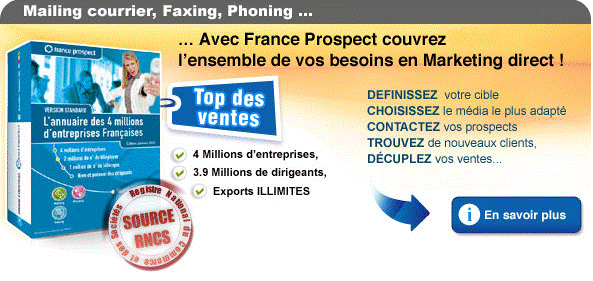
CD ROM Annuaire d'Entreprises France prospect (avec ou sans emails) : REMISE DE 10 % Avec le code réduction AUDEN872
|
10% de réduction sur vos envois d'emailing --> CLIQUEZ ICI Retour ŕ l'accueil, cliquez ici VPN Client Administrator Guide Release 4.0 May 2001 Corporate Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 526-4100 VPN Client Administrator Guide Release 4.0 May 2003 Customer Order Number: DOC-7815404= Text Part Number: 78-15404-02THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS. THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY. The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California. NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS” WITH ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE. IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. CCIP, CCSP, the Cisco Arrow logo, the Cisco Powered Network mark, the Cisco Systems Verified logo, Cisco Unity, Follow Me Browsing, FormShare, iQ Net Readiness Scorecard, Networking Academy, and ScriptShare are trademarks of Cisco Systems, Inc.; Changing the Way We Work, Live, Play, and Learn, The Fastest Way to Increase Your Internet Quotient, and iQuick Study are service marks of Cisco Systems, Inc.; and Aironet, ASIST, BPX, Catalyst, CCDA, CCDP, CCIE, CCNA, CCNP, Cisco, the Cisco Certified Internetwork Expert logo, Cisco IOS, the Cisco IOS logo, Cisco Press, Cisco Systems, Cisco Systems Capital, the Cisco Systems logo, Empowering the Internet Generation, Enterprise/Solver, EtherChannel, EtherSwitch, Fast Step, GigaStack, Internet Quotient, IOS, IP/TV, iQ Expertise, the iQ logo, LightStream, MGX, MICA, the Networkers logo, Network Registrar, Packet, PIX, Post-Routing, Pre-Routing, RateMUX, Registrar, SlideCast, SMARTnet, StrataView Plus, Stratm, SwitchProbe, TeleRouter, TransPath, and VCO are registered trademarks of Cisco Systems, Inc. and/or its affiliates in the U.S. and certain other countries. All other trademarks mentioned in this document or Web site are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (0303R) VPN Client Administrator Guide Copyright © 2003 Cisco Systems, Inc. All rights reserved.iii VPN Client Administrator Guide 78-15404-02 C O N T E N T S Preface vii Audience vii Organization viii Related Documentation ix VPN 3000 Series Concentrator Documentation ix Other References ix Conventions x Data Formats x Obtaining Documentation xi Cisco.com xi Documentation CD-ROM xi Ordering Documentation xi Documentation Feedback xii Obtaining Technical Assistance xii Cisco.com xii Technical Assistance Center xiii Cisco TAC Website xiii Cisco TAC Escalation Center xiii Obtaining Additional Publications and Information xiv C H A P T E R 1 Configuration Information for an Administrator 1-1 VPN 3000 Series Concentrators Configuration Information 1-1 Configuring a VPN 3000 Concentrator for Remote Access Users 1-1 Completing Quick Configuration 1-2 Creating an IPSec Group 1-2 Creating VPN Client User Profiles 1-3 Configuring VPN Client Users for Digital Certificate Authorization 1-3 Configuring VPN Client Firewall Policy—Windows Only 1-5 Overview 1-5 Firewall Configuration Scenarios 1-8 Defining a Filter and Rules to Use with Firewalls for CPP 1-10 Configuring the VPN 3000 Concentrator to Enforce Firewall Usage on the VPN Client 1-11 Setting up Cisco Integrated Client Firewall (CIC) for CPP 1-12 Custom Vendor Codes 1-12Contents iv VPN Client Administrator Guide 78-15404-02 Obtaining Firewall Troubleshooting Information 1-13 Notifying Remote Users of a Client Update 1-14 Setting up Local LAN Access for the VPN Client 1-15 Configuring the VPN Concentrator for Client Backup Servers 1-17 Configuring NAT Traversal for the VPN Client 1-17 Global Configuration 1-17 Configuring Entrust Entelligence for the VPN Client—Windows Only 1-18 Setting up the VPN Client for Authentication using Smart Cards—Windows Only 1-20 C H A P T E R 2 Preconfiguring the VPN Client for Remote Users 2-1 Profiles 2-1 File Format for All Profile Files 2-2 Making a Parameter Read Only 2-2 Creating a Global Profile 2-2 Features Controlled by Global Profile 2-2 Global Profile Configuration Parameters 2-4 DNS Suffixes and the VPN Client—Windows 2000 and Windows XP Only 2-12 Setting Up RADIUS SDI Extended Authentication 2-15 Creating Connection Profiles 2-16 Features Controlled by Connection Profiles 2-16 Creating a .pcf file for a Connection Profile 2-18 Naming the Connection Profile 2-18 Connection Profile Configuration Parameters 2-18 Distributing Configured VPN Client Software to Remote Users 2-25 Separate Distribution 2-25 Distribution with the VPN Client Software 2-26 C H A P T E R 3 Configuring Automatic VPN Initiation—Windows Only 3-1 Creating Automatic VPN Initiation in the vpnclient.ini File 3-3 Preparation 3-3 What You Have to Do 3-3 Verifying Automatic VPN Initiation Configuration 3-5 C H A P T E R 4 Using the VPN Client Command-Line Interface 4-1 CLI Commands 4-1 Displaying a List of VPN Client Commands 4-1 Starting a Connection—vpnclient connect 4-1 Displaying a Notification—vpnclient notify 4-4 Displaying an Automatic VPN Initiation Configuration—Windows Only 4-4Contents v VPN Client Administrator Guide 78-15404-02 Suspending/Resuming Stateful Firewall (Windows Only) 4-5 Ending a Connection—vpnclient disconnect 4-6 Displaying Information About Your Connection—vpnclient stat 4-6 Return Codes 4-10 Application Example—Windows Only 4-12 C H A P T E R 5 Customizing the VPN Client Software 5-1 Customizing the VPN Client GUI for Windows 5-2 Areas Affected by Customizing the VPN Client 5-2 Installation Bitmap 5-2 Program Menu Titles and Text 5-3 VPN Client 5-4 Setup Bitmap—setup.bmp 5-5 Creating the oem.ini File 5-5 Sample oem.ini File 5-5 oem.ini File Keywords and Values 5-6 Customizing the VPN Client Using an MSI Transform 5-10 Creating the Transform 5-10 OEM.INI File and MSI 5-15 Installing the VPN Client using the Transform 5-15 Installing the VPN Client Without User Interaction 5-16 Silent Installation Using InstallShield 5-16 Silent Installation Using MSI 5-17 Launching SetMTU with Silent Installation 5-17 Customizing the VPN Client GUI for Mac OS X 5-18 C H A P T E R 6 Troubleshooting and Programmer Notes 6-1 Troubleshooting the VPN Client 6-1 Gathering Information for Customer Support 6-1 If Your Operating System is Windows 98, 98 SE, ME, 2000, or XP 6-1 If Your Operating System is Windows NT or Windows 2000 6-2 If Your Operating System is Mac OS X 6-3 Solving Common Problems 6-4 Shutting Down on Windows 98 6-4 Booting Automatically Starts up Dial-up Networking on Windows 95 6-4 Changing the MTU Size 6-4 Changing the MTU Size—Windows 6-4 Changing the MTU Size—Linux, Solaris, and Mac OS X 6-5Contents vi VPN Client Administrator Guide 78-15404-02 Delete With Reason 6-6 Configuring Delete with Reason on the VPN Concentrator 6-7 Start Before Logon and GINAs—Windows Only 6-7 Fallback Mode 6-7 Incompatible GINAs 6-8 Programmer Notes 6-8 Testing the Connection 6-8 Command Line Switches for ipsecdialer Command—Windows Only 6-9 IKE Proposals 6-10 C H A P T E R 7 Windows Installer (MSI) Information 7-1 Differences Between InstallShield and MSI 7-1 Starting the VPN Client MSI 7-2 Alternative Ways to Launch MSI 7-2 Launching MSI via Command Line 7-2 Launching MSI via the MSI Icon 7-2 Logging During Installation 7-3 IN D E Xvii VPN Client Administrator Guide 78-15404-02 Preface This VPN Client Administrator Guide tells you how to set up selected features of the Cisco VPN Client for users. This manual supplements the information provided in accompanying documentation for the Cisco VPN devices that work with the VPN Client. The chapters and sections in this manual apply to all platforms supported by the Cisco VPN Client unless otherwise specified. The VPN Client is a software client that lets users: • Connect to a Cisco VPN device • Capture, filter, and display messages generated by the VPN Client software • Enroll for and manage certificates • Remove the VPN Client software from the program menu (for InstallShield installation only) • Manually change the size of the maximum transmission unit (see “Changing the MTU Size”) For information about how to use this application, see the VPN Client User Guide for your platform. In this administrator guide, the term Cisco VPN device refers to the following Cisco products: • Cisco VPN 3000 Series Concentrator • Cisco Secure PIX Firewall devices • IOS platform devices, such as the Cisco 7100 Series Routers Audience We assume you are an experienced system administrator or network administrator with appropriate education and training, who knows how to install, configure, and manage internetworking systems. You should be familiar with system configuration and management for the platform you are administering.viii VPN Client Administrator Guide 78-15404-02 Preface Organization The VPN Administrator Guide is organized as follows: Chapter Title Description Chapter 1 Configuration Information for an Administrator Explains how to configure a VPN 3000 Concentrator for remote access, personal firewalls, local LAN access, backup servers, NAT-T. Also describes how to configure a VPN Client to work with Entrust Entelligence and smart cards. Chapter 2 Preconfiguring the VPN Client for Remote Users Shows how to create global and user profiles. Chapter 3 Configuring Automatic VPN Initiation—Windows Only Describes auto initiation and how to configure the vpnclient.ini file for auto initiation. Chapter 4 Using the VPN Client Command-Line Interface Explains how to use the command-line interface (CLI) to connect to a VPN device, how to disconnect from a VPN device, and how to get status information from a VPN device. You can use these commands in batch mode. Chapter 5 Customizing the VPN Client Software Describes how to use your own names and icons for the VPN Client applications instead of Cisco Systems names. Also describes how to install and reboot the VPN Client software without user interaction, called silent mode. Chapter 6 Troubleshooting and Programmer Notes Lists troubleshooting techniques. Describes how to use the SetMTU application. Chapter 7 Windows Installer (MSI) Information Lists the differences between InstallShield and MSI, describes alternative ways to start MSI, explains logging and upgrading.ix VPN Client Administrator Guide 78-15404-02 Preface Related Documentation Related Documentation This administrator guide is a companion to the following VPN Client user guides: • VPN Client User Guide for Windows, Release 4.0— explains to Windows VPN Client users how to install the VPN Client for Windows software, configure connection entries, connect to Cisco VPN devices, manage VPN connections, and enroll for digital certificates. • VPN Client User Guide for Mac OS X, Release 4.0— explains to Mac VPN Client users how to install the VPN Client for Mac software, configure connection entries, connect to Cisco VPN devices, manage VPN connections, and enroll for digital certificates. The VPN Client on the Macintosh platform can be managed through the GUI or the command-line interface. • VPN Client User Guide for Linux and Solaris, Release 4.0— explains to Linux and Solaris VPN Client users how to install the VPN Client software, configure connection entries, connect to Cisco VPN devices, manage VPN connections, and enroll for digital certificates. The VPN Client on the Linux and Solaris platforms is managed only through the command-line interface. • Also the VPN Client includes an online HTML-based help system that you can access through a browser in several ways: clicking the Help icon on the Cisco Systems VPN Client programs menu (Start>Programs>Cisco Systems VPN Client>Help), pressing F1 while using the applications, or clicking the Help button on screens that include it. • Release Notes for the Cisco VPN Client Version 4.0—includes information relevant to all platforms. To view the latest version of the VPN Client documentation on the Cisco Web site, go to the following site and click on VPN Clients. http://www.cisco.com/univercd/cc/td/doc/product/vpn/index.htm VPN 3000 Series Concentrator Documentation The VPN 3000 Concentrator Getting Started, Release 4.0 guide explains how to unpack and install the VPN 3000 Concentrator, and how to configure the minimal parameters. This is known as Quick Config. The VPN 3000 Concentrator Reference Volume I: Configuration, Release 4.0 explains how to start and use the VPN 3000 Concentrator Manager. It details the Configuration screens and explains how to configure your device beyond the minimal parameters you set during quick configuration. The VPN 3000 Concentrator Reference Volume II: Administration and Monitoring, Release 4.0 provides guidelines for administering and monitoring the VPN 3000 Concentrator. It explains and defines all functions available in the Administration and Monitoring screens of the VPN 3000 Concentrator Manager. Appendixes to this manual provide troubleshooting guidance and explain how to access and use the alternate command-line interface. The VPN 3000 Concentrator Manager (the Manager) also includes online help that you can access by clicking the Help icon on the toolbar in the Manager window. Other References Other useful references include: • Cisco Systems, Dictionary of Internetworking Terms and Acronyms. Cisco Press: 2001. • Virtual Private Networking: An Overview. Microsoft Corporation: 1999. (Available from Microsoft website.)x VPN Client Administrator Guide 78-15404-02 Preface Conventions • www.ietf.org for Internet Engineering Task Force (IETF) Working Group drafts on IP Security Protocol (IPSec). • www.whatis.com, a web reference site with definitions for computer, networking, and data communication terms. Conventions This document uses the following conventions: Notes use the following conventions: Note Means reader take note. Notes contain helpful suggestions or references to material not covered in the publication. Cautions use the following conventions: Caution Means reader be careful. Cautions alert you to actions or conditions that could result in equipment damage or loss of data. Data Formats As you configure and manage the system, enter data in the following formats unless the instructions indicate otherwise: Convention Description boldface font User actions and commands are in boldface. italic font Arguments for which you supply values are in italics. screen font Terminal sessions and information the system displays are in screen font. boldface screen font Information you must enter is in boldface screen font in the command-line interface (for example, vpnclient stat). italic screen font Arguments for which you supply values are in italic screen font. Type of Data Format IP Addresses IP addresses use 4-byte dotted decimal notation (for example, 192.168.12.34); as the example indicates, you can omit leading zeros in a byte position. Subnet Masks and Wildcard Masks Subnet masks use 4-byte dotted decimal notation (for example, 255.255.255.0). Wildcard masks use the same notation (for example, 0.0.0.255); as the example illustrates, you can omit leading zeros in a byte position.xi VPN Client Administrator Guide 78-15404-02 Preface Obtaining Documentation Obtaining Documentation Cisco provides several ways to obtain documentation, technical assistance, and other technical resources. These sections explain how to obtain technical information from Cisco Systems. Cisco.com You can access the most current Cisco documentation on the World Wide Web at this URL: http://www.cisco.com/univercd/home/home.htm You can access the Cisco website at this URL: http://www.cisco.com International Cisco web sites can be accessed from this URL: http://www.cisco.com/public/countries_languages.shtml Documentation CD-ROM Cisco documentation and additional literature are available in a Cisco Documentation CD-ROM package, which may have shipped with your product. The Documentation CD-ROM is updated monthly and may be more current than printed documentation. The CD-ROM package is available as a single unit or through an annual subscription. Registered Cisco.com users can order the Documentation CD-ROM (product number DOC-CONDOCCD=) through the online Subscription Store: http://www.cisco.com/go/subscription Ordering Documentation You can find instructions for ordering documentation at this URL: http://www.cisco.com/univercd/cc/td/doc/es_inpck/pdi.htm MAC Addresses MAC addresses use 6-byte hexadecimal notation (for example, 00.10.5A.1F.4F.07). Hostnames Hostnames use legitimate network hostname or end-system name notation (for example, VPN01). Spaces are not allowed. A hostname must uniquely identify a specific system on a network. Text Strings Text strings use upper- and lower-case alphanumeric characters. Most text strings are case-sensitive (for example, simon and Simon represent different usernames). In most cases, the maximum length of text strings is 48 characters. Port Numbers Port numbers use decimal numbers from 0 to 65535. No commas or spaces are permitted in a number. Type of Data Formatxii VPN Client Administrator Guide 78-15404-02 Preface Obtaining Technical Assistance You can order Cisco documentation in these ways: • Registered Cisco.com users (Cisco direct customers) can order Cisco product documentation from the Networking Products MarketPlace: http://www.cisco.com/en/US/partner/ordering/index.shtml • Registered Cisco.com users can order the Documentation CD-ROM (Customer Order Number DOCCD-NA-12XYR or DOCCD-NA-4XYR)) through the online Subscription Store: http://www.cisco.com/go/subscription • Nonregistered Cisco.com users can order documentation through a local account representative by calling Cisco Systems Corporate Headquarters (California, U.S.A.) at 408 526-7208 or, elsewhere in North America, by calling 800 553-NETS (6387). Documentation Feedback You can submit comments electronically on Cisco.com. On the Cisco Documentation home page, click Feedback at the top of the page. You can e-mail your comments to bug-doc@cisco.com. You can submit your comments by mail by using the response card behind the front cover of your document or by writing to the following address: Cisco Systems Attn: Customer Document Ordering 170 West Tasman Drive San Jose, CA 95134-9883 We appreciate your comments. Obtaining Technical Assistance Cisco provides Cisco.com, which includes the Cisco Technical Assistance Center (TAC) Website, as a starting point for all technical assistance. Customers and partners can obtain online documentation, troubleshooting tips, and sample configurations from the Cisco TAC website. Cisco.com registered users have complete access to the technical support resources on the Cisco TAC website, including TAC tools and utilities. Cisco.com Cisco.com offers a suite of interactive, networked services that let you access Cisco information, networking solutions, services, programs, and resources at any time, from anywhere in the world. Cisco.com provides a broad range of features and services to help you with these tasks: • Streamline business processes and improve productivity • Resolve technical issues with online support • Download and test software packages • Order Cisco learning materials and merchandise • Register for online skill assessment, training, and certification programsxiii VPN Client Administrator Guide 78-15404-02 Preface Obtaining Technical Assistance To obtain customized information and service, you can self-register on Cisco.com at this URL: http://www.cisco.com Technical Assistance Center The Cisco TAC is available to all customers who need technical assistance with a Cisco product, technology, or solution. Two levels of support are available: the Cisco TAC website and the Cisco TAC Escalation Center. The avenue of support that you choose depends on the priority of the problem and the conditions stated in service contracts, when applicable. We categorize Cisco TAC inquiries according to urgency: • Priority level 4 (P4)—You need information or assistance concerning Cisco product capabilities, product installation, or basic product configuration. • Priority level 3 (P3)—Your network performance is degraded. Network functionality is noticeably impaired, but most business operations continue. • Priority level 2 (P2)—Your production network is severely degraded, affecting significant aspects of business operations. No workaround is available. • Priority level 1 (P1)—Your production network is down, and a critical impact to business operations will occur if service is not restored quickly. No workaround is available. Cisco TAC Website You can use the Cisco TAC website to resolve P3 and P4 issues yourself, saving both cost and time. The site provides around-the-clock access to online tools, knowledge bases, and software. To access the Cisco TAC website, go to this URL: http://www.cisco.com/tac All customers, partners, and resellers who have a valid Cisco service contract have complete access to the technical support resources on the Cisco TAC website. Some services on the Cisco TAC website require a Cisco.com login ID and password. If you have a valid service contract but do not have a login ID or password, go to this URL to register: http://tools.cisco.com/RPF/register/register.do If you are a Cisco.com registered user, and you cannot resolve your technical issues by using the Cisco TAC website, you can open a case online at this URL: http://www.cisco.com/en/US/support/index.html If you have Internet access, we recommend that you open P3 and P4 cases through the Cisco TAC website so that you can describe the situation in your own words and attach any necessary files. Cisco TAC Escalation Center The Cisco TAC Escalation Center addresses priority level 1 or priority level 2 issues. These classifications are assigned when severe network degradation significantly impacts business operations. When you contact the TAC Escalation Center with a P1 or P2 problem, a Cisco TAC engineer automatically opens a case. To obtain a directory of toll-free Cisco TAC telephone numbers for your country, go to this URL: http://www.cisco.com/warp/public/687/Directory/DirTAC.shtmlxiv VPN Client Administrator Guide 78-15404-02 Preface Obtaining Additional Publications and Information Before calling, please check with your network operations center to determine the level of Cisco support services to which your company is entitled: for example, SMARTnet, SMARTnet Onsite, or Network Supported Accounts (NSA). When you call the center, please have available your service agreement number and your product serial number. Obtaining Additional Publications and Information Information about Cisco products, technologies, and network solutions is available from various online and printed sources. • The Cisco Product Catalog describes the networking products offered by Cisco Systems as well as ordering and customer support services. Access the Cisco Product Catalog at this URL: http://www.cisco.com/en/US/products/products_catalog_links_launch.html • Cisco Press publishes a wide range of networking publications. Cisco suggests these titles for new and experienced users: Internetworking Terms and Acronyms Dictionary, Internetworking Technology Handbook, Internetworking Troubleshooting Guide, and the Internetworking Design Guide. For current Cisco Press titles and other information, go to Cisco Press online at this URL: http://www.ciscopress.com • Packet magazine is the Cisco monthly periodical that provides industry professionals with the latest information about the field of networking. You can access Packet magazine at this URL: http://www.cisco.com/en/US/about/ac123/ac114/about_cisco_packet_magazine.html • iQ Magazine is the Cisco monthly periodical that provides business leaders and decision makers with the latest information about the networking industry. You can access iQ Magazine at this URL: http://business.cisco.com/prod/tree.taf%3fasset_id=44699&public_view=true&kbns=1.html • Internet Protocol Journal is a quarterly journal published by Cisco Systems for engineering professionals involved in the design, development, and operation of public and private internets and intranets. You can access the Internet Protocol Journal at this URL: http://www.cisco.com/en/US/about/ac123/ac147/about_cisco_the_internet_protocol_journal.html • Training—Cisco offers world-class networking training, with current offerings in network training listed at this URL: http://www.cisco.com/en/US/learning/le31/learning_recommended_training_list.htmlC H A P T E R 1-1 VPN Client Administrator Guide 78-15404-02 1 Configuration Information for an Administrator This chapter provides information to a network administrator that supplements the VPN Client User Guide for your platform and the VPN 3000 Series Concentrator Reference Volume I: Configuration. This chapter includes the following major topics: • VPN 3000 Series Concentrators Configuration Information • Configuring Entrust Entelligence for the VPN Client—Windows Only • Setting up the VPN Client for Authentication using Smart Cards—Windows Only VPN 3000 Series Concentrators Configuration Information We recommend that you carefully read the chapter on “User Management,” VPN 3000 Series Concentrator Reference Volume I: Configuration. The “User Management” chapter contains complete information on setting up remote users to connect through the IPSec tunnel, and also explains how to use features such as setting up a client banner, firewalls, split tunneling, and so on. This section covers the following tasks: • Configuring a VPN 3000 Concentrator for Remote Access Users • Configuring VPN Client Firewall Policy—Windows Only • Notifying Remote Users of a Client Update • Setting up Local LAN Access for the VPN Client • Configuring the VPN Concentrator for Client Backup Servers • Configuring NAT Traversal for the VPN Client Configuring a VPN 3000 Concentrator for Remote Access Users Before VPN Client users can access the remote network through a VPN 3000 Concentrator, you must complete the following tasks on the VPN 3000 Concentrator: • Complete all the steps in quick configuration, as a minimum. • Create and assign attributes to an IPSec group. • Create and assign attributes to VPN Client users as members of the IPSec group. • Configure VPN Client users who are using digital certificates instead of pre-shared keys for authentication.1-2 VPN Client Administrator Guide 78-15404-02 Chapter 1 Configuration Information for an Administrator VPN 3000 Series Concentrators Configuration Information Completing Quick Configuration For steps in quick configuration, refer to VPN 3000 Series Concentrator Getting Started or Quick Configuration online help. Be sure to perform the following tasks. • Configure and enable both Ethernet interfaces 1 and 2 (Private and Public) with appropriate IP addresses and filters. • Configure a DNS server and default gateway. • Enable IPSec as one of the tunneling protocols (the default). • Enter a group name and password for an IPSec group. • Configure at least one method for assigning user IP addresses. • Configure authentication servers for group and user authentication. These instructions assume the internal server for both, but you can set up any of the external servers instead. • Save the configuration. Creating an IPSec Group During the Quick Configuration, you can automatically create an IPSec group. If you want to add an IPSec group or modify one, follow the procedure in this section. Refer to “User Management” in the VPN 3000 Series Concentrator Reference Volume I: Configuration, or the online help, for details on configuring groups. You may want to set base-group attributes before you create an IPSec group; see the Configuration | User Management | Base Group screen. We suggest you carefully review the General Parameters and IPSec Parameters on that screen. If you use external user authentication, base-group attributes are especially important since they govern all attributes that the external server does not provide. The VPN Client uses the IPSec protocol for creating and using secure tunnels. IPSec has two authentication phases: first for the group, then for the user. These instructions assume that you are using the VPN 3000 Concentrator internal authentication server for both group and user authentication. Use the Configuration | User Management | Groups | Add screen to create an IPSec group: Step 1 Under the Identity tab, enter a Group Name and Password. VPN Client users need these to configure a connection entry and connect via the VPN Client; see “Gathering Information You Need” in Chapter 2 of the VPN Client User Guide for your platform. Step 2 Next, select a method of authentication. The Type parameter determines the group authentication method, Internal or External. Internal groups are configured on the VPN Concentrator. If you select External, you must configure an external RADIUS server to authenticate and provide appropriate group attributes. Step 3 Under the General tab | Tunneling Protocols, be sure IPSec is checked. Step 4 Under the IPSec tab | IPSec SA, select ESP-3DES-MD5 to require Triple-DES authentication. Alternatively, you could choose ESP-DES-MD5, which uses DES authentication and provides a minimum level of security. Or, to use AES, select one of the AES protocols, such as ESP-AES128-SHA. AES is the most secure.1-3 VPN Client Administrator Guide 78-15404-02 Chapter 1 Configuration Information for an Administrator VPN 3000 Series Concentrators Configuration Information Note To create or customize the Security Association (SA), see the Configuration | Policy Management | Traffic Management | Security Associations screens. Step 5 Under IPSec > Authentication, choose the method you use for the members of the group; for example, Internal or RADIUS. If you choose an authentication method other than None or Internal, be sure to configure the external authentication server appropriately and supply users with the appropriate information for installing the VPN Client. Step 6 To require users to enter a password each time they log in, we suggest that you not check Allow Password Storage on Client, which is on the Client Config tab. Not checking this parameter provides greater security. Step 7 To add the group, click Add, and then save the configuration. Creating VPN Client User Profiles For details on configuring VPN Client users within a group, see “User Management,” in the VPN 3000 Series Concentrator Reference Volume I: Configuration. Use the Configuration | User Management | Users | Add or Modify screen to configure a VPN Client user: Step 1 Enter a User Name, Password, and Verify Password. VPN Client users need a user name and password to authenticate when they connect to the VPN Concentrator; see “Gathering Information You Need” in Chapter 2 of the VPN Client User Guide for your platform. Step 2 Under Group, select the group name you configured under the section “Creating an IPSec Group.” Step 3 Carefully review and configure other attributes under General and IPSec. Note that if you are adding a user, the Inherit? checkboxes refer to base-group attributes; if you are modifying a user, the checkboxes refer to the user’s assigned-group attributes. Step 4 Click Add or Apply, and save the configuration. Configuring VPN Client Users for Digital Certificate Authorization Use the following procedure to configure the VPN 3000 Concentrator for IPSec client connections using digital certificates. • Activate an IKE SA. • Configure a security association (SA) to use the VPN 3000 Concentrator’s identity certificate. • Create a new group for clients connecting with certificates. • Add VPN Client users to the new group. • For details refer to the VPN 3000 Series Concentrator Reference Volume I: Configuration: – On configuring IKE proposals, see “Tunneling Protocols.” – On configuring SAs, see “Policy Management.” – On configuring groups and users, see “User Management.” 1-4 VPN Client Administrator Guide 78-15404-02 Chapter 1 Configuration Information for an Administrator VPN 3000 Series Concentrators Configuration Information Follow these steps: Step 1 Use the Configuration | System | Tunneling Protocols | IPSec | IKE Proposals screen to activate an IKE proposal for certificates: a. Activate one of the IKE protocols such as CiscoVPNClient-3DES-MD5-RSA-DH5, CiscoVPNClient-3DES-SHA-DSA-DH5, or CiscoVPNClient-AES128-SHA. Note To use AES, move the AES proposal(s) to the top of the list. You must be running Release 3.6 or higher of the VPN Client software to use AES. b. If you do not want to modify one of the standard proposals, copy an active proposal and give it a new name; for example, copy the CiscoVPNClient-3DES-MD5-RSA-DH5 and name it “IKE-Proposal for digital certificate use.” c. Click Security Associations, which takes you to the next step. Step 2 Use the Configuration | Policy Management | Traffic Management | Security Associations screen to create a new SA. You can use the Security Associations link on the IKE Proposals screen. a. Add a new SA. For example, name it “Security association for digital certificate use.” b. Change the Digital Certificates parameter to identify the VPN 3000 Concentrator’s digital certificate. This is the only field that you need to change. Step 3 Use the Configuration | User Management | Groups | Add or Modify screen to configure a group for using digital certificates: a. To use the Organizational Unit to configure the group, under the Identity tab, enter a group name that is the same as the OU field of the certificate(s) for this group. For example, if the OU in the VPN Client certificate is Finance, you would enter Finance as the group name. The OU is a field of the ASN.1 Distinguished Name (DN). Enter password and verify it. or Alternatively, you can configure a policy for certificate group matching. To use this approach, go to Configuration | Policy Management | Certificate Group Matching | Policy. For instructions on creating rules, see VPN 3000 Series Concentrator Reference I: Configuration for this section or refer to online help. b. Under the IPSec tab > IPSec SA, select the IPSec SA you created in step 2; for example, “Security association for digital certificate use.” c. Under IPSec tab > Authentication, select the method you use for user authentication; for example, Internal. If you select an external authentication method, such as RADIUS, be sure to configure the external authentication server appropriately and supply users with the appropriate entries for the “Gathering the Information You Need” section in Chapter 2 of the VPN Client User Guide for your platform. d. Click Add or Apply, and save the configuration. Step 4 Use the Configuration | User Management | Users | Add or Modify | Identity screen to configure VPN Client users for digital certificates: a. As the group name, enter the group you have set up in step 3 as the group parameter; continuing the example, you would enter Finance. b. Click Add or Apply, and save the configuration.1-5 VPN Client Administrator Guide 78-15404-02 Chapter 1 Configuration Information for an Administrator VPN 3000 Series Concentrators Configuration Information Configuring VPN Client Firewall Policy—Windows Only To provide a higher level of security, the VPN Client can either enforce the operation of a supported firewall or receive a pushed down stateful firewall policy for Internet bound traffic. This section includes the following topics: • how firewalls work with the VPN Client • list of the personal firewall products that the VPN Client can enforce for Internet traffic • how to configure a stateful firewall policy on a VPN Concentrator for the VPN Client to enforce Overview This section summarizes how a network administrator can control personal firewall features from a VPN 3000 Concentrator operating as the Secure Gateway communicating policy information to the VPN Client running on a Windows platform. Optional versus Required Configuration Option The VPN Concentrator can require that a VPN Client use a designated firewall configuration or make this configuration optional. Making a designated firewall configuration optional gives a VPN Client user a chance to install the desired firewall on the client PC. When the VPN Client tries to connect, it notifies the VPN Concentrator about any firewalls installed on the client PC. The VPN Concentrator sends back information about what firewall the VPN Client must use. If the firewall configuration is optional, the VPN Concentrator can notify the VPN Client that there is a mismatch but still allow the VPN Client to establish a tunnel. The optional feature thus lets the network administrator of the VPN Client maintain the tunneled connection while obtaining and installing the required firewall. Stateful Firewall (Always On) The VPN Client configuration option Stateful Firewall (Always On) is enabled on the VPN Client. This configuration option is not negotiated. The policy is not controlled from the VPN Concentrator. The VPN Client user enables this option on the VPN Client under the Options menu or while the VPN Client is active by right-clicking on the VPN Client icon and selecting the option. When enabled, this feature allows no inbound sessions from all networks, whether or not a VPN connection is in effect. Also, the firewall is active for both tunneled and nontunneled traffic. Users who enable this feature cannot have a server running on their PC and their system can no longer respond to PING requests. There are two exceptions to allowing no inbound traffic. The first is DHCP, which sends requests to the DHCP server out one port but receives responses from DHCP through a different port. For DHCP, the stateful firewall allows inbound traffic. The second is ESP (VPN data). The stateful firewall allows ESP traffic from the secure gateway, because ESP rules are packet filters and not session-based filters. Stateful Firewall (Always On) is the most basic VPN Client firewall and provides the highest level of security. However, it is also the least flexible, since it blocks almost all incoming traffic and does not allow outbound traffic to be limited. Note The Always On personal firewall allows inbound access from the internal (tunneled) network to ensure that your internal applications work properly, while still providing additional protection for non tunneled traffic.1-6 VPN Client Administrator Guide 78-15404-02 Chapter 1 Configuration Information for an Administrator VPN 3000 Series Concentrators Configuration Information Cisco Integrated Client The VPN Client on the Windows platform includes a stateful firewall that incorporates Zone Labs technology. This firewall is used for both the Stateful Firewall (Always On) feature and the Centralized Protection Policy (see “Centralized Protection Policy (CPP)”). This firewall is transparent to the VPN Client user, and is called “Cisco Integrated Client Firewall” or CIC. While the “Always On” option lets the VPN Client user choose to have basic firewall protection in effect, CPP lets an administrator define rules to enforce for inbound/outbound Internet traffic during split tunneling operation. Since tunnel everything already forces all traffic back through the tunnel, CPP is not used for tunnel everything. Centralized Protection Policy (CPP) Centralized Protection Policy (CPP) also known as firewall push policy, lets a network administrator define a set of rules for allowing or dropping Internet traffic while the VPN Client is tunneled in to the VPN Concentrator. A network administrator defines this policy on the VPN Concentrator, and the policy is sent to the VPN Client during connection negotiation. The VPN Client passes the policy to the Cisco Integrated Client, which then enforces the policy. If the client user has already selected the “Always On” option, any more restrictive rules are enforced for Internet traffic while the tunnel is established. Since CIC includes a stateful firewall module, most configurations block all inbound traffic and permit either all outbound traffic or traffic through specific TCP and UDP ports outbound. Cisco Integrated Client, Zone Alarm, and Zone Alarm Pro firewalls can assign firewall rules. CPP rules are in effect during split tunneling and help protect the VPN Client PC from Internet attacks by preventing servers from running and by blocking any inbound connections unless they are associated with outbound connections. CPP provides more flexibility than the Stateful Firewall (Always On) feature, since with CPP, you can refine the ports and protocols that you want to permit. Policy Configured on the Remote PC—Personal Firewall Enforcement As an alternative to CPP, a network manager can define policy on the personal firewall that is installed on the same PC as the VPN Client. This approach accommodates situations where there is already a firewall set up and in use on the PC. The VPN Client then polls the personal firewall every 30 seconds to make sure it is running and if it is not, terminates the secure connection to the VPN Concentrator. In this case, the VPN Concentrator does not define the firewall policy. The only contact the VPN Client has with the firewall is polling it to ascertain that it is running, a capability known as Are You There (AYT). Currently, the VPN Client supports the following personal firewalls: • BlackIce Defender • Cisco Intrusion Prevention Security Agent • Sygate Personal Firewall • Sygate Personal Firewall Pro • Sygate Security Agent • ZoneAlarm • ZoneAlarmPro1-7 VPN Client Administrator Guide 78-15404-02 Chapter 1 Configuration Information for an Administrator VPN 3000 Series Concentrators Configuration Information Zone Labs Integrity Agent and Integrity Server (IA/IS) The Zone Labs Integrity solution secures remote PCs on Windows platforms. This feature is a client/server solution that comprises four components: Integrity Server (IS)—located on a central organization’s network, IS maintains policies for the firewall on the remote VPN Client PCs. A network manager defines the policy on the IS, the IS downloads the policy to the Integrity Agent (IA) on the remote PC through a secure tunnel activated through the VPN Concentrator. The IS monitors the PC to ensure enforcement of the policy. The IS also communicates with the VPN Concentrator to establish/terminate connections, exchange session and user information, and report status information. Integrity Agent (IA)—on the remote PC enforces the protection policies it receives from IS and communicates with IS to exchange policy and status information. The IA also communicates with the VPN Client on the remote PC to obtain server addresses and to exchange status information with the VPN Concentrator. VPN Concentrator—provides the means for configuring firewall functionality by group. It reports the IS’s IP address and other VPN session-related information to the VPN Client, which passes it on to the IA. The VPN Concentrator also communicates with the IS to establish and terminate sessions, exchange session and user information, and request and acquire authentication status. VPN Client—on the remote PC gets the IS addresses and information from the VPN Concentrator and passes it to the IA. The VPN Client also gets and reports status information from the IA and terminates sessions. Once the connection is up and IS has communicated the firewall policy to IA, then IS and IA keep in touch though a heartbeat mechanism. Table 1-1 Summary and Comparison of Firewall Configurations Product/Policy Where Defined Security/Flexibility What it Does/When Used Stateful Firewall (Always on) VPN Client Option Blocks all unauthorized inbound traffic; least flexible (no application awareness) Blocks all inbound traffic, all networks with few exceptions. Centralized Protection Policy (CPP) with Cisco Integrated Client (CIC) Policy pushed; central control Centrally controlled. Determined by traffic filters and rules defined on VPN Concentrator Used with split tunneling to protect VPN Client PC and private network from incoming traffic from the Internet. (Tunnel everything already blocks all nontunneled traffic.) ZoneAlarm and ZoneAlarm Pro with CPP Policy pushed; central control Centrally controlled. Determined by traffic filters and rules defined on VPN Concentrator Used with split tunneling to protect VPN Client PC and private network from unauthorized incoming and outbound traffic from/to the Internet when a tunnel is active.1-8 VPN Client Administrator Guide 78-15404-02 Chapter 1 Configuration Information for an Administrator VPN 3000 Series Concentrators Configuration Information Firewall Configuration Scenarios This section shows three sample firewall configurations. Each diagram shows the parameter settings in effect on the VPN Concentrator as well as the firewall product and policy in effect on the VPN Client. Cisco Integrated Client Figure 1-1 shows a typical configuration for Cisco Integrated Client, in which the policy (CPP) is pushed to the VPN Client. This policy blocks inbound traffic from the Internet while split tunneling is in use. Traffic from the private network is not blocked, however. Figure 1-1 Cisco Integrated Client ZoneAlarm ZoneAlarm Pro BlackIce Agent /Defender Sygate Personal Sygate Pro Sygate Security Agent Cisco Intrusion Prevention Security Agent Policy defined on VPN Client PC (AYT) Determined by traffic filters and rules defined on VPN Client PC Used when personal firewall is installed on the VPN Client and policy is not pushed. No specific policy is enforced. Client/Server Firewall—Zone Labs Integrity Policy pushed from Integrity Server (IS) Most secure and flexible central control of firewall policies. Enforces centralized corporate role-based policies on the VPN Client PC. Lets administrator monitor and enforce application control and prevent unauthorized inbound/outbound traffic. Table 1-1 Summary and Comparison of Firewall Configurations (continued) Product/Policy Where Defined Security/Flexibility What it Does/When Used 67447 Private network VPN Concentrator (VPNC) Require Firewall Cisco Integrated Client Firewall Policy Pushed (CPP) Filter/rules = drop all inbound; forward any outbound VPN Client PC Integrated Firewall Policy from VPNC Internet1-9 VPN Client Administrator Guide 78-15404-02 Chapter 1 Configuration Information for an Administrator VPN 3000 Series Concentrators Configuration Information Remote Firewall Figure 1-2 shows a configuration in which the policy is set up on a personal firewall on the PC. In this case, Are You There (AYT) is the policy. The VPN Client polls the firewall every 30 seconds to ensure that it is still running and if it is not, the VPN Client terminates the session. Figure 1-2 Remote Firewall Determines Policy Client/Server Approach Figure 1-3 shows a sample configuration for Zone Labs Integrity. 67448 Private network VPN Concentrator (VPNC) Require firewall Specific firewall selected Policy set up on remote PC's firewall VPN Client PC ZoneAlarm, BlackICE,Custom, etc. Firewall defines and maintains policy VPN Client polls (AYT) Internet1-10 VPN Client Administrator Guide 78-15404-02 Chapter 1 Configuration Information for an Administrator VPN 3000 Series Concentrators Configuration Information Figure 1-3 Client/Server—Integration With Zone Labs Integrity Server Defining a Filter and Rules to Use with Firewalls for CPP When you want the VPN Concentrator to push the firewall policy to the VPN Client, you must first define the policy on the VPN Concentrator. To do this you need to create a filter and add rules to the filter on the public network. The VPN 3000 Concentrator provides a default filter you can use for CPP by selecting it from the menu. The name of this filter is “Firewall Filter for VPN Client (Default)”. This filter allows all outbound traffic and drops all inbound traffic. Firewall filters are session filters, rather than packet filters. This means that for an “allow all outbound/drop all inbound” rule, the CPP policy lets inbound responses come from outbound sessions only from IP protocols TCP, UDP, and ICMP. These protocols are the only protocols that are “stateful.” Most administrators will want to use a rule that blocks all inbound traffic and either permits all outbound traffic or limits outbound traffic to specific TCP and UDP ports. For complete information on creating filters and adding rules in general, see VPN 3000 Series Concentrator Reference Volume I: Configuration, Configuration | Policy Management | Traffic Management. Example 1-1 Creating a Filter for a Firewall Policy allowing the VPN Client to Act as a Web Server This example shows step-by-step how to add a filter that allows outbound traffic to any protocol and to allow inbound traffic from HTTP but none of the other protocols. In this way, you can enable your VPN Client to become a Web server. 67449 Private network VPN Concentrator (VPNC) Knows address of IS Provides User ID/Session ID/Port to IS Sends User ID/Session ID/Port to VPN Client Integrity Server (IS) Gets User ID, Session ID, and Port from VPNC Provides connection information to VPNC Establishes policy; pushes policy to Integrity Agent (IA) VPN Client PC Integrity Agent (IA) IA installed and running VPNC and VPN Client negotiate VPNC passes User ID/Session ID/Port to Integrity Server VPN Client -- initializes IA with cached info --passes User ID/Session ID to IA IA connects with IS; gets firewall policy from IS IA starts enforcing policy VPN Client polls IA every 30 seconds If Firewall terminates, VPN connection dropped VPN Client uninitializes IA Caches policy Internet1-11 VPN Client Administrator Guide 78-15404-02 Chapter 1 Configuration Information for an Administrator VPN 3000 Series Concentrators Configuration Information Step 1 First, create a rule that allows inbound traffic only from HTTP. To do this, go to Configuration | Policy Management | Traffic Management | Rules. Step 2 Click Add a. For the Rule Name, enter the name, such as FW-Allow incoming HTTP. b. For Action, choose Forward. c. For Protocol, choose TCP. d. For TCP/UDP Destination Port, choose HTTP(80). e. Click Add. Step 3 Next add a filter that drops all inbound traffic except from HTTP but forwards any outbound traffic while connected through a tunnel. To do this, under Traffic Management, click Filters. a. Click the Add Filter box. b. Enter the filter name, such as FW-Allow Incoming HTTP, and select the defaults for the remaining parameters. c. Click Add, which brings up the Actions screen. d. On this screen, highlight the rule you made in Step 2 and click Add to move it to the Current Rules in Filter column. Do the same for the Any Out (forward/out) rule. e. Click Done. Step 4 Save the configuration. This filter now is available under Base Group and Groups for you to select for the CPP policy. Configuring the VPN 3000 Concentrator to Enforce Firewall Usage on the VPN Client This section shows how to configure the VPN Concentrator to require the VPN Client to enforce the use of a personal firewall on the VPN Client PC. On the VPN 3000 Concentrator side, you configure the Base Group or a specific group of users to enforce a personal firewall policy on the VPN Client side. Use the following general procedure. Step 1 To configure firewalls for the Base Group, choose Configuration | User Management | Base Group or to configure firewalls for a specific group, choose Configuration | User Management | Groups. Step 2 To add a firewall, do one of the following: • For the Base Group, choose the Client FW tab. • To create a new group for a firewall configuration, click Add Group and then click the Client FW tab. • To add a firewall to an existing group, highlight the group name, click Modify Group, and click the Client FW tab. Step 3 To require a firewall, under the Firewall Setting attribute, choose Firewall Required. Step 4 Under the Firewall attribute, choose a firewall from the Firewall pull-down menu. If the firewall you are using is not on the list, you must use Custom. Step 5 Choose the Firewall Policy: Policy defined by the remote firewall (AYT) or Policy pushed (CPP). (See the next section.)1-12 VPN Client Administrator Guide 78-15404-02 Chapter 1 Configuration Information for an Administrator VPN 3000 Series Concentrators Configuration Information For complete information, refer to VPN 3000 Series Concentrator Reference Volume I: Configuration, the section “User Management” or the VPN 3000 Concentrator Network Manager’s online help. Setting up Cisco Integrated Client Firewall (CIC) for CPP Step 1 Under Client FW tab on Firewall Setting, choose Firewall Required. Step 2 On the Firewall pull-down menu, choose Cisco Integrated Client Firewall. Step 3 On Firewall Policy, click Policy Pushed and select a filter that contains firewall policy rules. You can choose the default firewall filter or one that you have configured for a special purpose (see “Defining a Filter and Rules to Use with Firewalls for CPP”). Setting up a Client/Server Firewall —Zone Labs Integrity Step 1 Configure firewall policy on the Integrity Server (IS), following Zone Labs documentation. Step 2 On the VPN Concentrator, go to Configuration | System | Servers | Firewall Server. For the Zone Labs Integrity Server, enter the host name or IP address and the port number. Step 3 Under Configuration | User Management | Base Group or Groups | Client FW tab (see “Defining a Filter and Rules to Use with Firewalls for CPP”), configure the following: a. Firewall Setting = Firewall Required b. Firewall = Zone Labs Integrity c. Firewall Policy = Policy from Server Step 4 Save the configuration. Custom Vendor Codes On the VPN 3000 Concentrator, you can configure a custom firewall. Currently there are no supported firewall configurations that you cannot choose from the menu on the VPN Concentrator. This feature is mainly for future use. Nevertheless, the following table lists the vendor codes and products that are currently supported. Table 1-2 Custom Vendor and Product codes Vendor Vendor Code Products Product Code Cisco Systems 1 Cisco Integrated Client (CIC) 1 Zone Labs 2 Zone Alarm 1 ZoneAlarm Pro 2 Zone Labs Integrity 3 NetworkICE 3 BlackIce Defender 1 Sygate 4 Sygate Personal Firewall 11-13 VPN Client Administrator Guide 78-15404-02 Chapter 1 Configuration Information for an Administrator VPN 3000 Series Concentrators Configuration Information Obtaining Firewall Troubleshooting Information This section describes two ways to obtain information about firewall negotiations: through the IPSec Log or a notification from the VPN Concentrator. Examining the IPSec Log One way to see what is happening during tunnel negotiation between the VPN Client and the VPN Concentrator is to examine messages in the IPSec Log on the VPN Client. You can use the Log Viewer application to do this (for information on using Log Viewer, refer to the VPN Client User Guide for Windows, Chapter 5). During tunnel negotiation, the VPN Client initiates the firewall exchange by sending the VPN Concentrator a list of firewalls installed and running on the PC, if any. The VPN Concentrator then sends messages indicating its firewall requirements to the VPN Client. Following is an example of this exchange. First, the request from the VPN Client to the VPN Concentrator: Next, the responses from the VPN Concentrator: Notifications If the VPN Client and VPN Concentrator firewall configurations do not match, the VPN Concentrator notifies the VPN Client when the VPN Client user attempts to connect. If the firewall configuration is required, the connection attempt fails; if the firewall configuration is optional, the tunnel comes up. Sygate Pro 2 Sygate Security Agent 3 Cisco 5 Cisco Intrustion Prevention Security Agent 1 Table 1-2 Custom Vendor and Product codes (continued) Vendor Vendor Code Products Product Code1-14 VPN Client Administrator Guide 78-15404-02 Chapter 1 Configuration Information for an Administrator VPN 3000 Series Concentrators Configuration Information Figure 1-4 Firewall Mismatch Notification Notifying Remote Users of a Client Update You can notify VPN Client users when it is time to update the VPN Client software on their remote systems. The notification can include a location containing the client update (the update does not happen automatically). Use the Client Update procedure at the VPN 3000 Concentrator to configure a client notification: Step 1 To enable Client Update, go to Configuration | System | Client Update and click Enable. Step 2 At the Configuration | System | Client Update | Enable screen, check Enabled (the default) and then click Apply. Step 3 On the Configuration | System | Client Update | screen, click Entries. Step 4 On the Entries screen, click Add. Step 5 For Client Type, enter the operating systems to notify: • Windows includes all Windows based platforms • Win9X includes Windows 95, Windows 98, and Windows ME platforms • WinNT includes Windows NT 4.0, Windows 2000, and Windows XP platforms • Linux • Solaris • Mac OS X1-15 VPN Client Administrator Guide 78-15404-02 Chapter 1 Configuration Information for an Administrator VPN 3000 Series Concentrators Configuration Information Note The VPN 3000 Concentrator sends a separate notification message for each entry in a Client Update list. Therefore your client update entries must not overlap. For example, the value Windows includes all Windows platforms, and the value WinNT includes Windows NT 4.0, Windows 2000 and Windows XP platforms. So you would not include both Windows and WinNT. To find out the client types and version information, click on the lock icon at the top left corner of the Cisco Systems VPN Client main window and choose About VPN Client. Step 6 In the URL field, enter the URL that contains the notification. To activate the Launch button on the VPN Client Notification, the message must include the protocol HTTP or HTTPS and the server address of the site that contains the update. The message can also include the directory and filename of the update, for example, http://www.oz.org/upgrades/clientupdate. If you do not want to activate the Launch button for the remote user, you do not need to include a protocol in the message. In the Revisions field, enter a comma separated list of client revisions that do not need the update because they are already using the latest software. For example, the value 3.6.5 (Rel), 4.0 (Rel) identifies the releases that are compliant; all other VPN Clients need to upgrade. Step 7 Click Add. The Notification dialog box appears when the remote user first connects to the VPN device or when the user clicks the Notifications button on the Connection Status dialog box. When the notification pops up, on the VPN Client, click Launch on the Notification dialog box to open a default browser and access the URL containing the update. Setting up Local LAN Access for the VPN Client Remote users with Cable or DSL access from home might have home networks for sharing files and printers. You can configure local LAN access for remote users so that they can access resources on the LAN at the client side and still maintain the secure connection to the central site (through the IPSec tunnel). Before you begin, you should carefully read the section on split tunneling in the VPN 3000 Series Concentrator Reference Volume 1: Configuration. See the section explaining Configuration | User Management | Groups | Add or Modify | IPSec tab. Configuring local LAN access involves the following general steps: • Enabling local LAN access on the VPN Client • Enabling local LAN access in specific groups on the VPN 3000 Concentrator • Adding the accessible networks to a network list (or using the default network address). Use the following procedure: Step 1 On the VPN Client, enable the Allow Local LAN Access parameter. When creating or modifying a connection entry, display the Transport tab and check Allow Local LAN Access.1-16 VPN Client Administrator Guide 78-15404-02 Chapter 1 Configuration Information for an Administrator VPN 3000 Series Concentrators Configuration Information Figure 1-5 Setting the Allow Local LAN Access Parameter on the VPN Client Step 2 On the VPN 3000 Concentrator, either add a new group or modify an existing group as follows: a. To configure local LAN access for a specific group, go to Configuration | User Management | Groups. b. Choose either Add to add a new group or Modify to enable Local LAN for an existing group. c. Go to the Client Config tab. d. At the Split Tunneling Policy attribute, under Value, click the Tunnel everything radio button and then click Allow the networks in list to bypass the tunnel. This enables local LAN access on the VPN Client. e. At the Split Tunneling Network List, under Value, choose the network list you have created for local LAN access, if any. VPN Client Local LAN is the default and is assigned the address 0.0.0.0/0.0.0.0. This IP address allows access to all hosts on the client side LAN without regard to the network addressing configured on that network. Since this local LAN access is limited to only one local network, if you have multiple network cards in the client PC, you can access only the network in which the VPN Client has established the VPN connection. For information on creating a network list, see VPN 3000 Series Concentrator Reference Volume I: Configuration, “Configuration | Policy Management | Traffic Management | Network Lists”. Note When the VPN Client is connected and configured for local LAN access, you cannot print or browse by name on the local LAN. When the VPN Client is disconnected, you can print or browse by name. You can browse or print by IP Address. To print, you can change the properties for the network printer to use the IP Address instead of names. For example instead of the syntax \\sharename\printername, use \\x.x.x.x\printername, where x.x.x.x is an IP address. To print and browse by name, you can use an LMHOSTS file. To do this, add the IP addresses and local 1-17 VPN Client Administrator Guide 78-15404-02 Chapter 1 Configuration Information for an Administrator VPN 3000 Series Concentrators Configuration Information hostnames to a text file named LMHOSTS and place it on all your local PCs in the \Windows directory. The PC’s TCP/IP stack then uses the IP address to hostname mapping in the LMHOSTS file to resolve the name when printing or browsing. This approach requires that all local hosts have a static IP address; or if you are using DHCP, you must configure local hosts to always get the same IP address. Example LMHOSTS file: 192.168.1.100 MKPC 192.168.1.101 SBPC 192.168.1.101 LHPC Configuring the VPN Concentrator for Client Backup Servers This section shows how to configure a group on the VPN Concentrator to automatically push new backup server information to a VPN Client. Step 1 On the VPN Concentrator, go to Configuration | User Management | Group. Step 2 To add a new group, click Add or to modify an existing group, highlight it in the box and click Modify. Step 3 Go to the Client Config tab. Step 4 For IPSec Backup Servers, select Use List Below from the drop-down menu. Step 5 Enter a list of up to 10 IPSec backup servers in high to low priority order. Step 6 Type each server address or name on a single line into the IPSec Backup Servers box. Step 7 Click Apply and then save the configuration. Configuring NAT Traversal for the VPN Client NAT Traversal (NAT-T) lets the VPN Concentrator establish IPSec tunnels with a VPN Client when there is a NAT device between them. It does this by encapsulating ESP traffic in UDP datagrams, which provides ESP with the port information that NAT devices require. You can configure NAT-T globally on the VPN Concentrator, which then activates NAT-T for all groups configured on the VPN Concentrator. Global Configuration To configure NAT-T globally, follow these steps on the VPN Concentrator: Step 1 Go to Configuration | System | Tunneling Protocols| IPSec | NAT Transparency and check the IPSec over NAT-T check box. Step 2 Click Apply and then save the configuration. Next configure the following parameters on the VPN Client. Step 1 Go to Options > Properties > General.1-18 VPN Client Administrator Guide 78-15404-02 Chapter 1 Configuration Information for an Administrator Configuring Entrust Entelligence for the VPN Client—Windows Only Step 2 Check Enable Transparent Tunneling check box. Step 3 Click the Allow IPSec over UDP (NAT/PAT) radio button. Configuring Entrust Entelligence for the VPN Client—Windows Only This section explains how to set up a VPN Client to access Entrust Entelligence to obtain an Entrust identity certificate. It also provides information for using the VPN Client software with Entrust. For Entrust installation and configuration information, see your Entrust documentation—Entrust Entelligence Quick Start Guide or Entrust Entelligence online help. Use the following procedure: Step 1 Install Entrust Entelligence software on the remote user’s PC. You should install the Entrust Entelligence software before you install the VPN Client. The order is important when the VPN Client is using start before logon and Entrust SignOn at the same time. For information about what happens when both of these features are configured on the VPN Client, refer to VPN Client User Guide for Windows, Chapter 5. Step 2 As part of Entust Entelligence installation, create a new Entrust profile, using the Create Entrust Profile Wizard. To create an Entrust Entelligence profile, you need the following information: • The Entrust Entelligence reference number • The Entrust Entelligence authorization code • The name of a directory for storing the profile • A name for the profile • A password, following the rules set by the Entrust administrator Step 3 Optionally install Entrust SignOn, following the instructions in the Entrust documentation. a. As part of Entrust SignOn installation, you see the Entrust Options dialog box. (See Figure 1-6.) b. Make sure that you check Always prompt me to confirm this login information. Checking this box causes the Entrust SignOn login dialog box to pause and allow the VPN connection to come up before the remote user enters the NT logon information.1-19 VPN Client Administrator Guide 78-15404-02 Chapter 1 Configuration Information for an Administrator Configuring Entrust Entelligence for the VPN Client—Windows Only Figure 1-6 Entrust Options SignOn Tab Step 4 After creating a profile, log out of Entrust Entelligence. Step 5 Install the VPN Client software. Step 6 Create a new connection entry that includes authenticating using an Entrust certificate. For instructions see section “Configuring an Entrust Certificate for Authentication,” in Chapter 4 of VPN Client User Guide for Windows. Note The VPN Client relies on an up-to-date Entrust DLL file. The name of this file is kmpapi32.dll. If you are using Entrust Entelligence version 5.1, the DLL file is up to date. If you have version 4.0 or 5.0 installed on the VPN Client system, then the DLL file is not up to date. If “Entelligence Certificate (Entrust)” does not appear in the Certificate menu on the VPN Client, you probably do not have the latest version of the DLL file, which ships with the VPN Client software. To update the kmpapi32.dll file, copy it to the VPN Client system from the Release medium and place it in the Windows default system directory. For Windows NT, Windows 2000 and Windows XP systems, this directory is c:\WinNT\System32. For Windows 9x and Windows ME, the directory is \Windows\System.1-20 VPN Client Administrator Guide 78-15404-02 Chapter 1 Configuration Information for an Administrator Setting up the VPN Client for Authentication using Smart Cards—Windows Only Setting up the VPN Client for Authentication using Smart Cards—Windows Only The VPN Client supports authentication via a certificate stored on a smart card. Once you create a connection entry and choose the certificate for authentication, the VPN Client user needs to insert the smart card into its reader. Once the VPN Client connection is initiated, the user is prompted to enter a PIN or passcode to obtain access to the smart card. The private key stays on the smart card and is never accessible without entering the PIN or passcode. Also, in most cases, there is a limit to how many times someone can try to enter the PIN or passcode after which there is a lock on the card. Explaining how to configure VPN Client authentication for every smart card vendor is beyond the scope of this documentation. You must follow documentation from your smart card vendor to obtain this information. In general: Step 1 Under Key Options, when you are performing web-based certificate enrollment, choose your smart card provider from the pull-down menu. Step 2 For Key usage choose Signature and verify that Create new key set is selected. Step 3 Install the certificate. The keys are generated on the smart card and a copy of the certificate is stored in the Microsoft store on your PC and listed on the VPN Client Certificates tab. Step 4 Go to the Conection Entry > Modify dialog, and do the following: a. Open the Authentication tab and check the Certificate Authentication radio button b. Display the drop-down Name menu and click the smartcard certificate. Now a VPN Client user can complete authentication only when the smart card is inserted in its reader that is plugged into the proper port on the PC and when the user enters the correct PIN or passcode. Note With most vendors, when the smart card is not plugged in, the Certificates tab still displays the certificate. However when disconnected, e-token by Aladdin removes the certificate from the list. The certificate appears in the list only when the e-token is inserted and active.C H A P T E R 2-1 VPN Client Administrator Guide 78-15404-02 2 Preconfiguring the VPN Client for Remote Users This chapter explains how to prepare configurations for remote users and how to distribute them. This chapter includes the following sections: • Profiles • Creating a Global Profile • Creating Connection Profiles Profiles Groups of configuration parameters define the connection entries that remote users use to connect to a VPN device. Together these parameters form files called profiles. There are two profiles: a global profile and an individual profile. • A global profile sets rules for all remote users; it contains parameters for the VPN Client as a whole. The name of the global profile file is vpnclient.ini. • Individual profiles contain the parameter settings for each connection entry and are unique to that connection entry. Individual profiles have a .pcf extension. Profiles get created in two ways: 1. When an administrator or a remote user creates connection entries using the VPN Client graphical user interface (Windows and Macintosh only) 2. When you create profiles using a text editor In the first case, the remote user is also creating a file that can be edited through a text editor. You can start with a profile file generated through the GUI and edit it. This approach lets you control some parameters that are not available in the VPN Client GUI application. For example, auto-initiation or dial-up wait for third-party dialers. The default location for individual profiles is: • For Windows platforms—C:\Program Files\Cisco Systems\VPN Client\Profiles. • For the Linux, Solaris, and Mac OS X platforms— /etc/CiscoSystemsVPNClient/Profiles/ This chapter explains how to create and edit the vpnclient.ini and individual profiles. Both files use the same conventions.2-2 VPN Client Administrator Guide 78-15404-02 Chapter 2 Preconfiguring the VPN Client for Remote Users Creating a Global Profile Note The easiest way to create a profile for the Windows platforms is to run the VPN Client and use the VPN Client GUI to configure the parameters. When you have created a profile in this way, you can copy the .pcf file to a distribution disk for your remote users. This approach eliminates errors you might introduce by typing the parameters and the group password gets automatically converted to an encrypted format. File Format for All Profile Files The vpnclient.ini and .pcf files follow normal Windows.ini file format: • Use a semicolon (;) to begin a comment. • Place section names within brackets [section name]; they are not case sensitive. • Use key names to set values for parameters; keyword = value. Keywords without values, or unspecified keywords, use VPN Client defaults. Keywords can be in any order and are not case sensitive, although using lower and uppercase makes them more readable. Making a Parameter Read Only To make a parameter read-only so that the client user cannot change it within the VPN Client applications, precede the parameter name with an exclamation mark (!). This controls what the user can do within the VPN Client applications only. You cannot prevent someone from editing the global or .pcf file and removing the read-only designator. Creating a Global Profile The name of the global profile is vpnclient.ini. This file is located in the following directories: • For Windows platforms—C:\Program Files\Cisco Systems\VPN Client directory • For the Linux, Solaris, and Mac OS X platforms— /etc/CiscoSystemsVPNClient/vpnclient.ini These are the default locations created during installation. Features Controlled by Global Profile The vpnclient.ini file controls the following features on all VPN Client platforms: • Start before logon • Automatic disconnect upon log off • Control of logging services by class • Certificate enrollment • Identity of a proxy server for routing HTTP traffic • Identity of an application to launch upon connect • Missing group warning message • Logging levels for log classes • RADIUS SDI extended authentication behavior2-3 VPN Client Administrator Guide 78-15404-02 Chapter 2 Preconfiguring the VPN Client for Remote Users Creating a Global Profile • GUI parameters—appearance and behavior of GUI applications The vpnclient.ini file controls the following additional features in the Windows platform: • Location of the Entrust.ini file • List of GINAs that are not compatible with the VPN Client • Auto initiation • Setting of the Stateful Firewall option • The method to use in adding suffixes to domain names on Windows 2000 and Windows XP platforms • When working with a third-party dialer, time to wait after receiving an IP address before initiating an IKE tunnel • Network proxy server for routing HTTP traffic • Application launching • DNS suffixes • Force Network Login, which forces a user on Windows NT, Windows 2000, or Windows XP to log out and log back in to the network without using cached credentials Sample vpnclient.ini file Note Profiles for the VPN Client are interchangeable between platforms. Keywords that are specific to the Windows platform are ignored by other platforms. This sample file shows what you might see if you open it with a text editor [main] IncompatibleGinas=PALGina.dll,theirgina.dll RunAtLogon=0 EnableLog=1 DialerDisconnect=1 AutoInitiationEnable=1 AutoInitiationRetryInterval=1 AutoInitiationList=techsupport,admin [techsupport] Network=175.55.0.0 Mask=255.255.0.0 ConnectionEntry=ITsupport [admin] Network=176.55.0.0 Mask=255.255.0.0 ConnectionEntry=Administration [LOG.IKE] LogLevel=1 [LOG.CM] LogLevel=1 [LOG.PPP] LogLevel=2 [LOG.DIALER] LogLevel=2 [LOG.CVPND] LogLevel=1 [LOG.CERT] LogLevel=0 [LOG.IPSEC]2-4 VPN Client Administrator Guide 78-15404-02 Chapter 2 Preconfiguring the VPN Client for Remote Users Creating a Global Profile LogLevel=3 [LOG.FIREWALL] LogLevel=1 [LOG.CLI] LogLevel=1 [CertEnrollment] SubjectName=Alice Wonderland Company=University of OZ Department=International Relations State=Massachusetts Country=US Email=AliceW@UOZ.com CADomainName=CertsAreUs CAHostAddress=10.10.10.10 CACertificate=CAU [Application Launcher] Enable=1 Command=c:\apps\apname.exe [ForceNetLogin] Force=1 Wait=10 DefaultMsg=You will be logged off in 10 seconds Separator=************************************** [GUI] WindowWidth=578 WindowHeight=367 WindowX=324 WindowY=112 VisibleTab=0 ConnectionAttribute=0 AdvancedView=1 DefaultConnectionEntry=ACME MinimizeOnConnect=1 UseWindowSettings=1 ShowToolTips=1 ShowConnectHistory=1 The rest of this section explains the parameters that can appear in the vpnclient.ini file, what they mean, and how to use them. Global Profile Configuration Parameters Table 2-1 lists all parameters, keywords, and values. It also includes the parameter name as used in the VPN Client GUI application if it exists, and where to configure it in the application. Each parameter can be configured on all VPN Client platforms unless specified.2-5 VPN Client Administrator Guide 78-15404-02 Chapter 2 Preconfiguring the VPN Client for Remote Users Creating a Global Profile Table 2-1 vpnclient.ini file parameters .ini Parameter (Keyword) VPN Client Parameter Description Values VPN Client GUI Configuration Location(s) [main] Required keyword to identify main section. [main] Enter exactly as shown, as first entry in the file. Does not appear in GUI DialupWait Specifies the number of seconds to wait between receiving an IP address from a third-party dialer such as General Packet Radio Services (GPRS) before initiating an IKE tunnel. This grants enough time for the connection to go through on the first attempt. After the keyword and equal sign, enter the number of seconds to wait. For example: DialupWait=1 Default number = 0. Does not appear in GUI IncompatibleGinas (Windows-only) Lists Graphical Identification and Authentication dynamic link libraries (GINA.DLLs) that are not compatible with Cisco’s GINA. Adding a GINA to the list causes the VPN Client to leave the GINA alone during installation and use fallback mode. The VPN Client goes into fallback mode only if RunAtLogon = 1. Otherwise, the Client GINA is never installed. (See “Installing the VPN Client Without User Interaction”. After the keyword and equal sign, enter the name(s) of the GINAs, separated by commas. For example: IncompatibleGinas= PALgina.dll, Yourgina.dll, Theirgina.dll Do not enclose the name in quotes. Does not appear in GUI MissingGroupDialog Controls the pop up window warning that occurs when a user tries to connect without setting the group name in a preshared connection. 0= (default) Do not show the warning message. 1=Show the warning message. Does not appear in GUI RunAtLogon (Windows-only) Specifies whether to start the VPN Client connection before users log on to their Microsoft network. Available only for the Windows NT platform (Windows NT 4.0, Windows 2000 and Windows XP). This feature is sometimes known as the NT Logon feature. 0 = Disable (default) 1 = Enable Options > Windows Logon Properties > Enable start before logon EntrustIni= (Windows-only) Locates the entrust.ini file if it is in a location that is different from the default.ini file. The default location is the base Windows system directory. Complete pathname of location Does not appear in GUI2-6 VPN Client Administrator Guide 78-15404-02 Chapter 2 Preconfiguring the VPN Client for Remote Users Creating a Global Profile DialerDisconnect= (Windows-only) Determines whether to automatically disconnect upon logging off a Windows NT platform (Windows NT 4.0, Windows 2000 and Windows XP). Disabling this parameter lets the VPN connection remain when the user logs off, allowing that user to log back in without having to establish another connection. 0 = Disable 1 = Enable (default disconnect on logoff) Options > Windows Logon Properties > Disconnect VPN connection when logging off There are limitations to DialerDisconnect. For example, in the case of MS DUN, the RAS (PPP) connection might go down when the user logs off. For more information about this specific case, see the following URL: http://support.microsoft.com/support/kb/articles/Q158/9/09.asp?LN=EN-US&SD=gn&FR=0&qry=RAS%20AND%20LOGOFF&rn k=2&src=DHCS_MSPSS_gn_SRCH&SPR=NTW40 EnableLog= Determines whether to override log settings for the classes that use the logging services. By default, logging is turned on. This parameter lets a user disable logging without having to set the log levels to zero for each of the classes. By disabling logging you can improve the performance of the client system. 0 = Disable 1 = Enable (default) Log > Enable/Disable StatefulFirewall= (Windows-only) Determines whether the stateful firewall is always on. When enabled, the stateful firewall always on feature allows no inbound sessions from all networks, whether a VPN connection is in effect or not. Also, the firewall is active for both tunneled and nontunneled traffic. 0 = Disable (default) 1 = Enable Options > Stateful Firewall (Always On) StatefulFirewallAllow ICMP (Windows only) Controls whether StatefulFirewall (Always On) allows ICMP traffic. Some DHCP Servers use ICMP pings to detect if the DHCP client PCs are up so that the lease can be revoked or retained. 0 = Disable (default) 1 = Enable Does not appear in the GUI. AutoInitiationEnable (Windows-only) Enables auto initiation, which is an automated method for establishing a wireless VPN connection in a LAN environment. For information on this feature see Configuring Automatic VPN Initiation—Windows Only 0 = Disable (default) 1 = Enable Options > Automatic VPN Initiation AutoInitiationRetryInterval (Windows-only) Specifies the time to wait, in minutes, before retrying auto initiation after a connection attempt failure. 1 to 10 minutes Default = 1 minute Options > Automatic VPN Initiation Table 2-1 vpnclient.ini file parameters (continued) .ini Parameter (Keyword) VPN Client Parameter Description Values VPN Client GUI Configuration Location(s)2-7 VPN Client Administrator Guide 78-15404-02 Chapter 2 Preconfiguring the VPN Client for Remote Users Creating a Global Profile AutoInitiationRetryIntervalType (Windows-only) Changes the retry interval from minutes (the default) to seconds. The range in seconds is 5-600. 0 = minutes (default) 1 = seconds Options > Automatic VPN Initiation AutoInitiationList (Windows-only) Identifies auto initiation-related section names within the vpnclient.ini file. The vpnclient.ini file can contain a maximum of 64 auto initiation list entries. A list of section names separated by commas; for example: SJWLAN, RTPWLAN, CHWLAN Does not appear in GUI [section name] (of an item in the AutoInitiationList) (Windows-only) Each section contains a network address, network mask, connection entry name, and a connect flag. The network and mask values identify a subnet. The connection entry identifies a connection profile (.pcf file). The connect flag specifies whether to auto initiate the connection. Section name in brackets Network = IP address Mask = Subnet mask ConnectionEntry = name of a connection entry (profile) Connect = 1 or 0 0 = Do not auto initiate the connection 1 = Auto initiate the connection (the default) Example: [SJWLAN] Network=110.110.110.0 Mask=255.255.0.0 ConnectionEntry=SantaJuan WirelessLAN Does not appear in GUI For each class that follows, use the LogLevel= parameter to set the logging level [LOG.IKE] Identifies the Internet Key Exchange class for setting the logging level. [LOG.IKE] Enter exactly as shown. Log > Settings [LOG.CM] Identifies the Connection Manager class for setting the logging level. [LOG.CM] Enter exactly as shown. Log > Settings [LOG.XAUTH] Identifies the Extend authorization class for setting the logging level. [LOG.XAUTH] Enter exactly as shown. Log > Settings [LOG.PPP] (Windows-only) Identifies the PPP class for setting the logging level. [LOG.PPP] Enter exactly as shown. Log > Settings [LOG.CVPND] Identifies the Cisco VPN Daemon class for setting the logging level. [LOG.CVPND] Enter exactly as shown. Log > Settings [LOG.CERT] Identifies the Certificate Management class for setting the logging level. [LOG.CERT] Enter exactly as shown. Log > Settings [LOG.IPSEC] Identifies the IPSec module class for setting the logging level. [LOG.IPSEC] Enter exactly as shown. Log > Settings [LOG.FIREWALL] (Windows-only) Identifies the FWAPI class for setting the logging level. [LOG.FIREWALL] Enter exactly as shown Log > Settings Table 2-1 vpnclient.ini file parameters (continued) .ini Parameter (Keyword) VPN Client Parameter Description Values VPN Client GUI Configuration Location(s)2-8 VPN Client Administrator Guide 78-15404-02 Chapter 2 Preconfiguring the VPN Client for Remote Users Creating a Global Profile [LOG.CLI] Identifies the Command-Line Interface class for setting the logging level. [LOG.CLI] Enter exactly as shown Log > Settings [LOG.GUI] Identifies the Graphical User Interface class for setting the logging level. [LOG.GUI] Enter exactly as shown Log > Settings LogLevel= Determines the log level for individual classes that use logging services. By default, the log level for all classes is Low. You can use this parameter to override the default setting for the preceding [LOG] parameters. The VPN Client supports log levels from 1 (lowest) to 15 (highest). Default = 1 To set logging levels, you must first enable logging: EnableLog=1. Log > Settings [CertEnrollment] Required keyword to identify the Certificate Enrollment section. [CertEnrollment] Enter exactly as shown. Does not appear in GUI SubjectName= Identifies the username associated with this certificate. Maximum of 519 alphanumeric characters. Certificates > Enroll Certificate Enrollment form Company= Identifies the company or organization of the certificate owner. Maximum of 129 alphanumeric characters. Certificates > Enroll Certificate Enrollment form Department= Identifies the department or organizational unit of the certificate owner. If matching by IPSec group in a VPN 3000 Concentrator, must match the group name in the configuration. Maximum of 129 alphanumeric characters. Certificates > Enroll Certificate Enrollment form State= Identifies the state or province of the certificate owner. Maximum of 129 alphanumeric characters. Certificates > Enroll Certificate Enrollment form Country= Identifies the two-letter code identifying the country of this certificate owner. Maximum of 2 alphanumeric characters. Certificates > Enroll Certificate Enrollment form Email= Identifies the certificate owner’s email address. Maximum of 129 alphanumeric characters. Certificates > Enroll Certificate Enrollment form IPAddress Identifies the IP address of the system of the certificate owner. Internet address in dotted decimal notation. Certificates > Enroll Certificate Enrollment form Domain Identifies the fully qualified domain name of the host that is serving the certificate owner. Maximum of 129 alphanumeric characters. Certificates > Enroll Certificate Enrollment form Table 2-1 vpnclient.ini file parameters (continued) .ini Parameter (Keyword) VPN Client Parameter Description Values VPN Client GUI Configuration Location(s)2-9 VPN Client Administrator Guide 78-15404-02 Chapter 2 Preconfiguring the VPN Client for Remote Users Creating a Global Profile CADomainName= Identifies the domain name that the certificate authority belongs to; for network enrollment. Maximum of 129 alphanumeric characters. Certificates > Enroll Certificate Enrollment form CAHostAddress= Identifies the IP address or hostname of the certificate authority. Internet hostname or IP address in dotted decimal notation. Maximum of 129 alphanumeric characters. Certificates > Enroll Certificate Enrollment form CACertificate= Identifies the name of the self-signed certificate issued by the certificate authority. Maximum of 519 alphanumeric characters. Note: The VPNClient GUI ignores a read-only setting on this parameter. Certificates > Enroll Certificate Enrollment form NetworkProxy= (Windows-only) Identifies a proxy server you can use to route HTTP traffic. Using a network proxy can help prevent intrusions into your private network. IP address in dotted decimal notation or domain name. Maximum of 519 alphanumeric characters. The proxy setting sometimes has a port associated with it. Example:10.10.10.10:8080 Does not appear in GUI [ApplicationLauncher] (Windows-only) (No VPN Client field) Required keyword to identify Application Launcher section. [ApplicationLauncher] Enter exactly as shown, as first entry in the section. Does not appear in GUI Enable= (Windows-only) Use this parameter to allow VPN Client users to launch an application when connecting to the private network. 0 = Disabled (default) 1 = Enabled Disabled means no launching. Options> Application Launcher Command= (Windows-only) The name of the application to be launched. This variable includes the pathname to the command, and the name of the command complete with arguments. command string Maximum 512 alphanumeric characters. Example: c:\auth\swtoken.exe. Options> Application Launcher> Application [DNS] (Windows-only) (No VPN Client field) Required keyword to identify DNS section. [DNS] Enter exactly as shown, as first entry in the section. Does not appear in GUI AppendOriginalSuffix= (Windows-only) Determines the way the VPN Client treats suffixes to domain names. See “DNS Suffixes and the VPN Client—Windows 2000 and Windows XP Only”, following this table. 0 = do nothing 1= append the primary DNS suffix to the suffix that the VPN Concentrator supplies. 2= append the primary and connection-specific DNS suffixes to the suffix that the VPN Concentrator supplies. Does not appear in GUI Table 2-1 vpnclient.ini file parameters (continued) .ini Parameter (Keyword) VPN Client Parameter Description Values VPN Client GUI Configuration Location(s)2-10 VPN Client Administrator Guide 78-15404-02 Chapter 2 Preconfiguring the VPN Client for Remote Users Creating a Global Profile [RadiusSDI] Required keyword to identify the RADIUS SDI extended authentication (XAuth) section. Configure this section to enable a VPN Client to handle Radius SDI authentication the same as native SDI authentication, which makes authentication easier for VPN Client users to authenticate using SDI. Enter exactly as shown. Does not appear in GUI. QuestionSubStr Uniquely identifies question-type RADIUS SDI Xauth prompts. Enter text up to 32 bytes in length. The default text is a question mark. Example: “Are you prepared to have the system generate your PIN? (y/n):” Response: ____________ The question appears in the GUI during extended authentication. It is followed by a Response field. NewPinSubStr Uniquely identifies new PIN RADIUS SDI Xauth prompts. Enter text up to 32 bytes in length. Default text is “new PIN.” Example: “Enter a new PIN of 4 to 8 digits.” Appears in the GUI during extended authentication. NewPasscodeSubStr Uniquely identifies new passcode RADIUS Xauth prompts. Enter text up to 32 bytes in length. Default text is “new passcode.” Example: “PIN accepted. Wait for the token code to change, then enter the new passcode” Appears in the GUI during extended authentication. [Netlogin] (windows-only Identifies the Force Network Login section of the vpnclient.ini file. This feature forces a user on Windows NT, Windows 2000, and Windows XP to log out and log back in to the network without using cached credentials. Enter exactly as shown; this is required as part of the feature. Does not appear in the GUI. Note You cannot use this feature with Start Before Logon. If users are connecting via dialup (RAS), you should add the registry key described in the Microsoft article: http://support.microsoft.com/default.aspx?scid=kb;en-us;Q158909. Adding the registry key assures that the RAS connection does not drop when the user gets logged off. Table 2-1 vpnclient.ini file parameters (continued) .ini Parameter (Keyword) VPN Client Parameter Description Values VPN Client GUI Configuration Location(s)2-11 VPN Client Administrator Guide 78-15404-02 Chapter 2 Preconfiguring the VPN Client for Remote Users Creating a Global Profile Force (windows-only) Specifies what action to take for the Force Network Login feature. This parameter is required for this feature. 0 = (default) Do not force the user to log out and log in. 1 = Force user to log out when the Wait time is reached unless an option is selected. 2 = Disconnect VPN session upon reaching the Wait time unless an option is selected. 3 = Wait for the user to select Connect or Disconnect. Does not appear in the GUI. Wait (windows-only) Determines the number of seconds to wait before performing an action specified by the Force parameter. This parameter is optional. x number of seconds. The default is 5 seconds. Does not appear in the GUI. DefaultMsg (windows-only) Specifies a message to display before performing the action specified by the Force parameter. Message can vary according to setting of Force. This parameter is optional. Ascii text up to 1023 bytes. Default message = You will soon be disconnected. Does not appear in the GUI. Separator (windows-only) Specifies the separator text that separates banner text from the message. If no banner exists, the separator is not displayed. This parameter is optional. Ascii text up to 511 bytes. Default separator = ------------ Does not appear in the GUI. [GUI] Required keyword to identify the section of the file that lets you control features of the Graphical User Interface application. [GUI] Enter exactly as shown, as first entry in the section. Does not appear in the GUI. DefaultConnectionEntry Specifies the name of the connection entry for the VPN Client to use to initiate a connection, unless otherwise indicated. ConnectionEntryName Connection Entries > Add/Modify > Set as default entry. WindowWidth Controls the width of the window. Default = 578 pixels Manual control WindowHeight Controls the height of the window. Default = 367 pixels Manual control WindowX Controls the X coordinate of the window. 0 to 1024 pixels Default = 324 Where the window appears horizontally relative to your monitor’s screen WindowY Controls the Y coordinate of the window. 0 to 768 pixels Default = 112 Where the window appears vertically relative to your monitor’s screen Table 2-1 vpnclient.ini file parameters (continued) .ini Parameter (Keyword) VPN Client Parameter Description Values VPN Client GUI Configuration Location(s)2-12 VPN Client Administrator Guide 78-15404-02 Chapter 2 Preconfiguring the VPN Client for Remote Users Creating a Global Profile DNS Suffixes and the VPN Client—Windows 2000 and Windows XP Only When a command or program such as ping server123 passes a hostname without a suffix to a Windows 2000 or Windows XP platform, Windows 2000/XP has to convert the name into a fully-qualified domain name (FQDN). The Windows operating system has two methods for adding suffixes to domain names: Method 1 and Method 2. This section describes these two methods. Method 1—Primary and Connection-Specific DNS Suffixes A primary DNS suffix is global across all adapters. A connection-specific DNS suffix is only for a specific connection (adapter), so that each connection can have a different DNS suffix. Identifying a Primary DNS Suffix A primary suffix comes from the computer name. To find or assign a primary DNS suffix, use the following procedure according to your operating system: VisibleTab Tracks which tab is currently visible in the advanced mode main dialog; an index. Connection Entries Certificates Log VPN Client main dialog ConnectionAttibute Indicates the current setting for the status bar display. The status bar is the line area at the bottom of the dialog that shows the state of the connection (connect/not connected), if connected, the name of the connection entry on the left and what the status is on the right. If you click on the arrow on the right end of the status bar, the right part of the status bar changes. This value records the current display selection. VPN Client main dialog > status bar AdvancedView Toggles between Advanced and Simple modes of operation. Simple Mode = 0 Advanced Mode = 1 (default) Main menu > Options menu > Advanced/ Simple Mode MinimizeOnConnect Controls whether to minimize to a system tray icon upon connection to a VPN device. 0 = Do not minimize 1 = Do minimize (default) Main menu > Options > Preferences > Hide upon connect UseWindowSettings Controls whether to save windows settings. 0 = No 1 = Yes (default) Main menu > Options > Preferences > Save window settings ShowTooltips Controls whether to display the tool tips. 0 = No 1 = Yes (default) Main menu > Options > Preferences > Enable tooltips ShowConnectHistory Controls whether to display the connection history dialog during connection negotiation. 0 = No (default) 1 = Yes Main menu > Options > Preferences > Enable Connection History Display Table 2-1 vpnclient.ini file parameters (continued) .ini Parameter (Keyword) VPN Client Parameter Description Values VPN Client GUI Configuration Location(s)2-13 VPN Client Administrator Guide 78-15404-02 Chapter 2 Preconfiguring the VPN Client for Remote Users Creating a Global Profile On Windows 2000 Step 1 On a Windows 2000 desktop, right click the My Computer icon, and select Properties from the menu. The System Properties dialog displays. Step 2 Open the Network Identification tab. The entry next to Full Computer Name identifies the computer’s name and DNS suffix on this screen, for example, SILVER-W2KP.tango.dance.com. The part after the first dot is the primary DNS suffix, in this example: tango.dance.com. Step 3 To change the primary DNS suffix, click Properties on the Network Identification tab. The Identification Changes dialog displays. Step 4 Click More.... This action displays the DNS Suffix and Net BIOS Computer Name dialog. The Primary DNS suffix of this computer entry identifies the primary suffix. You can edit this entry. On Windows XP Step 1 Right click My Computer, and select Properties from the menu. The System Properties dialog displays. Step 2 Open the Computer Name tab. The entry next to Full Computer Name identifies the computer’s name and DNS suffix on this screen (for example, SILVER-W2KP.tango.dance.com). The part after the first dot is the primary DNS suffix (in this example: tango.dance.com). Step 3 To change the primary DNS suffix, click Change on the Computer Name tab. The Computer Name Changes dialog displays. Step 4 Click More.... This action displays the DNS Suffix and Net BIOS Computer Name dialog. The Primary DNS suffix of this computer entry identifies the primary suffix. You can edit this entry. Identifying a Connection-Specific DNS Suffix You can identify a connection-specific DNS suffix in one of two ways. 1. The connection-specific DNS value is listed as the DNS suffix for the selected connection on the Advanced TCP/IP Settings dialog. Note The following instructions are for a Windows 2000 platform. There may be slight variations on a Windows XP platform. To display the Advanced TCP/IP Settings dialog, use the following procedure: Step 1 Right click the My Network Places icon to display the Properties dialog, which lists your connections.2-14 VPN Client Administrator Guide 78-15404-02 Chapter 2 Preconfiguring the VPN Client for Remote Users Creating a Global Profile Step 2 Double-click on a connection (for example, local) to display its Properties dialog. The connection uses the checked components, such as those shown in Figure 2-1, which shows components of a connection named Local Area Connection. Figure 2-1 Displaying Properties for a Connection Step 3 Double-click Internet Protocol (TCP/IP) to reveal its properties. Step 4 Select Advanced. Step 5 Display the DNS tab and look at DNS suffix for this connection box. If the box is empty, you can have it assigned by the DHCP Server. a. To identify the connection-specific suffix assigned by the DHCP Server, use the ipconfig /all command (Alternative 2, below) and for the DNS Server address. 2. The connection-specific DNS value is listed in the output from the ipconfig /all command, executed at the command-line prompt. Look under Windows 2000 IP Configuration for DNS Suffix Search List. Under Ethernet Adapter Connection Name, look for Connection-specific DNS Suffix. Method 2—User Supplied DNS Suffix For this method, you can provide specific suffixes. You can view and change suffixes in the DNS tab of the connection properties page. The Append these DNS suffixes (in order) edit box supplies the name that you can edit. The values you provide here are global to all adapters.2-15 VPN Client Administrator Guide 78-15404-02 Chapter 2 Preconfiguring the VPN Client for Remote Users Creating a Global Profile VPN Client Behavior When the VPN Client establishes a VPN tunnel to the VPN central device (for example, the VPN 3000 Concentrator), the VPN Client uses Method 2 without regard for the method that the Windows platform uses. If the Windows platform is using Method 2, the VPN Client appends the suffix provided by the VPN central device. This is the default behavior and works correctly with no problem. However if Windows is using Method 1, the VPN Client does not append the primary or connection-specific suffix. To fix this problem, you can set the AppendOriginalSuffix option in the vpnclient.ini file. In Table 2-1, the [DNS] section contains this option: [DNS] AppendOriginalSuffix Option=1: In this case, the VPN Client appends the primary DNS suffix to the suffix provided by the VPN Concentrator. While the tunnel is established, Windows has two suffixes: one provided by the VPN Concentrator and the primary DNS suffix. AppendOriginalSuffix Option=2: In this case, the VPN Client appends the primary and connection-specific DNS suffixes to the suffix provided by the VPN Concentrator. While the tunnel is established, Windows has three suffixes: one provided by the VPN Concentrator, the primary DNS suffix, and the connection-specific DNS suffix. Note If Windows is using Method 2, adding these values to the vpnclient.ini file has no effect. The VPN Client sets these values every time a tunnel is established and then restores the original configuration when tearing down the tunnel. Setting Up RADIUS SDI Extended Authentication You can configure the VPN Client to handle RADIUS SDI authentication the same way it handles “native” SDI authentication, which is more seamless and easier to use. With this configuration, users do not have to deal with the RSA SecurID software interface; the VPN Client software directly interfaces with the RSA SecureID software for the user. To enable intelligent handling of RADIUS SDI authentication, you must configure one profile (.pcf) parameter and possibly three global (vpnclient.ini) parameters: • In the vpnclient.ini file, enter the following information. (For complete information on these parameters, see Table 2-1.) – RadiusSDI—identifies the configuration section for RADIUS SDI – A question sub-string to identify question prompts (e.g. “?”) – A new PIN sub-string to identify prompts for a new PIN – A new passcode sub-string to identify prompts for a new passcode • In the profile (connection entry) file under the Main section, enter the parameter “RadiusSDI = 1”. (See Table 2-2.) Now when the request comes in to the VPN Client, the software identifies it as a RADIUS SDI extended authentication request and knows how to process the request.2-16 VPN Client Administrator Guide 78-15404-02 Chapter 2 Preconfiguring the VPN Client for Remote Users Creating Connection Profiles Creating Connection Profiles The VPN Client uses parameters that must be uniquely configured for each remote user of the private network. Together these parameters make up a user profile, which is contained in a profile configuration file (.pcf file) in the VPN Client user’s local file system in the following directories: • For Windows platforms—Program Files\Cisco Systems\VPN Client\Profiles (if the software installed in the default location) • For the Linux, Solaris, and Mac OS X platforms— /etc/CiscoSystemsVPNClient/Profiles/ These parameters include the remote server address, IPSec group name and password, use of a log file, use of backup servers, and automatic Internet connection via Dial-Up Networking. Each connection entry has its own .pcf file. For example, if you have three connection entries, named Doc Server, Documentation, and Engineering, the Profiles directory shows the list of .pcf files. Figure 2-2 shows the directory structure for the user profile in the Windows platforms. Figure 2-2 List of .pcf files Features Controlled by Connection Profiles A connection profile (.pcf file) controls the following features on all platforms): • Description of the connection profile • The remote server address • Authentication type • Name of IPSec group containing the remote user • Group password • Connecting to the Internet via dial-up networking • Name of remote user • Remote user’s password • Backup servers • Split DNS • Type of dial-up networking connection • Transparent tunneling2-17 VPN Client Administrator Guide 78-15404-02 Chapter 2 Preconfiguring the VPN Client for Remote Users Creating Connection Profiles • TCP tunneling port • Allowing of local LAN access • Enabling of IKE and ESP keepalives • Setting of peer response time-out • Certificate parameters for a certificate connection • Setting of certificate chain • Diffie-Hellman group • Verification of the DN of a peer certificate • RADIUS SDI extended authentication setting • Use of SDI hardware token setting • Split DNS setting • Use legacy IKE port setting A connection profile (.pcf file) controls the following additional features on the Windows platform: • Dial-Up networking phone book entry for Microsoft • Command string for connecting through an ISP • NT domain • Logging on to Microsoft Network and credentials • Change the default IKE port from 500/4500 (must be explicitly added) • Enable Force Network Login, which forces a user on Windows NT, Windows 2000, and Windows XP to log out and then log back in to the network without using cached credentials Sample .pcf file Note Connection profiles for the VPN Client are interchangeable between platforms. Keywords that are specific to the Windows platform are ignored by other platforms. When you open the Doc Server.pcf file, it looks like the example below. This is a connection entry that uses preshared keys. Note that the enc_ prefix (for example, enc_GroupPwd) indicates that the value for that parameter is encrypted. [main] Description=connection to TechPubs server Host=10.10.99.30 AuthType=1 GroupName=docusers GroupPwd= enc_GroupPwd=158E47893BDCD398BF863675204775622C494B39523E5CB65434D3C851ECF2DCC8BD488857EFA FDE1397A95E01910CABECCE4E040B7A77BF EnableISPConnect=0 ISPConnectType=0 ISPConnect= ISPCommand= Username=alice SaveUserPassword=0 UserPassword= enc_UserPassword= NTDomain=2-18 VPN Client Administrator Guide 78-15404-02 Chapter 2 Preconfiguring the VPN Client for Remote Users Creating Connection Profiles EnableBackup=1 BackupServer=Engineering1, Engineering2, Engineering 3, Engineering4 EnableMSLogon=0 MSLogonType=0 EnableNat=1 EnableLocalLAN=0 TunnelingMode=0 TCPTunnelingPort=10000 CertStore=0 CertName= CertPath= CertSubjectName SendCertChain=0 VerifyCertDN=CN=”ID Cert”,OU*”Cisco”,ISSUER-CN!=”Entrust”,ISSURE-OU!*”wonderland” DHGroup=2 PeerTimeOut=90 ForceNetLogin=1 You can configure the VPN Client for remote users by creating a profile configuration file for each connection entry and distribute the .pcf files with the VPN Client software. These configuration files can include all, or only some, of the parameter settings. Users must configure those settings not already configured. You can also distribute the VPN Client to users without a configuration file and let them configure it on their own. In this case, when they complete their configuration using the VPN Client program, they are in effect creating a .pcf file for each connection entry, which they can edit and share. To protect system security you should not include key security parameters such as the IPSec group password, authentication username, or authentication password in .pcf files for remote users. Note Whatever preconfiguring you provide, you must supply users with the information they need to configure the VPN Client. See “Gathering Information You Need” in Chapter 2 of the VPN Client User Guide for your platform. Creating a .pcf file for a Connection Profile Each user requires a unique configuration file. Use Notepad or another ASCII text editor to create and edit each file. Save as a text-only file with no formatting. Naming the Connection Profile For a Windows platform, you can create profile names that contain spaces. However, if you want to distribute profiles to other platforms (Linux, Mac OS X, or Solaris), the name cannot contain spaces. Connection Profile Configuration Parameters Table 2-2 lists all parameters, keywords, and values. It also includes the VPN Client parameter name (if it exists) that corresponds to the keyword and where it is configured on the VPN Client GUI. You can configure each parameter on all VPN Client platforms unless specified.2-19 VPN Client Administrator Guide 78-15404-02 Chapter 2 Preconfiguring the VPN Client for Remote Users Creating Connection Profiles Table 2-2 .pcf file parameters .pcf Parameter (Keyword) VPN Client Parameter Description Values VPN Client Configuration Location(s) [main] (No VPN Client field) Required keyword to identify main section. [main] As the first entry in the file, enter exactly as shown. Does not appear in GUI Description= Description A line of text that describes this connection entry. Optional. Any text. Maximum 246 alphanumeric characters. Connection Entry> New/Modify Host= Remote server address The hostname or IP address of the Cisco remote access server (a VPN device) to which remote users connect. Internet hostname, or IP address in dotted decimal notation. Maximum 255 alphanumeric characters. Connection Entry > New/Modify AuthType= Authentication type The authentication type of this user: 1 = Pre-shared keys (default) 3 = Digital Certificate using an RSA signature. Connection Entry > New/Modify > Authentication GroupName= Group Name The name of the IPSec group that contains this user. Used with pre-shared keys. The exact name of the IPSec group configured on the VPN device. Maximum 32 alphanumeric characters. Case-sensitive. Connection Entry > New/Modify > Authentication GroupPwd= Group Password The password for the IPSec group that contains this user. Used with pre-shared keys. The first time the VPN Client reads this password, it replaces it with an encypted one (enc_GroupPwd). The exact password for the IPSec group configured on the VPN device. Minimum of 4, maximum 32 alphanumeric characters. Case-sensitive clear text. Connection Entry > New/Modify > Authentication encGroupPwd= The password for the IPSec group that contains the user. Used with preshared keys. This is the scrambled version of the GroupPwd. Binary data represented as alphanumeric text. Does not appear in GUI. EnableISPConnect= (Windows-only) Connect to the Internet via Dial-Up Networking Specifies whether the VPN Client automatically connects to an ISP before initiating the IPSec connection; determines whether to use PppType parameter. 0 = Disable (default) 1 = Enable The VPN Client GUI ignores a read-only setting on this parameter. Connection Entry > New/Modify >Dial-Up > Connect to the Internet via dial-up2-20 VPN Client Administrator Guide 78-15404-02 Chapter 2 Preconfiguring the VPN Client for Remote Users Creating Connection Profiles ISPConnectType= (Windows-only) Dial-Up Networking connection entry type Identifies the type to use: ISPConnect or ISPCommand. 0 = ISPConnect (default) 1 = ISPCommand The VPN Client GUI ignores a read-only setting on this parameter. Connection Entry > New/Modify >Dial-Up > (choosing either DUN or Third Party (command) ISPConnect= (Windows-only) Dial-Up Networking Phonebook Entry (Microsoft) Use this parameter to dial into the Microsoft network; dials the specified dial-up networking phone book entry for the user’s connection. Applies only if EnableISPconnect=1 and ISPConnectType=0. phonebook_name This variable is the name of the phone book entry for DUN – maximum of 256 alphanumeric characters. The VPN Client GUI ignores a read-only setting on this parameter. Connection Entry > New/Modify >Dial-Up > Microsoft Dial-Up Networking > Phonebook ISPCommand= (Windows-only) Dial-Up Networking Phonebook Entry (command) Use this parameter to specify a command to dial the user’s ISP dialer. Applies only if EnableISPconnect=1 and ISPConnectType=1. command string This variable includes the pathname to the command and the name of the command complete with arguments; for example: c:\isp\ispdialer.exe dialEngineering Maximum 512 alphanumeric characters. Connection Entry > New/Modify >Dial-Up > Third party dialup program > Application Username= User Authentication: Username The name that authenticates a user as a valid member of the IPSec group specified in GroupName. The exact username. Case-sensitive, clear text, maximum of 32 characters. The VPN Client prompts the user for this value during user authentication. Connection Entry > New/Modify > Authentication UserPassword= User Authentication: Password The password used during extended authentication. The first time the VPN Client reads this password, it saves it in the file as the enc_UserPassword and deletes the clear-text version. If SaveUserPassword is disabled, then the VPN Client deletes the UserPassword and does not create an encrypted version. You should only modify this parameter manually if there is no GUI interface to manage profiles. Maximum of 32 alphanumeric characters, case sensitive. Connection Entry > New/Modify > Authentication Table 2-2 .pcf file parameters (continued) .pcf Parameter (Keyword) VPN Client Parameter Description Values VPN Client Configuration Location(s)2-21 VPN Client Administrator Guide 78-15404-02 Chapter 2 Preconfiguring the VPN Client for Remote Users Creating Connection Profiles encUserPassword Scrambled version of the user’s password Binary data represented as alphanumeric text. Does not appear in GUI. SaveUserPassword Determines whether or not the user password or its encrypted version are valid in the profile. This value is pushed down from the VPN device. 0 = (default) do not allow user to save password information locally. 1 = allow user to save password locally. Does not appear in GUI. NTDomain= (Windows-only) User Authentication: Domain The NT Domain name configured for the user’s IPSec group. Applies only to user authentication via a Windows NT Domain server. NT Domain name. Maximum 14 alphanumeric characters. Underbars are not allowed. Connection Entry > New/Modify EnableBackup= Enable backup server(s) Specifies whether to use backup servers if the primary server is not available. 0 = Disable (default) 1 = Enable Connection Entry > New/Modify > Backup Servers BackupServer= (Backup server list) List of hostnames or IP addresses of backup servers. Applies only if EnableBackup=1. Legitimate Internet hostnames, or IP addresses in dotted decimal notation. Separate multiple entries by commas. Maximum of 255 characters in length. Connection Entry > New/Modify > Backup Servers EnableMSLogon= (Windows-only) Logon to Microsoft Network. Specifies that users log on to a Microsoft network. Applies only to systems running Windows 9x. 0 = Disable 1 = Enable (Default) Connection Entry > New/Modify > Microsoft Logon This is available only on Windows 98 and Windows ME. MSLogonType= (Windows-only) Use default system logon credentials. Prompt for network logon credentials. Specifies whether the Microsoft network accepts the user’s Windows username and password for logon, or whether the Microsoft network prompts for a username and password. Applies only if EnableMSLogon=1. 0 = (default) Use default system logon credentials; i.e., use the Windows logon username and password. 1 = Prompt for network logon username and password. Connection Entry > New/Modify > Microsoft Logon This is available only on Windows 98 and Windows ME. Table 2-2 .pcf file parameters (continued) .pcf Parameter (Keyword) VPN Client Parameter Description Values VPN Client Configuration Location(s)2-22 VPN Client Administrator Guide 78-15404-02 Chapter 2 Preconfiguring the VPN Client for Remote Users Creating Connection Profiles EnableNat= Enable Transparent Tunneling. Allows secure transmission between the VPN Client and a secure gateway through a router serving as a firewall, which may also be performing NAT or PAT. 0 = Disable 1 = Enable (default) Connection Entry > New/Modify > Transport TunnelingMode= Specifies the mode of transparent tunneling, over UDP or over TCP; must match that used by the secure gateway with which you are connecting. 0 = UDP (default) 1 = TCP Connection Entry > New/Modify > Transport TCPTunnelingPort= Specifies the TCP port number, which must match the port number configured on the secure gateway. Port number from 1 through 65545 Default = 10000 Connection Entry> New/Modify > Transport EnableLocalLAN= Allow Local LAN Access. Specifies whether to enable access to resources on a local LAN at the Client site while connected through a secure gateway to a VPN device at a central site. 0 = Disable (default) 1 = Enable Connection Entry > New/Modify > Transport PeerTimeout= Peer response timeout The number of seconds to wait before terminating a connection because the VPN device on the other end of the tunnel is not responding. Number of seconds Minimum = 30 seconds Maximum = 480 seconds Default = 90 seconds Connection Entry > New/Modify > Transport CertStore= Certificate Store Identifies the type of store containing the configured certificate. 0 = No certificate (default) 1 = Cisco 2 = Microsoft The VPN Client GUI ignores a read-only (!) setting on this parameter. (See note) Windows GUI Does not appear in GUI. You can view on Certificates tab. Mac OS X GUI Connection Entry > New/Modify > Transport Note Normally, if a parameter is marked as read only, the GUI disables the checkbox or edit box so users can not change the value of the parameter. However, this is not true for Certificate parameters. These values cannot be overwritten in the file. Users can change them in the GUI display, but these changes are not saved. CertName= Certificate Name Identifies the certificate used to connect to a VPN device. Maximum 129 alphanumeric characters The VPN Client GUI ignores a read-only setting on this parameter. Certificates > View Table 2-2 .pcf file parameters (continued) .pcf Parameter (Keyword) VPN Client Parameter Description Values VPN Client Configuration Location(s)2-23 VPN Client Administrator Guide 78-15404-02 Chapter 2 Preconfiguring the VPN Client for Remote Users Creating Connection Profiles CertPath= The complete pathname of the directory containing the certificate file. Maximum 259 alphanumeric characters The VPN Client GUI ignores a read-only setting on this parameter. Certificates > Import CertSubjectName The fully qualified distinguished name (DN) of certificate’s owner. If present, the VPN Dialer enters the value for this parameter. Either do not include this parameter or leave it blank. The VPN Client GUI ignores a read-only setting on this parameter. Certificates > View CertSerialHash A hash of the certificate’s complete contents, which provides a means of validating the authenticity of the certificate. If present, the VPN Dialer enters the value for this parameter. Either do not include this parameter or leave it blank. The VPN Client GUI ignores a read-only setting on this parameter. Certificates > View SendCertChain Sends the chain of CA certificates between the root certificate and the identity certificate plus the identity certificate to the peer for validation of the identity certificate. 0 = disable (default) 1 = enable • Connection Entry > New/Modify • Certificates > Export VerifyCertDN Prevents a user from connecting to a valid gateway by using a stolen but valid certificate and a hijacked IP address. If the attempt to verify the domain name of the peer certificate fails, the client connection also fails. Include any certificate DN values of both subject and issuer: You can use all valid ASCII characters including -_@<>()., as well as wildcards. See example: Does not appear in GUI Example: VerifyCertDN=CN=”ID Cert”,OU*”Cisco”,ISSUER-CN!=”Entrust”,ISSUER-OU!*”wonderland” CN=”ID Cert”—Specifies an exact match on the CN. OU*”Cisco”—Specifies any OU that contains the string “Cisco”. ISSUER-CN!”Entrust”—Specifies that the Issuer CN must not equal “Entrust”. ISSUER-OU!*”wonderland”—Specifies that the Issuer OU must not contain “wonderland”. DHGroup Allows a network administrator to override the default group value on a VPN device used to generate Diffie- Hellman key pairs. 1 = modp group 1 2 = modp group 2 (default) 5 = modp group 5 Note: This value is preset only for pre-shared keys; for a certificate-authenticated connection, the DHGroup number is negotiated. Does not appear in GUI Table 2-2 .pcf file parameters (continued) .pcf Parameter (Keyword) VPN Client Parameter Description Values VPN Client Configuration Location(s)2-24 VPN Client Administrator Guide 78-15404-02 Chapter 2 Preconfiguring the VPN Client for Remote Users Creating Connection Profiles RadiusSDI Tells the VPN Client to assume that Radius SDI is being used for extended authentication (XAuth). 0 = No (default) 1 = Yes If this parameter is enabled, the prompts in the GUI for SDI authentication are from Radius SDI and configured using parameters in the vpnclient.ini file. SDIUseHardwareToken Enables a connection entry to avoid using RSA SoftID software. 0 = Yes, use RSA SoftID (default) 1 = No, ignore RSA SoftID software installed on the PC. Does not appear in GUI EnableSplitDNS Determines whether the connection entry is using splitDNS, which can direct packets in clear text over the Internet to domains served through an external DNS or through an IPSec tunnel to domains served by a corporate DNS. This feature is configured on the VPN 3000 Concentrator and is used in a split-tunneling connection. Note You must also enable this feature on the VPN device you are connecting to. 0 = No 1 = Yes (default) Does not appear in GUI Table 2-2 .pcf file parameters (continued) .pcf Parameter (Keyword) VPN Client Parameter Description Values VPN Client Configuration Location(s)2-25 VPN Client Administrator Guide 78-15404-02 Chapter 2 Preconfiguring the VPN Client for Remote Users Creating Connection Profiles Distributing Configured VPN Client Software to Remote Users When you have created the VPN Client profile configuration file, you can distribute it to users separately or as part of the VPN Client software. Separate Distribution To distribute the configuration file separately and have users import it to the VPN Client after they have installed it on their PCs, follow these steps: Note For the Mac OS X platform, the configuration file is placed in the Profiles folder before the VPN Client is installed. See Chapter 2 of the VPN Client User Guide for Mac OS X for more information. Step 1 Distribute the appropriate profile files to users on whatever media you prefer. Step 2 Supply users with necessary configuration information. UseLegacyIKEPort Changes the default IKE port from 500/4500 to dynamic ports to be used during all connections. You must explicitly enter this parameter into the .pcf file. 0 = Turn off the legacy setting; use dynamic ports with cTCP. 1 = (default) Maintain the legacy setting 500/4500. This lets TCP/UDP work easily with VPN devices that support cTCP. This setting enables interoperability with VPN devices that expect the VPN Client to use static port assignments. Enabling this parameter inhibits interoperability with certain versions of Windows. Does not appear in GUI ForceNetlogin (windows-only) Enables the Force Net Login feature for this connection profile. 0 = Do not force the user to log out and log in (default). 1 = Force user to log out when the Wait time is reached unless an option is selected. 2 = Disconnect VPN session upon reaching the Wait time unless an option is selected. 3 = Wait for the user to select Connect or Disconnect. Does not appear in GUI Table 2-2 .pcf file parameters (continued) .pcf Parameter (Keyword) VPN Client Parameter Description Values VPN Client Configuration Location(s)2-26 VPN Client Administrator Guide 78-15404-02 Chapter 2 Preconfiguring the VPN Client for Remote Users Creating Connection Profiles Step 3 Instruct users to: a. Install the VPN Client according to the instructions in the VPN Client User Guide for your platform. b. Start the VPN Client and follow the instructions in Chapter 5 of the VPN Client User Guide for your platform. See the section “Importing a VPN Client Configuration File.” (Windows-only) c. Finish configuring the VPN Client according to the instructions in Chapter 4of the VPN Client User Guide for your platform. d. Connect to the private network, and enter parameters according to the instructions in Chapter 5 of the VPN Client User Guide for your platform. Distribution with the VPN Client Software If the vpnclient.ini file is bundled with the VPN Client software when it is first installed, it automatically configures the VPN Client during installation. You can also distribute the profile files (one .pcf file for each connection entry) as preconfigured connection profiles for automatic configuration. To distribute preconfigured copies of the VPN Client software to users for installation, perform the following steps: Step 1 Copy the VPN Client software files from the distribution CD-ROM into each directory where you created an vpnclient.ini (global) file and separate connection profiles for a set of users. Note For the Mac OS X platform, preconfigured files are placed in the Profiles and Resources folders before the VPN Client is installed. The vpnclient.ini file is placed in the installer directory. See Chapter 2 of the VPN Client User Guide for Mac OS X for more information. Step 2 Prepare and distribute the bundled software. CD-ROM or network distribution: Be sure the vpnclient.ini file and profile files are in the same directory with all the CD-ROM image files. You can have users install from this directory through a network connection; or you can copy all files to a new CD-ROM for distribution; or you can create a self-extracting ZIP file that contains all the files from this directory, and have users download it, and then install the software. Step 3 Supply users with any other necessary configuration information and instructions. See Chapter 2 of the VPN Client User Guide for your platform.C H A P T E R 3-1 VPN Client Administrator Guide 78-15404-02 3 Configuring Automatic VPN Initiation—Windows Only Note Before you begin, we highly recommend that you read “SAFE: Wireless LAN Security in Depth,” which you can access at http://www.cisco.com/go/safe This document analyzes the best practices of implementing security for wireless LANs using VPNs. For a sample configuration demonstrating complete step-by-step instructions covering the group/user configuration on the VPN Concentrator, auto initiation configuration on the VPN Client, and wireless configuration in the Aironet, refer to the TAC technical note “Configuring Automatic VPN Initiation on a Cisco VPN Client in a Wireless LAN Environment.” Automatic VPN initiation (auto initiation) provides secure connections within an on-site wireless LAN (WLAN) environment through a VPN Concentrator. When auto initiation is configured on the VPN Client, the VPN Client: • Becomes active immediately when a user starts his/her PC or when the PC becomes active after being on standby or hibernating • Detects that the PC has an IP address defined as requiring auto initiation • Establishes a VPN tunnel to the VPN Concentrator defined for its network, prompts the user to authenticate, and allows that user network access It is worth mentioning that although auto initiation was designed for wireless environments, you can use it in any networking environment. Auto initiation provides a generic way for the VPN Client to auto initiate a connection whether the VPN Client PC is based on specific networks or not. Figure 3-1 depicts a simple network configuration that employs VPN for securing on-site WLANs. The VPN 3000 Concentrators, which may or may not be using load balancing, provide the gateway between the untrusted and the trusted networks. The DHCP Server can be on either side of the VPN 3000 Concentrator. VPN Client users with laptops that have wireless NIC cards can connect through access points (APs) throughout the campus or building and tunnel to the trusted 30.30.30.x network from the untrusted 10.10.10.x network. The network administrator can set this type of scenario up to be largely transparent to the VPN Client user. Note You can set up auto initiation configurations that both include and exclude networks for auto initiation.3-2 VPN Client Administrator Guide 78-15404-02 Chapter 3 Configuring Automatic VPN Initiation—Windows Only Figure 3-1 Auto Initiation Scenario In Figure 3-1 the trusted (wired) network, numbered 30.30.30, is at the top of the diagram with a VPN Concentrator separating it from other networks considered untrusted. The untrusted networks contain wireless subnets, such as 20.20.A.x and 20.20.B.x. Every device on the untrusted network must use a VPN tunnel to access resources on the trusted network. Access to a DHCP server must be available to provide the devices on the untrusted network with initial IP connectivity to the VPN Concentrator. The figure shows the placement of the DHCP server as optional, since it can be placed either on the untrusted network or on the trusted network with DHCP Relay enabled in the VPN Concentrator. To configure auto initiation for users on the network, you add parameters to the VPN Client’s global profile (vpnclient.ini). For information on how to create or use a global profile, see “Creating a Global Profile.” Using the VPN Client GUI, users can only enable/disable auto initiation and change the retry interval. These features are available through the Options menu when auto initiation has been configured through the global profile. If auto initiation is not configured, these options do not appear in the Options menu. For a complete explanation of how auto initiation appears to the VPN Client user, see Cisco VPN Client User Guide for Windows, “Using Automatic VPN Initiation.” The auto initiation feature can be used in WLAN environments containing NIC cards and access points from any vendor. 71727 RADIUS Server DHCP Server Optional placement 30.30.30.3 30.30.30.2 10.10.10.1 30.30.30.1 Trusted Untrusted File Server 30.30.30.4 30.30.30.X network DHCP Server 10.10.10.2 20.20.A.1 (AP) 20.20.A.X network 10.10.10.X network 20.20.A.2 (AP) 20.20.A.3 30.30.30.5 (VPN assigned) VPN 3000s (load balancing) Routed network 20.20.B.1 (AP) 20.20.B.X network 20.20.B.2 (AP) 20.20.B.3 30.30.30.6 (VPN assigned)3-3 VPN Client Administrator Guide 78-15404-02 Chapter 3 Configuring Automatic VPN Initiation—Windows Only Creating Automatic VPN Initiation in the vpnclient.ini File Creating Automatic VPN Initiation in the vpnclient.ini File This section shows how to create or edit the vpnclient.ini file to activate auto initiation on a VPN Client. Preparation Before you begin, you should gather the information you need to configure auto initiation: • The network IP addresses for the client network • The subnet mask for the client network • The names for all connection entries that users are using for their connections What You Have to Do To configure auto initiation, you must add the following keywords and values in the [Main] section of the vpnclient.ini global profile file: • AutoInitiationEnable—enables or disables auto initiation. To enable auto initiation, enter 1. To disable it, enter 0. • AutoInitiationRetryInterval—specifies the number of minutes to wait before retrying an auto initiation connection. The range is 1 to 10 minutes or 5 to 600 seconds. If you do not include this parameter in the file, the default retry interval is one minute. • AutoInitiationRetryIntervalType—specifies whether the retry AutoInitiationRetryInterval parameter is displayed in minutes or seconds. The default is minutes. • AutoInitiationList—provides a series of section names, each of which contains a network address, a subnet mask, a connection entry name, and optionally, a connect flag. You can include a maximum of 64 section (network) entries. – The section name is the name of an entry in the auto initiation list (within brackets) – The network and subnet mask identify a subnet – The connection entry specifies a connection profile (.pcf file) configured for auto initiation. – The connect flag, if present, indicates the action to take if there is a match. If the Connect parameter is set to 1, the VPN Client should auto initiate; if 0, the VPN Client should not auto initiate. The default setting is 1. This parameter is optional. You can use it to exclude certain network ranges from auto initiation. For example, you might want to address a situation where Mobile IP and VPN software clients co-exist on client PCs and you want the VPN Client to auto initiate when not on a corporate subnet. In general, when configuring exceptions with the Connect parameter, you might want to place the network ranges you are excluding before those that should auto initiate. More importantly, the software processes the list in the order specified in the vpnclient.ini file. When it matches an entry in the list, the software stops searching and the Connect setting of that entry determines whether to auto initiate or do nothing. So if you put the Connect = 1 entries first, the software never reaches the Connect=0 entries. It is also important to order the entries in the list by the uniqueness of the network and subnet mask. You should list the more unique entries first. For example, an entry with a network/mask that specifies a match on 10.10.200.* should come before a network/mask that specifies a match on 10.10.*.*. If not, the software matches 10.10.*.* and never reaches 10.10.200.* Here is an example of an entry in an auto initiation list that excludes the network from auto initiating:3-4 VPN Client Administrator Guide 78-15404-02 Chapter 3 Configuring Automatic VPN Initiation—Windows Only Creating Automatic VPN Initiation in the vpnclient.ini File [Franklin] Network=10.10.200.0 Subnet=255.255.255.0 ConnectionEntry=robron Connect=0 Example 3-1 Section of vpnclient.ini File for Auto Initiation Suppose a sales manager travels among three locations (Chicago, Denver, and Laramie) within a corporation, attending sales meetings, and wants to securely and easily initiate a wireless connection at these locations. The vpnclient.ini contains the entries shown in this example. The connection entry named in each network section points to the individual’s profile (.pcf) for that on-site wireless LAN network. [Main] AutoInitiationEnable=1 AutoInitiationRetryInterval=3 AutoInitiationList=ChicagoWLAN,DenverWLAN,LaramieWLAN [ChicagoWLAN] Network=110.110.110.0 Mask=255.255.255.0 ConnectionEntry=Chicago (points to a connection profile named chicago.pcf) [DenverWLAN] Network=220.220.220.0 Mask=255.255.255.0 ConnectionEntry=Denver (points to a connection profile named denver.pcf) [LaramieWLAN] Network=221.221.221.0 Mask=255.255.255.0 ConnectionEntry=Laramie (points to a connection profile named laramie.pcf) Example 3-2 Section of vpnclient File for Auto Initiation that excludes and includes auto initiation In this example, the exceptions (more specific) network addresses appear first in the vpnclient.ini file followed by the connection entries for auto initiation. The connection entries for auto initiation do not need to include the Connect parameter. [Main] AutoInitiationEnable=1 AutoInitiationRetryInterval=3 AutoInitiationList=NetworkAExceptions,NetworkA,NetworkBexceptions,NetworkB [NetworkAExceptions] Network=192.168.0.0 Mask=255.255.255.0 ConnectionEntry=VPNprofileA1 Connect=0 [NetworkA] Network=192.0.0.0 Mask=255.0.0.0 ConnectionEntry=VPNprofileA2 [NetworkBExceptions] Network=161.200.100.0 Mask=255.255.255.0 ConnectionEntry=VPNprofileB1 Connect=0 [NetworkB] Network=161.200.0.0 Mask=255.255.0.0 ConnectionEntry=VPNprofileB23-5 VPN Client Administrator Guide 78-15404-02 Chapter 3 Configuring Automatic VPN Initiation—Windows Only Creating Automatic VPN Initiation in the vpnclient.ini File Verifying Automatic VPN Initiation Configuration To verify that you have configured auto initiation correctly, open the VPN Client GUI application and perform the following steps: Step 1 Display the Options menu, and select Automatic VPN Initiation. Step 2 On the Automatic VPN Initiation dialog, verify that Enable automatic VPN initiation is selected. If not, then click to select it. Step 3 Click Apply to close the window. Alternatively you can verify the auto initiation configuration from the command line by executing the following command: vpnclient verify autoinitconfig This display shows configuration information for each setting plus a list of your network entries.3-6 VPN Client Administrator Guide 78-15404-02 Chapter 3 Configuring Automatic VPN Initiation—Windows Only Creating Automatic VPN Initiation in the vpnclient.ini FileC H A P T E R 4-1 VPN Client Administrator Guide 78-15404-02 4 Using the VPN Client Command-Line Interface This chapter explains how to use the VPN Client command-line interface (CLI) to connect to a Cisco VPN device, generate statistical reports, and disconnect from the device. You can create your own script files that use the CLI commands to perform routine tasks, such as connect to a corporate server, run reports, and then disconnect from the server. CLI Commands This section lists each command, its syntax, and gives sample output for each command. It is organized by task. Displaying a List of VPN Client Commands To display a list of all VPN Client commands, go to the directory that contains the VPN Client software, and enter the vpnclient command at the command-line prompt: Note The vpnclient command lists all the commands and parameters available for your platform. Not all commands and parameters are available on all platforms. Starting a Connection—vpnclient connect To start a connection, enter the following command: vpnclient connect |