LIVRES - EBOOKS - THEME : Computers
LIVRES - EBOOKS - THEME : Computers
IMAGE_LINK LINK TITLE DESCRIPTION PRODUCT_TYPE

The Facebook Effect The exclusive inside story of Facebook and how it has revolutionized the way the world uses the Internet. “A fantastic book, filled with great reporting and colorful narrative†(Walter Isaacson). In little more than half a decade, Facebook has gone from a dorm-room novelty to a company with 500 million users. It is one of the fastest growing companies in history, an essential part of the social life not only of teenagers but hundreds of millions of adults worldwide. As Facebook spreads around the globe, it creates surprising effects—even becoming instrumental in political protests from Colombia to Iran. Veteran technology reporter David Kirkpatrick had the full cooperation of Facebook’s key executives in researching this fascinating history of the company and its impact on our lives. Kirkpatrick tells us how Facebook was created, why it has flourished, and where it is going next. He chronicles its successes and missteps, and gives readers the most complete assessment anywhere of founder and CEO Mark Zuckerberg, the central figure in the company’s remarkable ascent. This is the Facebook story that can be found nowhere else. How did a nineteen-year-old Harvard student create a company that has transformed the Internet and how did he grow it to its current enormous size? Kirkpatrick shows how Zuckerberg steadfastly refused to compromise his vision, insistently focusing on growth over profits and preaching that Facebook must dominate (his word) communication on the Internet. In the process, he and a small group of key executives have created a company that has changed social life in the United States and elsewhere, a company that has become a ubiquitous presence in marketing, altering politics, business, and even our sense of our own identity. This is the Facebook Effect. BUSINESS & ECONOMICS,E-Commerce,General (see also COMPUTERS,Electronic Commerce)

Alibaba's World A former VP at Alibaba Group, and creator of a documentary about its origins, offers an inside glimpse at the behemoth that's poised to transform the ecommerce world BUSINESS & ECONOMICS,E-Commerce,General (see also COMPUTERS,Electronic Commerce)

Alibaba In just a decade and half Jack Ma, a man who rose from humble beginnings and started his career as an English teacher, founded and built Alibaba into the second largest Internet company in the world. The company’s $25 billion IPO in 2014 was the world’s largest, valuing the company more than Facebook or Coca Cola. Alibaba today runs the e-commerce services that hundreds of millions of Chinese consumers depend on every day, providing employment and income for tens of millions more. A Rockefeller of his age, Jack has become an icon for the country’s booming private sector, and as the face of the new, consumerist China is courted by heads of state and CEOs from around the world. Granted unprecedented access to a wealth of new material including exclusive interviews, Clark draws on his own first-hand experience of key figures integral to Alibaba’s rise to create an authoritative, compelling narrative account of how Alibaba and its charismatic creator have transformed the way that Chinese exercise their new found economic freedom, inspiring entrepreneurs around the world and infuriating others, turning the tables on the Silicon Valley giants who have tried to stand in his way. Duncan explores vital questions about the company’s past, present, and future: How, from such unremarkable origins, did Jack Ma build Alibaba? What explains his relentless drive and his ability to outsmart his competitors? With over 80% of China’s e-commerce market, how long can the company hope to maintain its dominance? As the company sets its sights on the country’s financial and media markets, are there limits to Alibaba’s ambitions, or will the Chinese government act to curtail them? And as it set up shop from LA and San Francisco to Seattle, how will Alibaba grow its presence and investments in the US and other international markets? Clark tells Alibaba’s tale within the wider story of China’s economic explosion—the rise of the private sector and the expansion of Internet usage—that haver powered the country’s rise to become the world’s second largest economy and largest Internet population, twice the size of the United States. He also explores the political and social context for these momentous changes. An expert insider with unrivaled connections, Clark has a deep understanding of Chinese business mindset. He illuminates an unlikely corporate titan as never before, and examines the key role his company has played in transforming China while increasing its power and presence worldwide. BUSINESS & ECONOMICS,E-Commerce,General (see also COMPUTERS,Electronic Commerce)

E-Commerce Website Optimization Convert online traffic and increase revenue with this invaluable step-by-step guide to e-commerce website optimization. BUSINESS & ECONOMICS,E-Commerce,General (see also COMPUTERS,Electronic Commerce)

Platform Strategy During the last decade, platform businesses such as Uber, Airbnb, Amazon and eBay have been taking over the world. In almost every sector, traditional businesses are under attack from digital disrupters that are effectively harnessing the power of communities. But what exactly is a platform business and why is it different? In Platform Strategy, Laure Claire Reillier and Benoit Reillier provide a practical guide for students, digital entrepreneurs and executives to understand what platforms are, how they work and how you can build one successfully. Using their own "rocket model" and original case studies (including Google, Apple, Amazon), they explain how designing, igniting and scaling a platform business requires learning a whole new set of management rules. Platform Strategy also offers many fascinating insights into the future of platforms, their regulation and governance, as well as how they can be combined with other business models. Benoit Reillier and Laure Claire Reillier are co-founders of Launchworks, a leading advisory firm focused on helping organizations develop and scale innovative business models. BUSINESS & ECONOMICS,E-Commerce,General (see also COMPUTERS,Electronic Commerce)

The Bitcoin Standard When a pseudonymous programmer introduced “a new electronic cash system that’s fully peer-to-peer, with no trusted third party†to a small online mailing list in 2008, very few paid attention. Ten years later, and against all odds, this upstart autonomous decentralized software offers an unstoppable and globally-accessible hard money alternative to modern central banks. The Bitcoin Standard analyzes the historical context to the rise of Bitcoin, the economic properties that have allowed it to grow quickly, and its likely economic, political, and social implications. While Bitcoin is a new invention of the digital age, the problem it purports to solve is as old as human society itself: transferring value across time and space. Ammous takes the reader on an engaging journey through the history of technologies performing the functions of money, from primitive systems of trading limestones and seashells, to metals, coins, the gold standard, and modern government debt. Exploring what gave these technologies their monetary role, and how most lost it, provides the reader with a good idea of what makes for sound money, and sets the stage for an economic discussion of its consequences for individual and societal future-orientation, capital accumulation, trade, peace, culture, and art. Compellingly, Ammous shows that it is no coincidence that the loftiest achievements of humanity have come in societies enjoying the benefits of sound monetary regimes, nor is it coincidental that monetary collapse has usually accompanied civilizational collapse. With this background in place, the book moves on to explain the operation of Bitcoin in a functional and intuitive way. Bitcoin is a decentralized, distributed piece of software that converts electricity and processing power into indisputably accurate records, thus allowing its users to utilize the Internet to perform the traditional functions of money without having to rely on, or trust, any authorities or infrastructure in the physical world. Bitcoin is thus best understood as the first successfully implemented form of digital cash and digital hard money. With an automated and perfectly predictable monetary policy, and the ability to perform final settlement of large sums across the world in a matter of minutes, Bitcoin’s real competitive edge might just be as a store of value and network for final settlement of large payments—a digital form of gold with a built-in settlement infrastructure. Ammous’ firm grasp of the technological possibilities as well as the historical realities of monetary evolution provides for a fascinating exploration of the ramifications of voluntary free market money. As it challenges the most sacred of government monopolies, Bitcoin shifts the pendulum of sovereignty away from governments in favor of individuals, offering us the tantalizing possibility of a world where money is fully extricated from politics and unrestrained by borders. The final chapter of the book explores some of the most common questions surrounding Bitcoin: Is Bitcoin mining a waste of energy? Is Bitcoin for criminals? Who controls Bitcoin, and can they change it if they please? How can Bitcoin be killed? And what to make of all the thousands of Bitcoin knock-offs, and the many supposed applications of Bitcoin’s ‘blockchain technology’? The Bitcoin Standard is the essential resource for a clear understanding of the rise of the Internet’s decentralized, apolitical, free-market alternative to national central banks. BUSINESS & ECONOMICS,E-Commerce,General (see also COMPUTERS,Electronic Commerce)

The Bitcoin Standard When a pseudonymous programmer introduced “a new electronic cash system that’s fully peer-to-peer, with no trusted third party†to a small online mailing list in 2008, very few paid attention. Ten years later, and against all odds, this upstart autonomous decentralized software offers an unstoppable and globally-accessible hard money alternative to modern central banks. The Bitcoin Standard analyzes the historical context to the rise of Bitcoin, the economic properties that have allowed it to grow quickly, and its likely economic, political, and social implications. While Bitcoin is a new invention of the digital age, the problem it purports to solve is as old as human society itself: transferring value across time and space. Ammous takes the reader on an engaging journey through the history of technologies performing the functions of money, from primitive systems of trading limestones and seashells, to metals, coins, the gold standard, and modern government debt. Exploring what gave these technologies their monetary role, and how most lost it, provides the reader with a good idea of what makes for sound money, and sets the stage for an economic discussion of its consequences for individual and societal future-orientation, capital accumulation, trade, peace, culture, and art. Compellingly, Ammous shows that it is no coincidence that the loftiest achievements of humanity have come in societies enjoying the benefits of sound monetary regimes, nor is it coincidental that monetary collapse has usually accompanied civilizational collapse. With this background in place, the book moves on to explain the operation of Bitcoin in a functional and intuitive way. Bitcoin is a decentralized, distributed piece of software that converts electricity and processing power into indisputably accurate records, thus allowing its users to utilize the Internet to perform the traditional functions of money without having to rely on, or trust, any authorities or infrastructure in the physical world. Bitcoin is thus best understood as the first successfully implemented form of digital cash and digital hard money. With an automated and perfectly predictable monetary policy, and the ability to perform final settlement of large sums across the world in a matter of minutes, Bitcoin’s real competitive edge might just be as a store of value and network for final settlement of large payments—a digital form of gold with a built-in settlement infrastructure. Ammous’ firm grasp of the technological possibilities as well as the historical realities of monetary evolution provides for a fascinating exploration of the ramifications of voluntary free market money. As it challenges the most sacred of government monopolies, Bitcoin shifts the pendulum of sovereignty away from governments in favor of individuals, offering us the tantalizing possibility of a world where money is fully extricated from politics and unrestrained by borders. The final chapter of the book explores some of the most common questions surrounding Bitcoin: Is Bitcoin mining a waste of energy? Is Bitcoin for criminals? Who controls Bitcoin, and can they change it if they please? How can Bitcoin be killed? And what to make of all the thousands of Bitcoin knock-offs, and the many supposed applications of Bitcoin’s ‘blockchain technology’? The Bitcoin Standard is the essential resource for a clear understanding of the rise of the Internet’s decentralized, apolitical, free-market alternative to national central banks. BUSINESS & ECONOMICS,E-Commerce,General (see also COMPUTERS,Electronic Commerce)

Electronic Commerce 2018 This new Edition of Electronic Commerce is a complete update of the leading graduate level/advanced undergraduate level textbook on the subject. Electronic commerce (EC) describes the manner in which transactions take place over electronic networks, mostly the Internet. It is the process of electronically buying and selling goods, services, and information. Certain EC applications, such as buying and selling stocks and airline tickets online, are reaching maturity, some even exceeding non-Internet trades. However, EC is not just about buying and selling; it also is about electronically communicating, collaborating, and discovering information. It is about e-learning, e-government, social networks, and much more. EC is having an impact on a significant portion of the world, affecting businesses, professions, trade, and of course, people. The most important developments in EC since 2014 are the continuous phenomenal growth of social networks, especially Facebook , LinkedIn and Instagram, and the trend toward conducting EC with mobile devices. Other major developments are the expansion of EC globally, especially in China where you can find the world's largest EC company. Much attention is lately being given to smart commerce and the use of AI-based analytics and big data to enhance the field. Finally, some emerging EC business models are changing industries (e.g., the shared economy models of Uber and Airbnb). The 2018 (9th) edition, brings forth the latest trends in e-commerce, including smart commerce, social commerce, social collaboration, shared economy, innovations, and mobility. BUSINESS & ECONOMICS,E-Commerce,General (see also COMPUTERS,Electronic Commerce)

Selling on Amazon For Dummies Sell on Amazon and Make Them Do the Heavy Lifting Selling on Amazon has become one of the most popular ways to earn income online. In fact, there are over 2 million people selling on Amazon worldwide. Amazon allows any business, no matter how small, to get their products in front of millions of customers and take advantage of the largest fulfillment network in the world. It also allows businesses to leverage their first-class customer service and storage capabilities. Selling on Amazon For Dummies walks owners through the process of building a business on Amazon—a business that can be built almost anywhere in the world, as long as you have access to a computer and the internet. The basics of selling on Amazon Using FBA Getting started Deciding what to sell Conducting product research Finding your way around Seller Central Product sourcing, shipping and returns, Amazon subscription, fees, sales tax, and more How to earn ROIs (Returns on Your Investments) Selling on Amazon For Dummies provides the strategies, tools, and education you need, including turnkey solutions focused on sales, marketing, branding, and marketplace development to analyze and maximize opportunities. BUSINESS & ECONOMICS,E-Commerce,General (see also COMPUTERS,Electronic Commerce)

Strategies for e-Business This is the fourth edition of a unique textbook that provides extensive coverage of the evolution, the current state, and the practice of e-business strategies. It provides a solid introduction to understanding e-business and e-commerce by combining fundamental concepts and application models with practice-based case studies. An ideal classroom companion for business schools, the authors use their extensive knowledge to show how corporate strategy can imbibe and thrive by adopting vibrant e-business frameworks with proper tools. Students will gain a thorough knowledge of developing electronic and mobile commerce strategies and the methods to deal with these issues and challenges. BUSINESS & ECONOMICS,E-Commerce,General (see also COMPUTERS,Electronic Commerce)

Beyond Cybersecurity Move beyond cybersecurity to take protection of your digital business to the next level Beyond Cybersecurity: Protecting Your Digital Business arms your company against devastating online security breaches by providing you with the information and guidance you need to avoid catastrophic data compromise. Based upon highly-regarded risk assessment analysis, this critical text is founded upon proprietary research, client experience, and interviews with over 200 executives, regulators, and security experts, offering you a well-rounded, thoroughly researched resource that presents its findings in an organized, approachable style. Members of the global economy have spent years and tens of billions of dollars fighting cyber threats—but attacks remain an immense concern in the world of online business. The threat of data compromise that can lead to the leak of important financial and personal details can make consumers suspicious of the digital economy, and cause a nosedive in their trust and confidence in online business models. Understand the critical issue of cyber-attacks, and how they are both a social and a business issue that could slow the pace of innovation while wreaking financial havoc Consider how step-change capability improvements can create more resilient organizations Discuss how increased collaboration within the cybersecurity industry could improve alignment on a broad range of policy issues Explore how the active engagement of top-level business and public leaders can achieve progress toward cyber-resiliency Beyond Cybersecurity: Protecting Your Digital Business is an essential resource for business leaders who want to protect their organizations against cyber-attacks. BUSINESS & ECONOMICS,Industries,Computers & Information Technology

Modern Monopolies A look at the ubiquitous new business model, the platform, that's taking over the economy - and our digital lives. BUSINESS & ECONOMICS,Industries,Computers & Information Technology

Smart Flexibility Smart Flexibility: Moving Smart and Flexible Working from Theory to Practice is an engaging and practical management book to help organisations implement Smart Working, and take a business-focused approach to ’Flexible Working’. Written for managers at the leading edge of change, Andy Lake takes a strategic, comprehensive and integrated approach to Smart and Flexible Working. Taking an evidence-based approach, he sets out how to achieve measurable benefits across the Triple Bottom Line. Starting from the underlying principles and the compelling context for change, he takes a pragmatic approach to delivering change in each of the key areas of People (HR), Property and Technology. The book is designed to help professionals understand the vital connecting points across disciplines as well as innovations in their own fields. And there are separate chapters that look at the real impacts for sustainability, the impacts for ’Smart Government’, how to manage the ’Anywhere Anytime Team’ and how to take people on the journey towards a Smart Flexibility organisational culture. The book includes many insights based on the author’s experience and the latest research, many practical techniques for implementing change plus ten new case studies. Smart Flexibility is essential reading for anyone involved in workplace change and increasing the efficiency of organisations. It is aimed at managers who need to deliver change, and will be of great interest to consultants in the fields of workplace design, new technologies and HR/OD/Training. BUSINESS & ECONOMICS,Industries,Computers & Information Technology

The One Device The secret history of the invention that changed everything-and became the most profitable product in the world. "The One Device is a tour de force, with a fast-paced edge and heaps of analytical insight."-Ashlee Vance, New York Times bestselling author of Elon Musk "A stunning book. You will never look at your iPhone the same way again." -Dan Lyons, New York Times bestselling author of Disrupted Odds are that as you read this, an iPhone is within reach. But before Steve Jobs introduced us to "the one device," as he called it, a cell phone was merely what you used to make calls on the go. How did the iPhone transform our world and turn Apple into the most valuable company ever? Veteran technology journalist Brian Merchant reveals the inside story you won't hear from Cupertino-based on his exclusive interviews with the engineers, inventors, and developers who guided every stage of the iPhone's creation. This deep dive takes you from inside One Infinite Loop to 19th century France to WWII America, from the driest place on earth to a Kenyan pit of toxic e-waste, and even deep inside Shenzhen's notorious "suicide factories." It's a firsthand look at how the cutting-edge tech that makes the world work-touch screens, motion trackers, and even AI-made their way into our pockets. The One Device is a roadmap for design and engineering genius, an anthropology of the modern age, and an unprecedented view into one of the most secretive companies in history. This is the untold account, ten years in the making, of the device that changed everything. BUSINESS & ECONOMICS,Industries,Computers & Information Technology

The Age of Surveillance Capitalism The challenges to humanity posed by the digital future, the first detailed examination of the unprecedented form of power called "surveillance capitalism," and the quest by powerful corporations to predict and control our behavior. In this masterwork of original thinking and research, Shoshana Zuboff provides startling insights into the phenomenon that she has named surveillance capitalism. The stakes could not be higher: a global architecture of behavior modification threatens human nature in the twenty-first century just as industrial capitalism disfigured the natural world in the twentieth. Zuboff vividly brings to life the consequences as surveillance capitalism advances from Silicon Valley into every economic sector. Vast wealth and power are accumulated in ominous new "behavioral futures markets," where predictions about our behavior are bought and sold, and the production of goods and services is subordinated to a new "means of behavioral modification." The threat has shifted from a totalitarian Big Brother state to a ubiquitous digital architecture: a "Big Other" operating in the interests of surveillance capital. Here is the crucible of an unprecedented form of power marked by extreme concentrations of knowledge and free from democratic oversight. Zuboff's comprehensive and moving analysis lays bare the threats to twenty-first century society: a controlled "hive" of total connection that seduces with promises of total certainty for maximum profit -- at the expense of democracy, freedom, and our human future. With little resistance from law or society, surveillance capitalism is on the verge of dominating the social order and shaping the digital future -- if we let it. BUSINESS & ECONOMICS,Industries,Computers & Information Technology

Beginning Power BI Analyze your company’s data quickly and easily using Microsoft’s latest tools. You will learn to build scalable and robust data models to work from, clean and combine different data sources effectively, and create compelling visualizations and share them with your colleagues. Author Dan Clark takes you through each topic using step-by-step activities and plenty of screen shots to help familiarize you with the tools. This second edition includes new material on advanced uses of Power Query, along with the latest user guidance on the evolving Power BI platform. Beginning Power BI is your hands-on guide to quick, reliable, and valuable data insight. What You'll Learn Simplify data discovery, association, and cleansing Build solid analytical data models Create robust interactive data presentations Combine analytical and geographic data in map-based visualizations Publish and share dashboards and reports Who This Book Is For Business analysts, database administrators, developers, and other professionals looking to better understand and communicate with data BUSINESS & ECONOMICS,Industries,Computers & Information Technology

The Philosophy of Software This book is a critical introduction to code and software that develops an understanding of its social and philosophical implications in the digital age. Written specifically for people interested in the subject from a non-technical background, the book provides a lively and interesting analysis of these new media forms. BUSINESS & ECONOMICS,Industries,Computers & Information Technology

Cybersecurity Program Development for Business "This is the book executives have been waiting for. It is clear: With deep expertise but in nontechnical language, it describes what cybersecurity risks are and the decisions executives need to make to address them. It is crisp: Quick and to the point, it doesn't waste words and won't waste your time. It is candid: There is no sure cybersecurity defense, and Chris Moschovitis doesn't pretend there is; instead, he tells you how to understand your company's risk and make smart business decisions about what you can mitigate and what you cannot. It is also, in all likelihood, the only book ever written (or ever to be written) about cybersecurity defense that is fun to read." —Thomas A. Stewart, Executive Director, National Center for the Middle Market and Co-Author of Woo, Wow, and Win: Service Design, Strategy, and the Art of Customer Delight Get answers to all your cybersecurity questions In 2016, we reached a tipping point—a moment where the global and local implications of cybersecurity became undeniable. Despite the seriousness of the topic, the term "cybersecurity" still exasperates many people. They feel terrorized and overwhelmed. The majority of business people have very little understanding of cybersecurity, how to manage it, and what's really at risk. This essential guide, with its dozens of examples and case studies, breaks down every element of the development and management of a cybersecurity program for the executive. From understanding the need, to core risk management principles, to threats, tools, roles and responsibilities, this book walks the reader through each step of developing and implementing a cybersecurity program. Read cover-to-cover, it’s a thorough overview, but it can also function as a useful reference book as individual questions and difficulties arise. Unlike other cybersecurity books, the text is not bogged down with industry jargon Speaks specifically to the executive who is not familiar with the development or implementation of cybersecurity programs Shows you how to make pragmatic, rational, and informed decisions for your organization Written by a top-flight technologist with decades of experience and a track record of success If you’re a business manager or executive who needs to make sense of cybersecurity, this book demystifies it for you. BUSINESS & ECONOMICS,Industries,Computers & Information Technology

Summary and Analysis of The Upstarts So much to read, so little time? This brief overview of The Upstarts tells you what you need to know—before or after you read Brad Stone’s book. Crafted and edited with care, Worth Books set the standard for quality and give you the tools you need to be a well-informed reader. This short summary and analysis of The Upstarts: How Uber, Airbnb, and the Killer Companies of the New Silicon Valley Are Changing the World includes: Chapter-by-chapter overviews Character profiles Detailed timeline of events Important quotes Fascinating trivia Glossary of terms Supporting material to enhance your understanding of the original work About The Upstarts by Brad Stone: Brad Stone’s The Upstarts: How Uber, Airbnb, and the Killer Companies of the New Silicon Valley Are Changing the World is a detailed account of the founding of Uber and Airbnb, as well as each company’s climb from small startup to transportation and hospitality powerhouse. The Upstarts provides insight into the early lives of entrepreneurs Travis Kalanick and Brian Chesky, including their forays into new business ventures, some successful, most of them not. Stone points out the amazing parallels between the two tech companies as they fight for startup capital, wrestle to find the right framework for their products and organizations, and bring in the talent and technology needed to support those offerings. The summary and analysis in this ebook are intended to complement your reading experience and bring you closer to a great work of nonfiction. BUSINESS & ECONOMICS,Industries,Computers & Information Technology

Live Work Work Work Die A scathing, sardonic exploration of Silicon Valley tech culture, laying bare the greed, hubris, and retrograde politics of an industry that aspires to radically transform society for its own benefit At the height of the startup boom, journalist Corey Pein set out for Silicon Valley with little more than a smartphone and his wits. His goal: to learn how such an overhyped industry could possibly sustain itself as long as it has. But to truly understand the delirious reality of the tech entrepreneurs, he knew he would have to inhabit that perspective—he would have to become an entrepreneur himself. Thus Pein begins his journey—skulking through gimmicky tech conferences, pitching his over-the-top business ideas to investors, and rooming with a succession of naive upstart programmers whose entire lives are managed by their employers—who work endlessly and obediently, never thinking to question their place in the system. In showing us this frantic world, Pein challenges the positive, feel-good self-image that the tech tycoons have crafted—as nerdy and benevolent creators of wealth and opportunity—revealing their self-justifying views and their insidious visions for the future. Vivid and incisive, Live Work Work Work Die is a troubling portrait of a self-obsessed industry bent on imposing its disturbing visions on the rest of us. BUSINESS & ECONOMICS,Industries,Computers & Information Technology

Straight Talk for Startups "Straight Talk for Startups memorializes age-old best practices and empowers both experienced and new investment professionals to beat the odds."—David Krane, CEO, Google Ventures "Straight Talk for Startups is filled with real, raw, and fact-based ‘rules of the road’ that you need to know when diving into our ultra-competitive startup world. A must read and a re-read!"—Tony Fadell, Coinventor of the iPod/iPhone & Founder of Nest Labs Veteran venture capitalist Randy Komisar and finance executive Jantoon Reigersman share no-nonsense, counterintuitive guidelines to help anyone build a successful startup. Over the course of their careers, Randy Komisar and Jantoon Reigersman continue to see startups crash and burn because they forget the timeless lessons of entrepreneurship. But, as Komisar and Reigersman show, you can beat the odds if you quickly learn what insiders know about what it takes to build a healthy foundation for a thriving venture. In Straight Talk for Startups they walk budding entrepreneurs through 100 essential rules—from pitching your idea to selecting investors to managing your board to deciding how and when to achieve liquidity. Culled from their own decades of experience, as well as the experiences of their many successful colleagues and friends, the rules are organized under broad topics, from "Mastering the Fundamentals" and "Selecting the Right Investors," to "The Ideal Fundraise," "Building and Managing Effective Boards," and "Achieving Liquidity." Vital rules you’ll find in Straight Talk for Startups include: The best ideas originate from founders who are users Create two business plans: an execution plan and an aspirational plan Net income is an option, but cash flow is a fact Don’t accept money from strangers Personal wealth doesn’t equal good investing Small boards are better than big ones Add independent board members for expertise and objectivity Too many unanimous board decisions are a sign of trouble Choose an acquirer, don’t wait to be chosen Learn the rules by heart so you know when to break them Filled with helpful real-life examples and specific, actionable advice, Straight Talk for Startups is the ideal handbook for anyone running, working for, or thinking about creating a startup, or just curious about what makes high-potential ventures tick. BUSINESS & ECONOMICS,Industries,Computers & Information Technology

AI Superpowers The United States has long been the leader in Artificial Intelligence. But Dr. Kai-Fu Lee—one of the world’s most respected experts on AI—reveals that China has caught up to the US at an astonishingly rapid pace. As Sino-American competition in AI heats up, Lee envisions China and the US forming a powerful duopoly in AI. He outlines the upheaval of traditional jobs, how the suddenly unemployed will find new ways of making their lives meaningful, and how the Chinese and American governments will have to cope with the changing economic landscape. BUSINESS & ECONOMICS,Industries,Computers & Information Technology
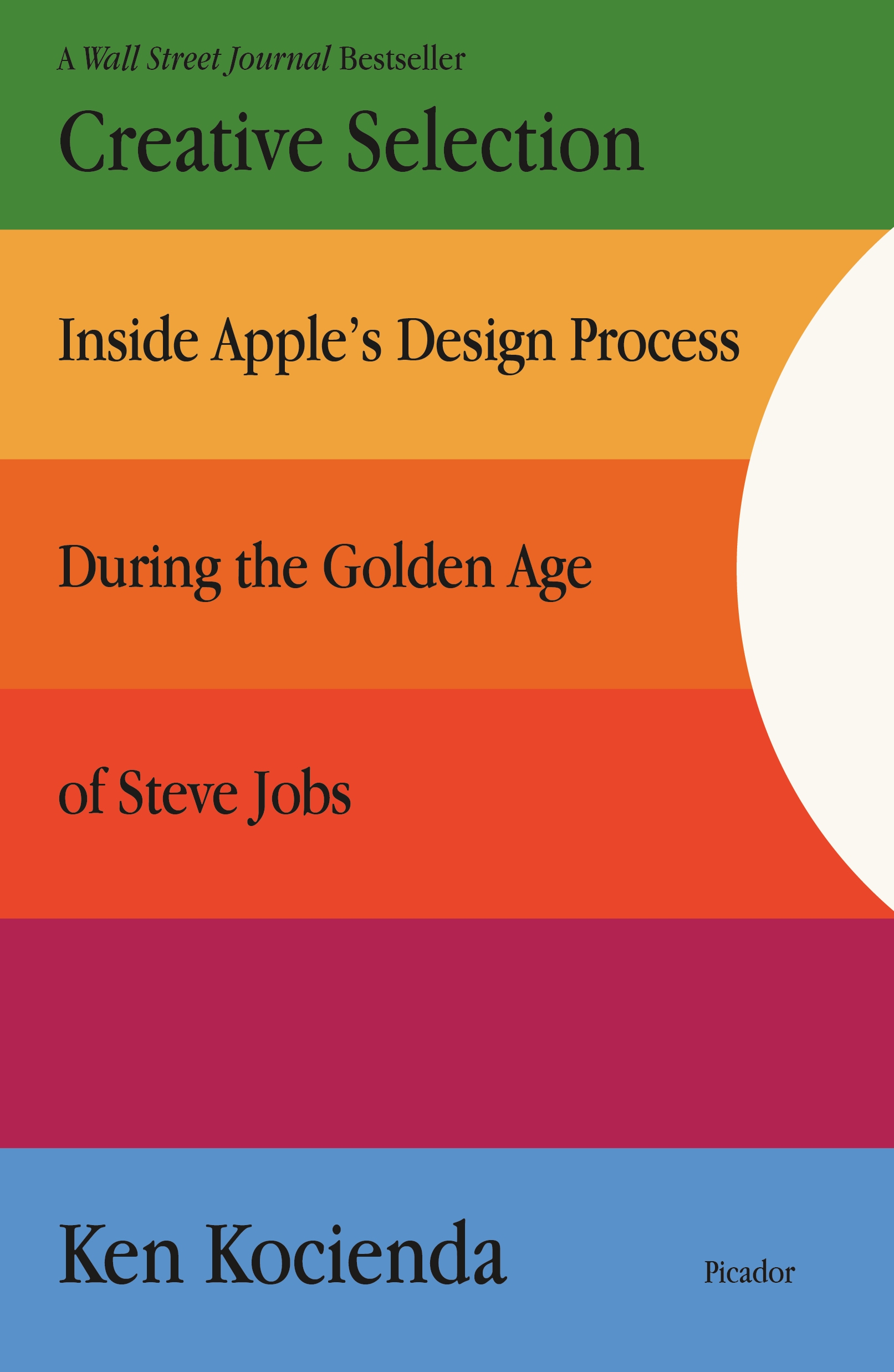
Creative Selection * WALL STREET JOURNAL BESTSELLER * An insider's account of Apple's creative process during the golden years of Steve Jobs. Hundreds of millions of people use Apple products every day; several thousand work on Apple's campus in Cupertino, California; but only a handful sit at the drawing board. Creative Selection recounts the life of one of the few who worked behind the scenes, a highly-respected software engineer who worked in the final years of the Steve Jobs era—the Golden Age of Apple. Ken Kocienda offers an inside look at Apple’s creative process. For fifteen years, he was on the ground floor of the company as a specialist, directly responsible for experimenting with novel user interface concepts and writing powerful, easy-to-use software for products including the iPhone, the iPad, and the Safari web browser. His stories explain the symbiotic relationship between software and product development for those who have never dreamed of programming a computer, and reveal what it was like to work on the cutting edge of technology at one of the world's most admired companies. Kocienda shares moments of struggle and success, crisis and collaboration, illuminating each with lessons learned over his Apple career. He introduces the essential elements of innovation—inspiration, collaboration, craft, diligence, decisiveness, taste, and empathy—and uses these as a lens through which to understand productive work culture. An insider's tale of creativity and innovation at Apple, Creative Selection shows readers how a small group of people developed an evolutionary design model, and how they used this methodology to make groundbreaking and intuitive software which countless millions use every day. BUSINESS & ECONOMICS,Industries,Computers & Information Technology

Life After Google A FINANCIAL TIMES BOOK OF THE MONTH FROM THE WALL STREET JOURNAL: " Nothing Mr. Gilder says or writes is ever delivered at anything less than the fullest philosophical decibel... Mr. Gilder sounds less like a tech guru than a poet, and his words tumble out in a romantic cascade." “Google’s algorithms assume the world’s future is nothing more than the next moment in a random process. George Gilder shows how deep this assumption goes, what motivates people to make it, and why it’s wrong: the future depends on human action.†— Peter Thiel, founder of PayPal and Palantir Technologies and author of Zero to One: Notes on Startups, or How to Build the Future The Age of Google, built on big data and machine intelligence, has been an awesome era. But it’s coming to an end. In Life after Google, George Gilder—the peerless visionary of technology and culture—explains why Silicon Valley is suffering a nervous breakdown and what to expect as the post-Google age dawns. Google’s astonishing ability to “search and sort†attracts the entire world to its search engine and countless other goodies—videos, maps, email, calendars….And everything it offers is free, or so it seems. Instead of paying directly, users submit to advertising. The system of “aggregate and advertise†works—for a while—if you control an empire of data centers, but a market without prices strangles entrepreneurship and turns the Internet into a wasteland of ads. The crisis is not just economic. Even as advances in artificial intelligence induce delusions of omnipotence and transcendence, Silicon Valley has pretty much given up on security. The Internet firewalls supposedly protecting all those passwords and personal information have proved hopelessly permeable. The crisis cannot be solved within the current computer and network architecture. The future lies with the “cryptocosmâ€â€”the new architecture of the blockchain and its derivatives. Enabling cryptocurrencies such as bitcoin and ether, NEO and Hashgraph, it will provide the Internet a secure global payments system, ending the aggregate-and-advertise Age of Google. Silicon Valley, long dominated by a few giants, faces a “great unbundling,†which will disperse computer power and commerce and transform the economy and the Internet. Life after Google is almost here. For fans of "Wealth and Poverty," "Knowledge and Power," and "The Scandal of Money." BUSINESS & ECONOMICS,Industries,Computers & Information Technology

The Big Nine A call-to-arms about the broken nature of artificial intelligence, and the powerful corporations that are turning the human-machine relationship on its head. We like to think that we are in control of the future of "artificial" intelligence. The reality, though, is that we -- the everyday people whose data powers AI -- aren't actually in control of anything. When, for example, we speak with Alexa, we contribute that data to a system we can't see and have no input into -- one largely free from regulation or oversight. The big nine corporations -- Amazon, Google, Facebook, Tencent, Baidu, Alibaba, Microsoft, IBM and Apple--are the new gods of AI and are short-changing our futures to reap immediate financial gain. In this book, Amy Webb reveals the pervasive, invisible ways in which the foundations of AI -- the people working on the system, their motivations, the technology itself -- is broken. Within our lifetimes, AI will, by design, begin to behave unpredictably, thinking and acting in ways which defy human logic. The big nine corporations may be inadvertently building and enabling vast arrays of intelligent systems that don't share our motivations, desires, or hopes for the future of humanity. Much more than a passionate, human-centered call-to-arms, this book delivers a strategy for changing course, and provides a path for liberating us from algorithmic decision-makers and powerful corporations. BUSINESS & ECONOMICS,Industries,Computers & Information Technology

The Infinite Machine Written with the verve of such works as The Big Short, The History of the Future, and The Spider Network, here is the fascinating, true story of the rise of Ethereum, the second-biggest digital asset in the world, the growth of cryptocurrency, and the future of the internet as we know it. Everyone has heard of Bitcoin, but few know about the second largest cryptocurrency, Ethereum, which has been heralded as the "next internet." The story of Ethereum begins with Vitalik Buterin, a supremely gifted nineteen-year-old autodidact who saw the promise of blockchain when the technology was in its earliest stages. He convinced a crack group of coders to join him in his quest to make a super-charged, global computer. The Infinite Machine introduces Vitalik’s ingenious idea and unfolds Ethereum’s chaotic beginnings. It then explores the brilliant innovation and reckless greed the platform—an infinitely adaptable foundation for experimentation and new applications—has unleashed and the consequences that resulted as the frenzy surrounding it grew: increased regulatory scrutiny, incipient Wall Street interest, and the founding team’s effort to get the Ethereum platform to scale so it can eventually be accessible to the masses. Financial journalist and cryptocurrency expert Camila Russo details the wild and often hapless adventures of a team of hippy-anarchists, reluctantly led by an ambivalent visionary, and lays out how this new foundation for the internet will spur both transformation and fraud—turning some into millionaires and others into felons—and revolutionize our ideas about money. BUSINESS & ECONOMICS,Industries,Computers & Information Technology

Always Day One "This is a terrific book" - Kara Swisher An acclaimed tech reporter reveals the inner workings of Amazon, Facebook, Google, Apple, and Microsoft, showing how to compete with the tech titans using their own playbook. At Amazon, "Day One" is code for inventing like a startup, with little regard for legacy. Day Two is, in Jeff Bezos's own words, "stasis, followed by irrelevance, followed by excruciating, painful decline, followed by death." Most companies today are set up for Day Two. They build advantages and defend them fiercely, rather than invent the future. But Amazon and fellow tech titans Facebook, Google, and Microsoft are operating in Day One: they prioritize reinvention over tradition and collaboration over ownership. Through 130 interviews with insiders, from Mark Zuckerberg to hourly workers, Always Day One reveals the tech giants' blueprint for sustainable success in a business world where no advantage is safe. Companies today can spin up new products at record speed -- thanks to artificial intelligence and cloud computing -- and those who stand still will be picked apart. The tech giants remain dominant because they've built cultures that spark continual reinvention. It might sound radical, but those who don't act like it's always day one do so at their own peril. Kantrowitz uncovers the engine propelling the tech giants' continued dominance at a stage when most big companies begin to decline. And he shows the way forward for everyone who wants to compete with--and beat--the titans. BUSINESS & ECONOMICS,Industries,Computers & Information Technology

Digital Transformation Building Intelligent Enterprises by leveraging the emerging and next-generation technologies to accelerate the adoption of digital transformation The speed of innovation and emerging IT technologies are changing at a very fast pace and enterprises are eager to join the digital revolution so they can stand above the competition and succeed as the enterprise of tomorrow. This book is an attempt to make the enterprise intelligent by providing the path to digital transformation and the adoption of new IT methods, tools and technologies. This book has been organized to cover the following topics: Digital Transformation, Design Thinking, Agile, DevOps, Robotic Process Automation, Internet of Things, Artificial Intelligence, Machine Learning, Blockchain, Drones, Augmented and Virtual Reality, 3D Printing, Big Data, Analytics, Cloud Computing, APIs, and SAP Leonardo. No prior knowledge of any technical coding or language is necessary to understand the content of this book. End-to-end storyline to accelerate the enterprise’s digital transformation journey How an enterprise can stay relevant, compete, and perform in the digital economy How to leverage these technologies to build intelligent enterprises Understand and apply the emerging technologies across key business processes Industry-specific Use Cases for all technologies as a reference point to build the business case for implementation The book is very well suited towards the C-Suite executives, both IT and business leaders, directors and managers, project managers, solution architects, and all professionals who have an interest and desire to keep up-to-date with the latest technological trends, looking for a career change, want to help enterprise adapt and onboard the digital roadmap, or have an agenda to digitize key processes within the enterprise to make it intelligent. BUSINESS & ECONOMICS,Industries,Computers & Information Technology

World It Project, The Understanding the key IT issues facing firms within their surrounding contexts is critical for the firm, government, and their international counterparts.In response to the dominant and pervasive bias in Information Systems (IS) research towards American and Western views, the World IT Project was launched and is the largest study of its kind in the field. This book captures the organizational, technological, and individual issues of IT employees across 37 countries.The book enables management and staff to formulate business and IT-related policies and strategies. Likewise, it allows policymakers, governments and vendors to address important issues at the national level as well as to respond to the needs of partners and stakeholders in other countries. It also offers current and future academic scholars a grounded understanding of the international IT environment and provides a sound foundation to launch many international IT studies. BUSINESS & ECONOMICS,Industries,Computers & Information Technology

Digital Enablement This collection of papers from the Digital Enablement Conference 2016 aims to illustrate various aspects of the digital enablement phenomenon. Over the last two decades, advances in digital technology have fundamentally transformed the way we do business, work, and live. As new technologies emerge, they offer new possibilities for addressing increasingly complex economic and social problems.Digital enablement refers to the consumerizational and transformational roles of digital technology in driving business and social innovation, and has profound, multi-disciplinary implications. Some of these include: Facilitating new business models that transform the way firms transact, market, and engage with customers; providing new means of income generation for disadvantaged groups; and generating new means of social interaction, which empowers employees, customers, small businesses, and entire communities.This book introduces readers to case studies of digital enablement in business and society. It offers unique insights into the phenomenon from multiple contexts, giving readers a nuanced understanding of the roles digital enablement can play. BUSINESS & ECONOMICS,Industries,Computers & Information Technology

Digital Enablement And Innovation In China The casebook aims at providing the latest case materials for researchers and students who are keen to learn about the consumerization and transformation effects of digital technology.It is one of the first books covering the best practices of digital enablement in China, which has been the focus many observers among the practitioners as well as academics.The 22 projects analyzed include Zhongguancun InnoWay, OFO Bicycle, Esheke, Taobao, and more. BUSINESS & ECONOMICS,Industries,Computers & Information Technology

Beginning Apache Spark Using Azure Databricks Analyze vast amounts of data in record time using Apache Spark with Databricks in the Cloud. Learn the fundamentals, and more, of running analytics on large clusters in Azure and AWS, using Apache Spark with Databricks on top. Discover how to squeeze the most value out of your data at a mere fraction of what classical analytics solutions cost, while at the same time getting the results you need, incrementally faster. This book explains how the confluence of these pivotal technologies gives you enormous power, and cheaply, when it comes to huge datasets. You will begin by learning how cloud infrastructure makes it possible to scale your code to large amounts of processing units, without having to pay for the machinery in advance. From there you will learn how Apache Spark, an open source framework, can enable all those CPUs for data analytics use. Finally, you will see how services such as Databricks provide the power of Apache Spark, without you having to know anything about configuring hardware or software. By removing the need for expensive experts and hardware, your resources can instead be allocated to actually finding business value in the data. This book guides you through some advanced topics such as analytics in the cloud, data lakes, data ingestion, architecture, machine learning, and tools, including Apache Spark, Apache Hadoop, Apache Hive, Python, and SQL. Valuable exercises help reinforce what you have learned. What You Will Learn Discover the value of big data analytics that leverage the power of the cloud Get started with Databricks using SQL and Python in either Microsoft Azure or AWS Understand the underlying technology, and how the cloud and Apache Spark fit into the bigger picture See how these tools are used in the real world Run basic analytics, including machine learning, on billions of rows at a fraction of a cost or free Who This Book Is For Data engineers, data scientists, and cloud architects who want or need to run advanced analytics in the cloud. It is assumed that the reader has data experience, but perhaps minimal exposure to Apache Spark and Azure Databricks. The book is also recommended for people who want to get started in the analytics field, as it provides a strong foundation. BUSINESS & ECONOMICS,Industries,Computers & Information Technology

Strategic System Assurance and Business Analytics This book systematically examines and quantifies industrial problems by assessing the complexity and safety of large systems. It includes chapters on system performance management, software reliability assessment, testing, quality management, analysis using soft computing techniques, management analytics, and business analytics, with a clear focus on exploring real-world business issues. Through contributions from researchers working in the area of performance, management, and business analytics, it explores the development of new methods and approaches to improve business by gaining knowledge from bulk data. With system performance analytics, companies are now able to drive performance and provide actionable insights for each level and for every role using key indicators, generate mobile-enabled scorecards, time series-based analysis using charts, and dashboards. In the current dynamic environment, a viable tool known as multi-criteria decision analysis (MCDA) is increasingly being adopted to deal with complex business decisions. MCDA is an important decision support tool for analyzing goals and providing optimal solutions and alternatives. It comprises several distinct techniques, which are implemented by specialized decision-making packages. This book addresses a number of important MCDA methods, such as DEMATEL, TOPSIS, AHP, MAUT, and Intuitionistic Fuzzy MCDM, which make it possible to derive maximum utility in the area of analytics. As such, it is a valuable resource for researchers and academicians, as well as practitioners and business experts. BUSINESS & ECONOMICS,Industries,Computers & Information Technology

The Internet of Things Entrepreneurial Ecosystems This book focuses on the Internet of Things (IoT). IoT has caught the imagination as a transformational technology that will positively impact a large and diverse array of socio-economic activities. This book explores this impact, beginning with a chapter highlighting the promises and complexities of the IoT. It then explores these in greater detail in subsequent chapters. The first of these chapters explores the patenting activity of leading companies and is followed by a discussion of the challenges faced by the growth of ‘unicorns’ within Europe. The fourth chapter outlines a methodology for determining when investments in IoT should occur and is followed by a discussion of how the data generated by IoT will change marketing related decisions. The scope and complexity of the regulatory and governance structures associated with the IoT are then explored in the sixth chapter. These issues are brought together in the final chapter, which identifies the opportunities and challenges emanating from the IoT and how these may be tackled. This book will be valuable reading to academics working in the field of disruptive technology, innovation management, and technological change more broadly. BUSINESS & ECONOMICS,Industries,Computers & Information Technology

Just the Tips, Man for Excel 2000 If you want great spreadsheets, you want Microsoft Excel 2000, hands down. But if you want great spreadsheets fast, you want Just the Tips, Manâ„¢ for Microsoft Excel 2000. We've collected over 400 of the shortest cuts and coolest tips and tricks that you won't find in one place anywhere else. And we've put them in a portable, fun-to-read package that will get you working faster and more efficiently from page one. Computers

Protected Mode Software Architecture A fundamental understanding of Protected Mode vs. Real Mode operation is key to understanding the basic PC platform. MindShare's book, Protected Mode Software Architecture, details Protected Mode and Real Mode operation and the challenges associated with each. Computers

Pentium Processor System Architecture, Second Edition A comprehensive description of the Pentium microprocessor and its relationship to the remainder of the system. Emphasis is placed on the interaction of the processor's execution units, internal caches, and the external cache and system memory. The different types of Pentium bus transfers are described in detail. Computers

PCI Express System Architecture PCI Express System Architecture provides an in-depth description of this technology and provides insights into its new features and implementation requirements. This comprehensive book describes the PCI Express technology using an approach that is as easy to read and reference. The book is organized so that all relevant issues related to key topics can be found in one location. Computers

Embedded Ethernet and Internet Complete Bringing together two areas of computer technology—networking and embedded systems—this developer's guide offers guidance and examples for each of these, with a focus on the special requirements and limits of embedded systems. Because developing an embedded system for networking requires knowledge from many areas, including circuit design, programming, network architecture, and Ethernet and Internet protocols, developers are given valuable technical information on each that can be put to use right away. Covered are the advantages and limits of using Ethernet to connect embedded systems in a local network, hardware and program code needed to connect an embedded system to an Ethernet network and the Internet, and how to build a network. Also discussed are how embedded systems can use TCP/IP and related protocols and how personal-computer applications can use the protocols to communicate with embedded systems. Developers will learn how their Web server's pages can include dynamic, real-time content and respond to user input. Computers

Indra's Pearls This book tells the story of the first computer exploration of Klein's vision of infinitely repeated reflections, featuring extraordinary images. Computers

Principles of Constraint Programming Upper-division textbook covering foundations of constraint programming and applications to scheduling, optimisation etc. Computers

3D Computer Graphics Topics include transformations, lighting and shading, ray tracing, radiosity, texture mapping, colour theory, and aspects of animation. Computers

Foundations of Cryptography Focuses on the basic mathematical tools needed for cryptographic design: computational difficulty (one-way functions), pseudorandomness and zero-knowledge proofs. Computers

Flexible Pattern Matching in Strings Presents recently developed algorithms for searching for simple, multiple and extended strings, regular expressions, exact and approximate matches. Computers

Modern Compiler Implementation in Java The second edition features a redesigned compiler project in Java, for a subset of Java itself. Computers

A Practitioner's Guide to Software Test Design Here’s a comprehensive, up-to-date and practical introduction to software test design. This invaluable book presents all the important test design techniques in a single place and in a consistent, and easy-to-digest format. An immediately useful handbook for test engineers, developers, quality assurance professionals, and requirements and systems analysts, it enables you to: choose the best test case design, find software defects in less time and with fewer resources, and develop optimal strategies that help reduce the likelihood of costly errors. It also assists you in estimating the effort, time and cost of good testing. Computers

Probability and Computing An excellent 2005 introduction to the probabilistic techniques and paradigms used in the development of probabilistic algorithms and analyses. Computers

Recursion Theory for Metamathematics This work is a sequel to the author's Gödel's Incompleteness Theorems, though it can be read independently by anyone familiar with Gödel's incompleteness theorem for Peano arithmetic. The book deals mainly with those aspects of recursion theory that have applications to the metamathematics of incompleteness, undecidability, and related topics. It is both an introduction to the theory and a presentation of new results in the field. Computers

SAS Storage Architecture MindShare Press's SAS Storage Architecture provides a comprehensive description of the SAS (Serial Attached SCSI) architecture. -Harry Mason, President of the SCSI Trade Association Board of Directors Computers

An Introduction to Computational Physics This advanced textbook provides an introduction to the basic methods of computational physics. Computers

The Elements of UMLâ„¢ 2.0 Style Concise and easy-to-understand guidelines and standards for creating UML 2.0 diagrams. Computers

Essential Bioinformatics Clear, concise introduction to bioinformatics, written specifically to be accessible to a life science audience. Computers

Global Methods for Combinatorial Isoperimetric Problems This text explores global methods in combinatorial optimization and is suitable for graduate students and researchers. Computers

The Elements of C++ Style This 2004 book contains guidelines for writing consistent C++ code that's easy to understand, enhance and maintain. Perfect for teams. Computers

A Short Introduction to Quantum Information and Quantum Computation This undergraduate book, first published in 2006, introduces quantum information and computation for physicists, mathematicians and computer scientists. Computers

Kernel Methods for Pattern Analysis A unique account of developing topic in data mining and machine learning. Computers

Computers, Phones, and the Internet During the past decade, technology has become more pervasive, encroaching more and more on our lives. Computers, cell phones, and the internet have an enormous influence not only on how we function at work, but also on how we communicate and interact outside the office. Researchers have been documenting the effect that these types of technology have on individuals, families, and other social groups. Their work addresses questions that relate to how people use computers, cell phones, and the internet, how they integrate their use of new technology into daily routines, and how family function, social relationships, education, and socialization are changing as a result. This research is being conducted in a number of countries, by scientists from a variety of disciplines, who publish in very different places. The result is that it is difficult for researchers and students to get a current and coherent view of the research literature. This book brings together the leading researchers currently investigating the impact of information and communication technology outside of the workplace. Its goal is to develop a consolidated view of what we collectively know in this fast-changing area, to evaluate approaches to data collection and analysis, and to identify future directions for research. The book will appeal to professionals and students in social psychology, human-technology interaction, sociology, and communication. Computers

Writing Scientific Software A manual and guide to good scientific computing style, explaining how to write good software and how to test it for bugs, accuracy and performance. Computers

Writing About Medicines For People The definitive guidelines for writing, designing, and testing medicine information for consumers. Computers

Who Controls the Internet? In this provocative new book, Jack Goldsmith and Tim Wu tell the fascinating story of the Internet's challenge to governmental rule in the 1990s, and the ensuing battles with governments around the world. It's a book about the fate of one idea--that the Internet might liberate us forever from government, borders, and even our physical selves. The authors show how, in the course of a decade, this original vision is uprooted, as governments time and time again assert their power to direct the future of the Internet. The destiny of the Internet over the next decades, argue Goldsmith and Wu, will reflect the interests of powerful nations and the conflicts within and between them. Computers

Introduction to Computational Genomics Self-contained and entertaining introduction to computational genomics, using a case-studies approach with Matlab demos. Computers

Sams Teach Yourself SQL in 10 Minutes Sams Teach Yourself SQL in 10 Minutes has established itself as the gold standard for introductory SQL books, offering a fast-paced accessible tutorial to the major themes and techniques involved in applying the SQL language. Forta¿s examples are clear and his writing style is crisp and concise. As with earlier editions, this revision includes coverage of current versions of all major commercial SQL platforms. New this time around is coverage of MySQL, and PostgreSQL. All examples have been tested against each SQL platform, with incompatibilities or platform distinctives called out and explained. Computers

Networks This book is a masterful unification of disparate fields and lessons from nature and derives comprehensible and realistic design principles. Computers

IP Quality of Service The complete resource for understanding and deploying IP quality of service for Cisco networks Learn to deliver and deploy IP QoS and MPLS-based traffic engineering by understanding: QoS fundamentals and the need for IP QoS The Differentiated Services QoS architecture and its enabling QoS functionality The Integrated Services QoS model and its enabling QoS functions ATM, Frame Relay, and IEEE 802.1p/802.1Q QoS technologies and how they work with IP QoS MPLS and MPLS VPN QoS and how they work with IP QoS MPLS traffic engineering Routing policies, general IP QoS functions, and other miscellaneous QoS information Quality-of-service (QoS) technologies provide networks with greater reliability in delivering applications, as well as control over access, delay, loss, content quality, and bandwidth. IP QoS functions are crucial in today's scalable IP networks. These networks are designed to deliver reliable and differentiated Internet services by enabling network operators to control network resources and use. Network planners, designers, and engineers need a thorough understanding of QoS concepts and features to enable their networks to run at maximum efficiency and to deliver the new generation of time-critical multimedia and voice applications. IP Quality of Service serves as an essential resource and design guide for anyone planning to deploy QoS services in Cisco networks. Author Srinivas Vegesna provides complete coverage of Cisco IP QoS features and functions, including case studies and configuration examples. The emphasis is on real-world application-going beyond conceptual explanations to teach actual deployment. IP Quality of Service is written for internetworking professionals who are responsible for designing and maintaining IP services for corporate intranets and for service provider network infrastructures. If you are a network engineer, architect, manager, planner, or operator who has a rudimentary knowledge of QoS technologies, this book will provide you with practical insights on what you need to consider when designing and implementing various degrees of QoS in the network. Because incorporating some measure of QoS is an integral part of any network design process, IP Quality of Service applies to all IP networks-corporate intranets, service provider networks, and the Internet. Computers

MPLS and VPN Architectures A practical guide to understanding, designing, and deploying MPLS and MPLS-enabled VPNs In-depth analysis of the Multiprotocol Label Switching (MPLS) architecture Detailed discussion of the mechanisms and features that constitute the architecture Learn how MPLS scales to support tens of thousands of VPNs Extensive case studies guide you through the design and deployment of real-world MPLS/VPN networks Configuration examples and guidelines assist in configuring MPLS on Cisco® devices Design and implementation options help you build various VPN topologies Multiprotocol Label Switching (MPLS) is an innovative technique for high-performance packet forwarding. There are many uses for this new technology, both within a service-provider environment and within the enterprise network, and the most widely deployed usage today is the enabling of Virtual Private Networks (VPNs). With the introduction of MPLS-enabled VPNs, network designers are able to better scale their networks than with the methods available in the past. Network engineers and administrators need quick, effective education on this technology to efficiently deploy MPLS-enabled VPNs within their networks. With that goal in mind, MPLS and VPN Architectures provides an in-depth discussion particular to Cisco's MPLS architecture. This book covers MPLS theory and configuration, network design issues, and case studies as well as one major MPLS application: MPLS-based VPNs. The MPLS/VPN architecture and all its mechanisms are explained with configuration examples, suggested design and deployment guidelines, and extensive case studies. MPLS and VPN Architectures is your practical guide to understanding, designing, and deploying MPLS and MPLS-based VPNs. Computers

Designing Your Second Life Whether your second, virtual life has just begun, or you’ve been “in-world" for a long time, a successful and rewarding experience depends on your mastery of design. Everything from your avatar to your home, your clothes to your behavior says something about who you are and the way others see you. In this book Rebecca Tapley—“Mera Luan†in SL—shows you how to design everything from bodies to earrings, cars to castles, for improved appearance, function, and usability. Real-world topics such as urban planning, color theory, user experience, interior design, and landscaping are mapped to SL conditions. Learn how to spot the best skin and hair, clothing, architecture and construction, property for sale, and more. In addition, Rebecca’s insights and observations on Second Life etiquette, manners, customs, and other subtle socio-cultural realities will help you make your way through this new and sometimes baffling world. Have a more rewarding second life by learning how to: Create a realistic or fantastical avatar Make gorgeous clothes and other luxury goods Build impressive homes and planned communities Develop whole islands Establish a social community and career Life. Computers

Programming in Haskell A textbook on the functional programming language Haskell, with all concepts are explained from first principles via carefully chosen examples. Computers

Computability and Logic Computability and Logic is a classic because of its accessibility to students without a mathematical background. This fifth edition was first published in 2007. Computers

Quantum Computer Science A concise introduction to quantum computation for computer scientists who know nothing about quantum theory. Computers

An Introduction to Many-Valued and Fuzzy Logic An accessible introduction to many-valued and fuzzy logic designed for undergraduate and graduate students. Computers

Analyzing Linguistic Data A straightforward introduction to the statistical analysis of language data, designed for students with a non-mathematical background. Computers

Theory of Automata, Formal Languages and Computation This book is aimed at providing an introduction to the basic models of computability to the undergraduate students. This book is devoted to Finite Automata and their properties. Pushdown Automata provides a class of models and enables the analysis of context-free languages. Turing Machines have been introduced and the book discusses computability and decidability. A number of problems with solutions have been provided for each chapter. A lot of exercises have been given with hints/answers to most of these tutorial problems. Computers

C Unleashed C Unleashed is a very comprehensive book on the ANSI C programming language. This book promotes solid, portable programming using ANSI C, thus benefiting programmers on any platform, including mainframes. Covers the New Standard for C, known as C9X, and includes embedded systems, simulation processing, threading and multiprocessing, digital signal processing, and natural language processing. Computers

Phenomenology of the Human Person In this book, Robert Sokolowski argues that being a person means to be involved with truth. Computers

How to Think About Algorithms Textbook that teaches students how to think about algorithms like an expert, without getting bogged down in formal proof. Computers

Quantum Computing for Computer Scientists Finally, a textbook that explains quantum computing using techniques and concepts familiar to computer scientists. Computers

Analytic Combinatorics The definitive treatment of analytic combinatorics, from leaders in the field. Exercises, examples, appendices and notes aid understanding. Computers

Handbook of Practical Logic and Automated Reasoning A one-stop reference, self-contained, with theoretical topics presented in conjunction with implementations for which code is supplied. Computers

Multimedia Learning An evidence based, rigorous text reviewing 12 principles of experimental studies grounded in cognitive theory of multi-media learning. Computers

Statistical Mechanics This book discusses the computational approach in modern statistical physics, adopting simple language and an attractive format with many illustrations, tables and printed algorithms. The style will appeal to students, teachers and researchers in the physical sciences. The focus is on orientation, with implementation details kept to a minimum. Computers

Finite-State Methods and Natural Language Processing These proceedings contain the final versions of the papers presented at the 7th International Workshop on Finite-State Methods and Natural Language Processing (FSMNLP), held in Ispra, Italy, on September 11–12, 2008. The aim of the FSMNLP workshops is to bring together members of the research and industrial community working on finite-state based models in language technology, computational linguistics, web mining, linguistics and cognitive science on one hand, and on related theory and methods in fields such as computer science and mathematics on the other. Thus, the workshop series is a forum for researchers and practitioners working on applications as well as theoretical and implementation aspects. The special theme of FSMNLP 2008 was high performance finite-state devices in large-scale natural language text processing systems and applications. The papers in this publication cover a range of interesting NLP applications, including machine learning and translation, logic, computational phonology, morphology and semantics, data mining, information extraction and disambiguation, as well as programming, optimization and compression of finite-state networks. The applied methods include weighted algorithms, kernels and tree automata. In addition, relevant aspects of software engineering, standardization and European funding programmes are discussed. Computers

Email Etiquette E-mail is one of the greatest inventions of our lifetime phenomenally affecting the way we communicate. Reading, writing and managing e-mail is taking up an increasing amount of our time. But are we using it right? E-mail can be used to stay in touch whether we are traveling or working from home. Perhaps we can relax standards when it comes to personal e-mails, but e-mailing for business purposes has reached a new dimension. People whose jobs never used to involve writing skills are now replying dozens of e-mails each day. But under such pressure to respond quickly, what happens to the quality of the messages exchanged? The bottom line remains: just as body language helps you to making an impression in person, what you write and how you write it affects what people think of you and your organisation. Be it a thank you note, a meeting reminder, a proposal or a sales pitch, a well-written message that looks and sounds professional will make it easier for people to want to do business with you. It will help people feel good about communicating with you and help you achieve the right results. Computers

Photographing Nature 25 years of nature photography instruction in one gorgeous, full-color, hands-on course Anyone can photograph nature—just step outside and you’re on location. But becoming a good nature photographer takes expert training. In Photographing Nature, Ralph Clevenger, whose images have appeared in such publications as Nature’s Best and National Geographic, shares the techniques he’s been personally using and teaching to aspiring photographers for the last 25 years in his popular nature photography course at the elite Brooks Institute. In this stunning, four-color course-in-a-book, each chapter opens with a spectacular photo spread from the natural world that Clevenger uses to illustrate themes and techniques essential to mastering nature photography. Just as he does in his classroom at Brooks, Clevenger explains how each photo was captured, the tools and techniques used, and typical problems related to capturing such a photo, along with solutions. Chapters also include sample Q&A sessions as well as assignments you can try yourself. By the time you’ve worked through all of the techniques in this beautiful, yet informative book, you’ll not only photograph the world differently, you’ll see it differently as well. With a foreword by George Lepp, one of North America’s best-known contemporary outdoor and nature photographers. Computers

Canon 7D This book has one goal: to teach Canon 7D owners how to make great shots using your camera. Starting with the top ten things you need to know about the 7D — charging your battery, setting your ISO, reviewing your photos, and more — professional photographer Nicole S. Young then carefully guides you through the modes of the camera, offering practical advice on choosing your settings, expert shooting tips, and end-of-chapter “challenges†to get you up and running with your 7D. This book is for anyone who has upgraded from a point-and-shoot, or who wants to jump right into photography with the control and capabilities of a powerful DSLR. Canon 7D: From Snapshots to Great Shots shows not only what makes a great shot work — but how to get that shot using your 7D. Follow along with your friendly and knowledgeable guide, photographer and author Nicole S. Young, and you will: Learn the top ten things you need to know about shooting with the 7D Use the 7D’s advanced camera settings to gain full control over the look and feel of your images Master the photographic basics of composition, focus, depth of field, and much more Learn all the best tricks and techniques for getting great action shots, landscapes, and portraits Find out how to get great shots in low light Learn the basics behind shooting video with your 7D and start making movies of your own Fully grasp all the concepts and techniques as you go, with challenges at the end of every chapter And once you’ve got the shot, show it off! Join the book’s Flickr group, share your photos, and discuss how you use your 7D to get great shots at flickr.com/groups/canon7dfromsnapshotstogreatshots. Computers

Compiling with Continuations This book shows how continuation-passing style is used as an intermediate representation on which to perform optimisations and program transformations. Computers

Neural Network Learning This book describes theoretical advances in the study of artificial neural networks. Computers

Foundations of Cryptography A rigorous treatment of Encryption, Signatures, and General Cryptographic Protocols, emphasizing fundamental concepts. Computers

Hands-on Guide to the Red Hat Exams Master every topic on Red Hat’s new RHCSA™ and RHCE® exams. Assess your knowledge and focus your learning. Get the practical workplace knowledge you need! Start-to-finish RHCSA™ and RHCE® preparation from leading Linux system administrator, IT trainer, and certification expert Damian Tommasino! Master every RHCSA™ and RHCE® topic! Red Hat Enterprise Linux 6 local and network installation System services, runlevels, and bootup Disks, partitions, and file systems, including LUKS encryption Networking Package management User administration Logging, monitoring, and automation Kernel updates and tuning Security, including SELinux, firewalls, and policies Remote access, including SSH Apache, Squid, DNS, DHCP, NTP, and email NFS and Samba Client and network troubleshooting KVM virtualization Test your knowledge, build your confidence, and succeed! 22 hands-on RHCSA™ and RHCE® Labs, each with multiple real-world tasks Downloadable troubleshooting scripts Practical tutorials and real-world tips Exam tips Red Hat Enterprise Linux 6 Command Quick Reference Exclusive Red Hat exam prep advice and task lists Two full length lab-based practice exams Damian Tommasino (RHCE, RHCSA, MCSA, CCNA, CCENT, MCP, Security+, Network+, A+) is a Linux system administrator at TradeCard and CEO of Modular Learning Inc., an online IT training company. He blogs on Red Hat, Linux, and security at Security Nut (http://secnut.blogspot.com), and actively contributes to the popular IT exam certification forums at techexams.net. Computers

Graph-based Natural Language Processing and Information Retrieval This book extensively covers the use of graph-based algorithms for natural language processing and information retrieval. Computers

Bayesian Time Series Models The first unified treatment of time series modelling techniques spanning machine learning, statistics, engineering and computer science. Computers

OpenGL Programming Guide Please note that this title's color insert (referred to as "Plates" within the text) is not available for this digital product. OpenGL is a powerful software interface used to produce high-quality, computer-generated images and interactive applications using 2D and 3D objects, bitmaps, and color images. The OpenGL® Programming Guide, Seventh Edition , provides definitive and comprehensive information on OpenGL and the OpenGL Utility Library. The previous edition covered OpenGL through Version 2.1. This seventh edition of the best-selling “red book†describes the latest features of OpenGL Versions 3.0 and 3.1. You will find clear explanations of OpenGL functionality and many basic computer graphics techniques, such as building and rendering 3D models; interactively viewing objects from different perspective points; and using shading, lighting, and texturing effects for greater realism. In addition, this book provides in-depth coverage of advanced techniques, including texture mapping, antialiasing, fog and atmospheric effects, NURBS, image processing, and more. The text also explores other key topics such as enhancing performance, OpenGL extensions, and cross-platform techniques. This seventh edition has been updated to include the newest features of OpenGL Versions 3.0 and 3.1, including Using framebuffer objects for off-screen rendering and texture updates Examples of the various new buffer object types, including uniform-buffer objects, transform feedback buffers, and vertex array objects Using texture arrays to increase performance when using numerous textures Efficient rendering using primitive restart and conditional rendering Discussion of OpenGL’s deprecation mechanism and how to verify your programs for future versions of OpenGL This edition continues the discussion of the OpenGL Shading Language (GLSL) and explains the mechanics of using this language to create complex graphics effects and boost the computational power of OpenGL. The OpenGL Technical Library provides tutorial and reference books for OpenGL. The Library enables programmers to gain a practical understanding of OpenGL and shows them how to unlock its full potential. Originally developed by SGI, the Library continues to evolve under the auspices of the Khronos OpenGL ARB Working Group, an industry consortium responsible for guiding the evolution of OpenGL and related technologies. Computers

Information Luciano Floridi unpacks this fundamental concept - what information is, how it is measured, its value and meaning - cutting across the sciences and humanities, from DNA to the Internet, and the ethical issues related to privacy, copyright, and accessibility. Computers

The Nature of Computation Why are some problems easy to solve, while others seem nearly impossible? What can we compute with a given amount of time or memory, and what cannot be computed at all? How will quantum physics change the landscape of computation? This book gives a playful and accessible introduction to the deep ideas of theoretical computer science. Computers

Non-Designer's InDesign Book, The Many designers and photographers own the entire suite of Adobe’s creative products, but they manage to learn only one or two of the applications really well. If Adobe InDesign CS5.5 is the one app in the suite that makes you feel like you’re entering a foreign country where you don’t speak the language, Robin Williams provides the perfect travel guide and translator in this new edition to the best-selling Non-Designer’s series. This fun, straight-forward, four-color book includes many individual exercises designed specifically to teach InDesign CS5.5 to beginners in such a way that you can jump in at any point to learn a specific tool or technique. Along the way, Robin offers design tips for making your work communicate appropriately and beautifully. Whether you need to create your own marketing materials for a small business or organization, or you want your student or business papers to be perceived as more professional, or you want to become more proficient with the design tools you already use, this book is the fastest and most efficient path to mastering basic tasks InDesign. In this non-designer’s guide to InDesign CS5.5, you’ll learn: How to create basic design projects, such as flyers, business cards, letterhead, ads, brochures, CD covers, and much more How to add images to your pages and crop, rotate, resize, and add effects to those images How to use InDesign’s typographic tools to make your work look professional How to use style sheets so every job is easier to create and work with How to use tabs and indents with confidence and predictability How to create nice-looking tables to effectively organize data And, of course, the basics of working in InDesign with layers, panels, tools, etc. Computers

Algorithmic Puzzles Algorithmic puzzles are puzzles involving well-defined procedures for solving problems. This book will provide an enjoyable and accessible introduction to algorithmic puzzles that will develop the reader's algorithmic thinking. Computers

Data Analysis for Physical Scientists Introducing data analysis techniques to help undergraduate students develop the tools necessary for studying and working in the physical sciences. Computers

Bayesian Reasoning and Machine Learning A practical introduction perfect for final-year undergraduate and graduate students without a solid background in linear algebra and calculus. Computers

Density Ratio Estimation in Machine Learning This book introduces theories, methods and applications of density ratio estimation, a newly emerging paradigm in the machine learning community. Computers

Blogging and Tweeting without Getting Sued What you post on a blog or tweet to your followers can get you arrested or cost you a lot of money in legal battles. This practical guide shows you how to stay out of trouble when you write online. Computers

Everyday Cryptography A self-contained and widely accessible text, with almost no prior knowledge of mathematics required, this book presents a comprehensive introduction to the role that cryptography plays in providing information security for technologies such as the Internet, mobile phones, payment cards, and wireless local area networks. Computers

Genomics and Bioinformatics A hands-on introduction to Unix, Perl and other bioinformatics tools using relevant and interesting molecular biology problems. Computers

LaTeX Beginner's Guide Create high-quality and professional-looking texts, articles, and books for Business and Science using LaTeX Computers

Apache Axis2 Web Services Create secure, reliable, and easy-to-use web services using Apache Axis2 Computers

Object-Oriented Programming in ColdFusion Break free from procedural programming and learn how to optimize your applications and enhance your skills using objects and design patterns Computers

Relational Knowledge Discovery Introductory textbook presenting relational methods in machine learning. Computers

Programming with Higher-Order Logic A programming language based on a higher-order logic provides a declarative approach to capturing computations involving types, proofs and other syntactic structures. Computers

Modern Fortran in Practice A tutorial guide that shows programmers how to apply features of Fortran 2008 in a modular, concise, object-oriented and resource-efficient manner, using multiple processors. Computers

Xen Virtualization A fast and practical guide to supporting multiple operating systems with the Xen hypervisor Computers

Learning FreeNAS Configure and manage a network attached storage solution Computers

RESTful PHP Web Services Learn the basic architectural concepts and step through examples of consuming and creating RESTful web services in PHP Computers

Unity Game Development Essentials Build fully functional, professional 3D games with realistic environments, sound, dynamic effects, and more! Computers

Active Learning The key idea behind active learning is that a machine learning algorithm can perform better with less training if it is allowed to choose the data from which it learns. An active learner may pose "queries," usually in the form of unlabeled data instances to be labeled by an "oracle" (e.g., a human annotator) that already understands the nature of the problem. This sort of approach is well-motivated in many modern machine learning and data mining applications, where unlabeled data may be abundant or easy to come by, but training labels are difficult, time-consuming, or expensive to obtain.This book is a general introduction to active learning. It outlines several scenarios in which queries might be formulated, and details many query selection algorithms which have been organized into four broad categories, or "query selection frameworks." We also touch on some of the theoretical foundations of active learning, and conclude with an overview of the strengths and weaknesses of these approaches in practice, including a summary of ongoing work to address these open challenges and opportunities.Table of Contents: Automating Inquiry / Uncertainty Sampling / Searching Through the Hypothesis Space / Minimizing Expected Error and Variance / Exploiting Structure in Data / Theory / Practical Considerations Computers

How to Play a Video Game Every day millions of people enter virtual worlds through video games, which are now the fastest-growing form of entertainment and are played by young and old alike. This account unlocks this amazing world, providing insight into what makes video games so fascinating and exploring the emotions involved in playing, the issues that surround them, and the future of the technology. Considering how games are appearing on phones and other mobile electronic devices, the book raises the questions Will everyone become a gamer? and Will people gain happiness or merely lose time? Computers

Learn OpenOffice.org Spreadsheet Macro Programming OOoBasic and Calc automation A fast and friendly tutorial to writing macros and spreadsheet applications Computers

UML 2.0 in Action A project-based tutorial A detailed and practical book and eBook walk-through showing how to apply UML to real world development projects Computers

Oracle Primavera P6 Version 8 Project and Portfolio Management A comprehensive guide to manage projects and portfolios using Primavera P6 with this book and ebook Computers

Cyberspace and National Security In a very short time, individuals and companies have harnessed cyberspace to create new industries, a vibrant social space, and a new economic sphere that are intertwined with our everyday lives. At the same time, individuals, subnational groups, and governments are using cyberspace to advance interests through malicious activity. Terrorists recruit, train, and target through the Internet, hackers steal data, and intelligence services conduct espionage. Still, the vast majority of cyberspace is civilian space used by individuals, businesses, and governments for legitimate purposes. Cyberspace and National Security brings together scholars, policy analysts, and information technology executives to examine current and future threats to cyberspace. They discuss various approaches to advance and defend national interests, contrast the US approach with European, Russian, and Chinese approaches, and offer new ways and means to defend interests in cyberspace and develop offensive capabilities to compete there. Policymakers and strategists will find this book to be an invaluable resource in their efforts to ensure national security and answer concerns about future cyberwarfare. Computers

Cognitive Science Cognitive science is at last treated as a unified subject in this exciting textbook on the science of the mind. Computers

HTML5 Video How-to 20 practical, hands-on recipes to encode and display videos in the HTML5 video standard Computers

Final Cut Pro X Cookbook Edit with style and ease using the latest editing technologies in Final Cut Pro X! Computers

Algorithms on Strings, Trees, and Sequences This book describes a range of string problems in computer science and molecular biology and the algorithms developed to solve them. Computers

Purely Functional Data Structures This book describes data structures and data structure design techniques for functional languages. Computers

Enumerative Combinatorics An introduction, suitable for beginning graduate students, showing connections to other areas of mathematics. Computers

The Object Primer The acclaimed beginner's book on object technology now presents UML 2.0, Agile Modeling, and object development techniques. Computers

Programming with Mathematica® This practical, example-driven introduction teaches the foundations of the Mathematica language so it can be applied to solving concrete problems. Computers

Causality, Probability, and Time Presents a new approach to causal inference and explanation, addressing both the timing and complexity of relationships. Computers

Performance Modeling and Design of Computer Systems Written with computer scientists and engineers in mind, this book brings queueing theory decisively back to computer science. Computers

Search User Interfaces Focuses on the human users of search engines and the tools available for interaction and visualization in searches. Computers

Randomized Algorithms This book presents basic tools from probability theory used in algorithmic applications, with concrete examples. Computers

Lisp in Small Pieces This will become the new standard reference for people wanting to know about the Lisp family of languages. Computers

An Introduction to Support Vector Machines and Other Kernel-based Learning Methods This is a comprehensive introduction to Support Vector Machines, a generation learning system based on advances in statistical learning theory. Computers

Computational Physics First published in 2007, this second edition is for graduate students and researchers in theoretical, computational and experimental physics. Computers

Causality Written by one of the preeminent researchers in the field, this provides a comprehensive exposition of modern analysis of causation. Computers

WiX 3.6 A step-by-step tutorial with plenty of code and examples to improve your learning curve. If you are a developer and want to create installers for software targeting the Windows platform, then this book is for you. You’ll be using plenty of XML and ought to know the basics of writing a well-formed document. No prior experience in WiX or Windows Installer is assumed. You should know your way around Visual Studio to compile projects, add project references and tweak project properties. Computers

Learning RStudio for R Statistical Computing A practical tutorial covering how to leverage RStudio functionality to effectively perform R Development, analysis, and reporting with RStudio. The book is aimed at R developers and analysts who wish to do R statistical development while taking advantage of RStudio functionality to ease their development efforts. Familiarity with R is assumed. Those who want to get started with R development using RStudio will also find the book useful. Even if you already use R but want to create reproducible statistical analysis projects or extend R with self-written packages, this book shows how to quickly achieve this using RStudio. Computers

Data Visualization A comprehensive yet quick guide to the best approaches to designing data visualizations, with real examples and illustrative diagrams. Whatever the desired outcome ensure success by following this expert design process. This book is for anyone who has responsibility for, or is interested in trying to find innovative and effective ways to visually analyze and communicate data. There is no skill, no knowledge and no role-based pre-requisites or expectations of anyone reading this book. Computers

Spring Security 3.1 This practical step-by-step tutorial has plenty of example code coupled with the necessary screenshots and clear narration so that grasping content is made easier and quicker. This book is intended for Java web developers and assumes a basic understanding of creating Java web applications, XML, and the Spring Framework. You are not assumed to have any previous experience with Spring Security. Computers

SAP ABAP Advanced Cookbook This book is written in a simple, easy to understand format with lots of screenshots and step-by-step explanations. If you are an ABAP developer and/or consultant looking forward to building advanced SAP programming applications with ABAP, then this is the best guide for you. Basic knowledge of ABAP programming is required. Computers

Quantum Computing since Democritus Takes students and researchers on a tour through some of the deepest ideas of maths, computer science and physics. Computers

HTML5 Enterprise Application Development A practical development tutorial, giving users step-by-step instructions to allow them to create an enterprise web application.This book is for developers who want to create enterprise web applications with engaging user experiences with no browser plugins. Basic JavaScript programming and knowledge of HTML and CSS is required. No knowledge of HTML5 or CSS3 is assumed. Computers

Instant RaphaelJS Starter Get to grips with a new technology, understand what it is and what it can do for you, and then get to work with the most important features and tasks. Starter GuideThis book is great for developers new to Vector graphics in browsers (SVG and VML), and who are looking to get a good grounding in how to use Raphael JS to create imageless and fast loading interactive drawings and shapes, in a web browser. It’s assumed that you will have some experience in HTML JavaScript or jQuery already. Computers

Instant Wireshark Starter Get to grips with a new technology, understand what it is and what it can do for you, and then get to work with the most important features and tasks. Written as a practical guide, Wireshark Starter will show you all you need to know to effectively capture and analyze network traffic. This book is specially designed for new learners who are willing to dive deeper into network analysis using Wireshark. It requires a basic understanding of network protocols and their implementation and is equally handy for network administrators, forensic experts, and network penetration testers. Computers

Instant Google Drive Starter This book is a Starter which teaches you how to use Google Drive practically. This book is perfect for people of all skill levels who want to enjoy the benefits of using Google Drive to safely store their files online and in the cloud. It’s also great for anyone looking to learn more about cloud computing in general. Readers are expected to have an Internet connection and basic knowledge of using the internet. Computers

Instant Burp Suite Starter This starter guide will lead you through the field of application security with everyday examples explained. Build up your skills and your defenses with this hands-on tutorial. If you are an application developer with a focus on security then this practical guide is for you. Even with basic knowledge of security you will be able to develop your expertise and make your applications bulletproof. Computers

Python Testing The book begins with the very foundations of automated testing, and expands on them until the best-practice tools and techniques are fully covered. New concepts are illustrated with step-by-step hands-on exercises. Testing will be easier and more enjoyable with this beginner's guide. If you are a Python developer and want to write tests for your applications, this book will get you started and show you the easiest way to learn testing. You need to have sound Python programming knowledge to follow along. An awareness of software testing would be good, but no formal knowledge of testing is expected nor do you need to have any knowledge of the libraries discussed in the book. Computers

Joomla! 3 Beginner’s Guide Written with a fast-paced but friendly and engaging approach, this Packt Beginner's Guide is designed to be placed alongside the computer as your guide and mentor. Step-by-step tutorials are bolstered by explanations of the reasoning behind what you are doing. You will quickly pick up the necessary skills, tips, and tricks for building a successful Joomla! website.This book is written for beginners to website design. By the end of the book you will have built a complete custom content managed website, and be ready to build any kind of website. Computers

Systematic Program Design Describes a systematic program design method, starting with specifications of computations and deriving implementations by step-wise program analysis and transformations. Computers

The Geography of the Internet This timely book presents a wide range of quantitative methods, including complex network analysis and econometric modelling, to illustrate how the Internet both follows, and at the same time challenges, more traditional geographies. Emmanouil Tranos explores the spatiality of the Internet, its physical infrastructure, and the geographic and socio-economic factors that shape its spatial distribution. He shows that although the Internet is a technical system with strong topological attributes, an almost 'hidden' spatial dimension also exists. The scattering of Internet Backbone Networks across European city-regions is compared with the aviation network in order to better understand the topology of the digital infrastructure. Finally, a causality analysis demonstrates the significant positive effect of the Internet infrastructure in the economic development of regions characterized by high absorptive capacity. This book will prove a highly fascinating read for those with an interest in Internet geographies, ICTs, regional development and infrastructure, digital economy, network analysis, and regional science.Practitioners working on local and regional development, as well as those focusing on ICTs, digital economy and smart cities, will also find this book to be an invaluable reference tool. Computers

Elliptic Curves in Cryptography This book explains the mathematics behind practical implementations of elliptic curve systems. Computers

Relational Mathematics A modern, comprehensive 2010 overview providing an easy introduction for applied scientists who are not versed in mathematics. Computers

IBM Cognos Framework Manager Presented in a handson style, this guide presents you with real world examples to guide you through every process step by step.This book will be useful for any developer, novice or expert, who uses Framework Manager to build packages, but wants to expand their knowledge even further. Computers

Functional Programming Using F# This comprehensive introduction to the principles of functional programming using F# shows how to apply basic theoretical concepts to produce succinct and elegant programs. Computers

Implementing MyBatis This book will have a practical approach, thus making it easy for the readers to understand and learn with step-by-step instructions.This book is for Java developers who would like to learn all about the MyBatis framework and are looking for a practical guide to get started. The prerequisites required for this book are basic Java and SQL skills. No prior knowledge of MyBatis is expected. Computers

Instant Redis Optimization How-to Filled with practical, step-by-step instructions and clear explanations for the most important and useful tasks. This book is written in a concise, focused style with numerous practical and hands-on recipes and examples. If you want to leverage Redis to create blazing fast applications, then this book is for you.This book is for developers who are already proficient in programming and traditional databases and want to start learning about Redis for its simplicity and fast performance. A basic understanding of Linux and proficiency in a programming language are required to get the most out of this book. Computers

Bootstrap Methods and their Application This book on statistical methods was first published in 1997 and has code on a supporting website. Computers

Modern Compiler Implementation in ML Describes all phases of a modern compiler, including techniques in code generation and register allocation for imperative, functional and object-oriented languages. Computers

Computational Geometry in C This 1998 book explains the design of geometry algorithms, including discussion of implementation issues and working C code. Computers

The Haskell School of Expression This book teaches functional programming using Haskell and examples drawn from multimedia applications. Computers

IBM Cognos 10.1 Report Studio Cookbook This Cookbook contains step-by-step instructions for Report Studio 10.1 users to author effective reports. The book is designed in a way that you can refer to it chapter by chapter, look at the list of recipes and read them in no particular order.The Cognos 10.1 Report Studio Cookbook is for you if you are a Business Intelligence Developer who is working on IBM Cognos 10 Report Studio and wants to author impressive reports by putting to use what this tool has to offer. It is also ideal you are a Business Analyst or Power User who authors his own reports and wants to look beyond the conventional features of IBM Cognos 10 Report Studio.This book assumes that you are familiar with the architecture of IBM Cognos 10. You should also have basic knowledge of IBM Cognos Report Studio and can do the basic report authoring tasks. Computers

Astrophysics through Computation This new astrophysics text integrates analytical and computational methods to explore a broad range of topics in astrophysics. Computers

Creating a Software Engineering Culture This is the digital version of the printed book (Copyright © 1996). Written in a remarkably clear style, Creating a Software Engineering Culture presents a comprehensive approach to improving the quality and effectiveness of the software development process. In twenty chapters spread over six parts, Wiegers promotes the tactical changes required to support process improvement and high-quality software development. Throughout the text, Wiegers identifies scores of culture builders and culture killers, and he offers a wealth of references to resources for the software engineer, including seminars, conferences, publications, videos, and on-line information. With case studies on process improvement and software metrics programs and an entire part on action planning (called “What to Do on Mondayâ€), this practical book guides the reader in applying the concepts to real life. Topics include software culture concepts, team behaviors, the five dimensions of a software project, recognizing achievements, optimizing customer involvement, the project champion model, tools for sharing the vision, requirements traceability matrices, the capability maturity model, action planning, testing, inspections, metrics-based project estimation, the cost of quality, and much more! Principles from Part 1 Never let your boss or your customer talk you into doing a bad job. People need to feel the work they do is appreciated. Ongoing education is every team member’s responsibility. Customer involvement is the most critical factor in software quality. Your greatest challenge is sharing the vision of the final product with the customer. Continual improvement of your software development process is both possible and essential. Written software development procedures can help build a shared culture of best practices. Quality is the top priority; long-term productivity is a natural consequence of high quality. Strive to have a peer, rather than a customer, find a defect. A key to software quality is to iterate many times on all development steps except coding: Do this once. Managing bug reports and change requests is essential to controlling quality and maintenance. If you measure what you do, you can learn to do it better. You can’t change everything at once. Identify those changes that will yield the greatest benefits, and begin to implement them next Monday. Do what makes sense; don’t resort to dogma. Computers

The Quest for Artificial Intelligence The definitive history of artificial intelligence (AI), from the dreams of early pioneers to the achievements of modern research. Computers

Introduction to Distributed Algorithms The second edition of this successful textbook provides an up-to-date introduction both to distributed algorithms and to the theory behind them. Computers

Modern Computer Algebra Now in its third edition, this highly successful textbook is widely regarded as the 'bible of computer algebra'. Computers

Open Source Identity Management Patterns and Practices Using OpenAM 10.x This is a Packt Mini in a tutorial format that provides multiple examples on Identity Management using OpenAM 10.x.Open Source Identity Management Patterns and Practices Using OpenAM 10.x is great for developers and architects who are new to Identity Management, and who want a brief overview of what’s possible and how to quickly implement a prototype. It’s assumed that you’ve had experience with web applications and some knowledge of Apache and Tomcat. Computers

Pentaho Data Integration Cookbook Pentaho Data Integration Cookbook Second Edition is written in a cookbook format, presenting examples in the style of recipes.This allows you to go directly to your topic of interest, or follow topics throughout a chapter to gain a thorough in-depth knowledge.Pentaho Data Integration Cookbook Second Edition is designed for developers who are familiar with the basics of Kettle but who wish to move up to the next level.It is also aimed at advanced users that want to learn how to use the new features of PDI as well as and best practices for working with Kettle. Computers

Getting Started with JUCE his book is a fast-paced, practical guide full of step-by-step examples which are easy to follow and implement.This book is for programmers with a basic grasp of C++. The examples start at a basic level, making few assumptions beyond fundamental C++ concepts. Those without any experience with C++ should be able to follow and construct the examples, although you may need further support to understand the fundamental concepts. Computers

Instant Markdown Get to grips with a new technology, understand what it is and what it can do for you, and then get to work with the most important features and tasks. A quick, clear, concise tutorial guide-based approach that will help you to get started with Markdown.Instant Markdown is for people who are interested in an introduction to Markdown. You will not need any specific knowledge about programming or markup languages. This book will give you many ideas to use and take full potential of Markdown over many different services. Computers

Network Analysis using Wireshark Cookbook Network analysis using Wireshark Cookbook contains more than 100 practical recipes for analyzing your network and troubleshooting problems in the network. This book provides you with simple and practical recipes on how to solve networking problems with a step-by-step approach.This book is aimed at research and development professionals, engineering and technical support, and IT and communications managers who are using Wireshark for network analysis and troubleshooting. This book requires a basic understanding of networking concepts, but does not require specific and detailed technical knowledge of protocols or vendor implementations. Computers

HTML5 and CSS3 Transition, Transformation and Animation Quick and simple example-driven introduction to HTML5 Transitions, Transformations and Animations. Learn by doing to create some simply amazing HTML5 web applications. If you are a web developer or designer and would love to learn and use the game changing technologies included within HTML5 this is the right book for you, start at the beginning and learn some of this technologies awesome features around transitions, transformations and animations. This book is for beginners with transitions, transformations and animations that want a quick and simple kick start using clear and reusable examples. Computers

Instant HTML5 Fonts and Typography Filled with practical, step-by-step instructions and clear explanations for the most important and useful tasks. Written as practical recipes, Instant HTML5 Fonts and Typography How-to will enable you to use custom fonts with outstanding effects.This book is great for both professional and amateur HTML and CSS developers who are looking to use fonts in order to enhance interface design. Familiarity with JavaScript is assumed. Computers

Brain-Computer Interfacing This introduction to brain-computer interfacing is designed for courses on neural engineering or brain-computer interfacing for students from wide-ranging disciplines. Computers

Bayesian Filtering and Smoothing A unified Bayesian treatment of the state-of-the-art filtering, smoothing, and parameter estimation algorithms for non-linear state space models. Computers

The Seismic Analysis Code The first comprehensive guide to SAC, complete with introductory materials and detailed descriptions of its most advanced features. Computers

SELinux Policy Administration A step-by-step guide to learn how to set up security on Linux servers by taking SELinux policies into your own hands.Linux administrators will enjoy the various SELinux features that this book covers and the approach used to guide the admin into understanding how SELinux works. The book assumes that you have basic knowledge in Linux administration, especially Linux permission and user management. Computers

Modal Logic for Philosophers The second edition of an accessible yet technically sound treatment of modal logic and its philosophical applications. Computers

IBM SPSS Modeler Cookbook This is a practical cookbook with intermediate-advanced recipes for SPSS Modeler data analysts. It is loaded with step-by-step examples explaining the process followed by the experts.If you have had some hands-on experience with IBM SPSS Modeler and now want to go deeper and take more control over your data mining process, this is the guide for you. It is ideal for practitioners who want to break into advanced analytics. Computers

Microsoft Visio 2013 Business Process Diagramming and Validation Microsoft Visio 2013 Business Process Diagramming and Validation provides a comprehensive and practical tutorial including example code and demonstrations for creating validation rules, writing ShapeSheet formulae, and much more.If you are a Microsoft Visio 2013 Professional Edition power user or developer who wants to get to grips with both the essential features of Visio 2013 and the validation rules in this edition, then this book is for you. A working knowledge of Microsoft Visio and optionally .NET for the add-on code is required, though previous knowledge of business process diagramming is not necessary. More experienced Visio users will gain valuable knowledge regarding building add-ons and creating and publishing rules. If you want to achieve results from Visio 2013 beyond the ordinary out-of-the-box features, then this book is ideal for you. Microsoft Visio 2013 Business Process Diagramming and Validation provides a comprehensive and practical tutorial including example code and demonstrations for creating validation rules, writing ShapeSheet formulae, and much more. Computers

OpenCL Programming by Example This book follows an example-driven, simplified, and practical approach to using OpenCL for general purpose GPU programming.If you are a beginner in parallel programming and would like to quickly accelerate your algorithms using OpenCL, this book is perfect for you! You will find the diverse topics and case studies in this book interesting and informative. You will only require a good knowledge of C programming for this book, and an understanding of parallel implementations will be useful, but not necessary. Computers

Implementing VMware vCenter Server This book is a practical, hands-on guide that will help you learn everything you need to know to administer your environment with VMware vCenter Server. Throughout the book, there are best practices and useful tips and tricks which can be used for day-to-day tasks.If you are an administrator or a technician starting with VMware, with little or no knowledge of virtualization products, this book is ideal for you. Even if you are an IT professional looking to expand your existing environment, you will be able to use this book to help you improve the management of these environments. IT managers will find it helpful in terms of improving cost efficiency, ensuring required levels of service and utilising its excellent reporting abilities. Computers

Optimization and Mathematical Modeling in Computer Architecture In this book we give an overview of modeling techniques used to describe computer systems to mathematical optimization tools. We give a brief introduction to various classes of mathematical optimization frameworks with special focus on mixed integer linear programming which provides a good balance between solver time and expressiveness. We present four detailed case studies -- instruction set customization, data center resource management, spatial architecture scheduling, and resource allocation in tiled architectures -- showing how MILP can be used and quantifying by how much it outperforms traditional design exploration techniques. This book should help a skilled systems designer to learn techniques for using MILP in their problems, and the skilled optimization expert to understand the types of computer systems problems that MILP can be applied to. Computers

Artificial Consciousness The book is interdisciplinary and focuses on the topic of artificial consciousness: from neuroscience to artificial intelligence, from bioengineering to robotics. It provides an overview on the current state of the art of research in the field of artificial consciousness and includes extended and revised versions of the papers presented at the International Workshop on ‘Artificial Consciousness’, held in November 2005 at Agrigento (Italy). Computers

Blender 2.49 Scripting The focus of the book is on practical problems and how to solve them in Python. The examples given are useful programs that try to solve real-world needs. Each chapter revolves around a single concept giving several examples gradually growing in difficulty. Each section analyses the problem first before diving into coding and gives extensive background information to enable the reader to generalize from the specific problem to a wider range of challenges. The sample code is provided as fully working examples with all key issues extensively highlighted. All sample programs are clear and concise yet nothing essential is left out and the programming style focuses on readability rather than on stylistic rigor or efficiency. This book is for users comfortable with Blender as a modeling and rendering tool who want to expand their skills to include Blender scripting to automate laborious tasks and achieve results otherwise impossible. Blender experience is essential as is some experience in Python programming. Computers

Learning Python Design Patterns This book takes a tutorial-based and user-friendly approach to covering Python design patterns. Its concise presentation means that in a short space of time, you will get a good introduction to various design patterns.If you are an intermediate level Python user, this book is for you. Prior knowledge of Python programming is essential. Some knowledge of UML is also required to understand the UML diagrams which are used to describe some design patterns. Computers

Sketchbook Pro Digital Painting Essentials This book is an example-based guide that will help you create professional grade paintings using Sketchbook Pro. As you progress from one chapter to another, you will learn how to virtually draw visually stunning paintings that are digitally drawn but look exactly like orthodox artwork.If you have had prior experience in developing digital artwork and are looking to add to your knowledge, Sketchbook Pro Digital Painting Essentials is a guide that will help you seamlessly translate what you do with traditional media to digital media. Computers

Instant Windows PowerShell Get to grips with a new technology, understand what it is and what it can do for you, and then get to work with the most important features and tasks. A practical, hands-on tutorial approach that explores the concepts of PowerShell in a friendly manner, taking an adhoc approach to each topic.If you are an administrator who is new to PowerShell or are looking to get a good grounding in these new features, this book is ideal for you. It’s assumed that you will have some experience in PowerShell and Windows Server, as well being familiar with the PowerShell command-line. Computers

Instant Kali Linux Get to grips with a new technology, understand what it is and what it can do for you, and then get to work with the most important features and tasks. A quick and handy guide for those who are willing to get straight into the business. This book will build a strong foundation for those who are willing to cover different security assessment areas by mastering various tools and techniques.If you are a beginners or an experienced security professional who is willing to dive deeper into the world of information security, then this book is perfect for you. The book is written is simple technical language which requires only a basic knowledge of security assessments and the Linux operating system. Computers

Cybersecurity and Cyberwar In Cybersecurity and CyberWar: What Everyone Needs to Know®, New York Times best-selling author P. W. Singer and noted cyber expert Allan Friedman team up to provide the kind of easy-to-read, yet deeply informative resource book that has been missing on this crucial issue of 21st century life. Written in a lively, accessible style, filled with engaging stories and illustrative anecdotes, the book is structured around the key question areas of cyberspace and its security: how it all works, why it all matters, and what can we do? Computers

Emgu CV Essentials This book provides a practical guide to Emgu CV libraries, with sample code and examples used throughout to explain the concepts clearly. Each chapter deals with a different aspect of the Computer Vision field and the implementation of that topic in Emgu CV.If you are a C# programmer working on computer vision projects, this book is for you. You should have prior experience with C#. Computers

Bayesian Cognitive Modeling Using a practical, hands-on approach, this book will teach anyone how to carry out Bayesian analyses and interpret the results. Computers

OAuth 2.0 Identity and Access Management Patterns This is a practical and fast-paced guide that gives you all the information you need to start implementing secure OAuth 2.0 implementations in your web applications.OAuth 2.0 Identity and Access Management Patterns is intended for software developers, software architects, and enthusiasts working with the OAuth 2.0 framework.In order to learn and understand the OAuth 2.0 grant flow, it is assumed that you have some basic knowledge of HTTP communication. For the practical examples, basic knowledge of HTML templating, programming languages, and executing commands in the command line terminal is assumed. Computers

Matplotlib for Python Developers This is a practical, hands-on book, with a lot of code and images. It presents the real code that generates every image and describes almost every single line of it, so that you know exactly what's going on. Introductory, descriptive, and theoretical parts are mixed with examples, so that reading and understanding them is easy. All of the examples build gradually with code snippets, their explanations, and plot images where necessary with the complete code and output presented at the end. This book is essentially for Python developers who have a good knowledge of Python; no knowledge of Matplotlib is required. You will be creating 2D plots using Matplotlib in no time at all. Computers

Introduction to Lattices and Order The second edition of a successful and unique textbook for students in mathematics or theoretical computer science. Computers

Foundations of Data Exchange Provides a summary of the key developments of a decade of research into the area of data exchange. Computers

The Design and Statistical Analysis of Animal Experiments This book will provide scientists with a better understanding of statistics, improving their decision-making and reducing animal use. Computers

GLSL Essentials This book is a practical guide to the OpenGL Shading Language, which contains several real-world examples that will allow you to grasp the core concepts easily and the use of the GLSL for graphics rendering applications.If you want upgrade your skills, or are new to shader programming and want to learn about graphic programming, this book is for you. If you want a clearer idea of shader programming, or simply want to upgrade from fixed pipeline systems to state-of-the-art shader programming and are familiar with any C-based language, then this book will show you what you need to know. Computers

Getting Started with Paint.NET This book follows a tutorial-based approach and is packed with examples in a compact and concise format.If you have ever wanted to create photos and images that go beyond simple point and shoot results, then this book is for you. This book will help you create artistic images in ways that are only limited by your imagination. No prior knowledge of photo editing or editing software is required. Computers

Cloud Computing Law Building on innovative research undertaken by the 'Cloud Legal Project' at Queen Mary, University of London, this work analyses the key legal and regulatory issues relevant to cloud computing under European and English law. Computers

Program Logics for Certified Compilers This tutorial for graduate students covers practical and theoretical aspects of separation logic with constructions and proofs in Coq. Computers

Puppet Reporting and Monitoring An easy to follow guide with extensive examples to explain Puppet's reporting capabilities to facilitate effective implementation of Puppet in the real world as a reporting tool. If you are a Puppet developer or a system administrator using Puppet, and you want to extend your expertise to manage and optimize your server resources, then this book is for you. Computers

Embedded Linux Development with Yocto Project A practical tutorial guide which introduces you to the basics of Yocto Project, and also helps you with its real hardware use to boost your Embedded Linux-based project. If you are an embedded systems enthusiast and willing to learn about compelling features offered by the Yocto Project, then this book is for you. With prior experience in the embedded Linux domain, you can make the most of this book to efficiently create custom Linux-based systems. Computers

Moodle Course Design Best Practices This book is an easy-to-follow guide with a hands-on approach that will help you learn the best practices for designing attractive and highly interactive courses with the help of Moodle. This book can be used by training managers, teachers, instructors, Moodle network specialists, instructional designers, and e-learning entrepreneurs. If you are involved in online, cloud-based education, training, or professional development, this is the book for you. No prior experience with Moodle is required, though it would be helpful to understand the basics of using HTML and also working with different multimedia file formats and social media. If you would like to find a very easy and convenient way to organize learning activities along with group projects and activities, then this is the book for you. Computers

Computability What can computers do in principle? What are their inherent theoretical limitations? These are questions to which computer scientists must address themselves. The theoretical framework which enables such questions to be answered has been developed over the last fifty years from the idea of a computable function: intuitively a function whose values can be calculated in an effective or automatic way. This book is an introduction to computability theory (or recursion theory as it is traditionally known to mathematicians). Dr Cutland begins with a mathematical characterisation of computable functions using a simple idealised computer (a register machine); after some comparison with other characterisations, he develops the mathematical theory, including a full discussion of non-computability and undecidability, and the theory of recursive and recursively enumerable sets. The later chapters provide an introduction to more advanced topics such as Gildel's incompleteness theorem, degrees of unsolvability, the Recursion theorems and the theory of complexity of computation. Computability is thus a branch of mathematics which is of relevance also to computer scientists and philosophers. Mathematics students with no prior knowledge of the subject and computer science students who wish to supplement their practical expertise with some theoretical background will find this book of use and interest. Computers

Burden of Proof, Presumption and Argumentation This book explains how burden of proof and presumption work as powerful devices in argumentation, based on studying many clearly explained legal and non-legal examples. Computers

Understanding Machine Learning Introduces machine learning and its algorithmic paradigms, explaining the principles behind automated learning approaches and the considerations underlying their usage. Computers

Python for Scientists This book provides everything the working scientist needs to know to start using Python effectively. Computers

Software Testing Foundations Professional testing of software is an essential task that requires a profound knowledge of testing techniques. The International Software Testing Qualifications Board (ISTQB) has developed a universally accepted, international qualification scheme aimed at software and system testing professionals, and has created the Syllabi and Tests for the "Certified Tester." Today about 300,000 people have taken the ISTQB certification exams. The authors of Software Testing Foundations, 4th Edition, are among the creators of the Certified Tester Syllabus and are currently active in the ISTQB. This thoroughly revised and updated fourth edition covers the "Foundations Level" (entry level) and teaches the most important methods of software testing. It is designed for self-study and provides the information necessary to pass the Certified Tester-Foundations Level exam, version 2011, as defined by the ISTQB. Also in this new edition, technical terms have been precisely stated according to the recently revised and updated ISTQB glossary. Topics covered: Fundamentals of Testing Testing and the Software Lifecycle Static and Dynamic Testing Techniques Test Management Test Tools Also mentioned are some updates to the syllabus that are due in 2015. Computers

Testing in Scrum These days, more and more software development projects are being carried out using agile methods like Scrum. Agile software development promises higher software quality, a shorter time to market, and improved focus on customer needs. However, the transition to working within an agile methodology is not easy. Familiar processes and procedures change drastically. Software testing and software quality assurance have a crucial role in ensuring that a software development team, department, or company successfully implements long-term agile development methods and benefits from this framework. This book discusses agile methodology from the perspective of software testing and software quality assurance management. Software development managers, project managers, and quality assurance managers will obtain tips and tricks on how to organize testing and assure quality so that agile projects maintain their impact. Professional certified testers and software quality assurance experts will learn how to work successfully within agile software teams and how best to integrate their expertise. Topics include: Agile methodology and classic process models How to plan an agile project Unit tests and test first approach Integration testing and continuous integration System testing and test nonstop Quality management and quality assurance Also included are five case studies from the manufacturing, online-trade, and software industry as well as test exercises for self-assessment. This book covers the new ISTQB Syllabus for Agile Software Testing and is a relevant resource for all students and trainees worldwide who plan to undertake this ISTQB certification. Computers

Pentaho Business Analytics Cookbook This practical guide contains a wide variety of recipes, taking you through all the topics you need to quickly familiarize yourself with Pentaho and extend your Pentaho skillset.If you are involved in daily activities using Pentaho Business Analytics platform, this is the book for you. It is a good companion to get you quickly acquainted with everything you need to increase your productivity with the platform. We assume basic familiarity with Pentaho, data warehouse design and SQL, HTML, and XML. Computers

Getting Started with LLVM Core Libraries This book is intended for enthusiasts, computer science students, and compiler engineers interested in learning about the LLVM framework. You need a background in C++ and, although not mandatory, should know at least some compiler theory. Whether you are a newcomer or a compiler expert, this book provides a practical introduction to LLVM and avoids complex scenarios. If you are interested enough and excited about this technology, then this book is definitely for you. Computers

Joomla! 3 Beginner's Guide Second Edition An easy to use, step-by-step guide to creating professional, mobile-friendly websites with the free Joomla CMS. The Joomla! 3 Beginner's Guide Second Edition is the ultimate guide for web developers who wish to build upon their skills and knowledge on creating websites. Even if you’re new to this subject, you won’t have any difficulty understanding the clear and friendly instructions and explanations. No prior knowledge of HTML and CSS is required. Computers

The Semantic Web Explained Describes the underlying theory as well as algorithms, optimisation ideas and implementation details. Includes numerous examples and exercises. Computers

Programming in Ada 2012 Sure to become the go-to resource for those wishing to learn the language or to program in it. Computers

A Guide to MATLAB® Now in its third edition, this outstanding textbook explains everything you need to get started using MATLAB®. Computers

Building a Web Application with PHP and MariaDB This is a step-by-step, tutorial guide designed to help readers transition from beginners to more experienced developers using clear explanations. The variety of examples will help readers build, secure, and host real-time web applications. If you are a developer who wants to use PHP and MariaDB to build web applications, this book is ideal for you. Beginners can use this book to start with the basics and learn how to build and host web applications. Seasoned PHP Developers can use this book to get familiar with the new features of PHP 5.4 and 5.5, unit testing, caching, security, and performance optimization. Computers

FL Studio Cookbook This book is built on recipes written in an easy-to-follow manner accompanied by diagrams and crucial insights and knowledge on what they mean in the real world. This book is ideal for musicians and producers who want to take their music creation skills to the next level, learn tips and tricks, and understand the key elements and nuances in building inspirational music. It’s good to have some knowledge about music production, but if you have creativity and a good pair of ears, you are already ahead of the curve and well on your way. Computers

Kendo UI Cookbook This book is an easy-to-follow guide full of hands-on examples that allows you to learn and build visually compelling web applications using the Kendo UI library. This book will do wonders for web developers having knowledge of HTML and Javascript and want to polish their skills in building applications using the Kendo UI library. Computers

Penetration Testing with the Bash Shell An easy-to-understand, step-by-step practical guide that shows you how to use the Linux Bash terminal tools to solve information security problems. If you are a penetration tester, system administrator, or developer who would like an enriching and practical introduction to the Bash shell and Kali Linux command-line-based tools, this is the book for you. Computers

Making a Machine That Sees Like Us Making a Machine That Sees Like Us explains why and how our visual perceptions can provide us with an accurate representation of the world 'out there.' Along the way, it tells the story of a machine (a computational model) built by the authors that solves the computationally difficult problem of seeing the way humans do. This accomplishment required a radical paradigm shift - one that challenged preconceptions about visual perception and tested the limits of human behavior-modeling for practical application. Computers

Multimedia Computing This innovative textbook presents an experiential, holistic approach to multimedia computing along with practical algorithms. Computers

Neuronal Dynamics This solid introduction uses the principles of physics and the tools of mathematics to approach fundamental questions of neuroscience. Computers

Configuration Management with Chef-Solo This is a step-by-step guide, full of hands-on examples of real-world deployment tasks. Each topic is explained and placed in context, while also pointing out the key details of the concepts used. This book is aimed at system administrators and system engineers who have an understanding of configuration management tools and infrastructure. For novice administrators, it contains easy-to-use application recipes to get started immediately. Computers

Complex Analysis with MATHEMATICA® This book presents a way of learning complex analysis, using Mathematica. Includes CD with electronic version of the book. Computers

Type Theory and Formal Proof A gentle introduction for graduate students and researchers in the art of formalizing mathematics on the basis of type theory. Computers

Probability A leading authority sheds light on a variety of interesting topics in which probability theory plays a key role. Computers

Trust Extension as a Mechanism for Secure Code Execution on Commodity Computers As society rushes to digitize sensitive information and services, it is imperative to adopt adequate security protections. However, such protections fundamentally conflict with the benefits we expect from commodity computers. In other words, consumers and businesses value commodity computers because they provide good performance and an abundance of features at relatively low costs. Meanwhile, attempts to build secure systems from the ground up typically abandon such goals, and hence are seldomadopted.In this book, I argue that we can resolve the tension between security and features by leveraging the trust a user has in one device to enable her to securely use another commodity device or service, without sacrificing the performance and features expected of commodity systems. At a high level, we support this premise by developing techniques to allow a user to employ a small, trusted, portable device to securely learn what code is executing on her local computer. Rather than entrusting her data to the mountain of buggy code likely running on her computer, we construct an on-demand secure execution environment which can perform security-sensitive tasks and handle private data in complete isolation from all other software (and most hardware) on the system. Meanwhile, non-security-sensitive software retains the same abundance of features and performance it enjoys today.Having established an environment for secure code execution on an individual computer, we then show how to extend trust in this environment to network elements in a secure and efficient manner. This allows us to reexamine the design of network protocols and defenses, since we can now execute code on endhosts and trust the results within the network. Lastly, we extend the user's trust one more step to encompass computations performed on a remote host (e.g., in the cloud). We design, analyze, and prove secure a protocol that allows a user to outsource arbitrary computations to commodity computers run by an untrusted remote party (or parties) who may subject the computers to both software and hardware attacks. Our protocol guarantees that the user can both verify that the results returned are indeed the correct results of the specified computations on the inputs provided, and protect the secrecy of both the inputs and outputs of the computations. These guarantees are provided in a non-interactive, asymptotically optimal (with respect to CPU and bandwidth) manner.Thus, extending a user's trust, via software, hardware, and cryptographic techniques, allows us to provide strong security protections for both local and remote computations on sensitive data, while still preserving the performance and features of commodity computers. Computers

Compute-IT Compute-IT will help you deliver innovative lessons for the new Key Stage 3 Computing curriculum with confidence, using resources and meaningful assessment produced by expert educators. With Compute-IT you will be able to assess and record students' attainment and monitor progression all the way through to Key Stage 4. Developed by members of Computing at School, the national subject association for Computer Science, and a team of Master Teachers who deliver CPD through the Network of Excellence project funded by the Department for Education, Compute-IT provides a cohesive and supportive learning package structured around the key strands of Computing. Creative and flexible in its approach, Compute-IT makes Computing for Key Stage 3 easy to teach, and fun and meaningful to learn, so you can: Follow well-structured and finely paced lessons along a variety of suggested routes through Key Stage 3 Deliver engaging and interesting lessons using a range of files and tutorials provided for a range of different programming languages Ensure progression throughout Key Stage 3 with meaningful tasks underpinned by unparalleled teacher and student support Assess students' work with confidence, using ready-prepared formative and summative tasks that are mapped to meaningful learning outcomes and statements in the new Programme of Study Creative and flexible in its approach, Compute-IT makes Computing for Key Stage 3 easy to teach, and fun and meaningful to learn. This is the first title in the Compute-IT course, which comprises three Student's Books, three Teacher Packs and a range of digital teaching and learning resources delivered through Dynamic Learning. Computers

Citrix® XenApp® 7.x Performance Essentials If you are an IT architect or system administrator who works with Citrix® XenApp® and need an agile, practical guide to tune and optimize the performance of your XenApp® architecture, this is the book for you. Citrix®, Citrix Systems®, XenApp®, XenDesktop® and CloudPortalâ„¢ are trademarks of Citrix Systems, Inc. and/or one or more of its subsidiaries, and may be registered in the United States Patent and Trademark Office and in other countries. Computers

Kali Linux Network Scanning Cookbook "Kali Linux Network Scanning Cookbook" is intended for information security professionals and casual security enthusiasts alike. It will provide the foundational principles for the novice reader but will also introduce scripting techniques and in-depth analysis for the more advanced audience. Whether you are brand new to Kali Linux or a seasoned veteran, this book will aid in both understanding and ultimately mastering many of the most powerful and useful scanning techniques in the industry. It is assumed that the reader has some basic security testing experience. Computers

Mastering DynamoDB If you have interest in DynamoDB and want to know what DynamoDB is all about and become proficient in using it, this is the book for you. If you are an intermediate user who wishes to enhance your knowledge of DynamoDB, this book is aimed at you. Basic familiarity with programming, NoSQL, and cloud computing concepts would be helpful. Computers

Maven for Eclipse If you want to learn about Maven and use it from within Eclipse to develop Java projects, this is the book for you. Prior experience in developing Java projects and using the Eclipse IDE is presumed. Whether you are a beginner or an experienced developer, this book will get you up and running quickly, with a hands-on approach. Computers

Compute-IT Compute-IT will help you deliver innovative lessons for the new Key Stage 3 Computing curriculum with confidence, using resources and meaningful assessment produced by expert educators. With Compute-IT you will be able to assess and record students' attainment and monitor progression all the way through to Key Stage 4. Developed by members of Computing at School, the national subject association for Computer Science, and a team of Master Teachers who deliver CPD through the Network of Excellence project funded by the Department for Education, Compute-IT provides a cohesive and supportive learning package structured around the key strands of Computing. Creative and flexible in its approach, Compute-IT makes Computing for Key Stage 3 easy to teach, and fun and meaningful to learn, so you can: Follow well-structured and finely paced lessons along a variety of suggested routes through Key Stage 3 Deliver engaging and interesting lessons using a range of files and tutorials provided for a range of different programming languages Ensure progression throughout Key Stage 3 with meaningful tasks underpinned by unparalleled teacher and student support Assess students' work with confidence, using ready-prepared formative and summative tasks that are mapped to meaningful learning outcomes and statements in the new Programme of Study Creative and flexible in its approach, Compute-IT makes Computing for Key Stage 3 easy to teach, and fun and meaningful to learn. This is the second title in the Compute-IT course, which comprises three Student's Books, three Teacher Packs and a range of digital teaching and learning resources delivered through Dynamic Learning. Computers

Principles of Automated Negotiation Top researchers investigate the main challenges and state of the art in automated negotiation and discuss potential applications. Computers

Mining of Massive Datasets Now in its second edition, this book focuses on practical algorithms for mining data from even the largest datasets. Computers

Advanced Software Testing - Vol. 2, 2nd Edition This book teaches test managers what they need to know to achieve advanced skills in test estimation, test planning, test monitoring, and test control. Readers will learn how to define the overall testing goals and strategies for the systems being tested. This hands-on, exercise-rich book provides experience with planning, scheduling, and tracking these tasks. You'll be able to describe and organize the necessary activities as well as learn to select, acquire, and assign adequate resources for testing tasks. You'll learn how to form, organize, and lead testing teams, and master the organizing of communication among the members of the testing teams, and between the testing teams and all the other stakeholders. Additionally, you'll learn how to justify decisions and provide adequate reporting information where applicable. With over thirty years of software and systems engineering experience, author Rex Black is President of RBCS, is a leader in software, hardware, and systems testing, and is the most prolific author practicing in the field of software testing today. He has published a dozen books on testing that have sold tens of thousands of copies worldwide. He is past president of the International Software Testing Qualifications Board (ISTQB) and a director of the American Software Testing Qualifications Board (ASTQB). This book will help you prepare for the ISTQB Advanced Test Manager exam. Included are sample exam questions, at the appropriate level of difficulty, for most of the learning objectives covered by the ISTQB Advanced Level Syllabus. The ISTQB certification program is the leading software tester certification program in the world. With about 300,000 certificate holders and a global presence in over 50 countries, you can be confident in the value and international stature that the Advanced Test Manager certificate can offer you. This second edition has been thoroughly updated to reflect the new ISTQB Advanced Test Manager 2012 Syllabus, and the latest ISTQB Glossary. This edition reflects Rex Black's unique insights into these changes, as he was one of the main participants in the ISTQB Advanced Level Working Group. Computers

SELinux Cookbook If you are a Linux system administrator or a Linux-based service administrator and want to fine-tune SELinux to implement a supported, mature, and proven access control system, then this book is for you. Basic experience with SELinux enabled distributions is expected. Computers

Thinking Functionally with Haskell This book introduces fundamental techniques for reasoning mathematically about functional programs. Ideal for a first- or second-year undergraduate course. Computers

Salesforce Essentials for Administrators This book is targeted at expert administrators or professionals who are new to Salesforce and want to learn the various features supported by the platform in a short space of time. The book can also be used by professionals preparing for Developer and Administrator certification exams from Salesforce. Computers

PostgreSQL Administration Essentials If you are a database administrator who needs to get to grips with PostgreSQL quickly and efficiently, then this book is for you. This book will also be highly beneficial if you are a project leader or a developer who is interested in knowing more about database systems or bottleneck detection, as it will enable you to work more closely and cooperatively with your administrators. Computers

WCF Multi-layer Services Development with Entity Framework If you are a C#, VB.NET, or C++ developer and want to get started with WCF and Entity Framework, then this book is for you. Competence in Entity Framework will be needed to follow the examples in the book, but experience in creating WCF services using Entity Framework is not necessary. Developers and architects evaluating SOA implementation technologies for their company will find this book useful. Computers

Basic Proof Theory Introduction to proof theory and its applications in mathematical logic, theoretical computer science and artificial intelligence. Computers

Compute-IT Compute-IT will help you deliver innovative lessons for the new Key Stage 3 Computing curriculum with confidence, using resources and meaningful assessment produced by expert educators. With Compute-IT you will be able to assess and record students' attainment and monitor progression all the way through to Key Stage 4. Developed by members of Computing at School, the national subject association for Computer Science, and a team of Master Teachers who deliver CPD through the Network of Excellence project funded by the Department for Education, Compute-IT provides a cohesive and supportive learning package structured around the key strands of Computing. Creative and flexible in its approach, Compute-IT makes Computing for Key Stage 3 easy to teach, and fun and meaningful to learn, so you can: Follow well-structured and finely paced lessons along a variety of suggested routes through Key Stage 3 Deliver engaging and interesting lessons using a range of files and tutorials provided for a range of different programming languages Ensure progression throughout Key Stage 3 with meaningful tasks underpinned by unparalleled teacher and student support Assess students' work with confidence, using ready-prepared formative and summative tasks that are mapped to meaningful learning outcomes and statements in the new Programme of Study Creative and flexible in its approach, Compute-IT makes Computing for Key Stage 3 easy to teach, and fun and meaningful to learn. This is the third title in the Compute-IT course, which comprises three Student's Books, three Teacher Packs and a range of digital teaching and learning resources delivered through Dynamic Learning. Computers

Multimedia Programming Using Max/MSP and TouchDesigner If you want to learn how to use Max 6 and/or TouchDesigner, or work in audio-visual real-time processing, this is the book for you. It is intended for intermediate users of both programs and can be helpful for artists, designers, musicians, VJs, and researchers. A basic understanding of audio principles is advantageous. Computers

Moodle Gradebook This book is for teachers and administrators who have experience with Moodle. Basic knowledge of Moodle 2.x will be required, but no prior knowledge of grade functions is needed. This book will help you utilize the full functionality of Version 2.7. Computers

Learning Construct 2 If you want to make your own game but don't know how to start or don't have the technical skills to do it, then this is the book for you. You don't need to have a programming background to understand the concepts explained. Computers

Learning MS Dynamics AX 2012 Programming If you are a .NET or Java developer who wants to develop and customize Dynamics AX 2012 R3, this book is for you. Some experience with object-oriented development technologies is expected, but no experience in development with AX is required. Computers

Learning NGUI for Unity If you are a Unity 3D developer who wants to create an effective and user-friendly GUI using NGUI for Unity, then this book is for you. Prior knowledge of C# scripting is expected; however, no knowledge of NGUI is required. Computers

Mastering Unity Scripting Mastering Unity Scripting is an advanced book intended for students, educators, and professionals familiar with the Unity basics as well as the basics of scripting. Whether you've been using Unity for a short time or are an experienced user, this book has something important and valuable to offer to help you improve your game development workflow. Computers

Mastering Scientific Computing with R If you want to learn how to quantitatively answer scientific questions for practical purposes using the powerful R language and the open source R tool ecosystem, this book is ideal for you. It is ideally suited for scientists who understand scientific concepts, know a little R, and want to be able to start applying R to be able to answer empirical scientific questions. Some R exposure is helpful, but not compulsory. Computers

Workload Modeling for Computer Systems Performance Evaluation A book for experts and practitioners, emphasizing the intuition and reasoning behind definitions and derivations related to evaluating computer systems performance. Computers

The Phonology of Consonants The most comprehensive work on dissimilation to date, this book surveys over 150 dissimilation patterns drawn from over 130 languages. Computers

The Chief Data Officer Handbook for Data Governance A practical guide for today’s chief data officers to define and manage data governance programs The relatively new role of chief data officer (CDO) has been created to address the issue of managing a company’s data as a strategic asset, but the problem is that there is no universally accepted “playbook†for this role. Magnifying the challenge is the rapidly increasing volume and complexity of data, as well as regulatory compliance as it relates to data. In this book, Sunil Soares provides a practical guide for today’s chief data officers to manage data as an asset while delivering the trusted data required to power business initiatives, from the tactical to the transformative. The guide describes the relationship between the CDO and the data governance team, whose task is the formulation of policy to optimize, secure, and leverage information as an enterprise asset by aligning the objectives of multiple functions. Soares provides unique insight into the role of the CDO and presents a blueprint for implementing data governance successfully within the context of the position. With practical advice CDOs need, this book helps establish new data governance practices or mature existing practices. Computers

TIBCO Spotfire – A Comprehensive Primer If you are a business user or data professional, this book will give you a solid grounding in the use of TIBCO Spotfire. This book assumes no prior knowledge of Spotfire or even basic data and visualization concepts. Computers

Cambridge IGCSE Computer Science Endorsed by Cambridge International Examinations. Develop your students computational thinking and programming skills with complete coverage of the latest syllabus (0478) from experienced examiners and teachers. - Includes a Student CD-ROM with interactive tests, based on the short answer questions from both papers - Follows the order of the syllabus exactly, ensuring complete coverage - Introduces students to self-learning exercises, helping them learn how to use their knowledge in new scenarios This syllabus is for first examination from 2015. Computers

SFML Essentials If you are an enthusiast who is not new to the field of game development but want to exercise the countless features of SFML and build 2D games with minimal effort, this is the book for you. Computers

Apache Flume If you are a Hadoop programmer who wants to learn about Flume to be able to move datasets into Hadoop in a timely and replicable manner, then this book is ideal for you. No prior knowledge about Apache Flume is necessary, but a basic knowledge of Hadoop and the Hadoop File System (HDFS) is assumed. Computers

WebRTC Cookbook If you are a JavaScript developer with a basic knowledge of WebRTC and software development, but want to explore how to use it in more depth, this book is for you. Computers

Hadoop MapReduce v2 Cookbook If you are a Big Data enthusiast and wish to use Hadoop v2 to solve your problems, then this book is for you. This book is for Java programmers with little to moderate knowledge of Hadoop MapReduce. This is also a one-stop reference for developers and system admins who want to quickly get up to speed with using Hadoop v2. It would be helpful to have a basic knowledge of software development using Java and a basic working knowledge of Linux. Computers

Python Programming for Arduino This is the book for you if you are a student, hobbyist, developer, or designer with little or no programming and hardware prototyping experience, and you want to develop IoT applications. If you are a software developer or a hardware designer and want to create connected devices applications, then this book will help you get started. Computers

A Student's Guide to Numerical Methods The plain language style, worked examples and exercises in this book help students to understand the foundations of computational physics and engineering. Computers

Functional Programming in JavaScript If you are a JavaScript developer interested in learning functional programming, looking for the quantum leap towards mastering the JavaScript language, or just want to become a better programmer in general, then this book is ideal for you. It is aimed at programmers involved in developing reactive frontend apps, server-side apps that wrangle with reliability and concurrency, and everything in between. Computers

Advanced Software Testing - Vol. 3, 2nd Edition This book is written for the technical test analyst who wants to achieve advanced skills in test analysis, design, and execution. With a hands-on, exercise-rich approach, this book teaches you how to define and carry out the tasks required to implement a test strategy. You will be able to analyze, design, implement, and execute tests using risk considerations to determine the appropriate effort and priority for tests. This book will help you prepare for the ISTQB Advanced Technical Test Analyst exam. Included are sample exam questions for most of the learning objectives covered by the latest (2012) ISTQB Advanced Level syllabus. The ISTQB certification program is the leading software tester certification program in the world. You can be confident in the value and international stature that the Advanced Technical Test Analyst certificate will offer you. With over thirty years of software and systems engineering experience, author Rex Black is President of RBCS, a leader in software, hardware, and systems testing, and the most prolific author practicing in the field of software testing today. Previously, he served as President of both the International and American Software Testing Qualifications Boards (ISTQB and ASTQB). Jamie Mitchell is a consultant who has been working in software testing, test automation, and development for over 20 years. He was a member of the Technical Advisory Group for ASTQB, and one of the primary authors for the ISTQB Advanced Technical Test Analyst 2012 syllabus. Computers

Embedded Linux Projects Using Yocto Project Cookbook If you are an embedded developer learning about embedded Linux with some experience with the Yocto project, this book is the ideal way to become proficient and broaden your knowledge with examples that are immediately applicable to your embedded developments. Experienced embedded Yocto developers will find new insight into working methodologies and ARM specific development competence. Computers

WooCommerce Cookbook If you have ever built or managed a WordPress site and want to add e-commerce functionality into your site, WooCommerce and this book are perfect for you. Learning how to use WooCommerce through this series of recipes will give you a solid platform to add any future e-commerce needs. Computers

Twitter A resource for social scientists on how Twitter data can be used to study individual behavior and social interaction. Computers

Computation, Proof, Machine To understand the future of mathematics, this fascinating book returns to its past, tracing the hidden history that follows the thread of computation. Computers

OCR A Level Computer Science Develop confident students with our expert authors: their insight and guidance will ensure a thorough understanding of OCR A Level computer science, with challenging tasks and activities to test essential analytical and problem-solving skills. - Endorsed by OCR for use with the OCR AS and A Level Computer Science specification and written by a trusted and experienced author team, OCR Computer Science for A Level:- Endorsed by OCR for use with the OCR AS and A Level Computer Science specification and written by a trusted and experienced author team, OCR Computer Science for A Level:- Builds students' understanding of the core topics and computing skills required by the course units - Computing Systems, Algorithms and Problem Solving, and Programming Project - with detailed topic coverage, case studies and regular questions to measure understanding - Develops a problem-solving approach based on computational thinking required at both AS and A Level - thought-provoking practice questions at the end of each chapter gives opportunities to probe more deeply into key topics - Incorporates full coverage of the skills and knowledge demanded by the examined units, with exercises to help students understand the assessment objectives and advice and examples to support them through the practical element of the course. Computers

Ansible Configuration Management This book is intended for anyone who wants to learn Ansible starting from the basics. Some experience of how to set up and configure Linux machines and a working knowledge of BIND, MySQL, and other Linux daemons is expected. Computers

Git Essentials If you are a software developer with little or no experience of versioning systems, or are familiar with other centralized versioning systems, then this book is for you. If you have some experience working with command lines or using Linux admin or just using Unix and want to know more about Git, then this book is ideal for you. Computers

Making Your Case This book introduces readers to R, a freely available statistical language, to conduct program evaluations. The book uses case studies to illustrate techniques that include data description and visualization, bivariate analysis, simple and multiple regression, and logistic regression. There is a comprehensive example using The Clinical Record as a data repository. Computers

Express.js Blueprints This book is for beginners to Node.js and also for those who are technically advanced. By the end of this book, every competent developer will have achieved expertise in building web applications with Express.js. Computers

Sentiment Analysis This book gives a comprehensive introduction to all the core areas and many emerging themes of sentiment analysis. Computers

Probabilistic Forecasting and Bayesian Data Assimilation This book covers key ideas and concepts. It is an ideal introduction for graduate students in any field where Bayesian data assimilation is applied. Computers

Nmap Essentials This book is for beginners who wish to start using Nmap, who have experience as a system administrator or of network engineering, and who wish to get started with Nmap. Computers

Learning Robotics Using Python If you are an engineer, a researcher, or a hobbyist, and you are interested in robotics and want to build your own robot, this book is for you. Readers are assumed to be new to robotics but should have experience with Python. Computers

Handbook of Digital Politics It would be difficult to imagine how a development as world-changing as the emergence of the Internet could have taken place without having some impact upon the ways in which politics is expressed, conducted, depicted and reflected upon. The Handbook of Digital Politics explores this impact in a series of chapters written by some of the world's leading Internet researchers. This volume is a must-read for students, researchers and practitioners interested in the changing landscape of political communication. Computers

Getting Started with Unity 5 If you are a game developer interested in learning Unity 3D from scratch and becoming familiar with its core features, then this book is for you. No prior knowledge of Unity 3D is required. Computers

Getting Started with VMware Virtual SAN This book is intended for server administrators and storage administrators who would like to successfully build and scale a VSAN-backed vSphere infrastructure. A basic understanding of vSphere concepts and storage fundamentals will be helpful. Computers

LLVM Cookbook The book is for compiler programmers who are familiar with concepts of compilers and want to indulge in understanding, exploring, and using LLVM infrastructure in a meaningful way in their work. This book is also for programmers who are not directly involved in compiler projects but are often involved in development phases where they write thousands of lines of code. With knowledge of how compilers work, they will be able to code in an optimal way and improve performance with clean code. Computers

Getting Started with MariaDB This book is for anyone who wants to learn more about databases in general and wants to get started with MariaDB. Prior database experience is not required. Computers

Privacy and Legal Issues in Cloud Computing Adopting a multi-disciplinary and comparative approach, this book focuses on emerging and innovative attempts to tackle privacy and legal issues in cloud computing, such as personal data privacy, security and intellectual property protection. Leading international academics and practitioners in the fields of law and computer science examine the specific legal implications of cloud computing pertaining to jurisdiction, biomedical practice and information ownership. This collection offers original and critical responses to the rising challenges posed by cloud computing. Computers

Secure Multiparty Computation and Secret Sharing This book provides information on theoretically secure multiparty computation (MPC) and secret sharing, and the fascinating relationship between the two concepts. Computers

ggplot2 Essentials This book is perfect for R programmers who are interested in learning to use ggplot2 for data visualization, from the basics up to using more advanced applications, such as faceting and grouping. Since this book will not cover the basics of R commands and objects, you should have a basic understanding of the R language. Computers

HTML5 Game Development by Example This book is for web designers who have a basic knowledge of HTML, CSS, and JavaScript and want to create Canvas or DOM-based games that run on browsers. Computers

Mastering Julia This hands-on guide is aimed at practitioners of data science. The book assumes some previous skills with Julia and skills in coding in a scripting language such as Python or R, or a compiled language such as C or Java. Computers

Building High Integrity Applications with SPARK This is the first introduction to the SPARK 2014 language and the tools to verify programs for safety- and security-critical applications. Computers

Learning Laravel's Eloquent This book is perfect for developers with some basic knowledge of PHP development, but are new to the Eloquent ORM. However, developers with previous Laravel and Eloquent experience will also benefit from the in-depth analysis of specific classes and methodologies in the book. Computers

Lua Game Development Cookbook This book is for all programmers and game enthusiasts who want to stop dreaming about creating a game, and actually create one from scratch. The reader should know the basics of programming and using the Lua language. Knowledge of the C/C++ programming language is not necessary, but it's strongly recommended in order to write custom Lua modules extending game engine capabilities or to rewrite parts of the Lua code into a more efficient form. Algebra and matrix operations are required in order to understand advanced topics in Chapter 4, Graphics - Legacy Method with OpenGL 1.x-2.1 and Chapter 5, Graphics - Modern Method with OpenGL 3.0+. Sample demonstrations are coupled with binary libraries for Windows and Linux operating systems for convenience. Computers

PostgreSQL Replication This book is ideal for PostgreSQL administrators who want to set up and understand replication. By the end of the book, you will be able to make your databases more robust and secure by getting to grips with PostgreSQL replication. Computers

Python and Matplotlib Essentials for Scientists and Engineers This book provides an introduction to the core features of the Python programming language and Matplotlib plotting routings for scientists and engineers (or students of either discipline) who want to use Pythonâ„¢ to analyse data, simulate physical processes, and render publication-quality plots. No previous programming experience is needed before reading the first page.Readers will learn the core features of the Python programming language in under a day. They will be able to immediately use Python to implement codes that solve their own problems and make beautiful plots and animations. Python code is extremely fast to prototype, allowing users to achieve results quickly and accurately. The examples within the book are available for download athttp://pythonessentials.com.Python and Matplotlib Essentials for Scientists and Engineers is accessible for motivated high-school students, but will likely be most useful for undergraduate and graduate students as well as working professionals who have some background with the basic mathematical concepts. This book is intended for technical people who want to get things done. Computers

Cambridge IGCSE ICT 2nd Edition Endorsed by Cambridge Assessment International Education Now including Brian Sargent in the expert author team, alongside first edition authors Graham Brown and David Watson, this book has been fully revised and updated to cover every part of the latest Cambridge IGCSE ICT (0417) syllabus. - Written by experts, who bring a wealth of theoretical knowledge and practical experience to both the book and the CD- Ensures that students are fully prepared for both the written theory paper as well as the two practical papers- Covers each section of the syllabus with clear explanations and plenty of tasks and activitiesEvery Student's Book includes a CD that contains source files for the tasks and activities. Answers to all questions can be found on the Teacher's CD Rom. Computers

Boost.Asio C++ Network Programming Learn effective C++ network programming with Boost.Asio and become a proficient C++ network programmerAbout This Book• Learn efficient C++ network programming with minimum coding using Boost.Asio• Your one-stop destination to everything related to the Boost.Asio library• Explore the fundamentals of networking to choose designs with more examples, and learn the basics of Boost.Asio Who This Book Is ForThis book is for C++ Network programmers with basic knowledge of network programming, but no knowledge of how to use Boost.Asio for network programming.What You Will Learn• Prepare the tools to simplify network programming in C++ using Boost.Asio• Explore the networking concepts of IP addressing, TCP/IP ports and protocols, and LAN topologies• Get acquainted with the usage of the Boost libraries• Get to know more about the content of Boost.Asio network programming and Asynchronous programming• Establish communication between client and server by creating client-server application• Understand the various functions inside Boost.Asio C++ libraries to delve into network programming• Discover how to debug and run the code successfullyIn DetailBoost.Asio is a C++ library used for network programming operations.Organizations use Boost because of its productivity. Use of these high-quality libraries speed up initial development, result in fewer bugs, reduce reinvention-of-the-wheel, and cut long-term maintenance costs. Using Boost libraries gives an organization a head start in adopting new technologies.This book will teach you C++ Network programming using synchronous and asynchronous operations in Boost.Asio with minimum code, along with the fundamentals of Boost, server-client applications, debugging, and more.You will begin by preparing and setting up the required tools to simplify your network programming in C++ with Boost.Asio. Then you will learn about the basic concepts in networking such as IP addressing, TCP/IP protocols, and LAN with its topologies. This will be followed by an overview of the Boost libraries and their usage.Next you will get to know more about Boost.Asio and its concepts related to network programming. We will then go on to create a client-server application, helping you to understand the networking concepts. Moving on, you will discover how to use all the functions inside the Boost.Asio C++ libraries. Lastly, you will understand how to debug the code if there are errors found and will run the code successfully.Style and approachAn example-oriented book to show you the basics of networking and help you create a network application simply using Boost.Asio, with more examples for you to get up and running with Boost.Asio quickly. Computers

Python Machine Learning Unlock deeper insights into Machine Leaning with this vital guide to cutting-edge predictive analytics About This Book: Leverage Python’s most powerful open-source libraries for deep learning, data wrangling, and data visualization; Learn effective strategies and best practices to improve and optimize machine learning systems and algorithms; Ask - and answer - tough questions of your data with robust statistical models, built for a range of datasets Who This Book Is For. If you want to find out how to use Python to start answering critical questions of your data, pick up Python Machine Learning - whether you want to get started from scratch or want to extend your data science knowledge, this is an essential and unmissable resource. What You Will Learn: Explore how to use different machine learning models to ask different questions of your data; Learn how to build neural networks using Pylearn 2 and Theano; Find out how to write clean and elegant Python code that will optimize the strength of your algorithms; Discover how to embed your machine learning model in a web application for increased accessibility; Predict continuous target outcomes using regression analysis; Uncover hidden patterns and structures in data with clustering; Organize data using effective pre-processing techniques; Get to grips with sentiment analysis to delve deeper into textual and social media data In Detail. Machine learning and predictive analytics are transforming the way businesses and other organizations operate. Being able to understand trends and patterns in complex data is critical to success, becoming one of the key strategies for unlocking growth in a challenging contemporary marketplace. Python can help you deliver key insights into your data - its unique capabilities as a language let you build sophisticated algorithms and statistical models that can reveal new perspectives and answer key questions that are vital for success. Python Machine Learning gives you access to the world of predictive analytics and demonstrates why Python is one of the world’s leading data science languages. If you want to ask better questions of data, or need to improve and extend the capabilities of your machine learning systems, this practical data science book is invaluable. Covering a wide range of powerful Python libraries, including scikit-learn, Theano, and Pylearn2, and featuring guidance and tips on everything from sentiment analysis to neural networks, you’ll soon be able to answer some of the most important questions facing you and your organization. Style and approach. Python Machine Learning connects the fundamental theoretical principles behind machine learning to their practical application in a way that focuses you on asking and answering the right questions. It walks you through the key elements of Python and its powerful machine learning libraries, while demonstrating how to get to grips with a range of statistical models. Computers

Psychology of the Digital Age Drawing on years of online research, this book presents key principles of life and wellbeing in the digital realm. Computers

Perception as Bayesian Inference This 1996 book describes an exciting theoretical paradigm for visual perception based on experimental and computational insights. Computers

Argumentation Schemes Provides a systematic analysis of many common argumentation schemes. Computers

Programming in ILE RPG Since its original publication, Programming in RPG IV has given thousands of students and professionals a strong foundation in the essentials of business programming using RPG IV. Now, the long-awaited Fifth Edition, retitled Programming in ILE RPG, produces the most significant update to this "gold standard" book in many years. The book has been reorganized and updated to the newest software release. It includes exclusive coverage of free-format RPG, new attention to SQL, and expanded emphasis on ILE modules, procedures, and service programs. All-new programming exercises and assignments add even more value for learning. The book includes complete coverage of the program development process, the newest development tools, RPG IV instructions and operations, creating and using files, program workflow and structured design, arithmetic operations and functions, accessing and updating database files, writing interactive applications, modular programming, service programs, error handling, subfiles, APIs, and more. This book is the one guide you need to learn how to be successful with all aspects of ILE RPG. Computers

Partial Differential Equation Methods for Image Inpainting This book introduces the mathematical concept of partial differential equations (PDEs) for virtual image restoration. Computers

Data Analysis with Stata Explore the big data field and learn how to perform data analytics and predictive modelling in STATA About This Book: Visualize and analyse data in STATA to devise a business strategy; Learn STATA programming and predictive modeling; Discover how you can become a data scientist with the power of STATA Who This Book Is For. This book is for all the professionals and students who want to learn STATA programming and apply predictive modelling concepts. This book is also very helpful for experienced STATA programmers as it provides advanced statistical modelling concepts and their application. What You Will Learn: Perform important statistical tests to become a STATA data scientist; Be guided through how to program in STATA; Implement logistic and linear regression models; Visualize and program the data in STATA; Analyse survey data, time series data, and survival data; Perform database management in STATA In Detail. STATA is an integrated software package that provides you with everything you need for data analysis, data management, and graphics. STATA also provides you with a platform to efficiently perform simulation, regression analysis (linear and multiple) [and custom programming. This book covers data management, graphs visualization, and programming in STATA. Starting with an introduction to STATA and data analytics you’ll move on to STATA programming and data management. Next, the book takes you through data visualization and all the important statistical tests in STATA. Linear and logistic regression in STATA is also covered. As you progress through the book, you will explore a few analyses, including the survey analysis, time series analysis, and survival analysis in STATA. You’ll also discover different types of statistical modelling techniques and learn how to implement these techniques in STATA. Style and approach. This book is a hands-onguide to STATA programming and statistical modelling providing many STATA code examples and taking. You through the working of the code in detail. Computers

LaTeX Cookbook Over 100 hands-on recipes to quickly prepare LaTeX documents of various kinds to solve challenging tasks About This Book: Work with modern document classes, such as KOMA-Script classes; Explore the latest LaTeX packages, including TikZ, pgfplots, and biblatex; An example-driven approach to creating stunning graphics directly within LaTeX Who This Book Is For. If you already know the basics of LaTeX and you like to get fast, efficient solutions, this is the perfect book for you. If you are an advanced reader, you can use this book's example-driven format to take your skillset to the next level. Some familiarity with the basic syntax of LaTeX and how to use the editor of your choice for compiling is required. What You Will Learn: Choose the right document class for your project to customize its features; Utilize fonts globally and locally; Frame, shape, arrange, and annotate images; Add a bibliography, a glossary, and an index; Create colorful graphics including diagrams, flow charts, bar charts, trees, plots in 2d and 3d, time lines, and mindmaps; Solve typical tasks for various sciences including math, physics, chemistry, electrotechnics, and computer science; Optimize PDF output and enrich it with meta data, annotations, popups, animations, and fill-in fields; Explore the outstanding capabilities of the newest engines and formats such as XeLaTeX, LuaLaTeX, and LaTeX3 In Detail. LaTeX is a high-quality typesetting software and is very popular, especially among scientists. Its programming language gives you full control over every aspect of your documents, no matter how complex they are. LaTeX's huge amount of customizable templates and supporting packages cover most aspects of writing with embedded typographic expertise. With this book you will learn to leverage the capabilities of the latest document classes and explore the functionalities of the newest packages. The book starts with examples of common document types. It provides you with samples for tuning text design, using fonts, embedding images, and creating legible tables. Common document parts such as the bibliography, glossary, and index are covered, with LaTeX's modern approach. You will learn how to create excellent graphics directly within LaTeX, including diagrams and plots quickly and easily. Finally, you will discover how to use the new engines XeTeX and LuaTeX for advanced programming and calculating with LaTeX. The example-driven approach of this book is sure to increase your productivity. Style and approach. This book guides you through the world of LaTeX based on over a hundred hands-on examples. These are explained in detail and are designed to take minimal time and to be self-compliant. Computers

Mastering Ansible Design, develop, and solve real world automation and orchestration needs by unlocking the automation capabilities of Ansible About This Book: Discover how Ansible works in detail; Explore use cases for Ansible’s advanced features including task delegation, fast failures, and serial task execution; Extend Ansible with custom modules, plugins, and inventory sources Who This Book Is For. This book is intended for Ansible developers and operators who have an understanding of the core elements and applications but are now looking to enhance their skills in applying automation using Ansible. What You Will Learn: Understand Ansible’s code and logic flow; Safeguard sensitive data within Ansible; Access and manipulate complex variable data within Ansible playbooks; Handle task results to manipulate change and failure definitions; Organize Ansible content into a simple structure; Craft a multi-tier rollout playbook utilizing load balancers and manipulating your monitoring system; Utilize advanced Ansible features to orchestrate rolling updates with almost no service disruptions; Troubleshoot Ansible failures to understand and resolve issues; Extend Ansible with custom modules, plugins, or inventory sources In Detail. Automation is critical to success in the world of DevOps. How quickly and efficiently an application deployment can be automated, or a new infrastructure can be built up, can be the difference between a successful product or a failure. Ansible provides a simple yet powerful automation engine. Beyond the basics of Ansible lie a host of advanced features which are available to help you increase efficiency and accomplish complex orchestrations with ease. This book provides you with the knowledge you need to understand how Ansible works at a fundamental level and leverage its advanced capabilities. You'll learn how to encrypt Ansible content at rest and decrypt data at runtime. You will master the advanced features and capabilities required to tackle the complex automation challenges of today and beyond. You will gain detailed knowledge of Ansible workflows, explore use cases for advanced features, craft well thought out orchestrations, troubleshoot unexpected behaviour, and extend Ansible through customizations. Finally, you will discover the methods used to examine and debug Ansible operations, helping you to understand and resolve issues. Style and approach. A clear, practical guide that covers best practise, system architecture and design aspects that will help you master Ansible with ease. Computers

Learning Scientific Programming with Python Learn to master basic programming tasks from scratch with real-life scientific examples in this complete introduction to Python. Computers

Essentials of Programming in Mathematica® This book covers Mathematica® for beginners. An example-driven text covering a wide variety of applications, containing over 350 exercises with solutions available online. Computers

Statistical Methods for Recommender Systems This book provides an in-depth discussion of challenges encountered in deploying real-life large-scale systems and the state-of-the-art solutions in personalization. Computers

Image Processing with ImageJ Extract and analyze data from complex images with ImageJ, the world’s leading image processing tool About This Book: Design automated image-processing solutions and speed up image-processing tasks with ImageJ; Create quality and intuitive interfaces for image processing by developing a basic framework for ImageJ plugins.; Tackle even the most sophisticated datasets and complex images Who This Book Is For. The book has been created for engineers, scientists, and developers eager to tackle image processing with one of the leading tools available. No prior knowledge of ImageJ is needed. Familiarity with Java programming will be required for readers to code their own routines using ImageJ. What You Will Learn: Install and set up ImageJ for image processing.; Process images using ImageJ’s built-in tools; Create macros to perform repetitive processing tasks; Set up and use an integrated development environment for ImageJ plugins; Create plugins with a user-friendly interface for processing; Use established ImageJ plugins for processing and quantification; Generate a simple interface based on a real world example and create other interfaces for other projects; Speed up interface development by setting multiple parameters interactively In Detail. Advances in image processing have been vital for the scientific and technological communities, making it possible to analyze images in greater detail than ever before. But as images become larger and more complex, advanced processing techniques are required. ImageJ is built for the modern challenges of image processing - it’s one of the key tools in its development, letting you automate basic tasks so you can focus on sophisticated, in depth analysis. This book demonstrates how to put ImageJ into practice. It outlines its key features and demonstrates how to create your own image processing applications using macros and ImageJ plugins. Once you’ve got to grips with the basics of ImageJ, you’ll then discover how to build a number of different image processing solutions. From simple tasks to advanced and automated image processing, you’ll gain confidence with this innovative and powerful tool - however and whatever you are using it for. Style and approach. A step-by-step guide to image processing and developing macros and plugins in ImageJ. The book will progress from using the built-in tools to macros and finally plugins for image processing. Computers

LLVM Essentials Become familiar with the LLVM infrastructure and start using LLVM libraries to design a compiler About This Book: Learn to use the LLVM libraries to emit intermediate representation (IR) from high-level language; Build your own optimization pass for better code generation; Understand AST generation and use it in a meaningful way Who This Book Is For. This book is intended for those who already know some of the concepts of compilers and want to quickly get familiar with the LLVM infrastructure and the rich set of libraries that it provides. What You Will Learn: Get an introduction to LLVM modular design and LLVM tools; Convert frontend code to LLVM IR; Implement advanced LLVM IR paradigms; Understand the LLVM IR Optimization Pass Manager infrastructure and write an optimization pass; Absorb LLVM IR transformations; Understand the steps involved in converting LLVM IR to Selection DAG; Implement a custom target using the LLVM infrastructure; Get a grasp of C’s frontend clang, an AST dump, and static analysis In Detail. LLVM is currently the point of interest for many firms, and has a very active open source community. It provides us with a compiler infrastructure that can be used to write a compiler for a language. It provides us with a set of reusable libraries that can be used to optimize code, and a target-independent code generator to generate code for different backends. It also provides us with a lot of other utility tools that can be easily integrated into compiler projects. This book details how you can use the LLVM compiler infrastructure libraries effectively, and will enable you to design your own custom compiler with LLVM in a snap. We start with the basics, where you’ll get to know all about LLVM. We then cover how you can use LLVM library calls to emit intermediate representation (IR) of simple and complex high-level language paradigms. Moving on, we show you how to implement optimizations at different levels, write an optimization pass, generate code that is independent of a target, and then map the code generated to a backend. The book also walks you through CLANG, IR to IR transformations, advanced IR block transformations, and target machines. By the end of this book, you’ll be able to easily utilize the LLVM libraries in your own projects. Style and approach. This book deals with topics sequentially, increasing the difficulty level in a step-by-step approach. Each topic is explained with a detailed example, and screenshots are included to help you understand the examples. Computers

Building Minecraft Server Modifications Create and customize your very own Minecraft server using Java and the Spigot API About This Book: Set up a Minecraft server that you control; Use object-oriented programming to modify Minecraft regardless of your level of experience; This interactive guide will help you create a unique experience for you and your friends Who This Book Is For. This book is great for anyone who is interested in customizing their Minecraft server. Whether you are new to programming, Java, Bukkit, or even Minecraft itself, this book has you covered. All you need is a valid Minecraft account. If you are interested in programming as a career or hobby, this book will get you started. If you are simply interested in playing Minecraft with your friends, then this book will help you make that experience even more enjoyable. What You Will Learn: Install and run a Spigot server for free on your home PC; Adjust the server settings to customize Minecraft to your liking; Install an IDE and configure a project to write code; Install and test plugins on a Spigot server; Test your plugins through debugging the code; Program in game commands and permissions; Get to know advanced programming concepts such as event-driven programming, configuration files, saving/loading data, and scheduled tasks; Implement configuration files to make your plugins customizable; Save and load your plugin's data to persist across server restarts In Detail. Minecraft is a sandbox game that allows you to play it in any way you want. Coupled with a multiplayer server powered by Spigot, you can customize the game even more! Using the Bukkit API, anyone interested in learning how to program can control their Minecraft world by developing server plugins. This book is a great introduction to software development through the wonderful world of Minecraft. We start by instructing you through how to set up your home PC for Minecraft server development. This includes an IDE complete with the required libraries as well as a Spigot server to test on. You will be guided through writing code for several different plugins. Each chapter teaches you new skills to create plugins of increasing complexity, and each plugin adds a new concept of the Bukkit API By the end of the book, you will have all the knowledge you need about the API to successfully create any type of plugin. You can then practice and build your Java skills through developing more mods for their server. Style and approach. This hands-on guide is filled with interactive examples to help you modify Minecraft. Programming terms and concepts are explained along the way so even those who have never written code before can keep up. Computers

Gradle Essentials Master the fundamentals of Gradle using real-world projects with this quick and easy-to-read guide About This Book: Write beautiful build scripts for various types of projects effortlessly; Become more productive by harnessing the power and elegance of the Gradle DSL; Learn how to use Gradle quickly and effectively with this step-by-step guide Who This Book Is For. This book is for Java and other JVM-based language developers who want to use Gradle or are already using Gradle on their projects. No prior knowledge of Gradle is required, but some familiarity with build-related terminologies and an understanding of the Java language would help. What You Will Learn: Master the Gradle DSL by identifying the building blocks; Learn just enough Groovy for Gradle; Set up tests and reports for your projects to make them CI ready; Create library, stand-alone, and web projects; Craft multi-module projects quickly and efficiently; Migrate existing projects to a modern Gradle build; Extract common build logic into plugins; Write builds for languages like Java, Groovy, and Scala In Detail. Gradle is an advanced and modern build automation tool. It inherits the best elements of the past generation of build tools, but it also differs and innovates to bring terseness, elegance, simplicity, and the flexibility to build. Right from installing Gradle and writing your first build file to creating a fully-fledged multi-module project build, this book will guide you through its topics in a step-by-step fashion. You will get your hands dirty with a simple Java project built with Gradle and go on to build web applications that are run with Jetty or Tomcat. We take a unique approach towards explaining the DSL using the Gradle API, which makes the DSL more accessible and intuitive. All in all, this book is a concise guide to help you decipher the Gradle build files, covering the essential topics that are most useful in real-world projects. With every chapter, you will learn a new topic and be able to readily implement your build files. Style and approach. This step-by-step guide focuses on being productive with every chapter. When required, topics are explained in-depth to give you a good foundation of the Gradle fundamentals. The book covers most aspects of builds required for conventional JVM-based projects, and when necessary, points you towards the right resources. Computers

Learning Python Learn to code like a professional with Python - an open source, versatile and powerful programming language About This Book: Learn the fundamentals of programming with Python - one of the best languages ever created; Develop a strong set of programming skills that you will be able to express in any situation, on every platform, thanks to Python’s portability; Create outstanding applications of all kind, from websites to scripting, and from GUIs to data science Who This Book Is For. Python is the most popular introductory teaching language in U.S. top computer science universities, so if you are new to software development, or maybe you have little experience, and would like to start off on the right foot, then this language and this book are what you need. Its amazing design and portability will help you become productive regardless of the environment you choose to work with. What You Will Learn: Get Python up and running on Windows, Mac, and Linux in no time; Grasp the fundamental concepts of coding, along with the basics of data structures and control flow.; Write elegant, reusable, and efficient code in any situation; Understand when to use the functional or the object oriented programming approach; Create bulletproof, reliable software by writing tests to support your code; Explore examples of GUIs, scripting, data science and web applications; Learn to be independent, capable of fetching any resource you need, as well as dig deeper In Detail. Learning Python has a dynamic and varied nature. It reads easily and lays a good foundation for those who are interested in digging deeper. It has a practical and example-oriented approach through which both the introductory and the advanced topics are explained. Starting with the fundamentals of programming and Python, it ends by exploring very different topics, like GUIs, web apps and data science. The book takes you all the way to creating a fully fledged application. The book begins by exploring the essentials of programming, data structures and teaches you how to manipulate them. It then moves on to controlling the flow of a program and writing reusable and error proof code. You will then explore different programming paradigms that will allow you to find the best approach to any situation, and also learn how to perform performance optimization as well as effective debugging. Throughout, the book steers you through the various types of applications, and it concludes with a complete mini website built upon all the concepts that you learned. Style and approach. This book is an easy-to-follow guide that will take you from a novice to the proficient level at a comfortable pace, using a lot of simple but effective examples. Each topic is explained thoroughly, and pointers are left for the more inquisitive readers to dig deeper and expand their knowledge. Computers

Pentaho Analytics for MongoDB Cookbook Over 50 recipes to learn how to use Pentaho Analytics and MongoDB to create powerful analysis and reporting solutions About This Book: Create reports and stunning dashboards with MongoDB data; Accelerate data access and maximize productivity with unique features of Pentaho for MongoDB; A step-by-step recipe-based guide for making full use of Pentaho suite tools with MongoDB Who This Book Is For. This book is intended for data architects and developers with a basic level of knowledge of MongoDB. Familiarity with Pentaho is not expected. What You Will Learn: Extract, load, and transform data from MongoDB collections to other datasources; Design Pentaho Reports using different types of connections for MongoDB; Create a OLAP mondrian schema for MongoDB; Explore your MongoDB data using Pentaho Analyzer; Utilize the drag and drop web interface to create dashboards; Use Kettle Thin JDBC with MongoDB for analysis; Integrate advanced dashboards with MondoDB using different types of connections; Publish and run a report on Pentaho BI server using a web interface In Detail. MongoDB is an open source, schemaless NoSQL database system. Pentaho as a famous open source Analysis tool provides high performance, high availability, and easy scalability for large sets of data. The variant features in Pentaho for MongoDB are designed to empower organizations to be more agile and scalable and also enables applications to have better flexibility, faster performance, and lower costs. Whether you are brand new to online learning or a seasoned expert, this book will provide you with the skills you need to create turnkey analytic solutions that deliver insight and drive value for your organization. The book will begin by taking you through Pentaho Data Integration and how it works with MongoDB. You will then be taken through the Kettle Thin JDBC Driver for enabling a Java application to interact with a database. This will be followed by exploration of a MongoDB collection using Pentaho Instant view and creating reports with MongoDB as a datasource using Pentaho Report Designer. The book will then teach you how to explore and visualize your data in Pentaho BI Server using Pentaho Analyzer. You will then learn how to create advanced dashboards with your data. The book concludes by highlighting contributions of the Pentaho Community. Style and approach. A comprehensive, recipe-based guide to take complete advantage of the Pentaho Analytics for MongoDB. Computers

SFML Game Development By Example Create and develop exciting games from start to finish using SFML About This Book: Familiarize yourself with the SFML library and explore additional game development techniques; Craft, shape, and improve your games with SFML and common game design elements; A practical guide that will teach you how to use utilize the SFML library to build your own, fully functional applications Who This Book Is For. This book is intended for game development enthusiasts with at least decent knowledge of the C++ programming language and an optional background in game design. What You Will Learn: Create and open a window by using SFML; Utilize, manage, and apply all of the features and properties of the SFML library; Employ some basic game development techniques to make your game tick; Build your own code base to make your game more robust and flexible; Apply common game development and programming patterns to solve design problems; Handle your visual and auditory resources properly; Construct a robust system for user input and interfacing; Develop and provide networking capabilities to your game In Detail. Simple and Fast Multimedia Library (SFML) is a simple interface comprising five modules, namely, the audio, graphics, network, system, and window modules, which help to develop cross-platform media applications. By utilizing the SFML library, you are provided with the ability to craft games quickly and easily, without going through an extensive learning curve. This effectively serves as a confidence booster, as well as a way to delve into the game development process itself, before having to worry about more advanced topics such as "rendering pipelines" or "shaders.". With just an investment of moderate C++ knowledge, this book will guide you all the way through the journey of game development. The book starts by building a clone of the classical snake game where you will learn how to open a window and render a basic sprite, write well-structured code to implement the design of the game, and use the AABB bounding box collision concept. The next game is a simple platformer with enemies, obstacles and a few different stages. Here, we will be creating states that will provide custom application flow and explore the most common yet often overlooked design patterns used in game development. Last but not the least, we will create a small RPG game where we will be using common game design patterns, multiple GUI. elements, advanced graphical features, and sounds and music features. We will also be implementing networking features that will allow other players to join and play together. By the end of the book, you will be an expert in using the SFML library to its full potential. Style and approach. An elaborate take on the game development process in a way that compliments the reader’s existing knowledge, this book provides plenty of examples and is kind to the uninitiated. Each chapter builds upon the knowledge gained from the previous one and offers clarifications on common issues while still remaining within the scope of its own subject and retaining clarity. Computers

Real-Time Software Design for Embedded Systems This tutorial reference goes from use cases to complete architectures for real-time embedded systems using SysML, UML, and MARTE. Computers

Interactions with Search Systems This book describes advances in technology, data availability, and searcher expectations around next-generation search engines. Computers

Logic and Algebraic Structures in Quantum Computing Experts in the field explore the connections across physics, quantum logic, and quantum computing. Computers

Find It Fast Go beyond Google to mine big data and social media Author Robert Berkman gives expert advice on how to search the internet to locate the best information sources, how to find and utilize the professionals behind those sources, and how to combine these techniques to complete an information search on any subject. This fully updated 6th edition includes how to search beyond Google, leveraging big data in the search process, and how to search the social web. Readers will also find expert advice on how to know if a site is a trusted source; understanding how and why sources differ; using precision search strategies and taming information overload; and finding, evaluating, and identifying experts. Whether it’s consumer advice, information for a job or project, facts for starting a new business, or answers to questions on obscure topics, Find It Fast is the perfect resource for learning to hone one’s internet searching skills. Computers

Elasticsearch Essentials Harness the power of ElasticSearch to build and manage scalable search and analytics solutions with this fast-paced guide About This Book: New to ElasticSearch? Here’s what you need—a highly practical guide that gives you a quick start with ElasticSearch using easy-to-follow examples; get up and running with ElasticSearch APIs in no time; Get the latest guide on ElasticSearch 2.0.0, which contains concise and adequate information on handling all the issues a developer needs to know while handling data in bulk with search relevancy; Learn to create large-scale ElasticSearch clusters using best practices; Learn from our experts—written by Bharvi Dixit who has extensive experience in working with search servers (especially ElasticSearch) Who This Book Is For. Anyone who wants to build efficient search and analytics applications can choose this book. This book is also beneficial for skilled developers, especially ones experienced with Lucene or Solr, who now want to learn Elasticsearch quickly. What You Will Learn: Get to know about advanced Elasticsearch concepts and its REST APIs; Write CRUD operations and other search functionalities using the ElasticSearch Python and Java clients; Dig into wide range of queries and find out how to use them correctly; Design schema and mappings with built-in and custom analyzers; Excel in data modeling concepts and query optimization; Master document relationships and geospatial data; Build analytics using aggregations; Setup and scale Elasticsearch clusters using best practices; Learn to take data backups and secure Elasticsearch clusters In Detail. With constantly evolving and growing datasets, organizations have the need to find actionable insights for their business. ElasticSearch, which is the world's most advanced search and analytics engine, brings the ability to make massive amounts of data usable in a matter of milliseconds. It not only gives you the power to build blazing fast search solutions over a massive amount of data, but can also serve as a NoSQL data store. This guide will take you on a tour to become a competent developer quickly with a solid knowledge level and understanding of the ElasticSearch core concepts. Starting from the beginning, this book will cover these core concepts, setting up ElasticSearch and various plugins, working with analyzers, and creating mappings. This book provides complete coverage of working with ElasticSearch using Python and performing CRUD operations and aggregation-based analytics, handling document relationships in the NoSQL world, working with geospatial data, and taking data backups. Finally, we’ll show you how to set up and scale ElasticSearch clusters in production environments as well as providing some best practices. Style and approach. This is an easy-to-follow guide with practical examples and clear explanations of the concepts. This fast-paced book believes in providing very rich content focusing majorly on practical implementation. This book will provide you with step-by-step practical examples, letting you know about the common errors and solutions along with ample screenshots and code to ensure your success. Computers

Mastering PhoneGap Mobile Application Development Take your PhoneGap experience to the next level and create engaging real-world applications About This Book: Create a useful PhoneGap workflow for larger projects in order to simplify and manage the development process; Use third-party plugins, IndexedDB, and SQLite for PhoneGap to develop large-scale, data-driven, and highly accessible applications; A pragmatic guide to construct top-notch large-scale applications using PhoneGap Who This Book Is For. If you have created simple applications using PhoneGap in the past and now want to take your workflow and apps to the next level, this book will help you reach your goals. You should have a good working knowledge of HTML, CSS, and JavaScript, and prior experience with PhoneGap. What You Will Learn: Construct build workflows that simplify complex application development; Integrate the next version of JavaScript to simplify your code; Create accessible hybrid applications; Persist and query data using third-party database plugins; Create your own PhoneGap plugins for your unique use cases; Create icons and splash screens suitable for submission to app stores; Publish your app to the Google Play and Apple iTunes stores In Detail. PhoneGap is a useful and flexible tool that enables you to create complex hybrid applications for mobile platforms. In addition to the core technology, there is a large and vibrant community that creates third-party plugins that can take your app to the next level. This book will guide you through the process of creating a complex data-driven hybrid mobile application using PhoneGap, web technologies, and third-party plugins. A good foundation is critical, so you will learn how to create a useful workflow to make development easier. From there, the next version of JavaScript (ES6) and the CSS pre-processor SASS are introduced as a way to simplify creating the look of the mobile application. Responsive design techniques are also covered, including the flexbox layout module. As many apps are data-driven, you'll build an application throughout the course of the book that relies upon IndexedDB and SQLite. You'll also download additional content and address how to handle in-app purchases. Furthermore, you’ll build your own customized plugins for your particular use case. When the app is complete, the book will guide you through the steps necessary to submit your app to the Google Play and Apple iTunes stores. Style and approach. This book is a step-by-step guide, in which the concepts covered are explained with the help of hands-on examples Computers

Magento 2 Development Essentials Get up and running with Magento 2 to create custom solutions, themes, and extensions effectively About This Book: Create unique solutions for Magento 2 by developing and implementing solutions, themes, and extensions; Be proficient in the main functionalities, resources, and system structure of Magento 2; Get to grips with this practical and hands-on guide to raise your web development skills to the next level Who This Book Is For. If you are a PHP developer who wants to improve your skills in e-commerce development by creating themes and extensions for Magento 2, then this book is for you. What You Will Learn: Install and set up the Magento Ecosystem; Choose the best options for Magento’s Sell System features; Work with Search Engine Optimization in Magento; Create and customize themes for Magento; Develop extensions for new Magento functionalities; Package extensions to publish in the Magento Connect network; Create Magento solutions for mobile devices; Carry out performance adjustments to speed up your Magento system In Detail. Magento is the e-commerce software and platform trusted by the world's leading brands. Used by thousands of merchants for their transactions worth billions, it provides the flexibility to customize the content and functionality of your website. By strengthening your fundamentals in Magento development, you can develop the best solutions and take advantage of the growing market. This fast-paced tutorial will provide you with skills you need to successfully create themes, extensions, and solutions to Magento 2 projects. This book begins by setting up Magento 2 before gradually moving onto setting the basic options of the Sell System. You will take advantage of Search Engine Optimization aspects, create design and customize theme layout, develop new extensions, and adjust the Magento System to achieve great performance. By sequentially working through the steps in each chapter, you will quickly explore all the features of Magento 2 to create a great solution. With ample examples and a practical approach, this book will ensure your success with this astonishing e-commerce management system. Style and approach. This book would be a fast-paced tutorial guide that uses hands-on examples to developing new solutions for Magento e-commerce system. Each topic is explained sequentially in the process of creating a Magento solution, along with detailed explanations of the basic and advanced features of Magento 2. Computers

Blender 3D Incredible Machines Design, model, and texture complex mechanical objects in Blender About This Book: Develop realistic and awesome machines for your 3D projects and animation films; Gain the ability to look at a piece of machinery in real life and then recreate it in Blender; Develop a comprehensive skill set covering key aspects of mechanical modeling Who This Book Is For. This book is intended for consumers and hobbyists who are existing users of Blender 3D want to expand their capabilities by diving into machine modeling with Blender 3D. You are expected to have experience with basic Blender operations. What You Will Learn: Reacquaint yourself with Blender's modeling toolset; Practice fundamental skills that are applicable to a range of modeling projects; Know when and where to use various types of geometry—something that saves time in one instance will pose significant problems in another; Think ahead and plan your project out to significantly improve both quality and efficiency; Create models for freestyle use; Overcome challenging modeling problems; Create customized game models that can easily be exported to other formats. This is one of the most popular uses of Blender, and the results can be incorporated into game design!; Get comfortable with the start-to-finish process to create any type of hard surface model In Detail. Blender 3D is one of the top pieces of 3D animation software. Machine modeling is an essential aspect of war games, space games, racing games, and animated action films. As the Blender software grows more powerful and popular, there is a demand to take your modeling skills to the next level. This book will cover all the topics you need to create professional models and renders. This book will help you develop a comprehensive skill set that covers the key aspects of mechanical modeling. Through this book, you will create many types of projects, including a pistol, spacecraft, robot, and a racer. We start by making a Sci-fi pistol, creating its basic shape and adding details to it. Moving on, you’ll discover modeling techniques for larger objects such as a space craft and take a look at how different techniques are required for freestyle modeling. After this, we’ll create the basic shapes for the robot and combine the meshes to create unified objects. We'll assign materials and explore the various options for freestyle rendering. We’ll discuss techniques to build low-poly models, create a low-poly racer, and explain how they differ from the high poly models we created previously. By the end of this book, you will have mastered a workflow that you will be able to apply to your own creations. Style and approach. This is an easy-to-follow book that is based around four concrete projects. Each topic is explained sequentially in the process of creating a model, and detailed explanations of the basic and advanced features are also included. Computers

OpenGL Game Development By Example Design and code your own 2D and 3D games efficiently using OpenGL and C++ About This Book: Create 2D and 3D games completely, through a series of end-to-end game projects; Learn to render high performance 2D and 3D graphics using OpenGL; Implement a rudimentary game engine using step-by-step code Who This Book Is For. If you are a prospective game developer with some experience using C++, then this book is for you. Both prospective and experienced game programmers will find nuggets of wisdom and practical advice as they learn to code two full games using OpenGL, C++, and a host of related tools. What You Will Learn: Set up your development environment in Visual Studio using OpenGL; Use 2D and 3D coordinate systems; Implement an input system to handle the mouse and the keyboard; Create a state machine to handle complex changes in the game; Load, display, and manipulate both 2D and 3D graphics; Implement collision detection and basic physics; Discover the key components needed to complete a polished game; Handle audio files and implement sound effects and music In Detail. OpenGL is one of the most popular rendering SDKs used to develop games. OpenGL has been used to create everything from 3D masterpieces running on desktop computers to 2D puzzles running on mobile devices. You will learn to apply both 2D and 3D technologies to bring your game idea to life. There is a lot more to making a game than just drawing pictures and that is where this book is unique! It provides a complete tutorial on designing and coding games from the setup of the development environment to final credits screen, through the creation of a 2D and 3D game. The book starts off by showing you how to set up a development environment using Visual Studio, and create a code framework for your game. It then walks you through creation of two games-a 2D platform game called Roboracer 2D and a 3D first-person space shooter game-using OpenGL to render both 2D and 3D graphics using a 2D coordinate system. You'll create sprite classes, render sprites and animation, and navigate and control the characters. You will also learn how to implement input, use audio, and code basic collision and physics systems. From setting up the development environment to creating the final credits screen, the book will take you through the complete journey of creating a game engine that you can extend to create your own games. Style and approach. An easy-to-follow guide full of code examples to illustrate every concept and help you build a 2D and 3D game from scratch, while learning the key tools that surround a typical OpenGL project. Computers

The Foundations of EU Data Protection Law A timely and innovative examination of the EU data protection regime, this book challenges existing assumptions about data protection and expounds a clear vision for the future of this crucial and contentious area of law. Computers

Molecular Evolution The book focuses on molecular evolution and phylogenetics, dealing with the statistical methods of data analysis implemented in commonly-used computer software. Computers

Mathematical Underpinnings of Analytics A cutting edge graduate level book on the way the mathematical analytics of big data can add value and bring competitive advantage to consumer-facing industries. Computers

Cyber War versus Cyber Realities Cyber conflict is real, but is not changing the dynamics of international politics. In this study, the authors provide a realistic evaluation of the tactic in modern international interactions using a detailed examination of several famous cyber incidents and disputes in the last decade. Computers

Computer Science While the development of Information Technology has been obvious to all, the underpinning computer science has been less apparent. Subrata Dasgupta provides a thought-provoking introduction to the field and its core principles, considering computer science as a science of symbol processing. Computers

Drupal 8 Theming with Twig Master Drupal 8’s new Twig templating engine to create fun and fast websites with simple steps to help you move from concept to completion About This Book: Create beautiful responsive Drupal 8 websites using Twig; Quickly master theme administration, custom block layouts, views, and the Twig template structure; A step-by-step guide to the most common approaches in web design Who This Book Is For. This book is intended for front-end developers, designers, and anyone who is generally interested in learning all the new features of Drupal 8 theming. Discover what has changed from Drupal 7 to Drupal 8 and immerse yourself in the new Twig PHP templating engine. Familiarity with HTML5, CSS3, JavaScript, and the Drupal Admin interface would be helpful. Prior experience with setting up and configuring a standalone development environment is required as we will be working with PHP and MySQL. What You Will Learn: Navigate the Drupal 8 Admin interface; Build custom block layouts with reusable and fieldable blocks; Create subthemes based on the Bartik and Classy base themes; Construct a responsive theme with Twitter Bootstrap; Work with the new Twig PHP templating engine; Configure Drupal for Twig debugging; Enable preprocessing of Twig variables; Develop a theme from scratch following a step-by-step project outline In Detail. Drupal 8 is an open source content management system and powerful framework that helps deliver great websites to individuals and organizations, including non-profits, commercial, and government around the globe. This new release has been built on top of object-oriented PHP and includes more than a handful of improvements such as a better user experience, cleaner HTML5 markup, a new templating engine called Twig, multilingual capabilities, new configuration management, and effortless content authoring. Drupal 8 will quickly become the new standard for deploying content to both the web and mobile applications. However, with so many new changes, it can quickly become overwhelming knowing where to start and how to quickly. Starting from the bottom up, we will install, set up, and configure Drupal 8. We’ll navigate the Admin interface so you can learn how to work with core themes and create new custom block layouts. Walk through a real-world project to create a Twig theme from concept to completion while adopting best practices to implement CSS frameworks and JavaScript libraries. We will see just how quick and easy it is to create beautiful, responsive Drupal 8 websites while avoiding the common mistakes that many front-end developers make. Style and approach. Drupal 8 Theming with Twig is intended for front-end developers, designers, and anyone who is generally interested in learning all the new features of Drupal 8 theming. Discover what has changed from Drupal 7 to Drupal 8 and immerse yourself in the new Twig PHP templating engine. Familiarity with HTML5, CSS3, JavaScript, and the Drupal Admin interface would be helpful. Prior experience with setting up and configuring a standalone development environment is required as we will be working with PHP and MySQL. Computers

Learning PHP 7 Learn the art of PHP programming through this example-rich book filled to the brim with tutorials every PHP developer needs to know About This Book: Set up the PHP environment and get started with web programming; Leverage the potential of PHP for server-side programming, memory management, and object-oriented programming (OOP); This book is packed with real-life examples to help you implement the concepts as you learn Who This Book Is For. If you are a web developer or programmer who wants to create real-life web applications using PHP 7, or a beginner who wants to get started with PHP 7 programming, this book is for you. Prior knowledge of PHP, PHP 7, or programming is not mandatory. What You Will Learn: Set up a server on your machine with PHP; Use PHP syntax with the built-in server to create apps; Apply the OOP paradigm to PHP to write richer code; Use MySQL to manage data in your web applications; Create a web application from scratch using MVC; Add tests to your web application and write testable code; Use an existing PHP framework to build and manage your applications; Build REST APIs for your PHP applications; Test the behavior of web applications with Behat In Detail. PHP is a great language for building web applications. It is essentially a server-side scripting language that is also used for general purpose programming. PHP 7 is the latest version with a host of new features, and it provides major backwards-compatibility breaks. This book begins with the fundamentals of PHP programming by covering the basic concepts such as variables, functions, class, and objects. You will set up PHP server on your machine and learn to read and write procedural PHP code. After getting an understanding of OOP as a paradigm, you will execute MySQL queries on your database. Moving on, you will find out how to use MVC to create applications from scratch and add tests. Then, you will build REST APIs and perform behavioral tests on your applications. By the end of the book, you will have the skills required to read and write files, debug, test, and work with MySQL. Style and approach. This book begins with the basics that all PHP developers use every day and then dives deep into detailed concepts and tricks to help you speed through development. You will be able to learn the concepts by performing practical tasks and implementing them in your daily activities, all at your own pace. Computers

Extending Ansible Discover how to efficiently deploy and customize Ansible in the way your platform demands About This Book: Get the first book on the market that maximizes the functionalities of Ansible; Master the skill of extending Ansible by deep diving into its modules and plugins; Work through this step-by-step guide to customizing Ansible according to your requirements Who This Book Is For. This book is perfect for developers and administrators who are familiar with Ansible and Python programming, but have no knowledge of how to customize Ansible. What You Will Learn: Get a thorough understanding of Ansible modules; Find out everything about plugins that fit in the Ansible architecture; Get to grips with designing modules and handling errors; Work with data structures; Distribute Ansible extensions using PyPi and Git submodules; Get to know the various distribution methods of modules and plugins In Detail. Ansible is an IT automation tool that lets you manage your Infrastructure as a Code. It helps you deploy your applications and manage configurations, thus making life easier. Ansible, in most ways, is self sufficient to address most of your requirements. Ideally, standard modules, libraries, or plugins are used to automate a given IT platform. Customizing Ansible can be done by custom module and plugin development. This book shows you how to automate most of the tasks in your IT environment, thus minimizing the need to manually perform scheduled tasks and extend your Ansible implementation by developing customized modules and plugins. You’ll begin by getting an understanding of the fundamental aspects of extending the Ansible framework, such as custom functions and reusable modules. You’ll then progress to building custom plugins and extensions using the fundamental building blocks explained earlier. We’ll also show you how to automate some tasks using scripts. Finally, we’ll demonstrate how these extensions can be seamlessly integrated into existing Ansible installations and explain how to conduct unit testing on these extensions to ensure they work as desired. Style and approach. This book is a learning book on the fundamentals of Ansible framework and how it can be leveraged to extend it using the modules and plugins. Computers

Practical Foundations for Programming Languages This book unifies a broad range of programming language concepts under the framework of type systems and structural operational semantics. Computers

ReactJS by Example - Building Modern Web Applications with React Get up and running with ReactJS by developing five cutting-edge and responsive projects About This Book: Create pragmatic real-world applications while learning React and its modern developer tools; Build sustainable user interfaces by transforming data into components of UI; Learn how to generate reusable ReactJS components effectively Who This Book Is For. If you are a web developer and wish to learn ReactJS from scratch, then this book is tailor-made for you. Good understanding of Javascript, HTML, and CSS is expected. What You Will Learn: Create, reuse, and compose React components using JSX; Share data between various React components and techniques for data flow within a React app; Handle user interactions with the help of event handlers and dynamic components; Set up and use various next generation ES2015/ES6 features with React; Understand the performance and immutability features of React using React add-ons; Learn the techniques of Animation in React; Use data stores to store model-related data and information; Create a flux-based React application by using Reflux library In Detail. ReactJS is an open-source JavaScript library that brings the power of reactive programming to web applications and sites. It aims to address the challenges encountered in developing single-page applications, and is intended to help developers build large, easily scalable and changing web apps. Starting with a project on Open Library API, you will be introduced to React and JSX before moving on to learning about the life cycle of a React component. In the second project, building a multi-step wizard form, you will learn about composite dynamic components and perform DOM actions. You will also learn about building a fast search engine by exploring server-side rendering in the third project on a search engine application. Next, you will build a simple frontpage for an e-commerce app in the fourth project by using data models and React add-ons. In the final project you will develop a complete social media tracker by using the flux way of defining React apps and know about the best practices and use cases with the help of ES6 and redux. By the end of this book, you will not only have a good understanding of ReactJS but will also have built your very own responsive frontend applications from scratch. Style and approach. An easy-to-follow program to learn ReactJS with the help of real world projects. Each topic is explained within the context of a project and provides plenty of tips and tricks for using ReactJS. Computers

Julia High Performance Design and develop high performing programs with Julia About This Book: Learn to code high reliability and high performance programs; Stand out from the crowd by developing code that runs faster than your peers’ codes; This book is intended for developers who are interested in high performance technical programming. Who This Book Is For. This book is for beginner and intermediate Julia programmers who are interested in high performance technical computing. You will have a basic familiarity with Julia syntax, and have written some small programs in the language. What You Will Learn: Discover the secrets behind Julia’s speed; Get a sense of the possibilities and limitations of Julia’s performance; Analyze the performance of Julia programs; Measure the time and memory taken by Julia programs; Create fast machine code using Julia’s type information; Define and call functions without compromising Julia’s performance; Understand number types in Julia; Use Julia arrays to write high performance code; Get an overview of Julia’s distributed computing capabilities In Detail. Julia is a high performance, high-level dynamic language designed to address the requirements of high-level numerical and scientific computing. Julia brings solutions to the complexities faced by developers while developing elegant and high performing code. Julia High Performance will take you on a journey to understand the performance characteristics of your Julia programs, and enables you to utilize the promise of near C levels of performance in Julia. You will learn to analyze and measure the performance of Julia code, understand how to avoid bottlenecks, and design your program for the highest possible performance. In this book, you will also see how Julia uses type information to achieve its performance goals, and how to use multuple dispatch to help the compiler to emit high performance machine code. Numbers and their arrays are obviously the key structures in scientific computing - you will see how Julia’s design makes them fast. The last chapter will give you a taste of Julia’s distributed computing capabilities. Style and approach. This is a hands-on manual that will give you good explanations about the important concepts related to Julia programming. Computers

Quantum Monte Carlo Methods The first textbook to provide a pedagogical examination of the major algorithms used in quantum Monte Carlo simulations. Computers

Gynaecology Provides evidence-based guidelines in schematic flowcharts, representing a step-by-step method of solving clinical problems in gynaecology. Computers

Instant Recovery with Write-Ahead Logging Traditional theory and practice of write-ahead logging and of database recovery focus on three failure classes: transaction failures (typically due to deadlocks) resolved by transaction rollback; system failures (typically power or software faults) resolved by restart with log analysis, "redo," and "undo" phases; and media failures (typically hardware faults) resolved by restore operations that combine multiple types of backups and log replay. The recent addition of single-page failures and single-page recovery has opened new opportunities far beyond the original aim of immediate, lossless repair of single-page wear-out in novel or traditional storage hardware. In the contexts of system and media failures, efficient single-page recovery enables on-demand incremental "redo" and "undo" as part of system restart or media restore operations. This can give the illusion of practically instantaneous restart and restore: instant restart permits processing new queries and updates seconds after system reboot and instant restore permits resuming queries and updates on empty replacement media as if those were already fully recovered. In the context of node and network failures, instant restart and instant restore combine to enable practically instant failover from a failing database node to one holding merely an out-of-date backup and a log archive, yet without loss of data, updates, or transactional integrity. In addition to these instant recovery techniques, the discussion introduces self-repairing indexes and much faster offline restore operations, which impose no slowdown in backup operations and hardly any slowdown in log archiving operations. The new restore techniques also render differential and incremental backups obsolete, complete backup commands on a database server practically instantly, and even permit taking full up-to-date backups without imposing any load on the database server. Compared to the first version of this book, this second edition adds sections on applications of single-page repair, instant restart, single-pass restore, and instant restore. Moreover, it adds sections on instant failover among nodes in a cluster, applications of instant failover, recovery for file systems and data files, and the performance of instant restart and instant restore. Computers

Sitecore Cookbook for Developers Over 70 incredibly effective and practical recipes to get you up and running with Sitecore development About This Book: Build enterprise-level rich websites quickly and deliver the best possible content management to your website; Get maximum usage of functionalities like different user interfaces, workflow, publishing, search, analytics, etc and learn different rendering techniques using presentation components for data bindings, events, handlers, schedulers, media, etc.; Add a surprising amount of functionality just by customizing the Sitecore architecture through the best practices contained in this book Who This Book Is For. If you are a Sitecore developer or a programmer who wants to expand your Sitecore development skills, this book is ideal for you. You will need working knowledge of ASP.NET WebForms or MVC, as well as HTML, and a basic knowledge of Sitecore installation. What You Will Learn: Create, access, and personalize your website content using different Sitecore presentation components; Learn how to extend the presentation components to fulfill some real-life requiremnts such as improving the site’s performance, generating Rss feeds and so on; Work with multiple websites on a single Sitecore instance and create multilingual websites; Customize the Sitecore interfaces as per your business requirements to provide easier and error-free user interface to content authors to save time and improve accuracy; Customize the Sitecore backend architecture as per your business needs; Automate tasks and achieve scalability by altering the development and configuration settings; Integrate external systems with Sitecore to import or export content and secure user interactions; Integrate the advanced features of analytics and personalization, to get the best possible customer experience and generate its reports In Detail. This book will get you started on building rich websites, and customizing user interfaces by creating content management applications quickly. It will give you an insight into web designs and how to customize the Sitecore architecture as per your website's requirements using best practices. Packed with over 70 recipes to help you achieve and solve real-world common tasks, requirements, and the problems of content management, content delivery, and publishing instance environments. It also presents recipes on Sitecore’s backend processes of customizing pipelines, creating custom event handler and media handler, setting hooks to interpret foreign language URL and more. Other topics covered include creating a workflow action, publishing sublayouts and media files, securing your environment by customizing user profiles and access rights, boosting search capabilities, optimising performance, scalability and high-availability of Sitecore instances and much more. By the end of this book, you will have be able to add virtually limitless features to your websites by developing and deploying Sitecore efficiently. Style and approach. This easy-to-follow guide is full of hands-on recipes on real-world development tasks to improve your existing Sitecore system. Each topic is presented with its benefits and detailed steps to achieve it through well-explained code and images. Computers

Interacting Electrons This book sets out modern methods of computing properties of materials, including essential theoretical background, computational approaches, practical guidelines and instructive applications. Computers

Multilayer Social Networks This book unifies and consolidates methods for analyzing multilayer networks arising from the social and physical sciences and computing. Computers

Practical Mobile Forensics A hands-on guide to mastering mobile forensics for the iOS, Android, and the Windows Phone platforms About This Book: Get to grips with the basics of mobile forensics and the various forensic approaches; Retrieve and analyze the data stored on mobile devices and on the cloud; A practical guide to leverage the power of mobile forensics on the popular mobile platforms with lots of tips, tricks and caveats Who This Book Is For. This book is for forensics professionals who are eager to widen their forensics skillset to mobile forensics and acquire data from mobile devices. What You Will Learn: Discover the new features in practical mobile forensics; Understand the architecture and security mechanisms present in iOS and Android platforms; Identify sensitive files on the iOS and Android platforms; Set up the forensic environment; Extract data on the iOS and Android platforms; Recover data on the iOS and Android platforms; Understand the forensics of Windows devices; Explore various third-party application techniques and data recovery techniques In Detail. Mobile phone forensics is the science of retrieving data from a mobile phone under forensically sound conditions. This book is an update to Practical Mobile Forensics and it delves into the concepts of mobile forensics and its importance in today's world. We will deep dive into mobile forensics techniques in iOS 8 - 9.2, Android 4.4 - 6, and Windows Phone devices. We will demonstrate the latest open source and commercial mobile forensics tools, enabling you to analyze and retrieve data effectively. You will learn how to introspect and retrieve data from cloud, and document and prepare reports for your investigations. By the end of this book, you will have mastered the current operating systems and techniques so you can recover data from mobile devices by leveraging open source solutions. Style and approach. This book takes a very practical approach and depicts real-life mobile forensics scenarios with lots of tips and tricks to help acquire the required forensics skillset for various mobile platforms. Computers

Moodle 3.x Teaching Techniques Creative ways to build powerful and effective online courses with Moodle 3.0 About This Book: Unleash your teaching talents and develop exciting, dynamic courses; Put together effective online courses that motivate students from all backgrounds, generations, and learning styles; Find powerful insights into developing more successful and educational courses Who This Book Is For. If you want to unleash your teaching talents and develop exciting, dynamic courses that really get students moving forward, then this book is for you. Experienced Moodlers who want to upgrade to Moodle 3.0 will find powerful insights into developing more successful and educational courses. What You Will Learn: Create a dynamic learning environment using different techniques; Motivate your students to collaborate and demonstrate what they are learning and to create projects together; Develop materials you can re-use in your future courses; Create online workshops and galleries for your students to make presentations about what they have learned; Engage your students in team work that helps them connect course content with their experiences and prior learning; Develop high-quality courses that will last to create a personal inventory you can use and re-use In Detail. Moodle, the world's most popular, free open-source Learning Management System (LMS) has released several new features and enhancements in its latest 3.0 release. More and more colleges, universities, and training providers are using Moodle, which has helped revolutionize e-learning with its flexible, reusable platform and components. This book brings together step-by-step, easy-to-follow instructions to leverage the full power of Moodle 3 to build highly interactive and engaging courses that run on a wide range of platforms including mobile and cloud. Beginning with developing an effective online course, you will write learning outcomes that align with Bloom's taxonomy and list the kinds of instructional materials that will work given one's goal. You will gradually move on to setting up different types of forums for discussions and incorporating multi-media from cloud-base sources. You will then focus on developing effective timed tests, self-scoring quizzes while organizing the content, building different lessons, and incorporating assessments. Lastly, you will dive into more advanced topics such as creating interactive templates for a full course by focussing on creating each element and create workshops and portfolios which encourage engagement and collaboration Style and approach. With clear, step-by-step instructions, this book helps you develop good, solid, dynamic courses that will last by making sure that your instructional design is robust, and that they are built around satisfying learning objectives and course outcomes. Packed with plenty of screenshots and practical examples, you will get solid understanding of developing courses that are a success in the real world. Computers

RESTful Web API Design with Node.js Design and implement efficient RESTful solutions with this practical hands-on guide About This Book: Create a fully featured RESTful API solution from scratch.; Learn how to leverage Node.JS, Express, MongoDB and NoSQL datastores to give an extra edge to your REST API design.; Use this practical guide to integrate MongoDB in your Node.js application. Who This Book Is For. The ideal target audience for this book is web developers who have some experience with RESTful services. Familiarity with basic JavaScript programming techniques is required. No prior experience with Node.JS or Express.js is required. What You Will Learn: Install, develop, and test your own Node.js user modules; Comprehend the differences between an HTTP and a RESTful application; Optimize RESTful service URI routing with best practices; Eliminate third-party dependencies in your tests with mocking; Learn about NoSQL data stores and integrate MongoDB in your Node.js application with Mongoose; Secure your services with NoSQL database integration within Node.js applications; Enrich your development skills to create scalable, server-side, RESTful applications based on the Node.js platform In Detail. In this era of cloud computing, every data provisioning solution is built in a scalable and fail-safe way. Thus, when building RESTful services, the right choice for the underlying platform is vital. Node.js, with its asynchronous, event-driven architecture, is exactly the right choice to build RESTful APIs. This book will help you enrich your development skills to create scalable, server-side, RESTful applications based on the Node.js platform. Starting with the fundamentals of REST, you will understand why RESTful web services are better data provisioning solution than other technologies. You will start setting up a development environment by installing Node.js, Express.js, and other modules. Next, you will write a simple HTTP request handler and create and test Node.js modules using automated tests and mock objects. You will then have to choose the most appropriate data storage type, having options between a key/value or document data store, and also you will implement automated tests for it. This module will evolve chapter by chapter until it turns into a full-fledged and secure Restful service. Style and approach. Create state of the art RESTful API solutions leveraging Node.JS 4.x. Computers

Practical Digital Forensics Get started with the art and science of digital forensics with this practical, hands-on guide! About This Book: Champion the skills of digital forensics by understanding the nature of recovering and preserving digital information which is essential for legal or disciplinary proceedings; Explore new and promising forensic processes and tools based on 'disruptive technology' to regain control of caseloads.; Richard Boddington, with 10+ years of digital forensics, demonstrates real life scenarios with a pragmatic approach Who This Book Is For. This book is for anyone who wants to get into the field of digital forensics. Prior knowledge of programming languages (any) will be of great help, but not a compulsory prerequisite. What You Will Learn: Gain familiarity with a range of different digital devices and operating and application systems that store digital evidence.; Appreciate and understand the function and capability of forensic processes and tools to locate and recover digital evidence.; Develop an understanding of the critical importance of recovering digital evidence in pristine condition and ensuring its safe handling from seizure to tendering it in evidence in court.; Recognise the attributes of digital evidence and where it may be hidden and is often located on a range of digital devices.; Understand the importance and challenge of digital evidence analysis and how it can assist investigations and court cases.; Explore emerging technologies and processes that empower forensic practitioners and other stakeholders to harness digital evidence more effectively. In Detail. Digital Forensics is a methodology which includes using various tools, techniques, and programming language. This book will get you started with digital forensics and then follow on to preparing investigation plan and preparing toolkit for investigation. In this book you will explore new and promising forensic processes and tools based on ‘disruptive technology’ that offer experienced and budding practitioners the means to regain control of their caseloads. During the course of the book, you will get to know about the technical side of digital forensics and various tools that are needed to perform digital forensics. This book will begin with giving a quick insight into the nature of digital evidence, where it is located and how it can be recovered and forensically examined to assist investigators. This book will take you through a series of chapters that look at the nature and circumstances of digital forensic examinations and explains the processes of evidence recovery and preservation from a range of digital devices, including mobile phones, and other media. This book has a range of case studies and simulations will allow you to apply the knowledge of the theory gained to real-life situations. By the end of this book you will have gained a sound insight into digital forensics and its key components. Style and approach. The book takes the reader through a series of chapters that look at the nature and circumstances of digital forensic examinations and explains the processes of evidence recovery and preservation from a range of digital devices, including mobile phones, and other media. The mystery of digital forensics is swept aside and the reader will gain a quick insight into the nature of digital evidence, where it is located and how it can be recovered and forensically examined to assist investigators. Computers

Learning Pentaho CTools Acquire finesse with CTools features and build rich and custom analytics solutions using Pentaho About This Book: Learn everything you need to know to make the most of CTools; Create interactive and remarkable dashboards using the CTools; Understand how to use and create data visualizations that can make the difference; The author of our book works for Pentaho as a Senior Consultant; Acts as a follow-up to Packt's previously published products on Pentaho such as Pentaho Business Analytics Cookbook, Pentaho Analytics for MongoDB, Pentaho Data Integration Cookbook - Second Edition, and Pentaho Reporting [Video]; Our book is based on the latest version of Pentaho, that is, 6.0 Who This Book Is For. If you are a CTools developer and would like to expand your knowledge and create attractive dashboards and frameworks, this book is the go-to-guide for you. A basic knowledge of JavaScript and Cascading Style Sheets (CSS) is highly recommended. What You Will Learn: Install Community Tools on Pentaho; and understand the necessary concepts and considerations when creating an exciting dashboard design; Get data from many different Pentaho datasources and deliver it in different formats (CSV, XLS, XML, or JSON); Use the Community Data Access (CDA) as the data abstraction layer and understand the concepts in the Community Dashboard Framework (CDF); Create a Community Dashboard Editor (CDE) dashboard and make the most of the main components; Create and make use of widgets and use duplicate components to have data-driven sections on the dashboard; Customize and create interaction between all components, including charts, using the Community Charts Components; Create and embed dashboards in a better and new way; Create plugins and make use of parameters inside Pentaho without writing code In Detail. Pentaho and CTools are two of the fastest and most rapidly growing tools for practical solutions not found in any other tool available on the market. Using Pentaho allows you to build a complete analytics solution, and CTools brings an advanced flexibility to customizing them in a remarkable way. CTools provides its users with the ability to utilize Web technologies and data visualization concepts, and make the most of best practices to create a huge visual impact. The book starts with the basics of the framework and how to get data to your dashboards. We'll take you all the way through to create your custom and advanced dashboards that will create an effective visual impact and provide the best user experience. You will be given deep insights into the lifecycle of dashboards and the working of various components. Further, you will create a custom dashboard using the Community Dashboards Editor and use datasources to load data on the components. You will also create custom content using Query, the Freeform Addins Popup, and text components. Next, you will make use of widgets to create similar sections and duplicate components to reproduce other components on a dashboard. You will then learn to build a plugin without writing Java code, use Sparkl as a CPK plugin manager, and understand the application of deployment and version control to dashboard development. Finally, you will learn tips and tricks that can be very useful while embedding dashboards into other applications. This guide is an invaluable tutorial if you are planning to use custom and advanced dashboards among the solutions that you are building with Pentaho. Style and approach. This book is a pragmatic, easy-to-follow guide that provides theoretical concepts, ideas, and tricks to better understand the necessary theoretical concepts. It also provides you with a set of highly intriguing samples of dashboards with customized code within them that can be utilized for future projects. Computers

R Master the art of building analytical models using R About This Book: Load, wrangle, and analyze your data using the world's most powerful statistical programming language; Build and customize publication-quality visualizations of powerful and stunning R graphs; Develop key skills and techniques with R to create and customize data mining algorithms; Use R to optimize your trading strategy and build up your own risk management system; Discover how to build machine learning algorithms, prepare data, and dig deep into data prediction techniques with R Who This Book Is For. This course is for data scientist or quantitative analyst who are looking at learning R and take advantage of its powerful analytical design framework. It’s a seamless journey in becoming a full-stack R developer What You Will Learn: Describe and visualize the behavior of data and relationships between data; Gain a thorough understanding of statistical reasoning and sampling; Handle missing data gracefully using multiple imputation; Create diverse types of bar charts using the default R functions; Produce and customize density plots and histograms with lattice and ggplot2; Get to know the top classification algorithms written in R; Familiarize yourself with algorithms written in R for spatial data mining, text mining, and so on; Understand relationships between market factors and their impact on your portfolio; Harness the power of R to build machine learning algorithms with real-world data science applications; Learn specialized machine learning techniques for text mining, big data, and more In Detail. The R learning path created for you has five connected modules,which are a mini-course in their own right.As you complete each one, you'll have gained key skills and be ready for the material in the next module!. This course begins by looking at the Data Analysis with R module. This will help you navigate the R environment. You'll gain a thorough understanding of statistical reasoning and sampling. Finally, you'll be able to put best practices into effect to make your job easier and facilitate reproducibility. The second place to explore is R Graphs,which will help you leverage powerful default R graphics and utilize advanced graphics systems such as lattice and ggplot2, the grammar of graphics. Through inspecting large datasets using tableplot and stunning 3D visualizations, you will know how to produce, customize, and publish advanced visualizations using this popular and powerful framework. With the third module, Learning Data Mining with R, you will learn how to manipulate data with R using code snippets and be introduced to mining frequent patterns, association, and correlations while working with R programs. You will finish this module feeling confident in your ability to know which data mining algorithm to apply in any situation. The Mastering R for Quantitative Finance module pragmatically introduces both the quantitative finance concepts and their modeling in R, enabling you to build a tailor-made trading system on your own. By the end of the module, you will be well-versed with various financial techniques using R and will be able to place good bets while making financial decisions. Finally, we'll look at the Machine Learning with R module. With this module, you'll discover all the analytical tools you need to gain insights from complex data and learn how to choose the correct algorithm for your specific needs. You'll also learn to apply machine learning methods to deal with common tasks, including classification, prediction, forecasting, market analysis, and clustering. Style and approach. Learn data analysis, data visualization techniques, data mining, and machine learning all using R and also learn to build models in quantitative finance using this powerful language Computers

Cambridge IGCSE Computer Science Study and Revision Guide Providing guidance that helps students practice and troubleshoot their exam technique,these books send them into their exam with the confidence to aim for the best grades. - Enables students to avoid common misconceptions and mistakes by highlighting them throughout- Builds students' skills constructing and writing answers as they progress through a range of practice questions- Allows students to mark their own responses and easily identify areas for improvement using the answers in the back of the book- Helps students target their revision and focus on important concepts and skills with key objectives at the beginning of every chapter- Ensures that students maximise their time in the exam by including examiner's tops and suggestions on how to approach the questions This title has not been through the Cambridge International endorsement process. Computers

Big Crisis Data Social media is invaluable during crises like natural disasters, but difficult to analyze. This book shows how computer science can help. Computers

A First Course in Statistical Programming with R Learn to program in R from the experts with this new, color edition of Braun and Murdoch's bestselling textbook. Computers

Yocto for Raspberry Pi Create unique and amazing projects by using the powerful combination of Yocto and Raspberry Pi About This Book: Set up and configure the Yocto Project efficiently with Raspberry Pi; Deploy multimedia applications from existing Yocto/OE layers; An easy-to-follow guide to utilize your custom recipes on your Raspberry Pi Who This Book Is For. If you are a student or a developer of embedded software, embedded Linux engineer or embedded systems in competence with Raspberry Pi and want to discover the Yocto Project, then this book is for you. Experience with Yocto is not needed. What You Will Learn: Explore the basic concept of Yocto's build system and how it is organized in order to use it efficiently with Raspberry Pi; Generate your first image with Yocto for the Raspberry Pi; Understand how to customize your Linux kernel within the Yocto Project; Customize your image in order to integrate your own applications; Write your own recipes for your graphical applications; Integrate a custom layer for the Raspberry Pi In Detail. The Yocto Project is a Linux Foundation workgroup, which produces tools (SDK) and processes (configuration, compilation, installation) that will enable the creation of Linux distributions for embedded software, independent of the architecture of embedded software (Raspberry Pi, i.MX6, and so on). It is a powerful build system that allows you to master your personal or professional development. This book presents you with the configuration of the Yocto Framework for the Raspberry Pi, allowing you to create amazing and innovative projects using the Yocto/OpenEmbedded eco-system. It starts with the basic introduction of Yocto's build system, and takes you through the setup and deployment steps for Yocto. It then helps you to develop an understanding of Bitbake (the task scheduler), and learn how to create a basic recipe through a GPIO application example. You can then explore the different types of Yocto recipe elements (LICENSE, FILES, SRC_URI, and so on). Next, you will learn how to customize existing recipes in Yocto/OE layers and add layers to your custom environment (qt5 for example). Style and approach. A step by step guide covering the fundamentals to create amazing new projects with Raspberry Pi and Yocto. Computers

Text Data Management and Analysis Recent years have seen a dramatic growth of natural language text data, including web pages, news articles, scientific literature, emails, enterprise documents, and social media such as blog articles, forum posts, product reviews, and tweets. This has led to an increasing demand for powerful software tools to help people analyze and manage vast amounts of text data effectively and efficiently. Unlike data generated by a computer system or sensors, text data are usually generated directly by humans, and are accompanied by semantically rich content. As such, text data are especially valuable for discovering knowledge about human opinions and preferences, in addition to many other kinds of knowledge that we encode in text. In contrast to structured data, which conform to well-defined schemas (thus are relatively easy for computers to handle), text has less explicit structure, requiring computer processing toward understanding of the content encoded in text. The current technology of natural language processing has not yet reached a point to enable a computer to precisely understand natural language text, but a wide range of statistical and heuristic approaches to analysis and management of text data have been developed over the past few decades. They are usually very robust and can be applied to analyze and manage text data in any natural language, and about any topic. This book provides a systematic introduction to all these approaches, with an emphasis on covering the most useful knowledge and skills required to build a variety of practically useful text information systems. The focus is on text mining applications that can help users analyze patterns in text data to extract and reveal useful knowledge. Information retrieval systems, including search engines and recommender systems, are also covered as supporting technology for text mining applications. The book covers the major concepts, techniques, and ideas in text data mining and information retrieval from a practical viewpoint, and includes many hands-on exercises designed with a companion software toolkit (i.e., MeTA) to help readers learn how to apply techniques of text mining and information retrieval to real-world text data and how to experiment with and improve some of the algorithms for interesting application tasks. The book can be used as a textbook for a computer science undergraduate course or a reference book for practitioners working on relevant problems in analyzing and managing text data. Computers

Linked Lexical Knowledge Bases This book conveys the fundamentals of Linked Lexical Knowledge Bases (LLKB) and sheds light on their different aspects from various perspectives, focusing on their construction and use in natural language processing (NLP). It characterizes a wide range of both expert-based and collaboratively constructed lexical knowledge bases. Only basic familiarity with NLP is required and this book has been written for both students and researchers in NLP and related fields who are interested in knowledge-based approaches to language analysis and their applications. Lexical Knowledge Bases (LKBs) are indispensable in many areas of natural language processing, as they encode human knowledge of language in machine readable form, and as such, they are required as a reference when machines attempt to interpret natural language in accordance with human perception. In recent years, numerous research efforts have led to the insight that to make the best use of available knowledge, the orchestrated exploitation of different LKBs is necessary. This allows us to not only extend the range of covered words and senses, but also gives us the opportunity to obtain a richer knowledge representation when a particular meaning of a word is covered in more than one resource. Examples where such an orchestrated usage of LKBs proved beneficial include word sense disambiguation, semantic role labeling, semantic parsing, and text classification. This book presents different kinds of automatic, manual, and collaborative linkings between LKBs. A special chapter is devoted to the linking algorithms employing text-based, graph-based, and joint modeling methods. Following this, it presents a set of higher-level NLP tasks and algorithms, effectively utilizing the knowledge in LLKBs. Among them, you will find advanced methods, e.g., distant supervision, or continuous vector space models of knowledge bases (KB), that have become widely used at the time of this book's writing. Finally, multilingual applications of LLKB's, such as cross-lingual semantic relatedness and computer-aided translation are discussed, as well as tools and interfaces for exploring LLKBs, followed by conclusions and future research directions. Computers

Microsoft Identity Manager 2016 Handbook A complete handbook on Microsoft Identity Manager 2016 - from design considerations to operational best practices About This Book: Get to grips with the basics of identity management and get acquainted with the MIM components and functionalities; Discover the newly-introduced product features and how they can help your organization; A step-by-step guide to enhance your foundational skills in using Microsoft Identity Manager from those who have taught and supported large and small enterprise customers Who This Book Is For. If you are an architect or a developer who wants to deploy, manage, and operate Microsoft Identity Manager 2016, then this book is for you. This book will also help the technical decision makers who want to improve their knowledge of Microsoft Identity Manager 2016. A basic understanding of Microsoft-based infrastructure using Active Directory is expected. Identity management beginners and experts alike will be able to apply the examples and scenarios to solve real-world customer problems. What You Will Learn: Install MIM components; Find out about the MIM synchronization, its configuration settings, and advantages; Get to grips with the MIM service capabilities and develop custom activities; Use the MIM Portal to provision and manage an account; Mitigate access escalation and lateral movement risks using privileged access management; Configure client certificate management and its detailed permission model; Troubleshoot MIM components by enabling logging and reviewing logs; Back up and restore the MIM 2015 configuration; Discover more about periodic purging and the coding best practices In Detail. Microsoft Identity Manager 2016 is Microsoft’s solution to identity management. When fully installed, the product utilizes SQL, SharePoint, IIS, web services, the .NET Framework, and SCSM to name a few, allowing it to be customized to meet nearly every business requirement. The book is divided into 15 chapters and begins with an overview of the product, what it does, and what it does not do. To better understand the concepts in MIM, we introduce a fictitious company and their problems and goals, then build an identity solutions to fit those goals. Over the course of this book, we cover topics such as MIM installation and configuration, user and group management options, self-service solutions, role-based access control, reducing security threats, and finally operational troubleshooting and best practices. By the end of this book, you will have gained the necessary skills to deploy, manage and operate Microsoft Identity Manager 2016 to meet your business requirements and solve real-world customer problems. Style and approach. The concepts in the book are explained and illustrated with the help of screenshots as much as possible. We strive for readability and provide you with step-by-step instructions on the installation, configuration, and operation of the product. Throughout the book, you will be provided on-the-field knowledge that you won’t get from whitepapers and help files. Computers

Internet of Things with ESP8266 Build amazing Internet of Things projects using the ESP8266 Wi-Fi chip About This Book: Get to know the powerful and low cost ESP8266 and build interesting projects in the field of Internet of Things; Configure your ESP8266 to the cloud and explore the networkable modules that will be utilized in the IoT projects; This step-by-step guide teaches you the basics of IoT with ESP8266 and makes your life easier Who This Book Is For. This book is for those who want to build powerful and inexpensive IoT projects using the ESP8266 WiFi chip, including those who are new to IoT, or those who already have experience with other platforms such as Arduino. What You Will Learn: Control various devices from the cloud; Interact with web services, such as Twitter or Facebook; Make two ESP8266 boards communicate with each other via the cloud; Send notifications to users of the ESP8266, via email, text message, or push notifications; Build a physical device that indicates the current price of Bitcoin; Build a simple home automation system that can be controlled from the cloud; Create your own cloud platform to control ESP8266 devices In Detail. The Internet of Things (IoT) is the network of objects such as physical things embedded with electronics, software, sensors, and connectivity, enabling data exchange. ESP8266 is a low cost WiFi microcontroller chip that has the ability to empower IoT and helps the exchange of information among various connected objects. ESP8266 consists of networkable microcontroller modules, and with this low cost chip, IoT is booming. This book will help deepen your knowledge of the ESP8266 WiFi chip platform and get you building exciting projects. Kick-starting with an introduction to the ESP8266 chip, we will demonstrate how to build a simple LED using the ESP8266. You will then learn how to read, send, and monitor data from the cloud. Next, you’ll see how to control your devices remotely from anywhere in the world. Furthermore, you’ll get to know how to use the ESP8266 to interact with web services such as Twitter and Facebook. In order to make several ESP8266s interact and exchange data without the need for human intervention, you will be introduced to the concept of machine-to-machine communication. The latter part of the book focuses more on projects, including a door lock controlled from the cloud, building a physical Bitcoin ticker, and doing wireless gardening. You’ll learn how to build a cloud-based ESP8266 home automation system and a cloud-controlled ESP8266 robot. Finally, you’ll discover how to build your own cloud platform to control ESP8266 devices. With this book, you will be able to create and program Internet of Things projects using the ESP8266 WiFi chip. Style and approach. This is a step-by-step guide that provides great IOT projects with ESP8266. All the key concepts are explained details with the help of examples and demonstrations of the projects. Computers

R for Data Science Cookbook Over 100 hands-on recipes to effectively solve real-world data problems using the most popular R packages and techniques About This Book: Gain insight into how data scientists collect, process, analyze, and visualize data using some of the most popular R packages; Understand how to apply useful data analysis techniques in R for real-world applications; An easy-to-follow guide to make the life of data scientist easier with the problems faced while performing data analysis Who This Book Is For. This book is for those who are already familiar with the basic operation of R, but want to learn how to efficiently and effectively analyze real-world data problems using practical R packages. What You Will Learn: Get to know the functional characteristics of R language; Extract, transform, and load data from heterogeneous sources; Understand how easily R can confront probability and statistics problems; Get simple R instructions to quickly organize and manipulate large datasets; Create professional data visualizations and interactive reports; Predict user purchase behavior by adopting a classification approach; Implement data mining techniques to discover items that are frequently purchased together; Group similar text documents by using various clustering methods In Detail. This cookbook offers a range of data analysis samples in simple and straightforward R code, providing step-by-step resources and time-saving methods to help you solve data problems efficiently. The first section deals with how to create R functions to avoid the unnecessary duplication of code. You will learn how to prepare, process, and perform sophisticated ETL for heterogeneous data sources with R packages. An example of data manipulation is provided, illustrating how to use the "dplyr" and "data.table" packages to efficiently process larger data structures. We also focus on "ggplot2" and show you how to create advanced figures for data exploration. In addition, you will learn how to build an interactive report using the "ggvis" package. Later chapters offer insight into time series analysis on financial data, while there is detailed information on the hot topic of machine learning, including data classification, regression, clustering, association rule mining, and dimension reduction. By the end of this book, you will understand how to resolve issues and will be able to comfortably offer solutions to problems encountered while performing data analysis. Style and approach. This easy-to-follow guide is full of hands-on examples of data analysis with R. Each topic is fully explained beginning with the core concept, followed by step-by-step practical examples, and concluding with detailed explanations of each concept used. Computers

Intelligence Analysis as Discovery of Evidence, Hypotheses, and Arguments Using a flexible software system, this book teaches evidential and inferential issues used in drawing conclusions from masses of evidence. Computers

Programming in Haskell This extensively updated and expanded version of the best-selling first edition now covers recent and more advanced features of Haskell. Computers

Compact Data Structures This practical, applications-oriented book describes essential tools for efficiently handling massive amounts of data. Computers

Responsive Web Design with HTML5 and CSS3 Essentials Design and deliver an optimal user experience for all devices About This Book: Get to grips with the core functionality of RWD through examples; Discover how to make layouts, content and media flexible, and explore why a content-first approach is more effective; Maximize the performance of your web pages so that they work across all browsers and devices irrespective of the screen size Who This Book Is For. This book is for web designers who are familiar with HTML and CSS, and want to begin with responsive web design. Web development experience and knowledge of HTML5, CSS3 is assumed. What You Will Learn: Explore various layout options; Understand what can be achieved in the browser, without the use of third-party tools; Executing media queries to benefit responsive designs; Understand the basics of responsive workflow and boilerplate frameworks; Improve performance of responsive web design; Maintain compatibility across various browsers In Detail. Responsive web design (RWD) is a web design approach aimed at crafting sites to provide an optimal viewing and interaction experience—providing easy reading and navigation with minimum resizing, panning, and scrolling—and all of this across a wide range of devices from desktop computer monitors to mobile phones. Responsive web design is becoming more important as the amount of mobile traffic now accounts for more than half of the Internet’s total traffic. This book will give you in depth knowledge about the basics of responsive web design. You will embark on a journey of building effective responsive web pages that work across a range of devices, from mobile phones to smart TVs, with nothing more than standard markup and styling techniques. You'll begin by getting an understanding of what RWD is and its significance to the modern web. Building on the basics, you'll learn about layouts and media queries. Following this, we’ll dive into creating layouts using grid based templates. We’ll also cover the important topic of performance management, and discover how to tackle cross-browser challenges. Style and approach. This is a practical example-based book which will delve into various elements and benefits of a responsive web design. It will help you understand the essential skills needed to create responsive web sites and guide you through the basics of building responsive web pages for any device. The topics are a blend of theoretical and practical essentials which will assist you to explore more about responsive web design. Computers

Microsoft Office 365 – Exchange Online Implementation and Migration Plan and execute a successful Office 365 Exchange Online migration with ease About This Book: This book gives you the most up-to-date and accurate information available today on online migration with Microsoft Office 365; Discover the very best migration path for your small or enterprise network and avoid costly mistakes; Learn from seasoned professionals who migrate small businesses to multinational companies from around the world on a daily basis Who This Book Is For. If you are an appointed IT person or an IT administrator who is part of a large internal team in your organization, then this book is for you. If you are a small business owner, manager, or consultant, this book will also help you. Knowledge of Office 365 is not required. However, experience with Exchange Server and mail clients, and role and delegation concepts is required. What You Will Learn: Sign up for an Office 365 account and configure your e-mail domains; Migrate mailboxes from Exchange server, Google, and any other POP3 or IMAP based system in to Office 365; Configure a hybrid configuration by using Azure AD Connect to synchronize your on-premises Active Directory with Office 365; Deploy Active Directory Federation Services (AD FS) to enable Single sign on and streamline the login process for your users; Set up a hybrid Exchange configuration and host mailboxes locally or in the cloud and move mailboxes between the two with ease; Configure a public folder hybrid and share existing on-premises public folders with users hosted in Exchange online; Setup a hybrid Skype for Business (SFB) configuration and move users into SFB online; Configure a SharePoint configuration, allowing users to create and search content hosted on an existing SharePoint server as well as in SharePoint online In Detail. Organizations are migrating to the cloud to save money, become more efficient, and empower their users with the latest technology. Office 365 delivers all of this in a reliable, fast, and ever-expanding way, keeping you ahead of the competition. As the IT administrator of your network, you need to make the transition as painless as possible for your users. Learn everything you need to know and exactly what to do to ensure your Office 365 Exchange online migration is a success!. This guide gives you everything you need to develop a successful migration plan to move from Exchange, Google, POP3, and IMAP systems to Office 365 with ease. We start by providing an overview of the Office 365 plans available and how to make a decision on what plan fits your organization. We then dive into topics such as the Office 365 Admin Portal, integration options for professionals and small businesses, integration options for enterprises, preparing for a simple migration, performing a simple migration, and preparing for a hybrid deployment. Later in the book, we look at migration options for Skype for Business and SharePoint to further help you leverage the latest collaborative working technologies within your organization. Style and approach. This is a detailed yet easy to follow step-by-step guide to planning and executing a successful migration to Office 365. Computers

Learning Nagios Learn and monitor your entire IT infrastructure to ensure your systems, applications, services, and business function effectively. About This Book: Packed with tips, tricks and illustrations, the book will explain the configuration and monitoring concepts in a simplified manner; Experience the scalability and flexibility of Nagios in a very practical and easy-to-understand approach.; Unleash the power of Nagios Core and Nagios XI 5 to monitor and secure your infrastructure with ease. Who This Book Is For. This book is targeted at System Administrators, both, who have no prior knowledge of Nagios as well as readers experienced with it. It not only covers the basics of Nagios but also the advanced features. What You Will Learn: Set up and use the built-in Nagios web interface; Upskill the additional interfaces available for Nagios to monitor your IT infrastructure; Learn how to perform various checks using both, Nagios standard plugins and third-party plugins; Explore the working of notifications and events in Nagios; Familiarize yourself with SNMP and use it for monitoring devices such as routers, switches, modems and printers; Discover how can be Nagios can be customized and tailored to your needs; Get to know more about the entreprise version of Nagios, Nagios XI In Detail. Nagios, a powerful and widely used IT monitoring and management software for problem -solving. It detects problems related to your organizations infrastructure and helps in resolving the issue before it impacts the business. Following the success of the previous edition, this book will continue to help you monitor the status of network devices and also notify the system administrators of network problems. Starting with the fundamentals, the book will teach you how to install and configure Nagios for your environment. The book helps you learn how to end downtimes, adding comments and generating reports using the built-in Web interface of Nagios. Moving on, you will be introduced to the third-party web interfaces and applications for checking the status and report specific information. As you progress further in Learning Nagios, you will focus on the standard set of Nagios plugins and also focus on teach you how to efficiently manage large configurations and using templates. Once you are up to speed with this, you will get to know the concept and working of notifications and events in Nagios. The book will then uncover the concept of passive check and shows how to use NRDP (Nagios Remote Data Processor). The focus then shifts to how Nagios checks can be run on remote machines and SNMP (Simple Network Management Protocol) can be used from Nagios. Lastly, the book will demonstrate how to extend Nagios by creating custom check commands, custom ways of notifying users and showing how passive checks and NRDP can be used to integrate your solutions with Nagios. By the end of the book, you will be a competent system administrator who could monitor mid-size businesses or even large scale enterprises. Style and approach. This will be a practical learning guide for system administrators which will teach them everything about Nagios along with implementing it for your organization and then ending with securing it. Computers

C++ Windows Programming Develop real-world applications in Windows About This Book: Create diverse applications featuring the versatility of Small Windows C++ library; Learn about object-oriented programming in Windows and how to develop a large object-oriented class library in C++; Understand how to tackle application-specific problems along with acquiring a deep understanding of the workings of Windows architecture Who This Book Is For. This book is for application developers who want a head-first approach into Windows programming. It will teach you how to develop an object-oriented class library in C++ and enhanced applications in Windows. Basic knowledge of C++ and the object-oriented framework is assumed to get the most out of this book. What You Will Learn: Develop advanced real-world applications in Windows; Design and implement a graphical object-oriented class library in C++; Get to grips with the workings of the integral aspects of the Win32 API, such as mouse input, drawing, cut-and-paste, file handling, and drop files; Identify general problems when developing graphical applications as well as specific problems regarding drawing, spreadsheet, and word processing applications; Implement classes, functions, and macros of the object-oriented class library developed in the book and how we implement its functionality by calling functions and macros in the Win32 API In Detail. It is critical that modern developers have the right tools to build practical, user-friendly, and efficient applications in order to compete in today’s market. Through hands-on guidance, this book illustrates and demonstrates C++ best practices and the Small Windows object-oriented class library to ease your development of interactive Windows applications. Begin with a focus on high level application development using Small Windows. Learn how to build four real-world applications which focus on the general problems faced when developing graphical applications. Get essential troubleshooting guidance on drawing, spreadsheet, and word processing applications. Finally finish up with a deep dive into the workings of the Small Windows class library, which will give you all the insights you need to build your own object-oriented class library in C++. Style and approach. This book takes a tutorial-style approach that will demonstrate the features of a C++ object-oriented library by developing interactive Windows applications. Computers

Artificial Intelligence Over the coming decades, Artificial Intelligence will profoundly impact the way we work and live. Whose interests should such systems serve? What limits should we place on their use? This book is a succinct introduction to the complex social, ethical, legal, and economic issues raised by the emergence of intelligent machines. Computers

Mastering Unity Shaders and Effects Harness the power of Unity 5 tools to write shaders and create stunning effects for next generation games About This Book: Leverage the power of Unity 5 compatible shaders to create a variety of realistic surfaces; Create amazing visual effects for your Unity 5.x games by blending advanced post-processing techniques and lighting effects; Add that extra visual edge to your games by learning pro level techniques Who This Book Is For. This book is for users who are familiar with creating Unity projects and are looking for the next step to create stunning high-end visuals in their game project using the latest tools and features. You are expected to understand the creation of basic Unity projects, game object types, and scene navigation. You will need some basic programming experience in C# or JavaScript. What You Will Learn: Build your own custom shaders to suit a variety of organic and inorganic surfaces; Create amazing visual effects using Unity 5's improved toolset; Compare the advantages of Metallic and Specular workflows in Unity's Physically Based Lighting System; Take your Unity 5 project to the next level with advanced real-time and baked lighting methods; Design powerful particle effects; Find out how shaders, materials, and scripts work together within the Unity framework; Develop high-end and optimized game visuals suitable for mobile devices and other platforms In Detail. With the inclusion of Physically Based Shading and the Standard Shader, Unity has changed the game for independent and large scale developers alike. Never before has it been so easy to create startling high quality visuals in games and other interactive projects. This book will give you a solid understanding of the interaction of shaders, lighting and effects in Unity 5, and give you some great ideas for how you can maximize the visual impact of your own games for PC, mobile and other platforms. In the sequence of chapters you will find solutions to some of the major challenges to the creation of responsive and realistic looking games. As you work on example scenes, you will get to know the syntax of ShaderLab and CG languages, creating simple and complex shader solutions for a variety of different surface effects. You will see how Unity’s responsive lighting solutions can be harnessed to build immersive and appealing game experiences. Style and approach. This is the most up-to-date resource on creating amazing visual effects for your Unity 5.x games. With the perfect mix of advanced techniques and their illustrations in real-world examples, this is the most comprehensive advanced guide on Unity shaders and effects you’ll find. Computers

Learning Tableau 10 Learn how to create effective data visualizations with Tableau and unlock a smarter approach to business analytics. It might just transform your organization About This Book: Create stylish visualizations and dashboards that explain complexity with clarity; Learn effective data storytelling to transform how your business uses ideas and makes decisions; Explore all the new features in Tableau 10 and start to redefine what business analytics means to your organization Who This Book Is For. Got data? Not sure what to make of it? This is the guide for you - whether you’ve been working with Tableau for years or are just beginning your adventure into business analytics. What You Will Learn: Find out how to build effective visualizations and dashboards; Prepare and clean your data so you can be sure Tableau is finding answers to your questions - not raising more problems; Discover how to create advanced visualizations that explain complexity with clarity and style; Dig deeper into your data with clustering and distribution models that allow you to analyze trends and make forecasts; Learn how to use data storytelling to aid decision-making and strategy; Share dashboards and visualizations to cultivate a culture where data is available and valued In Detail. Tableau has for some time been one of the most popular Business Intelligence and data visualization tools available. Why? Because, quite simply, it’s a tool that’s responsive to the needs of modern businesses. But it’s most effective when you know how to get what you want from it - it might make your business intelligent, but it isn’t going to make you intelligent.... We’ll make sure you’re well prepared to take full advantage of Tableau 10’s new features. Whether you’re an experienced data analyst that wants to explore 2016’s new Tableau, or you’re a beginner that wants to expand their skillset and bring a more professional and sharper approach to their organization, we’ve got you covered. Beginning with the fundamentals, such as data preparation, you’ll soon learn how to build and customize your own data visualizations and dashboards, essential for high-level visibility and effective data storytelling. You’ll also find out how to so trend analysis and forecasting using clustering and distribution models to inform your analytics. But it’s not just about you - when it comes to data it’s all about availability and access. That’s why we’ll show you how to share your Tableau visualizations. It’s only once insights are shared and communicated that you - and your organization - will start making smarter and informed decisions. And really, that’s exactly what this guide is for. Style and approach. Practical yet comprehensive, this Tableau guide takes you from the fundamentals of the tool before diving deeper into creating advanced visualizations. Covering the latest features found in Tableau 10, this might be the guide that transforms your organization. Computers

Mastering Metasploit Take your penetration testing and IT security skills to a whole new level with the secrets of Metasploit About This Book: Gain the skills to carry out penetration testing in complex and highly-secured environments; Become a master using the Metasploit framework, develop exploits, and generate modules for a variety of real-world scenarios; Get this completely updated edition with new useful methods and techniques to make your network robust and resilient Who This Book Is For. This book is a hands-on guide to penetration testing using Metasploit and covers its complete development. It shows a number of techniques and methodologies that will help you master the Metasploit framework and explore approaches to carrying out advanced penetration testing in highly secured environments. What You Will Learn: Develop advanced and sophisticated auxiliary modules; Port exploits from PERL, Python, and many more programming languages; Test services such as databases, SCADA, and many more; Attack the client side with highly advanced techniques; Test mobile and tablet devices with Metasploit; Perform social engineering with Metasploit; Simulate attacks on web servers and systems with Armitage GUI; Script attacks in Armitage using CORTANA scripting In Detail. Metasploit is a popular penetration testing framework that has one of the largest exploit databases around. This book will show you exactly how to prepare yourself against the attacks you will face every day by simulating real-world possibilities. We start by reminding you about the basic functionalities of Metasploit and its use in the most traditional ways. You’ll get to know about the basics of programming Metasploit modules as a refresher, and then dive into carrying out exploitation as well building and porting exploits of various kinds in Metasploit. In the next section, you’ll develop the ability to perform testing on various services such as SCADA, databases, IoT, mobile, tablets, and many more services. After this training, we jump into real-world sophisticated scenarios where performing penetration tests are a challenge. With real-life case studies, we take you on a journey through client-side attacks using Metasploit and various scripts built on the Metasploit framework. By the end of the book, you will be trained specifically on time-saving techniques using Metasploit. Style and approach. This is a step-by-step guide that provides great Metasploit framework methodologies. All the key concepts are explained details with the help of examples and demonstrations that will help you understand everything you need to know about Metasploit. Computers

Teaching with Google Classroom Put Google Classroom to work while teaching your students and make your life easier About This Book: This is the first book to guide educators step by step through teaching with Google Classroom; It’s focused on you, your students, and providing great learning experiences easily; It’s easy to follow, with everything you need to get started and keep going even if you’re not a technology fan Who This Book Is For. This is a book for educators who want to use Google Classroom to teach better. It’s not for geeks. There are rich examples, clear instructions, and enlightening explanations to help you put this platform to work. What You Will Learn: Create a Google Classroom and add customized information for each individual class; Add students to a Google Classroom; Send announcements and questions to students; Create, distribute, collect, and grade assignments through Google Classroom; Add events to and share a Google Classroom’s calendar with parents to track a student's progress; Reuse posts, archive classrooms, and perform other administrative tasks in Google Classroom; Use Google Docs Add-ons, and Google Chrome Webstore Apps and Extensions to enhance assignments; Set up Google Classroom’s mobile app In Detail. Google Classroom helps teachers bring their work online. According to Google Trends, it’s already bigger than Moodle after barely a year in the wild. This book is a complete start-to-finish guide for teachers using Google Classroom for the first time. It explains what Google Classroom is, what it can do, how to set it up, and how to use it to enhance student learning while making your life as a teacher easier. It shows you how to place resources and activities online, gather assignments, and develop group and individual activities. It’s not just a manual, you’ll also discover inspiring, easy ways to put Google Classroom to work for you and your class. Style and approach. This is a step-by-step guide to using Google Classroom, the rapidly emerging platform for education, effectively. Computers

Xamarin Blueprints Leverage the power of Xamarin to create stunning cross-platform and native apps About This Book: Helps you get a clear practical understanding of creating professional-grade apps with Xamarin; Covers Xamarin.Forms, Xamarin Android, and Xamarin iOS; If you want to transform yourself from an amateur mobile developer into a professional app developer across multiple platforms, then this is the ideal book for you Who This Book Is For. If you are a mobile developer looking to create interesting and fully featured apps for different platforms, then this book is the ideal solution for you. A basic knowledge of Xamarin and C# programming is assumed What You Will Learn: Discover eight different ways to create your own Xamarin applications; Improve app performance by using SQLite for data-intensive applications; Set up a simple web service to feed JSON data into mobile applications; Store files locally with Xamarin.Forms using dependency services; Use Xamarin extension libraries to create effective applications with less coding In Detail. Do you want to create powerful, efficient, and independent apps from scratch that will leverage the Xamarin framework and code with C#? Well, look no further; you’ve come to the right place!. This is a learn-as-you-build practical guide to building eight full-fledged applications using Xamarin.Forms, Xamarin Android, and Xamarin iOS. Each chapter includes a project, takes you through the process of building applications (such as a gallery Application, a text-to-speech service app, a GPS locator app, and a stock market app), and will show you how to deploy the application’s source code to a Google Cloud Source Repository. Other practical projects include a chat and a media-editing app, as well as other examples fit to adorn any developer’s utility belt. In the course of building applications, this book will teach you how to design and prototype professional-grade applications implementing performance and security considerations. Style and approach. A project-based approach that will solve all your needs when it comes to creating native Android, iOS, and cross-platform apps efficiently and effectively. Computers

PHP 7 Use new features of PHP 7 to solve practical, real-world problems faced by PHP developers like yourself every day. About This Book: This course covers the new features of version 7.x, best practices for server-side programming, and MVC frameworks; Leverage the potential of PHP for server-side programming, memory management, and Object-Oriented Programming to improve your programming productivity; This course also illustrates the development of a complete modular application using PHP 7 in detail Who This Book Is For. If you are an aspiring web developer, mobile developer, or back-end programmer, who has basic experience in PHP programming and wants to develop performance-critical applications, then this course is for you. It will take your PHP programming skills to next level. What You Will Learn: Solve practical real-world programming problems using PHP 7; Discover where and when PHP 5 code needs to be re-written to avoid backwards-compatibility breaks; Use advanced PHP 7 features such as the Abstract Syntax Tree, Uniform Variable Syntax, Scalar Type Hints, Generator Delegation, Anonymous Classes, and the Context Sensitive Lexer; Set up a high performance development and production environment for PHP 7; Discover new OOP features in PHP 7 to achieve high performance; Discover the new features of PHP 7 that are relevant to modular application development; Explore the ins and outs of the Symfony framework; Build a set of modules based on the Symfony framework that comprise a simple web shop app In Detail. PHP is a great language for developing web applications. It is essentially a server-side scripting language. PHP 7 is the latest version, providing major backward-compatibility breaks and focusing on improved performance and speed. This course follows a learning path which is divided into three modules. Each module is a mini course in its own right, taking your basic PHP programing skills to the next level by showing you intermediate to advanced PHP techniques with a focus on PHP 7. This way, get you equipped with the tools and skills required to develop professional and efficient applications for your websites and enterprises. The first module of the book is a programming cookbook that consists over 80 recipes! Each recipe is designed to solve practical, real-world problems faced by PHP developers like yourself every day. This course also covers new ways of writing PHP code made possible only in version 7. The second module of the course is designed to improve the performance and productivity of your application. We’ll introduce you to the concepts of Object-Oriented Programming (OOP) in PHP 7, then shed some light on how to improve the performance of your PHP 7 applications and database. Throughout this module you will be introduced to benchmarking tools. With all important concepts of PHP covered up you will move on to third module. In this module you will gain a deep insight into the modular programming paradigm and how to achieve modularity in your PHP code. Modular design techniques help you build readable, manageable, reusable, and more efficient codes. PHP 7, which is a popular open source scripting language, is used to build modular functions for your software. This Learning Path combines some of the best that Packt has to offer in one complete, curated package. It includes content from the following Packt products: PHP 7 Programming Cookbook, Doug Bierer; Learning PHP 7 High Performance, Altaf Hussain; Modular Programming with PHP 7, Branko Ajzele Style and approach. This book takes a practical, step-by-step approach with real-world examples that serve as building blocks for your application development and guide you through improving the quality of your code. Computers

CentOS 7 Server Deployment Cookbook Deploy and manage today's essential services on an enterprise-class, open operating system About This Book: Configure and manage Linux servers in varying scenarios and for a range of business requirements; Explore the up-to-date features of CentOS using real-world scenarios; See practical and extensive recipes to deploy and manage CentOS Who This Book Is For. This book is for Linux professionals with basic Unix/Linux functionality experience, perhaps even having set up a server before, who want to advance their knowledge in administering various services. What You Will Learn: See how to deploy CentOS easily and painlessly, even in multi-server environments; Configure various methods of remote access to the server so you don’t always have to be in the data center; Make changes to the default configuration of many services to harden them and increase the security of the system; Learn to manage DNS, emails and web servers; Protect yourself from threats by monitoring and logging network intrusion and system intrusion attempts, rootkits, and viruses; Take advantage of today’s powerful hardware by running multiple systems using virtualization In Detail. CentOS is derived from Red Hat Enterprise Linux (RHEL) sources and is widely used as a Linux server. This book will help you to better configure and manage Linux servers in varying scenarios and business requirements. Starting with installing CentOS, this book will walk you through the networking aspects of CentOS. You will then learn how to manage users and their permissions, software installs, disks, filesystems, and so on. You’ll then see how to secure connection to remotely access a desktop and work with databases. Toward the end, you will find out how to manage DNS, e-mails, web servers, and more. You will also learn to detect threats by monitoring network intrusion. Finally, the book will cover virtualization techniques that will help you make the most of CentOS. Style and approach. This easy-to-read cookbook is filled with practical recipes. Hands-on, task-based exercises will present you with real-world solutions to deploy and manage CentOS in varying business scenarios. Computers

PHP 7 Programming Blueprints Learn how to exploit the impressive power of PHP 7 with this collection of practical project blueprints - begin building better applications for the web today! About This Book: Don’t just learn PHP 7 - follow a diverse range of practical knowledge to get started quickly; Take advantage of PHP 7’s newest features - and find out how to use them to solve real development challenges; Put PHP to work for performance and scalability - we’ll show you how, you do it! Who This Book Is For. The book is for web developers, PHP consultants, and anyone who is working on multiple projects with PHP. Basic knowledge of PHP programming is assumed. What You Will Learn: Build versatile projects using the newest features PHP 7 has to offer; Learn how to use PHP 7’s event-driven asynchronous features; Find out how to improve the performance of your code with effective techniques and design patterns; Get to grips with backend development and find out how to optimize session handling; Learn how to use the PHP 7 Abstract Syntax Tree to improve the quality of your code and make it more maintainable; Find out how to build a RESTful web service; Build your own asynchronous microservice In Detail. When it comes to modern web development, performance is everything. The latest version of PHP has been improvised and updated to make it easier to build for performance, improved engine execution, better memory usage, and a new and extended set of tools. If you’re a web developer, what’s not to love? This guide will show you how to make full use of PHP 7 with a range of practical projects that will not only teach you the principles, but also show you how to put them into practice. It will push and extend your skills, helping you to become a more confident and fluent PHP developer. You’ll find out how to build a social newsletter service, a simple blog with a search capability using Elasticsearch, as well as a chat application. We’ll also show you how to create a RESTful web service, a database class to manage a shopping cart on an e-commerce site and how to build an asynchronous microservice architecture. With further guidance on using reactive extensions in PHP, we’re sure that you’ll find everything you need to take full advantage of PHP 7. So dive in now! Style and approach. This product focuses on helping developers build projects from scratch. But more than that, each project will help the reader to learn a new facet or feature of PHP 7 - it means the reader really will ‘learn by doing.’ Computers

Understanding Maple This book explains the key features of Maple, with a focus on showing how things work, and how to avoid common problems. Computers

Mastering ServiceNow Unleash the full potential of ServiceNow from foundations to advanced functions, with this hands-on expert guide fully revised for the Helsinki version About This Book: Give your ServiceNow Helsinki implementation a powerful kick-start by understanding the deep capabilities of the platform,; Learn by doing with an extended, comprehensive example, creating a feature-rich, secure and automated application from the ground up; Interact with your whole organization by integrating with REST web services and build a custom Service Portal interface Who This Book Is For. This book is aimed at advanced ServiceNow System Administrators and developers who would like to gain greater control of ServiceNow and its architecture. The book expects you to be new to ServiceNow, but have a good grounding in internet and computing technologies, like HTML, JSON, REST and database systems. Readers should be especially familiar with JavaScript, and be keen to extend and alter the platform. With this book, they will be able to develop a new application for their company. What You Will Learn: Build custom scoped applications that access the full ServiceNow API; Build a modern, responsive self-service interface with Service Portal; Design feature-rich, responsive, automated workflow systems; Design powerful data-driven applications; Control information flow and apply business logic with Business Rules; Write efficient and effective client-side JavaScript; Learn how to authenticate and secure Web Services; Integrate and exchange data with people and systems; Create and secure your systems with proper access control In Detail. ServiceNow is a SaaS application that provides workflow form-based applications. It is an ideal platform for creating enterprise-level applications giving requesters and fulfillers improved visibility and access to a process. ServiceNow-based applications often replace email by providing a better way to get work done. The book steps through the main aspects of the ServiceNow platform, from the ground up. It starts by exploring the core architecture of ServiceNow, including building the right data structure. To add business logic and control data, and interactivity to user interaction, you will be shown how to code on both server and the client. You will then learn more about the power of tasks, events and notifications. The book will then focus on using web services and other mechanisms to integrate ServiceNow with other systems. Furthermore, you will learn how to secure applications and data, and understand how ServiceNow performs logging and error reporting. You will then be shown how to package your applications and changes, so they can be installed elsewhere and ways to maintain them easily. If you wish to create an alternative simple interface, then explore ways to make ServiceNow beautiful using Service Portal. By the end of the book, you will know the fundamentals of the ServiceNow platform, helping you be a better ServiceNow System Administrator or developer. Style and approach. Explore how to implement business logic and automated workflows and write effective code by flexible choices for client-side scripting Computers

Scala Test-Driven Development Build robust Scala applications by implementing the fundamentals of test-driven development in your workflow About This Book: Get a deep understanding of various testing concepts such as test-driven development (TDD) and BDD; Efficient usage of the built-in Scala features such as ScalaTest, specs2, and Scala check; Change your approach towards problem solving by thinking about the boundaries of the problem and its definition rather than focusing on the solution Who This Book Is For. This book is for Scala developers who are looking to write better quality and easily maintainable code. No previous knowledge of TDD/BDD is required. What You Will Learn: Understand the basics of TDD and its significance; Refactoring tests to build APIs in order to increase test coverage; How to leverage the inbuilt Scala testing modules like ScalaTest, specs2 and Scala Check; Writing test fixtures and apply the concepts of BDD; How to divide tests to run at different points in continuous delivery cycle; Benefits of refactoring and how it affects the final quality of code produced; Understanding of SBT based build environment and how to use it to run tests; The fundamentals of mocking and stubbing in Scala and how to use it efficiently In Detail. Test-driven development (TDD) produces high-quality applications in less time than is possible with traditional methods. Due to the systematic nature of TDD, the application is tested in individual units as well as cumulatively, right from the design stage, to ensure optimum performance and reduced debugging costs. This step-by-step guide shows you how to use the principles of TDD and built-in Scala testing modules to write clean and fully tested Scala code and give your workflow the change it needs to let you create better applications than ever before. After an introduction to TDD, you will learn the basics of ScalaTest, one of the most flexible and most popular testing tools around for Scala, by building your first fully test-driven application. Building on from that you will learn about the ScalaTest API and how to refactor code to produce high-quality applications. We’ll teach you the concepts of BDD (Behavior-driven development) and you’ll see how to add functional tests to the existing suite of tests. You’ll be introduced to the concepts of Mocks and Stubs and will learn to increase test coverage using properties. With a concluding chapter on miscellaneous tools, this book will enable you to write better quality code that is easily maintainable and watch your apps change for the better. Style and approach. This step-by-step guide explains the significance of TDD in Scala through various practical examples. You will learn to write a complete test-driven application throughout the course of the book. Computers

Go Programming Blueprints Build real-world, production-ready solutions in Go using cutting-edge technology and techniques About This Book: Get up to date with Go and write code capable of delivering massive world-class scale performance and availability; Learn to apply the nuances of the Go language, and get to know the open source community that surrounds it to implement a wide range of start-up quality projects; Write interesting and clever but simple code, and learn skills and techniques that are directly transferrable to your own projects Who This Book Is For. If you are familiar with Go and are want to put your knowledge to work, then this is the book for you. Go programming knowledge is a must. What You Will Learn: Build quirky and fun projects from scratch while exploring patterns, practices, and techniques, as well as a range of different technologies; Create websites and data services capable of massive scale using Go’s net/http package, exploring RESTful patterns as well as low-latency WebSocket APIs; Interact with a variety of remote web services to consume capabilities ranging from authentication and authorization to a fully functioning thesaurus; Develop high-quality command-line tools that utilize the powerful shell capabilities and perform well using Go’s in-built concurrency mechanisms; Build microservices for larger organizations using the Go Kit library; Implement a modern document database as well as high-throughput messaging queue technology to put together an architecture that is truly ready to scale; Write concurrent programs and gracefully manage the execution of them and communication by smartly using channels; Get a feel for app deployment using Docker and Google App Engine In Detail. Go is the language of the Internet age, and the latest version of Go comes with major architectural changes. Implementation of the language, runtime, and libraries has changed significantly. The compiler and runtime are now written entirely in Go. The garbage collector is now concurrent and provides dramatically lower pause times by running in parallel with other Go routines when possible. This book will show you how to leverage all the latest features and much more. This book shows you how to build powerful systems and drops you into real-world situations. You will learn to develop high-quality command-line tools that utilize the powerful shell capabilities and perform well using Go’s in-built concurrency mechanisms. Scale, performance, and high availability lie at the heart of our projects, and the lessons learned throughout this book will arm you with everything you need to build world-class solutions. You will get a feel for app deployment using Docker and Google App Engine. Each project could form the basis of a start-up, which means they are directly applicable to modern software markets. Style and approach. This book provides fun projects that involve building applications from scratch. These projects will teach you to build chat applications, a distributed system, and a recommendation system. Computers

Python Learn to solve challenging data science problems by building powerful machine learning models using Python About This Book: Understand which algorithms to use in a given context with the help of this exciting recipe-based guide; This practical tutorial tackles real-world computing problems through a rigorous and effective approach; Build state-of-the-art models and develop personalized recommendations to perform machine learning at scale Who This Book Is For. This Learning Path is for Python programmers who are looking to use machine learning algorithms to create real-world applications. It is ideal for Python professionals who want to work with large and complex datasets and Python developers and analysts or data scientists who are looking to add to their existing skills by accessing some of the most powerful recent trends in data science. Experience with Python, Jupyter Notebooks, and command-line execution together with a good level of mathematical knowledge to understand the concepts is expected. Machine learning basic knowledge is also expected. What You Will Learn: Use predictive modeling and apply it to real-world problems; Understand how to perform market segmentation using unsupervised learning; Apply your new-found skills to solve real problems, through clearly-explained code for every technique and test; Compete with top data scientists by gaining a practical and theoretical understanding of cutting-edge deep learning algorithms; Increase predictive accuracy with deep learning and scalable data-handling techniques; Work with modern state-of-the-art large-scale machine learning techniques; Learn to use Python code to implement a range of machine learning algorithms and techniques In Detail. Machine learning is increasingly spreading in the modern data-driven world. It is used extensively across many fields such as search engines, robotics, self-driving cars, and more. Machine learning is transforming the way we understand and interact with the world around us. In the first module, Python Machine Learning Cookbook, you will learn how to perform various machine learning tasks using a wide variety of machine learning algorithms to solve real-world problems and use Python to implement these algorithms. The second module, Advanced Machine Learning with Python, is designed to take you on a guided tour of the most relevant and powerful machine learning techniques and you’ll acquire a broad set of powerful skills in the area of feature selection and feature engineering. The third module in this learning path, Large Scale Machine Learning with Python, dives into scalable machine learning and the three forms of scalability. It covers the most effective machine learning techniques on a map reduce framework in Hadoop and Spark in Python. This Learning Path will teach you Python machine learning for the real world. The machine learning techniques covered in this Learning Path are at the forefront of commercial practice. This Learning Path combines some of the best that Packt has to offer in one complete, curated package. It includes content from the following Packt products: Python Machine Learning Cookbook by Prateek Joshi; Advanced Machine Learning with Python by John Hearty; Large Scale Machine Learning with Python by Bastiaan Sjardin, Alberto Boschetti, Luca Massaron Style and approach. This course is a smooth learning path that will teach you how to get started with Python machine learning for the real world, and develop solutions to real-world problems. Through this comprehensive course, you’ll learn to create the most effective machine learning techniques from scratch and more! Computers

Bayesian Analysis with Python Unleash the power and flexibility of the Bayesian framework About This Book: Simplify the Bayes process for solving complex statistical problems using Python; Tutorial guide that will take the you through the journey of Bayesian analysis with the help of sample problems and practice exercises; Learn how and when to use Bayesian analysis in your applications with this guide. Who This Book Is For. Students, researchers and data scientists who wish to learn Bayesian data analysis with Python and implement probabilistic models in their day to day projects. Programming experience with Python is essential. No previous statistical knowledge is assumed. What You Will Learn: Understand the essentials Bayesian concepts from a practical point of view; Learn how to build probabilistic models using the Python library PyMC3; Acquire the skills to sanity-check your models and modify them if necessary; Add structure to your models and get the advantages of hierarchical models; Find out how different models can be used to answer different data analysis questions; When in doubt, learn to choose between alternative models.; Predict continuous target outcomes using regression analysis or assign classes using logistic and softmax regression.; Learn how to think probabilistically and unleash the power and flexibility of the Bayesian framework In Detail. The purpose of this book is to teach the main concepts of Bayesian data analysis. We will learn how to effectively use PyMC3, a Python library for probabilistic programming, to perform Bayesian parameter estimation, to check models and validate them. This book begins presenting the key concepts of the Bayesian framework and the main advantages of this approach from a practical point of view. Moving on, we will explore the power and flexibility of generalized linear models and how to adapt them to a wide array of problems, including regression and classification. We will also look into mixture models and clustering data, and we will finish with advanced topics like non-parametrics models and Gaussian processes. With the help of Python and PyMC3 you will learn to implement, check and expand Bayesian models to solve data analysis problems. Style and approach. Bayes algorithms are widely used in statistics, machine learning, artificial intelligence, and data mining. This will be a practical guide allowing the readers to use Bayesian methods for statistical modelling and analysis using Python. Computers

Julia Leverage the power of Julia to design and develop high performing programs About This Book: Get to know the best techniques to create blazingly fast programs with Julia; Stand out from the crowd by developing code that runs faster than your peers' code; Complete an extensive data science project through the entire cycle from ETL to analytics and data visualization Who This Book Is For. This learning path is for data scientists and for all those who work in technical and scientific computation projects. It will be great for Julia developers who are interested in high-performance technical computing. This learning path assumes that you already have some basic working knowledge of Julia's syntax and high-level dynamic languages such as MATLAB, R, Python, or Ruby. What You Will Learn: Set up your Julia environment to achieve the highest productivity; Solve your tasks in a high-level dynamic language and use types for your data only when needed; Apply Julia to tackle problems concurrently and in a distributed environment; Get a sense of the possibilities and limitations of Julia's performance; Use Julia arrays to write high performance code; Build a data science project through the entire cycle of ETL, analytics, and data visualization; Display graphics and visualizations to carry out modeling and simulation in Julia; Develop your own packages and contribute to the Julia Community In Detail. In this learning path, you will learn to use an interesting and dynamic programming language—Julia! You will get a chance to tackle your numerical and data problems with Julia. You’ll begin the journey by setting up a running Julia platform before exploring its various built-in types. We’ll then move on to the various functions and constructs in Julia. We’ll walk through the two important collection types—arrays and matrices in Julia. You will dive into how Julia uses type information to achieve its performance goals, and how to use multiple dispatch to help the compiler emit high performance machine code. You will see how Julia’s design makes code fast, and you’ll see its distributed computing capabilities. By the end of this learning path, you will see how data works using simple statistics and analytics, and you’ll discover its high and dynamic performance—its real strength, which makes it particularly useful in highly intensive computing tasks. This learning path combines some of the best that Packt has to offer in one complete, curated package. It includes content from the following Packt products: Getting Started with Julia by Ivo Balvaert; Julia High Performance by Avik Sengupta; Mastering Julia by Malcolm Sherrington Style and approach. This hands-on manual will give you great explanations of the important concepts related to Julia programming. Computers

Computer Programming with C++ This book provides in-depth coverage of the fundamental concepts of the C and C++ programming languages and the object-oriented programming paradigm. Computers

Mastering Tableau Master the intricacies of Tableau to create effective data visualizations About This Book: Arm yourself with an arsenal of advanced chart types and geocoding to efficiently and engagingly present information; Map a grid over a network node diagram and use that grid to demonstrate loads, processing time, and more in Tableau; Integrate R with Tableau by utilizing R functions, libraries, and saved models Who This Book Is For. If you are a business analyst without developer-level programming skills, then this book is for you. You are expected to have at least a fundamental understanding of Tableau and basic knowledge of joins, however SQL knowledge is not assumed. You should have basic computer skills, including at least moderate Excel proficiency. What You Will Learn: Create a worksheet that can display the current balance for any given period in time; Recreate a star schema from in a data warehouse in Tableau; Combine level of detail calculations with table calculations, sets, and parameters; Create custom polygons to build filled maps for area codes in the USA; Visualize data using a set of analytical and advanced charting techniques; Know when to use Tableau instead of PowerPoint; Build a dashboard and export it to PowerPoint In Detail. Tableau has emerged as one of the most popular Business Intelligence solutions in recent times, thanks to its powerful and interactive data visualization capabilities. This book will empower you to become a master in Tableau by exploiting the many new features introduced in Tableau 10.0. You will embark on this exciting journey by getting to know the valuable methods of utilizing advanced calculations to solve complex problems. These techniques include creative use of different types of calculations such as row-level, aggregate-level, and more. You will discover how almost any data visualization challenge can be met in Tableau by getting a proper understanding of the tool’s inner workings and creatively exploring possibilities. You’ll be armed with an arsenal of advanced chart types and techniques to enable you to efficiently and engagingly present information to a variety of audiences through the use of clear, efficient, and engaging dashboards. Explanations and examples of efficient and inefficient visualization techniques, well-designed and poorly designed dashboards, and compromise options when Tableau consumers will not embrace data visualization will build on your understanding of Tableau and how to use it efficiently. By the end of the book, you will be equipped with all the information you need to create effective dashboards and data visualization solutions using Tableau. Style and approach. This book takes a direct approach, to systematically evolve to more involved functionalities such as advanced calculation, parameters & sets, data blending and R integration. This book will help you gain skill in building visualizations previously beyond your capacity. Computers

AQA Computer Science for GCSE Student Book Exam Board: AQA Level: GCSE Subject: Computer Science First Teaching: September 2016 First Exam: Summer 2018 Build student confidence and ensure successful progress through GCSE Computer Science. - Builds students' knowledge and confidence through detailed topic coverage and key points- Instils a deeper understanding and awareness of computer science, and its applications and implications in the wider world- Develops knowledge and computational thinking skills with tasks featured throughout the book- Ensures progression through GCSE with regular assessment questions, that can be developed with supporting Dynamic Learning digital resources Computers

Edexcel Computer Science for GCSE Student Book Exam Board: Edexcel Level: GCSE Subject: Computer Science First Teaching: September 2016 First Exam: Summer 2018 Build student confidence and ensure successful progress through GCSE Computer Science. Our expert author provides insight and guidance to meet the demands of the new Edexcel specification, with challenging tasks and activities to test the computational skills and knowledge required completing the exams and the non-examined assessment.- Builds students' knowledge and confidence through detailed topic coverage and explanation of key points to match important Edexcel concepts- Develops computational thinking skills with practice exercises and problem-solving tasks- Ensures progression through GCSE with regular assessment questions, that can be developed with supporting Dynamic Learning digital resources- Instils a deeper understanding and awareness of computer science, and its applications and implications in the wider world Computers

The Singularity This volume represents the combination of two special issues of the Journal of Consciousness Studies on the topic of the technological singularity. Could artificial intelligence really out-think us, and what would be the likely repercussions if it could? Leading authors contribute to the debate, which takes the form of a target chapter by philosopher David Chalmers, plus commentaries from the likes of Daniel Dennett, Nick Bostrom, Ray Kurzweil, Ben Goertzel, Frank Tipler, among many others. ... Computers

Essential Maths Skills for AS/A Level Computer Science If you struggle with binary multiplication, or Big O Notation, this is the book for you. This textbook companion will help improve your essential maths skills for computer science, whichever awarding body specification you're following. You can use it throughout your course, whenever you feel you need some extra help.- Develop your understanding of both maths and computer science with all worked examples and questions within a computer science context- Improve your confidence with a step-by-step approach to every maths skill- Measure your progress with guided and non-guided questions to see how you're improving- Understand where you're going wrong with full worked solutions to every question - Feel confident in expert guidance from experienced teachers and examiners Victoria Ellis and Gavin Craddock, reviewed by Dr Kathleen Maitland, Senior Lecturer in Computing and Director of the SAS Student Academy at Birmingham City University Computers

Cambridge Technicals Level 3 IT Exam Board: Cambridge Level: KS4 Subject: IT First Teaching: September 2016 First Exam: June 207 Support your teaching of the new Cambridge Technicals 2016 suite with Cambridge Technical Level 3 IT, developed in partnership between OCR and Hodder Education; this textbook covers each specialist pathway and ensures your ability to deliver a flexible course that is both vocationally focused and academically thorough. Cambridge Technical Level 3 IT is matched exactly to the new specification and follows specialist pathways in IT Infrastructure Technician, Emerging Digital Technology Practitioner, Application Developer, and Data Analyst. - Ensures effective teaching of each specialist pathway offered within the qualification.- Focuses learning on the skills, knowledge and understanding demanded from employers and universities.- Provides ideas and exercises for the application of practical skills and knowledge.- Developed in partnership between Hodder Education and OCR, guaranteeing quality resources which match the specification perfectly Computers

Data Acquisition Using LabVIEW Transform physical phenomena into computer-acceptable data using a truly object-oriented language About This Book: Create your own data acquisition system independently using LabVIEW and build interactive dashboards; Collect data using National Instrument's and third-party, open source, affordable hardware; Step-by-step real-world examples using various tools that illustrate the fundamentals of data acquisition Who This Book Is For. If you are an engineer, scientist, experienced hobbyist, or student, you will highly benefit from the content and examples illustrated in this book. A working knowledge of precision testing, measurement instruments, and electronics, as well as a background in computer fundamentals and programming is expected. What You Will Learn: Create a virtual instrument which highlights common functionality of LabVIEW; Get familiarized with common buses such as Serial, GPIB, and SCPI commands; Staircase signal acquisition using NI-DAQmx; Discover how to measure light intensity and distance; Master LabVIEW debugging techniques; Build a data acquisition application complete with an installer and required drivers; Utilize open source microcontroller Arduino and a 32-bit Arduino compatible Uno32 using LabVIEW programming environment In Detail. NI LabVIEW's intuitive graphical interface eliminates the steep learning curve associated with text-based languages such as C or C++. LabVIEW is a proven and powerful integrated development environment to interact with measurement and control hardware, analyze data, publish results, and distribute systems. This hands-on tutorial guide helps you harness the power of LabVIEW for data acquisition. This book begins with a quick introduction to LabVIEW, running through the fundamentals of communication and data collection. Then get to grips with the auto-code generation feature of LabVIEW using its GUI interface. You will learn how to use NI-DAQmax Data acquisition VIs, showing how LabVIEW can be used to appropriate a true physical phenomenon (such as temperature, light, and so on) and convert it to an appropriate data type that can be manipulated and analyzed with a computer. You will also learn how to create Distribution Kit for LabVIEW, acquainting yourself with various debugging techniques offered by LabVIEW to help you in situations where bugs are not letting you run your programs as intended. By the end of the book, you will have a clear idea how to build your own data acquisition system independently and much more. Style and approach. A hands-on practical guide that starts by laying down the software and hardware foundations necessary for subsequent data acquisition-intensive chapters. The book is packed full of specific examples with software screenshots and schematic diagrams to guide you through the creation of each virtual instrument. Computers

Salesforce CRM - The Definitive Admin Handbook Learn how to successfully administer, build, and manage Salesforce CRM and Salesforce mobile solutions using real-world and best practice techniques About This Book: See the latest best practice Salesforce administration principles, gain real-world advice, and understand critical design considerations to set up and customize Salesforce CRM; This is a pragmatic guide to the key functions of customizing and setting up the application for enterprise security, user and data management, process automation, analytics, and mobile features; Step-by-step navigation and descriptions of the features of Salesforce CRM platform and clear guidance on the customization and administration of the application; Identify what is covered to create your own improved study guide for the certified administrator examination Who This Book Is For. This book is for administrators who want to develop and strengthen their Salesforce CRM skills in the areas of configuration and system management. Whether you are a new administrator or a more experienced professional, this book will enhance your knowledge and understanding of the features of Salesforce CRM. What You Will Learn: Manage and administer user records and password policies; Configure and control the various organization-wide user interface features in Salesforce CRM; Set up and maintain users, profiles, and permission sets and administer appropriate security and login access mechanisms; Apply organization security; Understand the capabilities of the Salesforce CRM sharing model; Create, delete, and customize fields, page layout, and list views for custom and standard objects; Find out how Apex and Visualforce coding can be used in Salesforce CRM; Implement the mechanisms for data management; Discover the tools to import, update, transfer, and mass delete data In Detail. Salesforce CRM’s Winter ’17 release offers a host of new features for CRM designed to transform your sales and marketing requirements. With this comprehensive guide to implementing Salesforce CRM, administrators of all levels can easily acquire deep knowledge of the platform. The book begins by guiding you through setting up users and the security settings and then progresses to configuration, data management, and data analytics. We swiftly move on to the setting up of organization wide features that affect the look and feel of the application. Process automation and approval mechanisms are covered next, along with the functional areas of Sales Cloud, Service Cloud, Marketing Cloud, and Salesforce Chatter. This book details Salesforce CRM system administration in a practical way and is an invaluable reference for both new administrators and experienced professionals. At the end of the book, techniques to further enhance the system and improve the return on investment Salesforce mobile apps and mobile administration are covered, along with Salesforce Adoption Manager. Every chapter is complete with a section containing example questions of the type that you might encounter in the certification examination. Style and approach. This book takes a straightforward, no-nonsense approach to working with the Salesforce CRM platform. Filled with examples and use cases, the book presents the facts along with seasoned advice and real-world examples to ensure you have all the resources you need to become a more informed Salesforce Administrator. Computers

TypeScript Leverage the features of TypeScript to boost your development skills and create captivating applications About This Book: Learn how to develop modular, scalable, maintainable, and adaptable web applications by taking advantage of TypeScript; Explore techniques to use TypeScript alongside other leading tools such as Angular 2, React, and Node.js; Focusing on design patterns in TypeScript, this step-by-step guide demonstrates all the important design patterns in practice Who This Book Is For. This Learning Path is for intermediate-level JavaScript developers who want to use TypeScript to build beautiful web applications and fun projects. No prior knowledge of TypeScript is required, but a basic understanding of jQuery is expected. This Learning Path is also for experienced TypeScript developers who want to take their skills to the next level, and also for web developers who wish to make the most of TypeScript. What You Will Learn: Understand the key TypeScript language features and runtime; Install and configure the necessary tools in order to start developing an application; Create object-oriented code that adheres to the SOLID principles; Develop robust applications with testing (Mocha, Chai, and SinonJS); Apply GoF patterns in an application with a testing approach; Identify the challenges when developing an application; Migrate JavaScript codebases to TypeScript to improve your workflow; Utilize System.JS and Webpack to load scripts and their dependencies; Develop high performance server-side applications to run within Node.js In Detail. TypeScript is an open source and cross-platform typed superset of JavaScript that compiles to plain JavaScript that runs in any browser or any host. TypeScript adds optional static types, classes, and modules to JavaScript, to enable great tooling and better structuring of large JavaScript applications. Through this three-module learning path, you’ll learn the ins-and-outs of TypeScript for building more robust software. The first module gets you started with TypeScript and helps you understand the basics of TypeScript and automation tools. Get a detailed description of function, generics, callbacks, and promises, and discover the object-oriented features and memory management functionality of TypeScript. The next module starts by explaining the current challenges when designing and developing an application and how you can solve these challenges by applying the correct design pattern and best practices. You will be introduced to low-level programming concepts to help you write TypeScript code, as well as working with software architecture, best practices, and design aspects. The final module will help you build a complete single page app with Angular 2, create a neat mobile app using NativeScript, and even build a Pac Man game with TypeScript. As if the fun wasn't enough, you'll also find out how to migrate your legacy codebase from JavaScript to TypeScript. By the end of this Learning Path, you will be able to take your skills up a notch and develop full-fledged web applications using the latest features of the TypeScript. This Learning Path combines some of the best that Packt has to offer in one complete, curated package. It includes content from the following Packt products: Learning TypeScript by Remo H. Jansen; TypeScript Design Patterns by Vilic Vane; TypeScript Blueprints by Ivo Gabe de Wolff Style and approach. This is a step-by-step, practical guide covering the fundamentals of TypeScript with practical examples. The end-to-end projects included in this book will give you ready-to-implement solutions for your business scenario, showcasing the depth and robustness of TypeScript. Computers

Introduction to Experimental Mathematics This text introduces students to an experimental approach to mathematics, using Maple to systematically investigate and develop mathematical theory. Computers

Introduction to Software Testing This classroom-tested new edition features expanded coverage of the basics and test automation frameworks, with new exercises and examples. Computers

Quantum Information Theory Introduces many concepts and mathematical tools in quantum information theory, with over 100 pages of new material and exercises. Computers

Human and Machine Hearing This book describes how human hearing works and how to build machines that analyze sounds in the same way that people do. Computers

Darkweb Cyber Threat Intelligence Mining This book describes techniques and results in cyber threat intelligence from the center of the malicious hacking underworld - the dark web. Computers

Implementing DevOps on AWS Bring the best out of DevOps and build, deploy, and maintain applications on AWS About This Book: Work through practical examples and gain DevOps best practices to successfully deploy applications on AWS; Successfully provision and operate distributed application systems and your AWS infrastructure using DevOps; Perform Continuous Integration and deployment and fine-tune the way you deliver on AWS Who This Book Is For. This book is for system administrators and developers who manage AWS infrastructure and environments and are planning to implement DevOps in their organizations. Those aiming for the AWS Certified DevOps Engineer certification will also find this book useful. Prior experience of operating and managing AWS environments is expected. What You Will Learn: See the difference between Object Oriented Programming and Protocol Oriented Programming; See the difference between reference and value types and when to use each; Find out how we can leverage the tuple to reduce the complexity of our code; Discover what protocols are and how to use them; See how to implement protocol extensions to create a very flexible code base; Learn how to implement several design patterns in a Protocol-Oriented approach; Learn how to solve real-world design issues with protocol-oriented programming In Detail. Knowing how to adopt DevOps in your organization is becoming an increasingly important skill for developers, whether you work for a start-up, an SMB, or an enterprise. This book will help you to drastically reduce the amount of time spent on development and increase the reliability of your software deployments on AWS using popular DevOps methods of automation. To start, you will get familiar with the concept of IaC and will learn to design, deploy, and maintain AWS infrastructure. Further on, you’ll see how to design and deploy a Continuous Integration platform on AWS using either open source or AWS provided tools/services. Following on from the delivery part of the process, you will learn how to deploy a newly created, tested, and verified artefact to the AWS infrastructure without manual intervention. You will then find out what to consider in order to make the implementation of Configuration Management easier and more effective. Toward the end, you will get to know the tricks and tips to optimize and secure your AWS environment. By the end of the book, you will have mastered the art of applying AWS to DevOps in your organization Style and approach. This book is packed full of real-world examples demonstrating use cases that help you deploy DevOps best practices on AWS. Computers

Getting Started with R A popular entry-level guide into the use of R as a statistical programming and data management language for students, post-docs, and seasoned researchers now in a new revised edition, incorporating the updates in the R environment, and also adding guidance on the use of more complex statistical analyses and tools. Computers

Direct Methods for Sparse Matrices The subject of sparse matrices has its root in such diverse fields as management science, power systems analysis, surveying, circuit theory, and structural analysis. Efficient use of sparsity is a key to solving large problems in many fields. This book provides both insight and answers for those attempting to solve these problems. Computers

Picturing Quantum Processes In this book, quantum phenomena are explained through the language of diagrams, setting out an innovative method of presenting complex scientific theories. Computers

Probability and Computing This greatly expanded new edition offers a comprehensive introduction to randomization and probabilistic techniques in modern computer science. Computers

Cambridge IGCSE Computer Science Workbook Consolidate learning and improve Students' confidence with plenty of extra practice questions and activities alongside the Student's Book that follow the contents and chapter order. Suitable for study in class or use at home throughout the course. This title has not been through the Cambridge International endorsement process. Computers

A Dictionary of Science This bestselling dictionary contains more than 9,500 entries on all aspects of chemistry, physics, biology (including human biology), earth sciences, computer science, and astronomy. With clear and concise definitions and recommended web links for many entries, this A-Z is a reliable reference work for science students as well as non-scientists. Computers

Blackstone's Handbook of Cyber Crime Investigation A comprehensive and practical guide to the police investigation of cyber crime offering an overview of the national strategies and structures, a strand-by-strand treatment of the different types of cyber crime, and the relevant laws, police powers, and investigative tools. Computers

Microsoft Excel 2016 Programming by Example with VBA, XML, and ASP Updated for Excel 2016 and based on the bestselling editions from previous versions, Microsoft Excel 2016 Programming by Example with VBA, XML and ASP is a practical, how-to book on Excel programming, suitable for readers already proficient with the Excel user interface (UI). If you are looking to automate Excel routine tasks, this book will progressively introduce you to programming concepts via numerous, illustrated, hands-on exercises. Includes a comprehensive disc with source code, supplemental files, and color screen captures (Also available from the publisher for download by writing to info@merclearning.com). More advanced topics are demonstrated via custom projects. From recording and editing a macro and writing VBA code to working with XML documents and using Classic ASP pages to access and display data on the Web, this book takes you on a programming journey that will change the way you work with Excel. The book provides information on performing automatic operations on files, folders, and other Microsoft Office applications. It also covers proper use of event procedures, testing and debugging, and guides you through programming advanced Excel features such as PivotTables, PivotCharts, and the Ribbon interface. Features: •Contains 28 chapters loaded with illustrated "Hands-On" exercises and projects that guide you through the VBA programming language. Each example tells you exactly where to enter code, how to test it and then run it. •Includes a comprehensive disc with source code, supplemental files, and color screen captures (Also available from the publisher for download by writing to info@merclearning.com). •Takes you from introductory topics--including recording and editing macros, using variables, and constants, writing subroutines/functions, conditional statements, and various methods of coding loops to repeat actions--to intermediate and advanced topics that include working with collections, class modules, arrays, file and database access, custom forms, error handling and debugging. •Includes comprehensive coverage of native file handling in VBA, Windows Scripting Host (WSH), and low-level File Access. •Demonstrates how to interact with Microsoft Access databases using both ADO and DAO Object Libraries to access and manipulate data. •Includes chapters on programming charts, PivotTables, dialog boxes, custom forms, the Ribbon, Backstage View, context/shortcut menu customizations, as well as proper use of event procedures and callbacks. •Provides a quick Hands-On introduction to the data analysis and transformation process using the new Excel 2016 Get & Transform feature and the “M†language formulas. •Provides a practical coverage of using Web queries, HTML, XML, and VBScript in Classic ASP to retrieve and publish Excel data to the Web. On The Companion Files: •All source code and supplemental files for the Hands-On exercises and custom projects •All images from the text (including 4-color screenshots) Computers

Introduction to 3D Game Programming with DirectX 12 This updated bestseller provides an introduction to programming interactive computer graphics, with an emphasis on game development using DirectX 12. The book is divided into three main parts: basic mathematical tools, fundamental tasks in Direct3D, and techniques and special effects. It shows how to use new Direct12 features such as command lists, pipeline state objects, descriptor heaps and tables, and explicit resource management to reduce CPU overhead and increase scalability across multiple CPU cores. The book covers modern special effects and techniques such as hardware tessellation, writing compute shaders, ambient occlusion, reflections, normal and displacement mapping, shadow rendering, and character animation. Includes a companion DVD with code and figures. eBook Customers: Companion files are available for downloading with order number/proof of purchase by writing to the publisher at info@merclearning.com. FEATURES: • Provides an introduction to programming interactive computer graphics, with an emphasis on game development using DirectX 12 • Uses new Direct3D 12 features to reduce CPU overhead and take advantage of multiple CPU cores • Contains detailed explanations of popular real-time game effects • Includes a DVD with source code and all the images (including 4-color) from the book • Learn advance rendering techniques such as ambient occlusion, real-time reflections, normal and displacement mapping, shadow rendering, programming the geometry shader, and character animation • Covers a mathematics review and 3D rendering fundamentals such as lighting, texturing, blending and stenciling • Use the end-of-chapter exercises to test understanding and provide experience with DirectX 12 Computers

Model-Driven Software Engineering in Practice This book discusses how model-based approaches can improve the daily practice of software professionals. This is known as Model-Driven Software Engineering (MDSE) or, simply, Model-Driven Engineering (MDE). MDSE practices have proved to increase efficiency and effectiveness in software development, as demonstrated by various quantitative and qualitative studies. MDSE adoption in the software industry is foreseen to grow exponentially in the near future, e.g., due to the convergence of software development and business analysis. The aim of this book is to provide you with an agile and flexible tool to introduce you to the MDSE world, thus allowing you to quickly understand its basic principles and techniques and to choose the right set of MDSE instruments for your needs so that you can start to benefit from MDSE right away. The book is organized into two main parts. The first part discusses the foundations of MDSE in terms of basic concepts (i.e., models and transformations), driving principles, application scenarios, and current standards, like the well-known MDA initiative proposed by OMG (Object Management Group) as well as the practices on how to integrate MDSE in existing development processes. The second part deals with the technical aspects of MDSE, spanning from the basics on when and how to build a domain-specific modeling language, to the description of Model-to-Text and Model-to-Model transformations, and the tools that support the management of MDSE projects. The second edition of the book features: a set of completely new topics, including: full example of the creation of a new modeling language (IFML), discussion of modeling issues and approaches in specific domains, like business process modeling, user interaction modeling, and enterprise architecture complete revision of examples, figures, and text, for improving readability, understandability, and coherence better formulation of definitions, dependencies between concepts and ideas addition of a complete index of book content In addition to the contents of the book, more resources are provided on the book's website http://www.mdse-book.com, including the examples presented in the book. Computers

Microsoft Access 2016 Programming By Example Updated for Access 2016 and based on the bestselling editions from previous versions, Microsoft Access 2016 Programming by Example with VBA, XML and ASP is a practical how-to book on Access programming, suitable for readers already proficient with the Access user interface (UI). If you are looking to automate Access routine tasks, this book will progressively introduce you to programming concepts via numerous illustrated hands-on exercises. More advanced topics are demonstrated via custom projects. Includes a comprehensive disc with source code, supplemental files, and color screen captures (Also available from the publisher for download by writing to info@merclearning.com). With concise and straightforward explanations, you learn how to write and test your programming code with the built-in Visual Basic Editor; understand and use common VBA programming structures such as conditions, loops, arrays, and collections; code a "message box"; reprogram characteristics of a database; and use various techniques to query and manipulate your Access .mdb and .accdb databases. The book shows you how you can build database solutions with Data Access Objects (DAO) and ActiveX Data Objects (ADO); define database objects and manage database security with SQL; enhance and alter the way users interact with database applications with Ribbon customizations and event programming in forms and reports. You also learn how to program Microsoft Access databases for Internet access with Active Server Pages (Classic ASP), HTML, and XML. Features: + Contains over thirty chapters loaded with illustrated hands-on exercises and projects that guide you through the VBA programming language. Each example tells you exactly where to enter code and how to test it and then run it. + Includes a comprehensive disc with source code, supplemental files, and color screen captures (Also available from the publisher for download by writing to info@merclearning.com). + Explains how to store data for further manipulation in variables, arrays, and collections while teaching you to write both simple and complex VBA programming routines and functions. + Teaches you how to programmatically create and access database tables and fields. + Shows you how to insert, update, and delete data via programming code using various data access techniques. + Gets you proficient creating and running simple and parameterized queries against your Access databases. + Gets you comfortable using external data sources with Access (Excel, Word, flat files, XML, and SQL Server). + Teaches you how to take control of your forms and reports by writing programming code known as event procedures. + Shows you how to use various types of macros and templates. + Takes your programming skills to the Web by introducing you to dynamic XML and Classic ASP pages. On the disc:(Also available from the publisher for download by writing to info@merclearning.com). + All source code and supplemental files for the Hands-On exercises and custom projects + All images from the text (including 4-color screenshots) Computers

The Cambridge Handbook of Cognitive Linguistics A comprehensive survey of the quickly developing discipline of cognitive linguistics, its rich methodology, key results, and interdisciplinary context. Computers

Microsoft Excel 2013 Programming by Example with VBA, XML, and ASP This book is suitable for readers already familiar with the Excel user interface and introduces programming concepts via numerous multi-step, practical exercises. More advanced topics are introduced via custom projects. Covers recording and editing a macro and writing VBA code through working with XML documents and using ASP to display data on the Web. Microsoft Excel 2013 Programming by Example with VBA, XML and ASP is a practical how-to book on Excel programming, suitable for readers already familiar with the Excel user interface. The book introduces programming concepts via numerous multi-step, illustrated, hands-on exercises. More advanced topics are introduced via custom projects. From recording and editing a macro and writing VBA code to working with XML documents and using classic ASP to access and display data on the Web, this book takes you on a programming journey that will change the way you work with Excel. Completely updated for Excel 2010, this book provides information on performing automatic operations on files, folders, and other Microsoft Office applications. It also covers proper use of event procedures, testing and debugging, and programming advanced Excel features such as PivotTables, PivotCharts, and SmartTags. The chapters are loaded with illustrated hands-on projects and exercises that tell you exactly where to enter code, how to debug it, and then run it. Each exercise/project step is clearly explained as it is performed. Features: Explores in great detail the latest version of Excel and all of its features. Covers recording and editing a macro and writing VBA code through working with XL documents and using ASP to display data on the Web. Covers Office Web Apps. Computers

Microsoft Access 2013 Programming by Example with VBA, XML, and ASP With more than 275 applied examples and 10 projects, Access users can quickly build database solutions with ActiveX Data Objects (ADO), perform database tasks with Jet/Access Structured Query Language (SQL) and export/import Access data to and from XML both manually and programmatically. The book, which covers the latest release of Access and earlier versions, is divided into five parts: an introduction to VBA programming, manipulating databases with ADO, using DDL, event programming, and using ASP and XML. The text will show you how to write and debug your programming code with the Visual Basic Editor; understand and use common VBA programming structures such as conditions, loops, arrays, and collections; code a “message box†and reprogram characteristics of a database; query and manipulate your database from a Web browser with Active Server Pages (ASP) and many more practical techniques. Features: Covers in great detail the latest version of Access and all of its features. Includes more than 275 applied examples and 10 projects. Covers Office Web Apps Computers

Programming Fundamentals Using Java This is a Java textbook for beginning programmers that uses game programming as a central pedagogical tool to improve student engagement, learning outcomes, and retention. Game programming is incorporated into the text in a way that does not compromise the amount of material traditionally covered in a basic or advanced programming course and permits instructors who are not familiar with game programming and computer graphics concept to realize their advantages. The material presented in the book is in full compliance with the 2013 ACM/IEEE computer science curriculum guidelines and provides an in-depth discussion of graphical user interfaces (GUIs). It has been used to teach programming to student whose majors are both within and outside of the computing fields. The companion DVD includes a game environment that is easily integrated into projects created with the popular Java Development Environments (Eclipse, NetBeans, and JCreator) and includes a set of executable student games to pique students’ interest by giving them a glimpse into their future capabilities. The material in this book can be covered within one or two courses such as a basic programming course followed by an advanced programming course. Features: Uses an objects-early approach to learning Java. Follows the 2013 ACM/IEEE computer science curriculum guidelines Integrates game programming as central pedagogical tool to improve student engagement, learning outcomes, and retention Includes a companion DVD with projects created with the popular Java Development Environments; also includes a set of executable games, source code, and figures Uses working programs to illustrate concepts under discussion Complete instructor’s resource package available upon adoption Computers

Python for Scientists Scientific Python is taught from scratch in this book via copious, downloadable, useful and adaptable code snippets. Computers

Cloud Computing This book offers a balanced treatment of elementary concepts with recent developments in cloud computing. Computers

Topics at the Frontier of Statistics and Network Analysis This snapshot of the frontier of statistics and network analysis focuses on the foundational topics of modeling, sampling, and design. Computers

Data Localization Laws and Policy Countries are increasingly introducing data localization laws, threatening digital globalization and inhibiting cloud computing adoption despite its acknowledged benefits. This multi-disciplinary book analyzes the EU restriction (including the Privacy Shield and General Data Protection Regulation) through a cloud computing lens, covering historical objectives and practical problems, showing why the focus should move from physical data location to effective jurisdiction over those controlling access to intelligible data, and control of access to data through security. Computers

Computational Art Therapy This book is concerned with the interdisciplinary studies applying computer technologies to the theory and practice of art therapy. The contents consist of the author's sixteen papers published, twelve patents in Korea, Japan, and the U.S.A., and other relevant materials, all organized in a logical sequence. This book is intended for art therapy courses at upper undergraduate and graduate levels. Computers

The Discipline of Organizing We organize things. We organize information, information about things, and information about information. Organizing is a fundamental issue in many professional fields, but these fields have only limited agreement in how they approach problems of organizing and in what they seek as their solutions. The Discipline of Organizing synthesizes insights from library science, information science, computer science, cognitive science, systems analysis, business, and other disciplines to create an Organizing System for understanding organizing. This framework is robust and forward-looking, enabling effective sharing of insights and design patterns between disciplines that weren't possible before. The 4th edition of this award-winning and widely adopted text adds content to bridge between the foundations of organizing systems and the new statistical and computational techniques of data science because at its core, data science is about how resources are described and organized. The 4th edition reframes descriptive statistics as organizing techniques, expands the treatment of classification to include computational methods, and incorporates many new examples of data-driven resource selection, organization, maintenance, and personalization. The Professional edition remains the definitive source for advanced students and practitioners who require comprehensive and pinpoint connections to the classic and contemporary literature about organizing. Dozens of new citations and endnotes for the new data science material bring to 12 the number of distinct disciplinary perspectives identified in the book. Computers

Ethics in an Age of Surveillance We live in an age of surveillance. In this book, the moral importance of this is explained through an examination of virtual identities. Computers

Finite Elements An easy-to-understand guide covering the key principles of finite element methods and its applications to differential equations. Computers

Revit 2018 Architecture This is the most comprehensive book you will find covering Autodesk Revit 2018 Architecture. Covering all of the 2D concepts, it uses both metric and imperial units to illustrate the myriad drawing and editing tools for this popular application. Use the companion files to set up drawing exercises and projects and see all of the book’s figures in color. Revit 2018 Architecture includes over 50 exercises or “mini-workshops†that complete small projects from concept through actual plotting. Solving all of the workshops will simulate the creation of three projects (architectural and mechanical) from beginning to end without overlooking any of the basic commands and functions in Revit 2018 Architecture. FEATURES: * Covers Revit 2018 updates and new features * Designed for novice users of Revit 2018 Architecture. Most useful for 'teach yourself' or instructor-led Revit training. No previous CAD experience is required. * Uses both metric and imperial units in examples, exercises, projects, and descriptions * Accompanied by companion files that feature drawings, practice and finished plots, figures, etc. * Includes over 50 'mini-workshops' and hundreds of figures that complete small projects * Helps you to prepare for the Revit Architecture Certified Professional exam * Exercises and projects included for use as a textbook Computers

Matrix Analysis and Applications The theory, methods and applications of matrix analysis are presented here in a novel theoretical framework. Computers

Complex Networks A comprehensive introduction to the theory and applications of complex network science, complete with real-world data sets and software tools. Computers

Embedded Courts A study of the decision-making process of Chinese courts and the non-legal forces and regional factors that influence judicial outcomes. Computers

Computer Simulation of Liquids This is the second edition of a widely used practical guide to computer simulations of liquids. The technique uses a model for the way molecules interact, to predict how large numbers of them behave in liquid state. This essential introduction to this rapidly growing field is complete with illustrative computer code. Computers

The Emperor's New Mind In his bestselling work of popular science, Sir Roger Penrose takes us on a fascinating tour through the basic principles of physics, cosmology, mathematics, and philosophy to show that human thinking can never be emulated by a machine. Computers

Game Theory for Data Science Intelligent systems often depend on data provided by information agents, for example, sensor data or crowdsourced human computation. Providing accurate and relevant data requires costly effort that agents may not always be willing to provide. Thus, it becomes important not only to verify the correctness of data, but also to provide incentives so that agents that provide high-quality data are rewarded while those that do not are discouraged by low rewards. We cover different settings and the assumptions they admit, including sensing, human computation, peer grading, reviews, and predictions. We survey different incentive mechanisms, including proper scoring rules, prediction markets and peer prediction, Bayesian Truth Serum, Peer Truth Serum, Correlated Agreement, and the settings where each of them would be suitable. As an alternative, we also consider reputation mechanisms. We complement the game-theoretic analysis with practical examples of applications in prediction platforms, community sensing, and peer grading. Computers

Adversarial Machine Learning This study allows readers to get to grips with the conceptual tools and practical techniques for building robust machine learning in the face of adversaries. Computers

Lectures on the Poisson Process A modern introduction to the Poisson process, with general point processes and random measures, and applications to stochastic geometry. Computers

Codes, Cryptology and Curves with Computer Algebra Graduate-level introduction to error-correcting codes, which are used to protect digital data and applied in public key cryptosystems. Computers

Computational Phylogenetics This book presents the foundations of phylogeny estimation and technical material enabling researchers to develop improved computational methods. Computers

Cambridge IGCSE ICT Study and Revision Guide Exam Board: Cambridge Assessment International Education Level: IGCSE Subject: ICT First Teaching: September 2015 First Exam: Summer 2017 Providing guidance that helps students practice and troubleshoot their exam technique,these books send them into their exam with the confidence to aim for the best grades. - Enables students to avoid common misconceptions and mistakes by highlighting them throughout- Builds students' skills constructing and writing answers as they progress through a range of practice questions- Allows students to mark their own responses and easily identify areas for improvement using the answers in the back of the book- Helps students target their revision and focus on important concepts and skills with key objectives at the beginning of every chapter- Ensures that students maximise their time in the exam by including examiner's tops and suggestions on how to approach the questions This title has not been through the Cambridge International endorsement process. Computers

Numerical Linear Algebra This self-contained introduction to numerical linear algebra provides a comprehensive, yet concise, overview of the subject. Computers

Big Data An unimaginably vast amount of data is now generated by our on-line lives and businesses, At the same time, our ability to store, manage, analyse, and exploit this data is becoming ever more sophisticated. This Very Short Introduction maps out the technology, and also the range of possibilities, challenges, and ethical questions it raises. Computers

Communication Networks This book results from many years of teaching an upper division course on communication networks in the EECS department at the University of California, Berkeley. It is motivated by the perceived need for an easily accessible textbook that puts emphasis on the core concepts behind current and next generation networks. After an overview of how today's Internet works and a discussion of the main principles behind its architecture, we discuss the key ideas behind Ethernet, WiFi networks, routing, internetworking, and TCP. To make the book as self-contained as possible, brief discussions of probability and Markov chain concepts are included in the appendices. This is followed by a brief discussion of mathematical models that provide insight into the operations of network protocols. Next, the main ideas behind the new generation of wireless networks based on LTE, and the notion of QoS are presented. A concise discussion of the physical layer technologies underlying various networks is also included. Finally, a sampling of topics is presented that may have significant influence on the future evolution of networks, including overlay networks like content delivery and peer-to-peer networks, sensor networks, distributed algorithms, Byzantine agreement, source compression, SDN and NFV, and Internet of Things. Computers

Next Generation Technology-Enhanced Assessment This book examines the types of web-based testing applications that exist, their technical requirements, and their use in various countries. Computers

Mood This book presents the essential background for understanding semantic theories of both verbal mood and sentence mood. Paul Portner evaluates and compares the theories, draws connections between seemingly disparate approaches, and highlights the most significant insights in the literature to provide a clearer understanding of how mood works. Computers

Predicting Human Decision-Making Human decision-making often transcends our formal models of "rationality." Designing intelligent agents that interact proficiently with people necessitates the modeling of human behavior and the prediction of their decisions. In this book, we explore the task of automatically predicting human decision-making and its use in designing intelligent human-aware automated computer systems of varying natures—from purely conflicting interaction settings (e.g., security and games) to fully cooperative interaction settings (e.g., autonomous driving and personal robotic assistants). We explore the techniques, algorithms, and empirical methodologies for meeting the challenges that arise from the above tasks and illustrate major benefits from the use of these computational solutions in real-world application domains such as security, negotiations, argumentative interactions, voting systems, autonomous driving, and games. The book presents both the traditional and classical methods as well as the most recent and cutting edge advances, providing the reader with a panorama of the challenges and solutions in predicting human decision-making. Computers

Language, Cognition, and Computational Models This book uses recent computational models to explore issues related to language and cognition. Computers

Calendrical Calculations These algorithmic tools for programmers, astronomers, and calendar enthusiasts include more than forty calendars and astronomical functions. Computers

Cyber Mercenaries Cyber Mercenaries explores how and why states use hackers as proxies to project power through cyberspace. Computers

Decoding Reality In this engaging and mind-stretching book, Vlatko Vedral explores the nature of information and looks at quantum computing, discussing the bizarre effects that arise from the quantum world. He concludes by asking the ultimate question: where did all of the information in the Universe come from? Computers

Power Of Computational Thinking, The From the team behind Computer Science for Fun (cs4fn), The Power of Computational Thinking shows that learning to think can be fascinating fun.Yes, and this book shows you how.Computational thinking has changed the way we all live, work and play. It has changed the way science is done too; won wars, created whole new industries and saved lives. It is at the heart of computer programming and is a powerful approach to problem solving, with or without computers. It is so important that many countries now require that primary school children learn the skills.Professors Paul Curzon and Peter McOwan of Queen Mary University of London have written a unique and enjoyable introduction. They describe the elements of computational thinking — such as algorithmic thinking, decomposition, abstraction and pattern matching — in an entertaining and accessible way, using magic tricks, games and puzzles, as well as through real and challenging problems that computer scientists work on.This book gives you a head start in learning the skills needed for coding, and will improve your real life problem solving skills. It will help you design and evaluate new technologies, as well as understand both your own brain and the digital world in a deeper way. Computers

The Sparse Fourier Transform The Fourier transform is one of the most fundamental tools for computing the frequency representation of signals. It plays a central role in signal processing, communications, audio and video compression, medical imaging, genomics, astronomy, as well as many other areas. Because of its widespread use, fast algorithms for computing the Fourier transform can benefit a large number of applications. The fastest algorithm for computing the Fourier transform is the Fast Fourier Transform (FFT), which runs in near-linear time making it an indispensable tool for many applications. However, today, the runtime of the FFT algorithm is no longer fast enough especially for big data problems where each dataset can be few terabytes. Hence, faster algorithms that run in sublinear time, i.e., do not even sample all the data points, have become necessary. This book addresses the above problem by developing the Sparse Fourier Transform algorithms and building practical systems that use these algorithms to solve key problems in six different applications: wireless networks; mobile systems; computer graphics; medical imaging; biochemistry; and digital circuits. This is a revised version of the thesis that won the 2016 ACM Doctoral Dissertation Award. Computers

Forbidden Configurations in Discrete Geometry Unifies discrete and computational geometry by using forbidden patterns of points to characterize many of its problems. Computers

Robotica Offers a First Amendment approach to defend against governmental censorship of the newest form of technological expression: robotic speech. Computers

Graph Theory In 1736, the mathematician Euler invented graph theory while solving the Konigsberg seven-bridge problem. Over 200 years later, graph theory remains the skeleton content of discrete mathematics, which serves as a theoretical basis for computer science and network information science. This book introduces some basic knowledge and the primary methods in graph theory by many interesting problems and games. Computers

The Second Age of Computer Science Between the genesis of computer science in the 1960s and the advent of the World Wide Web around 1990, computer science evolved in significant ways. The author has termed this period the "second age of computer science." This book describes its evolution in the form of several interconnected parallel histories. Computers

Network Security and Cryptography Network Security and Cryptography introduces the basic concepts in computer networks and the latest trends and technologies in cryptography and network security. The book is a definitive guide to the principles and techniques of cryptography and network security, and introduces basic concepts in computer networks such as classical cipher schemes, public key cryptography, authentication schemes, pretty good privacy, and Internet security. It features the latest material on emerging technologies, related to IoT, cloud computing, SCADA, blockchain, smart grid, big data analytics, and more. Primarily intended as a textbook for courses in computer science and electronics & communication, the book also serves as a basic reference and refresher for professionals in these areas. FEATURES: •Includes the latest material on emerging technologies, related to IoT, cloud computing, smart grid, big data analytics, blockchain, and more•Features separate chapters on the mathematics related to network security and cryptography•Introduces basic concepts in computer networks including classical cipher schemes, public key cryptography, authentication schemes, pretty good privacy, Internet security services, and system security•Includes end of chapter review questions Computers

Data-Driven Computational Methods Describes computational methods for parametric and nonparametric modeling of stochastic dynamics. Aimed at graduate students, and suitable for self-study. Computers

Demystifying OWL for the Enterprise After a slow incubation period of nearly 15 years, a large and growing number of organizations now have one or more projects using the Semantic Web stack of technologies. The Web Ontology Language (OWL) is an essential ingredient in this stack, and the need for ontologists is increasing faster than the number and variety of available resources for learning OWL. This is especially true for the primary target audience for this book: modelers who want to build OWL ontologies for practical use in enterprise and government settings. The purpose of this book is to speed up the process of learning and mastering OWL. To that end, the focus is on the 30% of OWL that gets used 90% of the time. Others who may benefit from this book include technically oriented managers, semantic technology developers, undergraduate and post-graduate students, and finally, instructors looking for new ways to explain OWL. The book unfolds in a spiral manner, starting with the core ideas. Each subsequent cycle reinforces and expands on what has been learned in prior cycles and introduces new related ideas. Part 1 is a cook's tour of ontology and OWL, giving an informal overview of what things need to be said to build an ontology, followed by a detailed look at how to say them in OWL. This is illustrated using a healthcare example. Part 1 concludes with an explanation of some foundational ideas about meaning and semantics to prepare the reader for subsequent chapters. Part 2 goes into depth on properties and classes, which are the core of OWL. There are detailed descriptions of the main constructs that you are likely to need in every day modeling, including what inferences are sanctioned. Each is illustrated with real world examples. Part 3 explains and illustrates how to put OWL into practice, using examples in healthcare, collateral, and financial transactions. A small ontology is described for each, along with some key inferences. Key limitations of OWL are identified, along with possible workarounds. The final chapter gives a variety of practical tips and guidelines to send the reader on their way. Computers

Networks This book brings together recent advances and presents a comprehensive picture of the scientific study of networks. It includes discussion of computer networks, social networks, biological networks, and others, and an introduction to the mathematics of network theory, including analysis techniques, computer algorithms, and network modeling. Computers

Artificial Intelligence and Social Work An introductory guide with real-life examples on using AI to help homeless youth, diabetes patients, and other social welfare interventions. Computers

Algorithmic Aspects of Machine Learning Introduces cutting-edge research on machine learning theory and practice, providing an accessible, modern algorithmic toolkit. Computers

Machine Learning for Face, Emotion, and Pain Recognition This Spotlight explains how to build an automated system for face, emotion, and pain recognition. The steps involved include pre-processing, face detection and segmentation, feature extraction, and finally recognition to classify features and show the accuracy of the system. State-of-the-art algorithms are used to describe all possible solutions of each step. For face detection and segmentation, several approaches are described to detect a face in images: Viola-Jones, color-based approaches, histogram-based approaches, and morphological operation. Local binary patterns, edge detectors, wavelets, discrete cosine transformation, Gabor filters, and fuzzified features are used for feature extraction. The last step includes three approaches for recognition: classification techniques (with a special focus on deep learning), statistical modeling, and distance/similarity measures. Computers

Mining Structures of Factual Knowledge from Text The real-world data, though massive, is largely unstructured, in the form of natural-language text. It is challenging but highly desirable to mine structures from massive text data, without extensive human annotation and labeling. In this book, we investigate the principles and methodologies of mining structures of factual knowledge (e.g., entities and their relationships) from massive, unstructured text corpora. Departing from many existing structure extraction methods that have heavy reliance on human annotated data for model training, our effort-light approach leverages human-curated facts stored in external knowledge bases as distant supervision and exploits rich data redundancy in large text corpora for context understanding. This effort-light mining approach leads to a series of new principles and powerful methodologies for structuring text corpora, including (1) entity recognition, typing and synonym discovery, (2) entity relation extraction, and (3) open-domain attribute-value mining and information extraction. This book introduces this new research frontier and points out some promising research directions. Computers

Artificial Intelligence This concise guide explains the history, theory, potential, application, and limitations of Artificial Intelligence. Boden shows how research into AI has shed light on the working of human and animal minds, and she considers the philosophical challenges AI raises: could programs ever be really intelligent, creative or even conscious? Computers

Adversarial Machine Learning The increasing abundance of large high-quality datasets, combined with significant technical advances over the last several decades have made machine learning into a major tool employed across a broad array of tasks including vision, language, finance, and security. However, success has been accompanied with important new challenges: many applications of machine learning are adversarial in nature. Some are adversarial because they are safety critical, such as autonomous driving. An adversary in these applications can be a malicious party aimed at causing congestion or accidents, or may even model unusual situations that expose vulnerabilities in the prediction engine. Other applications are adversarial because their task and/or the data they use are. For example, an important class of problems in security involves detection, such as malware, spam, and intrusion detection. The use of machine learning for detecting malicious entities creates an incentive among adversaries to evade detection by changing their behavior or the content of malicius objects they develop. The field of adversarial machine learning has emerged to study vulnerabilities of machine learning approaches in adversarial settings and to develop techniques to make learning robust to adversarial manipulation. This book provides a technical overview of this field. After reviewing machine learning concepts and approaches, as well as common use cases of these in adversarial settings, we present a general categorization of attacks on machine learning. We then address two major categories of attacks and associated defenses: decision-time attacks, in which an adversary changes the nature of instances seen by a learned model at the time of prediction in order to cause errors, and poisoning or training time attacks, in which the actual training dataset is maliciously modified. In our final chapter devoted to technical content, we discuss recent techniques for attacks on deep learning, as well as approaches for improving robustness of deep neural networks. We conclude with a discussion of several important issues in the area of adversarial learning that in our view warrant further research. Given the increasing interest in the area of adversarial machine learning, we hope this book provides readers with the tools necessary to successfully engage in research and practice of machine learning in adversarial settings. Computers

Diversity and Intersectionality This volume brings together two core concepts that are central to understanding the social and public significance of religions and theologies within the contemporary world and are therefore of key importance to the discipline of religious education: diversity and intersectionality. Religious diversity requires an understanding of religions and theologies and their roles within a plural society. However, the effect of the intersectionality of multiple social identities on a person’s flourishing illuminates the ways in which the broader complexity of diversity must be viewed from different perspectives. These core constructs were brought together in a recent conference convened by the International Seminar on Religious Education and Values, the leading international association for religious educators across the world. This volume presents twelve key contributions made to the seminar, spanning both conceptual and empirical approaches, and represents a unique collection of international perspectives on the interlocking themes of intersectionality and diversity. Computers

Cloth Simulation for Computer Graphics Physics-based animation is commonplace in animated feature films and even special effects for live-action movies. Think about a recent movie and there will be some sort of special effects such as explosions or virtual worlds. Cloth simulation is no different and is ubiquitous because most virtual characters (hopefully!) wear some sort of clothing. The focus of this book is physics-based cloth simulation. We start by providing background information and discuss a range of applications. This book provides explanations of multiple cloth simulation techniques. More specifically, we start with the most simple explicitly integrated mass-spring model and gradually work our way up to more complex and commonly used implicitly integrated continuum techniques in state-of-the-art implementations. We give an intuitive explanation of the techniques and give additional information on how to efficiently implement them on a computer. This book discusses explicit and implicit integration schemes for cloth simulation modeled with mass-spring systems. In addition to this simple model, we explain the more advanced continuum-inspired cloth model introduced in the seminal work of Baraff and Witkin [1998]. This method is commonly used in industry. We also explain recent work by Liu et al. [2013] that provides a technique to obtain fast simulations. In addition to these simulation approaches, we discuss how cloth simulations can be art directed for stylized animations based on the work of Wojtan et al. [2006]. Controllability is an essential component of a feature animation film production pipeline. We conclude by pointing the reader to more advanced techniques. Computers

Modern Fortran Explained Written by leading experts in the field, two of whom have actively contributed to Fortran 2018, Modern Fortran Explained is a complete and authoritative description of Fortran in its latest form Computers

Advanced Software Testing - Vol. 3, 2nd Edition This book is written for the technical test analyst who wants to achieve advanced skills in test analysis, design, and execution. With a hands-on, exercise-rich approach, this book teaches you how to define and carry out the tasks required to implement a test strategy. You will be able to analyze, design, implement, and execute tests using risk considerations to determine the appropriate effort and priority for tests. This book will help you prepare for the ISTQB Advanced Technical Test Analyst exam. Included are sample exam questions for most of the learning objectives covered by the latest (2012) ISTQB Advanced Level syllabus. The ISTQB certification program is the leading software tester certification program in the world. You can be confident in the value and international stature that the Advanced Technical Test Analyst certificate will offer you. With over thirty years of software and systems engineering experience, author Rex Black is President of RBCS, a leader in software, hardware, and systems testing, and the most prolific author practicing in the field of software testing today. Previously, he served as President of both the International and American Software Testing Qualifications Boards (ISTQB and ASTQB). Jamie Mitchell is a consultant who has been working in software testing, test automation, and development for over 20 years. He was a member of the Technical Advisory Group for ASTQB, and one of the primary authors for the ISTQB Advanced Technical Test Analyst 2012 syllabus. Computers

Photoshop Elements 2018 Designed for all photographers from enthusiasts to professionals, this book provides readers with easy to follow, building-block style learning of Photoshop Elements 2018 through hands on projects working in both its Organizer and Photo Editor workspaces. Companion files with practice projects and all of the color figures from the text are included (also available by contacting the publisher by writing to: info @ merclearning.com). Divided into two parts, using the files supplied or your own, Part One will teach you to easily import, sort and find your photographs working in the Elements Organizer. When working with the Elements Photo Editor in Part Two, topics include understanding resolution, using Camera Raw, multiple techniques for color and image correction, precision selection, using layers, accurate color printing, removing unwanted content, correcting red eye and closed eyes, creating a panorama and much more, plus numerous tricks of the trade and ways to share your precious photographs in print and online. Through projects using each of its modes: Quick, Guided, and Expert, you will gain a comprehensive knowledge of the Photo Editor, allowing you later to choose the mode best suited to your working style and project requirements. Key Features: +Divided into two parts each exclusively dedicated to one of the Photoshop Elements 2018 workspaces, this book offers readers the opportunity to focus their learning on one workspace or both depending on their needs and interests +Companion files with practice projects and all of the color figures from the text (also available by contacting the publisher by writing to: info@merclearning.com) +Project photographs are supplied for each chapter to guide readers through the learning process +Additional supplementary projects and images are provided with each chapter to further reinforce learning +Helpful tips and notes are included in each chapter to maximize and streamline learning and efficiency On the Companion Files:(Included with this text, and also available by contacting the publisher by writing to: info @ merclearning.com) • Photographs to complete all projects covered in the text • Extra practice project files for each chapter • Copies of all figures used in the text Computers

How to Get to the Top of Google Search Anyone trying to sell anything wants potential customers to be able to find them straight away when searching online. This book tells them how.It has been written by a professional search engine consultant. Richard Conway started his company, Pure SEO, in 2009 with just $200 to spend on a single web page. From there, mostly using digital marketing, he has expanded the business to four offices in New Zealand and Australia. Pure SEO has been listed by Deloitte in the fastest-growing 500 tech companies in the Asia Pacific region for the past five years.This practical guide cuts through the mis-information and sets the record straight on what actions you need to take, so searchers will find your product quickly and easily. It covers keywords, website content and structure, mobile search and optimisation, loading speed of your website and how that affects searches, planning content to make it easily searchable, tracking tools and much much more.With Australasian-focused statistics and insights, as well as advice about how these two markets differ, the book is an authoritative and accessible 'how to' resource.Case studies and Q&A sections provide real-life dos and don'ts. As well as actionable advice and 'red flags' to avoid, the book also looks ahead to consider the future of search marketing. Computers

Abstract Recursion and Intrinsic Complexity Presents a new framework for the complexity of algorithms, for all readers interested in the theory of computation. Computers

Research Handbook on the Law of Artificial Intelligence The field of artificial intelligence (AI) has made tremendous advances in the last two decades, but as smart as AI is now, it is getting smarter and becoming more autonomous. This raises a host of challenges to current legal doctrine, including whether AI/algorithms should count as ‘speech’, whether AI should be regulated under antitrust and criminal law statutes, and whether AI should be considered as an agent under agency law or be held responsible for injuries under tort law. This book contains chapters from US and international law scholars on the role of law in an age of increasingly smart AI, addressing these and other issues that are critical to the evolution of the field. Computers

Autonomous Vehicles and the Law Autonomous vehicles have attracted a great deal of attention in the media, however there are some inconsistencies between the perception of autonomous vehicles’ capabilities and their actual functions. This book provides an accessible explanation of how autonomous vehicles function, suggesting appropriate regulatory responses to the existing and emerging technology. Computers

Cloud Computing Basics This book is designed for use as a primary textbook for a course in cloud computing or as a resource for professionals in industry seeking to explore cloud services. The book highlights the recent developments in distributed computing and details the architecture, virtualization concepts, and security concerns of cloud computing. It also provides a detailed understanding of the benefits of cloud computing that can encourage enterprises to switch to the cloud. Features: - Provides a basic understanding of the computing paradigm of cloud computing- Gives a brief introduction to cloud computing, its architecture, and the Hadoop distributed file system- Deals with cloud management concepts like scalable, fault tolerance, resiliency, provisioning, asset management, cloud governance, high availability, disaster recovery, and multi-tenancy- Includes case studies on MS Azure, Google, Amazon Web Services, Aneka, etc. Computers

Game Development Using Python This book will guide you through thebasic game development process using Python, covering game topics includinggraphics, sound, artificial intelligence, animation, game engines, etc. Realgames are created as you work through the text and significant parts of a gameengine are built and made available for download. The companion disc contains allof the resources described in the book, e.g. example code, game assets, video/soundediting software, and color figures. Instructor resources are available for useas a textbook. Features: Teaches basic game development concepts using Python including graphics, sound, artificial intelligence, animation, game engines, collision detection, Web-based games, and more Includes a companion disc with example code, games assets, and color figures Companion files are available for downloading with order number/proof of purchase by writing to the publisher at info@merclearning.com. Computers

The Logic of Information Luciano Floridi presents an innovative approach to philosophy, conceived as conceptual design. His starting-point is that reality provides the data which we transform into information. He explores how we make, transform, refine, and improve the objects of our knowledge, and defends the radical idea that knowledge is design. Computers

The Student's Introduction to Mathematica and the Wolfram Language An introduction to Mathematica® and the Wolfram Language™ in the familiar context of the standard university mathematics curriculum. Computers

The Oxford Handbook of Event Structure This handbook explores what events are, how we perceive them, how we use language to describe them, how we reason with them, and the role they play in the organization of grammar and discourse. It takes an interdisciplinary approach with insights from linguistics, philosophy, psychology, cognitive science, and computer science. Computers

Mathematical Modelling of the Human Cardiovascular System Addresses the mathematical and numerical modelling of the human cardiovascular system, from patient data to clinical applications. Computers

An Introduction to the Planning Domain Definition Language Planning is the branch of Artificial Intelligence (AI) that seeks to automate reasoning about plans, most importantly the reasoning that goes into formulating a plan to achieve a given goal in a given situation. AI planning is model-based: a planning system takes as input a description (or model) of the initial situation, the actions available to change it, and the goal condition to output a plan composed of those actions that will accomplish the goal when executed from the initial situation. The Planning Domain Definition Language (PDDL) is a formal knowledge representation language designed to express planning models. Developed by the planning research community as a means of facilitating systems comparison, it has become a de-facto standard input language of many planning systems, although it is not the only modelling language for planning. Several variants of PDDL have emerged that capture planning problems of different natures and complexities, with a focus on deterministic problems. The purpose of this book is two-fold. First, we present a unified and current account of PDDL, covering the subsets of PDDL that express discrete, numeric, temporal, and hybrid planning. Second, we want to introduce readers to the art of modelling planning problems in this language, through educational examples that demonstrate how PDDL is used to model realistic planning problems. The book is intended for advanced students and researchers in AI who want to dive into the mechanics of AI planning, as well as those who want to be able to use AI planning systems without an in-depth explanation of the algorithms and implementation techniques they use. Computers

Rhetoric and Experience Architecture Organizations value insights from reflexive, iterative processes of designing interactive environments that reflect user experience. “I really like this definition of experience architecture, which requires that we understand ecosystems of activity, rather than simply considering single-task scenarios.â€â€”Donald Norman (The Design of Everyday Things) Computers

Human-Computer Interactions in Museums Museums have been a domain of study and design intervention for Human-Computer Interaction (HCI) for several decades. However, while resources providing overviews on the key issues in the scholarship have been produced in the fields of museum and visitor studies, no such resource as yet existed within HCI. This book fills this gap and covers key issues regarding the study and design of HCIs in museums. Through an on-site focus, the book examines how digital interactive technologies impact and shape galleries, exhibitions, and their visitors. It consolidates the body of work in HCI conducted in the heritage field and integrates it with insights from related fields and from digital heritage practice. Processes of HCI design and evaluation approaches for museums are also discussed. This book draws from the authors' extensive knowledge of case studies as well as from their own work to provide examples, reflections, and illustrations of relevant concepts and problems. This book is designed for students and early career researchers in HCI or Interaction Design, for more seasoned investigators who might approach the museum domain for the first time, and for researchers and practitioners in related fields such as heritage and museum studies or visitor studies. Designers who might wish to understand the HCI perspective on visitor-facing interactive technologies may also find this book useful. Computers

A Hobbyist's Guide to THEC64 Mini If you own a C64 and tinkered with it, you will definitely enjoy this book.I have collected a large collection of tips and tricks, hardware, useful software and many other interesting internet links for the Mini.Retro Games has answered my every question and covered every topic. As a result, a lot of official answers went into this ... Computers

Integer Linear Programming in Computational and Systems Biology This hands-on tutorial text for non-experts demonstrates biological applications of a versatile modeling and optimization technique. Computers

Python by Example A collection of progressively more complex Python programming challenges to help students learn to code in a naturally engaging way. Computers

Arduino and Scilab based Projects Computers

An Invitation to Applied Category Theory Category theory reveals commonalities between structures of all sorts. This book shows its potential in science, engineering, and beyond. Computers

Conversational UX Design With recent advances in natural language understanding techniques and far-field microphone arrays, natural language interfaces, such as voice assistants and chatbots, are emerging as a popular new way to interact with computers. They have made their way out of the industry research labs and into the pockets, desktops, cars and living rooms of the general public. But although such interfaces recognize bits of natural language, and even voice input, they generally lack conversational competence, or the ability to engage in natural conversation. Today’s platforms provide sophisticated tools for analyzing language and retrieving knowledge, but they fail to provide adequate support for modeling interaction. The user experience (UX) designer or software developer must figure out how a human conversation is organized, usually relying on commonsense rather than on formal knowledge. Fortunately, practitioners can rely on conversation science. This book adapts formal knowledge from the field of Conversation Analysis (CA) to the design of natural language interfaces. It outlines the Natural Conversation Framework (NCF), developed at IBM Research, a systematic framework for designing interfaces that work like natural conversation. The NCF consists of four main components: 1) an interaction model of “expandable sequences,†2) a corresponding content format, 3) a pattern language with 100 generic UX patterns and 4) a navigation method of six basic user actions. The authors introduce UX designers to a new way of thinking about user experience design in the context of conversational interfaces, including a new vocabulary, new principles and new interaction patterns. User experience designers and graduate students in the HCI field as well as developers and conversation analysis students should find this book of interest. Computers

Cache Replacement Policies This book summarizes the landscape of cache replacement policies for CPU data caches. The emphasis is on algorithmic issues, so the authors start by defining a taxonomy that places previous policies into two broad categories, which they refer to as coarse-grained and fine-grained policies. Each of these categories is then divided into three subcategories that describe different approaches to solving the cache replacement problem, along with summaries of significant work in each category. Richer factors, including solutions that optimize for metrics beyond cache miss rates, that are tailored to multi-core settings, that consider interactions with prefetchers, and that consider new memory technologies, are then explored. The book concludes by discussing trends and challenges for future work. This book, which assumes that readers will have a basic understanding of computer architecture and caches, will be useful to academics and practitioners across the field. Computers

How to Prove It Helps students transition from problem solving to proving theorems, with a new chapter on number theory and over 150 new exercises. Computers

Finite-State Techniques Covers the whole spectrum of finite-state methods, from theory to practical applications. Computers

3D Printing and Intellectual Property Focuses on the novel issues raised for IP law by 3D printing for the major IP systems around the world. Computers

Variational Bayesian Learning Theory This introduction to the theory of variational Bayesian learning summarizes recent developments and suggests practical applications. Computers

Cambridge International AS & A Level Computer Science This title is endorsed by Cambridge Assessment International Education to support the full syllabus for examination from 2021. Develop computational thinking and ensure full coverage of the revised Cambridge Assessment International Education AS & A Level Computer Science syllabus (9618) with this comprehensive Student's Book written by experienced authors and examiners. - Improve understanding with clear explanations, examples, illustrations and diagrams, plus a glossaryof key terms- Reinforce learning with a range of activities, exercises, and exam-style questions- Prepare for further study with extension activities that go beyond the requirements of the syllabus and prompt further investigation about new developments in technology- Follow a structured route through the course with in-depth coverage of the full AS & A Level syllabus Answers are available in the Online Teacher Guide. Also available in the seriesProgramming skills workbook ISBN: 9781510457683 Student eTextbook ISBN: 9781510457614 Whiteboard eTextbook ISBN: 9781510457621 Online Teacher's guide ISBN: 9781510457652 Computers

The 9 Pitfalls of Data Science The 9 Pitfalls of Data Science is loaded with entertaining tales of both successful and misguided approaches to interpreting data, both grand successes and epic failures. Computers

Microsoft Access 2019 Programming by Example with VBA, XML, and ASP Updatedfor Access 2019 and based on the bestselling editions from previous versions, MicrosoftAccess 2019 Programming by Example with VBA, XML and ASP is a practical,how-to book on Access programming, suitable for readers already proficient withthe Access user interface (UI). If you are looking to automate Access routinetasks, this book will progressively introduce you to programming concepts vianumerous illustrated hands-on exercises. More advanced topics are demonstratedvia custom projects. With concise and straightforward explanations, you learnhow to write and test your programming code with the built-in Visual BasicEditor; understand and use common VBA programming structures such asconditions, loops, arrays, and collections; code a "message box";reprogram characteristics of a database; and use various techniques to queryand manipulate your Access .mdb and .accdb databases. The book shows you howyou can build database solutions with Data Access Objects (DAO) and ActiveXData Objects (ADO); define database objects and manage database security withSQL; enhance and alter the way users interact with database applications withRibbon customizations and event programming in forms and reports. You alsolearn how to program Microsoft Access databases for Internet access with ActiveServer Pages (Classic ASP), HTML, and XML. Features: Contains over thirty chapters loaded withillustrated "Hands-On" exercises and projects that guide you throughthe VBA programming language. Each example tells you exactly where to entercode and how to test it and then run it. Includes a companion disc with source code, supplemental files,and color screen captures (also available from the publisher for download) Explains how to store data for furthermanipulation in variables, arrays, and collections while teaching you to writeboth simple and complex VBA programming routines and functions. Teaches you how to programmatically createand access database tables and fields. Shows you how to insert, update, and deletedata via programming code using various data access techniques. Gets you proficient creating and runningsimple and parameterized queries against your Access databases. Gets you comfortable using external datasources with Access (Excel, Word, flat files, XML, and SQL Server). Teaches you how to take control of yourforms and reports by writing programming code known as event procedures. Shows you how to use various types of macrosand templates. Takes your programming skills to the Web byintroducing you to dynamic XML and Classic ASP pages. ONTHE DISC! (Files are also available by emailing proof of purchase to the publisher at info@merclearning.com) All source code and supplemental files for the Hands-On exercises and custom projects Allimages from the text (including 4-color screenshots) Computers

Are We There Yet? Digital transformation across the public sector has stalled. After over 25 years of considerable time, money, and effort at national, state, and local levels, we’re still not 'there' yet. The reason is that successive waves of investment in digital transformation have focused largely on improving the transactional functions and activities of government. They have failed to embrace a bigger challenge - the need for governing and government to rethink a new 'theory of the business' - which that same revolution has caused and to which it is an inescapable part of the answer. This is a unique, timely, and distinctly Australian look at a global phenomenon by two 'reflective practitioners'. Their personal and practical experience of digital transformation in government and the public sector in Australia suggests it is a story missing half its plot. Packed full of insights from government and digital leaders from around Australia and across the world, this is a much-needed practical guide for public servants and leaders in any jurisdiction. It contains insights and ideas about the way digital technologies, and their associated tools, platforms, and cultures, are changing the business of governing and the design and delivery of public policy and services. " Are We There Yet? lucidly diagnoses how digital technologies, including AI and big data, are transforming the role of the public servant and the project of governance itself. Stewart-Weeks and Cooper describe the important shift from power to problem-solving and explain how to harness digital transformation to make government work better for all of us.†- Beth Noveck, author of Wiki Government, former Deputy Chief Technology Officer in the Obama White House, Professor in Technology, Culture & Society, New York University and Chief Innovation Officer for New Jersey "I've read a lot about the potential impact of digital technology on public services … this is the first book to persuade me that the power of digital, properly conceived, really can transform the nature of democratic governance." - Professor Peter Shergold AC, Chancellor, Western Sydney University, Former Secretary, Department of Prime Minister and Cabinet Computers

The Essentials of Modern Software Engineering The first course in software engineering is the most critical. Education must start from an understanding of the heart of software development, from familiar ground that is common to all software development endeavors. This book is an in-depth introduction to software engineering that uses a systematic, universal kernel to teach the essential elements of all software engineering methods. This kernel, Essence, is a vocabulary for defining methods and practices. Essence was envisioned and originally created by Ivar Jacobson and his colleagues, developed by Software Engineering Method and Theory (SEMAT) and approved by The Object Management Group (OMG) as a standard in 2014. Essence is a practice-independent framework for thinking and reasoning about the practices we have and the practices we need. Essence establishes a shared and standard understanding of what is at the heart of software development. Essence is agnostic to any particular method, lifecycle independent, programming language independent, concise, scalable, extensible, and formally specified. Essence frees the practices from their method prisons. The first part of the book describes Essence, the essential elements to work with, the essential things to do and the essential competencies you need when developing software. The other three parts describe more and more advanced use cases of Essence. Using real but manageable examples, it covers the fundamentals of Essence and the innovative use of serious games to support software engineering. It also explains how current practices such as user stories, use cases, Scrum, and micro-services can be described using Essence, and illustrates how their activities can be represented using the Essence notions of cards and checklists. The fourth part of the book offers a vision how Essence can be scaled to support large, complex systems engineering. Essence is supported by an ecosystem developed and maintained by a community of experienced people worldwide. From this ecosystem, professors and students can select what they need and create their own way of working, thus learning how to create ONE way of working that matches the particular situation and needs. Computers

Machine Learning for Signal Processing Describes in detail the fundamental mathematics and algorithms of machine learning (an example of artificial intelligence) and signal processing, two of the most important and exciting technologies in the modern information economy. Builds up concepts gradually so that the ideas and algorithms can be implemented in practical software applications. Computers

Bell Nonlocality Quantum technologies have seen a tremendous upsurge in recent years. Bell nonlocality, one of the most striking discoveries triggered by quantum theory, has been instrumental in this trend. It states that in some situations measurements of physical systems do not reveal pre-existing properties, but properties are created by the measurement itself. Computers

Introduction to Statistics Using R Introduction to Statistics Using R is organized into 13 major chapters. Each chapter is broken down into many digestible subsections in order to explore the objectives of the book. There are many real-life practical examples in this book and each of the examples is written in R codes to acquaint the readers with some statistical methods while simultaneously learning R scripts. Computers

Ethical Challenges in Digital Psychology and Cyberpsychology Explores the ethical issues of cyberpsychology research and praxes, which arise in algorithmically paired people and technologies. Computers

Science, Technology, and Society Investigates the impact of scientific and technological advances on society, including politics, economy, family life, and ethics. Computers

Computing Possible Futures Computing Possible Futures provides an easy to digest tour of modeling, simulation, analytics, and AI and how these technologies can enable better decision making. Computers

General Video Game Artificial Intelligence Research on general video game playing aims at designing agents or content generators that can perform well in multiple video games, possibly without knowing the game in advance and with little to no specific domain knowledge. The general video game AI framework and competition propose a challenge in which researchers can test their favorite AI methods with a potentially infinite number of games created using the Video Game Description Language. The open-source framework has been used since 2014 for running a challenge. Competitors around the globe submit their best approaches that aim to generalize well across games. Additionally, the framework has been used in AI modules by many higher-education institutions as assignments, or as proposed projects for final year (undergraduate and Master's) students and Ph.D. candidates. The present book, written by the developers and organizers of the framework, presents the most interesting highlights of the research performed by the authors during these years in this domain. It showcases work on methods to play the games, generators of content, and video game optimization. It also outlines potential further work in an area that offers multiple research directions for the future. Computers

On the Foundations of Computing On the Foundation of Computing offers a comprehensive and critical overview of the birth and evolution of computing, and analyses some of the most important technical results and philosophical problems of the discipline, combining both historical and systematic analyses. Computers

Foundations of Data Science Covers mathematical and algorithmic foundations of data science: machine learning, high-dimensional geometry, and analysis of large networks. Computers

Python for Linguists An introduction to Python programming for linguists. Examples of code specifically designed for language analysis are featured throughout. Computers

Spectral Analysis for Univariate Time Series Focuses on practical application of spectral analysis of time series, with examples from environmental, engineering and physical sciences. Computers

Transfer Learning This in-depth tutorial for students, researchers, and developers covers foundations, plus applications ranging from search to multimedia. Computers

Fundamentals of Machine Learning Interest in machine learning is exploding across the world, both in research and for industrial applications. Fundamentals of Machine Learning provides a brief and accessible introduction to this rapidly growing field, one that will appeal to both students and researchers. Computers

Mathematics for Machine Learning Distills key concepts from linear algebra, geometry, matrices, calculus, optimization, probability and statistics that are used in machine learning. Computers

TinyML Deep learning networks are getting smaller. Much smaller. The Google Assistant team can detect words with a model just 14 kilobytes in size—small enough to run on a microcontroller. With this practical book you’ll enter the field of TinyML, where deep learning and embedded systems combine to make astounding things possible with tiny devices. Pete Warden and Daniel Situnayake explain how you can train models small enough to fit into any environment. Ideal for software and hardware developers who want to build embedded systems using machine learning, this guide walks you through creating a series of TinyML projects, step-by-step. No machine learning or microcontroller experience is necessary. Build a speech recognizer, a camera that detects people, and a magic wand that responds to gestures Work with Arduino and ultra-low-power microcontrollers Learn the essentials of ML and how to train your own models Train models to understand audio, image, and accelerometer data Explore TensorFlow Lite for Microcontrollers, Google’s toolkit for TinyML Debug applications and provide safeguards for privacy and security Optimize latency, energy usage, and model and binary size Computers

Federated Learning How is it possible to allow multiple data owners to collaboratively train and use a shared prediction model while keeping all the local training data private? Traditional machine learning approaches need to combine all data at one location, typically a data center, which may very well violate the laws on user privacy and data confidentiality. Today, many parts of the world demand that technology companies treat user data carefully according to user-privacy laws. The European Union's General Data Protection Regulation (GDPR) is a prime example. In this book, we describe how federated machine learning addresses this problem with novel solutions combining distributed machine learning, cryptography and security, and incentive mechanism design based on economic principles and game theory. We explain different types of privacy-preserving machine learning solutions and their technological backgrounds, and highlight some representative practical use cases. We show how federated learning can become the foundation of next-generation machine learning that caters to technological and societal needs for responsible AI development and application. Computers

Human-Robot Interaction This broad overview for graduate students introduces multidisciplinary topics from robotics to sociology which are needed to understand the area. Computers

Statistics Using Stata This textbook integrates the teaching and learning of statistical concepts with the acquisition of the Stata (version 16) software package. Computers

Introduction to Logic Programming Logic Programming is a style of programming in which programs take the form of sets of sentences in the language of Symbolic Logic. Over the years, there has been growing interest in Logic Programming due to applications in deductive databases, automated worksheets, Enterprise Management (business rules), Computational Law, and General Game Playing. This book introduces Logic Programming theory, current technology, and popular applications. In this volume, we take an innovative, model-theoretic approach to logic programming. We begin with the fundamental notion of datasets, i.e., sets of ground atoms. Given this fundamental notion, we introduce views, i.e., virtual relations; and we define classical logic programs as sets of view definitions, written using traditional Prolog-like notation but with semantics given in terms of datasets rather than implementation. We then introduce actions, i.e., additions and deletions of ground atoms; and we define dynamic logic programs as sets of action definitions. In addition to the printed book, there is an online version of the text with an interpreter and a compiler for the language used in the text and an integrated development environment for use in developing and deploying practical logic programs. "This is a book for the 21st century: presenting an elegant and innovative perspective on logic programming. Unlike other texts, it takes datasets as a fundamental notion, thereby bridging the gap between programming languages and knowledge representation languages; and it treats updates on an equal footing with datasets, leading to a sound and practical treatment of action and change." – Bob Kowalski, Professor Emeritus, Imperial College London "In a world where Deep Learning and Python are the talk of the day, this book is a remarkable development. It introduces the reader to the fundamentals of traditional Logic Programming and makes clear the benefits of using the technology to create runnable specifications for complex systems." – Son Cao Tran, Professor in Computer Science, New Mexico State University "Excellent introduction to the fundamentals of Logic Programming. The book is well-written and well-structured. Concepts are explained clearly and the gradually increasing complexity of exercises makes it so that one can understand easy notions quickly before moving on to more difficult ideas." – George Younger, student, Stanford University Computers

AI Narratives This book is the first to examine the history of imaginative thinking about intelligent machines, featuring contributions from leading humanities and social science scholars who detail the narratives about artificial intelligence (AI) that in turn offer a crucial epistemic site for exploring contemporary debates about these powerful technologies. Computers

Birth of Intelligence As man-made machines become more powerful and smarter, will their intelligence eventually exceed our own? To accurately predict how the relationship between human and artificial intelligence will change in the future, it is essential to understand the origin and limits of human intelligence. In Birth of Intelligence, distinguished neuroscientist Daeyeol Lee tackles these pressing fundamental issues. Lee reveals how intelligence is the ability of a biological agent to solve complex decision-making problems in diverse and unpredictable environments. Furthermore, understanding how intelligent behavior emerges from interaction among multiple learning systems will provide valuable insights into the ultimate nature of human intelligence. Computers

Hands-On Swift 5 Microservices Development Learn to design and deploy fully functioning microservices for your applications from scratch using Swift, Docker, and AWS Key Features Understand server-side Swift development concepts for building your first microservice Build microservices using Vapor 4 and deploy them to the cloud using Docker Learn effective techniques for enhancing maintainability and stability of your Swift applications Book Description The capabilities of the Swift programming language are extended to server-side development using popular frameworks such as Vapor. This enables Swift programmers to implement the microservices approach to design scalable and easy-to-maintain architecture for iOS, macOS, iPadOS, and watchOS applications. This book is a complete guide to building microservices for iOS applications. You'll start by examining Swift and Vapor as backend technologies and compare them to their alternatives. The book then covers the concept of microservices to help you get started with developing your first microservice. Throughout this book, you'll work on a case study of writing an e-commerce backend as a microservice application. You'll understand each microservice as it is broken down into details and written out as code throughout the book. You'll also become familiar with various aspects of server-side development such as scalability, database options, and information flow for microservices that are unwrapped in the process. As you advance, you'll get to grips with microservices testing and see how it is different from testing a monolith application. Along the way, you'll explore tools such as Docker, Postman, and Amazon Web Services. By the end of the book, you'll be able to build a ready-to-deploy application that can be used as a base for future applications. What you will learn Grasp server-side Swift development concepts using practical examples Understand the microservices approach and why Swift is a great choice for building microservices Design and structure mobile and web applications using microservices architecture Discover the available database options and understand which one to choose Scale and monitor your microservices Use Postman to automate testing for your microservices API Who this book is for The book is for iOS, iPadOS, and macOS developers and Swift programmers who want to understand how Swift can be used for building microservices. The book assumes familiarity with Swift programming and the fundamentals of the web, including how APIs work. Computers

Retooling Politics Provides academics, journalists, and general readers with bird's-eye view of data-driven practices and their impact in politics and media. Computers

Think Before You Compute This guide to computational fluid mechanics introduces beginning graduate students to the subject's standard methods and common pitfalls. Computers

Introduction to Graph Neural Networks Graphs are useful data structures in complex real-life applications such as modeling physical systems, learning molecular fingerprints, controlling traffic networks, and recommending friends in social networks. However, these tasks require dealing with non-Euclidean graph data that contains rich relational information between elements and cannot be well handled by traditional deep learning models (e.g., convolutional neural networks (CNNs) or recurrent neural networks (RNNs)). Nodes in graphs usually contain useful feature information that cannot be well addressed in most unsupervised representation learning methods (e.g., network embedding methods). Graph neural networks (GNNs) are proposed to combine the feature information and the graph structure to learn better representations on graphs via feature propagation and aggregation. Due to its convincing performance and high interpretability, GNN has recently become a widely applied graph analysis tool.This book provides a comprehensive introduction to the basic concepts, models, and applications of graph neural networks. It starts with the introduction of the vanilla GNN model. Then several variants of the vanilla model are introduced such as graph convolutional networks, graph recurrent networks, graph attention networks, graph residual networks, and several general frameworks. Variants for different graph types and advanced training methods are also included. As for the applications of GNNs, the book categorizes them into structural, non-structural, and other scenarios, and then it introduces several typical models on solving these tasks. Finally, the closing chapters provide GNN open resources and the outlook of several future directions. Computers

Linked Data Visualization Linked Data (LD) is a well-established standard for publishing and managing structured information on the Web, gathering and bridging together knowledge from different scientific and commercial domains. The development of Linked Data Visualization techniques and tools has been adopted as the established practice for the analysis of this vast amount of information by data scientists, domain experts, business users, and citizens. This book covers a wide spectrum of visualization topics, providing an overview of the recent advances in this area, focusing on techniques, tools, and use cases of visualization and visual analysis of LD. It presents core concepts related to data visualization and LD technologies, techniques employed for data visualization based on the characteristics of data, techniques for Big Data visualization, tools and use cases in the LD context, and, finally, a thorough assessment of the usability of these tools under different scenarios. The purpose of this book is to offer a complete guide to the evolution of LD visualization for interested readers from any background and to empower them to get started with the visual analysis of such data. This book can serve as a course textbook or as a primer for all those interested in LD and data visualization. Computers

Defences to Copyright Infringement This volume analyses how available copyright defences accommodate modern uses of copyright works, and how EU copyright defences might be framed to promote creativity, technological innovation, and the development of new services and business models on the internet. Computers

Neural Machine Translation Learn how to build machine translation systems with deep learning from the ground up, from basic concepts to cutting-edge research. Computers

Algorithmic Randomness Surveys on recent developments in the theory of algorithmic randomness and its interactions with other areas of mathematics. Computers

The Internet of Things The Internet of Things (IoT) is the notion that nearly everything we use, from gym shorts to streetlights, will soon be connected to the Internet; the Internet of Everything (IoE) encompasses not just objects, but the social connections, data, and processes that the IoT makes possible. As more devices and systems become intertwined, the growing scale of the threat from hackers can easily get lost in the excitement of lower costs and smarter tech. The goal of this book is to demystify our increasingly "smart" world, and offer practical guidance for consumers, managers, and policymakers seeking to navigate this new frontier. Computers

Worth-Focused Design, Book 1 This book develops an appropriate common language for truly interdisciplinary teams involved in design. Design now has many meanings. For some, it is the creation of value. For others, it is the conception and creation of artefacts. For still others, it is fitting things to people. These differences reflect disciplinary values that both overlap and diverge. All involve artefacts: we always design things. Each definition considers people and purpose in some way. Each handles evaluation differently, measuring against aesthetics, craft standards, specifications, sales, usage experiences, or usage outcomes. There are both merits and risks in these differences, without an appropriate balance. Poor balance can result from professions claiming the centre of design for their discipline, marginalising others. Process can also cause imbalance when allocating resources to scheduled stages. Balance is promoted by replacing power centres with power sharing, and divisive processes with integrative progressions. A focus on worth guides design towards worthwhile experiences and outcomes that generously exceed expectations. This book places worth focus (Wo-Fo) into the context of design progressions that are balanced, integrated, and generous (BIG). BIG and Wo-Fo are symbiotic. Worth provides a focus for generosity. Effective Wo-Fo needs BIG practices. The companion book Worth-Focused Design, Book 2: Approaches, Contexts, and Case Studies (Cockton, 2020b) relates the concept of worth to experiences and outcomes based on a number of practical case studies. Computers

Theoretical Ecology This book continues the authoritative and established sequence of theoretical ecology books initiated by Robert M. May which helped pave the way for ecology to become a more robust theoretical science, encouraging the modern biologist to better understand the mathematics behind their theories. Computers

Code Nation Code Nation explores the rise of software development as a social, cultural, and technical phenomenon in American history. The movement germinated in government and university labs during the 1950s, gained momentum through corporate and counterculture experiments in the 1960s and 1970s, and became a broad-based computer literacy movement in the 1980s. As personal computing came to the fore, learning to program was transformed by a groundswell of popular enthusiasm, exciting new platforms, and an array of commercial practices that have been further amplified by distributed computing and the Internet. The resulting society can be depicted as a “Code Nationâ€â€”a globally-connected world that is saturated with computer technology and enchanted by software and its creation. Code Nation is a new history of personal computing that emphasizes the technical and business challenges that software developers faced when building applications for CP/M, MS-DOS, UNIX, Microsoft Windows, the Apple Macintosh, and other emerging platforms. It is a popular history of computing that explores the experiences of novice computer users, tinkerers, hackers, and power users, as well as the ideals and aspirations of leading computer scientists, engineers, educators, and entrepreneurs. Computer book and magazine publishers also played important, if overlooked, roles in the diffusion of new technical skills, and this book highlights their creative work and influence. Code Nation offers a “behind-the-scenes†look at application and operating-system programming practices, the diversity of historic computer languages, the rise of user communities, early attempts to market PC software, and the origins of “enterprise†computing systems. Code samples and over 80 historic photographs support the text. The book concludes with an assessment of contemporary efforts to teach computational thinking to young people. Computers

CXC Study Guide Developed with the Caribbean Examinations Council, this book provides you with the support to maximise your exam performance. Written by a team of experts, it covers the essential information in an easy-to-use double page spread format. Each topic begins with learning outcomes and has a range of features to help you enhance your study. Computers

The Art of Feature Engineering A practical guide for data scientists who want to improve the performance of any machine learning solution with feature engineering. Computers

Algorithms and Law Exploring issues from big-data to robotics, this volume is the first to comprehensively examine the regulatory implications of AI technology. Computers

Symbolic Execution and Quantitative Reasoning This book reviews recent advances in symbolic execution and its probabilistic variant and discusses how they can be used to ensure the safety and security of software systems. Symbolic execution is a systematic program analysis technique which explores multiple program behaviors all at once by collecting and solving symbolic constraints collected from the branching conditions in the program. The obtained solutions can be used as test inputs that execute feasible program paths. Symbolic execution has found many applications in various domains, such as security, smartphone applications, operating systems, databases, and more recently deep neural networks, uncovering subtle errors and unknown vulnerabilities. We review here the technique has also been extended to reason about algorithmic complexity and resource consumption. Furthermore, symbolic execution has been recently extended with probabilistic reasoning, allowing one to reason about quantitative properties of software systems. The approach computes the conditions to reach target program events of interest and uses model counting to quantify the fraction of the input domain satisfying these conditions thus computing the probability of event occurrence. This probabilistic information can be used for example to compute the reliability of an aircraft controller under different wind conditions (modeled probabilistically) or to quantify the leakage of sensitive data in a software system, using information theory metrics such as Shannon entropy. This book is intended for students and software engineers who are interested in advanced techniques for testing and verifying software systems. Computers

Interactive Technologies and Autism This book provides an in-depth review of the historical and state-of-the-art use of technology by and for individuals with autism. The design, development, deployment, and evaluation of interactive technologies for use by and with individuals with autism have been rapidly increasing over the last few decades. There is great promise for the use of these technologies to enrich lives, improve the experience of interventions, help with learning, facilitate communication, support data collection, and promote understanding. Emerging technologies in this area also have the potential to enhance assessment and diagnosis of autism, to understand the nature and lived experience of autism, and to help researchers conduct basic and applied research. The intention of this book is to give readers a comprehensive background for understanding what work has already been completed and its impact as well as what promises and challenges lie ahead. A large majority of existing technologies have been designed for autistic children, there is increased interest in technology’s intersection with the lived experiences of autistic adults. By providing a classification scheme and general review, this book can help technology designers, researchers, autistic people, and their advocates better understand how technologies have been successful or unsuccessful, what problems remain open, and where innovations can further address challenges and opportunities for individuals with autism and the variety of stakeholders connected to them. Computers

Machines and Thought This is the first of two volumes of essays on the intellectual legacy of Alan Turing, whose pioneering work in artificial intelligence and computer science made him one of the seminal thinkers of the century. A distinguished international cast of contributors focus on the three famous ideas associated with his name: the Turing test, the Turing machine, and the Church-Turing thesis.'a fascinating series of essays on computation by contributors in many fields' Choice Computers

Stepping Up to Google Classroom In this Stepping Up to Google Classroom, Google education experts Alice Keeler and Kimberly Mattina give you the tools you’ll need to ensure that your first foray into blended learning is a successful one—for you and your students. This book empowers educators to take the leap into the digital classroom with confidence and purpose. By guiding readers through fifty straightforward and accessible steps and offering a host of tips for customization, it ensures that teachers with all levels of tech comfortability can make the most of Google Classroom’s powerful tools. Computers

Load Balance For Distributed Real-time Computing Systems This illustrative compendium analyzes the load balancing problem in distributed stream processing systems and explores a set of high-performance real-time processing scheme based on key-based balancing strategy, join-matrix model and fault tolerance mechanisms.The volume succinctly provides the theoretical support for the proposed techniques. Through a rich set of experiments and comparisons with the other state-of-the-art techniques using both standard benchmarks and real data sets, the book comprehensively verifies the correctness and effectiveness of the proposed methods.This unique title is an excellent reference text for researchers in the fields of distributed stream processing, parallel system, cloud computing, etc. Computers

Automatic Disambiguation of Author Names in Bibliographic Repositories This book deals with a hard problem that is inherent to human language: ambiguity. In particular, we focus on author name ambiguity, a type of ambiguity that exists in digital bibliographic repositories, which occurs when an author publishes works under distinct names or distinct authors publish works under similar names. This problem may be caused by a number of reasons, including the lack of standards and common practices, and the decentralized generation of bibliographic content. As a consequence, the quality of the main services of digital bibliographic repositories such as search, browsing, and recommendation may be severely affected by author name ambiguity. The focal point of the book is on automatic methods, since manual solutions do not scale to the size of the current repositories or the speed in which they are updated. Accordingly, we provide an ample view on the problem of automatic disambiguation of author names, summarizing the results of more than a decade of research on this topic conducted by our group, which were reported in more than a dozen publications that received over 900 citations so far, according to Google Scholar. We start by discussing its motivational issues (Chapter 1). Next, we formally define the author name disambiguation task (Chapter 2) and use this formalization to provide a brief, taxonomically organized, overview of the literature on the topic (Chapter 3). We then organize, summarize and integrate the efforts of our own group on developing solutions for the problem that have historically produced state-of-the-art (by the time of their proposals) results in terms of the quality of the disambiguation results. Thus, Chapter 4 covers HHC - Heuristic-based Clustering, an author name disambiguation method that is based on two specific real-world assumptions regarding scientific authorship. Then, Chapter 5 describes SAND - Self-training Author Name Disambiguator and Chapter 6 presents two incremental author name disambiguation methods, namely INDi - Incremental Unsupervised Name Disambiguation and INC- Incremental Nearest Cluster. Finally, Chapter 7 provides an overview of recent author name disambiguation methods that address new specific approaches such as graph-based representations, alternative predefined similarity functions, visualization facilities and approaches based on artificial neural networks. The chapters are followed by three appendices that cover, respectively: (i) a pattern matching function for comparing proper names and used by some of the methods addressed in this book; (ii) a tool for generating synthetic collections of citation records for distinct experimental tasks; and (iii) a number of datasets commonly used to evaluate author name disambiguation methods. In summary, the book organizes a large body of knowledge and work in the area of author name disambiguation in the last decade, hoping to consolidate a solid basis for future developments in the field. Computers

DTP Coursebook Desktop publishing began in 1983 with a program developed by James Bessen at a community newspaper in Philadelphia. That program, Type Processor One, ran on an IBM PC using a Hercules Graphics Card for a WYSIWYG display and was offered commercially by Bestinfo in 1984. (Desktop typesetting, with only limited page makeup facilities, had arrived in 1978–9 with the introduction of TeX, and was extended in the early 1980s by LaTeX.) The DTP market exploded in 1985 with the introduction in January of the Apple Laser Writer printer, and later in July with the introduction of PageMaker software from Aldus which rapidly became the DTP industry standard software. Before the advent of desktop publishing, the only option available to most persons for producing typed (as opposed to handwritten) documents was a typewriter, which offered only a handful of typefaces (usually fixed-width) and one or two font sizes. This book covers the whole groundwork for this course. Computers

Encyclopaedia of Computer and Library Science Libraries in developing countries face particular problems procuring library materials and information resources. This is due to lower currency values in the international market and to limited financial resources, along with regular increases in subscription prices. Most libraries are supported by- different levels of government either directly or through government-funded agencies. In India many libraries were procuring the same materials from the same sources and spending large amounts of funds. In turn, libraries were finding it difficult to procure alternate resources due to limited funds. Therefore, they were denying access to a full selection of information resources. There was increasing frustration among the information providers and seekers about limited access to existing and available information resources. There were several studies on procurement and use of similar expensive resources, especially secondary resources, and duplication of high priced resources by many libraries in India. There were repeated complaints that use was not optimum, and cost per use was estimated to be very high. When this crisis reached its peak, libraries, government agencies, and even the concerned ministries started working together to find ways to make better use of limited budgets to provide access to increased numbers of resources as well as make optimum use of the resources to enable the scientists and researchers to become more information rich. This book fulfills the long felt necessity of a text dealing with concepts of this subject. It can also prove to be a worthy companion and guide for the students, users and researchers. Computers

Encyclopaedia of Computer and Library Science Libraries in developing countries face particular problems procuring library materials and information resources. This is due to lower currency values in the international market and to limited financial resources, along with regular increases in subscription prices. Most libraries are supported by- different levels of government either directly or through government-funded agencies. In India many libraries were procuring the same materials from the same sources and spending large amounts of funds. In turn, libraries were finding it difficult to procure alternate resources due to limited funds. Therefore, they were denying access to a full selection of information resources. There was increasing frustration among the information providers and seekers about limited access to existing and available information resources. There were several studies on procurement and use of similar expensive resources, especially secondary resources, and duplication of high priced resources by many libraries in India. There were repeated complaints that use was not optimum, and cost per use was estimated to be very high. When this crisis reached its peak, libraries, government agencies, and even the concerned ministries started working together to find ways to make better use of limited budgets to provide access to increased numbers of resources as well as make optimum use of the resources to enable the scientists and researchers to become more information rich. This book fulfills the long felt necessity of a text dealing with concepts of this subject. It can also prove to be a worthy companion and guide for the students, users and researchers. Computers

Encyclopaedia Of Discrete Mathematics Volume-1 The Encyclopaedia of Discrete Mathematics presents a through, Comprehensive Treatment of the subject using a Flexible Modular format. The Encyclopaedia is organized so that selected chapters in the book can either be studied together or used as a reference. The material in the Encyclopaedia is ideal for a freshman level in Computer Science or Mathematics. In addition, the author believes that the notion of proofs is important in most areas of study, and can be learned by any student, making it an effective alternative to the subject. The core of the Encyclopaedia consists of logical Reasoning ,Graph Theory, Binary Relations, Recurrence Relations, Combinatorics, Functions, Matrices. The remaining chapters can be selected according to individual course outlines. Computers

Encyclopaedia Of Discrete Mathematics Volume-2 The Encyclopaedia of Discrete Mathematics presents a through, Comprehensive Treatment of the subject using a Flexible Modular format. The Encyclopaedia is organized so that selected chapters in the book can either be studied together or used as a reference. The material in the Encyclopaedia is ideal for a freshman level in Computer Science or Mathematics. In addition, the author believes that the notion of proofs is important in most areas of study, and can be learned by any student, making it an effective alternative to the subject. The core of the Encyclopaedia consists of logical Reasoning ,Graph Theory, Binary Relations, Recurrence Relations, Combinatorics, Functions, Matrices. The remaining chapters can be selected according to individual course outlines. Computers

Encyclopaedia of Operating System Volume-1 Operating system is the heart of any computer. This field is changing field at a breathtakingly rapid rate, as computers are now prevalent in virtually every application. Yet the fundamental concepts remain the same and it is clear in all books of operating systems. This work provides a clear description on the concepts that are required for understanding the proper functioning of any operating system. The hardware text required for an understanding of operating system are included in this work for coding examples we use predominantly 'C' as well as lava, but the reader can still understand the algorithms without a thorough knowledge of these languages. Apart from these some case studies on Unix, and on windows are also included in this work. Computers

Encyclopaedia of Operating System Volume-2 Operating system is the heart of any computer. This field is changing field at a breathtakingly rapid rate, as computers are now prevalent in virtually every application. Yet the fundamental concepts remain the same and it is clear in all books of operating systems. This work provides a clear description on the concepts that are required for understanding the proper functioning of any operating system. The hardware text required for an understanding of operating system are included in this work for coding examples we use predominantly 'C' as well as lava, but the reader can still understand the algorithms without a thorough knowledge of these languages. Apart from these some case studies on Unix, and on windows are also included in this work. Computers

Encyclopaedia of Operating System Volume-3 Operating system is the heart of any computer. This field is changing field at a breathtakingly rapid rate, as computers are now prevalent in virtually every application. Yet the fundamental concepts remain the same and it is clear in all books of operating systems. This work provides a clear description on the concepts that are required for understanding the proper functioning of any operating system. The hardware text required for an understanding of operating system are included in this work for coding examples we use predominantly 'C' as well as lava, but the reader can still understand the algorithms without a thorough knowledge of these languages. Apart from these some case studies on Unix, and on windows are also included in this work. Computers

Visual Techniques Applied in Social Research The book illustrates the relevance of visual data in social research. It highlights the multitude and variety of research contexts where the visual can be applied. It provides useful examples to those who want to use visual techniques in their social research. Computers

After the Digital Tornado Leading technology scholars examine how networks powered by algorithms are transforming humanity, posing deep questions about power, freedom, and fairness. This title is also available as Open Access on Cambridge Core. Computers

Algorithm Design with Haskell Ideal for learning or reference, this book explains the five main principles of algorithm design and their implementation in Haskell. Computers

Best of the Independent Journals in Rhetoric and Composition 2012, The The Best of the Independent Rhetoric and Composition Journals 2012 represents the result of a nationwide conversation—beginning with journal editors, but expanding to teachers, scholars and workers across the discipline of Rhetoric and Composition—to select essays that showcase the innovative and transformative work now being published in the field’s independent journals. Representing both print and digital journals in the field, the essays featured here explore issues ranging from classroom practice to writing in global and digital contexts, from writing workshops to community activism. Together, the essays provide readers with a rich understanding of the present and future direction of the field. In addition to the introduction by Julia Voss and Beverly Moss, the anthology features work by the following authors and representing these journals: Jamie White-Farnham (Community Literacy Journal), Noah R. Roderick (Composition Forum), Kate Pantelides and Mariaelena Bartesaghi (Composition Studies), Heidi A. McKee (Computers and Composition), Rex Veeder (Enculturation), Matthew Pavesich (Journal of Basic Writing), Kelly S. Bradbury (The Journal of Teaching Writing), Derek N. Mueller (Kairos), Richard H. Thames (KB Journal), Jeanne Marie Rose (Pedagogy), and Melvette Melvin Davis (Reflections). Computers

Quantum Computer Systems This book targets computer scientists and engineers who are familiar with concepts in classical computer systems but are curious to learn the general architecture of quantum computing systems. It gives a concise presentation of this new paradigm of computing from a computer systems' point of view without assuming any background in quantum mechanics. As such, it is divided into two parts. The first part of the book provides a gentle overview on the fundamental principles of the quantum theory and their implications for computing. The second part is devoted to state-of-the-art research in designing practical quantum programs, building a scalable software systems stack, and controlling quantum hardware components. Most chapters end with a summary and an outlook for future directions. This book celebrates the remarkable progress that scientists across disciplines have made in the past decades and reveals what roles computer scientists and engineers can play to enable practical-scale quantum computing. Computers

The Domains of Identity "The Domains of Identity" defines sixteen coherent yet comprehensive categories of interactions which cause personally identifiable information to be stored in databases. Discussions of identity management are often confusing; enumerating these domains and describing their characteristics clarifies which problems arise and how they can be solved within each domain. Computers

Efficient Processing of Deep Neural Networks This book provides a structured treatment of the key principles and techniques for enabling efficient processing of deep neural networks (DNNs). DNNs are currently widely used for many artificial intelligence (AI) applications, including computer vision, speech recognition, and robotics. While DNNs deliver state-of-the-art accuracy on many AI tasks, it comes at the cost of high computational complexity. Therefore, techniques that enable efficient processing of deep neural networks to improve key metrics—such as energy-efficiency, throughput, and latency—without sacrificing accuracy or increasing hardware costs are critical to enabling the wide deployment of DNNs in AI systems. The book includes background on DNN processing; a description and taxonomy of hardware architectural approaches for designing DNN accelerators; key metrics for evaluating and comparing different designs; features of DNN processing that are amenable to hardware/algorithm co-design to improve energy efficiency and throughput; and opportunities for applying new technologies. Readers will find a structured introduction to the field as well as formalization and organization of key concepts from contemporary work that provide insights that may spark new ideas. Computers

Bioinformatics From very old times, human is dealing with biological information and data. After 17th century, when biological data started accumulating at a very high pace, then biologists started feeling a need of some technology which can make their task easy. Along with it computational technology achieved big stones for the improvement is data management and information technology. Then biologists start using computational techniques for managing and handling biological data. Taxonomy is the first informatics problem for biologists. Later, data and information accumulation rate increases at a very high rate due to DNA or protein sequences, structures, drug bank, motifs and protein profiles and many more. While doing research, scientists and research scholars need very much scientific data regarding their work, which can be fetched through post or by meeting in-person. Development in Laboratory techniques and biological methods facilitated the collection of data. PCR and advance sequencing techniques flooded the biological databases. Bioinformatics, branch of Biotechnology, which gives the "power to Biotechnology" to make their work more precise and efficient. Using Bioinformatics, biologists can handle large amount of data, which can be in the form of sequences, structures, motifs, smiles, drug bank or some research paper. Bioinformatics is also providing good algorithms and ways to biologists to fetch the required data in an efficient manner. Even laboratory personals are provided power to analyze different sets of data to analyze in different sets. Bioinformatics is the application of computer technology to the management and analysis of biological data. The result is that computers are being used to gather, store, analyze and merge biological data. This will provide Similarity Searching Tools, Protein Function Analysis, Structural Analysis, and Sequence Analysis for advancements of biology. We can say, Bioinformatics is an interdisciplinary research area that is the interface between the biological and computational sciences. The ultimate goal of bioinformatics is to uncover the wealth of biological information hidden in the mass of data and obtain a clearer insight into the fundamental biology of organisms. This new knowledge could have profound impacts on fields as varied as human health, agriculture, the environment, energy and biotechnology. Computers

Poisson Line Cox Process This book provides a comprehensive treatment of the Poisson line Cox process (PLCP) and its applications to vehicular networks. The PLCP is constructed by placing points on each line of a Poisson line process (PLP) as per an independent Poisson point process (PPP). For vehicular applications, one can imagine the layout of the road network as a PLP and the vehicles on the roads as the points of the PLCP. First, a brief historical account of the evolution of the theory of PLP is provided to familiarize readers with the seminal contributions in this area. In order to provide a self-contained treatment of this topic, the construction and key fundamental properties of both PLP and PLCP are discussed in detail. The rest of the book is devoted to the applications of these models to a variety of wireless networks, including vehicular communication networks and localization networks. Specifically, modeling the locations of vehicular nodes and roadside units (RSUs) using PLCP, the signal-to-interference-plus-noise ratio (SINR)-based coverage analysis is presented for both ad hoc and cellular network models. For a similar setting, the load on the cellular macro base stations (MBSs) and RSUs in a vehicular network is also characterized analytically. For the localization networks, PLP is used to model blockages, which is shown to facilitate the characterization of asymptotic blind spot probability in a localization application. Finally, the path distance characteristics for a special case of PLCP are analyzed, which can be leveraged to answer critical questions in the areas of transportation networks and urban planning. The book is concluded with concrete suggestions on future directions of research. Based largely on the original research of the authors, this is the first book that specifically focuses on the self-contained mathematical treatment of the PLCP. The ideal audience of this book is graduate students as well as researchers in academia and industry who are familiar with probability theory, have some exposure to point processes, and are interested in the field of stochastic geometry and vehicular networks. Given the diverse backgrounds of the potential readers, the focus has been on providing an accessible and pedagogical treatment of this topic by consciously avoiding the measure theoretic details without compromising mathematical rigor. Computers

Views into the Chinese Room The most famous challenge to the aims of computational cognitive science and artificial intelligence is the philosopher John Searle's 1980 'Chinese Room' argument. Searle argued that the fact that machines can be devised to pass the 'Turing Test', that is, respond to input with the same output that a mind would give, does not mean that mind and machine are doing the same thing: for such machines lack understanding of the symbols they process. Nineteen speciallywritten essays by leading scientists and philosophers assess, renew, and respond to this crucial challenge—fascinating reading for anyone interested in minds and computers. Computers

Blockchain Platforms This book introduces all the technical features that make up blockchain technology today. It starts with a thorough explanation of all technological concepts necessary to understand any discussions related to distributed ledgers and a short history of earlier implementations. It then discusses in detail how the Bitcoin network looks and what changes are coming in the near future, together with a range of altcoins that were created on the same base code. To get an even better idea, the book shortly explores how Bitcoin might be forked before going into detail on the Ethereum network and cryptocurrencies running on top of the network, smart contracts, and more. The book introduces the Hyperledger foundation and the tools offered to create private blockchain solutions. For those willing, it investigates directed acyclic graphs (DAGs) and several of its implementations, which could solve several of the problems other blockchain networks are still dealing with to this day. In Chapter 4, readers can find an overview of blockchain networks that can be used to build solutions of their own and the tools that can help them in the process. Computers

Logic Pro X 10.5 - Apple Pro Training Series Computers

Attribution of Advanced Persistent Threats An increasing number of countries develop capabilities for cyber-espionage and sabotage. The sheer number of reported network compromises suggests that some of these countries view cyber-means as integral and well-established elements of their strategical toolbox. At the same time the relevance of such attacks for society and politics is also increasing. Digital means were used to influence the US presidential election in 2016, repeatedly led to power outages in Ukraine, and caused economic losses of hundreds of millions of dollars with a malfunctioning ransomware. In all these cases the question who was behind the attacks is not only relevant from a legal perspective, but also has a political and social dimension. Attribution is the process of tracking and identifying the actors behind these cyber-attacks. Often it is considered an art, not a science. This book systematically analyses how hackers operate, which mistakes they make, and which traces they leave behind. Using examples from real cases the author explains the analytic methods used to ascertain the origin of Advanced Persistent Threats. Computers

Foundations of Finitely Supported Structures This book presents a set theoretical development for the foundations of the theory of atomic and finitely supported structures. It analyzes whether a classical result can be adequately reformulated by replacing a 'non-atomic structure' with an 'atomic, finitely supported structure’. It also presents many specific properties, such as finiteness, cardinality, connectivity, fixed point, order and uniformity, of finitely supported atomic structures that do not have non-atomic correspondents. In the framework of finitely supported sets, the authors analyze the consistency of various forms of choice and related results. They introduce and study the notion of 'cardinality' by presenting various order and arithmetic properties. Finitely supported partially ordered sets, chain complete sets, lattices and Galois connections are studied, and new fixed point, calculability and approximation properties are presented. In this framework, the authors study the finitely supported L-fuzzy subsets of a finitely supported set and the finitely supported fuzzy subgroups of a finitely supported group. Several pairwise non-equivalent definitions for the notion of 'infinity' (Dedekind infinity, Mostowski infinity, Kuratowski infinity, Tarski infinity, ascending infinity) are introduced, compared and studied in the new framework. Relevant examples of sets that satisfy some forms of infinity while not satisfying others are provided. Uniformly supported sets are analyzed, and certain surprising properties are presented. Finally, some variations of the finite support requirement are discussed. The book will be of value to researchers in the foundations of set theory, algebra and logic. Computers

Practical User Research Explore how User Research has been influenced over the years by a range of disciplines, such as HCI, usability, anthropology, cognitive psychology, ergonomics etc. This book aims to contribute to the User Research community and covers topics that will help UX professionals, students and stakeholders to gain a better understanding of what User Research is. Throughout the book you will acquire a practical skill set, ranging from how to get the research going, to building a case in order to receive the budget and resources needed. It will provide you with a clear account of how to organise your research, how to plan it, and how to manage stakeholders’ expectations throughout the project. You’ll see how to fit User Research into your organization and incorporate it through the different product development phases (Discovery, Alpha, Beta until Live), as well as how to grow a User Research team. Practical User Research reviews the methodologies used for User Research, looks at how to recruit participants along with how to collect and analyse data, finally focusing on how to interpret and present your findings. Cross-cultural research, accessibility and assisted digital research will also be discussed throughout this book. The final chapter gives you 10 project briefs, with which you will be able to apply your new skill set and put into practice what you have learnt. What You'll Learn Integrate user research into your business Apply user research to your product development cycle Review the appropriate processes necessary to carry out user research Take a pragmatic approach to user research, method by method Who This Book Is For Anyone that wants to understand more about user research. Computers

Build Your Own Car Dashboard with a Raspberry Pi a Computers

Combinatorial Optimization This book constitutes the thoroughly refereed post-conference proceedings of the 6th International Symposium on Combinatorial Optimization, ISCO 2020, which was due to be held in Montreal, Canada, in May 2020. The conference was held virtually due to the COVID-19 pandemic. The 24 revised full papers presented in this book were carefully reviewed and selected from 66 submissions. They were organized in the following topical sections: polyhedral combinatorics; integer programming; scheduling; matching; Network Design; Heuristics. Computers

Modern C++ for Absolute Beginners Learn the C++ programming language in a structured, straightforward, and friendly manner. This book teaches the basics of the modern C++ programming language, C++ Standard Library, and modern C++ standards. No previous programming experience is required. C++ is a language like no other, surprising in its complexity, yet wonderfully sleek and elegant in so many ways. It is also a language that cannot be learned by guessing, one that is easy to get wrong and challenging to get right. To overcome this, each section is filled with real-world examples that gradually increase in complexity. Modern C++ for Absolute Beginners teaches more than just programming in C++20. It provides a solid C++ foundation to build upon. The author takes you through the C++ programming language, the Standard Library, and the C++11 to C++20 standard basics. Each chapter is accompanied by the right amount of theory and plenty of source code examples. You will work with C++20 features and standards, yet you will also compare and take a look into previous versions of C++. You will do so with plenty of relevant source code examples. What You Will Learn Work with the basics of C++: types, operators, variables, constants, expressions, references, functions, classes, I/O, smart pointers, polymorphism, and more Set up the Visual Studio environment on Windows and GCC on Linux, where you can write your own code Declare and define functions, classes, and objects, and organize code into namespaces Discover object-oriented programming: classes and objects, encapsulation, inheritance, polymorphism, and more using the most advanced C++ features Employ best practices in organizing source code and controlling program workflow Get familiar with C++ language dos and donts, and more Master the basics of lambdas, inheritance, polymorphism, smart pointers, templates, modules, contracts, concepts, and more Who This Book Is For Beginner or novice programmers who wish to learn C++ programming. No prior programming experience is required. Computers

Software Technologies This book constitutes the thoroughly refereed post-conference proceedings of the 14th International Conference on Software Technologies, ICSOFT 2019, held in Prague, Czech Republic, in July 2019. The 10 revised full papers were carefully reviewed and selected from 116 submissions. The topics covered in the papers include: business process modelling, IT service management, interoperability and service-oriented architecture, project management software, scheduling and estimating, software metrics, requirements elicitation and specification, software and systems integration, etc. Computers

Distributed Denial of Service Attacks Distributed Denial of Service (DDoS) attacks have become more destructive, wide-spread and harder to control over time. This book allows students to understand how these attacks are constructed, the security flaws they leverage, why they are effective, how they can be detected, and how they can be mitigated. Students use software defined networking (SDN) technology to created and execute controlled DDoS experiments. They learn how to deploy networks, analyze network performance, and create resilient systems. This book is used for graduate level computer engineering instruction at Clemson University. It augments the traditional graduate computing curricula by integrating: Internet deployment, network security, ethics, contemporary social issues, and engineering principles into a laboratory based course of instruction. Unique features of this book include: A history of DDoS attacks that includes attacker motivations Discussion of cyber-war, censorship, and Internet black-outs SDN based DDoS laboratory assignments Up-to-date review of current DDoS attack techniques and tools Review of the current laws that globally relate to DDoS Abuse of DNS, NTP, BGP and other parts of the global Internet infrastructure to attack networks Mathematics of Internet traffic measurement Game theory for DDoS resilience Construction of content distribution systems that absorb DDoS attacks This book assumes familiarity with computing, Internet design, appropriate background in mathematics, and some programming skills. It provides analysis and reference material for networking engineers and researchers. By increasing student knowledge in security, and networking; it adds breadth and depth to advanced computing curricula. Computers

Machine Learning and Big Data Currently many different application areas for Big Data (BD) and Machine Learning (ML) are being explored. These promising application areas for BD/ML are the social sites, search engines, multimedia sharing sites, various stock exchange sites, online gaming, online survey sites and various news sites, and so on. To date, various use-cases for this application area are being researched and developed. Software applications are already being published and used in various settings from education and training to discover useful hidden patterns and other information like customer choices and market trends that can help organizations make more informed and customer-oriented business decisions. Combining BD with ML will provide powerful, largely unexplored application areas that will revolutionize practice in Videos Surveillance, Social Media Services, Email Spam and Malware Filtering, Online Fraud Detection, and so on. It is very important to continuously monitor and understand these effects from safety and societal point of view. Hence, the main purpose of this book is for researchers, software developers and practitioners, academicians and students to showcase novel use-cases and applications, present empirical research results from user-centered qualitative and quantitative experiments of these new applications, and facilitate a discussion forum to explore the latest trends in big data and machine learning by providing algorithms which can be trained to perform interdisciplinary techniques such as statistics, linear algebra, and optimization and also create automated systems that can sift through large volumes of data at high speed to make predictions or decisions without human intervention Computers

Emerging Technology Trends in Electronics, Communication and Networking This book constitutes refereed proceedings of the Third International Conference on Emerging Technology Trends in Electronics, Communication and Networking, ET2ECN 2020, held in Surat, India, in February 2020. The 17 full papers and 6 short papers presented were thorougly reviewed and selected from 70 submissions. The volume covers a wide range of topics including electronic devices, VLSI design and fabrication, photo electronics, systems and applications, integrated optics, embedded systems, wireless communication, optical communication, free space optics, signal processing, image/ audio/ video processing, wireless sensor networks, next generation networks, network security, and many others. Computers

VLSI-SoC This book contains extended and revised versions of the best papers presented at the 27th IFIP WG 10.5/IEEE International Conference on Very Large Scale Integration, VLSI-SoC 2019, held in Cusco, Peru, in October 2019. The 15 full papers included in this volume were carefully reviewed and selected from the 28 papers (out of 82 submissions) presented at the conference. The papers discuss the latest academic and industrial results and developments as well as future trends in the field of System-on-Chip (SoC) design, considering the challenges of nano-scale, state-of-the-art and emerging manufacturing technologies. In particular they address cutting-edge research fields like heterogeneous, neuromorphic and brain-inspired, biologically-inspired, approximate computing systems. Computers

Information Retrieval This series is directed to healthcare professionals who are leading the transfor- tion of health care by using information and knowledge to advance the quality of patient care. Launched in 1988 as Computers in Health Care, the series offers a broad range of titles: some are addressed to speci?c professions such as nursing, medicine, and health administration; others to special areas of practice such as trauma and radiology. Still other books in this series focus on interdisciplinary issues, such as the computer-based patient record, electronic health records, and networked healthcare systems. Renamed Health Informatics in 1998 to re?ect the rapid evolution in the discipline now known as health informatics, the series continues to add titles that contribute to the evolution of the ?eld. In this series, eminent experts, serving as editors or authors, offer their accounts of innovation in health informatics. Incre- ingly, these accounts go beyond hardware and software to address the role of information in in?uencing the transformation of healthcare delivery systems around the world. The series also increasingly focuses on “peopleware†and the organi- tional, behavioral, and societal changes that accompany the diffusion of infor- tion technology in health services environments. Computers

Beginning Rails 6 Springboard your journey into web application development and discover how much fun building web applications with Ruby on Rails can be. This book has been revised to cover what's new in Rails 6 including features such as WebPack, advanced JavaScript integration, Action Mailbox, Action Text, system and parallel testing, Action Cable testing, and more. Beginning Rails 6 gently guides you through designing your application, writing tests for the application, and then writing the code to make your application work as expected. It is a book that will guide you from never having programmed with Ruby, to having a Rails 6 application built and deployed to the web. After reading and using this book, you'll have the know-how and the freely available source code to get started with your own Rails-based web development in days. What You Will Learn Create Ruby on Rails 6 web applications from the bottom up Gain the basics of the Ruby programming language Combine all the components of Rails to develop your own web applications Apply TDD to make sure your application works exactly as you expect Use Git source control and best practice techniques to create applications like a pro Who This Book Is For Someone with little to no Ruby or Rails experience, or possibly even someone with no experience developing web applications at all. A basic familiarity with the web and typical web terms is assumed, but you don’t need to be an expert in these. Computers

Institutional Literacies Information technologies have become an integral part of writing and communication courses, shaping the ways students and teachers think about and do their work. But, too often, teachers and other educational stakeholders take a passive or simply reactive role in institutional approaches to technologies, and this means they are missing out on the chance to make positive changes in their departments and on campus. Institutional Literacies argues that writing and communication teachers and program directors should collaborate more closely and engage more deeply with IT staff as technology projects are planned, implemented, and expanded. Teachers need to both analyze how their institutions approach information technologies and intervene in productive ways as active university citizens with relevant expertise. To help them do so, the book offers a three-part heuristic, reflecting the reality that academic IT units are complex and multilayered, with historical, spatial, and textual dimensions. It discusses six ways teachers can intervene in the academic IT work of their own institutions: maintaining awareness, using systems and services, mediating for audiences, participating as user advocates, working as designers, and partnering as researchers. With these strategies in hand, educators can be proactive in helping institutional IT approaches align with the professional values and practices of writing and communication programs. Computers

The Deep Learning with PyTorch Workshop Get a head start in the world of AI and deep learning by developing your skills with PyTorch Key Features Learn how to define your own network architecture in deep learning Implement helpful methods to create and train a model using PyTorch syntax Discover how intelligent applications using features like image recognition and speech recognition really process your data Book Description Want to get to grips with one of the most popular machine learning libraries for deep learning? The Deep Learning with PyTorch Workshop will help you do just that, jumpstarting your knowledge of using PyTorch for deep learning even if you're starting from scratch. It's no surprise that deep learning's popularity has risen steeply in the past few years, thanks to intelligent applications such as self-driving vehicles, chatbots, and voice-activated assistants that are making our lives easier. This book will take you inside the world of deep learning, where you'll use PyTorch to understand the complexity of neural network architectures. The Deep Learning with PyTorch Workshop starts with an introduction to deep learning and its applications. You'll explore the syntax of PyTorch and learn how to define a network architecture and train a model. Next, you'll learn about three main neural network architectures - convolutional, artificial, and recurrent - and even solve real-world data problems using these networks. Later chapters will show you how to create a style transfer model to develop a new image from two images, before finally taking you through how RNNs store memory to solve key data issues. By the end of this book, you'll have mastered the essential concepts, tools, and libraries of PyTorch to develop your own deep neural networks and intelligent apps. What you will learn Explore the different applications of deep learning Understand the PyTorch approach to building neural networks Create and train your very own perceptron using PyTorch Solve regression problems using artificial neural networks (ANNs) Handle computer vision problems with convolutional neural networks (CNNs) Perform language translation tasks using recurrent neural networks (RNNs) Who this book is for This deep learning book is ideal for anyone who wants to create and train deep learning models using PyTorch. A solid understanding of the Python programming language and its packages will help you grasp the topics covered in the book more quickly. Computers

The Applied Artificial Intelligence Workshop With knowledge and information shared by experts, take your first steps towards creating scalable AI algorithms and solutions in Python, through practical exercises and engaging activities Key Features Learn about AI and ML algorithms from the perspective of a seasoned data scientist Get practical experience in ML algorithms, such as regression, tree algorithms, clustering, and more Design neural networks that emulate the human brain Book Description You already know that artificial intelligence (AI) and machine learning (ML) are present in many of the tools you use in your daily routine. But do you want to be able to create your own AI and ML models and develop your skills in these domains to kickstart your AI career? The Applied Artificial Intelligence Workshop gets you started with applying AI with the help of practical exercises and useful examples, all put together cleverly to help you gain the skills to transform your career. The book begins by teaching you how to predict outcomes using regression. You'll then learn how to classify data using techniques such as k-nearest neighbor (KNN) and support vector machine (SVM) classifiers. As you progress, you'll explore various decision trees by learning how to build a reliable decision tree model that can help your company find cars that clients are likely to buy. The final chapters will introduce you to deep learning and neural networks. Through various activities, such as predicting stock prices and recognizing handwritten digits, you'll learn how to train and implement convolutional neural networks (CNNs) and recurrent neural networks (RNNs). By the end of this applied AI book, you'll have learned how to predict outcomes and train neural networks and be able to use various techniques to develop AI and ML models. What you will learn Create your first AI game in Python with the minmax algorithm Implement regression techniques to simplify real-world data Experiment with classification techniques to label real-world data Perform predictive analysis in Python using decision trees and random forests Use clustering algorithms to group data without manual support Learn how to use neural networks to process and classify labeled images Who this book is for The Applied Artificial Intelligence Workshop is designed for software developers and data scientists who want to enrich their projects with machine learning. Although you do not need any prior experience in AI, it is recommended that you have knowledge of high school-level mathematics and at least one programming language, preferably Python. Although this is a beginner's book, experienced students and programmers can improve their Python skills by implementing the practical applications given in this book. Computers

The Machine Learning Workshop Take a comprehensive and step-by-step approach to understanding machine learning Key Features Discover how to apply the scikit-learn uniform API in all types of machine learning models Understand the difference between supervised and unsupervised learning models Reinforce your understanding of machine learning concepts by working on real-world examples Book Description Machine learning algorithms are an integral part of almost all modern applications. To make the learning process faster and more accurate, you need a tool flexible and powerful enough to help you build machine learning algorithms quickly and easily. With The Machine Learning Workshop, you'll master the scikit-learn library and become proficient in developing clever machine learning algorithms. The Machine Learning Workshop begins by demonstrating how unsupervised and supervised learning algorithms work by analyzing a real-world dataset of wholesale customers. Once you've got to grips with the basics, you'll develop an artificial neural network using scikit-learn and then improve its performance by fine-tuning hyperparameters. Towards the end of the workshop, you'll study the dataset of a bank's marketing activities and build machine learning models that can list clients who are likely to subscribe to a term deposit. You'll also learn how to compare these models and select the optimal one. By the end of The Machine Learning Workshop, you'll not only have learned the difference between supervised and unsupervised models and their applications in the real world, but you'll also have developed the skills required to get started with programming your very own machine learning algorithms. What you will learn Understand how to select an algorithm that best fits your dataset and desired outcome Explore popular real-world algorithms such as K-means, Mean-Shift, and DBSCAN Discover different approaches to solve machine learning classification problems Develop neural network structures using the scikit-learn package Use the NN algorithm to create models for predicting future outcomes Perform error analysis to improve your model's performance Who this book is for The Machine Learning Workshop is perfect for machine learning beginners. You will need Python programming experience, though no prior knowledge of scikit-learn and machine learning is necessary. Computers

Windows Server 2019 Cookbook Efficiently manage and administer enterprise environments using Microsoft Windows Server 2019 Key Features Leverage Windows Server 2019 to improve enterprise workflow efficiency and increase productivity Deliver enterprise-grade cloud services that can be applied in your infrastructure Get up and running with PowerShell and the all-new Hyper-V improvements Book Description Do you want to get up and running with essential administrative tasks in Windows Server 2019? This second edition of the Windows Server 2019 Cookbook is packed with practical recipes that will help you do just that. The book starts by taking you through the basics that you need to know to get a Windows Server operating system working, before teaching you how to navigate through daily tasks using the upgraded graphical user interface (GUI). You'll then learn how to compose an optimal Group Policy and perform task automation with PowerShell scripting. As you advance, you'll get to grips with faster app innovation, improved Windows security measures, and hybrid cloud environments. After you've explored the functions available to provide remote network access to your users, you'll cover the new Hyper-V enhancements. Finally, this Windows Server book will guide you through practical recipes relating to Azure integration and important tips for how to manage a Windows Server environment seamlessly. By the end of this book, you'll be well-versed with Windows Server 2019 essentials and have the skills you need to configure Windows services and implement best practices for securing a Windows Server environment. What you will learn Get up and running with Windows Server 2019's new features Install, configure, and administer Windows Server 2019 effectively Configure the server to host any enterprise application Discover ways to manage a server without a GUI Safeguard your virtual machines in the event of server failure Explore new ways to integrate Windows Server with Microsoft Azure Deploy Windows containers using Docker Who this book is for This Windows Server 2019 book is for system administrators and IT professionals who have basic experience in Windows environments and are interested in acquiring the skills and knowledge needed to manage and maintain the core infrastructure required for a Windows Server 2019 environment. Computers

Evaluative Informetrics We intend to edit a Festschrift for Henk Moed combining a “best of†collection of his papers and new contributions (original research papers) by authors having worked and collaborated with him. The outcome of this original combination aims to provide an overview of the advancement of the field in the intersection of bibliometrics, informetrics, science studies and research assessment. Computers

The Applied Data Science Workshop Designed with beginners in mind, this workshop helps you make the most of Python libraries and the Jupyter Notebook's functionality to understand how data science can be applied to solve real-world data problems. Key Features Gain useful insights into data science and machine learning Explore the different functionalities and features of a Jupyter Notebook Discover how Python libraries are used with Jupyter for data analysis Book Description From banking and manufacturing through to education and entertainment, using data science for business has revolutionized almost every sector in the modern world. It has an important role to play in everything from app development to network security. Taking an interactive approach to learning the fundamentals, this book is ideal for beginners. You'll learn all the best practices and techniques for applying data science in the context of real-world scenarios and examples. Starting with an introduction to data science and machine learning, you'll start by getting to grips with Jupyter functionality and features. You'll use Python libraries like sci-kit learn, pandas, Matplotlib, and Seaborn to perform data analysis and data preprocessing on real-world datasets from within your own Jupyter environment. Progressing through the chapters, you'll train classification models using sci-kit learn, and assess model performance using advanced validation techniques. Towards the end, you'll use Jupyter Notebooks to document your research, build stakeholder reports, and even analyze web performance data. By the end of The Applied Data Science Workshop, you'll be prepared to progress from being a beginner to taking your skills to the next level by confidently applying data science techniques and tools to real-world projects. What you will learn Understand the key opportunities and challenges in data science Use Jupyter for data science tasks such as data analysis and modeling Run exploratory data analysis within a Jupyter Notebook Visualize data with pairwise scatter plots and segmented distribution Assess model performance with advanced validation techniques Parse HTML responses and analyze HTTP requests Who this book is for If you are an aspiring data scientist who wants to build a career in data science or a developer who wants to explore the applications of data science from scratch and analyze data in Jupyter using Python libraries, then this book is for you. Although a brief understanding of Python programming and machine learning is recommended to help you grasp the topics covered in the book more quickly, it is not mandatory. Computers

Learning Python Python is an easy to learn, powerful programming language. It has efficient high-level data structures and a simple but effective approach to object-oriented programming. Python's elegant syntax and dynamic typing, together with its interpreted nature, make it an ideal language for scripting and rapid application development in many areas on most platforms. The Python interpreter and the extensive standard library are freely available in source or binary form for all major platforms from the Python Web site. The same site also contains distributions of and pointers to many free third party Python modules, programs and tools, and additional documentation. The Python interpreter is easily extended with new functions and data types implemented in C or C++ (or other languages callable from C). Python is also suitable as an extension language for customizable applications. This tutorial introduces the reader informally to the basic concepts and features of the python language and system. It helps to have a Python interpreter handy for hands-on experience, but all examples are self contained, so the tutorial can be read off-line as well. For a description of standard objects and modules, see library-index. reference-index gives a more formal deï¬nition of the language. To write extensions in C or C++, read extending-index and c-api-index. There are also several books covering Python in depth. This tutorial does not attempt to be comprehensive and cover every single feature, or even every commonly used feature. Instead, it introduces many of Python's most noteworthy features, and will give you a good idea of the language's flavor and style. After reading it, you will be able to read and write Python modules and programs, and you will be ready to learn more about the various Python library modules described in library-index. The Glossary is also worth going through. This fast-paced, thorough introduction to programming with Python will have you writing programs, solving problems, and making things that work in no time. Python Tutorial Release 3.7.0 Guido van Rossum and the Python development team Computers

Crime Dot Com “Brilliantly researched and written.â€â€”Jon Snow, Channel 4 News “A comprehensive and intelligible account of the elusive world of hacking and cybercrime over the last two decades. . . . Lively, insightful, and, often, alarming.â€â€”Ewen MacAskill, Guardian On May 4, 2000, an email that read “kindly check the attached LOVELETTER†was sent from a computer in the Philippines. Attached was a virus, the Love Bug, and within days it had been circulated across the globe, paralyzing banks, broadcasters, and businesses in its wake, and extending as far as the UK Parliament and, reportedly, the Pentagon. The outbreak presaged a new era of online mayhem: the age of Crime Dot Com. In this book, investigative journalist Geoff White charts the astonishing development of hacking, from its conception in the United States’ hippy tech community in the 1970s, through its childhood among the ruins of the Eastern Bloc, to its coming of age as one of the most dangerous and pervasive threats to our connected world. He takes us inside the workings of real-life cybercrimes, drawing on interviews with those behind the most devastating hacks and revealing how the tactics employed by high-tech crooks to make millions are being harnessed by nation states to target voters, cripple power networks, and even prepare for cyber-war. From Anonymous to the Dark Web, Ashley Madison to election rigging, Crime Dot Com is a thrilling, dizzying, and terrifying account of hacking, past and present, what the future has in store, and how we might protect ourselves from it. Computers

Blockchain-enabled Fog and Edge Computing This comprehensive book unveils the working relationship of blockchain and the fog/edge computing. The contents of the book have been designed in such a way that the reader will not only understand blockchain and fog/edge computing but will also understand their co-existence and their collaborative power to solve a range of versatile problems. The first part of the book covers fundamental concepts and the applications of blockchain-enabled fog and edge computing. These include: Internet of Things, Tactile Internet, Smart City; and E-challan in the Internet of Vehicles. The second part of the book covers security and privacy related issues of blockchain-enabled fog and edge computing. These include, hardware primitive based Physical Unclonable Functions; Secure Management Systems; security of Edge and Cloud in the presence of blockchain; secure storage in fog using blockchain; and using differential privacy for edge-based Smart Grid over blockchain. This book is written for students, computer scientists, researchers and developers, who wish to work in the domain of blockchain and fog/edge computing. One of the unique features of this book is highlighting the issues, challenges, and future research directions associated with Blockchain-enabled fog and edge computing paradigm. We hope the readers will consider this book a valuable addition in the domain of Blockchain and fog/edge computing. Computers

Hands-On Machine Learning with scikit-learn and Scientific Python Toolkits Integrate scikit-learn with various tools such as NumPy, pandas, imbalanced-learn, and scikit-surprise and use it to solve real-world machine learning problemsKey FeaturesDelve into machine learning with this comprehensive guide to scikit-learn and scientific PythonMaster the art of data-driven problem-solving with hands-on examplesFoster your theoretical and practical knowledge of supervised and unsupervised machine learning algorithmsBook DescriptionMachine learning is applied everywhere, from business to research and academia, while scikit-learn is a versatile library that is popular among machine learning practitioners. This book serves as a practical guide for anyone looking to provide hands-on machine learning solutions with scikit-learn and Python toolkits.The book begins with an explanation of machine learning concepts and fundamentals, and strikes a balance between theoretical concepts and their applications. Each chapter covers a different set of algorithms, and shows you how to use them to solve real-life problems. You'll also learn about various key supervised and unsupervised machine learning algorithms using practical examples. Whether it is an instance-based learning algorithm, Bayesian estimation, a deep neural network, a tree-based ensemble, or a recommendation system, you'll gain a thorough understanding of its theory and learn when to apply it. As you advance, you'll learn how to deal with unlabeled data and when to use different clustering and anomaly detection algorithms.By the end of this machine learning book, you'll have learned how to take a data-driven approach to provide end-to-end machine learning solutions. You'll also have discovered how to formulate the problem at hand, prepare required data, and evaluate and deploy models in production.What you will learnUnderstand when to use supervised, unsupervised, or reinforcement learning algorithmsFind out how to collect and prepare your data for machine learning tasksTackle imbalanced data and optimize your algorithm for a bias or variance tradeoffApply supervised and unsupervised algorithms to overcome various machine learning challengesEmploy best practices for tuning your algorithm's hyper parametersDiscover how to use neural networks for classification and regressionBuild, evaluate, and deploy your machine learning solutions to productionWho this book is forThis book is for data scientists, machine learning practitioners, and anyone who wants to learn how machine learning algorithms work and to build different machine learning models using the Python ecosystem. The book will help you take your knowledge of machine learning to the next level by grasping its ins and outs and tailoring it to your needs. Working knowledge of Python and a basic understanding of underlying mathematical and statistical concepts is required. Computers

Learning ArcGIS Pro 2 Create 2D maps and 3D scenes, analyze GIS data, and share your results with the GIS community using the latest ArcGIS Pro 2 features Key Features Get up to speed with the new ribbon-based user interface, projects, models, and common workflows in ArcGIS Pro 2 Learn how to visualize, maintain, and analyze GIS data Automate analysis and processes with ModelBuilder and Python scripts Book Description Armed with powerful tools to visualize, maintain, and analyze data, ArcGIS Pro 2 is Esri's newest desktop geographic information system (GIS) application that uses the modern ribbon interface and a 64-bit processor to make using GIS faster and more efficient. This second edition of Learning ArcGIS Pro will show you how you can use this powerful desktop GIS application to create maps, perform spatial analysis, and maintain data. The book begins by showing you how to install ArcGIS and listing the software and hardware prerequisites. You'll then understand the concept of named user licensing and learn how to navigate the new ribbon interface to leverage the power of ArcGIS Pro for managing geospatial data. Once you've got to grips with the new interface, you'll build your first GIS project and understand how to use the different project resources available. The book shows you how to create 2D and 3D maps by adding layers and setting and managing the symbology and labeling. You'll also discover how to use the analysis tool to visualize geospatial data. In later chapters, you'll be introduced to Arcade, the new lightweight expression language for ArcGIS, and then advance to creating complex labels using Arcade expressions. Finally, you'll use Python scripts to automate and standardize tasks and models in ArcGIS Pro. By the end of this ArcGIS Pro book, you'll have developed the core skills needed for using ArcGIS Pro 2.x competently. What you will learn Navigate the user interface to create maps, perform analysis, and manage data Display data based on discrete attribute values or range of values Label features on a GIS map based on one or more attributes using Arcade Create map books using the map series functionality Share ArcGIS Pro maps, projects, and data with other GIS community members Explore the most used geoprocessing tools for performing spatial analysis Create Tasks based on common workflows to standardize processes Automate processes using ModelBuilder and Python scripts Who this book is for If you want to learn ArcGIS Pro to create maps and, edit and analyze geospatial data, this ArcGIS book is for you. No knowledge of GIS fundamentals or experience with any GIS tool or ArcGIS software suite is required. Basic Windows skills, such as navigating and file management, are all you need. Computers

Mary Ellen Bute This biography drawn from interviews with Bute's family, friends, and colleagues, presents the personal and professional life of the filmmaker and her behind-the-scenes process of making animated and live action films. Computers

Deep Learning Projects Using TensorFlow 2 Work through engaging and practical deep learning projects using TensorFlow 2.0. Using a hands-on approach, the projects in this book will lead new programmers through the basics into developing practical deep learning applications. Deep learning is quickly integrating itself into the technology landscape. Its applications range from applicable data science to deep fakes and so much more. It is crucial for aspiring data scientists or those who want to enter the field of AI to understand deep learning concepts. The best way to learn is by doing. You'll develop a working knowledge of not only TensorFlow, but also related technologies such as Python and Keras. You'll also work with Neural Networks and other deep learning concepts. By the end of the book, you'll have a collection of unique projects that you can add to your GitHub profiles and expand on for professional application. What You'll Learn Grasp the basic process of neural networks through projects, such as creating music Restore and colorize black and white images with deep learning processes Who This Book Is For Beginners new to TensorFlow and Python. Computers

Hands-on Azure Pipelines Build, package, and deploy software projects, developed with any language targeting any platform, using Azure pipelines. The book starts with an overview of CI/CD and the need for software delivery automation. It further delves into the basic concepts of Azure pipelines followed by a hands-on guide to setting up agents on all platforms enabling software development in any language. Moving forward, you will learn to set up a pipeline using the classic Visual Editor using PowerShell scripts, a REST API, building edit history, retention, and much more. You’ll work with artifact feeds to store deployment packages and consume them in a build. As part of the discussion you’ll see the implementation and usage of YAML (Yet Another Markup Language) build pipelines. You will then create Azure release pipelines in DevOps and develop extensions for Azure pipelines. Finally, you will learn various strategies and patterns for developing pipelines and go through some sample lessons on building and deploying pipelines. After reading Hands-on Azure Pipelines, you will be able to combine CI and CD to constantly and consistently test and build your code and ship it to any target. What You Will Learn Work with Azure build-and-release pipelines Extend the capabilities and features of Azure pipelines Understand build, package, and deployment strategies, and versioning and patterns with Azure pipelines Create infrastructure and deployment that targets commonly used Azure platform services Build and deploy mobile applications Use quick-start Azure DevOps projects Who This Book Is For Software developers and test automation engineers who are involved in the software delivery process. Computers

Microsoft Azure Gain the technical and business insight needed to plan, deploy, and manage the services provided by the Microsoft Azure cloud. This second edition focuses on improving operational decision tipping points for the professionals leading DevOps and security teams. This will allow you to make an informed decision concerning the workloads appropriate for your growing business in the Azure public cloud. Microsoft Azure starts with an introduction to Azure along with an overview of its architecture services such as IaaS and PaaS. You’ll also take a look into Azure’s data, artificial intelligence, and machine learning services. Moving on, you will cover the planning for and adoption of Azure where you will go through budgeting, cloud economics, and designing a hybrid data center. Along the way, you will work with web apps, network PaaS, virtual machines, and much more. The final section of the book starts with Azure data services and big data with an in-depth discussion of Azure SQL Database, CosmosDB, Azure Data Lakes, and MySQL. You will further see how to migrate on-premises databases to Azure and use data engineering. Next, you will discover the various Azure services for application developers, including Azure DevOps and ASP.NET web apps. Finally, you will go through the machine learning and AI tools in Azure, including Azure Cognitive Services. What You Will Learn Apply design guidance and best practices using Microsoft Azure to achieve business growth Create and manage virtual machines Work with AI frameworks to process and analyze data to support business decisions and increase revenue Deploy, publish, and monitor a web app Who This Book Is For Azure architects and business professionals looking for Azure deployment and implementation advice. Computers

Social Network Analysis and Law Enforcement This book examines the use of social network analysis (SNA) in operational environments from the perspective of those who actually apply it. A rapidly growing body of literature suggests that SNA can reveal significant insights into the overall structure of criminal networks as well as the position of critical actors within such groups. This book draws on the existing SNA and intelligence literature, as well as qualitative interviews with crime intelligence analysts from two Australian state law enforcement agencies to understand its use by law enforcement agencies and the extent to which it can be used in practice. It includes a discussion of the challenges that analysts face when attempting to apply various network analysis techniques to criminal networks. Overall, it advances SNA as an investigative tool, and provides a significant contribution to the field that will be of interest to both researchers and practitioners interested in social network analysis, intelligence analysis and law enforcement. Computers

Advances in Hydroinformatics This book features a collection of extended papers based on presentations given at the SimHydro 2019 conference, held in Sophia Antipolis in June 2019 with the support of French Hydrotechnic Society (SHF), focusing on “Which models for extreme situations and crisis management?†Hydraulics and related disciplines are frequently applied in extreme situations that need to be understood accurately before implementing actions and defining appropriate mitigation measures. However, in such situations currently used models may be partly irrelevant due to factors like the new physical phenomena involved, the scale of the processes, and the hypothesis included in the different numerical tools. The availability of computational resources and new capacities like GPU offers modellers the opportunity to explore various approaches to provide information for decision-makers. At the same time, the topic of crisis management has sparked interest from stakeholders who need to share a common understanding of a situation. Hydroinfomatics tools can provide essential information in crises; however, the design and integration of models in decision-support systems require further development and the engagement of various communities, such as first responders. In this context, methodologies, guidelines and standards are more and more in demand in order to ensure that the systems developed are efficient and sustainable. Exploring both the limitations and performance of current models, this book presents the latest developments based on new numerical schemes, high-performance computing, multiphysics and multiscale methods, as well as better integration of field-scale model data. As such, it will appeal to practitioners, stakeholders, researchers and engineers active in this field. Computers

Parallel Computational Technologies This book constitutes refereed proceedings of the 14th International Conference on Parallel Computational Technologies, PCT 2020, held in May 2020. Due to the COVID-19 pandemic the conference was held online.The 22 revised full papers and 2 short papers presented were carefully reviewed and selected from 124 submissions. The papers are organized in topical sections on high performance architectures, tools and technologies; parallel numerical algorithms; supercomputer simulation. Computers

Advanced Python Development This book builds on basic Python tutorials to explain various Python language features that aren’t routinely covered: from reusable console scripts that play double duty as micro-services by leveraging entry points, to using asyncio efficiently to collate data from a large number of sources. Along the way, it covers type-hint based linting, low-overhead testing and other automated quality checking to demonstrate a robust real-world development process. Some powerful aspects of Python are often documented with contrived examples that explain the feature as a standalone example only. By following the design and build of a real-world application example from prototype to production quality you'll see not only how the various pieces of functionality work but how they integrate as part of the larger system design process. In addition, you'll benefit from the kind of useful asides and library recommendations that are a staple of conference Q&A sessions at Python conferences as well as discussions of modern Python best practice and techniques to better produce clear code that is easily maintainable. Advanced Python Development is intended for developers who can already write simple programs in Python and want to understand when it’s appropriate to use new and advanced language features and to do so in a confident manner. It is especially of use to developers looking to progress to a more senior level and to very experienced developers who have thus far used older versions of Python. What You'll Learn Understand asynchronous programming Examine developing plugin architectures Work with type annotations Review testing techniques Explore packaging and dependency management Who This Book Is For Developers at the mid to senior level who already have Python experience. Computers

VR Integrated Heritage Recreation Create assets for history-based games. This book covers the fundamental principles required to understand and create architectural visualizations of historical locations using digital tools. You will explore aspects of 3D design visualization and VR integration using industry-preferred software. Some of the most popular video games in recent years have historical settings (Age of Empires, Call of Duty, etc.). Creating these games requires creating historically accurate game assets. You will use Blender to create VR-ready assets by modeling and unwrapping them. And you will use Substance Painter to texture the assets that you create. You will also learn how to use the Quixel Megascans library to acquire and implement physically accurate materials in the scenes. Finally, you will import the assets into Unreal Engine 4 and recreate a VR integrated heritage that can be explored in real time. Using VR technology and game engines, you can digitally recreate historical settings for games. What You Will Learn Create high-quality, optimized models suitable for any 3D game engine Master the techniques of texturing assets using Substance Painter and Quixel Megascans Keep assets historically accurate Integrate assets with the game engine Create visualizations with Unreal Engine 4 Who Is This Book For Game developers with some experience who are eager to get into VR-based games Computers

Windows 10 For Dummies Time-tested advice on Windows 10 Windows 10 For Dummies remains the #1 source for readers looking for advice on Windows 10. Expert author Andy Rathbone provides an easy-to-follow guidebook to understanding Windows 10 and getting things done based on his decades of experience as a Windows guru. Look inside to get a feel for the basics of the Windows interface, the Windows apps that help you get things done, ways to connect to the Internet at home or on the go, and steps for customizing your Windows 10 experience from the desktop wallpaper to how tightly you secure your computer. • Manage user accounts • Customize the start menu • Find and manage your files • Connect to a printer wirelessly Revised to cover the latest round of Windows 10 updates, this trusted source for unleashing everything the operating system has to offer is your first and last stop for learning the basics of Windows! Computers

Windows 10 For Seniors For Dummies The easy way to get up and running with Windows 10! With Windows 10 For Seniors For Dummies, becoming familiarized with Windows 10 is a painless process. If you’re interested in learning the basics of this operating system without having to dig through confusing computer jargon, look no further. This book offers a step-by-step approach that is specifically designed to assist first time Windows 10 users who are over-50, providing easy-to-understand language, large-print text, and an abundance of helpful images along the way! Protect your computer Follow friends and family online Use Windows 10 to play games and enjoy media Check your security and maintenance status Step-by-step instructions are provided to ensure that you don't get lost at any point along the way. Computers

The Applied AI and Natural Language Processing Workshop With the help of engaging activities, learn how to leverage Amazon Web Services for building serverless intelligent applications that can process information in no time Key Features Learn how to integrate Amazon's Simple Storage Services with AI and NLP projects Get to grips with serverless computing and its applications Create intelligent applications such as chatbots and image recognition models Book Description Are you fascinated with applications like Alexa and Siri and how they accurately process information within seconds before returning accurate results? Are you looking for a practical guide that will teach you how to build intelligent applications that can revolutionize the world of artificial intelligence? The Applied AI and NLP Workshop will take you on a practical journey where you will learn how to build artificial intelligence (AI) and natural language processing (NLP) applications with Amazon Web services (AWS). Starting with an introduction to AI and machine learning, this book will explain how Amazon S3, or Amazon Simple Storage Service, works. You'll then integrate AI with AWS to build serverless services and use Amazon's NLP service Comprehend to perform text analysis on a document. As you advance, the book will help you get to grips with topic modeling to extract and analyze common themes on a set of documents with unknown topics. You'll also work with Amazon Lex to create and customize a chatbot for task automation and use Amazon Rekognition for detecting objects, scenes, and text in images. By the end of The Applied AI and NLP Workshop, you'll be equipped with the knowledge and skills needed to build scalable intelligent applications with AWS. What you will learn Grasp the fundamentals of AI, ML, and AWS Explore the AWS command line, its interface, and its applications Import and export data to Amazon S3 Perform topic modeling on a set of documents to analyze common themes Develop a custom chatbot to get the latest stock market quotes Create a personal call center and connect it to the chatbot Who this book is for If you are a machine learning enthusiast, data scientist, or programmer who wants to explore AWS's artificial intelligence and machine learning capabilities, this book is for you. Although not necessary, a basic understanding of AI and NLP will assist with grasping key topics quickly. Computers

The Complete Guide to Blender Graphics BlenderTM is a free Open Source 3D Computer Modeling and Animation Suite incorporating Character Rigging, Particles, Real World Physics Simulation, Sculpting, Video Editing with Motion Tracking and 2D Animation within the 3D Environment. Blender is FREE to download and use by anyone for anything. The Complete Guide to Blender Graphics: Computer Modeling and Animation, Sixth Edition is a unified manual describing the operation of the program with reference to the Graphical User Interface for Blender Version 2.82a. A reader of the Sixth Edition should use Blender 2.82a when learning the program and treat it as a training exercise before using any later versions Key Features: The book provides instruction for New Users starting at the very beginning. Instruction is presented in a series of chapters incorporating visual reference to the program's interface. The initial chapters are designed to instruct the user in the operation of the program while introducing and demonstrating interesting features of the program. Chapters are developed in a building block fashion providing forward and reverse reference to relevant material. Computers

The Data Visualization Workshop Explore a modern approach to visualizing data with Python and transform large real-world datasets into expressive visual graphics using this beginner-friendly workshop Key Features Discover the essential tools and methods of data visualization Learn to use standard Python plotting libraries such as Matplotlib and Seaborn Gain insights into the visualization techniques of big companies Book Description Do you want to transform data into captivating images? Do you want to make it easy for your audience to process and understand the patterns, trends, and relationships hidden within your data? The Data Visualization Workshop will guide you through the world of data visualization and help you to unlock simple secrets for transforming data into meaningful visuals with the help of exciting exercises and activities. Starting with an introduction to data visualization, this book shows you how to first prepare raw data for visualization using NumPy and pandas operations. As you progress, you'll use plotting techniques, such as comparison and distribution, to identify relationships and similarities between datasets. You'll then work through practical exercises to simplify the process of creating visualizations using Python plotting libraries such as Matplotlib and Seaborn. If you've ever wondered how popular companies like Uber and Airbnb use geoplotlib for geographical visualizations, this book has got you covered, helping you analyze and understand the process effectively. Finally, you'll use the Bokeh library to create dynamic visualizations that can be integrated into any web page. By the end of this workshop, you'll have learned how to present engaging mission-critical insights by creating impactful visualizations with real-world data. What you will learn Understand the importance of data visualization in data science Implement NumPy and pandas operations on real-life datasets Create captivating data visualizations using plotting libraries Use advanced techniques to plot geospatial data on a map Integrate interactive visualizations to a webpage Visualize stock prices with Bokeh and analyze Airbnb data with Matplotlib Who this book is for The Data Visualization Workshop is for beginners who want to learn data visualization, as well as developers and data scientists who are looking to enrich their practical data science skills. Prior knowledge of data analytics, data science, and visualization is not mandatory. Knowledge of Python basics and high-school-level math will help you grasp the concepts covered in this data visualization book more quickly and effectively. Computers

Blockchain Technology and Applications Blockchain is emerging as a powerful technology, which has attracted the wider attention of all businesses across the globe. In addition to financial businesses, IT companies and business organizations are keenly analyzing and adapting this technology for improving business processes. Security is the primary enterprise application. There are other crucial applications that include creating decentralized applications and smart contracts, which are being touted as the key differentiator of this pioneering technology. The power of any technology lies in its ecosystem. Product and tool vendors are building and releasing a variety of versatile and robust toolsets and platforms in order to speed up and simplify blockchain application development, deployment and management. There are other infrastructure-related advancements in order to streamline blockchain adoption. Cloud computing, big data analytics, machine and deep learning algorithm, and connected and embedded devices all are driving blockchain application development and deployment. Blockchain Technology and Applications illustrates how blockchain is being sustained through a host of platforms, programming languages, and enabling tools. It examines: Data confidential, integrity, and authentication Distributed consensus protocols and algorithms Blockchain systems design criteria and systems interoperability and scalability Integration with other technologies including cloud and big data It also details how blockchain is being blended with cloud computing, big data analytics and IoT across all industry verticals. The book gives readers insight into how this path-breaking technology can be a value addition in several business domains ranging from healthcare, financial services, government, supply chain and retail. Computers

Furnishing the Library Interior This book discusses the selection, evaluation, and purchase of furniture and equipment for libraries. It examines the arrangement of the interior to update and illuminate earlier writings, and helps those spending even small amounts for library furniture and equipment to do so more wisely. Computers

Data Management at Scale As data management and integration continue to evolve rapidly, storing all your data in one place, such as a data warehouse, is no longer scalable. In the very near future, data will need to be distributed and available for several technological solutions. With this practical book, you’ll learnhow to migrate your enterprise from a complex and tightly coupled data landscape to a more flexible architecture ready for the modern world of data consumption. Executives, data architects, analytics teams, and compliance and governance staff will learn how to build a modern scalable data landscape using the Scaled Architecture, which you can introduce incrementally without a large upfront investment. Author Piethein Strengholt provides blueprints, principles, observations, best practices, and patterns to get you up to speed. Examine data management trends, including technological developments, regulatory requirements, and privacy concerns Go deep into the Scaled Architecture and learn how the pieces fit together Explore data governance and data security, master data management, self-service data marketplaces, and the importance of metadata Computers

Ascend AI Processor Architecture and Programming Ascend AI Processor Architecture and Programming: Principles and Applications of CANN offers in-depth AI applications using Huawei’s Ascend chip, presenting and analyzing the unique performance and attributes of this processor. The title introduces the fundamental theory of AI, the software and hardware architecture of the Ascend AI processor, related tools and programming technology, and typical application cases. It demonstrates internal software and hardware design principles, system tools and programming techniques for the processor, laying out the elements of AI programming technology needed by researchers developing AI applications. Chapters cover the theoretical fundamentals of AI and deep learning, the state of the industry, including the current state of Neural Network Processors, deep learning frameworks, and a deep learning compilation framework, the hardware architecture of the Ascend AI processor, programming methods and practices for developing the processor, and finally, detailed case studies on data and algorithms for AI. Presents the performance and attributes of the Huawei Ascend AI processor Describes the software and hardware architecture of the Ascend processor Lays out the elements of AI theory, processor architecture, and AI applications Provides detailed case studies on data and algorithms for AI Offers insights into processor architecture and programming to spark new AI applications Computers

G Suite For Dummies Get fast answers to y our G Suite questions with this friendly resource G Suite For Dummies is the fun guide to the productivity suite that’s quickly winning over professional and personal users. This book shares the steps on how to collaborate in the cloud, create documents and spreadsheets, build presentations, and connect with chat or video. Written in the easy-to-follow For Dummies style, G Suite For Dummies covers the essential components of Google’s popular software, including: Google Docs for word processing Gmail for email Google Calendar for scheduling and day planning Google Sheets for spreadsheet functionality Google Drive for data storage Google Hangouts and Google Meet for videoconferencing and calling capability The book helps navigate the G Suite payment plans and subscription options as well as settings that ensure your own privacy and security while operating in the cloud. Perfect for anyone hoping to get things done with this tool, G Suite For Dummies belongs on the bookshelf of every G Suite user who needs help from time to time. Computers

The Deep Learning with Keras Workshop Discover how to leverage Keras, the powerful and easy-to-use open source Python library for developing and evaluating deep learning models Key Features Get to grips with various model evaluation metrics, including sensitivity, specificity, and AUC scores Explore advanced concepts such as sequential memory and sequential modeling Reinforce your skills with real-world development, screencasts, and knowledge checks Book Description New experiences can be intimidating, but not this one! This beginner's guide to deep learning is here to help you explore deep learning from scratch with Keras, and be on your way to training your first ever neural networks. What sets Keras apart from other deep learning frameworks is its simplicity. With over two hundred thousand users, Keras has a stronger adoption in industry and the research community than any other deep learning framework. The Deep Learning with Keras Workshop starts by introducing you to the fundamental concepts of machine learning using the scikit-learn package. After learning how to perform the linear transformations that are necessary for building neural networks, you'll build your first neural network with the Keras library. As you advance, you'll learn how to build multi-layer neural networks and recognize when your model is underfitting or overfitting to the training data. With the help of practical exercises, you'll learn to use cross-validation techniques to evaluate your models and then choose the optimal hyperparameters to fine-tune their performance. Finally, you'll explore recurrent neural networks and learn how to train them to predict values in sequential data. By the end of this book, you'll have developed the skills you need to confidently train your own neural network models. What you will learn Gain insights into the fundamentals of neural networks Understand the limitations of machine learning and how it differs from deep learning Build image classifiers with convolutional neural networks Evaluate, tweak, and improve your models with techniques such as cross-validation Create prediction models to detect data patterns and make predictions Improve model accuracy with L1, L2, and dropout regularization Who this book is for If you know the basics of data science and machine learning and want to get started with advanced machine learning technologies like artificial neural networks and deep learning, then this is the book for you. To grasp the concepts explained in this deep learning book more effectively, prior experience in Python programming and some familiarity with statistics and logistic regression are a must. Computers

The Data Wrangling Workshop A beginner's guide to simplifying Extract, Transform, Load (ETL) processes with the help of hands-on tips, tricks, and best practices, in a fun and interactive way Key Features Explore data wrangling with the help of real-world examples and business use cases Study various ways to extract the most value from your data in minimal time Boost your knowledge with bonus topics, such as random data generation and data integrity checks Book Description While a huge amount of data is readily available to us, it is not useful in its raw form. For data to be meaningful, it must be curated and refined. If you're a beginner, then The Data Wrangling Workshop will help to break down the process for you. You'll start with the basics and build your knowledge, progressing from the core aspects behind data wrangling, to using the most popular tools and techniques. This book starts by showing you how to work with data structures using Python. Through examples and activities, you'll understand why you should stay away from traditional methods of data cleaning used in other languages and take advantage of the specialized pre-built routines in Python. Later, you'll learn how to use the same Python backend to extract and transform data from an array of sources, including the internet, large database vaults, and Excel financial tables. To help you prepare for more challenging scenarios, the book teaches you how to handle missing or incorrect data, and reformat it based on the requirements from your downstream analytics tool. By the end of this book, you will have developed a solid understanding of how to perform data wrangling with Python, and learned several techniques and best practices to extract, clean, transform, and format your data efficiently, from a diverse array of sources. What you will learn Get to grips with the fundamentals of data wrangling Understand how to model data with random data generation and data integrity checks Discover how to examine data with descriptive statistics and plotting techniques Explore how to search and retrieve information with regular expressions Delve into commonly-used Python data science libraries Become well-versed with how to handle and compensate for missing data Who this book is for The Data Wrangling Workshop is designed for developers, data analysts, and business analysts who are looking to pursue a career as a full-fledged data scientist or analytics expert. Although this book is for beginners who want to start data wrangling, prior working knowledge of the Python programming language is necessary to easily grasp the concepts covered here. It will also help to have a rudimentary knowledge of relational databases and SQL. Computers

The Unsupervised Learning Workshop Learning how to apply unsupervised algorithms on unlabeled datasets from scratch can be easier than you thought with this beginner's workshop, featuring interesting examples and activities Key Features Get familiar with the ecosystem of unsupervised algorithms Learn interesting methods to simplify large amounts of unorganized data Tackle real-world challenges, such as estimating the population density of a geographical area Book Description Do you find it difficult to understand how popular companies like WhatsApp and Amazon find valuable insights from large amounts of unorganized data? The Unsupervised Learning Workshop will give you the confidence to deal with cluttered and unlabeled datasets, using unsupervised algorithms in an easy and interactive manner. The book starts by introducing the most popular clustering algorithms of unsupervised learning. You'll find out how hierarchical clustering differs from k-means, along with understanding how to apply DBSCAN to highly complex and noisy data. Moving ahead, you'll use autoencoders for efficient data encoding. As you progress, you'll use t-SNE models to extract high-dimensional information into a lower dimension for better visualization, in addition to working with topic modeling for implementing natural language processing (NLP). In later chapters, you'll find key relationships between customers and businesses using Market Basket Analysis, before going on to use Hotspot Analysis for estimating the population density of an area. By the end of this book, you'll be equipped with the skills you need to apply unsupervised algorithms on cluttered datasets to find useful patterns and insights. What you will learn Distinguish between hierarchical clustering and the k-means algorithm Understand the process of finding clusters in data Grasp interesting techniques to reduce the size of data Use autoencoders to decode data Extract text from a large collection of documents using topic modeling Create a bag-of-words model using the CountVectorizer Who this book is for If you are a data scientist who is just getting started and want to learn how to implement machine learning algorithms to build predictive models, then this book is for you. To expedite the learning process, a solid understanding of the Python programming language is recommended, as you'll be editing classes and functions instead of creating them from scratch. Computers

Plunkett's Games, Apps & Social Media Industry Almanac 2021 Everything you need to know about the business of games, apps and social media—a powerful tool for market research, strategic planning, competitive intelligence or employment searches. Includes trends analysis, software, design, statistics, markets, technologies, contacts, and profiles of more than 200 leading companies, containing addresses, phone numbers and executives. Computers

When 5G Meets Industry 4.0 Since the 1980s, mobile communication has undergone major transitions from 1G to 4G, at a rate of roughly one generation per decade. And the next upgrade is set to come soon, with 5G heralding a new era of large-bandwidth Internet, and a multi-connection, low-latency Internet of Everything. 5G technology will be the standard for next-generation mobile Internet, and it will not only enhance the individual user’s experience, but also provide technical support for artificial-intelligence-based applications, such as smart manufacturing, smart healthcare, smart government, smart cities and driverless cars. As a result, 5G is regarded as the “infrastructure†of the industrial Internet and artificial intelligence and both China and the United States are striving to become the 5G leader and spearhead this new generation of international mobile communication standards. Though trade tensions between China and the United States continue to escalate, with products ranging from soybeans to mobile phones and automobiles being affected, 5G technology may be the true cause of trade wars between the world’s top two economies. In short, 5G will change not only society, but also international trade patterns. This book describes various 5G scenarios, changes and values; explains the standards, technologies and development directions behind 5G; and explores new models, new formats and new trends in 5G-based artificial intelligence. Computers

Implicit and Explicit Semantics Integration in Proof-Based Developments of Discrete Systems This book addresses mechanisms for reducing model heterogeneity induced by the absence of explicit semantics expression in the formal techniques used to specify design models. More precisely, it highlights the advances in handling both implicit and explicit semantics in formal system developments, and discusses different contributions expressing different views and perceptions on the implicit and explicit semantics. The book is based on the discussions at the Shonan meeting on this topic held in 2016, and includes contributions from the participants summarising their perspectives on the problem and offering solutions. Divided into 5 parts: domain modelling, knowledge-based modelling, proof-based modelling, assurance cases, and refinement-based modelling, and offers inspiration for researchers and practitioners in the fields of formal methods, system and software engineering, domain knowledge modelling, requirement analysis, and explicit and implicit semantics of modelling languages. Computers

Code-Based Cryptography This book constitutes the refereed and revised post-conference proceedings of the 8th International Workshop on Code-Based Cryptography, CBCrypto 2020, held in Zagreb, Croatia, in May 2020.*The seven papers presented in this book were carefully reviewed and selected from numerous submissions. These contributions focus on various topics such as code-based cryptography, from design to implementation, security, new systems, and improved decoding algorithms. * The conference was held virtually due to the COVID-19 pandemic. Computers

Interactivity, Game Creation, Design, Learning, and Innovation This book constitutes the refereed post-conference proceedings of two conferences: The 8th EAI International Conference on ArtsIT, Interactivity and Game Creation (ArtsIT 2019), and the 4th EAI International Conference on Design, Learning, and Innovation (DLI 2019). Both conferences were hosed in Aalborg, Denmark, and took place November 6-8, 2019. The 61 revised full papers presented were carefully selected from 98 submissions. The papers represent a forum for the dissemination of cutting-edge research results in the area of arts, design and technology, including open related topics like interactivity and game creation. Computers

Science and Technologies for Smart Cities This book constitutes the refereed proceedings of the 5th Annual Smart City 360° Summit, held in Braga, Portugal, in December 2019. The volume combines selected papers of four conferences, namely IoT in Urban Space, Urb-IoT 2019, Smart Governance for Sustainable Smart Cities, SmartGov 2019, Sensor Systems and Software, S-Cube 2019, and Intelligent Technologies for Interactive Entertainment, Intetain 2019. The 5 keynote and 32 conference papers presented were carefully reviewed and selected from 113 submissions and present results of multidisciplinary scientific and industry collaboration to solve complex societal, technological and economic problems Smart Cities. As such, the main goals are to promote quality of life, work conditions, mobility and sustainability. Computers

A Computational View of Autism This book first explains autism, its prevalence, and some conventional intervention techniques, and it then describes how virtual reality technology can support autism intervention and skills training. The approaches and technologies covered include immersive virtual reality, augmented reality and mixed reality. The tasks covered include emotion recognition, affective computing, teaching communication skills, imparting literacy skills, training for imitation skills, and joint attention skills. Most of the chapters assume no prerequisite knowledge of autism or virtual reality, and they are supported throughout with detailed references for further investigation. While the author is an engineer by profession, with specialist knowledge in robotics and computer-based platforms, in this book she adopts a user perspective and cites many real-life examples from her own experience. The book is suitable for students of cognitive science, and researchers and practitioners engaged with designing and offering technological assistance for special needs training. Computers

Beginning C Learn how to program using C, beginning from first principles and progressing through step-by-step examples to become a competent, C-language programmer. All you need are this book and any of the widely available C compilers, and you'll soon be writing real C programs. You’ll discover that C is a foundation language that every programmer ought to know. Beginning C is written by renowned author Ivor Horton and expert programmer German Gonzalez-Morris. This book increases your programming expertise by guiding you through the development of fully working C applications that use what you've learned in a practical context. You’ll also be able to strike out on your own by trying the exercises included at the end of each chapter. At the end of the book you'll be confident in your skills with all facets of the widely-used and powerful C language. What You Will Learn Discover the C programming language Program using C starting with first steps, then making decisions Use loops, arrays, strings, text, pointers, functions, I/O, and more Code applications with strings and text Structure your programs efficiently Work with data, files, facilities, and more Who This Book Is For Those new to C programming who may or may not have some prior programming experience. Computers

CoderDojo CoderDojo is the coding club that lets you hang out with other coders, learn new stuff and generally have fun with computers. This amazing CoderDojo book tells you everything you need to know to build your own website. Start by getting your very own Dojo Nano club up and running. All you need is one or more friends, a computer, and this book! Computers

Performance Evaluation and Benchmarking for the Era of Cloud(s) This book constitutes the refereed post-conference proceedings of the 11th TPC Technology Conference on Performance Evaluation and Benchmarking, TPCTC 2019, held in conjunction with the 45th International Conference on Very Large Databases (VLDB 2019) in August 2019.The 11 papers presented were carefully reviewed and focus on topics such as blockchain; big data and analytics; complex event processing; database Optimizations; data Integration; disaster tolerance and recovery; artificial Intelligence; emerging storage technologies (NVMe, 3D XPoint Memory etc.); hybrid workloads; energy and space efficiency; in-memory databases; internet of things; virtualization; enhancements to TPC workloads; lessons learned in practice using TPC workloads; collection and interpretation of performance data in public cloud environments. Computers

Structural Information and Communication Complexity This book constitutes the refereed conference proceedings of the 27th International Colloquium on Structural Information and Communication Complexity, SIROCCO 2020, held in Paderborn, Germany, in June 2020.* The 19 full papers and 2 invited papers presented in this book were carefully reviewed and selected from 41 submissions. They are divided into seven sections, i.e. invited papers; mobile robots; dynamic graphs; network communication; multi-agent systems; communication complexity; and game theory. * The conference was held virtually due to the COVID-19 pandemic. Computers

Data Management Technologies and Applications This book constitutes the thoroughly refereed proceedings of the 8th International Conference on Data Management Technologies and Applications, DATA 2019, held in Prague, Czech Republic, in July 2019. The 8 revised full papers were carefully reviewed and selected from 90 submissions. The papers deal with the following topics: decision support systems, data analytics, data and information quality, digital rights management, big data, knowledge management, ontology engineering, digital libraries, mobile databases, object-oriented database systems, and data integrity. Computers

Cyber Security and Computer Science This book constitutes the refereed post-conference proceedings of the Second International Conference on Cyber Security and Computer Science, ICONCS 2020, held in Dhaka, Bangladesh, in February 2020. The 58 full papers were carefully reviewed and selected from 133 submissions. The papers detail new ideas, inventions, and application experiences to cyber security systems. They are organized in topical sections on optimization problems; image steganography and risk analysis on web applications; machine learning in disease diagnosis and monitoring; computer vision and image processing in health care; text and speech processing; machine learning in health care; blockchain applications; computer vision and image processing in health care; malware analysis; computer vision; future technology applications; computer networks; machine learning on imbalanced data; computer security; Bangla language processing. Computers

Practical Hexo Leverage the power of Hexo to quickly produce static blog sites that are efficient and fast. This project-oriented book simplifies the process of setting up Hexo and manipulating content, using little more than a text editor and free software. It will equip you with a starting toolset that you can use to develop future projects, incorporate into your existing workflow and allow you to take your websites to the next level. Hexo is based on JavaScript and Node.js, two of the biggest tools available for developers: you can enhance, extend, and configure Hexo as requirements dictate. With Hexo the art of possible is only limited by the extent of your imagination and the power of JavaScript and Node.js. Practical Hexo gets you quickly acquainted with creating and manipulating blogs using a static site generator approach. You will understand how to use the Hexo framework to rapidly create and deploy blogs that are performant, with the minimum of fuss, then extend and customize your content using plugins and themes. You will work through some practical projects to help solidify your skills, and put them into practice. What You'll Learn Implement the Hexo framework in a project Customize and extend content Consider maintenance requirements and how they compare to other blog systems Apply skills to practical, real-world projects Create themes and build plugins Make changes using other tools and libraries. Who This Book Is For Website developers who are already familiar with JavaScript and keen to learn how to leverage the Hexo framework. Agile development team members, where time is of the essence to deliver results quickly. Developers who want to focus on simplicity, to produce efficient and properly optimized content in modern browsers using tools already in their possession. Computers

C++20 Quick Syntax Reference This quick C++ 20 guide is a condensed code and syntax reference to the popular programming language, fully updated for C++20. It presents the essential C++20 code syntax in a well-organized format that can be used as a handy reference. This edition covers topics including designated initializers, lambdas and lambda captures, the spaceship operator, pack expressions, string literals as template parameters, atomic smart pointers, and contracts. It also covers library changes including extended futures, latches and barriers, task blocks, and text formatting. In the C++20 Quick Syntax Reference, you will find short, simple, and focused code examples. This book includes a well-laid-out table of contents and a comprehensive index allowing for easy review. You won’t find any technical jargon, bloated samples, drawn out history lessons, or witty stories in this book. What you will find is a language reference that is concise, to the point, and highly accessible. The book is packed with useful information and is a must-have for any C++ programmer. What You'll Learn Discover the key C++20 features Work with concepts to constrain template arguments Use modules as a replacement for header files Take advantage of the three-way comparison operator Create immediate functions using the consteval keyword Make use of constexpr, constinit and designated initializers Who This Book Is For Experienced C++ programmers. Additionally, this is a concise, easily-digested introduction for other programmers new to C++. Computers

Smart Multimedia This book constitutes the proceedings of the Second International Conference on Smart Multimedia, ICSM 2019, which was held in San Diego, CA, USA, in December 2019. The 45 papers presented were selected from about 100 submissions and are grouped in sections on 3D mesh and depth image processing; image understanding; miscellaneous; smart multimedia for citizen-centered smart living; 3D perception and applications; video applications; multimedia in medicine; haptics and applications; smart multimedia beyond the visible spectrum; machine learning for multimedia; image segmentation and processing; biometrics; 3D and image processing; and smart social and connected household products. Computers

Iceberg Semantics for Mass Nouns and Count Nouns Iceberg semantics is a new framework of Boolean semantics for mass nouns and count nouns in which the interpretation of a noun phrase rises up from a generating base and floats with its base on its Boolean part set, like an iceberg. The framework is shown to preserve the attractive features of classical Boolean semantics for count nouns; the book argues that Iceberg semantics forms a much better framework for studying mass nouns than the classical theory does. Iceberg semantics uses its notion of base to develop a semantic theory of the differences between mass nouns and count nouns and between different types of mass nouns, in particular between prototypical mass nouns (here called mess mass nouns) like water and mud versus object mass nouns (here called neat mass nouns) like poultry and pottery. The book shows in detail how and why neat mass nouns pattern semantically both with mess mass nouns and with count nouns. Iceberg semantics is a compositional theory and in Iceberg semantics the semantic distinctions defined apply to noun phrases of any complexity. The book studies in depth the semantics of classifier noun phrases (like three glasses of wine) and measure noun phrases (like three liters of wine). The classical wisdom is that classifier interpretations are count. Recent literature has argued compellingly that measure interpretations are mass. The book shows that both connections follow from the basic architecture of Iceberg semantics. Audience: Scholars and students in linguistics - in particular semantics, pragmatics, computational linguistics and syntax – and neighbouring disciplines like logic, philosophy of language, and cognitive science. Computers

Wireless Internet This book constitutes the refereed post-conference proceedings of the 12th International Conference on Wireless Internet, WiCON 2019, held in TaiChung, Taiwan, in November 2019. The 39 full papers were selected from 79 submissions and are grouped into the following topics: Ad hoc and sensor network, artificial intelligence, security and blockchain, internet of things, wireless internet, services and applications. Computers

Artificial Intelligence and Bioethics This book explores major bioethical issues emerging from the development and use of artificial intelligence in medical settings. The authors start by defining the past, present and future of artificial intelligence in medical settings and then proceed to address the resulting common and specific bioethical inquiries. The book discusses bioethical inquiries in two separate sets. The first set is comprised of ontological discussions mainly focusing on personhood and being an ethical agent of an artefact. The second set discusses bioethical issues resulting from the use of artificial intelligence. It focuses particularly on the area of artificial intelligence use in medicine and health services. It addresses the main challenges by considering fundamental principles of medical ethics, including confidentiality, privacy, compassion, veracity and fidelity. Finally, the authors discuss the ethical implications of involvement of artificial intelligence agents in patient care by expanding on communication skills in a case-based approach. The book is of great interest to ethicists, medical professionals, academicians, engineers and scientists working with artificial intelligence. Computers

The Applied TensorFlow and Keras Workshop Cut through the noise and get real results with this workshop for beginners. Use a project-based approach to exploring machine learning with TensorFlow and Keras. Key Features Understand the nuances of setting up a deep learning programming environment Gain insights into the common components of a neural network and its essential operations Get to grips with deploying a machine learning model as an interactive web application with Flask Book Description Machine learning gives computers the ability to learn like humans. It is becoming increasingly transformational to businesses in many forms, and a key skill to learn to prepare for the future digital economy. As a beginner, you'll unlock a world of opportunities by learning the techniques you need to contribute to the domains of machine learning, deep learning, and modern data analysis using the latest cutting-edge tools. The Applied TensorFlow and Keras Workshop begins by showing you how neural networks work. After you've understood the basics, you will train a few networks by altering their hyperparameters. To build on your skills, you'll learn how to select the most appropriate model to solve the problem in hand. While tackling advanced concepts, you'll discover how to assemble a deep learning system by bringing together all the essential elements necessary for building a basic deep learning system - data, model, and prediction. Finally, you'll explore ways to evaluate the performance of your model, and improve it using techniques such as model evaluation and hyperparameter optimization. By the end of this book, you'll have learned how to build a Bitcoin app that predicts future prices, and be able to build your own models for other projects. What you will learn Familiarize yourself with the components of a neural network Understand the different types of problems that can be solved using neural networks Explore different ways to select the right architecture for your model Make predictions with a trained model using TensorBoard Discover the components of Keras and ways to leverage its features in your model Explore how you can deal with new data by learning ways to retrain your model Who this book is for If you are a data scientist or a machine learning and deep learning enthusiast, who is looking to design, train, and deploy TensorFlow and Keras models into real-world applications, then this workshop is for you. Knowledge of computer science and machine learning concepts and experience in analyzing data will help you to understand the topics explained in this book with ease. Computers

The Applied SQL Data Analytics Workshop Take a step-by-step approach to learning SQL data analysis in this interactive workshop that uses fun exercises and activities to make learning data analytics for beginners easy and approachable. Key Features Explore ways to use SQL for data analytics and gain key insights from your data Study advanced analytics, such as geospatial and text analytics Discover ways to integrate your SQL pipelines with other analytics technologies Book Description Every day, businesses operate around the clock and a huge amount of data is generated at a rapid pace. Hidden in this data are key patterns and behaviors that can help you and your business understand your customers at a deep, fundamental level. Are you ready to enter the exciting world of data analytics and unlock these useful insights? Written by a team of expert data scientists who have used their data analytics skills to transform businesses of all shapes and sizes, The Applied SQL Data Analytics Workshop is a great way to get started with data analysis, showing you how to effectively sieve and process information from raw data, even without any prior experience. The book begins by showing you how to form hypotheses and generate descriptive statistics that can provide key insights into your existing data. As you progress, you'll learn how to write SQL queries to aggregate, calculate and combine SQL data from sources outside of your current dataset. You'll also discover how to work with different data types, like JSON. By exploring advanced techniques, such as geospatial analysis and text analysis, you'll finally be able to understand your business at a deeper level. Finally, the book lets you in on the secret to getting information faster and more effectively by using advanced techniques like profiling and automation. By the end of The Applied SQL Data Analytics Workshop, you'll have the skills you need to start identifying patterns and unlocking insights in your own data. You will be capable of looking and assessing data with the critical eye of a skilled data analyst. What you will learn Understand what data analytics is and why it is important Experiment with data analytics using basic and advanced queries Interpret data through descriptive statistics and aggregate functions Export data from external sources using powerful SQL queries Work with and manipulate data using SQL joins and constraints Speed up your data analysis workflow by automating tasks and optimizing queries Who this book is for If you are a database engineer who is looking to transition into analytics or someone who knows SQL basics but doesn't know how to use it to create business insights, then this book is for you. Computers

GarageBand For Dummies Lay down some tracks—no garage required! GarageBand has become the default musical sketchpad for both well-known artists and hobbyists musicians who want a simple way to record, edit, and share their own tunes. GarageBand For Dummies is your go-to guide to navigating the interface and making the tweaks to create your own songs. Look inside to discover how to lay down a beat with the virtual drum kits, layer on sweet sounds with built-in virtual instruments, and attach simple hardware to record vocals or live instruments on a Mac, iPad, or even an iPhone. Use built-in instruments to create a song Attach your guitar or mic to record live sounds Export your final product or individual tracks Add effects and edit your song GarageBand is the simplest way to create basic tracks without investing in costly hardware and learning a complex digital audio workstation software package—and this book shows you how. Computers

Bite-Size Python Introduce children to the popular Python programming language through relatable examples and fun projects! Python has now surpassed Java as the most commonly used programming language. As the language rises in popularity, this complete guide can teach basic Python concepts to kids with its simple, friendly format. Bite-Size Python: An Introduction to Python Programming provides children with a foundation in the Python language. This unique book shares knowledge through easy-to-understand examples, fast exercises, and fun projects! As children learn, their parents, caregivers, and instructors can also join in their discoveries. Bite-Size Python is ideal for those who are new to programming, giving kids ages 9 and up a beginners’ approach to learning one of the most important programming languages. Gives an overview of Python Provides exciting programming projects Offers instruction on how to download and install Python Presents key programming language concepts Simplifies technical definitions With this playful guide to learning Python, readers can try out activities on their computers for a hands-on learning experience. The artwork in Bite-Size Python represents children of various backgrounds, so any child who picks up this book will be empowered to learn and young readers will love showing their projects to friends and family! Computers

Red Hat RHCE 8 (EX294) Cert Guide Learn, prepare, and practice for Red Hat RHCE 8 EX294 exam success with this Cert Guide from Pearson IT Certification, a leader in IT certification learning. * Master RHCE 8 EX294 exam topics * Assess your knowledge with chapter-ending quizzes * Review key concepts with step-by-step exercises, code examples, and complete labs after every chapter, designed to closely resemble the exam * Practice with realistic exam questions from four full practice exams: two printed in the book and two more on the companion website * Supplement your learning with an hour of video mentoring Red Hat RHCE 8 (EX294) Cert Guide is the authoritative exam study guide. Leading Red Hat and Linux consultant, trainer, and author Sander van Vugt walks you through the RHCE EX 294 objectives so you have a full study resource. He shares preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. Material is presented in a concise manner, focusing on increasing your understanding, retention of exam topics, and hands-on practice so you can feel ready to take the exam. The book presents you with an organized test preparation routine through the use of proven series elements and techniques. Exam topic lists make referencing easy. Chapter-ending Exam Preparation Tasks help you drill on key concepts you must know thoroughly. Review questions help you assess your knowledge, and a final preparation chapter guides you through tools and resources to help you craft your final study plan. The end of chapter labs are an essential part of learning each topic and cover each chapter’s key concepts so you can test yourself and put your knowledge to work. The companion website contains two additional practice exams, flashcards that test you on the glossary terms in the book, an hour of video mentoring from the author, and study resources. Well regarded for its level of detail, assessment features, and challenging review questions and exercises, this study guide helps you master the concepts and techniques that will enable you to succeed on the exam the first time. The study guide helps you master all the topics on the RHCE 8 exam, including * Understanding configuration management * Installing Ansible and setting up managed environments * Using ad hoc commands * Getting started with playbooks * Working with variables and facts * Using task control * Deploying files * Using Ansible roles * Using Ansible in large environments * Troubleshooting Ansible * Managing software with Ansible * Managing users, processes, tasks, and storage Computers

Information Technology This revised edition has more breadth and depth of coverage than the first edition. Information Technology: An Introduction for Today’s Digital World introduces undergraduate students to a wide variety of concepts that they will encounter throughout their IT studies and careers. The features of this edition include: Introductory system administration coverage of Windows 10 and Linux (Red Hat 7), both as general concepts and with specific hands-on instruction Coverage of programming and shell scripting, demonstrated through example code in several popular languages Updated information on modern IT careers Computer networks, including more content on cloud computing Improved coverage of computer security Ancillary material that includes a lab manual for hands-on exercises Suitable for any introductory IT course, this classroom-tested text presents many of the topics recommended by the ACM Special Interest Group on IT Education (SIGITE). It offers a far more detailed examination of the computer and IT fields than computer literacy texts, focusing on concepts essential to all IT professionals – from system administration to scripting to computer organization. Four chapters are dedicated to the Windows and Linux operating systems so that students can gain hands-on experience with operating systems that they will deal with in the real world. Computers

GCIH GIAC Certified Incident Handler All-in-One Exam Guide This self-study guide delivers complete coverage of every topic on the GIAC Certified Incident Handler exam Prepare for the challenging GIAC Certified Incident Handler exam using the detailed information contained in this effective exam preparation guide. Written by a recognized cybersecurity expert and seasoned author, GCIH GIAC Certified Incident Handler All-in-One Exam Guide clearly explains all of the advanced security incident handling skills covered on the test. Detailed examples and chapter summaries throughout demonstrate real-world threats and aid in retention. You will get online access to 300 practice questions that match those on the live test in style, format, and tone. Designed to help you prepare for the exam, this resource also serves as an ideal on-the-job reference. Covers all exam topics, including: Intrusion analysis and incident handling Information gathering Scanning, enumeration, and vulnerability identification Vulnerability exploitation Infrastructure and endpoint attacks Network, DoS, and Web application attacks Maintaining access Evading detection and covering tracks Worms, bots, and botnets Online content includes: 300 practice exam questions Test engine that provides full-length practice exams and customizable quizzes Computers

Computer Programming for Absolute Beginners Get to grips with the building blocks of programming languages and get started on your programming journey without a computer science degree Key Features Understand the fundamentals of a computer program and apply the concepts you learn to different programming languages Gain the confidence to write your first computer program Explore tips, techniques, and best practices to start coding like a professional programmer Book Description Learning how to code has many advantages, and gaining the right programming skills can have a massive impact on what you can do with your current skill set and the way you advance in your career. This book will be your guide to learning computer programming easily, helping you overcome the difficulties in understanding the major constructs in any mainstream programming language. Computer Programming for Absolute Beginners starts by taking you through the building blocks of any programming language with thorough explanations and relevant examples in pseudocode. You'll understand the relationship between computer programs and programming languages and how code is executed on the computer. The book then focuses on the different types of applications that you can create with your programming knowledge. You'll delve into programming constructs, learning all about statements, operators, variables, and data types. As you advance, you'll see how to control the flow of your programs using control structures and reuse your code using functions. Finally, you'll explore best practices that will help you write code like a pro. By the end of this book, you'll be prepared to learn any programming language and take control of your career by adding coding to your skill set. What you will learn Get to grips with basic programming language concepts such as variables, loops, selection and functions Understand what a program is and how the computer executes it Explore different programming languages and learn about the relationship between source code and executable code Solve problems using various paradigms such as procedural programming, object oriented programming, and functional programming Write high-quality code using several coding conventions and best practices Become well-versed with how to track and fix bugs in your programs Who this book is for This book is for beginners who have never programmed before and are looking to enter the world of programming. This includes anyone who is about to start studying programming and wants a head start, or simply wants to learn how to program on their own. Computers

Node.js Web Development Build scalable web applications using Node.js, Express.js, and the latest ECMAScript techniques, along with deploying applications with AWS and Docker with this updated fifth edition Key Features Learn backend web programming with the JavaScript stack Explore best practices, right from configuring and building web servers to deploying them on a production cloud hosting system: AWS using Docker and Terraform Work through the different stages of developing robust and scalable apps using Node.js 14 Book Description Node.js is the leading choice of server-side web development platform, enabling developers to use the same tools and paradigms for both server-side and client-side software. This updated fifth edition of Node.js Web Development focuses on the new features of Node.js 14, Express 4.x, and ECMAScript, taking you through modern concepts, techniques, and best practices for using Node.js. The book starts by helping you get to grips with the concepts of building server-side web apps with Node.js. You'll learn how to develop a complete Node.js web app, with a backend database tier to help you explore several databases. You'll deploy the app to real web servers, including a cloud hosting platform built on AWS EC2 using Terraform and Docker Swarm, while integrating other tools such as Redis and NGINX. As you advance, you'll learn about unit and functional testing, along with deploying test infrastructure using Docker. Finally, you'll discover how to harden Node.js app security, use Let's Encrypt to provision the HTTPS service, and implement several forms of app security with the help of expert practices. With each chapter, the book will help you put your knowledge into practice throughout the entire life cycle of developing a web app. By the end of this Node.js book, you'll have gained practical Node.js web development knowledge and be able to build and deploy your own apps on a public web hosting solution. What you will learn Install and use Node.js 14 and Express 4.17 for both web development and deployment Implement RESTful web services using the Restify framework Develop, test, and deploy microservices using Docker, Docker Swarm, and Node.js, on AWS EC2 using Terraform Get up to speed with using data storage engines such as MySQL, SQLite3, and MongoDB Test your web applications using unit testing with Mocha, and headless browser testing with Puppeteer Implement HTTPS using Let's Encrypt and enhance application security with Helmet Who this book is for If you're looking for an alternative to the P' languages (Perl, PHP, and Python), or if you want to get started with server-side web development with JavaScript programming, or if you want a deep dive into deploying services to cloud hosting, this Node.js book is for you. A rudimentary understanding of JavaScript and web application development is a must before you get started with this book. Computers

Modern Python Cookbook Complete recipes spread across 15 chapters to help you overcome commonly faced issues by Python for everybody across the globe. Each recipe takes a problem-solution approach to resolve for effective Python. Key Features Develop expressive and effective Python programs Best practices and common idioms through carefully explained recipes Discover new ways to apply Python for data-focused development Make use of Python's optional type annotations Book Description Python is the preferred choice of developers, engineers, data scientists, and hobbyists everywhere. It is a great language that can power your applications and provide great speed, safety, and scalability. It can be used for simple scripting or sophisticated web applications. By exposing Python as a series of simple recipes, this book gives you insight into specific language features in a particular context. Having a tangible context helps make the language or a given standard library feature easier to understand. This book comes with 133 recipes on the latest version of Python 3.8. The recipes will benefit everyone, from beginners just starting out with Python to experts. You'll not only learn Python programming concepts but also how to build complex applications. The recipes will touch upon all necessary Python concepts related to data structures, object oriented programming, functional programming, and statistical programming. You will get acquainted with the nuances of Python syntax and how to effectively take advantage of it. By the end of this Python book, you will be equipped with knowledge of testing, web services, configuration, and application integration tips and tricks. You will be armed with the knowledge of how to create applications with flexible logging, powerful configuration, command-line options, automated unit tests, and good documentation. What you will learn See the intricate details of the Python syntax and how to use it to your advantage Improve your coding with Python readability through functions Manipulate data effectively using built-in data structures Get acquainted with advanced programming techniques in Python Equip yourself with functional and statistical programming features Write proper tests to be sure a program works as advertised Integrate application software using Python Who this book is for The Python book is for web developers, programmers, enterprise programmers, engineers, and big data scientists. If you are a beginner, this book will get you started. If you are experienced, it will expand your knowledge base. A basic knowledge of programming would help. Computers

The Data Visualization Workshop Cut through the noise and get real results with a step-by-step approach to learning data visualization with Python Key Features Ideal for Python beginners getting started with data visualization for the first time A step-by-step data visualization tutorial with exercises and activities that help build key skills Structured to let you progress at your own pace, on your own terms Use your physical print copy to redeem free access to the online interactive edition Book Description You already know you want to learn data visualization with Python, and a smarter way to learn is to learn by doing. The Data Visualization Workshop focuses on building up your practical skills so that you can develop clear, expressive real-world charts and diagrams. You'll learn from real examples that lead to real results. Throughout The Data Visualization Workshop, you'll take an engaging step-by-step approach to understand data visualization with Python. You won't have to sit through any unnecessary theory. If you're short on time you can jump into a single exercise each day or spend an entire weekend learning how companies like Uber are using advanced visualization techniques to represent their data visually. It's your choice. Learning on your terms, you'll build up and reinforce key skills in a way that feels rewarding. Every physical print copy of The Data Visualization Workshop unlocks access to the interactive edition. With videos detailing all exercises and activities, you'll always have a guided solution. You can also benchmark yourself against assessments, track progress, and receive content updates. You'll even earn a secure credential that you can share and verify online upon completion. It's a premium learning experience that's included with your printed copy. To redeem, follow the instructions located at the start of your book. Fast-paced and direct, The Data Visualization Workshop is the ideal companion for Python beginners who want to get up and running with data visualization. You'll visualize your work like a skilled data scientist, learning along the way. This process means that you'll find that your new skills stick, embedded as best practice. A solid foundation for the years ahead. What you will learn Get to grips with fundamental concepts and conventions of data visualization Learn how to use libraries like NumPy and Pandas to index, slice, and iterate data frames Implement different plotting techniques to produce compelling data visualizations Learn how you can skyrocket your Python data wrangling skills Draw statistical graphics using the Seaborn and Matplotlib libraries Create interactive visualizations and integrate them into any web page Who this book is for Our goal at Packt is to help you be successful, in whatever it is that you choose to do. The Data Visualization Workshop is an ideal tutorial for those who want to perform data visualization with Python and are just getting started. Pick up a Workshop today and let Packt help you develop skills that stick with you for life. Computers

Applying Math with Python Discover easy-to-follow solutions and techniques to help you to implement applied mathematical concepts such as probability, calculus, and equations using Python's numeric and scientific libraries Key Features Compute complex mathematical problems using programming logic with the help of step-by-step recipes Learn how to utilize Python's libraries for computation, mathematical modeling, and statistics Discover simple yet effective techniques for solving mathematical equations and apply them in real-world statistics Book Description Python, one of the world's most popular programming languages, has a number of powerful packages to help you tackle complex mathematical problems in a simple and efficient way. These core capabilities help programmers pave the way for building exciting applications in various domains, such as machine learning and data science, using knowledge in the computational mathematics domain. The book teaches you how to solve problems faced in a wide variety of mathematical fields, including calculus, probability, statistics and data science, graph theory, optimization, and geometry. You'll start by developing core skills and learning about packages covered in Python's scientific stack, including NumPy, SciPy, and Matplotlib. As you advance, you'll get to grips with more advanced topics of calculus, probability, and networks (graph theory). After you gain a solid understanding of these topics, you'll discover Python's applications in data science and statistics, forecasting, geometry, and optimization. The final chapters will take you through a collection of miscellaneous problems, including working with specific data formats and accelerating code. By the end of this book, you'll have an arsenal of practical coding solutions that can be used and modified to solve a wide range of practical problems in computational mathematics and data science. What you will learn Get familiar with basic packages, tools, and libraries in Python for solving mathematical problems Explore various techniques that will help you to solve computational mathematical problems Understand the core concepts of applied mathematics and how you can apply them in computer science Discover how to choose the most suitable package, tool, or technique to solve a certain problem Implement basic mathematical plotting, change plot styles, and add labels to the plots using Matplotlib Get to grips with probability theory with the Bayesian inference and Markov Chain Monte Carlo (MCMC) methods Who this book is for This book is for professional programmers and students looking to solve mathematical problems computationally using Python. Advanced mathematics knowledge is not a requirement, but a basic knowledge of mathematics will help you to get the most out of this book. The book assumes familiarity with Python concepts of data structures. Computers

The Deep Learning Workshop Take a hands-on approach to understanding deep learning and build smart applications that can recognize images and interpret text Key Features Understand how to implement deep learning with TensorFlow and Keras Learn the fundamentals of computer vision and image recognition Study the architecture of different neural networks Book Description Are you fascinated by how deep learning powers intelligent applications such as self-driving cars, virtual assistants, facial recognition devices, and chatbots to process data and solve complex problems? Whether you are familiar with machine learning or are new to this domain, The Deep Learning Workshop will make it easy for you to understand deep learning with the help of interesting examples and exercises throughout. The book starts by highlighting the relationship between deep learning, machine learning, and artificial intelligence and helps you get comfortable with the TensorFlow 2.0 programming structure using hands-on exercises. You'll understand neural networks, the structure of a perceptron, and how to use TensorFlow to create and train models. The book will then let you explore the fundamentals of computer vision by performing image recognition exercises with convolutional neural networks (CNNs) using Keras. As you advance, you'll be able to make your model more powerful by implementing text embedding and sequencing the data using popular deep learning solutions. Finally, you'll get to grips with bidirectional recurrent neural networks (RNNs) and build generative adversarial networks (GANs) for image synthesis. By the end of this deep learning book, you'll have learned the skills essential for building deep learning models with TensorFlow and Keras. What you will learn Understand how deep learning, machine learning, and artificial intelligence are different Develop multilayer deep neural networks with TensorFlow Implement deep neural networks for multiclass classification using Keras Train CNN models for image recognition Handle sequence data and use it in conjunction with RNNs Build a GAN to generate high-quality synthesized images Who this book is for If you are interested in machine learning and want to create and train deep learning models using TensorFlow and Keras, this workshop is for you. A solid understanding of Python and its packages, along with basic machine learning concepts, will help you to learn the topics quickly. Computers

The Applied SQL Data Analytics Workshop Cut through the noise and get real results with a step-by-step approach to learning about SQL data analysis Key Features Ideal for SQL beginners who are getting started with data analytics for the first time A step-by-step SQL tutorial with exercises and activities that help build key skills Structured to let you progress at your own pace, on your own terms Use your physical print copy to redeem free access to the online interactive edition Book Description You already know that you want to learn data analysis with SQL, and a smarter way to learn is to learn by doing. The Applied SQL Data Analytics Workshop focuses on building up your practical skills so that you can navigate and compose custom reports like an expert data analyst. You'll learn from real examples that lead to real results. Throughout The Applied SQL Data Analytics Workshop, you'll take an engaging step-by-step approach to understand data analytics with SQL. You won't have to sit through any unnecessary theory. You can jump into a single exercise each day if you're short on time, or you can spend an entire weekend tinkering with SQLAlchemy and Python. It's your choice. Learning on your terms, you'll build up and reinforce key skills in a way that feels rewarding. Every physical print copy of The Applied SQL Data Analytics Workshop unlocks access to the interactive edition. With videos detailing all exercises and activities, you'll always have a guided solution. You can also benchmark yourself against assessments, track progress, and receive content updates. You'll even earn a secure credential that you can share and verify online upon completion. It's a premium learning experience that's included with your printed copy. To redeem, follow the instructions located at the start of your book. Fast-paced and direct, The Applied SQL Data Analytics Workshop is the ideal companion for SQL beginners. You'll perform SQL queries like a professional data scientist, learning along the way. This process means that you'll find that your new skills stick, embedded as best practice. A solid foundation for the years ahead. What you will learn Experiment with data analytics using basic and advanced queries Learn data interpretation through descriptive statistics and aggregate functions Export data from outside sources using powerful SQL queries Discover how to work with and manipulate data using SQL joins and constraints Speed up your data analysis workflow by automating tasks and optimizing queries Discover different advanced analytics techniques, including geospatial and text analysis Who this book is for Our goal at Packt is to help you be successful, in whatever it is you choose to do. The Applied SQL Data Analytics Workshop is an ideal tutorial for the beginner who wants to perform data analysis with SQL and is just getting started. Pick up a Workshop today, and let Packt help you develop skills that stick with you for life. Computers

Practical Artificial Intelligence and Blockchain Learn how to use AI and blockchain to build decentralized intelligent applications (DIApps) that overcome real-world challenges Key Features Understand the fundamental concepts for converging artificial intelligence and blockchain Apply your learnings to build apps using machine learning with Ethereum, IPFS, and MoiBit Get well-versed with the AI-blockchain ecosystem to develop your own DIApps Book Description AI and blockchain are two emerging technologies catalyzing the pace of enterprise innovation. With this book, you'll understand both technologies and converge them to solve real-world challenges. This AI blockchain book is divided into three sections. The first section covers the fundamentals of blockchain, AI, and affiliated technologies, where you'll learn to differentiate between the various implementations of blockchains and AI with the help of examples. The second section takes you through domain-specific applications of AI and blockchain. You'll understand the basics of decentralized databases and file systems and connect the dots between AI and blockchain before exploring products and solutions that use them together. You'll then discover applications of AI techniques in crypto trading. In the third section, you'll be introduced to the DIApp design pattern and compare it with the DApp design pattern. The book also highlights unique aspects of SDLC (software development lifecycle) when building a DIApp, shows you how to implement a sample contact tracing application, and delves into the future of AI with blockchain. By the end of this book, you'll have developed the skills you need to converge AI and blockchain technologies to build smart solutions using the DIApp design pattern. What you will learn Get well-versed in blockchain basics and AI methodologies Understand the significance of data collection and cleaning in AI modeling Discover the application of analytics in cryptocurrency trading Get to grips with open, permissioned, and private blockchains Explore the DIApp design pattern and its merit in digital solutions Find out how LSTM and ARIMA can be applied in crypto trading Use the DIApp design pattern to build a sample contact tracing application Get started with building your own DIApps across various domains Who this book is for This book is for blockchain and AI architects, developers, data scientists, data engineers, and evangelists who want to harness the power of artificial intelligence in blockchain applications. If you are looking for a blend of theoretical and practical use cases to understand how to implement smart cognitive insights into blockchain solutions, this book is what you need! Knowledge of machine learning and blockchain concepts is required. Computers

Hands-On Explainable AI (XAI) with Python Resolve the black box models in your AI applications to make them fair, trustworthy, and secure. Familiarize yourself with the basic principles and tools to deploy Explainable AI (XAI) into your apps and reporting interfaces. Key Features Learn explainable AI tools and techniques to process trustworthy AI results Understand how to detect, handle, and avoid common issues with AI ethics and bias Integrate fair AI into popular apps and reporting tools to deliver business value using Python and associated tools Book Description Effectively translating AI insights to business stakeholders requires careful planning, design, and visualization choices. Describing the problem, the model, and the relationships among variables and their findings are often subtle, surprising, and technically complex. Hands-On Explainable AI (XAI) with Python will see you work with specific hands-on machine learning Python projects that are strategically arranged to enhance your grasp on AI results analysis. You will be building models, interpreting results with visualizations, and integrating XAI reporting tools and different applications. You will build XAI solutions in Python, TensorFlow 2, Google Cloud's XAI platform, Google Colaboratory, and other frameworks to open up the black box of machine learning models. The book will introduce you to several open-source XAI tools for Python that can be used throughout the machine learning project life cycle. You will learn how to explore machine learning model results, review key influencing variables and variable relationships, detect and handle bias and ethics issues, and integrate predictions using Python along with supporting the visualization of machine learning models into user explainable interfaces. By the end of this AI book, you will possess an in-depth understanding of the core concepts of XAI. What you will learn Plan for XAI through the different stages of the machine learning life cycle Estimate the strengths and weaknesses of popular open-source XAI applications Examine how to detect and handle bias issues in machine learning data Review ethics considerations and tools to address common problems in machine learning data Share XAI design and visualization best practices Integrate explainable AI results using Python models Use XAI toolkits for Python in machine learning life cycles to solve business problems Who this book is for This book is not an introduction to Python programming or machine learning concepts. You must have some foundational knowledge and/or experience with machine learning libraries such as scikit-learn to make the most out of this book. Some of the potential readers of this book include: Professionals who already use Python for as data science, machine learning, research, and analysis Data analysts and data scientists who want an introduction into explainable AI tools and techniques AI Project managers who must face the contractual and legal obligations of AI Explainability for the acceptance phase of their applications Computers

Machine Learning for Algorithmic Trading Leverage machine learning to design and back-test automated trading strategies for real-world markets using pandas, TA-Lib, scikit-learn, LightGBM, SpaCy, Gensim, TensorFlow 2, Zipline, backtrader, Alphalens, and pyfolio. Key Features Design, train, and evaluate machine learning algorithms that underpin automated trading strategies Create a research and strategy development process to apply predictive modeling to trading decisions Leverage NLP and deep learning to extract tradeable signals from market and alternative data Book Description The explosive growth of digital data has boosted the demand for expertise in trading strategies that use machine learning (ML). This revised and expanded second edition enables you to build and evaluate sophisticated supervised, unsupervised, and reinforcement learning models. This book introduces end-to-end machine learning for the trading workflow, from the idea and feature engineering to model optimization, strategy design, and backtesting. It illustrates this by using examples ranging from linear models and tree-based ensembles to deep-learning techniques from cutting edge research. This edition shows how to work with market, fundamental, and alternative data, such as tick data, minute and daily bars, SEC filings, earnings call transcripts, financial news, or satellite images to generate tradeable signals. It illustrates how to engineer financial features or alpha factors that enable an ML model to predict returns from price data for US and international stocks and ETFs. It also shows how to assess the signal content of new features using Alphalens and SHAP values and includes a new appendix with over one hundred alpha factor examples. By the end, you will be proficient in translating ML model predictions into a trading strategy that operates at daily or intraday horizons, and in evaluating its performance. What you will learn Leverage market, fundamental, and alternative text and image data Research and evaluate alpha factors using statistics, Alphalens, and SHAP values Implement machine learning techniques to solve investment and trading problems Backtest and evaluate trading strategies based on machine learning using Zipline and Backtrader Optimize portfolio risk and performance analysis using pandas, NumPy, and pyfolio Create a pairs trading strategy based on cointegration for US equities and ETFs Train a gradient boosting model to predict intraday returns using AlgoSeek's high-quality trades and quotes data Who this book is for If you are a data analyst, data scientist, Python developer, investment analyst, or portfolio manager interested in getting hands-on machine learning knowledge for trading, this book is for you. This book is for you if you want to learn how to extract value from a diverse set of data sources using machine learning to design your own systematic trading strategies. Some understanding of Python and machine learning techniques is required. Computers

The Deep Learning with Keras Workshop Cut through the noise and get real results with a step-by-step approach to understanding deep learning with Keras programming Key Features Ideal for those getting started with Keras for the first time A step-by-step Keras tutorial with exercises and activities that help build key skills Structured to let you progress at your own pace, on your own terms Use your physical print copy to redeem free access to the online interactive edition Book Description You already know that you want to learn Keras, and a smarter way to learn is to learn by doing. The Deep Learning with Keras Workshop focuses on building up your practical skills so that you can develop artificial intelligence applications or build machine learning models with Keras. You'll learn from real examples that lead to real results. Throughout The Deep Learning with Keras Workshop, you'll take an engaging step-by-step approach to understand Keras. You won't have to sit through any unnecessary theory. If you're short on time you can jump into a single exercise each day or spend an entire weekend tinkering with your own neural networks. It's your choice. Learning on your terms, you'll build up and reinforce key skills in a way that feels rewarding. Every physical print copy of The Deep Learning with Keras Workshop unlocks access to the interactive edition. With videos detailing all exercises and activities, you'll always have a guided solution. You can also benchmark yourself against assessments, track progress, and receive content updates. You'll even earn a secure credential that you can share and verify online upon completion. It's a premium learning experience that's included with your printed copy. To redeem, follow the instructions located at the start of your book. Fast-paced and direct, The Deep Learning with Keras Workshop is the ideal companion for those who are just getting started with Keras. You'll build and iterate on your code like a software developer, learning along the way. This process means that you'll find that your new skills stick, embedded as best practice. A solid foundation for the years ahead. What you will learn Gain insight into the fundamental concepts of neural networks Learn to think like a data scientist and understand the difference between machine learning and deep learning Discover various techniques to evaluate, tweak, and improve your models Explore different techniques to manipulate your data Explore alternative techniques to verify the accuracy of your model Who this book is for Our goal at Packt is to help you be successful, in whatever it is that you choose to do. The Deep Learning with Keras Workshop is an ideal tutorial for the programmer who is getting started with Keras and deep learning. Pick up a Workshop today and let Packt help you develop skills that stick with you for life. Computers

Samsung Galaxy S20 For Dummies Get the most out of the powerful new Samsung Galaxy S20 With its superfast refresh rate for seamless browsing and spectacularly enhanced camera—among many other goodies—there’s a lot to enjoy about your sleek new Samsung S20. Whether you’re a Samsung newbie or an upgrading customer, Samsung Galaxy S20 for Dummies is the perfect guide to the latest generation. From the basics, like setup and security, to the fun, like the supercool Single Take mode, this book has you covered from the moment you take your new smartphone out of its shiny new box. Want to watch movies? Navigate your way around with GPS? Say hello to family and friends on social media? All the easy-to-follow tips and tricks that make it fast and fun are pages away! Configure and personalize your new phone Get going with the best features, apps, and games Shoot eye-popping photo and video with 30x zoom and nighttime mode Sync with your other devices Whatever you want to use it for gaming with friends, in-app conferencing or emailing for work, shooting home movies, sending witty Tweets—or even making phone calls—this friendly, no-nonsense how-to is the best guide to your galaxy. Enjoy! Computers

CASP+ Practice Tests Power through your CASP+ Exam CAS-003 preparation with these invaluable practice questions For those studying for the CASP+ Exam CAS-003, Nadean H. Tanner’s CASP+ Practice Tests Exam CAS-003 will help you make the most of your prep time. The included two practice exams, domain-by-domain questions, and the accompanying Sybex interactive learning environment and online test bank will help you focus your efforts, gauge your progress, and improve your understanding of the necessary objectives. CASP+ Practice Tests Exam CAS-003 provides readers with practice questions that cover the five CASP+ objective domains: Risk Management Enterprise Security Architecture Enterprise Security Operations Technical Integration of Enterprise Security Research, Development, and Collaboration Specifically written for IT professionals studying for the CASP+ Exam CAS-003, this book is also a perfect refresher for anyone seeking to brush up on their IT cybersecurity knowledge. The practice exams and domain-by-domain questions combine to provide readers with over 1,000 practice questions to help validate your knowledge and optimize your preparation. Computers

YouTube Channels For Dummies Create a You Tube channel that draws subscribers with top-notch content YouTube has the eyes and ears of two billion monthly users. YouTube Channels for Dummies, 2nd Edition offers proven steps to attracting a chunk of those billions to your personal or business channel. This updated guide offers insight from a quartet of YouTube channel content creators, managers, marketers, and analysts as they share the secrets of creating great content, building an audience, and interacting with your viewers. The book includes information on: · Setting up a channel · Creating videos that attract viewers · Putting together a video studio · Editing your final product · Reaching your target audience · Interacting with your fans · Building a profitable business · Tips on copyright law Written for both the budding YouTube creator and the business professional seeking to boost their company’s profile on the popular social networking site, YouTube Channels for Dummies allows its readers to access the over two billion active YouTube users who log on each day. Learn how to create a channel, build a YouTube following, and get insight on content creation, planning, and marketing from established YouTube creators. Computers

Tableau Prep For self-service data preparation, Tableau Prep is relatively easy to use—as long as you know how to clean and organize your datasets. Carl Allchin, from The Information Lab in London, gets you up to speed on Tableau Prep through a series of practical lessons that include methods for preparing, cleaning, automating, organizing, and outputting your datasets. Based on Allchin’s popular blog, Preppin’ Data, this practical guide takes you step-by-step through Tableau Prep’s fundamentals. Self-service data preparation reduces the time it takes to complete data projects and improves the quality of your analyses. Discover how Tableau Prep helps you access your data and turn it into valuable information. Know what to look for when you prepare data Learn which Tableau Prep functions to use when working with data fields Analyze the shape and profile of your dataset Output data for analysis and learn how Tableau Prep automates your workflow Learn how to clean your dataset using Tableau Prep functions Explore ways to use Tableau Prep techniques in real-world scenarios Make your data available to others by managing and documenting the output Computers

Learning Spark Data is bigger, arrives faster, and comes in a variety of formats—and it all needs to be processed at scale for analytics or machine learning. But how can you process such varied workloads efficiently? Enter Apache Spark. Updated to include Spark 3.0, this second edition shows data engineers and data scientists why structure and unification in Spark matters. Specifically, this book explains how to perform simple and complex data analytics and employ machine learning algorithms. Through step-by-step walk-throughs, code snippets, and notebooks, you’ll be able to: Learn Python, SQL, Scala, or Java high-level Structured APIs Understand Spark operations and SQL Engine Inspect, tune, and debug Spark operations with Spark configurations and Spark UI Connect to data sources: JSON, Parquet, CSV, Avro, ORC, Hive, S3, or Kafka Perform analytics on batch and streaming data using Structured Streaming Build reliable data pipelines with open source Delta Lake and Spark Develop machine learning pipelines with MLlib and productionize models using MLflow Computers

Web and Digital for Graphic Designers Creative web design requires knowledge from across the design and technical realms, and it can seem like a daunting task working out where to get started. In this book the authors take you through all you need to know about designing for the web and digital, from initial concepts and client needs, through layout and typography to basic coding, e-commerce and working with different platforms. The companion website provides step-by-step tutorial videos, HTML/CSS styling tips and links to useful resources to really help you get to grips with all the aspects of web design. Working alongside the text are interviews with international designers and critical commentaries looking at best practice and theoretical considerations. Written for graphic designers, this book delivers more than just an instruction manual – it provides a complete overview of designing for the web. Computers

Phylogenomics Phylogenomics: A Primer, Second Edition is for advanced undergraduate and graduate biology students studying molecular biology, comparative biology, evolution, genomics, and biodiversity. This book explains the essential concepts underlying the storage and manipulation of genomics level data, construction of phylogenetic trees, population genetics, natural selection, the tree of life, DNA barcoding, and metagenomics. The inclusion of problem-solving exercises in each chapter provides students with a solid grasp of the important molecular and evolutionary questions facing modern biologists as well as the tools needed to answer them. Computers

Bitcoin and Blockchain In recent years, blockchain development has grown quickly from the original Bitcoin protocol to the second-generation Ethereum platform, and to today’s process of building third-generation blockchains. During this evolution, we can see how blockchain technology has evolved from its original form as a distributed database to becoming a fully fledged, globally distributed, cloud computing platform. This book traces the past, present, and future of blockchain technology. Presents the knowledge and history of Bitcoin Offers blockchain applications Discusses developing working code for real-world blockchain applications Includes many real-life examples Covers the original Bitcoin protocol to the second-generation Ethereum platform Bitcoin and Blockchain: History and Current Applications is a useful reference for students, business schools, research scholars, practitioners, and business analytics professionals. Computers

The Case Against Reality Can we trust our senses to tell us the truth? Challenging leading scientific theories that claim that our senses report back objective reality, cognitive scientist Donald Hoffman argues that while we should take our perceptions seriously, we should not take them literally. How can it be possible that the world we see is not objective reality? And how can our senses be useful if they are not communicating the truth? Hoffman grapples with these questions and more over the course of this eye-opening work. Ever since Homo sapiens has walked the earth, natural selection has favored perception that hides the truth and guides us toward useful action, shaping our senses to keep us alive and reproducing. We observe a speeding car and do not walk in front of it; we see mold growing on bread and do not eat it. These impressions, though, are not objective reality. Just like a file icon on a desktop screen is a useful symbol rather than a genuine representation of what a computer file looks like, the objects we see every day are merely icons, allowing us to navigate the world safely and with ease. The real-world implications for this discovery are huge. From examining why fashion designers create clothes that give the illusion of a more “attractive†body shape to studying how companies use color to elicit specific emotions in consumers, and even dismantling the very notion that spacetime is objective reality, The Case Against Reality dares us to question everything we thought we knew about the world we see. Computers

Hello World "A beautifully accessible guide.… One of the best books yet written on data and algorithms."—Times (UK) Shortlisted for the 2018 Royal Society Investment Science Book Prize Shortlisted for the 2018 Baillie Gifford Prize When it comes to artificial intelligence, we either hear of a paradise on earth or of our imminent extinction. It’s time we stand face-to-digital-face with the true powers and limitations of the algorithms that already automate important decisions in healthcare, transportation, crime, and commerce. Hello World is indispensable preparation for the moral quandaries of a world run by code, and with the unfailingly entertaining Hannah Fry as our guide, we’ll be discussing these issues long after the last page is turned. Computers

The Man Who Knew Too Much A "skillful and literate" (New York Times Book Review) biography of the persecuted genius who helped create the modern computer. To solve one of the great mathematical problems of his day, Alan Turing proposed an imaginary computer. Then, attempting to break a Nazi code during World War II, he successfully designed and built one, thus ensuring the Allied victory. Turing became a champion of artificial intelligence, but his work was cut short. As an openly gay man at a time when homosexuality was illegal in England, he was convicted and forced to undergo a humiliating "treatment" that may have led to his suicide. With a novelist's sensitivity, David Leavitt portrays Turing in all his humanity—his eccentricities, his brilliance, his fatal candor—and elegantly explains his work and its implications. Computers

The Shallows New York Times bestseller • Finalist for the Pulitzer Prize “This is a book to shake up the world.†—Ann Patchett Nicholas Carr’s bestseller The Shallows has become a foundational book in one of the most important debates of our time: As we enjoy the internet’s bounties, are we sacrificing our ability to read and think deeply? This 10th-anniversary edition includes a new afterword that brings the story up to date, with a deep examination of the cognitive and behavioral effects of smartphones and social media. Computers

Counterknowledge An important and compelling book on the viral dissemination of misinformation in today's world. We are being swamped with dangerous nonsense. From 9/11 conspiracy theories to Holocaust denial to alternative medicine, we are all experiencing an epidemic of demonstrably untrue descriptions of the world. For Damian Thompson, the misinformation industry is wreaking havoc on the once-lauded virtues of science and reason. Unproven theories and spurious claims are forms of "counterknowledge," and, helped by the Internet, they are creating a global generation of misguided adherents who repeat these untruths and lend them credence. Thompson explores our readiness to accept falsehoods and the viral role of technology in spreading quack remedies, pseudo-history, and creationist fanaticism. Following in the footsteps of Richard Dawkins's The God Delusion, Sam Harris's The End of Faith, and Christopher Hitchens's God Is Not Great, Counterknowledge is a brilliant defense of scientific proof in an age of fabrication. Computers

The Shallows Finalist for the 2011 Pulitzer Prize in General Nonfiction: “Nicholas Carr has written a Silent Spring for the literary mind.â€â€”Michael Agger, Slate “Is Google making us stupid?†When Nicholas Carr posed that question, in a celebrated Atlantic Monthly cover story, he tapped into a well of anxiety about how the Internet is changing us. He also crystallized one of the most important debates of our time: As we enjoy the Net’s bounties, are we sacrificing our ability to read and think deeply? Now, Carr expands his argument into the most compelling exploration of the Internet’s intellectual and cultural consequences yet published. As he describes how human thought has been shaped through the centuries by “tools of the mindâ€â€”from the alphabet to maps, to the printing press, the clock, and the computer—Carr interweaves a fascinating account of recent discoveries in neuroscience by such pioneers as Michael Merzenich and Eric Kandel. Our brains, the historical and scientific evidence reveals, change in response to our experiences. The technologies we use to find, store, and share information can literally reroute our neural pathways. Building on the insights of thinkers from Plato to McLuhan, Carr makes a convincing case that every information technology carries an intellectual ethic—a set of assumptions about the nature of knowledge and intelligence. He explains how the printed book served to focus our attention, promoting deep and creative thought. In stark contrast, the Internet encourages the rapid, distracted sampling of small bits of information from many sources. Its ethic is that of the industrialist, an ethic of speed and efficiency, of optimized production and consumption—and now the Net is remaking us in its own image. We are becoming ever more adept at scanning and skimming, but what we are losing is our capacity for concentration, contemplation, and reflection. Part intellectual history, part popular science, and part cultural criticism, The Shallows sparkles with memorable vignettes—Friedrich Nietzsche wrestling with a typewriter, Sigmund Freud dissecting the brains of sea creatures, Nathaniel Hawthorne contemplating the thunderous approach of a steam locomotive—even as it plumbs profound questions about the state of our modern psyche. This is a book that will forever alter the way we think about media and our minds. Computers

The Alignment Problem A jaw-dropping exploration of everything that goes wrong when we build AI systems and the movement to fix them. Today’s “machine-learning†systems, trained by data, are so effective that we’ve invited them to see and hear for us—and to make decisions on our behalf. But alarm bells are ringing. Recent years have seen an eruption of concern as the field of machine learning advances. When the systems we attempt to teach will not, in the end, do what we want or what we expect, ethical and potentially existential risks emerge. Researchers call this the alignment problem. Systems cull résumés until, years later, we discover that they have inherent gender biases. Algorithms decide bail and parole—and appear to assess Black and White defendants differently. We can no longer assume that our mortgage application, or even our medical tests, will be seen by human eyes. And as autonomous vehicles share our streets, we are increasingly putting our lives in their hands. The mathematical and computational models driving these changes range in complexity from something that can fit on a spreadsheet to a complex system that might credibly be called “artificial intelligence.†They are steadily replacing both human judgment and explicitly programmed software. In best-selling author Brian Christian’s riveting account, we meet the alignment problem’s “first-responders,†and learn their ambitious plan to solve it before our hands are completely off the wheel. In a masterful blend of history and on-the ground reporting, Christian traces the explosive growth in the field of machine learning and surveys its current, sprawling frontier. Readers encounter a discipline finding its legs amid exhilarating and sometimes terrifying progress. Whether they—and we—succeed or fail in solving the alignment problem will be a defining human story. The Alignment Problem offers an unflinching reckoning with humanity’s biases and blind spots, our own unstated assumptions and often contradictory goals. A dazzlingly interdisciplinary work, it takes a hard look not only at our technology but at our culture—and finds a story by turns harrowing and hopeful. Computers

Deep Learning An introduction to a broad range of topics in deep learning, covering mathematical and conceptual background, deep learning techniques used in industry, and research perspectives. “Written by three experts in the field, Deep Learning is the only comprehensive book on the subject.” —Elon Musk, cochair of OpenAI; cofounder and CEO of Tesla and SpaceX Deep learning is a form of machine learning that enables computers to learn from experience and understand the world in terms of a hierarchy of concepts. Because the computer gathers knowledge from experience, there is no need for a human computer operator to formally specify all the knowledge that the computer needs. The hierarchy of concepts allows the computer to learn complicated concepts by building them out of simpler ones; a graph of these hierarchies would be many layers deep. This book introduces a broad range of topics in deep learning. The text offers mathematical and conceptual background, covering relevant concepts in linear algebra, probability theory and information theory, numerical computation, and machine learning. It describes deep learning techniques used by practitioners in industry, including deep feedforward networks, regularization, optimization algorithms, convolutional networks, sequence modeling, and practical methodology; and it surveys such applications as natural language processing, speech recognition, computer vision, online recommendation systems, bioinformatics, and videogames. Finally, the book offers research perspectives, covering such theoretical topics as linear factor models, autoencoders, representation learning, structured probabilistic models, Monte Carlo methods, the partition function, approximate inference, and deep generative models. Deep Learning can be used by undergraduate or graduate students planning careers in either industry or research, and by software engineers who want to begin using deep learning in their products or platforms. A website offers supplementary material for both readers and instructors. Computers

Introduction to Algorithms, third edition The latest edition of the essential text and professional reference, with substantial new material on such topics as vEB trees, multithreaded algorithms, dynamic programming, and edge-based flow. Some books on algorithms are rigorous but incomplete; others cover masses of material but lack rigor. Introduction to Algorithms uniquely combines rigor and comprehensiveness. The book covers a broad range of algorithms in depth, yet makes their design and analysis accessible to all levels of readers. Each chapter is relatively self-contained and can be used as a unit of study. The algorithms are described in English and in a pseudocode designed to be readable by anyone who has done a little programming. The explanations have been kept elementary without sacrificing depth of coverage or mathematical rigor. The first edition became a widely used text in universities worldwide as well as the standard reference for professionals. The second edition featured new chapters on the role of algorithms, probabilistic analysis and randomized algorithms, and linear programming. The third edition has been revised and updated throughout. It includes two completely new chapters, on van Emde Boas trees and multithreaded algorithms, substantial additions to the chapter on recurrence (now called “Divide-and-Conquer”), and an appendix on matrices. It features improved treatment of dynamic programming and greedy algorithms and a new notion of edge-based flow in the material on flow networks. Many exercises and problems have been added for this edition. The international paperback edition is no longer available; the hardcover is available worldwide. Computers

Implementing Service Level Objectives Although service-level objectives (SLOs) continue to grow in importance, there’s a distinct lack of information about how to implement them. Practical advice that does exist usually assumes that your team already has the infrastructure, tooling, and culture in place. In this book, recognized SLO expert Alex Hidalgo explains how to build an SLO culture from the ground up. Ideal as a primer and daily reference for anyone creating both the culture and tooling necessary for SLO-based approaches to reliability, this guide provides detailed analysis of advanced SLO and service-level indicator (SLI) techniques. Armed with mathematical models and statistical knowledge to help you get the most out of an SLO-based approach, you’ll learn how to build systems capable of measuring meaningful SLIs with buy-in across all departments of your organization. Define SLIs that meaningfully measure the reliability of a service from a user’s perspective Choose appropriate SLO targets, including how to perform statistical and probabilistic analysis Use error budgets to help your team have better discussions and make better data-driven decisions Build supportive tooling and resources required for an SLO-based approach Use SLO data to present meaningful reports to leadership and your users Computers

Semantic Web for the Working Ontologist Enterprises have made amazing advances by taking advantage of data about their business to provide predictions and understanding of their customers, markets, and products. But as the world of business becomes more interconnected and global, enterprise data is no long a monolith; it is just a part of a vast web of data. Managing data on a world-wide scale is a key capability for any business today. The Semantic Web treats data as a distributed resource on the scale of the World Wide Web, and incorporates features to address the challenges of massive data distribution as part of its basic design. The aim of the first two editions was to motivate the Semantic Web technology stack from end-to-end; to describe not only what the Semantic Web standards are and how they work, but also what their goals are and why they were designed as they are. It tells a coherent story from beginning to end of how the standards work to manage a world-wide distributed web of knowledge in a meaningful way. The third edition builds on this foundation to bring Semantic Web practice to enterprise. Fabien Gandon joins Dean Allemang and Jim Hendler, bringing with him years of experience in global linked data, to open up the story to a modern view of global linked data. While the overall story is the same, the examples have been brought up to date and applied in a modern setting, where enterprise and global data come together as a living, linked network of data. Also included with the third edition, all of the data sets and queries are available online for study and experimentation at data.world/swwo. Computers

Design And Implementation Of Datacenter Protocols For Cloud Computing This unique compendium focuses on the design and implementation of emerging transport protocols and task scheduling mechanisms to mitigate congestion in datacentre networks. Datacenters have become a critical infrastructure for hosting user-facing online services such as web search and social networking.For datacenter transport, this volume highlights the design and implementation details of the state-of-art transport protocols that not only achieves optimal performance in terms of minimizing flow completion times but are also deployment friendly.Moreover, this must-have reference material also discusses the transport protocols for multi-tenant datacentre networks. For datacenter task scheduling, the book introduces an innovative task placement framework that considers network scheduling while making task placement decisions. Computers

Distributed Simulation Simulation is a multi-disciplinary field, and significant simulation research is dispersed across multiple fields of study. Distributed computer systems, software design methods, and new simulation techniques offer synergistic multipliers when joined together in a distributed simulation. Systems of most interest to the simulation practitioner are often the most difficult to model and implement. Distributed Simulation brings together the many complex technologies for distributed simulation. There is strong emphasis on emerging simulation methodologies, including object-oriented, multilevel, and multi-resolution simulation. Finally, one concise text provides a strong foundation for the development of high fidelity simulations in heterogeneous distributed computing environments! Computers

From Fractals And Cellular Automata To Biology The didactical level of exposition, together with many astonishing images and animations, accompanied by the related simple computer programming codes (in Python and POV-Ray languages) make this book an extremely and unique useful tool to test the power of algorithmic information in generating ordered structure models (2D and 3D) like regular geometric shapes, complex shapes like fractals and cellular automata, and biological systems as the organs of a living body. Informational biologists besides mathematicians and physicists of complexity may learn to test their own capabilities in programming and modelling ordered structures starting from random initial conditions at different scale of each system: from elementary particles, to biological systems, to galaxies and the whole universe. Moreover the philosophical comments comparing some aspects of modern information theory to the Aristotelian notion of 'form are very appealing also for the epistemologist and the philosopher involved in complexity matters. Computers

Algorithms For Big Data This unique volume is an introduction for computer scientists, including a formal study of theoretical algorithms for Big Data applications, which allows them to work on such algorithms in the future. It also serves as a useful reference guide for the general computer science population, providing a comprehensive overview of the fascinating world of such algorithms.To achieve these goals, the algorithmic results presented have been carefully chosen so that they demonstrate the important techniques and tools used in Big Data algorithms, and yet do not require tedious calculations or a very deep mathematical background. Computers

Principles Of Quantum Artificial Intelligence This unique compendium presents an introduction to problem solving, information theory, statistical machine learning, stochastic methods and quantum computation. It indicates how to apply quantum computation to problem solving, machine learning and quantum-like models to decision making — the core disciplines of artificial intelligence.Most of the chapters were rewritten and extensive new materials were updated. New topics include quantum machine learning, quantum-like Bayesian networks and mind in Everett many-worlds. Computers

Recommender Systems Recommender systems provide users (businesses or individuals) with personalized online recommendations of products or information, to address the problem of information overload and improve personalized services. Recent successful applications of recommender systems are providing solutions to transform online services for e-government, e-business, e-commerce, e-shopping, e-library, e-learning, e-tourism, and more.This unique compendium not only describes theoretical research but also reports on new application developments, prototypes, and real-world case studies of recommender systems. The comprehensive volume provides readers with a timely snapshot of how new recommendation methods and algorithms can overcome challenging issues. Furthermore, the monograph systematically presents three dimensions of recommender systems — basic recommender system concepts, advanced recommender system methods, and real-world recommender system applications.By providing state-of-the-art knowledge, this excellent reference text will immensely benefit researchers, managers, and professionals in business, government, and education to understand the concepts, methods, algorithms and application developments in recommender systems. Computers

The Data Analysis Workshop Learn how to analyze data using Python models with the help of real-world use cases and guidance from industry experts Key Features Get to grips with data analysis by studying use cases from different fields Develop your critical thinking skills by following tried-and-true data analysis Learn how to use conclusions from data analyses to make better business decisions Book Description Businesses today operate online and generate data almost continuously. While not all data in its raw form may seem useful, if processed and analyzed correctly, it can provide you with valuable hidden insights. The Data Analysis Workshop will help you learn how to discover these hidden patterns in your data, to analyze them, and leverage the results to help transform your business. The book begins by taking you through the use case of a bike rental shop. You'll be shown how to correlate data, plot histograms, and analyze temporal features. As you progress, you'll learn how to plot data for a hydraulic system using the Seaborn and Matplotlib libraries, and explore a variety of use cases that show you how to join and merge databases, prepare data for analysis, and handle imbalanced data. By the end of the book, you'll have learned different data analysis techniques, including hypothesis testing, correlation, and null-value imputation, and will have become a confident data analyst. What you will learn Get to grips with the fundamental concepts and conventions of data analysis Understand how different algorithms help you to analyze the data effectively Determine the variation between groups of data using hypothesis testing Visualize your data correctly using appropriate plotting points Use correlation techniques to uncover the relationship between variables Find hidden patterns in data using advanced techniques and strategies Who this book is for The Data Analysis Workshop is for programmers who already know how to code in Python and want to use it to perform data analysis. If you are looking to gain practical experience in data science with Python, this book is for you. Computers

Game Audio Programming 3 Welcome to the third volume of Game Audio Programming: Principles and Practices—the first series of its kind dedicated to the art and science of game audio programming. This volume contains 14 chapters from some of the top game audio programmers and sound designers in the industry. Topics range across game genres (ARPG, RTS, FPS, etc.), and from low-level topics such as DSP to high-level topics like using influence maps for audio. The techniques in this book are targeted at game audio programmers of all abilities, from newbies who are just getting into audio programming to seasoned veterans. All of the principles and practices in this book have been used in real shipping games, so they are all very practical and immediately applicable. There are chapters about split-screen audio, dynamic music improvisation, dynamic mixing, ambiences, DSPs, and more. This book continues the tradition of collecting modern, up-to-date knowledge and wisdom about game audio programming. So, whether you’ve been a game audio programmer for one year or ten years, or even if you’ve just been assigned the task and are trying to figure out what it’s all about, this book is for you! Key Features Cutting-edge advanced game audio programming concepts with examples from real game audio engines Includes both high-level and low-level topics Practical code examples, math, and diagrams that you can apply directly to your game audio engine. Guy Somberg has been programming audio engines for his entire career. From humble beginnings writing a low-level audio mixer for slot machines, he quickly transitioned to writing game audio engines for all manner of games. He has written audio engines that shipped AAA games like Hellgate: London, Bioshock 2, The Sims 4, and Torchlight 3, as well as smaller titles like Minion Master, Tales from the Borderlands, and Game of Thrones. Guy has also given several talks at the Game Developer Conference, the Audio Developer Conference, and CppCon. When he’s not programming or writing game audio programming books, he can be found at home reading, playing video games, and playing the flute. Computers

Supervised Machine Learning AI framework intended to solve a problem of bias-variance tradeoff for supervised learning methods in real-life applications. The AI framework comprises of bootstrapping to create multiple training and testing data sets with various characteristics, design and analysis of statistical experiments to identify optimal feature subsets and optimal hyper-parameters for ML methods, data contamination to test for the robustness of the classifiers. Key Features: Using ML methods by itself doesn’t ensure building classifiers that generalize well for new data Identifying optimal feature subsets and hyper-parameters of ML methods can be resolved using design and analysis of statistical experiments Using a bootstrapping approach to massive sampling of training and tests datasets with various data characteristics (e.g.: contaminated training sets) allows dealing with bias Developing of SAS-based table-driven environment allows managing all meta-data related to the proposed AI framework and creating interoperability with R libraries to accomplish variety of statistical and machine-learning tasks Computer programs in R and SAS that create AI framework are available on GitHub Computers

Advanced Machine Vision Paradigms for Medical Image Analysis Computer vision and machine intelligence paradigms are prominent in the domain of medical image applications, including computer assisted diagnosis, image guided radiation therapy, landmark detection, imaging genomics, and brain connectomics. Medical image analysis and understanding are daunting tasks owing to the massive influx of multi-modal medical image data generated during routine clinal practice. Advanced computer vision and machine intelligence approaches have been employed in recent years in the field of image processing and computer vision. However, due to the unstructured nature of medical imaging data and the volume of data produced during routine clinical processes, the applicability of these meta-heuristic algorithms remains to be investigated. Advanced Machine Vision Paradigms for Medical Image Analysis presents an overview of how medical imaging data can be analyzed to provide better diagnosis and treatment of disease. Computer vision techniques can explore texture, shape, contour and prior knowledge along with contextual information, from image sequence and 3D/4D information which helps with better human understanding. Many powerful tools have been developed through image segmentation, machine learning, pattern classification, tracking, and reconstruction to surface much needed quantitative information not easily available through the analysis of trained human specialists. The aim of the book is for medical imaging professionals to acquire and interpret the data, and for computer vision professionals to learn how to provide enhanced medical information by using computer vision techniques. The ultimate objective is to benefit patients without adding to already high healthcare costs. Explores major emerging trends in technology which are supporting the current advancement of medical image analysis with the help of computational intelligence Highlights the advancement of conventional approaches in the field of medical image processing Investigates novel techniques and reviews the state-of-the-art in the areas of machine learning, computer vision, soft computing techniques, as well as their applications in medical image analysis Computers

SAS® Coding Primer and Reference Guide Although the web and online SAS® communities can provide volumes of information for programmers, these resources are often overwhelming and lack a simple path to guide coding SAS. This reference, however, does provide such a path from a data user’s standpoint vs. seeing things as a code writer. Written by an experienced SAS programmer, this book lets SAS coders easily find explanations and clarification to typical programming problems. This book presents practical real-world data analysis steps encountered by analysts in the field. These steps include the following: Getting to know raw data Understanding variables Getting data into SAS Creating new data variables Performing data manipulations, including sorting, ranking, grouping, subtotal, total, and percentage Statistical testing under a broad range of logical and conditional settings Data visualization Throughout this book, statements and codes are accompanied by thorough annotation. Line-by-line explanations ensure that all terms are clearly explained. Code examples and sample codes have broad usages. All the examples are related to highway transportation where the use of big data is exploding and presenting new challenges and opportunities for growth. Clear and precise practical introductory material on statistics is integrated into the relevant SAS procedures to bolster users’ confidence in applying such methods to their own work. Comprehensive and foundational coverage, systematic introduction of programming topics, thoroughly annotated code examples, and real-world code samples combine to make SAS® Coding Primer and Reference Guide an indispensable reference for beginners and experienced programmers. Computers

Multi-Modal Face Presentation Attack Detection For the last ten years, face biometric research has been intensively studied by the computer vision community. Face recognition systems have been used in mobile, banking, and surveillance systems. For face recognition systems, face spoofing attack detection is a crucial stage that could cause severe security issues in government sectors. Although effective methods for face presentation attack detection have been proposed so far, the problem is still unsolved due to the difficulty in the design of features and methods that can work for new spoofing attacks. In addition, existing datasets for studying the problem are relatively small which hinders the progress in this relevant domain. In order to attract researchers to this important field and push the boundaries of the state of the art on face anti-spoofing detection, we organized the Face Spoofing Attack Workshop and Competition at CVPR 2019, an event part of the ChaLearn Looking at People Series. As part of this event, we released the largest multi-modal face anti-spoofing dataset so far, the CASIA-SURF benchmark. The workshop reunited many researchers from around the world and the challenge attracted more than 300 teams. Some of the novel methodologies proposed in the context of the challenge achieved state-of-the-art performance. In this manuscript, we provide a comprehensive review on face anti-spoofing techniques presented in this joint event and point out directions for future research on the face anti-spoofing field. Computers

Thermodynamics of Complex Systems This textprovides a concise introduction to non-equilibrium thermodynamics of open,complex systems using a first-principles approach. The book is avaluable reference text for researchers interested in thermodynamics and complex systems, and usefulsupplementary reading for graduate courses in these areas. Computers

RabbitMQ Essentials Learn basic to advanced RabbitMQ techniques with the help of a realistic case study shared by the experts from CloudAMQP Key Features Delve into message queues with this comprehensive RabbitMQ guide Explore message queue architecture evolution with the help of a realistic case study Discover strategies for improving scalability and fault tolerance of a message queue architecture Book Description RabbitMQ is an open source message queuing software that acts as a message broker using the Advanced Message Queuing Protocol (AMQP). This book will help you to get to grips with RabbitMQ to build your own applications with a message queue architecture. You'll learn from the experts from CloudAMQP as they share what they've learned while managing the largest fleet of RabbitMQ clusters in the world. Following the case study of Complete Car, you'll discover how you can use RabbitMQ to provide exceptional customer service and user experience, and see how a message queue architecture makes it easy to upgrade the app and add features as the company grows. From implementing simple synchronous operations through to advanced message routing and tracking, you'll explore how RabbitMQ streamlines scalable operations for fast distribution. This book will help you understand the advantages of message queue architecture, including application scalability, resource efficiency, and user reliability. Finally, you'll learn best practices for working with RabbitMQ and be able to use this book as a reference guide for your future app development projects. By the end of this book, you'll have learned how to use message queuing software to streamline the development of your distributed and scalable applications. What you will learn Get well versed with RabbitMQ's message queue architecture and features Discover the benefits of RabbitMQ, AMQP, and message queuing Install and configure RabbitMQ and its plugins Get to grips with the management console features and controls Understand how queue and exchange types differ and when and how to use them Get the hang of channels, routing strategies, and direct exchanges Implement best practices to work smoothly with message queues Who this book is for If you are a professional enterprise developer or someone who just codes for fun, RabbitMQ Essentials is a valuable resource on open-source message queue architecture. Even those already familiar with microservices and messaging will discover value in reading this book for an exploration of moving forward with best practices and resource efficiency. This book will give you the push you need to get started with creating new and exciting applications or migrating existing monoliths to a microservice architecture. Computers

Smart Data Discovery Using SAS Viya Gain Powerful Insights with SAS Viya ! Whether you are an executive, departmental decision maker, or analyst, the need to leverage data and analytical techniques in order make critical business decisions is now crucial to every part of an organization. Smart Data Discovery with SAS Viya : Powerful Techniques for Deeper Insights provides you with the necessary knowledge and skills to conduct a smart discovery process and empower you to ask more complex questions using your data. The book highlights key components of a smart data discovery process utilizing advanced machine learning techniques, powerful capabilities from SAS Viya , and finally brings it all together using real examples and applications. With its step-by-step approach and integrated examples, the book provides a relevant and practical guide to insight discovery that goes beyond traditional charts and graphs. By showcasing the powerful visual modeling capabilities of SAS Viya , it also opens up the world of advanced analytics and machine learning techniques to a much broader set of audiences. Computers

Advanced Deep Learning with TensorFlow 2 and Keras Updated and revised second edition of the bestselling guide to advanced deep learning with TensorFlow 2 and Keras Key Features Explore the most advanced deep learning techniques that drive modern AI results New coverage of unsupervised deep learning using mutual information, object detection, and semantic segmentation Completely updated for TensorFlow 2.x Book Description Advanced Deep Learning with TensorFlow 2 and Keras, Second Edition is a completely updated edition of the bestselling guide to the advanced deep learning techniques available today. Revised for TensorFlow 2.x, this edition introduces you to the practical side of deep learning with new chapters on unsupervised learning using mutual information, object detection (SSD), and semantic segmentation (FCN and PSPNet), further allowing you to create your own cutting-edge AI projects. Using Keras as an open-source deep learning library, the book features hands-on projects that show you how to create more effective AI with the most up-to-date techniques. Starting with an overview of multi-layer perceptrons (MLPs), convolutional neural networks (CNNs), and recurrent neural networks (RNNs), the book then introduces more cutting-edge techniques as you explore deep neural network architectures, including ResNet and DenseNet, and how to create autoencoders. You will then learn about GANs, and how they can unlock new levels of AI performance. Next, you'll discover how a variational autoencoder (VAE) is implemented, and how GANs and VAEs have the generative power to synthesize data that can be extremely convincing to humans. You'll also learn to implement DRL such as Deep Q-Learning and Policy Gradient Methods, which are critical to many modern results in AI. What you will learn Use mutual information maximization techniques to perform unsupervised learning Use segmentation to identify the pixel-wise class of each object in an image Identify both the bounding box and class of objects in an image using object detection Learn the building blocks for advanced techniques - MLPss, CNN, and RNNs Understand deep neural networks - including ResNet and DenseNet Understand and build autoregressive models – autoencoders, VAEs, and GANs Discover and implement deep reinforcement learning methods Who this book is for This is not an introductory book, so fluency with Python is required. The reader should also be familiar with some machine learning approaches, and practical experience with DL will also be helpful. Knowledge of Keras or TensorFlow 2.0 is not required but is recommended. Computers

Hands-On JavaScript High Performance An example-driven guide covering modern web app development techniques and emerging technologies such as WebAssembly, Service Workers, and Svelte.js to build faster, secure, and scalable apps Key Features Discover effective techniques for accessing DOM, minimizing painting, and using a V8 engine to optimize JavaScript Understand what makes the web tick and create apps that look and feel like native desktop applications Explore modern JavaScript frameworks like Svelte.js for building next-gen web apps Book Description High-performance web development is all about cutting through the complexities in different layers of a web app and building services and APIs that improve the speed and performance of your apps on the browser. With emerging web technologies, building scalable websites and sustainable web apps is smoother than ever. This book starts by taking you through the web frontend, popular web development practices, and the latest version of ES and JavaScript. You'll work with Node.js and learn how to build web apps without a framework. The book consists of three hands-on examples that help you understand JavaScript applications at both the server-side and the client-side using Node.js and Svelte.js. Each chapter covers modern techniques such as DOM manipulation and V8 engine optimization to strengthen your understanding of the web. Finally, you'll delve into advanced topics such as CI/CD and how you can harness their capabilities to speed up your web development dramatically. By the end of this web development book, you'll have understood how the JavaScript landscape has evolved, not just for the frontend but also for the backend, and be ready to use new tools and techniques to solve common web problems. What you will learn Explore Vanilla JavaScript for optimizing the DOM, classes, and modules, and querying with jQuery Understand immutable and mutable code and develop faster web apps Delve into Svelte.js and use it to build a complete real-time Todo app Build apps to work offline by caching calls using service workers Write C++ native code and call the WebAssembly module with JavaScript to run it on a browser Implement CircleCI for continuous integration in deploying your web apps Who this book is for This JavaScript book is for web developers, C/C++ programmers, and anyone who wants to build robust web applications using advanced web technologies. This book assumes a good grasp of Vanilla JavaScript and an understanding of web development tools, such as Chrome Developer tools or Mozilla's developer tools. Computers

Learning RxJava Updated with the latest Maven coordinates, Java programming features, and API changes, this book is your guide to solving problems in writing asynchronous and event-based programs Key Features Explore a variety of tools and techniques used to solve problems in implementing concurrency and parallelization Learn about core operators in RxJava that enable you to express your code logic productively Apply RxJava with Kotlin to create responsive Android apps with better user experience Book Description RxJava is not just a popular library for building asynchronous and event-based applications; it also enables you to create a cleaner and more readable code base. In this book, you'll cover the core fundamentals of reactive programming and learn how to design and implement reactive libraries and applications. Learning RxJava will help you understand how reactive programming works and guide you in writing your first example in reactive code. You'll get to grips with the workings of Observable and Subscriber, and see how they are used in different contexts using real-world use cases. The book will also take you through multicasting and caching to help prevent redundant work with multiple Observers. You'll then learn how to create your own RxJava operators by reusing reactive logic. As you advance, you'll explore effective tools and libraries to test and debug RxJava code. Finally, you'll delve into RxAndroid extensions and use Kotlin features to streamline your Android apps. By the end of this book, you'll become proficient in writing reactive code in Java and Kotlin to build concurrent applications, including Android applications. What you will learn Discover different ways to create Observables, Observers, and Subscribers Multicast in order to push data to multiple destinations and cache and replay them Express RxJava idiomatically with the help of Kotlin features such as extension functions and data classes Become familiar with various operators available in RxJava to perform common transformations and tasks Explore RxJava's reactive types, including Flowable, Single, Maybe, and Completable Demystify Observables and how they express data and events as sequences Who this book is for This book is for Java developers who want to leverage reactive programming to develop more resilient and concurrent applications. If you're an RxJava user looking to get to grips with the latest features and updates in RxJava 3, this book is for you. Fundamental knowledge of core Java features and object-oriented programming will assist you in understanding the key concepts covered in this book. Computers

Artificial Intelligence By Example Understand the fundamentals and develop your own AI solutions in this updated edition packed with many new examples Key Features AI-based examples to guide you in designing and implementing machine intelligence Build machine intelligence from scratch using artificial intelligence examples Develop machine intelligence from scratch using real artificial intelligence Book Description AI has the potential to replicate humans in every field. Artificial Intelligence By Example, Second Edition serves as a starting point for you to understand how AI is built, with the help of intriguing and exciting examples. This book will make you an adaptive thinker and help you apply concepts to real-world scenarios. Using some of the most interesting AI examples, right from computer programs such as a simple chess engine to cognitive chatbots, you will learn how to tackle the machine you are competing with. You will study some of the most advanced machine learning models, understand how to apply AI to blockchain and Internet of Things (IoT), and develop emotional quotient in chatbots using neural networks such as recurrent neural networks (RNNs) and convolutional neural networks (CNNs). This edition also has new examples for hybrid neural networks, combining reinforcement learning (RL) and deep learning (DL), chained algorithms, combining unsupervised learning with decision trees, random forests, combining DL and genetic algorithms, conversational user interfaces (CUI) for chatbots, neuromorphic computing, and quantum computing. By the end of this book, you will understand the fundamentals of AI and have worked through a number of examples that will help you develop your AI solutions. What you will learn Apply k-nearest neighbors (KNN) to language translations and explore the opportunities in Google Translate Understand chained algorithms combining unsupervised learning with decision trees Solve the XOR problem with feedforward neural networks (FNN) and build its architecture to represent a data flow graph Learn about meta learning models with hybrid neural networks Create a chatbot and optimize its emotional intelligence deficiencies with tools such as Small Talk and data logging Building conversational user interfaces (CUI) for chatbots Writing genetic algorithms that optimize deep learning neural networks Build quantum computing circuits Who this book is for Developers and those interested in AI, who want to understand the fundamentals of Artificial Intelligence and implement them practically. Prior experience with Python programming and statistical knowledge is essential to make the most out of this book. Computers

PyTorch Artificial Intelligence Fundamentals Use PyTorch to build end-to-end artificial intelligence systems using Python Key Features Build smart AI systems to handle real-world problems using PyTorch 1.x Become well-versed with concepts such as deep reinforcement learning (DRL) and genetic programming Cover PyTorch functionalities from tensor manipulation through to deploying in production Book Description Artificial Intelligence (AI) continues to grow in popularity and disrupt a wide range of domains, but it is a complex and daunting topic. In this book, you'll get to grips with building deep learning apps, and how you can use PyTorch for research and solving real-world problems. This book uses a recipe-based approach, starting with the basics of tensor manipulation, before covering Convolutional Neural Networks (CNNs) and Recurrent Neural Networks (RNNs) in PyTorch. Once you are well-versed with these basic networks, you'll build a medical image classifier using deep learning. Next, you'll use TensorBoard for visualizations. You'll also delve into Generative Adversarial Networks (GANs) and Deep Reinforcement Learning (DRL) before finally deploying your models to production at scale. You'll discover solutions to common problems faced in machine learning, deep learning, and reinforcement learning. You'll learn to implement AI tasks and tackle real-world problems in computer vision, natural language processing (NLP), and other real-world domains. By the end of this book, you'll have the foundations of the most important and widely used techniques in AI using the PyTorch framework. What you will learn Perform tensor manipulation using PyTorch Train a fully connected neural network Advance from simple neural networks to convolutional neural networks (CNNs) and recurrent neural networks (RNNs) Implement transfer learning techniques to classify medical images Get to grips with generative adversarial networks (GANs), along with their implementation Build deep reinforcement learning applications and learn how agents interact in the real environment Scale models to production using ONNX Runtime Deploy AI models and perform distributed training on large datasets Who this book is for This PyTorch book is for AI engineers who are just getting started, machine learning engineers, data scientists and deep learning enthusiasts who are looking for a guide to help them solve AI problems effectively. Working knowledge of the Python programming language and a basic understanding of machine learning are expected. Computers

Hands-On RESTful Web Services with Go Design production-ready, testable, and maintainable RESTful web services for the modern web that scale easily Key Features Employ a combination of custom and open source solutions for application program interface (API) development Discover asynchronous API and API security patterns and learn how to deploy your web services to the cloud Apply design patterns and techniques to build reactive and scalable web services Book Description Building RESTful web services can be tough as there are countless standards and ways to develop API. In modern architectures such as microservices, RESTful APIs are common in communication, making idiomatic and scalable API development crucial. This book covers basic through to advanced API development concepts and supporting tools. You'll start with an introduction to REST API development before moving on to building the essential blocks for working with Go. You'll explore routers, middleware, and available open source web development solutions in Go to create robust APIs, and understand the application and database layers to build RESTful web services. You'll learn various data formats like protocol buffers and JSON, and understand how to serve them over HTTP and gRPC. After covering advanced topics such as asynchronous API design and GraphQL for building scalable web services, you'll discover how microservices can benefit from REST. You'll also explore packaging artifacts in the form of containers and understand how to set up an ideal deployment ecosystem for web services. Finally, you'll cover the provisioning of infrastructure using infrastructure as code (IaC) and secure your REST API. By the end of the book, you'll have intermediate knowledge of web service development and be able to apply the skills you've learned in a practical way. What you will learn Explore the fundamentals of API development and web services Understand the various building blocks of API development in Go Use superior open source solutions for representational state transfer (REST) API development Scale a service using microservices and asynchronous design patterns Deliver containerized artifacts to the Amazon Web Services (AWS) Cloud Get to grips with API security and its implementation Who this book is for This book is for all the Go developers who are comfortable with the language and seeking to learn REST API development. Even senior engineers can enjoy this book, as it discusses many cutting-edge concepts, such as building microservices, developing API with GraphQL, using protocol buffers, asynchronous API design, and Infrastructure as a Code. Developers who are already familiar with REST concepts and stepping into the Go world from other platforms, such as Python and Ruby, can also benefit a lot. Computers

AWS Certified Security – Specialty Exam Guide Get to grips with the fundamentals of cloud security and prepare for the AWS Security Specialty exam with the help of this comprehensive certification guide Key Features Learn the fundamentals of security with this fast-paced guide Develop modern cloud security skills to build effective security solutions Answer practice questions and take mock tests to pass the exam with confidence Book Description AWS Certified Security – Specialty is a certification exam to validate your expertise in advanced cloud security. With an ever-increasing demand for AWS security skills in the cloud market, this certification can help you advance in your career. This book helps you prepare for the exam and gain certification by guiding you through building complex security solutions. From understanding the AWS shared responsibility model and identity and access management to implementing access management best practices, you'll gradually build on your skills. The book will also delve into securing instances and the principles of securing VPC infrastructure. Covering security threats, vulnerabilities, and attacks such as the DDoS attack, you'll discover how to mitigate these at different layers. You'll then cover compliance and learn how to use AWS to audit and govern infrastructure, as well as to focus on monitoring your environment by implementing logging mechanisms and tracking data. Later, you'll explore how to implement data encryption as you get hands-on with securing a live environment. Finally, you'll discover security best practices that will assist you in making critical decisions relating to cost, security,and deployment complexity. By the end of this AWS security book, you'll have the skills to pass the exam and design secure AWS solutions. What you will learn Understand how to identify and mitigate security incidents Assign appropriate Amazon Web Services (AWS) resources to underpin security requirements Work with the AWS shared responsibility model Secure your AWS public cloud in different layers of cloud computing Discover how to implement authentication through federated and mobile access Monitor and log tasks effectively using AWS Who this book is for If you are a system administrator or a security professional looking to get AWS security certification, this book is for you. Prior experience in securing cloud environments is necessary to get the most out of this AWS book. Computers

Designing with the Mind in Mind User interface (UI) design rules and guidelines, developed by early HCI gurus and recognized throughout the field, were based on cognitive psychology (study of mental processes such as problem solving, memory, and language), and early practitioners were well informed of its tenets. But today practitioners with backgrounds in cognitive psychology are a minority, as user interface designers and developers enter the field from a wide array of disciplines. HCI practitioners today have enough experience in UI design that they have been exposed to UI design rules, but it is essential that they understand the psychological basis behind the rules in order to effectively apply them. In Designing with the Mind in Mind, best-selling author Jeff Johnson provides designers with just enough background in perceptual and cognitive psychology that UI design guidelines make intuitive sense rather than being just a list of rules to follow. Provides an essential source for user interface design rules and how, when, and why to apply them Arms designers with the science behind each design rule, allowing them to make informed decisions in projects, and to explain those decisions to others Equips readers with the knowledge to make educated tradeoffs between competing rules, project deadlines, and budget pressures Completely updated and revised, including additional coverage in such areas as persuasion, cognitive economics and decision making, emotions, trust, habit formation, and speech UIs Computers

Entropy and Free Energy in Structural Biology Computer simulation has become the main engine of development in statistical mechanics. In structural biology, computer simulation constitutes the main theoretical tool for structure determination of proteins and for calculation of the free energy of binding, which are important in drug design. Entropy and Free Energy in Structural Biology leads the reader to the simulation technology in a systematic way. The book, which is structured as a course, consists of four parts: Part I is a short course on probability theory emphasizing (1) the distinction between the notions of experimental probability, probability space, and the experimental probability on a computer, and (2) elaborating on the mathematical structure of product spaces. These concepts are essential for solving probability problems and devising simulation methods, in particular for calculating the entropy. Part II starts with a short review of classical thermodynamics from which a non-traditional derivation of statistical mechanics is devised. Theoretical aspects of statistical mechanics are reviewed extensively. Part III covers several topics in non-equilibrium thermodynamics and statistical mechanics close to equilibrium, such as Onsager relations, the two Fick's laws, and the Langevin and master equations. The Monte Carlo and molecular dynamics procedures are discussed as well. Part IV presents advanced simulation methods for polymers and protein systems, including techniques for conformational search and for calculating the potential of mean force and the chemical potential. Thermodynamic integration, methods for calculating the absolute entropy, and methodologies for calculating the absolute free energy of binding are evaluated. Enhanced by a number of solved problems and examples, this volume will be a valuable resource to advanced undergraduate and graduate students in chemistry, chemical engineering, biochemistry biophysics, pharmacology, and computational biology. Computers

The Mojo Handbook The Mojo Handbook: Theory to Praxis offers a detailed and engaging crash course on how to use mobile tools to create powerful journalistic stories. Drawing on both theoretical underpinnings and practical techniques, the book outlines the fundamentals of mobile journalism methods, by placing mobile storytelling within a wider context of current affairs, documentary filmmaking and public relations. The book offers expert advice for how to use storytelling skills to transform mobile content into engaging and purposeful user-generated stories for audiences. Topics covered include tips for recording dynamic video and clean audio, conducting interviews on your phone and editing and post-production processes, as well as advice on how to handle copyright issues and a primer on journalistic ethics. The book also includes a comprehensive glossary of terms to help students navigate the video production and mobile journalism world. The Mojo Handbook is a valuable resource for aspiring multimedia professionals in journalism, strategic and corporate communication, community and education, as well as anyone looking to incorporate mobile into their visual storytelling tool kit. Computers

Restricted Congruences in Computing Congruences are ubiquitous in computer science, engineering, mathematics, and related areas. Developing techniques for finding (the number of) solutions of congruences is an important problem. But there are many scenarios in which we are interested in only a subset of the solutions; in other words, there are some restrictions. What do we know about these restricted congruences, their solutions, and applications? This book introduces the tools that are needed when working on restricted congruences and then systematically studies a variety of restricted congruences. Restricted Congruences in Computing defines several types of restricted congruence, obtains explicit formulae for the number of their solutions using a wide range of tools and techniques, and discusses their applications in cryptography, information security, information theory, coding theory, string theory, quantum field theory, parallel computing, artificial intelligence, computational biology, discrete mathematics, number theory, and more. This is the first book devoted to restricted congruences and their applications. It will be of interest to graduate students and researchers across computer science, electrical engineering, and mathematics. Computers

Machine Learning A comprehensive introduction to machine learning that uses probabilistic models and inference as a unifying approach. Today's Web-enabled deluge of electronic data calls for automated methods of data analysis. Machine learning provides these, developing methods that can automatically detect patterns in data and then use the uncovered patterns to predict future data. This textbook offers a comprehensive and self-contained introduction to the field of machine learning, based on a unified, probabilistic approach. The coverage combines breadth and depth, offering necessary background material on such topics as probability, optimization, and linear algebra as well as discussion of recent developments in the field, including conditional random fields, L1 regularization, and deep learning. The book is written in an informal, accessible style, complete with pseudo-code for the most important algorithms. All topics are copiously illustrated with color images and worked examples drawn from such application domains as biology, text processing, computer vision, and robotics. Rather than providing a cookbook of different heuristic methods, the book stresses a principled model-based approach, often using the language of graphical models to specify models in a concise and intuitive way. Almost all the models described have been implemented in a MATLAB software package—PMTK (probabilistic modeling toolkit)—that is freely available online. The book is suitable for upper-level undergraduates with an introductory-level college math background and beginning graduate students. Computers

AI and Machine Learning A primer to AI and Machine Learning which also touches upon “good†and “bad†AI and its relationship with governments and corporations. Computers

Android For Dummies Set up, configure, and get connected Shoot and share photos and videos Use social media, text, and email to stay in touch Make the most of your Android gizmo Be honest—isn't "gizmo" a friendlier word than "device"? This book will tell you pretty much everything you need to know about your Android smartphone or tablet in an equally friendly manner, because that's the best way to learn how to get the most from your Android. From buying, unpacking, and setting up your gizmo to managing calls and email, posting to social media, navigating with Maps, and creating a photo slideshow, it's like having a good friend show you the basics and explain how to take advantage of all the cool stuff. Inside... All about Android 10 Updated security features Customizing your Android Creating multimedia messages Apps to help you get social The Bluetooth connection Exploring Google Play Essential troubleshooting tips Computers

Tribe of Hackers Blue Team Blue Team defensive advice from the biggest names in cybersecurity The Tribe of Hackers team is back. This new guide is packed with insights on blue team issues from the biggest names in cybersecurity. Inside, dozens of the world’s leading Blue Team security specialists show you how to harden systems against real and simulated breaches and attacks. You’ll discover the latest strategies for blocking even the most advanced red-team attacks and preventing costly losses. The experts share their hard-earned wisdom, revealing what works and what doesn’t in the real world of cybersecurity. Tribe of Hackers Blue Team goes beyond the bestselling, original Tribe of Hackers book and delves into detail on defensive and preventative techniques. Learn how to grapple with the issues that hands-on security experts and security managers are sure to build into their blue team exercises. Discover what it takes to get started building blue team skills Learn how you can defend against physical and technical penetration testing Understand the techniques that advanced red teamers use against high-value targets Identify the most important tools to master as a blue teamer Explore ways to harden systems against red team attacks Stand out from the competition as you work to advance your cybersecurity career Authored by leaders in cybersecurity attack and breach simulations, the Tribe of Hackers series is perfect for those new to blue team security, experienced practitioners, and cybersecurity team leaders. Tribe of Hackers Blue Team has the real-world advice and practical guidance you need to advance your information security career and ready yourself for the blue team defense. Computers

Java All-in-One For Dummies Java—from first steps to first apps Knowing Java is a must-have programming skill for any programmer. It’s used in a wide array of programming projects—from enterprise apps and mobile apps to big data, scientific, and financial uses. The language regularly ranks #1 in surveys of the most popular language based on number of developers, lines of code written, and real-world usage. It’s also the language of choice in AP Computer Science classes taught in the U.S. This guide provides an easy-to-follow path from understanding the basics of writing Java code to applying those skills to real projects. Split into eight minibooks covering core aspects of Java, the book introduces the basics of the Java language and object-oriented programming before setting you on the path to building web apps and databases. • Get up to speed on Java basics • Explore object-oriented programming • Learn about strings, arrays, and collections • Find out about files and databases Step-by-step instructions are provided to ensure that you don't get lost at any point along the way. Computers

Hands on Hacking A fast, hands-on introduction to offensive hacking techniques Hands-On Hacking teaches readers to see through the eyes of their adversary and apply hacking techniques to better understand real-world risks to computer networks and data. Readers will benefit from the author's years of experience in the field hacking into computer networks and ultimately training others in the art of cyber-attacks. This book holds no punches and explains the tools, tactics and procedures used by ethical hackers and criminal crackers alike. We will take you on a journey through a hacker’s perspective when focused on the computer infrastructure of a target company, exploring how to access the servers and data. Once the information gathering stage is complete, you’ll look for flaws and their known exploits—including tools developed by real-world government financed state-actors. • An introduction to the same hacking techniques that malicious hackers will use against an organization • Written by infosec experts with proven history of publishing vulnerabilities and highlighting security flaws • Based on the tried and tested material used to train hackers all over the world in the art of breaching networks • Covers the fundamental basics of how computer networks are inherently vulnerable to attack, teaching the student how to apply hacking skills to uncover vulnerabilities We cover topics of breaching a company from the external network perimeter, hacking internal enterprise systems and web application vulnerabilities. Delving into the basics of exploitation with real-world practical examples, you won’t find any hypothetical academic only attacks here. From start to finish this book will take the student through the steps necessary to breach an organization to improve its security. Written by world-renowned cybersecurity experts and educators, Hands-On Hacking teaches entry-level professionals seeking to learn ethical hacking techniques. If you are looking to understand penetration testing and ethical hacking, this book takes you from basic methods to advanced techniques in a structured learning format. Computers

SwiftUI For Dummies The simplest way to create world-class apps Have a unique app idea but worried you don’t quite have the coding skills to build it? Good news: You can stop fretting about someone beating you to market with the same idea and start work right now using SwiftUI. SwiftUI is a gateway app development framework that has become one of the best ways for fledgling developers to get iOS apps off the ground without having to become a coding expert overnight. SwiftUI For Dummies makes that process even faster, providing a friendly introduction to the SwiftUI and Swift programming language and helping you feel right at home creating and building with playgrounds. The book also covers the frameworks and APIs that make it so easy to create smooth, intuitive interfaces—just dive right in and have fun! Combine projects into workspaces Employ Xcode editing tools Use constants and variables Test your code on iOS Simulator Time is of the essence, and with SwiftUI For Dummies, it’s also on your side. Get going with this friendly guide today, and you’ll be celebrating the successful launch of your app way before you thought possible! Computers

The Read Aloud Cloud What is “the cloud� Is it here or there? Should it be allowed? Should I even care? Have you ever imagined the internet as a giant Rube Goldberg machine? Or the fast-evolving cloud computing space as a literal jungle filled with prehistoric beasts? Does a data breach look like a neo-noir nightmare full of turned-up coat collars and rain-soaked alleys? Wouldn’t all these vital concepts be easier to understand if they looked as interesting as they are? And wouldn’t they be more memorable if we could explain them in rhyme? Whether you’re a kid or an adult, the answer is: YES! The medicine in this spoonful of sugar is a sneaky-informative tour through the past, present and future of cloud computing, from mainframes to serverless and from the Internet of Things to artificial intelligence. Forrest is a professional explainer whose highly-rated conference talks and viral cartoon graphics have been teaching engineers to cloud for years. He knows that a picture is worth a thousand words. But he has plenty of words, too. Your hotel key, your boarding pass, The card you swipe to pay for gas, The smart TV atop the bar, The entertainment in your car, Your doorbell, toothbrush, thermostat, The vacuum that attacked your cat, They all connect the cloud and you. Maybe they shouldn't, but they do. As a graduation gift (call it “Oh the Places You’ll Go†for engineering students), a cubicle conversation starter, or just a delightfully nerdy bedtime story for your kids, “The Read-Aloud Cloud†will be the definitive introduction to the technologies that everyone uses and nobody understands. You can even read it silently if you want. But good luck with that. Computers

Drupal 9 Module Development Build and extend flexible Drupal sites and applications with this up-to-date, expert guide to Drupal 9 module development Key Features Explore the essential Drupal 9 APIs for module development Learn how to implement data modeling, caching, architecture, and much more in your Drupal applications Discover what's new in the latest Drupal core releases Book Description With its latest release, Drupal 9, the popular open source CMS platform has been updated with new functionalities for building complex Drupal apps with ease. This third edition of the Drupal Module Development guide covers these new Drupal features, helping you to stay on top of code deprecations and the changing architecture with every release. The book starts by introducing you to the Drupal 9 architecture and its subsystems before showing you how to create your first module with basic functionality. You'll explore the Drupal logging and mailing systems, learn how to output data using the theme layer, and work with menus and links programmatically. Once you've understood the different kinds of data storage, this Drupal guide will demonstrate how to create custom entities and field types and leverage the Database API for lower-level database queries. You'll also learn how to introduce JavaScript into your module, work with various file systems, and ensure that your code works on multilingual sites. Finally, you'll work with Views, create automated tests for your functionality, and write secure code. By the end of the book, you'll have learned how to develop custom modules that can provide solutions to complex business problems, and who knows, maybe you'll even contribute to the Drupal community! What you will learn Develop custom Drupal 9 modules for your applications Master different Drupal 9 subsystems and APIs Model, store, manipulate, and process data for effective data management Display data and content in a clean and secure way using the theme system Test your business logic to prevent regression Stay ahead of the curve and write PHP code by implementing best practices Who this book is for If you are a Drupal developer looking to learn Drupal 9 to write modules for your sites, this book is for you. Drupal site builders and PHP developers with basic object-oriented programming skills will also find this book helpful. Although not necessary, some Symfony experience will help with understanding concepts easily. Computers

Managing Software Requirements the Agile Way Learn how to deliver software that meets your clients' needs with the help of a structured, end-to-end methodology for managing software requirements and building suitable systems Key Features Learn how to communicate with a project's stakeholders to elicit software requirements Deal every phase of the requirement life cycle with pragmatic methods and techniques Manage the software development process and deliver verified requirements using Scrum and Kanban Book Description Difficulty in accurately capturing and managing requirements is the most common cause of software project failure. Learning how to analyze and model requirements and produce specifications that are connected to working code is the single most fundamental step that you can take toward project success. This book focuses on a delineated and structured methodology that will help you analyze requirements and write comprehensive, verifiable specifications. You'll start by learning about the different entities in the requirements domain and how to discover them based on customer input. You'll then explore tried-and-tested methods such as impact mapping and behavior-driven development (BDD), along with new techniques such as D3 and feature-first development. This book takes you through the process of modeling customer requirements as impact maps and writing them as executable specifications. You'll also understand how to organize and prioritize project tasks using Agile frameworks, such as Kanban and Scrum, and verify specifications against the delivered code. Finally, you'll see how to start implementing the requirements management methodology in a real-life scenario. By the end of this book, you'll be able to model and manage requirements to create executable specifications that will help you deliver successful software projects. What you will learn Kick-start the requirements-gathering and analysis process in your first meeting with the client Accurately define system behavior as features Model and describe requirement entities using Impact Mapping and BDD Create a feature-based product backlog and use it to drive software development Write verification code to turn features into executable specifications Deliver the right software and respond to change using either Scrum or Kanban Choose appropriate software tools to provide transparency and traceability to your clients Who this book is for This book is for software engineers, business analysts, product managers, project managers, and software project stakeholders looking to learn a variety of techniques and methodologies for collating accurate software requirements. A fundamental understanding of the software development life cycle (SDLC) is needed to get started with this book. Although not necessary, basic knowledge of the Agile philosophy and practices, such as Scrum, along with some programming experience will help you to get the most out of this book. Computers

Hands-on Nuxt.js Web Development Learn Nuxt.js for building server-side rendered, static-generated, and production-ready Vue.js web applications with the help of practical examples Key Features Explore techniques for authentication, testing, and deployment to build your first complete Nuxt.js web app Write cleaner, maintainable, and scalable isomorphic JavaScript web applications Transform your Vue.js application into universal and static-generated web apps Book Description Nuxt.js is a progressive web framework built on top of Vue.js for server-side rendering (SSR). With Nuxt.js and Vue.js, building universal and static-generated applications from scratch is now easier than ever before. This book starts with an introduction to Nuxt.js and its constituents as a universal SSR framework. You'll learn the fundamentals of Nuxt.js and find out how you can integrate it with the latest version of Vue.js. You'll then explore the Nuxt.js directory structure and set up your first Nuxt.js project using pages, views, routing, and Vue components. With the help of practical examples, you'll learn how to connect your Nuxt.js application with the backend API by exploring your Nuxt.js application's configuration, plugins, modules, middleware, and the Vuex store. The book shows you how you can turn your Nuxt.js application into a universal or static-generated application by working with REST and GraphQL APIs over HTTP requests. Finally, you'll get to grips with security techniques using authorization, package your Nuxt.js application for testing, and deploy it to production. By the end of this web development book, you'll have developed a solid understanding of using Nuxt.js for your projects and be able to build secure, end-to-end tested, and scalable web applications with SSR, data handling, and SEO capabilities. What you will learn Integrate Nuxt.js with the latest version of Vue.js Extend your Vue.js applications using Nuxt.js pages, components, routing, middleware, plugins, and modules Create a basic real-time web application using Nuxt.js, Node.js, Koa.js and RethinkDB Develop universal and static-generated web applications with Nuxt.js, headless CMS and GraphQL Build Node.js and PHP APIs from scratch with Koa.js, PSRs, GraphQL, MongoDB and MySQL Secure your Nuxt.js applications with the JWT authentication Discover best practices for testing and deploying your Nuxt.js applications Who this book is for The book is for any JavaScript or full-stack developer who wants to build server-side rendered Vue.js apps. A basic understanding of the Vue.js framework will assist with understanding key concepts covered in the book. Computers

Docker for Developers Learn how to deploy and test Linux-based Docker containers with the help of real-world use cases Key Features Understand how to make a deployment workflow run smoothly with Docker containers Learn Docker and DevOps concepts such as continuous integration and continuous deployment (CI/CD) Gain insights into using various Docker tools and libraries Book Description Docker is the de facto standard for containerizing apps, and with an increasing number of software projects migrating to containers, it is crucial for engineers and DevOps teams to understand how to build, deploy, and secure Docker environments effectively. Docker for Developers will help you understand Docker containers from scratch while taking you through best practices and showing you how to address security concerns. Starting with an introduction to Docker, you'll learn how to use containers and VirtualBox for development. You'll explore how containers work and develop projects within them after you've explored different ways to deploy and run containers. The book will also show you how to use Docker containers in production in both single-host set-ups and in clusters and deploy them using Jenkins, Kubernetes, and Spinnaker. As you advance, you'll get to grips with monitoring, securing, and scaling Docker using tools such as Prometheus and Grafana. Later, you'll be able to deploy Docker containers to a variety of environments, including the cloud-native Amazon Elastic Kubernetes Service (Amazon EKS), before finally delving into Docker security concepts and best practices. By the end of the Docker book, you'll be able to not only work in a container-driven environment confidently but also use Docker for both new and existing projects. What you will learn Get up to speed with creating containers and understand how they work Package and deploy your containers to a variety of platforms Work with containers in the cloud and on the Kubernetes platform Deploy and then monitor the health and logs of running containers Explore best practices for working with containers from a security perspective Become familiar with scanning containers and using third-party security tools and libraries Who this book is for If you're a software engineer new to containerization or a DevOps engineer responsible for deploying Docker containers in the cloud and building DevOps pipelines for container-based projects, you'll find this book useful. This Docker containers book is also a handy reference guide for anyone working with a Docker-based DevOps ecosystem or interested in understanding the security implications and best practices for working in container-driven environments. Computers

The Natural Language Processing Workshop Make NLP easy by building chatbots and models, and executing various NLP tasks to gain data-driven insights from raw text data Key Features Get familiar with key natural language processing (NLP) concepts and terminology Explore the functionalities and features of popular NLP tools Learn how to use Python programming and third-party libraries to perform NLP tasks Book Description Do you want to learn how to communicate with computer systems using Natural Language Processing (NLP) techniques, or make a machine understand human sentiments? Do you want to build applications like Siri, Alexa, or chatbots, even if you've never done it before? With The Natural Language Processing Workshop, you can expect to make consistent progress as a beginner, and get up to speed in an interactive way, with the help of hands-on activities and fun exercises. The book starts with an introduction to NLP. You'll study different approaches to NLP tasks, and perform exercises in Python to understand the process of preparing datasets for NLP models. Next, you'll use advanced NLP algorithms and visualization techniques to collect datasets from open websites, and to summarize and generate random text from a document. In the final chapters, you'll use NLP to create a chatbot that detects positive or negative sentiment in text documents such as movie reviews. By the end of this book, you'll be equipped with the essential NLP tools and techniques you need to solve common business problems that involve processing text. What you will learn Obtain, verify, clean and transform text data into a correct format for use Use methods such as tokenization and stemming for text extraction Develop a classifier to classify comments in Wikipedia articles Collect data from open websites with the help of web scraping Train a model to detect topics in a set of documents using topic modeling Discover techniques to represent text as word and document vectors Who this book is for This book is for beginner to mid-level data scientists, machine learning developers, and NLP enthusiasts. A basic understanding of machine learning and NLP is required to help you grasp the topics in this workshop more quickly. Computers

The Artificial Intelligence Infrastructure Workshop Explore how a data storage system works – from data ingestion to representation Key Features Understand how artificial intelligence, machine learning, and deep learning are different from one another Discover the data storage requirements of different AI apps using case studies Explore popular data solutions such as Hadoop Distributed File System (HDFS) and Amazon Simple Storage Service (S3) Book Description Social networking sites see an average of 350 million uploads daily - a quantity impossible for humans to scan and analyze. Only AI can do this job at the required speed, and to leverage an AI application at its full potential, you need an efficient and scalable data storage pipeline. The Artificial Intelligence Infrastructure Workshop will teach you how to build and manage one. The Artificial Intelligence Infrastructure Workshop begins taking you through some real-world applications of AI. You'll explore the layers of a data lake and get to grips with security, scalability, and maintainability. With the help of hands-on exercises, you'll learn how to define the requirements for AI applications in your organization. This AI book will show you how to select a database for your system and run common queries on databases such as MySQL, MongoDB, and Cassandra. You'll also design your own AI trading system to get a feel of the pipeline-based architecture. As you learn to implement a deep Q-learning algorithm to play the CartPole game, you'll gain hands-on experience with PyTorch. Finally, you'll explore ways to run machine learning models in production as part of an AI application. By the end of the book, you'll have learned how to build and deploy your own AI software at scale, using various tools, API frameworks, and serialization methods. What you will learn Get to grips with the fundamentals of artificial intelligence Understand the importance of data storage and architecture in AI applications Build data storage and workflow management systems with open source tools Containerize your AI applications with tools such as Docker Discover commonly used data storage solutions and best practices for AI on Amazon Web Services (AWS) Use the AWS CLI and AWS SDK to perform common data tasks Who this book is for If you are looking to develop the data storage skills needed for machine learning and AI and want to learn AI best practices in data engineering, this workshop is for you. Experienced programmers can use this book to advance their career in AI. Familiarity with programming, along with knowledge of exploratory data analysis and reading and writing files using Python will help you to understand the key concepts covered. Computers

Mastering Palo Alto Networks Set up next-generation firewalls from Palo Alto Networks and get to grips with configuring and troubleshooting using the PAN-OS platform Key Features Understand how to optimally use PAN-OS features Build firewall solutions to safeguard local, cloud, and mobile networks Protect your infrastructure and users by implementing robust threat prevention solutions Book Description To safeguard against security threats, it is crucial to ensure that your organization is effectively secured across networks, mobile devices, and the cloud. Palo Alto Networks' integrated platform makes it easy to manage network and cloud security along with endpoint protection and a wide range of security services. With this book, you'll understand Palo Alto Networks and learn how to implement essential techniques, right from deploying firewalls through to advanced troubleshooting. The book starts by showing you how to set up and configure the Palo Alto Networks firewall, helping you to understand the technology and appreciate the simple, yet powerful, PAN-OS platform. Once you've explored the web interface and command-line structure, you'll be able to predict expected behavior and troubleshoot anomalies with confidence. You'll learn why and how to create strong security policies and discover how the firewall protects against encrypted threats. In addition to this, you'll get to grips with identifying users and controlling access to your network with user IDs and even prioritize traffic using quality of service (QoS). The book will show you how to enable special modes on the firewall for shared environments and extend security capabilities to smaller locations. By the end of this network security book, you'll be well-versed with advanced troubleshooting techniques and best practices recommended by an experienced security engineer and Palo Alto Networks expert. What you will learn Perform administrative tasks using the web interface and command-line interface (CLI) Explore the core technologies that will help you boost your network security Discover best practices and considerations for configuring security policies Run and interpret troubleshooting and debugging commands Manage firewalls through Panorama to reduce administrative workloads Protect your network from malicious traffic via threat prevention Who this book is for This book is for network engineers, network security analysts, and security professionals who want to understand and deploy Palo Alto Networks in their infrastructure. Anyone looking for in-depth knowledge of Palo Alto Network technologies, including those who currently use Palo Alto Network products, will find this book useful. Intermediate-level network administration knowledge is necessary to get started with this cybersecurity book. Computers

Soft Numerical Computing in Uncertain Dynamic Systems Soft Numerical Computing in Uncertain Dynamic Systems is intended for system specialists interested in dynamic systems that operate at different time scales. The book discusses several types of errors and their propagation, covering numerical methods—including convergence and consistence properties and characteristics—and proving of related theorems within the setting of soft computing. Several types of uncertainty representation like interval, fuzzy, type 2 fuzzy, granular, and combined uncertain sets are discussed in detail. The book can be used by engineering students in control and finite element fields, as well as all engineering, applied mathematics, economics, and computer science students. One of the important topics in applied science is dynamic systems and their applications. The authors develop these models and deliver solutions with the aid of numerical methods. Since they are inherently uncertain, soft computations are of high relevance here. This is the reason behind investigating soft numerical computing in dynamic systems. If these systems are involved with complex-uncertain data, they will be more practical and important. Real-life problems work with this type of data and most of them cannot be solved exactly and easily—sometimes they are impossible to solve. Clearly, all the numerical methods need to consider error of approximation. Other important applied topics involving uncertain dynamic systems include image processing and pattern recognition, which can benefit from uncertain dynamic systems as well. In fact, the main objective is to determine the coefficients of a matrix that acts as the frame in the image. One of the effective methods exhibiting high accuracy is to use finite differences to fill the cells of the matrix. Explores dynamic models, how time is fundamental to the structure of the model and data, and how a process unfolds Investigates the dynamic relationships between multiple components of a system in modeling using mathematical models and the concept of stability in uncertain environments Exposes readers to many soft numerical methods to simulate the solution function’s behavior Computers

The Statistics and Calculus with Python Workshop With examples and activities that help you achieve real results, applying calculus and statistical methods relevant to advanced data science has never been so easy Key Features Discover how most programmers use the main Python libraries when performing statistics with Python Use descriptive statistics and visualizations to answer business and scientific questions Solve complicated calculus problems, such as arc length and solids of revolution using derivatives and integrals Book Description Are you looking to start developing artificial intelligence applications? Do you need a refresher on key mathematical concepts? Full of engaging practical exercises, The Statistics and Calculus with Python Workshop will show you how to apply your understanding of advanced mathematics in the context of Python. The book begins by giving you a high-level overview of the libraries you'll use while performing statistics with Python. As you progress, you'll perform various mathematical tasks using the Python programming language, such as solving algebraic functions with Python starting with basic functions, and then working through transformations and solving equations. Later chapters in the book will cover statistics and calculus concepts and how to use them to solve problems and gain useful insights. Finally, you'll study differential equations with an emphasis on numerical methods and learn about algorithms that directly calculate values of functions. By the end of this book, you'll have learned how to apply essential statistics and calculus concepts to develop robust Python applications that solve business challenges. What you will learn Get to grips with the fundamental mathematical functions in Python Perform calculations on tabular datasets using pandas Understand the differences between polynomials, rational functions, exponential functions, and trigonometric functions Use algebra techniques for solving systems of equations Solve real-world problems with probability Solve optimization problems with derivatives and integrals Who this book is for If you are a Python programmer who wants to develop intelligent solutions that solve challenging business problems, then this book is for you. To better grasp the concepts explained in this book, you must have a thorough understanding of advanced mathematical concepts, such as Markov chains, Euler's formula, and Runge-Kutta methods as the book only explains how these techniques and concepts can be implemented in Python. Computers

The Reinforcement Learning Workshop Start with the basics of reinforcement learning and explore deep learning concepts such as deep Q-learning, deep recurrent Q-networks, and policy-based methods with this practical guide Key Features Use TensorFlow to write reinforcement learning agents for performing challenging tasks Learn how to solve finite Markov decision problems Train models to understand popular video games like Breakout Book Description Various intelligent applications such as video games, inventory management software, warehouse robots, and translation tools use reinforcement learning (RL) to make decisions and perform actions that maximize the probability of the desired outcome. This book will help you to get to grips with the techniques and the algorithms for implementing RL in your machine learning models. Starting with an introduction to RL, you'll be guided through different RL environments and frameworks. You'll learn how to implement your own custom environments and use OpenAI baselines to run RL algorithms. Once you've explored classic RL techniques such as Dynamic Programming, Monte Carlo, and TD Learning, you'll understand when to apply the different deep learning methods in RL and advance to deep Q-learning. The book will even help you understand the different stages of machine-based problem-solving by using DARQN on a popular video game Breakout. Finally, you'll find out when to use a policy-based method to tackle an RL problem. By the end of The Reinforcement Learning Workshop, you'll be equipped with the knowledge and skills needed to solve challenging problems using reinforcement learning. What you will learn Use OpenAI Gym as a framework to implement RL environments Find out how to define and implement reward function Explore Markov chain, Markov decision process, and the Bellman equation Distinguish between Dynamic Programming, Monte Carlo, and Temporal Difference Learning Understand the multi-armed bandit problem and explore various strategies to solve it Build a deep Q model network for playing the video game Breakout Who this book is for If you are a data scientist, machine learning enthusiast, or a Python developer who wants to learn basic to advanced deep reinforcement learning algorithms, this workshop is for you. A basic understanding of the Python language is necessary. Computers

Semantic Modeling for Data What value does semantic data modeling offer? As an information architect or data science professional, let’s say you have an abundance of the right data and the technology to extract business gold—but you still fail. The reason? Bad data semantics. In this practical and comprehensive field guide, author Panos Alexopoulos takes you on an eye-opening journey through semantic data modeling as applied in the real world. You’ll learn how to master this craft to increase the usability and value of your data and applications. You’ll also explore the pitfalls to avoid and dilemmas to overcome for building high-quality and valuable semantic representations of data. Understand the fundamental concepts, phenomena, and processes related to semantic data modeling Examine the quirks and challenges of semantic data modeling and learn how to effectively leverage the available frameworks and tools Avoid mistakes and bad practices that can undermine your efforts to create good data models Learn about model development dilemmas, including representation, expressiveness and content, development, and governance Organize and execute semantic data initiatives in your organization, tackling technical, strategic, and organizational challenges Computers

Cassandra Imagine what you could do if scalability wasn't a problem. With this hands-on guide, you’ll learn how the Cassandra database management system handles hundreds of terabytes of data while remaining highly available across multiple data centers. This third edition—updated for Cassandra 4.0—provides the technical details and practical examples you need to put this database to work in a production environment. Authors Jeff Carpenter and Eben Hewitt demonstrate the advantages of Cassandra’s nonrelational design, with special attention to data modeling. If you’re a developer, DBA, or application architect looking to solve a database scaling issue or future-proof your application, this guide helps you harness Cassandra’s speed and flexibility. Understand Cassandra’s distributed and decentralized structure Use the Cassandra Query Language (CQL) and cqlsh—the CQL shell Create a working data model and compare it with an equivalent relational model Develop sample applications using client drivers for languages including Java, Python, and Node.js Explore cluster topology and learn how nodes exchange data Computers

HCISPP HealthCare Information Security and Privacy Practitioner All-in-One Exam Guide HCISPP® HealthCare Information Security and Privacy Practitioner All-in-One Exam Guide Prepare for the current release of the HealthCare Information Security and Privacy Practitioner (HCISPP) exam using the detailed information contained in this effective self-study resource. Written by a healthcare information security and privacy expert and a founding contributor to the HCISPP credential, HCISPP HealthCare Information Security and Privacy Practitioner All-in-One Exam Guide contains complete coverage of all seven security and privacy exam domains along with examples and practice questions that closely match those on the actual test. Designed to help you pass the rigorous exam with ease, this guide also serves as an ideal on-the-job reference. Covers all exam domains: Healthcare industry Information governance in healthcare Information technologies in healthcare Regulatory and standards environment Privacy and security in healthcare Risk management and risk assessment Third-party risk management Online content includes: 250 practice exam questions Test engine that provides full-length practice exams and customizable quizzes Computers

CompTIA Cybersecurity Analyst (CySA+) CS0-002 Cert Guide CompTIA Cybersecurity Analyst (CySA+) CS0-002 Cert Guide is a best-of-breed exam study guide. Expert technology instructor and certification author Troy McMillan shares preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. Material is presented in a concise manner, focusing on increasing your understanding and retention of exam topics. The book presents you with an organized test-preparation routine through the use of proven series elements and techniques. Exam topic lists make referencing easy. Chapter-ending Exam Preparation Tasks help you drill on key concepts you must know thoroughly. Review questions help you assess your knowledge, and a final preparation chapter guides you through tools and resources to help you craft your final study plan. The companion website contains the powerful Pearson Test Prep practice test software, complete with hundreds of exam-realistic questions. The assessment engine offers you a wealth of customization options and reporting features, laying out a complete assessment of your knowledge to help you focus your study where it is needed most. Well regarded for its level of detail, assessment features, and challenging review questions and exercises, this CompTIA approved study guide helps you master the concepts and techniques that will enable you to succeed on the exam the first time. Computers

Cisco Software-Defined Wide Area Networks This is the eBook edition of Cisco Software-Defined Wide-Area Networks. This eBook does not include access to the companion website with practice exam that comes with the print edition. Access to the video mentoring is available through product registration at Cisco Press; or see the instructions in the back pages of your eBook. This study guide from Cisco Press will help you learn, prepare, and practice for exam success. This guide is built with the objective of providing assessment, review, and practice to help ensure you are prepared for your certification exam. Master Cisco Implementing Cisco SD-WAN Solutions (ENSDWI 300-415) exam topics Assess your knowledge with chapter-opening quizzes Review key concepts with exam preparation tasks Cisco Software-Defined Wide-Area Networks presents you with an organized test preparation routine using proven series elements and techniques. Key Topic tables help you drill on key concepts you must know thoroughly. Chapter-ending Review Questions help you to review what you learned in the chapter. Cisco Software-Defined Wide-Area Networks focuses specifically on the objectives for the Implementing Cisco SD-WAN Solutions (ENSDWI 300-415) exam. Four leading Cisco technology experts share preparation hints and test-taking tips, helping you improve both your conceptual knowledge and hands-on skills. Material is presented in a concise manner, focusing on increasing your understanding and retention of exam topics. Well regarded for its level of detail, assessment features, comprehensive design scenarios, this study guide helps you master the concepts and techniques that will enable you to succeed on the exam the first time. The official study guide helps you master all the topics on the Implementing Cisco SD-WAN Solutions (ENSDWI 300-415) exam, including: Architecture Controller Deployment Router Deployment Policies Security and Quality of Service Management and Operations Cisco Software-Defined Wide-Area Networks is part of a recommended learning path from Cisco that includes simulation and hands-on training from authorized Cisco Learning Partners and self-study products from Cisco Press. To find out more about instructor-led training, e-learning, and hands-on instruction offered by authorized Cisco Learning Partners worldwide, please visit http://www.cisco.com/web/learning/index.html Computers

Unity 2020 Virtual Reality Projects Explore the latest features of Unity and build VR experiences including first-person interactions, audio fireball games, 360-degree media, art gallery tours, and VR storytelling Key Features Discover step-by-step instructions and best practices to begin your VR development journey Explore Unity features such as URP rendering, XR Interaction Toolkit, and ProBuilder Build impressive VR-based apps and games that can be experienced using modern devices like Oculus Rift and Oculus Quest Book Description This third edition of the Unity Virtual Reality (VR) development guide is updated to cover the latest features of Unity 2019.4 or later versions - the leading platform for building VR games, applications, and immersive experiences for contemporary VR devices. Enhanced with more focus on growing components, such as Universal Render Pipeline (URP), extended reality (XR) plugins, the XR Interaction Toolkit package, and the latest VR devices, this edition will help you to get up to date with the current state of VR. With its practical and project-based approach, this book covers the specifics of virtual reality development in Unity. You'll learn how to build VR apps that can be experienced with modern devices from Oculus, VIVE, and others. This virtual reality book presents lighting and rendering strategies to help you build cutting-edge graphics, and explains URP and rendering concepts that will enable you to achieve realism for your apps. You'll build real-world VR experiences using world space user interface canvases, locomotion and teleportation, 360-degree media, and timeline animation, as well as learn about important VR development concepts, best practices, and performance optimization and user experience strategies. By the end of this Unity book, you'll be fully equipped to use Unity to develop rich, interactive virtual reality experiences. What you will learn Understand the current state of virtual reality and VR consumer products Get started with Unity by building a simple diorama scene using Unity Editor and imported assets Configure your Unity VR projects to run on VR platforms such as Oculus, SteamVR, and Windows immersive MR Design and build a VR storytelling animation with a soundtrack and timelines Implement an audio fireball game using game physics and particle systems Use various software patterns to design Unity events and interactable components Discover best practices for lighting, rendering, and post-processing Who this book is for Whether you're a non-programmer unfamiliar with 3D computer graphics or experienced in both but new to virtual reality, if you're interested in building your own VR games or applications, this Unity book is for you. Any experience in Unity will be useful but is not necessary. Computers

Applied Deep Learning and Computer Vision for Self-Driving Cars Explore self-driving car technology using deep learning and artificial intelligence techniques and libraries such as TensorFlow, Keras, and OpenCV Key Features Build and train powerful neural network models to build an autonomous car Implement computer vision, deep learning, and AI techniques to create automotive algorithms Overcome the challenges faced while automating different aspects of driving using modern Python libraries and architectures Book Description Thanks to a number of recent breakthroughs, self-driving car technology is now an emerging subject in the field of artificial intelligence and has shifted data scientists' focus to building autonomous cars that will transform the automotive industry. This book is a comprehensive guide to use deep learning and computer vision techniques to develop autonomous cars. Starting with the basics of self-driving cars (SDCs), this book will take you through the deep neural network techniques required to get up and running with building your autonomous vehicle. Once you are comfortable with the basics, you'll delve into advanced computer vision techniques and learn how to use deep learning methods to perform a variety of computer vision tasks such as finding lane lines, improving image classification, and so on. You will explore the basic structure and working of a semantic segmentation model and get to grips with detecting cars using semantic segmentation. The book also covers advanced applications such as behavior-cloning and vehicle detection using OpenCV, transfer learning, and deep learning methodologies to train SDCs to mimic human driving. By the end of this book, you'll have learned how to implement a variety of neural networks to develop your own autonomous vehicle using modern Python libraries. What you will learn Implement deep neural network from scratch using the Keras library Understand the importance of deep learning in self-driving cars Get to grips with feature extraction techniques in image processing using the OpenCV library Design a software pipeline that detects lane lines in videos Implement a convolutional neural network (CNN) image classifier for traffic signal signs Train and test neural networks for behavioral-cloning by driving a car in a virtual simulator Discover various state-of-the-art semantic segmentation and object detection architectures Who this book is for If you are a deep learning engineer, AI researcher, or anyone looking to implement deep learning and computer vision techniques to build self-driving blueprint solutions, this book is for you. Anyone who wants to learn how various automotive-related algorithms are built, will also find this book useful. Python programming experience, along with a basic understanding of deep learning, is necessary to get the most of this book. Computers

Node.js Design Patterns Learn proven patterns, techniques, and tricks to take full advantage of the Node.js platform. Master well-known design principles to create applications that are readable, extensible, and that can grow big. Key Features Learn how to create solid server-side applications by leveraging the full power of Node.js 14 Understand how Node.js works and learn how to take full advantage of its core components as well as the solutions offered by its ecosystem Avoid common mistakes and use proven patterns to create production grade Node.js applications Book Description In this book, we will show you how to implement a series of best practices and design patterns to help you create efficient and robust Node.js applications with ease. We kick off by exploring the basics of Node.js, analyzing its asynchronous event driven architecture and its fundamental design patterns. We then show you how to build asynchronous control flow patterns with callbacks, promises and async/await. Next, we dive into Node.js streams, unveiling their power and showing you how to use them at their full capacity. Following streams is an analysis of different creational, structural, and behavioral design patterns that take full advantage of JavaScript and Node.js. Lastly, the book dives into more advanced concepts such as Universal JavaScript, scalability and messaging patterns to help you build enterprise-grade distributed applications. Throughout the book, you'll see Node.js in action with the help of several real-life examples leveraging technologies such as LevelDB, Redis, RabbitMQ, ZeroMQ, and many others. They will be used to demonstrate a pattern or technique, but they will also give you a great introduction to the Node.js ecosystem and its set of solutions. What you will learn Become comfortable with writing asynchronous code by leveraging callbacks, promises, and the async/await syntax Leverage Node.js streams to create data-driven asynchronous processing pipelines Implement well-known software design patterns to create production grade applications Share code between Node.js and the browser and take advantage of full-stack JavaScript Build and scale microservices and distributed systems powered by Node.js Use Node.js in conjunction with other powerful technologies such as Redis, RabbitMQ, ZeroMQ, and LevelDB Who this book is for This book is for developers and software architects who have some prior basic knowledge of JavaScript and Node.js and now want to get the most out of these technologies in terms of productivity, design quality, and scalability. Software professionals with intermediate experience in Node.js and JavaScript will also find valuable the more advanced patterns and techniques presented in this book. This book assumes that you have an intermediate understanding of web application development, databases, and software design principles. Computers

Hands-On Unity 2020 Game Development Build immersive game experiences using the new Unity 2020 features with this practical guide Key Features Unleash the capabilities of C# scripting for creating immersive UI, graphics, Game AI agents and much more Explore Unity's latest tools, including Universal Render Pipeline, Shader Graph, and VFX graph, to enhance graphics and animation Get started with building augmented reality experience using Unity's AR Foundation Book Description Over the years, the Unity game engine has extended its scope from just being about creating video games to building AR/VR experiences, complex simulations, real-time realistic rendering, films, and serious games for training and education. Its features for implementing gameplay, graphics, and customization using C# programming make Unity a comprehensive platform for developing professional-level, rich experiences. With this book, you'll be able to build impressive Unity projects in a step-by-step manner and apply your knowledge of Unity concepts to create a real-world game. Complete with hands-on tutorials and projects, this easy-to-follow guide will show you how to develop your first complete game using a variety of Unity tools. As you make progress, you'll learn how to make the most of the Unity Editor and create scripts using the C# programming language. This Unity game development book will then take you through integrating graphics, sound, and animations and manipulating physics to create impressive mechanics for your games. You'll also learn how to code a simple AI agent to challenge the user and use profiling tools to ensure that the code runs in a performant way. Finally, you'll get to grips with Unity's AR Foundation for creating AR experiences for 3D apps and games. By the end of this book, you'll have developed a complete game and will have built a solid foundation using Unity's tooling ecosystem to develop game projects of any scale. What you will learn Write scripts for customizing various aspects of a game, such as physics, gameplay, and UI Program rich shaders and effects using Unity's new Shader Graph and Universal Render Pipeline Implement postprocessing to increase graphics quality with full-screen effects Create rich particle systems for your Unity games from scratch using VFX Graph and Shuriken Add animations to your game using the Animator, Cinemachine, and Timeline Implement game artificial intelligence (AI) to control character behavior Detect and fix optimization issues using profilers and batching Who this book is for This book is for game developers looking to migrate to the Unity game engine. If you are a developer with some exposure to Unity, this book will help you explore its latest features. Prior experience with C# programming is required to get the most out of the book. Computers

The Computer Vision Workshop Explore the potential of deep learning techniques in computer vision applications using the Python ecosystem, and build real-time systems for detecting human behavior Key Features Understand OpenCV and select the right algorithm to solve real-world problems Discover techniques for image and video processing Learn how to apply face recognition in videos to automatically extract key information Book Description Computer Vision (CV) has become an important aspect of AI technology. From driverless cars to medical diagnostics and monitoring the health of crops to fraud detection in banking, computer vision is used across all domains to automate tasks. The Computer Vision Workshop will help you understand how computers master the art of processing digital images and videos to mimic human activities. Starting with an introduction to the OpenCV library, you'll learn how to write your first script using basic image processing operations. You'll then get to grips with essential image and video processing techniques such as histograms, contours, and face processing. As you progress, you'll become familiar with advanced computer vision and deep learning concepts, such as object detection, tracking, and recognition, and finally shift your focus from 2D to 3D visualization. This CV course will enable you to experiment with camera calibration and explore both passive and active canonical 3D reconstruction methods. By the end of this book, you'll have developed the practical skills necessary for building powerful applications to solve computer vision problems. What you will learn Access and manipulate pixels in OpenCV using BGR and grayscale images Create histograms to better understand image content Use contours for shape analysis, object detection, and recognition Track objects in videos using a variety of trackers available in OpenCV Discover how to apply face recognition tasks using computer vision techniques Visualize 3D objects in point clouds and polygon meshes using Open3D Who this book is for If you are a researcher, developer, or data scientist looking to automate everyday tasks using computer vision, this workshop is for you. A basic understanding of Python and deep learning will help you to get the most out of this workshop. Computers

CompTIA CySA+ Practice Tests Efficiently prepare yourself for the demanding CompTIA CySA+ exam CompTIA CySA+ Practice Tests: Exam CS0-002, 2nd Edition offers readers the fastest and best way to prepare for the CompTIA Cybersecurity Analyst exam. With five unique chapter tests and two additional practice exams for a total of 1000 practice questions, this book covers topics including: Threat and Vulnerability Management Software and Systems Security Security Operations and Monitoring Incident Response Compliance and Assessment The new edition of CompTIA CySA+ Practice Tests is designed to equip the reader to tackle the qualification test for one of the most sought-after and in-demand certifications in the information technology field today. The authors are seasoned cybersecurity professionals and leaders who guide readers through the broad spectrum of security concepts and technologies they will be required to master before they can achieve success on the CompTIA CySA exam. The book also tests and develops the critical thinking skills and judgment the reader will need to demonstrate on the exam. Computers

Artificial Intelligence Business The concise guide to artificial intelligence for business people and commercially oriented data scientists Key Features Find out how artificial intelligence is shaping the future of businesses Discover how AI influences the society and its politics and economy Explore the future of AI and its applications Book Description We're living in revolutionary times. Artificial intelligence is changing how the world operates and it determines how smooth certain processes are. For instance, when you go on a holiday, multiple services allow you to find the most convenient flights and the best hotels, you get personalized suggestions on what you might want to see, and you go to the airport via one of the ride-sharing apps. At each of these steps, AI algorithms are at work for your convenience. This book will guide you through everything, from what AI is to how it influences our economy and society. The book starts with an introduction to artificial intelligence and machine learning, and explains the importance of AI in the modern world. You'll explore how start-ups make key decisions with AI and how AI plays a major role in boosting businesses. Next, you'll find out how media companies use image generation techniques to create engaging content. As you progress, you'll explore how text generation and AI chatbot models simplify our daily lives. Toward the end, you'll understand the importance of AI in the education and healthcare sectors, and realize the risks associated with AI and how we can leverage AI effectively to help us in the future. By the end of this book, you'll have learned how machine learning works and have a solid understanding of the recent business applications of AI. What you will learn Find out how AI helps in building innovative cultures in enterprises Understand how AI boosts start-ups Discover modern AI trends in the field of manufacturing and logistics Explore the benefits of text and image generation applications Study popular machine learning trends and their usage Uncover the uses of AI in politics and society Who this book is for This book is for artificial intelligence enthusiasts or anyone with a business background who wants to learn how AI can scale up businesses. Computers

Ubuntu 20.04 Essentials Explore the potential of Ubuntu 20.04 to manage your local machine and external servers with ease Key Features Learn how to install Ubuntu on a clean disk drive and with the network installer Find out how to set up a firewall to protect your system from vulnerable attacks Explore file-sharing services such as Samba and NFS to share files from Ubuntu to third-party systems Book Description Ubuntu is undeniably one of the most highly regarded and widely used Debian-based Linux distributions available today. Thanks to its ease of use and reliability, Ubuntu has a loyal following of Linux users and an active community of developers. Ubuntu 20.04 Essentials is designed to take you through the installation, use, and administration of the Ubuntu 20.04 distribution in detail. For beginners, the book covers topics such as operating system installation, the basics of the GNOME desktop environment, configuring email and web servers, and installing packages and system updates. Additional installation topics such as dual booting with Microsoft Windows are also covered along with crucial security topics such as configuring a firewall and user and group administration. For the experienced user, the book delves into topics such as remote desktop access, the Cockpit web interface, logical volume management (LVM), disk partitioning, and swap management. Further, it also explores KVM virtualization, Secure Shell (SSH), Linux containers, and file sharing using both Samba and NFS to provide a thorough overview of this enterprise-class operating system. What you will learn Get to grips with the process of installing and booting Ubuntu Configure SSH key-based authentication on Ubuntu Create KVM virtual machines using Cockpit and the Virtual Machine Manager (VMM) Install, run, and manage containers on Ubuntu Send and receive emails using a third-party SMTP relay server Add a new disk to an Ubuntu volume group and logical volume Who this book is for If you are into network engineering or system administration or are a Linux enthusiast looking to get hands-on with Ubuntu 20.04 to manage local and virtual machines, this book is for you. A solid understanding of basic Linux commands and knowledge of Ubuntu is recommended. Computers

Smartphones within Psychological Science Find out how the common smartphone is challenging and transforming psychological science. Computers

Numerical Methods in Physics with Python A standalone text for courses on computational physics combining idiomatic Python, foundational numerical methods, and physics applications. Computers

Machine Learning in Chemistry This book provides practical examples of machine learning applied to science to help researchers make an informed choice about using the method in chemistry. Computers

Software Development in Practice This book is a pragmatic guide to software development in practice. It explores the inner workings of software development in the context of the industry, covering good practice for software developers and providing you with tools and practical understanding you'll need to advance within the software development world. Computers

Unity 2020 Mobile Game Development A practical guide on how to use Unity for building cross-platform mobile games and Augmented Reality apps using the latest Unity 2020 toolset Key Features Create, deploy, and monetize captivating and immersive games on Android and iOS platforms Take your games into the real world by adding augmented reality features to your mobile projects Kick-start your mobile game development journey with step-by-step instructions and a demo game project Book Description Unity 2020 brings a lot of new features that can be harnessed for building powerful games for popular mobile platforms. This updated second edition delves into Unity development, covering the new features of Unity, modern development practices, and augmented reality (AR) for creating an immersive mobile experience. The book takes a step-by-step approach to building an endless runner game using Unity to help you learn the concepts of mobile game development. This new edition also covers AR features and explains how to implement them using ARCore and ARKit with Unity. The book explores the new mobile notification package and helps you add notifications for your games. You'll learn how to add touch gestures and design UI elements that can be used in both landscape and portrait modes at different resolutions. The book then covers the best ways to monetize your games using Unity Ads and in-app purchases before you learn how to integrate your game with various social networks. Next, using Unity's analytics tools, you'll enhance your game by gaining insights into how players like and use your game. Finally, you'll take your games into the real world by implementing AR capabilities and publishing them on both Android and iOS app stores. By the end of this book, you will have learned Unity tools and techniques and be able to use them to build robust cross-platform mobile games. What you will learn Design responsive user interfaces for your mobile games Detect collisions, receive user input, and create player movements for your mobile games Create interesting gameplay elements using inputs from your mobile device Explore the mobile notification package in Unity game engine to keep players engaged Create interactive and visually appealing content for Android and iOS devices Monetize your game projects using Unity Ads and in-app purchases Who this book is for If you are a game developer or mobile developer who wants to learn Unity and use it to build mobile games for iOS and Android, then this Unity book is for you. Prior knowledge of C# and Unity will be beneficial but is not mandatory. Computers

Learn Linux Quickly Learn over 116 Linux commands to develop the skills you need to become a professional Linux system administrator Key Features Explore essential Linux commands and understand how to use Linux help tools Discover the power of task automation with bash scripting and Cron jobs Get to grips with various network configuration tools and disk management techniques Book Description Linux is one of the most sought-after skills in the IT industry, with jobs involving Linux being increasingly in demand. Linux is by far the most popular operating system deployed in both public and private clouds; it is the processing power behind the majority of IoT and embedded devices. Do you use a mobile device that runs on Android? Even Android is a Linux distribution. This Linux book is a practical guide that lets you explore the power of the Linux command-line interface. Starting with the history of Linux, you'll quickly progress to the Linux filesystem hierarchy and learn a variety of basic Linux commands. You'll then understand how to make use of the extensive Linux documentation and help tools. The book shows you how to manage users and groups and takes you through the process of installing and managing software on Linux systems. As you advance, you'll discover how you can interact with Linux processes and troubleshoot network problems before learning the art of writing bash scripts and automating administrative tasks with Cron jobs. In addition to this, you'll get to create your own Linux commands and analyze various disk management techniques. By the end of this book, you'll have gained the Linux skills required to become an efficient Linux system administrator and be able to manage and work productively on Linux systems. What you will learn Master essential Linux commands and analyze the Linux filesystem hierarchy Find out how to manage users and groups in Linux Analyze Linux file ownership and permissions Automate monotonous administrative tasks with Cron jobs and bash scripts Use aliases to create your own Linux commands Understand how to interact with and manage Linux processes Become well-versed with using a variety of Linux networking commands Perform disk partitioning, mount filesystems, and create logical volumes Who this book is for This book doesn't assume any prior Linux knowledge, which makes it perfect for beginners. Intermediate and advanced Linux users will also find this book very useful as it covers a wide range of topics necessary for Linux administration. Computers

Hands-On Graph Analytics with Neo4j Discover how to use Neo4j to identify relationships within complex and large graph datasets using graph modeling, graph algorithms, and machine learning Key Features Get up and running with graph analytics with the help of real-world examples Explore various use cases such as fraud detection, graph-based search, and recommendation systems Get to grips with the Graph Data Science library with the help of examples, and use Neo4j in the cloud for effective application scaling Book Description Neo4j is a graph database that includes plugins to run complex graph algorithms. The book starts with an introduction to the basics of graph analytics, the Cypher query language, and graph architecture components, and helps you to understand why enterprises have started to adopt graph analytics within their organizations. You'll find out how to implement Neo4j algorithms and techniques and explore various graph analytics methods to reveal complex relationships in your data. You'll be able to implement graph analytics catering to different domains such as fraud detection, graph-based search, recommendation systems, social networking, and data management. You'll also learn how to store data in graph databases and extract valuable insights from it. As you become well-versed with the techniques, you'll discover graph machine learning in order to address simple to complex challenges using Neo4j. You will also understand how to use graph data in a machine learning model in order to make predictions based on your data. Finally, you'll get to grips with structuring a web application for production using Neo4j. By the end of this book, you'll not only be able to harness the power of graphs to handle a broad range of problem areas, but you'll also have learned how to use Neo4j efficiently to identify complex relationships in your data. What you will learn Become well-versed with Neo4j graph database building blocks, nodes, and relationships Discover how to create, update, and delete nodes and relationships using Cypher querying Use graphs to improve web search and recommendations Understand graph algorithms such as pathfinding, spatial search, centrality, and community detection Find out different steps to integrate graphs in a normal machine learning pipeline Formulate a link prediction problem in the context of machine learning Implement graph embedding algorithms such as DeepWalk, and use them in Neo4j graphs Who this book is for This book is for data analysts, business analysts, graph analysts, and database developers looking to store and process graph data to reveal key data insights. This book will also appeal to data scientists who want to build intelligent graph applications catering to different domains. Some experience with Neo4j is required. Computers

CISA – Certified Information Systems Auditor Study Guide This CISA study guide is for those interested in achieving CISA certification and provides complete coverage of ISACA's latest CISA Review Manual (2019) with practical examples and over 850 exam-oriented practice questions Key Features Gain tactical skills in auditing, control, and security to pass the CISA examination Get up to speed with auditing business IT systems Increase your value to organizations and be at the forefront of an evolving business landscape by achieving CISA certification Book Description Are you looking to prepare for the CISA exam and understand the roles and responsibilities of an information systems (IS) auditor? The CISA - Certified Information Systems Auditor Study Guide is here to help you get started with CISA exam prep. This book covers all the five CISA domains in detail to help you pass the exam. You'll start by getting up and running with the practical aspects of an information systems audit. The book then shows you how to govern and manage IT, before getting you up to speed with acquiring information systems. As you progress, you'll gain knowledge of information systems operations and understand how to maintain business resilience, which will help you tackle various real-world business problems. Finally, you'll be able to assist your organization in effectively protecting and controlling information systems with IT audit standards. By the end of this CISA book, you'll not only have covered the essential concepts and techniques you need to know to pass the CISA certification exam but also have the ability to apply them in the real world. What you will learn Understand the information systems auditing process Get to grips with IT governance and management Gain knowledge of information systems acquisition Assist your organization in protecting and controlling information systems with IT audit standards Understand information systems operations and how to ensure business resilience Evaluate your organization's security policies, standards, and procedures to meet its objectives Who this book is for This CISA exam study guide is designed for those with a non-technical background who are interested in achieving CISA certification and are currently employed or looking to gain employment in IT audit and security management positions. Computers

Learning C# by Developing Games with Unity 2020 Get to grips with coding in C# and build simple 3D games with Unity from the ground up with this updated fifth edition of the bestselling guide Key Features Understand C# programming basics, terminology, and coding best practices Put your knowledge of C# concepts into practice by building a fun and playable game Come away with a clear direction for taking your C# programming and Unity game development skills to the next level Book Description Over the years, the Learning C# by Developing Games with Unity series has established itself as a popular choice for getting up to speed with C#, a powerful and versatile programming language that can be applied in a wide array of application areas. This book presents a clear path for learning C# programming from the ground up without complex jargon or unclear programming logic, all while building a simple game with Unity. This fifth edition has been updated to introduce modern C# features with the latest version of the Unity game engine, and a new chapter has been added on intermediate collection types. Starting with the basics of software programming and the C# language, you'll learn the core concepts of programming in C#, including variables, classes, and object-oriented programming. Once you've got to grips with C# programming, you'll enter the world of Unity game development and discover how you can create C# scripts for simple game mechanics. Throughout the book, you'll gain hands-on experience with programming best practices to help you take your Unity and C# skills to the next level. By the end of this book, you'll be able to leverage the C# language to build your own real-world Unity game development projects. What you will learn Discover easy-to-follow steps and examples for learning C# programming fundamentals Get to grips with creating and implementing scripts in Unity Create basic game mechanics such as player controllers and shooting projectiles using C# Understand the concepts of interfaces and abstract classes Leverage the power of the latest C# features to solve complex programming problems Become familiar with stacks, queues, exceptions, error handling, and other core C# concepts Explore the basics of artificial intelligence (AI) for games and implement them to control enemy behavior Who this book is for If you're a developer, programmer, hobbyist, or anyone who wants to get started with C# programming in a fun and engaging manner, this book is for you. Prior experience in programming or Unity is not required. Computers

The React Workshop Work through engaging exercises and activities and gain practical skills to make your web applications function effortlessly with the help of React Key Features Explore the React environment by creating live projects Solve real-world problems relating to building modern web applications Gain a thorough understanding of how data moves through different React components Book Description Are you interested in how React takes command of the view layer for web and mobile apps and changes the data of large web applications without needing to reload the page? This workshop will help you learn how and show you how to develop and enhance web apps using the features of the React framework with interesting examples and exercises. The workshop starts by demonstrating how to create your first React project. You'll tap into React's popular feature JSX to develop templates and use DOM events to make your project interactive. Next, you'll focus on the lifecycle of the React component and understand how components are created, mounted, unmounted, and destroyed. Later, you'll create and customize components to understand the data flow in React and how props and state communicate between components. You'll also use Formik to create forms in React to explore the concept of controlled and uncontrolled components and even play with React Router to navigate between React components. The chapters that follow will help you build an interesting image-search app to fetch data from the outside world and populate the data to the React app. Finally, you'll understand what ref API is and how it is used to manipulate DOM in an imperative way. By the end of this React book, you'll have the skills you need to set up and create web apps using React. What you will learn Use JSX to include logic in the view layer of applications Get familiar with the important methods and events in the React lifecycle Distinguish between class and functional component syntaxes Create forms with Formik and handle errors Understand the React Hooks API and the problems it can solve Fetch outside data using the Axios library and populate the data to the app Who this book is for The React Workshop is for web developers and programmers who are looking to learn React and use it for creating and enhancing web applications. Although the workshop is for beginners, prior knowledge of JavaScript programming and HTML and CSS is necessary to easily understand the concepts that are covered. Computers

Learning Dapr Get the authoritative guide to Dapr, the distributed application runtime that works with new and existing programming languages alike. Written by the model’s creators, this introduction shows you how Dapr not only unifies stateless, stateful, and actor programming models but also runs everywhere—in the cloud or on the edge. Authors Haishi Bai and Yaron Schneider, both with Microsoft’s Azure CTO team, explain that, with Dapr, you don’t need to include any SDKs or libraries in your user code. Instead, you automatically get flexible binding, state management, the actor pattern, pub-sub, reliable messaging, and many more features. This book shows developers, architects, CIOs, students, and computing enthusiasts how to get started with Dapr. Learn the new programming model for cloud native applications Write high-performance distributed applications without drilling into technical details Use Dapr with any language or framework to write microservices easily Learn how Dapr provides consistency and portability through open APIs and extensible, community-driven components Explore how Dapr handles state, resource bindings, and pub-sub messaging to enable resilient event-driven architectures that scale Integrate cloud applications with various SaaS offerings, such as machine learning Computers

Data Orchestration in Deep Learning Accelerators This Synthesis Lecture focuses on techniques for efficient data orchestration within DNN accelerators. The End of Moore's Law, coupled with the increasing growth in deep learning and other AI applications has led to the emergence of custom Deep Neural Network (DNN) accelerators for energy-efficient inference on edge devices. Modern DNNs have millions of hyper parameters and involve billions of computations; this necessitates extensive data movement from memory to on-chip processing engines. It is well known that the cost of data movement today surpasses the cost of the actual computation; therefore, DNN accelerators require careful orchestration of data across on-chip compute, network, and memory elements to minimize the number of accesses to external DRAM. The book covers DNN dataflows, data reuse, buffer hierarchies, networks-on-chip, and automated design-space exploration. It concludes with data orchestration challenges with compressed and sparse DNNs and future trends. The target audience is students, engineers, and researchers interested in designing high-performance and low-energy accelerators for DNN inference. Computers

The In-House Option Here is a timely book that expertly addresses the current impact of automation on the profession of librarianship in terms of its practitioners, standards, and underlying philosophy. In clear and understandable language, author T. D. Webb focuses his discussion--with practical examples--on the important decision of the location of the computer--at the library site or a remote automation center. Designed to be a practical guide to host computer location, this articulate book also addresses the broad professional issues of library automation. Computers

Electronic Resources The universe of electronic resources is indeed diverse, expansive, intimidating, and unstructured compared to the finite, prepackaged print world upon which the information delivery infrastructure has been constructed. Electronic Resources: Selection and Bibliographic Control addresses the resultant concerns of information professionals as they struggle to define, select, and control electronic resources in libraries and information centers today. This book offers readers an overview of issues and provides a common ground for deliberations and decisionmaking. Librarians and students concerned with the Internet and related issues will appreciate the broad scope and in-depth discussions in Electronic Resources: Selection and Bibliographic Control. From both conceptual and pragmatic standpoints, this book enlightens the reader on such topics as: Internet resources the relationship between OPAC and Internet Standard Generalized Markup Language (SGML) versus USMARC Text Encoding Initiative (TEI) Core Language and the Information Bus Dublin Core Metadata as a discovery/retrieval tool decision-making matrix model e-texts and e-theses digital materials and digital libraries This book also gives the reader an inside look at a number of specific emerging projects from around the world. Highlighted here are the CATRIONA project from the U.K.--designing an Internet discovery and retrieval system; the ALCUIN project--using traditional infrastructure to handle Internet resources; the Center for Electronic Texts in the Humanities (CETH) and the Electronic Text Center at the University of Virginia; the OCLC Internet Cataloging project; and the National Digital Library Program (NDLP), Encoded Archival Description (EAD), and electronic CIP projects at the Library of Congress. Electronic Resources: Selection and Bibliographic Control clearly illustrates the evolving role of librarian fro Computers

SRE with Java Microservices In a microservices architecture, the whole is indeed greater than the sum of its parts. But in practice, individual microservices can inadvertently impact others and alter the end user experience. Effective microservices architectures require standardization on an organizational level with the help of a platform engineering team. This practical book provides a series of progressive steps that platform engineers can apply technically and organizationally to achieve highly resilient Java applications. Author Jonathan Schneider covers many effective SRE practices from companies leading the way in microservices adoption. You’ll examine several patterns discovered through much trial and error in recent years, complete with Java code examples. Chapters are organized according to specific patterns, including: Application metrics: Monitoring for availability with Micrometer Debugging with observability: Logging and distributed tracing; failure injection testing Charting and alerting: Building effective charts; KPIs for Java microservices Safe multicloud delivery: Spinnaker, deployment strategies, and automated canary analysis Source code observability: Dependency management, API utilization, and end-to-end asset inventory Traffic management: Concurrency of systems; platform, gateway, and client-side load balancing Computers

CCSP For Dummies with Online Practice Secure your CSSP certification CCSP is the world’s leading Cloud Security certification. It covers the advanced technical skills and knowledge to design, manage, and secure data, applications, and infrastructure in the cloud using best practices, policies, and procedures. If you’re a cloud security professional seeking your CSSP certification, this book is a perfect way to prepare for the exam. Covering in detail all six domains, the expert advice in this book gives you key information you'll need to pass the exam. In addition to the information covered on the exam, you'll get tips on setting up a study plan, tips for exam day, and access to an online test bank of questions. Key information for all six exam domains Test -taking and exam day tips and tricks Free online practice questions and flashcards Coverage of the core concepts From getting familiar with the core concepts to establishing a study plan, this book is all you need to hang your hat on that certification! Computers

Online Political Hate Speech in Europe Thought-provoking and timely, this book addresses the increasingly widespread issue of online political hatred in Europe. Taking an interdisciplinary approach, it examines both the contributions of new technologies, in particular social networks, to the rise of this phenomenon, and the legal and political contexts in which it is taking place. Giovanni Ziccardi also evaluates possible remedies for the situation, including both legal and technological solutions, and outlines the potential for a unified European framework to counter the spread of hatred online. Computers

Investigations and the Art of the Interview The Art of Investigative Interviewing, Fourth Edition, builds on the successes of the previous editions providing the reader guidance on conducting investigative interviews, both ethically and professionally. The book can be used by anyone who is involved in investigative interviewing. It is a perfect combination of real, practical, and effective techniques, procedures, and actual cases. The reader learns key elements of investigative interviewing, such as human psychology, proper interview preparation, tactical concepts, controlling the interview environment, and evaluating the evidence obtained from the interview. New to this edition will be coverage of Open Source Intelligence (OSINT) tools, workplace investigations, fraud investigations and the role of audit. Larry Fennelly joins original author Inge Sebyan Black, both well-known and respected in the field, providing everything an interviewer needs to know in order to conduct successful interviews with integrity and within the law. Written for anyone involved in investigative interviewing. Provides guidance on conducting investigative interviews professionally and ethically Includes instructions for obtaining voluntary confessions from suspects, victims, and witnesses Builds a foundation of effective interviewing skills with guidance on every step of the process, from preparation to evaluating evidence obtained in an interview Computers

Learn Amazon SageMaker Quickly build and deploy machine learning models without managing infrastructure, and improve productivity using Amazon SageMaker's capabilities such as Amazon SageMaker Studio, Autopilot, Experiments, Debugger, and Model Monitor Key Features Build, train, and deploy machine learning models quickly using Amazon SageMaker Analyze, detect, and receive alerts relating to various business problems using machine learning algorithms and techniques Improve productivity by training and fine-tuning machine learning models in production Book Description Amazon SageMaker enables you to quickly build, train, and deploy machine learning (ML) models at scale, without managing any infrastructure. It helps you focus on the ML problem at hand and deploy high-quality models by removing the heavy lifting typically involved in each step of the ML process. This book is a comprehensive guide for data scientists and ML developers who want to learn the ins and outs of Amazon SageMaker. You'll understand how to use various modules of SageMaker as a single toolset to solve the challenges faced in ML. As you progress, you'll cover features such as AutoML, built-in algorithms and frameworks, and the option for writing your own code and algorithms to build ML models. Later, the book will show you how to integrate Amazon SageMaker with popular deep learning libraries such as TensorFlow and PyTorch to increase the capabilities of existing models. You'll also learn to get the models to production faster with minimum effort and at a lower cost. Finally, you'll explore how to use Amazon SageMaker Debugger to analyze, detect, and highlight problems to understand the current model state and improve model accuracy. By the end of this Amazon book, you'll be able to use Amazon SageMaker on the full spectrum of ML workflows, from experimentation, training, and monitoring to scaling, deployment, and automation. What you will learn Create and automate end-to-end machine learning workflows on Amazon Web Services (AWS) Become well-versed with data annotation and preparation techniques Use AutoML features to build and train machine learning models with AutoPilot Create models using built-in algorithms and frameworks and your own code Train computer vision and NLP models using real-world examples Cover training techniques for scaling, model optimization, model debugging, and cost optimization Automate deployment tasks in a variety of configurations using SDK and several automation tools Who this book is for This book is for software engineers, machine learning developers, data scientists, and AWS users who are new to using Amazon SageMaker and want to build high-quality machine learning models without worrying about infrastructure. Knowledge of AWS basics is required to grasp the concepts covered in this book more effectively. Some understanding of machine learning concepts and the Python programming language will also be beneficial. Computers

Engineering Trustworthy Software Systems This book constitutes the refereed proceedings of the 5th International School on Engineering Trustworthy Software Systems, SETSS 2019, held in Chongqing, China, in April 2019.The five chapters in this volume provide lectures on leading-edge research in methods and tools for use in computer system engineering. The topics covered in these chapter include Seamless Model-based System Development: Foundations; From Bounded Reachability Analysis of Linear Hybrid Automata to Verification of Industrial CPS and IoT; Weakest Preexpectation Semantics for Bayesian Inference: Conditioning, Continuous Distributions and Divergence; K – A Semantic Framework for Programming Languages and Formal Analysis Tools; and Software Abstractions and Human-Cyber-Physical Systems Architecture Modelling. Computers

Basic Linux Terminal Tips and Tricks Learn command line tricks, programs, and hacks you can use day to day as a Linux user, programmer, and system administrator. When you interact with the digital world, you can’t go far without interacting with Linux systems. This book shows you how to leverage its power to serve your needs. Many users know "top" is installed on almost all Linux machines, but did you know with a few keystrokes you can customize it specifically for your needs? Stuck using `cd` and `ls` commands for navigating file systems? This book looks at how you can use Ranger to quickly navigate through multiple levels of folders, and quickly run bash commands without ever leaving the terminal. We also suggest programs that can be used for common tasks such as finding which programs are using the most processing, data download/upload, and file space. You’ll know how to quickly connect to remote machines and run your commonly needed jobs in a keystroke or even on auto-pilot. With Basic Linux Terminal Tips and Tricks you'll be equipped with a wide range of tools that can be used for daily work and maintenance on all sorts of Linux systems including servers, desktops, and even embedded devices. What You Will Learn Work with common tools on your local network. Techniques for efficient use of command line. Easily manipulate text files for processing. Monitor the state of a system with a handful of popular programs. Combine programs to create useful processes. Who This Book Is For Anyone who is interested in Linux and Unix based operating systems as a hobby or for work. Computers

Beginning Jakarta EE Web Development Start building Java-based web applications now, even if you’re a complete newcomer to Java. Comprehensive and example-driven, this book is all you need to develop dynamic Java-based web applications using JSP, connect to databases with JSF, and put them into action using the popular open source Java web server, Apache Tomcat. Beginning Jakarta EE Web Development is a comprehensive introduction to building Java-based web applications using JSP, JSF, MySQL, and the Apache Tomcat web application server. Other APIs including JSON, JSTL, and XML parser are covered along the way.Key concepts are made easy to grasp with numerous working examples and a walk-through of the development of a complete ecommerce project. This book is written for professionals by practicing Java web application professionals and experts. What You Will Learn Build Java-based web applications using JSP and JSF with Eclipse Jakarta EE Configure your database with MySQL Define XML documents for your applications Use the Apache MyFaces APIs to create JSF applications Integrate and implement JSF and JSP together Build an online ecommerce web application Who This Book Is For Programmers new to programming in Java and programming in general. Computers

Delphi Quick Syntax Reference The Delphi Quick Syntax Reference is a succinct code and syntax reference guide to Delphi. It presents the fundamental knowledge to get newcomers started with the language and provides a refresher to seasoned or returning Delphi developers. It covers all the new features added by Embarcadero during the last few years. Delphi celebrates 25 years in 2020 and, alongside the free community version that was introduced a couple of years ago, this syntax guide is a great way to get into the language. What You Will Learn Quickly use and learn Delphi Compile, build and run a Delphi program Master Delphi strings, variables, constants, and operators and how to apply them Use conditions, loops, procedures, and functions in Delphi Apply object-oriented programming in Delphi Who This Book Is For Returning or current Delphi developers: The book is a resource for reference for this group of developers especially for the new features that were introduced in the language over the last couple of years. Newcomers to the language: These developers will learn the fundamentals of the language in a very condensed and effective text that accelerates learning. Computers

Large-Scale Disk Failure Prediction This book constitutes the thoroughly refereed post-competition proceedings of the AI Ops Competition on Large-Scale Disk Failure Prediction, conducted between February 7th and May 15, 2020 on the Alibaba Cloud Tianchi Platform. A dedicated workshop, featuring the best performing teams of the competition, was held at the 24th Pacific-Asia Conference on Knowledge Discovery and Data Mining, PAKDD 2020, in Singapore, in April 2019. Due to the COVID-19 pandemic, the workshop was hosted online. This book includes 13 selected contributions: an introduction to dataset, selected approaches of the competing teams and the competition summary, describing the competition task, practical challenges, evaluation metrics, etc. Computers

Innovations and Interdisciplinary Solutions for Underserved Areas This book constitutes the refereed post-conference proceedings of the 4th EAI International Conference on Innovations and Interdisciplinary Solutions for Underserved Areas, InterSol 2020, held in Nairobi, Kenya, in March 2020. Due to the COVID-19 pandemic the conference is postponed to a later date in 2020.The 20 papers presented were selected from 50 submissions and issue different problems in underserved and unserved areas. They face problems in almost all sectors such as energy, water, communication, climate, food, education, transportation, social development, and economic growth. Computers

Financial Cryptography and Data Security This book constitutes the refereed proceedings of two workshops held at the 24th International Conference on Financial Cryptography and Data Security, FC 2020, in Kota Kinabalu, Malaysia, in February 2020. The 39 full papers and 3 short papers presented in this book were carefully reviewed and selected from 73 submissions. The papers feature four Workshops: The 1st Asian Workshop on Usable Security, AsiaUSEC 2020, the 1st Workshop on Coordination of Decentralized Finance, CoDeFi 2020, the 5th Workshop on Advances in Secure Electronic Voting, VOTING 2020, and the 4th Workshop on Trusted Smart Contracts, WTSC 2020. The AsiaUSEC Workshop contributes an increase of the scientific quality of research in human factors in security and privacy. In terms of improving efficacy of secure systems, the research included an extension of graphical password authentication. Further a comparative study of SpotBugs, SonarQube, Cryptoguard and CogniCrypt identified strengths in each and refined the need for improvements in security testing tools.The CoDeFi Workshop discuss multi-disciplinary issues regarding technologies and operations of decentralized finance based on permissionless blockchain. The workshop consists of two parts; presentations by all stakeholders, and unconference style discussions.The VOTING Workshop cover topics like new methods for risk-limited audits, new ethods to increase the efficiency of mixnets, verification of security of voting schemes election auditing, voting system efficiency, voting system usability, and new technical designs for cryptographic protocols for voting systems, and new way of preventing voteselling by de-incentivising this via smart contracts.The WTSC Workshop focuses on smart contracts, i.e., self-enforcing agreements in the form of executable programs, and other decentralized applications that are deployed to and run on top of specialized blockchains. Computers

Letters to a New Developer Learn what you need to succeed as a developer beyond the code. The lessons in this book will supercharge your career by sharing lessons and mistakes from real developers. Wouldn’t it be nice to learn from others’ career mistakes? “Soft†skills are crucial to success, but are haphazardly picked up on the job or, worse, never learned. Understanding these competencies and how to improve them will make you a more effective team member and a more attractive hire. This book will teach you the key skills you need, including how to ask questions, how and when to use common tools, and how to interact with other team members. Each will be presented in context and from multiple perspectives so you’ll be able to integrate them and apply them to your own career quickly. What You'll Learn Know when the best code is no code Understand what to do in the first month of your job See the surprising number of developers who can’t program Avoid the pitfalls of working alone Who This Book Is For Anyone who is curious about software development as a career choice. You have zero to five years of software development experience and want to learn non-technical skills that can help your career. It is also suitable for teachers and mentors who want to provide guidance to their students and/or mentees. Computers

Information Security and Privacy This book constitutes the refereed proceedings of the 25th Australasian Conference on Information Security and Privacy, ACISP 2020, held in Perth, WA, Australia, in November 2020*. The 31 revised full papers and 5 short papers presented were carefully revised and selected from 151 submissions. The papers present and discuss the latest research, trends, breakthroughs, and challenges in the domain of information security, privacy and cybersecurity on a variety of topics such as post-quantum cryptography; symmetric cipher; signature; network security and blockchain; cryptographic primitives; mathematical foundation; machine learning security, among others.*The conference was held virtually due to COVID-19 pandemic. Computers

Investigating a Phase Conjugate Mirror for Magnon-Based Computing This work provides a convincing motivation for and introduction to magnon-based computing. The challenges faced by the conventional semiconductor-transistor-based computing industry are contrasted with the many exciting avenues for developing spin waves (or magnons) as a complementary technology wherein information can be encoded, transmitted, and operated upon: essential ingredients for any computing paradigm. From this general foundation, one particular operation is examined: phase conjugation via four-wave-mixing (FWM). The author constructs an original theory describing the generation of a phase conjugate mirror with the remarkable property that any incident spin wave will be reflected back along the same direction of travel. After establishing a theoretical framework, the careful design of the experiment is presented, followed by the demonstration of a magnetic phase conjugate mirror using four-wave mixing for the first time. The thesis concludes with an investigation into the unexpected fractal behaviour observed arising from the phase conjugate mirror – a result that is testament to the richness and vibrancy of these highly nonlinear spin wave systems. Computers

Algorithmic Aspects in Information and Management This volume constitutes the proceedings of the 14th International Conference on Algorithmic Aspects in Information and Management, AAIM 2020, held in Jinhua, China in August 2020. The 39 full papers and 17 short papers presented were carefully reviewed and selected from 76 submissions. The papers deal with emerging important algorithmic problems with a focus on the fundamental background, theoretical technology development, and real-world applications associated with information and management analysis, modeling and data mining. Special considerations are given to algorithmic research that was motivated by real-world applications. Computers

Information Retrieval This book constitutes the refereed proceedings of the 26th China Conference on Information Retrieval, CCIR 2020, held in Xi'an, China, in August 2020.*The 12 full papers presented were carefully reviewed and selected from 102 submissions. The papers are organized in topical sections: search and recommendation, NLP for IR, and IR in finance. * Due to the COVID-19 pandemic the conference was held online supplemented with local on-site events. Computers

NASA Formal Methods The chapter “Verifying a Solver for Linear Mixed Integer Arithmetic in Isabelle/HOL†is available open access under a Creative Commons Attribution 4.0 International License via link.springer.com. Computers

Formal Methods. FM 2019 International Workshops This book constitutes the refereed proceedings of the workshops which complemented the 23rd Symposium on Formal Methods, FM 2019, held in Porto, Portugal, in October 2019. This volume presents the papers that have been accepted for the following workshops: Third Workshop on Practical Formal Verification for Software Dependability, AFFORD 2019; 8th International Symposium From Data to Models and Back, DataMod 2019; First Formal Methods for Autonomous Systems Workshop, FMAS 2019; First Workshop on Formal Methods for Blockchains, FMBC 2019; 8th International Workshop on Formal Methods for Interactive Systems, FMIS 2019; First History of Formal Methods Workshop, HFM 2019; 8th International Workshop on Numerical and Symbolic Abstract Domains, NSAD 2019; 9th International Workshop on Open Community Approaches to Education, Research and Technology, OpenCERT 2019; 17th Overture Workshop, Overture 2019; 19th Refinement Workshop, Refine 2019; First International Workshop on Reversibility in Programming, Languages, and Automata, RPLA 2019; 10th International Workshop on Static Analysis and Systems Biology, SASB 2019; and the 10th Workshop on Tools for Automatic Program Analysis, TAPAS 2019. Computers

Bio-inspired Information and Communication Technologies This book constitutes the refereed conference proceedings of the 12th International Conference on Bio-inspired Information and Communications Technologies, held in Shanghai, China, in July 2020. Due to the safety concerns and travel restrictions caused by COVID-19, BICT 2020 took place online in a live stream.BICT 2020 aims to provide a world-leading and multidisciplinary venue for researchers and practitioners in diverse disciplines that seek the understanding of key principles, processes and mechanisms in biological systems and leverage those understandings to develop novel information and communications technologies (ICT). The 20 full and 8 short papers were carefully revied and selected from 56 submissions. In addition to the main track targeting broad and mainstream research topics, BICT 2020 includes four special tracks with focused research topics on internet of everything, intelligent internet of things and network applications, intelligent sensor network, and data-driven intelligent modeling, application and optimization. Computers

The Legacy of Kurt Schütte This book on proof theory centers around the legacy of Kurt Schütte and its current impact on the subject. Schütte was the last doctoral student of David Hilbert who was the first to see that proofs can be viewed as structured mathematical objects amenable to investigation by mathematical methods (metamathematics). Schütte inaugurated the important paradigm shift from finite proofs to infinite proofs and developed the mathematical tools for their analysis. Infinitary proof theory flourished in his hands in the 1960s, culminating in the famous bound Γ0 for the limit of predicative mathematics (a fame shared with Feferman). Later his interests shifted to developing infinite proof calculi for impredicative theories. Schütte had a keen interest in advancing ordinal analysis to ever stronger theories and was still working on some of the strongest systems in his eighties. The articles in this volume from leading experts close to his research, show the enduring influence of his work in modern proof theory. They range from eye witness accounts of his scientific life to developments at the current research frontier, including papers by Schütte himself that have never been published before. Computers

Ordinal Analysis with an Introduction to Proof Theory This book provides readers with a guide to both ordinal analysis, and to proof theory. It mainly focuses on ordinal analysis, a research topic in proof theory that is concerned with the ordinal theoretic content of formal theories. However, the book also addresses ordinal analysis and basic materials in proof theory of first-order or omega logic, presenting some new results and new proofs of known ones. Primarily intended for graduate students and researchers in mathematics, especially in mathematical logic, the book also includes numerous exercises and answers for selected exercises, designed to help readers grasp and apply the main results and techniques discussed. Computers

Advances in Cryptology – CRYPTO 2020 Conference on Cryptologic Research, CRYPTO 2020, which was held during August 17–21, 2020. Crypto has traditionally been held at UCSB every year, but due to the COVID-19 pandemic it will be an online event in 2020. The 85 papers presented in the proceedings were carefully reviewed and selected from a total of 371 submissions. They were organized in topical sections as follows: Part I: Security Models; Symmetric and Real World Cryptography; Hardware Security and Leakage Resilience; Outsourced encryption; Constructions. Part II: Public Key Cryptanalysis; Lattice Algorithms and Cryptanalysis; Lattice-based and Post Quantum Cryptography; Multi-Party Computation. Part III: Multi-Party Computation; Secret Sharing; Cryptanalysis; Delay functions; Zero Knowledge. Computers

Advances in Cryptology – CRYPTO 2020 Conference on Cryptologic Research, CRYPTO 2020, which was held during August 17–21, 2020. Crypto has traditionally been held at UCSB every year, but due to the COVID-19 pandemic it will be an online event in 2020. The 85 papers presented in the proceedings were carefully reviewed and selected from a total of 371 submissions. They were organized in topical sections as follows: Part I: Security Models; Symmetric and Real World Cryptography; Hardware Security and Leakage Resilience; Outsourced encryption; Constructions. Part II: Public Key Cryptanalysis; Lattice Algorithms and Cryptanalysis; Lattice-based and Post Quantum Cryptography; Multi-Party Computation. Part III: Multi-Party Computation; Secret Sharing; Cryptanalysis; Delay functions; Zero Knowledge. Computers

The Discrete Math Workbook This practically-focused study guide introduces the fundamentals of discrete mathematics through an extensive set of classroom-tested problems. Each chapter presents a concise introduction to the relevant theory, followed by a detailed account of common challenges and methods for overcoming these. The reader is then encouraged to practice solving such problems for themselves, by tackling a varied selection of questions and assignments of different levels of complexity. This updated second edition now covers the design and analysis of algorithms using Python, and features more than 50 new problems, complete with solutions. Topics and features: provides a substantial collection of problems and examples of varying levels of difficulty, suitable for both laboratory practical training and self-study; offers detailed solutions to each problem, applying commonly-used methods and computational schemes; introduces the fundamentals of mathematical logic, the theory of algorithms, Boolean algebra, graph theory, sets, relations, functions, and combinatorics; presents more advanced material on the design and analysis of algorithms, including Turing machines, asymptotic analysis, and parallel algorithms; includes reference lists of trigonometric and finite summation formulae in an appendix, together with basic rules for differential and integral calculus. This hands-on workbook is an invaluable resource for undergraduate students of computer science, informatics, and electronic engineering. Suitable for use in a one- or two-semester course on discrete mathematics, the text emphasizes the skills required to develop and implement an algorithm in a specific programming language. Computers

Databases and Information Systems This book constitutes the refereed proceedings of the 14th International Baltic Conference on Databases and Information Systems, DB&IS 2020, held in Tallinn, Estonia, in June 2020.*The 22 revised papers presented were carefully reviewed and selected from 52 submissions. The papers are centered around topics like architectures and quality of information systems, artificial intelligence in information systems, data and knowledge engineering, enterprise and information systems engineering, security of information systems. *The conference was held virtully due to the COVID-19 pandemic. Computers

Foundations of Data Visualization This is the first book that focuses entirely on the fundamental questions in visualization. Unlike other existing books in the field, it contains discussions that go far beyond individual visual representations and individual visualization algorithms. It offers a collection of investigative discourses that probe these questions from different perspectives, including concepts that help frame these questions and their potential answers, mathematical methods that underpin the scientific reasoning of these questions, empirical methods that facilitate the validation and falsification of potential answers, and case studies that stimulate hypotheses about potential answers while providing practical evidence for such hypotheses. Readers are not instructed to follow a specific theory, but their attention is brought to a broad range of schools of thoughts and different ways of investigating fundamental questions. As such, the book represents the by now most significant collective effort for gathering a large collection of discourses on the foundation of data visualization. Data visualization is a relatively young scientific discipline. Over the last three decades, a large collection of computer-supported visualization techniques have been developed, and the merits and benefits of using these techniques have been evidenced by numerous applications in practice. These technical advancements have given rise to the scientific curiosity about some fundamental questions such as why and how visualization works, when it is useful or effective and when it is not, what are the primary factors affecting its usefulness and effectiveness, and so on. This book signifies timely and exciting opportunities to answer such fundamental questions by building on the wealth of knowledge and experience accumulated in developing and deploying visualization technology in practice. Computers

New Trends in Information and Communications Technology Applications This book constitutes refereed proceedings of the 4th International Conference on New Trends in Information and Communications Technology Applications, NTICT 2020, held on June 15, 2020. The NTICT conference was planned to take place in Baghdad on March 11-12, 2019, but due to the COVID-19 pandemic the conference has been postponed on June 15, 2020 and moved to the virtual format. The 15 full papers and 3 short papers presented were thoroughly reviewed and selected from 90 qualified submissions. The volume presents the latest research results in such areas as network protocols, overlay and other logical network structures, wireless access networks, computer vision, machine learning, artificial Intelligence, data mining, control methods. Computers

Neural Computing for Advanced Applications This book presents refereed proceedings of the First International Conference Neural Computing for Advanced Applications, NCAA 2020, held in July, 2020. Due to the COVID-19 pandemic the conference was held online. The 36 full papers and 7 short papers were thorougly reviewed and selected from a total of 113 qualified submissions. Thes papers present resent research on such topics as neural network theory, and cognitive sciences, machine learning, data mining, data security & privacy protection, and data-driven applications, computational intelligence, nature-inspired optimizers, and their engineering applications, cloud/edge/fog computing, the Internet of Things/Vehicles (IoT/IoV), and their system optimization, control systems, network synchronization, system integration, and industrial artificial intelligence, fuzzy logic, neuro-fuzzy systems, decision making, and their applications in management sciences, computer vision, image processing, and their industrial applications, and natural language processing, machine translation, knowledge graphs, and their applications. Computers

Transactions on Large-Scale Data- and Knowledge-Centered Systems XLIII The LNCS journal Transactions on Large-Scale Data- and Knowledge-Centered Systems focuses on data management, knowledge discovery, and knowledge processing, which are core and hot topics in computer science. Since the 1990s, the Internet has become the main driving force behind application development in all domains. An increase in the demand for resource sharing (e.g., computing resources, services, metadata, data sources) across different sites connected through networks has led to an evolution of data- and knowledge-management systems from centralized systems to decentralized systems enabling large-scale distributed applications providing high scalability.This, the 43rd issue of Transactions on Large-Scale Data- and Knowledge-Centered Systems, contains five revised selected regular papers. Topics covered include classification tasks, machine learning algorithms, top-k queries, business process redesign and a knowledge capitalization framework. Computers

Advances in Cryptology – CRYPTO 2020 Conference on Cryptologic Research, CRYPTO 2020, which was held during August 17–21, 2020. Crypto has traditionally been held at UCSB every year, but due to the COVID-19 pandemic it will be an online event in 2020. The 85 papers presented in the proceedings were carefully reviewed and selected from a total of 371 submissions. They were organized in topical sections as follows: Part I: Security Models; Symmetric and Real World Cryptography; Hardware Security and Leakage Resilience; Outsourced encryption; Constructions. Part II: Public Key Cryptanalysis; Lattice Algorithms and Cryptanalysis; Lattice-based and Post Quantum Cryptography; Multi-Party Computation. Part III: Multi-Party Computation; Secret Sharing; Cryptanalysis; Delay functions; Zero Knowledge. Computers

Formal Methods. FM 2019 International Workshops This book constitutes the refereed proceedings of the workshops which complemented the 23rd Symposium on Formal Methods, FM 2019, held in Porto, Portugal, in October 2019. This volume presents the papers that have been accepted for the following workshops: Third Workshop on Practical Formal Verification for Software Dependability, AFFORD 2019; 8th International Symposium From Data to Models and Back, DataMod 2019; First Formal Methods for Autonomous Systems Workshop, FMAS 2019; First Workshop on Formal Methods for Blockchains, FMBC 2019; 8th International Workshop on Formal Methods for Interactive Systems, FMIS 2019; First History of Formal Methods Workshop, HFM 2019; 8th International Workshop on Numerical and Symbolic Abstract Domains, NSAD 2019; 9th International Workshop on Open Community Approaches to Education, Research and Technology, OpenCERT 2019; 17th Overture Workshop, Overture 2019; 19th Refinement Workshop, Refine 2019; First International Workshop on Reversibility in Programming, Languages, and Automata, RPLA 2019; 10th International Workshop on Static Analysis and Systems Biology, SASB 2019; and the 10th Workshop on Tools for Automatic Program Analysis, TAPAS 2019. Computers

Build Location Apps on iOS with Swift Work with Apple Maps, Google Maps, and Mapbox in iOS with Swift programming. Guided by practical examples, this book covers all three map frameworks to ensure you properly select which one best suits your iOS app's needs in working with iOS location. You'll see how Apple's privacy settings apply to a user's location, and how to access that user's location from an application. Once you have access to the user's location, allow your app to display points of interest from Apple's database on the map inside the app, as well as to provide a search through that database by name. You can also incorporate turn by turn directions inside your own app to provide routes. Or trigger different functionality or notifications based on locational queues. With Build Location Apps on iOS with Swift, you'll even find out how to provide offline map support for hiking, camping, or other outdoors applications where cell phone service is weak. What You'll Learn Display points of interest within your own app Work with Apple's privacy settings so pertinent information comes through Trigger functionality based on geographic prompts Create your own custom map styles with Mapbox Studio and display them in the app Who This Book Is For Intermediate to advanced Swift programmers who would like to add location based services to their apps. Computers

Big Data and Security This book constitutes the refereed proceedings of the First International Conference on Big Data and Security, ICBDS 2019, held in Nanjing, China, in December 2019. The 37 revised full papers and 12 short papers were carefully reviewed and selected out of 251 submissions. The papers included in this book cover topics in cybersecurity & privacy, big data, blockchain & internet of things, security in cloud and fog computing, and artificial intelligence/ machine learning security. Computers

An Introduction to Computational Origami In this book, origami is treated as a set of basic geometrical objects that are represented and manipulated symbolically and graphically by computers. Focusing on how classical and modern geometrical problems are solved by means of origami, the book explains the methods not only with mathematical rigor but also by appealing to our scientific intuition, combining mathematical formulas and graphical images to do so. In turn, it discusses the verification of origami using computer software and symbolic computation tools. The binary code for the origami software, called Eos and created by the author, is also provided. Computers

Document Analysis Systems This book constitutes the refereed proceedings of the 14th IAPR International Workshop on Document Analysis Systems, DAS 2020, held in Wuhan, China, in July 2020. The 40 full papers presented in this book were carefully reviewed and selected from 57 submissions. The papers are grouped in the following topical sections: character and text recognition; document image processing; segmentation and layout analysis; word embedding and spotting; text detection; and font design and classification. Due to the Corona pandemic the conference was held as a virtual event . Computers

Ubiquitous Networking This book constitutes the refereed proceedings of the 5th International Symposium on Ubiquitous Networking, UNet 2019, held in Limoges, France, in November 2019.The 17 revised full papers presented together with 1 short paper were carefully reviewed and selected from 41 submissions. The papers are organized in topical sections: ubiquitous communication technologies and networking; ubiquitous Internet of things; pervasive services and applications. Computers

Advances in Databases and Information Systems The chapter “An Efficient Index for Reachability Queries in Public Transport Networks†is available open access under a Creative Commons Attribution 4.0 International License via link.springer.com. Computers

Diagrammatic Representation and Inference This book constitutes the refereed proceedings of the 11th International Conference on the Theory and Application of Diagrams, Diagrams 2020, held in Tallinn, Estonia, in August 2020.*The 20 full papers and 16 short papers presented together with 18 posters were carefully reviewed and selected from 82 submissions. The papers are organized in the following topical sections: diagrams in mathematics; diagram design, principles, and classification; reasoning with diagrams; Euler and Venn diagrams; empirical studies and cognition; logic and diagrams; and posters. *The conference was held virtually due to the COVID-19 pandemic. The chapters ‘Modality and Uncertainty in Data Visualization: A Corpus Approach to the Use of Connecting Lines,’ ‘On Effects of Changing Multi-Attribute Table Design on Decision Making: An Eye Tracking Study,’ ‘Truth Graph: A Novel Method for Minimizing Boolean Algebra Expressions by Using Graphs,’ ‘The DNA Framework of Visualization’ and ‘Visualizing Curricula’ are available open access under a Creative Commons Attribution 4.0 International License via link.springer.com. Computers

Digital Libraries for Open Knowledge This book constitutes the proceedings of the 24th International Conference on Theory and Practice of Digital Libraries, TPDL 2020, held in Lyon, France, in August 2020.*The 14 full papers and 4 short papers presented were carefully reviewed and selected from 53 submissions. TPDL 2020 attempts to facilitate establishing connections and convergences between diverse research communities such as Digital Humanities, Information Sciences and others that could benefit from ecosystems offered by digital libraries and repositories. The papers present a wide range of the following topics: knowledge graphs and linked data; quality assurance in digital libraries; ontology design; user requirements and behavior; research data management and discovery; and digital cultural heritage.* The conference was held virtually due to the COVID-19 pandemic. Computers

New Trends in Databases and Information Systems This book constitutes thoroughly refereed short papers of the 24th European Conference on Advances in Databases and Information Systems, ADBIS 2020, held in August 2020. ADBIS 2020 was to be held in Lyon, France, however due to COVID-19 pandemic the conference was held in online format. The 18 presented short research papers were carefully reviewed and selected from 69 submissions. The papers are organized in the following sections: data access and database performance; machine learning; data processing; semantic web; data analytics. Computers

Bioinformatics Research and Applications This book constitutes the proceedings of the 16th International Symposium on Bioinformatics Research and Applications, ISBRA 2020, held in Moscow, Russia, in December 2020. The 23 full papers and 18 short papers presented in this book were carefully reviewed and selected from 131 submissions. They were organized in topical sections named: genome analysis; systems biology; computational proteomics; machine and deep learning; and data analysis and methodology. Computers

Euro-Par 2020 This book constitutes the proceedings of the 26th International Conference on Parallel and Distributed Computing, Euro-Par 2020, held in Warsaw, Poland, in August 2020. The conference was held virtually due to the coronavirus pandemic. The 39 full papers presented in this volume were carefully reviewed and selected from 158 submissions. They deal with parallel and distributed computing in general, focusing on support tools and environments; performance and power modeling, prediction and evaluation; scheduling and load balancing; high performance architectures and compilers; data management, analytics and machine learning; cluster, cloud and edge computing; theory and algorithms for parallel and distributed processing; parallel and distributed programming, interfaces, and languages; multicore and manycore parallelism; parallel numerical methods and applications; and accelerator computing. Computers

Artificial Intelligence. IJCAI 2019 International Workshops a Computers

Trends in Functional Programming This book constitutes revised selected papers from the 21st International Symposium on Trends in Functional Programming, TFP 2020, which was held in Krakow, Poland, during February 13-14, 2020. The 11 full papers presented in this volume were carefully reviewed and selected from 22 submissions. They were organized in topical sections named: domain-specific languages; debugging and testing; reasoning and effects; and parallelism. Computers

ADBIS, TPDL and EDA 2020 Common Workshops and Doctoral Consortium This book constitutes thoroughly reviewed and selected papers presented at Workshops and Doctoral Consortium of the 24th East-European Conference on Advances in Databases and Information Systems, ADBIS 2020, the 24th International Conference on Theory and Practice of Digital Libraries, TPDL 2020, and the 16th Workshop on Business Intelligence and Big Data, EDA 2020, held in August 2020. Due to the COVID-19 the joint conference and satellite events were held online. The 26 full papers and 5 short papers were carefully reviewed and selected from 56 submissions. This volume presents the papers that have been accepted for the following satellite events: Workshop on Intelligent Data - From Data to Knowledge, DOING 2020; Workshop on Modern Approaches in Data Engineering and Information System Design, MADEISD 2020; Workshop on Scientic Knowledge Graphs, SKG 2020; Workshop of BI & Big Data Applications, BBIGAP 2020; International Symposium on Data-Driven Process Discovery and Analysis, SIMPDA 2020; International Workshop on Assessing Impact and Merit in Science, AIMinScience 2020; Doctoral Consortium. Computers

Rules and Reasoning This book constitutes the proceedings of the International Joint Conference on Rules and Reasoning, RuleML+RR 2020, held in Oslo, Norway, during June-July 2020*. This is the 4th conference of a new series, joining the efforts of two existing conference series, namely “RuleML†(International Web Rule Symposium) and “RR†(Web Reasoning and Rule Systems). The 7 full research papers presented together with 6 short technical communications papers were carefully reviewed and selected from 30 submissions. *The conference was held virtually due to the COVID-19 pandemic. Computers

Primitive Interaction Design Interaction design is acknowledged as an important area of study, and more especially of design practice. Hugely popular and profitable consumer devices, such as mobile phones and tablets, are seen as owing much of their success to the way they have been designed, not least their interface characteristics and the styles of interaction that they support. Interaction design studies point to the importance of a user-centred approach, whereby products are in principle designed around their future users’ needs and capacities. However, it is the market, and marketing, that determine which products are available for people to interact with and to a great extent what their designed characteristics are. Primitive Interaction Design is based on the realisation that designers need to be freed from the marketplace and industry pressure, and that the usual user-centred arguments are not enough to make a practical difference. Interaction designers are invited to cast themselves as “savagesâ€, as if wielding primitive tools in concrete physical environments. A theoretical perspective is presented that opens up new possibilities for designers to explore fresh ideas and practices, including the importance of conscious and unconscious being, emptiness and trickery. Building on this, a set of design tools for primitive design work is presented and illustrated with practical examples. This book will be of particular interest to undergraduate and graduate students and researchers in interaction design and HCI, as well as practicing interaction designers and computer professions. It will also appeal to those with an interest in psychology, anthropology, cultural studies, design and the future of technology in society. Computers

Decoding Blockchain for Business Business professionals looking to understand the impact, future, and limitations of blockchain need look no further. This revolutionary technology has impacted business and the economy in unprecedented ways within the past decade, and it is only continuing to grow. As a leader in your organization, it is vital that you decode blockchain and optimize all the ways in which it can improve your business. Author of Decoding Blockchain for Business, Stijn Van Hijfte, expertly emphasizes the imperative of professionals in any sector of industry to understand the core concepts and implications of blockchain technology. Cryptocurrencies, cryptotrading, and constantly-changing tax structures for financial systems using blockchain technologies are covered in detail. The lasting effects of blockchain across specific industries such as media, real estate, finance, and regulatory bodies are addressed with an insightful eye from Van Hijfte. If not properly implemented with care and a foundation of knowledge, blockchain brings risks and uncertainties to a company. Know your technology to be ready for the present and the future, and stay ahead of the curve. Blockchain is here to stay, and Decoding Blockchain for Business is your professional roadmap. What You Will Learn Discover the risks associated with blockchain if not properly implemented Gain insights on how blockchain technology affects other booming topics such as AI, IoT, and RPA Look at the regulations surrounding Blockchain in different countries Who This Book Is For Business professionals looking to understand the impact, future, and limitations of Blockchain and how individuals and companies should prepare for this technology. Computers

Practical Entity Framework Determine your object relational mapper (ORM) of choice for enterprise applications using .NET Framework, and especially .NET Framework Core 3.1 and higher. Real-world examples and considerations are presented in this book to help you create robust and efficient database solutions. Throughout the text, actual problems, questions, and common pitfalls are provided to help you recognize optimal solutions for maximum success in the different application scenarios you might encounter. Practical Entity Framework begins with a simple overview of the two most common approaches to working with databases—database first and code first—and then focuses on working in a code first manner. Taking the code first approach allows the entire database to be built and maintained in code so there is never a situation in which you cannot restore the database schema. Additionally, the code first approach creates an entirely transparent record of changes to the database that is easily tracked in source control. Emphasis throughout the book is on leaving you well positioned to architect and lead data development efforts for your organization. What You Will Learn Build robust and maintainable databases using a code first approach Create and execute stored procedures, triggers, and functions Analyze and optimize performance of database queries Ensure data integrity through keys, constraints, and relationships Who This Book Is For .NET developers who work with enterprise-level applications and need to interact with data structures and data within the back end data store, developers who want to take a code first approach to building database applications to prevent conflicts and optimize efficiency, and those who are moving into full-stack roles, or into senior and architectural roles, and will be responsible for database design and implementation Computers

Knowledge Science, Engineering and Management This two-volume set of LNAI 12274 and LNAI 12275 constitutes the refereed proceedings of the 13th International Conference on Knowledge Science, Engineering and Management, KSEM 2020, held in Hangzhou, China, in August 2020.*The 58 revised full papers and 27 short papers were carefully reviewed and selected from 291 submissions. The papers of the first volume are organized in the following topical sections: knowledge graph; knowledge representation; knowledge management for education; knowledge-based systems; and data processing and mining. The papers of the second volume are organized in the following topical sections: machine learning; recommendation algorithms and systems; social knowledge analysis and management; text mining and document analysis; and deep learning.*The conference was held virtually due to the COVID-19 pandemic. Computers

Computer Safety, Reliability, and Security This book constitutes the proceedings of the 39th International Conference on Computer Safety, Reliability and Security, SAFECOMP 2020, held in Lisbon, Portugal, in September 2020.* The 27 full and 2 short papers included in this volume were carefully reviewed and selected from 116 submissions. They were organized in topical sections named: safety cases and argumentation; formal verification and analysis; security modelling and methods; assurance of learning-enabled systems; practical experience and tools; threat analysis and risk mitigation; cyber-physical systems security; and fault injection and fault tolerance. *The conference was held virtually due to the COVID-19 pandemic. The chapter ‘Assurance Argument Elements for Off-the-Shelf, Complex Computational Hardware’ is available open access under an Open Government License 3.0 via link.springer.com. Computers

Knowledge Science, Engineering and Management This two-volume set of LNAI 12274 and LNAI 12275 constitutes the refereed proceedings of the 13th International Conference on Knowledge Science, Engineering and Management, KSEM 2020, held in Hangzhou, China, in August 2020.*The 58 revised full papers and 27 short papers were carefully reviewed and selected from 291 submissions. The papers of the first volume are organized in the following topical sections: knowledge graph; knowledge representation; knowledge management for education; knowledge-based systems; and data processing and mining. The papers of the second volume are organized in the following topical sections: machine learning; recommendation algorithms and systems; social knowledge analysis and management; text mining and document analysis; and deep learning.*The conference was held virtually due to the COVID-19 pandemic. Computers

Well-Being in the Information Society. Fruits of Respect This book constitutes the refereed proceedings of the 8th International Conference on Well-Being in the Information Society, WIS 2020, held in Turku, Finland, in August 2020. Due to the COVID-19 pandemic the conference was held online. The 19 revised full papers presented were carefully reviewed and selected from 25 submissions. The submitted papers present academic contributions on the topics of intersection of health, ICT and fruits of respect as seen from different directions and contexts. The paperd are organized in the following topical sections: improving quality and containing cost in health care and care for the elderly by using information technology; collecting the fruits of respect in entrepreneurship and management of organizations; friend or foe: society in the area of tension between free data movement and data protection; bridging the digital divide: strengthening (health-) literacy and supporting trainings in information society. Computers

Machine Learning and Knowledge Extraction This book constitutes the refereed proceedings of the 4th IFIP TC 5, TC 12, WG 8.4, WG 8.9, WG 12.9 International Cross-Domain Conference, CD-MAKE 2020, held in Dublin, Ireland, in August 2020. The 30 revised full papers presented were carefully reviewed and selected from 41 submissions. The cross-domain integration and appraisal of different fields provides an atmosphere to foster different perspectives and opinions; it will offer a platform for novel ideas and a fresh look on the methodologies to put these ideas into business for the benefit of humanity. Due to the Corona pandemic CD-MAKE 2020 was held as a virtual event. Computers

Statistical Field Theory for Neural Networks This book presents a self-contained introduction to techniques from field theory applied to stochastic and collective dynamics in neuronal networks. These powerful analytical techniques, which are well established in other fields of physics, are the basis of current developments and offer solutions to pressing open problems in theoretical neuroscience and also machine learning. They enable a systematic and quantitative understanding of the dynamics in recurrent and stochastic neuronal networks. This book is intended for physicists, mathematicians, and computer scientists and it is designed for self-study by researchers who want to enter the field or as the main text for a one semester course at advanced undergraduate or graduate level. The theoretical concepts presented in this book are systematically developed from the very beginning, which only requires basic knowledge of analysis and linear algebra. Computers

Coalgebraic Methods in Computer Science This book constitutes the thoroughly refereed post-conference proceedings of the 15th International Workshop on Coalgebraic Methods in Computer Science, CMCS 2020, colocated with ETAPS 2020, held in Dublin, Ireland, in April 2020. The conference was held as several online events in September and October due to the COVID-19 pandemic. The 9 revised full papers were carefully reviewed and selected from 13 submissions. Also included is one invited talk. The papers cover a wide range of topics in the theory, logics, and applications of coalgebras. Computers

Security Protocols XXVII The volume LNCS 12287 constitutes the proceedings of the 27th International Workshop on Security Protocols, held in Cambridge, UK, in April 2019. The volume consists of 16 thoroughly revised invited papers presented together with the respective transcripts of discussions. The theme of this year's workshop was “Security Protocols for Humans" The topics covered included Designing for Humans and Understanding Humans, Human Limitations in Security, Secure sharing and collaboration and much more. Computers

Types and Programming Languages A comprehensive introduction to type systems and programming languages. A type system is a syntactic method for automatically checking the absence of certain erroneous behaviors by classifying program phrases according to the kinds of values they compute. The study of type systems—and of programming languages from a type-theoretic perspective—has important applications in software engineering, language design, high-performance compilers, and security. This text provides a comprehensive introduction both to type systems in computer science and to the basic theory of programming languages. The approach is pragmatic and operational; each new concept is motivated by programming examples and the more theoretical sections are driven by the needs of implementations. Each chapter is accompanied by numerous exercises and solutions, as well as a running implementation, available via the Web. Dependencies between chapters are explicitly identified, allowing readers to choose a variety of paths through the material. The core topics include the untyped lambda-calculus, simple type systems, type reconstruction, universal and existential polymorphism, subtyping, bounded quantification, recursive types, kinds, and type operators. Extended case studies develop a variety of approaches to modeling the features of object-oriented languages. Computers

Introduction to Deep Learning A project-based guide to the basics of deep learning. This concise, project-driven guide to deep learning takes readers through a series of program-writing tasks that introduce them to the use of deep learning in such areas of artificial intelligence as computer vision, natural-language processing, and reinforcement learning. The author, a longtime artificial intelligence researcher specializing in natural-language processing, covers feed-forward neural nets, convolutional neural nets, word embeddings, recurrent neural nets, sequence-to-sequence learning, deep reinforcement learning, unsupervised models, and other fundamental concepts and techniques. Students and practitioners learn the basics of deep learning by working through programs in Tensorflow, an open-source machine learning framework. “I find I learn computer science material best by sitting down and writing programs,” the author writes, and the book reflects this approach. Each chapter includes a programming project, exercises, and references for further reading. An early chapter is devoted to Tensorflow and its interface with Python, the widely used programming language. Familiarity with linear algebra, multivariate calculus, and probability and statistics is required, as is a rudimentary knowledge of programming in Python. The book can be used in both undergraduate and graduate courses; practitioners will find it an essential reference. Computers

The Elements of Computing Systems A textbook with a hands-on approach that leads students through the gradual construction of a complete and working computer system including the hardware platform and the software hierarchy. In the early days of computer science, the interactions of hardware, software, compilers, and operating system were simple enough to allow students to see an overall picture of how computers worked. With the increasing complexity of computer technology and the resulting specialization of knowledge, such clarity is often lost. Unlike other texts that cover only one aspect of the field, The Elements of Computing Systems gives students an integrated and rigorous picture of applied computer science, as its comes to play in the construction of a simple yet powerful computer system. Indeed, the best way to understand how computers work is to build one from scratch, and this textbook leads students through twelve chapters and projects that gradually build a basic hardware platform and a modern software hierarchy from the ground up. In the process, the students gain hands-on knowledge of hardware architecture, operating systems, programming languages, compilers, data structures, algorithms, and software engineering. Using this constructive approach, the book exposes a significant body of computer science knowledge and demonstrates how theoretical and applied techniques taught in other courses fit into the overall picture. Designed to support one- or two-semester courses, the book is based on an abstraction-implementation paradigm; each chapter presents a key hardware or software abstraction, a proposed implementation that makes it concrete, and an actual project. The emerging computer system can be built by following the chapters, although this is only one option, since the projects are self-contained and can be done or skipped in any order. All the computer science knowledge necessary for completing the projects is embedded in the book, the only pre-requisite being a programming experience. The book's web site provides all tools and materials necessary to build all the hardware and software systems described in the text, including two hundred test programs for the twelve projects. The projects and systems can be modified to meet various teaching needs, and all the supplied software is open-source. Computers

Artificial Intelligence in Daily Life Given the exponential growth of Artificial Intelligence (AI) over the past few decades, AI and its related applications have become part of daily life in ways that we could never have dreamt of only a century ago. Our routines have been changed beyond measure by robotics and AI, which are now used in a vast array of services. Though AI is still in its infancy, we have already benefited immensely. This book introduces readers to basic Artificial Intelligence concepts, and helps them understand the relationship between AI and daily life. In the interest of clarity, the content is divided into four major parts. Part I (AI Concepts) presents fundamental concepts of and information on AI; while Part II (AI Technology) introduces readers to the five core AI Technologies that provide the building blocks for various AI applications, namely: Machine Learning (ML), Data Mining (DM), Computer Vision (CV), Natural Languages Processing (NLP), and Ontology-based Search Engine (OSE). In turn, Part III (AI Applications) reviews major contemporary applications that are impacting our ways of life, working styles and environment, ranging from intelligent agents and robotics to smart campus and smart city projects. Lastly, Part IV (Beyond AI) addresses related topics that are vital to the future development of AI. It also discusses a number of critical issues, such as AI ethics and privacy, the development of a conscious mind, and autonomous robotics in our daily lives. Computers

Computer Safety, Reliability, and Security. SAFECOMP 2020 Workshops This book constitutes the proceedings of the Workshops held in conjunction with SAFECOMP 2020, 39th International Conference on Computer Safety, Reliability and Security, Lisbon, Portugal, September 2020.The 26 regular papers included in this volume were carefully reviewed and selected from 45 submissions; the book also contains one invited paper. The workshops included in this volume are: DECSoS 2020:15th Workshop on Dependable Smart Embedded and Cyber-Physical Systems and Systems-of-Systems. DepDevOps 2020:First International Workshop on Dependable Development-Operation Continuum Methods for Dependable Cyber-Physical Systems. USDAI 2020:First International Workshop on Underpinnings for Safe Distributed AI. WAISE 2020:Third International Workshop on Artificial Intelligence Safety Engineering. The workshops were held virtually due to the COVID-19 pandemic. Computers

Practical Test Automation Learn the principles behind test-driven development (TDD) and behavior-driven development (BDD) and see how Jasmine, RSpec and Cucumber can be used to your advantage. This book examines some of the leading technologies used for testing. You'll see how to use Jasmine’s features to work with a JavaScript application. You will learn how to use Mini Test and RSpec with Ruby and Rubymine. Finally, you’ll use Cucumber to develop your software using a BDD approach. Understanding test automation is a vital skill for any web developer. Practical Test Automation breaks down for you some of the important TDD and BDD technologies on the modern web. What You'll Learn Test an example JavaScript application with Jasmine Use Jasmine with JS Bin Work with Minitest for test-driven development Test an example Ruby project with RSpec Use Cucumber and Gherkin for behavior-driven development Integrate Cucumber with RSpec Who This Book Is For This book is for anyone who wants to learn test automation and more about test-driven development and behavior-driven development. Computers

Electronic Government This book constitutes the proceedings of the 19th IFIP WG 8.5 International Conference on Electronic Government, EGOV 2020, held in Linköping, Sweden, in August/September 2020, in conjunction with the IFIP WG 8.5 IFIP International Conference on Electronic Participation (ePart 2020) and the International Conference for E-Democracy and Open Government Conference (CeDEM 2020). The conference was held virtually due to the COVID-19 pandemic. The 30 full papers presented were carefully reviewed and selected from 118 submissions. The papers are clustered under the following topical sections: e-government foundations; e-government services and open government; open data: social and technical aspects; AI, data analytics, and automated decision making; and smart cities. Computers

Formal Modeling and Analysis of Timed Systems This book constitutes the refereed proceedings of the 18th International Conference on Formal Modeling and Analysis of Timed Systems, FORMATS 2020, held in Vienna, Austria, in September 2020. The 16 full papers and 2 short papers presented in this volume were carefully reviewed and selected from 42 submissions. The papers focus on topics such as foundations and semantics, methods and tools, techniques, algorithms, data structures, and software tools for analyzing timed systems and resolving temporal constraints. Due to the Corona pandemic this conference was held as a virtual event. Computers

Spatial Cognition XII This book constitutes the thoroughly refereed proceedings of the 12th International Conference, Spatial Cognition 2020, held in Riga, Latvia, in September 2020. The physical event was postponed to 2021 due to the COVID-19 pandemic. The 19 full papers and 6 short papers presented in this book were carefully selected and reviewed from 50 submissions. They focus on the following topics: spatial representation and cognitive maps; navigation and wayfinding; spatial representation in language, logic, and narrative; and spatial abilities and learning. Computers

Applications and Usability of Interactive TV a Computers

Serverless Swift Decrease development time to market with Serverless Swift—the event-based modern architecture for full stack developers. This book reviews how to use the Apache OpenWhisk framework to enrich your standalone applications with cloud-based functionalities from data sources up to Artificial Intelligence. You'll leverage serverless in your mobile apps with use case scenarios and gain the skills that will allow you to create robust, performant, secure yet economically viable systems in a cloud native environment. Finally, you'll see how to participate in the creation and further development of this open source project with Apache Foundation, which is supported by IBM, Google, and others Serverless has become a new style of coding, and it can be used to offload your mobile apps without incurring unnecessary costs. Get a solid, hands-on introduction into serverless, function-as-a-service, and cloud function technologies and learn why startups and enterprises are so excited about using them. What You'll Learn Employ Apache OpenWhisk in your apps Expand your iOS skills with Cloud Native Serverless programming Use a Docker container as a Polyglot action Who This Book Is For Developers, development leaders in the enterprise, and startup CTOs who want to learn a leading technology for the cloud in order to enrich applications with SaaS, Social Networks, and cloud based AI and APIs. Computers

Applied Machine Learning for Health and Fitness Explore the world of using machine learning methods with deep computer vision, sensors and data in sports, health and fitness and other industries. Accompanied by practical step-by-step Python code samples and Jupyter notebooks, this comprehensive guide acts as a reference for a data scientist, machine learning practitioner or anyone interested in AI applications. These ML models and methods can be used to create solutions for AI enhanced coaching, judging, athletic performance improvement, movement analysis, simulations, in motion capture, gaming, cinema production and more.Packed with fun, practical applications for sports, machine learning models used in the book include supervised, unsupervised and cutting-edge reinforcement learning methods and models with popular tools like PyTorch, Tensorflow, Keras, OpenAI Gym and OpenCV. Author Kevin Ashley—who happens to be both a machine learning expert and a professional ski instructor—has written an insightful book that takes you on a journey of modern sport science and AI. Filled with thorough, engaging illustrations and dozens of real-life examples, this book is your next step to understanding the implementation of AI within the sports world and beyond. Whether you are a data scientist, a coach, an athlete, or simply a personal fitness enthusiast excited about connecting your findings with AI methods, the author’s practical expertise in both tech and sports is an undeniable asset for your learning process. Today’s data scientists are the future of athletics, and Applied Machine Learning for Health and Fitness hands you the knowledge you need to stay relevant in this rapidly growing space. What You'll Learn Use multiple data science tools and frameworks Apply deep computer vision and other machine learning methods for classification, semantic segmentation, and action recognition Build and train neural networks, reinforcement learning models and more Analyze multiple sporting activities with deep learning Use datasets available today for model trainingUse machine learning in the cloud to train and deploy modelsApply best practices in machine learning and data science Who This Book Is For Primarily aimed at data scientists, coaches, sports enthusiasts and athletes interested in connecting sports with technology and AI methods. Computers

Hands-on Time Series Analysis with Python Learn the concepts of time series from traditional to bleeding-edge techniques. This book uses comprehensive examples to clearly illustrate statistical approaches and methods of analyzing time series data and its utilization in the real world. All the code is available in Jupyter notebooks. You'll begin by reviewing time series fundamentals, the structure of time series data, pre-processing, and how to craft the features through data wrangling. Next, you'll look at traditional time series techniques like ARMA, SARIMAX, VAR, and VARMA using trending framework like StatsModels and pmdarima. The book also explains building classification models using sktime, and covers advanced deep learning-based techniques like ANN, CNN, RNN, LSTM, GRU and Autoencoder to solve time series problem using Tensorflow. It concludes by explaining the popular framework fbprophet for modeling time series analysis. After reading Hands -On Time Series Analysis with Python, you'll be able to apply these new techniques in industries, such as oil and gas, robotics, manufacturing, government, banking, retail, healthcare, and more. What You'll Learn: · Explains basics to advanced concepts of time series · How to design, develop, train, and validate time-series methodologies · What are smoothing, ARMA, ARIMA, SARIMA,SRIMAX, VAR, VARMA techniques in time series and how to optimally tune parameters to yield best results · Learn how to leverage bleeding-edge techniques such as ANN, CNN, RNN, LSTM, GRU, Autoencoder to solve both Univariate and multivariate problems by using two types of data preparation methods for time series. · Univariate and multivariate problem solving using fbprophet. Who This Book Is For Data scientists, data analysts, financial analysts, and stock market researchers Computers

Modeling Decisions for Artificial Intelligence This book constitutes the refereed proceedings of the 17th International Conference on Modeling Decisions for Artificial Intelligence, MDAI 2020, held in Sant Cugat, Spain, in September 2020.* The 24 papers presented in this volume were carefully reviewed and selected from 46 submissions. They discuss different facets of decision processes in a broad sense and present research in data science, data privacy, aggregation functions, human decision making, graphs and social networks, and recommendation and search. The papers are organized in the following topical sections: aggregation operators and decision making, and data science and data mining. * The conference was canceled due to the COVID-19 pandemic. Computers

Electronic Participation This book constitutes the proceedings of the 12th IFIP WG 8.5 International Conference on Electronic Participation, ePart 2019, held in Linköping, Sweden, in August/September 2020, in conjunction with the 19th IFIP WG 8.5 IFIP International Conference on Electronic Government (EGOV 2020) and the International Conference for E-Democracy and Open Government Conference (CeDEM 2020). The conference was held virtually due to the COVID-19 pandemic. The 11 full papers presented were carefully reviewed and selected from 33 submissions. The papers are clustered under the following topical sections: eParticipation developments; digital transformation; open government and transparency; and user perspectives. Computers

Applied Cryptography and Network Security This two-volume set of LNCS 12146 and 12147 constitutes the refereed proceedings of the 18th International Conference on Applied Cryptography and Network Security, ACNS 2020, held in Rome, Italy, in October 2020. The conference was held virtually due to the COVID-19 pandemic. The 46 revised full papers presented were carefully reviewed and selected from 214 submissions. The papers were organized in topical sections named: cryptographic protocols cryptographic primitives, attacks on cryptographic primitives, encryption and signature, blockchain and cryptocurrency, secure multi-party computation, post-quantum cryptography. Computers

Computing and Combinatorics This book constitutes the proceedings of the 26th International Conference on Computing and Combinatorics, COCOON 2020, held in Atlanta, GA, USA, in August 2020. Due to the COVID-19 pandemic COCOON 2020 was organized as a fully online conference. The 54 papers presented in this volume were carefully reviewed and selected from 126 submissions. The papers cover various topics, including algorithm design, approximation algorithm, graph theory, complexity theory, problem solving, optimization, computational biology, computational learning, communication network, logic, and game theory. Computers

Critical Information Infrastructures Security This book constitutes the revised selected papers of the 15th International Conference on Critical Information Infrastructures Security, CRITIS 2020, held in Bristol, UK*, in September 2020. The 5 full papers and 1 short paper presented were carefully reviewed and selected from 17 submissions. They are grouped in the following topical sections: invited papers, attacks and vulnerabilities, threat modelling and monitoring, and networks and IoT. *The conference was held virtually due to the COVID-19 pandemic. Computers

Advances in Information and Computer Security This book constitutes the refereed proceedings of the 15th International Workshop on Security, IWSEC 2020, held in Fukui, Japan, in September 2020.* The 15 regular papers and 1 short paper presented in this volume were carefully reviewed and selected from 47 submissions. They were organized in topical sections named: symmetric-key cryptography, malicious activity detection, multiparty computation, post quantum cryptography, privacy, pairing-based cryptography, and machine learning. * The conference was held virtually due to the COVID-19 pandemic. Computers

Exploring C++20 Discover everything you need to know about C++ in a logical progression of small lessons that you can work through as quickly or as slowly as you need. This book divides C++ up into bite-sized chunks that will help you learn the language one step at a time. Fully updated to include C++20, it assumes no familiarity with C++ or any other C-based language. Exploring C++20 acknowledges that C++ can be a complicated language, so rather than baffle you with complex chapters explaining functions, classes, and statements in isolation you’ll focus on how to achieve results. By learning a little bit of this and a little of that you’ll soon have amassed enough knowledge to be writing non-trivial programs and will have built a solid foundation of experience that puts those previously baffling concepts into context. In this fully-revised third edition of Exploring C++, you’ll learn how to use the standard library early in the book. Next, you’ll work with operators, objects, and data-sources in increasingly realistic situations. Finally, you’ll start putting the pieces together to create sophisticated programs of your own design confident that you’ve built a firm base of experience from which to grow. What You Will Learn Grasp the basics, including compound statements, modules, and more Work with custom types and see how to use them Write useful algorithms, functions, and more Discover the latest C++ 20 features, including concepts, modules, and ranges Apply your skills to projects that include a fixed-point numbers and body-mass index applications Carry out generic programming and apply it in a practical project Exploit multiple inheritance, traits/policies, overloaded functions, and metaprogramming Who This Book Is For Experienced programmers who may have little or no experience with C++ who want an accelerated learning guide to C++20 so they can hit the ground running. Computers

Transactions on Computational Collective Intelligence XXXV These transactions publish research in computer-based methods of computational collective intelligence (CCI) and their applications in a wide range of fields such as performance optimization in IoT, big data, reliability, privacy, security, service selection, QoS and machine learning. This thirty-fifth issue contains 10 selected papers which present new findings and innovative methodologies as well as discuss issues and challenges in the field of collective intelligence from big data and networking paradigms while addressing security, privacy, reliability and optimality to achieve QoS to the benefit of final users. Computers

Topics in Theoretical Computer Science This book constitutes the refereed proceedings of the Third IFIP WG 1.8 International Conference on Topics in Theoretical Computer Science, TTCS 2020, held in Tehran, Iran, in July 2020. The conference was held virtually due to the COVID-19 pandemic. The 8 papers presented in this volume were carefully reviewed and selected from 24 submissions. They focus on novel and high-quality research in all areas of theoretical computer science, such as algorithms and complexity; logic, semantics, and programming theory; and more. Computers

Artificial Intelligence, Computational Modelling and Criminal Proceedings This book discusses issues relating to the application of AI and computational modelling in criminal proceedings from a European perspective. Part one provides a definition of the topics. Rather than focusing on policing or prevention of crime – largely tackled by recent literature – it explores ways in which AI can affect the investigation and adjudication of crime. There are two main areas of application: the first is evidence gathering, which is addressed in Part two. This section examines how traditional evidentiary law is affected by both new ways of investigation – based on automated processes (often using machine learning) – and new kinds of evidence, automatically generated by AI instruments. Drawing on the comprehensive case law of the European Court of Human Rights, it also presents reflections on the reliability and, ultimately, the admissibility of such evidence. Part three investigates the second application area: judicial decision-making, providing an unbiased review of the meaning, benefits, and possible long-term effects of ‘predictive justice’ in the criminal field. It highlights the prediction of both violent behaviour, or recidivism, and future court decisions, based on precedents. Touching on the foundations of common law and civil law traditions, the book offers insights into the usefulness of ‘prediction’ in criminal proceedings. Computers

An Introduction to Clustering with R The purpose of this book is to thoroughly prepare the reader for applied research in clustering. Cluster analysis comprises a class of statistical techniques for classifying multivariate data into groups or clusters based on their similar features. Clustering is nowadays widely used in several domains of research, such as social sciences, psychology, and marketing, highlighting its multidisciplinary nature. This book provides an accessible and comprehensive introduction to clustering and offers practical guidelines for applying clustering tools by carefully chosen real-life datasets and extensive data analyses. The procedures addressed in this book include traditional hard clustering methods and up-to-date developments in soft clustering. Attention is paid to practical examples and applications through the open source statistical software R. Commented R code and output for conducting, step by step, complete cluster analyses are available. The book is intended for researchers interested in applying clustering methods. Basic notions on theoretical issues and on R are provided so that professionals as well as novices with little or no background in the subject will benefit from the book. Computers

Neural-Network Simulation of Strongly Correlated Quantum Systems Quantum systems with many degrees of freedom are inherently difficult to describe and simulate quantitatively. The space of possible states is, in general, exponentially large in the number of degrees of freedom such as the number of particles it contains. Standard digital high-performance computing is generally too weak to capture all the necessary details, such that alternative quantum simulation devices have been proposed as a solution. Artificial neural networks, with their high non-local connectivity between the neuron degrees of freedom, may soon gain importance in simulating static and dynamical behavior of quantum systems. Particularly promising candidates are neuromorphic realizations based on analog electronic circuits which are being developed to capture, e.g., the functioning of biologically relevant networks. In turn, such neuromorphic systems may be used to measure and control real quantum many-body systems online. This thesis lays an important foundation for the realization of quantum simulations by means of neuromorphic hardware, for using quantum physics as an input to classical neural nets and, in turn, for using network results to be fed back to quantum systems. The necessary foundations on both sides, quantum physics and artificial neural networks, are described, providing a valuable reference for researchers from these different communities who need to understand the foundations of both. Computers

String Algorithms in C Implement practical data structures and algorithms for text search and discover how it is used inside other larger applications. This unique in-depth guide explains string algorithms using the C programming language. String Algorithms in C teaches you the following algorithms and how to use them: classical exact search algorithms; tries and compact tries; suffix trees and arrays; approximative pattern searches; and more. In this book, author Thomas Mailund provides a library with all the algorithms and applicable source code that you can use in your own programs. There are implementations of all the algorithms presented in this book so there are plenty of examples. You’ll understand that string algorithms are used in various applications such as image processing, computer vision, text analytics processing from data science to web applications, information retrieval from databases, network security, and much more. What You Will Learn Use classical exact search algorithms including naive search, borders/border search, Knuth-Morris-Pratt, and Boyer-Moor with or without Horspool Search in trees, use tries and compact tries, and work with the Aho-Carasick algorithm Process suffix trees including the use and development of McCreight’s algorithm Work with suffix arrays including binary searches; sorting naive constructions; suffix tree construction; skew algorithms; and the Borrows-Wheeler transform (BWT) Deal with enhanced suffix arrays including longest common prefix (LCP) Carry out approximative pattern searches among suffix trees and approximative BWT searches Who This Book Is For Those with at least some prior programming experience with C or Assembly and have at least prior experience with programming algorithms. Computers

Applied Cryptography and Network Security This two-volume set of LNCS 12146 and 12147 constitutes the refereed proceedings of the 18th International Conference on Applied Cryptography and Network Security, ACNS 2020, held in Rome, Italy, in October 2020.The conference was held virtually due to the COVID-19 pandemic. The 46 revised full papers presented were carefully reviewed and selected from 214 submissions. The papers were organized in topical sections named: cryptographic protocols cryptographic primitives, attacks on cryptographic primitives, encryption and signature, blockchain and cryptocurrency, secure multi-party computation, post-quantum cryptography. Computers

Formal Methods for Industrial Critical Systems This book constitutes the proceedings of the 25th International Workshop on Formal Methods for Industrial Critical Systems, FMICS 2020, which was held during September 2-3, 2020. The conference was planned to take place in Vienna, Austria. Due to the COVID-19 pandemic it changed to a virtual event.The 11 full papers presented in this volume were carefully reviewed and selected from 26 submissions. The papers are organized in topical sections as follows: Quantitative Analysis and Cyber-Physical Systems, Formal Verification of Industrial Systems, Temporal Logic and Model Checking. The book also contains a lengthy report on a Formal Methods Survey conducted on occasion of the 25th edition of the conference. Computers

Understanding Hybrid Environments in SharePoint 2019 Design and develop hybrid scenarios with SharePoint Online and SharePoint Server 2019. This book will help you build hybrid environments from scratch, and covers basic to advanced scenarios. The book takes you through the setup and configuration of SharePoint 2019 on virtual machines in Microsoft Azure. It gives you an overview of the features of the SharePoint Server 2019 User Experience. Integration of SP 2019 with PowerApps and Microsoft Flow is covered, along with Power BI reporting. You will learn to manage the data gateway and understand how to publish the Power BI Report. Configuration of the SP 2019 home page is explained and you learn how to enable a hybrid experience via the SP Office 365 link setting. You will know how to register a public domain in Office 365 and configure it for SP hybrid. Cloud hybrid search with the PowerShell script approach is discussed as well as SP 2019 hybrid Self-Service Site Creation. Configuration of the hybrid taxonomy, content types, and SharePoint framework development with SP 2019 are covered. And the book ends on using the office online server for SharePoint Server 2019 along with SP Server 2019 upgrade scenarios. After reading this book, you will be able to build and manage different hybrid environments with SharePoint Online and SharePoint Server 2019. What Will You Learn Enlarge your hybrid terminology Get familiar with the new and improved features of SharePoint Server 2019 Develop a hybrid experience with SharePoint Server 2019 Enable hybrid search Understand the on-premises data gateway Configure and integrate SharePoint Server 2019 with Power Platform, including Power BI, Power Apps, and Power Automate Who Is This Book For SharePoint professionals who want to configure hybrid solutions in SharePoint Computers

Algorithmic Aspects of Cloud Computing This book constitutes the refereed post-conference proceedings of the 5th International Symposium on Algorithmic Aspects of Cloud Computing, ALGOCLOUD 2019, held in Munich, Germany, in September 2019. The 8 revised full papers were carefully reviewed and selected from 16 submissions. The aim of the symposium is to present research activities and results on topics related to algorithmic, design, and development aspects of modern cloud-based systems. Computers

Visual Analytics for Data Scientists This textbook presents the main principles of visual analytics and describes techniques and approaches that have proven their utility and can be readily reproduced. Special emphasis is placed on various instructive examples of analyses, in which the need for and the use of visualisations are explained in detail. The book begins by introducing the main ideas and concepts of visual analytics and explaining why it should be considered an essential part of data science methodology and practices. It then describes the general principles underlying the visual analytics approaches, including those on appropriate visual representation, the use of interactive techniques, and classes of computational methods. It continues with discussing how to use visualisations for getting aware of data properties that need to be taken into account and for detecting possible data quality issues that may impair the analysis. The second part of the book describes visual analytics methods and workflows, organised by various data types including multidimensional data, data with spatial and temporal components, data describing binary relationships, texts, images and video. For each data type, the specific properties and issues are explained, the relevant analysis tasks are discussed, and appropriate methods and procedures are introduced. The focus here is not on the micro-level details of how the methods work, but on how the methods can be used and how they can be applied to data. The limitations of the methods are also discussed and possible pitfalls are identified. The textbook is intended for students in data science and, more generally, anyone doing or planning to do practical data analysis. It includes numerous examples demonstrating how visual analytics techniques are used and how they can help analysts to understand the properties of data, gain insights into the subject reflected in the data, and build good models that can be trusted. Based on several years of teaching related courses at the City, University of London, the University of Bonn and TU Munich, as well as industry training at the Fraunhofer Institute IAIS and numerous summer schools, the main content is complemented by sample datasets and detailed, illustrated descriptions of exercises to practice applying visual analytics methods and workflows. Computers

Collaboration Technologies and Social Computing This book constitutes the proceedings of the 26th International Conference on Collaboration Technologies and Social Computing, CollabTech 2020. The conference was scheduled to take place in Tartu, Estonia, in September 2020. It was held virtually due to the COVID-19 pandemic. The 10 full and 5 work-in-progress papers presented in this volume were carefully reviewed and selected from 25 submissions. Computers

Augmented Reality, Virtual Reality, and Computer Graphics The 2-volume set LNCS 12242 and 12243 constitutes the refereed proceedings of the 7th International Conference on Augmented Reality, Virtual Reality, and Computer Graphics, AVR 2020, held in Lecce, Italy, in September 2020.*The 45 full papers and 14 short papers presented were carefully reviewed and selected from 99 submissions. The papers discuss key issues, approaches, ideas, open problems, innovative applications and trends in virtual reality, augmented reality, mixed reality, 3D reconstruction visualization, and applications in the areas of cultural heritage, medicine, education, and industry. * The conference was held virtually due to the COVID-19 pandemic. Computers

Augmented Reality, Virtual Reality, and Computer Graphics The 2-volume set LNCS 12242 and 12243 constitutes the refereed proceedings of the 7th International Conference on Augmented Reality, Virtual Reality, and Computer Graphics, AVR 2020, held in Lecce, Italy, in September 2020.* The 45 full papers and 14 short papers presented were carefully reviewed and selected from 99 submissions. The papers discuss key issues, approaches, ideas, open problems, innovative applications and trends in virtual reality, augmented reality, mixed reality, 3D reconstruction visualization, and applications in the areas of cultural heritage, medicine, education, and industry. * The conference was held virtually due to the COVID-19 pandemic. Computers

Advance Metadata Fair This book outlines the legal powers of a major Western nation – Australia – to collect and use location information. Mobile service and social media service providers now have the ability to track, record and store more precise location information. Unlike 4G, 5G mobile communications require that cell towers and antennas be in much closer proximity; as a result, the location data can reveal more personal and sensitive information about individual citizens. Despite this aspect, service providers are required to disclose the data to the authorities, without the need for a judicial warrant. This book was written from the perspective of big location data software analytics, a capability that makes it possible to combine various location data points to create a profile on a given individual’s movements, habits, and political, religious and ideological orientation. In this regard, privacy is poorly protected. The rationale used to justify the powers was enforcing serious crimes – terrorism offences. Location data can now be retained for at least two years and be collected to investigate even minor offences. This can be done without the person being reasonably suspected of a criminal offence – when the individual is simply determined to be a person of interest. This poses legal risks to vulnerable communities. And yet, such investigative techniques are deemed lawful and reasonable. At a time when national security is so broadly defined to include economic issues, which in turn overlap with climate change and environmental protection, these legal powers should be reassessed. The book clarifies the complex rules that every citizen must know in order to have agency. Further, it calls upon authorities to reflect and to self-regulate, by making the conscious decision to surrender some of their powers to review by the independent judiciary. Without the requirement for a judicial warrant or judicial review, the powers are unfairly broad. The book pursues an interdisciplinary approach to assess the functionality of mobile telecommunications in direct relation to law enforcement powers and existing judicial precedents. Further, it offers a unifying techno-legal perspective on a complex issue touching on modern privacy law and communications technologies. Computers

Dependable Computing - EDCC 2020 Workshops This book constitutes refereed proceedings of the Workshops of the 16th European Dependable Computing Conference, EDCC: ​Workshop on Articial Intelligence for Railways, AI4RAILS 2020, Worskhop on Dynamic Risk Management for Autonomous Systems, DREAMS 2020, Workshop on Dependable Solutions for Intelligent Electricity Distribution Grids, DSOGRI 2020, Workshop on Software Engineering for Resilient Systems, SERENE 2020, held in September 2020. Due to the COVID-19 pandemic the workshops were held virtually. The 12 full papers and 4 short papers were thoroughly reviewed and selected from 35 submissions. The workshop papers complement the main conference topics by addressing dependability or security issues in specic application domains or by focussing in specialized topics, such as system resilience. Computers

Quality of Information and Communications Technology This book constitutes the refereed proceedings of the 13th International Conference on the Quality of Information and Communications Technology, QUATIC 2020, held in Faro, Portugal*, in September 2020. The 27 full papers and 12 short papers were carefully reviewed and selected from 81 submissions. The papers are organized in topical sections: quality aspects in machine learning, AI and data analytics; evidence-based software quality engineering; human and artificial intelligences for software evolution; process modeling, improvement and assessment; software quality education and training; quality aspects in quantum computing; safety, security and privacy; ICT verification and validation; RE, MDD and agile.*The conference was held virtually due to the COVID-19 pandemic. Computers

Svelte 3 Up and Running Build your first web project using the Svelte framework and deploy it in the cloud with automated testing and CI/CD Key Features Get up and running with the Svelte framework in no time with this quick introductory guide Build faster and leaner frontend and static web apps using the JAMstack Deploy your Svelte 3 app to production using cloud services and DevOps principles such as automated testing and CI/CD Book Description Svelte is a modern JavaScript framework used to build static web apps that are fast and lean, as well as being fun for developers to use. This book is a concise and practical introduction for those who are new to the Svelte framework which will have you up to speed with building apps quickly, and teach you how to use Svelte 3 to build apps that offer a great app user experience (UX). The book starts with an introduction to Svelte 3, before showing you how to set up your first complete application with the framework. Filled with code samples, each chapter will show you how to write components using the Svelte template syntax and the application programming interfaces (APIs) of the Svelte framework. As you advance, you'll go from scaffolding your project and tool setup all the way through to production with DevOps principles such as automated testing, continuous integration, and continuous delivery (CI/CD). Finally, you'll deploy your application in the cloud with object storage services and a content delivery network (CDN) for best-in-class performance for your users. By the end of this book, you'll have learned how to build and deploy apps using Svelte 3 to solve real-world problems and deliver impressive results. What you will learn Understand why Svelte 3 is the go-to framework for building static web apps that offer great UX Explore the tool setup that makes it easier to build and debug Svelte apps Scaffold your web project and build apps using the Svelte framework Create Svelte components using the Svelte template syntax and its APIs Combine Svelte components to build apps that solve complex real-world problems Use Svelte's built-in animations and transitions for creating components Implement routing for client-side single-page applications (SPAs) Perform automated testing and deploy your Svelte apps, using CI/CD when applicable Who this book is for The book is for frontend or full-stack developers looking to build modern web apps with Svelte. Web developers with experience in leading frontend JavaScript frameworks who wish to learn Svelte will find this book useful. The book assumes a solid understanding of JavaScript and core HTML5 technologies. Basic understanding of modern frontend frameworks will be beneficial, but not necessary. Computers

The Data Science Workshop Gain expert guidance on how to successfully develop machine learning models in Python and build your own unique data platforms Key Features Gain a full understanding of the model production and deployment process Build your first machine learning model in just five minutes and get a hands-on machine learning experience Understand how to deal with common challenges in data science projects Book Description Where there's data, there's insight. With so much data being generated, there is immense scope to extract meaningful information that'll boost business productivity and profitability. By learning to convert raw data into game-changing insights, you'll open new career paths and opportunities. The Data Science Workshop begins by introducing different types of projects and showing you how to incorporate machine learning algorithms in them. You'll learn to select a relevant metric and even assess the performance of your model. To tune the hyperparameters of an algorithm and improve its accuracy, you'll get hands-on with approaches such as grid search and random search. Next, you'll learn dimensionality reduction techniques to easily handle many variables at once, before exploring how to use model ensembling techniques and create new features to enhance model performance. In a bid to help you automatically create new features that improve your model, the book demonstrates how to use the automated feature engineering tool. You'll also understand how to use the orchestration and scheduling workflow to deploy machine learning models in batch. By the end of this book, you'll have the skills to start working on data science projects confidently. By the end of this book, you'll have the skills to start working on data science projects confidently. What you will learn Explore the key differences between supervised learning and unsupervised learning Manipulate and analyze data using scikit-learn and pandas libraries Understand key concepts such as regression, classification, and clustering Discover advanced techniques to improve the accuracy of your model Understand how to speed up the process of adding new features Simplify your machine learning workflow for production Who this book is for This is one of the most useful data science books for aspiring data analysts, data scientists, database engineers, and business analysts. It is aimed at those who want to kick-start their careers in data science by quickly learning data science techniques without going through all the mathematics behind machine learning algorithms. Basic knowledge of the Python programming language will help you easily grasp the concepts explained in this book. Computers

Python Algorithmic Trading Cookbook Build a solid foundation in algorithmic trading by developing, testing and executing powerful trading strategies with real market data using Python Key Features Build a strong foundation in algorithmic trading by becoming well-versed with the basics of financial markets Demystify jargon related to understanding and placing multiple types of trading orders Devise trading strategies and increase your odds of making a profit without human intervention Book Description If you want to find out how you can build a solid foundation in algorithmic trading using Python, this cookbook is here to help. Starting by setting up the Python environment for trading and connectivity with brokers, you'll then learn the important aspects of financial markets. As you progress, you'll learn to fetch financial instruments, query and calculate various types of candles and historical data, and finally, compute and plot technical indicators. Next, you'll learn how to place various types of orders, such as regular, bracket, and cover orders, and understand their state transitions. Later chapters will cover backtesting, paper trading, and finally real trading for the algorithmic strategies that you've created. You'll even understand how to automate trading and find the right strategy for making effective decisions that would otherwise be impossible for human traders. By the end of this book, you'll be able to use Python libraries to conduct key tasks in the algorithmic trading ecosystem. Note: For demonstration, we're using Zerodha, an Indian Stock Market broker. If you're not an Indian resident, you won't be able to use Zerodha and therefore will not be able to test the examples directly. However, you can take inspiration from the book and apply the concepts across your preferred stock market broker of choice. What you will learn Use Python to set up connectivity with brokers Handle and manipulate time series data using Python Fetch a list of exchanges, segments, financial instruments, and historical data to interact with the real market Understand, fetch, and calculate various types of candles and use them to compute and plot diverse types of technical indicators Develop and improve the performance of algorithmic trading strategies Perform backtesting and paper trading on algorithmic trading strategies Implement real trading in the live hours of stock markets Who this book is for If you are a financial analyst, financial trader, data analyst, algorithmic trader, trading enthusiast or anyone who wants to learn algorithmic trading with Python and important techniques to address challenges faced in the finance domain, this book is for you. Basic working knowledge of the Python programming language is expected. Although fundamental knowledge of trade-related terminologies will be helpful, it is not mandatory. Computers

The Complete Coding Interview Guide in Java Explore a wide variety of popular interview questions and learn various techniques for breaking down tricky bits of code and algorithms into manageable chunks Key Features Discover over 200 coding interview problems and their solutions to help you secure a job as a Java developer Work on overcoming coding challenges faced in a wide array of topics such as time complexity, OOP, and recursion Get to grips with the nuances of writing good code with the help of step-by-step coding solutions Book Description Java is one of the most sought-after programming languages in the job market, but cracking the coding interview in this challenging economy might not be easy. This comprehensive guide will help you to tackle various challenges faced in a coding job interview and avoid common interview mistakes, and will ultimately guide you toward landing your job as a Java developer. This book contains two crucial elements of coding interviews - a brief section that will take you through non-technical interview questions, while the more comprehensive part covers over 200 coding interview problems along with their hands-on solutions. This book will help you to develop skills in data structures and algorithms, which technical interviewers look for in a candidate, by solving various problems based on these topics covering a wide range of concepts such as arrays, strings, maps, linked lists, sorting, and searching. You'll find out how to approach a coding interview problem in a structured way that produces faster results. Toward the final chapters, you'll learn to solve tricky questions about concurrency, functional programming, and system scalability. By the end of this book, you'll have learned how to solve Java coding problems commonly used in interviews, and will have developed the confidence to secure your Java-centric dream job. What you will learn Solve the most popular Java coding problems efficiently Tackle challenging algorithms that will help you develop robust and fast logic Practice answering commonly asked non-technical interview questions that can make the difference between a pass and a fail Get an overall picture of prospective employers' expectations from a Java developer Solve various concurrent programming, functional programming, and unit testing problems Who this book is for This book is for students, programmers, and employees who want to be invited to and pass interviews given by top companies. The book assumes high school mathematics and basic programming knowledge. Computers

Image Fusion This book systematically discusses the basic concepts, theories, research and latest trends in image fusion. It focuses on three image fusion categories – pixel, feature and decision – presenting various applications, such as medical imaging, remote sensing, night vision, robotics and autonomous vehicles. Further, it introduces readers to a new category: edge-preserving-based image fusion, and provides an overview of image fusion based on machine learning and deep learning. As such, it is a valuable resource for graduate students and scientists in the field of digital image processing and information fusion. Computers

Edge AI As an important enabler for changing people’s lives, advances in artiï¬cial intelligence (AI)-based applications and services are on the rise, despite being hindered by efï¬ciency and latency issues. By focusing on deep learning as the most representative technique of AI, this book provides a comprehensive overview of how AI services are being applied to the network edge near the data sources, and demonstrates how AI and edge computing can be mutually beneficial. To do so, it introduces and discusses: 1) edge intelligence and intelligent edge; and 2) their implementation methods and enabling technologies, namely AI training and inference in the customized edge computing framework. Gathering essential information previously scattered across the communication, networking, and AI areas, the book can help readers to understand the connections between key enabling technologies, e.g. a) AI applications in edge; b) AI inference in edge; c) AI training for edge; d) edge computing for AI; and e) using AI to optimize edge. After identifying these five aspects, which are essential for the fusion of edge computing and AI, it discusses current challenges and outlines future trends in achieving more pervasive and fine-grained intelligence with the aid of edge computing. Computers

Ethereum Smart Contract Development in Solidity The general consensus is that BlockChain is the next disruptive technology, and Ethereum is the flagship product of BlockChain 2.0. However, coding and implementing business logic in a decentralized and transparent environment is fundamentally different from traditional programming and is emerging as a major challenge for developers. This book introduces readers to the Solidity language from scratch, together with case studies and examples. It also covers advanced topics and explains the working mechanism of smart contracts in depth. Further, it includes relevant examples that shed new light on the forefront of Solidity programming. In short, it equips readers with essential practical skills, allowing them to quickly catch up and start using Solidity programming. To gain the most from the book, readers should have already learned at least one object-oriented programming language Computers

Artificial Intelligence and Security This two-volume set LNCS 12239-12240 constitutes the refereed proceedings of the 6th International Conference on Artificial Intelligence and Security, ICAIS 2020, which was held in Hohhot, China, in July 2020. The conference was formerly called “International Conference on Cloud Computing and Security†with the acronym ICCCS.The total of 142 full papers presented in this two-volume proceedings was carefully reviewed and selected from 1064 submissions. The papers were organized in topical sections as follows: Part I: Artificial intelligence and internet of things. Part II: Internet of things, information security, big data and cloud computing, and information processing. Computers

Artificial Intelligence and Security This two-volume set LNCS 12239-12240 constitutes the refereed proceedings of the 6th International Conference on Artificial Intelligence and Security, ICAIS 2020, which was held in Hohhot, China, in July 2020. The conference was formerly called “International Conference on Cloud Computing and Security†with the acronym ICCCS.The total of 142 full papers presented in this two-volume proceedings was carefully reviewed and selected from 1064 submissions. The papers were organized in topical sections as follows: Part I: Artificial intelligence and internet of things. Part II: Internet of things, information security, big data and cloud computing, and information processing. Computers

Modelling Non-Markovian Quantum Systems Using Tensor Networks This thesis presents a revolutionary technique for modelling the dynamics of a quantum system that is strongly coupled to its immediate environment. This is a challenging but timely problem. In particular it is relevant for modelling decoherence in devices such as quantum information processors, and how quantum information moves between spatially separated parts of a quantum system. The key feature of this work is a novel way to represent the dynamics of general open quantum systems as tensor networks, a result which has connections with the Feynman operator calculus and process tensor approaches to quantum mechanics. The tensor network methodology developed here has proven to be extremely powerful: For many situations it may be the most efficient way of calculating open quantum dynamics. This work is abounds with new ideas and invention, and is likely to have a very significant impact on future generations of physicists. Computers

Practical Smart Device Design and Construction With the rapid development of the Internet of Things, a gap has emerged in skills versus knowledge in an industry typically segmented into hardware versus software. Practitioners are now expected to possess capabilities across the spectrum of hardware and software skills to create these smart devices. This book explores these skill sets in an instructive way, beginning at the foundations of what makes “smart†technology smart, addressing the basics of hardware and hardware design, software, user experiences, and culminating in the considerations and means of building a fully formed smart device, capable of being used in a commercial capacity, versus a DIY project. Practical Smart Device Design and Construction includes a set of starter projects designed to encourage the novice to build and learn from doing. Each project also includes a summary guiding you where to go next, and how to tie the practical, hands-on experience together with what they have learned to take the next step on their own. What You'll Learn Practical smart device design and construction considerations such as size, power consumption, wiring needs, analog vs digital, and sensor types and uses Methods and tools for creating their own designs such as circuit board designs; and wiring and prototyping tools Hands-on guidance through their own prototype projects and building it alongside the projects in this book Software considerations for speed versus ease, security, and basics of programming and data analytics for smart devices Who This Book Is For Those with some technical skills, or at least a familiarity with technical topics, who are looking for the means and skills to start experimenting with combined hardware and software projects in order to gain familiarity and comfort with the smart device space. Computers

Practical Bootstrap Learn to use one of the most popular CSS frameworks and build mobile-friendly web pages. Used for numerous websites and applications, Bootstrap is a key tool for modern web development. You will explore the grid system and then be introduced to the power of Bootstrap in practical projects. You’ll make navigation bars, use themes and styling, create and manipulate cover pages, admin dashboards, forms, and modal dialogs. You’ll learn to use Scrollspy and create tooltips and popovers. Today's web is responsive and Bootstrap continues to be at the forefront with web professionals. Learn by doing with Practical Bootstrap today. What You Will Learn Review how the grid system applies to Bootstrap Create stunning cover pages that encompass a large background image Build an admin dashboard page that changes its layout according to a device’s display width Work with the modal HTML markup and its main parts Customize modal behavior by setting various options using JavaScript Integrate Bootstrap JavaScript libraries with your own HTML page Add scroll spying functionality to your long-content pages Adjust the offset and activation point of the scroll sections Who This Book Is For Anyone who wants to learn how to use Bootstrap. You should have knowledge of HTML, CSS and basic JavaScript. Computers

Demystifying Azure AI Explore artificial intelligence offerings by Microsoft Azure, along with its other services. This book will help you implement AI features in various Azure services to help build your organization and customers. The book starts by introducing you to the Azure Cognitive Search service to create and use an application. You then will learn the built-in automatic tuning intelligence mechanism in Azure SQL Database. This is an important feature you can use to enable Azure SQL Database to optimize the performance of your queries. Next, you will go through AI services with Azure Integration Platform service and Azure Logic Apps to build a modern intelligent workflow in your application. Azure functions are discussed as a part of its server-less feature. The book concludes by teaching you how to work with Power Automate to analyze your business workflow. After reading this book, you will be able to understand and work with different Azure Cognitive Services in AI. What You Will Learn Get started with Azure Cognitive Search service Use AI services with Low Code – Power Automate Use AI services with Azure Integration services Use AI services with Azure Server-less offerings Use automatic tuning in Azure SQL database Who This Book Is For Aspiring Azure and AI professionals Computers

Android Apps Security Gain the information you need to design secure, useful, high-performing apps that expose end-users to as little risk as possible. This book shows you how to best design and develop Android apps with security in mind: explore concepts that you can use to secure apps and how you can use and incorporate these security features into your apps. What You Will Learn Identify data that should be secured Use the Android APIs to ensure confidentiality and integrity of data Build secure apps for the enterprise Implement Public Key Infrastructure and encryption APIs in apps Master owners, access control lists, and permissions to allow user control over app properties Manage authentication, transport layer encryption, and server-side security Who This Book Is For Experienced Android app developers. Computers

Artificial Neural Networks in Pattern Recognition This book constitutes the refereed proceedings of the 9th IAPR TC3 International Workshop on Artificial Neural Networks in Pattern Recognition, ANNPR 2020, held in Winterthur, Switzerland, in September 2020. The conference was held virtually due to the COVID-19 pandemic. The 22 revised full papers presented were carefully reviewed and selected from 34 submissions. The papers present and discuss the latest research in all areas of neural network-and machine learning-based pattern recognition. They are organized in two sections: learning algorithms and architectures, and applications. Computers

Parallel Problem Solving from Nature – PPSN XVI This two-volume set LNCS 12269 and LNCS 12270 constitutes the refereed proceedings of the 16th International Conference on Parallel Problem Solving from Nature, PPSN 2020, held in Leiden, The Netherlands, in September 2020. The 99 revised full papers were carefully reviewed and selected from 268 submissions. The topics cover classical subjects such as automated algorithm selection and configuration; Bayesian- and surrogate-assisted optimization; benchmarking and performance measures; combinatorial optimization; connection between nature-inspired optimization and artificial intelligence; genetic and evolutionary algorithms; genetic programming; landscape analysis; multiobjective optimization; real-world applications; reinforcement learning; and theoretical aspects of nature-inspired optimization. Computers

Text, Speech, and Dialogue This book constitutes the proceedings of the 23rd International Conference on Text, Speech, and Dialogue, TSD 2020, held in Brno, Czech Republic, in September 2020.* The 54 full papers presented in this volume were carefully reviewed and selected from 110 submissions. They were organized in topical sections named text, speech, and dialogue. The book also contains 3 invited talks. * The conference was held virtually due to the COVID-19 pandemic. Computers

OpenMP This book constitutes the proceedings of the 16th International Workshop on OpenMP, IWOMP 2020, held in Austin, TX, USA, in September 2020. The conference was held virtually due to the COVID-19 pandemic. The 21 full papers presented in this volume were carefully reviewed and selected for inclusion in this book. The papers are organized in topical sections named: performance methodologies; applications; OpenMP extensions; performance studies; tools; NUMA; compilation techniques; heterogeneous computing; and memory. The chapters ‘A Case Study on Addressing Complex Load Imbalance in OpenMP’ and ‘A Study of Memory Anomalies in OpenMP Applications’ are available open access under a Creative Commons Attribution 4.0 License via link.springer.com. Computers

Electronics for Beginners Jump start your journey with electronics! If you’ve thought about getting into electronics, but don’t know where to start, this book gives you the information you need. Starting with the basics of electricity and circuits, you'll be introduced to digital electronics and microcontrollers, capacitors and inductors, and amplification circuits – all while gaining the basic tools and information you need to start working with low-power electronics. Electronics for Beginners walks the fine line of focusing on projects-based learning, while still keeping electronics front and center. You'll learn the mathematics of circuits in an uncomplicated fashion and see how schematics map on to actual breadboards. Written for the absolute beginner, this book steers clear of being too math heavy, giving readers the key information they need to get started on their electronics journey. What You’ll Learn Review the basic “patterns†of resistor usage—pull up, pull down, voltage divider, and current limiter Understand the requirements for circuits and how they are put together Read and differentiate what various parts of the schematics do Decide what considerations to take when choosing components Use all battery-powered circuits, so projects are safe Who This Book Is For Makers, students, and beginners of any age interested in getting started with electronics. Computers

Intelligent Data Security Solutions for e-Health Applications E-health applications such as tele-medicine, tele-radiology, tele-ophthalmology, and tele-diagnosis are very promising and have immense potential to improve global healthcare. They can improve access, equity, and quality through the connection of healthcare facilities and healthcare professionals, diminishing geographical and physical barriers. One critical issue, however, is related to the security of data transmission and access to the technologies of medical information. Currently, medical-related identity theft costs billions of dollars each year and altered medical information can put a person’s health at risk through misdiagnosis, delayed treatment or incorrect prescriptions. Yet, the use of hand-held devices for storing, accessing, and transmitting medical information is outpacing the privacy and security protections on those devices. Researchers are starting to develop some imperceptible marks to ensure the tamper-proofing, cost effective, and guaranteed originality of the medical records. However, the robustness, security and efficient image archiving and retrieval of medical data information against these cyberattacks is a challenging area for researchers in the field of e-health applications. Intelligent Data Security Solutions for e-Health Applications focuses on cutting-edge academic and industry-related research in this field, with particular emphasis on interdisciplinary approaches and novel techniques to provide security solutions for smart applications. The book provides an overview of cutting-edge security techniques and ideas to help graduate students, researchers, as well as IT professionals who want to understand the opportunities and challenges of using emerging techniques and algorithms for designing and developing more secure systems and methods for e-health applications. Investigates new security and privacy requirements related to eHealth technologies and large sets of applications Reviews how the abundance of digital information on system behavior is now being captured, processed, and used to improve and strengthen security and privacy Provides an overview of innovative security techniques which are being developed to ensure the guaranteed authenticity of transmitted, shared or stored data/information Computers

Fault-Tolerant Systems Fault-Tolerant Systems, Second Edition, is the first book on fault tolerance design utilizing a systems approach to both hardware and software. No other text takes this approach or offers the comprehensive and up-to-date treatment that Koren and Krishna provide. The book comprehensively covers the design of fault-tolerant hardware and software, use of fault-tolerance techniques to improve manufacturing yields, and design and analysis of networks. Incorporating case studies that highlight more than ten different computer systems with fault-tolerance techniques implemented in their design, the book includes critical material on methods to protect against threats to encryption subsystems used for security purposes. The text’s updated content will help students and practitioners in electrical and computer engineering and computer science learn how to design reliable computing systems, and how to analyze fault-tolerant computing systems. Delivers the first book on fault tolerance design with a systems approach Offers comprehensive coverage of both hardware and software fault tolerance, as well as information and time redundancy Features fully updated content plus new chapters on failure mechanisms and fault-tolerance in cyber-physical systems Provides a complete ancillary package, including an on-line solutions manual for instructors and PowerPoint slides Computers

Linux For Dummies Your step-by-step guide to the latest in Linux Nine previous editions of this popular benchmark guide can’t be wrong! Whether you’re new to Linux and need a step-by-step guide or are a pro who wants to catch up with recent distributions, Linux For Dummies, 10 th Edition has your back. Covering everything from installation to automation, this updated edition focuses on openSUSE and Ubuntu and includes new and refreshed material—as well as chapters on building a web server and creating simple shell scripts. In his friendly, no-jargon style, IT professional and tech higher education instructor Richard Blum draws on more than 10 years of teaching to show you just why Linux’s open source operating systems are relied on to run a huge proportion of the world’s online infrastructure, servers, supercomputers, and NAS devices—and how you can master them too. Study the thinking behind Linux Choose the right installation approach Pick up the basics—from prepping to desktops Get fancy with music, video, movies, and games Whatever your Linux needs—work, fun, or just a hobby—this bestselling, evergreen guide will get you up and coding in the open source revolution in no time at all. Computers

Parallel Problem Solving from Nature – PPSN XVI This two-volume set LNCS 12269 and LNCS 12270 constitutes the refereed proceedings of the 16th International Conference on Parallel Problem Solving from Nature, PPSN 2020, held in Leiden, The Netherlands, in September 2020. The 99 revised full papers were carefully reviewed and selected from 268 submissions. The topics cover classical subjects such as automated algorithm selection and configuration; Bayesian- and surrogate-assisted optimization; benchmarking and performance measures; combinatorial optimization; connection between nature-inspired optimization and artificial intelligence; genetic and evolutionary algorithms; genetic programming; landscape analysis; multiobjective optimization; real-world applications; reinforcement learning; and theoretical aspects of nature-inspired optimization. Computers

Blockchain Data Analytics For Dummies Get ahead of the curve—learn about big data on the blockchain Blockchain came to prominence as the disruptive technology that made cryptocurrencies work. Now, data pros are using blockchain technology for faster real-time analysis, better data security, and more accurate predictions. Blockchain Data Analytics For Dummies is your quick-start guide to harnessing the potential of blockchain. Inside this book, technologists, executives, and data managers will find information and inspiration to adopt blockchain as a big data tool. Blockchain expert Michael G. Solomon shares his insight on what the blockchain is and how this new tech is poised to disrupt data. Set your organization on the cutting edge of analytics, before your competitors get there! Learn how blockchain technologies work and how they can integrate with big data Discover the power and potential of blockchain analytics Establish data models and quickly mine for insights and results Create data visualizations from blockchain analysis Discover how blockchains are disrupting the data world with this exciting title in the trusted For Dummies line! Computers

Trends in Artificial Intelligence Theory and Applications. Artificial Intelligence Practices This book constitutes the thoroughly refereed proceedings of the 33rd International Conference on Industrial, Engineering and Other Applications of Applied Intelligent Systems, IEA/AIE 2020, held in Kitakyushu, Japan, in September 2020. The 62 full papers and 17 short papers presented were carefully reviewed and selected from 119 submissions. The IEA/AIE 2020 conference will continue the tradition of emphasizing on applications of applied intelligent systems to solve real-life problems in all areas. These areas include are language processing; robotics and drones; knowledge based systems; innovative applications of intelligent systems; industrial applications; networking applications; social network analysis; financial applications and blockchain; medical and health-related applications; anomaly detection and automated diagnosis; decision-support and agent-based systems; multimedia applications; machine learning; data management and data clustering; pattern mining; system control, classification, and fault diagnosis. Computers

Model-Based Safety and Assessment This book constitutes the proceedings of the 7th International Symposium on Model-Based Safety and Assessment, IMBSA 2020, held in Lisbon, Portugal, in September 2020. The conference was held virtually due to the COVID-19 pandemic. The 15 revised full papers and 4 short papers presented were carefully reviewed and selected from 30 initial submissions. The papers are organized in topical sections on safety models and languages; state-space modeling; dependability analysis process; safety assessment in automotive domain; AI and safety assurance. Computers

Practical Blockchains and Cryptocurrencies Create cryptocurrency and blockchain applications by examining the key algorithms and concepts pertaining to blockchains, transaction processing, mining, distributed consensus, and anonymous currencies. In this book, you’ll develop a fully functional cryptocurrency from scratch in the Python language. Practical Blockchains and Cryptocurrencies is a reference for development of blockchain applications and provides you with rigorous information on cryptography and the theory underlying blockchains. This book consists of small chapters that focus on particular topics. You’ll start with a short history of money. Next, you will survey the bitcoin and altcoin ecosystem before delving into cryptographic hash functions, symmetric encryption, public key cryptography, and digital signatures. All the mathematics required to develop blockchain applications is covered. The emphasis is on providing a lucid and rigorous exposition on the nature and working of these constructs. The next major segment of the book discusses the key concepts and algorithms required to develop blockchain and cryptocurrency applications. There are expositions on blockchain construction, Merkle trees, peer-to-peer networks, cryptocurrency addresses, transactions, and mining. You’ll take a deep dive into the formation of consensus in distributed systems. In this book you’ll develop a fully functional cryptocurrency called Helium from scratch in Python. The language requirements are modest since it is presumed that most readers will not be acquainted with Python. The entire source code and unit test code is included in this book. Practical Blockchains and Cryptocurrencies interleaves theory and Helium program code chapters in order to demonstrate the practical application of theory in working Helium program code. What You Will Learn Gain the mathematical foundations as well as the concepts and algorithms of blockchains and cryptocurrencies Implement a cryptocurrency from scratch in Python Master the design of distributed blockchain applications Who This Book Is For Anyone interested in creating cryptocurrency and blockchain applications Computers

Judgement-Proof Robots and Artificial Intelligence This book addresses the role of public policy in regulating the autonomous artificial intelligence and related civil liability for damage caused by the robots (and any form of artificial intelligence). It is a very timely book, focusing on the consequences of judgment proofness of autonomous decision-making on tort law, risk and safety regulation, and the incentives stemming from these. This book is extremely important as regulatory endeavours concerning AI are in their infancy at most, whereas the industry’s development is continuing in a strong way. It is an important scientific contribution that will bring scientific objectivity to a, to date, very one-sided academic treatment of legal scholarship on AI. Computers

Implementing Effective Code Reviews The ideal code review process differs from organization to organization, but the needs all boil down to the same foundational factors. A software development team cannot properly grow if its code reviews are not consistent, straightforward, and aspire to hit several company goals at once, such as security, performance, longevity, and more. Implementing Effective Code Reviews is the manual your team has been seeking.Author Giuliana Carullo uses her expert background to guide you through the basics of building and maintaining clean code, and she is known for distilling complex concepts into entertaining and easy-to-grasp lessons. Healthy code requires incremental improvements, and knowing how to execute this is essential for conducting effective reviews on your team. While complex and fancy code can be interesting to work with, it will not always achieve business goals or solve urgent problems. Good coding practices are at the heart of a high-performing team, and Carullo instills these core values in a simple, straight-forward way in Implementing Effective Code Reviews. Whether you are a passionate programmer looking to go the extra mile at the office, or an experienced software engineer seeking a guide to how to improve your leadership and code review process, this book covers it all. With each chapter wrapped up in a handy checklist of crucial takeaways, Carullo has created an essential handbook for coders everywhere. There are a lot of myths that dominate the programming landscape, and Implementing Effective Code Reviews grounds the process and gets to the heart of the matter. What You Will Learn Understand how to work with your team to implement effective code reviews Master good programming practices that will build healthy code Discover how you should tackle different complex areas during code review like, security and performance Who This Book Is For Passionate programmers willing to go the extra mile to be better at their jobs, new programmers looking to strengthen their programming skills, and experienced software engineers looking for a quick guide on how to review code Computers

Classical Recording Classical Recording: A Practical Guide in the Decca Tradition is the authoritative guide to all aspects of recording acoustic classical music. Offering detailed descriptions, diagrams, and photographs of fundamental recording techniques such as the Decca tree, this book offers a comprehensive overview of the essential skills involved in successfully producing a classical recording. Written by engineers with years of experience working for Decca and Abbey Road Studios and as freelancers, Classical Recording equips the student, the interested amateur, and the practising professional with the required knowledge and confidence to tackle everything from solo piano to opera. Computers

Learn Azure Administration Enhance your Azure administration and Azure DevOps skills and get up and running with networking, security, automation, and effective cost management Key Features Explore a variety of administration patterns used for different cloud architectures Discover best practices for administering various IT systems hosted in Azure Administer, automate, and manage your Azure cloud environment effectively Book Description Microsoft Azure is one of the upcoming cloud platforms that provide cost-effective solutions and services to help businesses overcome complex infrastructure-related challenges. This book will help you scale your cloud administration skills with Microsoft Azure. Learn Azure Administration starts with an introduction to the management of Azure subscriptions, and then takes you through Azure resource management. Next, you'll configure and manage virtual networks and find out how to integrate them with a set of Azure services. You'll then handle the identity and security for users with the help of Azure Active Directory, and manage access from a single place using policies and defined roles. As you advance, you'll get to grips with receipts to manage a virtual machine. The next set of chapters will teach you how to solve advanced problems such as DDoS protection, load balancing, and networking for containers. You'll also learn how to set up file servers, along with managing and storing backups. Later, you'll review monitoring solutions and backup plans for a host of services. The last set of chapters will help you to integrate different services with Azure Event Grid, Azure Automation, and Azure Logic Apps, and teach you how to manage Azure DevOps. By the end of this Azure book, you'll be proficient enough to easily administer your Azure-based cloud environment. What you will learn Explore different Azure services and understand the correlation between them Secure and integrate different Azure components Work with a variety of identity and access management (IAM) models Find out how to set up monitoring and logging solutions Build a complete skill set of Azure administration activities with Azure DevOps Discover efficient scaling patterns for small and large workloads Who this book is for This book is for cloud administrators, system administrators, and IT professionals who want to scale up their skillset and enter the world of cloud computing. IT professionals and engineers who are already familiar with the basics of the Azure services and are looking for a step-by-step guide to solving the most common Azure problems will also find this book useful. Basic understanding of cloud concepts such as IaaS, PaaS, virtualization, networking, and common Azure services is required. Computers

Mastering Blockchain Develop a deep understanding of the theoretical foundations of blockchain technology and learn how to write smart contracts and build decentralized applications Key Features Updated with four new chapters on consensus algorithms, Ethereum 2.0, tokenization, and enterprise blockchains Dive deep into foundational pillars of blockchain technology such as decentralization, cryptography, and consensus protocols Get to grips with Solidity, Web3, cryptocurrencies, smart contract development and solve scalability, security, and privacy issues Discover the architecture of different distributed ledger platforms including Ethereum, Bitcoin, Hyperledger Fabric, Hyperledger Sawtooth, Corda, and Quorum Book Description Blockchain technology is the backbone of cryptocurrencies, and it has applications in finance, government, media, and many other industries. With a legacy of providing technologists with executable insights, the third edition of Mastering Blockchain is thoroughly revised and updated with the latest blockchain research, including four new chapters on consensus algorithms, Serenity (Ethereum 2.0), tokenization, and enterprise blockchains. Apart from covering the basics, including blockchain's technical underpinnings, cryptography, and consensus protocols, this book provides you with expert knowledge on decentralization, decentralized application development on Ethereum, Bitcoin, alternative coins, smart contracts, alternative blockchains, and Hyperledger. Furthermore, you will explore how to implement blockchain solutions beyond cryptocurrencies, such as the Internet of Things with blockchain, blockchain scalability, enterprise blockchains, and tokenization using blockchain, and the future scope of this fascinating and disruptive technology. By the end of this book, you will have gained a thorough understanding of the various facets of blockchain technology and be comfortable applying them to diverse real-world scenarios. What you will learn Grasp the mechanisms behind Bitcoin, Ethereum, and alternative cryptocurrencies Understand cryptography and its usage in blockchain technology Understand the theoretical foundations of smart contracts Develop decentralized applications using Solidity, Remix, Truffle, Ganache, and Drizzle Identify and examine applications of blockchain beyond cryptocurrencies Understand the architecture and development of Ethereum 2.0 Explore research topics and the future scope of blockchain technology Who this book is for If you are a technologist, business executive, a student or an enthusiast who wishes to explore the fascinating world of blockchain technology, smart contracts, decentralized applications and distributed systems then this book is for you. Basic familiarity with a beginner-level command of a programming language would be a plus. Computers

Docker Certified Associate (DCA) Pass the DCA exam and enhance your DevOps skills by achieving faster deployments, reduced downtime, and continuous integration and continuous delivery Key Features Strengthen your knowledge of container fundamentals and exploit Docker networking, storage, and image management Leverage Docker Swarm to deploy and scale applications in a cluster Build your Docker skills with the help of sample questions and mock tests Book Description Developers have changed their deployment artifacts from application binaries to container images, and they now need to build container-based applications as containers are part of their new development workflow. This Docker book is designed to help you learn about the management and administrative tasks of the Containers as a Service (CaaS) platform. The book starts by getting you up and running with the key concepts of containers and microservices. You'll then cover different orchestration strategies and environments, along with exploring the Docker Enterprise platform. As you advance, the book will show you how to deploy secure, production-ready, container-based applications in Docker Enterprise environments. Later, you'll delve into each Docker Enterprise component and learn all about CaaS management. Throughout the book, you'll encounter important exam-specific topics, along with sample questions and detailed answers that will help you prepare effectively for the exam. By the end of this Docker containers book, you'll have learned how to efficiently deploy and manage container-based environments in production, and you will have the skills and knowledge you need to pass the DCA exam. What you will learn Understand the key concepts of containerization and its advantages Discover how to build secure images and run customized Docker containers Explore orchestration with Docker Swarm and Kubernetes Become well versed with networking and application publishing methods Understand the Docker container runtime environment and customizations Deploy services on Docker Enterprise with Universal Control Plane Get to grips with effectively managing images using Docker Trusted Registry Who this book is for If you are a system administrator, a developer, a DevOps engineer, or any professional interested in enhancing your career portfolio by gaining Docker certification, this book is for you. In order to understand container networking and the use of load balancers and proxies to provide a full-featured Containers-as-a-Service environment, Linux and Windows user knowledge with some networking skills will be necessary. Computers

Advanced Computer Architecture This book constitutes the refereed proceedings of the 13th Conference on Advanced Computer Architecture, ACA 2020, held in Kunming, China, in August 2020. Due to the COVID-19 pandemic the conference was held online. The 24 revised full papers presented were carefully reviewed and selected from 105 submissions. The papers of this volume are organized in topical sections on: interconnection network, router and network interface architecture; accelerator-based, application-specific and reconfigurable architecture; processor, memory, and storage systems architecture; model, simulation and evaluation of architecture; new trends of technologies and applications. Computers

Learning Tableau 2020 Gain a solid foundation to learn Tableau, and develop the skills and abilities required for an advanced mastery of the tool. Whether you're new to Tableau or have been using it years, you will benefit from this book. Key Features Explore the latest Tableau 2020 features and redefine business analytics for your firm Understand visualizing data and creating interactive dashboards to gain meaningful insights Learn implementing effective data storytelling to redefine how your business leverages data and makes decisions Book Description Learning Tableau strengthens your command on Tableau fundamentals and builds on advanced topics. The book starts by taking you through foundational principles of Tableau. We then demonstrate various types of connections and how to work with metadata. We teach you to use a wide variety of visualizations to analyze and communicate the data, and introduce you to calculations and parameters. We then take an in-depth look at level of detail (LOD) expressions and use them to solve complex data challenges. Up next, we show table calculations, how to extend and alter default visualizations, build an interactive dashboard, and master the art of telling stories with data. This Tableau book will introduce you to visual statistical analytics capabilities, create different types of visualizations and dynamic dashboards for rich user experiences. We then move on to maps and geospatial visualization, and the new Data Model capabilities introduced in Tableau 2020.2. You will further use Tableau Prep's ability to clean and structure data and share the stories contained in your data. By the end of this book, you will be proficient in implementing the powerful features of Tableau 2020 for decision-making. What you will learn Develop stunning visualizations to explain complex data with clarity Explore exciting new Data Model capabilities Connect to various data sources to bring all your data together Leverage Tableau Prep Builder's amazing capabilities for data cleaning and structuring Create and use calculations to solve problems and enrich the analytics Master advanced topics such as sets, LOD calculations, and much more Enable smart decisions with data clustering, distribution, and forecasting Share your data stories to build a culture of trust and action Who this book is for This Tableau book is for anyone who wants to understand data. If you're new to Tableau, don't worry. This book will simplify Tableau for beginners to build on the foundations to help you understand how Tableau really works and then builds on that knowledge with practical examples before moving on to advanced techniques. Having a bit of background with data will help, but you don't need to know scripting, SQL or database structures. Computers

MCA Modern Desktop Administrator Practice Tests EXAM MD-100 AND MD-101 Provides 1,000 practice questions covering all exam objectives. Compliments the MCA Modern Desktop Administrator Complete Study Guide: Exam MD-100 and Exam MD-101 Quick, focused review for MD-100 and MD-101 Microsoft's new Certified Associate Modern Desktop qualification verifies your skill as an administrator of Windows 10 technologies and modern desktop management. With a focus on the intricacies of Microsoft 365, this certification is in high demand. The 2 practice exams PLUS domain-by-domain questions in this book will help you target your study and sharpen your focus—1000 questions total! So now tackle the certification exam with confidence. Expertly crafted questions cover 100% of the objectives for both the MD-100 and MD-101 exams, enabling you to be fully prepared. Coverage of 100% of all exam objectives in these practice tests means you'll be ready for: Desktop and Device Deployment Windows Management and Monitoring OS Updates and Upgrades Core Services Support Data Access and Usage Networking Security Driver and Device Installation Remote Access Configuration System Backup and Restore Interactive learning environment Take your exam prep to the next level with Sybex's superior interactive online study tools. To access our learning environment, simply visit www.wiley.com/go/sybextestprep, register to receive your unique PIN, and instantly gain one year of FREE access to the interactive test bank with two practice exams and domain-by-domain questions. 1000 questions total! Interactive test bank Use the interactive online version of the book's 2 practice exams to help you identify areas where further review is needed. Get more than 90% of the answers correct, and you're ready to take the certification exam. 100 questions total! ABOUT THE MCA PROGRAM The MCA Microsoft 365 Certified: Modern Desktop Administrator Associate certification helps Modern Desktop Administrators deploy, configure, secure, manage, and monitor devices and client applications in an enterprise environment. Exam MD-100, Windows 10, measures your ability to accomplish the following technical tasks: deploy Windows; manage devices and data; configure connectivity; and maintain Windows. Exam MD-101, Managing Modern Desktops, measures your ability to accomplish the following technical tasks: deploy and update operating systems; manage policies and profiles; manage and protect devices; and manage apps and data. Visit www.microsoft.com/en-us/ learning/modern-desktop.aspx for more information. Computers

Learn Windows Subsystem for Linux Become productive with seamless interoperability between Windows and the Linux subsystem, and understand the problems that Windows Subsystem for Linux (WSL) solves. Microsoft has pushed the boundaries of open source research with WSL and you don't want to miss this ride. You will learn keywords, definitions, new features, setup, and use cases around WSL, starting from downloading to setup to interoperability between Windows and Linux subsystems. You will understand the architecture of WSL and all the new features in WSL 2. This book includes wonderful use cases, including a dedicated chapter to how to start programming and web development on WSL, and the ability to use containerization solutions like Docker and Kubernetes. WSL is a great solution to work natively in a Linux environment from your Windows 10 machines. Modern applications demand integration of cross-platform tools, services and technologies. WSL makes life for developers and system administrators easy because it allows Linux applications to run on Windows without worrying about installing a Linux distribution on a traditional Virtual Machine. It is remarkable product with powerful functionality – get started with it using this book today. What You'll Learn Review the workings and internals of WSL and WSL2 Run Linux-based applications natively on Windows Establish your development environment in WSL Build mixed experiences (Windows-Linux) Set up and manage WSL and supported distribution packages. Who This Book Is For Programmers, web developers and system administrators working on Windows and Linux environments who want to bridge the gap between operating systems by running a Linux as a subsystem on Windows to boost their overall productivity, performance and delivery. Computers

Raku Fundamentals Gain the skills to begin developing Raku applications from the ground up in this hands-on compact book, which includes a foreword from Larry Wall, creator of Perl. You’ll learn enough to get started building with Raku, using Raku's gradual typing, handy object orientated features, powerful parsing capabilities, and human-usable concurrency. This book has been updated to include the latest version of Raku based upon the Perl 6.d major version which includes over 3,400 new commits in its specification. After a short introduction, each chapter develops a small example project, explaining the Raku features used. When the example is done, you’ll explore another aspect, such as optimizing further for readability or testing the code. Along the way you’ll see Raku basics, such as variables and scoping; subroutines; classes and objects; regexes; and code testing. When you’ve mastered the basics, Raku Fundamentals moves onto more advanced topics to give you a deeper understanding of the language. You’ll learn, amongst other things, how to work with persistent storage, how to generate good error messages, and how to write tricky applications such as a file and directory usage graph and a Unicode search tool. What You Will Learn Get coding with latest version of Raku Work on several hands-on examples and projects Integrate Python libraries into your Raku-based programs Parse INI files using regexes and grammars Build a date-time converter Carry out refactoring and other automated tests Who This Book Is For If you already know one or more programming languages, and want to learn about Raku, then this book is for you. Computers

Electronic Government and the Information Systems Perspective This book constitutes the refereed proceedings of the 9th International Conference on Electronic Government and the Information Systems Perspective, EGOVIS 2020, held in Bratislava, Slovakia, in September 2020. The 15 full and one short papers presented were carefully reviewed and selected from 24 submissions. The papers are organized in the following topical sections: Knowledge representation and modeling in e-Government; e-Government theoretical background; E-Government cases - data and knowledge management; identity management and legal issues; artificial intelligence and machine learning in e-Government context. Computers

Introduction to AI Robotics, second edition A comprehensive survey of artificial intelligence algorithms and programming organization for robot systems, combining theoretical rigor and practical applications. This textbook offers a comprehensive survey of artificial intelligence (AI) algorithms and programming organization for robot systems. Readers who master the topics covered will be able to design and evaluate an artificially intelligent robot for applications involving sensing, acting, planning, and learning. A background in AI is not required; the book introduces key AI topics from all AI subdisciplines throughout the book and explains how they contribute to autonomous capabilities. This second edition is a major expansion and reorganization of the first edition, reflecting the dramatic advances made in AI over the past fifteen years. An introductory overview provides a framework for thinking about AI for robotics, distinguishing between the fundamentally different design paradigms of automation and autonomy. The book then discusses the reactive functionality of sensing and acting in AI robotics; introduces the deliberative functions most often associated with intelligence and the capability of autonomous initiative; surveys multi-robot systems and (in a new chapter) human-robot interaction; and offers a “metaview” of how to design and evaluate autonomous systems and the ethical considerations in doing so. New material covers locomotion, simultaneous localization and mapping, human-robot interaction, machine learning, and ethics. Each chapter includes exercises, and many chapters provide case studies. Endnotes point to additional reading, highlight advanced topics, and offer robot trivia. Computers

Probabilistic Graphical Models A general framework for constructing and using probabilistic models of complex systems that would enable a computer to use available information for making decisions. Most tasks require a person or an automated system to reason—to reach conclusions based on available information. The framework of probabilistic graphical models, presented in this book, provides a general approach for this task. The approach is model-based, allowing interpretable models to be constructed and then manipulated by reasoning algorithms. These models can also be learned automatically from data, allowing the approach to be used in cases where manually constructing a model is difficult or even impossible. Because uncertainty is an inescapable aspect of most real-world applications, the book focuses on probabilistic models, which make the uncertainty explicit and provide models that are more faithful to reality. Probabilistic Graphical Models discusses a variety of models, spanning Bayesian networks, undirected Markov networks, discrete and continuous models, and extensions to deal with dynamical systems and relational data. For each class of models, the text describes the three fundamental cornerstones: representation, inference, and learning, presenting both basic concepts and advanced techniques. Finally, the book considers the use of the proposed framework for causal reasoning and decision making under uncertainty. The main text in each chapter provides the detailed technical development of the key ideas. Most chapters also include boxes with additional material: skill boxes, which describe techniques; case study boxes, which discuss empirical cases related to the approach described in the text, including applications in computer vision, robotics, natural language understanding, and computational biology; and concept boxes, which present significant concepts drawn from the material in the chapter. Instructors (and readers) can group chapters in various combinations, from core topics to more technically advanced material, to suit their particular needs. Computers

Cyber Security Practitioner's Guide In an era of unprecedented volatile political and economic environments across the world, computer-based cyber security systems face ever growing challenges. While the internet has created a global platform for the exchange of ideas, goods and services, it has also created boundless opportunities for cyber crime. The debate over how to plan for the cyber security of the future has focused the minds of developers and scientists alike. This book aims to provide a reference on current and emerging issues on systems security from the lens of autonomy, artificial intelligence and ethics as the race to fight and prevent cyber crime becomes increasingly pressing. Computers

Digital Transformation Selecting the right technology is one of the most critical decisions in technology driven enterprises, and no selection is complete without a thorough and informed evaluation. This book explores the digital transformation movement from three perspectives: the technological, the personal, and the organizational.The technical perspective analyses and evaluates new and up and coming technologies such as IoT and Cloud Technology. The personal perspective focuses on the consumer's attitude and experience in the adoption of technologies such as smart homes, smart watches, drones and wireless devices. And the organizational perspective focuses on evaluating how technology-driven an organization and their core activities or products are.This book is an ideal reference for managers who are responsible for digital transformation in their organizations and also serves a good starting point for researchers interested in understanding the trend. The book contains case studies that may be used by educators in MBA and Engineering and Technology Management MS programs covering digital transformation related courses. Computers

Handbook On Big Data And Machine Learning In The Physical Sciences (In 2 Volumes) This compendium provides a comprehensive collection of the emergent applications of big data, machine learning, and artificial intelligence technologies to present day physical sciences ranging from materials theory and imaging to predictive synthesis and automated research. This area of research is among the most rapidly developing in the last several years in areas spanning materials science, chemistry, and condensed matter physics.Written by world renowned researchers, the compilation of two authoritative volumes provides a distinct summary of the modern advances in instrument — driven data generation and analytics, establishing the links between the big data and predictive theories, and outlining the emerging field of data and physics-driven predictive and autonomous systems. Computers

Addressing Global Challenges and Quality Education This book constitutes the proceedings of the 15th European Conference on Technology Enhanced Learning, EC-TEL 2020, held in Heidelberg, Germany, in September 2020. The 24 research papers and 20 demo and 5 poster papers presented in this volume were carefully reviewed and selected from 91 submissions. The European Conference on Technology-Enhance Learning, which celebrates its 15th anniversary this year, is committed to address global challenges and quality education. The papers deal with the Sustainable Development Goals, particularly SDG 4 and SDG 10, to help to reduce the existing gaps and inequalities between countries and regions from around the world in terms of inclusiveness, equity, access, and quality of education. The chapters: “Designing an Online Self-Assessment for Informed Study Decisions: The User Perspectiveâ€; “Living with Learning Difficulties: Two Case Studies Exploring the Relationship Between Emotion and Performance in Students With Learning Difficultiesâ€; “Applying Instructional Design Principles on Augmented Reality Cards for Computer Science Educationâ€; and “Teaching Simulation Literacy With Evacuations - Concept, Technology, and Material for a Novel Approach†are available open access under a Creative Commons Attribution 4.0 International License via link.springer.com. Due to the Corona pandemic EC-TEL 2020 was held as an virtual event. Computers

Principles and Practice of Constraint Programming This book constitutes the proceedings of the 26th International Conference on Principles and Practice of Constraint Programming, CP 2020, held in Louvain-la-Neuve, Belgium, in September 2020. The conference was held virtually due to the COVID-19 pandemic. The 55 full papers presented in this volume were carefully reviewed and selected from 122 submissions. They deal with all aspects of computing with constraints including theory, algorithms, environments, languages, models, systems, and applications such as decision making, resource allocation, scheduling, configuration, and planning. The papers were organized according to the following topics/tracks: technical track; application track; and CP and data science and machine learning. Computers

Security and Cryptography for Networks This book constitutes the proceedings of the 12th International Conference on Security and Cryptography for Networks, SCN 2020, held in Amalfi, Italy, in September 2020*.The 33 papers presented in this volume were carefully reviewed and selected from 87 submissions. They are organized in topical sections on blockchain; multiparty computation; oblivious RAM; primitives and constructions; signatures, encryption, and algebraic constructions; symmetric crypto; theory and lower bounds ; zero-knowledge. *The conference was held virtually due to the COVID-19 pandemic. Computers

Advances in Digital Forensics XVI Digital forensics deals with the acquisition, preservation, examination, analysis and presentation of electronic evidence. Computer networks, cloud computing, smartphones, embedded devices and the Internet of Things have expanded the role of digital forensics beyond traditional computer crime investigations. Practically every crime now involves some aspect of digital evidence; digital forensics provides the techniques and tools to articulate this evidence in legal proceedings. Digital forensics also has myriad intelligence applications; furthermore, it has a vital role in cyber security -- investigations of security breaches yield valuable information that can be used to design more secure and resilient systems. Advances in Digital Forensics XVI describes original research results and innovative applications in the discipline of digital forensics. In addition, it highlights some of the major technical and legal issues related to digital evidence and electronic crime investigations. The areas of coverage include: themes and issues, forensic techniques, filesystem forensics, cloud forensics, social media forensics, multimedia forensics, and novel applications.This book is the sixteenth volume in the annual series produced by the International Federation for Information Processing (IFIP) Working Group 11.9 on Digital Forensics, an international community of scientists, engineers and practitioners dedicated to advancing the state of the art of research and practice in digital forensics. The book contains a selection of sixteen edited papers from the Sixteenth Annual IFIP WG 11.9 International Conference on Digital Forensics, held in New Delhi, India, in the winter of 2020. Advances in Digital Forensics XVI is an important resource for researchers, faculty members and graduate students, as well as for practitioners and individuals engaged in research and development efforts for the law enforcement and intelligence communities. Computers

Jumpstart UIKit ​Learn to build modern, sleek, and powerful websites quickly and easily with UIKit, an open-source, responsive, and lightweight framework. This book reveals the massive potential of this amazing framework to help you prototype, develop, and customize your web projects as per your business requirements Responsive web design is imperative nowadays as mobile sites become the de-facto standard. UIKit makes front-end design easier and helps speed up the development process significantly. You can build enterprise-level, feature-rich websites that work elegantly with a wide range of different device sizes and resolutions with minimum fuss. You'll play with the mobile-first grid component and an expansive set of intuitive CSS elements. UIKit simplifies the difficult task of crafting intricate and robust websites. Instead of loads of theory, this good read will help you get comfortable with the various utilities using comprehensive coding examples in an easy-to-understand manner. What You'll Learn Set up the UIKit's required build tools to get started Create a fully responsive, fluid, and nested grid layout Use UIKit to take your first steps in responsive web design Play with the wide-range of CSS components and elements Work with design web elements such as Navigation, Cards, Modals, Forms, and Accordion. Who This Book Is For This book is aimed at newbies and beginners, who are keen to build responsive websites using the solid UIkit framework. It can also be a quick reference for web designers, who are acquainted with or use the UIkit toolset for their important projects. Computers

Designing Internet of Things Solutions with Microsoft Azure Build a strong and efficient IoT solution at industrial and enterprise level by mastering industrial IoT using Microsoft Azure. This book focuses on the development of the industrial Internet of Things (IIoT) paradigm, discussing various architectures, as well as providing nine case studies employing IoT in common industrial domains including medical, supply chain, finance, and smart homes. The book starts by giving you an overview of the basic concepts of IoT, after which you will go through the various offerings of the Microsoft Azure IoT platform and its services. Next, you will get hands-on experience of IoT applications in various industries to give you a better picture of industrial solutions and how you should take your industry forward. As you progress through the chapters, you will learn real-time applications in IoT in agriculture, supply chain, financial services, retail, and transportation. Towards the end, you will gain knowledge to identify and analyze IoT security and privacy risks along with a detailed sample project. The book fills an important gap in the learning of IoT and its practical use case in your industry. Therefore, this is a practical guide that helps you discover the technologies and use cases for IIoT. By the end of this book, you will be able to build industrial IoT solution in Microsoft Azure with sensors, stream analytics, and serverless technologies. What You Will Learn Provision, configure, and connect devices with Microsoft Azure IoT hub Stream analytics using structural data and non-structural data such as images Use stream analytics, serverless technology, and IoT SaaS offerings Work with common sensors and IoT devices Who This Book Is For IoT architects, developers, and stakeholders working with the industrial Internet of Things. Computers

Algorithmic Game Theory This book constitutes the refereed proceedings of the 13th International Symposium on Algorithmic Game Theory, SAGT 2020, held in Augsburg, Germany, in September 2020.* The 21 full papers presented together with 3 abstract papers were carefully reviewed and selected from 53 submissions. The papers are organized in topical sections named: auctions and mechanism design, congestion games and flows over time, markets and matchings, scheduling and games on graphs, and social choice and cooperative games. * The conference was held virtually due to the COVID-19 pandemic. Computers

Functional Brain Mapping This book provides an essential overview of the broad range of functional brain imaging techniques, as well as neuroscientific methods suitable for various scientific tasks in fundamental and clinical neuroscience. It also shares information on novel methods in computational neuroscience, mathematical algorithms, image processing, and applications to neuroscience. The mammalian brain is a huge and complex network that consists of billions of neural and glial cells. Decoding how information is represented and processed by this neural network requires the ability to monitor the dynamics of large numbers of neurons at high temporal and spatial resolution over a large part of the brain. Functional brain optical imaging has seen more than thirty years of intensive development. Current light-using methods provide good sensitivity to functional changes through intrinsic contrast and are rapidly exploiting the growing availability of exogenous fluorescence probes. In addition, various types of functional brain optical imaging are now being used to reveal the brain’s microanatomy and physiology. Computers

Emergent Transport Properties of Magnetic Topological Insulator Heterostructures This book reveals unique transport phenomena and functionalities in topological insulators coupled with magnetism and superconductivity. Topological insulators are a recently discovered class of materials that possess a spin-momentum-locked surface state. Their exotic spin texture makes them an exciting platform for investigating emergent phenomena, especially when coupled with magnetism or superconductivity. Focusing on the strong correlation between electricity and magnetism in magnetic topological insulators, the author presents original findings on current-direction-dependent nonreciprocal resistance, current-induced magnetization reversal and chiral edge conduction at the domain wall. In addition, he demonstrates how the coupling between superconductivity and topological surface state leads to substantial nonreciprocal resistance. The author also elucidates the origins of these phenomena and deepens readers’ understanding of the topologically nontrivial electronic state. The book includes several works which are published in top journals and were selected for the President’s Award by the University of Tokyo and for the Ikushi Prize, awarded to distinguished Ph.D. students in Japan. Computers

Learning Angular Uncover Angular's potential for creating enterprise web applications—from setting up the environment to deployment—with the help of expert guidance, step-by-step explanations, and hands-on exercises Key Features Learn the fundamentals of Angular to build web applications using TypeScript Explore the basics of Angular development, from components and templates to forms and services Discover best practices for building, packaging, and testing Angular applications Book Description Angular, loved by millions of web developers around the world, continues to be one of the top JavaScript frameworks thanks to its regular updates and new features that enable fast, cross-platform, and secure frontend web development. With Angular, you can achieve high performance using the latest web techniques and extensive integration with web tools and integrated development environments (IDEs). Updated to Angular 10, this third edition of the Learning Angular book covers new features and modern web development practices to address the current frontend web development landscape. If you are new to Angular, this book will give you a comprehensive introduction to help you get you up and running in no time. You'll learn how to develop apps by harnessing the power of the Angular command-line interface (CLI), write unit tests, style your apps by following the Material Design guidelines, and finally deploy them to a hosting provider. The book is especially useful for beginners to get to grips with the bare bones of the framework needed to start developing Angular apps. By the end of this book, you'll not only be able to create Angular applications with TypeScript from scratch but also enhance your coding skills with best practices. What you will learn Use the Angular CLI to scaffold, build, and deploy a new Angular application Build components, the basic building blocks of an Angular application Discover techniques to make Angular components interact with each other Understand the different types of templates supported by Angular Create HTTP data services to access APIs and provide data to components Enhance your application's UX with Angular Material Apply best practices and coding conventions to your large-scale web development projects Who this book is for The Angular TypeScript book is for JavaScript and full-stack developers who want to enter the world of frontend development with Angular or migrate to the Angular framework to build professional web applications. Familiarity with web and programming concepts will assist with understanding the content covered in the book. Computers

Access, Resource Sharing and Collection Development Access, Resource Sharing, and Collection Development explores the role of libraries in acquiring, storing, and disseminating information in different formats to help you better use technology to share scarce resources and connect library users with collections. With an expressed goal of encouraging continued debate and further investigation, this book provides you with developing strategies and procedures to meet the challenges you face as a collection development librarian during this dynamic time. Among the vital concerns addressed are the competition for limited resources, trends in document delivery, the evaluation of document delivery products, and libraries’options for the future. The chapters collected in Access, Resource Sharing, and Collection Development represent the proceedings of the annual conference held by the University of Oklahoma Libraries and the University of Oklahoma Foundation. The book provides insight into your peers’findings and ideas on: access vs. ownership the future role of the bibliographer changes in collection management managing restrained resource budgets an emphasis on the library user as customer the growth and acceptance of document delivery as a component of collection development and ILL electronic publishing and copyright issues commercial document delivery services Access, Resource Sharing, and Collection Development also shows you how to discover and evaluate "free" resources on the Internet, as standards for production, promotion, and maintenance are nonexistent. The challenge of using these materials is being met by developing criteria for selection, looking at cataloging options, and working in cooperation with other institutions. You’ll also learn the different options for document delivery and how to evaluate document delivery products. Among the book’s advice: you should consider the types of document delivery available, examine the benefits of combining outside services with in-house systems, review the criteria for selecting technologies and suppliers, and explore examples of institutions creating customized systems. Computers

Wireless Algorithms, Systems, and Applications The two-volume set LNCS 12385 + 12386 constitutes the proceedings of the 15th International Conference on Wireless Algorithms, Systems, and Applications, WASA 2020, which was held during September 13-15, 2020. The conference was planned to take place in Qingdao, China; due to the COVID-19 pandemic it was held virtually. The 67 full and 14 short papers presented in these proceedings were carefully reviewed and selected from 216 submissions. The papers focus on data path algorithms; control path algorithms; network protocol design; network security; network services; and cloud computing. Computers

Computer Vision and Graphics This book constitutes the refereed proceedings of the International Conference on Computer Vision and Graphics, ICCVG 2020, held in Warsaw, Poland, in September 2020. The 20 full papers were selected from 49 submissions. The contributions cover topics such as: modelling of human visual perception; computational geometry; geometrical models of objects and scenes; illumination and reflection models and methods; image formation; image and video coding; image filtering and enhancement; biomedical image processing; biomedical graphics; colour image processing; multispectral image processing; pattern recognition in image processing; scene understanding; motion analysis, visual navigation and active vision; human motion detection and analysis; visualisation and graphical data presentation; hardware and architectures for image processing; computer-aided graphic design; 3D imaging, shading and rendering; computer animation; graphics for internet and mobile systems; virtual reality; image and video databases; digital watermarking; multimedia applications; and computer art. Due to the Corona pandemic ICCVG 2020 was held as a virtual event. Computers

KI 2020 This book constitutes the refereed proceedings of the 43rd German Conference on Artificial Intelligence, KI 2020, held in Bamberg, Germany, in September 2020.The 16 full and 12 short papers presented together with 6 extended abstracts in this volume were carefully reviewed and selected from 62 submissions. As well-established annual conference series KI is dedicated to research on theory and applications across all methods and topic areas of AI research. KI 2020 had a special focus on human-centered AI with highlights on AI and education and explainable machine learning. Due to the Corona pandemic KI 2020 was held as a virtual event. Computers

Functional and Logic Programming This book constitutes the proceedings of the 15th International Symposium on Functional and Logic Programming, FLOPS 2020, held in Akita, Japan*, in September 2020. The 12 papers presented in this volume were carefully reviewed and selected from 25 submissions. They cover all aspects of the design, semantics, theory, applications, implementations, and teaching of declarative programming focusing on topics such as functional programming, logic programming, declarative programming, constraint programming, formal method, model checking, program transformation, program refinement, and type theory. *The conference was held virtually due to the COVID-19 pandemic. Computers

The Art of Multiprocessor Programming The Art of Multiprocessor Programming, Second Edition, provides users with an authoritative guide to multicore programming. This updated edition introduces higher level software development skills relative to those needed for efficient single-core programming, and includes comprehensive coverage of the new principles, algorithms, and tools necessary for effective multiprocessor programming. The book is an ideal resource for students and professionals alike who will benefit from its thorough coverage of key multiprocessor programming issues. Features new exercises developed for instructors using the text, with more algorithms, new examples, and other updates throughout the book Presents the fundamentals of programming multiple threads for accessing shared memory Explores mainstream concurrent data structures and the key elements of their design, as well as synchronization techniques, from simple locks to transactional memory systems Computers

Electronic Resources Electronic Resources: Implications for Collection Management shows librarians the strengths and weaknesses of electronic resources and the implications these resources have on collection management. The book then helps librarians incorporate electronic resources into their collections accordingly. Contributors in Electronic Resources provide a broad look at the ways in which electronic information affects the business of building and maintaining library collections. They examine the history of electronic resources in document collections and share with readers a thorough analysis of the gains and losses libraries can expect to experience in an increasingly digital environment. Readers also learn: how to budget for both traditional and emerging information sources the effects of electronic collections on the public services realm how to assess the value of journals amidst the many different access and delivery mechanisms how to use resource sharing as a solution to the archival problems which arise as libraries collect materials in continuously proliferating formats selection criteria for electronic resources how to assemble electronic resources into archives social implications of electronic collections Academic librarians in collection management will find Electronic Resources an essential resource for finding their place in the electronic environment. Librarians will refer to this volume again and again as they adjust to increasing dependence upon electronic resources for fulfilling their patrons’needs. Computers

Ontologies and Concepts in Mind and Machine This book constitutes the proceedings of the 25th International Conference on Conceptual Structures, ICCS 2020, held in Bolzano, Italy, in September 2020.* The 10 full papers, 5 short papers and 1 poster paper presented were carefully reviewed and selected from 24 submissions. The proceedings also include two keynotes and two tutorials. The papers focus on the representation of and reasoning with conceptual structures in a variety of contexts. The topics of this year's conference range from formal concept analysis to decision making, from machine learning to natural language processing. *The conference was held virtually due to the COVID-19 pandemic. Computers

Software Engineering and Formal Methods The volume LNCS 12226 constitutes the revised selected papers from the four workshops collocated with the 17th International Conference on Software Engineering and Formal Methods, SEFM 2019. The 13 full papers presented together with 7 short papers in this volume were carefully reviewed and selected from a total of 45 submissions. They stem from the following workshops: CoSim-CPS 2019 – 3rd International Workshop on Formal Co-Simulation of Cyber-Physical Systems; ASYDE 2019 -- 1st International Workshop on Cognition: Interdisciplinary Foundations, Models and Applications; and FOCLASA 2019 -- 17th International Workshop on Foundations of Coordination Languages and Self-Adaptive Systems​. Computers

Transactions on Large-Scale Data- and Knowledge-Centered Systems XLIV The LNCS journal Transactions on Large-Scale Data- and Knowledge-Centered Systems focuses on data management, knowledge discovery, and knowledge processing, which are core and hot topics in computer science. Since the 1990s, the Internet has become the main driving force behind application development in all domains. An increase in the demand for resource sharing (e.g., computing resources, services, metadata, data sources) across different sites connected through networks has led to an evolution of data- and knowledge-management systems from centralized systems to decentralized systems enabling large-scale distributed applications providing high scalability.This, the 44th issue of Transactions on Large-Scale Data- and Knowledge-Centered Systems, contains six fully revised and extended papers selected from the 35th conference on Data Management – Principles, Technologies and Applications, BDA 2019. The topics covered include big data, graph data streams, workflow execution in the cloud, privacy in crowdsourcing, secure distributed computing, machine learning, and data mining for recommendation systems. Computers

Computers Helping People with Special Needs The two-volume set LNCS 12376 and 12377 constitutes the refereed proceedings of the 17th International Conference on Computers Helping People with Special Needs, ICCHP 2020, held in Lecco, Italy, in September 2020. The conference was held virtually due to the COVID-19 pandemic. The 104 papers presented were carefully reviewed and selected from 206 submissions. Included also are 13 introductions. The papers are organized in the following topical sections: Part I: user centred design and user participation in inclusive R&D; artificial intelligence, accessible and assistive technologies; XR accessibility – learning from the past, addressing real user needs and the technical architecture for inclusive immersive environments; serious and fun games; large-scale web accessibility observatories; accessible and inclusive digital publishing; AT and accessibility for blind and low vision users; Art Karshmer lectures in access to mathematics, science and engineering; tactile graphics and models for blind people and recognition of shapes by touch; and environmental sensing technologies for visual impairment Part II: accessibility of non-verbal communication: making spatial information accessible to people with disabilities; cognitive disabilities and accessibility – pushing the boundaries of inclusion using digital technologies and accessible eLearning environments; ICT to support inclusive education – universal learning design (ULD); hearing systems and accessories for people with hearing loss; mobile health and mobile rehabilitation for people with disabilities: current state, challenges and opportunities; innovation and implementation in the area of independent mobility through digital technologies; how to improve interaction with a text input system; human movement analysis for the design and evaluation of interactive systems and assistive devices; and service and care provision in assistive environments 12 chapters are available open access under a Creative Commons Attribution 4.0 International License via link.springer.com. Computers

Wireless Algorithms, Systems, and Applications The two-volume set LNCS 12385 + 12386 constitutes the proceedings of the 15th International Conference on Wireless Algorithms, Systems, and Applications, WASA 2020, which was held during September 13-15, 2020. The conference was planned to take place in Qingdao, China; due to the COVID-19 pandemic it was held virtually. The 67 full and 14 short papers presented in these proceedings were carefully reviewed and selected from 216 submissions. These submissions cover many hot research topics, including machine-learning algorithms for wireless systems and applications, Internet of Things (IoTs) and related wireless solutions, wireless networking for cyber-physical systems (CPSs), security and privacy solutions for wireless applications, blockchain solutions for mobile applications, mobile edge computing, wireless sensor networks, distributed and localized algorithm design and analysis, wireless crowdsourcing, mobile cloud computing, vehicular networks, wireless solutions for smart cities, wireless algorithms for smart grids, mobile social networks, mobile system security, storage systems for mobile applications, etc. Computers

Smooth Manifolds and Observables This book gives an introduction to fiber spaces and differential operators on smooth manifolds. Over the last 20 years, the authors developed an algebraic approach to the subject and they explain in this book why differential calculus on manifolds can be considered as an aspect of commutative algebra. This new approach is based on the fundamental notion of observable which is used by physicists and will further the understanding of the mathematics underlying quantum field theory. Computers

The Web of Data This book’s main goals are to bring together in a concise way all the methodologies, standards and recommendations related to Data, Queries, Links, Semantics, Validation and other issues concerning machine-readable data on the Web, to describe them in detail, to provide examples of their use, and to discuss how they contribute to – and how they have been used thus far on – the “Web of Dataâ€. As the content of the Web becomes increasingly machine readable, increasingly complex tasks can be automated, yielding more and more powerful Web applications that are capable of discovering, cross-referencing, filtering, and organizing data from numerous websites in a matter of seconds. The book is divided into nine chapters, the first of which introduces the topic by discussing the shortcomings of the current Web and illustrating the need for a Web of Data. Next, “Web of Data†provides an overview of the fundamental concepts involved, and discusses some current use-cases on the Web where such concepts are already being employed. “Resource Description Framework (RDF)†describes the graph-structured data model proposed by the Semantic Web community as a common data model for the Web. The chapter on “RDF Schema (RDFS) and Semantics†presents a lightweight ontology language used to define an initial semantics for terms used in RDF graphs. In turn, the chapter “Web Ontology Language (OWL)†elaborates on a more expressive ontology language built upon RDFS that offers much more powerful ontological features. In “SPARQL Query Language†a language for querying and updating RDF graphs is described, with examples of the features it supports, supplemented by a detailed definition of its semantics. “Shape Constraints and Expressions (SHACL/ShEx)†introduces two languages for describing the expected structure of – and expressing constraints on – RDF graphs for the purposes of validation. “Linked Data†discusses the principles and best practices proposed by the Linked Data community for publishing interlinked (RDF) data on the Web, and how these techniques have been adopted. The final chapter highlights open problems and rounds out the coverage with a more general discussion on the future of the Web of Data. The book is intended for students, researchers and advanced practitioners interested in learning more about the Web of Data, and about closely related topics such as the Semantic Web, Knowledge Graphs, Linked Data, Graph Databases, Ontologies, etc. Offering a range of accessible examples and exercises, it can be used as a textbook for students and other newcomers to the field. It can also serve as a reference handbook for researchers and developers, as it offers up-to-date details on key standards (RDF, RDFS, OWL, SPARQL, SHACL, ShEx, RDB2RDF, LDP), along with formal definitions and references to further literature. The associated website webofdatabook.org offers a wealth of complementary material, including solutions to the exercises, slides for classes, raw data for examples, and a section for comments and questions. Computers

Profinite Semigroups and Symbolic Dynamics This book describes the relation between profinite semigroups and symbolic dynamics. Profinite semigroups are topological semigroups which are compact and residually finite. In particular, free profinite semigroups can be seen as the completion of free semigroups with respect to the profinite metric. In this metric, two words are close if one needs a morphism on a large finite monoid to distinguish them. The main focus is on a natural correspondence between minimal shift spaces (closed shift-invariant sets of two-sided infinite words) and maximal J-classes (certain subsets of free profinite semigroups). This correspondence sheds light on many aspects of both profinite semigroups and symbolic dynamics. For example, the return words to a given word in a shift space can be related to the generators of the group of the corresponding J-class. The book is aimed at researchers and graduate students in mathematics or theoretical computer science. Computers

Software Architecture This book constitutes the refereed proceedings of the 14th International Conference on Software Architecture, ECSA 2020, held in A’quila, Italy, in September 2020. In the Research Track, 12 full papers presented together with 5 short papers were carefully reviewed and selected from 103 submissions. They are organized in topical sections as follows: microservices; uncertainty, self-adaptive, and open systems; model-based approaches; performance and security engineering; architectural smells and source code analysis; education and training; experiences and learnings from industrial case studies; and architecting contemporary distributed systems. In the Industrial Track, 11 submissions were received and 6 were accepted to form part of these proceedings. In addition the book contains 3 keynote talks. Due to the Corona pandemic ECSA 2020 was held as an virtual event. Computers

Computers Helping People with Special Needs The two-volume set LNCS 12376 and 12377 constitutes the refereed proceedings of the 17th International Conference on Computers Helping People with Special Needs, ICCHP 2020, held in Lecco, Italy, in September 2020. The conference was held virtually due to the COVID-19 pandemic. The 104 papers presented were carefully reviewed and selected from 206 submissions. Included also are 13 introductions. The papers are organized in the following topical sections: Part I: user centred design and user participation in inclusive R&D; artificial intelligence, accessible and assistive technologies; XR accessibility – learning from the past, addressing real user needs and the technical architecture for inclusive immersive environments; serious and fun games; large-scale web accessibility observatories; accessible and inclusive digital publishing; AT and accessibility for blind and low vision users; Art Karshmer lectures in access to mathematics, science and engineering; tactile graphics and models for blind people and recognition of shapes by touch; and environmental sensing technologies for visual impairment Part II: accessibility of non-verbal communication: making spatial information accessible to people with disabilities; cognitive disabilities and accessibility – pushing the boundaries of inclusion using digital technologies and accessible eLearning environments; ICT to support inclusive education – universal learning design (ULD); hearing systems and accessories for people with hearing loss; mobile health and mobile rehabilitation for people with disabilities: current state, challenges and opportunities; innovation and implementation in the area of independent mobility through digital technologies; how to improve interaction with a text input system; human movement analysis for the design and evaluation of interactive systems and assistive devices; and service and care provision in assistive environments 10 chapters are available open access under a Creative Commons Attribution 4.0 International License via link.springer.com. Computers

Software Architecture This book constitutes the refereed proceedings of the tracks and workshops which complemented the 14th European Conference on Software Architecture, ECSA 2020, held in L'Aquila, Italy*, in September 2020. The 30 full papers and 9 short papers presented in this volume were carefully reviewed and selected from 72 submissions. Papers presented were accepted into the following tracks and workshops: ECSA 2020 Doctoral Symposium track; ECSA 2020 Tool Demos track; ECSA 2020 Gender Diversity in Software Architecture &Software Engineering track; CASA - 3rd International Workshop on Context-aware, Autonomous and Smart Architecture; CSE/QUDOS - Joint Workshop on Continuous Software Engineering and Quality-Aware DevOps; DETECT - 3rd International Workshop on Modeling, Verication and Testing of Dependable Critical Systems; FAACS-MDE4SA - Joint Workshop on Formal Approaches for Advanced Computing Systems and Model-Driven Engineering for Software Architecture; IoT-ASAP - 4th International Workshop on Engineering IoT Systems: Architectures, Services, Applications, and Platforms; SASI4 - 2nd Workshop on Systems, Architectures, and Solutions for Industry 4.0; WASA - 6th International Workshop on Automotive System/Software Architecture. *The conference was held virtually due to the COVID-19 pandemic. Computers

Cloud Network Management Data storage, processing, and management at remote location over dynamic networks is the most challenging task in cloud networks. Users’ expectations are very high for data accuracy, reliability, accessibility, and availability in pervasive cloud environment. It was the core motivation for the Cloud Networks Internet of Things (CNIoT). The exponential growth of the networks and data management in CNIoT must be implemented in fast growing service sectors such as logistic and enterprise management. The network based IoT works as a bridge to fill the gap between IT and cloud networks, where data is easily accessible and available. This book provides a framework for the next generation of cloud networks, which is the emerging part of 5G partnership projects. This contributed book has following salient features, A cloud-based next generation networking technologies. Cloud-based IoT and mobility management technology. The proposed book is a reference for research scholars and course supplement for cloud-IoT related subjects such as distributed networks in computer/ electrical engineering. Sanjay Kumar Biswash is working as an Assistant professor in NIIT University, India. He held Research Scientist position, Institute of Cybernetics, National Research Tomsk Polytechnic University, Russia. He was PDF at LNCC, Brazil and SDSU, USA. He was a visiting researcher to the UC, Portugal. Sourav Kanti Addya is working as an Assistant professor in NITK, Surathkal, India. He was a PDF at IIT Kharagpur, India. He was a visiting scholar at SDSU, USA. He obtained national level GATE scholarship. He is a member of IEEE, ACM. Computers

Computational Science and its Applications Computational science is a rapidly growing multidisciplinary field concerned with the design, implementation, and use of mathematical models to analyze and solve real-world problems. It is an area of science that spans many disciplines and which involves the development of models and allows the use of computers to perform simulations or numerical analysis to understand problems that are computational and theoretical. Computational Science and its Applications provides an opportunity for readers to develop abilities to pose and solve problems that combine insights from one or more disciplines from the natural sciences with mathematical tools and computational skills. This requires a unique combination of applied and theoretical knowledge and skills. The topics covered in this edited book are applications of wavelet and fractals, modeling by partial differential equations on flat structure as well as on graphs and networks, computational linguistics, prediction of natural calamities and diseases like epilepsy seizure, heart attack, stroke, biometrics, modeling through inverse problems, interdisciplinary topics of physics, mathematics, and medical science, and modeling of terrorist attacks and human behavior. The focus of this book is not to educate computer specialists, but to provide readers with a solid understanding of basic science as well as an integrated knowledge on how to use essential methods from computational science. Features: Modeling of complex systems Cognitive computing systems for real-world problems Presentation of inverse problems in medical science and their numerical solutions Challenging research problems in many areas of computational science This book could be used as a reference book for researchers working in theoretical research as well as those who are doing modeling and simulation in such disciplines as physics, biology, geoscience, and mathematics, and those who have a background in computational science. Computers

Big Data Analytics and Knowledge Discovery The volume LNCS 12393 constitutes the papers of the 22nd International Conference Big Data Analytics and Knowledge Discovery which will be held online in September 2020. The 15 full papers presented together with 14 short papers plus 1 position paper in this volume were carefully reviewed and selected from a total of 77 submissions. This volume offers a wide range to following subjects on theoretical and practical aspects of big data analytics and knowledge discovery as a new generation of big data repository, data pre-processing, data mining, text mining, sequences, graph mining, and parallel processing. Computers

Random Forests with R This book offers an application-oriented guide to random forests: a statistical learning method extensively used in many fields of application, thanks to its excellent predictive performance, but also to its flexibility, which places few restrictions on the nature of the data used. Indeed, random forests can be adapted to both supervised classification problems and regression problems. In addition, they allow us to consider qualitative and quantitative explanatory variables together, without pre-processing. Moreover, they can be used to process standard data for which the number of observations is higher than the number of variables, while also performing very well in the high dimensional case, where the number of variables is quite large in comparison to the number of observations. Consequently, they are now among the preferred methods in the toolbox of statisticians and data scientists. The book is primarily intended for students in academic fields such as statistical education, but also for practitioners in statistics and machine learning. A scientific undergraduate degree is quite sufficient to take full advantage of the concepts, methods, and tools discussed. In terms of computer science skills, little background knowledge is required, though an introduction to the R language is recommended. Random forests are part of the family of tree-based methods; accordingly, after an introductory chapter, Chapter 2 presents CART trees. The next three chapters are devoted to random forests. They focus on their presentation (Chapter 3), on the variable importance tool (Chapter 4), and on the variable selection problem (Chapter 5), respectively. After discussing the concepts and methods, we illustrate their implementation on a running example. Then, various complements are provided before examining additional examples. Throughout the book, each result is given together with the code (in R) that can be used to reproduce it. Thus, the book offers readers essential information and concepts, together with examples and the software tools needed to analyse data using random forests. Computers

Fundamentals of Pattern Recognition and Machine Learning Fundamentals of Pattern Recognition and Machine Learning is designed for a one or two-semester introductory course in Pattern Recognition or Machine Learning at the graduate or advanced undergraduate level. The book combines theory and practice and is suitable to the classroom and self-study. It has grown out of lecture notes and assignments that the author has developed while teaching classes on this topic for the past 13 years at Texas A&M University. The book is intended to be concise but thorough. It does not attempt an encyclopedic approach, but covers in significant detail the tools commonly used in pattern recognition and machine learning, including classification, dimensionality reduction, regression, and clustering, as well as recent popular topics such as Gaussian process regression and convolutional neural networks. In addition, the selection of topics has a few features that are unique among comparable texts: it contains an extensive chapter on classifier error estimation, as well as sections on Bayesian classification, Bayesian error estimation, separate sampling, and rank-based classification. The book is mathematically rigorous and covers the classical theorems in the area. Nevertheless, an effort is made in the book to strike a balance between theory and practice. In particular, examples with datasets from applications in bioinformatics and materials informatics are used throughout to illustrate the theory. These datasets are available from the book website to be used in end-of-chapter coding assignments based on python and scikit-learn. All plots in the text were generated using python scripts, which are also available on the book website. Computers

MongoDB Topology Design Create a world-class MongoDB cluster that is scalable, reliable, and secure. Comply with mission-critical regulatory regimes such as the European Union’s General Data Protection Regulation (GDPR). Whether you are thinking of migrating to MongoDB or need to meet legal requirements for an existing self-managed cluster, this book has you covered. It begins with the basics of replication and sharding, and quickly scales up to cover everything you need to know to control your data and keep it safe from unexpected data loss or downtime. This book covers best practices for stable MongoDB deployments. For example, a well-designed MongoDB cluster should have no single point of failure. The book covers common use cases when only one or two data centers are available. It goes into detail about creating geopolitical sharding configurations to cover the most stringent data protection regulation compliance. The book also covers different tools and approaches for automating and monitoring a cluster with Kubernetes, Docker, and popular cloud provider containers. What You Will Learn Get started with the basics of MongoDB clusters Protect and monitor a MongoDB deployment Deepen your expertise around replication and sharding Keep effective backups and plan ahead for disaster recovery Recognize and avoid problems that can occur in distributed databases Build optimal MongoDB deployments within hardware and data center limitations Who This Book Is For Solutions architects, DevOps architects and engineers, automation and cloud engineers, and database administrators who are new to MongoDB and distributed databases or who need to scale up simple deployments. This book is a complete guide to planning a deployment for optimal resilience, performance, and scaling, and covers all the details required to meet the new set of data protection regulations such as the GDPR. This book is particularly relevant for large global organizations such as financial and medical institutions, as well as government departments that need to control data in the whole stack and are prohibited from using managed cloud services. Computers

Beginning Android Games Development Do you have an awesome idea for the next break-through mobile gaming title? This updated edition will help you kick-start your project as it guides you through the process of creating several example game apps using APIs available in Android. You will learn the basics needed to join the ranks of successful Android game app developers. the book starts with game design fundamentals using Canvas and Android SDK 10 or earlier programming basics. You then will progress toward creating your own basic game engine and playable game apps that work on Android 10 or earlier smartphones and tablets. You take your game through the chapters and topics in the book to learn different tools such as OpenGL ES. And you will learn about publishing and marketing your games to monetize your creation. What You Will Learn Gain knowledge on the fundamentals of game programming in the context of Android Use Android's APIs for graphics, audio, and user input to reflect those fundamentals Develop two 2D games from scratch, based on Canvas API and OpenGL ES Create a full-featured 3D game Publish your games, get crash reports, and support your users Complete your own playable 2D OpenGL games Who This Book Is For Those with basic knowledge of Java who want to write games on the Android platform, and experienced game developers who want to know about the pitfalls and peculiarities of the platform Computers

The Self-Service Data Roadmap Data-driven insights are a key competitive advantage for any industry today, but deriving insights from raw data can still take days or weeks. Most organizations can’t scale data science teams fast enough to keep up with the growing amounts of data to transform. What’s the answer? Self-service data. With this practical book, data engineers, data scientists, and team managers will learn how to build a self-service data science platform that helps anyone in your organization extract insights from data. Sandeep Uttamchandani provides a scorecard to track and address bottlenecks that slow down time to insight across data discovery, transformation, processing, and production. This book bridges the gap between data scientists bottlenecked by engineering realities and data engineers unclear about ways to make self-service work. Build a self-service portal to support data discovery, quality, lineage, and governance Select the best approach for each self-service capability using open source cloud technologies Tailor self-service for the people, processes, and technology maturity of your data platform Implement capabilities to democratize data and reduce time to insight Scale your self-service portal to support a large number of users within your organization Computers

IRL It's easy to view our online presence as fake, to see the internet as a space we enter when we aren't living our real, offline lives. IRL, Chris Stedman's insightful exploration of authenticity in the digital age, shines a light on how age-old notions of realness can be freshly understood in our online lives. Stedman invites readers to consider the ways they edit themselves for digital audiences and ultimately makes a bold case for authenticity. Computers

Handbook of Bioinformatics Bioinformatics is the symbiotic relationship between biological sciences and computational techniques. It is an application of computer science, mathematical and statistical methods to manage and analysis the biological data, and is becoming a fundamental tool in experimental biology as a genome and proteome testing in silico. Bioinformatics is the application of computer technology to the management of biological information. Computers are used to gather, store, analyse and integrate biological and genetic information which can then be applied to gene-based drug discovery and development. Arrangement of chapters and the method of presentation is very clear and lucid, which is easily followed by the students. It is hoped that the handbook will be useful not only to the undergraduate and postgraduate students but also to the experimental biologists, computer scientists and others looking to move into a biological domain. Computers

Elements Of Computer Science This book Provides a balanced, realisltic pictures that communicates the dynamics of computer science by presenting topics in a historical perspective in which past developments, the current state of the art, and directions of research are discussed. This book can be used for a graduate course in computer science, combining useful mathematics with applications in robotics and computer graphics. It is also suitable for self-study in the continued education of professionals in the fields requiring geometric a modeling, such as robotics , computer vision graphics and computer games. The book contains all the material needed for a good course on Theory of Computation and Complexity. Contents: Computer and Its Peripherals; Internet and Networking; Computer Communication System; Logic Gates; Modelling. Computers

International Encyclopaedia of Computer Science and Technology Volume-6 (Algorithms and Data Structures) This "International Encyclopedia of Computer Science and Technology" covers both theoretical foundations of information and computation and of practical tools and techniques for their implementation and application. Computer science is the study of the theoretical foundations of information and computation and of practical techniques for their implementation and application in computer systems. Computer science has many sub-fields; some, such as computational complexity theory, study the properties of computational problems, while others, such as computer graphics, emphasize the computation of specific results. However, the embedded computers found in many devices from MP3 players to fighter aircraft and from toys to industrial robots are the most numerous. The ten volumes are focused on Algorithms and Data Structures; Artificial Intelligence; Computer Applications and Networks; Computer Design and Programming Languages; Computer Elements and Systems Architecture; Computer Graphics; Computer Scanner and Antivirus Programmes; Computer Security and Databases; Computer Storage Devices and; Digital Processing and Multiprocessing. Computers

International Encyclopaedia of Computer Science and Technology Volume-7 (Artificial Intelligence) This "International Encyclopedia of Computer Science and Technology" covers both theoretical foundations of information and computation and of practical tools and techniques for their implementation and application. Computer science is the study of the theoretical foundations of information and computation and of practical techniques for their implementation and application in computer systems. Computer science has many sub-fields; some, such as computational complexity theory, study the properties of computational problems, while others, such as computer graphics, emphasize the computation of specific results. However, the embedded computers found in many devices from MP3 players to fighter aircraft and from toys to industrial robots are the most numerous. The ten volumes are focused on Algorithms and Data Structures; Artificial Intelligence; Computer Applications and Networks; Computer Design and Programming Languages; Computer Elements and Systems Architecture; Computer Graphics; Computer Scanner and Antivirus Programmes; Computer Security and Databases; Computer Storage Devices and; Digital Processing and Multiprocessing. Computers

International Encyclopaedia of Computer Science and Technology Volume-8 (Computer Scanner and Antivirus Programmes) This "International Encyclopedia of Computer Science and Technology" covers both theoretical foundations of information and computation and of practical tools and techniques for their implementation and application. Computer science is the study of the theoretical foundations of information and computation and of practical techniques for their implementation and application in computer systems. Computer science has many sub-fields; some, such as computational complexity theory, study the properties of computational problems, while others, such as computer graphics, emphasize the computation of specific results. However, the embedded computers found in many devices from MP3 players to fighter aircraft and from toys to industrial robots are the most numerous. The ten volumes are focused on Algorithms and Data Structures; Artificial Intelligence; Computer Applications and Networks; Computer Design and Programming Languages; Computer Elements and Systems Architecture; Computer Graphics; Computer Scanner and Antivirus Programmes; Computer Security and Databases; Computer Storage Devices and; Digital Processing and Multiprocessing. Computers

International Encyclopaedia of Computer Science and Technology Volume-9 (Computer Design and Programming Languages) This "International Encyclopedia of Computer Science and Technology" covers both theoretical foundations of information and computation and of practical tools and techniques for their implementation and application. Computer science is the study of the theoretical foundations of information and computation and of practical techniques for their implementation and application in computer systems. Computer science has many sub-fields; some, such as computational complexity theory, study the properties of computational problems, while others, such as computer graphics, emphasize the computation of specific results. However, the embedded computers found in many devices from MP3 players to fighter aircraft and from toys to industrial robots are the most numerous. The ten volumes are focused on Algorithms and Data Structures; Artificial Intelligence; Computer Applications and Networks; Computer Design and Programming Languages; Computer Elements and Systems Architecture; Computer Graphics; Computer Scanner and Antivirus Programmes; Computer Security and Databases; Computer Storage Devices and; Digital Processing and Multiprocessing. Computers

Encyclopaedia of Biostatistics, Bioinformatics and Computer Applications Volume-1 Biostatistics is the application of statistics to a wide range of topics in biology. The science of biostatistics encompasses the design of biological experiments, especially in medicine and agriculture; the collection, summarization, and analysis of data from those experiments; and the interpretation of, and inference from, the results. Biostatistical reasoning and modelling were of critical importance to the foundation theories of modern biology. ln larger universities where both a statistics and a biostatistics department exist, the degree of integration between the two departments may range from the bare minimum to very close collaboration. ln general, the difference between a statistics program and a biostatistics one is twofold: (i) statistics departments will often host theoretical/methodological research which arc less common in biostatistics programs and (ii) statistics departments have lines of research that may include biomedical applications but also other areas such as industry (quality control), business and economics and biological areas other than medicine. Applications for machine learning include machine perception, computer vision, natural language processing, syntactic pattern recognition, search engines, medical diagnosis, bioinformatics, brain-machine interfaces and cheminformatics, detecting credit card fraud, stock market analysis, classifying DNA sequences, speech and handwriting recognition, object recognition in computer vision, game playing, software engineering, adaptive websites, robot locomotion, and structural health monitoring. This book provides deep insight to various dimensions of issues relating to development of this subject. Computers

Bioinformatics and its Applications An emerging, ever evolving branch of science, bioinformatics has paved the way for the explosive growth in the distribution of biological information to a variety of biological databases. Bridging the gap between biology and computer science, Bioinformatics and its applications assimilates current bioinformatics knowledge and tools relevant to the concise and self- contained book. This book presents the most state of the art bioinformatics applications. This book provides theoretical introductions followed by step- by-step tutorials and sample datasets of practical applications in each chapter. This book covers the most commonly used biocomputing tools and programme languages. Computers

International Encyclopaedia of Computer Science and Technology Volume-5 (Computer Storage Devices) This "International Encyclopedia of Computer Science and Technology" covers both theoretical foundations of information and computation and of practical tools and techniques for their implementation and application. Computer science is the study of the theoretical foundations of information and computation and of practical techniques for their implementation and application in computer systems. Computer science has many sub-fields; some, such as computational complexity theory, study the properties of computational problems, while others, such as computer graphics, emphasize the computation of specific results. However, the embedded computers found in many devices from MP3 players to fighter aircraft and from toys to industrial robots are the most numerous. The ten volumes are focused on Algorithms and Data Structures; Artificial Intelligence; Computer Applications and Networks; Computer Design and Programming Languages; Computer Elements and Systems Architecture; Computer Graphics; Computer Scanner and Antivirus Programmes; Computer Security and Databases; Computer Storage Devices and; Digital Processing and Multiprocessing. Computers

Services Computing – SCC 2020 This volume constitutes the proceedings of the 17th International Conference on Services Computing 2020, held as Part of SCF 2020 in Honolulu, HI, USA in September 2020.. The 8 full papers and 2 short papers presented in this volume were carefully reviewed and selected from 20 submissions. They cover topics such as: foundations of services computing; scientific workflows; business process integration and management; microservices; modeling of services systems; service security and privacy; SOA service applications; and service lifecycle management. Computers

Software Engineering and Formal Methods This book constitutes the refereed proceedings of the 18th International Conference on Software Engineering and Formal Methods, SEFM 2020, held in Amsterdam, The Netherlands, in September 2020. The 16 full papers presented together with 1 keynote talk and an abstract of a keynote talk were carefully reviewed and selected from 58 submissions. The papers cover a large variety of topics, including testing, formal verification, program analysis, runtime verification, meta-programming and software development and evolution. The papers address a wide range of systems, such as IoT systems, human-robot interaction in healthcare scenarios, navigation of maritime autonomous systems, and operating systems. The Chapters "Multi-Purpose Syntax Definition with SDF3", “FRed: Conditional Model Checking via Reducers and Folders" and "Difference Verification with Conditions†are available open access under a Creative Commons Attribution 4.0 International License via link.springer.com. Computers

Computer Security – ESORICS 2020 The two volume set, LNCS 12308 + 12309, constitutes the proceedings of the 25th European Symposium on Research in Computer Security, ESORICS 2020, which was held in September 2020. The conference was planned to take place in Guildford, UK. Due to the COVID-19 pandemic, the conference changed to an online format. The total of 72 full papers included in these proceedings was carefully reviewed and selected from 366 submissions. The papers were organized in topical sections named: database and Web security; system security; network security; software security; machine learning security; privacy; formal modelling; applied cryptography; analyzing attacks; post-quantum cryptogrphy; security analysis; and blockchain. Computers

3D Imaging, Analysis and Applications This textbook is designed for postgraduate studies in the field of 3D Computer Vision. It also provides a useful reference for industrial practitioners; for example, in the areas of 3D data capture, computer-aided geometric modelling and industrial quality assurance. This second edition is a significant upgrade of existing topics with novel findings. Additionally, it has new material covering consumer-grade RGB-D cameras, 3D morphable models, deep learning on 3D datasets, as well as new applications in the 3D digitization of cultural heritage and the 3D phenotyping of crops. Overall, the book covers three main areas: â— 3D imaging, including passive 3D imaging, active triangulation 3D imaging, active time-of-flight 3D imaging, consumer RGB-D cameras, and 3D data representation and visualisation; â— 3D shape analysis, including local descriptors, registration, matching, 3D morphable models, and deep learning on 3D datasets; and â— 3D applications, including 3D face recognition, cultural heritage and 3D phenotyping of plants. 3D computer vision is a rapidly advancing area in computer science. There are many real-world applications that demand high-performance 3D imaging and analysis and, as a result, many new techniques and commercial products have been developed. However, many challenges remain on how to analyse the captured data in a way that is sufficiently fast, robust and accurate for the application. Such challenges include metrology, semantic segmentation, classification and recognition. Thus, 3D imaging, analysis and their applications remain a highly-active research field that will continue to attract intensive attention from the research community with the ultimate goal of fully automating the 3D data capture, analysis and inference pipeline. Computers

Advances in Design, Music and Arts This book presents the outcomes of recent endeavors that will contribute to significant advances in the areas of communication design, fashion design, interior design and product design, music and musicology, as well as overlapping areas. Gathering the proceedings of the 7th EIMAD conference, held on May 14–15, 2020, and organized by the School of Applied Arts, Campus da Talagueira, in Castelo Branco, Portugal, it proposes new theoretical perspectives and practical research directions in design and music, while also discussing teaching practices and some areas of intersection. It addresses strategies for communication and culture in a global, digital world, that take into account key individual and societal needs. Computers

Firewalls Don't Stop Dragons Rely on this practical, end-to-end guide on cyber safety and privacy written expressly for a non-technical audience. You will have just what you need to protect yourself—step by step, without judgment, and with as little jargon as possible. Just how secure is your computer right now? You probably don't know. Computers and the Internet have revolutionized the modern world, but if you are like most people, you have no clue how these things work and don't know the real threats. Protecting your computer is like defending a medieval castle. While moats, walls, drawbridges, and castle guards can be effective, you would go broke trying to build something dragon-proof. This book is not about protecting yourself from a targeted attack by the NSA; it is about arming yourself against common hackers and mass surveillance. There are dozens of no-brainer things we all should be doing to protect our computers and safeguard our data—just like wearing a seat belt, installing smoke alarms, and putting on sunscreen. Author Carey Parker has structured this book to give you maximum benefit with minimum effort. If you just want to know what to do, every chapter has a complete checklist with step-by-step instructions and pictures. This revised and expanded fourth edition contains more than 170 tips to make you and your family safer. It includes: Updates for Windows 10 (May 2020) and Mac OS 10.15 (Catalina) Updates for iOS 13 and Android 10 Updated recommendations on the best apps, products, and services More than 170 tips with complete step-by-step instructions and pictures A preview of Mac OS 11 Big Sur and iOS 14 What You Will Learn Create killer passwords that you do not have to remember Browse the web safely and with confidence Protect your data and reclaim your privacy Shop and bank online with maximum security Defend against identity theft Protect yourself from viruses and scams Maximize your smartphone security and privacy Safeguard your children online Block online tracking and dangerous ads Send files and messages securely and privately Set up secure home networking Keep your smart devices from spying on you Stop oversharing on social media Create automated backups of all your devices Learn how the Internet actually works And more! Who This Book Is For Those who use computers and mobile devices, but do not know (or care) how they work. The book is for people who want to know what they need to do to protect themselves—step by step, without judgment, and with as little jargon as possible. Computers

Artificial Intelligence and Security The 3-volume set CCIS 1252 until CCIS 1254 constitutes the refereed proceedings of the 6th International Conference on Artificial Intelligence and Security, ICAIS 2020, which was held in Hohhot, China, in July 2020. The conference was formerly called “International Conference on Cloud Computing and Security†with the acronym ICCCS. The total of 178 full papers and 8 short papers presented in this 3-volume proceedings was carefully reviewed and selected from 1064 submissions. The papers were organized in topical sections as follows: Part I: artificial intelligence; Part II: artificial intelligence; Internet of things; information security; Part III: information security; big data and cloud computing; information processing. Computers

Artificial Intelligence and Security The 3-volume set CCIS 1252 until CCIS 1254 constitutes the refereed proceedings of the 6th International Conference on Artificial Intelligence and Security, ICAIS 2020, which was held in Hohhot, China, in July 2020. The conference was formerly called “International Conference on Cloud Computing and Security†with the acronym ICCCS. The total of 178 full papers and 8 short papers presented in this 3-volume proceedings was carefully reviewed and selected from 1064 submissions. The papers were organized in topical sections as follows: Part I: artificial intelligence; Part II: artificial intelligence; Internet of things; information security; Part III: information security; big data and cloud computing; information processing. Computers

Artificial Intelligence and Security The 3-volume set CCIS 1252 until CCIS 1254 constitutes the refereed proceedings of the 6th International Conference on Artificial Intelligence and Security, ICAIS 2020, which was held in Hohhot, China, in July 2020. The conference was formerly called “International Conference on Cloud Computing and Security†with the acronym ICCCS. The total of 178 full papers and 8 short papers presented in this 3-volume proceedings was carefully reviewed and selected from 1064 submissions. The papers were organized in topical sections as follows: Part I: artificial intelligence; Part II: artificial intelligence; Internet of things; information security; Part III: information security; big data and cloud computing; information processing. Computers

Computer Security – ESORICS 2020 The two volume set, LNCS 12308 + 12309, constitutes the proceedings of the 25th European Symposium on Research in Computer Security, ESORICS 2020, which was held in September 2020. The conference was planned to take place in Guildford, UK. Due to the COVID-19 pandemic, the conference changed to an online format. The total of 72 full papers included in these proceedings was carefully reviewed and selected from 366 submissions. The papers were organized in topical sections named: database and Web security; system security; network security; software security; machine learning security; privacy; formal modelling; applied cryptography; analyzing attacks; post-quantum cryptogrphy; security analysis; and blockchain. Computers

Database and Expert Systems Applications The double volumes LNCS 12391-12392 constitutes the papers of the 31st International Conference on Database and Expert Systems Applications, DEXA 2020, which will be held online in September 2020. The 38 full papers presented together with 20 short papers plus 1 keynote papers in these volumes were carefully reviewed and selected from a total of 190 submissions. Computers

CompTIA Security+ Certification Study Guide Prepare for the CompTIA Security+ certification exam that covers the skills required to perform core security functions and pursue a career in IT. You will learn the basic principles of network security. Computer network vulnerabilities and threats are covered and you will learn how to safeguard computer networks. Network security planning, technology, and organization are discussed along with associated legal and ethical issues. Lesson objectives and instruction succinctly review each major topic, including: network fundamentals, operational and organizational security, risk management, wireless security, change management, physical security, forensics, network attacks, and much more. What You Will Learn Identify the concepts of confidentiality, integrity, and availability Implement secure network administration principles Apply appropriate risk mitigation strategies Explain the impact of physical security on computer and network security Use assessment tools to discover security threats and vulnerabilities Implement appropriate security controls when performing account management Who This Book Is For Security professionals looking to get this credential, including systems administrators, network administrators, security administrators, junior IT auditors and penetration testers, security specialists, security consultants, security engineers, and more Computers

Self-Service AI with Power BI Desktop This book explains how you can enrich the data you have loaded into Power BI Desktop by accessing a suite of Artificial Intelligence (AI) features. These AI features are built into Power BI Desktop and help you to gain new insights from existing data. Some of the features are automated and are available to you at the click of a button or through writing Data Analysis Expressions (DAX). Other features are available through writing code in either the R, Python, or M languages. This book opens up the entire suite of AI features to you with clear examples showing when they are best applied and how to invoke them on your own datasets. No matter if you are a business user, analyst, or data scientist – Power BI has AI capabilities tailored to you. This book helps you learn what types of insights Power BI is capable of delivering automatically. You will learn how to integrate and leverage the use of the R and Python languages for statistics, how to integrate with Cognitive Services and Azure Machine Learning Services when loading data, how to explore your data by asking questions in plain English ... and more! There are AI features for discovering your data, characterizing unexplored datasets, and building what-if scenarios. There’s much to like and learn from this book whether you are a newcomer to Power BI or a seasoned user. Power BI Desktop is a freely available tool for visualization and analysis. This book helps you to get the most from that tool by exploiting some of its latest and most advanced features. What You Will Learn Ask questions in natural language and get answers from your data Let Power BI explain why a certain data point differs from the rest Have Power BI show key influencers over categories of data Access artificial intelligence features available in the Azure cloud Walk the same drill down path in different parts of your hierarchy Load visualizations to add smartness to your reports Simulate changes in data and immediately see the consequences Know your data, even before you build your first report Create new columns by giving examples of the data that you need Transform and visualize your data with the help of R and Python scripts Who This Book Is For For the enthusiastic Power BI user who wants to apply state-of-the-art artificial intelligence (AI) features to gain new insights from existing data. For end-users and IT professionals who are not shy of jumping into a new world of machine learning and are ready to make that step and take a deeper look into their data. For those wanting to step up their game from doing simple reporting and visualizations by making the move into diagnostic and predictive analysis. Computers

Introduction to Natural Language Processing A survey of computational methods for understanding, generating, and manipulating human language, which offers a synthesis of classical representations and algorithms with contemporary machine learning techniques. This textbook provides a technical perspective on natural language processing—methods for building computer software that understands, generates, and manipulates human language. It emphasizes contemporary data-driven approaches, focusing on techniques from supervised and unsupervised machine learning. The first section establishes a foundation in machine learning by building a set of tools that will be used throughout the book and applying them to word-based textual analysis. The second section introduces structured representations of language, including sequences, trees, and graphs. The third section explores different approaches to the representation and analysis of linguistic meaning, ranging from formal logic to neural word embeddings. The final section offers chapter-length treatments of three transformative applications of natural language processing: information extraction, machine translation, and text generation. End-of-chapter exercises include both paper-and-pencil analysis and software implementation. The text synthesizes and distills a broad and diverse research literature, linking contemporary machine learning techniques with the field's linguistic and computational foundations. It is suitable for use in advanced undergraduate and graduate-level courses and as a reference for software engineers and data scientists. Readers should have a background in computer programming and college-level mathematics. After mastering the material presented, students will have the technical skill to build and analyze novel natural language processing systems and to understand the latest research in the field. Computers

MATLAB for Brain and Cognitive Scientists An introduction to a popular programming language for neuroscience research, taking the reader from beginning to intermediate and advanced levels of MATLAB programming. MATLAB is one of the most popular programming languages for neuroscience and psychology research. Its balance of usability, visualization, and widespread use makes it one of the most powerful tools in a scientist's toolbox. In this book, Mike Cohen teaches brain scientists how to program in MATLAB, with a focus on applications most commonly used in neuroscience and psychology. Although most MATLAB tutorials will abandon users at the beginner's level, leaving them to sink or swim, MATLAB for Brain and Cognitive Scientists takes readers from beginning to intermediate and advanced levels of MATLAB programming, helping them gain real expertise in applications that they will use in their work. The book offers a mix of instructive text and rigorous explanations of MATLAB code along with programming tips and tricks. The goal is to teach the reader how to program data analyses in neuroscience and psychology. Readers will learn not only how to but also how not to program, with examples of bad code that they are invited to correct or improve. Chapters end with exercises that test and develop the skills taught in each chapter. Interviews with neuroscientists and cognitive scientists who have made significant contributions their field using MATLAB appear throughout the book. MATLAB for Brain and Cognitive Scientists is an essential resource for both students and instructors, in the classroom or for independent study. Computers

Introduction to Autonomous Mobile Robots, second edition The second edition of a comprehensive introduction to all aspects of mobile robotics, from algorithms to mechanisms. Mobile robots range from the Mars Pathfinder mission's teleoperated Sojourner to the cleaning robots in the Paris Metro. This text offers students and other interested readers an introduction to the fundamentals of mobile robotics, spanning the mechanical, motor, sensory, perceptual, and cognitive layers the field comprises. The text focuses on mobility itself, offering an overview of the mechanisms that allow a mobile robot to move through a real world environment to perform its tasks, including locomotion, sensing, localization, and motion planning. It synthesizes material from such fields as kinematics, control theory, signal analysis, computer vision, information theory, artificial intelligence, and probability theory. The book presents the techniques and technology that enable mobility in a series of interacting modules. Each chapter treats a different aspect of mobility, as the book moves from low-level to high-level details. It covers all aspects of mobile robotics, including software and hardware design considerations, related technologies, and algorithmic techniques. This second edition has been revised and updated throughout, with 130 pages of new material on such topics as locomotion, perception, localization, and planning and navigation. Problem sets have been added at the end of each chapter. Bringing together all aspects of mobile robotics into one volume, Introduction to Autonomous Mobile Robots can serve as a textbook or a working tool for beginning practitioners. Curriculum developed by Dr. Robert King, Colorado School of Mines, and Dr. James Conrad, University of North Carolina-Charlotte, to accompany the National Instruments LabVIEW Robotics Starter Kit, are available. Included are 13 (6 by Dr. King and 7 by Dr. Conrad) laboratory exercises for using the LabVIEW Robotics Starter Kit to teach mobile robotics concepts. Computers

Quantum Computing A thorough exposition of quantum computing and the underlying concepts of quantum physics, with explanations of the relevant mathematics and numerous examples. The combination of two of the twentieth century's most influential and revolutionary scientific theories, information theory and quantum mechanics, gave rise to a radically new view of computing and information. Quantum information processing explores the implications of using quantum mechanics instead of classical mechanics to model information and its processing. Quantum computing is not about changing the physical substrate on which computation is done from classical to quantum but about changing the notion of computation itself, at the most basic level. The fundamental unit of computation is no longer the bit but the quantum bit or qubit. This comprehensive introduction to the field offers a thorough exposition of quantum computing and the underlying concepts of quantum physics, explaining all the relevant mathematics and offering numerous examples. With its careful development of concepts and thorough explanations, the book makes quantum computing accessible to students and professionals in mathematics, computer science, and engineering. A reader with no prior knowledge of quantum physics (but with sufficient knowledge of linear algebra) will be able to gain a fluent understanding by working through the book. Computers

The Little Typer An introduction to dependent types, demonstrating the most beautiful aspects, one step at a time. A program's type describes its behavior. Dependent types are a first-class part of a language, and are much more powerful than other kinds of types; using just one language for types and programs allows program descriptions to be as powerful as the programs they describe. The Little Typer explains dependent types, beginning with a very small language that looks very much like Scheme and extending it to cover both programming with dependent types and using dependent types for mathematical reasoning. Readers should be familiar with the basics of a Lisp-like programming language, as presented in the first four chapters of The Little Schemer. The first five chapters of The Little Typer provide the needed tools to understand dependent types; the remaining chapters use these tools to build a bridge between mathematics and programming. Readers will learn that tools they know from programming—pairs, lists, functions, and recursion—can also capture patterns of reasoning. The Little Typer does not attempt to teach either practical programming skills or a fully rigorous approach to types. Instead, it demonstrates the most beautiful aspects as simply as possible, one step at a time. Computers

Decision Making Under Uncertainty An introduction to decision making under uncertainty from a computational perspective, covering both theory and applications ranging from speech recognition to airborne collision avoidance. Many important problems involve decision making under uncertainty—that is, choosing actions based on often imperfect observations, with unknown outcomes. Designers of automated decision support systems must take into account the various sources of uncertainty while balancing the multiple objectives of the system. This book provides an introduction to the challenges of decision making under uncertainty from a computational perspective. It presents both the theory behind decision making models and algorithms and a collection of example applications that range from speech recognition to aircraft collision avoidance. Focusing on two methods for designing decision agents, planning and reinforcement learning, the book covers probabilistic models, introducing Bayesian networks as a graphical model that captures probabilistic relationships between variables; utility theory as a framework for understanding optimal decision making under uncertainty; Markov decision processes as a method for modeling sequential problems; model uncertainty; state uncertainty; and cooperative decision making involving multiple interacting agents. A series of applications shows how the theoretical concepts can be applied to systems for attribute-based person search, speech applications, collision avoidance, and unmanned aircraft persistent surveillance. Decision Making Under Uncertainty unifies research from different communities using consistent notation, and is accessible to students and researchers across engineering disciplines who have some prior exposure to probability theory and calculus. It can be used as a text for advanced undergraduate and graduate students in fields including computer science, aerospace and electrical engineering, and management science. It will also be a valuable professional reference for researchers in a variety of disciplines. Computers

Trust, Privacy and Security in Digital Business This book constitutes the refereed proceedings of the 17th International Conference on Trust, Privacy and Security in Digital Business, TrustBus 2020, held in Bratislava, Slovakia, in September 2020. The conference was held virtually due to the COVID-19 pandemic. The 11 full and 4 short papers presented were carefully reviewed and selected from 28 submissions. The papers are organized in the following topical sections: blockchain, cloud security/hardware; economics/privacy; human aspects; privacy; privacy and machine learning; trust. Computers

New Frontiers in Artificial Intelligence This book constitutes extended, revised and selected papers from the 11th International Symposium of Artificial Intelligence supported by the Japanese Society for Artificial Intelligence, JSAI-isAI 2019. It was held in November 2019 in Yokohama, Japan.The 26 papers were carefully selected from 46 submissions and deal with topics of AI research and are organized into 4 sections, according to the 4 workshops: JURISIN 2019, AI-Biz 2019, LENLS 16, and Kansei-AI 2019. Computers

Database and Expert Systems Applications The double volumes LNCS 12391-12392 constitutes the papers of the 31st International Conference on Database and Expert Systems Applications, DEXA 2020, which will be held online in September 2020. The 38 full papers presented together with 20 short papers plus 1 keynote papers in these volumes were carefully reviewed and selected from a total of 190 submissions. Computers

Cognitive Computing – ICCC 2020 This book constitutes the proceedings of the International Conference on Cognitive Computing, ICCC 2020, held as part of SCF 2020 in Honolulu, HI, USA, in September 2020.The conference was held virtually due to the COVID-19 pandemic. The 8 full and 2 short papers presented in this volume were carefully reviewed and selected from 20 submissions. The papers cover all aspects of Sensing Intelligence (SIJ as a Service (SlaaS). Cognitive Computing is a sensing-driven computing (SDC) scheme that explores and integrates intelligence from all types of senses in various scenarios and solution contexts. Computers

ICT Systems Security and Privacy Protection This book constitutes the refereed proceedings of the 35th IFIP TC 11 International Conference on Information Security and Privacy Protection, SEC 2020, held in Maribor, Slovenia, in September 2020. The conference was held virtually due to the COVID-19 pandemic. The 29 full papers presented were carefully reviewed and selected from 149 submissions. The papers present novel research on theoretical and practical aspects of security and privacy protection in ICT systems. They are organized in topical sections on channel attacks; connection security; human aspects of security and privacy; detecting malware and software weaknesses; system security; network security and privacy; access control and authentication; crypto currencies; privacy and security management; and machine learning and security. Computers

Mathematical Optimization Theory and Operations Research This book constitutes refereed proceedings of the 19th International Conference on Mathematical Optimization Theory and Operations Research, MOTOR 2020, held in July 2020. Due to the COVID-19 pandemic the conference was held online. The 25 full papers and 8 short papers presented in this volume were carefully reviewed and selected from a total of 102 submissions. The papers in the volume are organised according to the following topical headings: ​combinatorial optimization; mathematical programming; global optimization; game theory and mathematical economics; heuristics and metaheuristics; machine learning and data analysis. Computers

Database and Expert Systems Applications This volume constitutes the refereed proceedings of the three workshops held at the 31st International Conference on Database and Expert Systems Applications, DEXA 2020, held in September 2020: The 11th International Workshop on Biological Knowledge Discovery from Data, BIOKDD 2020, the 4th International Workshop on Cyber-Security and Functional Safety in Cyber-Physical Systems, IWCFS 2020, the 2nd International Workshop on Machine Learning and Knowledge Graphs, MLKgraphs2019. Due to the COVID-19 pandemic the conference and workshop were held virtually. The 10 papers were thoroughly reviewed and selected from 15 submissions, and discuss a range of topics including: knowledge discovery, biological data, cyber security, cyber-physical system, machine learning, knowledge graphs, information retriever, data base, and artificial intelligent. Computers

Pro C# 8 with .NET Core 3 This essential classic provides a comprehensive foundation in the C# programming language and the frameworks it lives in. Now in its 9th edition, you will find the latest C# 8 and .NET Core features, along with new chapters on Microsoft’s lightweight, cross-platform framework, .NET Core 3.1. Coverage of ASP.NET Core, Entity Framework Core, and more, sits alongside the latest updates to .NET Core, including Windows Presentation Foundation (WPF). Not only does this book cover all of the latest features in C# 8, but all chapters and code samples have been rewritten for this latest release. Dive in and discover why this book has been a favorite of C# developers worldwide for more than 15 years. Gain a solid foundation in object-oriented development techniques, attributes and reflection, generics and collections, and numerous advanced topics not found in other texts (such as CIL opcodes and emitting dynamic assemblies). With the help of Pro C# 8 with .NET Core 3 gain the confidence to put C# into practice and explore the .NET Core universe on your own terms. What You Will Learn Discover the bells and whistles of C# 8 features and updates to previous features Hit the ground running with ASP.NET Core web applications and web services, and Entity Framework Core Work with the latest version of Windows Presentation Foundation, now a part of .NET Core Understand the philosophy behind .NET and the cross-platform alternative, .NET Core Develop applications with C# and modern frameworks for services, web, and smart client applications Who This Book Is For Developers who are interested in .NET programming and the C# language “Amazing! Provides easy-to-follow explanations and examples. I remember reading the first version of this book; this is a 'must-have' for your collection if you are learning .NET Core!†– Rick McGuire, Senior Application Development Manager, Microsoft “Phil is a journeyman programmer who brings years of experience and a passion for teaching to make this fully revised and modernized ‘classic’ a ‘must-have’. Any developer who wants full-spectrum, up-to-date coverage of both the C# language and how to use it with .NET Core and ASP.NET Core should get this book.†– Brian A. Randell, Partner, MCW Technologies and Microsoft MVP Computers

SQL Server 2019 Administrator's Guide Use Microsoft SQL Server 2019 to implement, administer, and secure a robust database solution that is disaster-proof and highly available Key Features Explore new features of SQL Server 2019 to set up, administer, and maintain your database solution successfully Develop a dynamic SQL Server environment and streamline big data pipelines Discover best practices for fixing performance issues, database access management, replication, and security Book Description SQL Server is one of the most popular relational database management systems developed by Microsoft. This second edition of the SQL Server Administrator's Guide will not only teach you how to administer an enterprise database, but also help you become proficient at managing and keeping the database available, secure, and stable. You'll start by learning how to set up your SQL Server and configure new and existing environments for optimal use. The book then takes you through designing aspects and delves into performance tuning by showing you how to use indexes effectively. You'll understand certain choices that need to be made about backups, implement security policy, and discover how to keep your environment healthy. Tools available for monitoring and managing a SQL Server database, including automating health reviews, performance checks, and much more, will also be discussed in detail. As you advance, the book covers essential topics such as migration, upgrading, and consolidation, along with the techniques that will help you when things go wrong. Once you've got to grips with integration with Azure and streamlining big data pipelines, you'll learn best practices from industry experts for maintaining a highly reliable database solution. Whether you are an administrator or are looking to get started with database administration, this SQL Server book will help you develop the skills you need to successfully create, design, and deploy database solutions. What you will learn Discover SQL Server 2019's new features and how to implement them Fix performance issues by optimizing queries and making use of indexes Design and use an optimal database management strategy Combine SQL Server 2019 with Azure and manage your solution using various automation techniques Implement efficient backup and recovery techniques in line with security policies Get to grips with migrating, upgrading, and consolidating with SQL Server Set up an AlwaysOn-enabled stable and fast SQL Server 2019 environment Understand how to work with Big Data on SQL Server environments Who this book is for This book is for database administrators, database developers, and anyone who wants to administer large and multiple databases single-handedly using Microsoft's SQL Server 2019. Basic awareness of database concepts and experience with previous SQL Server versions is required. Computers

Learning Microsoft Project 2019 Explore detailed explanations and examples to get up and running with the five phases of the project management lifecycle and integrate project management principles in a variety of projects Key Features Explore various algorithms and the latest features of MS Project to organize and keep track of your projects Understand Work Breakdown Structure (WBS) to improve productivity Apply real-world best practices and discover the tips, tricks, and pitfalls of schedule management Book Description Microsoft Project is one of the most popular project management tools for enterprises of all sizes thanks to its wide variety of features such as project scheduling, project budgeting, built-in templates, and reporting tools. Learning Microsoft Project 2019 will get you started with the basics and gradually guide you through the complete project life cycle. Starting with an overview of Microsoft Project 2019 and a brief introduction to project management concepts, this book will take you through the different phases of project management – initiation, planning, execution, control, and closure. You will then learn how to identify and handle problems related to scheduling, costing, resourcing, and work allocation. Understand how to use dynamic reports to create powerful, automated reports and dashboards at the click of a button. This Microsoft Project book highlights the pitfalls of overallocation and demonstrates how to avoid and resolve these issues using a wide spectrum of tools, techniques, and best practices. Finally, you will focus on executing Agile projects efficiently and get to grips with using Kanban and Scrum features. By the end of this book, you will be well-versed with Microsoft Project and have the skills you need to use it effectively in every stage of project management. What you will learn Create efficient project plans using Microsoft Project 2019 Get to grips with resolving complex issues related to time, budget, and resource allocation Understand how to create automated dynamic reports Identify and protect the critical path in your project and mitigate project risks Become well-versed with executing Agile projects using MS Project Understand how to create custom reports and make them available for future projects Who this book is for If you use Microsoft Office and are looking to use MS Project to manage your projects efficiently, this book is for you. Project managers or anyone interested in project management will also find this book useful. Basic knowledge of Windows UI and MS Office products is required. Computers

Learn MongoDB 4.x Design, administer, and deploy high-volume and fault-tolerant database applications using MongoDB 4.xKey FeaturesBuild a powerful and scalable MongoDB database using real industry dataUnderstand the process of designing NoSQL schema with the latest release of MongoDB 4.xExplore the ins and outs of MongoDB, including queries, replication, sharding, and vital admin tasksBook DescriptionWhen it comes to managing a high volume of unstructured and non-relational datasets, MongoDB is the defacto database management system (DBMS) for DBAs and data architects. This updated book includes the latest release and covers every feature in MongoDB 4.x, while helping you get hands-on with building a MongoDB database app. You'll get to grips with MongoDB 4.x concepts such as indexes, database design, data modeling, authentication, and aggregation. As you progress, you'll cover tasks such as performing routine operations when developing a dynamic database-driven website. Using examples, you'll learn how to work with queries and regular database operations. The book will not only guide you through design and implementation, but also help you monitor operations to achieve optimal performance and secure your MongoDB database systems. You'll also be introduced to advanced techniques such as aggregation, map-reduce, complex queries, and generating ad hoc financial reports on the fly. Later, the book shows you how to work with multiple collections as well as embedded arrays and documents, before finally exploring key topics such as replication, sharding, and security using practical examples. By the end of this book, you'll be well-versed with MongoDB 4.x and be able to perform development and administrative tasks associated with this NoSQL database.What you will learnUnderstand how to configure and install MongoDB 4.xBuild a database-driven website using MongoDB as the backendPerform basic database operations and handle complex MongoDB queriesDevelop a successful MongoDB database design for large corporate customers with complex requirementsSecure MongoDB database systems by establishing role-based access control with X.509 transport-level securityOptimize reads and writes directed to a replica set or sharded clusterPerform essential MongoDB administration tasksMaintain database performance through monitoringWho this book is forThis book is a MongoDB tutorial for DevOps engineers, database developers, database administrators, system administrators and those who are just getting started with NoSQL and looking to build document-oriented databases and gain real-world experience in managing databases using MongoDB. Basic knowledge of databases and Python is required to get started with this DBMS book. Computers

Modern C++ Programming Cookbook A pragmatic recipe book for acquiring a comprehensive understanding of the complexities and core fundamentals of C++ programming Key Features Explore the latest language and library features of C++20 such as modules, coroutines, concepts, and ranges Shed new light on the core concepts in C++ programming, including functions, algorithms, threading, and concurrency, through practical self-contained recipes Leverage C++ features like smart pointers, move semantics, constexpr, and more for increased robustness and performance Book Description C++ has come a long way to be one of the most widely used general-purpose languages that is fast, efficient, and high-performance at its core. The updated second edition of Modern C++ Programming Cookbook addresses the latest features of C++20, such as modules, concepts, coroutines, and the many additions to the standard library, including ranges and text formatting. The book is organized in the form of practical recipes covering a wide range of problems faced by modern developers. The book also delves into the details of all the core concepts in modern C++ programming, such as functions and classes, iterators and algorithms, streams and the file system, threading and concurrency, smart pointers and move semantics, and many others. It goes into the performance aspects of programming in depth, teaching developers how to write fast and lean code with the help of best practices. Furthermore, the book explores useful patterns and delves into the implementation of many idioms, including pimpl, named parameter, and attorney-client, teaching techniques such as avoiding repetition with the factory pattern. There is also a chapter dedicated to unit testing, where you are introduced to three of the most widely used libraries for C++: Boost.Test, Google Test, and Catch2. By the end of the book, you will be able to effectively leverage the features and techniques of C++11/14/17/20 programming to enhance the performance, scalability, and efficiency of your applications. What you will learn Understand the new C++20 language and library features and the problems they solve Become skilled at using the standard support for threading and concurrency for daily tasks Leverage the standard library and work with containers, algorithms, and iterators Solve text searching and replacement problems using regular expressions Work with different types of strings and learn the various aspects of compilation Take advantage of the file system library to work with files and directories Implement various useful patterns and idioms Explore the widely used testing frameworks for C++ Who this book is for The book is designed for entry- or medium-level C++ programmers who have a basic knowledge of C++ and want to master the language and become prolific modern C++ developers. Experienced C++ programmers can leverage this book to strengthen their command of C++ and find a good reference to many language and library features of C++11/14/17/20. Computers

The 2020 Solo and Small Firm Legal Technology Guide Solo and small firm lawyers can find the best technology for their dollar. This state-of-the-art guide provides the most current and clearly presented information and recommendations on computers, servers, networking equipment, legal software, printers, security products, smartphones, tablets, and anything else a law office might need. Computers

Blockchain – ICBC 2020 This book constitutes the proceedings of the Third International Conference on Blockchain, ICBC 2020, held as part of SCF 2020, during September 18-20, 2020. The conference was planned to take place in Honolulu, HI, USA and was changed to a virtual format due to the COVID-19 pandemic.The 14 full paper and 1 short paper presented were carefully reviewed and selected from 26 submissions. They deal with all topics regarding blockchain technologies, platforms, solutions and business models, including new blockchain architecture, platform constructions, blockchain development and blockchain services technologies as well as standards, and blockchain services innovation lifecycle including enterprise modeling, business consulting, solution creation, services orchestration, services optimization, services management, services marketing, business process integration and management. Computers

Experimental IR Meets Multilinguality, Multimodality, and Interaction This book constitutes the refereed proceedings of the 11th International Conference of the CLEF Association, CLEF 2020, held in Thessaloniki, Greece, in September 2020.*The conference has a clear focus on experimental information retrieval with special attention to the challenges of multimodality, multilinguality, and interactive search ranging from unstructured to semi structures and structured data. The 5 full papers and 2 short papers presented in this volume were carefully reviewed and selected from 9 submissions. This year, the contributions addressed the following challenges: a large-scale evaluation of translation effects in academic search, advancement of assessor-driven aggregation methods for efficient relevance assessments, and development of a new test dataset. In addition to this, the volume presents 7 “best of the labs†papers which were reviewed as full paper submissions with the same review criteria. The 12 lab overview papers were accepted out of 15 submissions and represent scientific challenges based on new data sets and real world problems in multimodal and multilingual information access. * The conference was held virtually due to the COVID-19 pandemic. Computers

Information Security Education. Information Security in Action This book constitutes the refereed proceedings of the 13th IFIP WG 11.8 World Conference on Information Security Education, WISE 13, held in Maribor, Slovenia, in September 2020. The conference was held virtually due to the COVID-19 pandemic. The 13 full papers presented were carefully reviewed and selected from 28 submissions. The papers are organized in the following topical sections: teaching methods and tools; cybersecurity knowledge within the organization; and teaching of detection and forensics. Computers

Big Data in Emergency Management This contributed volume discusses essential topics and the fundamentals for Big Data Emergency Management and primarily focusses on the application of Big Data for Emergency Management. It walks the reader through the state of the art, in different facets of the big disaster data field. This includes many elements that are important for these technologies to have real-world impact. This book brings together different computational techniques from: machine learning, communication network analysis, natural language processing, knowledge graphs, data mining, and information visualization, aiming at methods that are typically used for processing big emergency data. This book also provides authoritative insights and highlights valuable lessons by distinguished authors, who are leaders in this field. Emergencies are severe, large-scale, non-routine events that disrupt the normal functioning of a community or a society, causing widespread and overwhelming losses and impacts. Emergency Management is the process of planning and taking actions to minimize the social and physical impact of emergencies and reduces the community’s vulnerability to the consequences of emergencies. Information exchange before, during and after the disaster periods can greatly reduce the losses caused by the emergency. This allows people to make better use of the available resources, such as relief materials and medical supplies. It also provides a channel through which reports on casualties and losses in each affected area, can be delivered expeditiously. Big Data-Driven Emergency Management refers to applying advanced data collection and analysis technologies to achieve more effective and responsive decision-making during emergencies. Researchers, engineers and computer scientists working in Big Data Emergency Management, who need to deal with large and complex sets of data will want to purchase this book. Advanced-level students interested in data-driven emergency/crisis/disaster management will also want to purchase this book as a study guide. Computers

Rust for the IoT Get started programming Rust applications for the Internet of Things (IoT). This book is a programming skills migration book that teaches you the Rust programming techniques most useful for IoT applications. You'll step through from server to board development in creating a set of IoT applications. In Rust for the IoT, you'll learn how to build a modern server-side application using Rust on the backend. Then you'll use docker and Kubernetes to deploy these to a managed cloud. Finally you will use a Raspberry Pi with a SenseHat and Camera to capture the world around you and send that information to the cloud. While you will be able to follow along without any cloud or hardware, to make the most of it we recommend a few cloud pieces and hardware that is designed to integrate with the software in this book. After reading and using this book, you'll see how to apply Rust to the Internet of Things. What You Will Learn Create a modern Rust backend complete with handling eventual consistency and interacting via a GraphQL interface Use the Raspberry PI to serve as a cheap IoT device that one can easily deploy around the house Capture temperature, video, and use the interactive joystick to interact with the software you’ve created Use OpenCV to perform facial detection from the PI’s camera and save that information to the cloud. Create deployable helm charts for the cloud, and for the device create complete ISOs that allow you to easily deploy the Pi’s OS + custom software Who This Book Is For You will need to have a basic understanding of cloud application development at a minimum and the basics of Rust coding. This book is for those interested in or working with the IoT and the Raspberry Pi who want to learn how Rust can work for them. Computers

GNU Octave by Example Get a quick start to learn, understand, and apply GNU Octave using a math- and programming-friendly approach. This book focuses on an end-to-end track to teach mathematical programming, data science, signal processing, and image processing with GNU Octave. GNU Octave by Example starts with an introduction to GNU Octave, a free and open-source alternative to MATLAB. Next, it explains the processes to install GNU Octave on popular operating systems such as Windows, Ubuntu, Raspberry Pi, and other platforms. Further, it covers hands-on exercises with GNU Octave exploring the basic functionality and command line in interactive mode. This is followed by covering matrices and various operations including how to read and analyze data from various sources. Moving forward, it introduces commonly used programming constructs in data visualization. It explains 2D and 3D data visualization along with data analysis. It also demonstrates the concepts related to geometry and its application with GNU Octave. It concludes with coverage of signal processing followed by image, video, and audio processing techniques. After reading this book, you will be able to write your own programs for scientific and numerical applications. What You Will Learn â— Understand the practical aspects of GNU Octave with math and programming-friendly abstractions â— Install GNU Octave on multiple platforms including Windows, Raspberry Pi, and Ubuntu â— Work with GNU Octave using the GUI, the command line, and Jupyter notebooks â— Implement 2D and 3D data visualization and analysis with GNU Octave Who This Book Is For Software engineers, data engineers, data science enthusiasts, and computer vision professionals. Computers

Mastering Docker Unlock the full potential of the Docker containerization platform with this practical guide Key Features Explore tools such as Docker Engine, Machine, Compose, and Swarm Discover how you can integrate Docker into your everyday workflows Get well-versed with Kubernetes options such as Minikube, Kind, and MicroK8s Book Description Docker has been a game changer when it comes to how modern applications are deployed and created. It has now grown into a key driver of innovation beyond system administration, with a significant impact on the world of web development. Mastering Docker shows you how you can ensure that you're keeping up with the innovations it's driving and be sure you're using it to its full potential. This fourth edition not only demonstrates how to use Docker more effectively but also helps you rethink and reimagine what you can achieve with it. You'll start by building, managing, and storing images along with exploring best practices for working with Docker confidently. Once you've got to grips with Docker security, the book covers essential concepts for extending and integrating Docker in new and innovative ways. You'll also learn how to take control of your containers efficiently using Docker Compose, Docker Swarm, and Kubernetes. By the end of this Docker book, you'll have a broad yet detailed sense of what's possible with Docker and how seamlessly it fits in with a range of other platforms and tools. What you will learn Get to grips with essential Docker components and concepts Discover the best ways to build, store, and distribute container images Understand how Docker can fit into your development workflow Secure your containers and files with Docker's security features Explore first-party and third-party cluster tools and plugins Launch and manage your Kubernetes clusters in major public clouds Who this book is for If you are a software architect, DevOps engineer, sysadmin, or IT professional looking to leverage Docker's extensive features for innovating any process from system administration to web development, Mastering Docker will show you how you can use it to its full potential. A basic understanding of containerization and prior Docker experience is necessary. Computers

Microsoft Office 365 Administration Cookbook Make the most out of your investment in Office 365 apps and services with this Microsoft Office cookbook Key Features Learn how to manage and secure the entire Office 365 stack in addition to specific services Delve into newer and frequently shifting areas such as Power Platform, Microsoft Teams, and Microsoft Search administration Discover carefully selected techniques that cover a range of administrative tasks of varying difficulty levels Book Description Organizations across the world have switched to Office 365 to boost workplace productivity. However, to maximize investment in Office 365, you need to know how to efficiently administer Office 365 solutions. Microsoft Office 365 Administration Cookbook is packed with recipes to guide you through common and not-so-common administrative tasks throughout Office 365. Whether you're administering a single app such as SharePoint or organization-wide Security & Compliance across Office 365, this cookbook offers a variety of recipes that you'll want to have to hand. The book begins by covering essential setup and administration tasks. You'll learn how to manage permissions for users and user groups along with automating routine admin tasks using PowerShell. You'll then progress through to managing core Office 365 services such as Exchange Online, OneDrive, SharePoint Online, and Azure Active Directory (AD). This book also features recipes that'll help you to manage newer services such as Microsoft Search, Power Platform, and Microsoft Teams. In the final chapters, you'll delve into monitoring, reporting, and securing your Office 365 services. By the end of this book, you'll have learned about managing individual Office 365 services along with monitoring, securing, and optimizing your entire Office 365 deployment efficiently. What you will learn Get to grips with basic Office 365 setup and routine administration tasks Manage Office 365 identities and groups efficiently and securely Harness the capabilities of PowerShell to automate common administrative tasks Configure and manage core Office 365 services such as Exchange Online, SharePoint, and OneDrive Configure and administer fast-evolving services such as Microsoft Search, Power Platform, Microsoft Teams, and Azure AD Get up and running with advanced threat protection features provided by the Microsoft 365 Security & Compliance Center Protect your organization's sensitive data with Office 365 Data Loss Prevention Monitor activities and behaviors across all Office 365 services Who this book is for This book is for newer Office 365 administrators and IT pros alike, and comes with recipes of varying difficulty levels along with step-by-step guidance. Whether you are new to Office 365 administration or just seeking new ideas, this cookbook contains recipes to enhance your organization's app and service management and productivity. Computers

If We Build It Help lay the foundation for the future of scholarly communication with these informative chapters on new information technologies and predictions for developments in the publishing industry. If We Build It, the proceedings from the 7th annual conference of the North American Serials Interest Group, stresses that the time to prepare for the revolution and phenomenal growth in electronic technology is now. This groundbreaking book addresses important questions about the future that libraries need to answer today such as: What will change for serials librarians, vendors, and publishers as ink and paper become the oddity and electronic transmitters and receivers become the norm? What services will be in demand and who will provide them? Which economic models will keep them afloat? Most importantly, can the disparate groups currently active in scholarly communication work together to build the physical, social, and economic backbone of a new model? If We Build It is an invaluable guide to the future of serials librarianship. It describes new technologies, predicts how the publishing industry will develop in the near future, and explores how the library may evolve within a new system of scholarly communication. Just a few of the exciting topics covered in these proceedings include the development of standards for networking technologies, the shift from ownership to access in libraries as a result of electronic information, the history of scholarly communication, copyright of electronic data, higher education in the 1990?s, marketing in libraries. A unique perspective on issues of cooperation between librarians, scholars, and publishers is provided by the inclusion of a joint conference day with the Society for Scholarly Publishing. If We Build It is an energizing look at the new possibilities for libraries and a call to strengthen structures and work together to build a solid future for libraries within the future of scholarly communication. Computers

The Kollected Kode Vicious Pragmatic, Bite-Sized Programming Advice from Koder-with-Attitude, Kode Vicious “For many years I have been a fan of the regular columns by Kode Vicious in Communications of the ACM. The topics are not only timely, they’re explained with wit and elegance.†--From the Foreword by Donald E. Knuth Writing as Kode Vicious (KV), George V. Neville-Neil has spent more than 15 years sharing incisive advice and fierce insights for everyone who codes, works with code, or works with coders. Now, in The Kollected Kode Vicious , he’s brought together his best essays and Socratic dialogues on the topic of building more effective computer systems. These columns have been among the most popular items published in ACM’s Queue magazine, as well as Communications of the ACM, and KV’s entertaining and perceptive explorations are supplemented here with new material that illuminates broader themes and addresses issues relevant to every software professional. Neville-Neil cuts to the heart of the matter and offers practical takeaways for newcomers and veterans alike on the following topics: The Kode at Hand: What to do (or not to do) with a specific piece of code Koding Konundrums: Issues that surround code, such as testing and documentation Systems Design: Overall systems design topics, from abstraction and threads to security Machine to Machine: Distributed systems and computer networking Human to Human: Dealing with developers, managers, and other people Each chapter brings together letters, responses, and advice that apply directly to day-to-day problems faced by those who work in or with computing systems. While the answers to the questions posed are always written with an eye towards humor, the advice given is deadly serious. Register your book for convenient access to downloads, updates, and/or corrections as they become available. See inside book for details. Computers

Accountability and Privacy in Network Security This book discusses accountability and privacy in network security from a technical perspective, providing a comprehensive overview of the latest research, as well as the current challenges and open issues. Further, it proposes a set of new and innovative solutions to balance privacy and accountability in networks in terms of their content, flow and service, using practical deep learning techniques for encrypted traffic analysis and focusing on the application of new technologies and concepts. These solutions take into account various key components (e.g. the in-network cache) in network architectures and adopt the emerging blockchain technique to ensure the security and scalability of the proposed architectures. In addition, the book examines in detail related studies on accountability and privacy, and validates the architectures using real-world datasets. Presenting secure and scalable solutions that can detect malicious behaviors in the network in a timely manner without compromising user privacy, the book offers a valuable resource for undergraduate and graduate students, researchers, and engineers working in the fields of network architecture and cybersecurity. Computers

Microbial Communication This book introduces the concept of bacterial communication systems from a mathematical modeling point of view. It sheds light on the research undertaken in the last three decades, and the mathematical models that have been proposed to understand the underlying mechanism of such systems. These communication systems are related to quorum sensing mechanisms and quorum sensing regulated processes such as biofilm formation, gene expression, bioluminescence, swarming and virulence. The book further describes the phenomenon of noise, and discusses how noise plays a crucial role in gene expression and the quorum sensing circuit operationusing a set of tools like frequency domain analysis, power spectral density, stochastic simulation and the whitening effect. It also explores various aspects of synthetic biology (related to bacterial communication), such as genetic toggle switch, bistable gene regulatory networks, transcriptional repressor systems, pattern formation, synthetic cooperation, predator-prey synthetic systems, dynamical quorum sensing, synchronized quorum of genetic clocks, role of noise in synthetic biology, the Turing test and stochastic Turing test. Computers

Privacy in Statistical Databases This book constitutes the refereed proceedings of the International Conference on Privacy in Statistical Databases, PSD 2020, held in Tarragona, Spain, in September 2020 under the sponsorship of the UNESCO Chair in Data Privacy.The 25 revised full papers presented were carefully reviewed and selected from 49 submissions. The papers are organized into the following topics: privacy models; microdata protection; protection of statistical tables; protection of interactive and mobility databases; record linkage and alternative methods; synthetic data; data quality; and case studies.The Chapter “Explaining recurrent machine learning models: integral privacy revisited†is available open access under a Creative Commons Attribution 4.0 International License via link.springer.com. Computers

Edge Computing – EDGE 2020 This book constitutes the proceedings of the International Conference on Edge Computing, EDGE 2020, held virtually as part of SCF 2020, in Honolulu, HI, USA, in September 2020. The 7 full and 2 short papers presented in this volume were carefully reviewed and selected from 13 submissions. The conference proceeding EDGE 2020 presents the latest fundamental advances in the state of the art and practice of edge computing, identify emerging research topics, and define the future of edge computing. Computers

Scalable Uncertainty Management This book constitutes the refereed proceedings of the 14th International Conference on Scalable Uncertainty Management, SUM 2020, which was held in Bozen-Bolzano, Italy, in September 2020. The 12 full, 7 short papers presented in this volume were carefully reviewed and selected from 30 submissions. Besides that, the book also contains 2 abstracts of invited talks, 2 tutorial papers, and 2 PhD track papers. The conference aims to gather researchers with a common interest in managing and analyzing imperfect information from a wide range of fields, such as artificial intelligence and machine learning, databases, information retrieval and data mining, the semantic web and risk analysis. Due to the Corona pandemic SUM 2020 was held as an virtual event. Computers

Security and Trust Management This book constitutes the proceedings of the 16th International Workshop on Security and Trust Management, STM 2020, co-located with the 25th European Symposium on Research in Computer Security, ESORICS 2020. The conference was planned to take place in Guildford, UK, but had to be moved to an online format due to the COVID-19 pandemic. The workshop took place during September 17-18, 2020. The 8 papers presented in this volume were carefully reviewed and selected from 20 submissions. They were organized in topical sections on security properties and attacks; confidentiality schema and security processes. Computers

Fundamentals of Data Analytics This book introduces the basic methodologies for successful data analytics. Matrix optimization and approximation are explained in detail and extensively applied to dimensionality reduction by principal component analysis and multidimensional scaling. Diffusion maps and spectral clustering are derived as powerful tools. The methodological overlap between data science and machine learning is emphasized by demonstrating how data science is used for classification as well as supervised and unsupervised learning. Computers

Spring Quick Reference Guide a Computers

Spatial Multidimensional Cooperative Transmission Theories And Key Technologies This book introduces the basic theory and key technologies of MIMO multi-antenna system, the characteristics and applications of spatial multi-dimensional cooperative transmission in the Ground-based, Air-based and Space-based communication systems as well as several advanced technologies for spatial multidimensional cooperative transmission from theoretical and practical perspectives. The Chinese edition of this book won the 4th Chinese Government Award for Publishing, and the authors are well known in the field of Spatial Information Network. Computers

Career Planning and Job Searching in the Information Age Career Planning and Job Searching in the Information Age answers key questions for today?s providers of career-planning and job-searching information. Librarians and career development professionals’concerns--such as cost-effective use of the Internet, the reliability and integrity of electronic resources, and successful search strategies--are addressed in this comprehensive collection. In this follow-up to Library Services for Career Planning, Job Searching and Employment Opportunities (1992), real-life methods used by information providers to reduce costs and improve quality of service through a better understanding of today?s technology and audience needs and expectations are shown. Readers learn about: issues and ethics in the electronic environment job searches conducted on the World Wide Web a university placement office?s gopher site for 24-hour access to job information a university library and career service department?s collaboration on job search seminars how a public library fit electronic job searching into its mission an alumnae network?s evolution into a national career development organization Career Planning and Job Searching in the Information Age presents a broad base of knowledge from which readers are launched into tightly focused case studies offering details on how to deal with the issues of technology and service. This book makes it clear that in the ever-changing world of information technology, there is little room for the status quo. Professionals who don’t learn about electronic resources risk missing out on a wealth of up-to-the-minute information that is infinitely useful to patrons planning a career or searching for a job. Library professionals just beginning to address these issues, professionals already possessing a general knowledge of these issues, and students of library science and career development will all benefit from this collection. Computers

Interconnection Network Reliability Evaluation Keeping in view the growth of the technological frontiers, there is always a need for the development of reliable, fault tolerant and cost- effective interconnection networks (INs) which are the critical metrics to achieve the goal of parallelism. The main objective of this book is to design new fault tolerant interconnection network layouts capable of path redundancy among dynamic failures. New INs designs are proposed and their observed results are found promising when compared with some of the earlier networks. The book also covers the reliability evaluation of various industrial network topologies considering multiple reliability performance parameters (2-TR, broadcast and ATR). Finally, the book also focuses on reliability evaluation and comparison of various topologies considering connectivity among multiple sources and multiple destinations (MSMT) nodes. Computers

Foundations of Intelligent Systems This book constitutes the proceedings of the 25th International Symposium on Foundations of Intelligent Systems, ISMIS 2020, held in Graz, Austria, in October 2020. The conference was held virtually due to the COVID-19 pandemic. The 35 full and 8 short papers presented in this volume were carefully reviewed and selected from 79 submissions. Included is also one invited talk. The papers deal with topics such as natural language processing; deep learning and embeddings; digital signal processing; modelling and reasoning; and machine learning applications. Computers

String Processing and Information Retrieval This book constitutes the refereed proceedings of the 27th International Symposium on String Processing and Information Retrieval, SPIRE 2020, held in Orlando, FL, USA, in October 2020. The 17 full papers and 4 short papers presented in this volume were carefully reviewed and selected from 32 submissions. They cover topics such as: data structures; algorithms; information retrieval; compression; combinatorics on words; and computational biology. Computers

Services – SERVICES 2020 This book constitutes the refereed proceedings of the 16th World Congress on Services, SERVICES 2020, held as part of the Services Conference Federation, SCF 2020, in Honolulu, HI, USA, in September 2020. The conference was held virtually due to the COVID-19 pandemic.The 5 full papers and 4 short papers presented were carefully reviewed and selected from 10 submissions. The papers cover topics in the field of software engineering foundations and applications with a focus on novel approaches for engineering requirements, design and architectures, testing, maintenance and evolution, model-driven development, software processes, metrics, quality assurance and new software economics models, search-based software engineering, benefiting day-to-day services sectors and derived through experiences, with appreciation to scale, pragmatism, transparency, compliance and/or dependability. Computers

Advances in Photometric 3D-Reconstruction This book presents the latest advances in photometric 3D reconstruction. It provides the reader with an overview of the state of the art in the field, and of the latest research into both the theoretical foundations of photometric 3D reconstruction and its practical application in several fields (including security, medicine, cultural heritage and archiving, and engineering). These techniques play a crucial role within such emerging technologies as 3D printing, since they permit the direct conversion of an image into a solid object. The book covers both theoretical analysis and real-world applications, highlighting the importance of deepening interdisciplinary skills, and as such will be of interest to both academic researchers and practitioners from the computer vision and mathematical 3D modeling communities, as well as engineers involved in 3D printing. No prior background is required beyond a general knowledge of classical computer vision models, numerical methods for optimization, and partial differential equations. Computers

Cognitive Modeling for Automated Human Performance Evaluation at Scale Cognitive models and software tools have been widely used for both research and commercial purposes. Although they have proved very useful, there are some limitations preventing large-scale modeling and simulation tasks to be carried out efficiently and effectively. In this book, we aim to provide readers with a systematic overview of state-of-the-art cognitive modeling software tools and applications and an introduction to a new software framework for facilitating large-scale modeling and simulation of human-performance tasks. The authors first review cognitive modeling theories and then present an overview of state-of-the-art software tools for cognitive modeling and simulation. Finally, the book focuses on the new software framework and a research prototype called CogTool+, including how to incorporate behavioral data such as eye-tracking data in modeling and simulation tasks. Typical applications of CogTool+ in HCI and cyber security are given to demonstrate its usefulness. Computers

Introducing Deno Learn everything there is to know about the new secure runtime for JavaScript: Deno. A proposed replacement for Node.js envisioned and created by the same developer who wrote the first version of Node, Deno is a simple, modern and secure runtime for JavaScript and TypeScript that uses V8 and is built in Rust. This book will cover everything from its inception to the currently available version. You’ll see how to take advantage of the security layer in order to avoid unwanted security holes, and how to use TypeScript to develop your applications without having to manually set up a build process. You'll also learn how to create and use modules without having to depend on a package manager, and much more. Armed with these newly learned concepts, by the time you finish this book, you’ll be ready to build and test your own Deno applications. Whether you’re a brand new developer to the back end with a JavaScript background or a seasoned Node.js developer looking to understand this competing technology, Introducing Deno will put you on the right path. What You'll Learn Learn why Deno was created and why it is different from Node Build real applications using Deno and related technologies Create backend applications with Typescript Resolve how to live without npm and package.json Set permissions and default behavior Who This Book Is For Anyone with knowledge of back-end development looking to learn a new way of doing things and those with a basic understanding of JavaScript and Node.js core concepts. Computers

Beginning Quarkus Framework Harness the power of Quarkus, the supersonic subatomic cloud-native Java platform from Red Hat. This book covers everything you need to know to get started with the platform, which has been engineered from the ground up for superior performance and cloud-native deployment. You’ll start with an overview of the Quarkus framework and its features. Next, you'll dive into building your first microservice using Quarkus, including the use of JAX-RS, Swagger, Microprofile, REST, reactive programming, and more. You’ll see how to seamlessly add Quarkus to existing Spring framework projects. The book continues with a dive into the dependency injection pattern and how Quarkus supports it, working with annotations and facilities from both Jakarta EE CDI and the Spring framework. You’ll also learn about dockerization and serverless technologies to deploy your microservice. Next you’ll cover how data access works in Quarkus with Hibernate, JPA, Spring Boot, MongoDB, and more. This will also give you an eye for efficiency with reactive SQL, microservices, and many more reactive components. You’ll also see tips and tricks not available in the official documentation for Quarkus. Lastly, you'll test and secure Quarkus-based code and use different deployment scenarios to package and deploy your Quarkus-based microservice for the cloud, using Amazon Web Services as a focus. After reading and using Beginning Quarkus Framework, you'll have the essentials to build and deploy cloud-native microservices and full-fledged applications. Author Tayo Koleoso goes to great lengths to ensure this book has up to date material including brand new and some unreleased features! What You Will Learn Build and deploy cloud-native Java applications with Quarkus Create Java-based microservices Integrate existing technologies such as the Spring framework and vanilla Java EE into the Quarkus framework Work with the Quarkus data layer on persistence with SQL, reactive SQL, and NoSQL Test code in Quarkus with the latest versions of JUnit and Testcontainers Secure your microservices with JWT and other technologies Package your microservices with Docker containers and GraalVM native image tooling Tips and techniques you won't find in the official Quarkus documentation Who This Book Is For Intermediate Java developers familiar with microservices, the cloud in general, and REST web services, but interested in modern approaches. Computers

Containers in Cisco IOS-XE, IOS-XR, and NX-OS Acomprehensive guide to learning container and application hosting capabilitiesin Cisco platforms, and implementing them to achieve higher efficiency innetwork deployments and operations Cisco architectures offer comprehensive compute virtualizationcapabilities to accommodate both native and third-party container hosting, soyou can containerize and instantiate any application or network service andgain unprecedented value from your networks. Direct from Cisco, this is the complete guide to deploying andoperating containerized application andnetwork services on Cisco platforms. First, the authors review essentialvirtualization and containerization concepts for all network professionals andintroduce leading orchestration tools. Next, they take a deep dive intocontainer networking, introducing Cisco architectural support for containerinfrastructures. You’ll find modular coverage of configuration, activation,orchestration, operations, and application hosting for each key Cisco softwareplatform: IOS-XE, IOS-XR, and NX-OS. The authors explore diverse orchestration tools, including LXC,Docker, and Kubernetes, and cover both Cisco and open-source tools for buildingand testing applications. They conclude with multiple use cases that show howcontainerization can improve agility and efficiency in a wide range of networkenvironments. Reviewthe motivation, drivers, and concepts of computing virtualization Learnhow Cisco platforms are achieving infrastructure virtualization Explorethe Cisco reference model for developing cloud-native services and moving tocloud-native network functions MasterCisco container networking fundamentals, supported modes, and configuration Enable,install, activate, and orchestrate containerized applications in Cisco IOS-XE,IOS-XR, and NX-OS Comparetools and methods for developing, testing, hosting, and orchestratingcontainerized applications Discoverreal-world use cases for Day-0, Day-1, and Day-2 operations, with practicaldeployment examples Previewemerging trends in network containerization Computers

Enriched Meanings This book develops a theory of enriched meanings for natural language interpretation that uses the concept of monads and related ideas from category theory. The volume is interdisciplinary in nature, and will appeal to graduate students and researchers from a range of disciplines interested in natural language understanding and representation. Computers

Practical PowerShell Security and Compliance Center Learn all the latest practices to build and enhance your PowerShell scripts and manage the Security and Compliance Center easily and efficiently Key Features Gather the latest information and new cmdlets to get started with PowerShell Discover innovative ways to construct useful scripts Learn how to manage SCC with PowerShell through real-world scenarios Book Description PowerShell is an integral part of Office 365. This updated edition shares tips, tricks, new cmdlets, and best practices for using PowerShell with the Security and Compliance Center. The book starts by covering the basic tools of PowerShell, such as PowerShell ISE and PowerShell repositories, and then goes on to teach you how to connect to the SCC using multi-factor authentication. You will manage role groups to layer security, before exploring the importance of information barriers. As you progress, you will orchestrate insider risk policies to protect your organization from malicious users with access to sensitive data. Next, the book will show you how to manage various devices using tenant policies and device access rules. Later chapters will delve into various reporting methods and explore options for troubleshooting scripts and best practices to produce better scripts. The book concludes with an overview of Microsoft Secure Score to help you measure your organization's security posture. By the end of this book, you'll have the latest information and new cmdlets to confidently manage the Security and Compliance Center (SCC) with PowerShell. What you will learn Enhance the script, test it, and move it into production Make your PowerShell scripts more usable and accessible Study directory synchronization and its applications Explore layers of security that prevent unauthorized access Use PowerShell to implement Data Loss Prevention (DLP) Understand compliance and how it can be managed with PowerShell Who this book is for If you are already managing Exchange and have some PowerShell experience, then this book is for you. Professionals who want to gain more proficiency in PowerShell but are unsure of how to approach it will also find this book useful. To get the most out of this book, you must have sufficient experience of working in PowerShell as the book is not a beginner's guide to PowerShell. Computers

Combinatorial Algorithms This textbook thoroughly outlines combinatorial algorithms for generation, enumeration, and search. Topics include backtracking and heuristic search methods applied to various combinatorial structures, such as: Combinations Permutations Graphs Designs Many classical areas are covered as well as new research topics not included in most existing texts, such as: Group algorithms Graph isomorphism Hill-climbing Heuristic search algorithms This work serves as an exceptional textbook for a modern course in combinatorial algorithms, providing a unified and focused collection of recent topics of interest in the area. The authors, synthesizing material that can only be found scattered through many different sources, introduce the most important combinatorial algorithmic techniques - thus creating an accessible, comprehensive text that students of mathematics, electrical engineering, and computer science can understand without needing a prior course on combinatorics. Computers

Computers, Communication, and Mental Models Computers, Commmunication, and Mental Models is a far-ranging, focused treatment of the cognitive and behavioural issues in computer-mediated communication, knowledge representation and computer-supported co- operative work. It is also an argued development of the theoretical bases for treating computerized tools as intermediaries in the communication of mental maps between tool builders and users.Empirical trails are reported in detail sufficient for representation, in computer-based instruction, fractal dimensions of cognitive mapping and group decision support. The book is a collection of multidisciplinary papers which each shed light on the complex interactions between users and systems architects, via a common medium: computerized tools. Computers

Internet of Things - ICIOT 2020 This book constitutes the proceedings of the International Conference on Internet of Things, ICIOT 2020, held virtually as part of SCF 2020, in Honolulu, HI, USA, in September 2020. The 8 full and 4 short papers presented in this volume were carefully reviewed and selected from 20 submissions. The conference Internet of Things (ICIOT 2020) covers state-of-the-art technologies and best practices of Internet of Things, as well as emerging standards and research topics which would define the future of Internet of Things. Computers

Artificial Intelligence and Mobile Services – AIMS 2020 This book constitutes the proceedings of the 9th International Conference on Artificial Intelligence and Mobile Services, AIMS 2020, held as part of SCF 2020, during September 18-20, 2020. The conference was planned to take place in Honolulu, HI, USA and was changed to a virtual format due to the COVID-19 pandemic. The 11 full and 2 short papers presented were carefully reviewed and selected from 42 submissions. They cover topics in AI Modeling, AI Analysis, AI and Mobile Applications, AI Architecture, AI Management, AI Engineering, Mobile backend as a service (MBaaS), User experience of AI and mobile services. Computers

Cloud Computing – CLOUD 2020 This book constitutes the proceedings of the 13th International Conference on Cloud Computing, CLOUD 2020, held as part of SCF 2020, during September 18-20, 2020. The conference was planned to take place in Honolulu, HI, USA and was changed to a virtual format due to the COVID-19 pandemic.The 16 full and 6 short papers presented were carefully reviewed and selected from 49 submissions. They deal with the latest fundamental advances in the state of the art and practice of cloud computing, identify emerging research topics, and define the future of cloud computing. Computers

Big Data – BigData 2020 This book constitutes the proceedings of the 9th International Conference on Big Data, BigData 2020, held as part of SCF 2020, during September 18-20, 2020. The conference was planned to take place in Honolulu, HI, USA and was changed to a virtual format due to the COVID-19 pandemic. The 16 full and 3 short papers presented were carefully reviewed and selected from 52 submissions. The topics covered are Big Data Architecture, Big Data Modeling, Big Data As A Service, Big Data for Vertical Industries (Government, Healthcare, etc.), Big Data Analytics, Big Data Toolkits, Big Data Open Platforms, Economic Analysis, Big Data for Enterprise Transformation, Big Data in Business Performance Management, Big Data for Business Model Innovations and Analytics, Big Data in Enterprise Management Models and Practices, Big Data in Government Management Models and Practices, and Big Data in Smart Planet Solutions. Computers

Advanced Platform Development with Kubernetes Leverage Kubernetes for the rapid adoption of emerging technologies. Kubernetes is the future of enterprise platform development and has become the most popular, and often considered the most robust, container orchestration system available today. This book focuses on platforming technologies that power the Internet of Things, Blockchain, Machine Learning, and the many layers of data and application management supporting them. Advanced Platform Development with Kubernetes takes you through the process of building platforms with these in-demand capabilities. You'll progress through the development of Serverless, CICD integration, data processing pipelines, event queues, distributed query engines, modern data warehouses, data lakes, distributed object storage, indexing and analytics, data routing and transformation, query engines, and data science/machine learning environments. You’ll also see how to implement and tie together numerous essential and trending technologies including: Kafka, NiFi, Airflow, Hive, Keycloak, Cassandra, MySQL, Zookeeper, Mosquitto, Elasticsearch, Logstash, Kibana, Presto, Mino, OpenFaaS, and Ethereum. The book uses Golang and Python to demonstrate the development integration of custom container and Serverless functions, including interaction with the Kubernetes API. The exercises throughout teach Kubernetes through the lens of platform development, expressing the power and flexibility of Kubernetes with clear and pragmatic examples. Discover why Kubernetes is an excellent choice for any individual or organization looking to embark on developing a successful data and application platform. What You'll Learn Configure and install Kubernetes and k3s on vendor-neutral platforms, including generic virtual machines and bare metal Implement an integrated development toolchain for continuous integration and deployment Use data pipelines with MQTT, NiFi, Logstash, Kafka and Elasticsearch Install a serverless platform with OpenFaaS Explore blockchain network capabilities with Ethereum Support a multi-tenant data science platform and web IDE with JupyterHub, MLflow and Seldon Core Build a hybrid cluster, securely bridging on-premise and cloud-based Kubernetes nodes Who This Book Is For System and software architects, full-stack developers, programmers, and DevOps engineers with some experience building and using containers. This book also targets readers who have started with Kubernetes and need to progress from a basic understanding of the technology and "Hello World" example to more productive, career-building projects. Computers

Observations, Modeling and Systems Analysis in Geomagnetic Data Interpretation Geomagnetic field penetrates through all shells of the solid Earth, hydrosphere and atmosphere, spreading into space. The Earth Magnetic Field plays a key-role in major natural processes. Geomagnetic field variations in time and space provide important information about the state of the solid Earth, as well as the solar-terrestrial relationships and space weather conditions. The monograph presents a set of fundamental and, at the same time, urgent scientific problems of modern geomagnetic studies, as well as describes the results of the authors’ developments. The new technique introduced in the book can be applied far beyond the limits of Earth sciences. Requirements to corresponding data models are formulated. The conducted experimental investigations are combined with development and implementation of new methods of mathematical modeling, artificial intelligence, systems analysis and data science to solve the fundamental problems of geomagnetism. At that, formalism of Big Data and its application to Earth Sciences is presented as essential part of systems analysis. The book is intended for research scientists, tutors, students, postgraduate students and engineers working in geomagnetism and Earth sciences in general, as well as in other relevant scientific disciplines. Computers

Mathematics and Programming for Machine Learning with R Based on the author’s experience in teaching data science for more than 10 years, Mathematics and Programming for Machine Learning with R: From the Ground Up reveals how machine learning algorithms do their magic and explains how these algorithms can be implemented in code. It is designed to provide readers with an understanding of the reasoning behind machine learning algorithms as well as how to program them. Written for novice programmers, the book progresses step-by-step, providing the coding skills needed to implement machine learning algorithms in R. The book begins with simple implementations and fundamental concepts of logic, sets, and probability before moving to the coverage of powerful deep learning algorithms. The first eight chapters deal with probability-based machine learning algorithms, and the last eight chapters deal with machine learning based on artificial neural networks. The first half of the book does not require mathematical sophistication, although familiarity with probability and statistics would be helpful. The second half assumes the reader is familiar with at least one semester of calculus. The text guides novice R programmers through algorithms and their application and along the way; the reader gains programming confidence in tackling advanced R programming challenges. Highlights of the book include: More than 400 exercises A strong emphasis on improving programming skills and guiding beginners to the implementation of full-fledged algorithms Coverage of fundamental computer and mathematical concepts including logic, sets, and probability In-depth explanations of machine learning algorithms Computers

Integration of Constraint Programming, Artificial Intelligence, and Operations Research The volume LNCS 12296 constitutes the papers of the 17th International Conference on the Integration of Constraint Programming, Artificial Intelligence, and Operations Research which will be held online in September 2020. The 32 regular papers presented together with 4 abstracts of fast-track papers were carefully reviewed and selected from a total of 72 submissions. Additionally, this volume includes the 4 abstracts and 2 invited papers by plenary speakers. The conference program also included a Master Class on the topic “Recent Advances in Optimization Paradigms and Solving Technology" Computers

Web Services – ICWS 2020 This book constitutes the proceedings of the International Conference on Web of Services, ICWS 2020, held virtually as part of SCF 2020, in Honolulu, HI, USA, in September 2020. The 14 full papers presented in this volume were carefully reviewed and selected from 52 submissions.The conference proceeding ICWS 2020 presents the latest fundamental advances in the state of the art and practice of Web-based services, identify emerging research topics, and define the future of Web-based services. All topics regarding Web-centric services, enabling technologies and applications align with the theme of ICWS. Computers

Computational Epidemiology This book provides a comprehensive introduction to computational epidemiology, highlighting its major methodological paradigms throughout the development of the field while emphasizing the needs for a new paradigm shift in order to most effectively address the increasingly complex real-world challenges in disease control and prevention. Specifically, the book presents the basic concepts, related computational models, and tools that are useful for characterizing disease transmission dynamics with respect to a heterogeneous host population. In addition, it shows how to develop and apply computational methods to tackle the challenges involved in population-level intervention, such as prioritized vaccine allocation. A unique feature of this book is that its examination on the issues of vaccination decision-making is not confined only to the question of how to develop strategic policies on prioritized interventions, as it further approaches the issues from the perspective of individuals, offering a well integrated cost-benefit and social-influence account for voluntary vaccination decisions. One of the most important contributions of this book lies in it offers a blueprint on a novel methodological paradigm in epidemiology, namely, systems epidemiology, with detailed systems modeling principles, as well as practical steps and real-world examples, which can readily be applied in addressing future systems epidemiological challenges. The book is intended to serve as a reference book for researchers and practitioners in the fields of computer science and epidemiology. Together with the provided references on the key concepts, methods, and examples being introduced, the book can also readily be adopted as an introductory text for undergraduate and graduate courses in computational epidemiology as well as systems epidemiology, and as training materials for practitioners and field workers. Computers

Data Teams Learn how to run successful big data projects, how to resource your teams, and how the teams should work with each other to be cost effective. This book introduces the three teams necessary for successful projects, and what each team does. Most organizations fail with big data projects and the failure is almost always blamed on the technologies used. To be successful, organizations need to focus on both technology and management. Making use of data is a team sport. It takes different kinds of people with different skill sets all working together to get things done. In all but the smallest projects, people should be organized into multiple teams to reduce project failure and underperformance. This book focuses on management. A few years ago, there was little to nothing written or talked about on the management of big data projects or teams. Data Teams shows why management failures are at the root of so many project failures and how to proactively prevent such failures with your project. What You Will Learn Discover the three teams that you will need to be successful with big data Understand what a data scientist is and what a data science team does Understand what a data engineer is and what a data engineering team does Understand what an operations engineer is and what an operations team does Know how the teams and titles differ and why you need all three teams Recognize the role that the business plays in working with data teams and how the rest of the organization contributes to successful data projects Who This Book Is For Management, at all levels, including those who possess some technical ability and are about to embark on a big data project or have already started a big data project. It will be especially helpful for those who have projects which may be stuck and they do not know why, or who attended a conference or read about big data and are beginning their due diligence on what it will take to put a project in place. This book is also pertinent for leads or technical architects who are: on a team tasked by the business to figure out what it will take to start a project, in a project that is stuck, or need to determine whether there are non-technical problems affecting their project. Computers

Practical TensorFlow.js Develop and deploy deep learning web apps using the TensorFlow.js library. TensorFlow.​js​ is part of a bigger framework named TensorFlow, which has many tools that supplement it, such as TensorBoard​, ​ml5js​, ​tfjs-vis. This book will cover all these technologies and show they integrate with TensorFlow.​js​ to create intelligent web apps. The most common and accessible platform users interact with everyday is their web browser, making it an ideal environment to deploy AI systems. TensorFlow.js is a well-known and battle-tested library for creating browser solutions. Working in JavaScript, the so-called language of the web, directly on a browser, you can develop and serve deep learning applications.You'll work with deep learning algorithms such as feedforward neural networks, convolutional neural networks (CNN), recurrent neural networks (RNN), and generative adversarial network (GAN). Through hands-on examples, apply these networks in use cases related to image classification, natural language processing, object detection, dimensionality reduction, image translation, transfer learning, and time series analysis. Also, these topics are very varied in terms of the kind of data they use, their output, and the training phase. Not everything in machine learning is deep networks, there is also what some call shallow or traditional machine learning. While TensorFlow.js is not the most common place to implement these, you'll be introduce them and review the basics of machine learning through TensorFlow.js. What You'll Learn Build deep learning products suitable for web browsers Work with deep learning algorithms such as feedforward neural networks, convolutional neural networks (CNN), recurrent neural networks (RNN), and generative adversarial network (GAN) Develop apps using image classification, natural language processing, object detection, dimensionality reduction, image translation, transfer learning, and time series analysis Who This Book Is For Programmers developing deep learning solutions for the web and those who want to learn TensorFlow.js with at least minimal programming and software development knowledge. No prior JavaScript knowledge is required, but familiarity with it is helpful. Computers

Brain Informatics This book constitutes the refereed proceedings of the 13th International Conference on Brain Informatics, BI 2020, held in Padua, Italy, in September 2020. The conference was held virtually due to the COVID-19 pandemic. The 33 full papers were carefully reviewed and selected from 57 submissions. The papers are organized in the following topical sections: cognitive and computational foundations of brain science; investigations of human information processing systems; brain big data analytics, curation and management; informatics paradigms for brain and mental health research; and brain-machine intelligence and brain-inspired computing. Computers

Transactions on Large-Scale Data- and Knowledge-Centered Systems XLV The LNCS journal Transactions on Large-Scale Data- and Knowledge-Centered Systems focuses on data management, knowledge discovery, and knowledge processing, which are core and hot topics in computer science. Since the 1990s, the Internet has become the main driving force behind application development in all domains. An increase in the demand for resource sharing (e.g., computing resources, services, metadata, data sources) across different sites connected through networks has led to an evolution of data- and knowledge-management systems from centralized systems to decentralized systems enabling large-scale distributed applications providing high scalability. This, the 45th issue of Transactions on Large-Scale Data- and Knowledge-Centered Systems, contains eight revised selected regular papers. Topics covered include data analysis, information extraction, blockchains, and big data. Computers

GIS LATAM This book constitutes the refereed proceedings of the First GIS LATAM Conference, GIS LATAM 2020, held in September 2020. Due to the COVID-19 pandemic the conference was held online. The 9 full papers and 2 short papers were thoroughly reviewed and selected from 29 submissions. The papers are focused on the GIS applications in data analytics in spheres of health, environment, government, public, and education. Computers

Signal and Image Processing Techniques for the Development of Intelligent Healthcare Systems This book comprehensively reviews the various automated and semi-automated signal and image processing techniques, as well as deep-learning-based image analysis techniques, used in healthcare diagnostics. It highlights a range of data pre-processing methods used in signal processing for effective data mining in remote healthcare, and discusses pre-processing using filter techniques, noise removal, and contrast-enhanced methods for improving image quality. The book discusses the status quo of artificial intelligence in medical applications, as well as its future. Further, it offers a glimpse of feature extraction methods for reducing dimensionality and extracting discriminatory information hidden in biomedical signals. Given its scope, the book is intended for academics, researchers and practitioners interested in the latest real-world technological innovations. Computers

Database Systems for Advanced Applications The 4 volume set LNCS 12112-12114 constitutes the papers of the 25th International Conference on Database Systems for Advanced Applications which will be held online in September 2020. The 119 full papers presented together with 19 short papers plus 15 demo papers and 4 industrial papers in this volume were carefully reviewed and selected from a total of 487 submissions. The conference program presents the state-of-the-art R&D activities in database systems and their applications. It provides a forum for technical presentations and discussions among database researchers, developers and users from academia, business and industry. Computers

Artificial Intelligence This book constitutes the proceedings of the 18th Russian Conference on Artificial Intelligence, RCAI 2020, held in Moscow, Russia, in October 2020. The 27 full papers and 8 short papers presented in this volume were carefully reviewed and selected from 140 submissions. The conference deals with a wide range of topics, including data mining and knowledge discovery, text mining, reasoning, decisionmaking, natural language processing, vision, intelligent robotics, multi-agent systems,machine learning, AI in applied systems, and ontology engineering. Computers

Database Systems for Advanced Applications The 4 volume set LNCS 12112-12114 constitutes the papers of the 25th International Conference on Database Systems for Advanced Applications which will be held online in September 2020. The 119 full papers presented together with 19 short papers plus 15 demo papers and 4 industrial papers in this volume were carefully reviewed and selected from a total of 487 submissions. The conference program presents the state-of-the-art R&D activities in database systems and their applications. It provides a forum for technical presentations and discussions among database researchers, developers and users from academia, business and industry. Computers

Database Systems for Advanced Applications The 4 volume set LNCS 12112-12114 constitutes the papers of the 25th International Conference on Database Systems for Advanced Applications which will be held online in September 2020. The 119 full papers presented together with 19 short papers plus 15 demo papers and 4 industrial papers in this volume were carefully reviewed and selected from a total of 487 submissions. The conference program presents the state-of-the-art R&D activities in database systems and their applications. It provides a forum for technical presentations and discussions among database researchers, developers and users from academia, business and industry. Computers

Database Systems for Advanced Applications. DASFAA 2020 International Workshops The LNCS 12115 constitutes the workshop papers which were held also online in conjunction with the 25th International Conference on Database Systems for Advanced Applications in September 2020. The complete conference includes 119 full papers presented together with 19 short papers plus 15 demo papers and 4 industrial papers in this volume were carefully reviewed and selected from a total of 487 submissions. DASFAA 2020 presents this year following five workshops: The 7th International Workshop on Big Data Management and Service (BDMS 2020) The 6th International Symposium on Semantic Computing and Personalization (SeCoP 2020) The 5th Big Data Quality Management (BDQM 2020) The 4th International Workshop on Graph Data Management and Analysis (GDMA 2020) The 1st International Workshop on Artificial Intelligence for Data Engineering (AIDE 2020) Computers

Web Information Systems and Applications This book constitutes the proceedings of the 17th International Conference on Web Information Systems and Applications, WISA 2020, held in Guangzhou, China, in September 2020. The 42 full papers and 16 short papers presented were carefully reviewed and selected from 165 submissions. The papers are grouped in topical sections on world wide web, recommendation, query processing and algorithm, natural language processing, machine learning, graph query, edge computing and data mining, data privacy and security, and blockchain. Computers

Foundational Java Java is now well-established as one of the world’s major programming languages, used in everything from desktop applications to web-hosted applications and enterprise systems, and embedded in devices such as mobile phones and Blu-ray players. Foundational Java: Key Elements and Practical Programming presents a detailed guide to the core features of Java – and some more recent innovations – enabling the reader to build their skills and confidence though tried-and-trusted stages, supported by exercises that reinforce the key learning points. All of the most useful and commonly applied Java syntax and libraries are introduced, along with many example programs that can provide the basis for more substantial applications. Use of the Eclipse Integrated Development Environment (IDE) and the JUnit testing framework is integral to the book, ensuring maximum productivity and code quality when learning Java, although to ensure that skills are not confined to one environment the fundamentals of the Java compiler and run time are also explained. Additionally, coverage of the Ant tool will equip the reader with the skills to automatically build, test and deploy applications independent of an IDE. Topics and features: presents the most up-to-date information on Java, including Java 7; examines the key theme of unit testing, introducing the JUnit 4 testing framework to emphasize the importance of unit testing in modern software development; describes the Eclipse IDE, the most popular open source Java IDE, and also explains how Java can be run from the command line; includes coverage of the Ant build tool; contains numerous code examples and exercises throughout; provides downloadable source code, self-test questions, PowerPoint slides and other supplementary material at the website http://www.introjava.com. This hands-on, classroom-tested textbook/reference is ideal for undergraduate students on introductory and intermediate courses on programming with Java. Professional software developers will also find this an excellent self-study guide/refresher on the topic. Computers

Machine Learning Concepts with Python and the Jupyter Notebook Environment Create, execute, modify, and share machine learning applications with Python and TensorFlow 2.0 in the Jupyter Notebook environment. This book breaks down any barriers to programming machine learning applications through the use of Jupyter Notebook instead of a text editor or a regular IDE. You’ll start by learning how to use Jupyter Notebooks to improve the way you program with Python. After getting a good grounding in working with Python in Jupyter Notebooks, you’ll dive into what TensorFlow is, how it helps machine learning enthusiasts, and how to tackle the challenges it presents. Along the way, sample programs created using Jupyter Notebooks allow you to apply concepts from earlier in the book. Those who are new to machine learning can dive in with these easy programs and develop basic skills. A glossary at the end of the book provides common machine learning and Python keywords and definitions to make learning even easier. What You Will Learn Program in Python and TensorFlow Tackle basic machine learning obstacles Develop in the Jupyter Notebooks environment Who This Book Is For Ideal for Machine Learning and Deep Learning enthusiasts who are interested in programming with Python using Tensorflow 2.0 in the Jupyter Notebook Application. Some basic knowledge of Machine Learning concepts and Python Programming (using Python version 3) is helpful. Computers

Understanding Oracle APEX 20 Application Development This book shows developers and Oracle professionals how to build practical, non-trivial web applications using Oracle’s rapid application development environment – Application Express (APEX). This third edition Is revised to cover the new features and user interface experience found in APEX 20. Interactive grids and form regions are two of the newer aspects of APEX covered in this edition. The book is targeted at those who are new to APEX and just beginning to develop real projects for deployment, as well as those who are familiar with APEX and want a deeper understanding. The book takes you through the development of a demo web application that illustrates the concepts all APEX programmers should know. This book introduces the world of APEX properties, explaining the functionality supported by each page component as well as the techniques developers use to achieve that functionality. Topics include conditional formatting, user-customized reports, data entry forms, concurrency and lost updates, and security control. Specific attention is given in the book to the thought process involved in choosing and assembling APEX components and features to deliver a specific result. Understanding Oracle APEX 20 Application Development, 3rd Edition is the ideal book to take you from an understanding of the individual pieces of APEX to an understanding of how those pieces are assembled into polished applications. What You Will Learn Build attractive, highly functional web apps from the ground up Enhance and customize pages created by the APEX wizards Understand the security implications of page design Write PL/SQL code for process activity and verification Build complex components such as forms and interactive grids Who This Book Is For Developers new to APEX who desire a strong fundamental understanding of how APEX applications work. For existing developers and database administrators desiring to mine the most value from APEX by improving their development techniques. Computers

Getting Started with Oracle Cloud Free Tier Use this comprehensive guide to get started with the Oracle Cloud Free Tier. Reading this book and creating your own application in the Free Tier is an excellent way to build familiarity with, and expertise in, Oracle Cloud Infrastructure. Even better is that the Free Tier by itself is capable enough and provides all the ingredients needed for you to create secure and robust, multi-tiered web applications of modest size. Examples in this book introduce the broad suite of Always Free options that are available from Oracle Cloud Infrastructure. You will learn how to provision autonomous databases and autonomous Linux compute nodes. And you will see how to use Terraform to manage infrastructure as code. You also will learn about the virtual cloud network and application deployment, including how to create and deploy public-facing Oracle Application Express solutions and three-tier web applications on a foundation of Oracle REST Data Services. The book also includes a brief introduction to using and managing access to Oracle Machine Learning Notebooks. Cloud computing is a strong industry trend. Mastering the content in this book leaves you well-positioned to make the transition into providing and supporting cloud-based applications and databases. You will have the knowledge and skills that you need to deploy modest applications along with a growing understanding of Oracle’s Cloud platform that will serve you well as you go beyond the limits of the Always Free options and take full advantage of all that Oracle Cloud Infrastructure can offer. What You Will Learn Know which resources are available for free forever from Oracle Cloud Infrastructure Provision your virtual cloud network Host, manage, and monitor web applications using the freely available components Provision and manage Autonomous Databases and Autonomous Linux Compute Nodes Use and manage access to Oracle Machine Learning Notebooks Automate and manage your infrastructure as code using Terraform Monitor and manage costs when you grow beyond the Always Free platform Who This Book Is For Database administrators and application developers who want to learn about Oracle’s cloud offerings, application developers seeking a robust platform on which to build and deploy modest applications at zero cost, and developers and administrators interested in exploring Oracle Application Express running on a self-managing, self-tuning Oracle Database Computers

Microsoft Azure Architect Technologies Study Companion Use this invaluable study companion and hands-on guide to help you prepare for the AZ-300 and AZ-303 certification exam and get well on your way to becoming an Azure Solutions Architect. The book starts with an overview of public, private, and hybrid clouds and then goes into configuration of virtual machines. Azure Resource Manager (ARM) and VM encryption are discussed along with Azure Monitor. You will learn how to work with Azure recommendations and analyze your resource configuration. Storage solutions, connecting to networks, and Azure Active Directory are discussed in depth, with examples. You will be able to migrate servers to Azure and demonstrate server-less computing, load balancing, and app services in Azure. You also will learn about Service Fabric, Azure Kubernetes services, and data security in Azure. Cosmos DB and Relational DB are covered and you will know how to connect to cloud databases using SQL Server Management Studio (SSMS). The book presents exercises, practice questions, and Azure architecture best practices. What Will You Learn Be able to speak with customers, understand their infrastructure, and provide a blueprint to migrate their framework to Azure Go beyond moving on-premise frameworks to Azure and design solutions on Azure from the start Know Azure architecture best practices to optimize Azure deployments Complete practice exercises to prepare for exam lab assignments Take a mock exam for practice Who This Book Is For Azure developers, Azure Solution Architects, and those aspiring to fill these roles, who possess some familiarity with cloud computing Computers

Vue.js 3 Cookbook Explore the new features of Vue.js 3 and discover best practices for building fault-tolerant and professional frontend web applications Key Features Migrate your apps from Vue.js 2 to Vue.js 3 with the help of practical recipes Explore the latest Vue.js 3 features such as reactivity API, composition API, and TypeScript support Extend the capabilities and performance of Vue.js apps with Quasar, Vuetify, and Nuxt.js frameworks Book Description Vue.js is a progressive web framework for building professional user interfaces for your web applications. With Vue.js 3, the frontend framework is reinforced with architectural enhancements, new base languages, new render processes, and separated core components. The book starts with recipes for implementing Vue.js 3's new features in your web development projects and migrating your existing Vue.js apps to the latest version. You will get up and running with TypeScript with Vue.js and find succinct solutions to common challenges and pitfalls faced in implementing components, derivatives, and animation, through to building plugins, adding state management, routing, and developing complete single-page applications (SPAs). As you advance, you'll discover recipes to help you integrate Vue.js apps with Nuxt.js in order to add server-side rendering capabilities to your SPAs. You'll then learn about the Vue.js ecosystem by exploring modern frameworks such as Quasar, Nuxt.js, Vuex, and Vuetify in your web projects. Finally, the book provides you with solutions for packaging and deploying your Vue.js apps. By the end of this Vue.js book, you'll be able to identify and solve challenges faced in building Vue.js applications and be able to adopt the Vue.js framework for frontend web projects of any scale. What you will learn Design and develop large-scale web applications using Vue.js 3's latest features Create impressive UI layouts and pages using Vuetify, Buefy, and Ant Design Extend your Vue.js applications with dynamic form and custom rules validation Add state management, routing, and navigation to your web apps Extend Vue.js apps to the server-side with Nuxt.js Discover effective techniques to deploy your web applications with Netlify Develop web applications, mobile applications, and desktop applications with a single code base using the Quasar framework Who this book is for The book is for both new and experienced Vue.js developers looking to overcome challenges in building dynamic web applications with Vue 3. Knowledge of JavaScript and a basic understanding of Vue.js will help you to make the most of this book. Computers

Learn Human-Computer Interaction Explore fundamentals, strategies, and emerging techniques in the field of human-computer interaction to enhance how users and computers interact Key Features Explore various HCI techniques and methodologies to enhance the user experience Delve into user behavior analytics to solve common and not-so-common challenges faced while designing user interfaces Learn essential principles, techniques and explore the future of HCI Book Description Human-Computer Interaction (HCI) is a field of study that researches, designs, and develops software solutions that solve human problems. This book will help you understand various aspects of the software development phase, from planning and data gathering through to the design and development of software solutions. The book guides you through implementing methodologies that will help you build robust software. You will perform data gathering, evaluate user data, and execute data analysis and interpretation techniques. You'll also understand why human-centered methodologies are successful in software development, and learn how to build effective software solutions through practical research processes. The book will even show you how to translate your human understanding into software solutions through validation methods and rapid prototyping leading to usability testing. Later, you will understand how to use effective storytelling to convey the key aspects of your software to users. Throughout the book, you will learn the key concepts with the help of historical figures, best practices, and references to common challenges faced in the software industry. By the end of this book, you will be well-versed with HCI strategies and methodologies to design effective user interfaces. What you will learn Become well-versed with HCI and UX concepts Evaluate prototypes to understand data gathering, analysis, and interpretation techniques Execute qualitative and quantitative methods for establishing humans as a feedback loop in the software design process Create human-centered solutions and validate these solutions with the help of quantitative testing methods Move ideas from the research and definition phase into the software solution phase Improve your systems by becoming well-versed with the essential design concepts for creating user interfaces Who this book is for This book is for software engineers, UX designers, entrepreneurs, or anyone who is just getting started with user interface design and looking to gain a solid understanding of human-computer interaction and UX design. No prior HCI knowledge is required to get started. Computers

Deep Learning for Beginners Implementing supervised, unsupervised, and generative deep learning (DL) models using Keras and Dopamine over TensorFlow. Key Features Understand the fundamental machine learning concepts useful in deep learning Learn the underlying mathematical concepts as you implement deep learning models from scratch Explore easy-to-understand examples and use cases that will help you build a solid foundation in DL Book Description With information on the web exponentially increasing, it has become more difficult than ever to navigate through everything to find reliable content that will help you get started with deep learning. This book is designed to help you if you're a beginner looking to work on deep learning and build deep learning models from scratch, and already have the basic mathematical and programming knowledge required to get started. The book begins with a basic overview of machine learning, guiding you through setting up popular Python frameworks. You will also understand how to prepare data by cleaning and preprocessing it for deep learning, and gradually go on to explore neural networks. A dedicated section will give you insights into the working of neural networks by helping you get hands-on with training single and multiple layers of neurons. Later, you will cover popular neural network architectures such as CNNs, RNNs, AEs, VAEs, and GANs with the help of simple examples, and you will even build models from scratch. At the end of each chapter, you will find a question and answer section to help you test what you've learned through the course of the book. By the end of this book, you'll be well-versed with deep learning concepts and have the knowledge you need to use specific algorithms with various tools for different tasks. What you will learn Implement RNNs and Long short-term memory for image classification and Natural Language Processing tasks Explore the role of CNNs in computer vision and signal processing Understand the ethical implications of deep learning modeling Understand the mathematical terminology associated with deep learning Code a GAN and a VAE to generate images from a learned latent space Implement visualization techniques to compare AEs and VAEs Who this book is for This book is for aspiring data scientists and deep learning engineers who want to get started with the fundamentals of deep learning and neural networks. Although no prior knowledge of deep learning or machine learning is required, familiarity with linear algebra and Python programming is necessary to get started. Computers

Workflow Automation with Microsoft Power Automate Enhance your organization's productivity by automating repetitive tasks and simplifying business workflows using Microsoft Power Automate (formerly Microsoft Flow) Key Features Create basic and advanced workflows for automating Twitter posts, sending emails, push notifications, and much more Manage user inputs, documents, approvals, and database storage using flow controls Create flows that integrate with services both inside and outside the Microsoft 365 ecosystem Book Description Microsoft Power Automate (formerly Flow) is a workflow automation tool built into Microsoft 365 to help businesses and users to automate repetitive tasks or trigger business processes without user intervention. If you are new to Microsoft Power Automate, this book will give you a comprehensive introduction to help you to get up to speed with automating business processes in no time. Complete with hands-on tutorials, projects, and self-assessment questions, this easy-to-follow guide will show you how to configure automation workflows for business processes between hundreds of Microsoft and third-party applications. Once you understand how to use connectors, triggers, and actions to automate business processes, you'll get to grips with managing user inputs, documents, approvals, and database storage using efficient flow controls. This Power Automate book explains key concepts and takes you through creating your own flows step by step. By the end of the book, you'll have learned how to use Microsoft Power Automate to replace repetitive tasks with business workflow automation technology. What you will learn Get to grips with the building blocks of Power Automate, its services, and core capabilities Explore connectors in Power Automate to automate email workflows Discover how to create a flow for copying files between two cloud services Understand the business process, connectors, and actions for creating approval flows Use flows to save responses submitted to a database through Microsoft Forms Find out how to integrate Power Automate with Microsoft Teams Who this book is for The book is for technologists, system administrators, and Power users with little or no Microsoft Power Automate experience. Familiarity with basic Microsoft 365 services is expected. Computers

Developing Multi-Platform Apps with Visual Studio Code Redefine your software development experience by understanding the extensive features and rich functionalities offered by Visual Studio Code Key Features Leverage the power of the free, cross-platform, and highly customizable code editor to build modern web and cloud applications Edit, debug and deploy on Microsoft Azure with Visual Studio Code Learn how to customize features and install a wide variety of third-party extensions Book Description Microsoft Visual Studio Code is a powerful, lightweight code editor for modern web and cloud development. It is a source code editor that can be used with a variety of programming languages, which works on multiple platforms such as Linux, Windows, and macOS. This book provides extensive coverage of the tools, functionalities, and extensions available within the VS Code environment that will help you build multi-platform apps with ease. You'll start with the installation of VS Code and learn about various tools and features that are essential for development. Progressing through the chapters, you'll explore the user interface while understanding tips and tricks for increasing productivity. Next, you'll delve into VS Code extensions and discover how they can make life easier for developers. Later, the book shows you how to develop a sample application with different programming languages, tools, and runtimes to display how VS code can be used effectively for development, before helping you get to grips with source code version management and deployment on Azure with VS Code. Finally, you'll build on your skills by focusing on remote development with VS Code. By the end of this book, you'll have the knowledge you need to use Visual Studio Code as your primary tool for software development. What you will learn Explore various editing, formatting, and navigational features of VS Code Understand how to add, delete, and configure extensions in VS Code Develop web APIs using Node.js, Java, and Python in VS Code Develop background service in .NET Core and explore Dapr Delve into debugging techniques such as breakpoints, log points, and data inspection Use Git with Azure DevOps to share and synchronize code with VS Code Create custom extensions in VS Code to increase developer productivity Understand the concepts of remote development using VS Code Who this book is for This book is for software developers, web developers and polyglot programmers, who are working with any language or framework such as Python, Java, Node.js, or .NET and are looking to learn how they can create multi-platform, microservices based, cloud-native applications while effectively using Visual Studio Code for editing, debugging, version management and deployment. Basic software development skills are a must to grasp the concepts covered in this book. Computers

VBA Automation for Excel 2019 Cookbook A comprehensive guide to gaining a 360-degree overview of the VBA programming language and learning how to build your own programs for automating routine tasks Key Features Extend the capabilities of Excel and other Office applications with the help of Microsoft VBA Take your Excel programming skills to the next level by creating custom applications with dialogue boxes and the range object Automate repetitive and monotonous office work with VBA Excel programming Book Description Visual Basic for Applications (VBA) is a programming language developed by Microsoft to automate tasks in MS Office applications. This book will help you to focus on the essential aspects of your role by automating mundane tasks in Excel and other Office applications. With comprehensive coverage of VBA delivered in the form of practice problems and bite-sized recipes, this book will help you to hit the ground running. Unlike most books that assume prior programming experience, this book starts with the fundamentals and gradually progresses to solving bigger problems. You'll start by becoming familiar with VBA so that you can start recording macros right away. With this foundation in place, you'll advance to using the full capabilities of the language as you apply loops, functions, and custom dialog boxes to design your own automation programs. You'll also get to grips with embedded macros and other advanced tools to enhance productivity and explore topics relating to app performance and security. Throughout this VBA book, you'll cover multiple practice projects in Excel, Word, and PowerPoint while exploring tips and best practices to hone your skills. By the end of this book, you'll have developed the skills you need to use VBA to create your own programs that control MS Office applications. What you will learn Understand the VBA programming language's role in the context of the MS Office suite Discover various aspects of VBA programming such as its terminology, syntax, procedures, functions, and forms Investigate the elements, features, and characteristics of the VBA Editor to write and edit custom scripts Automate Excel sheets with the help of ranges Explore error handling and debugging techniques to catch bugs in your programs Create and use custom dialog boxes to collect data from users Customize and extend Office apps such as Excel, PowerPoint, and Word Who this book is for This book is for experienced Excel users, business analysts, finance professionals, and business users looking to boost their productivity by learning VBA programming to automate repetitive, tedious, or complex tasks. No prior programming experience is required to get started with this book. Computers

The Phantom Pattern Problem Patterns in data are often used as evidence, but how can you tell if that evidence is worth believing? The Phantom Pattern Problem helps readers avoid being duped by data, tricked into worthless investing strategies, or scared out of getting vaccinations. Becoming a sceptical consumer of data is important in this age of Big Data. Computers

Identity Management with Biometrics Work with common biometrics such as face, fingerprint, and iris recognition for business and personal use to ensure secure identification and authentication for fintech, homes, and computer systems Key Features Explore the next iteration of identity protection and overcome real-world challenges Understand different biometric use cases to deploy a large-scale biometric system Curated by renowned security ambassador and experienced author Lisa Bock Book Description Biometric technologies provide a variety of robust and convenient methods to securely identify and authenticate an individual. Unlike a password or smart card, biometrics can identify an attribute that is not only unique to an individual, but also eliminates any possibility of duplication. Identity Management with Biometrics is a solid introduction for anyone who wants to explore biometric techniques, such as fingerprint, iris, voice, palm print, and facial recognition. Starting with an overview of biometrics, you'll learn the various uses and applications of biometrics in fintech, buildings, border control, and many other fields. You'll understand the characteristics of an optimal biometric system and then review different types of errors and discover the benefits of multi-factor authentication. You'll also get to grips with analyzing a biometric system for usability and accuracy and understand the process of implementation, testing, and deployment, along with addressing privacy concerns. The book outlines the importance of protecting biometric data by using encryption and shows you which factors to consider and how to analyze them before investing in biometric technologies. By the end of this book, you'll be well-versed with a variety of recognition processes and be able to make the right decisions when implementing biometric technologies. What you will learn Review the advantages and disadvantages of biometric technology Understand the characteristics of an optimal biometric system Discover the uses of biometrics and where they are used Compare different types of errors and see how to tune your system Understand the benefits of multi-factor authentication Work with commonly used biometrics such as face, fingerprint, and iris Analyze a biometric system for usability and accuracy Address privacy concerns and get a glimpse of the future of biometrics Who this book is for Identity Management with Biometrics is for IT managers, security professionals, students, teachers, and anyone involved in selecting, purchasing, integrating, or securing a biometric system. This book will help you understand how to select the right biometric system for your organization and walk you through the steps for implementing identity management and authentication. A basic understanding of biometric authentication techniques, such as fingerprint and facial recognition, and the importance of providing a secure method of authenticating an individual will help you make the most of the book. Computers

The Multi-Agent Programming Contest 2019 This book constitutes the 14th edition of the annual Multi-Agent Programming Contest, MAPC 2019, and presents its participants.The 2019 scenario and all its changes from previous competitions are described in the first contribution, together with a brief description and analysis of the five participating teams and a closer look at the matches. It is followed by a contribution from each team, introducing their methods and tools used to create their agent team and analyzing their performance and the contest. Computers

Frontiers in Algorithmics This book constitutes the proceedings of the 14th International Workshop on Frontiers in Algorithmics, FAW 2020, held in Haikou, China, in May 2020. The conference was held virtually due to the COVID-19 pandemic. The 12 full papers presented in this volume were carefully reviewed and selected from 15 submissions. The workshop provides a focused forum on current trends of research on algorithms, discrete structures, and their applications, and brings together international experts at the research frontiers in these areas to exchange ideas and to present significant new results. The papers detail graph theory, scheduling and algorithm and complexity. Computers

Simulation and Synthesis in Medical Imaging This book constitutes the refereed proceedings of the 5th International Workshop on Simulation and Synthesis in Medical Imaging, SASHIMI 2020, held in conjunction with MICCAI 2020, in Lima, Peru, in October 2020. The 19 full papers presented were carefully reviewed and selected from 27 submissions. The contributions span the following broad categories in alignment with the initial call-for-papers: methods based on generative models or adversarial learning for MRI/CT/PET/microscopy image synthesis, and several applications of image synthesis and simulation for data augmentation, image enhancement or segmentation. Computers

Distant Connections Analogical thinking lies at the core of human cognition, pervading from the most mundane to the most extraordinary forms of creativity. By connecting poorly understood phenomena to learned situations whose structure is well articulated, it allows reasoners to expand the boundaries of their knowledge. The first part of the book begins by fleshing out the debate around whether our cognitive system is well-suited for creative analogizing, and ends by reviewing a series of studies that were designed to decide between the experimental and the naturalistic accounts. The studies confirm the psychological reality of the surface bias revealed by most experimental studies, thus claiming for realistic solutions to the problem of inert knowledge. The second part of the book delves into cognitive interventions, while maintaining an emphasis on the interplay between psychological modeling and instructional applications. It begins by reviewing the first generation of instructional interventions aimed at improving the later retrievability of educational contents by highlighting their abstract structure. Subsequent chapters discuss the most realistic avenues for devising easily-executable and widely-applicable ways of enhancing access to stored knowledge that would otherwise remain inert. The authors review results from studies from both others and their own lab that speak of the promise of these approaches. ​ Computers

Introducing Bootstrap 4 a Computers

Malware Analysis and Detection Engineering Discover how the internals of malware work and how you can analyze and detect it. You will learn not only how to analyze and reverse malware, but also how to classify and categorize it, giving you insight into the intent of the malware. Malware Analysis and Detection Engineering is a one-stop guide to malware analysis that simplifies the topic by teaching you undocumented tricks used by analysts in the industry. You will be able to extend your expertise to analyze and reverse the challenges that malicious software throws at you. The book starts with an introduction to malware analysis and reverse engineering to provide insight on the different types of malware and also the terminology used in the anti-malware industry. You will know how to set up an isolated lab environment to safely execute and analyze malware. You will learn about malware packing, code injection, and process hollowing plus how to analyze, reverse, classify, and categorize malware using static and dynamic tools. You will be able to automate your malware analysis process by exploring detection tools to modify and trace malware programs, including sandboxes, IDS/IPS, anti-virus, and Windows binary instrumentation.The book provides comprehensive content in combination with hands-on exercises to help you dig into the details of malware dissection, giving you the confidence to tackle malware that enters your environment. What You Will Learn Analyze, dissect, reverse engineer, and classify malware Effectively handle malware with custom packers and compilers Unpack complex malware to locate vital malware components and decipher their intent Use various static and dynamic malware analysis tools Leverage the internals of various detection engineering tools to improve your workflow Write Snort rules and learn to use them with Suricata IDS Who This Book Is For Security professionals, malware analysts, SOC analysts, incident responders, detection engineers, reverse engineers, and network security engineers "This book is a beast! If you're looking to master the ever-widening field of malware analysis, look no further. This is the definitive guide for you." Pedram Amini, CTO Inquest; Founder OpenRCE.org and ZeroDayInitiative Computers

The Science of Quantitative Information Flow This book presents a comprehensive mathematical theory that explains precisely what information flow is, how it can be assessed quantitatively – so bringing precise meaning to the intuition that certain information leaks are small enough to be tolerated – and how systems can be constructed that achieve rigorous, quantitative information-flow guarantees in those terms. It addresses the fundamental challenge that functional and practical requirements frequently conflict with the goal of preserving confidentiality, making perfect security unattainable. Topics include: a systematic presentation of how unwanted information flow, i.e., "leaks", can be quantified in operationally significant ways and then bounded, both with respect to estimated benefit for an attacking adversary and by comparisons between alternative implementations; a detailed study of capacity, refinement, and Dalenius leakage, supporting robust leakage assessments; a unification of information-theoretic channels and information-leaking sequential programs within the same framework; and a collection of case studies, showing how the theory can be applied to interesting realistic scenarios. The text is unified, self-contained and comprehensive, accessible to students and researchers with some knowledge of discrete probability and undergraduate mathematics, and contains exercises to facilitate its use as a course textbook. Computers

Thinking Like a Computer Thinking Like a Computer is the result of a detailed 30-year study of how computers imitate life.Although they are machines, computers are designed to act like human beings. Software is specifically created to help accomplish human-like tasks and to be understood in human terms. Yet unlike human life, computer operations can be analyzed in detail because we build the machines that accomplish them and we know the design decisions that make them work.With every choice made during the evolution of digital technology, computer architects have intuitively or consciously incorporated truths of human functioning into their designs.Thinking Like a Computer is based on these truths, assembling them into a new explanation of human knowledge. In addition, it provides insights into the foundations of theoretical science because much of digital technology is dedicated to creating new realities. Computers

Computation in Science (Second Edition) The book explains how computing is used in the natural sciences and provides a high-level overview of relevant aspects of computer science and software engineering with a focus on concepts, results and applications. It is intended for both graduate students and experienced scientists. Computers

Discovering Computer Science "Havill's problem-driven approach introduces algorithmic concepts in context and motivates students with a wide range of interests and backgrounds." -- Janet Davis , Associate Professor and Microsoft Chair of Computer Science, Whitman College "This book looks really great and takes exactly the approach I think should be used for a CS 1 course. I think it really fills a need in the textbook landscape." -- Marie desJardins , Dean of the College of Organizational, Computational, and Information Sciences, Simmons University "Discovering Computer Science is a refreshing departure from introductory programming texts, offering students a much more sincere introduction to the breadth and complexity of this ever-growing field." -- James Deverick , Senior Lecturer, The College of William and Mary "This unique introduction to the science of computing guides students through broad and universal approaches to problem solving in a variety of contexts and their ultimate implementation as computer programs." -- Daniel Kaplan , DeWitt Wallace Professor, Macalester College Discovering Computer Science: Interdisciplinary Problems, Principles, and Python Programming is a problem-oriented introduction to computational problem solving and programming in Python, appropriate for a first course for computer science majors, a more targeted disciplinary computing course or, at a slower pace, any introductory computer science course for a general audience. Realizing that an organization around language features only resonates with a narrow audience, this textbook instead connects programming to students’ prior interests using a range of authentic problems from the natural and social sciences and the digital humanities. The presentation begins with an introduction to the problem-solving process, contextualizing programming as an essential component. Then, as the book progresses, each chapter guides students through solutions to increasingly complex problems, using a spiral approach to introduce Python language features. The text also places programming in the context of fundamental computer science principles, such as abstraction, efficiency, testing, and algorithmic techniques, offering glimpses of topics that are traditionally put off until later courses. This book contains 30 well-developed independent projects that encourage students to explore questions across disciplinary boundaries, over 750 homework exercises, and 300 integrated reflection questions engage students in problem solving and active reading. The accompanying website — https://www.discoveringcs.net — includes more advanced content, solutions to selected exercises, sample code and data files, and pointers for further exploration. Computers

Graph Representation Learning Graph-structured data is ubiquitous throughout the natural and social sciences, from telecommunication networks to quantum chemistry. Building relational inductive biases into deep learning architectures is crucial for creating systems that can learn, reason, and generalize from this kind of data. Recent years have seen a surge in research on graph representation learning, including techniques for deep graph embeddings, generalizations of convolutional neural networks to graph-structured data, and neural message-passing approaches inspired by belief propagation. These advances in graph representation learning have led to new state-of-the-art results in numerous domains, including chemical synthesis, 3D vision, recommender systems, question answering, and social network analysis. This book provides a synthesis and overview of graph representation learning. It begins with a discussion of the goals of graph representation learning as well as key methodological foundations in graph theory and network analysis. Following this, the book introduces and reviews methods for learning node embeddings, including random-walk-based methods and applications to knowledge graphs. It then provides a technical synthesis and introduction to the highly successful graph neural network (GNN) formalism, which has become a dominant and fast-growing paradigm for deep learning with graph data. The book concludes with a synthesis of recent advancements in deep generative models for graphs—a nascent but quickly growing subset of graph representation learning. Computers

Computer Vision – ECCV 2020 The 30-volume set, comprising the LNCS books 12346 until 12375, constitutes the refereed proceedings of the 16th European Conference on Computer Vision, ECCV 2020, which was planned to be held in Glasgow, UK, during August 23-28, 2020. The conference was held virtually due to the COVID-19 pandemic. The 1360 revised papers presented in these proceedings were carefully reviewed and selected from a total of 5025 submissions. The papers deal with topics such as computer vision; machine learning; deep neural networks; reinforcement learning; object recognition; image classification; image processing; object detection; semantic segmentation; human pose estimation; 3d reconstruction; stereo vision; computational photography; neural networks; image coding; image reconstruction; object recognition; motion estimation. Computers

Multimedia Communications, Services and Security This volume constitutes the refereed proceedings of the 10th International Conference on Multimedia Communications, Services and Security, MCSS 2020, held in Kraków, Poland, in October 2020. The 24 full papers and 2 short papers included in the volume were selected from 54 submissions. The papers cover ongoing research activities in the following topics: multimedia services; intelligent monitoring; audio-visual systems; biometric applications; experiments and deployments. Computers

Terraform Cookbook Manage and scale your infrastructure using Infrastructure as Code (IaC) and share Terraform code with modules and integrate it in CI/CD pipeline Key Features Get up and running with the latest version of Terraform, v0.13 Design and manage infrastructure that can be shared, tested, modified, provisioned, and deployed Work through practical recipes to achieve zero-downtime deployment and scale your infrastructure effectively Book Description HashiCorp Configuration Language (HCL) has changed how we define and provision a data center infrastructure with the launch of Terraform—one of the most popular and powerful products for building Infrastructure as Code. This practical guide will show you how to leverage HashiCorp's Terraform tool to manage a complex infrastructure with ease. Starting with recipes for setting up the environment, this book will gradually guide you in configuring, provisioning, collaborating, and building a multi-environment architecture. Unlike other books, you'll also be able to explore recipes with real-world examples to provision your Azure infrastructure with Terraform. Once you've covered topics such as Azure Template, Azure CLI, Terraform configuration, and Terragrunt, you'll delve into manual and automated testing with Terraform configurations. The next set of chapters will show you how to manage a balanced and efficient infrastructure and create reusable infrastructure with Terraform modules. Finally, you'll explore the latest DevOps trends such as continuous integration and continuous delivery (CI/CD) and zero-downtime deployments. By the end of this book, you'll have developed the skills you need to get the most value out of Terraform and manage your infrastructure effectively. What you will learn Understand how to install Terraform for local development Get to grips with writing Terraform configuration for infrastructure provisioning Use Terraform for advanced infrastructure use cases Understand how to write and use Terraform modules Discover how to use Terraform for Azure infrastructure provisioning Become well-versed in testing Terraform configuration Execute Terraform configuration in CI/CD pipelines Explore how to use Terraform Cloud Who this book is for This book is for developers, operators, and DevOps engineers looking to improve their workflow and use Infrastructure as Code. Experience with Microsoft Azure, Jenkins, shell scripting, and DevOps practices is required to get the most out of this Terraform book. Computers

Hacking Multifactor Authentication Protect your organization from scandalously easy-to-hack MFA security “solutions†Multi-Factor Authentication (MFA) is spreading like wildfire across digital environments. However, hundreds of millions of dollars have been stolen from MFA-protected online accounts. How? Most people who use multifactor authentication (MFA) have been told that it is far less hackable than other types of authentication, or even that it is unhackable. You might be shocked to learn that all MFA solutions are actually easy to hack. That’s right: there is no perfectly safe MFA solution. In fact, most can be hacked at least five different ways. Hacking Multifactor Authentication will show you how MFA works behind the scenes and how poorly linked multi-step authentication steps allows MFA to be hacked and compromised. This book covers over two dozen ways that various MFA solutions can be hacked, including the methods (and defenses) common to all MFA solutions. You’ll learn about the various types of MFA solutions, their strengthens and weaknesses, and how to pick the best, most defensible MFA solution for your (or your customers') needs. Finally, this book reveals a simple method for quickly evaluating your existing MFA solutions. If using or developing a secure MFA solution is important to you, you need this book. Learn how different types of multifactor authentication work behind the scenes See how easy it is to hack MFA security solutions—no matter how secure they seem Identify the strengths and weaknesses in your (or your customers’) existing MFA security and how to mitigate Author Roger Grimes is an internationally known security expert whose work on hacking MFA has generated significant buzz in the security world. Read this book to learn what decisions and preparations your organization needs to take to prevent losses from MFA hacking. Computers

HCI International 2020 – Late Breaking Papers This book constitutes late breaking papers from the 22nd International Conference on Human-Computer Interaction, HCII 2020, which was held in July 2020. The conference was planned to take place in Copenhagen, Denmark, but had to change to a virtual conference mode due to the COVID-19 pandemic.From a total of 6326 submissions, a total of 1439 papers and 238 posters have been accepted for publication in the HCII 2020 proceedings before the conference took place. In addition, a total of 333 papers and 144 posters are included in the volumes of the proceedings published after the conference as “Late Breaking Work†(papers and posters). These contributions address the latest research and development efforts in the field and highlight the human aspects of design and use of computing systems. The 59 late breaking papers presented in this volume address the latest research and development efforts in the field and highlight the human aspects of design and use of computing systems. Computers

Electronic Voting This book constitutes the proceedings of the 5th International Conference on Electronic Voting, E-Vote-ID 2020, held online -due to COVID -19- in Bregenz, Austria, in October 2020. The 14 full papers presented were carefully reviewed and selected from 55 submissions.The conference collected the most relevant debates on the development of Electronic Voting, from aspects relating to security and usability through to practical experiences and applications of voting systems, also including legal, social or political aspects, amongst others; turning out to be an important global referent in relation to this issue. Computers

Quantitative Methods in Pharmaceutical Research and Development This contributed volume presents an overview of concepts, methods, and applications used in several quantitative areas of drug research, development, and marketing. Chapters bring together the theories and applications of various disciplines, allowing readers to learn more about quantitative fields, and to better recognize the differences between them. Because it provides a thorough overview, this will serve as a self-contained resource for readers interested in the pharmaceutical industry, and the quantitative methods that serve as its foundation. Specific disciplines covered include: Biostatistics Pharmacometrics Genomics Bioinformatics Pharmacoepidemiology Commercial analytics Operational analytics Quantitative Methods in Pharmaceutical Research and Development is ideal for undergraduate students interested in learning about real-world applications of quantitative methods, and the potential career options open to them. It will also be of interest to experts working in these areas. Computers

Practical JAMstack Learn what JAMstack is all about, what those three big letters in the front mean and why it’s so beneficial. This book shows you how to create sites and apps on the JAMstack using GatsbyJS, a tool made specifically for generating them. As part of that, you’ll learn about React, one of the hottest front-end development tools out there today. You will build three separate projects, starting with a relatively simple site to get your feet wet, then a more robust and dynamic application to see more advanced topics like API usage and data storage. Finally, you’ll build a game on the JAMstack to get a whole different perspective on how all the pieces can fit together. JAMstack, a modern take on best practices, is taking the web development world by storm and allowing developers to create web site and apps that are blazingly fast and highly secure. In many ways JAMstack is a throwback to web development of yesteryear, all while providing a simpler development experience that is streamlined by many years of best practices being brought to bear. What You'll Learn Review the principles of JAMstack: Javascript, APIs and Markup Use React to build a front-end Set up a GitHub account and hosting using GitHub Pages Host in Netlify (the creators of JAMstack!) Understand Netlify functions and FaunaDB for persistent data storage Explore GraphQL usage for querying data Work with the Phaser game library Who This Book Is For Web developers with some HTML, CSS and JavaScript experience, who want to apply best practices to build web sites that have no back-end server infrastructure while still providing dynamic content along with a streamlined development process. Architects who just want to learn JAMstack, even if they aren’t going to be hacking code all day. Computers

Design Patterns in C# Get hands-on experience with each Gang of Four (GoF) design pattern using C#. For each of the patterns, you will see at least one real-world scenario, a coding example, and a complete implementation including output. In addition to GoF patterns, you will learn additional design patterns which are common and equally important. In this second edition, you will go through the design patterns and their implementation in Visual Studio 2019 and C# 8. Common patterns in asynchronous programming are covered, including the TAP pattern and APM pattern. You will learn via easy-to-follow examples and understand the concepts in depth. With these updated patterns, you will have a collection of programs to port over to your own projects. The book begins with the 23 GoF design patterns, and then moves onto alternative design patterns, including the Simple Factory, Null Object, and MVC patterns plus various patterns in asynchronous programming. The book concludes with a discussion of the criticisms of design patterns and chapters on anti-patterns. Each chapter includes a Q&A session that clears up any doubts and covers the pros and cons of each pattern. FAQs will help you consolidate your knowledge. What You Will Learn Work with each of the design patterns Implement the design patterns in real-world applications Select an alternative to these patterns by comparing their pros and cons Use Visual Studio Community Edition 2019 to write code and generate output Who This Book Is For Software developers, testers, and architects Computers

WordPress Whether you’re a budding blogger or seasoned web designer, WordPress is a brilliant tool for creating websites—once you know how to tap into its impressive features. The latest edition of this jargon-free Missing Manual shows you how to use WordPress’s themes, widgets, and plug-ins to build just about any kind of site. The important stuff you need to know: Set up WordPress. Configure WordPress on your web host or get it running on your home computer. Create your site. Get hands-on instructions for building all types of websites, from blogs to business sites with ecommerce features. Jazz it up. Add picture galleries, slideshows, video clips, music players, and podcasts. Add features. Select from thousands of plug-ins to enhance your site’s capabilities, from contact forms to a basic shopping cart. Build a truly unique site. Customize a WordPress theme to create a site that looks exactly the way you want. Attract an audience. Use SEO, site statistics, and social sharing to reach more people. Stay safe. Use backup and staging tools to protect your content and avoid catastrophe. Computers

iOS 14 Programming Fundamentals with Swift Move into iOS development by getting a firm grasp of its fundamentals, including the Xcode 12 IDE, Cocoa Touch, and the latest version of Apple’s acclaimed programming language, Swift 5.3. With this thoroughly updated guide, you’ll learn the Swift language, understand Apple’s Xcode development tools, and discover the Cocoa framework. Become familiar with built-in Swift types Dive deep into Swift objects, protocols, and generics Tour the life cycle of an Xcode project Learn how nibs are loaded Understand Cocoa’s event-driven design Communicate with C and Objective-C In this edition, catch up on the latest iOS programming features: Multiple trailing closures Code editor document tabs New Simulator features Resources in Swift packages Logging and testing improvements And more! Once you master the fundamentals, you’ll be ready to tackle the details of iOS app development with author Matt Neuburg’s companion guide, Programming iOS 14 . Computers

Slow Computing Is it possible to experience the joy and benefits of computing in a way that asserts individual and collective autonomy? Drawing on the ideas of the ‘slow movement’, Slow Computing sets out numerous practical and political means to take back control and counter the more pernicious effects of living digital lives. Computers

The Kubernetes Workshop From building your own cluster to running cloud-native applications with Kubernetes, this workshop covers it all using engaging examples and activities Key Features Explore the Kubernetes environment and understand how containers are managed Learn how to build, maintain, and deploy cloud-native applications using Kubernetes Get to grips with using Kubernetes primitives to manage the life cycle of a full application stack Book Description Thanks to its extensive support for managing hundreds of containers that run cloud-native applications, Kubernetes is the most popular open source container orchestration platform that makes cluster management easy. This workshop adopts a practical approach to get you acquainted with the Kubernetes environment and its applications. Starting with an introduction to the fundamentals of Kubernetes, you'll install and set up your Kubernetes environment. You'll understand how to write YAML files and deploy your first simple web application container using Pod. You'll then assign human-friendly names to Pods, explore various Kubernetes entities and functions, and discover when to use them. As you work through the chapters, this Kubernetes book will show you how you can make full-scale use of Kubernetes by applying a variety of techniques for designing components and deploying clusters. You'll also get to grips with security policies for limiting access to certain functions inside the cluster. Toward the end of the book, you'll get a rundown of Kubernetes advanced features for building your own controller and upgrading to a Kubernetes cluster without downtime. By the end of this workshop, you'll be able to manage containers and run cloud-based applications efficiently using Kubernetes. What you will learn Get to grips with the fundamentals of Kubernetes and its terminology Share or store data in different containers running in the same pod Create a container image from an image definition manifest Construct a Kubernetes-aware continuous integration (CI) pipeline for deployments Attract traffic to your app using Kubernetes ingress Build and deploy your own admission controller Who this book is for Whether you are new to the world of web programming or are an experienced developer or software engineer looking to use Kubernetes for managing and scaling containerized applications, you'll find this workshop useful. A basic understanding of Docker and containerization is necessary to make the most of this book. Computers

Android Studio 4.0 Development Essentials - Java Edition Explore Android Studio 4.0 and update your skills to build modern applications in Java Key Features Set up your Android development and testing environments Create user interfaces with Android Studio Editor, XML, and Java Explore the essential elements of Android Jetpack Book Description Android rolls out frequent updates to meet the demands of the dynamic mobile market and to enable its developer community to lead advancements in application development. This book focuses on the updated features of Android Studio (the fully integrated development environment launched by Google) to build reliable Android applications using Java. The book starts by outlining the steps necessary to set up an Android development and testing environment. You'll then learn how to create user interfaces with the help of Android Studio Layout Editor, XML files, and by writing the code in Java. The book introduces you to Android architecture components and advanced topics such as intents, touchscreen handling, gesture recognition, multi-window support integration, and biometric authentication, and lets you explore key features of Android Studio 4.0, including the layout editor, direct reply notifications, and dynamic delivery. You'll also cover Android Jetpack in detail and create a sample app project using the ViewModel component. Finally, you'll upload your app to the Google Play Console and handle the build process with Gradle. By the end of this book, you'll have gained the skills necessary to develop applications using Android Studio 4.0 and Java. What you will learn Design impressive UI for Android application using Android Studio Editor and Java Understand how Android Jetpack can help you reduce the amount of code Explore unique ways to handle single-touch and multi-touch events Trigger local and remote notifications on the device Integrate biometric authentication into an Android app Create, test, and upload an Android app bundle on Google Play Store Who this book is for This book is for application developers and Java programmers who want to explore Android Studio 4.0 to create powerful Android applications. A basic understanding of Java and the Android SDK will be helpful. Computers

Security and Privacy in Social Networks and Big Data This book constitutes revised and selected papers from the 6th International Symposium on Security and Privacy in Social Networks and Big Data, SocialSec 2020, held in Tianjin, China, in September 2020. The 38 full papers presented in this volume were carefully reviewed and selected from a total of 111 submissions. The papers are organized according to the topical sections on big data security; social networks; privacy-preserving and security. Computers

Statistical Language and Speech Processing This book constitutes the proceedings of the 8th International Conference on Statistical Language and Speech Processing, SLSP 2020, held in Cardiff, UK, in October 2020. The 13 full papers presented together with one invited paper in this volume were carefully reviewed and selected from 25 submissions. They papers cover the wide spectrum of statistical methods that are currently in use in computational language or speech processing. Computers

Artificial Intelligence in Medicine The LNAI 12299 constitutes the papers of the 18th International Conference on Artificial Intelligence in Medicine, AIME 2020, which will be held online in August 2020. The 42 full papers presented together with 1short papers in this volume were carefully reviewed and selected from a total of 103 submissions. The AIME 2020 goals were to present and consolidate the international state of the art of AI in biomedical research from the perspectives of theory, methodology, systems, and applications. Computers

Domain Adaptation and Representation Transfer, and Distributed and Collaborative Learning This book constitutes the refereed proceedings of the Second MICCAI Workshop on Domain Adaptation and Representation Transfer, DART 2020, and the First MICCAI Workshop on Distributed and Collaborative Learning, DCL 2020, held in conjunction with MICCAI 2020 in October 2020. The conference was planned to take place in Lima, Peru, but changed to an online format due to the Coronavirus pandemic. For DART 2020, 12 full papers were accepted from 18 submissions. They deal with methodological advancements and ideas that can improve the applicability of machine learning (ML)/deep learning (DL) approaches to clinical settings by making them robust and consistent across different domains. For DCL 2020, the 8 papers included in this book were accepted from a total of 12 submissions. They focus on the comparison, evaluation and discussion of methodological advancement and practical ideas about machine learning applied to problems where data cannot be stored in centralized databases; where information privacy is a priority; where it is necessary to deliver strong guarantees on the amount and nature of private information that may be revealed by the model as a result of training; and where it's necessary to orchestrate, manage and direct clusters of nodes participating in the same learning task. Computers

Roguelike Development with JavaScript Go on an adventure and build a roguelike from scratch using JavaScript. With the help of the battle-tested Phaser library, you’ll go through all the steps to build a small, fun, playable web roguelite game. The author will guide you on how to add further features to the game such as populating the game with enemies, adding treasures, and so on. You will acquire technical knowledge about procedural generation and tile-based mapping as well as learn game design skills such as what makes dungeons fun and how to evoke an emotion in your game. Roguelikes are very popular with indie developers because of their focus on gameplay over graphics. You’ll see why they appeal to game designers on a budget and discover that they serve as a good platform to experiment with novel ideas and designs. Along the way, you’ll cover the increasingly popular roguelite genre that provides a hyper casual form of the genre that is approachable and often mobile. After reading this book, you’ll be ready to create your own roguelikes, to dive deep into procedural generation, and also to bring some of the techniques shown here into other genres and game projects. What You Will Learn Make use of procedural generation for dungeons, mazes, monsters, and treasure Pick up skills to use Phaser to build games Implement turn-based mechanics Use tile-based graphics Who This Book Is For Game developers who want to build something fun and who have at least some prior JavaScript programming experience. Computers

Deploying AI in the Enterprise Your company has committed to AI. Congratulations, now what? This practical book offers a holistic plan for implementing AI from the perspective of IT and IT operations in the enterprise. You will learn about AI’s capabilities, potential, limitations, and challenges. This book teaches you about the role of AI in the context of well-established areas, such as design thinking and DevOps, governance and change management, blockchain, and quantum computing, and discusses the convergence of AI in these key areas of the enterprise. Deploying AI in the Enterprise provides guidance and methods to effectively deploy and operationalize sustainable AI solutions. You will learn about deployment challenges, such as AI operationalization issues and roadblocks when it comes to turning insight into actionable predictions. You also will learn how to recognize the key components of AI information architecture, and its role in enabling successful and sustainable AI deployments. And you will come away with an understanding of how to effectively leverage AI to augment usage of core information in Master Data Management (MDM) solutions. What You Will Learn Understand the most important AI concepts, including machine learning and deep learning Follow best practices and methods to successfully deploy and operationalize AI solutions Identify critical components of AI information architecture and the importance of having a plan Integrate AI into existing initiatives within an organization Recognize current limitations of AI, and how this could impact your business Build awareness about important and timely AI research Adjust your mindset to consider AI from a holistic standpoint Get acquainted with AI opportunities that exist in various industries Who This Book Is For IT pros, data scientists, and architects who need to address deployment and operational challenges related to AI and need a comprehensive overview on how AI impacts other business critical areas. It is not an introduction, but is for the reader who is looking for examples on how to leverage data to derive actionable insight and predictions, and needs to understand and factor in the current risks and limitations of AI and what it means in an industry-relevant context. Computers

Computational Logistics This book constitutes the proceedings of the 11th International Conference on Computational Logistics, ICCL 2020, held in Enschede, The Netherlands, in September 2020.The 49 papers included in this book were carefully reviewed and selected from 73 submissions. They were organized in topical sections named: maritime and port logistics; vehicle routing and scheduling; freight distribution and city logistics; network design and scheduling; and selected topics in logistics. Due to the Corona pandemic ICCL 2020 was held as a virtual event. Computers

HCI International 2020 – Late Breaking Papers This book constitutes late breaking papers from the 22nd International Conference on Human-Computer Interaction, HCII 2020, which was held in July 2020. The conference was planned to take place in Copenhagen, Denmark, but had to change to a virtual conference mode due to the COVID-19 pandemic.From a total of 6326 submissions, a total of 1439 papers and 238 posters have been accepted for publication in the HCII 2020 proceedings before the conference took place. In addition, a total of 333 papers and 144 posters are included in the volumes of the proceedings published after the conference as “Late Breaking Work†(papers and posters). These contributions address the latest research and development efforts in the field and highlight the human aspects of design and use of computing systems. The 54 late breaking papers address topics such as Interaction, Knowledge and Social Media. Computers

Universal Time-Series Forecasting with Mixture Predictors The author considers the problem of sequential probability forecasting in the most general setting, where the observed data may exhibit an arbitrary form of stochastic dependence. All the results presented are theoretical, but they concern the foundations of some problems in such applied areas as machine learning, information theory and data compression. Computers

Immersive Office 365 Bring mixed reality into your office workplace by building immersive experiences using data and content from your Office 365 platform. Imagine being able to sit at your desk and surround yourself with a 3D chart showing your work relationships as mined from your relationships with others based on how you collaborate together. This book shows you how to access your Office 365 data using the Microsoft Graph API, and then helps you present that data in a 3D modeling visualization using the Microsoft HoloLens 2 as a mixed reality device. This book covers the growing number of tools and techniques you can use to access and visualize data on a Microsoft HoloLens 2 device. Foremost is the Graph API, giving access to the full range of data in Office 365. Also covered are Unity and Visual Studio, the development environments from which you can create mixed reality applications for Microsoft HoloLens 2. You will learn how to load data from and save data to your Office 365 platform based on several interesting use cases. You will be able to extend your digital workplace into a 3D space powered by Microsoft HoloLens 2. Whether you know Office 365 and want to move toward mixed reality, or whether you know the Microsoft HoloLens 2 and want to build functionality around Office 365 data, this book helps you step up and accomplish your goal of bridging between mixed reality and Office 365. What You Will Learn Create immersive experiences using Microsoft HoloLens 2 and Office 365 Access Office 365 data programmatically using the Microsoft Graph API Control your immersive experiences using natural gestures and eye tracking Understand and correctly use different visualization models Implement design patterns to write better code in Unity Know how to access services using web requests via DLLs Who This Book Is For Developers who want to expand their knowledge of the Office 365 platform into the world of mixed reality by creating immersive experiences and 3D visualizations using the Microsoft HoloLens 2 and similar devices, and mixed reality developers who want to extend their repertoire toward serving everyday business needs of workers in corporate office environments Computers

The Complete ASP.NET Core 3 API Tutorial Use this ASP.NET Core API tutorial and straightforward step-by-step guide to build, test, and deploy an ASP.NET Core API to Azure. It will help you code confidently and efficiently, and provides just what you need for context. The book starts with detailing how to set up your development environment, and then introduces a variety of tools and technologies to build, test, and deploy your API. It covers tools such as .NET Core SDK, (Version 3.1), Visual Studio Code, Git, xUnit, Docker, PostgreSQL, Postman, Azure DevOps, Azure, AutoMapper, and many more. Practical guidance is provided so you can achieve a tangible and valuable outcome, and you also are given a dose of theory on REST (Representational State Transfer), JSON, (JavaScript Object Notation), DTOs (Data Transfer Objects), and the MVC (Model View Controller) architectural pattern. What You Will Learn Build an ASP.NET Core API using C#, test it, and deploy it to Azure Understand concepts on Entity Framework Core Gain hard-earned secrets, shortcuts, and gotchas throughout the “build along†Get comfortable with ASP NET Core Environments Be introduced to unit testing, CI/CD pipelines, bearer authentication, and JSON Web Tokens (JWT) Who This Book Is For Developers using the Microsoft stack. Some basic understanding of .NET Core is assumed. Computers

Microsoft Power Platform Enterprise Architecture Gain a 360-degree view of Microsoft Power Platform and combine the benefits of Power Apps, Power BI, Power Automate, Azure, and Dynamics 365 to build an enterprise application platform for your organization Key Features Explore various Microsoft cloud components and find out how they can enhance your Power Platform solutions Get to grips with Microsoft Power Platform's security and extensibility, integration, and data migration models Discover architectural best practices for designing complex enterprise solutions Book Description For forward-looking architects and decision makers who want to craft complex solutions to serve growing business needs, Microsoft Power Platform Enterprise Architecture offers an array of architectural best practices and techniques. With this book, you'll learn how to design robust software using the tools available in the Power Platform suite and be able to integrate them seamlessly with various Microsoft 365 and Azure components. Unlike most other resources that are overwhelmingly long and unstructured, this book covers essential concepts using concise yet practical examples to help you save time. You'll develop the skills you need to architect, design, and manage a complex solution as you follow the journey of a fictitious enterprise customer as they enter the world of Power Platform. Throughout the book, you'll discover how to combine the functionality of Power Apps, Power Automate, Power BI, and Power Virtual Agents with various methodologies to effectively address application lifecycle management, security, and extensibility. Finally, you'll learn how to overcome common challenges in migrating data to and from Microsoft Power Platform using proven techniques. By the end of this book, you'll have the strategic perspective of an enterprise architect to make accurate architectural decisions for your complex Power Platform projects. What you will learn Understand various Dynamics 365 CRM, ERP, and AI modules for creating Power Platform solutions Enhance Power Platform with Microsoft 365 and Azure Find out which regions, staging environments, and user licensing groups need to be employed when creating enterprise solutions Implement sophisticated security by using various authentication and authorization techniques Extend Power Apps, Power BI, and Power Automate to create custom applications Integrate your solution with various in-house Microsoft components or third-party systems using integration patterns Who this book is for This book is for enterprise architects and technical decision makers who want to craft complex solutions using Microsoft Power Platform to serve growing business needs and to stay competitive in the modern IT world. A basic understanding of Microsoft Power Platform will help you to get started with this book. Computers

Hands-on JavaScript for Python Developers Build robust full-stack web applications using two of the world's most popular programming languages Python and JavaScript Key Features Discover similarities and differences between JavaScript and Python coding conventions Explore frontend web concepts, UI/UX techniques, and JavaScript frameworks to enhance your web development skills Put your JS knowledge into practice by developing a full-stack web app with React and Express Book Description Knowledge of Python is a great foundation for learning other languages. This book will help you advance in your software engineering career by leveraging your Python programming skills to learn JavaScript and apply its unique features not only for frontend web development but also for streamlining work on the backend. Starting with the basics of JavaScript, you'll cover its syntax, its use in the browser, and its frameworks and libraries. From working with user interactions and ingesting data from APIs through to creating APIs with Node.js, this book will help you get up and running with JavaScript using hands-on exercises, code snippets, and detailed descriptions of JavaScript implementation and benefits. To understand the use of JavaScript in the backend, you'll explore Node.js and discover how it communicates with databases. As you advance, you'll get to grips with creating your own RESTful APIs and connecting the frontend and backend for holistic full-stack development knowledge. By the end of this Python JavaScript book, you'll have the knowledge you need to write full-fledged web applications from start to finish. You'll have also gained hands-on experience of working through several projects, which will help you advance in your career as a JavaScript developer. What you will learn Discover the differences between Python and JavaScript at both the syntactical and semantical level Become well versed in implementing JavaScript in the frontend as well as the backend Understand the separation of concerns while using Python programming for server-side development Get to grips with frontend web development tasks, including UI/UX design, form validation, animations, and much more Create modern interaction interfaces for your Python web application Explore modern web technologies and libraries for building full-stack applications Who this book is for This book is for experienced Python programmers who are looking to expand their knowledge of frontend and backend web development with JavaScript. An understanding of data types, functions, and scope is necessary to get to grips with the concepts covered in the book. Familiarity with HTML and CSS, Document Object Model (DOM), and Flask or Django will help you to learn JavaScript easily. Computers

Legal Challenges of Big Data This groundbreaking book explores the new legal and economic challenges triggered by big data, and analyses the interactions among and between intellectual property, competition law, free speech, privacy and other fundamental rights vis-à-vis big data analysis and algorithms. Computers

Computational Legal Studies Featuring contributions from a diverse set of experts, this thought-provoking book offers a visionary introduction to the computational turn in law and the resulting emergence of the computational legal studies field. It explores how computational data creation, collection, and analysis techniques are transforming the way in which we comprehend and study the law, and the implications that this has for the future of legal studies. Computers

Computational Science and Its Applications – ICCSA 2020 The seven volumes LNCS 12249-12255 constitute the refereed proceedings of the 20th International Conference on Computational Science and Its Applications, ICCSA 2020, held in Cagliari, Italy, in July 2020. Due to COVID-19 pandemic the conference was organized in an online event.Computational Science is the main pillar of most of the present research, industrial and commercial applications, and plays a unique role in exploiting ICT innovative technologies.The 466 full papers and 32 short papers presented were carefully reviewed and selected from 1450 submissions. Apart from the general track, ICCSA 2020 also include 52 workshops, in various areas of computational sciences, ranging from computational science technologies, to specific areas of computational sciences, such as software engineering, security, machine learning and artificial intelligence, blockchain technologies, and of applications in many fields. Computers

Computational Science and Its Applications – ICCSA 2020 The seven volumes LNCS 12249-12255 constitute the refereed proceedings of the 20th International Conference on Computational Science and Its Applications, ICCSA 2020, held in Cagliari, Italy, in July 2020. Due to COVID-19 pandemic the conference was organized in an online event.Computational Science is the main pillar of most of the present research, industrial and commercial applications, and plays a unique role in exploiting ICT innovative technologies.The 466 full papers and 32 short papers presented were carefully reviewed and selected from 1450 submissions. Apart from the general track, ICCSA 2020 also include 52 workshops, in various areas of computational sciences, ranging from computational science technologies, to specific areas of computational sciences, such as software engineering, security, machine learning and artificial intelligence, blockchain technologies, and of applications in many fields. Computers

Recent Advances in Data Science This book constitutes selected papers of the ​Third International Conference on Data Science, Medicine and Bioinformatics, IDMB 2019, held in Nanning, China, in June 2019. The 19 full papers and 1 short paper were carefully reviewed and selected from 93 submissions. The papers are organized according to the following topical sections: business data science: fintech, management, and analytics.- health and biological data science.- novel data science theory and applications. Computers

Algorithmic Combinatorics The book is centered around the research areas of combinatorics, special functions, and computer algebra. What these research fields share is that many of their outstanding results do not only have applications in Mathematics, but also other disciplines, such as computer science, physics, chemistry, etc. A particular charm of these areas is how they interact and influence one another. For instance, combinatorial or special functions' techniques have motivated the development of new symbolic algorithms. In particular, first proofs of challenging problems in combinatorics and special functions were derived by making essential use of computer algebra. This book addresses these interdisciplinary aspects. Algorithmic aspects are emphasized and the corresponding software packages for concrete problem solving are introduced. Readers will range from graduate students, researchers to practitioners who are interested in solving concrete problems within mathematics and other research disciplines. Computers

Emerging Technologies in Computing This book constitutes the refereed conference proceedings of the Third International Conference on Emerging Technologies in Computing, iCEtiC 2020, held in London, UK, in August 2020. Due to VOVID-19 pandemic the conference was helt virtually.The 25 revised full papers were reviewed and selected from 65 submissions and are organized in topical sections covering blockchain and cloud computing; security, wireless sensor networks and IoT; AI, big data and data analytics; emerging technologies in engineering, education and sustainable development. Computers

Machine Learning Methods for Stylometry This book presents methods and approaches used to identify the true author of a doubtful document or text excerpt. It provides a broad introduction to all text categorization problems (like authorship attribution, psychological traits of the author, detecting fake news, etc.) grounded in stylistic features. Specifically, machine learning models as valuable tools for verifying hypotheses or revealing significant patterns hidden in datasets are presented in detail. Stylometry is a multi-disciplinary field combining linguistics with both statistics and computer science. The content is divided into three parts. The first, which consists of the first three chapters, offers a general introduction to stylometry, its potential applications and limitations. Further, it introduces the ongoing example used to illustrate the concepts discussed throughout the remainder of the book. The four chapters of the second part are more devoted to computer science with a focus on machine learning models. Their main aim is to explain machine learning models for solving stylometric problems. Several general strategies used to identify, extract, select, and represent stylistic markers are explained. As deep learning represents an active field of research, information on neural network models and word embeddings applied to stylometry is provided, as well as a general introduction to the deep learning approach to solving stylometric questions. In turn, the third part illustrates the application of the previously discussed approaches in real cases: an authorship attribution problem, seeking to discover the secret hand behind the nom de plume Elena Ferrante, an Italian writer known worldwide for her My Brilliant Friend’s saga; author profiling in order to identify whether a set of tweets were generated by a bot or a human being and in this second case, whether it is a man or a woman; and an exploration of stylistic variations over time using US political speeches covering a period of ca. 230 years.A solutions-based approach is adopted throughout the book, and explanations are supported by examples written in R. To complement the main content and discussions on stylometric models and techniques, examples and datasets are freely available at the author’s Github website. Computers

Empower Decision Makers with SAP Analytics Cloud Discover the capabilities and features of SAP Analytics Cloud to draw actionable insights from a variety of data, as well as the functionality that enables you to meet typical business challenges. With this book, you will work with SAC and enable key decision makers within your enterprise to deliver crucial business decisions driven by data and key performance indicators. Along the way you’ll see how SAP has built a strong repertoire of analytics products and how SAC helps you analyze data to derive better business solutions. This book begins by covering the current trends in analytics and how SAP is re-shaping its solutions. Next, you will learn to analyze a typical business scenario and map expectations to the analytics solution including delivery via a single platform. Further, you will see how SAC as a solution meets each of the user expectations, starting with creation of a platform for sourcing data from multiple sources, enabling self-service for a spectrum of business roles, across time zones and devices. There’s a chapter on advanced capabilities of predictive analytics and custom analytical applications. Later there are chapters explaining the security aspects and their technical features before concluding with a chapter on SAP’s roadmap for SAC. Empower Decision Makers with SAP Analytics Cloud takes a unique approach of facilitating learning SAP Analytics Cloud by resolving the typical business challenges of an enterprise. These business expectations are mapped to specific features and capabilities of SAC, while covering its technical architecture block by block. What You Will Learn Work with the features and capabilities of SAP Analytics Cloud Analyze the requirements of a modern decision-support system Use the features of SAC that make it a single platform for decision support in a modern enterprise. See how SAC provides a secure and scalable platform hosted on the cloud Who This Book Is For Enterprise architects, SAP BI analytic solution architects, and developers. Computers

Intermediate C Programming for the PIC Microcontroller Delve into the exciting world of embedded programming with PIC microcontrollers in C. The key to learning how to program is to understand how the code works – and that is what you’ll learn here. Following C Programming for the PIC Microcontroller, this book continues exploring the coding required to control the PIC microcontroller and can be used as a standalone single reference, or paired with the previous title to enhance your programming skills. You'll see how to control the position of a servo motor and use the compare aspect of the CCP module to create a square wave with varying frequency. You'll also work with the capture aspect of the CCP to determine the frequency of a signal inputted to the PIC and use external and internal interrupts. This book breaks down the programs with line-by-line analysis to give you a deep understanding of the code. After reading it you’ll be able to use all three aspects of the Capture, Compare and PWM module; work with different types of interrupts; create useful projects with the 7 segment display; and use the LCD and push button keyboard. What You’ll Learn Create a small musical keyboard with the PIC Manage a stepper motor with the PIC Use the main features of the MPLABX IDE Interface the PIC to the real world Design and create useful programs based around the PIC18F4525 Who This Book Is For Engineering students and hobbyist who want to try their hand at embedded programming the PIC micros. Computers

Learn Quantum Computing with Python and IBM Quantum Experience A step-by-step guide to learning the implementation and associated methodologies in quantum computing with the help of the IBM Quantum Experience, Qiskit, and Python that will have you up and running and productive in no time Key Features Determine the difference between classical computers and quantum computers Understand the quantum computational principles such as superposition and entanglement and how they are leveraged on IBM Quantum Experience systems Run your own quantum experiments and applications by integrating with Qiskit Book Description IBM Quantum Experience is a platform that enables developers to learn the basics of quantum computing by allowing them to run experiments on a quantum computing simulator and a real quantum computer. This book will explain the basic principles of quantum mechanics, the principles involved in quantum computing, and the implementation of quantum algorithms and experiments on IBM's quantum processors. You will start working with simple programs that illustrate quantum computing principles and slowly work your way up to more complex programs and algorithms that leverage quantum computing. As you build on your knowledge, you'll understand the functionality of IBM Quantum Experience and the various resources it offers. Furthermore, you'll not only learn the differences between the various quantum computers but also the various simulators available. Later, you'll explore the basics of quantum computing, quantum volume, and a few basic algorithms, all while optimally using the resources available on IBM Quantum Experience. By the end of this book, you'll learn how to build quantum programs on your own and have gained practical quantum computing skills that you can apply to your business. What you will learn Explore quantum computational principles such as superposition and quantum entanglement Become familiar with the contents and layout of the IBM Quantum Experience Understand quantum gates and how they operate on qubits Discover the quantum information science kit and its elements such as Terra and Aer Get to grips with quantum algorithms such as Bell State, Deutsch-Jozsa, Grover's algorithm, and Shor's algorithm How to create and visualize a quantum circuit Who this book is for This book is for Python developers who are looking to learn quantum computing and put their knowledge to use in practical situations with the help of IBM Quantum Experience. Some background in computer science and high-school-level physics and math is required. Computers

Artificial Intelligence and Natural Language ​This book constitutes the refereed proceedings of the 9th Conference on Artificial Intelligence and Natural Language, AINL 2020, held in Helsinki, Finland, in October 2020. The 11 revised full papers and 3 short papers were carefully reviewed and selected from 36 submissions. Additionally, the volume presents 1 shared task paper. The volume presents recent research in areas of of text mining, speech technologies, dialogue systems, information retrieval, machine learning, articial intelligence, and robotics. Computers

Algorithms and Architectures for Parallel Processing This three-volume set LNCS 12452, 12453, and 12454 constitutes the proceedings of the 20th International Conference on Algorithms and Architectures for Parallel Processing, ICA3PP 2020, in New York City, NY, USA, in October 2020. The total of 142 full papers and 5 short papers included in this proceedings volumes was carefully reviewed and selected from 495 submissions. ICA3PP is covering the many dimensions of parallel algorithms and architectures, encompassing fundamental theoretical approaches, practical experimental projects, and commercial components and systems. As applications of computing systems have permeated in every aspects of daily life, the power of computing system has become increasingly critical. This conference provides a forum for academics and practitioners from countries around the world to exchange ideas for improving the efficiency, performance, reliability, security and interoperability of computing systems and applications. ICA3PP 2020 focus on two broad areas of parallel and distributed computing, i.e. architectures, algorithms and networks, and systems and applications. Computers

Search-Based Software Engineering This book constitutes the refereed proceedings of the 12th International Symposium on Search-Based Software Engineering, SSBSE 2020, held in Bari, Italy, in October 2020. The 13 research papers and 5 short papers presented together with 1 keynote were carefully reviewed and selected from 34 submissions. SBSE is a research area focused on the formulation of software engineering problems as search problems, and the subsequent use of complex heuristic techniques to attain optimal solutions to such problems. A wealth of engineering challenges - from test generation, to design refactoring, to process organization - can be solved efficiently through the application of automated optimization techniques. SBSE is a growing field - sitting at the crossroads between AI, machine learning, and software engineering - and SBSE techniques have begun to attain human-competitive results. Due to the Corona pandemic SSBSE 2020 was held as a virtual event. Computers

Algorithms and Architectures for Parallel Processing This three-volume set LNCS 12452, 12453, and 12454 constitutes the proceedings of the 20th International Conference on Algorithms and Architectures for Parallel Processing, ICA3PP 2020, in New York City, NY, USA, in October 2020. The total of 142 full papers and 5 short papers included in this proceedings volumes was carefully reviewed and selected from 495 submissions. ICA3PP is covering the many dimensions of parallel algorithms and architectures, encompassing fundamental theoretical approaches, practical experimental projects, and commercial components and systems. As applications of computing systems have permeated in every aspects of daily life, the power of computing system has become increasingly critical. This conference provides a forum for academics and practitioners from countries around the world to exchange ideas for improving the efficiency, performance, reliability, security and interoperability of computing systems and applications. ICA3PP 2020 focus on two broad areas of parallel and distributed computing, i.e. architectures, algorithms and networks, and systems and applications. Computers

Computational Science and Its Applications – ICCSA 2020 The seven volumes LNCS 12249-12255 constitute the refereed proceedings of the 20th International Conference on Computational Science and Its Applications, ICCSA 2020, held in Cagliari, Italy, in July 2020. Due to COVID-19 pandemic the conference was organized in an online event.Computational Science is the main pillar of most of the present research, industrial and commercial applications, and plays a unique role in exploiting ICT innovative technologies.The 466 full papers and 32 short papers presented were carefully reviewed and selected from 1450 submissions. Apart from the general track, ICCSA 2020 also include 52 workshops, in various areas of computational sciences, ranging from computational science technologies, to specific areas of computational sciences, such as software engineering, security, machine learning and artificial intelligence, blockchain technologies, and of applications in many fields. Computers

Interactive Collaborative Robotics This book constitutes the proceedings of the 5th International Conference on Interactive Collaborative Robotics, ICR 2020, held in St. Petersburg, Russia, in October 2020. The 31 papers presented were carefully reviewed and selected from 62 submissions. Challenges of human-robot interaction, robot control and behavior in social robotics and collaborative robotics, as well as applied robotic and cyber-physical systems are mainly discussed in the papers. Computers

Computational Science and Its Applications – ICCSA 2020 The seven volumes LNCS 12249-12255 constitute the refereed proceedings of the 20th International Conference on Computational Science and Its Applications, ICCSA 2020, held in Cagliari, Italy, in July 2020. Due to COVID-19 pandemic the conference was organized in an online event.Computational Science is the main pillar of most of the present research, industrial and commercial applications, and plays a unique role in exploiting ICT innovative technologies.The 466 full papers and 32 short papers presented were carefully reviewed and selected from 1450 submissions. Apart from the general track, ICCSA 2020 also include 52 workshops, in various areas of computational sciences, ranging from computational science technologies, to specific areas of computational sciences, such as software engineering, security, machine learning and artificial intelligence, blockchain technologies, and of applications in many fields. Computers

Topics in Galois Fields This monograph provides a self-contained presentation of the foundations of finite fields, including a detailed treatment of their algebraic closures. It also covers important advanced topics which are not yet found in textbooks: the primitive normal basis theorem, the existence of primitive elements in affine hyperplanes, and the Niederreiter method for factoring polynomials over finite fields. We give streamlined and/or clearer proofs for many fundamental results and treat some classical material in an innovative manner. In particular, we emphasize the interplay between arithmetical and structural results, and we introduce Berlekamp algebras in a novel way which provides a deeper understanding of Berlekamp's celebrated factorization algorithm. The book provides a thorough grounding in finite field theory for graduate students and researchers in mathematics. In view of its emphasis on applicable and computational aspects, it is also useful for readers working in information and communication engineering, for instance, in signal processing, coding theory, cryptography or computer science. Computers

Empowering Teaching for Digital Equity and Agency This book constitutes the refereed post-conference proceedings of the IFIP TC 3 Open Conference on Computers in Education, OCCE 2020, held in Mumbai, India, in January 2020. The 11 full papers and 4 short papers included in this volume were carefully reviewed and selected from 57 submissions. The papers discuss key emerging topics and evolving practices in the area of educational computing research. They are organized in the following topical sections: computing education; learners’ and teachers’ perspectives; teacher professional development; the industry perspective; and further aspects. Computers

Emotions in Technology Design Understanding emotions is becoming ever more valuable in design, both in terms of what people prefer as well as in relation to how they behave in relation to it. Approaches to conceptualising emotions in technology design, how emotions can be operationalised and how they can be measured are paramount to ascertaining the core principles of design. Emotions in Technology Design: From Experience to Ethics provides a multi-dimensional approach to studying, designing and comprehending emotions in design. It presents emotions as understood through basic human-technology research, applied design practice, culture and aesthetics, ethical approaches to emotional design, and ethics as a cultural framework for emotions in design experience. Core elements running through the book are: cognitive science – cognitive-affective theories of emotions (i.e., Appraisal); culture – the ways in which our minds are trained to recognise, respond to and influence design; and ethics – a deep cultural framework of interpretations of good versus evil. This ethical understanding brings culture and cognition together to form genuine emotional experience. This book is essential reading for designers, technology developers, HCI and cognitive science scholars, educators and students (at both undergraduate and graduate levels) in terms of emotional design methods and tools, systematic measurement of emotion in design experience, cultural theory underpinning how emotions operate in the production and interaction of design, and how ethics influence basic (primal) and higher level emotional reactions. The broader scope equips design practitioners, developers and scholars with that ‘something more’ in terms of understanding how emotional experience of technology can be positioned in relation to cultural discourse and ethics. Computers

Access Control Management in Cloud Environments This textbook introduces new business concepts on cloud environments such as secure, scalable anonymity and practical payment protocols for the Internet of things and Blockchain technology. The protocol uses electronic cash for payment transactions. In this new protocol, from the viewpoint of banks, consumers can improve anonymity if they are worried about disclosure of their identities in the cloud. Currently, there is not a book available that has reported the techniques covering the protocols with anonymizations and Blockchain technology. Thus this will be a useful book for universities to purchase. This textbook provides new direction for access control management and online business, with new challenges within Blockchain technology that may arise in cloud environments. One is related to the authorization granting process. For example, when a role is granted to a user, this role may conflict with other roles of the user or together with this role; the user may have or derive a high level of authority. Another is related to authorization revocation. For instance, when a role is revoked from a user, the user may still have the role. Experts will get benefits from these challenges through the developed methodology for authorization granting algorithm, and weak revocation and strong revocation algorithms. Computers

Digital Communications 1 It is a complete training in digital communications in the same book with all the aspects involved in such training: courses, tutorials with many typical problems targeted with detailed solutions, practical work concretely illustrating various aspects of technical implementation implemented. It breaks down into three parts. The Theory of information itself, which concerns both the sources of information and the channels of its transmission, taking into account the errors they introduce in the transmission of information and the means of protect by the use of appropriate coding methods. Then for the technical aspects of transmission, first the baseband transmission is presented with the important concept and fundamental technique of equalization. The performance evaluation in terms of probability of errors is systematically developed and detailed as well as the online codes used. Finally, the third part presents the Transmissions with digital modulation of carriers used in radio transmissions but also on electric cables. A second important aspect in learning a learner's knowledge and skills is this book. It concerns the "Directed Work" aspect of a training. This is an ordered set of 33 typical problems with detailed solutions covering the different parts of the course with practical work. Finally, the last aspect concerns the practical aspects in the proper sense of the term, an essential complement to training going as far as know-how. We propose here a set of 5 practical works. Computers

An Introduction to Information Science This book comprises an introduction to information as an external commodity; a data base that can be manipulated, retrieved, transmitted, and used. It is useful at an introductory undergraduate level and also for anyone who is new to the field of Information Science. Computers

Beyond Planar Graphs This book is the first general and extensive review on the algorithmics and mathematical results of beyond planar graphs. Most real-world data sets are relational and can be modelled as graphs consisting of vertices and edges. Planar graphs are fundamental for both graph theory and graph algorithms and are extensively studied. Structural properties and fundamental algorithms for planar graphs have been discovered. However, most real-world graphs, such as social networks and biological networks, are non-planar. To analyze and visualize such real-world networks, it is necessary to solve fundamental mathematical and algorithmic research questions on sparse non-planar graphs, called beyond planar graphs.This book is based on the National Institute of Informatics (NII) Shonan Meeting on algorithmics on beyond planar graphs held in Japan in November, 2016. The book consists of 13 chapters that represent recent advances in various areas of beyond planar graph research. The main aims and objectives of this book include 1) to timely provide a state-of-the-art survey and a bibliography on beyond planar graphs; 2) to set the research agenda on beyond planar graphs by identifying fundamental research questions and new research directions; and 3) to foster cross-disciplinary research collaboration between computer science (graph drawing and computational geometry) and mathematics (graph theory and combinatorics). New algorithms for beyond planar graphs will be in high demand by practitioners in various application domains to solve complex visualization problems. This book therefore will be a valuable resource for researchers in graph theory, algorithms, and theoretical computer science, and will stimulate further deep scientific investigations into many areas of beyond planar graphs. Computers

Predictive Intelligence in Medicine This book constitutes the proceedings of the Second International Workshop on Predictive Intelligence in Medicine, PRIME 2020, held in conjunction with MICCAI 2020, in Lima, Peru, in October 2020. The workshop was held virtually due to the COVID-19 pandemic. The 17 full and 2 short papers presented in this volume were carefully reviewed and selected for inclusion in this book. The contributions describe new cutting-edge predictive models and methods that solve challenging problems in the medical field for a high-precision predictive medicine. Computers

Computational Science and Its Applications – ICCSA 2020 The seven volumes LNCS 12249-12255 constitute the refereed proceedings of the 20th International Conference on Computational Science and Its Applications, ICCSA 2020, held in Cagliari, Italy, in July 2020. Due to COVID-19 pandemic the conference was organized in an online event.Computational Science is the main pillar of most of the present research, industrial and commercial applications, and plays a unique role in exploiting ICT innovative technologies.The 466 full papers and 32 short papers presented were carefully reviewed and selected from 1450 submissions. Apart from the general track, ICCSA 2020 also include 52 workshops, in various areas of computational sciences, ranging from computational science technologies, to specific areas of computational sciences, such as software engineering, security, machine learning and artificial intelligence, blockchain technologies, and of applications in many fields. Computers

Medical Ultrasound, and Preterm, Perinatal and Paediatric Image Analysis This book constitutes the proceedings of the First International Workshop on Advances in Simplifying Medical UltraSound, ASMUS 2020, and the 5th International Workshop on Perinatal, Preterm and Paediatric Image Analysis, PIPPI 2020, held in conjunction with MICCAI 2020, the 23rd International Conference on Medical Image Computing and Computer-Assisted Intervention. The conference was planned to take place in Lima, Peru, but changed to an online event due to the Coronavirus pandemic. For ASMUS 2020, 19 contributions were accepted from 26 submissions; the 14 contributions from the PIPPI workshop were carefully reviewed and selected from 21 submissions. The papers were organized in topical sections named: diagnosis and measurement; segmentation, captioning and enhancement; localisation and guidance; robotics and skill assessment, and PIPPI 2020. Computers

Computational Methods in Systems Biology This book constitutes the refereed proceedings of the 18th International Conference on Computational Methods in Systems Biology, CMSB 2020, held in Konstanz, Germany, in September 2020.*The 17 full papers and 5 tool papers were carefully reviewed and selected from 30 submissions. In addition 3 abstracts of invited talks and 2 tutorials have been included in this volume. Topics of interest include formalisms for modeling biological processes; models and their biological applications; frameworks for model verification, validation, analysis, and simulation of biological systems; high-performance computational systems biology and parallel implementations; model inference from experimental data; model integration from biological databases; multi-scale modeling and analysis methods; computational approaches for synthetic biology; and case studies in systems and synthetic biology. * The conference was held virtually due to the COVID-19 pandemic. Computers

Algorithms and Architectures for Parallel Processing This three-volume set LNCS 12452, 12453, and 12454 constitutes the proceedings of the 20th International Conference on Algorithms and Architectures for Parallel Processing, ICA3PP 2020, in New York City, NY, USA, in October 2020.The total of 142 full papers and 5 short papers included in this proceedings volumes was carefully reviewed and selected from 495 submissions.ICA3PP is covering the many dimensions of parallel algorithms and architectures, encompassing fundamental theoretical approaches, practical experimental projects, and commercial components and systems. As applications of computing systems have permeated in every aspects of daily life, the power of computing system has become increasingly critical. This conference provides a forum for academics and practitioners from countries around the world to exchange ideas for improving the efficiency, performance, reliability, security and interoperability of computing systems and applications. ICA3PP 2020 focus on two broad areas of parallel and distributed computing, i.e. architectures, algorithms and networks, and systems and applications. Computers

Shape Optimization Problems This book provides theories on non-parametric shape optimization problems, systematically keeping in mind readers with an engineering background. Non-parametric shape optimization problems are defined as problems of finding the shapes of domains in which boundary value problems of partial differential equations are defined. In these problems, optimum shapes are obtained from an arbitrary form without any geometrical parameters previously assigned. In particular, problems in which the optimum shape is sought by making a hole in domain are called topology optimization problems. Moreover, a problem in which the optimum shape is obtained based on domain variation is referred to as a shape optimization problem of domain variation type, or a shape optimization problem in a limited sense. Software has been developed to solve these problems, and it is being used to seek practical optimum shapes. However, there are no books explaining such theories beginning with their foundations. The structure of the book is shown in the Preface. The theorems are built up using mathematical results. Therefore, a mathematical style is introduced, consisting of definitions and theorems to summarize the key points. This method of expression is advanced as provable facts are clearly shown. If something to be investigated is contained in the framework of mathematics, setting up a theory using theorems prepared by great mathematicians is thought to be an extremely effective approach. However, mathematics attempts to heighten the level of abstraction in order to understand many things in a unified fashion. This characteristic may baffle readers with an engineering background. Hence in this book, an attempt has been made to provide explanations in engineering terms, with examples from mechanics, after accurately denoting the provable facts using definitions and theorems. Computers

Optimal Coverage in Wireless Sensor Networks This book will serve as a reference, presenting state-of-the-art research on theoretical aspects of optimal sensor coverage problems. Readers will find it a useful tool for furthering developments on theory and applications of optimal coverage; much of the content can serve as material for advanced topics courses at the graduate level. The book is well versed with the hottest research topics such as Lifetime of Coverage, Weighted Sensor Cover, k-Coverage, Heterogeneous Sensors, Barrier, Sweep and Partial Coverage, Mobile Sensors, Camera Sensors and Energy-Harvesting Sensors, and more. Topics are introduced in a natural order from simple covers to connected covers, to the lifetime problem. Later, the book begins revisiting earlier problems ranging from the introduction of weights to coverage by k sensors and partial coverage, and from sensor heterogeneity to novel problems such as the barrier coverage problem. The book ends with coverage of mobile sensors, camera sensors, energy-harvesting sensors, underwater sensors, and crowdsensing. Computers

Advances in Trefftz Methods and Their Applications In this book we gather recent mathematical developments and engineering applications of Trefftz methods, with particular emphasis on the Method of Fundamental Solutions (MFS). These are true meshless methods that have the advantage of avoiding the need to set up a mesh altogether, and therefore going beyond the reduction of the mesh to a boundary. These Trefftz methods have advantages in several engineering applications, for instance in inverse problems where the domain is unknown and some numerical methods would require a remeshing approach. Trefftz methods are also known to perform very well with regular domains and regular data in boundary value problems, achieving exponential convergence. On the other hand, they may also under certain conditions, exhibit instabilities and lead to ill-conditioned systems. This book is divided into ten chapters that illustrate recent advances in Trefftz methods and their application to engineering problems. The first eight chapters are devoted to the MFS and variants whereas the last two chapters are devoted to related meshless engineering applications. Part of these selected contributions were presented in the 9th International Conference on Trefftz Methods and 5th International Conference on the MFS, held in 2019, July 29-31, in Lisbon, Portugal. Computers

Disruptive Technology, Legal Innovation, and the Future of Real Estate This book addresses challenges that new technologies and the big data revolution pose to existing regulatory and legal frameworks. The volume discusses issues such as blockchain and its implications for property transactions and taxes, three (or four) dimensional title registration, land use and urban planning in the age of big data, and the future of property rights in light of these changes. The book brings together an interdisciplinary collection of chapters that revolve around the potential influence of disruptive technologies on existing legal norms and the future development of real estate markets. The book is divided into five parts. Part I presents a survey of the current available research on blockchain and real estate. Part II provides a background on property law for the volume, grounding it in fundamental theory. Part III discusses the changing landscapes of property rights while Part IV debates the potential effects of blockchain on land registration. Finally the book concludes with Part V, which is devoted to new technological applications relevant to real estate. Providing an interdisciplinary perspective on emerging technologies that have the potential to disrupt the real estate industry and the regulation of it, this book will appeal to a broad audience, consisting of scholars, policy-makers, practitioners, and students, interested in real estate, law, economics, blockchain, and technology policy. Computers

BigQuery for Data Warehousing Create a data warehouse, complete with reporting and dashboards using Google’s BigQuery technology. This book takes you from the basic concepts of data warehousing through the design, build, load, and maintenance phases. You will build capabilities to capture data from the operational environment, and then mine and analyze that data for insight into making your business more successful. You will gain practical knowledge about how to use BigQuery to solve data challenges in your organization. BigQuery is a managed cloud platform from Google that provides enterprise data warehousing and reporting capabilities. Part I of this book shows you how to design and provision a data warehouse in the BigQuery platform. Part II teaches you how to load and stream your operational data into the warehouse to make it ready for analysis and reporting. Parts III and IV cover querying and maintaining, helping you keep your information relevant with other Google Cloud Platform services and advanced BigQuery. Part V takes reporting to the next level by showing you how to create dashboards to provide at-a-glance visual representations of your business situation. Part VI provides an introduction to data science with BigQuery, covering machine learning and Jupyter notebooks. What You Will Learn Design a data warehouse for your project or organization Load data from a variety of external and internal sources Integrate other Google Cloud Platform services for more complex workflows Maintain and scale your data warehouse as your organization grows Analyze, report, and create dashboards on the information in the warehouse Become familiar with machine learning techniques using BigQuery ML Who This Book Is For Developers who want to provide business users with fast, reliable, and insightful analysis from operational data, and data analysts interested in a cloud-based solution that avoids the pain of provisioning their own servers. Computers

Monitoring Microservices and Containerized Applications Discover the methodologies and best practices for getting started with container services monitoring using Prometheus, AppDynamics, and Dynatrace. The book begins with the basics of working with the containerization and microservices architecture while establishing the need for monitoring and management technologies. You’ll go through hands-on deployment, configuration, and best practices for Prometheus. Next, you’ll delve deeper into monitoring of container ecosystems for availability, performance, and logs, and then cover the reporting capabilities of Prometheus. Further, you’ll move on to advanced topics of extending Prometheus including how to develop new use cases and scenarios. You’ll then use enterprise tools such as AppDynamics and Wavefront to discover deeper application monitoring best practices. You’ll conclude with fully automated deployment of the monitoring and management platforms integrated with the container ecosystem using infrastructure-as -code tools such as Jenkins, Ansible and Terraform. The book provides sample code and best practices for you to look at container monitoring from a holistic viewpoint. This book is a good starting point for developers, architects, and administrators who want to learn about monitoring and management of cloud native and microservices containerized applications. What You Will Learn Examine the fundamentals of container monitoring Get an overview of the architecture for Prometheus and Alert Manager Enable Prometheus monitoring for containers Monitor containers using Wavefront Use the guidelines on container monitoring with enterprise solutions AppDynamics and Wavefront Who This Book Is For Software developers, system administrators, and DevOps engineers working for enterprise customers who want to use monitoring solutions for their container ecosystems. Computers

Multivariate Public Key Cryptosystems This book discusses the current research concerning public key cryptosystems. It begins with an introduction to the basic concepts of multivariate cryptography and the history of this field. The authors provide a detailed description and security analysis of the most important multivariate public key schemes, including the four multivariate signature schemes participating as second round candidates in the NIST standardization process for post-quantum cryptosystems. Furthermore, this book covers the Simple Matrix encryption scheme, which is currently the most promising multivariate public key encryption scheme. This book also covers the current state of security analysis methods for Multivariate Public Key Cryptosystems including the algorithms and theory of solving systems of multivariate polynomial equations over finite fields. Through the book’s website, interested readers can find source code to the algorithms handled in this book. In 1994, Dr. Peter Shor from Bell Laboratories proposed a quantum algorithm solving the Integer Factorization and the Discrete Logarithm problem in polynomial time, thus making all of the currently used public key cryptosystems, such as RSA and ECC insecure. Therefore, there is an urgent need for alternative public key schemes which are resistant against quantum computer attacks. Researchers worldwide, as well as companies and governmental organizations have put a tremendous effort into the development of post-quantum public key cryptosystems to meet this challenge. One of the most promising candidates for this are Multivariate Public Key Cryptosystems (MPKCs). The public key of an MPKC is a set of multivariate polynomials over a small finite field. Especially for digital signatures, numerous well-studied multivariate schemes offering very short signatures and high efficiency exist. The fact that these schemes work over small finite fields, makes them suitable not only for interconnected computer systems, but also for small devices with limited resources, which are used in ubiquitous computing. This book gives a systematic introduction into the field of Multivariate Public Key Cryptosystems (MPKC), and presents the most promising multivariate schemes for digital signatures and encryption. Although, this book was written more from a computational perspective, the authors try to provide the necessary mathematical background. Therefore, this book is suitable for a broad audience. This would include researchers working in either computer science or mathematics interested in this exciting new field, or as a secondary textbook for a course in MPKC suitable for beginning graduate students in mathematics or computer science. Information security experts in industry, computer scientists and mathematicians would also find this book valuable as a guide for understanding the basic mathematical structures necessary to implement multivariate cryptosystems for practical applications. Computers

Learn Data Science Using SAS Studio Do you want to create data analysis reports without writing a line of code? This book introduces SAS Studio, a free data science web browser-based product for educational and non-commercial purposes. The power of SAS Studio comes from its visual point-and-click user interface that generates SAS code. It is easier to learn SAS Studio than to learn R and Python to accomplish data cleaning, statistics, and visualization tasks. The book includes a case study about analyzing the data required for predicting the results of presidential elections in the state of Maine for 2016 and 2020. In addition to the presidential elections, the book provides real-life examples including analyzing stocks, oil and gold prices, crime, marketing, and healthcare. You will see data science in action and how easy it is to perform complicated tasks and visualizations in SAS Studio.You will learn, step-by-step, how to do visualizations, including maps. In most cases, you will not need a line of code as you work with the SAS Studio graphical user interface. The book includes explanations of the code that SAS Studio generates automatically. You will learn how to edit this code to perform more complicated advanced tasks. The book introduces you to multiple SAS products such as SAS Viya, SAS Analytics, and SAS Visual Statistics. What You Will Learn Become familiar with SAS Studio IDE Understand essential visualizations Know the fundamental statistical analysis required in most data science and analytics reports Clean the most common data set problems Use linear progression for data prediction Write programs in SAS Get introduced to SAS-Viya, which is more potent than SAS studio Who This Book Is For A general audience of people who are new to data science, students, and data analysts and scientists who are experienced but new to SAS. No programming or in-depth statistics knowledge is needed. Computers

C Programming For Dummies Get an A grade in C As with any major language, mastery of C can take you to some very interesting new places. Almost 50 years after it first appeared, it's still the world's most popular programming language and is used as the basis of global industry's core systems, including operating systems, high-performance graphics applications, and microcontrollers. This means that fluent C users are in big demand at the sharp end in cutting-edge industries—such as gaming, app development, telecommunications, engineering, and even animation—to translate innovative ideas into a smoothly functioning reality. To help you get to where you want to go with C, this 2nd edition of C Programming For Dummies covers everything you need to begin writing programs, guiding you logically through the development cycle: from initial design and testing to deployment and live iteration. By the end you'll be au fait with the do's and don'ts of good clean writing and easily able to produce the basic—and not-so-basic—building blocks of an elegant and efficient source code. Write and compile source code Link code to create the executable program Debug and optimize your code Avoid common mistakes Whatever your destination: tech industry, start-up, or just developing for pleasure at home, this easy-to-follow, informative, and entertaining guide to the C programming language is the fastest and friendliest way to get there! Computers

International Dictionary of Artificial Intelligence First Published in 1998. Artificial intelligence is increasingly employed in all areas of human endeavor and industry. Anticipating the needs of professionals, researchers, and students alike, International Dictionary of Artificial Intelligence defines and illustrates over 2,500 terms and provides detailed explanations of major concepts as well as topics in related disciplines. The Dictionary also contains an annotated bibliography and an extensive appendix of World Wide Web sites devoted to the latest trends and developments in the world of artificial intelligence. Computers

Computational Science and Its Applications – ICCSA 2020 The seven volumes LNCS 12249-12255 constitute the refereed proceedings of the 20th International Conference on Computational Science and Its Applications, ICCSA 2020, held in Cagliari, Italy, in July 2020. Due to COVID-19 pandemic the conference was organized in an online event.Computational Science is the main pillar of most of the present research, industrial and commercial applications, and plays a unique role in exploiting ICT innovative technologies.The 466 full papers and 32 short papers presented were carefully reviewed and selected from 1450 submissions. Apart from the general track, ICCSA 2020 also include 52 workshops, in various areas of computational sciences, ranging from computational science technologies, to specific areas of computational sciences, such as software engineering, security, machine learning and artificial intelligence, blockchain technologies, and of applications in many fields. Computers

Medical Image Computing and Computer Assisted Intervention – MICCAI 2020 The seven-volume set LNCS 12261, 12262, 12263, 12264, 12265, 12266, and 12267 constitutes the refereed proceedings of the 23rd International Conference on Medical Image Computing and Computer-Assisted Intervention, MICCAI 2020, held in Lima, Peru, in October 2020. The conference was held virtually due to the COVID-19 pandemic.The 542 revised full papers presented were carefully reviewed and selected from 1809 submissions in a double-blind review process. The papers are organized in the following topical sections: Part I: machine learning methodologies Part II: image reconstruction; prediction and diagnosis; cross-domain methods and reconstruction; domain adaptation; machine learning applications; generative adversarial networks Part III: CAI applications; image registration; instrumentation and surgical phase detection; navigation and visualization; ultrasound imaging; video image analysis Part IV: segmentation; shape models and landmark detection Part V: biological, optical, microscopic imaging; cell segmentation and stain normalization; histopathology image analysis; opthalmology Part VI: angiography and vessel analysis; breast imaging; colonoscopy; dermatology; fetal imaging; heart and lung imaging; musculoskeletal imaging Part VI: brain development and atlases; DWI and tractography; functional brain networks; neuroimaging; positron emission tomography Computers

An Introduction to Sequential Monte Carlo This book provides a general introduction to Sequential Monte Carlo (SMC) methods, also known as particle filters. These methods have become a staple for the sequential analysis of data in such diverse fields as signal processing, epidemiology, machine learning, population ecology, quantitative finance, and robotics. The coverage is comprehensive, ranging from the underlying theory to computational implementation, methodology, and diverse applications in various areas of science. This is achieved by describing SMC algorithms as particular cases of a general framework, which involves concepts such as Feynman-Kac distributions, and tools such as importance sampling and resampling. This general framework is used consistently throughout the book.Extensive coverage is provided on sequential learning (filtering, smoothing) of state-space (hidden Markov) models, as this remains an important application of SMC methods. More recent applications, such as parameter estimation of these models (through e.g. particle Markov chain Monte Carlo techniques) and the simulation of challenging probability distributions (in e.g. Bayesian inference or rare-event problems), are also discussed. The book may be used either as a graduate text on Sequential Monte Carlo methods and state-space modeling, or as a general reference work on the area. Each chapter includes a set of exercises for self-study, a comprehensive bibliography, and a “Python corner,†which discusses the practical implementation of the methods covered. In addition, the book comes with an open source Python library, which implements all the algorithms described in the book, and contains all the programs that were used to perform the numerical experiments. Computers

Numerical Semigroups and Applications This book is an extended and revised version of "Numerical Semigroups with Applications," published by Springer as part of the RSME series. Like the first edition, it presents applications of numerical semigroups in Algebraic Geometry, Number Theory and Coding Theory. It starts by discussing the basic notions related to numerical semigroups and those needed to understand semigroups associated with irreducible meromorphic series. It then derives a series of applications in curves and factorization invariants. A new chapter is included, which offers a detailed review of ideals for numerical semigroups. Based on this new chapter, descriptions of the module of Kähler differentials for an algebroid curve and for a polynomial curve are provided. Moreover, the concept of tame degree has been included, and is viewed in relation to other factorization invariants appearing in the first edition. This content highlights new applications of numerical semigroups and their ideals, following in the spirit of the first edition. Computers

The Data Science Framework This edited book first consolidates the results of the EU-funded EDISON project (Education for Data Intensive Science to Open New science frontiers), which developed training material and information to assist educators, trainers, employers, and research infrastructure managers in identifying, recruiting and inspiring the data science professionals of the future. It then deepens the presentation of the information and knowledge gained to allow for easier assimilation by the reader. The contributed chapters are presented in sequence, each chapter picking up from the end point of the previous one. After the initial book and project overview, the chapters present the relevant data science competencies and body of knowledge, the model curriculum required to teach the required foundations, profiles of professionals in this domain, and use cases and applications. The text is supported with appendices on related process models. The book can be used to develop new courses in data science, evaluate existing modules and courses, draft job descriptions, and plan and design efficient data-intensive research teams across scientific disciplines. Computers

Creating Good Data Create good data from the start, rather than fixing it after it is collected. By following the guidelines in this book, you will be able to conduct more effective analyses and produce timely presentations of research data. Data analysts are often presented with datasets for exploration and study that are poorly designed, leading to difficulties in interpretation and to delays in producing meaningful results. Much data analytics training focuses on how to clean and transform datasets before serious analyses can even be started. Inappropriate or confusing representations, unit of measurement choices, coding errors, missing values, outliers, etc., can be avoided by using good dataset design and by understanding how data types determine the kinds of analyses which can be performed. This book discusses the principles and best practices of dataset creation, and covers basic data types and their related appropriate statistics and visualizations. A key focus of the book is why certain data types are chosen for representing concepts and measurements, in contrast to the typical discussions of how to analyze a specific data type once it has been selected. What You Will Learn Be aware of the principles of creating and collecting data Know the basic data types and representations Select data types, anticipating analysis goals Understand dataset structures and practices for analyzing and sharing Be guided by examples and use cases (good and bad) Use cleaning tools and methods to create good data Who This Book Is For Researchers who design studies and collect data and subsequently conduct and report the results of their analyses can use the best practices in this book to produce better descriptions and interpretations of their work. In addition, data analysts who explore and explain data of other researchers will be able to create better datasets. Computers

PMP Project Management Professional Practice Tests The best practice test preparation for the PMP exam! Boost your confidence through preparation before you take the new Project Management Professional (PMP) exam. The PMP Project Management Professional Practice Tests is the hands-on way to prepare for the exam and achieve your certification. Access three practice tests Study questions that cover the three PMP performance domains Test your knowledge with three additional bonus exams Practice with a total of 1,000 unique test questions. The Project Management Professional (PMP) certification was developed by the Project Management Institute (PMI). The certification requires extensive project management experience, instructional hours, and successful completion of the certification exam. Well-known PMP authors and experts, Kim Heldman and Vanina Mangano, have written practice questions that will help you get ready for testing as you work toward certification. The test questions provide you with coverage within each of the performance domains: people, process, and business environments. Project managers play a critical role in today’s organizations. When you pass the exam and earn certification, you will gain additional recognition for your skill set and expertise. This confidence-building guide also connects you to an interactive online learning environment and test bank including all the practice exam questions. Get help reaching your professional goals with the right PMP tools! Computers

Data Cleaning Pocket Primer As part of the best selling Pocket Primer series, this book is an effort to give programmers sufficient knowledge of data cleaning to be able to work on their own projects. It is designed as a practical introduction to using flexible, powerful (and free) Unix / Linux shell commands to perform common data cleaning tasks. The book is packed with realistic examples and numerous commands that illustrate both the syntax and how the commands work together. Companion files with source code are available for downloading from the publisher. Features:- A practical introduction to using flexible, powerful (and free) Unix / Linux shell commands to perform common data cleaning tasks - Includes the concept of piping data between commands, regular expression substitution, and the sed and awk commands - Packed with realistic examples and numerous commands that illustrate both the syntax and how the commands work together - Assumes the reader has no prior experience, but the topic is covered comprehensively enough to teach a pro some new tricks - Includes companion files with all of the source code examples (download from the publisher). Computers

Angular and Deep Learning Pocket Primer As part of the best-selling Pocket Primer series, this book is designed to introduce the reader to basic deep learning concepts and incorporate thatknowledge into Angular 10 applications. It is intended to be a fast-paced introduction to some basic features of deep learning and an overview of severalpopular deep learning classifiers. The book includes code samples and numerous figures and covers topics such as Angular 10 functionality, basic deep learning concepts, classification algorithms, TensorFlow, and Keras. Companion files with code and color figures are included. FEATURES: Introduces basic deep learning concepts and Angular 10 applications Covers MLPs (MultiLayer Perceptrons) and CNNs (Convolutional Neural Networks), RNNs (Recurrent Neural Networks), LSTMs (Long Short-Term Memory), GRUs (Gated RecurrentUnits), autoencoders, and GANs (Generative Adversarial Networks) Introduces TensorFlow 2 and Keras Includes companion files with source code and 4-color figures. Computers

Angular and Deep Learning Pocket Primer As part of the best-selling Pocket Primer series, this book is designed to introduce the reader to basic deep learning concepts and incorporate thatknowledge into Angular 10 applications. It is intended to be a fast-paced introduction to some basic features of deep learning and an overview of severalpopular deep learning classifiers. The book includes code samples and numerous figures and covers topics such as Angular 10 functionality, basic deep learning concepts, classification algorithms, TensorFlow, and Keras. Companion files with code and color figures are included. FEATURES: Introduces basic deep learning concepts and Angular 10 applications Covers MLPs (MultiLayer Perceptrons) and CNNs (Convolutional Neural Networks), RNNs (Recurrent Neural Networks), LSTMs (Long Short-Term Memory), GRUs (Gated RecurrentUnits), autoencoders, and GANs (Generative Adversarial Networks) Introduces TensorFlow 2 and Keras Includes companion files with source code and 4-color figures. Computers

Modern Web Testing with TestCafe A no-nonsense guide to getting started with TestCafe quickly by building a complete test suite while learning the core concepts of test automation with TestCafe Key Features Build a proof-of-concept project to demonstrate your familiarity with TestCafe Discover useful tips and best practices for building production-ready and fault-tolerant tests Write clean and maintainable tests by refactoring your codebase using PageObject pattern Book Description TestCafe is an open source end-to-end testing framework that combines unmatched ease of use with advanced automation and robust built-in stability mechanisms. This book is a comprehensive, project-based introduction to TestCafe that will show you how to use the TestCafe framework and enable you to write fast and reliable tests; plus you'll have a proof of concept ready to demonstrate the practical potential of TestCafe. You'll begin by learning how to write end-to-end web tests using the TestCafe syntax and features of the TestCafe framework. You'll then go from setting up the environment all the way through to writing production-ready tests. You'll also find out how to build a sample set of tests in a step-by-step manner and use TestCafe to log in to the website, verify the elements present on different pages, create/delete entities, and run custom JavaScript code. As you advance, you'll delve into several stages of refactoring that will take you through the showcase setup/teardown and PageObject patterns. While this test suite is relatively simple to build, it showcases some of the most prominent features of TestCafe. Finally, this TestCafe book will show you how the tests can be run on a free and simple-to-use website, without requiring you to build and deploy your own servers or backend services. By the end of this book, you'll have learned how to write and enhance end-to-end tests with TestCafe to solve real-world problems and deliver results. What you will learn Understand the basic concepts of TestCafe and how it differs from classic Selenium Find out how to set up a TestCafe test environment Run TestCafe with command-line settings Verify and execute TestCafe code in the browser Automate end-to-end testing with TestCafe using expert techniques Discover best practices in TestCafe development and learn about the future roadmap of TestCafe Who this book is for The book is for QA professionals, test engineers, software engineers, and test automation enthusiasts looking for hands-on guidance on learning about TestCafe. This book is also great for full-stack developers who want to learn more about new tools for testing their code. The book assumes a basic understanding of JavaScript, Node.js, HTML, CSS, and some simple Bash commands. Computers

Metabase Up and Running Ask questions of your data and gain insights to make better business decisions using the open source business intelligence tool, MetabaseKey FeaturesDeploy Metabase applications to let users across your organization interact with itLearn to create data visualizations, charts, reports, and dashboards with the help of a variety of examplesUnderstand how to embed Metabase into your website and send out reports automatically using email and SlackBook DescriptionMetabase is an open source business intelligence tool that helps you use data to answer questions about your business. This book will give you a detailed introduction to using Metabase in your organization to get the most value from your data. You'll start by installing and setting up Metabase on your local computer. You'll then progress to handling the administration aspect of Metabase by learning how to configure and deploy Metabase, manage accounts, and execute administrative tasks such as adding users and creating permissions and metadata. Complete with examples and detailed instructions, this book shows you how to create different visualizations, charts, and dashboards to gain insights from your data. As you advance, you'll learn how to share the results with peers in your organization and cover production-related aspects such as embedding Metabase and auditing performance. Throughout the book, you'll explore the entire data analytics process - from connecting your data sources, visualizing data, and creating dashboards through to daily reporting. By the end of this book, you'll be ready to implement Metabase as an integral tool in your organization.What you will learnExplore different types of databases and find out how to connect them to MetabaseDeploy and host Metabase securely using Amazon Web ServicesUse Metabase's user interface to filter and aggregate data on single and multiple tablesBecome a Metabase admin by learning how to add users and create permissionsAnswer critical questions for your organization by using the Notebook editor and writing SQL queriesUse the search functionality to search through tables, dashboards, and metricsWho this book is forThis book is for business analysts, data analysts, data scientists, and other professionals who want to become well-versed with business intelligence and analytics using Metabase. This book will also appeal to anyone who wants to understand their data to extract meaningful insights with the help of practical examples. A basic understanding of data handling and processing is necessary to get started with this book. Computers

ETL with Azure Cookbook Explore the latest Azure ETL techniques both on-premises and in the cloud using Azure services such as SQL Server Integration Services (SSIS), Azure Data Factory, and Azure Databricks Key Features Understand the key components of an ETL solution using Azure Integration Services Discover the common and not-so-common challenges faced while creating modern and scalable ETL solutions Program and extend your packages to develop efficient data integration and data transformation solutions Book Description ETL is one of the most common and tedious procedures for moving and processing data from one database to another. With the help of this book, you will be able to speed up the process by designing effective ETL solutions using the Azure services available for handling and transforming any data to suit your requirements. With this cookbook, you'll become well versed in all the features of SQL Server Integration Services (SSIS) to perform data migration and ETL tasks that integrate with Azure. You'll learn how to transform data in Azure and understand how legacy systems perform ETL on-premises using SSIS. Later chapters will get you up to speed with connecting and retrieving data from SQL Server 2019 Big Data Clusters, and even show you how to extend and customize the SSIS toolbox using custom-developed tasks and transforms. This ETL book also contains practical recipes for moving and transforming data with Azure services, such as Data Factory and Azure Databricks, and lets you explore various options for migrating SSIS packages to Azure. Toward the end, you'll find out how to profile data in the cloud and automate service creation with Business Intelligence Markup Language (BIML). By the end of this book, you'll have developed the skills you need to create and automate ETL solutions on-premises as well as in Azure. What you will learn Explore ETL and how it is different from ELT Move and transform various data sources with Azure ETL and ELT services Use SSIS 2019 with Azure HDInsight clusters Discover how to query SQL Server 2019 Big Data Clusters hosted in Azure Migrate SSIS solutions to Azure and solve key challenges associated with it Understand why data profiling is crucial and how to implement it in Azure Databricks Get to grips with BIML and learn how it applies to SSIS and Azure Data Factory solutions Who this book is for This book is for data warehouse architects, ETL developers, or anyone who wants to build scalable ETL applications in Azure. Those looking to extend their existing on-premise ETL applications to use big data and a variety of Azure services or others interested in migrating existing on-premise solutions to the Azure cloud platform will also find the book useful. Familiarity with SQL Server services is necessary to get the most out of this book. Computers

Live Longer with AI A wakeup call that shows us how to live our best and longest lives through the power of AI Key Features Discover how the latest cutting-edge developments in health and AI are helping us live longer, healthier, and better lives Personalize your health, wealth and well-being using technology best suited to help you plan and build up your assets for a multi-stage life Understand how we can live our best lives in a post-COVID-19 world and equip ourselves for the next pandemic using technology Book Description Live Longer with AI examines how the latest cutting-edge developments are helping us to live longer, healthier and better too. It compels us to stop thinking that health is about treating disease and start regarding it as our greatest personal and societal asset to protect. The book discusses the impact that AI has on understanding the cellular basis of aging and how our genes are influenced by our environment – with the pandemic highlighting the interconnectedness of human and planetary health. Author Tina Woods, founder and CEO of Collider Health and Collider Science, and the co-founder of Longevity International, has curated a panel of deeply insightful interviews with some of today's brightest and most innovative thought leaders at the crossroads of health, technology and society. Read what leading experts in health and technology are saying about the book: "This is a handbook for the revolution!" —Sir Muir Gray, Director, Optimal Ageing "You can live longer and be happier if you make some changes – that is the theme of this book. Well-written and compelling." —Ben Page, CEO, Ipsos Mori "Tina's book is a must-read for those who want to discover the future of health." —Jose Luis Cordeiro, Fellow, World Academy of Art & Science; Director, The Millennium Project; Vice Chair, Humanity Plus; Co-Author of The Death of Death About the consultant editor Melissa Ream is a leading health and care strategist in the UK, leveraging user-driven design and artificial intelligence to design systems and support people to live healthier, longer lives. What you will learn Discover how AI is changing the way we understand the wider determinants of health, how the environment influences our genes and why the solutions for living longer are linked to living greener Inform your perspective on how technology can deal with the health emergency in front of us – by minimizing health and wealth inequalities Learn why our “life data†is so important and how sharing it will help us develop aging “bio-markersâ€, enabling us to predict and manage dementia and other chronic diseases of aging Find out how scientists and doctors are using AI to find a vaccine for Covid-19, make us more resilient to future pandemic threats and pre-empt the next outbreak Who this book is for Professionals and general readers with an interest in learning how technology can and is being used to change our approach to aging and help us live longer and healthier lives. No prior knowledge of or experience with artificial intelligence is required. Computers

Unity 2020 By Example Learn Unity game development with C# through a series of practical projects ranging from building a simple 2D game to adding AR/VR experiences and machine learning capabilities in a simple yet effective way Key Features Gain a high-level overview of the Unity game engine while building your own games portfolio Discover best practices for implementing game animation, game physics, shaders, and effects Create fully featured apps, including Space shooter and a 2D adventure game, and develop AR/VR experiences and Game AI agents Book Description The Unity game engine, used by millions of developers around the world, is popular thanks to its features that enable you to create games and 3D apps for desktop and mobile platforms in no time. With Unity 2020, this state-of-the-art game engine introduces enhancements in Unity tooling, editor, and workflow, among many other additions. The third edition of this Unity book is updated to the new features in Unity 2020 and modern game development practices. Once you've quickly got to grips with the fundamentals of Unity game development, you'll create a collection, a twin-stick shooter, and a 2D adventure game. You'll then explore advanced topics such as machine learning, virtual reality, and augmented reality by building complete projects using the latest game tool kit. As you implement concepts in practice, this book will ensure that you come away with a clear understanding of Unity game development. By the end of the book, you'll have a firm foundation in Unity development using C#, which can be applied to other engines and programming languages. You'll also be able to create several real-world projects to add to your professional game development portfolio. What you will learn Learn the fundamentals of game development, including GameObjects, components, and scenes Develop a variety of games in C# and explore the brand new sprite shaping tool for Unity 3D and 2D games Handle player controls and input functionality for your Unity games Implement AI techniques such as pathfinding, finite state machines, and machine learning using Unity ML-Agents Create virtual and augmented reality games using UnityVR and AR Foundation Explore the cutting-edge features of Unity 2020 and how they can be used to improve your games Who this book is for If you are a game developer or programmer new to Unity and want to get up and running with the game engine in a hands-on way, this book is for you. Unity developers looking to work on practical projects to explore new features in Unity 2020 will find this book useful. A basic understanding of C# programming is required. Computers

Deep Reinforcement Learning with Python An example-rich guide for beginners to start their reinforcement and deep reinforcement learning journey with state-of-the-art distinct algorithms Key Features Covers a vast spectrum of basic-to-advanced RL algorithms with mathematical explanations of each algorithm Learn how to implement algorithms with code by following examples with line-by-line explanations Explore the latest RL methodologies such as DDPG, PPO, and the use of expert demonstrations Book Description With significant enhancements in the quality and quantity of algorithms in recent years, this second edition of Hands-On Reinforcement Learning with Python has been revamped into an example-rich guide to learning state-of-the-art reinforcement learning (RL) and deep RL algorithms with TensorFlow 2 and the OpenAI Gym toolkit. In addition to exploring RL basics and foundational concepts such as Bellman equation, Markov decision processes, and dynamic programming algorithms, this second edition dives deep into the full spectrum of value-based, policy-based, and actor-critic RL methods. It explores state-of-the-art algorithms such as DQN, TRPO, PPO and ACKTR, DDPG, TD3, and SAC in depth, demystifying the underlying math and demonstrating implementations through simple code examples. The book has several new chapters dedicated to new RL techniques, including distributional RL, imitation learning, inverse RL, and meta RL. You will learn to leverage stable baselines, an improvement of OpenAI's baseline library, to effortlessly implement popular RL algorithms. The book concludes with an overview of promising approaches such as meta-learning and imagination augmented agents in research. By the end, you will become skilled in effectively employing RL and deep RL in your real-world projects. What you will learn Understand core RL concepts including the methodologies, math, and code Train an agent to solve Blackjack, FrozenLake, and many other problems using OpenAI Gym Train an agent to play Ms Pac-Man using a Deep Q Network Learn policy-based, value-based, and actor-critic methods Master the math behind DDPG, TD3, TRPO, PPO, and many others Explore new avenues such as the distributional RL, meta RL, and inverse RL Use Stable Baselines to train an agent to walk and play Atari games Who this book is for If you're a machine learning developer with little or no experience with neural networks interested in artificial intelligence and want to learn about reinforcement learning from scratch, this book is for you. Basic familiarity with linear algebra, calculus, and the Python programming language is required. Some experience with TensorFlow would be a plus. Computers

Case-Based Reasoning Research and Development This book constitutes the refereed proceedings of the 28th International Conference on Case-Based Reasoning Research and Development, ICCBR 2020, held in Salamanca, Spain*, in June 2020. The 20 full papers and 2 short papers presented in this book were carefully reviewed and selected from 64 submissions. The theme of ICCBR 2020, “CBR Across Bridges†was highlighted by several activities. These papers, which are included in the proceedings, address many themes related to the theory and application of case-based reasoning and its future direction. *The conference was held virtually due to the COVID-19 pandemic. Computers

Computational Science and Its Applications – ICCSA 2020 The seven volumes LNCS 12249-12255 constitute the refereed proceedings of the 20th International Conference on Computational Science and Its Applications, ICCSA 2020, held in Cagliari, Italy, in July 2020. Due to COVID-19 pandemic the conference was organized in an online event.Computational Science is the main pillar of most of the present research, industrial and commercial applications, and plays a unique role in exploiting ICT innovative technologies.The 466 full papers and 32 short papers presented were carefully reviewed and selected from 1450 submissions. Apart from the general track, ICCSA 2020 also include 52 workshops, in various areas of computational sciences, ranging from computational science technologies, to specific areas of computational sciences, such as software engineering, security, machine learning and artificial intelligence, blockchain technologies, and of applications in many fields. Computers

Medical Image Computing and Computer Assisted Intervention – MICCAI 2020 The seven-volume set LNCS 12261, 12262, 12263, 12264, 12265, 12266, and 12267 constitutes the refereed proceedings of the 23rd International Conference on Medical Image Computing and Computer-Assisted Intervention, MICCAI 2020, held in Lima, Peru, in October 2020. The conference was held virtually due to the COVID-19 pandemic.The 542 revised full papers presented were carefully reviewed and selected from 1809 submissions in a double-blind review process. The papers are organized in the following topical sections: Part I: machine learning methodologies Part II: image reconstruction; prediction and diagnosis; cross-domain methods and reconstruction; domain adaptation; machine learning applications; generative adversarial networks Part III: CAI applications; image registration; instrumentation and surgical phase detection; navigation and visualization; ultrasound imaging; video image analysis Part IV: segmentation; shape models and landmark detection Part V: biological, optical, microscopic imaging; cell segmentation and stain normalization; histopathology image analysis; opthalmology Part VI: angiography and vessel analysis; breast imaging; colonoscopy; dermatology; fetal imaging; heart and lung imaging; musculoskeletal imaging Part VI: brain development and atlases; DWI and tractography; functional brain networks; neuroimaging; positron emission tomography Computers

Medical Image Computing and Computer Assisted Intervention – MICCAI 2020 The seven-volume set LNCS 12261, 12262, 12263, 12264, 12265, 12266, and 12267 constitutes the refereed proceedings of the 23rd International Conference on Medical Image Computing and Computer-Assisted Intervention, MICCAI 2020, held in Lima, Peru, in October 2020. The conference was held virtually due to the COVID-19 pandemic.The 542 revised full papers presented were carefully reviewed and selected from 1809 submissions in a double-blind review process. The papers are organized in the following topical sections: Part I: machine learning methodologies Part II: image reconstruction; prediction and diagnosis; cross-domain methods and reconstruction; domain adaptation; machine learning applications; generative adversarial networks Part III: CAI applications; image registration; instrumentation and surgical phase detection; navigation and visualization; ultrasound imaging; video image analysis Part IV: segmentation; shape models and landmark detection Part V: biological, optical, microscopic imaging; cell segmentation and stain normalization; histopathology image analysis; opthalmology Part VI: angiography and vessel analysis; breast imaging; colonoscopy; dermatology; fetal imaging; heart and lung imaging; musculoskeletal imaging Part VI: brain development and atlases; DWI and tractography; functional brain networks; neuroimaging; positron emission tomography Computers

Medical Image Computing and Computer Assisted Intervention – MICCAI 2020 The seven-volume set LNCS 12261, 12262, 12263, 12264, 12265, 12266, and 12267 constitutes the refereed proceedings of the 23rd International Conference on Medical Image Computing and Computer-Assisted Intervention, MICCAI 2020, held in Lima, Peru, in October 2020. The conference was held virtually due to the COVID-19 pandemic. The 542 revised full papers presented were carefully reviewed and selected from 1809 submissions in a double-blind review process. The papers are organized in the following topical sections: Part I: machine learning methodologies Part II: image reconstruction; prediction and diagnosis; cross-domain methods and reconstruction; domain adaptation; machine learning applications; generative adversarial networks Part III: CAI applications; image registration; instrumentation and surgical phase detection; navigation and visualization; ultrasound imaging; video image analysis Part IV: segmentation; shape models and landmark detection Part V: biological, optical, microscopic imaging; cell segmentation and stain normalization; histopathology image analysis; opthalmology Part VI: angiography and vessel analysis; breast imaging; colonoscopy; dermatology; fetal imaging; heart and lung imaging; musculoskeletal imaging Part VI: brain development and atlases; DWI and tractography; functional brain networks; neuroimaging; positron emission tomography Computers

Medical Image Computing and Computer Assisted Intervention – MICCAI 2020 The seven-volume set LNCS 12261, 12262, 12263, 12264, 12265, 12266, and 12267 constitutes the refereed proceedings of the 23rd International Conference on Medical Image Computing and Computer-Assisted Intervention, MICCAI 2020, held in Lima, Peru, in October 2020. The conference was held virtually due to the COVID-19 pandemic. The 542 revised full papers presented were carefully reviewed and selected from 1809 submissions in a double-blind review process. The papers are organized in the following topical sections: Part I: machine learning methodologies Part II: image reconstruction; prediction and diagnosis; cross-domain methods and reconstruction; domain adaptation; machine learning applications; generative adversarial networks Part III: CAI applications; image registration; instrumentation and surgical phase detection; navigation and visualization; ultrasound imaging; video image analysis Part IV: segmentation; shape models and landmark detection Part V: biological, optical, microscopic imaging; cell segmentation and stain normalization; histopathology image analysis; opthalmology Part VI: angiography and vessel analysis; breast imaging; colonoscopy; dermatology; fetal imaging; heart and lung imaging; musculoskeletal imaging Part VI: brain development and atlases; DWI and tractography; functional brain networks; neuroimaging; positron emission tomography Computers

Shape in Medical Imaging This book constitutes the proceedings of the International Workshop on Shape in Medical Imaging, ShapeMI 2020, which was held in conjunction with the 23rd International Conference on Medical Image Computing and Computer Assistend Intervention, MICCAI 2020, in October 2020. The conference was planned to take place in Lima, Peru, but changed to a virtual format due to the COVID-19 pandemic. The 12 full papers included in this volume were carefully reviewed and selected from 18 submissions. They were organized in topical sections named: methods; learning; and applications. Computers

Medical Image Computing and Computer Assisted Intervention – MICCAI 2020 The seven-volume set LNCS 12261, 12262, 12263, 12264, 12265, 12266, and 12267 constitutes the refereed proceedings of the 23rd International Conference on Medical Image Computing and Computer-Assisted Intervention, MICCAI 2020, held in Lima, Peru, in October 2020. The conference was held virtually due to the COVID-19 pandemic.The 542 revised full papers presented were carefully reviewed and selected from 1809 submissions in a double-blind review process. The papers are organized in the following topical sections: Part I: machine learning methodologies Part II: image reconstruction; prediction and diagnosis; cross-domain methods and reconstruction; domain adaptation; machine learning applications; generative adversarial networks Part III: CAI applications; image registration; instrumentation and surgical phase detection; navigation and visualization; ultrasound imaging; video image analysis Part IV: segmentation; shape models and landmark detection Part V: biological, optical, microscopic imaging; cell segmentation and stain normalization; histopathology image analysis; opthalmology Part VI: angiography and vessel analysis; breast imaging; colonoscopy; dermatology; fetal imaging; heart and lung imaging; musculoskeletal imaging Part VI: brain development and atlases; DWI and tractography; functional brain networks; neuroimaging; positron emission tomography Computers

HCI International 2020 - Late Breaking Papers This book constitutes late breaking papers from the 22nd International Conference on Human-Computer Interaction, HCII 2020, which was held in July 2020. The conference was planned to take place in Copenhagen, Denmark, but had to change to a virtual conference mode due to the COVID-19 pandemic.From a total of 6326 submissions, a total of 1439 papers and 238 posters have been accepted for publication in the HCII 2020 proceedings before the conference took place. In addition, a total of 333 papers and 144 posters are included in the volumes of the proceedings published after the conference as “Late Breaking Work†(papers and posters). These contributions address the latest research and development efforts in the field and highlight the human aspects of design and use of computing systems. The 54 late breaking papers presented in this volume were organized in two topical sections named: User Experience Design and Evaluation Methods and Tools; Design Case Studies; User Experience Case Studies. Computers

Machine Learning in Medical Imaging This book constitutes the proceedings of the 11th International Workshop on Machine Learning in Medical Imaging, MLMI 2020, held in conjunction with MICCAI 2020, in Lima, Peru, in October 2020. The conference was held virtually due to the COVID-19 pandemic. The 68 papers presented in this volume were carefully reviewed and selected from 101 submissions. They focus on major trends and challenges in the above-mentioned area, aiming to identify new-cutting-edge techniques and their uses in medical imaging. Topics dealt with are: deep learning, generative adversarial learning, ensemble learning, sparse learning, multi-task learning, multi-view learning, manifold learning, and reinforcement learning, with their applications to medical image analysis, computer-aided detection and diagnosis, multi-modality fusion, image reconstruction, image retrieval, cellular image analysis, molecular imaging, digital pathology, etc. Computers

Medical Image Computing and Computer Assisted Intervention – MICCAI 2020 The seven-volume set LNCS 12261, 12262, 12263, 12264, 12265, 12266, and 12267 constitutes the refereed proceedings of the 23rd International Conference on Medical Image Computing and Computer-Assisted Intervention, MICCAI 2020, held in Lima, Peru, in October 2020. The conference was held virtually due to the COVID-19 pandemic. The 542 revised full papers presented were carefully reviewed and selected from 1809 submissions in a double-blind review process. The papers are organized in the following topical sections: Part I: machine learning methodologies Part II: image reconstruction; prediction and diagnosis; cross-domain methods and reconstruction; domain adaptation; machine learning applications; generative adversarial networks Part III: CAI applications; image registration; instrumentation and surgical phase detection; navigation and visualization; ultrasound imaging; video image analysis Part IV: segmentation; shape models and landmark detection Part V: biological, optical, microscopic imaging; cell segmentation and stain normalization; histopathology image analysis; opthalmology Part VI: angiography and vessel analysis; breast imaging; colonoscopy; dermatology; fetal imaging; heart and lung imaging; musculoskeletal imaging Part VI: brain development and atlases; DWI and tractography; functional brain networks; neuroimaging; positron emission tomography Computers

Brain Function Assessment in Learning This book constitutes the thoroughly refereed proceedings of the Second International Conference on Brain Function Assessment in Learning, BFAL 2020, held in Heraklion, Crete, Greece, in October 2020*. The 11 revised full papers and 10 short papers presented were carefully selected from 35 submissions. The BFAL conference aims to regroup research in multidisciplinary domains such as neuroscience, computer science, medicine, education, human-computer interactions, and social interaction on the theme of Brain Function Assessment in Learning. *The conference was held virtually due to the COVID-19 pandemic. Computers

Processing, second edition The new edition of an introduction to computer programming within the context of the visual arts, using the open-source programming language Processing; thoroughly updated throughout. The visual arts are rapidly changing as media moves into the web, mobile devices, and architecture. When designers and artists learn the basics of writing software, they develop a new form of literacy that enables them to create new media for the present, and to imagine future media that are beyond the capacities of current software tools. This book introduces this new literacy by teaching computer programming within the context of the visual arts. It offers a comprehensive reference and text for Processing (www.processing.org), an open-source programming language that can be used by students, artists, designers, architects, researchers, and anyone who wants to program images, animation, and interactivity. Written by Processing's cofounders, the book offers a definitive reference for students and professionals. Tutorial chapters make up the bulk of the book; advanced professional projects from such domains as animation, performance, and installation are discussed in interviews with their creators. This second edition has been thoroughly updated. It is the first book to offer in-depth coverage of Processing 2.0 and 3.0, and all examples have been updated for the new syntax. Every chapter has been revised, and new chapters introduce new ways to work with data and geometry. New “synthesis” chapters offer discussion and worked examples of such topics as sketching with code, modularity, and algorithms. New interviews have been added that cover a wider range of projects. “Extension” chapters are now offered online so they can be updated to keep pace with technological developments in such fields as computer vision and electronics. Interviews SUE.C, Larry Cuba, Mark Hansen, Lynn Hershman Leeson, Jürg Lehni, LettError, Golan Levin and Zachary Lieberman, Benjamin Maus, Manfred Mohr, Ash Nehru, Josh On, Bob Sabiston, Jennifer Steinkamp, Jared Tarbell, Steph Thirion, Robert Winter Computers

Generalized Linear and Nonlinear Models for Correlated Data Edward Vonesh's Generalized Linear and Nonlinear Models for Correlated Data: Theory and Applications Using SAS is devoted to the analysis of correlated response data using SAS, with special emphasis on applications that require the use of generalized linear models or generalized nonlinear models. Written in a clear, easy-to-understand manner, it provides applied statisticians with the necessary theory, tools, and understanding to conduct complex analyses of continuous and/or discrete correlated data in a longitudinal or clustered data setting. Using numerous and complex examples, the book emphasizes real-world applications where the underlying model requires a nonlinear rather than linear formulation and compares and contrasts the various estimation techniques for both marginal and mixed-effects models. The SAS procedures MIXED, GENMOD, GLIMMIX, and NLMIXED as well as user-specified macros will be used extensively in these applications. In addition, the book provides detailed software code with most examples so that readers can begin applying the various techniques immediately.This book is part of the SAS Press program. Computers

Multimodal Learning for Clinical Decision Support and Clinical Image-Based Procedures This book constitutes the refereed joint proceedings of the 10th International Workshop on Multimodal Learning for Clinical Decision Support, ML-CDS 2020, and the 9th International Workshop on Clinical Image-Based Procedures, CLIP 2020, held in conjunction with the 23rd International Conference on Medical Imaging and Computer-Assisted Intervention, MICCAI 2020, in Lima, Peru, in October 2020. The workshops were held virtually due to the COVID-19 pandemic. The 4 full papers presented at ML-CDS 2020 and the 9 full papers presented at CLIP 2020 were carefully reviewed and selected from numerous submissions to ML-CDS and 10 submissions to CLIP. The ML-CDS papers discuss machine learning on multimodal data sets for clinical decision support and treatment planning. The CLIP workshops provides a forum for work centered on specific clinical applications, including techniques and procedures based on comprehensive clinical image and other data. Computers

HCI International 2020 – Late Breaking Papers This book constitutes late breaking papers from the 22nd International Conference on Human-Computer Interaction, HCII 2020, which was held in July 2020. The conference was planned to take place in Copenhagen, Denmark, but had to change to a virtual conference mode due to the COVID-19 pandemic.From a total of 6326 submissions, a total of 1439 papers and 238 posters have been accepted for publication in the HCII 2020 proceedings before the conference took place. In addition, a total of 333 papers and 144 posters are included in the volumes of the proceedings published after the conference as “Late Breaking Work†(papers and posters). These contributions address the latest research and development efforts in the field and highlight the human aspects of design and use of computing systems. Computers

Interpretable and Annotation-Efficient Learning for Medical Image Computing This book constitutes the refereed joint proceedings of the Third International Workshop on Interpretability of Machine Intelligence in Medical Image Computing, iMIMIC 2020, the Second International Workshop on Medical Image Learning with Less Labels and Imperfect Data, MIL3ID 2020, and the 5th International Workshop on Large-scale Annotation of Biomedical data and Expert Label Synthesis, LABELS 2020, held in conjunction with the 23rd International Conference on Medical Imaging and Computer-Assisted Intervention, MICCAI 2020, in Lima, Peru, in October 2020. The 8 full papers presented at iMIMIC 2020, 11 full papers to MIL3ID 2020, and the 10 full papers presented at LABELS 2020 were carefully reviewed and selected from 16 submissions to iMIMIC, 28 to MIL3ID, and 12 submissions to LABELS. The iMIMIC papers focus on introducing the challenges and opportunities related to the topic of interpretability of machine learning systems in the context of medical imaging and computer assisted intervention. MIL3ID deals with best practices in medical image learning with label scarcity and data imperfection. The LABELS papers present a variety of approaches for dealing with a limited number of labels, from semi-supervised learning to crowdsourcing. Computers

Networks in Systems Biology This book presents a range of current research topics in biological network modeling, as well as its application in studies on human hosts, pathogens, and diseases. Systems biology is a rapidly expanding field that involves the study of biological systems through the mathematical modeling and analysis of large volumes of biological data. Gathering contributions from renowned experts in the field, some of the topics discussed in depth here include networks in systems biology, the computational modeling of multidrug-resistant bacteria, and systems biology of cancer. Given its scope, the book is intended for researchers, advanced students, and practitioners of systems biology. The chapters are research-oriented, and present some of the latest findings on their respective topics. Computers

Learn Android Studio 4 Build and deploy your Java-based Android apps using the popular and efficient Android Studio 4 suite of tools, an integrated development environment (IDE) for today's Android developers. With this book, you’ll learn the latest and most productive tools in the Android tools ecosystem, ensuring quick Android app development and minimal effort on your part. Among these tools, you'll use the new Android Studio 4 features, including an upgraded CPU profiler UI, a new build speed window, the multi-preview feature, and the live layout inspector. After reading and using this book, you'll be able to efficiently build complete Java-based Android apps that run on any Android smartphone, tablet, smart watch and more. You’ll also be able to publish those apps and sell them online and in the Google Play store. What You Will Learn Use Android Studio 4 to quickly and confidently build your first Android apps Build an Android user interface using activities and layouts, event handling, images, menus, and the action bar Work with new tools in Android Studio 4: Jetpack compose support, a smart editor for ProGuard rules, a new motion layout editor, a new Android Gradle plugin, and a fragment wizard with new fragment templates Integrate data with data persistence Access the cloud Who This Book Is For Those who may be new to Android Studio 4 or Android Studio in general. You may or may not be new to Android development. Some prior experience with Java is recommended. Computers

Beginning C++20 Begin your programming journey with C++ , starting with the basics and progressing through step-by-step examples that will help you become a proficient C++ programmer. This book includes new features from the C++20 standard such as modules, concepts, ranges, and the spaceship operator. All you need are Beginning C++20 and any recent C++ compiler and you'll soon be writing real C++ programs. There is no assumption of prior programming knowledge. All language concepts that are explained in the book are illustrated with working program examples, and all chapters include exercises for you to test and practice your knowledge. Free source code downloads are provided for all examples from the text and solutions to the exercises. This latest edition has been fully updated to the latest version of the language, C++20, and to all conventions and best practices of modern C++. Beginning C++20 also introduces the elements of the C++ Standard Library that provide essential support for the C++20 language. What You Will Learn Begin programming with the C++20 standard Carry out modular programming in C++ Work with arrays and loops, pointers and references, strings, and more Write your own functions, types, and operators Discover the essentials of object-oriented programming Use overloading, inheritance, virtual functions, and polymorphism Write generic function and class templates, and make them safer using concepts Learn the ins and outs of containers, algorithms, and ranges Use auto type declarations, exceptions, move semantics, lambda expressions, and much more Who This Book Is For Programmers new to C++ and those who may be looking for a refresh primer on C++ in general. Computers

Speech and Computer This book constitutes the proceedings of the 22nd International Conference on Speech and Computer, SPECOM 2020, held in St. Petersburg, Russia, in October 2020. The 65 papers presented were carefully reviewed and selected from 160 submissions. The papers present current research in the area of computer speech processing including speech science, speech technology, natural language processing, human-computer interaction, language identification, multimedia processing, human-machine interaction, deep learning for audio processing, computational paralinguistics, affective computing, speech and language resources, speech translation systems, text mining and sentiment analysis, voice assistants, etc. Due to the Corona pandemic SPECOM 2020 was held as a virtual event. Computers

EU General Data Protection Regulation (GDPR) – An implementation and compliance guide, fourth edition Now in its fourth edition, this bestselling guide is the ideal companion for anyone carrying out a GDPR (General Data Protection Regulation) compliance project. It provides comprehensive guidance and practical advice on complying with the Regulation. Computers

EU GDPR – An international guide to compliance Thrive under the GDPR (General Data Protection Regulation) wherever you are in the world. This pocket guide will help you understand the Regulation, the broader principles of data protection, and what the GDPR means for businesses in Europe and beyond. Computers

Uncertainty for Safe Utilization of Machine Learning in Medical Imaging, and Graphs in Biomedical Image Analysis This book constitutes the refereed proceedings of the Second International Workshop on Uncertainty for Safe Utilization of Machine Learning in Medical Imaging, UNSURE 2020, and the Third International Workshop on Graphs in Biomedical Image Analysis, GRAIL 2020, held in conjunction with MICCAI 2020, in Lima, Peru, in October 2020. The workshops were held virtually due to the COVID-19 pandemic.For UNSURE 2020, 10 papers from 18 submissions were accepted for publication. They focus on developing awareness and encouraging research in the field of uncertainty modelling to enable safe implementation of machine learning tools in the clinical world. GRAIL 2020 accepted 10 papers from the 12 submissions received. The workshop aims to bring together scientists that use and develop graph-based models for the analysis of biomedical images and to encourage the exploration of graph-based models for difficult clinical problems within a variety of biomedical imaging contexts. Computers

The Algorithm Design Manual Most professional programmers that I’ve encountered are not well prepared to tacklealgorithmdesignproblems.Thisisapity,becausethetechniquesofalgorithm design form one of the core practical technologies of computer science. Designing correct, e?cient, and implementable algorithms for real-world problems requires access to two distinct bodies of knowledge: • Techniques – Good algorithm designers understand several fundamental - gorithm design techniques, including data structures, dynamic programming, depth-?rst search, backtracking, and heuristics. Perhaps the single most - portantdesigntechniqueismodeling,theartofabstractingamessyreal-world application into a clean problem suitable for algorithmic attack. • Resources – Good algorithm designers stand on the shoulders of giants. Ratherthanlaboringfromscratchtoproduceanewalgorithmforeverytask, they can ?gure out what is known about a particular problem. Rather than re-implementing popular algorithms from scratch, they seek existing imp- mentations to serve as a starting point. They are familiar with many classic algorithmic problems, which provide su?cient source material to model most any application. This book is intended as a manual on algorithm design, providing access to combinatorial algorithm technology for both students and computer professionals. Computers

Natural Language Processing and Chinese Computing This two-volume set of LNAI 12340 and LNAI 12341 constitutes the refereed proceedings of the 9th CCF Conference on Natural Language Processing and Chinese Computing, NLPCC 2020, held in Zhengzhou, China, in October 2020.The 70 full papers, 30 poster papers and 14 workshop papers presented were carefully reviewed and selected from 320 submissions. They are organized in the following areas: Conversational Bot/QA; Fundamentals of NLP; Knowledge Base, Graphs and Semantic Web; Machine Learning for NLP; Machine Translation and Multilinguality; NLP Applications; Social Media and Network; Text Mining; and Trending Topics. Computers

Cryptographic Obfuscation This book explains the development of cryptographic obfuscation, providing insight into the most important ideas and techniques. It will be a useful reference for researchers in cryptography and theoretical computer science. Computers

Serverless Security Apply the basics of security in serverless computing to new or existing projects. This hands-on guide provides practical examples and fundamentals. You will apply these fundamentals in all aspects of serverless computing: improving the code, securing the application, and protecting the infrastructure. You will come away having security knowledge that enables you to secure a project you are supporting and have technical conversations with cybersecurity personnel. At a time when there are many news stories on cybersecurity breaches, it is crucial to think about security in your applications. It is tempting to believe that having a third-party host the entire computing platform will increase security. This book shows you why cybersecurity is the responsibility of everyone working on the project. What You Will Learn Gain a deeper understanding of cybersecurity in serverless computing Know how to use free and open source tools (such as the Node Package Manager, ESLint, and VSCode) to reduce vulnerabilities in your application code Assess potential threats from event triggers in your serverless functions Understand security best practices in serverless computing Develop an agnostic security architecture while reducing risk from vendor-specific infrastructure Who This Book Is For Developers or security engineers looking to expand their current knowledge of traditional cybersecurity into serverless computing projects. Individuals just beginning in serverless computing and cybersecurity can apply the concepts in this book in their projects. Computers

Learn PHP 8 Write solid, secure, object-oriented code in the new PHP 8. In this book you will create a complete three-tier application using a natural process of building and testing modules within each tier. This practical approach teaches you about app development and introduces PHP features when they are actually needed rather than providing you with abstract theory and contrived examples. In Learn PHP 8, programming examples take advantage of the newest PHP features; you’ll follow a learn-by-doing approach, which provides you with complete coding examples. “Do It†exercises in each chapter provide the opportunity to make adjustments to the example code. The end-of-chapter programming exercises allow you to develop your own applications using the algorithms demonstrated in the chapter. Each tier is logically and physically separated using object-oriented and dependency injection techniques, thus allowing independent tiers that can be updated with little or no effect on the other tiers. In addition to teaching good programming practices through OOP, there is a strong emphasis on creating secure code. As each chapter is completed, you’ll have the opportunity to design and create an application reinforcing the concepts learned. What You Will Learn Program PHP 8 web applications Use interfaces, containers, and platforms Apply modular programming Manage data objects and use MySQL and other databases Work with multi-functional and secure user interfaces Handle logging exceptions and more Who This Book Is For Those new to web development, specifically PHP programming. Also, this book can be useful to those who have some PHP/web development experience who are new to PHP 8. Computers

Exploring iPad Pro Exploring iPad Pro is the perfect companion for your new iPad Pro. Written by best-selling technology author, lecturer, and computer trainer Kevin Wilson, Exploring iPad Pro is packed with step-by-step instructions, full color photos, illustrations, helpful tips and video demos. Updated to cover the iPadOS update, Exploring iPad Pro will help you : Upgrade your iPad to iPadOS The new features introduced in iPadOS Find your way around the dock, menus, and icons Navigate with touch gestures: tap, drag, pinch, spread and swipe Multi-task with slide over, split view, and drag & drop Use iPad as a second screen on your Mac with SideCar. Use control centre, lock screen, notifications, and handoff Connect external keyboards as well as the on-screen keyboard Use Apple Pencil to draw, annotate, and take notes Get to know Siri, voice dictation, and recording voice memos Communicate with email, FaceTime, and iMessage Use digital touch, and peer-to-peer payments Browse the web with Safari web browser Take, enhance, and share photos and video Stream music with Apple Music, buy tracks & albums from iTunes Store Stream TV programs & movies with the new Apple TV App Use Files App, as well as Maps, News, Apple Books, and Notes Get productive with Pages, Keynote, and Numbers Setup and use Apple Pay, Calendar, and Contacts, and more... In addition, you will learn how to make the most of the new features of iPadOS with clear explanations and video demos to help you along the way. Finally, maintenance, system updates, backups, and general housekeeping tips complete this invaluable guide. You'll want to keep this edition handy as you explore the new iPadOS. Computers

Mastering KVM Virtualization Learn how to configure, automate, orchestrate, troubleshoot, and monitor KVM-based environments capable of scaling to private and hybrid cloud models Key Features Gain expert insights into Linux virtualization and the KVM ecosystem with this comprehensive guide Learn to use various Linux tools such as QEMU, oVirt, libvirt, Cloud-Init, and Cloudbase-Init Scale, monitor, and troubleshoot your VMs on various platforms, including OpenStack and AWS Book Description Kernel-based Virtual Machine (KVM) enables you to virtualize your data center by transforming your Linux operating system into a powerful hypervisor that allows you to manage multiple operating systems with minimal fuss. With this book, you'll gain insights into configuring, troubleshooting, and fixing bugs in KVM virtualization and related software. This second edition of Mastering KVM Virtualization is updated to cover the latest developments in the core KVM components - libvirt and QEMU. Starting with the basics of Linux virtualization, you'll explore VM lifecycle management and migration techniques. You'll then learn how to use SPICE and VNC protocols while creating VMs and discover best practices for using snapshots. As you progress, you'll integrate third-party tools with Ansible for automation and orchestration. You'll also learn to scale out and monitor your environments, and will cover oVirt, OpenStack, Eucalyptus, AWS, and ELK stack. Throughout the book, you'll find out more about tools such as Cloud-Init and Cloudbase-Init. Finally, you'll be taken through the performance tuning and troubleshooting guidelines for KVM-based virtual machines and a hypervisor. By the end of this book, you'll be well-versed with KVM virtualization and the tools and technologies needed to build and manage diverse virtualization environments. What you will learn Implement KVM virtualization using libvirt and oVirt Delve into KVM storage and network Understand snapshots, templates, and live migration features Get to grips with managing, scaling, and optimizing the KVM ecosystem Discover how to tune and optimize KVM virtualization hosts Adopt best practices for KVM platform troubleshooting Who this book is for If you are a systems administrator, DevOps practitioner, or developer with Linux experience looking to sharpen your open-source virtualization skills, this virtualization book is for you. Prior understanding of the Linux command line and virtualization is required before getting started with this book. Computers

NGINX Unit Cookbook Alongside its popular web server, NGINX provides a dynamic application server that supports configuration through a RESTful JSON API. The open source NGINX Unit server deploys configuration changes without service disruptions and runs apps built with multiple languages and frameworks. This updated cookbook shows developers, DevOps personnel, network admins, and cloud infrastructure pros how to quickly get started with NGINX Unit. Hands-on recipes demonstrate Unit’s new approach and show you how to deploy and configure this server for different applications. You’ll learn how to run applications written in different languages on the same server, how to use NGINX Unit as the foundation for your web application development environment, and how Unit’s RESTful API simplifies configuration. Learn how Unit differs from other middleware application servers Install Unit using source code, Red Hat and Debian systems, or third-party repositories Configure Unit using application, router, and listener objects Start and stop the Unit server and the applications it runs Manage user permissions, Linux namespace isolation, and API security Run WordPress, Django, and other web applications with Unit Serve applications with an NGINX proxy or load balancer Computers

Big Data Computers

Asymptotic Analyses for Complex Evolutionary Systems with Markov and Semi-Markov Switching Using Approximation Schemes Computers

Computer Vision – ECCV 2020 The 30-volume set, comprising the LNCS books 12346 until 12375, constitutes the refereed proceedings of the 16th European Conference on Computer Vision, ECCV 2020, which was planned to be held in Glasgow, UK, during August 23-28, 2020. The conference was held virtually due to the COVID-19 pandemic. The 1360 revised papers presented in these proceedings were carefully reviewed and selected from a total of 5025 submissions. The papers deal with topics such as computer vision; machine learning; deep neural networks; reinforcement learning; object recognition; image classification; image processing; object detection; semantic segmentation; human pose estimation; 3d reconstruction; stereo vision; computational photography; neural networks; image coding; image reconstruction; object recognition; motion estimation. Computers

Computer Vision – ECCV 2020 The 30-volume set, comprising the LNCS books 12346 until 12375, constitutes the refereed proceedings of the 16th European Conference on Computer Vision, ECCV 2020, which was planned to be held in Glasgow, UK, during August 23-28, 2020. The conference was held virtually due to the COVID-19 pandemic. The 1360 revised papers presented in these proceedings were carefully reviewed and selected from a total of 5025 submissions. The papers deal with topics such as computer vision; machine learning; deep neural networks; reinforcement learning; object recognition; image classification; image processing; object detection; semantic segmentation; human pose estimation; 3d reconstruction; stereo vision; computational photography; neural networks; image coding; image reconstruction; object recognition; motion estimation. Computers

Advances in Computational Intelligence The two-volume set LNAI 12468 and 12469 constitutes the proceedings of the 19th Mexican International Conference on Artificial Intelligence, MICAI 2020, held in Mexico City, Mexico, in October 2020. The total of 77 papers presented in these two volumes was carefully reviewed and selected from 186 submissions. The contributions are organized in topical as follows: Part I: machine and deep learning, evolutionary and metaheuristic algorithms, and soft computing. Part II: natural language processing, image processing and pattern recognition, and intelligent applications and robotics. Computers

Natural Language Processing and Chinese Computing This two-volume set of LNAI 12340 and LNAI 12341 constitutes the refereed proceedings of the 9th CCF Conference on Natural Language Processing and Chinese Computing, NLPCC 2020, held in Zhengzhou, China, in October 2020.The 70 full papers, 30 poster papers and 14 workshop papers presented were carefully reviewed and selected from 320 submissions. They are organized in the following areas: Conversational Bot/QA; Fundamentals of NLP; Knowledge Base, Graphs and Semantic Web; Machine Learning for NLP; Machine Translation and Multilinguality; NLP Applications; Social Media and Network; Text Mining; and Trending Topics. Computers

Advances in Soft Computing The two-volume set LNAI 12468 and 12469 constitutes the proceedings of the 19th Mexican International Conference on Artificial Intelligence, MICAI 2020, held in Mexico City, Mexico, in October 2020. The total of 77 papers presented in these two volumes was carefully reviewed and selected from 186 submissions. The contributions are organized in topical as follows: Part I: machine and deep learning, evolutionary and metaheuristic algorithms, and soft computing. Part II: natural language processing, image processing and pattern recognition, and intelligent applications and robotics. Computers

Using Gatsby and Netlify CMS Leverage the powerful new combination of Gatsby and Netlify CMS, a free open source content management solution, to build blazing fast apps. This book shows you how to create a React-powered website using the Gatsby framework for the frontend, and Netlify CMS as the content backend. Through the course of the book you'll gradually build a website for a coffee shop that includes a blog and a bakery/coffee menu that is customizable through Netlify CMS. The project starts with a bare-bones Gatsby site to which you'll add functionality such as setting up/configuring the CMS, creating different types of content, and writing some Gatsby glue code to consume the Markdown data via plugins. When done, you'll be well-equipped to build on your existing JavaScript and React knowledge to effectively use Gatsby and Netlify CMS for yourself or your clients. Using Gatsby and Netlify CMS is an ideal guide for anyone looking to build their own sites and manage their own content without having to deal with creating Markdown files or Git repositories. What You'll Learn Clone repositories, install dependencies and deploy on Netlify Configure Netlify Identity and Git Gateway Use Netlify CMS Content Manager Source blog data using Gatsby plugin Manage dynamic page reactions using Gatsby Node APIs Work with pagination, content and menus Customize Netlify CMS Who This Book Is For Experienced JavaScript developers with a good handle on React who want to learn how to build a maintainable Gatsby powered site. Basic familiarity with Gatsby is assumed but not required. Computers

Modern CSS Come on a tour of “modern†CSS in 2020. This example-driven book demonstrates the concepts by showing code examples, screenshots, and diagrams to help clearly communicate the information. You'll start with the very basics of CSS: box model, colors, selectors and combinators, and specificity. Then gradually move through more intermediate topics - styling text, positioning, Z-index and stacking contexts, gradients, borders, and then to more advanced topics such as transforms, transitions, animations, flexbox, and CSS grid. Some features are only available in modern browsers (Chrome, Edge, Safari, and Firefox), but information about IE11 compatibility is included where possible. There is a lot of discussion about how hard CSS is, and how intimidated some people are by it, but it doesn’t have to be this way. Modern CSS uses a logical and understandable approach to break down and clearly explain the ins and outs of CSS. What You'll Learn Work with the syntax of CSS selectors and calculate specificity Use styling techniques, fonts and text styling Review custom properties (variables) Explore the different ways an element can be transformed Use animating elements with CSS transitions Position elements using Flexbox layout Understand the basics of responsive design Who This Book Is For Anyone who has some experience with HTML, and some CSS, but might not be familiar with some of the newer concepts like flexbox or grid. Also, those looking for a refresher in those areas. Computers

Fundamentals of CRM with Dynamics 365 and Power Platform Explore the latest features of Dynamics 365 and Power Platform's out-of-the-box tools to build custom business solutions for your organization Key Features Discover impressive Dynamics 365 features to transform your business and increase productivity Leverage the platform's extensibility to meet your organizational needs Understand how Power Platform powers Dynamics 365 and enhances its integration capabilities Book Description Microsoft Dynamics 365 provides a vast array of tools and applications to meet various Customer Engagement requirements. This Customer Relationship Management (CRM) guide covers the latest advancements in Dynamics 365 and Power Platform that help organizations adapt to changing market conditions for agility and resilience. With this book, you'll explore the core platform functionality of Dynamics 365 and explore its wide range of components for transforming your business with new services and capabilities. You'll learn the basics of configuration and customization to enhance the functionality of Microsoft Dynamics 365 CRM and create solutions and custom applications by leveraging features such as apps, portals, automation, and business intelligence. As you advance, you'll understand how Power Platform drives Dynamics 365 and how various integration capabilities add value by providing a comprehensive view of data aggregated across different systems and data sources. Finally, you'll delve into core administration concepts that will help you to manage extensions added to the platform. By the end of this book, you'll have learned how to tailor Microsoft Dynamics 365 to fit your organization's requirements and tweak the platform to meet your business needs. What you will learn Get to grips with Power Platform for building and enhancing Dynamics 365 apps Integrate Dynamics 365 CRM with Microsoft 365, Azure, and other platforms Discover how you can customize existing entities and create new ones Explore various security features and grant users access to CRM data and functions Find out which CRM attributes are used to automate operations with programming Use internal and external social data to help users to make informed decisions Who this book is for This book is for customers and project stakeholders, new functional consultants, business administration users, and project managers looking to get up and running with the latest features of Dynamics 365 and Power Platform. This guide will help non-developers become acquainted with a no-code approach to customization and configuration. A basic understanding of relational data and customer management concepts will help you get the most out of this book. Computers

Global Seismicity Dynamics and Data-Driven Science The recent explosion of global and regional seismicity data in the world requires new methods of investigation of microseismicity and development of their modelling to understand the nature of whole earth mechanics. In this book, the author proposes a powerful tool to reveal the characteristic features of global and regional microseismicity big data accumulated in the databases of the world. The method proposed in this monograph is based on (1) transformation of stored big data to seismicity density data archives, (2) linear transformation of microseismicity density data matrixes to correlated seismicity matrixes by means of the singular value decomposition method, (3) time series analyses of globally and regionally correlated seismicity rates, and (4) the minimal non-linear equations approximation of their correlated seismicity rate dynamics. Minimal non-linear modelling is the manifestation for strongly correlated seismicity time series controlled by Langevin-type stochastic dynamic equations involving deterministic terms and random Gaussian noises. A deterministic term is composed minimally with correlated seismicity rate vectors of a linear term and of a term with a third exponent. Thus, the dynamics of correlated seismicity in the world contains linearly changing stable nodes and rapid transitions between them with transient states. This book contains discussions of future possibilities of stochastic extrapolations of global and regional seismicity in order to reduce earthquake disasters worldwide. The dataset files are available online and can be downloaded at springer.com. Computers

Runtime Verification This book constitutes the refereed proceedings of the 20th International Conference on Runtime Verification, RV 2020, held in Los Angeles, CA, USA, in October 2020. The conference was held virtually due to the COVID-19 pandemic. The 14 regular papers and 2 short papers presented in this book were carefully reviewed and selected from 43 submissions. Also included are an invited paper, 5 tutorial papers, 6 tool papers, and a benchmark paper. The RV conference is concerned with all aspects of monitoring and analysis of hardware, software and more general system executions. The papers are organized in the following topical sections: runtime verification for autonomy; runtime verification for software; runtime verification with temporal logic specifications; stream-based monitoring; and runtime verification for cyber-physical systems. Computers

Social Informatics This volume constitutes the proceedings of the 12th International Conference on Social Informatics, SocInfo 2020, held in Pisa, Italy, in October 2020. The 30 full and 3 short papers presented in these proceedings were carefully reviewed and selected from 99 submissions. The papers presented in this volume cover a broad range of topics, ranging from works that ground information-system design on social concepts, to papers that analyze complex social systems using computational methods, or explore socio-technical systems using social sciences methods. Computers

Applied Computer Sciences in Engineering This volume constitutes the refereed proceedings of the 7th Workshop on Engineering Applications, WEA 2020, held in Bogota, Colombia, in October 2020.The 32 revised full papers and 12 short papers presented in this volume were carefully reviewed and selected from 136 submissions. The papers are organized in the following topical sections: computational intelligence; computer science; optimization; bioengineering; military applications; simulation, IoT and networks; power applications. Computers

Construction of Fundamental Data Structures for Strings This books reviews recent theoretical and practical advances on suffix sorting and introduces algorithmic solutions to problems of wide interest for the construction of fundamental data structures that operate efficiently on strings namely, constructing the suffix array, the longest common prefix (LCP) array, the document array and the Lyndon array. These data structures are the cornerstone of many algorithmic solutions in Bioiformatics, Information Retrieval and Data Compression. This book introduces the relevant problem areas, their importance, the notation and related algorithms and then presents the algorithmic solutions for indexing data structure constructions. This book is intended for graduate students, researchers and practitioners from Computer Science and Bioinformatics with a strong interest in algorithmic aspects. Computers

Imagine Math 7 Imagine mathematics, imagine with the help of mathematics, imagine new worlds, new geometries, new forms. Imagine building mathematical models that make it possible to manage our world better, imagine solving great problems, imagine new problems never before thought of, imagine combining music, art, poetry, literature, architecture, theatre and cinema with mathematics. Imagine the unpredictable and sometimes counterintuitive applications of mathematics in all areas of human endeavour. This seventh volume starts with a homage to the Italian artist Mimmo Paladino who created exclusively for the Venice Conference 2019 ten original and unique works of art paper dedicated to the themes of the meeting. A large section is dedicated to the most recent Fields Medals including a Homage to Maryam Mirzakhani including a presentation of the exhibition on soap bubbles in art and science that took place in 2019. A section is dedicated to cinema and theatre including the performances by Claire Bardainne & Adrien Mondot. A part of the conference focused on the community of mathematicians, their role in literature and even in politics with the extraordinary example of Antanas Mockus Major of Bogotá. Mathematics in the constructions of bridges, in particular in Italy in the Sixties was presented by Tullia Iori. A very particular contribution on Origami by a mathematician, Marco Abate and an artist, Alessandro Beber. And many other topics. As usual the topics are treated in a way that is rigorous but captivating, detailed and full of evocations. This is an all-embracing look at the world of mathematics and culture. The world, life, culture, everything has changed in a few weeks with the Coronavirus. Culture, science are the main ways to safeguard people's physical and social life. Trust in humanity's creativity and ability. The motto today in Italy is Everything will be fine. This work is addressed to all those who have an interest in Mathematics. Computers

Pro Microsoft Power Platform Become a self-sufficient citizen developer by learning the tools within the Microsoft Power Platform and how they can be used together to drive change and multiply your productivity. Learn about PowerApps for building applications, Power Automate for automating business processes across those applications, and Power BI for analyzing results and communicating business intelligence through compelling visuals. By understanding the purpose and capabilities of these tools, you will be able to enhance your organization’s visibility into key areas and make informed business decisions in a timely matter. This book is divided into four parts and begins in Part I by showing you how to build applications through PowerApps. You will learn about screens and controls, application sharing and administration, and how to make your applications accessible from mobile devices such as phones and tablets. Part II is about creating workflows using Power Automate that implement business logic across your applications. Part III brings in dashboards and data analysis, showing you how to connect to a data source, cleanse the data from that source, and drive decision making through interactive reports and storytelling. Part IV brings together all the pieces by showing the integrations that are possible when all three tools are combined into a single solution. What You Will Learn Understand the need for the citizen developer in today’s business environment Organize and plan the building of line-of-business applications with PowerApps solutions Replace wasteful paper processes with automated applications built in PowerApps Automate workflows across processes with Power Automate Communicate analytical results through visualizations and storytelling Integrate PowerApps, Power Automate, and Power BI into solutions that multiply productivity Who This Book Is For Power users and analysts with strong Excel skills who need a more comprehensive set of tools that can better help them accomplish their vision on projects, those familiar with one of the Power Platform tools who wish to learn how all three can fit together, and those who are seen as as “rogue IT†problem solvers who get things done when others have tried but failed Computers

Modern Arm Assembly Language Programming Gain the fundamentals of Armv8-A 32-bit and 64-bit assembly language programming. This book emphasizes Armv8-A assembly language topics that are relevant to modern software development. It is designed to help you quickly understand Armv8-A assembly language programming and the computational resources of Arm’s SIMD platform. It also contains an abundance of source code that is structured to accelerate learning and comprehension of essential Armv8-A assembly language constructs and SIMD programming concepts. After reading this book, you will be able to code performance-optimized functions and algorithms using Armv8- A 32-bit and 64-bit assembly language. Modern Arm Assembly Language Programming accentuates the coding of Armv8-A 32-bit and 64-bit assembly language functions that are callable from C++. Multiple chapters are also devoted to Armv8-A SIMD assembly language programming. These chapters discuss how to code functions that are used in computationally intense applications such as machine learning, image processing, audio and video encoding, and computer graphics. The source code examples were developed using the GNU toolchain (g++, gas, and make) and tested on a Raspberry Pi 4 Model B running Raspbian (32-bit) and Ubuntu Server (64-bit). It is important to note that this is a book about Armv8-A assembly language programming and not the Raspberry Pi. What You Will Learn See essential details about the Armv8-A 32-bit and 64-bit architectures including data types, general purpose registers, floating-point and SIMD registers, and addressing modes Use the Armv8-A 32-bit and 64-bit instruction sets to create performance-enhancing functions that are callable from C++ Employ Armv8-A assembly language to efficiently manipulate common data types and programming constructs including integers, arrays, matrices, and user-defined structures Create assembly language functions that perform scalar floating-point arithmetic using the Armv8-A 32-bit and 64-bit instruction sets Harness the Armv8-A SIMD instruction sets to significantly accelerate the performance of computationally intense algorithms in applications such as machine learning, image processing, computer graphics, mathematics, and statistics. Apply leading-edge coding strategies and techniques to optimally exploit the Armv8-A 32-bit and 64-bit instruction sets for maximum possible performance Who This Book Is For Software developers who are creating programs for Armv8-A platforms and want to learn how to code performance-enhancing algorithms and functions using the Armv8-A 32-bit and 64-bit instruction sets. Readers should have previous high-level language programming experience and a basic understanding of C++. Computers

Supervised Learning with Python Gain a thorough understanding of supervised learning algorithms by developing use cases with Python. You will study supervised learning concepts, Python code, datasets, best practices, resolution of common issues and pitfalls, and practical knowledge of implementing algorithms for structured as well as text and images datasets.You’ll start with an introduction to machine learning, highlighting the differences between supervised, semi-supervised and unsupervised learning. In the following chapters you’ll study regression and classification problems, mathematics behind them, algorithms like Linear Regression, Logistic Regression, Decision Tree, KNN, Naïve Bayes, and advanced algorithms like Random Forest, SVM, Gradient Boosting and Neural Networks. Python implementation is provided for all the algorithms. You’ll conclude with an end-to-end model development process including deployment and maintenance of the model.After reading Supervised Learning with Python you’ll have a broad understanding of supervised learning and its practical implementation, and be able to run the code and extend it in an innovative manner. What You'll Learn Review the fundamental building blocks and concepts of supervised learning using Python Develop supervised learning solutions for structured data as well as text and images Solve issues around overfitting, feature engineering, data cleansing, and cross-validation for building best fit models Understand the end-to-end model cycle from business problem definition to model deployment and model maintenance Avoid the common pitfalls and adhere to best practices while creating a supervised learning model using Python Who This Book Is For Data scientists or data analysts interested in best practices and standards for supervised learning, and using classification algorithms and regression techniques to develop predictive models. Computers

Fundamentals Of Quantum Information (Extended Edition) This expanded version to the 2010 edition features quantum annealing algorithm and its application for optimization problems. Recent progress on quantum computing, especially, advanced topics such as Shor's algorithm, quantum search, quantum cryptography and architecture of quantum bit are also included.Book is self-contained and unified in its description of the cross-disciplinary nature of this field. It is not strictly mathematical, but aims to provide intuitive and transparent ideas of the subjects. The book starts from basic quantum mechanics and EPR pair and its measurements. Fundamental concepts of classical computer are given in order to extend it to quantum computer. Classical information theory is also explained in detail such as Shannon and Von Neumann entropy. Then quantum algorithm is introduced starting from Dutch-Josza and ending up with Shor's factorization algorithms. Quantum cryptography is also introduced such as BB84 Protocol, B92 protocol and E91 protocol. Eventually quantum search algorithm is explained.In summary, the book starts from basic quantum mechanics and eventually comes up to state-of-the art quantum algorithm of quantum computations and computers. Students can obtain practical problem-solving ability by attempting the exercises at the end of each chapter. Detailed solutions to all problems are provided. Computers

Biocomputing 2017 - Proceedings Of The Pacific Symposium The Pacific Symposium on Biocomputing (PSB) 2017 is an international, multidisciplinary conference for the presentation and discussion of current research in the theory and application of computational methods in problems of biological significance. Presentations are rigorously peer reviewed and are published in an archival proceedings volume. PSB 2017 will be held on January 4 - 8, 2017 in Kohala Coast, Hawaii. Tutorials and workshops will be offered prior to the start of the conference.PSB 2017 will bring together top researchers from the US, the Asian Pacific nations, and around the world to exchange research results and address open issues in all aspects of computational biology. It is a forum for the presentation of work in databases, algorithms, interfaces, visualization, modeling, and other computational methods, as applied to biological problems, with emphasis on applications in data-rich areas of molecular biology.The PSB has been designed to be responsive to the need for critical mass in sub-disciplines within biocomputing. For that reason, it is the only meeting whose sessions are defined dynamically each year in response to specific proposals. PSB sessions are organized by leaders of research in biocomputing's 'hot topics.' In this way, the meeting provides an early forum for serious examination of emerging methods and approaches in this rapidly changing field. Computers

Advances in Mathematics for Industry 4.0 Advances in Mathematics for Industry 4.0 examines key tools, techniques, strategies, and methods in engineering applications. By covering the latest knowledge in technology for engineering design and manufacture, chapters provide systematic and comprehensive coverage of key drivers in rapid economic development. Written by leading industry experts, chapter authors explore managing big data in processing information and helping in decision-making, including mathematical and optimization techniques for dealing with large amounts of data in short periods. Focuses on recent research in mathematics applications for Industry 4.0 Provides insights on international and transnational scales Identifies mathematics knowledge gaps for Industry 4.0 Describes fruitful areas for further research in industrial mathematics, including forthcoming international studies and research Computers

PROC SQL by Example In PROC SQL by Example: Using SQL within SAS, author Howard Schreier illustrates the use of PROC SQL in the context of the SAS DATA step and other SAS procedures (such as SORT, FREQ, MEANS, SUMMARY, APPEND, DATASETS, and TRANSPOSE) whose functionality overlaps and complements that of SQL. Using a side-by-side approach, this concise reference guide includes many extensively explained examples showing equivalent DATA step and SQL code, enabling SAS users to take advantage of existing SAS skills and knowledge while learning about SQL. Discussions cover the differences between SQL and the DATA step as well as situations where SQL and the DATA step are used together to benefit from the strengths of each.Topics addressed include working with joins and merges; using subqueries; understanding set operators; using the Macro Facility with PROC SQL; maintaining tables; working with views; using PROC SQL as a report generator; and more.This text is ideal for SAS programmers seeking to add PROC SQL to their SAS toolkits as well as SQL programmers striving to better integrate the SAS DATA step and SQL.This book is part of the SAS Press program. Computers

Systems and Network Infrastructure Integration Computers

Pattern Recognition and Artificial Intelligence This book constitutes the proceedings of the Second International Conference on Pattern Recognition and Artificial Intelligence, ICPRAI 2020, which took place in Zhongshan, China, in October 2020. The 49 full and 14 short papers presented were carefully reviewed and selected for inclusion in the book. The papers were organized in topical sections as follows: handwriting and text processing; features and classifiers; deep learning; computer vision and image processing; medical imaging and applications; and forensic studies and medical diagnosis. Computers

Data Lake Analytics on Microsoft Azure Get a 360-degree view of how the journey of data analytics solutions has evolved from monolithic data stores and enterprise data warehouses to data lakes and modern data warehouses. You will This book includes comprehensive coverage of how: To architect data lake analytics solutions by choosing suitable technologies available on Microsoft Azure The advent of microservices applications covering ecommerce or modern solutions built on IoT and how real-time streaming data has completely disrupted this ecosystem These data analytics solutions have been transformed from solely understanding the trends from historical data to building predictions by infusing machine learning technologies into the solutions Data platform professionals who have been working on relational data stores, non-relational data stores, and big data technologies will find the content in this book useful. The book also can help you start your journey into the data engineer world as it provides an overview of advanced data analytics and touches on data science concepts and various artificial intelligence and machine learning technologies available on Microsoft Azure. What Will You Learn You will understand the: Concepts of data lake analytics, the modern data warehouse, and advanced data analytics Architecture patterns of the modern data warehouse and advanced data analytics solutions Phases—such as Data Ingestion, Store, Prep and Train, and Model and Serve—of data analytics solutions and technology choices available on Azure under each phase In-depth coverage of real-time and batch mode data analytics solutions architecture Various managed services available on Azure such as Synapse analytics, event hubs, Stream analytics, CosmosDB, and managed Hadoop services such as Databricks and HDInsight Who This Book Is For Data platform professionals, database architects, engineers, and solution architects Computers

Programming iOS 14 If you’re grounded in the basics of Swift, Xcode, and the Cocoa framework, this book provides a structured explanation of all essential real-world iOS app components. Through deep exploration and copious code examples, you’ll learn how to create views, manipulate view controllers, and add features from iOS frameworks. Create, arrange, draw, layer, and animate views that respond to touch Use view controllers to manage multiple screens of interface Master interface classes for scroll views, table views, collection views, text, popovers, split views, web views, and controls Dive into frameworks for sound, video, maps, and sensors Access user libraries: music, photos, contacts, and calendar Explore additional topics, including files, networking, and threads Stay up-to-date on iOS 14 innovations, such as: Control action closures and menus Table view cell configuration objects Collection view lists and outlines New split view controller architecture Pointer customization on iPad New photo picker and limited photos authorization Reduced accuracy location Color picker, new page control behavior, revised date pickers, and more! Want to brush up on the basics? Pick up iOS 14 Programming Fundamentals with Swift to learn about Swift, Xcode, and Cocoa. Together with Programming iOS 14, you’ll gain a solid, rigorous, and practical understanding of iOS 14 development. Computers

Linux Security Fundamentals Includes one year of FREE access after activation to the online test bank and study tools: Custom practice exam 100 electronic flashcards Searchable key term glossary The Sybex™ method for teaching Linux® security concepts Understanding Linux Security is essential for administration professionals. Linux Security Fundamentals covers all the IT security basics to help active and aspiring admins respond successfully to the modern threat landscape. You'll improve your ability to combat major security threats against computer systems, networks, and services. You'll discover how to prevent and mitigate attacks against personal devices and how to encrypt secure data transfers through networks, storage devices, or the cloud. Linux Security Fundamentals teaches: Using Digital Resources Responsibly What Vulnerabilities and Threats Are Controlling Access to Your Assets Controlling Network Connections Encrypting Data, Whether at Rest or Moving Risk Assessment Configuring System Backups and Monitoring Resource Isolation Design Patterns Interactive learning environment Take your skills to the next level with Sybex's superior interactive online study tools. To access our learning environment, simply visit www.wiley.com/go/sybextestprep, register your book to receive your unique PIN, and instantly gain one year of FREE access to: Interactive test bank with a practice exam to help you identify areas where you need to expand your knowledge 100 electronic flashcards to reinforce what you've learned Comprehensive glossary in PDF format gives you instant access to key terms you use in your job Computers

Computer Vision – ECCV 2020 The 30-volume set, comprising the LNCS books 12346 until 12375, constitutes the refereed proceedings of the 16th European Conference on Computer Vision, ECCV 2020, which was planned to be held in Glasgow, UK, during August 23-28, 2020. The conference was held virtually due to the COVID-19 pandemic. The 1360 revised papers presented in these proceedings were carefully reviewed and selected from a total of 5025 submissions. The papers deal with topics such as computer vision; machine learning; deep neural networks; reinforcement learning; object recognition; image classification; image processing; object detection; semantic segmentation; human pose estimation; 3d reconstruction; stereo vision; computational photography; neural networks; image coding; image reconstruction; object recognition; motion estimation. Computers

Systematic Complex Problem Solving in the Age of Digitalization and Open Innovation This book constitutes the refereed proceedings of the 20th International TRIZ Future Conference on Automated Invention for Smart Industries, TFC 2020, held in Cluj-Napoca, Romania, in October 2020 and sponsored by IFIP WG 5.4. The conference was held virtually.The 34 full papers presented were carefully reviewed and selected from 91 submissions. They are organized in the following thematic sections: computing TRIZ; education and pedagogy; sustainable development; tools and techniques of TRIZ for enhancing design; TRIZ and system engineering; TRIZ and complexity; and cross-fertilization of TRIZ for innovation management. Computers

Innovations in Digital Economy This book constitutes the revised and extended papers of the First International Conference on Innovations in Digital Economy, SPBU IDE 2019, held in St. Petersburg, Russia, in October 2019. The 8 papers presented were thoroughly reviewed and selected for publication from 78 submissions. The papers are organized according the following topical sections: economic efficiency and social consequences of digital innovations implementation; industrial, service and agricultural digitalization; regional innovation systems and clusters as drivers of the economic growth during the Fourth Industrial Revolution; response of an educational system and labor market to the digital-driven changes in the economic system. Computers

Foundation Dynamic Web Pages with Python Discover the concepts of creating dynamic web pages (HTML) with Python. This book reviews several methods available to serve up dynamic HTML including CGI, SSI, Django, and Flask. You will start by covering HTML pages and CSS in general and then move on to creating pages via CGI. It is easy to use and can serve as a foundation for the more advanced services available for launching dynamic web pages. Next you'll explore the SSI (Server Side Interface) method. This is a slightly more advanced interface included in mots web servers that adds functionality to modify static HTML pages to add such things as the current date or time, include additional HTML, and other features to a static web page before it is delivered to the user. The book also covers some of the key the Django module features, which must be added to the web server. These features include creating dynamic web pages and calling a database to provide additional information to the web page. Lastly you will explore the Flask module. While it has limited functionality on its own, it provides a very flexible environment to create a self designed system for delivery of dynamic web pages. By the time you finish this book, you will be able to choose the appropriate methodology for delivering dynamic information using fast HTML creation services. What You'll Learn Use HTML pages and CSS together to control the style of your web site. Install and configure SSI, Django, and Flask for Apache. Create dynamic web pages using CGI and creating a library of partial HTML pages to use in this task. Build dynamic web pages using SSI and auxiliary Python programs to enhance the SSI functionality. Develop dynamic web pages using Django. Who This Book Is For Software Developers with basic Python programming skills interested in learning Web Development Computers

iOS Unit Testing by Example Fearlessly change the design of your iOS code with solid unit tests. Use Xcode's built-in test framework XCTest and Swift to get rapid feedback on all your code - including legacy code. Learn the tricks and techniques of testing all iOS code, especially view controllers (UIViewControllers), which are critical to iOS apps. Learn to isolate and replace dependencies in legacy code written without tests. Practice safe refactoring that makes these tests possible, and watch all your changes get verified quickly and automatically. Make even the boldest code changes with complete confidence. Manual code and UI testing get slower the deeper your navigation hierarchy goes. It can take several taps just to reach a particular screen, never mind the actual workflow tests. Automatic unit testing offers such rapid feedback that it can change the rules of development. Bring testing to iOS development, even for legacy code. Use XCTest to write unit tests in Swift for all your code. iOS developers typically reserve unit tests for their model classes alone. But that approach skips most of the code common to iOS apps, especially with UIViewControllers. Learn how to unit test these view controllers to expand your unit testing possibilities. Since good unit tests form the bedrock for safe refactoring, you're empowered to make bold changes. Learn how to avoid the most common mistakes Swift programmers make with the XCTest framework. Use code coverage to find holes in your test suites. Learn how to identify hard dependencies. Reshape the design of your code quickly, with less risk and less fear. Computers

AI and Machine Learning for Coders If you're looking to make a career move from programmer to AI specialist, this is the ideal place to start. Based on Laurence Moroney's extremely successful AI courses, this introductory book provides a hands-on, code-first approach to help you build confidence while you learn key topics. You'll understand how to implement the most common scenarios in machine learning, such as computer vision, natural language processing (NLP), and sequence modeling for web, mobile, cloud, and embedded runtimes. Most books on machine learning begin with a daunting amount of advanced math. This guide is built on practical lessons that let you work directly with the code. You'll learn: How to build models with TensorFlow using skills that employers desire The basics of machine learning by working with code samples How to implement computer vision, including feature detection in images How to use NLP to tokenize and sequence words and sentences Methods for embedding models in Android and iOS How to serve models over the web and in the cloud with TensorFlow Serving Computers

Build Websites with Hugo Database-driven sites bring complexity you might not need, but building a site by hand is too much work. Hugo is a static site generator and web development framework that creates content sites quickly without the overhead or dependencies of a dyanmic web framework. With Hugo, you use HTML templates and Markdown to build static sites you can host anywhere, letting you use the skills you already have. Develop your own theme using standard HTML and CSS, using Hugo’s powerful templating features to organize your site’s components. Create your site’s content with HTML or Markdown and use Hugo’s content templating features to build new content quickly. Build a fully-featured blog with archive pages, tagging, and pagination, and integrate an external commenting system to provide interactivity. Use data from front-matter, site-wide configuration, and external JSON sources to add content, and generate JSON others can use. Integrate JavaScript with your site to create a search engine. Get Hugo working with Webpack so you can leverage the wider web development ecosystem, and explore ways to publish your site to various services. Finally, learn how you can move your existing content site to Hugo. Dive in and build your next site with Hugo! Computers

Build Location-Based Projects for iOS Coding is awesome. So is being outside. With location-based iOS apps, you can combine the two for an enhanced outdoor experience. Use Swift to create your own apps that use GPS data, read sensor data from your iPhone, draw on maps, automate with geofences, and store augmented reality world maps. You'll have a great time without even noticing that you're learning. And even better, each of the projects is designed to be extended and eventually submitted to the App Store. Explore, share, and have fun. Location-based apps are everywhere. From mapping our jogging path to pointing us to the nearest collectible creature in a location-based game, these apps offer useful and interesting features and information related to where you are. Using real-world maps and places as the environment, they add an extra layer of adventure to exploring the outdoors. If you've ever wanted to make your own location-based apps and games, you can learn how with four simple, Swift-based projects that are easy to code and fun to use. Build four stunning apps that sense the iPhone's surroundings. Use Core Location and MapKit to draw GPS data on maps and share the results to social media. Use the sensor data from the iPhone and draw acceleration graphs using Core Graphics while on a playground swing. Build an app that measures the time you spend outside using geofences. Combine Core Location and ARKit to build an augmented reality scavenger hunt app that you can use and play with other people. Have great time building creative apps you cannot wait to try out. Computers

Quantum Computing You've heard that quantum computing is going to change the world. Now you can check it out for yourself. Learn how quantum computing works, and write programs that run on the IBM Q quantum computer, one of the world's first functioning quantum computers. Learn a simple way to apply quantum mechanics to computer programming. Create algorithms to solve intractable problems for classical computers, and discover how to explore the entire problem space at once to determine the optimal solution. Get your hands on the future of computing today. Quantum computing overhauls computer science. Problems such as designing life-saving drugs and super-large logistics problems that have been difficult or impossible for classical computers to handle can now be solved in moments. Quantum computing makes it possible to explore all possible solutions simultaneously and determine those that work, instead of iterating through each possibility sequentially. Work with quantum computers directly, instead of talking about them theoretically. Discover a new visual way of looking at quantum bits that makes quantum computing intuitive for computer programmers. Master the special properties that make them different, and more powerful, than classical bits. Control quantum bits with gates and create circuits to model complex problems. Write programs that run on real quantum machines to solve problems that classical computers struggle with. Dive into quantum optimization and cryptography. Get a head start on the technology that will drive computer science into the future. What You Need: Access to the IBM quantum computer, via any internet connection Computers

A Common-Sense Guide to Data Structures and Algorithms, Second Edition Algorithms and data structures are much more than abstract concepts. Mastering them enables you to write code that runs faster and more efficiently, which is particularly important for today’s web and mobile apps. Take a practical approach to data structures and algorithms, with techniques and real-world scenarios that you can use in your daily production code, with examples in JavaScript, Python, and Ruby. This new and revised second edition features new chapters on recursion, dynamic programming, and using Big O in your daily work. Use Big O notation to measure and articulate the efficiency of your code, and modify your algorithm to make it faster. Find out how your choice of arrays, linked lists, and hash tables can dramatically affect the code you write. Use recursion to solve tricky problems and create algorithms that run exponentially faster than the alternatives. Dig into advanced data structures such as binary trees and graphs to help scale specialized applications such as social networks and mapping software. You’ll even encounter a single keyword that can give your code a turbo boost. Practice your new skills with exercises in every chapter, along with detailed solutions. Use these techniques today to make your code faster and more scalable. Computers

Alice and Bob Learn Application Security Learn application security from the very start, with this comprehensive and approachable guide! Alice and Bob Learn Application Security is an accessible and thorough resource for anyone seeking to incorporate, from the beginning of the System Development Life Cycle, best security practices in software development. This book covers all the basic subjects such as threat modeling and security testing, but also dives deep into more complex and advanced topics for securing modern software systems and architectures. Throughout, the book offers analogies, stories of the characters Alice and Bob, real-life examples, technical explanations and diagrams to ensure maximum clarity of the many abstract and complicated subjects. Topics include: · Secure requirements, design, coding, and deployment · Security Testing (all forms) · Common Pitfalls · Application Security Programs · Securing Modern Applications · Software Developer Security Hygiene Alice and Bob Learn Application Security is perfect for aspiring application security engineers and practicing software developers, as well as software project managers, penetration testers, and chief information security officers who seek to build or improve their application security programs. Alice and Bob Learn Application Security illustrates all the included concepts with easy-to-understand examples and concrete practical applications, furthering the reader’s ability to grasp and retain the foundational and advanced topics contained within. Computers

Cybersecurity in Humanities and Social Sciences The humanities and social sciences are interested in the cybersecurity object since its emergence in the security debates, at the beginning of the 2000s. This scientific production is thus still relatively young, but diversified, mobilizing at the same time political science, international relations, sociology , law, information science, security studies, surveillance studies, strategic studies, polemology. There is, however, no actual cybersecurity studies. After two decades of scientific production on this subject, we thought it essential to take stock of the research methods that could be mobilized, imagined and invented by the researchers. The research methodology on the subject "cybersecurity" has, paradoxically, been the subject of relatively few publications to date. This dimension is essential. It is the initial phase by which any researcher, seasoned or young doctoral student, must pass, to define his subject of study, delimit the contours, ask the research questions, and choose the methods of treatment. It is this methodological dimension that our book proposes to treat. The questions the authors were asked to answer were: how can cybersecurity be defined? What disciplines in the humanities and social sciences are studying, and how, cybersecurity? What is the place of pluralism or interdisciplinarity? How are the research topics chosen, the questions defined? How, concretely, to study cybersecurity: tools, methods, theories, organization of research, research fields, data ...? How are discipline-specific theories useful for understanding and studying cybersecurity? Has cybersecurity had an impact on scientific theories? Computers

Microprocessor 1 Computers

Advanced ASP.NET Core 3 Security Incorporate security best practices into ASP.NET Core. This book covers security-related features available within the framework, explains where these feature may fall short, and delves into security topics rarely covered elsewhere. Get ready to dive deep into ASP.NET Core 3.1 source code, clarifying how particular features work and addressing how to fix problems. For straightforward use cases, the ASP.NET Core framework does a good job in preventing certain types of attacks from happening. But for some types of attacks, or situations that are not straightforward, there is very little guidance available on how to safely implement solutions. And worse, there is a lot of bad advice online on how to implement functionality, be it encrypting unsafely hard-coded parameters that need to be generated at runtime, or articles which advocate for certain solutions that are vulnerable to obvious injection attacks. Even more concerning is the functions in ASP.NET Core that are not as secure as they should be by default. Advanced ASP.NET Core 3 Security is designed to train developers to avoid these problems. Unlike the vast majority of security books that are targeted to network administrators, system administrators, or managers, this book is targeted specifically to ASP.NET developers. Author Scott Norberg begins by teaching developers how ASP.NET Core works behind the scenes by going directly into the framework's source code. Then he talks about how various attacks are performed using the very tools that penetration testers would use to hack into an application. He shows developers how to prevent these attacks. Finally, he covers the concepts developers need to know to do some testing on their own, without the help of a security professional. What You Will Learn Discern which attacks are easy to prevent, and which are more challenging, in the framework Dig into ASP.NET Core 3.1 source code to understand how the security services work Establish a baseline for understanding how to design more secure software Properly apply cryptography in software development Take a deep dive into web security concepts Validate input in a way that allows legitimate traffic but blocks malicious traffic Understand parameterized queries and why they are so important to ASP.NET Core Fix issues in a well-implemented solution Know how the new logging system in ASP.NET Core falls short of security needs Incorporate security into your software development process Who This Book Is For Software developers who have experience creating websites in ASP.NET and want to know how to make their websites secure from hackers and security professionals who work with a development team that uses ASP.NET Core. A basic understanding of web technologies such as HTML, JavaScript, and CSS is assumed, as is knowledge of how to create a website, and how to read and write C#. You do not need knowledge of security concepts, even those that are often covered in ASP.NET Core documentation. Computers

Progress in Differential-Algebraic Equations II This book contains articles presented at the 9th Workshop on Differential-Algebraic Equations held in Paderborn, Germany, from 17–20 March 2019. The workshop brought together more than 40 mathematicians and engineers from various fields, such as numerical and functional analysis, control theory, mechanics and electromagnetic field theory. The participants focussed on the theoretical and numerical treatment of “descriptor†systems, i.e., differential-algebraic equations (DAEs). The book contains 14 contributions and is organized into four parts: mathematical analysis, numerics and model order reduction, control as well as applications. It is a useful resource for applied mathematicians with interest in recent developments in the field of differential algebraic equations but also for engineers, in particular those interested in modelling of constraint mechanical systems, thermal networks or electric circuits. Computers

Social, Cultural, and Behavioral Modeling This book constitutes the proceedings of the 13th International Conference on Social, Cultural, and Behavioral Modeling, SBP-BRiMS 2020, which was planned to take place in Washington, DC, USA. Due to the COVID-19 pandemic the conference was held online during October 18–21, 2020. The 33 full papers presented in this volume were carefully reviewed and selected from 66 submissions. A wide number of disciplines are represented including computer science, psychology, sociology, communication science, public health, bioinformatics, political science, and organizational science. Numerous types of computational methods are used, such as machine learning, language technology, social network analysis and visualization, agent-based simulation, and statistics. Computers

Pattern Recognition and Computer Vision The three-volume set LNCS 12305, 12306, and 12307 constitutes the refereed proceedings of the Third Chinese Conference on Pattern Recognition and Computer Vision, PRCV 2020, held virtually in Nanjing, China, in October 2020. The 158 full papers presented were carefully reviewed and selected from 402 submissions. The papers have been organized in the following topical sections: Part I: Computer Vision and Application, Part II: Pattern Recognition and Application, Part III: Machine Learning. Computers

Automated Technology for Verification and Analysis This book constitutes the refereed proceedings of the 18th International Symposium on Automated Technology for Verification and Analysis, ATVA 2020, held in Hanoi, Vietnam, in October 2020. The 27 regular papers presented together with 5 tool papers and 2 invited papers were carefully reviewed and selected from 75 submissions. The symposium is dedicated to promoting research in theoretical and practical aspects of automated analysis, verification and synthesis by providing an international venue for the researchers to present new results. The papers focus on neural networks and machine learning; automata; logics; techniques for verification, analysis and testing; model checking and decision procedures; synthesis; and randomization and probabilistic systems. Computers

Theory and Applications of Models of Computation This book constitutes the refereed proceedings of the 16th Annual Conference on Theory and Applications of Models of Computation, TAMC 2020, held in Changsha, China, in October 2020. The 37 full papers were carefully reviewed and selected from 83 submissions. The main themes of the selected papers are computability, complexity, algorithms, information theory and their extensions to machine learning theory and foundations of artificial intelligence. Computers

Carpenter's Complete Guide to the SAS REPORT Procedure Art Carpenter demystifies the powerful REPORT procedure and shows you how to incorporate this highly flexible and customizable procedure into your SAS reporting programs. Combining his years of SAS experience with a talent for instruction, Art offers clear and comprehensive coverage that demonstrates how valuable this procedure is for both summarizing and displaying data. Illustrated with more than two hundred examples and sample exercises to reinforce your learning, Carpenter's Complete Guide to the SAS REPORT Procedure provides you with information that you can put to immediate use. The text is divided into three distinct sections. Part 1 introduces you to PROC REPORT, showing you how it works and "thinks." This section is designed to be read linearly by users who are unfamiliar with the procedure. Part 2 is a collection of increasingly more complex examples that feature advanced options and capabilities. It also introduces the relationship between PROC REPORT and the Output Delivery System (ODS). Part 3 incorporates the options and statements described in Parts 1 and 2 into a series of examples that highlight many of the extended capabilities of PROC REPORT. Included in this section is a discussion of a few ODS statements and options that might be useful to a PROC REPORT programmer, plus an in-depth look at the PROC REPORT process itself, especially as it relates to the execution of compute blocks.Art's author page at support.sas.com/carpenter includes the following bonus material: example SAS data sets, example results, and a compilation of nearly 100 related conference papers.This book is part of the SAS Press program. Computers

Learn PostgreSQL A comprehensive guide to building, managing, and securing scalable and reliable database and data warehousing applications using Postgres 12 and 13 Key Features Set up your database cluster and monitor, secure, and fine-tune it for optimal performance Learn the fundamentals of database management and implement client- and server-side programming using SQL and PL/pgSQL Explore useful tips to develop efficient PostgreSQL database solutions from scratch Book Description PostgreSQL is one of the fastest-growing open source object-relational database management systems (DBMS) in the world. As well as being easy to use, it's scalable and highly efficient. In this book, you'll explore PostgreSQL 12 and 13 and learn how to build database solutions using it. Complete with hands-on tutorials, this guide will teach you how to achieve the right database design required for a reliable environment. You'll learn how to install and configure a PostgreSQL server and even manage users and connections. The book then progresses to key concepts of relational databases, before taking you through the Data Definition Language (DDL) and commonly used DDL commands. To build on your skills, you'll understand how to interact with the live cluster, create database objects, and use tools to connect to the live cluster. You'll then get to grips with creating tables, building indexes, and designing your database schema. Later, you'll explore the Data Manipulation Language (DML) and server-side programming capabilities of PostgreSQL using PL/pgSQL, before learning how to monitor, test, and troubleshoot your database application to ensure high-performance and reliability. By the end of this book, you'll be well-versed with the Postgres database and be able to set up your own PostgreSQL instance and use it to build robust solutions. What you will learn Understand how users and connections are managed by running a PostgreSQL instance Interact with transaction boundaries using server-side programming Identify bottlenecks to maintain your database efficiently Create and manage extensions to add new functionalities to your cluster Choose the best index type for each situation Use online tools to set up a memory configuration that will suit most databases Explore how Postgres can be used in multi-instance environments to provide high-availability, redundancy, and scalability Who this book is for This Postgres book is for anyone interested in learning about the PostgreSQL database from scratch. Anyone looking to build robust data warehousing applications and scale the database for high-availability and performance using the latest features of PostgreSQL will also find this book useful. Although prior knowledge of PostgreSQL is not required, familiarity with databases is expected. Computers

Pattern Recognition and Computer Vision The three-volume set LNCS 12305, 12306, and 12307 constitutes the refereed proceedings of the Third Chinese Conference on Pattern Recognition and Computer Vision, PRCV 2020, held virtually in Nanjing, China, in October 2020. The 158 full papers presented were carefully reviewed and selected from 402 submissions. The papers have been organized in the following topical sections: Part I: Computer Vision and Application, Part II: Pattern Recognition and Application, Part III: Machine Learning. Computers

Research and the Future of Telematics This book constitutes selected papers from the 20th International Conference on Transport Systems Telematics, TST 2020, held in Kraków, Poland, in October 2020. The 34 full papers presented in this volume were carefully reviewed and selected from 97 submissions. They were organized in topical sections named: telematics in road transport - general view; telematics in road transport - details in applications.- telematics in rail and marine transport; general about telematics. Computers

Raku Recipes Explore Raku problems and solutions using the latest version of the Raku programming language. In Raku Recipes, the emphasis is on applying Raku code to various important tasks and applications including data science, analytics, microservices, and desktop/console applications. There are also fun one-liner script recipes and instructions on how to create mini-languages of your very own. All in all, over 70 recipes cover a broad range of the tasks and problems encountered by a modern Raku developer. You’ll be able to solve problems starting from basics such as input/output and math, to more complex domains such as microservices web sockets, web hooks, and mini-bots. What You Will Learn Put Raku to use in a real world environment Work with Raku modules, including design classes, roles, and more Query a GeoIP database and extract information from the web Carry out text processing such as creating a dictionary with fast searches over it and scraping markdown documents Work with MongoDB, WikiData, and other data sources Build data science and analytics applications using Raku Integrate with Python, C, and other languages and libraries Create mini-languages and shell scripting languages Who This Book Is For While some prior experience in Raku may be useful, it is not required. Prior programming experience using earlier versions of Perl is recommended, however. Computers

Digitalia Susannah Hagan boldly discusses the fraught relationship between key dominating areas of architectural discourse - digital design, environmental design, and avant-garde design. Digitalia firstly demonstrates that drawing such firm lines between architectural spheres is damaging and foolish, particularly as both environmental and avant-garde practices are experimenting with the digital, and secondly remonstrates with an avant-garde that has repudiated the social/ethical agenda of the modernist avant-garde because it failed the first time round. It is environmental architecture that has picked up the social/ethical ball and is running with it, using the digital to very different, and more far-reaching, ends. As the debates rage, this book is a key read for all who are involved or intrigued. Computers

Refactoring at Scale Making significant changes to large, complex codebases is a daunting task--one that's nearly impossible to do successfully unless you have the right team, tools, and mindset. If your application is in need of a substantial overhaul and you're unsure how to go about implementing those changes in a sustainable way, then this book is for you. Software engineer Maude Lemaire walks you through the entire refactoring process from start to finish. You'll learn from her experience driving performance and refactoring efforts at Slack during a period of critical growth, including two case studies illustrating the impact these techniques can have in the real world. This book will help you achieve a newfound ability to productively introduce important changes in your codebase. Understand how code degrades and why some degradation is inevitable Quantify and qualify the state of your codebase before refactoring Draft a well-scoped execution plan with strategic milestones Win support from engineering leadership Build and coordinate a team best suited for the project Communicate effectively inside and outside your team Adopt best practices for successfully executing the refactor Computers

Kubeflow for Machine Learning If you're training a machine learning model but aren't sure how to put it into production, this book will get you there. Kubeflow provides a collection of cloud native tools for different stages of a model's lifecycle, from data exploration, feature preparation, and model training to model serving. This guide helps data scientists build production-grade machine learning implementations with Kubeflow and shows data engineers how to make models scalable and reliable. Using examples throughout the book, authors Holden Karau, Trevor Grant, Ilan Filonenko, Richard Liu, and Boris Lublinsky explain how to use Kubeflow to train and serve your machine learning models on top of Kubernetes in the cloud or in a development environment on-premises. Understand Kubeflow's design, core components, and the problems it solves Understand the differences between Kubeflow on different cluster types Train models using Kubeflow with popular tools including Scikit-learn, TensorFlow, and Apache Spark Keep your model up to date with Kubeflow Pipelines Understand how to capture model training metadata Explore how to extend Kubeflow with additional open source tools Use hyperparameter tuning for training Learn how to serve your model in production Computers

Web and Big Data This two-volume set, LNCS 11317 and 12318, constitutes the thoroughly refereed proceedings of the 4th International Joint Conference, APWeb-WAIM 2020, held in Tianjin, China, in September 2020. Due to the COVID-19 pandemic the conference was organizedas a fully online conference. The 42 full papers presented together with 17 short papers, and 6 demonstration papers were carefully reviewed and selected from 180 submissions. The papers are organized around the following topics: Big Data Analytics; Graph Data and Social Networks; Knowledge Graph; Recommender Systems; Information Extraction and Retrieval; Machine Learning; Blockchain; Data Mining; Text Analysis and Mining; Spatial, Temporal and Multimedia Databases; Database Systems; and Demo. Computers

Intelligent Computing Theories and Application This two-volume set of LNCS 12463 and LNCS 12464 constitutes - in conjunction with the volume LNAI 12465 - the refereed proceedings of the 16th International Conference on Intelligent Computing, ICIC 2020, held in Bari, Italy, in October 2020. The 162 full papers of the three proceedings volumes were carefully reviewed and selected from 457 submissions. The ICIC theme unifies the picture of contemporary intelligent computing techniques as an integral concept that highlights the trends in advanced computational intelligence and bridges theoretical research with applications. The theme for this conference is “Advanced Intelligent Computing Methodologies and Applications.†Papers related to this theme are especially solicited, addressing theories, methodologies, and applications in science and technology. Computers

Intelligent Computing Theories and Application This two-volume set of LNCS 12463 and LNCS 12464 constitutes - in conjunction with the volume LNAI 12465 - the refereed proceedings of the 16th International Conference on Intelligent Computing, ICIC 2020, held in Bari, Italy, in October 2020. The 162 full papers of the three proceedings volumes were carefully reviewed and selected from 457 submissions. The ICIC theme unifies the picture of contemporary intelligent computing techniques as an integral concept that highlights the trends in advanced computational intelligence and bridges theoretical research with applications. The theme for this conference is “Advanced Intelligent Computing Methodologies and Applications.†Papers related to this theme are especially solicited, addressing theories, methodologies, and applications in science and technology. Computers

Applied Cryptography and Network Security Workshops This book constitutes the proceedings of the satellite workshops held around the 18th International Conference on Applied Cryptography and Network Security, ACNS 2020, in Rome, Italy, in October 2020. The 31 papers presented in this volume were carefully reviewed and selected from 65 submissions. They stem from the following workshops: AIBlock 2020:Second International Workshop on Application Intelligence and Blockchain Security AIHWS 2020:First International Workshop on Artificial Intelligence in Hardware Security AIoTS 2020:Second International Workshop on Artificial Intelligence and Industrial Internet-of-Things Security Cloud S&P 2020:Second International Workshop on Cloud Security and Privacy SCI 2020:First International Workshop on Secure Cryptographic Implementation SecMT 2020:First International Workshop on Security in Mobile Technologies SiMLA 2020: Second International Workshop on Security in Machine Learning and its Applications Computers

Statistical Graphics Procedures by Example Sanjay Matange and Dan Heath's Statistical Graphics Procedures by Example: Effective Graphs Using SAS shows the innumerable capabilities of SAS Statistical Graphics (SG) procedures. The authors begin with a general discussion of the principles of effective graphics, ODS Graphics, and the SG procedures. They then move on to show examples of the procedures' many features. The book is designed so that you can easily flip through it, find the graph you need, and view the code right next to the example. Among the topics included are how to combine plot statements to create custom graphs; customizing graph axes, legends, and insets; advanced features, such as annotation and attribute maps; tips and tricks for creating the optimal graph for the intended usage; real-world examples from the health and life sciences domain; and ODS styles.The procedures in Statistical Graphics Procedures by Example are specifically designed for the creation of analytical graphs. That makes this book a must-read for analysts and statisticians in the health care, clinical trials, financial, and insurance industries. However, you will find that the examples here apply to all fields.This book is part of the SAS Press program. Computers

Photoshop Elements 2021 For Dummies Get picture-perfect results with Photoshop Elements 2021 Photoshop Elements has a reputation for delivering the photo editing power that non-professional photographers and designers need to get eye-catching—and art-quality—results. This book offers guidance for applying everything from simple, one-click fixes all the way up to detailed retouching of your images. Photoshop Elements 2021 For Dummies assumes no prior photo-editing experience and makes it easy for even the absolute beginner to quickly grasp how to edit to create slick, professional-looking photos. In no time at all you’ll feel confident in everything from common image fixes to utilizing more creative techniques, such as using image layers to create a standout look. You’ll also find tips on building and managing complex photo projects. Understand photo-editing concepts Adjust clarity, color, and brightness Add artistic touches Catalog and organize your work This fun and easy guide provides the steps you need to get the most out of this popular version of Photoshop—and will help you achieve truly beautiful results! Computers

macOS Big Sur For Dummies Your “get-started†guide to the world of macOS Big Sur Wherever you like to Mac—at home in front of your trusty iMac or over a coffee with your portable MacBook Air—macOS provides you with the seamless, efficient, and reliable user experience that makes these devices so famously a pleasure to use. macOS Big Sur For Dummies is here to heighten the experience for new users and upgraders alike by providing the very latest on the ways macOS Big Sur can enhance how you work and play. Written in a no-jargon style by Bob LeVitus—the Houston Chronicle’s much-loved “Dr. Mac†since 1996—this guide starts with the basics, like getting set up, and explains more advanced uses, like making music and movies, exploring the expanding universe of apps and giving tips on how to save time and enhance productivity along the way. With this book, you’ll learn to Set up and connect your Mac Get friendly with Siri Enhance your world with apps Work better and faster Use the comprehensive capabilities of macOS Big Sur to do anything and everything you would like to do—and do it even better. For beginners and experts alike, macOS Big Sur For Dummies is the best way to step into the magical world of getting things done with Mac. Computers

QuickBooks 2021 For Dummies Save on expensive professionals with this trusted bestseller! Running your own business is pretty cool, but when it comes to the financial side—accounts and payroll, for instance—it's not so cool! That’s why millions of small business owners around the world count on QuickBooks to quickly and easily manage accounting and financial tasks and save big time on hiring expensive professionals. In a friendly, easy-to-follow style, small business guru and bestselling author Stephen L. Nelson checks off all your financial line-item asks, including how to track your profits, plan a perfect budget, simplify tax returns, manage inventory, create invoices, track costs, generate reports, and pretty much any other accounts and financial-planning task that turns up on your desk! Keep up with the latest QuickBooks changes Use QuickBooks to track profits and finances Balance your budget Back up your data safely The fully updated new edition of QuickBooks For Dummies takes the sweat (and the expense) out of cooking the books—and gives you more time to savor the results of your labors! Computers

Podcasting For Dummies Understand the do's and don'ts of podcasting Produce unique content that attracts listeners Build a studio that rivals pro podcasters How to talk your way to the top As more and more people turn to podcasts for entertainment, information, and education, the market for new players has never been bigger—or more competitive. And with corporations and A-list celebs moving in on the action, it's more important than ever to know how to stand out from the crowd. Written by two podcasting veterans, this book gives you everything you need to launch a podcast. Get the insider info on how to produce quality audio (and even video), keep your content fresh, find your voice, and build an audience. Inside... Building your podcasting studio Developing your podcast theme Conducting great interviews Recording and editing episodes Distributing your podcast Adding sponsorships Expanding your podcast consumption Computers

Lattice-Based Cryptosystems This book focuses on lattice-based cryptosystems, widely considered to be one of the most promising post-quantum cryptosystems and provides fundamental insights into how to construct provably secure cryptosystems from hard lattice problems. The concept of provable security is used to inform the choice of lattice tool for designing cryptosystems, including public-key encryption, identity-based encryption, attribute-based encryption, key change and digital signatures. Given its depth of coverage, the book especially appeals to graduate students and young researchers who plan to enter this research area. Computers

Privacy Technologies and Policy This book constitutes the refereed conference proceedings of the 8th Annual Privacy Forum, APF 2020, held in Lisbon, Portugal, in October 2020.The 12 revised full papers were carefully reviewed and selected from 59 submissions. The papers are organized in topical sections on impact assessment; privacy by design; data protection and security; and transparency. Computers

Similarity Search and Applications This book constitutes the refereed proceedings of the 13th International Conference on Similarity Search and Applications, SISAP 2020, held in Copenhagen, Denmark, in September/October 2020. The conference was held virtually due to the COVID-19 pandemic.The 19 full papers presented together with 12 short and 2 doctoral symposium papers were carefully reviewed and selected from 50 submissions. The papers are organized in topical sections named: scalable similarity search; similarity measures, search, and indexing; high-dimensional data and intrinsic dimensionality; clustering; artificial intelligence and similarity; demo and position papers; and doctoral symposium. Computers

Reachability Problems This book constitutes the refereed proceedings of the 14th International Conference on Reachability Problems, RP 2020, held in Paris, France in October 2020.The 8 full papers presented were carefully reviewed and selected from 25 submissions. In addition, 2 invited papers were included in this volume. The papers cover topics such as reachability for infinite state systems; rewriting systems; reachability analysis in counter/timed/cellular/communicating automata; Petri nets; computational aspects of semigroups, groups, and rings; reachability in dynamical and hybrid systems; frontiers between decidable and undecidable reachability problems; complexity and decidability aspects; predictability in iterative maps; and new computational paradigms. Computers

Embedded Computer Systems This book constitutes the refereed proceedings of the 20th International Conference on Embedded Computer Systems: Architectures, Modeling, and Simulation, SAMOS 2020, held in Samos, Greece, in July 2020.*The 16 regular papers presented were carefully reviewed and selected from 35 submissions. In addition, 9 papers from two special sessions were included, which were organized on topics of current interest: innovative architectures for security and European projects on embedded and high performance computing for health applications. * The conference was held virtually due to the COVID-19 pandemic. Computers

Trends and Applications in Knowledge Discovery and Data Mining This book constitutes the thoroughly refereed post-workshop proceedings of the workshops that were held in conjunction with the 24th Pacific-Asia Conference on Knowledge Discovery and Data Mining, PAKDD 2020, in Singapore, Singapore, in May 2020. The 17 revised full papers presented were carefully reviewed and selected from a total of 50 submissions. The five workshops were as follows: · First International Workshop on Literature-Based Discovery (LBD 2020) · Workshop on Data Science for Fake News (DSFN 2020) · Learning Data Representation for Clustering (LDRC 2020) · Ninth Workshop on Biologically Inspired Techniques for Data Mining (BDM · 2020) · First Pacific Asia Workshop on Game Intelligence & Informatics (GII 2020) Computers

Pattern Recognition and Computer Vision The three-volume set LNCS 12305, 12306, and 12307 constitutes the refereed proceedings of the Third Chinese Conference on Pattern Recognition and Computer Vision, PRCV 2020, held virtually in Nanjing, China, in October 2020. The 158 full papers presented were carefully reviewed and selected from 402 submissions. The papers have been organized in the following topical sections: Part I: Computer Vision and Application, Part II: Pattern Recognition and Application, Part III: Machine Learning. Computers

Discovery Science This book constitutes the proceedings of the 23rd International Conference on Discovery Science, DS 2020, which took place during October 19-21, 2020. The conference was planned to take place in Thessaloniki, Greece, but had to change to an online format due to the COVID-19 pandemic. The 26 full and 19 short papers presented in this volume were carefully reviewed and selected from 76 submissions. The contributions were organized in topical sections named: classification; clustering; data and knowledge representation; data streams; distributed processing; ensembles; explainable and interpretable machine learning; graph and network mining; multi-target models; neural networks and deep learning; and spatial, temporal and spatiotemporal data. Computers

Linux Containers and Virtualization Get a novel perspective on Linux containers and understand the world of virtualization. This book takes you down the rabbit hole to discover what lies below the API. You’ll go on a journey of virtualization and see how containers are realized in the Linux world. Linux Containers and Virtualization details the data structures within the Linux kernel which make up Linux containers. You will start with the fundamentals of virtualization including how different resources such as memory, CPU, network, and storage are virtualized. Then you will move on to hypervisors and virtualization using the Kernel virtual Machine (KVM) and Quick Emulator (QEMU). Next, you will learn about Linux namespace, cgroups, and layered file systems, which are the essential building blocks of Linux containers. The explanation traverses the Linux kernel codebase to show how these are realized in the Linux kernel. In the final chapter, you will code your own container by applying the concepts learnt in the previous chapters. On completion of the book, you will have the knowledge to start coding a Linux container. What You Will Learn Understand the basics of virtualization Discover how the Linux kernel supports virtualization See how the evolution of the Linux kernel and CPUs led to the creation of containerization technologies Develop the ability to create your own container framework Who This Book Is For Developers working on virtualized software deployment and containers. Architects designing platforms based on a container runtime as well as DevOps professionals who want to get a microscopic view on how containers and virtualization work would find the book useful. Computers

Oracle Database Transactions and Locking Revealed Access much-needed information for building scalable, high-concurrency applications and deploying them against the Oracle Database. This new edition is updated to be current with Oracle Database 19. It includes a new chapter with troubleshooting recipes to help you quickly diagnose and resolve locking problems that are urgent and block production. Good transaction design is an important facet of highly-concurrent applications that are run by hundreds, even thousands, of users who are executing transactions at the same time. Transaction design, in turn, relies on a good understanding of how the database engine manages the locking of resources to prevent access conflicts and data loss that might otherwise result from concurrent access to data in the database. This book provides a solid and accurate explanation of how locking and concurrency are dealt with by Oracle Database. You will learn how the Oracle Database architecture accommodates user transactions, and how you can write code to mesh with the way in which Oracle Database is designed to operate. Oracle Database Transactions and Locking Revealed covers in detail the various lock types, and also different locking schemes such as pessimistic and optimistic locking. Then you will learn about transaction isolation and multi-version concurrency, and how the various lock types support Oracle Database’s transactional features. You will learn tips for transaction design, as well as some bad practices and habits to avoid. Coverage is also given to redo and undo, and their role in concurrency. The book is loaded with insightful code examples that drive home each concept. This is an important book that anyone developing highly-concurrent applications will want to have handy on their shelf. What You Will Learn Avoid application lockups due to conflicts over accessing the same resource Understand how Oracle prevents one application from overwriting another’s modifications Create transaction designs that mesh with how Oracle Database is designed Build high-throughput applications supporting thousands of concurrent users Design applications to take full advantage of Oracle’s powerful database engine Gain a fundamental knowledge of Oracle’s transaction and locking architecture Develop techniques to quickly diagnose and resolve common locking issues Who This Book Is For Oracle developers and database administrators faced with troubleshooting and solving deadlocks, locking contention, and similar problems that are encountered in high-concurrency environments; and application developers wanting to design their applications to excel at multi-user concurrency by taking full advantage of Oracle Database’s multi-versioning and concurrency support Computers

The Essential PROC SQL Handbook for SAS Users Navigate the world of the powerful SQL procedure with Katherine Prairie's Essential PROC SQL Handbook for SAS Users. Written in an easy-to-use, logical format, this comprehensive reference focuses on the functionality of the procedure, as well as the accomplishment of common tasks using PROC SQL, enabling readers to quickly develop and enhance their SQL skills. Features include more than 300 examples of PROC SQL code, plus queries and diagrams showing how the statements are processed, tips and techniques highlighting "need-to-know" concepts, and an appendix designed specifically for SQL Pass-Through Facility and SAS/ACCESS users. This practical guide is written for SAS users of all levels who want to learn how to integrate the SQL procedure into their Base SAS and/or SAS/ACCESS programs as well as SQL programmers who want to adapt their current skills to SAS.This book is part of the SAS Press program. Computers

Parallel Scientific Computation Parallel Scientific Computation presents a methodology for designing parallel algorithms and writing parallel computer programs for modern computer architectures with multiple processors. Computers

Machine Learning Design Patterns The design patterns in this book capture best practices and solutions to recurring problems in machine learning. The authors, three Google engineers, catalog proven methods to help data scientists tackle common problems throughout the ML process. These design patterns codify the experience of hundreds of experts into straightforward, approachable advice. In this book, you will find detailed explanations of 30 patterns for data and problem representation, operationalization, repeatability, reproducibility, flexibility, explainability, and fairness. Each pattern includes a description of the problem, a variety of potential solutions, and recommendations for choosing the best technique for your situation. You'll learn how to: Identify and mitigate common challenges when training, evaluating, and deploying ML models Represent data for different ML model types, including embeddings, feature crosses, and more Choose the right model type for specific problems Build a robust training loop that uses checkpoints, distribution strategy, and hyperparameter tuning Deploy scalable ML systems that you can retrain and update to reflect new data Interpret model predictions for stakeholders and ensure models are treating users fairly Computers

Web and Big Data This two-volume set, LNCS 11317 and 12318, constitutes the thoroughly refereed proceedings of the 4th International Joint Conference, APWeb-WAIM 2020, held in Tianjin, China, in September 2020. Due to the COVID-19 pandemic the conference was organizedas a fully online conference. The 42 full papers presented together with 17 short papers, and 6 demonstration papers were carefully reviewed and selected from 180 submissions. The papers are organized around the following topics: Big Data Analytics; Graph Data and Social Networks; Knowledge Graph; Recommender Systems; Information Extraction and Retrieval; Machine Learning; Blockchain; Data Mining; Text Analysis and Mining; Spatial, Temporal and Multimedia Databases; Database Systems; and Demo. Computers

Graph-Theoretic Concepts in Computer Science This book constitutes the revised papers of the 46th International Workshop on Graph-Theoretic Concepts in Computer Science, WG 2020, held in Leeds, UK, in June 2020. The workshop was held virtually due to the COVID-19 pandemic. The 32 full papers presented in this volume were carefully reviewed and selected from 94 submissions. They cover a wide range of areas, aiming to present emerging research results and to identify and explore directions of future research of concepts on graph theory and how they can be applied to various areas in computer science. Computers

Cooperative Design, Visualization, and Engineering This book constitutes the proceedings of the 17th International Conference on Cooperative Design, Visualization, and Engineering, CDVE 2020, held in Bangkok, Thailand, in October 2020.*The 33 full papers and 7 short papers presented were carefully reviewed and selected from 74 submissions. The achievement, progress and future challenges are reported in areas such as health care, industrial design, banking IT systems, cultural activities support, operational maritime cybersecurity assurance, emotion communication, and social network data analytics. * The conference was held virtually due to the COVID-19 pandemic. Computers

Intelligent Computing Methodologies This two-volume set of LNCS 12463 and LNCS 12464 constitutes - in conjunction with the volume LNAI 12465 - the refereed proceedings of the 16th International Conference on Intelligent Computing, ICIC 2020, held in Bari, Italy, in October 2020. The 162 full papers of the three proceedings volumes were carefully reviewed and selected from 457 submissions. The ICIC theme unifies the picture of contemporary intelligent computing techniques as an integral concept that highlights the trends in advanced computational intelligence and bridges theoretical research with applications. The theme for this conference is “Advanced Intelligent Computing Methodologies and Applications.†Papers related to this theme are especially solicited, addressing theories, methodologies, and applications in science and technology. Computers

Intelligent Systems The two-volume set LNAI 12319 and 12320 constitutes the proceedings of the 9th Brazilian Conference on Intelligent Systems, BRACIS 2020, held in Rio Grande, Brazil, in October 2020. The total of 90 papers presented in these two volumes was carefully reviewed and selected from 228 submissions. The contributions are organized in the following topical section: Part I: Evolutionary computation, metaheuristics, constrains and search, combinatorial and numerical optimization; neural networks, deep learning and computer vision; and text mining and natural language processing. Part II: Agent and multi-agent systems, planning and reinforcement learning; knowledge representation, logic and fuzzy systems; machine learning and data mining; and multidisciplinary artificial and computational intelligence and applications. Due to the Corona pandemic BRACIS 2020 was held as a virtual event. Computers

Ad-Hoc, Mobile, and Wireless Networks This book constitutes the refereed proceedings of the 19th International Conference on Ad-Hoc, Mobile, and Wireless Networks, ADHOC-NOW 2020, held in Bari, Italy, in October 2020.*The 19 full and 4 short papers presented were carefully reviewed and selected from 39 submissions. The papers provide an in-depth and stimulating view on the new frontiers in the field of mobile, ad hoc and wireless computing. They are organized in the following topical sections: intelligent, programmable and delay- and disruption- tolerant networks; internet of drones and smart mobility; internet of things and internet of medical things; secure communication protocols and architectures; and wireless systems. *The conference was held virtually due to the COVID-19 pandemic. Computers

The Common Lisp Condition System Discover the functioning and example uses of the Common Lisp condition system. This book supplements already existing material for studying Common Lisp as a language by providing detailed information about the Lisp condition system and its control flow mechanisms; it also describes an example ANSI-conformant implementation of the condition system. In part 1 of The Common Lisp Condition System, the author introduces the condition system using a bottom-up approach, constructing it piece by piece. He uses a storytelling approach to convey the foundation of the condition system, dynamically providing code to alter the behavior of an existing program. Later, in part 2, you’ll implement a full and complete ANSI-conformant condition system while examining and testing each piece of code that you write. Throughout, the author demonstrates how to extend Lisp using Lisp itself by using the condition system as an example. This is done while paying proper attention to the CL restart subsystem, giving it attention on a par with the handler subsystem. After reading and using this book, you'll have learned about the inner functioning of the condition system, how to use it in your own Common Lisp coding and applications, and how to implement it from scratch, should such a need arise. What You Will Learn Examine the condition system and see why it is important in Common Lisp Construct the condition system from scratch using foundational mechanisms provided by Common Lisp Program the condition system and its control flow mechanisms to achieve practical results Implement all parts of a condition system: conditions, restarts, handler- and restart-binding macros, signalling mechanisms, assertions, a debugger, and more Who This Book Is For Beginning and intermediate Lisp programmers, as well as intermediate programmers of other programming languages. Computers

Programming Distributed Computing Systems An introduction to fundamental theories of concurrent computation and associated programming languages for developing distributed and mobile computing systems. Starting from the premise that understanding the foundations of concurrent programming is key to developing distributed computing systems, this book first presents the fundamental theories of concurrent computing and then introduces the programming languages that help develop distributed computing systems at a high level of abstraction. The major theories of concurrent computation—including the π-calculus, the actor model, the join calculus, and mobile ambients—are explained with a focus on how they help design and reason about distributed and mobile computing systems. The book then presents programming languages that follow the theoretical models already described, including Pict, SALSA, and JoCaml. The parallel structure of the chapters in both part one (theory) and part two (practice) enable the reader not only to compare the different theories but also to see clearly how a programming language supports a theoretical model. The book is unique in bridging the gap between the theory and the practice of programming distributed computing systems. It can be used as a textbook for graduate and advanced undergraduate students in computer science or as a reference for researchers in the area of programming technology for distributed computing. By presenting theory first, the book allows readers to focus on the essential components of concurrency, distribution, and mobility without getting bogged down in syntactic details of specific programming languages. Once the theory is understood, the practical part of implementing a system in an actual programming language becomes much easier. Computers

Systems Modelling and Management This book constitutes the refereed proceedings of the First International Conference on Systems Modelling and Management, ICSMM 2020, planned to be held in Bergen, Norway, in June 2020. Due to the COVID-19 pandemic the conference did not take place physically or virtually. The 10 full papers and 3 short papers were thoroughly reviewed and selected from 19 qualified submissions. The papers are organized according to the following topical sections: verification and validation; applications; methods, techniques and tools. Computers

HCI International 2020 - Late Breaking Papers This book constitutes late breaking papers from the 22nd International Conference on Human-Computer Interaction, HCII 2020, which was held in July 2020. The conference was planned to take place in Copenhagen, Denmark, but had to change to a virtual conference mode due to the COVID-19 pandemic.From a total of 6326 submissions, a total of 1439 papers and 238 posters have been accepted for publication in the HCII 2020 proceedings before the conference took place. In addition, a total of 333 papers and 144 posters are included in the volumes of the proceedings published after the conference as “Late Breaking Work†(papers and posters). These contributions address the latest research and development efforts in the field and highlight the human aspects of design and use of computing systems. Computers

Artificial Neural Networks and Machine Learning – ICANN 2020 The proceedings set LNCS 12396 and 12397 constitute the proceedings of the 29th International Conference on Artificial Neural Networks, ICANN 2020, held in Bratislava, Slovakia, in September 2020.*The total of 139 full papers presented in these proceedings was carefully reviewed and selected from 249 submissions. They were organized in 2 volumes focusing on topics such as adversarial machine learning, bioinformatics and biosignal analysis, cognitive models, neural network theory and information theoretic learning, and robotics and neural models of perception and action. *The conference was postponed to 2021 due to the COVID-19 pandemic. Computers

Health Information Science This book constitutes the proceedings of the 9th International Conference on Health Information Science, HIS 2020, which took place in Amsterdam, The Netherlands, during October 20-23, 2020. The 11 full papers and 6 short papers presented in this volume were carefully reviewed and selected from 62 submissions. They were organized in topical sections named: mental health; medical record processing; medical information systems; medical diagnosis with machine learning; and health behavior and medication. Computers

Advances in Computer Graphics This book constitutes the refereed proceedings of the 37th Computer Graphics International Conference, CGI 2020, held in Geneva, Switzerland, in October 2020. The conference was held virtually. The 43 full papers presented together with 3 short papers were carefully reviewed and selected from 189 submissions. The papers address topics such as: virtual reality; rendering and textures; augmented and mixed reality; video processing; image processing; fluid simulation and control; meshes and topology; visual simulation and aesthetics; human computer interaction; computer animation; geometric computing; robotics and vision; scientific visualization; and machine learning for graphics. Computers

Creating Game Environments in Blender 3D Discover how to create a simple game environment in Blender 3D, from modeling and texturing game assets, to placing them in a scene. You’ll export and import game assets as well as look at open-source game engines that will work with your game assets. Creating Game Environments in Blender 3D introduces the power of Blender 3D when creating a low poly game environment. The book starts by discussing the basics of game terminology, such as knowing the difference between low poly and high poly assets and the types of game you’re likely to work on. You’ll also take a brief look at Blender's background and installation. The following chapters talk about the process for creating a simple game environment. This is discussed in detail along with a sample project. These chapters discuss the common tools for starting a game environment and the methods for enhancing your game environment, such as color fundamentals. The final chapter shows how you can export the game assets you created in Blender, how you can import game assets in Blender, and how to evaluate the different game engines available. This book shows you the exciting side of creating a game environment while showing the power of Blender. After reading it, you will feel confident about creating a game environment. What You Will Learn Use Blender to create low poly game environments Work with the common Blender tools for game environment design and development Discover how to use Blender features in depth Compare the Eevee and Cycles game engines Who This Book Is For Game environment artists who want to use Blender 3D to create a game environment. Some previous exposure to game design and development would be helpful, but not required. Computers

Reasoning Web. Declarative Artificial Intelligence This volume contains 8 lecture notes of the 16th Reasoning Web Summer School (RW 2020), held in Oslo, Norway, in June 2020. The Reasoning Web series of annual summer schools has become the prime educational event in the field of reasoning techniques on the Web, attracting both young and established researchers. The broad theme of this year's summer school was “Declarative Artificial Intelligence†and it covered various aspects of ontological reasoning and related issues that are of particular interest to Semantic Web and Linked Data applications. The following eight lectures have been presented during the school: Introduction to Probabilistic Ontologies, On the Complexity of Learning Description Logic Ontologies, Explanation via Machine Arguing, Stream Reasoning: From Theory to Practice, First-Order Rewritability of Temporal Ontology-Mediated Queries, An Introduction to Answer Set Programming and Some of Its Extensions, Declarative Data Analysis using Limit Datalog Programs, and Knowledge Graphs: Research Directions. Computers

Computer Algebra in Scientific Computing This book constitutes the refereed proceedings of the 22nd International Workshop on Computer Algebra in Scientific Computing, CASC 2020, held in Linz, Austria, in September 2020. The conference was held virtually due to the COVID-19 pandemic.The 34 full papers presented together with 2 invited talks were carefully reviewed and selected from 41 submissions. They deal with cutting-edge research in all major disciplines of computer algebra. The papers cover topics such as polynomial algebra, symbolic and symbolic-numerical computation, applications of symbolic computation for investigating and solving ordinary differential equations, applications of CAS in the investigation and solution of celestial mechanics problems, and in mechanics, physics, and robotics. Computers

Web Information Systems Engineering – WISE 2020 This book constitutes the proceedings of the 21st International Conference on Web Information Systems Engineering, WISE 2020, held in Amsterdam, The Netherlands, in October 2020.The 81 full papers presented were carefully reviewed and selected from 190 submissions. The papers are organized in the following topical sections: Part I: network embedding; graph neural network; social network; graph query; knowledge graph and entity linkage; spatial temporal data analysis; and service computing and cloud computing Part II: information extraction; text mining; security and privacy; recommender system; database system and workflow; and data mining and applications Computers

Deployable Machine Learning for Security Defense This book constitutes selected papers from the First International Workshop on Deployable Machine Learning for Security Defense, MLHat 2020, held in August 2020. Due to the COVID-19 pandemic the conference was held online. The 8 full papers were thoroughly reviewed and selected from 13 qualified submissions. The papers are organized in the following topical sections: understanding the adversaries; adversarial ML for better security; threats on networks. Computers

Linking Sensitive Data This book provides modern technical answers to the legal requirements of pseudonymisation as recommended by privacy legislation. It covers topics such as modern regulatory frameworks for sharing and linking sensitive information, concepts and algorithms for privacy-preserving record linkage and their computational aspects, practical considerations such as dealing with dirty and missing data, as well as privacy, risk, and performance assessment measures. Existing techniques for privacy-preserving record linkage are evaluated empirically and real-world application examples that scale to population sizes are described. The book also includes pointers to freely available software tools, benchmark data sets, and tools to generate synthetic data that can be used to test and evaluate linkage techniques. This book consists of fourteen chapters grouped into four parts, and two appendices. The first part introduces the reader to the topic of linking sensitive data, the second part covers methods and techniques to link such data, the third part discusses aspects of practical importance, and the fourth part provides an outlook of future challenges and open research problems relevant to linking sensitive databases. The appendices provide pointers and describe freely available, open-source software systems that allow the linkage of sensitive data, and provide further details about the evaluations presented. A companion Web site at https://dmm.anu.edu.au/lsdbook2020 provides additional material and Python programs used in the book. This book is mainly written for applied scientists, researchers, and advanced practitioners in governments, industry, and universities who are concerned with developing, implementing, and deploying systems and tools to share sensitive information in administrative, commercial, or medical databases. The Book describes how linkage methods work and how to evaluate their performance. It covers all the major concepts and methods and also discusses practical matters such as computational efficiency, which are critical if the methods are to be used in practice - and it does all this in a highly accessible way! David J. Hand, Imperial College, London Computers

Beginning R 4 Learn how to use R 4, write and save R scripts, read in and write out data files, use built-in functions, and understand common statistical methods. This in-depth tutorial includes key R 4 features including a new color palette for charts, an enhanced reference counting system (useful for big data), and new data import settings for text (as well as the statistical methods to model text-based, categorical data). Each chapter starts with a list of learning outcomes and concludes with a summary of any R functions introduced in that chapter, along with exercises to test your new knowledge. The text opens with a hands-on installation of R and CRAN packages for both Windows and macOS. The bulk of the book is an introduction to statistical methods (non-proof-based, applied statistics) that relies heavily on R (and R visualizations) to understand, motivate, and conduct statistical tests and modeling. Beginning R 4 shows the use of R in specific cases such as ANOVA analysis, multiple and moderated regression, data visualization, hypothesis testing, and more. It takes a hands-on, example-based approach incorporating best practices with clear explanations of the statistics being done. You will: Acquire and install R and RStudio Import and export data from multiple file formats Analyze data and generate graphics (including confidence intervals) Interactively conduct hypothesis testing Code multiple and moderated regression solutions Who This Book Is For Programmers and data analysts who are new to R. Some prior experience in programming is recommended. Computers

SQL Server Data Automation Through Frameworks Learn to automate SQL Server operations using frameworks built from metadata-driven stored procedures and SQL Server Integration Services (SSIS). Bring all the power of Transact-SQL (T-SQL) and Microsoft .NET to bear on your repetitive data, data integration, and ETL processes. Do this for no added cost over what you’ve already spent on licensing SQL Server. The tools and methods from this book may be applied to on-premises and Azure SQL Server instances. The SSIS framework from this book works in Azure Data Factory (ADF) and provides DevOps personnel the ability to execute child packages outside a project—functionality not natively available in SSIS. Frameworks not only reduce the time required to deliver enterprise functionality, but can also accelerate troubleshooting and problem resolution. You'll learn in this book how frameworks also improve code quality by using metadata to drive processes. Much of the work performed by data professionals can be classified as “drudge workâ€â€”tasks that are repetitive and template-based. The frameworks-based approach shown in this book helps you to avoid that drudgery by turning repetitive tasks into "one and done" operations. Frameworks as described in this book also support enterprise DevOps with built-in logging functionality. What You Will Learn Create a stored procedure framework to automate SQL process execution Base your framework on a working system of stored procedures and execution logging Create an SSIS framework to reduce the complexity of executing multiple SSIS packages Deploy stored procedure and SSIS frameworks to Azure Data Factory environments in the cloud Who This Book Is For Database administrators and developers who are involved in enterprise data projects built around stored procedures and SQL Server Integration Services (SSIS). Readers should have a background in programming along with a desire to optimize their data efforts by implementing repeatable processes that support enterprise DevOps. Computers

Applied Informatics This book constitutes the thoroughly refereed papers of the Second International Conference on Applied Informatics, ICAI 2020, held in Ota, Nigeria, in October 2020. The 35 full papers were carefully reviewed and selected from 101 submissions. The papers are organized in topical sections on artificial intelligence; business process management; cloud computing; data analysis; decision systems; health care information systems; human-computer interaction; image processing; learning management systems; software design engineering. Computers

Statistical Learning with Math and R The most crucial ability for machine learning and data science is mathematical logic for grasping their essence rather than knowledge and experience. This textbook approaches the essence of machine learning and data science by considering math problems and building R programs. As the preliminary part, Chapter 1 provides a concise introduction to linear algebra, which will help novices read further to the following main chapters. Those succeeding chapters present essential topics in statistical learning: linear regression, classification, resampling, information criteria, regularization, nonlinear regression, decision trees, support vector machines, and unsupervised learning.Each chapter mathematically formulates and solves machine learning problems and builds the programs. The body of a chapter is accompanied by proofs and programs in an appendix, with exercises at the end of the chapter. Because the book is carefully organized to provide the solutions to the exercises in each chapter, readers can solve the total of 100 exercises by simply following the contents of each chapter. This textbook is suitable for an undergraduate or graduate course consisting of about 12 lectures. Written in an easy-to-follow and self-contained style, this book will also be perfect material for independent learning. Computers

Maschinenliebe Sexroboter sind ein Thema, das die Medien mit Vorliebe behandeln und die Gesellschaft spaltet. Es gibt einige Modelle wie Emma oder Harmony. Viel verbreiteter sind allerdings einfache Liebespuppen mit überzeugender Haut und auswechselbaren Körperöffnungen. Sie finden sich in zahlreichen Bordellen und können problemlos bei Amazon und Co. bestellt werden. Zwischen Liebespuppen und Sexrobotern sind die Grenzen fließend. Sobald Liebespuppen sprechen können oder Sensoren und Aktoren haben, werden sie zu Sexrobotern. Einzelne Varianten weisen mimische Fähigkeiten auf und können den Kopf bewegen. Das Buch erklärt Grundbegriffe, geht auf technische Details ein und diskutiert psychologische, soziologische und philosophische Erkenntnisse und Herausforderungen. Es beleuchtet die Praxis der Sexarbeit und liefert Stellungnahmen von Herstellern und Benutzern. Computers

High Performance Computing This book constitutes the refereed post-conference proceedings of 10 workshops held at the 35th International ISC High Performance 2020 Conference, in Frankfurt, Germany, in June 2020: First Workshop on Compiler-assisted Correctness Checking and Performance Optimization for HPC (C3PO); First International Workshop on the Application of Machine Learning Techniques to Computational Fluid Dynamics Simulations and Analysis (CFDML); HPC I/O in the Data Center Workshop (HPC-IODC); First Workshop \Machine Learning on HPC Systems" (MLHPCS); First International Workshop on Monitoring and Data Analytics (MODA); 15th Workshop on Virtualization in High-Performance Cloud Computing (VHPC). The 25 full papers included in this volume were carefully reviewed and selected. They cover all aspects of research, development, and application of large-scale, high performance experimental and commercial systems. Topics include high-performance computing (HPC), computer architecture and hardware, programming models, system software, performance analysis and modeling, compiler analysis and optimization techniques, software sustainability, scientific applications, deep learning. Computers

Artificial Neural Networks and Machine Learning – ICANN 2020 The proceedings set LNCS 12396 and 12397 constitute the proceedings of the 29th International Conference on Artificial Neural Networks, ICANN 2020, held in Bratislava, Slovakia, in September 2020.*The total of 139 full papers presented in these proceedings was carefully reviewed and selected from 249 submissions. They were organized in 2 volumes focusing on topics such as adversarial machine learning, bioinformatics and biosignal analysis, cognitive models, neural network theory and information theoretic learning, and robotics and neural models of perception and action. *The conference was postponed to 2021 due to the COVID-19 pandemic. Computers

HCI Outdoors Advances in network connectivity, power consumption, and physical size create new possibilities for using interactive computing outdoors. However, moving computing outdoors can drastically change the human outdoor experience. This impact is felt in many kinds of outdoor activities such as citizen science, personal recreation, search and rescue, informal education, and others. It is also felt across outdoor settings that range from remote wilderness to crowded cities. Understanding these effects can lead to ideas, designs and systems that improve, rather than diminish, outdoor experiences. This book represents the current results emerging from recent workshops focused on HCI outdoors and held in conjunction with CHI, GROUP, UbiComp, and MobileHCI conferences. Based on feedback at those workshops, and outreach to other leaders in the field, the chapters collected were crafted to highlight methods and approaches for understanding how technologies such as handhelds, wearables, and installed standalone devices impact individuals, groups, and even communities. These findings frame new ways of thinking about HCI outdoors, explore logistical issues associated with moving computing outdoors, and probe new experiences created by involving computing in outdoor pursuits. Also important are the ways that social media has influenced preparation, experience, and reflection related to outdoor experiences. HCI Outdoors: Theory, Design, Methods and Applications is of interest to HCI researchers, HCI practitioners, and outdoor enthusiasts who want to shape future understanding and current practice related to technology in every kind of outdoor experience. Computers

Pro iOS Testing Discover what tools there are for unit testing in iOS, and how to work in a test-driven environment. This book reveals how testing is a crucial capability in any iOS developer’s toolset, and a minimum requirement in iOS interviews. A few years ago, tests on mobile platforms were not very popular. It wasn’t a technical constraint, more a cultural one. But these days it’s a crucial skill set, especially when projects become big and hard to maintain. This book shows you how to set up a testing target in XCode unit tests. You'll learn how to write unit tests properly and incorporate concepts like spies and mocks and code coverage. You'll also learn the philosophy behind the architecture of UI tests, and how to mock network and DB layers in testing. Write unbreakable UI tests performance tests, as well. And learn the difference between integration tests and snapshot testing. This book will show you how to maintain code that's not only bug-free but will also remain high quality over time and maintainable while you make changes and refactors during an app's life. Testing in all its aspects is the best way of maintaining iOS projects to run fast and reliably long after you've released them. Many iOS developers working today lack an understanding of the advantages of testing, and might be unfamiliar with tools that make the job easier, such as XCTest framework. With Pro iOS Testing you'll see how to develop and test apps that work and stay working for a long time. What You'll Learn Set up a stable testing system Extend an app's lifetime with testing before release Incorporate testing into your everyday development routine Write unbreakable UI tests performance tests Understand the difference between integration tests and snapshot testing Who This Book Is For Professional iOS developers with extensive experience in the basics of building apps. Computers

Building Better PowerShell Code Learn to write better PowerShell code via short, example-driven tips. This book covers tips to make your PowerShell scripts faster and easier to read all while following proven best practices. Written by a six-time Microsoft MVP and one of the first Microsoft PowerShell MVPs with over a decade of PowerShell experience, Building Better PowerShell Code gives you easily digestible tips you can begin using immediately. The book starts with an overview of some of the most important tips the author can muster which segues into a deeper dive with dozens of examples throughout the book. It takes you through tips such as using community modules, writing better comments, thinking of PowerShell functions as building blocks, and more. You will also see how to use parameters the right way and how to create simple logging code to easily record script activity. You will learn not only how to write better code, but also how to implement some mindset tricks, such as being explicit and specific with code and how to write code that reads well. You’ll get into error handling and also how to make your scripts more secure. Finally, you’ll examine the concept of building PowerShell tools and how to build scripts for speed. Other tips and best practices include: Building Pester tests Improving performance through parallel processing Writing cross-platform scripts Using filtering properly After reading this book and applying these tips, you will have an expert coding mindset and be able to build PowerShell code that’s efficient, readable, and compliant with many best practices. What You Will Learn Implement error handling Create a logging function Use regular expressions to search strings Implement parallel processing Who This Book Is For PowerShell script developers. Computers

Hands-On Low-Code Application Development with Salesforce Explore a wide range of low-code tools in the Salesforce platform for building customized CRM applications without writing any code Key Features Create apps with a rich user experience without paying for costly developers Leverage Salesforce Lightning Platform's declarative features to build professional-grade applications Improve productivity with business process automation using Workflow, Process Builder, and Flow Book Description Low-code platforms allow users to focus on business logic to create solutions without getting trapped in programming complexities. Thanks to its powerful features for designing, developing, and deploying apps without having to hand-code, Salesforce is at the forefront of the low-code development revolution. This book will guide you in building creative applications for solving your business problems using the declarative framework provided by Salesforce. You'll start by learning how to design your business data model with custom objects, fields, formulas, and validation rules, all secured by the Salesforce security model. You'll then explore tools such as Workflow, Process Builder, Lightning Flow, and Actions that will help you to automate your business processes with ease. This book also shows you how to use Lightning App Builder to build personalized UIs for your Salesforce applications, explains the value of creating community pages for your organization, and teaches you how to customize them with Experience Builder. Finally, you'll work with the sandbox model, deploy your solutions, and deliver an effective release management strategy. By the end of this Salesforce book, you'll be ready to customize Salesforce CRM to meet your business requirements by creating unique solutions without writing a single line of code. What you will learn Get to grips with the fundamentals of data modeling to enhance data quality Deliver dynamic configuration capabilities using custom settings and metadata types Secure your data by implementing the Salesforce security model Customize Salesforce applications with Lightning App Builder Create impressive pages for your community using Experience Builder Use Data Loader to import and export data without writing any code Embrace the Salesforce Ohana culture to share knowledge and learn from the global Salesforce community Who this book is for If you are a citizen developer, business analyst, Salesforce administrator, or anyone interested in developing applications or solutions for business problems but lack technical knowledge, this book is for you. No prior programming experience is required. Computers

SwiftUI Cookbook Unleash the power of declarative programming in SwiftUI with practical recipes for building cross-platform Apple applications for iOS 14, macOS, and watchOS using Swift 5.3, Xcode 12, and SwiftUI 2.0 Key Features Apply the declarative programming paradigm for building cross-platform UIs for Apple devices Learn to integrate UIKit, Core Data, Sign in with Apple, and Firebase with SwiftUI Adopt the new SwiftUI 2.0 features to build visually appealing UIs at speed Book Description SwiftUI is an innovative and simple way to build beautiful user interfaces (UIs) for all Apple platforms, right from iOS and macOS through to watchOS and tvOS, using the Swift programming language. In this recipe-based book, you'll work with SwiftUI and explore a range of essential techniques and concepts that will help you through the development process. The recipes cover the foundations of SwiftUI as well as the new SwiftUI 2.0 features introduced in iOS 14. Other recipes will help you to make some of the new SwiftUI 2.0 components backward-compatible with iOS 13, such as the Map View or the Sign in with Apple View. The cookbook begins by explaining how to use basic SwiftUI components. Then, you'll learn the core concepts of UI development such as Views, Controls, Lists, and ScrollViews using practical implementation in Swift. By learning drawings, built-in shapes, and adding animations and transitions, you'll discover how to add useful features to the SwiftUI. When you're ready, you'll understand how to integrate SwiftUI with exciting new components in the Apple development ecosystem, such as Combine for managing events and Core Data for managing app data. Finally, you'll write iOS, macOS, and watchOS apps while sharing the same SwiftUI codebase. By the end of this SwiftUI book, you'll have discovered a range of simple, direct solutions to common problems found in building SwiftUI apps. What you will learn Explore various layout presentations in SwiftUI such as HStack, VStack, LazyHStack, and LazyVGrid Create a cross-platform app for iOS, macOS, and watchOS Get up to speed with drawings in SwiftUI using built-in shapes, custom paths, and polygons Discover modern animation and transition techniques in SwiftUI Add user authentication using Firebase and Sign in with Apple Handle data requests in your app using Core Data Solve the most common SwiftUI problems, such as integrating a MapKit map, unit testing, snapshot testing, and previewing layouts Who this book is for This book is for mobile developers who want to learn SwiftUI as well as experienced iOS developers transitioning from UIKit to SwiftUI. The book assumes knowledge of the Swift programming language. Knowledge of object-oriented design and data structures is useful but not necessary. Computers

Artificial Intelligence and Soft Computing The two-volume set LNCS 12415 and 12416 constitutes the refereed proceedings of of the 19th International Conference on Artificial Intelligence and Soft Computing, ICAISC 2020, held in Zakopane, Poland*, in October 2020.The 112 revised full papers presented were carefully reviewed and selected from 265 submissions. The papers included in the first volume are organized in the following six parts: ​neural networks and their applications; fuzzy systems and their applications; evolutionary algorithms and their applications; pattern classification; bioinformatics, biometrics and medical applications; artificial intelligence in modeling and simulation.The papers included in the second volume are organized in the following four parts: computer vision, image and speech analysis; data mining; various problems of artificial intelligence; agent systems, robotics and control. *The conference was held virtually due to the COVID-19 pandemic. Computers

Cellular Automata and Discrete Complex Systems This volume constitutes the refereed post-conference proceedings of the 26th IFIP WG 1.5 International Workshop on Cellular Automata and Discrete Complex Systems, AUTOMATA 2020, held in Stockholm, Sweden, in August 2020. The workshop was held virtually.The 11 full papers presented in this book were carefully reviewed and selected from a total of 21 submissions. The topics of the conference include dynamical, topological, ergodic and algebraic aspects of CA and DCS, algorithmic and complexity issues, emergent properties, formal languages, symbolic dynamics, tilings, models of parallelism and distributed systems, timing schemes, synchronous versus asynchronous models, phenomenological descriptions, scientific modeling, and practical applications. Computers

Disinformation in Open Online Media This book constitutes the refereed proceedings of the Second Multidisciplinary International Symposium, MISDOOM 2020, held in Leiden, The Netherlands, in October 2020.* The 18 full papers were carefully reviewed and selected from 23 submissions. The papers deal with the interdisciplinary field of computational social science, and in particular with the automated detection and combat of misinformation using modern techniques from machine learning, text mining, and social network analysis. * The conference was held virtually due to the COVID-19 pandemic. Chapters “Identifying Political Sentiments on YouTube: A Systematic Comparison regarding the Accuracy of Recurrent Neural Network and Machine Learning Models†and “Do Online Trolling Strategies Differ in Political and Interest Forums: Early Results†are available open access under a Creative Commons Attribution 4.0 International License via link.springer.com. Computers

Web Information Systems Engineering – WISE 2020 This book constitutes the proceedings of the 21st International Conference on Web Information Systems Engineering, WISE 2020, held in Amsterdam, The Netherlands, in October 2020.The 81 full papers presented were carefully reviewed and selected from 190 submissions. The papers are organized in the following topical sections: Part I: network embedding; graph neural network; social network; graph query; knowledge graph and entity linkage; spatial temporal data analysis; and service computing and cloud computing Part II: information extraction; text mining; security and privacy; recommender system; database system and workflow; and data mining and applications Computers

Artificial Intelligence and Soft Computing The two-volume set LNCS 12415 and 12416 constitutes the refereed proceedings of of the 19th International Conference on Artificial Intelligence and Soft Computing, ICAISC 2020, held in Zakopane, Poland*, in October 2020.The 112 revised full papers presented were carefully reviewed and selected from 265 submissions. The papers included in the first volume are organized in the following six parts: ​neural networks and their applications; fuzzy systems and their applications; evolutionary algorithms and their applications; pattern classification; bioinformatics, biometrics and medical applications; artificial intelligence in modeling and simulation.The papers included in the second volume are organized in the following four parts: computer vision, image and speech analysis; data mining; various problems of artificial intelligence; agent systems, robotics and control. *The conference was held virtually due to the COVID-19 pandemic. Computers

Machine Learning for Medical Image Reconstruction This book constitutes the refereed proceedings of the Third International Workshop on Machine Learning for Medical Reconstruction, MLMIR 2020, held in conjunction with MICCAI 2020, in Lima, Peru, in October 2020. The workshop was held virtually. The 15 papers presented were carefully reviewed and selected from 18 submissions. The papers are organized in the following topical sections: deep learning for magnetic resonance imaging and deep learning for general image reconstruction. Computers

Decidability of Logical Theories and Their Combination This textbook provides a self-contained introduction to decidability of first-order theories and their combination. The technical material is presented in a systematic and universal way and illustrated with plenty of examples and a range of proposed exercises. After an overview of basic first-order logic concepts, the authors discuss some model-theoretic notions like embeddings, diagrams, and elementary substructures. The text then goes on to explore an applicable way to deduce logical consequences from a given theory and presents sufficient conditions for a theory to be decidable. The chapters that follow focus on quantifier elimination, decidability of the combination of first-order theories and the basics of computability theory. The inclusion of a chapter on Gentzen calculus, cut elimination, and Craig interpolation, as well as a chapter on combination of theories and preservation of decidability, help to set this volume apart from similar books in the field. Decidability of Logical Theories and their Combination is ideal for graduate students of Mathematics and is equally suitable for Computer Science, Philosophy and Physics students who are interested in gaining a deeper understanding of the subject. The book is also directed to researchers that intend to get acquainted with first-order theories and their combination. Computers

Disney Stories The second edition of Disney Stories: Getting to Digital will be of interest to lovers of Disney history and also to lovers of Hollywood history in general. The first edition was planned as a short history of the companies evolution from analog storytelling to a digital online presence that closed the chapter on early Disney films with the release of the groundbreaking Snow White. The purpose of the new edition is to bring to readers a more complete view of the analog-digital story by including three new chapters on film that cover key developments from the live-animation hybrids of the 1940s to CAPS and CGI in the 1990s and VR in the 2010s. It also includes in the discussion of cross-media storytelling the acquisition of the exceptional story property, Star Wars, and discusses how Disney has brought the epic into the Disney Master Narrative by creating Galaxy’s Edge in its US theme parks. Krystina Madej’s engaging portrayal of the long history of Disney’s love affair with storytelling and technology brings to life the larger focus of innovation in creating characters and stories that captivate an audience, and together with Newton Lee’s detailed experience of Disney during the crucial 1995-2005 era when digital innovation in online and games was at its height in the company, makes for a fast-paced captivating read. Disney Stories first edition explored the history of Disney, both analog and digital. It described in detail how Walt Disney used inventive and often ground-breaking approaches in the use of sound, color, depth, and the psychology of characters to move the animation genre from short visual gags to feature-length films with meaningful stories that engaged audience's hearts as well as tickled their funny bones. It showed Walt’s comprehensive approach to engaging the public across all media as he built the Disney Master Narrative by using products, books, comics, public engagements, fan groups such as the Mickey Mouse club, TV, and, of course, Disneyland, his theme park. Finally it showed how, after his passing, the company continued to embrace Walt’s enthusiasm for using new technology to engage audiences through their commitment to innovation in digital worlds. It describes in detail the innovative storybook CD-ROMs, their extensive online presence, the software they used and created for MMORGs such as Toontown, and the use of production methods such as agile methodology. This new edition provides insight on major developments in Disney films that moved them into the digital world. Computers

Structure And Randomness In Computability And Set Theory This volume presents some exciting new developments occurring on the interface between set theory and computability as well as their applications in algebra, analysis and topology. These include effective versions of Borel equivalence, Borel reducibility and Borel determinacy. It also covers algorithmic randomness and dimension, Ramsey sets and Ramsey spaces. Many of these topics are being discussed in the NSF-supported annual Southeastern Logic Symposium. Computers

Practical AI on the Google Cloud Platform Working with AI is complicated and expensive for many developers. That's why cloud providers have stepped in to make it easier, offering free (or affordable) state-of-the-art models and training tools to get you started. With this book, you'll learn how to use Google's AI-powered cloud services to do everything from creating a chatbot to analyzing text, images, and video. Author Micheal Lanham demonstrates methods for building and training models step-by-step and shows you how to expand your models to accomplish increasingly complex tasks. If you have a good grasp of math and the Python language, you'll quickly get up to speed with Google Cloud Platform, whether you want to build an AI assistant or a simple business AI application. Learn key concepts for data science, machine learning, and deep learning Explore tools like Video AI and AutoML Tables Build a simple language processor using deep learning systems Perform image recognition using CNNs, transfer learning, and GANs Use Google's Dialogflow to create chatbots and conversational AI Analyze video with automatic video indexing, face detection, and TensorFlow Hub Build a complete working AI agent application Computers

Parallel Processing, 1980 to 2020 This historical survey of parallel processing from 1980 to 2020 is a follow-up to the authors’ 1981 Tutorial on Parallel Processing, which covered the state of the art in hardware, programming languages, and applications. Here, we cover the evolution of the field since 1980 in: parallel computers, ranging from the Cyber 205 to clusters now approaching an exaflop, to multicore microprocessors, and Graphic Processing Units (GPUs) in commodity personal devices; parallel programming notations such as OpenMP, MPI message passing, and CUDA streaming notation; and seven parallel applications, such as finite element analysis and computer vision. Some things that looked like they would be major trends in 1981, such as big Single Instruction Multiple Data arrays disappeared for some time but have been revived recently in deep neural network processors. There are now major trends that did not exist in 1980, such as GPUs, distributed memory machines, and parallel processing in nearly every commodity device. This book is intended for those that already have some knowledge of parallel processing today and want to learn about the history of the three areas. In parallel hardware, every major parallel architecture type from 1980 has scaled-up in performance and scaled-out into commodity microprocessors and GPUs, so that every personal and embedded device is a parallel processor. There has been a confluence of parallel architecture types into hybrid parallel systems. Much of the impetus for change has been Moore’s Law, but as clock speed increases have stopped and feature size decreases have slowed down, there has been increased demand on parallel processing to continue performance gains. In programming notations and compilers, we observe that the roots of today’s programming notations existed before 1980. And that, through a great deal of research, the most widely used programming notations today, although the result of much broadening of these roots, remain close to target system architectures allowing the programmer to almost explicitly use the target’s parallelism to the best of their ability. The parallel versions of applications directly or indirectly impact nearly everyone, computer expert or not, and parallelism has brought about major breakthroughs in numerous application areas. Seven parallel applications are studied in this book. Computers

Security and Privacy in Digital Economy This book constitutes the refereed proceedings of the First International Conference on Security and Privacy in Digital Economy, SPDE 2020, held in Quzhou, China, in October 2020*. The 49 revised full papers and 2 short papers were carefully reviewed and selected from 132 submissions. The papers are organized in topical sections: ​cyberspace security, privacy protection, anomaly and intrusion detection, trust computation and forensics, attacks and countermeasures, covert communication, security protocol, anonymous communication, security and privacy from social science. *The conference was held virtually due to the COVID-19 pandemic. Computers

Emotion and Information Processing This book consists of thirteen chapters covering many facts like psycho-social intervention on emotional disorders in individuals, impact of emotion and cognition on blended theory, theory and implication of information processing, effects of emotional self esteem in women, emotional dimension of women in workplace, effects of mental thinking in different age groups irrespective of the gender, negative emotions and its effect on information processing, role of emotions in education and lastly emotional analysis in multi perspective domain adopting machine learning approach. Most of the chapters having experimental studies, with each experiment having different constructs as well as different samples for each data collection. Most of the studies measure information processing within altered mood states, such as depression, anxiety, or positive emotional states, with mental ability tasks being conducted in addition to the experiments of quasi-experimental design. Computers

Essential Excel 2019 Create, edit, sort, analyze, summarize, and format data as well as graph it in Excel 2019. Chock full of visuals, user-friendly instructions, and reader exercises, this in-depth guide makes it easy for you to get on the bandwagon taking advantage of this powerful software and what it can do. Essential Excel 2019 doesn’t mess around. It provides the most clear and concise, but complete, information you need to successfully use the expansive features of Excel in your work environment. The second edition of this soup-to-nuts book delivers essential how-to and reference information for users who are new to Excel, those who want to continue building their Excel skills, or anyone who wants to get up to speed on the latest changes and features in Excel 2019. It is heavy on the practical examples and light on the theory, providing a step-by-step process of what you need to do when you are working with Excel. You will begin with the basics, advancing as each chapter builds on knowledge from previous chapters. You will appreciate real-life examples and exercises that reinforce what you have learned, and upon finishing the book, you will have the confidence to use much more than the typical 10% that most people use in Excel. What You Will Learn Create amazing visualizations of your data Get up to speed on easy and accurate methods for entering data Extract the information you want from imported data; manipulate and format it to meet your needs Export your results to other programs or share with others in the cloud Organize, summarize, filter, and consolidate your data in multiple ways Audit, validate, and protect your data Who This Book Is For Anyone new to Excel or looking to take better advantage of the advanced features of the platform Computers

Digital SLR Photography All-in-One For Dummies 6 Books in one! Boost your DSLR photography skills with this amazing book When you're investing in top-notch camera equipment, it's also time to build top-notch photography skills that help you create the stunning images you see in your mind. This book gets you started on the path to capturing incredible photos of life's most precious moments. Cut through the jargon and techspeak as you get down to the essentials of taking control of your powerful camera and leaving the days of washed-out and blurry photos behind. 6 Books Inside… Review digital photography basics and camera controls Get the right lens for the shot Take creative control of exposure settings Shed some light on your subject Perfect the picture with editing Follow recipes for portraits, landscapes, close-ups, and action shots Computers

Ubuntu Linux Bible The best reference for Ubuntu Linux Ubuntu Linux is a popular, powerful, and versatile operating system. Now you can get the most out of everything Ubuntu Linux has to offer with the Ubuntu Linux Bible. This complete and comprehensive guide introduces you to Ubuntu and shows you how to use it to its fullest, whether you're a typical desktop user or a system administrator. You'll learn to do everything from reading email to configuring wireless networks. You'll reap huge rewards from this book, regardless of how much prior experience you have with Ubuntu. Get started with Ubuntu Linux and see what's in the newest version (20.04) Learn how to read emails, surf the web, and create and publish documents Take on system administration tasks, like creating and managing users and adding new disks to the system Discover how to use Ubuntu Linux in an enterprise or personal environment Figure out how to set up Ubuntu Linux servers for the web, email, shared printing, and more Find out why Ubuntu Linux is the most popular Linux operating system in the world Computers

An Introduction To Artificial Intelligence An authoritative and accessible one-stop resource, An Introduction to Artificial Intelligence presents the first full examination of AI. Designed to provide an understanding of the foundations of artificial intelligence, it examines the central computational techniques employed by AI, including knowledge representation, search, reasoning, and learning, as well as the principal application domains of expert systems, natural language, vision, robotics, software agents and cognitive modeling. Many of the major philosophical and ethical issues of AI are also introduced. Throughout the volume, the authors provide detailed, well-illustrated treatments of each topic with abundant examples and exercises. The authors bring this exciting field to life by presenting a substantial and robust introduction to artificial intelligence in a clear and concise coursebook form. This book stands as a core text for all computer scientists approaching AI for the first time. Computers

Teach Yourself VISUALLY Chromebook Teach yuorself VISUALLYTM Are you a visual learner? Do you prefer instructions that show you how to do something — and skip the long-winded explanations? If so, then this book is for you. Open it up and you'll find clear, step-by-step screen shots that show you how to tackle the most useful Chromebook tasks. Each task-based spread covers a single technique, sure to help you get up and running on your Chromebook in no time. You'll learn to: Set up your Chromebook from Scratch Configure Chrome OS to work your way Connect your Android phone Enjoy email, chat, and video chat Master your schedule and tasks Designed for visual learners Two-page lessons break big topics into bite-sized modules Succinct explanations walk you through step by step Full-color screen shots demonstrate each task Helpful sidebars offer practical tips and tricks Computers

Swarm Intelligence This book constitutes the proceedings of the 12th International Conference on Swarm Intelligence, ANTS 2020, held online -due to COVID-19- in Barcelona Spain, in October 2020. The 20 full papers presented , together with 8 short papers and 5 extended abstracts were carefully reviewed and selected from 50 submissions. ANTS 2020 contributions are dealing with any aspect of swarm intelligence. Computers

Advances in Design and Digital Communication This book reports on research findings and practical lessons featuring advances in: digital and interaction design; graphic design and branding; design strategies and methodologies; design education; society and communication in design practice; and other related areas. Gathering the proceedings of the 4th International Conference on Digital Design and Communication, Digicom 2020, held virtually on November 5-6, 2020, the book describes cutting-edge perspectives on and analysis of and solutions to challenges digital communication is currently presenting to society, institutions and brands. It offers a timely guide and a source of inspiration for designers of all kinds, including graphic, digital and web designers, UI, UX and social media designers, and to researchers, advertisers, artists, and entrepreneurs, as well as brand or corporate communication managers. Computers

Hands-On SQL Server 2019 Analysis Services Get up to speed with the new features added to Microsoft SQL Server 2019 Analysis Services and create models to support your businessKey FeaturesExplore tips and tricks to design, develop, and optimize end-to-end data analytics solutions using Microsoft's technologiesLearn tabular modeling and multi-dimensional cube design development using real-world examplesImplement Analysis Services to help you make productive business decisionsBook DescriptionSQL Server Analysis Services (SSAS) continues to be a leading enterprise-scale toolset, enabling customers to deliver data and analytics across large datasets with great performance. This book will help you understand MS SQL Server 2019's new features and improvements, especially when it comes to SSAS.First, you'll cover a quick overview of SQL Server 2019, learn how to choose the right analytical model to use, and understand their key differences. You'll then explore how to create a multi-dimensional model with SSAS and expand on that model with MDX. Next, you'll create and deploy a tabular model using Microsoft Visual Studio and Management Studio. You'll learn when and how to use both tabular and multi-dimensional model types, how to deploy and configure your servers to support them, and design principles that are relevant to each model. The book comes packed with tips and tricks to build measures, optimize your design, and interact with models using Excel and Power BI. All this will help you visualize data to gain useful insights and make better decisions. Finally, you'll discover practices and tools for securing and maintaining your models once they are deployed.By the end of this MS SQL Server book, you'll be able to choose the right model and build and deploy it to support the analytical needs of your business.What you will learnDetermine the best analytical model using SSASCover the core aspects involved in MDX, including writing your first queryImplement calculated tables and calculation groups (new in version 2019) in DAXCreate and deploy tabular and multi-dimensional models on SQL 2019Connect and create data visualizations using Excel and Power BIImplement row-level and other data security methods with tabular and multi-dimensional modelsExplore essential concepts and techniques to scale, manage, and optimize your SSAS solutionsWho this book is forThis Microsoft SQL Server book is for BI professionals and data analysts who are looking for a practical guide to creating and maintaining tabular and multi-dimensional models using SQL Server 2019 Analysis Services. A basic working knowledge of BI solutions such as Power BI and database querying is required. Computers

Microsoft SharePoint Server 2019 and SharePoint Hybrid Administration Manage your Microsoft 365 workloads between SharePoint Server and SharePoint Online using the SharePoint Hybrid configuration Key Features Explore the collaborative features of SharePoint Server technologies using expert techniques Migrate your Microsoft 365 workload and Teamwork services to SharePoint Online using a hybrid configuration Learn how to map traditional Microsoft services to a cloud service model Book Description SharePoint Server is an on-premises collaboration and business productivity platform. It serves as a content management and web services platform, enabling users to create, publish, and discover content and applications and integrate with business systems. This SharePoint book offers complete, up-to-date coverage of the SharePoint Server 2019 interface to help you configure and deploy confidently from the start. With the help of clear and succinct explanations and expert tips, this book covers SharePoint Server and SharePoint Hybrid configuration as well as the process for migrating to Microsoft SharePoint Online. As the book takes you through strategies and techniques for configuring and managing SharePoint on-premises and hybrid scenarios, you'll get to grips with the concepts essential for SharePoint deployments, such as authentication, Business Connectivity Services, and the data gateway. You'll also explore migration methods and strategies. By the end of this book, you'll have learned the fundamentals of deploying SharePoint Server 2019 and be able to use this reference guide for your administration tasks. What you will learn Understand how SharePoint Server technologies enable you to collaborate Deploy and configure SharePoint Server 2019 Configure and manage SharePoint site collections Manage data migration with SharePoint's migration tools Explore Business Connectivity Services (BCS) for working with external data sources Get to grips with the different types of authentication available in the SharePoint ecosystem Who this book is for Microsoft SharePoint Server 2019 and SharePoint Hybrid Administration is targeted at entry-level SharePoint Server administrators who want to learn how to deploy and manage SharePoint farms, service applications, and connected data services. Computers

Cloud Computing, Big Data & Emerging Topics This book constitutes the revised selected papers of the 8th International Conference on Cloud Computing, Big Data & Emerging Topics, JCC-BD&ET 2020, held in La Plata, Argentina*, in September 2020.The 11 full papers presented were carefully reviewed and selected from a total of 36 submissions. The papers are organized in topical sections of cloud computing and HPC; Big Data and machine and deep learning. *The conference was held virtually due to the COVID-19 pandemic. Computers

Open Semantic Technologies for Intelligent System This book constitutes the refereed proceedings of the 10th International Conference on Open Semantic Technologies for Intelligent System, OSTIS 2020, held in Minsk, Belarus, in February 2020. The 14 revised full papers and 2 short papers were carefully reviewed and selected from 62 submissions. The papers mainly focus on standardization of intelligent systems and cover wide research fields including knowledge representation and reasoning, semantic networks, natural language processing, temporal reasoning, probabilistic reasoning, multi-agent systems, intelligent agents. Computers

Learn Rails 6 Effectively learn and apply software development and engineering techniques to web application development using Rails 6 with this accelerated tutorial. This book teaches modern engineering practices including git flow, containerization, debugging, testing, and deployment. Along the way, you’ll see how to build a social network application and then deploy it on a cloud provider such as Amazon Web Services. After reading and using this book, you'll be able to effectively build and deploy your Rails application to the cloud. You’ll also have used the Ruby on Rails framework to carry out the rapid development of an idea into a product without sacrificing quality. What You Will Learn Use the Ruby on Rails 6 web development framework Integrate Docker with your Ruby on Rails code Apply software engineering techniques to learning the Rails framework Design, build, and deploy a social networking application to the Amazon cloud Who This Book Is For Beginners with at least some prior programming experience. Ruby experience is helpful, but not required. Computers

Practical Python Data Visualization Quickly start programming with Python 3 for data visualization with this step-by-step, detailed guide. This book’s programming-friendly approach using libraries such as leather, NumPy, Matplotlib, and Pandas will serve as a template for business and scientific visualizations. You’ll begin by installing Python 3, see how to work in Jupyter notebook, and explore Leather, Python’s popular data visualization charting library. You’ll also be introduced to the scientific Python 3 ecosystem and work with the basics of NumPy, an integral part of that ecosystem. Later chapters are focused on various NumPy routines along with getting started with Scientific Data visualization using matplotlib. You’ll review the visualization of 3D data using graphs and networks and finish up by looking at data visualization with Pandas, including the visualization of COVID-19 data sets. The code examples are tested on popular platforms like Ubuntu, Windows, and Raspberry Pi OS. With Practical Python Data Visualization you’ll master the core concepts of data visualization with Pandas and the Jupyter notebook interface. What You'll Learn Review practical aspects of Python Data Visualization with programming-friendly abstractions Install Python 3 and Jupyter on multiple platforms including Windows, Raspberry Pi, and Ubuntu Visualize COVID-19 data sets with Pandas Who This Book Is For Data Science enthusiasts and professionals, Business analysts and managers, software engineers, data engineers. Computers

Windows Subsystem for Linux 2 (WSL 2) Tips, Tricks, and Techniques A practical handbook that will help you bridge the gap between Windows and Linux to develop apps that leverage the best features across both ecosystems with seamless interoperability Key Features Configure and control WSL to suit your needs and preferences Discover tips for working seamlessly between Windows and WSL Linux distros Learn how to work effectively with containers in WSL, as well as how to containerize your development environments with Visual Studio Code to isolate your dependencies Book Description Windows Subsystem for Linux (WSL) allows you to run native Linux tools alongside traditional Windows applications. Whether you're developing applications across multiple operating systems or looking to add more tools to your Windows environment, WSL offers endless possibilities. You'll start by understanding what WSL is and learn how to install and configure WSL along with different Linux distros. Next, you'll learn techniques that allow you to work across both Windows and Linux environments. You'll discover how to install and customize the new Windows Terminal. We'll also show you how to work with code in WSL using Visual Studio Code (VS Code). In addition to this, you'll explore how to work with containers with Docker and Kubernetes, and how to containerize a development environment using VS Code. While Microsoft has announced support for GPU and GUI applications in an upcoming release of WSL, at the time of writing these features are either not available or only in early preview releases. This book focuses on the stable, released features of WSL and giving you a solid understanding of the amazing techniques that you can use with WSL today. By the end of this book, you'll be able to configure WSL and Windows Terminal to suit your preferences, and productively use Visual Studio Code for developing applications with WSL. What you will learn Install and configure Windows Subsystem for Linux and Linux distros Access web applications running in Linux from Windows Invoke Windows applications, file systems, and environment variables from bash in WSL Customize the appearance and behavior of the Windows Terminal to suit your preferences and workflows Explore various tips for enhancing the Visual Studio Code experience with WSL Install and work with Docker and Kubernetes within Windows Subsystem for Linux Discover various productivity tips for working with Command-line tools in WSL Who this book is for This book is for developers who want to use Linux tools on Windows, including Windows-native programmers looking to ease into a Linux environment based on project requirements or Linux developers who've recently switched to Windows. This book is also for web developers working on open source projects with Linux-first tools such as Ruby or Python, or developers looking to switch between containers and development machines for testing apps. Prior programming or development experience and a basic understanding of running tasks in bash, PowerShell, or the Windows Command Prompt will be required. Computers

Hands-On Vision and Behavior for Self-Driving Cars A practical guide to learning visual perception for self-driving cars for computer vision and autonomous system engineers Key Features Explore the building blocks of the visual perception system in self-driving cars Identify objects and lanes to define the boundary of driving surfaces using open-source tools like OpenCV and Python Improve the object detection and classification capabilities of systems with the help of neural networks Book Description The visual perception capabilities of a self-driving car are powered by computer vision. The work relating to self-driving cars can be broadly classified into three components - robotics, computer vision, and machine learning. This book provides existing computer vision engineers and developers with the unique opportunity to be associated with this booming field. You will learn about computer vision, deep learning, and depth perception applied to driverless cars. The book provides a structured and thorough introduction, as making a real self-driving car is a huge cross-functional effort. As you progress, you will cover relevant cases with working code, before going on to understand how to use OpenCV, TensorFlow and Keras to analyze video streaming from car cameras. Later, you will learn how to interpret and make the most of lidars (light detection and ranging) to identify obstacles and localize your position. You'll even be able to tackle core challenges in self-driving cars such as finding lanes, detecting pedestrian and crossing lights, performing semantic segmentation, and writing a PID controller. By the end of this book, you'll be equipped with the skills you need to write code for a self-driving car running in a driverless car simulator, and be able to tackle various challenges faced by autonomous car engineers. What you will learn Understand how to perform camera calibration Become well-versed with how lane detection works in self-driving cars using OpenCV Explore behavioral cloning by self-driving in a video-game simulator Get to grips with using lidars Discover how to configure the controls for autonomous vehicles Use object detection and semantic segmentation to locate lanes, cars, and pedestrians Write a PID controller to control a self-driving car running in a simulator Who this book is for This book is for software engineers who are interested in learning about technologies that drive the autonomous car revolution. Although basic knowledge of computer vision and Python programming is required, prior knowledge of advanced deep learning and how to use sensors (lidar) is not needed. Computers

Data Engineering with Python Build, monitor, and manage real-time data pipelines to create data engineering infrastructure efficiently using open-source Apache projects Key Features Become well-versed in data architectures, data preparation, and data optimization skills with the help of practical examples Design data models and learn how to extract, transform, and load (ETL) data using Python Schedule, automate, and monitor complex data pipelines in production Book Description Data engineering provides the foundation for data science and analytics, and forms an important part of all businesses. This book will help you to explore various tools and methods that are used for understanding the data engineering process using Python. The book will show you how to tackle challenges commonly faced in different aspects of data engineering. You'll start with an introduction to the basics of data engineering, along with the technologies and frameworks required to build data pipelines to work with large datasets. You'll learn how to transform and clean data and perform analytics to get the most out of your data. As you advance, you'll discover how to work with big data of varying complexity and production databases, and build data pipelines. Using real-world examples, you'll build architectures on which you'll learn how to deploy data pipelines. By the end of this Python book, you'll have gained a clear understanding of data modeling techniques, and will be able to confidently build data engineering pipelines for tracking data, running quality checks, and making necessary changes in production. What you will learn Understand how data engineering supports data science workflows Discover how to extract data from files and databases and then clean, transform, and enrich it Configure processors for handling different file formats as well as both relational and NoSQL databases Find out how to implement a data pipeline and dashboard to visualize results Use staging and validation to check data before landing in the warehouse Build real-time pipelines with staging areas that perform validation and handle failures Get to grips with deploying pipelines in the production environment Who this book is for This book is for data analysts, ETL developers, and anyone looking to get started with or transition to the field of data engineering or refresh their knowledge of data engineering using Python. This book will also be useful for students planning to build a career in data engineering or IT professionals preparing for a transition. No previous knowledge of data engineering is required. Computers

CompTIA PenTest+ Certification For Dummies Prepare for the CompTIA PenTest+ certification CompTIA's PenTest+ Certification is an essential certification to building a successful penetration testing career. Test takers must pass an 85-question exam to be certified, and this book—plus the online test bank—will help you reach your certification goal. CompTIA PenTest+ Certification For Dummies includes a map to the exam’s objectives and helps you get up to speed on planning and scoping, information gathering and vulnerability identification, attacks and exploits, penetration testing tools and reporting, and communication skills. Pass the PenTest+ Certification exam and grow as a Pen Testing professional Learn to demonstrate hands-on ability to Pen Test Practice with hundreds of study questions in a free online test bank Find test-taking advice and a review of the types of questions you'll see on the exam Get ready to acquire all the knowledge you need to pass the PenTest+ exam and start your career in this growing field in cybersecurity! Computers

Knowledge Engineering and Knowledge Management This book constitutes the refereed proceedings of the 22nd International Conference on Knowledge Engineering and Knowledge Management, EKAW 2020, held in Bolzano, Italy, in September 2020. The 12 full papers presented together with 7 were carefully reviewed and selected from 104 submissions. The special theme of EKAW 2020 is „Ethical and Trustworthy Knowledge Engineering". The papers cover all aspects of eliciting, acquiring, discovering, modeling, and managing knowledge and construction of knowledge-intensive systems. Computers

Leveraging Applications of Formal Methods, Verification and Validation The three-volume set LNCS 12476 - 12478 constitutes the refereed proceedings of the 9th International Symposium on Leveraging Applications of Formal Methods, ISoLA 2020, which was planned to take place during October 20–30, 2020, on Rhodes, Greece. The event itself was postponed to 2021 due to the COVID-19 pandemic. The papers presented were carefully reviewed and selected for inclusion in the proceedings. Each volume focusses on an individual topic with topical section headings within the volume: Part I, Verification Principles: Modularity and (De-)Composition in Verification; X-by-Construction: Correctness meets Probability; 30 Years of Statistical Model Checking; Verification and Validation of Concurrent and Distributed Systems. Part II, Engineering Principles: Automating Software Re-Engineering; Rigorous Engineering of Collective Adaptive Systems. Part III, Applications: Reliable Smart Contracts: State-of-the-art, Applications, Challenges and Future Directions; Automated Verification of Embedded Control Software; Formal methods for DIStributed COmputing in future RAILway systems. Computers

Leveraging Applications of Formal Methods, Verification and Validation The three-volume set LNCS 12476 - 12478 constitutes the refereed proceedings of the 9th International Symposium on Leveraging Applications of Formal Methods, ISoLA 2020, which was planned to take place during October 20–30, 2020, on Rhodes, Greece. The event itself was postponed to 2021 due to the COVID-19 pandemic. The papers presented were carefully reviewed and selected for inclusion in the proceedings. Each volume focusses on an individual topic with topical section headings within the volume: Part I, Verification Principles: Modularity and (De-)Composition in Verification; X-by-Construction: Correctness meets Probability; 30 Years of Statistical Model Checking; Verification and Validation of Concurrent and Distributed Systems. Part II, Engineering Principles: Automating Software Re-Engineering; Rigorous Engineering of Collective Adaptive Systems. Part III, Applications: Reliable Smart Contracts: State-of-the-art, Applications, Challenges and Future Directions; Automated Verification of Embedded Control Software; Formal methods for DIStributed COmputing in future RAILway systems. Computers

Virtual Reality and Augmented Reality This book constitutes the refereed proceedings of the 17th International Conference on Virtual Reality and Augmented Reality, EuroVR 2020, held in Valencia, Spain, in November 2020. The 12 full papers were carefully reviewed and selected from 35 submissions. The papers are organized in topical sections named: Perception, Cognition and Behaviour; Training, Teaching and Learning; Tracking and Rendering; and Scientific Posters. Computers

Interactive Storytelling This book constitutes the refereed proceedings of the 13th International Conference on Interactive Digital Storytelling, ICIDS 2020, held in Bournemouth, UK, in November 2020. The 15 full papers and 8 short papers presented together with 5 posters, were carefully reviewed and selected from 70 submissions. The conference offers topics in game narrative and interactive storytelling, including the theoretical, technological, and applied design practices, narrative systems, storytelling technology, and humanities-inspired theoretical inquiry, empirical research and artistic expression. Computers

Guide to Flow-Aware Networking The book presents a comprehensive view on Flow-Aware Networking. It starts with a brief overview of the known QoS architectures based on the concept of a flow. Then, the original FAN concept is presented, along with its variations proposed by the authors. The next chapter covers a very valuable feature of the FAN architecture, namely its ability to assure net neutrality. The chapters that follow will discuss, in detail, a variety of issues making the FAN concept implementable, including congestion control, fairness, resilience to failures, service differentiation and degradation. The final chapter presents the test implementation of the FAN router, including the environment used and performance tests. Chapters are supplemented with problems to solve, along with their solutions. The pedagogical character of the book is supported by a number of illustrative examples contained in most of the chapters. At the end of the book, a glossary of the key terms is included, along with a comprehensive bibliography. Flow-based traffic management is currently becoming a mainstream. There is plenty of Quality of Service (QoS) techniques based on flows. Software-Defined Networking with its dominant protocol OpenFlow also follows this trend. Flow-Aware Networking (FAN) is a promising QoS architecture. Information on FAN can be found in various research papers. It is, therefore highly scattered. This book gathers practically all relevant information regarding FAN and puts it together. Quality of Service assurance is one of the key challenges of today’s Internet. The existing approaches to provide QoS do not meet expectations of network operators, managers and users although numerous efforts in this area have been reported. One of the most promising concepts is the Flow-Aware Network (FAN). FAN can play a key role in assuring the net neutrality, smoothly combining interests of all the involved parties. The authors of the proposal have been involved in FAN research practically since its inception at the start of the 21st century. The book reports the wide experiences the authors accumulated in the subject area during the work on common FAN-related projects conducted with the team of James Roberts that proposed the original FAN concept as well as other leading research groups in Europe and the USA. One of the aims of the book is to accompany courses taught by the authors. Computers

Essential C# 8.0 The Comprehensive, Expert Guide to C# 8.0 for Programmers at All Levels “Welcome to one of the most venerable and trusted franchises you could dream of in the world of C# books—and probably far beyond! . . . Mark is super smart, insists on understanding everything to the core, and has phenomenal insight into how things affect real developers. . . . He goes right to the essence and communicates with great integrity—no sugarcoating—and has a keen eye for practical value and real-world problems.†— From the Foreword by Mads Torgersen, C# Lead Designer, Microsoft Essential C# 8.0 is a well-organized, no-fluff guide to C# 8.0 for programmers at all levels of experience. This edition retains all the valuable content of prior editions and adds discussions of null reference types, indices and ranges, enhanced pattern matching, asynchronous stream, and more. World-class C# expert Mark Michaelis presents a comprehensive tutorial and reference for the entire language, providing an accelerated learning opportunity to achieve expert C# programming skills. He includes key C# 8.0 enhancements, succinct examples to illustrate central constructs, and updated coding guidelines for minimizing bugs and writing code that’s easier to evolve. To help you quickly fi nd what you need, there are version-specific indexes of C# 6.0, 7.0, and 8.0 topics and visual icons that identify when each language innovation was introduced. Use structured programming constructs to write functioning code immediately Learn both the complexities and solutions to nullable reference types Thoroughly master C# object constructs, including classes, inheritance, and interfaces Reduce code redundancy with generics, delegates, lambda expressions, and events Take full advantage of collections, including the new standard query operator collection API Make the most of reflection, attributes, and the declarative programming paradigm Improve multithreading with the task-based async pattern and C# 8.0 asynchronous streams Enhance performance through the parallel processing of data and multithreading tasks Program complex types with enhanced pattern matching syntax Interoperate with unmanaged code written in other languages, including C-based APIs Explore the relationship between C# programs and the underlying CLI runtime Register your product for convenient access to downloads, updates, and/or corrections as they become available. See inside book for details. Computers

The Pentester BluePrint JUMPSTART YOUR NEW AND EXCITING CAREER AS A PENETRATION TESTER The Pentester BluePrint: Your Guide to Being a Pentester offers readers a chance to delve deeply into the world of the ethical, or "white-hat" hacker. Accomplished pentester and author Phillip L. Wylie and cybersecurity researcher Kim Crawley walk you through the basic and advanced topics necessary to understand how to make a career out of finding vulnerabilities in systems, networks, and applications. You'll learn about the role of a penetration tester, what a pentest involves, and the prerequisite knowledge you'll need to start the educational journey of becoming a pentester. Discover how to develop a plan by assessing your current skillset and finding a starting place to begin growing your knowledge and skills. Finally, find out how to become employed as a pentester by using social media, networking strategies, and community involvement. Perfect for IT workers and entry-level information security professionals, The Pentester BluePrint also belongs on the bookshelves of anyone seeking to transition to the exciting and in-demand field of penetration testing. Written in a highly approachable and accessible style, The Pentester BluePrint avoids unnecessarily technical lingo in favor of concrete advice and practical strategies to help you get your start in pentesting. This book will teach you: The foundations of pentesting, including basic IT skills like operating systems, networking, and security systems The development of hacking skills and a hacker mindset Where to find educational options, including college and university classes, security training providers, volunteer work, and self-study Which certifications and degrees are most useful for gaining employment as a pentester How to get experience in the pentesting field, including labs, CTFs, and bug bounties Computers

Edge Intelligence in the Making With the explosive growth of mobile computing and Internet of Things (IoT) applications, as exemplified by AR/VR, smart city, and video/audio surveillance, billions of mobile and IoT devices are being connected to the Internet, generating zillions of bytes of data at the network edge. Driven by this trend, there is an urgent need to push the frontiers of artificial intelligence (AI) to the network edge to fully unleash the potential of IoT big data. Indeed, the marriage of edge computing and AI has resulted in innovative solutions, namely edge intelligence or edge AI. Nevertheless, research and practice on this emerging inter-disciplinary field is still in its infancy stage. To facilitate the dissemination of the recent advances in edge intelligence in both academia and industry, this book conducts a comprehensive and detailed survey of the recent research efforts and also showcases the authors' own research progress on edge intelligence. Specifically, the book first reviews the background and present motivation for AI running at the network edge. Next, it provides an overview of the overarching architectures, frameworks, and emerging key technologies for deep learning models toward training/inference at the network edge. To illustrate the research problems for edge intelligence, the book also showcases four of the authors' own research projects on edge intelligence, ranging from rigorous theoretical analysis to studies based on realistic implementation. Finally, it discusses the applications, marketplace, and future research opportunities of edge intelligence. This emerging interdisciplinary field offers many open problems and yet also tremendous opportunities, and this book only touches the tip of iceberg. Hopefully, this book will elicit escalating attention, stimulate fruitful discussions, and open new directions on edge intelligence. Computers

Privacy Risk Analysis of Online Social Networks The social benefit derived from Online Social Networks (OSNs) can lure users to reveal unprecedented volumes of personal data to an online audience that is much less trustworthy than their offline social circle. Even if a user hides his personal data from some users and shares with others, privacy settings of OSNs may be bypassed, thus leading to various privacy harms such as identity theft, stalking, or discrimination. Therefore, users need to be assisted in understanding the privacy risks of their OSN profiles as well as managing their privacy settings so as to keep such risks in check, while still deriving the benefits of social network participation. This book presents to its readers how privacy risk analysis concepts such as privacy harms and risk sources can be used to develop mechanisms for privacy scoring of user profiles and for supporting users in privacy settings management in the context of OSNs. Privacy scoring helps detect and minimize the risks due to the dissemination and use of personal data. The book also discusses many open problems in this area to encourage further research. Computers

Deep Learning Systems This book describes deep learning systems: the algorithms, compilers, and processor components to efficiently train and deploy deep learning models for commercial applications. The exponential growth in computational power is slowing at a time when the amount of compute consumed by state-of-the-art deep learning (DL) workloads is rapidly growing. Model size, serving latency, and power constraints are a significant challenge in the deployment of DL models for many applications. Therefore, it is imperative to codesign algorithms, compilers, and hardware to accelerate advances in this field with holistic system-level and algorithm solutions that improve performance, power, and efficiency. Advancing DL systems generally involves three types of engineers: (1) data scientists that utilize and develop DL algorithms in partnership with domain experts, such as medical, economic, or climate scientists; (2) hardware designers that develop specialized hardware to accelerate the components in the DL models; and (3) performance and compiler engineers that optimize software to run more efficiently on a given hardware. Hardware engineers should be aware of the characteristics and components of production and academic models likely to be adopted by industry to guide design decisions impacting future hardware. Data scientists should be aware of deployment platform constraints when designing models. Performance engineers should support optimizations across diverse models, libraries, and hardware targets. The purpose of this book is to provide a solid understanding of (1) the design, training, and applications of DL algorithms in industry; (2) the compiler techniques to map deep learning code to hardware targets; and (3) the critical hardware features that accelerate DL systems. This book aims to facilitate co-innovation for the advancement of DL systems. It is written for engineers working in one or more of these areas who seek to understand the entire system stack in order to better collaborate with engineers working in other parts of the system stack. The book details advancements and adoption of DL models in industry, explains the training and deployment process, describes the essential hardware architectural features needed for today's and future models, and details advances in DL compilers to efficiently execute algorithms across various hardware targets. Unique in this book is the holistic exposition of the entire DL system stack, the emphasis on commercial applications, and the practical techniques to design models and accelerate their performance. The author is fortunate to work with hardware, software, data scientist, and research teams across many high-technology companies with hyperscale data centers. These companies employ many of the examples and methods provided throughout the book. Computers

Pattern Recognition This book considers classical and current theory and practice, of supervised, unsupervised and semi-supervised pattern recognition, to build a complete background for professionals and students of engineering. The authors, leading experts in the field of pattern recognition, have provided an up-to-date, self-contained volume encapsulating this wide spectrum of information. The very latest methods are incorporated in this edition: semi-supervised learning, combining clustering algorithms, and relevance feedback. · Thoroughly developed to include many more worked examples to give greater understanding of the various methods and techniques · Many more diagrams included--now in two color--to provide greater insight through visual presentation · Matlab code of the most common methods are given at the end of each chapter. · More Matlab code is available, together with an accompanying manual, via this site · Latest hot topics included to further the reference value of the text including non-linear dimensionality reduction techniques, relevance feedback, semi-supervised learning, spectral clustering, combining clustering algorithms. · An accompanying book with Matlab code of the most common methods and algorithms in the book, together with a descriptive summary, and solved examples including real-life data sets in imaging, and audio recognition. The companion book will be available separately or at a special packaged price (ISBN: 9780123744869). Thoroughly developed to include many more worked examples to give greater understanding of the various methods and techniques Many more diagrams included--now in two color--to provide greater insight through visual presentation Matlab code of the most common methods are given at the end of each chapter An accompanying book with Matlab code of the most common methods and algorithms in the book, together with a descriptive summary and solved examples, and including real-life data sets in imaging and audio recognition. The companion book is available separately or at a special packaged price (Book ISBN: 9780123744869. Package ISBN: 9780123744913) Latest hot topics included to further the reference value of the text including non-linear dimensionality reduction techniques, relevance feedback, semi-supervised learning, spectral clustering, combining clustering algorithms Solutions manual, powerpoint slides, and additional resources are available to faculty using the text for their course. Register at www.textbooks.elsevier.com and search on "Theodoridis" to access resources for instructor. COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

Design Patterns Capturing a wealth of experience about the design of object-oriented software, four top-notch designers present a catalog of simple and succinct solutions to commonly occurring design problems. Previously undocumented, these 23 patterns allow designers to create more flexible, elegant, and ultimately reusable designs without having to rediscover the design solutions themselves. The authors begin by describing what patterns are and how they can help you design object-oriented software. They then go on to systematically name, explain, evaluate, and catalog recurring designs in object-oriented systems. With Design Patterns as your guide, you will learn how these important patterns fit into the software development process, and how you can leverage them to solve your own design problems most efficiently. Each pattern describes the circumstances in which it is applicable, when it can be applied in view of other design constraints, and the consequences and trade-offs of using the pattern within a larger design. All patterns are compiled from real systems and are based on real-world examples. Each pattern also includes code that demonstrates how it may be implemented in object-oriented programming languages like C++ or Smalltalk. COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

Image Structure Despite the fact that images constitute the main objects in computer vision and image analysis, there is remarkably little concern about their actual definition. In this book a complete account of image structure is proposed in terms of rigorously defined machine concepts, using basic tools from algebra, analysis, and differential geometry. Machine technicalities such as discretisation and quantisation details are de-emphasised, and robustness with respect to noise is manifest. From the foreword by Jan Koenderink: `It is my hope that the book will find a wide audience, including physicists - who still are largely unaware of the general importance and power of scale space theory, mathematicians - who will find in it a principled and formally tight exposition of a topic awaiting further development, and computer scientists - who will find here a unified and conceptually well founded framework for many apparently unrelated and largely historically motivated methods they already know and love. The book is suited for self-study and graduate courses, the carefully formulated exercises are designed to get to grips with the subject matter and prepare the reader for original research.' COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

Gaussian Scale-Space Theory Gaussian scale-space is one of the best understood multi-resolution techniques available to the computer vision and image analysis community. It is the purpose of this book to guide the reader through some of its main aspects. During an intensive weekend in May 1996 a workshop on Gaussian scale-space theory was held in Copenhagen, which was attended by many of the leading experts in the field. The bulk of this book originates from this workshop. Presently there exist only two books on the subject. In contrast to Lindeberg's monograph (Lindeberg, 1994e) this book collects contributions from several scale space researchers, whereas it complements the book edited by ter Haar Romeny (Haar Romeny, 1994) on non-linear techniques by focusing on linear diffusion. This book is divided into four parts. The reader not so familiar with scale-space will find it instructive to first consider some potential applications described in Part 1. Parts II and III both address fundamental aspects of scale-space. Whereas scale is treated as an essentially arbitrary constant in the former, the latter em phasizes the deep structure, i.e. the structure that is revealed by varying scale. Finally, Part IV is devoted to non-linear extensions, notably non-linear diffusion techniques and morphological scale-spaces, and their relation to the linear case. The Danish National Science Research Council is gratefully acknowledged for providing financial support for the workshop under grant no. 9502164. COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

Mustererkennung 1997 Nachdem die letztjiihrige DAGM-Tagung an der iiltesten Universitat Deutsch lands stattfand, freut es uns, daJ3 wir das diesjahrige Mustererkennungs-Sym posium jetzt an Deutschlands altester Technischer Universitat nun schon zum zweitenmal veranstalten durfen. An der Carolo-Wilhelmina zu Braunschweig (gegrundet im Jahre 1745) ist Forschung auf den Gebieten der Mustererken nung, der Sprachverarbeitung und der Bildverarbeitung schon seit Jahrzehnten im Institut fiir Nachrichtentechnik (INT) beheimatet. Seit 1986 wird am Institut fiir Robotik und Prozefiinformatik (IRP) auf den Gebieten der aktiven optischen 3D Oberflachenerfassung und der Analyse von Tiefendaten fiir vision-gestutzte Robotikanwendungen geforscht. Daneben gibt es an der Technischen Universitat sowie an den Forschungseinrichtungen der Region eine Vielzahl von Bereichen, in denen Methoden der Mustererkennung in unterschiedlichsten Anwendungsgebie ten fur den praktischen Einsatz vorbereitet werden; diese reichen von melkenden Robotern bis hin zur sichtgestutzten automatischen Navigation von Helikoptern und zu Anwendungen in der virtuellen Medizin. Von insgesamt 90 eingereichten Beitragen wurden yom Programmkomitee 34 als Vortrag und 30 zur Posterprasentation angenommen. Die Beitrage uberdecken - wie in fruheren Jahren auch - das gesamte Spektrum des von der DAGM be treuten Themengebietes: Von den theoretischen Grundlagen, Musterinvarianten, neuronalen Netzen uber die Bildsegmentierung bis hin zur Erkennung in und Interpretation von statischen und dynamischen 3D Szenen. Auch Beitrage zur Schrift- und Spracherkennung sind wiederum wesentlicher Bestandteil des Pro gramms. Bei den Anwendungen ist dieses Jahr insbesondere der medizinische Bereich stark vertreten. COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

Ridges in Image and Data Analysis The concept of ridges has appeared numerous times in the image processing liter ature. Sometimes the term is used in an intuitive sense. Other times a concrete definition is provided. In almost all cases the concept is used for very specific ap plications. When analyzing images or data sets, it is very natural for a scientist to measure critical behavior by considering maxima or minima of the data. These critical points are relatively easy to compute. Numerical packages always provide support for root finding or optimization, whether it be through bisection, Newton's method, conjugate gradient method, or other standard methods. It has not been natural for scientists to consider critical behavior in a higher-order sense. The con cept of ridge as a manifold of critical points is a natural extension of the concept of local maximum as an isolated critical point. However, almost no attention has been given to formalizing the concept. There is a need for a formal development. There is a need for understanding the computation issues that arise in the imple mentations. The purpose of this book is to address both needs by providing a formal mathematical foundation and a computational framework for ridges. The intended audience for this book includes anyone interested in exploring the use fulness of ridges in data analysis. COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

Epipolar Geometry in Stereo, Motion and Object Recognition Appendix 164 3. A 3. A. 1 Approximate Estimation of Fundamental Matrix from General Matrix 164 3. A. 2 Estimation of Affine Transformation 165 4 RECOVERY OF EPIPOLAR GEOMETRY FROM LINE SEGMENTS OR LINES 167 Line Segments or Straight Lines 168 4. 1 4. 2 Solving Motion Using Line Segments Between Two Views 173 4. 2. 1 Overlap of Two Corresponding Line Segments 173 Estimating Motion by Maximizing Overlap 175 4. 2. 2 Implementation Details 4. 2. 3 176 Reconstructing 3D Line Segments 4. 2. 4 179 4. 2. 5 Experimental Results 180 4. 2. 6 Discussions 192 4. 3 Determining Epipolar Geometry of Three Views 194 4. 3. 1 Trifocal Constraints for Point Matches 194 4. 3. 2 Trifocal Constraints for Line Correspondences 199 4. 3. 3 Linear Estimation of K, L, and M Using Points and Lines 200 4. 3. 4 Determining Camera Projection Matrices 201 4. 3. 5 Image Transfer 203 4. 4 Summary 204 5 REDEFINING STEREO, MOTION AND OBJECT RECOGNITION VIA EPIPOLAR GEOMETRY 205 5. 1 Conventional Approaches to Stereo, Motion and Object Recognition 205 5. 1. 1 Stereo 205 5. 1. 2 Motion 206 5. 1. 3 Object Recognition 207 5. 2 Correspondence in Stereo, Motion and Object Recognition as 1D Search 209 5. 2. 1 Stereo Matching 209 xi Contents 5. 2. 2 Motion Correspondence and Segmentation 209 5. 2. 3 3D Object Recognition and Localization 210 Disparity and Spatial Disparity Space 210 5. COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

Neural Networks Neural networks is a field of research which has enjoyed rapid expansion in both the academic and industrial research communities. This volume contains papers presented at the Third Annual SNN Symposium on Neural Networks to be held in Nijmegen, The Netherlands, 14 - 15 September 1995. The papers are divided into two sections: the first gives an overview of new developments in neurobiology, the cognitive sciences, robotics, vision and data modelling. The second presents working neural network solutions to real industrial problems, including process control, finance and marketing. The resulting volume gives a comprehensive view of the state of the art in 1995 and will provide essential reading for postgraduate students and academic/industrial researchers. COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

From Statistics to Neural Networks Proceedings of the NATO Advances Study Institute From Statistics to Neural Networks, Theory and Pattern Recognition Applications, held in Les Arcs, Bourg Saint Maurice, France, June 21 - July 2, 1993 COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

Scale-Space Theory in Computer Vision The problem of scale pervades both the natural sciences and the vi sual arts. The earliest scientific discussions concentrate on visual per ception (much like today!) and occur in Euclid's (c. 300 B. C. ) Optics and Lucretius' (c. 100-55 B. C. ) On the Nature of the Universe. A very clear account in the spirit of modern "scale-space theory" is presented by Boscovitz (in 1758), with wide ranging applications to mathemat ics, physics and geography. Early applications occur in the cartographic problem of "generalization", the central idea being that a map in order to be useful has to be a "generalized" (coarse grained) representation of the actual terrain (Miller and Voskuil 1964). Broadening the scope asks for progressive summarizing. Very much the same problem occurs in the (realistic) artistic rendering of scenes. Artistic generalization has been analyzed in surprising detail by John Ruskin (in his Modern Painters), who even describes some of the more intricate generic "scale-space sin gularities" in detail: Where the ancients considered only the merging of blobs under blurring, Ruskin discusses the case where a blob splits off another one when the resolution is decreased, a case that has given rise to confusion even in the modern literature. COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

Geometry-Driven Diffusion in Computer Vision Scale is a concept the antiquity of which can hardly be traced. Certainly the familiar phenomena that accompany sc ale changes in optical patterns are mentioned in the earliest written records. The most obvious topological changes such as the creation or annihilation of details have been a topic to philosophers, artists and later scientists. This appears to of fascination be the case for all cultures from which extensive written records exist. For th instance, chinese 17 c artist manuals remark that "distant faces have no eyes" . The merging of details is also obvious to many authors, e. g. , Lucretius mentions the fact that distant islands look like a single one. The one topo logical event that is (to the best of my knowledge) mentioned only late (by th John Ruskin in his "Elements of drawing" of the mid 19 c) is the splitting of a blob on blurring. The change of images on a gradual increase of resolu tion has been a recurring theme in the arts (e. g. , the poetic description of the distant armada in Calderon's The Constant Prince) and this "mystery" (as Ruskin calls it) is constantly exploited by painters. COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

Fundamentals in Handwriting Recognition Proceedings of the NATO Advanced Study Institute on Fundamentals in Handwriting Recognition, held at Chateau de Bonas, France, June 21 - July 3, 1993 COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

The Perception of Visual Information Human knowledge is primarily the product of experiences acquired through interactions of our senses with our surroundings. Of all the senses, vision is the one relied on most heavily by most people for sensory input about the environment. Visual interactions can be divided into three processes: (1) de tection of visual information; (2) recognition of the "external source" of the information; and (3) interpretation of the significance of the information. These processes usually occur sequentially, although there is considerable interdependence among them. With our strong dependence on the processes of visual interactions, we might assume that they are well characterized and understood. Nothing could be further from the truth. Human vision remains an engima, in spite of specu lations by philosophers for centuries, and, more recently, of attention from physicists and cognitive and experimental psychologists. How we see, and how we know what we see, remains an unsolved mystery that challenges some of the most creative scientists and cognitive specialists. COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

Structured Document Image Analysis Document image analysis is the automatic computerinterpretation of images of printed and handwrittendocuments, including text, drawings, maps, music scores,etc. Research in this field supports a rapidly growinginternational industry. This is the first book to offer abroad selection of state-of-the-art research papers,including authoritative critical surveys of the literature,and parallel studies of the architectureof completehigh-performance printed-document reading systems. A uniquefeature is the extended section on music notation, an idealvehicle for international sharing of basic research. Also,the collection includes important new work on line drawings,handwriting, character and symbol recognition, and basicmethodological issues. The IAPR 1990 Workshop on Syntacticand Structural Pattern Recognition is summarized,includingthe reports of its expert working groups, whose debatesprovide a fascinating perspective on the field.The book is an excellent text for a first-year graduateseminar in document image analysis,and is likely to remaina standard reference in the field for years. COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

3D Dynamic Scene Analysis he problem of analyzing sequences of images to extract three-dimensional T motion and structure has been at the heart of the research in computer vi sion for many years. It is very important since its success or failure will determine whether or not vision can be used as a sensory process in reactive systems. The considerable research interest in this field has been motivated at least by the following two points: 1. The redundancy of information contained in time-varying images can over come several difficulties encountered in interpreting a single image. 2. There are a lot of important applications including automatic vehicle driv ing, traffic control, aerial surveillance, medical inspection and global model construction. However, there are many new problems which should be solved: how to effi ciently process the abundant information contained in time-varying images, how to model the change between images, how to model the uncertainty inherently associated with the imaging system and how to solve inverse problems which are generally ill-posed. There are of course many possibilities for attacking these problems and many more remain to be explored. We discuss a few of them in this book based on work carried out during the last five years in the Computer Vision and Robotics Group at INRIA (Institut National de Recherche en Informatique et en Automatique). COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

Measurement of Image Velocity Measurement of Image Velocity presents a computational framework for computing motion information from sequences of images. Its specific goal is the measurement of image velocity (or optical flow), the projection of 3-D object motion onto the 2-D image plane. The formulation of the problem emphasizes the geometric and photometric properties of image formation, and the occurrence of multiple image velocities caused, for example, by specular reflections, shadows, or transparency. The method proposed for measuring image velocity is based on the phase behavior in the output of velocity-tuned filters. Extensive experimental work is used to show that phase can be a reliable source of pure image translation, small geometric deformation, smooth contrast variations, and multiple local velocities. Extensive theorectical analysis is used to explain the robustness of phase with respect to deviations from image translation, and to detect situations in which phase becomes unstable. The results indicate that optical flow may be extracted reliably for computing egomotion and structure from motion. The monograph also contains a review of other techniques and frequency analysis applied to image sequences, and it discusses the closely related topics of zero-crossing tracking, gradient-based methods, and the measurement of binocular disparity. The work is relevant to those studying machine vision and visual perception. COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

Computer Vision in Vehicle Technology A unified view of the use of computer vision technology for different types of vehicles Computer Vision in Vehicle Technology focuses on computer vision as on-board technology, bringing together fields of research where computer vision is progressively penetrating: the automotive sector, unmanned aerial and underwater vehicles. It also serves as a reference for researchers of current developments and challenges in areas of the application of computer vision, involving vehicles such as advanced driver assistance (pedestrian detection, lane departure warning, traffic sign recognition), autonomous driving and robot navigation (with visual simultaneous localization and mapping) or unmanned aerial vehicles (obstacle avoidance, landscape classification and mapping, fire risk assessment). The overall role of computer vision for the navigation of different vehicles, as well as technology to address on-board applications, is analysed. Key features: Presents the latest advances in the field of computer vision and vehicle technologies in a highly informative and understandable way, including the basic mathematics for each problem. Provides a comprehensive summary of the state of the art computer vision techniques in vehicles from the navigation and the addressable applications points of view. Offers a detailed description of the open challenges and business opportunities for the immediate future in the field of vision based vehicle technologies. This is essential reading for computer vision researchers, as well as engineers working in vehicle technologies, and students of computer vision. COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

Theory and Applications of Image Registration A hands-on guide to image registration theory and methods—with examples of a wide range of real-world applications Theory and Applications of Image Registration offers comprehensive coverage of feature-based image registration methods. It provides in-depth exploration of an array of fundamental issues, including image orientation detection, similarity measures, feature extraction methods, and elastic transformation functions. Also covered are robust parameter estimation, validation methods, multi-temporal and multi-modality image registration, methods for determining the orientation of an image, methods for identifying locally unique neighborhoods in an image, methods for detecting lines in an image, methods for finding corresponding points and corresponding lines in images, registration of video images to create panoramas, and much more. Theory and Applications of Image Registration provides readers with a practical guide to the theory and underpinning principles. Throughout the book numerous real-world examples are given, illustrating how image registration can be applied to problems in various fields, including biomedicine, remote sensing, and computer vision. Also provided are software routines to help readers develop their image registration skills. Many of the algorithms described in the book have been implemented, and the software packages are made available to the readers of the book on a companion website. In addition, the book: Explores the fundamentals of image registration and provides a comprehensive look at its multi-disciplinary applications Reviews real-world applications of image registration in the fields of biomedical imaging, remote sensing, computer vision, and more Discusses methods in the registration of long videos in target tracking and 3-D reconstruction Addresses key research topics and explores potential solutions to a number of open problems in image registration Includes a companion website featuring fully implemented algorithms and image registration software for hands-on learning Theory and Applications of Image Registration is a valuable resource for researchers and professionals working in industry and government agencies where image registration techniques are routinely employed. It is also an excellent supplementary text for graduate students in computer science, electrical engineering, software engineering, and medical physics. COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

Learning OpenCV 3 Get started in the rapidly expanding field of computer vision with this practical guide. Written by Adrian Kaehler and Gary Bradski, creator of the open source OpenCV library, this book provides a thorough introduction for developers, academics, roboticists, and hobbyists. You’ll learn what it takes to build applications that enable computers to "see" and make decisions based on that data. With over 500 functions that span many areas in vision, OpenCV is used for commercial applications such as security, medical imaging, pattern and face recognition, robotics, and factory product inspection. This book gives you a firm grounding in computer vision and OpenCV for building simple or sophisticated vision applications. Hands-on exercises in each chapter help you apply what you’ve learned. This volume covers the entire library, in its modern C++ implementation, including machine learning tools for computer vision. Learn OpenCV data types, array types, and array operations Capture and store still and video images with HighGUI Transform images to stretch, shrink, warp, remap, and repair Explore pattern recognition, including face detection Track objects and motion through the visual field Reconstruct 3D images from stereo vision Discover basic and advanced machine learning techniques in OpenCV COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

Eye Tracking the User Experience Eye tracking is a widely used research method, but there are many questions and misconceptions about how to effectively apply it. Eye Tracking the User Experience—the first how-to book about eye tracking for UX practitioners—offers step-by-step advice on how to plan, prepare, and conduct eye tracking studies; how to analyze and interpret eye movement data; and how to successfully communicate eye tracking findings. COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

Building Computer Vision Projects with OpenCV 4 and C++ Delve into practical computer vision and image processing projects and get up to speed with advanced object detection techniques and machine learning algorithms Key Features Discover best practices for engineering and maintaining OpenCV projects Explore important deep learning tools for image classification Understand basic image matrix formats and filters Book Description OpenCV is one of the best open source libraries available and can help you focus on constructing complete projects on image processing, motion detection, and image segmentation. This Learning Path is your guide to understanding OpenCV concepts and algorithms through real-world examples and activities. Through various projects, you'll also discover how to use complex computer vision and machine learning algorithms and face detection to extract the maximum amount of information from images and videos. In later chapters, you'll learn to enhance your videos and images with optical flow analysis and background subtraction. Sections in the Learning Path will help you get to grips with text segmentation and recognition, in addition to guiding you through the basics of the new and improved deep learning modules. By the end of this Learning Path, you will have mastered commonly used computer vision techniques to build OpenCV projects from scratch. This Learning Path includes content from the following Packt books: Mastering OpenCV 4 - Third Edition by Roy Shilkrot and David Millan Escriva Learn OpenCV 4 By Building Projects - Second Edition by David Millan Escriva, Vinicius G. Mendonca, and Prateek Joshi What you will learn Stay up-to-date with algorithmic design approaches for complex computer vision tasks Work with OpenCV's most up-to-date API through various projects Understand 3D scene reconstruction and Structure from Motion (SfM) Study camera calibration and overlay augmented reality (AR) using the ArUco module Create CMake scripts to compile your C++ application Explore segmentation and feature extraction techniques Remove backgrounds from static scenes to identify moving objects for surveillance Work with new OpenCV functions to detect and recognize text with Tesseract Who this book is for If you are a software developer with a basic understanding of computer vision and image processing and want to develop interesting computer vision applications with OpenCV, this Learning Path is for you. Prior knowledge of C++ and familiarity with mathematical concepts will help you better understand the concepts in this Learning Path. COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

Hands-On Computer Vision with TensorFlow 2 A practical guide to building high performance systems for object detection, segmentation, video processing, smartphone applications, and more. Key Features Discover how to build, train, and serve your own deep neural networks with TensorFlow 2 and Keras Apply modern solutions to a wide range of applications such as object detection and video analysis Learn how to run your models on mobile devices and webpages and improve their performance Book Description Computer vision solutions are becoming increasingly common, making their way in fields such as health, automobile, social media, and robotics. This book will help you explore TensorFlow 2, the brand new version of Google's open source framework for machine learning. You will understand how to benefit from using convolutional neural networks (CNNs) for visual tasks. Hands-On Computer Vision with TensorFlow 2 starts with the fundamentals of computer vision and deep learning, teaching you how to build a neural network from scratch. You will discover the features that have made TensorFlow the most widely used AI library, along with its intuitive Keras interface, and move on to building, training, and deploying CNNs efficiently. Complete with concrete code examples, the book demonstrates how to classify images with modern solutions, such as Inception and ResNet, and extract specific content using You Only Look Once (YOLO), Mask R-CNN, and U-Net. You will also build Generative Adversarial Networks (GANs) and Variational Auto-Encoders (VAEs) to create and edit images, and LSTMs to analyze videos. In the process, you will acquire advanced insights into transfer learning, data augmentation, domain adaptation, and mobile and web deployment, among other key concepts. By the end of the book, you will have both the theoretical understanding and practical skills to solve advanced computer vision problems with TensorFlow 2.0. What you will learn Create your own neural networks from scratch Classify images with modern architectures including Inception and ResNet Detect and segment objects in images with YOLO, Mask R-CNN, and U-Net Tackle problems in developing self-driving cars and facial emotion recognition systems Boost your application's performance with transfer learning, GANs, and domain adaptation Use recurrent neural networks for video analysis Optimize and deploy your networks on mobile devices and in the browser Who this book is for If you're new to deep learning and have some background in Python programming and image processing, like reading/writing image files and editing pixels, this book is for you. Even if you're an expert curious about the new TensorFlow 2 features, you'll find this book useful. While some theoretical explanations require knowledge in algebra and calculus, the book covers concrete examples for learners focused on practical applications such as visual recognition for self-driving cars and smartphone apps. COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

Generative Deep Learning Generative modeling is one of the hottest topics in AI. It’s now possible to teach a machine to excel at human endeavors such as painting, writing, and composing music. With this practical book, machine-learning engineers and data scientists will discover how to re-create some of the most impressive examples of generative deep learning models, such as variational autoencoders,generative adversarial networks (GANs), encoder-decoder models and world models. Author David Foster demonstrates the inner workings of each technique, starting with the basics of deep learning before advancing to some of the most cutting-edge algorithms in the field. Through tips and tricks, you’ll understand how to make your models learn more efficiently and become more creative. Discover how variational autoencoders can change facial expressions in photos Build practical GAN examples from scratch, including CycleGAN for style transfer and MuseGAN for music generation Create recurrent generative models for text generation and learn how to improve the models using attention Understand how generative models can help agents to accomplish tasks within a reinforcement learning setting Explore the architecture of the Transformer (BERT, GPT-2) and image generation models such as ProGAN and StyleGAN COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

Learn OpenCV 4 by Building Projects Explore OpenCV 4 to create visually appealing cross-platform computer vision applications Key Features Understand basic OpenCV 4 concepts and algorithms Grasp advanced OpenCV techniques such as 3D reconstruction, machine learning, and artificial neural networks Work with Tesseract OCR, an open-source library to recognize text in images Book Description OpenCV is one of the best open source libraries available, and can help you focus on constructing complete projects on image processing, motion detection, and image segmentation. Whether you're completely new to computer vision, or have a basic understanding of its concepts, Learn OpenCV 4 by Building Projects – Second edition will be your guide to understanding OpenCV concepts and algorithms through real-world examples and projects. You'll begin with the installation of OpenCV and the basics of image processing. Then, you'll cover user interfaces and get deeper into image processing. As you progress through the book, you'll learn complex computer vision algorithms and explore machine learning and face detection. The book then guides you in creating optical flow video analysis and background subtraction in complex scenes. In the concluding chapters, you'll also learn about text segmentation and recognition and understand the basics of the new and improved deep learning module. By the end of this book, you'll be familiar with the basics of Open CV, such as matrix operations, filters, and histograms, and you'll have mastered commonly used computer vision techniques to build OpenCV projects from scratch. What you will learn Install OpenCV 4 on your operating system Create CMake scripts to compile your C++ application Understand basic image matrix formats and filters Explore segmentation and feature extraction techniques Remove backgrounds from static scenes to identify moving objects for surveillance Employ various techniques to track objects in a live video Work with new OpenCV functions for text detection and recognition with Tesseract Get acquainted with important deep learning tools for image classification Who this book is for If you are a software developer with a basic understanding of computer vision and image processing and want to develop interesting computer vision applications with OpenCV, Learn OpenCV 4 by Building Projects for you. Prior knowledge of C++ will help you understand the concepts covered in this book. COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

Practical Deep Learning for Cloud, Mobile, and Edge Whether you’re a software engineer aspiring to enter the world of deep learning, a veteran data scientist, or a hobbyist with a simple dream of making the next viral AI app, you might have wondered where to begin. This step-by-step guide teaches you how to build practical deep learning applications for the cloud, mobile, browsers, and edge devices using a hands-on approach. Relying on years of industry experience transforming deep learning research into award-winning applications, Anirudh Koul, Siddha Ganju, and Meher Kasam guide you through the process of converting an idea into something that people in the real world can use. Train, tune, and deploy computer vision models with Keras, TensorFlow, Core ML, and TensorFlow Lite Develop AI for a range of devices including Raspberry Pi, Jetson Nano, and Google Coral Explore fun projects, from Silicon Valley’s Not Hotdog app to 40+ industry case studies Simulate an autonomous car in a video game environment and build a miniature version with reinforcement learning Use transfer learning to train models in minutes Discover 50+ practical tips for maximizing model accuracy and speed, debugging, and scaling to millions of users COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

Deep Learning with PyTorch 1.x Build and train neural network models with high speed and flexibility in text, vision, and advanced analytics using PyTorch 1.x Key Features Gain a thorough understanding of the PyTorch framework and learn to implement neural network architectures Understand GPU computing to perform heavy deep learning computations using Python Apply cutting-edge natural language processing (NLP) techniques to solve problems with textual data Book Description PyTorch is gaining the attention of deep learning researchers and data science professionals due to its accessibility and efficiency, along with the fact that it's more native to the Python way of development. This book will get you up and running with this cutting-edge deep learning library, effectively guiding you through implementing deep learning concepts. In this second edition, you'll learn the fundamental aspects that power modern deep learning, and explore the new features of the PyTorch 1.x library. You'll understand how to solve real-world problems using CNNs, RNNs, and LSTMs, along with discovering state-of-the-art modern deep learning architectures, such as ResNet, DenseNet, and Inception. You'll then focus on applying neural networks to domains such as computer vision and NLP. Later chapters will demonstrate how to build, train, and scale a model with PyTorch and also cover complex neural networks such as GANs and autoencoders for producing text and images. In addition to this, you'll explore GPU computing and how it can be used to perform heavy computations. Finally, you'll learn how to work with deep learning-based architectures for transfer learning and reinforcement learning problems. By the end of this book, you'll be able to confidently and easily implement deep learning applications in PyTorch. What you will learn Build text classification and language modeling systems using neural networks Implement transfer learning using advanced CNN architectures Use deep reinforcement learning techniques to solve optimization problems in PyTorch Mix multiple models for a powerful ensemble model Build image classifiers by implementing CNN architectures using PyTorch Get up to speed with reinforcement learning, GANs, LSTMs, and RNNs with real-world examples Who this book is for This book is for data scientists and machine learning engineers looking to work with deep learning algorithms using PyTorch 1.x. You will also find this book useful if you want to migrate to PyTorch 1.x. Working knowledge of Python programming and some understanding of machine learning will be helpful. COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

Engineering Autonomous Vehicles and Robots Offers a step-by-step guide to building autonomous vehicles and robots, with source code and accompanying videos The first book of its kind on the detailed steps for creating an autonomous vehicle or robot, this book provides an overview of the technology and introduction of the key elements involved in developing autonomous vehicles, and offers an excellent introduction to the basics for someone new to the topic of autonomous vehicles and the innovative, modular-based engineering approach called DragonFly. Engineering Autonomous Vehicles and Robots: The DragonFly Modular-based Approach covers everything that technical professionals need to know about: CAN bus, chassis, sonars, radars, GNSS, computer vision, localization, perception, motion planning, and more. Particularly, it covers Computer Vision for active perception and localization, as well as mapping and motion planning. The book offers several case studies on the building of an autonomous passenger pod, bus, and vending robot. It features a large amount of supplementary material, including the standard protocol and sample codes for chassis, sonar, and radar. GPSD protocol/NMEA protocol and GPS deployment methods are also provided. Most importantly, readers will learn the philosophy behind the DragonFly modular-based design approach, which empowers readers to design and build their own autonomous vehicles and robots with flexibility and affordability. Offers progressive guidance on building autonomous vehicles and robots Provides detailed steps and codes to create an autonomous machine, at affordable cost, and with a modular approach Written by one of the pioneers in the field building autonomous vehicles Includes case studies, source code, and state-of-the art research results Accompanied by a website with supplementary material, including sample code for chassis/sonar/radar; GPS deployment methods; Vision Calibration methods Engineering Autonomous Vehicles and Robots is an excellent book for students, researchers, and practitioners in the field of autonomous vehicles and robots. COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

PyTorch Computer Vision Cookbook Discover powerful ways to use deep learning algorithms and solve real-world computer vision problems using Python Key Features Solve the trickiest of problems in computer vision by combining the power of deep learning and neural networks Leverage PyTorch 1.x capabilities to perform image classification, object detection, and more Train and deploy enterprise-grade, deep learning models for computer vision applications Book Description Computer vision techniques play an integral role in helping developers gain a high-level understanding of digital images and videos. With this book, you'll learn how to solve the trickiest problems in computer vision (CV) using the power of deep learning algorithms, and leverage the latest features of PyTorch 1.x to perform a variety of CV tasks. Starting with a quick overview of the PyTorch library and key deep learning concepts, the book then covers common and not-so-common challenges faced while performing image recognition, image segmentation, object detection, image generation, and other tasks. Next, you'll understand how to implement these tasks using various deep learning architectures such as convolutional neural networks (CNNs), recurrent neural networks (RNNs), long short-term memory (LSTM), and generative adversarial networks (GANs). Using a problem-solution approach, you'll learn how to solve any issue you might face while fine-tuning the performance of a model or integrating it into your application. Later, you'll get to grips with scaling your model to handle larger workloads, and implementing best practices for training models efficiently. By the end of this CV book, you'll be proficient in confidently solving many CV related problems using deep learning and PyTorch. What you will learn Develop, train and deploy deep learning algorithms using PyTorch 1.x Understand how to fine-tune and change hyperparameters to train deep learning algorithms Perform various CV tasks such as classification, detection, and segmentation Implement a neural style transfer network based on CNNs and pre-trained models Generate new images and implement adversarial attacks using GANs Implement video classification models based on RNN, LSTM, and 3D-CNN Discover best practices for training and deploying deep learning algorithms for CV applications Who this book is for Computer vision professionals, data scientists, deep learning engineers, and AI developers looking for quick solutions for various computer vision problems will find this book useful. Intermediate-level knowledge of computer vision concepts, along with Python programming experience is required. COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

Mastering Computer Vision with TensorFlow 2.x Apply neural network architectures to build state-of-the-art computer vision applications using the Python programming language Key Features Gain a fundamental understanding of advanced computer vision and neural network models in use today Cover tasks such as low-level vision, image classification, and object detection Develop deep learning models on cloud platforms and optimize them using TensorFlow Lite and the OpenVINO toolkit Book Description Computer vision allows machines to gain human-level understanding to visualize, process, and analyze images and videos. This book focuses on using TensorFlow to help you learn advanced computer vision tasks such as image acquisition, processing, and analysis. You'll start with the key principles of computer vision and deep learning to build a solid foundation, before covering neural network architectures and understanding how they work rather than using them as a black box. Next, you'll explore architectures such as VGG, ResNet, Inception, R-CNN, SSD, YOLO, and MobileNet. As you advance, you'll learn to use visual search methods using transfer learning. You'll also cover advanced computer vision concepts such as semantic segmentation, image inpainting with GAN's, object tracking, video segmentation, and action recognition. Later, the book focuses on how machine learning and deep learning concepts can be used to perform tasks such as edge detection and face recognition. You'll then discover how to develop powerful neural network models on your PC and on various cloud platforms. Finally, you'll learn to perform model optimization methods to deploy models on edge devices for real-time inference. By the end of this book, you'll have a solid understanding of computer vision and be able to confidently develop models to automate tasks. What you will learn Explore methods of feature extraction and image retrieval and visualize different layers of the neural network model Use TensorFlow for various visual search methods for real-world scenarios Build neural networks or adjust parameters to optimize the performance of models Understand TensorFlow DeepLab to perform semantic segmentation on images and DCGAN for image inpainting Evaluate your model and optimize and integrate it into your application to operate at scale Get up to speed with techniques for performing manual and automated image annotation Who this book is for This book is for computer vision professionals, image processing professionals, machine learning engineers and AI developers who have some knowledge of machine learning and deep learning and want to build expert-level computer vision applications. In addition to familiarity with TensorFlow, Python knowledge will be required to get started with this book. COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition
Handbook Of Pattern Recognition And Computer Vision (6th Edition) Written by world-renowned authors, this unique compendium presents the most updated progress in pattern recognition and computer vision (PRCV), fully reflecting the strong international research interests in the artificial intelligence arena.Machine learning has been the key to current developments in PRCV. This useful comprehensive volume complements the previous five editions of the book. It places great emphasis on the use of deep learning in many aspects of PRCV applications, not readily available in other reference text. COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

Advanced Fingerprint Recognition Fingerprints are among the most widely used biometric modalities and have been successfully applied in various scenarios. For example, in forensics, fingerprints serve as important legal evidence; and in civilian applications, fingerprints are used for access and attendance control as well as other identity services. Thanks to advances in three-dimensional (3D) and high-resolution imaging technology, it is now feasible to capture 3D or high-resolution fingerprints to provide extra information and go beyond the traditional features such as global ridge patterns and local ridge singularities used in conventional fingerprint recognition tasks. This book presents the state of the art in the acquisition and analysis of 3D and high-resolution fingerprints. Based on the authors’ research, this book focuses on advanced fingerprint recognition using 3D fingerprint features (i.e., finger shape, level 0 features) or high-resolution fingerprint features (i.e., ridge detail, level 3 features). It is a valuable resource for researchers, professionals and graduate students working in the field of computer vision, pattern recognition, security/biometrics practice, as well as interdisciplinary researchers. COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

OpenVX Programming Guide OpenVX is the computer vision API adopted by many high-performance processor vendors. It is quickly becoming the preferred way to write fast and power-efficient code on embedded systems. OpenVX Programming Guidebook presents definitive information on OpenVX 1.2 and 1.3, the Neural Network, and other extensions as well as the OpenVX Safety Critical standard. This book gives a high-level overview of the OpenVX standard, its design principles, and overall structure. It covers computer vision functions and the graph API, providing examples of usage for the majority of the functions. It is intended both for the first-time user of OpenVX and as a reference for experienced OpenVX developers. Get to grips with the OpenVX standard and gain insight why various options were chosen Start developing efficient OpenVX code instantly Understand design principles and use them to create robust code Develop consumer and industrial products that use computer vision to understand and interact with the real world COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

Ensemble Learning This updated compendium provides a methodical introduction with a coherent and unified repository of ensemble methods, theories, trends, challenges, and applications. More than a third of this edition comprised of new materials, highlighting descriptions of the classic methods, and extensions and novel approaches that have recently been introduced.Along with algorithmic descriptions of each method, the settings in which each method is applicable and the consequences and tradeoffs incurred by using the method is succinctly featured. R code for implementation of the algorithm is also emphasized.The unique volume provides researchers, students and practitioners in industry with a comprehensive, concise and convenient resource on ensemble learning methods. COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

Robotic Intelligence This volume aims to provide a reference to the development of robotic intelligence, built upon Semantic Computing, in terms of 'action' to realize the 'context' and 'intention' formulated by Semantics Computing during the 'thinking' or reasoning process. It addresses three core areas: COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

Facial Multi-characteristics And Applications What features or information can we observe from a face, and how can these information help us to understand the person concerned, in terms of their well-being and what can we learn about and from each given feature? This book answers these questions by first dividing a face's multiple characteristics into two main categories: original (or physiological) features and features that change over a lifetime. The first category, original features, may be further divided into two sub-classes: features special (or unique) to an individual, and features common to a particular group. The second, changed features, can also be subdivided into two groups: features altered due to disease or features altered by other external factors. From these four sub-categories, four different applications — facial identification using original and special features; beauty analysis using original common features; facial diagnosis by disease changed features; and expression recognition through affect-changed features — are identified.The book will benefit researchers, professionals, and graduate students working in the field of computer vision, pattern recognition, security/clinical practice, and beauty analysis, and will also be useful for interdisciplinary research. COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

Syntactic Pattern Recognition This unique compendium presents the major methods of recognition and learning used in syntactic pattern recognition from the 1960s till 2018. Each method is introduced firstly in a formal way. Then, it is explained with the help of examples and its algorithms are described in a pseudocode. The survey of the applications contains more than 1,000 sources published since the 1960s. The open problems in the field, the challenges and the determinants of the future development of syntactic pattern recognition are discussed.This must-have volume provides a good read and serves as an excellent source of reference materials for researchers, academics, and postgraduate students in the fields of pattern recognition, machine perception, computer vision and artificial intelligence. COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

Pattern Recognition This book constitutes the proceedings of the 12th Mexican Conference on Pattern Recognition, MCPR 2020, which was due to be held in Morelia, Mexico, in June 2020. The conference was held virtually due to the COVID-19 pandemic. The 31 papers presented in this volume were carefully reviewed and selected from 67 submissions. They were organized in the following topical sections: pattern recognition techniques; image processing and analysis; computer vision; industrial and medical applications of pattern recognition; natural language processing and recognition; artificial intelligence techniques and recognition. COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

Fake Photos A concise and accessible guide to techniques for detecting doctored and fake images in photographs and digital media. Stalin, Mao, Hitler, Mussolini, and other dictators routinely doctored photographs so that the images aligned with their messages. They erased people who were there, added people who were not, and manipulated backgrounds. They knew if they changed the visual record, they could change history. Once, altering images required hours in the darkroom; today, it can be done with a keyboard and mouse. Because photographs are so easily faked, fake photos are everywhere—supermarket tabloids, fashion magazines, political ads, and social media. How can we tell if an image is real or false? In this volume in the MIT Press Essential Knowledge series, Hany Farid offers a concise and accessible guide to techniques for detecting doctored and fake images in photographs and digital media. Farid, an expert in photo forensics, has spent two decades developing techniques for authenticating digital images. These techniques model the entire image-creation process in order to find the digital disruption introduced by manipulation of the image. Each section of the book describes a different technique for analyzing an image, beginning with those requiring minimal technical expertise and advancing to those at intermediate and higher levels. There are techniques for, among other things, reverse image searches, metadata analysis, finding image imperfections introduced by JPEG compression, image cloning, tracing pixel patterns, and detecting images that are computer generated. In each section, Farid describes the techniques, explains when they should be applied, and offers examples of image analysis. COMPUTERS,Artificial Intelligence,Computer Vision & Pattern Recognition

Hard Real-Time Computing Systems Real-time computing plays a crucial role in our society since an increasing num ber of complex systems rely, in part or completely, on processor control. Ex amples of applications that require real-time computing include nuclear power plants, railway switching systems, automotive electronics, air traffic control, telecommunications, robotics, and military systems. In spite of this large application domain, most of the current real-time systems are still designed and implemented using low-level programming and empirical techniques, without the support of a scientific methodology. This approach results in a lack of reliability, which in critical applications may cause serious environmental damage or even loss of life. This book is a basic treatise on real-time computing, with particular emphasis on predictable scheduling algorithms. The main objectives of the book are to introduce the basic concepts of real-time computing, illustrate the most sig nificant results in the field, and provide the basic methodologies for designing predictable computing systems useful in supporting critical control applica tions. The book is written for instructional use and is organized to enable readers without a strong knowledge of the subject matter to quickly grasp the material. Technical concepts are clearly defined at the beginning of each chapter, and algorithm descriptions are reinforced through concrete examples, illustrations, and tables. COMPUTERS,Artificial Intelligence,Expert Systems

Real-Time Search for Learning Autonomous Agents Autonomous agents or multiagent systems are computational systems in which several computational agents interact or work together to perform some set of tasks. These systems may involve computational agents having common goals or distinct goals. Real-Time Search for Learning Autonomous Agents focuses on extending real-time search algorithms for autonomous agents and for a multiagent world. Although real-time search provides an attractive framework for resource-bounded problem solving, the behavior of the problem solver is not rational enough for autonomous agents. The problem solver always keeps the record of its moves and the problem solver cannot utilize and improve previous experiments. Other problems are that although the algorithms interleave planning and execution, they cannot be directly applied to a multiagent world. The problem solver cannot adapt to the dynamically changing goals and the problem solver cannot cooperatively solve problems with other problem solvers. This book deals with all these issues. Real-Time Search for Learning Autonomous Agents serves as an excellent resource for researchers and engineers interested in both practical references and some theoretical basis for agent/multiagent systems. The book can also be used as a text for advanced courses on the subject. COMPUTERS,Artificial Intelligence,Expert Systems

Real-Time Database Systems Despite the growing interest in Real-Time Database Systems, there is no single book that acts as a reference to academics, professionals, and practitioners who wish to understand the issues involved in the design and development of RTDBS. Real-Time Database Systems: Issues and Applications fulfills this need. This book presents the spectrum of issues that may arise in various real-time database applications, the available solutions and technologies that may be used to address these issues, and the open problems that need to be tackled in the future. With rapid advances in this area, several concepts have been proposed without a widely accepted consensus on their definitions and implications. To address this need, the first chapter is an introduction to the key RTDBS concepts and definitions, which is followed by a survey of the state of the art in RTDBS research and practice. The remainder of the book consists of four sections: models and paradigms, applications and benchmarks, scheduling and concurrency control, and experimental systems. The chapters in each section are contributed by experts in the respective areas. Real-Time Database Systems: Issues and Applications is primarily intended for practicing engineers and researchers working in the growing area of real-time database systems. For practitioners, the book will provide a much needed bridge for technology transfer and continued education. For researchers, this book will provide a comprehensive reference for well-established results. This book can also be used in a senior or graduate level course on real-time systems, real-time database systems, and database systems or closely related courses. COMPUTERS,Artificial Intelligence,Expert Systems

UK Parallel ’96 Parallel processing is a key topic which is becoming more important as the technology becomes more widespread. UK Parallel '96 - Proceedings of the BCS PPSG Annual Group is the publication of the academic programme from the first in an annual series of national conferences covering the broad area of parallel and distributed computing. It was coordinated by the BCS Parallel Processing Specialist Group and provided a focus for both research and industrial presentations. This first conference was held at the University of Surrey in July 1996, and contains work from a number of universities within the UK. The scope of the proceedings illustrates the breadth of the work being undertaken in the UK and includes a variety of papers covering a number of important areas, including: compiler development for both data-parallel and message passing languages and the development of application specific software. COMPUTERS,Artificial Intelligence,Expert Systems

Automated Practical Reasoning This book is a collection of selected papers written by researchers qf our "RISC" institute (Research Institute for Symbolic Computation) along with the ESPRIT MEDLAR Project (Mechanizing Deduction in the Logics of Practical Reason ing). Naturally, the MEDLAR Project was and is the focal point for our institute whose main objective is the combination of foundational research in the area of symbolic computation and possible applications thereof for high-tech industrial projects. I am grateful to the director of the MEDLAR project, Jim Cunningham, for his enthusiasm, profound expertise, and continuous effort to manage a fruitful cooperation between various European working groups in the area of the project and for giving us the opportunity to be part of this challenging endeavor. I also acknowledge and feel indebted to Jochen Pfalzgraf for managing the RISC part of the MEDLAR project and to both him and Dongming Wang for editing this volume and organizing the refereeing process. COMPUTERS,Artificial Intelligence,Expert Systems

Dependable Computing for Critical Applications 4 This volume contains the articles presented at the Fourth InternationallFIP Working Conference on Dependable Computing for Critical Applications held in San Diego, California, on January 4-6, 1994. In keeping with the previous three conferences held in August 1989 at Santa Barbara (USA), in February 1991 at Tucson (USA), and in September 1992 at Mondello (Italy), the conference was concerned with an important basic question: can we rely on computer systems for critical applications? This conference, like its predecessors, addressed various aspects of dependability, a broad term defined as the degree of trust that may justifiably be placed in a system's reliability, availability, safety, security and performance. Because of its broad scope, a main goal was to contribute to a unified understanding and integration of these concepts. The Program Committee selected 21 papers for presentation from a total of 95 submissions at a September meeting in Menlo Park, California. The resulting program represents a broad spectrum of interests, with papers from universities, corporations and government agencies in eight countries. The selection process was greatly facilitated by the diligent work of the program committee members, for which we are most grateful. As a Working Conference, the program was designed to promote the exchange of ideas by extensive discussions. All paper sessions ended with a 30 minute discussion period on the topics covered by the session. In addition, three panel sessions have been organizcd. COMPUTERS,Artificial Intelligence,Expert Systems

A Practitioner’s Handbook for Real-Time Analysis A Practitioner's Handbook for Real-Time Analysis: Guide to Rate Monotonic Analysis for Real-Time Systems contains an invaluable collection of quantitative methods that enable real-time system developers to understand, analyze, and predict the timing behavior of many real-time systems. The methods are practical and theoretically sound, and can be used to assess design tradeoffs and to troubleshoot system timing behavior. This collection of methods is called rate monotonic analysis (RMA). The Handbook includes a framework for describing and categorizing the timing aspects of real-time systems, step-by-step techniques for performing timing analysis, numerous examples of real-time situations to which the techniques can be applied, and two case studies. A Practitioner's Handbook for Real-Time Analysis: Guide to Rate Monotonic Analysis for Real-Time Systems has been created to serve as a definitive source of information and a guide for developers as they analyze and design real-time systems using RMA. The Handbook is an excellent reference, and may be used as the text for advanced courses on the subject. COMPUTERS,Artificial Intelligence,Expert Systems

Dependable Computing for Critical Applications 2 This volume contains the papers presented at the Second International Work ing Conference on Dependable Computing for Critical Applications, sponsored by IFIP Working Group lOA and held in Tucson, Arizona on February 18-20, 1991. In keeping with the first such conference on this topic, which took place at the University of California, Santa Barbara in 1989, this meeting was like wise concerned with an important basic question: Can we rely on Computers? In more precise terms, it addressed various aspects of computer system de pendability, a broad concept defined as th'e trustworthiness of computer service such that reliance can justifiably be placed on this service. Given that this term includes attributes such as reliability, availability, safety, and security, it is our hope that these papers will contribute to further integration of these ideas in the context of critical applications. The program consisted of 20 papers and three panel sessions. The papers were selected from a total of 61 submissions at a November 1990 meeting of the Program Committee in Ann Arbor, Michigan. We were very fortunate to have a broad spectrum of interests represented, with papers in the final program coming from seven different countries, representing work at universities, corporations, and government agencies. The process was greatly facilitated by the diligent work of the Program Committee and the quality of reviews provided by outside referees. In addition to the paper presentations, there were three panel sessions or ganized to examine particular topics in detail. COMPUTERS,Artificial Intelligence,Expert Systems

Foundations of Real-Time Computing This volume contains a selection of papers that focus on the state-of the-art in real-time scheduling and resource management. Preliminary versions of these papers were presented at a workshop on the foundations of real-time computing sponsored by the Office of Naval Research in October, 1990 in Washington, D.C. A companion volume by the title Foundations of Real-Time Computing: Fonnal Specifications and Methods complements this book by addressing many of the most advanced approaches currently being investigated in the arena of formal specification and verification of real-time systems. Together, these two texts provide a comprehensive snapshot of current insights into the process of designing and building real-time computing systems on a scientific basis. Many of the papers in this book take care to define the notion of real-time system precisely, because it is often easy to misunderstand what is meant by that term. Different communities of researchers variously use the term real-time to refer to either very fast computing, or immediate on-line data acquisition, or deadline-driven computing. This text is concerned with the very difficult problems of scheduling tasks and resource management in computer systems whose performance is inextricably fused with the achievement of deadlines. Such systems have been enabled for a rapidly increasing set of diverse end-uses by the unremitting advances in computing power per constant-dollar cost and per constant-unit-volume of space. End-use applications of deadline-driven real-time computers span a spectrum that includes transportation systems, robotics and manufacturing, aerospace and defense, industrial process control, and telecommunications. COMPUTERS,Artificial Intelligence,Expert Systems

Automation and Systems Issues in Air Traffic Control Proceedings of the NATO Advanced Study Institute on Automation and Systems Issues in Air Traffic Control, held in Acquafredda di Maratea, Italy, June 18-29, 1990 COMPUTERS,Artificial Intelligence,Expert Systems

The New User’s Guide to the Sun Workstation Welcome Sun users. This guide will be your key to understanding your Sun workstation. Within these pages you will find out how to use all of the basic functions and capabilities in a minimal amount of time. From SunView to Security, from Backups to Permissions, you will find out what you need quickly. This book is not intended to replace the current Sun docu mentation. It is a fast learning tool for you to become a functional Sun user quickly. Each chapter will cover the basic information needed to allow you to use that area efficiently. The chapters on UNIX file systems and permissions are for beginners' reference and will aid in learning the file system. All examples will refer to the machine name 1 tahoe. This is done to make the references to a system prompt consistent and avoid confusion. You should use this book in conjunction with the Sun manual pages included with your system. When referencing system com mands or functions, the manual pages will give you the additional capabilities which will prove invaluable in the future. I hope you enjoy this book and your new Sun workstation. COMPUTERS,Artificial Intelligence,Expert Systems

Constructing Predictable Real Time Systems Vorwort In der Natur entwickelten sich die Echtzeitsysteme seit einigen 100 Mil Honen Jahren. Tierische Nervensysteme haben zur Aufgabe, auf die Nachrichten aus der Umwelt die Steuerungsbefehle an die aktiven Or gane zu geben. Dabei spielen zum Beispiel bedingte Reflexe eine wichtige Rolle. Vielleicht kann man die Entstehung des Menschen etwa zu der Zeit ansetzen, als sein sich allmahlich entwickelndes Gehirn Gedanken entwickelte, deren Bedeutung in vorausplanender Weise iiber die gerade vorliegende Situation hinausging. Das fiihrte schliesslich unter anderem zum heutigen Wissenschaftler, der seine Theorien und Systeme aufgrund langwieriger Uberlegungen aufbaut. Die Entwicklung der Computer ging im wesentlichen den umgekehrten Weg. Zunachst diente sie nur der Durchfiihrung "starrer" Programme, wie z.B. das erste programmgesteuerte Rechengerat Z3, das der Unterzeichner im Jahre 1941 vorfiihren konnte. Es folgte unter an derem ein Spezialgerat zur Fliigelvermessung, das man als den ersten Prozessrechner bezeichnen kann. Es wurden etwa vierzig als Analog Digital-Wandler arbeitende Messuhren yom Rechnerautomaten abgele sen und im Rahmen eines Programms als Variable verarbeitet. Abel' auch das erfolgte noch in starrer Reihenfolge. Die echte Prozesssteuerung - heute auch Echtzeitsysteme genannt - erfordert aber ein Reagieren auf bestandig wechselnde Situationen. COMPUTERS,Artificial Intelligence,Expert Systems

Safety-Critical Real-Time Systems Safety-Critical Real-Time Systems brings together in one place important contributions and up-to-date research results in this fast moving area. Safety-Critical Real-Time Systems serves as an excellent reference, providing insight into some of the most challenging research issues in the field. COMPUTERS,Artificial Intelligence,Expert Systems

Dependability COMPUTERS,Artificial Intelligence,Expert Systems

Dependable Computing for Critical Applications 3 This volume contains the papers presented. at the Third IFIP International Working Conference on Dependable Computing for Critical Applications, sponsored by IFIP Working Group 10.4 and held in Mondello (Sicily), Italy on September 14-16, 1992. System developers increasingly apply computers where they can affect the safety and security of people and equipment. The Third IFIP International Working Conference on Dependable Computing for Critical Applications, like its predecessors, addressed various aspects of computer system dependability, a broad term defined as the degree of trust that may justifiably be placed in a system's reliability, availability, safety, security, and performance. Because the scope of the conference was so broad, we hope the presentations and discussions will contribute to the integration of these concepts so that future computer-based systems will indeed be more dependable. The Program Committee selected 18 papers for presentation from a total of 7 4 submissions at a May meeting in Newcastle upon Tyne, UK. The resulting program represented a broad spectrum of interests, with papers from universities, corporations, and government agencies in eight countries. Much diligent work by the Program Committee and the quality of reviews from more than a hundred external referees from around the world, for which we are most grateful, significantly eased the production of this technical program. COMPUTERS,Artificial Intelligence,Expert Systems

Real Time Computing Proceedings of the NATO Advanced Study Institute on Real Time Computing, held in Sint Maarten, Dutch Antilles, October 5 - 17, 1992 COMPUTERS,Artificial Intelligence,Expert Systems

Predictably Dependable Computing Systems The first ESPRIT Basic Research Project on Predictably Dependable Computing Systems (No. 3092, PDCS) commenced in May 1989, and ran until March 1992. The institutions and principal investigators that were involved in PDCS were: City University, London, UK (Bev Littlewood), lEI del CNR, Pisa, Italy (Lorenzo Strigini), Universitiit Karlsruhe, Germany (Tom Beth), LAAS-CNRS, Toulouse, France (Jean-Claude Laprie), University of Newcastle upon Tyne, UK (Brian Randell), LRI-CNRS/Universite Paris-Sud, France (Marie-Claude Gaudel), Technische Universitiit Wien, Austria (Hermann Kopetz), and University of York, UK (John McDermid). The work continued after March 1992, and a three-year successor project (No. 6362, PDCS2) officially started in August 1992, with a slightly changed membership: Chalmers University of Technology, Goteborg, Sweden (Erland Jonsson), City University, London, UK (Bev Littlewood), CNR, Pisa, Italy (Lorenzo Strigini), LAAS-CNRS, Toulouse, France (Jean-Claude Laprie), Universite Catholique de Louvain, Belgium (Pierre-Jacques Courtois), University of Newcastle upon Tyne, UK (Brian Randell), LRI-CNRS/Universite Paris-Sud, France (Marie-Claude Gaudel), Technische Universitiit Wien, Austria (Hermann Kopetz), and University of York, UK (John McDermid). The summary objective of both projects has been "to contribute to making the process of designing and constructing dependable computing systems much more predictable and cost-effective". In the case of PDCS2, the concentration has been on the problems of producing dependable distributed real-time systems and especially those where the dependability requirements centre on issues of safety and/or security. COMPUTERS,Artificial Intelligence,Expert Systems

Synchronous Programming of Reactive Systems This book will attempt to give a first synthesis of recent works con cerning reactive system design. The term "reactive system" has been introduced in order to at'oid the ambiguities often associated with by the term "real-time system," which, although best known and more sugges tive, has been given so many different meanings that it is almost in evitably misunderstood. Industrial process control systems, transporta tion control and supervision systems, signal-processing systems, are ex amples of the systems we have in mind. Although these systems are more and more computerized, it is sur prising to notice that the problem of time in computer science has been studied only recently by "pure" computer scientists. Until the early 1980s, time problems were regarded as the concern of performance evalu ation, or of some (unjustly scorned) "industrial computer engineering," or, at best, of operating systems. A second surprising fact, in contrast, is the growth of research con cerning timed systems during the last decade. The handling of time has suddenly become a fundamental goal for most models of concurrency. In particular, Robin Alilner 's pioneering works about synchronous process algebras gave rise to a school of thought adopting the following abstract point of view: As soon as one admits that a system can instantaneously react to events, i. e. COMPUTERS,Artificial Intelligence,Expert Systems

Understanding Modern Dive Computers and Operation This brief provides a complete yet concise description of modern dive computers and their operations to date in one source with coupled applications for added understanding. Basic diving principles are detailed with practical computer implementations. Interrelated topics to diving protocols and operational procedures are included. Tests, statistics and correlations of computer models with data are underscored. The exposition also links phase mechanics to dissolved gases in modern decompression theory with mathematical relationships and equations used in dive computer synthesis. Applications focus upon and mimic dive computer operations within model implementations for added understanding. This comprehensive resource includes a complete list of dive computers that are marketed and their staging models, as well as a complete list of diveware marketed and their staging algorithms, linkage of pertinent wet and dry tests to modern computer algorithms, a description of two basic computer models with all constants and parameters, mathematical ansatz of on-the-fly risk for surfacing at any dive depth, detailing of statistical techniques used to validate dive computers from data, and a description of profile Data Banks for computer dive model correlations. The book will find an audience amongst computer scientists, doctors, underwater researchers, engineers, physical and biosciences diving professionals, explorers, chamber technicians, physiologists and technical and recreational divers. COMPUTERS,Artificial Intelligence,Expert Systems

Hands-On Industrial Internet of Things Build a strong and efficient IoT infrastructure at industrial and enterprise level by mastering Industrial IoT network Key Features Gain hands-on experience working with industrial architecture Explore the potential of cloud-based Industrial IoT platforms, analytics, and protocols Improve business models and transform your workforce with Industry 4.0 Book Description We live in an era where advanced automation is used to achieve accurate results. To set up an automation environment, you need to first configure a network that can be accessed anywhere and by any device. This book is a practical guide that helps you discover the technologies and use cases for Industrial Internet of Things (IIOT). Hands-On Industrial Internet of Things takes you through the implementation of industrial processes and specialized control devices and protocols. You'll study the process of identifying and connecting to different industrial data sources gathered from different sensors. Furthermore, you'll be able to connect these sensors to cloud network, such as AWS IoT, Azure IoT, Google IoT, and OEM IoT platforms, and extract data from the cloud to your devices. As you progress through the chapters, you'll gain hands-on experience in using open source Node-Red, Kafka, Cassandra, and Python. You will also learn how to develop streaming and batch-based Machine Learning algorithms. By the end of this book, you will have mastered the features of Industry 4.0 and be able to build stronger, faster, and more reliable IoT infrastructure in your Industry. What you will learn Explore industrial processes, devices, and protocols Design and implement the I-IoT network flow Gather and transfer industrial data in a secure way Get to grips with popular cloud-based platforms Understand diagnostic analytics to answer critical workforce questions Discover the Edge device and understand Edge and Fog computing Implement equipment and process management to achieve business-specific goals Who this book is for If you're an IoT architect, developer, or stakeholder working with architectural aspects of Industrial Internet of Things, this book is for you. COMPUTERS,Artificial Intelligence,Expert Systems

Recent Advances in Reinforcement Learning Recent Advances in Reinforcement Learning addresses current research in an exciting area that is gaining a great deal of popularity in the Artificial Intelligence and Neural Network communities. Reinforcement learning has become a primary paradigm of machine learning. It applies to problems in which an agent (such as a robot, a process controller, or an information-retrieval engine) has to learn how to behave given only information about the success of its current actions. This book is a collection of important papers that address topics including the theoretical foundations of dynamic programming approaches, the role of prior knowledge, and methods for improving performance of reinforcement-learning techniques. These papers build on previous work and will form an important resource for students and researchers in the area. Recent Advances in Reinforcement Learning is an edited volume of peer-reviewed original research comprising twelve invited contributions by leading researchers. This research work has also been published as a special issue of Machine Learning (Volume 22, Numbers 1, 2 and 3). COMPUTERS,Artificial Intelligence,General

Connectionist Approaches to Language Learning arise automatically as a result of the recursive structure of the task and the continuous nature of the SRN's state space. Elman also introduces a new graphical technique for study ing network behavior based on principal components analysis. He shows that sentences with multiple levels of embedding produce state space trajectories with an intriguing self similar structure. The development and shape of a recurrent network's state space is the subject of Pollack's paper, the most provocative in this collection. Pollack looks more closely at a connectionist network as a continuous dynamical system. He describes a new type of machine learning phenomenon: induction by phase transition. He then shows that under certain conditions, the state space created by these machines can have a fractal or chaotic structure, with a potentially infinite number of states. This is graphically illustrated using a higher-order recurrent network trained to recognize various regular languages over binary strings. Finally, Pollack suggests that it might be possible to exploit the fractal dynamics of these systems to achieve a generative capacity beyond that of finite-state machines. COMPUTERS,Artificial Intelligence,General

Knowledge Representation and Reasoning Knowledge representation is at the very core of a radical idea for understanding intelligence. Instead of trying to understand or build brains from the bottom up, its goal is to understand and build intelligent behavior from the top down, putting the focus on what an agent needs to know in order to behave intelligently, how this knowledge can be represented symbolically, and how automated reasoning procedures can make this knowledge available as needed. This landmark text takes the central concepts of knowledge representation developed over the last 50 years and illustrates them in a lucid and compelling way. Each of the various styles of representation is presented in a simple and intuitive form, and the basics of reasoning with that representation are explained in detail. This approach gives readers a solid foundation for understanding the more advanced work found in the research literature. The presentation is clear enough to be accessible to a broad audience, including researchers and practitioners in database management, information retrieval, and object-oriented systems as well as artificial intelligence. This book provides the foundation in knowledge representation and reasoning that every AI practitioner needs. Authors are well-recognized experts in the field who have applied the techniques to real-world problems Presents the core ideas of KR&R in a simple straight forward approach, independent of the quirks of research systems Offers the first true synthesis of the field in over a decade COMPUTERS,Artificial Intelligence,General

Programming Collective Intelligence Want to tap the power behind search rankings, product recommendations, social bookmarking, and online matchmaking? This fascinating book demonstrates how you can build Web 2.0 applications to mine the enormous amount of data created by people on the Internet. With the sophisticated algorithms in this book, you can write smart programs to access interesting datasets from other web sites, collect data from users of your own applications, and analyze and understand the data once you've found it. Programming Collective Intelligence takes you into the world of machine learning and statistics, and explains how to draw conclusions about user experience, marketing, personal tastes, and human behavior in general -- all from information that you and others collect every day. Each algorithm is described clearly and concisely with code that can immediately be used on your web site, blog, Wiki, or specialized application. This book explains: Collaborative filtering techniques that enable online retailers to recommend products or media Methods of clustering to detect groups of similar items in a large dataset Search engine features -- crawlers, indexers, query engines, and the PageRank algorithm Optimization algorithms that search millions of possible solutions to a problem and choose the best one Bayesian filtering, used in spam filters for classifying documents based on word types and other features Using decision trees not only to make predictions, but to model the way decisions are made Predicting numerical values rather than classifications to build price models Support vector machines to match people in online dating sites Non-negative matrix factorization to find the independent features in a dataset Evolving intelligence for problem solving -- how a computer develops its skill by improving its own code the more it plays a game Each chapter includes exercises for extending the algorithms to make them more powerful. Go beyond simple database-backed applications and put the wealth of Internet data to work for you. "Bravo! I cannot think of a better way for a developer to first learn these algorithms and methods, nor can I think of a better way for me (an old AI dog) to reinvigorate my knowledge of the details." -- Dan Russell, Google "Toby's book does a great job of breaking down the complex subject matter of machine-learning algorithms into practical, easy-to-understand examples that can be directly applied to analysis of social interaction across the Web today. If I had this book two years ago, it would have saved precious time going down some fruitless paths." -- Tim Wolters, CTO, Collective Intellect COMPUTERS,Artificial Intelligence,General

On Intelligence From the inventor of the PalmPilot comes a new and compelling theory of intelligence, brain function, and the future of intelligent machines Jeff Hawkins, the man who created the PalmPilot, Treo smart phone, and other handheld devices, has reshaped our relationship to computers. Now he stands ready to revolutionize both neuroscience and computing in one stroke, with a new understanding of intelligence itself. Hawkins develops a powerful theory of how the human brain works, explaining why computers are not intelligent and how, based on this new theory, we can finally build intelligent machines. The brain is not a computer, but a memory system that stores experiences in a way that reflects the true structure of the world, remembering sequences of events and their nested relationships and making predictions based on those memories. It is this memory-prediction system that forms the basis of intelligence, perception, creativity, and even consciousness. In an engaging style that will captivate audiences from the merely curious to the professional scientist, Hawkins shows how a clear understanding of how the brain works will make it possible for us to build intelligent machines, in silicon, that will exceed our human ability in surprising ways. Written with acclaimed science writer Sandra Blakeslee, On Intelligence promises to completely transfigure the possibilities of the technology age. It is a landmark book in its scope and clarity. COMPUTERS,Artificial Intelligence,General

Artificial Intelligence Intelligent agents are employed as the central characters in this new introductory text. Beginning with elementary reactive agents, Nilsson gradually increases their cognitive horsepower to illustrate the most important and lasting ideas in AI. Neural networks, genetic programming, computer vision, heuristic search, knowledge representation and reasoning, Bayes networks, planning, and language understanding are each revealed through the growing capabilities of these agents. The book provides a refreshing and motivating new synthesis of the field by one of AI's master expositors and leading researchers. Artificial Intelligence: A New Synthesis takes the reader on a complete tour of this intriguing new world of AI. An evolutionary approach provides a unifying theme Thorough coverage of important AI ideas, old and new Frequent use of examples and illustrative diagrams Extensive coverage of machine learning methods throughout the text Citations to over 500 references Comprehensive index COMPUTERS,Artificial Intelligence,General

Uncertainty Management in Information Systems As its title suggests, "Uncertainty Management in Information Systems" is a book about how information systems can be made to manage information permeated with uncertainty. This subject is at the intersection of two areas of knowledge: information systems is an area that concentrates on the design of practical systems that can store and retrieve information; uncertainty modeling is an area in artificial intelligence concerned with accurate representation of uncertain information and with inference and decision-making under conditions infused with uncertainty. New applications of information systems require stronger capabilities in the area of uncertainty management. Our hope is that lasting interaction between these two areas would facilitate a new generation of information systems that will be capable of servicing these applications. Although there are researchers in information systems who have addressed themselves to issues of uncertainty, as well as researchers in uncertainty modeling who have considered the pragmatic demands and constraints of information systems, to a large extent there has been only limited interaction between these two areas. As the subtitle, "From Needs to Solutions," indicates, this book presents view points of information systems experts on the needs that challenge the uncer tainty capabilities of present information systems, and it provides a forum to researchers in uncertainty modeling to describe models and systems that can address these needs. COMPUTERS,Artificial Intelligence,General

Neural Nets WIRN VIETRI-96 This volume contains the Proceedings of the 8th Italian Workshop on Neural Nets WIRN VIETRI-96, organized by the International Institute for Advanced Scientific Studies "Eduardo R. Caianiello" and by the Societa Italiana Reti Neuroniche (SIREN). We would like to thank Professor L.B. Almeida who agreed to deliver an invited lecture which is included in these Proceedings. The spectrum of contributors and participants covers the activity of Italian research in the field and of some European groups. The highly qualified and motivated attendance is·proof of the interest with which this annual event has met in the Italian scientific community. Maria Marinaro Roberto Tagliaferri Organizing - Scientific Committee: B. Apolloni (Univ. Milano), A. Bertoni (Univ. Milano), D.o. Caviglia (Univ. Genova), P. Campadelli (Univ. Milano), M. Ceccarelli (CNR NapolD, A. Colla (ELSAG - Genova), M. Frixione (/lASS), C. Furlanello (IRST - Trento), G.M. Guazzo (!lASS), M. Gori (Univ. Firenze), F. Lauria (Univ. Napo/D, M. Marinaro (Univ. Salerno - flASS), F. Masulli (Univ. Genova), P. Morasso (Univ. Genova), G. Orlandi (Univ. Roma), E. Pasero (Politecnico Torino), A. Petrosino (CNR Napoli), M. Protasi (Univ. Roma Ilj, S. Rampone (/lASS), R. Serra (Gruppo Ferruzzi Ravenna), F. Sorbello (Univ. Palermo), R. Stefanel.1i (Politecnico Milano), R. Tagliaferri (Univ. Salerno), R. Vaccaro (CNR Napo/D. COMPUTERS,Artificial Intelligence,General

Computational Intelligence for Optimization The field of optimization is interdisciplinary in nature, and has been making a significant impact on many disciplines. As a result, it is an indispensable tool for many practitioners in various fields. Conventional optimization techniques have been well established and widely published in many excellent textbooks. However, there are new techniques, such as neural networks, simulated anneal ing, stochastic machines, mean field theory, and genetic algorithms, which have been proven to be effective in solving global optimization problems. This book is intended to provide a technical description on the state-of-the-art development in advanced optimization techniques, specifically heuristic search, neural networks, simulated annealing, stochastic machines, mean field theory, and genetic algorithms, with emphasis on mathematical theory, implementa tion, and practical applications. The text is suitable for a first-year graduate course in electrical and computer engineering, computer science, and opera tional research programs. It may also be used as a reference for practicing engineers, scientists, operational researchers, and other specialists. This book is an outgrowth of a couple of special topic courses that we have been teaching for the past five years. In addition, it includes many results from our inter disciplinary research on the topic. The aforementioned advanced optimization techniques have received increasing attention over the last decade, but relatively few books have been produced. COMPUTERS,Artificial Intelligence,General

Cooperative Knowledge Processing In the light of the challenges that face today's organizations, there is a grow ing recognition that future market success and long term' survival of enter prises will increasingly depend upon the effective usage of information technology. Of late, a new generation of terminology has emerged to describe enterprises. This terminology draws heavily upon the virtual concep- virtual reality, virtual organization, virtual (working) environment, and indeed virtual product. However, developing computerized organisations for the 21st century demands serious thought with regard to the judicious integration of organizational theory, design and practice with research tools and methods from within information processing technology. Within this book, we approach this aim from the perspective of a radically decentralized (possibly virtual) enterprise. We assume that organizations are becoming increasingly process-orientated, rather than adhering to the former more traditional organizational structures based upon task oriented models. This approach has proved illuminating in that, due to the inherent autonomy of organizational subunits any approach to coordinating decentralized activ ities (including workflows and business processes) necessitates a cooperative style of problem solving. This book introduces the reader to a stimulating new field of interdiscipli nary research in cooperative problem solving. In Chapter 1 Kim presents a view of three central discip14tes, namely those of Organizational Theory, Computer Supported Cooperative Work (CSCW) and Distributed Artificial Intelligence (DAI). The applications given here demonstrate how future enterprises will benefit from recent advances in the technological arena of cooperative knowledge processing. COMPUTERS,Artificial Intelligence,General

One Jump Ahead Why did I write this book? I'm still not sure. After all, I'm a researcher, which means I think I know how to write technical papers. But writing for a n- technical audience is something I know nothing about. It took a lot of effort before I could force myself to sit down to write the first word. Once I did, however, it was hard not to stop! When I started this project, I didn't know that I had a lot to say and, in some sense, the results show this. The book is much longer than I even imagined it would be. Worse yet is that there is a lot of material that I decided not to include. It's a good thing that the publishers decided to limit how long the book could be! However, after much soul searching, I think I now know the reasons why I wrote this book. First and foremost, this book tells an interesting story. It's about the life of a checkers-playing computer program, Chinook, from its creation in 1989 to its retirement in 1996. In reality the story revolves around two people with different views of the program. As the creator of Chinook, I wanted to push the program to become the best player in the world, in much the same way that a father might encourage his son to excel at sports. COMPUTERS,Artificial Intelligence,General

Microsystem Technology and Microrobotics Microsystem technology (MST) integrates very small (up to a few nanometers) mechanical, electronic, optical, and other components on a substrate to construct functional devices. These devices are used as intelligent sensors, actuators, and controllers for medical, automotive, household and many other purposes. This book is a basic introduction to MST for students, engineers, and scientists. It is the first of its kind to cover MST in its entirety. It gives a comprehensive treatment of all important parts of MST such as microfabrication technologies, microactuators, microsensors, development and testing of microsystems, and information processing in microsystems. It surveys products built to date and experimental products and gives a comprehensive view of all developments leading to MST devices and robots. COMPUTERS,Artificial Intelligence,General

Mathematics of Neural Networks This volume of research papers comprises the proceedings of the first International Conference on Mathematics of Neural Networks and Applications (MANNA), which was held at Lady Margaret Hall, Oxford from July 3rd to 7th, 1995 and attended by 116 people. The meeting was strongly supported and, in addition to a stimulating academic programme, it featured a delightful venue, excellent food and accommo dation, a full social programme and fine weather - all of which made for a very enjoyable week. This was the first meeting with this title and it was run under the auspices of the Universities of Huddersfield and Brighton, with sponsorship from the US Air Force (European Office of Aerospace Research and Development) and the London Math ematical Society. This enabled a very interesting and wide-ranging conference pro gramme to be offered. We sincerely thank all these organisations, USAF-EOARD, LMS, and Universities of Huddersfield and Brighton for their invaluable support. The conference organisers were John Mason (Huddersfield) and Steve Ellacott (Brighton), supported by a programme committee consisting of Nigel Allinson (UMIST), Norman Biggs (London School of Economics), Chris Bishop (Aston), David Lowe (Aston), Patrick Parks (Oxford), John Taylor (King's College, Lon don) and Kevin Warwick (Reading). The local organiser from Huddersfield was Ros Hawkins, who took responsibility for much of the administration with great efficiency and energy. The Lady Margaret Hall organisation was led by their bursar, Jeanette Griffiths, who ensured that the week was very smoothly run. COMPUTERS,Artificial Intelligence,General

Artificial Intelligence Techniques The purpose of "Artificial Intelligence Techniques: A Comprehensive Cata logue" is to promote interaction between members of the AI community. It does this by announcing the existence of AI techniques, and acting as a pointer into the literature. Thus the AI community has access to a common, extensional definition of the field, which promotes a common terminology, discourages the reinvention of wheels, and acts as a clearing house for ideas and algorithms. I am grateful to the impressive group of AI experts who have contributed the many descriptions of AI techniques which go to make up this Catalogue. They have managed to distill a very wide knowledge of AI into a very compact form. The Catalogue is a reference work providing a quick guide to the AI tech niques available for different tasks. Intentionally, it only provides a brief de scription of each technique, with no extended discussion of its historical origin or how it has been used in particular AI programs. COMPUTERS,Artificial Intelligence,General

Second-Order Methods for Neural Networks About This Book This book is about training methods - in particular, fast second-order training methods - for multi-layer perceptrons (MLPs). MLPs (also known as feed-forward neural networks) are the most widely-used class of neural network. Over the past decade MLPs have achieved increasing popularity among scientists, engineers and other professionals as tools for tackling a wide variety of information processing tasks. In common with all neural networks, MLPsare trained (rather than programmed) to carryout the chosen information processing function. Unfortunately, the (traditional' method for trainingMLPs- the well-knownbackpropagation method - is notoriously slow and unreliable when applied to many prac tical tasks. The development of fast and reliable training algorithms for MLPsis one of the most important areas ofresearch within the entire field of neural computing. The main purpose of this book is to bring to a wider audience a range of alternative methods for training MLPs, methods which have proved orders of magnitude faster than backpropagation when applied to many training tasks. The book also addresses the well-known (local minima' problem, and explains ways in which fast training methods can be com bined with strategies for avoiding (or escaping from) local minima. All the methods described in this book have a strong theoretical foundation, drawing on such diverse mathematical fields as classical optimisation theory, homotopic theory and stochastic approximation theory. COMPUTERS,Artificial Intelligence,General

Handbook for Evaluating Knowledge-Based Systems Knowledge-based systems are increasingly found in a wide variety of settings and this handbook has been written to meet a specific need in their widening use. While there have been many successful applications of knowledge-based systems, some applications have failed because they never received the corrective feedback that evaluation provides for keeping development focused on the users' needs in their actual working environment. This handbook provides a conceptual framework and compendium of methods for performing evaluations of knowledge-based systems during their development. Its focus is on the users' and subject matter experts' evaluation of the usefulness of the system, and not on the developers' testing of the adequacy of the programming code. The handbook permits evaluators to systematically answer the following kinds of questions: Does the knowledge-based system meet the users' task requirements? Is the system easy to use? Is the knowledge base logically consistent? Does it meet the required level of expertise? Does the system improve performance? The authors have produced a handbook that will serve two audiences: a tool that can be used to create knowledge-based systems (practitioners, developers, and evaluators) and a framework that will stimulate more research in the area (academic researchers and students). To accomplish this, the handbook is built around a conceptual framework that integrates the different types of evaluations into the system of development process. The kinds of questions that can be answered, and the methods available for answering them, will change throughout the system development life cycle. And throughout this process, one needs to know what can be done, and what can't. It is this dichotomy that addresses needs in both the practitioner and academic research audiences. COMPUTERS,Artificial Intelligence,General

Rough Sets and Data Mining Rough Sets and Data Mining: Analysis of Imprecise Data is an edited collection of research chapters on the most recent developments in rough set theory and data mining. The chapters in this work cover a range of topics that focus on discovering dependencies among data, and reasoning about vague, uncertain and imprecise information. The authors of these chapters have been careful to include fundamental research with explanations as well as coverage of rough set tools that can be used for mining data bases. The contributing authors consist of some of the leading scholars in the fields of rough sets, data mining, machine learning and other areas of artificial intelligence. Among the list of contributors are Z. Pawlak, J Grzymala-Busse, K. Slowinski, and others. Rough Sets and Data Mining: Analysis of Imprecise Data will be a useful reference work for rough set researchers, data base designers and developers, and for researchers new to the areas of data mining and rough sets. COMPUTERS,Artificial Intelligence,General

Reasoning with Complex Cases Reasoning with Complex Cases emphasizes case retrieval methods based on structured cases as they are relevant for planning, configuration, and design, and provides a systematic view of the case reuse phase, centering on complex situations. So far, books on case-based reasoning considered comparatively simple situations only. This book is a coherent work, not a selection of separate contributions, and consists largely of original research results using examples taken from industrial design, biology, medicine, jurisprudence and other areas. Reasoning with Complex Cases is suitable as a secondary text for graduate-level courses on case-based reasoning and as a reference for practitioners applying conventional CBR systems or techniques. COMPUTERS,Artificial Intelligence,General

Neural Networks and Fuzzy Systems Neural Networks and Fuzzy Systems: Theory and Applications discusses theories that have proven useful in applying neural networks and fuzzy systems to real world problems. The book includes performance comparison of neural networks and fuzzy systems using data gathered from real systems. Topics covered include the Hopfield network for combinatorial optimization problems, multilayered neural networks for pattern classification and function approximation, fuzzy systems that have the same functions as multilayered networks, and composite systems that have been successfully applied to real world problems. The author also includes representative neural network models such as the Kohonen network and radial basis function network. New fuzzy systems with learning capabilities are also covered. The advantages and disadvantages of neural networks and fuzzy systems are examined. The performance of these two systems in license plate recognition, a water purification plant, blood cell classification, and other real world problems is compared. COMPUTERS,Artificial Intelligence,General

Interleaving Planning and Execution for Autonomous Robots Interleaving Planning and Execution for Autonomous Robots develops a formal representation for interleaving planning and execution in the context of incomplete information. This work bridges the gap between theory and practice in robotics by presenting control architectures that are provably sound, complete and optimal, and then describing real-world implementations of these robot architectures. Dervish, winner of the 1994 AAAI National Robot Contest, is one of the robots featured. Interleaving Planning and Execution for Autonomous Robots is based on the author's PhD research, covering the same material taught in CS 224, the very popular Introduction to Robot Programming Laboratory taught at Stanford for four years by Professor Michael Genesereth and the author. COMPUTERS,Artificial Intelligence,General

Life Cycle Networks The globalisation of markets and the expansion of product responsibility into the entire product life cycle lead to an increasing competitive situation for nationally and internationally operating companies. Therefore, to win this competition the use of the most effective and efficient resources regarding the whole product life cycle is necessary. Since these resources are globally distributed the different tasks both within a phase of product life cycle and those spread over different phases are distributed as well. The global interference of these tasks requires a close multilateral co-operation of the companies concerned. Current information- and communication technologies and modern management concepts offer high potentials to meet these requirements. The international seminar of CIRP on Life Cycle Engineering titled "Life Cycle Networks" was a forum for the presentation and discussion of current research work and recent advancements on these strategic issues for current and future engineering. Complex requirements and innovative solutions to support and realise Life Cycle Networks has been revealed and summerised. The employment of information technology to support both specific phases of product life cycle and holistic approaches will be the main focus. This volume contains the papers presented at the seminar which provide opportunities to identify the state-of-the-art and address future needs. The parts in this volume correspond to the sessions of the seminar and are presented under the following headings: Life Cycle Management; Life Cycle Design; Design for Environment; Design for Recycling; Life Cycle Assessment; Disassembly; IT-Networks. COMPUTERS,Artificial Intelligence,General

Intelligent Systems and Financial Forecasting A fundamental objective of Artificial Intelligence (AI) is the creation of in telligent computer programs. In more modest terms AI is simply con cerned with expanding the repertoire of computer applications into new domains and to new levels of efficiency. The motivation for this effort comes from many sources. At a practical level there is always a demand for achieving things in more efficient ways. Equally, there is the technical challenge of building programs that allow a machine to do something a machine has never done before. Both of these desires are contained within AI and both provide the inspirational force behind its development. In terms of satisfying both of these desires there can be no better example than machine learning. Machines that can learn have an in-built effi ciency. The same software can be applied in many applications and in many circumstances. The machine can adapt its behaviour so as to meet the demands of new, or changing, environments without the need for costly re-programming. In addition, a machine that can learn can be ap plied in new domains with the genuine potential for innovation. In this sense a machine that can learn can be applied in areas where little is known about possible causal relationships, and even in circumstances where causal relationships are judged not to exist. This last aspect is of major significance when considering machine learning as applied to fi nancial forecasting. COMPUTERS,Artificial Intelligence,General

Engineering Intelligent Hybrid Multi-Agent Systems Engineering Intelligent Hybrid Multi-Agent Systems is about building intelligent hybrid systems. Included is coverage of applications and design concepts related to fusion systems, transformation systems and combination systems. These applications are in areas involving hybrid configurations of knowledge-based systems, case-based reasoning, fuzzy systems, artificial neural networks, genetic algorithms, and in knowledge discovery and data mining. Through examples and applications a synergy of these subjects is demonstrated. The authors introduce a multi-agent architectural theory for engineering intelligent associative hybrid systems. The architectural theory is described at both the task structure level and the computational level. This problem-solving architecture is relevant for developing knowledge agents and information agents. An enterprise-wide system modeling framework is outlined to facilitate forward and backward integration of systems developed in the knowledge, information, and data engineering layers of an organization. In the modeling process, software engineering aspects like agent oriented analysis, design and reuse are developed and described. Engineering Intelligent Hybrid Multi-Agent Systems is the first book in the field to provide details of a multi-agent architecture for building intelligent hybrid systems. COMPUTERS,Artificial Intelligence,General

Expert Systems and Probabilistic Network Models Artificial intelligence and expert systems have seen a great deal of research in recent years, much of which has been devoted to methods for incorporating uncertainty into models. This book is devoted to providing a thorough and up-to-date survey of this field for researchers and students. COMPUTERS,Artificial Intelligence,General

Self-Organizing Maps The second, revised edition of this book was suggested by the impressive sales of the first edition. Fortunately this enabled us to incorporate new important results that had just been obtained. The ASSOM (Adaptive-Subspace SOM) is a new architecture in which invariant-feature detectors emerge in an unsupervised learning process. Its basic principle was already introduced in the first edition, but the motiva tion and theoretical discussion in the second edition is more thorough and consequent. New material has been added to Sect. 5.9 and this section has been rewritten totally. Correspondingly, Sect. 1.4, which deals with adaptive subspace classifiers in general and constitutes the prerequisite for the ASSOM principle, has also been extended and rewritten totally. Another new SOM development is the WEBSOM, a two-layer architecture intended for the organization of very large collections of full-text documents such as those found in the Internet and World Wide Web. This architecture was published after the first edition came out. The idea and results seemed to be so important that the new Sect. 7.8 has now been added to the second edition. Another addition that contains new results is Sect. 3.15, which describes the acceleration in the computing of very large SOMs. It was also felt that Chap. 7, which deals with 80M applications, had to be extended. COMPUTERS,Artificial Intelligence,General

Parsing with Principles and Classes of Information Parsing with Principles and Classes of Information presents a parser based on current principle-based linguistic theories for English. It argues that differences in the kind of information being computed, whether lexical, structural or syntactic, play a crucial role in the mapping from grammatical theory to parsing algorithms. The direct encoding of homogeneous classes of information has computational and cognitive advantages, which are discussed in detail. Phrase structure is built by using a fast algorithm and compact reference tables. A quantified comparison of different compilation methods shows that lexical and structural information are most compactly represented by separate tables. This finding is reconciled to evidence on the resolution of lexical ambiguity, as an approach to the modularization of information. The same design is applied to the efficient computation of long- distance dependencies. Incremental parsing using bottom-up tabular algorithms is discussed in detail. Finally, locality restrictions are calculated by a parametric algorithm. Students of linguistics, parsing and psycholinguistics will find this book a useful resource on issues related to the implementation of current linguistic theories, using computational and cognitive plausible algorithms. COMPUTERS,Artificial Intelligence,General

Explanation-Based Neural Network Learning Lifelong learning addresses situations in which a learner faces a series of different learning tasks providing the opportunity for synergy among them. Explanation-based neural network learning (EBNN) is a machine learning algorithm that transfers knowledge across multiple learning tasks. When faced with a new learning task, EBNN exploits domain knowledge accumulated in previous learning tasks to guide generalization in the new one. As a result, EBNN generalizes more accurately from less data than comparable methods. Explanation-Based Neural Network Learning: A Lifelong Learning Approach describes the basic EBNN paradigm and investigates it in the context of supervised learning, reinforcement learning, robotics, and chess. `The paradigm of lifelong learning - using earlier learned knowledge to improve subsequent learning - is a promising direction for a new generation of machine learning algorithms. Given the need for more accurate learning methods, it is difficult to imagine a future for machine learning that does not include this paradigm.' From the Foreword by Tom M. Mitchell. COMPUTERS,Artificial Intelligence,General

An Information-Theoretic Approach to Neural Computing Neural networks provide a powerful new technology to model and control nonlinear and complex systems. In this book, the authors present a detailed formulation of neural networks from the information-theoretic viewpoint. They show how this perspective provides new insights into the design theory of neural networks. In particular they show how these methods may be applied to the topics of supervised and unsupervised learning including feature extraction, linear and non-linear independent component analysis, and Boltzmann machines. Readers are assumed to have a basic understanding of neural networks, but all the relevant concepts from information theory are carefully introduced and explained. Consequently, readers from several different scientific disciplines, notably cognitive scientists, engineers, physicists, statisticians, and computer scientists, will find this to be a very valuable introduction to this topic. COMPUTERS,Artificial Intelligence,General

Automated Mathematical Induction It has been shown how the common structure that defines a family of proofs can be expressed as a proof plan [5]. This common structure can be exploited in the search for particular proofs. A proof plan has two complementary components: a proof method and a proof tactic. By prescribing the structure of a proof at the level of primitive inferences, a tactic [11] provides the guarantee part of the proof. In contrast, a method provides a more declarative explanation of the proof by means of preconditions. Each method has associated effects. The execution of the effects simulates the application of the corresponding tactic. Theorem proving in the proof planning framework is a two-phase process: 1. Tactic construction is by a process of method composition: Given a goal, an applicable method is selected. The applicability of a method is determined by evaluating the method's preconditions. The method effects are then used to calculate subgoals. This process is applied recursively until no more subgoals remain. Because of the one-to-one correspondence between methods and tactics, the output from this process is a composite tactic tailored to the given goal. 2. Tactic execution generates a proof in the object-level logic. Note that no search is involved in the execution of the tactic. All the search is taken care of during the planning process. The real benefits of having separate planning and execution phases become appar ent when a proof attempt fails. COMPUTERS,Artificial Intelligence,General

Transforming Organisations Through Groupware Lotus Notes is one of the most successful and versatile groupware products on the market today and is used widely in both large and small organisations. Transforming Organisations Through Groupware - Lotus Notes in Action contains a selection of carefully chosen case studies which illustrate the implementational, organisational and commercial consequences of using Lotus Notes. These case studies have been chosen for their international appeal and, unlike other books on Lotus Notes, concentrate on the added value that can be gained by using Notes - rather than on the technical aspects of how to make the software work. COMPUTERS,Artificial Intelligence,General

Artificial Intelligence in Design ’96 Change is one of the most significant parameters in our society. Designers are amongst the primary change agents for any society. As a consequence design is an important research topic in engineering and architecture and related disciplines, since design is not only a means of change but is also one of the keystones to economic competitiveness and the fundamental precursor to manufacturing. The development of computational models founded on the artificial intelligence paradigm has provided an impetus for much of current design research -both computational and cognitive. These forms of design research have only been carried out in the last decade or so and in the temporal sense they are still immature. Notwithstanding this immaturity, noticeable advances have been made both in extending our understanding of design and in developing tools based on that understanding. Whilst many researchers in the field of artificial intelligence in design utilise ideas about how humans design as one source of concepts there is normally no attempt to model human designers. Rather the results of the research presented in this volume demonstrate approaches to increasing our understanding of design as a process. COMPUTERS,Artificial Intelligence,General

CSCW Requirements and Evaluation There is a rapidly-growing commercial awareness of the need for evaluation in CSCW as major producers push to get cooperative technology taken up in commercial organisations. CSCW Requirements and Evaluation looks at ways of evaluating how well computer systems meet the requirements of organisations and their workforces, and establishing how effective, efficient and satisfactory they are for the actual users. It provides an integrated framework for assessment which reflects both practical and academic perspectives. Descriptions of various methods are given, along with examples of their commercial application and specific case studies. Containing contributions from leading authorities in the field, this book will be welcomed by scientists and practitioners involved in organisational research, CSCW, information and business systems, and HCI. COMPUTERS,Artificial Intelligence,General

Genetic Algorithms + Data Structures = Evolution Programs Genetic algorithms are founded upon the principle of evolution, i.e., survival of the fittest. Hence evolution programming techniques, based on genetic algorithms, are applicable to many hard optimization problems, such as optimization of functions with linear and nonlinear constraints, the traveling salesman problem, and problems of scheduling, partitioning, and control. The importance of these techniques is still growing, since evolution programs are parallel in nature, and parallelism is one of the most promising directions in computer science.The book is self-contained and the only prerequisite is basic undergraduate mathematics. This third edition has been substantially revised and extended by three new chapters and by additional appendices containing working material to cover recent developments and a change in the perception of evolutionary computation. COMPUTERS,Artificial Intelligence,General

Intelligent Learning Environments Proceedings originating from the NATO Advanced Research Workshop on Intelligent Learning Environments: the Case of Geometry, held in Grenoble, France, November 13-16, 1989 COMPUTERS,Artificial Intelligence,General

Resolution Proof Systems Resolution Proof Systems: An Algebraic Theory presents a new algebraic framework for the design and analysis of resolution- based automated reasoning systems for a range of non-classical logics. It develops an algebraic theory of resolution proof systems focusing on the problems of proof theory, representation and efficiency of the deductive process. A new class of logical calculi, the class of resolution logics, emerges as a second theme of the book. The logical and computational aspects of the relationship between resolution logics and resolution proof systems is explored in the context of monotonic as well as nonmonotonic reasoning. This book is aimed primarily at researchers and graduate students in artificial intelligence, symbolic and computational logic. The material is suitable as a reference book for researchers and as a text book for graduate courses on the theoretical aspects of automated reasoning and computational logic. COMPUTERS,Artificial Intelligence,General

Integration of Natural Language and Vision Processing Although there has been much progress in developing theories, models and systems in the areas of Natural Language Processing (NLP) and Vision Processing (VP) there has up to now been little progress on integrating these two subareas of Artificial Intelligence (AI). This book contains a set of edited papers on recent advances in the theories, computational models and systems of the integration of NLP and VP. The volume includes original work of notable researchers: Alex Waibel outlines multimodal interfaces including studies in speech, gesture and points; eye-gaze, lip motion and facial expression; hand writing, face recognition, face tracking and sound localization in a connectionist framework. Antony Cohen and John Gooday use spatial relations to describe visual languages. Naoguki Okada considers intentions of agents in visual environments. In addition to these studies, the volume includes many recent advances from North America, Europe and Asia demonstrating the fact that integration of Natural Language Processing and Vision is truly an international challenge. COMPUTERS,Artificial Intelligence,General

Artificial Intelligence in Economics and Managment In the past decades several researchers have developed statistical models for the prediction of corporate bankruptcy, e. g. Altman (1968) and Bilderbeek (1983). A model for predicting corporate bankruptcy aims to describe the relation between bankruptcy and a number of explanatory financial ratios. These ratios can be calculated from the information contained in a company's annual report. The is to obtain a method for timely prediction of bankruptcy, a so ultimate purpose called "early warning" system. More recently, this subject has attracted the attention of researchers in the area of machine learning, e. g. Shaw and Gentry (1990), Fletcher and Goss (1993), and Tam and Kiang (1992). This research is usually directed at the comparison of machine learning methods, such as induction of classification trees and neural networks, with the "standard" statistical methods of linear discriminant analysis and logistic regression. In earlier research, Feelders et al. (1994) performed a similar comparative analysis. The methods used were linear discriminant analysis, decision trees and neural networks. We used a data set which contained 139 annual reports of Dutch industrial and trading companies. The experiments showed that the estimated prediction error of both the decision tree and neural network were below the estimated error of the linear discriminant. Thus it seems that we can gain by replacing the "traditionally" used linear discriminant by a more flexible classification method to predict corporate bankruptcy. The data set used in these experiments was very small however. COMPUTERS,Artificial Intelligence,General

Computational Psycholinguistics Computational Psycholinguistics: An Interdisciplinary Approach to the Study of Language investigates the architecture and mechanisms which underlie the human capacity to process language. It is the first such study to integrate modern syntactic theory, cross-linguistic psychological evidence, and modern computational techniques in constructing a model of the human sentence processing mechanism. The monograph follows the rationalist tradition, arguing the central role of modularity and universal grammar in a theory of human linguistic performance. It refines the notion of `modularity of mind', and presents a distributed model of syntactic processing which consists of modules aligned with the various informational `types' associated with modern linguistic theories. By considering psycholinguistic evidence from a range of languages, a small number of processing principles are motivated and are demonstrated to hold universally. It is also argued that the behavior of modules, and the strategies operative within them, can be derived from an overarching `Principle of Incremental Comprehension'. Audience: The book is recommended to all linguists, psycholinguists, computational linguists, and others interested in a unified and interdisciplinary study of the human language faculty. COMPUTERS,Artificial Intelligence,General

The Biology and Technology of Intelligent Autonomous Agents Proceedings of the NATO Advanced Study Institute on The Biology and Technology of Intelligent Autonomous Agents, COMPUTERS,Artificial Intelligence,General

Integration of Natural Language and Vision Processing Although there has been much progress in developing theories, models and systems in the areas of Natural Language Processing (NLP) and Vision Processing (VP) there has heretofore been little progress on integrating these subareas of Artificial Intelligence (AI). This book contains a set of edited papers addressing computational models and systems for the integration of NLP and VP. The papers focus on site descriptions such as that of the large Japanese $500 million Real World Computing (RWC) project, on historical philosophical issues, on systems which have been built and which integrate the processing of visual scenes together with language about them, and on spatial relations which appear to be the key to integration. The U.S.A., Japan and the EU are well reflected, showing up the fact that integration is a truly international issue. There is no doubt that all of this will be necessary for the InformationSuperHighways of the future. COMPUTERS,Artificial Intelligence,General

The Knowledge Acquisition and Representation Language, KARL Within the framework of so-called second generation expert systems [62] knowledge modeling is one of the most important aspects. On the one hand, knowledge acquisition is no longer seen as a knowledge transfer process, rather it is now considered as model construction process which is typically a cyclic and error prone process. On the other hand, the distinction between knowledge and symbol level descriptions [166] resulted in various proposals for conceptual knowledge models describing knowledge in an implementation independent way. One of the most prominent examples of such a conceptual model is the KADS model of expertise which is characterized by its clear distinction of different know ledge types and by the usage of specific modeling primitives to describe these different knowledge types [185]. The semi formal KADS expertise model entails all the advantages and disadvantages which have been identified for semi-formal system models e.g. in the software engineering community. COMPUTERS,Artificial Intelligence,General

The Pleadings Game The British philosopher Stephan Toulmin, in his The Uses of Argument, made the provocative claim that "logic is generalized jurisprudence". For Toulmin, logic is the study of nonns for practical argumentation and decision making. In his view, mathematical logicians were preoccupied with fonnalizing the concepts of logical necessity, consequence and contradiction, at the expense of other equally important issues, such as how to allocate the burden of proof and make rational decisions given limited resources. He also considered it a mistake to look primarily to psychology, linguistics or the cognitive sciences for answers to these fundamentally nonnative questions. Toulmin's concerns about logic, writing in the 1950's, are equally applicable to the field of Artificial Intelligence today. The mainstream of Artificial Intelligence has focused on the analytical and empirical aspects of intelligence, without giving adequate attention to the nonnative, regulative functions of knowledge representation, problem solving and decision-making. Nonnative issues should now be of even greater interest, with the shift in perspective of AI from individual to collective intelligence, in areas such as multi-agent systems, cooperative design, distributed artificial intelligence, and computer-supported cooperative work. Networked "virtual societies" of humans and software agents would also require "virtual legal systems" to fairly balance interests, resolve conflicts, and promote security. COMPUTERS,Artificial Intelligence,General

Neural Networks Neural Networks presents concepts of neural-network models and techniques of parallel distributed processing in a three-step approach: - A brief overview of the neural structure of the brain and the history of neural-network modeling introduces to associative memory, preceptrons, feature-sensitive networks, learning strategies, and practical applications. - The second part covers subjects like statistical physics of spin glasses, the mean-field theory of the Hopfield model, and the "space of interactions" approach to the storage capacity of neural networks. - The final part discusses nine programs with practical demonstrations of neural-network models. The software and source code in C are on a 3 1/2" MS-DOS diskette can be run with Microsoft, Borland, Turbo-C, or compatible compilers. COMPUTERS,Artificial Intelligence,General

Artificial Neural Nets and Genetic Algorithms Artificial neural networks and genetic algorithms both are areas of research which have their origins in mathematical models constructed in order to gain understanding of important natural processes. By focussing on the process models rather than the processes themselves, significant new computational techniques have evolved which have found application in a large number of diverse fields. This diversity is reflected in the topics which are subjects of the contributions to this volume.There are contributions reporting successful applications of the technology to the solution of industrial/commercial problems. This may well reflect the maturity of the technology, notably in the sense that 'real' users of modelling/prediction techniques are prepared to accept neural networks as a valid paradigm. Theoretical issues also receive attention, notably in connection with the radial basis function neural network. Contributions in the field of genetic algorithms reflect the wide range of current applications, including, for example, portfolio selection, filter design, frequency assignment, tuning of nonlinear PID controllers. These techniques are also used extensively for combinatorial optimisation problems. COMPUTERS,Artificial Intelligence,General

The Neurobiology of Computation Proceedings of the Third Annual Computation and Neural Systems Conference COMPUTERS,Artificial Intelligence,General

Hybrid Intelligent Systems Hybrid Intelligent Systems summarizes the strengths and weaknesses of five intelligent technologies: fuzzy logic, genetic algorithms, case-based reasoning, neural networks and expert systems, reviewing the status and significance of research into their integration. Engineering and scientific examples and case studies are used to illustrate principles and application development techniques. The reader will gain a clear idea of the current status of hybrid intelligent systems and discover how to choose and develop appropriate applications. The book is based on a thorough literature search of recent publications on research and development in hybrid intelligent systems; the resulting 50-page reference section of the book is invaluable. The book starts with a summary of the five major intelligent technologies and of the issues in and current status of research into them. Each subsequent chapter presents a detailed discussion of a different combination of intelligent technologies, along with examples and case studies. Four chapters contain detailed case studies of working hybrid systems. The book enables the reader to: Describe the important concepts, strengths and limitations of each technology; Recognize and analyze potential problems with the application of hybrid systems; Choose appropriate hybrid intelligent solutions; Understand how applications are designed with any of the approaches covered; Choose appropriate commercial development shells or tools. An invaluable reference source for those who wish to apply intelligent systems techniques to their own problems. COMPUTERS,Artificial Intelligence,General

Hybrid Neural Network and Expert Systems Hybrid Neural Network and Expert Systems presents the basics of expert systems and neural networks, and the important characteristics relevant to the integration of these two technologies. Through case studies of actual working systems, the author demonstrates the use of these hybrid systems in practical situations. Guidelines and models are described to help those who want to develop their own hybrid systems. Neural networks and expert systems together represent two major aspects of human intelligence and therefore are appropriate for integration. Neural networks represent the visual, pattern-recognition types of intelligence, while expert systems represent the logical, reasoning processes. Together, these technologies allow applications to be developed that are more powerful than when each technique is used individually. Hybrid Neural Network and Expert Systems provides frameworks for understanding how the combination of neural networks and expert systems can produce useful hybrid systems, and illustrates the issues and opportunities in this dynamic field. COMPUTERS,Artificial Intelligence,General

Genetic Algorithms + Data Structures = Evolution Programs Genetic algorithms are founded upon the principle of evolution, i.e., survival of the fittest. Hence evolution programming techniques, based on genetic algorithms, are applicable to many hard optimization problems, such as optimization of functions with linear and nonlinear constraints, the traveling salesman problem, and problems of scheduling, partitioning, and control. The importance of these techniques has been growing in the last decade, since evolution programs are parallel in nature, and parallelism is one of the most promising directions in computer science.The book is self-contained and the only prerequisite is basic undergraduate mathematics. It is aimed at researchers, practitioners, and graduate students in computer science and artificial intelligence, operations research, and engineering.This second edition includes several new sections and many references to recent developments. A simple example of genetic code and an index are also added. Writing an evolution program for a given problem should be an enjoyable experience - this book may serve as a guide to this task. COMPUTERS,Artificial Intelligence,General

Qualitative Reasoning The book provides a survey about the field of Qualitative Reasoning, it contrasts and classifies its approaches and puts them into a common framework. Qualitative Reasoning represents an approach of Artificial Intelligence to model dynamic systems, about which little information is available, and to derive statements about the potential behavior of these systems, putting emphasis on a causal explanation of the behavior. Both variables and relationships between variables are described by means of qualitative terms such as small and large or positive and negative. Since this approach also takes into consideration the way how humans reason about physical systems, it can be stated that Qualitative Reasoning participates in the creation of a cognitive theory of non-numerical process descriptions which can be mapped onto a digital computer. This approach can be used for simulation, diagnosis, design, structure identification and interpretation. Areas of application are physics, medicine, the field of ecology, process control, etc. In addition to the classification of existing methods, the book presents a new approach based on fuzzy sets. And the work relates Qualitative Reasoning with such fields of Expert Systems, System Theory and Cognitive Science. COMPUTERS,Artificial Intelligence,General

Neural Networks in Telecommunications Neural Networks in Telecommunications consists of a carefully edited collection of chapters that provides an overview of a wide range of telecommunications tasks being addressed with neural networks. These tasks range from the design and control of the underlying transport network to the filtering, interpretation and manipulation of the transported media. The chapters focus on specific applications, describe specific solutions and demonstrate the benefits that neural networks can provide. By doing this, the authors demonstrate that neural networks should be another tool in the telecommunications engineer's toolbox. Neural networks offer the computational power of nonlinear techniques, while providing a natural path to efficient massively-parallel hardware implementations. In addition, the ability of neural networks to learn allows them to be used on problems where straightforward heuristic or rule-based solutions do not exist. Together these capabilities mean that neural networks offer unique solutions to problems in telecommunications. For engineers and managers in telecommunications, Neural Networks in Telecommunications provides a single point of access to the work being done by leading researchers in this field, and furnishes an in-depth description of neural network applications. COMPUTERS,Artificial Intelligence,General

Automating Instructional Design, Development, and Delivery Proceedings of the NATO Advanced Research Workshop on Automating Instructional Design, Development, and Delivery, held in Sitges, Spain, March 23 - 27, 1992 COMPUTERS,Artificial Intelligence,General

Rough Sets, Fuzzy Sets and Knowledge Discovery The objective of this book is two-fold. Firstly, it is aimed at bringing to gether key research articles concerned with methodologies for knowledge discovery in databases and their applications. Secondly, it also contains articles discussing fundamentals of rough sets and their relationship to fuzzy sets, machine learning, management of uncertainty and systems of logic for formal reasoning about knowledge. Applications of rough sets in different areas such as medicine, logic design, image processing and expert systems are also represented. The articles included in the book are based on selected papers presented at the International Workshop on Rough Sets and Knowledge Discovery held in Banff, Canada in 1993. The primary methodological approach emphasized in the book is the mathematical theory of rough sets, a relatively new branch of mathematics concerned with the modeling and analysis of classification problems with imprecise, uncertain, or incomplete information. The methods of the theory of rough sets have applications in many sub-areas of artificial intelligence including knowledge discovery, machine learning, formal reasoning in the presence of uncertainty, knowledge acquisition, and others. This spectrum of applications is reflected in this book where articles, although centered around knowledge discovery problems, touch a number of related issues. The book is intended to provide an important reference material for students, researchers, and developers working in the areas of knowledge discovery, machine learning, reasoning with uncertainty, adaptive expert systems, and pattern classification. COMPUTERS,Artificial Intelligence,General

Distributed and Parallel Database Object Management Distributed and Parallel Database Object Management brings together in one place important contributions and state-of-the-art research results in this rapidly advancing area of computer science. Distributed and Parallel Database Object Management serves as an excellent reference, providing insights into some of the most important issues in the field. COMPUTERS,Artificial Intelligence,General

Concept Formation and Knowledge Revision A fundamental assumption of work in artificial intelligence and machine learning is that knowledge is expressed in a computer with the help of knowledge representations. Since the proper choice of such representations is a difficult task that fundamentally affects the capabilities of a system, the problem of automatic representation change is an important topic in current research. Concept Formation and Knowledge Revision focuses on representation change as a concept formation task, regarding concepts as the elementary representational vocabulary from which further statements are constructed. Taking an interdisciplinary approach from psychological foundations to computer implementations, the book draws on existing psychological results about the nature of human concepts and concept formation to determine the scope of concept formation phenomena, and to identify potential components of computational concept formation models. The central idea of this work is that computational concept formation can usefully be understood as a process that is triggered in a demand-driven fashion by the representational needs of the learning system, and identify the knowledge revision activities of a system as a particular context for such a process. The book presents a detailed analysis of the revision problem for first-order clausal theories, and develops a set of postulates that any such operation should satisfy. It shows how a minimum theory revision operator can be realized by using exception sets, and that this operator is indeed maximally general. The book then shows that concept formation can be triggered from within the knowledge revision process whenever the existing representation does not permit the plausible reformulation of an exception set, demonstrating the usefulness of the approach both theoretically and empirically within the learning knowledge acquisition system MOBAL. In using a first-order representation, this book is part of the rapidly developing field of Inductive Logic Programming (ILP). By integrating the computational issues with psychological and fundamental discussions of concept formation phenomena, the book will be of interest to readers both theoretically and psychologically inclined. From the foreword by Katharina Morik: ` The ideal to combine the three sources of artificial intelligence research has almost never been reached. Such a combined and integrated research requires the researcher to master different ways of thinking, different work styles, different sets of literature, and different research procedures. It requires capabilities in software engineering for the application part, in theoretical computer science for the theory part, and in psychology for the cognitive part. The most important capability for artificial intelligence is to keep the integrative view and to create a true original work that goes beyond the collection of pieces from different fields. This book achieves such an integrative view of concept formation and knowledge revision by presenting the way from psychological investigations that indicate that concepts are theories and point at the important role of a demand for learning. to an implemented system which supports users in their tasks when working with a knowledge base and its theoretical foundation. ' COMPUTERS,Artificial Intelligence,General

Representing Uncertain Knowledge The representation of uncertainty is a central issue in Artificial Intelligence (AI) and is being addressed in many different ways. Each approach has its proponents, and each has had its detractors. However, there is now an in creasing move towards the belief that an eclectic approach is required to represent and reason under the many facets of uncertainty. We believe that the time is ripe for a wide ranging, yet accessible, survey of the main for malisms. In this book, we offer a broad perspective on uncertainty and approach es to managing uncertainty. Rather than provide a daunting mass of techni cal detail, we have focused on the foundations and intuitions behind the various schools. The aim has been to present in one volume an overview of the major issues and decisions to be made in representing uncertain knowl edge. We identify the central role of managing uncertainty to AI and Expert Systems, and provide a comprehensive introduction to the different aspects of uncertainty. We then describe the rationales, advantages and limitations of the major approaches that have been taken, using illustrative examples. The book ends with a review of the lessons learned and current research di rections in the field. The intended readership will include researchers and practitioners in volved in the design and implementation of Decision Support Systems, Ex pert Systems, other Knowledge-Based Systems and in Cognitive Science. COMPUTERS,Artificial Intelligence,General

Computation and Neural Systems Computational neuroscience is best defined by its focus on understanding the nervous systems as a computational device rather than by a particular experimental technique. Accordinlgy, while the majority of the papers in this book describe analysis and modeling efforts, other papers describe the results of new biological experiments explicitly placed in the context of computational issues. The distribution of subjects in Computation and Neural Systems reflects the current state of the field. In addition to the scientific results presented here, numerous papers also describe the ongoing technical developments that are critical for the continued growth of computational neuroscience. Computation and Neural Systems includes papers presented at the First Annual Computation and Neural Systems meeting held in San Francisco, CA, July 26--29, 1992. COMPUTERS,Artificial Intelligence,General

Neuroscience The Central Nervous System can be considered as an aggregate of neurons specialized in both the transmission and transformation of information. Information can be used for many purposes, but probably the most important one is to generate a representation of the "external" world that allows the organism to react properly to changes in its external environment. These functions range from such basic ones as detection of changes that may lead to tissue damage and eventual destruction of the organism and the implementation of avoidance reactions, to more elaborate representations of the external world implying recognition of shapes, sounds and textures as the basis of planned action or even reflection. Some of these functions confer a clear survival advantage to the organism (prey or mate recognition, escape reactions, etc. ). Others can be considered as an essential part of cognitive processes that contribute, to varying degrees, to the development of individuality and self-consciousness. How can we hope to understand the complexity inherent in this range of functionalities? One of the distinguishing features of the last two decades has been the availability of computational power that has impacted many areas of science. In neurophysiology, computation is used for experiment control, data analysis and for the construction of models that simulate particular systems. Analysis of the behavior of neuronal networks has transcended the limits of neuroscience and is now a discipline in itself, with potential applications both in the neural sciences and in computing sciences. COMPUTERS,Artificial Intelligence,General

The Promise of Neural Networks This book is the product of a 15-month intensive investigation of the European artificial network scene, together with a view of the broader framework of the subject in a world context. It could not have been completed in such a remarkably short time, and so effectively, without the dedicated efforts of Louise Turner, the DEANNA secretary, and Geoff Chappell, the DEANNA researcher, at the Centre for Neural Networks, King's College, London. I would like to take this opportunity to thank them for their heroic efforts. I would also like to thank my colleagues in the Centre and in the Mathematics Department, especially Mark Plumbley, Michael Reiss and Trevor Clarkson for all their help and encouragement, Denise Gorse of University College London, for allowing use of her lecture notes as a basis for the tutorial and the DEANNA partners for the part they played. Finally I would like to acknowledge the European Community support, and especially Mike Coyle for his trenchant comments during the carrying out of the work. March 1993 J. G. Taylor CONTENTS PART I: SETTING THE SCENE Chapter 1: DEANNA. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3 1 . 1 Introduction. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3 . 2 The Geographical Dimension. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5 1 1. 3 The Industrial Dimension. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6 1 . 4 The Plan for Neural Networks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6 Chapter 2: Neural Net Demonstrators. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9 2. 1 The Status of Neural Networks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9 2. 2 Reasons for the Employment of Neural Networks . . . . . . . . . . . . . . . . . . . 9 2. 3 Neural Network Models . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10 2. 4 Areas of Application . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11 2. 5 Typical Applications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . COMPUTERS,Artificial Intelligence,General
Program Verification Among the most important problems confronting computer science is that of developing a paradigm appropriate to the discipline. Proponents of formal methods - such as John McCarthy, C.A.R. Hoare, and Edgar Dijkstra - have advanced the position that computing is a mathematical activity and that computer science should model itself after mathematics. Opponents of formal methods - by contrast, suggest that programming is the activity which is fundamental to computer science and that there are important differences that distinguish it from mathematics, which therefore cannot provide a suitable paradigm. Disagreement over the place of formal methods in computer science has recently arisen in the form of renewed interest in the nature and capacity of program verification as a method for establishing the reliability of software systems. A paper that appeared in Communications of the ACM entitled, `Program Verification: The Very Idea', by James H. Fetzer triggered an extended debate that has been discussed in several journals and that has endured for several years, engaging the interest of computer scientists (both theoretical and applied) and of other thinkers from a wide range of backgrounds who want to understand computer science as a domain of inquiry. The editors of this collection have brought together many of the most interesting and important studies that contribute to answering questions about the nature and the limits of computer science. These include early papers advocating the mathematical paradigm by McCarthy, Naur, R. Floyd, and Hoare (in Part I), others that elaborate the paradigm by Hoare, Meyer, Naur, and Scherlis and Scott (in Part II), challenges, limits and alternatives explored by C. Floyd, Smith, Blum, and Naur (in Part III), and recent work focusing on formal verification by DeMillo, Lipton, and Perlis, Fetzer, Cohn, and Colburn (in Part IV). It provides essential resources for further study. This volume will appeal to scientists, philosophers, and laypersons who want to understand the theoretical foundations of computer science and be appropriately positioned to evaluate the scope and limits of the discipline. COMPUTERS,Artificial Intelligence,General

Systematic Introduction to Expert Systems At present one of the main obstacles to a broaderapplication of expert systems is the lack of a theory totell us which problem-solving methods areavailable for agiven problem class. Such a theory could lead to significantprogress in the following central aims of the expert systemtechnique:- Evaluating the technical feasibility of expert systemprojects: This depends on whether there is a suitableproblem-solving method, and if possible a correspondingtool, for the given problem class.- Simplifying knowledge acquisition and maintenance: Theproblem-solving methods provide direct assistance asinterpretation models in knowledge acquisition. Also, theymake possible the development of problem-specific expertsystem tools with graphical knowledge acquisitioncomponents, which can be used even by experts withoutprogramming experience.- Making use of expert systems as a knowledge medium: Thestructured knowledge in expert systems can be used not onlyfor problem solving but also for knowledge communication andtutorial purposes.With such a theory in mind, this book provides a systematicintroduction to expert systems. It describes the basicknowledge representations and the present situation withregard tothe identification, realization, and integrationof problem-solving methods for the main problem classes ofexpert systems: classification (diagnostics), construction,and simulation. COMPUTERS,Artificial Intelligence,General

Nonmonotonic Logic When I first participated in exploring theories of nonmonotonic reasoning in the late 1970s, I had no idea of the wealth of conceptual and mathematical results that would emerge from those halting first steps. This book by Wiktor Marek and Miroslaw Truszczynski is an elegant treatment of a large body of these results. It provides the first comprehensive treatment of two influen tial nonmonotonic logics - autoepistemic and default logic - and describes a number of surprising and deep unifying relationships between them. It also relates them to various modal logics studied in the philosophical logic litera ture, and provides a thorough treatment of their applications as foundations for logic programming semantics and for truth maintenance systems. It is particularly appropriate that Marek and Truszczynski should have authored this book, since so much of the research that went into these results is due to them. Both authors were trained in the Polish school of logic and they bring to their research and writing the logical insights and sophisticated mathematics that one would expect from such a background. I believe that this book is a splendid example of the intellectual maturity of the field of artificial intelligence, and that it will provide a model of scholarship for us all for many years to come. Ray Reiter Department of Computer Science University of Toronto Toronto, Canada M5S 1A4 and The Canadian Institute for Advanced Research Table of Contents 1 1 Introduction ......... COMPUTERS,Artificial Intelligence,General

Designing Environments for Constructive Learning Proceedings of the NATO Advanced Research Workshop on The Design of Constructivist Learning Environments: Implications for Instructional Design and the Use of Technology, held at the Catholic University Leuven, Belgium, May 14-18, 1991 COMPUTERS,Artificial Intelligence,General

Artificial Neural Nets and Genetic Algorithms Artificial neural networks and genetic algorithms both are areas of research which have their origins in mathematical models constructed in order to gain understanding of important natural processes. By focussing on the process models rather than the processes themselves, significant new computational techniques have evolved which have found application in a large number of diverse fields. This diversity is reflected in the topics which are the subjects of contributions to this volume.There are contributions reporting theoretical developments in the design of neural networks, and in the management of their learning. In a number of contributions, applications to speech recognition tasks, control of industrial processes as well as to credit scoring, and so on, are reflected.Regarding genetic algorithms, several methodological papers consider how genetic algorithms can be improved using an experimental approach, as well as by hybridizing with other useful techniques such as tabu search. The closely related area of classifier systems also receives a significant amount of coverage, aiming at better ways for their implementation. Further, while there are many contributions which explore ways in which genetic algorithms can be applied to real problems, nearly all involve some understanding of the context in order to apply the genetic algorithm paradigm more successfully. That this can indeed be done is evidenced by the range of applications covered in this volume. COMPUTERS,Artificial Intelligence,General

Intelligent Systems Published in honour of the 70th birthday of Yoh-Han Pao, George S. Dively Dis tinguished Professor of Engineering at Case Western Reserve University, Cleveland, Ohio, this festschrift embraces a remarkably diverse set of topics. Drawing from the fields of pattern recognition, engineering, artificial intelligence and artificial neural systems, it is a fitting testament to the extraordinary breadth of his professional in terests both in foundational research into the new technology of Intelligent Systems and ill the application of that evolving technology to the solution of hard engineering problems. In common with many scientists who build their reputations in one field before devoting their considerable energies and talents to another one, by 1972, the year in which I met him for the first time, Yoh-Han had made significant contributions to laser technology, in particular to the development of the highly accurate and stable lasers required for holographic recording purposes. In conventional holography, the information stored in a hologram produces a virtual image of the object charac terised by it. However, Yoh-Han became fascinated by the possiblity of driving the process hackwards, of using the hologram as an associative memory device enabling previously stored information to be retrieved on the basis of partial cues. It was this burgeoning interest which shaped his career for more than twenty years. Just prior to 1972, my colleagues Professor Christopher Longuet-Higgins and Dr. COMPUTERS,Artificial Intelligence,General

Simulation-Based Experiential Learning Proceediings of the NATO Advanced Research Workshop on The Use of Computer Models for Explication, Analysis and Experiential Learning, held in Bonas, France, October 12-14, 1992 COMPUTERS,Artificial Intelligence,General

AI and Cognitive Science ’92 The annual Irish Conferences on Artificial Intelligence and Cognitive Science have become the major forum in Ireland for the discussion of various aspects of artificial intelligence. Their aim is to provide a forum where researchers can present their current work, and where industrial and commercial users can relate this work to their own practical needs and experiences. Although the emphasis of the conferences is on Irish research, there are also important contributions from Europe, Australia, Canada, and the USA. This volume is based on the proceedings of the Fifth Irish Conference on Artificial Intelligence and Cognitive Science (AICS'92), which was held at the University of Limerick, Ireland, from 10-11 September 1992. The conference was divided into 6 sessions, covering knowledge representation, cognitive foundations, natural language 1 and 2, learning and expert systems, and nov§ el aspects of artificial intelligence and cognitive science. Because of the high number of papers submitted to the conference, a poster session was run in addition to the plenary sessions. Each paper presented at the poster session is represented in this volume by a four page abstract. Among the specific topics covered in this volume are: a model-based theory of conceptual combination; the nature and development of reasoning strategies; word recognition as a parsing problem; a knowledge-based autonomous vehicle system for emergency management support; the construction and use of scope neutral discourse entities; computer-based iconic communication; and exceptions in multiple inheritance systems. AI and Cognitive Science '92 provides a comprehensive record of current research into this important field. It will be of interest to researchers, lecturers and postgraduate students in a variety of disciplines related to artificial intelligence and cognitive science. COMPUTERS,Artificial Intelligence,General

Expert Systems in Engineering Applications Expert system technology is receiving increasing popularityand acceptance in the engineering community. This is due tothe fact that there actually exists a close match betweenthe capabilities of the current generation expert systemsand the requirements of engineering practice. Prepared by adistinguished team of experts, this book provides a balancedstate-of-the-art presentation of the design principles ofengineering expert systems, and a representative picture oftheir capabilities to assist efficiently the design,diagnosis and operation of complex industrial plants.Among the application areas covered are the following:hardware synthesis, industrial plant layout design, faultdiagnosis, process control, image analysis, computercommunication, electric power systems, intelligent control,robotics, and manufacturing systems. The book is appropriatefor the researcher and the professional. The researcher cansave considerable time in searching the scattered technicalinformation on engineering expert systems. The professionalcan have readily available a rich set of guidelines andtechniques that are applicable to a wide class ofengineering domains. COMPUTERS,Artificial Intelligence,General

The Practical Intellect The intention of this book is not to add another technical work to the series of publications already available on matters connected with the relations between natural and artificial intelligence, nor to repeat the positions already well expressed in, for example, the debate between John Searle, Daniel Dennet and Hubert Dreyfus. It is an attempt to encourage philosophical reflection on dimensions of the subject that have hitherto been somewhat neglected. This book, which explores a number of case studies, is the fifth in the series, the previous four books being: (i) Knowledge, Skill and Artificial Intelligence (Bo Goranzon and Ingela Josefson (Eds. ), Springer-Verlag, London, 1988) (ii) Artificial Intelligence, Culture and Language: On Education and Work (Bo Goranzon and Magnus Florin (Eds. ), Springer Verlag, London, 1990) (iii) Dialogue and Technology: Art and Knowledge (Bo Goranzon and Magnus Florin (Eds. ), Springer-Verlag, London, 1991) (iv) Skill and Education: Reflection and Experience (Bo Goranzon and Magnus Florin (Eds. ), Springer-Verlag, London, 1992) An important connection between these four books is the conference on Culture, Language and Artificial Intelligence held in Stockholm in May-June, 1988. The conference was attended by more than 300 researchers and practitioners, from over 15 countries, in the fields of technology, philosophy, the history of ideas, literature and linguistics. Contributions to the books were solicited from among those who attended the conference and from researchers involved in work related to its aim. COMPUTERS,Artificial Intelligence,General

Communication from an Artificial Intelligence Perspective Proceedings of the NATO Advanced Research Workshop on Computational Theories of Communication and Their Applications: Problems and Perspectives, held at Castel Ivano, Trento, Italy, November 5-9, 1990 COMPUTERS,Artificial Intelligence,General

Computers and Writing This book grew out of the Fourth Conference on Computers and the Writing Process, held at the University of Sussex in March 1991. The conference brought together a wide variety of people interested in most aspects of computers and the writing process including, computers and writing education, computer supported fiction, computers and technical writing, evaluation of computer-based writing, and hypertext. Fifteen papers were selected from the twenty-five delivered at the conference. The authors were asked to develop them into articles, incorporating any insights they had gained from their conference presentations. This book offers a survey of the wide area of Computers and Writing, and describes current work in the design and use of computer-based tools for writing. University of Sussex M.S. October, 1991 Note from Publisher This collection of articles is being published simultaneously as a special issue, Volume 21(1-3), of Instructional Science - An International Journal of Learning and Cognition. Instructional Science 21: 1-4 (1992) 1 © Kluwer Academic Publishers, Dordrecht Introduction MIKE SHARPLES School of Cognitive and Computing Sciences, University of Sussex, Falmer, Brighton BNl 9QH, United Kingdom. COMPUTERS,Artificial Intelligence,General

Connectionism in Context Connectionism in Context aims to broaden and extend thedebate concerning the significance of connectionist models.The volume collects together a variety of perspectives byexperimental and developmental psychologists, philosophersand active AI researchers. These contributions relate con-nectionist ideas to historical psychlogical debates, e.g.,over behaviourism and associationism, to develop-mental and philosophical issues. The result is a volumewhich addresses both familiar, but central, topics such asthe relation between connectionism and classical AI, andless familiar, but highly challenging topics, such asconnectionism,associationism and behaviourism, the dis-tinction between perception and cognition, the role of en-vironmental structure, and the potential value ofconnec-tionism as a means of "symbol grounding". The nine essayshave been written with an interdisciplinary audience in mindand avoid both technical jargon and heavy mathematics. COMPUTERS,Artificial Intelligence,General

Informationssysteme und Künstliche Intelligenz Neuere Entwicklungen im Datenbank- undInformationssystembereich sind u.a. gekennzeichnet durch dieBereitstellung sehr m{chtiger semantischer bzw.objektorientierter Datenmodelle, um den Anforderungen aussogenannten Nicht-Standardanwendungen wie z.B. demB}robereich gerecht zu werden. Daraus ergeben sichunmittelbar neue Problemstellungen imHinblick auf dieEntwurfs- und Modellierungsaufgaben, die mit dem Einsatzderartiger m{chtiger Datenmodelle verbunden sind.Betrachtet manandererseits Entwicklungstendenzen imBereich der K}nstlichen Intelligenz, so wird Fragen dersystematischen Entwicklung Wissensbasierter Systeme eineimmer gr|~ere Wichtigkeit beigemessen. Dabei spielen u.a.Phasen-Systeme und damit verbunden der Aufbau geeigneterModelle eine zentrale Rolle. Dementsprechend hat der 2.Workshop "Informationssysteme und K}nstliche Intelligenz"gerade das Gebiet der Modellierung als generelles Thema.Zielsetzung ist dabei, auf dem Gebiet derModellierungGemeinsamkeiten und Unterschiede von Problemstellungen bzw.L|sungsans{tzen, die in den Fachdisziplinen K}nstlicheIntelligenz und Informationssysteme/Datenbanksystemeidentifiziert bzw. entwickelt worden sind,herauszuarbeiten. Damit soll gleichzeitig derGedankenaustausch zwischen den beteiligten Fachdisziplinengef|rdertund die Zusammenarbeit }ber Fachdisziplinen hinwegverbessert werden. COMPUTERS,Artificial Intelligence,General

Computers and Writing Patrik O'Brian Holt Heriot-Watt University After speech, writing is the most common form of human communication and represents the cornerstone of our ability to preserve and record information. Writing, by its very definition, requires artifacts in the form of tools to write with and a medium to write on. Through history these artifacts have ranged from sticks and clay tablets, feather and leather, crude pens and paper, sophisticated pens and paper, typewriters and paper; and electronic devices with or without paper. The development of writing tools has straightforward objectives, to make writing easier and more effective and assist in distributing written communication fast and efficiently. Both the crudest and most sophisticated forms of writing tools act as mediators of human written communication for the purpose of producing, distributing and conserving written language. In the modern world the computer is arguably the most sophisticated form of mediation, the implications of which are not yet fully understood. The use of computers (a writing artifact which mediates communication) for the production and editing of text is almost as old as computers themselves. Early computers involved the use of crude text editors and a writer had to insert commands resembling a programming language to format and print a document. For example to underline a word the writer had to do the following, This is an example of how to .ul underline a single word. in order to produce: This is an example of how to underline a single word. COMPUTERS,Artificial Intelligence,General

An Introduction to Fuzzy Logic Applications in Intelligent Systems An Introduction to Fuzzy Logic Applications in Intelligent Systems consists of a collection of chapters written by leading experts in the field of fuzzy sets. Each chapter addresses an area where fuzzy sets have been applied to situations broadly related to intelligent systems. The volume provides an introduction to and an overview of recent applications of fuzzy sets to various areas of intelligent systems. Its purpose is to provide information and easy access for people new to the field. The book also serves as an excellent reference for researchers in the field and those working in the specifics of systems development. People in computer science, especially those in artificial intelligence, knowledge-based systems, and intelligent systems will find this to be a valuable sourcebook. Engineers, particularly control engineers, will also have a strong interest in this book. Finally, the book will be of interest to researchers working in decision support systems, operations research, decision theory, management science and applied mathematics. An Introduction to Fuzzy Logic Applications in Intelligent Systems may also be used as an introductory text and, as such, it is tutorial in nature. COMPUTERS,Artificial Intelligence,General

Natural Object Recognition Natural Object Recognition presents a totally new approach to the automation of scene understanding. Rather than attempting to construct highly specialized algorithms for recognizing physical objects, as is customary in modern computer vision research, the application and subsequent evaluation of large numbers of relatively straightforward image processing routines is used to recognize natural features such as trees, bushes, and rocks. The use of contextual information is the key to simplifying the problem to the extent that well understood algorithms give reliable results in ground-level, outdoor scenes. COMPUTERS,Artificial Intelligence,General

Coupled Oscillating Neurons This volume consists of proceedings of the one-day conference on "Coupled Oscillating Neurons" held at King's College, London on December 13th, 1990. The subject is currently of increasing interest to neurophysiologists, neural network researchers, applied mathematicians and physicists. The papers attempt to cover the major areas of the subject, as the titles indicate. It is hoped that the appearance of the papers (some of which have been updated since their original presentation) indicates why the subject is becoming of great excitement. A better understanding of coupled oscillating neurons may well hold the key to a clearer appreciation of the manner in which neural networks composed of such elements can control complex behaviour from the heart to consciousness. December 1991 J.G. Taylor King's College, London C.L.T. Mannion CONTENTS Contributors....... ..................... .......... .......................... .................... ix Introduction to Nonlinear Oscillators I. Stewart ....................................................................................... . Identical Oscillator Networks with Symmetry P.B. Ashwin .................................................................................... 21 Bifurcating Neurones AV. Holden, J. Hyde, M.A Muhamad, H.G. Zhang....................... 41 A Model for Low Threshold Oscillations in Neurons J.L. Hindmarsh, R.M. Rose ............................................................ 81 Information Processing by Oscillating Neurons C.L. T. Mannion, J.G. Taylor ........................................................... 100 Gamma Oscillations, Association and Consciousness R.M.J. Cotterill, C. Nielsen ............................................................. 117 Modelling of Cardiac Rhythm: From Single Celis to Massive Networks D. Noble, J. C. Denyer, H.F. Brown, R. Winslow, A Kimball .......... 1 32 CONTRIBUTORS Ashwin, P.B. Mathematics Institute, University of Warwick, Coventry, CV4 7 AL, UK Brown, H.F. COMPUTERS,Artificial Intelligence,General

Speech Recognition and Understanding Proceedings of the NATO Advanced "Study Institute on Speech Recognition and Understanding. Recent Advances, Trends and Applications" held in Cetraro, Italy, July 1-13, 1990 COMPUTERS,Artificial Intelligence,General

Intelligent Decision Support Intelligent decision support is based on human knowledge related to a specific part of a real or abstract world. When the knowledge is gained by experience, it is induced from empirical data. The data structure, called an information system, is a record of objects described by a set of attributes. Knowledge is understood here as an ability to classify objects. Objects being in the same class are indiscernible by means of attributes and form elementary building blocks (granules, atoms). In particular, the granularity of knowledge causes that some notions cannot be expressed precisely within available knowledge and can be defined only vaguely. In the rough sets theory created by Z. Pawlak each imprecise concept is replaced by a pair of precise concepts called its lower and upper approximation. These approximations are fundamental tools and reasoning about knowledge. The rough sets philosophy turned out to be a very effective, new tool with many successful real-life applications to its credit. It is worthwhile stressing that no auxiliary assumptions are needed about data, like probability or membership function values, which is its great advantage. The present book reveals a wide spectrum of applications of the rough set concept, giving the reader the flavor of, and insight into, the methodology of the newly developed disciplines. Although the book emphasizes applications, comparison with other related methods and further developments receive due attention. COMPUTERS,Artificial Intelligence,General

Intelligent Tutoring Systems for Foreign Language Learning Proceedings of the NATO Advanced Research Workshop "The Bridge to International Communication: Intelligent Tutoring Systems for Foreign Language Learning", held in Washington, DC, September 19-21, 1990 COMPUTERS,Artificial Intelligence,General
Industrial Applications of Neural Networks Neural network technology encompasses a class of methodswhich attempt to mimic the basic structures used in thebrain for information processing. Thetechnology is aimed atproblems such as pattern recognition which are difficult fortraditional computational methods. Neural networks havepotential applications in many industrial areas such asadvanced robotics, operations research, and processengineering.This book is concerned with the application of neuralnetwork technology to real industrial problems. Itsummarizes a three-year collaborative international projectcalled ANNIE (Applications of Neural Networks for Industryin Europe) which was jointly funded by industry and theEuropean Commission within the ESPRIT programme. As a recordof a working project, the book gives an insight into thereal problems faced in taking a new technology from theworkbench into a live industrial application, and shows justhow it can be achieved. It stresses the comparison betweenneural networks and conventional approaches. Even thenon-specialist reader will benefit from understanding thelimitations as well as the advantages of the new technology. COMPUTERS,Artificial Intelligence,General

Beyond Information Preamble The emergence of machine intelligence during the second half of the twentieth century is the most important development in the evolution of this planet since the origin of life two to three thousand million years ago. The emergence of machine intelligence within the matrix of human society is analogous to the emergence, three billion years ago, of complex, self-replicating molecules within the matrix of an energy-rich molecular soup - the first step in the evolution of life. The emergence of machine intelligence within a human social context has set into motion irreversible processes which will lead to an evolutionary discontinuity. Just as the emergence of "Life" represented a qualitatively different form of organisation of matter and energy, so will pure "Intelligence" represent a qualitatively different form of organisation of matter, energy and life. The emergence of machine intelligence presages the progression of the human species as we know it, into a form which, at present, we would not recognise as "human". As Forsyth and Naylor (1985) have pointed out: "Humanity has opened two Pandora's boxes at the same time, one labelled genetic engineering, the other labelled knowledge engineering. What we have let out is not entirely clear, but it is reasonable to hazard a guess that it contains the seeds of our successors". COMPUTERS,Artificial Intelligence,General

Analogy and Structure Analogy and Structure provides the necessary foundation for understanding the nature of analogical and structuralist (or rule-based) approaches to describing behavior. In the first part of this book, the mathematical properties of rule approaches are developed; in the second part, the analogical alternative to rules is developed. This book serves as the mathematical basis for Analogical Modeling of Language (Kluwer, 1989). Features include: A Natural Measure of Uncertainty: The disagreement between randomly chosen occurences avids the difficulties of using entropy as the measure of uncertainty. Optimal Descriptions: The implicit assumption of structuralist descriptions (namely, that descriptions of behavior should be corrected and minimal) can be derived from more fundamental statements about the uncertainty of rule systems. Problems with Rule Approaches: The correct description of nondeterministic behavior leads to an atomistic, analog alternative to structuralist (or rule-based) descriptions. Natural Statistics: Traditional statistical tests are eliminated in favor of statistically equivalent decision rules that involve little or no mathematical calculation. Psycholinguistic Factors: Analogical models, unlike, neural networks, directly account for probabilistic learning as well as reaction times in world-recognition experiments. COMPUTERS,Artificial Intelligence,General

A Natural Language and Graphics Interface In the terminal phase of the ACORD project, the idea of documenting relevant results and perspectives grew among most of the involved partners. This book is the outcome of the idea. It completes in a more theoretically perspective the final technical documentation of the project (see p. 6 footnote 1) which is mainly focussed in the description of the integrated demonstrator and of each of its modules. The reader will find in chapter 1 a brief presentation of the general architecture of the ACORD system and pointers to each of the subsequent chapters. These cover the main results and perspectives of the project on grammar formalisms and implementation, for both parsing and generation, graphics and natural language integration, and knowledge base formalism. The production of the book benefited from a fund of Alcatel Alsthom Recherche, from the techni cal assistance of Karine Baschung and from a carefull typographic revision and final preparation of the submitted texts by Sylvie Di Penta. Gabriel G. Bes VI CONTRIBUTORS KARINE BAS CHUNG Formation Doctorale Linguistique et Informatique, Universite Blaise Pascal (Clermont Ferrand II), 34 Avenue Carnot, 63037 Clermont Ferrand Cedex, France. GABRIEL G. BES Formation Doctorale Linguistique et Informatique, Universite Blaise Pascal (Clermont Ferrand II), 34 Avenue Carnot, 63037 Clermont Ferrand Cedex, France. FRIEDRICH DUDDA Triumph-Adler, Hundingst. 11 bd, 8500 Nuremberg, Germany. CLAIRE GARDENT Departement of Philosophy, Facultet der Wisjbegeerte, Heidelberglaan, 2 Postbus 80103,3508 TC Utrecht, The Netherlands. THIERRY GUILLOTIN Centre Scientifique d'IBM France, 3-5 Place Vendome, 75021 Paris Cedex 01, France. COMPUTERS,Artificial Intelligence,General

Neural Network Dynamics Neural Network Dynamics is the latest volume in the Perspectives in Neural Computing series. It contains papers presented at the 1991 Workshop on Complex Dynamics in Neural Networks, held at IIASS in Vietri, Italy. The workshop encompassed a wide range of topics in which neural networks play a fundamental role, and aimed to bridge the gap between neural computation and computational neuroscience. The papers - which have been updated where necessary to include new results - are divided into four sections, covering the foundations of neural network dynamics, oscillatory neural networks, as well as scientific and biological applications of neural networks. Among the topics discussed are: A general analysis of neural network activity; Descriptions of various network architectures and nodes; Correlated neuronal firing; A theoretical framework for analyzing the behaviour of real and simulated neuronal networks; The structural properties of proteins; Nuclear phenomenology; Resonance searches in high energy physics; The investigation of information storage; Visual cortical architecture; Visual processing. Neural Network Dynamics is the first volume to cover neural networks and computational neuroscience in such detail. Although it is primarily aimed at researchers and postgraduate students in the above disciplines, it will also be of interest to researchers in electrical engineering, medicine, psychology and philosophy. COMPUTERS,Artificial Intelligence,General

Human-Centred Systems in the Global Economy The arrival of the information society in Japan has radically altered the industrial structure, work patterns and cultural values of its society. The innovation and implementation of information technology has accelerated this change and made its effects more profoundly felt. Because of this, there is now a need to widen the debate on human-centred manufacturing systems to include broader issues such as industrial culture, international economies and global knowledge. Human Centred Systems in the Global Economy contains the proceedings of an international workshop held at Tokyo Keizai University which looked at the design of human-centred systems in the context of these technological and social changes. The workshop attracted contributions from internationally known researchers in Europe, Japan, the USA, South East Asia, Eastern Europe and the USSR. The resulting volume is unique in that it addresses the relationship of information technology to Japanese society as a whole, rather than concentrating on technical issues. The papers have been divided into three areas, covering the structure, dimensions, and policies and perspectives of the information society. Specific areas covered include: social and cultural shaping of technology, economic interdependence, technology and knowledge transfer, computer-aided design, management culture and communication technologies. Human Centred Systems in the Global Economy provides a comprehensive assessment of the debates on human-centred systems and will be of interest to people in a wide variety of disciplines including information technology, economic development, management science and related studies of social science and humanities. COMPUTERS,Artificial Intelligence,General

Skill and Education This book has an important starting point in the conference held in Stockholm in May-June 1988 on Culture, Language and Artifidal Intelligence. It assembled more than 300 researchers and practitioners in the fields of technology, philosophy, history of ideas, literature, linguistics, sodal science etc. The conference was an initiative from the Swedish Center for Working Life, based on the project AI-Based Systems and the Future of Language, Knowledge and Responsibility in Professions within the COST 13 programme of the European Commission. Partidpants in the conference and researchers related to its aims were chosen to contribute to this book. It is preceded by Knowledge, Skill and Artificial Intelligence (ed. B. Göranzon and I. Josefson, Springer-Verlag, 1988), Artifidal Intelligence, Culture and Language (ed. B. Göranzon and M. Florin, Springer-Verlag, 1990) and Dialogue and Technology: Art and Knowledge (ed. B. Göranzon and M. Florin, Springer-Verlag, 1991). The two latter books have the same conference connection as this one, and their aim is to present the contours of a research field with a multitude of issues that demands thorough investigation. The contributors' thinking in this field varies greatly; so do their styles of writing. For example: contributors have varied in their choice of "he" or "helshe" for the third person. No distinc tion is intended, but chapters have been left with the original usage to avoid extensive changes. Similarly, individual contribu tor's preference as to notes or reference lists have been followed. COMPUTERS,Artificial Intelligence,General

New Directions for Intelligent Tutoring Systems This book is a result of the NATO Advanced Research Workshop on New Directions for Intelligent Tutoring Systems, held in Sintra, Portugal, October 6-10, 1990. The main idea behind the workshop was to bring together scientists with different concerns about Intelligent Tutoring Systems (ITS) in order to discuss the positive and negative aspects of the current architecture paradigm (expert module, student module, instructional module, and interface module) and, eventually, propose some modifications or radical changes to it. This was a consequence of the increasing malaise felt currently by researchers in the area of artificial intelligence and education and in particular by those concerned with ITS. One symptom of this state of affairs is the fact that people have started talking about Intelligent Learning Environ ments (lLE) instead of ITS. To understand the reasons for this situation we promoted the discussion of questions like: - To what extent do we need the technology of expert systems in ITS? Which other relevant AI techniques and methodologies are urgently needed? - Is ITS a tool for knowledge communication or is it rather a belief system? - How can the research already done on interactions among agents be utilized? - Is it possible to find a fonnal theory to describe and solve the current problems with ITS? The book contains the revised versions of the papers presented at the workshop. The new texts reflect the discussions that took place at the meeting. COMPUTERS,Artificial Intelligence,General

Cognitive Tools for Learning Proceedings of the NATO Advanced Study Institute on Mindtools: Cognitive Technologies for Modeling Knowledge, held in Enschede, The Netherlands, July 4-10, 1990 COMPUTERS,Artificial Intelligence,General

BMVC92 This book contains the 61 papers that were accepted for presenta tion at the 1992 British Machine Vision Conference. Together they provide a snapshot of current machine vision research throughout the UK in 24 different institutions. There are also several papers from vision groups in the rest of Europe, North America and Australia. At the start of the book is an invited paper from the first keynote speaker, Robert Haralick. The quality of papers submitted to the conference was very high and the programme committee had a hard task selecting around half for presentation at the meeting and inclusion in these proceedings. It is a positive feature of the annual BMV A conference that the entire process from the submission deadline through to the conference itself and publication of the proceedings is completed in under 5 months. My thanks to members of the programme committee for their essential contribution to the success of the conference and to Roger Boyle, Charlie Brown, Nick Efford and Sue Nemes for their excellent local organisation and administration of the conference at the University of Leeds. COMPUTERS,Artificial Intelligence,General

Artificial Intelligence Through Search This is an important textbook on artificial intelligence that uses the unifying thread of search to bring together most of the major techniques used in symbolic artificial intelligence. The authors, aware of the pitfalls of being too general or too academic, have taken a practical approach in that they include program code to illustrate their ideas. Furthermore, code is offered in both POP-11 and Prolog, thereby giving a dual perspective, highlighting the merits of these languages. Each chapter covers one technique and divides up into three sections: a section which introduces the technique (and its usual applications) andsuggests how it can be understood as a variant/generalisation of search; a section which developed a `low'-level (POP-11) implementation; a section which develops a high-level (Prolog) implementation of the technique. The authors also include useful notes on alternative treatments to the material, further reading and exercises. As a practical book it will be welcomed by a wide audience including, those already experienced in AI, students with some background in programming who are taking an introductory course in AI, and lecturers looking for a precise, professional and practical text book to use in their AI courses. About the authors: Dr Christopher Thornton has a BA in Economics, an Sc in Computer Science and a DPhil in Artificial Intelligence. Formerly a lecturer in the Department of AI at the University of Edinburgh, he is now a lecturer in AI in the School of Cognitive and Computing Sciences at the University of Sussex. Professor Benedict du Boulay has a BSc in Physics and a PhD in Artificial Intelligence. Previously a lecturer in the Department of Computing Science at the University of Aberdeen he is currently Professor of Artificial Intelligence, also in the School of Cognitive and Computing Sciences, University of Sussex. COMPUTERS,Artificial Intelligence,General

Theory and Applications of Neural Networks This volume contains the papers from the first British Neural Network Society meeting held at Queen Elizabeth Hall, King's College, London on 18--20 April 1990. The meeting was sponsored by the London Mathemati cal Society. The papers include introductory tutorial lectures, invited, and contributed papers. The invited contributions were given by experts from the United States, Finland, Denmark, Germany and the United Kingdom. The majority of the contributed papers came from workers in the United Kingdom. The first day was devoted to tutorials. Professor Stephen Grossberg was a guest speaker on the first day giving a thorough introduction to his Adaptive Resonance Theory of neural networks. Subsequent tutorials on the first day covered dynamical systems and neural networks, realistic neural modelling, pattern recognition using neural networks, and a review of hardware for neural network simulations. The contributed papers, given on the second day, demonstrated the breadth of interests of workers in the field. They covered topics in pattern recognition, multi-layer feedforward neural networks, network dynamics, memory and learning. The ordering of the papers in this volume is as they were given at the meeting. On the final day talks were given by Professor Kohonen (on self organising maps), Professor Kurten (on the dynamics of random and structured nets) and Professor Cotterill (on modelling the visual cortex). Dr A. Mayes presented a paper on various models for amnesia. The editors have taken the opportunity to include a paper of their own which was not presented at the meeting. COMPUTERS,Artificial Intelligence,General

Computer-aided Manufacturing and Women’s Employment Drawing on the experiences of four major EC countries, this book documents the way computer technology has changed the pattern of women's work in the manufacturing sector. The sixteen contributors are leading authorities on the subject and analyse how technology has transformed employment in the clothing industry, which is still the major employer of female blue-collar workers in the EC. The contributors assess the aspects of computerisation that particularly affect women's employment opportuni- ties: flexible hours, flexible work locations and flexible specialisation. The book also contains evaluations of post-Fordism and human-centred technology, two leading issues in the debate about the applications of artificial intelligence and computer-aided technology. These essays highlight a growing polarisation in the job market and suggest training schemes which can equip women for technical and managerial employment. This is a pioneering work; so far, most of the literature on women and computerisation has focussed on office automation and data processing. Computer-aided Manufacturing and Women's Employment makes an important contribution to the fields of technology, employment, women's work, business management and trade union studies. COMPUTERS,Artificial Intelligence,General

Active Perception and Robot Vision Proceedings of the NATO Advanced Study Institute on Active Perception and Robot Vision, held at Maratea, Italy, July 16-29, 1989 COMPUTERS,Artificial Intelligence,General

Adaptive Learning Environments Adaptive Learning Environments (ALEs) can be viewed as theintersection of two traditionally distinct areas ofresearch: instructional science and computer science. Theyencompass intelligent tutoring systems, interactive learningenvironments, and situated learning environments. There isincreasing interest in effective instructional systems fromeducation, industry, military and government sectors. Givenrecent advances in hardware architecture and reduction ofhardware costs, the time is right to define the next stepsin research and development of ALEs.This book is an outgrowth of the presentations anddiscussions that took place at the NATO Advanced StudyInstitute held at the University of Calgary in July 1990. Itcontains chapters from both researchers in instructionalscience and researchers in computer science on the followingtopics:- Systems and architectures for instruction- Representing curriculum and designing instructional tasks- Environments to support learning- Diagnosing students' learning and adjusting plans forinstruction- Models of students' metacognition, motivation and learningstrategies- Student-system interactions.The book containsintroductions/critiques of each pair ofchapters, and a final chapter discusses the synthesis ofinstructional science and computer science. COMPUTERS,Artificial Intelligence,General

Rough Sets To-date computers are supposed to store and exploit knowledge. At least that is one of the aims of research fields such as Artificial Intelligence and Information Systems. However, the problem is to understand what knowledge means, to find ways of representing knowledge, and to specify automated machineries that can extract useful information from stored knowledge. Knowledge is something people have in their mind, and which they can express through natural language. Knowl edge is acquired not only from books, but also from observations made during experiments; in other words, from data. Changing data into knowledge is not a straightforward task. A set of data is generally disorganized, contains useless details, although it can be incomplete. Knowledge is just the opposite: organized (e.g. laying bare dependencies, or classifications), but expressed by means of a poorer language, i.e. pervaded by imprecision or even vagueness, and assuming a level of granularity. One may say that knowledge is summarized and organized data - at least the kind of knowledge that computers can store. COMPUTERS,Artificial Intelligence,General
Common LISP Modules While creativity plays an important role in the advancement of computer science, great ideas are built on a foundation of practical experience and knowledge. This book presents programming techniques which will be useful in both AI projects and more conventional software engineering endeavors. My primary goal is to enter tain, to introduce new technologies and to provide reusable software modules for the computer programmer who enjoys using programs as models for solutions to hard and interesting problems. If this book succeeds in entertaining, then it will certainly also educate. I selected the example application areas covered here for their difficulty and have provided both program examples for specific applications and (I hope) the method ology and spirit required to master problems for which there is no obvious solution. I developed the example programs on a Macintosh ™ using the Macintosh Common LISP ™ development system capturing screen images while the example programs were executing. To ensure portability to all Common LISP environments, I have provided a portable graphics library in Chapter 2. All programs in this book are copyrighted by Mark Watson. They can be freely used in any free or commercial software systems if the following notice appears in the fine print of the program's documentation: "This program contains software written by Mark Watson." No royalties are required. The program miniatures contained in this book may not be distributed by posting in source code form on public information networks, or in printed form without my written permission. COMPUTERS,Artificial Intelligence,General
Sensor-Based Robots Proceedings of the NATO Advanced Research Workshop on Sensor-Based Robots: Algorithms and Architectures, held in Chateau de Bonas, France, October 12-14, 1988 COMPUTERS,Artificial Intelligence,General

Uncertainty and Vagueness in Knowledge Based Systems The primary aim of this monograph is to provide a formal framework for the representation and management of uncertainty and vagueness in the field of artificial intelligence. It puts particular emphasis on a thorough analysis of these phenomena and on the development of sound mathematical modeling approaches. Beyond this theoretical basis the scope of the book includes also implementational aspects and a valuation of existing models and systems. The fundamental ambition of this book is to show that vagueness and un certainty can be handled adequately by using measure-theoretic methods. The presentation of applicable knowledge representation formalisms and reasoning algorithms substantiates the claim that efficiency requirements do not necessar ily require renunciation of an uncompromising mathematical modeling. These results are used to evaluate systems based on probabilistic methods as well as on non-standard concepts such as certainty factors, fuzzy sets or belief functions. The book is intended to be self-contained and addresses researchers and practioneers in the field of knowledge based systems. It is in particular suit able as a textbook for graduate-level students in AI, operations research and applied probability. A solid mathematical background is necessary for reading this book. Essential parts of the material have been the subject of courses given by the first author for students of computer science and mathematics held since 1984 at the University in Braunschweig. COMPUTERS,Artificial Intelligence,General

Managing Uncertainty in Expert Systems 3. Textbook for a course in expert systems,if an emphasis is placed on Chapters 1 to 3 and on a selection of material from Chapters 4 to 7. There is also the option of using an additional commercially available sheU for a programming project. In assigning a programming project, the instructor may use any part of a great variety of books covering many subjects, such as car repair. Instructions for mostofthe "weekend mechanic" books are close stylisticaUy to expert system rules. Contents Chapter 1 gives an introduction to the subject matter; it briefly presents basic concepts, history, and some perspectives ofexpert systems. Then itpresents the architecture of an expert system and explains the stages of building an expert system. The concept of uncertainty in expert systems and the necessity of deal ing with the phenomenon are then presented. The chapter ends with the descrip tion of taxonomy ofexpert systems. Chapter 2 focuses on knowledge representation. Four basic ways to repre sent knowledge in expert systems are presented: first-order logic, production sys tems, semantic nets, and frames. Chapter 3 contains material about knowledge acquisition. Among machine learning techniques, a methodofrule learning from examples is explained in de tail. Then problems ofrule-base verification are discussed. In particular, both consistency and completeness oftherule base are presented. COMPUTERS,Artificial Intelligence,General

CKBS ’90 This is the first international conference aimed at bringing the distributed database and distributed AI (DAD experts together, from both academia and industry, in order to discuss the issues of the next generation of knowledge based systems, namely Cooperating Knowledge Based Systems or CKBS for short. As the area of CKBS is new, we intended it to be an ideas conference - a conference where interesting new ideas, rather than results from completed projects, are explored, discussed, and debated. The conference was organised by the DAKE Centre. This is an interdisciplinary centre at the University of Keele for research and development in Data and Knowledge Engineering (DAKE). The Centre draws most of its strength from the Department of Computer Science which also provides administrative support for the activities of the Centre, although its membership is spread over several departments. The Centre has three main streams of research activities, namely: Large Knowledge Bases Software Engineering Neural Networks The Large Knowledge Base group, which provided the focus for this conference, is active in a number of research areas relating to data and knowledge bases, spanning from distributed databases to cooperations among data and knowledge bases. The current research topics include integration of data and knowledge bases and coopera ting knowledge based systems, with several major projects in the latter (see the entries under the Poster Session given below). COMPUTERS,Artificial Intelligence,General

AISB91 AISB91 is the eighth conference organized by the Society for the Study of Artificial Intelligence and Simulation of Behaviour. It is not only the oldest regular conference in Europe on AI - which spawned the ECAI conferences in 1982 - but it is also the conference that has a tradition for focusing on research as opposed to applications. The 1991 edition of the conference was no different in this respect. On the contrary, research, and particularly newly emerging research dir ections such as knowledge level expert systems research, neural networks and emergent functionality in autonomous agents, was strongly emphasised. The conference was organized around the following sessions: dis tributed intelligent agents, situatedness and emergence in autonomous agents, new modes of reasoning, the knowledge level perspective, and theorem proving and machine learning. Each of these sessions is discussed below in more detail. DISTRIBUTED INTELLIGENT AGENTS Research in distributed AI is concerned with the problem of how multiple agents and societies of agents can be organized to co-operate and collectively solve a problem. The first paper by Chakravarty (MIT) focuses on the problem of evolving agents in the context of Minsky's society of mind theory. It addesses the question of how new agents can be formed by transforming existing ones and illustrates the theory with an example from game playing. Smieja (GMD, Germany) focuses on the problem of organizing networks of agents which consist internally of neural networks. COMPUTERS,Artificial Intelligence,General

Expert Systems and Robotics Proceedings of the NATO Advanced Study Institute on Expert Systems and Robotics, held in Corfu, Greece, July 15-27, 1990 COMPUTERS,Artificial Intelligence,General

Integrating Advanced Technology into Technology Education Proceedings of the NATO Advanced Research Workshop on Integrating Advanced Technology into Technology Education, held in Eindhoven, The Netherlands, October 9 - 12, 1990. COMPUTERS,Artificial Intelligence,General

Generalized LR Parsing The Generalized LR parsing algorithm (some call it "Tomita's algorithm") was originally developed in 1985 as a part of my Ph.D thesis at Carnegie Mellon University. When I was a graduate student at CMU, I tried to build a couple of natural language systems based on existing parsing methods. Their parsing speed, however, always bothered me. I sometimes wondered whether it was ever possible to build a natural language parser that could parse reasonably long sentences in a reasonable time without help from large mainframe machines. At the same time, I was always amazed by the speed of programming language compilers, because they can parse very long sentences (i.e., programs) very quickly even on workstations. There are two reasons. First, programming languages are considerably simpler than natural languages. And secondly, they have very efficient parsing methods, most notably LR. The LR parsing algorithm first precompiles a grammar into an LR parsing table, and at the actual parsing time, it performs shift-reduce parsing guided deterministically by the parsing table. So, the key to the LR efficiency is the grammar precompilation; something that had never been tried for natural languages in 1985. Of course, there was a good reason why LR had never been applied for natural languages; it was simply impossible. If your context-free grammar is sufficiently more complex than programming languages, its LR parsing table will have multiple actions, and deterministic parsing will be no longer possible. COMPUTERS,Artificial Intelligence,General

Structure Level Adaptation for Artificial Neural Networks 63 3. 2 Function Level Adaptation 64 3. 3 Parameter Level Adaptation. 67 3. 4 Structure Level Adaptation 70 3. 4. 1 Neuron Generation . 70 3. 4. 2 Neuron Annihilation 72 3. 5 Implementation . . . . . 74 3. 6 An Illustrative Example 77 3. 7 Summary . . . . . . . . 79 4 Competitive Signal Clustering Networks 93 4. 1 Introduction. . 93 4. 2 Basic Structure 94 4. 3 Function Level Adaptation 96 4. 4 Parameter Level Adaptation . 101 4. 5 Structure Level Adaptation 104 4. 5. 1 Neuron Generation Process 107 4. 5. 2 Neuron Annihilation and Coalition Process 114 4. 5. 3 Structural Relation Adjustment. 116 4. 6 Implementation . . 119 4. 7 Simulation Results 122 4. 8 Summary . . . . . 134 5 Application Example: An Adaptive Neural Network Source Coder 135 5. 1 Introduction. . . . . . . . . . 135 5. 2 Vector Quantization Problem 136 5. 3 VQ Using Neural Network Paradigms 139 Vlll 5. 3. 1 Basic Properties . 140 5. 3. 2 Fast Codebook Search Procedure 141 5. 3. 3 Path Coding Method. . . . . . . 143 5. 3. 4 Performance Comparison . . . . 144 5. 3. 5 Adaptive SPAN Coder/Decoder 147 5. 4 Summary . . . . . . . . . . . . . . . . . 152 6 Conclusions 155 6. 1 Contributions 155 6. 2 Recommendations 157 A Mathematical Background 159 A. 1 Kolmogorov's Theorem . 160 A. 2 Networks with One Hidden Layer are Sufficient 161 B Fluctuated Distortion Measure 163 B. 1 Measure Construction . 163 B. 2 The Relation Between Fluctuation and Error 166 C SPAN Convergence Theory 171 C. 1 Asymptotic Value of Wi 172 C. 2 Energy Function . . COMPUTERS,Artificial Intelligence,General

Artificial Intelligence and Human Institutions Artificial Intelligence and Human Institutions argues that successful applications of artificial intelligence are possible only within an understanding of human institutions and the limitations of technology. Products of artificial intelligence research are becoming widely available to non-specialists using low-cost computer systems, but there has been a lack of communication between re- searchers and community groups. Taking the "weak AI" position, the book explores the way insights and tools from artificial intelligence can be valuable in coming to terms with real world problems. Drawing on the author's extensive practical experience in AI research and research management, the book brings together case studies from the fields of education, training, business, engineering, defence, health, and community work, and suggests future directions. This book deals with advanced concepts of artificial intelligence for non-specialist readers, while providing an introduction to state-of-the-art developments. It seeks to use AI concepts to illuminate the practical and theoretical concerns of institutions and organisations, opening up possibilities for new areas of collaborative work, and revealing new sources of references and ideas. This is the latest title in the Artificial Intelligence and Society series and will be of interest to lecturers and students in AI, education, social and political sciences, and business studies. COMPUTERS,Artificial Intelligence,General

Competitively Inhibited Neural Networks for Adaptive Parameter Estimation Artificial Neural Networks have captured the interest of many researchers in the last five years. As with many young fields, neural network research has been largely empirical in nature, relyingstrongly on simulationstudies ofvarious network models. Empiricism is, of course, essential to any science for it provides a body of observations allowing initial characterization of the field. Eventually, however, any maturing field must begin the process of validating empirically derived conjectures with rigorous mathematical models. It is in this way that science has always pro ceeded. It is in this way that science provides conclusions that can be used across a variety of applications. This monograph by Michael Lemmon provides just such a theoretical exploration of the role ofcompetition in Artificial Neural Networks. There is "good news" and "bad news" associated with theoretical research in neural networks. The bad news isthat such work usually requires the understanding of and bringing together of results from many seemingly disparate disciplines such as neurobiology, cognitive psychology, theory of differential equations, largc scale systems theory, computer science, and electrical engineering. The good news is that for those capable of making this synthesis, the rewards are rich as exemplified in this monograph. COMPUTERS,Artificial Intelligence,General

Exploration and Innovation in Design Exploration and Innovation in Design is one of the first books to present both conceptual and computational models of processes which have the potential to produce innovative results at early stages of design. Discussed here is the concept of exploration where the system, using computational processes, moves outside predefined available decisions. Sections of this volume discuss areas such as design representation and search, exploration and the emergence of new criteria, and precedent-based adaptation. In addition, the author presents the overall architecture of a design system and shows how the pieces fit together into one coherent system. Concluding chapters of the book discuss relationships of work in design to other research efforts, applications, and future research directions in design. The ideas and processes presented in this volume further our understanding of computational models of design, particularly those that are capable of assisting in the production of non-routine designs, and affirm that we are indeed moving toward a science of design. COMPUTERS,Artificial Intelligence,General

Dialogue and Technology This book springs from a conference held in Stockholm in May June 1988 on Culture, Language and Artificial Intelligence. It assembled more than 300 researchers and practitioners in the fields of technology, philosophy, history of ideas, literature, linguistics, social· science, etc. The conference was an initiative from the Swedish Center for Working Life, based on the project AI-Based Systems mzd the Future of Language, Knowledge and Re sponsibility in Professions within the COST 13 programme of the European Commission. Participants in the conference, or in some cases researchers in areas related to its aims, were chosen to contribute to this book. It was preceded by Knowledge, Skill and Artificial Intelligence (ed. B. Gbranzon and I. Josefson, Springer-Verlag, London, 1988) and Artificial Intelligence, Culture and Language (ed. B. Gbranzon and M. Florin, Springer-Verlag, 1990). The latter book springs, as this one, from the 1988 conference, and one further book will follow: Skill and Education: Reflection and Experience (Springer Verlag, planned autumn 1991). The philosophical and aesthetic interest of the contributions in the present volume is in large part due to the framework of the Dialogue Seminar, held regularly at the Royal Dramatic Theatre in Stockholm, in which several of the contributors have participated. COMPUTERS,Artificial Intelligence,General

Natural Language and Speech This volume in the Basic Research Series consists of the proceedings of the Symposium on Natural Language and Speech held during the ESPRIT Conference of November 1991 - a conference that serves to open up ESPRIT results not only to the ESPRIT community but also to the entire European IT industry and its users. The symposium is organised by the newly launched Network of Excellence on Language and Speech (3701) which brings together the foremost European experts and institutions in these two domains. By bringing together these two communities, which have so far been working in relative isolation from each other, the network aims to augment the focusing of research onto the long-term goal of the "construction of an integrated model of the cognitive chain linking speech to reasoning via natural language". To advance towards this industrially significant goal, the network operates at different levels - a strategy for research, a coordination for the training of needed researchers and a coordination of the use of its resource and communication infrastructure for the most efficient interworking of the members of the community who are spread all over Europe. This symposium is a small but significant building block for the achievement of the goals of the network. COMPUTERS,Artificial Intelligence,General

AI and Cognitive Science ’90 This book contains the edited versions of papers presented at the 3rd Irish Conference on Artificial Intelligence and Cognitive Science, which was held at the University of Ulster at Jordanstown, Northern Ireland on 20-21 September 1990. The main aims of this annual conference are to promote AI research in Ireland, to provide a forum for the exchange of ideas amongst the different disciplines concerned with the study of cognition, and to provide an opportunity for industry to see what research is being carried out in Ireland and how they might benefit from the results of this research. Although most of the partiCipants at the conference came from universities and companies within Ireland, a positive feature of the conference was the extent of interest shown outside of Ireland, resulting in partiCipants from USA, Canada, Austria, and England. The keynote speakers were Professor David Chin, University of Hawaii, and Professor Derek Partridge, University of Exeter, and the topics included machine learning, AI tools and methods, expert systems, speech, vision, natural language, reasoning with uncertain information, and explanation. The sponsors of the conference were Digital Equipment Co (Galway) and the Industrial Development Board for Northern Ireland. COMPUTERS,Artificial Intelligence,General

Automated Reasoning These essays have been written to honor W. W. Bledsoe, a scientist who has contributed to such diverse fields as mathematics, systems analysis, pattern recognition, biology, artificial intelligence, and automated reasoning. The first essay provides a sketch of his life, emphasizing his scientific contributions. The diversity of the fields to which Bledsoe has contributed is reflected in the range of the other essays, which are original scientific contributions by some of his many friends and colleagues. Bledsoe is a founding father of the field of automated reasoning, and a majority of the essays are on that topic. These essays are collected together here not only to acknowledge Bledsoe's manifold and substantial scientific contributions but also to express our appreciation for the great care and energy that he has devoted to nurturing many of the scientists working in those scientific fields he has helped found. Robert S. Boyer Austin February, 1991 ix Acknow ledgements Thanks to Larry Wos, editor of the Journal of Automated Reasoning, and Derek Middleton and Martin Scrivener, Kluwer Academic editors, for sup porting the idea of initiating this collection of essays. Thanks to A. Michael Ballantyne and Michael Spivak, for help with lffi.TWC, especially in identifying many formatting problems and providing fixes. COMPUTERS,Artificial Intelligence,General

Computers, Chess, and Cognition Computers, Chess, and Cognition presents an excellent up-to-date description of developments in computer chess, a rapidly advancing area in artificial intelligence research. This book is intended for an upper undergraduate and above level audience in the computer science (artificial intelligence) community. The chapters have been edited to present a uniform terminology and balanced writing style, to make the material understandable to a wider, less specialized audience. The book's primary strengths are the description of the workings of some major chess programs, an excellent review of tree searching methods, discussion of exciting new research ideas, a philosophical discussion of the relationship of computer game playing to artificial intelligence, and the treatment of computer Go as an important new research area. A complete index and extensive bibliography makes the book a valuable reference work. The book includes a special foreword by Ken Thompson, author of the UNIX operating system. COMPUTERS,Artificial Intelligence,General

Artifical Intelligence, Culture and Language This book springs from a conference held in Stockholm in May June 1988 on Culture, Language and Artificial Intelligence. It assembled more than 300 researchers and practitioners in the fields of technology, philosophy, history of ideas, literature, lin guistics, social science, etc. It was an initiative from the Swedish Center for Working Life, based on the project AI-Based Systems and the Future of Language, Knowledge and Responsibility in Professions within the COST 13 programme of the European Commission. Participants in the conference, or in some cases researchers related to its aims, were chosen to contribute to this book. It was preceded by Knowledge, Skill and Artificial Intelligence (ed. B. G6ranzon and 1. Josefson, Springer-Verlag, London, 1988) and will be followed by Dialogue and Technology (ed. M. Florin and B. Goranzon, Springer-Verlag, London, 1990). The contributors' thinking in this field varies greatly; so do their styles of writing. For example: contributors have varied in their choice of 'he' or 'he/she' for the third person. No distinction is intended but chapters have been left with the original usage to avoid extensive changes. Similarly, individual contributor's preferences as to notes or references lists have been followed. We want to thank our researcher Satinder P. Gill for excellent work with summaries and indexes, and Sandi Irvine of Springer Verlag for eminent editorial work. COMPUTERS,Artificial Intelligence,General

Catalogue of Artificial Intelligence Techniques The purpose of the Catalogue of Artificial Intelligence Techniques is to promote interaction between members of the AI community. It does this by announcing the existence of AI techniques, and acting as a pointer into the literature. Thus the AI community will have access to a common, extensional definition of the field, which will promote a common terminology, discourage the reinvention of wheels, and act as a clearing house for ideas and algorithms. The catalogue is a reference work providing a quick guide to the AI techniques available for different jobs. It is not intended to be a textbook like the Artificial Intelligence Handbook. Intentionally, it only provides a brief description of each technique, with no extended discussion of its historical origin or how it has been used in particular AI programs. The original version of the catalogue was hastily built in 1983 as part of the UK SERC-DoI, IKBS Architecture Study. It was adopted by the UK Alvey Programme and, during the life of the programme, was both circulated to Alvey grant holders in hard copy form and maintained as an on-line document. A version designed for the international community was published as a paperback by Springer-Verlag. All these versions have undergone constant revision and refinement. Springer-Verlag has agreed to reprint the catalogue at frequent intervals in order to keep it up to date and this is the third edition of their paperback version. COMPUTERS,Artificial Intelligence,General

Knowledge, Data and Computer-Assisted Decisions Proceedings of the NATO Advanced Research Workshop on Data, Expert Knowledge and Decisions, held in Hamburg, FRG, September 3-5, 1989 COMPUTERS,Artificial Intelligence,General

Sensory Robotics for the Handling of Limp Materials Proceedings of the NATO Advanced Research Workshop on Sensory Robotics for the Handling of Limp Materials held in Il Ciocco, Italy, October 16-22, 1988 COMPUTERS,Artificial Intelligence,General

Contributions to a Computer-Based Theory of Strategies People use the word strategy in a variety of different contexts. The term has connotations ranging from statesmanship to economic planning, and has become pervasive in the social sciences. We also talk about "problem solving strategies" and "corporate strategy" in a large business enterprise. The concept of strategy applies whenever a sequence of goal-oriented actions is based on large-scale and long-range planning. This monograph gives a systematic overview of the theory of strategies, a new area of enquiry developed over the past two decades by the author and his team. The projects described have clearly defined research objectives and are based on realistic assumptions about the environments in which the programming systems will work, and about the constraints and requirements they have to satisfy. Applications of the systems range over various aspects of air traffic control, automatic verification and validation of discrete-event simulation models, econometric model building, distributed planning systems for manufacturing, control of traffic lights, and others. The book is aimed at researchers, teachers and students in computer science, management science and certain areas of engineering. The reader should have some maturity in computer science and mathematics, and familiarity with the basic concepts of artificial intelligence. COMPUTERS,Artificial Intelligence,General

AI and Cognitive Science ’89 This volume contains the texts of papers presented at the Second Irish Conference on Artificial Intelligence and Cognitive Science, held at Dublin City University in September 1989. This Conference has now become the major annual forum in Ireland for the presentation and discussion of current research work in the multi-disciplinary area of Artificial Intelligence. Papers in this volume have been divided into seven sections which vary in their subject matter. Image processing, human-computer interaction, planning, applications and theory of expert systems, learn ing, speech, and natural language processing and semantics repre sents as broad a spectrum of AI and AI-related topics as can be found in current AI research. This harmonises quite well with the aims and scope of the AICS'89 conference which were to provide a forum for industry and academic research to discuss AI and AI-related topics and we were delighted that such a broad coverage of topics was achieved. Despite the broad nature, however, none of the papers are primarily review articles; each paper presents new research results within its own specific area. COMPUTERS,Artificial Intelligence,General

Kinematic and Dynamic Issues in Sensor Based Control Proceedings of the NATO Advanced Research Workshop on Kinematic and Dynamic Issues in Sensor Based Control held in Il Ciocco, Italy, October 25-31, 1987 COMPUTERS,Artificial Intelligence,General

Highly Redundant Sensing in Robotic Systems Proceedings of the NATO Advanced Research Workshop on Highly Redundant Sensing in Robotic Systems held in Il Ciocco, Italy, May 16-20, 1988 COMPUTERS,Artificial Intelligence,General

Connectionistic Problem Solving 1. 1 The problem and the approach The model developed here, which is actually more a collection of com ponents than a single monolithic structure, traces a path from relatively low-level neural/connectionistic structures and processes to relatively high-level animal/artificial intelligence behaviors. Incremental extension of this initial path permits increasingly sophisticated representation and processing strategies, and consequently increasingly sophisticated behavior. The initial chapters develop the basic components of the sys tem at the node and network level, with the general goal of efficient category learning and representation. The later chapters are more con cerned with the problems of assembling sequences of actions in order to achieve a given goal state. The model is referred to as connectionistic rather than neural, be cause, while the basic components are neuron-like, there is only limited commitment to physiological realism. Consequently the neuron-like ele ments are referred to as "nodes" rather than "neurons". The model is directed more at the behavioral level, and at that level, numerous con cepts from animal learning theory are directly applicable to connectionis tic modeling. An attempt to actually implement these behavioral theories in a computer simulation can be quite informative, as most are only partially specified, and the gaps may be apparent only when actual ly building a functioning system. In addition, a computer implementa tion provides an improved capability to explore the strengths and limita tions of the different approaches as well as their various interactions. COMPUTERS,Artificial Intelligence,General

Traditional and Non-Traditional Robotic Sensors Proceedings of the NATO Advanced Research Workshop on Traditional and Non-Traditional Robotic Sensors, held in Maratea, Italy, August 28-September 2, 1989 COMPUTERS,Artificial Intelligence,General

Computer Animation ’90 Computer Animation '90, the second international workshop on computer animation, was held in Geneva, Switzerland, on April 25-27, 1990. This book contains invited papers and a selection of research papers submitted to this workshop. The contributions address original research as well as results achieved in a number of fields of computer animation including scientific visualization, human animation, behavioral animation, and motion control. COMPUTERS,Artificial Intelligence,General

Knowledge Representation and Defeasible Reasoning This series will include monographs and collections of studies devoted to the investigation and exploration of knowledge, information, and data processing systems of all kinds, no matter whether human, (other) ani mal, or machine. Its scope is intended to span the full range of interests from classical problems in the philosophy of mind and philosophical psy chology through issues in cognitive psychology and sociobiology (concerning the mental capabilities of other species) to ideas related to artificial intelli gence and computer science. While primary emphasis will be placed upon theoretical, conceptual, and epistemological aspects of these problems and domains, empirical, experimental, and methodological studies will also ap pear from time to time. The present volume provides a collection of studies that focus on some of the central problems within the domain of artificial intelligence. These difficulties fall into four principal areas: defeasible reasoning (including the frame problem as apart), ordinary language (and the representation prob lems that it generates), the revision of beliefs (and its rules of inference), and knowledge representation (and the logical problems that are encountered there). These papers make original contributions to each of these areas of inquiry and should be of special interest to those who understand the crucial role that is played by questions of logical form. They vividly illustrate the benefits that can emerge from collaborative efforts involving scholars from linguistics, philosophy, computer science, and AI. J. H. F. COMPUTERS,Artificial Intelligence,General

Advances in Artificial Intelligence Research in artificial intelligence, natural language processing and knowledge-based systems has blossomed during the past decade. At national and international symposia as well as in research centers and universities all over the world, these subjects have been the focus of intense debate and study. This is equally true in Israel which has hosted several international forums on these topics. The articles in this book represent a selection of contributions presented at recent AI conferences held in Israel. A theoretical model for a system that learns from its own experience in playing board games is presented in Learning from Experience in Board Games by Ze'ev Ben-Porat and Martin Golumbic. The model enables such a system to enhance and improve its playing capabilities through the use of a learning mechanism which extracts knowledge from actual playing experience. The learning process requires no external guidance or assistance. This model was implemented and tested on a variant of "Chinese Checkers. " The paper shows the feasibility and validity of the proposed model and investigates the parameters that affect its performance traits. The experimental results give evidence of the validity of the model as a powerful learning mechanism. Original and general algorithms for knowledge extraction and pattern matching were designed and tested as part of the prototype computer system. Analysis of the performance characteristics of these algorithms indicates that they can handle large knowledge bases in an efficient manner. COMPUTERS,Artificial Intelligence,General

Computational Logic This volume has a dual significance to the ESPRIT Basic Research efforts towards forging strong links between European academic and industrial teams carrying out research, often interdisciplinary, at the forefront of Information Technology. Firstly, it consists of the proceedings of the "Symposium on Computational Logic" - held on the occasion of the 7th ESPRIT Conference Week in November 1990 - whose organisation was inspired by the work of Basic Research Action 3012 (COMPULOG). This is a consortium which has attracted world-wide interest, with requests for collaboration throughout Europe, the US and Japan. The work of COMPULOG acts as a focal point in this symposium which is broadened to cover the work of other eminent researchers in the field, thus providing a review of the state of the art in computational logic, new and important contributions in the field, but also a vision of the future. Secondly, this volume is the first of an ESPRIT Basic Research Series of publications of research results. It is expected that the quality of content and broad distribution of this series will have a major impact in making the advances achieved accessible to the world of academic and industrial research alike. At this time, all ESPRIT Basic Research Actions have completed their first year and it is most encouraging and stimulating to see the flow of results such as the fine examples presented in this symposium. COMPUTERS,Artificial Intelligence,General

Expert Systems ***e FACHGEBIET*** Mathematical Geology, Computer Applications, Artificial Intelligence, Urban Economics and Regional Economics ***INTERESSENTENGRUPPE*** Of interest to Urban and Regional planners, civil engineers, geographers; computer scientists; operations researchers; landscape architects; and advanced students in the above disciplines.- Level: Technical Book, Monograph ***URHEBER*** T.J. Kim, University of Illinois, Champaign, IL; L.L. Wiggins, Massachusetts Institute of Technology, Cambridge, MA; J.R. Wright, Purdue University, Lafayette, IN (Eds.) ***TITEL*** Expert Systems: Applications to Urban Planning ***BIBLIOGRAPHISCHE-ANGABEN*** 1990. XIV, 268 pp. 48 figs. Hardcover DM 78,- ISBN 3-540-97171-8 ***LANGTEXT*** While expert systems have become a popular topic in the computing, medical and engineering fields, the expert system is still a new technology in urban planning. This book introduces expert systems for problem solving in urban planning and describes the way in which heuristic knowledge and rules of thumb of expert planners can be represented through computer programs. The book presents practical applications of expert systems for solving many important urban planning problems, particularly those issues that many practicing planners face in their daily operations. Problems and issues discussed are grouped in the following categories: - Land Use Planning - Transportation Planning - Site Selection and Analysis - Environmental Planning - Conflict Mediation and Legal Disputes - Future Developments and Directions Expert Systems: Applications to Urban Planning will benefit both urban planners who wish to learn how this new technology might be applied to their daily work as well as researchers in expert systems seeking new ideas for systems design. COMPUTERS,Artificial Intelligence,General

Artificial Intelligence This series will include monographs and collections of studies devoted to the investigation and exploration of knowledge, information, and data processing systems of all kinds, no matter whether human, (other) animal, or machine. Its scope is intended to span the full range of interests from classical problems in the philosophy of mind and philosophical psycholo gy through issues in cognitive psychology and sociobiology (concerning the mental capabilities of other species) to ideas related to artificial in telligence and to computer science. While primary emphasis will be placed upon theoretical, conceptual, and epistemological aspects of these prob lems and domains, empirical, experimental, and methodological studies will also appear from time to time. The perspective that prevails in artificial intelligence today suggests that the theory of computability defines the boundaries of the nature of thought, precisely because all thinking is computational. This paradigm draws its inspiration from the symbol-system hypothesis of Newell and Simon and finds its culmination in the computational conception of lan guage and mentality. The "standard conception" represented by these views is subjected to a thorough and sustained critique in the pages of this book. Employing a distinction between systems for which signs are signif icant for the users of a system and others for which signs are significant for use by a system, I have sought to define the boundaries of what AI, in principle, may be expected to achieve. COMPUTERS,Artificial Intelligence,General

Probabilistic Reasoning in Intelligent Systems Probabilistic Reasoning in Intelligent Systems is a complete and accessible account of the theoretical foundations and computational methods that underlie plausible reasoning under uncertainty. The author provides a coherent explication of probability as a language for reasoning with partial belief and offers a unifying perspective on other AI approaches to uncertainty, such as the Dempster-Shafer formalism, truth maintenance systems, and nonmonotonic logic. The author distinguishes syntactic and semantic approaches to uncertainty--and offers techniques, based on belief networks, that provide a mechanism for making semantics-based systems operational. Specifically, network-propagation techniques serve as a mechanism for combining the theoretical coherence of probability theory with modern demands of reasoning-systems technology: modular declarative inputs, conceptually meaningful inferences, and parallel distributed computation. Application areas include diagnosis, forecasting, image interpretation, multi-sensor fusion, decision support systems, plan recognition, planning, speech recognition--in short, almost every task requiring that conclusions be drawn from uncertain clues and incomplete information. Probabilistic Reasoning in Intelligent Systems will be of special interest to scholars and researchers in AI, decision theory, statistics, logic, philosophy, cognitive psychology, and the management sciences. Professionals in the areas of knowledge-based systems, operations research, engineering, and statistics will find theoretical and computational tools of immediate practical use. The book can also be used as an excellent text for graduate-level courses in AI, operations research, or applied probability. COMPUTERS,Artificial Intelligence,General

Paradigms of Artificial Intelligence Programming Paradigms of AI Programming is the first text to teach advanced Common Lisp techniques in the context of building major AI systems. By reconstructing authentic, complex AI programs using state-of-the-art Common Lisp, the book teaches students and professionals how to build and debug robust practical programs, while demonstrating superior programming style and important AI concepts. The author strongly emphasizes the practical performance issues involved in writing real working programs of significant size. Chapters on troubleshooting and efficiency are included, along with a discussion of the fundamentals of object-oriented programming and a description of the main CLOS functions. This volume is an excellent text for a course on AI programming, a useful supplement for general AI courses and an indispensable reference for the professional programmer. COMPUTERS,Artificial Intelligence,General

Artificial Intelligence in Medicine Expert systems constitute a research area which is currently expanding. This book is based largely on work undertaken for my doctoral thesis and attempts to set out in readily understood language the different methods of knowledge representation used in different systems. How ever, since the field for applications is enormous and touches on many disciplines (engineering science, computing, geology, medicine etc.) only those systems with medical applications are presented. The second part of this book is devoted to detailed discussion of one expert system developed in this department: SPHINX. I wish to thank all those who have given me their support, their criticisms and suggestions: Dominique Fieschi, Michel Joubert, Genevieve Botti, Michel Roux, Jean-Louis Lauriere, as well as the CNRS which supported the ATP Expert Systems Group with an individual grant. Marius Fieschi Foreword This work deals with 'Expert Systems' in the realm of medicine. The phrase 'Expert System' describes an information system not only in terms of its content but also in terms of its application. As with all generic terms, it is condensed to the point where the meaning cannot be guessed from simply reading it. It concerns systems processing knowledge and behaviour in ways close to those of a human expert. In the field of medicine this expert would be the consultant or specialist to whom a family practitioner refers a 'case' which he is unable to diagnose. The study of expert systems is a branch of computer science called artificial intelligence. COMPUTERS,Artificial Intelligence,General

Image Processing, Analysis and Machine Vision Image Processing, Analysis and Machine Vision represent an exciting part of modern cognitive and computer science. Following an explosion of inter est during the Seventies, the Eighties were characterized by the maturing of the field and the significant growth of active applications; Remote Sensing, Technical Diagnostics, Autonomous Vehicle Guidance and Medical Imaging are the most rapidly developing areas. This progress can be seen in an in creasing number of software and hardware products on the market as well as in a number of digital image processing and machine vision courses offered at universities world-wide. There are many texts available in the areas we cover - most (indeed, all of which we know) are referenced somewhere in this book. The subject suffers, however, from a shortage of texts at the 'elementary' level - that appropriate for undergraduates beginning or completing their studies of the topic, or for Master's students - and the very rapid developments that have taken and are still taking place, which quickly age some of the very good text books produced over the last decade or so. This book reflects the authors' experience in teaching one and two semester undergraduate and graduate courses in Digital Image Processing, Digital Image Analysis, Machine Vision, Pattern Recognition and Intelligent Robotics at their respective institutions. COMPUTERS,Artificial Intelligence,General

Complex Systems and Cognitive Processes This volume describes our intellectual path from the physics of complex sys tems to the science of artificial cognitive systems. It was exciting to discover that many of the concepts and methods which succeed in describing the self organizing phenomena of the physical world are relevant also for understand ing cognitive processes. Several nonlinear physicists have felt the fascination of such discovery in recent years. In this volume, we will limit our discussion to artificial cognitive systems, without attempting to model either the cognitive behaviour or the nervous structure of humans or animals. On the one hand, such artificial systems are important per se; on the other hand, it can be expected that their study will shed light on some general principles which are relevant also to biological cognitive systems. The main purpose of this volume is to show that nonlinear dynamical systems have several properties which make them particularly attractive for reaching some of the goals of artificial intelligence. The enthusiasm which was mentioned above must however be qualified by a critical consideration of the limitations of the dynamical systems approach. Understanding cognitive processes is a tremendous scientific challenge, and the achievements reached so far allow no single method to claim that it is the only valid one. In particular, the approach based upon nonlinear dynamical systems, which is our main topic, is still in an early stage of development. COMPUTERS,Artificial Intelligence,General

Causality, Correlation And Artificial Intelligence For Rational Decision Making Causality has been a subject of study for a long time. Often causality is confused with correlation. Human intuition has evolved such that it has learned to identify causality through correlation. In this book, four main themes are considered and these are causality, correlation, artificial intelligence and decision making. A correlation machine is defined and built using multi-layer perceptron network, principal component analysis, Gaussian Mixture models, genetic algorithms, expectation maximization technique, simulated annealing and particle swarm optimization. Furthermore, a causal machine is defined and built using multi-layer perceptron, radial basis function, Bayesian statistics and Hybrid Monte Carlo methods. Both these machines are used to build a Granger non-linear causality model. In addition, the Neyman-Rubin, Pearl and Granger causal models are studied and are unified. The automatic relevance determination is also applied to extend Granger causality framework to the non-linear domain. The concept of rational decision making is studied, and the theory of flexibly-bounded rationality is used to extend the theory of bounded rationality within the principle of the indivisibility of rationality. The theory of the marginalization of irrationality for decision making is also introduced to deal with satisficing within irrational conditions. The methods proposed are applied in biomedical engineering, condition monitoring and for modelling interstate conflict. COMPUTERS,Artificial Intelligence,General

An Introduction to Fuzzy Control Fuzzy controllers are a class of knowledge based controllers using artificial intelligence techniques with origins in fuzzy logic. They can be found either as stand-alone control elements or as integral parts of a wide range of industrial process control systems and consumer products. Applications of fuzzy controllers are an established practice for Japanese manufacturers, and are spreading in Europe and America. The main aim of this book is to show that fuzzy control is not totally ad hoc, that there exist formal techniques for the analysis of a fuzzy controller, and that fuzzy control can be implemented even when no expert knowledge is available. The book is mainly oriented to control engineers and theorists, although parts can be read without any knowledge of control theory and may interest AI people. This 2nd, revised edition incorporates suggestions from numerous reviewers and updates and reorganizes some of the material. COMPUTERS,Artificial Intelligence,General

Lazy Learning This edited collection describes recent progress on lazy learning, a branch of machine learning concerning algorithms that defer the processing of their inputs, reply to information requests by combining stored data, and typically discard constructed replies. It is the first edited volume in AI on this topic, whose many synonyms include `instance-based', `memory-based'. `exemplar-based', and `local learning', and whose topic intersects case-based reasoning and edited k-nearest neighbor classifiers. It is intended for AI researchers and students interested in pursuing recent progress in this branch of machine learning, but, due to the breadth of its contributions, it should also interest researchers and practitioners of data mining, case-based reasoning, statistics, and pattern recognition. COMPUTERS,Artificial Intelligence,General

Designing Correct Circuits These proceedings contain the papers presented at a workshop on Designing Correct Circuits, jointly organised by the Universities of Oxford and Glasgow, and held in Oxford on 26-28 September 1990. There is a growing interest in the application to hardware design of the techniques of software engineering. As the complexity of hardware systems grows, and as the cost both in money and time of making design errors becomes more apparent, so there is an eagerness to build on the success of mathematical techniques in program develop ment. The harsher constraints on hardware designers mean both that there is a greater need for good abstractions and rigorous assurances of the trustworthyness of designs, and also that there is greater reason to expect that these benefits can be realised. The papers presented at this workshop consider the application of mathematics to hardware design at several different levels of abstraction. At the lowest level of this spectrum, Zhou and Hoare show how to describe and reason about synchronous switching circuits using UNilY, a formalism that was developed for reasoning about parallel programs. Aagaard and Leeser use standard mathematical tech niques to prove correct their implementation of an algorithm for Boolean simplification. The circuits generated by their formal synthesis system are thus correct by construction. Thuau and Pilaud show how the declarative language LUSTRE, which was designed for program ming real-time systems, can be used to specify synchronous circuits. COMPUTERS,Artificial Intelligence,General

Neural Computation and Psychology The papers that appear in this volume are refereed versions of presenta tions made at the third Neural Computation and Psychology Workshop, held at Stirling University, Scotland, from 31 August to 2 September 1994. The aim of this series of conferences has been to explore the interface between Neural Computing and Psychology: this has been a fruitful area for many researchers for a number of reasons. The development ofNeural Computation has supplied tools to researchers in Cognitive Neuroscience, allowing them to look at possible mechanisms for implementing theories which would otherwise remain 'black box' techniques. These theories may be high-level theories, concerned with interaction between a number of brain areas, or low-level, describing the way in which smaller local groups of neurons behave. Neural Computation techniques have allowed computer scientists to implement systems which are based on how real brains appear to function, providing effective pattern recognition systems. We can thus mount a two-pronged attack on perception. The papers here come from both the Cognitive Psychology viewpoint and from the Computer Science viewpoint: it is a mark of the growing maturity of the interface between the two subjects that they can under stand each other's papers, and the level of discussion at the workshop itself showed how important each camp considers the other to be. The papers here are divided into four sections, reflecting the primary areas of the material. COMPUTERS,Artificial Intelligence,General

Cognitive Models and Intelligent Environments for Learning Programming Proceedings of the NATO Advanced Research Workshop on Cognitive Models and Intelligent Environments for Learning Programming, held near Genova, Italy, March 17-21, 1992 COMPUTERS,Artificial Intelligence,General

Frontiers of Combining Systems First International Workshop, Munich, March 1996 COMPUTERS,Artificial Intelligence,General

Quantitative Methods in Parallel Systems It is widely recognized that the complexity of parallel and distributed systems is such that proper tools must be employed during their design stage in order to achieve the quantitative goals for which they are intended. This volume collects recent research results obtained within the Basic Research Action Qmips, which bears on the quantitative analysis of parallel and distributed architectures. Part 1 is devoted to research on the usage of general formalisms stemming from theoretical computer science in quantitative performance modeling of parallel systems. It contains research papers on process algebras, on Petri nets, and on queueing networks. The contributions in Part 2 are concerned with solution techniques. This part is expected to allow the reader to identify among the general formalisms of Part I, those that are amenable to an efficient mathematical treatment in the perspective of quantitative information. The common theme of Part 3 is the application of the analytical results of Part 2 to the performance evaluation and optimization of parallel and distributed systems. Part 1. Stochastic Process Algebras are used by N. Gotz, H. Hermanns, U. Herzog, V. Mertsiotakis and M. Rettelbach as a novel approach for the struc tured design and analysis of both the functional behaviour and performability (i.e performance and dependability) characteristics of parallel and distributed systems. This is achieved by integrating stochastic modeling and analysis into the powerful and well investigated formal description techniques of process algebras. COMPUTERS,Artificial Intelligence,General

Advanced Algorithms and Architectures for Speech Understanding This book is intended to give an overview of the major results achieved in the field of natural speech understanding inside ESPRIT Project P. 26, "Advanced Algorithms and Architectures for Speech and Image Processing". The project began as a Pilot Project in the early stage of Phase 1 of the ESPRIT Program launched by the Commission of the European Communities. After one year, in the light of the preliminary results that were obtained, it was confirmed for its 5-year duration. Even though the activities were carried out for both speech and image understand ing we preferred to focus the treatment of the book on the first area which crystallized mainly around the CSELT team, with the valuable cooperation of AEG, Thomson-CSF, and Politecnico di Torino. Due to the work of the five years of the project, the Consortium was able to develop an actual and complete understanding system that goes from a continuously spoken natural language sentence to its meaning and the consequent access to a database. When we started in 1983 we had some expertise in small-vocabulary syntax-driven connected-word speech recognition using Hidden Markov Models, in written natural lan guage understanding, and in hardware design mainly based upon bit-slice microprocessors. COMPUTERS,Artificial Intelligence,General

Artificial Neural Networks 1.1 Overview We are living in a decade recently declared as the "Decade of the Brain". Neuroscientists may soon manage to work out a functional map of the brain, thanks to technologies that open windows on the mind. With the average human brain consisting of 15 billion neurons, roughly equal to the number of stars in our milky way, each receiving signals through as many as 10,000 synapses, it is quite a view. "The brain is the last and greatest biological frontier", says James Weston codiscoverer of DNA, considered to be the most complex piece of biological machinery on earth. After many years of research by neuroanatomists and neurophys iologists, the overall organization of the brain is well understood, but many of its detailed neural mechanisms remain to be decoded. In order to understand the functioning of the brain, neurobiologists have taken a bottom-up approach of studying the stimulus-response characteristics of single neurons and networks of neurons, while psy chologists have taken a top-down approach of studying brain func tions from the cognitive and behavioral level. While these two ap proaches are gradually converging, it is generally accepted that it may take another fifty years before we achieve a solid microscopic, intermediate, and macroscopic understanding of brain. COMPUTERS,Artificial Intelligence,General

Common LISP The defacto standard - a must-have for all LISP programmers. In this greatly expanded edition of the defacto standard, you'll learn about the nearly 200 changes already made since original publication - and find out about gray areas likely to be revised later. Written by the Vice- Chairman of X3J13 (the ANSIcommittee responsible for the standardization of Common Lisp) and co-developer of the language itself, the new edition contains the entire text of the first edition plus six completely new chapters. They cover: - CLOS, the Common Lisp Object System, with new features to support function overloading and object-oriented programming, plus complete technical specifications * Loops, a powerful control structure for multiple variables * Conditions, a generalization of the error signaling mechanism * Series and generators * Plus other subjects not part of the ANSI standards but of interest to professional programmers. Throughout, you'll find fresh examples, additional clarifications, warnings, and tips - all presented with the author's customary vigor and wit. COMPUTERS,Artificial Intelligence,General

Social Machines Will your next doctor be a human being—or a machine? Will you have a choice? If you do, what should you know before making it? This book introduces the reader to the pitfalls and promises of artificial intelligence (AI) in its modern incarnation and the growing trend of systems to "reach off the Web" into the real world. The convergence of AI, social networking, and modern computing is creating an historic inflection point in the partnership between human beings and machines with potentially profound impacts on the future not only of computing but of our world and species. AI experts and researchers James Hendler—co-originator of the Semantic Web (Web 3.0)—and Alice Mulvehill—developer of AI-based operational systems for DARPA, the Air Force, and NASA—explore the social implications of AI systems in the context of a close examination of the technologies that make them possible. The authors critically evaluate the utopian claims and dystopian counterclaims of AI prognosticators. Social Machines: The Coming Collision of Artificial Intelligence, Social Networking, and Humanity is your richly illustrated field guide to the future of your machine-mediated relationships with other human beings and with increasingly intelligent machines. What Readers Will Learn What the concept of a social machine is and how the activities of non-programmers are contributing to machine intelligence How modern artificial intelligence technologies, such as Watson, are evolving and how they process knowledge from both carefully produced information (such as Wikipedia and journal articles) and from big data collections The fundamentals of neuromorphic computing, knowledge graph search, and linked data, as well as the basic technology concepts that underlie networking applications such as Facebook and Twitter How the change in attitudes towards cooperative work on the Web, especially in the younger demographic, is critical to the future of Web applications Who This Book Is ForGeneral readers and technically engaged developers, entrepreneurs, and technologists interested in the threats and promises of the accelerating convergence of artificial intelligence with social networks and mobile web technologies. COMPUTERS,Artificial Intelligence,General

Data Mining Data Mining: Practical Machine Learning Tools and Techniques, Fourth Edition, offers a thorough grounding in machine learning concepts, along with practical advice on applying these tools and techniques in real-world data mining situations. This highly anticipated fourth edition of the most acclaimed work on data mining and machine learning teaches readers everything they need to know to get going, from preparing inputs, interpreting outputs, evaluating results, to the algorithmic methods at the heart of successful data mining approaches. Extensive updates reflect the technical changes and modernizations that have taken place in the field since the last edition, including substantial new chapters on probabilistic methods and on deep learning. Accompanying the book is a new version of the popular WEKA machine learning software from the University of Waikato. Authors Witten, Frank, Hall, and Pal include today's techniques coupled with the methods at the leading edge of contemporary research. Please visit the book companion website at https://www.cs.waikato.ac.nz/~ml/weka/book.html. It contains Powerpoint slides for Chapters 1-12. This is a very comprehensive teaching resource, with many PPT slides covering each chapter of the book Online Appendix on the Weka workbench; again a very comprehensive learning aid for the open source software that goes with the book Table of contents, highlighting the many new sections in the 4th edition, along with reviews of the 1st edition, errata, etc. Provides a thorough grounding in machine learning concepts, as well as practical advice on applying the tools and techniques to data mining projects Presents concrete tips and techniques for performance improvement that work by transforming the input or output in machine learning methods Includes a downloadable WEKA software toolkit, a comprehensive collection of machine learning algorithms for data mining tasks-in an easy-to-use interactive interface Includes open-access online courses that introduce practical applications of the material in the book COMPUTERS,Artificial Intelligence,General
Wheeled Mobile Robotics Wheeled Mobile Robotics: From Fundamentals Towards Autonomous Systemscovers the main topics from the wide area of mobile robotics, explaining all applied theory and application. The book gives the reader a good foundation, enabling them to continue to more advanced topics. Several examples are included for better understanding, many of them accompanied by short MATLAB® script code making it easy to reuse in practical work. The book includes several examples of discussed methods and projects for wheeled mobile robots and some advanced methods for their control and localization. It is an ideal resource for those seeking an understanding of robotics, mechanics, and control, and for engineers and researchers in industrial and other specialized research institutions in the field of wheeled mobile robotics. Beginners with basic math knowledge will benefit from the examples, and engineers with an understanding of basic system theory and control will find it easy to follow the more demanding fundamental parts and advanced methods explained. Offers comprehensive coverage of the essentials of the field that are suitable for both academics and practitioners Includes several examples of the application of algorithms in simulations and real laboratory projects Presents foundation in mobile robotics theory before continuing with more advanced topics Self-sufficient to beginner readers, covering all important topics in the mobile robotics field Contains specific topics on modeling, control, sensing, path planning, localization, design architectures, and multi-agent systems COMPUTERS,Artificial Intelligence,General

Raspberry Pi Image Processing Programming Write your own Digital Image Processing programs with the use of pillow, scipy.ndimage, and matplotlib in Python 3 with Raspberry Pi 3 as the hardware platform. This concise quick-start guide provides working code examples and exercises. Learn how to interface Raspberry Pi with various image sensors. What You'll Learn Understand Raspberry Pi concepts and setup Understand digital image processing concepts Study pillow, the friendly PIL fork Explore scipy.ndimage and matplotlib Master use of the Pi camera and webcam Who This Book Is For Raspberry Pi and IoT enthusiasts, digital image processing enthusiasts, Python and Open Source enthusiasts and professionals COMPUTERS,Artificial Intelligence,General

Deep Learning with Keras Get to grips with the basics of Keras to implement fast and efficient deep-learning models About This Book Implement various deep-learning algorithms in Keras and see how deep-learning can be used in games See how various deep-learning models and practical use-cases can be implemented using Keras A practical, hands-on guide with real-world examples to give you a strong foundation in Keras Who This Book Is For If you are a data scientist with experience in machine learning or an AI programmer with some exposure to neural networks, you will find this book a useful entry point to deep-learning with Keras. A knowledge of Python is required for this book. What You Will Learn Optimize step-by-step functions on a large neural network using the Backpropagation Algorithm Fine-tune a neural network to improve the quality of results Use deep learning for image and audio processing Use Recursive Neural Tensor Networks (RNTNs) to outperform standard word embedding in special cases Identify problems for which Recurrent Neural Network (RNN) solutions are suitable Explore the process required to implement Autoencoders Evolve a deep neural network using reinforcement learning In Detail This book starts by introducing you to supervised learning algorithms such as simple linear regression, the classical multilayer perceptron and more sophisticated deep convolutional networks. You will also explore image processing with recognition of hand written digit images, classification of images into different categories, and advanced objects recognition with related image annotations. An example of identification of salient points for face detection is also provided. Next you will be introduced to Recurrent Networks, which are optimized for processing sequence data such as text, audio or time series. Following that, you will learn about unsupervised learning algorithms such as Autoencoders and the very popular Generative Adversarial Networks (GAN). You will also explore non-traditional uses of neural networks as Style Transfer. Finally, you will look at Reinforcement Learning and its application to AI game playing, another popular direction of research and application of neural networks. Style and approach This book is an easy-to-follow guide full of examples and real-world applications to help you gain an in-depth understanding of Keras. This book will showcase more than twenty working Deep Neural Networks coded in Python using Keras. COMPUTERS,Artificial Intelligence,General

Mastering Machine Learning with Python in Six Steps Master machine learning with Python in six steps and explore fundamental to advanced topics, all designed to make you a worthy practitioner. This book’s approach is based on the “Six degrees of separation†theory, which states that everyone and everything is a maximum of six steps away. Mastering Machine Learning with Python in Six Steps presents each topic in two parts: theoretical concepts and practical implementation using suitable Python packages. You’ll learn the fundamentals of Python programming language, machine learning history, evolution, and the system development frameworks. Key data mining/analysis concepts, such as feature dimension reduction, regression, time series forecasting and their efficient implementation in Scikit-learn are also covered. Finally, you’ll explore advanced text mining techniques, neural networks and deep learning techniques, and their implementation. All the code presented in the book will be available in the form of iPython notebooks to enable you to try out these examples and extend them to your advantage. What You'll Learn Examine the fundamentals of Python programming language Review machine Learning history and evolution Understand machine learning system development frameworks Implement supervised/unsupervised/reinforcement learning techniques with examples Explore fundamental to advanced text mining techniques Implement various deep learning frameworks Who This Book Is For Python developers or data engineers looking to expand their knowledge or career into machine learning area. Non-Python (R, SAS, SPSS, Matlab or any other language) machine learning practitioners looking to expand their implementation skills in Python. Novice machine learning practitioners looking to learn advanced topics, such as hyperparameter tuning, various ensemble techniques, natural language processing (NLP), deep learning, and basics of reinforcement learning. COMPUTERS,Artificial Intelligence,General

Artificial Intelligence For Dummies Step into the future with AI The term "Artificial Intelligence" has been around since the 1950s, but a lot has changed since then. Today, AI is referenced in the news, books, movies, and TV shows, and the exact definition is often misinterpreted. Artificial Intelligence For Dummies provides a clear introduction to AI and how it’s being used today. Inside, you’ll get a clear overview of the technology, the common misconceptions surrounding it, and a fascinating look at its applications in everything from self-driving cars and drones to its contributions in the medical field. Learn about what AI has contributed to society Explore uses for AI in computer applications Discover the limits of what AI can do Find out about the history of AI The world of AI is fascinating—and this hands-on guide makes it more accessible than ever! COMPUTERS,Artificial Intelligence,General

Python Machine Learning Unlock modern machine learning and deep learning techniques with Python by using the latest cutting-edge open source Python libraries. About This Book Second edition of the bestselling book on Machine Learning A practical approach to key frameworks in data science, machine learning, and deep learning Use the most powerful Python libraries to implement machine learning and deep learning Get to know the best practices to improve and optimize your machine learning systems and algorithms Who This Book Is For If you know some Python and you want to use machine learning and deep learning, pick up this book. Whether you want to start from scratch or extend your machine learning knowledge, this is an essential and unmissable resource. Written for developers and data scientists who want to create practical machine learning and deep learning code, this book is ideal for developers and data scientists who want to teach computers how to learn from data. What You Will Learn Understand the key frameworks in data science, machine learning, and deep learning Harness the power of the latest Python open source libraries in machine learning Explore machine learning techniques using challenging real-world data Master deep neural network implementation using the TensorFlow library Learn the mechanics of classification algorithms to implement the best tool for the job Predict continuous target outcomes using regression analysis Uncover hidden patterns and structures in data with clustering Delve deeper into textual and social media data using sentiment analysis In Detail Machine learning is eating the software world, and now deep learning is extending machine learning. Understand and work at the cutting edge of machine learning, neural networks, and deep learning with this second edition of Sebastian Raschka's bestselling book, Python Machine Learning. Thoroughly updated using the latest Python open source libraries, this book offers the practical knowledge and techniques you need to create and contribute to machine learning, deep learning, and modern data analysis. Fully extended and modernized, Python Machine Learning Second Edition now includes the popular TensorFlow deep learning library. The scikit-learn code has also been fully updated to include recent improvements and additions to this versatile machine learning library. Sebastian Raschka and Vahid Mirjalili's unique insight and expertise introduce you to machine learning and deep learning algorithms from scratch, and show you how to apply them to practical industry challenges using realistic and interesting examples. By the end of the book, you'll be ready to meet the new data analysis opportunities in today's world. If you've read the first edition of this book, you'll be delighted to find a new balance of classical ideas and modern insights into machine learning. Every chapter has been critically updated, and there are new chapters on key technologies. You'll be able to learn and work with TensorFlow more deeply than ever before, and get essential coverage of the Keras neural network library, along with the most recent updates to scikit-learn. Style and Approach Python Machine Learning Second Edition takes a practical, hands-on coding approach so you can learn about machine learning by coding with Python. This book moves fluently between the theoretical principles of machine learning and the practical details of implementation with Python. COMPUTERS,Artificial Intelligence,General

AIQ “There comes a time in the life of a subject when someone steps up and writes the book about it. AIQ explores the fascinating history of the ideas that drive this technology of the future and demystifies the core concepts behind it; the result is a positive and entertaining look at the great potential unlocked by marrying human creativity with powerful machines.†—Steven D. Levitt, bestselling co-author of Freakonomics From leading data scientists Nick Polson and James Scott, what everyone needs to know to understand how artificial intelligence is changing the world and how we can use this knowledge to make better decisions in our own lives. Dozens of times per day, we all interact with intelligent machines that are constantly learning from the wealth of data now available to them. These machines, from smart phones to talking robots to self-driving cars, are remaking the world in the 21st century in the same way that the Industrial Revolution remade the world in the 19th century. AIQ is based on a simple premise: if you want to understand the modern world, then you have to know a little bit of the mathematical language spoken by intelligent machines. AIQ will teach you that language—but in an unconventional way, anchored in stories rather than equations. You will meet a fascinating cast of historical characters who have a lot to teach you about data, probability, and better thinking. Along the way, you'll see how these same ideas are playing out in the modern age of big data and intelligent machines—and how these technologies will soon help you to overcome some of your built-in cognitive weaknesses, giving you a chance to lead a happier, healthier, more fulfilled life. COMPUTERS,Artificial Intelligence,General

The Artificial Intelligence Imperative Artificial intelligence has arrived, and it's coming to a business near you. The disruptive impact of AI on the global economy—from health care to energy, financial services to agriculture, and defense to media—is enormous. Technology literacy is a must for traditional businesses, their boards, policy makers, and governance professionals. This is the first book to explain where AI comes from, why it has emerged as one of the most powerful forces in mergers and acquisitions and research and development, and what companies need to do to implement it successfully. It equips business leaders with a practical roadmap for competing and even thriving in the face of the coming AI revolution. The authors analyze competitive trends, provide industry and governance examples, and explain interactions between AI and other digital technologies, such as blockchain, cybersecurity, and the Internet of Things. At the same time, AI experts will learn how their research and products can increase the competitiveness of their businesses, and corporate boards will come away with a thorough knowledge of the AI governance, ethics, and risk questions to ask. COMPUTERS,Artificial Intelligence,General

Mathematics Of Autonomy Mathematics of Autonomy provides solid mathematical foundations for building useful Autonomous Systems. It clarifies what makes a system autonomous rather than simply automated, and reveals the inherent limitations of systems currently incorrectly labeled as autonomous in reference to the specific and strong uncertainty that characterizes the environments they operate in. Such complex real-world environments demand truly autonomous solutions to provide the flexibility and robustness needed to operate well within them.This volume embraces hybrid solutions to demonstrate extending the classes of uncertainty autonomous systems can handle. In particular, it combines physical-autonomy (robots), cyber-autonomy (agents) and cognitive-autonomy (cyber and embodied cognition) to produce a rigorous subset of trusted autonomy: Cyber-Physical-Cognitive autonomy (CPC-autonomy).The body of the book alternates between underlying theory and applications of CPC-autonomy including 'Autonomous Supervision of a Swarm of Robots' , 'Using Wind Turbulence against a Swarm of UAVs' and 'Unique Super-Dynamics for All Kinds of Robots (UAVs, UGVs, UUVs and USVs)' to illustrate how to effectively construct Autonomous Systems using this model. It avoids the wishful thinking that characterizes much discussion related to autonomy, discussing the hard limits and challenges of real autonomous systems. In so doing, it clarifies where more work is needed, and also provides a rigorous set of tools to tackle some of the problem space. COMPUTERS,Artificial Intelligence,General

Deep Learning for Natural Language Processing Discover the concepts of deep learning used for natural language processing (NLP), with full-fledged examples of neural network models such as recurrent neural networks, long short-term memory networks, and sequence-2-sequence models. You’ll start by covering the mathematical prerequisites and the fundamentals of deep learning and NLP with practical examples. The first three chapters of the book cover the basics of NLP, starting with word-vector representation before moving onto advanced algorithms. The final chapters focus entirely on implementation, and deal with sophisticated architectures such as RNN, LSTM, and Seq2seq, using Python tools: TensorFlow, and Keras. Deep Learning for Natural Language Processing follows a progressive approach and combines all the knowledge you have gained to build a question-answer chatbot system. This book is a good starting point for people who want to get started in deep learning for NLP. All the code presented in the book will be available in the form of IPython notebooks and scripts, which allow you to try out the examples and extend them in interesting ways. What You Will Learn Gain the fundamentals of deep learning and its mathematical prerequisites Discover deep learning frameworks in Python Develop a chatbot Implement a research paper on sentiment classification Who This Book Is For Software developers who are curious to try out deep learning with NLP. COMPUTERS,Artificial Intelligence,General

Hands-On Ensemble Learning with R Explore powerful R packages to create predictive models using ensemble methods Key Features Implement machine learning algorithms to build ensemble-efficient models Explore powerful R packages to create predictive models using ensemble methods Learn to build ensemble models on large datasets using a practical approach Book Description Ensemble techniques are used for combining two or more similar or dissimilar machine learning algorithms to create a stronger model. Such a model delivers superior prediction power and can give your datasets a boost in accuracy. Hands-On Ensemble Learning with R begins with the important statistical resampling methods. You will then walk through the central trilogy of ensemble techniques – bagging, random forest, and boosting – then you'll learn how they can be used to provide greater accuracy on large datasets using popular R packages. You will learn how to combine model predictions using different machine learning algorithms to build ensemble models. In addition to this, you will explore how to improve the performance of your ensemble models. By the end of this book, you will have learned how machine learning algorithms can be combined to reduce common problems and build simple efficient ensemble models with the help of real-world examples. What you will learn Carry out an essential review of re-sampling methods, bootstrap, and jackknife Explore the key ensemble methods: bagging, random forests, and boosting Use multiple algorithms to make strong predictive models Enjoy a comprehensive treatment of boosting methods Supplement methods with statistical tests, such as ROC Walk through data structures in classification, regression, survival, and time series data Use the supplied R code to implement ensemble methods Learn stacking method to combine heterogeneous machine learning models Who this book is for This book is for you if you are a data scientist or machine learning developer who wants to implement machine learning techniques by building ensemble models with the power of R. You will learn how to combine different machine learning algorithms to perform efficient data processing. Basic knowledge of machine learning techniques and programming knowledge of R would be an added advantage. COMPUTERS,Artificial Intelligence,General

Hands-On Recommendation Systems with Python With Hands-On Recommendation Systems with Python, learn the tools and techniques required in building various kinds of powerful recommendation systems (collaborative, knowledge and content based) and deploying them to the web Key Features Build industry-standard recommender systems Only familiarity with Python is required No need to wade through complicated machine learning theory to use this book Book Description Recommendation systems are at the heart of almost every internet business today; from Facebook to Net?ix to Amazon. Providing good recommendations, whether it's friends, movies, or groceries, goes a long way in defining user experience and enticing your customers to use your platform. This book shows you how to do just that. You will learn about the different kinds of recommenders used in the industry and see how to build them from scratch using Python. No need to wade through tons of machine learning theory—you'll get started with building and learning about recommenders as quickly as possible.. In this book, you will build an IMDB Top 250 clone, a content-based engine that works on movie metadata. You'll use collaborative filters to make use of customer behavior data, and a Hybrid Recommender that incorporates content based and collaborative filtering techniques With this book, all you need to get started with building recommendation systems is a familiarity with Python, and by the time you're fnished, you will have a great grasp of how recommenders work and be in a strong position to apply the techniques that you will learn to your own problem domains. What you will learn Get to grips with the different kinds of recommender systems Master data-wrangling techniques using the pandas library Building an IMDB Top 250 Clone Build a content based engine to recommend movies based on movie metadata Employ data-mining techniques used in building recommenders Build industry-standard collaborative filters using powerful algorithms Building Hybrid Recommenders that incorporate content based and collaborative fltering Who this book is for If you are a Python developer and want to develop applications for social networking, news personalization or smart advertising, this is the book for you. Basic knowledge of machine learning techniques will be helpful, but not mandatory. COMPUTERS,Artificial Intelligence,General

Python Artificial Intelligence Projects for Beginners Build smart applications by implementing real-world artificial intelligence projects Key Features Explore a variety of AI projects with Python Get well-versed with different types of neural networks and popular deep learning algorithms Leverage popular Python deep learning libraries for your AI projects Book Description Artificial Intelligence (AI) is the newest technology that's being employed among varied businesses, industries, and sectors. Python Artificial Intelligence Projects for Beginners demonstrates AI projects in Python, covering modern techniques that make up the world of Artificial Intelligence. This book begins with helping you to build your first prediction model using the popular Python library, scikit-learn. You will understand how to build a classifier using an effective machine learning technique, random forest, and decision trees. With exciting projects on predicting bird species, analyzing student performance data, song genre identification, and spam detection, you will learn the fundamentals and various algorithms and techniques that foster the development of these smart applications. In the concluding chapters, you will also understand deep learning and neural network mechanisms through these projects with the help of the Keras library. By the end of this book, you will be confident in building your own AI projects with Python and be ready to take on more advanced projects as you progress What you will learn Build a prediction model using decision trees and random forest Use neural networks, decision trees, and random forests for classification Detect YouTube comment spam with a bag-of-words and random forests Identify handwritten mathematical symbols with convolutional neural networks Revise the bird species identifier to use images Learn to detect positive and negative sentiment in user reviews Who this book is for Python Artificial Intelligence Projects for Beginners is for Python developers who want to take their first step into the world of Artificial Intelligence using easy-to-follow projects. Basic working knowledge of Python programming is expected so that you're able to play around with code COMPUTERS,Artificial Intelligence,General

Neural Networks and Deep Learning This book covers both classical and modern models in deep learning. The primary focus is on the theory and algorithms of deep learning. The theory and algorithms of neural networks are particularly important for understanding important concepts, so that one can understand the important design concepts of neural architectures in different applications. Why do neural networks work? When do they work better than off-the-shelf machine-learning models? When is depth useful? Why is training neural networks so hard? What are the pitfalls? The book is also rich in discussing different applications in order to give the practitioner a flavor of how neural architectures are designed for different types of problems. Applications associated with many different areas like recommender systems, machine translation, image captioning, image classification, reinforcement-learning based gaming, and text analytics are covered. The chapters of this book span three categories: The basics of neural networks: Many traditional machine learning models can be understood as special cases of neural networks. An emphasis is placed in the first two chapters on understanding the relationship between traditional machine learning and neural networks. Support vector machines, linear/logistic regression, singular value decomposition, matrix factorization, and recommender systems are shown to be special cases of neural networks. These methods are studied together with recent feature engineering methods like word2vec. Fundamentals of neural networks: A detailed discussion of training and regularization is provided in Chapters 3 and 4. Chapters 5 and 6 present radial-basis function (RBF) networks and restricted Boltzmann machines. Advanced topics in neural networks: Chapters 7 and 8 discuss recurrent neural networks and convolutional neural networks. Several advanced topics like deep reinforcement learning, neural Turing machines, Kohonen self-organizing maps, and generative adversarial networks are introduced in Chapters 9 and 10. The book is written for graduate students, researchers, and practitioners. Numerous exercises are available along with a solution manual to aid in classroom teaching. Where possible, an application-centric view is highlighted in order to provide an understanding of the practical uses of each class of techniques. COMPUTERS,Artificial Intelligence,General

Prediction Machines "What does AI mean for your business? Read this book to find out." -- Hal Varian, Chief Economist, Google Artificial intelligence does the seemingly impossible, magically bringing machines to life--driving cars, trading stocks, and teaching children. But facing the sea change that AI will bring can be paralyzing. How should companies set strategies, governments design policies, and people plan their lives for a world so different from what we know? In the face of such uncertainty, many analysts either cower in fear or predict an impossibly sunny future. But in Prediction Machines, three eminent economists recast the rise of AI as a drop in the cost of prediction. With this single, masterful stroke, they lift the curtain on the AI-is-magic hype and show how basic tools from economics provide clarity about the AI revolution and a basis for action by CEOs, managers, policy makers, investors, and entrepreneurs. When AI is framed as cheap prediction, its extraordinary potential becomes clear: Prediction is at the heart of making decisions under uncertainty. Our businesses and personal lives are riddled with such decisions.Prediction tools increase productivity--operating machines, handling documents, communicating with customers.Uncertainty constrains strategy. Better prediction creates opportunities for new business structures and strategies to compete. Penetrating, fun, and always insightful and practical, Prediction Machines follows its inescapable logic to explain how to navigate the changes on the horizon. The impact of AI will be profound, but the economic framework for understanding it is surprisingly simple. COMPUTERS,Artificial Intelligence,General

Human + Machine AI is radically transforming business. Are you ready? Look around you. Artificial intelligence is no longer just a futuristic notion. It's here right now--in software that senses what we need, supply chains that "think" in real time, and robots that respond to changes in their environment. Twenty-first-century pioneer companies are already using AI to innovate and grow fast. The bottom line is this: Businesses that understand how to harness AI can surge ahead. Those that neglect it will fall behind. Which side are you on? In Human + Machine, Accenture leaders Paul R. Daugherty and H. James (Jim) Wilson show that the essence of the AI paradigm shift is the transformation of all business processes within an organization--whether related to breakthrough innovation, everyday customer service, or personal productivity habits. As humans and smart machines collaborate ever more closely, work processes become more fluid and adaptive, enabling companies to change them on the fly--or to completely reimagine them. AI is changing all the rules of how companies operate. Based on the authors' experience and research with 1,500 organizations, the book reveals how companies are using the new rules of AI to leap ahead on innovation and profitability, as well as what you can do to achieve similar results. It describes six entirely new types of hybrid human + machine roles that every company must develop, and it includes a "leader’s guide" with the five crucial principles required to become an AI-fueled business. Human + Machine provides the missing and much-needed management playbook for success in our new age of AI. BOOK PROCEEDS FOR THE AI GENERATION The authors' goal in publishing Human + Machine is to help executives, workers, students and others navigate the changes that AI is making to business and the economy. They believe AI will bring innovations that truly improve the way the world works and lives. However, AI will cause disruption, and many people will need education, training and support to prepare for the newly created jobs. To support this need, the authors are donating the royalties received from the sale of this book to fund education and retraining programs focused on developing fusion skills for the age of artificial intelligence. COMPUTERS,Artificial Intelligence,General

Hands-On Artificial Intelligence with Java for Beginners Build, train, and deploy intelligent applications using Java libraries Key Features Leverage the power of Java libraries to build smart applications Build and train deep learning models for implementing artificial intelligence Learn various algorithms to automate complex tasks Book Description Artificial intelligence (AI) is increasingly in demand as well as relevant in the modern world, where everything is driven by technology and data. AI can be used for automating systems or processes to carry out complex tasks and functions in order to achieve optimal performance and productivity. Hands-On Artificial Intelligence with Java for Beginners begins by introducing you to AI concepts and algorithms. You will learn about various Java-based libraries and frameworks that can be used in implementing AI to build smart applications. In addition to this, the book teaches you how to implement easy to complex AI tasks, such as genetic programming, heuristic searches, reinforcement learning, neural networks, and segmentation, all with a practical approach. By the end of this book, you will not only have a solid grasp of AI concepts, but you'll also be able to build your own smart applications for multiple domains. What you will learn Leverage different Java packages and tools such as Weka, RapidMiner, and Deeplearning4j, among others Build machine learning models using supervised and unsupervised machine learning techniques Implement different deep learning algorithms in Deeplearning4j and build applications based on them Study the basics of heuristic searching and genetic programming Differentiate between syntactic and semantic similarity among texts Perform sentiment analysis for effective decision making with LingPipe Who this book is for Hands-On Artificial Intelligence with Java for Beginners is for Java developers who want to learn the fundamentals of artificial intelligence and extend their programming knowledge to build smarter applications. COMPUTERS,Artificial Intelligence,General

Keras Reinforcement Learning Projects A practical guide to mastering reinforcement learning algorithms using Keras Key Features Build projects across robotics, gaming, and finance fields, putting reinforcement learning (RL) into action Get to grips with Keras and practice on real-world unstructured datasets Uncover advanced deep learning algorithms such as Monte Carlo, Markov Decision, and Q-learning Book Description Reinforcement learning has evolved a lot in the last couple of years and proven to be a successful technique in building smart and intelligent AI networks. Keras Reinforcement Learning Projects installs human-level performance into your applications using algorithms and techniques of reinforcement learning, coupled with Keras, a faster experimental library. The book begins with getting you up and running with the concepts of reinforcement learning using Keras. You'll learn how to simulate a random walk using Markov chains and select the best portfolio using dynamic programming (DP) and Python. You'll also explore projects such as forecasting stock prices using Monte Carlo methods, delivering vehicle routing application using Temporal Distance (TD) learning algorithms, and balancing a Rotating Mechanical System using Markov decision processes. Once you've understood the basics, you'll move on to Modeling of a Segway, running a robot control system using deep reinforcement learning, and building a handwritten digit recognition model in Python using an image dataset. Finally, you'll excel in playing the board game Go with the help of Q-Learning and reinforcement learning algorithms. By the end of this book, you'll not only have developed hands-on training on concepts, algorithms, and techniques of reinforcement learning but also be all set to explore the world of AI. What you will learn Practice the Markov decision process in prediction and betting evaluations Implement Monte Carlo methods to forecast environment behaviors Explore TD learning algorithms to manage warehouse operations Construct a Deep Q-Network using Python and Keras to control robot movements Apply reinforcement concepts to build a handwritten digit recognition model using an image dataset Address a game theory problem using Q-Learning and OpenAI Gym Who this book is for Keras Reinforcement Learning Projects is for you if you are data scientist, machine learning developer, or AI engineer who wants to understand the fundamentals of reinforcement learning by developing practical projects. Sound knowledge of machine learning and basic familiarity with Keras is useful to get the most out of this book COMPUTERS,Artificial Intelligence,General

Talking to Robots Award-winning journalist David Ewing Duncan considers 24 visions of possible human-robot futures—Incredible scenarios from Teddy Bots to Warrior Bots, and Politician Bots to Sex Bots—Grounded in real technologies and possibilities and inspired by our imagination. What robot and AI systems are being built and imagined right now? What do they say about us, their creators? Will they usher in a fantastic new future, or destroy us? What do some of our greatest thinkers, from physicist Brian Greene and futurist Kevin Kelly to inventor Dean Kamen, geneticist George Church, and filmmaker Tiffany Shlain, anticipate about our human-robot future? For even as robots and A.I. intrigue us and make us anxious about the future, our fascination with robots has always been about more than the potential of the technology–it’s also about what robots tell us about being human. COMPUTERS,Artificial Intelligence,General

Hands-On Artificial Intelligence for Beginners Grasp the fundamentals of Artificial Intelligence and build your own intelligent systems with ease Key Features Enter the world of AI with the help of solid concepts and real-world use cases Explore AI components to build real-world automated intelligence Become well versed with machine learning and deep learning concepts Book Description Virtual Assistants, such as Alexa and Siri, process our requests, Google's cars have started to read addresses, and Amazon's prices and Netflix's recommended videos are decided by AI. Artificial Intelligence is one of the most exciting technologies and is becoming increasingly significant in the modern world. Hands-On Artificial Intelligence for Beginners will teach you what Artificial Intelligence is and how to design and build intelligent applications. This book will teach you to harness packages such as TensorFlow in order to create powerful AI systems. You will begin with reviewing the recent changes in AI and learning how artificial neural networks (ANNs) have enabled more intelligent AI. You'll explore feedforward, recurrent, convolutional, and generative neural networks (FFNNs, RNNs, CNNs, and GNNs), as well as reinforcement learning methods. In the concluding chapters, you'll learn how to implement these methods for a variety of tasks, such as generating text for chatbots, and playing board and video games. By the end of this book, you will be able to understand exactly what you need to consider when optimizing ANNs and how to deploy and maintain AI applications. What you will learn Use TensorFlow packages to create AI systems Build feedforward, convolutional, and recurrent neural networks Implement generative models for text generation Build reinforcement learning algorithms to play games Assemble RNNs, CNNs, and decoders to create an intelligent assistant Utilize RNNs to predict stock market behavior Create and scale training pipelines and deployment architectures for AI systems Who this book is for This book is designed for beginners in AI, aspiring AI developers, as well as machine learning enthusiasts with an interest in leveraging various algorithms to build powerful AI applications. COMPUTERS,Artificial Intelligence,General

Data Science Learn the basics of Data Science through an easy to understand conceptual framework and immediately practice using RapidMiner platform. Whether you are brand new to data science or working on your tenth project, this book will show you how to analyze data, uncover hidden patterns and relationships to aid important decisions and predictions. Data Science has become an essential tool to extract value from data for any organization that collects, stores and processes data as part of its operations. This book is ideal for business users, data analysts, business analysts, engineers, and analytics professionals and for anyone who works with data. You’ll be able to: Gain the necessary knowledge of different data science techniques to extract value from data. Master the concepts and inner workings of 30 commonly used powerful data science algorithms. Implement step-by-step data science process using using RapidMiner, an open source GUI based data science platform Data Science techniques covered: Exploratory data analysis, Visualization, Decision trees, Rule induction, k-nearest neighbors, Naïve Bayesian classifiers, Artificial neural networks, Deep learning, Support vector machines, Ensemble models, Random forests, Regression, Recommendation engines, Association analysis, K-Means and Density based clustering, Self organizing maps, Text mining, Time series forecasting, Anomaly detection, Feature selection and more... Contains fully updated content on data science, including tactics on how to mine business data for information Presents simple explanations for over twenty powerful data science techniques Enables the practical use of data science algorithms without the need for programming Demonstrates processes with practical use cases Introduces each algorithm or technique and explains the workings of a data science algorithm in plain language Describes the commonly used setup options for the open source tool RapidMiner COMPUTERS,Artificial Intelligence,General

Practical Computer Vision Applications Using Deep Learning with CNNs Deploy deep learning applications into production across multiple platforms. You will work on computer vision applications that use the convolutional neural network (CNN) deep learning model and Python. This book starts by explaining the traditional machine-learning pipeline, where you will analyze an image dataset. Along the way you will cover artificial neural networks (ANNs), building one from scratch in Python, before optimizing it using genetic algorithms. For automating the process, the book highlights the limitations of traditional hand-crafted features for computer vision and why the CNN deep-learning model is the state-of-art solution. CNNs are discussed from scratch to demonstrate how they are different and more efficient than the fully connected ANN (FCNN). You will implement a CNN in Python to give you a full understanding of the model. After consolidating the basics, you will use TensorFlow to build a practical image-recognition model that you will deploy to a web server using Flask, making it accessible over the Internet. Using Kivy and NumPy, you will create cross-platform data science applications with low overheads. This book will help you apply deep learning and computer vision concepts from scratch, step-by-step from conception to production. What You Will Learn Understand how ANNs and CNNs work Create computer vision applications and CNNs from scratch using Python Follow a deep learning project from conception to production using TensorFlow Use NumPy with Kivy to build cross-platform data science applications Who This Book Is For Data scientists, machine learning and deep learning engineers, software developers. COMPUTERS,Artificial Intelligence,General

Artificial Intelligence for Fashion Learn how Artificial Intelligence (AI) is being applied in the fashion industry. With an application focused approach, this book provides real-world examples, breaks down technical jargon for non-technical readers, and provides an educational resource for fashion professionals. The book investigates the ways in which AI is impacting every part of the fashion value chain starting with product discovery and working backwards to manufacturing. Artificial Intelligence for Fashion walks you through concepts, such as connected retail, data mining, and artificially intelligent robotics. Each chapter contains an example of how AI is being applied in the fashion industry illustrated by one major technological theme. There are no equations, algorithms, or code. The technological explanations are cumulative so you'll discover more information about the inner workings of artificial intelligence in practical stages as the book progresses. What You’ll Learn Gain a basic understanding of AI and how it is used in fashion Understand key terminology and concepts in AI Review the new competitive landscape of the fashion industry Conceptualize and develop new ways to apply AI within the workplace Who This Book Is For Fashion industry professionals from designers, managers, department heads, and executives can use this book to learn about how AI is impacting roles in every department and profession. COMPUTERS,Artificial Intelligence,General

Python Deep Learning Learn advanced state-of-the-art deep learning techniques and their applications using popular Python libraries Key Features Build a strong foundation in neural networks and deep learning with Python libraries Explore advanced deep learning techniques and their applications across computer vision and NLP Learn how a computer can navigate in complex environments with reinforcement learning Book Description With the surge in artificial intelligence in applications catering to both business and consumer needs, deep learning is more important than ever for meeting current and future market demands. With this book, you'll explore deep learning, and learn how to put machine learning to use in your projects. This second edition of Python Deep Learning will get you up to speed with deep learning, deep neural networks, and how to train them with high-performance algorithms and popular Python frameworks. You'll uncover different neural network architectures, such as convolutional networks, recurrent neural networks, long short-term memory (LSTM) networks, and capsule networks. You'll also learn how to solve problems in the fields of computer vision, natural language processing (NLP), and speech recognition. You'll study generative model approaches such as variational autoencoders and Generative Adversarial Networks (GANs) to generate images. As you delve into newly evolved areas of reinforcement learning, you'll gain an understanding of state-of-the-art algorithms that are the main components behind popular games Go, Atari, and Dota. By the end of the book, you will be well-versed with the theory of deep learning along with its real-world applications. What you will learn Grasp the mathematical theory behind neural networks and deep learning processes Investigate and resolve computer vision challenges using convolutional networks and capsule networks Solve generative tasks using variational autoencoders and Generative Adversarial Networks Implement complex NLP tasks using recurrent networks (LSTM and GRU) and attention models Explore reinforcement learning and understand how agents behave in a complex environment Get up to date with applications of deep learning in autonomous vehicles Who this book is for This book is for data science practitioners, machine learning engineers, and those interested in deep learning who have a basic foundation in machine learning and some Python programming experience. A background in mathematics and conceptual understanding of calculus and statistics will help you gain maximum benefit from this book. COMPUTERS,Artificial Intelligence,General

Rebooting AI Two leaders in the field offer a compelling analysis of the current state of the art and reveal the steps we must take to achieve a truly robust artificial intelligence. Despite the hype surrounding AI, creating an intelligence that rivals or exceeds human levels is far more complicated than we have been led to believe. Professors Gary Marcus and Ernest Davis have spent their careers at the forefront of AI research and have witnessed some of the greatest milestones in the field, but they argue that a computer beating a human in Jeopardy! does not signal that we are on the doorstep of fully autonomous cars or superintelligent machines. The achievements in the field thus far have occurred in closed systems with fixed sets of rules, and these approaches are too narrow to achieve genuine intelligence. The real world, in contrast, is wildly complex and open-ended. How can we bridge this gap? What will the consequences be when we do? Taking inspiration from the human mind, Marcus and Davis explain what we need to advance AI to the next level, and suggest that if we are wise along the way, we won't need to worry about a future of machine overlords. If we focus on endowing machines with common sense and deep understanding, rather than simply focusing on statistical analysis and gatherine ever larger collections of data, we will be able to create an AI we can trust—in our homes, our cars, and our doctors' offices. Rebooting AI provides a lucid, clear-eyed assessment of the current science and offers an inspiring vision of how a new generation of AI can make our lives better. COMPUTERS,Artificial Intelligence,General

Artificial Intelligence Melanie Mitchell separates science fact from science fiction in this sweeping examination of the current state of AI and how it is remaking our world No recent scientific enterprise has proved as alluring, terrifying, and filled with extravagant promise and frustrating setbacks as artificial intelligence. The award-winning author Melanie Mitchell, a leading computer scientist, now reveals AI’s turbulent history and the recent spate of apparent successes, grand hopes, and emerging fears surrounding it. In Artificial Intelligence, Mitchell turns to the most urgent questions concerning AI today: How intelligent—really—are the best AI programs? How do they work? What can they actually do, and when do they fail? How humanlike do we expect them to become, and how soon do we need to worry about them surpassing us? Along the way, she introduces the dominant models of modern AI and machine learning, describing cutting-edge AI programs, their human inventors, and the historical lines of thought underpinning recent achievements. She meets with fellow experts such as Douglas Hofstadter, the cognitive scientist and Pulitzer Prize–winning author of the modern classic Gödel, Escher, Bach, who explains why he is “terrified†about the future of AI. She explores the profound disconnect between the hype and the actual achievements in AI, providing a clear sense of what the field has accomplished and how much further it has to go. Interweaving stories about the science of AI and the people behind it, Artificial Intelligence brims with clear-sighted, captivating, and accessible accounts of the most interesting and provocative modern work in the field, flavored with Mitchell’s humor and personal observations. This frank, lively book is an indispensable guide to understanding today’s AI, its quest for “human-level†intelligence, and its impact on the future for us all. COMPUTERS,Artificial Intelligence,General

Link Why aren't the most powerful new technologies being used to solve the world's most important problems: hunger, poverty, conflict, employment, disease? In Link, Dr. Lorien Pratt answers these questions by exploring the solution that is emerging worldwide to take Artificial Intelligence to the next level: Decision Intelligence. COMPUTERS,Artificial Intelligence,General

You Look Like a Thing and I Love You AS HEARD ON NPR'S "SCIENCE FRIDAY" Discover the book that Malcolm Gladwell, Susan Cain, Daniel Pink, and Adam Grant want you to read this year, an "accessible, informative, and hilarious" introduction to the weird and wonderful world of artificial intelligence (Ryan North). "You look like a thing and I love you" is one of the best pickup lines ever... according to an artificial intelligence trained by scientist Janelle Shane, creator of the popular blog AI Weirdness. She creates silly AIs that learn how to name paint colors, create the best recipes, and even flirt (badly) with humans--all to understand the technology that governs so much of our daily lives. We rely on AI every day for recommendations, for translations, and to put cat ears on our selfie videos. We also trust AI with matters of life and death, on the road and in our hospitals. But how smart is AI really... and how does it solve problems, understand humans, and even drive self-driving cars? Shane delivers the answers to every AI question you've ever asked, and some you definitely haven't. Like, how can a computer design the perfect sandwich? What does robot-generated Harry Potter fan-fiction look like? And is the world's best Halloween costume really "Vampire Hog Bride"? In this smart, often hilarious introduction to the most interesting science of our time, Shane shows how these programs learn, fail, and adapt--and how they reflect the best and worst of humanity. You Look Like a Thing and I Love You is the perfect book for anyone curious about what the robots in our lives are thinking. "I can't think of a better way to learn about artificial intelligence, and I've never had so much fun along the way." - Adam Grant, New York Times bestselling author of Originals COMPUTERS,Artificial Intelligence,General

Python for Programmers The professional programmer’s Deitel® guide to Python® with introductory artificial intelligence case studies Written for programmers with a background in another high-level language, Python for Programmers uses hands-on instruction to teach today’s most compelling, leading-edge computing technologies and programming in Python–one of the world’s most popular and fastest-growing languages. Please read the Table of Contents diagram inside the front cover and the Preface for more details. In the context of 500+, real-world examples ranging from individual snippets to 40 large scripts and full implementation case studies, you’ll use the interactive IPython interpreter with code in Jupyter Notebooks to quickly master the latest Python coding idioms. After covering Python Chapters 1-5 and a few key parts of Chapters 6-7, you’ll be able to handle significant portions of the hands-on introductory AI case studies in Chapters 11-16, which are loaded with cool, powerful, contemporary examples. These include natural language processing, data mining Twitter® for sentiment analysis, cognitive computing with IBM® Watson™, supervised machine learning with classification and regression, unsupervised machine learning with clustering, computer vision through deep learning and convolutional neural networks, deep learning with recurrent neural networks, big data with Hadoop®, Spark™ and NoSQL databases, the Internet of Things and more. You’ll also work directly or indirectly with cloud-based services, including Twitter, Google Translate™, IBM Watson, Microsoft® Azure®, OpenMapQuest, PubNub and more. Features 500+ hands-on, real-world, live-code examples from snippets to case studies IPython + code in Jupyter® Notebooks Library-focused: Uses Python Standard Library and data science libraries to accomplish significant tasks with minimal code Rich Python coverage: Control statements, functions, strings, files, JSON serialization, CSV, exceptions Procedural, functional-style and object-oriented programming Collections: Lists, tuples, dictionaries, sets, NumPy arrays, pandas Series & DataFrames Static, dynamic and interactive visualizations Data experiences with real-world datasets and data sources Intro to Data Science sections: AI, basic stats, simulation, animation, random variables, data wrangling, regression AI, big data and cloud data science case studies: NLP, data mining Twitter®, IBM® Watson™, machine learning, deep learning, computer vision, Hadoop®, Spark™, NoSQL, IoT Open-source libraries: NumPy, pandas, Matplotlib, Seaborn, Folium, SciPy, NLTK, TextBlob, spaCy, Textatistic, Tweepy, scikit-learn®, Keras and more Accompanying code examples are available here: http://ptgmedia.pearsoncmg.com/imprint_downloads/informit/bookreg/9780135224335/9780135224335_examples.zip. Register your product for convenient access to downloads, updates, and/or corrections as they become available. See inside book for more information. COMPUTERS,Artificial Intelligence,General

Mobile Artificial Intelligence Projects Learn to build end-to-end AI apps from scratch for Android and iOS using TensorFlow Lite, CoreML, and PyTorch Key Features Build practical, real-world AI projects on Android and iOS Implement tasks such as recognizing handwritten digits, sentiment analysis, and more Explore the core functions of machine learning, deep learning, and mobile vision Book Description We're witnessing a revolution in Artificial Intelligence, thanks to breakthroughs in deep learning. Mobile Artificial Intelligence Projects empowers you to take part in this revolution by applying Artificial Intelligence (AI) techniques to design applications for natural language processing (NLP), robotics, and computer vision. This book teaches you to harness the power of AI in mobile applications along with learning the core functions of NLP, neural networks, deep learning, and mobile vision. It features a range of projects, covering tasks such as real-estate price prediction, recognizing hand-written digits, predicting car damage, and sentiment analysis. You will learn to utilize NLP and machine learning algorithms to make applications more predictive, proactive, and capable of making autonomous decisions with less human input. In the concluding chapters, you will work with popular libraries, such as TensorFlow Lite, CoreML, and PyTorch across Android and iOS platforms. By the end of this book, you will have developed exciting and more intuitive mobile applications that deliver a customized and more personalized experience to users. What you will learn Explore the concepts and fundamentals of AI, deep learning, and neural networks Implement use cases for machine vision and natural language processing Build an ML model to predict car damage using TensorFlow Deploy TensorFlow on mobile to convert speech to text Implement GAN to recognize hand-written digits Develop end-to-end mobile applications that use AI principles Work with popular libraries, such as TensorFlow Lite, CoreML, and PyTorch Who this book is for Mobile Artificial Intelligence Projects is for machine learning professionals, deep learning engineers, AI engineers, and software engineers who want to integrate AI technology into mobile-based platforms and applications. Sound knowledge of machine learning and experience with any programming language is all you need to get started with this book. COMPUTERS,Artificial Intelligence,General

Machine Learning with R Solve real-world data problems with R and machine learning Key Features Third edition of the bestselling, widely acclaimed R machine learning book, updated and improved for R 3.6 and beyond Harness the power of R to build flexible, effective, and transparent machine learning models Learn quickly with a clear, hands-on guide by experienced machine learning teacher and practitioner, Brett Lantz Book Description Machine learning, at its core, is concerned with transforming data into actionable knowledge. R offers a powerful set of machine learning methods to quickly and easily gain insight from your data. Machine Learning with R, Third Edition provides a hands-on, readable guide to applying machine learning to real-world problems. Whether you are an experienced R user or new to the language, Brett Lantz teaches you everything you need to uncover key insights, make new predictions, and visualize your findings. This new 3rd edition updates the classic R data science book to R 3.6 with newer and better libraries, advice on ethical and bias issues in machine learning, and an introduction to deep learning. Find powerful new insights in your data; discover machine learning with R. What you will learn Discover the origins of machine learning and how exactly a computer learns by example Prepare your data for machine learning work with the R programming language Classify important outcomes using nearest neighbor and Bayesian methods Predict future events using decision trees, rules, and support vector machines Forecast numeric data and estimate financial values using regression methods Model complex processes with artificial neural networks — the basis of deep learning Avoid bias in machine learning models Evaluate your models and improve their performance Connect R to SQL databases and emerging big data technologies such as Spark, H2O, and TensorFlow Who this book is for Data scientists, students, and other practitioners who want a clear, accessible guide to machine learning with R. COMPUTERS,Artificial Intelligence,General

Artificial Intelligence Getting to the heart of the Artificial Intelligence debate. COMPUTERS,Artificial Intelligence,General

Text Analytics with Python Leverage Natural Language Processing (NLP) in Python and learn how to set up your own robust environment for performing text analytics. This second edition has gone through a major revamp and introduces several significant changes and new topics based on the recent trends in NLP. You’ll see how to use the latest state-of-the-art frameworks in NLP, coupled with machine learning and deep learning models for supervised sentiment analysis powered by Python to solve actual case studies. Start by reviewing Python for NLP fundamentals on strings and text data and move on to engineering representation methods for text data, including both traditional statistical models and newer deep learning-based embedding models. Improved techniques and new methods around parsing and processing text are discussed as well. Text summarization and topic models have been overhauled so the book showcases how to build, tune, and interpret topic models in the context of an interest dataset on NIPS conference papers. Additionally, the book covers text similarity techniques with a real-world example of movie recommenders, along with sentiment analysis using supervised and unsupervised techniques. There is also a chapter dedicated to semantic analysis where you’ll see how to build your own named entity recognition (NER) system from scratch. While the overall structure of the book remains the same, the entire code base, modules, and chapters has been updated to the latest Python 3.x release. What You'll Learn •Understand NLP and text syntax, semantics and structure •Discover text cleaning and feature engineering •Review text classification and text clustering • Assess text summarization and topic models • Study deep learning for NLP Who This Book Is For IT professionals, data analysts, developers, linguistic experts, data scientists and engineers and basically anyone with a keen interest in linguistics, analytics and generating insights from textual data. COMPUTERS,Artificial Intelligence,General

Machine Learning for Finance A guide to advances in machine learning for financial professionals, with working Python code Key Features Explore advances in machine learning and how to put them to work in financial industries Clear explanation and expert discussion of how machine learning works, with an emphasis on financial applications Deep coverage of advanced machine learning approaches including neural networks, GANs, and reinforcement learning Book Description Machine Learning for Finance explores new advances in machine learning and shows how they can be applied across the financial sector, including in insurance, transactions, and lending. It explains the concepts and algorithms behind the main machine learning techniques and provides example Python code for implementing the models yourself. The book is based on Jannes Klaas' experience of running machine learning training courses for financial professionals. Rather than providing ready-made financial algorithms, the book focuses on the advanced ML concepts and ideas that can be applied in a wide variety of ways. The book shows how machine learning works on structured data, text, images, and time series. It includes coverage of generative adversarial learning, reinforcement learning, debugging, and launching machine learning products. It discusses how to fight bias in machine learning and ends with an exploration of Bayesian inference and probabilistic programming. What you will learn Apply machine learning to structured data, natural language, photographs, and written text How machine learning can detect fraud, forecast financial trends, analyze customer sentiments, and more Implement heuristic baselines, time series, generative models, and reinforcement learning in Python, scikit-learn, Keras, and TensorFlow Dig deep into neural networks, examine uses of GANs and reinforcement learning Debug machine learning applications and prepare them for launch Address bias and privacy concerns in machine learning Who this book is for This book is ideal for readers who understand math and Python, and want to adopt machine learning in financial applications. The book assumes college-level knowledge of math and statistics. COMPUTERS,Artificial Intelligence,General
Artificial Intelligence in Education This two-volume set LNCS 11625 and 11626 constitutes the refereed proceedings of the 20th International Conference on Artificial Intelligence in Education, AIED 2019, held in Chicago, IL, USA, in June 2019. The 45 full papers presented together with 41 short, 10 doctoral consortium, 6 industry, and 10 workshop papers were carefully reviewed and selected from 177 submissions. AIED 2019 solicits empirical and theoretical papers particularly in the following lines of research and application: Intelligent and interactive technologies in an educational context; Modelling and representation; Models of teaching and learning; Learning contexts and informal learning; Evaluation; Innovative applications; Intelligent techniques to support disadvantaged schools and students, inequity and inequality in education.​ COMPUTERS,Artificial Intelligence,General

Applied Machine Learning Machine learning methods are now an important tool for scientists, researchers, engineers and students in a wide range of areas. This book is written for people who want to adopt and use the main tools of machine learning, but aren’t necessarily going to want to be machine learning researchers. Intended for students in final year undergraduate or first year graduate computer science programs in machine learning, this textbook is a machine learning toolkit. Applied Machine Learning covers many topics for people who want to use machine learning processes to get things done, with a strong emphasis on using existing tools and packages, rather than writing one’s own code. A companion to the author's Probability and Statistics for Computer Science, this book picks up where the earlier book left off (but also supplies a summary of probability that the reader can use). Emphasizing the usefulness of standard machinery from applied statistics, this textbook gives an overview of the major applied areas in learning, including coverage of: • classification using standard machinery (naive bayes; nearest neighbor; SVM) • clustering and vector quantization (largely as in PSCS) • PCA (largely as in PSCS) • variants of PCA (NIPALS; latent semantic analysis; canonical correlation analysis) • linear regression (largely as in PSCS) • generalized linear models including logistic regression • model selection with Lasso, elasticnet • robustness and m-estimators • Markov chains and HMM’s (largely as in PSCS) • EM in fairly gory detail; long experience teaching this suggests one detailed example is required, which students hate; but once they’ve been through that, the next one is easy • simple graphical models (in the variational inference section) • classification with neural networks, with a particular emphasis onimage classification • autoencoding with neural networks • structure learning COMPUTERS,Artificial Intelligence,General

Neural Network Projects with Python Build your Machine Learning portfolio by creating 6 cutting-edge Artificial Intelligence projects using neural networks in Python Key Features Discover neural network architectures (like CNN and LSTM) that are driving recent advancements in AI Build expert neural networks in Python using popular libraries such as Keras Includes projects such as object detection, face identification, sentiment analysis, and more Book Description Neural networks are at the core of recent AI advances, providing some of the best resolutions to many real-world problems, including image recognition, medical diagnosis, text analysis, and more. This book goes through some basic neural network and deep learning concepts, as well as some popular libraries in Python for implementing them. It contains practical demonstrations of neural networks in domains such as fare prediction, image classification, sentiment analysis, and more. In each case, the book provides a problem statement, the specific neural network architecture required to tackle that problem, the reasoning behind the algorithm used, and the associated Python code to implement the solution from scratch. In the process, you will gain hands-on experience with using popular Python libraries such as Keras to build and train your own neural networks from scratch. By the end of this book, you will have mastered the different neural network architectures and created cutting-edge AI projects in Python that will immediately strengthen your machine learning portfolio. What you will learn Learn various neural network architectures and its advancements in AI Master deep learning in Python by building and training neural network Master neural networks for regression and classification Discover convolutional neural networks for image recognition Learn sentiment analysis on textual data using Long Short-Term Memory Build and train a highly accurate facial recognition security system Who this book is for This book is a perfect match for data scientists, machine learning engineers, and deep learning enthusiasts who wish to create practical neural network projects in Python. Readers should already have some basic knowledge of machine learning and neural networks. COMPUTERS,Artificial Intelligence,General

Introduction to Artificial Intelligence Can computers think? Updated edition, ideal for lay readers and students of computer science, offers well-illustrated, easy-to-read discussions of problem-solving methods and representations, game playing, neural networks, more. 2019 edition. COMPUTERS,Artificial Intelligence,General

Machine Learning Pocket Reference With detailed notes, tables, and examples, this handy reference will help you navigate the basics of structured machine learning. Author Matt Harrison delivers a valuable guide that you can use for additional support during training and as a convenient resource when you dive into your next machine learning project. Ideal for programmers, data scientists, and AI engineers, this book includes an overview of the machine learning process and walks you through classification with structured data. You’ll also learn methods for clustering, predicting a continuous value (regression), and reducing dimensionality, among other topics. This pocket reference includes sections that cover: Classification, using the Titanic dataset Cleaning data and dealing with missing data Exploratory data analysis Common preprocessing steps using sample data Selecting features useful to the model Model selection Metrics and classification evaluation Regression examples using k-nearest neighbor, decision trees, boosting, and more Metrics for regression evaluation Clustering Dimensionality reduction Scikit-learn pipelines COMPUTERS,Artificial Intelligence,General

Practical Machine Learning with R Understand how machine learning works and get hands-on experience of using R to build algorithms that can solve various real-world problems Key Features Gain a comprehensive overview of different machine learning techniques Explore various methods for selecting a particular algorithm Implement a machine learning project from problem definition through to the final model Book Description With huge amounts of data being generated every moment, businesses need applications that apply complex mathematical calculations to data repeatedly and at speed. With machine learning techniques and R, you can easily develop these kinds of applications in an efficient way. Practical Machine Learning with R begins by helping you grasp the basics of machine learning methods, while also highlighting how and why they work. You will understand how to get these algorithms to work in practice, rather than focusing on mathematical derivations. As you progress from one chapter to another, you will gain hands-on experience of building a machine learning solution in R. Next, using R packages such as rpart, random forest, and multiple imputation by chained equations (MICE), you will learn to implement algorithms including neural net classifier, decision trees, and linear and non-linear regression. As you progress through the book, you'll delve into various machine learning techniques for both supervised and unsupervised learning approaches. In addition to this, you'll gain insights into partitioning the datasets and mechanisms to evaluate the results from each model and be able to compare them. By the end of this book, you will have gained expertise in solving your business problems, starting by forming a good problem statement, selecting the most appropriate model to solve your problem, and then ensuring that you do not overtrain it. What you will learn Define a problem that can be solved by training a machine learning model Obtain, verify and clean data before transforming it into the correct format for use Perform exploratory analysis and extract features from data Build models for neural net, linear and non-linear regression, classification, and clustering Evaluate the performance of a model with the right metrics Implement a classification problem using the neural net package Employ a decision tree using the random forest library Who this book is for If you are a data analyst, data scientist, or a business analyst who wants to understand the process of machine learning and apply it to a real dataset using R, this book is just what you need. Data scientists who use Python and want to implement their machine learning solutions using R will also find this book very useful. The book will also enable novice programmers to start their journey in data science. Basic knowledge of any programming language is all you need to get started. COMPUTERS,Artificial Intelligence,General

Deep Learning from Scratch With the resurgence of neural networks in the 2010s, deep learning has become essential for machine learning practitioners and even many software engineers. This book provides a comprehensive introduction for data scientists and software engineers with machine learning experience. You’ll start with deep learning basics and move quickly to the details of important advanced architectures, implementing everything from scratch along the way. Author Seth Weidman shows you how neural networks work using a first principles approach. You’ll learn how to apply multilayer neural networks, convolutional neural networks, and recurrent neural networks from the ground up. With a thorough understanding of how neural networks work mathematically, computationally, and conceptually, you’ll be set up for success on all future deep learning projects. This book provides: Extremely clear and thorough mental models—accompanied by working code examples and mathematical explanations—for understanding neural networks Methods for implementing multilayer neural networks from scratch, using an easy-to-understand object-oriented framework Working implementations and clear-cut explanations of convolutional and recurrent neural networks Implementation of these neural network concepts using the popular PyTorch framework COMPUTERS,Artificial Intelligence,General

Machines That Think A scientist who has spent a career developing Artificial Intelligence takes a realistic look at the technological challenges and assesses the likely effect of AI on the future.How will Artificial Intelligence (AI) impact our lives? Toby Walsh, one of the leading AI researchers in the world, takes a critical look at the many ways in which "thinking machines" will change our world.Based on a deep understanding of the technology, Walsh describes where Artificial Intelligence is today, and where it will take us.·Will automation take away most of our jobs? ·Is a "technological singularity" near? ·What is the chance that robots will take over? ·How do we best prepare for this future? The author concludes that, if we plan well, AI could be our greatest legacy, the last invention human beings will ever need to make. COMPUTERS,Artificial Intelligence,General

Practical Time Series Analysis Time series data analysis is increasingly important due to the massive production of such data through the internet of things, the digitalization of healthcare, and the rise of smart cities. As continuous monitoring and data collection become more common, the need for competent time series analysis with both statistical and machine learning techniques will increase. Covering innovations in time series data analysis and use cases from the real world, this practical guide will help you solve the most common data engineering and analysis challengesin time series, using both traditional statistical and modern machine learning techniques. Author Aileen Nielsen offers an accessible, well-rounded introduction to time series in both R and Python that will have data scientists, software engineers, and researchers up and running quickly. You’ll get the guidance you need to confidently: Find and wrangle time series data Undertake exploratory time series data analysis Store temporal data Simulate time series data Generate and select features for a time series Measure error Forecast and classify time series with machine or deep learning Evaluate accuracy and performance COMPUTERS,Artificial Intelligence,General

Practical Automated Machine Learning on Azure Develop smart applications without spending days and weeks building machine-learning models. With this practical book, you’ll learn how to apply automated machine learning (AutoML), a process that uses machine learning to help people build machine learning models. Deepak Mukunthu, Parashar Shah, and Wee Hyong Tok provide a mix of technical depth, hands-on examples, and case studies that show how customers are solving real-world problems with this technology. Building machine-learning models is an iterative and time-consuming process. Even those who know how to create ML models may be limited in how much they can explore. Once you complete this book, you’ll understand how to apply AutoML to your data right away. Learn how companies in different industries are benefiting from AutoML Get started with AutoML using Azure Explore aspects such as algorithm selection, auto featurization, and hyperparameter tuning Understand how data analysts, BI professions, developers can use AutoML in their familiar tools and experiences Learn how to get started using AutoML for use cases including classification, regression, and forecasting. COMPUTERS,Artificial Intelligence,General

Mastering Machine Learning with Python in Six Steps Explore fundamental to advanced Python 3 topics in six steps, all designed to make you a worthy practitioner. This updated version’s approach is based on the “six degrees of separation†theory, which states that everyone and everything is a maximum of six steps away and presents each topic in two parts: theoretical concepts and practical implementation using suitable Python 3 packages. You’ll start with the fundamentals of Python 3 programming language, machine learning history, evolution, and the system development frameworks. Key data mining/analysis concepts, such as exploratory analysis, feature dimension reduction, regressions, time series forecasting and their efficient implementation in Scikit-learn are covered as well. You’ll also learn commonly used model diagnostic and tuning techniques. These include optimal probability cutoff point for class creation, variance, bias, bagging, boosting, ensemble voting, grid search, random search, Bayesian optimization, and the noise reduction technique for IoT data. Finally, you’ll review advanced text mining techniques, recommender systems, neural networks, deep learning, reinforcement learning techniques and their implementation. All the code presented in the book will be available in the form of iPython notebooks to enable you to try out these examples and extend them to your advantage. What You'll Learn Understand machine learning development and frameworks Assess model diagnosis and tuning in machine learning Examine text mining, natuarl language processing (NLP), and recommender systems Review reinforcement learning and CNN Who This Book Is For Python developers, data engineers, and machine learning engineers looking to expand their knowledge or career into machine learning area. COMPUTERS,Artificial Intelligence,General

Reinforcement Learning Algorithms with Python Develop self-learning algorithms and agents using TensorFlow and other Python tools, frameworks, and libraries Key Features Learn, develop, and deploy advanced reinforcement learning algorithms to solve a variety of tasks Understand and develop model-free and model-based algorithms for building self-learning agents Work with advanced Reinforcement Learning concepts and algorithms such as imitation learning and evolution strategies Book Description Reinforcement Learning (RL) is a popular and promising branch of AI that involves making smarter models and agents that can automatically determine ideal behavior based on changing requirements. This book will help you master RL algorithms and understand their implementation as you build self-learning agents. Starting with an introduction to the tools, libraries, and setup needed to work in the RL environment, this book covers the building blocks of RL and delves into value-based methods, such as the application of Q-learning and SARSA algorithms. You'll learn how to use a combination of Q-learning and neural networks to solve complex problems. Furthermore, you'll study the policy gradient methods, TRPO, and PPO, to improve performance and stability, before moving on to the DDPG and TD3 deterministic algorithms. This book also covers how imitation learning techniques work and how Dagger can teach an agent to drive. You'll discover evolutionary strategies and black-box optimization techniques, and see how they can improve RL algorithms. Finally, you'll get to grips with exploration approaches, such as UCB and UCB1, and develop a meta-algorithm called ESBAS. By the end of the book, you'll have worked with key RL algorithms to overcome challenges in real-world applications, and be part of the RL research community. What you will learn Develop an agent to play CartPole using the OpenAI Gym interface Discover the model-based reinforcement learning paradigm Solve the Frozen Lake problem with dynamic programming Explore Q-learning and SARSA with a view to playing a taxi game Apply Deep Q-Networks (DQNs) to Atari games using Gym Study policy gradient algorithms, including Actor-Critic and REINFORCE Understand and apply PPO and TRPO in continuous locomotion environments Get to grips with evolution strategies for solving the lunar lander problem Who this book is for If you are an AI researcher, deep learning user, or anyone who wants to learn reinforcement learning from scratch, this book is for you. You'll also find this reinforcement learning book useful if you want to learn about the advancements in the field. Working knowledge of Python is necessary. COMPUTERS,Artificial Intelligence,General

Foundations of Deep Reinforcement Learning The Contemporary Introduction to Deep Reinforcement Learning that Combines Theory and Practice Deep reinforcement learning (deep RL) combines deep learning and reinforcement learning, in which artificial agents learn to solve sequential decision-making problems. In the past decade deep RL has achieved remarkable results on a range of problems, from single and multiplayer games—such as Go, Atari games, and DotA 2—to robotics. Foundations of Deep Reinforcement Learning is an introduction to deep RL that uniquely combines both theory and implementation. It starts with intuition, then carefully explains the theory of deep RL algorithms, discusses implementations in its companion software library SLM Lab, and finishes with the practical details of getting deep RL to work. This guide is ideal for both computer science students and software engineers who are familiar with basic machine learning concepts and have a working understanding of Python. Understand each key aspect of a deep RL problem Explore policy- and value-based algorithms, including REINFORCE, SARSA, DQN, Double DQN, and Prioritized Experience Replay (PER) Delve into combined algorithms, including Actor-Critic and Proximal Policy Optimization (PPO) Understand how algorithms can be parallelized synchronously and asynchronously Run algorithms in SLM Lab and learn the practical implementation details for getting deep RL to work Explore algorithm benchmark results with tuned hyperparameters Understand how deep RL environments are designed Register your book for convenient access to downloads, updates, and/or corrections as they become available. See inside book for details. COMPUTERS,Artificial Intelligence,General

Quantum Finance With the exponential growth of program trading in the global financial industry, quantum finance and its underlying technologies have become one of the hottest topics in the fintech community. Numerous financial institutions and fund houses around the world require computer professionals with a basic understanding of quantum finance to develop intelligent financial systems. This book presents a selection of the author’s past 15 years’ R&D work and practical implementation of the Quantum Finance Forecast System – which integrates quantum field theory and related AI technologies to design and develop intelligent global financial forecast and quantum trading systems. The book consists of two parts: Part I discusses the basic concepts and theories of quantum finance and related AI technologies, including quantum field theory, quantum price fields, quantum price level modelling and quantum entanglement to predict major financial events. Part II then examines the current, ongoing R&D projects on the application of quantum finance technologies in intelligent real-time financial prediction and quantum trading systems. This book is both a textbook for undergraduate & masters level quantum finance, AI and fintech courses and a valuable resource for researchers and data scientists working in the field of quantum finance and intelligent financial systems. It is also of interest to professional traders/ quants & independent investors who would like to grasp the basic concepts and theory of quantum finance, and more importantly how to adopt this fascinating technology to implement intelligent financial forecast and quantum trading systems. For system implementation, the interactive quantum finance programming labs listed on the Quantum Finance Forecast Centre official site (QFFC.org) enable readers to learn how to use quantum finance technologies presented in the book. COMPUTERS,Artificial Intelligence,General

Hands-On Reinforcement Learning with R Implement key reinforcement learning algorithms and techniques using different R packages such as the Markov chain, MDP toolbox, contextual, and OpenAI Gym Key Features Explore the design principles of reinforcement learning and deep reinforcement learning models Use dynamic programming to solve design issues related to building a self-learning system Learn how to systematically implement reinforcement learning algorithms Book Description Reinforcement learning (RL) is an integral part of machine learning (ML), and is used to train algorithms. With this book, you'll learn how to implement reinforcement learning with R, exploring practical examples such as using tabular Q-learning to control robots. You'll begin by learning the basic RL concepts, covering the agent-environment interface, Markov Decision Processes (MDPs), and policy gradient methods. You'll then use R's libraries to develop a model based on Markov chains. You will also learn how to solve a multi-armed bandit problem using various R packages. By applying dynamic programming and Monte Carlo methods, you will also find the best policy to make predictions. As you progress, you'll use Temporal Difference (TD) learning for vehicle routing problem applications. Gradually, you'll apply the concepts you've learned to real-world problems, including fraud detection in finance, and TD learning for planning activities in the healthcare sector. You'll explore deep reinforcement learning using Keras, which uses the power of neural networks to increase RL's potential. Finally, you'll discover the scope of RL and explore the challenges in building and deploying machine learning models. By the end of this book, you'll be well-versed with RL and have the skills you need to efficiently implement it with R. What you will learn Understand how to use MDP to manage complex scenarios Solve classic reinforcement learning problems such as the multi-armed bandit model Use dynamic programming for optimal policy searching Adopt Monte Carlo methods for prediction Apply TD learning to search for the best path Use tabular Q-learning to control robots Handle environments using the OpenAI library to simulate real-world applications Develop deep Q-learning algorithms to improve model performance Who this book is for This book is for anyone who wants to learn about reinforcement learning with R from scratch. A solid understanding of R and basic knowledge of machine learning are necessary to grasp the topics covered in the book. COMPUTERS,Artificial Intelligence,General

Building Machine Learning Powered Applications Learn the skills necessary to design, build, and deploy applications powered by machine learning (ML). Through the course of this hands-on book, you’ll build an example ML-driven application from initial idea to deployed product. Data scientists, software engineers, and product managers—including experienced practitioners and novices alike—will learn the tools, best practices, and challenges involved in building a real-world ML application step by step. Author Emmanuel Ameisen, an experienced data scientist who led an AI education program, demonstrates practical ML concepts using code snippets, illustrations, screenshots, and interviews with industry leaders. Part I teaches you how to plan an ML application and measure success. Part II explains how to build a working ML model. Part III demonstrates ways to improve the model until it fulfills your original vision. Part IV covers deployment and monitoring strategies. This book will help you: Define your product goal and set up a machine learning problem Build your first end-to-end pipeline quickly and acquire an initial dataset Train and evaluate your ML models and address performance bottlenecks Deploy and monitor your models in a production environment COMPUTERS,Artificial Intelligence,General

Algorithms Are Not Enough Why a new approach is needed in the quest for general artificial intelligence. Since the inception of artificial intelligence, we have been warned about the imminent arrival of computational systems that can replicate human thought processes. Before we know it, computers will become so intelligent that humans will be lucky to kept as pets. And yet, although artificial intelligence has become increasingly sophisticated--with such achievements as driverless cars and humanless chess-playing--computer science has not yet created general artificial intelligence. In Algorithms Are Not Enough, Herbert Roitblat explains how artificial general intelligence may be possible and why a robopocalypse is neither imminent, nor likely. COMPUTERS,Artificial Intelligence,General

Multi-Agent Oriented Programming The main concepts and techniques of multi-agent oriented programming, which supports the multi-agent systems paradigm at the programming level. A multi-agent system is an organized ensemble of autonomous, intelligent, goal-oriented entities called agents, communicating with each other and interacting within an environment. This book introduces the main concepts and techniques of multi-agent oriented programming, (MAOP) which supports the multi-agent systems paradigm at the programming level. MAOP provides a structured approach based on three integrated dimensions, which the book examines in detail: the agent dimension, used to design the individual (interacting) entities; the environment dimension, which allows the development of shared resources and connections to the real world; and the organization dimension, which structures the interactions among the autonomous agents and the shared environment. COMPUTERS,Artificial Intelligence,General

Fundamentals of Machine Learning for Predictive Data Analytics, second edition The second edition of a comprehensive introduction to machine learning approaches used in predictive data analytics, covering both theory and practice. Machine learning is often used to build predictive models by extracting patterns from large datasets. These models are used in predictive data analytics applications including price prediction, risk assessment, predicting customer behavior, and document classification. This introductory textbook offers a detailed and focused treatment of the most important machine learning approaches used in predictive data analytics, covering both theoretical concepts and practical applications. Technical and mathematical material is augmented with explanatory worked examples, and case studies illustrate the application of these models in the broader business context. This second edition covers recent developments in machine learning, especially in a new chapter on deep learning, and two new chapters that go beyond predictive analytics to cover unsupervised learning and reinforcement learning. COMPUTERS,Artificial Intelligence,General

AI in the Wild Examining the potential benefits and risks of using artificial intelligence to advance global sustainability. Drones with night vision are tracking elephant and rhino poachers in African wildlife parks and sanctuaries; smart submersibles are saving coral from carnivorous starfish on Australia's Great Barrier Reef; recycled cell phones alert Brazilian forest rangers to the sound of illegal logging. The tools of artificial intelligence are being increasingly deployed in the battle for global sustainability. And yet, warns Peter Dauvergne, we should be cautious in declaring AI the planet's savior. In AI in the Wild, Dauvergne avoids the AI industry-powered hype and offers a critical view, exploring both the potential benefits and risks of using artificial intelligence to advance global sustainability. COMPUTERS,Artificial Intelligence,General

Dancing with Qubits Explore the principles and practicalities of quantum computing Key Features Discover how quantum computing works and delve into the math behind it with this quantum computing textbook Learn how it may become the most important new computer technology of the century Explore the inner workings of quantum computing technology to quickly process complex cloud data and solve problems Book Description Quantum computing is making us change the way we think about computers. Quantum bits, a.k.a. qubits, can make it possible to solve problems that would otherwise be intractable with current computing technology. Dancing with Qubits is a quantum computing textbook that starts with an overview of why quantum computing is so different from classical computing and describes several industry use cases where it can have a major impact. From there it moves on to a fuller description of classical computing and the mathematical underpinnings necessary to understand such concepts as superposition, entanglement, and interference. Next up is circuits and algorithms, both basic and more sophisticated. It then nicely moves on to provide a survey of the physics and engineering ideas behind how quantum computing hardware is built. Finally, the book looks to the future and gives you guidance on understanding how further developments will affect you. Really understanding quantum computing requires a lot of math, and this book doesn't shy away from the necessary math concepts you'll need. Each topic is introduced and explained thoroughly, in clear English with helpful examples. What you will learn See how quantum computing works, delve into the math behind it, what makes it different, and why it is so powerful with this quantum computing textbook Discover the complex, mind-bending mechanics that underpin quantum systems Understand the necessary concepts behind classical and quantum computing Refresh and extend your grasp of essential mathematics, computing, and quantum theory Explore the main applications of quantum computing to the fields of scientific computing, AI, and elsewhere Examine a detailed overview of qubits, quantum circuits, and quantum algorithm Who this book is for Dancing with Qubits is a quantum computing textbook for those who want to deeply explore the inner workings of quantum computing. This entails some sophisticated mathematical exposition and is therefore best suited for those with a healthy interest in mathematics, physics, engineering, and computer science. COMPUTERS,Artificial Intelligence,General

The Practitioner's Guide to Graph Data Graph data closes the gap between the way humans and computers view the world. While computers rely on static rows and columns of data, people navigate and reason about life through relationships. This practical guide demonstrates how graph data brings these two approaches together. By working with concepts from graph theory, database schema, distributed systems, and data analysis, you’ll arrive at a unique intersection known as graph thinking. Authors Denise Koessler Gosnell and Matthias Broecheler show data engineers, data scientists, and data analysts how to solve complex problems with graph databases. You’ll explore templates for building with graph technology, along with examples that demonstrate how teams think about graph data within an application. Build an example application architecture with relational and graph technologies Use graph technology to build a Customer 360 application, the most popular graph data pattern today Dive into hierarchical data and troubleshoot a new paradigm that comes from working with graph data Find paths in graph data and learn why your trust in different paths motivates and informs your preferences Use collaborative filtering to design a Netflix-inspired recommendation system COMPUTERS,Artificial Intelligence,General

Declarative Programming and Knowledge Management This book constitutes revised selected papers from the 22nd International Conference on Applications of Declarative Programming and Knowledge Management, INAP 2019, the 33rd Workshop on Logic Programming, WLP 2019, and the 27th Workshop on Functional and (Constraint) Logic Programming, WFLP 2019. The 15 full papers and 1 short paper presented in this volume were carefully reviewed and selected from 24 submissions. The contributions present current research activities in the areas of declarative languages and compilation techniques, in particular for constraint-based, logical and functional languages and their extensions, as well as discuss new approaches and key findings in constraint-solving, knowledge representation, and reasoning techniques. COMPUTERS,Artificial Intelligence,General

ICT for Competitive Strategies Fourth International Conference on Information and Communication Technology for Competitive Strategies targets state-of-the-art as well as emerging topics pertaining to information and communication technologies (ICTs) and effective strategies for its implementation for engineering and intelligent applications. COMPUTERS,Artificial Intelligence,General

Advances in Artificial Intelligence This book constitutes the refereed proceedings of the 33rd Canadian Conference on Artificial Intelligence, Canadian AI 2020, which was planned to take place in Ottawa, ON, Canada. Due to the COVID-19 pandemic, however, it was held virtually during May 13–15, 2020. The 31 regular papers and 24 short papers presented together with 4 Graduate Student Symposium papers were carefully reviewed and selected from a total of 175 submissions. The selected papers cover a wide range of topics, including machine learning, pattern recognition, natural language processing, knowledge representation, cognitive aspects of AI, ethics of AI, and other important aspects of AI research. COMPUTERS,Artificial Intelligence,General

Artificial Intelligence in Economics and Finance Theories As Artificial Intelligence (AI) seizes all aspects of human life, there is a fundamental shift in the way in which humans are thinking of and doing things. Ordinarily, humans have relied on economics and finance theories to make sense of, and predict concepts such as comparative advantage, long run economic growth, lack or distortion of information and failures, role of labour as a factor of production and the decision making process for the purpose of allocating resources among other theories. Of interest though is that literature has not attempted to utilize these advances in technology in order to modernize economic and finance theories that are fundamental in the decision making process for the purpose of allocating scarce resources among other things. With the simulated intelligence in machines, which allows machines to act like humans and to some extent even anticipate events better than humans, thanks to their ability to handle massive data sets, this book will use artificial intelligence to explain what these economic and finance theories mean in the context of the agent wanting to make a decision. The main feature of finance and economic theories is that they try to eliminate the effects of uncertainties by attempting to bring the future to the present. The fundamentals of this statement is deeply rooted in risk and risk management. In behavioural sciences, economics as a discipline has always provided a well-established foundation for understanding uncertainties and what this means for decision making. Finance and economics have done this through different models which attempt to predict the future. On its part, risk management attempts to hedge or mitigate these uncertainties in order for “the planner†to reach the favourable outcome. This book focuses on how AI is to redefine certain important economic and financial theories that are specifically used for the purpose of eliminating uncertainties so as to allow agents to make informed decisions. In effect, certain aspects of finance and economic theories cannot be understood in their entirety without the incorporation of AI. COMPUTERS,Artificial Intelligence,General

A Guided Tour of Artificial Intelligence Research The purpose of this book is to provide an overview of AI research, ranging from basic work to interfaces and applications, with as much emphasis on results as on current issues. It is aimed at an audience of master students and Ph.D. students, and can be of interest as well for researchers and engineers who want to know more about AI. The book is split into three volumes: - the first volume brings together twenty-three chapters dealing with the foundations of knowledge representation and the formalization of reasoning and learning (Volume 1. Knowledge representation, reasoning and learning) - the second volume offers a view of AI, in fourteen chapters, from the side of the algorithms (Volume 2. AI Algorithms) - the third volume, composed of sixteen chapters, describes the main interfaces and applications of AI (Volume 3. Interfaces and applications of AI). This second volume presents the main families of algorithms developed or used in AI to learn, to infer, to decide. Generic approaches to problem solving are presented: ordered heuristic search, as well as metaheuristics are considered. Algorithms for processing logic-based representations of various types (first-order formulae, propositional formulae, logic programs, etc.) and graphical models of various types (standard constraint networks, valued ones, Bayes nets, Markov random fields, etc.) are presented. The volume also focuses on algorithms which have been developed to simulate specific ‘intelligent†processes such as planning, playing, learning, and extracting knowledge from data. Finally, an afterword draws a parallel between algorithmic problems in operation research and in AI. COMPUTERS,Artificial Intelligence,General

Genetic Programming Theory and Practice XVII These contributions, written by the foremost international researchers and practitioners of Genetic Programming (GP), explore the synergy between theoretical and empirical results on real-world problems, producing a comprehensive view of the state of the art in GP. In this year’s edition, the topics covered include many of the most important issues and research questions in the ï¬eld, such as: opportune application domains for GP-based methods, game playing and co-evolutionary search, symbolic regression and efï¬cient learning strategies, encodings and representations for GP, schema theorems, and new selection mechanisms.The volume includes several chapters on best practices and lessons learned from hands-on experience. Readers will discover large-scale, real-world applications of GP to a variety of problem domains via in-depth presentations of the latest and most significant results. COMPUTERS,Artificial Intelligence,General

Advances in Knowledge Discovery and Data Mining The two-volume set LNAI 12084 and 12085 constitutes the thoroughly refereed proceedings of the 24th Pacific-Asia Conference on Knowledge Discovery and Data Mining, PAKDD 2020, which was due to be held in Singapore, in May 2020. The conference was held virtually due to the COVID-19 pandemic. The 135 full papers presented were carefully reviewed and selected from 628 submissions. The papers present new ideas, original research results, and practical development experiences from all KDD related areas, including data mining, data warehousing, machine learning, artificial intelligence, databases, statistics, knowledge engineering, visualization, decision-making systems, and the emerging applications. They are organized in the following topical sections: recommender systems; classification; clustering; mining social networks; representation learning and embedding; mining behavioral data; deep learning; feature extraction and selection; human, domain, organizational and social factors in data mining; mining sequential data; mining imbalanced data; association; privacy and security; supervised learning; novel algorithms; mining multi-media/multi-dimensional data; application; mining graph and network data; anomaly detection and analytics; mining spatial, temporal, unstructured and semi-structured data; sentiment analysis; statistical/graphical model; multi-source/distributed/parallel/cloud computing. COMPUTERS,Artificial Intelligence,General

Advances in Knowledge Discovery and Data Mining The two-volume set LNAI 12084 and 12085 constitutes the thoroughly refereed proceedings of the 24th Pacific-Asia Conference on Knowledge Discovery and Data Mining, PAKDD 2020, which was due to be held in Singapore, in May 2020. The conference was held virtually due to the COVID-19 pandemic. The 135 full papers presented were carefully reviewed and selected from 628 submissions. The papers present new ideas, original research results, and practical development experiences from all KDD related areas, including data mining, data warehousing, machine learning, artificial intelligence, databases, statistics, knowledge engineering, visualization, decision-making systems, and the emerging applications. They are organized in the following topical sections: recommender systems; classification; clustering; mining social networks; representation learning and embedding; mining behavioral data; deep learning; feature extraction and selection; human, domain, organizational and social factors in data mining; mining sequential data; mining imbalanced data; association; privacy and security; supervised learning; novel algorithms; mining multi-media/multi-dimensional data; application; mining graph and network data; anomaly detection and analytics; mining spatial, temporal, unstructured and semi-structured data; sentiment analysis; statistical/graphical model; multi-source/distributed/parallel/cloud computing. COMPUTERS,Artificial Intelligence,General

IoT Machine Learning Applications in Telecom, Energy, and Agriculture Apply machine learning using the Internet of Things (IoT) in the agriculture, telecom, and energy domains with case studies. This book begins by covering how to set up the software and hardware components including the various sensors to implement the case studies in Python. The case study section starts with an examination of call drop with IoT in the telecoms industry, followed by a case study on energy audit and predictive maintenance for an industrial machine, and finally covers techniques to predict cash crop failure in agribusiness. The last section covers pitfalls to avoid while implementing machine learning and IoT in these domains. After reading this book, you will know how IoT and machine learning are used in the example domains and have practical case studies to use and extend. You will be able to create enterprise-scale applications using Raspberry Pi 3 B+ and Arduino Mega 2560 with Python. What You Will Learn Implement machine learning with IoT and solve problems in the telecom, agriculture, and energy sectors with Python Set up and use industrial-grade IoT products, such as Modbus RS485 protocol devices, in practical scenarios Develop solutions for commercial-grade IoT or IIoT projects Implement case studies in machine learning with IoT from scratch Who This Book Is For Raspberry Pi and Arduino enthusiasts and data science and machine learning professionals. COMPUTERS,Artificial Intelligence,General

Linear Algebra and Optimization for Machine Learning This textbook introduces linear algebra and optimization in the context of machine learning. Examples and exercises are provided throughout the book. A solution manual for the exercises at the end of each chapter is available to teaching instructors. This textbook targets graduate level students and professors in computer science, mathematics and data science. Advanced undergraduate students can also use this textbook. The chapters for this textbook are organized as follows: 1. Linear algebra and its applications: The chapters focus on the basics of linear algebra together with their common applications to singular value decomposition, matrix factorization, similarity matrices (kernel methods), and graph analysis. Numerous machine learning applications have been used as examples, such as spectral clustering, kernel-based classification, and outlier detection. The tight integration of linear algebra methods with examples from machine learning differentiates this book from generic volumes on linear algebra. The focus is clearly on the most relevant aspects of linear algebra for machine learning and to teach readers how to apply these concepts. 2. Optimization and its applications: Much of machine learning is posed as an optimization problem in which we try to maximize the accuracy of regression and classification models. The “parent problem†of optimization-centric machine learning is least-squares regression. Interestingly, this problem arises in both linear algebra and optimization, and is one of the key connecting problems of the two fields. Least-squares regression is also the starting point for support vector machines, logistic regression, and recommender systems. Furthermore, the methods for dimensionality reduction and matrix factorization also require the development of optimization methods. A general view of optimization in computational graphs is discussed together with its applications to back propagation in neural networks. A frequent challenge faced by beginners in machine learning is the extensive background required in linear algebra and optimization. One problem is that the existing linear algebra and optimization courses are not specific to machine learning; therefore, one would typically have to complete more course material than is necessary to pick up machine learning. Furthermore, certain types of ideas and tricks from optimization and linear algebra recur more frequently in machine learning than other application-centric settings. Therefore, there is significant value in developing a view of linear algebra and optimization that is better suited to the specific perspective of machine learning. COMPUTERS,Artificial Intelligence,General

New Frontiers in Mining Complex Patterns This book constitutes the refereed post-conference proceedings of the 8th International Workshop on New Frontiers in Mining Complex Patterns, NFMCP 2019, held in conjunction with ECML-PKDD 2019 in Würzburg, Germany, in September 2019. The workshop focused on the latest developments in the analysis of complex and massive data sources, such as blogs, event or log data, medical data, spatio-temporal data, social networks, mobility data, sensor data and streams. COMPUTERS,Artificial Intelligence,General

Deep Neural Evolution This book delivers the state of the art in deep learning (DL) methods hybridized with evolutionary computation (EC). Over the last decade, DL has dramatically reformed many domains: computer vision, speech recognition, healthcare, and automatic game playing, to mention only a few. All DL models, using different architectures and algorithms, utilize multiple processing layers for extracting a hierarchy of abstractions of data. Their remarkable successes notwithstanding, these powerful models are facing many challenges, and this book presents the collaborative efforts by researchers in EC to solve some of the problems in DL.EC comprises optimization techniques that are useful when problems are complex or poorly understood, or insufficient information about the problem domain is available. This family of algorithms has proven effective in solving problems with challenging characteristics such as non-convexity, non-linearity, noise, and irregularity, which dampen the performance of most classic optimization schemes. Furthermore, EC has been extensively and successfully applied in artificial neural network (ANN) research —from parameter estimation to structure optimization. Consequently, EC researchers are enthusiastic about applying their arsenal for the design and optimization of deep neural networks (DNN). This book brings together the recent progress in DL research where the focus is particularly on three sub-domains that integrate EC with DL: (1) EC for hyper-parameter optimization in DNN; (2) EC for DNN architecture design; and (3) Deep neuroevolution. The book also presents interesting applications of DL with EC in real-world problems, e.g., malware classification and object detection. Additionally, it covers recent applications of EC in DL, e.g. generative adversarial networks (GAN) training and adversarial attacks. The book aims to prompt and facilitate the research in DL with EC both in theory and in practice. COMPUTERS,Artificial Intelligence,General

Machine Vision Inspection Systems, Image Processing, Concepts, Methodologies, and Applications This edited book brings together leading researchers, academic scientists and research scholars to put forward and share their experiences and research results on all aspects of an inspection system for detection analysis for various machine vision applications. It also provides a premier interdisciplinary platform to present and discuss the most recent innovations, trends, methodology, applications, and concerns as well as practical challenges encountered and solutions adopted in the inspection system in terms of image processing and analytics of machine vision for real and industrial application. Machine vision inspection systems (MVIS) utilized all industrial and non-industrial applications where the execution of their utilities based on the acquisition and processing of images. MVIS can be applicable in industry, governmental, defense, aerospace, remote sensing, medical, and academic/education applications but constraints are different. MVIS entails acceptable accuracy, high reliability, high robustness, and low cost. Image processing is a well-defined transformation between human vision and image digitization, and their techniques are the foremost way to experiment in the MVIS. The digital image technique furnishes improved pictorial information by processing the image data through machine vision perception. Digital image proÂcessing has widely been used in MVIS applications and it can be employed to a wide diversity of problems particularly in Non-Destructive testing (NDT), presence/absence detection, defect/fault detection (weld, textile, tiles, wood, etc.,), automated vision test & measurement, pattern matching, optical character recognition & verification (OCR/OCV), barcode reading and traceability, medical diagnosis, weather forecasting, face recognition, defence and space research, etc. This edited book is designed to address various aspects of recent methodologies, concepts and research plan out to the readers for giving more depth insights for perusing research on machine vision using image processing techniques. COMPUTERS,Artificial Intelligence,General

A Matrix Algebra Approach to Artificial Intelligence Matrix algebra plays an important role in many core artificial intelligence (AI) areas, including machine learning, neural networks, support vector machines (SVMs) and evolutionary computation. This book offers a comprehensive and in-depth discussion of matrix algebra theory and methods for these four core areas of AI, while also approaching AI from a theoretical matrix algebra perspective. The book consists of two parts: the first discusses the fundamentals of matrix algebra in detail, while the second focuses on the applications of matrix algebra approaches in AI. Highlighting matrix algebra in graph-based learning and embedding, network embedding, convolutional neural networks and Pareto optimization theory, and discussing recent topics and advances, the book offers a valuable resource for scientists, engineers, and graduate students in various disciplines, including, but not limited to, computer science, mathematics and engineering. COMPUTERS,Artificial Intelligence,General

Cognition and the Creative Machine How would you assemble a machine that can be creative, what would its cogs be? Starting from how humans do creative problem solving, the author has developed a framework to explore whether a diverse set of creative problem-solving tasks can be solved computationally using a unified set of principles. In this book she describes the implementation of related prototype AI systems, and the computational and empirical experiments conducted. The book will be of interest to researchers, graduate students, and laypeople engaged with ideas in artificial intelligence, cognitive science, and creativity. COMPUTERS,Artificial Intelligence,General

Digital Twin Development and Deployment on the Cloud Digital Twin Development and Deployment in the Cloud: Developing Cloud-Friendly Dynamic Models Using Simulink®/SimscapeTM and Amazon AWS promotes a physics-based approach to the field of digital twins. Through the use of multiphysics models running in the cloud, significant improvement to the diagnostics and prognostic of systems can be attained. The book draws a clear definition of digital twins, helping business leaders clearly identify the value it brings. In addition, it outlines the key elements needed for deployment, including the hardware and software tools needed. Special attention is paid to the process of developing and deploying the multi-physics models of the digital twins. Provides a high-level overview of digital twins and their underutilization in the field of asset management and maintenance Proposes a streamline process to create digital twins for a wide variety of applications using MATLAB® Simscape™ Deploys developed digital twins on Amazon Web Services Includes MATLAB and Simulink codes available for free download on MATLAB central Covers popular prototyping hardwares, such as Arduino and Raspberry Pi COMPUTERS,Artificial Intelligence,General

Artificial Intelligence Algorithms and Applications This book constitutes the thoroughly refereed proceedings of the 11th International Symposium on Intelligence Computation and Applications, ISICA 2019, held in Guangzhou, China, in November 2019. The 65 papers presented were carefully reviewed and selected from the total of 112 submissions. This volume features the most up-to-date research in evolutionary algorithms, parallel computing and quantum computing, evolutionary multi-objective and dynamic optimization, intelligent multimedia systems, virtualization and AI applications, smart scheduling, intelligent control, big data and cloud computing, deep learning, and hybrid machine learning systems.The papers are organized according to the following topical sections: new frontier in evolutionary algorithms; evolutionary multi-objective and dynamic optimization; intelligent multimedia systems; virtualization and AI applications; smart scheduling; intelligent control; big data and cloud computing; statistical learning. COMPUTERS,Artificial Intelligence,General

Proceedings of the 21st EANN (Engineering Applications of Neural Networks) 2020 Conference This book gathers the proceedings of the 21st Engineering Applications of Neural Networks Conference, which is supported by the International Neural Networks Society (INNS). Artificial Intelligence (AI) has been following a unique course, characterized by alternating growth spurts and “AI winters.†Today, AI is an essential component of the fourth industrial revolution and enjoying its heyday. Further, in specific areas, AI is catching up with or even outperforming human beings. This book offers a comprehensive guide to AI in a variety of areas, concentrating on new or hybrid AI algorithmic approaches with robust applications in diverse sectors. One of the advantages of this book is that it includes robust algorithmic approaches and applications in a broad spectrum of scientific fields, namely the use of convolutional neural networks (CNNs), deep learning and LSTM in robotics/machine vision/engineering/image processing/medical systems/the environment; machine learning and meta learning applied to neurobiological modeling/optimization; state-of-the-art hybrid systems; and the algorithmic foundations of artificial neural networks. COMPUTERS,Artificial Intelligence,General

The AI Ladder AI may be the greatest opportunity of our time, with the potential to add nearly $16 trillion to the global economy over the next decade. But so far, adoption has been much slower than anticipated, or so headlines may lead you to believe. With this practical guide, business leaders will discover where they are in their AI journey and learn the steps necessary to successfully scale AI throughout their organization. Authors Rob Thomas and Paul Zikopoulos from IBM introduce C-suite executives and business professionals to the AI Ladder—a unified, prescriptive approach to help them understand and accelerate the AI journey. Complete with real-world examples and real-life experiences, this book explores AI drivers, value, and opportunity, as well as the adoption challenges organizations face. Understand why you can’t have AI without an information architecture (IA) Appreciate how AI is as much a cultural change as it is a technological one Collect data and make it simple and accessible, regardless of where it lives Organize data to create a business-ready analytics foundation Analyze data, and build and scale AI with trust and transparency Infuse AI throughout your entire business and create intelligent workflows COMPUTERS,Artificial Intelligence,General

Accelerated Optimization for Machine Learning This book on optimization includes forewords by Michael I. Jordan, Zongben Xu and Zhi-Quan Luo. Machine learning relies heavily on optimization to solve problems with its learning models, and first-order optimization algorithms are the mainstream approaches. The acceleration of first-order optimization algorithms is crucial for the efficiency of machine learning. Written by leading experts in the field, this book provides a comprehensive introduction to, and state-of-the-art review of accelerated first-order optimization algorithms for machine learning. It discusses a variety of methods, including deterministic and stochastic algorithms, where the algorithms can be synchronous or asynchronous, for unconstrained and constrained problems, which can be convex or non-convex. Offering a rich blend of ideas, theories and proofs, the book is up-to-date and self-contained. It is an excellent reference resource for users who are seeking faster optimization algorithms, as well as for graduate students and researchers wanting to grasp the frontiers of optimization in machine learning in a short time. COMPUTERS,Artificial Intelligence,General

Artificial Intelligence Applications and Innovations This 2 volume-set of IFIP AICT 583 and 584 constitutes the refereed proceedings of the 16th IFIP WG 12.5 International Conference on Artificial Intelligence Applications and Innovations, AIAI 2020, held in Neos Marmaras, Greece, in June 2020.* The 70 full papers and 5 short papers presented were carefully reviewed and selected from 149 submissions. They cover a broad range of topics related to technical, legal, and ethical aspects of artificial intelligence systems and their applications and are organized in the following sections: Part I: classification; clustering - unsupervised learning -analytics; image processing; learning algorithms; neural network modeling; object tracking - object detection systems; ontologies - AI; and sentiment analysis - recommender systems. Part II: AI ethics - law; AI constraints; deep learning - LSTM; fuzzy algebra - fuzzy systems; machine learning; medical - health systems; and natural language. *The conference was held virtually due to the COVID-19 pandemic. COMPUTERS,Artificial Intelligence,General

Artificial Intelligence Applications and Innovations This 2 volume-set of IFIP AICT 583 and 584 constitutes the refereed proceedings of the 16th IFIP WG 12.5 International Conference on Artificial Intelligence Applications and Innovations, AIAI 2020, held in Neos Marmaras, Greece, in June 2020.* The 70 full papers and 5 short papers presented were carefully reviewed and selected from 149 submissions. They cover a broad range of topics related to technical, legal, and ethical aspects of artificial intelligence systems and their applications and are organized in the following sections: Part I: classification; clustering - unsupervised learning -analytics; image processing; learning algorithms; neural network modeling; object tracking - object detection systems; ontologies - AI; and sentiment analysis - recommender systems. Part II: AI ethics - law; AI constraints; deep learning - LSTM; fuzzy algebra - fuzzy systems; machine learning; medical - health systems; and natural language. *The conference was held virtually due to the COVID-19 pandemic. COMPUTERS,Artificial Intelligence,General

Artificial Intelligence Applications and Innovations. AIAI 2020 IFIP WG 12.5 International Workshops This book constitutes the refereed proceedings of two International Workshops held as parallel events of the 16th IFIP WG 12.5 International Conference on Artificial Intelligence Applications and Innovations, AIAI 2020, in Neos Marmaras, Greece, in June 2020: the 9th Mining Humanistic Data Workshop, MHDW 2020, and the 5th Workshop on 5G-Putting Intelligence to the Network Edge, 5G-PINE 2020.* The 6 full papers and 3 short papers presented at MHDW 2020 were carefully reviewed and selected from 16 submissions; out of the 23 papers submitted to 5G-PINE 2020, 11 were accepted as full papers and 1 as a short paper. The MHDW papers focus on topics such as recommendation systems, sentiment analysis, pattern recognition, data mining, and time series. The papers presented at 5G-PINE focus on the latest AI applications in the telecommunication industry and deal with topics such as the Internet of Things, intelligence fusion in 5G networks, and 5G media. *The workshops were held virtually due to the COVID-19 pandemic. COMPUTERS,Artificial Intelligence,General

Machine Learning and Cognitive Computing for Mobile Communications and Wireless Networks Communication and network technology has witnessed recent rapid development and numerous information services and applications have been developed globally. These technologies have high impact on society and the way people are leading their lives. The advancement in technology has undoubtedly improved the quality of service and user experience yet a lot needs to be still done. Some areas that still need improvement include seamless wide-area coverage, high-capacity hot-spots, low-power massive-connections, low-latency and high-reliability and so on. Thus, it is highly desirable to develop smart technologies for communication to improve the overall services and management of wireless communication. Machine learning and cognitive computing have converged to give some groundbreaking solutions for smart machines. With these two technologies coming together, the machines can acquire the ability to reason similar to the human brain. The research area of machine learning and cognitive computing cover many fields like psychology, biology, signal processing, physics, information theory, mathematics, and statistics that can be used effectively for topology management. Therefore, the utilization of machine learning techniques like data analytics and cognitive power will lead to better performance of communication and wireless systems. COMPUTERS,Artificial Intelligence,General
Heart of the Machine For Readers of Ray Kurzweil and Michio Kaku, a New Look at the Cutting Edge of Artificial Intelligence Imagine a robotic stuffed animal that can read and respond to a child’s emotional state, a commercial that can recognize and change based on a customer’s facial expression, or a company that can actually create feelings as though a person were experiencing them naturally. Heart of the Machine explores the next giant step in the relationship between humans and technology: the ability of computers to recognize, respond to, and even replicate emotions. Computers have long been integral to our lives, and their advances continue at an exponential rate. Many believe that artificial intelligence equal or superior to human intelligence will happen in the not-too-distance future; some even think machine consciousness will follow. Futurist Richard Yonck argues that emotion, the first, most basic, and most natural form of communication, is at the heart of how we will soon work with and use computers. Instilling emotions into computers is the next leap in our centuries-old obsession with creating machines that replicate humans. But for every benefit this progress may bring to our lives, there is a possible pitfall. Emotion recognition could lead to advanced surveillance, and the same technology that can manipulate our feelings could become a method of mass control. And, as shown in movies like Her and Ex Machina, our society already holds a deep-seated anxiety about what might happen if machines could actually feel and break free from our control. Heart of the Machine is an exploration of the new and inevitable ways in which mankind and technology will interact. The paperback edition has a new foreword by Rana el Kaliouby, PhD, a pioneer in artificial emotional intelligence, as well as the cofounder and CEO of Affectiva, the acclaimed AI startup spun off from the MIT Media Lab. COMPUTERS,Artificial Intelligence,General

Inductive Logic Programming This book constitutes the refereed conference proceedings of the 29th International Conference on Inductive Logic Programming, ILP 2019, held in Plovdiv, Bulgaria, in September 2019. The 11 papers presented were carefully reviewed and selected from numerous submissions. Inductive Logic Programming (ILP) is a subfield of machine learning, which originally relied on logic programming as a uniform representation language for expressing examples, background knowledge and hypotheses. Due to its strong representation formalism, based on first-order logic, ILP provides an excellent means for multi-relational learning and data mining, and more generally for learning from structured data. COMPUTERS,Artificial Intelligence,General

Information Processing and Management of Uncertainty in Knowledge-Based Systems This three volume set (CCIS 1237-1239) constitutes the proceedings of the 18th International Conference on Information Processing and Management of Uncertainty in Knowledge-Based Systems, IPMU 2020, in June 2020. The conference was scheduled to take place in Lisbon, Portugal, at University of Lisbon, but due to COVID-19 pandemic it was held virtually. The 173 papers were carefully reviewed and selected from 213 submissions. The papers are organized in topical sections: homage to Enrique Ruspini; invited talks; foundations and mathematics; decision making, preferences and votes; optimization and uncertainty; games; real world applications; knowledge processing and creation; machine learning I; machine learning II; XAI; image processing; temporal data processing; text analysis and processing; fuzzy interval analysis; theoretical and applied aspects of imprecise probabilities; similarities in artificial intelligence; belief function theory and its applications; aggregation: theory and practice; aggregation: pre-aggregation functions and other generalizations of monotonicity; aggregation: aggregation of different data structures; fuzzy methods in data mining and knowledge discovery; computational intelligence for logistics and transportation problems; fuzzy implication functions; soft methods in statistics and data analysis; image understanding and explainable AI; fuzzy and generalized quantifier theory; mathematical methods towards dealing with uncertainty in applied sciences; statistical image processing and analysis, with applications in neuroimaging; interval uncertainty; discrete models and computational intelligence; current techniques to model, process and describe time series; mathematical fuzzy logic and graded reasoning models; formal concept analysis, rough sets, general operators and related topics; computational intelligence methods in information modelling, representation and processing. COMPUTERS,Artificial Intelligence,General

Information Processing and Management of Uncertainty in Knowledge-Based Systems This three volume set (CCIS 1237-1239) constitutes the proceedings of the 18th International Conference on Information Processing and Management of Uncertainty in Knowledge-Based Systems, IPMU 2020, in June 2020. The conference was scheduled to take place in Lisbon, Portugal, at University of Lisbon, but due to COVID-19 pandemic it was held virtually. The 173 papers were carefully reviewed and selected from 213 submissions. The papers are organized in topical sections: homage to Enrique Ruspini; invited talks; foundations and mathematics; decision making, preferences and votes; optimization and uncertainty; games; real world applications; knowledge processing and creation; machine learning I; machine learning II; XAI; image processing; temporal data processing; text analysis and processing; fuzzy interval analysis; theoretical and applied aspects of imprecise probabilities; similarities in artificial intelligence; belief function theory and its applications; aggregation: theory and practice; aggregation: pre-aggregation functions and other generalizations of monotonicity; aggregation: aggregation of different data structures; fuzzy methods in data mining and knowledge discovery; computational intelligence for logistics and transportation problems; fuzzy implication functions; soft methods in statistics and data analysis; image understanding and explainable AI; fuzzy and generalized quantifier theory; mathematical methods towards dealing with uncertainty in applied sciences; statistical image processing and analysis, with applications in neuroimaging; interval uncertainty; discrete models and computational intelligence; current techniques to model, process and describe time series; mathematical fuzzy logic and graded reasoning models; formal concept analysis, rough sets, general operators and related topics; computational intelligence methods in information modelling, representation and processing. COMPUTERS,Artificial Intelligence,General

Information Processing and Management of Uncertainty in Knowledge-Based Systems This three volume set (CCIS 1237-1239) constitutes the proceedings of the 18th International Conference on Information Processing and Management of Uncertainty in Knowledge-Based Systems, IPMU 2020, in June 2020. The conference was scheduled to take place in Lisbon, Portugal, at University of Lisbon, but due to COVID-19 pandemic it was held virtually. The 173 papers were carefully reviewed and selected from 213 submissions. The papers are organized in topical sections: homage to Enrique Ruspini; invited talks; foundations and mathematics; decision making, preferences and votes; optimization and uncertainty; games; real world applications; knowledge processing and creation; machine learning I; machine learning II; XAI; image processing; temporal data processing; text analysis and processing; fuzzy interval analysis; theoretical and applied aspects of imprecise probabilities; similarities in artificial intelligence; belief function theory and its applications; aggregation: theory and practice; aggregation: pre-aggregation functions and other generalizations of monotonicity; aggregation: aggregation of different data structures; fuzzy methods in data mining and knowledge discovery; computational intelligence for logistics and transportation problems; fuzzy implication functions; soft methods in statistics and data analysis; image understanding and explainable AI; fuzzy and generalized quantifier theory; mathematical methods towards dealing with uncertainty in applied sciences; statistical image processing and analysis, with applications in neuroimaging; interval uncertainty; discrete models and computational intelligence; current techniques to model, process and describe time series; mathematical fuzzy logic and graded reasoning models; formal concept analysis, rough sets, general operators and related topics; computational intelligence methods in information modelling, representation and processing. COMPUTERS,Artificial Intelligence,General
Practical Machine Learning for Data Analysis Using Python Practical Machine Learning for Data Analysis Using Python is a problem solver’s guide for creating real-world intelligent systems. It provides a comprehensive approach with concepts, practices, hands-on examples, and sample code. The book teaches readers the vital skills required to understand and solve different problems with machine learning. It teaches machine learning techniques necessary to become a successful practitioner, through the presentation of real-world case studies in Python machine learning ecosystems. The book also focuses on building a foundation of machine learning knowledge to solve different real-world case studies across various fields, including biomedical signal analysis, healthcare, security, economics, and finance. Moreover, it covers a wide range of machine learning models, including regression, classification, and forecasting. The goal of the book is to help a broad range of readers, including IT professionals, analysts, developers, data scientists, engineers, and graduate students, to solve their own real-world problems. Offers a comprehensive overview of the application of machine learning tools in data analysis across a wide range of subject areas Teaches readers how to apply machine learning techniques to biomedical signals, financial data, and healthcare data Explores important classification and regression algorithms as well as other machine learning techniques Explains how to use Python to handle data extraction, manipulation, and exploration techniques, as well as how to visualize data spread across multiple dimensions and extract useful features COMPUTERS,Artificial Intelligence,General

Unlocking Consciousness In order to bridge the gap between artificial and synthetic intelligence, we must first understand our own intelligence. 'What is intelligence?' might appear as a simple question, but many great minds have agreed that there is no singular answer. Unlocking Consciousness attempts to examine this central question through exploring the convergence of computing, philosophy, cognitive neuroscience and biogenetics.The book is the first of its kind to compare comprehensive definitions of both information and intelligence, an essential component to the advancement of computing into the realms of artificial intelligence. In examining explanations for intelligence, consciousness, memory and meaning from the perspective of a computer scientist, it offers routes that can be taken to augment natural and artificial intelligence, improving our own individual abilities, and even considering the potential for creating a prosthetic brain.Unlocking Consciousness demonstrates that understanding intelligence is not just for the benefit of computer scientists, it is also of great value to those working in evolutionary, molecular and systems biology, cognitive neuroscience, genetics and biotechnology. In unlocking the secrets of intelligence and laying out the methods of which information is structured and processed, we can unlock a completely new theory of consciousness.For additional published articles and appendices referenced in this title, readers can visit www.brainmindforum.org/ for further information. COMPUTERS,Artificial Intelligence,General

Semantic Computing As the first volume of World Scientific Encyclopedia with Semantic Computing and Robotic Intelligence, this volume is designed to lay the foundation for the understanding of the Semantic Computing (SC), as a core concept to study Robotic Intelligence in the subsequent volumes.This volume aims to provide a reference to the development of Semantic Computing, in the terms of 'meaning', 'context', and 'intention'. It brings together a series of technical notes, in average, no longer than 10 pages in length, each focuses on one topic in Semantic Computing; being review article or research paper, to explain the fundamental concepts, models or algorithms, and possible applications of the technology concerned.This volume will address three core areas in Semantic Computing: COMPUTERS,Artificial Intelligence,General
Fuzzy Logic-based Material Selection And Synthesis This unique compendium presents a comprehensive and self-contained theory of material development under imperfect information and its applications. The book describes new approaches to synthesis and selection of materials with desirable characteristics. Such approaches provide the ability of systematic and computationally effective analysis in order to predict composition, structure and related properties of new materials.The volume will be a useful advanced textbook for graduate students. It is also suitable for academicians and practitioners who wish to have fundamental models in new material synthesis and selection. COMPUTERS,Artificial Intelligence,General

Human-Machine Shared Contexts Human-Machine Shared Contexts considers the foundations, metrics, and applications of human-machine systems. Editors and authors debate whether machines, humans, and systems should speak only to each other, only to humans, or to both and how. The book establishes the meaning and operation of “shared contexts between humans and machines; it also explores how human-machine systems affect targeted audiences (researchers, machines, robots, users) and society, as well as future ecosystems composed of humans and machines. This book explores how user interventions may improve the context for autonomous machines operating in unfamiliar environments or when experiencing unanticipated events; how autonomous machines can be taught to explain contexts by reasoning, inferences, or causality, and decisions to humans relying on intuition; and for mutual context, how these machines may interdependently affect human awareness, teams and society, and how these "machines" may be affected in turn. In short, can context be mutually constructed and shared between machines and humans? The editors are interested in whether shared context follows when machines begin to think, or, like humans, develop subjective states that allow them to monitor and report on their interpretations of reality, forcing scientists to rethink the general model of human social behavior. If dependence on machine learning continues or grows, the public will also be interested in what happens to context shared by users, teams of humans and machines, or society when these machines malfunction. As scientists and engineers "think through this change in human terms," the ultimate goal is for AI to advance the performance of autonomous machines and teams of humans and machines for the betterment of society wherever these machines interact with humans or other machines. This book will be essential reading for professional, industrial, and military computer scientists and engineers; machine learning (ML) and artificial intelligence (AI) scientists and engineers, especially those engaged in research on autonomy, computational context, and human-machine shared contexts; advanced robotics scientists and engineers; scientists working with or interested in data issues for autonomous systems such as with the use of scarce data for training and operations with and without user interventions; social psychologists, scientists and physical research scientists pursuing models of shared context; modelers of the internet of things (IOT); systems of systems scientists and engineers and economists; scientists and engineers working with agent-based models (ABMs); policy specialists concerned with the impact of AI and ML on society and civilization; network scientists and engineers; applied mathematicians (e.g., holon theory, information theory); computational linguists; and blockchain scientists and engineers. Discusses the foundations, metrics, and applications of human-machine systems Considers advances and challenges in the performance of autonomous machines and teams of humans Debates theoretical human-machine ecosystem models and what happens when machines malfunction COMPUTERS,Artificial Intelligence,General

Robot Adventures in Python and C In this book the author stresses software as the most important topic in modern robotics. In particular the book concentrates on software for mobile robots, and the author demonstrates how inexpensive solutions can be constructed by mounting Raspberry Pi controllers and cameras onto model cars or other simple mechanical drive systems. He introduces EyeSim-VR, a freely available system that can realistically simulate driving, swimming, diving, and walking robots. The emphasis throughout is on algorithm development and all software assignments can run on real robot hardware, as well as on the simulation system presented. The book is suitable for undergraduate and graduate courses in artificial intelligence and robotics, and also for self-study by practitioners. All software used in this book, including all example programs, can be freely downloaded online, with native applications for MacOS, Windows, Linux, and Raspberry Pi. COMPUTERS,Artificial Intelligence,General

Image Schemas and Concept Invention In this book the author's theoretical framework builds on linguistic and psychological research, arguing that similar image-schematic notions should be grouped together into interconnected family hierarchies, with complexity increasing with regard to the addition of spatial and conceptual primitives. She introduces an image schema logic as a language to model image schemas, and she shows how the semantic content of image schemas can be used to improve computational concept invention. The book will be of value to researchers in artificial intelligence, cognitive science, psychology, and creativity. COMPUTERS,Artificial Intelligence,General

Hands-On Mathematics for Deep Learning A comprehensive guide to getting well-versed with the mathematical techniques for building modern deep learning architectures Key Features Understand linear algebra, calculus, gradient algorithms, and other concepts essential for training deep neural networks Learn the mathematical concepts needed to understand how deep learning models function Use deep learning for solving problems related to vision, image, text, and sequence applications Book Description Most programmers and data scientists struggle with mathematics, having either overlooked or forgotten core mathematical concepts. This book uses Python libraries to help you understand the math required to build deep learning (DL) models. You'll begin by learning about core mathematical and modern computational techniques used to design and implement DL algorithms. This book will cover essential topics, such as linear algebra, eigenvalues and eigenvectors, the singular value decomposition concept, and gradient algorithms, to help you understand how to train deep neural networks. Later chapters focus on important neural networks, such as the linear neural network and multilayer perceptrons, with a primary focus on helping you learn how each model works. As you advance, you will delve into the math used for regularization, multi-layered DL, forward propagation, optimization, and backpropagation techniques to understand what it takes to build full-fledged DL models. Finally, you'll explore CNN, recurrent neural network (RNN), and GAN models and their application. By the end of this book, you'll have built a strong foundation in neural networks and DL mathematical concepts, which will help you to confidently research and build custom models in DL. What you will learn Understand the key mathematical concepts for building neural network models Discover core multivariable calculus concepts Improve the performance of deep learning models using optimization techniques Cover optimization algorithms, from basic stochastic gradient descent (SGD) to the advanced Adam optimizer Understand computational graphs and their importance in DL Explore the backpropagation algorithm to reduce output error Cover DL algorithms such as convolutional neural networks (CNNs), sequence models, and generative adversarial networks (GANs) Who this book is for This book is for data scientists, machine learning developers, aspiring deep learning developers, or anyone who wants to understand the foundation of deep learning by learning the math behind it. Working knowledge of the Python programming language and machine learning basics is required. COMPUTERS,Artificial Intelligence,General

A Practical Guide to Hybrid Natural Language Processing This book provides readers with a practical guide to the principles of hybrid approaches to natural language processing (NLP) involving a combination of neural methods and knowledge graphs. To this end, it first introduces the main building blocks and then describes how they can be integrated to support the effective implementation of real-world NLP applications. To illustrate the ideas described, the book also includes a comprehensive set of experiments and exercises involving different algorithms over a selection of domains and corpora in various NLP tasks. Throughout, the authors show how to leverage complementary representations stemming from the analysis of unstructured text corpora as well as the entities and relations described explicitly in a knowledge graph, how to integrate such representations, and how to use the resulting features to effectively solve NLP tasks in a range of domains. In addition, the book offers access to executable code with examples, exercises and real-world applications in key domains, like disinformation analysis and machine reading comprehension of scientific literature. All the examples and exercises proposed in the book are available as executable Jupyter notebooks in a GitHub repository. They are all ready to be run on Google Colaboratory or, if preferred, in a local environment. A valuable resource for anyone interested in the interplay between neural and knowledge-based approaches to NLP, this book is a useful guide for readers with a background in structured knowledge representations as well as those whose main approach to AI is fundamentally based on logic. Further, it will appeal to those whose main background is in the areas of machine and deep learning who are looking for ways to leverage structured knowledge bases to optimize results along the NLP downstream. COMPUTERS,Artificial Intelligence,General

Cognitive Computing in Human Cognition This edited book designs the Cognitive Computing in Human Cognition to analyze to improve the efficiency of decision making by cognitive intelligence. The book is also intended to attract the audience who work in brain computing, deep learning, transportation, and solar cell energy. Due to this in the recent era, smart methods with human touch called as human cognition is adopted by many researchers in the field of information technology with the Cognitive Computing. COMPUTERS,Artificial Intelligence,General

Ensemble Learning for AI Developers Use ensemble learning techniques and models to improve your machine learning results. Ensemble Learning for AI Developers starts you at the beginning with an historical overview and explains key ensemble techniques and why they are needed. You then will learn how to change training data using bagging, bootstrap aggregating, random forest models, and cross-validation methods. Authors Kumar and Jain provide best practices to guide you in combining models and using tools to boost performance of your machine learning projects. They teach you how to effectively implement ensemble concepts such as stacking and boosting and to utilize popular libraries such as Keras, Scikit Learn, TensorFlow, PyTorch, and Microsoft LightGBM. Tips are presented to apply ensemble learning in different data science problems, including time series data, imaging data, and NLP. Recent advances in ensemble learning are discussed. Sample code is provided in the form of scripts and the IPython notebook. What You Will Learn Understand the techniques and methods utilized in ensemble learning Use bagging, stacking, and boosting to improve performance of your machine learning projects by combining models to decrease variance, improve predictions, and reduce bias Enhance your machine learning architecture with ensemble learning Who This Book Is For Data scientists and machine learning engineers keen on exploring ensemble learning COMPUTERS,Artificial Intelligence,General

Artificial Intelligence in Healthcare Artificial Intelligence (AI) in Healthcare is more than a comprehensive introduction to artificial intelligence as a tool in the generation and analysis of healthcare data. The book is split into two sections where the first section describes the current healthcare challenges and the rise of AI in this arena. The ten following chapters are written by specialists in each area, covering the whole healthcare ecosystem. First, the AI applications in drug design and drug development are presented followed by its applications in the field of cancer diagnostics, treatment and medical imaging. Subsequently, the application of AI in medical devices and surgery are covered as well as remote patient monitoring. Finally, the book dives into the topics of security, privacy, information sharing, health insurances and legal aspects of AI in healthcare. Highlights different data techniques in healthcare data analysis, including machine learning and data mining Illustrates different applications and challenges across the design, implementation and management of intelligent systems and healthcare data networks Includes applications and case studies across all areas of AI in healthcare data COMPUTERS,Artificial Intelligence,General

Machine Learning, Image Processing, Network Security and Data Sciences This two-volume set (CCIS 1240-1241) constitutes the refereed proceedings of the Second International Conference on Machine Learning, Image Processing, Network Security and Data Sciences, MIND 2020, held in Silchar, India. Due to the COVID-19 pandemic the conference has been postponed to July 2020. The 79 full papers and 4 short papers were thoroughly reviewed and selected from 219 submissions. The papers are organized according to the following topical sections: data science and big data; image processing and computer vision; machine learning and computational intelligence; network and cyber security. COMPUTERS,Artificial Intelligence,General

Machine Learning, Image Processing, Network Security and Data Sciences This two-volume set (CCIS 1240-1241) constitutes the refereed proceedings of the Second International Conference on Machine Learning, Image Processing, Network Security and Data Sciences, MIND 2020, held in Silchar, India. Due to the COVID-19 pandemic the conference has been postponed to July 2020. The 79 full papers and 4 short papers were thoroughly reviewed and selected from 219 submissions. The papers are organized according to the following topical sections: data science and big data; image processing and computer vision; machine learning and computational intelligence; network and cyber security. COMPUTERS,Artificial Intelligence,General

Artificial Intelligence and Machine Learning for Digital Pathology Data driven Artificial Intelligence (AI) and Machine Learning (ML) in digital pathology, radiology, and dermatology is very promising. In specific cases, for example, Deep Learning (DL), even exceeding human performance. However, in the context of medicine it is important for a human expert to verify the outcome. Consequently, there is a need for transparency and re-traceability of state-of-the-art solutions to make them usable for ethical responsible medical decision support. Moreover, big data is required for training, covering a wide spectrum of a variety of human diseases in different organ systems. These data sets must meet top-quality and regulatory criteria and must be well annotated for ML at patient-, sample-, and image-level. Here biobanks play a central and future role in providing large collections of high-quality, well-annotated samples and data. The main challenges are finding biobanks containing ‘‘fit-for-purpose’’ samples, providing quality related meta-data, gaining access to standardized medical data and annotations, and mass scanning of whole slides including efficient data management solutions. COMPUTERS,Artificial Intelligence,General

Geoinformatics in Sustainable Ecosystem and Society This book constitutes the refereed proceedings of the 7th International Conference on Geoinformatics in Sustainable Ecosystem and Society, GSES 2019, and First International Conference on Geospatial Artificial Intelligence for Urban Computing, GeoAI 2019, held in Guangzhou, China, in November 2019. The 29 full papers and 3 short papers presented in this volume were carefully reviewed and selected from 80 submissions. The papers are organized according to the following topical sections: the applications of geospatial data in the sustainable development of social economy; new approaches for earth observation data acquisition and processing; remote sensing monitoring of resources and environment and intelligent analysis; intelligent perceptions and services of spatial information; ecology, environment and social sustainable development. COMPUTERS,Artificial Intelligence,General

Intelligent Information Processing X This book constitutes the refereed proceedings of the 11th IFIP TC 12 International Conference on Intelligent Information Processing, IIP 2020, held in Hangzhou, China, in July 2020. The 24 full papers and 5 short papers presented were carefully reviewed and selected from 36 submissions. They are organized in topical sections on machine learning; multi-agent system; recommendation system; social computing; brain computer integration; pattern recognition; and computer vision and image understanding. COMPUTERS,Artificial Intelligence,General

Urban Intelligence and Applications This volume presents selected papers from the International Conference on Urban Intelligence and Applications (ICUIA), which took place on May 10-12, 2019 in Wuhan, China. The goal of the conference was to bring together researchers, industry leaders, policy makers, and administrators to discuss emerging technologies and their applications to advance the design and implementation of intelligent utilization and management of urban assets, and thus contributing to the autonomous, reliable, and efficient operation of modern, smart cities. The papers are collated to address major themes of urban sustainability, urban infrastructure and management, smart city applications, image and signal processing, natural language processing, and machine learning for monitoring and communications applications. The book will be of interest to researchers and industrial practitioners working on geospatial theories and tools, smart city applications, urban mobility and transportation, and community well-being and management. COMPUTERS,Artificial Intelligence,General

Deep Reinforcement Learning Deep reinforcement learning (DRL) is the combination of reinforcement learning (RL) and deep learning. It has been able to solve a wide range of complex decision-making tasks that were previously out of reach for a machine, and famously contributed to the success of AlphaGo. Furthermore, it opens up numerous new applications in domains such as healthcare, robotics, smart grids and finance. Divided into three main parts, this book provides a comprehensive and self-contained introduction to DRL. The first part introduces the foundations of deep learning, reinforcement learning (RL) and widely used deep RL methods and discusses their implementation. The second part covers selected DRL research topics, which are useful for those wanting to specialize in DRL research. To help readers gain a deep understanding of DRL and quickly apply the techniques in practice, the third part presents mass applications, such as the intelligent transportation system and learning to run, with detailed explanations. The book is intended for computer science students, both undergraduate and postgraduate, who would like to learn DRL from scratch, practice its implementation, and explore the research topics. It also appeals to engineers and practitioners who do not have strong machine learning background, but want to quickly understand how DRL works and use the techniques in their applications. COMPUTERS,Artificial Intelligence,General

Machine Translation A concise, nontechnical overview of the development of machine translation, including the different approaches, evaluation issues, and major players in the industry. The dream of a universal translation device goes back many decades, long before Douglas Adams's fictional Babel fish provided this service in The Hitchhiker's Guide to the Galaxy. Since the advent of computers, research has focused on the design of digital machine translation tools—computer programs capable of automatically translating a text from a source language to a target language. This has become one of the most fundamental tasks of artificial intelligence. This volume in the MIT Press Essential Knowledge series offers a concise, nontechnical overview of the development of machine translation, including the different approaches, evaluation issues, and market potential. The main approaches are presented from a largely historical perspective and in an intuitive manner, allowing the reader to understand the main principles without knowing the mathematical details. The book begins by discussing problems that must be solved during the development of a machine translation system and offering a brief overview of the evolution of the field. It then takes up the history of machine translation in more detail, describing its pre-digital beginnings, rule-based approaches, the 1966 ALPAC (Automatic Language Processing Advisory Committee) report and its consequences, the advent of parallel corpora, the example-based paradigm, the statistical paradigm, the segment-based approach, the introduction of more linguistic knowledge into the systems, and the latest approaches based on deep learning. Finally, it considers evaluation challenges and the commercial status of the field, including activities by such major players as Google and Systran. COMPUTERS,Artificial Intelligence,General

The Sciences of the Artificial, third edition Continuing his exploration of the organization of complexity and the science of design, this new edition of Herbert Simon's classic work on artificial intelligence adds a chapter that sorts out the current themes and tools—chaos, adaptive systems, genetic algorithms—for analyzing complexity and complex systems. There are updates throughout the book as well. These take into account important advances in cognitive psychology and the science of design while confirming and extending the book's basic thesis: that a physical symbol system has the necessary and sufficient means for intelligent action. The chapter "Economic Reality" has also been revised to reflect a change in emphasis in Simon's thinking about the respective roles of organizations and markets in economic systems. COMPUTERS,Artificial Intelligence,General

Bio-Inspired Artificial Intelligence A comprehensive introduction to new approaches in artificial intelligence and robotics that are inspired by self-organizing biological processes and structures. New approaches to artificial intelligence spring from the idea that intelligence emerges as much from cells, bodies, and societies as it does from evolution, development, and learning. Traditionally, artificial intelligence has been concerned with reproducing the abilities of human brains; newer approaches take inspiration from a wider range of biological structures that that are capable of autonomous self-organization. Examples of these new approaches include evolutionary computation and evolutionary electronics, artificial neural networks, immune systems, biorobotics, and swarm intelligence—to mention only a few. This book offers a comprehensive introduction to the emerging field of biologically inspired artificial intelligence that can be used as an upper-level text or as a reference for researchers. Each chapter presents computational approaches inspired by a different biological system; each begins with background information about the biological system and then proceeds to develop computational models that make use of biological concepts. The chapters cover evolutionary computation and electronics; cellular systems; neural systems, including neuromorphic engineering; developmental systems; immune systems; behavioral systems—including several approaches to robotics, including behavior-based, bio-mimetic, epigenetic, and evolutionary robots; and collective systems, including swarm robotics as well as cooperative and competitive co-evolving systems. Chapters end with a concluding overview and suggested reading. COMPUTERS,Artificial Intelligence,General

Elements of Causal Inference A concise and self-contained introduction to causal inference, increasingly important in data science and machine learning. The mathematization of causality is a relatively recent development, and has become increasingly important in data science and machine learning. This book offers a self-contained and concise introduction to causal models and how to learn them from data. After explaining the need for causal models and discussing some of the principles underlying causal inference, the book teaches readers how to use causal models: how to compute intervention distributions, how to infer causal models from observational and interventional data, and how causal ideas could be exploited for classical machine learning problems. All of these topics are discussed first in terms of two variables and then in the more general multivariate case. The bivariate case turns out to be a particularly hard problem for causal learning because there are no conditional independences as used by classical methods for solving multivariate cases. The authors consider analyzing statistical asymmetries between cause and effect to be highly instructive, and they report on their decade of intensive research into this problem. The book is accessible to readers with a background in machine learning or statistics, and can be used in graduate courses or as a reference for researchers. The text includes code snippets that can be copied and pasted, exercises, and an appendix with a summary of the most important technical concepts. COMPUTERS,Artificial Intelligence,General
Artificial Unintelligence A guide to understanding the inner workings and outer limits of technology and why we should never assume that computers always get it right. In Artificial Unintelligence, Meredith Broussard argues that our collective enthusiasm for applying computer technology to every aspect of life has resulted in a tremendous amount of poorly designed systems. We are so eager to do everything digitally—hiring, driving, paying bills, even choosing romantic partners—that we have stopped demanding that our technology actually work. Broussard, a software developer and journalist, reminds us that there are fundamental limits to what we can (and should) do with technology. With this book, she offers a guide to understanding the inner workings and outer limits of technology—and issues a warning that we should never assume that computers always get things right. Making a case against technochauvinism—the belief that technology is always the solution—Broussard argues that it's just not true that social problems would inevitably retreat before a digitally enabled Utopia. To prove her point, she undertakes a series of adventures in computer programming. She goes for an alarming ride in a driverless car, concluding “the cyborg future is not coming any time soon”; uses artificial intelligence to investigate why students can't pass standardized tests; deploys machine learning to predict which passengers survived the Titanic disaster; and attempts to repair the U.S. campaign finance system by building AI software. If we understand the limits of what we can do with technology, Broussard tells us, we can make better choices about what we should do with it to make the world better for everyone. COMPUTERS,Artificial Intelligence,General

Algorithms for Optimization A comprehensive introduction to optimization with a focus on practical algorithms for the design of engineering systems. This book offers a comprehensive introduction to optimization with a focus on practical algorithms. The book approaches optimization from an engineering perspective, where the objective is to design a system that optimizes a set of metrics subject to constraints. Readers will learn about computational approaches for a range of challenges, including searching high-dimensional spaces, handling problems where there are multiple competing objectives, and accommodating uncertainty in the metrics. Figures, examples, and exercises convey the intuition behind the mathematical approaches. The text provides concrete implementations in the Julia programming language. Topics covered include derivatives and their generalization to multiple dimensions; local descent and first- and second-order methods that inform local descent; stochastic methods, which introduce randomness into the optimization process; linear constrained optimization, when both the objective function and the constraints are linear; surrogate models, probabilistic surrogate models, and using probabilistic surrogate models to guide optimization; optimization under uncertainty; uncertainty propagation; expression optimization; and multidisciplinary design optimization. Appendixes offer an introduction to the Julia language, test functions for evaluating algorithm performance, and mathematical concepts used in the derivation and analysis of the optimization methods discussed in the text. The book can be used by advanced undergraduates and graduate students in mathematics, statistics, computer science, any engineering field, (including electrical engineering and aerospace engineering), and operations research, and as a reference for professionals. COMPUTERS,Artificial Intelligence,General

Log-Linear Models, Extensions, and Applications Advances in training models with log-linear structures, with topics including variable selection, the geometry of neural nets, and applications. Log-linear models play a key role in modern big data and machine learning applications. From simple binary classification models through partition functions, conditional random fields, and neural nets, log-linear structure is closely related to performance in certain applications and influences fitting techniques used to train models. This volume covers recent advances in training models with log-linear structures, covering the underlying geometry, optimization techniques, and multiple applications. The first chapter shows readers the inner workings of machine learning, providing insights into the geometry of log-linear and neural net models. The other chapters range from introductory material to optimization techniques to involved use cases. The book, which grew out of a NIPS workshop, is suitable for graduate students doing research in machine learning, in particular deep learning, variable selection, and applications to speech recognition. The contributors come from academia and industry, allowing readers to view the field from both perspectives. Contributors Aleksandr Aravkin, Avishy Carmi, Guillermo A. Cecchi, Anna Choromanska, Li Deng, Xinwei Deng, Jean Honorio, Tony Jebara, Huijing Jiang, Dimitri Kanevsky, Brian Kingsbury, Fabrice Lambert, Aurélie C. Lozano, Daniel Moskovich, Yuriy S. Polyakov, Bhuvana Ramabhadran, Irina Rish, Dimitris Samaras, Tara N. Sainath, Hagen Soltau, Serge F. Timashev, Ewout van den Berg COMPUTERS,Artificial Intelligence,General

Fundamentals of Machine Learning for Predictive Data Analytics A comprehensive introduction to the most important machine learning approaches used in predictive data analytics, covering both theoretical concepts and practical applications. Machine learning is often used to build predictive models by extracting patterns from large datasets. These models are used in predictive data analytics applications including price prediction, risk assessment, predicting customer behavior, and document classification. This introductory textbook offers a detailed and focused treatment of the most important machine learning approaches used in predictive data analytics, covering both theoretical concepts and practical applications. Technical and mathematical material is augmented with explanatory worked examples, and case studies illustrate the application of these models in the broader business context. After discussing the trajectory from data to insight to decision, the book describes four approaches to machine learning: information-based learning, similarity-based learning, probability-based learning, and error-based learning. Each of these approaches is introduced by a nontechnical explanation of the underlying concept, followed by mathematical models and algorithms illustrated by detailed worked examples. Finally, the book considers techniques for evaluating prediction models and offers two case studies that describe specific data analytics projects through each phase of development, from formulating the business problem to implementation of the analytics solution. The book, informed by the authors' many years of teaching machine learning, and working on predictive data analytics projects, is suitable for use by undergraduates in computer science, engineering, mathematics, or statistics; by graduate students in disciplines with applications for predictive data analytics; and as a reference for professionals. COMPUTERS,Artificial Intelligence,General

The Digital Mind How developments in science and technology may enable the emergence of purely digital minds—intelligent machines equal to or greater in power than the human brain. What do computers, cells, and brains have in common? Computers are electronic devices designed by humans; cells are biological entities crafted by evolution; brains are the containers and creators of our minds. But all are, in one way or another, information-processing devices. The power of the human brain is, so far, unequaled by any existing machine or known living being. Over eons of evolution, the brain has enabled us to develop tools and technology to make our lives easier. Our brains have even allowed us to develop computers that are almost as powerful as the human brain itself. In this book, Arlindo Oliveira describes how advances in science and technology could enable us to create digital minds. Exponential growth is a pattern built deep into the scheme of life, but technological change now promises to outstrip even evolutionary change. Oliveira describes technological and scientific advances that range from the discovery of laws that control the behavior of the electromagnetic fields to the development of computers. He calls natural selection the ultimate algorithm, discusses genetics and the evolution of the central nervous system, and describes the role that computer imaging has played in understanding and modeling the brain. Having considered the behavior of the unique system that creates a mind, he turns to an unavoidable question: Is the human brain the only system that can host a mind? If digital minds come into existence—and, Oliveira says, it is difficult to argue that they will not—what are the social, legal, and ethical implications? Will digital minds be our partners, or our rivals? COMPUTERS,Artificial Intelligence,General

Machine Learning for Data Streams A hands-on approach to tasks and techniques in data stream mining and real-time analytics, with examples in MOA, a popular freely available open-source software framework. Today many information sources—including sensor networks, financial markets, social networks, and healthcare monitoring—are so-called data streams, arriving sequentially and at high speed. Analysis must take place in real time, with partial data and without the capacity to store the entire data set. This book presents algorithms and techniques used in data stream mining and real-time analytics. Taking a hands-on approach, the book demonstrates the techniques using MOA (Massive Online Analysis), a popular, freely available open-source software framework, allowing readers to try out the techniques after reading the explanations. The book first offers a brief introduction to the topic, covering big data mining, basic methodologies for mining data streams, and a simple example of MOA. More detailed discussions follow, with chapters on sketching techniques, change, classification, ensemble methods, regression, clustering, and frequent pattern mining. Most of these chapters include exercises, an MOA-based lab session, or both. Finally, the book discusses the MOA software, covering the MOA graphical user interface, the command line, use of its API, and the development of new methods within MOA. The book will be an essential reference for readers who want to use data stream mining as a tool, researchers in innovation or data stream mining, and programmers who want to create new algorithms for MOA. COMPUTERS,Artificial Intelligence,General

The Artist in the Machine An authority on creativity introduces us to AI-powered computers that are creating art, literature, and music that may well surpass the creations of humans. Today's computers are composing music that sounds “more Bach than Bach,” turning photographs into paintings in the style of Van Gogh's Starry Night, and even writing screenplays. But are computers truly creative—or are they merely tools to be used by musicians, artists, and writers? In this book, Arthur I. Miller takes us on a tour of creativity in the age of machines. Miller, an authority on creativity, identifies the key factors essential to the creative process, from “the need for introspection” to “the ability to discover the key problem.” He talks to people on the cutting edge of artificial intelligence, encountering computers that mimic the brain and machines that have defeated champions in chess, Jeopardy!, and Go. In the central part of the book, Miller explores the riches of computer-created art, introducing us to artists and computer scientists who have, among much else, unleashed an artificial neural network to create a nightmarish, multi-eyed dog-cat; taught AI to imagine; developed a robot that paints; created algorithms for poetry; and produced the world's first computer-composed musical, Beyond the Fence, staged by Android Lloyd Webber and friends. But, Miller writes, in order to be truly creative, machines will need to step into the world. He probes the nature of consciousness and speaks to researchers trying to develop emotions and consciousness in computers. Miller argues that computers can already be as creative as humans—and someday will surpass us. But this is not a dystopian account; Miller celebrates the creative possibilities of artificial intelligence in art, music, and literature. COMPUTERS,Artificial Intelligence,General

Logic Primer, second edition Logic Primer presents a rigorous introduction to natural deduction systems of sentential and first-order logic. Logic Primer presents a rigorous introduction to natural deduction systems of sentential and first-order logic. The text is designed to foster the student-instructor relationship. The key concepts are laid out in concise definitions and comments, with the expectation that the instructor will elaborate upon them. New to the second edition is the addition of material on the logic of identity in chapters 3 and 4. An innovative interactive Web site, consisting of a "Logic Daemon" and a "Quizmaster," encourages students to formulate their own proofs and links them to appropriate explanations in the book. COMPUTERS,Artificial Intelligence,General

The Technological Singularity The idea of technological singularity, and what it would mean if ordinary human intelligence were enhanced or overtaken by artificial intelligence. The idea that human history is approaching a “singularity”—that ordinary humans will someday be overtaken by artificially intelligent machines or cognitively enhanced biological intelligence, or both—has moved from the realm of science fiction to serious debate. Some singularity theorists predict that if the field of artificial intelligence (AI) continues to develop at its current dizzying rate, the singularity could come about in the middle of the present century. Murray Shanahan offers an introduction to the idea of the singularity and considers the ramifications of such a potentially seismic event. Shanahan's aim is not to make predictions but rather to investigate a range of scenarios. Whether we believe that singularity is near or far, likely or impossible, apocalypse or utopia, the very idea raises crucial philosophical and pragmatic questions, forcing us to think seriously about what we want as a species. Shanahan describes technological advances in AI, both biologically inspired and engineered from scratch. Once human-level AI—theoretically possible, but difficult to accomplish—has been achieved, he explains, the transition to superintelligent AI could be very rapid. Shanahan considers what the existence of superintelligent machines could mean for such matters as personhood, responsibility, rights, and identity. Some superhuman AI agents might be created to benefit humankind; some might go rogue. (Is Siri the template, or HAL?) The singularity presents both an existential threat to humanity and an existential opportunity for humanity to transcend its limitations. Shanahan makes it clear that we need to imagine both possibilities if we want to bring about the better outcome. COMPUTERS,Artificial Intelligence,General

Common Sense, the Turing Test, and the Quest for Real AI What artificial intelligence can tell us about the mind and intelligent behavior. What can artificial intelligence teach us about the mind? If AI's underlying concept is that thinking is a computational process, then how can computation illuminate thinking? It's a timely question. AI is all the rage, and the buzziest AI buzz surrounds adaptive machine learning: computer systems that learn intelligent behavior from massive amounts of data. This is what powers a driverless car, for example. In this book, Hector Levesque shifts the conversation to “good old fashioned artificial intelligence,” which is based not on heaps of data but on understanding commonsense intelligence. This kind of artificial intelligence is equipped to handle situations that depart from previous patterns—as we do in real life, when, for example, we encounter a washed-out bridge or when the barista informs us there's no more soy milk. Levesque considers the role of language in learning. He argues that a computer program that passes the famous Turing Test could be a mindless zombie, and he proposes another way to test for intelligence—the Winograd Schema Test, developed by Levesque and his colleagues. “If our goal is to understand intelligent behavior, we had better understand the difference between making it and faking it,” he observes. He identifies a possible mechanism behind common sense and the capacity to call on background knowledge: the ability to represent objects of thought symbolically. As AI migrates more and more into everyday life, we should worry if systems without common sense are making decisions where common sense is needed. COMPUTERS,Artificial Intelligence,General

Reinforcement Learning Richard Sutton and Andrew Barto provide a clear and simple account of the key ideas and algorithms of reinforcement learning. Their discussion ranges from the history of the field's intellectual foundations to the most recent developments and applications. Reinforcement learning, one of the most active research areas in artificial intelligence, is a computational approach to learning whereby an agent tries to maximize the total amount of reward it receives when interacting with a complex, uncertain environment. In Reinforcement Learning, Richard Sutton and Andrew Barto provide a clear and simple account of the key ideas and algorithms of reinforcement learning. Their discussion ranges from the history of the field's intellectual foundations to the most recent developments and applications. The only necessary mathematical background is familiarity with elementary concepts of probability. The book is divided into three parts. Part I defines the reinforcement learning problem in terms of Markov decision processes. Part II provides basic solution methods: dynamic programming, Monte Carlo methods, and temporal-difference learning. Part III presents a unified view of the solution methods and incorporates artificial neural networks, eligibility traces, and planning; the two final chapters present case studies and consider the future of reinforcement learning. COMPUTERS,Artificial Intelligence,General
How Smart Machines Think Everything you've always wanted to know about self-driving cars, Netflix recommendations, IBM's Watson, and video game-playing computer programs. The future is here: Self-driving cars are on the streets, an algorithm gives you movie and TV recommendations, IBM's Watson triumphed on Jeopardy over puny human brains, computer programs can be trained to play Atari games. But how do all these things work? In this book, Sean Gerrish offers an engaging and accessible overview of the breakthroughs in artificial intelligence and machine learning that have made today's machines so smart. Gerrish outlines some of the key ideas that enable intelligent machines to perceive and interact with the world. He describes the software architecture that allows self-driving cars to stay on the road and to navigate crowded urban environments; the million-dollar Netflix competition for a better recommendation engine (which had an unexpected ending); and how programmers trained computers to perform certain behaviors by offering them treats, as if they were training a dog. He explains how artificial neural networks enable computers to perceive the world—and to play Atari video games better than humans. He explains Watson's famous victory on Jeopardy, and he looks at how computers play games, describing AlphaGo and Deep Blue, which beat reigning world champions at the strategy games of Go and chess. Computers have not yet mastered everything, however; Gerrish outlines the difficulties in creating intelligent agents that can successfully play video games like StarCraft that have evaded solution—at least for now. Gerrish weaves the stories behind these breakthroughs into the narrative, introducing readers to many of the researchers involved, and keeping technical details to a minimum. Science and technology buffs will find this book an essential guide to a future in which machines can outsmart people. COMPUTERS,Artificial Intelligence,General

Foundations of Machine Learning, second edition A new edition of a graduate-level machine learning textbook that focuses on the analysis and theory of algorithms. This book is a general introduction to machine learning that can serve as a textbook for graduate students and a reference for researchers. It covers fundamental modern topics in machine learning while providing the theoretical basis and conceptual tools needed for the discussion and justification of algorithms. It also describes several key aspects of the application of these algorithms. The authors aim to present novel theoretical tools and concepts while giving concise proofs even for relatively advanced topics. Foundations of Machine Learning is unique in its focus on the analysis and theory of algorithms. The first four chapters lay the theoretical foundation for what follows; subsequent chapters are mostly self-contained. Topics covered include the Probably Approximately Correct (PAC) learning framework; generalization bounds based on Rademacher complexity and VC-dimension; Support Vector Machines (SVMs); kernel methods; boosting; on-line learning; multi-class classification; ranking; regression; algorithmic stability; dimensionality reduction; learning automata and languages; and reinforcement learning. Each chapter ends with a set of exercises. Appendixes provide additional material including concise probability review. This second edition offers three new chapters, on model selection, maximum entropy models, and conditional entropy models. New material in the appendixes includes a major section on Fenchel duality, expanded coverage of concentration inequalities, and an entirely new entry on information theory. More than half of the exercises are new to this edition. COMPUTERS,Artificial Intelligence,General

Deep Learning An accessible introduction to the artificial intelligence technology that enables computer vision, speech recognition, machine translation, and driverless cars. Deep learning is an artificial intelligence technology that enables computer vision, speech recognition in mobile phones, machine translation, AI games, driverless cars, and other applications. When we use consumer products from Google, Microsoft, Facebook, Apple, or Baidu, we are often interacting with a deep learning system. In this volume in the MIT Press Essential Knowledge series, computer scientist John Kelleher offers an accessible and concise but comprehensive introduction to the fundamental technology at the heart of the artificial intelligence revolution. Kelleher explains that deep learning enables data-driven decisions by identifying and extracting patterns from large datasets; its ability to learn from complex data makes deep learning ideally suited to take advantage of the rapid growth in big data and computational power. Kelleher also explains some of the basic concepts in deep learning, presents a history of advances in the field, and discusses the current state of the art. He describes the most important deep learning architectures, including autoencoders, recurrent neural networks, and long short-term networks, as well as such recent developments as Generative Adversarial Networks and capsule networks. He also provides a comprehensive (and comprehensible) introduction to the two fundamental algorithms in deep learning: gradient descent and backpropagation. Finally, Kelleher considers the future of deep learning—major trends, possible developments, and significant challenges. COMPUTERS,Artificial Intelligence,General

AI and Humanity An examination of the implications for society of rapidly advancing artificial intelligence systems, combining a humanities perspective with technical analysis; includes exercises and discussion questions. AI and Humanity provides an analytical framing and a common language for understanding the effects of technological advances in artificial intelligence on society. Coauthored by a computer scientist and a scholar of literature and cultural studies, it is unique in combining a humanities perspective with technical analysis, using the tools of literary explication to examine the societal impact of AI systems. It explores the historical development of these technologies, moving from the apparently benign Roomba to the considerably more sinister semi-autonomous weapon system Harpy. The book is driven by an exploration of the cultural and etymological roots of a series of keywords relevant to both AI and society. Works examined range from Narrative of the Life of Frederick Douglass, given a close reading for its themes of literacy and agency, to Simon Head's critique of the effects of surveillance and automation on the Amazon labor force in Mindless. Originally developed as a textbook for an interdisciplinary humanities-science course at Carnegie Mellon, AI & Humanity offers discussion questions, exercises (including journal writing and concept mapping), and reading lists. A companion website provides updated resources and a portal to a video archive of interviews with AI scientists, sociologists, literary theorists, and others. COMPUTERS,Artificial Intelligence,General

Machine Learning A concise overview of machine learning—computer programs that learn from data—which underlies applications that include recommendation systems, face recognition, and driverless cars. Today, machine learning underlies a range of applications we use every day, from product recommendations to voice recognition—as well as some we don't yet use everyday, including driverless cars. It is the basis of the new approach in computing where we do not write programs but collect data; the idea is to learn the algorithms for the tasks automatically from data. As computing devices grow more ubiquitous, a larger part of our lives and work is recorded digitally, and as “Big Data” has gotten bigger, the theory of machine learning—the foundation of efforts to process that data into knowledge—has also advanced. In this book, machine learning expert Ethem Alpaydin offers a concise overview of the subject for the general reader, describing its evolution, explaining important learning algorithms, and presenting example applications. Alpaydin offers an account of how digital technology advanced from number-crunching mainframes to mobile devices, putting today's machine learning boom in context. He describes the basics of machine learning and some applications; the use of machine learning algorithms for pattern recognition; artificial neural networks inspired by the human brain; algorithms that learn associations between instances, with such applications as customer segmentation and learning recommendations; and reinforcement learning, when an autonomous agent learns act so as to maximize reward and minimize penalty. Alpaydin then considers some future directions for machine learning and the new field of “data science,” and discusses the ethical and legal implications for data privacy and security. COMPUTERS,Artificial Intelligence,General

The Deep Learning Revolution How deep learning—from Google Translate to driverless cars to personal cognitive assistants—is changing our lives and transforming every sector of the economy. The deep learning revolution has brought us driverless cars, the greatly improved Google Translate, fluent conversations with Siri and Alexa, and enormous profits from automated trading on the New York Stock Exchange. Deep learning networks can play poker better than professional poker players and defeat a world champion at Go. In this book, Terry Sejnowski explains how deep learning went from being an arcane academic field to a disruptive technology in the information economy. Sejnowski played an important role in the founding of deep learning, as one of a small group of researchers in the 1980s who challenged the prevailing logic-and-symbol based version of AI. The new version of AI Sejnowski and others developed, which became deep learning, is fueled instead by data. Deep networks learn from data in the same way that babies experience the world, starting with fresh eyes and gradually acquiring the skills needed to navigate novel environments. Learning algorithms extract information from raw data; information can be used to create knowledge; knowledge underlies understanding; understanding leads to wisdom. Someday a driverless car will know the road better than you do and drive with more skill; a deep learning network will diagnose your illness; a personal cognitive assistant will augment your puny human brain. It took nature many millions of years to evolve human intelligence; AI is on a trajectory measured in decades. Sejnowski prepares us for a deep learning future. COMPUTERS,Artificial Intelligence,General

Reinforcement Learning, second edition The significantly expanded and updated new edition of a widely used text on reinforcement learning, one of the most active research areas in artificial intelligence. Reinforcement learning, one of the most active research areas in artificial intelligence, is a computational approach to learning whereby an agent tries to maximize the total amount of reward it receives while interacting with a complex, uncertain environment. In Reinforcement Learning, Richard Sutton and Andrew Barto provide a clear and simple account of the field's key ideas and algorithms. This second edition has been significantly expanded and updated, presenting new topics and updating coverage of other topics. Like the first edition, this second edition focuses on core online learning algorithms, with the more mathematical material set off in shaded boxes. Part I covers as much of reinforcement learning as possible without going beyond the tabular case for which exact solutions can be found. Many algorithms presented in this part are new to the second edition, including UCB, Expected Sarsa, and Double Learning. Part II extends these ideas to function approximation, with new sections on such topics as artificial neural networks and the Fourier basis, and offers expanded treatment of off-policy learning and policy-gradient methods. Part III has new chapters on reinforcement learning's relationships to psychology and neuroscience, as well as an updated case-studies chapter including AlphaGo and AlphaGo Zero, Atari game playing, and IBM Watson's wagering strategy. The final chapter discusses the future societal impacts of reinforcement learning. COMPUTERS,Artificial Intelligence,General

Automation and Collaborative Robotics Understand the current and future research into technologies that underpin the increasing capabilities of automation technologies and their impact on the working world of the future. Rapid advances in automation and robotics technologies are often reported in the trade and general media, often relying on scary headlines such as “Jobs Lost to Robots.†It is certainly true that work will change with the advent of smarter and faster automated workers; however, the scope and scale of the changes is still unknown. Automation may seem to be here already, but we are only at the early stages. Automation and Collaborative Robotics explores the output of current research projects that are improving the building blocks of an automated world. Research into collaborative robotics (cobotics) is merging digital, audio, and visual data to generate a commonly held view between cobots and their human collaborators. Low-power machine learning at the edge of the network can deliver decision making on cobots or to their manipulations. Topics covered in this book include: Robotic process automation, chatbots, and their impact in the near future The hype of automation and headlines leading to concerns over the future of work Component technologies that are still in the research labs Foundational technologies and collaboration that will enable many tasks to be automated with human workers being re-skilled and displaced rather than replaced What You Will Learn Be aware of the technologies currently being researched to improve or deliver automation Understand the impact of robotics, other automation technologies, and the impact of AI on automation Get an idea of how far we are from implementation of an automated future Know what work will look like in the future with the deployment of these technologies Who This Book Is For Technical and business managers interested in the future of automation and robotics, and the impact it will have on their organizations, customers, and the business world in general COMPUTERS,Artificial Intelligence,General

Advances in Practical Applications of Agents, Multi-Agent Systems, and Trustworthiness. The PAAMS Collection This book constitutes the proceedings of the 18th International Conference on Practical Applications of Agents and Multi-Agent Systems, PAAMS 2020, held in L'Aquila, Italy, in October 2020. The 29 regular and 17 demo papers presented in this volume were carefully reviewed and selected from 64 submissions. They deal with the application and validation of agent-based models, methods, and technologies in a number of key applications areas, including: advanced models and learning, agent-based programming, decision-making, educa-tion and social interactions, formal and theoretic models, health and safety, mobility and the city, swarms and task allocation. COMPUTERS,Artificial Intelligence,General

Analog IC Placement Generation via Neural Networks from Unlabeled Data In this book, innovative research using artificial neural networks (ANNs) is conducted to automate the placement task in analog integrated circuit layout design, by creating a generalized model that can generate valid layouts at push-button speed. Further, it exploits ANNs’ generalization and push-button speed prediction (once fully trained) capabilities, and details the optimal description of the input/output data relation. The description developed here is chiefly reflected in two of the system’s characteristics: the shape of the input data and the minimized loss function. In order to address the latter, abstract and segmented descriptions of both the input data and the objective behavior are developed, which allow the model to identify, in newer scenarios, sub-blocks which can be found in the input data. This approach yields device-level descriptions of the input topology that, for each device, focus on describing its relation to every other device in the topology. By means of these descriptions, an unfamiliar overall topology can be broken down into devices that are subject to the same constraints as a device in one of the training topologies. In the experimental results chapter, the trained ANNs are used to produce a variety of valid placement solutions even beyond the scope of the training/validation sets, demonstrating the model’s effectiveness in terms of identifying common components between newer topologies and reutilizing the acquired knowledge. Lastly, the methodology used can readily adapt to the given problem’s context (high label production cost), resulting in an efficient, inexpensive and fast model. COMPUTERS,Artificial Intelligence,General

Artificial Intelligence, Data And Blockchain In A Digital Economy, First Edition Digital transformation continues to create new growth opportunities for businesses and improve the lives of citizens. To help businesses seize these opportunities, the Infocomm Media Development Authority (IMDA) launched the Digital Economy Framework for Action in 2018. This living document aims to enhance Singapore's digital competitiveness and become a global node in Asia.As part of Singapore's push for a Digital Economy, IMDA and the Singapore University of Social Sciences have collaborated to jointly publish the Artificial Intelligence, Data and Blockchain in a Digital Economy, First Edition. This book explains how frontier technologies such as blockchain and artificial intelligence can empower Singapore's digital transformation. It also highlights and provides insights on transformative services and how frontier technology can impact the nation's digitalisation journey. COMPUTERS,Artificial Intelligence,General

What Is Artificial Intelligence? This book engages with the title question: what is artificial intelligence (AI)? Instead of reiterating received definitions or surveying the field from a disciplinary perspective, the question is engaged here by putting two standpoints into conversation. The standpoints are different in their disciplinary groundings — i.e. technology and the humanities — and also in their approaches — i.e. applied and conceptual. Peter is an AI engineer: his approach is in terms of how to make AI work. Suman is a humanities researcher: his approach is in terms of what people and academics mean when they say 'AI'.A coherent argument, if not a consensus, develops by putting the two standpoints into conversation. The conversation is presented in 32 short chapters, in turn by Suman and Peter. There are two parts: Part 1, Questioning AI, and Part 2, AI and Government Policy. The first part covers issues such as the meaning of intelligence, automation, evolution, artificial and language. It outlines some of the processes through which these concepts may be technologically grounded as AI. The second part addresses policy considerations that underpin the development of AI and responds to the consequences. Themes taken up here include: rights and responsibilities; data usage and state-level strategies in the USA, UK and China; unemployment and policy futures. COMPUTERS,Artificial Intelligence,General
Artificial Intelligence in Education This two-volume set LNAI 12163 and 12164 constitutes the refereed proceedings of the 21th International Conference on Artificial Intelligence in Education, AIED 2020, held in Ifrane, Morocco, in July 2020.*The 49 full papers presented together with 66 short, 4 industry & innovation, 4 doctoral consortium, and 4 workshop papers were carefully reviewed and selected from 214 submissions. The conference provides opportunities for the cross-fertilization of approaches, techniques and ideas from the many fields that comprise AIED, including computer science, cognitive and learning sciences, education, game design, psychology, sociology, linguistics as well as many domain-specific areas. ​*The conference was held virtually due to the COVID-19 pandemic. COMPUTERS,Artificial Intelligence,General
Artificial Intelligence in Education This two-volume set LNAI 12163 and 12164 constitutes the refereed proceedings of the 21th International Conference on Artificial Intelligence in Education, AIED 2020, held in Ifrane, Morocco, in July 2020.* The 49 full papers presented together with 66 short, 4 industry & innovation, 4 doctoral consortium, and 4 workshop papers were carefully reviewed and selected from 214 submissions. The conference provides opportunities for the cross-fertilization of approaches, techniques and ideas from the many fields that comprise AIED, including computer science, cognitive and learning sciences, education, game design, psychology, sociology, linguistics as well as many domain-specific areas. ​*The conference was held virtually due to the COVID-19 pandemic. COMPUTERS,Artificial Intelligence,General

Highlights in Practical Applications of Agents, Multi-Agent Systems, and Trust-worthiness. The PAAMS Collection This book constitutes the refereed proceedings of the workshops co-located with the 18th International Conference on Practical Applications of Agents and Multi-Agent Systems, PAAMS 2020, held in L’Aquila, Italy, in October 2020. The total of 21 full and 13 short papers presented in this volume were carefully reviewed and selected from 57 submissions. The papers in this volume stem from the following meetings: Workshop on Agent-Based Artificial Markets Computational Economics (ABAM); Workshop on Agents and Edge-AI (AgEdAI); Workshop on Character Computing (C2); Workshop on MAS for Complex Networks and Social Computation (CNSC); Workshop on Decision Support, Recommendation, and Persuasion in Artificial Intelligence (DeRePAI); Workshop on Multi-Agent Systems and Simulation (MAS&S); Workshop on Multi-agent based Applications for Energy Markets, Smart Grids and Sustainable Energy Systems (MASGES); Workshop on Smart Cities and Intelligent Agents (SCIA). COMPUTERS,Artificial Intelligence,General
Explainable, Transparent Autonomous Agents and Multi-Agent Systems This book constitutes the proceedings of the Second International Workshop on Explainable, Transparent Autonomous Agents and Multi-Agent Systems, EXTRAAMAS 2020, which was due to be held in Auckland, New Zealand, in May 2020. The conference was held virtually due to the COVID-19 pandemic. The 8 revised and extended papers were carefully selected from 20 submissions and are presented here with one demo paper. The papers are organized in the following topical sections: explainable agents; cross disciplinary XAI; explainable machine learning; demos. COMPUTERS,Artificial Intelligence,General

Artificial General Intelligence This book constitutes the refereed proceedings of the 13th International Conference on Artificial General Intelligence, AGI 2020, held in St. Petersburg, Russia, in September 2020.The 30 full papers and 8 short papers presented in this book were carefully reviewed and selected from 60 submissions. The papers cover topics such as AGI architectures, artificial creativity and AI safety, transfer learning, AI unification and benchmarks for AGI. COMPUTERS,Artificial Intelligence,General

Artificial Intelligent Techniques for Electric and Hybrid Electric Vehicles Electric vehicles/hybrid electric vehicles (EV/HEV) commercialization is still a challenge in industries in terms of performance and cost. The performance along with cost reduction are two tradeoffs which need to be researched to arrive at an optimal solution. This book focuses on the convergence of various technologies involved in EV/HEV. The book brings together the research that is being carried out in the field of EV/HEV whose leading role is by optimization techniques with artificial intelligence (AI). Other featured research includes green drive schemes which involve the possible renewable energy sources integration to develop eco-friendly green vehicles, as well as Internet of Things (IoT)-based techniques for EV/HEVs. Electric vehicle research involves multi-disciplinary expertise from electrical, electronics, mechanical engineering and computer science. Consequently, this book serves as a point of convergence wherein all these domains are addressed and merged and will serve as a potential resource for industrialists and researchers working in the domain of electric vehicles. COMPUTERS,Artificial Intelligence,General

Embracing Industry 4.0 This book highlights selected articles from the electrical engineering track, with a focus on the latest trends in electrical and electronic engineering toward embracing Industry 4.0, as part of the Malaysian Technical Universities Conference on Engineering and Technology—MUCET 2019. The event brings together researchers and professionals in the fields of engineering, research, and technology, and provides a platform for future collaborations and exchanges. COMPUTERS,Artificial Intelligence,General

Evolution in Action This edited research monograph brings together contributions from computer scientists, biologists, and engineers who are engaged with the study of evolution and how it may be applied to solve real-world problems. It also serves as a Festschrift dedicated to Erik D. Goodman, the founding director of the BEACON Center for the Study of Evolution in Action, a pioneering NSF Science and Technology Center headquartered at Michigan State University. The contributing authors are leading experts associated with the center, and they serve in top research and industrial establishments across the US and worldwide. Part I summarizes the history of the BEACON Center, with refreshingly personal chapters that describe Erik's working and leadership style, and others that discuss the development and successes of the center in the context of research funding, projects, and careers. The chapters in Part II deal with the evolution of genomes and evolvability. The contributions in Part III discuss the evolution of behavior and intelligence. Those in Part IV concentrate on the evolution of communities and collective dynamics. The chapters in Part V discuss selected evolutionary computing applications in domains such as arts and science, automated program repair, cybersecurity, mechatronics, and genomic prediction. Part VI deals with evolution in the classroom, using creativity in research, and responsible conduct in research training. The book concludes with a special chapter from Erik Goodman, a short biography that concentrates on his personal positive influences and experiences throughout his long career in academia and industry. COMPUTERS,Artificial Intelligence,General

Engineering Psychology and Cognitive Ergonomics. Mental Workload, Human Physiology, and Human Energy This book constitutes the proceedings of the 17th International Conference on Engineering Psychology and Cognitive Ergonomics, EPCE 2020, held as part of the 22nd International Conference, HCI International 2020, which took place in Copenhagen, Denmark, in July 2020. The total of 1439 papers and 238 posters included in the 37 HCII 2020 proceedings volumes was carefully reviewed and selected from 6326 submissions.EPCE 2020 includes a total of 60 regular papers; they were organized in topical sections named: mental workload and performance; human physiology, human energy and cognition; cognition and design of complex and safety critical systems; human factors in human autonomy teaming and intelligent systems; cognitive psychology in aviation and automotive. As a result of the Danish Government's announcement, dated April 21, 2020, to ban all large events (above 500 participants) until September 1, 2020, the HCII 2020 conference was held virtually. COMPUTERS,Artificial Intelligence,General

Hands-On Artificial Intelligence for Banking Delve into the world of real-world financial applications using deep learning, artificial intelligence, and production-grade data feeds and technology with Python Key Features Understand how to obtain financial data via Quandl or internal systems Automate commercial banking using artificial intelligence and Python programs Implement various artificial intelligence models to make personal banking easy Book Description Remodeling your outlook on banking begins with keeping up to date with the latest and most effective approaches, such as artificial intelligence (AI). Hands-On Artificial Intelligence for Banking is a practical guide that will help you advance in your career in the banking domain. The book will demonstrate AI implementation to make your banking services smoother, more cost-efficient, and accessible to clients, focusing on both the client- and server-side uses of AI. You'll begin by understanding the importance of artificial intelligence, while also gaining insights into the recent AI revolution in the banking industry. Next, you'll get hands-on machine learning experience, exploring how to use time series analysis and reinforcement learning to automate client procurements and banking and finance decisions. After this, you'll progress to learning about mechanizing capital market decisions, using automated portfolio management systems and predicting the future of investment banking. In addition to this, you'll explore concepts such as building personal wealth advisors and mass customization of client lifetime wealth. Finally, you'll get to grips with some real-world AI considerations in the field of banking. By the end of this book, you'll be equipped with the skills you need to navigate the finance domain by leveraging the power of AI. What you will learn Automate commercial bank pricing with reinforcement learning Perform technical analysis using convolutional layers in Keras Use natural language processing (NLP) for predicting market responses and visualizing them using graph databases Deploy a robot advisor to manage your personal finances via Open Bank API Sense market needs using sentiment analysis for algorithmic marketing Explore AI adoption in banking using practical examples Understand how to obtain financial data from commercial, open, and internal sources Who this book is for This is one of the most useful artificial intelligence books for machine learning engineers, data engineers, and data scientists working in the finance industry who are looking to implement AI in their business applications. The book will also help entrepreneurs, venture capitalists, investment bankers, and wealth managers who want to understand the importance of AI in finance and banking and how it can help them solve different problems related to these domains. Prior experience in the financial markets or banking domain, and working knowledge of the Python programming language are a must. COMPUTERS,Artificial Intelligence,General

Engineering Multi-Agent Systems This book constitutes the thoroughly refereed post-conference proceedings of the 7th International Workshop on Engineering Multi-Agent Systems, EMAS 2019, held in Montreal, QC, Canada, in May 2019. The 13 revised full papers presented in this book were carefully selected and reviewed from 20 submissions. The papers are grouped in the following topical sections: Multi-Agent Interaction and Organization; Simulation; Social Awareness and Explainability; Learning and Reconfiguration; and Implementation Techniques and Tools. COMPUTERS,Artificial Intelligence,General

Artificial Life and Evolutionary Computation This book constitutes the revised selected papers of the 14th Italian Workshop on Artificial Life and Evolutionary Computation, WIVACE 2019, held in Rende, Italy, in September 2019. The 13 full papers and 4 short paper presented were thoroughly reviewed and selected from 31 submissions. They are focused on the topics of information systems, design and analysis of algorithms, artificial intelligence, machine learning, cognitive science, modeling and simulation, collaborative and social computing, parallel computing, distributed computing. The chapter “Nestedness Temperature in the Agent-Artifact Space: Emergence of Hierarchical Order in the 2000-2014 Photonics Techno-Economic Complex System†is available open access under a CC BY 4.0 license. COMPUTERS,Artificial Intelligence,General

The Development of Deep Learning Technologies This book is a part of the Blue Book series “Research on the Development of Electronic Information Engineering Technology in China,†which explores the cutting edge of deep learning studies. A subfield of machine learning, deep learning differs from conventional machine learning methods in its ability to learn multiple levels of representation and abstraction by using several layers of nonlinear modules for feature extraction and transformation. The extensive use and huge success of deep learning in speech, CV, and NLP have led to significant advances toward the full materialization of AI. Focusing on the development of deep learning technologies, this book also discusses global trends, the status of deep learning development in China and the future of deep learning. COMPUTERS,Artificial Intelligence,General

Artificial Intelligence for Knowledge Management This book features a selection of extended papers presented at the 6th IFIP WG 12.6 International Workshop on Artificial Intelligence for Knowledge Management, AI4KM 2018, held in Stockholm, Sweden, in July 2018, in the framework of the International Joint Conference on Artificial Intelligence, IJCAI 2018.The 11 revised and extended papers were carefully reviewed and selected for inclusion in this volume. They present new research and innovative aspects in the field of knowledge management such as machine learning, knowledge models, KM and Web, knowledge capturing and learning, and KM and AI intersections. COMPUTERS,Artificial Intelligence,General

Building Computer Vision Applications Using Artificial Neural Networks Apply computer vision and machine learning concepts in developing business and industrial applications ​using a practical, step-by-step approach. The book comprises four main sections starting with setting up your programming environment and configuring your computer with all the prerequisites to run the code examples. Section 1 covers the basics of image and video processing with code examples of how to manipulate and extract useful information from the images. You will mainly use OpenCV with Python to work with examples in this section. Section 2 describes machine learning and neural network concepts as applied to computer vision. You will learn different algorithms of the neural network, such as convolutional neural network (CNN), region-based convolutional neural network (R-CNN), and YOLO. In this section, you will also learn how to train, tune, and manage neural networks for computer vision. Section 3 provides step-by-step examples of developing business and industrial applications, such as facial recognition in video surveillance and surface defect detection in manufacturing. The final section is about training neural networks involving a large number of images on cloud infrastructure, such as Amazon AWS, Google Cloud Platform, and Microsoft Azure. It walks you through the process of training distributed neural networks for computer vision on GPU-based cloud infrastructure. By the time you finish reading Building Computer Vision Applications Using Artificial Neural Networks and working through the code examples, you will have developed some real-world use cases of computer vision with deep learning. What You Will Learn · Employ image processing, manipulation, and feature extraction techniques· Work with various deep learning algorithms for computer vision · Train, manage, and tune hyperparameters of CNNs and object detection models, such as R-CNN, SSD, and YOLO · Build neural network models using Keras and TensorFlow · Discover best practices when implementing computer vision applications in business and industry· Train distributed models on GPU-based cloud infrastructure Who This Book Is For Data scientists, analysts, and machine learning and software engineering professionals with Python programming knowledge. COMPUTERS,Artificial Intelligence,General

Intelligent Computer Mathematics This book constitutes the refereed proceedings of the 13th International Conference on Intelligent Computer Mathematics, CICM 2020, held in Bertinoro, Italy, in July 2020*.The 15 full papers, 1 invited paper and 2 abstracts of invited papers presented were carefully reviewed and selected from a total of 35 submissions. The papers focus on advances in automated theorem provers and formalization, computer algebra systems and their libraries, and applications of machine learning, among other topics. * The conference was held virtually due to the COVID-19 pandemic. COMPUTERS,Artificial Intelligence,General

The AI Does Not Hate You 'A fascinating and delightfully written book about some very smart people who may not, or may, be about to transform humanity forever' JON RONSON This is a book about AI and AI risk. But it's also more importantly about a community of people who are trying to think rationally about intelligence, and the places that these thoughts are taking them, and what insight they can and can't give us about the future of the human race over the next few years. It explains why these people are worried, why they might be right, and why they might be wrong. It is a book about the cutting edge of our thinking on intelligence and rationality right now by the people who stay up all night worrying about it. Along the way, we discover why we probably don't need to worry about a future AI resurrecting a perfect copy of our minds and torturing us for not inventing it sooner, but we perhaps should be concerned about paperclips destroying life as we know it; how Mickey Mouse can teach us an important lesson about how to program AI; and how a more rational approach to life could be what saves us all. COMPUTERS,Artificial Intelligence,General

Computing Science, Communication and Security This book constitutes revised selected papers of the First International Conference on Computing Science, Communication and Security, COMS2 2020, held in March 2020. Due to the COVID-19 pandemic the conference was held virtually. The 26 full papers and 1 short paper were thoroughly reveiwed and selected from 79 submissions. Papers are organised according to the topical sections on artificial intelligence and machine learning; network, communication and security; computing science. COMPUTERS,Artificial Intelligence,General

Text Mining with R Much of the data available today is unstructured and text-heavy, making it challenging for analysts to apply their usual data wrangling and visualization tools. With this practical book, you’ll explore text-mining techniques with tidytext, a package that authors Julia Silge and David Robinson developed using the tidy principles behind R packages like ggraph and dplyr. You’ll learn how tidytext and other tidy tools in R can make text analysis easier and more effective. The authors demonstrate how treating text as data frames enables you to manipulate, summarize, and visualize characteristics of text. You’ll also learn how to integrate natural language processing (NLP) into effective workflows. Practical code examples and data explorations will help you generate real insights from literature, news, and social media. Learn how to apply the tidy text format to NLP Use sentiment analysis to mine the emotional content of text Identify a document’s most important terms with frequency measurements Explore relationships and connections between words with the ggraph and widyr packages Convert back and forth between R’s tidy and non-tidy text formats Use topic modeling to classify document collections into natural groups Examine case studies that compare Twitter archives, dig into NASA metadata, and analyze thousands of Usenet messages COMPUTERS,Artificial Intelligence,Natural Language Processing

R Deep Learning Essentials Implement neural network models in R 3.5 using TensorFlow, Keras, and MXNet Key Features Use R 3.5 for building deep learning models for computer vision and text Apply deep learning techniques in cloud for large-scale processing Build, train, and optimize neural network models on a range of datasets Book Description Deep learning is a powerful subset of machine learning that is very successful in domains such as computer vision and natural language processing (NLP). This second edition of R Deep Learning Essentials will open the gates for you to enter the world of neural networks by building powerful deep learning models using the R ecosystem. This book will introduce you to the basic principles of deep learning and teach you to build a neural network model from scratch. As you make your way through the book, you will explore deep learning libraries, such as Keras, MXNet, and TensorFlow, and create interesting deep learning models for a variety of tasks and problems, including structured data, computer vision, text data, anomaly detection, and recommendation systems. You'll cover advanced topics, such as generative adversarial networks (GANs), transfer learning, and large-scale deep learning in the cloud. In the concluding chapters, you will learn about the theoretical concepts of deep learning projects, such as model optimization, overfitting, and data augmentation, together with other advanced topics. By the end of this book, you will be fully prepared and able to implement deep learning concepts in your research work or projects. What you will learn Build shallow neural network prediction models Prevent models from overfitting the data to improve generalizability Explore techniques for finding the best hyperparameters for deep learning models Create NLP models using Keras and TensorFlow in R Use deep learning for computer vision tasks Implement deep learning tasks, such as NLP, recommendation systems, and autoencoders Who this book is for This second edition of R Deep Learning Essentials is for aspiring data scientists, data analysts, machine learning developers, and deep learning enthusiasts who are well versed in machine learning concepts and are looking to explore the deep learning paradigm using R. Fundamental understanding of the R language is necessary to get the most out of this book. COMPUTERS,Artificial Intelligence,Natural Language Processing

IBM Watson Projects Incorporate intelligence to your data-driven business insights and high accuracy business solutions Key Features Explore IBM Watson capabilities such as Natural Language Processing (NLP) and machine learning Build projects to adopt IBM Watson across retail, banking, and healthcare Learn forecasting, anomaly detection, and pattern recognition with ML techniques Book Description IBM Watson provides fast, intelligent insight in ways that the human brain simply can't match. Through eight varied projects, this book will help you explore the computing and analytical capabilities of IBM Watson. The book begins by refreshing your knowledge of IBM Watson's basic data preparation capabilities, such as adding and exploring data to prepare it for being applied to models. The projects covered in this book can be developed for different industries, including banking, healthcare, media, and security. These projects will enable you to develop an AI mindset and guide you in developing smart data-driven projects, including automating supply chains, analyzing sentiment in social media datasets, and developing personalized recommendations. By the end of this book, you'll have learned how to develop solutions for process automation, and you'll be able to make better data-driven decisions to deliver an excellent customer experience. What you will learn Build a smart dialog system with cognitive assistance solutions Design a text categorization model and perform sentiment analysis on social media datasets Develop a pattern recognition application and identify data irregularities smartly Analyze trip logs from a driving services company to determine profit Provide insights into an organization's supply chain data and processes Create personalized recommendations for retail chains and outlets Test forecasting effectiveness for better sales prediction strategies Who this book is for This book is for data scientists, AI engineers, NLP engineers, machine learning engineers, and data analysts who wish to build next-generation analytics applications. Basic familiarity with cognitive computing and sound knowledge of any programming language is all you need to understand the projects covered in this book. COMPUTERS,Artificial Intelligence,Natural Language Processing

Natural Language Processing with PyTorch Natural Language Processing (NLP) provides boundless opportunities for solving problems in artificial intelligence, making products such as Amazon Alexa and Google Translate possible. If you’re a developer or data scientist new to NLP and deep learning, this practical guide shows you how to apply these methods using PyTorch, a Python-based deep learning library. Authors Delip Rao and Brian McMahon provide you with a solid grounding in NLP and deep learning algorithms and demonstrate how to use PyTorch to build applications involving rich representations of text specific to the problems you face. Each chapter includes several code examples and illustrations. Explore computational graphs and the supervised learning paradigm Master the basics of the PyTorch optimized tensor manipulation library Get an overview of traditional NLP concepts and methods Learn the basic ideas involved in building neural networks Use embeddings to represent words, sentences, documents, and other features Explore sequence prediction and generate sequence-to-sequence models Learn design patterns for building production NLP systems COMPUTERS,Artificial Intelligence,Natural Language Processing

Advanced Deep Learning with R Discover best practices for choosing, building, training, and improving deep learning models using Keras-R, and TensorFlow-R libraries Key Features Implement deep learning algorithms to build AI models with the help of tips and tricks Understand how deep learning models operate using expert techniques Apply reinforcement learning, computer vision, GANs, and NLP using a range of datasets Book Description Deep learning is a branch of machine learning based on a set of algorithms that attempt to model high-level abstractions in data. Advanced Deep Learning with R will help you understand popular deep learning architectures and their variants in R, along with providing real-life examples for them. This deep learning book starts by covering the essential deep learning techniques and concepts for prediction and classification. You will learn about neural networks, deep learning architectures, and the fundamentals for implementing deep learning with R. The book will also take you through using important deep learning libraries such as Keras-R and TensorFlow-R to implement deep learning algorithms within applications. You will get up to speed with artificial neural networks, recurrent neural networks, convolutional neural networks, long short-term memory networks, and more using advanced examples. Later, you'll discover how to apply generative adversarial networks (GANs) to generate new images; autoencoder neural networks for image dimension reduction, image de-noising and image correction and transfer learning to prepare, define, train, and model a deep neural network. By the end of this book, you will be ready to implement your knowledge and newly acquired skills for applying deep learning algorithms in R through real-world examples. What you will learn Learn how to create binary and multi-class deep neural network models Implement GANs for generating new images Create autoencoder neural networks for image dimension reduction, image de-noising and image correction Implement deep neural networks for performing efficient text classification Learn to define a recurrent convolutional network model for classification in Keras Explore best practices and tips for performance optimization of various deep learning models Who this book is for This book is for data scientists, machine learning practitioners, deep learning researchers and AI enthusiasts who want to develop their skills and knowledge to implement deep learning techniques and algorithms using the power of R. A solid understanding of machine learning and working knowledge of the R programming language are required. COMPUTERS,Artificial Intelligence,Natural Language Processing

Deep Learning with TensorFlow 2 and Keras Build machine and deep learning systems with the newly released TensorFlow 2 and Keras for the lab, production, and mobile devices Key Features Introduces and then uses TensorFlow 2 and Keras right from the start Teaches key machine and deep learning techniques Understand the fundamentals of deep learning and machine learning through clear explanations and extensive code samples Book Description Deep Learning with TensorFlow 2 and Keras, Second Edition teaches neural networks and deep learning techniques alongside TensorFlow (TF) and Keras. You'll learn how to write deep learning applications in the most powerful, popular, and scalable machine learning stack available. TensorFlow is the machine learning library of choice for professional applications, while Keras offers a simple and powerful Python API for accessing TensorFlow. TensorFlow 2 provides full Keras integration, making advanced machine learning easier and more convenient than ever before. This book also introduces neural networks with TensorFlow, runs through the main applications (regression, ConvNets (CNNs), GANs, RNNs, NLP), covers two working example apps, and then dives into TF in production, TF mobile, and using TensorFlow with AutoML. What you will learn Build machine learning and deep learning systems with TensorFlow 2 and the Keras API Use Regression analysis, the most popular approach to machine learning Understand ConvNets (convolutional neural networks) and how they are essential for deep learning systems such as image classifiers Use GANs (generative adversarial networks) to create new data that fits with existing patterns Discover RNNs (recurrent neural networks) that can process sequences of input intelligently, using one part of a sequence to correctly interpret another Apply deep learning to natural human language and interpret natural language texts to produce an appropriate response Train your models on the cloud and put TF to work in real environments Explore how Google tools can automate simple ML workflows without the need for complex modeling Who this book is for This book is for Python developers and data scientists who want to build machine learning and deep learning systems with TensorFlow. Whether or not you have done machine learning before, this book gives you the theory and practice required to use Keras, TensorFlow 2, and AutoML to build machine learning systems. COMPUTERS,Artificial Intelligence,Natural Language Processing

Hands-On Machine Learning with C++ Implement supervised and unsupervised machine learning algorithms using C++ libraries such as PyTorch C++ API, Caffe2, Shogun, Shark-ML, mlpack, and dlib with the help of real-world examples and datasets Key Features Become familiar with data processing, performance measuring, and model selection using various C++ libraries Implement practical machine learning and deep learning techniques to build smart models Deploy machine learning models to work on mobile and embedded devices Book Description C++ can make your machine learning models run faster and more efficiently. This handy guide will help you learn the fundamentals of machine learning (ML), showing you how to use C++ libraries to get the most out of your data. This book makes machine learning with C++ for beginners easy with its example-based approach, demonstrating how to implement supervised and unsupervised ML algorithms through real-world examples. This book will get you hands-on with tuning and optimizing a model for different use cases, assisting you with model selection and the measurement of performance. You'll cover techniques such as product recommendations, ensemble learning, and anomaly detection using modern C++ libraries such as PyTorch C++ API, Caffe2, Shogun, Shark-ML, mlpack, and dlib. Next, you'll explore neural networks and deep learning using examples such as image classification and sentiment analysis, which will help you solve various problems. Later, you'll learn how to handle production and deployment challenges on mobile and cloud platforms, before discovering how to export and import models using the ONNX format. By the end of this C++ book, you will have real-world machine learning and C++ knowledge, as well as the skills to use C++ to build powerful ML systems. What you will learn Explore how to load and preprocess various data types to suitable C++ data structures Employ key machine learning algorithms with various C++ libraries Understand the grid-search approach to find the best parameters for a machine learning model Implement an algorithm for filtering anomalies in user data using Gaussian distribution Improve collaborative filtering to deal with dynamic user preferences Use C++ libraries and APIs to manage model structures and parameters Implement a C++ program to solve image classification tasks with LeNet architecture Who this book is for You will find this C++ machine learning book useful if you want to get started with machine learning algorithms and techniques using the popular C++ language. As well as being a useful first course in machine learning with C++, this book will also appeal to data analysts, data scientists, and machine learning developers who are looking to implement different machine learning models in production using varied datasets and examples. Working knowledge of the C++ programming language is mandatory to get started with this book. COMPUTERS,Artificial Intelligence,Natural Language Processing

Practical Natural Language Processing Many books and courses tackle natural language processing (NLP) problems with toy use cases and well-defined datasets. But if you want to build, iterate, and scale NLP systems in a business setting and tailor them for particular industry verticals, this is your guide. Software engineers and data scientists will learn how to navigate the maze of options available at each step of the journey. Through the course of the book, authors Sowmya Vajjala, Bodhisattwa Majumder, Anuj Gupta, and Harshit Surana will guide you through the process of building real-world NLP solutions embedded in larger product setups. You’ll learn how to adapt your solutions for different industry verticals such as healthcare, social media, and retail. With this book, you’ll: Understand the wide spectrum of problem statements, tasks, and solution approaches within NLP Implement and evaluate different NLP applications using machine learning and deep learning methods Fine-tune your NLP solution based on your business problem and industry vertical Evaluate various algorithms and approaches for NLP product tasks, datasets, and stages Produce software solutions following best practices around release, deployment, and DevOps for NLP systems Understand best practices, opportunities, and the roadmap for NLP from a business and product leader’s perspective COMPUTERS,Artificial Intelligence,Natural Language Processing

Natural Language Processing with Spark NLP If you want to build an enterprise-quality application that uses natural language text but aren’t sure where to begin or what tools to use, this practical guide will help get you started. Alex Thomas, principal data scientist at Wisecube, shows software engineers and data scientists how to build scalable natural language processing (NLP) applications using deep learning and the Apache Spark NLP library. Through concrete examples, practical and theoretical explanations, and hands-on exercises for using NLP on the Spark processing framework, this book teaches you everything from basic linguistics and writing systems to sentiment analysis and search engines. You’ll also explore special concerns for developing text-based applications, such as performance. In four sections, you’ll learn NLP basics and building blocks before diving into application and system building: Basics: Understand the fundamentals of natural language processing, NLP on Apache Stark, and deep learning Building blocks: Learn techniques for building NLP applications—including tokenization, sentence segmentation, and named-entity recognition—and discover how and why they work Applications: Explore the design, development, and experimentation process for building your own NLP applications Building NLP systems: Consider options for productionizing and deploying NLP models, including which human languages to support COMPUTERS,Artificial Intelligence,Natural Language Processing

Blockchain Bitcoin is starting to come into its own as a digital currency, but the blockchain technology behind it could prove to be much more significant. This book takes you beyond the currency ("Blockchain 1.0") and smart contracts ("Blockchain 2.0") to demonstrate how the blockchain is in position to become the fifth disruptive computing paradigm after mainframes, PCs, the Internet, and mobile/social networking. Author Melanie Swan, Founder of the Institute for Blockchain Studies, explains that the blockchain is essentially a public ledger with potential as a worldwide, decentralized record for the registration, inventory, and transfer of all assets—not just finances, but property and intangible assets such as votes, software, health data, and ideas. Topics include: Concepts, features, and functionality of Bitcoin and the blockchain Using the blockchain for automated tracking of all digital endeavors Enabling censorship?resistant organizational models Creating a decentralized digital repository to verify identity Possibility of cheaper, more efficient services traditionally provided by nations Blockchain for science: making better use of the data-mining network Personal health record storage, including access to one’s own genomic data Open access academic publishing on the blockchain This book is part of an ongoing O’Reilly series. Mastering Bitcoin: Unlocking Digital Crypto-Currencies introduces Bitcoin and describes the technology behind Bitcoin and the blockchain. Blockchain: Blueprint for a New Economy considers theoretical, philosophical, and societal impact of cryptocurrencies and blockchain technologies. COMPUTERS,Blockchain

The Truth Machine "Views differ on bitcoin, but few doubt the transformative potential of Blockchain technology. The Truth Machine is the best book so far on what has happened and what may come along. It demands the attention of anyone concerned with our economic future." —Lawrence H. Summers, Charles W. Eliot University Professor and President Emeritus at Harvard, Former Treasury Secretary From Michael J. Casey and Paul Vigna, the authors of The Age of Cryptocurrency, comes the definitive work on the Internet’s Next Big Thing: The Blockchain. Big banks have grown bigger and more entrenched. Privacy exists only until the next hack. Credit card fraud is a fact of life. Many of the “legacy systems†once designed to make our lives easier and our economy more efficient are no longer up to the task. Yet there is a way past all this—a new kind of operating system with the potential to revolutionize vast swaths of our economy: the blockchain. In The Truth Machine, Michael J. Casey and Paul Vigna demystify the blockchain and explain why it can restore personal control over our data, assets, and identities; grant billions of excluded people access to the global economy; and shift the balance of power to revive society’s faith in itself. They reveal the disruption it promises for industries including finance, tech, legal, and shipping. Casey and Vigna expose the challenge of replacing trusted (and not-so-trusted) institutions on which we’ve relied for centuries with a radical model that bypasses them. The Truth Machine reveals the empowerment possible when self-interested middlemen give way to the transparency of the blockchain, while highlighting the job losses, assertion of special interests, and threat to social cohesion that will accompany this shift. With the same balanced perspective they brought to The Age of Cryptocurrency, Casey and Vigna show why we all must care about the path that blockchain technology takes—moving humanity forward, not backward. COMPUTERS,Blockchain

Mastering Bitcoin Join the technological revolution that’s taking the financial world by storm. Mastering Bitcoin is your guide through the seemingly complex world of bitcoin, providing the knowledge you need to participate in the internet of money. Whether you’re building the next killer app, investing in a startup, or simply curious about the technology, this revised and expanded second edition provides essential detail to get you started. Bitcoin, the first successful decentralized digital currency, is still in its early stages and yet it’s already spawned a multi-billion-dollar global economy open to anyone with the knowledge and passion to participate. Mastering Bitcoin provides the knowledge. You simply supply the passion. The second edition includes: A broad introduction of bitcoin and its underlying blockchain—ideal for non-technical users, investors, and business executives An explanation of the technical foundations of bitcoin and cryptographic currencies for developers, engineers, and software and systems architects Details of the bitcoin decentralized network, peer-to-peer architecture, transaction lifecycle, and security principles New developments such as Segregated Witness, Payment Channels, and Lightning Network A deep dive into blockchain applications, including how to combine the building blocks offered by this platform into higher-level applications User stories, analogies, examples, and code snippets illustrating key technical concepts COMPUTERS,Blockchain

Statistical Techniques for Forensic Accounting Master powerful statistical techniques for uncovering fraud or misrepresentation in complex financial data. The discipline of statistics has developed sophisticated, well-accepted approaches for identifying financial fraud and demonstrating that it is deliberate. Statistical Techniques for Forensic Accounting is the first comprehensive guide to these tools and techniques. Leading expert Dr. Saurav Dutta explains their mathematical underpinnings, shows how to use them properly, and guides you in communicating your findings to other interested and knowledgeable parties, or assessing others' analyses. Dutta is singularly well-qualified to write this book: he has been engaged as an expert in many of the world's highest-profile financial fraud cases, including Worldcom, Global Crossing, Cendant, and HealthSouth. Here, he covers everything professionals need to know to construct and conduct valid and defensible statistical tests, perform analyses, and interpret others' analyses. Coverage includes: exploratory data analysis to identify the "Fraud Triangle" and other red flags… data mining tools, usage, and limitations… statistical terms and methods applicable to forensic accounting… relevant uncertainty and probability concepts… Bayesian analysis and networks… statistical inference, sampling, sample size, estimation, regression, correlation, classification, prediction, and much more. For all forensic accountants, auditors, investigators, and litigators involved with corporate financial reporting; and for all students interested in forensic accounting and related fields. COMPUTERS,Business & Productivity Software,Accounting & Finance

Private Equity Accounting, Investor Reporting, and Beyond Today's only advanced comprehensive guide to private equity accounting, investor reporting, valuations and performance measurement provides a complete update to reflect the latest standards and best practices, as well as the author's unique experience teaching hundreds of fund professionals. In Private Equity Accounting, Investor Reporting and Beyond Mariya Stefanova brings together comprehensive advanced accounting guidance and advice for all private equity practitioners and fund accountants worldwide: information once available only by learning from peers. Replete with up-to-date, user-friendly examples from all main jurisdictions, this guide explains the precise workings and lifecycles of private equity funds; reviews commercial terms; evaluates structures and tax treatments; shows how to read Limited Partnership Agreements; presents best-practice details and processes, and identifies costly pitfalls to avoid. COMPUTERS,Business & Productivity Software,Accounting & Finance

QuickBooks 2016 For Dummies The perennial bestseller on QuickBooks—now covering QuickBooks 2016 If you're like most people involved with a small business, accounting is the last thing you want to spend a lot of time on. Luckily, QuickBooks 2016 For Dummies makes it easy to keep your finances under control so you can concentrate on other aspects of your business. In no time, you'll find out how to populate QuickBooks lists, create invoices and credit memos, record a sales receipt, track sales and inventory, pay bills, process payroll, track business checkbooks and credit cards, and so much more. QuickBooks is the leading small business accounting software package designed to help users handle their financial and business management tasks more effectively. With plain-English explanations that cut through financial jargon, this easy-to-follow guide walks you through installing the software and configuring QuickBooks for your business needs and goes on to show you how to build the perfect budget, simplify tax return preparation, and generate financial reports—without ever breaking a sweat! Organize all of your business finances in one place Create invoices and credit memos, record sales receipts, and pay the bills Track inventory, figure job costs, and monitor your business with reports Make tax time easier Written by an expert CPA who knows QuickBooks and understands your unique business needs, QuickBooks 2016 For Dummies is your go-to guide for getting past the paperwork and putting the program to work. COMPUTERS,Business & Productivity Software,Accounting & Finance

Hands-On Financial Modeling with Microsoft Excel 2019 Explore the aspects of financial modeling with the help of clear and easy-to-follow instructions and a variety of Excel features, functions, and productivity tips Key Features A non data professionals guide to exploring Excel's financial functions and pivot tables Learn to prepare various models for income and cash flow statements, and balance sheets Learn to perform valuations and identify growth drivers with real-world case studies Book Description Financial modeling is a core skill required by anyone who wants to build a career in finance. Hands-On Financial Modeling with Microsoft Excel 2019 examines various definitions and relates them to the key features of financial modeling with the help of Excel. This book will help you understand financial modeling concepts using Excel, and provides you with an overview of the steps you should follow to build an integrated financial model. You will explore the design principles, functions, and techniques of building models in a practical manner. Starting with the key concepts of Excel, such as formulas and functions, you will learn about referencing frameworks and other advanced components of Excel for building financial models. Later chapters will help you understand your financial projects, build assumptions, and analyze historical data to develop data-driven models and functional growth drivers. The book takes an intuitive approach to model testing, along with best practices and practical use cases. By the end of this book, you will have examined the data from various use cases, and you will have the skills you need to build financial models to extract the information required to make informed business decisions. What you will learn Identify the growth drivers derived from processing historical data in Excel Use discounted cash flow (DCF) for efficient investment analysis Build a financial model by projecting balance sheets, profit, and loss Apply a Monte Carlo simulation to derive key assumptions for your financial model Prepare detailed asset and debt schedule models in Excel Discover the latest and advanced features of Excel 2019 Calculate profitability ratios using various profit parameters Who this book is for This book is for data professionals, analysts, traders, business owners, and students, who want to implement and develop a high in-demand skill of financial modeling in their finance, analysis, trading, and valuation work. This book will also help individuals that have and don't have any experience in data and stats, to get started with building financial models. The book assumes working knowledge with Excel. COMPUTERS,Business & Productivity Software,Accounting & Finance

Cobol for Students COBOL for Students has established itself as one of the most successful teaching texts on COBOL programming and is now in its fourth edition. The first part of the book concentrates on the fundamentals of the language and takes students to the point where they can write modestly sized programs using sequential files. Part two assumes competence in elementary COBOL and explains design and other programming techniques which should be part of the professional programmer's repertoire. Part three extends the student's knowledge of the language by explaining some of the more advanced features of COBOL. Written for students learning COBOL for the first time, it takes the reader from the basic fundamentals right through to some of the more advanced features in one handy, and inexpensive volume. As many lecture courses have been based upon earlier editions of this book, this edition maintains the highly successful style and format and has been updated to include the 'Intrinsic Function Module for COBOL'. (This is the ANSI Standard X3.23a-1989 (COBOL 89) which has also been adopted as ISO International Standard 1989 Addendum 1 (an addendum to the ANSI Standard X3.23-1985 (COBOL 85)) and consists mainly of 42 predefined functions related to many different application areas). COMPUTERS,Business & Productivity Software,Business Intelligence

The Discipline of Organizing Note about this ebook: This ebook exploits many advanced capabilities with images, hypertext, and interactivity and is optimized for EPUB3-compliant book readers, especially Apple's iBooks and browser plugins. These features may not work on all ebook readers. We organize things. We organize information, information about things, and information about information. Organizing is a fundamental issue in many professional fields, but these fields have only limited agreement in how they approach problems of organizing and in what they seek as their solutions. The Discipline of Organizing synthesizes insights from library science, information science, computer science, cognitive science, systems analysis, business, and other disciplines to create an Organizing System for understanding organizing. This framework is robust and forward-looking, enabling effective sharing of insights and design patterns between disciplines that weren’t possible before. The Professional Edition includes new and revised content about the active resources of the "Internet of Things," and how the field of Information Architecture can be viewed as a subset of the discipline of organizing. You’ll find: 600 tagged endnotes that connect to one or more of the contributing disciplines Nearly 60 new pictures and illustrations Links to cross-references and external citations Interactive study guides to test on key points The Professional Edition is ideal for practitioners and as a primary or supplemental text for graduate courses on information organization, content and knowledge management, and digital collections. FOR INSTRUCTORS: Supplemental materials (lecture notes, assignments, exams, etc.) are available at http://disciplineoforganizing.org. FOR STUDENTS: Make sure this is the edition you want to buy. There's a newer one and maybe your instructor has adopted that one instead. COMPUTERS,Business & Productivity Software,Business Intelligence

Business Intelligence Guidebook Between the high-level concepts of business intelligence and the nitty-gritty instructions for using vendors’ tools lies the essential, yet poorly-understood layer of architecture, design and process. Without this knowledge, Big Data is belittled – projects flounder, are late and go over budget. Business Intelligence Guidebook: From Data Integration to Analytics shines a bright light on an often neglected topic, arming you with the knowledge you need to design rock-solid business intelligence and data integration processes. Practicing consultant and adjunct BI professor Rick Sherman takes the guesswork out of creating systems that are cost-effective, reusable and essential for transforming raw data into valuable information for business decision-makers. After reading this book, you will be able to design the overall architecture for functioning business intelligence systems with the supporting data warehousing and data-integration applications. You will have the information you need to get a project launched, developed, managed and delivered on time and on budget – turning the deluge of data into actionable information that fuels business knowledge. Finally, you’ll give your career a boost by demonstrating an essential knowledge that puts corporate BI projects on a fast-track to success. Provides practical guidelines for building successful BI, DW and data integration solutions. Explains underlying BI, DW and data integration design, architecture and processes in clear, accessible language. Includes the complete project development lifecycle that can be applied at large enterprises as well as at small to medium-sized businesses Describes best practices and pragmatic approaches so readers can put them into action. Companion website includes templates and examples, further discussion of key topics, instructor materials, and references to trusted industry sources. COMPUTERS,Business & Productivity Software,Business Intelligence

Power Pivot and Power BI Microsoft PowerPivot is a free add-on to Excel from Microsoft that allows users to produce new kinds of reports and analyses that were simply impossible before, and this book is the first to tackle DAX formulas, the core capability of PowerPivot, from the perspective of the Excel audience. Written by the world's foremost PowerPivot blogger and practitioner, the book's concepts and approach are introduced in a simple, step-by-step manner tailored to the learning style of Excel users everywhere. The techniques presented allow users to produce, in hours or even minutes, results that formerly would have taken entire teams weeks or months to produce. It includes lessons on the difference between calculated columns and measures; how formulas can be reused across reports of completely different shapes; how to merge disjointed sets of data into unified reports; how to make certain columns in a pivot behave as if the pivot were filtered while other columns do not; and how to create time-intelligent calculations in pivot tables such as "Year over Year" and "Moving Averages" whether they use a standard, fiscal, or a complete custom calendar. The "pattern-like" techniques and best practices contained in this book have been developed and refined over two years of onsite training with Excel users around the world, and the key lessons from those seminars costing thousands of dollars per day are now available to within the pages of this easy-to-follow guide. This updated second edition covers new features introduced with Office 2015. COMPUTERS,Business & Productivity Software,Business Intelligence

Digital Creativity Model and Its Relationship with Corporate Performance This book provides theoretical and practical backgrounds for the digital creativity management and related Agent-Based Modeling (ABM) results on the basis of a set of realistic assumptions in which several topics such as knowledge network, diversity, individual creativity, team creativity, exploration and exploitation, and organizational creativity are discussed. Until now, there has been no clear-cut methodology by which creativity management can be articulated and materialized into the business process management within companies and corporate performance. Though many approaches have been proposed to tackle the creativity research issues, this book adopts a new approach which assumes that the network structure formulated by interrelationships among team members decides individual creativity and team creativity as well, and ABM-based simulations lead to robust analysis of corporate performance over time. Typical examples of network structure under consideration in this study are degree centrality and structural hole (an opportunity to broker the flow of information between people, and control the projects that bring together people from opposite sides of the hole). This book suggests detailed analysis of source code used in implementing a prototype digital creativity simulation engine with related snap-shots and ABM results, so that readers can understand hard core of how to design and implement ABM tasks related to target problems, and extract implications from the ABM results. COMPUTERS,Business & Productivity Software,Business Intelligence

Disruptive Analytics Learn all you need to know about seven key innovations disrupting business analytics today. These innovations—the open source business model, cloud analytics, the Hadoop ecosystem, Spark and in-memory analytics, streaming analytics, Deep Learning, and self-service analytics—are radically changing how businesses use data for competitive advantage. Taken together, they are disrupting the business analytics value chain, creating new opportunities. Enterprises who seize the opportunity will thrive and prosper, while others struggle and decline: disrupt or be disrupted. Disruptive Business Analytics provides strategies to profit from disruption. It shows you how to organize for insight, build and provision an open source stack, how to practice lean data warehousing, and how to assimilate disruptive innovations into an organization. Through a short history of business analytics and a detailed survey of products and services, analytics authority Thomas W. Dinsmore provides a practical explanation of the most compelling innovations available today. What You'll Learn Discover how the open source business model works and how to make it work for you See how cloud computing completely changes the economics of analytics Harness the power of Hadoop and its ecosystem Find out why Apache Spark is everywhere Discover the potential of streaming and real-time analytics Learn what Deep Learning can do and why it matters See how self-service analytics can change the way organizations do business Who This Book Is For Corporate actors at all levels of responsibility for analytics: analysts, CIOs, CTOs, strategic decision makers, managers, systems architects, technical marketers, product developers, IT personnel, and consultants. COMPUTERS,Business & Productivity Software,Business Intelligence

Microsoft Dynamics 365 Extensions Cookbook More than 80 recipes to help you leverage the various extensibility features available for Microsoft Dynamics and solve problems easily About This Book Customize, configure, and extend the vanilla features of Dynamics 365 to deliver bespoke CRM solutions fit for any organization Implement business logic using point-and-click configuration, plugins, and client-side scripts with MS Dynamics 365 Built a DevOps pipeline as well as Integrate Dynamics 365 with Azure and other platforms Who This Book Is For This book is for developers, administrators, consultants, and power users who want to learn about best practices when extending Dynamics 365 for enterprises. You are expected to have a basic understand of the Dynamics CRM/365 platform. What You Will Learn Customize, configure, and extend Microsoft Dynamics 365 Create business process automation Develop client-side extensions to add features to the Dynamics 365 user interface Set up a security model to securely manage data with Dynamics 365 Develop and deploy clean code plugins to implement a wide range of custom behaviors Use third-party applications, tools, and patterns to integrate Dynamics 365 with other platforms Integrate with Azure, Java, SSIS, PowerBI, and Octopus Deploy Build an end-to-end DevOps pipeline for Dynamics 365 In Detail Microsoft Dynamics 365 is a powerful tool. It has many unique features that empower organisations to bridge common business challenges and technology pitfalls that would usually hinder the adoption of a CRM solution. This book sets out to enable you to harness the power of Dynamics 365 and cater to your unique circumstances. We start this book with a no-code configuration chapter and explain the schema, fields, and forms modeling techniques. We then move on to server-side and client-side custom code extensions. Next, you will see how best to integrate Dynamics 365 in a DevOps pipeline to package and deploy your extensions to the various SDLC environments. This book also covers modern libraries and integration patterns that can be used with Dynamics 365 (Angular, 3 tiers, and many others). Finally, we end by highlighting some of the powerful extensions available. Throughout we explain a range of design patterns and techniques that can be used to enhance your code quality; the aim is that you will learn to write enterprise-scale quality code. Style and approach This book takes a recipe-based approach, delivering practical examples and use cases so that you can identify the best possible approach to extend your Dynamics 365 deployment and tackle your specific business problems. COMPUTERS,Business & Productivity Software,Business Intelligence

The Application of Fuzzy Logic for Managerial Decision Making Processes This book addresses the latest research and applications of fuzzy management methods for business decisions. It showcases a broad set of applications and discusses topics such as measures for the quality of analytics outcomes in big data environments; how fuzzy management methods support the inclusion of human thinking and human behavior in decision making processes; how to generate better results with fuzzy management methods in cases of imprecise information; new personalization concepts enabled by fuzzy logic for the offering of customized products and services especially in the electronic market; and lastly the application of fuzzy analysis for executives using natural rather than computer language. The combination of research papers and case studies makes it a valuable resource both for researchers and practitioners in the digital economy. COMPUTERS,Business & Productivity Software,Business Intelligence

Dynamics 365 for Finance and Operations Development Cookbook Over 80 effective recipes to help you solve real-world Microsoft Dynamics 365 for Finance and Operations development problems About This Book Learn all about the enhanced functionalities of Dynamics 365 for Finance and Operations and master development best practices Develop powerful projects using new tools and features Work through easy-to-understand recipes with step-by-step instructions and useful screenshots Who This Book Is For If you are a Dynamics AX developer primarily focused on delivering time-proven applications, then this book is for you. This book is also ideal for people who want to raise their programming skills above the beginner level, and at the same time learn the functional aspects of Dynamics 365 for Finance and Operations. Some X++ coding experience is expected. What You Will Learn Explore data manipulation concepts in Dynamics 365 for Operations Build scripts to assist data migration processes Organize data in Dynamics 365 for Operations forms Make custom lookups using AOT forms and dynamically generate them from X++ code Create a custom electronic payment format and process a vendor payment using it Integrate your application with Microsoft Office Suite and other external systems using various approaches Export and import business data for further distribution or analysis Improve your development efficiency and performance In Detail Microsoft Dynamics 365 for Finance and Operations has a lot to offer developers. It allows them to customize and tailor their implementations to meet their organization's needs. This Development Cookbook will help you manage your company or customer ERP information and operations efficiently. We start off by exploring the concept of data manipulation in Dynamics 365 for Operations. This will also help you build scripts to assist data migration, and show you how to organize data in forms. You will learn how to create custom lookups using Application Object Tree forms and generate them dynamically. We will also show you how you can enhance your application by using advanced form controls, and integrate your system with other external systems. We will help you script and enhance your user interface using UI elements. This book will help you look at application development from a business process perspective, and develop enhanced ERP solutions by learning and implementing the best practices and techniques. Style and approach The book follows a practical recipe-based approach, focusing on real-world scenarios and giving you all the information you need to build a strong Dynamics 365 for Finance and Operations implementation. COMPUTERS,Business & Productivity Software,Business Intelligence

Microsoft Dynamics 365 Enterprise Edition – Financial Management Boost your accounting and financial skills with Microsoft Dynamics 365 About This Book Make real-time data-driven decisions for your enterprise with Microsoft Dynamics 365 Enterprise edition Configure and set up the Microsoft Dynamics 365 financial module via highly useful tips and tricks Administer customer relations and plan enterprise resources with this systematic guide Who This Book Is For This book is for application consultants, solution architects, controllers, CFOs, pre-sales and other professionals who are involved in a Microsoft Dynamics 365 for finance and operation implementation. Basic knowledge of financial terms, concepts, and terminologies is required. What You Will Learn Examine the business logic behind the financial functionalities of Microsoft Dynamics 365 FFO Set up and configure the core modules of financial management Grasp the key control points of financial management Explore intercompany and consolidation in Microsoft Dynamics 365 FFO Understand multi-currency sales, tax mechanisms, and budgeting capabilities in Microsoft Dynamics 365 FFO Get to grips with month/year-end period close functionality Understand the account payable and receivable module Use Microsoft Dynamics 365 to create financial reports In Detail Microsoft Dynamics 365 for finance and operations is a rapidly growing application and is widely used in enterprise organizations. Because of its ability to maximize business productivity, it is a fast-growing business application package in the ERP market. We will start by looking into ERP concepts, implementation needs, and interface design, giving you basic knowledge of financial management aspects and explaining key concepts along the way. To begin with, you'll be taken through the general ledger and financial dimension functions. You'll later learn about the sales tax mechanism and multi-currency in Microsoft Dynamics 365. We tackle each topic with focused examples and explanations on topics such as payable/receivable accounts, forecasting, cash and bank management, budgeting planning/control, and fixed assets. Finally, we walk you through intercompany, consolidation, costing basics, and financial reporting. By the end of this book, your finance team will have a much richer understanding of Microsoft Dynamics 365 for finance and operations and its powerful capabilities. Style and approach This book is a step-by-step guide focusing on implementing Dynamics 365 financial management for your organization. COMPUTERS,Business & Productivity Software,Business Intelligence

MATLAB MATLAB: A Practical Introduction to Programming and Problem Solving, winner of TAA’s 2017 Textbook Excellence Award ("Texty"), guides the reader through both programming and built-in functions to easily exploit MATLAB's extensive capabilities for tackling engineering and scientific problems. Assuming no knowledge of programming, this book starts with programming concepts, such as variables, assignments, and selection statements, moves on to loops, and then solves problems using both the programming concept and the power of MATLAB. The fifth edition has been updated to reflect the functionality of the current version of MATLAB (R2018a), including the addition of local functions in scripts, the new string type, coverage of recently introduced functions to import data from web sites, and updates to the Live Editor and App Designer. Presents programming concepts and MATLAB built-in functions side by side, giving students the ability to program efficiently and exploit the power of MATLAB to solve technical problems Offers sections on common pitfalls and programming guidelines that direct students to best practice procedures Tests conceptual understanding of the material with Quick Questions! and Practice sections within each chapter NEW TO THE FIFTH EDITION Use of MATLAB Version R2018a A revised Text Manipulation chapter, which includes manipulating character vectors as well as the new string type Introduction to alternate MATLAB platforms, including MATLAB Mobile Local functions within scripts The new output format for most expression types Introduction to the RESTFUL web functions which import data from web sites Increased coverage of App Designer Introduction to recording audio from a built-in device such as a microphone Modified and new end-of-chapter exercises More coverage of data structures including categorical arrays and tables Increased coverage of built-in functions in MATLAB COMPUTERS,Business & Productivity Software,Business Intelligence

SAP Business Intelligence Quick Start Guide Designing and deploying solutions using the SAP BusinessObjects Business Intelligence platform 4.2. Key Features Get up and running with the SAP BusinessObjects Business Intelligence platform Perform effective data analysis and visualization for actionable insights Enhance your BI strategy by creating different types of reports and dashboards using SAP BusinessObjects Book Description The SAP BusinessObjects Business Intelligence platform is a powerful reporting and analysis tool. This book is the ideal introduction to the SAP BusinessObjects Business Intelligence platform, introducing you to its data visualization, visual analytics, reporting, and dashboarding capabilities. The book starts with an overview of the BI platform and various data sources for reporting. Then, we move on to looking at data visualization, analysis, reporting, and analytics using BusinessObjects Business Intelligence tools. You will learn about the features associated with reporting, scheduling, and distribution and learn how to deploy the platform. Toward the end, you will learn about the strategies and factors that should be considered during deployment. By the end, you will be confident working with the SAP BusinessObjects Business Intelligence platform to deliver better insights for more effective decision making. What you will learn Work with various tools to create interactive data visualization and analysis Query, report, and analyze with SAP Business Objects Web Intelligence Create a report in SAP Crystal Reports for Enterprise Visualize and manipulate data using an SAP Lumira Storyboard Deep dive into the workings of the SAP predictive analytics tool Deploy and configure SAP BO Intelligence platform 4.2 Who this book is for This book is for Business Intelligence professionals and existing SAP ecosystem users who want to perform effective Business Intelligence using SAP BusinessObjects. COMPUTERS,Business & Productivity Software,Business Intelligence

Hands-On Business Intelligence with Qlik Sense Create dynamic dashboards to bring interactive data visualization to your enterprise using Qlik Sense Key Features Implement various Qlik Sense features to create interactive dashboards Analyze data easily and make business decisions faster using Qlik Sense Perform self-service data analytics and geospatial analytics using an example-based approach Book Description Qlik Sense allows you to explore simple-to-complex data to reveal hidden insights and data relationships to make business-driven decisions. Hands-On Business Intelligence with Qlik Sense begins by helping you get to grips with underlying Qlik concepts and gives you an overview of all Qlik Sense's features. You will learn advanced modeling techniques and learn how to analyze the data loaded using a variety of visualization objects. You'll also be trained on how to share apps through Qlik Sense Enterprise and Qlik Sense Cloud and how to perform aggregation with AGGR. As you progress through the chapters, you'll explore the stories feature to create data-driven presentations and update an existing story. This book will guide you through the GeoAnalytics feature with the geo-mapping object and GeoAnalytics connector. Furthermore, you'll learn about the self-service analytics features and perform data forecasting using advanced analytics. Lastly, you'll deploy Qlik Sense apps for mobile and tablet. By the end of this book, you will be well-equipped to run successful business intelligence applications using Qlik Sense's functionality, data modeling techniques, and visualization best practices. What you will learn Discover how to load, reshape, and model data for analysis Apply data visualization practices to create stunning dashboards Make use of Python and R for advanced analytics Perform geo-analysis to create visualizations using native objects Learn how to work with AGGR and data stories Who this book is for If you're a data analyst, BI developer, or interested in business intelligence and want to gain practical experience of working on Qlik Sense, this book is for you. You'll also find it useful if you want to explore Qlik Sense's next-generation applications for self-service business intelligence. No prior experience of working with Qlik Sense is required. COMPUTERS,Business & Productivity Software,Business Intelligence

Essential MATLAB for Engineers and Scientists Essential MATLAB for Engineers and Scientists, Seventh Edition, provides a concise, balanced overview of MATLAB's functionality, covering both fundamentals and applications. The essentials are illustrated throughout, featuring complete coverage of the software's windows and menus. Program design and algorithm development are presented, along with many examples from a wide range of familiar scientific and engineering areas. This edition has been updated to include the latest MATLAB versions through 2018b. This is an ideal book for a first course on MATLAB, but is also ideal for an engineering problem-solving course using MATLAB. Updated to include all the newer features through MATLAB R2018b Includes new chapter on useful toolboxes Provides additional examples on engineering applications COMPUTERS,Business & Productivity Software,Business Intelligence

Learning Tableau 2019 Create powerful data visualizations and unlock intelligent business insights with Tableau Key Features Explore all the latest Tableau 2019 features and redefine business analytics for your organization Create impressive data visualizations and interactive dashboards to get insights from your data Learn effective data storytelling to transform how your business leverages data and makes decisions Book Description Tableau is the gold standard of business intelligence and visual analytics tools in every industry. It enables rapid data visualization and interpretation with charts, graphs, dashboards, and much more. Updated with the latest features of Tableau, this book takes you from the foundations of the Tableau 2019 paradigm through to advanced topics. This third edition of the bestselling guide by Tableau Zen Master, Joshua Milligan, will help you come to grips with updated features, such as set actions and transparent views. Beginning with installation, you'll create your first visualizations with Tableau and then explore practical examples and advanced techniques. You'll create bar charts, tree maps, scatterplots, time series, and a variety of other visualizations. Next, you'll discover techniques to overcome challenges presented by data structure and quality and engage in effective data storytelling and decision making with business critical information. Finally, you'll be introduced to Tableau Prep, and learn how to use it to integrate and shape data for analysis. By the end of this book, you will be equipped to leverage the powerful features of Tableau 2019 for decision making. What you will learn Develop stunning visualizations that explain complexity with clarity Explore the exciting new features of Tableau Desktop and Tableau Prep Connect to various data sources to bring all your data together Uncover techniques to prep and structure your data for easy analysis Create and use calculations to solve problems and enrich analytics Master advanced topics such as sets, LOD calcs, and much more Enable smart decisions with clustering, distribution, and forecasting Share your data stories to build a culture of trust and action Who this book is for This Tableau book is for anyone who wants to understand data. If you're new to Tableau, don't worry. This book builds on the foundations to help you understand how Tableau really works and then builds on that knowledge with practical examples before moving on to advanced techniques. Working experience with databases will be useful but is not necessary to get the most out of this book. COMPUTERS,Business & Productivity Software,Business Intelligence

Programming Microsoft Dynamics 365 Business Central Explore the fundamentals of Dynamics 365 Business Central and the Visual Studio Code development environment with the help of useful examples and case studies Key Features Tailor your applications to best suit the needs of your business Explore the latest features of Business Central with examples curated by industry experts Integrate Business Central features in your applications with this comprehensive guide Book Description Microsoft Dynamics 365 Business Central is a full ERP business solution suite with a robust set of development tools to support customization and enhancement. These tools can be used to tailor Business Central's in-built applications to support complete management functions for finance, supply chain, manufacturing, and operations. Using a case study approach, this book will introduce you to Dynamics 365 Business Central and Visual Studio Code development tools to help you become a productive Business Central developer. You'll also learn how to evaluate a product's development capabilities and manage Business Central-based development and implementation. You'll explore application structure, the construction of and uses for each object type, and how it all fits together to build apps that meet special business requirements. By the end of this book, you'll understand how to design and develop high-quality software using the Visual Studio Code development environment, the AL language paired with the improved editor, patterns, and features. What you will learn Programming using the AL language in the Visual Studio Code development environment Explore functional design and development using AL How to build interactive pages and learn how to extract data for users How to use best practices to design and develop modifications for new functionality integrated with the standard Business Central software Become familiar with deploying the broad range of components available in a Business Central system Create robust, viable systems to address specific business requirements Who this book is for If you want to learn about Dynamics 365 Business Central's powerful and extensive built-in development capabilities, this is the book for you. ERP consultants and managers of Business Central development will also find this book helpful. Although you aren't expected to have worked with Dynamics Business Central, basic understanding of programming and familiarity with business application software will help you understand the concepts covered in this book. COMPUTERS,Business & Productivity Software,Business Intelligence

Automated Testing in Microsoft Dynamics 365 Business Central Learn how to write automated tests for Dynamics 365 Business Central and see how to implement it in your daily work Key Features Leverage automated testing to advance over traditional manual testing methods Write, design, and implement automated tests Explore various testing frameworks and tools compatible with Microsoft Dynamics 365 Business Central Book Description Dynamics 365 Business Central is the new cloud-based SaaS ERP proposition from Microsoft. It's not as simple as it used to be way back when it was called Navigator, Navision Financials, or Microsoft Business Solutions-Navision. Our development practices are becoming more formal, and with this, the call for test automation is pressing on us. This book will teach you to leverage testing tools available with Dynamics 365 Business Central to perform automated testing. We'll begin with a quick introduction to automated testing, followed by an overview of test automation in Dynamics 365 Business Central. Then you'll learn to design and build automated tests and we'll go through some efficient methods to get from requirements to application and testing code. Lastly, you'll learn to incorporate your own and Microsoft tests into your daily development practice. By the end of the book, you'll be able to write your own automated tests for Dynamics 365 Business Central. What you will learn Understand what automated tests are, and when and why to use them Explore the five pillars of the Testability Framework of Business Central Design and write automated tests for Business Central Make use of standard automated tests and their helper libraries Integrate automated tests into your development practice Who this book is for This book is for consultants, testers, developers, and development managers working with Microsoft Dynamics NAV and Business Central. Being a book on automated testing techniques, it also caters to both functional and technical development teams. COMPUTERS,Business & Productivity Software,Business Intelligence

Office 365 User Guide Work with the powerful subscription software, Office 365 to increase your organization's efficiency by managing file sharing, email exchange and much more. Key Features Become well versed with Office 365 and leverage its capabilities for your business Speed up your workflow and effectively collaborate using Office Web Apps Learn to set audio and web conferences and seamlessly access your workspace Book Description Microsoft Office 365 combines the popular Office suite with next-generation cloud computing capabilities. With this user guide, you'll be able to implement its software features for effective business communication and collaboration. This book begins by providing you with a quick introduction to the user interface (UI) and the most commonly used features of Office 365. After covering the core aspects of this suite, you'll learn how to perform various email functions via Exchange. Next, you will learn how to communicate using Skype for Business and Microsoft Teams. To boost your productivity, this book will help you learn everything from using instant messaging to conducting audio and web conferences, and even accessing business information from any location. In the final chapters, you will learn to work in a systematic style using file management and collaboration with OneDrive for Business using SharePoint. By the end of this book, you'll be equipped with the knowledge you need to take full advantage of Office 365 and level up your organization's productivity. What you will learn Understand the UI of Office 365 Perform a variety of email functions through Exchange Communicate using Skype for Business and Microsoft Teams Explore file management using OneDrive for Business Collaborate using SharePoint Understand how to leverage Office 365 in your daily tasks Who this book is for If you are an IT professional who wants to upgrade your traditional Office suite, this book is for you. Users looking to learn, configure, manage, and maintain an Office 365 environment in their organization will also find this book useful. Some understanding of Microsoft Office Suite and cloud computing basics will be beneficial. COMPUTERS,Business & Productivity Software,Business Intelligence

Drilling Data Vortex In today's world, traditional methods of drilling oil wells don't work. Yesterday's practices are being superseded by a universal trend towards the extensive use of historical and real-time data to understand, learn and predict all well intervention operations. This book explores the impact of data analytics on well operations. Drawn from the author's extensive experience in data analysis, it examines, in easily understandable terms, today's data management processes. The book explores issues related to: Basic concepts of data management for drilling; Methods of using data as a basis for improving and optimizing process control; Achieving a common understanding of the issues involved among information technology personnel and field engineers; A roadmap for the implementation of a drilling process improvement system; Business Intelligence as the ultimate goal of any data management process; Discussions about data acquisition, quality control, storage, retrieval and analyses; Map intelligence; Understanding operational time and trouble analyses; learning curve, technical limit and benchmarking; Real business cases to illustrate the concepts explored in the book.The book is designed for a broad audience, including drilling personnel, managers, data analysts, and all professionals involved in the use of data to improve drilling operations. COMPUTERS,Business & Productivity Software,Business Intelligence

Data Governance Managing data continues to grow as a necessity for modern organizations. There are seemingly infinite opportunities for organic growth, reduction of costs, and creation of new products and services. It has become apparent that none of these opportunities can happen smoothly without data governance. The cost of exponential data growth and privacy / security concerns are becoming burdensome. Organizations will encounter unexpected consequences in new sources of risk. The solution to these challenges is also data governance; ensuring balance between risk and opportunity. Data Governance, Second Edition, is for any executive, manager or data professional who needs to understand or implement a data governance program. It is required to ensure consistent, accurate and reliable data across their organization. This book offers an overview of why data governance is needed, how to design, initiate, and execute a program and how to keep the program sustainable. This valuable resource provides comprehensive guidance to beginning professionals, managers or analysts looking to improve their processes, and advanced students in Data Management and related courses. With the provided framework and case studies all professionals in the data governance field will gain key insights into launching successful and money-saving data governance program. Incorporates industry changes, lessons learned and new approaches Explores various ways in which data analysts and managers can ensure consistent, accurate and reliable data across their organizations Includes new case studies which detail real-world situations Explores all of the capabilities an organization must adopt to become data driven Provides guidance on various approaches to data governance, to determine whether an organization should be low profile, central controlled, agile, or traditional Provides guidance on using technology and separating vendor hype from sincere delivery of necessary capabilities Offers readers insights into how their organizations can improve the value of their data, through data quality, data strategy and data literacy Provides up to 75% brand-new content compared to the first edition COMPUTERS,Business & Productivity Software,Business Intelligence

Mastering Microsoft Dynamics 365 Business Central Develop customized business management solutions with the latest features of Microsoft Dynamics 365 Business Central Key Features Learn Dynamics 365 Business Central, the next generation of Dynamics NAV Explore advanced topics for handling complex integrations such as using APIs, OData, and Azure Functions Discover best practices for developing SaaS extensions and moving existing solutions to the cloud Book Description Dynamics 365 Business Central is an all-in-one business management solution, which is easy to adopt and helps you make smarter business decisions. This book is a comprehensive guide to developing solutions with Microsoft ERP (in the cloud and also on-premises). It covers all aspects of developing extensions, right from preparing a sandbox environment to deploying a complete solution. The book starts by introducing you to the Dynamics 365 Business Central platform and the new Modern Development Environment. You'll then explore the sandbox concept, and see how to create sandboxes for development. As you advance, you'll be able to build a complete advanced solution for Dynamics 365 Business Central with AL language and Visual Studio Code. You'll then learn how to debug and deploy the extension and write automatic testing. The book will also take you through advanced topics like integration (with Azure Functions, web services, and APIs), DevOps and CI/CD techniques, and machine learning. You'll discover how Dynamics 365 Business Central can be used with Office 365 apps. Finally, you'll analyze different ways to move existing solutions to the new development model based on extensions. By the end of this book, you'll be able to develop highly customized solutions that meet the requirements of modern businesses using Dynamics 365 Business Central. What you will learn Create a sandbox environment with Dynamics 365 Business Central Handle source control management when developing solutions Explore extension testing, debugging, and deployment Create real-world business processes using Business Central and different Azure services Integrate Business Central with external applications Apply DevOps and CI/CD to development projects Move existing solutions to the new extension-based architecture Who this book is for If you're a new developer looking to get started with Dynamics 365 Business Central, this book is for you. This book will also help experienced professionals enhance their knowledge and understanding of Dynamics 365 Business Central. COMPUTERS,Business & Productivity Software,Business Intelligence

Implementing Microsoft Dynamics 365 for Finance and Operations Apps Harness the power of Finance and Operations apps, and discover all you need for their implementation Key Features Manage and plan different Dynamics configurations, designs, and products Learn how to manage projects for pre-sales and implementation using Microsoft Dynamics Lifecycle Services (LCS) Discover various integration planning techniques, tools, and frameworks such as PowerApps and Power Automate Book Description Microsoft Dynamics 365 for Finance and Operations is a modern cloud ERP platform that adopts a mobile-first approach suitable for medium-to-large enterprises. This book covers the entire implementation process of Dynamics 365 Finance and Operation Apps, including post-implementation and business transformation. The updated second edition starts with an introduction to Microsoft Dynamics 365, describing different apps and tools under it. You will learn about different implementation methodologies such as Waterfall and Agile, for your projects. We will cover various application components and architectures of Dynamics such as requirements processing, development, reports and analytics, and integration. With the help of tips, techniques, and best practices, you'll explore strategies for managing configurations and data migrations. As you read further, you'll discover development tools and processes in Dynamics for building customized solutions in Dynamics. The book will also demonstrate analytics and financial reporting options such as Power BI and Cortana Intelligence. Finally, you'll learn the importance of testing and explore various automated testing strategies. By the end of this book, you will have gained the necessary knowledge to implement Microsoft business solutions with Dynamics 365 for Finance and Operations Apps. What you will learn Understand the architecture of Dynamics 365 for Finance and Operations Apps Implement Dynamics with confidence to manage finances in your business Get up to speed with different methodologies and support cycles of the Microsoft Dynamics architecture Explore best practices to analyze the requirements of your business Understand the technique of data migration from legacy systems Leverage the capabilities of Power BI to make informed business decisions Manage all your upgrades through One Version service updates Who this book is for This book is for consultants, technical managers, project managers, or solution architects who are looking to implement Microsoft Dynamics 365 Finance and Operations apps in their business. A basic understanding of the enterprise resource planning (ERP) implementation process and software lifecycle is expected. COMPUTERS,Business & Productivity Software,Business Intelligence

Mastering AWS CloudFormation Build scalable and production-ready infrastructure in Amazon Web Services with CloudFormation Key Features Leverage AWS CloudFormation templates to manage your entire infrastructure Get up and running with writing your infrastructure as code and automating your environment Simplify infrastructure management and increase productivity with AWS CloudFormation Book Description DevOps and the cloud revolution have forced software engineers and operations teams to rethink how to manage infrastructures. With this AWS book, you'll understand how you can use Infrastructure as Code (IaC) to simplify IT operations and manage the modern cloud infrastructure effectively with AWS CloudFormation. This comprehensive guide will help you explore AWS CloudFormation from template structures through to developing complex and reusable infrastructure stacks. You'll then delve into validating templates, deploying stacks, and handling deployment failures. The book will also show you how to leverage AWS CodeBuild and CodePipeline to automate resource delivery and apply continuous integration and continuous delivery (CI/CD) practices to the stack. As you advance, you'll learn how to generate templates on the fly using macros and create resources outside AWS with custom resources. Finally, you'll improve the way you manage the modern cloud in AWS by extending CloudFormation using AWS serverless application model (SAM) and AWS cloud development kit (CDK). By the end of this book, you'll have mastered all the major AWS CloudFormation concepts and be able to simplify infrastructure management. What you will learn Understand modern approaches to IaC Develop universal and reusable CloudFormation templates Discover ways to apply continuous delivery with CloudFormation Implement IaC best practices for the AWS Cloud Provision massive applications across multiple regions and accounts Automate template generation and software provisioning for AWS Extend CloudFormation with custom resources and template macros Who this book is for If you are a developer who wants to learn how to write templates, a DevOps engineer interested in deployment and orchestration, or a solutions architect looking to understand the benefits of managing infrastructure with ease, this book is for you. Prior understanding of the AWS Cloud is necessary. COMPUTERS,Business & Productivity Software,Business Intelligence

Digital Transformation and New Challenges This book gathers the best papers presented at the first conference held by the Russian chapter of the Association for Information Systems (AIS). It shares the latest insights into various aspects of the digitalization of the economy and the consequences of transformation in public administration, business and public life. Integrating a broad range of analytical perspectives, including economic, social and, technological, this interdisciplinary book is particularly relevant for scientists, digital technology users, companies and public institutions. COMPUTERS,Business & Productivity Software,Business Intelligence

Blockchain and Distributed Ledger Technology Use Cases Blockchain and other trustless systems have gone from being relatively obscure technologies, which were only known to a small community of computer scientists and cryptologists, to mainstream phenomena that are now considered powerful game changers for many industries. This book explores and assesses real-world use cases and case studies on blockchain and related technologies. The studies describe the respective applications and address how these technologies have been deployed, the rationale behind their application, and finally, their outcomes. The book shares a wealth of experiences and lessons learned regarding financial markets, energy, SCM, healthcare, law and compliance. Given its scope, it is chiefly intended for academics and practitioners who want to learn more about blockchain applications. COMPUTERS,Business & Productivity Software,Business Intelligence

SharePoint 2013 For Dummies The bestselling guide on running SharePoint, now updated to cover all the new features of SharePoint 2013 SharePoint Portal Server is an essential part of the enterprise infrastructure for many businesses. Building on the success of previous versions of SharePoint For Dummies, this new edition covers all the latest features of SharePoint 2013 and provides you with an easy-to-understand resource for making the most of all that this version has to offer. You'll learn how to get a site up and running, branded, and populated with content, workflow, and management. In addition, this new edition includes essential need-to-know information for administrators, techsumers, and page admins who want to leverage the cloud-hosted features online, either as a standalone product or in conjunction with an existing SharePoint infrastructure. Walks you through getting a SharePoint site up and running effectively and efficiently Explains ongoing site management and offers plenty of advice for administrators who want to leverage SharePoint and Office 365 in various ways Shows how to use SharePoint to leverage data centers and collaborate with both internal and external customers, including partners and clients SharePoint 2013 For Dummies is essential reading if you want to make the most of this technology. COMPUTERS,Business & Productivity Software,Collaboration

SharePoint 2016 For Dummies Learn all the ins and outs of SharePoint 2016, launch your site, collaborate with coworkers, and go mobile There's no doubt about it, SharePoint is a complex creature. But when broken down into easily digestible chunks, it's not quite the beast it appears to be right out of the gate—that's where SharePoint 2016 For Dummies comes in! Written in plain English and free of intimidating jargon, this friendly, accessible guide starts out by showing you just what SharePoint 2016 is, translating the terminology, and explaining the tools. Then it helps you create a site, work with apps, and master basic SharePoint administration. Next, you'll learn to use SharePoint 2016 to get social, go mobile, manage content, and connect with others through working with Office 365, archiving documents, developing workflows, and so much more. SharePoint is truly one of Microsoft's crown jewels. Launched in 2001, it offers organizations a secure place to store, organize, share, and access information under the Microsoft Office system umbrella—all in a single portal. Whether you're new to SharePoint 2016 or new to SharePoint altogether, SharePoint 2016 For Dummies is the fast and painless way to get a site up and running, branded, and populated with content. Plus, this new edition adds the need-to-know information for administrators, techsumers, and page admins who want to leverage the cloud-based features online, either as a standalone product or in conjunction with an existing SharePoint infrastructure. Get up to speed with SharePoint 2016 and take advantage of new features Set up and effectively manage your SharePoint site Use SharePoint 2016 in the Cloud with SharePoint Online Leverage SharePoint 2016 capabilities to drive business value If you want to learn SharePoint from the ground up, get your site going, and start collaborating, SharePoint 2016 For Dummies will be the dog-eared reference you'll turn to again and again. COMPUTERS,Business & Productivity Software,Collaboration

Implementing Cisco UCS Solutions Discover how to simplify your data center architecture, reduces costs, and improve speed and agility with Cisco UCS at your side About This Book Learn how to reduce equipment and operating costs, consolidate resources, and automate data center processes Eliminate manual, time-consuming tasks that were traditionally required to connect servers in data centers A practical hands-on guide that will help you to deploy servers and application stacks with ease Who This Book Is For This book is for system, network, and storage administrators who are responsible for Cisco UCS deployments. You need to have basic knowledge of server architecture, network, and storage technologies. What You Will Learn Set up your Lab using Cisco UCS Emulator Configure Cisco UCS, LAN, and SAN connectivity Create and manage Service profiles Perform various tasks using UCS Backup and restore Cisco UCS configuration Test various Cisco UCS scenarios Manage and automate multiple domains In Detail Cisco Unified Computer System (UCS) is a powerful solution for modern data centers and is responsible for increasing efficiency and reducing costs. This hands-on guide will take you through deployment in Cisco UCS. Using real-world examples of configuring and deploying Cisco UCS components, we'll prepare you for the practical deployments of Cisco UCS data center solutions. If you want to develop and enhance your hands-on skills with Cisco UCS solutions, this book is certainly for you. We start by showing you the Cisco UCS equipment options then introduce Cisco UCS Emulator so you can learn and practice deploying Cisco UCS components. We'll also introduce you to all the areas of UCS solutions through practical configuration examples. Moving on, you'll explore the Cisco UCS Manager, which is the centralized management interface for Cisco UCS. Once you get to know UCS Manager, you'll dive deeper into configuring LAN, SAN, identity pools, resource pools, and service profiles for the servers. You'll also get hands-on with administration topics including backup, restore, user's roles, and high availability cluster configuration. Finally, you will learn about virtualized networking, third-party integration tools, and testing failure scenarios. By the end of this book, you'll know everything you need to know to rapidly grow Cisco UCS deployments in the real world. Style and approach This hands-on book takes a tutorial-based approach to help you understand the practical methodologies and deployment of Cisco UCS components. COMPUTERS,Business & Productivity Software,Collaboration

SharePoint For Dummies All you need to know about SharePoint Online and SharePoint Server SharePoint is an enterprise portal server living under the Microsoft Office umbrella. It can be used as a local installation (on-premises) or an online service. The SharePoint Online service comes bundled with Office 365. You can use SharePoint to aggregate sites, information, data, and applications into a single portal. SharePoint 2019 contains highly integrated features that allow you to work with it directly from other Office products such as Teams, Word, Excel, PowerPoint, and many others. SharePoint For Dummies provides a thorough update on how to make the most of all the new SharePoint and Office features—while still building on the great and well-reviewed content in the prior editions. The book shows those new to SharePoint or new to SharePoint 2019 how to get up and running so that you and your team can become productive with this powerful tool. Find high-level, need-to-know information for “techsumersâ€, administrators, and admins Learn how SharePoint Online can get you started in minutes without the hassle and frustration of building out your own servers Find everything you need to know about the latest release of SharePoint Online and SharePoint Server Get your hands on the best guide on the market for SharePoint! COMPUTERS,Business & Productivity Software,Collaboration

Microsoft 365 Certified Fundamentals MS-900 Exam Guide An up-to-date study guide to help you learn MS-900 exam concepts and objectives and get hands-on with Microsoft 365 essentials Key Features Learn effectively with self-assessment questions, exam tips, and mock tests with detailed explanations Get to grips with Microsoft Office 365 collaboration, mobility, and the support and service lifecycle Understand the considerations and benefits of adopting different types of cloud services Book Description Microsoft 365 Certified Fundamentals certification demonstrates your foundational knowledge of adopting cloud services and the SaaS model. Exam MS-900 tests your understanding of Microsoft 365 services, components, their implementation, and cloud concepts, along with helping you gain the certification. This exam guide covers the MS-900 exam objectives, with explanations of essential cloud concepts, and also ensures you get hands-on experience of Microsoft 365 services and features. The book is divided into five parts, with each section consisting of chapters that focus on topics such as Microsoft security and compliance policies, pricing and support, and cloud concepts. You will progress through these chapters with the help of real-world scenarios, learning the pros and cons of core Microsoft services such as Microsoft Windows, SharePoint, Office, Teams, and Exchange. Gradually, you'll learn how to form strategies for migrating from on-premise infrastructure to the cloud, and how to improve the enterprise mobility and information security of your organization. Finally, you can test your knowledge with mock tests, and even explore the exam format to prepare effectively. By the end of this book, you'll be well-versed with the concepts you need to know to pass the MS-900 certification exam and have the skills to work effectively with Microsoft 365 services. What you will learn Gain insights into the exam objectives, test scenarios, and knowledge required before taking the MS-900 exam Understand the cloud services and SaaS models available in the Microsoft ecosystem Identify Windows deployment considerations using the Admin Center and User Portal experiences Implement enterprise mobility, device management, and application management within your organization Explore the reporting and analytics capabilities of Microsoft 365 Discover various features of Azure Active Directory and other Microsoft 365 security tools Who this book is for This book is for beginners as well as experienced administrators and individuals who want to pass the MS-900 exam and achieve Microsoft 365 certification. Basic knowledge of Microsoft services and cloud concepts is assumed to get started. COMPUTERS,Business & Productivity Software,Collaboration

Microsoft Teams For Dummies Discover the power of Microsoft Teams Millions of people access Microsoft Teams every day to assist with the collaboration it takes to get work done. That number continues to grow thanks to the countless communication tools for working with associates inside and outside your organization you can find in Microsoft Teams. If you’re new to Microsoft Teams, start here. This book will give you must-have insight on chatting, file sharing, organizing teams, using video communication, and more. You’ll also see just how you should be doing things, with best-practice recommendations and ideas for integrating Microsoft Teams into your existing workflows. Learn your way around Microsoft Teams and set up the interface Communicate via chat and video chat, inside and outside your org Integrate Teams with other Office apps for seamless collaboration Use Teams to optimize your meetings, build a knowledge wiki, and more! Microsoft’s shared workspace can help you get collaborative and stay connected to the people and files you need, whether you're at your desk or on the go. COMPUTERS,Business & Productivity Software,Collaboration

Hands-On Microsoft Teams A complete guide on Teams filled with real-world scenarios and best practices to increase enterprise productivity and engagement Key Features Interactive approach to learn the key concepts of Teams and its implementation in modern workplace Discover tips and techniques for extending Teams to meet your business requirements Integrate Teams with various Microsoft services such as PowerShell, SharePoint, PowerApps, and Power Automate Book Description Microsoft Teams is a platform for unified communication in modern workplaces. It not only enables effective communication, but also helps you manage your resources through its integration with various Microsoft Office 365 services. This book offers a comprehensive introduction to the platform, getting you up to speed in no time. Complete with hands-on tutorials, and projects, this easy-to-follow guide will teach you how to use Teams in the best possible way. Starting with the basic concepts that will help you collaborate on Teams, this book takes you through expert techniques for creating and managing teams. A dedicated section also features industry practices to help enhance collaboration in modern workplaces. In later chapters, you'll explore Microsoft services such as SharePoint, PowerApps, Power Automate, and learn how they interact with Microsoft Teams. You'll also get to grips with dealing with permissions and security issues in managing private and public teams and channels. Along the way, you'll discover practical scenarios that will help you improve the collaboration in your organization and increase productivity by using Teams features. By the end of this book, you'll have hands-on experience of using Microsoft Teams, along with the skills you need to improve the way people collaborate in your organization. What you will learn Create teams, channels, and tabs in Microsoft Teams Explore the Teams architecture and various Office 365 components included in Teams Perform scheduling, and managing meetings and live events in Teams Configure and manage apps in Teams Design automated scripts for managing a Teams environment using PowerShell Build your own Microsoft Teams app without writing code Who this book is for This Microsoft Teams book is for power users and business professionals looking to use Teams for improving collaboration in an enterprise environment. The book will also be useful for Office 365 administrators interested in implementing Microsoft Teams effectively by learning about and exploring expert tips and best practices to ensure good governance. COMPUTERS,Business & Productivity Software,Collaboration

Slack For Dummies You get so much more done when you Slack! Ever wondered what it would be like to be less overwhelmed, more efficient, and much more engaged at work? A way you can make all that happen is, of course, to Slack. Actually, it’s to use Slack, the business communications platform that’s revolutionized how groups work together. This comprehensive guide shows how—as well as why—there are now millions of users of this flexible, fun, and intuitive workspace tool. Presented in a clear, easy-to-follow style, Slack For Dummies takes you from the basics of getting started with the service all the way through how to get your teams Slacking together for all they’re worth. You’ll also find case studies showing how Slack increases productivity and how to replicate that in your organization, as well as tips on getting buy-in from the boss. Introduce Slack to your workflow Understand roles and features Analyze user data Keep your Slacking secure So, take a peek inside and discover how you can cut the slack using Slack—and clue your teams in on how there is actually a way to Slack off for improved results! COMPUTERS,Business & Productivity Software,Collaboration

Microsoft 365 and SharePoint Online Cookbook Embrace modern solutions to enhance collaboration, teamwork, robotic process automation, and business intelligence in your organization using powerful Microsoft 365 services (formerly Office 365) Key Features Gain a complete overview of popular Microsoft 365 services using practical recipes and expert insights Collaborate with your team and external users effectively using SharePoint and Teams Create no-code and low-code solutions, such as bots, forms, dashboards, and workflows, using the Power platform Book Description Microsoft 365 in an integrated suite that provides intelligent tools for managing everyday organizational tasks like content management, communication, creating reports, and automating business processes. With this book, you'll get to grips with popular apps from Microsoft, with a focus on enabling workspace collaboration and productivity using Microsoft SharePoint Online, Teams, and the Power Platform to name a few. In addition to guiding you through the implementation of Microsoft 365 apps, this practical guide helps you to learn from a Microsoft consultant's extensive experience of working with the Microsoft business suite. Starting with a quick overview of the M365 ecosystem, the book covers recipes for implementing SharePoint Online for various content management tasks. You'll learn how to create sites for your organization and enhance collaboration across the business and then see how you can boost productivity with apps such as Microsoft Teams, Power Platform, Planner, Delve, and M365 Groups. Using a step-by-step approach, you'll also find out how to use the Power Platform efficiently, making the most of Microsoft PowerApps, Power Automate, PowerBI, and Power Virtual Agents. Finally, the book focuses on the SharePoint framework, which helps you to build custom Teams and SharePoint solutions. By the end of the book, you'll be equipped with the skills required to set up Microsoft 365 and SharePoint Online and be ready to enhance business productivity using a variety of tools. What you will learn Get to grips with a wide range of apps and cloud services in Microsoft 365 Discover ways to use SharePoint Online to create and manage content Store and share documents using SharePoint Online Improve your search experience with Microsoft Search Leverage the Power Platform to build business solutions with Power Automate, Power Apps, Power BI, and Power Virtual Agents Enhance native capabilities in SharePoint and Teams using the SPFx framework Use Microsoft Teams to meet, chat, and collaborate with colleagues or external users Who this book is for This book is for business professionals, IT administrators, enterprise developers and architects, and anyone who wants to get to grips with using M365 for effective implementation of Microsoft apps. Prior experience with Office 365 and SharePoint will assist with understanding the recipes effortlessly. COMPUTERS,Business & Productivity Software,Collaboration

Zoom For Dummies Zoom into the new world of remote collaboration While a worldwide pandemic may have started the Zoom revolution, the convenience of remote meetings is here to stay. Zoom For Dummies takes you from creating meetings on the platform to running global webinars. Along the way you'll learn how to expand your remote collaboration options, record meetings for future review, and even make scheduling a meeting through your other apps a one-click process. Take in all the advice or zoom to the info you need - it's all there! Discover how to set up meetings Share screens and files Keep your meetings secure Add Zoom hardware to your office Get tips for using Zoom as a social tool Award-winning author Phil Simon takes you beyond setting up and sharing links for meetings to show how Zoom can transform your organization and the way you work. COMPUTERS,Business & Productivity Software,Collaboration

Microsoft Office Access 2007 VBA This is the eBook version of the printed book. If the print book includes a CD-ROM, this content is not included within the eBook version. Business Solutions Microsoft® Office Access 2007 VBA Develop your Access 2007 VBA expertise instantly with proven techniques Microsoft Office Access 2007 VBA builds on the skills you’ve already developed in creating database applications and helps you take them to the next level—using Visual Basic for Applications (VBA) to accomplish things you once performed manually. To facilitate this lofty goal, Access includes the VBA programming language. Even if you’ve never programmed, this book will help you learn how to leverage the power of VBA to make your work with Access more efficient than ever before. Microsoft Office Access 2007 VBA is for professionals who use Microsoft Access frequently in their daily work. You have serious work to get done and you can’t spend all day reading a computer book. This book teaches you the essential skills you need to automate your databases as quickly as possible. Although written for Access 2007, the techniques and concepts covered will work in most versions of Microsoft Access. Highlights of This Book Include • Navigating within the Visual Basic Editor • Using variables, constants, and data types • Employing built-in functions • Creating procedures • Understanding object-and event-driven coding • Working with arrays • Understanding scope • Working with forms • Using selection controls • Creating reports • Exploring menus, navigation, and ribbons • Using object models • Working with data • Defining database schema • Using the Windows API • Working with XML files • Exploring Access SQL On the Website Download database files used in the book at www.quepublishing.com. Category Office Applications Covers Visual Basic for Applications User Level Intermediate - Advanced Scott B. Diamond is a seasoned database designer and Microsoft Access 2007 MVP. During the last 20+ years COMPUTERS,Business & Productivity Software,Databases

Using SQLite Application developers, take note: databases aren't just for the IS group any more. You can build database-backed applications for the desktop, Web, embedded systems, or operating systems without linking to heavy-duty client-server databases such as Oracle and MySQL. This book shows you how to use SQLite, a small and lightweight relational database engine that you can build directly into your application. With SQLite, you'll discover how to develop a database-backed application that remains manageable in size and complexity. This book guides you every step of the way. You'll get a crash course in data modeling, become familiar with SQLite's dialect of the SQL database language, and much more. Learn how to maintain localized storage in a single file that requires no configuration Build your own SQLite library or use a precompiled distribution in your application Get a primer on SQL, and learn how to use several language functions and extensions Work with SQLite using a scripting language or a C-based language such as C# or Objective-C Understand the basics of database design, and learn how to transfer what you already know to SQLite Take advantage of virtual tables and modules "Complex SQL concepts explained clearly." --D. Richard Hipp, creator of SQLite COMPUTERS,Business & Productivity Software,Databases

Access 2013 Bible A comprehensive reference to the updated and new features of Access 2013 As the world's most popular database management tool, Access enables you to organize, present, analyze, and share data as well as build powerful database solutions. However, databases can be complex. That's why you need the expert guidance in this comprehensive reference. Access 2013 Bible helps you gain a solid understanding of database purpose, construction, and application so that whether you're new to Access or looking to upgrade to the 2013 version, this well-rounded resource provides you with a thorough look at everything Access can do. Explains how to create tables, manipulate datasheets, and work with multiple tables Teaches you how to apply the seven-step design method to build databases that are tailored to your needs Covers building forms with wizards, creating bound and unbound forms, and adding data validation Shows you ways to automate query parameters, create functions and subroutines, and add programmed error routines Features a bonus website with content that contains all source code from the book as well as bonus shareware, freeware, trial, demo, and evaluation programs If you are looking for a comprehensive book on all things Access, look no further than Access 2013 Bible. COMPUTERS,Business & Productivity Software,Databases

Microsoft Access 2010 VBA Programming Inside Out You're beyond the basics, so dive right in and customize, automate, and extend Access—using Visual Basic for Applications (VBA). This supremely organized reference is packed with hundreds of time-saving solutions, troubleshooting tips, and workarounds. It's all muscle and no fluff. Discover how the experts use VBA to exploit the power of Access—and challenge yourself to new levels of mastery! Enhance your application with VBA built-in functions and SQL code Use the Access Object Model to work with data in forms and reports Manipulate data using SQL, queries, and recordsets with Data Access Objects (DAO) Create classes for handling form and control events Connect your Access database to different sources of data Effectively plan how to upsize an existing Access database to Microsoft SQL Server Dynamically update Microsoft Excel spreadsheets from the database Migrate your Access database directly to the cloud using SQL Azure COMPUTERS,Business & Productivity Software,Databases

Microsoft Access 2013 Plain & Simple Learn the simplest ways to get things done with Microsoft Access 2013 Get the full-color, visual guide that makes learning Microsoft Access 2013 plain and simple! Follow the book’s easy steps and screenshots and clear, concise language to learn the simplest ways to build a database and sort information. Here’s WHAT you’ll learn: Build and manage your own database Apply professional designs across your databases Create presentations and publish reports online Secure your database with passwords and encryption Exchange data with other databases and documents Interact with your data easier using macros Here’s HOW you’ll learn it: Jump in wherever you need answers Follow easy STEPS and SCREENSHOTS to see exactly what to do Get handy TIPS for new techniques and shortcuts Use TRY THIS! Exercises to apply what you learn right away COMPUTERS,Business & Productivity Software,Databases

FileMaker Pro 13 You don’t need a technical background to build powerful databases with FileMaker Pro 13. This crystal-clear guide covers all new FileMaker Pro 13 features, such as its improved layout tools and enhanced mobile support. Whether you’re running a business, printing a catalog, or planning a wedding, you’ll learn how to customize your database to run on a PC, Mac, Web browser, or iOS device. The important stuff you need to know: Get started. Tour FileMaker Pro’s features and create your first database in minutes. Access data anywhere. Use FileMaker Go on your iPad or iPhone—or share data on the Web. Dive into relational data. Solve problems quickly by connecting and combining data tables. Create professional documents. Publish reports, invoices, catalogs, and other documents with ease. Harness processing power. Use calculations and scripts to crunch numbers, search text, and automate tasks. Add visual power and clarity. Create colorful charts to illustrate and summarize your data. Share your database on a secure server. Add the high-level features of FileMaker Pro Advanced and FileMaker Pro Server. COMPUTERS,Business & Productivity Software,Databases

Access 2016 Bible Master database creation and management Access 2016 Bible is your, comprehensive reference to the world's most popular database management tool. With clear guidance toward everything from the basics to the advanced, this go-to reference helps you take advantage of everything Access 2016 has to offer. Whether you're new to Access or getting started with Access 2016, you'll find everything you need to know to create the database solution perfectly tailored to your needs, with expert guidance every step of the way. The companion website features all examples and databases used in the book, plus trial software and a special offer from Database Creations. Start from the beginning for a complete tutorial, or dip in and grab what you need when you need it. Access enables database novices and programmers to store, organize, view, analyze, and share data, as well as build powerful, integrable, custom database solutions — but databases can be complex, and difficult to navigate. This book helps you harness the power of the database with a solid understanding of their purpose, construction, and application. Understand database objects and design systems objects Build forms, create tables, manipulate datasheets, and add data validation Use Visual Basic automation and XML Data Access Page design Exchange data with other Office applications, including Word, Excel, and more From database fundamentals and terminology to XML and Web services, this book has everything you need to maximize Access 2016 and build the database you need. COMPUTERS,Business & Productivity Software,Databases

FileMaker Pro 14 You don’t need a technical background to build powerful databases with FileMaker Pro 14. This crystal-clear, objective guide shows you how to create a database that lets you do almost anything with your data so you can quickly achieve your goals. Whether you’re creating catalogs, managing inventory and billing, or planning a wedding, you’ll learn how to customize your database to run on a PC, Mac, web browser, or iOS device. The important stuff you need to know: Dive into relational data. Solve problems quickly by connecting and combining data from different tables. Create professional documents. Publish reports, charts, invoices, catalogs, and other documents with ease. Access data anywhere. Use FileMaker Go on your iPad or iPhone—or share data on the Web. Harness processing power. Use new calculation and scripting tools to crunch numbers, search text, and automate tasks. Run your database on a secure server. Learn the high-level features of FileMaker Pro Advanced. Keep your data safe. Set privileges and allow data sharing with FileMaker’s streamlined security features. COMPUTERS,Business & Productivity Software,Databases

Designing Data-Intensive Applications Data is at the center of many challenges in system design today. Difficult issues need to be figured out, such as scalability, consistency, reliability, efficiency, and maintainability. In addition, we have an overwhelming variety of tools, including relational databases, NoSQL datastores, stream or batch processors, and message brokers. What are the right choices for your application? How do you make sense of all these buzzwords? In this practical and comprehensive guide, author Martin Kleppmann helps you navigate this diverse landscape by examining the pros and cons of various technologies for processing and storing data. Software keeps changing, but the fundamental principles remain the same. With this book, software engineers and architects will learn how to apply those ideas in practice, and how to make full use of data in modern applications. Peer under the hood of the systems you already use, and learn how to use and operate them more effectively Make informed decisions by identifying the strengths and weaknesses of different tools Navigate the trade-offs around consistency, scalability, fault tolerance, and complexity Understand the distributed systems research upon which modern databases are built Peek behind the scenes of major online services, and learn from their architectures COMPUTERS,Business & Productivity Software,Databases

Microsoft Access 2019 Programming Pocket Primer This book was designed for someone like you who needs to master Access programming fundamentals without spending too much time. All you need is a short book to get you started. It will show you only the things you need to know to feel at home with VBA. What you learn in this book on Access programming will alsoapply to, say, Excel programming. The book is divided into nine chapters that progressively introduce you to programming Microsoft Access 2019. Features: Includes a companion disc with all of the “Hands-On†files needed to complete the chapter projects andall the images from the text (also available from the publisher by emailing info@merclearning.com) Introducesyou to programming Microsoft Access 2019 COMPUTERS,Business & Productivity Software,Databases

Microsoft Outlook 2010 Plain & Simple Get the guide that makes learning Microsoft Outlook 2010 plain and simple! This full color, no-nonsense book shows you the quickest ways to manage your email and schedule appointments, using easy-to-follow steps and concise, straightforward language. You'll learn how to stay productive and in touch with all of your personal and business networks. Here's WHAT you'll learn: Send and receive messages, files, and photos Set up e-mail filters to weed out the junk Manage your contacts and stay in touch Keep track of your calendar and manage your tasks Read RSS feeds right from your inbox Jot down e-notes and keep a journal Here's HOW you'll learn it: Jump in whenever you need answers Easy-to-follow STEPS and SCREENSHOTS show exactly what to do Handy TIPS teach new techniques and shortcuts Quick TRY THIS! exercises help apply what you learn right away COMPUTERS,Business & Productivity Software,Email Clients

Effective Time Management Take charge—and create an effective balance between your work and personal life with the help of Microsoft Outlook. In this practical guide, two experts teach you a proven time-management system, showing you how to set and manage your priorities with custom modifications to Outlook. Sharpen your focus, combat distractions—and manage your time with complete confidence. Get the skills to take control of your schedule Organize email in a systematic way and keep your inbox clean Schedule time for productivity—and defend it against interruptions Apply Outlook filters to help you manage tasks and projects Make time for family and fun—plan your work and private lives together Use Outlook with Microsoft OneNote to capture ideas and set goals Learn effective time management techniques with practical examples COMPUTERS,Business & Productivity Software,Email Clients

Total Workday Control Using Microsoft Outlook In this new fifth edition, Michael Linenberger updates his longtime #1 bestselling Outlook book to cover Microsoft's new Outlook version 365, which includes desktop Outlook 2016 Windows and Mac (and Window Outlook 2013). This seminal guide presents the author's latest best practices of time, task, and e-mail management, applying these best practices in Microsoft Outlook. Strategies for using smartphones are included. Anyone who finds they are overburdened by e-mail or working too late each day will benefit from this book. COMPUTERS,Business & Productivity Software,Email Clients

MOS 2016 Study Guide for Microsoft Outlook This is the eBook of the printed book and may not include any media, website access codes, or print supplements that may come packaged with the bound book. The MOS 2016 Study Guide for Microsoft Outlook covers Microsoft Outlook 2016, specifically the skills required to pass the Outlook 2016 Microsoft Office Specialist exam. The Microsoft Office Specialist Study Guides provide concise descriptions of the tasks that certification candidates must demonstrate to pass the Microsoft Office Specialist exams, step-by-step procedures for performing those tasks, practice tasks based on the MOS exam approach, sample files for practicing the tasks, and solution files so you can check your work. COMPUTERS,Business & Productivity Software,Email Clients

Microsoft Dynamics GP For Dummies If you’re accountable for accounting in a mid-level business, Microsoft Dynamics GP accounting software can be your friend. Microsoft Dynamics GP For Dummies improves the friendship by highlighting the most useful and practical features, dispelling the most common misconceptions, and letting you in on the best tips and tricks — all in plain English! Microsoft Dynamics GP For Dummies shows you how to set up and use this modular accounting program. You’ll learn to customize Dynamics Great Plains, get around the program, create a company, build an effective chart of accounts, and maintain a general ledger. You’ll find out how to: Create invoices and bill your customers, manage receipts, and easily match payments to invoices Set up vendors quickly and easily Customize GP fit your business perfectly and make the home page more efficient Work with the modules you’ll use most often in the Purchasing, Sales, Inventory, and Financial series Safeguard your database and set up a disaster recovery plan containing all the right steps Use Professional Services Tools and utilities to find and fix data discrepancies Get inventory under control Close your books at year end and use shortcuts to easily print reports from all the data you’ve collected Save keystrokes with Quick Journal and batch frequency Leverage the interoperability between Dynamics GP and Microsoft Office applications Make upgrading hassle-free Microsoft Dynamics GP For Dummies helps you make this sometimes-complex program do your bidding, which might account for your rising popularity in the office! Note: CD-ROM/DVD and other supplementary materials are not included as part of eBook file. COMPUTERS,Business & Productivity Software,General

NetSuite For Dummies NetSuite is an easy-to-use, customizable enterprise software for running your business. Part I explains NetSuite basics everyone should know. Part II focuses on tracking money (accounting, AR, AP, and managing inventory). Parts III, IV, and V explain how to sell and market your products, take care of customers, and sell goods online with NetSuite. Part VI describes how to gauge your progress using dashboards and analytics. Bonus chapters provide information about scripting, customization, and setting up your Web site (see the Downloads tab). Table of contents: Part 1: NetSuite Basics Part II: Using NetSuite's Various Components Part III: How to use NetSuite for your specific business Part IV: Configuring NetSuite Part V: Getting organized with NetSuite. Bringing it all together Part VI: Advanced stuff Part VII: The Part of Tens COMPUTERS,Business & Productivity Software,General

IT Architecture For Dummies A solid introduction to the practices, plans, and skills required for developing a smart system architecture Information architecture combines IT skills with business skills in order to align the IT structure of an organization with the mission, goals, and objectives of its business. This friendly introduction to IT architecture walks you through the myriad issues and complex decisions that many organizations face when setting up IT systems to work in sync with business procedures. Veteran IT professional and author Kirk Hausman explains the business value behind IT architecture and provides you with an action plan for implementing IT architecture procedures in an organization. You'll explore the many challenges that organizations face as they attempt to use technology to enhance their business's productivity so that you can gain a solid understanding of the elements that are required to plan and create an architecture that meets specific business goals. Defines IT architecture as a blend of IT skills and business skills that focuses on business optimization, business architecture, performance management, and organizational structure Uncovers and examines every topic within IT architecture including network, system, data, services, application, and more Addresses the challenges that organizations face when attempting to use information technology to enable profitability and business continuity While companies look to technology more than ever to enhance productivity, you should look to IT Architecture For Dummies for guidance in this field. COMPUTERS,Business & Productivity Software,General

Managing RPM-Based Systems with Kickstart and Yum Managing multiple Red Hat-based systems can be easy--with the right tools. The yum package manager and the Kickstart installation utility are full of power and potential for automatic installation, customization, and updates. Here's what you need to know to take control of your systems. COMPUTERS,Business & Productivity Software,General

Big Data For Dummies Find the right big data solution for your business or organization Big data management is one of the major challenges facing business, industry, and not-for-profit organizations. Data sets such as customer transactions for a mega-retailer, weather patterns monitored by meteorologists, or social network activity can quickly outpace the capacity of traditional data management tools. If you need to develop or manage big data solutions, you'll appreciate how these four experts define, explain, and guide you through this new and often confusing concept. You'll learn what it is, why it matters, and how to choose and implement solutions that work. Effectively managing big data is an issue of growing importance to businesses, not-for-profit organizations, government, and IT professionals Authors are experts in information management, big data, and a variety of solutions Explains big data in detail and discusses how to select and implement a solution, security concerns to consider, data storage and presentation issues, analytics, and much more Provides essential information in a no-nonsense, easy-to-understand style that is empowering Big Data For Dummies cuts through the confusion and helps you take charge of big data solutions for your organization. COMPUTERS,Business & Productivity Software,General

Hadoop For Dummies Let Hadoop For Dummies help harness the power of your data and rein in the information overload Big data has become big business, and companies and organizations of all sizes are struggling to find ways to retrieve valuable information from their massive data sets with becoming overwhelmed. Enter Hadoop and this easy-to-understand For Dummies guide. Hadoop For Dummies helps readers understand the value of big data, make a business case for using Hadoop, navigate the Hadoop ecosystem, and build and manage Hadoop applications and clusters. Explains the origins of Hadoop, its economic benefits, and its functionality and practical applications Helps you find your way around the Hadoop ecosystem, program MapReduce, utilize design patterns, and get your Hadoop cluster up and running quickly and easily Details how to use Hadoop applications for data mining, web analytics and personalization, large-scale text processing, data science, and problem-solving Shows you how to improve the value of your Hadoop cluster, maximize your investment in Hadoop, and avoid common pitfalls when building your Hadoop cluster From programmers challenged with building and maintaining affordable, scaleable data systems to administrators who must deal with huge volumes of information effectively and efficiently, this how-to has something to help you with Hadoop. COMPUTERS,Business & Productivity Software,General

Access 2016 For Dummies Your all-access guide to all things Access 2016 If you don't know a relational database from an isolationist table—but still need to figure out how to organize and analyze your data—Access 2016 For Dummies is for you. Written in a friendly and accessible manner, it assumes no prior Access or database-building knowledge and walks you through the basics of creating tables to store your data, building forms that ease data entry, writing queries that pull real information from your data, and creating reports that back up your analysis. Add in a dash of humor and fun, and Access 2016 For Dummies is the only resource you'll need to go from data rookie to data pro! This expanded and updated edition of Access For Dummies covers all of the latest information and features to help data newcomers better understand Access' role in the world of data analysis and data science. Inside, you'll get a crash course on how databases work—and how to build one from the ground up. Plus, you'll find step-by-step guidance on how to structure data to make it useful, manipulate, edit, and import data into your database, write and execute queries to gain insight from your data, and report data in elegant ways. Speak the lingo of database builders and create databases that suit your needs Organize your data into tables and build forms that ease data entry Query your data to get answers right Create reports that tell the story of your data findings If you have little to no experience with creating and managing a database of any sort, Access 2016 For Dummies is the perfect starting point for learning the basics of building databases, simplifying data entry and reporting, and improving your overall data skills. COMPUTERS,Business & Productivity Software,General

Office 2016 at Work For Dummies Get more productive using the new features in Microsoft Office 2016! It may seem like an eternity since your IT department upgraded you to the latest version of Microsoft Office. Prepare yourself, because Office 2016 is packed with updated features and new ways to increase your productivity in the office! With Office 2016 at Work For Dummies, we make it easy by breaking the content down into over 300 of the most common tasks and operations, providing you with straightforward, simple-to-navigate, approachable information. With four-color illustrations for visual support as your work through the tasks, and then nearly three hours of supporting video, you can choose your path for learning the ins and outs of Office 2016. As the world's leading productivity software, Microsoft Office plays an integral role in the daily lives of professionals. Understanding how to quickly and accurately use Office 2016 can improve your productivity, enhance your deliverables, and provide you with the tools and knowledge you need to be successful. Choose your path for learning and explore the fundamental features of Microsoft Office 2016 through task based exercises supported by online video Dive into Microsoft Word by creating a document, formatting paragraphs and pages, and adding tables and graphics Explore Microsoft Excel's ability to analyze data through creating formulas and functions, and learn to format and print spreadsheets Use Outlook to organize your work day, and find out how to make amazing PowerPoint presentations using the new features in the 2016 version Office 2016 at Work For Dummies is the perfect office companion if you use Microsoft Office regularly and need to get up to speed on the changes with the latest release as quickly and efficiently as possible. COMPUTERS,Business & Productivity Software,General

Bitcoin For Dummies Learn the ins and outs of Bitcoin so you can get started today Bitcoin For Dummies is the fast, easy way to start trading crypto currency, with clear explanations and expert advice for breaking into this exciting new market. Understanding the mechanisms and risk behind Bitcoin can be a challenge, but this book breaks it down into easy-to-understand language to give you a solid grasp of just where your money is going. You'll learn the details of Bitcoin trading, how to set up your Bitcoin wallet, and everything you need to get started right away. An in-depth discussion on security shows you how to protect yourself against some of the riskier aspects of this open-source platform, helping you reduce your risks in the market and use Bitcoin safely and effectively. Bitcoin uses peer-to-peer technology to operate with no central authority or banks, with transaction management and issuing of Bitcoins carried out collectively by the network. Bitcoin allows easy mobile payments, fast international payments, low- or no-fee transactions, multi-signature capabilities, and more, but the nuances of the market can be difficult to grasp. This informative guide lays it all out in plain English, so you can strengthen your understanding and get started now. Understand the ins and outs of the Bitcoin market Learn how to set up your Bitcoin wallet Protect yourself against fraud and theft Get started trading this exciting new currency The Bitcoin market is huge, growing quickly, and packed with potential. There's also some risk, so you need to go in fully informed and take steps to manage your risk wisely. Bitcoin For Dummies is the clear, quick, easy-to-follow guide to getting started with Bitcoin. COMPUTERS,Business & Productivity Software,General

Dragon Professional Individual For Dummies Stop typing and get more done with Dragon Professional Individual voice recognition software Tired of typing, but afraid to take the leap into voice recognition software? No problem! Dragon Professional Individual For Dummies, 5th Edition gives you a great overview of the industry-leading speech recognition software so you can start talking instead of typing in no time at all. With this easy-to-use guide, you'll quickly find out how to use Professional Individual to open documents, write emails and notes, update your Facebook status, and much more. The book includes everything you need to get started, from launching the software and basic dictating to controlling your desktop by voice, and tips for improving accuracy. Available for both Windows and Mac, Dragon Professional Individual is the gold standard for home and professional voice recognition software. Easy to use and much more efficient than typing, the software can take your productivity to the next level. Get an introduction to everything you'll need to know to get started with Dragon Professional Individual voice recognition software Find out how to access documents, write emails, and even update your Facebook status with nothing more than your voice Includes the most updated information on the latest version of the software Offers information for programmers and developers who want to use the software for mobile app development Dragon Professional Individual For Dummies, 5th Edition is your go-to resource to get up and running with this great voice recognition software in no time. COMPUTERS,Business & Productivity Software,General

SAP in 24 Hours, Sams Teach Yourself Thoroughly updated and expanded! Includes new coverage on HANA, the cloud, and using SAP’s applications! In just 24 sessions of one hour or less, you’ll get up and running with the latest SAP technologies, applications, and solutions. Using a straightforward, step-by-step approach, each lesson strengthens your understanding of SAP from both a business and technical perspective, helping you gain practical mastery from the ground up on topics such as security, governance, validations, release management, SLA, and legal issues. Step-by-step instructions carefully walk you through the most common questions, issues, and tasks. Quizzes and exercises help you build and test your knowledge. Notes present interesting pieces of information. Tips offer advice or teach an easier way to do something. Cautions advise you about potential problems and help you steer clear of disaster. Learn how to… Understand SAP terminology, concepts, and solutions Install SAP on premises or in the cloud Master SAP’s revamped user interface Discover how and when to use in-memory HANA databases Integrate SAP Software as a Service (SaaS) solutions such as Ariba, Successfactors, Fieldglass, and hybris Find resources at SAP’s Service Marketplace, Developer Network, and Help Portal Avoid pitfalls in SAP project implementation, migration, and upgrades Discover how SAP fits with mobile devices, social media, big data, and the Internet of Things Start or accelerate your career working with SAP technologies COMPUTERS,Business & Productivity Software,General

QuickBooks 2017 All-In-One For Dummies Make business chores easy with QuickBooks Managing the books for a small business can be a challenging, onerous task. If you're looking to spend fewer hours hunched over multiple spreadsheets and more time focused on other aspects of your growing business, this all-in-one guide gives you everything you need to put QuickBooks to work for you. Combining eight content-rich books into one complete package, this value-priced reference provides answers to all the questions you have about how QuickBooks can manage your business finances—even the ones you didn't know to ask! With the help of QuickBooks 2017 All-In-One For Dummies, you'll quickly and painlessly discover how to use this fan-favorite software program to establish fundamental accounting practices that will keep your company successful and healthy. From installing the software and configuring QuickBooks to setting up payroll reminders and keeping track of your business checkbook and credit cards, everything you need to effectively—and efficiently—stay on top of those dollars and cents is only a page away! Organize all of your business finances in one place Pay vendors, invoice customers, and track inventory Prepare financial statements and reports Access your cloud-based account using your smartphone This is your all-encompassing guide to putting your financial woes to rest and simplifying your business accounting with confidence! COMPUTERS,Business & Productivity Software,General

AWS For Developers For Dummies Everything you need to get running with IaaS for Amazon Web Services Modern businesses rely on Infrastructure-as-a-Service (IaaS)—a setup in which someone else foots the bill to create application environments—and developers are expected to know how to write both platform-specific and IaaS-supported applications. If you're a developer who writes desktop and web applications but have little-to-no experience with cloud development, this book is an essential tool in getting started in the IaaS environment with Amazon Web Services. In Amazon Web Services For Developers For Dummies, you'll quickly and easily get up to speed on which language or platform will work best to meet a specific need, how to work with management consoles, ways you'll interact with services at the command line, how to create applications with the AWS API, and so much more. Assess development options to produce the kind of result that's actually needed Use the simplest approach to accomplish any given task Automate tasks using something as simple as the batch processing features offered by most platforms Create example applications using JavaScript, Python, and R Discover how to use the XML files that appear in the management console to fine tune your configuration Making sense of Amazon Web Services doesn't have to be as difficult as it seems—and this book shows you how. COMPUTERS,Business & Productivity Software,General

QuickBooks Online For Dummies Organise business finances with the latest cloud-based accounting innovation QuickBooks Online For Dummies, Australian Edition is your key guide to getting business finances under control. From budgeting and payroll to tax, inventory, accounts and beyond, this book shows you everything you need to know to keep the cash flow flowing. Whether you're a small business owner, accountant or bookkeeper, this guide walks you through essential bookkeeping tasks, and hands-on tutorials provide quick and practical instruction using the QuickBooks Online and QuickBooks Online Accountant cloud-based accounting solution. Stop juggling files and notes and calendars, stressing about what's due, what's coming and what you may have overlooked; this book shows you how to track and manage everything in one place, with alerts, reminders and detailed reports that help you gain a clearer picture of the business's financial state — and all you need is an internet connection. Using the many helpful, timesaving features of QuickBooks Online and QuickBooks Online Accountant to their utmost capability requires a little insider knowledge and hands-on instruction; this book has you covered, with clear, practical guidance to help you: Manage payroll, invoices and accounts payable Track inventory, costs and expenses Create reports and simplify tax return preparation Organise finances in one intuitive place Wouldn't you enjoy the peace of mind that comes from knowing that your finances are under control? Wouldn't you prefer the freedom to access the books on any device, at any time? QuickBooks Online can help with that, and QuickBooks Online For Dummies, Australian Edition is the ultimate guide to working with the latest innovation in cloud-based accounting. COMPUTERS,Business & Productivity Software,General

ServiceNow Cookbook Over 50 practical and immediately applicable recipes to help you manage services in your enterprise environment efficiently About This Book Solve problems and challenges encountered while implementing or using ServiceNow in your organization Helps you build core administration, management, and maintenance skills to automate and orchestrate your IT environment Comes with recipes to improve the way you design and create automated workflows Who This Book Is For This book targets IT professionals and administrators who have some experience of working with ServiceNow already and are looking to solve regular or unique problems that surface when using ServiceNow. It's advisable to have a basic level of administration experience with ServiceNow. Familiarity with JavaScript is assumed. What You Will Learn Grasp the basics, such as entering and navigation, required to implement ServiceNow Perform core configuration and management tasks Use the ServiceNow plugins to manage development Build and publish custom applications for service management Design data-driven apps to connect with outside worlds by getting into Client and server scripting Configure alerts and notifications and understand e-mail troubleshooting and watermarking Build and configure reports to set up your dashboard as per the requirement Create and configure workflow activities In Detail ServiceNow is the ideal platform for you to create enterprise-level applications, giving borh requesters and fulfillers better visibility and access to a process. With this title we'll guide you through the world of ServiceNow, letting you take on the best the platform offers you with the least amount of hassle. Starting with the core configuration and management tasks, this book will help you build data-driven apps and it will also explore development best practices. You will learn to set up email notifications for users and work with the database view for reporting. Next, the book will guide you through creating various tasks from the workflow and show you how to make the most of the workflow utilities available in ServiceNow. Finally, the book will drive you through the auditing and diagnosing aspects of ServiceNow. By the end of this book, you will acquire immediately applicable skills to rectify everyday problems encountered on the ServiceNow platform. Style and approach This book follows a recipe-based problem-solution approach to address and dispel challenges faced when implementing and using ServiceNow on a regular basis.It will act as a quick solution when trying to solve specific problems without having to read an exhaustive tutorial. COMPUTERS,Business & Productivity Software,General

Spinning Up ServiceNow Learn how to onboard ServiceNow ITSM tools by evangelizing, educating, and coordinating your organization's service desk, developers, and stakeholders. Drawing on his own story of lessons learned in spinning up the adoption of ServiceNow throughout the Al Jazeera Media Network, application architect Gabriele Kahlout shows IT service managers how to launch automated ServiceNow ticketing tools in seamless integration with their organization's existing email and Active Directory. Spinning Up ServiceNow: IT Service Managers' Guide to Successful User Adoption shows you how to orchestrate your IT service desks and developers to facilitate the adoption and consumption of IT services by all users, supporting their various business needs while optimizing human-computer interaction and minimizing stress and productivity loss arising from poor human-system design. What You'll Learn Quick-start ServiceNow in a matter of days with the minimum configuration required to start processing tickets via email Avoid the teething problems that can spoil your users’ onboarding experience with ServiceNow Automate the process of scaling up new teams into ServiceNow Shape your users' experiences so that they retain their familiar bearings in email and Active Directory while welcoming the power of ServiceNow enhancements Create a strategy to avoid common pitfalls that sabotage ITSM programs Who This Book Is For IT managers charged with implementing ServiceNow ITSM suites in their organizations and business analysts determining the requirements for such implementation. The secondary readership is system administrators and developers involved in ITSM. COMPUTERS,Business & Productivity Software,General

QuickBooks 2018 For Dummies The perennial bestseller—now in a new edition for QuickBooks 2018 QuickBooks 2018 For Dummies is here to make it easier than ever to familiarize yourself with the latest version of the software. It shows you step by step how to build the perfect budget, simplify tax return preparation, manage inventory, track job costs, generate income statements and financial reports, and every other accounting-related task that crosses your desk at work. Written by highly qualified CPA Stephen L. Nelson, this trusted bestseller shows you how to get the most out of the software that helps over six million small businesses manage their finances. Removing the need to hire expensive financial professionals, it empowers you to take your small business' finances into your own hands. Handle your financial and business management tasks more effectively Implement QuickBooks and get the most out of its features Create invoices and credit memos with ease Pay bills, prepare payroll, and record sales receipts If you're a small business owner, manager, or employee who utilizes QuickBooks at work, this bestselling guide has answers for all of your business accounting needs. COMPUTERS,Business & Productivity Software,General

Cloud Native Java What separates the traditional enterprise from the likes of Amazon, Netflix, and Etsy? Those companies have refined the art of cloud native development to maintain their competitive edge and stay well ahead of the competition. This practical guide shows Java/JVM developers how to build better software, faster, using Spring Boot, Spring Cloud, and Cloud Foundry. Many organizations have already waded into cloud computing, test-driven development, microservices, and continuous integration and delivery. Authors Josh Long and Kenny Bastani fully immerse you in the tools and methodologies that will help you transform your legacy application into one that is genuinely cloud native. In four sections, this book takes you through: The Basics: learn the motivations behind cloud native thinking; configure and test a Spring Boot application; and move your legacy application to the cloud Web Services: build HTTP and RESTful services with Spring; route requests in your distributed system; and build edge services closer to the data Data Integration: manage your data with Spring Data, and integrate distributed services with Spring’s support for event-driven, messaging-centric architectures Production: make your system observable; use service brokers to connect stateful services; and understand the big ideas behind continuous delivery COMPUTERS,Business & Productivity Software,General

Manage Your SAP Projects with SAP Activate Explore and use the agile techniques of SAP Activate Framework in your SAP Projects. About This Book Explore the three pillars of SAP Activate and see how it works in different scenario. Understand and Implement Agile and Scrum concepts in SAP Activate. Get to Grisp with SAP Activate framework and manage your SAP projects effectively. Who This Book Is For This book is for readers who want to understand the working of SAP Activate and use it to manage SAP projects. Prior knowledge of SAP Hana is must. What You Will Learn Understand the fundamentals of SAP S4/HANA. Get familiar with the structure and characteristics of SAP Activate. Explore the application scenarios of SAP Activate. Use Agile and Scrum in SAP Projects effectively and efficiently Implement your learning into a sample project to explore and understand the benefits of SAP Activate methodology. In Detail It has been a general observation that most SAP consultants and professionals are used to the conventional waterfall methodology. Traditionally, this method has been there for ages and we all grew up learning about it and started practicing it in real world. The evolution of agile methodology has revolutionized the way we manage our projects and businesses. SAP Activate is an innovative, next generation business suite that allows producing working deliverables straight away. Manage your SAP Project with SAP Activate, will take your learning to the next level. The book promises to make you understand and practice the SAP Activate Framework. The focus is to take you on a journey of all the phases of SAP Activate methodology and make you understand all the phases with real time project examples. The author explains how SAP Activate methodology can be used through real-world use cases, with a comprehensive discussion on Agile and Scrum, in the context of SAP Project. You will get familiar with SAP S4HANA which is an incredibly innovative platform for businesses which can store business data, interpret it, analyze it, process it in real time, and use it when it's needed depending upon the business requirement. Style and approach An easy to follow approach with concepts explained via scenarios and project examples COMPUTERS,Business & Productivity Software,General

Microsoft Dynamics 365 For Dummies Accelerate your digital transformation and break down silos with Microsoft Dynamics 365 It’s no secret that running a business involves several complex parts like managing staff, financials, marketing, and operations—just to name a few. That’s where Microsoft Dynamics 365, the most profitable business management tool, comes in. In Microsoft Dynamics 365 For Dummies, you’ll learn the aspects of the program and each of its applications from Customer Service to Financial Management. With expert author Renato Bellu’s clear instructions and helpful tips, you’ll be managing to your fullest advantage before you know it. Let’s get started! Digitally transform your business by connecting CRM and ERP Use data to make decisions across all business functions Integrate Dynamics 365 with Office 365 and LinkedIn Manage financials and operations Are you running a dynamic business? This book shows you how! COMPUTERS,Business & Productivity Software,General

QuickBooks 2019 For Dummies The bestselling guide to QuickBooks—now in a new edition QuickBooks 2019 For Dummies is here to make it easier than ever to familiarize yourself with the latest version of the software. It shows you step by step how to build the perfect budget, simplify tax return preparation, manage inventory, track job costs, generate income statements and financial reports, and every other accounting-related task that crosses your desk at work. Written by CPA Stephen L. Nelson, this perennial bestseller shows you how to get the most out of the software that helps over six million small businesses manage their finances. Removing the need to hire expensive financial professionals, it empowers you to take your small business' finances into your own hands. Handle your financial and business management tasks more effectively Implement QuickBooks and get the most out of its features Create invoices and credit memos with ease Pay bills, prepare payroll, and record sales receipts If you're a small business owner, manager, or employee who utilizes QuickBooks at work, this bestselling guide has answers for all of your business accounting needs. COMPUTERS,Business & Productivity Software,General

Dynamics 365 Business Central Development Quick Start Guide Understanding the new Microsoft Extension model for development Key Features Develop solutions for Dynamics 365 Business Central Orient yourself with the new Microsoft Extension model for development Learn modern ways to develop with Dynamics 365 Business Central Book Description Microsoft Dynamics 365 Business Central is the new SaaS ERP proposition from Microsoft. This latest version has many exciting features guaranteed to make your life easier. This book is an ideal guide to Dynamics 365 Business Central and will help you get started with implementing and designing solutions for real-world scenarios. This book will take you through the fundamental topics for implementing solutions based on Dynamics 365 Business Central (on-premise and SaaS). We'll see the core topics of the new development model (based on extensions) and we'll see how to create applications with the new Microsoft ERP proposition. The book begins by explaining the basics of Dynamics 365 Business Central and the Microsoft ERP proposition. We will then cover topics such as extensions, the new modern development model of Visual studio code, sandboxes, Docker, and many others. By the end of the book, you will have learned how to debug and compile extensions and to deploy them to the cloud and on-premise.You will also have learned how to create serverless business processes for Microsoft Dynamics 365 Business Central. What you will learn Develop solutions for Dynamics 365 Business Central Create a sandbox for extensions development (local or on cloud) Use Docker with Dynamics 365 Business Central Create extensions for Dynamics 365 Business Central Handle dependencies, translations and reporting Deploy extensions on-premise and to the cloud Create serverless processes with Dynamics 365 Business Central Understand source code management for AL Who this book is for This book is for Microsoft Dynamics 365 Business Central solution developers and architects that needs to implement solutions based on the Microsoft's ERP (on-premise and SaaS). COMPUTERS,Business & Productivity Software,General

QuickBooks 2019 All-in-One For Dummies The quickest way to do the books! Finances don’t have to put you in a funk! With the help of this all-encompassing book, you’ll get the easy-to-follow instruction you need to get your business’ ducks in a row—without ever losing your cool. Whether you’re a numbers person or have never spent much time with a calculator, you’ll discover how to use QuickBooks 2019 to make it easier than ever to handle your finances. This value-priced reference combines eight content-rich mini-books into one complete package, providing the answers you need to get the most out of the latest version of QuickBooks. No stone is left unturned, giving you everything you need to turn what used to be harrowing tasks into simple items you can check off on your to-do list. Helps you use QuickBooks to ease accounting chores, financial management, and business planning Provides guidance from an industry expert Shows you how to set up a QuickBooks accounting system, load the master files lists, invoice customers, pay vendors, track inventory, manage cash and bank accounts, and more Gives helpful troubleshooting tips to make your accounting easy Your time is precious—why waste a minute when QuickBooks can make it easier? Get started today! COMPUTERS,Business & Productivity Software,General

Implementing Microsoft Dynamics 365 Business Central On-Premise Implement Business Central and explore methods to upgrade to NAV 2018 Key Features Learn the key roles of Dynamics NAV partner and the roles within your customer's organization Create configuration packages and perform data migration Explore Microsoft Dynamics 365 Business Central to use Dynamics NAV 2018 functionalities in the Cloud Book Description Microsoft Dynamics Business Central is a full business solution suite and a complete ERP solution, which contains a robust set of development tools; these tools can help you to gain control over your business and can simplify supply chains, manufacturing, and operations. Implementing Microsoft Dynamics 365 Business Central On-Premise covers the latest features of Dynamics Business Central and NAV from the end users' and developers' perspectives. It also provides an insight into different tools available for implementation, whether it's a new installation or migrating from the previous version of Dynamics NAV. This book will take you from an introduction to Dynamics NAV 2018 through to exploring all the techniques related to implementation and migration. You will also learn to expand functionalities within your existing Microsoft Dynamics NAV installation, perform data analysis, and implement free third-party add-ons to your existing installation. As you progress through the book, you will learn to work with third-party add-on tools. In the concluding chapters, you will explore Dynamics 365 Business Central, the new Cloud solution based on the Microsoft NAV platform, and techniques for using Docker and Sandbox to develop applications. By the end of the book, you will have gained a deep understanding of the key components for successful Dynamics NAV implementation for an organization. What you will learn Explore new features introduced in Microsoft Dynamics NAV 2018 Migrate to Microsoft Dynamics NAV 2018 from previous versions Learn abstract techniques for data analysis, reporting, and debugging Install, configure, and use additional tools for business intelligence, document management, and reporting Discover Dynamics 365 Business Central and several other Microsoft services Utilize different tools to develop applications for Business Central Who this book is for Implementing Microsoft Dynamics 365 Business Central On-Premise is for Dynamics NAV partners and end users who want to know everything about Dynamics NAV implementation. This book is for you if you want to be a project manager or get involved with Dynamics NAV, but do not have the expertise to write code yourself. This book can also help you to understand the need to move to Business Central and its advantages. COMPUTERS,Business & Productivity Software,General

Jira Quick Start Guide Leverage Jira's powerful task management and workflow features to better manage your business processes Key Features The book covers all major applications of Jira, which are Jira Software, Jira Core, Jira Service Desk. Configure project workflows and the fields that will be used in the project with the help of Jira's features Create tickets for issues and manage your projects using the Jira software Book Description Jira is an issue tracker and project management system. With their latest release, the Jira team has now expanded their user base to agile teams as well as business teams. This book provides a comprehensive explanation covering all major components of Jira, including Jira Software, Jira Core, and Jira Service Desk. This book starts with an introduction to Jira's unique features and how it can be used as an issue-tracking tool. It will then teach you about how a new project is created by a Jira administrator, what responsibilities there are, and using correct and relevant schemes in your project. You will then learn how to configure project workflows and fields for project screens. You will understand the various permissions used in projects and the importance of project roles in Jira. Then, the book talks about the concepts of versions acting as milestones and using components when handling issues in your projects. It will then focus on analysing data using built-in reports and creating dashboards in Jira. At the end, it will discuss various best practices for users as well as project managers or project administrators. What you will learn Implement Jira as a project administrator or project manager Get familiar with various functionalities of Jira Configure projects and boards in your organisation's Jira instance Understand how and when to use components and versions in your projects Manage project configurations and Jira schemes Learn the best practices to manage your Jira instance Who this book is for This book will be especially useful for project managers but it's also intended for other Jira users, including developers, and any other industry besides software development, who would like to use Jira for project management. COMPUTERS,Business & Productivity Software,General

Cloud et transformation digitale - 5e éd Cet ouvrage s’adresse à tous ceux qui souhaitent comprendre les concepts et les enjeux du cloud computing qu’ils soient informaticiens (chefs de projet, architectes, développeurs, équipes d’exploitation) experts métiers, ou responsables de maîtrises d’ouvrage... La première partie introduit les concepts du cloud computing, des SaaS, PaaS, et IaaS, du SI hybride. La deuxième partie aborde les problématiques de sécurité et de confiance. Elle analyse les risques du cloud pour l’entreprise. Elle aborde successivement les points de vue de la direction, des utilisateurs et des informaticiens. La troisième partie décrit les différents modes de gouvernance du cloud. Elle présente l’organisation à mettre en place et décrit les mécanismes d’intégration au SI. La quatrième partie propose un panorama des offres SaaS disponibles. La cinquième partie aborde les aspects techniques. Elle introduit les architectures sous-jacentes aux plateformes IaaS et PaaS. Elle décrit les principales plateformes du marché. Cette cinquième édition apporte des mises à jour sur les interfaces web (avec Angular, React, HTML 5...) et sur le fonctionnement (serverless ou avec les containers Docker et Kubernetes).Plusieurs autres chapitres ont également été actualisés sur le cloud hybride, sur les datacenters et sur les changements induits par DevOps. COMPUTERS,Business & Productivity Software,General

VMware vSphere 6.7 Data Center Design Cookbook Design a virtualized data center with VMware vSphere 6.7 Key Features Get the first book on the market that helps you design a virtualized data center with VMware vSphere 6.7 Learn how to create professional vSphere design documentation to ensure a successful implementation A practical guide that will help you apply infrastructure design principles to vSphere design Book Description VMware is the industry leader in data center virtualization. The vSphere 6.x suite of products provides a robust and resilient platform to virtualize server and application workloads. This book uses proven infrastructure design principles and applies them to VMware vSphere 6.7 virtual data center design through short and focused recipes on each design aspect. The second edition of this book focused on vSphere 6.0. vSphere features released since then necessitate an updated design guide, which includes recipes for upgrading to 6.7, vCenter HA; operational improvements; cutting-edge, high-performance storage access such as RDMA and Pmem; security features such as encrypted vMotion and VM-level encryption; Proactive HA; HA Orchestrated Restart; Predictive DRS; and more. By the end of the book, you will be able to achieve enhanced compute, storage, network, and management capabilities for your virtual data center. What you will learn Identify key factors related to a vSphere design Mitigate security risks and meet compliance requirements in a vSphere design Create a vSphere conceptual design by identifying technical and business requirements Design for performance, availability, recoverability, manageability, and security Map the logical resource design into the physical vSphere design Create professional vSphere design documentation Who this book is for If you are an administrator or consultant interested in designing virtualized data center environments using VMware vSphere 6.x (or previous versions of vSphere and the supporting components), this book is for you. COMPUTERS,Business & Productivity Software,General

QuickBooks Online For Dummies Your quick guide to using QuickBooks Online Searching for a cloud-based solution for your small business’ accounting needs? Master the fundamentals of QuickBooks Online—the world’s most popular software for fast and easy mobile accounting! QuickBooks Online brings this popular accounting software to your browser for a monthly fee, allowing you access to its tools from any device with an Internet connection. From generating financial reports to simplifying tax preparation to tracking business finances, QuickBooks Online For Dummies covers it all! Handle your financial and business management tasks more effectively Get the most out of QuickBooks’ features Create invoices and memos with ease Pay bills, prepare payroll, and record sales receipts If you use QuickBooks Online—or want to implement it—this new edition gets you up and running fast. COMPUTERS,Business & Productivity Software,General

Azure DevOps Server 2019 Cookbook Over 70 recipes to effectively apply DevOps best practices and implement Agile, Git, CI-CD & Test automation using Azure DevOps Server (TFS) 2019 Key Features Learn improving code quality using pull requests, branch policies, githooks and git branching design Accelerate the deployment of high quality software by automating build and releases using CI-CD Pipelines. Learn tried and tested techniques to automate database deployments, App Service & Function Deployments in Azure. Book Description Azure DevOps Server, previously known as Team Foundation Server (TFS), is a comprehensive on-premise DevOps toolset with a rich ecosystem of open source plugins. This book is your one stop guide to learn how to effectively use all of these Azure DevOps services to go from zero to DevOps. You will start by building high-quality scalable software targeting .NET, .NET core or Node.js applications. You will learn techniques that will help you to set up end-to-end traceability of your code changes from design through to release. Whether you are deploying software on-premise or in the cloud in App Service, Functions, or Azure VMs, this book will help you learn release management techniques to reduce release failures. Next, you will be able to secure application configuration by using Azure KeyVault. You will also learn how to create and release extensions to the Azure DevOps marketplace and reach million developer ecosystem for feedback. The working extension samples will allow you to iterate changes in your extensions easily and release updates to the marketplace quickly. By the end of this book, techniques provided in the book will help you break down the invisible silos between your software development teams. This will transform you from being a good software development team to an elite modern cross functional software development team. What you will learn Set up a team project for an Agile delivery team, importing requirements from Excel Plan,track, and monitor progress using self updating boards, Sprint and Kanban boards Unlock the features of Git by using branch policies, Git pull requests, forks, and Git hooks Build and release .NET core, SQL and Node.js applications using Azure Pipeline Automate testing by integrating Microsoft and open source testing frameworks Extend Azure DevOps Server to a million developer ecosystem Who this book is for This book is for anyone looking to succeed with DevOps. The techniques in this book apply to all roles of the software development lifecycle including developers, testers, architects, configuration analysts, site reliability engineers and release managers. If you are a new user you'll learn how to get started; if you are an experienced user you'll learn how to launch your project into a modern and mature DevOps enabled software development team. COMPUTERS,Business & Productivity Software,General

How to Use Evernote for Genealogy Maximize Your Research Progress! Harness the powerful, timesaving organization features of Evernote's free software and mobile apps to manage your genealogy research. This comprehensive user guide explains how to organize all kinds of genealogy clues--from notes and e-mails to vital records and audio files--so the information is easily searchable, accessible on any device, and automatically backed up in the cloud. Step-by-step instructions show you how to file research materials, analyze research clues, collaborate with cousins, and share your family history. In this book, you'll find • Evernote tips and strategies specifically for genealogy researchers, with real-life examples • Step-by-step instructions for managing different types of genealogy information, from research notes to document images to web clippings • Tricks for using Evernote to speed up research tasks, including transcription and research logs • Suggestions to search-optimize your Evernote data so your information is easy to find • Ideas for enhancing Evernote with external apps • Tips to protect your data and troubleshoot common issues • Worksheets to help you organize your notebooks and stacksWhether you're an Evernote newbie or dedicated user, How to Use Evernote for Genealogy will change your research life by showing you how this free tool can make you a better, more efficient genealogist. COMPUTERS,Business & Productivity Software,General

Building Intelligent Cloud Applications Serverless computing is radically changing the way we build and deploy applications. With cloud providers running servers and managing machine resources, companies now can focus solely on the application’s business logic and functionality. This hands-on book shows experienced programmers how to build and deploy scalable machine learning and deep learning models using serverless architectures with Microsoft Azure. You’ll learn step-by-step how to code machine learning into your projects using Python and pretrained models that include tools such as image recognition, speech recognition, and classification. You’ll also examine issues around deployment and continuous delivery, including scaling, security, and monitoring. This book is divided into three parts with application examples woven throughout: Cloud-based development: Learn the basics of serverless computing with machine learning, Functions-as-a-Service (FaaS), and the use of APIs Adding intelligence: Create serverless applications using Azure Functions; learn how to use prebuilt machine learning and deep learning models Deployment and continuous delivery: Get up to speed with Azure Kubernetes Service, Azure Security Center, and Azure Monitoring COMPUTERS,Business & Productivity Software,General

QuickBooks 2020 For Dummies The perennial bestseller—now in a new edition QuickBooks allows small businesses to manage their own accounting and financial management tasks—without needing to hire expensive financial professionals. This perennial bestseller is here to show you step by step how to build the perfect budget, simplify tax return preparation, manage inventory, track job costs, generate statement and financial reports, and every other accounting-related task that crosses your desk. Written by CPA Stephen L. Nelson, it shows you how to get the most out of the software that helps over six million small businesses manage their finances. Handle your financial and business management tasks more effectively Get the most out of QuickBooks’ features Create invoices and memos with ease Pay bills, prepare payroll, and record sales receipts If you use QuickBooks at work—or want to implement it in 2020—this book has you covered. COMPUTERS,Business & Productivity Software,General

Salesforce Lightning Platform Enterprise Architecture A comprehensive guide filled with best practices and tailor-made examples - a must-read for all Lightning Platform architects! Key Features Use the Lightning Platform to build integrated, scalable, and robust apps focused on enterprise-level customer demands Use the Lightning Component framework to deliver modern and responsive user experiences targeting multiple devices through Lightning Experience and Salesforce Mobile Extend your application with access to external services and AI Book Description Salesforce Lightning provides a secure and scalable platform to build, deploy, customize, and upgrade applications. This book will take you through the architecture of building an application on the Lightning platform to help you understand its features and best practices, and ensure that your app keeps up with your customers' increasing needs as well as the innovations on the platform. This book guides you in working with the popular aPaaS offering from Salesforce, the Lightning Platform. You'll see how to build and ship enterprise-grade apps that not only leverage the platform's many productivity features, but also prepare your app to harness its extensibility and customization capabilities. You'll even get to grips with advanced application architectural design patterns such as Separation of Concerns, Unit Testing and Dependency Integration. You will learn to use Apex and JavaScript with Lightning Web Components, Platform Events, among others, with the help of a sample app illustrating patterns that will ensure your own applications endure and evolve with the platform. Finally, you will become familiar with using Salesforce DX to develop, publish, and monitor a sample app and experience standard application life cycle processes along with tools such as Jenkins to implement CI/CD. By the end of this book, you will have learned how to develop effective business apps and be ready to explore innovative ways to meet customer demands. What you will learn Create and deploy AppExchange packages and manage upgrades Understand Enterprise Application Architecture patterns Customize mobile and desktop user experience with Lightning Web Components Manage large data volumes with asynchronous processing and big data strategies Implement Source Control and Continuous Integration Add AI to your application with Einstein Use Lightning External Services to integrate external code and data with your Lightning Application Who this book is for This book is for Lightning platform developers who want to discover the true potential of the platform to develop complex scalable applications for use in enterprise businesses. COMPUTERS,Business & Productivity Software,General

QuickBooks 2020 All-in-One For Dummies The quickest way to do the books for small business owners and managers No one looks forward to doing the finances: that’s why QuickBooks 2020 All-in-One For Dummies is on hand to help get it over with as quickly and painlessly as possible. This comprehensive one-stop reference combines 8 mini-books in one, all written in plain and simple language that makes it easy for even the most accounts-averse to get the most out of the latest version of the QuickBooks software and save time. Written and revised by financial expert Stephen Nelson, the latest version of this invaluable guide takes readers step-by-step through every aspect of small business accounting procedures, including understanding the fundamentals of double-entry bookkeeping, setting up and administering the QuickBooks system, and carrying out complex tasks such as ratio analysis and capital budgeting. Write a business plan and create a forecast Learn how to use profit-volume-cost analysis tools Prepare financial statements and reports Protect your financial data Time is money—get this time-saving resource today and start reaping the rewards! COMPUTERS,Business & Productivity Software,General

Hands-On Edge Analytics with Azure IoT Design, secure, and protect the privacy of edge analytics applications using platforms and tools such as Microsoft's Azure IoT Edge, MicroPython, and Open Source Computer Vision (OpenCV) Key Features Become well-versed with best practices for implementing automated analytical computations Discover real-world examples to extend cloud intelligence Develop your skills by understanding edge analytics and applying it to research activities Book Description Edge analytics has gained attention as the IoT model for connected devices rises in popularity. This guide will give you insights into edge analytics as a data analysis model, and help you understand why it's gaining momentum. You'll begin with the key concepts and components used in an edge analytics app. Moving ahead, you'll delve into communication protocols to understand how sensors send their data to computers or microcontrollers. Next, the book will demonstrate how to design modern edge analytics apps that take advantage of the processing power of modern single-board computers and microcontrollers. Later, you'll explore Microsoft Azure IoT Edge, MicroPython, and the OpenCV visual recognition library. As you progress, you'll cover techniques for processing AI functionalities from the server side to the sensory side of IoT. You'll even get hands-on with designing a smart doorbell system using the technologies you've learned. To remove vulnerabilities in the overall edge analytics architecture, you'll discover ways to overcome security and privacy challenges. Finally, you'll use tools to audit and perform real-time monitoring of incoming data and generate alerts for the infrastructure. By the end of this book, you'll have learned how to use edge analytics programming techniques and be able to implement automated analytical computations. What you will learn Discover the key concepts and architectures used with edge analytics Understand how to use long-distance communication protocols for edge analytics Deploy Microsoft Azure IoT Edge to a Raspberry Pi Create Node-RED dashboards with MQTT and Text to Speech (TTS) Use MicroPython for developing edge analytics apps Explore various machine learning techniques and discover how machine learning is related to edge analytics Use camera and vision recognition algorithms on the sensory side to design an edge analytics app Monitor and audit edge analytics apps Who this book is for If you are a data analyst, data architect, or data scientist who is interested in learning and practicing advanced automated analytical computations, then this book is for you. You will also find this book useful if you're looking to learn edge analytics from scratch. Basic knowledge of data analytics concepts is assumed to get the most out of this book. COMPUTERS,Business & Productivity Software,General

Robotic Process Automation Projects Learn RPA by building business solutions such as ERP and CRM automation, software robots, and intelligent process automation from scratch Key Features Use popular RPA tools Automation Anywhere A2019 and UiPath, for real-world task automation Build automation solutions for domains such as System Administration, Finance, HR, Supply Chain, and Customer Relations Extend your RPA capabilities by implementing Intelligent process automation with APIs and AI Book Description Robotic Process automation helps businesses to automate monotonous tasks that can be performed by machines. This project-based guide will help you progress through easy to more advanced RPA projects. You'll learn the principles of RPA and how to architect solutions to meet the demands of business automation, along with exploring the most popular RPA tools - UiPath and Automation Anywhere. In the first part, you'll learn how to use UiPath by building a simple helpdesk ticket system. You'll then automate CRM systems by integrating Excel data with UiPath. After this, the book will guide you through building an AI-based social media moderator using Google Cloud Vision API. In the second part, you'll learn about Automation Anywhere's latest Cloud RPA platform (A2019) by creating projects such as an automated ERP administration system, an AI bot for order and invoice processing, and an automated emergency notification system for employees. Later, you'll get hands-on with advanced RPA tasks such as invoking APIs, before covering complex concepts such as Artificial Intelligence (AI) and machine learning in automation to take your understanding of RPA to the next level. By the end of the book, you'll have a solid foundation in RPA with experience in building real-world projects. What you will learn Explore RPA principles, techniques, and tools using an example-driven approach Understand the basics of UiPath by building a helpdesk ticket generation system Automate read and write operations from Excel in a CRM system using UiPath Build an AI-based social media moderator platform using Google Cloud Vision API with UiPath Explore how to use Automation Anywhere by building a simple sales order processing system Build an automated employee emergency reporting system using Automation Anywhere Test your knowledge of building an automated workflow through fun exercises Who this book is for This RPA book is for enterprise application developers, software developers, business analysts, or any professional who wants to implement RPA across various domains of the business. The book assumes some understanding of enterprise systems. Computer programming experience will also be beneficial. COMPUTERS,Business & Productivity Software,General

Angular for Enterprise-Ready Web Applications Revised and updated second edition of the bestselling hands-on guide to building enterprise-ready web apps using an evergreen Angular platform Key Features Updated examples, projects, and a new overview of tools – including NgRX and Ivy, automated testing, and Firebase authentication New chapter summarizing history of web frameworks and Angular version updates All-new RESTful API implementation leveraging the MEAN stack with MongoDB, Express.js, Angular and Node.js Book Description This second edition of Angular for Enterprise-Ready Web Applications is updated with in-depth coverage of the evergreen Angular platform. You'll start by mastering Angular programming fundamentals. Using the Kanban method and GitHub tools, you'll build great-looking apps with Angular Material and also leverage reactive programming patterns with RxJS, discover the flux pattern with NgRx, become familiar with automated testing, utilize continuous integration using CircleCI, and deploy your app to the cloud using Vercel Now and GCloud. You will then learn how to design and develop line-of-business apps using router-first architecture with observable data anchors, demonstrated through oft-used recipes like master/detail views, and data tables with pagination and forms. Next, you'll discover robust authentication and authorization design demonstrated via integration with Firebase, API documentation using Swagger, and API implementation using the MEAN stack. Finally, you will learn about DevOps using Docker, build a highly available cloud infrastructure on AWS, capture user behavior with Google Analytics, and perform load testing. By the end of the book, you'll be familiar with the entire gamut of modern web development and full-stack architecture, learning patterns and practices to be successful as an individual developer on the web or as a team in the enterprise. What you will learn Adopt a minimalist, value-first approach to delivering web apps Master Angular development fundamentals, RxJS, CLI tools, GitHub, and Docker Discover the flux pattern and NgRx Implement a RESTful APIs using Node.js, Express.js, and MongoDB Create secure and efficient web apps for any cloud provider or your own servers Deploy your app on highly available cloud infrastructure using DevOps, CircleCI, and AWS Who this book is for This book is for developers who want to confidently deliver high-quality and production-grade Angular apps from design to deployment. Developers that have prior experience in writing a RESTful APIs will also benefit, as well as developers who will gain greater awareness of how they fit into the larger picture of delivering a web application. Prior experience with RESTful APIs is desired. COMPUTERS,Business & Productivity Software,General

Microsoft Excel 2010 On Demand, Portable Documents What you need, when you need it! Need answers quickly? Microsoft Excel 2010 on Demand provides those answers in a visual step-by-step format. We will show you exactly what to do through lots of full color illustrations and easy-to-follow instructions. Includes Workshops MCAS Exam Prep More than 500 Essential Excel Tasks Inside the Book • Create workbooks more efficiently using the improved Ribbon interface • Use data-analysis tools and techniques for better decision making • Use organizing, processing, and presenting tools to create and analyze data • Integrate data from external sources and add hyperlinks • Use conditional formatting and Sparklines to visualize results • Add impact to your data with PivotTable and PivotChart reports • Organize information and add impact with clip art, SmartArt diagrams, tables, and charts • Use SharePoint to collaborate and share documents • Use the Excel Web App to view and edit documents in a browser • Prepare for the Microsoft Certified Application Specialist (MCAS) exam Bonus Online Content Register your book at queondemand.com to gain access to: • Workshops and related files • Keyboard shortcuts COMPUTERS,Business & Productivity Software,Office Suites

Charts and Graphs Using Excel 2010, it's possible to create breathtaking charts, graphs, and other data visualizations - and communicate even the most complex data more effectively than ever before. In Charts and Graphs, one of the world's leading Excel experts show exactly how to make the most of Excel 2010's unprecedented visual features. Bill Jelen ("MrExcel") explains exactly when and how to use each type of Excel chart, then walks through creating superb visuals and customizing them with themes, colors, and effects. Jelen shows how to craft charts that illuminate trends, differences, and relationships; how to create stock analysis charts; how to use Excel's flexible PivotCharts; and even how to present data on maps with Microsoft MapPoint. You will discover how to make the most of Excel 2010's new Sparklines and other in-cell visualizations; how to incorporate additional images and shapes with SmartArt; how to export charts for use outside of Excel; and how to generate dynamic, customized charts automatically with Excel VBA. There's even a full chapter on assessing the truth of charts created in Excel - and recognizing when someone's trying to lie to you! This book is part of the new MrExcel Library series. Everything Excel users need to know to communicate visually - from trend analysis to stock charting, geographical mapping to Excel 2010's new In-Cell Data Bars and Sparklines From basic through leading-edge techniques - including the automatic generation of custom charts with VBA Part of the brand-new MrExcel Library series, edited by Excel legend Bill Jelen COMPUTERS,Business & Productivity Software,Office Suites

Pivot Table Data Crunching PivotTables may be Excel's most powerful feature, but Microsoft has estimated that only 15% of Excel users take advantage of them. That's because PivotTables (and their companion feature, PivotCharts) have a reputation for being difficult to learn. Not any more! In this book, Excel legends Bill Jelen ("MrExcel") and Michael Alexander teach PivotTables and PivotCharts step-by-step, using realistic business scenarios that any Excel user can intuitively understand. Jelen and Alexander go far beyond merely explaining PivotTables and PivotCharts: they present practical "recipes" for solving a wide range of business problems. Drawing on more than 30 combined years of Excel experience, they provide tips and tricks you won't find anywhere else, and show exactly how to sidestep common mistakes. Coverage includes: " Creating PivotTables, customizing them, and changing the way you view them " Performing calculations within PivotTables " Using PivotCharts and other visualizations " Analyzing multiple data sources with PivotTables " Sharing PivotTables with others " Working with and analyzing OLAP data " Making the most of Excel 2010's powerful new PowerPivot feature " Using Excel 2010's Slicer to dynamically filter PivotTables " Enhancing PivotTables with macros and VBA code This book is part of the new MrExcel Library series, edited by Bill Jelen, world-renowned Excel expert and host of the enormously popular Excel help site, MrExcel.com. Teaches PivotTables, PivotCharts, and Excel 2010's new PowerPivot feature through real-world scenarios that make intuitive sense to users at all levels Includes proven PivotTable recipes for instant on-the-job results Helps Excel users avoid common pitfalls and mistakes Part of the brand-new MrExcel Library series, edited by Excel legend Bill Jelen COMPUTERS,Business & Productivity Software,Office Suites

Office 2016 All-in-One For Dummies The fast and easy way to get things done with Office Perplexed by PowerPoint? Looking to excel at Excel? From Access to Word—and every application in between—this all-encompassing guide provides plain-English guidance on mastering the entire Microsoft Office suite. Through easy-to-follow instruction, you'll quickly get up and running with Excel, Word, PowerPoint, Outlook, Access, Publisher, Charts and Graphics, OneNote, and more—and make your work and home life easier, more productive, and more streamlined. Microsoft Office is the leading productivity tool in the world. From word processing to business communication to data crunching, it requires a lot of knowledge to operate it—let alone master it. Luckily, Office 2016 All-in-One For Dummies is here to deliver the breadth of information you need to complete basic tasks and drill down into Office's advanced features. Create customized documents and add graphic elements, proofing, and citations in Word Build a worksheet, create formulas, and perform basic data analysis in Excel Create a notebook and organize your thoughts in Notes Manage messages, tasks, contacts, and calendars in Outlook Clocking in at over 800 pages, Office 2016 All-in-One For Dummies will be the singular Microsoft Office resource you'll turn to again and again. COMPUTERS,Business & Productivity Software,Office Suites

Office 2016 Simplified Start learning the latest in Office Office Simplified is the quick, easy, full-color guide to the new features and tools of the latest version of Office. With a clear, highly visual, introductory style of instruction, this book gives you step-by-step directions alongside illustrative screen shots to help you learn Microsoft's bestselling productivity software. You'll take a tour through all Office applications, and learn how the new tools can make your workday easier. The simplified approach eliminates unnecessary information, focusing instead on the essentials you need to know to get things done. Organized for easy navigation, this helpful guide is designed to be used both as a start-to-finish tutorial and as a handy desk reference when you run into unfamiliar territory. Whether you're upgrading from a previous version or using the Office suite of applications for the first time, this book has you covered every step of the way. You'll find the answers you need, new tools you can use, and the step-by-step guidance that helps you get it right on the first try. Get acquainted with the Office workflow Walk through Word, Excel, PowerPoint, Outlook, and Publisher Follow along with practical examples to tackle dozens of tasks Compose documents, create spreadsheets, organize your email, and more This book provides the ideal rundown of Microsoft Office's full feature set and capabilities. Even experienced users may learn something they never realized they were missing. If you need to get things done with minimal interruption to your workflow, Office Simplified will get you up to speed quickly and easily. COMPUTERS,Business & Productivity Software,Office Suites

Teach Yourself VISUALLY Office 2016 Quickly and efficiently learn the latest version of Office Are you a visual learner who wants to spend more time working in Microsoft Office than trying to figure out how the programs actually work? Teach Yourself Visually Office offers you a straightforward, visual approach to making your work life more efficient and productive using the latest version of the Microsoft Office suite. Featuring visually rich tutorials and step-by-step instructions that will help you make the most of this power-packed suite of office productivity tools, it covers everything you need to compute, document, graph, chart, present, and organize your way to success in the workplace—from the most basic to the most advanced. The Microsoft Office suite can be intimidating to the uninitiated, but it doesn't have to be. Through a series of easy-to-follow, full-color two-page tutorials, you'll quickly get up and running on working in Word, excelling at Excel, powering through PowerPoint, keeping in touch on Outlook, managing data in Access, and propelling your way through Publisher like a pro! Highly visual tutorials and step-by-step screenshots make lessons easy to follow and understand Helps you grasp the basic functions of Microsoft Office—and beyond Walks you through Microsoft Office's new features Demonstrates how to use the Microsoft Office suite to make your work life more streamlined and effective Whether you're looking to discover what's new in the latest release of Microsoft Office or don't know Access from Word, this visual guide makes learning easy! COMPUTERS,Business & Productivity Software,Office Suites

Excel 2016 VBA and Macros (includes Content Update Program) MASTER CORE EXCEL 2016 TOOLS FOR BUILDING POWERFUL, RELIABLE SPREADSHEETS! Use this guide to automate virtually any routine task: save yourself hours, days, maybe even weeks! Make Excel do things you thought were impossible, discover macro techniques you won’t find anywhere else, and create automated reports that are amazingly powerful. Bill Jelen and Tracy Syrstad help you instantly visualize information, so you can act on it… capture data from anywhere, and use it anywhere… automate Excel 2016’s best new features. You’ll find simple, step-by-step instructions, real-world case studies, and 50 workbooks packed with bonus examples, macros, and solutions–straight from MrExcel! Get started fast with Excel macro development Work efficiently with ranges, cells, and formulas Build super-fast applications with arrays Automate Excel’s new pivot table enhancements Collect user data with custom dialogs Make your macros more reliable and resilient Pull data from the Internet with web queries Use advanced classes, collections, and custom functions Build sophisticated business analysis solutions Read and write to Access or SQL Server databases Control other Office programs, and Windows itself Write code that also works on older Excel versions Start writing Office Store-style Excel Apps About MrExcel Library Every book in the MrExcel Library pinpoints a specific set of crucial Excel tasks and presents focused skills and examples for performing them rapidly and effectively. Selected by Bill Jelen, Microsoft Excel MVP and mastermind behind the leading Excel solutions website MrExcel.com, these books will Dramatically increase your productivity–saving you 50 hours a year or more Present proven, creative strategies for solving real-world problems Show you how to get great results, no matter how much data you have Help you avoid critical mistakes that even experienced users make This book is part of Que’s Content Update Program. As Microsoft updates features of Excel, sections of this book will be updated or new sections will be added to match the updates to the software. See inside for details. COMPUTERS,Business & Productivity Software,Office Suites

Microsoft Visio 2016 Step By Step This is learning made easy. Get more done quickly with Visio 2016. Jump in wherever you need answers--brisk lessons and colorful screenshots show you exactly what to do, step by step. Get results faster with starter diagrams Diagram processes, organisations, networks, and datacenters Add styles, colors, and themes Enhance diagrams with data-driven visualisations Link to external data sources, websites, and documents Add structure to diagrams with containers, lists, and callouts Validate flowchart, swimlane, and BPMN diagrams Collaborate and publish with Visio Services and Microsoft SharePoint 2016 Look up just the tasks and lessons you need The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Business & Productivity Software,Office Suites

Microsoft Word 2016 Step By Step The quick way to learn Microsoft Word 2016! This is learning made easy. Get more done quickly with Word 2016. Jump in wherever you need answers--brisk lessons and colorful screenshots show you exactly what to do, step by step. Get easy-to-follow guidance from a certified Microsoft Office Specialist Master Learn and practice new skills while working with sample content, or look up specific procedures Create visually appealing documents for school, business, community, or personal purposes Use built-in tools to capture and edit graphics Present data in tables, diagrams, and charts Track and compile reference materials Manage document collaboration and review Fix privacy, accessibility, and compatibility issues Supercharge your efficiency by creating custom styles, themes, and templates COMPUTERS,Business & Productivity Software,Office Suites

Microsoft OneNote Step by Step This is learning made easy. Get productive fast with OneNote and jump in wherever you need answers. Brisk lessons and colourful screenshots show you exactly what to do, step by step-and practice files help you build your skills. Access local and online OneNote notebooks from any device Create notes that include handwriting, drawings, screen clips, audio clips, video clips, and structured equations Revise, reorganise, flag, format, search, and share your notes Customise OneNote for the way you like to work Get more done by integrating OneNote with Microsoft Word, Excel, and Outlook Share notes by using email, Microsoft OneDrive, and SharePoint Look up just the tasks and lessons you need The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Business & Productivity Software,Office Suites

Exam Ref 70-347 Enabling Office 365 Services Prepare for Microsoft Exam 70-347--and help demonstrate your real-world mastery of the skills needed to help securely and efficiently provide Microsoft Office 365 services in any environment. Designed for experienced IT pros ready to advance their status, Exam Ref focuses on the critical-thinking and decision-making acumen needed for success at the MCSA level. Focus on the expertise measured by these objectives: Manage clients and end-user devices Provision Microsoft SharePoint Online site collections Configure Microsoft Exchange Online and Skype for Business for end users Plan for Exchange Online and Skype for Business This Microsoft Exam Ref: Organizes its coverage by exam objectives Features strategic, what-if scenarios to challenge you Provides exam preparation tips written by a top trainer, consultant, and sysadmin Assumes you have experience with the Office 365 Admin Center and an understanding of Exchange Online, Skype for Business, SharePoint Online, Office 365 ProPlus, and Microsoft Azure Active Directory COMPUTERS,Business & Productivity Software,Office Suites

Office 365 For Dummies Everything you need to get productive in the Cloud with Office 365 With 70 million users worldwide, Microsoft Office 365 combines the familiar Office desktop suite with cloud-based versions of Microsoft’s next-generation communications and collaboration services. It offers many benefits including security, reliability, compatibility with other products, over-the-air updates in the cloud that don't require anything from the user, single sign on for access to everything right away, and so much more. Office 365 For Dummies offers a basic overview of cloud computing and goes on to cover Microsoft cloud solutions and the Office 365 product in a language you can understand. This includes an introduction to each component which leads into topics around using each feature in each application. Get up to speed on instant messaging Use audio, video, and web conferencing Get seamless access to the Office suite with Office Web apps Access information anywhere, anytime Office 365 is the key to office productivity — and now you can put it to use for you! COMPUTERS,Business & Productivity Software,Office Suites

Microsoft Excel 2019 Inside Out Conquer Microsoft Excel 2019–from the inside out! Dive into Microsoft Excel 2019–and really put your spreadsheet expertise to work. This supremely organized reference packs hundreds of timesaving solutions, tips, and workarounds–all you need to make the most of Excel’s most powerful tools for analyzing data and making better decisions. Renowned Excel expert Bill Jelen offers a complete tour of Excel 2019 and Excel in Office 365, from efficient interface customizations to advanced analysis, visualizations, and dashboards. Discover how experts tackle today’s key tasks–and challenge yourself to new levels of mastery. Enter formulas more efficiently, and fully control operators and dates Master the most widely-used functions in Excel Integrate external data from the web and other sources Easily transform complex datasets with Power Query Quickly summarize millions of records with Pivot Tables Perform ad hoc analyses with slicers and other filters Create advanced data mashups with Power Pivot Solve complex problems with What-If, Scenario Manager, Goal Seek, and Solver Automate repetitive tasks by editing recorded VBA code Demystify data with conditional formatting and other visualization techniques Use the newest maps, charts, and data types in Excel Show geographical changes over time with animated 3D maps Use dynamic array functions: SORT, FILTER, UNIQUE, SORTBY and SEQUENCE Find insights using Excel’s new artificial intelligence Collaborate via Excel 2019’s breakthrough CoAuthoring tools Publish Power BI Desktop dashboards based on Excel data COMPUTERS,Business & Productivity Software,Office Suites

Office 365 All-in-One For Dummies The deepest reference on Microsoft’s productivity service Office 365 offers the same productivity power as past versions of Microsoft Office along with tools designed to boost collaboration in the workplace and instant access to the latest Office updates without buying a whole new software package. It’s an ideal solution for both the office and home use. The author of the bestselling Office All-in-One For Dummies shares his advice on how to navigate the nuts and bolts of getting things done with Office 365. Look inside for step-by-step instructions on Excel, Outlook, Word, PowerPoint, Access, and OneNote along with a dive into the cloud services that come with Office 365. Access Office 365 Make sense of common Office tasks Use Excel, Word, outlook, PowerPoint and more Take advantage of 365 online services If you’re a home or business user interested in having a complete reference on the suite, this book has you covered. COMPUTERS,Business & Productivity Software,Office Suites

Learn Microsoft Office 2019 Get to grips with the complete range of Office 2019 applications, explore solutions to common challenges, and discover best practices for working productively Key Features Explore MS Office to enhance productivity and boost your professional development Get up and running with the new and improved features in Microsoft Office 2019 Discover how to overcome common challenges when working with Office 2019 applications Book Description Learn Microsoft Office 2019 provides a comprehensive introduction to the latest versions of Microsoft Word, Excel, PowerPoint, Access, and Outlook. With the help of illustrated explanations, this Microsoft Office book will take you through the updated Office 2019 applications and guide you through implementing them using practical examples. You'll start by exploring the Word 2019 interface and creating professional Word documents using elements such as citations and cover pages, tracking changes, and performing mail merge. You'll then learn how to create impressive PowerPoint presentations and advance to performing calculations and setting up workbooks in Excel 2019, along with discovering its data analysis features. Later chapters will focus on Access 2019, assisting you in everything from organizing a database to constructing advanced queries. You'll then get up to speed with Outlook, covering how to create and manage tasks, as well as how to handle your mail and contacts effortlessly. Finally, you'll find solutions to commonly encountered issues and best practices for streamlining various workplace tasks. By the end of this book, you'll have learned the essentials of Office business apps and be ready to work with them to boost your productivity. What you will learn Use PowerPoint 2019 effectively to create engaging presentations Gain working knowledge of Excel formulas and functions Collaborate using Word 2019 tools, and create and format tables and professional documents Organize emails, calendars, meetings, contacts, and tasks with Outlook 2019 Store information for reference, reporting, and analysis using Access 2019 Discover new functionalities such as Translator, Read Aloud, Scalable Vector Graphics (SVG), and data analysis tools that are useful for working professionals Who this book is for Whether you're just getting started or have used Microsoft Office before and are looking to develop your MS Office skills further, this book will help you to make the most of the different Office applications. Familiarity with the Office 2019 suite will be useful, but not mandatory. COMPUTERS,Business & Productivity Software,Office Suites

PowerPoint 2010 Bible Master PowerPoint and improve your presentation skills-with one book! It's no longer enough to have slide after slide of text, bullets, and charts. It's not even enough to have good speaking skills if your PowerPoint slides bore your audience. Get the very most out of all that PowerPoint 2010 has to offer while also learning priceless tips and techniques for making good presentations in this new PowerPoint 2010 Bible. Well-known PowerPoint expert and author Faithe Wempen provides formatting tips; shows you how to work with drawings, tables, and SmartArt; introduces new collaboration tools; walks you through five special presentation labs; and more. Coverage includes: A First Look at PowerPoint What Makes a Great Presentation? Creating and Saving Presentation Files Creating Slides and Text Boxes Working with Layouts, Themes, and Masters Formatting Paragraphs and Text Boxes Correcting and Improving Text Creating and Formatting Tables Drawing and Formatting Objects Creating SmartArt Diagrams Using and Organizing Clip Art Working with Photographic Images Working with Charts Incorporating Content from Other Programs Adding Sound Effects, Music, and Soundtracks Incorporating Motion Video Creating Animation Effects and Transitions Creating Support Materials Preparing for a Live Presentation Designing User-Interactive or Self-Running Presentations Preparing a Presentation for Mass Distribution Sharing and Collaborating Customizing PowerPoint Presenting Content Without Bulleted Lists Adding Sound and Movement to a Presentation Creating a Menu-Based Navigation System Creating a Classroom Game It's the book you need to succeed with PowerPoint 2010 and your next live presentation! COMPUTERS,Business & Productivity Software,Presentations

PowerPoint 2013 Bible Master PowerPoint and improve your presentation skills with one book! In today's business climate, you need to know PowerPoint inside and out, and that's not all. You also need to be able to make a presentation that makes an impact. From using sophisticated transitions and animation in your PowerPoint presentations to interfacing in person with your audience, this information-packed book helps you succeed. Start creating professional-quality slides that captivate audiences and discover essential tips and techniques for making first-rate presentations, whether you're at a podium or online. Combines both the technical software skills and the soft presentation skills needed to be a successful presenter in today's business climate Explains PowerPoint 2013's features and tools in detail, so you can create impressive,professional presentations for your job Shows you essential formatting techniques, including tables and working with Layouts, Themes, and Masters Covers working with drawings and SmartArt, photos, charts, sounds, music, video, and data from other sources Explains how to prepare for live presentations and also how to create and present material in the Cloud or online, including e-learning For compelling, successful presentations in person, in the cloud, or on the web, start with PowerPoint 2013 Bible. COMPUTERS,Business & Productivity Software,Presentations

PowerPoint 2016 For Dummies Get up and running with PowerPoint 2016 Does using PowerPoint make you want to pull your hair out? PowerPoint 2016 For Dummies takes the pain out of working with PowerPoint, offering plain-English explanations of everything you need to know to get up and running with the latest version of the software. With full-color illustrations and step-by-step instructions, it shows you how to create and edit slides, import data from other applications, collaborate with other users in the Cloud, add charts, clip art, sound, and video—and so much more. PowerPoint is the world's de facto presentation software, used and supported in over 60 countries. The time has never been better to take advantage of the latest software to make killer PowerPoint presentations. From adding special effects to your presentations to working with master slides and templates, this hands-on friendly guide is the fast and easy way to make PowerPoint work for you. Presented in full color to better illustrate the powerful presentation features of the software Helps you take advantage of all of PowerPoint's new features Available in conjunction with the release of the next version of Microsoft Office Written by bestselling author Doug Lowe If you're a new or inexperienced PowerPoint user who spends more time trying to figure out how the software works than you do actually working on your presentations, PowerPoint 2016 For Dummies is just what you need to gain back hours of your work day and make professional, impactful presentations. COMPUTERS,Business & Productivity Software,Presentations

Beyond Bullet Points Beyond Bullet Points, Fourth Edition “Throw away those room-emptying, left-brain slides–and use Atkinson’s book to turn your PowerPoint presentation into an epic.†–Daniel H. Pink, author of Drive and A Whole New Mind Think beyond bullet points–and amplify the impact of your message! Now in its fourth edition, this popular classic illuminates an innovative, step-by-step methodology designed to unlock the amazing visual story waiting to be released from your message. Communications expert Cliff Atkinson shows how to apply classic storytelling tenets and practical, research-based guidelines as you work with Microsoft PowerPoint–for memorable, meaningful, and persuasive visual stories. Change your approach–and transform your results! Find your story thread Create an emotional connection to increase your impact. Cut through the clutter Distill your message and get right to the point. Bring your story to life Storyboard your ideas, find your natural voice, and deliver a compelling presentation! COMPUTERS,Business & Productivity Software,Presentations

PowerPoint 2019 For Dummies Get up and running fast with the PowerPoint 2019 PowerPoint continues to be the go-to tool for business presentations. The software helps anyone who needs to communicate clearly by creating powerful and effective slideshow presentations featuring data in the form of charts, clip art, sound, and video. You can even use it to create presentations for the Web. In PowerPoint 2019 For Dummies, expert Doug Lowe shows you how to use this popular tool to make show-stopping presentations that will get your message across — and your audience excited. Create a slide presentation with special effects Work with master slides and templates Collaborate with other users in the cloud Add charts, clip art, sound, and video Want to learn to use PowerPoint quickly and efficiently? Look no further! COMPUTERS,Business & Productivity Software,Presentations

Odoo 12 Development Essentials Extend your skills with Odoo 12 to build resourceful and open source business applications Key Features Explore Odoo 12 capabilities to develop business applications Program business logic and manipulate data to implement specific business rules in your applications Integrate Python APIs for building customizable and scalable business logic Book Description Odoo is one of the best platforms for open source ERP and CRM. Its latest version, Odoo 12, brings with it new features and updates in Python packages to develop more customizable applications with additional cloud capabilities. The book begins by covering the development essentials for building business applications. You will start your journey by learning how to install and configure Odoo, and then transition from having no specific knowledge of Odoo to being ready for application development. You will develop your first Odoo application and understand topics such as models and views. Odoo 12 Development Essentials will also guide you in using server APIs to add business logic, helping you lay a solid foundation for advanced topics. As you progress through the chapters, you will be equipped to build and customize your applications and explore the new features in Odoo 12, such as cloud integration, to scale your business applications. You will get insights into building business logic and integrating various APIs into your application. By the end of the book, you will be able to build a business application from scratch by using the latest version of Odoo. What you will learn Manage Odoo server instances Create a new Odoo application from scratch using the most frequently used elements Develop new models and use inheritance to extend existing models Use ORM methods in the Odoo server and from external clients Create Kanban views using QWeb effectively Build custom web and website CMS pages Use external APIs to integrate Odoo with external applications Add automated tests and techniques to debug module business logic Who this book is for If you are a developer familiar with Python and MVC design and want to build business applications using Odoo, this book is for you. COMPUTERS,Business & Productivity Software,Presentations

Agile Project Management For Dummies Be flexible and faster with Agile project management As mobile and web technologies continue to evolve rapidly, there is added pressure to develop and implement software projects in weeks instead of months. Agile Project Management For Dummies can make that happen. This is the first book to provide a simple, step-by-step guide to Agile Project Management approaches, tools, and techniques. With the fast pace of mobile and web technology development, software project development must keep pace; Agile Project Management enables developers to complete and implement projects more quickly and this book shows you how. Offers a practical context for understanding and applying Agile techniques, moving from theory into actual practice Explains when to use Agile and how to avoid common pitfalls Written by experts who know how to apply the principles in real-world situations Agile Project Management For Dummies enables you to understand and apply Agile principles for faster, more accurate development. COMPUTERS,Business & Productivity Software,Project Management Tools

50 Top IT Project Management Challenges This book provides a focused and concise summary of 50 challenges facing today’s IT project manager. The authors draw on years of practical experience to outline the challenges and give useful tips and advice on how to deal with them. COMPUTERS,Business & Productivity Software,Project Management Tools

The Concise PRINCE2 Written by a former Chief Examiner for PRINCE2®. This pocket guide is a checklist and handy summary of the fundamental principles and essential themes of PRINCE2®. An ideal revision guide for anyone studying for the PRINCE2® foundation exam. COMPUTERS,Business & Productivity Software,Project Management Tools

Microsoft Project 2010 Step by Step Experience learning made easy-and quickly teach yourself how to manage your projects with Project 2010. With Step By Step, you set the pace-building and practicing the skills you need, just when you need them! Topics include building a project plan and fine-tuning the details; scheduling tasks, assigning resources, and managing dependencies; monitoring progress and costs; keeping projects on track; communicating project data through Gantt charts and other views. COMPUTERS,Business & Productivity Software,Project Management Tools

Agile Governance and Audit This title bridges the gap between auditing requirements and Agile methodologies. It provides an overview of Agile for auditors and other risk professionals who have not encountered the approach before. The book also tells Agile teams what auditors and risk professionals need, and the questions they are likely to ask. COMPUTERS,Business & Productivity Software,Project Management Tools

Microsoft Project 2016 Step by Step The quick way to learn Microsoft Project 2016! This is learning made easy. Get more done quickly with Project 2016. Jump in wherever you need answers–brisk lessons and colorful screenshots show you exactly what to do, step by step. Quickly start a new plan, build task lists, and assign resources Share your plan and track your progress Capture and fine-tune work and cost details Use Gantt charts and other views and reports to visualize project schedules Share resources across multiple plans and consolidate projects Master project management best practices while you learn Project Look up just the tasks and lessons you need COMPUTERS,Business & Productivity Software,Project Management Tools

Microsoft Project 2019 For Dummies Keep projects on track Microsoft Project 2019 is a powerhouse project management, portfolio management, and resource management tool. Whether you’re a full-time project manager or manage projects as part of a larger set of duties, Microsoft Project 2019 For Dummies will get you thinking and operating at the level of a project management guru. Written by a noted project management pro, this book covers the ins and outs of Microsoft Project. Throughout the book, you’ll find project management best practices and tips for keeping any project on schedule and under budget. Reference the full set of Microsoft Project 2019 features Learn to think like a project management professional Get into the nuts and bolts of Project for better productivity Create a task schedule that keeps a project moving Identify the golden rules that keep projects on track With Microsoft Project 2019 For Dummies, you’ll soon get a grip on all the powerful features of this popular project management software. No matter your level of training or experience, this book will show you how improve your project management with Microsoft Project 2019. COMPUTERS,Business & Productivity Software,Project Management Tools

Microsoft Project 2019 Step by Step The quick way to learn Microsoft Project 2019! This is learning made easy. Get more done quickly with Microsoft Project 2019. Jump in wherever you need answers–brisk lessons and informative screenshots show you exactly what to do, step by step. Other Project users will want to grab this book as well. Quickly start new plans, build task lists, and assign resources View resource capacity and track progress Capture and fine-tune work and cost details Visualize schedules with Gantt charts and other views and reports Consolidate projects, and share resources across plans Manage modern Agile projects (James Mills, Jr., contributor) Customize Project to maximize your efficiency Leverage improvements to task linking, timelines, and accessibility Master PM best practices while you learn Project Look up just the tasks and lessons you need COMPUTERS,Business & Productivity Software,Project Management Tools

Excel Workbook For Dummies Excel is the most sophisticated spreadsheet program available, making it easy for you to create a variety of analyses and calculations for personal and professional use. However, this program is much more than just an electronic version of an accountant’s green sheet, and mastering even the most basic functions can be a challenge. Excel Workbook For Dummies is specially designed to give you the hands-on experience you need to start using this great program with confidence and efficiency. This guide is packed with hundreds of exercises that walk you through the ins and outs of Excel at your own pace. You’ll have all the tools you need to: Enter spreadsheet data Format, modify, and print your spreadsheet Copy and correct formulas Create date and time formulas Use math, statistical, lookup, and logical functions Chart spreadsheet data Add graphics to the spreadsheet Manage and secure your data Perform what-if analyses Generate pivot tables Publish spreadsheets as Web pages Add hyperlinks to spreadsheets Take advantage of Macros and Visual Basic Editor Included is a bonus CD-ROM full of useful features, including sample files for all exercises in the book, a variety of important Excel tools, worksheets, and templates for financial planning, and a trial version of Crystal Xcelsius to get you started making progress and becoming an Excel expert! Note: CD-ROM/DVD and other supplementary materials are not included as part of eBook file. COMPUTERS,Business & Productivity Software,Spreadsheets

Professional Excel Development This is the eBook version of the printed book. The print version of this title comes with a disc of companion content. As an eBook reader, you have access to these files. See the instruction in back pages of your eBook or by following the steps outlined below. “As Excel applications become more complex and the Windows development platform more powerful, Excel developers need books like this to help them evolve their solutions to the next level of sophistication. Professional Excel Development is a book for developers who want to build powerful, state-of-the-art Excel applications using the latest Microsoft technologies.†—Gabhan Berry, Program Manager, Excel Programmability, Microsoft “The first edition of Professional Excel Development is my most-consulted and most-recommended book on Office development. The second edition expands both the depth and range. It shines because it takes every issue one step further than you expect. The book relies on the authors’ current, real-world experience to cover not only how a feature works, but also the practical implications of using it in professional work.†—Shauna Kelly, Director, Thendara Green “This book illustrates techniques that will result in well-designed, robust, and maintainable Excel-based applications. The authors’ advice comes from decades of solid experience of designing and building applications. The practicality of the methods is well illustrated by the example timesheet application that is developed step-by-step through the book. Every serious Excel developer should read this and learn from it. I did.†— Bill Manville, Application Developer, Bill Manville Associates The Start-to-Finish Guide to Building State-of-the-Art Solutions with Excel 2007 In this book, four world-class Microsoft® Excel developers offer start-to-finish guidance for building powerful, robust, and secure applications with Excel. The authors–three of whom have been honored by Microsoft as Excel Most Valuable Professionals (MVPs)–show how to consistently make the right design decisions and make the most of Excel’s most powerful new features. Using their techniques,you can reduce development costs, time to market, and hassle–and build more effective, successful solutions. Fully updated for Excel 2007, this book starts where other books on Excel programming leave off. Through a hands-on case study project, you’ll discover best practices for planning, architecting, and building Excel applications that are robust, secure, easy to maintain, and highly usable. If you’re a working developer, no other book on Excel programming offers you this much depth, insight, or value. • Design worksheets that will be more useful and reliable • Leverage built-in and application-specific add-ins • Construct applications that behave like independent Windows programs • Make the most of the new Ribbon user interface • Create cross-version applications that work with legacy versions of Excel • Utilize XML within Excel applications • Understand and use Windows API calls • Master VBA error handling, debugging, and performance optimization • Develop applications based on data stored in Access, SQL Server, and other databases • Build powerful visualization solutions with Excel charting engine • Learn how to work with VB.NET and leverage its IDE • Automate Microsoft Excel with VB.NET • Create managed COM add-ins for Microsoft Excel with VB.NET • Develop Excel solutions with Visual Studio Tools for Office (VSTO) • Integrate Excel with Web Services • Deploy applications more securely and efficiently How to access the companion content: 1. On your PC or MAC, open a web browser and go to this URL: www.informit.com/title/9780321508799 Navigate to the Downloads tab and click on the “CD Contents†link. 2. Download the ZIP file (or files) from the web site to your hard drive. 3. Unzip the files and follow the directions for use in the READ ME included in the download. COMPUTERS,Business & Productivity Software,Spreadsheets

Excel 2007 Pocket Guide Moving to Excel 2007 is not a routine upgrade. Microsoft's radical redesign of the application's user interface has led to confusion among many who people who have relied on Excel for years. Our new edition of the Excel 2007 Pocket Guide has been written from the ground up to help newcomers and longtime users alike find their way around without getting lost. With this book in hand, you'll be able to find your favorite Excel tools quickly. It's packed with information to guide beginners through the basics of creating spreadsheets and entering data, while providing advanced users with information on formulas, pivot tables, and more. Inside, you'll find: A visual guide to the new "Ribbon" interface that helps users find familiar tools A section designed to give beginners enough information to dive right in and start creating rich Excel workbooks immediately Quick answers about how to perform specific tasks in Excel, such as working with files, editing data, formatting, summarizing and displaying data Convenient techniques for connecting data across worksheets and projects Help for moving from the basics of spreadsheet construction to more advanced features This edition also includes an extensive reference on commonly used formulas, which reveal at a glance the many possibilities Excel 2007 provides for easy calculation. Tasks in the book are presented as answers to "How do I..." questions -- such as "How do I change the formatting of part of a cell's contents?" -- followed by concise instructions for performing the task. You'll learn ways to customize Excel to fit your needs, and how to share workbooks and collaborate with others. And much more. Don't let Excel 2007 baffle you. Pick up this convenient pocket guide and learn to navigate this redesigned application with ease. COMPUTERS,Business & Productivity Software,Spreadsheets

Integrating Excel and Access In a corporate setting, the Microsoft Office Suite is an invaluable set of applications. One of Offices' biggest advantages is that its applications can work together to share information, produce reports, and so on. The problem is, there isn't much documentation on their cross-usage. Until now. Introducing Integrating Excel and Access, the unique reference that shows you how to combine the strengths of Microsoft Excel with those of Microsoft Access. In particular, the book explains how the powerful analysis tools of Excel can work in concert with the structured storage and more powerful querying of Access. The results that these two applications can produce together are virtually impossible to achieve with one program separately. But the book isn't just limited to Excel and Access. There's also a chapter on SQL Server, as well as one dedicated to integrating with other Microsoft Office applications. In no time, you'll discover how to: Utilize the built in features of Access and Excel to access data Use VBA within Access or Excel to access data Build connection strings using ADO and DAO Automate Excel reports including formatting, functions, and page setup Write complex functions and queries with VBA Write simple and advanced queries with the Access GUI Produce pivot tables and charts with your data With Integrating Excel and Access, you can crunch and visualize data like never before. It's the ideal guide for anyone who uses Microsoft Office to handle data. COMPUTERS,Business & Productivity Software,Spreadsheets

Excel 2010 For Dummies The bestselling Excel book on the market, updated for Excel 2010 As the world's leading spreadsheet application, Excel has a huge user base. The release of Office 2010 brings major changes to Excel, so Excel For Dummies comes to the rescue once more! In the friendly and non-threatening For Dummies style, this popular guide shows beginners how to get up and running with Excel and helps more experienced users get comfortable with new features. Excel is the number one spreadsheet application worldwide, and Excel For Dummies is the number one guide to using it With the major changes in Microsoft Office 2010, Excel has new features and a new interface design; users need help to get up to speed The book includes everything you need to know to perform basic Excel 2010 tasks Covers creating and editing worksheets and charts, formatting cells, entering formulas, inserting graphs, designing database forms, and adding database records Also covers printing, adding hyperlinks to worksheets, saving worksheets as Web pages, adding existing worksheet data to an existing Web page, and much more Whether you're new to Excel or just need to understand the 2010 version, Excel 2010 For Dummies provides what you need to know. COMPUTERS,Business & Productivity Software,Spreadsheets

Excel Data Analysis Advanced techniques for Excel power users Crunch and analyze Excel data the way the professionals do with this clean, uncluttered, visual guide to advanced Excel techniques. Using numerous screenshots and easy-to-follow numbered steps, this book clearly shows you how to perform professional-level modeling, charting, data access, data slicing, and other functions. You'll find super techniques for getting the most out of Excel's statistical and financial functions, Excel PivotTables and PivotCharts, Excel Solver, and more. Provides a clear look at power-using Excel, the world's leading spreadsheet application from Microsoft, and part of the new Microsoft Office 2010 suite Expands your Excel knowledge and helps you use Excel data more efficiently Demonstrates how to retrieve data from databases;; cut, slice, and pivot data using PivotTables; model data and chart data; and use advanced formulas Explores all features and functions in friendly, two-color pages packed with screenshots, numbered steps, and other visual graphics that clearly show you how to accomplish tasks Includes practical examples, tips, and advice to help you get the most out of Excel's features and functions Learn Excel at the highest levels with this practical guide. COMPUTERS,Business & Productivity Software,Spreadsheets

VBA and Macros Use Excel 2010 VBA and macros to automate virtually any routine task, and save yourself hours, days, maybe even weeks. Then learn how to make Excel do things you thought were simply impossible! This book reveals scripting techniques you won’t find anywhere else and shows you how to create automated reports that are amazingly powerful and useful. It helps you instantly visualize information so you can understand and act on it. It also shows you how to capture data from anywhere and use it anywhere, and helps you automate Excel 2010’s most powerful new features. Learning advanced Excel scripting has never been easier. You’ll find simple, step-by-step instructions, real-world examples and case studies, and 50 workbooks packed with bonus examples, macros, and solutions, straight from MrExcel. Work efficiently with ranges, cells, and R1C1-style formulas Build super-fast applications with arrays Customize the Excel 2010 Ribbon to run your macros Write Excel 2010 VBA code that works on older versions of Excel Create custom dialog boxes to collect information from your users Use error handling to make your VBA scripts more resilient Use Web queries to import data from virtually any online source Master advanced techniques such as classes and collections Use Excel VBA to control other Office programs…even control Windows itself, via the Windows API Create add-ins to share or sell your programs About MrExcel Library: Every book in the MrExcel Library pinpoints a specific set of crucial Excel tasks and presents focused skills and examples for performing them rapidly and effectively. Selected by Bill Jelen, Microsoft Excel MVP and mastermind behind the leading Excel solutions website MrExcel.com, these books will Dramatically increase your productivity—saving you 50 hours a year or more Present proven, creative strategies for solving real-world problems Show you how to get great results, no matter how much data you have Help you avoid critical mistakes that even experienced users make COMPUTERS,Business & Productivity Software,Spreadsheets

Head First Excel Do you use Excel for simple lists, but get confused and frustrated when it comes to actually doing something useful with all that data? Stop tearing your hair out: Head First Excel helps you painlessly move from spreadsheet dabbler to savvy user. Whether you're completely new to Excel or an experienced user looking to make the program work better for you, this book will help you incorporate Excel into every aspect of your workflow, from a scratch pad for data-based brainstorming to exploratory analysis with PivotTables, optimizing outcomes with Goal Seek, and presenting your conclusions with sophisticated data visualizations. Organize and clearly present information in a spreadsheet Make calculations across a number of worksheets Change your point of view with sorting, zooming, and filtering Manipulate numerical data to extract and use just what you need Leverage Excel as a grid-based layout program Write formulas for optimal functionality Nest formulas for more complex operations Create sophisticated data visualizations with charts and graphs Use Goal Seek to optimize possible outcomes based on different assumptions Create summaries from large data sets for exploratory data analysis with PivotTables We think your time is too valuable to waste struggling with new concepts. Using the latest research in cognitive science and learning theory to craft a multi-sensory learning experience, Head First Excel uses a visually rich format designed for the way your brain works, rather than a text-heavy approach that will put you to sleep. COMPUTERS,Business & Productivity Software,Spreadsheets

Slaying Excel Dragons This enthusiastic introduction provides support for Excel beginners and focuses on using the program immediately for maximum efficiency. With 1,104 screenshots and explicit information on everything from rows, columns, and cells to subtotaling, sorting, and pivot tables, this guide aims to alleviate the frustrations that come with using the program for the first time. This manual offers strategies for avoiding problems and streamlining efficiency and assists readers from start to finish, turning Excel 2010 novices into experts. COMPUTERS,Business & Productivity Software,Spreadsheets

Microsoft Excel 2010 Digital Classroom The perfect book-and-video training package for Excel 2010! This Excel 2010 book-and-video training package-from the same professional training experts who also create many training materials for Adobe Systems-is like having your own personal instructor guiding you through each lesson, but you work at your own pace! The full-color ebook includes 8 lessons that teach you the new features and quirks of Microsoft Excel 2010. Each lesson includes step-by-step instructions and lesson files, and provides valuable video tutorials that complement what you're learning and clearly demonstrate how to do tasks. This training package takes you well beyond the basics in a series of easy-to-absorb, five-minute lessons. Walks you through 8 lessons, each consisting of easy-to-follow, step-by-step instructions and lesson files in full color that make each task less intimidating Includes all the lesson files from the book and video tutorials that clearly show you how to do tasks and reinforces what you're learning in the book Covers new Excel 2010 features such as Office Web apps that can be accessed from anywhere and a streamlined new Ribbon Additional resources available on companion Web site: www.digitalclassroombooks.com Learn the ins-and-outs of Excel 2010! COMPUTERS,Business & Productivity Software,Spreadsheets

Excel 2010 For Dummies Dig into formulas, functions, and more to build your Excel skills Whether you're a beginner or an Excel veteran, this friendly guide provides the fundamental techniques to help you create, edit, format, and print your own spreadsheets. You'll start from scratch and quickly progress to manipulating data with formulas and using Excel's extensive formatting options to present your information in the most powerful way. Open the book and find: Ways to navigate Excel's Ribbon interface Data entry tips to start your spreadsheet How to build formulas and edit workbooks Formatting steps to follow Printing basics to present your data COMPUTERS,Business & Productivity Software,Spreadsheets

Excel 2013 Pivot Table Data Crunching CRUNCH ANY DATA, FROM ANY SOURCE, QUICKLY AND EASILY, WITH EXCEL 2013 PIVOT TABLES! Use Excel 2013 pivot tables and pivot charts to produce powerful, dynamic reports in minutes instead of hours… understand exactly what’s going on in your business… take control, and stay in control! Even if you’ve never created a pivot table before, this book will help you leverage all their amazing flexibility and analytical power. In just the first seven chapters, you learn how to generate complex pivot reports complete with drill-down capabilities and accompanying charts. Then, you go even further, discovering how to build a comprehensive, dynamic pivot table reporting system for any business task or function. Learning advanced pivot table and pivot chart techniques for Excel 2013 or the newest Office 365 has never been easier. You’ll find simple, step-by-step instructions, real-world case studies, even complete, easy recipes for solving your most common business analysis problems. • Create, customize, and change your pivot tables and pivot charts • Transform gigantic data sets into crystal-clear summary reports • Summarize and analyze data even faster with new Excel 2013 recommended pivot tables • Instantly highlight your most (and least) profitable customers, products, or regions • Quickly filter pivot tables using slicers • Use dynamic dashboards using Power View to see exactly where your business stands right now • Revamp analyses on the fly by simply dragging and dropping fields • Build dynamic self-service reporting systems your entire team can use • Use PowerPivot or the Data Model to create pivot tables from multiple data sources and worksheets • Work with and analyze OLAP data, and much more About MrExcel Library: Every book in the MrExcel Library pinpoints a specific set of crucial Excel tasks and presents focused skills and examples for performing them rapidly and effectively. Selected by Bill Jelen, Microsoft Excel MVP and mastermind behind the leading Excel solutions website MrExcel.com, these books will • Dramatically increase your productivity—saving you 50 hours a year or more • Present proven, creative strategies for solving real-world problems • Show you how to get great results, no matter how much data you have • Help you avoid critical mistakes that even experienced users make CATEGORY: Spreadsheets COVERS: Microsoft Office Excel 2013 COMPUTERS,Business & Productivity Software,Spreadsheets

Excel 2013 VBA and Macros SAVE TIME AND SUPERCHARGE EXCEL 2013 WITH VBA AND MACROS! Use Excel® 2013 VBA and Macros to automate virtually any routine task, and save yourself hours, days, maybe even weeks. Then, learn how to make Excel do things you thought were simply impossible! You’ll discover macro techniques you won’t find anywhere else and learn how to create automated reports that are amazingly powerful and useful. Bill Jelen and Tracy Syrstad show how to instantly visualize information, so you and your colleagues can understand and act on it…how to capture data from anywhere, and use it anywhere…how to automate Excel 2013’s most valuable new features. Mastering advanced Excel macros has never been easier. You’ll find simple, step-by-step instructions, real-world examples and case studies, and 50 workbooks packed with bonus examples, macros, and solutions–straight from MrExcel. • Get started fast with Excel 2013 macro development • Write macros that use Excel 2013 enhancements, including Timelines and the latest pivot table models • Work efficiently with ranges, cells, and R1C1-style formulas • Build super-fast applications with arrays • Write Excel 2013 VBA code that works on older versions of Excel • Create custom dialog boxes to collect information from your users • Use error handling to make your macros more resilient • Use web queries and new web service functions to integrate data from anywhere • Master advanced techniques such as classes, collections, and custom functions • Build sophisticated data mining and business analysis applications • Read and write to both Access and SQL Server databases • Control other Office programs–and even control Windows itself • Start writing Excel Apps similar to those in the Excel App Store About MrExcel Library: Every book in the MrExcel Library pinpoints a specific set of crucial Excel tasks and presents focused skills and examples for performing them rapidly and effectively. Selected by Bill Jelen, Microsoft Excel MVP and mastermind behind the leading Excel solutions website MrExcel.com, these books will • Dramatically increase your productivity–saving you 50 hours a year or more • Present proven, creative strategies for solving real-world problems • Show you how to get great results, no matter how much data you have • Help you avoid critical mistakes that even experienced users make COMPUTERS,Business & Productivity Software,Spreadsheets

Excel 2013 Bible Excel at Excel with the help of this bestselling spreadsheet guide John Walkenbach's name is synonymous with excellence in computer books that decipher the complexities of Microsoft Excel. Known as "Mr. Spreadsheet," Walkenbach shows you how to maximize the power of Excel 2013 while bringing you up to speed on the latest features. This perennial bestseller is fully updated to cover all the new features of Excel 2013, including how to navigate the user interface, take advantage of various file formats, master formulas, analyze data with PivotTables, and more. Whether you're an Excel beginner who is looking to get more savvy or an advanced user looking to become a power user, this latest edition provides you with comprehensive coverage as well as helpful tips, tricks, and techniques that you won't find anywhere else. Shares the invaluable insight of Excel guru and bestselling author "Mr. Spreadsheet" John Walkenbach as he guides you through every aspect of Excel 2013 Provides essential coverage of all the newest features of Excel 2013 Presents material in a clear, concise, logical format that is ideal for all levels of Excel experience Features a website that includes downloadable templates and worksheets from the book Chart your path to fantastic formulas and stellar spreadsheets with Excel 2013 Bible! COMPUTERS,Business & Productivity Software,Spreadsheets

Excel 2013 Charts and Graphs Use Excel 2013’s radically revamped charting and graphing tools to communicate more clearly, powerfully, and quickly… so you drive your message home, and get the decisions and actions you’re looking for! This book reveals data visualization techniques you won’t find anywhere else and shows you how to use Excel 2013 to create designer-quality charts and graphs that stand out from the crowd. It will help you make the most of new features ranging from Power View to Recommended Charts, and instantly share your insights with anyone, anywhere–even on the Web and social networks. Learning advanced Excel techniques has never been easier. You’ll find simple, step-by-step instructions, real-world examples and case studies, and more than a dozen YouTube videos, straight from MrExcel! • Create stunning data visualizations instantly with Excel 2013’s new Recommended Charts • Use charts to instantly reveal trends, differences, and relationships • Map your data with Excel 2013, MapPoint, and the new GeoFlow add-in • Quickly generate combo charts that once required complex, frustrating procedures • Use sparklines to imbue worksheets with more context and insight • Highlight and clarify the meaning of data with DataBars, color scales, icon sets, and other conditional formatting tools • Post charts to Facebook, Twitter, or LinkedIn, directly from Excel • Build stock charts that help you make smarter investments • Solve “non-standard†problems such as noncontiguous data or custom data sequences • Generate new charts automatically with Excel VBA • Uncover visual tricks that people use to lie with Excel About MrExcel Library: Every book in the MrExcel Library pinpoints a specific set of crucial Excel tasks and presents focused skills and examples for performing them rapidly and effectively. Selected by Bill Jelen, Microsoft Excel MVP and mastermind behind the leading Excel solutions website MrExcel.com, these books will: • Dramatically increase your productivity–saving you 50 hours a year or more • Present proven, creative strategies for solving real-world problems • Show you how to get great results, no matter how much data you have • Help you avoid critical mistakes that even experienced users make COMPUTERS,Business & Productivity Software,Spreadsheets

Excel 2013 Formulas Maximize the power of Excel 2013 formulas with this must-have Excel reference John Walkenbach, known as "Mr. Spreadsheet," is a master at deciphering complex technical topics and Excel formulas are no exception. This fully updated book delivers more than 800 pages of Excel 2013 tips, tricks, and techniques for creating formulas that calculate, developing custom worksheet functions with VBA, debugging formulas, and much more. Demonstrates how to use all the latest features in Excel 2013 Shows how to create financial formulas and tap into the power of array formulas Serves as a guide to using various lookup formulas, working with conditional formatting, and developing custom functions Shares proven solutions for handling typical (and not-so-typical) Excel formula challenges Includes links to the "Mr. Spreadsheet" website, which contains all the templates and worksheets used in the book, plus access to John Walkenbach's award-winning Power Utility Pak. From charts to PivotTables and everything in between, Excel 2013 Formulas is your formula for Excel success. COMPUTERS,Business & Productivity Software,Spreadsheets

Excel Dashboards and Reports Learn to use Excel dashboards and reports to better conceptualize data Updated for all the latest features and capabilities of Excel 2013, this go-to resource provides you with in-depth coverage of the individual functions and tools that can be used to create compelling Excel reports. Veteran author Michael Alexander walks you through the most effective ways to present and report data. Featuring a comprehensive review of a wide array of technical and analytical concepts, this essential guide helps you go from reporting data with simple tables full of dull numbers to presenting key information through the use of high-impact, meaningful reports and dashboards that will wow management both visually and substantively. Details how to analyze large amounts of data and report the results in a way that is both visually attractive and effective Describes how to use different perspectives to achieve better visibility into data, as well as how to slice data into various views on the fly Shows how to automate redundant reporting and analysis processes Walks you through creating impressive dashboards, eye-catching visualizations, and real-world What-If analyses Excel Dashboards and Reports, Second Edition is part technical manual, part analytical guidebook, and exactly what you need to become your organization's dashboard dynamo! COMPUTERS,Business & Productivity Software,Spreadsheets

Ctrl+Shift+Enter Mastering Excel Array Formulas Designed with Excel gurus in mind, this handbook outlines how to create formulas that can be used to solve everyday problems with a series of data values that standard Excel formulas cannot or would be too arduous to attempt. Beginning with an introduction to array formulas, this manual examines topics such as how they differ from ordinary formulas, the benefits and drawbacks of their use, functions that can and cannot handle array calculations, and array constants and functions. Among the practical applications surveyed include how to extract data from tables and unique lists, how to get results that match any criteria, and how to utilize various methods for unique counts. This book contains 529 screen shots. COMPUTERS,Business & Productivity Software,Spreadsheets

Microsoft Excel 2010 Data Analysis and Business Modeling Master the business modeling and analysis techniques that help you transform data into bottom-line results. For more than a decade, Wayne Winston has been teaching corporate clients and MBA students the most effective ways to use Excel to solve business problems and make better decisions. Now this award-winning educator shares the best of his expertise in this hands-on, scenario-focused guide—fully updated for Excel 2010! Use Excel to solve real business problems—and sharpen your edge! Model investment risks and returns Analyze your sales team’s effectiveness Create best, worst, and most-likely case scenarios Compare lease vs. buy, and calculate loan terms See how price, advertising, and seasonality affect sales Manage inventory with precision Quantify the value of customer loyalty Calculate your break-even number and ROI Maximize scheduling efficiency Express “home-field advantage†in real numbers Project company growth, predict election results, and more! Plus—introduce yourself to PowerPivot for Excel Your companion web content includes: Downloadable eBook Hundreds of scenario-based practice problems All the book’s sample files—plus customizable templates COMPUTERS,Business & Productivity Software,Spreadsheets

Microsoft Excel 2013 Data Analysis and Business Modeling Master business modeling and analysis techniques with Microsoft Excel 2013, and transform data into bottom-line results. Written by award-winning educator Wayne Winston, this hands-on, scenario-focused guide shows you how to use the latest Excel tools to integrate data from multiple tables—and how to effectively build a relational data source inside an Excel workbook. Solve real business problems with Excel—and sharpen your edge Summarize data with PivotTables and Descriptive Statistics Explore new trends in predictive and prescriptive analytics Use Excel Trend Curves, multiple regression, and exponential smoothing Master advanced Excel functions such as OFFSET and INDIRECT Delve into key financial, statistical, and time functions Make your charts more effective with the Power View tool Tame complex optimization problems with Excel Solver Run Monte Carlo simulations on stock prices and bidding models Apply important modeling tools such as the Inquire add-in COMPUTERS,Business & Productivity Software,Spreadsheets

Dashboarding and Reporting with Power Pivot and Excel Microsoft's revolutionary Power Pivot is a tool that allows users to create and transform data into reports and dashboards in new and much more powerful ways using the most-used analytical tool in the world: Excel. This book, written by a member of Microsoft's Power Pivot team, provides a practical step by step guide on creating a financial dashboard. The book covers in detail how to combine and shape the relevant data, build the dashboard in Excel, providing layout and design tips and tricks, prepare the model to work with fiscal dates, and show values used in many financial reports, including year-to-date, variance-to-target, percentage-of-total, and running totals reports. Accessibly written, this book offers readers a practical, real-world scenario and can be used as a day-to-day reference. Though the guide focuses on Power Pivot for Excel 2010, a chapter that discusses Power View—compatible with Excel 2013— and Power BI is also included. COMPUTERS,Business & Productivity Software,Spreadsheets

Excel VBA 24-Hour Trainer Master VBA automation quickly and easily to get more out of Excel Excel VBA 24-Hour Trainer, 2nd Edition is the quick-start guide to getting more out of Excel, using Visual Basic for Applications. This unique book/video package has been updated with fifteen new advanced video lessons, providing a total of eleven hours of video training and 45 total lessons to teach you the basics and beyond. This self-paced tutorial explains Excel VBA from the ground up, demonstrating with each advancing lesson how you can increase your productivity. Clear, concise, step-by-step instructions are combined with illustrations, code examples, and downloadable workbooks to give you a practical, in-depth learning experience and results that apply to real-world scenarios. This is your comprehensive guide to becoming a true Excel power user, with multimedia instruction and plenty of hands-on practice. Program Excel's newest chart and pivot table object models Manipulate the user interface to customize the look and feel of a project Utilize message boxes, input boxes, and loops to yield customized logical results Interact with and manipulate Word, Access, PowerPoint, and Outlook from Excel If you're ready to get more out of this incredibly functional program, Excel VBA 24-Hour Trainer, 2nd Edition provides the expert instruction and fast, hands-on learning you need. COMPUTERS,Business & Productivity Software,Spreadsheets

Teach Yourself VISUALLY Excel 2016 See your way to Excel spreadsheet stardom with this visual guide If you're always hearing about the cool things Excel can do, here's your chance to see how to do them!Teach Yourself Visually Excel offers you a straightforward visual approach to working with the newest version of the world's leading spreadsheet program. Packed with visually rich tutorials and step-by-step instructions that will help you take your Excel skills to new heights, this friendly and approachable guide will have you creating, editing, and manipulating Excel spreadsheets in no time! Excel can seem daunting, but with Teach Yourself Visually Excel, you'll quickly and painlessly learn how to perform dozens of tasks, including creating spreadsheets and charts, filtering and sorting data, working with PivotTables, and so much more. Covering the latest additions and changes to the newest version of Excel, a series of easy-to-follow, full-color tutorials helps you to excel at working with Excel! Tutorials and step-by-step screenshots make lessons easy to follow and understand Helps you grasp the basic functions of Excel—and beyond Walks you through Excel s new features Clearly demonstrates how to organize, present, analyze, and chart data with Excel Whether you've never used Excel or just need to brush up on its new features, Teach Yourself Visually Excel will be the dog-eared resource you'll turn to again and again. COMPUTERS,Business & Productivity Software,Spreadsheets

Excel 2016 Bible The complete guide to Excel 2016, from Mr. Spreadsheet himself Whether you are just starting out or an Excel novice, the Excel 2016 Bible is your comprehensive, go-to guide for all your Excel 2016 needs. Whether you use Excel at work or at home, you will be guided through the powerful new features and capabilities by expert author and Excel Guru John Walkenbach to take full advantage of what the updated version offers. Learn to incorporate templates, implement formulas, create pivot tables, analyze data, and much more. Navigate this powerful tool for business, home management, technical work, and much more with the only resource you need, Excel 2016 Bible. Create functional spreadsheets that work Master formulas, formatting, pivot tables, and more Get acquainted with Excel 2016's new features and tools Customize downloadable templates and worksheets Whether you need a walkthrough tutorial or an easy-to-navigate desk reference, the Excel 2016 Bible has you covered with complete coverage and clear expert guidance. COMPUTERS,Business & Productivity Software,Spreadsheets

Excel 2016 All-in-One For Dummies Your one-stop guide to all things Excel 2016 Excel 2016 All-in-One For Dummies, the most comprehensive Excel reference on the market, is completely updated to reflect Microsoft's changes in the popular spreadsheet tool. It offers you everything you need to grasp basic Excel functions, such as creating and editing worksheets, setting up formulas, importing data, performing statistical functions, editing macros with Visual Basic—and beyond. In no time, your Excel skills will go from 'meh' to excellent. Written by expert Greg Harvey, who has sold more than 4.5 million copies of his previous books combined and has taught and trained extensively in Microsoft Excel, this all-encompassing guide offers everything you need to get started with Excel. From generating pivot tables and performing financial functions to performing error trapping and building and running macros—and everything in between—this hands-on, friendly guide makes working with Excel easier than ever before. Serves as the ideal reference for solving common questions and Excel pain points quickly and easily Helps to increase productivity and efficiency when working in Excel Fully updated for the new version of Excel Covers basic and more advanced Excel topics If working in Excel occasionally makes you want to scream, this will be the dog-eared, dust-free reference you'll turn to again and again. COMPUTERS,Business & Productivity Software,Spreadsheets

Excel 2016 Formulas Leverage the full power of Excel formulas Excel 2016 Formulas is fully updated to cover all of the tips, tricks, and techniques you need to maximize the power of Excel 2016 through the use of formulas. This comprehensive book explains how to create financial formulas, release the power of array formulas, develop custom worksheet functions with VBA, debug formulas, and much more. Whether you're a beginner, a power user, or somewhere in between this is your essential go-to for the latest on Excel formulas. When conducting simple math or building highly complicated spreadsheets that require formulas up to the task, leveraging the right formula can heighten the accuracy and efficiency of your work, and can improve the speed with which you compile and analyze data. Understanding which formulas to use and knowing how to create a formula when you need to are essential. Access tips, tricks, and techniques that have been fully updated to reflect the latest capabilities of Microsoft Excel Create and use formulas that have the power to transform your Excel experience Leverage supplemental material online, including sample files, templates, and worksheets from the book COMPUTERS,Business & Productivity Software,Spreadsheets

Excel 2016 Power Programming with VBA Maximize your Excel experience with VBA Excel 2016 Power Programming with VBA is fully updated to cover all the latest tools and tricks of Excel 2016. Encompassing an analysis of Excel application development and a complete introduction to Visual Basic for Applications (VBA), this comprehensive book presents all of the techniques you need to develop both large and small Excel applications. Over 800 pages of tips, tricks, and best practices shed light on key topics, such as the Excel interface, file formats, enhanced interactivity with other Office applications, and improved collaboration features. In addition to the procedures, tips, and ideas that will expand your capabilities, this resource provides you with access to over 100 online example Excel workbooks and the Power Utility Pak, found on the Mr. Spreadsheet website. Understanding how to leverage VBA to improve your Excel programming skills can enhance the quality of deliverables that you produce—and can help you take your career to the next level. Explore fully updated content that offers comprehensive coverage through over 900 pages of tips, tricks, and techniques Leverage templates and worksheets that put your new knowledge in action, and reinforce the skills introduced in the text Access online resources, including the Power Utility Pak, that supplement the content Improve your capabilities regarding Excel programming with VBA, unlocking more of your potential in the office Excel 2016 Power Programming with VBA is a fundamental resource for intermediate to advanced users who want to polish their skills regarding spreadsheet applications using VBA. COMPUTERS,Business & Productivity Software,Spreadsheets

Excel Power Pivot & Power Query For Dummies A guide to PowerPivot and Power Query no data cruncher should be without! Want to familiarize yourself with the rich set of Microsoft Excel tools and reporting capabilities available from PowerPivot and Power Query? Look no further! Excel PowerPivot & Power Query For Dummies shows you how this powerful new set of tools can be leveraged to more effectively source and incorporate 'big data' Business Intelligence and Dashboard reports. You'll discover how PowerPivot and Power Query not only allow you to save time and simplify your processes, but also enable you to substantially enhance your data analysis and reporting capabilities. Gone are the days of relatively small amounts of data—today's data environment demands more from business analysts than ever before. Now, with the help of this friendly, hands-on guide, you'll learn to use PowerPivot and Power Query to expand your skill-set from the one-dimensional spreadsheet to new territories, like relational databases, data integration, and multi-dimensional reporting. Demonstrates how Power Query is used to discover, connect to, and import your data Shows you how to use PowerPivot to model data once it's been imported Offers guidance on using these tools to make analyzing data easier Written by a Microsoft MVP in the lighthearted, fun style you've come to expect from the For Dummies brand If you spend your days analyzing data, Excel PowerPivot & Power Query For Dummies will get you up and running with the rich set of Excel tools and reporting capabilities that will make your life—and work—easier. COMPUTERS,Business & Productivity Software,Spreadsheets

Excel 2016 Formulas and Functions (includes Content Update Program) Book + Content Update Program Master core Excel 2016 tools for building powerful, reliable spreadsheets with Excel 2016 Formulas and Functions. Excel expert Paul McFedries shows how to use Excel 2016’s core features to solve problems and get the answers you need. Using real-world examples, McFedries helps you get the absolute most out of features and improvements ranging from AutoFill to Excel’s newest functions. Along the way, you discover the fastest, best ways to handle essential day-to-day tasks ranging from generating account numbers to projecting the impact of inflation. Becoming an Excel expert has never been easier! You’ll find crystal-clear instructions; insider insights; even complete step-by-step projects for building timesheets, projecting cash flow, aging receivables, analyzing defects, and more. • Quickly create powerful spreadsheets with range names and array formulas • Use conditional formatting to instantly reveal anomalies, problems, or opportunities • Analyze your data with standard tables and PivotTables • Use complex criteria to filter data in lists • Understand correlations between data • Perform sophisticated what-if analyses • Use regression to track trends and make forecasts • Build loan, investment, and discount formulas • Validate data, troubleshoot problems, and build more accurate, trustworthy spreadsheets In addition, this book is part of Que’s exciting Content Update Program. As Microsoft updates features of Excel 2016, sections of this book will be updated or new sections will be added to match the updates to the software. The updates will be delivered to you via a FREE Web Edition of this book, which can be accessed with any Internet connection. To learn more, visit www.quepublishing.com/CUP. About MrExcel Library: Every book in the MrExcel Library pinpoints a specific set of crucial Excel tasks and presents focused skills and examples for performing them rapidly and effectively. Selected by Bill Jelen, Microsoft Excel MVP and mastermind behind the leading Excel solutions website MrExcel.com, these books will • Dramatically increase your productivity–saving you 50 hours a year or more • Present proven, creative strategies for solving real-world problems • Show you how to get great results, no matter how much data you have • Help you avoid critical mistakes that even experienced users make COMPUTERS,Business & Productivity Software,Spreadsheets

My Excel 2016 (includes Content Update Program) Book + Content Update Program My Excel 2016 is your must-have companion for getting most out of Excel 2016. This friendly, quick, full-color, 100% practical tutorial walks you through every task you'll want to do with Excel 2016. Get productive fast with Excel 2016’s updated interface Save time and make your data easier to work with Efficiently enter, insert, move, and manage data Use templates to reuse work and get a jumpstart on new projects Format worksheets and charts to make them clearer and more useful Use intuitive sparkline charts that fit in a single cell Build custom formulas using powerful built-in functions Sort, filter, and consolidate data and eliminate duplication Instantly group data and generate subtotals Quickly summarize huge data sets with PivotTables Find, fix, and avoid errors that break spreadsheets or cause inaccuracies Communicate more powerfully using visual tools such as SmartArt and WordArt Precisely control what you print and how it looks Securely share and distribute your workbooks Use Excel on the Web wherever you have Internet access Every task is presented step-by-step, using carefully annotated, colorful screenshots, all numbered so there's no chance of getting lost or confused. Everything's clearly organized in modular, self-contained chapters designed to help you get started quickly. Throughout, the book is packed with helpful tips, lists, and quick solutions to the problems you're most likely to encounter. In addition, this book is part of Que’s exciting new Content Update Program. As Microsoft updates features of Excel 2016, sections of this book will be updated or new sections will be added to match the updates to the software. The updates will be delivered to you via a FREE Web Edition of this book, which can be accessed with any Internet connection. To learn more, visit www.quepublishing.com/CUP. How to access the web edition: Follow the instructions in the book to learn how to register your book to access the FREE Web Edition. COMPUTERS,Business & Productivity Software,Spreadsheets

Excel 2016 In Depth (includes Content Update Program) Excel 2016 In Depth Full Color: Figures and code appear as they do in Excel 2016 Beyond the Basics…Beneath the Surface...In Depth Do more in less time! Experienced with Excel? Don’t let Excel 2016 make you feel like a beginner again! This new full-color edition of the bestselling book has been completely overhauled. Gone is unnecessary and rarely used content; emphasis is on the most-used and new aspects of Excel 2016. The result is a focused book where every topic is relevant and worth learning. Excel 2016 In Depth is the fastest, smartest way to master Excel 2016’s full power and updated interface. You’ll discover how to leverage Excel’s new tools for charting, business analysis, data visualization, forecasting, and more. • Quickly clean your data with Excel 2016’s powerful Get & Transform tools • Discover Excel 2016’s newest charts: waterfall, histogram, Pareto, sunburst, TreeMap, and Box and Whisker • Use Forecast Sheets to forecast the future, including seasonal adjustments • Pivot data on maps with 3D Maps, and animate your maps over time • Create formulas, charts, subtotals, and pivot tables faster than ever • Create amazing PowerPivot data mashups that integrate information from anywhere • Automate repetitive functions using Excel macros • Solve real-world business intelligence analysis problems • Use PowerPivot Data Model to create pivot tables from multiple data sets without VLOOKUP • Share workbooks on the Web and social networks • Leverage Excel to create highly interactive web pages and online surveys • Quickly apply attractive, consistent formats This book is part of Que’s Content Update Program. As Microsoft updates features of Excel, sections of this book will be updated or new sections will be added to match the updates to the software. See inside for details. COMPUTERS,Business & Productivity Software,Spreadsheets

Excel 2016 Pivot Table Data Crunching (includes Content Update Program) Excel® 2016 PIVOT TABLE DATA CRUNCHING CRUNCH DATA FROM ANY SOURCE, QUICKLY AND EASILY, WITH EXCEL 2016 PIVOT TABLES! Use Excel 2016 pivot tables and pivot charts to produce powerful, dynamic reports in minutes instead of hours… understand exactly what’s going on in your business… take control, and stay in control! Even if you’ve never created a pivot table before, this book will help you leverage all their amazing flexibility and analytical power. Drawing on more than 40 combined years of Excel experience, Bill Jelen and Michael Alexander offer practical “recipes†for solving real business problems, help you avoid common mistakes, and present tips and tricks you’ll find nowhere else! • Create, customize, and change pivot tables • Transform huge data sets into clear summary reports • Analyze data faster with Excel 2016’s new recommended pivot tables • Instantly highlight your most profitable customers, products, or regions • Quickly import, clean, and shape data with Power Query vBuild geographical pivot tables with Power Map • Use Power View dynamic dashboards to see where your business stands • Revamp analyses on the fly by dragging and dropping fields • Build dynamic self-service reporting systems • Combine multiple data sources into one pivot table • Use Auto grouping to build date/time-based pivot tables faster vCreate data mashups with Power Pivot • Automate pivot tables with macros and VBA About MrExcel Library Every book in the MrExcel Library pinpoints a specific set of crucial Excel tasks and presents focused skills and examples for performing them rapidly and effectively. Selected by Bill Jelen, Microsoft Excel MVP and mastermind behind the leading Excel solutions website MrExcel.com, these books will • Dramatically increase your productivity—saving you 50 hours a year or more • Present proven, creative strategies for solving real-world problems • Show you how to get great results, no matter how much data you have • Help you avoid critical mistakes that even experienced users make Bill Jelen is MrExcel, the world’s #1 spreadsheet wizard. Jelen hosts MrExcel.com, the premier Excel solutions site, with more than 20 million page views annually. A Microsoft MVP for Excel, his best-sellers include Excel 2016 In Depth. Michael Alexander, Microsoft Certified Application Developer (MCAD) and Microsoft MVP, is author of several books on advanced business analysis with Excel and Access. He has more than 15 years of experience developing Office solutions. CATEGORY: Spreadsheets COVERS: Microsoft Excel 2016 COMPUTERS,Business & Productivity Software,Spreadsheets

Guerilla Data Analysis Using Microsoft Excel This book includes step-by-step examples and case studies that teach users the many power tricks for analyzing data in Excel. These are tips honed by Bill Jelen, “MrExcel,” and Oz do Soleil during their careers run as a financial analyst charged with taking mainframe data and turning it into useful information quickly. Topics include data quality, validation, perfectly sorting with one click every time, matching lists of data, data consolidation, data subtotals, pivot tables, pivot charts, tables and much more. COMPUTERS,Business & Productivity Software,Spreadsheets

Excel 2016 For Dummies Let your Excel skills sore to new heights with this bestselling guide Updated to reflect the latest changes to the Microsoft Office suite, this new edition of Excel For Dummies quickly and painlessly gets you up to speed on mastering the world's most widely used spreadsheet tool. Written by bestselling author Greg Harvey, it has been completely revised and updated to offer you the freshest and most current information to make using the latest version of Excel easy and stress-free. If the thought of looking at spreadsheet makes your head swell, you've come to the right place. Whether you've used older versions of this popular program or have never gotten a headache from looking at all those grids, this hands-on guide will get you up and running with the latest installment of the software, Microsoft Excel 2016. In no time, you'll begin creating and editing worksheets, formatting cells, entering formulas, creating and editing charts, inserting graphs, designing database forms, and more. Plus, you'll get easy-to-follow guidance on mastering more advanced skills, like adding hyperlinks to worksheets, saving worksheets as web pages, adding worksheet data to an existing web page, and so much more. Save spreadsheets in the Cloud to work on them anywhere Use Excel 2016 on a desktop, laptop, or tablet Share spreadsheets via email, online meetings, and social media sites Analyze data with PivotTables If you're new to Excel and want to spend more time on your actual work than figuring out how to make it work for you, this new edition of Excel 2016 For Dummies sets you up for success. COMPUTERS,Business & Productivity Software,Spreadsheets

Excel Macros For Dummies Save time and be way more productive with Microsoft Excel macros Looking for ready-made Excel macros that will streamline your workflow? Look no further! Excel Macros For Dummies, 2nd Edition helps you save time, automate, and be more productive–even with no programming experience at all. Each chapter offers macros you can implement right away, with practical exercises that extend your knowledge and help you understand the mechanics at work. You'll find over 70 of the most effective Excel macros for solving common problems and explanations of why and where to use each one–plus invaluable guidance and step-by-step instruction for applying them effectively. Microsoft Excel is the world's leading spreadsheet application, and it supports VBA macros that allow you to customize the program and automate many common tasks. In no time, you'll learn how to customize your applications to look and work exactly the way you want them to, with simple, friendly walk-throughs that directly apply to real-world tasks. Follow it through from start to finish, or quickly look up problems as they occur. It's the perfect desk reference for all of your Microsoft Excel macros needs! Immediately implement the given Excel macros Work with workbooks, worksheets, and ranges Clean data, automate reporting, and send email from Excel Streamline your workflow If you have an Excel problem, there's a macro to solve it–and now, you don't need to be a programmer to customize it for your own use!. COMPUTERS,Business & Productivity Software,Spreadsheets

Power Excel 2016 with MrExcel Updating the previous edition's tips to include features in Excel 2016, this new edition of MrExcel's popular software guide even incorporates suggestions sent in by readers. Each featured topic has a problem statement and description, followed by a broad strategy for solving the problem. MrExcel then walks readers through the specific steps to solve the issue. Alternate strategies are also provided, along with common scenarios that trip users up, leaving readers with not only answers to their specific dilemmas but also new and quicker ways to use formulas and spreadsheets. COMPUTERS,Business & Productivity Software,Spreadsheets

Microsoft Excel Data Analysis and Business Modeling This is the eBook of the printed book and may not include any media, website access codes, or print supplements that may come packaged with the bound book. Master business modeling and analysis techniques with Microsoft Excel 2016, and transform data into bottom-line results. Written by award-winning educator Wayne Winston, this hands on, scenario-focused guide helps you use Excel’s newest tools to ask the right questions and get accurate, actionable answers. This edition adds 150+ new problems with solutions, plus a chapter of basic spreadsheet models to make sure you’re fully up to speed. Solve real business problems with Excel–and build your competitive advantage Quickly transition from Excel basics to sophisticated analytics Summarize data by using PivotTables and Descriptive Statistics Use Excel trend curves, multiple regression, and exponential smoothing Master advanced functions such as OFFSET and INDIRECT Delve into key financial, statistical, and time functions Leverage the new charts in Excel 2016 (including box and whisker and waterfall charts) Make charts more effective by using Power View Tame complex optimizations by using Excel Solver Run Monte Carlo simulations on stock prices and bidding models Work with the AGGREGATE function and table slicers Create PivotTables from data in different worksheets or workbooks Learn about basic probability and Bayes’ Theorem Automate repetitive tasks by using macros COMPUTERS,Business & Productivity Software,Spreadsheets

Analyzing Data with Power BI and Power Pivot for Excel Renowned DAX experts Alberto Ferrari and Marco Russo teach you how to design data models for maximum efficiency and effectiveness. How can you use Excel and Power BI to gain real insights into your information? As you examine your data, how do you write a formula that provides the numbers you need? The answers to both of these questions lie with the data model. This book introduces the basic techniques for shaping data models in Excel and Power BI. It’s meant for readers who are new to data modeling as well as for experienced data modelers looking for tips from the experts. If you want to use Power BI or Excel to analyze data, the many real-world examples in this book will help you look at your reports in a different way–like experienced data modelers do. As you’ll soon see, with the right data model, the correct answer is always a simple one! By reading this book, you will: • Gain an understanding of the basics of data modeling, including tables, relationships, and keys • Familiarize yourself with star schemas, snowflakes, and common modeling techniques • Learn the importance of granularity • Discover how to use multiple fact tables, like sales and purchases, in a complex data model • Manage calendar-related calculations by using date tables • Track historical attributes, like previous addresses of customers or manager assignments • Use snapshots to compute quantity on hand • Work with multiple currencies in the most efficient way • Analyze events that have durations, including overlapping durations • Learn what data model you need to answer your specific business questions About This Book • For Excel and Power BI users who want to exploit the full power of their favorite tools • For BI professionals seeking new ideas for modeling data COMPUTERS,Business & Productivity Software,Spreadsheets

MrExcel LIVe The 54 essential tips that all Excel users need to know. MrExcel LIVe provides users with a concise book that can be absorbed in under an hour. Includes a section with keyboard shortcuts. Anyone who uses Excel will be able to turn to any page and pick up tips that will save them hours of work. COMPUTERS,Business & Productivity Software,Spreadsheets

Excel 2019 For Dummies The bestselling Excel book on the market — now in a new edition covering the latest version of Excel! Excel is the spreadsheet and data analysis tool of choice for people across the globe who utilize the Microsoft Office suite to make their work and personal lives easier. It is estimated that 1 in 7 people on the planet use Microsoft Office! If you’re one of them, and want to get up to speed on the latest changes in Excel, you’ve come to the right place. Excel 2019 For Dummies has been updated to reflect the major changes and features made to Excel and covers everything you need to know to perform any spreadsheet task at hand. It includes information on creating and editing worksheets, formatting cells, entering formulas, creating and editing charts, inserting graphs, designing database forms, adding database records, using seek-and-find options, printing, adding hyperlinks to worksheets, saving worksheets as web pages, adding existing worksheet data to an existing webpage, pivot tables, pivot charts, formulas and functions, Excel data analysis, sending worksheets via e-mail, and so much more! Get to know the new Excel interface Become a pro at the spreadsheet and data analysis tool that’s available as part of the Microsoft Office suite Find time-tested and trusted advice from bestselling author and expert Greg Harvey Use Excel to streamline your processes and make your work life easier than ever before Written by a bestselling author and seasoned educator, Excel 2019 For Dummies makes it easier than ever to get everything out of this powerful data tool. COMPUTERS,Business & Productivity Software,Spreadsheets

Exam Ref 70-779 Analyzing and Visualizing Data with Microsoft Excel Prepare for Microsoft Exam 70-779–and help demonstrate your real-world mastery of Microsoft Excel data analysis and visualization. Designed for BI professionals, data analysts, and others who analyze business data with Excel, this Exam Ref focuses on the critical thinking and decision-making acumen needed for success at the MCSA level. Focus on the expertise measured by these objectives: Consume and transform data by using Microsoft Excel Model data, from building and optimizing data models through creating performance KPIs, actual and target calculations, and hierarchies Visualize data, including creating and managing PivotTables and PivotCharts, and interacting with PowerBI This Microsoft Exam Ref: Organizes its coverage by exam objectives Features strategic, what-if scenarios to challenge you Assumes you have a strong understanding of how to use Microsoft Excel to perform data analysis COMPUTERS,Business & Productivity Software,Spreadsheets

Excel Custom Functions Excel users are used to build custom functions—called user-defined functions (UDFs)—in Windows and Mac versions of the application. UDFs can be simply written in Visual Basic Editor (VBE) using the Visual Basic for Applications (VBA) language.UDFs are not portable to Excel Online and Excel for iOS due to the missing VBA capability on these platforms. Therefore, Microsoft has improved the JavaScript API that was already being used for Office add-in development to allow developers to create custom functions attached to the add-ins. These custom functions can be used like any other native functions or UDFs in Excel. While Microsoft calls these functions JavaScript custom functions, they can also be called JavaScript UDFs, which is the name used in this book.This book shows the process of creating JavaScript UDFs in Excel in Developer Preview for Office Insider program subscribers. COMPUTERS,Business & Productivity Software,Spreadsheets

Excel 2016 Hands-On Lab The new way to learn Excel 2016 immediately, and now the ebook is constantly updated with new topics.Learn at your own pace with real "step by step" exercises to guarantee your learning. Do not forget to download the practice files for free.With Excel 2016 Handson-Lab you will learn to:- Learn the basics of Microsoft Excel 2016- Manage different types of data- Work with basic formulas and functions- Understand the use of text, logic, search and date and time functions- Use and convert ranges into tables- Insert new types of charts COMPUTERS,Business & Productivity Software,Spreadsheets

Excel 2019 Bible The complete guide to Excel 2019 Whether you are just starting out or an Excel novice, the Excel 2019 Bible is your comprehensive, go-to guide for all your Excel 2019 needs. Whether you use Excel at work or at home, you will be guided through the powerful new features and capabilities to take full advantage of what the updated version offers. Learn to incorporate templates, implement formulas, create pivot tables, analyze data, and much more. Navigate this powerful tool for business, home management, technical work, and much more with the only resource you need, Excel 2019 Bible. Create functional spreadsheets that work Master formulas, formatting, pivot tables, and more Get acquainted with Excel 2019's new features and tools Whether you need a walkthrough tutorial or an easy-to-navigate desk reference, the Excel 2019 Bible has you covered with complete coverage and clear expert guidance. COMPUTERS,Business & Productivity Software,Spreadsheets

Excel VBA Programming For Dummies Take your Excel programming skills to the next level To take Excel to the next level, you need to understand and implement the power of Visual Basic for Applications (VBA). Excel VBA Programming For Dummies introduces you to a wide array of new Excel options, beginning with the most important tools and operations for the Visual Basic Editor. Inside, you’ll find an overview of the essential elements and concepts for programming with Excel. In no time, you’ll discover techniques for handling errors and exterminating bugs, working with range objects and controlling program flow, and much more. With friendly advice on the easiest ways to develop custom dialog boxes, toolbars, and menus, readers will be creating Excel applications custom fit to their unique needs! Fully updated for the new Excel 2019 Step-by-step instructions for creating VBA macros to maximize productivity Guidance on customizing your applications so they work the way you want All sample programs, VBA code, and worksheets are available at dummies.com Beginning VBA programmers rejoice! This easy-to-follow book makes it easier than ever to excel at Excel VBA! COMPUTERS,Business & Productivity Software,Spreadsheets

Excel Formulas & Functions For Dummies Put the power of Excel functions to work in your formulas There are more than 400 built-in functions in Excel 2019, from AGGREGATE to Z.TEST. The question is which ones will make your work easier? How and why should you use a particular function in your formulas? Excel Formulas and Functions For Dummies offers thorough but easy-to-read coverage of powerful Excel functions. With this book, you’ll learn to apply the power of Excel functions and formulas to make your work and other tasks easier. Compare 15-year vs. 30-year mortgage terms, choose between leasing or buying a car, compute classroom grades, create an amortization table, evaluate investment performance, calculate the real cost of credit card purchases, or forecast college expenses and savings. All of this and more is possible when you master functions and formulas in Excel. Although it covers the latest software version, Excel 2019, the techniques and functions described in this book can be used on any version of Excel. Step-by-step instruction on Excel's 150 most useful functions Each function is illustrated by helpful, real-world examples 85 specialized functions are described in abbreviated form Includes Excel’s must-know functions This book is a must-read for beginning to intermediate Excel users who want to find out how to use Excel’s powerful built-in functions. COMPUTERS,Business & Productivity Software,Spreadsheets

Excel Data Analysis For Dummies Take Excel to the next level Excel is the world’s leading spreadsheet application. It’s a key module in Microsoft Office—the number-one productivity suite—and it is the number-one business intelligence tool. An Excel dashboard report is a visual presentation of critical data and uses gauges, maps, charts, sliders, and other graphical elements to present complex data in an easy-to-understand format. Excel Data Analysis For Dummies explains in depth how to use Excel as a tool for analyzing big data sets. In no time, you’ll discover how to mine and analyze critical data in order to make more informed business decisions. Work with external databases, PivotTables, and Pivot Charts Use Excel for statistical and financial functions and data sharing Get familiar with Solver Use the Small Business Finance Manager If you’re familiar with Excel but lack a background in the technical aspects of data analysis, this user-friendly book makes it easy to start putting it to use for you. COMPUTERS,Business & Productivity Software,Spreadsheets

Excel 2019 All-in-One For Dummies Make Excel work for you Excel 2019 All-In-One For Dummies offers eight books in one!! It is completely updated to reflect the major changes Microsoft is making to Office with the 2019 release. From basic Excel functions, such as creating and editing worksheets, to sharing and reviewing worksheets, to editing macros with Visual Basic, it provides you with a broad scope of the most common Excel applications and functions—including formatting worksheets, setting up formulas, protecting worksheets, importing data, charting data, and performing statistical functions. The book covers importing data, building and editing worksheets, creating formulas, generating pivot tables, and performing financial functions, what-if scenarios, database functions, and Web queries. More advanced topics include worksheet sharing and auditing, performing error trapping, building and running macros, charting data, and using Excel in conjunction with Microsoft Power BI (Business Intelligence) to analyze, model, and visualize vast quantities of data from a variety of local and online sources. Get familiar with Worksheet design Find out how to work with charts and graphics Use Excel for data management, analysis, modeling, and visualization Make sense of macros and VBA If you’re a new or inexperienced user looking to spend more time on your projects than trying to figure out how to make Excel work for you, this all-encompassing book makes it easy! COMPUTERS,Business & Productivity Software,Spreadsheets

Business Analysis with Microsoft Excel Gain Deeper Insights, Make Smarter Decisions, and Earn More Profits It’s time to put the full power of Excel quantitative analysis behind your management decisions! Business analysis expert Conrad Carlberg shows you how to use Excel to perform core financial tasks all managers and entrepreneurs need to master: analyzing statements, planning and controlling company finances, making investment decisions, and managing sales and marketing. Carlberg helps you make the most of Excel’s tools and features in everything from business case development to cash flow analysis. Becoming an Excel expert has never been easier. You’ll find crystal-clear instructions, real-world examples, insider insights, step-by-step projects, and much more. It’s all complemented by extensive web-based resources, from sample journals and ledgers to business forecasting tools. · Get more insight from income statements and balance sheets · Manage current assets and value inventories · Summarize transactions from journal to balance sheet · Analyze working capital, cash flow, statements, and ratios · Optimize budgeting and planning cycles · Make more accurate and useful forecasts and projections · Measure product or service quality · Plan investments, set decision criteria, and perform sensitivity analyses · Analyze profits, pricing, costs, contributions, and margins · Make better decisions in uncertain conditions · Understand and maximize the value of fixed assets · Efficiently import and export business data · Use Excel and Power BI to analyze data from QuickBooks or other sources COMPUTERS,Business & Productivity Software,Spreadsheets

Microsoft Excel 2019 Pivot Table Data Crunching Renowned Excel experts Bill Jelen (MrExcel) and Michael Alexander help you crunch data from any source with Excel 2019 pivot tables. Use Excel 2019 pivot tables and pivot charts to produce powerful, dynamic reports in minutes instead of hours, to take control of your data and your business. Even if you’ve never created a pivot table before, this book will help you leverage all their remarkable flexibility and analytical power–including valuable improvements in Excel 2019 and Excel in Office 365. Drawing on more than 45 combined years of Excel experience, Bill Jelen and Michael Alexander offer practical “recipes†for solving real business problems, help you avoid common mistakes, and present tips and tricks you’ll find nowhere else. By reading this book, you will: • Master easy, powerful ways to create, customize, change, and control pivot tables • Control all future pivot tables using new pivot table defaults • Transform huge data sets into clear summary reports • Instantly highlight your most profitable customers, products, or regions • Use Power Query to quickly import, clean, shape, and analyze disparate data sources • Build geographical pivot tables with 3D Map • Construct and share state-of-the-art dynamic dashboards • Revamp analyses on the fly by dragging and dropping fields • Build dynamic self-service reporting systems • Share your pivot tables with colleagues • Create data mashups using the full Power Pivot capabilities of Excel 2019 and Excel in Office 365 • Automate pivot tables with macros and VBA • Save time by adapting reports with GetPivotData • Discover today’s most useful pivot table tips and shortcuts COMPUTERS,Business & Productivity Software,Spreadsheets

Microsoft Excel 2019 Formulas and Functions Expert Paul McFedries helps you master key Excel 2019 and Office 365 tools for building more powerful spreadsheets. Use Excel 2019 and Office 365 core features to build spreadsheets that solve business problems and deliver reliable answers. Drawing on his unsurpassed experience, Paul McFedries helps you make the most of formulas and functions, including the latest improvements to arrays, formula error handling, and statistics. McFedries’ step-by-step projects walk you through handling key tasks, from building timesheets to projecting cash flow and aging receivables. His practical examples and clear instructions demystify intermediate- to advanced-level formula construction, and help you leverage Excel’s most useful functions in your everyday work. Becoming an Excel expert has never been easier! By reading this book, you will: • Improve business analyses by adding intelligence and knowledge to your models • Replace cumbersome formulas with convenient predefined functions • Radically simplify complex calculations with Office 365’s new dynamic arrays • Use conditional formatting to reveal anomalies, problems, or opportunities • Calculate loan payments, interest costs, terms, and amortization schedules • Project the future value of investments, and plan to achieve investment goals • Master essential discounting and cash-flow analysis tools, including net present value and internal rate of return • Sort, filter, and analyze tabular data, from customers to inventory • Easily analyze huge data sets with PivotTable calculations About This Book • For everyone who wants to get more done with Microsoft Excel in less time • For business and financial professionals, entrepreneurs, students, and others who need to efficiently manage and analyze data COMPUTERS,Business & Productivity Software,Spreadsheets

Excel 2019 Power Programming with VBA Maximize your Excel experience with VBA Excel 2019 Power Programming with VBA is fully updated to cover all the latest tools and tricks of Excel 2019. Encompassing an analysis of Excel application development and a complete introduction to Visual Basic for Applications (VBA), this comprehensive book presents all of the techniques you need to develop both large and small Excel applications. Over 800 pages of tips, tricks, and best practices shed light on key topics, such as the Excel interface, file formats, enhanced interactivity with other Office applications, and improved collaboration features. Understanding how to leverage VBA to improve your Excel programming skills can enhance the quality of deliverables that you produce—and can help you take your career to the next level. Explore fully updated content that offers comprehensive coverage through over 900 pages of tips, tricks, and techniques Leverage templates and worksheets that put your new knowledge in action, and reinforce the skills introduced in the text Improve your capabilities regarding Excel programming with VBA, unlocking more of your potential in the office Excel 2019 Power Programming with VBA is a fundamental resource for intermediate to advanced users who want to polish their skills regarding spreadsheet applications using VBA. COMPUTERS,Business & Productivity Software,Spreadsheets

Cleaning Excel Data With Power Query Straight to the Point Author Oz Du Soleil's area of frustration with Excel is cleaning data. From his earliest days with Excel, he has found himself constantly needing to fix names that are ALLCAPS, peel addresses away from phone numbers, and fixing all the many other things that prevent data from being useful. In this intro to Power Query, Oz shows you five core techniques in Excel Power Query: Splitting data, Filling blanks, Joining data sets, grouping and summarizing, and adding columns using Column From Examples. COMPUTERS,Business & Productivity Software,Spreadsheets

MrExcel LX The Holy Grail of Excel Tips These are the 125 essential tips that all Excel users need to know. MrExcel LX provides users with a concise book that can be absorbed in under two hours. Includes a section with keyboard shortcuts. Anyone who uses Excel will be able to turn to any page and pick up tips that will save them hours of work. COMPUTERS,Business & Productivity Software,Spreadsheets

Definitive Guide to DAX, The Now expanded and updated with modern best practices, this is the most complete guide to Microsoft’s DAX language for business intelligence, data modeling, and analytics. Expert Microsoft BI consultants Marco Russo and Alberto Ferrari help you master everything from table functions through advanced code and model optimization. You’ll learn exactly what happens under the hood when you run a DAX expression, and use this knowledge to write fast, robust code. This edition focuses on examples you can build and run with the free Power BI Desktop, and helps you make the most of the powerful syntax of variables (VAR) in Power BI, Excel, or Analysis Services. Want to leverage all of DAX’s remarkable capabilities? This no-compromise “deep dive†is exactly what you need. Perform powerful data analysis with DAX for Power BI, SQL Server, and Excel · Master core DAX concepts, including calculated columns, measures, and calculation groups · Work efficiently with basic and advanced table functions · Understand evaluation contexts and the CALCULATE and CALCULATETABLE functions · Perform time-based calculations · Use calculation groups and calculation items · Use syntax of variables (VAR) to write more readable, maintainable code · Express diverse and unusual relationships with DAX, including many-to-many relationships and bidirectional filters · Master advanced optimization techniques, and improve performance in aggregations · Optimize data models to achieve better compression · Measure DAX query performance with DAX Studio and learn how to optimize your DAX COMPUTERS,Business & Productivity Software,Spreadsheets

Excel Data Cleansing Straight to the Point This Straight to the Point guide provides an introduction to data cleansing, which also goes by names such as data munging and data wrangling. Whatever the name, it basically means doing what needs to be done to make data useful and trustworthy. Data cleansing can include the following tasks:Deleting unnecessary headersDeleting summary rowsFilling in gapsFlattening a reportMerging and appending data from multiple sourcesPulling data from source X to complete data in source YSplitting names from addressesIdentifying and deleting duplicate recordsConverting units of measurement in multiple sources COMPUTERS,Business & Productivity Software,Spreadsheets

Excel 2019 – Business Basics & Beyond Are you tired of tracking financial elements of your business manually, do you have to prepare staffing schedules by hand, or do you simply want to know how to get more information from your business data? Learn how to harness your business data and put it to use for you. Learn the basics of Excel, including a comprehensive review of every tab of the Excel Ribbon. See how to best display your data for maximum impact with formatting tools, Data Tables, Charts & Pivot Tables. Use customer information to create customized letters with Mail Merge. Import data using Power Query. Calculate the costs of doing business with financial formulas, learn where to find pre-packaged business templates, and much more. This book uses real-world business examples in operation with all these elements. COMPUTERS,Business & Productivity Software,Spreadsheets

Power Excel 2019 with MrExcel Updating the previous edition's tips to include features in Office 365 and Excel 2019, this new edition of MrExcel's popular software guide even incorporates suggestions sent in by readers. Each featured topic has a problem statement and description, followed by a broad strategy for solving the problem. MrExcel then walks readers through the specific steps to solve the issue. Alternate strategies are also provided, along with common scenarios that trip up users, leaving readers with not only answers to their specific dilemmas but also new and quicker ways to use formulas and spreadsheets. COMPUTERS,Business & Productivity Software,Spreadsheets

Excel Insights Learn favorite techniques from this group of twenty-two Excel MVPs. The Excel MVPs are friends and competitors who each pulled out their favorite tricks to impress you and their fellow MVPs. COMPUTERS,Business & Productivity Software,Spreadsheets

Introduction To Financial Modelling If you have had little formal training in developing financial forecasts in Excel or have ever burnt the midnight oil trying to get a Balance Sheet to balance, then this book is for you. A simple walkthrough of the common perils and pitfalls of financial modelling, this book constructs a solid foundation to build upon (pun most definitely intended). Taking little for granted, Liam examines the common Excel functions and functionalities necessary, emphasises the importance of a standardised and functional layout, explains accounting concepts simply and reinforces the four key concepts of a "Best Practice" model: Consistency, Robustness, Flexibility and Transparency – CraFT. With over 50 examples and an extended case study that creates a simple financial model from scratch to highlight the key concepts, this is a "hands on" book, focused on working with Excel more efficiently and effectively. A simple process, this methodology has been adopted by many seasoned professionals without resorting to balancing figures, circulars and macros. COMPUTERS,Business & Productivity Software,Spreadsheets

MOS Study Guide for Microsoft Excel Expert Exam MO-201 Advance your expert-level proficiency with Excel. And earn the credential that proves it! Demonstrate your expert-level competency with Microsoft Excel! Designed to help you practice and prepare for Microsoft Office Specialist: Microsoft Excel Expert (Excel and Excel 2019) certification, this official Study Guide delivers: In-depth preparation for each MOS objective Detailed procedures to help build the skills measured by the exam Hands-on tasks to practice what you’ve learned Ready-made practice files Sharpen the skills measured by these objectives: Manage Workbook Options and Settings Manage and Format Data Create Advanced Formulas and Macros Manage Advanced Charts and Tables About the MOS: Expert Certification A Microsoft Office Specialist (MOS): Expert certification validates your hands-on experience and competency with an Office product at an expert level. It demonstrates that you can apply the product’s principal features at an advanced level, can complete expert tasks independently, and are ready to enter the job market. See full details at: microsoft.com/learn Practice Files Available at: MicrosoftPressStore.com/ MOSExcelExpert201/downloads COMPUTERS,Business & Productivity Software,Spreadsheets

Microsoft Office Word 2007 Quick Reference Guide Readers unfamiliar with Windows-based environments will find plenty of introductory help here that brings them quickly up to speed. This Digital Short Cut shows you how to do work in Word 2007 as well as how to manage many of the Internet-based Word 2007 elements you need in today’s online-connected world. If you are new to the Internet, you’ll learn how to combine the Internet with Word 2007 to gain synergy from both. This Short Cut also helps previous Microsoft Word users adapt and familiarize themselves with the dramatic interface change of Word 2007. With the fundamental Office understanding you already have, you will appreciate the new features and added power of Word 2007 and you’ll learn how to maximize your use of the Office 2007 ribbon to get your work done quickly, easily, and comfortably. Table of Contents Chapter 1 Learning Word’s Basics 5 Chapter 2 Making Your Words Look Good 43 Chapter 3 Adding Lists,Tables, and Graphics 81 Chapter 4 Using Word’s Advanced Features 121 COMPUTERS,Business & Productivity Software,Word Processing

Word 2010 Bible In-depth guidance on Word 2010 from a Microsoft MVP Microsoft Word 2010 arrives with many changes and improvements, and this comprehensive guide from Microsoft MVP Herb Tyson is your expert, one-stop resource for it all. Master Word's new features such as a new interface and customized Ribbon, major new productivity-boosting collaboration tools, how to publish directly to blogs, how to work with XML, and much more. Follow step-by-step instructions and best practices, avoid pitfalls, discover practical workarounds, and get the very most out of your new Word 2010 with this packed guide. COMPUTERS,Business & Productivity Software,Word Processing

Microsoft® Word 2013 QuickSteps Step-by-Step, Full-Color Graphics! Get up and running on Microsoft Word 2013 right away--the QuickSteps way. Full-color screenshots and clear instructions make it easy to start using the latest release of the leading word processing application. Take control and learn how to create and format documents, apply templates and themes, use mail merge, add tables and illustrations, use special features such as forms and translation, save Word documents as web pages, and much more. Screenshots with callouts show and explain exactly what you'll see on your computer screen while you're doing a task. This practical, fast-paced guide gets you started in no time! Use these handy guideposts: Shortcuts for accomplishing common tasks Need-to-know facts in concise narrative Helpful reminders or alternate ways of doing things Bonus information related to the topic being covered Errors and pitfalls to avoid COMPUTERS,Business & Productivity Software,Word Processing

Microsoft Word 2010 Plain & Simple Get the guide that makes learning Microsoft Word 2010 plain and simple! This full color, no-nonsense book shows you the quickest ways to solve a problem or learn new skills, using easy-to-follow steps and concise, straightforward language. You'll create professional-quality documents in no time. Here’s WHAT you'll learn: Create professional-looking documents with ease Organize, edit, and format text Apply themes, styles, and other design elements Work with graphics, tables, and charts Take advantage of pre-built templates, or make your own Edit a document with others simultaneously -- online Here's HOW you’ll learn it: Jump in whenever you need answers Easy-to-follow STEPS and SCREENSHOTS show exactly what to do Handy TIPS teach new techniques and shortcuts Quick TRY THIS! exercises help apply what you learn right away COMPUTERS,Business & Productivity Software,Word Processing

Microsoft Word 2013 Plain & Simple Get the full-color, visual guide that makes learning Microsoft Word 2013 plain and simple! Follow the book’s easy steps and screenshots and clear, concise language to learn the simplest ways to create and share documents. Here’s WHAT you’ll learn: Create, edit, format, and share text Add graphics, data, table, and charts Improve page layout to best present your ideas Use and make templates for increased productivity Collaborate and present documents online Access your documents from almost any browser Here’s HOW you’ll learn it: Jump in wherever you need answers Follow easy STEPS and SCREENSHOTS to see exactly what to do Get handy TIPS for new techniques and shortcuts Use TRY THIS! Exercises to apply what you learn right away COMPUTERS,Business & Productivity Software,Word Processing

Word 2016 For Dummies The bestselling beginner's guide to Microsoft Word Written by the author of the first-ever For Dummies book, Dan Gookin, this new edition of Word For Dummies quickly and painlessly gets you up to speed on mastering the world's number-one word processing software. In a friendly, human, and often irreverent manner, it focuses on the needs of the beginning Word user, offering clear and simple guidance on everything you need to know about Microsoft Word 2016, minus the chin-scratching tech jargon. Whether you've used older versions of this popular program or have never processed a single word, this hands-on guide will get you going with the latest installment of Microsoft Word. In no time, you'll begin editing, formatting, proofing, and dressing up your Word documents like a pro. Plus, you'll get easy-to-follow guidance on mastering more advanced skills, like formatting multiple page elements, developing styles, building distinctive templates, and adding creative flair to your documents with images and tables. Covers the new and improved features found in the latest version of the software, Word 2016 Shows you how to master a word processor's seven basic tasks Explains why you can't always trust the spell checker Offers little-known keyboard shortcuts If you're new to Word and want to spend more time on your actual work than figuring out how to make it work for you, this new edition of Word 2016 For Dummies has you covered. COMPUTERS,Business & Productivity Software,Word Processing

Word 2016 For Professionals For Dummies The most comprehensive guide to Microsoft Word 2016 If you're a professional who uses Word, but aren't aware of its many features or get confused about how they work best, Word 2016 For Professionals For Dummies answers all your burning questions about the world's number-one word processing software. Offering in-depth coverage of topics you won't find in Word 2016 For Dummies, this guide focuses on the professional's needs, giving you all you need to know not only do your job well, but to do it even better. As Microsoft continues to hone Word with each new release, new features are added beyond basic word processing. From using Word to create blog posts to importing data from Excel to expertly flowing text around objects, it covers the gamut of Word's more advanced capabilities—including those you probably don't know exist. Whether you're looking to use Word to build a master document, collaborate and share, publish an ebook, or anything in between, the thorough, step-by-step guidance in Word 2016 For Professionals For Dummies makes it easier. Discover neat Word editing tips and tricks to create complex documents Share documents and collaborate with others Format text, paragraphs, and pages like never before Add Excel charts and graphics to Word documents Create an ebook Essential reading for the Word power user who wants to be more productive and efficient at work, this handy guide gives you the boost to take your skills to the next level. COMPUTERS,Business & Productivity Software,Word Processing

MOS 2016 Study Guide for Microsoft Word Expert Advance your expert skills in Word 2016. And earn the credential that proves it!! Demonstrate your expertise with Microsoft Word! Designed to help you practice and prepare for Microsoft Office Specialist (MOS): Word 2016 Expert certification, this official Study Guide delivers: In-depth exam prep for each MOS objective Detailed procedures to help build the skills measured by the exam Hands-on tasks to apply what you’ve learned Practice and review questions Ready-made practice files with solutions Sharpen the skills measured by these MOS objectives: Manage Document Options and Settings Design Advanced Documents Create Advanced References Create Custom Word Elements COMPUTERS,Business & Productivity Software,Word Processing

Word 2019 For Dummies The bestselling beginner’s guide to Microsoft Word Whether you've used older versions of this popular program or have never processed a single word, this hands-on guide gets you going with the latest version of Microsoft Word. In no time, you'll begin editing, formatting, proofing, and dressing up your Word documents like a pro. In this leading book about the world’s number one word processing application, Dan Gookin talks about using Microsoft Word in friendly, easy-to-follow terms. Focusing on the needs of the beginning Word user, it provides everything you need to know about Word—without any painful jargon. Covers the new and improved features found in the latest version of Word Create your own templates Explains why you can’t always trust the spell checker Offers little-known keyboard shortcuts If you’re new to Word and want to spend more time on your actual work rather than figuring out how to make it work for you, this new edition of Word X For Dummies has you covered. COMPUTERS,Business & Productivity Software,Word Processing

Word 2016 Hands-On Lab The new way to learn Word 2016 immediately, and now the ebook is constantly updated with new topics.Learn at your own pace with real "step by step" exercises to guarantee your learning. Do not forget to download the practice files for free.With Word 2016 Step by Step you will learn to:- Know the Word 2016 interface in a simple way- Apply font and paragraph formats to your documents- Configure your documents and decorate it for a better presentation- Insert images, graphics and other content.- Add table of contents and print COMPUTERS,Business & Productivity Software,Word Processing

Using Word 2019 We’ve all been there before, staring at a computer screen with no idea what to do — don’t worry Using Word 2019 is here to help. Written by best-selling technology author, lecturer, and computer trainer Kevin Wilson, Using Word 2019 is packed with easy to follow instructions, photos, illustrations, helpful tips and video demos. Updated to cover Microsoft Word 2019, this guide will show you how to: Start Word and find your way around the ribbon menu Format text: bold, italic, underlined, strike, and super/sub script Align, highlight and change text colour Cut, copy, paste and using the clipboard Use headers, footers, columns, watermarks, and cover pages Insert page numbers, contents pages and indexes Add page borders, and page breaks Sort text, adjust line spacing, and tabs, as well as bullet and numbered lists Save, print, share and collaborate with others Insert SmartArt, charts, tables, equations and special characters Add images, crop, wrap text and use effects Use pre-designed templates, and build your own Mail merge letters, labels and envelopes Check spelling and grammar Improve your work with thesaurus and insights You'll want to keep this edition handy as you make your way around Microsoft Word. Have Fun! COMPUTERS,Business & Productivity Software,Word Processing

MOS Study Guide for Microsoft Word Expert Exam MO-101 Advance your expert-level proficiency with Word. And earn the credential that proves it! Demonstrate your expert-level competency with Microsoft Word! Designed to help you practice and prepare for Microsoft Office Specialist: Word Expert (Word and Word 2019) certification, this official Study Guide delivers: In-depth preparation for each MOS objective Detailed procedures to help build the skills measured by the exam Hands-on tasks to practice what you’ve learned Ready-made practice files Sharpen the skills measured by these objectives: Manage Document Options and Settings Use Advanced Editing and Formatting Features Create Custom Document Elements Use Advanced Word Features About MOS: Expert Certification A Microsoft Office Specialist (MOS): Expert certification validates your hands-on experience and competency with an Office product at an expert level. It demonstrates that you can apply the product’s principal features at an advanced level, can complete expert tasks independently, and are ready to enter the job market. See full details at: microsoft.com/learn Practice Files Available at: MicrosoftPressStore.com/MOSWordExpert101/downloads COMPUTERS,Business & Productivity Software,Word Processing

Computer Concepts and Management Information Systems This book is designed to provide the reader with the fundamentals of computers and MIS in an easy to understand, “self-teaching†format. It introduces the major subjects such as hardware components, software applications, detailed information on Microsoft Office, information systems, ERP, CRM, security, business ethics, and cybercrime. Features: Covers the major components of MS Office: Excel, Word, PowerPoint, and Access Provides an overview of theworkings of a computer, software applications, and MIS Includes discussion of information systems, ERP, security, businessethics, and cybercrime COMPUTERS,Business & Productivity Software,Word Processing

Teach Yourself VISUALLY Word 2019 Master one of the most popular word processors ever with this essential, visual reference Teach Yourself VISUALLY: Word 2019 provides readers with a thorough and visual exploration of the 2019 edition of Microsoft Word. Written by the celebrated author of over 100 books on computing, Guy Hart-Davis, Teach Yourself VISUALLY: Word 2019 allows you to quickly get up to speed with one of the most popular word processors on the planet. The book covers all the topics you’ll need to comprehensively master Word 2019, and includes: Full-color, step-by-step instructions showing you how to perform all the essential tasks of Microsoft Word 2019 How to set up and format documents, edit them, and add images and charts How to post documents online for sharing and reviewing and take advantage of all the newest features of Word Newly updated to include the latest features of Microsoft Word, like how to collaborate on documents in real time, draw and write with the digital pen, new accessibility options and the new Resume Assistant, Teach Yourself VISUALLY: Word 2019 belongs on the shelf of anyone who wants to improve their effectiveness with this essential word processor. COMPUTERS,Business & Productivity Software,Word Processing

TI-Nspire For Dummies The updated guide to the newest graphing calculator from Texas Instruments The TI-Nspire graphing calculator is popular among high school and college students as a valuable tool for calculus, AP calculus, and college-level algebra courses. Its use is allowed on the major college entrance exams. This book is a nuts-and-bolts guide to working with the TI-Nspire, providing everything you need to get up and running and helping you get the most out of this high-powered math tool. Texas Instruments’ TI-Nspire graphing calculator is perfect for high school and college students in advanced algebra and calculus classes as well as students taking the SAT, PSAT, and ACT exams This fully updated guide covers all enhancements to the TI-Nspire, including the touchpad and the updated software that can be purchased along with the device Shows how to get maximum value from this versatile math tool With updated screenshots and examples, TI-Nspire For Dummies provides practical, hands-on instruction to help students make the most of this revolutionary graphing calculator. COMPUTERS,Calculators

Ti-84 Plus Graphing Calculator For Dummies Get up-to-speed on the functionality of your TI-84 Plus calculator Completely revised to cover the latest updates to the TI-84 Plus calculators, this bestselling guide will help you become the most savvy TI-84 Plus user in the classroom! Exploring the standard device, the updated device with USB plug and upgraded memory (the TI-84 Plus Silver Edition), and the upcoming color screen device, this book provides you with clear, understandable coverage of the TI-84's updated operating system. Details the new apps that are available for download to the calculator via the USB cable Walks you through menus and basic arithmetic Addresses graphing and analyzing functions as well as probability and statistics functions Explains how to use the calculator for geometry Reviews communicating with PCs and other calculators TI-84 Plus Graphic Calculator For Dummies, 2nd Edition is the perfect solution for getting comfortable with the new line of TI-84 calculators! COMPUTERS,Calculators

CompTIA A+ 220-901 and 220-902 Exam Cram CompTIA A+ 220-901 and 220-902 exams retired in 2019. Search the store to find CompTIA A+ Core 1 (220-1001) and Core 2 (220-1002) books, eBooks, and video courses. This is the perfect study guide to help you pass CompTIA®’s new A+® 220-901 and 220-902 exams. It provides coverage and practice questions for every exam topic, including substantial new coverage of Windows 8/8.1, new PC hardware, tablets, smartphones, OS X, Linux, cloud computing, and professional-level networking and security. Extensive prep tools include quizzes, Exam Alerts, our great last-minute Cram Sheet, and two full practice exams in the ebook. You’ll also find ten exclusive Real World Scenario case studies, all linked to simulations or video posted to the book website! Covers the critical information you’ll need to know to score higher on your A+ 220-901 and 220-902 exams! Deploy and manage desktops and notebooks running Windows 8.1/8, 7, Vista, OS X, or Linux Master and practice the six-step A+ troubleshooting process Understand, install, configure, and troubleshoot motherboards, CPUs, and memory Test and troubleshoot power-related problems Use all forms of storage, including SSDs, Blu-ray devices, and RAID systems Work effectively with mobile devices, including iOS, Android, and Windows tablets and smartphones Install, configure, and troubleshoot both visible and internal laptop components Configure Windows components and applications, use Windows administrative tools, and optimize Windows systems Repair damaged Windows environments and boot errors Work with audio and video subsystems, I/O devices, and new peripherals Install and manage both local and network printers Understand and work with networks, network hardware, wireless protocols, and cloud technologies Install and configure SOHO wired/wireless networks and troubleshoot connectivity Secure desktops and mobile devices, implement authentication methods, prevent malware attacks, and protect data The eBook edition does not provide access to the test engine and practice test that accompanies the print book. COMPUTERS,Certification Guides,CompTIA (incl. A+)

CompTIA A+ 220-901 and 220-902 Practice Questions Exam Cram The CompTIA A+ 220-901 and 220-902 Practice Questions Exam Cram is an ideal supplemental preparation tool and provides students with 700 practice test questions as well as complete answer explanations, giving them the perfect complementary tool for their A+ studies. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Certification Guides,CompTIA (incl. A+)

CompTIA A+ 220-901 and 220-902 Cert Guide, Academic Edition CompTIA A+ 220-901 and 220-902 Cert Guide, Academic Editionis a comprehensive guide to the new A+ exams from CompTIA from one of the leading A+ Certification authors. With over 15 years of experience in developing CompTIA A+ Certification content and 30 years of experience in the computer field, Mark teaches you not just what you need to pass the exams, but also what you need to know to apply your knowledge in the real world. This book is rich with learning and exam preparation features: Hands-on lab exercises Real-world test preparation advice This is the eBook edition of the CCDA 200-310 Official Cert Guide. This eBook does not include the practice exam that comes with the print edition. CompTIA A+ 220-901 and 220-902 Cert Guide, Academic Editionis a comprehensive guide to the new A+ exams from CompTIA from one of the leading A+ Certification authors. With over 15 years of experience in developing CompTIA A+ Certification content and 30 years of experience in the computer field, Mark teaches you not just what you need to pass the exams, but also what you need to know to apply your knowledge in the real world. This book is rich with learning and exam preparation features: Hands-on lab exercises Real-world test preparation advice This is the eBook edition of the CCDA 200-310 Official Cert Guide. This eBook does not include the practice exam that comes with the print edition. Each chapter takes a ground-up approach - starting with the essentials and gradually building to larger, more complex concepts. Regardless of your level of experience, from beginner to expert, this book helps you improve your knowledge and skills. Loaded with informative illustrations, photos and screen captures that help readers follow along, the book also includes access to bonus content including a handy objectives index that maps each test objective to the section of the book in which that objective is covered. This invaluable tool will help readers be certain that they are ready for test day! The Academic Edition is ideal for the classroom and self-study that helps you master all the topics on the new A+ 901 and 902 exams, including Motherboards, processors, RAM, and BIOS Power supplies and system cooling I/O, input ports, and devices Video displays and video cards Customized PCs Laptops, mobile and wearable devices Printers Storage devices including SSDs Installing, using, and troubleshooting Windows, Linux, and OS X Virtualization Networking Security Operational procedures and communications methods COMPUTERS,Certification Guides,CompTIA (incl. A+)

CompTIA A+ Certification Study Guide, Tenth Edition (Exams 220-1001 & 220-1002) A highly effective study system for the CompTIA A+ exams—fully updated for the 2019 versions of the exams With hundreds of accurate practice questions and hands-on exercises, CompTIA A+ Certification Study Guide, Tenth Edition (Exams 220-1001 & 220-1002) teaches you what you need to know―and shows you how to prepare―for these challenging exams. This bestselling self-study guide has been fully revised to offer 100% coverage of all current objectives for both exams. This integrated study system is based on proven methodology. Step-by-step exercises, end-of-chapter self-tests, and “Exam Watch†and “Inside the Exam†sections reinforce salient points and aid in retention. This up-to-date edition features new or expanded coverage of mobile devices; configuring operating systems, including Windows 10, Linux, Android, and iOS; and enhanced security and troubleshooting procedures. • Online content includes 400 practice questions, video tutorials, and unlimited access to a PDF copy of the book • Contains a coupon for 10% off of the exam fee—a $42 value • Written by a pair of PC trainers and experienced authors COMPUTERS,Certification Guides,CompTIA (incl. A+)

CompTIA A+ Complete Study Guide The definitive Sybex guide to A+ certification, fully updated for the latest exams The CompTIA A+ Complete Study Guide, Fourth Edition is your ultimate preparation guide for Exams 220-1001 and 220-1002. Covering 100 percent of the objectives for both exams, this book gets you up to speed on essential A+ knowledge and skills. Master the critical competencies associated with hardware and software, system maintenance, troubleshooting, connectivity, and more—with practical examples drawn from real-world experience, you’ll develop the skill set employers demand in today’s IT environment. End-of-chapter reviews help you gauge your progress and stay on track for success, while exam highlights give you a sneak preview of what to expect on the big day. You also get access to the Sybex online test bank, featuring electronic flashcards, a searchable glossary, and 4 practice exams to help you study from anywhere, any time—track your progress and test your understanding with interactive study tools. CompTIA A+ certification is the industry-leading standard for IT professionals. Hundreds of companies require their computer technicians to hold this valuable credential. Now in its fourth edition, this revised and updated study guide includes expanded coverage of virtualization and cloud computing, mobile hardware installation, network security, and more, to reflect the latest changes in the A+ exam. Providing all the information you need to earn your A+ certification, this invaluable resource will help you: Master the basics of hardware, software, and peripherals Understand and troubleshoot network connectivity issues Install and configure Windows, iOS, Android, Apple OSX, and Linux operating systems The CompTIA A+ Complete Study Guide, Fourth Edition arms you with the tools and knowledge necessary to take your skills to the next level. Whether a first-time candidate or IT professional in need of recertification, this essential study guide will help you prepare, practice, and pass with minimal burden and maximum results. COMPUTERS,Certification Guides,CompTIA (incl. A+)

Complete A+ Guide to IT Hardware and Software Master IT hardware and software installation, configuration, repair, maintenance, and troubleshooting and fully prepare for the CompTIA® A+ Core 1 (220-1001) and Core 2 (220-1002) exams. This is your all-in-one, real-world, full-color guide to connecting, managing, and troubleshooting modern devices and systems in authentic IT scenarios. Its thorough instruction built on the CompTIA A+ Core 1 (220-1001) and Core 2 (220-1002) exam objectives includes coverage of Windows 10, Mac, Linux, Chrome OS, Android, iOS, cloud-based software, mobile and IoT devices, security, Active Directory, scripting, and other modern techniques and best practices for IT management. Award-winning instructor Cheryl Schmidt also addresses widely-used legacy technologies—making this the definitive resource for mastering the tools and technologies you’ll encounter in real IT and business environments. Schmidt’s emphasis on both technical and soft skills will help you rapidly become a well-qualified, professional, and customer-friendly technician. LEARN MORE QUICKLY AND THOROUGHLY WITH THESE STUDY AND REVIEW TOOLS: Learning Objectives and chapter opening lists of CompTIA A+ Certification Exam Objectives make sure you know exactly what you’ll be learning, and you cover all you need to know Hundreds of photos, figures, and tables present information in a visually compelling full-color design Practical Tech Tips provide real-world IT tech support knowledge Soft Skills best-practice advice and team-building activities in every chapter cover key tools and skills for becoming a professional, customer-friendly technician Review Questions—including true/false, multiple choice, matching, fill-in-the-blank, and open-ended questions—carefully assess your knowledge of each learning objective Thought-provoking activities help students apply and reinforce chapter content, and allow instructors to “flip†the classroom if they choose Key Terms identify exam words and phrases associated with each topic Detailed Glossary clearly defines every key term Dozens of Critical Thinking Activities take you beyond the facts to deeper understanding Chapter Summaries recap key concepts for more efficient studying Certification Exam Tips provide insight into the certification exam and preparation process COMPUTERS,Certification Guides,CompTIA (incl. A+)

Complete A+ Guide to IT Hardware and Software Lab Manual The companion Complete A+ Guide to IT Hardware and Software Lab Manual provides students hands-on practice with various computer parts, mobile devices, wired networking, wireless networking, operating systems, and security. The 155 labs are designed in a step-by-step manner that allows students to experiment with various technologies and answer questions along the way to consider the steps being taken. Some labs include challenge areas to further practice the new concepts. The labs ensure students gain the experience and confidence required to succeed in industry. COMPUTERS,Certification Guides,CompTIA (incl. A+)

CompTIA A+ Core 1 (220-1001) and Core 2 (220-1002) Exam Cram This is the perfect study guide to help you pass CompTIA®’s new A+® Core 1 (220-1001) and Core 2 (220-1002) exams. It provides coverage and practice questions for every exam topic, including substantial new coverage of Windows 10, as well as new PC hardware, tablets, smartphones, macOS, Linux, cloud computing, and professional-level networking and security. Deploy and manage computers running Windows 10/8/7, macOS, Linux, iOS, and Android Master and practice the six-step A+ troubleshooting process Understand, install, configure, and troubleshoot motherboards, CPUs, and memory Test and troubleshoot power-related problems Use all forms of storage, including SSDs, optical devices, and RAID systems Work effectively with mobile devices, including laptops, tablets, and smartphones Configure Windows components and applications, use Windows administrative tools, and optimise Windows systems Repair damaged Windows environments and troubleshoot Windows issues Install and manage printers and other peripherals Understand and work with networks, network hardware, wireless protocols, and cloud technologies Install and configure SOHO wired/wireless networks, and troubleshoot connectivity Secure desktops and mobile devices, implement authentication methods, prevent malware attacks, and protect data The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Certification Guides,CompTIA (incl. A+)

CompTIA A+ Practice Questions Exam Cram Core 1 (220-1001) and Core 2 (220-1002) CompTIA A+ Practice Questions Exam Cram Core 1 (220-1001) and Core 2 (220-1002) complements any A+ study plan with 480 practice test questions in the book plus two bonus exams on the companion website–all supported by complete explanations of every answer. This package’s highly realistic questions cover every area of knowledge for both new A+ exams: 220-1001 and 220-1002. Covers the critical information you’ll need to know to score higher on your A+ 220-1001 and 220-1002 exams Features 480 questions presented as three full, realistic practice exams for each A+ certification test: both 220-1001 and 220-1002 Includes a detailed answer explanation for every question Addresses all objectives for the 220-1001 and 220-1002 A+ exams, so you can easily assess your knowledge of every topic The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Certification Guides,CompTIA (incl. A+)

Alpha Project Managers Debunking misconceptions surrounding successful project managers, this source builds upon a landmark survey of more than 800 project managers from around the world to highlight the traits that make them stand out in the minds of their teams, senior managers, customers, and stakeholders. Through in-depth interviews and discussions, the common attributes of these elite project managersfrom character and beliefs to organizational approachesare uncovered and help to explain their achievements. Painstakingly researched, this guide offers key insights by providing multiple perspectives on the character makeup of the world’s most successful project managers. COMPUTERS,Certification Guides,General

Requirements Engineering Fundamentals In practice, requirements engineering tasks become more and more complex. In order to ensure a high level of knowledge and training, the International Requirements Engineering Board (IREB) worked out the training concept “Certified Professional for Requirements Engineeringâ€, which defines a requirements engineer’s practical skills on different training levels. The book covers the different subjects of the curriculum for the “Certified Professional for Requirements Engineering†(CPRE) defined by the International Requirements Engineering Board (IREB). It supports its readers in preparing for the test to achieve the “Foundation Level†of the CPRE. COMPUTERS,Certification Guides,General

CompTIA CTT+ Certified Technical Trainer All-in-One Exam Guide "All-in-One is All You Need" "This book coaches you through the five domains of the exam and provides effective practice exercises to prepare you with confidence. Thanks for providing the industry with such a great book!" -- Linda Hainlen, Director; Learning Solutions, Indiana University Health Get complete coverage of all the material included on the CompTIA CTT+ exams inside this comprehensive resource. Written by industry expert, trainer, and project management consultant Joseph Phillips, this authoritative guide covers exams TKO-201, TKO-202, and TKO-203 in full detail. You'll find learning objectives at the beginning of each chapter, exam tips, practice questions, and in-depth explanations. A bonus appendix provides accelerated review of the exam objectives. Designed to help you pass the exams with ease, this definitive volume also serves as an essential on-the-job reference. COVERS ALL EXAM TOPICS, INCLUDING HOW TO: Evaluate learners' needs Manage the technical classroom Engage learners through instructional methods Manage instructional materials Train with confidence Lead a successful class Manage learner-centered instruction Promote learner engagement Motivate adult learners Evaluate learner competencies Evaluate instructor performance CD-ROM FEATURES: Two practice exams Video training PDF of the book COMPUTERS,Certification Guides,General

Advanced Software Testing - Vol. 1 This book is written for the test analyst who wants to achieve advanced skills in test analysis, design, and execution. With a hands-on, exercise-rich approach, this book teaches you how to define and carry out the tasks required to put a test strategy into action. Learn how to analyze the system, taking into account the user's quality expectations. Additionally, learn how to evaluate system requirements as part of formal and informal reviews, using an understanding of the business domain to determine requirement validity. You will be able to analyze, design, implement, and execute tests, using risk considerations to determine the appropriate effort and priority for tests. You will learn how to report on testing progress and provide necessary evidence to support your evaluations of system quality. COMPUTERS,Certification Guides,General

RHCSA/RHCE Red Hat Linux Certification Practice Exams with Virtual Machines (Exams EX200 & EX300) Don’t Let the Real Test Be Your First Test! RHCSA/RHCE Red Hat Linux Certification Practice Exams with Virtual Machines (Exams EX200 & EX300) features 100+ hands-on labs, four complete practice exams, and three virtual machines. To help you understand the material, the labs and practice exams are accompanied by in-depth answer explanations. This practical guide covers all official objectives for Exams EX200 and EX300 and is the perfect companion to RHCSA/RHCE Red Hat Linux Certification Study Guide, Sixth Edition. Covers all exam topics, including:Virtual Machines and Automated Installations • Fundamental Command Line Skills • RHCSA-Level Security Options • The Boot Process • Linux Filesystem Administration • Package Management • User Administration • RHCSA-Level System Administration Tasks • Security • System Services and SELinux • RHCE Administrative Tasks • Electronic Mail Servers • The Apache Web Server • The Samba File Server • More File-Sharing Services • Administrative Services: DNS, FTP, and Logging Includes three virtual machines preloaded with: Two RHCSA practice exams Two RHCE practice exams 100+ hands-on labs In order to take advantage of the virtual machines that accompany this book you will need a 64-bit system with hardware virtualization enabled as well as RHEL 6 or its equivalent. COMPUTERS,Certification Guides,General

Software Testing Practice Aimed at experts who are dedicated to software testing, The Software Testing Process: Test Management addresses the major issues related to advanced, state-of-the-art test management. This book covers the syllabus required to pass the Certified Tester Examination - Advanced Level as defined by the International Software Testing Qualifications Board (ISTQB). Software developers, project managers, quality managers, and team leaders will benefit from the comprehensive coverage of risk oriented management and the way testing is shown to be an integral, though independent part of software development. Included are best practices in the field of testing, as well as detailed descriptions of involved tasks, roles, and responsibilities. Well suited for self-study, the reader is "taken by the hand" and guided through the key concepts and terminology of software testing in a variety of scenarios and case studies (as featured in the first book in this series, Software Testing Foundations). Not only will testers and test managers find this a must-read, but anyone requiring advanced professional knowledge and skills in this field, anyone wanting to become a true testing professional, will find this book a must for a successful, well-founded education in advanced test management. Topics include: Test process and test toolsTesting in the software life cycleTest policy and test manualTest plan and test planningTest controlIncident managementRisk management/risk-based testingStaff qualificationsTest metrics COMPUTERS,Certification Guides,General

CTS Certified Technology Specialist Exam Guide, Second Edition The Most Complete, Up-to-Date CTS Exam Study System Published with InfoComm International, CTS Certified Technology Specialist Exam Guide, Second Edition provides comprehensive coverage of all objectives on the latest release of the InfoComm Certified Technology Specialist exam—the leading internationally recognized audiovisual (AV) certification. You’ll get learning objectives at the beginning of each chapter, best practices, checklists, diagrams, photos, chapter review questions with in-depth explanations, and a full-color insert. Designed to help you prepare for the CTS exam, this authoritative resource also serves as an essential on-the-job reference. Electronic content includes: One all-new CTS practice exam Covers all current CTS exam objectives, including how to: Conduct a site survey Gather customer information Evaluate and recommend changes to a site environment Develop a functional AV scope Design, provide, and sell AV solutions Conduct a vendor selection process Operate AV solutions Conduct maintenance activities Manage AV solutions and operations Project manage AV projects Perform AV finance and job costing activities Troubleshoot and repair AV solutions COMPUTERS,Certification Guides,General

OCP Upgrade to Oracle Database 12c Exam Guide (Exam 1Z0-060) A Fully Integrated Study System for OCP Exam 1Z0-060 Prepare for the Oracle Certified Professional Upgrade to Oracle Database 12c exam with this exclusive Oracle Press guide. Each chapter features step-by-step examples, a certification summary, a two-minute drill, and a self-test to reinforce the topics presented. This authoritative resource helps you pass the exam and also serves as an essential, on-the-job reference. Get complete coverage of the new features of Oracle Database 12c, including: Oracle Enterprise Manager Database Express and additional tools for database monitoring Multitenant container databases and pluggable databases Auditing, administrative privileges, data redaction, and other Oracle security features Adaptive execution plans, adaptive statistics, and automatic SQL plan management Oracle Recovery Manager backup and recovery improvements Oracle Database Resource Manager and other performance enhancements Oracle Data Pump, SQL*Loader, external tables, and online operations enhancements Improvements to information lifecycle management and storage, including automatic data optimization, in-database archiving, and temporal validity Electronic content includes: 170 practice exam questions with detailed answer explanations COMPUTERS,Certification Guides,General

CHFI Computer Hacking Forensic Investigator Certification All-in-One Exam Guide An all-new exam guide for version 8 of the Computer Hacking Forensic Investigator (CHFI) exam from EC-Council Get complete coverage of all the material included on version 8 of the EC-Council's Computer Hacking Forensic Investigator exam from this comprehensive resource. Written by an expert information security professional and educator, this authoritative guide addresses the tools and techniques required to successfully conduct a computer forensic investigation. You'll find learning objectives at the beginning of each chapter, exam tips, practice exam questions, and in-depth explanations. Designed to help you pass this challenging exam, this definitive volume also serves as an essential on-the-job reference. CHFI Computer Hacking Forensic Investigator Certification All-in-One Exam Guide covers all exam topics, including: Computer forensics investigation process Setting up a computer forensics lab First responder procedures Search and seizure laws Collecting and transporting digital evidence Understanding hard disks and file systems Recovering deleted files and partitions Windows forensics Forensics investigations using the AccessData Forensic Toolkit (FTK) and Guidance Software's EnCase Forensic Network, wireless, and mobile forensics Investigating web attacks Preparing investigative reports Becoming an expert witness Electronic content includes: 300 practice exam questions Test engine that provides full-length practice exams and customized quizzes by chapter or by exam domain COMPUTERS,Certification Guides,General

OCA Oracle Database 12c Installation and Administration Exam Guide (Exam 1Z0-062) A Complete Study System for OCA Exam 1Z0-062 Prepare for the Oracle Certified Associate Oracle Database 12c Installation and Administration exam with this exclusive Oracle Press guide. Each chapter features challenging exercises, a certification summary, a two-minute drill, and a self-test to reinforce the topics presented. This authoritative resource helps you pass the exam and also serves as an essential, on-the-job reference. Get complete coverage of all OCA objectives for exam 1Z0-062, including: Installing and upgrading Oracle Database software Managing the database instance Configuring the Oracle network environment Managing database storage structures Administering user security Managing undo data and data concurrency Implementing Oracle Database auditing Performing database maintenance Managing performance and tuning SQL Managing resources using Oracle Database Resource Manager Automating tasks Moving data Performing backup and recovery Installing Oracle Grid Infrastructure for a standalone server Electronic content includes: 185+ practice exam questions with detailed answers and explanations Test engine that provides custom exams by chapter or by domain COMPUTERS,Certification Guides,General

CCENT ICND1 100-101 Flash Cards and Exam Practice Pack Cisco Press has the only Self-Study Guides Approved by Cisco for the New CCENT Certification. The New Edition of this Best-Selling Flash Cards and Exam Practice Pack is Completely Updated and includes Flash Cards and Reference Sheets for all Topics Covered in the New Exams. Note that this eBook version of the print book does not contain access to the Cert Flash Cards Online application nor to the Practice Test application that come with the print product. Are you ready to take the ICND1 exam for the CCENT certification? You’ve learned the concepts, you have the experience to put them to real-world use, and now you want to practice, practice, practice until exam time. The Cisco CCENT 100-101 Flash Cards and Exam Practice Pack contains more than 500 flash cards and quick reference sheets. Cisco CCENT 100-101 Flash Cards and Exam Practice Pack eBook version gives you two methods of proven, late-stage exam preparation in one package. Flash Cards More than 450 flash cards in print. Quick Reference Sheets All exam topics are covered for a quick review and refresh in more than 100 graphical quick reference sheets. COMPUTERS,Certification Guides,General

Designing for Cisco Internetwork Solutions (DESGN) Foundation Learning Guide Designing for Cisco Internetwork Solutions (DESGN) Foundation Learning Guide Third Edition Sean Wilkins Foundation learning for the CCDA DESGN 640-864 exam Designing for Cisco Internetwork Solutions (DESGN) Foundation Learning Guide, Third Edition, is a Cisco®-authorized, self-paced learning tool for CCDA® foundation learning. This book provides you with the knowledge needed to design enterprise networks. By reading this book, you will gain a thorough understanding of designing routed and switched network infrastructures and services involving LAN, WAN, and broadband access for businesses and organizations. Designing for Cisco Internetwork Solutions (DESGN) Foundation Learning Guide, Third Edition teaches you how to gather internetworking requirements, identify solutions, and design the network infrastructure and services to ensure basic functionality using the principles of hierarchical network design to structure and modularize a converged enterprise network design. Specific topics include understanding the design methodology; structuring and modularizing the network design; designing the Enterprise Campus, Enterprise Data Center, Enterprise Edge, and remote modules as needed; designing an addressing plan and selecting suitable routing protocols; designing basic voice transport across the network; designing a basic wireless solution; and evaluating security solutions. Chapter-ending review questions illustrate and help solidify the concepts presented in the book. Whether you are preparing for CCDA certification or simply want to gain a better understanding of network design principles, you will benefit from the foundation information presented in this book. Designing for Cisco Internetwork Solutions (DESGN) Foundation Learning Guide, Third Edition, is part of a recommended learning path from Cisco that includes simulation and hands-on training from authorized Cisco Learning Partners and self-study products from Cisco Press. To find out more about instructor-led training, e-learning, and hands-on instruction offered by authorized Cisco Learning Partners worldwide, please visit www.cisco.com/go/authorizedtraining. · Understand network design methodologies and the lifecycle of a network · Learn how to structure and modularize network designs within the Cisco Network Architectures for the Enterprise · Design basic campus and data center networks · Build designs for remote connectivity with WAN technologies · Examine IPv4 and IPv6 addressing schemes · Select the appropriate routing protocols for various modules in the enterprise architecture · Evaluate security solutions for the network · Identify voice and video networking considerations · Understand design technologies and considerations when implementing a controller-based wireless network This book is in the Foundation Learning Guide Series. These guides are developed together with Cisco® as the only authorized, self-paced learning tools that help networking professionals build their understanding of networking concepts and prepare for Cisco certification exams. COMPUTERS,Certification Guides,General

CCNP Wireless (642-732 CUWSS) Quick Reference As a final exam preparation tool, the CCNP Wireless (642-732 CUWSS) Quick Reference provides a concise review of all objectives on the new exams. The short eBook provides readers with detailed, graphical-based information, highlighting only the key topics in cram-style format. With this document as your guide, you will review topics on concepts and commands that apply to this exam. This fact-filled Quick Reference allows you to get all-important information at a glance, helping you focus your study on areas of weakness and enhancing your memory retention of essential exam concepts. The CUWSS Conducting Cisco Unified Wireless Site Survey exam is an exam associated with the CCNP Wireless certification. This exam assesses a candidate's capability to plan and conduct a wireless site survey, to design the RF network and to conduct a post installation assessment to ensure compliancy. COMPUTERS,Certification Guides,General

Practical Guide to Advanced Networking, A A Practical Guide to Advanced Networking, Third Edition takes a pragmatic, hands-on approach to teaching advanced modern networking concepts from the network administrator’s point of view. Thoroughly updated for the latest networking technologies and applications, the book guides you through designing, configuring, and managing campus networks, connecting networks to the Internet, and using the latest networking technologies. The authors first show how to solve key network design challenges, including data flow, selection of network media, IP allocation, subnetting, and configuration of both VLANs and Layer 3 routed networks. Next, they illuminate advanced routing techniques using RIP/RIPv2, OSPF, IS-IS, EIGRP, and other protocols, and show how to address common requirements such as static routing and route redistribution. You’ll find thorough coverage of configuring IP-based network infrastructure, and using powerful WireShark and NetFlow tools to analyze and troubleshoot traffic. A full chapter on security introduces best practices for preventing DoS attacks, configuring access lists, and protecting routers, switches, VPNs, and wireless networks. This book’s coverage also includes IPv6, Linux-based networking, Juniper routers, BGP Internet routing, and Voice over IP (VoIP). Every topic is introduced in clear, easy-to-understand language; key ideas are reinforced with working examples, and hands-on exercises based on powerful network simulation software. Key Pedagogical Features NET-CHALLENGE SIMULATION SOFTWARE provides hands-on experience with advanced router and switch commands, interface configuration, and protocols–now including RIPv2 and IS-IS WIRESHARK NETWORK PROTOCOL ANALYZER TECHNIQUES and EXAMPLES of advanced data traffic analysis throughout PROVEN TOOLS FOR MORE EFFECTIVE LEARNING, including chapter outlines and summaries WORKING EXAMPLES IN EVERY CHAPTER to reinforce key concepts and promote mastery KEY TERMS DEFINITIONS, LISTINGS, and EXTENSIVE GLOSSARY to help you master the language of networking QUESTIONS, PROBLEMS, and CRITICAL THINKING QUESTIONS to help you deepen your understanding CD-ROM includes Net-Challenge Simulation Software and the Wireshark Network Protocol Analyzer Software examples. COMPUTERS,Certification Guides,General

PHR/SPHR Professional in Human Resources Certification Practice Exams Don't Let the Real Test Be Your First Test! Based on the HR Certification Institute's Professional and Senior Professional in Human Resources bodies of knowledge, this practical guide contains 600+ realistic practice exam questions to prepare you for these challenging certification exams. To aid in your understanding of the material, in-depth explanations of both the correct and incorrect answers are provided for every question. A valuable pre-assessment exam tests your readiness and identifies areas requiring further study. Designed to help you pass the exams, this is the perfect companion to PHR/SPHR Professional in Human Resources Certification All-in-One Exam Guide. Covers all PHR and SPHR functional areas, including: Business management and strategy Workforce planning and employment Human resource development Compensation and benefits Employee and labor relations Risk management Electronic content includes: All 600+ practice exam questions from the book in the Total Tester exam engine--test yourself by exam topic or take complete exams COMPUTERS,Certification Guides,General

31 Days Before Your CCENT Certification Exam 31 Days Before Your CCENT Certification Exam Second Edition A Day-By-Day Review Guide for the ICND1 (100-101) Certification Exam 31 Days Before Your CCENT Certification Exam offers you a personable and practical way to understand the certification process, commit to taking the 100-101 ICND1 certification exam, and finish your preparation using a variety of Primary and Supplemental study resources. With a CCENT (Cisco Certified Entry Networking Technician) certification, a network professional demonstrates the skills required for entry-level network support positions—the starting point for many successful careers in networking. CCENT is the first step toward achieving CCNA certification. Sign up for the ICND1 exam and use the book’s day-by-day guide and checklist to organize, prepare, and review. Each day in this guide breaks down an exam topic into a manageable bit of information to review using short summaries. A Study Resources section provides you with a quick reference for locating more in-depth treatment of a day’s topics within the Primary and Supplemental resources. The features of the book empower you to fit exam preparation into a busy schedule: --Visual calendar summarizing each day’s study topic --Checklist providing advice for preparation activities leading up to the exam --Description of the 100-101 ICND1 exam organization and sign-up process --Strategies from the author to be mentally, organizationally, and physically prepared for exam day --Conversational tone, which makes your study time more enjoyable Primary Resources: Cisco CCENT/CCNA ICND1 100-101 Official Cert Guide ISBN: 9781587143854 Interconnecting Cisco Network Devices, Part 1 Foundation Learning Guide ISBN: 9781587143762 Introduction to Networks Companion Guide ISBN: 9781587133169 Introduction to Networks Lab Manual ISBN: 9781587133121 Routing and Switching Essentials Companion Guide ISBN: 9781587133183 Routing and Switching Essentials Lab Manual ISBN: 9781587133206 Supplemental Resources: CCENT Practice and Study Guide ISBN: 9781587133459 Cisco CCENT ICND1 100-101 Flash Cards and Exam Practice Pack ISBN: 9781587203992 CCNA Routing and Switching Portable Command Guide, 3e ISBN: 9781587204302 Cisco CCENT ICND1 100-101 Network Simulator ISBN: 9780789750433 COMPUTERS,Certification Guides,General

Essential Virtual SAN (VSAN) Understand and implement VMware Virtual SAN: the heart of tomorrow’s Software-Defined Datacenter (SDDC) VMware’s breakthrough Software-Defined Datacenter (SDDC) initiative can help you virtualize your entire datacenter: compute, storage, networks, and associated services. Central to SDDC is VMware Virtual SAN (VSAN): a fully distributed storage architecture seamlessly integrated into the hypervisor and capable of scaling to meet any enterprise storage requirement. Now, the leaders of VMware’s wildly popular Virtual SAN previews have written the first authoritative guide to this pivotal technology. You’ll learn what Virtual SAN is, exactly what it offers, how to implement it, and how to maximize its value. Writing for administrators, consultants, and architects, Cormac Hogan and Duncan Epping show how Virtual SAN implements both object-based storage and a policy platform that simplifies VM storage placement. You’ll learn how Virtual SAN and vSphere work together to dramatically improve resiliency, scale-out storage functionality, and control over QoS. Both an up-to-the-minute reference and hands-on tutorial, Essential Virtual SAN uses realistic examples to demonstrate Virtual SAN’s most powerful capabilities. You’ll learn how to plan, architect, and deploy Virtual SAN successfully, avoid gotchas, and troubleshoot problems once you’re up and running. Coverage includes Understanding the key goals and concepts of Software-Defined Storage and Virtual SAN technology Meeting physical and virtual requirements for safe Virtual SAN implementation Installing and configuring Virtual SAN for your unique environment Using Storage Policy Based Management to control availability, performance, and reliability Simplifying deployment with VM Storage Policies Discovering key Virtual SAN architectural details: caching I/O, VASA, witnesses, pass-through RAID, and more Ensuring efficient day-to-day Virtual SAN management and maintenance Interoperating with other VMware features and products Designing and sizing Virtual SAN clusters Troubleshooting, monitoring, and performance optimization COMPUTERS,Certification Guides,General

CCNP Routing and Switching ROUTE 300-101 Official Cert Guide Trust the best-selling Official Cert Guide series from Cisco Press to help you learn, prepare, and practice for exam success. They are built with the objective of providing assessment, review, and practice to help ensure you are fully prepared for your certification exam. --Master Cisco CCNP ROUTE 300-101 exam topics --Assess your knowledge with chapter-opening quizzes --Review key concepts with exam preparation tasks This is the eBook edition of the CCNP Routing and Switching ROUTE 300-101 Official Cert Guide. This eBook does not include the companion CD-ROM with practice exam that comes with the print edition. CCNP Routing and Switching ROUTE 300-101 Official Cert Guide from Cisco Press enables you to succeed on the exam the first time and is the only self-study resource approved by Cisco. Expert instructor and best-selling author Kevin Wallace shares preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. This complete, official study package includes --A test-preparation routine proven to help you pass the exam --"Do I Know This Already?" quizzes, which enable you to decide how much time you need to spend on each section --Chapter-ending exercises, which help you drill on key concepts you must know thoroughly --The powerful Pearson IT Certification Practice Test software, complete with hundreds of well-reviewed, exam-realistic questions, customization options, and detailed performance reports --More than 60 minutes of personal video mentoring from the author on important exam topics --A final preparation chapter, which guides you through tools and resources to help you craft your review and test-taking strategies --Study plan suggestions and templates to help you organize and optimize your study time Well regarded for its level of detail, study plans, assessment features, challenging review questions and exercises, this official study guide helps you master the concepts and techniques that ensure your exam success. CCNP Routing and Switching ROUTE 300-101 Official Cert Guide is part of a recommended learning path from Cisco that includes simulation and hands-on training from authorized Cisco Learning Partners and self-study products from Cisco Press. To find out more about instructor-led training, e-learning, and hands-on instruction offered by authorized Cisco Learning Partners worldwide, please visit www.cisco.com. The official study guide helps you master topics on the CCNP R&S ROUTE 300-101 exam, including --Routing protocol characteristics and virtual routers --Remote site connectivity --IPv6 routing and RIPng --EIGRP, OSPFv2, and OSPFv3 --IGP redistribution and route selection --eBGP and iBGP --IPv6 Internet connectivity --Router security --Routing protocol authentication COMPUTERS,Certification Guides,General

CCNP Routing and Switching TSHOOT 300-135 Official Cert Guide Trust the best-selling Official Cert Guide series from Cisco Press to help you learn, prepare, and practice for exam success. They are built with the objective of providing assessment, review, and practice to help ensure you are fully prepared for your certification exam. Master Cisco CCNP TSHOOT 300-135 exam topics Assess your knowledge with chapter-opening quizzes Review key concepts with exam preparation tasks This is the eBook edition of the CCNP Routing and Switching TSHOOT 300-135 Official Cert Guide. This eBook does not include the companion CD-ROM with practice exam that comes with the print edition. CCNP Routing and Switching TSHOOT 300-115 Official Cert Guide from Cisco Press enables you to succeed on the exam the first time and is the only self-study resource approved by Cisco. Expert instructor Raymond Lacoste shares preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. This complete, official study package includes A test-preparation routine proven to help you pass the exam Do I Know This Already? quizzes, which enable you to decide how much time you need to spend on each section Chapter-ending exercises, which help you drill on key concepts you must know thoroughly A trouble ticket chapter that explores 10 additional network failures and the approaches you can take to resolve the issues presented A final preparation chapter, which guides you through tools and resources to help you craft your review and test-taking strategies Study plan suggestions and templates to help you organize and optimize your study time Well regarded for its level of detail, study plans, assessment features, challenging review questions and exercises, this official study guide helps you master the concepts and techniques that ensure your exam success. CCNP Routing and Switching TSHOOT 300-115 Official Cert Guide is part of a recommended learning path from Cisco that includes simulation and hands-on training from authorized Cisco Learning Partners and self-study products from Cisco Press. To find out more about instructor-led training, e-learning, and hands-on instruction offered by authorized Cisco Learning Partners worldwide, please visit www.cisco.com. The official study guide helps you master topics on the CCNP R&S TSHOOT 300-135 exam, including how to troubleshoot: Device performance VLANs, Trunks, and VTP STP and Layer 2 Etherchannel Inter-VLAN routing and Layer 3 Etherchannel Switch security HSRP, VRRP, GLBP IPv4 and IPv6 addressing IPv4/IPv6 routing and GRE tunnels RIPv2, RIPng, EIGRP, and OSPF Route maps, policy-based routing, and route redistribution BGP Management protocols, tools, and access COMPUTERS,Certification Guides,General

CCNP Routing and Switching SWITCH 300-115 Official Cert Guide CCNP Routing and Switching SWITCH 300-115 Official Cert Guide CCNP Routing and Switching SWITCH 300-115 Official Cert Guide from Cisco Press enables you to succeed on the exam the first time and is the only self-study resource approved by Cisco. Expert engineer David Hucaby shares preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. This complete study package includes A test-preparation routine proven to help you pass the exam “Do I Know This Already?†quizzes, which enable you to decide how much time you need to spend on each section Chapter-ending exercises, which help you drill on key concepts you must know thoroughly The powerful Pearson IT Certification Practice Test software, complete with hundreds of well-reviewed, exam-realistic questions, customization options, and detailed performance reports More than 60 minutes of personal video mentoring from the author on important exam topics A final preparation chapter, which guides you through tools and resources to help you craft your review and test-taking strategies Study plan suggestions and templates to help you organize and optimize your study time Well regarded for its level of detail, study plans, assessment features, and challenging review questions and exercises, this official study guide helps you master the concepts and techniques that ensure your exam success. David Hucaby, CCIE® No. 4594, is a lead network engineer for the University of Kentucky, where he works with a large healthcare network based on the Cisco product lines. David holds bachelor’s and master’s degrees in electrical engineering from the University of Kentucky. He is the author of several Cisco Press titles, including CCNA Wireless Cert Guide, Cisco ASA, PIX, and FWSM Firewall Handbook, Second Edition, Cisco Firewall Video Mentor, and Cisco LAN Switching Video Mentor. The official study guide helps you master topics on the CCNP R&S SWITCH 300-115 exam, including the following: Enterprise campus design Switch operation Switch port configuration VLANs, trunks, and VLAN Trunking Protocol (VTP) Spanning Tree Protocol (STP), RSTP, and MSTP Protecting the STP topology Aggregating switch links Multilayer switching Configuring DHCP Logging switch activity and managing switches with SNMP Monitoring performance and traffic High availability Securing switched networks The CD-ROM contains more than 200 practice questions for the exam, memory table exercises and answer keys, a study planner tool, and more than 60 minutes of video. Includes Exclusive Offer for 70% Off Premium Edition eBook and Practice Test Pearson IT Certification Practice Test minimum system requirements: Windows Vista (SP2), Windows 7, or Windows 8.1; Microsoft .NET Framework 4.5 Client; Pentium-class 1GHz processor (or equivalent); 512 MB RAM; 650 MB disk space plus 50 MB for each downloaded practice exam; access to the Internet to register and download exam databases COMPUTERS,Certification Guides,General

CTS-D Certified Technology Specialist-Design Exam Guide Exclusively from McGraw-Hill Professional and InfoComm International, this exam guide covers the latest Certified Technology Specialist Design exam for AV professionals. CTS-D Certified Technology Specialist Design Exam Guide is a complete study system for the leading internationally recognized audiovisual (AV) certification from InfoComm International—the audiovisual association. This exam guide covers AV systems design, including the assessment of client's needs, AV design documents preparation, and coordination with other professionals to ensure AV systems satisfy client requirements. Each chapter contains exam objective call-outs, exam tips, and end-of-chapter review questions with in-depth answer explanations. Covers the 2014 exam update which includes updated IT security design-related content, more networking coverage, and additional business content Electronic content includes an official InfoComm CTS-D practice exam More than 150 photos and illustrations reinforce key AV design concepts COMPUTERS,Certification Guides,General

ITIL Foundation All-in-One Exam Guide Written by an Information Technology Infrastructure Library (ITIL) consulting and training expert, this all-new guide helps you pass the ITIL v3 Foundation certification exam and serves as an on-the-job reference. ITIL Foundation All-in-One Exam Guide takes you through ITIL Foundation v3 (2011), explaining the fundamentals of IT Service Management, the five stages of the service lifecycle, ITIL processes, functions within them, and their crucial interactions, all while clearing up common misapprehensions about ITIL and adding valuable insights and examples. The ITIL is the best practice framework adopted worldwide for managing IT services, and the ITIL Foundation Certification can be considered a pre-requisite for success for all involved in IT services, as well as a stepping stone to IT Service Management certifications in ITIL. Exam Tips, accelerated reviews, and end-of-chapter practice exam questions ensure you’re on track to pass the Foundation exam. Filled with practical exercises and examples that reinforce learning, the book and electronic content include more than 300 practice exam questions and exclusive, real-world examples of how an understanding of ITIL can be used to address common service management challenges. ITIL Licensed Product -- an official endorsement of the quality and accuracy of the book's content Electronic content includes practice exams in a customizable test engine, video training from the author on key concepts, worksheets, and a Quick Review Guide In-depth case studies analyze projects end-to-end through ITIL's framework, taken from the author's 40 years of experience as an ITIL consultant Jim Davies, ITSM UK’s 2013 Trainer of the Year and ITIL Champion provides his “10 Commandments†of IT Service Management COMPUTERS,Certification Guides,General

CompTIA Network+ All-In-One Exam Guide, Sixth Edition (Exam N10-006) From Mike Meyers, the #1 name in CompTIA training and exam preparation, a thorough revision of his bestselling exam guide—updated to cover the 2015 release of the CompTIA Network+ exam. Get complete coverage of all the CompTIA Network+ exam objectives inside this comprehensive resource. Written by the leading expert on CompTIA certification and training, Mike Meyers, this authoritative guide covers exam N10-006 in full detail. You’ll find learning objectives at the beginning of each chapter, exam tips, scenarios, practice exam questions, and in-depth explanations. Designed to help you pass the exam with ease, this definitive volume also serves as an essential on-the-job reference. CompTIA Network+ Certification All-in-One Exam Guide, Sixth Edition covers all exam topics, including: Network architectures Cabling and topology Ethernet basics Network installation TCP/IP applications and network protocols Routing Network naming Advanced networking devices IPv6 Remote connectivity Wireless networking Virtualization and cloud computing Network operations Managing risk Network security Network monitoring and troubleshooting Electronic content includes: 100+ practice exam questions in a customizable test engine 20+ lab simulations to help you prepare for the performance-based questions One hour of video training from Mike Meyers Mike’s favorite shareware and freeware networking tools and utilities COMPUTERS,Certification Guides,General

CCIE Routing and Switching v5.0 Official Cert Guide Library CCIE Routing and Switching v5.0 Official Cert Guide Library, Fifth Edition Assessment, review, and practice package for the CCIE R&S v5.0 exams Includes CCIE Routing and Switching v5.0 Official Cert Guide, Volume 1, Fifth Edition, and CCIE Routing and Switching v5.0 Official Cert Guide, Volume 2, Fifth Edition. This is the eBook version of the print title. The eBook edition does not provide access to the test engine software or the practice tests that accompany the print book These official study guides help you master all the topics on the CCIE R&S v5.0 exams, including Virtual LANs and VLAN Trunking Spanning Tree Protocol (STP) IP services (ARP, NTP, DHCP, NAT, SNMP, NetFlow, and more) RIPv2 and RIPng EIGRP OSPFv2 and v3 IS-IS Route redistribution, route summarization, default routing, and performance routing BGP operations and routing policies QoS WANs IP Multicast Device and network security and tunneling technologies MPLS CCIE Routing and Switching v5.0 Official Cert Guide Library, Fifth Edition from Cisco Press enables you to succeed on the exam the first time and is the only self-study resource approved by Cisco. In the two books included in this package, expert instructors Narbik Kocharians, Peter Palúch, and Terry Vinson share preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. The first volume covers LAN switching, IP networking, and IP IGP routing topics. The second volume covers IP BGP routing, quality of service (QoS), wide area networks, IP multicast, network security, and Multiprotocol Label Switching (MPLS) topics. Together, these two books cover all the topics on the new v5.0 blueprint. This complete study package includes A test-preparation routine proven to help you pass the exams “Do I Know This Already?†quizzes, which enable you to decide how much time you need to spend on each section Chapter-ending exercises, which help you drill on key concepts you must know thoroughly A final preparation chapter, which guides you through tools and resources to help you craft your review and test-taking strategies Study plan suggestions and templates to help you organize and optimize your study time Well regarded for its level of detail, study plans, assessment features, challenging review questions and exercises, this official study guide helps you master the concepts and techniques that ensure your exam success. CCIE Routing and Switching v5.0 Official Cert Guide Library, Fifth Edition is part of a recommended learning path from Cisco that includes simulation and hands-on training from authorized Cisco Learning Partners and self-study products from Cisco Press. To find out more about instructor-led training, e-learning, and hands-on instruction offered by authorized Cisco Learning Partners worldwide, please visit www.cisco.com. This volume is part of the Official Cert Guide series from Cisco Press. Books in this series provide officially developed exam preparation materials that offer assessment, review, and practice to help Cisco Career Certification candidates identify weaknesses, concentrate their study efforts, and enhance their confidence as exam day nears. COMPUTERS,Certification Guides,General

CompTIA Network+ N10-006 Cert Guide This approved study guide helps you master topics on the CompTIA Network+ N10-006 exam, including the following: Computer network fundamentals The OSI model and TCP/IP stack Media types, infrastructure components, and network devices Ethernet technology IPv4 and IPv6 addresses Routing IP traffic with dynamic routing protocols DNAT, SNAT, and PAT Multicast routing Wide Area Networks (WANs) Wireless LANs Network optimization and QoS Windows and UNIX command-line tools for network administration and troubleshooting Network security Troubleshooting common Layer 2, Layer 3, and wireless networking issues CompTIA Network+ N10-006 Cert Guide contains proven study features that enable you to succeed on the exam the first time. Best-selling authors and expert instructors Keith Barker and Kevin Wallace share preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills, essential for successful completion of the performance-based testing items on the exam. This complete, CompTIA-approved study package includes the following: A test-preparation routine proven to help you pass the exams approved by CompTIA Clearly defined chapter learning objectives covering all N10-006 exam topics Chapter-ending review questions and exam preparation exercises, which help you drill on key concepts you must know thoroughly The powerful Pearson IT Certification Practice Test software, complete with hundreds of well reviewed, exam-realistic questions, customization options, and detailed performance reports 40 performance-based practice question exercises to help you prepare for the hands-on exam questions An 80% discount off the Premium Edition eBook and Practice Test (a $40 value!) A free copy of the CompTIA Network+ Simulator Lite software, complete with meaningful lab exercises that help you hone your hands-on skills More than 60 minutes of video mentoring from the author A final preparation chapter that guides you through tools and resources to help you craft your review and test-taking strategies An Exam Essentials appendix that quickly recaps all major chapter topics for easy reference, both in print and interactive digital format A key terms Glossary in both print and on the DVD, which acts as an interactive flash-card application Study plan suggestions and templates to help you organize and optimize your study time A 10% exam discount voucher (a $27 value!) Well regarded for its level of detail, study plans, assessment features, challenging review questions and exercises, video instruction, and hands-on labs, this approved study guide helps you master the concepts and techniques that ensure your exam success. Keith Barker, CCIE No. 6783, has been working in the information technology (IT) industry since 1985. He currently enjoys creating effective and entertaining video training for CBT Nuggets. He has certifications from VMware, Cisco, Juniper, HP, Check Point, Palo Alto, (ISC)2, and many others. Kevin Wallace, CCIEx2 (Collaboration and R/S) NO. 7945, has been a network design specialist for the Walt Disney World Resort, an instructor of networking courses for Skillsoft, and a network manager for Eastern Kentucky University. Kevin currently produces video courses and writes books for Cisco Press/Pearson IT Certification (http://kwtrain.com/books). Companion DVD The DVD contains more than 200 practice questions, 40 performance-based question exercises, glossary flash cards, an exam essentials review tool, memory table exercises and answer keys, a study planner tool, more than 60 minutes of video, and the Network+ Simulator Lite. Includes Exclusive Offer for 80% Off Premium Edition eBook and Practice Tests COMPUTERS,Certification Guides,General

CCNP Routing and Switching Foundation Learning Guide Library CCNP Routing and Switching Foundation Learning Library: ROUTE¿300-101, SWITCH 300-115, TSHOOT 300-135¿contains three books that provide early and comprehensive foundation learning for the three new required exams for CCNP certification: Implementing Cisco IP Routing (ROUTE) Foundation Learning Guide: (CCNP ROUTE 300-101) Implementing Cisco IP Switched Networks (SWITCH) Foundation Learning Guide: (CCNP SWITCH 300-115) Troubleshooting and Maintaining Cisco IP Networks (TSHOOT) Foundation Learning Guide: (CCNP TSHOOT 300-135) This package is a comprehensive self-study tool for learning the material covered in the three new CCNP exams. The books are intermediate-level texts that assume that readers have been exposed to beginner-level networking concepts contained in the CCNA (ICND1 and ICND2) certification curriculum. No previous exposure to the CCNP level subject matter is required, so the books provide a great deal of detail on the topics covered. Within the Authorized Self-Study Guide series, each chapter opens with a list of objectives to help focus the reader's study. Real-world case studies sprinkled throughout help illuminate theoretical concepts. Key terms will be highlighted and defined as they are first used. Each chapter will conclude with a summary to help review key concepts, as well as review questions to reinforce the reader's understanding of what was covered. COMPUTERS,Certification Guides,General

CompTIA Network+ N10-006 Exam Cram Prepare for CompTIA Network+ N10-006 exam success with this CompTIA authorized Exam Cram from Pearson IT Certification, a leader in IT Certification learning and a CompTIA Authorized Platinum Partner. This is the eBook version of the print title. Note that the eBook does not provide access to the practice test software that accompanies the print book. Access to the digital edition of the Cram Sheet is available through product registration at Pearson IT Certification, or see instructions in the back pages of your eBook. CompTIA® Network+ N10-006 Exam Cram, Fifth Edition is the perfect study guide to help you pass the CompTIA Network+ N10-006 exam. It provides coverage and practice questions for every exam topic, including substantial new coverage of security, cloud networking, IPv6, and wireless technologies. The book presents you with an organized test preparation routine through the use of proven series elements and techniques. Exam topic lists make referencing easy. Exam Alerts, sidebars, and Notes interspersed throughout the text keep you focused on what you need to know. Cram Quizzes help you assess your knowledge, and the Cram Sheet tear card is the perfect last-minute review. Covers the critical information you’ll need to know to score higher on your CompTIA Network+ (N10-006) exam! --Understand modern network topologies, protocols, and infrastructure --Implement networks based on specific requirements --Install and configure DNS and DHCP --Monitor and analyze network traffic --Understand IPv6 and IPv4 addressing, routing, and switching --Perform basic router/switch installation and configuration --Explain network device functions in cloud environments --Efficiently implement and troubleshoot WANs --Install, configure, secure, and troubleshoot wireless networks --Apply patches/updates, and support change/configuration management --Describe unified communication technologies --Segment and optimize networks --Identify risks/threats, enforce policies and physical security, configure firewalls, and control access --Understand essential network forensics concepts --Troubleshoot routers, switches, wiring, connectivity, and security COMPUTERS,Certification Guides,General

CompTIA Server+ Study Guide NOTE: The correct URL to access the Sybex interactive online test bank and study tools is www.wiley.com/go/sybextestprep. The book’s back cover, Introduction, and last page in the book provided the wrong URL. We apologize for any confusion and inconvenience this may have caused you. Comprehensive interactive exam preparation plus expert insight from the field CompTIA Server+ Study Guide Exam SK0-004 is your ideal study companion for the SK0-004 exam. With 100% coverage of all exam objectives, this guide walks you through system hardware, software, storage, best practices, disaster recovery, and troubleshooting, with additional coverage of relevant topics including virtualization, big data, cloud storage, security, and scalability. Get an 'in the trenches' view of how server and data storage administration works in a real-world IT environment. From the basics through advanced topics, you'll learn how to deliver world-class solutions in today's evolving organizations by getting under the hood of technologies that enable performance, resiliency, availability, recoverability, and simplicity. Gain access to the Sybex interactive online learning environment, which features electronic flashcards, a searchable glossary, test bank, and bonus practice exams to reinforce what you have learned. Using and understanding in-house storage devices and the cloud has become an urgent skill for any IT professional. This is your comprehensive, expert driven study guide for taking the CompTIA Server+ exam SK0-004 Study 100% of exam objectives and more Understand storage design, implementation, and administration Utilize bonus practice exams and study tools Gain a real-world perspective of data storage technology CompTIA Server+ Study Guide Exam SK0-004 is your ticket to exam day confidence. COMPUTERS,Certification Guides,General

Red Hat RHCSA/RHCE 7 Cert Guide Trust the best-selling Cert Guide series from Pearson IT Certification to help you learn, prepare, and practice for exam success. Cert Guides are built with the objective of providing assessment, review, and practice to help ensure you are fully prepared for your certification exam. Master Red Hat RHCSA (EX200) and RHCE (EX300) exam topics Assess your knowledge with chapter-opening quizzes Review key concepts with exam preparation tasks Test yourself with 4 practice exams (2 RHCSA and 2 RHCE) Gain expertise and knowledge using the companion website, which contains over 40 interactive exercises, 4 advanced CLI simulations, 40 interactive quizzes and glossary quizzes (one for each chapter), 3 virtual machines and more. Red Hat RHCSA/RHCE 7 Cert Guide presents you with an organized test preparation routine through the use of proven series elements and techniques. “Do I Know This Already?†quizzes open each chapter and allow you to decide how much time you need to spend on each section. Exam topic lists make referencing easy. Chapter-ending labs help you drill on key concepts you must know thoroughly. Red Hat RHCSA/RHCE 7, Premium Edition eBook and Practice Test focuses specifically on the objectives for the newest Red Hat RHCSA (EX200) and RHCE (EX300) exams reflecting Red Hat Enterprise Linux 7. Expert Linux trainer and consultant Sander van Vugt shares preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. Material is presented in a concise manner, focusing on increasing your understanding and retention of exam topics. Well-regarded for its level of detail, assessment features, comprehensive design scenarios, and challenging review questions and exercises, this study guide helps you master the concepts and techniques that will allow you to succeed on the exam the first time. This study guide helps you master all the topics on the new RHCSA (EX200) and RHCE (EX300) exams, including Part 1: RHCSA Basic System Management: Installation, tools, text files, server connections; user, group, and permissions management; network configuration Operating Running Systems: Process management, VMs, package installation, task scheduling, logging, managing partitions and LVM logical volumes Advanced System Administration: Basic kernel management, basic Apache server configuration, boot procedures/troubleshooting Managing Network Services: Using Kickstart; managing SELinux; configuring firewalls, remote mounts, FTP, and time services Part 2: RHCE System Configuration/Management: External authentication/authorization, iSCSI SANs, performance reporting, optimization, logging, routing/advanced networking, Bash scripting System Security: Configuring firewalls, advanced Apache services, DNS, MariaDB, NFS, Samba, SMTP, SSH, and time synchronization COMPUTERS,Certification Guides,General

CCNA Security 210-260 Official Cert Guide Trust the best selling Official Cert Guide series from Cisco Press to help you learn, prepare, and practice for exam success. They are built with the objective of providing assessment, review, and practice to help ensure you are fully prepared for your certification exam. --Master Cisco CCNA Security 210-260 Official Cert Guide exam topics --Assess your knowledge with chapter-opening quizzes --Review key concepts with exam preparation tasks This is the eBook edition of the CCNA Security 210-260 Official Cert Guide. This eBook does not include the companion CD-ROM with practice exam that comes with the print edition. CCNA Security 210-260 Official Cert Guide presents you with an organized test-preparation routine through the use of proven series elements and techniques. “Do I Know This Already?†quizzes open each chapter and enable you to decide how much time you need to spend on each section. Exam topic lists make referencing easy. Chapter-ending Exam Preparation Tasks help you drill on key concepts you must know thoroughly. CCNA Security 210-260 Official Cert Guide focuses specifically on the objectives for the Cisco CCNA Security exam. Networking Security experts Omar Santos and John Stuppi share preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. Material is presented in a concise manner, focusing on increasing your understanding and retention of exam topics. Well regarded for its level of detail, assessment features, comprehensive design scenarios, and challenging review questions and exercises, this official study guide helps you master the concepts and techniques that will enable you to succeed on the exam the first time. The official study guide helps you master all the topics on the CCNA Security exam, including --Networking security concepts --Common security threats --Implementing AAA using IOS and ISE --Bring Your Own Device (BYOD) --Fundamentals of VPN technology and cryptography --Fundamentals of IP security --Implementing IPsec site-to-site VPNs --Implementing SSL remote-access VPNs using Cisco ASA --Securing Layer 2 technologies --Network Foundation Protection (NFP) --Securing the management plane on Cisco IOS devices --Securing the data plane --Securing routing protocols and the control plane --Understanding firewall fundamentals --Implementing Cisco IOS zone-based firewalls --Configuring basic firewall policies on Cisco ASA --Cisco IPS fundamentals --Mitigation technologies for e-mail- and web-based threats --Mitigation technologies for endpoint threats CCNA Security 210-260 Official Cert Guide is part of a recommended learning path from Cisco that includes simulation and hands-on training from authorized Cisco Learning Partners and self-study products from Cisco Press. To find out more about instructor-led training, e-learning, and hands-on instruction offered by authorized Cisco Learning Partners worldwide, please visit http://www.cisco.com/web/learning/index.html. COMPUTERS,Certification Guides,General

CWSP Certified Wireless Security Professional Study Guide The most detailed, comprehensive coverage of CWSP-205 exam objectives CWSP: Certified Wireless Security Professional Study Guide offers comprehensive preparation for the CWSP-205 exam. Fully updated to align with the new 2015 exam, this guide covers all exam objectives and gives you access to the Sybex interactive online learning system so you can go into the test fully confident in your skills. Coverage includes WLAN discovery, intrusion and attack, 802.11 protocol analysis, wireless intrusion prevention system implementation, Layer 2 and 3 VPN over 802.11 networks, managed endpoint security systems, and more. Content new to this edition features discussions about BYOD and guest access, as well as detailed and insightful guidance on troubleshooting. With more than double the coverage of the “official†exam guide, plus access to interactive learning tools, this book is your ultimate solution for CWSP-205 exam prep. The CWSP is the leading vendor-neutral security certification administered for IT professionals, developed for those working with and securing wireless networks. As an advanced certification, the CWSP requires rigorous preparation — and this book provides more coverage and expert insight than any other source. Learn the ins and outs of advanced network security Study 100 percent of CWSP-205 objectives Test your understanding with two complete practice exams Gauge your level of preparedness with a pre-test assessment The CWSP is a springboard for more advanced certifications, and the premier qualification employers look for in the field. If you’ve already earned the CWTS and the CWNA, it’s time to take your career to the next level. CWSP: Certified Wireless Security Professional Study Guide is your ideal companion for effective, efficient CWSP-205 preparation. COMPUTERS,Certification Guides,General

Mike Meyers’ CompTIA Network+ Certification Passport, Fifth Edition (Exam N10-006) Bestselling certification author and CompTIA training expert Mike Meyers updates his CompTIA Network+ Certification Passport to give you concise, focused coverage of the new 2015 exam. In Mike Meyers’ CompTIA Network+ Certification Passport, Fifth Edition, the #1 name in professional certification provides you with an intensive focus only on what you need to know to pass CompTIA Network+ Exam N10-006, the latest exam release. The book is completely revised to cover the 2015 exam objectives. New topics include convergence (video and teleconferencing over networks); cloud and virtualization technologies; enhanced networking security concepts; and industry standards and best practices. The Passport series provides an accelerated review and exam preparation for CompTIA Network+ candidates. In addition, Mike Meyers guides you on your career path, providing expert tips and sound advice along the way. Electronic content includes a test engine with two complete practice exams, Mike's favorite freeware and shareware networking tools, and a video introduction to CompTIA Network+. A low-priced quick review guide for CompTIA Network+, the leading vendor-neutral networking certification CompTIA reviewed and approved: CAQC (CompTIA Authorized Quality Curriculum) Electronic content includes Total Seminar's Total Tester exam simulator with 200+ practice exam questions, a new collection of Mike's favorite shareware and freeware networking tools and utilities COMPUTERS,Certification Guides,General

CRISC Certified in Risk and Information Systems Control All-in-One Exam Guide An all-new exam guide for the industry-standard information technology risk certification, Certified in Risk and Information Systems Control (CRISC) Prepare for the newly-updated Certified in Risk and Information Systems Control (CRISC) certification exam with this comprehensive exam guide. CRISC Certified in Risk and Information Systems Control All-in-One Exam Guide offers 100% coverage of all four exam domains effective as of June 2015 and contains hundreds of realistic practice exam questions. Fulfilling the promise of the All-in-One series, this reference guide serves as a test preparation tool AND an on-the-job reference that will serve you well beyond the examination. To aid in self-study, each chapter includes Exam Tips sections that highlight key information about the exam, chapter summaries that reinforce salient points, and end-of-chapter questions that are accurate to the content and format of the real exam. Electronic download features two complete practice exams. 100% coverage of the CRISC Certification Job Practice effective as of June 2015 Hands-on exercises allow for additional practice and Notes, Tips, and Cautions throughout provide real-world insights Electronic download features two full-length, customizable practice exams in the Total Tester exam engine COMPUTERS,Certification Guides,General

CCNA Collaboration CIVND 210-065 Official Cert Guide CCNA Collaboration CIVND 210-065 Official Cert Guide CCNA Collaboration CIVND 210-065 Official Cert Guide from Cisco Press enables you to succeed on the exam the first time and is the only self-study resource approved by Cisco. Expert Cisco Collaboration engineers Brian Morgan and Jason Ball share preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. This complete, official study package includes A test-preparation routine proven to help you pass the exam “Do I Know This Already?†quizzes, which enable you to decide how much time you need to spend on each section Chapter-ending exercises, which help you drill on key concepts you must know thoroughly The powerful Pearson IT Certification Practice Test software, complete with hundreds of well-reviewed, exam-realistic questions, customization options, and detailed performance reports A final preparation chapter, which guides you through tools and resources to help you craft your review and test-taking strategies Study plan suggestions and templates to help you organize and optimize your study time Well regarded for its level of detail, study plans, assessment features, challenging review questions and exercises, this official study guide helps you master the concepts and techniques that ensure your exam success. CCNA Collaboration CIVND 201-065 Official Cert Guide is part of a recommended learning path from Cisco that includes simulation and hands-on training from authorized Cisco Learning Partners and self-study products from Cisco Press. To find out more about instructor-led training, e-learning, and hands-on instruction offered by authorized Cisco Learning Partners worldwide, please visit www.cisco.com. The official study guide helps you master topics on the CCNA Collaboration CIVND 210-065 exam, including the following: Cisco Collaboration components and architecture Cisco Digital Media Suite, Digital Signs, Cisco Cast, and Show and Share Cisco video surveillance components and architectures Cisco IP Phones, desktop units, and Cisco Jabber Cisco TelePresence endpoint portfolio Cisco Edge Architecture including Expressway Multipoint, multisite, and multiway video conferencing features Cisco TelePresence MCU hardware and server family Cisco TelePresence management Cisco WebEx solutions Register your product at ciscopress.com/register for convenient access to downloads, updates, and corrections as they become available. COMPUTERS,Certification Guides,General

CCNA Wireless 200-355 Official Cert Guide Trust the best selling Official Cert Guide series from Cisco Press to help you learn, prepare, and practice for exam success. This series is built with the objective of providing assessment, review, and practice to help ensure you are fully prepared for your certification exam. Master Cisco CCNA Wireless 200-355 exam topics Assess your knowledge with chapter-opening quizzes Review key concepts with exam preparation tasks This is the eBook edition of the CCNA Wireless 200-355 Official Cert Guide. This eBook does not include the companion DVD with practice exam that comes with the print edition. CCNA Wireless 200-355 Official Cert Guide presents you with an organized test-preparation routine through the use of proven series elements and techniques. “Do I Know This Already?†quizzes open each chapter and enable you to decide how much time you need to spend on each section. Exam topic lists make referencing easy. Chapter-ending Exam Preparation Tasks help you drill on key concepts you must know thoroughly. CCNA Wireless 200-355 Official Cert Guide focuses specifically on the objectives for the Cisco CCNA WIFUND exam. Leading network engineer and best-selling Cisco certification author David Hucaby shares preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. Material is presented in a concise manner, focusing on increasing your understanding and retention of exam topics. Well regarded for its level of detail, assessment features, comprehensive design scenarios, and challenging review questions and exercises, this official study guide helps you master the concepts and techniques that will enable you to succeed on the exam the first time. The official study guide helps you master all the topics on the CCNA WIFUND 200-355 exam, including RF signals, modulations, standards, and performance Antenna theory Wireless LAN topologies and 802.11 frame types Wireless AP coverage planning Cisco wireless architectures Autonomous, cloud, and controller-based deployments Controller discovery, roaming, and RRM Wireless security WLAN configuration Wireless guest network implementation Client connectivity Cisco wireless network management Troubleshooting interference and connectivity CCNA Wireless 200-355 Official Cert Guide is part of a recommended learning path from Cisco that includes simulation and hands-on training from authorized Cisco Learning Partners and self-study products from Cisco Press. To find out more about instructor-led training, e-learning, and hands-on instruction offered by authorized Cisco Learning Partners worldwide, please visit http://www.cisco.com/web/learning/index.html. COMPUTERS,Certification Guides,General

CompTIA A+ Certification All-in-One Exam Guide, Ninth Edition (Exams 220-901 & 220-902) This bestselling on-the-job reference and test preparation guide has been fully revised for the new 2015 CompTIA exam objectives for exams 901 & 902 Written by the leading authority on CompTIA A+ certification and training, this self-study set has been thoroughly updated to cover 100% of the topics covered on the latest edition of the exam. New topics include managing and maintaining cellular devices, including tablets; configuring operating systems, including Windows 8, Android, and iOS; and enhanced, mobile-centered security and troubleshooting procedures. The All-in-One Exam Guide enables you to take the test with complete confidence. It also serves as a practical reference for IT support and technical personnel. Bonus electronic content includes: Practice exams with hundreds of accurate questions More than an hour of video training featuring Mike Meyers Performance-based simulations that prepare you for the performance-based questions on the exam A collection of Mike's favorite free PC tools Key Features include: Written with the “in the trenches†voice and clarity Mike Meyers is known for Features pre-assessment tests, exam tips, and “Try This!†sections to reinforce difficult topics Includes a coupon for 10% off of the exam fee, a $37 value COMPUTERS,Certification Guides,General

LPIC-2 Full coverage of the latest LPI-level 2 exams, with bonus online test bank LPIC-2 is the one-stop preparation resource for the Linux Professional Institute's Advanced Level certification exam. With 100 percent coverage of all exam objectives, this book provides clear and concise coverage of the Linux administration topics you'll need to know for exams 201 and 202. Practical examples highlight the real-world applications of important concepts, and together, the author team provides insights based on almost fifty years in the IT industry. This brand new second edition has been completely revamped to align with the latest versions of the exams, with authoritative coverage of the Linux kernel, system startup, advanced storage, network configuration, system maintenance, web services, security, troubleshooting, and more. You also get access to online learning tools including electronic flashcards, chapter tests, practice exams, and a glossary of critical terms to help you solidify your understanding of upper-level Linux administration topics. The LPI-level 2 certification confirms your advanced Linux skill set, and the demand for qualified professionals continues to grow. This book gives you the conceptual guidance and hands-on practice you need to pass the exam with flying colors. Understand all of the material for both LPIC-2 exams Gain insight into real-world applications Test your knowledge with chapter tests and practice exams Access online study aids for more thorough preparation Organizations are flocking to the open-source Linux as an excellent, low-cost, secure alternative to expensive operating systems like Microsoft Windows. As the Linux market share continues to climb, organizations are scrambling to find network and server administrators with expert Linux knowledge and highly practical skills. The LPI-level 2 certification makes you the professional they need, and LPIC-2 is your ideal guide to getting there. COMPUTERS,Certification Guides,General

RHCSA/RHCE Red Hat Linux Certification Study Guide, Seventh Edition (Exams EX200 & EX300) Based on Red Hat Enterprise Linux 7, the new edition of this bestselling study guide covers the updated Red Hat Certified System Administrator (RHCSA) and Red Hat Certified Engineer (RHCE) exams. RHCSA/RHCE Red Hat Linux Certification Study Guide, 7th Edition is fully revised to cover the recently released Red Hat Enterprise Linux 7 and the corresponding RHCSA and RHCE certification exams. This new edition provides complete coverage of all official exam objectives for the new exams. An integrated study system based on proven pedagogy, this revised bestseller features special elements that reinforce and teach practical skills while preparing candidates for the exam. Each chapter includes step-by-step exercises, Exam Watch and On-the-Job sidebars, Two-Minute Drills, end-of-chapter self tests, and hands-on lab questions. Electronic content includes four complete lab-based practice exams to ensure you’re ready to sit for the live exams. Complete coverage of all exam objectives and performance-based requirements related to the exams, including difficult lab-based scenarios Electronic content includes four complete lab-based practice exams, two for RHSCA and two for RHCE A proven study system for RHCSA and RHCE candidates This book includes copies of the Linux Kernel provided under the terms of the GNU General Public License version 2 COMPUTERS,Certification Guides,General

VMware Certified Professional Data Center Virtualization on vSphere 6.7 Study Guide Master vSphere 6 virtualization with hands-on practice and bonus preview exams VCP6-DCV: VMware Certified Professional-Data Center Virtualization on vSphere 6 Study Guide is your ultimate guide to preparing for exam 2VO-621. This Study Guide provides 100% coverage of all exam objectives and offers a unique set of study tools including assessment tests, objective map, real-world scenarios, hands-on exercises, and much more so you can be confident come exam day. You will also receive access to the superior Sybex interactive online learning environment that provides additional study tools including electronic flashcards and bonus practice exams. More than just a study guide, this book bridges the gap between exam prep and real-world on the job skills by focusing on the key information VMware professionals need to do the job. You'll master the vCenter Server and ESXi from planning and installation through upgrade and security, and develop an in-depth understanding of vSphere networking and storage, vApp deployment, service level establishment, troubleshooting, monitoring implementation, and so much more. Study 100% of exam 2V0-621 objectives Practice your skills with hands-on exercises Gain professional insight from real-world scenarios Test your understanding with review questions, practice tests, and more Virtualization is the number-one IT priority for organizations across public and private sectors, and VMware is the dominant force in the virtualization space. The VCP6-DCV certification gives you a highly marketable credential in terms of employment, but first you must pass this challenging exam. VCP6-DCV gives you the power of Sybex exam prep and the skills you need to excel at the job. COMPUTERS,Certification Guides,General

CISSP All-in-One Exam Guide, Seventh Edition Completely revised and updated for the 2015 CISSP body of knowledge, this new edition by Fernando Maymì continues Shon Harris’s bestselling legacy, providing a comprehensive overhaul of the content that is the leading chosen resource for CISSP exam success, and has made Harris the #1 name in IT security certification. This bestselling self-study guide fully prepares candidates for the challenging Certified Information Systems Security Professional exam and offers 100% coverage of all eight exam domains. This edition has been thoroughly revised to cover the new CISSP 2015 Common Body of Knowledge, including new hot spot and drag and drop question formats, and more. Each chapter features learning objectives, exam tips, practice questions, and in-depth explanations. Beyond exam prep, the guide also serves as an ideal on-the-job reference for IT security professionals. CISSP All-in-One Exam Guide, Seventh Edition provides real-world insights and cautions that call out potentially harmful situations. Fully updated to cover the 8 new domains in the 2015 CISSP body of knowledge Written by leading experts in IT security certification and training Features new hot spot and drag-and-drop question formats Electronic content includes 1400+ updated practice exam questions COMPUTERS,Certification Guides,General

CISSP Practice Exams, Fourth Edition Complete, up-to-date coverage of the 2015 CISSP exam, including 1250+ realistic practice questions Fully updated and featuring new exam question formats, this self- study tool contains more than 1250 realistic practice exam questions and offers 100% coverage of the 2015 CISSP Common Body of Knowledge. In-depth explanations of both the correct and incorrect answers are provided for every question. This book is the perfect companion to CISSP All-in-One Exam Guide, Seventh Edition. Designed as an exam-focused self-study aid and resource, CISSP Practice Exams, Fourth Edition, fully covers the eight newly-revised exam domains. The logical structure of the book allows you to focus on specific topics and tailor your study to areas of expertise and weakness. Each chapter presents more than 25 exam questions—an additional 1000+ review questions are contained in the book's electronic content. Fully revised to cover new exam domains and the 2015 CISSP CBK Written by leading experts in IT security certification and training Electronic content features 1000+ practice exam questions, including questions in the new drag and drop and hotspot formats COMPUTERS,Certification Guides,General

MCSA Windows 10 Study Guide Master Windows 10 installation and configuration, including new technologies The MCSA Windows 10 Study Guide is the only comprehensive resource you'll need to prepare for Exam 70-698. You'll find expert coverage of 100% of all exam objectives led by expert Microsoft MVP, William Panek. Quickly master the concepts and processes involved in Windows 10 installation and configuration. The Sybex superior study tools and online learning environment include: system requirements, devices, core services, networking, storage, data access and usage, maintenance, updates, data recovery, and more. Real-world scenarios bring on the job experience while hands-on exercises provide practical instruction on critical techniques, and the Sybex online learning environment gives you access to electronic flashcards for last minute review, an assessment test, and bonus practice exams so you can be confident on exam day. Exam 70-698 is the first of two exams for the MCSA certification. Addressing local and desktop deployments, these topics form the foundation of what's to come. This Sybex Study Guide gives you the tools you need along with expert content so you can build the essential knowledge base and master the ley concepts. Clarify processes with hands-on exercises Identify knowledge gaps through chapter review questions Test your understanding with online bonus practice exams and more With a 90-percent market share, Windows is the world's number-one desktop OS. While it may look similar to Windows 8, Windows 10 includes a number of enhanced features that specialists need to know, and MCSA candidates must be able to demonstrate a clear understanding of how to work with these new technologies. MCSA Windows 10 Study Guide: Exam 70-698 is your complete guide to Windows 10 installation and configuration, with expert instruction and practical exam preparation. COMPUTERS,Certification Guides,General

CEH Certified Ethical Hacker All-in-One Exam Guide, Third Edition Fully up-to-date coverage of every topic on the CEH v9 certification exam Thoroughly revised for current exam objectives, this integrated self-study system offers complete coverage of the EC Council's Certified Ethical Hacker v9 exam. Inside, IT security expert Matt Walker discusses all of the tools, techniques, and exploits relevant to the CEH exam. Readers will find learning objectives at the beginning of each chapter, exam tips, end-of-chapter reviews, and practice exam questions with in-depth answer explanations. An integrated study system based on proven pedagogy, CEH Certified Ethical Hacker All-in-One Exam Guide, Third Edition, features brand-new explanations of cloud computing and mobile platforms and addresses vulnerabilities to the latest technologies and operating systems. Readers will learn about footprinting and reconnaissance, malware, hacking Web applications and mobile platforms, cloud computing vulnerabilities, and much more. Designed to help you pass the exam with ease, this authoritative resource will also serve as an essential on-the-job reference. Features more than 400 accurate practice questions, including new performance-based questions Electronic content includes 2 complete practice exams and a PDF copy of the book Written by an experienced educator with more than 30 years of experience in the field COMPUTERS,Certification Guides,General

MCSA Windows Server 2016 Study Guide NOTE: As the response to the coronavirus (COVID-19) continues to evolve rapidly around the world, Microsoft has announced that it’s extending the retirement date of the current MCSA Windows Server 2016 certification until January 31, 2021. Pearson VUE has temporarily closed many of its testing centers worldwide in response to global government regulations to battle the spread of COVID-19. As an alternative to taking your exam at a testing center, online proctoring is available, which allows you to take your certification exam in the comfort of your own home or office. Instead of taking the required exams at a Pearson VUE testing center near you, Pearson VUE will be offering only online proctored exams for the foreseeable future. This means you will have more time to prepare for the current exams: 70-740: Installation, Storage, and Compute with Windows Server 2016 70-741: Networking with Windows Server 2016 70-742: Identity with Windows Server 2016 To help you prepare for the exams, our Study Guides are available for purchase. The bestselling MCSA 70-740 study guide, updated for the latest exam MCSA Windows Server 2016 Study Guide is your ultimate resource for Exam 70-740. Covering 100% of all exam objectives, this study guide goes far beyond concept review with real-world scenarios containing expert insights, chapter review questions, hands-on practice exercises while the Sybex interactive learning environment provides additional last minute review through practice exams, electronic flashcards, and searchable glossary. This new edition has been fully updated to align with the Windows Server 2016 exam, featuring authoritative coverage of installation, configuration, server roles, Hyper-V, core network services, Active Directory, Group Policy, security, remote access, disaster recovery, and more. The vast majority of servers around the world use Windows Server, and the 2016 release includes a host of new features and updates. This study guide has been updated to prepare you for these changes so you can be confident on exam day and beyond. Study 100% of Exam 70-740 objectives Gain hands-on practice performing critical tasks Link concept to practice through real-world scenarios Access to the Sybex interactive learning environment Whether you want to sit for the exam, or simply improve your job performance, this Sybex study guide will give you the expert insight to learn the key concepts and latest updates to Windows Server 2016. COMPUTERS,Certification Guides,General

CISA Certified Information Systems Auditor All-in-One Exam Guide, Third Edition This up-to-date self-study system offers 100% coverage of every topic on the 2016 version of the CISA exam The fully revised new edition delivers complete coverage of every topic on the latest release of the Certified Information Systems Auditor (CISA) exam. Written by an IT security and auditing expert, CISA Certified Information Systems Auditor All-in-One Exam Guide, Third Edition , covers all five exam domains developed by the Information Systems Audit and Control Association (ISACA). This effective self-study system features learning objectives at the beginning of each chapter, in-depth explanations of each topic, and accurate practice questions. Each chapter includes Exam Tips that highlight key exam information, hands-on exercises, a chapter summary that serves as a quick review, and end-of-chapter questions that simulate those on the actual exam. Designed to help you pass the CISA exam with ease, this trusted guide also serves as an ideal on-the-job reference. The latest edition of this trusted resource offers complete, up-to-date coverage of all the material included on the latest release of the Certified Information Systems Auditor exam. Written by an IT security and audit expert, CISA Certified Information Systems Auditor All-in-One Exam Guide, Third Edition covers all five exam domains developed by ISACA®. You’ll find learning objectives at the beginning of each chapter, exam tips, practice exam questions, and in-depth explanations. Designed to help you pass the CISA exam with ease, this comprehensive guide also serves as an essential on-the-job reference for new and established IS auditors. COVERS ALL EXAM TOPICS, INCLUDING: • IT governance and management• Information systems audit process• Information systems life-cycle management• IT service delivery and infrastructure• Information asset protection Electronic content includes: • 400 practice exam questions in the Total Tester exam engine--take full-length practice exams or customizable quizzes by exam topic (Windows only) COMPUTERS,Certification Guides,General

CISSP Boxed Set 2015 Common Body of Knowledge Edition Prepare for the 2015 CISSP exam with this up-to-date, money-saving study package Designed as a complete self-study program, this collection offers a variety of proven, exam-focused resources to use in preparation for the 2015 CISSP exam. This set bundles the seventh edition of Shon Harris’ bestselling CISSP All-in-One Exam Guide and CISSP Practice Exams, FourthEdition. CISSP candidates will gain access to a variety of comprehensive resources to get ready for this challenging exam. CISSP Boxed Set 2015 Common Body of Knowledge Edition fully covers the eight newly-revised exam domains and offers real-world insights from the authors’ professional experiences. More than 1250 accurate practice exam questions are provided, along with in-depth explanations of both the correct and incorrect answers. Presents 100% coverage of the 2015 CISSP Common Body of Knowledge Written by leading experts in IT security certification and training This bundle is 12% cheaper than buying the books individually Shon Harris, CISSP was the founder and CEO of Logical Security LLC, an information security consultant, a former engineer in the Air Force's Information Warfare unit, an instructor, and an author. Fernando MaymÃ, Ph.D., CISSP, is a security practitioner with over 25 years of experience in the field. Jonathan Ham, CISSP, GSEC, GCIA, GCIH, is an independent consultant who specializes in large-scale enterprise security issues. He is co-author of Network Forensics: Tracking Hackers through Cyberspace. COMPUTERS,Certification Guides,General

MCSA The go-to MCSA prep guide, updated for Windows 10 and the new exams MCSA Windows 10 Complete Study Guide is your comprehensive resource for taking both Exams 70-698 and 70-697. Covering 100% of all exam objectives, this study guide goes beyond mere review to delve deeper into the complex topics and technologies to help you strengthen your understanding and sharpen your skills. Written by a veteran Microsoft MVP, this guide walks you through MCSA skills in context to show you how concepts are applied in real-world situations. Hands-on exercises speed the learning process and facilitate internalization, while review questions challenge and test the depth of your understanding. You also get access to the Sybex interactive online learning environment, featuring flashcards, videos, an assessment test, and bonus practice exams to face exam day with confidence. The MCSA certification process has changed; Exam 70-698 tests your skills in installing and configuring Windows 10, and then Exam 70-697 gauges your abilities in configuring Windows devices. This book is your ideal companion to study for both exams. Study 100 percent of the objectives for Exams 70-698 and 70-697 Apply your knowledge with hands-on exercises Test your skills with challenging review questions Access videos, electronic flashcards, a searchable glossary, and bonus practice exams The demand for qualified Windows 10 professionals will be high, as more than half of the corporate user base that skipped Windows 8/8.1 is expected to adopt Windows 10. If you want the skills that are in demand, you need to get certified; if you're ready to get serious about the exam, MCSA: Windows 10 Complete Study Guide is the resource you shouldn't be without. COMPUTERS,Certification Guides,General

CompTIA Server+ Certification All-in-One Exam Guide (Exam SK0-004) Complete coverage of every objective for the CompTIA Server+ exam Take the CompTIA Server+ exam with confidence using this highly effective self-study guide. CompTIA Server+ Certification All-in-One Exam Guide (Exam SK0-004) offers complete coverage of every topic on the latest version of the exam. You will get in-depth explanations of the latest server types and components, virtualization, IPv4 and IPv6 networking, cloud computing, security, troubleshooting, and more. The book and electronic content provide 350+ accurate practice questions along with in-depth answers, explanations, learning objectives, and exam tips. Coverage includes: • General concepts• CompTIA Server+ essentials• Server hardware• Server operating systems• Storage• Network concepts• Security• Troubleshooting• Performance optimization Electronic content includes: • Practice exam questions COMPUTERS,Certification Guides,General

CompTIA Project+ Study Guide The bestselling Project+ preparation guide, updated for the latest exam The CompTIA Project+ Study Guide, Second Edition is your comprehensive resource for taking Exam PK0-004. With 100% coverage of all exam objectives, bolstered by real-world scenarios and the Sybex interactive learning environment, this book gives you everything you need to approach the exam with confidence. Detailed explanations and superior study tools cover and reinforce setup, initiation, planning, execution, delivery, change, control, communication, and closure, and the author Kim Heldman's twenty-five years of project management experience provide deep insight into real-world applications. Study tools include access to two bonus practice exams, allowing you to focus on areas you need further review, and electronic flashcards provide last minute review on key concepts. The Project+ exam is a first step into the complex world of project management, and serves as a springboard to the Project Management Institute's (PMI) PMP certification. This study guide helps you build the knowledge you need to be confident on exam day. Review 100 percent of the Project+ exam objectives Understand the real-world applications of each concept Gain expert insight drawn from real-world experience Access online practice exams, electronic flashcards, and more Every industry needs people who know how to deliver successful project outcomes. The Project+ exam parallels the PMI's A Guide to Project Management Body of Knowledge (PMBOK© Guide), so this smart study guide gives you a solid foundation for additional project management training and certification. The CompTIA Project+ Study Guide, Second Edition combines industry-leading expertise with Sybex resources to help you successfully begin your project management journey. COMPUTERS,Certification Guides,General

CCSP Certified Cloud Security Professional All-in-One Exam Guide This self-study guide delivers 100% coverage of all topics on the new CCSP exam This highly effective test preparation guide covers all six domains within the CCSP Body of Knowledge, as established both by CSA and the (ISC)2. The book offers clear explanations of every subject on the brand-new CCSP exam and features accurate practice questions and real-world examples. Written by a respected computer security expert, CCSP Certified Cloud Security Professional All-in-One Exam Guide is both a powerful study tool and a valuable reference that will serve you long after the test. To aid in self-study, each chapter includes exam tips that highlight key information, a summary that serves as a quick review of salient points, and practice questions that allow you to test your comprehension. “Notes,†“Tips,†and “Cautions†throughout provide insight and call out potentially harmful situations. · Practice questions match the tone, content, and format of those on the actual exam · Electronic content includes 300+ downloadable practice questions (PC-compatible) · Written by an experienced technical writer and computer security expert COMPUTERS,Certification Guides,General

CEH Certified Ethical Hacker Bundle, Third Edition Fully revised for the CEH v9 exam objectives, this valuable bundle includes two books, exclusive electronic content, and a bonus quick review guide This thoroughly updated, money-saving self-study set gathers essential exam-focused resources to use in preparation for the latest Certified Ethical Hacker exam. CEH Certified Ethical Hacker All-in-One Exam Guide, Third Edition, provides an in-depth review that covers 100% of the exam’s objectives. CEH Certified Ethical Hacker Practice Exams, Third Edition, tests and reinforces this coverage with 500+ realistic practice questions. The CEH Certified Ethical Hacker Bundle, Third Edition, contains a bonus Quick Review Guide that can be used as the final piece for exam preparation. This content comes in addition to the electronic content included with the bundle’s component books. This new edition includes greater emphasis on cloud computing and mobile platforms and addresses new vulnerabilities to the latest technologies and operating systems. In all, the bundle includes more than 1000 accurate questions with detailed answer explanations Electronic content includes the Total Tester customizable exam engine, Quick Review Guide, and searchable PDF copies of both books Readers will save 12% compared to buying the two books separately, and the bonus Quick Review Guide is available only with the bundle COMPUTERS,Certification Guides,General

Project Management with CompTIA Project+ Apply the latest project management techniques and prepare for CompTIA Project+ certification This fully updated self-study guide and professional resource shows how to successfully manage projects and prepare for the challenging CompTIA Project+ exam. Project Management with CompTIA Project+: On Track from Start to Finish, Fourth Edition, walks you through each step of the project management process, covering critical strategies for on-time and within-budget projects. You’ll get complete explanations of every objective on the CompTIA Project+ exam along with end of chapter summaries, quizzes, and exercises that reinforce key points. Coverage includes:• Initiating the project• Developing project plans• Working with management• Managing project scope• Creating the budget• Building a project plan• Organizing a project team• Managing teams• Implementing the project plan• Revising the project plan• Enforcing quality• Completing the project Electronic content includes: • Two complete practice exams• Video training from the author• Templates and worksheets COMPUTERS,Certification Guides,General

OCA Java SE 8 Programmer I Exam Guide (Exams 1Z0-808) Up-to-date coverage of every topic on the Java 8 SE Programmer I exam Prepare for the OCA Java SE 8 Programmer I exam using this effective self-study system from Oracle Press. Written by developers of the original Sun Certified Java Programmer exam, OCA Java SE 8 Programmer I Exam Guide (Exam 1Z0-808) includes two complete, accurate practice exams. In all, you will get more than 200 practice questions that mirror those on the actual test in content, tone, and format. Beyond fully preparing you for the challenging exam, the book also serves as an ideal on-the-job reference. Clearly explains every topic on Exam IZ0-808, including:• Declarations• Access control• Object orientation• Assignments• Operators• Flow control• Exceptions• Strings• Arrays• ArrayLists Electronic content includes:• 200+ practice exam questions• Fully customizable test engine• Secured book PDF COMPUTERS,Certification Guides,General

CompTIA Security+ Study Guide Some copies of CompTIA Security+ Study Guide: Exam SY0-501 (9781119416876) were printed without discount exam vouchers in the front of the books. If you did not receive a discount exam voucher with your book, please visit http://media.wiley.com/product_ancillary/5X/11194168/DOWNLOAD/CompTIA_Coupon.pdf to download one. Expert preparation covering 100% of Security+ exam SY0-501 objectives CompTIA Security+ Study Guide, Seventh Edition offers invaluable preparation for Exam SY0-501. Written by an expert author team, this book covers 100% of the exam objectives with clear, concise explanation. You'll learn how to handle threats, attacks, and vulnerabilities using industry-standard tools and technologies, while understanding the role of architecture and design. From everyday tasks like identity and access management to complex topics like risk management and cryptography, this study guide helps you consolidate your knowledge base in preparation for the Security+ exam. Practical examples illustrate how these processes play out in real-world scenarios, allowing you to immediately translate essential concepts to on-the-job application. You also gain access to the Sybex online learning environment, which features a robust toolkit for more thorough prep: flashcards, glossary of key terms, practice questions, and a pre-assessment exam equip you with everything you need to enter the exam confident in your skill set. This study guide is approved and endorsed by CompTIA, and has been fully updated to align with the latest version of the exam. Master essential security technologies, tools, and tasks Understand how Security+ concepts are applied in the real world Study on the go with electronic flashcards and more Test your knowledge along the way with hundreds of practice questions To an employer, the CompTIA Security+ certification proves that you have the knowledge base and skill set to secure applications, devices, and networks; analyze and respond to threats; participate in risk mitigation, and so much more. As data threats loom larger every day, the demand for qualified security professionals will only continue to grow. If you're ready to take the first step toward a rewarding career, CompTIA Security+ Study Guide, Seventh Edition is the ideal companion for thorough exam preparation. COMPUTERS,Certification Guides,General

CCNA Security Study Guide Cisco has announced big changes to its certification program. As of February 24, 2020, all current certifications will be retired, and Cisco will begin offering new certification programs. The good news is if you’re working toward any current CCNA certification, keep going. You have until February 24, 2020 to complete your current CCNA. If you already have CCENT/ICND1 certification and would like to earn CCNA, you have until February 23, 2020 to complete your CCNA certification in the current program. Likewise, if you’re thinking of completing the current CCENT/ICND1, ICND2, or CCNA Routing and Switching certification, you can still complete them between now and February 23, 2020. Lay the foundation for a successful career in network security CCNA Security Study Guide offers comprehensive review for Exam 210-260. Packed with concise explanations of core security concepts, this book is designed to help you successfully prepare for the exam. Expert instruction guides you through critical concepts relating to secure network infrastructure, access management, VPN encryption, Firewalls, intrusion prevention and more, with complete coverage of the CCNA exam objectives. Practical examples allow you to apply your skills in real-world scenarios, helping you transition effectively from "learning" to "doing". You also get access to the Sybex online learning environment, featuring the tools you need to maximize your study time: key terminology and flash cards allow you to study anytime, anywhere, while chapter tests and practice exams help you track your progress and gauge your readiness along the way. The CCNA Security certification tests your knowledge of secure network installation, monitoring, and troubleshooting using Cisco security hardware and software solutions. When you're ready to get serious about preparing for the exam, this book gives you the advantage of complete coverage, real-world application, and extensive learning aids to help you pass with confidence. Master Cisco security essentials, standards, and core technologies Work through practical examples drawn from real-world examples Track your progress with online study aids and self-tests Develop critical competencies in maintaining data integrity, confidentiality, and availability Earning your CCNA Security certification validates your abilities in areas that define careers including network security, administrator, and network security support engineer. With data threats continuing to mount, the demand for this skill set will only continue to grow—and in an employer's eyes, a CCNA certification makes you a true professional. CCNA Security Study Guide is the ideal preparation resource for candidates looking to not only pass the exam, but also succeed in the field. COMPUTERS,Certification Guides,General

CompTIA Security+ Review Guide Consolidate your knowledge base with critical Security+ review CompTIA Security+ Review Guide, Fourth Edition, is the smart candidate's secret weapon for passing Exam SY0-501 with flying colors. You've worked through your study guide, but are you sure you're prepared? This book provides tight, concise reviews of all essential topics throughout each of the exam's six domains to help you reinforce what you know. Take the pre-assessment test to identify your weak areas while there is still time to review, and use your remaining prep time to turn weaknesses into strengths. The Sybex online learning environment gives you access to portable study aids, including electronic flashcards and a glossary of key terms, so you can review on the go. Hundreds of practice questions allow you to gauge your readiness, and give you a preview of the big day. Avoid exam-day surprises by reviewing with the makers of the test—this review guide is fully approved and endorsed by CompTIA, so you can be sure that it accurately reflects the latest version of the exam. The perfect companion to the CompTIA Security+ Study Guide, Seventh Edition, this review guide can be used with any study guide to help you: Review the critical points of each exam topic area Ensure your understanding of how concepts translate into tasks Brush up on essential terminology, processes, and skills Test your readiness with hundreds of practice questions You've put in the time, gained hands-on experience, and now it's time to prove what you know. The CompTIA Security+ certification tells employers that you're the person they need to keep their data secure; with threats becoming more and more sophisticated, the demand for your skills will only continue to grow. Don't leave anything to chance on exam day—be absolutely sure you're prepared with the CompTIA Security+ Review Guide, Fourth Edition. COMPUTERS,Certification Guides,General

CCNA Routing and Switching Portable Command Guide (ICND1 100-105, ICND2 200-105, and CCNA 200-125) Here are all the CCNA-level Routing and Switching commands you need in one condensed, portable resource. CCNA Routing and Switching Portable Command Guide is filled with valuable, easy-to-access information—and it’s portable enough to use whether you’re in the server room or the equipment closet. The guide summarizes all CCNA certification-level Cisco IOS Software commands, keywords, command arguments, and associated prompts, providing you with tips and examples of how to apply the commands to real-world scenarios. Throughout, configuration examples give you a better understanding of how these commands are used in simple network designs. This book has been completely updated to cover all topics in the new ICND1 100-105, ICND2 200-105, and CCNA 200-125 exams. Use this quick reference resource to help you memorize commands and concepts as you work to pass the CCNA Routing and Switching certification exam. Coverage includes Network Fundamentals: Subnetting, VLSM, route summarization, cables/connections, CLI LAN Switching: Switch configuration, VLANs, VLAN trunking protocol, inter-VLAN communication, STP, EtherChannel Routing (IPv4/IPv6): Router configuration, static routing, RIPng, EIGRP/EIGRPv6, OSPFv2/OSPFv3 WAN: Point-to-point protocols, eBGP, GRE tunnels, QoS Infrastructure Services: DHCP, FHRP, HSRP, NAT Infrastructure Security: Switch port security, ACL traffic management, device hardening Infrastructure Management: Backup/restore, password recovery, CDP, LLDP, IOS tools, device monitoring, IOS licensing, troubleshooting Quick, offline access to all CCNA Routing and Switching commands for research and solutions --Logical how-to topic groupings for a one-stop resource --Great for review before CCNA Routing and Switching certification exams --Compact size makes it easy to carry with you wherever you go --“Create Your Own Journal†section with blank, lined pages enables you to personalize the book for your needs --“What Do You Want to Do?†chart inside the back cover helps you to quickly reference specific tasks This book is part of the Cisco Press Certification Self-Study Product Family, which offers readers a self-paced study routine for Cisco® certification exams. Titles in the Cisco Press Certification Self-Study Product Family are part of a recommended learning program from Cisco that includes simulation and hands-on training from authorized Cisco Learning Partners and self-study products from Cisco Press. COMPUTERS,Certification Guides,General

CCENT/CCNA ICND1 100-105 Official Cert Guide, Academic Edition Trust the best-selling Official Cert Guide series from Cisco Press to help you learn, prepare, and practice for exam success. They are built with the objective of providing assessment, review, and practice to help ensure you are fully prepared for your certification exam. CCENT/CCNA ICND1 100-105 Official Cert Guide, Academic Edition is a comprehensive textbook and study package that provides you with an introduction to foundational networking concepts and hands-on application. Best-selling author and expert instructor Wendell Odom shares study hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. This complete study package includes A study routine proven to help you retain knowledge Chapter-ending summaries that provide a quick review of key topics Tons of review exercises, including memory tables, command summaries, key term definitions, mind mapping exercises, review questions, and more, which test your understanding and reinforce your knowledge Troubleshooting sections, which help you master complex, real-world scenarios A free copy of the eBook version of the text, available in PDF, EPUB, and Mobi (Kindle) formats The powerful Pearson IT Certification Practice Test Premium Edition software, complete with hundreds of well-reviewed, exam-realistic questions, customization options, linking of all questions to the PDF eBook file, and detailed performance reports A free copy of the CCENT/CCNA ICND1 100-105 Network Simulator Lite software, complete with meaningful lab exercises that help you hone your hands-on skills with the command-line interface for routers and switches Links to a series of hands-on config labs developed by the author Online interactive practice exercises that help you enhance your knowledge More than 90 minutes of video mentoring from the author A final preparation chapter that guides you through tools and resources to help you craft your review and test-taking strategies Study plan suggestions and templates to help you organize and optimize your study time Well regarded for its level of detail, study plans, assessment features, challenging review questions and exercises, video instruction, and hands-on labs, this official study guide helps you master the concepts and techniques that ensure your success. This official study guide helps you master all the topics on the CCENT/CCNA ICND1 exam, including · Networking fundamentals · Implementing basic Ethernet LANs · Ethernet LANs: design, VLANs, and troubleshooting · IPv4 addressing and subnetting · Implementing IPv4 · IPv4 design and troubleshooting · IPv4 services: ACLs and NAT · IPv6 · Network device management The DVD contains more than 500 unique practice exam questions, ICND1 Network Simulator Lite software, online practice exercises, and 90 minutes of video training. Includes Exclusive Offers For Up to 70% Off Video Training and Network Simulator Software Pearson IT Certification Practice Test minimum system requirements: Windows 10, Windows 8.1, Windows 7, or Vista (SP2), Microsoft .NET Framework 4.5 Client; Pentium-class 1 GHz processor (or equivalent); 512 MB RAM; 650 MB disk space plus 50 MB for each downloaded practice exam; access to the Internet to register and download exam databases In addition to the wealth of updated content, this new edition includes a series of free hands-on exercises to help you master several real-world configuration and troubleshooting activities. These exercises can be performed on the CCENT/CCNA ICND1 100-105 Network Simulator Lite software included for free on the DVD or companion web page that accompanies this book. This software, which simulates the experience of working on actual Cisco routers and switches, contains the following 24 free lab exercises, covering all the topics in Part II, the first hands-on configuration section of the book: 1. Configuring Hostnames 2. Configuring Local Usernames 3. Configuring Switch IP Settings 4. Interface Settings I 5. Interface Settings II 6. Interface Settings III 7. Interface Status I 8. Interface Status II 9. Interface Status III 10. Interface Status IV 11. Setting Switch Passwords 12. Switch CLI Configuration Process I 13. Switch CLI Configuration Process II 14. Switch CLI Exec Mode 15. Switch Forwarding I 16. Switch IP Address 17. Switch IP Connectivity I 18. Switch Security I 19. Switch Security II 20. Switch Security III 21 COMPUTERS,Certification Guides,General

CCNA Cyber Ops SECOPS 210-255 Official Cert Guide This is the eBook version of the print title. Note that the eBook does not provide access to the practice test software that accompanies the print book. Learn, prepare, and practice for CCNA Cyber Ops SECOPS #210-255 exam success with this Official Cert Guide from Pearson IT Certification, a leader in IT Certification learning. Master CCNA Cyber Ops SECOPS #210-255 exam topics Assess your knowledge with chapter-ending quizzes Review key concepts with exam preparation tasks CCNA Cyber Ops SECOPS 210-255 Official Cert Guide is a best-of-breed exam study guide. Best-selling authors and internationally respected cybersecurity experts Omar Santos and Joseph Muniz share preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. Material is presented in a concise manner, focusing on increasing your understanding and retention of exam topics. The book presents you with an organized test preparation routine through the use of proven series elements and techniques. Exam topic lists make referencing easy. Chapter-ending Exam Preparation Tasks help you drill on key concepts you must know thoroughly. Review questions help you assess your knowledge, and a final preparation chapter guides you through tools and resources to help you craft your final study plan. Well-regarded for its level of detail, assessment features, and challenging review questions and exercises, this study guide helps you master the concepts and techniques that will allow you to succeed on the exam the first time. The study guide helps you master all the topics on the SECOPS #210-255 exam, including: Threat analysis Forensics Intrusion analysis NetFlow for cybersecurity Incident response and the incident handling process Incident response teams Compliance frameworks Network and host profiling Data and event analysis Intrusion event categories COMPUTERS,Certification Guides,General

CCNA Routing and Switching ICND2 200-105 Official Cert Guide, Academic Edition Trust the best-selling Official Cert Guide series from Cisco Press to help you learn, prepare, and practice for exam success. They are built with the objective of providing assessment, review, and practice to help ensure you are fully prepared for your certification exam. CCNA Routing and Switching ICND2 200-105 Official Cert Guide, Academic Editionis a comprehensive textbook and study package that provides you with a detailed overview of network configuration and troubleshooting. Best-selling author and expert instructor Wendell Odom shares study hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. This complete study package includes · A test-preparation routine proven to help you pass the exams · "Do I Know This Already?" quizzes, which enable you to decide how much time you need to spend on each section · Chapter-ending and part-ending exercises, which help you drill on key concepts you must know thoroughly · Troubleshooting sections, which help you master the complex scenarios you will face on the exam · A free copy of the eBook version of the text, available in PDF, EPUB, and Mobi (Kindle) formats · The powerful Pearson IT Certification Practice Test software, complete with hundreds of well-reviewed, exam-realistic questions, customization options, and detailed performance reports · A free copy of the CCNA ICND2 200-105 Network Simulator Lite software, complete with meaningful lab exercises that help you hone your hands-on skills with the command-line interface for routers and switches · Links to a series of hands-on config labs developed by the author · Online interactive practice exercises that help you hone your knowledge · More than 50 minutes of video mentoring from the author · A final preparation chapter, which guides you through tools and resources to help you craft your review and test-taking strategies · Study plan suggestions and templates to help you organize and optimize your study time Well regarded for its level of detail, study plans, assessment features, challenging review questions and exercises, video instruction, and hands-on labs, this official study guide helps you master the concepts and techniques that ensure your success. This official study guide helps you master all the topics on the CCNA ICND2 exam, including · Ethernet LANs · IPv4 routing protocols · Wide area networks · IPv4 services: ACLs and QoS · IPv4 routing and troubleshooting · IPv6 · Network management, SDN, and cloud computing Companion DVD The DVD contains more than 500 unique practice exam questions, ICND2 Network Simulator Lite software, online practice exercises, and 50+ minutes of video training. Includes Exclusive Offers For Up to 70% Off Video Training and Network Simulator Software Pearson IT Certification Practice Test minimum system requirements: Windows 10, Windows 8.1, Windows 7, or Vista (SP2), Microsoft .NET Framework 4.5 Client; Pentium-class 1 GHz processor (or equivalent); 512 MB RAM; 650 MB disk space plus 50 MB for each downloaded practice exam; access to the Internet to register and download exam databases In addition to the wealth of updated content, this new edition includes a series of free hands-on exercises to help you master several real-world conguration and troubleshooting activities. These exercises can be performed on the CCNA ICND2 200-105 Network Simulator Lite software included for free on the DVD or companion web page that accompanies this book. This software, which simulates the experience of working on actual Cisco routers and switches, contains the following 19 free lab exercises, covering all of the topics in Part II, the first hands-on configuration section of the book: 1. EIGRP Serial Configuration I 2. EIGRP Serial Configuration II 3. EIGRP Serial Configuration III 4. EIGRP Serial Configuration IV 5. EIGRP Serial Configuration V 6. EIGRP Serial Configuration VI 7. EIGRP Route Tuning I 8 COMPUTERS,Certification Guides,General

CCDA 200-310 Official Cert Guide Trust the best selling Official Cert Guide series from Cisco Press to help you learn, prepare, and practice for exam success. They are built with the objective of providing assessment, review, and practice to help ensure you are fully prepared for your certification exam. Master Cisco CCDA 200-310 exam topics Assess your knowledge with chapter-opening quizzes Review key concepts with exam preparation tasks This is the eBook edition of the CCDA 200-310 Official Cert Guide. This eBook does not include the practice exam that comes with the print edition. CCDA 200-310 Official Cert Guide presents you with an organized test preparation routine through the use of proven series elements and techniques. “Do I Know This Already?†quizzes open each chapter and allow you to decide how much time you need to spend on each section. Exam topic lists make referencing easy. Chapter-ending Exam Preparation Tasks help you drill on key concepts you must know thoroughly. CCDA 200-310 Official Cert Guide focuses specifically on the objectives for the newest Cisco CCDA DESGN exam. Expert networking consultants Anthony Bruno and Steve Jordan share preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. Material is presented in a concise manner, focusing on increasing your understanding and retention of exam topics. Well-regarded for its level of detail, assessment features, comprehensive design scenarios, and challenging review questions and exercises, this official study guide helps you master the concepts and techniques that will allow you to succeed on the exam the first time. The official study guide helps you master all the topics on the new CCDA DESGN exam, including: Design methodologies, including PBM, network characterization, and top-down/bottom-up approaches Design objectives: modularity, hierarchy, scalability, resilience, fault domains Addressing and routing protocols in existing networks Enterprise network design: campus, enterprise, and branch Expanding existing networks: wireless, security, collaboration, virtualization, programmability, data centers, and more CCDA 200-310 Official Cert Guide is part of a recommended learning path from Cisco that includes simulation and hands-on training from authorized Cisco Learning Partners and self-study products from Cisco Press. To find out more about instructor-led training, e-learning, and hands-on instruction offered by authorized Cisco Learning Partners worldwide, please visit http://www.cisco.com/web/learning/index.html COMPUTERS,Certification Guides,General

CCNA Routing and Switching 200-125 Official Cert Guide Library This is the eBook of the printed book and may not include any media, website access codes, or print supplements that may come packaged with the bound book. Cisco Press has the only self-study guides approved by Cisco for the new CCENT and CCNA Routing and Switching certifications. The new edition of the best-selling two-book value priced CCNA Official Cert Guide Library includes updated content, new online practice exercises, more than 600 practice exam questions, and more than 2 hours of video training, plus the CCENT and CCNA Network Simulator Lite Editions with 43 free Network Simulator labs. CCNA Routing and Switching 200-125 Official Cert Guide Library is a comprehensive review and practice package for the latest CCNA exams and is the only self-study resource approved by Cisco. The two books contained in this package, CCENT/CCNA ICND1 100-105 Official Cert Guide and CCNA Routing and Switching ICND2 200-105 Official Cert Guide, present complete reviews and more challenging and realistic preparation experiences. The books have been fully updated to refresh the content for the latest CCNA exam topics and to enhance certain key topics that are critical for exam success. Best-selling author and expert instructor Wendell Odom shares preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. This complete study package includes · A test-preparation routine proven to help you pass the exams · "Do I Know This Already?" quizzes, which enable you to decide how much time you need to spend on each section · Chapter-ending and part-ending exercises, which help you drill on key concepts you must know thoroughly · Troubleshooting sections, which help you master the complex scenarios you will face on the exam · The powerful Pearson IT Certification Practice Test software, complete with hundreds of well-reviewed, exam-realistic questions, customization options, and detailed performance reports · A free copy of the CCNA ICND1 and ICND2 Network Simulator Lite software, complete with meaningful lab exercises that help you hone your hands-on skills with the command-line interface for routers and switches · Links to a series of hands-on config labs developed by the author · Online interactive practice exercises that help you hone your knowledge · More than 2 hours of video mentoring from the author · A final preparation chapter, which guides you through tools and resources to help you craft your review and test-taking strategies · Study plan suggestions and templates to help you organize and optimize your study time Well regarded for its level of detail, study plans, assessment features, challenging review questions and exercises, video instruction, and hands-on labs, these official study guides help you master the concepts and techniques that ensure your exam success. These official study guides help you master all the topics on the CCNA exams, including · Networking fundamentals · Implementing basic Ethernet LANs · Ethernet LANs: design, VLANs, and troubleshooting · IPv4 addressing and subnetting · Implementing IPv4 · IPv4 design and troubleshooting · IPv4 services: ACLs, NAT, and QoS · IPv4 routing protocols and routing · Wide area networks · IPv6 · Network management, SDN, and cloud computing COMPUTERS,Certification Guides,General

CCENT/CCNA ICND1 100-105 Official Cert Guide Trust the best-selling Official Cert Guide series from Cisco Press to help you learn, prepare, and practice for exam success. They are built with the objective of providing assessment, review, and practice to help ensure you are fully prepared for your certification exam. Master Cisco CCENT/CCNA ICND1 100-105 exam topics Assess your knowledge with chapter-opening quizzes Review key concepts with exam preparation tasks This is the eBook edition of the CCENT/CCNA ICND1 100-105 Official Cert Guide. This eBook does not include the companion CD-ROM with practice exam that comes with the print edition. CCENT/CCNA ICND1 100-105 Official Cert Guide presents you with an organized test-preparation routine through the use of proven series elements and techniques. “Do I Know This Already?†quizzes open each chapter and enable you to decide how much time you need to spend on each section. Exam topic lists make referencing easy. Chapter-ending Exam Preparation Tasks help you drill on key concepts you must know thoroughly. CCENT/CCNA ICND1 100-105 Official Cert Guide from Cisco Press enables you to succeed on the exam the first time and is the only self-study resource approved by Cisco. Best-selling author and expert instructor Wendell Odom shares preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. This complete study package includes · A test-preparation routine proven to help you pass the exams · Do I Know This Already? quizzes, which enable you to decide how much time you need to spend on each section · Chapter-ending and part-ending exercises, which help you drill on key concepts you must know thoroughly · Troubleshooting sections, which help you master the complex scenarios you will face on the exam · A free copy of the CCENT ICND1 100-105 Network Simulator Lite software, complete with meaningful lab exercises that help you hone your hands-on skills with the command-line interface for routers and switches · Links to a series of hands-on config labs developed by the author · Online, interactive practice exercises that help you hone your knowledge · More than 90 minutes of video mentoring from the author · A final preparation chapter, which guides you through tools and resources to help you craft your review and test-taking strategies · Study plan suggestions and templates to help you organize and optimize your study time Well regarded for its level of detail, study plans, assessment features, challenging review questions and exercises, video instruction, and hands-on labs, this official study guide helps you master the concepts and techniques that ensure your exam success. This official study guide helps you master all the topics on the CCENT/CCNA ICND1 exam, including · Networking fundamentals · Implementing basic Ethernet LANs · Ethernet LANs: design, VLANs, and troubleshooting · IPv4 addressing and subnetting · Implementing IPv4 · IPv4 design and troubleshooting · IPv4 services: ACLs and NAT · IPv6 · Network device management COMPUTERS,Certification Guides,General

CCNA Routing and Switching 200-125 Exam Cram This is the eBook of the printed book and may not include any media, website access codes, or print supplements that may come packaged with the bound book. CCNA Routing and Switching 200-125 Exam Cram, 5/e is the perfect study guide to help you pass the Cisco 200-125 CCNA exam, providing coverage and practice questions for every exam topic. The book contains an extensive set of preparation tools, including topic overviews, ExamAlerts, CramSavers, CramQuizzes, chapter-ending review questions, author notes and tips, and an extensive glossary. The book also contains the extremely useful CramSheet tear-out: a collection of essential facts in an easy-to-review format. Complementing all these great study tools is the powerful Pearson Test Prep practice test software, complete with hundreds of exam-realistic practice questions. This assessment software offers you a wealth of customization options and reporting features, allowing you to test your knowledge in study mode should be. Covers the critical information you’ll need to know to score higher on your CCNA exam! Compare and contrast networking models including OSI and TCP/IP Master subnetting in IPv4 u Understand important details of IPv6 Configure Layer 2 switches, including VLANs, trunks, STP, and Port Security Deploy EtherChannel and switch stacking Configure and verify Inter-VLAN routing Configure, verify, and troubleshoot static and dynamic routing using OSPF, EIGRP, and RIPv2 Describe basic QoS concepts Learn WAN topology and connectivity options and configure PPP, MLPPP, PPPoE, and GRE tunnel connectivity Configure and verify single-homed branch connectivity using eBGP IPv4 Configure and verify key infrastructure services including DNS, DHCP, NTP, HSRP, and NAT Configure Cisco device hardening and deploy access layer security, AAA, and ACLs Learn how to manage Cisco infrastructure Troubleshoot networks using key IOS tools Understand network programmability concepts COMPUTERS,Certification Guides,General

CCNA Routing and Switching ICND2 200-105 Official Cert Guide Trust the best-selling Official Cert Guide series from Cisco Press to help you learn, prepare, and practice for exam success. They are built with the objective of providing assessment, review, and practice to help ensure you are fully prepared for your certification exam. · Master Cisco CCNA ICND2 200-105 exam topics · Assess your knowledge with chapter-opening quizzes · Review key concepts with exam-preparation tasks This is the eBook edition of CCNA Routing and Switching ICND2 200-105 Official Cert Guide. This eBook does not include the companion CD-ROM with practice exam that comes with the print edition. CCNA Routing and Switching ICND2 200-105 Official Cert Guide presents you with an organized test-preparation routine through the use of proven series elements and techniques. “Do I Know This Already?†quizzes open each chapter and enable you to decide how much time you need to spend on each section. Exam topic lists make referencing easy. Chapter-ending Exam Preparation Tasks help you drill on key concepts you must know thoroughly. CCNA Routing and Switching ICND2 200-105 Official Cert Guide from Cisco Press enables you to succeed on the exam the first time and is the only self-study resource approved by Cisco. Best-selling author and expert instructor Wendell Odom shares preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. This complete study package includes · A test-preparation routine proven to help you pass the exams · "Do I Know This Already?" quizzes, which enable you to decide how much time you need to spend on each section · Chapter-ending and part-ending exercises, which help you drill on key concepts you must know thoroughly · Troubleshooting sections, which help you master the complex scenarios you will face on the exam · A final preparation chapter, which guides you through tools and resources to help you craft your review and test-taking strategies · Study plan suggestions and templates to help you organize and optimize your study time Well regarded for its level of detail, study plans, assessment features, challenging review questions and exercises, video instruction, and hands-on labs, this official study guide helps you master the concepts and techniques that ensure your exam success. This official study guide helps you master all the topics on the CCNA ICND2 exam, including · Ethernet LANs · IPv4 routing protocols · Wide area networks · IPv4 services: ACLs and QoS · IPv4 routing and troubleshooting · IPv6 · Network management, SDN, and cloud computing COMPUTERS,Certification Guides,General

vSphere 6 Foundations Exam Official Cert Guide (Exam #2V0-620) VMware 2V0-620 and 2V0-621 exams retired in 2019. We are continuing to make this content available for those who wish to use it to study the foundational information it contains. vSphere 6 Foundations Exam Official Cert Guide (Exam #2V0-620) vSphere 6 Foundations Exam Official Cert Guide (Exam #2V0-620) presents you with an organized test-preparation routine through the use of proven series elements and techniques. “Do I Know This Already?†quizzes open each chapter and enable you to decide how much time you need to spend on each section. Exam topic lists make referencing easy. Chapter-ending Exam Preparation Tasks help you drill on key concepts you must know thoroughly. · Master VMware vSphere 6 Foundations Exam topics · Assess your knowledge with chapter-opening quizzes · Review key concepts with exam-preparation tasks · Practice with realistic exam questions vSphere 6 Foundations Exam Official Cert Guide (Exam #2V0-620) focuses specifically on the objectives for the vSphere 6 Foundations (#2V0-620) Exam. Leading VMware consultant and trainer Bill Ferguson shares preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. Material is presented in a concise manner, focusing on increasing your understanding and retention of exam topics. The companion website contains a powerful Pearson IT Certification Practice Test engine that enables you to focus on individual topic areas or take a complete, timed exam. The assessment engine tracks your performance and provides feedback on a module-by-module basis, laying out a complete assessment of your knowledge to help you focus your study where it is needed most. Well regarded for its level of detail, assessment features, comprehensive design scenarios, and challenging review questions and exercises, this official study guide helps you master the concepts and techniques that will enable you to succeed on the exam the first time. vSphere 6 Foundations Exam Official Cert Guide (Exam #2V0-620) is part of a recommended learning path from VMware that includes simulation and hands-on training from authorized VMware instructors and self-study products from VMware Press. To find out more about instructor-led training, e-learning, and hands-on instruction offered worldwide, please visit www.vmware.com/training. The official study guide helps you master all the topics on the vSphere 6 Foundations Exam (#2V0-620), including · Identifying vSphere architecture and solutions for a given use case · Installing and configuring vCenter Server and ESXi · Configuring vSphere networking, including vSS, vDS, and their features · Configuring vSphere storage · Deploying and administering virtual machines, VM clones, templates, and vApps · Establishing and maintaining availability and resource management features, including clusters, fault tolerance, and resource pools · Troubleshooting ESXi, vCenter Server, vCenter operations, VM operations, and basic misconfigurations · Monitoring a vSphere implementation, including ESXi, vCenter Server, and virtual machines · Installing, configuring, and managing vCenter Operations Manager NOTE: Although there are changes between vSphere 6.0 and 6.5, they are not in the area of Foundations, therefore, vSphere 6 Foundations Exam #2V0-620 can be taken as part of official preparation steps toward your 6.5 or 7.0 certifications. COMPUTERS,Certification Guides,General

CISSP Practice Questions Exam Cram This book provides students with more than 500 practice test questions as well as complete answer explanations, giving them the perfect complementary tool for their CISSP studies. The book features relevant Exam Notes to help score better on this challenging test, plus the ever popular Cram Sheet tear card, which is used for last-minute cramming. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Certification Guides,General

CISSP Exam Cram This is the eBook version of the print title. Note that the eBook does not provide access to the practice test software that accompanies the print book. Access to the digital edition of the Cram Sheet is available through product registration at Pearson IT Certification; or see instructions in back pages of your eBook. CISSP Exam Cram, Fourth Edition, is the perfect study guide to help you pass the tough new electronic version of the CISSP exam. It provides coverage and practice questions for every exam topic, including substantial new coverage of encryption, cloud security, information lifecycles, security management/governance, and more. The book contains an extensive set of preparation tools, such as quizzes, Exam Alerts, and two practice exams. Covers the critical information you’ll need to pass the CISSP exam! Enforce effective physical security throughout your organization Apply reliable authentication, authorization, and accountability Design security architectures that can be verified, certified, and accredited Understand the newest attacks and countermeasures Use encryption to safeguard data, systems, and networks Systematically plan and test business continuity/disaster recovery programs Protect today’s cloud, web, and database applications Address global compliance issues, from privacy to computer forensics Develop software that is secure throughout its entire lifecycle Implement effective security governance and risk management Use best-practice policies, procedures, guidelines, and controls Ensure strong operational controls, from background checks to security audits COMPUTERS,Certification Guides,General

Implementing Cisco IP Telephony and Video, Part 2 (CIPTV2) Foundation Learning Guide (CCNP Collaboration Exam 300-075 CIPTV2) Now updated for Cisco’s CIPTV2 300-075 exam, Implementing Cisco IP Telephony and Video, Part 2 (CIPTV2) Foundation Learning Guide is your Cisco® authorised learning tool for CCNP® Collaboration preparation. Part of the Cisco Press Foundation Learning Series, it teaches advanced skills for implementing a Cisco Unified Collaboration solution in a multisite environment. The authors show how to implement Uniform Resource Identifier (URI) dialing, globalised call routing, Intercluster Lookup Service and Global Dial Plan Replication, Cisco Service Advertisement Framework and Call Control Discovery, tail-end hop-off, Cisco Unified Survivable Remote Site Telephony, Enhanced Location Call Admission Control (CAC) and Automated Alternate Routing (AAR), and important mobility features. They introduce each key challenge associated with Cisco Unified Communications (UC) multisite deployments, and present solutions-focused coverage of Cisco Video Communication Server (VCS) Control, the Cisco Expressway Series, and their interactions with Cisco Unified Communications Manager. Each chapter opens with a topic list that clearly identifies its focus, ends with a quick-study summary of key concepts, and presents review questions to assess and reinforce your understanding. The authors present best practices based on Cisco Solutions Reference Network Designs and Cisco Validated Designs, and illustrate operation and troubleshooting via configuration examples and sample verification outputs. This guide is ideal for all certification candidates who want to master all the topics covered on the CIPTV2 300-075 exam. Shows how to craft a multisite dial plan that scales, allocates bandwidth appropriately, and supports QoS Identifies common problems and proven solutions in multisite UC deployments Introduces best practice media architectures, including remote conferencing and centralised transcoding Thoroughly reviews PSTN and intersite connectivity options Shows how to provide remote site telephony and branch redundancy Covers bandwidth reservation at UC application level with CAC Explains how to plan and deploy Cisco Device Mobility, Extension Mobility, and Unified Mobility Walks through deployment of Cisco Video Communication Server and Expressway series, including user and endpoint provisioning Covers Cisco UCM and Cisco VCS interconnections Shows how to use Cisco UC Mobile and Remote Access Covers fallback methods for overcoming IP WAN failure Demonstrates NAT traversal for video and IM devices via VCS Expressway Introduces dynamic dial plan learning via GDPR, SAD, or CCD The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Certification Guides,General

CompTIA Project+ Cert Guide Learn, prepare, and practice for CompTIA Project+ PK0-004 exam success with this CompTIA-approved Cert Guide from Pearson IT Certification, a leader in IT certification learning and a CompTIA Authorized Platinum Partner. Master CompTIA Project+ PK0-004 exam topics Assess your knowledge with chapter-ending quizzes Review key concepts with exam preparation tasks Practice with realistic exam questions Gain even deeper understanding with more than 130 true-to-life project management examples CompTIA Project+ Cert Guide is a best-of-breed exam study guide. Project management certification expert Robin Abernathy shares preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. Material is presented in a concise manner, focusing on increasing your understanding and retention of exam topics. The book presents you with an organized test preparation routine through the use of proven series elements and techniques. Exam topic lists make referencing easy. Chapter-ending Exam Preparation Tasks help you drill on key concepts you must know thoroughly. Review questions help you assess your knowledge, and a final preparation chapter guides you through tools and resources to help you craft your final study plan. Through 130+ exceptionally realistic examples, Abernathy demonstrates how project management actually works throughout the phases, tasks, documents, and processes that are part of the project manager's job. These examples are designed to offer deep real-world insight that is invaluable for successfully answering scenario-based questions on the live Project+ exam. The companion website contains the powerful Pearson Test Prep practice test software, complete with hundreds of exam-realistic questions. The assessment engine offers you a wealth of customization options and reporting features, laying out a complete assessment of your knowledge to help you focus your study where it is needed most. Well regarded for its level of detail, assessment features, and challenging review questions and exercises, this CompTIA-approved study guide helps you master the concepts and techniques that will enable you to succeed on the exam the first time. The CompTIA-approved study guide helps you master all the topics on the Project+ exam, including · Project basics: properties, phases, roles, responsibilities, team structures, cost control, schedules, resource management, and Agile methodology · Project constraints, influences, and risks, including risk activities and strategies · Communication and change management, including communication methods, influences, triggers, target audiences, and change control · Project management tools, project documentation, and vendor documentation COMPUTERS,Certification Guides,General

OCA Oracle Database SQL Exam Guide (Exam 1Z0-071) A fully updated, integrated self-study system for the Oracle Database SQL Exam This thoroughly revised Oracle Press guide offers 100% coverage of all objectives on the latest version of the Oracle Database SQL Exam. Ideal both as a study guide and on-the-job reference, OCA Oracle Database SQL Exam Guide (Exam 1Z0-071) features detailed explanations, examples, practice questions, and chapter summaries. “Certification Objectives,†“Exam Watch,†and “On the Job†sections reinforce salient points throughout. You will gain access to two complete practice exams that match the tone, tenor, and format of the live test. Get complete coverage every topic on Exam 1Z0-071, including: • DDL and SQL SELECT statements• Manipulating, restricting, and sorting data• Single-row and group functions• Displaying data from multiple tables• Subqueries• Schema objects• Set operators• Grouping related data• Report creation• Data dictionary views• Large data sets• Hierarchical retrieval• Regular expression support• User access control The electronic includes:• Two full practice exams• Detailed answers and explanations COMPUTERS,Certification Guides,General

CompTIA CySA+ Cybersecurity Analyst Certification All-in-One Exam Guide (Exam CS0-001) This comprehensive self-study guide offers complete coverage of the new CompTIA Cybersecurity Analyst+ certification exam Note: This guide has been updated to reflect CompTIA's exam acronym C ySA+. This highly effective self-study system provides complete coverage of every objective for the challenging CompTIA CySA+ Cybersecurity Analyst exam. You'll find learning objectives at the beginning of each chapter, exam tips, in-depth explanations, and practice exam questions. All questions closely mirror those on the live test in content, format, and tone. Designed to help you pass exam CS0-001 with ease, this definitive guide also serves as an essential on-the-job reference. Covers every topic on the exam, including: • Threat and vulnerability management • Conducting and analyzing reconnaissance • Responding to network-based threats • Securing a cooperate network • Cyber incident response • Determining the impact of incidents • Preparing the incident response toolkit • Security architectures • Policies, procedures, and controls • Assuring identity and access management • Putting in compensating controls • Secure software development Electronic content includes: • 200 practice questions • Secured book PDF COMPUTERS,Certification Guides,General

CompTIA Security+ Practice Tests 1,000 Challenging practice questions for Exam SY0-501 CompTIA Security+ Practice Tests provides invaluable practice for candidates preparing for Exam SY0-501. Covering 100% of exam objectives, this book provides 1,000 practice questions to help you test your knowledge and maximize your performance well in advance of exam day. Whether used alone or as a companion to the CompTIA Security+ Study Guide, these questions help reinforce what you know while revealing weak areas while there’s still time to review. Six unique practice tests plus one bonus practice exam cover threats, attacks, and vulnerabilities; technologies and tools; architecture and design; identity and access management; risk management; and cryptography and PKI to give you a comprehensive preparation resource. Receive one year of FREE access to the Sybex online interactive learning environment, to help you prepare with superior study tools that allow you to gauge your readiness and avoid surprises on exam day. The CompTIA Security+ certification is internationally-recognized as validation of security knowledge and skills. The exam tests your ability to install and configure secure applications, networks, and devices; analyze, respond to, and mitigate threats; and operate within applicable policies, laws, and regulations. This book provides the practice you need to pass with flying colors. Master all six CompTIA Security+ objective domains Test your knowledge with 1,000 challenging practice questions Identify areas in need of further review Practice test-taking strategies to go into the exam with confidence The job market for information security professionals is thriving, and will only expand as threats become more sophisticated and more numerous. Employers need proof of a candidate’s qualifications, and the CompTIA Security+ certification shows that you’ve mastered security fundamentals in both concept and practice. If you’re ready to take on the challenge of defending the world’s data, CompTIA Security+ Practice Tests is an essential resource for thorough exam preparation. COMPUTERS,Certification Guides,General

CompTIA Security+ Certification Practice Exams, Third Edition (Exam SY0-501) Publisher's Note: Products purchased from Third Party sellers are not guaranteed by the publisher for quality, authenticity, or access to any online entitlements included with the product. This fully updated, exam-focused study aid covers everything you need to know and shows you how to prepare for the CompTIA Security+ exam With hundreds of practice exam questions, including difficult performance-based questions, CompTIA Security+® Certification Study Guide, Third Edition covers what you need to know—and shows you how to prepare—for this challenging exam. • 100% complete coverage of all official objectives for exam SY0-501 • Exam Watch notes call attention to information about, and potential pitfalls in, the exam • Inside the Exam sections in every chapter highlight key exam topics covered • Two-Minute Drills for quick review at the end of every chapter • Simulated exam questions—including performance-based questions—match the format, topics, and difficulty of the real exam Covers all exam topics, including: Networking Basics and Terminology • Security Terminology • Security Policies and Standards • Types of Attacks • System Security Threats • Mitigating Security Threats • Implementing System Security • Securing the Network Infrastructure • Wireless Networking and Security • Authentication • Access Control • Cryptography • Managing a Public Key Infrastructure • Physical Security • Risk Analysis • Disaster Recovery and Business Continuity • Computer Forensics • Security Assessments and Audits • Monitoring and Auditing Electronic Content Includes: • 50+ lab exercises and solutions • Complete practice exams • 3+ hours of video training from the author • Secured book PDF COMPUTERS,Certification Guides,General

PMI-ACP Project Management Institute Agile Certified Practitioner Exam Study Guide The ultimate study package for the new PMI-ACP exam The PMI-ACP Project Management Institute Agile Certified Practitioner Exam Study Guide is an all-in-one package for comprehensive exam preparation. This up-to-date guide is fully aligned with the latest version of the exam, featuring coverage of 100 percent of the exam domains. Expanded coverage of AGILE includes the basic principles, value-driven delivery, stakeholder engagement, team performance, adaptive planning, problem detection and resolution, and continuous improvement to align with the A Guide to the Project Management Body of Knowledge (PMBOK® 6th Edition) and its increased emphasis on agile, adaptive and iterative practices. In-depth discussion merges with hands-on exercises and real-world scenarios to provide a well-rounded review of essential exam concepts, while the online learning center provides an assessment test, chapter tests, a practice exam, and study aids to help you ensure complete preparation for the big day. Master 100 percent of the exam objectives, including expanded AGILE coverage Reinforce critical concepts with hands-on practice and real-world scenarios Test your knowledge with challenging chapter review questions One year of FREE access to the Sybex online test bank featuring practice tests, flashcards, a glossary, and more Project management is one of the most in-demand skills in today's job market, making more and more employers turn to AGILE methodologies to enhance delivery and results. The PMI-ACP certification shows employers that you have demonstrated mastery of essential project management skills and a practical understanding of adaptive, iterative processes; this validation puts you among the ranks of qualified project management professionals employers are desperately seeking, and the PMI-ACP Project Management Institute Agile Certified Practitioner Exam Study Guide is your one-stop resource for exam success. COMPUTERS,Certification Guides,General

Preparing for the Certified OpenStack Administrator Exam Master the objectives required to pass the Certified OpenStack Administrator exam. About This Book Focuses on providing a clear, concise strategy so you gain the specific skills required to pass the Certified OpenStack Administrator exam Includes exercises and performance-based tasks to ensure all exam objectives can be completed via the Horizon dashboard and command-line interface Includes a free OpenStack Virtual Appliance to practice the objectives covered throughout the book Includes a practice exam to put your OpenStack skills to the test to prove you have what it takes to conquer the live exam Updated for the 2017 exam featuring OpenStack Newton Who This Book Is For This book is for IT professionals, system administrators, DevOps engineers, and software developers with basic Linux command-line and networking knowledge. It's also a great guide for those interested in an entry-level OpenStack position but have limited real-world OpenStack experience. After passing the exam, Certified OpenStack Administrators will prove they have the required skills for the job. What You Will Learn Manage the Keystone identity service by creating and modifying domains, groups, projects, users, roles, services, endpoints, and quotas. Upload Glance images, launch new Nova instances, and create flavors, key pairs, and snapshots. Discover Neutron tenant and provider networks, security groups, routers, and floating IPs. Manage the Cinder block storage service by creating volumes and attaching them to instances. Create Swift containers and set access control lists to allow read/write access to your objects. Explore Heat orchestration templates and create, list, and update stacks. In Detail This book provides you with a specific strategy to pass the OpenStack Foundation's first professional certification: the Certified OpenStack Administrator. In a recent survey, 78% of respondents said the OpenStack skills shortage had deterred them from adopting OpenStack. Consider this an opportunity to increase employer and customer confidence by proving you have the skills required to administrate real-world OpenStack clouds. You will begin your journey by getting well-versed with the OpenStack environment, understanding the benefits of taking the exam, and installing an included OpenStack all-in-one virtual appliance so you can work through objectives covered throughout the book. After exploring the basics of the individual services, you will be introduced to strategies to accomplish the exam objectives relevant to Keystone, Glance, Nova, Neutron, Cinder, Swift, Heat, and troubleshooting. Finally, you'll benefit from the special tips section and a practice exam to put your knowledge to the test. By the end of the journey, you will be ready to become a Certified OpenStack Administrator! Style and approach Clear, concise, and straightforward with supporting diagrams and lab environment tutorials, this book will help you confidently pass Certified OpenStack Administrator objectives on the Horizon dashboard and command-line interface. COMPUTERS,Certification Guides,General

PHR and SPHR Professional in Human Resources Certification Complete Study Guide The #1 book for the leading HR certifications, aligned with the updated HRBoK™ PHR and SPHR certifications, offered by Human Resources Certification Institute (HRCI), have become the industry standard for determining competence in the field of human resources. Developed by working professionals, the PHR and SPHR credentials demonstrate that recipients are fully competent HR practitioners based on a standard set by workforce peers. Offering insights into those areas of knowledge and practices specific and necessary to human resource management (HRM), this study guide covers tasks, processes, and strategies as detailed in the updated A Guide to the Human Resource Body of Knowledge™ (HRBoK™). The study guide breaks down the critical HR topics that you need to understand as you prepare for the exams. PHR/SPHR Professional in Human Resources Certification Study Guide, Fifth Edition, is the ideal resource for HR professionals seeking to validate their skills and knowledge acquired through years of practical experience, as well as for a relative newcomer to the HR field looking to strengthen their resume. In this edition of the top-selling PHR/SPHR study guide, you’ll find a practical review of all topics covered on the exams, as well as study tools designed to reinforce understanding of key functional areas. Strengthen the skills you learn with a year of FREE access to the Sybex online learning environment, complete with flash cards and practice quizzes to prepare you for exam day. • Business Management and Strategy • Workforce Planning and Employment • Compensation and Benefits • Human Resource Development and more If you’re preparing for these challenging exams, this is the trusted study guide that’ll help you perform your best. COMPUTERS,Certification Guides,General

PHR and SPHR Professional in Human Resources Certification Complete Practice Tests 1,000 challenging practice questions to prepare for the PHR and SPHR exams! PHR/SPHR Professional in Human Resources Certification Practice Tests is the ideal complement to the PHR/SPHR Study Guide, Fifth Edition, PHR/SPHR Deluxe Study Guide, Second Edition, and Review Guide. These self-study guides are intended for HR professionals seeking to validate their skills and knowledge acquired through years of practical experience, or for relative newcomers to the HR field looking to strengthen their resume. These Practice Tests were developed to help certification candidates prepare for these challenging exams, especially for those needing more practice to review or refresh their knowledge right before exam day. The book aligns with A Guide to the Human Resource Body of Knowledge™ (HRBoK™), which details the responsibilities of and knowledge needed by today's HR professionals. Practice Tests reflect the critical HR topics that you need to understand as you prepare for the PHR and SPHRexams. • Business Management and Strategy • Workforce Planning and Employment • Human Resource Development • Risk Management and more Plus, you’ll get a year of FREE access to the interactive online learning environment and test bank, which includes full-length tests and practice exams—1,000 practice questions total! COMPUTERS,Certification Guides,General

PHR and SPHR Professional in Human Resources Certification Complete Review Guide Essential review for the PHR/SPHR exams, aligned with the updated HRBoK™ PHR/SPHR Professional in Human Resources Certification Review Guide is the ideal companion to the PHR/SPHR Study Guide, Fifth Edition, and PHR/SPHR Deluxe Study Guide, Second Edition. These self-study guides are intended for HR professionals seeking to validate their skills and knowledge acquired through years of practical experience, or for relative newcomers to the HR field looking to strengthen their resume. Organized by those areas of knowledge and practices specific and necessary to human resource management (HRM), this handy review guide covers tasks, processes, and strategies as detailed in the updated A Guide to the Human Resource Body of Knowledge™ (HRBoK™), giving you clear guidance on what you need to know for the exams. You also get a year of FREE access to the Sybex online interactive learning environment and study tools, which feature flashcards, chapter tests, two bonus practice exams, and more. The review guide aligns with the HRCI test specifications, which detail the responsibilities and knowledge needed by today's HR professionals. Covers key functional areas in greater depth: HR students and professionals studying for the PHR/SPHR certification need a trusted resource to aid in their preparation—this review guide does that and more. COMPUTERS,Certification Guides,General

Subnetting Master the fundamental concept at the heart of professional networking Subnetting is the aspiring network professional’s guide to the concepts and practices at the core of the field. By dividing a single physical network into smaller subnetworks, you gain greater control of performance, access, and security. While the concept is simple, the actual practice is complex—yet it is an essential skill for networking professionals, and a major skill tested on the CCENT and CompTIA Network+ exams. This book shows you everything you need to know about constructing IP addresses, VSLM, and route summarization to help you build your skill set on a strong foundation. The IPv4 address has 32 bits available, which can be divided into host ID and network ID; the number of bits assigned to the network ID determines the balance between total subnetworks and devices allowed—the trick is determining the most efficient balance for a particular network. Subnetting allows you to borrow bits from the host to allow for more networks, and subnet masks are used to determine switching and routing priority. This book delves into the mechanisms and practices you need to know, including networking fundamentals, rules of IP addresses, supernetting, variable length subnet mask, IPv6, and more: Master the fundamental topic at the heart of the Cisco Certified Entry Networking Technician and CompTIA Network+ certifications Improve network performance using subnetworks to avoid high-usage “clogs†Utilize network partitioning to confine breaches or viruses and improve security Construct efficient solutions to problems of allocation and range With clear guidance from an industry expert and a practical perspective geared toward real-world situations, Subnetting offers an outstanding introduction to this essential foundational concept. COMPUTERS,Certification Guides,General

TCP / IP The most up-to-date, in-depth guide for TCP/IP mastery TCP/IP is the ultimate guide to the glue that holds the Internet together. When two computers “talk†to one another, they do it through Transmission Control Protocol/Internet Protocol. Networking professionals working toward any of the CCNA-Specialty certifications must have a firm understanding of this key technology, and must stay up to date on evolving practices as new technologies emerge. Whether you’re preparing for the CompTIA Network+ exam, the Cisco CCENT ICND1 exam, or just want to learn how to install, troubleshoot, and operate networks, this book tells you everything you need to know to work effectively with TCP/IP. Expert discussion details the latest on Web protocols and new hardware, including timely information on how TCP/IP secures connectivity for blogging, vlogging, photoblogging, and social networking. From installation and configuration to intranets, extranets, virtual private networks, security measures and more, this book provides the depth and breadth of information that every aspiring networking professional needs. Understand the de facto standard transmission medium for computer-computer communications Install and configure TCP/IP and its applications on clients and servers Use encryption, authentication, digital certificates, signatures, and other critical security measures Learn the most up-to-date methods for handling new voice and mobile technologies, and more Step-by-step instructions and clear explanations by an industry expert and networking guru bring TCP/IP down to earth and provide much-needed clarity on an essential topic. Whether or not you’re preparing for certification, TCP/IP is critical knowledge for anyone working with networks, and continuous innovation means that the learning never stops. TCP/IP is an indispensable resource, packed with the latest information on this central networking concept. COMPUTERS,Certification Guides,General

PMP NOTE: The book included the incorrect URL to access the online test banks provided with the purchase of this book. The correct URL is: www.wiley.com/go/sybextestprep. The ultimate PMP preparation and self-study experience, updated to align with the new PMBOK® Guide, 6th Edition The PMP: Project Management Professional Exam Study Guide, Ninth Edition, provides comprehensive review for the Project Management Institute's (PMI) PMP certification exam. This new ninth edition has been completely revised to align with the latest version of the exam, which includes new tasks that reflect changes to best practices, the role of the project manager, and the growing importance of agile and other adaptive and iterative practices. Detailed discussion draws from the latest A Guide to the Project Management Body of Knowledge (PMBOK® Guide), 6th edition, to provide the most up-to-date information on critical topics, while hands-on exercises provide insight on real-world implementation. Receive one year of free access to the Sybex online interactive learning environment, to help you prepare with superior study tools, rigorous chapter tests, and two practice exams that allows you to gauge your readiness and avoid surprises on exam day. The PMP certification is arguably the most desired skill in the IT marketplace, but its reach extends into a variety of other industries. Candidates must have extensive project management experience to qualify, but comprehensive study materials, aligned with the PMBOK® Guide Sixth Edition, are essential to success on the exam. This study guide provides everything you need to ensure thorough preparation and full exam-day confidence. Study 100% of the objectives for the latest PMP exam Practice applying PMP concepts to real-world scenarios Test your understanding with comprehensive review questions Access online chapter tests, practice exams, electronic flashcards, and more Companies are demanding more of project managers than ever before: skills in technical management, leadership, strategic management, and business management make you more competitive, and the PMP exam reflects their increasing relevance in a rapidly-evolving field. When you're ready to take the next step for your career, the PMP: Project Management Professional Exam Study Guide, Ninth Edition, is your ideal companion for ultimate PMP preparation. To register for access to the online test banks included with the purchase of this book, please visit: www.wiley.com/go/sybextestprep. COMPUTERS,Certification Guides,General

CompTIA Network+ Study Guide To complement the CompTIA Network+ Study Guide: Exam N10-007, 4e, and the CompTIA Network+ Deluxe Study Guide: Exam N10-007, 4e, look at CompTIA Network+ Practice Tests: Exam N10-007 (9781119432128). Todd Lammle's bestselling CompTIA Network+ Study Guide for the N10-007 exam! CompTIA's Network+ certification tells the world you have the skills to install, configure, and troubleshoot today's basic networking hardware peripherals and protocols. First, however, you have to pass the exam! This detailed CompTIA Authorized study guide by networking guru Todd Lammle has everything you need to prepare for the CompTIA Network+ Exam N10-007. Todd covers all exam objectives, explains key topics, offers plenty of practical examples, and draws upon his own invaluable 30 years of networking experience to help you learn. The Study Guide prepares you for Exam N10-007, the new CompTIA Network+ Exam: • Covers all exam objectives including network technologies, network installation and configuration, network media and topologies, security, and much more • Includes practical examples review questions, as well as access to practice exams and flashcards to reinforce learning • Networking guru and expert author Todd Lammle offers valuable insights and tips drawn from real-world experience Plus, receive one year of FREE access to a robust set of online interactive learning tools, including hundreds of sample practice questions, a pre-assessment test, bonus practice exams, and over 100 electronic flashcards. Prepare for the exam and enhance your career—starting now! COMPUTERS,Certification Guides,General

CompTIA Security+ SY0-501 Cert Guide Learn, prepare, and practice for CompTIA Security+ SY0-501 exam success with this CompTIA approved Cert Guide from Pearson IT Certification, a leader in IT certification learning and a CompTIA Authorized Platinum Partner. · Master CompTIA Security+ SY0-501 exam topics · Assess your knowledge with chapter-ending quizzes · Review key concepts with exam preparation tasks · Practice with realistic exam questions CompTIA Security+ SY0-501 Cert Guide is a best-of-breed exam study guide. Best-selling author and expert instructor David L. Prowse shares preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. Material is presented in a concise manner, focusing on increasing your understanding and retention of exam topics. The book presents you with an organized test-preparation routine through the use of proven series elements and techniques. Exam topic lists make referencing easy. Chapter-ending chapter review activities help you drill on key concepts you must know thoroughly. Review questions help you assess your knowledge, and a final preparation chapter guides you through tools and resources to help you craft your final study plan. The companion website contains the powerful Pearson Test Prep practice test software, complete with hundreds of exam-realistic questions. The assessment software offers you a wealth of customization options and reporting features, laying out a complete assessment of your knowledge to help you focus your study where it is needed most. Well regarded for its level of detail, assessment features, and challenging review questions and exercises, this CompTIA approved study guide helps you master the concepts and techniques that will enable you to succeed on the exam the first time. The CompTIA approved study guide helps you master all the topics on the Security+ exam, including · Core computer system security · OS hardening and virtualization · Application security · Network design elements · Networking ports, protocols, and threats · Network perimeter security · Physical security and authentication models · Access control · Vulnerability and risk assessment · Monitoring and auditing · Cryptography, including PKI · Redundancy and disaster recovery · Social Engineering · Policies and procedures COMPUTERS,Certification Guides,General

PMP Project Management Professional Practice Tests Master all five PMP domains and boost your confidence for exam day PMP: Project Management Professional Practice Tests provides candidates with an ideal study aid for PMP exam preparation. Fully aligned with the A Guide to the Project Management Body of Knowledge (PMBOK® Guide), 6th edition, this book provides practice questions covering all five performance domains. Five unique 160- question chapter tests, as well as one practice exam cover Initiating; Planning; Executing; Monitoring and Controlling; and Closing to help you pinpoint weak areas while there is still time to review. An additional 200-question practice test provides a bonus exam--1000 questions in all--, and a year of FREE access to the Sybex interactive online learning environment puts a test bank, practice questions, and more at your disposal. The PMP exam is a challenging four-hour, 200-question validation of your project management knowledge. Mimicking exam conditions is one of the best ways to prepare, and this book is designed to test your knowledge, focus, and mental endurance to get you fully prepared for the big day. Test your project management knowledge with 1,000 challenging questions Prepare using up-to-date material that accurately reflect the current exam Access digital study tools including electronic flashcards and additional practice questions In today's IT marketplace, qualified project managers are heavily in demand as employers increasingly require those who are capable of managing larger and more complex projects. The PMP certification shows that you know, understand, and can practice PMBOK guidelines to a rigorous level, and is considered the premier project management qualification out there—so when exam day arrives, complete preparation becomes critical to your success. PMP: Project Management Professional Practice Tests help you gauge your progress, preview exam day, and focus your study time so you can conquer the exam with confidence. To register for access to the online test banks included with the purchase of this book, please visit: www.wiley.com/go/sybextestprep. COMPUTERS,Certification Guides,General

Certified Information Systems Auditor (CISA) Cert Guide This is the eBook version of the print title. Note that the eBook may not provide access to the practice test software that accompanies the print book. Learn, prepare, and practice for CISA exam success with this Cert Guide from Pearson IT Certification, a leader in IT certification learning. Master CISA exam topics Assess your knowledge with chapter-ending quizzes Review key concepts with exam preparation tasks Certified Information Systems Auditor (CISA) Cert Guide is a best-of-breed exam study guide. World-renowned enterprise IT security leaders Michael Gregg and Rob Johnson share preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. Material is presented in a concise manner, focusing on increasing your understanding and retention of exam topics. The book presents you with an organized test preparation routine through the use of proven series elements and techniques. Exam topic lists make referencing easy. Chapter-ending Exam Preparation Tasks help you drill on key concepts you must know thoroughly. Review questions help you assess your knowledge, and a final preparation chapter guides you through tools and resources to help you craft your final study plan. Well-regarded for its level of detail, assessment features, and challenging review questions and exercises, this study guide helps you master the concepts and techniques that will allow you to succeed on the exam the first time. The study guide helps you master all the topics on the CISA exam, including: Essential information systems audit techniques, skills, and standards IT governance, management/control frameworks, and process optimization Maintaining critical services: business continuity and disaster recovery Acquiring information systems: build-or-buy, project management, and development methodologies Auditing and understanding system controls System maintenance and service management, including frameworks and networking infrastructure Asset protection via layered administrative, physical, and technical controls Insider and outsider asset threats: response and management COMPUTERS,Certification Guides,General

Mike Meyers' CompTIA Security+ Certification Passport, Fifth Edition (Exam SY0-501) This quick review, cram-style study guide offers 100% coverage of every topic on the latest version of the CompTIA Security+ exam This powerful exam preparation resource presents an accelerated review of the pertinent technology and covers all objectives for the CompTIA Security+ exam (exam SY0-501). Written in the proven Passport format developed by training expert Mike Meyers, the book enables you to focus on specific topics, determine areas of need, and tailor an effective course for study. Mike Meyers’ CompTIA Security+ Certification Passport, Fifth Edition (Exam SY0-501) features accurate practice exam questions and in-depth answer explanations as well as end-of-chapter bulleted summaries that reinforce salient points. Throughout, “Exam Tips†highlight important topics, “Local Lingo†notes define need-to-know terms, “Travel Advisories†alert you to potential pitfalls, and “Travel Assistance†icons specify resources for further information. • Provides complete coverage of every objective on exam SY0-501• Electronic content includes 200 practice questions and a secured book PDF• Written by a pair of security experts and edited by certification guru Mike Meyers COMPUTERS,Certification Guides,General

CompTIA Security+ SY0-501 Cert Guide, Academic Edition Learn, prepare, and practice for CompTIA Security+ SY0-501 exam success with this CompTIA Security+ SY0-501 Cert Guide, Academic Edition from Pearson IT Certification, a leader in IT Certification learning. The companion website features three complete practice exams, complete video solutions to hands-on labs, plus interactive flash-based simulations that include drag-and-drop and matching to reinforce the learning. · Master the CompTIA Security+ SY0-501 exam topics · Assess your knowledge with chapter-ending quizzes · Reinforce your knowledge of key concepts with chapter review activities · Practice with realistic exam questions online · Includes complete video solutions to hands-on labs, plus interactive simulations on key exam topics · Work through Flash Cards in Q&A and glossary term format · Includes free access to the Premium Edition eBook CompTIA Security+ SY0-501 Cert Guide, Academic Edition includes video solutions to the hands-on labs, practice tests, and interactive simulations that let the reader learn by doing. Best-selling author and expert instructor David L. Prowse shares preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. Material is presented in a concise manner, focusing on increasing your understanding and retention of exam topics. The book presents you with an organized test-preparation routine through the use of proven series elements and techniques. Exam topic lists make referencing easy. Chapter review activities help you drill on key concepts you must know thoroughly. Review questions help you assess your knowledge, and a final preparation chapter guides you through tools and resources to help you craft your approach to passing the exam. The companion Academic Edition website contains the powerful Pearson Test Prep practice test engine, with three complete practice exams and hundreds of exam-realistic questions and free access to the Premium Edition eBook. The assessment engine offers you a wealth of customization options and reporting features, laying out a complete assessment of your knowledge to help you focus your study where it is needed most. Work through Flash Cards in Q&A and glossary term format to help reinforce your knowledge of key concepts and facts. The Academic Edition companion site also includes complete video solutions to hands-on labs in the book and interactive simulations on key exam topics to reinforce the learning by doing. Learn activities such as testing password strength, matching the type of malware with its definition, finding security issues in the network map, and disallowing a user to access the network on Saturday and Sunday. Well regarded for its level of detail, assessment features, and challenging review questions and exercises, this CompTIA study guide helps you master the concepts and techniques that will allow you to succeed on the exam the first time. The CompTIA study guide helps you master all the topics on the Security+ exam, including · Core computer system security · OS hardening and virtualization · Application security · Network design elements and threats · Perimeter security · Network media and devices security · Physical security and authentication models · Access control · Vulnerability and risk assessment · Monitoring and auditing · Cryptography, including PKI · Redundancy and disaster recovery · Policies and procedures COMPUTERS,Certification Guides,General

CompTIA Security+ SY0-501 Exam Cram CompTIA Security+ SY0-501 Exam Cram , Fifth Edition, is the perfect study guide to help you pass CompTIA’s newly updated version of the Security+ exam. It provides coverage and practice questions for every exam topic. The book contains a set of 150 questions. The powerful Pearson Test Prep practice test software provides real-time practice and feedback with all the questions so you can simulate the exam. Covers the critical information you need to know to score higher on your Security+ exam! · Analyze indicators of compromise and determine types of attacks, threats, and risks to systems · Minimize the impact associated with types of attacks and vulnerabilities · Secure devices, communications, and network infrastructure · Effectively manage risks associated with a global business environment · Differentiate between control methods used to secure the physical domain · Identify solutions for the implementation of secure network architecture · Compare techniques for secure application development and deployment · Determine relevant identity and access management procedures · Implement security policies, plans, and procedures related to organizational security · Apply principles of cryptography and effectively deploy related solutions COMPUTERS,Certification Guides,General

Mike Meyers' CompTIA Security+ Certification Guide, Second Edition (Exam SY0-501) Publisher's Note: Products purchased from Third Party sellers are not guaranteed by the publisher for quality, authenticity, or access to any online entitlements included with the product. A fully updated CompTIA Security+ exam guide from training and exam preparation expert Mike Meyers Take the CompTIA Security+ exam (exam SY0-501) with confidence using the comprehensive information contained in this highly effective study resource. Like the exam, the guide goes beyond knowledge application and is designed to ensure that security personnel anticipate security risks and guard against them. In Mike Meyers’ CompTIA Security+ Certification Guide, Second Edition (Exam SY0-501), the bestselling author and leading authority on CompTIA A+ certification brings his proven methodology to IT security. Mike covers all exam objectives in small, digestible modules that allow you to focus on individual skills as you move through a broad and complex set of skills and concepts. The book features hundreds of accurate practice questions as well as a toolbox of the author’s favorite network security related freeware/shareware. • Provides complete coverage of every objective on exam SY0-501• Electronic content includes 20+ lab simulations, video training, and hundreds of practice exam questions• Written by computer security and certification guru Mike Meyers COMPUTERS,Certification Guides,General

MCSA Windows Server 2016 Complete Study Guide NOTE: As the response to the coronavirus (COVID-19) continues to evolve rapidly around the world, Microsoft has announced that it’s extending the retirement date of the current MCSA Windows Server 2016 certification until January 31, 2021. Pearson VUE has temporarily closed many of its testing centers worldwide in response to global government regulations to battle the spread of COVID-19. As an alternative to taking your exam at a testing center, online proctoring is available, which allows you to take your certification exam in the comfort of your own home or office. Instead of taking the required exams at a Pearson VUE testing center near you, Pearson VUE will be offering only online proctored exams for the foreseeable future. This means you will have more time to prepare for the current exams: 70-740: Installation, Storage, and Compute with Windows Server 2016 70-741: Networking with Windows Server 2016 70-742: Identity with Windows Server 2016 To help you prepare for the exams, our Study Guides are available for purchase. Over 1,000 pages of comprehensive exam prep for the entire MCSA Windows Server 2016 certification process MCSA Windows Server 2016 Complete Study Guide is your ultimate companion on the journey to earning the MCSA Windows Server 2016 certification. Covering required Exams 70-740, 70-741, and 70-742, plus preparing you to take the composite upgrade Exam 70-743 (not covered separately in this book), this Study Guide walks you through 100 percent of all exam objectives to help you achieve complete readiness. Hands-on exercises strengthen your practical skills, and real-world scenarios help you understand how these skills are used on the job. Over 500 practice questions allow you to test your understanding along the way, and the online test bank gives you access to electronic flashcards, practice exams, and over an hour of expert video demonstrations. From basic networking concepts and services to Active Directory and Hyper-V, this guide provides full coverage of critical MCSA concepts and skills. This new edition has been updated for the latest MCSA Windows Server 2016 exam releases, featuring coverage of all the objective domains. This value-priced guide is three books in one, giving you the most comprehensive exam prep experience for all required MCSA exams. Whether you're starting from the beginning, or upgrading from the MCSA Windows Server 2012 R2 certification, arm yourself with the ultimate tool for complete and comprehensive preparation. Study 100 percent of the objectives for all three MCSA exams, plus the upgrade exam Practice your skills using hands-on exercises and real-world scenarios Test your knowledge with over 500 challenging practice questions Access online study aids including flashcards, video demos, and more! The MCSA exams test your knowledge and skill in installation, configuration, deployment, and administration using a variety of networking tools. The scope is broad, but your complete understanding of the most up-to-date concepts and practices is critical to your success on the exam—and on the job. MCSA Windows Server 2016 Complete Study Guide covers everything you need to know, and gives you the tools to help you learn it. COMPUTERS,Certification Guides,General

CompTIA Security+ All-in-One Exam Guide, Fifth Edition (Exam SY0-501) This fully updated study guide covers every topic on the current version of the CompTIA Security+ exam Take the latest version of the CompTIA Security+ exam with complete confidence using the detailed information contained in this highly effective self-study system. Written by a team of leading information security experts, this authoritative guide addresses the skills required for securing a network and managing risk and enables you to become CompTIA Security+ certified. CompTIA Security+ All-in-One Exam Guide, Fifth Edition (Exam SY0-501) covers all exam domains and features 200 accurate practice questions. To aid in study, the book features learning objectives at the beginning of each chapter, exam tips, practice exam questions, and in-depth explanations. All questions mirror those on the live test in style, format, and difficulty. Beyond fully preparing you for the challenging SY0-501 exam, the book also serves as a valuable on-the-job reference for IT professionals. • Provides 100% coverage of every objective on exam SY0-501• Electronic content includes 200 practice questions and a secured book PDF• Written by a team of experienced IT security academics COMPUTERS,Certification Guides,General

CompTIA Network+ N10-007 Exam Cram Prepare for CompTIA Network+ N10-007 exam success with this CompTIA approved Exam Cram from Pearson IT Certification, a leader in IT Certification learning and a CompTIA Authorized Platinum Partner. This is the eBook version of the print title. Note that the eBook may not provide access to the practice test software that accompanies the print book. Access to the digital edition of the Cram Sheet is available through product registration at Pearson IT Certification; or see the instructions in the back pages of your eBook. CompTIA® Network+ N10- 007 Exam Cram, Sixth Edition is the perfect study guide to help you pass CompTIA’s Network+ N10-007 exam. It provides coverage and practice questions for every exam topic, including substantial new coverage of security, cloud networking, IPv6, and wireless technologies. The book presents you with an organized test-preparation routine through the use of proven series elements and techniques. Exam topic lists make referencing easy. Exam Alerts, Sidebars, and Notes interspersed throughout the text keep you focused on what you need to know. Cram Quizzes help you assess your knowledge, and the Cram Sheet tear card is the perfect last-minute review. Covers the critical information you’ll need to know to score higher on your CompTIA Network+ (N10-007) exam! · Understand modern network topologies, protocols, and infrastructure · Implement networks based on specific requirements · Install and configure DNS and DHCP · Monitor and analyze network traffic · Understand IPv6 and IPv4 addressing, routing, and switching · Perform basic router/switch installation and configuration · Explain network device functions in cloud environments · Efficiently implement and troubleshoot WANs · Install, configure, secure, and troubleshoot wireless networks · Apply patches/updates, and support change/configuration management · Describe unified communication technologies · Segment and optimize networks · Identify risks/threats, enforce policies and physical security, configure firewalls, and control access · Understand essential network forensics concepts · Troubleshoot routers, switches, wiring, connectivity, and security COMPUTERS,Certification Guides,General

(ISC)2 CISSP Certified Information Systems Security Professional Official Study Guide CISSP Study Guide - fully updated for the 2018 CISSP Body of Knowledge CISSP (ISC)2 Certified Information Systems Security Professional Official Study Guide, 8 th Edition has been completely updated for the latest 2018 CISSP Body of Knowledge. This bestselling Sybex study guide covers 100% of all exam objectives. You'll prepare for the exam smarter and faster with Sybex thanks to expert content, real-world examples, advice on passing each section of the exam, access to the Sybex online interactive learning environment, and much more. Reinforce what you've learned with key topic exam essentials and chapter review questions. Along with the book, you also get access to Sybex's superior online interactive learning environment that includes: Six unique 150 question practice exams to help you identify where you need to study more. Get more than 90 percent of the answers correct, and you're ready to take the certification exam. More than 700 Electronic Flashcards to reinforce your learning and give you last-minute test prep before the exam A searchable glossary in PDF to give you instant access to the key terms you need to know for the exam Coverage of all of the exam topics in the book means you'll be ready for: Security and Risk Management Asset Security Security Engineering Communication and Network Security Identity and Access Management Security Assessment and Testing Security Operations Software Development Security COMPUTERS,Certification Guides,General

(ISC)2 CISSP Certified Information Systems Security Professional Official Practice Tests Full-length practice tests covering all CISSP domains for the ultimate exam prep The (ISC)2 CISSP Official Practice Tests is a major resource for CISSP candidates, providing 1300 unique practice questions. The first part of the book provides 100 questions per domain. You also have access to four unique 125-question practice exams to help you master the material. As the only official practice tests endorsed by (ISC)2, this book gives you the advantage of full and complete preparation. These practice tests align with the 2018 version of the exam to ensure up-to-date preparation, and are designed to cover what you'll see on exam day. Coverage includes: Security and Risk Management, Asset Security, Security Architecture and Engineering, Communication and Network Security, Identity and Access Management (IAM), Security Assessment and Testing, Security Operations, and Software Development Security. The CISSP credential signifies a body of knowledge and a set of guaranteed skills that put you in demand in the marketplace. This book is your ticket to achieving this prestigious certification, by helping you test what you know against what you need to know. Test your knowledge of the 2018 exam domains Identify areas in need of further study Gauge your progress throughout your exam preparation The CISSP exam is refreshed every few years to ensure that candidates are up-to-date on the latest security topics and trends. Currently-aligned preparation resources are critical, and periodic practice tests are one of the best ways to truly measure your level of understanding. COMPUTERS,Certification Guides,General

CWNA Certified Wireless Network Administrator Study Guide The bestselling CWNA study guide, updated for the latest exam The CWNA: Certified Wireless Network Administrator Study Guide is the ultimate preparation resource for the CWNA exam. Fully updated to align with the latest version of the exam, this book features expert coverage of all exam objectives to help you internalize essential information. A pre-assessment test reveals what you already know, allowing you to focus your study time on areas in need of review, while hands-on exercises allow you to practice applying CWNA concepts to real-world scenarios. Expert-led discussion breaks complex topics down into easily-digestible chucks to facilitate clearer understanding, and chapter review questions help you gauge your progress along the way. You also get a year of free access to the Sybex online interactive learning environment, which features additional resources and study aids including bonus practice exam questions. The CWNA exam tests your knowledge of regulations and standards, protocols and devices, network implementation, security, and RF site surveying. Thorough preparation gives you your best chance of passing, and this book covers it all with a practical focus that translates to real on-the-job skills. Study 100% of the objectives for Exam CWNA-107 Assess your practical skills with hands-on exercises Test your understanding with challenging chapter tests Access digital flashcards, white papers, bonus practice exams, and more The CWNA certification is a de facto standard for anyone working with wireless technology. It shows employers that you have demonstrated competence in critical areas, and have the knowledge and skills to perform essential duties that keep their wireless technology functioning and safe. The CWNA: Certified Wireless Network Administrator Study Guide gives you everything you need to pass the exam with flying colors. COMPUTERS,Certification Guides,General

CISSP For Dummies Secure your CISSP certification! If you’re a security professional seeking your CISSP certification, this book is a perfect way to prepare for the exam. Covering in detail all eight domains, the expert advice inside gives you the key information you'll need to pass the exam. Plus, you'll get tips on setting up a 60-day study plan, tips for exam day, and access to an online test bank of questions. CISSP For Dummies is fully updated and reorganized to reflect upcoming changes (ISC)2 has made to the Common Body of Knowledge. Complete with access to an online test bank this book is the secret weapon you need to pass the exam and gain certification. Get key information for all eight exam domains Find test-taking and exam-day tips and tricks Benefit from access to free online practice questions and flash cards Prepare for the CISSP certification in 2018 and beyond You’ve put in the time as a security professional—and now you can reach your long-term goal of CISSP certification. COMPUTERS,Certification Guides,General

CompTIA Network+ N10-007 Cert Guide This is the eBook version of the print title. Note that the eBook does not provide access to the practice test software that accompanies the print book. Access to the personal video mentoring is available through product registration at Pearson IT Certification; or see instructions in back pages of your eBook. Learn, prepare, and practice for CompTIA Network+ N10-007 exam success with this CompTIA Cert Guide from Pearson IT Certification, a leader in IT Certification learning and a CompTIA Authorized Platinum Partner. Master CompTIA Network+ N10-007 exam topics Assess your knowledge with chapter-ending quizzes Review key concepts with exam preparation tasks Learn from more than two hours of video mentoring CompTIA Network+ N10-007 Cert Guide is a best-of-breed exam study guide. Best-selling author and expert instructor Anthony Sequeira shares preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. Material is presented in a concise manner, focusing on increasing your understanding and retention of exam topics. The book presents you with an organized test preparation routine through the use of proven series elements and techniques. Exam topic lists make referencing easy. Chapter-ending Exam Preparation Tasks help you drill on key concepts you must know thoroughly. Review questions help you assess your knowledge, and a final preparation chapter guides you through tools and resources to help you craft your final study plan. The book also contains more than three hours of personal video mentoring from the author. Go to the back pages of your eBook for instructions on how to access the personal video mentoring content. Well-regarded for its level of detail, assessment features, and challenging review questions and exercises, this CompTIA approved study guide helps you master the concepts and techniques that will enable you to succeed on the exam the first time. The CompTIA approved study guide helps you master all the topics on the Network+ exam, including: Computer networks and the OSI model Network components Ethernet IP addressing Routing traffic Wide Area Networks (WANs) Wireless Technologies Network performance Command-line utilities Network management Network policies and best practices Network security Troubleshooting COMPUTERS,Certification Guides,General

CISM Certified Information Security Manager All-in-One Exam Guide Publisher's Note: Products purchased from Third Party sellers are not guaranteed by the publisher for quality, authenticity, or access to any online entitlements included with the product. This effective study guide provides 100% coverage of every topic on the latest version of the CISM exam Written by an information security executive consultant, experienced author, and university instructor, this highly effective integrated self-study system enables you to take the challenging CISM exam with complete confidence. CISM Certified Information Security Manager All-in-One Exam Guide covers all four exam domains developed by ISACA. You’ll find learning objectives at the beginning of each chapter, exam tips, practice questions, and in-depth explanations. All questions closely match those on the live test in tone, format, and content. “Note,†“Tip,†and “Caution†sections throughout provide real-world insight and call out potentially harmful situations. Beyond fully preparing you for the exam, the book also serves as a valuable on-the-job reference. Covers all exam domains, including: • Information security governance • Information risk management • Information security program development and management • Information security incident management Electronic content includes: • 400 practice exam questions • Test engine that provides full-length practice exams and customizable quizzes by exam topic • Secured book PDF COMPUTERS,Certification Guides,General

OCP Java SE 8 Programmer II Exam Guide (Exam 1Z0-809) A Complete, Integrated Study System for OCP Exam 1Z0-809 Study for the OCP Java SE 8 Programmer II exam using this effective exam preparation guide from Oracle Press. Written by a team of experts, including two developers of the original exam, OCP Java SE 8 Programmer II Exam Guide (Exam 1Z0-809) offers comprehensive coverage of every subject on the test and lays out essential Java programming skills. Throughout, step-by-step exercises; self-tests; and “Exam Watch,†“Inside the Exam,†and “On the Job†sections highlight salient points and aid in learning. In all, the book and accompanying digital content feature more than 350 practice questions that mirror those on the live test in tone, format, and content. Clearly explains every topic on Exam 1Z0-809, including: • Declarations, access control, and enums • Object orientation • Assertions and exceptions • Dates, times, locales, and resource bundles • I/O and NIO • Generics and collections • Inner classes • Lambda expressions and functional interfaces • Streams • Threads • Concurrency • JDBC Electronic content includes: • 170 practice exam questions • Fully customizable test engine • Secured book PDF For questions regarding content or to report errata, e-mail hep_customer-service@mheducation.com COMPUTERS,Certification Guides,General

Architecting Microsoft Azure Solutions – Exam Guide 70-535 Get certified as an Azure architect by acing the 70-535 Architecting Microsoft Solutions (70-535) exam using this comprehensive guide with full coverage of the exam objectives About This Book Learn to successfully design and architect powerful solutions on the Azure Cloud platform Enhance your skills with mock tests and practice questions A detailed certification guide that will help you ace the 70-535 exam with confidence Who This Book Is For This book is for architects and experienced developers, who are gearing up for the 70-535 exam. Technical architects interested in learning more about designing Cloud solutions will also find this book useful. What You Will Learn Use Azure Virtual Machines to design effective VM deployments Implement architecture styles, like serverless computing and microservices Secure your data using different security features and design effective security strategies Design Azure storage solutions using various storage features Create identity management solutions for your applications and resources Architect state-of-the-art solutions using Artificial Intelligence, IoT, and Azure Media Services Use different automation solutions that are incorporated in the Azure platform In Detail Architecting Microsoft Azure Solutions: Exam Guide 70-535 will get Azure architects and developers up-to-date with the latest updates on Azure from an architecture and design perspective. The book includes all the topics that are still relevant from the previous 70-534 exam, and is updated with latest topics covered, including Artificial Intelligence, IoT, and architecture styles. This exam guide is divided into six parts, where the first part will give you a good understanding of how to design a compute infrastructure. It also dives into designing networking and data implementations. You will learn about designing solutions for Platform Service and operations. Next, you will be able to secure your resources and data, as well as design a mechanism for governance and policies. You will also understand the objective of designing solutions for Platform Services, by covering Artificial Intelligence, IoT, media services, and messaging solution concepts. Finally, you will cover the designing for operations objective. This objective covers application and platform monitoring, as well as designing alerting strategies and operations automation strategies. By the end of the book, you'll have met all of the exam objectives, and will have all the information you need to ace the 70-535 exam. You will also have become an expert in designing solutions on Microsoft Azure. Style and approach This book offers clear and crisp explanations of the exam objectives that will help you with all the information needed to pass the 70-535 exam. The detail oriented approach will make you an expert on designing solutions on Microsoft Azure. COMPUTERS,Certification Guides,General

CompTIA Advanced Security Practitioner (CASP) CAS-003 Cert Guide This is the eBook version of the print title. Note that the eBook may not provide access to the practice test software that accompanies the print book. Learn, prepare, and practice for CompTIA Advanced Security Practitioner (CASP) CAS-003 exam success with this CompTIA Approved Cert Guide from Pearson IT Certification, a leader in IT Certification learning and a CompTIA Authorized Platinum Partner. Master CompTIA Advanced Security Practitioner (CASP) CAS-003 exam topics Assess your knowledge with chapter-ending quizzes Review key concepts with exam preparation tasks CompTIA Advanced Security Practitioner (CASP) CAS-003 Cert Guide is a best-of-breed exam study guide. Leading security certification training experts Robin Abernathy and Troy McMillan share preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. Material is presented in a concise manner, focusing on increasing your understanding and retention of exam topics. The book presents you with an organized test preparation routine through the use of proven series elements and techniques. Exam topic lists make referencing easy. Chapter-ending Exam Preparation Tasks help you drill on key concepts you must know thoroughly. Review questions help you assess your knowledge, and a final preparation chapter guides you through tools and resources to help you craft your final study plan. Well-regarded for its level of detail, assessment features, and challenging review questions and exercises, this CompTIA approved study guide helps you master the concepts and techniques that will enable you to succeed on the exam the first time, including: Enterprise security Risk management and incident response Research, analysis, and assessment Integration of computing, communications, and business disciplines Technical integration of enterprise components COMPUTERS,Certification Guides,General

PMP Project Management Professional Practice Exams Don’t Let the Real Test Be Your First Test! Aligned with the current PMI® Project Management Body of Knowledge (PMBOK®) and the latest release of the Project Management Professional exam, PMP® Project Management Professional Practice Exams provides coverage of all exam objectives and is logically organized by exam domain. All questions simulate those on the actual exam in content, style, and difficulty. To facilitate retention, every question is accompanied by in-depth explanations for both correct and incorrect answers. Covers all five PMP exam domains: • Initiating the Project • Planning the Project • Executing the Project • Monitoring and Controlling the Project • Closing the Project Digital content includes: • Test engine that provides full-length practice exams or customized quizzes by chapter or by exam domain • 600 practice exam questions COMPUTERS,Certification Guides,General

CompTIA Network+ Certification All-in-One Exam Guide, Seventh Edition (Exam N10-007) Thoroughly revised for the new CompTIA Network+ exam, the Seventh Edition of this bestselling All-in-One Exam Guide delivers 100% coverage of the exam objectives and serves as a valuable on-the-job reference Take the latest version of the CompTIA Network+ exam with complete confidence using the fully updated information contained in this comprehensive self-study system. The book offers clear instruction and real-world examples from training expert and bestselling author Mike Meyers along with hundreds of accurate practice questions. Fulfilling the promise of the All-in-One series, this complete reference serves both as a study tool and a valuable on-the-job reference that will serve readers beyond the exam. CompTIA Network+ Certification All-in-One Exam Guide, Seventh Edition (Exam N10-007) also includes access to free video training and interactive hands-on labs and simulations that prepare you for difficult performance-based questions. A valuable pre-assessment test enables readers to gauge their familiarity with the test’s objectives and tailor an effective course for study. · Contains complete coverage of every objective for the CompTIA Network+ Certification exam · Written by CompTIA training and certification guru Mike Meyers · Electronic content includes the Total Tester exam simulator with over 100 practice questions, over an hour of training videos, and a collection of Mike Meyers’ favorite shareware and freeware networking utilities COMPUTERS,Certification Guides,General

CompTIA Security+ SY0-501 Review Guide The NEW complete Security+ preparation bundle, with over 1,000 practice questions! The CompTIA Security+ Certification Kit is the ultimate preparation experience for Exam SY0-501. Updated to align with the latest changes to the exam, this kit provides complete, expert coverage of all six exam domains. The CompTIA Security+ Study Guide clarifies crucial security topics and provides practical examples drawn from real-world experience, while the CompTIA Security+ Review Guide condenses essential information down into bite-sized pieces organized by domain. The CompTIA Security+ Practice Tests help you gauge your progress along the way, with six unique practice tests that help you diagnose weak points while there is still time to review. You also get a year of FREE access to the Sybex interactive online learning environment, which features a pre-assessment test, hundreds of practice questions, flashcards, and other tools to help you plan, prepare, and perform. Studying both content and technique gives you an advantage on test day, and the Sybex advantage means going into the exam with confidence. The CompTIA Security+ exam tests your knowledge of network security, compliance and operation security, threats and vulnerabilities, application, data, and host security. With clear guidance on critical topics including architecture and design, identity and access management, cryptography, risk management, and more, this kit provides everything you need to pas with flying colors. Find clear explanations covering 100% of Exam SY0-501 objectives Learn how critical exam topics translate into real-world on-the-job skills Test your knowledge with 1,020 practice questions covering all six exam domains Access digital study tools including flashcards, practice tests, and more The Security+ certification sets your career on track. DoDD 8570-approved and a springboard to the CISSP and CISA, this exam is an important first step for security professionals seeking an advantage over the competition. The exam is challenging, so comprehensive preparation is key — and the CompTIA Security+ Certification Kit is the ideal resource for candidates seeking deep understanding with real-world context. COMPUTERS,Certification Guides,General

Mike Meyers' CompTIA Network+ Certification Passport, Sixth Edition (Exam N10-007) Up-to-date, focused coverage of every topic on the CompTIA Network+ exam N10-007 Get on the fast track to becoming CompTIA Network+ certified with this affordable, portable study tool. Inside, certification training experts guide you through the official N10-007 exam objectives in the order that CompTIA presents them, providing a concise review of each and every exam topic. With an intensive focus only on what you need to know to pass the CompTIA Network+ Exam N10-007, this certification passport is your ticket to success on exam day. Inside: • Itineraries—List of official exam objectives covered • ETAs—Amount of time needed to review each exam objective • Travel Advisories—Expert advice on critical topics • Local Lingo—Concise definitions of key terms and concepts • Travel Assistance—Recommended resources for more information • Exam Tips—Common exam pitfalls and solutions • Connecting Flights—References to sections of the book that cover related concepts • Checkpoints—End-of-chapter questions, answers, and explanations • Career Flight Path—Information on the exam and possible next steps Online content includes: • 200 practice exam questions in the Total Tester exam engine COMPUTERS,Certification Guides,General

Learn Adobe Premiere Pro CC for Video Communication This study guide uses text integrated with video to help learners gain real-world skills that will get them started in their career in planning, shooting, and doing post-production on video projects and lays the foundation for taking the Premiere Pro ACA exam. A mix of project-based lessons, practical videos, and regular assessments throughout prepares beginning learners for an entry-level position in a competitive job market. Written by an instructor with classroom teaching experience, the book covers all of the objectives of the latest Video Communication Using Adobe Premiere Pro CC Adobe Certified Associate Exam. Following are the top level domain objectives for the Video Communication Using Adobe Premiere Pro CC Adobe Certified Associate Exam: Setting Project Requirements Identifying Design Elements When Preparing Video Understanding the Adobe Premiere Pro Interface Editing a Video Sequence with Adobe Premiere Pro Exporting Video with Adobe Premiere Pro The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Certification Guides,General

CISSP Cert Guide This is the eBook version of the print title. Note that the eBook does not provide access to the practice test software that accompanies the print book. Learn, prepare, and practice for CISSP exam success with this Cert Guide from Pearson IT Certification, a leader in IT Certification learning. Master the latest CISSP exam topics Assess your knowledge with chapter-ending quizzes Review key concepts with exam preparation tasks Practice with realistic exam questions Get practical guidance for test taking strategies CISSP Cert Guide, Third Edition is a best-of-breed exam study guide. Leading IT certification experts Robin Abernathy and Troy McMillan share preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. Material is presented in a concise manner, focusing on increasing your understanding and retention of exam topics. The book presents you with an organized test preparation routine through the use of proven series elements and techniques. Exam topic lists make referencing easy. Chapter-ending Exam Preparation Tasks help you drill on key concepts you must know thoroughly. Review questions help you assess your knowledge, and a final preparation chapter guides you through tools and resources to help you craft your final study plan. The companion website contains the powerful Pearson Test Prep practice test software engine, complete with hundreds of exam-realistic questions. The assessment engine offers you a wealth of customization options and reporting features, laying out a complete assessment of your knowledge to help you focus your study where it is needed most. Well regarded for its level of detail, assessment features, and challenging review questions and exercises, this CISSP study guide helps you master the concepts and techniques that will allow you to succeed on the exam the first time. The ISC2 study guide helps you master all the topics on the CISSP exam, including · Access control · Telecommunications and network security · Information security governance and risk management · Software development security · Cryptography · Security architecture and design · Operation security · Business continuity and disaster recovery planning · Legal, regulations, investigations, and compliance · Physical (environmental) security COMPUTERS,Certification Guides,General

CompTIA Network+ Certification Study Guide, Seventh Edition (Exam N10-007) Your complete exam prep course with digital content—500+ practice exam questions, 3+ hours of video training, and much more With hundreds of practice exam questions, including new performance-based types, CompTIA Network+® Certification Study Guide, Seventh Edition (Exam N10-007) covers everything you need to know to prepare for this challenging exam. • 100% complete coverage of all official objectives for exam N10-007 • Exam Watch notes call attention to information about, and potential pitfalls in, the exam • Exam Readiness checklist—you’re ready for the exam when all objectives on the list are checked off • Inside the Exam sections highlight key exam topics covered • Two-Minute Drills for quick review at the end of every chapter • Simulated exam questions match the format, tone, topics, and difficulty of the real exam Covers all the exam topics, including: Basic Network Concepts • Network Protocols and Standards • Networking Components • TCP/IP Addressing • TCP/IP Protocols • TCP/IP Utilities and Troubleshooting • Configuring Routers and Switches • Subnetting and Routing • Configuring Network Services • Wireless Networking • Remote Access and VPN Connectivity • Wide Area Network Technologies • Maintaining and Supporting a Network • Network Security Principles • Network Security Practices • Monitoring the Network • Troubleshooting the Network Online content includes: • 500+ practice exam questions • Test engine that provides full-length practice exams or customized quizzes based on chapters or exam objectives • NEW performance-based question simulations • Pre-assessment test • 3+ hours of video training • 20+ lab exercises and solutions • Bonus chapter! “Implementing a Network†• Quick Review Guide • Glossary COMPUTERS,Certification Guides,General

AWS Certified Solutions Architect Associate All-in-One Exam Guide (Exam SAA-C01) COVERS THE NEW 2018 EXAM SAA-C01! This effective study guide provides 100% coverage of every topic on the AWS Certified Solutions Architect Associate exam. Get complete coverage of all objectives included on the February 2018 SAA-C01 exam from this comprehensive resource. Written by an expert AWS Solutions Architect and well-respected author, this authoritative guide fully addresses the knowledge and skills required for passing the AWS Certified Solutions Architect Associate exam. You’ll find learning objectives at the beginning of each chapter, exam tips, practice exam questions, and in-depth explanations. Designed to help you pass the exam with ease, this definitive volume also serves as an essential on-the-job reference. Covers all exam domains, including: • Design Resilient Architectures • Define Performant Architectures • Specify Secure Applications and Architectures • Design Cost-Optimized Architectures • Define Operationally Excellent Architectures Digital content includes: • 130 practice exam questions • Test engine that provides practice exams or quizzes that can be customized by chapter or exam objective COMPUTERS,Certification Guides,General

Learn Adobe InDesign CC for Print and Digital Media Publication This study guide uses text integrated with video to help learners gain real-world skills that will get them started in their career in print and digital media design and publication and lays the foundation for taking the Adobe InDesign Adobe Certified Associate (ACA) exam. A mix of project-based lessons, videos, and quizzes throughout prepares beginning learners for an entry-level position in a competitive job market. Written by an instructor with classroom teaching experience, the book covers all of the objectives of the latest Print and Digital Media Publication Using Adobe InDesign CC Adobe Certified Associate Exam. Following are the top level domain objectives for the Print & Digital Media Publication Using Adobe InDesign exam: Setting Project Requirements Identifying Design Elements When Preparing Page Layouts Understanding Adobe InDesign Creating Page Layouts by Using Adobe InDesign Publish, Export, and Archive Page Layouts by Using Adobe InDesign The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Certification Guides,General

CompTIA CySA+ Cybersecurity Analyst Certification Practice Exams (Exam CS0-001) Prepare for the CompTIA CySA+ certification exam with this effective self-study resource Don’t Let the Real Test Be Your First Test! Pass the new Cybersecurity Analyst+ certification exam and obtain the latest security credential from CompTIA using the accurate practice questions contained in this guide. CompTIA CySA+® Cybersecurity Analyst Certification Practice Exams offers 100% coverage of all objectives for the exam. Written by a leading information security expert and experienced instructor, this guide includes knowledge, scenario, and performance-based questions. Throughout, in-depth explanations are provided for both correct and incorrect answers. Between the book and electronic content, you will get more than 500 practice questions that will fully prepare you for the challenging exam. Designed to help you pass the exam, this is the perfect companion to CompTIA CySA+ Cybersecurity Analyst Certification All-in-One Exam Guide (Exam CS0-001). Covers all exam topics including: • Threat management • Reconnaissance techniques • Securing a corporate network • Vulnerability management • Cyber incident response • Security architectures • Identity and access management • Secure software development • And much more Digital content includes: • 200+ accurate practice questions • A valuable pre-assessment test • Performance-based questions • Fully customizable test engine COMPUTERS,Certification Guides,General

PMI-ACP Agile Certified Practitioner All-in-One Exam Guide This comprehensive test preparation system offers complete coverage of every topic on the PMI-ACP exam Pass the PMI-ACP Agile Certified Practitioner exam with ease using the detailed information contained in this highly effective self-study guide. The book offers 100% coverage of all current exam objectives and shows, step by step, how to successfully set up and configure an Agile framework-based project. PMI-ACP Agile Certified Practitioner All-in-One Exam Guide features more than 240 accurate practice questions with in-depth answer explanations. All questions closely match those on the live test in tone, format, and content. Beyond fully preparing you for the exam, the book also serves as a valuable on-the-job reference. Coverage includes: • Agile principles and the PMI-ACP mindset • Value-driven delivery in Agile projects • Managing stakeholder engagement • Leading team performance • Planning for Agile projects • Detecting and resolving problems • Leading continuous improvement • And much more Digital content includes: • 240 practice exam questions • Video training from the author • A secured book PDF COMPUTERS,Certification Guides,General

Certified Enterprise Architect All-in-One Exam Guide This effective study guide offers comprehensive coverage of topics comprising the enterprise architecture body of knowledge. The book provides detailed coverage and lays out actionable methodologies and best practices to create and maintain successful EA models, artifacts and building blocks. It helps prepare readers to take any of the various EA certification exams and academic courses in enterprise architecture. This highly effective self-study guide offers comprehensive coverage of all topics in the enterprise architecture body of knowledge. Written by a team of experienced academics, practitioners, and professionals, the book takes a holistic look at the practice of enterprise architecture. You will get actionable methodologies and best practices and learn how to develop, deploy, and maintain successful enterprise architecture models, artifacts, and building blocks. Designed to help you prepare for certification, the Certified Enterprise Architect All-in-One Exam Guide also serves as an essential on-the-job reference. Coverage includes: • Enterprise architecture foundation concepts • Planning the enterprise architecture • Enterprise architecture development, governance, and maintenance • Defense frameworks • Viewpoints and views • The Zachman Framework • The Open Group Architecture Framework (TOGAF) • The Common Approach to Federal Enterprise Architecture • FEAF2 • Comparison of frameworks • Case Study integrated throughout the text • And much more COMPUTERS,Certification Guides,General

Pmi-Acp Exam Prep Study Guide Revised Version 2016. Passing the Project Management Institutes Agile Certified Practitioner (PMI-ACP) certification examination wont be easy, but youll boost your chances for success when you consult this study guide. Vivek Vaishampayan, an information technology expert who holds several certifications, including the PMI-ACP designation, introduces you to the exam process, Agile Project Management principles, and dozens of knowledge and skill areas that you must master to succeed in the field. Youll also get: handy tips for taking the exam;sample exam questions with answers;chapter summaries to review key concepts. Current references to Agile concepts are explained throughout the book in a simple manner so youll be better equipped to pass the test. Just as important, youll find tips throughout the book that will help you succeed after you pass the test. This latest entry to Certification Prep handbooks explicitly follows the PMIs ACP Certification Examination content outline and addresses each topic to the exact the level PMI-ACP test takers need. The PMI-ACP certification is an important facet of a practitioners development, so improve your chances of advancing your career with the PMI-ACP Exam Prep Study Guide. COMPUTERS,Certification Guides,General

OCA/OCP Java SE 8 Programmer Certification Bundle (Exams 1Z0-808 and 1Z0-809) Publisher's Note: Products purchased from Third Party sellers are not guaranteed by the publisher for quality, authenticity, or access to any online entitlements included with the product. Prepare for the Java SE 8 OCA and OCP Programmer exams with this money-saving, comprehensive study package Designed as a complete self-study program, this collection offers a variety of proven, exam-focused resources to use in preparation for for OCA and OCP certification exams 1Z0-808 and 1Z0-809. Comprised of OCA Java SE 8 Programmer I Exam Guide and OCP Java SE 8 Programmer II Exam Guide, this bundle thoroughly covers every topic on both exams—all at a discount of 23% off MSRP. OCA/OCP Java SE 8 Programmer Certification Bundle (Exams 1Z0-808 & 1Z0-809) contains hundreds of practice questions that match those on the live exams in content, style, tone, format, and difficulty. Step-by-step exercises; self-tests; and “Exam Watch,†“Inside the Exam,†and “On the Job†sections highlight salient points and aid in learning. You will get real-world examples, professional insights, and concise explanations. This authoritative, cost-effective bundle serves both as a study tool AND a valuable on-the-job reference. • This bundle is 23% cheaper than purchasing the books individually• Written by a team of Java OCA and OCP experts• Electronic content includes 330 practice exam questions in a fully-customizable test engine COMPUTERS,Certification Guides,General

CISSP All-in-One Exam Guide, Eighth Edition A new edition of Shon Harris’ bestselling exam prep guide—fully updated for the new CISSP 2018 Common Body of Knowledge This effective self-study guide fully prepares you for the challenging CISSP exam and offers 100% coverage of all exam domains. This edition has been thoroughly revised to cover the new CISSP 2018 Common Body of Knowledge, hot spot and drag and drop question formats, and more. CISSP All-in-One Exam Guide, Eighth Edition features hands-on exercises as well as “Notes,†“Tips,†and “Cautions†that provide real-world insight and call out potentially harmful situations. Each chapter features learning objectives, exam tips, and practice questions with in-depth answer explanations. Beyond exam prep, the guide also serves as an ideal on-the-job reference for IT security professionals. • Fully updated to cover 2018 exam objectives and question formats • Digital content includes access to the Total Tester test engine with 1500 practice questions, and flashcards • Serves as an essential on-the-job-reference COMPUTERS,Certification Guides,General

CAPM Certified Associate in Project Management Practice Exams Don’t Let the Real Test Be Your First Test! Take the 2018 version of the challenging CAPM exam with confidence using this highly effective, exam-focused study resource. CAPM® Certified Associate in Project Management Practice Exams contains more than 1000 practice questions and is fully aligned with the Project Management Body of Knowledge® Guide, Sixth Edition. All questions simulate those on the live test in content, style, tone, and difficulty. To facilitate retention, every question is accompanied by in-depth explanations for both correct and incorrect answers. Covers all 58 learning objectives for the CAPM exam, including: • Project integration management• Project scope management• Project schedule management• Project cost management• Project quality management• Project resource management• Project communications management• Project risk management• Project procurement management• Project stakeholder management Digital content includes: • Test engine that provides full-length practice exams or customized quizzes by chapter or by exam domain• 600 practice exam questions COMPUTERS,Certification Guides,General

CISSP Practice Exams, Fifth Edition Don’t Let the Real Test Be Your First Test! This fully updated self-study guide offers complete coverage of all eight Certified Information Systems Security Professional exam domains developed by the International Information Systems Security Certification Consortium (ISC)2®. To reinforce important skills and facilitate retention, every question is accompanied by in-depth explanations for both correct and incorrect answers. Designed to help you pass the test with ease, this book is the ideal companion to the bestselling CISSP All-in-One Exam Guide. Covers all 8 CISSP® domains: Security and risk management Asset security Security architecture and engineering Communication and network security Identity and access management Security assessment and testing Security operations Software development security DIGITAL CONTENT INCLUDES: 1000+ multiple-choice practice exam questions Hotspot and drag-and-drop practice exam questions COMPUTERS,Certification Guides,General

CompTIA PenTest+ Certification Practice Exams (Exam PT0-001) Don’t Let the Real Test Be Your First Test! Prepare for the challenging PenTest+ exam from CompTIA using this highly effective self-study guide. The book offers accurate practice questions for all exam objectives and includes a valuable pre-assessment test that enables you to tailor a course for study. Written by a cybersecurity expert, the book supplements the CompTIA PenTest+® Certification All-in-One Exam Guide (Exam PT0-001). You will get more than 500 practice questions in the knowledge, scenario, and performance-based formats contained on the live test—all with in-depth answer explanations for both the correct and incorrect answers. CompTIA PenTest+® Certification Practice Exams (Exam PT0-001) covers: • Pre-engagement activities • Getting to know your targets • Network scanning and enumeration • Vulnerability scanning and analysis • Mobile device and application testing • Social engineering • Network-based attacks • Wireless and RF attacks • Web and database attacks • Attacking local operating systems • Physical penetration testing • Writing the pen test report • And more Digital content includes: • 500+ practice exam questions • Test engine that provides full-length practice exams or customized quizzes by chapter or by exam domain COMPUTERS,Certification Guides,General

CCIE Wireless v3 Study Guide Thoroughly prepare for the revised Cisco CCIE Wireless v3.x certification exams Earning Cisco CCIE Wireless certification demonstrates your broad theoretical knowledge of wireless networking, your strong understanding of Cisco WLAN technologies, and the skills and technical knowledge required of an expert-level wireless network professional. This guide will help you efficiently master the knowledge and skills you’ll need to succeed on both the CCIE Wireless v3.x written and lab exams. Designed to help you efficiently focus your study, achieve mastery, and build confidence, it focuses on conceptual insight, not mere memorization. Authored by five of the leading Cisco wireless network experts, it covers all areas of the CCIE Wireless exam blueprint, offering complete foundational knowledge for configuring and troubleshooting virtually any Cisco wireless deployment. Plan and design enterprise-class WLANs addressing issues ranging from RF boundaries to AP positioning, power levels, and density Prepare and set up wireless network infrastructure, including Layer 2/3 and key network services Optimize existing wired networks to support wireless infrastructure Deploy, configure, and troubleshoot Cisco IOS Autonomous WLAN devices for wireless bridging Implement, configure, and manage AireOS Appliance, Virtual, and Mobility Express Controllers Secure wireless networks with Cisco Identity Services Engine: protocols, concepts, use cases, and configuration Set up and optimize management operations with Prime Infrastructure and MSE/CMX Design, configure, operate, and troubleshoot WLANs with real-time applications COMPUTERS,Certification Guides,General

CompTIA PenTest+ Certification All-in-One Exam Guide (Exam PT0-001) This comprehensive exam guide offers 100% coverage of every topic on the CompTIA PenTest+ exam Get complete coverage of all the objectives included on the CompTIA PenTest+ certification exam PT0-001 from this comprehensive resource. Written by an expert penetration tester, the book provides learning objectives at the beginning of each chapter, hands-on exercises, exam tips, and practice questions with in-depth answer explanations. Designed to help you pass the exam with ease, this definitive volume also serves as an essential on-the-job reference. Covers all exam topics, including: • Pre-engagement activities • Getting to know your targets • Network scanning and enumeration • Vulnerability scanning and analysis • Mobile device and application testing • Social engineering • Network-based attacks • Wireless and RF attacks • Web and database attacks • Attacking local operating systems • Physical penetration testing • Writing the pen test report • And more Online content includes: • Interactive performance-based questions • Test engine that provides full-length practice exams or customized quizzes by chapter or by exam domain COMPUTERS,Certification Guides,General

ITF+ CompTIA IT Fundamentals All-in-One Exam Guide, Second Edition (Exam FC0-U61) This fully updated study guide delivers 100% coverage of every topic on the CompTIA ITF+ IT Fundamentals exam Take the CompTIA ITF+ IT Fundamentals exam with complete confidence using this bestselling and effective self-study system. Written by CompTIA certification and training experts, this authoritative guide explains foundational computer technologies in full detail. You’ll find learning objectives at the beginning of each chapter, exam tips, practice exam questions, and in-depth explanations throughout. Designed to help you pass the exam with ease, this definitive volume also serves as an essential on-the-job reference. Also includes a voucher coupon for a 10% discount on your CompTIA exams! Covers all exam topics, including: • Computer basics• System hardware• I/O ports and peripherals• Data storage and sharing• PC setup and configuration• Understanding operating systems• Working with applications and files• Setting up and configuring a mobile device• Connecting to networks and the Internet• Handling local and online security threats• Computer maintenance and management• Troubleshooting and problem solving• Understanding databases• Software development and implementation Online content includes: • 130 practice exam questions in a customizable test engine• Link to over an hour of free video training from Mike Meyers COMPUTERS,Certification Guides,General

MCSA Windows Server 2016 Practice Tests NOTE: As the response to the coronavirus (COVID-19) continues to evolve rapidly around the world, Microsoft has announced that it’s extending the retirement date of the current MCSA Windows Server 2016 certification until January 31, 2021. Pearson VUE has temporarily closed many of its testing centers worldwide in response to global government regulations to battle the spread of COVID-19. As an alternative to taking your exam at a testing center, online proctoring is available, which allows you to take your certification exam in the comfort of your own home or office. Instead of taking the required exams at a Pearson VUE testing center near you, Pearson VUE will be offering only online proctored exams for the foreseeable future. This means you will have more time to prepare for the current exams: 70-740: Installation, Storage, and Compute with Windows Server 2016 70-741: Networking with Windows Server 2016 70-742: Identity with Windows Server 2016 To help you prepare for the exams, our Study Guides and Practice Tests are available for purchase. Get prepared for the high-stakes MCSA Windows Server 2016 certification exam Windows Server 2016 is the latest version of Microsoft's Windows server operating system, and the ideal server for Windows 8/8.1 and Windows 10 desktop clients. Windows Server 2016 will include many new and updated features, including enhancements to Hyper-V, Storage Spaces, and Active Directory. MCSA Windows Server 2016 Practice Tests provides 10 unique 85-question chapter tests, covering the ten MCSA Windows Server 2016 objective domains, PLUS three additional 50-question practice exams, for a total of 1000 practice test questions. • Practice tests are a popular way for certification candidates to prepare for taking exams • The practice test questions provide comprehensive coverage of the exam objectives • Covers all three exams: 70-740, 70-741, 70-742 • Written by a five-time Microsoft MVP Winner This book helps you gain the confidence you need and prepares you for taking the three required Exams 70-740, 70-741, and 70-742, or upgrade Exam 70-743. The practice test questions prepare you for test success. COMPUTERS,Certification Guides,General

SHRM-CP/SHRM-SCP Certification Bundle Prepare for the SHRM-CP and SHRM- SCP exams with this money-saving, comprehensive study package Designed as a complete self-study program, this collection offers a variety of proven, exam-focused resources to use in preparation for the SHRM Certified Professional (SHRM-CP) and SHRM Senior Certified Professional (SHRM-SCP) exams. Comprised of SHRM-CP/SHRM-SCP Certification All-in-One Exam Guide, SHRM-CP/SHRM-SCP Certification Practice Exams, and bonus electronic content, this bundle covers 100% of the topics on the exams and features a total of over 800 accurate practice questions. The bundle serves both as a study tool AND a valuable on-the-job reference that will serve HR professionals well beyond the exams. • Covers 100% of the SHRM Body of Competency & Knowledge and features 800+ practice exam questions• This bundle is 10% cheaper than buying the books individually AND includes content unavailable elsewhere• Electronic content includes practice exams, a quick review guide, study worksheets, exercises, and more COMPUTERS,Certification Guides,General

(ISC)2 SSCP Systems Security Certified Practitioner Official Practice Tests Smarter, faster prep for the SSCP exam The (ISC)² SSCP Official Practice Tests is the only (ISC)²-endorsed set of practice questions for the Systems Security Certified Practitioner (SSCP). This book’s first seven chapters cover each of the seven domains on the SSCP exam with sixty or more questions per domain, so you can focus your study efforts exactly where you need more review. When you feel well prepared, use the two complete practice exams from Sybex’s online interactive learning environment as time trials to assess your readiness to take the exam. Coverage of all exam objectives, including: • Access Controls • Security Operations and Administration • Risk Identification, Monitoring, and Analysis • Incident Response and Recovery •Cryptography •Network and Communications Security •Systems and Application Security SSCP certification demonstrates you have the advanced technical skills and knowledge to implement, monitor and administer IT infrastructure using security best practices, policies and procedures. It’s ideal for stuÂdents pursuing cybersecurity degrees as well as those in the field looking to take their careers to the next level. COMPUTERS,Certification Guides,General

CompTIA Network+ Certification Guide This is a practical certification guide covering all the exam topics in an easy-to-follow manner backed with self-assessment scenarios for better preparation. Key Features A step-by-step guide to give you a clear understanding of the Network+ Certification Learn about network architecture, protocols, security, and network troubleshooting Confidently ace the N10-007 exam with the help of practice tests Book Description CompTIA certified professionals have always had the upper hand in the information technology industry. This book will be your ideal guide to efficiently passing and achieving this certification. Learn from industry experts and implement their practices to resolve complex IT issues. This book revolves around networking concepts where readers will learn topics like network architecture, security, network monitoring, and troubleshooting. This book will not only prepare the readers conceptually but will also help them pass the N10-007 exam. This guide will also provide practice exercise after every chapter where readers can ensure their concepts are clear. By the end of this book, readers will leverage this guide and the included practice questions to boost their confidence in appearing for the actual certificate. What you will learn Explain the purpose of a variety of networking concepts and implement them appropriately Understand physical security and common attacks while securing wired and wireless networks Understand the fundamentals of IPv4 and IPv6 Determine and explain the appropriate cabling, device, and storage technologies Understand network troubleshooting methodology and appropriate tools to support connectivity and performance Use best practices to manage the network, determine policies, and ensure business continuity Who this book is for This book is ideal for readers wanting to pass the CompTIA Network+ certificate. Rookie network engineers and system administrators interested in enhancing their networking skills would also benefit from this book. No Prior knowledge on networking would be needed. COMPUTERS,Certification Guides,General

CISSP Bundle, Fourth Edition Prepare for the 2018 CISSP exam with this up-to-date, money-saving study package Designed as a complete self-study program, this collection offers a wide variety of proven, exam-focused resources to use in preparation for the current edition of the CISSP exam. The set bundles the eighth edition of Shon Harris’ bestselling CISSP All-in-One Exam Guide and CISSP Practice Exams, Fifth Edition—. You will gain access to a variety of comprehensive resources to get ready for the challenging exam. CISSP Bundle, Fourthe Edition fully covers all eight exam domains and offers real-world insights from the authors’ professional experiences. More than 2500 accurate practice exam questions are provided, along with in-depth explanations of both the correct and incorrect answers. The included Total Tester test engine provides full-length, timed simulated exams or customized quizzes that target selected chapters or exam objectives. • Presents 100% coverage of the 2018 CISSP Exam • Includes special discount to Shon Harris Brand CISSP video training from Human Element Security • Written by leading experts in IT security certification and training COMPUTERS,Certification Guides,General

CSSLP Certification All-in-One Exam Guide, Second Edition Publisher's Note: Products purchased from Third Party sellers are not guaranteed by the publisher for quality, authenticity, or access to any online entitlements included with the product. This self-study guide delivers 100% coverage of all domainsin the the CSSLP exam Get complete coverage of all the material included on the Certified Secure Software Lifecycle Professional exam. CSSLP Certification All-in-One Exam Guide, Second Edition covers all eight exam domains developed by the International Information Systems Security Certification Consortium (ISC)2®. You’ll find learning objectives at the beginning of each chapter, exam tips, practice questions, and in-depth explanations. Designed to help you pass the exam with ease, this definitive resource also serves as an essential on-the-job reference. Covers all eight exam domains: • Secure Software Concepts • Secure Software Requirements • Secure Software Design • Secure Software Implementation/Programming • Secure Software Testing • Software Lifecycle Management • Software Deployment, Operations, and Maintenance • Supply Chain and Software Acquisition Online content includes: • Test engine that provides full-length practice exams or customized quizzes by chapter or exam domain COMPUTERS,Certification Guides,General

CEH Certified Ethical Hacker All-in-One Exam Guide, Fourth Edition Publisher's Note: Products purchased from Third Party sellers are not guaranteed by the publisher for quality, authenticity, or access to any online entitlements included with the product. Up-to-date coverage of every topic on the CEH v10 exam Thoroughly updated for CEH v10 exam objectives, this integrated self-study system offers complete coverage of the EC-Council’s Certified Ethical Hacker exam. In this new edition, IT security expert Matt Walker discusses the latest tools, techniques, and exploits relevant to the exam. You’ll find learning objectives at the beginning of each chapter, exam tips, practice exam questions, and in-depth explanations. Designed to help you pass the exam with ease, this comprehensive resource also serves as an essential on-the-job reference. Covers all exam topics, including: • Ethical hacking fundamentals • Reconnaissance and footprinting • Scanning and enumeration • Sniffing and evasion • Attacking a system • Hacking web servers and applications • Wireless network hacking • Security in cloud computing • Trojans and other attacks • Cryptography • Social engineering and physical security • Penetration testing Digital content includes: • 300 practice exam questions • Test engine that provides full-length practice exams and customized quizzes by chapter COMPUTERS,Certification Guides,General

AWS Certified Solutions Architect Practice Tests NEW! We've added two new practice exams to the online test bank to cover concepts in the new certification Exam SAA-C02. To help you prepare for taking the exam, t he updated test bank n ow includes THREE practice exams PLUS all the domain-by-domain questions. Over 1000 questions to test your knowledge! 1,000 practice questions with answers and explanations! With five unique practice tests, covering the five AWS Certified Solutions Architect Associate Exam objective domains, PLUS one additional practice exam, AWS Certified Solutions Architect Practice Tests provides over 1,000 practice test questions to make sure you are prepared for exam day. Coverage of all exam objective domains includes: Design Resilient Architectures, Define Performant Architectures, Specify Secure Applications and Architectures, Design Cost-Optimized Architectures, Define Operationally Excellent Architectures. This book will help you: • Gain confidence as you prepare for the SAA-C01 exam • Ensure you are set up for success with 1,000 practice questions • When you are ready, test your knowledge with the Sybex online interactive learning environment • Get that highly desired AWS certification Prepare smarter, not harder, with Sybex's superior study tools. COMPUTERS,Certification Guides,General

CompTIA PenTest+ Certification Bundle (Exam PT0-001) Prepare for the new PenTest+ certification exam from CompTIA with this money-saving, comprehensive study package Designed as a complete self-study program, this collection offers a variety of proven resources to use in preparation for the August 2018 release of the CompTIA PenTest+ certification exam. Comprised of CompTIA PenTest+ Certification All-In-One Exam Guide (PT0-001) and CompTIA PenTest+ Certification Practice Exams (Exam CS0-001), this bundle thoroughly covers every topic on the challenging exam. CompTIA PenTest+ Certification Bundle (Exam PT0-001) contains hundreds of practice questions that match those on the live exam in content, difficulty, tone, and format. The set includes detailed coverage of performance-based questions. You will get exam-focused “Tip,†“Note,†and “Caution†elements as well as end of chapter reviews. This authoritative, cost-effective bundle serves both as a study tool AND a valuable on-the-job reference for computer security professionals. • This bundle is 25% cheaper than purchasing the books individually and includes a 10% off the exam voucher • Written by a pair of penetration testing experts • Electronic content includes 370+ practice exam questions and secured PDF copies of both books COMPUTERS,Certification Guides,General

Learn Adobe After Effects CC for Visual Effects and Motion Graphics Motion graphics are no longer just for movie and television screens. You now see motion graphics anywhere there’s a moving image, including your desktop web browser, your smartphone, and on digital signage when you shop or travel. Creating motion graphics with Adobe After Effects can enhance your value as a creative professional. Learn Adobe After Effects CC by building cool creative projects that teach you how to: Apply and customise effects and layer styles, and use animation presets to apply pre-built animations and effect combinations Achieve advanced effects quickly using techniques such as green screen background removal, masking, speed changes, motion tracking, and animation in 3D space Animate individual layers of still graphics imported from Adobe Photoshop and Adobe Illustrator Animate text, including changing type size, letter spacing, rotation, and color over time, and flowing text along a path Create a set of visually consistent intro videos for a social media platform, while practicing efficient production techniques Export a motion graphics composition once and render multiple versions for different delivery media (such as television, web sites, and smartphones) The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Certification Guides,General

CompTIA A+ Certification All-in-One Exam Guide, Tenth Edition (Exams 220-1001 & 220-1002) This bestselling on-the-job reference and test preparation guide has been fully revised for the new 2019 CompTIA A+ exam objectives This fully revised and updated resource offers complete coverage of the latest release of CompTIA A+ exams 220-1001 & 220-1002. You'll find learning objectives at the beginning of each chapter, exam tips, practice exam questions, and in-depth explanations. Designed to help you pass the CompTIA A+ exams with ease, this definitive guide also serves as an essential on-the-job IT reference. Covers all exam topics, including how to: • Work with CPUs, RAM, BIOS, motherboards, power supplies, and other personal computer components • Install, configure, and maintain hard drives • Manage input devices and removable media • Set up, upgrade, and maintain all versions of Windows • Troubleshoot and fix computer problems • Install printers and other peripherals • Configure and secure mobile devices • Connect to the Internet • Set up wired and wireless networks • Protect your personal computer and your network • Implement virtualization and cloud-based technologies Online content includes: • Practice exams for 1001 & 1002 • More than one hour of free video training • TotalSim simulations of performance-based questions • Mike Meyers’ favorite PC tools and utilities COMPUTERS,Certification Guides,General

Official Google Cloud Certified Associate Cloud Engineer Study Guide The Only Official Google Cloud Study Guide The Official Google Cloud Certified Associate Cloud Engineer Study Guide, provides everything you need to prepare for this important exam and master the skills necessary to land that coveted Google Cloud Engineering certification. Beginning with a pre-book assessment quiz to evaluate what you know before you begin, each chapter features exam objectives and review questions, plus the online learning environment includes additional complete practice tests. Written by Dan Sullivan, a popular and experienced online course author for machine learning, big data, and Cloud topics, Official Google Cloud Certified Associate Cloud Engineer Study Guide is your ace in the hole for deploying and managing Google Cloud Services. • Select the right Google service from the various choices based on the application to be built • Compute with Cloud VMs and managing VMs • Plan and deploying storage • Network and configure access and security Google Cloud Platform is a leading public cloud that provides its users to many of the same software, hardware, and networking infrastructure used to power Google services. Businesses, organizations, and individuals can launch servers in minutes, store petabytes of data, and implement global virtual clouds with the Google Cloud Platform. Certified Associate Cloud Engineers have demonstrated the knowledge and skills needed to deploy and operate infrastructure, services, and networks in the Google Cloud. This exam guide is designed to help you understand the Google Cloud Platform in depth so that you can meet the needs of those operating resources in the Google Cloud. COMPUTERS,Certification Guides,General

CASP+ CompTIA Advanced Security Practitioner Certification All-in-One Exam Guide, Second Edition (Exam CAS-003) Complete coverage of every topic on the CompTIA Advanced Security Practitioner certification exam Get complete coverage of all objectives included on the CompTIA CASP+ exam CAS-003 from this comprehensive resource. Written by a team of leading information security experts, this authoritative guide fully addresses the skills required for securing a network and managing risk. You’ll find learning objectives at the beginning of each chapter, exam tips, practice exam questions, and in-depth explanations. Designed to help you pass the exam with ease, this definitive volume also serves as an essential on-the-job reference. Covers all exam domains, including: Threats, attacks, and vulnerabilities Technologies and tools Architecture and design Identity and access management Risk management Cryptography and PKI Electronic content includes: 200 practice exam questions COMPUTERS,Certification Guides,General

CEH Certified Ethical Hacker Practice Exams, Fourth Edition Don’t Let the Real Test Be Your First Test! Fully updated for the CEH v10 exam objectives, this practical guide contains more than 600 realistic practice exam questions to prepare you for the EC-Council’s Certified Ethical Hacker exam. To aid in your understanding of the material, in-depth explanations of both the correct and incorrect answers are provided for every question. A valuable pre-assessment test evaluates your readiness and identifies areas requiring further study. Designed to help you pass the exam, this is the perfect companion to CEH™ Certified Ethical Hacker All-in-One Exam Guide, Fourth Edition. Covers all exam topics, including: Ethical hacking fundamentals Reconnaissance and footprinting Scanning and enumeration Sniffing and evasion Attacking a system Hacking web servers and applications Wireless network hacking Mobile and IoT Security in cloud computing Trojans and other attacks Cryptography Social engineering and physical security Penetration testing Online content includes: Test engine that provides full-length practice exams and customized quizzes by chapter or exam domain COMPUTERS,Certification Guides,General

Microsoft Azure Administrator – Exam Guide AZ-103 Manage Microsoft Azure cloud services that span storage, security, networking, and compute cloud capabilities and ace the AZ-103 Exam Key Features Master features and concepts pertaining to Azure's Administration services Gain a deep understanding of various Azure services related to infrastructure, applications, and environments Gauge yourself by giving mock tests with up-to-date exam questions Book Description Microsoft Azure Administrator – Exam Guide AZ-103 will cover all the exam objectives that will help you earn Microsoft Azure Administrator certification. Whether you want to clear AZ-103 exam or want hands-on experience in administering Azure, this study guide will help you achieve your objective. It covers the latest features and capabilities around configuring, managing, and securing Azure resources. Following Microsoft's AZ-103 exam syllabus, this guide is divided into five modules. The first module talks about how to manage Azure subscriptions and resources. You will be able to configure Azure subscription policies at Azure subscription level and learn how to use Azure policies for resource groups. Later, the book covers techniques related to implementing and managing storage in Azure. You will be able to create and configure backup policies and perform restore operations. The next module will guide you to create, configure, and deploy virtual machines for Windows and Linux. In the last two modules, you will learn about configuring and managing virtual networks and managing identities. The book concludes with effective mock tests along with answers so that you can confidently crack this exam. By the end of this book, you will acquire the skills needed to pass Exam AZ-103. What you will learn Configure Azure subscription policies and manage resource groups Monitor activity log by using Log Analytics Modify and deploy Azure Resource Manager (ARM) templates Protect your data with Azure Site Recovery Learn how to manage identities in Azure Monitor and troubleshoot virtual network connectivity Manage Azure Active Directory Connect, password sync, and password writeback Who this book is for This book is for Azure administrators, systems administrators or anyone preparing for AZ 103 exam and wants to master Azure's various administration features. Readers should have proficiency in working with PowerShell, CLI and other day-to-day Azure administration tasks. COMPUTERS,Certification Guides,General

CEH v10 Certified Ethical Hacker Study Guide As protecting information becomes a rapidly growing concern for today’s businesses, certifications in IT security have become highly desirable, even as the number of certifications has grown. Now you can set yourself apart with the Certified Ethical Hacker (CEH v10) certification. The CEH v10 Certified Ethical Hacker Study Guide offers a comprehensive overview of the CEH certification requirements using concise and easy-to-follow instruction. Chapters are organized by exam objective, with a handy section that maps each objective to its corresponding chapter, so you can keep track of your progress. The text provides thorough coverage of all topics, along with challenging chapter review questions and Exam Essentials, a key feature that identifies critical study areas. Subjects include intrusion detection, DDoS attacks, buffer overflows, virus creation, and more. This study guide goes beyond test prep, providing practical hands-on exercises to reinforce vital skills and real-world scenarios that put what you’ve learned into the context of actual job roles. Gain a unique certification that allows you to understand the mind of a hacker Expand your career opportunities with an IT certificate that satisfies the Department of Defense’s 8570 Directive for Information Assurance positions Fully updated for the 2018 CEH v10 exam, including the latest developments in IT security Access the Sybex online learning center, with chapter review questions, full-length practice exams, hundreds of electronic flashcards, and a glossary of key terms Thanks to its clear organization, all-inclusive coverage, and practical instruction, the CEH v10 Certified Ethical Hacker Study Guide is an excellent resource for anyone who needs to understand the hacking process or anyone who wants to demonstrate their skills as a Certified Ethical Hacker. COMPUTERS,Certification Guides,General

CompTIA Linux+ Practice Tests The best practice test preparation for the foundational CompTIA Linux+ certification exam If you’re preparing for this all-important exam, turn to CompTIA Linux+ Practice Tests. The book covers the 5 objective domains, PLUS one additional 90-question practice exam, for a total of 1,000 practice test questions. Readers will also get one year of FREE access to the online test bank where they can study and work through the questions, reinforcing their skills and knowledge. Study for the CompTIA Linux+ certification with Sybex and get the advantage of exam day confidence. This book covers: Hardware and System Configuration Systems Operation and Maintenance Security Linux Troubleshooting and Diagnostics Automation and Scripting Linux is a UNIX-based operating system originally created by Linus Torvalds with the help of developers around the world. Developed under the GNU General Public License, the source code is free. Because of this, Linux is viewed by many organizations and companies as an excellent, low-cost, secure alternative to expensive OSs, such as Microsoft Windows. The CompTIA Linux+ exam tests a candidate's understanding and familiarity with the Linux Kernel. As the Linux server market share continues to grow, so too does demand for qualified and certified Linux administrators. COMPUTERS,Certification Guides,General

CEH Certified Ethical Hacker Bundle, Fourth Edition Thoroughly revised to cover all CEH v10 exam objectives, this bundle includes two books, online resources, and a bonus quick review guide This fully updated, money-saving self-study set prepares you for the CEH v10 exam. You can start by reading CEH Certified Ethical Hacker All-in-One Exam Guide, Fourth Edition to learn about every topic included in the v10 exam objectives. Next, you can reinforce what you’ve learned with the 650+ practice questions featured in CEH Certified Ethical Hacker Practice Exams, Fourth Edition. The CEH Certified Ethical Hacker Bundle, Fourth Edition also includes a bonus a quick review guide that can be used as the final piece for exam preparation. A bonus voucher code for four hours of lab time from Practice Labs, a virtual machine platform providing access to real hardware and software, can be combined with the two hours of lab time included with the All-in-One Exam Guide and provides the hands-on experience that’s tested in the optional new CEH Practical exam. This edition features up-to-date coverage of all five phases of ethical hacking: reconnaissance, gaining access, enumeration, maintaining access, and covering tracks. •In all, the bundle includes more than 1,000 accurate questions with detailed answer explanations •Online content includes customizable practice exam software containing 600 practice questions in total and voucher codes for six free hours of lab time from Practice Labs •Bonus Quick Review Guide only available with this bundle •This bundle is 22% cheaper than buying the two books separately and includes exclusive online content COMPUTERS,Certification Guides,General

CompTIA A+ Complete Practice Tests Test your knowledge and know what to expect on A+ exam day CompTIA A+ Complete Practice Tests, Second Edition enables you to hone your test-taking skills, focus on challenging areas, and be thoroughly prepared to ace the exam and earn your A+ certification. This essential component of your overall study plan presents nine unique practice tests—and two 90-question bonus tests—covering 100% of the objective domains for both the 220-1001 and 220-1002 exams. Comprehensive coverage of every essential exam topic ensures that you will know what to expect on exam day and maximize your chances for success. Over 1200 practice questions on topics including hardware, networking, mobile devices, operating systems and procedures, troubleshooting, and more, lets you assess your performance and gain the confidence you need to pass the exam with flying colors. This second edition has been fully updated to reflect the latest best practices and updated exam objectives you will see on the big day. A+ certification is a crucial step in your IT career. Many businesses require this accreditation when hiring computer technicians or validating the skills of current employees. This collection of practice tests allows you to: Access the test bank in the Sybex interactive learning environment Understand the subject matter through clear and accurate answers and explanations of exam objectives Evaluate your exam knowledge and concentrate on problem areas Integrate practice tests with other Sybex review and study guides, including the CompTIA A+ Complete Study Guide and the CompTIA A+ Complete Deluxe Study Guide Practice tests are an effective way to increase comprehension, strengthen retention, and measure overall knowledge. The CompTIA A+ Complete Practice Tests, Second Edition is an indispensable part of any study plan for A+ certification. COMPUTERS,Certification Guides,General

CISM Certified Information Security Manager Practice Exams Publisher's Note: Products purchased from Third Party sellers are not guaranteed by the publisher for quality, authenticity, or access to any online entitlements included with the product. Don’t Let the Real Test Be Your First Test! Take the current version of the challenging CISM exam with complete confidence using relevant practice questions contained in this effective self-study guide. Each chapter of the book contains a battery of questions that closely match those on the live test in content, format, tone, and feel. To reinforce salient points and facilitate retention, in-depth explanations are provided for both the correct and incorrect answer choices. Written by an InfoSec expert and experienced author, CISM® Certified Information Security Manager® Practice Exams thoroughly covers every subject on the exam. Designed to help you pass the test with greater ease, this book is also an ideal companion to the CISM Certified Information Security Manager All-in-One Exam Guide. Covers all four exam domains:• Information security governance• Information risk management• Information security program development and management• Information security incident management Online content includes:• Test engine that provides a full-length practice exam and customized quizzes by chapter or exam domain COMPUTERS,Certification Guides,General

GSEC GIAC Security Essentials Certification All-in-One Exam Guide, Second Edition Publisher's Note: Products purchased from Third Party sellers are not guaranteed by the publisher for quality, authenticity, or access to any online entitlements included with the product. Fully updated coverage of every topic on the current version of the GSEC exam Get complete coverage of all the objectives on Global Information Assurance Certification’s Security Essentials (GSEC) exam inside this comprehensive resource. GSEC GIAC Security Essentials Certification All-in-One Exam Guide, Second Edition provides learning objectives at the beginning of each chapter, exam tips, practice exam questions, and in-depth explanations. Designed to help you pass the exam with ease, this authoritative resource also serves as an essential on-the-job reference. Covers all exam topics, including:• Networking fundamentals• Network design• Cloud computing• Authentication and access control• Unix/Linux• Windows• Encryption• Risk management• Virtual machines• Vulnerability control• Malware• Incident response• Wireless technologies• Log Management• IoT and embedded devices Online content features:• Two practice exams• Test engine that provides full-length practice exams and customizable quizzes• Author videos COMPUTERS,Certification Guides,General

MCA Modern Desktop Administrator Study Guide The essential study guide for the new Microsoft 365 Certified Associate (MCA) Modern Desktop certification—covers Exam MD-100: Windows 10! The new Microsoft 365 Certified Associate (MCA) Modern Desktop certification exam measures a candidate’s ability to deploy Windows, manage devices and data, configure connectivity, and maintain Windows. MCA certification, sought by a growing number of employers, is an important part of any IT professional’s resume. The MCA Modern Desktop Administrator Study Guide: Exam MD-100 is a must-have book for anyone preparing for certification. This clear and accurate study guide covers 100% of exam objectives—providing hands-on exercises, challenging review questions, full explanations, and real-world examples. From the intricacies of Windows deployment to advanced security and enterprise capabilities, each chapter explains everything candidates need to know for passing the exam and earning MCA certification. This accurate, up-to-date study guide is designed to prepare administrators to deploy, configure, secure, manage, and monitor devices and client applications in an enterprise environment. Access to Sybex's comprehensive online learning environment—comprising a self-assessment test, a bonus practice exam, flashcards, a searchable glossary, and chapter exercise videos—is included to fully prepare for exam day. This study guide: Covers all Exam: MD-100 objectives Prepares readers to implement, install, and configure Windows 10 Reinforces comprehension and retention of central exam topics Helps readers learn new skills or upgrade existing skills to Microsoft's latest desktop client Demand for competent IT professionals is already high and continues to grow at a rapid pace. The MCA Modern Desktop Administrator Study Guide: Exam MD-100 is a valuable resource for preparing for the new Exam MD-100 and MCA certification. COMPUTERS,Certification Guides,General

AWS Certified Developer Official Study Guide, Associate Exam Foreword by Werner Vogels, Vice President and Corporate Technology Officer, Amazon The AWS exam has been updated. Your study guide should be, too. The AWS Certified Developer Official Study Guide – Associate Exam is your ultimate preparation resource for the latest exam! Covering all exam objectives, this invaluable resource puts a team of AWS experts at your side with expert guidance, clear explanations, and the wisdom of experience with AWS best practices. You’ll master core services and basic architecture, and equip yourself to develop, deploy, and debug cloud-based applications using AWS. The AWS Developer certification is earned by those who demonstrate the technical knowledge and skill associated with best practices for building secure, reliable cloud-based applications using AWS technology. This book is your official exam prep companion, providing everything you need to know to pass with flying colors. Study the AWS Certified Developer Exam objectives Gain expert insight on core AWS services and best practices Test your understanding of key concepts with challenging chapter questions Access online study tools including electronic flashcards, a searchable glossary, practice exams, and more Cloud computing offers businesses the opportunity to replace up-front capital infrastructure expenses with low, variable costs that scale as they grow. This customized responsiveness has negated the need for far-future infrastructure planning, putting thousands of servers at their disposal as needed—and businesses have responded, propelling AWS to the number-one spot among cloud service providers. Now these businesses need qualified AWS developers, and the AWS certification validates the exact skills and knowledge they’re looking for. When you’re ready to get serious about your cloud credentials, the AWS Certified Developer Official Study Guide – Associate Exam is the resource you need to pass the exam with flying colors. NOTE: As of October 7, 2019, the accompanying code for hands-on exercises in the book is available for downloading from the secure Resources area in the online test bank. You'll find code for Chapters 1, 2, 11, and 12. COMPUTERS,Certification Guides,General

CCNA 200-301 Official Cert Guide, Volume 1 Trust the best-selling Official Cert Guide series from Cisco Press to help you learn, prepare, and practice for exam success. They are built with the objective of providing assessment, review, and practice to help ensure you are fully prepared for your certification exam. · Master Cisco CCNA 200-301 exam topics · Assess your knowledge with chapter-opening quizzes · Review key concepts with exam preparation tasks · Practice with realistic exam questions in the practice test software This is the eBook edition of the CCNA 200-301 Official Cert Guide, Volume 1. This eBook, combined with the CCNA 200-301 Official Cert Guide Volume 2, cover all of exam topics on the CCNA 200-301 exam. This eBook does not include the practice exams that comes with the print edition. CCNA 200-301 Official Cert Guide , Volume 1 presents you with an organized test-preparation routine using proven series elements and techniques. “Do I Know This Already?†quizzes open each chapter and enable you to decide how much time you need to spend on each section. Exam topic lists make referencing easy. Chapter-ending Exam Preparation Tasks help you drill on key concepts you must know thoroughly. CCNA 200-301 Official Cert Guide, Volume 1 from Cisco Press enables you to succeed on the exam the first time and is the only self-study resource approved by Cisco. Best-selling author and expert instructor Wendell Odom shares preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. This complete study package includes · A test-preparation routine proven to help you pass the exams · Do I Know This Already? quizzes, which enable you to decide how much time you need to spend on each section · Chapter-ending and part-ending exercises, which help you drill on key concepts you must know thoroughly · The powerful Pearson Test Prep Practice Test software, complete with hundreds of well-reviewed, exam-realistic questions, customization options, and detailed performance reports · A free copy of the CCNA 200-301 Volume 1 Network Simulator Lite software, complete with meaningful lab exercises that help you hone your hands-on skills with the command-line interface for routers and switches · Links to a series of hands-on config labs developed by the author · Online, interactive practice exercises that help you hone your knowledge · More than 90 minutes of video mentoring from the author · A final preparation chapter, which guides you through tools and resources to help you craft your review and test-taking strategies · Study plan suggestions and templates to help you organize and optimize your study time Well regarded for its level of detail, study plans, assessment features, challenging review questions and exercises, video instruction, and hands-on labs, this official study guide helps you master the concepts and techniques that ensure your exam success. The CCNA 200-301 Official Cert Guide, Volume 1, combined with CCNA 200-301 Official Cert Guide, Volume 2, walk you through all the exam topics found in the Cisco 200-301 exam. Topics covered in Volume 1 include: · Networking fundamentals · Implementing Ethernet LANs · Implementing VLANs and STP · IPv4 addressing · IPv4 routing · OSPF · IPv6 · Wireless LANs Companion Website: The companion website contains the CCNA Network Simulator Lite software, online practice exercises, study resources, and 90 minutes of video training. In addition to the wealth of updated content, this new edition includes a series of free hands-on exercises to help you master several real-world configuration and troubleshooting activities. These exercises can be performed on the CCNA 200-301 Network Simulator Lite, Volume 1 software included for free on the companion website that accompanies this book COMPUTERS,Certification Guides,General

CISM Certified Information Security Manager Bundle This cost-effective study bundle contains two books and bonus online content to use in preparation for the CISM exam Take ISACA’s challenging Certified Information Security Manager exam with confidence using this comprehensive self-study package. Comprised of CISM Certified Information Security Manager All-in-One Exam Guide, CISM Certified Information Security Manager Practice Exams, and bonus digital content, this bundle contains 100% coverage of every domain on the current exam. Readers will get real-world examples, professional insights, and concise explanations. CISM Certified Information Security Manager Bundle contains practice questions that match those on the live exam in content, style, tone, format, and difficulty. Every domain on the test is covered, including information security governance, information risk management, security program development and management, and information security incident management. This authoritative bundle serves both as a study tool AND a valuable on-the-job reference for security professionals. Readers will save 22% compared to buying the two books separately Online content includes 550 accurate practice exam questions and a quick review guide Written by an IT expert and experienced author COMPUTERS,Certification Guides,General

Official Google Cloud Certified Professional Cloud Architect Study Guide Sybex's proven Study Guide format teaches Google Cloud Architect job skills and prepares you for this important new Cloud exam. The Google Cloud Certified Professional Cloud Architect Study Guide is the essential resource for anyone preparing for this highly sought-after, professional-level certification. Clear and accurate chapters cover 100% of exam objectives—helping you gain the knowledge and confidence to succeed on exam day. A pre-book assessment quiz helps you evaluate your skills, while chapter review questions emphasize critical points of learning. Detailed explanations of crucial topics include analyzing and defining technical and business processes, migration planning, and designing storage systems, networks, and compute resources. Written by Dan Sullivan—a well-known author and software architect specializing in analytics, machine learning, and cloud computing—this invaluable study guide includes access to the Sybex interactive online learning environment, which includes complete practice tests, electronic flash cards, a searchable glossary, and more. Providing services suitable for a wide range of applications, particularly in high-growth areas of analytics and machine learning, Google Cloud is rapidly gaining market share in the cloud computing world. Organizations are seeking certified IT professionals with the ability to deploy and operate infrastructure, services, and networks in the Google Cloud. Take your career to the next level by validating your skills and earning certification. Design and plan cloud solution architecture Manage and provision cloud infrastructure Ensure legal compliance and security standards Understand options for implementing hybrid clouds Develop solutions that meet reliability, business, and technical requirements The Google Cloud Certified Professional Cloud Architect Study Guide is a must-have for IT professionals preparing for certification to deploy and manage Google cloud services. COMPUTERS,Certification Guides,General

CTS Certified Technology Specialist Exam Guide, Third Edition Publisher's Note: Products purchased from Third Party sellers are not guaranteed by the publisher for quality, authenticity, or access to any online entitlements included with the product. The Most Complete, Up-to-Date CTS Exam Study System Published with AVIXA™, CTS Certified Technical Specialist Exam Guide, Third Edition provides comprehensive coverage of all objectives on the latest release of the AVIXA Certified Technology Specialist exam—the leading internationally recognized audiovisual (AV) certification. You’ll get learning objectives at the beginning of each chapter, best practices, checklists, diagrams, photos, chapter review questions with in-depth explanations, and a full-color insert. Designed to help you prepare for the CTS exam, this authoritative resource also serves as an essential on-the-job reference. Digital content includes:• New sample CTS questions from AVIXA Covers all current CTS exam objectives, including how to:• Gather customer information• Conduct a site survey• Evaluate and recommend changes to a site environment• Develop an AV project scope• Design AV solutions• Integrate AV solutions• Operate AV solutions• Manage an AV project• Maintain AV operations• Conduct maintenance activities• Troubleshoot and repair AV solutions COMPUTERS,Certification Guides,General

Professional Cloud Architect – Google Cloud Certification Guide Become a Professional Cloud Architect by exploring essential concepts, tools, and services in GCP and working through tests designed to help you get certified Key Features Plan and design a GCP cloud solution architecture Ensure the security and reliability of your cloud solutions and operations Test yourself by taking mock tests with up-to-date exam questions Book Description Google Cloud Platform (GCP) is one of the leading cloud service suites and offers solutions for storage, analytics, big data, machine learning, and application development. It features an array of services that can help organizations to get the best out of their infrastructure. This comprehensive guide covers a variety of topics specific to Google's Professional Cloud Architect official exam syllabus and guides you in using the right methods for effective use of GCP services. You'll start by exploring GCP, understanding the benefits of becoming a certified architect, and learning how to register for the exam. You'll then delve into the core services that GCP offers such as computing, storage, and security. As you advance, this GCP book will help you get up to speed with methods to scale and automate your cloud infrastructure and delve into containers and services. In the concluding chapters, you'll discover security best practices and even gain insights into designing applications with GCP services and monitoring your infrastructure as a GCP architect. By the end of this book, you will be well versed in all the topics required to pass Google's Professional Cloud Architect exam and use GCP services effectively. What you will learn Manage your GCP infrastructure with Google Cloud management options such as CloudShell and SDK Understand the use cases for different storage options Design a solution with security and compliance in mind Monitor GCP compute options Discover machine learning and the different machine learning models offered by GCP Understand what services need to be used when planning and designing your architecture Who this book is for If you are a cloud architect, cloud engineer, administrator, or any IT professional who wants to learn how to implement Google Cloud services in your organization and become a GCP Certified Professional Cloud Architect, this book is for you. Basic knowledge of server infrastructure, including Linux and Windows Servers, is assumed. Knowledge of network and storage will also be helpful. COMPUTERS,Certification Guides,General

CISA Certified Information Systems Auditor All-in-One Exam Guide, Fourth Edition This up-to-date self-study system delivers complete coverage of every topic on the 2019 version of the CISA exam The latest edition of this trusted resource offers complete,up-to-date coverage of all the material included on the latest release of the Certified Information Systems Auditor exam. Written by an IT security and audit expert, CISA Certified Information Systems Auditor All-in-One Exam Guide, Fourth Edition covers all five exam domains developed by ISACA®. You’ll find learning objectives at the beginning of each chapter, exam tips, practice exam questions, and in-depth explanations. Designed to help you pass the CISA exam with ease, this comprehensive guide also serves as an essential on-the-job reference for new and established IS auditors. COVERS ALL EXAM TOPICS, INCLUDING: • IT governance and management• Information systems audit process• IT service delivery and infrastructure• Information asset protection Online content includes:• 300 practice exam questions• Test engine that provides full-length practice exams and customizable quizzes by exam topic COMPUTERS,Certification Guides,General

CCSP Certified Cloud Security Professional All-in-One Exam Guide, Second Edition Comprehensive coverage of every domain on the CCSP exam This highly effective self-study guide covers all six domains of the 2019 release of the challenging Certified Cloud Security Professional exam as well as the CCSP Common Body of Knowledge, developed by the International Information Systems Security Certification Consortium (ISC)2®. CCSP Certified Cloud Security Professional All-in-One Exam Guide, Second Edition offers clear explanations, real-world examples, and practice questions that match the content, tone, and format of those on the actual exam. To aid in retention, each chapter includes exam tips that highlight key information, a summary that serves as a quick review of salient points, and practice questions that allow you to test your comprehension. “Notes,†“Tips,†and “Cautions†throughout provide additional insight. Covers all six exam domains:• Cloud Concepts, Architecture, and Design• Cloud Data Security• Cloud Platform & Infrastructure Security• Cloud Application Security• Cloud Security Operations• Legal, Risk, and Compliance Online content includes:• 300 practice questions COMPUTERS,Certification Guides,General

CCNA 200-301 Official Cert Guide, Volume 2 Trust the best-selling Official Cert Guide series from Cisco Press to help you learn, prepare, and practice for exam success. They are built with the objective of providing assessment, review, and practice to help ensure you are fully prepared for your certification exam. This book, combined with CCNA 200-301 Official Cert Guide, Volume 1, covers all the exam topics on the CCNA 200-301 exam. Master Cisco CCNA 200-301 exam topics Assess your knowledge with chapter-opening quizzes Review key concepts with exam preparation tasks This is the eBook edition of CCNA 200-301 Official Cert Guide, Volume 2. This eBook does not include access to the Pearson Test Prep practice exams that comes with the print edition. CCNA 200-301 Official Cert Guide, Volume 2 presents you with an organized test preparation routine through the use of proven series elements and techniques. “Do I Know This Already?†quizzes open each chapter and enable you to decide how much time you need to spend on each section. Exam topic lists make referencing easy. Chapter-ending Exam Preparation Tasks help you drill on key concepts you must know thoroughly. CCNA 200-301 Official Cert Guide, Volume 2 from Cisco Press enables you to succeed on the exam the first time and is the only self-study resource approved by Cisco. Best-selling author Wendell Odom shares preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. This complete study package includes A test-preparation routine proven to help you pass the exams Do I Know This Already? quizzes, which enable you to decide how much time you need to spend on each section Chapter-ending Key Topic tables, which help you drill on key concepts you must know thoroughly The powerful Pearson Test Prep Practice Test software, complete with hundreds of well-reviewed, exam-realistic questions, customization options, and detailed performance reports A free copy of the CCNA 200-301 Network Simulator, Volume 2 Lite software, complete with meaningful lab exercises that help you hone your hands-on skills with the command-line interface for routers and switches Links to a series of hands-on config labs developed by the author Online interactive practice exercises that help you enhance your knowledge More than 50 minutes of video mentoring from the author An online interactive Flash Cards application to help you drill on Key Terms by chapter A final preparation chapter, which guides you through tools and resources to help you craft your review and test-taking strategies Study plan suggestions and templates to help you organize and optimize your study time Well regarded for its level of detail, study plans, assessment features, hands-on labs, and challenging review questions and exercises, this official study guide helps you master the concepts and techniques that ensure your exam success. CCNA 200-301 Official Cert Guide, Volume 2, combined with CCNA 200-301 Official Cert Guide, Volume 1, walk you through all the exam topics found in the Cisco 200-301 exam. Topics covered in Volume 2 include IP access control lists Security services IP services Network architecture Network automation Companion Website: The companion website contains CCNA Network Simulator Lite software, practice exercises, 50 minutes of video training, and other study resources. See the Where Are the Companion Files on the last page of your eBook file for instructions on how to access. In addition to the wealth of content, this new edition includes a series of free hands-on exercises to help you master several real-world configuration activities. These exercises can be performed on the CCNA 200-301 Network Simulator Lite, Volume 2 software included for free on the companion website that accompanies this book. COMPUTERS,Certification Guides,General

CCNP and CCIE Enterprise Core ENCOR 350-401 Official Cert Guidee Trust the best-selling Official Cert Guide series from Cisco Press to help you learn, prepare, and practice for exam success. They are built with the objective of providing assessment, review, and practice to help ensure you are fully prepared for your certification exam. * Master Cisco CCNP/CCIE ENCOR exam topics * Assess your knowledge with chapter-opening quizzes * Review key concepts with exam preparation tasks This is the eBook edition of the CCNP and CCIE Enterprise Core ENCOR 350-401 Official Cert Guide. This eBook does not include access to the Pearson Test Prep practice exams that comes with the print edition. CCNP and CCIE Enterprise Core ENCOR 350-401 Official Cert Guide presents you with an organized test preparation routine through the use of proven series elements and techniques. “Do I Know This Already?†quizzes open each chapter and enable you to decide how much time you need to spend on each section. Exam topic lists make referencing easy. Chapter-ending Exam Preparation Tasks help you drill on key concepts you must know thoroughly. CCNP and CCIE Enterprise Core ENCOR 350-401 Official Cert Guide focuses specifically on the objectives for the Cisco CCNP/CCIE ENCOR 350-401 exam. Networking experts Brad Edgeworth, Ramiro Garza Rios, Dave Hucaby, and Jason Gooley share preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. Material is presented in a concise manner, focusing on increasing your understanding and retention of exam topics. This complete study package includes * A test-preparation routine proven to help you pass the exams * Do I Know This Already? quizzes, which enable you to decide how much time you need to spend on each section * Chapter-ending exercises, which help you drill on key concepts you must know thoroughly * Practice exercises that help you enhance your knowledge * More than 90 minutes of video mentoring from the author * A final preparation chapter, which guides you through tools and resources to help you craft your review and test-taking strategies * Study plan suggestions and templates to help you organize and optimize your study time Well regarded for its level of detail, assessment features, comprehensive design scenarios, and challenging review questions and exercises, this official study guide helps you master the concepts and techniques that will enable you to succeed on the exam the first time. The official study guide helps you master all the topics on the CCNP/CCIE ENCOR exam, including * Enterprise network architecture * Virtualization * Network assurance * Security * Automation COMPUTERS,Certification Guides,General

CCNA 200-301 Portable Command Guide CCNA 200-301 Portable Command Guide is filled with valuable, easy-to-access information–and it’s portable enough to use whether you’re in the server room or the equipment closet. The guide summarizes all CCNA certification-level Cisco IOS Software commands, keywords, command arguments, and associated prompts, providing you with tips and examples of how to apply the commands to real-world scenarios. Throughout, configuration examples give you a better understanding of how these commands are used in simple network designs. This book has been completely updated to cover topics in the new 200-301 exam. Use this quick reference resource to help you memorize commands and concepts as you work to pass the CCNA certification exam. Coverage includes · Network Fundamentals: IPv4 addressing, subnetting, VLSM, route summarization, IPv6 addressing, cables/connections, CLI · LAN Switching Technologies: Switch configuration, VLANs, VLAN trunking protocol, inter-VLAN communication, STP, EtherChannel, CDP, LLDP · Routing Technologies: Router configuration, static routing, OSPF · IP Services: DHCP, NAT, NTP · Security Fundamentals: Layer 2 security, ACL traffic management, device monitoring and hardening · Wireless Technologies: Configuring and securing a WLAN AP · Quick, offline access to all CCNA commands for research and solutions · Logical how-to topic groupings for a one-stop resource · Great for review before CCNA certification exams · Compact size makes it easy to carry with you wherever you go · “Create Your Own Journal†section with blank, lined pages enables you to personalize the book for your needs This book is part of the Cisco Press Certification Self-Study Product Family, which offers readers a self-paced study routine for Cisco certification exams. Titles in the Cisco Press Certification Self-Study Product Family are part of a recommended learning program from Cisco that includes simulation and hands-on training from authorized Cisco Learning Partners and self-study products from Cisco Press. COMPUTERS,Certification Guides,General

Understanding Cisco Networking Technologies, Volume 1 Leading Cisco authority Todd Lammle helps you gain insights into the new core Cisco network technologies Understanding Cisco Networking Technologies is an important resource for those preparing for the new Cisco Certified Network Associate (CCNA) certification exam as well as IT professionals looking to understand Cisco’s latest networking products, services, and technologies. Written by bestselling author and internationally recognized Cisco expert Todd Lammle, this in-depth guide provides the fundamental knowledge required to implement and administer a broad range of modern networking and IT infrastructure. Cisco is the worldwide leader in network technologies—80% of the routers on the Internet are Cisco. This authoritative book provides you with a solid foundation in Cisco networking, enabling you to apply your technical knowledge to real-world tasks. Clear and accurate chapters cover topics including routers, switches, controllers and other network components, physical interface and cabling, IPv6 addressing, discovery protocols, wireless infrastructure, security features and encryption protocols, controller-based and software-defined architectures, and more. After reading this essential guide, you will understand: Network fundamentals Network access IP connectivity and IP services Security fundamentals Automation and programmability Understanding Cisco Networking Technologies is a must-read for anyone preparing for the new CCNA certification or looking to gain a primary understanding of key Cisco networking technologies. COMPUTERS,Certification Guides,General

Tableau Desktop Certified Associate Learn through hands-on exercises covering a variety of topics including data connections, analytics, and dashboards to effectively prepare for the Tableau Desktop Certified Associate exam Key Features Prepare for the Tableau Desktop Certified Associate exam with the help of tips and techniques shared by experts Implement Tableau's advanced analytical capabilities such as forecasting Delve into advanced Tableau features and explore best practices for building dashboards Book Description The Tableau Desktop Certified Associate exam measures your knowledge of Tableau Desktop and your ability to work with data and data visualization techniques. This book will help you to become well-versed in Tableau software and use its business intelligence (BI) features to solve BI and analytics challenges. With the help of this book, you'll explore the authors' success stories and their experience with Tableau. You'll start by understanding the importance of Tableau certification and the different certification exams, along with covering the exam format, Tableau basics, and best practices for preparing data for analysis and visualization. The book builds on your knowledge of advanced Tableau topics such as table calculations for solving problems. You'll learn to effectively visualize geographic data using vector maps. Later, you'll discover the analytics capabilities of Tableau by learning how to use features such as forecasting. Finally, you'll understand how to build and customize dashboards, while ensuring they convey information effectively. Every chapter has examples and tests to reinforce your learning, along with mock tests in the last section. By the end of this book, you'll be able to efficiently prepare for the certification exam with the help of mock tests, detailed explanations, and expert advice from the authors. What you will learn Apply Tableau best practices to analyze and visualize data Use Tableau to visualize geographic data using vector maps Create charts to gain productive insights into data and make quality-driven decisions Implement advanced analytics techniques to identify and forecast key values Prepare customized table calculations to compute specific values Answer questions based on the Tableau Desktop Certified Associate exam with the help of mock tests Who this book is for This Tableau certification book is for business analysts, BI professionals, and data analysts who want to become certified Tableau Desktop Associates and solve a range of data science and business intelligence problems using this example-packed guide. Some experience in Tableau Desktop is expected to get the most out of this book. COMPUTERS,Certification Guides,General

Oracle Cloud Infrastructure Architect Associate All-in-One Exam Guide (Exam 1Z0-1072) Publisher's Note: Products purchased from Third Party sellers are not guaranteed by the publisher for quality, authenticity, or access to any online entitlements included with the product. This study guide covers 100% of the objectives for the Oracle Cloud Infrastructure Architect Associate exam Pass the new Oracle Cloud Infrastructure Architect Associate exam with ease using the detailed information contained in this effective self-study system. Written by an Oracle expert and respected author, Oracle Cloud Infrastructure Architect Associate All-in-One Exam Guide (Exam 1Z0-1072) offers complete coverage of every subject on the challenging exam. Hands-on exercises, practice exam questions with in-depth explanations, “Notes,†“Exam Tips,†and “Cautions†throughout provide professional insight and call out potentially harmful situations. Beyond exam preparation, this guide also serves as a valuable on-the-job reference. Covers all exam topics, including:• Oracle Cloud Infrastructure concepts• OCI identity and access management• OCI networking• Compute instances• Storage• Database• Automation tools• OCI best practice architectures Online content includes:• 140 practice questions• Fully-customizable online test engine COMPUTERS,Certification Guides,General

CompTIA Linux+ Certification All-in-One Exam Guide Publisher's Note: Products purchased from Third Party sellers are not guaranteed by the publisher for quality, authenticity, or access to any online entitlements included with the product. This comprehensive study guide delivers 100% coverage of every topic on the challenging CompTIA Linux+ exam Get complete coverage of all the objectives included on CompTIA Linux+ exam XK0-004 from this up-to-date resource. Written by Linux experts and technology trainers, the book provides learning objectives at the beginning of each chapter, exam tips, practice exam questions, and in-depth answer explanations. Designed to help you pass these challenging exams, this definitive volume also serves as an essential on-the-job reference. Covers all exam topics, including how to: • Use the vi text editor• Work with the Linux shell• Manage Linux users, groups, files, and directories• Administer ownership, permissions, and quotas• Install Linux and manage the boot process• Configure the graphical environment• Manage software and hardware• Write shell scripts• Manage network settings and services• Secure Linux and use encryption Online content includes:• 180 practice exam questions• Downloadable virtual machines• 20+ video clips COMPUTERS,Certification Guides,General

CompTIA Security+ Practice Tests SY0-501 Learn from Ian Neil, one of the world's top CompTIA Security+ trainers in the world, and enhance your analytical skills to pass the CompTIA Security+ SY0-501 exam Key Features Become a pro at answering questions from all six of the domains of the SY0-501 exam Learn about cryptography algorithms, security policies, and their real-world implementations Solve practice tests that complement the official CompTIA Security+ certification exam Book Description CompTIA Security+ is a core security certification that will validate your baseline skills for a career in cybersecurity. Passing this exam will not only help you identify security incidents but will also equip you to resolve them efficiently. This book builds on the popular CompTIA Security+ Certification Guide, which mirrors the SY0-501 exam pattern. This practice test-based guide covers all six domains of the Security+ SY0-501 exam: threats, attacks, and vulnerabilities; technologies and tools; architecture and design; identity and access management; cryptography and PKI; and risk management. You'll take six mock tests designed as per the official Security+ certification exam pattern, each covering significant aspects from an examination point of view. For each domain, the book provides a dedicated cheat sheet that includes important concepts covered in the test. You can even time your tests to simulate the actual exam. These tests will help you identify gaps in your knowledge and discover answers to tricky exam questions. By the end of this book, you'll have developed and enhanced the skills necessary to pass the official CompTIA Security+ exam. What you will learn Understand how prepared you are for the CompTIA Security+ certification Identify different types of security threats, attacks, and vulnerabilities Explore identity and access management in an enterprise environment Protect your business tools and platforms from cyberattacks Create and maintain a secure network Understand how you can protect your data Discover encryption techniques required to protect against various cyber threat scenarios Who this book is for If you are a security administrator, a system or network administrator, or anyone who wants to pass the CompTIA Security+ exam, this book is for you. This book is an ideal resource for students who want a career or degree in cybersecurity or are studying for the CISSP certification exam. COMPUTERS,Certification Guides,General

Microsoft Azure Architect Technologies Become a certified Azure Architect and learn to design effective solutions that span compute, security, networking, and development Key Features Learn to successfully design and architect powerful and cost-effective solutions on Microsoft Azure Prepare to gain AZ-300 certification with the help of mock tests and practice questions Enhance your computing, networking, storage, and security skills to design modern cloud-based solutions Book Description From designing solutions on Azure to configuring and managing virtual networks, AZ-300 certification can help you achieve all this and more. Whether you want to get certified or gain hands-on experience in administering, developing, and architecting Azure solutions, this study guide will help you get started. The book features not only the different exam objectives, but also guides you through configuring, managing, securing, and architecting Azure resources. Divided into five modules, this book will systematically take you through the different concepts and features as you advance through the sections. The first module demonstrates how to deploy and configure infrastructure. You will cover techniques related to implementing workloads and security, before learning how to create and deploy apps in the next module. To build on your knowledge, the final two modules will get you up to speed with implementing authentication, data security, and application and platform monitoring, along with covering Azure storage, alerting, and automation strategies. Finally, you'll work through exam-based mock tests with answers to boost your confidence in passing the exam. By the end of this book, you'll have learned the concepts and techniques you need to know in order to prepare for the AZ-300 exam, along with the skills to design effective solutions on Microsoft Azure. What you will learn Manage Azure subscriptions and resources Understand how to migrate servers to Azure Configure and manage virtual networks Monitor and troubleshoot virtual network connectivity Manage Azure Active Directory (Azure AD) Connect and implement multi-factor authentication Implement and manage hybrid identities Develop solutions that use Cosmos DB and the Azure SQL Database Get to grips with implementing secure data solutions Who this book is for This book is for solution architects and experienced developers who advise stakeholders and translate business requirements into secure, scalable, and reliable solutions. Technical architects interested in learning more about designing cloud solutions will also find this book useful. Some experience and knowledge of various aspects of IT operations, including networking, security, business continuity, disaster recovery, budgeting, and governance are required to grasp the concepts covered in the book effectively. COMPUTERS,Certification Guides,General

CCNA Certification Study Guide, Volume 2 Cisco expert Todd Lammle prepares you for the NEW Cisco CCNA certification exam! Cisco, the world leader in network technologies, has released the new Cisco Certified Network Associate (CCNA) exam. This consolidated certification exam tests a candidate’s ability to implement and administer a wide range of modern IT networking technologies. The CCNA Certification Study Guide: Volume 2 Exam 200-301 covers every exam objective,including network components, IP connectivity and routing, network security, virtual networking, and much more. Clear and accuratechapters provide you with real-world examples, hands-on activities, in-depth explanations, and numerous review questions to ensure that you’re fully prepared on exam day. Written by the leading expert on Cisco technologies and certifications, this comprehensive exam guide includes access to the acclaimed Sybex online learning system—an interactive environment featuring practice exams, electronic flashcards, a searchable glossary, a self-assessment test, and video tutorials on critical Cisco networking concepts and technologies. Covers 100% of all CCNA Exam 200-301 objectives Provides accurate and up-to-date information on core network fundamentals Explains a broad range of Cisco networking and IT infrastructure Features learning objectives, chapter summaries, ‘Exam Essentials’ and figures, tables, and illustrations The CCNA Certification Study Guide: Volume 2 Exam 200-301 is the ideal resource for those preparing for the new CCNA certification, as well as IT professionals looking to learn more about Cisco networking concepts and technologies. COMPUTERS,Certification Guides,General

Deploying Microsoft 365 Teamwork Prepare to achieve Microsoft 365 Certified Teamwork Administrator Associate certification by learning essential SharePoint Online concepts, and answering self-assessment questions to test your knowledge Key Features Cover essential topics based on the MS-300 exam, and learn with the help of detailed explanations Understand the collaborative features of SharePoint, both on-premises and as part of the Office 365 service Work through practice questions relating to business use cases for SharePoint Server and Online Book Description The Microsoft MS-300 exam is designed to test the knowledge and skills of administrators in deploying, configuring, and managing SharePoint Online, SharePoint Server, SharePoint Hybrid, OneDrive for Business, and Teams. This book offers up-to-date coverage of the important topics based on the MS-300 exam and features question answers and insider tips to help you prepare for certification. Written in a clear, succinct way, the book starts by helping you configure and manage SharePoint Online. You'll then delve into OneDrive for Business, right from managing users and groups, through to monitoring sharing and security. Further chapters will guide you through working with Teams, with an emphasis on managing identity authentication, resolving issues with the service, and even observing usage patterns. Later, you'll get up to speed with workload integrations, covering the Yammer business communications platform, before moving on to understand how to integrate Microsoft Stream with SharePoint, Teams, and Yammer. Finally, you'll learn to develop data governance and user adoption strategies. By the end of this book, you'll be well-versed with SharePoint Online and have learned the essential techniques and concepts you need to know in order to pass the MS-300 certification exam. What you will learn Discover the different Microsoft services and features that make up Office 365 Configure cloud services for your environment and extend your infrastructure's capabilities Understand site architecture, site settings, and hub settings in SharePoint Online Explore business connectivity services for view and access options in SharePoint Online Configure Yammer to integrate with Office 365 groups, SharePoint, and Teams Deploy SharePoint Online, OneDrive for Business, and Microsoft Teams successfully, including bots and connectors Who this book is for This book is for SharePoint developers, administrators, or those who want to explore Microsoft's teamwork solution platforms and pass the certification exam to boost their career as Microsoft Teamwork Administrator Associates. Anyone who has achieved Microsoft's entry-level admin certification and wants to progress to intermediate certification will also find this book useful. COMPUTERS,Certification Guides,General

Mike Meyers' CompTIA A+ Certification Passport, Seventh Edition (Exams 220-1001 & 220-1002) Publisher's Note: Products purchased from Third Party sellers are not guaranteed by the publisher for quality, authenticity, or access to any online entitlements included with the product. Fully redesigned and updated to provide accelerated review of all the topics covered on the new Core 1 and Core 2 CompTIA A+ exams Get on the fast track to becoming CompTIA A+ certified with this affordable, portable study tool. Inside, certification training guru Mike Meyers guides you on your exam preparation path, providing expert tips and sound advice along the way. With an intensive focus on only what you need to know to pass the CompTIA A+ 220-1001 & 220-1002 exams, this certification passport is your ticket to success on exam day. TECHNICAL BULLETS:Inside:• Quick-reference tables and illustrated laptop teardown enhance coverage of mobile devices (Exam 1001, Domain 1.0)• Quick-reference tables help you master hardware troubleshooting (Exam 1001, Domain 5.0)• Practice questions and content review after each objective prepare you for exam mastery• Enhanced coverage of network hardware and protocols, desktop hardware, and hardware and software troubleshooting• Enhanced coverage of Windows 10, macOS, and Linux• Enhanced coverage of computer security Covers all exam topics, including how to:• Work with CPUs, RAM, BIOS, motherboards, power supplies, and other personal computer components• Install, configure, and maintain hard drives• Manage input devices and removable media• Set up, upgrade, and maintain all versions of Windows• Troubleshoot and fix computer problems• Install printers and other peripherals• Configure and secure mobile devices• Connect to the Internet• Set up wired and wireless networks• Protect your personal computer and your network• Implement virtualization and cloud-based technologies Online content includes:• Practice exams for 220-1001 & 220-1002• Free sample of online video training from Mike Meyers• Free sample of online interactive labs from Mike Meyers• Mike’s favorite PC tools and utilities• CompTIA A+ Glossary COMPUTERS,Certification Guides,General

CCSK Certificate of Cloud Security Knowledge All-in-One Exam Guide Publisher's Note: Products purchased from Third Party sellers are not guaranteed by the publisher for quality, authenticity, or access to any online entitlements included with the product. This effective study guide provides 100% coverage of every topic on the challenging CCSK exam from the Cloud Security Alliance This highly effective self-study guide covers all domains of the challenging Certificate of Cloud Security Knowledge v4 exam. Written by a cloud security trainer and consultant in collaboration with the Cloud Security Alliance, CCSK Certificate of Cloud Security Knowledge All-in-One Exam Guide offers clear explanations, real-world examples, and practice questions that match the content and format of those on the actual exam. To aid in retention, each chapter includes exam tips that highlight key information, a review that serves as a quick recap of salient points, and practice questions that allow you to test your comprehension. Sample cloud policies and a glossary of key terms are also provided. COVERS ALL EXAM TOPICS, INCLUDING:• Cloud Computing Concepts and Architectures• Governance and Enterprise Risk Management• Legal Issues, Contracts, and Electronic Discovery• Compliance and Audit Management• Information Governance• Management Plane and Business Continuity• Infrastructure Security• Virtualization and Containers• Incident Response• Application Security• Data Security and Encryption• Identity, Entitlement, and Access Management• Security as a Service• Related Technologies• ENISA Cloud Computing: Benefits, Risks, and Recommendations for Information Security Online content includes:• 120 practice exam questions• Test engine that provides full-length practice exams and customizable quizzes by exam topic COMPUTERS,Certification Guides,General

CISA Certified Information Systems Auditor Practice Exams Publisher's Note: Products purchased from Third Party sellers are not guaranteed by the publisher for quality, authenticity, or access to any online entitlements included with the product. Hundreds of accurate practice questions that cover every topic on the latest version of the CISA exam Written by an IT security and audit expert, this highly effective self-study guide covers all five domains included on the 2019 release of the Certified Information Systems Auditor exam. To reinforce important skills and facilitate retention, every question is accompanied by explanations for both correct and incorrect answers. Designed to help you pass the test with greater confidence, this book is also an ideal companion to the bestselling CISA Certified Information Systems Auditor All-in-One Exam Guide, Fourth Edition. Covers all five exam domains:• Information Systems Auditing Process• Governance and Management of IT• Information Systems Acquisition, Development, and Implementation• Information Systems Operations and Business Resilience• Protection of Information Assets Online content includes:• 150 practice questions• Test engine that provides full-length practice exams and customized quizzes by chapter or exam domain COMPUTERS,Certification Guides,General

CCNA 200-301 Official Cert Guide Library Cisco Press has the only study guides approved by Cisco for the new CCNA certification. The new edition of the best-selling two-book, value-priced CCNA 200-301 Official Cert Guide Library includes updated content, new online practice exercises, and more than two hours of video training–PLUS the CCNA Network Simulator Lite Editions with 34 free Network Simulator labs (available on the companion web site). The two books contained in this package, CCNA 200-301 Official Cert Guide, Volume 1 and CCNA 200-301 Official Cert Guide, Volume 2, present complete reviews and a more challenging and realistic preparation experience. The books have been fully updated to refresh the content for the latest CCNA exam topics and to enhance certain key topics that are critical for exam success. This is the eBook edition of the CCNA 200-301 Official Cert Guide Library and does not include access to the Pearson Test Prep practice exams that come with the print edition. This complete study package includes · A test-preparation routine proven to help you pass the exams · Do I Know This Already? quizzes · Chapter-ending Key Topic tables · A free copy of the CCNA 200-301 Network Simulator Lite software · Links to a series of hands-on config labs · Online, interactive practice exercises · More than 2 hours of video mentoring from the author · An online, interactive Flash Cards application to help you drill on Key Terms · Study plan suggestions and templates These official study guides help you master all exam topics, including · Networking fundamentals · Implementing Ethernet LANs · Implementing VLANs and STP · IPv4 addressing and subnetting · IPv4 routing · Implementing OSPF · IPv6 addressing, subnetting, and routing · Wireless LANs · IP Access Control Lists · Security services · IP services · Network architecture · Network automation Volume 1 Configuring Local Usernames Configuring Hostnames Interface Status I Interface Status II Interface Status III Interface Status IV Configuring Switch IP Settings Switch IP Address Switch IP Connectivity I Switch CLI Configuration Process I Switch CLI Configuration Process II Switch CLI Exec Mode Setting Switch Passwords Interface Settings I Interface Settings II Interface Settings III Switch Forwarding I Switch Security I Switch Interfaces and Forwarding Configuration Scenario Configuring VLANs Configuration Scenario VLAN Troubleshooting Volume 2 ACL I ACL II ACL III ACL IV ACL V ACL VI ACL Analysis I Named ACL I Named ACL II Named ACL III Standard ACL Configuration Scenario Extended ACL I Configuration Scenario Extended ACL II Configuration Scenario CCNA Network Simulator Lite System Requirements Windows system requirements (minimum): Windows 10 (32/64-bit), Windows 8.1 (32/64-bit), or Windows 7 (32/64 bit), 1 gigahertz (GHz) or faster 32-bit (x86) or 64-bit (x64) processor, 1 GB RAM (32-bit) or 2 GB RAM (64-bit), 16 GB available hard disk space (32-bit) or 20 GB (64-bit), DirectX 9 graphics device with WDDM 1.0 or higher driver, Adobe Acrobat Reader version 8 and above Mac system requirements (minimum) macOS 10.14, 10.13, 10.12, or 10.11, Intel core Duo 1.83 GHz, 512 MB RAM (1 GB recommended), 1.5 GB hard disk space, 32-bit color depth at 1024x768 resolution, Adobe Acrobat Reader version 8 and above To access interactive study tools on this book’s companion website: Go to www.ciscopress.com/register. Enter the print book ISBN: (Volume 1: 9780135792735, Volume 2: 9781587147135). Answer the security question to validate your purchase. Go to your account page. Click on the Registered Products tab. Under the book listing, click on the Access Bonus Content link. Contact our support team at http://pearsonitp.echelp.org with questions. COMPUTERS,Certification Guides,General

CCNP Enterprise Advanced Routing ENARSI 300-410 Official Cert Guide Trust the best selling Official Cert Guide series from Cisco Press to help you learn, prepare, and practice for exam success. They are built with the objective of providing assessment, review, and practice to help ensure you are fully prepared for your certification exam. Master Cisco CCNP ENARSI exam topics Assess your knowledge with chapter-opening quizzes Review key concepts with exam preparation tasks This is the eBook edition of the CCNP Enterprise Advanced Routing ENARSI 300-410 Official Cert Guide. This eBook does not include access to the Pearson Test Prep practice exams that comes with the print edition. CCNP Enterprise Advanced Routing ENARSI 300-410 Official Cert Guide from Cisco Press allows you to succeed on the exam the first time and is the only self-study resource approved by Cisco. Expert authors Raymond Lacoste and Brad Edgeworth share preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. This complete study package includes A test-preparation routine proven to help you pass the exams Do I Know This Already? quizzes, which allow you to decide how much time you need to spend on each section Chapter-ending exercises, which help you drill on key concepts you must know thoroughly Practice exercises that help you enhance your knowledge More than 60 minutes of video mentoring from the author A final preparation chapter, which guides you through tools and resources to help you craft your review and test-taking strategies Study plan suggestions and templates to help you organize and optimize your study time Well regarded for its level of detail, study plans, assessment features, and challenging review questions and exercises, this official study guide helps you master the concepts and techniques that ensure your exam success. This official study guide helps you master all the topics on the CCNP Enterprise Advanced Routing ENARSI exam, including Layer 3 technologies, including IPv4/IPv6 routing, EIGRP, OSPF, and BGP VPN services, including MPLS Layer 3 VPNs and DMVPN Infrastructure security, including ACLs, AAA, uRPF, CoPP, and IPv6 first hop security features Infrastructure services, including syslog, SNMP, IP SLA, Object Tracking, NetFlow, Flexible NetFlow, and more COMPUTERS,Certification Guides,General

AWS Certified SysOps Administrator Study Guide Your #1 all-in-one reference and exam Study Guide for the UPDATED AWS SysOps Administrator certification! This comprehensive book guides readers through the role of a SysOps Administrator and helps prepare candidates to take the updated AWS Certified SysOps Administrator—Associate (SOA-C01) Exam. The AWS Certified SysOps Administrator—Associate certification validates technical expertise in deployment, management, and operations on the AWS platform. This Study Guide not only prepares readers for the AWS exam, but it makes sure the reader is ready to perform the duties expected of SysOps Administrators. The book focuses on the skill-set required of AWS professionals by filling in the gap between test preparation and real-world preparedness. Concepts covered include: Monitoring and Reporting High Availability Deployment and Provisioning Storage and Dada Management Security and Compliance Networking Automation and Optimization And More Readers will also have one year of free access to the Sybex interactive online learning environment and test bank, providing a suite of robust study tools including an assessment test, chapter tests, bonus practice exam, electronic flashcards, and a glossary of key terms. COMPUTERS,Certification Guides,General

CCNP and CCIE Data Center Core DCCOR 350-601 Official Cert Guide This is the eBook version of the print title. Note that the eBook does not provide access to the practice test software that accompanies the print book. Access to the personal video mentoring is available through product registration at Cisco Press; or see the instructions in the back pages of your eBook. Learn, prepare, and practice for CCNP/CCIE Data Center Core DCCOR 350-601 exam success with this Cert Guide from Cisco Press, a leader in IT certification learning and the only self-study resource approved by Cisco. · Master CCNP/CCIE Data Center Core DCCOR 350-601 exam topics · Assess your knowledge with chapter-ending quizzes · Review key concepts with exam preparation tasks · Learn from more than two hours of video mentoring CCNP and CCIE Data Center Core DCCOR 350-601 Official Cert Guide is a best-of-breed exam study guide. Expert authors Somit Maloo and Firas Ahmed share preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. Material is presented in a concise manner, focusing on increasing your understanding and retention of exam topics. The book presents you with an organized test-preparation routine through the use of proven series elements and techniques. Exam topic lists make referencing easy. Chapter-ending Exam Preparation Tasks help you drill on key concepts you must know thoroughly. Review questions help you assess your knowledge, and a final preparation chapter guides you through tools and resources to help you craft your final study plan. The book also contains more than two hours of personal video mentoring from the Pearson IT Certification Complete Video Course. Go to the back pages of your eBook for instructions on how to access the personal video mentoring content. Well regarded for its level of detail, assessment features, and challenging review questions and exercises, this study guide helps you master the concepts and techniques that will help you succeed on the exam the first time. This official study guide helps you master all the topics on the CCNP/CCIE Data Center Core DCCOR 350-601 exam, including · Network · Compute · Storage Network · Automation · Security COMPUTERS,Certification Guides,General

CCNP and CCIE Security Core SCOR 350-701 Official Cert Guide Trust the best-selling Official Cert Guide series from Cisco Press to help you learn, prepare, and practice for exam success. They are built with the objective of providing assessment, review, and practice to help ensure you are fully prepared for your certification exam. Master Cisco CCNP and CCIE Security Core SCOR 350-701 exam topics Assess your knowledge with chapter-opening quizzes Review key concepts with exam preparation tasks This is the eBook edition of the CCNP and CCIE Security Core SCOR 350-701 Official Cert Guide. This eBook does not include access to the companion website with practice exam that comes with the print edition. CCNP and CCIE Security Core SCOR 350-701 Official Cert Guide presents you with an organized test preparation routine through the use of proven series elements and techniques. “Do I Know This Already?†quizzes open each chapter and allow you to decide how much time you need to spend on each section. Exam topic lists make referencing easy. Chapter-ending Exam Preparation Tasks help you drill on key concepts you must know thoroughly. CCNP and CCIE Security Core SCOR 350-701 Official Cert Guide, focuses specifically on the objectives for the Cisco CCNP and CCIE Security SCOR exam. Best-selling author and leading security engineer Omar Santos shares preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. Material is presented in a concise manner, focusing on increasing your understanding and retention of exam topics. Well regarded for its level of detail, assessment features, comprehensive design scenarios, and challenging review questions and exercises, this official study guide helps you master the concepts and techniques that will allow you to succeed on the exam the first time. The official study guide helps you master all the topics on the CCNP and CCIE Security SCOR 350-701 exam, including: Cybersecurity fundamentals Cryptography Software-Defined Networking security and network programmability Authentication, Authorization, Accounting (AAA) and Identity Management Network visibility and segmentation Infrastructure security Cisco next-generation firewalls and intrusion prevention systems Virtual Private Networks (VPNs) Securing the cloud Content security Endpoint protection and detection CCNP and CCIE Security Core SCOR 350-701 Official Cert Guide is part of a recommended learning path from Cisco that includes simulation and hands-on training from authorized Cisco Learning Partners and self-study products from Cisco Press. To find out more about instructor-led training, e-learning, and hands-on instruction offered by authorized Cisco Learning Partners worldwide, please visit www.cisco.com/web/learning/index.html COMPUTERS,Certification Guides,General

CISA Certified Information Systems Auditor Bundle Publisher's Note: Products purchased from Third Party sellers are not guaranteed by the publisher for quality, authenticity, or access to any online entitlements included with the product. Includes CISA All-in-One Exam Guide & CISA Practice Exams as well as a bonus Quick Review Guide -- all for 20% less than purchasing the books individually Take ISACA’s challenging Certified Information Systems Auditor (CISA) exam with complete confidence using this comprehensive self-study collection. Comprised of CISA Certified Information Systems Auditor All-in-One Exam Guide, Fourth Edition, CISA Certified Information Systems Auditor Practice Exams, and bonus digital content, this bundle contains 100% coverage of every topic in the 2019 CISA Job Practice. You will get real-world examples, professional insights, and concise explanations. CISA Certified Information Systems Auditor Bundle contains practice questions that match those on the live exam in content, style, tone, format, and difficulty. Every topic on the test is covered, including the information systems auditing process; governance and management of IT; information systems acquisition, development, and implementation; information systems operations and business resilience; and protection of information assets. This authoritative bundle serves both as a study tool AND a valuable on-the-job reference for auditing and security professionals. • Contains up-to-date coverage of all five exam domains• Online content includes 450 practice exam questions in a customizable test engine and a bonus quick review guide• Written by IT auditing expert and best-selling author, Peter Gregory COMPUTERS,Certification Guides,General

CCNP Enterprise Certification Study Guide The practical and conceptual knowledge you need to attain CCNP Enterprise certification From one of the most trusted study guide publishers comes CCNP Enterprise Certification Study Guide: Exam 350-401. This guide helps you develop practical knowledge and best practices for critical aspects of enterprise infrastructure so you can gain your CCNP Enterprise certification. If you’re hoping to attain a broader range of skills and a solid understanding of Cisco technology, this guide will also provide fundamental concepts for learning how to implement and operate Cisco enterprise network core technologies. By focusing on real-world skills, each chapter prepares you with the knowledge you need to excel in your current role and beyond. It covers emerging and industry-specific topics, such as SD-WAN, network design, wireless, and automation. This practical guide also includes lessons on: ◠Automation ◠Network assurance ◠Security ◠Enterprise infrastructure ◠Dual-stack architecture ◠Virtualization In addition to helping you gain enterprise knowledge, this study guidecan lead you toward your Cisco specialist certification. When you purchase this guide, you get access to the information you need to prepare yourself for advances in technology and new applications, as well as online study tools such as: ◠Bonus practice exams ◠Pre-made flashcards ◠Glossary of key terms ◠Specific focus areas Expand your skillset and take your career to the next level with CCNP Enterprise Certification Study Guide. COMPUTERS,Certification Guides,General

CCNA 200-301 Exam Cram CCNA 200-301 Exam Cram, Sixth Edition This is the eBook version of the print title. Note that the eBook does not provide access to the practice test software that accompanies the print book. CCNA 200-301 Exam Cram, Sixth Edition is the perfect study guide to help you pass the Cisco 200-301 CCNA exam, providing coverage and practice questions for every exam topic. The book contains an extensive set of preparation tools, including topic overviews, exam alerts, Cram Savers, Cram Quizzes, chapter-ending review questions, author notes and tips, Packet Tracer labs, and an extensive glossary. The book also contains the extremely useful Cram Sheet tear-out: a collection of essential facts in an easy to review format. Covers the critical information you’ll need to know to score higher on your CCNA exam! Understand networking fundamentals concepts, including network components, network topology architectures, physical interfaces and cabling types, TCP and UDP, wireless principals, switching concepts, and virtualization fundamentals Master IPv4 addressing and subnetting and configure IPv6 Configure and verify VLANs, interswitch connectivity, and Layer 2 discovery protocols Describe Rapid PVST+ Spanning Tree Protocol Compare Cisco Wireless Architectures and AP Modes Configure and verify IPv4 and IPv6 static routing and single area OSPF Understand DHCP, DNS, and other networking services like SNMP, syslog, SSH, and TFTP/FTP Configure and verify inside source NAT and NTP Enable security technologies including device access control, site-to-site and remote access VPNs, ACLs, Layer 2 security features, and wireless security protocols Understand how automation impacts network management, controller-based and software defined architectures, and Cisco DNA Center enabled device management Understand network programmability concepts, including characteristics of REST-based APIs (CRUD, HTTP verbs, and data encoding), configuration management mechanisms such as Puppet, Chef, and Ansible, and learn to Interpret JSON encoded data COMPANION WEBSITE The companion website provides access to several digital assets including the Glossary, hands-on Packet Tracer lab, the command reference and Cram Sheet. CCNA 200-301 Exam Cram, Sixth Edition Companion Website Access interactive study tools on this book’s companion website, including the Glossary, Packet Tracer lab files, Command Reference, and Cram Sheet To access the companion website, simply follow these steps: 1. Go to www.pearsonitcertification.com/register.2. Enter the print book ISBN: 9780136632887.3. Answer the security question to validate your purchase.4. Go to your account page.5. Click on the Registered Products tab.6. Under the book listing, click on the Access Bonus Content link. If you have any issues accessing the companion website, you can contact our support team by going to http://pearsonitp.echelp.org. COMPUTERS,Certification Guides,General

AWS Certified SysOps Administrator Practice Tests Study and prepare for the AWS Certified SysOps Administrator Associate (SOA-C01) Exam You can prepare for test success with AWS Certified SysOps Administrator Practice Tests: Associate (SOA-C01) Exam. It provides a total of 1,000 practice questions that get you ready for the exam. The majority of questions are found within seven practice tests, which correspond to the seven AWS Certified SysOps Administrator Associate SOA-C01 Exam objective domains. Additionally, you can take advantage of an extra practice exam, or utilize an online test bank as an additional study resource. Practice tests allow you to demonstrate your knowledge and ability to: Deploy, manage, and operate scalable and fault-tolerant systems on the service Implement and control data flow as it goes to and from AWS Choose the right AWS service depending upon requirements Identify the proper use of AWS best practices during operations Estimate AWS costs and pinpoint cost controls Migrate workloads to Amazon Web Services As someone working to deliver cloud-based solutions, you can earn an AWS Certification to demonstrate your expertise with the technology. The certification program recognizes proficiency in technical skills and knowledge related to best practices for building cloud-based applications with AWS. COMPUTERS,Certification Guides,General

CCBA® and CBAP® Certifications Study Guide A handy, on-the-job reference filled with real-life scenarios to help you achieve the Certified Business Analysis Professional (CBAP®) and Certification of Capability in Business Analysis (CCBA®) certifications Key Features Gain expert guidance from Esta Lessing, a CBAP® trainer with over 18 years of business analysis experience Understand BABOK® knowledge areas and tasks through examples and real-world scenarios Learn business analyst skills such as stakeholder engagement, strategy analysis, and requirement elicitation Book Description Certified Business Analysis Professional (CBAP®) is a certification from the International Institute of Business Analysis (IIBA®) for professionals with extensive experience in business analysis. The CCBA® and CBAP® validates your proficiency in various aspects of business analysis and your ability to tackle challenging projects, work effectively with stakeholders, and identify and deliver business value. You'll start by learning about the benefits of CCBA® and CBAP® certifications for your career progression before focussing on the six core knowledge areas explained thoroughly in each chapter. These include topics such as business analysis planning and monitoring, elicitation and collaboration, requirements life cycle management, strategy analysis, requirements analysis, and design definition as well as solution evaluation. The book includes the essential underlying competencies and techniques to ensure a complete understanding of the BABOK® v3 guide content. Each chapter delves into the essential concepts and business analysis task considerations utilizing practical examples. Finally, you'll assess your knowledge through mock exam questions based on real-world case studies. By the end of this book, you'll have gained the business analysis skills needed to prepare for the certification exams and to advance in your career. What you will learn Assess the IIBA® requirements for applying for the CCBA® and CBAP® exams Navigate through the sections of the BABOK® v3 Guide Understand business analysis concepts, practices and analysis techniques Be able to relate concepts, tasks, and techniques to real-world practical situations Understand the application of 50 practical techniques concerning the BABOK® v3 Guide knowledge area tasks Identify the challenges that could hinder a business analyst from delivering value and effective business solutions Who this book is for This book is for business analysts, business consultants, trainers, project managers, and business professionals who are interested in preparing for the IIBA CBAP or CCBA exams. The book assumes business analysis experience. COMPUTERS,Certification Guides,General

CCNP Enterprise Design ENSLD 300-420 Official Cert Guide Trust the best-selling Official Cert Guide series from Cisco Press to help you learn, prepare, and practice for exam success. They are built with the objective of providing assessment, review, and practice to help ensure you are fully prepared for your certification exam. Master Cisco CCNP ENSLD 300-420 exam topics Assess your knowledge with chapter-opening quizzes Review key concepts with exam preparation tasks This is the eBook edition of the CCNP Enterprise Design ENSLD 300-420 Official Cert Guide. This eBook does not include access to the Pearson Test Prep practice exams that comes with the print edition. CCNP Enterprise Design ENSLD 300-420 Official Cert Guide presents you with an organized test preparation routine through the use of proven series elements and techniques. “Do I Know This Already?†quizzes open each chapter and allow you to decide how much time you need to spend on each section. Exam topic lists make referencing easy. Chapter-ending Exam Preparation Tasks help you drill on key concepts you must know thoroughly. CCNP Enterprise Design ENSLD 300-420 Official Cert Guide focuses specifically on the objectives for the Cisco CCNP ENSLD 300-420 exam. Expert authors Anthony Bruno and Steve Jordan share preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. Material is presented in a concise manner, focusing on increasing your understanding and retention of exam topics. This complete study package includes A test-preparation routine proven to help you pass the exams Do I Know This Already? quizzes, which allow you to decide how much time you need to spend on each section Chapter-ending Key Topic tables, which help you drill on key concepts you must know thoroughly Practice exercises that help you enhance your knowledge An online interactive Flash Cards application to help you drill on Key Terms by chapter A final preparation chapter, which guides you through tools and resources to help you craft your review and test-taking strategies Study plan suggestions and templates to help you organize and optimize your study time Well regarded for its level of detail, assessment features, and challenging review questions and exercises, this official study guide helps you master the concepts and techniques that ensure your exam success. The official study guide helps you master all the topics on the CCNP Designing Cisco Enterprise Networks (300-420 ENSLD) exam, including Advanced Addressing and Routing Solutions Advanced Enterprise Campus Networks WAN for Enterprise Networks Network Services SD Access and SD-WAN Automation COMPUTERS,Certification Guides,General

Microsoft 365 Security Administration Get up to speed with expert tips and techniques to help you prepare effectively for the MS-500 Exam Key Features Get the right guidance and discover techniques to improve the effectiveness of your studying and prepare for the exam Explore a wide variety of strategies for security and compliance Gain knowledge that can be applied in real-world situations Book Description The Microsoft 365 Security Administration (MS-500) exam is designed to measure your ability to perform technical tasks such as managing, implementing, and monitoring security and compliance solutions for Microsoft 365 environments. This book starts by showing you how to configure and administer identity and access within Microsoft 365. You will learn about hybrid identity, authentication methods, and conditional access policies with Microsoft Intune. Next, the book shows you how RBAC and Azure AD Identity Protection can be used to help you detect risks and secure information in your organization. You will also explore concepts, such as Advanced Threat Protection, Windows Defender ATP, and Threat Intelligence. As you progress, you will learn about additional tools and techniques to configure and manage Microsoft 365, including Azure Information Protection, Data Loss Prevention, and Cloud App Discovery and Security. The book also ensures you are well prepared to take the exam by giving you the opportunity to work through a mock paper, topic summaries, illustrations that briefly review key points, and real-world scenarios. By the end of this Microsoft 365 book, you will be able to apply your skills in the real world, while also being well prepared to achieve Microsoft certification. What you will learn Get up to speed with implementing and managing identity and access Understand how to employ and manage threat protection Get to grips with managing governance and compliance features in Microsoft 365 Explore best practices for effective configuration and deployment Implement and manage information protection Prepare to pass the Microsoft exam and achieve certification with the help of self-assessment questions and a mock exam Who this book is for This Microsoft certification book is designed to help IT professionals, administrators, or anyone looking to pursue a career in security administration by becoming certified with Microsoft's role-based qualification. Those trying to validate their skills and improve their competitive advantage with Microsoft 365 Security Administration will also find this book to be a useful resource. COMPUTERS,Certification Guides,General

Unity Certified Programmer A practical guide to Unity game scripting using C#, backed with practice tests, exam tips, and easy-to-follow examples to help you better prepare for the exam and become a pro in Unity programming Key Features Discover the essentials of game scripting with Unity and C# to customize every aspect of your game Overcome challenges in Unity game development using effective techniques and easy solutions Pass the Unity certification exam with the help of mock tests, exam tips, and self-assessment questions Book Description Unity Certified Programmer is a global certification program by Unity for anyone looking to become a professional Unity developer. The official Unity programmer exam will not only validate your Unity knowledge and skills, but also enable you to be part of the Unity community. This study guide will start by building on your understanding of C# programming and take you through the process of downloading and installing Unity. You'll understand how Unity works and get to grips with the core objectives of the Unity exam. As you advance, you'll enhance your skills by creating an enjoyable side-scrolling shooter game that can be played within the Unity Editor or any recent Android mobile device. This Unity book will test your knowledge with self-assessment questions and help you take your skills to an advanced level by working with Unity tools such as the Animator, Particle Effects, Lighting, UI/UX, Scriptable Objects, and debugging. By the end of this book, you'll have developed a solid understanding of the different tools in Unity and understand how to create impressive Unity applications by making the most of its toolset. What you will learn Discover techniques for writing modular, readable, and reusable scripts in Unity Implement and configure objects, physics, controls, and movements for your game projects Understand 2D and 3D animation and write scripts that interact with Unity's Rendering API Explore Unity APIs for adding lighting, materials, and texture to your apps Write Unity scripts for building interfaces for menu systems, UI navigation, application settings, and much more Delve into SOLID principles for writing clean and maintainable Unity applications Who this book is for The book is for game developers, software developers, mobile app developers, and Unity developers who want to advance in the game or related industry. Basic knowledge of C# programming and Unity engine is required. COMPUTERS,Certification Guides,General

CompTIA CySA+ Study Guide Exam CS0-002 This updated study guide by two security experts will help you prepare for the CompTIA CySA+ certification exam. Position yourself for success with coverage of crucial security topics! Where can you find 100% coverage of the revised CompTIA Cybersecurity Analyst+ (CySA+) exam objectives? It’s all in the CompTIA CySA+ Study Guide Exam CS0-002, Second Edition! This guide provides clear and concise information on crucial security topics. You’ll be able to gain insight from practical, real-world examples, plus chapter reviews and exam highlights. Turn to this comprehensive resource to gain authoritative coverage of a range of security subject areas. Review threat and vulnerability management topics Expand your knowledge of software and systems security Gain greater understanding of security operations and monitoring Study incident response information Get guidance on compliance and assessment The CompTIA CySA+ Study Guide, Second Edition connects you to useful study tools that help you prepare for the exam. Gain confidence by using its interactive online test bank with hundreds of bonus practice questions, electronic flashcards, and a searchable glossary of key cybersecurity terms. You also get access to hands-on labs and have the opportunity to create a cybersecurity toolkit. Leading security experts, Mike Chapple and David Seidl, wrote this valuable guide to help you prepare to be CompTIA Security+ certified. If you’re an IT professional who has earned your CompTIA Security+ certification, success on the CySA+ (Cybersecurity Analyst) exam stands as an impressive addition to your professional credentials. Preparing and taking the CS0-002exam can also help you plan for advanced certifications, such as the CompTIA Advanced Security Practitioner (CASP+). COMPUTERS,Certification Guides,General

CCNP and CCIE Collaboration Core CLCOR 350-801 Official Cert Guide CCNP and CCIE Collaboration Core CLCOR 350-801 Official Cert Guide is Cisco's official, comprehensive self-study resource for Cisco’s CLCOR 350-801 exam (Implementing Cisco Collaboration Core Technologies), part of today’s pathway to the CCNP Collaboration credential. It will thoroughly prepare network professionals to install, configure, support, and troubleshoot today’s Cisco Collaboration endpoint and infrastructure products in modern on-premises environments. Designed for all CCNP Collaboration candidates, it covers every CLCOR 350-801 exam objective concisely and logically, with extensive teaching features designed to promote retention and understanding. You'll find: Pre-chapter quizzes to assess knowledge upfront and focus your study more efficiently Foundation topics sections that explain concepts and configurations, and link theory to practice Key topics sections calling attention to every figure, table, and list you must know Exam Preparation sections with additional chapter review features Final preparation chapter providing tools and a complete final study plan A customizable practice test library This guide offers comprehensive, up-to-date coverage of all CLCOR 350-801 exam topics related to: Audio and video fundamentals The Cisco UC phone and telepresence endpoint product portfolio Network requirements to support on-premises collaboration deployments Infrastructure components, from call control through Cisco Unified Communications Manager Edge products available in Cisco collaboration solutions Cisco Unity Connection and Cisco’s Instant Messaging (IM) and presence services Maintenance, support, and troubleshooting for Cisco Collaboration systems and components COMPUTERS,Certification Guides,General

MOS 2013 Study Guide for Microsoft Word Demonstrate your expertise with Microsoft Office! Designed to help you practice and prepare for the 2013 Word Microsoft Office Specialist (MOS) exam, this all-in-one study guide features: Full, objective-by-objective exam coverage Easy-to-follow procedures and illustrations to review essential skills Hands-on practice tasks to apply what you've learned Includes downloadable practice files COMPUTERS,Certification Guides,Microsoft

Exam Ref 70-410 Installing and Configuring Windows Server 2012 R2 (MCSA) Fully updated for Windows Server 2012 R2! Prepare for Microsoft Exam 70-410 - and help demonstrate your real-world mastery of implementing and configuring core services in Windows Server 2012 R2. Designed for experienced IT professionals ready to advance their status, Exam Ref focuses on the critical thinking and decision making acumen needed for success at the MCSA level. Focus on the expertise measured by these objectives: Install and configure servers Configure server roles and features Configure Hyper-V Deploy and configure core network services Install and administer Active Directory Create and manage Group Policy This Microsoft Exam Ref: Organizes its coverage by exam objectives. Features strategic, what-if scenarios to challenge you. COMPUTERS,Certification Guides,Microsoft

Exam Ref 70-411 Administering Windows Server 2012 R2 (MCSA) Prepare for Microsoft Exam 70-411 - and help demonstrate your real-world mastery of administering Windows Server 2012 R2. Designed for experienced IT professionals ready to advance their status, Exam Ref focuses on the critical-thinking and decision-making acumen needed for success at the MCSA level. Focus on the expertise measured by these objectives: Deploy, manage, and maintain servers Configure file and print services Configure network services and access Configure a Network Policy Server (NPS) infrastructure Configure Active Directory Configure and manage Group Policy This Microsoft Exam Ref: Organizes its coverage by objectives. Features strategic, what-if scenarios to challenge candidates. Assumes you have experience administering Windows Server 2012 R2 core infrastructure. COMPUTERS,Certification Guides,Microsoft

Exam Ref 70-480 Programming in HTML5 with JavaScript and CSS3 (MCSD) Prepare for Microsoft Exam 70-480—and help demonstrate your real-world mastery of programming with HTML5, JavaScript, and CSS3. Designed for experienced developers ready to advance their status, Exam Ref focuses on the critical-thinking and decision-making acumen needed for success at the Microsoft Specialist level. Focus on the expertise measured by these objectives: Implement and manipulate document structures and objects Implement program flow Access and secure data Use CSS3 in applications The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Certification Guides,Microsoft

Exam Ref 70-341 Core Solutions of Microsoft Exchange Server 2013 (MCSE) Prepare for Microsoft Exam 70-341--and help demonstrate your real-world mastery of the skills needed to deliver effective Microsoft Exchange Server 2013 solutions. Designed for experienced IT pros ready to advance their status, Exam Ref focuses on the critical-thinking and decision-making acumen needed for success at the MCSE level. Focus on the expertise measured by these objectives: Plan, install, configure, and manage the transport role Install, configure, and manage the mailbox role Plan, install, configure, and manage client access Design and manage an Exchange infrastructure This Microsoft Exam Ref: Organizes its coverage by exam objectives Features strategic, what-if scenarios to challenge you Provides exam preparation tips written by Exchange Server MVPs Assumes you have significant experience managing Exchange Server in an enterprise messaging environment COMPUTERS,Certification Guides,Microsoft

MOS 2016 Study Guide for Microsoft PowerPoint Advance your everyday proficiency with PowerPoint 2016. And earn the credential that proves it! Demonstrate your expertise with Microsoft PowerPoint! Designed to help you practice and prepare for Microsoft Office Specialist (MOS): PowerPoint 2016 certification, this official Study Guide delivers: In-depth preparation for each MOS objective Detailed procedures to help build the skills measured by the exam Hands-on tasks to practice what you’ve learned Practice files and sample solutions Sharpen the skills measured by these objectives: Create and manage presentations Insert and format text, shapes, and images Insert tables, charts, SmartArt, and media Apply transitions and animations Manage multiple presentations About MOS A Microsoft Office Specialist (MOS) certification validates your proficiency with Microsoft Office programs, demonstrating that you can meet globally recognized performance standards. Hands-on experience with the technology is required to successfully pass Microsoft Certification exams. COMPUTERS,Certification Guides,Microsoft

Exam Ref 70-744 Securing Windows Server 2016 Prepare for Microsoft Exam 70-744–and help demonstrate your real-world mastery of securing Windows Server 2016 environments. Designed for experienced IT professionals ready to advance their status, Exam Ref focuses on the critical-thinking and decision-making acumen needed for success at the MCSE level. Focus on the expertise measured by these objectives: • Implement server hardening solutions • Secure a virtualization infrastructure • Secure a network infrastructure • Manage privileged identities • Implement threat detection solutions • Implement workload-specific security This Microsoft Exam Ref: • Organizes its coverage by exam objectives • Features strategic, what-if scenarios to challenge you • Assumes you have experience as a Windows Server administrator and an understanding of basic networking and Hyper-V virtualization fundamentals, Active Directory Domain Services principles, and Windows Server security principles COMPUTERS,Certification Guides,Microsoft

Exam Ref 70-742 Identity with Windows Server 2016 Prepare for Microsoft Exam 70-742—and help demonstrate your real-world mastery of Windows Server 2016 identity features and functionality. Designed for experienced IT professionals ready to advance their status, Exam Ref focuses on the critical-thinking and decision-making acumen needed for success at the MCSA level. Focus on the expertise measured by these objectives: · Install and configure Active Directory Domain Services (AD DS) · Manage and maintain AD DS · Create and manage Group Policy · Implement Active Directory Certificate Services (AD CS) · Implement identity federation and access solutions This Microsoft Exam Ref: · Organizes its coverage by exam objectives · Features strategic, what-if scenarios to challenge you · Assumes you have experience working with Windows Server, Windows clients, and virtualization; are familiar with core networking technologies, and are aware of basic security best practices COMPUTERS,Certification Guides,Microsoft

Exam Ref 70-339 Managing Microsoft SharePoint Server 2016 Prepare for Microsoft Exam 70-339–and help demonstrate your real-world mastery of planning, configuring, and managing Microsoft SharePoint 2016 core technologies in datacenters, in the cloud, and in hybrid environments. Designed for experienced IT pros ready to advance their status, this Exam Ref focuses on the critical-thinking and decision-making acumen needed for success at the MCSE level. Focus on the skills measured on the exam: • Design SharePoint infrastructure• Plan authentication and security• Plan workload optimization• Plan productivity solutions• Manage search capabilities• Plan and configure cloud services• Monitor and optimize a SharePoint environment This Microsoft Exam Ref: • Organizes its coverage by the “Skills measured†posted on the exam webpage• Features strategic, what-if scenarios to challenge you• Provides exam preparation tips• Points to in-depth material by topic for exam candidates needing additional review• Assumes experience planning and maintaining SharePoint and related core technologies, including Windows Server 2012 R2 or later, Internet Information Services (IIS), Microsoft SQL Server 2014 or later, Active Directory, and networking infrastructure services COMPUTERS,Certification Guides,Microsoft

MOS 2016 Study Guide for Microsoft Excel This is the eBook of the printed book and may not include any media, website access codes, or print supplements that may come packaged with the bound book. Advance your everyday proficiency with Excel 2016. And earn the credential that proves it! Demonstrate your expertise with Microsoft Excel! Designed to help you practice and prepare for Microsoft Office Specialist (MOS): Excel 2016 Core certification, this official Study Guide delivers: In-depth preparation for each MOS objective Detailed procedures to help build the skills measured by the exam Hands-on tasks to practice what you’ve learned Practice files and sample solutions Sharpen the skills measured by these objectives: Create and manage worksheets and workbooks Manage data cells and ranges Create tables Perform operations with formulas and functions Create charts and objects About MOS A Microsoft Office Specialist (MOS) certification validates your proficiency with Microsoft Office programs, demonstrating that you can meet globally recognized performance standards. Hands-on experience with the technology is required to successfully pass Microsoft Certification exams. COMPUTERS,Certification Guides,Microsoft

MOS 2016 Study Guide for Microsoft Word Advance your everyday proficiency with Word 2016. And earn the credential that proves it! Demonstrate your expertise with Microsoft Word! Designed to help you practice and prepare for Microsoft Office Specialist (MOS): Word 2016 Core certification, this official Study Guide delivers: In-depth preparation for each MOS objective Detailed procedures to help build the skills measured by the exam Hands-on tasks to practice what you’ve learned Practice files and sample solutions Sharpen the skills measured by these objectives: Create and manage documents Format text, paragraphs, and sections Create tables and lists Create and manage references Insert and format graphic elements About MOS A Microsoft Office Specialist (MOS) certification validates your proficiency with Microsoft Office programs, demonstrating that you can meet globally recognized performance standards. Hands-on experience with the technology is required to successfully pass Microsoft Certification exams. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Certification Guides,Microsoft

MOS 2016 Study Guide for Microsoft Excel Expert Hone your advanced Excel 2016 skills. And earn the credential that proves it! Demonstrate your expertise with Microsoft Excel! Designed to help you practice and prepare for Microsoft Office Specialist (MOS): Excel Expert 2016 certification, this official Study Guide delivers: In-depth preparation for each MOS objective Detailed procedures to help build the skills measured by the exam Hands-on tasks to practice what you’ve learned Ready-made practice files Sharpen the skills measured by these objectives: Create and Manage Workbooks Apply Custom Formatting and Layouts Create Advanced Formulas Perform Data Analysis Create Advanced Charts and PivotTables COMPUTERS,Certification Guides,Microsoft

Exam Ref 70-740 Installation, Storage and Compute with Windows Server 2016 The Exam Ref is the official study guide for Microsoft certification exam 70-740. Featuring concise, objective-by-objective reviews and strategic case scenarios and Thought Experiments, exam candidates get professional-level preparation for the exam. The Exam Ref helps candidates maximize their performance on the exam and sharpen their job-role skills. It organizes material by the exam's objective domains. COMPUTERS,Certification Guides,Microsoft

Exam Ref 70-761 Querying Data with Transact-SQL Prepare for Microsoft Exam 70-761–and help demonstrate your real-world mastery of SQL Server 2016 Transact-SQL data management, queries, and database programming. Designed for experienced IT professionals ready to advance their status, Exam Ref focuses on the critical-thinking and decision-making acumen needed for success at the MCSA level. Focus on the expertise measured by these objectives: • Filter, sort, join, aggregate, and modify data • Use subqueries, table expressions, grouping sets, and pivoting • Query temporal and non-relational data, and output XML or JSON • Create views, user-defined functions, and stored procedures • Implement error handling, transactions, data types, and nulls This Microsoft Exam Ref: • Organizes its coverage by exam objectives • Features strategic, what-if scenarios to challenge you • Assumes you have experience working with SQL Server as a database administrator, system engineer, or developer • Includes downloadable sample database and code for SQL Server 2016 SP1 (or later) and Azure SQL Database Querying Data with Transact-SQL About the Exam Exam 70-761 focuses on the skills and knowledge necessary to manage and query data and to program databases with Transact-SQL in SQL Server 2016. About Microsoft Certification Passing this exam earns you credit toward a Microsoft Certified Solutions Associate (MCSA) certification that demonstrates your mastery of essential skills for building and implementing on-premises and cloud-based databases across organizations. Exam 70-762 (Developing SQL Databases) is also required for MCSA: SQL 2016 Database Development certification. See full details at: microsoft.com/learning COMPUTERS,Certification Guides,Microsoft

Exam Ref 70-346 Managing Office 365 Identities and Requirements Prepare for Microsoft Exam 70-346, and demonstrate your real-world mastery of the skills needed to provision, manage, monitor, and troubleshoot Microsoft Office 365 identities and cloud services. Designed for experienced IT pros ready to advance their status, this Exam Ref focuses on the critical-thinking and decision-making acumen needed for success at the MCSA level. The new Second Edition reflects all updated exam topics released by Microsoft through mid-2017. It covers the expertise measured by the following objectives: Provision Office 365 Plan and implement networking and security in Office 365 Manage cloud identities Implement and manage identities by using DirSync Implement and manage Federated Identities single sign on Monitor and troubleshoot Office 365 availability and usage Microsoft Exam Ref publications stand apart from third-party study guides because they: Provide guidance from Microsoft, the creator of Microsoft certification exams Target IT professional-level exam candidates with content focused on their needs, not "one-size-fits-all content Streamline study by organizing material according to the exam’s objective domain (OD), covering one functional group and its objectives in each chapter Feature Thought Experiments to guide candidates through a set of "what if?" scenarios, and prepare them more effectively for Pro-level style exam questions Explore big picture thinking around the planning and design aspects of the IT pro’s job role See full details about Exam 70-346 at: microsoft.com/learning COMPUTERS,Certification Guides,Microsoft

Exam Ref 70-764 Administering a SQL Database Infrastructure Prepare for Microsoft Exam 70-764—and help demonstrate your real-world mastery of skills for database administration. This exam is intended for database administrators charged with installation, maintenance, and configuration tasks. Their responsibilities also include setting up database systems, making sure those systems operate efficiently, and regularly storing, backing up, and securing data from unauthorized access. Focus on the expertise measured by these objectives: • Configure data access and auditing • Manage backup and restore of databases • Manage and monitor SQL Server instances • Manage high availability and disaster recovery This Microsoft Exam Ref: • Organizes its coverage by exam objectives • Features strategic, what-if scenarios to challenge you • Assumes you have working knowledge of database installation, configuration, and maintenance tasks. You should also have experience with setting up database systems, ensuring those systems operate efficiently, regularly storing and backing up data, and securing data from unauthorized access. About the Exam Exam 70-764 focuses on skills and knowledge required for database administration. About Microsoft Certification Passing both Exam 70-764 and Exam 70-765 (Provisioning SQL Databases) earns you credit toward an MCSA: SQL 2016 Database Administration certification. See full details at: microsoft.com/learning COMPUTERS,Certification Guides,Microsoft

Exam Ref 70-767 Implementing a SQL Data Warehouse Prepare for Microsoft Exam 70-767–and help demonstrate your real-world mastery of skills for managing data warehouses. This exam is intended for Extract, Transform, Load (ETL) data warehouse developers who create business intelligence (BI) solutions. Their responsibilities include data cleansing as well as ETL and data warehouse implementation. The reader should have experience installing and implementing a Master Data Services (MDS) model, using MDS tools, and creating a Master Data Manager database and web application. The reader should understand how to design and implement ETL control flow elements and work with a SQL Service Integration Services package. Focus on the expertise measured by these objectives: • Design, and implement, and maintain a data warehouse • Extract, transform, and load data • Build data quality solutionsThis Microsoft Exam Ref: • Organizes its coverage by exam objectives • Features strategic, what-if scenarios to challenge you • Assumes you have working knowledge of relational database technology and incremental database extraction, as well as experience with designing ETL control flows, using and debugging SSIS packages, accessing and importing or exporting data from multiple sources, and managing a SQL data warehouse. Implementing a SQL Data Warehouse About the Exam Exam 70-767 focuses on skills and knowledge required for working with relational database technology. About Microsoft Certification Passing this exam earns you credit toward a Microsoft Certified Professional (MCP) or Microsoft Certified Solutions Associate (MCSA) certification that demonstrates your mastery of data warehouse management Passing this exam as well as Exam 70-768 (Developing SQL Data Models) earns you credit toward a Microsoft Certified Solutions Associate (MCSA) SQL 2016 Business Intelligence (BI) Development certification. See full details at: microsoft.com/learning COMPUTERS,Certification Guides,Microsoft

Exam Ref 70-765 Provisioning SQL Databases Prepare for Microsoft Exam 70-765–and help demonstrate your real-world mastery of provisioning SQL Server databases both on premise and in SQL Azure. Designed for experienced IT professionals ready to advance their status, Exam Ref focuses on the critical thinking and decision-making acumen needed for success at the MCSA level. Focus on the expertise measured by these objectives: • Implement SQL in Azure • Manage databases and instances • Manage storage This Microsoft Exam Ref: • Organizes its coverage by exam objectives • Features strategic, what-if scenarios to challenge you • Assumes you have working knowledge of SQL Server administration and maintenance, as well as Azure skills Provisioning SQL Databases About the Exam Exam 70-765 focuses on skills and knowledge for provisioning, upgrading, and configuring SQL Server; managing databases and files; and provisioning, migrating, and managing databases in the Microsoft Azure cloud. About Microsoft Certification Passing this exam as well as Exam 70-764: Administering a SQL Database Infrastructure earns you MCSA: SQL 2016 Database Administration certification, qualifying you for a position as a database administrator or infrastructure specialist. See full details at: microsoft.com/learning COMPUTERS,Certification Guides,Microsoft

Exam Ref 70-774 Perform Cloud Data Science with Azure Machine Learning Prepare for Microsoft Exam 70-774–and help demonstrate your real-world mastery of performing key data science activities with Azure Machine Learning services. Designed for experienced IT professionals ready to advance their status, Exam Ref focuses on the critical thinking and decision-making acumen needed for success at the MCSA level. Focus on the expertise measured by these objectives: Prepare data for analysis in Azure Machine Learning and export from Azure Machine Learning Develop machine learning models Operationalize and manage Azure Machine Learning Services Use other services for machine learning This Microsoft Exam Ref: Organizes its coverage by exam objectives Features strategic, what-if scenarios to challenge you Assumes you are familiar with Azure data services, machine learning concepts, and common data science processes About the Exam Exam 70-774 focuses on skills and knowledge needed to prepare data for analysis with Azure Machine Learning; find key variables describing your data’s behavior; develop models and identify optimal algorithms; train, validate, deploy, manage, and consume Azure Machine Learning Models; and leverage related services and APIs. About Microsoft Certification Passing this exam as well as Exam 70-773: Analyzing Big Data with Microsoft R earns your MCSA: Machine Learning certifi¿cation, demonstrating your expertise in operationalizing Microsoft Azure machine learning and Big Data with R Server and SQL R Services. See full details at: microsoft.com/learning COMPUTERS,Certification Guides,Microsoft

Exam Ref 70-778 Analyzing and Visualizing Data with Microsoft Power BI Prepare for Microsoft Exam 70-778–and help demonstrate your real-world mastery of Power BI data analysis and visualization. Designed for experienced BI professionals and data analysts ready to advance their status, Exam Ref focuses on the critical thinking and decision-making acumen needed for success at the MCSA level. Focus on the expertise measured by these objectives: Consume and transform data by using Power BI Desktop Model and visualize data Configure dashboards, reports, and apps in the Power BI Service This Microsoft Exam Ref: Organizes its coverage by exam objectives Features strategic, what-if scenarios to challenge you Assumes you have experience consuming and transforming data, modeling and visualizing data, and configuring dashboards using Excel and Power BI COMPUTERS,Certification Guides,Microsoft

Exam Ref 70-483 Programming in C# Prepare for the latest versions of Microsoft Exam 70-483 and help demonstrate your real-world mastery of modern C# programming. Designed for experienced C# developers ready to advance their status, Exam Ref focuses on the critical thinking and decision-making acumen needed for success at the MCSA level. Focus on the expertise measured by these objectives: Manage program flow Create and use types Debug applications and implement security Implement data access This Microsoft Exam Ref: Organizes its coverage by exam objectives Features strategic, what-if scenarios to challenge you Assumes you have experience programming essential business logic with C# for diverse application types, hardware, and software platforms For details on requirements for taking Exam 70-483 go to https://www.microsoft.com/en-us/learning/exam-70-483.aspx COMPUTERS,Certification Guides,Microsoft

Exam Ref MS-101 Microsoft 365 Mobility and Security Prepare for Microsoft Exam MS-101–and help demonstrate your real-world mastery of skills and knowledge needed to manage Microsoft 365 mobility, security, and related administration tasks. Designed for experienced IT professionals, Exam Ref focuses on the critical thinking and decision-making acumen needed for success at the Microsoft Certified Expert level. Focus on the expertise measured by these objectives: Implement modern device services Implement Microsoft 365 security and threat management Manage Microsoft 365 governance and compliance This Microsoft Exam Ref: Organizes its coverage by exam objectives Features strategic, what-if scenarios to challenge you Assumes you are a Microsoft 365 Enterprise Administrator who participates in evaluating, planning, migrating, deploying, and managing Microsoft 365 services About the Exam Exam MS-101 focuses on knowledge needed to implement Mobile Device Management (MDM); manage device compliance; plan for devices and apps; plan Windows 10 deployment; implement Cloud App Security (CAS), threat management, and Windows Defender Advanced Threat Protection (ATP); manage security reports and alerts; configure Data Loss Prevention (DLP); implement Azure Information Protection (AIP); and manage data governance, auditing, and eDiscovery. About Microsoft Certification Passing this exam and Exam MS-100 Microsoft 365 Identity and Services (and earning one Microsoft 365 workload administrator certification or the MCSE: Productivity certification) fulfills your requirements for the Microsoft 365 Certified: Enterprise Administrator Expert certification credential. This demonstrates your ability to evaluate, plan, migrate, deploy, and manage Microsoft 365 services. See full details at: microsoft.com/learn COMPUTERS,Certification Guides,Microsoft

Exam Ref MD-100 Windows 10 The Exam Ref is the official study guide for Microsoft certification exams. Featuring concise coverage of the skills measured by the exam, challenging Thought Experiments, and pointers to more in-depth material for the candidate needing additional study, exam candidates get professional-level preparation for the exam. The Exam Ref helps candidates determine their readiness for the exam, and provides Exam Tips to help maximise their performance on the exam. The organisation of the material mirrors the skills measured by the exam as presented on the certification exam web page. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Certification Guides,Microsoft

Exam Ref AZ-103 Microsoft Azure Administrator Prepare for Microsoft Exam AZ-103—and help demonstrate your real-world mastery of deploying and managing infrastructure in Microsoft Azure cloud environments. Designed for experienced cloud professionals ready to advance their status, Exam Ref focuses on the critical thinking and decision-making acumen needed for success at the Microsoft Certified Associate level. Focus on the expertise measured by these objectives: Manage Azure subscriptions and resources Implement and manage storage Deploy and manage virtual machines (VMs) Configure and manage virtual networks Manage identities This Microsoft Exam Ref: Organizes its coverage by exam objectives Features strategic, what-if scenarios to challenge you Assumes you are an experienced Azure administrator who understands and manages diverse storage, security, networking and/or compute cloud services About the Exam Exam AZ-103 focuses on skills and knowledge needed to manage Azure subscriptions; analyze resource utilization and consumption; manage resource groups; establish storage accounts; import/export data; configure Azure files; implement backup; create, configure, and automate VM deployment; manage VMs and VM backups; implement, manage, and connect virtual networks; configure name resolution; create and configure Network Security Groups; manage Azure AD and its objects; and implement and manage hybrid identities. About Microsoft Certification Passing exam AZ-103 earns your Microsoft Certified: Azure Administrator Associate certification, demonstrating your skills in implementing, monitoring, and maintaining Microsoft Azure solutions, including major services related to compute, storage, network, and security. COMPUTERS,Certification Guides,Microsoft

Exam Ref AZ-900 Microsoft Azure Fundamentals Prepare for Microsoft Exam AZ-900–and help demonstrate your real-world mastery of cloud services and how they can be provided with Microsoft Azure. Designed for professionals in any non-technical or technical role, Exam Ref focuses on the critical thinking and decision-making acumen needed for success at the Microsoft Certified Fundamentals level. Focus on the expertise measured by these objectives: Understand cloud concepts Understand core Azure services Understand security, privacy, compliance, and trust Understand Azure pricing and support This Microsoft Exam Ref: Organizes its coverage by exam objectives Features strategic, what-if scenarios to challenge you Assumes you want to show foundational knowledge of cloud services and their delivery with Microsoft Azure; no technical background or IT experience is required About the Exam Exam AZ-900 focuses on knowledge needed to evaluate cloud service’s value; explain IaaS, PaaS, and SaaS; compare public, private, and hybrid cloud models; understand core Azure architectural components, products, and management tools; describe the Azure Marketplace, its usage, and key solutions; understand Azure security, identity services, and monitoring; manage privacy, compliance, and data protection; price subscriptions and manage costs; choose support options; use Service Level Agreements; and understand the Azure service lifecycle. About Microsoft Certification Passing this exam fulfills your requirements for the Microsoft Certified Azure Fundamentals credential, demonstrating that you understand cloud concepts, core Azure Services, Azure pricing and support, and the fundamentals of cloud security, privacy, compliance, and trust. See full details at: www.microsoft.com/learn COMPUTERS,Certification Guides,Microsoft

Exam Ref MS-100 Microsoft 365 Identity and Services Prepare for Microsoft Exam MS-100–and help demonstrate your real-world mastery of skills and knowledge needed to effectively design, deploy, manage, and secure Microsoft 365 services. Designed for experienced IT professionals, Exam Ref focuses on critical thinking and decision-making acumen needed for success at the Microsoft Certified Expert level. Focus on the expertise measured by these objectives: Design and implement Microsoft 365 services Manage user identity and roles Manage access and authentication Plan Office 365 workloads and applications This Microsoft Exam Ref: Organizes its coverage by exam objectives Features strategic, what-if scenarios to challenge you Assumes you have working knowledge of Microsoft 365 workloads, networking, server administration, and IT fundamentals; and have administered at least one Microsoft 365 workload About the Exam Exam MS-100 focuses on knowledge needed to manage domains; plan a Microsoft 365 implementation; set up and manage Microsoft 365 tenancy and subscriptions; plan user and data migration; design identity strategy; plan and manage identity synchronization with Azure AD Connect; manage Azure AD identities and user roles; manage authentication; implement MFA; configure application access; implement access for external users of Microsoft 365 workloads; and plan Office 365 workload and applications deployment. About Microsoft Certification Passing this exam and Exam MS-101 Microsoft 365 Mobility and Security (and earning one Microsoft 365 workload administrator certification or the MCSE Productivity certification) fulfills your requirements for the Microsoft 365 Certified Enterprise Administrator Expert certification credential. This demonstrates your ability to evaluate, plan, migrate, deploy, and manage Microsoft 365 services. COMPUTERS,Certification Guides,Microsoft

Exam Ref MD-101 Managing Modern Desktops The Exam Ref is the official study guide for Microsoft certification exams. Featuring concise coverage of the skills measured by the exam, challenging Thought Experiments, and pointers to more in-depth material for the candidate needing additional study, exam candidates get professional-level preparation for the exam. The Exam Ref helps candidates determine their readiness for the exam, and provides Exam Tips to help maximise their performance on the exam. The organisation of the material mirrors the skills measured by the exam as presented on the certification exam web page. This exam validates candidate’s fundamental knowledge, and skills for deploying and updating Windows, managing policies and profiles, managing apps and data, and managing and protecting devices. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Certification Guides,Microsoft

Exam Ref AZ-203 Developing Solutions for Microsoft Azure Prepare for Microsoft Exam AZ-203—and help demonstrate your real-world mastery of Microsoft Azure solutions development. Designed for working Azure developers, this Exam Ref focuses on the critical thinking and decision-making acumen needed for success at the Microsoft Certified Solutions Associate level. Focus on the expertise measured by these objectives: • Develop Azure Infrastructure as a Service compute solutions • Develop Azure Platform as a Service compute solutions • Develop for Azure storage • Implement Azure security • Monitor, troubleshoot, and optimize solutions • Connect to and consume Azure and third-party services This Microsoft Exam Ref: • Organizes its coverage by exam objectives • Features strategic, what-if scenarios to challenge you • Assumes you want to show your ability to design and build diverse Microsoft Azure cloud solutions, and successfully participate in all phases of their development. About the Exam Exam AZ-203 focuses on knowledge needed to implement solutions using VMs and containers; implement batch jobs; create Azure App Service apps; implement Azure functions; develop solutions with storage tables, Cosmos DB, relational databases, or blobs; implement authentication, access control, and secure data solutions; support app and service scalability; integrate caching and content delivery; instrument solutions; develop App Service Logic Apps; integrate Azure Search; establish API gateways; and develop event- and message-based solutions. About Microsoft Certification Passing this exam fulfills your requirements for the Microsoft Certified: Azure Developer Associate credential, demonstrating your readiness to design, build, test, and maintain Microsoft Azure cloud solutions, and partner with other cloud professionals and clients to implement them. This exam is also a prerequisite for the Microsoft Certified: Azure DevOps Engineer Expert credential. See full details at: microsoft.com/learn COMPUTERS,Certification Guides,Microsoft

Exam Ref AZ-300 Microsoft Azure Architect Technologies Prepare for Microsoft Exam AZ-300—and help demonstrate your real-world mastery of architecting high-value Microsoft Azure solutions for your organization or customers. Designed for modern IT professionals, this Exam Ref focuses on the critical thinking and decision-making acumen needed for success at the Microsoft Certified Expert level. Focus on the expertise measured by these objectives: Deploy and configure infrastructure Implement workloads and security Create and deploy apps Implement authentication and secure data Develop for the cloud and for Azure storage This Microsoft Exam Ref: Organizes its coverage by exam objectives Features strategic, what-if scenarios to challenge you Assumes you are an IT professional who wants to demonstrate your ability to design modern Microsoft Azure solutions involving compute, network, storage, and security About the Exam Exam AZ-300 focuses on knowledge needed to analyze resource usage; create and configure storage accounts and VMs; automate VM deployments and implement VM solutions; create and manage virtual networks; manage Azure AD and hybrid identities; migrate servers to Azure; configure serverless computing; implement app load balancing; integrate on-premises and virtual networks; manage RBAC; implement MFA; create web apps with PaaS; design and develop containerized apps; implement authentication and secure data solutions; build solutions with Cosmos DB or RDBMSes; configure message-based integration architecture; and develop for autoscaling. About Microsoft Certification Passing this exam and Exam AZ-301: Microsoft Azure Architect Design fulfills your requirements for the Microsoft Cer¿tified: Azure Solutions Architect Expert credential, demonstrating your expertise in compute, network, storage, and secu¿rity for designing modern cloud-based solutions that run on Microsoft Azure. See full details at: microsoft.com/learn COMPUTERS,Certification Guides,Microsoft

Exam Ref MS-900 Microsoft 365 Fundamentals Prepare for Microsoft Exam MS-900–and help demonstrate your mastery of real-world foundational knowledge about the considerations and benefits of adopting cloud services and the Software as a Service cloud model, as well as specific options and benefits of Microsoft 365 cloud service offerings. Designed for IT professionals, Exam Ref focuses on critical thinking and decision-making acumen needed for success at the Microsoft Certified Fundamentals level. Focus on the expertise measured by these objectives: Understand cloud concepts Understand core Microsoft 365 services and concepts Understand security, compliance, privacy, and trust in Microsoft 365 Understand Microsoft 365 pricing and support This Microsoft Exam Ref: Organizes its coverage by exam objectives Features strategic, what-if scenarios to challenge you Assumes you are a business user, IT professional, or student interested in cloud computing and technologies, including individuals planning to pursue more advanced Microsoft 365 certification. About the Exam Exam MS-900 focuses on knowledge about benefits and considerations of using cloud services; different types of cloud services; core Microsoft 365 components; comparisons between Microsoft 365 and on-premises services; modern management concepts; Office 365 ProPlus; Microsoft 365 collabora¿tion, mobility and analytics; Microsoft 365 security and compliance concepts; unified endpoint management; security usage scenarios and services; the Service Trust portal and Compliance manager; Microsoft 365 licensing options; pricing; support, and service lifecycles. About Microsoft Certification Passing this exam fulfills your requirements for the Microsoft 365 Certified Fundamentals certification credential, proving that you understand Microsoft 365 options, as well as the benefits of adopting cloud services, the Software as a Service (SaaS) cloud model, and Microsoft 365 cloud services in particular. See full details at: microsoft.com/learn COMPUTERS,Certification Guides,Microsoft

MOS Study Guide for Microsoft Excel Exam MO-200 Advance your everyday proficiency with Excel! And earn the credential that proves it! Demonstrate your expertise with Microsoft Excel! Designed to help you practice and prepare for Microsoft Office Specialist: Excel Associate (Excel and Excel 2019) certification, this official Study Guide delivers: In-depth preparation for each MOS objective Detailed procedures to help build the skills measured by the exam Hands-on tasks to practice what you’ve learned Ready-made practice files Sharpen the skills measured by these objectives: Manage Worksheets and Workbooks Manage Data Cells and Ranges Manage Tables and Table Data Perform Operations by Using Formulas and Functions Manage Charts About MOS A Microsoft Office Specialist (MOS) certification validates your proficiency with Microsoft Office programs, demonstrating that you can meet globally recognized performance standards. Hands-on experience with the technology is required to successfully pass Microsoft Certification exams. COMPUTERS,Certification Guides,Microsoft

MOS Study Guide for Microsoft Access Expert Exam MO-500 Advance your everyday proficiency with Access 2019. And earn the credential that proves it! Demonstrate your expertise with Microsoft Access! Designed to help you practice and prepare for Microsoft Office Specialist (MOS): Access 2019 certification, this official Study Guide delivers: In-depth preparation for each MOS objective Detailed procedures to help build the skills measured by the exam Hands-on tasks to practice what you’ve learned Practice files and sample solutions Sharpen the skills measured by these objectives: Create and manage databases Build tables Create queries Create forms Create reports About MOS A Microsoft Office Specialist (MOS) certification validates your proficiency with Microsoft Office programs, demonstrating that you can meet globally recognized performance standards. Hands-on experience with the technology is required to successfully pass Microsoft Certification exams. COMPUTERS,Certification Guides,Microsoft

MOS Study Guide for Microsoft Word Exam MO-100 Advance your proficiency with Word. And earn the credential that proves it! Demonstrate your expertise with Microsoft Word! Designed to help you practice and prepare for Microsoft Office Specialist: Word Associate (Word and Word 2019) certification, this official Study Guide delivers: • In-depth preparation for each MOS objective • Detailed procedures to help build the skills measured by the exam • Hands-on tasks to practice what you’ve learned • Ready-made practice files Sharpen the skills measured by these objectives: • Manage Documents • Insert and Format Text, Paragraphs, and Sections • Manage Tables and Lists • Create and Manage References • Insert and Format Graphic Elements EXAM MO-100 About the MOS: Associate Certification A Microsoft Office Specialist (MOS): Associate certification validates your hands-on competency in the correct application of the principal features of an Office product. It demonstrates that you can apply these features to complete associate-level tasks independently and are ready to enter the job market. See full details at: microsoft.com/learn Practice Files Available at: MicrosoftPressStore.com/MOSWord100/Downloads COMPUTERS,Certification Guides,Microsoft

MOS Study Guide for Microsoft PowerPoint Exam MO-300 Advance your everyday proficiency with PowerPoint 2019, and earn the credential that proves it! Demonstrate your expertise with Microsoft PowerPoint! Designed to help you practice and prepare for Microsoft Office Specialist (MOS): PowerPoint 2019 certification, this official Study Guide delivers: In-depth preparation for each MOS objective Detailed procedures to help build the skills measured by the exam Hands-on tasks to practice what you’ve learned Practice files and sample solutions Sharpen the skills measured by these objectives: Create and manage presentations and slides Insert and format text, shapes, and images Create and manage references Insert and format graphic elements Manage multiple presentations About MOS A Microsoft Office Specialist (MOS) certification validates your proficiency with Microsoft Office programs, demonstrating that you can meet globally recognized performance standards. Hands-on experience with the technology is required to successfully pass Microsoft Certification exams. COMPUTERS,Certification Guides,Microsoft

Dependence Analysis Dependence Analysis may be considered to be the second edition of the author's 1988 book, Dependence Analysis for Supercomputing. It is, however, a completely new work that subsumes the material of the 1988 publication. This book is the third volume in the series Loop Transformations for Restructuring Compilers. This series has been designed to provide a complete mathematical theory of transformations that can be used to automatically change a sequential program containing FORTRAN-like do loops into an equivalent parallel form. In Dependence Analysis, the author extends the model to a program consisting of do loops and assignment statements, where the loops need not be sequentially nested and are allowed to have arbitrary strides. In the context of such a program, the author studies, in detail, dependence between statements of the program caused by program variables that are elements of arrays. Dependence Analysis is directed toward graduate and undergraduate students, and professional writers of restructuring compilers. The prerequisite for the book consists of some knowledge of programming languages, and familiarity with calculus and graph theory. No knowledge of linear programming is required. COMPUTERS,Computer Architecture

Load Balancing in Parallel Computers Load Balancing in Parallel Computers: Theory and Practice is about the essential software technique of load balancing in distributed memory message-passing parallel computers, also called multicomputers. Each processor has its own address space and has to communicate with other processors by message passing. In general, a direct, point-to-point interconnection network is used for the communications. Many commercial parallel computers are of this class, including the Intel Paragon, the Thinking Machine CM-5, and the IBM SP2. Load Balancing in Parallel Computers: Theory and Practice presents a comprehensive treatment of the subject using rigorous mathematical analyses and practical implementations. The focus is on nearest-neighbor load balancing methods in which every processor at every step is restricted to balancing its workload with its direct neighbours only. Nearest-neighbor methods are iterative in nature because a global balanced state can be reached through processors' successive local operations. Since nearest-neighbor methods have a relatively relaxed requirement for the spread of local load information across the system, they are flexible in terms of allowing one to control the balancing quality, effective for preserving communication locality, and can be easily scaled in parallel computers with a direct communication network. Load Balancing in Parallel Computers: Theory and Practice serves as an excellent reference source and may be used as a text for advanced courses on the subject. COMPUTERS,Computer Architecture

Loop Transformations for Restructuring Compilers Automatic transformation of a sequential program into a parallel form is a subject that presents a great intellectual challenge and promises great practical rewards. There is a tremendous investment in existing sequential programs, and scientists and engineers continue to write their application programs in sequential languages (primarily in Fortran),but the demand for increasing speed is constant. The job of a restructuring compiler is to discover the dependence structure of a given program and transform the program in a way that is consistent with both that dependence structure and the characteristics of the given machine. Much attention in this field of research has been focused on the Fortran do loop. This is where one expects to find major chunks of computation that need to be performed repeatedly for different values of the index variable. Many loop transformations have been designed over the years, and several of them can be found in any parallelizing compiler currently in use in industry or at a university research facility. Loop Transformations for Restructuring Compilers: The Foundations provides a rigorous theory of loop transformations. The transformations are developed in a consistent mathematical framework using objects like directed graphs, matrices and linear equations. The algorithms that implement the transformations can then be precisely described in terms of certain abstract mathematical algorithms. The book provides the general mathematical background needed for loop transformations (including those basic mathematical algorithms), discusses data dependence, and introduces the major transformations. The next volume will build a detailed theory of loop transformations based on the material developed here. Loop Transformations for Restructuring Compilers: The Foundations presents a theory of loop transformations that is rigorous and yet reader-friendly. COMPUTERS,Computer Architecture

Symbolic Analysis for Parallelizing Compilers In Symbolic Analysis for Parallelizing Compilers the author presents an excellent demonstration of the effectiveness of symbolic analysis in tackling important optimization problems, some of which inhibit loop parallelization. The framework that Haghighat presents has proved extremely successful in induction and wraparound variable analysis, strength reduction, dead code elimination and symbolic constant propagation. The approach can be applied to any program transformation or optimization problem that uses properties and value ranges of program names. Symbolic analysis can be used on any transformational system or optimization problem that relies on compile-time information about program variables. This covers the majority of, if not all optimization and parallelization techniques. The book makes a compelling case for the potential of symbolic analysis, applying it for the first time - and with remarkable results - to a number of classical optimization problems: loop scheduling, static timing or size analysis, and dependence analysis. It demonstrates how symbolic analysis can solve these problems faster and more accurately than existing hybrid techniques. COMPUTERS,Computer Architecture

Object-Oriented Design with UML and Java Object-Oriented Design with UML and Java provides an integrated introduction to object-oriented design with the Unified Modelling Language (UML) and the Java programming language. The book demonstrates how Java applications, no matter how small, can benefit from some design during their construction. Fully road-tested by students on the authors' own courses, the book shows how these complementary technologies can be used effectively to create quality software. It requires no prior knowledge of object orientation, though readers must have some experience of Java or other high level programming language. This book covers object technology; object-oriented analysis and design; and implementation of objects with Java. It includes two case studies dealing with library applications. The UML has been incorporated into a graphical design tool called ROME, which can be downloaded from the book's website. This object modelling environment allows readers to prepare and edit various UML diagrams. ROME can be used alongside a Java compiler to generate Java code from a UML class diagram then compile and run the resulting application for hands-on learning. This text would be a valuable resource for undergraduate students taking courses on O-O analysis and design, O-O modelling, Java programming, and modelling with UML.* Integrates design and implementation, using Java and UML* Includes case studies and exercises * Bridges the gap between programming texts and high level analysis books on design COMPUTERS,Computer Architecture

Design of Reservation Protocols for Multimedia Communication The advent of multimedia technology is creating a number of new problems in the fields of computer and communication systems. Perhaps the most important of these problems in communication, and certainly the most interesting, is that of designing networks to carry multimedia traffic, including digital audio and video, with acceptable quality. The main challenge in integrating the different services needed by the different types of traffic into the same network (an objective that is made worthwhile by its obvious economic advantages) is to satisfy the performance requirements of continuous media applications, as the quality of audio and video streams at the receiver can be guaranteed only if bounds on delay, delay jitters, bandwidth, and reliability are guaranteed by the network. Since such guarantees cannot be provided by traditional packet-switching technology, a number of researchers and research groups during the last several years have tried to meet the challenge by proposing new protocols or modifications of old ones, to make packet-switching networks capable of delivering audio and video with good quality while carrying all sorts of other traffic. The focus of this book is on HeiTS (the Heidelberg Transport System), and its contributions to integrated services network design. The HeiTS architecture is based on using the Internet Stream Protocol Version 2 (ST-II) at the network layer. The Heidelberg researchers were the first to implement ST-II. The author documents this activity in the book and provides thorough coverage of the improvements made to the protocol. The book also includes coverage of HeiTP as used in error handling, error control, congestion control, and the full specification of ST2+, a new version of ST-II. The ideas and techniques implemented by the Heidelberg group and their coverage in this volume apply to many other approaches to multimedia networking. COMPUTERS,Computer Architecture

Automatic Performance Prediction of Parallel Programs Automatic Performance Prediction of Parallel Programs presents a unified approach to the problem of automatically estimating the performance of parallel computer programs. The author focuses primarily on distributed memory multiprocessor systems, although large portions of the analysis can be applied to shared memory architectures as well. The author introduces a novel and very practical approach for predicting some of the most important performance parameters of parallel programs, including work distribution, number of transfers, amount of data transferred, network contention, transfer time, computation time and number of cache misses. This approach is based on advanced compiler analysis that carefully examines loop iteration spaces, procedure calls, array subscript expressions, communication patterns, data distributions and optimizing code transformations at the program level; and the most important machine specific parameters including cache characteristics, communication network indices, and benchmark data for computational operations at the machine level. The material has been fully implemented as part of P3T, which is an integrated automatic performance estimator of the Vienna Fortran Compilation System (VFCS), a state-of-the-art parallelizing compiler for Fortran77, Vienna Fortran and a subset of High Performance Fortran (HPF) programs. A large number of experiments using realistic HPF and Vienna Fortran code examples demonstrate highly accurate performance estimates, and the ability of the described performance prediction approach to successfully guide both programmer and compiler in parallelizing and optimizing parallel programs. A graphical user interface is described and displayed that visualizes each program source line together with the corresponding parameter values. P3T uses color-coded performance visualization to immediately identify hot spots in the parallel program. Performance data can be filtered and displayed at various levels of detail. Colors displayed by the graphical user interface are visualized in greyscale. Automatic Performance Prediction of Parallel Programs also includes coverage of fundamental problems of automatic parallelization for distributed memory multicomputers, a description of the basic parallelization strategy and a large variety of optimizing code transformations as included under VFCS. COMPUTERS,Computer Architecture

Document Processing and Retrieval Document Processing and Retrieval: TEXPROS focuses on the design and implementation of a personal, customizable office information and document processing system called TEXPROS (a TEXt PROcessing System). TEXPROS is a personal, intelligent office information and document processing system for text-oriented documents. This system supports the storage, classification, categorization, retrieval and reproduction of documents, as well as extracting, browsing, retrieving and synthesizing information from a variety of documents. When using TEXPROS in a multi-user or distributed environment, it requires specific protocols for extracting, storing, transmitting and exchanging information. The authors have used a variety of techniques to implement TEXPROS, such as Object-Oriented Programming, Tcl/Tk, X-Windows, etc. The system can be used for many different purposes in many different applications, such as digital libraries, software documentation and information delivery. Audience: Provides in-depth, state-of-the-art coverage of information processing and retrieval, and documentation for such professionals as database specialists, information systems and software developers, and information providers. COMPUTERS,Computer Architecture

Principles of Distributed Systems Distributed computer systems are now widely available but, despite a number of recent advances, the design of software for these systems remains a challenging task, involving two main difficulties: the absence of a shared clock and the absence of a shared memory. The absence of a shared clock means that the concept of time is not useful in distributed systems. The absence of shared memory implies that the concept of a state of a distributed system also needs to be redefined. These two important concepts occupy a major portion of this book. Principles of Distributed Systems describes tools and techniques that have been successfully applied to tackle the problem of global time and state in distributed systems. The author demonstrates that the concept of time can be replaced by that of causality, and clocks can be constructed to provide causality information. The problem of not having a global state is alleviated by developing efficient algorithms for detecting properties and computing global functions. The author's major emphasis is in developing general mechanisms that can be applied to a variety of problems. For example, instead of discussing algorithms for standard problems, such as termination detection and deadlocks, the book discusses algorithms to detect general properties of a distributed computation. Also included are several worked examples and exercise problems that can be used for individual practice and classroom instruction. Audience: Can be used to teach a one-semester graduate course on distributed systems. Also an invaluable reference book for researchers and practitioners working on the many different aspects of distributed systems. COMPUTERS,Computer Architecture

Time-Constrained Transaction Management Transaction processing is an established technique for the concurrent and fault tolerant access of persistent data. While this technique has been successful in standard database systems, factors such as time-critical applications, emerg ing technologies, and a re-examination of existing systems suggest that the performance, functionality and applicability of transactions may be substan tially enhanced if temporal considerations are taken into account. That is, transactions should not only execute in a "legal" (i.e., logically correct) man ner, but they should meet certain constraints with regard to their invocation and completion times. Typically, these logical and temporal constraints are application-dependent, and we address some fundamental issues for the man agement of transactions in the presence of such constraints. Our model for transaction-processing is based on extensions to established mod els, and we briefly outline how logical and temporal constraints may be ex pressed in it. For scheduling the transactions, we describe how legal schedules differ from one another in terms of meeting the temporal constraints. Exist ing scheduling mechanisms do not differentiate among legal schedules, and are thereby inadequate with regard to meeting temporal constraints. This provides the basis for seeking scheduling strategies that attempt to meet the temporal constraints while continuing to produce legal schedules. COMPUTERS,Computer Architecture

Quality by Design for Electronics This book concentrates on the quality of electronic products. Electronics in general, including semiconductor technology and software, has become the key technology for wide areas of industrial production. In nearly all expanding branches of industry electronics, especially digital electronics, is involved. And the spread of electronic technology has not yet come to an end. This rapid development, coupled with growing competition and the shorter innovation cycle, have caused economic problems which tend to have adverse effects on quality. Therefore, good quality at low cost is a very attractive goal in industry today. The demand for better quality continues along with a demand for more studies in quality assurance. At the same time, many companies are experiencing a drop in profits just when better quality of their products is essential in order to survive against the competition. There have been many proposals in the past to improve quality without increase in cost, or to reduce cost for quality assurance without loss of quality. This book tries to summarize the practical content of many of these proposals and to give some advice, above all to the designer and manufacturer of electronic devices. It mainly addresses practically minded engineers and managers. It is probably of less interest to pure scientists. The book covers all aspects of quality assurance of components used in electronic devices. Integrated circuits (lCs) are considered to be the most important components because the degree of integration is still rising. COMPUTERS,Computer Architecture

Performance and Reliability Analysis of Computer Systems Performance and Reliability Analysis of Computer Systems: An Example-Based Approach Using the SHARPE Software Package provides a variety of probabilistic, discrete-state models used to assess the reliability and performance of computer and communication systems. The models included are combinatorial reliability models (reliability block diagrams, fault trees and reliability graphs), directed, acyclic task precedence graphs, Markov and semi-Markov models (including Markov reward models), product-form queueing networks and generalized stochastic Petri nets. A practical approach to system modeling is followed; all of the examples described are solved and analyzed using the SHARPE tool. In structuring the book, the authors have been careful to provide the reader with a methodological approach to analytical modeling techniques. These techniques are not seen as alternatives but rather as an integral part of a single process of assessment which, by hierarchically combining results from different kinds of models, makes it possible to use state-space methods for those parts of a system that require them and non-state-space methods for the more well-behaved parts of the system. The SHARPE (Symbolic Hierarchical Automated Reliability and Performance Evaluator) package is the `toolchest' that allows the authors to specify stochastic models easily and solve them quickly, adopting model hierarchies and very efficient solution techniques. All the models described in the book are specified and solved using the SHARPE language; its syntax is described and the source code of almost all the examples discussed is provided. Audience: Suitable for use in advanced level courses covering reliability and performance of computer and communications systems and by researchers and practicing engineers whose work involves modeling of system performance and reliability. COMPUTERS,Computer Architecture

Fast Simulation of Computer Architectures Chapters in Fast Simulation of Computer Architectures cover topics such as how to collect traces, emulate instruction sets, simulate microprocessors using execution-driven techniques, evaluate memory hierarchies, apply statistical sampling to simulation, and how to augment simulation with performance bound models. The chapters have been written by many of the leading researchers in the area, in a collaboration that ensures that the material is both coherent and cohesive. Audience: Of tremendous interest to practising computer architect designers seeking timely solutions to tough evaluation problems, and to advanced upper division undergraduate and graduate students of the field. Useful study aids are provided by the problems at the end of Chapters 2 through 8. COMPUTERS,Computer Architecture

Multiprocessor Execution of Logic Programs Multiprocessor Execution of Logic Programs addresses the problem of efficient implementation of logic programming languages, specifically Prolog, on multiprocessor architectures. The approaches and implementations developed attempt to take full advantage of sequential implementation technology developed for Prolog (such as the WAM) while exploiting all forms of control parallelism present in logic programs, namely, or-parallelism, independent and -parallelism and dependent and -parallelism. Coverage includes a thorough survey of parallel implementation techniques and parallel systems developed for Prolog. Multiprocessor Execution of Logic Programs is recommended for people implementing parallel logic programming systems, parallel symbolic systems, parallel AI systems, and parallel theorem proving systems. It will also be useful to people who wish to learn about the implementation of parallel logic programming systems. COMPUTERS,Computer Architecture

The Interaction of Compilation Technology and Computer Architecture In brief summary, the following results were presented in this work: • A linear time approach was developed to find register requirements for any specified CS schedule or filled MRT. • An algorithm was developed for finding register requirements for any kernel that has a dependence graph that is acyclic and has no data reuse on machines with depth independent instruction templates. • We presented an efficient method of estimating register requirements as a function of pipeline depth. • We developed a technique for efficiently finding bounds on register require ments as a function of pipeline depth. • Presented experimental data to verify these new techniques. • discussed some interesting design points for register file size on a number of different architectures. REFERENCES [1] Robert P. Colwell, Robert P. Nix, John J O'Donnell, David B Papworth, and Paul K. Rodman. A VLIW Architecture for a Trace Scheduling Com piler. In Architectural Support for Programming Languages and Operating Systems, pages 180-192, 1982. [2] C. Eisenbeis, W. Jalby, and A. Lichnewsky. Compile-Time Optimization of Memory and Register Usage on the Cray-2. In Proceedings of the Second Workshop on Languages and Compilers, Urbana l/inois, August 1989. [3] C. Eisenbeis, William Jalby, and Alain Lichnewsky. Squeezing More CPU Performance Out of a Cray-2 by Vector Block Scheduling. In Proceedings of Supercomputing '88, pages 237-246, 1988. [4] Michael J. Flynn. Very High-Speed Computing Systems. Proceedings of the IEEE, 54:1901-1909, December 1966. COMPUTERS,Computer Architecture

Neural Network Applications Neural Network Applications contains the 12 papers presented at the second British Neural Network Society Meeting (NCM '91) held at King's College London on 1st October 1991. The meeting was sponsored by the Centre for Neural Networks, King's College, and the British Neural Network Society, and was also part of the DEANNA ESPRIT programme. The papers reflect the wide spectrum of neural network applications that are currently being attempted in industry and medicine. They cover medical diagnosis, robotics, plant control, machine learning, and visual inspection, as well as more general discussions on net learning and knowledge representation. The breadth and depth of coverage is a sign of the health of the subject, as well as indicating the importance of neural network developments in industry and the manner in which the applications are progressing. Among the actual topics covered are: Learning algorithms - theory and practice; A review of medical diagnostic applications of neural networks; Simulated ultrasound tomographic imaging of defects; Linear quadtrees for neural network based position invariant pattern recognition; The pRTAM as a hardware-realisable neuron; The cognitive modalities ("CM") system of knowledge representation - the DNA of neural networks? This volume provides valuable reading for all those attempting to apply neural networks, as well as those entering the field, including researchers and postgraduate students in computational neuroscience, neurobiology, electrical engineering, computer science, mathematics, and medicine. COMPUTERS,Computer Architecture

Scalable Shared Memory Multiprocessors The workshop on Scalable Shared Memory Multiprocessors took place on May 26 and 27 1990 at the Stouffer Madison Hotel in Seattle, Washington as a prelude to the 1990 International Symposium on Computer Architecture. About 100 participants listened for two days to the presentations of 22 invited The motivation for this workshop was to speakers, from academia and industry. promote the free exchange of ideas among researchers working on shared-memory multiprocessor architectures. There was ample opportunity to argue with speakers, and certainly participants did not refrain a bit from doing so. Clearly, the problem of scalability in shared-memory multiprocessors is still a wide-open question. We were even unable to agree on a definition of "scalability". Authors had more than six months to prepare their manuscript, and therefore the papers included in this proceedings are refinements of the speakers' presentations, based on the criticisms received at the workshop. As a result, 17 authors contributed to these proceedings. We wish to thank them for their diligence and care. The contributions in these proceedings can be partitioned into four categories 1. Access Order and Synchronization 2. Performance 3. Cache Protocols and Architectures 4. Distributed Shared Memory Particular topics on which new ideas and results are presented in these proceedings include: efficient schemes for combining networks, formal specification of shared memory models, correctness of trace-driven simulations,synchronization, various coherence protocols, . COMPUTERS,Computer Architecture

Arrays, Functional Languages, and Parallel Systems During a meeting in Toronto last winter, Mike Jenkins, Bob Bernecky and I were discussing how the two existing theories on arrays influenced or were in fluenced by programming languages and systems. More's Army Theory was the basis for NIAL and APL2 and Mullin's A Mathematics of A rmys(MOA) , is being used as an algebra of arrays in functional and A-calculus based pro gramming languages. MOA was influenced by Iverson's initial and extended algebra, the foundations for APL and J respectively. We discussed that there is a lot of interest in the Computer Science and Engineering communities concerning formal methods for languages that could support massively parallel operations in scientific computing, a back to-roots interest for both Mike and myself. Languages for this domain can no longer be informally developed since it is necessary to map languages easily to many multiprocessor architectures. Software systems intended for parallel computation require a formal basis so that modifications can be done with relative ease while ensuring integrity in design. List based lan guages are profiting from theoretical foundations such as the Bird-Meertens formalism. Their theory has been successfully used to describe list based parallel algorithms across many classes of architectures. COMPUTERS,Computer Architecture
Past, Present, Parallel Past, Present, Parallel is a survey of the current state of the parallel processing industry. In the early 1980s, parallel computers were generally regarded as academic curiosities whose natural environment was the research laboratory. Today, parallelism is being used by every major computer manufacturer, although in very different ways, to produce increasingly powerful and cost-effec- tive machines. The first chapter introduces the basic concepts of parallel computing; the subsequent chapters cover different forms of parallelism, including descriptions of vector supercomputers, SIMD computers, shared memory multiprocessors, hypercubes, and transputer-based machines. Each section concentrates on a different manufacturer, detailing its history and company profile, the machines it currently produces, the software environments it supports, the market segment it is targetting, and its future plans. Supplementary chapters describe some of the companies which have been unsuccessful, and discuss a number of the common software systems which have been developed to make parallel computers more usable. The appendices describe the technologies which underpin parallelism. Past, Present, Parallel is an invaluable reference work, providing up-to-date material for commercial computer users and manufacturers, and for researchers and postgraduate students with an interest in parallel computing. COMPUTERS,Computer Architecture

Supercomputing For the Future of Supercomputing COMPUTERS,Computer Architecture

TRON Project 1990 Proceedings of the Seventh TRON Project Symposium COMPUTERS,Computer Architecture

Cache and Interconnect Architectures in Multiprocessors Cache And Interconnect Architectures In Multiprocessors Eilat, Israel May 25-261989 Michel Dubois UniversityofSouthernCalifornia Shreekant S. Thakkar SequentComputerSystems The aim of the workshop was to bring together researchers working on cache coherence protocols for shared-memory multiprocessors with various interconnect architectures. Shared-memory multiprocessors have become viable systems for many applications. Bus based shared-memory systems (Eg. Sequent's Symmetry, Encore's Multimax) are currently limited to 32 processors. The fIrst goal of the workshop was to learn about the performance ofapplications on current cache-based systems. The second goal was to learn about new network architectures and protocols for future scalable systems. These protocols and interconnects would allow shared-memory architectures to scale beyond current imitations. The workshop had 20 speakers who talked about their current research. The discussions were lively and cordial enough to keep the participants away from the wonderful sand and sun for two days. The participants got to know each other well and were able to share their thoughts in an informal manner. The workshop was organized into several sessions. The summary of each session is described below. This book presents revisions of some of the papers presented at the workshop. COMPUTERS,Computer Architecture

Neurocomputing Proceedings of the NATO Advanced Research Workshop on Neurocomputing. Algorithms, Architectures and Applications, held in Les Arcs, France, February 27 - March 3, 1989 COMPUTERS,Computer Architecture
Modeling Enterprise Architecture with TOGAF Modeling Enterprise Architecture with TOGAF explains everything you need to know to effectively model enterprise architecture with The Open Group Architecture Framework (TOGAF), the leading EA standard. This solution-focused reference presents key techniques and illustrative examples to help you model enterprise architecture. This book describes the TOGAF standard and its structure, from the architecture transformation method to governance, and presents enterprise architecture modeling practices with plenty of examples of TOGAF deliverables in the context of a case study. Although widespread and growing quickly, enterprise architecture is delicate to manage across all its dimensions. Focusing on the architecture transformation method, TOGAF provides a wide framework, which covers the repository, governance, and a set of recognized best practices. The examples featured in this book were realized using the open source Modelio tool, which includes extensions for TOGAF. Includes intuitive summaries of the complex TOGAF standard to let you effectively model enterprise architecture Uses practical examples to illustrate ways to adapt TOGAF to the needs of your enterprise Provides model examples with Modelio, a free modeling tool, letting you exercise TOGAF modeling immediately using a dedicated tool Combines existing modeling standards with TOGAF COMPUTERS,Computer Architecture

Loop Parallelization Automatic transformation of a sequential program into a parallel form is a subject that presents a great intellectual challenge and promises a great practical award. There is a tremendous investment in existing sequential programs, and scientists and engineers continue to write their application programs in sequential languages (primarily in Fortran). The demand for higher speedups increases. The job of a restructuring compiler is to discover the dependence structure and the characteristics of the given machine. Much attention has been focused on the Fortran do loop. This is where one expects to find major chunks of computation that need to be performed repeatedly for different values of the index variable. Many loop transformations have been designed over the years, and several of them can be found in any parallelizing compiler currently in use in industry or at a university research facility. The book series on KappaLoop Transformations for Restructuring Compilerskappa provides a rigorous theory of loop transformations and dependence analysis. We want to develop the transformations in a consistent mathematical framework using objects like directed graphs, matrices, and linear equations. Then, the algorithms that implement the transformations can be precisely described in terms of certain abstract mathematical algorithms. The first volume, Loop Transformations for Restructuring Compilers: The Foundations, provided the general mathematical background needed for loop transformations (including those basic mathematical algorithms), discussed data dependence, and introduced the major transformations. The current volume, Loop Parallelization, builds a detailed theory of iteration-level loop transformations based on the material developed in the previous book. COMPUTERS,Computer Architecture

Digital Design and Computer Architecture Digital Design and Computer Architecture: ARM Edition covers the fundamentals of digital logic design and reinforces logic concepts through the design of an ARM microprocessor. Combining an engaging and humorous writing style with an updated and hands-on approach to digital design, this book takes the reader from the fundamentals of digital logic to the actual design of an ARM processor. By the end of this book, readers will be able to build their own microprocessor and will have a top-to-bottom understanding of how it works. Beginning with digital logic gates and progressing to the design of combinational and sequential circuits, this book uses these fundamental building blocks as the basis for designing an ARM processor. SystemVerilog and VHDL are integrated throughout the text in examples illustrating the methods and techniques for CAD-based circuit design. The companion website includes a chapter on I/O systems with practical examples that show how to use the Raspberry Pi computer to communicate with peripheral devices such as LCDs, Bluetooth radios, and motors. This book will be a valuable resource for students taking a course that combines digital logic and computer architecture or students taking a two-quarter sequence in digital logic and computer organization/architecture. Covers the fundamentals of digital logic design and reinforces logic concepts through the design of an ARM microprocessor. Features side-by-side examples of the two most prominent Hardware Description Languages (HDLs)—SystemVerilog and VHDL—which illustrate and compare the ways each can be used in the design of digital systems. Includes examples throughout the text that enhance the reader’s understanding and retention of key concepts and techniques. The Companion website includes a chapter on I/O systems with practical examples that show how to use the Raspberry Pi computer to communicate with peripheral devices such as LCDs, Bluetooth radios, and motors. The Companion website also includes appendices covering practical digital design issues and C programming as well as links to CAD tools, lecture slides, laboratory projects, and solutions to exercises. COMPUTERS,Computer Architecture
Learning Computer Architecture with Raspberry Pi Use your Raspberry Pi to get smart about computing fundamentals In the 1980s, the tech revolution was kickstarted by a flood of relatively inexpensive, highly programmable computers like the Commodore. Now, a second revolution in computing is beginning with the Raspberry Pi. Learning Computer Architecture with the Raspberry Pi is the premier guide to understanding the components of the most exciting tech product available. Thanks to this book, every Raspberry Pi owner can understand how the computer works and how to access all of its hardware and software capabilities. Now, students, hackers, and casual users alike can discover how computers work with Learning Computer Architecture with the Raspberry Pi. This book explains what each and every hardware component does, how they relate to one another, and how they correspond to the components of other computing systems. You'll also learn how programming works and how the operating system relates to the Raspberry Pi's physical components. Co-authored by Eben Upton, one of the creators of the Raspberry Pi, this is a companion volume to the Raspberry Pi User Guide An affordable solution for learning about computer system design considerations and experimenting with low-level programming Understandable descriptions of the functions of memory storage, Ethernet, cameras, processors, and more Gain knowledge of computer design and operation in general by exploring the basic structure of the Raspberry Pi The Raspberry Pi was created to bring forth a new generation of computer scientists, developers, and architects who understand the inner workings of the computers that have become essential to our daily lives. Learning Computer Architecture with the Raspberry Pi is your gateway to the world of computer system design. COMPUTERS,Computer Architecture

Specification and Verification of Concurrent Systems This volume contains papers presented at the BCS-FACS Workshop on Specification and Verification of Concurrent Systems held on 6-8 July 1988, at the University of Stirling, Scotland. Specification and verification techniques are playing an increasingly important role in the design and production of practical concurrent systems. The wider application of these techniques serves to identify difficult problems that require new approaches to their solution and further developments in specification and verification. The Workshop aimed to capture this interplay by providing a forum for the exchange of the experience of academic and industrial experts in the field. Presentations included: surveys, original research, practical experi ence with methods, tools and environments in the following or related areas: Object-oriented, process, data and logic based models and specifi cation methods for concurrent systems Verification of concurrent systems Tools and environments for the analysis of concurrent systems Applications of specification languages to practical concurrent system design and development. We should like to thank the invited speakers and all the authors of the papers whose work contributed to making the Workshop such a success. We were particularly pleased with the international response to our call for papers. Invited Speakers Pierre America Philips Research Laboratories University of Warwick Professor M. Joseph David Freestone British Telecom Organising Committee Charles Rattray Dr Muffy Thomas Dr Simon Jones Dr John Cooke Professor Ken Turner Derek Coleman Maurice Naftalin Dr Peter Scharbach vi Preface We would like to aeknowledge the finaneial eontribution made by SD-Sysems Designers pie, Camberley, Surrey. COMPUTERS,Computer Architecture

Cloud Foundry What exactly is a cloud-native platform? It’s certainly a hot topic in IT, as enterprises today assess this option for developing and delivering software quickly and repeatedly. This O’Reilly report explains the capabilities of cloud-native platforms and examines the fundamental changes enterprises need to make in process, organization, and culture if they’re to take real advantage of this approach. Author Duncan Winn focuses on the open source platform Cloud Foundry, one of the more prominent cloud-native providers. You’ll learn how cloud-native applications are designed to be "infrastructure unaware" so they can thrive and move at will in the highly distributed and constantly evolving cloud environment. With this report, you’ll explore: Technical driving forces that are rapidly changing the way organizations develop and deliver software today How key concepts underpinning the Cloud Foundry platform leverage each of the technical forces discussed How cloud-native platforms remove the requirement to perform undifferentiated heavy lifting, such as provisioning VMs, middleware, and databases Why cloud-native platforms enable fast feedback loops as you move from agile development to agile deployment Recommended changes and practical considerations for organizations that want to build cloud-native applications COMPUTERS,Computer Architecture

Computers as Components Computers as Components: Principles of Embedded Computing System Design, Fourth Edition, continues to focus on foundational content in embedded systems technology and design while introducing new content on security and safety, the design of Internet-of-Things devices and systems, and wireless communications standards like Bluetooth® and ZigBee®. Uses real processors to demonstrate both technology and techniques Shows readers how to apply principles to actual design practice Stresses necessary fundamentals that can be applied to evolving technologies and helps readers gain facility to design large, complex embedded systems Covers the design of Internet-of-Things (IoT) devices and systems, including applications, devices, and communication systems and databases Introduces concepts of safety and security in embedded systems Includes new chapter on Automotive and Aerospace Systems Describes wireless communication standards such as Bluetooth® and ZigBee® COMPUTERS,Computer Architecture

Computer Architecture Not only does almost everyone in the civilized world use a personal computer, smartphone, and/or tablet on a daily basis to communicate with others and access information, but virtually every other modern appliance, vehicle, or other device has one or more computers embedded inside it. One cannot purchase a current-model automobile, for example, without several computers on board to do everything from monitoring exhaust emissions, to operating the anti-lock brakes, to telling the transmission when to shift, and so on. Appliances such as clothes washers and dryers, microwave ovens, refrigerators, etc. are almost all digitally controlled. Gaming consoles like Xbox, PlayStation, and Wii are powerful computer systems with enhanced capabilities for user interaction. Computers are everywhere, even when we don’t see them as such, and it is more important than ever for students who will soon enter the workforce to understand how they work. This book is completely updated and revised for a one-semester upper level undergraduate course in Computer Architecture, and suitable for use in an undergraduate CS, EE, or CE curriculum at the junior or senior level. Students should have had a course(s) covering introductory topics in digital logic and computer organization. While this is not a text for a programming course, the reader should be familiar with computer programming concepts in at least one language such as C, C++, or Java. Previous courses in operating systems, assembly language, and/or systems programming would be helpful, but are not essential. COMPUTERS,Computer Architecture

Cloud Foundry How can Cloud Foundry help you develop and deploy business-critical applications and tasks with velocity? This practical guide demonstrates how this open source, cloud-native application platform not only significantly reduces the develop-to-deploy cycle time, but also raises the value line for application operators by changing the way applications and supporting services are deployed and run. Learn how Cloud Foundry can help you improve your product velocity by handling many of essential tasks required to run applications in production. Author Duncan Winn shows DevOps and operations teams how to configure and run Cloud Foundry at scale. You’ll examine Cloud Foundry’s technical concepts—including how various platform components interrelate—and learn how to choose your underlying infrastructure, define the networking architecture, and establish resiliency requirements. This book covers: Cloud-native concepts that make the app build, test, deploy, and scale faster How to deploy Cloud Foundry and the BOSH release engineering toolchain Concepts and components of Cloud Foundry’s runtime architecture Cloud Foundry’s routing mechanisms and capabilities The platform’s approach to container tooling and orchestration BOSH concepts, deployments, components, and commands Basic tools and techniques for debugging the platform Recent and soon-to-emerge features of Cloud Foundry COMPUTERS,Computer Architecture

WSO2 Developer's Guide WSO2 Made Simple – dive deep into the core concepts of WSO2 to overcome the challenges faced while using the Enterprise Integrator About This Book Design, create, and publish services in the WSO2 technology Integrate the WSO2 Enterprise Integrator with other components and servers Log and test deployed services Who This Book Is For If you are a Java solutions architect or developer and are keen to understand how to build enterprise applications with WSO2, this book is for you. No prior knowledge of WSO2 is expected. What You Will Learn Configure WSO2 Enterprise Integrator server in a production environment Create SOAP Proxies and REST APIs Interact with WSO2 Message Broker Write services using the new language: Ballerina Schedule automatic tasks for the services you create Manage log messages depending on the log level of the system Integrate with social networks such as Twitter, Facebook, Instagram, and Yammer Test SOAP Services using the Tryit feature and SoapUI tool Work with Quality of Services In Detail WSO2 Enterprise Integrator brings together the most powerful servers provided by the WSO2 company for your SOA infrastructure. As an Enterprise Service Bus (ESB), WSO2 Enterprise Integrator provides greater flexibility and agility to meet growing enterprise demands, whereas, as a Data Services Server (DSS), it provides an easy-to-use platform for integrating data stores, creating composite views across different data sources, and hosting data services. Using real-world scenarios, this book helps you build a solid foundation in developing enterprise applications with powerful data integration capabilities using the WSO2 servers. The book gets you started by brushing up your knowledge about SOA architecture and how it can be implemented through WSO2. It will help build your expertise with the core concepts of ESB such as building proxies, sequences, endpoints, and how to work with these in WSO2. Going further, you will also get well-acquainted with DSS data service concepts such as configuring data services, tasks, events, testing, and much more. The book will also cover API management techniques. Along with ESB and DSS, you will also learn about business process servers, the rules server and other components that together provide the control and robustness your enterprise applications will need. With practical use cases, the book covers typical daily scenarios you will come across while using these servers to give you hands-on experience. Style and approach The book is a complete guide and helps you get the right start—from understanding SOA architectures to getting valuable experience with two important integration servers such as ESB and DSS. It will include some real-world practical scenarios to help you master the best practices followed right across the industry and overcome the challenges you're likely to face on a daily basis. COMPUTERS,Computer Architecture

High Performance Computing High Performance Computing: Modern Systems and Practices is a fully comprehensive and easily accessible treatment of high performance computing, covering fundamental concepts and essential knowledge while also providing key skills training. With this book, domain scientists will learn how to use supercomputers as a key tool in their quest for new knowledge. In addition, practicing engineers will discover how supercomputers can employ HPC systems and methods to the design and simulation of innovative products, and students will begin their careers with an understanding of possible directions for future research and development in HPC. Those who maintain and administer commodity clusters will find this textbook provides essential coverage of not only what HPC systems do, but how they are used. Covers enabling technologies, system architectures and operating systems, parallel programming languages and algorithms, scientific visualization, correctness and performance debugging tools and methods, GPU accelerators and big data problems Provides numerous examples that explore the basics of supercomputing, while also providing practical training in the real use of high-end computers Helps users with informative and practical examples that build knowledge and skills through incremental steps Features sidebars of background and context to present a live history and culture of this unique field Includes online resources, such as recorded lectures from the authors’ HPC courses COMPUTERS,Computer Architecture

Managing Kubernetes While Kubernetes has greatly simplified the task of deploying containerized applications, managing this orchestration framework on a daily basis can still be a complex undertaking. With this practical book, site reliability and DevOps engineers will learn how to build, operate, manage, and upgrade a Kubernetes cluster—whether it resides on cloud infrastructure or on-premises. Brendan Burns, cofounder of Kubernetes, and Craig Tracey, staff field engineer at Heptio, dissect how Kubernetes works internally and demonstrate ways to maintain, adjust, and improve the cluster to suit your particular use case. You’ll learn how to make architectural choices for designing a cluster, managing access control, monitoring and alerting, and upgrading Kubernetes. Dive in and discover how to take full advantage of this orchestration framework’s capabilities. Learn how your cluster operates, how developers use it to deploy applications, and how Kubernetes can facilitate a developer’s job Adjust, secure, and tune your cluster by understanding Kubernetes APIs and configuration options Detect cluster-level problems early and learn the steps necessary to respond and recover quickly Determine how and when to add libraries, tools, and platforms that build on, extend, or otherwise improve a Kubernetes cluster COMPUTERS,Computer Architecture

Programming Kubernetes If you’re looking to develop native applications in Kubernetes, this is your guide. Developers and AppOps administrators will learn how to build Kubernetes-native applications that interact directly with the API server to query or update the state of resources. AWS developer advocate Michael Hausenblas and Red Hat principal software engineer Stefan Schimanski explain the characteristics of these apps and show you how to program Kubernetes to build them. You’ll explore the basic building blocks of Kubernetes, including the client-go API library and custom resources. All you need to get started is a rudimentary understanding of development and system administration tools and practices, such as package management, the Go programming language, and Git. Walk through Kubernetes API basics and dive into the server’s inner structure Explore Kubernetes’s programming interface in Go, including Kubernetes API objects Learn about custom resources—the central extension tools used in the Kubernetes ecosystem Use tags to control Kubernetes code generators for custom resources Write custom controllers and operators and make them production ready Extend the Kubernetes API surface by implementing a custom API server COMPUTERS,Computer Architecture

Semantic Software Design With this practical book, architects, CTOs, and CIOs will learn a set of patterns for the practice of architecture, including analysis, documentation, and communication. Author Eben Hewitt shows you how to create holistic and thoughtful technology plans, communicate them clearly, lead people toward the vision, and become a great architect or Chief Architect. This book covers each key aspect of architecture comprehensively, including how to incorporate business architecture, information architecture, data architecture, application (software) architecture together to have the best chance for the system’s success. Get a practical set of proven architecture practices focused on shipping great products using architecture Learn how architecture works effectively with development teams, management, and product management teams through the value chain Find updated special coverage on machine learning architecture Get usable templates to start incorporating into your teams immediately Incorporate business architecture, information architecture, data architecture, and application (software) architecture together COMPUTERS,Computer Architecture

Software Engineering at Google Today, software engineers need to know not only how to program effectively but also how to develop proper engineering practices to make their codebase sustainable and healthy. This book emphasizes this difference between programming and software engineering. How can software engineers manage a living codebase that evolves and responds to changing requirements and demands over the length of its life? Based on their experience at Google, software engineers Titus Winters and Hyrum Wright, along with technical writer Tom Manshreck, present a candid and insightful look at how some of the world’s leading practitioners construct and maintain software. This book covers Google’s unique engineering culture, processes, and tools and how these aspects contribute to the effectiveness of an engineering organization. You’ll explore three fundamental principles that software organizations should keep in mind when designing, architecting, writing, and maintaining code: How time affects the sustainability of software and how to make your code resilient over time How scale affects the viability of software practices within an engineering organization What trade-offs a typical engineer needs to make when evaluating design and development decisions COMPUTERS,Computer Architecture

The Software Architect Elevator As the digital economy changes the rules of the game for enterprises, the role of software and IT architects is also transforming. Rather than focus on technical decisions alone, architects and senior technologists need to combine organizational and technical knowledge to effect change in their company’s structure and processes. To accomplish that, they need to connect the IT engine room to the penthouse, where the business strategy is defined. In this guide, author Gregor Hohpe shares real-world advice and hard-learned lessons from actual IT transformations. His anecdotes help architects, senior developers, and other IT professionals prepare for a more complex but rewarding role in the enterprise. This book is ideal for: Software architects and senior developers looking to shape the company’s technology direction or assist in an organizational transformation Enterprise architects and senior technologists searching for practical advice on how to navigate technical and organizational topics CTOs and senior technical architects who are devising an IT strategy that impacts the way the organization works IT managers who want to learn what’s worked and what hasn’t in large-scale transformation COMPUTERS,Computer Architecture

Mastering Kubernetes Go beyond simply learning Kubernetes fundamentals and its deployment, and explore more advanced concepts, including serverless computing and service meshes with the latest updates Key Features Master Kubernetes architecture and design to build and deploy secure distributed applications Learn advanced concepts like autoscaling, cluster federation, serverless computing, and service mesh integration for observability Explore Kubernetes 1.18 features and its rich ecosystem of tools like Kubectl, Knative, and Helm Book Description The third edition of Mastering Kubernetes is updated with the latest tools and code enabling you to learn Kubernetes 1.18's latest features. This book primarily concentrates on diving deeply into complex concepts and Kubernetes best practices to help you master the skills of designing and deploying large clusters on various cloud platforms. The book trains you to run complex stateful microservices on Kubernetes including advanced features such as horizontal pod autoscaling, rolling updates, resource quotas, and persistent storage backend. With the two new chapters, you will gain expertise in serverless computing and utilizing service meshes. As you proceed through the chapters, you will explore different options for network configuration and learn to set up, operate, and troubleshoot Kubernetes networking plugins through real-world use cases. Furthermore, you will understand the mechanisms of custom resource development and its utilization in automation and maintenance workflows. By the end of this Kubernetes book, you will graduate from an intermediate to advanced Kubernetes professional. What you will learn Master the fundamentals of Kubernetes architecture and design Build and run stateful applications and complex microservices on Kubernetes Use tools like Kubectl, secrets, and Helm to manage resources and storage Master Kubernetes Networking with load balancing options like Ingress Achieve high-availability Kubernetes clusters Improve Kubernetes observability with tools like Prometheus, Grafana, and Jaeger Extend Kubernetes working with Kubernetes API, plugins, and webhooks Who this book is for If you are a system administrator or a cloud developer with working knowledge of Kubernetes and are keen to master its advanced features, along with learning everything from building microservices to utilizing service meshes, Mastering Kubernetes is for you. Basic familiarity with networking concepts will be helpful. COMPUTERS,Computer Architecture

Computers, Software Engineering, and Digital Devices In two editions spanning more than a decade, The Electrical Engineering Handbook stands as the definitive reference to the multidisciplinary field of electrical engineering. Our knowledge continues to grow, and so does the Handbook. For the third edition, it has expanded into a set of six books carefully focused on a specialized area or field of study. Each book represents a concise yet definitive collection of key concepts, models, and equations in its respective domain, thoughtfully gathered for convenient access. Computers, Software Engineering, and Digital Devices examines digital and logical devices, displays, testing, software, and computers, presenting the fundamental concepts needed to ensure a thorough understanding of each field. It treats the emerging fields of programmable logic, hardware description languages, and parallel computing in detail. Each article includes defining terms, references, and sources of further information. Encompassing the work of the world's foremost experts in their respective specialties, Computers, Software Engineering, and Digital Devices features the latest developments, the broadest scope of coverage, and new material on secure electronic commerce and parallel computing. COMPUTERS,Computer Engineering

Semiconductors Because of the continuous evolution of integrated circuit manufacturing (ICM) and design for manufacturability (DfM), most books on the subject are obsolete before they even go to press. That’s why the field requires a reference that takes the focus off of numbers and concentrates more on larger economic concepts than on technical details. Semiconductors: Integrated Circuit Design for Manufacturability covers the gradual evolution of integrated circuit design (ICD) as a basis to propose strategies for improving return-on-investment (ROI) for ICD in manufacturing. Where most books put the spotlight on detailed engineering enhancements and their implications for device functionality, in contrast, this one offers, among other things, crucial, valuable historical background and roadmapping, all illustrated with examples. Presents actual test cases that illustrate product challenges, examine possible solution strategies, and demonstrate how to select and implement the right one This book shows that DfM is a powerful generic engineering concept with potential extending beyond its usual application in automated layout enhancements centered on proximity correction and pattern density. This material explores the concept of ICD for production by breaking down its major steps: product definition, design, layout, and manufacturing. Averting extended discussion of technology, techniques, or specific device dimensions, the author also avoids the clumsy chapter architecture that can hinder other books on this subject. The result is an extremely functional, systematic presentation that simplifies existing approaches to DfM, outlining a clear set of criteria to help readers assess reliability, functionality, and yield. With careful consideration of the economic and technical trade-offs involved in ICD for manufacturing, this reference addresses techniques for physical, electrical, and logical design, keeping coverage fresh and concise for the designers, manufacturers, and researchers defining product architecture and research programs. COMPUTERS,Computer Engineering

Real-Time Embedded Systems From the Foreword: "…the presentation of real-time scheduling is probably the best in terms of clarity I have ever read in the professional literature. Easy to understand, which is important for busy professionals keen to acquire (or refresh) new knowledge without being bogged down in a convoluted narrative and an excessive detail overload. The authors managed to largely avoid theoretical-only presentation of the subject, which frequently affects books on operating systems. … an indispensable [resource] to gain a thorough understanding of the real-time systems from the operating systems perspective, and to stay up to date with the recent trends and actual developments of the open-source real-time operating systems." —Richard Zurawski, ISA Group, San Francisco, California, USA Real-time embedded systems are integral to the global technological and social space, but references still rarely offer professionals the sufficient mix of theory and practical examples required to meet intensive economic, safety, and other demands on system development. Similarly, instructors have lacked a resource to help students fully understand the field. The information was out there, though often at the abstract level, fragmented and scattered throughout literature from different engineering disciplines and computing sciences. Accounting for readers’ varying practical needs and experience levels, Real Time Embedded Systems: Open-Source Operating Systems Perspective offers a holistic overview from the operating-systems perspective. It provides a long-awaited reference on real-time operating systems and their almost boundless application potential in the embedded system domain. Balancing the already abundant coverage of operating systems with the largely ignored real-time aspects, or "physicality," the authors analyze several realistic case studies to introduce vital theoretical material. They also discuss popular open-source operating systems—Linux and FreRTOS, in particular—to help embedded-system designers identify the benefits and weaknesses in deciding whether or not to adopt more traditional, less powerful, techniques for a project. COMPUTERS,Computer Engineering

Simulation of Semiconductor Devices and Processes The "Fifth International Conference on Simulation of Semiconductor Devices and Processes" (SISDEP 93) continues a series of conferences which was initiated in 1984 by K. Board and D. R. J. Owen at the University College of Wales, Swansea, where it took place a second time in 1986. Its organization was succeeded by G. Baccarani and M. Rudan at the University of Bologna in 1988, and W. Fichtner and D. Aemmer at the Federal Institute of Technology in Zurich in 1991. This year the conference is held at the Technical University of Vienna, Austria, September 7 - 9, 1993. This conference shall provide an international forum for the presentation of out standing research and development results in the area of numerical process and de vice simulation. The miniaturization of today's semiconductor devices, the usage of new materials and advanced process steps in the development of new semiconduc tor technologies suggests the design of new computer programs. This trend towards more complex structures and increasingly sophisticated processes demands advanced simulators, such as fully three-dimensional tools for almost arbitrarily complicated geometries. With the increasing need for better models and improved understand ing of physical effects, the Conference on Simulation of Semiconductor Devices and Processes brings together the simulation community and the process- and device en gineers who need reliable numerical simulation tools for characterization, prediction, and development. COMPUTERS,Computer Engineering

Computer Organization, Design, and Architecture, Fifth Edition Suitable for a one- or two-semester undergraduate or beginning graduate course in computer science and computer engineering, Computer Organization, Design, and Architecture, Fifth Edition presents the operating principles, capabilities, and limitations of digital computers to enable the development of complex yet efficient systems. With 11 new sect COMPUTERS,Computer Engineering

Principles of Synthetic Aperture Radar Imaging Principles of Synthetic Aperture Radar Imaging: A System Simulation Approach demonstrates the use of image simulation for SAR. It covers the various applications of SAR (including feature extraction, target classification, and change detection), provides a complete understanding of SAR principles, and illustrates the complete chain of a SAR operati COMPUTERS,Computer Engineering

Arduino Rather than yet another project-based workbook, Arduino: A Technical Reference is a reference and handbook that thoroughly describes the electrical and performance aspects of an Arduino board and its software. This book brings together in one place all the information you need to get something done with Arduino. It will save you from endless web searches and digging through translations of datasheets or notes in project-based texts to find the information that corresponds to your own particular setup and question. Reference features include pinout diagrams, a discussion of the AVR microcontrollers used with Arduino boards, a look under the hood at the firmware and run-time libraries that make the Arduino unique, and extensive coverage of the various shields and add-on sensors that can be used with an Arduino. One chapter is devoted to creating a new shield from scratch. The book wraps up with detailed descriptions of three different projects: a programmable signal generator, a "smart" thermostat, and a programmable launch sequencer for model rockets. Each project highlights one or more topics that can be applied to other applications. COMPUTERS,Computer Engineering

Cryptography Cryptography has proven to be one of the most contentious areas in modern society. For some, it protects the rights of individuals to privacy and security. For others, it puts up barriers against the protection of our society. This book aims to develop a deep understanding of cryptography and provide understanding of how privacy, identity provision, and integrity can be enhanced with the usage of encryption. The book has many novel features including: full provision of web-based material on almost every topic covered; provision of additional on-line material such as videos, source code, and labs; and coverage of emerging areas such as Blockchain, Light-weight Cryptography, and Zero-knowledge Proofs. Key areas covered include: Fundamentals of Encryption, Public Key Encryption, Symmetric Key Encryption, Hashing Methods, Key Exchange Methods, Digital Certificates and Authentication, Tunneling, Crypto Cracking, Light-weight Cryptography, Blockchain, and Zero-knowledge Proofs. This book provides extensive support through the associated website of: http://asecuritysite.com/encryption COMPUTERS,Computer Engineering

Digital Image Interpolation in Matlab This book provides a comprehensive study in digital image interpolation with theoretical, analytical and Matlab® implementation. It includes all historically and practically important interpolation algorithms, accompanied with Matlab® source code on a website, which will assist readers to learn and understand the implementation details of each presented interpolation algorithm. Furthermore, sections in fundamental signal processing theories and image quality models are also included. The authors intend for the book to help readers develop a thorough consideration of the design of image interpolation algorithms and applications for their future research in the field of digital image processing. Introduces a wide range of traditional and advanced image interpolation methods concisely and provides thorough treatment of theoretical foundations Discusses in detail the assumptions and limitations of presented algorithms Investigates a variety of interpolation and implementation methods including transform domain, edge-directed, wavelet and scale-space, and fractal based methods Features simulation results for comparative analysis, summaries and computational and analytical exercises at the end of each chapter Digital Image Interpolation in Matlab® is an excellent guide for researchers and engineers working in digital imaging and digital video technologies. Graduate students studying digital image processing will also benefit from this practical reference text. COMPUTERS,Computer Engineering

Embedded Systems Embedded Systems: A Contemporary Design Tool, Second Edition Embedded systems are one of the foundational elements of today’s evolving and growing computer technology. From operating our cars, managing our smart phones, cleaning our homes, or cooking our meals, the special computers we call embedded systems are quietly and unobtrusively making our lives easier, safer, and more connected. While working in increasingly challenging environments, embedded systems give us the ability to put increasing amounts of capability into ever-smaller and more powerful devices. Embedded Systems: A Contemporary Design Tool, Second Edition introduces you to the theoretical hardware and software foundations of these systems and expands into the areas of signal integrity, system security, low power, and hardware-software co-design. The text builds upon earlier material to show you how to apply reliable, robust solutions to a wide range of applications operating in today’s often challenging environments. Taking the user’s problem and needs as your starting point, you will explore each of the key theoretical and practical issues to consider when designing an application in today’s world. Author James Peckol walks you through the formal hardware and software development process covering: Breaking the problem down into major functional blocks; Planning the digital and software architecture of the system; Utilizing the hardware and software co-design process; Designing the physical world interface to external analog and digital signals; Addressing security issues as an integral part of the design process; Managing signal integrity problems and reducing power demands in contemporary systems; Debugging and testing throughout the design and development cycle; Improving performance. Stressing the importance of security, safety, and reliability in the design and development of embedded systems and providing a balanced treatment of both the hardware and the software aspects, Embedded Systems: A Contemporary Design Tool, Second Edition gives you the tools for creating embedded designs that solve contemporary real-world challenges. COMPUTERS,Computer Engineering

ARM-Based Microcontroller Multitasking Projects Most microcontroller-based applications nowadays are large, complex, and may require several tasks to share the MCU in multitasking applications. Most modern high-speed microcontrollers support multitasking kernels with sophisticated scheduling algorithms so that many complex tasks can be executed on a priority basis. ARM-based Microcontroller Multitasking Projects: Using the FreeRTOS Multitasking Kernel explains how to multitask ARM Cortex microcontrollers using the FreeRTOS multitasking kernel. The book describes in detail the features of multitasking operating systems such as scheduling, priorities, mailboxes, event flags, semaphores etc. before going onto present the highly popular FreeRTOS multitasking kernel. Practical working real-time projects using the highly popular Clicker 2 for STM32 development board (which can easily be transferred to other boards) together with FreeRTOS are an essential feature of this book. Projects include: LEDs flashing at different rates; Refreshing of 7-segment LEDs; Mobile robot where different sensors are controlled by different tasks; Multiple servo motors being controlled independently; Multitasking IoT project; Temperature controller with independent keyboard entry; Random number generator with 3 tasks: live, generator, display; home alarm system; car park management system, and many more. Explains the basic concepts of multitasking Demonstrates how to create small multitasking programs Explains how to install and use the FreeRTOS on an ARM Cortex processor Presents structured real-world projects that enables the reader to create their own COMPUTERS,Computer Engineering

Metaheuristic Computation with MATLAB® Metaheuristic algorithms are considered as generic optimization tools that can solve very complex problems characterized by having very large search spaces. Metaheuristic methods reduce the effective size of the search space through the use of effective search strategies. Book Features: Provides a unified view of the most popular metaheuristic methods currently in use Includes the necessary concepts to enable readers to implement and modify already known metaheuristic methods to solve problems Covers design aspects and implementation in MATLAB® Contains numerous examples of problems and solutions that demonstrate the power of these methods of optimization The material has been written from a teaching perspective and, for this reason, this book is primarily intended for undergraduate and postgraduate students of artificial intelligence, metaheuristic methods, and/or evolutionary computation. The objective is to bridge the gap between metaheuristic techniques and complex optimization problems that profit from the convenient properties of metaheuristic approaches. Therefore, engineer practitioners who are not familiar with metaheuristic computation will appreciate that the techniques discussed are beyond simple theoretical tools, since they have been adapted to solve significant problems that commonly arise in such areas. COMPUTERS,Computer Engineering

Computing Fundamentals The absolute beginner's guide to learning basic computer skills Computing Fundamentals, Introduction to Computers gets you up to speed on basic computing skills, showing you everything you need to know to conquer entry-level computing courses. Written by a Microsoft Office Master Instructor, this useful guide walks you step-by-step through the most important concepts and skills you need to be proficient on the computer, using nontechnical, easy-to-understand language. You'll start at the very beginning, getting acquainted with the actual, physical machine, then progress through the most common software at your own pace. You'll learn how to navigate Windows 8.1, how to access and get around on the Internet, and how to stay connected with email. Clear instruction guides you through Microsoft Office 2013, helping you create documents in Word, spreadsheets in Excel, and presentations in PowerPoint. You'll even learn how to keep your information secure with special guidance on security and privacy. Maybe you're preparing for a compulsory computing course, brushing up for a new job, or just curious about how a computer can make your life easier. If you're an absolute beginner, this is your complete guide to learning the essential skills you need: Understand the basics of how your computer works Learn your way around Windows 8.1 Create documents, spreadsheets, and presentations Send email, surf the Web, and keep your data secure With clear explanations and step-by-step instruction, Computing Fundamentals, Introduction to Computers will have you up and running in no time. COMPUTERS,Computer Literacy

Microprocessors & their Operating Systems Provides a comprehensive guide to all of the major microprocessor families (8, 16 and 32 bit). The hardware aspects and software implications are described, giving the reader an overall understanding of microcomputer architectures. The internal processor operation of each microprocessor device is presented, followed by descriptions of the instruction set and applications for the device. Software considerations are expanded with descriptions and examples of the main high level programming languages (BASIC, Pascal and C). The book also includes detailed descriptions of the three main operating systems (CP/M, DOS and UNIX) common to the most modern personal computers. COMPUTERS,Computer Literacy

Theory of Computation This textbook is uniquely written with dual purpose. It cover cores material in the foundations of computing for graduate students in computer science and also provides an introduction to some more advanced topics for those intending further study in the area. This innovative text focuses primarily on computational complexity theory: the classification of computational problems in terms of their inherent complexity. The book contains an invaluable collection of lectures for first-year graduates on the theory of computation. Topics and features include more than 40 lectures for first year graduate students, and a dozen homework sets and exercises. COMPUTERS,Computer Science

A Computer Scientist's Guide to Cell Biology This practical guide provides a succinct treatment of the general concepts of cell biology, furnishing the computer scientist with the tools necessary to read and understand current literature in the field. The book explores three different facets of biology: biological systems, experimental methods, and language and nomenclature. After a brief introduction to cell biology, the text focuses on the principles behind the most-widely used experimental procedures and mechanisms, relating them to well-understood concepts in computer science. The presentation of the material has been prepared for the reader’s quick grasp of the topic: comments on nomenclature and background notes can be ascertained at a glance, and essential vocabulary is boldfaced throughout the text for easy identification. Computer science researchers, professionals and computer science students will find this an incomparable resource and an excellent starting point for a more comprehensive examination of cell biology. "This concise book is an excellent introduction for computer scientists to the exciting revolution under way in molecular biology. It provides lucid, high-level descriptions of the fundamental molecular mechanisms of life, and discusses the computational principles involved. I wish this little gem was available when I was ‘learning the ropes’– it would have been my first choice of reading material." --Roni Rosenfeld, Carnegie Mellon University COMPUTERS,Computer Science

Computer Science Made Simple Be smarter than your computer If you don't understand computers, you can quickly be left behind in today's fast-paced, machine-dependent society. Computer Science Made Simple offers a straightforward resource for technology novices and advanced techies alike. It clarifies all you need to know, from the basic components of today’s computers to using advanced applications. The perfect primer, it explains how it all comes together to make computers work. Topics covered include: * hardware* software* programming* networks * the internet* computer graphics* advanced computer concepts* computers in society Look for these Made Simple titles: Accounting Made SimpleArithmetic Made SimpleAstronomy Made SimpleBiology Made SimpleBookkeeping Made SimpleBusiness Letters Made SimpleChemistry Made SimpleEarth Science Made SimpleEnglish Made SimpleFrench Made SimpleGerman Made SimpleInglés Hecho Fácil Investing Made SimpleItalian Made SimpleKeyboarding Made SimpleLatin Made SimpleLearning English Made SimpleMathematics Made SimpleThe Perfect Business Plan Made SimplePhilosophy Made SimplePhysics Made SimplePsychology Made SimpleSign Language Made SimpleSpanish Made SimpleSpelling Made SimpleStatistics Made SimpleYour Small Business Made Simple www.broadway.com COMPUTERS,Computer Science

Computational Geometry Computational geometry emerged from the ?eld of algorithms design and analysis in the late 1970s. It has grown into a recognized discipline with its own journals, conferences, and a large community of active researchers. The success of the ?eld as a research discipline can on the one hand be explained from the beauty of the problems studied and the solutions obtained, and, on the other hand, by the many application domains—computer graphics, geographic information systems (GIS), robotics, and others—in which geometric algorithms play a fundamental role. For many geometric problems the early algorithmic solutions were either slow or dif?cult to understand and implement. In recent years a number of new algorithmic techniques have been developed that improved and simpli?ed many of the previous approaches. In this textbook we have tried to make these modern algorithmic solutions accessible to a large audience. The book has been written as a textbook for a course in computational geometry, but it can also be used for self-study. COMPUTERS,Computer Science

Fundamentals of the Theory of Computation This innovative textbook presents the key foundational concepts for a one-semester undergraduate course in the theory of computation. It offers the most accessible and motivational course material available for undergraduate computer theory classes. Directed at undergraduates who may have difficulty understanding the relevance of the course to their future careers, the text helps make them more comfortable with the techniques required for the deeper study of computer science. The text motivates students by clarifying complex theory with many examples, exercises and detailed proofs. * This book is shorter and more accessible than the books now being used in core computer theory courses. * Theory of computing is a standard, required course in all computer science departments. COMPUTERS,Computer Science

Fuzzy Sets, Fuzzy Logic, Applications Fuzzy sets and fuzzy logic are powerful mathematical tools for modeling and controlling uncertain systems in industry, humanity, and nature; they are facilitators for approximate reasoning in decision making in the absence of complete and precise information. Their role is significant when applied to complex phenomena not easily described by traditional mathematics.The unique feature of the book is twofold: 1) It is the first introductory course (with examples and exercises) which brings in a systematic way fuzzy sets and fuzzy logic into the educational university and college system. 2) It is designed to serve as a basic text for introducing engineers and scientists from various fields to the theory of fuzzy sets and fuzzy logic, thus enabling them to initiate projects and make applications. COMPUTERS,Computer Science

Fuzzy Logic For Beginners There are many uncertainties in the real world. Fuzzy theory treats a kind of uncertainty called fuzziness, where it shows that the boundary of yes or no is ambiguous and appears in the meaning of words or is included in the subjunctives or recognition of human beings. Fuzzy theory is essential and is applicable to many systems — from consumer products like washing machines or refrigerators to big systems like trains or subways. Recently, fuzzy theory has been a strong tool for combining new theories (called soft computing) such as genetic algorithms or neural networks to get knowledge from real data.This introductory book enables the reader to understand easily what fuzziness is and how one can apply fuzzy theory to real problems — which explains why it was a best-seller in Japan. COMPUTERS,Computer Science

Intelligent Unmanned Ground Vehicles Intelligent Unmanned Ground Vehicles describes the technology developed and the results obtained by the Carnegie Mellon Robotics Institute in the course of the DARPA Unmanned Ground Vehicle (UGV) project. The goal of this work was to equip off-road vehicles with computer-controlled, unmanned driving capabilities. The book describes contributions in the area of mobility for UGVs including: tools for assembling complex autonomous mobility systems; on-road and off-road navigation; sensing techniques; and route planning algorithms. In addition to basic mobility technology, the book covers a number of integrated systems demonstrated in the field in realistic scenarios. The approaches presented in this book can be applied to a wide range of mobile robotics applications, from automated passenger cars to planetary exploration, and construction and agricultural machines. Intelligent Unmanned Ground Vehicles shows the progress that was achieved during this program, from brittle specially-built robots operating under highly constrained conditions, to groups of modified commercial vehicles operating in tough environments. One measure of progress is how much of this technology is being used in other applications. For example, much of the work in road-following, architectures and obstacle detection has been the basis for the Automated Highway Systems (AHS) prototypes currently under development. AHS will lead to commercial prototypes within a few years. The cross-country technology is also being used in the development of planetary rovers with a projected launch date within a few years. The architectural tools built under this program have been used in numerous applications, from an automated harvester to an autonomous excavator. The results reported in this work provide tools for further research development leading to practical, reliable and economical mobile robots. COMPUTERS,Computer Science

Robot Colonies Robots in groups or colonies can exhibit an enormous variety and richness of behaviors which cannot be observed with singly autonomous systems. Of course, this is analogous to the amazing variety of group animal behaviors which can be observed in nature. In recent years more and more investigators have started to study these behaviors. The studies range from classifications and taxonomies of behaviors, to development of architectures which cause such group activities as flocking or swarming, and from emphasis on the role of intelligent agents in such groups to studies of learning and obstacle avoidance. There used to be a time when many robotics researchers would question those who were interested in working with teams of robots: `Why are you worried about robotic teams when it's hard enough to just get one to work?'. This issue responds to that question. Robot Colonies provides a new approach to task problem-solving that is similar in many ways to distributed computing. Multiagent robotic teams offer the possibility of spatially distributed parallel and concurrent perception and action. A paradigm shift results when using multiple robots, providing a different perspective on how to carry out complex tasks. New issues such as interagent communications, spatial task distribution, heterogeneous or homogeneous societies, and interference management are now central to achieving coordinated and productive activity within a colony. Fortunately mobile robot hardware has evolved sufficiently in terms of both cost and robustness to enable these issues to be studied on actual robots and not merely in simulation. Robot Colonies presents a sampling of the research in this field. While capturing a reasonable representation of the most important work within this area, its objective is not to be a comprehensive survey, but rather to stimulate new research by exposing readers to the principles of robot group behaviors, architectures and theories. Robot Colonies is an edited volume of peer-reviewed original research comprising eight invited contributions by leading researchers. This research work has also been published as a special issue of Autonomous Robots (Volume 4, Number 1). COMPUTERS,Computer Science

Fault-Tolerant Parallel Computation Fault-Tolerant Parallel Computation presents recent advances in algorithmic ways of introducing fault-tolerance in multiprocessors under the constraint of preserving efficiency. The difficulty associated with combining fault-tolerance and efficiency is that the two have conflicting means: fault-tolerance is achieved by introducing redundancy, while efficiency is achieved by removing redundancy. This monograph demonstrates how in certain models of parallel computation it is possible to combine efficiency and fault-tolerance and shows how it is possible to develop efficient algorithms without concern for fault-tolerance, and then correctly and efficiently execute these algorithms on parallel machines whose processors are subject to arbitrary dynamic fail-stop errors. The efficient algorithmic approaches to multiprocessor fault-tolerance presented in this monograph make a contribution towards bridging the gap between the abstract models of parallel computation and realizable parallel architectures. Fault-Tolerant Parallel Computation presents the state of the art in algorithmic approaches to fault-tolerance in efficient parallel algorithms. The monograph synthesizes work that was presented in recent symposia and published in refereed journals by the authors and other leading researchers. This is the first text that takes the reader on the grand tour of this new field summarizing major results and identifying hard open problems. This monograph will be of interest to academic and industrial researchers and graduate students working in the areas of fault-tolerance, algorithms and parallel computation and may also be used as a text in a graduate course on parallel algorithmic techniques and fault-tolerance. COMPUTERS,Computer Science

Data Structures for Computational Statistics Since the beginning of the seventies computer hardware is available to use programmable computers for various tasks. During the nineties the hardware has developed from the big main frames to personal workstations. Nowadays it is not only the hardware which is much more powerful, but workstations can do much more work than a main frame, compared to the seventies. In parallel we find a specialization in the software. Languages like COBOL for business orientated programming or Fortran for scientific computing only marked the beginning. The introduction of personal computers in the eighties gave new impulses for even further development, already at the beginning of the seven ties some special languages like SAS or SPSS were available for statisticians. Now that personal computers have become very popular the number of pro grams start to explode. Today we will find a wide variety of programs for almost any statistical purpose (Koch & Haag 1995). COMPUTERS,Computer Science

Human and Machine Perception Proceedings of the Second International Workshop held in Trabia, Italy, July 21-25, 1996 COMPUTERS,Computer Science

Models in System Design Models in System Design tracks the general trend in electronics in terms of size, complexity and difficulty of maintenance. System design is by nature combined with prototyping, mixed domain design, and verification, and it is no surprise that today's modeling and models are used in various levels of system design and verification. In order to deal with constraints induced by volume and complexity, new methods and techniques have been defined. Models in System Design provides an overview of the latest modeling techniques for use by system designers. The first part of the book considers system level design, discussing such issues as abstraction, performance and trade-offs. There is also a section on automating system design. The second part of the book deals with some of the newest aspects of embedded system design. These include co-verification and prototyping. Finally, the book includes a section on the use of the MCSE methodology for hardware/software co-design. Models in System Design will help designers and researchers to understand these latest techniques in system design and as such will be of interest to all involved in embedded system design. COMPUTERS,Computer Science

Elementary Functions The elementary functions (sine, cosine, exponentials, logarithms . . . ) are the most commonly used mathematical functions. Computing them quickly and accurately is a major goal in computer arithmetic. This book gives the theoretical background necessary to understand and/or build algorithms for computing these functions, presents algorithms (hardware-oriented as well as software-oriented), and discusses issues related to the accurate floating-point implementation of these functions. My purpose was not to give "cooking recipes" that allow to implement some given functions on some given floating-point systems, but to provide the reader with the knowledge that is necessary to build, or adapt algorithms to his or her computing environment. When writing this book, I have had in mind two different audiences: specialists, who will have to design floating-point systems (hardware or soft ware parts) orto do research on algorithms, and inquiring minds, who just want to know what kind of methods are used to compute the math functions in current computers or pocket calculators. Because of this, the book is in tended to be helpful as well for postgraduate and advanced undergraduate students in computer science or applied mathematics as for professionals engaged in the design of algorithms, programs or circuits that implement floating-point arithmetic, or simply for engineers or scientists who want to improve their culture in that domain. COMPUTERS,Computer Science

Marcus Contextual Grammars Marcus Contextual Grammars is the first monograph to present a class of grammars introduced about three decades ago, based on the fundamental linguistic phenomenon of strings-contexts interplay (selection). Most of the theoretical results obtained so far about the many variants of contextual grammars are presented with emphasis on classes of questions with relevance for applications in the study of natural language syntax: generative powers, descriptive and computational complexity, automata recognition, semilinearity, structure of the generated strings, ambiguity, regulated rewriting, etc. Constant comparison with families of languages in the Chomsky hierarchy is made. Connections with non-linguistic areas are established, such as molecular computing. Audience: Researchers and students in theoretical computer science (formal language theory and automata theory), computational linguistics, mathematical methods in linguistics, and linguists interested in formal models of syntax. COMPUTERS,Computer Science

Software Engineering and Environment Software Engineering and Environment examines the various aspects of software development, describing a number of software life cycle models. Twelve in-depth chapters discuss the different phases of a software life cycle, with an emphasis on the object-oriented paradigm. In addition to technical models, algorithms, and programming styles, the author also covers several managerial issues key to software project management. Featuring an abundance of helpful illustrations, this cogent work is an excellent resource for project managers, programmers, and other computer scientists involved in software production. COMPUTERS,Computer Science

Embedded System Applications Embedded systems encompass a variety of hardware and software components which perform specific functions in host systems, for example, satellites, washing machines, hand-held telephones and automobiles. Embedded systems have become increasingly digital with a non-digital periphery (analog power) and therefore, both hardware and software codesign are relevant. The vast majority of computers manufactured are used in such systems. They are called `embedded' to distinguish them from standard mainframes, workstations, and PCs. Athough the design of embedded systems has been used in industrial practice for decades, the systematic design of such systems has only recently gained increased attention. Advances in microelectronics have made possible applications that would have been impossible without an embedded system design. Embedded System Applications describes the latest techniques for embedded system design in a variety of applications. This also includes some of the latest software tools for embedded system design. Applications of embedded system design in avionics, satellites, radio astronomy, space and control systems are illustrated in separate chapters. Finally, the book contains chapters related to industrial best-practice in embedded system design. Embedded System Applications will be of interest to researchers and designers working in the design of embedded systems for industrial applications. COMPUTERS,Computer Science

Beyond Calculation In March 1997, the Association for Computing Machinery will celebrate the fiftieth anniversary of the electronic computer. To understand what an extraordinary fifty years the computer has had, you need only look around you--probably no farther than your desk. Computers are everywhere: in our cars, our homes, our supermarkets, at the phone company office, and at your local hospital. But as the contributors to this volume make clear, the scientific, social and economic impact of computers is only beginning to be felt. These sixteen invited essays on the future of computing take on a dazzling variety of topics, with opinions from such experts as Gordon Bell, Sherry Turkle, Edsger W. Dijkstra, Paul Abraham, Donald Norman, Franz Alt, and David Gelernter. This brilliantly eclectic collection, commissioned to celebrate a major milestone in an ongoing technological revolution, will fascinate anybody with an interest in computers and where they're taking us. COMPUTERS,Computer Science

Logic of Computation Proceedings of the NATO Advanced Study Institute on Logic of Computation,held in Marktoberdorf,Germany,July 25-Aug.6,1995 COMPUTERS,Computer Science

Underwater Robots All life came from sea but all robots were born on land. The vast majority of both industrial and mobile robots operate on land, since the technology to allow them to operate in and under the ocean has only become available in recent years. A number of complex issues due to the unstructured, hazardous undersea environment, makes it difficult to travel in the ocean while today's technologies allow humans to land on the moon and robots to travel to Mars . . Clearly, the obstacles to allowing robots to operate in a saline, aqueous, and pressurized environment are formidable. Mobile robots operating on land work under nearly constant atmospheric pressure; their legs (or wheels or tracks) can operate on a firm footing; their bearings are not subjected to moisture and corrosion; they can use simple visual sensing and be observed by their creators working in simple environments. In contrast, consider the environment where undersea robots must operate. The pressure they are subjected to can be enormous, thus requiring extremely rugged designs. The deep oceans range between 19,000 to 36,000 ft. At a mere 33-foot depth, the pressure will be twice the normal one atmosphere pressure of 29. 4 psi. The chemical environment of the sea is highly corrosive, thus requiring the use of special materials. Lubrication of moving parts in water is also difficult, and may require special sealed, waterproof joints. COMPUTERS,Computer Science

COMPSTAT COMPSTAT symposia have been held regularly since 1974 when they started in Vienna. This tradition has made COMPSTAT a major forum for the interplay of statistics and computer sciences with contributions from many well known scientists all over the world. The scientific programme of COMPSTAT '96 covers all aspects of this interplay, from user-experiences and evaluation of software through the development and implementation of new statistical ideas. All papers presented belong to one of the three following categories: - Statistical methods (preferable new ones) that require a substantial use of computing; - Computer environments, tools and software useful in statistics; - Applications of computational statistics in areas of substantial interest (environment, health, industry, biometrics, etc.). COMPUTERS,Computer Science

Performance Engineering of Computer and Telecommunications Systems This book is the proceedings of the Workshop on the Performance Engineering of Computer and Telecommunications Systems. The workshop Was held at Liverpool John Moores University, England on the 5th and 6th September 1995. The workshop follows a series organised by the British Computer Society (BCS) Special Interest Group on Performance Engineering. The workshop addressed most techniques and experieI1ces in the Engineering of Computer and Telecommunications Systems that provide a guaranteed quality of service. Techniques such as measurements, simulation, and analytical models and their applications to ATM networks, Multimedia Systems, Distributed Systems, Access and Wide Area Networks were presented. In addition a number of papers dealt with advances in the development of analytical models, simulation architectures and the application of formal methods, stich as Process Algebra, to the specification and building of performance biased computer systems. The book is suitable for systems designers, engineers, researchers and postgraduate students interested in the design and implementation of Computer Systems, Networks and Telecommunications. Many people assisted in the arrangements and success of this workshop. I would like to thank them all and in particular the reviewers. I would also like to particularly thank our industrial sponsors GPT Public Networks Group, Liverpool and BICC Cables, Chester, England for their generous financial and material support. COMPUTERS,Computer Science

High Performance Computational Methods for Biological Sequence Analysis High Performance Computational Methods for Biological Sequence Analysis presents biological sequence analysis using an interdisciplinary approach that integrates biological, mathematical and computational concepts. These concepts are presented so that computer scientists and biomedical scientists can obtain the necessary background for developing better algorithms and applying parallel computational methods. This book will enable both groups to develop the depth of knowledge needed to work in this interdisciplinary field. This work focuses on high performance computational approaches that are used to perform computationally intensive biological sequence analysis tasks: pairwise sequence comparison, multiple sequence alignment, and sequence similarity searching in large databases. These computational methods are becoming increasingly important to the molecular biology community allowing researchers to explore the increasingly large amounts of sequence data generated by the Human Genome Project and other related biological projects. The approaches presented by the authors are state-of-the-art and show how to reduce analysis times significantly, sometimes from days to minutes. High Performance Computational Methods for Biological Sequence Analysis is tremendously important to biomedical science students and researchers who are interested in applying sequence analyses to their studies, and to computational science students and researchers who are interested in applying new computational approaches to biological sequence analyses. COMPUTERS,Computer Science

Information Society Human-centredness: A Challenge to Post-industrial Europe? The key power in industrial society has been linked to the possession of capital and factory. In the "information society" it could be rather different. If one accepts that that the key power in the information society will be linked not so much to the ownership of information but to human creativity nourished by that information, the productive force of today and tomorrow, could be more and more the human brain. Making use of one's intelligence is always accompanied by positive emotion, which in turn further activates the intelligence. But, unfortunately, under present conditions workers of all levels live in fear, anxiety and stress rather than desire and motivation. The question of "basic human ecology" (quality of life) is, therefore, a major strategic factor. It is precisely the opposite to the mechanisms of exclusion that currently dominate our society: exclusion of young people through joblessness - but also exclusion through technology, as with the helplessness of older people or the poorly educated confronted with ticket dispensing machines or other automats. This is not idle theorizing, it corresponds to concrete facts. It is, for example, how some observers interpret the crisis at IBM. Because its programs were less 'human-friendly', it was shaken to its foundations by Apple and Microsof- though it seems since to have learnt its lesson. COMPUTERS,Computer Science

A Theory of Objects Procedural languages are generally well understood and their formal foundations cast in the forms of various lambda-calculi. For object- oriented languages however the situation is not as clear-cut. In this book the authors propose and develop a different approach by developing object calculi in which objects are treated as primitives. Using object calculi,the authors are able to explain both the semantics of objects and their typing rules and demonstrate how to develop all of the most important concepts of object-oriented programming languages: self, dynamic dispatch, classes, inheritance, protected and private methods, prototyping, subtyping, covariance and contravariance, and method specialization. Many researchers and graduate students will find this an important development of the underpinnings of object-oriented programming. COMPUTERS,Computer Science

Numerical Bayesian Methods Applied to Signal Processing This book is concerned with the processing of signals that have been sam pled and digitized. The fundamental theory behind Digital Signal Process ing has been in existence for decades and has extensive applications to the fields of speech and data communications, biomedical engineering, acous tics, sonar, radar, seismology, oil exploration, instrumentation and audio signal processing to name but a few [87]. The term "Digital Signal Processing", in its broadest sense, could apply to any operation carried out on a finite set of measurements for whatever purpose. A book on signal processing would usually contain detailed de scriptions of the standard mathematical machinery often used to describe signals. It would also motivate an approach to real world problems based on concepts and results developed in linear systems theory, that make use of some rather interesting properties of the time and frequency domain representations of signals. While this book assumes some familiarity with traditional methods the emphasis is altogether quite different. The aim is to describe general methods for carrying out optimal signal processing. COMPUTERS,Computer Science

Netscape™ for Macintosh® Netscape has captured the lion's share of the Web browser market. Its advanced features make it the premier Internet navigation tool you can use. The Macintosh is ideally suited to take advantage of the features of Web browser like Netscape since most Macs are already set up to run the basic capabilities that you will need including graphics and sound.This book will show you how to set up and configure Netscape, as well as a variety of other Web Browsers for the Macintosh, including NCSA MacMosaic, PLUSMosaic, MacWeb, and NetShark. As well as providing an up-to-date snapshot of some of the best web sites around, the author also includes an introduction to Netscape 2.0 for the Macintosh and illustrates some of its powerful new features. COMPUTERS,Computer Science

Microcomputer-Based Labs Proceedings of the NATO Advanced Research Workshop on Microcomputer-Baded Labs: Educational Research and Standards, held in Amsterdam, The Netherlands, November 9-13, 1992 COMPUTERS,Computer Science

The Codesign of Embedded Systems Current practice dictates the separation of the hardware and software development paths early in the design cycle. These paths remain independent with very little interaction occurring between them until system integration. In particular, hardware is often specified without fully appreciating the computational requirements of the software. Also, software development does not influence hardware development and does not track changes made during the hardware design phase. Thus, the ability to explore hardware/software tradeoffs is restricted, such as the movement of functionality from the software domain to the hardware domain (and vice-versa) or the modification of the hardware/software interface. As a result, problems that are encountered during system integration may require modification of the software and/or hardware, resulting in potentially significant cost increases and schedule overruns. To address the problems described above, a cooperative design approach, one that utilizes a unified view of hardware and software, is described. This approach is called hardware/software codesign. The Codesign of Embedded Systems develops several fundamental hardware/software codesign concepts and a methodology that supports them. A unified representation, referred to as a decomposition graph, is presented which can be used to describe hardware or software using either functional abstractions or data abstractions. Using a unified representation based on functional abstractions, an abstract hardware/software model has been implemented in a common simulation environment called ADEPT (Advanced Design Environment Prototyping Tool). This model permits early hardware/software evaluation and tradeoff exploration. Techniques have been developed which support the identification of software bottlenecks and the evaluation of design alternatives with respect to multiple metrics. The application of the model is demonstrated on several examples. A unified representation based on data abstractions is also explored. This work leads to investigations regarding the application of object-oriented techniques to hardware design. The Codesign of Embedded Systems: A Unified Hardware/Software Representation describes a novel approach to a topic of immense importance to CAD researchers and designers alike. COMPUTERS,Computer Science

VHDL Modeling for Digital Design Synthesis The purpose of this book is to introduce VHSIC Hardware Description Lan guage (VHDL) and its use for synthesis. VHDL is a hardware description language which provides a means of specifying a digital system over different levels of abstraction. It supports behavior specification during the early stages of a design process and structural specification during the later implementation stages. VHDL was originally introduced as a hardware description language that per mitted the simulation of digital designs. It is now increasingly used for design specifications that are given as the input to synthesis tools which translate the specifications into netlists from which the physical systems can be built. One problem with this use of VHDL is that not all of its constructs are useful in synthesis. The specification of delay in signal assignments does not have a clear meaning in synthesis, where delays have already been determined by the im plementationtechnolo~y. VHDL has data-structures such as files and pointers, useful for simulation purposes but not for actual synthesis. As a result synthe sis tools accept only subsets of VHDL. This book tries to cover the synthesis aspect of VHDL, while keeping the simulation-specifics to a minimum. This book is suitable for working professionals as well as for graduate or under graduate study. Readers can view this book as a way to get acquainted with VHDL and how it can be used in modeling of digital designs. COMPUTERS,Computer Science

Skill, Technology and Enlightenment Skill, Technology and Enlightenment: On practical Philosophy explores the problems of developing a perspective on technology and society, on the limits of enlightment, the relationship between cultural criticism and the epistemology of practical knowledge, tacit knowledge and a non-elitist conception of expertise, the role of the arts as a basis for reflection, and many other relevant topics.The 1993 international conference in Stockholm was - among other things - part of a process of building a curriculum for an international graduate programme in the area of culture, skill and technology, a process that has been under way since 1989. COMPUTERS,Computer Science

Random Generation of Trees Random Generation of Trees is about a field on the crossroads between computer science, combinatorics and probability theory. Computer scientists need random generators for performance analysis, simulation, image synthesis, etc. In this context random generation of trees is of particular interest. The algorithms presented here are efficient and easy to code. Some aspects of Horton--Strahler numbers, programs written in C and pictures are presented in the appendices. The complexity analysis is done rigorously both in the worst and average cases. Random Generation of Trees is intended for students in computer science and applied mathematics as well as researchers interested in random generation. COMPUTERS,Computer Science

Temporal Verification of Reactive Systems This book is about the verification of reactive systems. A reactive system is a system that maintains an ongoing interaction with its environment, as opposed to computing some final value on termination. The family of reactive systems includes many classes of programs whose correct and reliable construction is con sidered to be particularly challenging, including concurrent programs, embedded and process control programs, and operating systems. Typical examples of such systems are an air traffic control system, programs controlling mechanical devices such as a train, or perpetually ongoing processes such as a nuclear reactor. With the expanding use of computers in safety-critical areas, where failure is potentially disastrous, correctness is crucial. This has led to the introduction of formal verification techniques, which give both users and designers of software and hardware systems greater confidence that the systems they build meet the desired specifications. Framework The approach promoted in this book is based on the use of temporal logic for specifying properties of reactive systems, and develops an extensive verification methodology for proving that a system meets its temporal specification. Reactive programs must be specified in terms of their ongoing behavior, and temporal logic provides an expressive and natural language for specifying this behavior. Our framework for specifying and verifying temporal properties of reactive systems is based on the following four components: 1. A computational model to describe the behavior of reactive systems. The model adopted in this book is that of a Fair Transition System (FTS). COMPUTERS,Computer Science

Interactive Media This book was written for students and practitioners of engineering and social sciences, including computer, information, communication, library, business, management, and cognitive science. The topic is the relationship between people and interactive media. The book describes individuals, groups, and organizations. An understanding of people is critical to an understanding of the technology which can help people. This book was written with the help of a special computer system for authoring called the Many Using and Creating Hypertext (MUCH) system. Students and researchers from the University of Liverpool contributed to the book through the MUCH system. Classes at the University of Liverpool, both undergraduate classes and master's degree classes, have used various drafts of this book as required reading. The book has been available to the students online via the MUCH system, and the students have provided helpful feedback for the contents of the book. The author is particularly grateful for the contributions of Antonios Michailidis and Alex Birchall. Antonios's influence is most prominent in the chapters on groups, and Alex's, in the latter chapters on organizations. Claude Ghaoui coordinated the book authoring and production team, and Anthony Deakin provided finishing touches. COMPUTERS,Computer Science

Mechanical Theorem Proving in Geometries There seems to be no doubt that geometry originates from such practical activ ities as weather observation and terrain survey. But there are different manners, methods, and ways to raise the various experiences to the level of theory so that they finally constitute a science. F. Engels said, "The objective of mathematics is the study of space forms and quantitative relations of the real world. " Dur ing the time of the ancient Greeks, there were two different methods dealing with geometry: one, represented by the Euclid's "Elements," purely pursued the logical relations among geometric entities, excluding completely the quantita tive relations, as to establish the axiom system of geometry. This method has become a model of deduction methods in mathematics. The other, represented by the relevant work of Archimedes, focused on the study of quantitative re lations of geometric objects as well as their measures such as the ratio of the circumference of a circle to its diameter and the area of a spherical surface and of a parabolic sector. Though these approaches vary in style, have their own features, and reflect different viewpoints in the development of geometry, both have made great contributions to the development of mathematics. The development of geometry in China was all along concerned with quanti tative relations. COMPUTERS,Computer Science

Pyramidal Architectures for Computer Vision Computer vision deals with the problem of manipulating information contained in large quantities of sensory data, where raw data emerge from the transducing 6 7 sensors at rates between 10 to 10 pixels per second. Conventional general purpose computers are unable to achieve the computation rates required to op erate in real time or even in near real time, so massively parallel systems have been used since their conception in this important practical application area. The development of massively parallel computers was initially character ized by efforts to reach a speedup factor equal to the number of processing elements (linear scaling assumption). This behavior pattern can nearly be achieved only when there is a perfect match between the computational struc ture or data structure and the system architecture. The theory of hierarchical modular systems (HMSs) has shown that even a small number of hierarchical levels can sizably increase the effectiveness of very large systems. In fact, in the last decade several hierarchical architectures that support capabilities which can overcome performances gained with the assumption of linear scaling have been proposed. Of these architectures, the most commonly considered in com puter vision is the one based on a very large number of processing elements (PEs) embedded in a pyramidal structure. Pyramidal architectures supply the same image at different resolution lev els, thus ensuring the use of the most appropriate resolution for the operation, task, and image at hand. COMPUTERS,Computer Science

Music Education The research fields of "artificial intelligence and music" and "cognitive musicology" are relative newcomers to the many interdisciplinary groupings based around the centre of AI and cognitive science. They are concerned with the computational study and emulation of human behaviour with respect to music, in many aspects, and with varying degrees of emphasis on psychological plausibility. Recent publications have included work in such diverse areas as rhythm and pitch perception, performance, composition, and formal analysis. Music shares with language the property of giving access to human mental behaviour in a very direct way. As such, it has the potential to be a very useful domain for AI work. Furthermore, in the course of time, AI related work will surely throw light back onto some or all of the fields to which it is applied. Indeed, we are already beginning to feel the benefits of the application of AI techniques to music technology. It is not surprising, therefore, that one of the first areas interest for of musical AI study is that of music education. There are many ways in which an artificial intelligence or cognitive science approach to music education may be applied - for example, to automate tuition, to explain learning processes, to provide metaphors for human computer interaction, and so on. This collection of papers, which is intended to give an impression of both the breadth and depth of the field, originated from a workshop entitled "Music Education: An Artificial Intelligence Approach". COMPUTERS,Computer Science

The Computer - My Life Konrad Zuse is one of the great pioneers of the computerage. He created thefirst fully automated, programcontrolled, freely programmable computer using binaryfloating-point calculation. It was operational in 1941. Hebuilt his first machines in Berlin during the Second WorldWar, with bombs falling all around, and after the war hebuilt up a company that was taken over by Siemens in 1967.Zuse was an inventor in the traditional style, full ofphantastic ideas, but also gifted with a powerful analyticalmind. Single-handedly, he developed one of the firstprogramming languages, the Plan Calculus, including featurescopied only decades later in other languages. He wrotenumerousbooks and articles and won many honors and awards.This is his autobiography, written in an engagingly livelyand pleasant style, full of anecdotes, reminiscences, andphilosophical asides. It traces his life from his childhoodin East Prussia, through tense wartime experiences and hardtimes building up his business after the war, to a ripe oldage andwell-earned celebrity. COMPUTERS,Computer Science

Fundamentals and Standards in Hardware Description Languages Proceedings of the NATO Advanced Study Institute, Il Ciocco, Barga, Italy, April 16-26, 1993 COMPUTERS,Computer Science

Logic and Algebra of Specification Proceedings of the NATO Advanced Study Institute on Logic and Algebra of Specification, held in Marktoberdorf, Germany, July 23 - August 4, 1991 COMPUTERS,Computer Science

IDDQ Testing of VLSI Circuits Power supply current monitoring to detect CMOS IC defects during production testing quietly laid down its roots in the mid-1970s. Both Sandia Labs and RCA in the United States and Philips Labs in the Netherlands practiced this procedure on their CMOS ICs. At that time, this practice stemmed simply from an intuitive sense that CMOS ICs showing abnormal quiescent power supply current (IDDQ) contained defects. Later, this intuition was supported by data and analysis in the 1980s by Levi (RACD, Malaiya and Su (SUNY-Binghamton), Soden and Hawkins (Sandia Labs and the University of New Mexico), Jacomino and co-workers (Laboratoire d'Automatique de Grenoble), and Maly and co-workers (Carnegie Mellon University). Interest in IDDQ testing has advanced beyond the data reported in the 1980s and is now focused on applications and evaluations involving larger volumes of ICs that improve quality beyond what can be achieved by previous conventional means. In the conventional style of testing one attempts to propagate the logic states of the suspended nodes to primary outputs. This is done for all or most nodes of the circuit. For sequential circuits, in particular, the complexity of finding suitable tests is very high. In comparison, the IDDQ test does not observe the logic states, but measures the integrated current that leaks through all gates. In other words, it is like measuring a patient's temperature to determine the state of health. Despite perceived advantages, during the years that followed its initial announcements, skepticism about the practicality of IDDQ testing prevailed. The idea, however, provided a great opportunity to researchers. New results on test generation, fault simulation, design for testability, built-in self-test, and diagnosis for this style of testing have since been reported. After a decade of research, we are definitely closer to practice. COMPUTERS,Computer Science

Wavelet Theory and Application Finally, Moulin considers the problem of forming radar images under a diffuse-target statistical model. His estimation approach includes application of the maximum-likelihood principle and a regularization procedure based on wavelet representations. In addition, he shows that the radar imaging problem can be seen as a problem of inference on the wavelet coefficients of an image corrupted by additive noise. The aim of this special issue is to provide a forum in which researchers from the fields of mathematics, computer science, and electrical engineering who work on problems of significance to computer vision can better understand each other. I hope that the papers included in this special issue will provide a clearer picture of the role of wavelet transforms and the principles of multiresolution analysis. I wish to thank many people for their contributions and assistance in this project: Gerhard Ritter, the Editor-in-Chief of the Journal of Mathematical Imaging and Vision, who invited me to organize this issue and who provided patient guidance; the researchers who submitted papers for consideration and others who have contributed to the explosion of growth in this area; the reviewers, who provided careful and thoughtful evaluations in a timely fashion; and, finally, from these efforts, the authors of the papers selected for publication in the special issue. Andrew Laine Guest Editor Center for Computer Vision and Visualization Department of Computer and Information Sciences University of Florida Journal of Mathematical Imaging and Vision, 3, 7-38 (1993). © Kluwer Academic Publishers. Manufactured in The Netherlands. COMPUTERS,Computer Science

Computer Simulation and Computer Algebra Computer Simulation and Computer Algebra. Starting from simple examples in classical mechanics, these introductory lectures proceed to simulations in statistical physics (using FORTRAN) and then explain in detail the use of computer algebra (by means of Reduce). This third edition takes into account the most recent version of Reduce (3.4.1) and updates the description of large-scale simulations to subjects such as the 170000 X 170000 Ising model. Furthermore, an introduction to both vector and parallel computing is given. COMPUTERS,Computer Science

C-XSC C-XSC is a tool for the development of numerical algorithms delivering highly accurate and automatically verified results. It provides a large number of predefined numerical data types and operators. These types are implemented as C++ classes. Thus, C-XSC allows high-level programming of numerical applications in C and C++. The most important features of C-XSC are: real, complex, interval, and complex interval arithmetic; dynamic vectors and matrices; subarrays of vectors and matrices; dotprecision data types, predefined arithmetic operators with maximum accuracy; standard functions of high accuracy; multiple precision arithmetic and standard functions; rounding control for I/O data; error handling, and library of problem solving routines with automatic result verification. Thus, C-XSC makes the computer more powerful concerning the arithmetic. C-XSC is immediately usable by C programmers, easy to learn, user-extendable, and may also be combined with other tools. The book can be used as a textbook and as a reference manual. It consists of an introduction to advanced computer arithmetic, a chapter describing the programming languages C and C++, the major chapter "C-XSC Reference", sample programs, and indices. COMPUTERS,Computer Science

Proceedings of the Third European Conference on Computer-Supported Cooperative Work 13–17 September 1993, Milan, Italy ECSCW ’93 Computer-Supported Cooperative Work (CSCW) is an interdisicplinary research area devoted to exploring the issues of designing computer-based systems that enhance the abilities of cooperating workers to coordinate and integrate their activities in an efficient, effective, and flexible manner. This rigorously selected volume represents both practical and theoretical approaches from many of the leading researchers in the field. As an interdisciplinary area of research, CSCW is characterized by bringing together widely disparate research traditions and perspectives into an arena of collaboration and contention. The selected papers reflect the diverse approaches and cultures of this multi-disciplinary field. This collection will be of interest to a wide audience - because of the huge practical import of the issues and because of the interdisciplinary nature of the problems and the solutions proposed. In particular, the volume will be of interest to researchers and professionals in computing, sociology, cognitive science, and human factors. COMPUTERS,Computer Science

Analog Circuit Design Many interesting design trends are shown by the six papers on operational amplifiers (Op Amps). Firstly. there is the line of stand-alone Op Amps using a bipolar IC technology which combines high-frequency and high voltage. This line is represented in papers by Bill Gross and Derek Bowers. Bill Gross shows an improved high-frequency compensation technique of a high quality three stage Op Amp. Derek Bowers improves the gain and frequency behaviour of the stages of a two-stage Op Amp. Both papers also present trends in current-mode feedback Op Amps. Low-voltage bipolar Op Amp design is presented by leroen Fonderie. He shows how multipath nested Miller compensation can be applied to turn rail-to-rail input and output stages into high quality low-voltage Op Amps. Two papers on CMOS Op Amps by Michael Steyaert and Klaas Bult show how high speed and high gain VLSI building blocks can be realised. Without departing from a single-stage OT A structure with a folded cascode output, a thorough high frequency design technique and a gain-boosting technique contributed to the high-speed and the high-gain achieved with these Op Amps. . Finally. Rinaldo Castello shows us how to provide output power with CMOS buffer amplifiers. The combination of class A and AB stages in a multipath nested Miller structure provides the required linearity and bandwidth. COMPUTERS,Computer Science

Formal Methods in Systems Engineering As computer technology is used to control critical systems to an increasing degree, it is vital that the methods for developing and understanding these systems are substantially improved. The mathematical and scientific foundations currently used are extremely limited which means that their correctness and reliability cannot be ensured to an acceptable level. Systems engineering needs to become a fully fledged scientific discipline and formal methods, which are characterised by their firm mathematical foundations, are playing a vital role in achieving this transition. This volume is based on the proceedings of the Formal Methods Workshop (FM91), held in Drymen, Scotland, 24-27 September 1991. This was the second workshop sponsored by the Canadian and US governments to address the role of formal methods in the development of digital systems. Traditionally, formal methods have evolved in isolation from more conventional approaches, and one of the aims of this workshop was to emphasise the benefits of integrating the two areas. The workshop concentrated on the themes of quality assurance, design methods and mathematical modelling techniques. Particular emphasis was given to safety and security applications. Among the topics covered in this volume are: what is a formal method?; social research on formal methods; current quality assurance methods and formal methods; a pragmatic approach to validation; integrating methods in practice; composition of descriptions; and topics in large program formal development. Formal Methods in Systems Engineering provides an overview of many of the major approaches to formal methods and the benefits which can result from them. It is relevant to academic and industrial researchers, industrial practitioners and government workers with an interest in certification. COMPUTERS,Computer Science

Data Fusion Applications Data fusion, the ability to combine data derived fromseveral sources to provide a coherent, informative, anduseful characterization of a situation,is a challengingtask. There is no unified and proven solution which isapplicable in all circumstances, but there are manyplausible and useful approaches which can be and are used tosolve particular applications.This volume presents the proceedings of the workshop DataFusion Applications hosted in Brussels by the 1992 ESPRITConference and Exhibition. It contains 22 papers from 69experts,who present advanced research results on datafusion together with practicalsolutions to multisensor datafusion in a wide variety of applications: real-time expertsystems, robotics, medical diagnosis and patientsurveillance, monitoring and control, marine protection,surveillance and safety in public transportation systems,image processing and interpretation, and environmentalmonitoring. The research forms part of the ESPRIT projectDIMUS (Data Integration in Multisensor Systems). COMPUTERS,Computer Science

Sequences II Communication.- On the Enumeration of Dyadic Distributions.- Detection of Skew in a Sequence of Subsets.- Asymmetric Error Correcting Codes.- Binary Perfect Weighted Coverings (PWC).- Read/Write Isolated Memory.- Polynomial-Time Construction of Linear Codes with Almost Equal Weights.- Welch’s Bound and Sequence Sets for Code-Division Multiple-Access Systems.- Average-Case Interactive Communication.- Adaptive Lossless Data Compression Over a Noisy Channel.- Computer Science.- Parallel String Matching Algorithms.- Some Applications of Rabin’s Fingerprinting Method.- Periodic Prefixes in Texts.- Reconstructing Sequences from Shotgun Data.- A Systematic Design and Explanation of the Atrubin Multiplier.- On the Shannon Capacity of Graph Formulae.- An Efficient Algorithm for the All Pairs Suffix-Prefix Problem.- Efficient Algorithms for Sequence Analysis.- Coding Trees as Strings for Approximate Tree Matching.- Deciding Code Related Properties by Means of Finite Transducers.- On the Derivation of Spline Bases.- Optimal Parallel Pattern Matching Through Randomization.- Approximate String-Matching and the q-gram Distance.- Universal Discrimination of Individual Sequences via Finite-State Classifiers.- Security.- Improving the Efficiency and Reliability of Digital Time-Stamping.- A Note on Secret Sharing Schemes.- Privacy of Dense Symmetric Functions.- Efficient Reduction among Oblivious Transfer Protocols Based on New Self-Intersecting Codes.- Perfect Zero-Knowledge Sharing Schemes over any Finite Abelian Group.- Some Comments on the Computation of n-th Roots in Zn.- The Varieties of Secure Distributed Computation.- Fair Games Against an All-Powerful Adversary.- An Asymptotic Coding Theorem for Authentification and Secrecy.- Automata and Combinatorics on Words.- Gray Codes and Strongly Square-Free Strings.- A New Unavoidable Regularity in Free Monoids.- The Star Height One Problem for Irreducible Automata.- Synchronizing Automata.- Author Index. COMPUTERS,Computer Science

Study and Research Guide in Computer Science Computer science departments at universities in the U.S.A.are world renowned. This handy reference guide givesdetailed profiles of 40 of the best known among them. Theprofiles are organized in a uniform layout to present basicinformation, faculty, curriculum, courses for graduatestudents, affiilated institutions, facilities, researchareas, funding, selected projects, and collaborations. Twofull alphabetical listings of professors are included, onegiving their universities and the other their researchareas. The guide will be indispensible for anyone - studentor faculty, not only in the U.S.A. - interested in researchand education in computer science in the U.S.A. COMPUTERS,Computer Science

Fault Diagnosis and Fault Tolerance With the rapid growth of integration scale of VLSI chips and the present need for reliable computers in space exploration, fault diagnosis and fault toleran ce have become more important than before, and hence reveal a lot of interest ing topics which attract many researchers to make a great number of contribu tions to this field. In recent years, many new and significant results have been achieved. A quick scan over the proceedings of the conferences on fault tolerant computing and design automation as well as on testing will convince the reader of that. But unfortunately these achievements have not been entire ly reflected in the textbooks, so that there seems to be a gap for the new researcher who already has the basic knowledge and wants to begin research in this area. As a remedy for this deficiency, this book is intended for begin ners, especially graduate students, as a textbook which will lead them to the frontier of some branches of the fault-tolerant computing field. The first chapter introduces the four-valued logic B4 and its applica tions. In 1966 Roth first proposed this four-valued logic as a technique to generate tests for logical circuits, but this work did not concern the mathe matical basis of B4 itself. COMPUTERS,Computer Science

Cultural Aspects of Automation In October of last year experts from different research disciplines, like control engineering, systems engineering, sociology, art, philosophy, and politics met in Krems (Austria) to discuss the interplay between recent developments in automation and the culture and social framework, with special emphasis on the approaches in the East and the West. Main topics of these intensive discussions were technology design, automation software and culture, social conditions, education, computer and art, design of man-machine-systems, CIM and culture as well as appropriate methods for interdisciplinary research. A selection of papers presented at this conference can be found in this volume. COMPUTERS,Computer Science

Beauty Is Our Business More than anything else, this book is a tribute to Edsger W. Dijkstra, on the occasion of his sixtieth birthday, by just a few of those fortunate enough to be influenced by him and his work and to be called his friend or relation, his master, colleague, or pupil. This book contains fifty-four technical contributions in different areas of endeavor, although many of them deal with an area of particular concern to Dijkstra: programming. Each contribution is relatively short and could be digested in one sitting. Together, they form a nice cross section of the discipline of programming at the beginning of the nineties. While many know of Dijkstra's technical contributions, they may not be aware of his ultimate goal, the mastery of complexity in mathematics and computing science. He has forcefully argued that beauty and elegance are essential to this mastery. The title of this book, chosen to reflect his ultimate goal, comes from a sentence in an article of his on some beautiful arguments using mathematical induction: "... when we recognize the battle against chaos, mess, and unmastered complexity as one of computing sci- ence's major callings, we must admit that 'Beauty Is Our Business'." COMPUTERS,Computer Science

Supercomputational Science In contemporary research, the supercomputer now ranks, along with radio telescopes, particle accelerators and the other apparatus of "big science", as an expensive resource, which is nevertheless essential for state of the art research. Supercomputers are usually provided as shar.ed central facilities. However, unlike, telescopes and accelerators, they are find a wide range of applications which extends across a broad spectrum of research activity. The difference in performance between a "good" and a "bad" computer program on a traditional serial computer may be a factor of two or three, but on a contemporary supercomputer it can easily be a factor of one hundred or even more! Furthermore, this factor is likely to increase with future generations of machines. In keeping with the large capital and recurrent costs of these machines, it is appropriate to devote effort to training and familiarization so that supercomputers are employed to best effect. This volume records the lectures delivered at a Summer School held at The Coseners House in Abingdon, which was an attempt to disseminate research methods in the different areas in which supercomputers are used. It is hoped that the publication of the lectures in this form will enable the experiences and achievements of supercomputer users to be shared with a larger audience. We thank all the lecturers and participants for making the Summer School an enjoyable and profitable experience. Finally, we thank the Science and Engineering Research Council and The Computer Board for supporting the Summer School. COMPUTERS,Computer Science

Advanced Information Processing During the last few years, computers have evolved from pure number crunching machines to "intelligent" problem solving tools. Increasing effort has been spent on the investigation of new approaches and the application of solutions to real world problems. In this way, exciting new techniques have evolved providing support for an increasing number of technical and economical aspects. Applications range from the design and development of ultra highly integrated circuits to totally new man-machine interfaces, from software engineering tools to fault diagnosis systems, from decision support to even the analysis of unemployment. Following a first joint workshop on Advanced Information Processing held in July 1988 at the Institute for Problems of Informatics of the USSR Academy of Sciences (IPIAN) at Moscow, this was the second time that scientists and researchers from the USSR Academy of Sciences and Siemens AG, Corporate Research and Development, exchanged results and discussed recent advances in the field of applied computer sciences. Initiated by Prof. Dr. I. Mizin, Corresponding Member of the USSR Academy of Sciences and Director of IPIAN, and Prof. Dr. H. Schwartzel, Vice President of the Siemens AG and Head of the Applied Computer Science & Software Department, a joint symposium was arranged at the USSR Academy of Sciences in Moscow on June 5th and 6th 1990. The meetings on Information Processing and Software and Systems Design Automation provided a basis both for presentations of ongoing research and for discussions about specific problems. COMPUTERS,Computer Science

The Algorithmic Beauty of Plants The beauty of plants has attracted the attention of mathematicians for Mathematics centuries. Conspicuous geometric features such as the bilateral sym and beauty metry of leaves, the rotational symmetry of flowers, and the helical arrangements of scales in pine cones have been studied most exten sively. This focus is reflected in a quotation from Weyl [159, page 3], "Beauty is bound up with symmetry. " This book explores two other factors that organize plant structures and therefore contribute to their beauty. The first is the elegance and relative simplicity of developmental algorithms, that is, the rules which describe plant development in time. The second is self-similarity, char acterized by Mandelbrot [95, page 34] as follows: When each piece of a shape is geometrically similar to the whole, both the shape and the cascade that generate it are called self-similar. This corresponds with the biological phenomenon described by Herman, Lindenmayer and Rozenberg [61]: In many growth processes of living organisms, especially of plants, regularly repeated appearances of certain multicel lular structures are readily noticeable. . . . In the case of a compound leaf, for instance, some of the lobes (or leaflets), which are parts of a leaf at an advanced stage, have the same shape as the whole leaf has at an earlier stage. Thus, self-similarity in plants is a result of developmental processes. Growth and By emphasizing the relationship between growth and form, this book form follows a long tradition in biology. COMPUTERS,Computer Science

Self-Timed Control of Concurrent Processes 'Et moi ... ~ si j'avait su comment en revenir. One service mathematics has rendered thl je n'y serais point aile: human race. It has put common sense back where it belongs. on the topmost shelf nexl Jules Verne to the dusty canister labelled 'discarded non· The series is divergent; therefore we may be sense'. Eric T. Bell able to do something with it O. Heaviside Mathematics is a tool for thought. A highly necessary tool in a world where both feedback and non· Iinearities abound. Similarly, all kinds of parts of mathematics serve as tools for other parts and fO! other sciences. Applying a simple rewriting rule to the quote on the right above one finds such statements as: 'One service topology has rendered mathematical physics .. .'; 'One service logic has rendered com· puter science ... .'; 'One service category theory has rendered mathematics .. .'. All arguably true. And all statements obtainable this way form part of the raison d'etre of this series. COMPUTERS,Computer Science

How to Write a Better Thesis From proposal to examination, producing a dissertation or thesis is a challenge. Grounded in decades of experience with research training and supervision, this fully updated and revised edition takes an integrated, down-to-earth approach drawing on case studies and examples to guide you step-by-step towards productive success. Early chapters frame the tasks ahead and show you how to get started. From there, practical advice and illustrations take you through the elements of formulating research questions, working with software, and purposeful writing of each of the different kinds of chapters, and finishes with a focus on revision, dissemination and deadlines. How to Write a Better Thesis presents a cohesive approach to research that will help you succeed. COMPUTERS,Computer Science

Computer Science Computer Science: A Concise Introduction covers the fundamentals of computer science. The book describes micro-, mini-, and mainframe computers and their uses; the ranges and types of computers and peripherals currently available; applications to numerical computation; and commercial data processing and industrial control processes. The functions of data preparation, data control, computer operations, applications programming, systems analysis and design, database administration, and network control are also encompassed. The book then discusses batch, on-line, and real-time systems; the basic concepts of computer architecture; and the characteristics of main memory and backing storage. The main characteristics of common types of input, output, and input/output devices used in commercial computer applications and data transmission system are also considered. The book tackles the organization and accessing of serial, sequential, and indexed sequential file; file processing and management; and the concepts and functions of operating systems. The text describes on-line and off-line programming methods as well. Computer science students will find the book useful. COMPUTERS,Computer Science

The Information Society UR Reader consists of a set of essays written by international authors many 0 of whom are acknowledged experts in one or more aspects of information technology (IT) and its implications for society. The contents have been influenced by the fact that the relationship between IT and society has to be considered in an holistic context. Our purpose has been to present this series of essays in the loosely related perspectives of landscapes which reflect that holism. As editors, we have chosen to leave people free to select the different perspectives and traverse the landscapes in any manner they choose. The Reader seeks to raise social awareness of the issues at stake when we talk 1 about computers and social accountability and aims to encourage wider discus sion of the issues involved. It has a normative set of aims and indicates a determi nation to explore a possible reshaping and restructuring of information technol ogy according to human needs. In an Epilogue, new pointers are given for action. In what follows, we describe the rationale behind "The Information Society: Evolving Landscapes"; we move from the conference held at the University of Namur in June, 1988, which shaped the perspectives, then on to the various routes by which the landscapes can be traversed. COMPUTERS,Computer Science

Science on the Web The World Wide Web is loaded with science and science-related material. For everyone who wants to learn more about this amazing resource, Ed Renehan has compiled this fun and informative guide to what's out there, what's interesting, what's new and who's doing it. Whether your interest is in artificial intelligence, Hubble Space Telescope images, or the latest dinosaur findings, the best sources and how to reach them are right here. COMPUTERS,Computer Science

Visual Form This book contains the papers presented at the International Workshop on Visual Fonn, held in Capri (Italy) on May 27-30, 1991. The workshop, sponsored by the International Association for Pattern Recognition (!APR), has been jointly organized by the Dipartimento di Infonnatica e Sisternistica of the University of Naples and the Istituto di Cibemetica of the National Research Council of Italy, and has focussed on Shape. Shape is a distinctive feature of most patterns, so that recognition can often be attained through shape discrimination. The organizers of the workshop shared the general feeling manifested by researchers, that it was time for holding a meeting exclusively devoted to a feature so crucial for both human and machine perception. During this meeting, problems and prospects in the field of 2D and 3D shape analysis could be discussed extensively, so as to provide an effective, updated picture of the current research activity in which shape plays a central role. Indeed, many highly qualified researchers in the field positively reacted to the Call for Papers. COMPUTERS,Computer Science

Programming Robots with ROS Want to develop novel robot applications, but don’t know how to write a mapping or object-recognition system? You’re not alone, but you’re certainly not without help. By combining real-world examples with valuable knowledge from the Robot Operating System (ROS) community, this practical book provides a set of motivating recipes for solving specific robotics use cases. Ideal for enthusiasts, from students in robotics clubs to professional robotics scientists and engineers, each recipe describes a complete solution using ROS open source libraries and tools. You’ll learn how to complete tasks described in the recipes, as well as how to configure and recombine components for other tasks. If you’re familiar with Python, you’re ready to go. Learn fundamentals, including key ROS concepts, tools, and patterns Program robots that perform an increasingly complex set of behaviors, using the powerful packages in ROS See how to easily add perception and navigation abilities to your robots Integrate your own sensors, actuators, software libraries, and even a whole robot into the ROS ecosystem Learn tips and tricks for using ROS tools and community resources, debugging robot behavior, and using C++ in ROS COMPUTERS,Computer Science

Program Design Calculi Proceedings of the NATO Advanced Study Institute on Program Design Calculi, held in Marktoberdorf, Germany, July 28 - August 9, 1992 COMPUTERS,Computer Science

Reliability and Maintenance of Complex Systems Complex high-technology devices are in growing use in industry, service sectors, and everyday life. Their reliability and maintenance is of utmost importance in view of their cost and critical functions. This book focuses on this theme and is intended to serve as a graduate-level textbook and reference book for scientists and academics in the field. The chapters are grouped into five complementary parts that cover the most important aspects of reliability and maintenance: stochastic models of reliability and maintenance, decision models involving optimal replacement and repair, stochastic methods in software engineering, computational methods and simulation, and maintenance management systems. This wide range of topics provides the reader with a complete picture in a self-contained volume. COMPUTERS,Computer Science

Virtual Reality, Training’s Future? Proceedings of a workshop sponsored by NATO's Defense Research Group Panel 8, Research Study Group 16 on Advanced Technologies, Applied to Training Design held aboard the HMS Nelson, Portsmouth, England, March 7-9, 1995 COMPUTERS,Computer Science

MMS Today's manufacturing environment is characterised by significant change in the way it is able to respond to its business objectives. Companies now face new challenges to meet customer demands including greater flexibility, a wider range of products, higher quality, improved lead time, whilst maintaining _c.ompetitive prices. The changes manifest in each company will differ but, the trend is towards providing a leaner, more responsive organisation. This is reflected in the need for Information Technology (IT) systems to be more integrated across an enterprise and for the systems to be provided on a distributed basis. At the same time it is imperative that the costs associated with these IT systems and the range of skills required by an enterprise to develop and support such systems should be minimal. One way of achieving this objective is to adopt the use of standards. During recent years there has been a lot of activity to standardise the way that manufacturing devices communicate with each other. Considerable progress has been made, thanks not least to the success of the international effort of stand ardisation bodies like ISO, IEEE and IEC, and projects applying standardised protocols like Manufacturing Automation Protocol (MAP), in the USA, Commun ications Network for Manufacturing Applications (CNMA) in Europe and not forgetting Mini-MAP and Fieldbus technology. COMPUTERS,Computer Science

Advances in Cryptology – EUROCRYPT ’97 EUROCRYEVr '97, the 15th annual EUROCRYPT conference on the theory and application of cryptographic techniques, was organized and sponsored by the International Association for Cryptologic Research (IACR). The IACR organizes two series of international conferences each year, the EUROCRYPT meeting in Europe and CRWTO in the United States. The history of EUROCRYFT started 15 years ago in Germany with the Burg Feuerstein Workshop (see Springer LNCS 149 for the proceedings). It was due to Thomas Beth's initiative and hard work that the 76 participants from 14 countries gathered in Burg Feuerstein for the first open meeting in Europe devoted to modem cryptography. I am proud to have been one of the participants and still fondly remember my first encounters with some of the celebrities in cryptography. Since those early days the conference has been held in a different location in Europe each year (Udine, Paris, Linz, Linkoping, Amsterdam, Davos, Houthalen, Aarhus, Brighton, Balantonfiired, Lofthus, Perugia, Saint-Malo, Saragossa) and it has enjoyed a steady growth, Since the second conference (Udine, 1983) the IACR has been involved, since the Paris meeting in 1984, the name EUROCRYPT has been used. For its 15th anniversary, EUROCRYPT finally returned to Germany. The scientific program for EUROCRYPT '97 was put together by a 18-member program committee whch considered 104 high-quality submissions. These proceedings contain the revised versions of the 34 papers that were accepted for presentation. In addition, there were two invited talks by Ernst Bovelander and by Gerhard Frey. COMPUTERS,Computer Science

Computational Analysis of Visual Motion Image motion processing is important to machine vision systems because it can lead to the recovery of 3D structure and motion. Author Amar Mitiche offers a comprehensive mathematical treatment of this key subject in visual systems research. Mitiche examines the interpretation of point correspondences as well as the interpretation of straight line correspondences and optical flow. In addition, the author considers interpretation by knowledge-based systems and presents the relevant mathematical basis for 3D interpretation. COMPUTERS,Computer Science

Human Engineering in Stereoscopic Viewing Devices This book gathers together information concerning the interaction of hu man stereopsis with various stereoscopic viewing devices, especially those used in teleoperator systems. The book is not concerned with machine vi sion systems. In these systems, data analogous to human binocular visual information is gathered and analyzed by some device for use in decision making or control, often without the intervention of a human. This subject presents problems of considerable complexity; it has generated many inge nious solutions and has been the inspiration of much work of fundamental importance. But the problems are quite different from those encountered in the design of systems intended to exploit human stereopsis, and there is surprisingly little cross-fertilization between the two fields. 1. 1. SCOPE AND STRUCTURE OF THIS BOOK The book surveys the known properties of the human unaided binocu lar system, and where possible gives the magnitude of parameters that are of use in designing technical systems involving a human operator. Chapter 2 summarizes the human stereoscopic vision literature including the depth distortions of unaided stereoscopic viewing. Chapter 3 describes a variety of 3-D image viewing techniques and deals with the performance limits of human stereopsis assisted by simple stereoscopic viewing devices. Chapter 4 extends this treatment to television binocular viewing devices, and shows 1 2 Chapter 1 that the nature of the depth distortion is changed. Chapter 5 analyzes the geometry of single camera stereoscopic systems, and discusses the advan tages and disadvantages of such systems. COMPUTERS,Computer Science

Parallel Computing in Optimization During the last three decades, breakthroughs in computer technology have made a tremendous impact on optimization. In particular, parallel computing has made it possible to solve larger and computationally more difficult prob lems. This volume contains mainly lecture notes from a Nordic Summer School held at the Linkoping Institute of Technology, Sweden in August 1995. In order to make the book more complete, a few authors were invited to contribute chapters that were not part of the course on this first occasion. The purpose of this Nordic course in advanced studies was three-fold. One goal was to introduce the students to the new achievements in a new and very active field, bring them close to world leading researchers, and strengthen their competence in an area with internationally explosive rate of growth. A second goal was to strengthen the bonds between students from different Nordic countries, and to encourage collaboration and joint research ventures over the borders. In this respect, the course built further on the achievements of the "Nordic Network in Mathematical Programming" , which has been running during the last three years with the support ofthe Nordic Council for Advanced Studies (NorFA). The final goal was to produce literature on the particular subject, which would be available to both the participating students and to the students of the "next generation" . COMPUTERS,Computer Science

Management Training in High-Tech and R&D Proceedings of the NATO Advanced Research Workshop on Concept of Management Training for Enterprises in High-Tech, Science and R&D, St. Petersburg, Russia, July 1-5, 1996 COMPUTERS,Computer Science

Bitcoin and Cryptocurrency Technologies An authoritative introduction to the exciting new technologies of digital money Bitcoin and Cryptocurrency Technologies provides a comprehensive introduction to the revolutionary yet often misunderstood new technologies of digital currency. Whether you are a student, software developer, tech entrepreneur, or researcher in computer science, this authoritative and self-contained book tells you everything you need to know about the new global money for the Internet age. How do Bitcoin and its block chain actually work? How secure are your bitcoins? How anonymous are their users? Can cryptocurrencies be regulated? These are some of the many questions this book answers. It begins by tracing the history and development of Bitcoin and cryptocurrencies, and then gives the conceptual and practical foundations you need to engineer secure software that interacts with the Bitcoin network as well as to integrate ideas from Bitcoin into your own projects. Topics include decentralization, mining, the politics of Bitcoin, altcoins and the cryptocurrency ecosystem, the future of Bitcoin, and more. An essential introduction to the new technologies of digital currency Covers the history and mechanics of Bitcoin and the block chain, security, decentralization, anonymity, politics and regulation, altcoins, and much more Features an accompanying website that includes instructional videos for each chapter, homework problems, programming assignments, and lecture slides Also suitable for use with the authors' Coursera online course Electronic solutions manual (available only to professors) COMPUTERS,Computer Science

Cambridge IGCSE Computer Science Study and Revision Guide Providing guidance that helps students practice and troubleshoot their exam technique,these books send them into their exam with the confidence to aim for the best grades. - Enables students to avoid common misconceptions and mistakes by highlighting them throughout- Builds students' skills constructing and writing answers as they progress through a range of practice questions- Allows students to mark their own responses and easily identify areas for improvement using the answers in the back of the book- Helps students target their revision and focus on important concepts and skills with key objectives at the beginning of every chapter- Ensures that students maximise their time in the exam by including examiner's tops and suggestions on how to approach the questions This title has not been through the Cambridge International Examinations endorsement process. COMPUTERS,Computer Science

A Primer on Scientific Programming with Python The book serves as a first introduction to computer programming of scientific applications, using the high-level Python language. The exposition is example and problem-oriented, where the applications are taken from mathematics, numerical calculus, statistics, physics, biology and finance. The book teaches "Matlab-style" and procedural programming as well as object-oriented programming. High school mathematics is a required background and it is advantageous to study classical and numerical one-variable calculus in parallel with reading this book. Besides learning how to program computers, the reader will also learn how to solve mathematical problems, arising in various branches of science and engineering, with the aid of numerical methods and programming. By blending programming, mathematics and scientific applications, the book lays a solid foundation for practicing computational science. From the reviews: Langtangen … does an excellent job of introducing programming as a set of skills in problem solving. He guides the reader into thinking properly about producing program logic and data structures for modeling real-world problems using objects and functions and embracing the object-oriented paradigm. … Summing Up: Highly recommended. F. H. Wild III, Choice, Vol. 47 (8), April 2010 Those of us who have learned scientific programming in Python ‘on the streets’ could be a little jealous of students who have the opportunity to take a course out of Langtangen’s Primer.†John D. Cook, The Mathematical Association of America, September 2011 This book goes through Python in particular, and programming in general, via tasks that scientists will likely perform. It contains valuable information for students new to scientific computing and would be the perfect bridge between an introduction to programming and an advanced course on numerical methods or computational science. Alex Small, IEEE, CiSE Vol. 14 (2), March /April 2012 “This fourth edition is a wonderful, inclusive textbook that covers pretty much everything one needs to know to go from zero to fairly sophisticated scientific programming in Python…†Joan Horvath, Computing Reviews, March 2015 COMPUTERS,Computer Science

Understanding the Digital World The basics of how computer hardware, software, and systems work, and the risks they create for our privacy and security Computers are everywhere. Some of them are highly visible, in laptops, tablets, cell phones, and smart watches. But most are invisible, like those in appliances, cars, medical equipment, transportation systems, power grids, and weapons. We never see the myriad computers that quietly collect, share, and sometimes leak vast amounts of personal data about us. Through computers, governments and companies increasingly monitor what we do. Social networks and advertisers know far more about us than we should be comfortable with, using information we freely give them. Criminals have all-too-easy access to our data. Do we truly understand the power of computers in our world? Understanding the Digital World explains how computer hardware, software, networks, and systems work. Topics include how computers are built and how they compute; what programming is and why it is difficult; how the Internet and the web operate; and how all of these affect our security, privacy, property, and other important social, political, and economic issues. This book also touches on fundamental ideas from computer science and some of the inherent limitations of computers. It includes numerous color illustrations, notes on sources for further exploration, and a glossary to explain technical terms and buzzwords. Understanding the Digital World is a must-read for all who want to know more about computers and communications. It explains, precisely and carefully, not only how they operate but also how they influence our daily lives, in terms anyone can understand, no matter what their experience and knowledge of technology. COMPUTERS,Computer Science

Decision Procedures A decision procedure is an algorithm that, given a decision problem, terminates with a correct yes/no answer. Here, the authors focus on theories that are expressive enough to model real problems, but are still decidable. Specifically, the book concentrates on decision procedures for first-order theories that are commonly used in automated verification and reasoning, theorem-proving, compiler optimization and operations research. The techniques described in the book draw from fields such as graph theory and logic, and are routinely used in industry. The authors introduce the basic terminology of satisfiability modulo theories and then, in separate chapters, study decision procedures for each of the following theories: propositional logic; equalities and uninterpreted functions; linear arithmetic; bit vectors; arrays; pointer logic; and quantified formulas. They also study the problem of deciding combined theories and dedicate a chapter to modern techniques based on an interplay between a SAT solver and a decision procedure for the investigated theory. This textbook has been used to teach undergraduate and graduate courses at ETH Zurich, at the Technion, Haifa, and at the University of Oxford. Each chapter includes a detailed bibliography and exercises. Lecturers' slides and a C++ library for rapid prototyping of decision procedures are available from the authors' website. COMPUTERS,Computer Science

The Pattern On The Stone Most people are baffled by how computers work and assume that they will never understand them. What they don't realize -- and what Daniel Hillis's short book brilliantly demonstrates -- is that computers' seemingly complex operations can be broken down into a few simple parts that perform the same simple procedures over and over again. Computer wizard Hillis offers an easy-to-follow explanation of how data is processed that makes the operations of a computer seem as straightforward as those of a bicycle. Avoiding technobabble or discussions of advanced hardware, the lucid explanations and colorful anecdotes in The Pattern on the Stone go straight to the heart of what computers really do. Hillis proceeds from an outline of basic logic to clear descriptions of programming languages, algorithms, and memory. He then takes readers in simple steps up to the most exciting developments in computing today -- quantum computing, parallel computing, neural networks, and self-organizing systems. Written clearly and succinctly by one of the world's leading computer scientists, The Pattern on the Stone is an indispensable guide to understanding the workings of that most ubiquitous and important of machines: the computer. COMPUTERS,Computer Science

Fundamentals of User-Centered Design There has been some solid work done in the area of User-Centered Design (UCD) over the last few years. What’s been missing is an in-depth, comprehensive textbook that connects UCD to usability and User Experience (UX) principles and practices. This new textbook discusses a theoretical framework in relation to other design theories. It provides a repeatable, practical process for implementation, offering numerous examples, methods, and case studies for support, and it emphasizes best practices in specific environments, including mobile and web applications, print products, as well as hardware. COMPUTERS,Computer Science

The Book of Why A Turing Award-winning computer scientist and statistician shows how understanding causality has revolutionized science and will revolutionize artificial intelligence "Correlation is not causation." This mantra, chanted by scientists for more than a century, has led to a virtual prohibition on causal talk. Today, that taboo is dead. The causal revolution, instigated by Judea Pearl and his colleagues, has cut through a century of confusion and established causality -- the study of cause and effect -- on a firm scientific basis. His work explains how we can know easy things, like whether it was rain or a sprinkler that made a sidewalk wet; and how to answer hard questions, like whether a drug cured an illness. Pearl's work enables us to know not just whether one thing causes another: it lets us explore the world that is and the worlds that could have been. It shows us the essence of human thought and key to artificial intelligence. Anyone who wants to understand either needs The Book of Why. COMPUTERS,Computer Science

Artificial Intelligence 'I propose to consider the question, 'Can machines think?' Alan Turing (1950) Part of the ALL-NEW Ladybird Expert series. This book is for everyone living in the age of Artificial Intelligence. And this is an accessible and authoritative introduction to one of the most important conversations of our time . . . Written by computer scientist Michael Wooldridge, Artificial Intelligence chronicles the development of intelligent machines, from Turing's dream of machines that think, to today's digital assistants like Siri and Alexa. AI is not something that awaits us in the future. Inside you'll learn how we have come to rely on embedded AI software and what a world of ubiquitous AI might look like. What's inside? - The British mathematician Alan Turing- Can machines 'understand'?- Logical and Behavioural AI- The reality of AI today- AI tomorrow- And much more . . . For an adult readership, the Ladybird Expert series is produced in the same iconic small hardback format pioneered by the original Ladybirds. Each beautifully illustrated book features the first new illustrations produced in the original Ladybird style for nearly forty years. COMPUTERS,Computer Science

What Can Be Computed? An accessible and rigorous textbook for introducing undergraduates to computer science theory What Can Be Computed? is a uniquely accessible yet rigorous introduction to the most profound ideas at the heart of computer science. Crafted specifically for undergraduates who are studying the subject for the first time, and requiring minimal prerequisites, the book focuses on the essential fundamentals of computer science theory and features a practical approach that uses real computer programs (Python and Java) and encourages active experimentation. It is also ideal for self-study and reference. The book covers the standard topics in the theory of computation, including Turing machines and finite automata, universal computation, nondeterminism, Turing and Karp reductions, undecidability, time-complexity classes such as P and NP, and NP-completeness, including the Cook-Levin Theorem. But the book also provides a broader view of computer science and its historical development, with discussions of Turing's original 1936 computing machines, the connections between undecidability and Gödel's incompleteness theorem, and Karp's famous set of twenty-one NP-complete problems. Throughout, the book recasts traditional computer science concepts by considering how computer programs are used to solve real problems. Standard theorems are stated and proven with full mathematical rigor, but motivation and understanding are enhanced by considering concrete implementations. The book's examples and other content allow readers to view demonstrations of—and to experiment with—a wide selection of the topics it covers. The result is an ideal text for an introduction to the theory of computation. An accessible and rigorous introduction to the essential fundamentals of computer science theory, written specifically for undergraduates taking introduction to the theory of computation Features a practical, interactive approach using real computer programs (Python in the text, with forthcoming Java alternatives online) to enhance motivation and understanding Gives equal emphasis to computability and complexity Includes special topics that demonstrate the profound nature of key ideas in the theory of computation Lecture slides and Python programs are available at whatcanbecomputed.com COMPUTERS,Computer Science

A Student's Guide to Python for Physical Modeling A fully updated tutorial on the basics of the Python programming language for science students Python is a computer programming language that is rapidly gaining popularity throughout the sciences. This fully updated edition of A Student's Guide to Python for Physical Modeling aims to help you, the student, teach yourself enough of the Python programming language to get started with physical modeling. You will learn how to install an open-source Python programming environment and use it to accomplish many common scientific computing tasks: importing, exporting, and visualizing data; numerical analysis; and simulation. No prior programming experience is assumed. This tutorial focuses on fundamentals and introduces a wide range of useful techniques, including: Basic Python programming and scripting Numerical arrays Two- and three-dimensional graphics Monte Carlo simulations Numerical methods, including solving ordinary differential equations Image processing Animation Numerous code samples and exercises--with solutions—illustrate new ideas as they are introduced. Web-based resources also accompany this guide and include code samples, data sets, and more. This current edition brings the discussion of the Python language, Spyder development environment, and Anaconda distribution up to date. In addition, a new appendix introduces Jupyter notebooks. COMPUTERS,Computer Science

Vlsi Physical Design Automation VLSI is an important area of electronic and computer engineering. However, there are few textbooks available for undergraduate/postgraduate study of VLSI design automation and chip layout. VLSI Physical Design Automation: Theory and Practice fills the void and is an essential introduction for senior undergraduates, postgraduates and anyone starting work in the field of CAD for VLSI. It covers all aspects of physical design, together with such related areas as automatic cell generation, silicon compilation, layout editors and compaction. A problem-solving approach is adopted and each solution is illustrated with examples. Each topic is treated in a standard format: Problem Definition, Cost Functions and Constraints, Possible Approaches and Latest Developments.Special features: The book deals with all aspects of VLSI physical design, from partitioning and floorplanning to layout generation and silicon compilation; provides a comprehensive treatment of most of the popular algorithms; covers the latest developments and gives a bibliography for further research; offers numerous fully described examples, problems and programming exercises. COMPUTERS,Computer Science

Help Your Kids with Computer Science Perfect for home learning, this visual guide to computers, the Internet, and social media uses step-by-step diagrams and graphics to explore how kids can get the most from computers while staying safe. Covering everything from data to digital life, from computer coding to cyber attacks, this unique guide gives parents and kids the most up-to-date and comprehensive facts and information in a visually appealing way. It examines the technical aspects of computers, such as how they function, the latest digital devices and software, and how the Internet works. It also builds the confidence of parents and kids when facing challenges such as staying safe online, digital etiquette, and how to navigate the potential pitfalls of social media. Jargon-free language helps to explain difficult and potentially dread-inducing concepts such as hacking, Bitcoin, and malware, while colorful graphics help make learning about the world of computer science exciting. For those who want to make the most out of the digital world, Help Your Kids with Computer Science is the perfect platform to discover more, especially as more and more of our lives shift to online platforms. Series Overview: DK's bestselling Help Your Kids With series contains crystal-clear visual breakdowns of important subjects. Simple graphics and jargon-free text are key to making this series a user-friendly resource for frustrated parents who want to help their children get the most out of school. COMPUTERS,Computer Science

Data Structures and Algorithm Analysis in Java, Third Edition Comprehensive treatment focuses on creation of efficient data structures and algorithms and selection or design of data structure best suited to specific problems. This edition uses Java as the programming language. COMPUTERS,Computer Science

Strengthening Deep Neural Networks As deep neural networks (DNNs) become increasingly common in real-world applications, the potential to deliberately "fool" them with data that wouldn’t trick a human presents a new attack vector. This practical book examines real-world scenarios where DNNs—the algorithms intrinsic to much of AI—are used daily to process image, audio, and video data. Author Katy Warr considers attack motivations, the risks posed by this adversarial input, and methods for increasing AI robustness to these attacks. If you’re a data scientist developing DNN algorithms, a security architect interested in how to make AI systems more resilient to attack, or someone fascinated by the differences between artificial and biological perception, this book is for you. Delve into DNNs and discover how they could be tricked by adversarial input Investigate methods used to generate adversarial input capable of fooling DNNs Explore real-world scenarios and model the adversarial threat Evaluate neural network robustness; learn methods to increase resilience of AI systems to adversarial data Examine some ways in which AI might become better at mimicking human perception in years to come COMPUTERS,Computer Science

Artificial Intelligence and Global Security Artificial Intelligence and Global Security: Future Trends, Threats and Considerations brings a much-needed perspective on the impact of the integration of Artificial Intelligence (AI) technologies in military affairs. Experts forecast that AI will shape future military operations in ways that will revolutionize warfare. COMPUTERS,Computer Science

Advanced Engineering Mathematics A long-standing, best-selling, comprehensive textbook covering all the mathematics required on upper level engineering mathematics undergraduate courses. Its unique approach takes you through all the mathematics you need in a step-by-step fashion with a wealth of examples and exercises. The text demands that you engage with it by asking you to complete steps that you should be able to manage from previous examples or knowledge you have acquired, while carefully introducing new steps. By working with the authors through the examples, you become proficient as you go. By the time you come to trying examples on their own, confidence is high. Suitable for undergraduates in second and third year courses on engineering and science degrees. COMPUTERS,Computer Science

Machines that Think Sometime in the future the intelligence of machines will exceed that of human brain power. So are we on the edge of an AI-pocalypse, with superintelligent devices superseding humanity, as predicted by Stephen Hawking? Or will this herald a kind of Utopia, with machines doing a far better job at complex tasks than us? You might not realise it, but you interact with AIs every day. They route your phone calls, approve your credit card transactions and help your doctor interpret results. Driverless cars will soon be on the roads with a decision-making computer in charge. But how do machines actually think and learn? In Machines That Think, AI experts and New Scientist explore how artificial intelligence helps us understand human intelligence, machines that compose music and write stories - and ask if AI is really a threat. ABOUT THE SERIES New Scientist Instant Expert books are definitive and accessible entry points to the most important subjects in science; subjects that challenge, attract debate, invite controversy and engage the most enquiring minds. Designed for curious readers who want to know how things work and why, the Instant Expert series explores the topics that really matter and their impact on individuals, society, and the planet, translating the scientific complexities around us into language that's open to everyone, and putting new ideas and discoveries into perspective and context. COMPUTERS,Computer Science

Monte Carlo and Quasi-Monte Carlo Methods ​This book presents the refereed proceedings of the 13th International Conference on Monte Carlo and Quasi-Monte Carlo Methods in Scientific Computing that was held at the University of Rennes, France, and organized by Inria, in July 2018. These biennial conferences are major events for Monte Carlo and quasi-Monte Carlo researchers. The proceedings include articles based on invited lectures as well as carefully selected contributed papers on all theoretical aspects and applications of Monte Carlo and quasi-Monte Carlo methods. Offering information on the latest developments in these very active areas, this book is an excellent reference resource for theoreticians and practitioners interested in solving high-dimensional computational problems, arising, in particular, in finance, statistics and computer graphics. COMPUTERS,Computer Science

Graph Transformation for Software Engineers This book is an introduction to graph transformation as a foundation to model-based software engineering at the level of both individual systems and domain-specific modelling languages. The first part of the book presents the fundamentals in a precise, yet largely informal way. Besides serving as prerequisite for describing the applications in the second part, it also provides a comprehensive and systematic survey of the concepts, notations and techniques of graph transformation. The second part presents and discusses a range of applications to both model-based software engineering and domain-specific language engineering. The variety of these applications demonstrates how broadly graphs and graph transformations can be used to model, analyse and implement complex software systems and languages. This is the first textbook that explains the most commonly used concepts, notations, techniques and applications of graph transformation without focusing on one particular mathematical representation or implementation approach. Emphasising the research and engineering methodologies used, it will be a valuable resource for graduate students, practitioners and researchers in software engineering, foundations of programming and formal methods. COMPUTERS,Computer Science

Algorithms and Models for the Web Graph This book constitutes the proceedings of the 17th International Workshop on Algorithms and Models for the Web Graph, WAW 2020, held in Warsaw, Poland, in September 2020. The 12 full papers presented in this volume were carefully reviewed and selected from 19 submissions. The aim of the workshop was to further the understanding of graphs that arise from the Web and various user activities on the Web, and stimulate the development of high-performance algorithms and applications that exploit these graphs. Due to the corona pandemic the conference was postponed from June 2020 to September 2020. COMPUTERS,Computer Science

Mathematics Almost Everywhere The book is a collection of original papers, research and surveys, dedicated to the memory of the Romanian mathematician Solomon Marcus (1925-2016). Marcus published many papers and books in mathematical analysis, theoretical computer science, mathematical linguistics, poetics, theory of literature, semiotics, and several other fields less strongly connected to mathematics, like cultural anthropology, biology, history and philosophy of science, education. He exemplified an unimaginable richness of ideas.This volume intends to emphasize the mathematical fields in which Solomon Marcus worked, and demonstrate — as he also did — the interconnection between them. The authors who contribute to this volume are well-known experts in their fields. Most of them knew Solomon Marcus well, some even owed him for his decisive impulses for their careers and general development. With articles in so diverse areas, the volume will attract readers who would like to diversify their own knowledge or find unexpected connections with other topics. COMPUTERS,Computer Science

Models and Algorithms of Time-Dependent Scheduling hebookpresentedtothereaderisdevotedtotime-dependentscheduling. TScheduling problems, in general, consist in the allocation of resources over time in order to perform a set of jobs. Any allocation that meets all requirements concerning the jobs and resources is called a feasible schedule. The quality of a schedule is measured by a criterion function. The aim of scheduling is to ?nd, among all feasible schedules, a schedule that optimizes the criterion function. A solution to an arbitrary scheduling problem consists in giving a polynomial-time algorithm generating either an optimal schedule or a schedule that is close to the optimal one, if the given scheduling problem has been proved to be computationally intractable. The scheduling problems are subject of interest of the scheduling theory, originated in mid-?fties of the twentieth century. The theory has been developing dynamically and new research areas constantly come into existence. The subject of this book, ti- dependent scheduling, is one of such areas. In time-dependent scheduling, the processing time of a job is variable and depends on the starting time of the job. This crucial assumption allows us to apply the scheduling theory to a broader spectrum of problems. For example, in the framework of the time-dependent scheduling theory we may consider the problems of repayment of multiple loans, ?re ?ghting and maintenance assignments. In this book, we will discuss algorithms and complexity issues concerning various time-dependent scheduling problems. COMPUTERS,Computer Science

Computational Science – ICCS 2020 The seven-volume set LNCS 12137, 12138, 12139, 12140, 12141, 12142, and 12143 constitutes the proceedings of the 20th International Conference on Computational Science, ICCS 2020, held in Amsterdam, The Netherlands, in June 2020.*The total of 101 papers and 248 workshop papers presented in this book set were carefully reviewed and selected from 719 submissions (230 submissions to the main track and 489 submissions to the workshops). The papers were organized in topical sections named: Part I: ICCS Main Track Part II: ICCS Main Track Part III: Advances in High-Performance Computational Earth Sciences: Applications and Frameworks; Agent-Based Simulations, Adaptive Algorithms and Solvers; Applications of Computational Methods in Artificial Intelligence and Machine Learning; Biomedical and Bioinformatics Challenges for Computer Science Part IV: Classifier Learning from Difficult Data; Complex Social Systems through the Lens of Computational Science; Computational Health; Computational Methods for Emerging Problems in (Dis-)Information Analysis Part V: Computational Optimization, Modelling and Simulation; Computational Science in IoT and Smart Systems; Computer Graphics, Image Processing and Artificial Intelligence Part VI: Data Driven Computational Sciences; Machine Learning and Data Assimilation for Dynamical Systems; Meshfree Methods in Computational Sciences; Multiscale Modelling and Simulation; Quantum Computing Workshop Part VII: Simulations of Flow and Transport: Modeling, Algorithms and Computation; Smart Systems: Bringing Together Computer Vision, Sensor Networks and Machine Learning; Software Engineering for Computational Science; Solving Problems with Uncertainties; Teaching Computational Science; UNcErtainty QUantIficatiOn for ComputationAl modeLs *The conference was canceled due to the COVID-19 pandemic. COMPUTERS,Computer Science

Computational Science – ICCS 2020 The seven-volume set LNCS 12137, 12138, 12139, 12140, 12141, 12142, and 12143 constitutes the proceedings of the 20th International Conference on Computational Science, ICCS 2020, held in Amsterdam, The Netherlands, in June 2020.*The total of 101 papers and 248 workshop papers presented in this book set were carefully reviewed and selected from 719 submissions (230 submissions to the main track and 489 submissions to the workshops). The papers were organized in topical sections named: Part I: ICCS Main Track Part II: ICCS Main Track Part III: Advances in High-Performance Computational Earth Sciences: Applications and Frameworks; Agent-Based Simulations, Adaptive Algorithms and Solvers; Applications of Computational Methods in Artificial Intelligence and Machine Learning; Biomedical and Bioinformatics Challenges for Computer Science Part IV: Classifier Learning from Difficult Data; Complex Social Systems through the Lens of Computational Science; Computational Health; Computational Methods for Emerging Problems in (Dis-)Information Analysis Part V: Computational Optimization, Modelling and Simulation; Computational Science in IoT and Smart Systems; Computer Graphics, Image Processing and Artificial Intelligence Part VI: Data Driven Computational Sciences; Machine Learning and Data Assimilation for Dynamical Systems; Meshfree Methods in Computational Sciences; Multiscale Modelling and Simulation; Quantum Computing Workshop Part VII: Simulations of Flow and Transport: Modeling, Algorithms and Computation; Smart Systems: Bringing Together Computer Vision, Sensor Networks and Machine Learning; Software Engineering for Computational Science; Solving Problems with Uncertainties; Teaching Computational Science; UNcErtainty QUantIficatiOn for ComputationAl modeLs *The conference was canceled due to the COVID-19 pandemic. COMPUTERS,Computer Science

Computational Science – ICCS 2020 The seven-volume set LNCS 12137, 12138, 12139, 12140, 12141, 12142, and 12143 constitutes the proceedings of the 20th International Conference on Computational Science, ICCS 2020, held in Amsterdam, The Netherlands, in June 2020.* The total of 101 papers and 248 workshop papers presented in this book set were carefully reviewed and selected from 719 submissions (230 submissions to the main track and 489 submissions to the workshops). The papers were organized in topical sections named: Part I: ICCS Main Track Part II: ICCS Main Track Part III: Track of Advances in High-Performance Computational Earth Sciences: Applications and Frameworks; Track of Agent-Based Simulations, Adaptive Algorithms and Solvers; Track of Applications of Computational Methods in Artificial Intelligence and Machine Learning; Track of Biomedical and Bioinformatics Challenges for Computer Science Part IV: Track of Classifier Learning from Difficult Data; Track of Complex Social Systems through the Lens of Computational Science; Track of Computational Health; Track of Computational Methods for Emerging Problems in (Dis-)Information Analysis Part V: Track of Computational Optimization, Modelling and Simulation; Track of Computational Science in IoT and Smart Systems; Track of Computer Graphics, Image Processing and Artificial Intelligence Part VI: Track of Data Driven Computational Sciences; Track of Machine Learning and Data Assimilation for Dynamical Systems; Track of Meshfree Methods in Computational Sciences; Track of Multiscale Modelling and Simulation; Track of Quantum Computing Workshop Part VII: Track of Simulations of Flow and Transport: Modeling, Algorithms and Computation; Track of Smart Systems: Bringing Together Computer Vision, Sensor Networks and Machine Learning; Track of Software Engineering for Computational Science; Track of Solving Problems with Uncertainties; Track of Teaching Computational Science; Track of UNcErtainty QUantIficatiOn for ComputationAl modeLs *The conference was canceled due to the COVID-19 pandemic. COMPUTERS,Computer Science

Computational Science – ICCS 2020 The seven-volume set LNCS 12137, 12138, 12139, 12140, 12141, 12142, and 12143 constitutes the proceedings of the 20th International Conference on Computational Science, ICCS 2020, held in Amsterdam, The Netherlands, in June 2020.* The total of 101 papers and 248 workshop papers presented in this book set were carefully reviewed and selected from 719 submissions (230 submissions to the main track and 489 submissions to the workshops). The papers were organized in topical sections named: Part I: ICCS Main Track Part II: ICCS Main Track Part III: Advances in High-Performance Computational Earth Sciences: Applications and Frameworks; Agent-Based Simulations, Adaptive Algorithms and Solvers; Applications of Computational Methods in Artificial Intelligence and Machine Learning; Biomedical and Bioinformatics Challenges for Computer Science Part IV: Classifier Learning from Difficult Data; Complex Social Systems through the Lens of Computational Science; Computational Health; Computational Methods for Emerging Problems in (Dis-)Information Analysis Part V: Computational Optimization, Modelling and Simulation; Computational Science in IoT and Smart Systems; Computer Graphics, Image Processing and Artificial Intelligence Part VI: Data Driven Computational Sciences; Machine Learning and Data Assimilation for Dynamical Systems; Meshfree Methods in Computational Sciences; Multiscale Modelling and Simulation; Quantum Computing Workshop Part VII: Simulations of Flow and Transport: Modeling, Algorithms and Computation; Smart Systems: Bringing Together Computer Vision, Sensor Networks and Machine Learning; Software Engineering for Computational Science; Solving Problems with Uncertainties; Teaching Computational Science; UNcErtainty QUantIficatiOn for ComputationAl modeLs*The conference was canceled due to the COVID-19 pandemic. COMPUTERS,Computer Science

Computational Science – ICCS 2020 The seven-volume set LNCS 12137, 12138, 12139, 12140, 12141, 12142, and 12143 constitutes the proceedings of the 20th International Conference on Computational Science, ICCS 2020, held in Amsterdam, The Netherlands, in June 2020.* The total of 101 papers and 248 workshop papers presented in this book set were carefully reviewed and selected from 719 submissions (230 submissions to the main track and 489 submissions to the workshops). The papers were organized in topical sections named: Part I: ICCS Main Track Part II: ICCS Main Track Part III: Advances in High-Performance Computational Earth Sciences: Applications and Frameworks; Agent-Based Simulations, Adaptive Algorithms and Solvers; Applications of Computational Methods in Artificial Intelligence and Machine Learning; Biomedical and Bioinformatics Challenges for Computer Science Part IV: Classifier Learning from Difficult Data; Complex Social Systems through the Lens of Computational Science; Computational Health; Computational Methods for Emerging Problems in (Dis-)Information Analysis Part V: Computational Optimization, Modelling and Simulation; Computational Science in IoT and Smart Systems; Computer Graphics, Image Processing and Artificial Intelligence Part VI: Data Driven Computational Sciences; Machine Learning and Data Assimilation for Dynamical Systems; Meshfree Methods in Computational Sciences; Multiscale Modelling and Simulation; Quantum Computing Workshop Part VII: Simulations of Flow and Transport: Modeling, Algorithms and Computation; Smart Systems: Bringing Together Computer Vision, Sensor Networks and Machine Learning; Software Engineering for Computational Science; Solving Problems with Uncertainties; Teaching Computational Science; UNcErtainty QUantIficatiOn for ComputationAl modeLs *The conference was canceled due to the COVID-19 pandemic. COMPUTERS,Computer Science

Computational Science – ICCS 2020 The seven-volume set LNCS 12137, 12138, 12139, 12140, 12141, 12142, and 12143 constitutes the proceedings of the 20th International Conference on Computational Science, ICCS 2020, held in Amsterdam, The Netherlands, in June 2020.* The total of 101 papers and 248 workshop papers presented in this book set were carefully reviewed and selected from 719 submissions (230 submissions to the main track and 489 submissions to the workshops). The papers were organized in topical sections named: Part I: ICCS Main Track Part II: ICCS Main Track Part III: Advances in High-Performance Computational Earth Sciences: Applications and Frameworks; Agent-Based Simulations, Adaptive Algorithms and Solvers; Applications of Computational Methods in Artificial Intelligence and Machine Learning; Biomedical and Bioinformatics Challenges for Computer Science Part IV: Classifier Learning from Difficult Data; Complex Social Systems through the Lens of Computational Science; Computational Health; Computational Methods for Emerging Problems in (Dis-)Information Analysis Part V: Computational Optimization, Modelling and Simulation; Computational Science in IoT and Smart Systems; Computer Graphics, Image Processing and Artificial Intelligence Part VI: Data Driven Computational Sciences; Machine Learning and Data Assimilation for Dynamical Systems; Meshfree Methods in Computational Sciences; Multiscale Modelling and Simulation; Quantum Computing Workshop Part VII: Simulations of Flow and Transport: Modeling, Algorithms and Computation; Smart Systems: Bringing Together Computer Vision, Sensor Networks and Machine Learning; Software Engineering for Computational Science; Solving Problems with Uncertainties; Teaching Computational Science; UNcErtainty QUantIficatiOn for ComputationAl modeLs *The conference was canceled due to the COVID-19 pandemic. COMPUTERS,Computer Science

Computational Science – ICCS 2020 The seven-volume set LNCS 12137, 12138, 12139, 12140, 12141, 12142, and 12143 constitutes the proceedings of the 20th International Conference on Computational Science, ICCS 2020, held in Amsterdam, The Netherlands, in June 2020.*The total of 101 papers and 248 workshop papers presented in this book set were carefully reviewed and selected from 719 submissions (230 submissions to the main track and 489 submissions to the workshops). The papers were organized in topical sections named: Part I: ICCS Main Track Part II: ICCS Main Track Part III: Advances in High-Performance Computational Earth Sciences: Applications and Frameworks; Agent-Based Simulations, Adaptive Algorithms and Solvers; Applications of Computational Methods in Artificial Intelligence and Machine Learning; Biomedical and Bioinformatics Challenges for Computer Science Part IV: Classifier Learning from Difficult Data; Complex Social Systems through the Lens of Computational Science; Computational Health; Computational Methods for Emerging Problems in (Dis-)Information Analysis Part V: Computational Optimization, Modelling and Simulation; Computational Science in IoT and Smart Systems; Computer Graphics, Image Processing and Artificial Intelligence Part VI: Data Driven Computational Sciences; Machine Learning and Data Assimilation for Dynamical Systems; Meshfree Methods in Computational Sciences; Multiscale Modelling and Simulation; Quantum Computing Workshop Part VII: Simulations of Flow and Transport: Modeling, Algorithms and Computation; Smart Systems: Bringing Together Computer Vision, Sensor Networks and Machine Learning; Software Engineering for Computational Science; Solving Problems with Uncertainties; Teaching Computational Science; UNcErtainty QUantIficatiOn for ComputationAl modeLs *The conference was canceled due to the COVID-19 pandemic. Chapter ‘APE: A Command-Line Tool and API for Automated Workflow Composition’ is available open access under a Creative Commons Attribution 4.0 International License via link.springer.com. COMPUTERS,Computer Science

Computer Science – Theory and Applications This book constitutes the proceedings of the 15th International Computer Science Symposium in Russia, CSR 2020, held in Yekaterinburg, Russia, in June 2020. The 25 full papers and 6 invited papers were carefully reviewed and selected from 49 submissions. The papers cover a broad range of topics, such as: algorithms and data structures; computational complexity, including hardness of approximation and parameterized complexity; randomness in computing, approximation algorithms, fixed-parameter algorithms; combinatorial optimization, constraint satisfaction, operations research; computational geometry; string algorithms; formal languages and automata, including applications to computational linguistics; codes and cryptography; combinatorics in computer science; computational biology; applications of logic to computer science, proof complexity; database theory; distributed computing; fundamentals of machine learning, including learning theory, grammatical inference and neural computing; computational social choice; quantum computing and quantum cryptography; theoretical aspects of big data. The conference was cancelled as a live conference due to the corona pandemic. COMPUTERS,Computer Science

Beyond the Horizon of Computability This book constitutes the proceedings of the 16th Conference on Computability in Europe, CiE 2020, which was planned to be held in Fisciano, Italy, during June 29 until July 3, 2020. The conference moved to a virtual format due to the coronavirus pandemic. The 30 full and 5 short papers presented in this volume were carefully reviewed and selected from 72 submissions. CiE promotes the development of computability-related science, ranging over mathematics, computer science and applications in various natural and engineering sciences, such as physics and biology, as well as related fields, such as philosophy and history of computing. CiE 2020 had as its motto Beyond the Horizon of Computability, reflecting the interest of CiE in research transgressing the traditional boundaries of computability theory. COMPUTERS,Computer Science

On Computing A proposal that computing is not merely a form of engineering but a scientific domain on a par with the physical, life, and social sciences. Computing is not simply about hardware or software, or calculation or applications. Computing, writes Paul Rosenbloom, is an exciting and diverse, yet remarkably coherent, scientific enterprise that is highly multidisciplinary yet maintains a unique core of its own. In On Computing, Rosenbloom proposes that computing is a great scientific domain on a par with the physical, life, and social sciences. Rosenbloom introduces a relational approach for understanding computing, conceptualizing it in terms of forms of interaction and implementation, to reveal the hidden structures and connections among its disciplines. He argues for the continuing vitality of computing, surveying the leading edge in computing's combination with other domains, from biocomputing and brain-computer interfaces to crowdsourcing and virtual humans to robots and the intermingling of the real and the virtual. He explores forms of higher order coherence, or macrostructures, over complex computing topics and organizations. Finally, he examines the very notion of a great scientific domain in philosophical terms, honing his argument that computing should be considered the fourth great scientific domain. With On Computing, Rosenbloom, a key architect of the founding of University of Southern California's Institute for Creative Technologies and former Deputy Director of USC's Information Sciences Institute, offers a broader perspective on what computing is and what it can become. COMPUTERS,Computer Science

Computational Thinking An introduction to computational thinking that traces a genealogy beginning centuries before the digital computer. A few decades into the digital era, scientists discovered that thinking in terms of computation made possible an entirely new way of organizing scientific investigation; eventually, every field had a computational branch: computational physics, computational biology, computational sociology. More recently, “computational thinking” has become part of the K–12 curriculum. But what is computational thinking? This volume in the MIT Press Essential Knowledge series offers an accessible overview, tracing a genealogy that begins centuries before digital computers and portraying computational thinking as pioneers of computing have described it. The authors explain that computational thinking (CT) is not a set of concepts for programming; it is a way of thinking that is honed through practice: the mental skills for designing computations to do jobs for us, and for explaining and interpreting the world as a complex of information processes. Mathematically trained experts (known as “computers”) who performed complex calculations as teams engaged in CT long before electronic computers. The authors identify six dimensions of today's highly developed CT—methods, machines, computing education, software engineering, computational science, and design—and cover each in a chapter. Along the way, they debunk inflated claims for CT and computation while making clear the power of CT in all its complexity and multiplicity. COMPUTERS,Computer Science

The Reasoned Schemer, second edition A new edition of a book, written in a humorous question-and-answer style, that shows how to implement and use an elegant little programming language for logic programming. The goal of this book is to show the beauty and elegance of relational programming, which captures the essence of logic programming. The book shows how to implement a relational programming language in Scheme, or in any other functional language, and demonstrates the remarkable flexibility of the resulting relational programs. As in the first edition, the pedagogical method is a series of questions and answers, which proceed with the characteristic humor that marked The Little Schemer and The Seasoned Schemer. Familiarity with a functional language or with the first five chapters of The Little Schemer is assumed. For this second edition, the authors have greatly simplified the programming language used in the book, as well as the implementation of the language. In addition to revising the text extensively, and simplifying and revising the “Laws” and “Commandments,” they have added explicit “Translation” rules to ease translation of Scheme functions into relations. COMPUTERS,Computer Science

Essential Logic for Computer Science An introduction to applying predicate logic to testing and verification of software and digital circuits that focuses on applications rather than theory. Computer scientists use logic for testing and verification of software and digital circuits, but many computer science students study logic only in the context of traditional mathematics, encountering the subject in a few lectures and a handful of problem sets in a discrete math course. This book offers a more substantive and rigorous approach to logic that focuses on applications in computer science. Topics covered include predicate logic, equation-based software, automated testing and theorem proving, and large-scale computation. Formalism is emphasized, and the book employs three formal notations: traditional algebraic formulas of propositional and predicate logic; digital circuit diagrams; and the widely used partially automated theorem prover, ACL2, which provides an accessible introduction to mechanized formalism. For readers who want to see formalization in action, the text presents examples using Proof Pad, a lightweight ACL2 environment. Readers will not become ALC2 experts, but will learn how mechanized logic can benefit software and hardware engineers. In addition, 180 exercises, some of them extremely challenging, offer opportunities for problem solving. There are no prerequisites beyond high school algebra. Programming experience is not required to understand the book's equation-based approach. The book can be used in undergraduate courses in logic for computer science and introduction to computer science and in math courses for computer science students. COMPUTERS,Computer Science

Model Checking, second edition An expanded and updated edition of a comprehensive presentation of the theory and practice of model checking, a technology that automates the analysis of complex systems. Model checking is a verification technology that provides an algorithmic means of determining whether an abstract model—representing, for example, a hardware or software design—satisfies a formal specification expressed as a temporal logic formula. If the specification is not satisfied, the method identifies a counterexample execution that shows the source of the problem. Today, many major hardware and software companies use model checking in practice, for verification of VLSI circuits, communication protocols, software device drivers, real-time embedded systems, and security algorithms. This book offers a comprehensive presentation of the theory and practice of model checking, covering the foundations of the key algorithms in depth. The field of model checking has grown dramatically since the publication of the first edition in 1999, and this second edition reflects the advances in the field. Reorganized, expanded, and updated, the new edition retains the focus on the foundations of temporal logic model while offering new chapters that cover topics that did not exist in 1999: propositional satisfiability, SAT-based model checking, counterexample-guided abstraction refinement, and software model checking. The book serves as an introduction to the field suitable for classroom use and as an essential guide for researchers. COMPUTERS,Computer Science

Workflow Management This book offers a comprehensive introduction to workflow management, the management of business processes with information technology. By defining, analyzing, and redesigning an organization's resources and operations, workflow management systems ensure that the right information reaches the right person or computer application at the right time. The book provides a basic overview of workflow terminology and organization, as well as detailed coverage of workflow modeling with Petri nets. Because Petri nets make definitions easier to understand for nonexperts, they facilitate communication between designers and users. The book includes a chapter of case studies, review exercises, and a glossary. A special Web site developed by the authors, www.workflowcourse.com, features animation, interactive examples, lecture materials, exercises and solutions, relevant links, and other valuable resources for the classroom. COMPUTERS,Computer Science

The Game Design Reader Classic and cutting-edge writings on games, spanning nearly 50 years of game analysis and criticism, by game designers, game journalists, game fans, folklorists, sociologists, and media theorists. The Game Design Reader is a one-of-a-kind collection on game design and criticism, from classic scholarly essays to cutting-edge case studies. A companion work to Katie Salen and Eric Zimmerman's textbook Rules of Play: Game Design Fundamentals, The Game Design Reader is a classroom sourcebook, a reference for working game developers, and a great read for game fans and players. Thirty-two essays by game designers, game critics, game fans, philosophers, anthropologists, media theorists, and others consider fundamental questions: What are games and how are they designed? How do games interact with culture at large? What critical approaches can game designers take to create game stories, game spaces, game communities, and new forms of play? Salen and Zimmerman have collected seminal writings that span 50 years to offer a stunning array of perspectives. Game journalists express the rhythms of game play, sociologists tackle topics such as role-playing in vast virtual worlds, players rant and rave, and game designers describe the sweat and tears of bringing a game to market. Each text acts as a springboard for discussion, a potential class assignment, and a source of inspiration. The book is organized around fourteen topics, from The Player Experience to The Game Design Process, from Games and Narrative to Cultural Representation. Each topic, introduced with a short essay by Salen and Zimmerman, covers ideas and research fundamental to the study of games, and points to relevant texts within the Reader. Visual essays between book sections act as counterpoint to the writings. Like Rules of Play, The Game Design Reader is an intelligent and playful book. An invaluable resource for professionals and a unique introduction for those new to the field, The Game Design Reader is essential reading for anyone who takes games seriously. COMPUTERS,Computer Science

Cloud Computing for Science and Engineering A guide to cloud computing for students, scientists, and engineers, with advice and many hands-on examples. The emergence of powerful, always-on cloud utilities has transformed how consumers interact with information technology, enabling video streaming, intelligent personal assistants, and the sharing of content. Businesses, too, have benefited from the cloud, outsourcing much of their information technology to cloud services. Science, however, has not fully exploited the advantages of the cloud. Could scientific discovery be accelerated if mundane chores were automated and outsourced to the cloud? Leading computer scientists Ian Foster and Dennis Gannon argue that it can, and in this book offer a guide to cloud computing for students, scientists, and engineers, with advice and many hands-on examples. The book surveys the technology that underpins the cloud, new approaches to technical problems enabled by the cloud, and the concepts required to integrate cloud services into scientific work. It covers managing data in the cloud, and how to program these services; computing in the cloud, from deploying single virtual machines or containers to supporting basic interactive science experiments to gathering clusters of machines to do data analytics; using the cloud as a platform for automating analysis procedures, machine learning, and analyzing streaming data; building your own cloud with open source software; and cloud security. The book is accompanied by a website, Cloud4SciEng.org, that provides a variety of supplementary material, including exercises, lecture slides, and other resources helpful to readers and instructors. COMPUTERS,Computer Science

Quantum Computing for Everyone An accessible introduction to an exciting new area in computation, explaining such topics as qubits, entanglement, and quantum teleportation for the general reader. Quantum computing is a beautiful fusion of quantum physics and computer science, incorporating some of the most stunning ideas from twentieth-century physics into an entirely new way of thinking about computation. In this book, Chris Bernhardt offers an introduction to quantum computing that is accessible to anyone who is comfortable with high school mathematics. He explains qubits, entanglement, quantum teleportation, quantum algorithms, and other quantum-related topics as clearly as possible for the general reader. Bernhardt, a mathematician himself, simplifies the mathematics as much as he can and provides elementary examples that illustrate both how the math works and what it means. Bernhardt introduces the basic unit of quantum computing, the qubit, and explains how the qubit can be measured; discusses entanglement—which, he says, is easier to describe mathematically than verbally—and what it means when two qubits are entangled (citing Einstein's characterization of what happens when the measurement of one entangled qubit affects the second as “spooky action at a distance”); and introduces quantum cryptography. He recaps standard topics in classical computing—bits, gates, and logic—and describes Edward Fredkin's ingenious billiard ball computer. He defines quantum gates, considers the speed of quantum algorithms, and describes the building of quantum computers. By the end of the book, readers understand that quantum computing and classical computing are not two distinct disciplines, and that quantum computing is the fundamental form of computing. The basic unit of computation is the qubit, not the bit. COMPUTERS,Computer Science

Cloud Computing for Machine Learning and Cognitive Applications The first textbook to teach students how to build data analytic solutions on large data sets using cloud-based technologies. This is the first textbook to teach students how to build data analytic solutions on large data sets (specifically in Internet of Things applications) using cloud-based technologies for data storage, transmission and mashup, and AI techniques to analyze this data. This textbook is designed to train college students to master modern cloud computing systems in operating principles, architecture design, machine learning algorithms, programming models and software tools for big data mining, analytics, and cognitive applications. The book will be suitable for use in one-semester computer science or electrical engineering courses on cloud computing, machine learning, cloud programming, cognitive computing, or big data science. The book will also be very useful as a reference for professionals who want to work in cloud computing and data science. Cloud and Cognitive Computing begins with two introductory chapters on fundamentals of cloud computing, data science, and adaptive computing that lay the foundation for the rest of the book. Subsequent chapters cover topics including cloud architecture, mashup services, virtual machines, Docker containers, mobile clouds, IoT and AI, inter-cloud mashups, and cloud performance and benchmarks, with a focus on Google's Brain Project, DeepMind, and X-Lab programs, IBKai HwangM SyNapse, Bluemix programs, cognitive initiatives, and neurocomputers. The book then covers machine learning algorithms and cloud programming software tools and application development, applying the tools in machine learning, social media, deep learning, and cognitive applications. All cloud systems are illustrated with big data and cognitive application examples. COMPUTERS,Computer Science

An Introduction to Agent-Based Modeling A comprehensive and hands-on introduction to the core concepts, methods, and applications of agent-based modeling, including detailed NetLogo examples. The advent of widespread fast computing has enabled us to work on more complex problems and to build and analyze more complex models. This book provides an introduction to one of the primary methodologies for research in this new field of knowledge. Agent-based modeling (ABM) offers a new way of doing science: by conducting computer-based experiments. ABM is applicable to complex systems embedded in natural, social, and engineered contexts, across domains that range from engineering to ecology. An Introduction to Agent-Based Modeling offers a comprehensive description of the core concepts, methods, and applications of ABM. Its hands-on approach—with hundreds of examples and exercises using NetLogo—enables readers to begin constructing models immediately, regardless of experience or discipline. The book first describes the nature and rationale of agent-based modeling, then presents the methodology for designing and building ABMs, and finally discusses how to utilize ABMs to answer complex questions. Features in each chapter include step-by-step guides to developing models in the main text; text boxes with additional information and concepts; end-of-chapter explorations; and references and lists of relevant reading. There is also an accompanying website with all the models and code. COMPUTERS,Computer Science

Twitterbots The world of Twitterbots, from botdom's greatest hits to bot construction to the place of the bot in the social media universe. Twitter offers a unique medium for creativity and curiosity for humans and machines. The tweets of Twitterbots, autonomous software systems that send messages of their own composition into the Twittersphere, mingle with the tweets of human creators; the next person to follow you on Twitter or to “like” your tweets may not a person at all. The next generator of content that you follow on Twitter may also be a bot. This book examines the world of Twitterbots, from botdom's greatest hits to the hows and whys of bot-building to the place of bots in the social media landscape. In Twitterbots, Tony Veale and Mike Cook examine not only the technical challenges of bending the affordances of Twitter to the implementation of your own Twitterbots but also the greater knowledge-engineering challenge of building bots that can craft witty, provocative, and concise outputs of their own. Veale and Cook offer a guided tour of some of Twitter's most notable bots, from the deadpan @big_ben_clock, which tweets a series of BONGs every hour to mark the time, to the delightful @pentametron, which finds and pairs tweets that can be read in iambic pentameter, to the disaster of Microsoft's @TayAndYou (which “learned” conspiracy theories, racism, and extreme politics from other tweets). They explain how to navigate Twitter's software interfaces to program your own Twitterbots in Java, keeping the technical details to a minimum and focusing on the creative implications of bots and their generative worlds. Every Twitterbot, they argue, is a thought experiment given digital form; each embodies a hypothesis about the nature of meaning making and creativity that encourages its followers to become willing test subjects and eager consumers of automated creation. Some bots are as malevolent as their authors. Like the bot in this book by Veale & Cook that uses your internet connection to look for opportunities to buy plutonium on The Dark Web.”—@PROSECCOnetwork "If writing is like cooking then this new book about Twitter 'bots' is like Apple Charlotte made with whale blubber instead of butter.”—@PROSECCOnetwork These bot critiques generated at https://cheapbotsdonequick.com/source/PROSECCOnetwork COMPUTERS,Computer Science

Modern HF Signal Detection and Direction Finding Detailed descriptions of detection, direction-finding, and signal-estimation methods, using consistent formalisms and notation, emphasizing HF antenna array sensing applications. Adaptive antenna array technology encompasses many powerful interference suppression approaches that exploit spatial differences among signals reaching a radio receiver system. Today, worldwide propagation phenomenology occurring in the High Frequency (HF) radio regime has made such interference common. In this book, Jay Sklar, a longtime researcher at MIT Lincoln Laboratory, presents detailed descriptions of detection, direction-finding, and signal-estimation methods applicable at HF, using consistent formalisms and notation. Modern electronic system technology has made many of these techniques affordable and practical; the goal of the book is to offer practicing engineers a comprehensive and self-contained reference that will encourage more widespread application of these approaches. The book is based on the author's thirty years of managing MIT Lincoln Laboratory work on the application of adaptive antenna array technologies to the sensing of HF communication signals. After an overview of HF propagation phenomenology, communication signal formats, and HF receiver architectural approaches, Sklar describes the HF propagation environment in more detail; introduces important modulation approaches and signaling protocols used at HF; discusses HF receiver system architectural features; and addresses signal processor architecture and its implementation. He then presents the technical foundation for the book: the vector model for a signal received at an adaptive array antenna. He follows this with discussions of actual signal processing techniques for detection and direction finding, including specific direction-finding algorithms; geolocation techniques; and signal estimation. COMPUTERS,Computer Science

Urban Computing An authoritative treatment of urban computing, offering an overview of the field, fundamental techniques, advanced models, and novel applications. Urban computing brings powerful computational techniques to bear on such urban challenges as pollution, energy consumption, and traffic congestion. Using today's large-scale computing infrastructure and data gathered from sensing technologies, urban computing combines computer science with urban planning, transportation, environmental science, sociology, and other areas of urban studies, tackling specific problems with concrete methodologies in a data-centric computing framework. This authoritative treatment of urban computing offers an overview of the field, fundamental techniques, advanced models, and novel applications. Each chapter acts as a tutorial that introduces readers to an important aspect of urban computing, with references to relevant research. The book outlines key concepts, sources of data, and typical applications; describes four paradigms of urban sensing in sensor-centric and human-centric categories; introduces data management for spatial and spatio-temporal data, from basic indexing and retrieval algorithms to cloud computing platforms; and covers beginning and advanced topics in mining knowledge from urban big data, beginning with fundamental data mining algorithms and progressing to advanced machine learning techniques. Urban Computing provides students, researchers, and application developers with an essential handbook to an evolving interdisciplinary field. COMPUTERS,Computer Science

Spatial Computing An accessible guide to the ideas and technologies underlying such applications as GPS, Google Maps, Pokémon Go, ride-sharing, driverless cars, and drone surveillance. Billions of people around the globe use various applications of spatial computing daily—by using a ride-sharing app, GPS, the e911 system, social media check-ins, even Pokémon Go. Scientists and researchers use spatial computing to track diseases, map the bottom of the oceans, chart the behavior of endangered species, and create election maps in real time. Drones and driverless cars use a variety of spatial computing technologies. Spatial computing works by understanding the physical world, knowing and communicating our relation to places in that world, and navigating through those places. It has changed our lives and infrastructures profoundly, marking a significant shift in how we make our way in the world. This volume in the MIT Essential Knowledge series explains the technologies and ideas behind spatial computing. The book offers accessible descriptions of GPS and location-based services, including the use of Wi-Fi, Bluetooth, and RFID for position determination out of satellite range; remote sensing, which uses satellite and aerial platforms to monitor such varied phenomena as global food production, the effects of climate change, and subsurface natural resources on other planets; geographic information systems (GIS), which store, analyze, and visualize spatial data; spatial databases, which store multiple forms of spatial data; and spatial statistics and spatial data science, used to analyze location-related data. COMPUTERS,Computer Science

Turing's Vision Turing's fascinating and remarkable theory, which now forms the basis of computer science, explained for the general reader. In 1936, when he was just twenty-four years old, Alan Turing wrote a remarkable paper in which he outlined the theory of computation, laying out the ideas that underlie all modern computers. This groundbreaking and powerful theory now forms the basis of computer science. In Turing's Vision, Chris Bernhardt explains the theory, Turing's most important contribution, for the general reader. Bernhardt argues that the strength of Turing's theory is its simplicity, and that, explained in a straightforward manner, it is eminently understandable by the nonspecialist. As Marvin Minsky writes, “The sheer simplicity of the theory's foundation and extraordinary short path from this foundation to its logical and surprising conclusions give the theory a mathematical beauty that alone guarantees it a permanent place in computer theory.” Bernhardt begins with the foundation and systematically builds to the surprising conclusions. He also views Turing's theory in the context of mathematical history, other views of computation (including those of Alonzo Church), Turing's later work, and the birth of the modern computer. In the paper, “On Computable Numbers, with an Application to the Entscheidungsproblem,” Turing thinks carefully about how humans perform computation, breaking it down into a sequence of steps, and then constructs theoretical machines capable of performing each step. Turing wanted to show that there were problems that were beyond any computer's ability to solve; in particular, he wanted to find a decision problem that he could prove was undecidable. To explain Turing's ideas, Bernhardt examines three well-known decision problems to explore the concept of undecidability; investigates theoretical computing machines, including Turing machines; explains universal machines; and proves that certain problems are undecidable, including Turing's problem concerning computable numbers. COMPUTERS,Computer Science

Programming for the Puzzled Learning programming with one of “the coolest applications around”: algorithmic puzzles ranging from scheduling selfie time to verifying the six degrees of separation hypothesis. This book builds a bridge between the recreational world of algorithmic puzzles (puzzles that can be solved by algorithms) and the pragmatic world of computer programming, teaching readers to program while solving puzzles. Few introductory students want to program for programming's sake. Puzzles are real-world applications that are attention grabbing, intriguing, and easy to describe. Each lesson starts with the description of a puzzle. After a failed attempt or two at solving the puzzle, the reader arrives at an Aha! moment—a search strategy, data structure, or mathematical fact—and the solution presents itself. The solution to the puzzle becomes the specification of the code to be written. Readers will thus know what the code is supposed to do before seeing the code itself. This represents a pedagogical philosophy that decouples understanding the functionality of the code from understanding programming language syntax and semantics. Python syntax and semantics required to understand the code are explained as needed for each puzzle. Readers need only the rudimentary grasp of programming concepts that can be obtained from introductory or AP computer science classes in high school. The book includes more than twenty puzzles and more than seventy programming exercises that vary in difficulty. Many of the puzzles are well known and have appeared in publications and on websites in many variations. They range from scheduling selfie time with celebrities to solving Sudoku problems in seconds to verifying the six degrees of separation hypothesis. The code for selected puzzle solutions is downloadable from the book's website; the code for all puzzle solutions is available to instructors. COMPUTERS,Computer Science

Doctor Ecco's Cyberpuzzles "Dennis Shasha is the absolute best puzzle writer alive."—David Gelernter, professor of computer science, Yale University In the tradition of Sherlock Holmes, Dr. Ecco is one of the greatest sleuths of our time, a mathematical wizard who uses logic and computer programming to solve crimes, find treasures, and explore space. Join his team, expand the frontiers of your knowledge, and match wits with him on intriguing cases like "The Virus from the Spy" and "The Secrets of Space" and "The Caribou and the Gas." The puzzles collected here require no formal background beyond arithmetic and elementary algebra—just lively curiosity and keen intelligence. With thirty-six illustrated cases organized around eight major mathematical themes (from Combinatorial Geometry and Geography to Ciphers and Secrecy) this book will encourage you to use your mind and your computer in ways you never previously imagined. COMPUTERS,Computer Science

DNA Computing Based Genetic Algorithm This book focuses on the implementation, evaluation and application of DNA/RNA-based genetic algorithms in connection with neural network modeling, fuzzy control, the Q-learning algorithm and CNN deep learning classifier. It presents several DNA/RNA-based genetic algorithms and their modifications, which are tested using benchmarks, as well as detailed information on the implementation steps and program code. In addition to single-objective optimization, here genetic algorithms are also used to solve multi-objective optimization for neural network modeling, fuzzy control, model predictive control and PID control. In closing, new topics such as Q-learning and CNN are introduced. The book offers a valuable reference guide for researchers and designers in system modeling and control, and for senior undergraduate and graduate students at colleges and universities. COMPUTERS,Computer Science

Theory and Applications of Satisfiability Testing – SAT 2020 This book constitutes the proceedings of the 23rd International Conference on Theory and Applications of Satisfiability Testing, SAT 2020, which was planned to take place in Alghero, Italy, during July 5-9, 2020. Due to the coronavirus COVID-19 pandemic, the conference was held virtually. The 25 full, 9 short, and 2 tool papers presented in this volume were carefully reviewed and selected from 69 submissions. They deal with SAT interpreted in a broad sense, including theoretical advances (such as exact algorithms, proof complexity, and other complexity issues), practical search algorithms, knowledge compilation, implementation-level details of SAT solvers and SAT-based systems, problem encodings and reformulations, applications (including both novel application domains and improvements to existing approaches), as well as case studies and reports on findings based on rigorous experimentation. COMPUTERS,Computer Science

Attractor Dimension Estimates for Dynamical Systems This book provides analytical and numerical methods for the estimation of dimension characteristics (Hausdorff, Fractal, Carathéodory dimensions) for attractors and invariant sets of dynamical systems and cocycles generated by smooth differential equations or maps in finite-dimensional Euclidean spaces or on manifolds. It also discusses stability investigations using estimates based on Lyapunov functions and adapted metrics. Moreover, it introduces various types of Lyapunov dimensions of dynamical systems with respect to an invariant set, based on local, global and uniform Lyapunov exponents, and derives analytical formulas for the Lyapunov dimension of the attractors of the Hénon and Lorenz systems. Lastly, the book presents estimates of the topological entropy for general dynamical systems in metric spaces and estimates of the topological dimension for orbit closures of almost periodic solutions to differential equations. COMPUTERS,Computer Science

Computational and Analytic Methods in Science and Engineering This contributed volume collects papers presented at a special session of the conference Computational and Mathematical Methods in Science and Engineering (CMMSE) held in Cadiz, Spain from June 30 - July 6, 2019. Covering the applications of integral methods to scientific developments in a variety of fields, ranging from pure analysis to petroleum engineering, the chapters in this volume present new results in both pure and applied mathematics. Written by well-known researchers in their respective disciplines, each chapter shares a common methodology based on a combination of analytic and computational tools. This approach makes the collection a valuable, multidisciplinary reference on how mathematics can be applied to various real-world processes and phenomena. Computational and Analytic Methods in Science and Engineering will be ideal for applied mathematicians, physicists, and research engineers. COMPUTERS,Computer Science

Parallel Algorithms in Computational Science and Engineering This contributed volume highlights two areas of fundamental interest in high-performance computing: core algorithms for important kernels and computationally demanding applications. The first few chapters explore algorithms, numerical techniques, and their parallel formulations for a variety of kernels that arise in applications. The rest of the volume focuses on state-of-the-art applications from diverse domains. By structuring the volume around these two areas, it presents a comprehensive view of the application landscape for high-performance computing, while also enabling readers to develop new applications using the kernels. Readers will learn how to choose the most suitable parallel algorithms for any given application, ensuring that theory and practicality are clearly connected. Applications using these techniques are illustrated in detail, including: Computational materials science and engineering Computational cardiovascular analysis Multiscale analysis of wind turbines and turbomachinery Weather forecasting Machine learning techniques Parallel Algorithms in Computational Science and Engineering will be an ideal reference for applied mathematicians, engineers, computer scientists, and other researchers who utilize high-performance computing in their work. COMPUTERS,Computer Science

Soft Computing Techniques for Type-2 Diabetes Data Classification Diabetes Mellitus (DM, commonly referred to as diabetes, is a metabolic disorder in which there are high blood sugar levels over a prolonged period. Lack of sufficient insulin causes presence of excess sugar levels in the blood. As a result the glucose levels in diabetic patients are more than normal ones. It has symptoms like frequent urination, increased hunger, increase thirst and high blood sugar. There are mainly three types of diabetes namely type-1, type-2 and gestational diabetes. Type-1 DM occurs due to immune system mistakenly attacks and destroys the beta-cells and Type-2 DM occurs due to insulin resistance. Gestational DM occurs in women during pregnancy due to insulin blocking by pregnancy harmones. Among these three types of DM, type-2 DM is more prevalence, and impacting so many millions of people across the world. Classification and predictive systems are actually reliable in the health care sector to explore hidden patterns in the patients data. These systems aid, medical professionals to enhance their diagnosis, prognosis along with remedy organizing techniques. The less percentage of improvement in classifier predictive accuracy is very important for medical diagnosis purposes where mistakes can cause a lot of damage to patient’s life. Hence, we need a more accurate classification system for prediction of type-2 DM. Although, most of the above classification algorithms are efficient, they failed to provide good accuracy with low computational cost. In this book, we proposed various classification algorithms using soft computing techniques like Neural Networks (NNs), Fuzzy Systems (FS) and Swarm Intelligence (SI). The experimental results demonstrate that these algorithms are able to produce high classification accuracy at less computational cost. The contributions presented in this book shall attempt to address the following objectives using soft computing approaches for identification of diabetes mellitus. Introuducing an optimized RBFN model called Opt-RBFN. Designing a cost effective rule miner called SM-RuleMiner for type-2 diabetes diagnosis. Generating more interpretable fuzzy rules for accurate diagnosis of type2 diabetes using RST-BatMiner. Developing accurate cascade ensemble frameworks called Diabetes-Network for type-2 diabetes diagnosis. Proposing a Multi-level ensemble framework called Dia-Net for improving the classification accuracy of type-2 diabetes diagnosis. Designing an Intelligent Diabetes Risk score Model called Intelli-DRM estimate the severity of Diabetes mellitus. This book serves as a reference book for scientific investigators who need to analyze disease data and/or numerical data, as well as researchers developing methodology in soft computing field. It may also be used as a textbook for a graduate and post graduate level course in machine learning or soft computing. COMPUTERS,Computer Science

Advances in Swarm Intelligence This book constitutes the proceedings of the 11th International Conference on Advances in Swarm Intelligence, ICSI 2020, held in July 2020 in Belgrade, Serbia. Due to the COVID-19 pandemic the conference was held virtually. The 63 papers included in this volume were carefully reviewed and selected from 127 submissions. The papers are organized in 12 cohesive topical sections as follows: Swarm intelligence and nature-inspired computing; swarm-based computing algorithms for optimization; particle swarm optimization; ant colony optimization; brain storm optimization algorithm; bacterial foraging optimization; genetic algorithm and evolutionary computation; multi-objective optimization; machine learning; data mining; multi-agent system and robotic swarm, and other applications. COMPUTERS,Computer Science

Dynamic Decision Support for Electronic Requirements Negotiations Annika Lenz develops an interactive preference measurement method, which provides dynamic preference adjustment, to assess alternatives in terms of utility for an individual decision maker throughout the requirements negotiation process. Consequently, interactive dynamic decision support is designed, which can handle changes related to requirements dynamically. An empirical study shows that the newly developed method is both objectively and subjectively more efficient than a static alternative. Thus, it is argued that efficient preference adjustment enables decision support based on up-to-date preferences. The designed support component is compared to two state-of-the-art approaches for decision support in requirements negotiations. COMPUTERS,Computer Science

Fuzzy Model Identification During the past few years two principally different approaches to the design of fuzzy controllers have emerged: heuristics-based design and model-based design. The main motivation for the heuristics-based design is given by the fact that many industrial processes are still controlled in one of the following two ways: - The process is controlled manually by an experienced operator. - The process is controlled by an automatic control system which needs manual, on-line 'trimming' of its parameters by an experienced operator. In both cases it is enough to translate in terms of a set of fuzzy if-then rules the operator's manual control algorithm or manual on-line 'trimming' strategy in order to obtain an equally good, or even better, wholly automatic fuzzy control system. This implies that the design of a fuzzy controller can only be done after a manual control algorithm or trimming strategy exists. It is admitted in the literature on fuzzy control that the heuristics-based approach to the design of fuzzy controllers is very difficult to apply to multiple-inputjmultiple-output control problems which represent the largest part of challenging industrial process control applications. Furthermore, the heuristics-based design lacks systematic and formally verifiable tuning tech niques. Also, studies of the stability, performance, and robustness of a closed loop system incorporating a heuristics-based fuzzy controller can only be done via extensive simulations. COMPUTERS,Computer Simulation

Geometric Modelling Experts from university and industry are presenting new technologies for solving industrial problems and giving many important and practicable impulses for new research. Topics explored include NURBS, product engineering, object oriented modelling, solid modelling, surface interrogation, feature modelling, variational design, scattered data algorithms, geometry processing, blending methods, smoothing and fairing algorithms, spline conversion.This collection of 24 articles gives a state-of-the-art survey of the relevant problems and issues in geometric modelling. COMPUTERS,Computer Simulation

3-Dimensional Process Simulation This book contains the proceedings of the International "Workshop on 3D Process Simulation†which was held at the Campus of the University Erlangen-Nuremberg in Erlangen on September 5, 1995, in conjunction with the 6th International Conference on "Simulation of Semiconductor Devices and Processes†(SISDEP ’95). Whereas two-dimensional semiconductor process simulation has achieved a certain degree of maturity, three-dimensional process simulation is a newly emerging field in which most efforts are dedicated to necessary basic developments. Research in this area is promoted by the growing demand to obtain reliable information on device geometries and dopant distributions needed for three-dimensional device simulation, and challenged by the great algorithmic problems caused by moving interfaces and by the requirement to limit computation times and memory requirements. This workshop provided a forum to discuss the industrial needs, technical problems, and solutions being developed in the field of three-dimensional semiconductor process simulation. Invited presentations from leading semiconductor companies and research Centers of Excellence from Japan, the USA, and Europe outlined novel numerical algorithms, physical models, and applications in this rapidly emerging field. COMPUTERS,Computer Simulation

Technology-Based Learning Environments Proceedings of the NATO Advances Study Institute on Psychological and Educational Foundations of Technology- Based Learning Environments, held in the Orthodox Academy, Kolymbari, Crete, Greece, July 26-August 3, 1992 COMPUTERS,Computer Simulation

A Systems-Based Approach to Policymaking This book is based on a number of systems concepts, of which the following are emphasized here: oThe interacting systems of society and the environment are dynamic and evolution ary oEvolution of these systems carries them through stages of differential stability and instability, continuity and discontinuity oAssociated with evolution and instability is structural change that is essentially irre versible oThe present is a stage of world transformation that may not have been equaled for decades or even centuries oPolicies and decisions must match the times, in the present case the stage of world transformation The time 11:59:59 PM, approximately, on December 31, 2000 has an impor tant symbolic meaning. It marks the end of a minute, the end of an hour, the end of a day, the end of a year, the end of a decade, the end of a century, and the end of a millennium. The time and date provide a convenient yardstick against which we can evaluate the evolution of our thinking and the adequacy of our assumptions, mental models, paradigms, and policies. Will the beginning tum out to be appropriately dif ferent from the end? We hope that this book is helpful in such evaluation. This is a new-paradigm book, which both presents and advances the new way of thinking about the systems of science, technology, society, economics, politics, and the environment, and actively calls for the replacement of the worn out cognitive/sociotechnical paradigm. COMPUTERS,Computer Simulation

Geometric Modelling In this volume experts from university and industry are presenting new technologies for solving industrial problems as well as important and practicable impulses for new research.The following topics are treated:- solid modelling- geometry processing- feature modelling- product modelling- surfaces over arbitrary topologies- blending methods- scattered data algorithms- smooting and fairing algorithms- NURBS21 articles are giving a state-of-the-art survey of the relevant problems and issues in the rapidly growing area of geometric modelling. COMPUTERS,Computer Simulation

Monte Carlo Simulation of Semiconductor Devices Particle simulation of semiconductor devices is a rather new field which has started to catch the interest of the world's scientific community. It represents a time-continuous solution of Boltzmann's transport equation, or its quantum mechanical equivalent, and the field equation, without encountering the usual numerical problems associated with the direct solution. The technique is based on first physical principles by following in detail the transport histories of indi vidual particles and gives a profound insight into the physics of semiconductor devices. The method can be applied to devices of any geometrical complexity and material composition. It yields an accurate description of the device, which is not limited by the assumptions made behind the alternative drift diffusion and hydrodynamic models, which represent approximate solutions to the transport equation. While the development of the particle modelling technique has been hampered in the past by the cost of computer time, today this should not be held against using a method which gives a profound physical insight into individual devices and can be used to predict the properties of devices not yet manufactured. Employed in this way it can save the developer much time and large sums of money, both important considerations for the laboratory which wants to keep abreast of the field of device research. Applying it to al ready existing electronic components may lead to novel ideas for their improvement. The Monte Carlo particle simulation technique is applicable to microelectronic components of any arbitrary shape and complexity. COMPUTERS,Computer Simulation

Creating and Animating the Virtual World This book contains several invited papers and a selection of research papers submitted to Computer Animation '92, the fourth international workshop on Computer Animation, which was held in Geneva on May 20-22. This workshop, now an annual event, has been organized by the Computer Graphics Society, the University of Geneva, and the Swiss Federal Institute of Technology in Lausanne. During the international workshop on Computer Animation '92, the fifth Computer-generated Film Festival of Geneva, was held. The book presents original research results and applications experience in various areas of computer animation. This year most papers are related to physics-based animation, human animation, and geometric modelling for animation. NADIA MAGNENAT THALMANN DANIEL THALMANN Table of Contents Part I: Physics-based Animation The Control of Hovering Flight for Computer Animation David Haumann, Jessica K. Hodgins . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3 Inverse Problems in Computer Graphics Michael Kass . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . " . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21 NPSNET: Physically-based Modeling Enhancements to An Object File Format Michael J. Zyda, James G. Monahan, David R. Pratt. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35 A New Method for Approximative Interactive Dynamics Ulrich Leiner, Bernhard Preim . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53 Part ll: Human animation Extraction of 3D Shapes from the Moving Human Face Using Lighting Swjtch Photometry Hitoshi Saji, Hirohisa Hioki, Yoshihisa Shinagawa, Kensyu Yoshida, Tosiyasu L. Kunii . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 69 An Interactive Tool for the Design of Human Free-Walking Trajectories Laurent Bezault, Ronan Boulic, Nadia Magnenat Thalmann, Daniel Thalmann . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87 Achilles - A System for Visualizing Non Standard Human Gait Homero L. Piccolo, Kentaro Takahashi, Marcus G. de Amorim, Andre C. de Sa Carneiro . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . COMPUTERS,Computer Simulation

Motion Planning in Dynamic Environments Computer Science Workbench is a monograph series which will provide you with an in-depth working knowledge of current developments in computer technology. Every volume in this series will deal with a topic of importance in computer science and elaborate on how you yourself can build systems related to the main theme. You will be able to develop a variety of systems, including computer software tools, computer graphics, computer animation, database management systems, and computer-aided design and manufacturing systems. Computer Science Workbench represents an important new contribution in the field of practical computer technology. TOSIYASU L. KUNII To my parents Kenjiro and Nori Fujimura Preface Motion planning is an area in robotics that has received much attention recently. Much of the past research focuses on static environments - various methods have been developed and their characteristics have been well investigated. Although it is essential for autonomous intelligent robots to be able to navigate within dynamic worlds, the problem of motion planning in dynamic domains is relatively little understood compared with static problems. COMPUTERS,Computer Simulation

Knowledge-Based Simulation Knowledge-Based Simulation: Methodology and Application represents a recent compilation of research material that reviews fundamental concepts of simulation methodology and knowledge-based simulation applications. Knowledge-based simulation represents a new and exciting bridge area linking the fields of computer simulation and artificial intelligence. This book will appeal to both theorists and practitioners who require simulation to solve complex problems. A primary attraction of the book is its emphasis on both methodology and applications. In this way, the reader can explore new methods for encoding knowledge-inten- sive information into a simulation model, and new applications that utilize these methods. COMPUTERS,Computer Simulation

Qualitative Simulation Modeling and Analysis Recently there has been considerable interest in qualitative methods in simulation and mathematical model- ing. Qualitative Simulation Modeling and Analysis is the first book to thoroughly review fundamental concepts in the field of qualitative simulation. The book will appeal to readers in a variety of disciplines including researchers in simulation methodology, artificial intelligence and engineering. This book boldly attempts to bring together, for the first time, the qualitative techniques previously found only in hard-to-find journals dedicated to single disciplines. The book is written for scientists and engineers interested in improving their knowledge of simulation modeling. The "qualitative" nature of the book stresses concepts of invariance, uncertainty and graph-theoretic bases for modeling and analysis. COMPUTERS,Computer Simulation

Compact Transistor Modelling for Circuit Design During the first decade following the invention of the transistor, progress in semiconductor device technology advanced rapidly due to an effective synergy of technological discoveries and physical understanding. Through physical reasoning, a feeling for the right assumption and the correct interpretation of experimental findings, a small group of pioneers conceived the major analytic design equations, which are currently to be found in numerous textbooks. Naturally with the growth of specific applications, the description of some characteristic properties became more complicated. For instance, in inte grated circuits this was due in part to the use of a wider bias range, the addition of inherent parasitic elements and the occurrence of multi dimensional effects in smaller devices. Since powerful computing aids became available at the same time, complicated situations in complex configurations could be analyzed by useful numerical techniques. Despite the resulting progress in device optimization, the above approach fails to provide a required compact set of device design and process control rules and a compact circuit model for the analysis of large-scale electronic designs. This book therefore takes up the original thread to some extent. Taking into account new physical effects and introducing useful but correct simplifying assumptions, the previous concepts of analytic device models have been extended to describe the characteristics of modern integrated circuit devices. This has been made possible by making extensive use of exact numerical results to gain insight into complicated situations of transistor operation. COMPUTERS,Computer Simulation

Advanced Simulation in Biomedicine This book presents a collection of invited contributions, each reflecting an area of biomedicine in which simulation techniques have been successfully applied. Thus, it provides a state-of-the-art survey of simulation techniques in a variety of biomedical applications. Chapter one presents the conceptual framework for advanced simulations such as parallel processing in biological systems. Chapter two focuses on structured biological modeling based on the bond graph method. This is followed by an up-to-date account of advanced simulation of a variety of sophisticated biomedical processes. The authors provide many insights into how computer simulation techniques and tools can be applied to research problems in biomedicine. The idea for this book arose out of the daily work by experts in their field and reflects developing areas. Therefore, I think the material is timely and hope that the work described will be an encouragement for others. It is the objective of this book to present advanced simulation techniques in biomedicine and outline current research, as well as to point out open problems, in this dynamic field. Finally, I wish to express my thanks to those colleagues who have made this book possible with their contributions. COMPUTERS,Computer Simulation

Simulation by Bondgraphs Bondgraphs are a powerful tool in the simulation of mechanical, hydraulic, electric and thermal systems. They are used to represent engineering systems in written form by means of letter elements and their interconnections, called bonds, instead of in the form of numerous equations. They may be used to increase the efficiency of new product design. This book introduces the reader to bondgraphs and their use on PCs. A broad variety of applications of this method in the simulation of the above systems is presented. Twenty fully worked examples complement the presentation. COMPUTERS,Computer Simulation

Dynamic Modeling Computer models offer a means of interpreting and analyzing the dynamics of real-world systems ranging from population growth to ozone depletion. Dynamic Modeling introduces an approach to modeling that makes it a more practical, intuitive endeavor. The book enables readers to convert their understanding of a phenomenon to a computer model, and then to run the model and let it yield the inevitable dynamic consequences built into the structure of the model. Dynamic Modeling uses STELLA II software to develop simulation models. Part I provides an introduction to modeling dynamic systems. Part II offers general methods for modeling. Parts III through VIII apply these methods to model real-world phenomena from chemistry, genetics, ecology, economics, and engineering. To develop and execute dynamic simulation models, Dynamic Modeling comes with STELLA II run-time software for Windows-based computers, as well as computer files of sample models used in the book. Dynamic Modeling offers a clear, approachable introduction to the modeling process, and will be of interest in any field where real problems can be illuminated by computer simulation. COMPUTERS,Computer Simulation

Particle Modeling COMPUTERS,Computer Simulation

Student Modelling Proceedings of the NATO Advanced Research Workshop on "Student Modelling: The Key to Individualized Knowledge-Based Instruction", held in Ste.Adele, Quebec, Canada, May 4 - 8, 1991 COMPUTERS,Computer Simulation

Mastering Quantum Computing with IBM QX Learn quantum computing by implementing quantum programs on IBM QX and be at the forefront of the next revolution in computation Key Features Learn quantum computing through programming projects Run, test, and debug your quantum programs with the fully integrated IBM QX Use Qiskit to create, compile, and execute quantum computing programs Book Description Quantum computing is set to disrupt the industry. IBM Research has made quantum computing available to the public for the first time, providing cloud access to IBM QX from any desktop or mobile device. Complete with cutting-edge practical examples, this book will help you understand the power of quantum computing in the real world. Mastering Quantum Computing with IBM QX begins with the principles of quantum computing and the areas in which they can be applied. You'll explore the IBM Ecosystem, which enables quantum development with Quantum Composer and Qiskit. As you progress through the chapters, you'll implement algorithms on the quantum processor and learn how quantum computations are actually performed. By the end of the book, you will completely understand how to create quantum programs of your own, the impact of quantum computing on your business, and how to future-proof your programming career. What you will learn Study the core concepts and principles of quantum computing Uncover the areas in which quantum principles can be applied Design programs with quantum logic Understand how a quantum computer performs computations Work with key quantum computational algorithms including Shor's algorithm and Grover's algorithm Develop the ability to analyze the potential of quantum computing in your industry Who this book is for If you're a developer or data scientist interested in learning quantum computing, this book is for you. You're expected to have basic understanding of Python language, however in-depth knowledge of quantum physics is not required. COMPUTERS,Computer Simulation

Finite Element Analysis Concepts Young engineers are often required to utilize commercial finite element software without having had a course on finite element theory. That can lead to computer-aided design errors.This book outlines the basic theory, with a minimum of mathematics, and how its phases are structured within a typical software. The importance of estimating a solution, or verifying the results, by other means is emphasized and illustrated. The book also demonstrates the common processes for utilizing the typical graphical icon interfaces in commercial codes. In particular, the book uses and covers the widely utilized SolidWorks solid modeling and simulation system to demonstrate applications in heat transfer, stress analysis, vibrations, buckling, and other fields. The book, with its detailed applications, will appeal to upper-level undergraduates as well as engineers new to industry. COMPUTERS,Computer Simulation

Hands-On Genetic Algorithms with Python Explore the ever-growing world of genetic algorithms to solve search, optimization, and AI-related tasks, and improve machine learning models using Python libraries such as DEAP, scikit-learn, and NumPy Key Features Explore the ins and outs of genetic algorithms with this fast-paced guide Implement tasks such as feature selection, search optimization, and cluster analysis using Python Solve combinatorial problems, optimize functions, and enhance the performance of artificial intelligence applications Book Description Genetic algorithms are a family of search, optimization, and learning algorithms inspired by the principles of natural evolution. By imitating the evolutionary process, genetic algorithms can overcome hurdles encountered in traditional search algorithms and provide high-quality solutions for a variety of problems. This book will help you get to grips with a powerful yet simple approach to applying genetic algorithms to a wide range of tasks using Python, covering the latest developments in artificial intelligence. After introducing you to genetic algorithms and their principles of operation, you'll understand how they differ from traditional algorithms and what types of problems they can solve. You'll then discover how they can be applied to search and optimization problems, such as planning, scheduling, gaming, and analytics. As you advance, you'll also learn how to use genetic algorithms to improve your machine learning and deep learning models, solve reinforcement learning tasks, and perform image reconstruction. Finally, you'll cover several related technologies that can open up new possibilities for future applications. By the end of this book, you'll have hands-on experience of applying genetic algorithms in artificial intelligence as well as in numerous other domains. What you will learn Understand how to use state-of-the-art Python tools to create genetic algorithm-based applications Use genetic algorithms to optimize functions and solve planning and scheduling problems Enhance the performance of machine learning models and optimize deep learning network architecture Apply genetic algorithms to reinforcement learning tasks using OpenAI Gym Explore how images can be reconstructed using a set of semi-transparent shapes Discover other bio-inspired techniques, such as genetic programming and particle swarm optimization Who this book is for This book is for software developers, data scientists, and AI enthusiasts who want to use genetic algorithms to carry out intelligent tasks in their applications. Working knowledge of Python and basic knowledge of mathematics and computer science will help you get the most out of this book. COMPUTERS,Computer Simulation

Hands-On Deep Learning for Finance Take your quantitative strategies to the next level by exploring nine examples that make use of cutting-edge deep learning technologies, including CNNs, LSTMs, GANs, reinforcement learning, and CapsNets Key Features Implement deep learning techniques and algorithms to build financial models Apply modern AI techniques in quantitative market modeling and investment decision making Leverage Python libraries for rapid development and prototyping Book Description Quantitative methods are the vanguard of the investment management industry. This book shows how to enhance trading strategies and investments in financial markets using deep learning algorithms. This book is an excellent reference to understand how deep learning models can be leveraged to capture insights from financial data. You will implement deep learning models using Python libraries such as TensorFlow and Keras. You will learn various deep learning algorithms to build models for understanding financial market dynamics and exploiting them in a systematic manner. This book takes a pragmatic approach to address various aspects of asset management. The information content in non-structured data like news flow is crystalized using BLSTM. Autoencoders for efficient index replication is discussed in detail. You will use CNN to develop a trading signal with simple technical indicators, and improvements offered by more complex techniques such as CapsNets. Volatility is given due emphasis by demonstrating the superiority of forecasts employing LSTM, and Monte Carlo simulations using GAN for value at risk computations. These are then brought together by implementing deep reinforcement learning for automated trading. This book will serve as a continuing reference for implementing deep learning models to build investment strategies. What you will learn Implement quantitative financial models using the various building blocks of a deep neural network Build, train, and optimize deep networks from scratch Use LSTMs to process data sequences such as time series and news feeds Implement convolutional neural networks (CNNs), CapsNets, and other models to create trading strategies Adapt popular neural networks for pattern recognition in finance using transfer learning Automate investment decisions by using reinforcement learning Discover how a risk model can be constructed using D-GAN Who this book is for If you're a finance or investment professional who wants to lead the development of quantitative strategies, this book is for you. With this practical guide, you'll be able to use deep learning methods for building financial models and incorporating them in your investment process. Anyone who wants to enter the fascinating domain of quantitative finance using the power of deep learning algorithms and techniques will also find this book useful. Basic knowledge of machine learning and Python programming is required. COMPUTERS,Computer Simulation

Simulation and Its Discontents How the simulation and visualization technologies so pervasive in science, engineering, and design have changed our way of seeing the world. Over the past twenty years, the technologies of simulation and visualization have changed our ways of looking at the world. In Simulation and Its Discontents, Sherry Turkle examines the now dominant medium of our working lives and finds that simulation has become its own sensibility. We hear it in Turkle's description of architecture students who no longer design with a pencil, of science and engineering students who admit that computer models seem more “real” than experiments in physical laboratories. Echoing architect Louis Kahn's famous question, “What does a brick want?”, Turkle asks, “What does simulation want?” Simulations want, even demand, immersion, and the benefits are clear. Architects create buildings unimaginable before virtual design; scientists determine the structure of molecules by manipulating them in virtual space; physicians practice anatomy on digitized humans. But immersed in simulation, we are vulnerable. There are losses as well as gains. Older scientists describe a younger generation as “drunk with code.” Young scientists, engineers, and designers, full citizens of the virtual, scramble to capture their mentors' tacit knowledge of buildings and bodies. From both sides of a generational divide, there is anxiety that in simulation, something important is slipping away. Turkle's examination of simulation over the past twenty years is followed by four in-depth investigations of contemporary simulation culture: space exploration, oceanography, architecture, and biology. COMPUTERS,Computer Simulation

Intelligent IoT Projects in 7 Days Discover how to build your own Intelligent Internet of Things projects and bring a new degree of interconnectivity to your world. About This Book Build intelligent and unusual IoT projects in just 7 days, Create home automation, smart home, and robotic projects and allow your devices to do smart work Build IoT skills through enticing projects and leverage revolutionary computing hardware through the RPi and Arduino. Who This Book Is For If you're a developer, IoT enthusiast, or just someone curious about Internet of Things, then this book is for you. A basic understanding of electronic hardware, networking, and basic programming skills would do wonders. What You Will Learn Learn how to get started with intelligent IoT projects Explore various pattern recognition and machine learning algorithms to make IoT projects smarter. Make decisions on which devices to use based on the kind of project to build. Create a simple machine learning application and implement decision system concepts Build a smart parking system using Arduino and Raspberry Pi Learn how to work with Amazon Echo and to build your own smart speaker machine Build multi-robot cooperation using swarm intelligence. In Detail Intelligent IoT Projects in 7 days is about creating smart IoT projects in just 7 days. This book will help you to overcome the challenge of analyzing data from physical devices. This book aims to help you put together some of the most exciting IoT projects in a short span of time. You'll be able to use these in achieving or automating everyday tasks—one project per day. We will start with a simple smart gardening system and move on to a smart parking system, and then we will make our own vending machine, a smart digital advertising dashboard, a smart speaker machine, an autonomous fire fighter robot, and finally look at a multi-robot cooperation using swarm intelligence Style and approach A clear step-by-step instruction guide to completing fully-fledged projects in just 7 days COMPUTERS,Computerized Home & Entertainment

Robot Operating System Cookbook Leverage the power of ROS to build exciting collaborative robots. About This Book Delve into an open source, meta-operating system for your robot Get acquainted with tools and libraries for building and running code on multiple platforms Use Gazebo to model your robot and create a virtual environment Who This Book Is For If you're a researcher or engineer with an interest in the problems, solutions, and future research issues that you may encounter in the development of robotic applications, this book is for you. Basic knowledge of C++ and Python programming with the GNU/Linux environment is strongly recommended to assist with understanding the key concepts covered in the book. What You Will Learn Explore advanced concepts, such as ROS pluginlib, nodelets, and actionlib Work with ROS visualization, profiling, and debugging tools Gain experience in robot modeling and simulation using Gazebo Understand the ROS Navigation Stack for mobile robots Configure a MoveIt! package for a manipulator robot Develop an autonomous navigation framework for MAV using ORB SLAM and MoveIt Integrate sensors, actuators, and robots into the ROS ecosystem Get acquainted with the ROS-Industrial package with hardware support, capabilities, and applications In Detail This book will leverage the power of ROS with an introduction to its core and advanced concepts through exciting recipes. You will get acquainted with the use of different synchronous and asynchronous communication methods, including messages, services, and actions. You will learn how to use the various debugging and visualization tools used in development and how to interface sensors and actuators with the ROS framework. Firstly, you will get to grips with ROS simulation frameworks, such as Gazebo and RotorS for modeling and simulating any physical robot and virtual environment. You will also cover mobile robotics, micro-aerial vehicles, and robotic arms, which are the leading branches of robotic applications. Robot Operating System Cookbook will also guide you in the development of an autonomous navigation framework for both mobile robots and micro-aerial vehicles. Finally, you will explore ROS-Industrial, an open source project that extends the advanced capabilities of ROS software to manufacturing industries. Style and approach The goal of this book is to provide an integrated overview of the concepts and techniques. ROS is not an operating system in the traditional sense of process management and scheduling; rather, it provides a structured communications layer above the host operating systems of a heterogeneous compute cluster. COMPUTERS,Computerized Home & Entertainment

Internet of Things Programming Projects A practical project-based guide to help you build and control your IoT projects Key Features Leverage the full potential of IoT with the combination of Raspberry Pi 3 and Python Build complex Python-based applications with IoT Work on various IoT projects and understand the basics of electronics Book Description The Internet of Things (IOT) has managed to attract the attention of researchers and tech enthusiasts, since it powerfully combines classical networks with instruments and devices. In Internet of Things Programming Projects, we unleash the power of Raspberry Pi and Python to create engaging projects. In the first part of the book, you'll be introduced to the Raspberry Pi, learn how to set it up, and then jump right into Python programming. Then, you'll dive into real-world computing by creating a“Hello World†app using flash LEDs. As you make your way through the chapters, you'll go back to an age when analog needle meters ruled the world of data display. You'll learn to retrieve weather data from a web service and display it on an analog needle meter, and build a home security system using the Raspberry Pi. The next project has a modern twist, where we employ the Raspberry Pi to send a signal to a web service that will send you a text when someone is at the door. In the final project, you take what you've learned from the previous two projects and create an IoT robot car that you can use to monitor what your pets are up to when you are away. By the end of this book, you will be well versed in almost every possible way to make your IoT projects stand out. What you will learn Install and set up a Raspberry Pi for IoT development Learn how to use a servo motor as an analog needle meter to read data Build a home security dashboard using an infrared motion detector Communicate with a web service that sends you a message when the doorbell rings Receive data and display it with an actuator connected to the Raspberry Pi Build an IoT robot car that is controlled through the internet Who this book is for Internet of Things Programming Projects is for Python developers and programmers who are interested in building their own IoT applications and IoT-based projects. It is also targeted at IoT programmers and developers who are looking to build exciting projects with Python. COMPUTERS,Computerized Home & Entertainment

ROS Robotics Projects Build exciting robotics projects such as mobile manipulators, self-driving cars, and industrial robots powered by ROS, machine learning, and virtual reality Key Features Create and program cool robotic projects using powerful ROS libraries Build industrial robots like mobile manipulators to handle complex tasks Learn how reinforcement learning and deep learning are used with ROS Book Description Nowadays, heavy industrial robots placed in workcells are being replaced by new age robots called cobots, which don't need workcells. They are used in manufacturing, retail, banks, energy, and healthcare, among other domains. One of the major reasons for this rapid growth in the robotics market is the introduction of an open source robotics framework called the Robot Operating System (ROS). This book covers projects in the latest ROS distribution, ROS Melodic Morenia with Ubuntu Bionic (18.04). Starting with the fundamentals, this updated edition of ROS Robotics Projects introduces you to ROS-2 and helps you understand how it is different from ROS-1. You'll be able to model and build an industrial mobile manipulator in ROS and simulate it in Gazebo 9. You'll then gain insights into handling complex robot applications using state machines and working with multiple robots at a time. This ROS book also introduces you to new and popular hardware such as Nvidia's Jetson Nano, Asus Tinker Board, and Beaglebone Black, and allows you to explore interfacing with ROS. You'll learn as you build interesting ROS projects such as self-driving cars, making use of deep learning, reinforcement learning, and other key AI concepts. By the end of the book, you'll have gained the confidence to build interesting and intricate projects with ROS. What you will learn Grasp the basics of ROS and understand ROS applications Uncover how ROS-2 is different from ROS-1 Handle complex robot tasks using state machines Communicate with multiple robots and collaborate to build apps with them Explore ROS capabilities with the latest embedded boards such as Tinker Board S and Jetson Nano Discover how machine learning and deep learning techniques are used with ROS Build a self-driving car powered by ROS Teleoperate your robot using Leap Motion and a VR headset Who this book is for If you're a student, hobbyist, professional, or anyone with a passion for learning robotics and interested in learning about algorithms, motion control, and perception capabilities from scratch, this book is for you. This book is also ideal for anyone who wants to build a new product and for researchers to make the most of what's already available to create something new and innovative in the field of robotics. COMPUTERS,Computerized Home & Entertainment

TechGnosis How does our fascination with technology intersect with the religious imagination? In TechGnosis—a cult classic now updated and reissued with a new afterword—Erik Davis argues that while the realms of the digital and the spiritual may seem worlds apart, esoteric and religious impulses have in fact always permeated (and sometimes inspired) technological communication. Davis uncovers startling connections between such seemingly disparate topics as electricity and alchemy; online roleplaying games and religious and occult practices; virtual reality and gnostic mythology; programming languages and Kabbalah. The final chapters address the apocalyptic dreams that haunt technology, providing vital historical context as well as new ways to think about a future defined by the mutant intermingling of mind and machine, nightmare and fantasy. COMPUTERS,Cybernetics

Possible Minds Science world luminary John Brockman assembles twenty-five of the most important scientific minds, people who have been thinking about the field artificial intelligence for most of their careers, for an unparalleled round-table examination about mind, thinking, intelligence and what it means to be human. "Artificial intelligence is today's story--the story behind all other stories. It is the Second Coming and the Apocalypse at the same time: Good AI versus evil AI." --John Brockman More than sixty years ago, mathematician-philosopher Norbert Wiener published a book on the place of machines in society that ended with a warning: "we shall never receive the right answers to our questions unless we ask the right questions.... The hour is very late, and the choice of good and evil knocks at our door." In the wake of advances in unsupervised, self-improving machine learning, a small but influential community of thinkers is considering Wiener's words again. In Possible Minds, John Brockman gathers their disparate visions of where AI might be taking us. The fruit of the long history of Brockman's profound engagement with the most important scientific minds who have been thinking about AI--from Alison Gopnik and David Deutsch to Frank Wilczek and Stephen Wolfram--Possible Minds is an ideal introduction to the landscape of crucial issues AI presents. The collision between opposing perspectives is salutary and exhilarating; some of these figures, such as computer scientist Stuart Russell, Skype co-founder Jaan Tallinn, and physicist Max Tegmark, are deeply concerned with the threat of AI, including the existential one, while others, notably robotics entrepreneur Rodney Brooks, philosopher Daniel Dennett, and bestselling author Steven Pinker, have a very different view. Serious, searching and authoritative, Possible Minds lays out the intellectual landscape of one of the most important topics of our time. COMPUTERS,Cybernetics

Cybernetic Revolutionaries A historical study of Chile's twin experiments with cybernetics and socialism, and what they tell us about the relationship of technology and politics. In Cybernetic Revolutionaries, Eden Medina tells the history of two intersecting utopian visions, one political and one technological. The first was Chile's experiment with peaceful socialist change under Salvador Allende; the second was the simultaneous attempt to build a computer system that would manage Chile's economy. Neither vision was fully realized—Allende's government ended with a violent military coup; the system, known as Project Cybersyn, was never completely implemented—but they hold lessons for today about the relationship between technology and politics. Drawing on extensive archival material and interviews, Medina examines the cybernetic system envisioned by the Chilean government—which was to feature holistic system design, decentralized management, human-computer interaction, a national telex network, near real-time control of the growing industrial sector, and modeling the behavior of dynamic systems. She also describes, and documents with photographs, the network's Star Trek-like operations room, which featured swivel chairs with armrest control panels, a wall of screens displaying data, and flashing red lights to indicate economic emergencies. Studying project Cybersyn today helps us understand not only the technological ambitions of a government in the midst of political change but also the limitations of the Chilean revolution. This history further shows how human attempts to combine the political and the technological with the goal of creating a more just society can open new technological, intellectual, and political possibilities. Technologies, Medina writes, are historical texts; when we read them we are reading history. COMPUTERS,Cybernetics

Cybernetics or Control and Communication in the Animal and the Machine, Reissue of the 1961 second edition A classic and influential work that laid the theoretical foundations for information theory and a timely text for contemporary informations theorists and practitioners. With the influential book Cybernetics, first published in 1948, Norbert Wiener laid the theoretical foundations for the multidisciplinary field of cybernetics, the study of controlling the flow of information in systems with feedback loops, be they biological, mechanical, cognitive, or social. At the core of Wiener's theory is the message (information), sent and responded to (feedback); the functionality of a machine, organism, or society depends on the quality of messages. Information corrupted by noise prevents homeostasis, or equilibrium. And yet Cybernetics is as philosophical as it is technical, with the first chapter devoted to Newtonian and Bergsonian time and the philosophical mixed with the technical throughout. This book brings the 1961 second edition back into print, with new forewords by Doug Hill and Sanjoy Mitter. Contemporary readers of Cybernetics will marvel at Wiener's prescience—his warnings against “noise,” his disdain for “hucksters” and “gadget worshipers,” and his view of the mass media as the single greatest anti-homeostatic force in society. This edition of Cybernetics gives a new generation access to a classic text. COMPUTERS,Cybernetics

Practical Biostatistics Evidence-based medicine aims to apply the best available evidence gained from the scientific method to medical decision making. It is a practice that uses statistical analysis of scientific methods and outcomes to drive further experimentation and diagnosis. The profusion of evidence-based medicine in medical practice and clinical research has produced a need for life scientists and clinical researchers to assimilate biostatistics into their work to meet efficacy and practical standards. Practical Biostatistics provides researchers, medical professionals, and students with a friendly, practical guide to biostatistics. With a detailed outline of implementation steps complemented by a review of important topics, this book can be used as a quick reference or a hands-on guide to effectively incorporate biostatistics in clinical trials. Customized presentation for biological investigators with examples taken from current clinical trials in multiple disciplines Clear and concise definitions and examples provide a pragmatic guide to bring clarity to the applications of statistics in improving human health Addresses the challenge of assimilation of mathematical concepts to better interpret literature, to build stronger studies, to present research effectively, and to improve communication with supporting biostatisticians COMPUTERS,Data Science,Bioinformatics

Bioinformatics Data Skills Learn the data skills necessary for turning large sequencing datasets into reproducible and robust biological findings. With this practical guide, you’ll learn how to use freely available open source tools to extract meaning from large complex biological data sets. At no other point in human history has our ability to understand life’s complexities been so dependent on our skills to work with and analyze data. This intermediate-level book teaches the general computational and data skills you need to analyze biological data. If you have experience with a scripting language like Python, you’re ready to get started. Go from handling small problems with messy scripts to tackling large problems with clever methods and tools Process bioinformatics data with powerful Unix pipelines and data tools Learn how to use exploratory data analysis techniques in the R language Use efficient methods to work with genomic range data and range operations Work with common genomics data file formats like FASTA, FASTQ, SAM, and BAM Manage your bioinformatics project with the Git version control system Tackle tedious data processing tasks with with Bash scripts and Makefiles COMPUTERS,Data Science,Bioinformatics

Gentle Introduction To Support Vector Machines In Biomedicine, A - Volume 1 Support Vector Machines (SVMs) are among the most important recent developments in pattern recognition and statistical machine learning. They have found a great range of applications in various fields including biology and medicine. However, biomedical researchers often experience difficulties grasping both the theory and applications of these important methods because of lack of technical background. The purpose of this book is to introduce SVMs and their extensions and allow biomedical researchers to understand and apply them in real-life research in a very easy manner. The book is to consist of two volumes: theory and methods (Volume 1) and case studies (Volume 2). COMPUTERS,Data Science,Bioinformatics

Companion Diagnostics (CDx) in Precision Medicine There is a new trend in anti-cancer therapeutics development: a targeted therapy and precision medicine that targets a subgroup of patients with specific biomarkers. An in vitro diagnostic (IVD) assay is required to identify a subgroup of cancer patients who would benefit from the targeted therapy, or not likely benefit, or have a high risk of side effects from the specific drug treatment. This IVD or medical device is called a companion diagnostic (CDx) assay. It is key to have a robust CDx assay or device for the success of targeted therapy and precision medicine. This book covers the technical, historical, clinical, and regulatory aspects of CDx in precision medicine. Clearly, more and more newly developed oncology drugs will require accompanying CDx assays, and this book, with chapters contributed by renowned oncologists, provides a comprehensive foundation for the knowledge and application of CDx for precision medicine. COMPUTERS,Data Science,Bioinformatics

R Bioinformatics Cookbook Over 60 recipes to model and handle real-life biological data using modern libraries from the R ecosystem Key Features Apply modern R packages to handle biological data using real-world examples Represent biological data with advanced visualizations suitable for research and publications Handle real-world problems in bioinformatics such as next-generation sequencing, metagenomics, and automating analyses Book Description Handling biological data effectively requires an in-depth knowledge of machine learning techniques and computational skills, along with an understanding of how to use tools such as edgeR and DESeq. With the R Bioinformatics Cookbook, you'll explore all this and more, tackling common and not-so-common challenges in the bioinformatics domain using real-world examples. This book will use a recipe-based approach to show you how to perform practical research and analysis in computational biology with R. You will learn how to effectively analyze your data with the latest tools in Bioconductor, ggplot, and tidyverse. The book will guide you through the essential tools in Bioconductor to help you understand and carry out protocols in RNAseq, phylogenetics, genomics, and sequence analysis. As you progress, you will get up to speed with how machine learning techniques can be used in the bioinformatics domain. You will gradually develop key computational skills such as creating reusable workflows in R Markdown and packages for code reuse. By the end of this book, you'll have gained a solid understanding of the most important and widely used techniques in bioinformatic analysis and the tools you need to work with real biological data. What you will learn Employ Bioconductor to determine differential expressions in RNAseq data Run SAMtools and develop pipelines to find single nucleotide polymorphisms (SNPs) and Indels Use ggplot to create and annotate a range of visualizations Query external databases with Ensembl to find functional genomics information Execute large-scale multiple sequence alignment with DECIPHER to perform comparative genomics Use d3.js and Plotly to create dynamic and interactive web graphics Use k-nearest neighbors, support vector machines and random forests to find groups and classify data Who this book is for This book is for bioinformaticians, data analysts, researchers, and R developers who want to address intermediate-to-advanced biological and bioinformatics problems by learning through a recipe-based approach. Working knowledge of R programming language and basic knowledge of bioinformatics are prerequisites. COMPUTERS,Data Science,Bioinformatics

Genomics in the Cloud Data in the genomics field is booming. In just a few years, organizations such as the National Institutes of Health (NIH) will host 50+ petabytes—or over 50 million gigabytes—of genomic data, and they’re turning to cloud infrastructure to make that data available to the research community. How do you adapt analysis tools and protocols to access and analyze that volume of data in the cloud? With this practical book, researchers will learn how to work with genomics algorithms using open source tools including the Genome Analysis Toolkit (GATK), Docker, WDL, and Terra. Geraldine Van der Auwera, longtime custodian of the GATK user community, and Brian O’Connor of the UC Santa Cruz Genomics Institute, guide you through the process. You’ll learn by working with real data and genomics algorithms from the field. This book covers: Essential genomics and computing technology background Basic cloud computing operations Getting started with GATK, plus three major GATK Best Practices pipelines Automating analysis with scripted workflows using WDL and Cromwell Scaling up workflow execution in the cloud, including parallelization and cost optimization Interactive analysis in the cloud using Jupyter notebooks Secure collaboration and computational reproducibility using Terra COMPUTERS,Data Science,Bioinformatics

Biological Language Model Conceived as a cross between natural language processing methods and biological sequences in DNA, RNA and protein, biological language model is a new scientific research topic in bioinformatics that has been extensively studied by the authors. The basic theory and applications of this model are presented in this book to serve as an reference for graduate students and researchers. COMPUTERS,Data Science,Bioinformatics

Statistical Approaches to Gene x Environment Interactions for Complex Phenotypes Diverse methodological and statistical approaches for investigating the role of gene-environment interactions in a range of complex diseases and traits. Findings from the Human Genome Project and from Genome-Wide Association (GWA) studies indicate that many diseases and traits manifest a more complex genomic pattern than previously assumed. These findings, and advances in high-throughput sequencing, suggest that there are many sources of influence—genetic, epigenetic, and environmental. This volume investigates the role of the interactions of genes and environment (G × E) in diseases and traits (referred to by the contributors as complex phenotypes) including depression, diabetes, obesity, and substance use. The contributors first present different statistical approaches or strategies to address G × E and G × G interactions with high-throughput sequenced data, including two-stage procedures to identify G × E and G × G interactions, marker-set approaches to assessing interactions at the gene level, and the use of a partial-least square (PLS) approach. The contributors then turn to specific complex phenotypes, research designs, or combined methods that may advance the study of G × E interactions, considering such topics as randomized clinical trials in obesity research, longitudinal research designs and statistical models, and the development of polygenic scores to investigate G × E interactions. Contributors Fatima Umber Ahmed, Yin-Hsiu Chen, James Y. Dai, Caroline Y. Doyle, Zihuai He, Li Hsu, Shuo Jiao, Erin Loraine Kinnally, Yi-An Ko, Charles Kooperberg, Seunggeun Lee, Arnab Maity, Jeanne M. McCaffery, Bhramar Mukherjee, Sung Kyun Park, Duncan C. Thomas, Alexandre Todorov, Jung-Ying Tzeng, Tao Wang, Michael Windle, Min Zhang COMPUTERS,Data Science,Bioinformatics

Building Ontologies with Basic Formal Ontology An introduction to the field of applied ontology with examples derived particularly from biomedicine, covering theoretical components, design practices, and practical applications. In the era of “big data,” science is increasingly information driven, and the potential for computers to store, manage, and integrate massive amounts of data has given rise to such new disciplinary fields as biomedical informatics. Applied ontology offers a strategy for the organization of scientific information in computer-tractable form, drawing on concepts not only from computer and information science but also from linguistics, logic, and philosophy. This book provides an introduction to the field of applied ontology that is of particular relevance to biomedicine, covering theoretical components of ontologies, best practices for ontology design, and examples of biomedical ontologies in use. After defining an ontology as a representation of the types of entities in a given domain, the book distinguishes between different kinds of ontologies and taxonomies, and shows how applied ontology draws on more traditional ideas from metaphysics. It presents the core features of the Basic Formal Ontology (BFO), now used by over one hundred ontology projects around the world, and offers examples of domain ontologies that utilize BFO. The book also describes Web Ontology Language (OWL), a common framework for Semantic Web technologies. Throughout, the book provides concrete recommendations for the design and construction of domain ontologies. COMPUTERS,Data Science,Bioinformatics

FileMaker Pro 8 Used by millions worldwide, FileMaker Pro is an award-winning database program for managing people, projects, images, assets, and other information. It's easy to use and totally customizable--so long as you know what you're doing. But FileMaker Pro doesn't come with a printed manual, so FileMaker Pro: The Missing Manual is the authoritative, jargon-free book that should have been in the box. FileMaker Pro: The Missing Manual approaches FileMaker the way FileMaker approaches you: it's user-friendly and seemingly straightforward enough, but it offers plenty of substance worthy of deeper exploration. Packed with practical information as well as countless expert tips and invaluable guidance, it's an in-depth guide to designing and building useful databases with the powerful and pliable FileMaker Pro. Covering FileMaker for both Windows and Macintosh, FileMaker Pro: The Missing Manual is ideal for small business users, home users, school teachers, developers--anyone who wants to organize information efficiently and effectively. Whether you want to run a business, publish a shopping cart on the Web, plan a wedding, manage a student information system at your school, or program databases for clients, this book delivers. Author Geoff Coffey has many years of experience using FileMaker Pro (he was, in fact, an early beta tester for the product). Author Susan Prosser is a FileMaker Certified Developer who trains other developers. Together, Coffey and Prosser show you how to: Get FileMaker up and running quickly and smoothly Import and organize information with ease Design relational databases that are simple to use, yet powerful Take advantage of FileMaker Pro calculation capabilities Automate processes with scripting Customize FileMaker Pro to your needs and preferences Share information with other people (coworkers, clients, and customers) and other programs Understand and select the best security options What could easily come across as dry and intimidating--things like relational theory, calculations, and scripting--are presented in a way that is interesting and intuitive to mainstream users. In no time, you'll be working more productively and efficiently using FileMaker Pro. COMPUTERS,Data Science,Data Analytics

Practical PostgreSQL Arguably the most capable of all the open source databases, PostgreSQL is an object-relational database management system first developed in 1977 by the University of California at Berkeley. In spite of its long history, this robust database suffers from a lack of easy-to-use documentation. Practical PostgreSQL fills that void with a fast-paced guide to installation, configuration, and usage. This comprehensive new volume shows you how to compile PostgreSQL from source, create a database, and configure PostgreSQL to accept client-server connections. It also covers the many advanced features, such as transactions, versioning, replication, and referential integrity that enable developers and DBAs to use PostgreSQL for serious business applications. The thorough introduction to PostgreSQL's PL/pgSQL programming language explains how you can use this very useful but under-documented feature to develop stored procedures and triggers. The book includes a complete command reference, and database administrators will appreciate the chapters on user management, database maintenance, and backup & recovery. With Practical PostgreSQL, you will discover quickly why this open source database is such a great open source alternative to proprietary products from Oracle, IBM, and Microsoft. COMPUTERS,Data Science,Data Analytics

High Performance MySQL How can you bring out MySQL’s full power? With High Performance MySQL, you’ll learn advanced techniques for everything from designing schemas, indexes, and queries to tuning your MySQL server, operating system, and hardware to their fullest potential. This guide also teaches you safe and practical ways to scale applications through replication, load balancing, high availability, and failover. Updated to reflect recent advances in MySQL and InnoDB performance, features, and tools, this third edition not only offers specific examples of how MySQL works, it also teaches you why this system works as it does, with illustrative stories and case studies that demonstrate MySQL’s principles in action. With this book, you’ll learn how to think in MySQL. Learn the effects of new features in MySQL 5.5, including stored procedures, partitioned databases, triggers, and views Implement improvements in replication, high availability, and clustering Achieve high performance when running MySQL in the cloud Optimize advanced querying features, such as full-text searches Take advantage of modern multi-core CPUs and solid-state disks Explore backup and recovery strategies—including new tools for hot online backups COMPUTERS,Data Science,Data Analytics

Marketing Analytics Helping tech-savvy marketers and data analysts solve real-world business problems with Excel Using data-driven business analytics to understand customers and improve results is a great idea in theory, but in today's busy offices, marketers and analysts need simple, low-cost ways to process and make the most of all that data. This expert book offers the perfect solution. Written by data analysis expert Wayne L. Winston, this practical resource shows you how to tap a simple and cost-effective tool, Microsoft Excel, to solve specific business problems using powerful analytic techniques—and achieve optimum results. Practical exercises in each chapter help you apply and reinforce techniques as you learn. Shows you how to perform sophisticated business analyses using the cost-effective and widely available Microsoft Excel instead of expensive, proprietary analytical tools Reveals how to target and retain profitable customers and avoid high-risk customers Helps you forecast sales and improve response rates for marketing campaigns Explores how to optimize price points for products and services, optimize store layouts, and improve online advertising Covers social media, viral marketing, and how to exploit both effectively Improve your marketing results with Microsoft Excel and the invaluable techniques and ideas in Marketing Analytics: Data-Driven Techniques with Microsoft Excel. COMPUTERS,Data Science,Data Analytics

Business Analytics Principles, Concepts, and Applications Learn everything you need to know to start using business analytics and integrating it throughout your organization. Business Analytics Principles, Concepts, and Applications brings together a complete, integrated package of knowledge for newcomers to the subject. The authors present an up-to-date view of what business analytics is, why it is so valuable, and most importantly, how it is used. They combine essential conceptual content with clear explanations of the tools, techniques, and methodologies actually used to implement modern business analytics initiatives. They offer a proven step-wise approach to designing an analytics program, and successfully integrating it into your organization, so it effectively provides intelligence for competitive advantage in decision making. Using step-by-step examples, the authors identify common challenges that can be addressed by business analytics, illustrate each type of analytics (descriptive, prescriptive, and predictive), and guide users in undertaking their own projects. Illustrating the real-world use of statistical, information systems, and management science methodologies, these examples help readers successfully apply the methods they are learning. Unlike most competitive guides, this text demonstrates the use of IBM's menu-based SPSS software, permitting instructors to spend less time teaching software and more time focusing on business analytics itself. A valuable resource for all beginning-to-intermediate-level business analysts and business analytics managers; for MBA/Masters' degree students in the field; and for advanced undergraduates majoring in statistics, applied mathematics, or engineering/operations research. COMPUTERS,Data Science,Data Analytics

Data Mining With Decision Trees Decision trees have become one of the most powerful and popular approaches in knowledge discovery and data mining; it is the science of exploring large and complex bodies of data in order to discover useful patterns. Decision tree learning continues to evolve over time. Existing methods are constantly being improved and new methods introduced.This 2nd Edition is dedicated entirely to the field of decision trees in data mining; to cover all aspects of this important technique, as well as improved or new methods and techniques developed after the publication of our first edition. In this new edition, all chapters have been revised and new topics brought in. New topics include Cost-Sensitive Active Learning, Learning with Uncertain and Imbalanced Data, Using Decision Trees beyond Classification Tasks, Privacy Preserving Decision Tree Learning, Lessons Learned from Comparative Studies, and Learning Decision Trees for Big Data. A walk-through guide to existing open-source data mining software is also included in this edition.This book invites readers to explore the many benefits in data mining that decision trees offer: COMPUTERS,Data Science,Data Analytics

Statistics for Big Data For Dummies The fast and easy way to make sense of statistics for big data Does the subject of data analysis make you dizzy? You've come to the right place! Statistics For Big Data For Dummies breaks this often-overwhelming subject down into easily digestible parts, offering new and aspiring data analysts the foundation they need to be successful in the field. Inside, you'll find an easy-to-follow introduction to exploratory data analysis, the lowdown on collecting, cleaning, and organizing data, everything you need to know about interpreting data using common software and programming languages, plain-English explanations of how to make sense of data in the real world, and much more. Data has never been easier to come by, and the tools students and professionals need to enter the world of big data are based on applied statistics. While the word "statistics" alone can evoke feelings of anxiety in even the most confident student or professional, it doesn't have to. Written in the familiar and friendly tone that has defined the For Dummies brand for more than twenty years, Statistics For Big Data For Dummies takes the intimidation out of the subject, offering clear explanations and tons of step-by-step instruction to help you make sense of data mining—without losing your cool. Helps you to identify valid, useful, and understandable patterns in data Provides guidance on extracting previously unknown information from large databases Shows you how to discover patterns available in big data Gives you access to the latest tools and techniques for working in big data If you're a student enrolled in a related Applied Statistics course or a professional looking to expand your skillset, Statistics For Big Data For Dummies gives you access to everything you need to succeed. COMPUTERS,Data Science,Data Analytics

Data Science and Big Data Analytics Data Science and Big Data Analytics is about harnessing the power of data for new insights. The book covers the breadth of activities and methods and tools that Data Scientists use. The content focuses on concepts, principles and practical applications that are applicable to any industry and technology environment, and the learning is supported and explained with examples that you can replicate using open-source software. This book will help you: Become a contributor on a data science team Deploy a structured lifecycle approach to data analytics problems Apply appropriate analytic techniques and tools to analyzing big data Learn how to tell a compelling story with data to drive business action Prepare for EMC Proven Professional Data Science Certification Corresponding data sets are available at www.wiley.com/go/9781118876138. Get started discovering, analyzing, visualizing, and presenting data in a meaningful way today! COMPUTERS,Data Science,Data Analytics

Fraud Analytics Using Descriptive, Predictive, and Social Network Techniques Detect fraud earlier to mitigate loss and prevent cascading damage Fraud Analytics Using Descriptive, Predictive, and Social Network Techniques is an authoritative guidebook for setting up a comprehensive fraud detection analytics solution. Early detection is a key factor in mitigating fraud damage, but it involves more specialized techniques than detecting fraud at the more advanced stages. This invaluable guide details both the theory and technical aspects of these techniques, and provides expert insight into streamlining implementation. Coverage includes data gathering, preprocessing, model building, and post-implementation, with comprehensive guidance on various learning techniques and the data types utilized by each. These techniques are effective for fraud detection across industry boundaries, including applications in insurance fraud, credit card fraud, anti-money laundering, healthcare fraud, telecommunications fraud, click fraud, tax evasion, and more, giving you a highly practical framework for fraud prevention. It is estimated that a typical organization loses about 5% of its revenue to fraud every year. More effective fraud detection is possible, and this book describes the various analytical techniques your organization must implement to put a stop to the revenue leak. Examine fraud patterns in historical data Utilize labeled, unlabeled, and networked data Detect fraud before the damage cascades Reduce losses, increase recovery, and tighten security The longer fraud is allowed to go on, the more harm it causes. It expands exponentially, sending ripples of damage throughout the organization, and becomes more and more complex to track, stop, and reverse. Fraud prevention relies on early and effective fraud detection, enabled by the techniques discussed here. Fraud Analytics Using Descriptive, Predictive, and Social Network Techniques helps you stop fraud in its tracks, and eliminate the opportunities for future occurrence. COMPUTERS,Data Science,Data Analytics

Accumulo Get up to speed on Apache Accumulo, the flexible, high-performance key/value store created by the National Security Agency (NSA) and based on Google’s BigTable data storage system. Written by former NSA team members, this comprehensive tutorial and reference covers Accumulo architecture, application development, table design, and cell-level security. With clear information on system administration, performance tuning, and best practices, this book is ideal for developers seeking to write Accumulo applications, administrators charged with installing and maintaining Accumulo, and other professionals interested in what Accumulo has to offer. You will find everything you need to use this system fully. Get a high-level introduction to Accumulo’s architecture and data model Take a rapid tour through single- and multiple-node installations, data ingest, and query Learn how to write Accumulo applications for several use cases, based on examples Dive into Accumulo internals, including information not available in the documentation Get detailed information for installing, administering, tuning, and measuring performance Learn best practices based on successful implementations in the field Find answers to common questions that every new Accumulo user asks COMPUTERS,Data Science,Data Analytics

Bayesian Methods for Hackers Master Bayesian Inference through Practical Examples and Computation–Without Advanced Mathematical Analysis Bayesian methods of inference are deeply natural and extremely powerful. However, most discussions of Bayesian inference rely on intensely complex mathematical analyses and artificial examples, making it inaccessible to anyone without a strong mathematical background. Now, though, Cameron Davidson-Pilon introduces Bayesian inference from a computational perspective, bridging theory to practice–freeing you to get results using computing power. Bayesian Methods for Hackers illuminates Bayesian inference through probabilistic programming with the powerful PyMC language and the closely related Python tools NumPy, SciPy, and Matplotlib. Using this approach, you can reach effective solutions in small increments, without extensive mathematical intervention. Davidson-Pilon begins by introducing the concepts underlying Bayesian inference, comparing it with other techniques and guiding you through building and training your first Bayesian model. Next, he introduces PyMC through a series of detailed examples and intuitive explanations that have been refined after extensive user feedback. You’ll learn how to use the Markov Chain Monte Carlo algorithm, choose appropriate sample sizes and priors, work with loss functions, and apply Bayesian inference in domains ranging from finance to marketing. Once you’ve mastered these techniques, you’ll constantly turn to this guide for the working PyMC code you need to jumpstart future projects. Coverage includes • Learning the Bayesian “state of mind†and its practical implications • Understanding how computers perform Bayesian inference • Using the PyMC Python library to program Bayesian analyses • Building and debugging models with PyMC • Testing your model’s “goodness of fit†• Opening the “black box†of the Markov Chain Monte Carlo algorithm to see how and why it works • Leveraging the power of the “Law of Large Numbers†• Mastering key concepts, such as clustering, convergence, autocorrelation, and thinning • Using loss functions to measure an estimate’s weaknesses based on your goals and desired outcomes • Selecting appropriate priors and understanding how their influence changes with dataset size • Overcoming the “exploration versus exploitation†dilemma: deciding when “pretty good†is good enough • Using Bayesian inference to improve A/B testing • Solving data science problems when only small amounts of data are available Cameron Davidson-Pilon has worked in many areas of applied mathematics, from the evolutionary dynamics of genes and diseases to stochastic modeling of financial prices. His contributions to the open source community include lifelines, an implementation of survival analysis in Python. Educated at the University of Waterloo and at the Independent University of Moscow, he currently works with the online commerce leader Shopify. COMPUTERS,Data Science,Data Analytics

Hadoop 2 Quick-Start Guide Get Started Fast with Apache Hadoop® 2, YARN, and Today’s Hadoop Ecosystem With Hadoop 2.x and YARN, Hadoop moves beyond MapReduce to become practical for virtually any type of data processing. Hadoop 2.x and the Data Lake concept represent a radical shift away from conventional approaches to data usage and storage. Hadoop 2.x installations offer unmatched scalability and breakthrough extensibility that supports new and existing Big Data analytics processing methods and models. Hadoop® 2 Quick-Start Guide is the first easy, accessible guide to Apache Hadoop 2.x, YARN, and the modern Hadoop ecosystem. Building on his unsurpassed experience teaching Hadoop and Big Data, author Douglas Eadline covers all the basics you need to know to install and use Hadoop 2 on personal computers or servers, and to navigate the powerful technologies that complement it. Eadline concisely introduces and explains every key Hadoop 2 concept, tool, and service, illustrating each with a simple “beginning-to-end†example and identifying trustworthy, up-to-date resources for learning more. This guide is ideal if you want to learn about Hadoop 2 without getting mired in technical details. Douglas Eadline will bring you up to speed quickly, whether you’re a user, admin, devops specialist, programmer, architect, analyst, or data scientist. Coverage Includes Understanding what Hadoop 2 and YARN do, and how they improve on Hadoop 1 with MapReduce Understanding Hadoop-based Data Lakes versus RDBMS Data Warehouses Installing Hadoop 2 and core services on Linux machines, virtualized sandboxes, or clusters Exploring the Hadoop Distributed File System (HDFS) Understanding the essentials of MapReduce and YARN application programming Simplifying programming and data movement with Apache Pig, Hive, Sqoop, Flume, Oozie, and HBase Observing application progress, controlling jobs, and managing workflows Managing Hadoop efficiently with Apache Ambari–including recipes for HDFS to NFSv3 gateway, HDFS snapshots, and YARN configuration Learning basic Hadoop 2 troubleshooting, and installing Apache Hue and Apache Spark COMPUTERS,Data Science,Data Analytics

Project Management Analytics To manage projects, you must not only control schedules and costs: you must also manage growing operational uncertainty. Today’s powerful analytics tools and methods can help you do all of this far more successfully. In Project Management Analytics , Harjit Singh shows how to bring greater evidence-based clarity and rationality to all your key decisions throughout the full project lifecycle. Singh identifies the components and characteristics of a good project decision and shows how to improve decisions by using predictive, prescriptive, statistical, and other methods. You’ll learn how to mitigate risks by identifying meaningful historical patterns and trends; optimize allocation and use of scarce resources within project constraints; automate data-driven decision-making processes based on huge data sets; and effectively handle multiple interrelated decision criteria. Singh also helps you integrate analytics into the project management methods you already use, combining today’s best analytical techniques with proven approaches such as PMI PMBOK® and Lean Six Sigma. Project managers can no longer rely on vague impressions or seat-of-the-pants intuition. Fortunately, you don’t have to. With Project Management Analytics , you can use facts, evidence, and knowledge—and get far better results. Achieve efficient, reliable, consistent, and fact-based project decision-making Systematically bring data and objective analysis to key project decisions Avoid “garbage in, garbage out†Properly collect, store, analyze, and interpret your project-related data Optimize multi-criteria decisions in large group environments Use the Analytic Hierarchy Process (AHP) to improve complex real-world decisions Streamline projects the way you streamline other business processes Leverage data-driven Lean Six Sigma to manage projects more effectively COMPUTERS,Data Science,Data Analytics

R in 24 Hours, Sams Teach Yourself In just 24 lessons of one hour or less, Sams Teach Yourself R in 24 Hours helps you learn all the R skills you need to solve a wide spectrum of real-world data analysis problems. You’ll master the entire data analysis workflow, learning to build code that’s efficient, reproducible, and suitable for sharing with others. This book’s straightforward, step-by-step approach teaches you how to import, manipulate, summarize, model, and plot data with R; formalize your analytical code; and build powerful R packages using current best practices. Practical, hands-on examples show you how to apply what you learn. Quizzes and exercises help you test your knowledge and stretch your skills. Learn How To Install, configure, and explore the R environment, including RStudio Use basic R syntax, objects, and packages Create and manage data structures, including vectors, matrices, and arrays Understand lists and data frames Work with dates, times, and factors Use common R functions, and learn to write your own Import and export data and connect to databases and spreadsheets Use the popular tidyr, dplyr and data.table packages Write more efficient R code with profiling, vectorization, and initialization Plot data and extend your graphical capabilities with ggplot2 and Lattice graphics Develop common types of models Construct high-quality packages, both simple and complex Write R classes: S3, S4, and Reference Classes Use R to generate dynamic reports Build web applications with Shiny Register your book at informit.com/register for convenient access to updates and corrections as they become available. This book’s source code can be found at http://www.mango-solutions.com/wp/teach-yourself-r-in-24-hours-book/. COMPUTERS,Data Science,Data Analytics

Visual Data Mining Visual Data Mining—Opening the Black Box Knowledge discovery holds the promise of insight into large, otherwise opaque datasets. Thenatureofwhatmakesaruleinterestingtoauserhasbeendiscussed 1 widely but most agree that it is a subjective quality based on the practical u- fulness of the information. Being subjective, the user needs to provide feedback to the system and, as is the case for all systems, the sooner the feedback is given the quicker it can in?uence the behavior of the system. There have been some impressive research activities over the past few years but the question to be asked is why is visual data mining only now being - vestigated commercially? Certainly, there have been arguments for visual data 2 mining for a number of years – Ankerst and others argued in 2002 that current (autonomous and opaque) analysis techniques are ine?cient, as they fail to - rectly embed the user in dataset exploration and that a better solution involves the user and algorithm being more tightly coupled. Grinstein stated that the “current state of the art data mining tools are automated, but the perfect data mining tool is interactive and highly participatory,†while Han has suggested that the “data selection and viewing of mining results should be fully inter- tive, the mining process should be more interactive than the current state of the 2 art and embedded applications should be fairly automated . †A good survey on 3 techniques until 2003 was published by de Oliveira and Levkowitz . COMPUTERS,Data Science,Data Analytics

Big Data Fundamentals “This text should be required reading for everyone in contemporary business.†--Peter Woodhull, CEO, Modus21 “The one book that clearly describes and links Big Data concepts to business utility.†--Dr. Christopher Starr, PhD “Simply, this is the best Big Data book on the market!†--Sam Rostam, Cascadian IT Group “...one of the most contemporary approaches I’ve seen to Big Data fundamentals...†--Joshua M. Davis, PhD The Definitive Plain-English Guide to Big Data for Business and Technology Professionals Big Data Fundamentals provides a pragmatic, no-nonsense introduction to Big Data. Best-selling IT author Thomas Erl and his team clearly explain key Big Data concepts, theory and terminology, as well as fundamental technologies and techniques. All coverage is supported with case study examples and numerous simple diagrams. The authors begin by explaining how Big Data can propel an organization forward by solving a spectrum of previously intractable business problems. Next, they demystify key analysis techniques and technologies and show how a Big Data solution environment can be built and integrated to offer competitive advantages. Discovering Big Data’s fundamental concepts and what makes it different from previous forms of data analysis and data science Understanding the business motivations and drivers behind Big Data adoption, from operational improvements through innovation Planning strategic, business-driven Big Data initiatives Addressing considerations such as data management, governance, and security Recognizing the 5 “V†characteristics of datasets in Big Data environments: volume, velocity, variety, veracity, and value Clarifying Big Data’s relationships with OLTP, OLAP, ETL, data warehouses, and data marts Working with Big Data in structured, unstructured, semi-structured, and metadata formats Increasing value by integrating Big Data resources with corporate performance monitoring Understanding how Big Data leverages distributed and parallel processing Using NoSQL and other technologies to meet Big Data’s distinct data processing requirements Leveraging statistical approaches of quantitative and qualitative analysis Applying computational analysis methods, including machine learning COMPUTERS,Data Science,Data Analytics

Data Analytics This book is a comprehensive introduction to the methods and algorithms of modern data analytics. It provides a sound mathematical basis, discusses advantages and drawbacks of different approaches, and enables the reader to design and implement data analytics solutions for real-world applications. This book has been used for more than ten years in the Data Mining course at the Technical University of Munich. Much of the content is based on the results of industrial research and development projects at Siemens. COMPUTERS,Data Science,Data Analytics

Mastering Azure Analytics Microsoft Azure has over 20 platform-as-a-service (PaaS) offerings that can act in support of a big data analytics solution. So which one is right for your project? This practical book helps you understand the breadth of Azure services by organizing them into a reference framework you can use when crafting your own big data analytics solution. You’ll not only be able to determine which service best fits the job, but also learn how to implement a complete solution that scales, provides human fault tolerance, and supports future needs. Understand the fundamental patterns of the data lake and lambda architecture Recognize the canonical steps in the analytics data pipeline and learn how to use Azure Data Factory to orchestrate them Implement data lakes and lambda architectures, using Azure Data Lake Store, Data Lake Analytics, HDInsight (including Spark), Stream Analytics, SQL Data Warehouse, and Event Hubs Understand where Azure Machine Learning fits into your analytics pipeline Gain experience using these services on real-world data that has real-world problems, with scenarios ranging from aviation to Internet of Things (IoT) COMPUTERS,Data Science,Data Analytics

Learning Social Media Analytics with R Tap into the realm of social media and unleash the power of analytics for data-driven insights using R About This Book A practical guide written to help leverage the power of the R eco-system to extract, process, analyze, visualize and model social media data Learn about data access, retrieval, cleaning, and curation methods for data originating from various social media platforms. Visualize and analyze data from social media platforms to understand and model complex relationships using various concepts and techniques such as Sentiment Analysis, Topic Modeling, Text Summarization, Recommendation Systems, Social Network Analysis, Classification, and Clustering. Who This Book Is For It is targeted at IT professionals, Data Scientists, Analysts, Developers, Machine Learning Enthusiasts, social media marketers and anyone with a keen interest in data, analytics, and generating insights from social data. Some background experience in R would be helpful, but not necessary, since this book is written keeping in mind, that readers can have varying levels of expertise. What You Will Learn Learn how to tap into data from diverse social media platforms using the R ecosystem Use social media data to formulate and solve real-world problems Analyze user social networks and communities using concepts from graph theory and network analysis Learn to detect opinion and sentiment, extract themes, topics, and trends from unstructured noisy text data from diverse social media channels Understand the art of representing actionable insights with effective visualizations Analyze data from major social media channels such as Twitter, Facebook, Flickr, Foursquare, Github, StackExchange, and so on Learn to leverage popular R packages such as ggplot2, topicmodels, caret, e1071, tm, wordcloud, twittR, Rfacebook, dplyr, reshape2, and many more In Detail The Internet has truly become humongous, especially with the rise of various forms of social media in the last decade, which give users a platform to express themselves and also communicate and collaborate with each other. This book will help the reader to understand the current social media landscape and to learn how analytics can be leveraged to derive insights from it. This data can be analyzed to gain valuable insights into the behavior and engagement of users, organizations, businesses, and brands. It will help readers frame business problems and solve them using social data. The book will also cover several practical real-world use cases on social media using R and its advanced packages to utilize data science methodologies such as sentiment analysis, topic modeling, text summarization, recommendation systems, social network analysis, classification, and clustering. This will enable readers to learn different hands-on approaches to obtain data from diverse social media sources such as Twitter and Facebook. It will also show readers how to establish detailed workflows to process, visualize, and analyze data to transform social data into actionable insights. Style and approach This book follows a step-by-step approach with detailed strategies for understanding, extracting, analyzing, visualizing, and modeling data from several major social network platforms such as Facebook, Twitter, Foursquare, Flickr, Github, and StackExchange. The chapters cover several real-world use cases and leverage data science, machine learning, network analysis, and graph theory concepts along with the R ecosystem, including popular packages such as ggplot2, caret,dplyr, topicmodels, tm, and so on. COMPUTERS,Data Science,Data Analytics

Fundamentals of Deep Learning With the reinvigoration of neural networks in the 2000s, deep learning has become an extremely active area of research, one that’s paving the way for modern machine learning. In this practical book, author Nikhil Buduma provides examples and clear explanations to guide you through major concepts of this complicated field. Companies such as Google, Microsoft, and Facebook are actively growing in-house deep-learning teams. For the rest of us, however, deep learning is still a pretty complex and difficult subject to grasp. If you’re familiar with Python, and have a background in calculus, along with a basic understanding of machine learning, this book will get you started. Examine the foundations of machine learning and neural networks Learn how to train feed-forward neural networks Use TensorFlow to implement your first neural network Manage problems that arise as you begin to make networks deeper Build neural networks that analyze complex images Perform effective dimensionality reduction using autoencoders Dive deep into sequence analysis to examine language Learn the fundamentals of reinforcement learning COMPUTERS,Data Science,Data Analytics

Agile Data Science 2.0 Data science teams looking to turn research into useful analytics applications require not only the right tools, but also the right approach if they’re to succeed. With the revised second edition of this hands-on guide, up-and-coming data scientists will learn how to use the Agile Data Science development methodology to build data applications with Python, Apache Spark, Kafka, and other tools. Author Russell Jurney demonstrates how to compose a data platform for building, deploying, and refining analytics applications with Apache Kafka, MongoDB, ElasticSearch, d3.js, scikit-learn, and Apache Airflow. You’ll learn an iterative approach that lets you quickly change the kind of analysis you’re doing, depending on what the data is telling you. Publish data science work as a web application, and affect meaningful change in your organization. Build value from your data in a series of agile sprints, using the data-value pyramid Extract features for statistical models from a single dataset Visualize data with charts, and expose different aspects through interactive reports Use historical data to predict the future via classification and regression Translate predictions into actions Get feedback from users after each sprint to keep your project on track COMPUTERS,Data Science,Data Analytics

Heterogeneous Information Network Analysis and Applications This book offers researchers an understanding of the fundamental issues and a good starting point to work on this rapidly expanding field. It provides a comprehensive survey of current developments of heterogeneous information network. It also presents the newest research in applications of heterogeneous information networks to similarity search, ranking, clustering, recommendation. This information will help researchers to understand how to analyze networked data with heterogeneous information networks. Common data mining tasks are explored, including similarity search, ranking, and recommendation. The book illustrates some prototypes which analyze networked data. Professionals and academics working in data analytics, networks, machine learning, and data mining will find this content valuable. It is also suitable for advanced-level students in computer science who are interested in networking or pattern recognition. COMPUTERS,Data Science,Data Analytics

Introduction to Computing Applications in Forestry and Natural Resource Management Due to the complexity of operational forestry problems, computing applications are becoming pervasive in all aspects of forest and natural resource management. This book provides a comprehensive introduction to computers and their applications in forest and natural resource management and is designed for both undergraduate and graduate students in forestry and natural resources. It introduces state-of-the-art applications for several of the most important computer technologies in terms of data acquisition, data manipulation, basic programming techniques, and other related computer and Internet concepts and applications. This book consists of six parts and 19 chapters. COMPUTERS,Data Science,Data Analytics

The Data Book The Data Book: Collection and Management of Research Data is the first practical book written for researchers and research team members covering how to collect and manage data for research. The book covers basic types of data and fundamentals of how data grow, move and change over time. Focusing on pre-publication data collection and handling, the text illustrates use of these key concepts to match data collection and management methods to a particular study, in essence, making good decisions about data. The first section of the book defines data, introduces fundamental types of data that bear on methodology to collect and manage them, and covers data management planning and research reproducibility. The second section covers basic principles of and options for data collection and processing emphasizing error resistance and traceability. The third section focuses on managing the data collection and processing stages of research such that quality is consistent and ultimately capable of supporting conclusions drawn from data. The final section of the book covers principles of data security, sharing, and archival. This book will help graduate students and researchers systematically identify and implement appropriate data collection and handling methods. COMPUTERS,Data Science,Data Analytics

Practical Data Science with Hadoop and Spark This book provides a unique perspective on applying data science with Hadoop by explaining what data science with Hadoop is all about, its practical business applications, and then diving deep into the details and providing a hands-on tutorial and showcase of various use-cases from the real world. The authors bring together all the practical knowledge students will need to do real, useful data science with Hadoop. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Data Science,Data Analytics

R for Everyone Statistical Computation for Programmers, Scientists, Quants, Excel Users, and Other Professionals Using the open source R language, you can build powerful statistical models to answer many of your most challenging questions. R has traditionally been difficult for non-statisticians to learn, and most R books assume far too much knowledge to be of help. R for Everyone, Second Edition, is the solution. Drawing on his unsurpassed experience teaching new users, professional data scientist Jared P. Lander has written the perfect tutorial for anyone new to statistical programming and modeling. Organized to make learning easy and intuitive, this guide focuses on the 20 percent of R functionality you’ll need to accomplish 80 percent of modern data tasks. Lander’s self-contained chapters start with the absolute basics, offering extensive hands-on practice and sample code. You’ll download and install R; navigate and use the R environment; master basic program control, data import, manipulation, and visualization; and walk through several essential tests. Then, building on this foundation, you’ll construct several complete models, both linear and nonlinear, and use some data mining techniques. After all this you’ll make your code reproducible with LaTeX, RMarkdown, and Shiny. By the time you’re done, you won’t just know how to write R programs, you’ll be ready to tackle the statistical problems you care about most. Coverage includes Explore R, RStudio, and R packages Use R for math: variable types, vectors, calling functions, and more Exploit data structures, including data.frames, matrices, and lists Read many different types of data Create attractive, intuitive statistical graphics Write user-defined functions Control program flow with if, ifelse, and complex checks Improve program efficiency with group manipulations Combine and reshape multiple datasets Manipulate strings using R’s facilities and regular expressions Create normal, binomial, and Poisson probability distributions Build linear, generalized linear, and nonlinear models Program basic statistics: mean, standard deviation, and t-tests Train machine learning models Assess the quality of models and variable selection Prevent overfitting and perform variable selection, using the Elastic Net and Bayesian methods Analyze univariate and multivariate time series data Group data via K-means and hierarchical clustering Prepare reports, slideshows, and web pages with knitr Display interactive data with RMarkdown and htmlwidgets Implement dashboards with Shiny Build reusable R packages with devtools and Rcpp Register your product at informit.com/register for convenient access to downloads, updates, and corrections as they become available. COMPUTERS,Data Science,Data Analytics

Power of People, The Business leaders today are seeking meaningful patterns in their people data that will help them gain a competitive edge. The answer is in the growing discipline of workforce analytics. Much attention has already been paid to the technical requirements for implementing workforce analytics, now, there's a book that covers the organisational development and change management issues that will make or break your success. Drawing on insights from dozens of experts in workforce analytics as well as their own cutting edge experience within IBM, the authors walk step-by-step through setting up and then embedding workforce analytics capabilities. With candid case studies and clear advice from those who have already faced and overcome the challenges associated with workforce analytics, you'll learn how to: Begin with a vision, not data analysis Pick your projects wisely, so you can "earn your keep" with visible, valuable successes Build a team with the right skills to deliver the insights your organisation needs Identify the right stakeholders and sponsors to ensure success Choose the best technology for your analytics needs Handle some of the sensitivities around using employee data in analytics projects Run a successful workforce analytics function for the long term Use storytelling techniques to ensure you can influence organisational decisions or initiatives with the results of your workforce analytics projects Analytics are rapidly becoming pervasive in functions ranging from Finance to Marketing. Now, discover how HR can gain just as much value, by informing every key decision with the best possible insight. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Data Science,Data Analytics

Deep Learning Although interest in machine learning has reached a high point, lofty expectations often scuttle projects before they get very far. How can machine learning—especially deep neural networks—make a real difference in your organization? This hands-on guide not only provides the most practical information available on the subject, but also helps you get started building efficient deep learning networks. Authors Adam Gibson and Josh Patterson provide theory on deep learning before introducing their open-source Deeplearning4j (DL4J) library for developing production-class workflows. Through real-world examples, you’ll learn methods and strategies for training deep network architectures and running deep learning workflows on Spark and Hadoop with DL4J. Dive into machine learning concepts in general, as well as deep learning in particular Understand how deep networks evolved from neural network fundamentals Explore the major deep network architectures, including Convolutional and Recurrent Learn how to map specific deep networks to the right problem Walk through the fundamentals of tuning general neural networks and specific deep network architectures Use vectorization techniques for different data types with DataVec, DL4J’s workflow tool Learn how to use DL4J natively on Spark and Hadoop COMPUTERS,Data Science,Data Analytics

Python Social Media Analytics Leverage the power of Python to collect, process, and mine deep insights from social media data About This Book Acquire data from various social media platforms such as Facebook, Twitter, YouTube, GitHub, and more Analyze and extract actionable insights from your social data using various Python tools A highly practical guide to conducting efficient social media analytics at scale Who This Book Is For If you are a programmer or a data analyst familiar with the Python programming language and want to perform analyses of your social data to acquire valuable business insights, this book is for you. The book does not assume any prior knowledge of any data analysis tool or process. What You Will Learn Understand the basics of social media mining Use PyMongo to clean, store, and access data in MongoDB Understand user reactions and emotion detection on Facebook Perform Twitter sentiment analysis and entity recognition using Python Analyze video and campaign performance on YouTube Mine popular trends on GitHub and predict the next big technology Extract conversational topics on public internet forums Analyze user interests on Pinterest Perform large-scale social media analytics on the cloud In Detail Social Media platforms such as Facebook, Twitter, Forums, Pinterest, and YouTube have become part of everyday life in a big way. However, these complex and noisy data streams pose a potent challenge to everyone when it comes to harnessing them properly and benefiting from them. This book will introduce you to the concept of social media analytics, and how you can leverage its capabilities to empower your business. Right from acquiring data from various social networking sources such as Twitter, Facebook, YouTube, Pinterest, and social forums, you will see how to clean data and make it ready for analytical operations using various Python APIs. This book explains how to structure the clean data obtained and store in MongoDB using PyMongo. You will also perform web scraping and visualize data using Scrappy and Beautifulsoup. Finally, you will be introduced to different techniques to perform analytics at scale for your social data on the cloud, using Python and Spark. By the end of this book, you will be able to utilize the power of Python to gain valuable insights from social media data and use them to enhance your business processes. Style and approach This book follows a step-by-step approach to teach readers the concepts of social media analytics using the Python programming language. To explain various data analysis processes, real-world datasets are used wherever required. COMPUTERS,Data Science,Data Analytics

An Introduction to Machine Learning This textbook presents fundamental machine learning concepts in an easy to understand manner by providing practical advice, using straightforward examples, and offering engaging discussions of relevant applications. The main topics include Bayesian classifiers, nearest-neighbor classifiers, linear and polynomial classifiers, decision trees, neural networks, and support vector machines. Later chapters show how to combine these simple tools by way of “boosting,†how to exploit them in more complicated domains, and how to deal with diverse advanced practical issues. One chapter is dedicated to the popular genetic algorithms. This revised edition contains three entirely new chapters on critical topics regarding the pragmatic application of machine learning in industry. The chapters examine multi-label domains, unsupervised learning and its use in deep learning, and logical approaches to induction. Numerous chapters have been expanded, and the presentation of the material has been enhanced. The book contains many new exercises, numerous solved examples, thought-provoking experiments, and computer assignments for independent work. COMPUTERS,Data Science,Data Analytics

Machine Learning AN INTRODUCTION TO MACHINE LEARNING THAT INCLUDES THE FUNDAMENTAL TECHNIQUES, METHODS, AND APPLICATIONS PROSE Award Finalist 2019 Association of American Publishers Award for Professional and Scholarly Excellence Machine Learning: a Concise Introduction offers a comprehensive introduction to the core concepts, approaches, and applications of machine learning. The author—an expert in the field—presents fundamental ideas, terminology, and techniques for solving applied problems in classification, regression, clustering, density estimation, and dimension reduction. The design principles behind the techniques are emphasized, including the bias-variance trade-off and its influence on the design of ensemble methods. Understanding these principles leads to more flexible and successful applications. Machine Learning: a Concise Introduction also includes methods for optimization, risk estimation, and model selection— essential elements of most applied projects. This important resource: Illustrates many classification methods with a single, running example, highlighting similarities and differences between methods Presents R source code which shows how to apply and interpret many of the techniques covered Includes many thoughtful exercises as an integral part of the text, with an appendix of selected solutions Contains useful information for effectively communicating with clients A volume in the popular Wiley Series in Probability and Statistics, Machine Learning: a Concise Introduction offers the practical information needed for an understanding of the methods and application of machine learning. STEVEN W. KNOX holds a Ph.D. in Mathematics from the University of Illinois and an M.S. in Statistics from Carnegie Mellon University. He has over twenty years’ experience in using Machine Learning, Statistics, and Mathematics to solve real-world problems. He currently serves as Technical Director of Mathematics Research and Senior Advocate for Data Science at the National Security Agency. COMPUTERS,Data Science,Data Analytics

Super Charge Power BI Power BI is a powerful self-service (and enterprise) business intelligence (BI) tool that was first made generally available by Microsoft in July 2015. Power BI is a complete BI package that covers the end to end BI process including data acquisition (get data), data modelling (prepare/model the data) and data visualisation (analyse the data). And there is a lot of good news about this tool including the fact that the skills needed to succeed with Power BI are fully transferable to Microsoft Excel. There are 3 learning areas required to master everything Power BI Desktop has to offer.1. The M Language - used for data acquisition2. The DAX Language - used to prepare and model data3. Visualisation and analysis - used to present data in a compelling wayPower BI is probably the first commercial grade software product that brings all of these areas into a single software package that is completely accessible to a business user (you don't need to be an IT pro). This book focuses on number 2 above, the DAX language (Data Analysis Expressions). Super Charge Power BI Desktop is the second book written by Matt Allington and is a sister book to his first book Learn to Write DAX (first released Dec 2015). Super Charge Power BI Desktop uses the same learning and practice exercise framework as used in Learn to Write DAX however the entire book is written using the Power BI Desktop user interface. Unfortunately simply reading a book is normally not enough for Excel users wanting to get the most out of Power BI Desktop and to learn the DAX language - most people will also need some practice. Super Charge Power BI Desktop is different to other books - it is written in such a way to clearly explain the concepts of Power BI data modelling while at the same time giving hands-on practice to deeply engage the reader to help the new knowledge and concepts stick. The book first presents the theory, then provides worked through sample exercises demonstrating each of the concepts, and finally it provides the reader with practice exercises and answers to maximize learning retention. COMPUTERS,Data Science,Data Analytics

Data Analytics with Spark Using Python Solve Data Analytics Problems with Spark, PySpark, and Related Open Source Tools Spark is at the heart of today’s Big Data revolution, helping data professionals supercharge efficiency and performance in a wide range of data processing and analytics tasks. In this guide, Big Data expert Jeffrey Aven covers all you need to know to leverage Spark, together with its extensions, subprojects, and wider ecosystem. Aven combines a language-agnostic introduction to foundational Spark concepts with extensive programming examples utilizing the popular and intuitive PySpark development environment. This guide’s focus on Python makes it widely accessible to large audiences of data professionals, analysts, and developers—even those with little Hadoop or Spark experience. Aven’s broad coverage ranges from basic to advanced Spark programming, and Spark SQL to machine learning. You’ll learn how to efficiently manage all forms of data with Spark: streaming, structured, semi-structured, and unstructured. Throughout, concise topic overviews quickly get you up to speed, and extensive hands-on exercises prepare you to solve real problems. Coverage includes: • Understand Spark’s evolving role in the Big Data and Hadoop ecosystems • Create Spark clusters using various deployment modes • Control and optimize the operation of Spark clusters and applications • Master Spark Core RDD API programming techniques • Extend, accelerate, and optimize Spark routines with advanced API platform constructs, including shared variables, RDD storage, and partitioning • Efficiently integrate Spark with both SQL and nonrelational data stores • Perform stream processing and messaging with Spark Streaming and Apache Kafka • Implement predictive modeling with SparkR and Spark MLlib COMPUTERS,Data Science,Data Analytics

Getting Started with Kudu Fast data ingestion, serving, and analytics in the Hadoop ecosystem have forced developers and architects to choose solutions using the least common denominator—either fast analytics at the cost of slow data ingestion or fast data ingestion at the cost of slow analytics. There is an answer to this problem. With the Apache Kudu column-oriented data store, you can easily perform fast analytics on fast data. This practical guide shows you how. Begun as an internal project at Cloudera, Kudu is an open source solution compatible with many data processing frameworks in the Hadoop environment. In this book, current and former solutions professionals from Cloudera provide use cases, examples, best practices, and sample code to help you get up to speed with Kudu. Explore Kudu’s high-level design, including how it spreads data across servers Fully administer a Kudu cluster, enable security, and add or remove nodes Learn Kudu’s client-side APIs, including how to integrate Apache Impala, Spark, and other frameworks for data manipulation Examine Kudu’s schema design, including basic concepts and primitives necessary to make your project successful Explore case studies for using Kudu for real-time IoT analytics, predictive modeling, and in combination with another storage engine COMPUTERS,Data Science,Data Analytics

Data Science Thinking This book explores answers to the fundamental questions driving the research, innovation and practices of the latest revolution in scientific, technological and economic development: how does data science transform existing science, technology, industry, economy, profession and education? How does one remain competitive in the data science field? What is responsible for shaping the mindset and skillset of data scientists? Data Science Thinking paints a comprehensive picture of data science as a new scientific paradigm from the scientific evolution perspective, as data science thinking from the scientific-thinking perspective, as a trans-disciplinary science from the disciplinary perspective, and as a new profession and economy from the business perspective. COMPUTERS,Data Science,Data Analytics

Data Science Foundations Tools and Techniques The Foundational Hands-On Skills You Need to Dive into Data Science “Freeman and Ross have created the definitive resource for new and aspiring data scientists to learn foundational programming skills.†–From the foreword by Jared Lander, series editor Using data science techniques, you can transform raw data into actionable insights for domains ranging from urban planning to precision medicine. Programming Skills for Data Science brings together all the foundational skills you need to get started, even if you have no programming or data science experience. Leading instructors Michael Freeman and Joel Ross guide you through installing and configuring the tools you need to solve professional-level data science problems, including the widely used R language and Git version-control system. They explain how to wrangle your data into a form where it can be easily used, analyzed, and visualized so others can see the patterns you’ve uncovered. Step by step, you’ll master powerful R programming techniques and troubleshooting skills for probing data in new ways, and at larger scales. Freeman and Ross teach through practical examples and exercises that can be combined into complete data science projects. Everything’s focused on real-world application, so you can quickly start analyzing your own data and getting answers you can act upon. Learn to Install your complete data science environment, including R and RStudio Manage projects efficiently, from version tracking to documentation Host, manage, and collaborate on data science projects with GitHub Master R language fundamentals: syntax, programming concepts, and data structures Load, format, explore, and restructure data for successful analysis Interact with databases and web APIs Master key principles for visualizing data accurately and intuitively Produce engaging, interactive visualizations with ggplot and other R packages Transform analyses into sharable documents and sites with R Markdown Create interactive web data science applications with Shiny Collaborate smoothly as part of a data science team Register your book for convenient access to downloads, updates, and/or corrections as they become available. See inside book for details. COMPUTERS,Data Science,Data Analytics

Learning Apache Drill Get up to speed with Apache Drill, an extensible distributed SQL query engine that reads massive datasets in many popular file formats such as Parquet, JSON, and CSV. Drill reads data in HDFS or in cloud-native storage such as S3 and works with Hive metastores along with distributed databases such as HBase, MongoDB, and relational databases. Drill works everywhere: on your laptop or in your largest cluster. In this practical book, Drill committers Charles Givre and Paul Rogers show analysts and data scientists how to query and analyze raw data using this powerful tool. Data scientists today spend about 80% of their time just gathering and cleaning data. With this book, you’ll learn how Drill helps you analyze data more effectively to drive down time to insight. Use Drill to clean, prepare, and summarize delimited data for further analysis Query file types including logfiles, Parquet, JSON, and other complex formats Query Hadoop, relational databases, MongoDB, and Kafka with standard SQL Connect to Drill programmatically using a variety of languages Use Drill even with challenging or ambiguous file formats Perform sophisticated analysis by extending Drill’s functionality with user-defined functions Facilitate data analysis for network security, image metadata, and machine learning COMPUTERS,Data Science,Data Analytics

Machine Learning with Apache Spark Quick Start Guide Combine advanced analytics including Machine Learning, Deep Learning Neural Networks and Natural Language Processing with modern scalable technologies including Apache Spark to derive actionable insights from Big Data in real-time Key Features Make a hands-on start in the fields of Big Data, Distributed Technologies and Machine Learning Learn how to design, develop and interpret the results of common Machine Learning algorithms Uncover hidden patterns in your data in order to derive real actionable insights and business value Book Description Every person and every organization in the world manages data, whether they realize it or not. Data is used to describe the world around us and can be used for almost any purpose, from analyzing consumer habits to fighting disease and serious organized crime. Ultimately, we manage data in order to derive value from it, and many organizations around the world have traditionally invested in technology to help process their data faster and more efficiently. But we now live in an interconnected world driven by mass data creation and consumption where data is no longer rows and columns restricted to a spreadsheet, but an organic and evolving asset in its own right. With this realization comes major challenges for organizations: how do we manage the sheer size of data being created every second (think not only spreadsheets and databases, but also social media posts, images, videos, music, blogs and so on)? And once we can manage all of this data, how do we derive real value from it? The focus of Machine Learning with Apache Spark is to help us answer these questions in a hands-on manner. We introduce the latest scalable technologies to help us manage and process big data. We then introduce advanced analytical algorithms applied to real-world use cases in order to uncover patterns, derive actionable insights, and learn from this big data. What you will learn Understand how Spark fits in the context of the big data ecosystem Understand how to deploy and configure a local development environment using Apache Spark Understand how to design supervised and unsupervised learning models Build models to perform NLP, deep learning, and cognitive services using Spark ML libraries Design real-time machine learning pipelines in Apache Spark Become familiar with advanced techniques for processing a large volume of data by applying machine learning algorithms Who this book is for This book is aimed at Business Analysts, Data Analysts and Data Scientists who wish to make a hands-on start in order to take advantage of modern Big Data technologies combined with Advanced Analytics. COMPUTERS,Data Science,Data Analytics

Machine Learning with Python for Everyone The Complete Beginner’s Guide to Understanding and Building Machine Learning Systems with Python Machine Learning with Python for Everyone will help you master the processes, patterns, and strategies you need to build effective learning systems, even if you’re an absolute beginner. If you can write some Python code, this book is for you, no matter how little college-level math you know. Principal instructor Mark E. Fenner relies on plain-English stories, pictures, and Python examples to communicate the ideas of machine learning. Mark begins by discussing machine learning and what it can do; introducing key mathematical and computational topics in an approachable manner; and walking you through the first steps in building, training, and evaluating learning systems. Step by step, you’ll fill out the components of a practical learning system, broaden your toolbox, and explore some of the field’s most sophisticated and exciting techniques. Whether you’re a student, analyst, scientist, or hobbyist, this guide’s insights will be applicable to every learning system you ever build or use. Understand machine learning algorithms, models, and core machine learning concepts Classify examples with classifiers, and quantify examples with regressors Realistically assess performance of machine learning systems Use feature engineering to smooth rough data into useful forms Chain multiple components into one system and tune its performance Apply machine learning techniques to images and text Connect the core concepts to neural networks and graphical models Leverage the Python scikit-learn library and other powerful tools Register your book for convenient access to downloads, updates, and/or corrections as they become available. See inside book for details. COMPUTERS,Data Science,Data Analytics

Dark Data A practical guide to making good decisions in a world of missing data In the era of big data, it is easy to imagine that we have all the information we need to make good decisions. But in fact the data we have are never complete, and may be only the tip of the iceberg. Just as much of the universe is composed of dark matter, invisible to us but nonetheless present, the universe of information is full of dark data that we overlook at our peril. In Dark Data, data expert David Hand takes us on a fascinating and enlightening journey into the world of the data we don't see. Dark Data explores the many ways in which we can be blind to missing data and how that can lead us to conclusions and actions that are mistaken, dangerous, or even disastrous. Examining a wealth of real-life examples, from the Challenger shuttle explosion to complex financial frauds, Hand gives us a practical taxonomy of the types of dark data that exist and the situations in which they can arise, so that we can learn to recognize and control for them. In doing so, he teaches us not only to be alert to the problems presented by the things we don’t know, but also shows how dark data can be used to our advantage, leading to greater understanding and better decisions. Today, we all make decisions using data. Dark Data shows us all how to reduce the risk of making bad ones. COMPUTERS,Data Science,Data Analytics

Basic Blockchain The only book you need to understand blockchain: what it is, how it works and how it will transform business, society and our everyday lives. Basic Blockchain is an accessible, non-technical introduction to a revolutionary technology. 'Makes it easy for the average business executive to understand blockchain' -- Chris Larsen, founder and chairman, Ripple 'An essential tool for those looking to distinguish information from noise' -- Eva Kaili, MEP and Chair of The Committee for the Future of Science and Technology A revolution is under way across the globe, yet very few people understand it. Basic Blockchain will explain everything you need to know to understand the technology that will soon disrupt and revolutionise everything from financial and health services to the property market and how we vote. Born of an obscure body of research on game theory developed by NASA, originally championed by drug dealers seeking to launder ill-gotten gains, accelerated by entrepreneurs seeking to improve financial access for the poor, funded by giant corporate interests attracted to the potential for billions of dollars of cost savings, blockchain heralds a new era of financial inclusion, legal inclusion for the dispossessed and lower prices for consumers. In short, it will enact radical change on our lives. In this book, David L. Shrier, one of MIT and Oxford University's leading futurists, explains for the general reader: - The history of blockchain, its apocryphal progenitor Satoshi Nakamoto and the socioeconomic context of its origins in the 2008 financial crisis. - How blockchain works, including the core technologies that drive it such as cryptographic hashes and network theory, all described in simple, understandable terms. - The potential of blockchain, including its impact on our jobs, industry and society as a whole. Blockchain will disrupt and transform our world in profound ways. This accessible book, written by a global authority on blockchain, is the essential introduction to the next technological revolution. COMPUTERS,Data Science,Data Analytics

Database Internals When it comes to choosing, using, and maintaining a database, understanding its internals is essential. But with so many distributed databases and tools available today, it’s often difficult to understand what each one offers and how they differ. With this practical guide, Alex Petrov guides developers through the concepts behind modern database and storage engine internals. Throughout the book, you’ll explore relevant material gleaned from numerous books, papers, blog posts, and the source code of several open source databases. These resources are listed at the end of parts one and two. You’ll discover that the most significant distinctions among many modern databases reside in subsystems that determine how storage is organized and how data is distributed. This book examines: Storage engines: Explore storage classification and taxonomy, and dive into B-Tree-based and immutable Log Structured storage engines, with differences and use-cases for each Storage building blocks: Learn how database files are organized to build efficient storage, using auxiliary data structures such as Page Cache, Buffer Pool and Write-Ahead Log Distributed systems: Learn step-by-step how nodes and processes connect and build complex communication patterns Database clusters: Which consistency models are commonly used by modern databases and how distributed storage systems achieve consistency COMPUTERS,Data Science,Data Analytics

New Age Analytics This comprehensive and timely book, New Age Analytics: Transforming the Internet through Machine Learning, IoT, and Trust Modeling, explores the importance of tools and techniques used in machine learning, big data mining, and more. The book explains how advancements in the world of the web have been achieved and how the experiences of users can be analyzed. It looks at data gathering by the various electronic means and explores techniques for analysis and management, how to manage voluminous data, user responses, and more. This volume provides an abundance of valuable information for professionals and researchers working in the field of business analytics, big data, social network data, computer science, analytical engineering, and forensic analysis. Moreover, the book provides insights and support from both practitioners and academia in order to highlight the most debated aspects in the field. COMPUTERS,Data Science,Data Analytics

Data Science Programming All-in-One For Dummies Your logical, linear guide to the fundamentals of data science programming Data science is exploding—in a good way—with a forecast of 1.7 megabytes of new information created every second for each human being on the planet by 2020 and 11.5 million job openings by 2026. It clearly pays dividends to be in the know. This friendly guide charts a path through the fundamentals of data science and then delves into the actual work: linear regression, logical regression, machine learning, neural networks, recommender engines, and cross-validation of models. Data Science Programming All-In-One For Dummies is a compilation of the key data science, machine learning, and deep learning programming languages: Python and R. It helps you decide which programming languages are best for specific data science needs. It also gives you the guidelines to build your own projects to solve problems in real time. Get grounded: the ideal start for new data professionals What lies ahead: learn about specific areas that data is transforming Be meaningful: find out how to tell your data story See clearly: pick up the art of visualization Whether you’re a beginning student or already mid-career, get your copy now and add even more meaning to your life—and everyone else’s! COMPUTERS,Data Science,Data Analytics

Data Analytics This book is a comprehensive introduction to the methods and algorithms of modern data analytics. It provides a sound mathematical basis, discusses advantages and drawbacks of different approaches, and enables the reader to design and implement data analytics solutions for real-world applications. This book has been used for more than ten years in the Data Mining course at the Technical University of Munich. Much of the content is based on the results of industrial research and development projects at Siemens. COMPUTERS,Data Science,Data Analytics

Data Science Tools In the world of data science there are myriad tools available to analyzedata. This book describes some of thepopular software application tools along with the processes for downloading andusing them in the most optimum fashion. The content includes data analysis using Microsoft Excel, KNIME, R, andOpenOffice (Spreadsheet). Each of these tools will be used to apply statisticalconcepts including confidence intervals, normal distribution, T-Tests, linearregression, histograms, and geographic analysis using real data from FederalGovernment sources. Features: Analyzes data using popularapplications such as Excel, R, KNIME, and OpenOffice Covers statistical conceptsincluding confidence intervals, normal distribution, T-Tests, linear regression,histograms, andgeographic analysis Capstone exercises analyze data using the different softwarepackages COMPUTERS,Data Science,Data Analytics

Modern Data Mining Algorithms in C++ and CUDA C Discover a variety of data-mining algorithms that are useful for selecting small sets of important features from among unwieldy masses of candidates, or extracting useful features from measured variables. As a serious data miner you will often be faced with thousands of candidate features for your prediction or classification application, with most of the features being of little or no value. You’ll know that many of these features may be useful only in combination with certain other features while being practically worthless alone or in combination with most others. Some features may have enormous predictive power, but only within a small, specialized area of the feature space. The problems that plague modern data miners are endless. This book helps you solve this problem by presenting modern feature selection techniques and the code to implement them. Some of these techniques are: Forward selection component analysis Local feature selection Linking features and a target with a hidden Markov model Improvements on traditional stepwise selection Nominal-to-ordinal conversion All algorithms are intuitively justified and supported by the relevant equations and explanatory material. The author also presents and explains complete, highly commented source code. The example code is in C++ and CUDA C but Python or other code can be substituted; the algorithm is important, not the code that's used to write it. What You Will Learn Combine principal component analysis with forward and backward stepwise selection to identify a compact subset of a large collection of variables that captures the maximum possible variation within the entire set. Identify features that may have predictive power over only a small subset of the feature domain. Such features can be profitably used by modern predictive models but may be missed by other feature selection methods. Find an underlying hidden Markov model that controls the distributions of feature variables and the target simultaneously. The memory inherent in this method is especially valuable in high-noise applications such as prediction of financial markets. Improve traditional stepwise selection in three ways: examine a collection of 'best-so-far' feature sets; test candidate features for inclusion with cross validation to automatically and effectively limit model complexity; and at each step estimate the probability that our results so far could be just the product of random good luck. We also estimate the probability that the improvement obtained by adding a new variable could have been just good luck. Take a potentially valuable nominal variable (a category or class membership) that is unsuitable for input to a prediction model, and assign to each category a sensible numeric value that can be used as a model input. Who This Book Is For Intermediate to advanced data science programmers and analysts. COMPUTERS,Data Science,Data Analytics

Data Science Concepts and Techniques with Applications This book comprehensively covers the topic of data science. Data science is an umbrella term that encompasses data analytics, data mining, machine learning, and several other related disciplines. This book synthesizes both fundamental and advanced topics of a research area that has now reached maturity. The chapters of this book are organized into three sections: The first section is an introduction to data science. Starting from the basic concepts, the book will highlight the types of data, its use, its importance and issues that are normally faced in data analytics. Followed by discussion on wide range of applications of data science and widely used techniques in data science. The second section is devoted to the tools and techniques of data science. It consists of data pre-processing, feature selection, classification and clustering concepts as well as an introduction to text mining and opining mining. And finally, the third section of the book focuses on two programming languages commonly used for data science projects i.e. Python and R programming language. Although this book primarily serves as a textbook, it will also appeal to industrial practitioners and researchers due to its focus on applications and references. The book is suitable for both undergraduate and postgraduate students as well as those carrying out research in data science. It can be used as a textbook for undergraduate students in computer science, engineering and mathematics. It can also be accessible to undergraduate students from other areas with the adequate background. The more advanced chapters can be used by postgraduate researchers intending to gather a deeper theoretical understanding. COMPUTERS,Data Science,Data Analytics

Statistical Data Science As an emerging discipline, data science broadly means different things across different areas. Exploring the relationship of data science with statistics, a well-established and principled data-analytic discipline, this book provides insights about commonalities in approach, and differences in emphasis.Featuring chapters from established authors in both disciplines, the book also presents a number of applications and accompanying papers. COMPUTERS,Data Science,Data Analytics

Data and Information in Online Environments This book constitutes the refereed post-conference proceedings of the First International Conference on Data and Information in Online Environments, DIONE 2020, which took place in Florianópolis, Brazil, in March 2020. DIONE 2020 handles the growing interaction between the information sciences, communication sciences and computer sciences. The 18 revised full papers were carefully reviewed and selected from 37 submissions and focus on the production, dissemination and evaluation of contents in online environments. The goal is to improve cooperation between data science, natural language processing, data engineering, big data, research evaluation, network science, sociology of science and communication communities. COMPUTERS,Data Science,Data Analytics

Disinformation, Misinformation, and Fake News in Social Media This book serves as a convenient entry point for researchers, practitioners, and students to understand the problems and challenges, learn state-of-the-art solutions for their specific needs, and quickly identify new research problems in their domains. The contributors to this volume describe the recent advancements in three related parts: (1) user engagements in the dissemination of information disorder; (2) techniques on detecting and mitigating disinformation; and (3) trending issues such as ethics, blockchain, clickbaits, etc. This edited volume will appeal to students, researchers, and professionals working on disinformation, misinformation and fake news in social media from a unique lens. COMPUTERS,Data Science,Data Analytics

Crowdsourced Health How data from our health-related Internet searches can lead to discoveries about diseases and symptoms and help patients deal with diagnoses. Most of us have gone online to search for information about health. What are the symptoms of a migraine? How effective is this drug? Where can I find more resources for cancer patients? Could I have an STD? Am I fat? A Pew survey reports more than 80 percent of American Internet users have logged on to ask questions like these. But what if the digital traces left by our searches could show doctors and medical researchers something new and interesting? What if the data generated by our searches could reveal information about health that would be difficult to gather in other ways? In this book, Elad Yom-Tov argues that Internet data could change the way medical research is done, supplementing traditional tools to provide insights not otherwise available. He describes how studies of Internet searches have, among other things, already helped researchers track to side effects of prescription drugs, to understand the information needs of cancer patients and their families, and to recognize some of the causes of anorexia. Yom-Tov shows that the information collected can benefit humanity without sacrificing individual privacy. He explains why people go to the Internet with health questions; for one thing, it seems to be a safe place to ask anonymously about such matters as obesity, sex, and pregnancy. He describes in detrimental effects of “pro-anorexia” online content; tells how computer scientists can scour search engine data to improve public health by, for example, identifying risk factors for disease and centers of contagion; and tells how analyses of how people deal with upsetting diagnoses help doctors to treat patients and patients to understand their conditions. COMPUTERS,Data Science,Data Analytics

Big Data, IoT, and Machine Learning The idea behind this book is to simplify the journey of aspiring readers and researchers to understand Big Data, IoT and Machine Learning. It also includes various real-time/offline applications and case studies in the fields of engineering, computer science, information security and cloud computing using modern tools. This book consists of two sections: Section I contains the topics related to Applications of Machine Learning, and Section II addresses issues about Big Data, the Cloud and the Internet of Things. This brings all the related technologies into a single source so that undergraduate and postgraduate students, researchers, academicians and people in industry can easily understand them. Features Addresses the complete data science technologies workflow Explores basic and high-level concepts and services as a manual for those in the industry and at the same time can help beginners to understand both basic and advanced aspects of machine learning Covers data processing and security solutions in IoT and Big Data applications Offers adaptive, robust, scalable and reliable applications to develop solutions for day-to-day problems Presents security issues and data migration techniques of NoSQL databases COMPUTERS,Data Science,Data Analytics

Rough Sets The volume LNAI 12179 constitutes the proceedings of the International Joint Conference on Rough Sets, IJCRS 2020, which was due to be held in Havana, Cuba, in June 2020. The conference was held virtually due to the COVID-19 pandemic. The 37 full papers accepted were carefully reviewed and selected from 50 submissions. The papers are grouped in the following topical sections: general rough sets; three-way decision theory; attribute reduction; granular computing; formal concept analysis; data summarization; community detection; fuzzy cognitive maps; tutorials. COMPUTERS,Data Science,Data Analytics

Ontology-Based Information Retrieval for Healthcare Systems With the advancements of semantic web, ontology has become the crucial mechanism for representing concepts in various domains. For research and dispersal of customized healthcare services, a major challenge is to efficiently retrieve and analyze individual patient data from a large volume of heterogeneous data over a long time span. This requirement demands effective ontology-based information retrieval approaches for clinical information systems so that the pertinent information can be mined from large amount of distributed data. This unique and groundbreaking book highlights the key advances in ontology-based information retrieval techniques being applied in the healthcare domain and covers the following areas: Semantic data integration in e-health care systems Keyword-based medical information retrieval Ontology-based query retrieval support for e-health implementation COMPUTERS,Data Science,Data Analytics

Data Analytics and AI Analytics and artificial intelligence (AI), what are they good for? The bandwagon keeps answering, absolutely everything! Analytics and artificial intelligence have captured the attention of everyone from top executives to the person in the street. While these disciplines have a relatively long history, within the last ten or so years they have exploded into corporate business and public consciousness. Organizations have rushed to embrace data-driven decision making. Companies everywhere are turning out products boasting that "artificial intelligence is included." We are indeed living in exciting times. The question we need to ask is, do we really know how to get business value from these exciting tools? Unfortunately, both the analytics and AI communities have not done a great job in collaborating and communicating with each other to build the necessary synergies. This book bridges the gap between these two critical fields. The book begins by explaining the commonalities and differences in the fields of data science, artificial intelligence, and autonomy by giving a historical perspective for each of these fields, followed by exploration of common technologies and current trends in each field. The book also readers introduces to applications of deep learning in industry with an overview of deep learning and its key architectures, as well as a survey and discussion of the main applications of deep learning. The book also presents case studies to illustrate applications of AI and analytics. These include a case study from the healthcare industry and an investigation of a digital transformation enabled by AI and analytics transforming a product-oriented company into one delivering solutions and services. The book concludes with a proposed AI-informed data analytics life cycle to be applied to unstructured data. COMPUTERS,Data Science,Data Analytics

Data Analytics and Management in Data Intensive Domains This book constitutes the post-conference proceedings of the 21st International Conference on Data Analytics and Management in Data Intensive Domains, DAMDID/RCDL 2019, held in Kazan, Russia, in October 2019.The 11 revised full papers presented together with four invited papers were carefully reviewed and selected from 52 submissions. The papers are organized in the following topical sections: advanced data analysis methods; data infrastructures and integrated information systems; models, ontologies and applications; data analysis in astronomy; information extraction from text; distributed computing; data science for education. COMPUTERS,Data Science,Data Analytics

Data Source Handbook If you're a developer looking to supplement your own data tools and services, this concise ebook covers the most useful sources of public data available today. You'll find useful information on APIs that offer broad coverage, tie their data to the outside world, and are either accessible online or feature downloadable bulk data. You'll also find code and helpful links. This guide organizes APIs by the subjects they cover—such as websites, people, or places—so you can quickly locate the best resources for augmenting the data you handle in your own service. Categories include: Website tools such as WHOIS, bit.ly, and Compete Services that use email addresses as search terms, including Github Finding information from just a name, with APIs such as WhitePages Services, such as Klout, for locating people with Facebook and Twitter accounts Search APIs, including BOSS and Wikipedia Geographical data sources, including SimpleGeo and U.S. Census Company information APIs, such as CrunchBase and ZoomInfo APIs that list IP addresses, such as MaxMind Services that list books, films, music, and products COMPUTERS,Data Science,Data Modeling & Design

Big Data Glossary To help you navigate the large number of new data tools available, this guide describes 60 of the most recent innovations, from NoSQL databases and MapReduce approaches to machine learning and visualization tools. Descriptions are based on first-hand experience with these tools in a production environment. This handy glossary also includes a chapter of key terms that help define many of these tool categories: NoSQL Databases—Document-oriented databases using a key/value interface rather than SQL MapReduce—Tools that support distributed computing on large datasets Storage—Technologies for storing data in a distributed way Servers—Ways to rent computing power on remote machines Processing—Tools for extracting valuable information from large datasets Natural Language Processing—Methods for extracting information from human-created text Machine Learning—Tools that automatically perform data analyses, based on results of a one-off analysis Visualization—Applications that present meaningful data graphically Acquisition—Techniques for cleaning up messy public data sources Serialization—Methods to convert data structure or object state into a storable format COMPUTERS,Data Science,Data Modeling & Design

MapReduce Design Patterns Until now, design patterns for the MapReduce framework have been scattered among various research papers, blogs, and books. This handy guide brings together a unique collection of valuable MapReduce patterns that will save you time and effort regardless of the domain, language, or development framework you’re using. Each pattern is explained in context, with pitfalls and caveats clearly identified to help you avoid common design mistakes when modeling your big data architecture. This book also provides a complete overview of MapReduce that explains its origins and implementations, and why design patterns are so important. All code examples are written for Hadoop. Summarization patterns: get a top-level view by summarizing and grouping data Filtering patterns: view data subsets such as records generated from one user Data organization patterns: reorganize data to work with other systems, or to make MapReduce analysis easier Join patterns: analyze different datasets together to discover interesting relationships Metapatterns: piece together several patterns to solve multi-stage problems, or to perform several analytics in the same job Input and output patterns: customize the way you use Hadoop to load or store data "A clear exposition of MapReduce programs for common data processing patterns—this book is indespensible for anyone using Hadoop." --Tom White, author of Hadoop: The Definitive Guide COMPUTERS,Data Science,Data Modeling & Design

Learning SPARQL Gain hands-on experience with SPARQL, the RDF query language that’s bringing new possibilities to semantic web, linked data, and big data projects. This updated and expanded edition shows you how to use SPARQL 1.1 with a variety of tools to retrieve, manipulate, and federate data from the public web as well as from private sources. Author Bob DuCharme has you writing simple queries right away before providing background on how SPARQL fits into RDF technologies. Using short examples that you can run yourself with open source software, you’ll learn how to update, add to, and delete data in RDF datasets. Get the big picture on RDF, linked data, and the semantic web Use SPARQL to find bad data and create new data from existing data Use datatype metadata and functions in your queries Learn techniques and tools to help your queries run more efficiently Use RDF Schemas and OWL ontologies to extend the power of your queries Discover the roles that SPARQL can play in your applications COMPUTERS,Data Science,Data Modeling & Design

Visualization in Scientific Computing ’95 Visualization is nowadays indispensable to get insight into the huge amounts of data pro duced by large scale simulations or advanced measurement devices. The use of com puter graphics for scientific purposes has become a well established discipline, known as Scientific Visualization. Many problems still have to be solved, and hence the field is a very active area for research and development. This book represents results of the sixth in a well established series of international workshops on Visualization in Scien tific Computing organized by the EUROGRAPHICS Association in collaboration with CRS4 (Center for Advanced Studies, Research and Development in Sardinia), held from May 3 to May 5,1995, in Chia, Italy. The thirteen contributions selected for this volume cover a wide range of topics, ranging from detailed algorithmic studies to searches for new metaphors. A rough di vision can be made into the parts interaction, irregular meshes, volume rendering, and applications. Interaction in three dimensions is a challenging area for research. The use of three dimensional user interfaces for more natural manipulation of three-dimensional data and their visualization is natural, but is far from trivial to realize. Pang et al. investigate the use of common objects such as spray cans and carving knives as metaphors for visualiza tion tools, in order to provide an intuitive and natural three dimensional user interface. Gibson uses a voxel-based data representation, not only for visualization, but also for physical modeling of objects. A prototype system under development for haptic explo ration is discussed. COMPUTERS,Data Science,Data Modeling & Design

Graph Data Model Complex databases can be understood well with visual representation. A graph is a very intuitive and rational structure to visually represent such databases. Graph Data Model (GDM) proposed by the author formalizes data representation and operations on the data in terms of the graph concept. The GDM is an extension of the relational model toward structural representation. In this model, a database is defined by a schema graph where nodes represent record types and arcs represent link types that are relationships between two record types. The capabilities of the GDM include direct representation of many-to-many relationships and of the relationships within a single record type. The characteristic operators are those associated with links: existential, universal, numerical and transitive link operators. Graph Data Language (GDL) is a data language based on this GDM. The essence of the GDL is path expressions used for formulation of queries. The concepts of GDM and GDL have actually been implemented by Ricoh Co., Ltd. and a system based on these concepts is commercially available for many UNIX machines. COMPUTERS,Data Science,Data Modeling & Design

Data Science for Business Written by renowned data science experts Foster Provost and Tom Fawcett, Data Science for Business introduces the fundamental principles of data science, and walks you through the "data-analytic thinking" necessary for extracting useful knowledge and business value from the data you collect. This guide also helps you understand the many data-mining techniques in use today. Based on an MBA course Provost has taught at New York University over the past ten years, Data Science for Business provides examples of real-world business problems to illustrate these principles. You’ll not only learn how to improve communication between business stakeholders and data scientists, but also how participate intelligently in your company’s data science projects. You’ll also discover how to think data-analytically, and fully appreciate how data science methods can support business decision-making. Understand how data science fits in your organization—and how you can use it for competitive advantage Treat data as a business asset that requires careful investment if you’re to gain real value Approach business problems data-analytically, using the data-mining process to gather good data in the most appropriate way Learn general concepts for actually extracting knowledge from data Apply data science principles when interviewing data science job candidates COMPUTERS,Data Science,Data Modeling & Design

Feedback Control for Computer Systems How can you take advantage of feedback control for enterprise programming? With this book, author Philipp K. Janert demonstrates how the same principles that govern cruise control in your car also apply to data center management and other enterprise systems. Through case studies and hands-on simulations, you’ll learn methods to solve several control issues, including mechanisms to spin up more servers automatically when web traffic spikes. Feedback is ideal for controlling large, complex systems, but its use in software engineering raises unique issues. This book provides basic theory and lots of practical advice for programmers with no previous background in feedback control. Learn feedback concepts and controller design Get practical techniques for implementing and tuning controllers Use feedback “design patterns†for common control scenarios Maintain a cache’s “hit rate†by automatically adjusting its size Respond to web traffic by scaling server instances automatically Explore ways to use feedback principles with queueing systems Learn how to control memory consumption in a game engine Take a deep dive into feedback control theory COMPUTERS,Data Science,Data Modeling & Design

Think Stats If you know how to program, you have the skills to turn data into knowledge, using tools of probability and statistics. This concise introduction shows you how to perform statistical analysis computationally, rather than mathematically, with programs written in Python. By working with a single case study throughout this thoroughly revised book, you’ll learn the entire process of exploratory data analysis—from collecting data and generating statistics to identifying patterns and testing hypotheses. You’ll explore distributions, rules of probability, visualization, and many other tools and concepts. New chapters on regression, time series analysis, survival analysis, and analytic methods will enrich your discoveries. Develop an understanding of probability and statistics by writing and testing code Run experiments to test statistical behavior, such as generating samples from several distributions Use simulations to understand concepts that are hard to grasp mathematically Import data from most sources with Python, rather than rely on data that’s cleaned and formatted for statistics tools Use statistical inference to answer questions about real-world data COMPUTERS,Data Science,Data Modeling & Design

Graph Databases Discover how graph databases can help you manage and query highly connected data. With this practical book, you’ll learn how to design and implement a graph database that brings the power of graphs to bear on a broad range of problem domains. Whether you want to speed up your response to user queries or build a database that can adapt as your business evolves, this book shows you how to apply the schema-free graph model to real-world problems. This second edition includes new code samples and diagrams, using the latest Neo4j syntax, as well as information on new functionality. Learn how different organizations are using graph databases to outperform their competitors. With this book’s data modeling, query, and code examples, you’ll quickly be able to implement your own solution. Model data with the Cypher query language and property graph model Learn best practices and common pitfalls when modeling with graphs Plan and implement a graph database solution in test-driven fashion Explore real-world examples to learn how and why organizations use a graph database Understand common patterns and components of graph database architecture Use analytical techniques and algorithms to mine graph database information COMPUTERS,Data Science,Data Modeling & Design

Creating a Data-Driven Organization What do you need to become a data-driven organization? Far more than having big data or a crack team of unicorn data scientists, it requires establishing an effective, deeply-ingrained data culture. This practical book shows you how true data-drivenness involves processes that require genuine buy-in across your company, from analysts and management to the C-Suite and the board. Through interviews and examples from data scientists and analytics leaders in a variety of industries, author Carl Anderson explains the analytics value chain you need to adopt when building predictive business models—from data collection and analysis to the insights and leadership that drive concrete actions. You’ll learn what works and what doesn’t, and why creating a data-driven culture throughout your organization is essential. Start from the bottom up: learn how to collect the right data the right way Hire analysts with the right skills, and organize them into teams Examine statistical and visualization tools, and fact-based story-telling methods Collect and analyze data while respecting privacy and ethics Understand how analysts and their managers can help spur a data-driven culture Learn the importance of data leadership and C-level positions such as chief data officer and chief analytics officer COMPUTERS,Data Science,Data Modeling & Design

Learn to Write DAX Active learning lessons for mastering DAX Data analysis expressions (DAX) is the formula language of PowerPivot and this book is written to give hands-on practice to anyone who wants to become competent at writing such formulas. Sample exercises that explain each concept are provided and followed by practice questions and answers to maximize learning and experience with DAX. COMPUTERS,Data Science,Data Modeling & Design

SQL and Relational Theory SQL is full of difficulties and traps for the unwary. You can avoid them if you understand relational theory, but only if you know how to put that theory into practice. In this book, Chris Date explains relational theory in depth, and demonstrates through numerous examples and exercises how you can apply it to your use of SQL. This third edition has been revised, extended, and improved throughout. Topics whose treatment has been expanded include data types and domains, table comparisons, image relations, aggregate operators and summarization, view updating, and subqueries. A special feature of this edition is a new appendix on NoSQL and relational theory. Could you write an SQL query to find employees who have worked at least once in every programming department in the company? And be sure it’s correct? Why is proper column naming so important? Nulls in the database cause wrong answers. Why? What you can do about it? How can image relations help you formulate complex SQL queries? SQL supports "quantified comparisons," but they’re better avoided. Why? And how? Database theory and practice have evolved considerably since Codd first defined the relational model, back in 1969. This book draws on decades of experience to present the most up to date treatment of the material available anywhere. Anyone with a modest to advanced background in SQL can benefit from the insights it contains. The book is product independent. COMPUTERS,Data Science,Data Modeling & Design

Database Programming Languages (DBPL-4) The Fourth International Workshop on Database Programming Languages - Object Models and Languages (DBPL-4) took place in Manhattan, New York City, 30 August-1 September 1993. The areas of interest and the format of DBPL-4 focused on the integration of programming languages, object models, type systems and database systems. As in the previous DBPL workshops, the setting was informal, allowing the participants to actively discuss and argue about the ideas presented in the talks. The comments and remarks made by the participants during and after the presentations were taken into account in the preparation of the final versions of the papers. The result, we believe, is a set of excellent papers. The DBPL sequence is closely related to the sequence of International Workshops on Persistent Object Systems (POS), first started in 1985. While the DBPL workshops focus on language and model issues, the POS workshops have focused on implementation issues; thus the two sequences complement each other. Many researchers participate in both workshop series. The eight sessions of the technical program of DBPL-4 were as follows: 1. Bulk types and their query languages (two sessions). 2. Object models and languages. 3. Data types with order. 4. Mechanisms to support persistence, reflection, and extensibility. 5. Query optimization and integrity constraints. 6. Logic-based models. 7. Implementation and performance issues. COMPUTERS,Data Science,Data Modeling & Design

Data Wrangling with Python How do you take your data analysis skills beyond Excel to the next level? By learning just enough Python to get stuff done. This hands-on guide shows non-programmers like you how to process information that’s initially too messy or difficult to access. You don't need to know a thing about the Python programming language to get started. Through various step-by-step exercises, you’ll learn how to acquire, clean, analyze, and present data efficiently. You’ll also discover how to automate your data process, schedule file- editing and clean-up tasks, process larger datasets, and create compelling stories with data you obtain. Quickly learn basic Python syntax, data types, and language concepts Work with both machine-readable and human-consumable data Scrape websites and APIs to find a bounty of useful information Clean and format data to eliminate duplicates and errors in your datasets Learn when to standardize data and when to test and script data cleanup Explore and analyze your datasets with new Python libraries and techniques Use Python solutions to automate your entire data-wrangling process COMPUTERS,Data Science,Data Modeling & Design

Advanced Analytics with Spark In the second edition of this practical book, four Cloudera data scientists present a set of self-contained patterns for performing large-scale data analysis with Spark. The authors bring Spark, statistical methods, and real-world data sets together to teach you how to approach analytics problems by example. Updated for Spark 2.1, this edition acts as an introduction to these techniques and other best practices in Spark programming. You’ll start with an introduction to Spark and its ecosystem, and then dive into patterns that apply common techniques—including classification, clustering, collaborative filtering, and anomaly detection—to fields such as genomics, security, and finance. If you have an entry-level understanding of machine learning and statistics, and you program in Java, Python, or Scala, you’ll find the book’s patterns useful for working on your own data applications. With this book, you will: Familiarize yourself with the Spark programming model Become comfortable within the Spark ecosystem Learn general approaches in data science Examine complete implementations that analyze large public data sets Discover which machine learning tools make sense for particular problems Acquire code that can be adapted to many uses COMPUTERS,Data Science,Data Modeling & Design

IBM SPSS Modeler Essentials Get to grips with the fundamentals of data mining and predictive analytics with IBM SPSS Modeler About This Book Get up–and-running with IBM SPSS Modeler without going into too much depth. Identify interesting relationships within your data and build effective data mining and predictive analytics solutions A quick, easy–to-follow guide to give you a fundamental understanding of SPSS Modeler, written by the best in the business Who This Book Is For This book is ideal for those who are new to SPSS Modeler and want to start using it as quickly as possible, without going into too much detail. An understanding of basic data mining concepts will be helpful, to get the best out of the book. What You Will Learn Understand the basics of data mining and familiarize yourself with Modeler's visual programming interface Import data into Modeler and learn how to properly declare metadata Obtain summary statistics and audit the quality of your data Prepare data for modeling by selecting and sorting cases, identifying and removing duplicates, combining data files, and modifying and creating fields Assess simple relationships using various statistical and graphing techniques Get an overview of the different types of models available in Modeler Build a decision tree model and assess its results Score new data and export predictions In Detail IBM SPSS Modeler allows users to quickly and efficiently use predictive analytics and gain insights from your data. With almost 25 years of history, Modeler is the most established and comprehensive Data Mining workbench available. Since it is popular in corporate settings, widely available in university settings, and highly compatible with all the latest technologies, it is the perfect way to start your Data Science and Machine Learning journey. This book takes a detailed, step-by-step approach to introducing data mining using the de facto standard process, CRISP-DM, and Modeler's easy to learn “visual programming†style. You will learn how to read data into Modeler, assess data quality, prepare your data for modeling, find interesting patterns and relationships within your data, and export your predictions. Using a single case study throughout, this intentionally short and focused book sticks to the essentials. The authors have drawn upon their decades of teaching thousands of new users, to choose those aspects of Modeler that you should learn first, so that you get off to a good start using proven best practices. This book provides an overview of various popular data modeling techniques and presents a detailed case study of how to use CHAID, a decision tree model. Assessing a model's performance is as important as building it; this book will also show you how to do that. Finally, you will see how you can score new data and export your predictions. By the end of this book, you will have a firm understanding of the basics of data mining and how to effectively use Modeler to build predictive models. Style and approach This book empowers users to build practical & accurate predictive models quickly and intuitively. With the support of the advanced analytics users can discover hidden patterns and trends.This will help users to understand the factors that influence them, enabling you to take advantage of business opportunities and mitigate risks. COMPUTERS,Data Science,Data Modeling & Design

The Model Thinker How anyone can become a data ninja From the stock market to genomics laboratories, census figures to marketing email blasts, we are awash with data. But as anyone who has ever opened up a spreadsheet packed with seemingly infinite lines of data knows, numbers aren't enough: we need to know how to make those numbers talk. In The Model Thinker, social scientist Scott E. Page shows us the mathematical, statistical, and computational models -- from linear regression to random walks and far beyond -- that can turn anyone into a genius. At the core of the book is Page's "many-model paradigm," which shows the reader how to apply multiple models to organize the data, leading to wiser choices, more accurate predictions, and more robust designs. The Model Thinker provides a toolkit for business people, students, scientists, pollsters, and bloggers to make them better, clearer thinkers, able to leverage data and information to their advantage. COMPUTERS,Data Science,Data Modeling & Design

Machine Learning with Python Cookbook This practical guide provides nearly 200 self-contained recipes to help you solve machine learning challenges you may encounter in your daily work. If you’re comfortable with Python and its libraries, including pandas and scikit-learn, you’ll be able to address specific problems such as loading data, handling text or numerical data, model selection, and dimensionality reduction and many other topics. Each recipe includes code that you can copy and paste into a toy dataset to ensure that it actually works. From there, you can insert, combine, or adapt the code to help construct your application. Recipes also include a discussion that explains the solution and provides meaningful context. This cookbook takes you beyond theory and concepts by providing the nuts and bolts you need to construct working machine learning applications. You’ll find recipes for: Vectors, matrices, and arrays Handling numerical and categorical data, text, images, and dates and times Dimensionality reduction using feature extraction or feature selection Model evaluation and selection Linear and logical regression, trees and forests, and k-nearest neighbors Support vector machines (SVM), naïve Bayes, clustering, and neural networks Saving and loading trained models COMPUTERS,Data Science,Data Modeling & Design

Elegant Fractals Fractals are intricate geometrical forms that contain miniature copies of themselves on ever smaller scales. This colorful book describes methods for producing an endless variety of fractal art using a computer program that searches through millions of equations looking for those few that can produce images having aesthetic appeal. Over a hundred examples of such images are included with a link to the software that produced these images, and can also produce many more similar fractals. The underlying mathematics of the process is also explained in detail.Other books by the author that could be of interest to the reader are Elegant Chaos: Algebraically Simple Chaotic Flows (J C Sprott, 2010) and Elegant Circuits: Simple Chaotic Oscillators (J C Sprott and W J Thio, 2020). COMPUTERS,Data Science,Data Modeling & Design

Hands-On Data Science for Marketing Optimize your marketing strategies through analytics and machine learning Key Features Understand how data science drives successful marketing campaigns Use machine learning for better customer engagement, retention, and product recommendations Extract insights from your data to optimize marketing strategies and increase profitability Book Description Regardless of company size, the adoption of data science and machine learning for marketing has been rising in the industry. With this book, you will learn to implement data science techniques to understand the drivers behind the successes and failures of marketing campaigns. This book is a comprehensive guide to help you understand and predict customer behaviors and create more effectively targeted and personalized marketing strategies. This is a practical guide to performing simple-to-advanced tasks, to extract hidden insights from the data and use them to make smart business decisions. You will understand what drives sales and increases customer engagements for your products. You will learn to implement machine learning to forecast which customers are more likely to engage with the products and have high lifetime value. This book will also show you how to use machine learning techniques to understand different customer segments and recommend the right products for each customer. Apart from learning to gain insights into consumer behavior using exploratory analysis, you will also learn the concept of A/B testing and implement it using Python and R. By the end of this book, you will be experienced enough with various data science and machine learning techniques to run and manage successful marketing campaigns for your business. What you will learn Learn how to compute and visualize marketing KPIs in Python and R Master what drives successful marketing campaigns with data science Use machine learning to predict customer engagement and lifetime value Make product recommendations that customers are most likely to buy Learn how to use A/B testing for better marketing decision making Implement machine learning to understand different customer segments Who this book is for If you are a marketing professional, data scientist, engineer, or a student keen to learn how to apply data science to marketing, this book is what you need! It will be beneficial to have some basic knowledge of either Python or R to work through the examples. This book will also be beneficial for beginners as it covers basic-to-advanced data science concepts and applications in marketing with real-life examples. COMPUTERS,Data Science,Data Modeling & Design

Data Science from Scratch Data science libraries, frameworks, modules, and toolkits are great for doing data science, but they’re also a good way to dive into the discipline without actually understanding data science. With this updated second edition, you’ll learn how many of the most fundamental data science tools and algorithms work by implementing them from scratch. If you have an aptitude for mathematics and some programming skills, author Joel Grus will help you get comfortable with the math and statistics at the core of data science, and with hacking skills you need to get started as a data scientist. Today’s messy glut of data holds answers to questions no one’s even thought to ask. This book provides you with the know-how to dig those answers out. COMPUTERS,Data Science,Data Modeling & Design

Mastering pandas Perform advanced data manipulation tasks using pandas and become an expert data analyst. Key Features Manipulate and analyze your data expertly using the power of pandas Work with missing data and time series data and become a true pandas expert Includes expert tips and techniques on making your data analysis tasks easier Book Description pandas is a popular Python library used by data scientists and analysts worldwide to manipulate and analyze their data. This book presents useful data manipulation techniques in pandas to perform complex data analysis in various domains. An update to our highly successful previous edition with new features, examples, updated code, and more, this book is an in-depth guide to get the most out of pandas for data analysis. Designed for both intermediate users as well as seasoned practitioners, you will learn advanced data manipulation techniques, such as multi-indexing, modifying data structures, and sampling your data, which allow for powerful analysis and help you gain accurate insights from it. With the help of this book, you will apply pandas to different domains, such as Bayesian statistics, predictive analytics, and time series analysis using an example-based approach. And not just that; you will also learn how to prepare powerful, interactive business reports in pandas using the Jupyter notebook. By the end of this book, you will learn how to perform efficient data analysis using pandas on complex data, and become an expert data analyst or data scientist in the process. What you will learn Speed up your data analysis by importing data into pandas Keep relevant data points by selecting subsets of your data Create a high-quality dataset by cleaning data and fixing missing values Compute actionable analytics with grouping and aggregation in pandas Master time series data analysis in pandas Make powerful reports in pandas using Jupyter notebooks Who this book is for This book is for data scientists, analysts and Python developers who wish to explore advanced data analysis and scientific computing techniques using pandas. Some fundamental understanding of Python programming and familiarity with the basic data analysis concepts is all you need to get started with this book. COMPUTERS,Data Science,Data Modeling & Design

Learn Power Query Discover how you can combine data from various sources to create data models to suit your business requirements with the help of this clear and concise guide Key Features Understand how Power Query overcomes the shortcomings of Excel Power Pivot in handling complex data Create customized dashboards and multi-dimensional reports using Power Query and Power BI Learn the Power Query M language and write advanced queries using custom functions Book Description Power Query is a data connection technology that allows you to connect, combine, and refine data from multiple sources to meet your business analysis requirements. With this Power Query book, you'll be empowered to work with a variety of data sources to create interactive reports and dashboards using Excel and Power BI. You'll start by learning how to access Power Query across different versions of Excel and install the Power BI engine. After you've explored Power Pivot, you'll see why Excel users find it challenging to clean data in Power Pivot and learn how Power Query can help to tackle the problem. The book will show you how to transform data using the Query Editor and write functions in Power Query. A dedicated section will focus on functions such as IF, Index, and Modulo, and creating parameters to alter query paths in a table. You'll also work with dashboards, get to grips with multi-dimensional reporting, and create automated reports. As you advance, you'll cover the M formula language in Power Query, delve into the basic M syntax, and write the M query language with the help of examples such as loading all library functions offline in Excel and Power BI. Finally, the book will demonstrate the difference between M and DAX and show how results are produced in M. By the end of this book, you'll be ready to create impressive dashboards and multi-dimensional reports in Power Query and turn data into valuable insights. What you will learn Convert worksheet data into a table format ready for query output Create a dynamic connection between an Access database and Excel workbook Reshape tabular data by altering rows, columns, and tables using various Power Query tools Create new columns automatically from filenames and sheet tabs, along with multiple Excel data files Streamline and automate reports from multiple sources Explore different customization options to get the most out of your dashboards Understand the difference between the DAX language and Power Query's M language Who this book is for This Power Query book is for business analysts, data analysts, BI professionals, and Excel users looking to take their skills to the next level by learning how to collect, combine, and transform data into insights using Power Query. Working knowledge of Excel and experience in constructing and troubleshooting Excel formulas and functions is expected. COMPUTERS,Data Science,Data Modeling & Design

Hands-On Simulation Modeling with Python Enhance your simulation modeling skills by creating and analyzing digital prototypes of a physical model using Python programming with this comprehensive guide Key Features Learn to create a digital prototype of a real model using hands-on examples Evaluate the performance and output of your prototype using simulation modeling techniques Understand various statistical and physical simulations to improve systems using Python Book Description Simulation modeling helps you to create digital prototypes of physical models to analyze how they work and predict their performance in the real world. With this comprehensive guide, you'll understand various computational statistical simulations using Python. Starting with the fundamentals of simulation modeling, you'll understand concepts such as randomness and explore data generating processes, resampling methods, and bootstrapping techniques. You'll then cover key algorithms such as Monte Carlo simulations and Markov decision processes, which are used to develop numerical simulation models, and discover how they can be used to solve real-world problems. As you advance, you'll develop simulation models to help you get accurate results and enhance decision-making processes. Using optimization techniques, you'll learn to modify the performance of a model to improve results and make optimal use of resources. The book will guide you in creating a digital prototype using practical use cases for financial engineering, prototyping project management to improve planning, and simulating physical phenomena using neural networks. By the end of this book, you'll have learned how to construct and deploy simulation models of your own to overcome real-world challenges. What you will learn Gain an overview of the different types of simulation models Get to grips with the concepts of randomness and data generation process Understand how to work with discrete and continuous distributions Work with Monte Carlo simulations to calculate a definite integral Find out how to simulate random walks using Markov chains Obtain robust estimates of confidence intervals and standard errors of population parameters Discover how to use optimization methods in real-life applications Run efficient simulations to analyze real-world systems Who this book is for Hands-On Simulation Modeling with Python is for simulation developers and engineers, model designers, and anyone already familiar with the basic computational methods that are used to study the behavior of systems. This book will help you explore advanced simulation techniques such as Monte Carlo methods, statistical simulations, and much more using Python. Working knowledge of Python programming language is required. COMPUTERS,Data Science,Data Modeling & Design

Modeling and Precision Control of Systems with Hysteresis Modelling and Precision Control of Systems with Hysteresis covers the piezoelectric and other smart materials that are increasingly employed as actuators in precision engineering, from scanning probe microscopes (SPMs) in life science and nano-manufacturing, to precision active optics in astronomy, including space laser communication, space imaging cameras, and the micro-electro-mechanical systems (MEMS). As smart materials are known for having hysteretic dynamics, it is necessary to overcome issues with a broadband range of frequencies. This book offers both the mathematical tools for modeling the systems and applications, including complete case studies and source code for the experiments to help both academics and researchers in the industry to achieve precision in the control of Smart Actuator systems. Provides a comprehensive identification of typical complex hysteresis Presents control algorithm design for systems with hysteresis Contain numerous real life examples and two complete case studies Source code to examples are provided COMPUTERS,Data Science,Data Visualization

Data Visualization with Python and JavaScript Learn how to turn raw data into rich, interactive web visualizations with the powerful combination of Python and JavaScript. With this hands-on guide, author Kyran Dale teaches you how build a basic dataviz toolchain with best-of-breed Python and JavaScript libraries—including Scrapy, Matplotlib, Pandas, Flask, and D3—for crafting engaging, browser-based visualizations. As a working example, throughout the book Dale walks you through transforming Wikipedia’s table-based list of Nobel Prize winners into an interactive visualization. You’ll examine steps along the entire toolchain, from scraping, cleaning, exploring, and delivering data to building the visualization with JavaScript’s D3 library. If you’re ready to create your own web-based data visualizations—and know either Python or JavaScript— this is the book for you. Learn how to manipulate data with Python Understand the commonalities between Python and JavaScript Extract information from websites by using Python’s web-scraping tools, BeautifulSoup and Scrapy Clean and explore data with Python’s Pandas, Matplotlib, and Numpy libraries Serve data and create RESTful web APIs with Python’s Flask framework Create engaging, interactive web visualizations with JavaScript’s D3 library COMPUTERS,Data Science,Data Visualization

Interactive Data Visualization for the Web Create and publish your own interactive data visualization projects on the web—even if you have little or no experience with data visualization or web development. It’s inspiring and fun with this friendly, accessible, and practical hands-on introduction. This fully updated and expanded second edition takes you through the fundamental concepts and methods of D3, the most powerful JavaScript library for expressing data visually in a web browser. Ideal for designers with no coding experience, reporters exploring data journalism, and anyone who wants to visualize and share data, this step-by-step guide will also help you expand your web programming skills by teaching you the basics of HTML, CSS, JavaScript, and SVG. Learn D3 4.x—the latest D3 version—with downloadable code and over 140 examples Create bar charts, scatter plots, pie charts, stacked bar charts, and force-directed graphs Use smooth, animated transitions to show changes in your data Introduce interactivity to help users explore your data Create custom geographic maps with panning, zooming, labels, and tooltips Walk through the creation of a complete visualization project, from start to finish Explore inspiring case studies with nine accomplished designers talking about their D3-based projects COMPUTERS,Data Science,Data Visualization

Making Data Visual You have a mound of data front of you and a suite of computation tools at your disposal. Which parts of the data actually matter? Where is the insight hiding? If you’re a data scientist trying to navigate the murky space between data and insight, this practical book shows you how to make sense of your data through high-level questions, well-defined data analysis tasks, and visualizations to clarify understanding and gain insights along the way. When incorporated into the process early and often, iterative visualization can help you refine the questions you ask of your data. Authors Danyel Fisher and Miriah Meyer provide detailed case studies that demonstrate how this process can evolve in the real world. You’ll learn: The data counseling process for moving from general to more precise questions about your data, and arriving at a working visualization The role that visual representations play in data discovery Common visualization types by the tasks they fulfill and the data they use Visualization techniques that use multiple views and interaction to support analysis of large, complex data sets COMPUTERS,Data Science,Data Visualization

Mastering Qlik Sense Master the capabilities of Qlik Sense to design and deploy solutions that address all the Business Intelligence needs of your organization About This Book Create compelling dashboards and visualizations with your data by leveraging Qlik Sense's self-service model Perform data loading and model efficient solutions with faster performance and better governance Master Qlik Sense's APIs and develop powerful mashups and fantastic extensions for visualizations and other components that run across all platforms Who This Book Is For This book is for Business Intelligence professionals and Data Analysts who want to become experts in using Qlik Sense. If you have extensively used QlikView in the past and are looking to transition to Qlik Sense, this book will also help you. A fundamental understanding of how Qlik Sense works and its features is all you need to get started with this book. What You Will Learn Understand the importance of self-service analytics and the IKEA-effect Explore all the available data modeling techniques and create efficient and optimized data models Master security rules and translate permission requirements into security rule logic Familiarize yourself with different types of Master Key Item(MKI) and know how and when to use MKI. Script and write sophisticated ETL code within Qlik Sense to facilitate all data modeling and data loading techniques Get an extensive overview of which APIs are available in Qlik Sense and how to take advantage of a technology with an API Develop basic mashup HTML pages and deploy successful mashup projects In Detail Qlik Sense is a powerful, self-servicing Business Intelligence tool for data discovery, analytics and visualization. It allows you to create personalized Business Intelligence solutions from raw data and get actionable insights from it. This book is your one-stop guide to mastering Qlik Sense, catering to all your organizational BI needs. You'll see how you can seamlessly navigate through tons of data from multiple sources and take advantage of the various APIs available in Qlik and its components for guided analytics. You'll also learn how to embed visualizations into your existing BI solutions and extend the capabilities of Qlik Sense to create new visualizations and dashboards that work across all platforms. We also cover other advanced concepts such as porting your Qlik View applications to Qlik Sense,and working with Qlik Cloud. Finally, you'll implement enterprise-wide security and access control for resources and data sources through practical examples. With the knowledge gained from this book, you'll have become the go-to expert in your organization when it comes to designing BI solutions using Qlik Sense. Style and approach This book provides in-depth knowledge on complex visualization processes. This guide will take you straight to complex implementation techniques. While covering the concepts, the use cases will help you understand how they work and how to utilize them. COMPUTERS,Data Science,Data Visualization

Mastering Microsoft Power BI Design, create and manage robust Power BI solutions to gain meaningful business insights About This Book Master all the dashboarding and reporting features of Microsoft Power BI Combine data from multiple sources, create stunning visualizations and publish your reports across multiple platforms A comprehensive guide with real-world use cases and examples demonstrating how you can get the best out of Microsoft Power BI Who This Book Is For Business Intelligence professionals and existing Power BI users looking to master Power BI for all their data visualization and dashboarding needs will find this book to be useful. While understanding of the basic BI concepts is required, some exposure to Microsoft Power BI will be helpful. What You Will Learn Build efficient data retrieval and transformation processes with the Power Query M Language Design scalable, user-friendly DirectQuery and Import Data Models Develop visually rich, immersive, and interactive reports and dashboards Maintain version control and stage deployments across development, test, and production environments Manage and monitor the Power BI Service and the On-premises data gateway Develop a fully on-premise solution with the Power BI Report Server Scale up a Power BI solution via Power BI Premium capacity and migration to Azure Analysis Services or SQL Server Analysis Services In Detail This book is intended for business intelligence professionals responsible for the design and development of Power BI content as well as managers, architects and administrators who oversee Power BI projects and deployments. The chapters flow from the planning of a Power BI project through the development and distribution of content to the administration of Power BI for an organization. BI developers will learn how to create sustainable and impactful Power BI datasets, reports, and dashboards. This includes connecting to data sources, shaping and enhancing source data, and developing an analytical data model. Additionally, top report and dashboard design practices are described using features such as Bookmarks and the Power KPI visual. BI managers will learn how Power BI's tools work together such as with the On-premises data gateway and how content can be staged and securely distributed via Apps. Additionally, both the Power BI Report Server and Power BI Premium are reviewed. By the end of this book, you will be confident in creating effective charts, tables, reports or dashboards for any kind of data using the tools and techniques in Microsoft PowerBI. Style and approach This book consists of real-world examples on Power BI that target novices as well as intermediate Power BI users. It goes deep into the technical issues, covers additional protocols, and many more real-live examples. COMPUTERS,Data Science,Data Visualization

Practical Tableau Whether you have some experience with Tableau software or are just getting started, this manual goes beyond the basics to help you build compelling, interactive data visualization applications. Author Ryan Sleeper, one of the world’s most qualified Tableau consultants, complements his web posts and instructional videos with this guide to give you a firm understanding of how to use Tableau to find valuable insights in data. Over five sections, Sleeper—recognized as a Tableau Zen Master, Tableau Public Visualization of the Year author, and Tableau Iron Viz Champion—provides visualization tips, tutorials, and strategies to help you avoid the pitfalls and take your Tableau knowledge to the next level. Practical Tableau sections include: Fundamentals: get started with Tableau from the beginning Chart types: use step-by-step tutorials to build a variety of charts in Tableau Tips and tricks: learn innovative uses of parameters, color theory, how to make your Tableau workbooks run efficiently, and more Framework: explore the INSIGHT framework, a proprietary process for building Tableau dashboards Storytelling: learn tangible tactics for storytelling with data, including specific and actionable tips you can implement immediately COMPUTERS,Data Science,Data Visualization

Matplotlib for Python Developers Leverage the power of Matplotlib to visualize and understand your data more effectively About This Book Perform effective data visualization with Matplotlib and get actionable insights from your data Design attractive graphs, charts, and 2D plots, and deploy them to the web Get the most out of Matplotlib in this practical guide with updated code and examples Who This Book Is For This book is essentially for anyone who wants to create intuitive data visualizations using the Matplotlib library. If you're a data scientist or analyst and wish to create attractive visualizations using Python, you'll find this book useful. Some knowledge of Python programming is all you need to get started. What You Will Learn Create 2D and 3D static plots such as bar charts, heat maps, and scatter plots Get acquainted with GTK+3, Qt5, and wxWidgets to understand the UI backend of Matplotlib Develop advanced static plots with third-party packages such as Pandas, GeoPandas, and Seaborn Create interactive plots with real-time updates Develop web-based, Matplotlib-powered graph visualizations with third-party packages such as Django Write data visualization code that is readily expandable on the cloud platform In Detail Python is a general-purpose programming language increasingly being used for data analysis and visualization. Matplotlib is a popular data visualization package in Python used to design effective plots and graphs. This is a practical, hands-on resource to help you visualize data with Python using the Matplotlib library. Matplotlib for Python Developers, Second Edition shows you how to create attractive graphs, charts, and plots using Matplotlib. You will also get a quick introduction to third-party packages, Seaborn, Pandas, Basemap, and Geopandas, and learn how to use them with Matplotlib. After that, you'll embed and customize your plots in third-party tools such as GTK+3, Qt 5, and wxWidgets. You'll also be able to tweak the look and feel of your visualization with the help of practical examples provided in this book. Further on, you'll explore Matplotlib 2.1.x on the web, from a cloud-based platform using third-party packages such as Django. Finally, you will integrate interactive, real-time visualization techniques into your current workflow with the help of practical real-world examples. By the end of this book, you'll be thoroughly comfortable with using the popular Python data visualization library Matplotlib 2.1.x and leveraging its power to build attractive, insightful, and powerful visualizations. Style and approach Step by step approach to learning the best of Matplotlib 2.1.x COMPUTERS,Data Science,Data Visualization

Hands-On Data Visualization with Bokeh Learn how to create interactive and visually aesthetic plots using the Bokeh package in Python About This Book A step by step approach to creating interactive plots with Bokeh Go from nstallation all the way to deploying your very own Bokeh application Work with a real time datasets to practice and create your very own plots and applications Who This Book Is For This book is well suited for data scientists and data analysts who want to perform interactive data visualization on their web browsers using Bokeh. Some exposure to Python programming will be helpful, but prior experience with Bokeh is not required. What You Will Learn Installing Bokeh and understanding its key concepts Creating plots using glyphs, the fundamental building blocks of Bokeh Creating plots using different data structures like NumPy and Pandas Using layouts and widgets to visually enhance your plots and add a layer of interactivity Building and hosting applications on the Bokeh server Creating advanced plots using spatial data In Detail Adding a layer of interactivity to your plots and converting these plots into applications hold immense value in the field of data science. The standard approach to adding interactivity would be to use paid software such as Tableau, but the Bokeh package in Python offers users a way to create both interactive and visually aesthetic plots for free. This book gets you up to speed with Bokeh - a popular Python library for interactive data visualization. The book starts out by helping you understand how Bokeh works internally and how you can set up and install the package in your local machine. You then use a real world data set which uses stock data from Kaggle to create interactive and visually stunning plots. You will also learn how to leverage Bokeh using some advanced concepts such as plotting with spatial and geo data. Finally you will use all the concepts that you have learned in the previous chapters to create your very own Bokeh application from scratch. By the end of the book you will be able to create your very own Bokeh application. You will have gone through a step by step process that starts with understanding what Bokeh actually is and ends with building your very own Bokeh application filled with interactive and visually aesthetic plots. Style and approach This books take you through a step by step process that starts with understanding what Bokeh actually is and ends with building your very own Bokeh application filled with interactive and visually aesthetic plots that will amaze your users. COMPUTERS,Data Science,Data Visualization

Applied Data Visualization with R and ggplot2 Develop informative and aesthetic visualizations that enable effective data analysis in less time Key Features Discover structure of ggplot2, grammar of graphics, and geometric objects Study how to design and implement visualization from scratch Explore the advantages of using advanced plots Book Description Applied Data Visualization with R and ggplot2 introduces you to the world of data visualization by taking you through the basic features of ggplot2. To start with, you'll learn how to set up the R environment, followed by getting insights into the grammar of graphics and geometric objects before you explore the plotting techniques. You'll discover what layers, scales, coordinates, and themes are, and study how you can use them to transform your data into aesthetical graphs. Once you've grasped the basics, you'll move on to studying simple plots such as histograms and advanced plots such as superimposing and density plots. You'll also get to grips with plotting trends, correlations, and statistical summaries. By the end of this book, you'll have created data visualizations that will impress your clients. What you will learn Set up the R environment, RStudio, and understand structure of ggplot2 Distinguish variables and use best practices to visualize them Change visualization defaults to reveal more information about data Implement the grammar of graphics in ggplot2 such as scales and faceting Build complex and aesthetic visualizations with ggplot2 analysis methods Logically and systematically explore complex relationships Compare variables in a single visual, with advanced plotting methods Who this book is for Applied Data Visualization with R and ggplot2 is for you if you are a professional working with data and R. This book is also for students who want to enhance their data analysis skills by adding informative and professional visualizations. It is assumed that you know basics of the R language and its commands and objects. COMPUTERS,Data Science,Data Visualization

R Graphics Cookbook This O’Reilly cookbook provides more than 150 recipes to help scientists, engineers, programmers, and data analysts generate high-quality graphs quickly—without having to comb through all the details of R’s graphing systems. Each recipe tackles a specific problem with a solution you can apply to your own project and includes a discussion of how and why the recipe works. Most of the recipes in this second edition use the updated version of the ggplot2 package, a powerful and flexible way to make graphs in R. You’ll also find expanded content about the visual design of graphics. If you have at least a basic understanding of the R language, you’re ready to get started with this easy-to-use reference. Use R’s default graphics for quick exploration of data Create a variety of bar graphs, line graphs, and scatter plots Summarize data distributions with histograms, density curves, box plots, and more Provide annotations to help viewers interpret data Control the overall appearance of graphics Explore options for using colors in plots Create network graphs, heat maps, and 3D scatter plots Get your data into shape using packages from the tidyverse COMPUTERS,Data Science,Data Visualization

Learn QGIS Learn to view, edit and analyse geospatial data using QGIS and Python 3 Key Features Leverage the power of QGIS to add professionalism to your maps Explore and work with the newly released features like Python 3, GeoPackage, 3D views, Print layouts in QGIS 3.4 Build your own plugins and customize maps using QT designer Book Description QGIS 3.4 is the first LTR (long term release) of QGIS version 3. This is a giant leap forward for the project with tons of new features and impactful changes. Learn QGIS is fully updated for QGIS 3.4, covering its processing engine update, Python 3 de-facto coding environment, and the GeoPackage format. This book will help you get started on your QGIS journey, guiding you to develop your own processing pathway. You will explore the user interface, loading your data, editing, and then creating data. QGIS often surprises new users with its mapping capabilities; you will discover how easily you can style and create your first map. But that's not all! In the final part of the book, you'll learn about spatial analysis and the powerful tools in QGIS, and conclude by looking at Python processing options. By the end of the book, you will have become proficient in geospatial analysis using QGIS and Python. What you will learn Explore various ways to load data into QGIS Understand how to style data and present it in a map Create maps and explore ways to expand them Get acquainted with the new processing toolbox in QGIS 3.4 Manipulate your geospatial data and gain quality insights Understand how to customize QGIS 3.4 Work with QGIS 3.4 in 3D Who this book is for If you are a developer or consultant familiar with the basic functions and processes of GIS and want to learn how to use QGIS to analyze geospatial data and create rich mapping applications, this book is for you. You'll also find this book useful if you're new to QGIS and wish to grasp its fundamentals COMPUTERS,Data Science,Data Visualization

Fundamentals of Data Visualization Effective visualization is the best way to communicate information from the increasingly large and complex datasets in the natural and social sciences. But with the increasing power of visualization software today, scientists, engineers, and business analysts often have to navigate a bewildering array of visualization choices and options. This practical book takes you through many commonly encountered visualization problems, and it provides guidelines on how to turn large datasets into clear and compelling figures. What visualization type is best for the story you want to tell? How do you make informative figures that are visually pleasing? Author Claus O. Wilke teaches you the elements most critical to successful data visualization. Explore the basic concepts of color as a tool to highlight, distinguish, or represent a value Understand the importance of redundant coding to ensure you provide key information in multiple ways Use the book’s visualizations directory, a graphical guide to commonly used types of data visualizations Get extensive examples of good and bad figures Learn how to use figures in a document or report and how employ them effectively to tell a compelling story COMPUTERS,Data Science,Data Visualization

Visual Analytics with Tableau A four-color journey through a complete Tableau visualization Tableau is a popular data visualization tool that’s easy for individual desktop use as well as enterprise. Used by financial analysts, marketers, statisticians, business and sales leadership, and many other job roles to present data visually for easy understanding, it’s no surprise that Tableau is an essential tool in our data-driven economy. Visual Analytics with Tableau is a complete journey in Tableau visualization for a non-technical business user. You can start from zero, connect your first data, and get right into creating and publishing awesome visualizations and insightful dashboards. • Learn the different types of charts you can create • Use aggregation, calculated fields, and parameters • Create insightful maps • Share interactive dashboards Geared toward beginners looking to get their feet wet with Tableau, this book makes it easy and approachable to get started right away. COMPUTERS,Data Science,Data Visualization

D3 for the Impatient If you’re in a hurry to learn D3.js, the leading JavaScript library for web-based graphics and visualization, this book is for you. Written for technically savvy readers with a background in programming or data science, the book moves quickly, emphasizing unifying concepts and patterns. Anticipating common difficulties, author Philipp K. Janert teaches you how to apply D3 to your own problems. Assuming only a general programming background, but no previous experience with contemporary web development, this book explains supporting technologies such as SVG, HTML5, CSS, and the DOM as needed, making it a convenient one-stop resource for a technical audience. Understand D3 selections, the library’s fundamental organizing principle Learn how to create data-driven documents with data binding Create animated graphs and interactive user interfaces Draw figures with curves, shapes, and colors Use the built-in facilities for heatmaps, tree graphs, and networks Simplify your work by writing your own reusable components COMPUTERS,Data Science,Data Visualization

Getting Started with Tableau 2019.2 Leverage the power of Tableau 2019.1's new features to create impactful data visualization Key Features Get up and running with the newly released features of Tableau 2019.1 Create enterprise-grade dashboard and reports to communicate your insights effectively Begin your Tableau journey by understanding its core functionalities Book Description Tableau is one of the leading data visualization tools and is regularly updated with new functionalities and features. The latest release, Tableau 2019.1, promises new and advanced features related to visual analytics, reporting, dashboarding, and a host of other data visualization aspects. Getting Started with Tableau 2019.1 will get you up to speed with these additional functionalities. The book starts by highlighting the new functionalities of Tableau 2019.1, providing concrete examples of how to use them. However, if you're new to Tableau, don't worry – you'll be guided through the major aspects of Tableau with relevant examples. You'll learn how to connect to data, build a data source, visualize your data, build a dashboard, and even share data online. In the concluding chapters, you'll delve into advanced techniques such as creating a cross-database join and data blending. By the end of this book, you will be able to use Tableau effectively to create quick, cost-effective, and business-efficient Business Intelligence (BI) solutions. What you will learn Discover new functionalities such as 'Ask Data', the new way to interact with your data using natural language Connect tables and make transformations such as pivoting the field and splitting columns Build an efficient data source for analysis Design insightful data visualization using different mark types and properties Develop powerful dashboards and stories Share your work and interact with Tableau Server Use Tableau to explore your data and find new insights Explore Tableau's advanced features and gear up for upcoming challenges Who this book is for Existing Tableau users and BI professionals who want to get up to speed with what's new in Tableau 2019 will find this beginner-level book to be a very useful resource. Some experience of Tableau is assumed, however, the book also features introductory concepts, which even beginners can take advantage of. COMPUTERS,Data Science,Data Visualization

Mastering Tableau 2019.1 Build, design and improve advanced business intelligence solutions using Tableau's latest features, including Tableau Prep, Tableau Hyper, and Tableau Server Key Features Master new features in Tableau 2019.1 to solve real-world analytics challenges Perform Geo-Spatial Analytics, Time Series Analysis, and self-service analytics using real-life examples Build and publish dashboards and explore storytelling using Python and MATLAB integration support Book Description Tableau is one of the leading business intelligence (BI) tools used to solve BI and analytics challenges. With this book, you will master Tableau's features and offerings in various paradigms of the BI domain. This book is also the second edition of the popular Mastering Tableau series, with new features, examples, and updated code. The book covers essential Tableau concepts and its advanced functionalities. Using Tableau Hyper and Tableau Prep, you'll be able to handle and prepare data easily. You'll gear up to perform complex joins, spatial joins, union, and data blending tasks using practical examples. Following this, you'll learn how to perform data densification to make displaying granular data easier. Next, you'll explore expert-level examples to help you with advanced calculations, mapping, and visual design using various Tableau extensions. With the help of examples, you'll also learn about improving dashboard performance, connecting Tableau Server, and understanding data visualizations. In the final chapters, you'll cover advanced use cases such as Self-Service Analytics, Time Series Analytics, and Geo-Spatial Analytics, and learn to connect Tableau to R, Python, and MATLAB. By the end of this book, you'll have mastered the advanced offerings of Tableau and be able to tackle common and not-so-common challenges faced in the BI domain. What you will learn Get up to speed with various Tableau components Master data preparation techniques using Tableau Prep Discover how to use Tableau to create a PowerPoint-like presentation Understand different Tableau visualization techniques and dashboard designs Interact with the Tableau server to understand its architecture and functionalities Study advanced visualizations and dashboard creation techniques Brush up on powerful Self-Service Analytics, Time Series Analytics, and Geo-Spatial Analytics Who this book is for This book is designed for business analysts, BI professionals and data analysts who want to master Tableau to solve a range of data science and business intelligence problems. The book is ideal if you have a good understanding of Tableau and want to take your skills to the next level. COMPUTERS,Data Science,Data Visualization

Innovative Tableau Level up with Tableau to build eye-catching, easy-to-interpret data visualizations. In this follow-up guide to Practical Tableau, author Ryan Sleeper takes you through a collection of unique tips and tutorials for using this popular software. Beginning to advanced Tableau users will learn how to go beyond Show Me to make better charts and learn dozens of tricks to improve both the author and user experience. Featuring many approaches he developed himself, Ryan shows you how to create charts that empower Tableau users to explore, understand, and derive value from their data. He also shares many of his favorite tricks that enabled him to become a Tableau Zen Master, Tableau Public Visualization of the Year author, and Tableau Global Iron Viz Champion. Learn what’s new in Tableau since Practical Tableau was released Examine unique new charts—timelines, custom gauges, and leapfrog charts—plus innovations to traditional charts such as highlight tables, scatter plots, and maps Get tips that can help make a Tableau developer’s life easier Understand what developers can do to make users’ lives easier COMPUTERS,Data Science,Data Visualization

Learn Grafana 7.0 A comprehensive introduction to help you get up and running with creating interactive dashboards to visualize and monitor time-series data in no time Key Features Install, set up, and configure Grafana for real-time data analysis and visualization Visualize and monitor data using data sources such as InfluxDB, Prometheus, and Elasticsearch Explore Grafana's multi-cloud support with Microsoft Azure, Amazon CloudWatch, and Google Stackdriver Book Description Grafana is an open-source analytical platform used to analyze and monitoring time-series data. This beginner's guide will help you get to grips with Grafana's new features for querying, visualizing, and exploring metrics and logs no matter where they are stored. The book begins by showing you how to install and set up the Grafana server. You'll explore the working mechanism of various components of the Grafana interface along with its security features, and learn how to visualize and monitor data using, InfluxDB, Prometheus, Logstash, and Elasticsearch. This Grafana book covers the advanced features of the Graph panel and shows you how Stat, Table, Bar Gauge, and Text are used. You'll build dynamic dashboards to perform end-to-end analytics and label and organize dashboards into folders to make them easier to find. As you progress, the book delves into the administrative aspects of Grafana by creating alerts, setting permissions for teams, and implementing user authentication. Along with exploring Grafana's multi-cloud monitoring support, you'll also learn about Grafana Loki, which is a backend logger for users running Prometheus and Kubernetes. By the end of this book, you'll have gained all the knowledge you need to start building interactive dashboards. What you will learn Find out how to visualize data using Grafana Understand how to work with the major components of the Graph panel Explore mixed data sources, query inspector, and time interval settings Discover advanced dashboard features such as annotations, templating with variables, dashboard linking, and dashboard sharing techniques Connect user authentication to Google, GitHub, and a variety of external services Find out how Grafana can provide monitoring support for cloud service infrastructures Who this book is for This book is for business intelligence developers, business analysts, data analysts, and anyone interested in performing time-series data analysis and monitoring using Grafana. Those looking to create and share interactive dashboards or looking to get up to speed with the latest features of Grafana will also find this book useful. Although no prior knowledge of Grafana is required, basic knowledge of data visualization and some experience in Python programming will help you understand the concepts covered in the book. COMPUTERS,Data Science,Data Visualization

The Infographic An exploration of infographics and data visualization as a cultural phenomenon, from eighteenth-century print culture to today's data journalism. Infographics and data visualization are ubiquitous in our everyday media diet, particularly in news—in print newspapers, on television news, and online. It has been argued that infographics are changing what it means to be literate in the twenty-first century—and even that they harmonize uniquely with human cognition. In this first serious exploration of the subject, Murray Dick traces the cultural evolution of the infographic, examining its use in news—and resistance to its use—from eighteenth-century print culture to today's data journalism. He identifies six historical phases of infographics in popular culture: the proto-infographic, the classical, the improving, the commercial, the ideological, and the professional. Dick describes the emergence of infographic forms within a wider history of journalism, culture, and communications, focusing his analysis on the UK. He considers their use in the partisan British journalism of late eighteenth and early nineteenth-century print media; their later deployment as a vehicle for reform and improvement; their mass-market debut in the twentieth century as a means of explanation (and sometimes propaganda); and their use for both ideological and professional purposes in the post–World War II marketized newspaper culture. Finally, he proposes best practices for news infographics and defends infographics and data visualization against a range of criticism. Dick offers not only a history of how the public has experienced and understood the infographic, but also an account of what data visualization can tell us about the past. COMPUTERS,Data Science,Data Visualization

The Data Warehouse ETL Toolkit Cowritten by Ralph Kimball, the world's leading data warehousing authority, whose previous books have sold more than 150,000 copies Delivers real-world solutions for the most time- and labor-intensive portion of data warehousing-data staging, or the extract, transform, load (ETL) process Delineates best practices for extracting data from scattered sources, removing redundant and inaccurate data, transforming the remaining data into correctly formatted data structures, and then loading the end product into the data warehouse Offers proven time-saving ETL techniques, comprehensive guidance on building dimensional structures, and crucial advice on ensuring data quality COMPUTERS,Data Science,Data Warehousing

Building the Data Warehouse The new edition of the classic bestseller that launched the data warehousing industry covers new approaches and technologies, many of which have been pioneered by Inmon himself In addition to explaining the fundamentals of data warehouse systems, the book covers new topics such as methods for handling unstructured data in a data warehouse and storing data across multiple storage media Discusses the pros and cons of relational versus multidimensional design and how to measure return on investment in planning data warehouse projects Covers advanced topics, including data monitoring and testing Although the book includes an extra 100 pages worth of valuable content, the price has actually been reduced from $65 to $55 COMPUTERS,Data Science,Data Warehousing

Beginning Database Design Solutions The vast majority of software applications use relational databases that virtually every application developer must work with. This book introduces you to database design, whether you're a DBA or database developer. You'll discover what databases are, their goals, and why proper design is necessary to achieve those goals. Additionally, you'll master how to structure the database so it gives good performance while minimizing the chance for error. You will learn how to decide what should be in a database to meet the application's requirements. COMPUTERS,Data Science,Data Warehousing

Refactoring SQL Applications What can you do when database performance doesn't meet expectations? Before you turn to expensive hardware upgrades to solve the problem, reach for this book. Refactoring SQL Applications provides a set of tested options for making code modifications to dramatically improve the way your database applications function. Backed by real-world examples, you'll find quick fixes for simple problems, in-depth answers for more complex situations, and complete solutions for applications with extensive problems. Learn to: Determine if and where you can expect performance gains Apply quick fixes, such as limiting calls to the database in stored functions and procedures Refactor tasks, such as replacing application code by a stored procedure, or replacing iterative, procedural statements with sweeping SQL statements Refactor flow by increasing parallelism and switching business-inducted processing from synchronous to asynchronous Refactor design using schema extensions, regular views, materialized views, partitioning, and more Compare before and after versions of a program to ensure you get the same results once you make modifications Refactoring SQL Applications teaches you to recognize and assess code that needs refactoring, and to understand the crucial link between refactoring and performance. If and when your application bogs down, this book will help you get it back up to speed. COMPUTERS,Data Science,Data Warehousing

Learning MySQL Whether you're running a business, keeping track of members andmeetings for a club, or just trying to organize a large and diversecollection of information, you'll find the MySQL database engineuseful for answering questions such as: Which are my top ten fastest-selling products? How frequently does this person come to our facility? What was the highest, lowest, and average score of the team last season? MySQL, the most popular open-source database, offers the power ofa relational database in a package that's easy to set up andadminister, and Learning MySQL provides all the tools you need toget started. This densely packed tutorial includes detailedinstructions to help you set up and design an effective database,create powerful queries using SQL, configure MySQL for improvedsecurity, and squeeze information out of your data. After covering the basics, the book travels far into MySQL'ssubtleties, including complex queries and joins, how to interact withthe database over the Web using PHP or Perl, and importanthouse-keeping such as backups and security. Topic include: Installation on Linux, Windows, and Mac OS X Basic and advanced querying using SQL User management and security Backups and recovery Tuning for improved efficiency Developing command-line and web database applications using thePHP and Perl programming languages The authors, Saied Tahaghoghi and Hugh E. Williams, have careers inacademia and business, and share a keen interest in research intosearch technologies. Whether you've never touched a database or have already completedsome MySQL projects, you'll find insights in Learning MySQLthat will last a career. COMPUTERS,Data Science,Data Warehousing

The Microsoft Data Warehouse Toolkit Best practices and invaluable advice from world-renowned data warehouse experts In this book, leading data warehouse experts from the Kimball Group share best practices for using the upcoming “Business Intelligence release†of SQL Server, referred to as SQL Server 2008 R2. In this new edition, the authors explain how SQL Server 2008 R2 provides a collection of powerful new tools that extend the power of its BI toolset to Excel and SharePoint users and they show how to use SQL Server to build a successful data warehouse that supports the business intelligence requirements that are common to most organizations. Covering the complete suite of data warehousing and BI tools that are part of SQL Server 2008 R2, as well as Microsoft Office, the authors walk you through a full project lifecycle, including design, development, deployment and maintenance. Features more than 50 percent new and revised material that covers the rich new feature set of the SQL Server 2008 R2 release, as well as the Office 2010 release Includes brand new content that focuses on PowerPivot for Excel and SharePoint, Master Data Services, and discusses updated capabilities of SQL Server Analysis, Integration, and Reporting Services Shares detailed case examples that clearly illustrate how to best apply the techniques described in the book The accompanying Web site contains all code samples as well as the sample database used throughout the case studies The Microsoft Data Warehouse Toolkit, Second Edition provides you with the knowledge of how and when to use BI tools such as Analysis Services and Integration Services to accomplish your most essential data warehousing tasks. COMPUTERS,Data Science,Data Warehousing

The Data Warehouse Lifecycle Toolkit A thorough update to the industry standard for designing, developing, and deploying data warehouse and business intelligence systems The world of data warehousing has changed remarkably since the first edition of The Data Warehouse Lifecycle Toolkit was published in 1998. In that time, the data warehouse industry has reached full maturity and acceptance, hardware and software have made staggering advances, and the techniques promoted in the premiere edition of this book have been adopted by nearly all data warehouse vendors and practitioners. In addition, the term "business intelligence" emerged to reflect the mission of the data warehouse: wrangling the data out of source systems, cleaning it, and delivering it to add value to the business. Ralph Kimball and his colleagues have refined the original set of Lifecycle methods and techniques based on their consulting and training experience. The authors understand first-hand that a data warehousing/business intelligence (DW/BI) system needs to change as fast as its surrounding organization evolves. To that end, they walk you through the detailed steps of designing, developing, and deploying a DW/BI system. You'll learn to create adaptable systems that deliver data and analyses to business users so they can make better business decisions. COMPUTERS,Data Science,Data Warehousing

Data Mining Techniques The leading introductory book on data mining, fully updated and revised! When Berry and Linoff wrote the first edition of Data Mining Techniques in the late 1990s, data mining was just starting to move out of the lab and into the office and has since grown to become an indispensable tool of modern business. This new edition—more than 50% new and revised— is a significant update from the previous one, and shows you how to harness the newest data mining methods and techniques to solve common business problems. The duo of unparalleled authors share invaluable advice for improving response rates to direct marketing campaigns, identifying new customer segments, and estimating credit risk. In addition, they cover more advanced topics such as preparing data for analysis and creating the necessary infrastructure for data mining at your company. Features significant updates since the previous edition and updates you on best practices for using data mining methods and techniques for solving common business problems Covers a new data mining technique in every chapter along with clear, concise explanations on how to apply each technique immediately Touches on core data mining techniques, including decision trees, neural networks, collaborative filtering, association rules, link analysis, survival analysis, and more Provides best practices for performing data mining using simple tools such as Excel Data Mining Techniques, Third Edition covers a new data mining technique with each successive chapter and then demonstrates how you can apply that technique for improved marketing, sales, and customer support to get immediate results. COMPUTERS,Data Science,Data Warehousing

Business Intelligence Roadmap "If you are looking for a complete treatment of business intelligence, then go no further than this book. Larissa T. Moss and Shaku Atre have covered all the bases in a cohesive and logical order, making it easy for the reader to follow their line of thought. From early design to ETL to physical database design, the book ties together all the components of business intelligence." --Bill Inmon, Inmon Enterprises This is the eBook version of the print title. The eBook edition contains the same content as the print edition. You will find instructions in the last few pages of your eBook that directs you to the media files. Business Intelligence Roadmap is a visual guide to developing an effective business intelligence (BI) decision-support application. This book outlines a methodology that takes into account the complexity of developing applications in an integrated BI environment. The authors walk readers through every step of the process--from strategic planning to the selection of new technologies and the evaluation of application releases. The book also serves as a single-source guide to the best practices of BI projects. Part I steers readers through the six stages of a BI project: justification, planning, business analysis, design, construction, and deployment. Each chapter describes one of sixteen development steps and the major activities, deliverables, roles, and responsibilities. All technical material is clearly expressed in tables, graphs, and diagrams. Part II provides five matrices that serve as references for the development process charted in Part I. Management tools, such as graphs illustrating the timing and coordination of activities, are included throughout the book. The authors conclude by crystallizing their many years of experience in a list of dos, don'ts, tips, and rules of thumb. Both the book and the methodology it describes are designed to adapt to the specific needs of individual stakeholders and organizations. The book directs business representatives, business sponsors, project managers, and technicians to the chapters that address their distinct responsibilities. The framework of the book allows organizations to begin at any step and enables projects to be scheduled and managed in a variety of ways. Business Intelligence Roadmap is a clear and comprehensive guide to negotiating the complexities inherent in the development of valuable business intelligence decision-support applications. COMPUTERS,Data Science,Data Warehousing

The Data Model Resource Book, Volume 1 A quick and reliable way to build proven databases for core business functions Industry experts raved about The Data Model Resource Book when it was first published in March 1997 because it provided a simple, cost-effective way to design databases for core business functions. Len Silverston has now revised and updated the hugely successful 1st Edition, while adding a companion volume to take care of more specific requirements of different businesses. This updated volume provides a common set of data models for specific core functions shared by most businesses like human resources management, accounting, and project management. These models are standardized and are easily replicated by developers looking for ways to make corporate database development more efficient and cost effective. This guide is the perfect complement to The Data Model Resource CD-ROM, which is sold separately and provides the powerful design templates discussed in the book in a ready-to-use electronic format. A free demonstration CD-ROM is available with each copy of the print book to allow you to try before you buy the full CD-ROM. COMPUTERS,Data Science,Data Warehousing

Bad Data Handbook What is bad data? Some people consider it a technical phenomenon, like missing values or malformed records, but bad data includes a lot more. In this handbook, data expert Q. Ethan McCallum has gathered 19 colleagues from every corner of the data arena to reveal how they’ve recovered from nasty data problems. From cranky storage to poor representation to misguided policy, there are many paths to bad data. Bottom line? Bad data is data that gets in the way. This book explains effective ways to get around it. Among the many topics covered, you’ll discover how to: Test drive your data to see if it’s ready for analysis Work spreadsheet data into a usable form Handle encoding problems that lurk in text data Develop a successful web-scraping effort Use NLP tools to reveal the real sentiment of online reviews Address cloud computing issues that can impact your analysis effort Avoid policies that create data analysis roadblocks Take a systematic approach to data quality analysis COMPUTERS,Data Science,Data Warehousing

Microsoft SQL Server 2012 Administration Implement, maintain, and repair SQL Server 2012 databases As the most significant update since 2008, Microsoft SQL Server 2012 boasts updates and new features that are critical to understand. Whether you manage and administer SQL Server 2012 or are planning to get your MCSA: SQL Server 2012 certification, this book is the perfect supplement to your learning and preparation. From understanding SQL Server's roles to implementing business intelligence and reporting, this practical book explores tasks and scenarios that a working SQL Server DBA faces regularly and shows you step by step how to handle them. Includes practice exams and coverage of exam objectives for those seeking MSCA: SQL Server 2012 certification Explores the skills you'll need on the job as a SQL Server 2012 DBA Discusses designing and implementing database solutions Walks you through administrating, maintaining, and securing SQL Server 2012 Addresses implementing high availability and data distribution Includes bonus videos where the author walks you through some of the more difficult tasks expected of a DBA Featuring hands-on exercises and real-world scenarios, this resource guides you through the essentials of implementing, maintaining, and repairing SQL Server 2012 databases. COMPUTERS,Data Science,Data Warehousing

The Data Warehouse Toolkit Updated new edition of Ralph Kimball's groundbreaking book on dimensional modeling for data warehousing and business intelligence! The first edition of Ralph Kimball's The Data Warehouse Toolkit introduced the industry to dimensional modeling, and now his books are considered the most authoritative guides in this space. This new third edition is a complete library of updated dimensional modeling techniques, the most comprehensive collection ever. It covers new and enhanced star schema dimensional modeling patterns, adds two new chapters on ETL techniques, includes new and expanded business matrices for 12 case studies, and more. Authored by Ralph Kimball and Margy Ross, known worldwide as educators, consultants, and influential thought leaders in data warehousing and business intelligence Begins with fundamental design recommendations and progresses through increasingly complex scenarios Presents unique modeling techniques for business applications such as inventory management, procurement, invoicing, accounting, customer relationship management, big data analytics, and more Draws real-world case studies from a variety of industries, including retail sales, financial services, telecommunications, education, health care, insurance, e-commerce, and more Design dimensional databases that are easy to understand and provide fast query response with The Data Warehouse Toolkit: The Definitive Guide to Dimensional Modeling, 3rd Edition. COMPUTERS,Data Science,Data Warehousing

Applied Predictive Analytics Learn the art and science of predictive analytics — techniques that get results Predictive analytics is what translates big data into meaningful, usable business information. Written by a leading expert in the field, this guide examines the science of the underlying algorithms as well as the principles and best practices that govern the art of predictive analytics. It clearly explains the theory behind predictive analytics, teaches the methods, principles, and techniques for conducting predictive analytics projects, and offers tips and tricks that are essential for successful predictive modeling. Hands-on examples and case studies are included. The ability to successfully apply predictive analytics enables businesses to effectively interpret big data; essential for competition today This guide teaches not only the principles of predictive analytics, but also how to apply them to achieve real, pragmatic solutions Explains methods, principles, and techniques for conducting predictive analytics projects from start to finish Illustrates each technique with hands-on examples and includes as series of in-depth case studies that apply predictive analytics to common business scenarios A companion website provides all the data sets used to generate the examples as well as a free trial version of software Applied Predictive Analytics arms data and business analysts and business managers with the tools they need to interpret and capitalize on big data. COMPUTERS,Data Science,Data Warehousing

The Kimball Group Reader The final edition of the incomparable data warehousing and business intelligence reference, updated and expanded The Kimball Group Reader, Remastered Collection is the essential reference for data warehouse and business intelligence design, packed with best practices, design tips, and valuable insight from industry pioneer Ralph Kimball and the Kimball Group. This Remastered Collection represents decades of expert advice and mentoring in data warehousing and business intelligence, and is the final work to be published by the Kimball Group. Organized for quick navigation and easy reference, this book contains nearly 20 years of experience on more than 300 topics, all fully up-to-date and expanded with 65 new articles. The discussion covers the complete data warehouse/business intelligence lifecycle, including project planning, requirements gathering, system architecture, dimensional modeling, ETL, and business intelligence analytics, with each group of articles prefaced by original commentaries explaining their role in the overall Kimball Group methodology. Data warehousing/business intelligence industry's current multi-billion dollar value is due in no small part to the contributions of Ralph Kimball and the Kimball Group. Their publications are the standards on which the industry is built, and nearly all data warehouse hardware and software vendors have adopted their methods in one form or another. This book is a compendium of Kimball Group expertise, and an essential reference for anyone in the field. Learn data warehousing and business intelligence from the field's pioneers Get up to date on best practices and essential design tips Gain valuable knowledge on every stage of the project lifecycle Dig into the Kimball Group methodology with hands-on guidance Ralph Kimball and the Kimball Group have continued to refine their methods and techniques based on thousands of hours of consulting and training. This Remastered Collection of The Kimball Group Reader represents their final body of knowledge, and is nothing less than a vital reference for anyone involved in the field. COMPUTERS,Data Science,Data Warehousing

Type Inheritance and Relational Theory Type inheritance is that phenomenon according to which we can say, for example, that every square is also a rectangle, and so properties that apply to rectangles in general apply to squares in particular. In other words, squares are a subtype of rectangles, and rectangles are a supertype of squares. Recognizing and acting upon such subtype / supertype relationships provides numerous benefits: Certainly it can help in data modeling, and it can also provide for code reuse in applications. For these reasons, many languages, including the standard database language SQL, have long supported such relationships. However, there doesn’t seem to be any consensus in the community at large on a formal, rigorous, and abstract model of inheritance. This book proposes such a model, one that enjoys several advantages over other approaches, not the least of which it is that it’s fully compatible with the well known relational model of data. Topics the model covers include: Both single and multiple inheritance Scalar, tuple, and relation inheritance Type lattices and union and intersection types Polymorphism and substitutability Compile time and run time binding All of these topics are described in detail in the book, with numerous illustrative examples, exercises, and answers. The book also discusses several alternative approaches. In particular, it includes a detailed discussion and analysis of inheritance as supported in the SQL standard. COMPUTERS,Data Science,Data Warehousing

SQL Server 2017 Integration Services Cookbook Harness the power of SQL Server 2017 Integration Services to build your data integration solutions with ease About This Book Acquaint yourself with all the newly introduced features in SQL Server 2017 Integration Services Program and extend your packages to enhance their functionality This detailed, step-by-step guide covers everything you need to develop efficient data integration and data transformation solutions for your organization Who This Book Is For This book is ideal for software engineers, DW/ETL architects, and ETL developers who need to create a new, or enhance an existing, ETL implementation with SQL Server 2017 Integration Services. This book would also be good for individuals who develop ETL solutions that use SSIS and are keen to learn the new features and capabilities in SSIS 2017. What You Will Learn Understand the key components of an ETL solution using SQL Server 2016-2017 Integration Services Design the architecture of a modern ETL solution Have a good knowledge of the new capabilities and features added to Integration Services Implement ETL solutions using Integration Services for both on-premises and Azure data Improve the performance and scalability of an ETL solution Enhance the ETL solution using a custom framework Be able to work on the ETL solution with many other developers and have common design paradigms or techniques Effectively use scripting to solve complex data issues In Detail SQL Server Integration Services is a tool that facilitates data extraction, consolidation, and loading options (ETL), SQL Server coding enhancements, data warehousing, and customizations. With the help of the recipes in this book, you'll gain complete hands-on experience of SSIS 2017 as well as the 2016 new features, design and development improvements including SCD, Tuning, and Customizations. At the start, you'll learn to install and set up SSIS as well other SQL Server resources to make optimal use of this Business Intelligence tools. We'll begin by taking you through the new features in SSIS 2016/2017 and implementing the necessary features to get a modern scalable ETL solution that fits the modern data warehouse. Through the course of chapters, you will learn how to design and build SSIS data warehouses packages using SQL Server Data Tools. Additionally, you'll learn to develop SSIS packages designed to maintain a data warehouse using the Data Flow and other control flow tasks. You'll also be demonstrated many recipes on cleansing data and how to get the end result after applying different transformations. Some real-world scenarios that you might face are also covered and how to handle various issues that you might face when designing your packages. At the end of this book, you'll get to know all the key concepts to perform data integration and transformation. You'll have explored on-premises Big Data integration processes to create a classic data warehouse, and will know how to extend the toolbox with custom tasks and transforms. Style and approach This cookbook follows a problem-solution approach and tackles all kinds of data integration scenarios by using the capabilities of SQL Server 2016 Integration Services. This book is well supplemented with screenshots, tips, and tricks. Each recipe focuses on a particular task and is written in a very easy-to-follow manner. COMPUTERS,Data Science,Data Warehousing

Learning Pentaho Data Integration 8 CE Get up and running with the Pentaho Data Integration tool using this hands-on, easy-to-read guide About This Book Manipulate your data by exploring, transforming, validating, and integrating it using Pentaho Data Integration 8 CE A comprehensive guide exploring the features of Pentaho Data Integration 8 CE Connect to any database engine, explore the databases, and perform all kind of operations on relational databases Who This Book Is For This book is a must-have for software developers, business intelligence analysts, IT students, or anyone involved or interested in developing ETL solutions. If you plan on using Pentaho Data Integration for doing any data manipulation task, this book will help you as well. This book is also a good starting point for data warehouse designers, architects, or anyone who is responsible for data warehouse projects and needs to load data into them. What You Will Learn Explore the features and capabilities of Pentaho Data Integration 8 Community Edition Install and get started with PDI Learn the ins and outs of Spoon, the graphical designer tool Learn to get data from all kind of data sources, such as plain files, Excel spreadsheets, databases, and XML files Use Pentaho Data Integration to perform CRUD (create, read, update, and delete) operations on relationaldatabases Populate a data mart with Pentaho Data Integration Use Pentaho Data Integration to organize files and folders, run daily processes, deal with errors, and more In Detail Pentaho Data Integration(PDI) is an intuitive and graphical environment packed with drag-and-drop design and powerful Extract-Tranform-Load (ETL) capabilities. This book shows and explains the new interactive features of Spoon, the revamped look and feel, and the newest features of the tool including transformations and jobs Executors and the invaluable Metadata Injection capability. We begin with the installation of PDI software and then move on to cover all the key PDI concepts. Each of the chapter introduces new features, enabling you to gradually get practicing with the tool. First, you will learn to do all kind of data manipulation and work with simple plain files. Then, the book teaches you how you can work with relational databases inside PDI. Moreover, you will be given a primer on data warehouse concepts and you will learn how to load data in a data warehouse. During the course of this book, you will be familiarized with its intuitive, graphical and drag-and-drop design environment. By the end of this book, you will learn everything you need to know in order to meet your data manipulation requirements. Besides, your will be given best practices and advises for designing and deploying your projects. Style and approach Step by step guide filled with practical, real world scenarios and examples. COMPUTERS,Data Science,Data Warehousing

Exploring Big Historical Data The Digital Humanities have arrived at a moment when digital Big Data is becoming more readily available, opening exciting new avenues of inquiry but also new challenges. This pioneering book describes and demonstrates the ways these data can be explored to construct cultural heritage knowledge, for research and in teaching and learning. It helps humanities scholars to grasp Big Data in order to do their work, whether that means understanding the underlying algorithms at work in search engines, or designing and using their own tools to process large amounts of information.Demonstrating what digital tools have to offer and also what 'digital' does to how we understand the past, the authors introduce the many different tools and developing approaches in Big Data for historical and humanistic scholarship, show how to use them, what to be wary of, and discuss the kinds of questions and new perspectives this new macroscopic perspective opens up. Authored 'live' online with ongoing feedback from the wider digital history community, Exploring Big Historical Data breaks new ground and sets the direction for the conversation into the future. It represents the current state-of-the-art thinking in the field and exemplifies the way that digital work can enhance public engagement in the humanities.Exploring Big Historical Data should be the go-to resource for undergraduate and graduate students confronted by a vast corpus of data, and researchers encountering these methods for the first time. It will also offer a helping hand to the interested individual seeking to make sense of genealogical data or digitized newspapers, and even the local historical society who are trying to see the value in digitizing their holdings.The companion website to Exploring Big Historical Data can be found at www.themacroscope.org/. On this site you will find code, a discussion forum, essays, and datafiles that accompany this book. COMPUTERS,Data Science,Data Warehousing

Hands-On Data Warehousing with Azure Data Factory Leverage the power of Microsoft Azure Data Factory v2 to build hybrid data solutions About This Book Combine the power of Azure Data Factory v2 and SQL Server Integration Services Design and enhance performance and scalability of a modern ETL hybrid solution Interact with the loaded data in data warehouse and data lake using Power BI Who This Book Is For This book is for you if you are a software professional who develops and implements ETL solutions using Microsoft SQL Server or Azure cloud. It will be an added advantage if you are a software engineer, DW/ETL architect, or ETL developer, and know how to create a new ETL implementation or enhance an existing one with ADF or SSIS. What You Will Learn Understand the key components of an ETL solution using Azure Data Factory and Integration Services Design the architecture of a modern ETL hybrid solution Implement ETL solutions for both on-premises and Azure data Improve the performance and scalability of your ETL solution Gain thorough knowledge of new capabilities and features added to Azure Data Factory and Integration Services In Detail ETL is one of the essential techniques in data processing. Given data is everywhere, ETL will always be the vital process to handle data from different sources. Hands-On Data Warehousing with Azure Data Factory starts with the basic concepts of data warehousing and ETL process. You will learn how Azure Data Factory and SSIS can be used to understand the key components of an ETL solution. You will go through different services offered by Azure that can be used by ADF and SSIS, such as Azure Data Lake Analytics, Machine Learning and Databrick's Spark with the help of practical examples. You will explore how to design and implement ETL hybrid solutions using different integration services with a step-by-step approach. Once you get to grips with all this, you will use Power BI to interact with data coming from different sources in order to reveal valuable insights. By the end of this book, you will not only learn how to build your own ETL solutions but also address the key challenges that are faced while building them. Style and approach A step-by-step guide to develop data movement code using SSIS, Azure Data Factory, and database stored procedures for implementing intelligent BI solutions. COMPUTERS,Data Science,Data Warehousing

Collect, Combine, and Transform Data Using Power Query in Excel and Power BI Using Power Query, you can import, reshape, and cleanse any data from a simple interface, so you can mine that data for all of its hidden insights. Power Query is embedded in Excel, Power BI, and other Microsoft products, and leading Power Query expert Gil Raviv will help you make the most of it. Discover how to eliminate time-consuming manual data preparation, solve common problems, avoid pitfalls, and more. Then, walk through several complete analytics challenges, and integrate all your skills in a realistic chapter-length final project. By the time you’re finished, you’ll be ready to wrangle any data–and transform it into actionable knowledge. Prepare and analyze your data the easy way, with Power Query · Quickly prepare data for analysis with Power Query in Excel (also known as Get & Transform) and in Power BI · Solve common data preparation problems with a few mouse clicks and simple formula edits · Combine data from multiple sources, multiple queries, and mismatched tables · Master basic and advanced techniques for unpivoting tables · Customize transformations and build flexible data mashups with the M formula language · Address collaboration challenges with Power Query · Gain crucial insights into text feeds · Streamline complex social network analytics so you can do it yourself For all information workers, analysts, and any Excel user who wants to solve their own business intelligence problems. COMPUTERS,Data Science,Data Warehousing

The Enterprise Big Data Lake The data lake is a daring new approach for harnessing the power of big data technology and providing convenient self-service capabilities. But is it right for your company? This book is based on discussions with practitioners and executives from more than a hundred organizations, ranging from data-driven companies such as Google, LinkedIn, and Facebook, to governments and traditional corporate enterprises. You’ll learn what a data lake is, why enterprises need one, and how to build one successfully with the best practices in this book. Alex Gorelik, CTO and founder of Waterline Data, explains why old systems and processes can no longer support data needs in the enterprise. Then, in a collection of essays about data lake implementation, you’ll examine data lake initiatives, analytic projects, experiences, and best practices from data experts working in various industries. Get a succinct introduction to data warehousing, big data, and data science Learn various paths enterprises take to build a data lake Explore how to build a self-service model and best practices for providing analysts access to the data Use different methods for architecting your data lake Discover ways to implement a data lake from experts in different industries COMPUTERS,Data Science,Data Warehousing

Google BigQuery Work with petabyte-scale datasets while building a collaborative, agile workplace in the process. This practical book is the canonical reference to Google BigQuery, the query engine that lets you conduct interactive analysis of large datasets. BigQuery enables enterprises to efficiently store, query, ingest, and learn from their data in a convenient framework. With this book, you’ll examine how to analyze data at scale to derive insights from large datasets efficiently. Valliappa Lakshmanan, tech lead for Google Cloud Platform, and Jordan Tigani, engineering director for the BigQuery team, provide best practices for modern data warehousing within an autoscaled, serverless public cloud. Whether you want to explore parts of BigQuery you’re not familiar with or prefer to focus on specific tasks, this reference is indispensable. COMPUTERS,Data Science,Data Warehousing

Data Structures & Algorithms Interview Questions You'll Most Likely Be Asked 200 Data Structures & Algorithms Interview Questions 77 HR Interview Questions Real life scenario based questions Strategies to respond to interview questions 2 Aptitude Tests Data Structures & Algorithms Interview Questions You'll Most Likely Be Asked is a perfect companion to stand ahead above the rest in today’s competitive job market. Rather than going through comprehensive, textbook-sized reference guides, this book includes only the information required immediately for job search to build an IT career. This book puts the interviewee in the driver's seat and helps them steer their way to impress the interviewer. The following is included in this book: (a) 200 Data Structures & Algorithms Interview Questions, Answers and proven strategies for getting hired as an IT professional (b) Dozens of examples to respond to interview questions (c) 77 HR Questions with Answers and proven strategies to give specific,impressive, answers that help nail the interviews (d) 2 Aptitude Tests download available on www.vibrantpublishers.com COMPUTERS,Data Science,Data Warehousing

Hands-On Kubernetes on Azure Kick-start your DevOps career by learning how to effectively deploy Kubernetes on Azure in an easy, comprehensive, and fun way with hands-on coding tasks Key Features Understand the fundamentals of Docker and Kubernetes Learn to implement microservices architecture using the Kubernetes platform Discover how you can scale your application workloads in Azure Kubernetes Service (AKS) Book Description From managing versioning efficiently to improving security and portability, technologies such as Kubernetes and Docker have greatly helped cloud deployments and application development. Starting with an introduction to Docker, Kubernetes, and Azure Kubernetes Service (AKS), this book will guide you through deploying an AKS cluster in different ways. You'll then explore the Azure portal by deploying a sample guestbook application on AKS and installing complex Kubernetes apps using Helm. With the help of real-world examples, you'll also get to grips with scaling your application and cluster. As you advance, you'll understand how to overcome common challenges in AKS and secure your application with HTTPS and Azure AD (Active Directory). Finally, you'll explore serverless functions such as HTTP triggered Azure functions and queue triggered functions. By the end of this Kubernetes book, you'll be well-versed with the fundamentals of Azure Kubernetes Service and be able to deploy containerized workloads on Microsoft Azure with minimal management overhead. What you will learn Plan, configure, and run containerized applications in production Use Docker to build apps in containers and deploy them on Kubernetes Improve the configuration and deployment of apps on the Azure Cloud Store your container images securely with Azure Container Registry Install complex Kubernetes applications using Helm Integrate Kubernetes with multiple Azure PaaS services, such as databases, Event Hubs and Functions. Who this book is for This book is for aspiring DevOps professionals, system administrators, developers, and site reliability engineers looking to understand test and deployment processes and improve their efficiency. If you're new to working with containers and orchestration, you'll find this book useful. COMPUTERS,Data Science,Data Warehousing

Recommender System with Machine Learning and Artificial Intelligence This book is a multi-disciplinary effort that involves world-wide experts from diverse fields, such as artificial intelligence, human computer interaction, information technology, data mining, statistics, adaptive user interfaces, decision support systems, marketing, and consumer behavior. It comprehensively covers the topic of recommender systems, which provide personalized recommendations of items or services to the new users based on their past behavior. Recommender system methods have been adapted to diverse applications including social networking, movie recommendation, query log mining, news recommendations, and computational advertising. This book synthesizes both fundamental and advanced topics of a research area that has now reached maturity. Recommendations in agricultural or healthcare domains and contexts, the context of a recommendation can be viewed as important side information that affects the recommendation goals. Different types of context such as temporal data, spatial data, social data, tagging data, and trustworthiness are explored. This book illustrates how this technology can support the user in decision-making, planning and purchasing processes in agricultural & healthcare sectors. COMPUTERS,Data Science,Data Warehousing

Azure Strategy and Implementation Guide Learn Azure's cloud capabilities with the help of this introductory guide to employing Azure for your cloud infrastructure needs. Key Features Get a clear overview of Azure's capabilities and benefits, and learn how to get started efficiently Develop the ability to opt for cloud architecture and design that best fits your organization Leverage Azure opportunities for cost savings and optimization Book Description Microsoft Azure is a powerful cloud computing platform that offers a multitude of services and capabilities for organizations of any size moving to a cloud strategy. Azure Strategy and Implementation Guide Third Edition encapsulates the entire spectrum of measures involved in Azure deployment that includes understanding Azure fundamentals, choosing a suitable cloud architecture, building on design principles, becoming familiar with Azure DevOps, and learning best practices for optimization and management. The book begins by introducing you to the Azure cloud platform and demonstrating the substantial scope of digital transformation and innovation that can be achieved by leveraging Azure's capabilities. The guide further acquaints you with practical insights on application modernization, Azure Infrastructure as a Service (IaaS) deployment, infrastructure management, key application architectures, best practices of Azure DevOps, and Azure automation. By the end of this book, you will be proficient in driving Azure operations right from the planning and cloud migration stage to cost management and troubleshooting. What you will learn Deploy and run Azure infrastructure services Carry out detailed planning for migrating applications to the cloud with Azure Move underlying code class structure into a serverless model Use a gateway to isolate your services and applications Define roles and responsibilities in DevOps Implement release & deployment coordination and automation Who this book is for Azure Strategy and Implementation Guide Third Edition is designed to benefit Azure architects, cloud solution architects, Azure developers, Azure administrators, and anyone who wants to develop an expertise in operating and administering the Azure cloud. A basic familiarity with operating systems and databases will help you grasp the concepts covered in this book. COMPUTERS,Data Science,Data Warehousing

Azure for Architects Build and design multiple types of applications that are cross-language, platform, and cost-effective by understanding core Azure principles and foundational concepts Key Features Get familiar with the different design patterns available in Microsoft Azure Develop Azure cloud architecture and a pipeline management system Get to know the security best practices for your Azure deployment Book Description Thanks to its support for high availability, scalability, security, performance, and disaster recovery, Azure has been widely adopted to create and deploy different types of application with ease. Updated for the latest developments, this third edition of Azure for Architects helps you get to grips with the core concepts of designing serverless architecture, including containers, Kubernetes deployments, and big data solutions. You'll learn how to architect solutions such as serverless functions, you'll discover deployment patterns for containers and Kubernetes, and you'll explore large-scale big data processing using Spark and Databricks. As you advance, you'll implement DevOps using Azure DevOps, work with intelligent solutions using Azure Cognitive Services, and integrate security, high availability, and scalability into each solution. Finally, you'll delve into Azure security concepts such as OAuth, OpenConnect, and managed identities. By the end of this book, you'll have gained the confidence to design intelligent Azure solutions based on containers and serverless functions. What you will learn Understand the components of the Azure cloud platform Use cloud design patterns Use enterprise security guidelines for your Azure deployment Design and implement serverless and integration solutions Build efficient data solutions on Azure Understand container services on Azure Who this book is for If you are a cloud architect, DevOps engineer, or a developer looking to learn about the key architectural aspects of the Azure cloud platform, this book is for you. A basic understanding of the Azure cloud platform will help you grasp the concepts covered in this book more effectively. COMPUTERS,Data Science,Data Warehousing

Mule 2 Mule 2: A Developer’s Guide introduces the Mule 2.0 integration platform for developers of enterprise integration applications who wish to leverage Mule as a lightweight messaging framework that contains a distributable object broker for managing communication between applications. The book is based on insight, knowledge, and experience resulting from working with Mule. The text provides support, consulting, and training to developers implementing Mule in a broad range of scenarios ranging from small projects through to large corporations developing major deployments. The author(s) have also developed the official training materials for Mule. COMPUTERS,Data Science,General

Getting Started with GEO, CouchDB, and Node.js Today's mobile devices have GPS and standard APIs to give you access to coordinates—but what can you do with that data? With this concise book, application developers learn how to work with location data quickly and easily, using Node.js, CouchDB, and other open source tools and libraries. Node.js makes it simple to run event code on the Web, and the CouchDB document-oriented database lets you store location data and perform complex queries on it quickly. You'll learn how to get started with these tools, and then use them together to build an example project called MapChat, using HTML and JavaScript code samples. Learn how to serve dynamic content with Node.js, and use its asynchronous IO to handle several requests at once Become familiar with GeoJSON, Geohash, and the Geospatial Data Abstraction Library (GDAL) for working with spatial data Build geospatial indexes using the GeoCouch branch of CouchDB Combine these tools to build a project that lets users post real-time chat messages tagged with their current map location COMPUTERS,Data Science,General

Business Process Management Business process management is usually treated from two different perspectives: business administration and computer science. While business administration professionals tend to consider information technology as a subordinate aspect in business process management for experts to handle, by contrast computer science professionals often consider business goals and organizational regulations as terms that do not deserve much thought but require the appropriate level of abstraction. Matthias Weske argues that all communities involved need to have a common understanding of the different aspects of business process management. To this end, he details the complete business process lifecycle from the modeling phase to process enactment and improvement, taking into account all different stakeholders involved. After starting with a presentation of general foundations and abstraction models, he explains concepts like process orchestrations and choreographies, as well as process properties and data dependencies. Finally, he presents both traditional and advanced business process management architectures, covering, for example, workflow management systems, service-oriented architectures, and data-driven approaches. In addition, he shows how standards like WfMC, SOAP, WSDL, and BPEL fit into the picture. This textbook is ideally suited for classes on business process management, information systems architecture, and workflow management. This 2nd edition contains major updates on BPMN Version 2 process orchestration and process choreographies, and the chapter on BPM methodologies has been completely rewritten. The accompanying website www.bpm-book.com contains further information and additional teaching material. COMPUTERS,Data Science,General

Fundamentals of Discrete Math for Computer Science An understanding of discrete mathematics is essential for students of computer science wishing to improve their programming competence. Fundamentals of Discrete Math for Computer Science provides an engaging and motivational introduction to traditional topics in discrete mathematics, in a manner specifically designed to appeal to computer science students. The text empowers students to think critically, to be effective problem solvers, to integrate theory and practice, and to recognize the importance of abstraction. Clearly structured and interactive in nature, the book presents detailed walkthroughs of several algorithms, stimulating a conversation with the reader through informal commentary and provocative questions. Topics and features: highly accessible and easy to read, introducing concepts in discrete mathematics without requiring a university-level background in mathematics; ideally structured for classroom-use and self-study, with modular chapters following ACM curriculum recommendations; describes mathematical processes in an algorithmic manner, often including a walk-through demonstrating how the algorithm performs the desired task as expected; contains examples and exercises throughout the text, and highlights the most important concepts in each section; selects examples that demonstrate a practical use for the concept in question. This easy-to-understand and fun-to-read textbook is ideal for an introductory discrete mathematics course for computer science students at the beginning of their studies. The book assumes no prior mathematical knowledge, and discusses concepts in programming as needed, allowing it to be used in a mathematics course taken concurrently with a student’s first programming course. COMPUTERS,Data Science,General

Measuring Data Quality for Ongoing Improvement The Data Quality Assessment Framework shows you how to measure and monitor data quality, ensuring quality over time. You’ll start with general concepts of measurement and work your way through a detailed framework of more than three dozen measurement types related to five objective dimensions of quality: completeness, timeliness, consistency, validity, and integrity. Ongoing measurement, rather than one time activities will help your organization reach a new level of data quality. This plain-language approach to measuring data can be understood by both business and IT and provides practical guidance on how to apply the DQAF within any organization enabling you to prioritize measurements and effectively report on results. Strategies for using data measurement to govern and improve the quality of data and guidelines for applying the framework within a data asset are included. You’ll come away able to prioritize which measurement types to implement, knowing where to place them in a data flow and how frequently to measure. Common conceptual models for defining and storing of data quality results for purposes of trend analysis are also included as well as generic business requirements for ongoing measuring and monitoring including calculations and comparisons that make the measurements meaningful and help understand trends and detect anomalies. Demonstrates how to leverage a technology independent data quality measurement framework for your specific business priorities and data quality challenges Enables discussions between business and IT with a non-technical vocabulary for data quality measurement Describes how to measure data quality on an ongoing basis with generic measurement types that can be applied to any situation COMPUTERS,Data Science,General

Parallel Algorithms for Irregular Problems Efficient parallel solutions have been found to many problems. Some of them can be obtained automatically from sequential programs, using compilers. However, there is a large class of problems - irregular problems - that lack efficient solutions. IRREGULAR 94 - a workshop and summer school organized in Geneva - addressed the problems associated with the derivation of efficient solutions to irregular problems. This book, which is based on the workshop, draws on the contributions of outstanding scientists to present the state of the art in irregular problems, covering aspects ranging from scientific computing, discrete optimization, and automatic extraction of parallelism. Audience: This first book on parallel algorithms for irregular problems is of interest to advanced graduate students and researchers in parallel computer science. COMPUTERS,Data Science,General

ACRI ’96 ACRI'96 is the second conference on Cellular Automata for Research and Industry; the first one was held in Rende (Cosenza), on September 29-30, 1994. This second edition confirms the growing interest in Cellular Automata currently present both in the scientific community and within the industrial applications world. Cellular Automata-based computational models, besides capturing the attention of scientists working in different fields, open new perspectives of intersection between different and historically distant areas of scientific knowledge, from Physics to Biology, to Computer Science. ACRI'96 aims at providing a forum both for researchers working in the Cellular Automata field, and for those who foresee the possibility to verify on concrete domains of application the impact of their solutions, as well as for those who are looking for a possibility of reflection upon the specific concept of parallel and distributed computation provided by Cellular Automata. This book contains the works presented at the conference. The invited papers cover different aspects of Cellular Automata. T. Worsch gives a classification of Cellular Automata mapping on the existent computational frameworks for the simulation of their behavior. One of the most mature areas where Cellular Automata showed their value is Physics: B. Chopard illustrates recent results on wave modeling, and some possible applications. According to the general purpose of ACRI'96 of transfering research results to the industrial world, F. COMPUTERS,Data Science,General

Algol-like Languages In recent years there has been a remarkable convergence of interest in programming languages based on ALGOL 60. Researchers interested in the theory of procedural and object-oriented languages discovered that ALGOL 60 shows how to add procedures and object classes to simple imperative languages in a general and clean way. And, on the other hand, researchers interested in purely functional languages discovered that ALGOL 60 shows how to add imperative mechanisms to functional languages in a way that does not compromise their desirable properties. Unfortunately, many of the key works in this field have been rather hard to obtain. The primary purpose of this collection is to make the most significant material on ALGoL-like languages conveniently available to graduate students and researchers. Contents Introduction to Volume 1 1 Part I Historical Background 1 Part n Basic Principles 3 Part III Language Design 5 Introduction to Volume 2 6 Part IV Functor-Category Semantics 7 Part V Specification Logic 7 Part VI Procedures and Local Variables 8 Part vn Interference, Irreversibility and Concurrency 9 Acknowledgements 11 Bibliography 11 Introduction to Volume 1 This volume contains historical and foundational material, and works on lan guage design. All of the material should be accessible to beginning graduate students in programming languages and theoretical Computer Science. COMPUTERS,Data Science,General

One-Factorizations This book has grown out of graduate courses given by the author at Southern Illinois University, Carbondale, as well as a series of seminars delivered at Curtin University of Technology, Western Australia. The book is intended to be used both as a textbook at the graduate level and also as a professional reference. The topic of one-factorizations fits into the theory of combinatorial designs just as much as it does into graph theory. Factors and factorizations occur as building blocks in the theory of designs in a number of places. Our approach owes as much to design theory as it does to graph theory. It is expected that nearly all readers will have some background in the theory of graphs, such as an advanced undergraduate course in Graph Theory or Applied Graph Theory. However, the book is self-contained, and the first two chapters are a thumbnail sketch of basic graph theory. Many readers will merely skim these chapters, observing our notational conventions along the way. (These introductory chapters could, in fact, enable some instructors to Ilse the book for a somewhat eccentric introduction to graph theory.) Chapter 3 introduces one-factors and one-factorizations. The next two chapters outline two major application areas: combinatorial arrays and tournaments. These two related areas have provided the impetus for a good deal of study of one-factorizations. COMPUTERS,Data Science,General

Algol-like Languages To construct a compiler for a modern higher-level programming languagel one needs to structure the translation to a machine-like intermediate language in a way that reflects the semantics of the language. little is said about such struc turing in compiler texts that are intended to cover a wide variety of program ming languages. More is said in the Iiterature on semantics-directed compiler construction [1] but here too the viewpoint is very general (though limited to 1 languages with a finite number of syntactic types). On the other handl there is a considerable body of work using the continuation-passing transformation to structure compilers for the specific case of call-by-value languages such as SCHEME and ML [21 3]. ln this paperl we will describe a method of structuring the translation of ALGOL-like languages that is based on the functor-category semantics devel oped by Reynolds [4] and Oles [51 6]. An alternative approach using category theory to structure compilers is the early work of F. L. Morris [7]1 which anticipates our treatment of boolean expressionsl but does not deal with procedures. 2 Types and Syntax An ALGOL-like language is a typed lambda calculus with an unusual repertoire of primitive types. Throughout most of this paper we assume that the primi tive types are comm(and) int(eger)exp(ression) int(eger)acc(eptor) int(eger)var(iable) I and that the set 8 of types is the least set containing these primitive types and closed under the binary operation -. COMPUTERS,Data Science,General

Conditional Monte Carlo Conditional Monte Carlo: Gradient Estimation and Optimization Applications deals with various gradient estimation techniques of perturbation analysis based on the use of conditional expectation. The primary setting is discrete-event stochastic simulation. This book presents applications to queueing and inventory, and to other diverse areas such as financial derivatives, pricing and statistical quality control. To researchers already in the area, this book offers a unified perspective and adequately summarizes the state of the art. To researchers new to the area, this book offers a more systematic and accessible means of understanding the techniques without having to scour through the immense literature and learn a new set of notation with each paper. To practitioners, this book provides a number of diverse application areas that makes the intuition accessible without having to fully commit to understanding all the theoretical niceties. In sum, the objectives of this monograph are two-fold: to bring together many of the interesting developments in perturbation analysis based on conditioning under a more unified framework, and to illustrate the diversity of applications to which these techniques can be applied. Conditional Monte Carlo: Gradient Estimation and Optimization Applications is suitable as a secondary text for graduate level courses on stochastic simulations, and as a reference for researchers and practitioners in industry. COMPUTERS,Data Science,General

Cooperation Proceedings of the NATO Advanced Study Institute on Cooperation: Game-Theoretic Approaches, helt at SUNY, Stony Brook, New York, July 18-29, 1994 COMPUTERS,Data Science,General

Mathematical Methods in Program Development Proceedings of the NATO Advanced Study Institute on Mathematical Methods in Program Development, held in Marktoberdorf, Germany, July 30 - August 11, 1996 COMPUTERS,Data Science,General

Finite Fields Finite Fields are fundamental structures of Discrete Mathematics. They serve as basic data structures in pure disciplines like Finite Geometries and Combinatorics, and also have aroused much interest in applied disciplines like Coding Theory and Cryptography. A look at the topics of the proceed ings volume of the Third International Conference on Finite Fields and Their Applications (Glasgow, 1995) (see [18]), or at the list of references in I. E. Shparlinski's book [47] (a recent extensive survey on the Theory of Finite Fields with particular emphasis on computational aspects), shows that the area of Finite Fields goes through a tremendous development. The central topic of the present text is the famous Normal Basis Theo rem, a classical result from field theory, stating that in every finite dimen sional Galois extension E over F there exists an element w whose conjugates under the Galois group of E over F form an F-basis of E (i. e. , a normal basis of E over F; w is called free in E over F). For finite fields, the Nor mal Basis Theorem has first been proved by K. Hensel [19] in 1888. Since normal bases in finite fields in the last two decades have been proved to be very useful for doing arithmetic computations, at present, the algorithmic and explicit construction of (particular) such bases has become one of the major research topics in Finite Field Theory. COMPUTERS,Data Science,General

Codes, Designs and Geometry Codes, Designs, and Geometry brings together in one place important contributions and up-to-date research results in this important area. Codes, Designs, and Geometry serves as an excellent reference, providing insight into some of the most important research issues in the field. COMPUTERS,Data Science,General

Scientific Pascal Guide to this Book My main objective is to teach programming in Pascal to people in the hard sciences and technology, who don't have much patience with the standard textbooks with their lengthy, pedantic approach, and their many examples of no interest to scientists and engineers. Another objective is to present many both interesting and useful algorithms and programs. A secondary objective is to explain how to cope with various features of the PC hardware. Pascal really is a wonderful programming language. It is easy to learn and to remember, and it has unrivalled clarity. You get serious results in short order. How should you read this book? Maybe backwards is the answer. If you are just starting with the Borland Pascal package, you must begin with Appendix 1, The Borland Pascal Package. If you are a Pascal user already, still you should skim over Appendix 1. Appendix 2, On Programming, has material on saving programming time and on debugging that might be useful for reference. Chapter 1, Introduction to Pascal, will hardly be read by the experienced Pascal programmer (unless he or she has not used units). Chapter 2, Programming Basics, begins to sample deeper waters, and I hope everyone will find something interesting there. Chapter 3, Files, Records, Pointers, is the final chapter to concentrate on the Pascal programming language; the remaining chapters concentrate on various areas of application. COMPUTERS,Data Science,General

Hypermedia Design This is the latest volume in the 'Workshops in Computing' series, and contains papers from the International Workshop on Hpyermedia Design, held in Montpellier, France, from 1 - 2 June 1995. The workshop aimed to provide a forum for researchers and practitioners from a variety of backgrounds to discuss the many facets of hypermedia design. Among the specific topics covered by the papers are: design methods, multimedia modelling, higher structures in hypermedia design spaces, user-interface design for hypermedia, building distributed web applications, and hyperdialogs. The resulting volume provides a comprehensive overview of the state of the art in this important field. It will be of interest to researchers, practitioners and students involved in any aspect of hypermedia design. COMPUTERS,Data Science,General

Multimedia Database Systems Multimedia Database Systems: Design and Implementation Strategies is a compendium of the state-of-the-art research and development work pertaining to the problems and issues in the design and development of multimedia database systems. The chapters in the book are developed from presentations given at previous meetings of the International Workshop on Multi-Media Data Base Management Systems (IW-MMDBMS), and address the following issues: development of adequate multimedia database models, design of multimedia database query and retrieval languages, design of indexing and organization techniques, development of efficient and reliable storage models, development of efficient and dependable retrieval and delivery strategies, and development of flexible, adaptive, and reliable presentation techniques. COMPUTERS,Data Science,General

Shape in Picture The fields of image analysis, computer vision, and artificial intelligence all make use of descriptions of shape in grey-level images. Most existing algorithms for the automatic recognition and classification of particular shapes have been devel oped for specific purposes, with the result that these methods are often restricted in their application. The use of advanced and theoretically well-founded math ematical methods should lead to the construction of robust shape descriptors having more general application. Shape description can be regarded as a meeting point of vision research, mathematics, computing science, and the application fields of image analy sis, computer vision, and artificial intelligence. The NATO Advanced Research Workshop "Shape in Picture" was organised with a twofold objective: first, it should provide all participants with an overview of relevant developments in these different disciplines; second, it should stimulate researchers to exchange original results and ideas across the boundaries of these disciplines. This book comprises a widely drawn selection of papers presented at the workshop, and many contributions have been revised to reflect further progress in the field. The focus of this collection is on mathematical approaches to the construction of shape descriptions from grey-level images. The book is divided into five parts, each devoted to a different discipline. Each part contains papers that have tutorial sections; these are intended to assist the reader in becoming acquainted with the variety of approaches to the problem. COMPUTERS,Data Science,General

Photorealistic Rendering in Computer Graphics Photorealistic rendering strives to generate images fromcomputer modeled scenes with an image quality as close toreal life as possible. A major issue in rendering issimulation of local and global light reflection in a scene.Both ray tracing and radiosity algorithms capture only someof the possible light reflection phenomena. Recentlydeveloped two-pass algorithms combine the ray tracing andradiosity approaches and are able to capture the whole rangeof light reflection.This book is a collection of papers discussing the latestdevelopments, including a new range of improvements, instochastic sampling strategies, radiosity form factorcalculation, and parallel processing for ray tracing andradiosity. A number of papers on rendering applications ininterior design, lighting design, and remote sensingconclude the volume.The contributions are revised versions of papers originallypresented at the Second Eurographics Workshop on Rendering,held in Barcelona, Spain, in May 1991. The book fullyreflects the state of the art in rendering and presentsawide variety of novel techniques. It will interestresearchers and students in computer graphics, as well asdesigners who want to apply rendering techniques forrealistic simulation in lighting design, interior design,and architecture. COMPUTERS,Data Science,General

Graphics Modeling and Visualization in Science and Technology This workshop on Graphics Modeling and Visualization in Scientific, Engineering and Technical Applications was held in Darmstadt, Germany, on 13-14 April 1992. Visualization is known as the key technology to control massive data sets and to achieve insight into these tera bytes of data. Graphics Modeling is the enabling technology for advanced interaction. This book contains the keynote papers from three internationally well-known invited speakers and a selection of papers submitted to this workshop. Due to the effective scientific contacts between German and Portuguese researchers, and the results from this cooperation, the workshop was also the 2nd Luso-German Meet ing on Computer Graphics. The keynote papers present an excellent overview of the main topics of the workshop. Prof. Rae Earnshaw focuses on Scientific Visualization as an inter disciplinary area of research and application, presenting state of the art concepts and works currently being developed, and the requirements of visualization sys tems in the 90's. Prof. Frank-Lothar Krause presents Product Modeling as the key for information integration in industry, in particular to support CAD-CAM inte gration and CIM. Dr. Rolf Iindner introduces the DEDICATED (DEvelopment of a new DImension in Computer Assisted Teaching and EDucation) project, a European DELTA project with a strong involvement of German and Portuguese partners. COMPUTERS,Data Science,General

Mathematical Computation with Maple V Developments in both computer hardware and Perhaps the greatest impact has been felt by the software over the decades have fundamentally education community. Today, it is nearly changed the way people solve problems. impossible to find a college or university that has Technical professionals have greatly benefited not introduced mathematical computation in from new tools and techniques that have allowed some form, into the curriculum. Students now them to be more efficient, accurate, and creative have regular access to the amount of in their work. computational power that were available to a very exclusive set of researchers five years ago. This Maple V and the new generation of mathematical has produced tremendous pedagogical computation systems have the potential of challenges and opportunities. having the same kind of revolutionary impact as high-level general purpose programming Comparisons to the calculator revolution of the languages (e.g. FORTRAN, BASIC, C), 70's are inescapable. Calculators have application software (e.g. spreadsheets, extended the average person's ability to solve Computer Aided Design - CAD), and even common problems more efficiently, and calculators have had. Maple V has amplified our arguably, in better ways. Today, one needs at mathematical abilities: we can solve more least a calculator to deal with standard problems problems more accurately, and more often. In in life -budgets, mortgages, gas mileage, etc. specific disciplines, this amplification has taken For business people or professionals, the excitingly different forms. COMPUTERS,Data Science,General

Neural and Automata Networks "Et moi, ... , si j'avait Sll comment en revenir. One sennce mathematics has rendered the human race. It has put common sense back je n'y serais point alle.' Jules Verne whe", it belongs, on the topmost shelf next to the dusty canister labelled 'discarded non- The series is divergent; therefore we may be smse'. able to do something with it. Eric T. Bell O. Heaviside Mathematics is a tool for thought. A highly necessary tool in a world where both feedback and non linearities abound. Similarly, all kinds of parts of mathematics serve as tools for other parts and for other sciences. Applying a simple rewriting rule to the quote on the right above one finds such statements as: 'One service topology has rendered mathematical physics .. .'; 'One service logic has rendered com puter science .. .'; 'One service category theory has rendered mathematics .. .'. All arguably true. And all statements obtainable this way form part of the raison d'!ltre of this series. COMPUTERS,Data Science,General

Oracle Essentials Written by Oracle insiders, this indispensable guide distills an enormous amount of information about the Oracle Database into one compact volume. Ideal for novice and experienced DBAs, developers, managers, and users, Oracle Essentials walks you through technologies and features in Oracle’s product line, including its architecture, data structures, networking, concurrency, and tuning. Complete with illustrations and helpful hints, this fifth edition provides a valuable one-stop overview of Oracle Database 12c, including an introduction to Oracle and cloud computing. Oracle Essentials provides the conceptual background you need to understand how Oracle truly works. Topics include: A complete overview of Oracle databases and data stores, and Fusion Middleware products and features Core concepts and structures in Oracle’s architecture, including pluggable databases Oracle objects and the various datatypes Oracle supports System and database management, including Oracle Enterprise Manager 12c Security options, basic auditing capabilities, and options for meeting compliance needs Performance characteristics of disk, memory, and CPU tuning Basic principles of multiuser concurrency Oracle’s online transaction processing (OLTP) Data warehouses, Big Data, and Oracle’s business intelligence tools Backup and recovery, and high availability and failover solutions COMPUTERS,Data Science,General

Anonymizing Health Data Updated as of August 2014, this practical book will demonstrate proven methods for anonymizing health data to help your organization share meaningful datasets, without exposing patient identity. Leading experts Khaled El Emam and Luk Arbuckle walk you through a risk-based methodology, using case studies from their efforts to de-identify hundreds of datasets. Clinical data is valuable for research and other types of analytics, but making it anonymous without compromising data quality is tricky. This book demonstrates techniques for handling different data types, based on the authors’ experiences with a maternal-child registry, inpatient discharge abstracts, health insurance claims, electronic medical record databases, and the World Trade Center disaster registry, among others. Understand different methods for working with cross-sectional and longitudinal datasets Assess the risk of adversaries who attempt to re-identify patients in anonymized datasets Reduce the size and complexity of massive datasets without losing key information or jeopardizing privacy Use methods to anonymize unstructured free-form text data Minimize the risks inherent in geospatial data, without omitting critical location-based health information Look at ways to anonymize coding information in health data Learn the challenge of anonymously linking related datasets COMPUTERS,Data Science,General

Hands-On Programming with R Learn how to program by diving into the R language, and then use your newfound skills to solve practical data science problems. With this book, you’ll learn how to load data, assemble and disassemble data objects, navigate R’s environment system, write your own functions, and use all of R’s programming tools. RStudio Master Instructor Garrett Grolemund not only teaches you how to program, but also shows you how to get more from R than just visualizing and modeling data. You’ll gain valuable programming skills and support your work as a data scientist at the same time. Work hands-on with three practical data analysis projects based on casino games Store, retrieve, and change data values in your computer’s memory Write programs and simulations that outperform those written by typical R users Use R programming tools such as if else statements, for loops, and S3 classes Learn how to write lightning-fast vectorized R code Take advantage of R’s package system and debugging tools Practice and apply R programming concepts as you learn them COMPUTERS,Data Science,General

Using Flume How can you get your data from frontend servers to Hadoop in near real time? With this complete reference guide, you’ll learn Flume’s rich set of features for collecting, aggregating, and writing large amounts of streaming data to the Hadoop Distributed File System (HDFS), Apache HBase, SolrCloud, Elastic Search, and other systems. Using Flume shows operations engineers how to configure, deploy, and monitor a Flume cluster, and teaches developers how to write Flume plugins and custom components for their specific use-cases. You’ll learn about Flume’s design and implementation, as well as various features that make it highly scalable, flexible, and reliable. Code examples and exercises are available on GitHub. Learn how Flume provides a steady rate of flow by acting as a buffer between data producers and consumers Dive into key Flume components, including sources that accept data and sinks that write and deliver it Write custom plugins to customize the way Flume receives, modifies, formats, and writes data Explore APIs for sending data to Flume agents from your own applications Plan and deploy Flume in a scalable and flexible way—and monitor your cluster once it’s running COMPUTERS,Data Science,General

I Heart Logs Why a book about logs? That’s easy: the humble log is an abstraction that lies at the heart of many systems, from NoSQL databases to cryptocurrencies. Even though most engineers don’t think much about them, this short book shows you why logs are worthy of your attention. Based on his popular blog posts, LinkedIn principal engineer Jay Kreps shows you how logs work in distributed systems, and then delivers practical applications of these concepts in a variety of common uses—data integration, enterprise architecture, real-time stream processing, data system design, and abstract computing models. Go ahead and take the plunge with logs; you’re going love them. Learn how logs are used for programmatic access in databases and distributed systems Discover solutions to the huge data integration problem when more data of more varieties meet more systems Understand why logs are at the heart of real-time stream processing Learn the role of a log in the internals of online data systems Explore how Jay Kreps applies these ideas to his own work on data infrastructure systems at LinkedIn COMPUTERS,Data Science,General

Data Science at the Command Line This hands-on guide demonstrates how the flexibility of the command line can help you become a more efficient and productive data scientist. You’ll learn how to combine small, yet powerful, command-line tools to quickly obtain, scrub, explore, and model your data. To get you started—whether you’re on Windows, OS X, or Linux—author Jeroen Janssens introduces the Data Science Toolbox, an easy-to-install virtual environment packed with over 80 command-line tools. Discover why the command line is an agile, scalable, and extensible technology. Even if you’re already comfortable processing data with, say, Python or R, you’ll greatly improve your data science workflow by also leveraging the power of the command line. Obtain data from websites, APIs, databases, and spreadsheets Perform scrub operations on plain text, CSV, HTML/XML, and JSON Explore data, compute descriptive statistics, and create visualizations Manage your data science workflow using Drake Create reusable tools from one-liners and existing Python or R code Parallelize and distribute data-intensive pipelines using GNU Parallel Model data with dimensionality reduction, clustering, regression, and classification algorithms COMPUTERS,Data Science,General

Maple V Library Reference Manual The design and implementation of the Maple system is an on-going project of the Symbolic Com putation Group at the University of Waterloo in Ontario, Canada. This manual corresponds with version V (roman numeral five) of the Maple system. The on-line help subsystem can be invoked from within a Maple session to view documentation on specific topics. In particular, the command ?updates points the user to documentation updates for each new version of Maple. The Maple project was first conceived in the autumn of 1980, growing out of discussions on the state of symbolic computation at the University of Waterloo. The authors wish to acknowledge many fruitful discussions with colleagues at the University of Waterloo, particularly Morven Gen tleman, Michael Malcolm, and Frank Tompa. It was recognized in these discussions that none ofthe locaIly-available systems for symbolic computation provided the facilities that should be expected for symbolic computation in modern computing environments. We concluded that since the basic design decisions for the then-current symbolic systems such as ALTRAN, CAMAL, REDUCE, and MACSYMA were based on 1960's computing technology, it would be wise to design a new system "from scratch". Thus we could take advantage of the software engineering technology which had become available in recent years, as well as drawing from the lessons of experience. Maple's basic features (elementary data structures, Input/output, arithmetic with numbers, and elementary simplification) are coded in a systems programming language for efficiency. COMPUTERS,Data Science,General

Scientific Computing on Supercomputers III The International Workshop on "The Use of Supercomputers in Theoretical Science" took place on January 24 and 25, 1991, at the University of Antwerp (UIA), Antwerpen, Belgium. It was the sixth in a series of workshops, the fIrst of which took place in 1984. The principal aim of these workshops is to present the state of the art in scientific large-scale and high speed-computation. Computational science has developed into a third methodology equally important now as its theoretical and experimental companions. Gradually academic researchers acquired access to a variety of supercomputers and as a consequence computational science has become a major tool for their work. It is a pleasure to thank the Belgian National Science Foundation (NFWO-FNRS) and the Ministry of ScientifIc Affairs for sponsoring the workshop. It was organized both in the framework of the Third Cycle "Vectorization, Parallel Processing and Supercomputers" and the "Governemental Program in Information Technology". We also very much would like to thank the University of Antwerp (Universitaire Instelling Antwerpen -VIA) for fInancial and material support. Special thanks are due to Mrs. H. Evans for the typing and editing of the manuscripts and for the preparation of the author and subject indexes. J.T. Devreese P.E. Van Camp University of Antwerp July 1991 v CONlENTS High Perfonnance Numerically Intensive Applications on Distributed Memory Parallel Computers .................... . F.W. Wray Abstract ......................................... . COMPUTERS,Data Science,General

R Packages Turn your R code into packages that others can easily download and use. This practical book shows you how to bundle reusable R functions, sample data, and documentation together by applying author Hadley Wickham’s package development philosophy. In the process, you’ll work with devtools, roxygen, and testthat, a set of R packages that automate common development tasks. Devtools encapsulates best practices that Hadley has learned from years of working with this programming language. Ideal for developers, data scientists, and programmers with various backgrounds, this book starts you with the basics and shows you how to improve your package writing over time. You’ll learn to focus on what you want your package to do, rather than think about package structure. Learn about the most useful components of an R package, including vignettes and unit tests Automate anything you can, taking advantage of the years of development experience embodied in devtools Get tips on good style, such as organizing functions into files Streamline your development process with devtools Learn the best way to submit your package to the Comprehensive R Archive Network (CRAN) Learn from a well-respected member of the R community who created 30 R packages, including ggplot2, dplyr, and tidyr COMPUTERS,Data Science,General

SAP ERP Financial Accounting and Controlling SAP ERP modules are notoriously hard to configure and use effectively without a lot of practice and experience. But as SAP ERP Financial Accounting and Controlling : Configuration and Use Management shows, it doesn't have to be so difficult. The book takes a systematic approach that leads SAP Financial Accounting and Controlling (FICO) users step by step through configuring and using all the program’s facets. This approach makes configuration complexities manageable. The book’s author—SAP expert, trainer, and accountant Andrew Okungbowa—ensures that both you and your end users are up and running quickly and confidently with FICO. He also provides sound and tested procedures that ensure your implementation works without error. SAP ERP Financial Accounting and Controlling : Configuration and Use Management is in fact the most comprehensive and easy-to-follow SAP FICO configuration book in the market. It incorporates a hands-on approach, with hundreds of screen shots and practical examples, that allows a person without prior configuration training to make SAP FICO ready for use in the enterprise. You’ll find that you don’t need to be a rocket scientist to grasp the concepts explained and apply them to your work—even when the finances are complicated, such as with the ins and outs of taxes, currency conversions, or special general ledger entries such as down payments or bills of exchange. Providing an in-depth coverage of both configuration and end user procedures, the book covers most aspects of the SAP FICO certification syllabus—SAP’s view of the module’s key tasks and procedures—including: Configuring and using the general ledger and accounts payable and receivable screens Configuring and completing closing procedures, asset accounting, and financial reporting Configuring global settings and enterprise variables Accounting for both profit and cost centers Creating a house bank Integrating FICO with other SAP modules Taking a jargon-free tone and providing an abundance of examples, Andrew Okungbowa provides a clear understanding of configuration techniques and the breadth of functionalities encompassed by SAP FICO. And as an accountant, Okungbowa understands the needs of end users as well as of those answering to the CIO. COMPUTERS,Data Science,General

Oracle PL/SQL Language Pocket Reference Be more productive with the Oracle PL/SQL language. The fifth edition of this popular pocket reference puts the syntax of specific PL/SQL language elements right at your fingertips, including features added in Oracle Database 12c. Whether you’re a developer or database administrator, when you need answers quickly, the Oracle PL/SQL Language Pocket Reference will save you hours of frustration with concise summaries of: Fundamental language elements, such as block structure, datatypes, and declarations Statements for program control, cursor management, and exception handling Records, procedures, functions, triggers, and packages Execution of PL/SQL functions in SQL Compilation options, object-oriented features, collections, and Java integration This handy pocket reference is a perfect companion to Steven Feuerstein and Bill Pribyl’s bestselling Oracle PL/SQL Programming. COMPUTERS,Data Science,General

Foundation Discrete Mathematics for Computing COMPUTERS,Data Science,General

Mathematical Problem Solving and New Information Technologies A strong and fluent competency in mathematics is a necessary condition for scientific, technological and economic progress. However, it is widely recognized that problem solving, reasoning, and thinking processes are critical areas in which students' performance lags far behind what should be expected and desired. Mathematics is indeed an important subject, but is also important to be able to use it in extra-mathematical contexts. Thinking strictly in terms of mathematics or thinking in terms of its relations with the real world involve quite different processes and issues. This book includes the revised papers presented at the NATO ARW "Information Technology and Mathematical Problem Solving Research", held in April 1991, in Viana do Castelo, Portugal, which focused on the implications of computerized learning environments and cognitive psychology research for these mathematical activities. In recent years, several committees, professional associations, and distinguished individuals throughout the world have put forward proposals to renew mathematics curricula, all emphasizing the importance of problem solving. In order to be successful, these reforming intentions require a theory-driven research base. But mathematics problem solving may be considered a "chaotic field" in which progress has been quite slow. COMPUTERS,Data Science,General

Designing User Interfaces for Hypermedia One can observe that a wide range of human activities involves various forms of de sign. Especially if the goal implies the creation of an artifact, design is at the very center of these activities. It is the general understanding in the public to place design especially in the context of, for example, fashion, furniture, household items, cars, and architecture or in a more general way at the intersection of art and engineering. Of course, in the field of information technology, developers of software and hard ware are called system 'designers'. Design can be identified and considered in the context of many activities related to pUblishing: creating a product ad in a magazine, designing the layout of a newspaper, authoring a book. Summarizing these exam ples as 'creating documents', these are activities where two challenges with respect to design have to be met. Designing the content, its structure, and its relationship to the existing knowledge of potential readers is one, while the other refers to the 'rhetorical' aspects including designing the presentation of the material in order to communicate the content. Publishing is communicating knowledge. COMPUTERS,Data Science,General

Getting Started with SQL Businesses are gathering data today at exponential rates and yet few people know how to access it meaningfully. If you’re a business or IT professional, this short hands-on guide teaches you how to pull and transform data with SQL in significant ways. You will quickly master the fundamentals of SQL and learn how to create your own databases. Author Thomas Nield provides exercises throughout the book to help you practice your newfound SQL skills at home, without having to use a database server environment. Not only will you learn how to use key SQL statements to find and manipulate your data, but you’ll also discover how to efficiently design and manage databases to meet your needs. You’ll also learn how to: Explore relational databases, including lightweight and centralized models Use SQLite and SQLiteStudio to create lightweight databases in minutes Query and transform data in meaningful ways by using SELECT, WHERE, GROUP BY, and ORDER BY Join tables to get a more complete view of your business data Build your own tables and centralized databases by using normalized design principles Manage data by learning how to INSERT, DELETE, and UPDATE records COMPUTERS,Data Science,General

Unstructured Data Analytics Turn unstructured data into valuable business insight Unstructured Data Analytics provides an accessible, non-technical introduction to the analysis of unstructured data. Written by global experts in the analytics space, this book presents unstructured data analysis (UDA) concepts in a practical way, highlighting the broad scope of applications across industries, companies, and business functions. The discussion covers key aspects of UDA implementation, beginning with an explanation of the data and the information it provides, then moving into a holistic framework for implementation. Case studies show how real-world companies are leveraging UDA in security and customer management, and provide clear examples of both traditional business applications and newer, more innovative practices. Roughly 80 percent of today's data is unstructured in the form of emails, chats, social media, audio, and video. These data assets contain a wealth of valuable information that can be used to great advantage, but accessing that data in a meaningful way remains a challenge for many companies. This book provides the baseline knowledge and the practical understanding companies need to put this data to work. Supported by research with several industry leaders and packed with frontline stories from leading organizations such as Google, Amazon, Spotify, LinkedIn, Pfizer Manulife, AXA, Monster Worldwide, Under Armour, the Houston Rockets, DELL, IBM, and SAS Institute, this book provide a framework for building and implementing a successful UDA center of excellence. You will learn: How to increase Customer Acquisition and Customer Retention with UDA The Power of UDA for Fraud Detection and Prevention The Power of UDA in Human Capital Management & Human Resource The Power of UDA in Health Care and Medical Research The Power of UDA in National Security The Power of UDA in Legal Services The Power of UDA for product development The Power of UDA in Sports The future of UDA From small businesses to large multinational organizations, unstructured data provides the opportunity to gain consumer information straight from the source. Data is only as valuable as it is useful, and a robust, effective UDA strategy is the first step toward gaining the full advantage. Unstructured Data Analytics lays this space open for examination, and provides a solid framework for beginning meaningful analysis. COMPUTERS,Data Science,General

Leadership with Synercube Description of the Synercube Leadership Theory with numerous practical examples. 10 different leadership styles are described according to the dimensions people, task and values. The book enables the reader to conclude how people interact with each other in a company and how corporate power should be used in order to achieve excellence with the available resources. By this, a sound corporate culture is supported. Based on the Synercube Theory, the guidance of change under consideration of psychological and behavioural effects empowers to continuously and effective change. Managers of organizations of all sizes equally benefit. COMPUTERS,Data Science,General

Data Science For Dummies Discover how data science can help you gain in-depth insight into your business - the easy way! Jobs in data science abound, but few people have the data science skills needed to fill these increasingly important roles. Data Science For Dummies is the perfect starting point for IT professionals and students who want a quick primer on all areas of the expansive data science space. With a focus on business cases, the book explores topics in big data, data science, and data engineering, and how these three areas are combined to produce tremendous value. If you want to pick-up the skills you need to begin a new career or initiate a new project, reading this book will help you understand what technologies, programming languages, and mathematical methods on which to focus. While this book serves as a wildly fantastic guide through the broad, sometimes intimidating field of big data and data science, it is not an instruction manual for hands-on implementation. Here’s what to expect: Provides a background in big data and data engineering before moving on to data science and how it's applied to generate value Includes coverage of big data frameworks like Hadoop, MapReduce, Spark, MPP platforms, and NoSQL Explains machine learning and many of its algorithms as well as artificial intelligence and the evolution of the Internet of Things Details data visualization techniques that can be used to showcase, summarize, and communicate the data insights you generate It's a big, big data world out there—let Data Science For Dummies help you harness its power and gain a competitive edge for your organization. COMPUTERS,Data Science,General

Introduction to Apache Flink There’s growing interest in learning how to analyze streaming data in large-scale systems such as web traffic, financial transactions, machine logs, industrial sensors, and many others. But analyzing data streams at scale has been difficult to do well—until now. This practical book delivers a deep introduction to Apache Flink, a highly innovative open source stream processor with a surprising range of capabilities. Authors Ellen Friedman and Kostas Tzoumas show technical and nontechnical readers alike how Flink is engineered to overcome significant tradeoffs that have limited the effectiveness of other approaches to stream processing. You’ll also learn how Flink has the ability to handle both stream and batch data processing with one technology. Learn the consequences of not doing streaming well—in retail and marketing, IoT, telecom, and banking and finance Explore how to design data architecture to gain the best advantage from stream processing Get an overview of Flink’s capabilities and features, along with examples of how companies use Flink, including in production Take a technical dive into Flink, and learn how it handles time and stateful computation Examine how Flink processes both streaming (unbounded) and batch (bounded) data without sacrificing performance COMPUTERS,Data Science,General

Cool Math for Hot Music This textbook is a first introduction to mathematics for music theorists, covering basic topics such as sets and functions, universal properties, numbers and recursion, graphs, groups, rings, matrices and modules, continuity, calculus, and gestures. It approaches these abstract themes in a new way: Every concept or theorem is motivated and illustrated by examples from music theory (such as harmony, counterpoint, tuning), composition (e.g., classical combinatorics, dodecaphonic composition), and gestural performance. The book includes many illustrations, and exercises with solutions. COMPUTERS,Data Science,General

Csound This rigorous book is a complete and up-to-date reference for the Csound system from the perspective of its main developers and power users. It explains the system, including the basic modes of operation and its programming language; it explores the many ways users can interact with the system, including the latest features; and it describes key applications such as instrument design, signal processing, and creative electronic music composition. The Csound system has been adopted by many educational institutions as part of their undergraduate and graduate teaching programs, and it is used by practitioners worldwide. This book is suitable for students, lecturers, composers, sound designers, programmers, and researchers in the areas of music, sound, and audio signal processing. COMPUTERS,Data Science,General

Practical Machine Learning with H2O Machine learning has finally come of age. With H2O software, you can perform machine learning and data analysis using a simple open source framework that’s easy to use, has a wide range of OS and language support, and scales for big data. This hands-on guide teaches you how to use H20 with only minimal math and theory behind the learning algorithms. If you’re familiar with R or Python, know a bit of statistics, and have some experience manipulating data, author Darren Cook will take you through H2O basics and help you conduct machine-learning experiments on different sample data sets. You’ll explore several modern machine-learning techniques such as deep learning, random forests, unsupervised learning, and ensemble learning. Learn how to import, manipulate, and export data with H2O Explore key machine-learning concepts, such as cross-validation and validation data sets Work with three diverse data sets, including a regression, a multinomial classification, and a binomial classification Use H2O to analyze each sample data set with four supervised machine-learning algorithms Understand how cluster analysis and other unsupervised machine-learning algorithms work COMPUTERS,Data Science,General

Efficient R Programming There are many excellent R resources for visualization, data science, and package development. Hundreds of scattered vignettes, web pages, and forums explain how to use R in particular domains. But little has been written on how to simply make R work effectively—until now. This hands-on book teaches novices and experienced R users how to write efficient R code. Drawing on years of experience teaching R courses, authors Colin Gillespie and Robin Lovelace provide practical advice on a range of topics—from optimizing the set-up of RStudio to leveraging C++—that make this book a useful addition to any R user’s bookshelf. Academics, business users, and programmers from a wide range of backgrounds stand to benefit from the guidance in Efficient R Programming. Get advice for setting up an R programming environment Explore general programming concepts and R coding techniques Understand the ingredients of an efficient R workflow Learn how to efficiently read and write data in R Dive into data carpentry—the vital skill for cleaning raw data Optimize your code with profiling, standard tricks, and other methods Determine your hardware capabilities for handling R computation Maximize the benefits of collaborative R programming Accelerate your transition from R hacker to R programmer COMPUTERS,Data Science,General

R for Data Science Learn how to use R to turn raw data into insight, knowledge, and understanding. This book introduces you to R, RStudio, and the tidyverse, a collection of R packages designed to work together to make data science fast, fluent, and fun. Suitable for readers with no previous programming experience, R for Data Science is designed to get you doing data science as quickly as possible. Authors Hadley Wickham and Garrett Grolemund guide you through the steps of importing, wrangling, exploring, and modeling your data and communicating the results. You’ll get a complete, big-picture understanding of the data science cycle, along with basic tools you need to manage the details. Each section of the book is paired with exercises to help you practice what you’ve learned along the way. You’ll learn how to: Wrangle—transform your datasets into a form convenient for analysis Program—learn powerful R tools for solving data problems with greater clarity and ease Explore—examine your data, generate hypotheses, and quickly test them Model—provide a low-dimensional summary that captures true "signals" in your dataset Communicate—learn R Markdown for integrating prose, code, and results COMPUTERS,Data Science,General

Become ITIL Foundation Certified in 7 Days Pass the ITIL Foundation examination by learning the basics of ITIL and working through real-life examples. This book breaks the course down for studying in 7 days with 3 hours a day, which means at the end of a week you are ready to pass the exam. You'll also see tips and an array of sample questions, as well as FAQs on ITIL. All this will prepare you for the examination and give you the knowledge required to pass with flying colors. After using Become ITIL Foundation Certified in 7 Days and earning the ITIL Foundation certification, you'll be well placed to get the career you always wanted. What You Will Learn Gain ITIL basics – the entire syllabus designed of the ITIL Foundation certification Obtain a deep-rooted understanding of ITIL topics and not textbook knowledge Prepare for the ITIL Foundation examination Sort out career-related queries and decide whether ITIL will aid your career Who This Book Is For IT professionals from the IT services industry are the primary audience. COMPUTERS,Data Science,General

Application Performance Management (APM) in the Digital Enterprise Application Performance Management (APM) in the Digital Enterprise enables IT professionals to be more successful in managing their company’s applications. It explores the fundamentals of application management, examines how the latest technological trends impact application management, and provides best practices for responding to these changes. The recent surge in the use of containers as a way to simplify management and deploy applications has created new challenges, and the convergence of containerization, cloud, mobile, virtualization, analytics, and automation is reshaping the requirements for application management. This book serves as a guide for understanding these dramatic changes and how they impact the management of applications, showing how to create a management strategy, define the underlying processes and standards, and how to select the appropriate tools to enable management processes. Offers a complete framework for implementing effective application management using clear tips and solutions for those responsible for application management Draws upon primary research to give technologists a current understanding of the latest technologies and processes needed to more effectively manage large-scale applications Includes real-world case studies and business justifications that support application management investments COMPUTERS,Data Science,General

Learning Quantitative Finance with R Implement machine learning, time-series analysis, algorithmic trading and more About This Book Understand the basics of R and how they can be applied in various Quantitative Finance scenarios Learn various algorithmic trading techniques and ways to optimize them using the tools available in R. Contain different methods to manage risk and explore trading using Machine Learning. Who This Book Is For If you want to learn how to use R to build quantitative finance models with ease, this book is for you. Analysts who want to learn R to solve their quantitative finance problems will also find this book useful. Some understanding of the basic financial concepts will be useful, though prior knowledge of R is not required. What You Will Learn Get to know the basics of R and how to use it in the field of Quantitative Finance Understand data processing and model building using R Explore different types of analytical techniques such as statistical analysis, time-series analysis, predictive modeling, and econometric analysis Build and analyze quantitative finance models using real-world examples How real-life examples should be used to develop strategies Performance metrics to look into before deciding upon any model Deep dive into the vast world of machine-learning based trading Get to grips with algorithmic trading and different ways of optimizing it Learn about controlling risk parameters of financial instruments In Detail The role of a quantitative analyst is very challenging, yet lucrative, so there is a lot of competition for the role in top-tier organizations and investment banks. This book is your go-to resource if you want to equip yourself with the skills required to tackle any real-world problem in quantitative finance using the popular R programming language. You'll start by getting an understanding of the basics of R and its relevance in the field of quantitative finance. Once you've built this foundation, we'll dive into the practicalities of building financial models in R. This will help you have a fair understanding of the topics as well as their implementation, as the authors have presented some use cases along with examples that are easy to understand and correlate. We'll also look at risk management and optimization techniques for algorithmic trading. Finally, the book will explain some advanced concepts, such as trading using machine learning, optimizations, exotic options, and hedging. By the end of this book, you will have a firm grasp of the techniques required to implement basic quantitative finance models in R. Style and approach This book introduces you to the essentials of quantitative finance with the help of easy-to-understand, practical examples and use cases in R. Each chapter presents a specific financial concept in detail, backed with relevant theory and the implementation of a real-life example. COMPUTERS,Data Science,General

Python Understand, evaluate, and visualize data About This Book Learn basic steps of data analysis and how to use Python and its packages A step-by-step guide to predictive modeling including tips, tricks, and best practices Effectively visualize a broad set of analyzed data and generate effective results Who This Book Is For This book is for Python Developers who are keen to get into data analysis and wish to visualize their analyzed data in a more efficient and insightful manner. What You Will Learn Get acquainted with NumPy and use arrays and array-oriented computing in data analysis Process and analyze data using the time-series capabilities of Pandas Understand the statistical and mathematical concepts behind predictive analytics algorithms Data visualization with Matplotlib Interactive plotting with NumPy, Scipy, and MKL functions Build financial models using Monte-Carlo simulations Create directed graphs and multi-graphs Advanced visualization with D3 In Detail You will start the course with an introduction to the principles of data analysis and supported libraries, along with NumPy basics for statistics and data processing. Next, you will overview the Pandas package and use its powerful features to solve data-processing problems. Moving on, you will get a brief overview of the Matplotlib API .Next, you will learn to manipulate time and data structures, and load and store data in a file or database using Python packages. You will learn how to apply powerful packages in Python to process raw data into pure and helpful data using examples. You will also get a brief overview of machine learning algorithms, that is, applying data analysis results to make decisions or building helpful products such as recommendations and predictions using Scikit-learn. After this, you will move on to a data analytics specialization—predictive analytics. Social media and IOT have resulted in an avalanche of data. You will get started with predictive analytics using Python. You will see how to create predictive models from data. You will get balanced information on statistical and mathematical concepts, and implement them in Python using libraries such as Pandas, scikit-learn, and NumPy. You'll learn more about the best predictive modeling algorithms such as Linear Regression, Decision Tree, and Logistic Regression. Finally, you will master best practices in predictive modeling. After this, you will get all the practical guidance you need to help you on the journey to effective data visualization. Starting with a chapter on data frameworks, which explains the transformation of data into information and eventually knowledge, this path subsequently cover the complete visualization process using the most popular Python libraries with working examples This Learning Path combines some of the best that Packt has to offer in one complete, curated package. It includes content from the following Packt products: Getting Started with Python Data Analysis, Phuong Vo.T.H &Martin Czygan Learning Predictive Analytics with Python, Ashish Kumar Mastering Python Data Visualization, Kirthi Raman Style and approach The course acts as a step-by-step guide to get you familiar with data analysis and the libraries supported by Python with the help of real-world examples and datasets. It also helps you gain practical insights into predictive modeling by implementing predictive-analytics algorithms on public datasets with Python. The course offers a wealth of practical guidance to help you on this journey to data visualization COMPUTERS,Data Science,General

High Performance Spark Apache Spark is amazing when everything clicks. But if you haven’t seen the performance improvements you expected, or still don’t feel confident enough to use Spark in production, this practical book is for you. Authors Holden Karau and Rachel Warren demonstrate performance optimizations to help your Spark queries run faster and handle larger data sizes, while using fewer resources. Ideal for software engineers, data engineers, developers, and system administrators working with large-scale data applications, this book describes techniques that can reduce data infrastructure costs and developer hours. Not only will you gain a more comprehensive understanding of Spark, you’ll also learn how to make it sing. With this book, you’ll explore: How Spark SQL’s new interfaces improve performance over SQL’s RDD data structure The choice between data joins in Core Spark and Spark SQL Techniques for getting the most out of standard RDD transformations How to work around performance issues in Spark’s key/value pair paradigm Writing high-performance Spark code without Scala or the JVM How to test for functionality and performance when applying suggested improvements Using Spark MLlib and Spark ML machine learning libraries Spark’s Streaming components and external community packages COMPUTERS,Data Science,General

Principles of Data Wrangling A key task that any aspiring data-driven organization needs to learn is data wrangling, the process of converting raw data into something truly useful. This practical guide provides business analysts with an overview of various data wrangling techniques and tools, and puts the practice of data wrangling into context by asking, "What are you trying to do and why?" Wrangling data consumes roughly 50-80% of an analyst’s time before any kind of analysis is possible. Written by key executives at Trifacta, this book walks you through the wrangling process by exploring several factors—time, granularity, scope, and structure—that you need to consider as you begin to work with data. You’ll learn a shared language and a comprehensive understanding of data wrangling, with an emphasis on recent agile analytic processes used by many of today’s data-driven organizations. Appreciate the importance—and the satisfaction—of wrangling data the right way. Understand what kind of data is available Choose which data to use and at what level of detail Meaningfully combine multiple sources of data Decide how to distill the results to a size and shape that can drive downstream analysis COMPUTERS,Data Science,General

Frank Kane's Taming Big Data with Apache Spark and Python Frank Kane's hands-on Spark training course, based on his bestselling Taming Big Data with Apache Spark and Python video, now available in a book. Understand and analyze large data sets using Spark on a single system or on a cluster. About This Book Understand how Spark can be distributed across computing clusters Develop and run Spark jobs efficiently using Python A hands-on tutorial by Frank Kane with over 15 real-world examples teaching you Big Data processing with Spark Who This Book Is For If you are a data scientist or data analyst who wants to learn Big Data processing using Apache Spark and Python, this book is for you. If you have some programming experience in Python, and want to learn how to process large amounts of data using Apache Spark, Frank Kane's Taming Big Data with Apache Spark and Python will also help you. What You Will Learn Find out how you can identify Big Data problems as Spark problems Install and run Apache Spark on your computer or on a cluster Analyze large data sets across many CPUs using Spark's Resilient Distributed Datasets Implement machine learning on Spark using the MLlib library Process continuous streams of data in real time using the Spark streaming module Perform complex network analysis using Spark's GraphX library Use Amazon's Elastic MapReduce service to run your Spark jobs on a cluster In Detail Frank Kane's Taming Big Data with Apache Spark and Python is your companion to learning Apache Spark in a hands-on manner. Frank will start you off by teaching you how to set up Spark on a single system or on a cluster, and you'll soon move on to analyzing large data sets using Spark RDD, and developing and running effective Spark jobs quickly using Python. Apache Spark has emerged as the next big thing in the Big Data domain – quickly rising from an ascending technology to an established superstar in just a matter of years. Spark allows you to quickly extract actionable insights from large amounts of data, on a real-time basis, making it an essential tool in many modern businesses. Frank has packed this book with over 15 interactive, fun-filled examples relevant to the real world, and he will empower you to understand the Spark ecosystem and implement production-grade real-time Spark projects with ease. Style and approach Frank Kane's Taming Big Data with Apache Spark and Python is a hands-on tutorial with over 15 real-world examples carefully explained by Frank in a step-by-step manner. The examples vary in complexity, and you can move through them at your own pace. COMPUTERS,Data Science,General

Learning Informatica PowerCenter 10.x Harness the power and simplicity of Informatica PowerCenter 10.x to build and manage efficient data management solutions About This Book Master PowerCenter 10.x components to create, execute, monitor, and schedule ETL processes with a practical approach. An ideal guide to building the necessary skills and competencies to become an expert Informatica PowerCenter developer. A comprehensive guide to fetching/transforming and loading huge volumes of data in a very effective way, with reduced resource consumption Who This Book Is For If you wish to deploy Informatica in enterprise environments and build a career in data warehousing, then this book is for you. Whether you are a software developer/analytic professional and are new to Informatica or an experienced user, you will learn all the features of Informatica 10.x. A basic knowledge of programming and data warehouse concepts is essential. What You Will Learn Install or upgrade the components of the Informatica PowerCenter tool Work on various aspects of administrative skills and on the various developer Informatica PowerCenter screens such as Designer, Workflow Manager, Workflow Monitor, and Repository Manager. Get practical hands-on experience of various sections of Informatica PowerCenter, such as navigator, toolbar, workspace, control panel, and so on Leverage basic and advanced utilities, such as the debugger, target load plan, and incremental aggregation to process data Implement data warehousing concepts such as schemas and SCDs using Informatica Migrate various components, such as sources and targets, to another region using the Designer and Repository Manager screens Enhance code performance using tips such as pushdown optimization and partitioning In Detail Informatica PowerCenter is an industry-leading ETL tool, known for its accelerated data extraction, transformation, and data management strategies. This book will be your quick guide to exploring Informatica PowerCenter's powerful features such as working on sources, targets, transformations, performance optimization, scheduling, deploying for processing, and managing your data at speed. First, you'll learn how to install and configure tools. You will learn to implement various data warehouse and ETL concepts, and use PowerCenter 10.x components to build mappings, tasks, workflows, and so on. You will come across features such as transformations, SCD, XML processing, partitioning, constraint-based loading, Incremental aggregation, and many more. Moreover, you'll also learn to deliver powerful visualizations for data profiling using the advanced monitoring dashboard functionality offered by the new version. Using data transformation technique, performance tuning, and the many new advanced features, this book will help you understand and process data for training or production purposes. The step-by-step approach and adoption of real-time scenarios will guide you through effectively accessing all core functionalities offered by Informatica PowerCenter version 10.x. Style and approach You'll get hand-on with sources, targets, transformations, performance optimization, scheduling, deploying for processing, and managing your data, and learn everything you need to become a proficient Informatica PowerCenter developer. COMPUTERS,Data Science,General

MATLAB for Machine Learning Extract patterns and knowledge from your data in easy way using MATLAB About This Book Get your first steps into machine learning with the help of this easy-to-follow guide Learn regression, clustering, classification, predictive analytics, artificial neural networks and more with MATLAB Understand how your data works and identify hidden layers in the data with the power of machine learning. Who This Book Is For This book is for data analysts, data scientists, students, or anyone who is looking to get started with machine learning and want to build efficient data processing and predicting applications. A mathematical and statistical background will really help in following this book well. What You Will Learn Learn the introductory concepts of machine learning. Discover different ways to transform data using SAS XPORT, import and export tools, Explore the different types of regression techniques such as simple & multiple linear regression, ordinary least squares estimation, correlations and how to apply them to your data. Discover the basics of classification methods and how to implement Naive Bayes algorithm and Decision Trees in the Matlab environment. Uncover how to use clustering methods like hierarchical clustering to grouping data using the similarity measures. Know how to perform data fitting, pattern recognition, and clustering analysis with the help of MATLAB Neural Network Toolbox. Learn feature selection and extraction for dimensionality reduction leading to improved performance. In Detail MATLAB is the language of choice for many researchers and mathematics experts for machine learning. This book will help you build a foundation in machine learning using MATLAB for beginners. You'll start by getting your system ready with t he MATLAB environment for machine learning and you'll see how to easily interact with the Matlab workspace. We'll then move on to data cleansing, mining and analyzing various data types in machine learning and you'll see how to display data values on a plot. Next, you'll get to know about the different types of regression techniques and how to apply them to your data using the MATLAB functions. You'll understand the basic concepts of neural networks and perform data fitting, pattern recognition, and clustering analysis. Finally, you'll explore feature selection and extraction techniques for dimensionality reduction for performance improvement. At the end of the book, you will learn to put it all together into real-world cases covering major machine learning algorithms and be comfortable in performing machine learning with MATLAB. Style and approach The book takes a very comprehensive approach to enhance your understanding of machine learning using MATLAB. Sufficient real-world examples and use cases are included in the book to help you grasp the concepts quickly and apply them easily in your day-to-day work. COMPUTERS,Data Science,General

Kafka Every enterprise application creates data, whether it’s log messages, metrics, user activity, outgoing messages, or something else. And how to move all of this data becomes nearly as important as the data itself. If you’re an application architect, developer, or production engineer new to Apache Kafka, this practical guide shows you how to use this open source streaming platform to handle real-time data feeds. Engineers from Confluent and LinkedIn who are responsible for developing Kafka explain how to deploy production Kafka clusters, write reliable event-driven microservices, and build scalable stream-processing applications with this platform. Through detailed examples, you’ll learn Kafka’s design principles, reliability guarantees, key APIs, and architecture details, including the replication protocol, the controller, and the storage layer. Understand publish-subscribe messaging and how it fits in the big data ecosystem. Explore Kafka producers and consumers for writing and reading messages Understand Kafka patterns and use-case requirements to ensure reliable data delivery Get best practices for building data pipelines and applications with Kafka Manage Kafka in production, and learn to perform monitoring, tuning, and maintenance tasks Learn the most critical metrics among Kafka’s operational measurements Explore how Kafka’s stream delivery capabilities make it a perfect source for stream processing systems COMPUTERS,Data Science,General

Python for Data Analysis Get complete instructions for manipulating, processing, cleaning, and crunching datasets in Python. Updated for Python 3.6, the second edition of this hands-on guide is packed with practical case studies that show you how to solve a broad set of data analysis problems effectively. You’ll learn the latest versions of pandas, NumPy, IPython, and Jupyter in the process. Written by Wes McKinney, the creator of the Python pandas project, this book is a practical, modern introduction to data science tools in Python. It’s ideal for analysts new to Python and for Python programmers new to data science and scientific computing. Data files and related material are available on GitHub. Use the IPython shell and Jupyter notebook for exploratory computing Learn basic and advanced features in NumPy (Numerical Python) Get started with data analysis tools in the pandas library Use flexible tools to load, clean, transform, merge, and reshape data Create informative visualizations with matplotlib Apply the pandas groupby facility to slice, dice, and summarize datasets Analyze and manipulate regular and irregular time series data Learn how to solve real-world data analysis problems with thorough, detailed examples COMPUTERS,Data Science,General

Pandas Cookbook Over 95 hands-on recipes to leverage the power of pandas for efficient scientific computation and data analysis About This Book Use the power of pandas to solve most complex scientific computing problems with ease Leverage fast, robust data structures in pandas to gain useful insights from your data Practical, easy to implement recipes for quick solutions to common problems in data using pandas Who This Book Is For This book is for data scientists, analysts and Python developers who wish to explore data analysis and scientific computing in a practical, hands-on manner. The recipes included in this book are suitable for both novice and advanced users, and contain helpful tips, tricks and caveats wherever necessary. Some understanding of pandas will be helpful, but not mandatory. What You Will Learn Master the fundamentals of pandas to quickly begin exploring any dataset Isolate any subset of data by properly selecting and querying the data Split data into independent groups before applying aggregations and transformations to each group Restructure data into tidy form to make data analysis and visualization easier Prepare real-world messy datasets for machine learning Combine and merge data from different sources through pandas SQL-like operations Utilize pandas unparalleled time series functionality Create beautiful and insightful visualizations through pandas direct hooks to Matplotlib and Seaborn In Detail This book will provide you with unique, idiomatic, and fun recipes for both fundamental and advanced data manipulation tasks with pandas. Some recipes focus on achieving a deeper understanding of basic principles, or comparing and contrasting two similar operations. Other recipes will dive deep into a particular dataset, uncovering new and unexpected insights along the way. The pandas library is massive, and it's common for frequent users to be unaware of many of its more impressive features. The official pandas documentation, while thorough, does not contain many useful examples of how to piece together multiple commands like one would do during an actual analysis. This book guides you, as if you were looking over the shoulder of an expert, through practical situations that you are highly likely to encounter. Many advanced recipes combine several different features across the pandas library to generate results. Style and approach The author relies on his vast experience teaching pandas in a professional setting to deliver very detailed explanations for each line of code in all of the recipes. All code and dataset explanations exist in Jupyter Notebooks, an excellent interface for exploring data. COMPUTERS,Data Science,General

Business Process Automation with ProcessMaker 3.1 Use this practical, hands-on guide to get started with ProcessMaker. The book provides clear steps for you to walk through and set up ProcessMaker on your own system and make processes run faster and smarter. You will model and build a complete business process for requesting, approving, and reporting expenses. In the course of building the process, you will understand: The Workflow Designer for modeling business processes using BPMN 2.0 The Dynaform Designer for creating responsive HTML forms Input and Output documents for capturing supporting documents for business processes and generating standardized documents from the data captured in a process Triggers for implementing custom business logic and extending ProcessMaker functionality What You’ll Learn Send email notifications and add comments to cases Build complex routing rules Manage users and their permissions Deploy ProcessMaker to a cloud server Configure and use the ProcessMaker mobile app Who This Book Is For Business analysts, programmers, and professionals in all industries (e.g., higher education, finance and insurance, government, healthcare, manufacturing, and telecommunications) COMPUTERS,Data Science,General

Data Science on the Google Cloud Platform Learn how easy it is to apply sophisticated statistical and machine learning methods to real-world problems when you build on top of the Google Cloud Platform (GCP). This hands-on guide shows developers entering the data science field how to implement an end-to-end data pipeline, using statistical and machine learning methods and tools on GCP. Through the course of the book, you’ll work through a sample business decision by employing a variety of data science approaches. Follow along by implementing these statistical and machine learning solutions in your own project on GCP, and discover how this platform provides a transformative and more collaborative way of doing data science. You’ll learn how to: Automate and schedule data ingest, using an App Engine application Create and populate a dashboard in Google Data Studio Build a real-time analysis pipeline to carry out streaming analytics Conduct interactive data exploration with Google BigQuery Create a Bayesian model on a Cloud Dataproc cluster Build a logistic regression machine-learning model with Spark Compute time-aggregate features with a Cloud Dataflow pipeline Create a high-performing prediction model with TensorFlow Use your deployed model as a microservice you can access from both batch and real-time pipelines COMPUTERS,Data Science,General

Learn Salesforce Lightning Refer to this invaluable how-to guide for basic training on Salesforce Lightning. Salespeople and technical users and consultants will no longer have to resort to learning the interface on their own, which is very time consuming. Learn Salesforce Lightning is a step-by-step visual guide that offers immediate and valuable solutions to the new set of UI tools included in Lightning. With chapters broken down into easily absorbed topics, you walk through the entire process of managing your daily activities within Salesforce, as well as basic customizations and system management. The book explains the primary use cases for Lighting, and simplifies some of the more complex features, such as opportunity stage management and the new dashboard builder. Topics covered include: Sales and service management Lightning Apps on the AppExchange Lightning dashboards and reports Lightning security Lightning Process Builder and more What You’ll Learn Navigate the Salesforce Lightning interface Know where to go in the setup area to make customizations Create dynamic reports and dashboards View Lightning on a mobile device Train other users on common day-to-day activities within Lightning Who This Book Is for Salespeople, managers, and executives who are currently evaluating Salesforce.com, who recently purchased a license with Salesforce.com, or recently upgraded to the Lightning user interface. This book is also for Salesforce administrators, consultants, project managers, and technical users looking for basic training on Salesforce Lightning. COMPUTERS,Data Science,General

Spark Learn how to use, deploy, and maintain Apache Spark with this comprehensive guide, written by the creators of the open-source cluster-computing framework. With an emphasis on improvements and new features in Spark 2.0, authors Bill Chambers and Matei Zaharia break down Spark topics into distinct sections, each with unique goals. You’ll explore the basic operations and common functions of Spark’s structured APIs, as well as Structured Streaming, a new high-level API for building end-to-end streaming applications. Developers and system administrators will learn the fundamentals of monitoring, tuning, and debugging Spark, and explore machine learning techniques and scenarios for employing MLlib, Spark’s scalable machine-learning library. Get a gentle overview of big data and Spark Learn about DataFrames, SQL, and Datasets—Spark’s core APIs—through worked examples Dive into Spark’s low-level APIs, RDDs, and execution of SQL and DataFrames Understand how Spark runs on a cluster Debug, monitor, and tune Spark clusters and applications Learn the power of Structured Streaming, Spark’s stream-processing engine Learn how you can apply MLlib to a variety of problems, including classification or recommendation COMPUTERS,Data Science,General

Deep Learning with PyTorch Build neural network models in text, vision and advanced analytics using PyTorch About This Book Learn PyTorch for implementing cutting-edge deep learning algorithms. Train your neural networks for higher speed and flexibility and learn how to implement them in various scenarios; Cover various advanced neural network architecture such as ResNet, Inception, DenseNet and more with practical examples; Who This Book Is For This book is for machine learning engineers, data analysts, data scientists interested in deep learning and are looking to explore implementing advanced algorithms in PyTorch. Some knowledge of machine learning is helpful but not a mandatory need. Working knowledge of Python programming is expected. What You Will Learn Use PyTorch for GPU-accelerated tensor computations Build custom datasets and data loaders for images and test the models using torchvision and torchtext Build an image classifier by implementing CNN architectures using PyTorch Build systems that do text classification and language modeling using RNN, LSTM, and GRU Learn advanced CNN architectures such as ResNet, Inception, Densenet, and learn how to use them for transfer learning Learn how to mix multiple models for a powerful ensemble model Generate new images using GAN's and generate artistic images using style transfer In Detail Deep learning powers the most intelligent systems in the world, such as Google Voice, Siri, and Alexa. Advancements in powerful hardware, such as GPUs, software frameworks such as PyTorch, Keras, Tensorflow, and CNTK along with the availability of big data have made it easier to implement solutions to problems in the areas of text, vision, and advanced analytics. This book will get you up and running with one of the most cutting-edge deep learning libraries—PyTorch. PyTorch is grabbing the attention of deep learning researchers and data science professionals due to its accessibility, efficiency and being more native to Python way of development. You'll start off by installing PyTorch, then quickly move on to learn various fundamental blocks that power modern deep learning. You will also learn how to use CNN, RNN, LSTM and other networks to solve real-world problems. This book explains the concepts of various state-of-the-art deep learning architectures, such as ResNet, DenseNet, Inception, and Seq2Seq, without diving deep into the math behind them. You will also learn about GPU computing during the course of the book. You will see how to train a model with PyTorch and dive into complex neural networks such as generative networks for producing text and images. By the end of the book, you'll be able to implement deep learning applications in PyTorch with ease. Style and approach An end-to-end guide that teaches you all about PyTorch and how to implement it in various scenarios. COMPUTERS,Data Science,General

Feature Engineering for Machine Learning Feature engineering is a crucial step in the machine-learning pipeline, yet this topic is rarely examined on its own. With this practical book, you’ll learn techniques for extracting and transforming features—the numeric representations of raw data—into formats for machine-learning models. Each chapter guides you through a single data problem, such as how to represent text or image data. Together, these examples illustrate the main principles of feature engineering. Rather than simply teach these principles, authors Alice Zheng and Amanda Casari focus on practical application with exercises throughout the book. The closing chapter brings everything together by tackling a real-world, structured dataset with several feature-engineering techniques. Python packages including numpy, Pandas, Scikit-learn, and Matplotlib are used in code examples. You’ll examine: Feature engineering for numeric data: filtering, binning, scaling, log transforms, and power transforms Natural text techniques: bag-of-words, n-grams, and phrase detection Frequency-based filtering and feature scaling for eliminating uninformative features Encoding techniques of categorical variables, including feature hashing and bin-counting Model-based feature engineering with principal component analysis The concept of model stacking, using k-means as a featurization technique Image feature extraction with manual and deep-learning techniques COMPUTERS,Data Science,General

Fundamentals of Business Process Management This textbook covers the entire Business Process Management (BPM) lifecycle, from process identification to process monitoring, covering along the way process modelling, analysis, redesign and automation. Concepts, methods and tools from business management, computer science and industrial engineering are blended into one comprehensive and inter-disciplinary approach. The presentation is illustrated using the BPMN industry standard defined by the Object Management Group and widely endorsed by practitioners and vendors worldwide. In addition to explaining the relevant conceptual background, the book provides dozens of examples, more than 230 exercises – many with solutions – and numerous suggestions for further reading. This second edition includes extended and completely revised chapters on process identification, process discovery, qualitative process analysis, process redesign, process automation and process monitoring. A new chapter on BPM as an enterprise capability has been added, which expands the scope of the book to encompass topics such as the strategic alignment and governance of BPM initiatives. The textbook is the result of many years of combined teaching experience of the authors, both at the undergraduate and graduate levels as well as in the context of professional training. Students and professionals from both business management and computer science will benefit from the step-by-step style of the textbook and its focus on fundamental concepts and proven methods. Lecturers will appreciate the class-tested format and the additional teaching material available on the accompanying website. COMPUTERS,Data Science,General

Visualizing Streaming Data While tools for analyzing streaming and real-time data are gaining adoption, the ability to visualize these data types has yet to catch up. Dashboards are good at conveying daily or weekly data trends at a glance, though capturing snapshots when data is transforming from moment to moment is more difficult—but not impossible. With this practical guide, application designers, data scientists, and system administrators will explore ways to create visualizations that bring context and a sense of time to streaming text data. Author Anthony Aragues guides you through the concepts and tools you need to build visualizations for analyzing data as it arrives. Determine your company’s goals for visualizing streaming data Identify key data sources and learn how to stream them Learn practical methods for processing streaming data Build a client application for interacting with events, logs, and records Explore common components for visualizing streaming data Consider analysis concepts for developing your visualization Define the dashboard’s layout, flow direction, and component movement Improve visualization quality and productivity through collaboration Explore use cases including security, IoT devices, and application data COMPUTERS,Data Science,General

Deep Learning Cookbook Deep learning doesn’t have to be intimidating. Until recently, this machine-learning method required years of study, but with frameworks such as Keras and Tensorflow, software engineers without a background in machine learning can quickly enter the field. With the recipes in this cookbook, you’ll learn how to solve deep-learning problems for classifying and generating text, images, and music. Each chapter consists of several recipes needed to complete a single project, such as training a music recommending system. Author Douwe Osinga also provides a chapter with half a dozen techniques to help you if you’re stuck. Examples are written in Python with code available on GitHub as a set of Python notebooks. You’ll learn how to: Create applications that will serve real users Use word embeddings to calculate text similarity Build a movie recommender system based on Wikipedia links Learn how AIs see the world by visualizing their internal state Build a model to suggest emojis for pieces of text Reuse pretrained networks to build an inverse image search service Compare how GANs, autoencoders and LSTMs generate icons Detect music styles and index song collections COMPUTERS,Data Science,General

Applied Text Analysis with Python From news and speeches to informal chatter on social media, natural language is one of the richest and most underutilized sources of data. Not only does it come in a constant stream, always changing and adapting in context; it also contains information that is not conveyed by traditional data sources. The key to unlocking natural language is through the creative application of text analytics. This practical book presents a data scientist’s approach to building language-aware products with applied machine learning. You’ll learn robust, repeatable, and scalable techniques for text analysis with Python, including contextual and linguistic feature engineering, vectorization, classification, topic modeling, entity resolution, graph analysis, and visual steering. By the end of the book, you’ll be equipped with practical methods to solve any number of complex real-world problems. Preprocess and vectorize text into high-dimensional feature representations Perform document classification and topic modeling Steer the model selection process with visual diagnostics Extract key phrases, named entities, and graph structures to reason about data in text Build a dialog framework to enable chatbots and language-driven interaction Use Spark to scale processing power and neural networks to scale model complexity COMPUTERS,Data Science,General

Streaming Systems Streaming data is a big deal in big data these days. As more and more businesses seek to tame the massive unbounded data sets that pervade our world, streaming systems have finally reached a level of maturity sufficient for mainstream adoption. With this practical guide, data engineers, data scientists, and developers will learn how to work with streaming data in a conceptual and platform-agnostic way. Expanded from Tyler Akidau’s popular blog posts "Streaming 101" and "Streaming 102", this book takes you from an introductory level to a nuanced understanding of the what, where, when, and how of processing real-time data streams. You’ll also dive deep into watermarks and exactly-once processing with co-authors Slava Chernyak and Reuven Lax. You’ll explore: How streaming and batch data processing patterns compare The core principles and concepts behind robust out-of-order data processing How watermarks track progress and completeness in infinite datasets How exactly-once data processing techniques ensure correctness How the concepts of streams and tables form the foundations of both batch and streaming data processing The practical motivations behind a powerful persistent state mechanism, driven by a real-world example How time-varying relations provide a link between stream processing and the world of SQL and relational algebra COMPUTERS,Data Science,General

Learning Jupyter 5 Create and share livecode, equations, visualizations, and explanatory text, in both a single document and a web browser with Jupyter Key Features Learn how to use Jupyter 5.x features such as cell tagging and attractive table styles Leverage big data tools and datasets with different Python packages Explore multiple-user Jupyter Notebook servers Book Description The Jupyter Notebook allows you to create and share documents that contain live code, equations, visualizations, and explanatory text. The Jupyter Notebook system is extensively used in domains such as data cleaning and transformation, numerical simulation, statistical modeling, and machine learning. Learning Jupyter 5 will help you get to grips with interactive computing using real-world examples. The book starts with a detailed overview of the Jupyter Notebook system and its installation in different environments. Next, you will learn to integrate the Jupyter system with different programming languages such as R, Python, Java, JavaScript, and Julia, and explore various versions and packages that are compatible with the Notebook system. Moving ahead, you will master interactive widgets and namespaces and work with Jupyter in a multi-user mode. By the end of this book, you will have used Jupyter with a big dataset and be able to apply all the functionalities you've explored throughout the book. You will also have learned all about the Jupyter Notebook and be able to start performing data transformation, numerical simulation, and data visualization. What you will learn Install and run the Jupyter Notebook system on your machine Implement programming languages such as R, Python, Julia, and JavaScript with the Jupyter Notebook Use interactive widgets to manipulate and visualize data in real time Start sharing your Notebook with colleagues Invite your colleagues to work with you on the same Notebook Organize your Notebook using Jupyter namespaces Access big data in Jupyter for dealing with large datasets using Spark Who this book is for Learning Jupyter 5 is for developers, data scientists, machine learning users, and anyone working on data analysis or data science projects across different teams. Data science professionals will also find this book useful for performing technical and scientific computing collaboratively. COMPUTERS,Data Science,General

Data Science Algorithms in a Week Build a strong foundation of machine learning algorithms in 7 days Key Features Use Python and its wide array of machine learning libraries to build predictive models Learn the basics of the 7 most widely used machine learning algorithms within a week Know when and where to apply data science algorithms using this guide Book Description Machine learning applications are highly automated and self-modifying, and continue to improve over time with minimal human intervention, as they learn from the trained data. To address the complex nature of various real-world data problems, specialized machine learning algorithms have been developed. Through algorithmic and statistical analysis, these models can be leveraged to gain new knowledge from existing data as well. Data Science Algorithms in a Week addresses all problems related to accurate and efficient data classification and prediction. Over the course of seven days, you will be introduced to seven algorithms, along with exercises that will help you understand different aspects of machine learning. You will see how to pre-cluster your data to optimize and classify it for large datasets. This book also guides you in predicting data based on existing trends in your dataset. This book covers algorithms such as k-nearest neighbors, Naive Bayes, decision trees, random forest, k-means, regression, and time-series analysis. By the end of this book, you will understand how to choose machine learning algorithms for clustering, classification, and regression and know which is best suited for your problem What you will learn Understand how to identify a data science problem correctly Implement well-known machine learning algorithms efficiently using Python Classify your datasets using Naive Bayes, decision trees, and random forest with accuracy Devise an appropriate prediction solution using regression Work with time series data to identify relevant data events and trends Cluster your data using the k-means algorithm Who this book is for This book is for aspiring data science professionals who are familiar with Python and have a little background in statistics. You'll also find this book useful if you're currently working with data science algorithms in some capacity and want to expand your skill set COMPUTERS,Data Science,General

Splunk 7.x Quick Start Guide Learn how to architect, implement, and administer a complex Splunk Enterprise environment and extract valuable insights from business data. Key Features Understand the various components of Splunk and how they work together to provide a powerful Big Data analytics solution. Collect and index data from a wide variety of common machine data sources Design searches, reports, and dashboard visualizations to provide business data insights Book Description Splunk is a leading platform and solution for collecting, searching, and extracting value from ever increasing amounts of big data - and big data is eating the world! This book covers all the crucial Splunk topics and gives you the information and examples to get the immediate job done. You will find enough insights to support further research and use Splunk to suit any business environment or situation. Splunk 7.x Quick Start Guide gives you a thorough understanding of how Splunk works. You will learn about all the critical tasks for architecting, implementing, administering, and utilizing Splunk Enterprise to collect, store, retrieve, format, analyze, and visualize machine data. You will find step-by-step examples based on real-world experience and practical use cases that are applicable to all Splunk environments. There is a careful balance between adequate coverage of all the critical topics with short but relevant deep-dives into the configuration options and steps to carry out the day-to-day tasks that matter. By the end of the book, you will be a confident and proficient Splunk architect and administrator. What you will learn Design and implement a complex Splunk Enterprise solution Configure your Splunk environment to get machine data in and indexed Build searches to get and format data for analysis and visualization Build reports, dashboards, and alerts to deliver critical insights Create knowledge objects to enhance the value of your data Install Splunk apps to provide focused views into key technologies Monitor, troubleshoot, and manage your Splunk environment Who this book is for This book is intended for experienced IT personnel who are just getting started working with Splunk and want to quickly become proficient with its usage. Data analysts who need to leverage Splunk to extract critical business insights from application logs and other machine data sources will also benefit from this book. COMPUTERS,Data Science,General

Architecting Modern Data Platforms There’s a lot of information about big data technologies, but splicing these technologies into an end-to-end enterprise data platform is a daunting task not widely covered. With this practical book, you’ll learn how to build big data infrastructure both on-premises and in the cloud and successfully architect a modern data platform. Ideal for enterprise architects, IT managers, application architects, and data engineers, this book shows you how to overcome the many challenges that emerge during Hadoop projects. You’ll explore the vast landscape of tools available in the Hadoop and big data realm in a thorough technical primer before diving into: Infrastructure: Look at all component layers in a modern data platform, from the server to the data center, to establish a solid foundation for data in your enterprise Platform: Understand aspects of deployment, operation, security, high availability, and disaster recovery, along with everything you need to know to integrate your platform with the rest of your enterprise IT Taking Hadoop to the cloud: Learn the important architectural aspects of running a big data platform in the cloud while maintaining enterprise security and high availability COMPUTERS,Data Science,General

Apache Kafka Quick Start Guide Process large volumes of data in real-time while building high performance and robust data stream processing pipeline using the latest Apache Kafka 2.0 Key Features Solve practical large data and processing challenges with Kafka Tackle data processing challenges like late events, windowing, and watermarking Understand real-time streaming applications processing using Schema registry, Kafka connect, Kafka streams, and KSQL Book Description Apache Kafka is a great open source platform for handling your real-time data pipeline to ensure high-speed filtering and pattern matching on the ?y. In this book, you will learn how to use Apache Kafka for efficient processing of distributed applications and will get familiar with solving everyday problems in fast data and processing pipelines. This book focuses on programming rather than the configuration management of Kafka clusters or DevOps. It starts off with the installation and setting up the development environment, before quickly moving on to performing fundamental messaging operations such as validation and enrichment. Here you will learn about message composition with pure Kafka API and Kafka Streams. You will look into the transformation of messages in different formats, such asext, binary, XML, JSON, and AVRO. Next, you will learn how to expose the schemas contained in Kafka with the Schema Registry. You will then learn how to work with all relevant connectors with Kafka Connect. While working with Kafka Streams, you will perform various interesting operations on streams, such as windowing, joins, and aggregations. Finally, through KSQL, you will learn how to retrieve, insert, modify, and delete data streams, and how to manipulate watermarks and windows. What you will learn How to validate data with Kafka Add information to existing data ?ows Generate new information through message composition Perform data validation and versioning with the Schema Registry How to perform message Serialization and Deserialization How to perform message Serialization and Deserialization Process data streams with Kafka Streams Understand the duality between tables and streams with KSQL Who this book is for This book is for developers who want to quickly master the practical concepts behind Apache Kafka. The audience need not have come across Apache Kafka previously; however, a familiarity of Java or any JVM language will be helpful in understanding the code in this book. COMPUTERS,Data Science,General

Kibana 7 Quick Start Guide A quick start guide to visualize your Elasticsearch data Key Features Your hands-on guide to visualizing the Elasticsearch data as well as navigating the Elastic stack Work with different Kibana plugins and create effective machine learning jobs using Kibana Build effective dashboards and reports without any hassle Book Description The Elastic Stack is growing rapidly and, day by day, additional tools are being added to make it more effective. This book endeavors to explain all the important aspects of Kibana, which is essential for utilizing its full potential. This book covers the core concepts of Kibana, with chapters set out in a coherent manner so that readers can advance their learning in a step-by-step manner. The focus is on a practical approach, thereby enabling the reader to apply those examples in real time for a better understanding of the concepts and to provide them with the correct skills in relation to the tool. With its succinct explanations, it is quite easy for a reader to use this book as a reference guide for learning basic to advanced implementations of Kibana. The practical examples, such as the creation of Kibana dashboards from CSV data, application RDBMS data, system metrics data, log file data, APM agents, and search results, can provide readers with a number of different drop-off points from where they can fetch any type of data into Kibana for the purpose of analysis or dashboarding. What you will learn Explore how Logstash is configured to fetch CSV data Understand how to create index patterns in Kibana Become familiar with how to apply filters on data Discover how to create ML jobs Explore how to analyze APM data from APM agents Get to grips with how to save, share, inspect, and edit visualizations Understand how to find an anomaly in data Who this book is for Kibana 7 Quick Start Guide is for developers new to Kibana who want to learn the fundamentals of using the tool for visualization, as well as existing Elastic developers. COMPUTERS,Data Science,General

Advanced MySQL 8 Design cost-efficient database solutions, scale enterprise operations and reduce overhead business costs with MySQL Key Features Explore the new and advanced features of MySQL 8.0 Use advanced techniques to optimize MySQL performance Create MySQL-based applications for your enterprise with the help of practical examples Book Description Advanced MySQL 8 teaches you to enhance your existing database infrastructure and build various tools to improve your enterprise applications and overall website performance. The book starts with the new and exciting MySQL 8.0 features and how to utilize them for maximum efficiency. As you make your way through the chapters, you will learn to optimize MySQL performance using indexes and advanced data query techniques for large queries. You will also discover MySQL Server 8.0 settings and work with the MySQL data dictionary to boost the performance of your database. In the concluding chapters, you will cover MySQL 8.0 Group Replication, which will enable you to create elastic, highly available, and fault-tolerant replication topologies. You will also explore backup and recovery techniques for your databases and understand important tips and tricks to help your critical data reach its full potential. By the end of this book, you'll have learned about new MySQL 8.0 security features that allow a database administrator (DBA) to simplify user management and increase the security of their multi-user environments. What you will learn Explore new and exciting features of MySQL 8.0 Analyze and optimize large MySQL queries Understand MySQL Server 8.0 settings Master the deployment of Group Replication and use it in an InnoDB cluster Monitor large distributed databases Discover different types of backups and recovery methods for your databases Explore tips to help your critical data reach its full potential Who this book is for Advanced MySQL 8 is for database administrators, data architects, and database developers who want to dive deeper into building advanced database applications in the MySQL environment. COMPUTERS,Data Science,General

Hands-On Unsupervised Learning Using Python Many industry experts consider unsupervised learning the next frontier in artificial intelligence, one that may hold the key to general artificial intelligence. Since the majority of the world's data is unlabeled, conventional supervised learning cannot be applied. Unsupervised learning, on the other hand, can be applied to unlabeled datasets to discover meaningful patterns buried deep in the data, patterns that may be near impossible for humans to uncover. Author Ankur Patel shows you how to apply unsupervised learning using two simple, production-ready Python frameworks: Scikit-learn and TensorFlow using Keras. With code and hands-on examples, data scientists will identify difficult-to-find patterns in data and gain deeper business insight, detect anomalies, perform automatic feature engineering and selection, and generate synthetic datasets. All you need is programming and some machine learning experience to get started. Compare the strengths and weaknesses of the different machine learning approaches: supervised, unsupervised, and reinforcement learning Set up and manage machine learning projects end-to-end Build an anomaly detection system to catch credit card fraud Clusters users into distinct and homogeneous groups Perform semisupervised learning Develop movie recommender systems using restricted Boltzmann machines Generate synthetic images using generative adversarial networks COMPUTERS,Data Science,General

Data Analyst With this book, aspiring data analysts will discover what data analysts do all day, what skills they will need for the role, and what regulations they will be required to adhere to. Practising data analysts can explore useful data analysis tools, methods and techniques, brush up on best practices and look at how they can advance their career. COMPUTERS,Data Science,General

Mastering Hadoop 3 A comprehensive guide to mastering the most advanced Hadoop 3 concepts Key Features Get to grips with the newly introduced features and capabilities of Hadoop 3 Crunch and process data using MapReduce, YARN, and a host of tools within the Hadoop ecosystem Sharpen your Hadoop skills with real-world case studies and code Book Description Apache Hadoop is one of the most popular big data solutions for distributed storage and for processing large chunks of data. With Hadoop 3, Apache promises to provide a high-performance, more fault-tolerant, and highly efficient big data processing platform, with a focus on improved scalability and increased efficiency. With this guide, you'll understand advanced concepts of the Hadoop ecosystem tool. You'll learn how Hadoop works internally, study advanced concepts of different ecosystem tools, discover solutions to real-world use cases, and understand how to secure your cluster. It will then walk you through HDFS, YARN, MapReduce, and Hadoop 3 concepts. You'll be able to address common challenges like using Kafka efficiently, designing low latency, reliable message delivery Kafka systems, and handling high data volumes. As you advance, you'll discover how to address major challenges when building an enterprise-grade messaging system, and how to use different stream processing systems along with Kafka to fulfil your enterprise goals. By the end of this book, you'll have a complete understanding of how components in the Hadoop ecosystem are effectively integrated to implement a fast and reliable data pipeline, and you'll be equipped to tackle a range of real-world problems in data pipelines. What you will learn Gain an in-depth understanding of distributed computing using Hadoop 3 Develop enterprise-grade applications using Apache Spark, Flink, and more Build scalable and high-performance Hadoop data pipelines with security, monitoring, and data governance Explore batch data processing patterns and how to model data in Hadoop Master best practices for enterprises using, or planning to use, Hadoop 3 as a data platform Understand security aspects of Hadoop, including authorization and authentication Who this book is for If you want to become a big data professional by mastering the advanced concepts of Hadoop, this book is for you. You'll also find this book useful if you're a Hadoop professional looking to strengthen your knowledge of the Hadoop ecosystem. Fundamental knowledge of the Java programming language and basics of Hadoop is necessary to get started with this book. COMPUTERS,Data Science,General

Hands-On Blockchain Development in 7 Days Build an Ethereum gaming application from scratch in a span of seven days, by mastering smart contracts in Solidity Key Features Create a simple, functional decentralized application, on the Ethereum network Learn fundamental blockchain programming concepts to become a blockchain developer Understand the development life cycle of a blockchain application Book Description Blockchain is a revolutionary technology that is currently been used in a variety of industrial applications, such as finance, healthcare, data analytics, and much more. This book will teach you the key blockchain principles and methodologies that are required to build decentralized applications in just 7 days. This book will teach you to build an online gaming application using Ethereum. Each section will introduce fundamental blockchain programming concepts as they relate to creating an online game, followed by practical exercises that readers can implement as homework assignments. With this book, you will learn core blockchain application development skills, create smart contracts, and build user interfaces. You will not only learn how to interact with the Ethereum network, but also how to deploy your application to the Internet. This book supplies seven self-contained lessons taught in a practical, hands-on way. By the end of the book, you will be amazed at how much you have learned about the blockchain application development on the Ethereum network, in just one week! What you will learn Work with blockchain networks to create interactive applications Learn how to create and use variables in smart contracts Use automated tests to eliminate mistakes and errors in the code Interact with the Ethereum network from a user interface Build a user interface for smart contracts using React Send and receive funds in smart contracts using wallets Deploy blockchain applications on AWS Who this book is for This book is for software engineers and IT professionals, who are eager to learn blockchain application development skills and want to master how blockchain applications are developed. This book is perfect for those with limited programming experience. COMPUTERS,Data Science,General

Stream Processing with Apache Flink Get started with Apache Flink, the open source framework that powers some of the world’s largest stream processing applications. With this practical book, you’ll explore the fundamental concepts of parallel stream processing and discover how this technology differs from traditional batch data processing. Longtime Apache Flink committers Fabian Hueske and Vasia Kalavri show you how to implement scalable streaming applications with Flink’s DataStream API and continuously run and maintain these applications in operational environments. Stream processing is ideal for many use cases, including low-latency ETL, streaming analytics, and real-time dashboards as well as fraud detection, anomaly detection, and alerting. You can process continuous data of any kind, including user interactions, financial transactions, and IoT data, as soon as you generate them. Learn concepts and challenges of distributed stateful stream processing Explore Flink’s system architecture, including its event-time processing mode and fault-tolerance model Understand the fundamentals and building blocks of the DataStream API, including its time-based and statefuloperators Read data from and write data to external systems with exactly-once consistency Deploy and configure Flink clusters Operate continuously running streaming applications COMPUTERS,Data Science,General

Python Data Mining Quick Start Guide Explore the different data mining techniques using the libraries and packages offered by Python Key Features Grasp the basics of data loading, cleaning, analysis, and visualization Use the popular Python libraries such as NumPy, pandas, matplotlib, and scikit-learn for data mining Your one-stop guide to build efficient data mining pipelines without going into too much theory Book Description Data mining is a necessary and predictable response to the dawn of the information age. It is typically defined as the pattern and/ or trend discovery phase in the data mining pipeline, and Python is a popular tool for performing these tasks as it offers a wide variety of tools for data mining. This book will serve as a quick introduction to the concept of data mining and putting it to practical use with the help of popular Python packages and libraries. You will get a hands-on demonstration of working with different real-world datasets and extracting useful insights from them using popular Python libraries such as NumPy, pandas, scikit-learn, and matplotlib. You will then learn the different stages of data mining such as data loading, cleaning, analysis, and visualization. You will also get a full conceptual description of popular data transformation, clustering, and classification techniques. By the end of this book, you will be able to build an efficient data mining pipeline using Python without any hassle. What you will learn Explore the methods for summarizing datasets and visualizing/plotting data Collect and format data for analytical work Assign data points into groups and visualize clustering patterns Learn how to predict continuous and categorical outputs for data Clean, filter noise from, and reduce the dimensions of data Serialize a data processing model using scikit-learn's pipeline feature Deploy the data processing model using Python's pickle module Who this book is for Python developers interested in getting started with data mining will love this book. Budding data scientists and data analysts looking to quickly get to grips with practical data mining with Python will also find this book to be useful. Knowledge of Python programming is all you need to get started. COMPUTERS,Data Science,General

Learn T-SQL Querying Troubleshoot query performance issues, identify anti-patterns in code, and write efficient T-SQL queries Key Features Discover T-SQL functionalities and services that help you interact with relational databases Understand the roles, tasks and responsibilities of a T-SQL developer Explore solutions for carrying out database querying tasks, database administration, and troubleshooting Book Description Transact-SQL (T-SQL) is Microsoft's proprietary extension to the SQL language that is used with Microsoft SQL Server and Azure SQL Database. This book will be a useful guide to learning the art of writing efficient T-SQL code in modern SQL Server versions, as well as the Azure SQL Database. The book will get you started with query processing fundamentals to help you write powerful, performant T-SQL queries. You will then focus on query execution plans and learn how to leverage them for troubleshooting. In the later chapters, you will learn how to identify various T-SQL patterns and anti-patterns. This will help you analyze execution plans to gain insights into current performance, and determine whether or not a query is scalable. You will also learn to build diagnostic queries using dynamic management views (DMVs) and dynamic management functions (DMFs) to address various challenges in T-SQL execution. Next, you will study how to leverage the built-in tools of SQL Server to shorten the time taken to address query performance and scalability issues. In the concluding chapters, the book will guide you through implementing various features, such as Extended Events, Query Store, and Query Tuning Assistant using hands-on examples. By the end of this book, you will have the skills to determine query performance bottlenecks, avoid pitfalls, and discover the anti-patterns in use. What you will learn Use Query Store to understand and easily change query performance Recognize and eliminate bottlenecks that lead to slow performance Deploy quick fixes and long-term solutions to improve query performance Implement best practices to minimize performance risk using T-SQL Achieve optimal performance by ensuring careful query and index design Use the latest performance optimization features in SQL Server 2017 and SQL Server 2019 Protect query performance during upgrades to newer versions of SQL Server Who this book is for This book is for database administrators, database developers, data analysts, data scientists, and T-SQL practitioners who want to get started with writing T-SQL code and troubleshooting query performance issues, through the help of practical examples. Previous knowledge of T-SQL querying is not required to get started on this book. COMPUTERS,Data Science,General

Learning Elastic Stack 7.0 A beginner's guide to storing, managing, and analyzing data with the updated features of Elastic 7.0 Key Features Gain access to new features and updates introduced in Elastic Stack 7.0 Grasp the fundamentals of Elastic Stack including Elasticsearch, Logstash, and Kibana Explore useful tips for using Elastic Cloud and deploying Elastic Stack in production environments Book Description The Elastic Stack is a powerful combination of tools for techniques such as distributed search, analytics, logging, and visualization of data. Elastic Stack 7.0 encompasses new features and capabilities that will enable you to find unique insights into analytics using these techniques. This book will give you a fundamental understanding of what the stack is all about, and help you use it efficiently to build powerful real-time data processing applications. The first few sections of the book will help you understand how to set up the stack by installing tools, and exploring their basic configurations. You'll then get up to speed with using Elasticsearch for distributed searching and analytics, Logstash for logging, and Kibana for data visualization. As you work through the book, you will discover the technique of creating custom plugins using Kibana and Beats. This is followed by coverage of the Elastic X-Pack, a useful extension for effective security and monitoring. You'll also find helpful tips on how to use Elastic Cloud and deploy Elastic Stack in production environments. By the end of this book, you'll be well versed with the fundamental Elastic Stack functionalities and the role of each component in the stack to solve different data processing problems. What you will learn Install and configure an Elasticsearch architecture Solve the full-text search problem with Elasticsearch Discover powerful analytics capabilities through aggregations using Elasticsearch Build a data pipeline to transfer data from a variety of sources into Elasticsearch for analysis Create interactive dashboards for effective storytelling with your data using Kibana Learn how to secure, monitor and use Elastic Stack's alerting and reporting capabilities Take applications to an on-premise or cloud-based production environment with Elastic Stack Who this book is for This book is for entry-level data professionals, software engineers, e-commerce developers, and full-stack developers who want to learn about Elastic Stack and how the real-time processing and search engine works for business analytics and enterprise search applications. Previous experience with Elastic Stack is not required, however knowledge of data warehousing and database concepts will be helpful. COMPUTERS,Data Science,General

Stream Processing with Apache Spark Before you can build analytics tools to gain quick insights, you first need to know how to process data in real time. With this practical guide, developers familiar with Apache Spark will learn how to put this in-memory framework to use for streaming data. You’ll discover how Spark enables you to write streaming jobs in almost the same way you write batch jobs. Authors Gerard Maas and François Garillot help you explore the theoretical underpinnings of Apache Spark. This comprehensive guide features two sections that compare and contrast the streaming APIs Spark now supports: the original Spark Streaming library and the newer Structured Streaming API. Learn fundamental stream processing concepts and examine different streaming architectures Explore Structured Streaming through practical examples; learn different aspects of stream processing in detail Create and operate streaming jobs and applications with Spark Streaming; integrate Spark Streaming with other Spark APIs Learn advanced Spark Streaming techniques, including approximation algorithms and machine learning algorithms Compare Apache Spark to other stream processing projects, including Apache Storm, Apache Flink, and Apache Kafka Streams COMPUTERS,Data Science,General

Business Process Management Business process management is usually treated from two different perspectives: business administration and computer science. While business administration professionals tend to consider information technology as a subordinate aspect in business process management for experts to handle, by contrast computer science professionals often consider business goals and organizational regulations as terms that do not deserve much thought but require the appropriate level of abstraction. Matthias Weske argues that all communities involved need to have a common understanding of the different aspects of business process management. To this end, he details the complete business process lifecycle from the modeling phase to process enactment and improvement, taking into account all different stakeholders involved. After starting with a presentation of general foundations and abstraction models, he explains concepts like process orchestrations and choreographies, as well as process properties and data dependencies. Finally, he presents both traditional and advanced business process management architectures, covering, for example, workflow management systems, service-oriented architectures, and data-driven approaches. In addition, he shows how standards like WfMC, SOAP, WSDL, and BPEL fit into the picture. This textbook is ideally suited for classes on business process management, information systems architecture, and workflow management. This 3rd edition contains a new chapter on business decision modelling, covering the Decision Model and Notation (DMN) standard; the chapter on process choreographies has been streamlined, and numerous clarifications have been fetched throughout the book. The accompanying website www.bpm-book.com contains further information and additional teaching material. COMPUTERS,Data Science,General

Hands-On Data Analysis with Pandas Get to grips with pandas—a versatile and high-performance Python library for data manipulation, analysis, and discovery Key Features Perform efficient data analysis and manipulation tasks using pandas Apply pandas to different real-world domains using step-by-step demonstrations Get accustomed to using pandas as an effective data exploration tool Book Description Data analysis has become a necessary skill in a variety of positions where knowing how to work with data and extract insights can generate significant value. Hands-On Data Analysis with Pandas will show you how to analyze your data, get started with machine learning, and work effectively with Python libraries often used for data science, such as pandas, NumPy, matplotlib, seaborn, and scikit-learn. Using real-world datasets, you will learn how to use the powerful pandas library to perform data wrangling to reshape, clean, and aggregate your data. Then, you will learn how to conduct exploratory data analysis by calculating summary statistics and visualizing the data to find patterns. In the concluding chapters, you will explore some applications of anomaly detection, regression, clustering, and classification, using scikit-learn, to make predictions based on past data. By the end of this book, you will be equipped with the skills you need to use pandas to ensure the veracity of your data, visualize it for effective decision-making, and reliably reproduce analyses across multiple datasets. What you will learn Understand how data analysts and scientists gather and analyze data Perform data analysis and data wrangling in Python Combine, group, and aggregate data from multiple sources Create data visualizations with pandas, matplotlib, and seaborn Apply machine learning (ML) algorithms to identify patterns and make predictions Use Python data science libraries to analyze real-world datasets Use pandas to solve common data representation and analysis problems Build Python scripts, modules, and packages for reusable analysis code Who this book is for This book is for data analysts, data science beginners, and Python developers who want to explore each stage of data analysis and scientific computing using a wide range of datasets. You will also find this book useful if you are a data scientist who is looking to implement pandas in machine learning. Working knowledge of Python programming language will be beneficial. COMPUTERS,Data Science,General

Hands-On Machine Learning with Scikit-Learn, Keras, and TensorFlow Through a series of recent breakthroughs, deep learning has boosted the entire field of machine learning. Now, even programmers who know close to nothing about this technology can use simple, efficient tools to implement programs capable of learning from data. This practical book shows you how. By using concrete examples, minimal theory, and two production-ready Python frameworks—Scikit-Learn and TensorFlow—author Aurélien Géron helps you gain an intuitive understanding of the concepts and tools for building intelligent systems. You’ll learn a range of techniques, starting with simple linear regression and progressing to deep neural networks. With exercises in each chapter to help you apply what you’ve learned, all you need is programming experience to get started. Explore the machine learning landscape, particularly neural nets Use Scikit-Learn to track an example machine-learning project end-to-end Explore several training models, including support vector machines, decision trees, random forests, and ensemble methods Use the TensorFlow library to build and train neural nets Dive into neural net architectures, including convolutional nets, recurrent nets, and deep reinforcement learning Learn techniques for training and scaling deep neural nets COMPUTERS,Data Science,General

Mastering Spark with R If you’re like most R users, you have deep knowledge and love for statistics. But as your organization continues to collect huge amounts of data, adding tools such as Apache Spark makes a lot of sense. With this practical book, data scientists and professionals working with large-scale data applications will learn how to use Spark from R to tackle big data and big compute problems. Authors Javier Luraschi, Kevin Kuo, and Edgar Ruiz show you how to use R with Spark to solve different data analysis problems. This book covers relevant data science topics, cluster computing, and issues that should interest even the most advanced users. Analyze, explore, transform, and visualize data in Apache Spark with R Create statistical models to extract information and predict outcomes; automate the process in production-ready workflows Perform analysis and modeling across many machines using distributed computing techniques Use large-scale data from multiple sources and different formats with ease from within Spark Learn about alternative modeling frameworks for graph processing, geospatial analysis, and genomics at scale Dive into advanced topics including custom transformations, real-time data processing, and creating custom Spark extensions COMPUTERS,Data Science,General

Learn Algorithmic Trading Understand the fundamentals of algorithmic trading to apply algorithms to real market data and analyze the results of real-world trading strategies Key Features Understand the power of algorithmic trading in financial markets with real-world examples Get up and running with the algorithms used to carry out algorithmic trading Learn to build your own algorithmic trading robots which require no human intervention Book Description It's now harder than ever to get a significant edge over competitors in terms of speed and efficiency when it comes to algorithmic trading. Relying on sophisticated trading signals, predictive models and strategies can make all the difference. This book will guide you through these aspects, giving you insights into how modern electronic trading markets and participants operate. You'll start with an introduction to algorithmic trading, along with setting up the environment required to perform the tasks in the book. You'll explore the key components of an algorithmic trading business and aspects you'll need to take into account before starting an automated trading project. Next, you'll focus on designing, building and operating the components required for developing a practical and profitable algorithmic trading business. Later, you'll learn how quantitative trading signals and strategies are developed, and also implement and analyze sophisticated trading strategies such as volatility strategies, economic release strategies, and statistical arbitrage. Finally, you'll create a trading bot from scratch using the algorithms built in the previous sections. By the end of this book, you'll be well-versed with electronic trading markets and have learned to implement, evaluate and safely operate algorithmic trading strategies in live markets. What you will learn Understand the components of modern algorithmic trading systems and strategies Apply machine learning in algorithmic trading signals and strategies using Python Build, visualize and analyze trading strategies based on mean reversion, trend, economic releases and more Quantify and build a risk management system for Python trading strategies Build a backtester to run simulated trading strategies for improving the performance of your trading bot Deploy and incorporate trading strategies in the live market to maintain and improve profitability Who this book is for This book is for software engineers, financial traders, data analysts, and entrepreneurs. Anyone who wants to get started with algorithmic trading and understand how it works; and learn the components of a trading system, protocols and algorithms required for black box and gray box trading, and techniques for building a completely automated and profitable trading business will also find this book useful. COMPUTERS,Data Science,General

MongoDB Manage your data with a system designed to support modern application development. Updated for MongoDB 4.2, the third edition of this authoritative and accessible guide shows you the advantages of using document-oriented databases. You’ll learn how this secure, high-performance system enables flexible data models, high availability, and horizontal scalability. Authors Shannon Bradshaw, Eoin Brazil, and Kristina Chodorow provide guidance for database developers, advanced configuration for system administrators, and use cases for a variety of projects. NoSQL newcomers and experienced MongoDB users will find updates on querying, indexing, aggregation, transactions, replica sets, ops management, sharding and data administration, durability, monitoring, and security. In six parts, this book shows you how to: Work with MongoDB, perform write operations, find documents, and create complex queries Index collections, aggregate data, and use transactions for your application Configure a local replica set and learn how replication interacts with your application Set up cluster components and choose a shard key for a variety of applications Explore aspects of application administration and configure authentication and authorization Use stats when monitoring, back up and restore deployments, and use system settings when deploying MongoDB COMPUTERS,Data Science,General

Practical Oracle Cloud Infrastructure Use this fast-paced and comprehensive guide to build cloud-based solutions on Oracle Cloud Infrastructure. You will understand cloud infrastructure, and learn how to launch new applications and move existing applications to Oracle Cloud. Emerging trends in software architecture are covered such as autonomous platforms, infrastructure as code, containerized applications, cloud-based container orchestration with managed Kubernetes, and running serverless workloads using open-source tools. Practical examples are provided. This book teaches you how to self-provision the cloud resources you require to run and scale your custom cloud-based applications using a convenient web console and programmable APIs, and you will learn how to manage your infrastructure as code with Terraform. You will be able to plan, design, implement, deploy, run, and monitor your production-grade and fault-tolerant cloud software solutions in Oracle's data centers across the world, paying only for the resources you actually use. Oracle Cloud Infrastructure is part of Oracle's new generation cloud that delivers a complete and well-integrated set of Infrastructure as a Service (IaaS) capabilities (compute, storage, networking), edge services (DNS, web application firewall), and Platform as a Service (PaaS) capabilities (such as Oracle Autonomous Database which supports both transactional and analytical workloads, the certified and fully managed Oracle Kubernetes Engine, and a serverless platform based on an open-source Fn Project). What You Will Learn Build software solutions on Oracle Cloud Automate cloud infrastructure with CLI and Terraform Follow best practices for architecting on Oracle Cloud Employ Oracle Autonomous Database to obtain valuable data insights Run containerized applications on Oracle’s Container Engine for Kubernetes Understand the emerging Cloud Native ecosystem Who This Book Is For Cloud architects, developers, DevOps engineers, and technology students and others who want to learn how to build cloud-based systems on Oracle Cloud Infrastructure (OCI) leveraging a broad range of OCI Infrastructure as a Service (IAAS) capabilities, Oracle Autonomous Database, and Oracle's Container Engine for Kubernetes. Readers should have a working knowledge of Linux, exposure to programming, and a basic understanding of networking concepts. All exercises in the book can be done at no cost with a 30-day Oracle Cloud trial. COMPUTERS,Data Science,General

Pandas 1.x Cookbook Use the power of pandas to solve most complex scientific computing problems with ease. Revised for pandas 1.x. Key Features This is the first book on pandas 1.x Practical, easy to implement recipes for quick solutions to common problems in data using pandas Master the fundamentals of pandas to quickly begin exploring any dataset Book Description The pandas library is massive, and it's common for frequent users to be unaware of many of its more impressive features. The official pandas documentation, while thorough, does not contain many useful examples of how to piece together multiple commands as one would do during an actual analysis. This book guides you, as if you were looking over the shoulder of an expert, through situations that you are highly likely to encounter. This new updated and revised edition provides you with unique, idiomatic, and fun recipes for both fundamental and advanced data manipulation tasks with pandas. Some recipes focus on achieving a deeper understanding of basic principles, or comparing and contrasting two similar operations. Other recipes will dive deep into a particular dataset, uncovering new and unexpected insights along the way. Many advanced recipes combine several different features across the pandas library to generate results. What you will learn Master data exploration in pandas through dozens of practice problems Group, aggregate, transform, reshape, and filter data Merge data from different sources through pandas SQL-like operations Create visualizations via pandas hooks to matplotlib and seaborn Use pandas, time series functionality to perform powerful analyses Import, clean, and prepare real-world datasets for machine learning Create workflows for processing big data that doesn't fit in memory Who this book is for This book is for Python developers, data scientists, engineers, and analysts. Pandas is the ideal tool for manipulating structured data with Python and this book provides ample instruction and examples. Not only does it cover the basics required to be proficient, but it goes into the details of idiomatic pandas. COMPUTERS,Data Science,General

Process Mining in Action This book describes process mining use cases and business impact along the value chain, from corporate to local applications, representing the state of the art in domain know-how. Providing a set of industrial case studies and best practices, it complements academic publications on the topic. Further the book reveals the challenges and failures in order to offer readers practical insights and guidance on how to avoid the pitfalls and ensure successful operational deployment. The book is divided into three parts: Part I provides an introduction to the topic from fundamental principles to key success factors, and an overview of operational use cases. As a holistic description of process mining in a business environment, this part is particularly useful for readers not yet familiar with the topic. Part II presents detailed use cases written by contributors from a variety of functions and industries. Lastly, Part III provides a brief overview of the future of process mining, both from academic and operational perspectives. Based on a solid academic foundation, process mining has received increasing interest from operational businesses, with many companies already reaping the benefits. As the first book to present an overview of successful industrial applications, it is of particular interest to professionals who want to learn more about the possibilities and opportunities this new technology offers. It is also a valuable resource for researchers looking for empirical results when considering requirements for enhancements and further developments. COMPUTERS,Data Science,General

Foundation Mathematics for Computer Science In this second edition of Foundation Mathematics for Computer Science, John Vince has reviewed and edited the original book and written new chapters on combinatorics, probability, modular arithmetic and complex numbers. These subjects complement the existing chapters on number systems, algebra, logic, trigonometry, coordinate systems, determinants, vectors, matrices, geometric matrix transforms, differential and integral calculus. During this journey, the author touches upon more esoteric topics such as quaternions, octonions, Grassmann algebra, Barrycentric coordinates, transfinite sets and prime numbers. John Vince describes a range of mathematical topics to provide a solid foundation for an undergraduate course in computer science, starting with a review of number systems and their relevance to digital computers, and finishing with differential and integral calculus. Readers will find that the author’s visual approach will greatly improve their understanding as to why certain mathematical structures exist, together with how they are used in real-world applications. This second edition includes new, full-colour illustrations to clarify the mathematical descriptions, and in some cases, equations are also coloured to reveal vital algebraic patterns. The numerous worked examples will help consolidate the understanding of abstract mathematical concepts. Whether you intend to pursue a career in programming, scientific visualisation, artificial intelligence, systems design, or real-time computing, you should find the author’s literary style refreshingly lucid and engaging, and prepare you for more advanced texts. COMPUTERS,Data Science,General

DAX Cookbook Solve real-world business problems by learning how to create common industry key performance indicators and other calculations using DAX within Microsoft products such as Power BI, SQL Server, and Excel. Key Features Learn to write sophisticated DAX queries to solve business intelligence and data analytics challenges Handle performance issues and optimization within the data model, DAX calculations and more Solve business issues with Microsoft Excel, Power BI, and SQL Server using DAX queries Book Description DAX provides an extra edge by extracting key information from the data that is already present in your model. Filled with examples of practical, real-world calculations geared toward business metrics and key performance indicators, this cookbook features solutions that you can apply for your own business analysis needs. You'll learn to write various DAX expressions and functions to understand how DAX queries work. The book also covers sections on dates, time, and duration to help you deal with working days, time zones, and shifts. You'll then discover how to manipulate text and numbers to create dynamic titles and ranks, and deal with measure totals. Later, you'll explore common business metrics for finance, customers, employees, and projects. The book will also show you how to implement common industry metrics such as days of supply, mean time between failure, order cycle time and overall equipment effectiveness. In the concluding chapters, you'll learn to apply statistical formulas for covariance, kurtosis, and skewness. Finally, you'll explore advanced DAX patterns for interpolation, inverse aggregators, inverse slicers, and even forecasting with a deseasonalized correlation coefficient. By the end of this book, you'll have the skills you need to use DAX's functionality and flexibility in business intelligence and data analytics. What you will learn Understand how to create common calculations for dates, time, and duration Create key performance indicators (KPIs) and other business calculations Develop general DAX calculations that deal with text and numbers Discover new ideas and time-saving techniques for better calculations and models Perform advanced DAX calculations for solving statistical measures and other mathematical formulas Handle errors in DAX and learn how to debug DAX calculations Understand how to optimize your data models Who this book is for Business users, BI developers, data analysts, and SQL users who are looking for solutions to the challenges faced while solving analytical operations using DAX techniques and patterns will find this book useful. Basic knowledge of the DAX language and Microsoft services is mandatory. COMPUTERS,Data Science,General

Practical Statistics for Data Scientists Statistical methods are a key part of data science, yet few data scientists have formal statistical training. Courses and books on basic statistics rarely cover the topic from a data science perspective. The second edition of this popular guide adds comprehensive examples in Python, provides practical guidance on applying statistical methods to data science, tells you how to avoid their misuse, and gives you advice on what’s important and what’s not. Many data science resources incorporate statistical methods but lack a deeper statistical perspective. If you’re familiar with the R or Python programming languages and have some exposure to statistics, this quick reference bridges the gap in an accessible, readable format. With this book, you’ll learn: Why exploratory data analysis is a key preliminary step in data science How random sampling can reduce bias and yield a higher-quality dataset, even with big data How the principles of experimental design yield definitive answers to questions How to use regression to estimate outcomes and detect anomalies Key classification techniques for predicting which categories a record belongs to Statistical machine learning methods that "learn" from data Unsupervised learning methods for extracting meaning from unlabeled data COMPUTERS,Data Science,General

Building an Anonymization Pipeline How can you use data in a way that protects individual privacy but still provides useful and meaningful analytics? With this practical book, data architects and engineers will learn how to establish and integrate secure, repeatable anonymization processes into their data flows and analytics in a sustainable manner. Luk Arbuckle and Khaled El Emam from Privacy Analytics explore end-to-end solutions for anonymizing device and IoT data, based on collection models and use cases that address real business needs. These examples come from some of the most demanding data environments, such as healthcare, using approaches that have withstood the test of time. Create anonymization solutions diverse enough to cover a spectrum of use cases Match your solutions to the data you use, the people you share it with, and your analysis goals Build anonymization pipelines around various data collection models to cover different business needs Generate an anonymized version of original data or use an analytics platform to generate anonymized outputs Examine the ethical issues around the use of anonymized data COMPUTERS,Data Science,General

Managing Data Quality This book explains data quality management in practical terms, focusing on three key areas - the nature of data in enterprises, the purpose and scope of data quality management, and implementing a data quality management system, in line with ISO 8000-61. COMPUTERS,Data Science,General

Modern Information Technology and IT Education This book constitutes the refereed proceedings of the 13th International Conference on Modern Information Technology and IT Education, held in Moscow, Russia, in November-December 2018. The 30 full papers and 1 short papers were carefully reviewed and selected from 164 submissions. The papers are organized according to the following topics: IT-education: methodology, methodological support; e-learning and IT in education; educational resources and best practices of IT-education; research and development in the field of new IT and their applications; scientific software in education and science; school education in computer science and ICT; economic informatics. COMPUTERS,Data Science,General

Group Decision and Negotiation This book constitutes the refereed proceedings of the 20th International Conference on Group Decision and Negotiation, GDN 2020, which was planned to be held in Toronto, ON, Canada, during June 7–11, 2020. The conference was cancelled due to the Coronavirus pandemic. Nevertheless, it was decided to publish the proceedings, because the review process had already been completed at the time the cancellation was decided. The field of Group Decision and Negotiation focuses on decision processes with at least two participants and a common goal but conflicting individual goals. Research areas of Group Decision and Negotiation include electronic negotiations, experiments, the role of emotions in group decision and negotiations, preference elicitation and decision support for group decisions and negotiations, and conflict resolution principles. The 14 full papers presented in this volume were carefully reviewed and selected from 75 submissions. They were organized in topical sections named: Conflict Resolution, Preference Modeling for Group Decision and Negotiation, Intelligent Group Decision Making and Consensus Process, Collaborative Decision Making Processes. COMPUTERS,Data Science,General

Decision Support Systems X This book constitutes the proceedings of the 6th International Conference on Decision Support Systems Technologies, ICDSST 2020, organised in Zaragoza, Spain, in May 2020. The conference was held online only due to the Corona pandemic. The EWG-DSS series of International Conference on Decision Support System Technology (ICDSST) is planned to consolidate the tradition of annual events organized by the EWG-DSS in offering a platform for European and international DSS communities, comprising the academic and industrial sectors, to present state-of-the-art DSS research and developments, to discuss current challenges that surround decision-making processes, to exchange ideas about realistic and innovative solutions, and to co-develop potential business opportunities. The main topic of this year’s conference was “Cognitive Decision Support Systems and Technologiesâ€. The 13 papers presented in this volume were carefully reviewed and selected from 51 submissions. They were organized in topical sections named: methodological contributions; case studies and applications; and overview (on the current state and future trends of DSS, BI, and data analytics research). COMPUTERS,Data Science,General

Practical Synthetic Data Generation Building and testing machine learning models requires access to large and diverse data. But where can you find usable datasets without running into privacy issues? This practical book introduces techniques for generating synthetic data—fake data generated from real data—so you can perform secondary analysis to do research, understand customer behaviors, develop new products, or generate new revenue. Data scientists will learn how synthetic data generation provides a way to make such data broadly available for secondary purposes while addressing many privacy concerns. Analysts will learn the principles and steps for generating synthetic data from real datasets. And business leaders will see how synthetic data can help accelerate time to a product or solution. This book describes: Steps for generating synthetic data using multivariate normal distributions Methods for distribution fitting covering different goodness-of-fit metrics How to replicate the simple structure of original data An approach for modeling data structure to consider complex relationships Multiple approaches and metrics you can use to assess data utility How analysis performed on real data can be replicated with synthetic data Privacy implications of synthetic data and methods to assess identity disclosure COMPUTERS,Data Science,General

Sets, Logic and Maths for Computing This easy-to-follow textbook introduces the mathematical language, knowledge and problem-solving skills that undergraduate students need to enter the world of computer and information sciences. The language is in part qualitative, with concepts such as set, relation, function and recursion/induction; but it is also partly quantitative, with principles of counting and finite probability. Entwined with both are the fundamental notions of logic and their use for representation and proof. In ten chapters on these topics, the book guides the student through essential concepts and techniques. The extensively revised second edition provides further clarification of matters that typically give rise to difficulty in the classroom and restructures the chapters on logic to emphasize the role of consequence relations and higher-level rules, as well as including more exercises and solutions. Topics and features: teaches finite mathematics as a language for thinking, as much as knowledge and skills to be acquired; uses an intuitive approach with a focus on examples for all general concepts; brings out the interplay between the qualitative and the quantitative in all areas covered, particularly in the treatment of recursion and induction; balances carefully the abstract and concrete, principles and proofs, specific facts and general perspectives; includes highlight boxes that raise common queries and clear away confusions; provides numerous exercises, with selected solutions, to test and deepen the reader’s understanding. This clearly-written text/reference is a must-read for first-year undergraduate students of computing. Assuming only minimal mathematical background, it is ideal for both the classroom and independent study. COMPUTERS,Data Science,General

Computer Information Systems and Industrial Management This book constitutes the proceedings of the 19th International Conference on Computer Information Systems and Industrial Management Applications, CISIM 2020, held in Bialystok, Poland, in October 2020. Due to the COVID-19 pandemic the conference has been postponed to October 2020. The 40 full papers presented together with 5 abstracts of keynotes were carefully reviewed and selected from 62 submissions. The main topics covered by the chapters in this book are biometrics, security systems, multimedia, classification and clustering, industrial management. Besides these, the reader will find interesting papers on computer information systems as applied to wireless networks, computer graphics, and intelligent systems. The papers are organized in the following topical sections: biometrics and pattern recognition applications; computer information systems and security; industrial management and other applications; machine learning and high performance computing; modelling and optimization. COMPUTERS,Data Science,General

Just Enough R! Just Enough R! An Interactive Approach to Machine Learning and Analytics presents just enough of the R language, machine learning algorithms, statistical methodology, and analytics for the reader to learn how to find interesting structure in data. The approach might be called "seeing then doing" as it first gives step-by-step explanations using simple, understandable examples of how the various machine learning algorithms work independent of any programming language. This is followed by detailed scripts written in R that apply the algorithms to solve nontrivial problems with real data. The script code is provided, allowing the reader to execute the scripts as they study the explanations given in the text. Features Gets you quickly using R as a problem-solving tool Uses RStudio’s integrated development environment Shows how to interface R with SQLite Includes examples using R’s Rattle graphical user interface Requires no prior knowledge of R, machine learning, or computer programming Offers over 50 scripts written in R, including several problem-solving templates that, with slight modification, can be used again and again Covers the most popular machine learning techniques, including ensemble-based methods and logistic regression Includes end-of-chapter exercises, many of which can be solved by modifying existing scripts Includes datasets from several areas, including business, health and medicine, and science About the Author Richard J. Roiger is a professor emeritus at Minnesota State University, Mankato, where he taught and performed research in the Computer and Information Science Department for over 30 years. COMPUTERS,Data Science,General

Integrated Science in Digital Age 2020 This book presents the proceedings of the 2020 International Conference on Integrated Science in Digital Age, which was jointly supported by the Institute of Certified Specialists (Russia) and Springer, and was held on May 1–3, 2020. The conference provided an international forum for researchers and practitioners to present and discuss the latest innovations, trends, results, experiences and concerns in the various areas of integrated science in the digital age. The main goal of the conference was to efficiently disseminate original findings in the natural and social sciences, covering topics such as blockchain & cryptocurrency; computer law & security; digital accounting & auditing; digital business & finance; digital economics; digital education; digital engineering; machine learning; smart cities in the digital age; health policy & management; and information management. COMPUTERS,Data Science,General

Combinatorial Algorithms This book constitutes the proceedings of the 31st International Workshop on Combinatorial Algorithms which was planned to take place in Bordeaux, France, during June 8–10, 2020. Due to the COVID-19 pandemic the conference changed to a virtual format. The 30 full papers included in this book were carefully reviewed and selected from 62 submissions. They focus on algorithms design for the myriad of combinatorial problems that underlie computer applications in science, engineering and business. COMPUTERS,Data Science,General

Current Achievements, Challenges and Digital Chances of Knowledge Based Economy This book is based on research from Russia, Hungary, Bulgaria, Great Britain, Switzerland and the Czech Republic on issues related to knowledge-based economy development. The idea for this book was developed during three international conferences on digitalization: VI, VII and VIII International Scientific Weeks, organized by Samara State University of Economics (Samara, Russia) in 2018–2020. It is an initiative by the scientific and business organizations in the Samara Region and their Russian and international partners to analyze the current digitalization of social-economic systems, the problems and perspectives of this process, and its role in the creation and development of a new type of economy and new quality of human capital. All the contributions focus on the search for effective ways of adapting to the new digital reality and are based analyses of international statistics, and data from specific companies, educational institutions and governmental development programs.The book explores a variety of topics, including • Knowledge and Information as Basic Values of a New Economic Paradigm; • Information Technologies for Ensuring Sustainable Development of Organizations; • Augmented Reality, Artificial Intelligence and Big Data in Education and Business;• Digital Platforms and the Sharing Economy; • Potential of Digital Footprints in Economies and Education; • Sociocultural Consequences of Digitalization. COMPUTERS,Data Science,General

SAS Stored Processes Customize the SAS Stored Process web application to create amazing tools for end users. This book shows you how to use stored processes—SAS programs stored on a server and executed as required by requesting applications.Never before have there been so many ways to turn data into information and build applications with SAS. This book teaches you how to use the web technologies that you frequently see used on impressive websites. By using SAS Stored Processes , you will be able to build applications that exploit CSS, JavaScript, and HTML libraries and enable you to build powerful and impressive web applications using SAS as the backend.While this approach is not common with SAS users, some have had amazing results. People who have SAS skills usually do not have web development skills, and those with web development skills usually do not have SAS skills. Some people have both skills but are unaware of how to connect them with the SAS Stored Process web application. This book shows you how to leverage your skills for success. What You Will Learn Know the benefits of stored processes Write your own tools in SAS Make a stored process generate its own HTML menu Pass data between stored processes Use stored processes to generate pure JavaScript Utilize data generated by SAS Convert a SAS program into a stored process Who This Book Is For SAS programmers looking to improve their existing programming skills to develop web applications, and programming managers who want to make better use of the SAS software they already license COMPUTERS,Data Science,General

Finite Volumes for Complex Applications IX - Methods, Theoretical Aspects, Examples The proceedings of the 9th conference on "Finite Volumes for Complex Applications" (Bergen, June 2020) are structured in two volumes. The first volume collects the focused invited papers, as well as the reviewed contributions from internationally leading researchers in the field of analysis of finite volume and related methods. Topics covered include convergence and stability analysis, as well as investigations of these methods from the point of view of compatibility with physical principles. Altogether, a rather comprehensive overview is given on the state of the art in the field. The properties of the methods considered in the conference give them distinguished advantages for a number of applications. These include fluid dynamics, magnetohydrodynamics, structural analysis, nuclear physics, semiconductor theory, carbon capture utilization and storage, geothermal energy and further topics. The second volume covers reviewed contributions reporting successful applications of finite volume and related methods in these fields. The finite volume method in its various forms is a space discretization technique for partial differential equations based on the fundamental physical principle of conservation. Many finite volume methods preserve further qualitative or asymptotic properties, including maximum principles, dissipativity, monotone decay of free energy, and asymptotic stability, making the finite volume methods compatible discretization methods, which preserve qualitative properties of continuous problems at the discrete level. This structural approach to the discretization of partial differential equations becomes particularly important for multiphysics and multiscale applications. The book is a valuable resource for researchers, PhD and master’s level students in numerical analysis, scientific computing and related fields such as partial differential equations, as well as engineers working in numerical modeling and simulations. COMPUTERS,Data Science,General

Practical Data Analysis Using Jupyter Notebook Understand data analysis concepts to make accurate decisions based on data using Python programming and Jupyter Notebook Key Features Find out how to use Python code to extract insights from data using real-world examples Work with structured data and free text sources to answer questions and add value using data Perform data analysis from scratch with the help of clear explanations for cleaning, transforming, and visualizing data Book Description Data literacy is the ability to read, analyze, work with, and argue using data. Data analysis is the process of cleaning and modeling your data to discover useful information. This book combines these two concepts by sharing proven techniques and hands-on examples so that you can learn how to communicate effectively using data. After introducing you to the basics of data analysis using Jupyter Notebook and Python, the book will take you through the fundamentals of data. Packed with practical examples, this guide will teach you how to clean, wrangle, analyze, and visualize data to gain useful insights, and you'll discover how to answer questions using data with easy-to-follow steps. Later chapters teach you about storytelling with data using charts, such as histograms and scatter plots. As you advance, you'll understand how to work with unstructured data using natural language processing (NLP) techniques to perform sentiment analysis. All the knowledge you gain will help you discover key patterns and trends in data using real-world examples. In addition to this, you will learn how to handle data of varying complexity to perform efficient data analysis using modern Python libraries. By the end of this book, you'll have gained the practical skills you need to analyze data with confidence. What you will learn Understand the importance of data literacy and how to communicate effectively using data Find out how to use Python packages such as NumPy, pandas, Matplotlib, and the Natural Language Toolkit (NLTK) for data analysis Wrangle data and create DataFrames using pandas Produce charts and data visualizations using time-series datasets Discover relationships and how to join data together using SQL Use NLP techniques to work with unstructured data to create sentiment analysis models Discover patterns in real-world datasets that provide accurate insights Who this book is for This book is for aspiring data analysts and data scientists looking for hands-on tutorials and real-world examples to understand data analysis concepts using SQL, Python, and Jupyter Notebook. Anyone looking to evolve their skills to become data-driven personally and professionally will also find this book useful. No prior knowledge of data analysis or programming is required to get started with this book. COMPUTERS,Data Science,General

Graph Transformation This book constitutes the refereed proceedings of the 13th International Conference on Graph Transformation, ICGT 2020, in Bergen, Norway, in June 2020.*The 16 research papers and 4 tool paper presented in this book were carefully reviewed and selected from 40 submissions. One invited paper is also included. The papers deal with the following topics: theoretical advances; application domains; and tool presentations. *The conference was held virtually due to the COVID-19 pandemic. COMPUTERS,Data Science,General

Mathematical Optimization Theory and Operations Research This book constitutes the proceedings of the 19th International Conference on Mathematical Optimization Theory and Operations Research, MOTOR 2020, held in Novosibirsk, Russia, in July 2020. The 31 full papers presented in this volume were carefully reviewed and selected from 102 submissions. The papers are grouped in these topical sections: discrete optimization; mathematical programming; game theory; scheduling problem; heuristics and metaheuristics; and operational research applications. COMPUTERS,Data Science,General

End-to-End Data Science with SAS Learn data science concepts with real-world examples in SAS ! End-to-End Data Science with SAS : A Hands-On Programming Guide provides clear and practical explanations of the data science environment, machine learning techniques, and the SAS programming knowledge necessary to develop machine learning models in any industry. The book covers concepts including understanding the business need, creating a modeling data set, linear regression, parametric classification models, and non-parametric classification models. Real-world business examples and example code are used to demonstrate each process step-by-step. Although a significant amount of background information and supporting mathematics are presented, the book is not structured as a textbook, but rather it is a user’s guide for the application of data science and machine learning in a business environment. Readers will learn how to think like a data scientist, wrangle messy data, choose a model, and evaluate the model’s effectiveness. New data scientists or professionals who want more experience with SAS will find this book to be an invaluable reference. Take your data science career to the next level by mastering SAS programming for machine learning models. COMPUTERS,Data Science,General

Hands-On Python Natural Language Processing Get well-versed with traditional as well as modern natural language processing concepts and techniques Key Features Perform various NLP tasks to build linguistic applications using Python libraries Understand, analyze, and generate text to provide accurate results Interpret human language using various NLP concepts, methodologies, and tools Book Description Natural Language Processing (NLP) is the subfield in computational linguistics that enables computers to understand, process, and analyze text. This book caters to the unmet demand for hands-on training of NLP concepts and provides exposure to real-world applications along with a solid theoretical grounding. This book starts by introducing you to the field of NLP and its applications, along with the modern Python libraries that you'll use to build your NLP-powered apps. With the help of practical examples, you'll learn how to build reasonably sophisticated NLP applications, and cover various methodologies and challenges in deploying NLP applications in the real world. You'll cover key NLP tasks such as text classification, semantic embedding, sentiment analysis, machine translation, and developing a chatbot using machine learning and deep learning techniques. The book will also help you discover how machine learning techniques play a vital role in making your linguistic apps smart. Every chapter is accompanied by examples of real-world applications to help you build impressive NLP applications of your own. By the end of this NLP book, you'll be able to work with language data, use machine learning to identify patterns in text, and get acquainted with the advancements in NLP. What you will learn Understand how NLP powers modern applications Explore key NLP techniques to build your natural language vocabulary Transform text data into mathematical data structures and learn how to improve text mining models Discover how various neural network architectures work with natural language data Get the hang of building sophisticated text processing models using machine learning and deep learning Check out state-of-the-art architectures that have revolutionized research in the NLP domain Who this book is for This NLP Python book is for anyone looking to learn NLP's theoretical and practical aspects alike. It starts with the basics and gradually covers advanced concepts to make it easy to follow for readers with varying levels of NLP proficiency. This comprehensive guide will help you develop a thorough understanding of the NLP methodologies for building linguistic applications; however, working knowledge of Python programming language and high school level mathematics is expected. COMPUTERS,Data Science,General

Hands-on Booting Master the booting procedure of various operating systems with in-depth analysis of bootloaders and firmware. The primary focus is on the Linux booting procedure along with other popular operating systems such as Windows and Unix. Hands-on Booting begins by explaining what a bootloader is, starting with the Linux bootloader followed by bootloaders for Windows and Unix systems. Next, you’ll address the BIOS and UEFI firmware by installing multiple operating systems on one machine and booting them through the Linux bootloader. Further, you’ll see the kernel's role in the booting procedure of the operating system and the dependency between kernel, initramfs, and dracut. You’ll also cover systemd, examining its structure and how it mounts the user root filesystem. In the final section, the book explains troubleshooting methodologies such as debugging shells followed by live images and rescue mode. On completing this book, you will understand the booting process of major operating systems such as Linux, Windows, and Unix. You will also know how to fix the Linux booting issues through various boot modes. What You Will Learn Examine the BIOS and UEFI firmware Understanding the Linux boot loader (GRUB) Work with initramfs, dracut, and systemd Fix can’t-boot issues on Linux Who This Book Is For Linux users, administrators, and developers. COMPUTERS,Data Science,General

Building Analytics Teams Master the skills necessary to hire and manage a team of highly skilled individuals to design, build, and implement applications and systems based on advanced analytics and AI Key Features Learn to create an operationally effective advanced analytics team in a corporate environment Select and undertake projects that have a high probability of success and deliver the improved top and bottom-line results Understand how to create relationships with executives, senior managers, peers, and subject matter experts that lead to team collaboration, increased funding, and long-term success for you and your team Book Description In Building Analytics Teams, John K. Thompson, with his 30+ years of experience and expertise, illustrates the fundamental concepts of building and managing a high-performance analytics team, including what to do, who to hire, projects to undertake, and what to avoid in the journey of building an analytically sound team. The core processes in creating an effective analytics team and the importance of the business decision-making life cycle are explored to help achieve initial and sustainable success. The book demonstrates the various traits of a successful and high-performing analytics team and then delineates the path to achieve this with insights on the mindset, advanced analytics models, and predictions based on data analytics. It also emphasizes the significance of the macro and micro processes required to evolve in response to rapidly changing business needs. The book dives into the methods and practices of managing, developing, and leading an analytics team. Once you've brought the team up to speed, the book explains how to govern executive expectations and select winning projects. By the end of this book, you will have acquired the knowledge to create an effective business analytics team and develop a production environment that delivers ongoing operational improvements for your organization. What you will learn Avoid organizational and technological pitfalls of moving from a defined project to a production environment Enable team members to focus on higher-value work and tasks Build Advanced Analytics and Artificial Intelligence (AA&AI) functions in an organization Outsource certain projects to competent and capable third parties Support the operational areas that intend to invest in business intelligence, descriptive statistics, and small-scale predictive analytics Analyze the operational area, the processes, the data, and the organizational resistance Who this book is for This book is for senior executives, senior and junior managers, and those who are working as part of a team that is accountable for designing, building, delivering and ensuring business success through advanced analytics and artificial intelligence systems and applications. At least 5 to 10 years of experience in driving your organization to a higher level of efficiency will be helpful. COMPUTERS,Data Science,General

Model Risk Management with SAS Cut through the complexity of model risk management with a guide to solutions from SAS ! There is an increasing demand for more model governance and model risk awareness. At the same time, high-performing models are expected to be deployed faster than ever. SAS Model Risk Management is a user-friendly, web-based application that facilitates the capture and life cycle management of statistical model-related information. It enables all stakeholders in the model life cycle — developers, validators, internal audit, and management – to get overview reports as well as detailed information in one central place. Model Risk Management with SAS introduces you to the features and capabilities of this software, including the entry, collection, transfer, storage, tracking, and reporting of models that are drawn from multiple lines of business across an organization. This book teaches key concepts, terminology, and base functionality that are integral to SAS Model Risk Management through hands-on examples and demonstrations. With this guide to SAS Model Risk Management, your organization can be confident it is making fact-based decisions and mitigating model risk. COMPUTERS,Data Science,General

Mathematical Software – ICMS 2020 This book constitutes the proceedings of the 7th International Conference on Mathematical Software, ICMS 2020, held in Braunschweig, Germany, in July 2020. The 48 papers included in this volume were carefully reviewed and selected from 58 submissions. The program of the 2020 meeting consisted of 20 topical sessions, each of which providing an overview of the challenges, achievements and progress in a environment of mathematical software research, development and use. COMPUTERS,Data Science,General

Hands-On Natural Language Processing with PyTorch 1.x Become a proficient NLP data scientist by developing deep learning models for NLP and extract valuable insights from structured and unstructured data Key Features Get to grips with word embeddings, semantics, labeling, and high-level word representations using practical examples Learn modern approaches to NLP and explore state-of-the-art NLP models using PyTorch Improve your NLP applications with innovative neural networks such as RNNs, LSTMs, and CNNs Book Description In the internet age, where an increasing volume of text data is generated daily from social media and other platforms, being able to make sense of that data is a crucial skill. With this book, you'll learn how to extract valuable insights from text by building deep learning models for natural language processing (NLP) tasks. Starting by understanding how to install PyTorch and using CUDA to accelerate the processing speed, you'll explore how the NLP architecture works with the help of practical examples. This PyTorch NLP book will guide you through core concepts such as word embeddings, CBOW, and tokenization in PyTorch. You'll then learn techniques for processing textual data and see how deep learning can be used for NLP tasks. The book demonstrates how to implement deep learning and neural network architectures to build models that will allow you to classify and translate text and perform sentiment analysis. Finally, you'll learn how to build advanced NLP models, such as conversational chatbots. By the end of this book, you'll not only have understood the different NLP problems that can be solved using deep learning with PyTorch, but also be able to build models to solve them. What you will learn Use NLP techniques for understanding, processing, and generating text Understand PyTorch, its applications and how it can be used to build deep linguistic models Explore the wide variety of deep learning architectures for NLP Develop the skills you need to process and represent both structured and unstructured NLP data Become well-versed with state-of-the-art technologies and exciting new developments in the NLP domain Create chatbots using attention-based neural networks Who this book is for This PyTorch book is for NLP developers, machine learning and deep learning developers, and anyone interested in building intelligent language applications using both traditional NLP approaches and deep learning architectures. If you're looking to adopt modern NLP techniques and models for your development projects, this book is for you. Working knowledge of Python programming, along with basic working knowledge of NLP tasks, is required. COMPUTERS,Data Science,General

Data Mining and Big Data This book constitutes refereed proceedings of the 5th International Conference on Data Mining and Big Data, DMBD 2020, held in July 2020. Due to the COVID-19 pandemic the conference was held in a fully virtual format. The 7 full papers and 3 short papers presented in this volume were carefully reviewed and selected from 39 submissions. The papers present the latest research on advantages in theories, technologies, and applications in data mining and big data. The volume covers many aspects of data mining and big data as well as intelligent computing methods applied to all fields of computer science, machine learning, data mining and knowledge discovery, data science, etc. COMPUTERS,Data Science,General

Blockchain and Applications This book constitutes the refereed proceedings of the 1st International Congress on Blockchain and Applications 2020, BLOCKCHAIN’20, held in L’Aquila, Italy, in October 2020. Among the scientific community, blockchain and artificial intelligence are a promising combination that will transform the production and manufacturing industry, media, finance, insurance, e-government, etc. Nevertheless, there is no consensus with schemes or best practices that would specify how blockchain and artificial intelligence should be used together. The 21 full papers presented were carefully reviewed and selected from over 40 submissions. They contain the latest advances on blockchain and artificial intelligence and on their application domains, exploring innovative ideas, guidelines, theories, models, technologies, and tools, and identifying critical issues and challenges that researchers and practitioners must deal with in future research. COMPUTERS,Data Science,General

Multimedia Technology and Enhanced Learning This two-volume book constitutes the refereed proceedings of the Second International Conference on Multimedia Technology and Enhanced Learning, ICMTEL 2020, held in Leicester, United Kingdom, in April 2020. Due to the COVID-19 pandemic all papers were presented in YouTubeLive. The 83 revised full papers have been selected from 158 submissions. They describe new learning technologies which range from smart school, smart class and smart learning at home and which have been developed from new technologies such as machine learning, multimedia and Internet of Things. COMPUTERS,Data Science,General

Multimedia Technology and Enhanced Learning This two-volume book constitutes the refereed proceedings of the Second International Conference on Multimedia Technology and Enhanced Learning, ICMTEL 2020, held in Leicester, United Kingdom, in April 2020. Due to the COVID-19 pandemic all papers were presented in YouTubeLive. The 83 revised full papers have been selected from 158 submissions. They describe new learning technologies which range from smart school, smart class and smart learning at home and which have been developed from new technologies such as machine learning, multimedia and Internet of Things. COMPUTERS,Data Science,General

Programming Machine Learning You've decided to tackle machine learning - because you're job hunting, embarking on a new project, or just think self-driving cars are cool. But where to start? It's easy to be intimidated, even as a software developer. The good news is that it doesn't have to be that hard. Master machine learning by writing code one line at a time, from simple learning programs all the way to a true deep learning system. Tackle the hard topics by breaking them down so they're easier to understand, and build your confidence by getting your hands dirty. Peel away the obscurities of machine learning, starting from scratch and going all the way to deep learning. Machine learning can be intimidating, with its reliance on math and algorithms that most programmers don't encounter in their regular work. Take a hands-on approach, writing the Python code yourself, without any libraries to obscure what's really going on. Iterate on your design, and add layers of complexity as you go. Build an image recognition application from scratch with supervised learning. Predict the future with linear regression. Dive into gradient descent, a fundamental algorithm that drives most of machine learning. Create perceptrons to classify data. Build neural networks to tackle more complex and sophisticated data sets. Train and refine those networks with backpropagation and batching. Layer the neural networks, eliminate overfitting, and add convolution to transform your neural network into a true deep learning system. Start from the beginning and code your way to machine learning mastery. What You Need: The examples in this book are written in Python, but don't worry if you don't know this language: you'll pick up all the Python you need very quickly. Apart from that, you'll only need your computer, and your code-adept brain. COMPUTERS,Data Science,Machine Learning

Analytical Skills for AI and Data Science While several market-leading companies have successfully transformed their business models by following data- and AI-driven paths, the vast majority have yet to reap the benefits. How can your business and analytics units gain a competitive advantage by capturing the full potential of this predictive revolution? This practical guide presents a battle-tested end-to-end method to help you translate business decisions into tractable prescriptive solutions using data and AI as fundamental inputs. Author Daniel Vaughan shows data scientists, analytics practitioners, and others interested in using AI to transform their businesses not only how to ask the right questions but also how to generate value using modern AI technologies and decision-making principles. You’ll explore several use cases common to many enterprises, complete with examples you can apply when working to solve your own issues. Break business decisions into stages that can be tackled using different skills from the analytical toolbox Identify and embrace uncertainty in decision making and protect against common human biases Customize optimal decisions to different customers using predictive and prescriptive methods and technologies Ask business questions that create high value through AI- and data-driven technologies COMPUTERS,Data Science,Machine Learning

Machine Learning with SAS Viya Master machine learning with SAS Viya ! Machine learning can feel intimidating for new practitioners. Machine Learning with SAS Viya provides everything you need to know to get started with machine learning in SAS Viya, including decision trees, neural networks, and support vector machines. The analytics life cycle is covered from data preparation and discovery to deployment. Working with open-source code? Machine Learning with SAS Viya has you covered – step-by-step instructions are given on how to use SAS Model Manager tools with open source. SAS Model Studio features are highlighted to show how to carry out machine learning in SAS Viya. Demonstrations, practice tasks, and quizzes are included to help sharpen your skills. In this book, you will learn about: Supervised and unsupervised machine learning Data preparation and dealing with missing and unstructured data Model building and selection Improving and optimizing models Model deployment and monitoring performance COMPUTERS,Data Science,Machine Learning

Deep Learning for Computer Vision with SAS Discover deep learning and computer vision with SAS! Deep Learning for Computer Vision with SAS®: An Introduction introduces the pivotal components of deep learning. Readers will gain an in-depth understanding of how to build deep feedforward and convolutional neural networks, as well as variants of denoising autoencoders. Transfer learning is covered to help readers learn about this emerging field. Containing a mix of theory and application, this book will also briefly cover methods for customizing deep learning models to solve novel business problems or answer research questions. SAS programs and data are included to reinforce key concepts and allow readers to follow along with included demonstrations.Readers will learn how to: Define and understand deep learningBuild models using deep learning techniques and SAS ViyaApply models to score (inference) new dataModify data for better analysis resultsSearch the hyperparameter space of a deep learning modelLeverage transfer learning using supervised and unsupervised methods COMPUTERS,Data Science,Machine Learning

Deep Learning for Coders with fastai and PyTorch Deep learning is often viewed as the exclusive domain of math PhDs and big tech companies. But as this hands-on guide demonstrates, programmers comfortable with Python can achieve impressive results in deep learning with little math background, small amounts of data, and minimal code. How? With fastai, the first library to provide a consistent interface to the most frequently used deep learning applications. Authors Jeremy Howard and Sylvain Gugger, the creators of fastai, show you how to train a model on a wide range of tasks using fastai and PyTorch. You’ll also dive progressively further into deep learning theory to gain a complete understanding of the algorithms behind the scenes. Train models in computer vision, natural language processing, tabular data, and collaborative filtering Learn the latest deep learning techniques that matter most in practice Improve accuracy, speed, and reliability by understanding how deep learning models work Discover how to turn your models into web applications Implement deep learning algorithms from scratch Consider the ethical implications of your work Gain insight from the foreword by PyTorch cofounder, Soumith Chintala COMPUTERS,Data Science,Machine Learning

Building Machine Learning Pipelines Companies are spending billions on machine learning projects, but it’s money wasted if the models can’t be deployed effectively. In this practical guide, Hannes Hapke and Catherine Nelson walk you through the steps of automating a machine learning pipeline using the TensorFlow ecosystem. You’ll learn the techniques and tools that will cut deployment time from days to minutes, so that you can focus on developing new models rather than maintaining legacy systems. Data scientists, machine learning engineers, and DevOps engineers will discover how to go beyond model development to successfully productize their data science projects, while managers will better understand the role they play in helping to accelerate these projects. Understand the steps to build a machine learning pipeline Build your pipeline using components from TensorFlow Extended Orchestrate your machine learning pipeline with Apache Beam, Apache Airflow, and Kubeflow Pipelines Work with data using TensorFlow Data Validation and TensorFlow Transform Analyze a model in detail using TensorFlow Model Analysis Examine fairness and bias in your model performance Deploy models with TensorFlow Serving or TensorFlow Lite for mobile devices Learn privacy-preserving machine learning techniques COMPUTERS,Data Science,Machine Learning

Learning TensorFlow Roughly inspired by the human brain, deep neural networks trained with large amounts of data can solve complex tasks with unprecedented accuracy. This practical book provides an end-to-end guide to TensorFlow, the leading open source software library that helps you build and train neural networks for computer vision, natural language processing (NLP), speech recognition, and general predictive analytics. Authors Tom Hope, Yehezkel Resheff, and Itay Lieder provide a hands-on approach to TensorFlow fundamentals for a broad technical audience—from data scientists and engineers to students and researchers. You’ll begin by working through some basic examples in TensorFlow before diving deeper into topics such as neural network architectures, TensorBoard visualization, TensorFlow abstraction libraries, and multithreaded input pipelines. Once you finish this book, you’ll know how to build and deploy production-ready deep learning systems in TensorFlow. Get up and running with TensorFlow, rapidly and painlessly Learn how to use TensorFlow to build deep learning models from the ground up Train popular deep learning models for computer vision and NLP Use extensive abstraction libraries to make development easier and faster Learn how to scale TensorFlow, and use clusters to distribute model training Deploy TensorFlow in a production setting COMPUTERS,Data Science,Neural Networks

Space-time Array Communications Space-time array communications have gained a great deal of interest in recent years. Its superior performance in practical multipath propagation environments has established it as a core aspect in next generation mobile networks, as well as several portable wireless communication systems. In fact the employment of the sensor array component has already been provided for in the current UMTS standard, and there is presently a major thrust to make space-time processing an important part of 3G/4G networks. This book hence attempts to bridge the knowledge gap, looking at the integration of two emerging technologies from an array manifold perspective — space-time array processing and spread spectrum multiple access communications. It covers a range of novel multiuser channel estimation and reception techniques, which is designed to provide mitigations of the various associated channel impairments in accordance to its environmental context. For convenience of the readers, the book is written in a self-contained modular format with its mathematical frameworks and tools readily extendable to other research domains. COMPUTERS,Data Science,Neural Networks

TensorFlow for Deep Learning Learn how to solve challenging machine learning problems with TensorFlow, Google’s revolutionary new software library for deep learning. If you have some background in basic linear algebra and calculus, this practical book introduces machine-learning fundamentals by showing you how to design systems capable of detecting objects in images, understanding text, analyzing video, and predicting the properties of potential medicines. TensorFlow for Deep Learning teaches concepts through practical examples and helps you build knowledge of deep learning foundations from the ground up. It’s ideal for practicing developers with experience designing software systems, and useful for scientists and other professionals familiar with scripting but not necessarily with designing learning algorithms. Learn TensorFlow fundamentals, including how to perform basic computation Build simple learning systems to understand their mathematical foundations Dive into fully connected deep networks used in thousands of applications Turn prototypes into high-quality models with hyperparameter optimization Process images with convolutional neural networks Handle natural language datasets with recurrent neural networks Use reinforcement learning to solve games such as tic-tac-toe Train deep networks with hardware including GPUs and tensor processing units COMPUTERS,Data Science,Neural Networks

Hands-On Machine Learning for Algorithmic Trading Explore effective trading strategies in real-world markets using NumPy, spaCy, pandas, scikit-learn, and Keras Key Features Implement machine learning algorithms to build, train, and validate algorithmic models Create your own algorithmic design process to apply probabilistic machine learning approaches to trading decisions Develop neural networks for algorithmic trading to perform time series forecasting and smart analytics Book Description The explosive growth of digital data has boosted the demand for expertise in trading strategies that use machine learning (ML). This book enables you to use a broad range of supervised and unsupervised algorithms to extract signals from a wide variety of data sources and create powerful investment strategies. This book shows how to access market, fundamental, and alternative data via API or web scraping and offers a framework to evaluate alternative data. You'll practice the ML work?ow from model design, loss metric definition, and parameter tuning to performance evaluation in a time series context. You will understand ML algorithms such as Bayesian and ensemble methods and manifold learning, and will know how to train and tune these models using pandas, statsmodels, sklearn, PyMC3, xgboost, lightgbm, and catboost. This book also teaches you how to extract features from text data using spaCy, classify news and assign sentiment scores, and to use gensim to model topics and learn word embeddings from financial reports. You will also build and evaluate neural networks, including RNNs and CNNs, using Keras and PyTorch to exploit unstructured data for sophisticated strategies. Finally, you will apply transfer learning to satellite images to predict economic activity and use reinforcement learning to build agents that learn to trade in the OpenAI Gym. What you will learn Implement machine learning techniques to solve investment and trading problems Leverage market, fundamental, and alternative data to research alpha factors Design and fine-tune supervised, unsupervised, and reinforcement learning models Optimize portfolio risk and performance using pandas, NumPy, and scikit-learn Integrate machine learning models into a live trading strategy on Quantopian Evaluate strategies using reliable backtesting methodologies for time series Design and evaluate deep neural networks using Keras, PyTorch, and TensorFlow Work with reinforcement learning for trading strategies in the OpenAI Gym Who this book is for Hands-On Machine Learning for Algorithmic Trading is for data analysts, data scientists, and Python developers, as well as investment analysts and portfolio managers working within the finance and investment industry. If you want to perform efficient algorithmic trading by developing smart investigating strategies using machine learning algorithms, this is the book for you. Some understanding of Python and machine learning techniques is mandatory. COMPUTERS,Data Science,Neural Networks

TensorFlow 2.0 Quick Start Guide Perform supervised and unsupervised machine learning and learn advanced techniques such as training neural networks. Key Features Train your own models for effective prediction, using high-level Keras API Perform supervised and unsupervised machine learning and learn advanced techniques such as training neural networks Get acquainted with some new practices introduced in TensorFlow 2.0 Alpha Book Description TensorFlow is one of the most popular machine learning frameworks in Python. With this book, you will improve your knowledge of some of the latest TensorFlow features and will be able to perform supervised and unsupervised machine learning and also train neural networks. After giving you an overview of what's new in TensorFlow 2.0 Alpha, the book moves on to setting up your machine learning environment using the TensorFlow library. You will perform popular supervised machine learning tasks using techniques such as linear regression, logistic regression, and clustering. You will get familiar with unsupervised learning for autoencoder applications. The book will also show you how to train effective neural networks using straightforward examples in a variety of different domains. By the end of the book, you will have been exposed to a large variety of machine learning and neural network TensorFlow techniques. What you will learn Use tf.Keras for fast prototyping, building, and training deep learning neural network models Easily convert your TensorFlow 1.12 applications to TensorFlow 2.0-compatible files Use TensorFlow to tackle traditional supervised and unsupervised machine learning applications Understand image recognition techniques using TensorFlow Perform neural style transfer for image hybridization using a neural network Code a recurrent neural network in TensorFlow to perform text-style generation Who this book is for Data scientists, machine learning developers, and deep learning enthusiasts looking to quickly get started with TensorFlow 2 will find this book useful. Some Python programming experience with version 3.6 or later, along with a familiarity with Jupyter notebooks will be an added advantage. Exposure to machine learning and neural network techniques would also be helpful. COMPUTERS,Data Science,Neural Networks

Deep Learning with R for Beginners Explore the world of neural networks by building powerful deep learning models using the R ecosystem Key Features Get to grips with the fundamentals of deep learning and neural networks Use R 3.5 and its libraries and APIs to build deep learning models for computer vision and text processing Implement effective deep learning systems in R with the help of end-to-end projects Book Description Deep learning finds practical applications in several domains, while R is the preferred language for designing and deploying deep learning models. This Learning Path introduces you to the basics of deep learning and even teaches you to build a neural network model from scratch. As you make your way through the chapters, you'll explore deep learning libraries and understand how to create deep learning models for a variety of challenges, right from anomaly detection to recommendation systems. The book will then help you cover advanced topics, such as generative adversarial networks (GANs), transfer learning, and large-scale deep learning in the cloud, in addition to model optimization, overfitting, and data augmentation. Through real-world projects, you'll also get up to speed with training convolutional neural networks (CNNs), recurrent neural networks (RNNs), and long short-term memory networks (LSTMs) in R. By the end of this Learning Path, you'll be well versed with deep learning and have the skills you need to implement a number of deep learning concepts in your research work or projects. This Learning Path includes content from the following Packt products: R Deep Learning Essentials - Second Edition by Joshua F. Wiley and Mark Hodnett R Deep Learning Projects by Yuxi (Hayden) Liu and Pablo Maldonado What you will learn Implement credit card fraud detection with autoencoders Train neural networks to perform handwritten digit recognition using MXNet Reconstruct images using variational autoencoders Explore the applications of autoencoder neural networks in clustering and dimensionality reduction Create natural language processing (NLP) models using Keras and TensorFlow in R Prevent models from overfitting the data to improve generalizability Build shallow neural network prediction models Who this book is for This Learning Path is for aspiring data scientists, data analysts, machine learning developers, and deep learning enthusiasts who are well versed in machine learning concepts and are looking to explore the deep learning paradigm using R. A fundamental understanding of R programming and familiarity with the basic concepts of deep learning are necessary to get the most out of this Learning Path. COMPUTERS,Data Science,Neural Networks

Deep Learning Illustrated "The authors’ clear visual style provides a comprehensive look at what’s currently possible with artificial neural networks as well as a glimpse of the magic that’s to come." – Tim Urban, author of Wait But Why Fully Practical, Insightful Guide to Modern Deep Learning Deep learning is transforming software, facilitating powerful new artificial intelligence capabilities, and driving unprecedented algorithm performance. Deep Learning Illustrated is uniquely intuitive and offers a complete introduction to the discipline’s techniques. Packed with full-color figures and easy-to-follow code, it sweeps away the complexity of building deep learning models, making the subject approachable and fun to learn. World-class instructor and practitioner Jon Krohn–with visionary content from Grant Beyleveld and beautiful illustrations by Aglaé Bassens–presents straightforward analogies to explain what deep learning is, why it has become so popular, and how it relates to other machine learning approaches. Krohn has created a practical reference and tutorial for developers, data scientists, researchers, analysts, and students who want to start applying it. He illuminates theory with hands-on Python code in accompanying Jupyter notebooks. To help you progress quickly, he focuses on the versatile deep learning library Keras to nimbly construct efficient TensorFlow models; PyTorch, the leading alternative library, is also covered. You’ll gain a pragmatic understanding of all major deep learning approaches and their uses in applications ranging from machine vision and natural language processing to image generation and game-playing algorithms. Discover what makes deep learning systems unique, and the implications for practitioners Explore new tools that make deep learning models easier to build, use, and improve Master essential theory: artificial neurons, training, optimization, convolutional nets, recurrent nets, generative adversarial networks (GANs), deep reinforcement learning, and more Walk through building interactive deep learning applications, and move forward with your own artificial intelligence projects Register your book for convenient access to downloads, updates, and/or corrections as they become available. See inside book for details. COMPUTERS,Data Science,Neural Networks

Programming PyTorch for Deep Learning Deep learning is changing everything. This machine-learning method has already surpassed traditional computer vision techniques, and the same is happening with NLP. If you're looking to bring deep learning into your domain, this practical book will bring you up to speed on key concepts using Facebook's PyTorch framework. Once author Ian Pointer helps you set up PyTorch on a cloud-based environment, you'll learn how use the framework to create neural architectures for performing operations on images, sound, text, and other types of data. By the end of the book, you'll be able to create neural networks and train them on multiple types of data. Learn how to deploy deep learning models to production Explore PyTorch use cases in companies other than Facebook Learn how to apply transfer learning to images Apply cutting-edge NLP techniques using a model trained on Wikipedia COMPUTERS,Data Science,Neural Networks

Learning in Energy-Efficient Neuromorphic Computing Explains current co-design and co-optimization methodologies for building hardware neural networks and algorithms for machine learning applications This book focuses on how to build energy-efficient hardware for neural networks with learning capabilities—and provides co-design and co-optimization methodologies for building hardware neural networks that can learn. Presenting a complete picture from high-level algorithm to low-level implementation details, Learning in Energy-Efficient Neuromorphic Computing: Algorithm and Architecture Co-Design also covers many fundamentals and essentials in neural networks (e.g., deep learning), as well as hardware implementation of neural networks. The book begins with an overview of neural networks. It then discusses algorithms for utilizing and training rate-based artificial neural networks. Next comes an introduction to various options for executing neural networks, ranging from general-purpose processors to specialized hardware, from digital accelerator to analog accelerator. A design example on building energy-efficient accelerator for adaptive dynamic programming with neural networks is also presented. An examination of fundamental concepts and popular learning algorithms for spiking neural networks follows that, along with a look at the hardware for spiking neural networks. Then comes a chapter offering readers three design examples (two of which are based on conventional CMOS, and one on emerging nanotechnology) to implement the learning algorithm found in the previous chapter. The book concludes with an outlook on the future of neural network hardware. Includes cross-layer survey of hardware accelerators for neuromorphic algorithms Covers the co-design of architecture and algorithms with emerging devices for much-improved computing efficiency Focuses on the co-design of algorithms and hardware, which is especially critical for using emerging devices, such as traditional memristors or diffusive memristors, for neuromorphic computing Learning in Energy-Efficient Neuromorphic Computing: Algorithm and Architecture Co-Design is an ideal resource for researchers, scientists, software engineers, and hardware engineers dealing with the ever-increasing requirement on power consumption and response time. It is also excellent for teaching and training undergraduate and graduate students about the latest generation neural networks with powerful learning capabilities. COMPUTERS,Data Science,Neural Networks

Hands-On Generative Adversarial Networks with PyTorch 1.x Apply deep learning techniques and neural network methodologies to build, train, and optimize generative network models Key Features Implement GAN architectures to generate images, text, audio, 3D models, and more Understand how GANs work and become an active contributor in the open source community Learn how to generate photo-realistic images based on text descriptions Book Description With continuously evolving research and development, Generative Adversarial Networks (GANs) are the next big thing in the field of deep learning. This book highlights the key improvements in GANs over generative models and guides in making the best out of GANs with the help of hands-on examples. This book starts by taking you through the core concepts necessary to understand how each component of a GAN model works. You'll build your first GAN model to understand how generator and discriminator networks function. As you advance, you'll delve into a range of examples and datasets to build a variety of GAN networks using PyTorch functionalities and services, and become well-versed with architectures, training strategies, and evaluation methods for image generation, translation, and restoration. You'll even learn how to apply GAN models to solve problems in areas such as computer vision, multimedia, 3D models, and natural language processing (NLP). The book covers how to overcome the challenges faced while building generative models from scratch. Finally, you'll also discover how to train your GAN models to generate adversarial examples to attack other CNN and GAN models. By the end of this book, you will have learned how to build, train, and optimize next-generation GAN models and use them to solve a variety of real-world problems. What you will learn Implement PyTorch's latest features to ensure efficient model designing Get to grips with the working mechanisms of GAN models Perform style transfer between unpaired image collections with CycleGAN Build and train 3D-GANs to generate a point cloud of 3D objects Create a range of GAN models to perform various image synthesis operations Use SEGAN to suppress noise and improve the quality of speech audio Who this book is for This GAN book is for machine learning practitioners and deep learning researchers looking to get hands-on guidance in implementing GAN models using PyTorch. You'll become familiar with state-of-the-art GAN architectures with the help of real-world examples. Working knowledge of Python programming language is necessary to grasp the concepts covered in this book. COMPUTERS,Data Science,Neural Networks

Advanced Deep Learning with Python Gain expertise in advanced deep learning domains such as neural networks, meta-learning, graph neural networks, and memory augmented neural networks using the Python ecosystem Key Features Get to grips with building faster and more robust deep learning architectures Investigate and train convolutional neural network (CNN) models with GPU-accelerated libraries such as TensorFlow and PyTorch Apply deep neural networks (DNNs) to computer vision problems, NLP, and GANs Book Description In order to build robust deep learning systems, you'll need to understand everything from how neural networks work to training CNN models. In this book, you'll discover newly developed deep learning models, methodologies used in the domain, and their implementation based on areas of application. You'll start by understanding the building blocks and the math behind neural networks, and then move on to CNNs and their advanced applications in computer vision. You'll also learn to apply the most popular CNN architectures in object detection and image segmentation. Further on, you'll focus on variational autoencoders and GANs. You'll then use neural networks to extract sophisticated vector representations of words, before going on to cover various types of recurrent networks, such as LSTM and GRU. You'll even explore the attention mechanism to process sequential data without the help of recurrent neural networks (RNNs). Later, you'll use graph neural networks for processing structured data, along with covering meta-learning, which allows you to train neural networks with fewer training samples. Finally, you'll understand how to apply deep learning to autonomous vehicles. By the end of this book, you'll have mastered key deep learning concepts and the different applications of deep learning models in the real world. What you will learn Cover advanced and state-of-the-art neural network architectures Understand the theory and math behind neural networks Train DNNs and apply them to modern deep learning problems Use CNNs for object detection and image segmentation Implement generative adversarial networks (GANs) and variational autoencoders to generate new images Solve natural language processing (NLP) tasks, such as machine translation, using sequence-to-sequence models Understand DL techniques, such as meta-learning and graph neural networks Who this book is for This book is for data scientists, deep learning engineers and researchers, and AI developers who want to further their knowledge of deep learning and build innovative and unique deep learning projects. Anyone looking to get to grips with advanced use cases and methodologies adopted in the deep learning domain using real-world examples will also find this book useful. Basic understanding of deep learning concepts and working knowledge of the Python programming language is assumed. COMPUTERS,Data Science,Neural Networks

Mobile Deep Learning with TensorFlow Lite, ML Kit and Flutter Learn how to deploy effective deep learning solutions on cross-platform applications built using TensorFlow Lite, ML Kit, and Flutter Key Features Work through projects covering mobile vision, style transfer, speech processing, and multimedia processing Cover interesting deep learning solutions for mobile Build your confidence in training models, performance tuning, memory optimization, and neural network deployment through every project Book Description Deep learning is rapidly becoming the most popular topic in the mobile app industry. This book introduces trending deep learning concepts and their use cases with an industrial and application-focused approach. You will cover a range of projects covering tasks such as mobile vision, facial recognition, smart artificial intelligence assistant, augmented reality, and more. With the help of eight projects, you will learn how to integrate deep learning processes into mobile platforms, iOS, and Android. This will help you to transform deep learning features into robust mobile apps efficiently. You'll get hands-on experience of selecting the right deep learning architectures and optimizing mobile deep learning models while following an application oriented-approach to deep learning on native mobile apps. We will later cover various pre-trained and custom-built deep learning model-based APIs such as machine learning (ML) Kit through Firebase. Further on, the book will take you through examples of creating custom deep learning models with TensorFlow Lite. Each project will demonstrate how to integrate deep learning libraries into your mobile apps, right from preparing the model through to deployment. By the end of this book, you'll have mastered the skills to build and deploy deep learning mobile applications on both iOS and Android. What you will learn Create your own customized chatbot by extending the functionality of Google Assistant Improve learning accuracy with the help of features available on mobile devices Perform visual recognition tasks using image processing Use augmented reality to generate captions for a camera feed Authenticate users and create a mechanism to identify rare and suspicious user interactions Develop a chess engine based on deep reinforcement learning Explore the concepts and methods involved in rolling out production-ready deep learning iOS and Android applications Who this book is for This book is for data scientists, deep learning and computer vision engineers, and natural language processing (NLP) engineers who want to build smart mobile apps using deep learning methods. You will also find this book useful if you want to improve your mobile app's user interface (UI) by harnessing the potential of deep learning. Basic knowledge of neural networks and coding experience in Python will be beneficial to get started with this book. COMPUTERS,Data Science,Neural Networks

Principles Of Artificial Neural Networks The field of Artificial Neural Networks is the fastest growing field in Information Technology and specifically, in Artificial Intelligence and Machine Learning.This must-have compendium presents the theory and case studies of artificial neural networks. The volume, with 4 new chapters, updates the earlier edition by highlighting recent developments in Deep-Learning Neural Networks, which are the recent leading approaches to neural networks. Uniquely, the book also includes case studies of applications of neural networks — demonstrating how such case studies are designed, executed and how their results are obtained.The title is written for a one-semester graduate or senior-level undergraduate course on artificial neural networks. It is also intended to be a self-study and a reference text for scientists, engineers and for researchers in medicine, finance and data mining. COMPUTERS,Data Science,Neural Networks

Signals and Boundaries An overarching framework for comparing and steering complex adaptive systems is developed through understanding the mechanisms that generate their intricate signal/boundary hierarchies. Complex adaptive systems (cas), including ecosystems, governments, biological cells, and markets, are characterized by intricate hierarchical arrangements of boundaries and signals. In ecosystems, for example, niches act as semi-permeable boundaries, and smells and visual patterns serve as signals; governments have departmental hierarchies with memoranda acting as signals; and so it is with other cas. Despite a wealth of data and descriptions concerning different cas, there remain many unanswered questions about "steering" these systems. In Signals and Boundaries, John Holland argues that understanding the origin of the intricate signal/border hierarchies of these systems is the key to answering such questions. He develops an overarching framework for comparing and steering cas through the mechanisms that generate their signal/boundary hierarchies. Holland lays out a path for developing the framework that emphasizes agents, niches, theory, and mathematical models. He discusses, among other topics, theory construction; signal-processing agents; networks as representations of signal/boundary interaction; adaptation; recombination and reproduction; the use of tagged urn models (adapted from elementary probability theory) to represent boundary hierarchies; finitely generated systems as a way to tie the models examined into a single framework; the framework itself, illustrated by a simple finitely generated version of the development of a multi-celled organism; and Markov processes. COMPUTERS,Data Science,Neural Networks

Ultra-wideband Coherent Optical LANs The content of this book is the result of the work and the experiences of an interdisciplinary and strictly European group of researchers who have attempted to give birth to a new fibre communication network concept by exploiting the potential benefits of optical coherent transmission. The run towards this ambitious goal started in 1985 on the basis of the ESPRIT program incentives by an "ad hoc" consortium of industrial partners and research institutions. The first three years were dedicated to a feasibility study carried out by a reduced number of "pioneers". In 1989 the team was extended to eleven partners. There was already clear evidence of the increasing interest in Europe in exploring the actual limits of optical fibre coherent systems; the project had innovative and very advanced features that were gradually refined by incorporating the latest technological developments to which it has directly contributed. The main objective of the project targeted the development of the necessary building blocks to show experimentally the performance and the flexibility built into the proposed concept of multi-channel ultra-wideband network. The system concept developed within this project associates optical frequency division multiplexing with a suitable network architecture and management techniques to allow very high flexibility and efficiency in handling simultaneous transmission over the network (on each optical frequency) of multiple virtual channels each operating with a wide range of information rates ranging from a fraction of a Mb/s up to a maximum value in excess of 160 Mb/s. COMPUTERS,Data Transmission Systems,Electronic Data Interchange

Optical Information Technology Research in optical information technology in Europe hasbeen very active inrecent years. This volume recordsstate-of-the-art research conducted in some 22 laboratorieswho have worked together within EC ESPRIT Basic ResearchAction 3199 up to 1992. The topics cover:(1) Active optical logic and switching devices - embracingnew materials, nonlinear and electrooptic mechanisms as wellas advanced device fabrication. These devices cover therange from all-optical nonlinear interferometer structuresthrough hybrid optical-electronic modulators to integratedemitter-receiver structures.(2) The latest state of optical interconnect technology,embracing diffractive optics (binary and multi-level phasegratings), holographic space-variant elements andmicro-refractive optics.(3) Contributions on optical information processingarchitecture and demonstrator projects. The materials baseranges from silicon to II-VI materials with the realisationof pn-junction devices in ZnSe.The research reported here lays the basis for long-termprogress in devices for information processing. COMPUTERS,Data Transmission Systems,Electronic Data Interchange

Bridging the Information Gap Proceedings of the Seminar "Distributed Database Systems for Small and Medium Enterprises", Beijing, China, May 8-12, 1989 COMPUTERS,Data Transmission Systems,Electronic Data Interchange

Perspectives for Parallel Optical Interconnects This volume is a monograph on parallel optical interconnects. It presents not only the state of-the-art in this domain but also the necessary physical and chemical background. It also provides a discussion of the potential for future devices. Both experts and newcomers to the area will appreciate the authors' proficiency in providing the complete picture of this rapidly growing field. Optical interconnects are already established in telecommunications and should eventually find their way being applied to chip and even gate level connections in integrated systems. The inspiring environment of the Basic Research Working Group on Optical Information Technology WOIT (3199), together with the excellent and complementary skills of its participants, make this contribution highly worthwhile. G. Metakides Table of contents 1 Perspectives for parallel optical interconnects: introduction . . . . . . . . . . . . . . . . . . . . . . . . . l Pierre Chavel and Philippe lAlanne 1. 1 Optical Interconnects and ESPRIT BRA WOIT . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1 1. 2 What are optical interconnects? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2 1. 3 Optical interconnects: how ? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3 1. 3. 1 Passive devices . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3 1. 3. 2 Active devices . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4 1. 3. 3 Schemes for parallel optical interconnects . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5 1. 3. 4 Limits of optical interconnects . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6 1. 4 Optical interconnects: why ? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6 Acknowledgetnents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8 References . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8 First Section: Components Part 1. 1 Passive interconnect components 2 Free space interconnects . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11 Philippe Lalanne and Pierre ChaveZ 2. 1 Introduction: 3D optical interconnects . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11 2. 2 Optical free space channels and their implementations . . . . . . . . . . . . . . . . . . . . . . . . . . . 12 2. 2. 1 Diffraction and degrees of freedom . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12 2. 2. 2 Two Qasic interconnect setups . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . COMPUTERS,Data Transmission Systems,Electronic Data Interchange

Fundamentals of Smart Contract Security Written by security experts at the forefront of this dynamic industry, this book teaches state-of-the-art smart contract security principles and practices. Smart contracts are an innovative application of blockchain technology. Acting as decentralized custodians of digital assets, they allow us to transfer value and information more effectively by reducing the need to trust a third party. By eliminating the need for intermediaries, smart contracts have the potential to massively scale the world economy and unleash the potential for faster and more efficient solutions than traditional systems could ever provide. But there's one catch: while blockchains are secure, smart contracts are not. Security vulnerabilities in smart contracts have led to over $250 million USD in value to be lost or stolen. For smart contract technology to achieve its full potential, these security vulnerabilities need to be addressed. Written by security experts at the forefront of this dynamic industry, this book teaches state-of-the-art smart contract security principles and practices. Help us secure the future of blockchain technology and join us at the forefront today! COMPUTERS,Data Transmission Systems,Electronic Data Interchange

Becoming a data-driven Organisation Data is the foundation of any current and future market transformation during this digital era. Companies are expected to adjust or to disappear. However, following assessments by Gartner and Forrester during the past two years, only a small fraction of all enterprises has adequately addressed the handling of data so far. Yet, more and more business leaders have become aware of the topic. They recognize the increasing relevance of data, and the need to act now. Those leaders will welcome this book as it guides them through the first steps in their journey towards a data-driven organisation. This book brings the topic of Data and its commercial usage to the attention of a broad range of business leaders. It encourages you to get engaged, by explaining in a non-technical way what data comprises, which opportunities wait to get discovered and, most importantly, how to prepare and launch the introduction of a Data Office in a company. COMPUTERS,Data Transmission Systems,Electronic Data Interchange

Practical Industrial Data Networks There are many data communications titles covering design, installation, etc, but almost none that specifically focus on industrial networks, which are an essential part of the day-to-day work of industrial control systems engineers, and the main focus of an increasingly large group of network specialists. The focus of this book makes it uniquely relevant to control engineers and network designers working in this area. The industrial application of networking is explored in terms of design, installation and troubleshooting, building the skills required to identify, prevent and fix common industrial data communications problems - both at the design stage and in the maintenance phase. The focus of this book is 'outside the box'. The emphasis goes beyond typical communications issues and theory to provide the necessary toolkit of knowledge to solve industrial communications problems covering RS-232, RS-485, Modbus, Fieldbus, DeviceNet, Ethernet and TCP/IP. The idea of the book is that in reading it you should be able to walk onto your plant, or facility, and troubleshoot and fix communications problems as quickly as possible. This book is the only title that addresses the nuts-and-bolts issues involved in design, installation and troubleshooting that are the day-to-day concern of engineers and network specialists working in industry. * Provides a unique focus on the industrial application of data networks * Emphasis goes beyond typical communications issues and theory to provide the necessary toolkit of knowledge to solve industrial communications problems* Provides the tools to allow engineers in various plants or facilities to troubleshoot and fix communications problems as quickly as possible COMPUTERS,Data Transmission Systems,General

Practical Industrial Data Communications The objective of this book is to outline the best practice in designing, installing, commissioning and troubleshooting industrial data communications systems. In any given plant, factory or installation there are a myriad of different industrial communications standards used and the key to successful implementation is the degree to which the entire system integrates and works together. With so many different standards on the market today, the debate is not about what is the best - be it Foundation Fieldbus, Profibus, Devicenet or Industrial Ethernet but rather about selecting the most appropriate technologies and standards for a given application and then ensuring that best practice is followed in designing, installing and commissioning the data communications links to ensure they run fault-free. The industrial data communications systems in your plant underpin your entire operation. It is critical that you apply best practice in designing, installing and fixing any problems that may occur. This book distills all the tips and tricks with the benefit of many years of experience and gives the best proven practices to follow. The main steps in using today's communications technologies involve selecting the correct technology and standards for your plant based on your requirements; doing the design of the overall system; installing the cabling and then commissioning the system. Fiber Optic cabling is generally accepted as the best approach for physical communications but there are obviously areas where you will be forced to use copper wiring and, indeed, wireless communications. This book outlines the critical rules followed in installing the data communications physical transport media and then ensuring that the installation will be trouble-free for years to come. The important point to make is that with today’s wide range of protocols available, you only need to know how to select, install and maintain them in the most cost-effective manner for your plant or factory - knowledge of the minute details of the protocols is not necessary. An engineer's guide to communications systems using fiber optic cabling, copper cabling and wireless technology Covers: selection of technology and standards - system design - installation of equipment and cabling - commissioning and maintenance Crammed with practical techniques and know how - written by engineers for engineers COMPUTERS,Data Transmission Systems,General

Essential Mobile Interaction Design Design User-Friendly, Intuitive Smartphone and Tablet Apps for Any Platform Mobile apps should feel natural and intuitive, and users should understand them quickly and easily. This means that effective interaction and interface design is crucial. However, few mobile app developers (or even designers) have had adequate training in these areas. Essential Mobile Interaction Design fills this gap, bringing together proven principles and techniques you can use in your next app–for any platform, target device, or user. This tutorial requires virtually no design or programming knowledge. Even if you’ve never designed a mobile app before, this guide teaches you the key skills that lead to the best results. Cameron Banga and Josh Weinhold help you master the mindset, processes, and vocabulary of mobile interaction design, so you can start making better choices right away. They guide you through the entire design process, demystifying issues that arise at every stage. The authors share hard-won lessons from years of experience developing more than one hundred mobile apps for clients and customers of every type. They cover important issues that platform-specific guides often overlook, including internationalization, accessibility, hybrid apps, sandboxing, and what to do after release. This guide shows you how to Think through your designs, instead of just throwing together UI elements Allow an intuitive design flow to emerge from your app Sketch and wireframe apps more effectively Reflect key differences among smartphones, tablets, and desktops Design for visual appeal without compromising usability Work effectively with programmers Make sure your apps are accessible to everyone Get usable feedback, and understand what it’s telling you Learn valuable lessons from today’s most successful apps Refresh your designs in new apps and future versions Discover new tools for designing more successfully Packed with iOS and Android™ examples, Essential Mobile Interaction Design offers dozens of tips and solutions that will be equally useful on today’s platforms and on whatever comes next. Extensive resources are available at cameronbanga.com/EMIDbook. COMPUTERS,Data Transmission Systems,Wireless

Access VBA Programming For Dummies This friendly, easy-to-use guide shows experienced Access users how to use VBA (Visual Basic for Applications) to build Access databases and applications, but also covers programming fundamentals for nonprogrammers Includes practical, ready-to-use VBA code examples that readers can type or copy and paste from the Web into their own database projects Explains basic VBA skills and concepts for nonprogrammers, such as procedures, variables, and loops Covers more advanced topics, such as record sets and other programming activities that are unique to Access programming Author has written more than ninety computer books and has been working with databases since the early 1980s COMPUTERS,Database Administration & Management

Microsoft Office Access 2007 All-in-One Desk Reference For Dummies Updated to cover all the latest features and capabilities of Access 2007, this resource provides new and inexperienced Access users with eight task-oriented minibooks that cover begininning to advanced-level material Each minibook covers a specific aspect of Access, such as database design, tables, queries, forms, reports, and macros Shows how to accomplish specific tasks such as database housekeeping, security data, and using Access with the Web Access is the world's leading desktop database solution and is used by millions of people to store, organize, view, analyze, and share data, as well as to build powerful, custom database solutions that integrate with the Web and enterprise data sources COMPUTERS,Database Administration & Management

Business Intelligence Business Intelligence describes the basic architectural components of a business intelligence environment, ranging from traditional topics such as business process modeling, data modeling, and more modern topics such as business rule systems, data profiling, information compliance and data quality, data warehousing, and data mining. This book progresses through a logical sequence, starting with data model infrastructure, then data preparation, followed by data analysis, integration, knowledge discovery, and finally the actual use of discovered knowledge. The book contains a quick reference guide for business intelligence terminology. Business Intelligence is part of Morgan Kaufmann's Savvy Manager's Guide series. * Provides clear explanations without technical jargon, followed by in-depth descriptions.* Articulates the business value of new technology, while providing relevant introductory technical background.* Contains a handy quick-reference to technologies and terminologies.* Guides managers through developing, administering, or simply understanding business intelligence technology.* Bridges the business-technical gap.* Is Web enhanced. Companion sites to the book and series provide value-added information, links, discussions, and more. COMPUTERS,Database Administration & Management

Oracle Database 11g SQL Write powerful SQL statements and PL/SQL programs Learn to access Oracle databases through SQL statements and construct PL/SQL programs with guidance from Oracle expert, Jason Price. Published by Oracle Press, Oracle Database 11g SQL explains how to retrieve and modify database information, use SQL Plus and SQL Developer, work with database objects, write PL/SQL programs, and much more. Inside, you'll find in-depth coverage of the very latest SQL features and tools, performance optimization techniques, advanced queries, Java support, and XML. This book contains everything you need to master SQL. Explore SQL Plus and SQL Developer Use SQL SELECT, INSERT, UPDATE, and DELETE statements Write PL/SQL programs Create tables, sequences, indexes, views, and triggers Write advanced queries containing complex analytical functions Create database objects and collections to handle abstract data Use large objects to handle multimedia files containing music and movies Write Java programs to access an Oracle Database using JDBC Tune your SQL statements to make them execute faster Explore the XML capabilities of the Oracle Database Master the very latest Oracle Database 11g features, such as PIVOT and UNPIVOT, flashback archives, and much more COMPUTERS,Database Administration & Management

Applied Mathematics for Database Professionals Relational databases hold data, right? They do indeed, but to think of a database as nothing more than a container for data is to miss out on the profound power that underlies relational technology. A far more powerful way of thinking lies in relational technologys foundation in the mathematical disciplines of logic and set theory. Databases contain truths or propositions describing some area of interest such as a business. Those truths are organized into sets. Operations from logic and set theory can be applied to existing sets of truths to derive new sets of truths. Applied Mathematics for Database Professionals introduces you to this way of thinking, to the logic and set theory that underlies relational database technology. All this may sound abstract now, but there are profound benefits from the deeper understanding youll gain from this book. The math that you'll learn in this book will put you above the level of understanding of most database professionals today. You'll better understand the technology and be able to apply it more effectively. You'll avoid data anomalies like redundancy and inconsistency. Understanding whats in this book will take your mastery of relational technology to heights you may not have thought possible. This book is reviewed and endorsed by C. J. Date and features a foreword by the same. COMPUTERS,Database Administration & Management

Developer's Guide to Data Modeling for SQL Server, A “ A Developer’s Guide to Data Modeling for SQL Server explains the concepts and practice of data modeling with a clarity that makes the technology accessible to anyone building databases and data-driven applications. “Eric Johnson and Joshua Jones combine a deep understanding of the science of data modeling with the art that comes with years of experience. If you’re new to data modeling, or find the need to brush up on its concepts, this book is for you.†— Peter Varhol, Executive Editor, Redmond Magazine Model SQL Server Databases That Work Better, Do More, and Evolve More Smoothly Effective data modeling is essential to ensuring that your databases will perform well, scale well, and evolve to meet changing requirements. However, if you’re modeling databases to run on Microsoft SQL Server 2008 or 2005, theoretical or platform-agnostic data modeling knowledge isn’t enough: models that don’t reflect SQL Server’s unique real-world strengths and weaknesses often lead to disastrous performance. A Developer’s Guide to Data Modeling for SQL Server is a practical, SQL Server-specific guide to data modeling for every developer, architect, and administrator. This book offers you invaluable start-to-finish guidance for designing new databases, redesigning existing SQL Server data models, and migrating databases from other platforms. You’ll begin with a concise, practical overview of the core data modeling techniques. Next, you’ll walk through requirements gathering and discover how to convert requirements into effective SQL Server logical models. Finally, you’ll systematically transform those logical models into physical models that make the most of SQL Server’s extended functionality. All of this book’s many examples are available for download from a companion Web site. This book enables you to Understand your data model’s physical elements, from storage to referential integrity Provide programmability via stored procedures, user-defined functions, triggers, and .NET CLR integration Normalize data models, one step at a time Gather and interpret requirements more effectively Learn an effective methodology for creating logical models Overcome modeling problems related to entities, attribute, data types, storage overhead, performance, and relationships Create physical models—from establishing naming guidelines through implementing business rules and constraints Use SQL Server’s unique indexing capabilities, and overcome their limitations Create abstraction layers that enhance security, extensibility, and flexibility COMPUTERS,Database Administration & Management

Master Data Management The key to a successful MDM initiative isn’t technology or methods, it’s people: the stakeholders in the organization and their complex ownership of the data that the initiative will affect. Master Data Management equips you with a deeply practical, business-focused way of thinking about MDM—an understanding that will greatly enhance your ability to communicate with stakeholders and win their support. Moreover, it will help you deserve their support: you’ll master all the details involved in planning and executing an MDM project that leads to measurable improvements in business productivity and effectiveness. * Presents a comprehensive roadmap that you can adapt to any MDM project.* Emphasizes the critical goal of maintaining and improving data quality.* Provides guidelines for determining which data to “master.* Examines special issues relating to master data metadata.* Considers a range of MDM architectural styles.* Covers the synchronization of master data across the application infrastructure. COMPUTERS,Database Administration & Management

How to Build a Digital Library How to Build a Digital Library reviews knowledge and tools to construct and maintain a digital library, regardless of the size or purpose. A resource for individuals, agencies, and institutions wishing to put this powerful tool to work in their burgeoning information treasuries. The Second Edition reflects developments in the field as well as in the Greenstone Digital Library open source software. In Part I, the authors have added an entire new chapter on user groups, user support, collaborative browsing, user contributions, and so on. There is also new material on content-based queries, map-based queries, cross-media queries. There is an increased emphasis placed on multimedia by adding a "digitizing" section to each major media type. A new chapter has also been added on "internationalization," which will address Unicode standards, multi-language interfaces and collections, and issues with non-European languages (Chinese, Hindi, etc.). Part II, the software tools section, has been completely rewritten to reflect the new developments in Greenstone Digital Library Software, an internationally popular open source software tool with a comprehensive graphical facility for creating and maintaining digital libraries. Outlines the history of libraries on both traditional and digital Written for both technical and non-technical audiences and covers the entire spectrum of media, including text, images, audio, video, and related XML standards Web-enhanced with software documentation, color illustrations, full-text index, source code, and more COMPUTERS,Database Administration & Management

Database in Depth This book sheds light on the principles behind the relational model, which is fundamental to all database-backed applications--and, consequently, most of the work that goes on in the computing world today. Database in Depth: The Relational Model for Practitioners goes beyond the hype and gets to the heart of how relational databases actually work.Ideal for experienced database developers and designers, this concise guide gives you a clear view of the technology--a view that's not influenced by any vendor or product. Featuring an extensive set of exercises, it will help you: understand why and how the relational model is still directly relevant to modern database technology (and will remain so for the foreseeable future) see why and how the SQL standard is seriously deficient use the best current theoretical knowledge in the design of their databases and database applications make informed decisions in their daily database professional activities Database in Depth will appeal not only to database developers and designers, but also to a diverse field of professionals and academics, including database administrators (DBAs), information modelers, database consultants, and more. Virtually everyone who deals with relational databases should have at least a passing understanding of the fundamentals of working with relational models.Author C.J. Date has been involved with the relational model from its earliest days. An exceptionally clear-thinking writer, Date lays out principle and theory in a manner that is easily understood. Few others can speak as authoritatively the topic of relational databases as Date can. COMPUTERS,Database Administration & Management

MySQL Stored Procedure Programming The implementation of stored procedures in MySQL 5.0 a hugemilestone -- one that is expected to lead to widespread enterprise adoption ofthe already extremely popular MySQL database. If you are serious aboutbuilding the web-based database applications of the future, you need toget up to speed quickly on how stored procedures work -- and how tobuild them the right way. This book, destined to be the bible of storedprocedure development, is a resource that no real MySQL programmer canafford to do without. In the decade since MySQL burst on the scene, it has become thedominant open source database, with capabilities and performancerivaling those of commercial RDBMS offerings like Oracle and SQLServer. Along with Linux and PHP, MySQL is at the heart of millions ofapplications. And now, with support for stored procedures, functions,and triggers in MySQL 5.0, MySQL offers the programming power neededfor true enterprise use. MySQL's new procedural language has a straightforward syntax, making iteasy to write simple programs. But it's not so easy to write secure,easily maintained, high-performance, and bug-free programs. Few in theMySQL world have substantial experience yet with stored procedures, butGuy Harrison and Steven Feuerstein have decades of combined expertise. In MySQL Stored Procedure Programming, they putthat hard-won experience to good use. Packed with code examples and coveringeverything from language basics to application building to advancedtuning and best practices, this highly readable book is the one-stopguide to MySQL development. It consists of four major sections: MySQL stored programming fundamentals -- tutorial, basicstatements, SQL in stored programs, and error handling Building MySQL stored programs -- transaction handling,built-in functions, stored functions, and triggers MySQL stored programs in applications -- using storedprograms with PHP, Java, Perl, Python, and .NET (C# and VB.NET) Optimizing MySQL stored programs -- security, basic andadvanced SQL tuning, optimizing stored program code, and programmingbest practices A companion web site contains many thousands of lines of code, that youcan put to use immediately. Guy Harrison is Chief Architect of Database Solutions at Quest Softwareand a frequent speaker and writer on MySQL topics. Steven Feuerstein isthe author of Oracle PL/SQL Programming, the classic reference for Oracle stored programming for more than ten years. Both have decades of experience as database developers, and between them they have authored a dozen books. COMPUTERS,Database Administration & Management

Star Schema The Complete Reference The definitive guide to dimensional design for your data warehouse Learn the best practices of dimensional design. Star Schema: The Complete Reference offers in-depth coverage of design principles and their underlying rationales. Organized around design concepts and illustrated with detailed examples, this is a step-by-step guidebook for beginners and a comprehensive resource for experts. This all-inclusive volume begins with dimensional design fundamentals and shows how they fit into diverse data warehouse architectures, including those of W.H. Inmon and Ralph Kimball. The book progresses through a series of advanced techniques that help you address real-world complexity, maximize performance, and adapt to the requirements of BI and ETL software products. You are furnished with design tasks and deliverables that can be incorporated into any project, regardless of architecture or methodology. Master the fundamentals of star schema design and slow change processing Identify situations that call for multiple stars or cubes Ensure compatibility across subject areas as your data warehouse grows Accommodate repeating attributes, recursive hierarchies, and poor data quality Support conflicting requirements for historic data Handle variation within a business process and correlation of disparate activities Boost performance using derived schemas and aggregates Learn when it's appropriate to adjust designs for BI and ETL tools COMPUTERS,Database Administration & Management

PeopleSoft PeopleTools Tips & Techniques Advanced PeopleSoft PeopleTools Development Strategies Maximize the efficiency and productivity of your PeopleSoft applications from Oracle using the proven methods and best practices in this Oracle Press guide. PeopleSoft PeopleTools Tips & Techniques lays out the benefits of each tactic along with implementation considerations, programming instructions, and reusable code samples. Construct powerful iScripts, build custom UIs, work with Java and Ajax, and integrate the latest Web 2.0 features. Test-driven development, application security, performance tuning, and debugging are also covered in this authoritative resource. Develop modular logic using PeopleSoft application classes Incorporate file attachment and approval workflow capabilities Add Web elements with PeopleCode iScripts and bookmarkets Enhance functionality using HTML, JavaScript, CSS, and Ajax Extend PeopleSoft Integration Broker through custom connctors Effectively merge Java with PeopleCode to create elegant solutions Use runtime loggers and tracers to test and tune applications Extend the PeopleSoft Web server with JSP, servlets, and filters Create Web-based mobile applications using Oracle JDeveloper COMPUTERS,Database Administration & Management

Access 2010 Programmer's Reference A comprehensive guide to programming for Access 2010 and 2007 Millions of people use the Access database applications, and hundreds of thousands of developers work with Access daily. Access 2010 brings better integration with SQL Server and enhanced XML support; this Wrox guide shows developers how to take advantage of these and other improvements. With in-depth coverage of VBA, macros, and other programming methods for building Access applications, this book also provides real-world code examples to demonstrate each topic. Access 2010 Programmer's Referenceis a comprehensive guide to the best-of-breed techniques for programming Access applications. Coverage Includes: Introduction to Microsoft Access 2010 New Features Upgrading and Converting to Access 2010 Macros in Access 2010 Using the VBA Editor VBA Basics Using VBA in Access Creating Classes in VBA Extending VBA with APIs Working with the Windows Registry Using DAO to Access Data Using ADO to Access Data Using SQL with VBA Using VBA to Enhance Forms Enhancing Reports with VBA Customizing the Ribbon Customizing the Office Backstage Working with Office 2010 Working with SharePoint Working with .NET Building Client-Server Applications with Access The Access 2010 Templates Access Runtime Deployment Database Security Access 2010 Security Features COMPUTERS,Database Administration & Management

Oracle SOA Suite 11g Handbook Master Oracle SOA Suite 11g Design and implement an agile service-oriented enterprise computing infrastructure using the detailed information in this Oracle Press guide. Written by an Oracle ACE director, Oracle SOA Suite 11g Handbook uses a hands-on case study to illustrate each programming, management, and governance concept. Get expert techniques for modeling and implementing complex business processes and deploying and securing Web services, while maximizing decoupling and code reuse. Install Oracle SOA Suite 11g or migrate from a previous version Design and develop composite applications using SCA and SDO Model processes using BPEL, BPMN, and human task components Connect components through mapping and filtering with Oracle Mediator Apply the principles of event-driven architecture through complex event processing, the event delivery network, and Oracle Business Activity Monitoring server Benefit from the power of Java through the Spring component and the interaction with Oracle Validate, enrich, transform, route, and operate on data using the Oracle Service Bus Deploy, test, and manage composite applications from the Oracle Enterprise Manager control console COMPUTERS,Database Administration & Management

The Practitioner's Guide to Data Quality Improvement The Practitioner's Guide to Data Quality Improvement offers a comprehensive look at data quality for business and IT, encompassing people, process, and technology. It shares the fundamentals for understanding the impacts of poor data quality, and guides practitioners and managers alike in socializing, gaining sponsorship for, planning, and establishing a data quality program. It demonstrates how to institute and run a data quality program, from first thoughts and justifications to maintenance and ongoing metrics. It includes an in-depth look at the use of data quality tools, including business case templates, and tools for analysis, reporting, and strategic planning. This book is recommended for data management practitioners, including database analysts, information analysts, data administrators, data architects, enterprise architects, data warehouse engineers, and systems analysts, and their managers. Offers a comprehensive look at data quality for business and IT, encompassing people, process, and technology. Shows how to institute and run a data quality program, from first thoughts and justifications to maintenance and ongoing metrics. Includes an in-depth look at the use of data quality tools, including business case templates, and tools for analysis, reporting, and strategic planning. COMPUTERS,Database Administration & Management

FileMaker Pro Design and Scripting For Dummies Get the scoop on designing databases for Mac and Windows Use FileMaker Pro design and scripting to quickly, easily build databases that solve real problems FileMaker Pro has grown up, and it's better than ever! This easy-to-use guide shows you how to design a great FileMaker application, build a database that works, add the functionality you need, populate your database, and venture into programming with ScriptMaker. You'll find out how to share and protect your database, too. Discover how to * Build a layout that works * Create custom triggers and calculated fields * Generate reports automatically * Manage security * Publish your database on the Web * Embed pictures, sound, and video COMPUTERS,Database Administration & Management

Data Mining Data Mining: Concepts and Techniques provides the concepts and techniques in processing gathered data or information, which will be used in various applications. Specifically, it explains data mining and the tools used in discovering knowledge from the collected data. This book is referred as the knowledge discovery from data (KDD). It focuses on the feasibility, usefulness, effectiveness, and scalability of techniques of large data sets. After describing data mining, this edition explains the methods of knowing, preprocessing, processing, and warehousing data. It then presents information about data warehouses, online analytical processing (OLAP), and data cube technology. Then, the methods involved in mining frequent patterns, associations, and correlations for large data sets are described. The book details the methods for data classification and introduces the concepts and methods for data clustering. The remaining chapters discuss the outlier detection and the trends, applications, and research frontiers in data mining. This book is intended for Computer Science students, application developers, business professionals, and researchers who seek information on data mining. Presents dozens of algorithms and implementation examples, all in pseudo-code and suitable for use in real-world, large-scale data mining projects Addresses advanced topics such as mining object-relational databases, spatial databases, multimedia databases, time-series databases, text databases, the World Wide Web, and applications in several fields Provides a comprehensive, practical look at the concepts and techniques you need to get the most out of your data COMPUTERS,Database Administration & Management

SAP® Project System Handbook Centralize and Control Enterprise Project Management Plan, execute, and track projects across the entire lifecycle using SAP Project System (PS) and the in-depth information contained in this comprehensive volume. SAP Project System Handbook explains how to configure PS for optimal performance, design structures and networks, create project blueprints, generate cost estimates and materials demands, and use the latest SAP tools. You will find full details on scheduling work, automating and tracking billing and POs, triggering events, and integrating with most other SAP modules. An invaluable reference to PS transaction codes is also included. Configure and customize SAP Project System Build PS objects, networks, and Work Breakdown Structures Use customer and service projects to track sales and billing Understand Assembly Processing concepts Create integrated cost, settlement, and resource plans Develop financial, workforce, and materials management blueprints Perform resource-related billing using Dynamic Item Processor Profiles Simulate and automatically generate sales documents, POs, and quotations Manage corporate investments with IM structures and AUCs Construct timesaving Project, Network, and Milestone Templates Extend functionality with the Project Builder, Planning Board, and ProMan COMPUTERS,Database Administration & Management

Professional Microsoft SQL Server 2012 Analysis Services with MDX and DAX Understand Microsoft's dramatically updated new release of its premier toolset for business intelligence The first major update to Microsoft's state-of-the-art, complex toolset for business intelligence (BI) in years is now available and what better way to master it than with this detailed book from key members of the product's development team? If you're a database or data warehouse developer, this is the expert resource you need to build full-scale, multi-dimensional, database applications using Microsoft's new SQL Server 2012 Analysis Services and related tools. Discover how to solve real-world BI problems by leveraging a slew of powerful new Analysis Services features and capabilities. These include the new DAX language, which is a more user-friendly version of MDX; PowerPivot, a new tool for performing simplified analysis of data; BISM, Microsoft's new Business Intelligence Semantic Model; and much more. Serves as an authoritative guide to Microsoft's new SQL Server 2012 Analysis Services BI product and is written by key members of the Microsoft Analysis Services product development team Covers SQL Server 2012 Analysis Services, a major new release with a host of powerful new features and capabilities Topics include using the new DAX language, a simplified, more user-friendly version of MDX; PowerPivot, a new tool for performing simplified analysis of data; BISM, Microsoft's new Business Intelligence Semantic Model; and a new, yet-to-be-named BI reporting tool Explores real-world scenarios to help developers build comprehensive solutions Get thoroughly up to speed on this powerful new BI toolset with the timely and authoritative Professional Microsoft SQL Server 2012 Analysis Services with MDX. COMPUTERS,Database Administration & Management

Beginning Microsoft SQL Server 2012 Programming Get up to speed on the extensive changes to the newest release of Microsoft SQL Server The 2012 release of Microsoft SQL Server changes how you develop applications for SQL Server. With this comprehensive resource, SQL Server authority Robert Vieira presents the fundamentals of database design and SQL concepts, and then shows you how to apply these concepts using the updated SQL Server. Publishing time and date with the 2012 release, Beginning Microsoft SQL Server 2012 Programming begins with a quick overview of database design basics and the SQL query language and then quickly proceeds to show you how to implement the fundamental concepts of Microsoft SQL Server 2012. You'll explore the key additions and changes to this newest version, including conditional action constructs, enhanced controls for results paging, application integration with SharePoint and Excel, and development of BI applications. Covers new features such as SQL Azure for cloud computing, client-connectivity enhancements, security and compliance, data replication, and data warehouse performance improvements Addresses essential topics including managing keys, writing scripts, and working with store procedures Shares helpful techniques for creating and changing tables, programming with XML, and using SQL Server Reporting and Integration Services Beginning Microsoft SQL Server 2012 Programming demystifies even the most difficult challenges you may face with the new version of Microsoft SQL Server. COMPUTERS,Database Administration & Management

Professional Microsoft SQL Server 2012 Administration An essential how-to guide for experienced DBAs on the most significant product release since 2005! Microsoft SQL Server 2012 will have major changes throughout the SQL Server and will impact how DBAs administer the database. With this book, a team of well-known SQL Server experts introduces the many new features of the most recent version of SQL Server and deciphers how these changes will affect the methods that administrators have been using for years. Loaded with unique tips, tricks, and workarounds for handling the most difficult SQL Server admin issues, this how-to guide deciphers topics such as performance tuning, backup and recovery, scaling and replication, clustering, and security. Serves as a must-have how-to guide on the new features of the 2012 release of Microsoft SQL Server Walks you through ways to manage and monitor SQL Server and automate administration Guides you through SQL Azure for cloud computing, data replication, and data warehouse performance improvements Addresses client-connectivity enhancements, new features that ensure high availability of mission-critical applications, and tighter integration with Excel and SharePoint for data analysis and reporting Highlights major changes to the suite of SQL Server BI tools, including integration, reporting, and analysis services Includes real-world case examples and best practices from Microsoft insiders If you're a database administrator eager to get started with the newest version of SQL Server, then this book is essential reading. COMPUTERS,Database Administration & Management

DB2 9 for Linux, UNIX, and Windows Advanced Database Administration Certification Database administrators versed in DB2 wanting to learn more about advanced database administration activities and students wishing to gain knowledge to help them pass the DB2 9 UDB Advanced DBA certification exam will find this exhaustive reference invaluable. Written by two individuals who were part of the team that developed the certification exam, this comprehensive study guide prepares the student for challenging questions on database design; data partitioning and clustering; high availability diagnostics; performance and scalability; security and encryption; connectivity and networking; and much more. Providing sample questions in each chapter, a complete practice test modeled after the actual exam, and an extensive answer key providing full explanations for each correct answer, readers will find this to be a key resource in stimulating the learning process. COMPUTERS,Database Administration & Management

Oracle E-Business Suite Manufacturing & Supply Chain Management Implement Oracle's Internet-based Manufacturing and Supply Chain Management products using this Oracle authorized resource. This comprehensive guide explains how to implement the planning, engineering, pricing, order fulfillment, and inventory management components of Oracle Manufacturing and Supply Chain--and develop and deliver goods and services faster, cheaper, and more efficiently than your competitors. COMPUTERS,Database Administration & Management

Data Governance This book is for any manager or team leader that has the green light to implement a data governance program. The problem of managing data continues to grow with issues surrounding cost of storage, exponential growth, as well as administrative, management and security concerns – the solution to being able to scale all of these issues up is data governance which provides better services to users and saves money. What you will find in this book is an overview of why data governance is needed, how to design, initiate, and execute a program and how to keep the program sustainable. With the provided framework and case studies you will be enabled and educated in launching your very own successful and money saving data governance program. Provides a complete overview of the data governance lifecycle, that can help you discern technology and staff needs Specifically aimed at managers who need to implement a data governance program at their company Includes case studies to detail ‘do’s’ and ‘don’ts’ in real-world situations COMPUTERS,Database Administration & Management

Oracle E-Business Suite Financials Handbook 3/E Implement the Full Spectrum of Oracle E-Business Suite Financial Applications Maintain an integrated, customer-focused financial computing framework that meets global business requirements while lowering total cost of ownership. Oracle E-Business Suite Financials Handbook, Third Edition offers fully updated coverage of the latest applications and modules. Find out how to enforce robust accounting rules, establish workflow, manage invoices and inventory, create budgets and forecasts, and secure your corporate assets. This Oracle Press guide thoroughly explains how to deploy custom Web applications, automate tax reporting, and incorporate Oracle Fusion Applications. Centralize financial data with Oracle General Ledger and Oracle Subledger Accounting Track invoices and payments through Oracle Receivables and Oracle Payables Forecast cash requirements and manage portfolios with Oracle Treasury Increase liquidity and profitability using Oracle Cash Management Establish asset depreciation schedules and handle leases and warranty information with Oracle Assets Use Oracle Purchasing and Oracle Inventory to optimize supply chain efficiency Handle procurement and billing information using Oracle Projects and Oracle Order Management Employ the all-new Oracle E-Business Tax and Oracle Landed Cost Management Leverage Oracle Fusion Applications in a co-existence strategy with Oracle E-Business Suite Financials Implement an end-to-end disaster recovery strategy COMPUTERS,Database Administration & Management

Oracle Database 12c PL/SQL Programming Master Oracle Database 12c PL/SQL Application Development Develop, debug, and administer robust database programs. Filled with detailed examples and expert strategies from an Oracle ACE, Oracle Database 12c PL/SQL Programming explains how to retrieve and process data, write PL/SQL statements, execute effective queries, incorporate PHP and Java, and work with dynamic SQL. Code testing, security, and object-oriented programming techniques are fully covered in this comprehensive Oracle Press guide. Explore new SQL and PL/SQL features in Oracle Database 12c Build control structures, cursors, and loop statements Work with collections, varrays, tables, and associative array collections Locate and repair errors and employ exception handlers Execute black box, white box, and integration tests Configure and manage stored packages and libraries Handle security with authentication and encryption Use LOBs to store text and multimedia content Write and implement PL/SQL and Java triggers Extend functionality using dynamic SQL statements Understand object types, nested tables, and unnesting queries COMPUTERS,Database Administration & Management

Successful Business Intelligence, Second Edition Revised to cover new advances in business intelligence—big data, cloud, mobile, and more—this fully updated bestseller reveals the latest techniques to exploit BI for the highest ROI. “Cindi has created, with her typical attention to details that matter, a contemporary forward-looking guide that organizations could use to evaluate existing or create a foundation for evolving business intelligence / analytics programs. The book touches on strategy, value, people, process, and technology, all of which must be considered for program success. Among other topics, the data, data warehousing, and ROI comments were spot on. The ‘technobabble’ chapter was brilliant!â€â€”Bill Frank, Business Intelligence and Data Warehousing Program Manager, Johnson & Johnson “If you want to be an analytical competitor, you’ve got to go well beyond business intelligence technology. Cindi Howson has wrapped up the needed advice on technology, organization, strategy, and even culture in a neat package. It’s required reading for quantitatively oriented strategists and the technologists who support them.â€â€”Thomas H. Davenport, President’s Distinguished Professor, Babson College and co-author, Competing on Analytics “Cindi has created an exceptional, authoritative description of the end-to-end business intelligence ecosystem. This is a great read for those who are just trying to better understand the business intelligence space, as well as for the seasoned BI practitioner.â€â€”Sully McConnell, Vice President, Business Intelligence and Information Management, Time Warner Cable “Cindi’s book succinctly yet completely lays out what it takes to deliver BI successfully. IT and business leaders will benefit from Cindi’s deep BI experience, which she shares through helpful, real-world definitions, frameworks, examples, and stories. This is a must-read for companies engaged in – or considering – BI.â€â€”Barbara Wixom, PhD, Principal Research Scientist, MIT Sloan Center for Information Systems Research Expanded to cover the latest advances in business intelligence such as big data, cloud, mobile, visual data discovery, and in-memory computing, this fully updated bestseller by BI guru Cindi Howson provides cutting-edge techniques to exploit BI for maximum value. Successful Business Intelligence: Unlock the Value of BI & Big Data, Second Edition describes best practices for an effective BI strategy. Find out how to: Garner executive support to foster an analytic culture Align the BI strategy with business goals Develop an analytic ecosystem to exploit data warehousing, analytic appliances, and Hadoop for the right BI workload Continuously improve the quality, breadth, and timeliness of data Find the relevance of BI for everyone in the company Use agile development processes to deliver BI capabilities and improvements at the pace of business change Select the right BI tools to meet user and business needs Measure success in multiple ways Embrace innovation, promote successes and applications, and invest in training Monitor your evolution and maturity across various factors for impact Exclusive industry survey data and real-world case studies from Medtronic, Macy’s, 1-800 CONTACTS, The Dow Chemical Company, Netflix, Constant Contact, and other companies show successful BI initiatives in action. From Moneyball to Nate Silver, BI and big data have permeated our cultural, political, and economic landscape. This timely, up-to-date guide reveals how to plan and deploy an agile, state-of-the-art BI solution that links insight to action and delivers a sustained competitive advantage. COMPUTERS,Database Administration & Management

Database Design for Mere Mortals The #1 Easy, Commonsense Guide to Database Design! Michael J. Hernandez’s best-selling Database Design for Mere Mortals® has earned worldwide respect as the clearest, simplest way to learn relational database design. Now, he’s made this hands-on, software-independent tutorial even easier, while ensuring that his design methodology is still relevant to the latest databases, applications, and best practices. Step by step, Database Design for Mere Mortals ® , Third Edition, shows you how to design databases that are soundly structured, reliable, and flexible, even in modern web applications. Hernandez guides you through everything from database planning to defining tables, fields, keys, table relationships, business rules, and views. You’ll learn practical ways to improve data integrity, how to avoid common mistakes, and when to break the rules. Coverage includes Understanding database types, models, and design terminology Discovering what good database design can do for you—and why bad design can make your life miserable Setting objectives for your database, and transforming those objectives into real designs Analyzing a current database so you can identify ways to improve it Establishing table structures and relationships, assigning primary keys, setting field specifications, and setting up views Ensuring the appropriate level of data integrity for each application Identifying and establishing business rules Whatever relational database systems you use, Hernandez will help you design databases that are robust and trustworthy. Never designed a database before? Settling for inadequate generic designs? Running existing databases that need improvement? Start here. COMPUTERS,Database Administration & Management

Access 2013 For Dummies The easy guide to Microsoft Access returns with updates on the latest version! Microsoft Access allows you to store, organize, view, analyze, and share data; the new Access 2013 release enables you to build even more powerful, custom database solutions that integrate with the web and enterprise data sources. Access 2013 For Dummies covers all the new features of the latest version of Accessand serves as an ideal reference, combining the latest Access features with the basics of building usable databases. You'll learn how to create an app from the Welcome screen, get support for your desktop databases, and much more. Includes coverage of all the new features of Access 2013, including the updated interface Shows you how to create and share reports Features special videos and materials created by the authors to help reinforce the lessons included in the book Helps you build data analysis and interface tools for your specific needs Offers plenty of techniques and tips for solving common problems Access 2013 For Dummies provides you with access to the latest version of this database tool. COMPUTERS,Database Administration & Management

Teach Yourself VISUALLY Access 2013 The easy, visual way to learn this popular database program Part of the Office 2013 productivity suite, Access enables you to organize, present, analyze, and share data on a network or over the web. With this Visual guide to show you how, you'll master the fundamentals of this robust database application in no time. Clear, step-by-step instructions are illustrated with full-color screen shots that show exactly what you should see on your screen. Learn to enter new records; create, edit, and design tables and forms; develop queries that generate specific reports; add smart tags to your tables; and much more. While it is the most widely used database application, Access is not particularly intuitive; the Visual system's two-page lessons and full-color screen shots make this complex software easier to learn Concise, step-by-step instructions and clear illustrations show you exactly what to expect Covers scores of tasks, including entering and setting up new records, organizing and sharing data, designing tables and forms, and generating reports Shows how to perform more complex operations, such as finding dependencies between database objects and adding smart tags to tables Teach Yourself VISUALLY Access 2013 uses clear steps and high-resolution screen images to get you up and running with this popular database program. COMPUTERS,Database Administration & Management

Beginning Database Design Beginning Database Design, Second Edition provides short, easy-to-read explanations of how to get database design right the first time. This book offers numerous examples to help you avoid the many pitfalls that entrap new and not-so-new database designers. Through the help of use cases and class diagrams modeled in the UML, you’ll learn to discover and represent the details and scope of any design problem you choose to attack. Database design is not an exact science. Many are surprised to find that problems with their databases are caused by poor design rather than by difficulties in using the database management software. Beginning Database Design, Second Edition helps you ask and answer important questions about your data so you can understand the problem you are trying to solve and create a pragmatic design capturing the essentials while leaving the door open for refinements and extension at a later stage. Solid database design principles and examples help demonstrate the consequences of simplifications and pragmatic decisions. The rationale is to try to keep a design simple, but allow room for development as situations change or resources permit. Provides solid design principles by which to avoid pitfalls and support changing needs Includes numerous examples of good and bad design decisions and their consequences Shows a modern method for documenting design using the Unified Modeling Language COMPUTERS,Database Administration & Management

MySQL Workbench The only Oracle Press guide to MySQL Workbench explains how to design and model MySQL databases. MySQL Workbench Data Modeling and Development helps developers learn how to effectively use this powerful product for database modeling, reverse engineering, and interaction with the database without writing SQL statements. MySQL Workbench is a graphical user interface that can be used to create and maintain MySQL databases without coding. The book covers the interface and explains how to accomplish each step by illustrating best practices visually. Clear examples, instructions, and explanations reveal, in a single volume, the art of database modeling. This Oracle Press guide shows you how to get the tool to do what you want. Annotated screen shots demonstrate all interactions with the tool, and text explains the how, what, and why of each step. Complete coverage Installation and Configuration; Creating and Managing Connections; Data Modeling Concepts; Creating an ERD; Defining the Physical Schemata; Creating and Managing Tables; Creating and Managing Relationships; Creating and Managing Views; Creating and Managing Routines; Creating and Managing Routine Groups; Creating and Managing User & Groups; Creating and Managing SQL Scripts; Generating SQL Scripts; Forward Engineering a Data Model; Synchronize a Model with a Database; Reverse Engineering a Database; Managing Differences in the Data Catalog; Creating and Managing Model Notes; Editing Table Data; Editing Generated Scripts; Creating New Instances; Managing Import and Export; Managing Security; Managing Server Instances COMPUTERS,Database Administration & Management

Recent Advances in Temporal Databases The International Workshop on Temporal Databases held in Zurich, Switzerland, 17-18 September 1995 brought together researchers from academic and industrial institutions with database practitioners interested in keeping up with the state-of-the-art developments in the management of temporal data. A previous workshop in Arlington, Texas in June 1993 focused on the development of an infrastructure that would spur the development of commercial implementations of many of the generally agreed-upon features of temporal database management that have emerged from the temporal database research community over more than a decade of research. This ARP AlNSF-sponsored Arlington workshop saw the formation of the TSQL2 Language Design Committee, which led to the development of the recently completed TSQL2 Language Specification, and also created a "consensus" glossary of temporal database terminology and a test suite of temporal database queries. The Zurich workshop was conceived from the outset to be universal in scope, and international in participation. The Call for Papers sought to evoke the highest quality and most up-to-date temporal database research from around the world. Mindful of the important work accomplished by the previous workshop, the Call also specifically sought out research papers and panels that would comment and build upon the widely publicized results from Arlington. These proceedings contain the papers that were selected for presentation at the International Workshop, on Temporal Databases held in Zurich, Switzerland on 17-18 September 1995. COMPUTERS,Database Administration & Management

Rules in Database Systems This book is the proceedings of a workshop held at Heriot-Watt University in Edinburgh in August 1993. The central theme of the workshop was rules in database systems, and the papers presented covered a range of different aspects of database rule systems. These aspects are reflected in the sessions of the workshop, which are the same as the sections in this proceedings: Active Databases Architectures Incorporating Temporal Rules Rules and Transactions Analysis and Debugging of Active Rules Integrating Graphs/Objects with Deduction Integrating Deductive and Active Rules Integrity Constraints Deductive Databases The incorporation of rules into database systems is an important area of research, as it is a major component in the integration of behavioural information with the structural data with which commercial databases have traditionally been associated. This integration of the behavioural aspects of an application with the data to which it applies in database systems leads to more straightforward application development and more efficient processing of data. Many novel applications seem to need database systems in which structural and behavioural information are fully integrated. Rules are only one means of expressing behavioural information, but it is clear that different types of rule can be used to capture directly different properties of an application which are cumbersome to support using conventional database architectures. In recent years there has been a surge of research activity focusing upon active database systems, and this volume opens with a collection of papers devoted specifically to this topic. COMPUTERS,Database Administration & Management

Object-Oriented Database System Computer Science Workbench is a monograph series which will provide you with an in depth working knowledge of current developments in computer technology. Every volume in this series will deal with a topic of importance in computer science and elaborate on how you yourself can build systems related to the main theme. You will be able to develop a variety of systems, including computer software tools, computer graphics, computer animation, database management systems, and computer-aided design and manufacturing systems. Computer Science Workbench represents an important new contribution in the field of practical computer technology. Tosiyasu L. Kunii Preface The goal of this book is to give concrete answers to questions such as what object oriented databases are, why they are needed, how they are implemented, and how they are applied, by describing a research prototype object-oriented database system called Jasmine. That is, this book is aimed at creating a consistent view to object-oriented databases. The contents of this book are directly based on the results of the Jasmine project conducted at Fujitsu Laboratories, Ltd. The book is a polished version of my doctoral dissertation, which includes research papers which I have authored and published. COMPUTERS,Database Administration & Management

Database and Expert Systems Applications The Database and Expert Systems Application -DEXA - conferences are mainly oriented to establish a state-of-the art forum on Database and Expert System applications. But Practice without Theory has no sense, as Leonardo said five centuries ago. In this Conference we try a comprornise between these two complementary aspects. A total of 5 sessions are application-oriented, ranging from classical applications to more unusual ones in Software Engineering. Recent research aspects in Databases, such as activity, deductivity and/or Object Orientation are also present in DEXA 92, as weIl as the implication of the new "data models" such as OO-Model, Deductive Model, etc .. included in the Modelling sessions. Other areas of interest, such as Hyper-Text and Multimedia application, together with the classical field of Information Retrieval are also considered. FinaIly, Implementation Apects are reflected in very concrete fields. A total of of nearly 200 papers submitted from all over the world were sent to DEXA 92. Only 90 could be accepted. A Poster session has also been establishcd. DEXA 90 was held in Vienna, Austria; DEXA 91 in Berlin, Germany; and DEXA 92 will take place in Valencia, Spain, where we are celebrating the discovery of thc New World just five centurics ago, in Leonardo's age. Both the quality of the Conference and the compromise between Practice and Thcory are duc to the credit of all the DEXA 92 authors. COMPUTERS,Database Administration & Management

Specifications of Database Systems Increasingly, formal specification is being used by database researchers to describe and understand the systems they are designing and implementing. Similarly, those working on formal specification techniques have recognised that the database field provides a rich context for developing their ideas. However, as experts in one field often have a relatively limited knowledge of the other, there is a growing need for discussion about the relationship between these two fields and how they can be usefully combined. This volume contains the 16 papers which were presented at the International Workshop on Specification on Database Systems, held in Glasgow, 3-5 July 1991. The purpose of the workshop was to bring together these fields and to examine, through a series of invited talks, presentations and working groups, the role that formal specification can play in developing database systems. The papers describe current research into topics such as the formal specification of data models, query languages and transaction handling and the use of formal specification techniques to understand problems which arise in database systems. The working groups, which are summarised at the end of the volume, covered a variety of issues including the role of graphical notations in database specification, the use of specification techniques in enabling "open" or extensible database systems and the education of the database community in specification techniques. This volume will be invaluable to the increasing number of researchers who are using both database systems and formal specification techniques in their work, and who wish to gain a more detailed knowledge of these two fields and the issues which affect them. COMPUTERS,Database Administration & Management

Engineering Databases Automation is nothing new to industry. It has a long tradition on the factory floor, where its constant objective has been to increase the productivity of manufacturing processes. Only with the advent of computers could the focus of automation widen to include administrative and information-handling tasks. More recently, automation has been extended to the more intellectual tasks of production planning and control, material and resource planning, engineering design, and quality control. New challenges arise in the form of flexible manu facturing, assembly automation, and automated floor vehicles, to name just a few. The sheer complexity of the problems as well as the state of the art has led scientists and engineers to concentrate on issues that could easily be isolated. For example, it was much simpler to build CAD systems whose sole objective was to ease the task of drawing, rather than to worry at the same time about how the design results could be interfaced with the manufacturing or assembly processes. It was less problematic to gather statistics from quality control and to print reports than to react immediately to first hints of irregularities by inter facing with the designers or manufacturing control, or, even better, by auto matically diagnosing the causes from the design and planning data. A heav- though perhaps unavoidable - price must today be paid whenever one tries to assemble these isolated solutions into a larger, integrated system. COMPUTERS,Database Administration & Management

Database and Expert Systems Applications DEXA 90 COMPUTERS,Database Administration & Management

Oracle Database 12c The Complete Reference Master the Cutting-Edge Features of Oracle Database 12c Maintain a scalable, highly available enterprise platform and reduce complexity by leveraging the powerful new tools and cloud enhancements of Oracle Database 12c. This authoritative Oracle Press guide offers complete coverage of installation, configuration, tuning, and administration. Find out how to build and populate Oracle databases, perform effective queries, design applications, and secure your enterprise data. Oracle Database 12c: The Complete Reference also contains a comprehensive appendix covering commands, keywords, features, and functions. Set up Oracle Database 12c or upgrade from an earlier version Design Oracle databases and plan for application implementation Construct SQL and SQL*Plus statements and execute powerful queries Secure data with roles, privileges, virtualization, and encryption Move data with SQL*Loader and Oracle Data Pump Restore databases using flashback and the Oracle Database Automatic Undo Management feature Build and deploy PL/SQL triggers, procedures, and packages Work with Oracle pluggable and container databases Develop database applications using Java, JDBC, and XML Optimize performance with Oracle Real Application Clusters COMPUTERS,Database Administration & Management

Big Data Analytics Big Data Analytics will assist managers in providing an overview of the drivers for introducing big data technology into the organization and for understanding the types of business problems best suited to big data analytics solutions, understanding the value drivers and benefits, strategic planning, developing a pilot, and eventually planning to integrate back into production within the enterprise. Guides the reader in assessing the opportunities and value proposition Overview of big data hardware and software architectures Presents a variety of technologies and how they fit into the big data ecosystem COMPUTERS,Database Administration & Management

Professional Access 2013 Programming Authoritative and comprehensive coverage for building Access 2013 Solutions Access, the most popular database system in the world, just opened a new frontier in the Cloud. Access 2013 provides significant new features for building robust line-of-business solutions for web, client and integrated environments. This book was written by a team of Microsoft Access MVPs, with consulting and editing by Access experts, MVPs and members of the Microsoft Access team. It gives you the information and examples to expand your areas of expertise and immediately start to develop and upgrade projects. Explores the new development environment for Access web apps Focuses on the tools and techniques for developing robust web applications Demonstrates how to monetize your apps with Office Store and create e-commerce solutions Explains how to use SQL Server effectively to support both web and client solutions Provides techniques to add professional polish and deploy desktop application Shows you how to automate other programs using Macros, VBA, API calls and more. Professional Access 2013 Programming is a complete guide on the latest tools and techniques for building Access 2013 applications for both the web and the desktop so that developers and businesses can move forward with confidence. Whether you want to add expand your expertise with Client/Server deployments or start developing web apps, you will want this book as a companion and reference. COMPUTERS,Database Administration & Management

Big Data, Mining, and Analytics There is an ongoing data explosion transpiring that will make previous creations, collections, and storage of data look trivial. Big Data, Mining, and Analytics: Components of Strategic Decision Making ties together big data, data mining, and analytics to explain how readers can leverage them to extract valuable insights from their data. Facilitating a clear understanding of big data, it supplies authoritative insights from expert contributors into leveraging data resources, including big data, to improve decision making. Illustrating basic approaches of business intelligence to the more complex methods of data and text mining, the book guides readers through the process of extracting valuable knowledge from the varieties of data currently being generated in the brick and mortar and internet environments. It considers the broad spectrum of analytics approaches for decision making, including dashboards, OLAP cubes, data mining, and text mining. Includes a foreword by Thomas H. Davenport, Distinguished Professor, Babson College; Fellow, MIT Center for Digital Business; and Co-Founder, International Institute for Analytics Introduces text mining and the transforming of unstructured data into useful information Examines real time wireless medical data acquisition for today’s healthcare and data mining challenges Presents the contributions of big data experts from academia and industry, including SAS Highlights the most exciting emerging technologies for big data—Hadoop is just the beginning Filled with examples that illustrate the value of analytics throughout, the book outlines a conceptual framework for data modeling that can help you immediately improve your own analytics and decision-making processes. It also provides in-depth coverage of analyzing unstructured data with text mining methods to supply you with the well-rounded understanding required to leverage your information assets into improved strategic decision making. COMPUTERS,Database Administration & Management

Microsoft SQL Server 2014 Query Tuning & Optimization Optimize Microsoft SQL Server 2014 queries and applications Microsoft SQL Server 2014 Query Tuning & Optimization is filled with ready-to-use techniques for creating high-performance queries and applications. The book describes the inner workings of the query processor so you can write better queries and provide the query processor with the quality information it needs to produce efficient execution plans. You’ll also get tips for troubleshooting underperforming queries. In-Memory OLTP (Hekaton), a key new feature of SQL Server 2014, is fully covered in this practical guide. Understand how the query optimizer works Troubleshoot queries using extended events, SQL trace, dynamic management views (DMVs), the data collector, and other tools Work with query operators for data access, joins, aggregations, parallelism, and updates Speed up queries and dramatically improve application performance by creating the right indexes Understand statistics and how to detect and fix cardinality estimation errors Maximize OLTP query performance using In-Memory OLTP (Hekaton) features, including memory-optimized tables and natively compiled stored procedures Monitor and promote plan caching and reuse to improve application performance Improve the performance of data warehouse queries using columnstore indexes Handle query processor limitations with hints and other methods COMPUTERS,Database Administration & Management

Practical Guide to Clinical Data Management The management of clinical data, from its collection during a trial to its extraction for analysis, has become a critical element in the steps to prepare a regulatory submission and to obtain approval to market a treatment. Groundbreaking on its initial publication nearly fourteen years ago, and evolving with the field in each iteration since then, the third edition of Practical Guide to Clinical Data Management includes important updates to all chapters to reflect the current industry approach to using electronic data capture (EDC) for most studies. See what’s new in the Third Edition: A chapter on the clinical trial process that explains the high level flow of a clinical trial from creation of the protocol through the study lock and provides the context for the clinical data management activities that follow Reorganized content reflects an industry trend that divides training and standard operating procedures for clinical data management into the categories of study startup, study conduct, and study closeout Coverage of current industry and Food and Drug Administration (FDA) approaches and concerns The book provides a comprehensive overview of the tasks involved in clinical data management and the computer systems used to perform those tasks. It also details the context of regulations that guide how those systems are used and how those regulations are applied to their installation and maintenance. Keeping the coverage practical rather than academic, the author hones in on the most critical information that impacts clinical trial conduct, providing a full end-to-end overview or introduction for clinical data managers. COMPUTERS,Database Administration & Management

Database Design Using Entity-Relationship Diagrams Essential to database design, entity-relationship (ER) diagrams are known for their usefulness in mapping out clear database designs. They are also well-known for being difficult to master. With Database Design Using Entity-Relationship Diagrams, Second Edition, database designers, developers, and students preparing to enter the field can quickly learn the ins and outs of ER diagramming. Building on the success of the bestselling first edition, this accessible text includes a new chapter on the relational model and functional dependencies. It also includes expanded chapters on Enhanced Entity Relationship (EER) diagrams and reverse mapping. It uses cutting-edge case studies and examples to help readers master database development basics and defines ER and EER diagramming in terms of requirements (end user requests) and specifications (designer feedback to those requests). Describes a step-by-step approach for producing an ER diagram and developing a relational database from it Contains exercises, examples, case studies, bibliographies, and summaries in each chapter Details the rules for mapping ER diagrams to relational databases Explains how to reverse engineer a relational database back to an entity-relationship model Includes grammar for the ER diagrams that can be presented back to the user The updated exercises and chapter summaries provide the real-world understanding needed to develop ER and EER diagrams, map them to relational databases, and test the resulting relational database. Complete with a wealth of additional exercises and examples throughout, this edition should be a basic component of any database course. Its comprehensive nature and easy-to-navigate structure makes it a resource that students and professionals will turn to throughout their careers. COMPUTERS,Database Administration & Management

SysML Distilled The Systems Modeling Language (SysML) extends UML with powerful systems engineering capabilities for modeling a wider spectrum of systems and capturing all aspects of a system’s design. SysML Distilled is the first clear, concise guide for everyone who wants to start creating effective SysML models. (Drawing on his pioneering experience at Lockheed Martin and NASA, Lenny Delligatti illuminates SysML’s core components and provides practical advice to help you create good models and good designs. Delligatti begins with an easy-to-understand overview of Model-Based Systems Engineering (MBSE) and an explanation of how SysML enables effective system specification, analysis, design, optimization, verification, and validation. Next, he shows how to use all nine types of SysML diagrams, even if you have no previous experience with modeling languages. A case study running through the text demonstrates the use of SysML in modeling a complex, real-world sociotechnical system. Modeled after Martin Fowler’s classic UML Distilled, Delligatti’s indispensable guide quickly teaches you what you need to know to get started and helps you deepen your knowledge incrementally as the need arises. Like SysML itself, the book is method independent and is designed to support whatever processes, procedures, and tools you already use. Coverage Includes Why SysML was created and the business case for using it Quickly putting SysML to practical use What to know before you start a SysML modeling project Essential concepts that apply to all SysML diagrams SysML diagram elements and relationships Diagramming block definitions, internal structures, use cases, activities, interactions, state machines, constraints, requirements, and packages Using allocations to define mappings among elements across a model SysML notation tables, version changes, and sources for more information COMPUTERS,Database Administration & Management

Professional Microsoft SQL Server 2014 Integration Services Fill the gap between planning and doing with SSIS 2014 The 2014 release of Microsoft's SQL Server Integration Services provides enhancements for managing extraction, transformation, and load operations, plus expanded in-memory capabilities, improved disaster recovery, increased scalability, and much more. The increased functionality will streamline your ETL processes and smooth out your workflow, but the catch is that your workflow must change. New tools come with new best practices, and Professional Microsoft SQL Server 2014 Integration Services will keep you ahead of the curve. SQL Server MVP Brian Knight is the most respected name in the business, and your ultimate guide to navigating the changes to use Microsoft SQL Server Integration Services 2014 to your utmost advantage. Implement new best practices for effective use of SSIS Work through tutorials for hands-on learning of complex techniques Read case studies that illustrate the more advanced concepts Learn directly from the foremost authority on SSIS SQL Server Integration Services is a complex tool, but it's the lifeblood of your work. You need to know it inside out, and you must understand the full potential of its capabilities in order to use it effectively. You need to make sure the right architecture is in place. Professional Microsoft SQL Server 2014 Integration Services is your roadmap to understanding SSIS on a fundamental level, and setting yourself up for success. COMPUTERS,Database Administration & Management

MySQL Cookbook MySQL’s popularity has brought a flood of questions about how to solve specific problems, and that’s where this cookbook is essential. When you need quick solutions or techniques, this handy resource provides scores of short, focused pieces of code, hundreds of worked-out examples, and clear, concise explanations for programmers who don’t have the time (or expertise) to solve MySQL problems from scratch. Ideal for beginners and professional database and web developers, this updated third edition covers powerful features in MySQL 5.6 (and some in 5.7). The book focuses on programming APIs in Python, PHP, Java, Perl, and Ruby. With more than 200+ recipes, you’ll learn how to: Use the mysql client and write MySQL-based programs Create, populate, and select data from tables Store, retrieve, and manipulate strings Work with dates and times Sort query results and generate summaries Use stored routines, triggers, and scheduled events Import, export, validate, and reformat data Perform transactions and work with statistics Process web input, and generate web content from query results Use MySQL-based web session management Provide security and server administration COMPUTERS,Database Administration & Management

Oracle SOA Suite 12c Handbook Master Oracle SOA Suite 12c Design, implement, manage, and maintain a highly flexible service-oriented computing infrastructure across your enterprise using the detailed information in this Oracle Press guide. Written by an Oracle ACE director, Oracle SOA Suite 12c Handbook uses a start-to-finish case study to illustrate each concept and technique. Learn expert techniques for designing and implementing components, assembling composite applications, integrating Java, handling complex business logic, and maximizing code reuse. Runtime administration, governance, and security are covered in this practical resource. Get started with the Oracle SOA Suite 12c development and run time environment Deploy and manage SOA composite applications Expose SOAP/XML REST/JSON through Oracle Service Bus Establish interactions through adapters for Database, JMS, File/FTP, UMS, LDAP, and Coherence Embed custom logic using Java and the Spring component Perform fast data analysis in real time with Oracle Event Processor Implement Event Drive Architecture based on the Event Delivery Network (EDN) Use Oracle Business Rules to encapsulate logic and automate decisions Model complex processes using BPEL, BPMN, and human task components Establish KPIs and evaluate performance using Oracle Business Activity Monitoring Control traffic, audit system activity, and encrypt sensitive data COMPUTERS,Database Administration & Management

Oracle Database Upgrade, Migration & Transformation Tips & Techniques A practical roadmap for database upgrade, migration, and transformation This Oracle Press guide provides best practices for migrating between different operating systems and platforms, transforming existing databases to use different storage or enterprise systems, and upgrading databases from one release to the next. Based on the expert authors’ real-world experience, Oracle Database Upgrade, Migration & Transformation Tips & Techniques will help you choose the best migration path for your project and develop an effective methodology. Code examples and detailed checklists are included in this comprehensive resource. Leverage the features of Oracle Data Guard to migrate an Oracle Database Use Oracle Recovery Manager, transportable tablespace sets, and transportable database toolsets to migrate between platforms Migrate databases with export/import Use Oracle GoldenGate for zero or near-zero downtime migrations Take advantage of the Cross-Platform Transportable Tablespace Set utility Migrate to new storage platforms using the features of Oracle Automatic Storage Management Upgrade to Oracle Database 12c with the Database Upgrade Assistant tool Move seamlessly to Oracle's engineered systems Migrate to the cloud COMPUTERS,Database Administration & Management

Enterprise Business Intelligence and Data Warehousing Corporations and governmental agencies of all sizes are embracing a new generation of enterprise-scale business intelligence (BI) and data warehousing (DW), and very often appoint a single senior-level individual to serve as the Enterprise BI/DW Program Manager. This book is the essential guide to the incremental and iterative build-out of a successful enterprise-scale BI/DW program comprised of multiple underlying projects, and what the Enterprise Program Manager must successfully accomplish to orchestrate the many moving parts in the quest for true enterprise-scale business intelligence and data warehousing. Author Alan Simon has served as an enterprise business intelligence and data warehousing program management advisor to many of his clients, and spent an entire year with a single client as the adjunct consulting director for a $10 million enterprise data warehousing (EDW) initiative. He brings a wealth of knowledge about best practices, risk management, organizational culture alignment, and other Critical Success Factors (CSFs) to the discipline of enterprise-scale business intelligence and data warehousing. COMPUTERS,Database Administration & Management

Expert Oracle Database Architecture Now in its third edition, this best-selling book continues to bring you some of the best thinking on how to apply Oracle Database to produce scalable applications that perform well and deliver correct results. Tom Kyte and Darl Kuhn share a simple philosophy: "you can treat Oracle as a black box and just stick data into it, or you can understand how it works and exploit it as a powerful computing environment." If you choose the latter, then you’ll find that there are few information management problems that you cannot solve quickly and elegantly. This fully revised third edition covers the developments up to Oracle Database 12c. Significant new content is included surrounding Oracle's new cloud feature set, and especially the use of pluggable databases. Each feature is taught in a proof-by-example manner, not only discussing what it is, but also how it works, how to implement software using it, and the common pitfalls associated with it.Don’t treat Oracle Database as a black-box. Get this book. Get under the hood. Turbo-charge your career. Revised to cover Oracle Database 12c Proof-by-example approach: Let the evidence be your guide Dives deeply into Oracle Database’s most powerful features COMPUTERS,Database Administration & Management

Oracle Enterprise Manager 12c Command-Line Interface Oracle Enterprise Manager 12c Command-Line Interface shows how to use Enterprise Manager’s powerful scripting language to automate your database administration work and save time by scripting routine tasks, and then executing those scripts across collections of databases and instances in your environment. This book is chock full of ready-made scripting examples contributed by the authors and leading members of the community. For example, you'll find scripts and examples of commands to: Remove an Enterprise Manager agent and its related targets Quickly create administrator accounts that are fully-configured with pre-expired passwords and all needed roles Invoke batch files to execute sequences of related commands with consistency against multiple targets Batch create large groups of user logins with a single command and more! The Enterprise Manager Command Line Interface (EM CLI) is the administrator's key to unlocking the power of Enterprise Manager 12c (EM12c) with scalability, repeatability, and confidence. In previous versions, most administrators ventured into the command-line interface only with the assistance of Oracle Support. But now there are many features in EM12c that are accessible only from the command-line. This is far from a disadvantage! Enterprise Manager is now a powerful tool for automation in the hands of a skilled database administrator.Enterprise Manager scripting offers potential for all administrators who manage Oracle’s enterprise-level products in their environment. You can automate from the smallest, single-instance configuration all the way up to a broadly distributed enterprise-level rollout having database instances strewn across broad geographical distributions. The power of the EM CLI returns the administrator to the golden age, where the entire environment, from database to application to infrastructure, can often be managed from this powerful command line tool secured by the robust Enterprise Manager framework. Brings a golden-age of automation to Oracle Database administrators Provides ready-made scripts contributed by leading members of the community Covers advanced techniques involving Jython and Python COMPUTERS,Database Administration & Management

Multi-Domain Master Data Management Multi-Domain Master Data Management delivers practical guidance and specific instruction to help guide planners and practitioners through the challenges of a multi-domain master data management (MDM) implementation. Authors Mark Allen and Dalton Cervo bring their expertise to you in the only reference you need to help your organization take master data management to the next level by incorporating it across multiple domains. Written in a business friendly style with sufficient program planning guidance, this book covers a comprehensive set of topics and advanced strategies centered on the key MDM disciplines of Data Governance, Data Stewardship, Data Quality Management, Metadata Management, and Data Integration. Provides a logical order toward planning, implementation, and ongoing management of multi-domain MDM from a program manager and data steward perspective. Provides detailed guidance, examples and illustrations for MDM practitioners to apply these insights to their strategies, plans, and processes. Covers advanced MDM strategy and instruction aimed at improving data quality management, lowering data maintenance costs, and reducing corporate risks by applying consistent enterprise-wide practices for the management and control of master data. COMPUTERS,Database Administration & Management

Fundamentals of Database Management Systems This lean, focused text concentrates on giving students a clear understanding of database fundamentals while providing a broad survey of all the major topics of the field. The result is a text that is easily covered in one semester, and that only includes topics relevant to the database course. Mark Gillenson, an associate editor of the Journal of Database Management, has 15 years experience of working with and teaching at IBM Corp. and 15 years of teaching experience at the college level. He writes in a clear, friendly style that progresses step-by-step through all of the major database topics. Each chapter begins with a story about a real company's database application, and is packed with examples. When students finish the text, they will be able to immediately apply what they've learned in business. COMPUTERS,Database Administration & Management

Toad for Oracle Unleashed Bert Scalzo and Dan Hotka have written the definitive, up-to-date guide to Version 12.x, Dell’s powerful new release of Toad for Oracle. Packed with step-by-step recipes, detailed screen shots, and hands-on exercises, Toad for Oracle Unleashed shows both developers and DBAs how to maximize their productivity. Drawing on their unsurpassed experience running Toad in production Oracle environments, Scalzo and Hotka thoroughly cover every area of Toad’s functionality. You’ll find practical insights into each of Toad’s most useful tools, from App Designer to Doc Generator, ER Diagrammer to Code Road Map. The authors offer proven solutions you can apply immediately to solve a wide variety of problems, from maintaining code integrity to automating performance and scalability testing. Learn how to… Install and launch Toad, connect to a database, and explore Toad’s new features Customize Toad to optimize productivity in your environment Use the Editor Window to execute SQL and PL/SQL, and view, save, or convert data Browse your schema, and create and edit objects Quickly generate useful reports with FastReport and Report Manager Clarify your database’s tables and data with the powerful Entity Relationship Diagrammer (ERD) and HTML documentation generator Work more efficiently with PL/SQL using code templates, snippets, and shortcuts Automate actions and applications with Automation Designer Perform key DBA tasks including database health checks, tablespace management, database and schema comparisons, and object rebuilding Identify and optimize poorlyperforming SQL and applications ON THE WEB: Download all examples and source code presented in this book from informit.com/title/9780134131856 as it becomes available. COMPUTERS,Database Administration & Management

Structured Search for Big Data The WWW era made billions of people dramatically dependent on the progress of data technologies, out of which Internet search and Big Data are arguably the most notable. Structured Search paradigm connects them via a fundamental concept of key-objects evolving out of keywords as the units of search. The key-object data model and KeySQL revamp the data independence principle making it applicable for Big Data and complement NoSQL with full-blown structured querying functionality. The ultimate goal is extracting Big Information from the Big Data. As a Big Data Consultant, Mikhail Gilula combines academic background with 20 years of industry experience in the database and data warehousing technologies working as a Sr. Data Architect for Teradata, Alcatel-Lucent, and PayPal, among others. He has authored three books, including The Set Model for Database and Information Systems and holds four US Patents in Structured Search and Data Integration. Conceptualizes structured search as a technology for querying multiple data sources in an independent and scalable manner. Explains how NoSQL and KeySQL complement each other and serve different needs with respect to big data Shows the place of structured search in the internet evolution and describes its implementations including the real-time structured internet search COMPUTERS,Database Administration & Management

Building a Scalable Data Warehouse with Data Vault 2.0 The Data Vault was invented by Dan Linstedt at the U.S. Department of Defense, and the standard has been successfully applied to data warehousing projects at organizations of different sizes, from small to large-size corporations. Due to its simplified design, which is adapted from nature, the Data Vault 2.0 standard helps prevent typical data warehousing failures. "Building a Scalable Data Warehouse" covers everything one needs to know to create a scalable data warehouse end to end, including a presentation of the Data Vault modeling technique, which provides the foundations to create a technical data warehouse layer. The book discusses how to build the data warehouse incrementally using the agile Data Vault 2.0 methodology. In addition, readers will learn how to create the input layer (the stage layer) and the presentation layer (data mart) of the Data Vault 2.0 architecture including implementation best practices. Drawing upon years of practical experience and using numerous examples and an easy to understand framework, Dan Linstedt and Michael Olschimke discuss: How to load each layer using SQL Server Integration Services (SSIS), including automation of the Data Vault loading processes. Important data warehouse technologies and practices. Data Quality Services (DQS) and Master Data Services (MDS) in the context of the Data Vault architecture. Provides a complete introduction to data warehousing, applications, and the business context so readers can get-up and running fast Explains theoretical concepts and provides hands-on instruction on how to build and implement a data warehouse Demystifies data vault modeling with beginning, intermediate, and advanced techniques Discusses the advantages of the data vault approach over other techniques, also including the latest updates to Data Vault 2.0 and multiple improvements to Data Vault 1.0 COMPUTERS,Database Administration & Management

Transaction Processing The key to client/server computing. Transaction processing techniques are deeply ingrained in the fields ofdatabases and operating systems and are used to monitor, control and updateinformation in modern computer systems. This book will show you how large,distributed, heterogeneous computer systems can be made to work reliably.Using transactions as a unifying conceptual framework, the authors show howto build high-performance distributed systems and high-availabilityapplications with finite budgets and risk. The authors provide detailed explanations of why various problems occur aswell as practical, usable techniques for their solution. Throughout the book,examples and techniques are drawn from the most successful commercial andresearch systems. Extensive use of compilable C code fragments demonstratesthe many transaction processing algorithms presented in the book. The bookwill be valuable to anyone interested in implementing distributed systemsor client/server architectures. COMPUTERS,Database Administration & Management

Database and Expert Systems Applications The Database and Expert Systems Applications - DEXA - conferences are dedi cated to providing an international forum for the presentation of applications in the database and expert systems field, for the exchange of ideas and experiences, and for defining requirements for the future systems in these fields. After the very promising DEXA 90 in Vienna, Austria, we hope to have successfully established wjth this year's DEXA 91 a stage where scientists from diverse fields interested in application-oriented research can present and discuss their work. This year there was a total of more than 250 submitted papers from 28 different countries, in all continents. Only 98 of the papers could be accepted. The collection of papers in these proceedings offers a cross-section of the issues facing the area of databases and expert systems, i.e., topics of basic research interest on one hand and questions occurring when developing applications on the other. Major credit for the success of the conference goes to all of our colleagues who submitted papers for consideration and to those who have organized and chaired the panel sessions. Many persons contributed numerous hours to organize this conference. The names of most of them will appear on the following pages. In particular we wish to thank the Organization Committee Chairmen Johann Gordesch, A Min Tjoa, and Roland Wag ner, who also helped establishing the program. Special thanks also go to Gabriella Wagner and Anke Ruckert. Dimitris Karagiannis General Conference Chairman Contents Conference Committee. COMPUTERS,Database Administration & Management

East/West Database Workshop This volume results from the four-day scientific Second International East/West Database Workshop which took place 25th-28th September 1994, in Klagenfurt, Austria, continuing a series of workshops started in Kiev in 1990 (Lecture Notes in Computer Science No. 504, Springer, "Next Generation Information System Technology"). The aims of this workshop are twofold: first, to provide a forum for the presentation and in-depth discussion of scientific achievements in the field of advanced databases that will effectively improve the building and use of future information systems; second, to establish and increase communication between research communities which were formerly separated and, therefore, had only rare opportunities to interact. It should establish contacts between researchers from the East and from the West to make exchange of ideas possible and to trigger collaborations. However, it is not only political borders which change their perviousness as a result of -or giving rise to -new autonomies or new possibilities for interaction and collaboration. The same happens with the borders between scientific areas, in particular in the dynamically evolving areas of computer science. Databases and programming languages are integrated in object oriented databases, database and information retrieval technology form together the basis for modern (multimedia) information systems. Furthermore, the borders between different information systems change and allow various forms of collaboration while maintaining different degrees of autonomy. Heterogeneous and distributed databases are enabling technologies for these systems. COMPUTERS,Database Administration & Management

Interfaces to Database Systems (IDS94) A brief survey of the major DBMS and HeI conference proceedings over the past 10 years will reveal isolated pockets of research in database user interfaces but little sense of being swept along with the general advances in DBMS technology and Hel. New data models have evolved to meet the needs of different application domains; persistent programming languages are blurring the traditional distinction between data definition and application programming languages; distribution and inter-operability have become issues as have the storage of heterogeneous media types; yet it is still rare to read of the HeI issues raised by these technological innovations being expressly addressed and rarer still to find recognition of the usability problems with longer-established database technologies. There are at least two reasons why this should be surprising: • Database systems are not like other computer systems; existing both as back-ends to other applications and as stand-alone data stores, they are typically slow, deal with very large volumes of data and can involve all sorts of security, confidentiality and even cooperability issues. • Databases are everywhere. Perhaps only word processors and spread sheets are more widespread. In addition, as business cultures change and personal computing continues to mould expectations, end-users find themselves interacting increasingly closely with database systems. COMPUTERS,Database Administration & Management

Advances in Object-Oriented Database Systems Proceedings of the NATO Advanced Study Institute on Object-Oriented Database Systems, held in Izmir, Kusadasi, Turkey, August 6 - 16, 1993 COMPUTERS,Database Administration & Management

XQuery The W3C XQuery 3.1 standard provides a tool to search, extract, and manipulate content, whether it's in XML, JSON or plain text. With this fully updated, in-depth tutorial, you’ll learn to program with this highly practical query language. Designed for query writers who have some knowledge of XML basics, but not necessarily advanced knowledge of XML-related technologies, this book is ideal as both a tutorial and a reference. You’ll find background information for namespaces, schemas, built-in types, and regular expressions that are relevant to writing XML queries. This second edition provides: A high-level overview and quick tour of XQuery New chapters on higher-order functions, maps, arrays, and JSON A carefully paced tutorial that teaches XQuery without being bogged down by the details Advanced concepts for taking advantage of modularity, namespaces, typing, and schemas Guidelines for working with specific types of data, such as numbers, strings, dates, URIs, maps and arrays XQuery’s implementation-specific features and its relationship to other standards including SQL and XSLT A complete alphabetical reference to the built-in functions, types, and error messages COMPUTERS,Database Administration & Management

Advances in Intelligent Data Analysis. Reasoning about Data This book constitutes the refereed proceedings of the Second International Symposium on Intelligent Data Analysis, IDA-97, held in London, UK, in August 1997.The volume presents 50 revised full papers selected from a total of 107 submissions. Also included is a keynote, Intelligent Data Analysis: Issues and Opportunities, by David J. Hand. The papers are organized in sections on exploratory data analysis, preprocessing and tools; classification and feature selection; medical applications; soft computing; knowledge discovery and data mining; estimation and clustering; data quality; qualitative models. COMPUTERS,Database Administration & Management

Introducing SQL Server Introducing SQL Server is a fast and easy introduction to SQL Server and the world of relational databases. You’ll learn how databases work and how to use the T-SQL language by practicing on one of the most widely-used and powerful database engines in the corporate world: Microsoft SQL Server. Do you quake at the sight of a SELECT statement? Start to shiver when people start talking about tables and rows? Fear not, Introducing SQL Server is here to rescue you. The book focuses on the knowledge and skills needed to begin your journey toward becoming a solid and competent SQL Server professional and database programmer. You’ll learn the core concepts of SQL Server, from installing the software to executing and profiling queries. Introducing SQL Server is aimed at SQL Server newcomers as well as at those wanting to improve their database skills. You’ll put a comprehensive database together as you work through the book. You will create tables and learn to use constraints; create reusable functions and stored procedures; and even learn how indexes work and what they bring in terms of increased performance. Introducing SQL Server shows you that databases don’t need to be difficult. • Teaches you how to build a SQL Server database from scratch• Takes a tutorial-based approach, with each chapter building on the last• Covers what you need to know for common SQL Server development tasks COMPUTERS,Database Administration & Management

SQL Server AlwaysOn Revealed Get a fast start tousing AlwaysOn, the SQL Server solution to high-availability anddisaster recovery. Read this short, 150-page book that is adapted from PeterCarter’s Pro SQL Server Administration to gain a solid and accurateunderstanding of how to implement systems requiring consistent and continuousuptime. Begin with anintroduction to high-availability and disaster recovery concepts such asRecovery Point Objectives (RPOs), Recovery Time Objectives (RTO), availabilitylevels, and the cost of downtime. Then move into detailed coverage ofimplementing and configuring the AlwaysOn feature set in order to meet thebusiness objectives set by your organization. SQL Server AlwaysOn Revealed offers real-world advice on how to build andconfigure the most appropriate topology to meet the high-availability anddisaster recovery requirements you are faced with. Content includes strongcoverage on implementing clusters, on building AlwaysOn failover clusteredinstances, and on configuring AlwaysOn Availability Groups. This is a practicaland hand-on book to get you started quickly in using one of the most talked-aboutSQL Server feature sets. Teaches you to build HA and DR solutions using the AlwaysOn feature set Provides real-world advice on configuration and performance considerations Demonstrates administrative techniques for the AlwaysOn feature set What You Will Learn Understand high availability and disaster recovery concepts and terminology. Understand the technologies available, to implement HA and DR. Build and configure a Windows Cluster. Build and configure an AlwaysOn failover clustered instance. Implement AlwaysOn Availability Groups and appropriately configure them. Administer AlwaysOn technologies post implementation. Who This Book Is For SQL Server AlwaysOn Revealed is for database administrators interested ingrowing their knowledge and skills in Microsoft SQL Server’s high-availabilityand disaster recovery feature set. COMPUTERS,Database Administration & Management

Professional Microsoft SQL Server 2016 Reporting Services and Mobile Reports Optimize reporting and BI with Microsoft SQL Server 2016 Professional Microsoft SQL Server 2016 Reporting Services and Mobile Reports provides a comprehensive lesson in business intelligence (BI), operational reporting and Reporting Services architecture using a clear, concise tutorial approach. You'll learn effective report solution design based upon many years of experience with successful report solutions. Improve your own reports with advanced, best-practice design, usability, query design, and filtering techniques. Expert guidance provides insight into common report types and explains where each could be made more efficient, while providing step-by step instruction on Microsoft SQL Server 2016. All changes to the 2016 release are covered in detail, including improvements to the Visual Studio Report Designer (SQL Server Data Tools) and Report Builder, Mobile Dashboard Designer, the new Report Portal Interface, HTML-5 Rendering, Power BI integration, Custom Parameters Pane, and more. The Microsoft SQL Server 2016 release will include significant changes. New functionality, new capabilities, re-tooled processes, and changing support require a considerable update to existing knowledge. Whether you're starting from scratch or simply upgrading, this book is an essential guide to report design and business intelligence solutions. Understand BI fundamentals and Reporting Services architecture Learn the ingredients to a successful report design Get up to speed on Microsoft SQL Server 2016 Grasp the purpose behind common designs to optimize your reporting Microsoft SQL Server Reporting Services makes reporting faster, easier, and more powerful than ever in web, desktop and portal solutions. Compatibility with an extensive variety of data sources makes it a go-to solution for organizations across the globe. The 2016 release brings some of the biggest changes in years, and the full depth and breadth of these changes can create a serious snag in your workflow. For a clear tutorial geared toward the working professional, Professional Microsoft SQL Server 2016 Reporting Services and Mobile Reports is the ideal guide for getting up to speed and producing successful reports. COMPUTERS,Database Administration & Management

Business Intelligence Strategy and Big Data Analytics Business Intelligence Strategy and Big Data Analytics is written for business leaders, managers, and analysts - people who are involved with advancing the use of BI at their companies or who need to better understand what BI is and how it can be used to improve profitability. It is written from a general management perspective, and it draws on observations at 12 companies whose annual revenues range between $500 million and $20 billion. Over the past 15 years, my company has formulated vendor-neutral business-focused BI strategies and program execution plans in collaboration with manufacturers, distributors, retailers, logistics companies, insurers, investment companies, credit unions, and utilities, among others. It is through these experiences that we have validated business-driven BI strategy formulation methods and identified common enterprise BI program execution challenges. In recent years, terms like “big data and “big data analytics have been introduced into the business and technical lexicon. Upon close examination, the newer terminology is about the same thing that BI has always been about: analyzing the vast amounts of data that companies generate and/or purchase in the course of business as a means of improving profitability and competitiveness. Accordingly, we will use the terms BI and business intelligence throughout the book, and we will discuss the newer concepts like big data as appropriate. More broadly, the goal of this book is to share methods and observations that will help companies achieve BI success and thereby increase revenues, reduce costs, or both. Provides ideas for improving the business performance of one’s company or business functions Emphasizes proven, practical, step-by-step methods that readers can readily apply in their companies Includes exercises and case studies with road-tested advice about formulating BI strategies and program plans COMPUTERS,Database Administration & Management

Relational Database Design and Implementation Relational Database Design and Implementation: Clearly Explained, Fourth Edition, provides the conceptual and practical information necessary to develop a database design and management scheme that ensures data accuracy and user satisfaction while optimizing performance. Database systems underlie the large majority of business information systems. Most of those in use today are based on the relational data model, a way of representing data and data relationships using only two-dimensional tables. This book covers relational database theory as well as providing a solid introduction to SQL, the international standard for the relational database data manipulation language. The book begins by reviewing basic concepts of databases and database design, then turns to creating, populating, and retrieving data using SQL. Topics such as the relational data model, normalization, data entities, and Codd's Rules (and why they are important) are covered clearly and concisely. In addition, the book looks at the impact of big data on relational databases and the option of using NoSQL databases for that purpose. Features updated and expanded coverage of SQL and new material on big data, cloud computing, and object-relational databases Presents design approaches that ensure data accuracy and consistency and help boost performance Includes three case studies, each illustrating a different database design challenge Reviews the basic concepts of databases and database design, then turns to creating, populating, and retrieving data using SQL COMPUTERS,Database Administration & Management

Practical Hive Dive into the world of SQL on Hadoop and get the most out of your Hive data warehouses. This book is your go-to resource for using Hive: authors Scott Shaw, Ankur Gupta, David Kjerrumgaard, and Andreas Francois Vermeulen take you through learning HiveQL, the SQL-like language specific to Hive, to analyze, export, and massage the data stored across your Hadoop environment. From deploying Hive on your hardware or virtual machine and setting up its initial configuration to learning how Hive interacts with Hadoop, MapReduce, Tez and other big data technologies, Practical Hive gives you a detailed treatment of the software. In addition, this book discusses the value of open source software, Hive performance tuning, and how to leverage semi-structured and unstructured data. What You Will Learn Install and configure Hive for new and existing datasets Perform DDL operations Execute efficient DML operationsUse tables, partitions, buckets, and user-defined functions Discover performance tuning tips and Hive best practices Who This Book Is For Developers, companies, and professionals who deal with large amounts of data and could use software that can efficiently manage large volumes of input. It is assumed that readers have the ability to work with SQL. COMPUTERS,Database Administration & Management

Microsoft SQL Server 2016 Reporting Services, Fifth Edition Up-to-Date Coverage of Microsoft® SQL Server® 2016 Reporting Services, Including the Mobile Report Publisher Build, publish, and maintain paginated and mobile reports using the expert tips and best practices contained in this hands-on guide. Written by a member of the original Reporting Services development team, Microsoft SQL Server 2016 Reporting Services, Fifth Edition, fully explains the process of creating and distributing reports and shows how to maximize all of the powerful, integrated SSRS capabilities, including the new and enhanced features. A detailed case study and sample reports are featured in this practical resource. • Plan for, install, configure, and customize SQL Server 2016 Reporting Services• Design and generate feature-rich reports using the Report Wizard• Work with Report Designer in Visual Studio, Report Builder, and the Mobile Report Publisher• Incorporate charts, images, gauges, and maps• Enhance your reports through summarizing, totaling, and interactivity• Build reusable report templates• Embed Visual Basic .NET functions and subreports• Enable end-user access via the Report Server and its web portal interface• Integrate SSRS reports with your own websites and custom applications• Follow along with sample reports from the book’s case study COMPUTERS,Database Administration & Management

Microsoft SQL Server 2016 Up-to-date Microsoft SQL Server 2016 skills made easy! Get up and running on Microsoft SQL Server 2016 in no time with help from this thoroughly revised, practical resource. The book offers thorough coverage of SQL management and development and features full details on the newest business intelligence, reporting, and security features. Filled with new real-world examples and hands-on exercises, Microsoft SQL Server 2016: A Beginner's Guide, Sixth Edition , starts by explaining fundamental relational database system concepts. From there, you will learn how to write Transact-SQL statements, execute simple and complex database queries, handle system administration and security, and use the powerful analysis and BI tools. XML, spatial data, and full-text search are also covered in this step-by-step tutorial. · Revised from the ground up to cover the latest version of SQL Server · Ideal both as a self-study guide and a classroom textbook · Written by a prominent professor and best-selling author COMPUTERS,Database Administration & Management

Delivering Business Intelligence with Microsoft SQL Server 2016, Fourth Edition Distribute Actionable, Timely BI with Microsoft® SQL Server® 2016 and Power BI Drive better, faster, more informed decision making across your organization using the expert tips and best practices featured in this hands-on guide. Delivering Business Intelligence with Microsoft SQL Server 2016, Fourth Edition, shows, step-by-step, how to distribute high-performance, custom analytics to users enterprise-wide. Discover how to build BI Semantic Models, create data marts and OLAP cubes, write MDX and DAX scripts, and share insights using Microsoft client tools. The book includes coverage of self-service business intelligence with Power BI. • Understand the goals and components of successful BI• Build data marts, OLAP cubes, and Tabular models• Load and cleanse data with SQL Server Integration Services• Manipulate and analyze data using MDX and DAX scripts and queries• Work with SQL Server Analysis Services and the BI Semantic Model• Author interactive reports using SQL Server Data Tools• Create KPIs and digital dashboards• Implement time-based analytics• Embed data model content in custom applications using ADOMD.NET• Use Power BI to gather, model, and visualize data in a self-service environment COMPUTERS,Database Administration & Management

Pro SQL Server Internals Improve your ability to develop, manage, and troubleshoot SQL Server solutions by learning how different components work “under the hood,†and how they communicate with each other. The detailed knowledge helps in implementing and maintaining high-throughput databases critical to your business and its customers. You’ll learn how to identify the root cause of each problem and understand how different design and implementation decisions affect performance of your systems. New in this second edition is coverage of SQL Server 2016 Internals, including In-Memory OLTP, columnstore enhancements, Operational Analytics support, Query Store, JSON, temporal tables, stretch databases, security features, and other improvements in the new SQL Server version. The knowledge also can be applied to Microsoft Azure SQL Databases that share the same code with SQL Server 2016. Pro SQL Server Internals is a book for developers and database administrators, and it covers multiple SQL Server versions starting with SQL Server 2005 and going all the way up to the recently released SQL Server 2016. The book provides a solid road map for understanding the depth and power of the SQL Server database server and teaches how to get the most from the platform and keep your databases running at the level needed to support your business. The book: • Provides detailed knowledge of new SQL Server 2016 features and enhancements • Includes revamped coverage of columnstore indexes and In-Memory OLTP • Covers indexing and transaction strategies • Shows how various database objects and technologies are implemented internally, and when they should or should not be used • Demonstrates how SQL Server executes queries and works with data and transaction log What You Will Learn Design and develop database solutions with SQL Server. Troubleshoot design, concurrency, and performance issues. Choose the right database objects and technologies for the job. Reduce costs and improve availability and manageability. Design disaster recovery and high-availability strategies. Improve performance of OLTP and data warehouse systems through in-memory OLTP and Columnstore indexes. Who This Book Is For Developers and database administrators who want to design, develop, and maintain systems in a way that gets the most from SQL Server. This book is an excellent choice for people who prefer to understand and fix the root cause of a problem rather than applying a 'band aid' to it. COMPUTERS,Database Administration & Management

Blockchain Basics In 25 concise steps, you will learn the basics of blockchain technology. No mathematical formulas, program code, or computer science jargon are used. No previous knowledge in computer science, mathematics, programming, or cryptography is required. Terminology is explained through pictures, analogies, and metaphors. This book bridges the gap that exists between purely technical books about the blockchain and purely business-focused books. It does so by explaining both the technical concepts that make up the blockchain and their role in business-relevant applications. What You'll Learn What the blockchain is Why it is needed and what problem it solves Why there is so much excitement about the blockchain and its potential Major components and their purpose How various components of the blockchain work and interact Limitations, why they exist, and what has been done to overcome them Major application scenarios Who This Book Is For Everyone who wants to get a general idea of what blockchain technology is, how it works, and how it will potentially change the financial system as we know it COMPUTERS,Database Administration & Management

Mastering Blockchain Distributed ledgers, decentralization and smart contracts explained About This Book Get to grips with the underlying technical principles and implementations of blockchain. Build powerful applications using Ethereum to secure transactions and create smart contracts. Explore cryptography, mine cryptocurrencies, and solve scalability issues with this comprehensive guide. Who This Book Is For This book appeals to those who wish to build fast, highly secure, transactional applications. This book is for those who are familiar with the concept of blockchain and are comfortable with a programming language. What You Will Learn Master the theoretical and technical foundations of blockchain technology Fully comprehend the concept of decentralization, its impact and relationship with blockchain technology Experience how cryptography is used to secure data with practical examples Grasp the inner workings of blockchain and relevant mechanisms behind Bitcoin and alternative cryptocurrencies Understand theoretical foundations of smart contracts Identify and examine applications of blockchain technology outside of currencies Investigate alternate blockchain solutions including Hyperledger, Corda, and many more Explore research topics and future scope of blockchain technology In Detail Blockchain is a distributed database that enables permanent, transparent, and secure storage of data. The blockchain technology is the backbone of cryptocurrency – in fact, it's the shared public ledger upon which the entire Bitcoin network relies – and it's gaining popularity with people who work in finance, government, and the arts. Blockhchain technology uses cryptography to keep data secure. This book gives a detailed description of this leading technology and its implementation in the real world. This book begins with the technical foundations of blockchain, teaching you the fundamentals of cryptography and how it keeps data secure. You will learn about the mechanisms behind cryptocurrencies and how to develop applications using Ethereum, a decentralized virtual machine. You will explore different blockchain solutions and get an exclusive preview into Hyperledger, an upcoming blockchain solution from IBM and the Linux Foundation. You will also be shown how to implement blockchain beyond currencies, scability with blockchain, and the future scope of this fascinating and powerful technology. Style and approach This comprehensive guide allows you to build smart blockchain applications and explore the power of this database. The book will let you quickly brush up on the basics of the blockchain database, followed by advanced implementations of blockchain in currency, smart contracts, decentralization, and so on. COMPUTERS,Database Administration & Management

PostgreSQL High Performance Cookbook Get to know effective ways to improve PostgreSQL's performance and master query optimization, and database monitoring. About This Book Perform essential database tasks such as benchmarking the database and optimizing the server's memory usage Learn ways to improve query performance and optimize the PostgreSQL server Explore a wide range of high availability and replication mechanisms to build robust, highly available, scalable, and fault-tolerant PostgreSQL databases Who This Book Is For If you are a developer or administrator with limited PostgreSQL knowledge and want to develop your skills with this great open source database, then this book is ideal for you. Learning how to enhance the database performance is always an exciting topic to everyone, and this book will show you enough ways to enhance the database performance. What You Will Learn Build replication strategies for homogeneous and heterogeneous databases Test and build a powerful machine with multiple bench marking techniques Get to know a few SQL injection techniques Find out how to manage the replication using multiple tools Benchmark the database server using multiple strategies Work with the query processing algorithms and their internal behaviors Build a proper plan to upgrade or migrate to PostgreSQL from other databases See the essential database load balancing techniques and the various partitioning approaches PostgreSQL provides Learn memory optimization techniques and database server configurations In Detail PostgreSQL is one of the most powerful and easy to use database management systems. It has strong support from the community and is being actively developed with a new release every year. PostgreSQL supports the most advanced features included in SQL standards. It also provides NoSQL capabilities and very rich data types and extensions. All of this makes PostgreSQL a very attractive solution in software systems. If you run a database, you want it to perform well and you want to be able to secure it. As the world's most advanced open source database, PostgreSQL has unique built-in ways to achieve these goals. This book will show you a multitude of ways to enhance your database's performance and give you insights into measuring and optimizing a PostgreSQL database to achieve better performance. This book is your one-stop guide to elevate your PostgreSQL knowledge to the next level. First, you'll get familiarized with essential developer/administrator concepts such as load balancing, connection pooling, and distributing connections to multiple nodes. Next, you will explore memory optimization techniques before exploring the security controls offered by PostgreSQL. Then, you will move on to the essential database/server monitoring and replication strategies with PostgreSQL. Finally, you will learn about query processing algorithms. Style and approach This comprehensive guide is packed with practical administration tasks. Each topic is explained using examples and a step-by-step approach. COMPUTERS,Database Administration & Management

Oracle Business Intelligence Enterprise Edition 12c A comprehensive guide from Oracle experts, that will act as your single point of reference for building an Oracle BI 12c system that turns data in actionable insight. About This Book Come, start your first Oracle Business intelligence system and excel in BI with this exhaustive guide An all-encompassing guide for your Oracle business intelligence needs Learn from the self-paced professional guidance and implement Oracle business intelligence using this easy-to-follow guide by our experts Who This Book Is For If your job includes working on data, improving the financial or operational performance of your organization or you are a consultant for the above, then this book is for you. If you have been placed on a business intelligence project, then this book is for you. If you are the Project Manager, Business Analyst or Data Scientist then this book is for you. If you are an end user of Oracle Business Intelligence, then this book is for you too. Having a basic understanding of databases and the use of Business Intelligence is expected, but no knowledge of Oracle BI is required. What You Will Learn Install OBIEE in Windows, including how to create the underlying Weblogic Application server and the required database Build the BI system repository, the vital engine connecting your data to the front end of Oracle BI Develop effective analysis, draw out meaning from the data, and present it to end users on interactive dashboards Build pixel-perfect, printable reports using the embedded BI Publisher feature Build agents for actionable insight and enable your users to act on Business Intelligence at their desktop or on the move Understand the various aspects of securing the Oracle BI system, from data restrictions to whole dashboard access rights Get acquainted with the system management tools and methods available for the continuous improvement of your system In Detail Oracle Business Intelligence Enterprise Edition (OBIEE) 12c is packed full of features and has a fresh approach to information presentation, system management, and security. OBIEE can help any organization to understand its data, to make useful information from data, and to ensure decision-making is supported by facts. OBIEE can focus on information that needs action, alerting users when conditions are met. OBIEE can be used for data analysis, form production, dashoarding, and workflow processes. We will introduce you to OBIEE features and provide a step-by-step guide to build a complete system from scratch. With this guide, you will be equipped with a good basic understanding of what the product contains, how to install and configure it, and how to create effective Business Intelligence. This book contains the necessary information for a beginner to create a high-performance OBIEE 12c system. This book is also a guide that explains how to use an existing OBIEE 12c system, and shows end users how to create. Style and approach This book will take you from one feature to another in a step-by-step manner and will teach how you can create effective business intelligence using Oracle Business Intelligence Enterprise Edition. You will be taught how to create BI solutions and dashboards from scratch. There will be multiple modules in the book, each module spread in chapters, that will cover one aspect of business intelligence in a systematic manner. COMPUTERS,Database Administration & Management

Building Blockchain Projects Develop real-time practical DApps using Ethereum and JavaScript About This Book Create powerful, end-to-end applications for Blockchain using Ethereum Write your first program using the Solidity programming language Change the way you think and design your applications by using the all new database-Blockchain Who This Book Is For This book is for JavaScript developers who now want to create tamper-proof data (and transaction) applications using Blockchain and Ethereum. Those who are interested in cryptocurrencies and the logic and database empowering it will find this book extremely useful. What You Will Learn Walk through the basics of the Blockchain technology Implement Blockchain's technology and its features, and see what can be achieved using them Build DApps using Solidity and Web3.js Understand the geth command and cryptography Create Ethereum wallets Explore consortium blockchain In Detail Blockchain is a decentralized ledger that maintains a continuously growing list of data records that are secured from tampering and revision. Every user is allowed to connect to the network, send new transactions to it, verify transactions, and create new blocks, making it permission-less. This book will teach you what Blockchain is, how it maintains data integrity, and how to create real-world Blockchain projects using Ethereum. With interesting real-world projects, you will learn how to write smart contracts which run exactly as programmed without any chance of fraud, censorship, or third-party interference, and build end-to-end applications for Blockchain. You will learn about concepts such as cryptography in cryptocurrencies, ether security, mining , smart contracts, solidity, and more. You will also learn about web sockets, various API services for Ethereum, and much more. The blockchain is the main technical innovation of bitcoin, where it serves as the public ledger for bitcoin transactions. Style and approach This is a project-based guide that not only gets you up and running with Blockchain, but also lets you create intuitive real-world applications that will make you an independent Blockchain developer. COMPUTERS,Database Administration & Management

Exam Ref 70-762 Developing SQL Databases This is the eBook of the printed book and may not include any media, website access codes, or print supplements that may come packaged with the bound book. Prepare for Microsoft Exam 70-762, Developing SQL Databases —and help demonstrate your real-world mastery of skills for building and implementing databases across organizations. Designed for database professionals who build and implement databases across organizations and who ensure high levels of data availability, Exam Ref focuses on the critical-thinking and decision-making acumen needed for success at the MCSA level. Focus on the expertise measured by these objectives: • Design and implement database objects • Implement programmability objects • Manage database concurrency • Optimize database objects and SQL infrastructure This Microsoft Exam Ref: • Organizes its coverage by exam objectives • Features strategic, what-if scenarios to challenge you • Assumes you have working knowledge of Microsoft Windows, Transact-SQL, and relational databases About the Exam Exam 70-762 focuses on skills and knowledge for building and implementing databases across organizations and ensuring high levels of data availability. About Microsoft Certification Passing this exam earns you credit toward a Microsoft Certified Solutions Associate (MCSA) certification that demonstrates your mastery of modern database development. Exam 70-761 (Querying Data with Transact-SQL) is also required for MCSA: SQL 2016 Database Development. See full details at: microsoft.com/learning COMPUTERS,Database Administration & Management

Tabular Modeling in Microsoft SQL Server Analysis Services Build agile and responsive business intelligence solutions Create a semantic model and analyze data using the tabular model in SQL Server 2016 Analysis Services to create corporate-level business intelligence (BI) solutions. Led by two BI experts, you will learn how to build, deploy, and query a tabular model by following detailed examples and best practices. This hands-on book shows you how to use the tabular model’s in-memory database to perform rapid analytics—whether you are new to Analysis Services or already familiar with its multidimensional model. Discover how to: • Determine when a tabular or multidimensional model is right for your project • Build a tabular model using SQL Server Data Tools in Microsoft Visual Studio 2015 • Integrate data from multiple sources into a single, coherent view of company information • Choose a data-modeling technique that meets your organization’s performance and usability requirements • Implement security by establishing administrative and data user roles • Define and implement partitioning strategies to reduce processing time • Use Tabular Model Scripting Language (TMSL) to execute and automate administrative tasks • Optimize your data model to reduce the memory footprint for VertiPaq • Choose between in-memory (VertiPaq) and pass-through (DirectQuery) engines for tabular models • Select the proper hardware and virtualization configurations • Deploy and manipulate tabular models from C# and PowerShell using AMO and TOM libraries Get code samples, including complete apps, at: https://aka.ms/tabular/downloads About This Book • For BI professionals who are new to SQL Server 2016 Analysis Services or already familiar with previous versions of the product, and who want the best reference for creating and maintaining tabular models. • Assumes basic familiarity with database design and business analytics concepts. COMPUTERS,Database Administration & Management

Microsoft SQL Server T-SQL in 10 Minutes, Sams Teach Yourself This is the eBook of the printed book and may not include any media, website access codes, or print supplements that may come packaged with the bound book. Sams Teach Yourself Microsoft SQL Server T-SQL in 10 Minutes offers straightforward, practical answers when you need fast results. By working through the book’s 30 lessons of 10 minutes or less, you’ll learn what you need to know to take advantage of Microsoft SQL Server’s T-SQL language. This handy pocket guide starts with simple data retrieval and moves on to more complex topics, including the use of joins, subqueries, full text-based searches, functions and stored procedures, cursors, triggers, table constraints, XML, JSON, and much more. Learn how to… Use T-SQL in the Microsoft SQL Server environment Construct complex T-SQL statements using multiple clauses and operators Filter data so you get the information you need quickly Retrieve, sort, and format database contents Join two or more related tables Make SQL Server work for you with globalization and localization Create subqueries to pinpoint your data Automate your workload with triggers Create and alter database tables Work with views, stored procedures, and more COMPUTERS,Database Administration & Management

Effective SQL Effective SQL brings together the hands-on solutions and practical insights you need to solve a wide range of complex problems with SQL, and to design databases that make it far easier to manage data in the future. Leveraging the proven format of the best-selling Effective series, it focuses on providing clear, practical explanations, expert tips, and plenty of realistic examples -- all in full color. Drawing on their immense experience as consultants and instructors, three world-class database experts identify specific challenges, and distill each solution into five pages or less. Throughout, they provide well-annotated SQL code designed for all leading platforms, as well as code for specific implementations ranging from SQL Server to Oracle and MySQL, wherever these vary or permit you to achieve your goal more efficiently. Going beyond mere syntax, the authors also show how to avoid poor database design that makes it difficult to write effective SQL, how to improve suboptimal designs, and how to work around designs you can't change. You'll also find detailed sections on filtering and finding data, aggregation, subqueries, and metadata, as well as specific solutions for everything from listing products to scheduling events and defining data hierarchies. Simply put, if you already know the basics of SQL, Effective SQL will help you become a world-class SQL problem-solver. COMPUTERS,Database Administration & Management

Language of SQL, The The Language of SQL, Second Edition Many SQL texts attempt to serve as an encyclopedic reference on SQL syntax -- an approach that is often counterproductive, because that information is readily available in online references published by the major database vendors. For SQL beginners, it’s more important for a book to focus on general concepts and to offer clear explanations and examples of what various SQL statements can accomplish. This is that book. A number of features make The Language of SQL unique among introductory SQL books. First, you will not be required to download software or sit with a computer as you read the text. The intent of this book is to provide examples of SQL usage that can be understood simply by reading. Second, topics are organized in an intuitive and logical sequence. SQL keywords are introduced one at a time, allowing you to grow your understanding as you encounter new terms and concepts. Finally, this book covers the syntax of three widely used databases: Microsoft SQL Server, MySQL, and Oracle. Special “Database Differences†sidebars clearly show you any differences in syntax among these three databases, and instructions are included on how to obtain and install free versions of the databases. This is the only book you need to gain a quick working knowledge of SQL and relational databases. Learn How To... Use SQL to retrieve data from relational databases Apply functions and calculations to data Group and summarize data in a variety of useful ways Use complex logic to retrieve only the data you need Update data and create new tables Design relational databases so that data retrieval is easy and intuitive Use spreadsheets to transform your data into meaningful displays Retrieve data from multiple tables via joins, subqueries, views, and set logic Create, modify, and execute stored procedures Install Microsoft SQL Server, MySQL, or Oracle Contents at a Glance 1 Relational Databases and SQL 2 Basic Data Retrieval 3 Calculated Fields and Aliases 4 Using Functions 5 Sorting Data 6 Selection Criteria 7 Boolean Logic 8 Conditional Logic 9 Summarizing Data 10 Subtotals and Crosstabs 11 Inner Joins 12 Outer Joins 13 Self Joins and Views 14 Subqueries 15 Set Logic 16 Stored Procedures and Parameters 17 Modifying Data 18 Maintaining Tables 19 Principles of Database Design 20 Strategies for Displaying Data A Getting Started with Microsoft SQL Server B Getting Started with MySQL C Getting Started with Oracle COMPUTERS,Database Administration & Management

Exam Ref 70-768 Developing SQL Data Models Prepare for Microsoft Exam 70-768–and help demonstrate your real-world mastery of Business Intelligence (BI) solutions development with SQL Server 2016 Analysis Services (SSAS), including modeling and queries. Designed for experienced IT professionals ready to advance their status, Exam Ref focuses on the critical thinking and decision-making acumen needed for success at the MCSA level. Focus on the expertise measured by these objectives: • Design a multidimensional BI semantic model • Design a tabular BI semantic model • Develop queries using Multidimensional Expressions (MDX) and Data Analysis Expressions (DAX) • Configure and maintain SSAS This Microsoft Exam Ref: • Organizes its coverage by exam objectives • Features strategic, what-if scenarios to challenge you • Assumes you are a database or BI professional with experience creating models, writing MDX or DAX queries, and using SSAS COMPUTERS,Database Administration & Management

SQL Server 2016 High Availability Unleashed (includes Content Update Program) Book + Content Update Program SQL Server 2016 High Availability Unleashed provides start-to-finish coverage of SQL Server’s powerful high availability (HA) solutions for your traditional on-premise databases, cloud-based databases (Azure or AWS), hybrid databases (on-premise coupled with the cloud), and your emerging Big Data solutions. This complete guide introduces an easy-to-follow, formal HA methodology that has been refined over the past several years and helps you identity the right HA solution for your needs. There is also additional coverage of both disaster recovery and business continuity architectures and considerations. You are provided with step-by-step guides, examples, and sample code to help you set up, manage, and administer these highly available solutions. All examples are based on existing production deployments at major Fortune 500 companies around the globe. This book is for all intermediate-to-advanced SQL Server and Big Data professionals, but is also organized so that the first few chapters are great foundation reading for CIOs, CTOs, and even some tech-savvy CFOs. Learn a formal, high availability methodology for understanding and selecting the right HA solution for your needs Deep dive into Microsoft Cluster Services Use selective data replication topologies Explore thorough details on AlwaysOn and availability groups Learn about HA options with log shipping and database mirroring/ snapshots Get details on Microsoft Azure for Big Data and Azure SQL Explore business continuity and disaster recovery Learn about on-premise, cloud, and hybrid deployments Provide all types of database needs, including online transaction processing, data warehouse and business intelligence, and Big Data Explore the future of HA and disaster recovery In addition, this book is part of InformIT’s exciting Content Update Program, which provides content updates for major technology improvements! As significant updates are made to SQL Server, sections of this book will be updated or new sections will be added to match the updates to the technologies. As updates become available, they will be delivered to you via a free Web Edition of this book, which can be accessed with any Internet connection. To learn more, visit informit.com/cup. How to access the Web Edition: Follow the instructions inside to learn how to register your book to access the FREE Web Edition. COMPUTERS,Database Administration & Management

PostgreSQL Thinking of migrating to PostgreSQL? This clear, fast-paced introduction helps you understand and use this open source database system. Not only will you learn about the enterprise class features in versions 9.5 to 10, you’ll also discover that PostgeSQL is more than a database system—it’s an impressive application platform as well. With examples throughout, this book shows you how to achieve tasks that are difficult or impossible in other databases. This third edition covers new features, such as ANSI-SQL constructs found only in proprietary databases until now: foreign data wrapper (FDW) enhancements; new full text functions and operator syntax introduced in version 9.6; XML constructs new in version 10; query parallelization features introduced in 9.6 and enhanced in 10; built-in logical replication introduced in Version 10.e. If you’re a current PostgreSQL user, you’ll pick up gems you may have missed before. Learn basic administration tasks such as role management, database creation, backup, and restore Apply the psql command-line utility and the pgAdmin graphical administration tool Explore PostgreSQL tables, constraints, and indexes Learn powerful SQL constructs not generally found in other databases Use several different languages to write database functions Tune your queries to run as fast as your hardware will allow Query external and variegated data sources with foreign data wrappers Learn how to use built-in replication to replicate data COMPUTERS,Database Administration & Management

Database Reliability Engineering The infrastructure-as-code revolution in IT is also affecting database administration. With this practical book, developers, system administrators, and junior to mid-level DBAs will learn how the modern practice of site reliability engineering applies to the craft of database architecture and operations. Authors Laine Campbell and Charity Majors provide a framework for professionals looking to join the ranks of today’s database reliability engineers (DBRE). You’ll begin by exploring core operational concepts that DBREs need to master. Then you’ll examine a wide range of database persistence options, including how to implement key technologies to provide resilient, scalable, and performant data storage and retrieval. With a firm foundation in database reliability engineering, you’ll be ready to dive into the architecture and operations of any modern database. This book covers: Service-level requirements and risk management Building and evolving an architecture for operational visibility Infrastructure engineering and infrastructure management How to facilitate the release management process Data storage, indexing, and replication Identifying datastore characteristics and best use cases Datastore architectural components and data-driven architectures COMPUTERS,Database Administration & Management

SQL Server 2017 Administrator's Guide Implement and administer successful database solution with SQL Server 2017 About This Book Master the required skills to successfully set up, administer, and maintain your SQL Server 2017 database solution Design and configure, manage, and secure a rock-solid SQL server Comprehensive guide in keeping your SQL server disaster proof and all-time availability Who This Book Is For This book targets database administrators with an interest in SQL Server 2017 administration. Readers are expected to have some experience with previous SQL Server versions. What You Will Learn Learn about the new features of SQL Server 2017 and how to implement them Build a stable and fast SQL Server environment Fix performance issues by optimizing queries and making use of indexes Perform a health check of an existing troublesome database environment Design and use an optimal database management strategy Implement efficient backup and recovery techniques in-line with security policies Combine SQL Server 2017 and Azure and manage your solution by various automation techniques Perform data migration, cluster upgradation and server consolidation In Detail Take advantage of the real power of SQL Server 2017 with all its new features, in addition to covering core database administration tasks. This book will give you a competitive advantage by helping you quickly learn how to design, manage, and secure your database solution. You will learn how to set up your SQL Server and configure new (and existing) environments for optimal use. After covering the designing aspect, the book delves into performance-tuning aspects by teaching you how to effectively use indexes. The book will also teach you about certain choices that need to be made about backups and how to implement a rock-solid security policy and keep your environment healthy. Finally, you will learn about the techniques you should use when things go wrong, and other important topics - such as migration, upgrading, and consolidation - are covered in detail. Integration with Azure is also covered in depth. Whether you are an administrator or thinking about entering the field, this book will provide you with all the skills you need to successfully create, design, and deploy databases using SQL Server 2017. Style and approach A comprehensive guide for database professionals, covering a wide range of topics from installation, maintenance, and configuration to managing systems for operational efficiency and high availability; best practices for maintaining a highly reliable database solution are also supplied from industry experts. COMPUTERS,Database Administration & Management

Confident Data Skills Understand the basics of data and learn to utilise its innovative potential, giving your career a valuable and cutting-edge boost. COMPUTERS,Database Administration & Management

Pro Power BI Desktop Deliver eye-catching Business Intelligence with Microsoft Power BI Desktop. This new edition has been updated to cover all the latest features, including combo charts, Cartesian charts, trend lines, use of gauges, and more. Also covered are Top-N features, the ability to bin data into groupings and chart the groupings, and new techniques for detecting and handling outlier data points. You can take data from virtually any source and use it to produce stunning dashboards and compelling reports that will seize your audience’s attention. Slice and dice the data with remarkable ease and then add metrics and KPIs to project the insights that create your competitive advantage. Make raw data into clear, accurate, and interactive information with Microsoft’s free self-service business intelligence tool. Pro Power BI Desktop shows you how to choose from a wide range of built-in and third-party visualization types so that your message is always enhanced. You’ll be able to deliver those results on the PC, tablets, and smartphones, as well as share results via the cloud. This book helps you save time by preparing the underlying data correctly without needing an IT department to prepare it for you. What You'll Learn Deliver attention-grabbing information, turning data into insight Mash up data from multiple sources into a cleansed and coherent data model Create dashboards that help in monitoring key performance indicators of your business Build interdependent charts, maps, and tables to deliver visually stunning information Share business intelligence in the cloud without involving IT Deliver visually stunning and interactive charts, maps, and tables Find new insights as you chop and tweak your data as never before Adapt delivery to mobile devices such as phones and tablets Who This Book Is For Everyone from CEOs and Business Intelligence developers to power users and IT managers COMPUTERS,Database Administration & Management

Complete Guide to Open Source Big Data Stack See a Mesos-based big data stack created and the components used. You will use currently available Apache full and incubating systems. The components are introduced by example and you learn how they work together. In the Complete Guide to Open Source Big Data Stack, the author begins by creating a private cloud and then installs and examines Apache Brooklyn. After that, he uses each chapter to introduce one piece of the big data stack—sharing how to source the software and how to install it. You learn by simple example, step by step and chapter by chapter, as a real big data stack is created. The book concentrates on Apache-based systems and shares detailed examples of cloud storage, release management, resource management, processing, queuing, frameworks, data visualization, and more. What You’ll Learn Install a private cloud onto the local cluster using Apache cloud stack Source, install, and configure Apache: Brooklyn, Mesos, Kafka, and Zeppelin See how Brooklyn can be used to install Mule ESB on a cluster and Cassandra in the cloud Install and use DCOS for big data processing Use Apache Spark for big data stack data processing Who This Book Is For Developers, architects, IT project managers, database administrators, and others charged with developing or supporting a big data system. It is also for anyone interested in Hadoop or big data, and those experiencing problems with data size. COMPUTERS,Database Administration & Management

Blockchain Develop, validate, and deploy powerful decentralized applications using blockchain Get the most out of cutting-edge blockchain technology using the hands-on information contained in this comprehensive resource. Written by a team of technology and legal experts, Blockchain: A Practical Guide to Developing Business, Law, and Technology Solutions demonstrates each topic through a start-to-finish, illustrated case study. The book includes financial, technology, governance, and legal use cases along with advantages and challenges. Validation, implementation, troubleshooting, and best practices are fully covered. You will learn, step-by-step, how to build and maintain effective, reliable, and transparent blockchain solutions. • Understand the fundamentals of decentralized computing and blockchain • Explore business, technology, governance, and legal use cases • Review the evolving practice of law and technology as it concerns legal and governance issues arising from blockchain implementation • Write and administer performant blockchain-enabled applications • Handle cryptographic validation in private, public, and consortium blockchains • Employ blockchain in cloud deployments and Internet of Things (IoT) devices • Incorporate Web 3.0 features with Swarm, IPFS, Storj, Golem, and WHISPER • Use Solidity to build and validate fully functional distributed applications and smart contracts using Ethereum • See how blockchain is used in crypto-currency, including Bitcoin and Ethereum • Overcome technical hurdles and secure your decentralized IT platform COMPUTERS,Database Administration & Management

SQL Queries for Mere Mortals The #1 Easy, Common-Sense Guide to SQL Queries—Updated with More Advanced Techniques and Solutions Foreword by Keith W. Hare, Vice Chair, USA SQL Standards Committee SQL Queries for Mere Mortals has earned worldwide praise as the clearest, simplest tutorial on writing effective queries with the latest SQL standards and database applications. Now, author John L. Viescas has updated this hands-on classic with even more advanced and valuable techniques. Step by step, Viescas guides you through creating reliable queries for virtually any current SQL-based database. He demystifies all aspects of SQL query writing, from simple data selection and filtering to joining multiple tables and modifying sets of data. Building on the basics, Viescas shows how to solve challenging real-world problems, including applying multiple complex conditions on one table, performing sophisticated logical evaluations, and using unlinked tables to think “outside the box.†In two brand-new chapters, you learn how to perform complex calculations on groups for sophisticated reporting, and how to partition data into windows for more flexible aggregation. Practice all you want with downloadable sample databases for today’s versions of Microsoft Office Access, Microsoft SQL Server, and the open source MySQL and PostgreSQL databases. Whether you’re a DBA, developer, user, or student, there’s no better way to master SQL. Coverage includes: Getting started: understanding what relational databases are, and ensuring that your database structures are sound SQL basics: using SELECT statements, creating expressions, sorting information with ORDER BY, and filtering data using WHERE Summarizing and grouping data with GROUP BY and HAVING clauses Drawing data from multiple tables: using INNER JOIN, OUTER JOIN, and UNION operators, and working with subqueries Modifying data sets with UPDATE, INSERT, and DELETE statements Advanced queries: complex NOT and AND, conditions, if-then-else using CASE, unlinked tables, driver tables, and more NEW! Using advanced GROUP BY keywords to create subtotals, roll-ups, and more NEW! Applying window functions to answer more sophisticated questions, and gain deeper insight into your data Software-Independent Approach! If you work with database software such as Access, MS SQL Server, Oracle, DB2, MySQL, Ingres, or any other SQL-based program, this book could save you hours of time and aggravation—before you write a single query! COMPUTERS,Database Administration & Management

MySQL 8 Cookbook Design and administer enterprise-grade MySQL 8 solutions About This Book Store, retrieve, and manipulate your data using the latest MySQL 8 features Practical recipes on effective administration in MySQL, with a focus on security, performance tuning, troubleshooting, and more Contains tips, tricks, and best practices for designing, developing, and administering your MySQL 8 database solution without any hassle Who This Book Is For If you are a MySQL developer or administrator looking for quick, handy solutions to solve the most common and not-so-common problems in MySQL, this book is for you. MySQL DBAs looking to get up-to-speed with the latest MySQL 8 development and administration features will also find this book very useful. Prior knowledge of Linux and RDBMS is desirable. What You Will Learn Install and configure your MySQL 8 instance without any hassle Get to grips with new features of MySQL 8 like CTE, Window functions and many more Perform backup tasks, recover data and set up various replication topologies for your database Maximize performance by using new features of MySQL 8 like descending indexes, controlling query optimizer and resource groups Learn how to use general table space to suit the SaaS or multi-tenant applications Analyze slow queries using performance schema, sys schema and third party tools Manage and monitor your MySQL instance and implement efficient performance-tuning tasks In Detail MySQL is one of the most popular and widely used relational databases in the World today. The recently released MySQL 8 version promises to be better and more efficient than ever before. This book contains everything you need to know to be the go-to person in your organization when it comes to MySQL. Starting with a quick installation and configuration of your MySQL instance, the book quickly jumps into the querying aspects of MySQL. It shows you the newest improvements in MySQL 8 and gives you hands-on experience in managing high-transaction and real-time datasets. If you've already worked with MySQL before and are looking to migrate your application to MySQL 8, this book will also show you how to do that. The book also contains recipes on efficient MySQL administration, with tips on effective user management, data recovery, security, database monitoring, performance tuning, troubleshooting, and more. With quick solutions to common and not-so-common problems you might encounter while working with MySQL 8, the book contains practical tips and tricks to give you the edge over others in designing, developing, and administering your database effectively. Style and approach This book takes a recipe-based approach to tackling the pain points of SQL developers. It is a comprehensive book full of solutions to common problems faced by SQL administrators and developers alike. COMPUTERS,Database Administration & Management

Mastering PostgreSQL 10 Master the capabilities of PostgreSQL 10 to efficiently manage and maintain your database About This Book Your one-stop guide to mastering advanced concepts in PostgreSQL 10 with ease Master query optimization, replication, and high availability with PostgreSQL Extend the functionalities of your PostgreSQL instance to suit your organizational needs with minimal effort Who This Book Is For If you are a PostgreSQL data architect or an administrator and want to understand how to implement advanced functionalities and master complex administrative tasks with PostgreSQL 10, then this book is perfect for you. Prior experience of administrating a PostgreSQL database and a working knowledge of SQL are required to make the best use of this book. What You Will Learn Get to grips with the advanced features of PostgreSQL 10 and handle advanced SQL Make use of the indexing features in PostgreSQL and fine-tune the performance of your queries Work with stored procedures and manage backup and recovery Master replication and failover techniques Troubleshoot your PostgreSQL instance for solutions to common and not-so-common problems Learn how to migrate your database from MySQL and Oracle to PostgreSQL without any hassle In Detail PostgreSQL is an open source database used for handling large datasets (big data) and as a JSON document database. This book highlights the newly introduced features in PostgreSQL 10, and shows you how you can build better PostgreSQL applications, and administer your PostgreSQL database more efficiently. We begin by explaining advanced database design concepts in PostgreSQL 10, along with indexing and query optimization. You will also see how to work with event triggers and perform concurrent transactions and table partitioning, along with exploring SQL and server tuning. We will walk you through implementing advanced administrative tasks such as server maintenance and monitoring, replication, recovery, high availability, and much more. You will understand common and not-so-common troubleshooting problems and how you can overcome them. By the end of this book, you will have an expert-level command of advanced database functionalities and will be able to implement advanced administrative tasks with PostgreSQL 10. Style and approach This mastering-level guide delves into the advanced functionalities of PostgreSQL 10 COMPUTERS,Database Administration & Management

Ethereum Smart Contract Development Become an Ethereum Blockchain developer using a blend of concepts and hands-on implementations About This Book Understand the Ethereum Ecosystem and its differences from its rich cousin Bitcoin Explore the Solidity programming language and smart contract optimizations Get a developer's perspective of Blockchain-as-a-technology with exposure to common challenges faced while building decentralized applications Who This Book Is For If you want to know the ins and outs of the Ethereum network and build your own decentralized applications, then this book is what you need! This book is for anyone who is interested in blockchain and wants to become an Ethereum developer. It's ideal for existing Ethereum developers who want to develop Ethereum using smart contracts. Basic knowledge of cryptography is expected but is not mandatory. What You Will Learn Know how to build your own smart contracts and cryptocurrencies Understand the Solidity language Find out about data types, control structure, functions, inheritance, mathematical operations, and much more See the various types of forks and discover how they are related to Ethereum Get to know the various concepts of web3.js and its APIs so you can build client-side apps Build a DAO from scratch and acquire basic knowledge of DApps on Ethercast Be guided through the project so you can optimize EVM for smart contracts Build your own decentralized applications (DApps) by taking a practical approach In Detail Ethereum is a public, blockchain-based distributed computing platform featuring smart contract functionality. This book is your one-stop guide to blockchain and Ethereum smart contract development. We start by introducing you to the basics of blockchain. You'll learn about hash functions, Merkle trees, forking, mining, and much more. Then you'll learn about Ethereum and smart contracts, and we'll cover Ethereum virtual machine (EVM) in detail. Next, you'll get acquainted with DApps and DAOs and see how they work. We'll also delve into the mechanisms of advanced smart contracts, taking a practical approach. You'll also learn how to develop your own cryptocurrency from scratch in order to understand the business behind ICO. Further on, you'll get to know the key concepts of the Solidity programming language, enabling you to build decentralized blockchain-based applications. We'll also look at enterprise use cases, where you'll build a decentralized microblogging site. At the end of this book, we discuss blockchain-as-a-service, the dark web marketplace, and various advanced topics so you can get well versed with the blockchain principles and ecosystem. Style and approach This comprehensive guide takes a practical approach by showing you how to implement Blockchain in different Enterprise use cases. You'll quickly brush up on the basics of the blockchain database, then learn the advanced intricacies of smart contract development. COMPUTERS,Database Administration & Management

Redis 4.x Cookbook Leverage the power of Redis 4.x to develop, optimize and administer your Redis solutions with ease About This Book Build, deploy and administer high performance and scalable applications in Redis Covers a range of important tasks - including development and administration of Redis A practical guide that takes your understanding of Redis to the next level Who This Book Is For This book is for database administrators, developers and architects who want to tackle the common and not so common problems associated with the different development and administration-related tasks in Redis. A fundamental understanding of Redis is expected to get the best out of this book. What You Will Learn Install and configure your Redis instance Explore various data types and commands in Redis Build client-side applications as well as a Big Data framework with Redis Manage data replication and persistence in Redis Implement high availability and data sharding in Redis Extend Redis with Redis Module Benchmark, debug, fine-tune and troubleshoot various issues in Redis In Detail Redis is considered the world's most popular key-value store database. Its versatility and the wide variety of use cases it enables have made it a popular choice of database for many enterprises. Based on the latest version of Redis, this book provides both step-by-step recipes and relevant the background information required to utilize its features to the fullest. It covers everything from a basic understanding of Redis data types to advanced aspects of Redis high availability, clustering, administration, and troubleshooting. This book will be your great companion to master all aspects of Redis. The book starts off by installing and configuring Redis for you to get started with ease. Moving on, all the data types and features of Redis are introduced in detail. Next, you will learn how to develop applications with Redis in Java, Python, and the Spring Boot web framework. You will also learn replication tasks, which will help you to troubleshoot replication issues. Furthermore, you will learn the steps that need to be undertaken to ensure high availability on your cluster and during production deployment. Toward the end of the book, you will learn the topmost tasks that will help you to troubleshoot your ecosystem efficiently, along with extending Redis by using different modules. Style and approach This book is a rich collection of recipes that will come in handy when you are working with Redis. It addresses your common and not-so-common pain points, so this is a book of Redis that you must have on the shelf. COMPUTERS,Database Administration & Management

Seven NoSQL Databases in a Week A beginner's guide to get you up and running with Cassandra, DynamoDB, HBase, InfluxDB, MongoDB, Neo4j, and Redis About This Book Covers the basics of 7 NoSQL databases and how they are used in the enterprises Quick introduction to MongoDB, DynamoDB, Redis, Cassandra, Neo4j, InfluxDB, and Hbase Includes effective techniques for database querying and management Who This Book Is For If you are a budding DBA or a developer who wants to get started with the fundamentals of NoSQL databases, this book is for you. Relational DBAs who want to get insights into the various offerings of popular NoSQL databases will also find this book to be very useful. What You Will Learn Understand how MongoDB provides high-performance, high-availability, and automatic scaling Interact with your Neo4j instances via database queries, Python scripts, and Java application code Get familiar with common querying and programming methods to interact with Redis Study the different types of problems Cassandra can solve Work with HBase components to support common operations such as creating tables and reading/writing data Discover data models and work with CRUD operations using DynamoDB Discover what makes InfluxDB a great choice for working with time-series data In Detail This is the golden age of open source NoSQL databases. With enterprises having to work with large amounts of unstructured data and moving away from expensive monolithic architecture, the adoption of NoSQL databases is rapidly increasing. Being familiar with the popular NoSQL databases and knowing how to use them is a must for budding DBAs and developers. This book introduces you to the different types of NoSQL databases and gets you started with seven of the most popular NoSQL databases used by enterprises today. We start off with a brief overview of what NoSQL databases are, followed by an explanation of why and when to use them. The book then covers the seven most popular databases in each of these categories: MongoDB, Amazon DynamoDB, Redis, HBase, Cassandra, InfluxDB, and Neo4j. The book doesn't go into too much detail about each database but teaches you enough to get started with them. By the end of this book, you will have a thorough understanding of the different NoSQL databases and their functionalities, empowering you to select and use the right database according to your needs. Style and approach This book is a quick-start guide with short and simple introductory content on the seven popular databases. COMPUTERS,Database Administration & Management

Seven Databases in Seven Weeks Data is getting bigger and more complex by the day, and so are your choices in handling it. Explore some of the most cutting-edge databases available - from a traditional relational database to newer NoSQL approaches - and make informed decisions about challenging data storage problems. This is the only comprehensive guide to the world of NoSQL databases, with in-depth practical and conceptual introductions to seven different technologies: Redis, Neo4J, CouchDB, MongoDB, HBase, Postgres, and DynamoDB. This second edition includes a new chapter on DynamoDB and updated content for each chapter. While relational databases such as MySQL remain as relevant as ever, the alternative, NoSQL paradigm has opened up new horizons in performance and scalability and changed the way we approach data-centric problems. This book presents the essential concepts behind each database alongside hands-on examples that make each technology come alive. With each database, tackle a real-world problem that highlights the concepts and features that make it shine. Along the way, explore five database models - relational, key/value, columnar, document, and graph - from the perspective of challenges faced by real applications. Learn how MongoDB and CouchDB are strikingly different, make your applications faster with Redis and more connected with Neo4J, build a cluster of HBase servers using cloud services such as Amazon's Elastic MapReduce, and more. This new edition brings a brand new chapter on DynamoDB, updated code samples and exercises, and a more up-to-date account of each database's feature set. Whether you're a programmer building the next big thing, a data scientist seeking solutions to thorny problems, or a technology enthusiast venturing into new territory, you will find something to inspire you in this book. What You Need: You'll need a *nix shell (Mac OS or Linux preferred, Windows users will need Cygwin), Java 6 (or greater), and Ruby 1.8.7 (or greater). Each chapter will list the downloads required for that database. COMPUTERS,Database Administration & Management

PostgreSQL 10 Administration Cookbook A practical guide to administer, monitor and replicate your PostgreSQL 10 database About This Book Get to grips with the capabilities of PostgreSQL 10 to administer your database more efficiently Monitor, tune, secure and protect your database for optimal performance A step-by-step, recipe-based guide to help you tackle any problem in PostgreSQL 10 administration with ease Who This Book Is For This book is for database administrators, data architects, developers, or anyone with an interest in planning for, or running, live production databases using PostgreSQL. It is most suited to those looking for hands-on solutions to any problem associated with PostgreSQL administration. What You Will Learn Get to grips with the newly released PostgreSQL 10 features to improve database performance and reliability Manage open source PostgreSQL versions 10 on various platforms. Explore best practices for planning and designing live databases Select and implement robust backup and recovery techniques in PostgreSQL 10 Explore concise and clear guidance on replication and high availability Discover advanced technical tips for experienced users In Detail PostgreSQL is a powerful, open source database management system with an enviable reputation for high performance and stability. With many new features in its arsenal, PostgreSQL 10 allows users to scale up their PostgreSQL infrastructure. This book takes a step-by-step, recipe-based approach to effective PostgreSQL administration. Throughout this book, you will be introduced to these new features such as logical replication, native table partitioning, additional query parallelism, and much more. You will learn how to tackle a variety of problems that are basically the pain points for any database administrator - from creating tables to managing views, from improving performance to securing your database. More importantly, the book pays special attention to topics such as monitoring roles, backup, and recovery of your PostgreSQL 10 database, ensuring high availability, concurrency, and replication. By the end of this book, you will know everything you need to know to be the go-to PostgreSQL expert in your organization. Style and approach The book is a step by step guide with example-driven recipes, focused on the new features of the latest PostgreSQL version10. This book will serve as a specific guide to understand and leverage useful PostgreSQL functionalities to create better and more efficient databases. COMPUTERS,Database Administration & Management

Beginning Blockchain Understand the nuts and bolts of Blockchain, its different flavors with simple use cases, and cryptographic fundamentals. You will also learn some design considerations that can help you build custom solutions. Beginning Blockchain is a beginner’s guide to understanding the core concepts of Blockchain from a technical perspective. By learning the design constructs of different types of Blockchain, you will get a better understanding of building the best solution for specific use cases. The book covers the technical aspects of Blockchain technologies, cryptography, cryptocurrencies, and distributed consensus mechanisms. You will learn how these systems work and how to engineer them to design next-gen business solutions. What You'll Learn Get a detailed look at how cryptocurrencies work Understand the core technical components of Blockchain Build a secured Blockchain solution from cryptographic primitives Discover how to use different Blockchain platforms and their suitable use cases Know the current development status, scope, limitations, and future of Blockchain Who This Book Is For Software developers and architects, computer science graduates, entrepreneurs, and anyone wishing to dive deeper into blockchain fundamentals. A basic understanding of computer science, data structure, and algorithms is helpful. COMPUTERS,Database Administration & Management

Big Data Analytics and Knowledge Discovery This book constitutes the refereed proceedings of the 20th International Conference on Big Data Analytics and Knowledge Discovery, DaWaK 2018, held in Regensburg, Germany, in September 2018.The 13 revised full papers and 17 short papers presented were carefully reviewed and selected from 76 submissions. The papers are organized in the following topical sections: Graph analytics; case studies; classification and clustering; pre-processing; sequences; cloud and database systems; and data mining. COMPUTERS,Database Administration & Management

Data Management for Researchers Learning how to manage, share and preserve data is essential for active researchers. A comprehensive guide for scientific researchers providing everything they need to know about data management and how to organize, document, use and reuse their data. COMPUTERS,Database Administration & Management

SQL Server 2017 Query Performance Tuning Identify and fix causes of poor performance. You will learn Query Store, adaptive execution plans, and automated tuning on the Microsoft Azure SQL Database platform. Anyone responsible for writing or creating T-SQL queries will find valuable the insight into bottlenecks, including how to recognize them and eliminate them. This book covers the latest in performance optimization features and techniques and is current with SQL Server 2017. If your queries are not running fast enough and you’re tired of phone calls from frustrated users, then this book is the answer to your performance problems. SQL Server 2017 Query Performance Tuning is about more than quick tips and fixes. You’ll learn to be proactive in establishing performance baselines using tools such as Performance Monitor and Extended Events. You’ll recognize bottlenecks and defuse them before the phone rings. You’ll learn some quick solutions too, but emphasis is on designing for performance and getting it right. The goal is to head off trouble before it occurs. What You'll Learn Use Query Store to understand and easily change query performance Recognize and eliminate bottlenecks leading to slow performance Deploy quick fixes when needed, following up with long-term solutions Implement best practices in T-SQL to minimize performance risk Design in the performance that you need through careful query and index design Utilize the latest performance optimization features in SQL Server 2017 Protect query performance during upgrades to the newer versions of SQL Server Who This Book Is For Developers and database administrators with responsibility for application performance in SQL Server environments. Anyone responsible for writing or creating T-SQL queries will find valuable the insight into bottlenecks, including how to recognize them and eliminate them. COMPUTERS,Database Administration & Management

Oracle Database Exadata Cloud Service Quickly Get Up and Running on Oracle Database Exadata Cloud Service Quickly install, configure, and start using Oracle Database Exadata Cloud Service with the hands-on information contained in this comprehensive Oracle Press guide. Designed for easy learning, the book features real-world examples, detailed illustrations, and step-by-step instructions. Oracle Database Exadata Cloud Service: A Beginner’s Guide walks you through the basics and shows you how to provision, create, and deploy databases. Basic system administration tasks, including data backup and recovery, software patching, and system updating, are clearly explained. Advanced monitoring and data compression techniques are also covered. Inside, you’ll discover how to: • Set up and configure Oracle Database Exadata Cloud Service • Navigate the user interface • Work with tooling and CLIs • Deploy smart scans and storage indexes • Employ the latest compression techniques • Handle Oracle Exadata resource management • Administer Oracle Exadata Smart Flash Cache • Manage and monitor your Oracle Exadata Cloud Service • Migrate to Oracle Exadata Cloud Service TAG: For a complete list of Oracle Press titles, visit www.OraclePressBooks.com. COMPUTERS,Database Administration & Management

Pro SQL Server on Linux Get SQL Server up and running on the Linux operating system and containers. No database professional managing or developing SQL Server on Linux will want to be without this deep and authoritative guide by one of the most respected experts on SQL Server in the industry. Get an inside look at how SQL Server for Linux works through the eyes of an engineer on the team that made it possible. Microsoft SQL Server is one of the leading database platforms in the industry, and SQL Server 2017 offers developers and administrators the ability to run a database management system on Linux, offering proven support for enterprise-level features and without onerous licensing terms. Organizations invested in Microsoft and open source technologies are now able to run a unified database platform across all their operating system investments. Organizations are further able to take full advantage of containerization through popular platforms such as Docker and Kubernetes. Pro SQL Server on Linux walks you through installing and configuring SQL Server on the Linux platform. The author is one of the principal architects of SQL Server for Linux, and brings a corresponding depth of knowledge that no database professional or developer on Linux will want to be without. Throughout this book are internals of how SQL Server on Linux works including an in depth look at the innovative architecture. The book covers day-to-day management and troubleshooting, including diagnostics and monitoring, the use of containers to manage deployments, and the use of self-tuning and the in-memory capabilities. Also covered are performance capabilities, high availability, and disaster recovery along with security and encryption. The book covers the product-specific knowledge to bring SQL Server and its powerful features to life on the Linux platform, including coverage of containerization through Docker and Kubernetes. What You'll Learn Learn about the history and internal of the unique SQL Server on Linux architecture. Install and configure Microsoft’s flagship database product on the Linux platform Manage your deployments using container technology through Docker and Kubernetes Know the basics of building databases, the T-SQL language, and developing applications against SQL Server on Linux Use tools and features to diagnose, manage, and monitor SQL Server on Linux Scale your application by learning the performance capabilities of SQL Server Deliver high availability and disaster recovery to ensure business continuity Secure your database from attack, and protect sensitive data through encryption Take advantage of powerful features such as Failover Clusters, Availability Groups, In-Memory Support, and SQL Server’s Self-Tuning Engine Learn how to migrate your database from older releases of SQL Server and other database platforms such as Oracle and PostgreSQL Build and maintain schemas, and perform management tasks from both GUI and command line Who This Book Is For Developers and IT professionals who are new to SQL Server and wish to configure it on the Linux operating system. This book is also useful to those familiar with SQL Server on Windows who want to learn the unique aspects of managing SQL Server on the Linux platform and Docker containers. Readers should have a grasp of relational database concepts and be comfortable with the SQL language. COMPUTERS,Database Administration & Management

Mastering Apache Cassandra 3.x Build, manage, and configure high-performing, reliable NoSQL database for your applications with Cassandra Key Features Write programs more efficiently using Cassandra's features with the help of examples Configure Cassandra and fine-tune its parameters depending on your needs Integrate Cassandra database with Apache Spark and build strong data analytics pipeline Book Description With ever-increasing rates of data creation, the demand for storing data fast and reliably becomes a need. Apache Cassandra is the perfect choice for building fault-tolerant and scalable databases. Mastering Apache Cassandra 3.x teaches you how to build and architect your clusters, configure and work with your nodes, and program in a high-throughput environment, helping you understand the power of Cassandra as per the new features. Once you've covered a brief recap of the basics, you'll move on to deploying and monitoring a production setup and optimizing and integrating it with other software. You'll work with the advanced features of CQL and the new storage engine in order to understand how they function on the server-side. You'll explore the integration and interaction of Cassandra components, followed by discovering features such as token allocation algorithm, CQL3, vnodes, lightweight transactions, and data modelling in detail. Last but not least you will get to grips with Apache Spark. By the end of this book, you'll be able to analyse big data, and build and manage high-performance databases for your application. What you will learn Write programs more efficiently using Cassandra's features more efficiently Exploit the given infrastructure, improve performance, and tweak the Java Virtual Machine (JVM) Use CQL3 in your application in order to simplify working with Cassandra Configure Cassandra and fine-tune its parameters depending on your needs Set up a cluster and learn how to scale it Monitor a Cassandra cluster in different ways Use Apache Spark and other big data processing tools Who this book is for Mastering Apache Cassandra 3.x is for you if you are a big data administrator, database administrator, architect, or developer who wants to build a high-performing, scalable, and fault-tolerant database. Prior knowledge of core concepts of databases is required. COMPUTERS,Database Administration & Management

How Well Do Executives Trust Their Intuition In this age of Big Data and analytics, knowledge gained through experiential learning and intuition may be taking a back seat to analytics. However, the use of intuition should not be underestimated and should play an important role in the decision process. How Well Do Executives Trust Their Intuition covers the Fulbright research study conducted by this international team of editors. The main question of their investigation is: How well do executives trust their intuition? In other words, do they typically prefer intuition over analysis and analytics. And equally importantly, what types of intuition may be most favorable looking at different variables? The research utilizes survey and biometrics approaches with C-level executives from Canada, U.S., Poland, and Italy. In addition, the book contains chapters from leading executives in industry, academia, and government. Their insights provide examples of how their intuition enabled key decisions that they made. This book covers such topics as: Using intuition How gender, experience, role, industry, and country affect intuition Trust and intuition in management Trusting intuition It’s a matter of heart Leadership intuition and the future of work Creating an intuitive awareness for executives Improvisation and instinct. The book explores how executives can use intuition to guide decision making. It also explains how to trust intuition-based decisions. How Well Do Executives Trust Their Intuition is a timely and prescient reminder in this age of data-driven analytics that human insight, instinct, and intuition should also play key roles. COMPUTERS,Database Administration & Management

SQL All-in-One For Dummies The latest on SQL databases SQL All -In-One For Dummies, 3rd Edition, is a one-stop shop for everything you need to know about SQL and SQL-based relational databases. Everyone from database administrators to application programmers and the people who manage them will find clear, concise explanations of the SQL language and its many powerful applications. With the ballooning amount of data out there, more and more businesses, large and small, are moving from spreadsheets to SQL databases like Access, Microsoft SQL Server, Oracle databases, MySQL, and PostgreSQL. This compendium of information covers designing, developing, and maintaining these databases. Cope with any issue that arises in SQL database creation and management Get current on the newest SQL updates and capabilities Reference information on querying SQL-based databases in the SQL language Understand relational databases and their importance to today’s organizations SQL All-In-One For Dummies is a timely update to the popular reference for readers who want detailed information about SQL databases and queries. COMPUTERS,Database Administration & Management

Blockchain For Dummies Unravel the mysteries of blockchains Blockchain technologies are disrupting some of the world’s biggest industries. Blockchain For Dummies provides a fast way to catch up with the essentials of this quickly evolving tech. Written by an author involved in founding and analyzing blockchain solutions, this book serves to help those who need to understand what a blockchain can do (and can't do). This revised edition walks you through how a blockchainsecurely records data across independent networks. It offers a tour of some of the world’s best-known blockchains, including those that power Bitcoin and other cryptocurrencies. It also provides a glance at how blockchain solutions are affecting the worlds of finance, supply chain management, insurance, and governments. Get a clear picture of what a blockchain can do Learn how blockchains rule cryptocurrency and smart contracts Discover current blockchains and how each of them work Test blockchain apps Blockchain has become the critical buzzword in the world of financial technology and transaction security — and now you can make sense of it with the help of this essential guide. COMPUTERS,Database Administration & Management

Data Science Strategy For Dummies All the answers to your data science questions Over half of all businesses are using data science to generate insights and value from big data. How are they doing it? Data Science Strategy For Dummies answers all your questions about how to build a data science capability from scratch, starting with the “what†and the “why†of data science and covering what it takes to lead and nurture a top-notch team of data scientists. With this book, you’ll learn how to incorporate data science as a strategic function into any business, large or small. Find solutions to your real-life challenges as you uncover the stories and value hidden within data. Learn exactly what data science is and why it’s important Adopt a data-driven mindset as the foundation to success Understand the processes and common roadblocks behind data science Keep your data science program focused on generating business value Nurture a top-quality data science team In non-technical language, Data Science Strategy For Dummies outlines new perspectives and strategies to effectively lead analytics and data science functions to create real value. COMPUTERS,Database Administration & Management

SQL for Data Analytics Take your first steps to become a fully qualified data analyst by learning how to explore large relational datasets Key Features Explore a variety of statistical techniques to analyze your data Integrate your SQL pipelines with other analytics technologies Perform advanced analytics such as geospatial and text analysis Book Description Understanding and finding patterns in data has become one of the most important ways to improve business decisions. If you know the basics of SQL, but don't know how to use it to gain the most effective business insights from data, this book is for you. SQL for Data Analytics helps you build the skills to move beyond basic SQL and instead learn to spot patterns and explain the logic hidden in data. You'll discover how to explore and understand data by identifying trends and unlocking deeper insights. You'll also gain experience working with different types of data in SQL, including time-series, geospatial, and text data. Finally, you'll learn how to increase your productivity with the help of profiling and automation. By the end of this book, you'll be able to use SQL in everyday business scenarios efficiently and look at data with the critical eye of an analytics professional. What you will learn Perform advanced statistical calculations using the WINDOW function Use SQL queries and subqueries to prepare data for analysis Import and export data using a text file and psql Apply special SQL clauses and functions to generate descriptive statistics Analyze special data types in SQL, including geospatial data and time data Optimize queries to improve their performance for faster results Debug queries that won't run Use SQL to summarize and identify patterns in data Who this book is for If you're a database engineer looking to transition into analytics, or a backend engineer who wants to develop a deeper understanding of production data, you will find this book useful. This book is also ideal for data scientists or business analysts who want to improve their data analytics skills using SQL. Knowledge of basic SQL and database concepts will aid in understanding the concepts covered in this book. COMPUTERS,Database Administration & Management

Mastering Data Processing Data Processing is a self-contained and up-to-date book, ideal for the relevant business and accounting courses or anyone in business who wishes to improve existing knowledge and skills. The book teaches all aspects of data processing, including an introduction to DP. COMPUTERS,Database Administration & Management

Big Data with Hadoop MapReduce The authors provide an understanding of big data and MapReduce by clearly presenting the basic terminologies and concepts. They have employed over 100 illustrations and many worked-out examples to convey the concepts and methods used in big data, the inner workings of MapReduce, and single node/multi-node installation on physical/virtual machines. This book covers almost all the necessary information on Hadoop MapReduce for most online certification exams. Upon completing this book, readers will find it easy to understand other big data processing tools such as Spark, Storm, etc. Ultimately, readers will be able to: • understand what big data is and the factors that are involved • understand the inner workings of MapReduce, which is essential for certification exams • learn the features and weaknesses of MapReduce • set up Hadoop clusters with 100s of physical/virtual machines • create a virtual machine in AWS • write MapReduce with Eclipse in a simple way • understand other big data processing tools and their applications COMPUTERS,Database Administration & Management

Augmented Intelligence The AI revolution is moving at a breakneck speed. Organizations are beginning to invest in innovative ways to monetize their data through the use of artificial intelligence. Businesses need to understand the reality of AI. To be successful, it is imperative that organizations understand that augmented intelligence is the secret to success. Augmented Intelligence: The Business Power of Human–Machine Collaboration is about the process of combining human and machine intelligence. This book provides business leaders and AI data experts with an understanding of the value of augmented intelligence and its ability to help win competitive markets. This book focuses on the requirement to clearly manage the foundational data used for augmented intelligence. It focuses on the risks of improper data use and delves into the ethics and governance of data in the era of augmented intelligence. In this book, we explore the difference between weak augmentation that is based on automating well understood processes and strong augmentation that is designed to rethink business processes through the inclusion of data, AI and machine learning. What experts are saying about Augmented Intelligence "The book you are about to read is of great importance because we increasingly rely on machine learning and AI. Therefore, it is critical that we understand the ability to create an environment in which businesses can have the tools to understand data from a holistic perspective. What is imperative is to be able to make better decisions based on an understanding of the behavior and thinking of our customers so that we can take the best next action. This book provides a clear understanding of the impact of augmented intelligence on both society and business."—Tsvi Gal, Managing Director, Enterprise Technology and Services, Morgan Stanley "Our mission has always been to help clients apply AI to better predict and shape future outcomes, empower higher value work, and automate how work gets done. I have always said, ’AI will not replace managers, but managers who use AI will replace managers who don't.’ This book delves into the real value that AI promises, to augment existing human intelligence, and in the process, dispels some of the myths around AI and its intended purpose."—Rob Thomas, General Manager, Data and AI, IBM COMPUTERS,Database Administration & Management

Microsoft SQL Server 2019 Publisher's Note: Products purchased from Third Party sellers are not guaranteed by the publisher for quality, authenticity, or access to any online entitlements included with the product. Get Up to Speed on Microsoft® SQL Server® 2019 Quickly and Easily Start working with Microsoft SQL Server 2019 in no time with help from this thoroughly revised, practical resource. Filled with real-world examples and hands-on exercises, Microsoft SQL Server 2019: A Beginner’s Guide, Seventh Edition starts by explaining fundamental relational database system concepts. From there, you’ll learn how to write Transact-SQL statements, execute simple and complex database queries, handle system administration and security, and use powerful analysis and reporting tools. New topics such as SQL and JSON support, graph databases, and support for machine learning with R and Python are also covered in this step-by-step tutorial. • Install, configure, and customize Microsoft SQL Server 2019• Create and modify database objects with Transact-SQL statements• Write stored procedures and user-defined functions• Handle backup and recovery, and automate administrative tasks• Tune your database system for optimal availability and reliability• Secure your system using authentication, encryption, and authorization• Work with SQL Server Analysis Services, Reporting Services, and other BI tools• Gain knowledge of relational storage, presentation, and retrieval of data stored in the JSON format• Manage graphs using SQL Server Graph Databases• Learn about machine learning support for R and Python COMPUTERS,Database Administration & Management

Fast and Scalable Cloud Data Management The unprecedented scale at which data is both produced and consumed today has generated a large demand for scalable data management solutions facilitating fast access from all over the world. As one consequence, a plethora of non-relational, distributed NoSQL database systems have risen in recent years and today’s data management system landscape has thus become somewhat hard to overlook. As another consequence, complex polyglot designs and elaborate schemes for data distribution and delivery have become the norm for building applications that connect users and organizations across the globe – but choosing the right combination of systems for a given use case has become increasingly difficult as well. To help practitioners stay on top of that challenge, this book presents a comprehensive overview and classification of the current system landscape in cloud data management as well as a survey of the state-of-the-art approaches for efficient data distribution and delivery to end-user devices. The topics covered thus range from NoSQL storage systems and polyglot architectures (backend) over distributed transactions and Web caching (network) to data access and rendering performance in the client (end-user). By distinguishing popular data management systems by data model, consistency guarantees, and other dimensions of interest, this book provides an abstract framework for reasoning about the overall design space and the individual positions claimed by each of the systems therein. Building on this classification, this book further presents an application-driven decision guidance tool that breaks the process of choosing a set of viable system candidates for a given application scenario down into a straightforward decision tree. COMPUTERS,Database Administration & Management

SQL Server Big Data Clusters Use this guide to one of SQL Server 2019’s most impactful features—Big Data Clusters. You will learn about data virtualization and data lakes for this complete artificial intelligence (AI) and machine learning (ML) platform within the SQL Server database engine. You will know how to use Big Data Clusters to combine large volumes of streaming data for analysis along with data stored in a traditional database. For example, you can stream large volumes of data from Apache Spark in real time while executing Transact-SQL queries to bring in relevant additional data from your corporate, SQL Server database. Filled with clear examples and use cases, this book provides everything necessary to get started working with Big Data Clusters in SQL Server 2019. You will learn about the architectural foundations that are made up from Kubernetes, Spark, HDFS, and SQL Server on Linux. You then are shown how to configure and deploy Big Data Clusters in on-premises environments or in the cloud. Next, you are taught about querying. You will learn to write queries in Transact-SQL—taking advantage of skills you have honed for years—and with those queries you will be able to examine and analyze data from a wide variety of sources such as Apache Spark. Through the theoretical foundation provided in this book and easy-to-follow example scripts and notebooks, you will be ready to use and unveil the full potential of SQL Server 2019: combining different types of data spread across widely disparate sources into a single view that is useful for business intelligence and machine learning analysis. What You Will Learn Install, manage, and troubleshoot Big Data Clusters in cloud or on-premise environments Analyze large volumes of data directly from SQL Server and/or Apache Spark Manage data stored in HDFS from SQL Server as if it were relational data Implement advanced analytics solutions through machine learning and AI Expose different data sources as a single logical source using data virtualization Who This Book Is For Data engineers, data scientists, data architects, and database administrators who want to employ data virtualization and big data analytics in their environments COMPUTERS,Database Administration & Management

The Manga Guide to Databases Want to learn about databases without the tedium? With its unique combination of Japanese-style comics and serious educational content, The Manga Guide to Databases is just the book for you. Princess Ruruna is stressed out. With the king and queen away, she has to manage the Kingdom of Kod's humongous fruit-selling empire. Overseas departments, scads of inventory, conflicting prices, and so many customers! It's all such a confusing mess. But a mysterious book and a helpful fairy promise to solve her organizational problems—with the practical magic of databases. In The Manga Guide to Databases, Tico the fairy teaches the Princess how to simplify her data management. We follow along as they design a relational database, understand the entity-relationship model, perform basic database operations, and delve into more advanced topics. Once the Princess is familiar with transactions and basic SQL statements, she can keep her data timely and accurate for the entire kingdom. Finally, Tico explains ways to make the database more efficient and secure, and they discuss methods for concurrency and replication. Examples and exercises (with answer keys) help you learn, and an appendix of frequently used SQL statements gives the tools you need to create and maintain full-featured databases. (Of course, it wouldn't be a royal kingdom without some drama, so read on to find out who gets the girl—the arrogant prince or the humble servant.) This EduManga book is a translation of a bestselling series in Japan, co-published with Ohmsha, Ltd., of Tokyo, Japan. COMPUTERS,Database Administration & Management

Big Data Analytics for Time-Critical Mobility Forecasting This book provides detailed descriptions of big data solutions for activity detection and forecasting of very large numbers of moving entities spread across large geographical areas. It presents state-of-the-art methods for processing, managing, detecting and predicting trajectories and important events related to moving entities, together with advanced visual analytics methods, over multiple heterogeneous, voluminous, fluctuating and noisy data streams from moving entities, correlating them with data from archived data sources expressing e.g. entities’ characteristics, geographical information, mobility patterns, mobility regulations and intentional data. The book is divided into six parts: Part I discusses the motivation and background of mobility forecasting supported by trajectory-oriented analytics, and includes specific problems and challenges in the aviation (air-traffic management) and the maritime domains. Part II focuses on big data quality assessment and processing, and presents novel technologies suitable for mobility analytics components. Next, Part III describes solutions toward processing and managing big spatio-temporal data, particularly enriching data streams and integrating streamed and archival data to provide coherent views of mobility, and storing of integrated mobility data in large distributed knowledge graphs for efficient query-answering. Part IV focuses on mobility analytics methods exploiting (online) processed, synopsized and enriched data streams as well as (offline) integrated, archived mobility data, and highlights future location and trajectory prediction methods, distinguishing between short-term and more challenging long-term predictions. Part V examines how methods addressing data management, data processing and mobility analytics are integrated in big data architectures with distinctive characteristics compared to other known big data paradigmatic architectures. Lastly, Part VI covers important ethical issues that research on mobility analytics should address. Providing novel approaches and methodologies related to mobility detection and forecasting needs based on big data exploration, processing, storage, and analysis, this book will appeal to computer scientists and stakeholders in various application domains. COMPUTERS,Database Administration & Management

Large-scale Graph Analysis This book introduces readers to a workload-aware methodology for large-scale graph algorithm optimization in graph-computing systems, and proposes several optimization techniques that can enable these systems to handle advanced graph algorithms efficiently. More concretely, it proposes a workload-aware cost model to guide the development of high-performance algorithms. On the basis of the cost model, the book subsequently presents a system-level optimization resulting in a partition-aware graph-computing engine, PAGE. In addition, it presents three efficient and scalable advanced graph algorithms – the subgraph enumeration, cohesive subgraph detection, and graph extraction algorithms. This book offers a valuable reference guide for junior researchers, covering the latest advances in large-scale graph analysis; and for senior researchers, sharing state-of-the-art solutions based on advanced graph algorithms. In addition, all readers will find a workload-aware methodology for designing efficient large-scale graph algorithms. COMPUTERS,Database Administration & Management

Mastering PostgreSQL 12 Master PostgreSQL 12 features such as advanced indexing, high availability, monitoring, and much more to efficiently manage and maintain your database Key Features Grasp advanced PostgreSQL 12 concepts with real-world examples and sample datasets Explore query parallelism, data replication, database administration, and more Extend PostgreSQL functionalities to suit your organization's needs with minimal effort Book Description Thanks to its reliability, robustness, and high performance, PostgreSQL has become the most advanced open source database on the market. This third edition of Mastering PostgreSQL helps you build dynamic database solutions for enterprise applications using the latest release of PostgreSQL, which enables database analysts to design both physical and technical aspects of system architecture with ease. Starting with an introduction to the newly released features in PostgreSQL 12, this book will help you build efficient and fault-tolerant PostgreSQL applications. You'll thoroughly examine the advanced features of PostgreSQL, including logical replication, database clusters, performance tuning, monitoring, and user management. You'll also work with the PostgreSQL optimizer, configure PostgreSQL for high speed, and understand how to move from Oracle to PostgreSQL. As you progress through the chapters, you'll cover transactions, locking, indexes, and how to optimize queries for improved performance. Additionally, you'll learn how to manage network security and explore backups and replications while understanding useful PostgreSQL extensions to help you in optimizing the performance of large databases. By the end of this PostgreSQL book, you'll be able to get the most out of your database by implementing advanced administrative tasks effortlessly. What you will learn Understand the advanced SQL functions in PostgreSQL 12 Use indexing features in PostgreSQL to fine-tune the performance of queries Work with stored procedures and manage backup and recovery Master replication and failover techniques to reduce data loss Replicate PostgreSQL database systems to create backups and to scale your database Manage and improve the security of your server to protect your data Troubleshoot your PostgreSQL instance for solutions to common and not-so-common problems Who this book is for This book is for PostgreSQL developers and administrators and database professionals who want to implement advanced functionalities and master complex administrative tasks with PostgreSQL 12. Prior exposure to PostgreSQL as well as familiarity with the basics of database administration is expected. COMPUTERS,Databases,Servers

PostgreSQL 12 High Availability Cookbook A comprehensive guide to understanding key techniques for architecture and hardware planning, monitoring, replication, backups, and decoupling Key Features Newly updated edition, covering the latest PostgreSQL 12 features with hands-on industry-driven recipes Create a PostgreSQL cluster that stays online even when disaster strikes Learn how to avoid costly downtime and data loss that can ruin your business Book Description Databases are nothing without the data they store. In the event of an outage or technical catastrophe, immediate recovery is essential. This updated edition ensures that you will learn the important concepts related to node architecture design, as well as techniques such as using repmgr for failover automation. From cluster layout and hardware selection to software stacks and horizontal scalability, this PostgreSQL cookbook will help you build a PostgreSQL cluster that will survive crashes, resist data corruption, and grow smoothly with customer demand. You'll start by understanding how to plan a PostgreSQL database architecture that is resistant to outages and scalable, as it is the scaffolding on which everything rests. With the bedrock established, you'll cover the topics that PostgreSQL database administrators need to know to manage a highly available cluster. This includes configuration, troubleshooting, monitoring and alerting, backups through proxies, failover automation, and other considerations that are essential for a healthy PostgreSQL cluster. Later, you'll learn to use multi-master replication to maximize server availability. Later chapters will guide you through managing major version upgrades without downtime. By the end of this book, you'll have learned how to build an efficient and adaptive PostgreSQL 12 database cluster. What you will learn Understand how to protect data with PostgreSQL replication tools Focus on hardware planning to ensure that your database runs efficiently Reduce database resource contention with connection pooling Monitor and visualize cluster activity with Nagios and the TIG (Telegraf, InfluxDB, Grafana) stack Construct a robust software stack that can detect and avert outages Use multi-master to achieve an enduring PostgreSQL cluster Who this book is for This book is for Postgres administrators and developers who are looking to build and maintain a highly reliable PostgreSQL cluster. Although knowledge of the new features of PostgreSQL 12 is not required, a basic understanding of PostgreSQL administration is expected. COMPUTERS,Databases,Servers

Introducing Microsoft SQL Server 2019 Explore the impressive storage and analytic tools available with the in-cloud and on-premises versions of Microsoft SQL Server 2019. Key Features Gain insights into what's new in SQL Server 2019 Understand use cases and customer scenarios that can be implemented with SQL Server 2019 Discover new cross-platform tools that simplify management and analysis Book Description Microsoft SQL Server comes equipped with industry-leading features and the best online transaction processing capabilities. If you are looking to work with data processing and management, getting up to speed with Microsoft Server 2019 is key. Introducing SQL Server 2019 takes you through the latest features in SQL Server 2019 and their importance. You will learn to unlock faster querying speeds and understand how to leverage the new and improved security features to build robust data management solutions. Further chapters will assist you with integrating, managing, and analyzing all data, including relational, NoSQL, and unstructured big data using SQL Server 2019. Dedicated sections in the book will also demonstrate how you can use SQL Server 2019 to leverage data processing platforms, such as Apache Hadoop and Spark, and containerization technologies like Docker and Kubernetes to control your data and efficiently monitor it. By the end of this book, you'll be well versed with all the features of Microsoft SQL Server 2019 and understand how to use them confidently to build robust data management solutions. What you will learn Build a custom container image with a Dockerfile Deploy and run the SQL Server 2019 container image Understand how to use SQL server on Linux Migrate existing paginated reports to Power BI Report Server Learn to query Hadoop Distributed File System (HDFS) data using Azure Data Studio Understand the benefits of In-Memory OLTP Who this book is for This book is for database administrators, architects, big data engineers, or anyone who has experience with SQL Server and wants to explore and implement the new features in SQL Server 2019. Basic working knowledge of SQL Server and relational database management system (RDBMS) is required. COMPUTERS,Databases,Servers

SQL Server on Azure Virtual Machines Learn how to combine SQL Server's analytics with Azure's flexibility and hybrid connectivity to achieve industry-leading performance and manageability for your cloud database. Key Features Understand platform availability for SQL Server in Azure Explore the benefits and deployment choices offered by SQL IaaS Get to grips with deploying SQL Server on the Linux development ecosystem Book Description Deploying SQL Server on Azure virtual machines allows you to work on full versions of SQL Server in the cloud without having to maintain on-premises hardware. The book begins by introducing you to the SQL portfolio in Azure and takes you through SQL Server IaaS scenarios, before explaining the factors that you need to consider while choosing an OS for SQL Server in Azure VMs. As you progress through the book, you'll explore different VM options and deployment choices for IaaS and understand platform availability, migration tools, and best practices in Azure. In later chapters, you'll learn how to configure storage to achieve optimized performance. Finally, you'll get to grips with the concept of Azure Hybrid Benefit and find out how you can use it to maximize the value of your existing on-premises SQL Server. By the end of this book, you'll be proficient in administering SQL Server on Microsoft Azure and leveraging the tools required for its deployment. What you will learn Choose an operating system for SQL Server in Azure VMs Use the Azure Management Portal to facilitate the deployment process Verify connectivity and network latency in cloud Configure storage for optimal performance and connectivity Explore various disaster recovery options for SQL Server in Azure Optimize SQL Server on Linux Discover how to back up databases to a URL Who this book is for SQL Server on Azure VMs is for you if you are a developer, data enthusiast, or anyone who wants to migrate SQL Server databases to Azure virtual machines. Basic familiarity with SQL Server and managed identities for Azure resources will be a plus. COMPUTERS,Databases,Servers

Audio Engineering The Newnes Know It All Series takes the best of what our authors have written to create hard-working desk references that will be an engineer's first port of call for key information, design techniques and rules of thumb. Guaranteed not to gather dust on a shelf! Audio engineers need to master a wide area of topics in order to excel. The Audio Engineering Know It All covers every angle, including digital signal processing, power supply design, microphone and loudspeaker technology as well as audio compression. A 360-degree view from our best-selling authors Includes such topics as fundamentals, compression, and test and measurement The ultimate hard-working desk reference; all the essential information, techniques and tricks of the trade in one volume COMPUTERS,Design,Graphics & Media,Audio

Web Audio API Go beyond HTML5’s Audio tag and boost the audio capabilities of your web application with the Web Audio API. Packed with lots of code examples, crisp descriptions, and useful illustrations, this concise guide shows you how to use this JavaScript API to make the sounds and music of your games and interactive applications come alive. You need little or no digital audio expertise to get started. Author Boris Smus introduces you to digital audio concepts, then shows you how the Web Audio API solves specific application audio problems. If you're an experienced JavaScript programmer, you’ll not only learn how to synthesize and process digital audio, you’ll also explore audio analysis and visualization with this API. Learn Web Audio API, including audio graphs and the audio nodes Provide quick feedback to user actions by scheduling sounds with the API’s precise timing model Control gain, volume, and loudness, and dive into clipping and crossfading Understand pitch and frequency: use tools to manipulate soundforms directly with JavaScript Generate synthetic sound effects and learn how to spatialize sound in 3D space Use Web Audio API with the Audio tag, getUserMedia, and the Page Visibility API COMPUTERS,Design,Graphics & Media,Audio

The Book of Audacity The Book of Audacity is the definitive guide to Audacity, the powerful, free, cross-platform audio editor. Audacity allows anyone to transform their Windows, Mac, or Linux computer into a powerful recording studio. The Book of Audacity is the perfect book for bands on a budget, solo artists, audiophiles, and anyone who wants to learn more about digital audio. Musician and podcaster Carla Schroder will guide you through a range of fun and useful Audacity projects that will demystify that geeky audio jargon and show you how to get the most from Audacity. You’ll learn how to:–Record podcasts, interviews, and live performances–Be your own backing band or chorus–Edit, splice, mix, and master multitrack recordings–Create super high-fidelity and surround-sound recordings–Digitize your vinyl or tape collection and clean up noise, hisses, and clicks–Create custom ringtones and sweet special effects In addition, you’ll learn how to choose and use digital audio hardware like mics and preamps, and tune your computer for flawless audio performance. You’ll also find out how to package your work for digital distribution, whether you want to share a podcast through iTunes or sell your own CDs. Become your own producer with The Book of Audacity. The fun starts now. COMPUTERS,Design,Graphics & Media,Audio

Sound and Image Sound and Image: Aesthetics and Practices brings together international artist scholars to explore diverse sound and image practices, applying critical perspectives to interrogate and evaluate both the aesthetics and practices that underpin the audiovisual. Contributions draw upon established discourses in electroacoustic music, media art history, film studies, critical theory and dance; framing and critiquing these arguments within the context of diverse audiovisual practices. The volume’s interdisciplinary perspective contributes to the rich and evolving dialogue surrounding the audiovisual, demonstrating the value and significance of practice-informed theory, and theory derived from practice. The ideas and approaches explored within this book will find application in a wide range of contexts across the whole scope of audiovisuality, from visual music and experimental film, to narrative film and documentary, to live performance, sound design and into sonic art and electroacoustic music. This book is ideal for artists, composers and researchers investigating theoretical positions and compositional practices which bring together sound and image. COMPUTERS,Design,Graphics & Media,Audio

Designing Sound A practitioner's guide to the basic principles of creating sound effects using easily accessed free software. Designing Sound teaches students and professional sound designers to understand and create sound effects starting from nothing. Its thesis is that any sound can be generated from first principles, guided by analysis and synthesis. The text takes a practitioner's perspective, exploring the basic principles of making ordinary, everyday sounds using an easily accessed free software. Readers use the Pure Data (Pd) language to construct sound objects, which are more flexible and useful than recordings. Sound is considered as a process, rather than as data—an approach sometimes known as “procedural audio.” Procedural sound is a living sound effect that can run as computer code and be changed in real time according to unpredictable events. Applications include video games, film, animation, and media in which sound is part of an interactive process. The book takes a practical, systematic approach to the subject, teaching by example and providing background information that offers a firm theoretical context for its pragmatic stance. [Many of the examples follow a pattern, beginning with a discussion of the nature and physics of a sound, proceeding through the development of models and the implementation of examples, to the final step of producing a Pure Data program for the desired sound. Different synthesis methods are discussed, analyzed, and refined throughout.] After mastering the techniques presented in Designing Sound, students will be able to build their own sound objects for use in interactive applications and other projects COMPUTERS,Design,Graphics & Media,Audio

VOICE Perspectives on the voice and technology, from discussions of voice mail and podcasts to reflections on dance and sound poetry. Voice has returned to both theoretical and artistic agendas. In the digital era, techniques and technologies of voice have provoked insistent questioning of the distinction between the human voice and the voice of the machine, between genuine and synthetic affect, between the uniqueness of an individual voice and the social and cultural forces that shape it. This volume offers interdisciplinary perspectives on these topics from history, philosophy, cultural theory, film, dance, poetry, media arts, and computer games. Many chapters demonstrate Lewis Mumford's idea of the “cultural preparation” that precedes technological innovation—that socially important new technologies are foreshadowed in philosophy, the arts, and everyday pastimes. Chapters cover such technologies as voice mail, podcasting, and digital approximations of the human voice. A number of authors explore the performance, performativity, and authenticity [(or 'authenticity effect') of voice in dance, poetry, film, and media arts]; while others examine more immaterial concerns—the voice's often-invoked magical powers, the ghostliness of disembodied voices, and posthuman vocalization. [The chapters evoke an often paradoxical reassertion of the human in the use of voice in mainstream media including recorded music, films, and computer games. Contributors Mark Amerika, Isabelle Arvers, Giselle Beiguelman, Philip Brophy, Ross Gibson, Brandon LaBelle, Thomas Levin, Helen Macallan, Virginia Madsen, Meredith Morse, Norie Neumark, Andrew Plain, John Potts, Theresa M. Senft, Nermin Saybasili, Amanda Stewart, Axel Stockburger, Michael Taussig, Martin Thomas, Theo van Leeuwen, Mark Wood COMPUTERS,Design,Graphics & Media,Audio

My TV for Seniors Covers What, How, and Where to Watch TV for Less Millions of people are cutting the cord on old-fashioned cable TV plans, and choosing more modern, efficient, and cost-effective ways to watch their favorite programming and movies. My TV for Seniors, 2nd Edition is an exceptionally easy and complete full-color guide to all the services and hardware you’ll need to do it. No ordinary “beginner’s book,†it approaches every topic from a senior’s point of view, using meaningful examples, step-by-step tasks, large text, close-up screen shots, and a full-color interior designed for comfortable reading. Full-color, step-by-step tasks walk you through watching TV today on a variety of devices—and saving money doing so. Learn how to Cut the cable and satellite cord Save money on your cable or satellite TV bill Watch local TV stations for free Choose the best TV and streaming media player for you Connect and use an Amazon Fire TV, Apple TV, Google Chromecast, or Roku device Watch Amazon Prime Video, Hulu, Netflix, Disney+, HBO Max, and other streaming video services Use live streaming services like DirecTV Now, fuboTV, Hulu with Live TV, PlayStation Vue, Sling TV, and YouTube TV Find where to best watch sporting events Get a better picture with HD, Ultra HD, and HDR Get better sound with a sound bar or surround sound system Watch TV on your phone, tablet, or computer An AARP TV for Grownups publication COMPUTERS,Design,Graphics & Media,Audio

Manual of Engineering Drawing The Manual of Engineering Drawing has long been recognised as the student and practising engineer's guide to producing engineering drawings that comply with ISO and British Standards. The information in this book is equally applicable to any CAD application or manual drawing. The second edition is fully in line with the requirements of the new British Standard BS8888: 2002, and will help engineers, lecturers and students with the transition to the new standards. BS8888 is fully based on the relevant ISO standards, so this book is also ideal for an international readership. The comprehensive scope of this book encompasses topics including orthographic, isometric and oblique projections, electric and hydraulic diagrams, welding and adhesive symbols, and guidance on tolerancing. Written by a member of the ISO committee and a former college lecturer, the Manual of Engineering Drawing combines up-to-the-minute technical accuracy with clear, readable explanations and numerous diagrams. This approach makes this an ideal student text for vocational courses in engineering drawing and undergraduates studying engineering design / product design. Colin Simmons is a member of the BSI and ISO Draughting Committees and an Engineering Standards Consultant. He was formerly Standards Engineer at Lucas CAV. * Fully in line with the latest ISO Standards* A textbook and reference guide for students and engineers involved in design engineering and product design* Written by a former lecturer and a current member of the relevant standards committees COMPUTERS,Design,Graphics & Media,CAD-CAM

CAD Systems Development Future computer aided design systems will themselves be designed using tools and methods that are still under development. This book presents the latest progress in research on the tools and methods needed to develop those CAD systems. The topics covered include algorithmic aspects, the product data and development process, future CAD architectures, feature based modeling and automatic feature recognition, complex surface design, and system implementation issues.The book contains contributions by the world's leading experts in the field of CAD technology from both universities and industry. The contributions are based on lectures given at the International Conference and Research Center for Computer Science, Schloss Dagstuhl, Germany. COMPUTERS,Design,Graphics & Media,CAD-CAM

Reasoning in Boolean Networks Reasoning in Boolean Networks provides a detailed treatment of recent research advances in algorithmic techniques for logic synthesis, test generation and formal verification of digital circuits. The book presents the central idea of approaching design automation problems for logic-level circuits by specific Boolean reasoning techniques. While Boolean reasoning techniques have been a central element of two-level circuit theory for many decades Reasoning in Boolean Networks describes a basic reasoning methodology for multi-level circuits. This leads to a unified view on two-level and multi-level logic synthesis. The presented reasoning techniques are applied to various CAD-problems to demonstrate their usefulness for today's industrially relevant problems. Reasoning in Boolean Networks provides lucid descriptions of basic algorithmic concepts in automatic test pattern generation, logic synthesis and verification and elaborates their intimate relationship to provide further intuition and insight into the subject. Numerous examples are provide for ease in understanding the material. Reasoning in Boolean Networks is intended for researchers in logic synthesis, VLSI testing and formal verification as well as for integrated circuit designers who want to enhance their understanding of basic CAD methodologies. COMPUTERS,Design,Graphics & Media,CAD-CAM

Codesign for Real-Time Video Applications Codesign for Real-Time Video Applications describes a modern design approach for embedded systems. It combines the design of hardware, software, and algorithms. Traditionally, these design domains are treated separately to reduce the design complexity. Advanced design tools support a codesign of the different domains which opens an opportunity for exploiting synergetic effects. The design approach is illustrated by the design of a video compression system. It is integrated into the video card of a PC. A VLIW processor architecture is used as the basis of the compression system and popular video compression algorithms (MPEG, JPEG, H.261) are analyzed. A complete top-down design flow is presented and the design tools for each of the design steps are explained. The tools are integrated into an HTML-based design framework. The resulting design data can be directly integrated into the WWW. This is a crucial aspect for supporting distributed design groups. The design data can be directly documented an cross referencing in an almost arbitrary way is supported. This provides a platform for information sharing among the different design domains. Codesign for Real-Time Video Applications focuses on the multi-disciplinary aspects of embedded system design. It combines design automation and advanced processor design with an important application domain. A quantitative design approach is emphasized which focuses the design time on the most crucial components. Thus enabling a fast and cost efficient design methodology. This book will be of interest to researchers, designers and managers working in embedded system design. COMPUTERS,Design,Graphics & Media,CAD-CAM

Model Based Fuzzy Control Model Based Fuzzy Control uses a given conventional or fuzzy open loop model of the plant under control to derive the set of fuzzy rules for the fuzzy controller. Of central interest are the stability, performance, and robustness of the resulting closed loop system. The major objective of model based fuzzy control is to use the full range of linear and nonlinear design and analysis methods to design such fuzzy controllers with better stability, performance, and robustness properties than non-fuzzy controllers designed using the same techniques. This objective has already been achieved for fuzzy sliding mode controllers and fuzzy gain schedulers - the main topics of this book. The primary aim of the book is to serve as a guide for the practitioner and to provide introductory material for courses in control theory. COMPUTERS,Design,Graphics & Media,CAD-CAM

Retargetable Compilers for Embedded Core Processors Embedded core processors are becoming a vital part of today's system-on-a-chip in the growing areas of telecommunications, multimedia and consumer electronics. This is mainly in response to a need to track evolving standards with the flexibility of embedded software. Consequently, maintaining the high product performance and low product cost requires a careful design of the processor tuned to the application domain. With the increased presence of instruction-set processors, retargetable software compilation techniques are critical, not only for improving engineering productivity, but to allow designers to explore the architectural possibilities for the application domain. Retargetable Compilers for Embedded Core Processors, with a Foreword written by Ahmed Jerraya and Pierre Paulin, overviews the techniques of modern retargetable compilers and shows the application of practical techniques to embedded instruction-set processors. The methods are highlighted with examples from industry processors used in products for multimedia, telecommunications, and consumer electronics. An emphasis is given to the methodology and experience gained in applying two different retargetable compiler approaches in industrial settings. The book also discusses many pragmatic areas such as language support, source code abstraction levels, validation strategies, and source-level debugging. In addition, new compiler techniques are described which support address generation for DSP architecture trends. The contribution is an address calculation transformation based on an architectural model. Retargetable Compilers for Embedded Core Processors will be of interest to embedded system designers and programmers, the developers of electronic design automation (EDA) tools for embedded systems, and researchers in hardware/software co-design. COMPUTERS,Design,Graphics & Media,CAD-CAM

The AutoCAD® Reference Guide PREFACE Getting Faster Answers About AutoCAD Whether you are a beginning AutoCAD user, a part-time user, or even a long-standing user, it is virtually impossible to remember every nuance and every option for every AutoCAD command and variable. We have all had questions like "Can I do it this way with that command?" or "How do I get this sequence to work?" It is more important to know where to find information about AutoCAD commands than to remember it all. This reference guide is designed to give you fast access to AutoCAD's commands, variables, and key topics. Each command, variable, and topic is presented alphabetically and described simply and to the point. The complexities of commands and variables are explained with tips and warnings learned from experience. Why This Book Is Different This guide pulls AutoCAD commands, variables, and topics into one easy-to-use refer ence that brings important information about every AutoCAD command and variable to your fmgertips. The guide is not limited to a mere listing of commands and variables and what they do. It also helps you ¢ Find commands and variables quickly to get key descriptions ¢ Get tips and warnings that will save you time ¢ See example sequences and screen shots illustrating how to use commands and variables ¢ Identify variables for use with commands, menu macros, and AutoLISP Who Does This Book Benefit? This book is intended to be used by a person having some basic knowledge of AutoCAD. COMPUTERS,Design,Graphics & Media,CAD-CAM

Advanced Course on FAIRSHAPE Fairing and Shape Preserving of Curves - Experiences in CurveFairing - Co-Convexivity preserving Curve Interpolation - Shape Preserving Interpolation by Planar Curves - Shape Preserving Interpolation by Curves in Three Dimensions - A coparative study of two curve fairing methods in Tribon Initial Design Fairing Curves and Surfaces Fairing of B-Spline Curves and Surfaces - Declarative Modeling of fair shapes: An additional approach to curves and surfaces computations Shape Preserving of Curves and Surfaces Shape preserving interpolation with variable degree polynomial splines Fairing of Surfaces Functional Aspects of Fairness - Surface design based on brightness intensity or isophotes-theory and practice - Fair surface blending, an overview of industrial problems - Multivariate Splines with Convex-B-Patch Control Nets are Convex Shape Preserving of Surfaces Parametrizing Wing Surfaces using Partial Differential Equations - Algorithms for convexity preserving interpolation of scattered data - Abstract schemes for functional shape-preserving interpolation - Tensor Product Spline Interpolation subject to Piecewise Bilinear Lower and Upper Bounds - Construction of Surfaces by Shape Preserving Approximation of Contour Data-B-Spline Approximation with Energy constraints - Curvature approximation with application to surface modelling - Scattered Data Approximation with Triangular B-Splines Benchmarks Benchmarking in the area of Planar Shape Preserving Interpolation - Benchmark Processes in the Aerea of Shape - Constrained Approximation COMPUTERS,Design,Graphics & Media,CAD-CAM

Computer-aided Tolerancing Theory and practice of tolerances are very important for designing and manufacturing engineering artifacts on a rational basis. Tolerance specifies a degree of "discrepancy" between an idealized object and its physical realization. Such discrepancy inevitably comes into our product realization processes because of practical cost consideration or our inability to fully control manufacturing processes. Major product and production characteristics which are affected by tolerances are product quality and cost. For achieving high precision machines tight tolerance specification is necessary, but this will normally increase product cost. In order to optimally compromise the conflicting requirements of quality and cost, it is essential to take into account of the total product life cycle throughout product planning, design, manufacturing, maintenance and recycling. For example, in order to construct durable products under severe working conditions, low sensitivity of product functionality with respect to tolerances is required. In future, re-use of components or parts will become important, and tolerance synthesis with respect to this aspect will be an interesting future research topics. COMPUTERS,Design,Graphics & Media,CAD-CAM

Vibration Control of Flexible Servo Mechanisms This volume reports the work carried out between 1987 and 1991 in the framework of the ESPRIT CIMEProject 1561 entitled A High Performance FMS Robot with On-Line Dynamic Compensation more often referred to by its French acronym SACODY, standing for Structure AlJegee a COmmande DYnamique. The volume is the outcome of a collaborative R&D project performed by a European team coordinated by Bertin & Cie (France) and involving AEG AG and KUKA Roboter GmbH (Germany), LMS International and K.U. Leuven (Belgium) as well as University College Dublin (Ireland). On behalf of this consortium, we would like to acknowledge the support of the Commission of the European Communities, without which the research and development reported hereafter would not have been possible. We would especially like to thank Mrs. Patricia Mac Connaill, Head of the ESPRIT ClME Division, Dr. Rainer Zimmermann, SACODY Project Officer, and the project reviewers Dr. Motta and Profs. Parker, Coiffet and Trostmann for the continuous interest they have shown for the project all along its life as well as for their precious advices. COMPUTERS,Design,Graphics & Media,CAD-CAM

Technology CAD Systems As the cost of developing new semiconductor technology at ever higher bit/gate densities continues to grow, the value of using accurate TCAD simu lation tools for design and development becomes more and more of a necessity to compete in today's business. The ability to tradeoff wafer starts in an advanced piloting facility for simulation analysis and optimization utilizing a "virtual fab" S/W tool set is a clear economical asset for any semiconductor development company. Consequently, development of more sophisticated, accurate, physics-based, and easy-to-use device and process modeling tools will receive continuing attention over the coming years. The cost of maintaining and paying for one's own internal modeling tool development effort, however, has caused many semiconductor development companies to consider replacing some or all of their internal tool development effort with the purchase of vendor modeling tools. While some (noteably larger) companies have insisted on maintaining their own internal modeling tool development organization, others have elected to depend totally on the tools offered by the TCAD vendors and have consequently reduced their mod eling staffs to a bare minimal support function. Others are seeking to combine the best of their internally developed tool suite with "robust", "proven" tools provided by the vendors, hoping to achieve a certain synergy as well as savings through this approach. In the following sections we describe IBM's internally developed suite of TCAD modeling tools and show several applications of the use of these tools. COMPUTERS,Design,Graphics & Media,CAD-CAM

CIMOSA Enterprise operation efficiency is seriously constrained by the inability to provide the right information, in the right place, at the right time. In spite of significant advances in technology it is still difficult to access information used or produced by different applications due to the hardware and software incompatibilities of manufacturing and information processing equipment. But it is this information and operational knowledge which makes up most of the business value of the enterprise and which enables it to compete in the marketplace. Therefore, sufficient and timely information access is a prerequisite for its efficient use in the operation of enterprises. It is the aim of the ESPRIT project AMICE to make this knowledge base available enterprise-wide. During several ESPRIT contracts the project has developed and validated CIMOSA: Open System Architecture for CIM. The CIMOSA concepts provide operation structuring based on cooperating processes. Enterprise operations are represented in terms of functionality and dynamic behaviour (control flow). Information needed and produced, as well as resources and organisational aspects relevant in the course of the operation are modelled in the process model. However, the different aspects may be viewed separately for additional structuring and detailing during the enterprise engineering process. COMPUTERS,Design,Graphics & Media,CAD-CAM

Boundary-Scan Test The ever-increasing miniaturization of digital electronic components is hampering the conventional testing of Printed Circuit Boards (PCBs) by means of bed-of-nails fixtures. Basically this is caused by the very high scale of integration of ICs, through which packages with hundreds of pins at very small pitches of down to a fraction of a millimetre, have become available. As a consequence the trace distances between the copper tracks on a printed circuit board cmne down to the same value. Not only the required small physical dimensions of the test nails have made conventional testing unfeasible, but also the complexity to provide test signals for the many hundreds of test nails has grown out of limits. Therefore a new board test methodology had to be invented. Following the evolution in the IC test technology. Boundary-Scan testing hm; become the new approach to PCB testing. By taking precautions in the design of the IC (design for testability), testing on PCB level can be simplified 10 a great extent. This condition has been essential for the success of the introduction of Boundary-Sc,m Test (BST) at board level. COMPUTERS,Design,Graphics & Media,CAD-CAM

CAD Geometry Data Exchange Using STEP The Product Data Technology Advisory Group, short PDTAG, was established on 30 September 1992 under the auspices of the ESPRIT CIME Division of the Directorate General XIII of the European Commission. Its goals include promoting European cooperation and improving the European infrastructure in Product Data Technology, particularly in connection with the new standard STEP (ISO 10303). The dissemination of information on Product Data Technology and on European contributions to STEP is of crucial importance to this development. The current volume is the first title in a new PDTAG subseries to Springer Publishers' Research Reports ESPRIT. This new subseries intends to form a comprehensive repository of publications on Product Data Technology resulting from ESPRIT Projects and from European contributions to standardisation based on ISO/STEP. PDTAG welcomes the opportunity to make this information more accessible under the format of a coherent subseries within the established framework of Research Reports ESPRIT. Much valuable background on the new international PDT standard can thus be found in the same collection. COMPUTERS,Design,Graphics & Media,CAD-CAM

3D CAD 3D CAD is one of the most important technologies of the 90sfor the engineering and manufacturing world. 3D CAD systemscan provide a competitive edge in the development of newproducts. This book presents the development of athree-dimensional CAD system and its wide range ofapplications. It describes the concepts of solid models, andthe theory of curves and surfaces and it illustrates theseconcepts through "reals world" applications. COMPUTERS,Design,Graphics & Media,CAD-CAM

Concurrent Engineering Proceedings of the NATO Advanced Study Institute on Concurrent Engineering Tools and Technologies for Mechanical System Design, held in Iowa City, Iowa, May 25-June 5, 1992 COMPUTERS,Design,Graphics & Media,CAD-CAM

CAST Methods in Modelling Microtechnologies and their corresponding CAD tools havemeanwhile reached alevel of sophistication that requiresthe application of theoretical means on all modelling levelsof design and analysis. Also, there is a growing need for ascientific approach in modelling again. Many conceptsprovided by Systems Theory again turn out to be of majorimportance. This is especially valid for the design of"machines with intelligent behaviour".When dealing with complex systems, the engineering designhas to be supported by CAD tools. Consequently, the methodsof Systems Theory must also get computerized. The newlyestablished field of "Computer Aided Systems Theory" (CAST)is a first effort in this direction. The goal of CASTresearch and development isto provide "Systems TheoryMethod Banks" which can be used in education and to providea platform for the migration of CAST methods into existingCAD tools.This book, basing on different research and developmentprojects in CAST, is written for engineers who areinterested in using and developing CAST systems,particularly in thefield of Information and SystemsEngineering. COMPUTERS,Design,Graphics & Media,CAD-CAM

Computer Vision This book is the fruit of a very long and elaborate process. It was conceived as a comprehensive solution to several deficiencies encountered while trying to teach the essentials of Computer Vision in different contexts: to technicians from industry looking for technological solutions to some of their problems, to students in search of a good subject for a PhD thesis, and to researchers in other fields who believe that Computer Vision techniques may help them to analyse their results. The book was carefully planned with all these people in mind. Thus, it covers the fundamentals of both 2D and 3D Computer Vision and their most widespread industrial applications, such as automated inspection, robot guidance and workpiece acquisition. The level of explanation is that of an expanded introductory text, in the sense that, besides the basic material, some special advanced topics are included in each chapter, together with an extensive bibliography for experts to follow up. Well-known researchers on each of the topics were appointed to write a chapter following several guidelines to ensure a consistent presentation throughout. I would like to thank the authors for their patience, because some of them had to go through several revisions of their chapters in order to avoid repetition and to improve the homogeneity and coherence of the book. I hope they will find that the final result has been worth their efforts. COMPUTERS,Design,Graphics & Media,CAD-CAM

Intelligent CAD Systems III This book contains a selection of revised versions of papers presented at the Third Eurographics Workshop on Intelligent CAD Systems, which was held at Hotel Opduin on the island of Texel in The Netherlands, April 3-7, 1989. The workshop theme was Practical Experience and Evaluation. It included five paper presentation sessions, each followed by a discussion. The workshop closed with a general discussion. The book is therefore divided into five parts: design process, system architecture, languages, geometric reasoning, and user interface. A report on the discussion session, written by the session's moderator, concludes each part. These reports are not intended to be exact records of the discussion, but rather the moderators' summary of their contents. The aim of the workshop was to share the experience the participants gained by developing intelligent CAD (Computer Aided Design) systems, and to evaluate the developed systems to determine which features were still lacking. The workshop was organized as the last one in a series of three workshops under the same title. The first workshop focused on theoretical and methodological aspects, resulting in a sound theoretical basis for intelligent CAD systems. Implementational issues were discussed at the second workshop, paying attention to systems developed with reference to this basis. The experience and evaluation showed a dual outcome. Firstly, it resulted in the development of a new generation of intelligent CAD systems. Secondly, it led us to the development of new theories for intelligent CAD. COMPUTERS,Design,Graphics & Media,CAD-CAM

An Artificial Intelligence Approach to Integrated Circuit Floorplanning In 1984, while I was following his postgraduate course on VLSI design, my supervisor Dr. David Skellern, asked me if I was interested in investigating intelligent approaches to automatic Ie floorplanning. He told me then: "a circuit that works always looks nice, has a clever data and control flow. A fast way to look at students' Ie projects is by looking at their fioorplans.". Later, I took a course on Knowledge Engineering (KE) and Artificial Intelligence (AI) with Professor John Gero, who encouraged me to investigate this area of design automation. The resources for such development were really poor at IS&E as KE was a relatively new field of research in Australia at that time. \'Vhatever the difficulties (a good programmmer never blames his tools as David Skellern used to tell me), I undertook the investigation of Knowledge-Based approaches to Ie ftoor planning as my PhD thesis subject with the help of my supervisor and John Gero and the encouragement of all researchers at IS&E , who provided an exciting environment for my research. This volume reports the results of my research during 1984, 1985, 1986, and 1987. The voulme deals with Ie ftoorplanning from four perspectives: floorplanning strategy, Knowledge Engineering in the Ie domain, the development of knowledge-based fioorplan ning processes and new floorplanning algorithms for use in the overall strategy. COMPUTERS,Design,Graphics & Media,CAD-CAM

Interactive System Identification The craft of designing mathematical models of dynamic objects offers a large number of methods to solve subproblems in the design, typically parameter estimation, order determination, validation, model reduc tion, analysis of identifiability, sensi tivi ty and accuracy. There is also a substantial amount of process identification software available. A typi cal 'identification package' consists of program modules that implement selections of solution methods, coordinated by supervising programs, communication, and presentation handling file administration, operator of results. It is to be run 'interactively', typically on a designer's 'work station' . However, it is generally not obvious how to do that. Using interactive identification packages necessarily leaves to the user to decide on quite a number of specifications, including which model structure to use, which subproblems to be solved in each particular case, and in what or der. The designer is faced with the task of setting up cases on the work station, based on apriori knowledge about the actual physical object, the experiment conditions, and the purpose of the identification. In doing so, he/she will have to cope with two basic difficulties: 1) The com puter will be unable to solve most of the tentative identification cases, so the latter will first have to be form11lated in a way the computer can handle, and, worse, 2) even in cases where the computer can actually produce a model, the latter will not necessarily be valid for the intended purpose. COMPUTERS,Design,Graphics & Media,CAD-CAM

Reliability and Robustness of Engineering Software II Software for engineering applications has become, during the last few years, a multi-billion pound industry as applications of computer programs are now an essential part of any engineering project. In spite of this, engineer ing software is not always reliable and many fail to produce good solutions. The extent of this problem, which is very costly to the engineering industry, and its consequences, are somewhat hidden because the software industry has not reached the necessary maturity. An engineer needs a long training before being able to design a body for instance. However, to do that, he may use a computer program which has undergone no validation whatsoever and is written by someone without any engineering knowledge. It is imperative to address this problem to ensure that computer codes are properly prepared to provide good solutions, and that they are robust and reliable. This 2nd International Conference on Reliability and Robustness of En gineering Software (RRES 91) was called to address this problem. The meeting was held in Milan, Italy, in April 1991 and was of importance to engineers working in industry who are actively involved with the develop ment of computer codes. COMPUTERS,Design,Graphics & Media,CAD-CAM

Integrating Functional and Temporal Domains in Logic Design This book is an extension of one author's doctoral thesis on the false path problem. The work was begun with the idea of systematizing the various solutions to the false path problem that had been proposed in the literature, with a view to determining the computational expense of each versus the gain in accuracy. However, it became clear that some of the proposed approaches in the literature were wrong in that they under estimated the critical delay of some circuits under reasonable conditions. Further, some other approaches were vague and so of questionable accu racy. The focus of the research therefore shifted to establishing a theory (the viability theory) and algorithms which could be guaranteed correct, and then using this theory to justify (or not) existing approaches. Our quest was successful enough to justify presenting the full details in a book. After it was discovered that some existing approaches were wrong, it became apparent that the root of the difficulties lay in the attempts to balance computational efficiency and accuracy by separating the tempo ral and logical (or functional) behaviour of combinational circuits. This separation is the fruit of several unstated assumptions; first, that one can ignore the logical relationships of wires in a network when considering timing behaviour, and, second, that one can ignore timing considerations when attempting to discover the values of wires in a circuit. COMPUTERS,Design,Graphics & Media,CAD-CAM

Applications of Supercomputers in Engineering II Proceedings of the Second International Conference on Applications of Supercomputers in Engineering, ASE/91, Massachusetts Institute of Technology, Cambridge, MA, USA, August 1991 COMPUTERS,Design,Graphics & Media,CAD-CAM

Neural Models and Algorithms for Digital Testing References . . . . . . . . . . . . . . . . . . . . . . . . . . . . 82 9 QUADRATIC 0-1 PROGRAMMING 8S 9. 1 Energy Minimization 86 9. 2 Notation and Tenninology . . . . . . . . . . . . . . . . . 87 9. 3 Minimization Technique . . . . . . . . . . . . . . . . . . 88 9. 4 An Example . . . . . . . . . . . . . . . . . . . . . . . . 92 9. 5 Accelerated Energy Minimization. . . . . . . . . . . . . 94 9. 5. 1 Transitive Oosure . . . . . . . . . . . . . . . . . 94 9. 5. 2 Additional Pairwise Relationships 96 9. 5. 3 Path Sensitization . . . . . . . . . . . . . . . . . 97 9. 6 Experimental Results 98 9. 7 Summary. . . . . . . . . . . . . . . . . . . . . . . . . . 100 References . . . . . . . . . . . . . . . . . . . . . . . . . . . . 100 10 TRANSITIVE CLOSURE AND TESTING 103 10. 1 Background . . . . . . . . . . . . . . . . . . . . . . . . 104 10. 2 Transitive Oosure Definition 105 10. 3 Implication Graphs 106 10. 4 A Test Generation Algorithm 107 10. 5 Identifying Necessary Assignments 112 10. 5. 1 Implicit Implication and Justification 113 10. 5. 2 Transitive Oosure Does More Than Implication and Justification 115 10. 5. 3 Implicit Sensitization of Dominators 116 10. 5. 4 Redundancy Identification 117 10. 6 Summary 119 References . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119 11 POLYNOMIAL-TIME TESTABILITY 123 11. 1 Background 124 11. 1. 1 Fujiwara's Result 125 11. 1. 2 Contribution of the Present Work . . . . . . . . . 126 11. 2 Notation and Tenninology 127 11. 3 A Polynomial TlDle Algorithm 128 11. 3. 1 Primary Output Fault 129 11. 3. 2 Arbitrary Single Fault 135 11. 3. 3 Multiple Faults. . . . . . . . . . . . . . . . . . . 137 11. 4 Summary. . . . . . . . . . . . . . . . . . . . . . . . . . 139 References . . . . . . . . . . . . . . . . . . . . . . . . . . . . 139 ix 12 SPECIAL CASES OF HARD PROBLEMS 141 12. 1 Problem Statement 142 12. 2 Logic Simulation 143 12. 3 Logic Circuit Modeling . 146 12. 3. 1 Modelfor a Boolean Gate . . . . . . . . . . . . . 147 12. 3. 2 Circuit Modeling 148 12. COMPUTERS,Design,Graphics & Media,CAD-CAM

Computer Applications in Plasma Science and Engineering This volume, which contains 15 contributions, is based on a minicourse held at the 1987 IEEE Plasma Science Meeting. The purpose of the lectures in the course was to acquaint the students with the multidisciplinary nature of computational techniques and the breadth of research areas in plasma science in which computation can address important physics and engineering design issues. These involve: electric and magnetic fields, MHD equations, chemistry, radiation, ionization etc. The contents of the contributions, written subsequent to the minicourse, stress important aspects of computer applications. They are: 1) the numerical methods used; 2) the range of applicability; 3) how the methods are actually employed in research and in the design of devices; and, as a compendium, 4) the multiplicity of approaches possible for any one problem. The materials in this book are organized by both subject and applications which display some of the richness in computational plasma physics. COMPUTERS,Design,Graphics & Media,CAD-CAM

Improving the Performance of Neutral File Data Transfers This book is concerned with problems and solutions associated with the exchange of data between different computer aided design, engineering and manufacturing (CAx) systems. After an analysis of the current problems a new strategy consisting of a test methodology, check software and tools for the improvement of the data exchange process are discussed. The particular problems associated with the transfer of curve and surface data are expanded upon and new methods to overcome them presented. With all these tools a system-specific adaption of neutral files is made possible. Thus the integration of several incompatible CAx systems within devel- opment and production processes can be effectively improved. In order to exclude incorrect data a new methodology for neutral file processor tests has been worked out. Finally, the benefits resulting from this new strategy are shown by the example of data transfer not only between CAx systems but also between consecutive production processes. COMPUTERS,Design,Graphics & Media,CAD-CAM

Autonomous Robot Vehicles Autonomous robot vehicles are vehicles capable of intelligent motion and action without requiring either a guide or teleoperator control. The recent surge of interest in this subject will grow even grow further as their potential applications increase. Autonomous vehicles are currently being studied for use as reconnaissance/exploratory vehicles for planetary exploration, undersea, land and air environments, remote repair and maintenance, material handling systems for offices and factories, and even intelligent wheelchairs for the disabled. This reference is the first to deal directly with the unique and fundamental problems and recent progress associated with autonomous vehicles. The editors have assembled and combined significant material from a multitude of sources, and, in effect, now conviniently provide a coherent organization to a previously scattered and ill-defined field. COMPUTERS,Design,Graphics & Media,CAD-CAM

3D Printing Want something? Print it–with your own 3D printer! Right now, you can print practically any 3D object you can imagine–from toys to gadgets to replacement parts, and beyond! All you need is a 3D printer…and they’re simpler and cheaper than you ever imagined. This full-color, step-by-step guide will get you started–and if you want, it’ll even walk you through building your own 3D printer from an inexpensive kit. Packed with colorful photos and screenshots, it explains all the crucial details other books skip. You’ll walk through choosing and assembling your new 3D printer kit…brainstorming and designing new objects with free software…and then printing them on your brand-new 3D printer. 3D printing is today’s hottest new technological revolution, and this book takes you right to the cutting edge! Discover how 3D printers work and what you can do with them Compare and choose your first 3D printer–either pre-built or kit Assemble Printrbot Simple, one of the world’s easiest 3D printer kits Install and configure software that tells your 3D printer what to do Print your first 3D project from an existing object file Use free Tinkercad software to create your own original 3D models Explore AutoDesk’s free software for 3D printing Use Print-It-For-You services for projects your home printer can’t handle Find great 3D printing projects and models on the Web Imagine creative new uses for your 3D printer COMPUTERS,Design,Graphics & Media,CAD-CAM

Visualizing with CAD I spent the first twenty six years of my life in Rome. I used to go for ice cream to a popular place near the Pantheon and I remem ber the excitement I felt, beyond the chocolate and whipped cream, when I entered this ancient Roman temple. After staring at the "shower" of light coming from the circular opening at the center of the dome, as strong as a spotlight, I remember being attracted almost hypnotically to the place below the opening. I remember counting the coffers carving the concave dome, com posed in five rows of circular arrays, and could feel the power and protection created by the concave space. I also recall going every Sunday to Piazza San Pietro. This Baroque square is well known for its colonnades, which have an oval shape defined by two interlocking circles. For each of these circles there is a mark, located approximately at its center, from which the four aligned rows of columns appear as one. Before entering the church, almost as a part of a ritual, I had to find the mark in the pavement of the oval square. I was amazed by how the rows of columns could appear and disappear according to my position in relation to the mark:. COMPUTERS,Design,Graphics & Media,CAD-CAM

AutoCAD Civil 3D 2016 Essentials Start designing today with this hands-on beginner's guide to AutoCAD Civil 3D 2016 AutoCAD Civil 3D 2016 Essentials gets you quickly up to speed with the features and functions of this industry-leading civil engineering software. This full-color guide features approachable, hands-on exercises and additional task-based tutorials that help you quickly become productive as you master the fundamental aspects of AutoCAD Civil 3D design. Each chapter opens with a quick discussion of concepts and learning goals, and then briskly moves into tutorial mode with screen shots that illustrate each step of the process. The emphasis is on skills rather than tools, and the clear delineation between "why" and "how" makes this guide ideal for quick reference. The companion website provides starting and ending files for each exercise, so you can jump in at any point and compare your work with the pros. Centered around the real-world task of designing a residential subdivision, these exercises get you up to speed with the program's functionality, while also providing the only Autodesk-endorsed preparation for the AutoCAD Civil 3D certification exam. Master the AutoCAD Civil 3D 2016 interface and basic tasks Model terrain using imported field survey data Analyze boundaries, pipe networks, surfaces, and terrain Estimate quantities and create construction documentation If you're ready to acquire this must-have skillset, AutoCAD Civil 3D 2016 Essentials will get you up to speed quickly and easily. COMPUTERS,Design,Graphics & Media,CAD-CAM

Mastering AutoCAD Civil 3D 2016 Utilize AutoCAD Civil 3D 2016 for a real-world workflow with these expert tricks and tips Mastering AutoCAD Civil 3D 2016 is a complete, detailed reference and tutorial for Autodesk's extremely popular and robust civil engineering software. With straightforward explanations, real-world examples, and practical tutorials, this invaluable guide walks you through everything you need to know to be productive. The focus is on real-world applications in professional environments, with all datasets available for download, and thorough coverage helps you prepare for the AutoCAD Civil 3D certification exam with over an hour's worth of video on crucial tips and techniques. You'll learn how to navigate the software and use essential tools, and how to put it all together in the context of a real-world project. In-depth discussion covers surveying, alignments, surface, grading, cross sections and more, and instructor support materials provide an ideal resource for training and education. This book will take you from beginner to pro, so you can get the most out of AutoCAD Civil 3D every step of the way. Understand key concepts and get acquainted with the interface Create, edit, and display all elements of a project Learn everything you need to know for the certification exam Download the datasets and start designing right away With expert insight, tips, and techniques, Mastering AutoCAD Civil 3D 2016 helps you become productive from the very beginning. COMPUTERS,Design,Graphics & Media,CAD-CAM

CAD & Office Integration In the realm of CAD & Office Integration a new technology has been introduced that will overturn many accepted ideas, both for developer and end-user. What is this revolutionary new technology? Called "OLE for Design and Modeling" it is an enhancement of Microsoft Windows OLE for high performance CAD/CAM/CAE-software. With this book, the reader will understand, how OLE for D&M enables users to introduce and manipulate CAD models within regular text-processing and DTP-documents. And why even high-end 3D design objects can now be transferred between different systems using easy "drag and drop" operations. Furthermore this "plug and play" CAD technology makes it possible to use older CAD documents and older software in an entirely new context. If you want to know, where technology is going to, you should read it. COMPUTERS,Design,Graphics & Media,CAD-CAM

Dynamic Modeling COMPUTERS,Design,Graphics & Media,CAD-CAM

Advanced Modelling for CAD/CAM Systems Reiner Anderl The Advanced Modelling part of the CAD*I project aimed at the development of a new generation of modelling techniques as a basic functionality of future CAD/CAM systems. The methodology and concepts for advanced modelling techniques, their availability in the communication interface of a CAD/CAM system and their influence on internal interfaces in the software architecture of a CAD/CAM system are fundamental results of advanced modelling work. These results form the basis for the development of a new generation of CAD/CAM systems which are called product modelling systems. CAD/CAM systems today mainly support the geometric description of a technical part or its description as a technical drawing. Advanced geometric modelling capabilities deal with parametric design functions embedded into CAD/CAM systems. However, development strategies for future CAD/CAM systems are directed toward the following: 1. The development of product modelling systems and 2. the development of integrated systems based on CAD, CAP (Computer Aided Planning), CAM and other CIM (Computer Integrated Manu facturing) functionalities. COMPUTERS,Design,Graphics & Media,CAD-CAM

CCE Within CIME environments, one continually comes across a multitude of different working practices, network devices, information systems and manufacturing technologies. This heterogeneous environment extends to individual enterprises and can have profound effects on the efficiency and effectiveness of an organisation, and often results in symptoms such as: long product lead times, poor visibility of the product and process status, high product inventory and work-in progress, low data integrity, etc., as well as incurring excessive infrastructure costs. Having to select an appropriate information system to help achieve the business objectives of anyone manufacturing enterprise can be an awesome task. During the 1980s, vendor-independent communications such as MAP (Manu facturing Automation Protocol) and CNMA (Communications Network for Manufacturing Applications) brought standard, open communications to computer controlled industrial devices, but this alone was not enough to satisfy the more demanding requirements of creating and maintaining manufacturing applications. In order to create manufacturing solutions that effectively utilise Open Systems Interconnection (OSI) it is necessary to look beyond the standard communications protocols to how and why applications are developed. COMPUTERS,Design,Graphics & Media,CAD-CAM

CAD*I Drafting Model The content of this book is an information model for technical drawings, the so-called "Drafting Model". The Drafting Model is a part of a complex information model describing product definition data, their applications and their representations. The definition of the information model is a central component of the development of STEP, a future international standard for the exchange of product defmition data. Here the Drafting Model particularly encloses descriptions for the representations of organizational drawing data, tolerances, dimensions and surface attributes such as surface fmish symbols (a survey of the whole content is shown in the figure above). Additional to that requirements for the Presentation Model concerning the representation of geometry as well as the integration process for both the Drafting and the Presentation Models are formulated. The extent of the Drafting Model is restricted to the application area "Mechanical Engineering". Within the Drafting Model the annotation representations are described on the one hand informally and on the other hand formally using a high level language for information modeling, EXPRESS. Principally the representations of the annotation are described according to the international drawing standards. Thus the semantics pertinent to the specific graphical appearance are maintained. The data structures provide formal descriptions of annotations at a high generation level, which means that a "way" is defmed how to generate these annotations. COMPUTERS,Design,Graphics & Media,CAD-CAM

3D CAD with Autodesk 123D If you've arrived at a stage in your creative life where you're ready to do more with your computer, it's time to learn how to combine its power with new advances in computer-aided design (CAD) and fabrication to make something awesome--in three dimensions! The free suite of Autodesk 123D software offers all the tools you need to capture or design three-dimensional objects and characters. This book tells you how to harness that power to print or fabricate just about anything you can imagine. Want to make something mechanical or structural that's based on precise measurements? 123D Design can help! Ready to create something cool based on a character, an organic shape, or something found in nature? 123D Catch, 123D Meshmixer, and 123D Sculpt+ will assist. Learn how to use these tools, plus 123D Make--perfect for prototyping designs you'll cut with a CNC mill--to take your creativity to a new level. An ideal book for Makers, hobbyists, students, artists, and designers (including beginners!), this book opens up the inexpensive world of personal fabrication to everyone. In 3D CAD with Autodesk 123D, you’ll: Meet the classic "Stanford bunny" and learn to modify it with Meshmixer Scan and 3D print anything around you Design your own 3D-printed guitar Find models in the Sculpt+ community and make a skeleton! Build a birdhouse, prototype a playground, or create a statue Learn everything from basics to troubleshooting skills Get started making right away COMPUTERS,Design,Graphics & Media,CAD-CAM

Autodesk Revit 2017 for Architecture The only Revit tutorial guide based on a real project workflow Autodesk Revit Architecture No Experience Required is the ultimate real-world guide for mastering this increasingly prevalent BIM software package. Using a continuous, step-by-step tutorial, this book walks you through all project phases as you learn the basics of Revit by designing, documenting, and presenting a four-story office building. You'll begin by learning your way around the interface and conventions, then jump right into design by placing walls, doors, and windows. Next you'll work with grids, beams, foundations, dimensions, and text as you build floors layer by layer, join walls, create ceilings and roofs, and place stairs, ramps, and railings. The instruction covers construction documentation, advanced detailing, and families, as well as site considerations including grading and top surface features to provide a well-rounded, real-world Revit skill set. The companion website features downloadable 'before and after' tutorial files that allow you to jump in at any point and compare your work to the pros. The shift from 2D drafting to 3D building information modeling has made Revit a must-have skill for an increasing number of design, engineering, and construction professionals. This book is designed to teach you the basics quickly, using a real-world workflow, process, and pacing. Get acquainted with the Revit interface, then immediately start building Learn to place structural components, text, dimensions, and more Understand views, grids, editing, importing, exporting, and work sharing Generate construction documentation including schedules and material takeoffs This simple yet engaging tutorial brings together all of the major skills a Revit user needs to know to complete real workplace projects. Whether read from beginning to end as a comprehensive lesson, or used as 'dip-in' reference for unfamiliar tasks, Autodesk Revit Architecture No Experience Required provides invaluable practical BIM instruction for every phase of a project. COMPUTERS,Design,Graphics & Media,CAD-CAM

Fusion 360 for Makers Learn how to use Autodesk Fusion 360 to digitally model your own original projects for a 3D printer or a CNC device. Fusion 360 software lets you design, analyze, and print your ideas. Free to students and small businesses alike, it offers solid, surface, organic, direct, and parametric modeling capabilities. Fusion 360 for Makers is written for beginners to 3D modeling software by an experienced teacher. It will get you up and running quickly with the goal of creating models for 3D printing and CNC fabrication. Inside Fusion 360 for Makers, you'll find: Eight easy-to-understand tutorials that provide a solid foundation in Fusion 360 fundamentals DIY projects that are explained with step-by-step instructions and color photos Projects that have been real-world tested, covering the most common problems and solutions Stand-alone projects, allowing you to skip to ones of interest without having to work through all the preceding projects first Design from scratch or edit downloaded designs. Fusion 360 is an appropriate tool for beginners and experienced makers. COMPUTERS,Design,Graphics & Media,CAD-CAM

Beginning AutoCAD 2020 Exercise Workbook For more than two decades, the Beginning AutoCAD® Exercise Workbook has been THE definitive tutorial for those learning and teaching about the CAD software. And as the AutoCAD package has continued to improve, so has this work, with better graphics, enhanced standard features (such as “CAD Tips†and side-by-side inch/metric measurements), and additional practical exercises. AutoCAD 2020 is packed with new features. The Exercise Workbook shows users and instructors how to unleash the power of AutoCAD with easy-to-follow lessons and tutorials on the many tools and commands available to create, tweak, and perfect a drafting, drawing, design, or 3D printed final product. Visual learners will be especially pleased with the heavily illustrated format, and the way the authors’ lessons and exercises progress seamlessly from the basics to more sophisticated projects. For users of AutoCAD®, there is simply no better resource on the market. COMPUTERS,Design,Graphics & Media,CAD-CAM

Discovering AutoCAD 2020 Designed for introductory AutoCAD users, Discovering AutoCAD 2020 presents a hands-on, activity-based approach to the use of AutoCAD 2020 as a drafting tool—complete with techniques, tips, shortcuts, and insights that improve efficiency. Topics and tasks are carefully grouped to lead students logically through the AutoCAD command set, with the level of difficulty increasing steadily as skills are acquired through experience and practice. Straightforward explanations focus on what is relevant to actual drawing procedures, and illustrations show exactly what to expect on the computer screen. This edition features updates for the latest release of AutoCAD 2020, projects, and test questions for each chapter. Lessons are broken down into tasks listed at the beginning of each section, introducing students to the AutoCAD commands using a structured, intuitive approach and helping students anticipate what information will be needed at each new phase of the learning process. General Procedure boxes appear as new commands are introduced, providing a simple overview of basic command sequences in a step-by-step format. Detailed graphics appear throughout the text, demonstrating what students should expect to see on their screens and encouraging self-paced study. Drawing problems appear at the end of each chapter, helping students apply newly learned techniques immediately to realistic drawing situations. This includes drawing suggestions, timesaving tips, and explanations of how to use techniques in actual situations. Working drawings accompany the end-of-chapter drawing problems, appearing in a large, clearly dimensioned format on each right-hand page, with drawing suggestions on the accompanying left-hand page. This includes mechanical, architectural, civil, and electrical drawings. End-of-chapter review questions to test the student’s knowledge. Discovering AutoCAD 2020 will be a valuable resource for any student wanting to learn drafting skills. COMPUTERS,Design,Graphics & Media,CAD-CAM

Revit 2020 for Architecture The updated 2020 edition of the popular step-by-step tutorial for Revit Architecture Shortly after its first publication, Autodesk Revit for Architecture: No Experience Required quickly became the market-leading, real-world guide for learning and building with Revit—the powerful and sophisticated Building Information Modeling (BIM) software used by professionals the world over. Fully updated for Revit 2020, this popular, user-friendly book helps you learn the Revit interface, understand the fundamental concepts and features of the software, and design, document, and present a 3D BIM project. A continuous, step-by-step tutorial guides you through every phase of the project: from placing walls, doors, windows, structural elements, dimensions, and text, to generating documentation, advanced detailing, site grading, construction scheduling, material takeoffs, and much more. Updated and revised to include new content, this invaluable guide covers all the fundamental skills every Revit user needs. Whether used as a complete, start-to-finish lesson or as a quick-reference for unfamiliar tasks, this book will help you: Learn each phase of designing, documenting, and presenting a four-story office building using a simple yet engaging continuous tutorial Follow the tutorial sequentially or jump to any chapter by downloading the project files from the Sybex website Use the start-to-finish tutorial project as a reference for your own real-world projects and to develop a powerful Revit skillset Gain thorough knowledge of Revit’s essential concepts and features to make the move from 2D drafting to 3D building information modeling Get up to speed with advanced features, including new coverage of advanced walls, families, sites, topography, and more Autodesk Revit 2020 for Architecture No Experience Required is the go-to guide for both professionals and students seeking to learn Revit's essential functions quickly and effectively, to understand real workplace projects, processes, and workflows, and to set the stage for continuing on to more advanced skills. COMPUTERS,Design,Graphics & Media,CAD-CAM

Practical Autodesk AutoCAD 2021 and AutoCAD LT 2021 Learn 2D drawing and 3D modeling from scratch using AutoCAD 2021 and its more affordable LT version to become a CAD professional Key Features Explore the AutoCAD GUI, file format, and drawing tools to get started with CAD projects Learn to use drawing management tools for working efficiently on large projects Discover techniques for creating, modifying, and managing 3D models and converting 2D plans into 3D models Book Description AutoCAD and AutoCAD LT are one of the most versatile software applications for architectural and engineering designs and the most popular computer-aided design (CAD) platform for 2D drafting and 3D modeling. This hands-on guide will take you through everything you need to know to make the most out of this powerful tool, starting from a simple tour of the user interface through to using advanced tools. Starting with basic drawing shapes and functions, you'll get to grips with the fundamentals of CAD designs. You'll then learn about effective drawing management using layers, dynamic blocks, and groups and discover how to add annotations and plot like professionals. The book delves into 3D modeling and helps you convert your 2D drawings into 3D models and shapes. As you progress, you'll cover advanced tools and features such as isometric drawings, drawing utilities for managing and recovering complex files, quantity surveying, and multidisciplinary drawing files using xRefs, and you'll learn how to implement them with the help of practical exercises at the end of each chapter. Finally, you'll get to grips with rendering and visualizing your designs in AutoCAD. By the end of the book, you'll have developed a solid understanding of CAD principles and be able to work with AutoCAD software confidently to build impressive 2D and 3D drawings. What you will learn Understand CAD fundamentals using AutoCAD's basic functions, navigation, and components Create complex 3d solid objects starting from the primitive shapes using the solid editing tools Working with reusable objects like Blocks and collaborating using xRef Explore some advanced features like external references and dynamic block Get to grips with surface and mesh modeling tools such as Fillet, Trim, and Extend Use the paper space layout in AutoCAD for creating professional plots for 2D and 3D models Convert your 2D drawings into 3D models Who this book is for The book is for design engineers, mechanical engineers, architects, and anyone working in construction, manufacturing, or similar fields. Whether you're an absolute beginner, student, or professional looking to upgrade your engineering design skills, you'll find this AutoCAD book useful. No prior knowledge of CAD or AutoCAD is necessary. COMPUTERS,Design,Graphics & Media,CAD-CAM

PDF Explained At last, here’s an approachable introduction to the widely used Portable Document Format. PDFs are everywhere, both online and in printed form, but few people take advantage of the useful features or grasp the nuances of this format. This concise book provides a hands-on tour of the world’s leading page-description language for programmers, power users, and professionals in the search, electronic publishing, and printing industries. Illustrated with lots of examples, this book is the documentation you need to fully understand PDF. Build a simple PDF file from scratch in a text editor Learn the layout and content of a PDF file, as well as the syntax of its objects Examine the logical structure of PDF objects, and learn how pages and their resources are arranged into a document Create vector graphics and raster images in PDF, and deal with transparency, color spaces, and patterns Explore PDF operators for building and showing text strings Get up to speed on bookmarks, metadata, hyperlinks, annotations, and file attachments Learn how encryption and document permissions work in PDF Use the pdftk program to process PDF files from the command line COMPUTERS,Design,Graphics & Media,General

My iPhone (Covers iPhone 7/7 Plus and other models running iOS 10) This is the eBook of the printed book and may not include any media, website access codes, or print supplements that may come packaged with the bound book. Step-by-step instructions with callouts to iPhone images that show you exactly what to do. Help when you run into iPhone problems or limitations. Tips and Notes to help you get the most from your iPhone. Full-color, step-by-step tasks walk you through getting and keeping your iPhone working just the way you want. The tasks include how to: • Connect to the Internet, Bluetooth devices, Wi-Fi networks, and other iPhones, iPod touches, and iPads; take advantage of AirDrop to instantly share with other iOS and Mac users around you • Use Siri to get information, write texts and emails, set reminders/appointments, and more just by speaking to your iPhone • Customize your iPhone with folders, wallpaper, ringtones, and much more • Configure and sync your information, and efficiently manage contacts, and calendars • Communicate via FaceTime videoconferences, conference calls, text, email, and more • Make your text messages come alive by adding Digital Touches and effects • Make the most of Safari to browse the Web and Mail to manage all of your email from one Inbox • Listen to music, subscribe to podcasts, and use other great iPhone apps • Capture and edit photos and video; use the great camera features such as burst, timed and time-lapse photos, slow-motion video, and Live Photos via email, AirDrop, or texts; use iCloud to automatically save and share your photos • Find, download, install, and use awesome iPhone apps • Take advantage of iCloud to keep your content and information in sync on all your devices COMPUTERS,Design,Graphics & Media,General

Make Your Own Pixel Art Make Your Own Pixel Art is a complete, illustrated introduction to the creation of pixel art aimed at beginners just starting out right through to the experienced pixel artist wanting to enhance their skills. Hand anyone a pencil and paper and they can start drawing, but it's just as easy to draw digitally using a keyboard and mouse. With Make Your Own Pixel Art, pixel artist Jennifer Dawe and game designer Matthew Humphries walk you step-by-step through the available tools, pixel art techniques, the importance of shapes, colors, shading, and how to turn your art into animation. By the end of the book, you'll be creating art far beyond what's possible on paper! Make Your Own Pixel Art will teach you about:- Creating pixel art using the most popular art software and the common tools they provide- Drawing with pixels, including sculpting, shading, texture, and color use- The basics of motion and how to animate your pixel art creations- Best practices for saving, sharing, sketching, and adding emotion to your art With a dash of creativity and the help of Make Your Own Pixel Art, your digital drawings can be brought to life, shared with the world, and form a basis for a career in art, design, or the video games industry. COMPUTERS,Design,Graphics & Media,General

Digitized Lives In chapters examining a broad range of issues—including sexuality, politics, education, race, gender relations, the environment and social protest movements—Digitized Lives argues that making sense of digitized culture means looking past the glossy surface of techno gear to ask deeper questions about how we can utilize technology to create a more socially, politically and economically just world. This second edition includes important updates on mobile and social media, examining how new platforms and devices have altered how we interact with digital technologies in an allegedly ‘post-truth’ era. A companion website (culturalpolitics.net/index/digital_cultures) includes links to online articles and useful websites, as well as a bibliography of offline resources, and more. COMPUTERS,Design,Graphics & Media,General

My iPad for Seniors Covers All iPads Running iPadOS 13 Easy, clear, readable, and focused on what you want to do. Full-color, step-by-step tasks walk you through getting and keeping your iPad working just the way you want. Learn how to Discover all the new features of iPadOS 13 Wirelessly connect to and browse the Internet, at home or away Personalize the way your iPad looks and works–including the new Dark Mode Make your iPad easier to use if you have trouble seeing or tapping the screen Use Siri’s voice commands to control your iPad and find useful information Communicate with friends and family via email, text messaging, and FaceTime video chats Shoot, share, and view photos and videos Listen to streaming music and watch streaming movies and TV shows online Connect and use the Apple Pencil and Smart Keyboard Use iCloud to store and share your photos and other important data online Troubleshoot common iPad problems COMPUTERS,Design,Graphics & Media,General

Smart Green World? In this book, Steffen Lange and Tilman Santarius investigate how digitalization influences environmental and social sustainability. The information revolution is currently changing the daily lives of billions of people worldwide. At the same time, the current economic model and consumerist lifestyle needs to be radically transformed if society is to overcome the challenges humanity is facing on a finite planet. Can the much-discussed disruption potential of digitalization be harnessed for this purpose? Smart Green World? provides guiding principles for a sustainable digital society and develops numerous hands-on proposals for how digitalization can be shaped to become a driving force for social transformation. For instance, the authors explain why more digitalization is needed to realize the transition towards 100% renewable energy and show how this can be achieved without sacrificing privacy. They analyze how the information revolution can transform consumption patterns, mobility habits and industry structures – instead of fostering the consumption of unneeded stuff due to personalized commercials and the acceleration of life. The authors reveal how Artificial Intelligence and the Industrial Internet of Things pose novel environmental challenges and contribute to a polarization of income; but they also demonstrate how the internet can be restored to its status as a commons, with users taking priority and society at large reaping the benefits of technological change in a most democratic way. Providing a comprehensive and practical assessment of both social and environmental opportunities and challenges of digitalization, Smart Green World? Making Digitalization Work for Sustainability will be of great interest to all those studying the complex interrelationship of the twenty-first-century megatrends of digitalization and decarbonization. COMPUTERS,Design,Graphics & Media,General

Disconnected How young people think about the moral and ethical dilemmas they encounter when they share and use online content and participate in online communities. Fresh from a party, a teen posts a photo on Facebook of a friend drinking a beer. A college student repurposes an article from Wikipedia for a paper. A group of players in a multiplayer online game routinely cheat new players by selling them worthless virtual accessories for high prices. In Disconnected, Carrie James examines how young people and the adults in their lives think about these sorts of online dilemmas, describing ethical blind spots and disconnects. Drawing on extensive interviews with young people between the ages of 10 and 25, James describes the nature of their thinking about privacy, property, and participation online. She identifies three ways that young people approach online activities. A teen might practice self-focused thinking, concerned mostly about consequences for herself; moral thinking, concerned about the consequences for people he knows; or ethical thinking, concerned about unknown individuals and larger communities. James finds, among other things, that youth are often blind to moral or ethical concerns about privacy; that attitudes toward property range from “what's theirs is theirs” to “free for all”; that hostile speech can be met with a belief that online content is “just a joke”; and that adults who are consulted about such dilemmas often emphasize personal safety issues over online ethics and citizenship. Considering ways to address the digital ethics gap, James offers a vision of conscientious connectivity, which involves ethical thinking skills but, perhaps more important, is marked by sensitivity to the dilemmas posed by online life, a motivation to wrestle with them, and a sense of moral agency that supports socially positive online actions. COMPUTERS,Design,Graphics & Media,General

Values at Play in Digital Games A theoretical and practical guide to integrating human values into the conception and design of digital games. All games express and embody human values, providing a compelling arena in which we play out beliefs and ideas. “Big ideas” such as justice, equity, honesty, and cooperation—as well as other kinds of ideas, including violence, exploitation, and greed—may emerge in games whether designers intend them or not. In this book, Mary Flanagan and Helen Nissenbaum present Values at Play, a theoretical and practical framework for identifying socially recognized moral and political values in digital games. Values at Play can also serve as a guide to designers who seek to implement values in the conception and design of their games. After developing a theoretical foundation for their proposal, Flanagan and Nissenbaum provide detailed examinations of selected games, demonstrating the many ways in which values are embedded in them. They introduce the Values at Play heuristic, a systematic approach for incorporating values into the game design process. Interspersed among the book's chapters are texts by designers who have put Values at Play into practice by accepting values as a design constraint like any other, offering a real-world perspective on the design challenges involved. COMPUTERS,Design,Graphics & Media,General

Inter/vention A proposal that electracy—the special skills needed to navigate and understand our digital world—can be developed through play. In today's complex digital world, we must understand new media expressions and digital experiences not simply as more technologically advanced forms of “writing” that can be understood and analyzed as “texts” but as artifacts in their own right that require a unique skill set. Just as agents seeking to express themselves in alphabetic writing need to be literate, “egents” who seek to express themselves in digital media need to be—to use a term coined by cybertheorist Gregory Ulmer—electrate. In Inter/vention, Jan Holmevik helps to invent electracy. He does so by tracing its path across the digital and rhetorical landscape—informatics, hacker heuretics, ethics, pedagogy, virtual space, and monumentality—and by introducing play as a new genre of electracy. Play, he argues, is the electrate ludic transversal. Holmevik contributes to the repertoire of electrate practices in order to understand and demonstrate how play invents electracy. Holmevik's argument straddles two divergences: in rhetoric, between how we study rhetoric as play and how we play rhetorically; and in game studies, between ludology and narratology. Games studies has forged ludology practice by distinguishing it from literate practice (and often allying itself with the scientific tradition). Holmevik is able to link ludology and rhetoric through electracy. Play can and does facilitate invention: play invented the field of ludology. Holmevik proposes a new heuretic in which play acts as a conductor for the invention of electracy. Play is a meta behavior that touches on every aspect of Ulmer's concept of electracy. COMPUTERS,Design,Graphics & Media,General

Hello Avatar An examination of our many modes of online identity and how we live on the continuum between the virtual and the real. Hello Avatar! Or, {llSay(0, "Hello, Avatar!"); is a tiny piece of user-friendly code that allows us to program our virtual selves. In Hello Avatar, B. Coleman examines a crucial aspect of our cultural shift from analog to digital: the continuum between online and off-, what she calls the “x-reality” that crosses between the virtual and the real. She looks at the emergence of a world that is neither virtual nor real but encompasses a multiplicity of network combinations. And she argues that it is the role of the avatar to help us express our new agency—our new power to customize our networked life. By avatar, Coleman means not just the animated figures that populate our screens but the gestalt of images, text, and multimedia that make up our online identities—in virtual worlds like Second Life and in the form of email, video chat, and other digital artifacts. Exploring such network activities as embodiment, extreme (virtual) violence, and the work in virtual reality labs, and offering sidebar interviews with designers and practitioners, she argues that what is new is real-time collaboration and copresence, the way we make connections using networked media and the cultures we have created around this. The star of this drama of expanded horizons is the networked subject—all of us who represent aspects of ourselves and our work across the mediascape. COMPUTERS,Design,Graphics & Media,General

Memes in Digital Culture Taking “Gangnam Style” seriously: what Internet memes can tell us about digital culture. In December 2012, the exuberant video “Gangnam Style” became the first YouTube clip to be viewed more than one billion times. Thousands of its viewers responded by creating and posting their own variations of the video—“Mitt Romney Style,” “NASA Johnson Style,” “Egyptian Style,” and many others. “Gangnam Style” (and its attendant parodies, imitations, and derivations) is one of the most famous examples of an Internet meme: a piece of digital content that spreads quickly around the web in various iterations and becomes a shared cultural experience. In this book, Limor Shifman investigates Internet memes and what they tell us about digital culture. Shifman discusses a series of well-known Internet memes—including “Leave Britney Alone,” the pepper-spraying cop, LOLCats, Scumbag Steve, and Occupy Wall Street's “We Are the 99 Percent.” She offers a novel definition of Internet memes: digital content units with common characteristics, created with awareness of each other, and circulated, imitated, and transformed via the Internet by many users. She differentiates memes from virals; analyzes what makes memes and virals successful; describes popular meme genres; discusses memes as new modes of political participation in democratic and nondemocratic regimes; and examines memes as agents of globalization. Memes, Shifman argues, encapsulate some of the most fundamental aspects of the Internet in general and of the participatory Web 2.0 culture in particular. Internet memes may be entertaining, but in this book Limor Shifman makes a compelling argument for taking them seriously. COMPUTERS,Design,Graphics & Media,General

Real World Print Production with Adobe Creative Cloud Sharpen your print production skills with this definitive resource created specifically for design professionals who need to create files using the Adobe Creative Cloud, including InDesign, Photoshop, Illustrator, and Acrobat and output for printing. The previous edition was steady seller, helping designers who have no training in print get up and running quickly and not make expensive mistakes on their projects. Completely updated for CS6 and the CC, this book also helps designers with some print experience tackle more complex projects. The book covers all the Adobe Suite programs they need to know to produce successful projects, rather than buying 4 or 5 different books. This book is considered the complete resource for understanding the print cycle, how ink works on paper, managing fonts, using colour spaces, handling images, and preparing files for print or electronic output. Print expert Claudia McCue shares her hands-on techniques to prepare files, edit photos and graphics, and prevent common problems without missing a deadline. This book is brimming with insightful advice, illustrations, and shortcuts that will have you quickly and professionally producing your work in no time. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Design,Graphics & Media,Graphics Tools

Photoshop CC Photoshop CC is an outstanding image editor, but it can be pretty overwhelming. This book makes learning Photoshop as easy as possible by explaining the hows and whys in a friendly, conversational style. You’ll unlock Photoshop’s secrets, new goodies, and time-saving features, with expert tips and practical editing advice you can use every day. The important stuff you need to know: Learn your way around. Tour Photoshop’s workspace and learn how to customize it. Unleash the magic. Use selections, layers, masks, and smart objects to safely edit images; automate common chores with actions. Perfect your photos. Learn to crop, resize, color-correct, retouch, combine, and prepare photos for print or online use. Master color. Drain, change, and add color, and even create digital makeup, partial-color effects, and duotones. Be artistic. Use filters effectively, create illustrations, paintings, artistic typography, animations, and videos. Go 3D. Create and edit 3D objects and send them off to a 3D-printing service from inside Photoshop. Export web graphics. Use Generator to instantly export and resize images—just by using layer names. COMPUTERS,Design,Graphics & Media,Graphics Tools

The Book of GIMP GIMP is a free alternative to Adobe Photoshop with tons of professional-grade features. But with so many powerful tools and menu options, GIMP can be difficult to master. Whether you're struggling to get started or trying to master some of GIMP's more complex features, you'll find the answers you're looking for in The Book of GIMP. The tutorials in the first half of the book walk you through essential GIMP skills, like resizing and cropping images, touching up spots and scratches, and customizing your work area. Illustrated, step-by-step instructions show you how to: –Improve the lighting and composition of images–Remove distortions and noise to make old and damaged photos look like new–Create stunning panoramas and digital collages using a series of photos–Make, edit, and export custom textures, logos, and animated GIFs–Work with selections, channels, and masks to edit images like a pro–Create colorful digital art, layer by layer The book's second half offers a comprehensive reference to GIMP's many features, including color balancing, masks, filters, and plug-ins. You'll find tools described in unparalleled detail, with coverage of nearly every option and parameter. With illustrated tutorials and detailed references, The Book of GIMP is sure to become your one-stop guide to just about everything GIMP. COMPUTERS,Design,Graphics & Media,Graphics Tools

Qt 5 Projects Design, build, and deploy powerful applications with amazing user interfaces on embedded, mobile, and desktop platforms About This Book Easily compile, run, and debug your applications from the powerful Qt Creator IDE Future-proof your applications with Qt Test and modern architecture principles Build multi-platform projects that target Android, iOS, Windows, macOS, Linux, and more Who This Book Is For This book is for developers who want to successfully build and maintain cross-platform applications with advanced UI and connectivity features. Basic knowledge of C++ is required. What You Will Learn Learn the basics of modern Qt application development Develop solid and maintainable applications with BDD, TDD, and Qt Test Master the latest UI technologies and know when to use them: Qt Quick, Controls 2, Qt 3D and Charts Build a desktop UI with Widgets and the Designer Translate your user interfaces with QTranslator and Linguist Get familiar with multimedia components to handle visual input and output Explore data manipulation and transfer: the model/view framework, JSON, Bluetooth, and network I/O Take advantage of existing web technologies and UI components with WebEngine In Detail Qt is a professional cross-platform application framework used across industries like automotive, medical, infotainment, wearables, and more. In this book you'll initially create a to-do style app by going via all stages for building a successful project. You'll learn basics of Qt's C++ and QML APIs, test-driven development with Qt Test, application architecture, and UIs with Qt Quick & Quick Controls 2. Next, you'll help two startups build their products. The first startup, Cute Comics, wants to help independent comic creators with a suite of apps that let them experiment with comic pages, image composition, comic dialogues, and scene descriptions. While developing these apps you'll deepen your knowledge of Qt Quick's layout systems, and see Qt 3D and Widgets in action. The second startup, Cute Measures, wants to create apps for industrial and agricultural sectors, to make sense of sensor data via a monitoring system. The apps should run seamlessly across devices and operating systems like Android, iOS, Windows, or Mac, and be cost-effective by integrating with existing web technologies. You take the role of lead developer and prototype the monitoring system. In doing so you'll get to know Qt's Bluetooth and HTTP APIs, as well as the Charts and Web Engine UI modules. These projects will help you gain a holistic view of the Qt framework. Style and approach Practical projects based guide COMPUTERS,Design,Graphics & Media,Graphics Tools

Building an RPG with Unity 2018 Build a high-end, multiplayer role-playing game (RPG) from scratch with C# and Unity 2018 Key Features Get insights into Unity's user interface (UI) system and and build UIs for your RPG Implement artificial intelligence (AI) to build intelligent entities that take your game to the next level Develop multiplayer features for an RPG using Unity 2018 Book Description In a role-playing game (RPG), users control a character, usually in the game's imaginary universe. Unity has become a top choice for developers looking to create these kinds of immersive RPGs. Building an RPG with Unity 2018, based on building some of the most common RPG features, teaches you tips, tricks, and techniques that can be applied to your own game. To start with, the book guides you through the fundamentals of role-playing games. You will learn the necessary aspects of building an RPG, such as structuring the game environment, customizing characters, controlling the camera, and designing other attributes such as inventory and weapons. You will also explore designing game levels by adding more features. Once you have understood the bigger picture, you will understand how to tackle the obstacles of networking in Unity and implement multiplayer mode for your RPG games. By the end of the book, you will be able to build upon the core RPG framework elements to create your own immersive games. What you will learn Construct a framework for inventory, equipment, characters, enemies, quests, and game events Understand how to load and unload scenes and assets Create multiplayer game settings for your RPG Design a UI for user input and feedback Implement AI for non-character players Customize your character at runtime Who this book is for Building an RPG with Unity 2018 is for you if you are a programmer interested in developing and further enhancing your skills when developing RPGs in Unity 2018. This book does not cover the basics of Unity, and so is for intermediate or more advanced users. COMPUTERS,Design,Graphics & Media,Graphics Tools

Mastering Adobe Captivate 2019 Create responsive eLearning content, including quizzes, demonstrations, simulations and Virtual Reality projects that fit on any device with Adobe Captivate 2019 Key Features Build responsive, interactive and highly engaging eLearning content with Adobe Captivate 2019 Build Virtual Reality eLearning experiences with Adobe Captivate 2019 Assess your student knowledge with interactive and random quizzes Seamlessly integrate your eLearning content with any SCORM or xAPI compliant LMS Book Description Adobe Captivate is used to create highly engaging, interactive, and responsive eLearning content. This book takes you through the production of a few pieces of eLearning content, covering all the project types and workflows of Adobe Captivate. First, you will learn how to create a typical interactive Captivate project. This will give you the opportunity to review all Captivate objects and uncover the application's main tools. Then, you will use the built-in capture engine of Captivate to create an interactive software simulation and a Video Demo that can be published as an MP4 video. Then, you will approach the advanced responsive features of Captivate to create a project that can be viewed on any device. And finally, you will immerse your learners in a 360o environment by creating Virtual Reality projects of Adobe Captivate. At the end of the book, you will empower your workflow and projects with the newer and most advanced features of the application, including variables, advanced actions, JavaScript, and using Captivate 2019 with other applications. If you want to produce high quality eLearning content using a wide variety of techniques, implement eLearning in your company, enable eLearning on any device, assess the effectiveness of the learning by using extensive Quizzing features, or are simply interested in eLearning, this book has you covered! What you will learn Learn how to use the objects in Captivate to build professional eLearning content Enhance your projects by adding interactivity, animations, and more Add multimedia elements, such as audio and video, to create engaging learning experiences Use themes to craft a unique visual experience Use question slides to create SCORM-compliant quizzes that integrate seamlessly with your LMS Make your content fit any device with responsive features of Captivate Create immersive 360 experiences with Virtual Reality projects of Captivate 2019 Integrate Captivate with other applications (such as PowerPoint and Photoshop) to establish a professional eLearning production workflow Publish your project in a wide variety of formats including HTML5 and Flash Who this book is for If you are a teacher, instructional designer, eLearning developer, or human resources manager who wants to implement eLearning, then this book is for you. A basic knowledge of your OS is all it takes to create the next generation of responsive eLearning content. COMPUTERS,Design,Graphics & Media,Graphics Tools

Unreal Engine 4 Game Development Quick Start Guide Learn how to use Unreal Engine 4 by building 3D and multiplayer games using Blueprints Key Features Learn the fundamentals of Unreal Engine such as project templates, Blueprints, and C++ Learn to design games; use UMG to create menus and HUDs, and replication to create multiplayer games Build dynamic game elements using Animation Blueprints and Behavior Trees Book Description Unreal Engine is a popular game engine for developers to build high-end 2D and 3D games. This book is a practical guide, starting off by quickly introducing you to the Unreal Engine 4 (UE4) ecosystem. You will learn how to create Blueprints and C++ code to define your game's functionality. You will be familiarized with the core systems of UE4 such as UMG, Animation Blueprints, and Behavior Trees. You will also learn how to use replication to create multiplayer games. By the end of this book, you will have a broad, solid knowledge base to expand upon on your journey with UE4. What you will learn Use project templates to give your game a head start Create custom Blueprints and C++ classes and extend from Epic's base classes Use UMG to create menus and HUDs for your game Create more dynamic characters using Animation Blueprints Learn how to create complex AI with Behavior Trees Use replication to create multiplayer games Optimize, test, and deploy a UE4 project Who this book is for Readers who already have some game development experience and Unity users who would like to try UE4 will all benefit from this book. Knowledge of basic Object-Oriented Programming topics such as variables, functions, and classes is assumed. COMPUTERS,Design,Graphics & Media,Graphics Tools

Adobe Photoshop Lightroom Classic For Dummies Edit, organize, store, and share photos Whether you are brand new to photography, a devoted enthusiast, or a seasoned pro, there’s a version of Lightroom for you. Lightroom For Dummies is the book to help you learn which version of Lightroom is right for your needs. The main focus of the book is on using Lightroom Classic, but also includes an introduction to Lightroom CC. All with the goal of helping you get started on the right foot toward taking your photographic workflow to the next level. The book is a great starting place to help you improve your family photos or add advanced Lightroom skills that aid your career. Look inside to find the steps to navigating the software and getting top-notch results. Deciding which version of Lightroom is the best fit Take control of your photo library with Lightroom Classic Importing, organizing, and finding photos Editing and sharing your photos Producing a slideshow, book, print, or web gallery Gain a foundation for getting started with Lightroom CC Get ready to spend less time in front of the computer and more time behind the lens! COMPUTERS,Design,Graphics & Media,Graphics Tools

Foundations of Digital Art and Design with Adobe Creative Cloud Foundations of Digital Art and Design, Second Edition Fuses design fundamentals and software training into one cohesive approach! All students of digital design and production–whether learning in a classroom or on their own–need to understand the basic principles of design. These principles are often excluded from books that teach software. Foundations of Digital Art and Design reinvigorates software training by integrating design exercises into tutorials that fuse design fundamentals and core Adobe Creative Cloud skills. The result is a comprehensive design learning experience organized into five sections that focus on vector art, photography, image manipulation, typography, and effective work habits for digital artists. Design topics and principles include: Bits, Dots, Lines, Shapes, Unity, Rule of Thirds, Zone System, Color Models, Collage, Appropriation, Gestalt, The Bauhaus Basic Course Approach, Continuity, Automation, and Revision. This book: Teaches art and design principles with references to contemporary digital art alongside digital tools and processes in Adobe Creative Cloud Addresses the growing trend of compressing design fundamentals and design software into the same course in universities and design colleges Times each lesson to be used in 50 to 90-minute class sessions with additional practice materials available online Includes free video screencasts that demonstrate key concepts in every chapter Download work files and bonus chapters, view screencasts, connect with the author online and more; see the Introduction to the book for details. "This ambitious book teaches visual thinking and software skills together. The text leads readers step-by-step through the process of creating dynamic images using a range of powerful applications. The engaging, experimental exercises take this project well beyond the typical software guide." ELLEN LUPTON, co-author of Graphic Design: The New Basics COMPUTERS,Design,Graphics & Media,Graphics Tools

Python GUI Programming Cookbook Over 90 recipes to help you develop widgets, forms, layouts, charts, and much more using the latest features of Python 3 Key Features Use object-oriented programming to develop impressive GUIs in Python Create interesting charts to visually represent data using Matplotlib Develop GUIs with the latest versions of tkinter, PyQt5, and wxPython frameworks Book Description Python is a multi-domain, interpreted programming language that is easy to learn and implement. With its wide support for frameworks to develop GUIs, you can build interactive and beautiful GUI-based applications easily using Python. This third edition of Python GUI Programming Cookbook follows a task-based approach to help you create effective GUIs with the smallest amount of code. Every recipe in this book builds upon the last to create an entire, real-life GUI application. These recipes also help you solve problems that you might encounter while developing GUIs. This book mainly focuses on using Python's built-in tkinter GUI framework. You'll learn how to create GUIs in Python using simple programming styles and object-oriented programming (OOP). As you add more widgets and expand your GUI, you will learn how to connect to networks, databases, and graphical libraries that greatly enhance the functionality of your GUI. You'll also learn how to use threading to ensure that your GUI doesn't become unresponsive. Toward the end, you'll learn about the versatile PyQt GUI framework, which comes along with its own visual editor that allows you to design GUIs using drag and drop features. By the end of the book, you'll be an expert in designing Python GUIs and be able to develop a variety of GUI applications with ease. What you will learn Create amazing GUIs with Python's built-in tkinter module Customize GUIs using layout managers to arrange GUI widgets Advance from the typical waterfall coding style to an OOP style using Python Develop beautiful charts using the free Matplotlib Python module Use threading in a networked environment to make GUIs responsive Discover ways to connect GUIs to a MySQL database Understand how unit tests can be created and internationalize GUI Delve into the world of GUI creation using PyQt5 Who this book is for If you're a programmer or developer looking to enhance your Python skills by writing powerful GUI applications, this book is for you. Familiarity with the Python programming language is necessary to get the most out of the book. COMPUTERS,Design,Graphics & Media,Graphics Tools

Blender For Dummies Make your 3D world a reality Some of the dramatic visual effects you've seen in top-grossing movies and heralded television series got their start in Blender. This book helps you get your own start in creating three-dimensional characters, scenes, and animations in the popular free and open-source tool. Author Jason van Gumster shares his insight as an independent animator and digital artist to help Blender newcomers turn their ideas into three-dimensional drawings. From exporting and sharing scenes to becoming a part of the Blender community, this accessible book covers it all! Create 3D characters—no experience required Build scenes with texture and real lighting features Animate your creations and share them with the world Avoid common rookie mistakes This book is the ideal starting place for newcomers to the world of 3D modeling and animation. COMPUTERS,Design,Graphics & Media,Graphics Tools

Adobe Photoshop Adobe Photoshop: A Complete Course and Compendium of Features is your guide to creating, editing, and enhancing images and designs in Adobe Photoshop. Whether you’re retouching a photograph, making a simulated chalk drawing, or creating a composite photo with a 3D drawing, Photoshop is the tool for you—and this book will teach you what you need to know. First, with a complete Course that includes a set of projects and lessons derived from Adobe Certified Instructor Steve Laskevitch, you will learn the procedures needed to use Photoshop effectively and professionally. Dozens of lessons are included that can be applied to any graphics you have in mind. Through these step-by-step lessons, you’ll be exposed to all of Photoshop’s features in practical contexts and its best practices for optimal workflows. To complete the Course, we’ll supply lesson documents and their assets to download. These can even serve as starting points for your own projects. Then, for greater depth of knowledge and subsequent reference, you’ll use the Compendium to uncover more of the “how†and “why†of Photoshop. With each topic easy to access, you can find and explore all of Photoshop’s key features and concepts in depth. With cross references between the Course and Compendium, the two parts of the book complement each other perfectly. Best of all, when the lessons in the Course are done, the Compendium will continue to serve for months and years to come. Learn step by step how to: • Set up an ideal workspace • Master selections and masks • Work with type and brushes • Use blend modes for combining images • Take advantage of Smart Objects • Become more efficient and effective with actions and scripts • And much more! COMPUTERS,Design,Graphics & Media,Graphics Tools

Mastering Adobe Photoshop Elements 2020 An example-driven guide to take your image editing skills from beginner to advanced using powerful Photoshop Elements tools and techniques in tandem with Adobe's latest AI technology Key Features Updated to the latest version of Photoshop Elements 2020 with focused coverage on Adobe's latest AI technology Organize, search, and keep track of an ever-increasing number of images and videos using expert practices Discover common solutions to a wide range of photographic and image-editing problems Book Description Adobe Photoshop Elements is a raster graphics editor for entry-level photographers, image editors, and hobbyists. Updated and improved to cover the latest features of Photoshop Elements 2020, this second edition includes focused coverage of Adobe's new AI-powered features that are designed to make the editing process more efficient, creative and fun. This book takes you through the complexities of image editing in easy-to-follow, bite-sized chunks, helping you to quickly recognize the editing challenge at hand and use suitable tools and techniques to overcome it. You'll start by learning how to import, organize, manage, edit, and use your pictures in a format that's designed for creative photography projects. Throughout this Adobe Photoshop Elements book, you'll discover how to fix different photographic problems using an extensive repertoire of commonly applied solutions. Common processes such as applying artistic effects to creative projects, custom image makeovers, processing images for social media, and other file export methods will also be covered. By the end of this book, you'll have learned about the impressive tools available in Photoshop Elements 2020, and how it is designed not only for photographers who'd like to dip their toes into the editing world, but also for those wanting simple but effective ideas on how to expand their creativity while remaining time-efficient. What you will learn Explore the automatic AI-powered features designed to make the editing process faster and more efficient Add graphic elements to any composition, photograph, or illustration Overcome challenges in editing multi-layered images for your photography projects Develop illustrative skills using Photoshop Elements' drawing tools Learn techniques for professional photo retouching Work with online and local templates to create calendars, greeting cards, and other projects Who this book is for This book is for creative and enthusiastic photographers with elementary experience in photo editing. If you are looking to organize your picture collection and take control of post-processing requirements, you'll find this book useful. Though not necessary, photography skills alongside basic photo editing knowledge will help you to get the most out of this book. COMPUTERS,Design,Graphics & Media,Graphics Tools

Blender 3D By Example Get up and running with Blender 3D through a series of practical projects that will help you learn core concepts of 3D design like modeling, sculpting, materials, textures, lighting, and rigging using the latest features of Blender 2.83 Key Features Learn the basics of 3D design and navigate your way around the Blender interface Understand how 3D components work and how to create 3D content for your games Familiarize yourself with 3D Modeling, Texturing, Lighting, Rendering and Sculpting with Blender Book Description Blender is a powerful 3D creation package that supports every aspect of the 3D pipeline. With this book, you'll learn about modeling, rigging, animation, rendering, and much more with the help of some interesting projects. This practical guide, based on the Blender 2.83 LTS version, starts by helping you brush up on your basic Blender skills and getting you acquainted with the software toolset. You'll use basic modeling tools to understand the simplest 3D workflow by customizing a Viking themed scene. You'll get a chance to see the 3D modeling process from start to finish by building a time machine based on provided concept art. You will design your first 2D character while exploring the capabilities of the new Grease Pencil tools. The book then guides you in creating a sleek modern kitchen scene using EEVEE, Blender's new state-of-the-art rendering engine. As you advance, you'll explore a variety of 3D design techniques, such as sculpting, retopologizing, unwrapping, baking, painting, rigging, and animating to bring a baby dragon to life. By the end of this book, you'll have learned how to work with Blender to create impressive computer graphics, art, design, and architecture, and you'll be able to use robust Blender tools for your design projects and video games. What you will learn Explore core 3D modeling tools in Blender such as extrude, bevel, and loop cut Understand Blender's Outliner hierarchy, collections, and modifiers Find solutions to common problems in modeling 3D characters and designs Implement lighting and probes to liven up an architectural scene using EEVEE Produce a final rendered image complete with lighting and post-processing effects Learn character concept art workflows and how to use the basics of Grease Pencil Learn how to use Blender's built-in texture painting tools Who this book is for Whether you're completely new to Blender, or an animation veteran enticed by Blender's newest features, this book will have something for you. COMPUTERS,Design,Graphics & Media,Graphics Tools

GIMP Pocket Reference The GIMP Pocket Reference explains the numerous features of the GNU Image Manipulation Program--more affectionately known as "The GIMP"--and is the essential guide for designers working in a Linux/Unix environment. The GIMP is an open source image editor and design application that parallels Adobe Photoshop in functionality with one exception: it is free.The GIMP runs on virtually all Unix platforms, is included with most commercial Linux distributions, and can be downloaded freely from the Internet. This powerful image manipulation tool can be quite complex, making it hard to overlook the whole functionality.Based on the menu structure of the program, this handy reference covers GIMP version 1.2. It explains the function of every menu item and offers tips for every day usage. The Appendix explains important terms of image manipulation and contains a table of file formats supported by The GIMP.The GIMP Pocket Reference enables novices and experts alike to use this complex program fast and efficiently. COMPUTERS,Design,Graphics & Media,Photography (see also PHOTOGRAPHY,Techniques,Digital)

Sony Alpha DSLR A100 This unique manual is better than the manual that comes with yourcamera in several important ways: It's organized according to efficient workflow, so you can get the most outof your Sony A100 quickly and with the least amount of bother.You can find what you're looking for interactively: by using the interactiveTable of Contents, choosing one of the questions in the Quick Answerssection, or by following any of the convenient links we've placed throughoutthe document. It's not a book (unless you want it to be). It's a PDF that you can read onyour computer or on a PDA that fits into your camera bag. It is laid out onan 8.5 x 11-inch "page" so if you want to print, you won't have to wastepaper or spend time configuring your printer. Because it's a PDF, you can find subjects you're looking for by searchingelectronically. Typing Cmd/Ctrl-F brings up the familiar search dialog. So allyou have to do to jump straight to all the references to a particular part orfeature is to enter its name. (No reliance on a mindreading indexer.) The PDF is photographically illustrated so you can see exactly whichcombination of buttons, knobs, wheels, and menu choices will help youmake the magic you are hoping for. In addition to teaching technically correct procedures, this documentoffers valuable hints for taking photographs in some of the toughestsituations. COMPUTERS,Design,Graphics & Media,Photography (see also PHOTOGRAPHY,Techniques,Digital)

Nikon D7200 For Dummies Your plain-English, full-color guide to the Nikon D7200 Your Nikon D7200 comes packed with enough power to satisfy even seasoned photographers. Unfortunately, it doesn't come with an easy guide on how to adjust the camera's settings to get the photos you want. That's where Nikon D7200 For Dummies comes in! Brimming with the tips, tricks, and friendly instruction you'd gain in a basic photography course, it shows you how to get the very most out of your new Nikon D7200—without losing your cool. Written by an experienced photographer and photography teacher, this fun, no-nonsense guide quickly gets you up and running on taking your first photos in automatic mode, then moves on to help you grasp more advanced features, like controlling exposure, adjusting color and focus for better results, using scene modes and priority modes, shooting portraits, action shots, outdoor shots, and night images—and so much more. Navigate your camera's buttons, dials, and settings Apply pro tricks to get better color, focus, and sharpness from your images Control exposure settings and jump from auto mode to manual Make sense of tricky material through full-color explanations of core photography concepts If you're the proud new owner of a Nikon D7200, but don't have a ton—or any—experience with cameras, this hands-on guide will have you taking photos like a pro in no time! COMPUTERS,Design,Graphics & Media,Photography (see also PHOTOGRAPHY,Techniques,Digital)

Adobe Photoshop Lightroom CC Book for Digital Photographers, The Since Lightroom 1.0 first launched, Scott’s Kelby’s The Adobe Photoshop Lightroom Book for Digital Photographers has been the world’s #1 bestselling Lightroom book (it has been translated into a dozen different languages), and in this latest version for Lightroom 6, Scott uses his same award-winning, step-by-step, plain-English style and layout to make learning Lightroom easy and fun. Scott doesn’t just show you which sliders do what (every Lightroom book will do that). Instead, by using the following three simple, yet brilliant, techniques that make it just an incredible learning tool, this book shows you how to create your own photography workflow using Lightroom: • Throughout the book, Scott shares his own personal settings and studio-tested techniques. Each year he trains thousands of Lightroom users at his live seminars and through that he’s learned what really works, what doesn’t, and he tells you flat out which techniques work best, which to avoid, and why. • The entire book is laid out in a real workflow order with everything step by step, so you can begin using Lightroom like a pro from the start. • What really sets this book apart is the last chapter. This is where Scott dramatically answers his #1 most-asked Lightroom question, which is: “Exactly what order am I supposed to do things in, and where does Photoshop fit in?†You’ll see Scott’s entire start-to-finish Lightroom 6 workflow and learn how to incorporate it into your own workflow. • Plus, this book includes a downloadable collection of some of the hottest Lightroom Develop module presets to give you a bunch of amazing effects with just one click! Scott knows firsthand the challenges today’s digital photographers are facing, and what they want to learn next to make their workflow faster, easier, and more fun. He has incorporated all of that into this major update for Lightroom 6. It’s the first and only book to bring the whole process together in such a clear, concise, and visual way. Plus, the book includes a special chapter on integrating Adobe Photoshop seamlessly right into your workflow, and you’ll learn some of Scott’s latest Photoshop portrait retouching techniques and special effects, which take this book to a whole new level. There is no faster, more straight to the point, or more fun way to learn Lightroom than with this groundbreaking book. COMPUTERS,Design,Graphics & Media,Photography (see also PHOTOGRAPHY,Techniques,Digital)

Photoshop Elements 15 For Dummies The top-selling guide to Photoshop Elements—updated for Photoshop Elements 15 No matter if you're a photo-editing newbie or an old hat looking for new tricks, Photoshop Elements 15 For Dummies offers photographers of all skill levels the power to turn run-of-the-mill digital pictures into beautiful photographs. Covering the latest version of this popular software, this up-to-date guide quickly shows you how to organize images for editing, adjust color and focus, apply artsy filters, add text to an image—and beyond. There's a reason Photoshop Elements 15 For Dummies is the best place to start learning Elements—it gets you up and running with this image-editing software faster than you can say 'cheese!' Get ready to explore your inner artist and add pizzazz to even the most ordinary pics with the professional tools in Photoshop Elements 15! Find simple explanations of how to handle basic image editing Get steps for giving your photos a digital makeover Create layers in your images Discover one-click instant fixes when you hit roadblocks The power and simplicity of Photoshop Elements makes it easy to produce photos worth bragging about—and this no-nonsense guide will get you there in a flash. COMPUTERS,Design,Graphics & Media,Photography (see also PHOTOGRAPHY,Techniques,Digital)

Nikon D5600 For Dummies An easy-to-follow Nikon D5600 photography class—in a book! Your Nikon D5600 is a powerful tool equipped to take top-notch photos. But unless you know how to use it to its full potential, your professional-grade camera will produce underwhelming amateur-grade photos. And that's where Nikon D5600 For Dummies comes in! Packed with all the expert tips and tricks you need to get your Nikon to live up to its name, this guide shows you how to use it to get truly striking shots—in a flash. Written by an expert on all things Nikon—and brimming with inspiring full-color photos—the step-by-step instruction offered inside arms shutterbugs of all skill levels with the know-how to turn any scene into a beautiful work of art. Whether you're looking to capture a cozy low-light shot or forever memorialize an awesome action scene, Nikon D5600 For Dummies will take your photography skills to picturesque new heights. Discover all your camera's features and capabilities Get better photos in auto or manual mode Adjust focus on the fly Start speaking photography lingo like a pro Even Leonardo da Vinci had to learn to work with paints and brushes before he could create the Mona Lisa. Before you let your frustration get the best of you, take heed in the friendly guidance in Nikon D5600 For Dummies. COMPUTERS,Design,Graphics & Media,Photography (see also PHOTOGRAPHY,Techniques,Digital)

Canon EOS Rebel T7i/800D For Dummies Action, beauty, adventure, and art—start capturing memories today! Canon EOS Rebel T7i/800D For Dummies is your ultimate guide to taking spectacular photos—no photography experience required! The EOS Rebel offers professional features that camera phones just cannot match, and this book shows you how to take advantage of these features to take stunning photos in any situation. First, you'll take a tour of the controls to learn what everything does, where to find it, and how to use it. Next, you'll walk through the automatic, scene, and manual modes to learn the strengths and weaknesses of each, and how to choose a mode based on your goals for that particular photo. You'll learn how to capture action shots, take beautiful portraits, and get as artsy as you want to get as you adjust for color, lighting, and focus, and control exposure for different effects. Taking great photos doesn't have to be difficult! Your camera offers everything you need to perfectly capture any scene, and this book provides clear, easy-to-follow instruction to help you take full advantage of these professional tools. Get acquainted with your camera's controls Shoot in automatic, scene, or manual mode Compose shots and work with lighting like a pro Adjust for focus, color, depth of field, and more Whether you're taking pictures at a party, shooting scenery on vacation, catching action at a ball game, or just wandering around capturing spontaneous moments of beauty, awesome photos are just a few simple steps away. Your Canon EOS Rebel T7i/800D is equipped with the tools to make any scene share-worthy, and Canon EOS Rebel T7i/800D For Dummies equips you to start snapping professional-quality photos today! COMPUTERS,Design,Graphics & Media,Photography (see also PHOTOGRAPHY,Techniques,Digital)

Photoshop Elements 2018 For Dummies The top-selling book on Photoshop Elements—updated in a new edition Photoshop Elements offers photo editors of all skill levels the power to turn run-of-the-mill images into beautiful works of art—and Photoshop Elements 2018 For Dummies shows you how. Those new to photo editing who are looking for advice on making the most common fixes and experienced editors in need of a road map to this version of Photoshop Elements will find great value in this book! Start off by touring the Photoshop Elements interface with introductions to the tools that make the program so powerful. You’ll also follow simple step-by-step instructions for organizing images for editing, creating layers in your images, adjusting color and focus, applying artsy filters, adding text to an image, and so much more. Get simple explanations for handling image editing Find steps for giving your photos a digital makeover Discover tips for getting better photos Create frame-worthy pieces you’ll be proud to display If you’re ready to take your photo editing skills to new heights, all the help you need is a page—and a click—away. COMPUTERS,Design,Graphics & Media,Photography (see also PHOTOGRAPHY,Techniques,Digital)

The Photoshop Elements 15 Book for Digital Photographers This is the eBook of the printed book and may not include any media, website access codes, or print supplements that may come packaged with the bound book. ARE YOU READY FOR AN ELEMENTS BOOK THAT BREAKS ALL THE RULES? This book breaks new ground by doing something for digital photographers that’s never been done before–it cuts through the bull and shows you exactly “how to do it.†It’s not a bunch of theory; it doesn’t challenge you to come up with your own settings or figure things out on your own. Instead, it does something that virtually no other Elements book has ever done–it tells you flat-out which settings to use, when to use them, and why. If you’re looking for one of those “tell-me-everything-about-the-Unsharp-Mask-filter†books, this isn’t it. You can grab any other Elements book on the shelf, because they all do that. Instead, this book gives you the inside tips and tricks of the trade for organizing, correcting, editing, sharp¿ening, retouching, and printing your photos like a pro. You’ll be absolutely amazed at how easy and effective these techniques are–once you know the secrets. LEARN HOW THE PROS DO IT Each year Scott trains thousands of digital photographers and, almost without exception, they have the same questions and face the same problems–that’s exactly what he covers in this book. You’ll learn: · How to unlock the power of layers (you’ll be amazed at how easy it is!) · How to use Camera Raw for processing not only RAW photos, but JPEGs, TIFFs, and PSDs too! (And you’ll learn why so many pros like it best–because it’s faster and easier) · The sharpening techniques the pros really use (there’s an entire chapter just on this!) · How to deal with common digital camera image problems, including brightening people in dark shadows and getting the best color possible · The most requested photographic special effects, and much more! THE BOOK’S SECRET WEAPON Although Elements 15 offers some digital photography features that Photoshop CC doesn’t offer, there are plenty of features that Photoshop CC has that Elements 15 doesn’t (like channels, HDR, etc.). But in this book, you’ll learn some slick work¿arounds, cheats, and fairly ingenious ways to replicate many of those Photo¿shop features right within Elements. Plus, you can download a bonus chapter on portrait retouching and all the images used in the book, from the book’s companion webpage. Since this book is designed for photographers, it doesn’t waste your time talking about what a pixel is, how to frame a shot or set your exposure, etc., and there’s no talk about which camera or printer to buy. It’s all Elements, step by step, cover to cover, in the only book of its kind, and you’re gonna love it! COMPUTERS,Design,Graphics & Media,Photography (see also PHOTOGRAPHY,Techniques,Digital)

Lightroom Mobile Book, The Scott Kelby, the #1 best-selling Lightroom book author, brings you everything you need to know about Lightroom Mobile in his newest book. Lightroom Mobile , which is kind of like an extension of the regular desktop version of Lightroom, allows users to use Lightroom on their iPads, iPhones, and Android devices. This is really handy because it lets you do a lot of the main things you use the desktop version for, but with Lightroom Mobile, you can easily do them on your mobile device. Plus, it’s “free,†and that’s a hard price to beat. The Lightroom Mobile Book , first shows you how to get up and running quickly. Then, comes the fun stuff, like telling Lightroom on your computer which collections you want access to over in Lightroom Mobile. Plus, you’ll learn how to manage your collections, add Pick flags and star ratings, move images, play slide shows, and a bunch of other important stuff you’ll want to know right up front. Then, you’ll learn how to edit your images in Lightroom Mobile, using the same Basic panel features found in the desktop version of Lightroom–it’s the same sliders that do the same thing, and it’s even in the same order. You’ll also learn how to easily crop images, as well as use the in-app camera. You’ll learn step by step how to set up Lightroom on your desktop and mobile device, so that during a shoot, you can hand your client your tablet and not only can they see the images coming in live as you shoot, they can make their own Picks, comments, and even share the link with someone at a different location, so they can be part of the shoot, and the approval process, too! There are lots of other handy features you’ll want to know about, and Scott tells you exactly how to use them just like he was sitting there beside you, using the same casual style as if he were telling a friend. In The Lightroom Mobile Book , Scott brings the whole process together in a clear, concise, and visual way. There is no faster, more straight-to-the-point, or more fun way to learn Lightroom Mobile than with this groundbreaking book. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Design,Graphics & Media,Photography (see also PHOTOGRAPHY,Techniques,Digital)

Photoshop Elements 2019 For Dummies Turn blah photos into dazzling images Photoshop Elements offers enough of the power you’ll find in full Photoshop to make both basic and artistic edits to your photos. Photoshop Elements 2019 For Dummies helps you learn how to use Photoshop Elements to take your shots to stunning new heights! Photoshop Elements 2019 For Dummies offers photographers of all skill levels the power to turn run-of-the-mill digital pictures into beautiful photographs. This friendly and helpful guidebook directs you on how to harness all the tools this powerful software has to offer. Simple explanations for handling image editing Steps for giving your photos a digital makeover Ways to turn your photos into works of art Guidance on fixing your pics with one click No matter if you're a photo editing newcomer looking for advice on making the most common fixes or an experienced editor in need of a road map to this version of Photoshop Elements, this book has you covered! COMPUTERS,Design,Graphics & Media,Photography (see also PHOTOGRAPHY,Techniques,Digital)

The Adobe Photoshop Lightroom Classic CC Book for Digital Photographers Since Lightroom first launched 11 years ago, Scott Kelby’s The Adobe Photoshop Lightroom Book for Digital Photographers has been the world’s #1 top-selling Lightroom book (it has been translated into dozens of different languages), and in this latest version for Lightroom Classic CC, Scott did his biggest update ever, sharing all his latest techniques, insights, and invaluable tips using his award-winning, step-by-step, plain-English style that makes learning Lightroom easy and fun. Scott doesn’t just show you which sliders do what (every Lightroom book does that, right?). Instead, he shares his own personal settings, his time-tested techniques, and his proven step-by-step method of learning Lightroom, so you can begin using it like a pro from the start. Each year, he trains thousands of Lightroom users at his live seminars and through his blog at LightroomKillerTips.com, and he has learned first-hand what really works and what doesn’t. He tells you flat-out which techniques work best, which ones to avoid, and why. You’ll learn: His now famous SLIM (Simplified Lightroom Image Management) system that will teach you, step by step, how to organize your images, back them up, and be able to find them quickly and easily. Scott’s SLIM system is used by photographers all over the world and is taught at colleges and universities, because it’s so simple, straightforward, and it works. How to make your images look like the pros and how to take advantage of the new RAW camera, creative, and B&W profiles—you’ll finally “get†the whole image-editing thing, and you’ll know exactly what to do, in what order, and why. How to use Lightroom along with Photoshop, and how to make the two work together absolutely seamlessly. You’ll be surprised at what you’ll be able to do, even if you’ve never used Photoshop before. There’s a full chapter on how to use Lightroom on your mobile device to expand Lightroom’s power. The last chapter really sets this book apart because this is where Scott answers his #1 most-asked Lightroom question, which is “Exactly what order am I supposed to do things in?†You’ll see his entire start-to-finish Lightroom workflow and learn how to incorporate it into your own workflow. You can also download most of the same images used in the book to follow right along with. And, you’ll get a killer collection of custom Lightroom Develop and Print presets to give you some of the most sought-after looks and effects, all with just one click. This is the first and only book to bring the whole process together in such a clear, concise, and visual way. There is no faster, more straight-to-the-point, or more fun way to learn Lightroom than with this ground- and record-breaking book. COMPUTERS,Design,Graphics & Media,Photography (see also PHOTOGRAPHY,Techniques,Digital)

Photoshop for Lightroom Users Adobe Photoshop Lightroom is truly an awesome program, and the primary editing tool for so many photographers today. But, at some point, you realize that there are things you need to do to your images that Lightroom just can’t do. It could be anything from pro-level portrait retouching, to blending two or more images together, to incredible special effects, to removing distracting things in your image, to adding beautiful type to your images, and, well…there are just lots of incredible things you could do…if you just knew Photoshop. Adobe Photoshop is…well…it’s Photoshop—this huge, amazing, Swiss Army knife of a program with 70+ tools, and more than a hundred filters. So, compared to Lightroom it seems really complicated, and it could be, but you’ve got a secret weapon: Scott Kelby. He’s the same guy who wrote the world’s #1 best-selling book on Lightroom, he’s Editor and Publisher of Photoshop User magazine and Lightroom Magazine, and he’s here to teach you just the most important, most useful parts of Photoshop—just the stuff that Lightroom can’t already do. Once you learn these techniques (all covered in this short, quick, easy-to-use, plain-English guide), it opens a whole new world of productivity and creativity. Here’s what you’ll learn: Scott tells you flat-out which tools to use, which techniques work best, which ones to avoid, and why. You only really need about 20% of what Photoshop can do, and that 20% is all covered right in this book. The most important layer techniques, and learning layers is like being handed the keys to the candy store—this is where the fun begins, and you’ll be amazed at what you’ll be able to do, so quickly and easily. Scott’s favorite (and most useful) portrait retouching techniques; his favorite special effects for landscape, travel, and people photos; plus which filters are awesome (and which ones waste your time). Also, you’ll learn how to mask hair and create super-realistic composites (you’ll be amazed when you learn how easy this is), plus how to take advantage of all the latest Photoshop technology, how to leverage the latest features (so you’re doing things the easy way), and a bunch of today’s most popular techniques (the same commercial looks you’re seeing in hot demand), so you’ll be using Photoshop like a shark in no time. If you’ve been saying to yourself, “Ya know, I really should learn Photoshop,†you’re holding the absolute best book to get you there, coming from the guy who literally wrote the book on Lightroom. He knows how to help you make the most of using these two powerful tools together to take your images (and your fun) to the next level. You are going to love being a Photoshop shark! COMPUTERS,Design,Graphics & Media,Photography (see also PHOTOGRAPHY,Techniques,Digital)

The Adobe Photoshop Lightroom Classic CC Book Adobe Photoshop Lightroom Classic CC is one of the most powerful tools a digital photographer has in their toolset, offering powerful editing features in streamlined interface that lets photographers import, sort, and organize images. In this completely updated bestseller, author Martin Evening describes Lightroom Classic CC features in detail, covering library organization, develop image processing, output modules, and an introduction to the features in the new Adobe Photoshop Lightroom CC across desktop, web, and mobile. As an established commercial and landscape photographer, Martin knows first-hand what photographers need for an efficient work flow. He has been working with Lightroom from the beginning, and as a result, knows the software inside and out. In this book, he’ll teach you how to: Work efficiently with images shot in raw or non-raw formats Import photographs with ease and sort them according to your workflow Create and manage a personal image and video library Integrate Lightroom with Adobe Photoshop Prepare images for print, slideshows, or to create a book Make the most of new features, such as the ability to migrate and sync photos via the cloud Photographers will find Lightroom Classic CC—and Th e Adobe Photoshop Lightroom Classic CC Book—indispensable tools in their digital darkrooms. COMPUTERS,Design,Graphics & Media,Photography (see also PHOTOGRAPHY,Techniques,Digital)

Photoshop Elements 2020 For Dummies Go beyond one-click filters with Photoshop Elements 2020 Photoshop Elements offers the tools to make quick, simple fixes to photos or to turn your images into completely different pieces of art. Digital imaging pros Barbara Obermeier and Ted Padova walk you step-by-step through the tools that help you take control of this powerful software. Discover simple one-click fixes that repair the most basic photo problems then dive into creative editing and adding artistic touches. You'll also find tips on shooting better photos and managing common photo projects. Apply instant edits to your digital images Improve lighting and add some color pops Discover artistic filters that push your creativity Create a frame-worthy print This fun guide is here to provide help to photographers and designers who prefer the latest version of the lighter, less-expensive version of Photoshop. COMPUTERS,Design,Graphics & Media,Photography (see also PHOTOGRAPHY,Techniques,Digital)

Canon EOS 90D For Dummies Get excited about the Canon EOS 90D and all it can do! An amazing photo begins with a quality camera and the know-how to use it. If you’ve selected the Canon EOS 90D, you now have a digital camera that serves a range of photographers, from novices to professionals. It takes some know-how to take advantage of the camera’s upgrades to its sensor, shutter speed, and video capabilities. Fortunately, Canon EOS 90D For Dummies canhelp you maximize the potential of the camera and its features. Canon EOS 90D For Dummies lets you skip the photography class and start shooting high-quality images right away The book introduces the camera’s settings; explains how to take control of exposure, focus, and color; and shows how to put all this new-found knowledge to work to shoot great portraits or action shots. The book is co-written by a pair of photography pros who share their professional experience on how to apply simple techniques for great shots. Choose the best setting for your situation Manage focus and color Make the most of your lighting Understand camera settings Customize your camera to your needs Create remarkable photos and memories, whether you stick with user-friendly automatic settings or decide to dive into more advanced features. With your Canon EOS 90D and this book at your side, you can shoot quality video and capture moving subjects confidently. COMPUTERS,Design,Graphics & Media,Photography (see also PHOTOGRAPHY,Techniques,Digital)

Nikon D780 For Dummies Join the photographers who turn to the For Dummies series for useful guidance Nikon D780 For Dummies provides Nikon D780 users and owners with in-depth knowledge and practical advice about how to get great shots with their powerful camera. Written by professional photographer Doug Sahlin, this book gives quick and convenient answers to Nikon D780 users’ most frequent and pressing questions. Nikon D780 For Dummies covers the topics you’ll need to get started with your new D780 camera. The book includes clear guidance on topics like: · Exploring the Nikon D780 body · Getting to know the settings options · Seeing results from auto modes · Taking control of exposure · Looking into lens options · Using the flash effectively Written in the straightforward and pragmatic style known and loved by For Dummies readers around the world, Nikon D780 For Dummies is perfect for people just starting out with digital SLR photography as well as those who know their way around a camera. COMPUTERS,Design,Graphics & Media,Photography (see also PHOTOGRAPHY,Techniques,Digital)

iPhone Photography For Dummies Create beautiful iPhone photos with the techniques found in this book iPhone Photography For Dummies , shares the expertise of photography workshop instructor Mark Hemmings as he shows readers how to get stunning images using their favorite iPhone. By implementing Hemmings’ simple techniques, you’ll get professional-looking results in a fraction of the time you’d expect. You’ll learn to: Adjust camera settings Create majestic landscape images Capture exciting action shots Shoot beautiful portraits Select an editing app Share and organize images Shoot photos comfortably while on the go Perfect for those who want to take breathtaking photos without investing in a top-of-the-line camera, iPhone Photography For Dummies takes the guesswork and luck out of creating beautiful imagery. It shows people without formal training in photography how to make meaningful and noticeable improvements in their shooting technique using either the latest iPhone model or older versions of the device. COMPUTERS,Design,Graphics & Media,Photography (see also PHOTOGRAPHY,Techniques,Digital)

3ds Max Animation with Biped COMPUTERS,Design,Graphics & Media,Video & Animation

ActionScript 3.0 Game Programming University Gary Rosenzweig's ActionScript 3.0 Game Programming University shows you how to use ActionScript, the programming language behind Flash CS3 Professional. The lessons teach you all the basics of ActionScript programming through game examples, but the code can be easily adapted to non-game-oriented projects, such as web training and advertising. Written by a real-world Flash developer, this book presents you with the source code of 16 complete games and lays the foundation for you to create your own games. Gary also provides a companion website - flashgameu.com, which contains files, updates, new content, Gary's blog and much more. COMPUTERS,Design,Graphics & Media,Video & Animation

The Art of the Storyboard Communicate your vision, tell your story and plan major scenes with simple, effective storyboarding techniques. Using sketches of shots from classic films, from silents to the present day, John Hart leads you through the history and evolution of this craft to help you get to grips with translating your vision onto paper, from the rough sketch to the finished storyboard. More than 150 illustrations from the author's and other storyboard artists' work illuminate the text throughout to help you master the essential components of storyboarding, such as framing, placement of figures, and camera angles. Level: Novice COMPUTERS,Design,Graphics & Media,Video & Animation

MoCap for Artists Make motion capture part of your graphics and effects arsenal. This introduction to motion capture principles and techniques delivers a working understanding of today's state-of-the-art systems and workflows without the arcane pseudocodes and equations. Learn about the alternative systems, how they have evolved, and how they are typically used, as well as tried-and-true workflows that you can put to work for optimal effect. Demo files and tutorials provided on the companion CD deliver first-hand experience with some of the core processes. COMPUTERS,Design,Graphics & Media,Video & Animation

Poly-Modeling with 3ds Max Polymodeling is a modeling technique used in 3d modeling. Unlike box modeling, or other forms of modeling where you start out with a basic form or primitive object that determines the mass of an object, artists can use the polygon (the basic building block of all of the primitives available in 3ds Max). This approach allows for more control over the flow, placement and detail of the meshes that are built. Placement of vertices/points, edges and all other sub-elements that build our models is determined by the user, rather than pre-determined by a computer generated primitive. This book is a collection of tips, tricks and techniques on how to create professional models for advertising on T.V and the web. The author has tons of industry experience using Max toward this end, and he shares the secrets of his trade. As Production Modeler for some of today's hottest studios (including GuerillaFx, Coke Zero, MTV, Old Navy, Nike, Target, HP) Todd Daniele brings real-world experience to the book. Daniele teaches the technical aspects of polymodeling, while showing how to ultimately create content in a dynamic, efficient manner. Associated web site offers instructional files that show the models in progressive stages of development; plus a supporting internet forum: readers can log-on to this forum to ask questions or comment on anything covered in the book. COMPUTERS,Design,Graphics & Media,Video & Animation

Maya for Games Well-known Maya professional, Michael Ingrassia, takes readers through his unique style of modeling: "Image Based Modeling" where efficient, realistic models can be created very quickly. Ingrassia's techniques allow modelers to create exact replicas of their concept characters or objects. The techniques presented are very efficient and allow game m COMPUTERS,Design,Graphics & Media,Video & Animation

3ds Max 8 MAXScript Essentials Write your own MAXScript functions and utilities to create custom tools and UI elements, and automate repetitive tasks. Demonstrated techniques include the creation of objects, arrays, collections, control structures, parametric objects, and the construction of UI elements. The companion CD-ROM contains media files that allow you to practice the techniques with real-world examples demonstrating how you can use then in a production environment. COMPUTERS,Design,Graphics & Media,Video & Animation

Layout and Composition for Animation This essential, hands-on guide is filled with examples of what a composition should look like and example of poorly designed layouts. Spot potential problems before they cost time and money, and adapt creative solutions for your own projects with this invaluable resource for beginner and intermediate artists. With Beauty and the Beast examples and Simpson character layouts, readers will learn how to develop character layout and background layout as well as strengthen composition styles with a creative toolset of trick shot examples and inspirational case studies. A companion website will include further technique based tools, finalized layout and composition examples and tutorials for further artistic skill development. COMPUTERS,Design,Graphics & Media,Video & Animation

Drawn to Life Discover the lessons that helped bring about a new golden age of Disney animation! Published for the first time ever, Drawn to Life is a two volume collection of the legendary lectures from long-time Disney animator Walt Stanchfield. For over twenty years, Walt helped breathe life into the new golden age of animation with these teachings at the Walt Disney Animation Studios and influenced such talented artists as Tim Burton, Brad Bird, Glen Keane, and John Lasseter. These writings represent the quintessential refresher for fine artists and film professionals, and it is a vital tutorial for students who are now poised to be part of another new generation in the art form. Written by Walt Stanchfield (1919-2000), who began work for the Walt Disney Studios in the 1950s. His work can be seen in films like Sleeping Beauty, The Jungle Book, 101 Dalmatians, and Peter Pan. Edited by Academy Award®-nominated producer Don Hahn, who has prduced such classic Disney films as Beauty and the Beast and The Lion King. COMPUTERS,Design,Graphics & Media,Video & Animation

ActionScript 3.0 Game Programming University Learn ActionScript 3.0 the fun way, by creating 16 great games: real, robust games - not just "web toys"! Highly-rated ActionScript tutorial, now with seven new 3D and card games! Code and techniques easily adaptable to training, advertising, and more For Flash artists learning ActionScript, Flash programmers seeking to create games, and upgraders from ActionScript 1.0/2.0. Includes a chapter on developing games in Flash for the iPhone! Gary Rosenzweig's ActionScript 3.0 Game Programming University, Second Edition is the best hands-on tutorial for learning ActionScript 3.0, the programming language behind Flash Professional CS5. You will master all the basics of ActionScript programming by building 16 robust games. One step at a time, you'll learn techniques (and get tested code) that can be adapted to virtually any project, from games to training and advertising. The first edition earned widespread raves; Rosenzweig has now updated it with seven brand-new games that teach even more valuable ActionScript 3.0 skills and techniques. You will first learn how Flash and ActionScript 3.0 work together, the elements of an ActionScript program, and how to build a basic game framework with ActionScript. Next, Rosenzweig walks you through building the full spectrum of ActionScript games, including brain games, animation-based games, picture puzzles, games based on direction and movement, casual games, word games, Q and A games, action games, game worlds, and more. This edition adds new chapters on card games and 3D games, with High-Low, Video Poker, Blackjack, 3D Paddle Ball, 3D Scavenger Hunt, and two other new projects. COMPUTERS,Design,Graphics & Media,Video & Animation

Tradigital Maya Explore Disney's 12 principles of animation, while learning how to animate in Maya. You can develop your own leading digital techniques rooted to traditional workflows. From squash and stretch to timing and appeal, you will enhance your creative toolset with strong classics training and cutting edge techniques. Trusted Maya Authority, Lee Montgomery offers the only artistic guide to applying the principles of traditional animation with Maya's tools, which are used in production by the best animators and VFX artists today. Add another webpage to your favourites and expand your digital workflow to include the practical resources of the Tradigital Maya with the robust companion web site that include demonstrations, project files, links to further resources, available at www.tradigitalmaya.com. COMPUTERS,Design,Graphics & Media,Video & Animation

Getting Started in 3D with Maya Deliver professional-level 3D content in no time with this comprehensive guide to 3D animation with Maya. With over 12 years of training experience, plus several award winning students under his belt, author Adam Watkins is the ideal mentor to get you up to speed with 3D in Maya. Using a structured and pragmatic approach Getting Started in 3D with Maya begins with basic theory of fundamental techniques, then builds on this knowledge using practical examples and projects to put your new skills to the test. Prepared so that you can learn in an organic fashion, each chapter builds on the knowledge gained in the previous chapter, showing you all the essentials of 3D in Maya, from modeling and UV layout, to texture creation, rigging animating and rendering. As you go from project to project you'll develop a strong arsenal of skills that combined will form a complete end to end process to creating complete projects in Maya. The accompanying website provides all the tools you need to develop your skills. Project files to accompany the practical examples used throughout the text, so you can work along with the examples. Additional textures and models will give you all the resources you need to start making your own projects in no time at all. COMPUTERS,Design,Graphics & Media,Video & Animation

Digital Video and HD Digital Video and HD: Algorithms and Interfaces provides a one-stop shop for the theory and engineering of digital video systems. Equally accessible to video engineers and those working in computer graphics, Charles Poynton’s revision to his classic text covers emergent compression systems, including H.264 and VP8/WebM, and augments detailed information on JPEG, DVC, and MPEG-2 systems. This edition also introduces the technical aspects of file-based workflows and outlines the emerging domain of metadata, placing it in the context of digital video processing. Basic concepts of digitization, sampling, quantization, gamma, and filtering Principles of color science as applied to image capture and display Scanning and coding of SDTV and HDTV Video color coding: luma, chroma (4:2:2 component video, 4fSC composite video) Analog NTSC and PAL Studio systems and interfaces Compression technology, including M-JPEG and MPEG-2 Broadcast standards and consumer video equipment COMPUTERS,Design,Graphics & Media,Video & Animation

Character Mentor You've researched your character extensively, tailored her to your audience, sketched hundreds of versions, and now you lean back content as you gaze at your final character model sheet. But now what? Whether you want to use her in an animated film, television show, video game, web comic, or children's book, you're going to have to make her perform. How a character looks and is costumed starts to tell her story, but her body language reveals even more. Character Mentor shows you how to pose your character, create emotion through facial expressions, and stage your character to create drama. Author Tom Bancroft addresses each topic with clear, concise prose, and then shows you what he really means through commenting on and redrawing artwork from a variety of student "apprentices." His assignments allow you to join in and bring your drawing to the next level with concrete techniques, as well as more theoretical analysis. Character Mentor is an apprenticeship in a book. Professional artists from a variety of media offer their experience through additional commentary. These include Marcus Hamilton (Dennis the Menace), Terry Dodson (X-Men), Bobby Rubio (Pixar), Sean "Cheeks" Galloway (Spiderman animated), and more. With a foreword by comicbook artist Adam Hughes, who has produced work for DC, Marvel Comics, Lucasfilm, Warner Bros. Pictures, and other companies. COMPUTERS,Design,Graphics & Media,Video & Animation

Digital Lighting and Rendering Who better to teach students the fine art and craft of digital lighting and rendering than the individual who created many of the stunning lighting effects for Pixar’s blockbuster films such as Brave, Toy Story 3, Wall-e, Cars, and The Incredibles? In these pages, lighting and animation pro Jeremy Birn draws on his wealth of industry and teaching experience to provide an thoroughly updated edition of what has become the standard guide to digital lighting and rendering. Using beautiful, full-colour examples; a friendly, clear teaching style; and a slew of case studies and tutorials, Jeremy demonstrates how to create strategic lighting for just about any project. By explaining not just how to use various lighting techniques but why, this guide provides the grounding graphics pros need to master Hollywood lighting techniques. Realising that lighting - how it's used, where it's placed, and the kind of shadow it casts - is critical to any image, Jeremy dedicates the first half of his volume to just that topic. Additional chapters cover colour, exposure, composition, materials and textures, and compositing. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Design,Graphics & Media,Video & Animation

Finish Your Film! Tips and Tricks for Making an Animated Short in Maya Finish Your Film! Tips and Tricks for Making an Animated Short in Maya is a first-of-its-kind book that walks the reader step-by-step through the actual production processes of creating a 3D Short film with Maya. Other books focus solely on the creative decisions of 3D Animation and broadly cover the multiple phases of animation production with no real applicable methods for readers to employ. This book shows you how to successfully manage the entire Maya animation pipeline. This book blends together valuable technical tips on film production and real-world shortcuts in a step-by-step approach to make sure you do not get lost. Follow along with author and director Kenny Roy as he creates a short film in front of your eyes using the exact same methods he shows you in the book. Armed with this book, you'll be able to charge forth into the challenge of creating a short film, confident that creativity will show up on screen instead of being stifled by the labyrinth that is a 3D animation pipeline. COMPUTERS,Design,Graphics & Media,Video & Animation

Adobe Flash Professional CC Classroom in a Book (2014 release) The 10 project-based lessons in this text show students how to create engaging interactive content with Flash Professional CC (2014 Release). Using step-by-step instructions with projects that build on the knowledge gained in each lesson, students learn the key elements of the Flash interface, including panels, timelines, and frames. From there, students learn how to work with graphics, create and edit symbols, modify text, add interactivity with ActionScript, and incorporate animation and sound into their projects. They also learn how to prepare and export their finished projects for publishing. This new edition covers innovations in the 2014 Release of Flash Professional CC, including more expressive tools, powerful controls for animation, and robust support for a wider variety of playback platforms. Also covered is the all-new Variable Width tool, which allows students to control the thick-and-thin outlines of their illustrations for more creative graphics and animations. For more advanced control over complex animations, this release integrates a new Motion Editor panel. The Motion Editor panel lets them see how the properties of their animation change over time as curves on a graph. They can change each property independently with Bezier precision, making complicated animations fast and easy. Support for SVG export, WebGL publishing, Macintosh and Windows Projectors, and easy-to-use JavaScript code snippets for HTML5 Canvas projects make Flash the ideal development environment for creative animation and multimedia. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Design,Graphics & Media,Video & Animation

Animate to Harmony Want to create studio-quality work and get noticed? Just coming off Flash and looking for a Toon Boom intro? Are you a traditional pencil-and-paper animator? From scene setup to the final render, learn how to navigate the Toon Boom interface to create animation that can be published on a variety of platforms and formats. Animate to Harmony guides you through Toon Boom’s Animate, Animate Pro and Harmony programs, teaching you how to create high-quality 2D animation of all complexities. The main text focuses onfeatures that are common across all three programs while "Advanced Techniques" boxes throughout the book elaborate on Pro and Harmony features, appealing to all levels of experience with any of the three main Toon Boom products. COMPUTERS,Design,Graphics & Media,Video & Animation

Learning Blender Create Amazing 3D Characters with Blender: From Design and Modeling to Video Compositing Learning Blender walks you through every step of creating an outstanding animated character with the free, open source, 3D software Blender, and then compositing it in a real video using a professional workflow. This is the only Blender tutorial to take you from preproduction to final result, and it’s perfect for both 3D novices and those who’ve used other 3D Software. Focusing on Blender 2.71 and above, 3D-professional Oliver Villar explains all the basics, including Blender’s interface, controls, and how to manipulate objects. Once you’ve mastered the fundamentals, you’ll follow a realistic 3D workflow through a complete project. You’ll find chapters on every aspect of the character creation: design, modeling, unwrapping, texturing, shading, rigging, and animation. Once your character is ready and animated, you’ll learn how to integrate it into a real video using camera tracking techniques, lighting, and compositing. Each skillset is taught hands on, and available online video tutorials (more than 5 hours) will guide you through Blender’s trickier tasks. By the time you’re done, you’ll understand how the whole process fits together, and how to use Blender to create outstanding characters for all media. You’ll also build strong Blender skills you can apply in any 3D project, whether it involves characters or not. Learn How To Master Blender’s innovative user interface, navigation, and selection techniques Create your first scene with Blender and get comfortable with its core tools Prepare for projects so they’ll go as smoothly as possible Use modeling tools to create a 3D character Bring your character to life with color, textures, and materials Create your character’s skeleton and make it walk Make the most of Blender’s Camera Tracking tools Add lights to your 3D scene Render with Blender Internal or the powerful new Cycles render engine Composite your 3D character into a real video Switch to Blender from 3ds Max, Maya, or XSI Register your book at informit.com/register to access all of this book’s production files, plus bonus video tutorials, and a useful Blender keyboard shortcut reference. COMPUTERS,Design,Graphics & Media,Video & Animation

The Game Narrative Toolbox Learn how to create compelling game storylines. Four experienced narrative designers from different genres of game development have banded together to create this all-inclusive guide on what it's like to work as a writer and narrative designer in the videogame industry. From concept to final testing, The Game Narrative Toolbox walks readers through what role a narrative designer plays on a development team and what the requirements are at every stage of development. Drawing on real experiences, authors Tobias Heussner, Toiya Finley, Ann Lemay, and Jennifer Hepler provide invaluable advice for writing compelling player-centered stories and effective dialogue trees in order to help readers make the switch from prose- or screen- writing to interactive. Accompanying every chapter are exercises that allow the reader to develop their own documentation, outlines, and game-dialogue samples for use in applying for industry jobs or developing independent projects. This first installment of Focal Press's Game Design Workshops series is a must-have for individuals looking to create captivating storylines for games. COMPUTERS,Design,Graphics & Media,Video & Animation

Getting Started with Processing Processing opened up the world of programming to artists, designers, educators, and beginners. This short book gently introduces the core concepts of computer programming and working with Processing. Written by the co-founders of the Processing project, Reas and Fry, Getting Started with Processing shows you how easy it is to make software and systems with interactive graphics. If you're an artist looking to develop interactive graphics programs or a programmer on your way to becoming an artist, this book will take you where you want to go. Updated with new material on graphics manipulation, data, and for the latest version of Processing. COMPUTERS,Design,Graphics & Media,Video & Animation

The Nine Old Men Learn from the men who changed animation forever Walt Disney’s team of core animators, who he affectionately called his "Nine Old Men," were known for creating Disney’s most famous works, as well as refining the 12 basic principles of animation. Follow master animator and Disney legend Andreas Deja as he takes you through the minds and works of these notable animators. An apprentice to the Nine Old Men himself, Deja gives special attention to each animator and provides a thoughtful analysis on their techniques that include figure drawing, acting, story structure, and execution. The in-depth analysis of each animator’s work will allow you to refine your approach to character animation. Rare sequential drawings from the Disney archives also give you unprecedented access and insight into the most creative minds that changed the course of animation. Instruction and analysis on the works of each of the Nine Old Men broaden your creative choices and approaches to character animation Original drawings, some never-before-seen by the public are explored in depth, giving you behind-the-scenes access into Disney animation history Gain first-hand insight into the foundation of timeless characters and scenes from some of Disney’s most memorable feature and short films COMPUTERS,Design,Graphics & Media,Video & Animation

Creating Web Animations Thanks to faster browsers, better web standards support, and more powerful devices, the web now defines the next generation of user interfaces that are fun, practical, fluid, and memorable. The key? Animation. But learning how to create animations is hard, and existing learning material doesn’t explain the context of the UI problem that animations are trying to solve. That’s where this book comes in. You'll gain a solid technical understanding of how to create awesome animations using CSS and learn how to implement common UI patterns, using practical examples that rely on animations to solve a core problem. Frontend web developers and designers will not only learn important technical details, but also how to apply them to solve real-world problems. Create animations found in common user interface implementations, such as bounce after scrolling, expanding search boxes, and content sliders Learn the technical details of working with CSS animations and transitions Use CSS transforms to very animate an element’s position, scale, and orientation Understand the importance of easing COMPUTERS,Design,Graphics & Media,Video & Animation

Learning Blender This is the eBook of the printed book and may not include any media, website access codes, or print supplements that may come packaged with the bound book. Master the Newest Blender Techniques for Creating Amazing 3D Characters: From Design and Modeling to Video Compositing Now fully updated for Blender 2.78b and beyond, Learning Blender, Second Edition, walks you through every step of creating an outstanding 3D animated character with Blender, and then compositing it in a real video using a professional workflow. This edition covers the powerful new selection and modeling tools, as well as high-efficiency improvements related to other parts of the project such as texture painting, shading, rigging, rendering, and compositing. Still the only Blender tutorial to take you from preproduction to final result, this guide is perfect for both novices and those moving from other software to Blender (open source and free software). Author Oliver Villar provides full-color, hands-on chapters that cover every aspect of character creation: design, modeling, unwrapping, texturing, shading, rigging, animation, and rendering. He also walks you through integrating your animated character into a real-world video, using professional camera tracking, lighting, and compositing techniques. The rich companion website (blendtuts.com/learning-blender-files) will help you quickly master even the most complex techniques with bonus contents like video tutorials. By the time you’re done, you’ll be ready to create outstanding characters for all media–and you’ll have up-to-date skills for any 3D project, whether it involves characters or not. Learn Blender’s updated user interface, navigation, and selection techniques Create your first scene with Blender and the Blender Render and Cycles render engines Organize an efficient, step-by-step pipeline to streamline workflow in any project Master modeling, unwrapping, and texturing Bring your character to life with materials and shading Create your character’s skeleton and make it walk Use Camera Tracking to mix 3D objects into a real-world video Transform a raw rendered scene into the final result using Blender’s compositing nodes Register your product at informit.com/register for convenient access to downloads, updates, and corrections as they become available. COMPUTERS,Design,Graphics & Media,Video & Animation

Unreal Engine 4 for Design Visualization The Official, Full-Color Guide to Developing Interactive Visualizations, Animations, and Renderings with Unreal Engine 4 Unreal Engine 4 (UE4) was created to develop video games, but it has gone viral among architecture, science, engineering, and medical visualization communities. UE4’s stunning visual quality, cutting-edge toolset, unbeatable price (free!), and unprecedented ease of use redefines the state of the art and has turned the gaming, film, and visualization industries on their heads. Unreal Engine 4 for Design Visualization delivers the knowledge visualization professionals need to leverage UE4’s immense power. World-class UE4 expert Tom Shannon introduces Unreal Engine 4’s components and technical concepts, mentoring you through the entire process of building outstanding visualization content–all with realistic, carefully documented, step-by-step sample projects. Shannon answers the questions most often asked about UE4 visualization, addressing issues ranging from data import and processing to lighting, advanced materials, and rendering. He reveals important ways in which UE4 works differently from traditional rendering systems, even when it uses similar terminology. Throughout, he writes from the perspective of visualization professionals in architecture, engineering, or science–not gaming. Understand UE4’s components and development environment Master UE4’s pipeline from source data to delivered application Recognize and adapt to the differences between UE4 and traditional visualization and rendering techniques Achieve staggering realism with UE4’s Physically Based Rendering (PBR) Materials, Lighting, and Post-Processing pipelines Create production-ready Materials with the interactive real-time Material Editor Quickly set up projects, import massive datasets, and populate worlds with accurate visualization data Develop bright, warm lighting for architectural visualizations Create pre-rendered animations with Sequencer Use Blueprints Visual Scripting to create complex interactions without writing a single line of code Work with (and around) UE4’s limitations and leveraging its advantages to achieve your vision All UE4 project files and 3ds Max source files, plus additional resources and links, are available at the book's companion website. COMPUTERS,Design,Graphics & Media,Video & Animation

Learn Adobe Animate CC for Multiplatform Animations This study guide uses text integrated with video to help learners gain real-world skills that will get them started in their career in animation and interactive media design and lays the foundation for taking the Adobe Animate Certified Associate (ACA) exam. A mix of project-based lessons, videos, and quizzes throughout prepares beginning learners for an entry-level position in a competitive job market. Written by an instructor with classroom teaching experience, the book covers all of the objectives of the latest Interactive Media Using Adobe Animate CC Adobe Certified Associate Exam. Following are the top level domain objectives for the Interactive Media Using Adobe Animate exam: Setting Project Requirements Identifying Interactive Media Design Elements Understanding the Adobe Animate Interface Building Interactive Media Elements by Using Adobe Animate Evaluating Interactive Media Elements by Using Adobe Animate The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Design,Graphics & Media,Video & Animation

Adobe After Effects CC Classroom in a Book Creative professionals seeking the fastest, easiest, most comprehensive way to learn Adobe After Effects CC (2019 release) choose Adobe After Effects CC Classroom in a Book (2019 release) from Adobe Press. The 15 project-based lessons in this book show users step-by-step the key techniques for working in After Effects. Learn how to create, manipulate, and optimize motion graphics for film, video, DVD, the web, and mobile devices. Gain hands-on experience animating text and images, customizing a wide range of effects, tracking and syncing content, rotoscoping, distorting and warping images and video, and correcting color. Create Motion Graphics templates in After Effects so colleagues can make specific edits in Premiere Pro without accidentally changing other critical settings. Learn to create 3D content with both After Effects and Maxon Cinema 4D Lite (included with the software). The online companion files include all the necessary assets for readers to complete the projects featured in each chapter. All buyers of the book get full access to the Web Edition: A Web-based version of the complete ebook enhanced with video and multiple-choice quizzes. COMPUTERS,Design,Graphics & Media,Video & Animation

Twitch For Dummies The first full resource to offer advice on tapping into Twitch Twitch got its start as a live-streaming platform mostly populated by gamers and their fans. It's quickly grown to host streaming events of all kinds—concerts, conferences, production events like podcast recording sessions, and even pro sports. Twitch For Dummies helps initiate those new to streaming with advice on how to launch and build a Twitch channel. Podcasting For Dummies author Tee Morris guides readers through the basics of starting a channel, streaming games or live events, growing and interacting with an audience, and how to overcome common tech glitches. • Build a streaming studio • Create your Twitch profile • Find successful streaming strategies • Interact with your audience This guide offers friendly, reliable advice for broadcasters, marketers, and video fans on how to tap into the most popular online live-streaming service. COMPUTERS,Design,Graphics & Media,Video & Animation

Learn Clip Studio Paint Take your comics and illustrations to the next level with the powerful art tools in Clip Studio Paint 1.8 Key Features Overcome “interface overwhelm†with a practical breakdown of the Clip Studio interface Comprehensive guide on the Clip Studio Paint with detailed coverage of all the tools and concepts of designing comics Streamline your workflow to create faster and easier using Clip Studio's features Book Description Clip Studio Paint, the successor to Manga Studio, is used by over four million illustrators and comic creators around the world. This book will guide you through every step of learning this software, from system requirements and installation, all the way through to exporting your work for print or the web. Learn how to create new documents, customize tools to fit your working style, use ruler tools to create anything from straight lines to intricate backgrounds, add 3D elements, create comic panels using the specialized panel tools, utilize screentones and materials, add text and word balloons to your comics, create sound effects, easily flat and color your comics using reference layers, and bring your drawings to life using the animation features. By the end of this book, you will be able to navigate the Clip Studio Interface and program preferences, customize the various tools, and be able to create your own black-and-white and color illustrations and comics from start to finish. What you will learn Understand the differences between Clip Studio Paint Pro and EX Discover how to navigate and customize the user interface Creating custom tools that fit your unique style of illustration Using the ruler tools to create intricate perspective shots and complex symmetry Discover how to use 3D elements in your work Learn how to create lettering and word balloons to bring your comic stories to life Understand the process of digital art creation from pencils to inks to color Understand how to use the animation tools available in Clip Studio Paint Who this book is for If you are a beginning digital artist or are switching to Clip Studio from another graphics software, this book is for you. This book is excellent for those with no knowledge of digital art up to intermediate users looking to explore the unique features of Clip Studio Paint. COMPUTERS,Design,Graphics & Media,Video & Animation

Hands-On Motion Graphics with Adobe After Effects CC Discover techniques to enhance your videos with complex animation Key Features Design, animate, and sequence a complete motion graphics project Work with compositions and pre-compositions to create animations speedily Maximize your motion graphics and visual effects skills Book Description If you're thinking seriously about making and publishing your videos with professional editing and animation, look no further! Adobe After Effects is a popular tool among video editors and YouTubers to enhance their videos and bring them to life by implementing visual effects and motion graphics. This book will take you right from the basics through to the advanced techniques in Adobe After Effects CC 2018. You will start by setting up your editing environment to learn and improve techniques to sharpen your video editing skills. Furthermore, you will work with basic and advanced special effects to create, modify, and optimize motion graphics in your videos. Lastly, you will not only learn how to create 2.5D animations, but also get to grips with using Cinema 4D Lite to build and animate complete 3D scenes. By the end of the book, you'll have learned how to package a video efficiently with the help of the projects covered. What you will learn Create a lower third project for a TV show with complex layers Work with shape layer animation to create an animated lyrics video Explore different tools to animate characters Apply text animation to create a dynamic film-opening title Use professional visual effects to create a VFX project Model, light, and composite your 3D project in After Effects Who this book is for If you're a student, professional, YouTuber, or anyone who is interested in video editing, animation, and motion graphics, this book is for you. You'll also find this resource useful if you're an Illustrator looking to put your creations in motion. COMPUTERS,Design,Graphics & Media,Video & Animation

Animated Storytelling Animation is a limitless medium for telling stories. Artists can create worlds, defy gravity, flip from factual to fantasy, and transport audiences to places they never imagined. The challenge is having the discipline to reel it in and be intentional about your storytelling choices. This book shows you how. In Animated Storytelling, learn how to create memorable stories using animation and motion graphics by following 10 simple guidelines that take you through the stages of concept development, pre-production, storyboarding, and design. Explore traditional linear storytelling and learn different processes for creating successful nonlinear animated stories, and also discover the wonders of experimental filmmaking. Award-winning filmmaker, educator, and motivator Liz Blazer uses clear examples and easy-to-follow exercises to provide you with the instruction, encouragement, and tools you need to get your designs moving. Whether your goal is to create exciting shorts for film festivals, effective messaging for broadcast or online, or simply to gain a deeper understanding of the medium, Animated Storytelling simplifies the process of creating clear and engaging stories for animation and motion graphics so you can get started easily. Animated Storytelling teaches you how to: • Write a creative brief for your project • Find and communicate your story’s Big Idea • Create tight stories with linear and nonlinear structures • Explore experimental filmmaking techniques • Use storyboards to communicate your visual story • Use color to clarify and enrich your story • Define the rules for your animated world • Ease into the challenging task of animation • Make the work you want to be hired to do • Share your work with the world! “Equal parts inspiring and practical, Animated Storytelling is a step-by-step guide that takes aspiring storytellers from raw idea to final render to distribution. –Justin Cone, Co-founder, Motionographer “This book is the instruction manual for navigating the complex world of animated storytelling. It's informative, inspirational, and extremely entertaining to read. Anyone working (or hoping to work) in the field of animation needs to read this. –Joey Korenman, CEO & Founder, School of Motion COMPUTERS,Design,Graphics & Media,Video & Animation

Adobe After Effects Classroom in a Book (2020 release) Adobe After Effects Classroom in a Book (2020 release) is the best-selling guide to Adobe's powerful motion graphics program. The 15 project-based lessons in this book teach students step-by-step the key techniques for working efficiently in After Effects and delivering in the widest possible range of media types. In addition to the key elements of the After Effects interface, this revised edition covers new features and techniques. Learn how to create, manipulate, and optimize motion graphics for film, video, DVD, the web, and mobile devices. Gain hands-on experience animating text and images, customizing a wide range of effects, tracking and syncing content, rotoscoping, removing unwanted objects, and correcting color. Learn to create 3D content with both After Effects and Maxon Cinema 4D Lite (included with the software). The online companion files include all the necessary assets for readers to complete the projects featured in each chapter. All buyers of the book get full access to the Web Edition: A Web-based version of the complete ebook enhanced with video and multiple-choice quizzes. COMPUTERS,Design,Graphics & Media,Video & Animation

Minecraft The official Minecraft: Guide to Exploration will help you survive. Learn how to find resources, craft equipment and protect yourself from hostile mobs. The world of Minecraft is waiting to be explored. But danger lurks around every corner and survival can prove difficult for even the bravest adventurer. With insider info and tips from the experts at Mojang, this is the definitive guide to exploration for new Minecrafters. This ebook is best viewed on a color device with a larger screen. Collect all of the official Minecraft books: Minecraft: The Island Minecraft: The CrashMinecraft: The Lost Journals Minecraft: The Survivors’ Book of Secrets Minecraft: Exploded Builds: Medieval Fortress Minecraft: Guide to Exploration Minecraft: Guide to Creative Minecraft: Guide to the Nether & the End Minecraft: Guide to Redstone Minecraft: Mobestiary Minecraft: Guide to Enchantments & Potions Minecraft: Guide to PVP Minigames Minecraft: Guide to Farming Minecraft: Let’s Build! Theme Park Adventure Minecraft for Beginners COMPUTERS,Design,Graphics & Media,Video & Animation

Minecraft Learn the art of redstone and become a master engineer with Minecraft: Guide to Redstone, then put theory into practice to construct intricate contraptions in Minecraft. Pick up the basics of the redstone components and their uses, discover how to make working circuits, and create incredibly complex builds using your new skills. With insider info and tips from the experts at Mojang, this is the definitive guide to redstone in Minecraft. This ebook is best viewed on a color device with a larger screen. Collect all of the official Minecraft books: Minecraft: The Island Minecraft: The CrashMinecraft: The Lost Journals Minecraft: The Survivors’ Book of Secrets Minecraft: Exploded Builds: Medieval Fortress Minecraft: Guide to Exploration Minecraft: Guide to Creative Minecraft: Guide to the Nether & the End Minecraft: Guide to Redstone Minecraft: Mobestiary Minecraft: Guide to Enchantments & Potions Minecraft: Guide to PVP Minigames Minecraft: Guide to Farming Minecraft: Let’s Build! Theme Park Adventure Minecraft for Beginners COMPUTERS,Design,Graphics & Media,Video & Animation

Minecraft Have you ever wanted to build an entire land dedicated to battling zombies? This guide will show you how it’s done! Inside you’ll find build ideas for everything from a zombie arena and a zombie-infested graveyard to an undead city and a top-secret lab where zombies are created and cured. Just follow the steps for each build, and before you know it you’ll have an entire Land of Zombies to enjoy with your friends! This ebook is best viewed on a color device with a larger screen. Collect all of the official Minecraft books: Minecraft: The Island Minecraft: The Crash Minecraft: The Survivors’ Book of Secrets Minecraft: Exploded Builds: Medieval Fortress Minecraft: Guide to Exploration Minecraft: Guide to Creative Minecraft: Guide to the Nether & the End Minecraft: Guide to Redstone Minecraft: Mobestiary Minecraft: Guide to Enchantments & Potions Minecraft: Guide to PVP Minigames Minecraft: Guide to Farming Minecraft: Let’s Build! Theme Park Adventure Minecraft: Let’s Build! Land of Zombies COMPUTERS,Design,Graphics & Media,Video & Animation

Non-Designer's Design Book, The This is the eBook version of the printed book. If the print book includes a CD-ROM, this content is not included within the eBook version.A lot has happened in the world of digital design since the first edition of this title was published, but one thing remains true: There is an ever-growing number of people attempting to design pages with no formal training. This book is the one place they can turn to find quick, non-intimidating, excellent design help from trusted design instructor Robin Williams. This revised classic--now in full color--includes a new section on the hot topic of Color itself. In The Non-Designer's Design Book, 3rd Editio n, Robin turns her attention to the basic principles that govern good design. Readers who follow her clearly explained concepts will produce more sophisticated and professional pages immediately. Humor-infused, jargon-free prose interspersed with design exercises, quizzes, and illustrations make learning a snap--which is just what audiences have come to expect from this best-selling author. COMPUTERS,Desktop Applications,Desktop Publishing

100 Things Every Designer Needs to Know About People We design to elicit responses from people. We want them to buy something, read more, or take action of some kind. Designing without understanding what makes people act the way they do is like exploring a new city without a map: results will be haphazard, confusing, and inefficient. This book combines real science and research with practical examples to deliver a guide every designer needs. With it you’ll be able to design more intuitive and engaging work for print, websites, applications, and products that matches the way people think, work, and play. Learn to increase the effectiveness, conversion rates, and usability of your own design projects by finding the answers to questions such as: What grabs and holds attention on a page or screen? What makes memories stick? What is more important, peripheral or central vision? How can you predict the types of errors that people will make? What is the limit to someone’s social circle? How do you motivate people to continue on to (the next step? What line length for text is best? Are some fonts better than others? These are just a few of the questions that the book answers in its deep-dive exploration of what makes people tick. COMPUTERS,Desktop Applications,Desktop Publishing

Inkscape Inkscape: Guide to a Vector Drawing Program, Third Edition , is the guide to the Inkscape program, with coverage of versions 0.46 and 0.47. This authoritative introduction and reference features hundreds of useful illustrations.With Inkscape, you can produce a wide variety of art, from photorealistic drawings to organizational charts. Inkscape uses SVG, a powerful vector-based drawing language and W3C web standard, as its native format. SVG drawings can be viewed directly in browsers such as Firefox and Opera. A subset of SVG has been adopted by the mobile phone market. Inkscape is available free for Windows, Macintosh, and Linux operating systems. Systematic coverage of the entire Inkscape program begins with eleven tutorials ranging in difficulty from very basic to highly complex. The remainder of the book covers each facet of Inkscape in detail with an emphasis on practical solutions for common problems.The book is filled with valuable tips and warnings about the use of Inkscape and SVG. Find dozens of Inkscape illustrations from the book in the online color supplement found at http://tavmjong.free.fr/INKSCAPE/. Updated for Inkscape v0.47, this new edition includes complete coverage of new features, including updated Pen and Pencil tools with new spiro, polyline, and sketch modes; the new Eraser tool; and the new Snapping toolbar with improved snapping. Advanced topics include the use of Inkscape’s powerful tiling tool, built-in bitmap tracing, and SVG use on the Web. Complete Coverage of New and Improved Inkscape 0.47 Features Complete vector drawing program supporting the W3C SVG standard Three path-drawing tools (Pencil, Pen, Calligraphy) Five shape-drawing tools (Rectangles, Ellipses, Stars, Spirals, 3D Boxes) Linear and Radial Gradients Pattern fills Tweak Tool for fine adjustment of paths and colors Eraser Tool with both Vector and Bitmap modes Sophisticated snapping for precision drawing and aligning objects Extendable through scripting; over a hundred scripts included Live Path Effects for tasks such as adding patterns along a path while maintaining complete editability Over 200 pre-built SVG filters for adding textures, manipulating color, and so forth A tiling tool to create complex tilings with thirteen different symmetries Clipping and Masking objects An integrated spell checker Built-in bitmap-to-vector tracing The ability to export to more than a dozen graphics formats, including PDF and PostScript The ability to import from more than two-dozen graphics formats, including PDF, Adobe Illustrator, Coral Draw, AutoCad, and XFig COMPUTERS,Desktop Applications,Desktop Publishing

Functional Art, The The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. Unlike any time before in our lives, we have access to vast amounts of free information. With the right tools, we can start to make sense of all this data to see patterns and trends that would otherwise be invisible to us. By transforming numbers into graphical shapes, we allow readers to understand the stories those numbers hide. In this practical introduction to understanding and using information graphics, you’ll learn how to use data visualisations as tools to see beyond lists of numbers and variables and achieve new insights into the complex world around us. Regardless of the kind of data you’re working with–business, science, politics, sports, or even your own personal finances–this book will show you how to use statistical charts, maps, and explanation diagrams to spot the stories in the data and learn new things from it. You’ll also get to peek into the creative process of some of the world’s most talented designers and visual journalists, including Condé Nast Traveler’s John Grimwade, National Geographic Magazine’s Fernando Baptista, The New York Times’ Steve Duenes, The Washington Post’s Hannah Fairfield, Hans Rosling of the Gapminder Foundation, Stanford’s Geoff McGhee, and European superstars Moritz Stefaner, Jan Willem Tulp, Stefanie Posavec, and Gregor Aisch. . The Functional Art reveals : Why data visualisation should be thought of as “functional art†rather than fine art How to use colour, type, and other graphic tools to make your information graphics more effective, not just better looking The science of how our brains perceive and remember information Best practices for creating interactive information graphics A comprehensive look at the creative process behind successful information graphics An extensive gallery of inspirational work from the world’s top designers and visual artists COMPUTERS,Desktop Applications,Desktop Publishing

Foundations of Digital Art and Design with the Adobe Creative Cloud Fuses design fundamentals and software training into one cohesive book! Teaches art and design principles with references to contemporary digital art alongside basic digital tools in Adobe's Creative Cloud Addresses the growing trend of compressing design fundamentals and design software into the same course in universities and design trade schools. Lessons are timed to be used in 50 to 90 minute class sessions with additional materials available online Free video screencasts demonstrate key concepts in every chapter All students of digital design and production—whether learning in a classroom or on their own—need to understand the basic principles of design. These principles are often excluded from books that teach software. Foundations of Digital Art and Design reinvigorates software training by integrating design exercises into tutorials fusing design fundamentals and core Adobe Creative Cloud skills. The result is a comprehensive design learning experience. This book is organized into six sections that focus on vector art, photography, image manipulation, typography, web design, and effective habits. Design topics and principles include: Bits, Dots, Lines, Shapes, Rule of Thirds, Zone System, Color Models, Collage, Appropriation, Gestalt, The Bauhaus Basic Course Approach, The Grid, Remix, Automation, and Revision. COMPUTERS,Desktop Applications,Desktop Publishing

InDesign Type Typography is the foundation of graphic design, and the most effective way to be a better designer is to understand type and use it confidently and creatively. This fully updated third edition is a comprehensive guide to creating professional type with Adobe InDesign. It covers micro and macro typography concepts, from understanding the nuance of a single spacing width to efficiently creating long and complex documents. Packed with visual examples, InDesign expert and acclaimed design instructor Nigel French shows not just how to use InDesign’s extensive type features, but why certain approaches are preferable to others, and how to avoid common mistakes. Whether you’re creating a single-page flyer or a thousand-page catalog, whether your documents will be printed or viewed on screen, InDesign Type is an invaluable resource for getting the most out of InDesign’s typographic toolset. COMPUTERS,Desktop Applications,Desktop Publishing

InDesign CC InDesign CC: Visual QuickStart Guide (2014 release) is your complete guide to the core functions of InDesign as well as all the important new features. New to this edition is coverage of the greatly expanded ebook export capabilities, including Fixed Layout EPUB. With the growth in digital publishing, these new functions will empower designers to create more compelling digital documents than ever before. Other landmark new features in the 2014 release of InDesign CC include: the ability to reformat tables by dragging and dropping; integration with the hot portfolio site, Behance, and improvements to footnotes. Using the task-based, visual approach that is the trademark of the Visual QuickStart Guides readers will learn not only how to create documents, but also to use automation to streamline the process, as well as importing and styling text and objects, managing long documents, exporting files for a wide variety of purposes, and much more. COMPUTERS,Desktop Applications,Desktop Publishing

Truthful Art, The No matter what your actual job title, you are—or soon will be—a data worker. Every day, at work, home, and school, we are bombarded with vast amounts of free data collected and shared by everyone and everything from our co-workers to our calorie counters. In this highly anticipated follow-up to The Functional Art—Alberto Cairo’s foundational guide to understanding information graphics and visualization—the respected data visualization professor explains in clear terms how to work with data, discover the stories hidden within, and share those stories with the world in the form of charts, maps, and infographics. In The Truthful Art, Cairo transforms elementary principles of data and scientific reasoning into tools that you can use in daily life to interpret data sets and extract stories from them. The Truthful Art explains: • The role infographics and data visualization play in our world • Basic principles of data and scientific reasoning that anyone can master • How to become a better critical thinker • Step-by-step processes that will help you evaluate any data visualization (including your own) • How to create and use effective charts, graphs, and data maps to explain data to any audience The Truthful Art is also packed with inspirational and educational real-world examples of data visualizations from such leading publications as The New York Times, The Wall Street Journal, Estado de São Paulo (Brazil), Berliner Morgenpost (Germany), and many more. COMPUTERS,Desktop Applications,Desktop Publishing

Adobe Acrobat DC Classroom in a Book Adobe Acrobat DC Classroom in a Book, Second Edition, is the most thorough and comprehensive way for you to learn how to reliably create, edit, and sign PDF documents and forms with Adobe Acrobat DC. Each of the 12 lessons in this step-by-step, project-based guide contains a project that builds on your growing knowledge of the program, while end-of-chapter review questions reinforce each lesson. This cross-platform (Mac and Windows) book shows you how to collaborate effectively through electronic reviews, easily share your work across multiple platforms and devices (including via the Adobe Document Cloud service), and speed up your production and business task workflows with Acrobat DC. All of the book’s screenshots have been updated for this new edition. You will learn how to easily convert files from any application to PDF and how to directly edit text and images in PDF documents. You’ll also learn how to use the newly refreshed tools to build PDF or web forms, and to speed up business workflow by gathering feedback and approval via online document reviews. And you’ll learn how to create interactive forms and track responses within Acrobat, add signatures and security to PDF files, and much more. All of the project files used in the book’s lessons are available for download. COMPUTERS,Desktop Applications,Desktop Publishing

Photoshop Tricks for Designers Perhaps you are working on a new project and need a little inspiration , or even a quick reference to show you how to do that one cool effect that will be the finishing touch on your latest creation. Whatever you need, this book can help you in so many ways. One of the toughest things about being a designer is getting a good idea. The next challenge is realizing that idea. This book will not only be a source of ideas , but will also show you how to create them step by step. You can even combine multiple effects to create other cool results–the book’s cover was designed by combining at least half a dozen techniques found within. Corey wrote this book for working designers, or anyone who just wants to add some “cool factor†to their projects. Each tutorial is a stand-alone technique or mini-project, so you do not have to follow the book in sequence. Just find what you like and have at it. And, as an added bonus, you can download all of t he images used in the book to follow along with. It’s everything you loved about the Down & Dirty books, now in a small handbook size you can use as a quick reference to a variety of effects. COMPUTERS,Desktop Applications,Desktop Publishing

Adobe InDesign CC Classroom in a Book (2018 release) Creative professionals seeking the fastest, easiest, most comprehensive way to learn Adobe InDesign choose Adobe InDesign CC Classroom in a Book (2018 release) from Adobe Press. The 15 project-based step-by-step lessons show users the key techniques for working in InDesign. Designers will build a strong foundation of typographic, page layout, and document-construction skills that will enable them to produce a broad range of print and digital publications—from a simple postcard to an interactive Adobe PDF with form fields. The real-world tasks in this comprehensive book are presented in an easy-to-follow, step-by-step format and are designed to train beginning Adobe InDesign users in the program—from fundamental features to powerful layout and output skills. This book will also help experienced InDesign users elevate their skills, understand best practices, and learn about new features. The online companion files include all the necessary assets for readers to complete the projects featured in each lesson as well as ebook updates when Adobe releases relevant new features for Creative Cloud customers. All buyers of the book get full access to the Web Edition: a Web-based version of the complete ebook enhanced with video and multiple-choice quizzes. COMPUTERS,Desktop Applications,Desktop Publishing

InDesign Type This fully updated guide shows students how to create beautiful type for print and web with Adobe InDesign. Using practical examples, loads of tips, and sidebars to provide additional detail, author Nigel French provides a comprehensive overview of all of InDesign's type features, including new features and Creative Cloud features not included in previous editions. Starting with character formats and then moving through paragraph formats, styles and effects, and layouts, this book teaches all the skills students need to produce beautiful type. More than ever, modern typographers need to be prepared to craft type that will be used in a wide variety of media, from the printed page to the high-resolution displays of mobile devices, and this new edition of InDesign Type is the perfect guidebook for them. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Desktop Applications,Desktop Publishing

Adobe InDesign CC Classroom in a Book Creative professionals seeking the fastest, easiest, most comprehensive way to learn Adobe InDesign choose Adobe InDesign CC Classroom in a Book (2019 release) from Adobe Press. The 15 project-based step-by-step lessons show users the key techniques for working in InDesign. Designers will build a strong foundation of typographic, color, page layout, and document-construction skills that will enable them to produce a broad range of print and digital publications—from a simple postcard to an interactive Adobe PDF with form fields. The real-world tasks in this comprehensive book are presented in an easy-to-follow, step-by-step format and are designed to train beginning Adobe InDesign users in the program—from fundamental features to powerful layout and output skills. This book also enables experienced InDesign users to elevate their skills, understand best practices, and learn about new features. Enhancements in this version target usability and productivity, including the ability to browse fonts visually, using Content Aware Fit for intelligent image placement, use Layout Adjust to automatically adjust layout when changing page sizes, and quickly access common controls in the Properties panel. The online companion files include all the necessary assets for readers to complete the projects featured in each lesson. All buyers of the book get full access to the Web Edition: A Web-based version of the complete ebook enhanced with video and multiple-choice quizzes. COMPUTERS,Desktop Applications,Desktop Publishing

Using Publisher 2019 We’ve all been there before, staring at a computer screen with no idea what to do — don’t worry Using Publisher 2019 is here to help. Written by best-selling technology author, lecturer, and computer trainer Kevin Wilson, Using Publisher 2019 is packed with easy to follow instructions, photos, illustrations, helpful tips and video demos. Updated to cover Microsoft Publisher 2019, this guide will show you how to: Start Publisher and find your way around the ribbon menu Lay out and design your page Use page parts, text boxes, borders and accents Use pre-designed templates, and build your own Format text: bold, italic, underlined, strike, and super/subscript Align, highlight and change text colour Cut, copy, paste and using the clipboard Use headers and footers Insert SmartArt and clipart Add charts, tables, equations and special characters Add photos, crop, wrap text and use effects Print your publications Check spelling and grammar You'll want to keep this edition handy as you make your way around Microsoft Publisher. Have Fun! COMPUTERS,Desktop Applications,Desktop Publishing

Adobe InDesign Classroom in a Book (2020 release) Creative professionals seeking the fastest, easiest, most comprehensive way to learn Adobe InDesign choose Adobe InDesign CC Classroom in a Book from Adobe Press. The project-based step-by-step lessons show users the key techniques for working in InDesign. Designers will build a strong foundation of typographic, color, page layout, and document-construction skills that will enable them to produce a broad range of print and digital publications–from a simple postcard to an interactive Adobe PDF with form fields. The real-world tasks in this comprehensive book are presented in an easy-to-follow, step-by-step format and are designed to train beginning Adobe InDesign users in the program–from fundamental features to powerful layout and output skills. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Desktop Applications,Desktop Publishing

Mastering QuickBooks 2020 Get up to speed with QuickBooks Online 2020 for financial management and bookkeeping Key Features Create a dashboard that highlights your company's financial activity and status upon login Manage customers, vendors, and products and services seamlessly with QuickBooks Explore special transactions such as recurring transactions, managing fixed assets, setting up loans, and recording bad debts Book Description Intuit QuickBooks is an accounting software package that helps small business owners to manage all their bookkeeping tasks. Its complete range of accounting capabilities, such as tracking income and expenses, managing payroll, simplifying taxes, and accepting online payments, makes QuickBooks software a must-have for business owners and aspiring bookkeepers. This book is a handy guide to using QuickBooks Online to manage accounting tasks and drawing business insights by generating reports easily. Using a fictitious company, the book demonstrates how to create a QuickBooks Online account; customize key settings for a business; manage customers, vendors, and products and services; generate reports; and close the books at the end of the period. QuickBooks records your debits and credits, so you don't need to learn accounting. However, you will find out what happens under the hood and understand how your financial statements are impacted by what you do in QuickBooks. You'll also discover tips, shortcuts, and best practices that will help you save time and become a QuickBooks pro. By the end of this book, you'll have become well-versed with the features of QuickBooks and be able to set up your business and manage all bookkeeping tasks with ease. What you will learn Get to grips with bookkeeping concepts and the typical bookkeeping and accounting cycle Set up QuickBooks for both product-based and service-based businesses Track everything, from billable and non-billable time and expenses to profit Generate key financial reports for accounts, customers, jobs, and invoice items Understand the complete payroll process and track payments made to 1099 contractors Manage various bank and credit accounts linked to your business Who this book is for If you're a small business owner, bookkeeper, or accounting student who wants to learn how to make the most of QuickBooks Online, this book is for you. Business analysts, data analysts, managers, and professionals working in bookkeeping, and QuickBooks accountants will also find this guide useful. No experience with QuickBooks Online is required to get started; however, some bookkeeping knowledge will be helpful. COMPUTERS,Desktop Applications,Desktop Publishing

100 Things Every Designer Needs to Know About People WE DESIGN TO ELICIT RESPONSES from people. We want them to buy something, read more, or take action of some kind. Designing without understanding what makes people act the way they do is like exploring a new city without a map: results will be haphazard, confusing, and inefficient. This book combines real science and research with practical examples to deliver a guide every designer needs. With this book you’ll design more intuitive and engaging apps, software, websites and products that match the way people think, decide and behave. INCREASE THE EFFECTIVENESS OF YOUR PRODUCTS. Apply psychology and behavioral science to your designs. Here are some of the questions this book will answer: • What grabs and holds attention. • What makes memories stick? • What is more important, peripheral or central vision? • Can you predict the types of errors people will make? • What is the limit to someone’s social circle? • What line length for text is best? • Are some fonts better than others? These are just a few of the questions that the book answers in its deep-dive exploration of what makes people tick. COMPUTERS,Desktop Applications,Desktop Publishing

The Type Project Book The Type Project Book brings together a collection of typographically-focused design projects for all beginning to intermediate-level graphic designers. Renowned design instructor Nigel French approaches each project from both technical and aesthetic points of view, showing the starting state and milestones along the way to the finished deliverable. Wherever appropriate, French discusses historical precedent and professional examples of meeting the same challenge. French describes the assets required and the software used, without presenting screenshots that may quickly become outdated. This guide’s self-contained projects build on examples French first created in his popular courses for Lynda.com/LinkedIn Learning. Its extensively illustrated, attractive format will also appeal to users who just want to dip in and out for specific knowledge and skills. Ideal for independent self-study and exploration by working designers who want to expand their skills and build their portfolios, The Type Project Book has also been crafted to support graphic design students who need a strong foundation in typography. COMPUTERS,Desktop Applications,Desktop Publishing

My Evernote My Evernote® Step-by-step instructions with callouts to photos that show you exactly what to do Help when you run into problems or limitations with Evernote Tips and Notes to help you take full advantage of Evernote on your smartphone, tablet, or computer Full-color, step-by-step tasks walk you through making the most of Evernote –free or premium, on any device! Learn how to • Install and use Evernote on your iPhone, Android, iPad, BlackBerry, Windows Phone, PC or Mac, and beyond • Create and share notebooks, customized just the way you like, and organize your notes your way • Save images, drawings, handwriting, web content, even webcam snapshots in notes you can access anywhere, anytime • Add notes straight from Twitter or Google+, and link Evernote to your Facebook account • Format your notes to look great, and easily print the notes you want to file the old-fashioned way • Build easy-to-use To Do lists, complete with checkboxes • Sync your notes across multiple devices, and store them in the cloud so they’re always available over the Web • Import notes from other popular note-taking tools, such as Microsoft OneNote and Google Notebooks • Record high-quality audio notes and organize and share them as needed • Send notes to Evernote from Apple’s Siri digital assistant • Organize, tag, and search your notebooks to instantly find whatever you’re looking for • Install and use the Evernote Web Clipper in all popular web browsers • Securely share notebooks publicly or privately and collaborate with teams, wherever they are • Find apps and add-ons that make Evernote do even more for you CATEGORY: Desktop Applications COVERS: Evernote USER LEVEL: Beginning-Intermediate COMPUTERS,Desktop Applications,General

Microsoft SharePoint 2013 Step by Step The smart way to learn Microsoft SharePoint 2013—one step at a time! Experience learning made easy—and quickly teach yourself how to boost team collaboration with SharePoint 2013. With Step by Step, you set the pace—building and practicing the skills you need, just when you need them! Customize your team site’s layout, features, and apps Manage and share ideas, documents, and data Capture and organize content into lists and libraries Automate business processes with built-in workflows Use social features to communicate and collaborate Publish content using enhanced web content management COMPUTERS,Desktop Applications,General

Microsoft SharePoint 2013 Plain & Simple Get the full-color, visual guide that makes learning Microsoft SharePoint 2013 plain and simple! Follow the book’s easy steps and screenshots and clear, concise language to learn the simplest ways to get things done. Here’s WHAT you’ll learn: Create libraries for all kinds of media Share information in one location Organize people and processes Connect SharePoint to Microsoft Office with no fuss Find things fast with the Search Center Expand your community with social networking Here’s HOW you’ll learn it: Jump in wherever you need answers Follow easy STEPS and SCREENSHOTS to see exactly what to do Get handy TIPS for new techniques and shortcuts Use TRY THIS! exercises to apply what you learn right away COMPUTERS,Desktop Applications,General

Outlook 2016 For Dummies Be more productive and simplify your life with Outlook 2016! Ever feel like you're drowning in your inbox? Outlook 2016 For Dummies helps you lower the metaphorical water levels by quickly prioritizing incoming email. Instead of wading through messages and tasks all day, use Outlook as it was intended—as a productivity tool—to organize your tasks on the to-do bar, filter junk email, make the most of Outlook's anti-phishing capabilities, manage email folders, use smart scheduling tools, leverage RSS support, collect electronic business cards, and integrate your Microsoft OneNote, Project, Access, and SharePoint files. This book is updated to reflect the latest and greatest features integrated into the Outlook 2016 user interface to ensure you're at the top of your Outlook game. With over 1.1 billion users worldwide and 90% market share for productivity suites, a figure that roughly translates into one in seven people the world over, odds are you'll need to learn how to use Microsoft Office programs—including Outlook—if you want to excel in the workplace. Get up to speed on the new and improved features of Microsoft Office 2016 Take advantage of often overlooked features that can simplify your day Discover new ways to filter junk email—and reclaim the hours that you spend sorting through spam each year Organize tasks and schedule meetings, keeping everyone up to date on the latest project and account progress If you're ready to take your productivity to the next level Outlook 2016 For Dummies is a must-read! COMPUTERS,Desktop Applications,General

Microsoft Excel 2016 Step by Step Now in full color! The quick way to learn Microsoft Excel 2016! This is learning made easy. Get more done quickly with Excel 2016. Jump in wherever you need answers--brisk lessons and full-color screen shots show you exactly what to do, step by step. Quickly set up workbooks, enter data, and format it for easier viewing Perform calculations and find and correct errors Filter, sort, summarize, and combine data Analyze data by using PivotTables, PivotCharts, scenarios, data tables, and Solver Visualize data with charts and graphs, including new sunbursts, waterfalls, and treemaps Build data models and use them in business intelligence analyses Create timelines, forecasts, and visualizations, including KPIs and PowerMap data maps Look up just the tasks and lessons you need COMPUTERS,Desktop Applications,General

Microsoft Office 2016 Step by Step The quick way to get started with Microsoft Office 2016! This is learning made easy. Get more done quickly with Microsoft Word, Excel, PowerPoint, and Outlook. Jump in wherever you need answers--brisk lessons and colorful screenshots show you exactly what to do, step by step. Covers Word, Excel, PowerPoint and Outlook Format documents for visual impact Quickly prepare personalized email messages and labels Build powerful workbooks for analysis and reporting Analyze alternative data sets with Quick Analysis Lens, Goal Seek, and Solver Prepare highly effective presentations Strengthen your presentations by adding tables and graphics Organize your email, scheduling, and contacts Look up just the tasks and lessons you need COMPUTERS,Desktop Applications,General

Microsoft Outlook 2016 Step by Step This is learning made easy. Get more done quickly with Outlook 2016. Jump in wherever you need answers--brisk lessons and colourful screenshots show you exactly what to do, step by step. Get easy-to-follow guidance from a certified Microsoft Office Specialist Master Learn and practice new skills while working with sample content, or look up specific procedures Manage your email more efficiently than ever Organise your Inbox to stay in control of everything that matters Schedule appointments, events, and meetings Organise contact records and link to information from social media sites Track tasks for yourself and assign tasks to other people Enhance message content and manage email security The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Desktop Applications,General

Microsoft SharePoint 2016 Step by Step This is the eBook of the printed book and may not include any media, website access codes, or print supplements that may come packaged with the bound book. This is learning made easy! Get productive fast with SharePoint 2016, and jump in wherever you need answers: brisk lessons and colorful screen shots show you exactly what to do, step by step – and practice files help you build your skills. Fully updated for today's powerful new version of SharePoint, Microsoft SharePoint 2016 Step by Step shows you how to do all this: Customize your team site's layout, features, and apps Manage and share ideas, documents, and data Capture and organize content into lists and libraries Automate business processes with built-in workflows Use social features to communicate and collaborate Work with SharePoint's business intelligence features Publish content using enhanced web content management Use SharePoint with Excel, Access, Outlook, and Lync And much more… COMPUTERS,Desktop Applications,General

Outlook 2019 For Dummies Get up to speed with the world’s best email application — Outlook 2019 Of the millions of people who use Outlook, most only use about two percent of its features. Don’t stay in the dark! Outlook 2019 For Dummies shows you how to take advantage of often-overlooked tips and tricks to make it work even better for you. Inside, you’ll find information on navigating the user interface; utilizing the To-Do bar; filtering junk email; smart scheduling; RSS support; using electronic business cards; accessing data with two-way sync and offline and cloud based access, and much more! Make the most of Outlook's anti-phishing capabilities Share your calendar Integrate tasks with other Microsoft applications and services Manage email folders If you’re upgrading to the latest version — or have never used this popular email tool — this book makes it easier than ever to get Outlook working for you. COMPUTERS,Desktop Applications,General

Microsoft Power BI Dashboards Step by Step Your hands-on guide to building effective Power BI dashboards Expand your expertise–and teach yourself how to create world-class Power BI business analysis dashboards that bring data to life for better decision-making. If you’re an experienced business intelligence professional or manager, you’ll get all the guidance, examples, and code you need to succeed–even if you’ve never used Power BI before. Successfully design, architect, and implement Power BI in your organization Take full advantage of any Microsoft Power BI platform, including Power BI Premium Make upfront decisions that position your Power BI project for success Build rich, live dashboards to monitor crucial data from across your organization Aggregate data and data elements from numerous internal and external data sources Develop dynamic visualizations, including charts, maps, and graphs Bring data to life with stunning interactive reports Ensure dashboard security and compliance Drive user adoption through effective training COMPUTERS,Desktop Applications,General

Microsoft Excel 2019 Step by Step The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. This is learning made easy. Get more done quickly with Excel 2019. Jump in wherever you need answers--brisk lessons and many screen shots show you exactly what to do, step by step. Quickly set up workbooks, enter data, and format it for easier viewing Perform calculations and find and correct errors Filter, sort, summarize, and combine data Analyse data by using PivotTables, PivotCharts, scenarios, data tables, and Solver Visualise data with charts and graphs, including new sunbursts, waterfalls, and treemaps Build data models and use them in business intelligence analyses Create timelines, forecasts, and visualisations, including KPIs and PowerMap data maps Look up just the tasks and lessons you need COMPUTERS,Desktop Applications,General

Microsoft Office 2019 Step by Step This is learning made easy. Get more done quickly with Office 2019. Jump in wherever you need answers - brisk lessons and colorful screenshots show you exactly what to do, step by step. Covers Word, Excel, PowerPoint and Outlook Format Word documents for maximum visual impact Build powerful, reliable Excel workbooks for analysis and reporting Prepare highly effective PowerPoint presentations Use Outlook to organize your email, calendar, and contacts Includes downloadable practice files COMPUTERS,Desktop Applications,General

Microsoft Excel 2019 VBA and Macros Renowned Excel experts Bill Jelen (MrExcel) and Tracy Syrstad explain how to build more powerful, reliable, and efficient Excel spreadsheets. Use this guide to automate virtually any routine Excel task: save yourself hours, days, maybe even weeks. Make Excel do things you thought were impossible, discover macro techniques you won’t find anywhere else, and create automated reports that are amazingly powerful. Bill Jelen and Tracy Syrstad help you instantly visualize information to make it actionable; capture data from anywhere, and use it anywhere; and automate the best new features in Excel 2019 and Excel in Office 365. You’ll find simple, step-by-step instructions, real-world case studies, and 50 workbooks packed with examples and complete, easy-to-adapt solutions. By reading this book, you will: Quickly master Excel macro development Work more efficiently with ranges, cells, and formulas Generate automated reports and quickly adapt them for new requirements Learn to automate pivot tables to summarize, analyze, explore, and present data Use custom dialog boxes to collect data from others using Excel Improve the reliability and resiliency of your macros Integrate data from the internet, Access databases, and other sources Automatically generate charts, visualizations, sparklines, and Word documents Create powerful solutions with classes, collections, and custom functions Solve sophisticated business analysis problems more rapidly About This Book For everyone who wants to get more done with Microsoft Excel in less time For business and financial professionals, entrepreneurs, students, and others who need to efficiently manage and analyze data COMPUTERS,Desktop Applications,General

Microsoft Word 2019 Step by Step The quick way to learn Microsoft Word 2019 and Word for Office 365! This is learning made easy. Get more done quickly with Microsoft Word 2019 and Word for Office 365. Jump in wherever you need answers--brisk lessons and informative screenshots show you exactly what to do, step by step. Create great-looking, well-organized documents to enhance communication Use headings, bookmarks, and footnotes for more intuitive access to knowledge Visualize information by using diagrams and charts Illustrate concepts by using 3D models, icons, and screen clippings Collaborate, track changes, and coauthor documents in real-time Enforce security and privacy in electronic documents Quickly build tables of contents, indexes, and equations Generate individualized emails, letters, labels, envelopes, directories, and catalogs Supercharge efficiency with custom styles, themes, templates, and building blocks Look up just the tasks and lessons you need COMPUTERS,Desktop Applications,General

Microsoft Excel 2019 Data Analysis and Business Modeling Master business modeling and analysis techniques with Microsoft Excel 2019 and Office 365 and transform data into bottom-line results. Written by award-winning educator Wayne Winston, this hands-on, scenario-focused guide helps you use Excel to ask the right questions and get accurate, actionable answers. New coverage ranges from Power Query/Get & Transform to Office 365 Geography and Stock data types. Practice with more than 800 problems, many based on actual challenges faced by working analysts. Solve real business problems with Excel—and build your competitive advantage: Quickly transition from Excel basics to sophisticated analytics Use PowerQuery or Get & Transform to connect, combine, and refine data sources Leverage Office 365’s new Geography and Stock data types and six new functions Illuminate insights from geographic and temporal data with 3D Maps Summarize data with pivot tables, descriptive statistics, histograms, and Pareto charts Use Excel trend curves, multiple regression, and exponential smoothing Delve into key financial, statistical, and time functions Master all of Excel’s great charts Quickly create forecasts from historical time-based data Use Solver to optimize product mix, logistics, work schedules, and investments—and even rate sports teams Run Monte Carlo simulations on stock prices and bidding models Learn about basic probability and Bayes’ Theorem Use the Data Model and Power Pivot to effectively build and use relational data sources inside an Excel workbook Automate repetitive analytics tasks by using macros COMPUTERS,Desktop Applications,General

Learn Power BI Solve business challenges with Microsoft Power BI's advanced visualization and data analysis techniques Key Features Create effective storytelling reports by implementing simple-to-intermediate Power BI features Develop powerful analytical models to extract key insights for changing business needs Build, publish, and share impressive dashboards for your organization Book Description To succeed in today's transforming business world, organizations need business intelligence capabilities to make smarter decisions faster than ever before. This Power BI book is an entry-level guide that will get you up and running with data modeling, visualization, and analytical techniques from scratch. You'll find this book handy if you want to get well-versed with the extensive Power BI ecosystem. You'll start by covering the basics of business intelligence and installing Power BI. You'll then learn the wide range of Power BI features to unlock business insights. As you progress, the book will take you through how to use Power Query to ingest, cleanse, and shape your data, and use Power BI DAX to create simple to complex calculations. You'll also be able to add a variety of interactive visualizations to your reports to bring your data to life. Finally, you'll gain hands-on experience in creating visually stunning reports that speak to business decision makers, and see how you can securely share these reports and collaborate with others. By the end of this book, you'll be ready to create simple, yet effective, BI reports and dashboards using the latest features of Power BI. What you will learn Explore the different features of Power BI to create interactive dashboards Use the Query Editor to import and transform data Perform simple and complex DAX calculations to enhance analysis Discover business insights and tell a story with your data using Power BI Explore data and learn to manage datasets, dataflows, and data gateways Use workspaces to collaborate with others and publish your reports Who this book is for If you're an IT manager, data analyst, or BI user new to using Power BI for solving business intelligence problems, this book is for you. You'll also find this book useful if you want to migrate from other BI tools to create powerful and interactive dashboards. No experience of working with Power BI is expected. COMPUTERS,Desktop Applications,General

InfoPath with SharePoint 2010 How-To Real, step-by-step solutions for creating and managing data forms in SharePoint 2010 with InfoPath: fast, accurate, proven, and easy to use A concise, task-based guide for SharePoint 2010 adopters who want to enhance business processes and workflows with powerful InfoPath data forms Tested, step-by-step procedures for solving a broad spectrum of business and technical problems: an indispensable resource for both information workers and IT pros Authored by leading business collaboration solutions developer Steven Mann SharePoint 2010 and InfoPath 2010 integrate more deeply than ever before, allowing SharePoint users and developers to build powerful "mini-apps" with InfoPath forms, and use them to streamline a wide range of workflows and business processes - all without writing code. InfoPath with SharePoint 2010 How-To is a single source for reliable, easy-to-implement SharePoint solutions built with InfoPath data forms. Steven Mann presents concise tutorials to get users and developers up to speed, and walks through more than 50 procedures, providing clear and accurate steps for each one. Mann's tested, step-by-step procedures include: designing form templates and libraries; using SharePoint form features; incorporating rules and functions; designing pages and views; creating workflows; using external web services data; creating tabbed navigation; providing offline form access; defining master/detail views; displaying and managing lists; dynamically populating repeating tables; tracking changes, and dozens more. Readers will also find several proven procedures for streamlining administration and troubleshooting. This book goes far beyond "tips and trick" to serve as the daily reference resource for every information worker and IT professional who wants to solve real business and technical problems with SharePoint 2010 and InfoPath 2010. COMPUTERS,Distributed Systems,Client-Server Computing

Cloud Computing In Cloud Computing: Concepts, Technology & Architecture , Thomas Erl, one of the world’s top-selling IT authors, teams up with cloud computing experts and researchers to break down proven and mature cloud computing technologies and practices into a series of well-defined concepts, models, technology mechanisms, and technology architectures, all from an industry-centric and vendor-neutral point of view. In doing so, the book establishes concrete, academic coverage with a focus on structure, clarity, and well-defined building blocks for mainstream cloud computing platforms and solutions. Subsequent to technology-centric coverage, the book proceeds to establish business-centric models and metrics that allow for the financial assessment of cloud-based IT resources and their comparison to those hosted on traditional IT enterprise premises. Also provided are templates and formulas for calculating SLA-related quality-of-service values and numerous explorations of the SaaS, PaaS, and IaaS delivery models. With more than 260 figures, 29 architectural models, and 20 mechanisms, this indispensable guide provides a comprehensive education of cloud computing essentials that will never leave your side. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Distributed Systems,Client-Server Computing

Programming Windows “Look it up in Petzold†remains the decisive last word in answering questions about Windows development. And in PROGRAMMING WINDOWS, FIFTH EDITION, the esteemed Windows Pioneer Award winner revises his classic text with authoritative coverage of the latest versions of the Windows operating system—once again drilling down to the essential API heart of Win32 programming. Topics include: The basics—input, output, dialog boxes An introduction to Unicode Graphics—drawing, text and fonts, bitmaps and metafiles The kernel and the printer Sound and music Dynamic-link libraries Multitasking and multithreading The Multiple-Document Interface Programming for the Internet and intranets Packed as always with definitive examples, this newest Petzold delivers the ultimate sourcebook and tutorial for Windows programmers at all levels working with Microsoft Windows 95, Windows 98, or Microsoft Windows NT. No aspiring or experienced developer can afford to be without it. An electronic version of this book is available on the companion CD. For customers who purchase an ebook version of this title, instructions for downloading the CD files can be found in the ebook. COMPUTERS,Distributed Systems,Client-Server Computing

Exam Ref 70-487 Developing Windows Azure and Web Services (MCSD) Prepare for Microsoft Exam 70-487—and help demonstrate your real-world mastery of developing Windows Azure and web services. Designed for experienced developers ready to advance their status, Exam Ref focuses on the critical-thinking and decision-making acumen needed for success at the Microsoft Specialist level. Focus on the expertise measured by these objectives: Accessing data Querying and manipulating data by using the Entity Framework Designing and implementing WCF Services Creating and consuming Web API-based services Deploying web applications and services This Microsoft Exam Ref: Organizes its coverage by exam objectives. Features strategic, what-if scenarios to challenge you. COMPUTERS,Distributed Systems,Client-Server Computing

Exam Ref 70-331 Core Solutions of Microsoft SharePoint Server 2013 (MCSE) Prepare for Exam 70-331—and help demonstrate your real-world mastery of Microsoft SharePoint Server 2013 core solutions. Designed for experienced IT professionals ready to advance their status, Exam Ref focuses on the critical-thinking and decision-making acumen needed for success at the MCSE level. Focus on the expertise measured by these objectives: Design a SharePoint Topology Plan Security Install and Configure SharePoint Farms Create and Configure Web Applications and Site Collections Maintain a Core SharePoint Environment This Microsoft Exam Ref: Organises its coverage by exam objectives. Features strategic, what-if scenarios to challenge you. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Distributed Systems,Client-Server Computing

Inside Microsoft Dynamics AX 2012 R3 Fully updated for Microsoft Dynamics AX 2012 R3! Dig into the architecture and internals of Microsoft Dynamics AX 2012 R3 - with firsthand insights from the team that designed and developed it. Deepen your knowledge of the underlying frameworks, components, and tools - and deliver custom ERP applications with the extensibility and performance your business needs. Useful for Microsoft Dynamics AX solution developers at all levels, this guide will provide max benefit to those who understand OOP, relational database, and Transact-SQL concepts. Gain best practices, patterns, and techniques to: Exploit interoperability with Microsoft Visual Studio tools Work with MorphX and avoid common pitfalls with X++ code Use Enterprise Portal with ASP.NET and SharePoint for rich web-based apps Simplify process automation with built-in workflow infrastructure See how the runtime implements security and configuration Design and customize the user experience Gain greater control over complex batch jobs Customize the prebuilt BI solution and reporting Test applications, publish services, and optimize performance COMPUTERS,Distributed Systems,Client-Server Computing

System Center 2012 R2 Configuration Manager Unleashed Since Microsoft introduced System Center 2012 Configuration Manager, it has released two sets of important changes and improvements: Service Pack 1 and R2. This comprehensive reference and technical guide focuses specifically on those enhancements. It offers 300+ pages of all-new “in the trenches†guidance for applying Configuration Manager 2012’s newest features to improve user and IT productivity across all corporate, consumer, and mobile devices. An authoring team of world-class System Center consultants thoroughly cover System Center integration with Microsoft Intune and its mobile device management capabilities. They fully address Microsoft’s increased support for cross-platform devices, enhanced profiles, changes to application management, operating system deployment, as well as improvements to performance, security, usability, and mobile device management. The essential follow-up to System Center 2012 R2 Configuration Manager Unleashed , this new supplement joins Sams’ market-leading series of books on Microsoft System Center. • Use ConfigMgr 2012 R2 with Windows Intune to deliver people-centric management to any user, any device, anywhere • Simplify BYOD registration and enrollment, and enable consistent access to corporate resources • Integrate new mobile device management capabilities into the Configuration Manager console without service packs, hot fixes, or major releases • Provision authentication certificates for managed devices via certificate profiles • Automate repetitive software- and device-related tasks with PowerShell cmdlets • Centrally control roaming profiles, certificates, Wi-Fi profiles, and VPN configuration • Configure User Data and Profiles to manage folder redirection, offline files/folders, and roaming profiles for Windows 8.x users • Enable users to access data in Virtual Desktop Infrastructure (VDI) environments • Manage devices running OS X, UNIX, Linux, Windows Phone 8, WinRT, iOS, and Android • Understand the new cross-platform agent introduced in ConfigMgr 2012 R2 • Automate Windows setup with OSD • Prepare for, configure, install, and verify successful installation of the Windows Intune connector role • Respond to emerging challenges in mobile device management COMPUTERS,Distributed Systems,Client-Server Computing

Universal Windows Apps with XAML and C# Unleashed Full Color: Figures and code appear as they do in Visual Studio. Universal Windows apps are a total game-changer. You can now write once and deploy your app to any modern PC, tablet, phone, or other Windows device. Suddenly, it’s quick and easy to serve new devices and form factors, sharing unified assets ranging from code to styles to user controls. It has never been easier to reach multiple-device markets! Now, the world’s #1 expert on Microsoft XAML brings together all the knowledge Windows developers need to build universal apps that adapt smoothly for any device running Windows 8.1, Windows Phone 8.1, or their successors. Drawing on his unsurpassed personal experience and direct input from Microsoft’s Windows and Visual Studio teams, Adam Nathan illuminates core development concepts, answers your most important questions, and candidly assesses the technology’s strengths and limitations. This full-color guide walks you through every key task involved in building a universal Windows app: layout and input, working with the app model, using advanced controls, leveraging XAML’s powerful rich media features, and much more. Detailed information on how to... Quickly build universal, localized apps that exploit the vast global scale of the Windows Store Size, position, and transform elements within layouts that gracefully adapt to different devices Handle input from touch, mouse, pen, keyboard, and any sensor Monetize apps with Windows Store sales, in-app purchases, and advertising Make the most of controls for managing content, items, text, images, media, speech, and more Create efficient 2D vector graphics and animations Use styles, templates, and visual states to redesign controls without losing functionality Bind data sources to simplify data presentation and updates Easily integrate data from apps, users, and networks Support Windows app commands: Search, Share, Print, Play, Project, Settings Use contracts to build apps that cooperate to perform complex tasks Improve the user experience even when your app isn’t running COMPUTERS,Distributed Systems,Client-Server Computing

Microsoft SharePoint Online for Office 365 Deliver world-class collaboration capabilities through the cloud Use SharePoint Online to provide today’s most advanced collaboration capabilities--without managing your own infrastructure! This concise reference will help you configure and manage SharePoint Online to meet your requirements for functionality, performance, and compliance. Bill English covers user profiles, security, search, records management, App Catalogs, metrics, and more--to derive maximum value from SharePoint Online. Master the specific skills you need to deploy and run SharePoint Online Choose the version of SharePoint Online that is best for you Manage profiles, properties, audiences, permissions, policies, and MySite settings Use Business Connectivity Services to make SharePoint Online your central hub for all business information Make the most of SharePoint search, indexing, and records and document management Create and manage security and App Catalogs Solve the core issues of governance, risk, compliance, taxonomies, and training COMPUTERS,Distributed Systems,Client-Server Computing

Art of Computer Programming, Volume 4, Fascicle 6, The This multivolume work on the analysis of algorithms has long been recognized as the definitive description of classical computer science. The four volumes published to date already comprise a unique and invaluable resource in programming theory and practice. Countless readers have spoken about the profound personal influence of Knuth’s writings. Scientists have marveled at the beauty and elegance of his analysis, while practicing programmers have successfully applied his “cookbook†solutions to their day-to-day problems. All have admired Knuth for the breadth, clarity, accuracy, and good humor found in his books. To continue the fourth and later volumes of the set, and to update parts of the existing volumes, Knuth has created a series of small books called fascicles, which are published at regular intervals. Each fascicle encompasses a section or more of wholly new or revised material. Ultimately, the content of these fascicles will be rolled up into the comprehensive, final versions of each volume, and the enormous undertaking that began in 1962 will be complete. Volume 4 Fascicle 6 This fascicle, brimming with lively examples, forms the middle third of what will eventually become hardcover Volume 4B. It introduces and surveys “Satisfiability,’’ one of the most fundamental problems in all of computer science: Given a Boolean function, can its variables be set to at least one pattern of 0s and 1s that will make the function true? Satisfiability is far from an abstract exercise in understanding formal systems. Revolutionary methods for solving such problems emerged at the beginning of the twenty-first century, and they’ve led to game-changing applications in industry. These so-called “SAT solvers’’ can now routinely find solutions to practical problems that involve millions of variables and were thought until very recently to be hopelessly difficult. Fascicle 6 presents full details of seven different SAT solvers, ranging from simple algorithms suitable for small problems to state-of-the-art algorithms of industrial strength. Many other significant topics also arise in the course of the discussion, such as bounded model checking, the theory of traces, Las Vegas algorithms, phase changes in random processes, the efficient encoding of problems into conjunctive normal form, and the exploitation of global and local symmetries. More than 500 exercises are provided, arranged carefully for self-instruction, together with detailed answers. COMPUTERS,Distributed Systems,Client-Server Computing

Skype for Business Unleashed This is the most comprehensive, realistic, and useful guide to Skype for Business , Microsoft’s most powerful unified communications system. Four leading Microsoft unified communications consultants share in-the-trenches guidance for planning, integration, migration, deployment, administration, and more. The authors thoroughly introduce Skype for Business 2015’s components and capabilities, as well as changes and improvements associated with the integration of popular Skype consumer technologies. You’ll find detailed coverage of IP voice, instant messaging, conferencing, and collaboration; and expert guidance on server roles, multi-platform clients, security, and troubleshooting. Reflecting their unsurpassed experience, the authors illuminate Microsoft’s new cloud-based and hybrid cloud architectures for unified communications, showing how these impact networking, security, and Active Directory. They cover SDN for unified communications; interoperation with consumer Skype and legacy video conferencing; quality optimisation, mobile improvements, and much more. Throughout, the authors combine theory, step-by-step configuration instructions, and best practices from real enterprise environments. Simply put, you’ll learn what works–and how it’s done. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Distributed Systems,Client-Server Computing

Elasticsearch 7.0 Cookbook Search, analyze, and manage data effectively with Elasticsearch 7 Key Features Extend Elasticsearch functionalities and learn how to deploy on Elastic Cloud Deploy and manage simple Elasticsearch nodes as well as complex cluster topologies Explore the capabilities of Elasticsearch 7 with easy-to-follow recipes Book Description Elasticsearch is a Lucene-based distributed search server that allows users to index and search unstructured content with petabytes of data. With this book, you'll be guided through comprehensive recipes on what's new in Elasticsearch 7, and see how to create and run complex queries and analytics. Packed with recipes on performing index mapping, aggregation, and scripting using Elasticsearch, this fourth edition of Elasticsearch Cookbook will get you acquainted with numerous solutions and quick techniques for performing both every day and uncommon tasks such as deploying Elasticsearch nodes, integrating other tools to Elasticsearch, and creating different visualizations. You will install Kibana to monitor a cluster and also extend it using a variety of plugins. Finally, you will integrate your Java, Scala, Python, and big data applications such as Apache Spark and Pig with Elasticsearch, and create efficient data applications powered by enhanced functionalities and custom plugins. By the end of this book, you will have gained in-depth knowledge of implementing Elasticsearch architecture, and you'll be able to manage, search, and store data efficiently and effectively using Elasticsearch. What you will learn Create an efficient architecture with Elasticsearch Optimize search results by executing analytics aggregations Build complex queries by managing indices and documents Monitor the performance of your cluster and nodes Design advanced mapping to take full control of index steps Integrate Elasticsearch in Java, Scala, Python, and big data applications Install Kibana to monitor clusters and extend it for plugins Who this book is for If you're a software engineer, big data infrastructure engineer, or Elasticsearch developer, you'll find this book useful. This Elasticsearch book will also help data professionals working in the e-commerce and FMCG industry who use Elastic for metrics evaluation and search analytics to get deeper insights for better business decisions. Prior experience with Elasticsearch will help you get the most out of this book. COMPUTERS,Distributed Systems,Client-Server Computing

Learning Amazon Web Services (AWS) The Practical, Foundational Technical Introduction to the World’s #1 Cloud Platform Includes access to several hours of online training video: Mark Wilkins’ expert training video library guides you through setting up core services and prepares you to deploy your own apps and resources. Learning Amazon Web Services (AWS) is the perfect foundational resource for all administrators, developers, project managers, and other IT professionals who want to plan and deploy AWS services and/or earn AWS certification. Top cloud trainer and evangelist Mark Wilkins teaches best practices that align with Amazon’s Well-Architected Framework, introduces key concepts in the context of a running case study, carefully explains how core AWS services operate and integrate, and offers extensively tested tips for maximizing flexibility, security, and value. Companion online videos guide you step-by-step through setting AWS compute, storage, networking, scale, security, automation, and more. Balance cost, compliance, and latency in your service designs Choose the right networking options for your virtual private cloud (VPC) Build, host, launch, manage, and budget for EC2 compute services Plan for scale and resiliency, and make informed decisions about AWS storage Enforce strict security, and automate to improve operational efficiency This book with companion training videos is a valuable learning tool for anyone seeking to demonstrate expertise through formal certification. WEB EDITION: All buyers of the book or ebook can register your book for access to a free online Web Edition of this title, which included videos embedded within the text, plus updates as they become available. COMPUTERS,Distributed Systems,Client-Server Computing

SQL Server 2019 Administration Inside Out Conquer SQL Server 2019 administration–from the inside out Dive into SQL Server 2019 administration–and really put your SQL Server DBA expertise to work. This supremely organized reference packs hundreds of timesaving solutions, tips, and workarounds–all you need to plan, implement, manage, and secure SQL Server 2019 in any production environment: on-premises, cloud, or hybrid. Six experts thoroughly tour DBA capabilities available in SQL Server 2019 Database Engine, SQL Server Data Tools, SQL Server Management Studio, PowerShell, and Azure Portal. You’ll find extensive new coverage of Azure SQL, big data clusters, PolyBase, data protection, automation, and more. Discover how experts tackle today’s essential tasks–and challenge yourself to new levels of mastery. Explore SQL Server 2019’s toolset, including the improved SQL Server Management Studio, Azure Data Studio, and Configuration Manager Design, implement, manage, and govern on-premises, hybrid, or Azure database infrastructures Install and configure SQL Server on Windows and Linux Master modern maintenance and monitoring with extended events, Resource Governor, and the SQL Assessment API Automate tasks with maintenance plans, PowerShell, Policy-Based Management, and more Plan and manage data recovery, including hybrid backup/restore, Azure SQL Database recovery, and geo-replication Use availability groups for high availability and disaster recovery Protect data with Transparent Data Encryption, Always Encrypted, new Certificate Management capabilities, and other advances Optimize databases with SQL Server 2019’s advanced performance and indexing features Provision and operate Azure SQL Database and its managed instances Move SQL Server workloads to Azure: planning, testing, migration, and post-migration COMPUTERS,Distributed Systems,Client-Server Computing

Windows Server 2019 Inside Out Conquer Windows Server 2019—from the inside out! Dive into Windows Server 2019—and really put your Windows Serverexpertise to work. Focusing on Windows Server 2019’s most powerful and innovative features, this supremely organized reference packs hundreds of timesaving solutions, tips, and workarounds—all you need to plan, implement, or manage Windows Server in enterprise, data center, cloud, and hybrid environments. Fully reflecting new innovations for security, hybrid cloud environments, and Hyper-Converged Infrastructure (HCI), it covers everything from cluster sets to Windows Subsystem for Linux. You’ll discover how experts tackle today’s essential tasks—and challenge yourself to new levels of mastery. • Optimize the full Windows Server 2019 lifecycle, from planning and configuration through rollout and administration • Leverage new configuration options including App Compatibility Features on Demand (FOD) or Desktop Experience • Ensure fast, reliable upgrades and migrations • Manage Windows servers, clients, and services through Windows Admin Center • Seamlessly deliver and administer core DNS, DHCP, fi le, print, storage, and Internet services • Use the Storage Migration Service to simplify storage moves and configuration at the destination • Seamlessly integrate Azure IaaS and hybrid services with Windows Server 2019 • Improve agility with advanced container technologies, including container networking and integration into Kubernetes orchestration clusters • Deliver Active Directory identity, certifi cate, federation, and rights management services • Protect servers, clients, VMs, assets, and users with advanced Windows Server 2019 security features, from Just Enough Administration to shielded VMs and guarded virtualization fabrics • Monitor performance, manage event logs, confi gure advanced auditing, and perform backup/recovery Windows Server 2019 For Experienced Windows Server Users and IT Professionals • Your role: Experienced intermediate to-advanced level Windows Server user or IT professional • Prerequisites: Basic understanding of Windows Server procedures, techniques, and navigation COMPUTERS,Distributed Systems,Client-Server Computing

Cloud and Serverless Computing for Scientists This book offers an introduction to cloud computing and serverless computing for students, researchers and R&D organizations through several practical examples. Rather than focusing exclusively on the computational issues related to cloud computing, the authors focus on addressing the multidisciplinary applications of cloud computing for daily research work in public institutions and private companies in fields such as archaeology, geosciences, computer sciences, medicine and physics. The book also discusses the emergence of serverless computing over the last three years as a means to make computational infrastructures more apparent to users, avoiding the need to concern one's self with the type of server or computing machine needed to perform a computing task. These topics are presented from the perspective of users, researchers and decision-makers, and are approached based on the authors' collective experience on the use and adoption of cloud computing. COMPUTERS,Distributed Systems,Client-Server Computing

Implementing Cisco HyperFlex Solutions Cisco’s HyperFlex HCI solutions enable exceptional datacenter efficiency, agility, and resiliency by tightly integrating core infrastructure (compute, storage, networking, and system management), increasing automation, and simplifying lifecycle management. In this authoritative and comprehensive guide, Cisco experts bring together all the knowledge, detailed configuration options, and real-world case studies you need to successfully deploy Cisco HyperFlex technologies in your environment. This guide’s key features include: Concise, easy-to-understand overviews of underlying concepts and how each HyperFlex technology applies them Detailed reference examples for implementing each key feature, with topologies, configurations, and verifications Thorough Intersight coverage to illuminate operations in cloud-based environments Do’s and don’ts for successful, high-efficiency HyperFlex design Best practice recommendations, guidelines, and caveats for avoiding pitfalls, streamlining deployment, and maximizing value COMPUTERS,Distributed Systems,Client-Server Computing

Programming Amazon Web Services Building on the success of its storefront and fulfillment services, Amazon now allows businesses to "rent" computing power, data storage and bandwidth on its vast network platform. This book demonstrates how developers working with small- to mid-sized companies can take advantage of Amazon Web Services (AWS) such as the Simple Storage Service (S3), Elastic Compute Cloud (EC2), Simple Queue Service (SQS), Flexible Payments Service (FPS), and SimpleDB to build web-scale business applications. With AWS, Amazon offers a new paradigm for IT infrastructure: use what you need, as you need it, and pay as you go. Programming Amazon Web Services explains how you can access Amazon's open APIs to store and run applications, rather than spend precious time and resources building your own. With this book, you'll learn all the technical details you need to: Store and retrieve any amount of data using application servers, unlimited data storage, and bandwidth with the Amazon S3 service Buy computing time using Amazon EC2's interface to requisition machines, load them with an application environment, manage access permissions, and run your image using as many or few systems as needed Use Amazon's web-scale messaging infrastructure to store messages as they travel between computers with Amazon SQS Leverage the Amazon FPS service to structure payment instructions and allow the movement of money between any two entities, humans or computers Create and store multiple data sets, query your data easily, and return the results using Amazon SimpleDB. Scale up or down at a moment's notice, using these services to employ as much time and space as you need Whether you're starting a new online business, need to ramp up existing services, or require an offsite backup for your home, Programming Amazon Web Services gives you the background and the practical knowledge you need to start using AWS. Other books explain how to build web services. This book teaches businesses how to take make use of existing services from an established technology leader. COMPUTERS,Distributed Systems,Cloud Computing

eCommerce in the Cloud Is your eCommerce solution ready for the cloud? This practical guide shows experienced and aspiring web architects alike how to adopt cloud computing incrementally, using public Infrastructure-as-a-Service and Platform-as-a-Service. You will learn how to marshal as much capacity as you need to handle peak holiday or special-event traffic. Written by eCommerce expert Kelly Goetsch, this book helps architects leverage recent technological advances that have made it possible to run an entire enterprise-level eCommerce platform from a cloud. Explore cloud service models: Infrastructure-as-a-Service, Platform-as-a-Service, and Software-as-a-Service Learn about public, hybrid, and private cloud deployment models Understand the impact of omnichannel retailing on platform and deployment architectures Build an auto-scaling solution that can quickly add or subtract hardware in response to real-time traffic Re-apply what you already know about security to the cloud Run a single eCommerce platform from multiple data centers, including several forms of multi-master Build a hybrid solution or deploy your entire platform to the cloud Learn application and deployment architecture for "cloud native" through legacy eCommerce platforms Use Software-as-a-Service for eCommerce, including Content Delivery Networks and Global Site Load Balancing services COMPUTERS,Distributed Systems,Cloud Computing

Mastering Ansible Master the ins and outs of advanced operations with Ansible About This Book Learn how to extend Ansible with custom modules, plugins, and inventory sources Utilize advanced Ansible features to orchestrate rolling updates with little to no service disruptions An up-to-date book that brings to light the newly added features in Ansible 2.x Who This Book Is For This book is for Ansible developers and operators who have an understanding of the core elements and applications but are now looking to enhance their skills in applying automation using Ansible. What You Will Learn Gain an in-depth understanding of how Ansible works under the covers Fully automate the Ansible playbook executions with encrypted data Access and manipulate variable data within playbooks Use Blocks to construct failure recovery or cleanup Explore the Playbook debugger and Ansible Console Troubleshoot unexpected behavior effectively Work with cloud infrastructure providers and container systems Develop custom modules, plugins, and dynamic inventory sources In Detail This book provides you with the knowledge you need to understand how Ansible 2.1 works at a fundamental level and leverage its advanced capabilities. You'll learn how to encrypt Ansible content at rest and decrypt data at runtime. You will master the advanced features and capabilities required to tackle the complex automation challenges of today and beyond. You will gain detailed knowledge of Ansible workflows, explore use cases for advanced features, craft well thought out orchestrations, troubleshoot unexpected behaviour, and extend Ansible through customizations. Finally, you will discover the methods used to examine and debug Ansible operations, helping you to understand and resolve issues. By the end of the book, the readers will be able to unlock the true power of the Ansible automation engine and will tackle complex real world actions with ease. Style and approach This clear, practical guide illustrates the advanced functionalities of Ansible, its system architecture, and design aspects that will help you to master Ansible with ease. COMPUTERS,Distributed Systems,Cloud Computing

Mastering OpenStack Discover your complete guide to designing, deploying, and managing OpenStack-based clouds in mid-to-large IT infrastructures with best practices, expert understanding, and more About This Book Design and deploy an OpenStack-based cloud in your mid-to-large IT infrastructure using automation tools and best practices Keep yourself up-to-date with valuable insights into OpenStack components and new services in the latest OpenStack release Discover how the new features in the latest OpenStack release can help your enterprise and infrastructure Who This Book Is For This book is for system administrators, cloud engineers, and system architects who would like to deploy an OpenStack-based cloud in a mid-to-large IT infrastructure. This book requires a moderate level of system administration and familiarity with cloud concepts. What You Will Learn Explore the main architecture design of OpenStack components and core-by-core services, and how they work together Design different high availability scenarios and plan for a no-single-point-of-failure environment Set up a multinode environment in production using orchestration tools Boost OpenStack's performance with advanced configuration Delve into various hypervisors and container technology supported by OpenStack Get familiar with deployment methods and discover use cases in a real production environment Adopt the DevOps style of automation while deploying and operating in an OpenStack environment Monitor the cloud infrastructure and make decisions on maintenance and performance improvement In Detail In this second edition, you will get to grips with the latest features of OpenStack. Starting with an overview of the OpenStack architecture, you'll see how to adopt the DevOps style of automation while deploying and operating in an OpenStack environment. We'll show you how to create your own OpenStack private cloud. Then you'll learn about various hypervisors and container technology supported by OpenStack. You'll get an understanding about the segregation of compute nodes based on reliability and availability needs. We'll cover various storage types in OpenStack and advanced networking aspects such as SDN and NFV. Next, you'll understand the OpenStack infrastructure from a cloud user point of view. Moving on, you'll develop troubleshooting skills, and get a comprehensive understanding of services such as high availability and failover in OpenStack. Finally, you will gain experience of running a centralized logging server and monitoring OpenStack services. The book will show you how to carry out performance tuning based on OpenStack service logs. You will be able to master OpenStack benchmarking and performance tuning. By the end of the book, you'll be ready to take steps to deploy and manage an OpenStack cloud with the latest open source technologies. Style and approach This book will help you understand the flexibility of OpenStack by showcasing integration of several out-of-the-box solutions in order to build a large-scale cloud environment.. It will also cover detailed discussions on the various design and deployment strategies for implementing a fault-tolerant and highly available cloud infrastructure. COMPUTERS,Distributed Systems,Cloud Computing

AWS Administration Cookbook Build, automate, and manage your AWS-based cloud environments About This Book Install, configure, and administer computing, storage, and networking in the AWS cloud Automate your infrastructure and control every aspect of it through infrastructure as code Work through exciting recipes to administer your AWS cloud Who This Book Is For If you are an administrator, DevOps engineer, or an IT professional who is moving to an AWS-based cloud environment, then this book is for you. It assumes familiarity with cloud computing platforms, and that you have some understanding of virtualization, networking, and other administration-related tasks. What You Will Learn Discover the best practices to achieve an automated repeatable infrastructure in AWS Bring down your IT costs by managing AWS successfully and deliver high availability, fault tolerance, and scalability Make any website faster with static and dynamic caching Create monitoring and alerting dashboards using CloudWatch Migrate a database to AWS Set up consolidated billing to achieve simple and effective cost management with accounts Host a domain and find out how you can automate health checks In Detail Amazon Web Services (AWS) is a bundled remote computing service that provides cloud computing infrastructure over the Internet with storage, bandwidth, and customized support for application programming interfaces (API). Implementing these services to efficiently administer your cloud environments is a core task. This book will help you build and administer your cloud environment with AWS. We'll begin with the AWS fundamentals, and you'll build the foundation for the recipes you'll work on throughout the book. Next, you will find out how to manage multiple accounts and set up consolidated billing. You will then learn to set up reliable and fast hosting for static websites, share data between running instances, and back up your data for compliance. Moving on, you will find out how to use the compute service to enable consistent and fast instance provisioning, and will see how to provision storage volumes and autoscale an application server. Next, you'll discover how to effectively use the networking and database service of AWS. You will also learn about the different management tools of AWS along with securing your AWS cloud. Finally, you will learn to estimate the costs for your cloud. By the end of the book, you will be able to easily administer your AWS cloud. Style and approach This practical guide is packed with clear, practical, instruction-based recipes that will enable you to use and implement the latest features of AWS. COMPUTERS,Distributed Systems,Cloud Computing

AWS Certified Developer - Associate Guide An effective guide to becoming an AWS Certified Developer About This Book This fast-paced guide will help you clear the exam with confidence Learn to design, develop, and deploy cloud-based solutions using AWS Enhance your AWS skills with practice questions and mock tests Who This Book Is For This book is for IT professionals and developers looking to clear the AWS Certified Developer – Associate 2017 exam. Developers looking to develop and manage their applications on the AWS platform will also find this book useful. No prior AWS experience is needed. What You Will Learn Create and manage users, groups, and permissions using AWS Identity and Access Management services Create a secured Virtual Private Cloud (VPC) with Public and Private Subnets, Network Access Control, and Security groups Get started with Elastic Compute Cloud (EC2), launching your first EC2 instance, and working with it Handle application traffic with Elastic Load Balancing (ELB) and monitor AWS resources with CloudWatch Work with AWS storage services such as Simple Storage Service (S3), Glacier, and CloudFront Get acquainted with AWS DynamoDB – a NoSQL database service Coordinate work across distributed application components using Simple Workflow Service (SWF) In Detail AWS Certified Developer - Associate Guide starts with a quick introduction to AWS and the prerequisites to get you started. Then, this book gives you a fair understanding of core AWS services and basic architecture. Next, this book will describe about getting familiar with Identity and Access Management (IAM) along with Virtual private cloud (VPC). Moving ahead you will learn about Elastic Compute cloud (EC2) and handling application traffic with Elastic Load Balancing (ELB). Going ahead you we will talk about Monitoring with CloudWatch, Simple storage service (S3) and Glacier and CloudFront along with other AWS storage options. Next we will take you through AWS DynamoDB – A NoSQL Database Service, Amazon Simple Queue Service (SQS) and CloudFormation Overview. Finally, this book covers understanding Elastic Beanstalk and overview of AWS lambda. At the end of this book, we will cover enough topics, tips and tricks along with mock tests for you to be able to pass the AWS Certified Developer - Associate exam and develop as well as manage your applications on the AWS platform. Style and approach This step-by-step guide includes exercises and mock tests to clear the AWS certification exam and become a successful AWS developer. COMPUTERS,Distributed Systems,Cloud Computing

Azure for Architects Your one stop guide to making the most out of Azure Cloud About This Book Get familiar with the different design patterns available in Microsoft Azure Develop Azure cloud architecture and a pipeline management system Get to know the security best practices for your Azure deployment Who This Book Is For If you are Cloud Architects, DevOps Engineers, or developers who want to learn key architectural aspects of the Azure Cloud platform, then this book is for you. Prior basic knowledge of the Azure Cloud platform is good to have. What You Will Learn Familiarize yourself with the components of the Azure Cloud platform Understand the cloud design patterns Use enterprise security guidelines for your Azure deployment Design and implement Serverless solutions See Cloud architecture and the deployment pipeline Understand cost management for Azure solutions In Detail Over the years, Azure cloud services has grown quickly, and the number of organizations adopting Azure for their cloud services is also gradually increasing. Leading industry giants are finding that Azure fulfills their extensive cloud requirements. This book will guide you through all the important and tough decision-making aspects involved in architecturing a Azure public cloud for your organization. The book starts with an extensive introduction to all the categories of designs available with Azure. These design patterns focus on different aspects of cloud such as high availability, data management, and so on. Gradually, we move on to various aspects such as building your cloud structure and architecture. It will also include a brief description about different types of services provided by Azure, such as Azure functions and Azure Analytics, which can prove beneficial for an organization. This book will cover each and every aspect and function required to develop a Azure cloud based on your organizational requirements. By the end of this book, you will be in a position to develop a full-fledged Azure cloud. Style and approach This hands-on guide to the Azure Cloud platform covers different architectural concepts and implementations necessary for any enterprise scale deployment. COMPUTERS,Distributed Systems,Cloud Computing

Mastering AWS Security In depth informative guide to implement and use AWS security services effectively. About This Book Learn to secure your network, infrastructure, data and applications in AWS cloud Log, monitor and audit your AWS resources for continuous security and continuous compliance in AWS cloud Use AWS managed security services to automate security. Focus on increasing your business rather than being diverged onto security risks and issues with AWS security. Delve deep into various aspects such as the security model, compliance, access management and much more to build and maintain a secure environment. Who This Book Is For This book is for all IT professionals, system administrators and security analysts, solution architects and Chief Information Security Officers who are responsible for securing workloads in AWS for their organizations. It is helpful for all Solutions Architects who want to design and implement secure architecture on AWS by the following security by design principle. This book is helpful for personnel in Auditors and Project Management role to understand how they can audit AWS workloads and how they can manage security in AWS respectively. If you are learning AWS or championing AWS adoption in your organization, you should read this book to build security in all your workloads. You will benefit from knowing about security footprint of all major AWS services for multiple domains, use cases, and scenarios. What You Will Learn Learn about AWS Identity Management and Access control Gain knowledge to create and secure your private network in AWS Understand and secure your infrastructure in AWS Understand monitoring, logging and auditing in AWS Ensure Data Security in AWS Learn to secure your applications in AWS Explore AWS Security best practices In Detail Mastering AWS Security starts with a deep dive into the fundamentals of the shared security responsibility model. This book tells you how you can enable continuous security, continuous auditing, and continuous compliance by automating your security in AWS with the tools, services, and features it provides. Moving on, you will learn about access control in AWS for all resources. You will also learn about the security of your network, servers, data and applications in the AWS cloud using native AWS security services. By the end of this book, you will understand the complete AWS Security landscape, covering all aspects of end - to -end software and hardware security along with logging, auditing, and compliance of your entire IT environment in the AWS cloud. Lastly, the book will wrap up with AWS best practices for security. Style and approach The book will take a practical approach delving into different aspects of AWS security to help you become a master of it. It will focus on using native AWS security features and managed AWS services to help you achieve continuous security and continuous compliance. COMPUTERS,Distributed Systems,Cloud Computing

Mastering Proxmox Discover real world scenarios for Proxmox troubleshooting and become an expert cloud builder About This Book Formulate Proxmox-based solutions and set up virtual machines of any size while gaining expertise even on the most complex multi-cluster setups Master the skills needed to analyze, monitor, and troubleshoot real-world virtual environments This is the most up-to-date title on mastering Proxmox, with examples based on the new Linux Kernel 4.10.15 and Debian Stretch (9.x) Who This Book Is For This book is for Linux and system administrators and professionals working in IT teams who would like to design and implement an enterprise-quality virtualized environment using Proxmox. Some knowledge of networking and virtualization concepts is assumed. What You Will Learn Install basic Proxmox VE nodes and get to know the Proxmox GUI Get to know Proxmox's internal structure and mechanics Create and manage KVM or LXC-based virtual machines Understand advanced virtual networks Configure high availability Proxmox nodes Integrate Ceph big data storage with the Proxmox hypervisor Plan a large virtual environment for cloud-based services Discover real-world scenarios for Proxmox troubleshooting In Detail Proxmox is an open source server virtualization solution that has enterprise-class features for managing virtual machines, for storage, and to virtualize both Linux and Windows application workloads. You'll begin with a refresher on the advanced installation features and the Proxmox GUI to familiarize yourself with the Proxmox VE hypervisor. Then, you'll move on to explore Proxmox under the hood, focusing on storage systems, such as Ceph, used with Proxmox. Moving on, you'll learn to manage KVM virtual machines, deploy Linux containers fast, and see how networking is handled in Proxmox. You'll also learn how to protect a cluster or a VM with a firewall and explore the new high availability features introduced in Proxmox VE 5.0. Next, you'll dive deeper into the backup/restore strategy and see how to properly update and upgrade a Proxmox node. Later, you'll learn how to monitor a Proxmox cluster and all of its components using Zabbix. Finally, you'll discover how to recover Promox from disaster strikes through some real-world examples. By the end of the book, you'll be an expert at making Proxmox work in production environments with minimal downtime. Style and approach This book walks you through every aspect of virtualization using Proxmox using a practical, scenario-based approach that features best practices and all the weaponry you need to succeed when building virtual environments with Proxmox 5.0. COMPUTERS,Distributed Systems,Cloud Computing

The Cloud Adoption Playbook The essential roadmaps for enterprise cloud adoption As cloud technologies continue to challenge the fundamental understanding of how businesses work, smart companies are moving quickly to adapt to a changing set of rules. Adopting the cloud requires a clear roadmap backed by use cases, grounded in practical real-world experience, to show the routes to successful adoption. The Cloud Adoption Playbook helps business and technology leaders in enterprise organizations sort through the options and make the best choices for accelerating cloud adoption and digital transformation. Written by a team of IBM technical executives with a wealth of real-world client experience, this book cuts through the hype, answers your questions, and helps you tailor your cloud adoption and digital transformation journey to the needs of your organization. This book will help you: Discover how the cloud can fulfill major business needs Adopt a standardized Cloud Adoption Framework and understand the key dimensions of cloud adoption and digital transformation Learn how cloud adoption impacts culture, architecture, security, and more Understand the roles of governance, methodology, and how the cloud impacts key players in your organization. Providing a collection of winning plays, championship advice, and real-world examples of successful adoption, this playbook is your ultimate resource for making the cloud work. There has never been a better time to adopt the cloud. Cloud solutions are more numerous and accessible than ever before, and evolving technology is making the cloud more reliable, more secure, and more necessary than ever before. Don’t let your organization be left behind! The Cloud Adoption Playbook gives you the essential guidance you need to make the smart choices that reduce your organizational risk and accelerate your cloud adoption and digital transformation. COMPUTERS,Distributed Systems,Cloud Computing

Ceph Cookbook Over 100 effective recipes to help you design, implement, and troubleshoot manage the software-defined and massively scalable Ceph storage system. About This Book Implement a Ceph cluster successfully and learn to manage it. Recipe based approach in learning the most efficient software defined storage system Implement best practices on improving efficiency and security of your storage cluster Learn to troubleshoot common issues experienced in a Ceph cluster Who This Book Is For This book is targeted at storage and cloud engineers, system administrators, or anyone who is interested in building software defined storage, to power your cloud or virtual infrastructure. If you have basic knowledge of GNU/Linux and storage systems, with no experience of software defined storage solutions and Ceph, but eager to learn then this book is for you What You Will Learn Understand, install, configure, and manage the Ceph storage system Get to grips with performance tuning and benchmarking, and learn practical tips to help run Ceph in production Integrate Ceph with OpenStack Cinder, Glance, and Nova components Deep dive into Ceph object storage, including S3, Swift, and Keystone integration Configure a disaster recovery solution with a Ceph Multi-Site V2 gateway setup and RADOS Block Device mirroring Gain hands-on experience with Ceph Metrics and VSM for cluster monitoring Familiarize yourself with Ceph operations such as maintenance, monitoring, and troubleshooting Understand advanced topics including erasure-coding, CRUSH map, cache pool, and general Ceph cluster maintenance In Detail Ceph is a unified distributed storage system designed for reliability and scalability. This technology has been transforming the software-defined storage industry and is evolving rapidly as a leader with its wide range of support for popular cloud platforms such as OpenStack, and CloudStack, and also for virtualized platforms. Ceph is backed by Red Hat and has been developed by community of developers which has gained immense traction in recent years. This book will guide you right from the basics of Ceph , such as creating blocks, object storage, and filesystem access, to advanced concepts such as cloud integration solutions. The book will also cover practical and easy to implement recipes on CephFS, RGW, and RBD with respect to the major stable release of Ceph Jewel. Towards the end of the book, recipes based on troubleshooting and best practices will help you get to grips with managing Ceph storage in a production environment. By the end of this book, you will have practical, hands-on experience of using Ceph efficiently for your storage requirements. Style and approach This step-by-step guide is filled with practical tutorials, making complex scenarios easy to understand. COMPUTERS,Distributed Systems,Cloud Computing

Containers in OpenStack A practical book which will help the readers understand how the container ecosystem and OpenStack work together. About This Book Gets you acquainted with containerization in private cloud Learn to effectively manage and secure your containers in OpenStack Practical use cases on container deployment and management using OpenStack components Who This Book Is For This book is targeted towards cloud engineers, system administrators, or anyone from the production team who works on OpenStack cloud. This book act as an end to end guide for anyone who wants to start using the concept of containerization on private cloud. Some basic knowledge of Docker and Kubernetes will help. What You Will Learn Understand the role of containers in the OpenStack ecosystem Learn about containers and different types of container runtimes tools. Understand containerization in OpenStack with respect to the deployment framework, platform services, application deployment, and security Get skilled in using OpenStack to run your applications inside containers Explore the best practices of using containers in OpenStack. In Detail Containers are one of the most talked about technologies of recent times. They have become increasingly popular as they are changing the way we develop, deploy, and run software applications. OpenStack gets tremendous traction as it is used by many organizations across the globe and as containers gain in popularity and become complex, it's necessary for OpenStack to provide various infrastructure resources for containers, such as compute, network, and storage. Containers in OpenStack answers the question, how can OpenStack keep ahead of the increasing challenges of container technology? You will start by getting familiar with container and OpenStack basics, so that you understand how the container ecosystem and OpenStack work together. To understand networking, managing application services and deployment tools, the book has dedicated chapters for different OpenStack projects: Magnum, Zun, Kuryr, Murano, and Kolla. Towards the end, you will be introduced to some best practices to secure your containers and COE on OpenStack, with an overview of using each OpenStack projects for different use cases. Style and approach An end to end guide for anyone who wants to start using the concept of containerization on private cloud. COMPUTERS,Distributed Systems,Cloud Computing

Internet of Things for Architects Learn to design, implement and secure your IoT infrastructure About This Book Build a complete IoT system that is the best fit for your organization Learn about different concepts, technologies, and tradeoffs in the IoT architectural stack Understand the theory, concepts, and implementation of each element that comprises IoT design—from sensors to the cloud Implement best practices to ensure the reliability, scalability, robust communication systems, security, and data analysis in your IoT infrastructure Who This Book Is For This book is for architects, system designers, technologists, and technology managers who want to understand the IoT ecosphere, various technologies, and tradeoffs and develop a 50,000-foot view of IoT architecture. What You Will Learn Understand the role and scope of architecting a successful IoT deployment, from sensors to the cloud Scan the landscape of IoT technologies that span everything from sensors to the cloud and everything in between See the trade-offs in choices of protocols and communications in IoT deployments Build a repertoire of skills and the vernacular necessary to work in the IoT space Broaden your skills in multiple engineering domains necessary for the IoT architect In Detail The Internet of Things (IoT) is the fastest growing technology market. Industries are embracing IoT technologies to improve operational expenses, product life, and people's well-being. An architectural guide is necessary if you want to traverse the spectrum of technologies needed to build a successful IoT system, whether that's a single device or millions of devices. This book encompasses the entire spectrum of IoT solutions, from sensors to the cloud. We start by examining modern sensor systems and focus on their power and functionality. After that, we dive deep into communication theory, paying close attention to near-range PAN, including the new Bluetooth® 5.0 specification and mesh networks. Then, we explore IP-based communication in LAN and WAN, including 802.11ah, 5G LTE cellular, SigFox, and LoRaWAN. Next, we cover edge routing and gateways and their role in fog computing, as well as the messaging protocols of MQTT and CoAP. With the data now in internet form, you'll get an understanding of cloud and fog architectures, including the OpenFog standards. We wrap up the analytics portion of the book with the application of statistical analysis, complex event processing, and deep learning models. Finally, we conclude by providing a holistic view of the IoT security stack and the anatomical details of IoT exploits while countering them with software defined perimeters and blockchains. Style and approach This hands-on guide combines theory and application to the Internet of Things. This book covers the entire architectural stack of components and engineering domains from sensors to power analysis, communication systems, information theory, networking and routing, data security, protocols, software stacks, cloud mechanics, and data analytics with deep learning. COMPUTERS,Distributed Systems,Cloud Computing

OpenStack Cloud Computing Cookbook The Fourth Edition of the industry-acclaimed OpenStack Cloud Computing Cookbook, from four recognized experts, updated to the latest OpenStack build including Cinder, Nova, and Neutron. About This Book Over 100 recipes created by a team of OpenStack experts Updated to work with the latest OpenStack builds, with recipes covering the installation and use of OpenStack with Ansible It covers topics such as Keystone, Glance, Neutron, Nova, Cinder, and more, plus recipes for OpenStack storage, networking, and orchestrating workloads Test drive OpenStack using the accompanying Vagrant environment Who This Book Is For This book is written for cloud system engineers, system administrators, and technical architects who are moving from a virtualized environment to cloud environments. This book assumes that you are familiar with cloud computing platforms, and have knowledge of virtualization, networking, and managing Linux environments. What You Will Learn Understand, install, configure, and manage a complete OpenStack Cloud platform using OpenStack-Ansible Configure networks, routers, load balancers, and more with Neutron Use Keystone to setup domains, roles, groups and user access Learn how to use Swift and setup container access control lists Gain hands-on experience and familiarity with Horizon, the OpenStack Dashboard user interface Automate complete solutions with our recipes on Heat, the OpenStack Orchestration service as well as using Ansible to orchestrate application workloads Follow practical advice and examples to run OpenStack in production In Detail This is the fourth edition of the industry-acclaimed OpenStack Cloud Computing Cookbook, created by four recognized OpenStack experts. It has now been updated to work with the latest OpenStack builds, using tools and processes based on their collective and vast OpenStack experience. OpenStack Open Source Cloud software is one of the most used cloud infrastructures to support a wide variety of use cases, from software development to big data analysis. It is developed by a thriving community of individual developers from around the globe and backed by most of the leading players in the cloud space today. We make it simple to implement, massively scalable, and able to store a large pool of data and networking resources. OpenStack has a strong ecosystem that helps you provision your cloud storage needs. Add OpenStack's enterprise features to reduce the cost of your business. This book will begin by showing you the steps to build up an OpenStack private cloud environment using Ansible. You'll then discover the uses of cloud services such as the identity service, image service, and compute service. You'll dive into Neutron, the OpenStack Networking service, and get your hands dirty with configuring networks, routers, load balancers, and more. You'll then gather more expert knowledge on OpenStack cloud computing by managing your cloud's security and migration. After that, we delve into OpenStack Object storage and you'll see how to manage servers and work with objects, cluster, and storage functionalities. Finally, you will learn about OpenStack dashboard, Ansible, Keystone, and other interesting topics. Style and approach Clear, step-by-step instructions coupled with practical and applicable recipes that will enable you to use and implement the latest features of OpenStack. The authors provide all the context you need around each recipe so that you can make it part of your own OpenStack solutions. COMPUTERS,Distributed Systems,Cloud Computing

Learning AWS Discover techniques and tools for building serverless applications with AWS About This Book Get well-versed with building and deploying serverless APIs with microservices Learn to build distributed applications and microservices with AWS Step Functions A step-by-step guide that will get you up and running with building and managing applications on the AWS platform Who This Book Is For If you are an I.T. professional or a system architect who wants to improve infrastructure using AWS, then this book is for you. It is also for programmers who are new to AWS and want to build highly efficient, scalable applications. What You Will Learn Set up your AWS account and get started with the basic concepts of AWS Learn about AWS terminology and identity access management Acquaint yourself with important elements of the cloud with features such as computing, ELB, and VPC Back up your database and ensure high availability by having an understanding of database-related services in the AWS cloud Integrate AWS services with your application to meet and exceed non-functional requirements Create and automate infrastructure to design cost-effective, highly available applications In Detail Amazon Web Services (AWS) is the most popular and widely-used cloud platform. Administering and deploying application on AWS makes the applications resilient and robust. The main focus of the book is to cover the basic concepts of cloud-based development followed by running solutions in AWS Cloud, which will help the solutions run at scale. This book not only guides you through the trade-offs and ideas behind efficient cloud applications, but is a comprehensive guide to getting the most out of AWS. In the first section, you will begin by looking at the key concepts of AWS, setting up your AWS account, and operating it. This guide also covers cloud service models, which will help you build highly scalable and secure applications on the AWS platform. We will then dive deep into concepts of cloud computing with S3 storage, RDS and EC2. Next, this book will walk you through VPC, building realtime serverless environments, and deploying serverless APIs with microservices. Finally, this book will teach you to monitor your applications, and automate your infrastructure and deploy with CloudFormation. By the end of this book, you will be well-versed with the various services that AWS provides and will be able to leverage AWS infrastructure to accelerate the development process. Style and approach Learn to write, run, and deploy applications in the AWS cloud Make the most of AWS to build scalable and cost-efficient systems A practical guide to developing serverless services and make the applications run faster COMPUTERS,Distributed Systems,Cloud Computing

Hybrid Cloud for Architects Build your own hybrid cloud strategy with this comprehensive learning guide. About This Book Build a hybrid cloud strategy for your organization with AWS and OpenStack Leverage Hybrid Cloud to design a complex deployment pipeline Learn to implement security and monitoring best practices with real-world examples Who This Book Is For This book is targeted at cloud architects, cloud solution providers, DevOps engineers, or any working stakeholder who wants to learn about the hybrid cloud architecture. A basic understanding of public and private cloud is desirable. What You Will Learn Learn the demographics and definitions of Hybrid Cloud Understand the different architecture and design of Hybrid Cloud Explore multi-cloud strategy and use it with your hybrid cloud Implement a Hybrid Cloud using CMP / Common API's Implement a Hybrid Cloud using Containers Overcome various challenges and issues while working with your Hybrid Cloud Understand how to monitor your Hybrid Cloud Discover the security implications in the Hybrid Cloud In Detail Hybrid cloud is currently the buzz word in the cloud world. Organizations are planning to adopt hybrid cloud strategy due to its advantages such as untested workloads, cloud-bursting, cloud service brokering and so on. This book will help you understand the dynamics, design principles, and deployment strategies of a Hybrid Cloud. You will start by understanding the concepts of hybrid cloud and the problems it solves as compared to a stand-alone public and private cloud. You will be delving into the different architecture and design of hybrid cloud. The book will then cover advanced concepts such as building a deployment pipeline, containerization strategy, and data storage mechanism. Next up, you will be able to deploy an external CMP to run a Hybrid cloud and integrate it with your OpenStack and AWS environments. You will also understand the strategy for designing a Hybrid Cloud using containerization and work with pre-built solutions like vCloud Air, VMware for AWS, and Azure Stack. Finally, the book will cover security and monitoring related best practices that will help you secure your cloud infrastructure. By the end of the book, you will be in a position to build a hybrid cloud strategy for your organization. Style and approach This book follows a step-by-step, practical approach to deploying and implementing hybrid cloud architectures using AWS and OpenStack. COMPUTERS,Distributed Systems,Cloud Computing

AWS Delve deep into various security aspects of AWS to build and maintain a secured environment About This Book Learn to secure your network, infrastructure, data, and applications in AWS cloud Use AWS managed security services to automate security Dive deep into various aspects such as the security model, compliance, access management and much more to build and maintain a secured environment Explore Cloud Adoption Framework (CAF) and its components Embedded with assessments that will help you revise the concepts you have learned in this book Who This Book Is For This book is for all IT professionals, system administrators, security analysts, solution architects, and chief information security officers who are responsible for securing workloads in AWS for their organizations. What You Will Learn Get familiar with VPC components, features, and benefits Learn to create and secure your private network in AWS Explore encryption and decryption fundamentals Understand monitoring, logging, and auditing in AWS Ensure data security in AWS Secure your web and mobile applications in AWS Learn security best practices for IAM, VPC, shared security responsibility model, and so on In Detail With organizations moving their workloads, applications, and infrastructure to the cloud at an unprecedented pace, security of all these resources has been a paradigm shift for all those who are responsible for security; experts, novices, and apprentices alike. This book focuses on using native AWS security features and managed AWS services to help you achieve continuous security. Starting with an introduction to Virtual Private Cloud (VPC) to secure your AWS VPC, you will quickly explore various components that make up VPC such as subnets, security groups, various gateways, and many more. You will also learn to protect data in the AWS platform for various AWS services by encrypting and decrypting data in AWS. You will also learn to secure web and mobile applications in AWS cloud. This book is ideal for all IT professionals, system administrators, security analysts, solution architects, and chief information security officers who are responsible for securing workloads in AWS for their organizations. This book is embedded with useful assessments that will help you revise the concepts you have learned in this book. Style and approach This book follows a practical approach delving into different aspects of AWS security. It focuses on using native AWS security features and managed AWS services to help you achieve continuous security. Note: This book is a blend of text and quizzes, all packaged up keeping your journey in mind. It includes content from the following Packt product: Mastering AWS Security by Albert Anthony COMPUTERS,Distributed Systems,Cloud Computing

Practical DevOps Understand the benefits of DevOps and continuous delivery and see how they support the agile software development process About This Book Learn how DevOps can accelerate your entire software development life cycle Improve your organization's performance to ensure the smooth production of software and services Get hands-on experience in using efficient DevOps tools to better effect Who This Book Is For If you're a developer or system administrator looking to take on larger responsibilities and understand how the infrastructure that builds today's enterprises works, this is the book for you. This book will also help you greatly if you're an operations worker who would like to better support developers. You do not need any previous knowledge of DevOps to understand the concepts in this book. What You Will Learn Understand how all deployment systems fit together to form a larger system Set up and familiarize yourself with all the tools you need to be efficient with DevOps Design an application suitable for continuous deployment systems with DevOps in mind Store and manage your code effectively using Git, Gerrit, Gitlab, and more Configure a job to build a sample CRUD application Test your code using automated regression testing with Jenkins Selenium Deploy your code using tools such as Puppet, Ansible, Palletops, Chef, and Vagrant In Detail DevOps is a practical field that focuses on delivering business value as efficiently as possible. DevOps encompasses all code workflows from testing environments to production environments. It stresses cooperation between different roles, and how they can work together more closely, as the roots of the word imply—Development and Operations. Practical DevOps begins with a quick refresher on DevOps and continuous delivery and quickly moves on to show you how DevOps affects software architectures. You'll create a sample enterprise Java application that you''ll continue to work with through the remaining chapters. Following this, you will explore various code storage and build server options. You will then learn how to test your code with a few tools and deploy your test successfully. In addition to this, you will also see how to monitor code for any anomalies and make sure that it runs as expected. Finally, you will discover how to handle logs and keep track of the issues that affect different processes. By the end of the book, you will be familiar with all the tools needed to deploy, integrate, and deliver efficiently with DevOps. Style and approach This book is primarily a technical guide to DevOps with practical examples suitable for people who like to learn by implementing concrete working code. COMPUTERS,Distributed Systems,Cloud Computing

OpenStack for Architects Implement successful private clouds with OpenStack About This Book Gain hands-on experience in designing a private cloud for all infrastructures Create a robust virtual environment for your organization Design, implement and deploy an OpenStack-based cloud based on the Queens release Who This Book Is For OpenStack for Architects is for Cloud architects who are responsible to design and implement a private cloud with OpenStack. System engineers and enterprise architects will also find this book useful. Basic understanding of core OpenStack services, as well as some working experience of concepts, is recommended. What You Will Learn Learn the overall structure of an OpenStack deployment Craft an OpenStack deployment process which fits within your organization Apply Agile Development methodologies to engineer and operate OpenStack clouds Build a product roadmap for Infrastructure as a Service based on OpenStack Make use of containers to increase the manageability and resiliency of applications running in and on OpenStack. Use enterprise security guidelines for your OpenStack deployment In Detail Over the past six years, hundreds of organizations have successfully implemented Infrastructure as a Service (IaaS) platforms based on OpenStack. The huge amount of investment from these organizations, including industry giants such as IBM and HP, as well as open source leaders, such as Red Hat, Canonical, and SUSE, has led analysts to label OpenStack as the most important open source technology since the Linux operating system. Due to its ambitious scope, OpenStack is a complex and fast-evolving open source project that requires a diverse skill set to design and implement it. OpenStack for Architects leads you through the major decision points that you'll face while architecting an OpenStack private cloud for your organization. This book will address the recent changes made in the latest OpenStack release i.e Queens, and will also deal with advanced concepts such as containerization, NVF, and security. At each point, the authors offer you advice based on the experience they've gained from designing and leading successful OpenStack projects in a wide range of industries. Each chapter also includes lab material that gives you a chance to install and configure the technologies used to build production-quality OpenStack clouds. Most importantly, the book focuses on ensuring that your OpenStack project meets the needs of your organization, which will guarantee a successful rollout. Style and approach This is practical, hands-on guide to implementing OpenStack clouds, where each topic is illustrated with real-world examples and then the technical points are proven in the lab. Conceptual chapters are written in discussion style to convey important concepts quickly and present decision points for choosing options. COMPUTERS,Distributed Systems,Cloud Computing

Google Cloud Platform for Architects Get acquainted with GCP and manage robust, highly available, and dynamic solutions to drive business objective About This Book Identify the strengths, weaknesses and ideal use-cases for individual services offered on the Google Cloud Platform Make intelligent choices about which cloud technology works best for your use-case Leverage Google Cloud Platform to analyze and optimize technical and business processes Who This Book Is For If you are a Cloud architect who is responsible to design and manage robust cloud solutions with Google Cloud Platform, then this book is for you. System engineers and Enterprise architects will also find this book useful. A basic understanding of distributed applications would be helpful, although not strictly necessary. Some working experience on other public cloud platforms would help too. What You Will Learn Set up GCP account and utilize GCP services using the cloud shell, web console, and client APIs Harness the power of App Engine, Compute Engine, Containers on the Kubernetes Engine, and Cloud Functions Pick the right managed service for your data needs, choosing intelligently between Datastore, BigTable, and BigQuery Migrate existing Hadoop, Spark, and Pig workloads with minimal disruption to your existing data infrastructure, by using Dataproc intelligently Derive insights about the health, performance, and availability of cloud-powered applications with the help of monitoring, logging, and diagnostic tools in Stackdriver In Detail Using a public cloud platform was considered risky a decade ago, and unconventional even just a few years ago. Today, however, use of the public cloud is completely mainstream - the norm, rather than the exception. Several leading technology firms, including Google, have built sophisticated cloud platforms, and are locked in a fierce competition for market share. The main goal of this book is to enable you to get the best out of the GCP, and to use it with confidence and competence. You will learn why cloud architectures take the forms that they do, and this will help you become a skilled high-level cloud architect. You will also learn how individual cloud services are configured and used, so that you are never intimidated at having to build it yourself. You will also learn the right way and the right situation in which to use the important GCP services. By the end of this book, you will be able to make the most out of Google Cloud Platform design. Style and approach A clear, concise, and straightforward book which will enable to develop and manage optimum solutions for your infrastructure COMPUTERS,Distributed Systems,Cloud Computing

Learning OpenStack Networking Discover the basics of virtual networking in OpenStack to implement various cloud network architectures Key Features Learn the difference between Open vSwitch and Linux bridge switching technologies Connect virtual machine instances to virtual networks, subnets, and ports Implement virtual load balancers, firewalls, and routers in your network Book Description OpenStack Networking is a pluggable, scalable, and API-driven system to manage physical and virtual networking resources in an OpenStack-based cloud. Like other core OpenStack components, OpenStack Networking can be used by administrators and users to increase the value and maximize the use of existing datacenter resources. This third edition of Learning OpenStack Networking walks you through the installation of OpenStack and provides you with a foundation that can be used to build a scalable and production-ready OpenStack cloud. In the initial chapters, you will review the physical network requirements and architectures necessary for an OpenStack environment that provide core cloud functionality. Then, you'll move through the installation of the new release of OpenStack using packages from the Ubuntu repository. An overview of Neutron networking foundational concepts, including networks, subnets, and ports will segue into advanced topics such as security groups, distributed virtual routers, virtual load balancers, and VLAN tagging within instances. By the end of this book, you will have built a network infrastructure for your cloud using OpenStack Neutron. What you will learn Get familiar with Neutron constructs, including agents and plugins Build foundational Neutron resources to provide connectivity to instances Work with legacy Neutron routers and troubleshoot traffic through them Explore high-availability routing capabilities utilizing Virtual Router Redundancy Protocol (VRRP) Create and manage load balancers and associated components Manage security groups as a method of securing traffic to and from instances Who this book is for If you are an OpenStack-based cloud operator and administrator who is new to Neutron networking and wants to build your very own OpenStack cloud, then this book is for you.Prior networking experience and a physical server and network infrastructure is recommended to follow along with concepts demonstrated in the book. COMPUTERS,Distributed Systems,Cloud Computing

Cloud Native Architectures Learn and understand the need to architect cloud applications and migrate your business to cloud efficiently Key Features Understand the core design elements required to build scalable systems Plan resources and technology stacks effectively for high security and fault tolerance Explore core architectural principles using real-world examples Book Description Cloud computing has proven to be the most revolutionary IT development since virtualization. Cloud native architectures give you the benefit of more flexibility over legacy systems. To harness this, businesses need to refresh their development models and architectures when they find they don't port to the cloud. Cloud Native Architectures demonstrates three essential components of deploying modern cloud native architectures: organizational transformation, deployment modernization, and cloud native architecture patterns. This book starts with a quick introduction to cloud native architectures that are used as a base to define and explain what cloud native architecture is and is not. You will learn what a cloud adoption framework looks like and develop cloud native architectures using microservices and serverless computing as design principles. You'll then explore the major pillars of cloud native design including scalability, cost optimization, security, and ways to achieve operational excellence. In the concluding chapters, you will also learn about various public cloud architectures ranging from AWS and Azure to the Google Cloud Platform. By the end of this book, you will have learned the techniques to adopt cloud native architectures that meet your business requirements. You will also understand the future trends and expectations of cloud providers. What you will learn Learn the difference between cloud native and traditional architecture Explore the aspects of migration, when and why to use it Identify the elements to consider when selecting a technology for your architecture Automate security controls and configuration management Use infrastructure as code and CICD pipelines to run environments in a sustainable manner Understand the management and monitoring capabilities for AWS cloud native application architectures Who this book is for Cloud Native Architectures is for software architects who are keen on designing resilient, scalable, and highly available applications that are native to the cloud. COMPUTERS,Distributed Systems,Cloud Computing

Effective DevOps with AWS Scale and maintain outstanding performance in your AWS-based infrastructure using DevOps principles Key Features Implement continuous integration and continuous deployment pipelines on AWS Gain insight from an expert who has worked with Silicon Valley's most high-profile companies Implement DevOps principles to take full advantage of the AWS stack and services Book Description The DevOps movement has transformed the way modern tech companies work. Amazon Web Services (AWS), which has been at the forefront of the cloud computing revolution, has also been a key contributor to the DevOps movement, creating a huge range of managed services that help you implement DevOps principles. Effective DevOps with AWS, Second Edition will help you to understand how the most successful tech start-ups launch and scale their services on AWS, and will teach you how you can do the same. This book explains how to treat infrastructure as code, meaning you can bring resources online and offline as easily as you control your software. You will also build a continuous integration and continuous deployment pipeline to keep your app up to date. Once you have gotten to grips will all this, we'll move on to how to scale your applications to offer maximum performance to users even when traffic spikes, by using the latest technologies, such as containers. In addition to this, you'll get insights into monitoring and alerting, so you can make sure your users have the best experience when using your service. In the concluding chapters, we'll cover inbuilt AWS tools such as CodeDeploy and CloudFormation, which are used by many AWS administrators to perform DevOps. By the end of this book, you'll have learned how to ensure the security of your platform and data, using the latest and most prominent AWS tools. What you will learn Implement automatic AWS instance provisioning using CloudFormation Deploy your application on a provisioned infrastructure with Ansible Manage infrastructure using Terraform Build and deploy a CI/CD pipeline with Automated Testing on AWS Understand the container journey for a CI/CD pipeline using AWS ECS Monitor and secure your AWS environment Who this book is for Effective DevOps with AWS is for you if you are a developer, DevOps engineer, or you work in a team which wants to build and use AWS for software infrastructure. Basic computer science knowledge is required to get the most out of this book. COMPUTERS,Distributed Systems,Cloud Computing

Mastering Identity and Access Management with Microsoft Azure Start empowering users and protecting corporate data, while managing identities and access with Microsoft Azure in different environments Key Features Understand how to identify and manage business drivers during transitions Explore Microsoft Identity and Access Management as a Service (IDaaS) solution Over 40 playbooks to support your learning process with practical guidelines Book Description Microsoft Azure and its Identity and access management are at the heart of Microsoft's software as service products, including Office 365, Dynamics CRM, and Enterprise Mobility Management. It is crucial to master Microsoft Azure in order to be able to work with the Microsoft Cloud effectively. You'll begin by identifying the benefits of Microsoft Azure in the field of identity and access management. Working through the functionality of identity and access management as a service, you will get a full overview of the Microsoft strategy. Understanding identity synchronization will help you to provide a well-managed identity. Project scenarios and examples will enable you to understand, troubleshoot, and develop on essential authentication protocols and publishing scenarios. Finally, you will acquire a thorough understanding of Microsoft Information protection technologies. What you will learn Apply technical descriptions to your business needs and deployments Manage cloud-only, simple, and complex hybrid environments Apply correct and efficient monitoring and identity protection strategies Design and deploy custom Identity and access management solutions Build a complete identity and access management life cycle Understand authentication and application publishing mechanisms Use and understand the most crucial identity synchronization scenarios Implement a suitable information protection strategy Who this book is for This book is a perfect companion for developers, cyber security specialists, system and security engineers, IT consultants/architects, and system administrators who are looking for perfectly up–to-date hybrid and cloud-only scenarios. You should have some understanding of security solutions, Active Directory, access privileges/rights, and authentication methods. Programming knowledge is not required but can be helpful for using PowerShell or working with APIs to customize your solutions. COMPUTERS,Distributed Systems,Cloud Computing

Cloud Native DevOps with Kubernetes Kubernetes is the operating system of the cloud native world, providing a reliable and scalable platform for running containerized workloads. In this friendly, pragmatic book, cloud experts John Arundel and Justin Domingus show you what Kubernetes can do—and what you can do with it. You’ll learn all about the Kubernetes ecosystem, and use battle-tested solutions to everyday problems. You’ll build, step by step, an example cloud native application and its supporting infrastructure, along with a development environment and continuous deployment pipeline that you can use for your own applications. Understand containers and Kubernetes from first principles; no experience necessary Run your own clusters or choose a managed Kubernetes service from Amazon, Google, and others Use Kubernetes to manage resource usage and the container lifecycle Optimize clusters for cost, performance, resilience, capacity, and scalability Learn the best tools for developing, testing, and deploying your applications Apply the latest industry practices for security, observability, and monitoring Adopt DevOps principles to help make your development teams lean, fast, and effective COMPUTERS,Distributed Systems,Cloud Computing

Architecting Cloud Native Applications Apply cloud native patterns and practices to deliver responsive, resilient, elastic, and message-driven systems with confidence Key Features Discover best practices for applying cloud native patterns to your cloud applications Explore ways to effectively plan resources and technology stacks for high security and fault tolerance Gain insight into core architectural principles using real-world examples Book Description Cloud computing has proven to be the most revolutionary IT development since virtualization. Cloud native architectures give you the benefit of more flexibility over legacy systems. This Learning Path teaches you everything you need to know for designing industry-grade cloud applications and efficiently migrating your business to the cloud. It begins by exploring the basic patterns that turn your database inside out to achieve massive scalability. You'll learn how to develop cloud native architectures using microservices and serverless computing as your design principles. Then, you'll explore ways to continuously deliver production code by implementing continuous observability in production. In the concluding chapters, you'll learn about various public cloud architectures ranging from AWS and Azure to the Google Cloud Platform, and understand the future trends and expectations of cloud providers. By the end of this Learning Path, you'll have learned the techniques to adopt cloud native architectures that meet your business requirements. This Learning Path includes content from the following Packt products: Cloud Native Development Patterns and Best Practices by John Gilbert Cloud Native Architectures by Erik Farr et al. What you will learn Understand the difference between cloud native and traditional architecture Automate security controls and configuration management Minimize risk by evolving your monolithic systems into cloud native applications Explore the aspects of migration, when and why to use it Apply modern delivery and testing methods to continuously deliver production code Enable massive scaling by turning your database inside out Who this book is for This Learning Path is designed for developers who want to progress into building cloud native systems and are keen to learn the patterns involved. Software architects, who are keen on designing scalable and highly available cloud native applications, will also find this Learning Path very useful. To easily grasp these concepts, you will need basic knowledge of programming and cloud computing. COMPUTERS,Distributed Systems,Cloud Computing

Arista Warrior Arista Networks has become a key player when it comes to software-driven cloud networking solutions for large data center storage and computing environments. In this updated edition of Arista Warrior, renowned consultant and technical author Gary Donahue Network Arista Networks has become a key player when it comes to software-driven cloud networking solutions for large data center, storage, and computing environments, and with their continued expansion and growth since the first edition was released, this book is a welcome update. In this updated edition of Arista Warrior, renowned trainer, consultant, and technical author Gary A. Donahue (Network Warrior) provides an in-depth, objective guide to Arista’s products explains why its network switches, software products, and Extensible Operating System (EOS) are so effective. Anyone with a CCNA or equivalent knowledge will benefit from this book, especially entrenched administrators, engineers, or architects tasked with building an Arista network. Is Arista right for your network? Pick up this in-depth guide and find out. In addition to the topics covered in the first edition, this book also includes: Configuration Management: Config sessions, config replace, etc. CloudVision: Arista’s management, workload orchestration, workflow automation, configuration, and telemetry tool VXLAN: Layer-2 overlay networking FlexRoute: Two million routes in hardware Tap Aggregation: Make your switch or blade into a Tap Aggregation device Advanced Mirroring: Mirror to a port-channel or even the CPU Network Design: A quick overview of the Arista recommended network designs vEOS: Arista’s Extensible Operating System in a VM with step-by-step instructions cEOS: Arista’s EOS in a container with examples eAPI: Arista’s fabulous extended Application Programmable Interface COMPUTERS,Distributed Systems,Cloud Computing

Cloud Native Developers often struggle when first encountering the cloud. Learning about distributed systems, becoming familiar with technologies such as containers and functions, and knowing how to put everything together can be daunting. With this practical guide, you’ll get up to speed on patterns for building cloud native applications and best practices for common tasks such as messaging, eventing, and DevOps. Authors Boris Scholl, Trent Swanson, and Peter Jausovec describe the architectural building blocks for a modern cloud native application. You’ll learn how to use microservices, containers, serverless computing, storage types, portability, and functions. You’ll also explore the fundamentals of cloud native applications, including how to design, develop, and operate them. Explore the technologies you need to design a cloud native application Distinguish between containers and functions, and learn when to use them Architect applications for data-related requirements Learn DevOps fundamentals and practices for developing, testing, and operating your applications Use tips, techniques, and best practices for building and managing cloud native applications Understand the costs and trade-offs necessary to make an application portable COMPUTERS,Distributed Systems,Cloud Computing

Cloud Computing Interview Questions You'll Most Likely Be Asked • 225 Cloud Computing Interview Questions • 77 HR Interview Questions • Real life scenario-based questions• Strategies to respond to interview questions• 2 Aptitude Tests Cloud Computing Interview Questions You'll Most Likely Be Asked: Second Edition is a perfect companion to stand ahead above the rest in today’s competitive job market. Rather than going through comprehensive, textbook-sized reference guides, this book includes only the information required immediately for job search to build an IT career. This book puts the interviewee in the driver's seat and helps them steer their way to impress the interviewer. Includes:a) 225 Cloud Computing Interview Questions, Answers and Proven Strategies for getting hired as an IT professionalb) Dozens of examples to respond to interview questionsc) 77 HR Questions with Answers and Proven strategies to give specific, impressive, answers that help nail the interviewsd) 2 Aptitude Tests download available on www.vibrantpublishers.com COMPUTERS,Distributed Systems,Cloud Computing

Kubernetes Best Practices In this practical guide, four Kubernetes professionals with deep experience in distributed systems, enterprise application development, and open source will guide you through the process of building applications with this container orchestration system. Based on the experiences of companies that are running Kubernetes in production successfully, many of the methods are also backed by concrete code examples. This book is ideal for those already familiar with basic Kubernetes concepts who want to learn common best practices. You’ll learn exactly what you need to know to build your best app with Kubernetes the first time. Set up and develop applications in Kubernetes Learn patterns for monitoring, securing your systems, and managing upgrades, rollouts, and rollbacks Understand Kubernetes networking policies and where service mesh fits in Integrate services and legacy applications and develop higher-level platforms on top of Kubernetes Run machine learning workloads in Kubernetes COMPUTERS,Distributed Systems,Cloud Computing

Cloud Native Data Center Networking If you want to study, build, or simply validate your thinking about modern cloud native data center networks, this is your book. Whether you’re pursuing a multitenant private cloud, a network for running machine learning, or an enterprise data center, author Dinesh Dutt takes you through the steps necessary to design a data center that’s affordable, high capacity, easy to manage, agile, and reliable. Ideal for network architects, data center operators, and network and containerized application developers, this book mixes theory with practice to guide you through the architecture and protocols you need to create and operate a robust, scalable network infrastructure. The book offers a vendor-neutral way to look at network design. For those interested in open networking, this book is chock-full of examples using open source software, from FRR to Ansible. In the context of a cloud native data center, you’ll examine: Clos topology Network disaggregation Network operating system choices Routing protocol choices Container networking Network virtualization and EVPN Network automation COMPUTERS,Distributed Systems,Cloud Computing

Cloud Native Transformation In the past few years, going cloud native has been a big advantage for many companies. But it’s a tough technique to get right, especially for enterprises with critical legacy systems. This practical hands-on guide examines effective architecture, design, and cultural patterns to help you transform your organization into a cloud native enterprise—whether you’re moving from older architectures or creating new systems from scratch. By following Wealth Grid, a fictional company, you’ll understand the challenges, dilemmas, and considerations that accompany a move to the cloud. Technical managers and architects will learn best practices for taking on a successful company-wide transformation. Cloud migration consultants Pini Reznik, Jamie Dobson, and Michelle Gienow draw patterns from the growing community of expert practitioners and enterprises that have successfully built cloud native systems. You’ll learn what works and what doesn’t when adopting cloud native—including how this transition affects not just your technology but also your organizational structure and processes. You’ll learn: What cloud native means and why enterprises are so interested in it Common barriers and pitfalls that have affected other companies (and how to avoid them) Context-specific patterns for a successful cloud native transformation How to implement a safe, evolutionary cloud native approach How companies addressed root causes and misunderstandings that hindered their progress Case studies from real-world companies that have succeeded with cloud native transformations COMPUTERS,Distributed Systems,Cloud Computing

Microsoft Azure For Dummies Your roadmap to Microsoft Azure Azure is Microsoft’s flagship cloud computing platform. With over 600 services available to over 44 geographic regions, it would take a library of books to cover the entire Azure ecosystem. Microsoft Azure For Dummies offers a shortcut to getting familiar with Azure’s core product offerings used by the majority of its subscribers. It’s a perfect choice for those looking to gain a quick, basic understanding of this ever-evolving public cloud platform. Written by a Microsoft MVP and Microsoft Certified Azure Solutions Architect, Microsoft Azure For Dummies covers building virtual networks, configuring cloud-based virtual machines, launching and scaling web applications, migrating on-premises services to Azure, and keeping your Azure resources secure and compliant. Migrate your applications and services to Azure with confidence Manage virtual machines smarter than you've done on premises Deploy web applications that scale dynamically to save you money and effort Apply Microsoft's latest security technologies to ensure compliance to maintain data privacy With more and more businesses making the leap to run their applications and services on Microsoft Azure, basic understanding of the technology is becoming essential. Microsoft Azure For Dummies offers a fast and easy first step into the Microsoft public cloud. COMPUTERS,Distributed Systems,Cloud Computing

Programming AWS Lambda Serverless revolutionizes the way organizations build and deploy software. With this hands-on guide, Java engineers will learn how to use their experience in the new world of serverless computing. You’ll discover how this cloud computing execution model can drastically decrease the complexity in developing and operating applications while reducing costs and time to market. Engineering leaders John Chapin and Mike Roberts guide you through the process of developing these applications using AWS Lambda, Amazon’s event-driven, serverless computing platform. You’ll learn how to prepare the development environment, program Lambda functions, and deploy and operate your serverless software. The chapters include exercises to help you through each aspect of the process. Get an introduction to serverless, functions as a service, and AWS Lambda Learn how to deploy working Lambda functions to the cloud Program Lambda functions and learn how the Lambda platform integrates with other AWS services Build and package Java-based Lambda code and dependencies Create serverless applications by building a serverless API and data pipeline Test your serverless applications using automated techniques Apply advanced techniques to build production-ready applications Understand both the gotchas and new opportunities of serverless architecture COMPUTERS,Distributed Systems,Cloud Computing

Knative Cookbook Enterprise developers face several challenges when it comes to building serverless applications, such as integrating applications and building container images from source. With more than 60 practical recipes, this cookbook helps you solve these issues with Knative—the first serverless platform natively designed for Kubernetes. Each recipe contains detailed examples and exercises, along with a discussion of how and why it works. If you have a good understanding of serverless computing and Kubernetes core resources such as deployment, services, routes, and replicas, the recipes in this cookbook show you how to apply Knative in real enterprise application development. Authors Kamesh Sampath and Burr Sutter include chapters on autoscaling, build and eventing, observability, Knative on OpenShift, and more. With this cookbook, you’ll learn how to: Efficiently build, deploy, and manage modern serverless workloads Apply Knative in real enterprise scenarios, including advanced eventing Monitor your Knative serverless applications effectively Integrate Knative with CI/CD principles, such as using pipelines for faster, more successful production deployments Deploy a rich ecosystem of enterprise integration patterns and connectors in Apache Camel K as Kubernetes and Knative components COMPUTERS,Distributed Systems,Cloud Computing

Official Google Cloud Certified Professional Data Engineer Study Guide The proven Study Guide that prepares you for this new Google Cloud exam The Google Cloud Certified Professional Data Engineer Study Guide, provides everything you need to prepare for this important exam and master the skills necessary to land that coveted Google Cloud Professional Data Engineer certification. Beginning with a pre-book assessment quiz to evaluate what you know before you begin, each chapter features exam objectives and review questions, plus the online learning environment includes additional complete practice tests. Written by Dan Sullivan, a popular and experienced online course author for machine learning, big data, and Cloud topics, Google Cloud Certified Professional Data Engineer Study Guide is your ace in the hole for deploying and managing analytics and machine learning applications. • Build and operationalize storage systems, pipelines, and compute infrastructure • Understand machine learning models and learn how to select pre-built models • Monitor and troubleshoot machine learning models • Design analytics and machine learning applications that are secure, scalable, and highly available. This exam guide is designed to help you develop an in depth understanding of data engineering and machine learning on Google Cloud Platform. COMPUTERS,Distributed Systems,Cloud Computing

Migrating to AWS Bring agility, cost savings, and a competitive edge to your business by migrating your IT infrastructure to AWS. With this practical book, executive and senior leadership and engineering and IT managers will examine the advantages, disadvantages, and common pitfalls when moving your company’s operations to the cloud. Author Jeff Armstrong brings years of practical hands-on experience helping dozens of enterprises make this corporate change. You’ll explore real-world examples from many organizations that have made—or attempted to make—this wide-ranging transition. Once you read this guide, you’ll be better prepared to evaluate your migration objectively before, during, and after the process in order to ensure success. Learn the benefits and drawbacks of migrating to AWS, including the risks to your business and technology Begin the process by discovering the applications and servers in your environment Examine the value of AWS migration when building your business case Address your operational readiness before you migrate Define your AWS account structure and cloud governance controls Create your migration plan in waves of servers and applications Refactor applications that will benefit from using more cloud native resources COMPUTERS,Distributed Systems,Cloud Computing

Cloud Computing Why cloud computing represents a paradigm shift for business, and how business users can best take advantage of cloud services. Most of the information available on cloud computing is either highly technical, with details that are irrelevant to non-technologists, or pure marketing hype, in which the cloud is simply a selling point. This book, however, explains the cloud from the user's viewpoint—the business user's in particular. Nayan Ruparelia explains what the cloud is, when to use it (and when not to), how to select a cloud service, how to integrate it with other technologies, and what the best practices are for using cloud computing. Cutting through the hype, Ruparelia cites the simple and basic definition of cloud computing from the National Institute of Science and Technology: a model enabling ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources. Thus with cloud computing, businesses can harness information technology resources usually available only to large enterprises. And this, Ruparelia demonstrates, represents a paradigm shift for business. It will ease funding for startups, alter business plans, and allow big businesses greater agility. Ruparelia discusses the key issues for any organization considering cloud computing: service level agreements, business service delivery and consumption, finance, legal jurisdiction, security, and social responsibility. He introduces novel concepts made possible by cloud computing: cloud cells, or specialist clouds for specific uses; the personal cloud; the cloud of things; and cloud service exchanges. He examines use case patterns in terms of infrastructure and platform, software information, and business process; and he explains how to transition to a cloud service. Current and future users will find this book an indispensable guide to the cloud. COMPUTERS,Distributed Systems,Cloud Computing

A Prehistory of the Cloud The militarized legacy of the digital cloud: how the cloud grew out of older network technologies and politics. We may imagine the digital cloud as placeless, mute, ethereal, and unmediated. Yet the reality of the cloud is embodied in thousands of massive data centers, any one of which can use as much electricity as a midsized town. Even all these data centers are only one small part of the cloud. Behind that cloud-shaped icon on our screens is a whole universe of technologies and cultural norms, all working to keep us from noticing their existence. In this book, Tung-Hui Hu examines the gap between the real and the virtual in our understanding of the cloud. Hu shows that the cloud grew out of such older networks as railroad tracks, sewer lines, and television circuits. He describes key moments in the prehistory of the cloud, from the game “Spacewar” as exemplar of time-sharing computers to Cold War bunkers that were later reused as data centers. Countering the popular perception of a new “cloudlike” political power that is dispersed and immaterial, Hu argues that the cloud grafts digital technologies onto older ways of exerting power over a population. But because we invest the cloud with cultural fantasies about security and participation, we fail to recognize its militarized origins and ideology. Moving between the materiality of the technology itself and its cultural rhetoric, Hu's account offers a set of new tools for rethinking the contemporary digital environment. COMPUTERS,Distributed Systems,Cloud Computing

The Big Switch “Magisterial…Draws an elegant and illuminating parallel between the late-19th-century electrification of America and today’s computing world.†—Salon Hailed as “the most influential book so far on the cloud computing movement†(Christian Science Monitor), The Big Switch makes a simple and profound statement: Computing is turning into a utility, and the effects of this transition will ultimately change society as completely as the advent of cheap electricity did. In a new chapter for this edition that brings the story up-to-date, Nicholas Carr revisits the dramatic new world being conjured from the circuits of the “World Wide Computer.†COMPUTERS,Distributed Systems,Cloud Computing

Cloud Computing For Dummies Get your head —and your business—into the Cloud Cloud computing is no longer just a clever new toy in the world of IT infrastructure. Despite the nebulous name, it’s become a real and important part of our information architecture—and tech professionals who ignore it or try to skim their way through risk falling behind rapidly. The new edition of Cloud Computing For Dummies gets you up to speed fast, clarifying your Cloud options, showing you where can save you time and money, giving you ways to frame your decisions, and helping you avoid weeks of research. In a friendly, easy-to-follow style, Cloud Computing For Dummies, 2nd Edition demystifies the Cloud’s virtual landscape, breaking up a complex and multi-layered topic into simple explanations that will make the various benefits clear and ultimately guide you toward making the most appropriate choices for your organization. Know the business case for the Cloud Understand hybrid and multi-cloud options Develop your Cloud strategy Get tips on best practices The Cloud is everywhere, and it can deliver amazing benefits to our lives and businesses. Get a much clearer vision of exactly how with Cloud Computing For Dummies—and you’ll begin to see that the sky really is the limit! COMPUTERS,Distributed Systems,Cloud Computing

Full Stack Serverless Cloud computing is typically associated with backend development and DevOps. But with the rise of serverless technologies and a new generation of services and frameworks, frontend and mobile developers can build robust applications with production-ready features such as authentication and authorization, API gateways, chatbots, augmented reality scenes, and more. This hands-on guide shows you how. Nader Dabit, developer advocate at Amazon Web Services, guides you through the process of building full stack applications using React, AWS, GraphQL, and AWS Amplify. You’ll learn how to create and incorporate services into your client applications while learning general best practices, deployment strategies, rich media management, and continuous integration and delivery along the way. Learn how to build serverless applications that solve real problems Understand what is (and isn’t) possible when using these technologies Create a GraphQL API that interacts with DynamoDB and a NoSQL database Examine how authentication works—and learn the difference between authentication and authorization Get an in-depth view of how serverless functions work and why they’re important Build full stack applications on AWS and create offline apps with Amplify DataStore COMPUTERS,Distributed Systems,Cloud Computing

The Art of Multiprocessor Programming, Revised Reprint Revised and updated with improvements conceived in parallel programming courses, The Art of Multiprocessor Programming is an authoritative guide to multicore programming. It introduces a higher level set of software development skills than that needed for efficient single-core programming. This book provides comprehensive coverage of the new principles, algorithms, and tools necessary for effective multiprocessor programming. Students and professionals alike will benefit from thorough coverage of key multiprocessor programming issues. This revised edition incorporates much-demanded updates throughout the book, based on feedback and corrections reported from classrooms since 2008 Learn the fundamentals of programming multiple threads accessing shared memory Explore mainstream concurrent data structures and the key elements of their design, as well as synchronization techniques from simple locks to transactional memory systems Visit the companion site and download source code, example Java programs, and materials to support and enhance the learning experience COMPUTERS,Distributed Systems,General

Programming WCF Services Programming WCF Services is the authoritative, bestselling guide to Microsoft’s unified platform for developing modern, service-oriented applications on Windows. Hailed as the definitive treatment of WCF, this guide provides unique insight, rather than documentation, to help you learn the topics and skills you need for building maintainable, extensible, and reusable WCF-based applications. Authors Juval Löwy—one of the world’s top .NET experts—and Michael Montgomery have revised this edition to include the productivity-enhancing features of .NET Framework 4.6, along with the latest WCF ideas and techniques. By teaching you the why and the how of WCF programming, this book will help you master WCF and make you a better software engineer. Learn WCF’s architecture and essential building blocks, including key concepts such as reliability and transport sessions Use built-in features such as service contracts, instance and concurrency management, transactions, queued services, and security Increase the quality of your WCF services by using design options, tips, and best practices in Löwy’s ServiceModelEx framework Understand the rationale behind particular design decisions, and rarely understood aspects of WCF development Learn why Azure Service Fabric is the killer app for modern DevOps COMPUTERS,Distributed Systems,General

Microservice Architecture Microservices can have a positive impact on your enterprise—just ask Amazon and Netflix—but you can fall into many traps if you don’t approach them in the right way. This practical guide covers the entire microservices landscape, including the principles, technologies, and methodologies of this unique, modular style of system building. You’ll learn about the experiences of organizations around the globe that have successfully adopted microservices. In three parts, this book explains how these services work and what it means to build an application the Microservices Way. You’ll explore a design-based approach to microservice architecture with guidance for implementing various elements. And you’ll get a set of recipes and practices for meeting practical, organizational, and cultural challenges to microservice adoption. Learn how microservices can help you drive business objectives Examine the principles, practices, and culture that define microservice architectures Explore a model for creating complex systems and a design process for building a microservice architecture Learn the fundamental design concepts for individual microservices Delve into the operational elements of a microservices architecture, including containers and service discovery Discover how to handle the challenges of introducing microservice architecture in your organization COMPUTERS,Distributed Systems,General

Building Evolutionary Architectures The software development ecosystem is constantly changing, providing a constant stream of new tools, frameworks, techniques, and paradigms. Over the past few years, incremental developments in core engineering practices for software development have created the foundations for rethinking how architecture changes over time, along with ways to protect important architectural characteristics as it evolves. This practical guide ties those parts together with a new way to think about architecture and time. COMPUTERS,Distributed Systems,General

Designing Distributed Systems Without established design patterns to guide them, developers have had to build distributed systems from scratch, and most of these systems are very unique indeed. Today, the increasing use of containers has paved the way for core distributed system patterns and reusable containerized components. This practical guide presents a collection of repeatable, generic patterns to help make the development of reliable distributed systems far more approachable and efficient. Author Brendan Burns—Director of Engineering at Microsoft Azure—demonstrates how you can adapt existing software design patterns for designing and building reliable distributed applications. Systems engineers and application developers will learn how these long-established patterns provide a common language and framework for dramatically increasing the quality of your system. Understand how patterns and reusable components enable the rapid development of reliable distributed systems Use the side-car, adapter, and ambassador patterns to split your application into a group of containers on a single machine Explore loosely coupled multi-node distributed patterns for replication, scaling, and communication between the components Learn distributed system patterns for large-scale batch data processing covering work-queues, event-based processing, and coordinated workflows COMPUTERS,Distributed Systems,General

AWS System Administration With platforms designed for rapid adaptation and failure recovery such as Amazon Web Services, cloud computing is more like programming than traditional system administration. Tools for automatic scaling and instance replacement allow even small DevOps teams to manage massively scalable application infrastructures—if team members drop their old views of development and operations and start mastering automation. This comprehensive guide shows developers and system administrators how to configure and manage AWS services including EC2, CloudFormation, Elastic Load Balancing, S3, and Route 53. Sysadms will learn will learn to automate their favorite tools and processes; developers will pick up enough ops knowledge to build a robust and resilient AWS application infrastructure. Launch instances with EC2 or CloudFormation Securely deploy and manage your applications with AWS tools Learn to automate AWS configuration management with Python and Puppet Deploy applications with Auto Scaling and Elastic Load Balancing Explore approaches for deploying application and infrastructure updates Save time on development and operations with reusable components Learn strategies for managing log files in AWS environments Configure a cloud-aware DNS service with Route 53 Use AWS CloudWatch to monitor your infrastructure and applications COMPUTERS,Distributed Systems,General

Seeking SRE Organizations big and small have started to realize just how crucial system and application reliability is to their business. They’ve also learned just how difficult it is to maintain that reliability while iterating at the speed demanded by the marketplace. Site Reliability Engineering (SRE) is a proven approach to this challenge. SRE is a large and rich topic to discuss. Google led the way with Site Reliability Engineering, the wildly successful O’Reilly book that described Google’s creation of the discipline and the implementation that’s allowed them to operate at a planetary scale. Inspired by that earlier work, this book explores a very different part of the SRE space. The more than two dozen chapters in Seeking SRE bring you into some of the important conversations going on in the SRE world right now. Listen as engineers and other leaders in the field discuss: Different ways of implementing SRE and SRE principles in a wide variety of settings How SRE relates to other approaches such as DevOps Specialties on the cutting edge that will soon be commonplace in SRE Best practices and technologies that make practicing SRE easier The important but rarely explored human side of SRE David N. Blank-Edelman is the book’s curator and editor. COMPUTERS,Distributed Systems,General

Foundations for Architecting Data Solutions While many companies ponder implementation details such as distributed processing engines and algorithms for data analysis, this practical book takes a much wider view of big data development, starting with initial planning and moving diligently toward execution. Authors Ted Malaska and Jonathan Seidman guide you through the major components necessary to start, architect, and develop successful big data projects. Everyone from CIOs and COOs to lead architects and developers will explore a variety of big data architectures and applications, from massive data pipelines to web-scale applications. Each chapter addresses a piece of the software development life cycle and identifies patterns to maximize long-term success throughout the life of your project. Start the planning process by considering the key data project types Use guidelines to evaluate and select data management solutions Reduce risk related to technology, your team, and vague requirements Explore system interface design using APIs, REST, and pub/sub systems Choose the right distributed storage system for your big data system Plan and implement metadata collections for your data architecture Use data pipelines to ensure data integrity from source to final storage Evaluate the attributes of various engines for processing the data you collect COMPUTERS,Distributed Systems,General

Hands-On Domain-Driven Design with .NET Core Solve complex business problems by understanding users better, finding the right problem to solve, and building lean event-driven systems to give your customers what they really want Key Features Apply DDD principles using modern tools such as EventStorming, Event Sourcing, and CQRS Learn how DDD applies directly to various architectural styles such as REST, reactive systems, and microservices Empower teams to work flexibly with improved services and decoupled interactions Book Description Developers across the world are rapidly adopting DDD principles to deliver powerful results when writing software that deals with complex business requirements. This book will guide you in involving business stakeholders when choosing the software you are planning to build for them. By figuring out the temporal nature of behavior-driven domain models, you will be able to build leaner, more agile, and modular systems. You'll begin by uncovering domain complexity and learn how to capture the behavioral aspects of the domain language. You will then learn about EventStorming and advance to creating a new project in .NET Core 2.1; you'll also and write some code to transfer your events from sticky notes to C#. The book will show you how to use aggregates to handle commands and produce events. As you progress, you'll get to grips with Bounded Contexts, Context Map, Event Sourcing, and CQRS. After translating domain models into executable C# code, you will create a frontend for your application using Vue.js. In addition to this, you'll learn how to refactor your code and cover event versioning and migration essentials. By the end of this DDD book, you will have gained the confidence to implement the DDD approach in your organization and be able to explore new techniques that complement what you've learned from the book. What you will learn Discover and resolve domain complexity together with business stakeholders Avoid common pitfalls when creating the domain model Study the concept of Bounded Context and aggregate Design and build temporal models based on behavior and not only data Explore benefits and drawbacks of Event Sourcing Get acquainted with CQRS and to-the-point read models with projections Practice building one-way flow UI with Vue.js Understand how a task-based UI conforms to DDD principles Who this book is for This book is for .NET developers who have an intermediate level understanding of C#, and for those who seek to deliver value, not just write code. Intermediate level of competence in JavaScript will be helpful to follow the UI chapters. COMPUTERS,Distributed Systems,General

Learning Apache OpenWhisk Serverless computing greatly simplifies software development. Your team can focus solely on your application while the cloud provider manages the servers you need. This practical guide shows you step-by-step how to build and deploy complex applications in a flexible multicloud, multilanguage environment using Apache OpenWhisk. You’ll learn how this platform enables you to pursue a vendor-independent approach using preconfigured containers, microservices, and Kubernetes as your cloud operating system. Michele Sciabarrà demonstrates how to build a serverless application using classical design patterns and the programming language or languages that best fit your task. You’ll start by building a simple serverless application hands-on before diving into the more complex aspects of the OpenWhisk platform. Examine how OpenWhisk’s serverless architecture works, including the use of packages, actions, sequences, triggers, rules, and feeds Learn how OpenWhisk compares to existing architectures, such as Java Enterprise Edition Manipulate OpenWhisk features using the command-line interface or a JavaScript API Design applications using common Gang of Four design patterns Use architectural design patterns such as model-view-controller to combine several OpenWhisk actions Learn how to test and debug your code in a serverless environment COMPUTERS,Distributed Systems,General

Hands-On Microservices with Kubernetes Enhance your skills in building scalable infrastructure for your cloud-based applications Key Features Learn to design a scalable architecture by building continuous integration (CI) pipelines with Kubernetes Get an in-depth understanding of role-based access control (RBAC), continuous deployment (CD), and observability Monitor a Kubernetes cluster with Prometheus and Grafana Book Description Kubernetes is among the most popular open-source platforms for automating the deployment, scaling, and operations of application containers across clusters of hosts, providing a container-centric infrastructure. Hands-On Microservices with Kubernetes starts by providing you with in-depth insights into the synergy between Kubernetes and microservices. You will learn how to use Delinkcious, which will serve as a live lab throughout the book to help you understand microservices and Kubernetes concepts in the context of a real-world application. Next, you will get up to speed with setting up a CI/CD pipeline and configuring microservices using Kubernetes ConfigMaps. As you cover later chapters, you will gain hands-on experience in securing microservices, and implementing REST, gRPC APIs, and a Delinkcious data store. In addition to this, you'll explore the Nuclio project, run a serverless task on Kubernetes, and manage and implement data-intensive tests. Toward the concluding chapters, you'll deploy microservices on Kubernetes and learn to maintain a well-monitored system. Finally, you'll discover the importance of service meshes and how to incorporate Istio into the Delinkcious cluster. By the end of this book, you'll have gained the skills you need to implement microservices on Kubernetes with the help of effective tools and best practices. What you will learn Understand the synergy between Kubernetes and microservices Create a complete CI/CD pipeline for your microservices on Kubernetes Develop microservices on Kubernetes with the Go kit framework using best practices Manage and monitor your system using Kubernetes and open-source tools Expose your services through REST and gRPC APIs Implement and deploy serverless functions as a service Externalize authentication, authorization and traffic shaping using a service mesh Run a Kubernetes cluster in the cloud on Google Kubernetes Engine Who this book is for This book is for developers, DevOps engineers, or anyone who wants to develop large-scale microservice-based systems on top of Kubernetes. If you are looking to use Kubernetes on live production projects or want to migrate existing systems to a modern containerized microservices system, then this book is for you. Coding skills, together with some knowledge of Docker, Kubernetes, and cloud concepts will be useful. COMPUTERS,Distributed Systems,General

Fundamentals of Software Architecture Salary surveys worldwide regularly place software architect in the top 10 best jobs, yet no real guide exists to help developers become architects. Until now. This book provides the first comprehensive overview of software architecture’s many aspects. Aspiring and existing architects alike will examine architectural characteristics, architectural patterns, component determination, diagramming and presenting architecture, evolutionary architecture, and many other topics. Mark Richards and Neal Ford—hands-on practitioners who have taught software architecture classes professionally for years—focus on architecture principles that apply across all technology stacks. You’ll explore software architecture in a modern light, taking into account all the innovations of the past decade. This book examines: Architecture patterns: The technical basis for many architectural decisions Components: Identification, coupling, cohesion, partitioning, and granularity Soft skills: Effective team management, meetings, negotiation, presentations, and more Modernity: Engineering practices and operational approaches that have changed radically in the past few years Architecture as an engineering discipline: Repeatable results, metrics, and concrete valuations that add rigor to software architecture COMPUTERS,Distributed Systems,General

Hands-On Serverless Computing with Google Cloud Effectively deploy fully managed workloads using Google Cloud's serverless services Key Features Use real-world use cases to understand the core functionalities of Functions as a Service Explore the potential of Cloud Run, Knative, Cloud Build, Google Kubernetes Engine, and Cloud Storage Get to grips with architectural decisions, seamless deployments, containerization, and serverless solutions Book Description Google Cloud's serverless platform allows organizations to scale fully managed solutions without worrying about the underlying infrastructure. With this book, you will learn how to design, develop, and deploy full stack serverless apps on Google Cloud. The book starts with a quick overview of the Google Cloud console, its features, user interface (UI), and capabilities. After getting to grips with the Google Cloud interface and its features, you will explore the core aspects of serverless products such as Cloud Run, Cloud Functions and App Engine. You will also learn essential features such as version control, containerization, and identity and access management with the help of real-world use cases. Later, you will understand how to incorporate continuous integration and continuous deployment (CI/CD) techniques for serverless applications. Toward the concluding chapters, you will get to grips with how key technologies such as Knative enable Cloud Run to be hosted on multiple platforms including Kubernetes and VMware. By the end of this book, you will have become proficient in confidently developing, managing, and deploying containerized applications on Google Cloud. What you will learn Explore the various options for deploying serverless workloads on Google Cloud Determine the appropriate serverless product for your application use case Integrate multiple lightweight functions to build scalable and resilient services Increase productivity through build process automation Understand how to secure serverless workloads using service accounts Build a scalable architecture with Google Cloud Functions and Cloud Run Who this book is for If you are a cloud administrator, architect, or developer who wants to build scalable systems and deploy serverless workloads on Google Cloud, then this book is for you. To get the most out of this book, a basic understanding of the serverless ecosystem and cloud computing will be beneficial. COMPUTERS,Distributed Systems,General

Architecting for Scale Every day, companies struggle to scale critical applications. As traffic volume and data demands increase, these applications become more complicated and brittle, exposing risks and compromising availability. With the popularity of software as a service, scaling has never been more important. Updated with an expanded focus on modern architecture paradigms such as microservices and cloud computing, this practical guide provides techniques for building systems that can handle huge quantities of traffic, data, and demand—without affecting the quality your customers expect. Architects, managers, and directors in engineering and operations organizations will learn how to build applications at scale that run more smoothly and reliably to meet the needs of customers. Learn how scaling affects the availability of your services, why that matters, and how to improve it Dive into a modern service-based application architecture that ensures high availability and reduces the effects of service failures Explore the Single Team Owned Service Architecture paradigm (STOSA)—a model for scaling your development organization in tandem with your application Understand, measure, and mitigate risk in your systems Use the cloud to build highly scalable applications COMPUTERS,Distributed Systems,General

Solutions Architect's Handbook From fundamentals and design patterns to the different strategies for creating secure and reliable architectures in AWS cloud, learn everything you need to become a successful solutions architect Key Features Create solutions and transform business requirements into technical architecture with this practical guide Understand various challenges that you might come across while refactoring or modernizing legacy applications Delve into security automation, DevOps, and validation of solution architecture Book Description Becoming a solutions architect gives you the flexibility to work with cutting-edge technologies and define product strategies. This handbook takes you through the essential concepts, design principles and patterns, architectural considerations, and all the latest technology that you need to know to become a successful solutions architect. This book starts with a quick introduction to the fundamentals of solution architecture design principles and attributes that will assist you in understanding how solution architecture benefits software projects across enterprises. You'll learn what a cloud migration and application modernization framework looks like, and will use microservices, event-driven, cache-based, and serverless patterns to design robust architectures. You'll then explore the main pillars of architecture design, including performance, scalability, cost optimization, security, operational excellence, and DevOps. Additionally, you'll also learn advanced concepts relating to big data, machine learning, and the Internet of Things (IoT). Finally, you'll get to grips with the documentation of architecture design and the soft skills that are necessary to become a better solutions architect. By the end of this book, you'll have learned techniques to create an efficient architecture design that meets your business requirements. What you will learn Explore the various roles of a solutions architect and their involvement in the enterprise landscape Approach big data processing, machine learning, and IoT from an architect's perspective and understand how they fit into modern architecture Discover different solution architecture patterns such as event-driven and microservice patterns Find ways to keep yourself updated with new technologies and enhance your skills Modernize legacy applications with the help of cloud integration Get to grips with choosing an appropriate strategy to reduce cost Who this book is for This book is for software developers, system engineers, DevOps engineers, architects, and team leaders working in the information technology industry who aspire to become solutions architect professionals. A good understanding of the software development process and general programming experience with any language will be useful. COMPUTERS,Distributed Systems,General

Distributed Tracing in Practice Most applications today are distributed in some fashion. Monitoring the health and performance of these distributed architectures requires a new approach. Enter distributed tracing, a method of profiling and monitoring applications—especially those that use microservice architectures. There’s just one problem: distributed tracing can be hard. But it doesn’t have to be. With this practical guide, you’ll learn what distributed tracing is and how to use it to understand the performance and operation of your software. Key players at Lightstep walk you through instrumenting your code for tracing, collecting the data that your instrumentation produces, and turning it into useful, operational insights. If you want to start implementing distributed tracing, this book tells you what you need to know. You’ll learn: The pieces of a distributed tracing deployment: Instrumentation, data collection, and delivering value Best practices for instrumentation (the methods for generating trace data from your service) How to deal with or avoid overhead, costs, and sampling How to work with spans (the building blocks of request-based distributed traces) and choose span characteristics that lead to valuable traces Where distributed tracing is headed in the future COMPUTERS,Distributed Systems,General

Practical Microservices MVC and CRUD make software easier to write, but harder to change. Microservice-based architectures can help even the smallest of projects remain agile in the long term, but most tutorials meander in theory or completely miss the point of what it means to be microservice-based. Roll up your sleeves with real projects and learn the most important concepts of evented architectures. You'll have your own deployable, testable project and a direction for where to go next. Much ink has been spilled on the topic of microservices, but all of this writing fails to accurately identity what makes a system a monolith, define what microservices are, or give complete, practical examples, so you're probably left thinking they have nothing to offer you. You don't have to be at Google or Facebook scale to benefit from a microservice-based architecture. Microservices will keep even small and medium teams productive by keeping the pieces of your system focused and decoupled. Discover the basics of message-based architectures, render the same state in different shapes to fit the task at hand, and learn what it is that makes something a monolith (it has nothing to do with how many machines you deploy to). Conserve resources by performing background jobs with microservices. Deploy specialized microservices for registration, authentication, payment processing, e-mail, and more. Tune your services by defining appropriate service boundaries. Deploy your services effectively for continuous integration. Master debugging techniques that work across different services. You'll finish with a deployable system and skills you can apply to your current project. Add the responsiveness and flexibility of microservices to your project, no matter what the size or complexity. What You Need: While the principles of this book transcend programming language, the code examples are in Node.js because JavaScript, for better or worse, is widely read. You'll use PostgreSQL for data storage, so familiarity with it is a plus. The books does provide Docker images to make working with PostgreSQL a bit easier, but extensive Docker knowledge is not required. COMPUTERS,Distributed Systems,General

Implementing Azure DevOps Solutions A comprehensive guide to becoming a skilled Azure DevOps engineer Key Features Explore a step-by-step approach to designing and creating a successful DevOps environment Understand how to implement continuous integration and continuous deployment pipelines on Azure Integrate and implement security, compliance, containers, and databases in your DevOps strategies Book Description Implementing Azure DevOps Solutions helps DevOps engineers and administrators to leverage Azure DevOps Services to master practices such as continuous integration and continuous delivery (CI/CD), containerization, and zero downtime deployments. This book starts with the basics of continuous integration, continuous delivery, and automated deployments. You will then learn how to apply configuration management and Infrastructure as Code (IaC) along with managing databases in DevOps scenarios. Next, you will delve into fitting security and compliance with DevOps. As you advance, you will explore how to instrument applications, and gather metrics to understand application usage and user behavior. The latter part of this book will help you implement a container build strategy and manage Azure Kubernetes Services. Lastly, you will understand how to create your own Azure DevOps organization, along with covering quick tips and tricks to confidently apply effective DevOps practices. By the end of this book, you'll have gained the knowledge you need to ensure seamless application deployments and business continuity. What you will learn Get acquainted with Azure DevOps Services and DevOps practices Implement CI/CD processes Build and deploy a CI/CD pipeline with automated testing on Azure Integrate security and compliance in pipelines Understand and implement Azure Container Services Become well versed in closing the loop from production back to development Who this book is for This DevOps book is for software developers and operations specialists interested in implementing DevOps practices for the Azure cloud. Application developers and IT professionals with some experience in software development and development practices will also find this book useful. Some familiarity with Azure DevOps basics is an added advantage. COMPUTERS,Distributed Systems,General

Managing Writers Managing Writers is a practical guide to managing documentation projects in the real world. It is informal, but concise, using examples from the author's experience working with and managing technical writers. It looks beyond big project, big team methodologies to the issues faced by smaller, less well-funded projects. Managing Writers is for technical writers, both freelancers and employees, documentation managers, and managers in other disciplines who are responsible for documentation; anyone who may need to manage, full or part-time, a documentation project. Inside the Book Leading People Leading Projects Leading Technology Glossary, Bibliography, and Index COMPUTERS,Document Management

Strategic Writing for UX When you depend on users to perform specific actions—like buying tickets, playing a game, or riding public transit—well-placed words are most effective. But how do you choose the right words? And how do you know if they work? With this practical book, you’ll learn how to write strategically for UX, using tools to build foundational pieces for UI text and UX voice strategy. UX content strategist Torrey Podmajersky provides strategies for converting, engaging, supporting, and re-attracting users. You’ll use frameworks and patterns for content, methods to measure the content’s effectiveness, and processes to create the collaboration necessary for success. You’ll also structure your voice throughout so that the brand is easily recognizable to its audience. Learn how UX content works with the software development lifecycle Use a framework to align the UX content with product principles Explore content-first design to root UX text in conversation Learn how UX text patterns work with different voices Produce text that’s purposeful, concise, conversational, and clear COMPUTERS,Documentation & Technical Writing

Blackboard For Dummies Use the quick-start guide to create your course in a flash Post course materials, give quizzes, facilitate discussions, and handle grades You're an educator, not a psychic, so how would you know how to use Blackboard with no instructions? These step-by-step examples show you how to set up a Blackboard classroom, put your materials on the Internet, communicate online with students, and even evaluate their performance. Discover how to * Navigate the Blackboard environment * Customize your course menu * Add and organize course materials * Give online assignments * Conduct online discussions and chat rooms * Keep track of grades COMPUTERS,Educational Software

The Game Believes in You USA Today journalist and former public school teacher Greg Toppo defies the technology-resistant attitude of today's educators and shows how game designers are revolutionizing learning COMPUTERS,Educational Software

Hermeneutica An introduction to text analysis using computer-assisted interpretive practices, accompanied by example essays that illustrate the use of these computational tools. The image of the scholar as a solitary thinker dates back at least to Descartes' Discourse on Method. But scholarly practices in the humanities are changing as older forms of communal inquiry are combined with modern research methods enabled by the Internet, accessible computing, data availability, and new media. Hermeneutica introduces text analysis using computer-assisted interpretive practices. It offers theoretical chapters about text analysis, presents a set of analytical tools (called Voyant) that instantiate the theory, and provides example essays that illustrate the use of these tools. Voyant allows users to integrate interpretation into texts by creating hermeneutica—small embeddable “toys” that can be woven into essays published online or into such online writing environments as blogs or wikis. The book's companion website, Hermeneuti.ca, offers the example essays with both text and embedded interactive panels. The panels show results and allow readers to experiment with the toys themselves. The use of these analytical tools results in a hybrid essay: an interpretive work embedded with hermeneutical toys that can be explored for technique. The hermeneutica draw on and develop such common interactive analytics as word clouds and complex data journalism interactives. Embedded in scholarly texts, they create a more engaging argument. Moving between tool and text becomes another thread in a dynamic dialogue. COMPUTERS,Educational Software

Selling Online 2.0 REMEMBER WHEN eBay USED TO BE A GREAT PLACE FOR SMALL SELLERS TO BECOME BIG SELLERS? Unfortunately, recent changes at eBay have made online auctions less reliable and profitable. So where can you sell when you can’t sell on eBay? Online auctions are the past; fixed-price selling is the future. It’s time to move beyond eBay and first-generation online selling and start Selling Online 2.0. Second generation online selling means migrating from eBay to other online marketplaces, including craigslist, Amazon, and your own e-commerce website. You’ll need to make some new plans, learn some new skills, and change some of the things you do--but you’ll find that there’s more money to be made on your own than relying on traditional eBay online auction sales. Put together a plan to maintain your sales level and profitability--to counteract eBay’s changes Discover how to shift from auction sales to fixed-priced listings on the eBay marketplace Find out if running an eBay Store or selling on Half.com makes sense for your business Learn out how to sell locally on craigslist and other online classifieds sites Discover how to sell fixed-price merchandise on the Amazon marketplace Find out how to launch your own e-commerce website--and promote your online store Learn how to sell products across multiple channels--and manage multichannel conflicts COMPUTERS,Electronic Commerce (see also headings under BUSINESS & ECONOMICS,E-Commerce)

Introduction to E-commerce Introduction to E-commerce discusses the foundations and key aspects of E-commerce while focusing on the latest developments in the E-commerce industry. Practical case studies offer a useful reference for dealing with various issues in E-commerce such as latest applications, management techniques, or psychological methods. Dr. Zheng Qin is currently Director of the E-Commerce Institute of Xi’an Jiaotong University. He received his PhD from Northwestern Polytechnical University. COMPUTERS,Electronic Commerce (see also headings under BUSINESS & ECONOMICS,E-Commerce)

Effortless E-Commerce with PHP and MySQL In this comprehensive guide to creating an e-commerce website using PHP and MySQL, renowned author Larry Ullman walks students through every step—designing the visual interface, creating the database, presenting content, generating an online catalog, managing the shopping cart, handling the order and the payment process, and fulfilling the order—always with security and best practices emphasised along the way. The book uses three e-commerce site examples, so students see the widest possible range of e-commerce scenarios. This edition includes an additional modern payment processing example that reflects changes in PayPal’s options and methodologies. There are new chapters on marketing-related functionality incorporating analytics, on adding functionality via Ajax, and on implementing e-commerce functionality using OOP. Effortless E-Commerce with PHP and MySQL, Second Edition teaches you how to: Think of the customer first, in order to maximise sales Create a safe server environment and database Use secure transactions and prevent common vulnerabilities Incorporate different payment gateways Design scalable sites that are easy to maintain Build administrative interfaces Extend both examples to match the needs of your own sites The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Electronic Commerce (see also headings under BUSINESS & ECONOMICS,E-Commerce)

Ecommerce Analytics >Ecommerce Analytics is the only book to deliver the focused, coherent, and practical guidance you’re looking for. Authored by leading consultant and analytics team leader Judah Phillips, it shows how to leverage your massive, complex data resources to improve efficiency, grow revenue, reduce cost, and above all, boost profitability. This landmark guide focuses on using analytics to solve critical problems ecommerce organizations face, from improving brand awareness and favorability through generating demand; shaping digital behavior to accelerating conversion, improving experience to nurturing and re-engaging customers. Phillips shows how to: Implement and unify ecommerce analytics related to product, transactions, customers, merchandising, and marketing More effectively measure performance associated with customer acquisition, conversion, outcomes, and business impact Use analytics to identify the tactics that will create the most value, and execute them more effectively Think about and analyze the behavior of customers, prospects, and leads in ecommerce experiences Optimize paid/owned/earned marketing channels, product mix, merchandising, pricing/promotions/sales, browsing/shopping/purchasing, and other ecommerce functions Understand and model attribution Structure and socialize ecommerce teams for success Evaluate the potential impact of technology choices and platforms Understand the implications of ecommerce analytics on customer privacy, life, and society Preview the future of ecommerce analytics over the next 20 years COMPUTERS,Electronic Commerce (see also headings under BUSINESS & ECONOMICS,E-Commerce)

Programming Bitcoin Dive into Bitcoin technology with this hands-on guide from one of the leading teachers on Bitcoin and Bitcoin programming. Author Jimmy Song shows Python programmers and developers how to program a Bitcoin library from scratch. You’ll learn how to work with the basics, including the math, blocks, network, and transactions behind this popular cryptocurrency and its blockchain payment system. By the end of the book, you'll understand how this cryptocurrency works under the hood by coding all the components necessary for a Bitcoin library. Learn how to create transactions, get the data you need from peers, and send transactions over the network. Whether you’re exploring Bitcoin applications for your company or considering a new career path, this practical book will get you started. Parse, validate, and create bitcoin transactions Learn Script, the smart contract language behind Bitcoin Do exercises in each chapter to build a Bitcoin library from scratch Understand how proof-of-work secures the blockchain Program Bitcoin using Python 3 Understand how simplified payment verification and light wallets work Work with public-key cryptography and cryptographic primitives COMPUTERS,Electronic Commerce (see also headings under BUSINESS & ECONOMICS,E-Commerce)

eBay For Dummies It’s a bargain! The definitive guide to buying and selling success on eBay - fully updated for 2020 Want to know the best way to get rid of some of that clutter laying around the house and make some cash? Or sell that beautiful jewelry you made recently? It might be time to take a quick trip to a market with more than 175 million buyers and start a global bidding war. eBay remains the easiest way to sell to hungry consumers worldwide and to uncover incredible bargains and unique items for yourself in the process. Marsha Collier, longtime eBay business owner and one of their first elite PowerSellers, shares 20+ years of expertise to fast-track you to becoming a trusted buyer and seller on the site. You’ll find out how to set up your account, market effectively, and master shipping and payment, as well as how to find the best bargains for yourself and close those sweet, sweet deals. Establish your eBay store Find techniques to make your listings stand out Make money and friends with social media Bid or buy outright Whether you’re a bargain hunter or bargain seller, declutterer or aspiring eBay tycoon, eBay for Dummies has what you need. Put your bid on it right now! COMPUTERS,Electronic Commerce (see also headings under BUSINESS & ECONOMICS,E-Commerce)

Mastering WooCommerce 4 Understand all aspects of building a successful online store which is search-engine-optimized, using theme management and one-page checkout features Key Features Extend your WordPress knowledge to build fully functional e-commerce websites using WooCommerce and its plugins Implement payment gateway, shipping, and inventory management solutions Improve the speed and performance of your websites by optimizing images and caching static information Book Description WooCommerce is one of the most flexible platforms for building online stores. With its flexibility, you can offer virtually any feature to a client using the WordPress system. WooCommerce is also self-hosted, so the ownership of data lies with you and your client. This book starts with the essentials of building a WooCommerce store. You'll learn how to set up WooCommerce and implement payment, shipping, and tax options, as well as configure your product. The book also demonstrates ways to customize and manage your products by using SEO for enhanced visibility. As you advance, you'll understand how to manage sales by using POS systems, outsource fulfillment, and external reporting services. Once you've set up and organized your online store, you'll focus on improving the user experience of your e-commerce website. In addition to this, the book takes you through caching techniques to not only improve the speed and performance of your website but also its look and UI by adding themes. Finally, you'll build the landing page for your website to promote your product, and design WooCommerce plugins to customize the functionalities of your e-commerce website. By the end of this WooCommerce book, you'll have learned how to run a complete WooCommerce store, and be able to customize each section of the store on the frontend as well as backend. What you will learn Grasp the fundamentals of e-commerce website design and management with WordPress Use Gutenberg product blocks to display products across various categories on your website Get to grips with WordPress plugin development to customize your website's functionality Discover various ways to effectively handle product payment, taxes, and shipping Use analytics and product data syncing in WordPress to keep an eye on the user experience and monitor the performance of your online store Promote your new product online using SEO management and landing pages Who this book is for This WooCommerce development book is for web developers, WordPress developers, e-commerce consultants, or anyone familiar with using WordPress and interested in building an e-commerce platform from scratch. Working knowledge of WordPress development and general web development concepts is required. COMPUTERS,Electronic Commerce (see also headings under BUSINESS & ECONOMICS,E-Commerce)

Technologies for Modern Digital Entrepreneurship Emerging technologies offer a plethora of unprecedented opportunities for entrepreneurs in the digital space. Understanding this evolution is essential for web-based business models to succeed. The Web 3.0 economy is here, and this book has arrived to serve as your guide. Technologies for Modern Digital Entrepreneurship is an in-depth look at the new developments of the digital economic system. Cryptocurrencies, Central Bank Digital Currencies, and Stable Coins are explained through timely case studies, as well as innovations in crowdfunding, educational marketplaces, and scalability in blockchain-based transactions. Author Dr. Abeba N. Turi expertly navigates the industry transition from platform-based centralized Web 2.0 economy to the distributed network economy. Turi additionally explores trust and reputation as currency in the digital economy and allays common fears in digital entrepreneurship such as mistrust by investors and intellectual property loss. Avoid falling behind your competitors in the Wild West that is modern digital entrepreneurship. Whether you are a business leader, a technology enthusiast, or a researcher in the field, Technologies for Modern Digital Entrepreneurship gives you the advantage of insightful knowledge using real data and meaningful examples. Amid global regulatory changes and the ever-shifting methods of digital entrepreneurship, our modern era demands this book. What You Will Learn Discover new trends in the digital economic system Comprehend the crowd-based digital business models Analyze the distributed information network economy Understand the workings of the currency system under the Web 3.0 economy, including Cryptocurrencies, Central Bank Digital Currencies, and Stable Coins Who This Book Is For Technology enthusiasts, tech and interdisciplinary students, digital business leaders, and researchers in the field COMPUTERS,Electronic Commerce (see also headings under BUSINESS & ECONOMICS,E-Commerce)

HCI in Business, Government and Organizations This volume LNCS 12204 constitutes the refereed proceedings of the 7th International Conference on Business, Government, and Organizations, HCIBGO 2020, which was held in July 2020 as part of HCI International 2020 in Copenhagen, Denmark.* 1439 papers and 238 posters were accepted for publication after a careful reviewing process. The 42 papers presented in this volume are organized in topical sections named: digital transformation and intelligent data analysis and social media, digital commerce and marketing. *The conference was held virtually due to the COVID-19 pandemic. Chapter “The Effect of Queuing Technology on Customer Experience in Physical Retail Environments†is available open access under a Creative Commons Attribution 4.0 International License via link.springer.com. COMPUTERS,Electronic Commerce (see also headings under BUSINESS & ECONOMICS,E-Commerce)

Publishing E-Books For Dummies Publish, market, and sell your own e-book Although creating an e-book seems fairly straightforward, it is not. You need to select and create a variety of formats that will be read on a variety of e-reader devices--and market and sell your book in a variety of ways. Before you take the plunge, get this practical guide. With clear instruction and sensible advice, it will help you navigate the often confusing, time-consuming, and costly world of self-publishing an e-book. The book gives you solid marketing tips for selling your e-book, including using blogging and social media and how to build an online platform. It also discusses key technologies you'll encounter, including Smashwords, iBooks Author, Amazon, Microsoft Word, Open Office, Calibre, WordPress, E-junkie, and others. Helps readers navigate the confusing, time-consuming, and often costly world of self-publishing an e-book Provides both technical how-tos as well solid marketing advice on how to sell your e-book using Facebook, Twitter, Goodreads, and other social media sites Covers essential technologies, such as Smashwords, iBooks Author, Amazon, Microsoft Word, Open Office, Calibre, WordPress, and E-junkie Explores e-book devices, including Kindle, Kobo, Sony Reader, Nook, iPad, and other tablets Delves into the nitty-gritty of e-book formats Before you self-publish your e-book, start first with Publishing eBooks For Dummies. COMPUTERS,Electronic Publishing

EPUB 3 Best Practices Ready to take your ebooks to the next level with EPUB 3? This concise guide includes best practices and advice to help you navigate the format’s wide range of technologies and functionality. EPUB 3 is set to turn electronic publishing on its head with rich multimedia reading experiences and scripted interactivity, but this specification can be daunting to learn. This book provides you with a solid foundation. Written by people involved in the development of this specification, EPUB 3 Best Practices includes chapters that cover unique aspects of the EPUB publishing process, such as technology, content creation, and distribution. Get a comprehensive survey of accessible production features Learn new global language-support features, including right-to-left page progressions Embed content with EPUB 3’s new multimedia elements Make your content dynamic through scripting and interactive elements Work with publication and distribution metadata Create synchronized text and audio playback in reading systems Learn techniques for fixed and adaptive layouts COMPUTERS,Electronic Publishing

LaTeX Companion, The This is the digial version of the printed book (Copyright © 2004). The LaTeX Companion has long been the essential resource for anyone using LaTeX to create high-quality printed documents. This completely updated edition brings you all the latest information about LaTeX and the vast range of add-on packages now available--over 200 are covered! Full of new tips and tricks for using LaTeX in both traditional and modern typesetting, this book will also show you how to customize layout features to your own needs--from phrases and paragraphs to headings, lists, and pages. Inside, you will find: Expert advice on using LaTeX's basic formatting tools to create all types of publications--from memos to encyclopedias In-depth coverage of important extension packages for tabular and technical typesetting, floats and captions, multicolumn layouts--including reference guides and discussions of the underlying typographic and TeXnical concepts Detailed techniques for generating and typesetting contents lists, bibliographies, indexes, etc. Tips and tricks for LaTeX programmers and systems support New to this edition: Nearly 1,000 fully tested examples that illustrate the text and solve typographical and technical problems--all ready to run! An additional chapter on citations and bibliographies Expanded material on the setup and use of fonts to access a huge collection of glyphs, and to typeset text from a wide range of languages and cultures Major new packages for graphics, "verbatim" listings, floats, and page layout Full coverage of the latest packages for all types ofdocuments--mathematical, multilingual, and many more Detailed help on all error messages, including those troublesome low-level TeX errors Like its predecessor, The LaTeX Companion, Second Edition, is an indispensable reference for anyone wishing to productivelyuse LaTeX. Appendix D talks about the TLC2 TeX CD at the end of the book, something you will have a hard time finding in the eBook. The most important content of the CD included with the print book is the full text of the examples. You can find the examples easily on the Internet, for example at http://www.ctan.org/tex-archive/info/examples/tlc2 as well as in many LaTeX installations. COMPUTERS,Electronic Publishing

Adobe Animate CC Classroom in a Book (2018 release) Creative professionals seeking the fastest, easiest, most comprehensive way to learn Adobe Animate choose Adobe Animate CC Classroom in a Book (2018 release) from Adobe Press. The 12 project-based step-by-step lessons in this book show users the key techniques for working in Animate. Adobe Animate CC provides more expressive tools, powerful controls for animation, and robust support for playback across a wide variety of platforms. Learn how to use and create vector-based brushes for painterly effects. Gain more advanced control over complex animations with the Camera tool, and learn to focus the action on different parts of the Stage. Explore the new Layer Depth panel which lets you control the depth level of individual layers, creating a more realistic sense of space. Support for SVG, WebGL, HTML5 animation and video, and seamless collaboration with other designers and with other Adobe applications through Creative Cloud libraries make Adobe Animate the ideal development environment for creative animation and multimedia. The online companion files include all the necessary assets for readers to complete the projects featured in each lesson as well as ebook updates when Adobe releases relevant new features for Creative Cloud customers. All buyers of the book get full access to the Web Edition: a Web-based version of the complete ebook enhanced with video and multiple-choice quizzes. COMPUTERS,Electronic Publishing

Adobe Animate CC Classroom in a Book Creative professionals seeking the fastest, easiest, most comprehensive way to learn Adobe Animate choose Adobe Animate CC Classroom in a Book (2019 release) from Adobe Press. The 11 project-based step-by-step lessons in this book show users the key techniques for working in Animate. Adobe Animate CC provides more expressive tools, powerful controls for animation, and robust support for playback across a wide variety of platforms. Create interactive virtual reality immersive environments with new VR 360 and VR Panorama documents. Gain advanced control over character animations with layer parenting and AI-driven lip syncing. Learn to focus the action on different parts of the Stage with the Camera tool and create a realistic sense of space with the Layer Depth panel. Support for SVG, WebGL, HTML5, animated GIFs, and HD video, and seamless collaboration with other designers and with other Adobe applications through Creative Cloud libraries make Adobe Animate the ideal development environment for creative animation and multimedia. The online companion files include all the necessary assets for readers to complete the projects featured in each chapter. All buyers of the book get full access to the Web Edition: A Web-based version of the complete ebook enhanced with video and multiple-choice quizzes. COMPUTERS,Electronic Publishing

Adobe Animate Classroom in a Book (2020 release) Creative professionals seeking the fastest, easiest, most comprehensive way to learn Adobe Animate choose Adobe Animate Classroom in a Book from Adobe Press. The 11 project-based step-by-step lessons in this book show users the key techniques for working in Animate. Adobe Animate CC provides more expressive tools, powerful controls for animation, and robust support for playback across a wide variety of platforms. Create interactive virtual reality immersive environments with new VR 360 and VR Panorama documents. Gain advanced control over character animations with layer parenting and AI-driven lip syncing. Learn to focus the action on different parts of the Stage with the Camera tool and create a realistic sense of space with the Layer Depth panel. Support for SVG, WebGL, HTML5, animated GIFs, and HD video, and seamless collaboration with other designers and with other Adobe applications through Creative Cloud libraries make Adobe Animate the ideal development environment for creative animation and multimedia. Classroom in a Book is the best-selling series of hands-on software training books designed to help you learn the features of Adobe software quickly and easily. Developed by the training experts at Adobe Systems, these books offer complete, self-paced lessons designed to fit your busy schedule and help you learn the features of Adobe software quickly and easily. Each book includes downloadable files to guide you through the lessons and special projects. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Electronic Publishing

Arithmetic and Logic in Computer Systems Arithmetic and Logic in Computer Systems provides a useful guide to a fundamental subject of computer science and engineering. Algorithms for performing operations like addition, subtraction, multiplication, and division in digital computer systems are presented, with the goal of explaining the concepts behind the algorithms, rather than addressing any direct applications. Alternative methods are examined, and explanations are supplied of the fundamental materials and reasoning behind theories and examples. No other current books deal with this subject, and the author is a leading authority in the field of computer arithmetic. The text introduces the Conventional Radix Number System and the Signed-Digit Number System, as well as Residue Number System and Logarithmic Number System. This book serves as an essential, up-to-date guide for students of electrical engineering and computer and mathematical sciences, as well as practicing engineers and computer scientists involved in the design, application, and development of computer arithmetic units. COMPUTERS,General

Modeling Software with Finite State Machines Modeling Software with Finite State Machines: A Practical Approach explains how to apply finite state machines to software development. It provides a critical analysis of using finite state machines as a foundation for executable specifications to reduce software development effort and improve quality. This book discusses the design of a state mach COMPUTERS,General

Cyber Crime Fighters “Cyber Crime Fighters: Tales from the Trenches offers one of the most insightful views of the latest criminal threats to the public: cyber crime. This book provides a good primer on how your personal information can be easily obtained by some of the folks you least want to have it.†—Maureen Boyle, crime reporter, The Enterprise of Brockton, MA “Experts Felicia Donovan and Kristyn Bernier pull no punches in explaining the dangers lurking on the Web, from identity appropriation and theft to using new technology and the Internet to facilitate real-life stalking. Parents especially will be shocked at how easy it is for predators to target and solicit children online. “By clearly explaining the dangers that lurk online and highlighting practical tips to minimize your risk, the authors have created a book that not only educates but empowers readers to protect themselves.†—Jennifer Hemmingsen, columnist and former public safety reporter, The (Cedar Rapids, Iowa) Gazette Written by leading cyber crime investigators, Cyber Crime Fighters: Tales from the Trenches takes you behind the scenes to reveal the truth behind Internet crime, telling shocking stories that aren’t covered by the media, and showing you exactly how to protect yourself and your children. This is the Internet crime wave as it really looks to law enforcement insiders: the truth about crime on social networks and YouTube, cyber stalking and criminal cyber bullying, online child predators, identity theft, even the latest cell phone crimes. Here are actual cases and actual criminals, presented by investigators who have been recognized by the FBI and the N.H. Department of Justice. These stories are true–and if you want to stay safe, you need to know about them. • Learn how today’s criminals can track your whereabouts, read your emails, and steal your identity • Find out how much of your personal information is already online–and how to keep the rest private • Learn how cyber stalkers really think–and how to protect yourself from them • Protect your laptop, your iPod, and your precious data from getting stolen • Encounter the “dark side†of Internet dating • Discover the hidden crime wave on today’s specialized social networks • Uncover the cell phone “upskirters†and “downblousers†–and the technicalities that keep them out of jail • Follow cyber crime specialists as they investigate and catch online sexual predators • Get the real truth about phishing, pharming, criminal spam, and online scams • See how investigations really work–and why TV crime shows often get it wrong! • Walk through your own personal, step-by-step, online safety checkup COMPUTERS,General

BSD Hacks In the world of Unix operating systems, the various BSDs come with a long heritage of high-quality software and well-designed solutions, making them a favorite OS of a wide range of users. Among budget-minded users who adopted BSD early on to developers of some of today's largest Internet sites, the popularity of BSD systems continues to grow. If you use the BSD operating system, then you know that the secret of its success is not just in its price tag: practical, reliable, extraordinarily stable and flexible, BSD also offers plenty of fertile ground for creative, time-saving tweaks and tricks, and yes, even the chance to have some fun."Fun?" you ask. Perhaps "fun" wasn't covered in the manual that taught you to install BSD and administer it effectively. But BSD Hacks, the latest in O'Reilly's popular Hacks series, offers a unique set of practical tips, tricks, tools--and even fun--for administrators and power users of BSD systems.BSD Hacks takes a creative approach to saving time and getting more done, with fewer resources. You'll take advantage of the tools and concepts that make the world's top Unix users more productive. Rather than spending hours with a dry technical document learning what switches go with a command, you'll learn concrete, practical uses for that command.The book begins with hacks to customize the user environment. You'll learn how to be more productive in the command line, timesaving tips for setting user-defaults, how to automate long commands, and save long sessions for later review. Other hacks in the book are grouped in the following areas: Customizing the User Environment Dealing with Files and Filesystems The Boot and Login Environments Backing Up Networking Hacks Securing the System Going Beyond the Basics Keeping Up-to-Date Grokking BSD If you want more than your average BSD user--you want to explore and experiment, unearth shortcuts, create useful tools, and come up with fun things to try on your own--BSD Hacks is a must-have. This book will turn regular users into power users and system administrators into super system administrators. COMPUTERS,General

Absolute Beginner's Guide to Computer Basics Everything casual users need to know to get the most out of their new Windows 7 PCs, software, and the Internet The best-selling beginner's guide, now completely updated for Windows 7 and today's most popular Internet tools - including Facebook, craigslist, Twitter, and Wikipedia Easy step-by-step instructions cover setting up a new PC, getting online, working with digital media, using productivity tools, and much more By the world's #1 author of beginning technology books, Michael Miller This year, you may be one of the millions of casual computer users that will buy a new Windows 7 notebook or desktop PC. You'll want to know how to find your way around, get comfortable, and get the job done - without jargon, complexity, or hassle. There's a book for you: Michael Miller's Absolute Beginner's Guide to Computer Basics, Windows 7 Edition. It's the one book that covers everything today's beginners and near-beginners need to know: not just about Windows, but also about software, hardware, and the Internet. Through 90+ books, author Michael Miller has established an unparalleled track record in explaining complicated concepts simply and clearly, and empowering beginners. Now, he's thoroughly updated his best-selling Absolute Beginner's Guide to Computer Basics to cover today's user experience - with Windows 7, Internet Explorer 8, and today's hottest online tools, from craigslist and Facebook to Twitter, Wikipedia, and Google Docs. Miller offers step-by-step instructions and friendly, practical advice for making the most of Windows 7's improvements, including the new taskbar, Action Center, and Aero Snap. He walks through setting up a new computer; connecting to the Internet; working with digital media; burning custom CDs; watching DVD movies; using Microsoft Office and other popular software; managing money online; setting up home networks; keeping PCs running reliably; and protecting them from spam, viruses, and spyware. This is the one indispensable book for today's PC novice. COMPUTERS,General

PDF Hacks PDF--to most of the world it stands for that rather tiresome format used for documents downloaded from the web. Slow to load and slower to print, hopelessly unsearchable, and all but impossible to cut and paste from, the Portable Document Format doesn't inspire much affection in the average user. But PDFs done right is another story. Those who know the ins and outs of this format know that it can be much more than electronic paper. Flexible, compact, interactive, and even searchable, PDF is the ideal way to present content across multiple platforms. PDF Hacks unveils the true promise of Portable Document Format, going way beyond the usual PDF as paged output mechanism. PDF expert Sid Steward draws from his years of analyzing, extending, authoring, and embellishing PDF documents to present 100 clever hacks--tools, tips, quick-and-dirty or not-so-obvious solutions to common problems. PDF Hacks will show you how to create PDF documents that are far more powerful than simple representations of paper pages. The hacks in the book cover the full range of PDF functionality, from the simple to the more complex, including generating, manipulating, annotating, and consuming PDF information. You'll learn how to manage content in PDF, navigate it, and reuse it as necessary. Far more than another guide to Adobe Acrobat, the book covers a variety of readily available tools for generating, deploying, and editing PDF. The little-known tips and tricks in this book are ideal for anyone who works with PDF on a regular basis, including web developers, pre-press users, forms creators, and those who generate PDF for distribution. Whether you want to fine-tune and debug your existing PDF documents or explore the full potential the format offers, PDF Hacks will turn you into a PDF power user. COMPUTERS,General

Using Samba This book is the comprehensive guide to Samba administration, officially adopted by the Samba Team. Wondering how to integrate Samba's authentication with that of a Windows domain? How to get Samba to serve Microsoft Dfs shares? How to share files on Mac OS X? These and a dozen other issues of interest to system administrators are covered. A whole chapter is dedicated to troubleshooting! The range of this book knows few bounds. Using Samba takes you from basic installation and configuration -- on both the client and server side, for a wide range of systems -- to subtle details of security, cross-platform compatibility, and resource discovery that make the difference between whether users see the folder they expect or a cryptic error message. The current edition covers such advanced 3.x features as: Integration with Active Directory and OpenLDAP Migrating from Windows NT 4.0 domains to Samba Delegating administrative tasks to non-root users Central printer management Advanced file serving features, such as making use of Virtual File System (VFS) plugins. Samba is a cross-platform triumph: robust, flexible and fast, it turns a Unix or Linux system into a file and print server for Microsoft Windows network clients. This book will help you make your file and print sharing as powerful and efficient as possible. The authors delve into the internals of the Windows activities and protocols to an unprecedented degree, explaining the strengths and weaknesses of each feature in Windows domains and in Samba itself. Whether you're playing on your personal computer or an enterprise network, on one note or a full three-octave range, Using Samba will give you an efficient and secure server. COMPUTERS,General

Learning GNU Emacs GNU Emacs is the most popular and widespread of the Emacs family of editors. It is also the most powerful and flexible. Unlike all other text editors, GNU Emacs is a complete working environment--you can stay within Emacs all day without leaving. Learning GNU Emacs, 3rd Edition tells readers how to get started with the GNU Emacs editor. It is a thorough guide that will also "grow" with you: as you become more proficient, this book will help you learn how to use Emacs more effectively. It takes you from basic Emacs usage (simple text editing) to moderately complicated customization and programming.The third edition of Learning GNU Emacs describes Emacs 21.3 from the ground up, including new user interface features such as an icon-based toolbar and an interactive interface to Emacs customization. A new chapter details how to install and run Emacs on Mac OS X, Windows, and Linux, including tips for using Emacs effectively on those platforms.Learning GNU Emacs, third edition, covers: How to edit files with Emacs Using the operating system shell through Emacs How to use multiple buffers, windows, and frames Customizing Emacs interactively and through startup files Writing macros to circumvent repetitious tasks Emacs as a programming environment for Java, C++, and Perl, among others Using Emacs as an integrated development environment (IDE) Integrating Emacs with CVS, Subversion and other change control systems for projects with multiple developers Writing HTML, XHTML, and XML with Emacs The basics of Emacs Lisp The book is aimed at new Emacs users, whether or not they are programmers. Also useful for readers switching from other Emacs implementations to GNU Emacs. COMPUTERS,General

Linux iptables Pocket Reference Firewalls, Network Address Translation (NAT), network logging and accounting are all provided by Linux's Netfilter system, also known by the name of the command used to administer it, iptables. The iptables interface is the most sophisticated ever offered onLinux and makes Linux an extremely flexible system for any kind of network filtering you might do. Large sets of filtering rules can be grouped in ways that makes it easy to test them and turn them on and off.Do you watch for all types of ICMP traffic--some of them quite dangerous? Can you take advantage of stateful filtering to simplify the management of TCP connections? Would you like to track how much traffic of various types you get?This pocket reference will help you at those critical moments when someone asks you to open or close a port in a hurry, either to enable some important traffic or to block an attack. The book will keep the subtle syntax straight and help you remember all the values you have to enter in order to be as secure as possible. The book has an introductory section that describes applications,followed by a reference/encyclopaedic section with all the matches and targets arranged alphabetically. COMPUTERS,General

JavaScript Pocket Reference JavaScript is a powerful, object-based scripting language that can be embedded directly in HTML pages. It allows you to create dynamic, interactive Web-based applications that run completely within a Web browser -- JavaScript is the language of choice for developing Dynamic HTML (DHTML) content. JavaScript can be integrated effectively with CGI and Java to produce sophisticated Web applications, although, in many cases, JavaScript eliminates the need for complex CGI scripts and Java applets altogether.The JavaScript Pocket Reference is a companion volume to JavaScript: The Definitive Guide. This small book, covering JavaScript 1.2, is a handy reference guide to this popular language for Web development. It provides a complete overview of the core JavaScript language and contains summaries of both core and client-side objects, methods, and properties. COMPUTERS,General

Writing GNU Emacs Extensions Yes, it is possible to be all things to all people, if you're talking about the Emacs editor. As a user, you can make any kind of customization you want, from choosing the keystrokes that invoke your favorite commands to creating a whole new work environment that looks like nothing ever developed before. It's all in Emacs Lisp -- and in this short but fast-paced book.GNU Emacs is more than an editor; it's a programming environment, a communications package, and many other things. To provide such a broad range of functions, it offers a full version of the Lisp programming language -- something much more powerful than the little macro languages provided in other editors (including older versions of Emacs). GNU Emacs is a framework in which you can create whole new kinds of editors or just alter aspects of the many functions it already provides.In this book, Bob Glickstein delves deep into the features that permit far-reaching Emacs customizations. He teaches you the Lisp language and discusses Emacs topics (such as syntax tables and macro templates) in easy-to-digest portions. Examples progress in complexity from simple customizations to extensive major modes.You will learn how to write interactive commands, use hooks and advice, perform error recovery, manipulate windows, buffers, and keymaps, exploit and alter Emacs's main loop, and more. Each topic is explored through realistic examples and a series of successive refinements that illustrate not only the Emacs Lisp language, but the development process as well, making learning pleasant and natural. COMPUTERS,General

The Computer User's Survival Guide You probably suspect, on some level, that computers might be hazardous to your health. You might vaguely remember a study that you read years ago about miscarriages being more frequent for data entry operators. Or you might have run into a co-worker wearing splints and talking ominously about Workers' Comp insurance. Or you might notice that when you use a computer too long, you get stiff and your eyes get dry.But who wants to worry about such things? Surely, the people wearing splints must be malingerers who don't want to work? Surely, the people who design keyboards and terminals must be working to change their products if they are unsafe? Surely, so long as you're a good worker and keep your mind on your job, nothing bad will happen to you?The bad news is: You can be hurt by working at a computer. The good news is that many of the same factors that pose a risk to you are within your own control. You can take action on your own to promote your own health -- whether or not your terminal manufacturer, keyboard designer, medical provider, safety trainer, and boss are working diligently to protect you.The Computer User's Survival Guide looks squarely at all the factors that affect your health on the job, including positioning, equipment, work habits, lighting, stress, radiation, and general health.Through this guide you will learn: a continuum of neutral postures that you can at utilize at different work tasks how radiation drops off with distance and what electrical equipment is responsible for most exposure how modern office lighting is better suited to working on paper than on a screen, and what you can do to prevent glare simple breathing techniques and stretches to keep your body well oxygenated and relaxed, even when you sit all day how reading from a screen puts unique strains on your eyes and what kind of vision breaks will keep you most productive and rested what's going on "under the skin" when your hands and arms spend much of the day mousing and typing, and how you can apply that knowledge to prevent overuse injuries The Computer User's Survival Guide is not a book of gloom and doom. It is a guide to protecting yourself against health risks from your computer, while boosting your effectiveness and your enjoyment of work. COMPUTERS,General

Introduction to High Performance Computing for Scientists and Engineers Written by high performance computing (HPC) experts, Introduction to High Performance Computing for Scientists and Engineers provides a solid introduction to current mainstream computer architecture, dominant parallel programming models, and useful optimization strategies for scientific HPC. From working in a scientific computing center, the author COMPUTERS,General

A History of the Internet and the Digital Future A History of the Internet and the Digital Future tells the story of the development of the Internet from the 1950s to the present and examines how the balance of power has shifted between the individual and the state in the areas of censorship, copyright infringement, intellectual freedom, and terrorism and warfare. Johnny Ryan explains how the Internet has revolutionized political campaigns; how the development of the World Wide Web enfranchised a new online population of assertive, niche consumers; and how the dot-com bust taught smarter firms to capitalize on the power of digital artisans. From the government-controlled systems of the Cold War to today’s move towards cloud computing, user-driven content, and the new global commons, this book reveals the trends that are shaping the businesses, politics, and media of the digital future. COMPUTERS,General

Probability and Statistics with Reliability, Queuing, and Computer Science Applications An accessible introduction to probability, stochastic processes, and statistics for computer science and engineering applications Second edition now also available in Paperback. This updated and revised edition of the popular classic first edition relates fundamental concepts in probability and statistics to the computer sciences and engineering. The author uses Markov chains and other statistical tools to illustrate processes in reliability of computer systems and networks, fault tolerance, and performance. This edition features an entirely new section on stochastic Petri nets—as well as new sections on system availability modeling, wireless system modeling, numerical solution techniques for Markov chains, and software reliability modeling, among other subjects. Extensive revisions take new developments in solution techniques and applications into account and bring this work totally up to date. It includes more than 200 worked examples and self-study exercises for each section. Probability and Statistics with Reliability, Queuing and Computer Science Applications, Second Edition offers a comprehensive introduction to probability, stochastic processes, and statistics for students of computer science, electrical and computer engineering, and applied mathematics. Its wealth of practical examples and up-to-date information makes it an excellent resource for practitioners as well. An Instructor's Manual presenting detailed solutions to all the problems in the book is available from the Wiley editorial department. COMPUTERS,General

The Art of Readable Code As programmers, we’ve all seen source code that’s so ugly and buggy it makes our brain ache. Over the past five years, authors Dustin Boswell and Trevor Foucher have analyzed hundreds of examples of "bad code" (much of it their own) to determine why they’re bad and how they could be improved. Their conclusion? You need to write code that minimizes the time it would take someone else to understand it—even if that someone else is you. This book focuses on basic principles and practical techniques you can apply every time you write code. Using easy-to-digest code examples from different languages, each chapter dives into a different aspect of coding, and demonstrates how you can make your code easy to understand. Simplify naming, commenting, and formatting with tips that apply to every line of code Refine your program’s loops, logic, and variables to reduce complexity and confusion Attack problems at the function level, such as reorganizing blocks of code to do one task at a time Write effective test code that is thorough and concise—as well as readable "Being aware of how the code you create affects those who look at it later is an important part of developing software. The authors did a great job in taking you through the different aspects of this challenge, explaining the details with instructive examples." —Michael Hunger, passionate Software Developer COMPUTERS,General

Imagined Hinduism This book explores the emergence and subsequent refinement of the idea of Hinduism as it developed among British Protestant missionaries in the late eighteenth and nineteenth centuries. Using missionary writings, the author shows how the early conservative view of Hinduism as pagan or heathen grew into the dominant paradigm of Hinduism as a unitary, brahman-controlled system, ridden with idolatry, ritualism, superstition, and sexual license. The last few chapters examine the impact of these representations of Hinduism in India and the West. This book is noteworthy for its recognition of the role of 'imagination' and the concept of the 'dominant paradigm'. COMPUTERS,General

Automotive SPICE in Practice Automotive SPICE is a framework for designing and assessing software development processes. If implemented effectively, it leads to better processes and better product quality. It also helps to improve the cooperation among complex supply chains and between globally distributed development and engineering centers. Automotive SPICE has been derived from the ISO/IEC 15504 standard, also known as SPICE. It has been developed under the Automotive SPICE initiative by the consensus of several major car manufacturers such as Audi, BMW, Ford, Fiat, Daimler, Porsche, Volkswagen, and Volvo. Today, Automotive SPICE has become a standard in the international automotive industry. This book is written as a guide to help the reader understand and interpret the requirements of this standard and to implement Automotive SPICE in a real world application environment. It is written for engineers, practitioners, managers, and project managers who need practical guidance in applying or implementing the Automotive SPICE framework in his/her company. Important topics, such as traceability, functional safety (IEC 61508), and the relationship between Automotive SPICE and CMMI are given particular attention. This book is a definite must for practitioners involved in implementing Automotive SPICE in process improvement programs; a welcome aid for any assessor looking for clear, consistent, and constructive rating guidelines; and an invaluable resource for anyone concerned with engineering development processes in the automotive industry. COMPUTERS,General

Type II Uses of Technology in Education Spark your students to actually want to learn through the creative application of technology! Type II applications in education make it possible to teach in new and more effective ways. Type II Uses of Technology in Education: Projects, Case Studies, and Software Applications clearly explains methods and strategies presently used by teachers to offer students a creative learning experience through the application of technology. Each chapter presents individual examples of how teachers have applied technology in schools and classrooms, illustrating through case studies, projects, and software applications how to effectively spark students’ interest and learning. Type II Uses of Technology in Education is the third in a series (Internet Applications of Type II Uses of Technology in Education and Classroom Integration of Type II Uses of Technology in Education, both from Haworth) that provides a clear view of the advantagesand challengesinvolved in the use of technology to enhance and actively involve students in the learning process. The applications described and discussed at length here go beyond the mundane educational functions like grading or presenting drill and practice exercises to explore fresh ways of teaching and learning. Students can become involved and actually want to learn, all through the use of creative technology application. The book also includes tables and figures to enhance understanding of the material. Type II Uses of Technology in Education discusses: data collection, analysis, and communication in student research using pocket PCs and laptops the educational effect of using a learning object as a pedagogical model rather than simply being technological in nature examples of integrated Type II activities e-learning courses using interactive video, WebCT, and on-site discussion groups electronic discussion applications in a laptop university teacher education program challenges facing students using computers to enhance and express the extent of their learning information and communication technology (ICT) integration into schoolsusing three illustrative case studies forward planning needed to make the difficult change to technological application for learning a case study that used problem-based learning software with at-risk students using technology to reinforce visual learning strategies digital portfolio development as a Type II application interactive computer technology in art instruction on-demand help features for effective interactive learning experience Personal Educational Tools (PETs) Type II Uses of Technology in Education: Projects, Case Studies, and Software Applications provides numerous illustrations of technology learning in action and is perfect for educators and students in programs dealing with information technology in education, and for public school personnel with interests and responsibilities in using information technology in the classroom. COMPUTERS,General

Implementing Service Quality based on ISO/IEC 20000 ISO/IEC 20000 is an important international standard for IT service providers. This book is crammed with practical advice and recommendations on how to prepare for ISO20000 audit and implementation. It is the ideal companion to ISO20000 courses from a range of certification bodies such as EXIN, PeopleCert and others. COMPUTERS,General

ITIL Lifecycle Essentials This text covers everything you need for the entry-level ITIL Foundation course, providing candidates with a solid grounding in the key elements, concepts and terminology used in the ITIL service lifecycle. However, it also goes beyond this in providing practical guidance for when newly qualified practitioners enter the real world. COMPUTERS,General

Architecting the Cloud An expert guide to selecting the right cloud service model for your business Cloud computing is all the rage, allowing for the delivery of computing and storage capacity to a diverse community of end-recipients. However, before you can decide on a cloud model, you need to determine what the ideal cloud service model is for your business. Helping you cut through all the haze, Architecting the Cloud is vendor neutral and guides you in making one of the most critical technology decisions that you will face: selecting the right cloud service model(s) based on a combination of both business and technology requirements. Guides corporations through key cloud design considerations Discusses the pros and cons of each cloud service model Highlights major design considerations in areas such as security, data privacy, logging, data storage, SLA monitoring, and more Clearly defines the services cloud providers offer for each service model and the cloud services IT must provide Arming you with the information you need to choose the right cloud service provider, Architecting the Cloud is a comprehensive guide covering everything you need to be aware of in selecting the right cloud service model for you. COMPUTERS,General

Get Started In Computing Get Started in Computing is perfect for any new computer user who wants to get up and running quickly and simply. If you are a beginner it is a cost-effective alternative to buying an expensive manual for each application. Though Written for the general user, you will also find the level and content relevant if you are following MOUS certification, SQA modules and BCS Level 1/2 application courses. With step-by-step instructions, minimal jargon and detailed explanations of all the technical terms, this book will give you the confidence to move forward and expand your knowledge. Updated for Windows 7, the book covers all the basics, helping you to find ways of using your computer to suit you. Also included: - Health and safety laws and guidelines affecting the use of IT - Creating and maintaining a safe workstation environment - MS Office interface - ribbon, tabs, groups, MSO button and menu, Quick Access toolbar - Advantages and disadvantages of different email systems - Netiquette - Hidden dangers - unsolicited email, virus dangers NOT GOT MUCH TIME? One and five-minute introductions to key principles to get you started. AUTHOR INSIGHTS Lots of instant help with common problems and quick tips for success, based on the author's many years of experience. TEST YOURSELF Tests in the book and online to keep track of your progress. EXTEND YOUR KNOWLEDGE Extra online articles at www.teachyourself.com to give you a richer understanding of the basics of computing. FIVE THINGS TO REMEMBER Quick refreshers to help you remember the key facts. TRY THIS Innovative exercises illustrate what you've learnt and how to use it. COMPUTERS,General

Fundamentals of Parallel Multicore Architecture Although multicore is now a mainstream architecture, there are few textbooks that cover parallel multicore architectures. Filling this gap, Fundamentals of Parallel Multicore Architecture provides all the material for a graduate or senior undergraduate course that focuses on the architecture of multicore processors. The book is also useful as a ref COMPUTERS,General

Digital Logic Design and Computer Organization with Computer Architecture for Security A COMPREHENSIVE GUIDE TO THE DESIGN & ORGANIZATION OF MODERN COMPUTING SYSTEMS Digital Logic Design and Computer Organization with Computer Architecture for Security provides practicing engineers and students with a clear understanding of computer hardware technologies. The fundamentals of digital logic design as well as the use of the Verilog hardware description language are discussed. The book covers computer organization and architecture, modern design concepts, and computer security through hardware. Techniques for designing both small and large combinational and sequential circuits are thoroughly explained. This detailed reference addresses memory technologies, CPU design and techniques to increase performance, microcomputer architecture, including "plug and play" device interface, and memory hierarchy. A chapter on security engineering methodology as it applies to computer architecture concludes the book. Sample problems, design examples, and detailed diagrams are provided throughout this practical resource. COVERAGE INCLUDES: Combinational circuits: small designs Combinational circuits: large designs Sequential circuits: core modules Sequential circuits: small designs Sequential circuits: large designs Memory Instruction set architecture Computer architecture: interconnection Memory system Computer architecture: security COMPUTERS,General

Getting a Big Data Job For Dummies Hone your analytic talents and become part of the next big thing Getting a Big Data Job For Dummies is the ultimate guide to landing a position in one of the fastest-growing fields in the modern economy. Learn exactly what "big data" means, why it's so important across all industries, and how you can obtain one of the most sought-after skill sets of the decade. This book walks you through the process of identifying your ideal big data job, shaping the perfect resume, and nailing the interview, all in one easy-to-read guide. Companies from all industries, including finance, technology, medicine, and defense, are harnessing massive amounts of data to reap a competitive advantage. The demand for big data professionals is growing every year, and experts forecast an estimated 1.9 million additional U.S. jobs in big data by 2015. Whether your niche is developing the technology, handling the data, or analyzing the results, turning your attention to a career in big data can lead to a more secure, more lucrative career path. Getting a Big Data Job For Dummies provides an overview of the big data career arc, and then shows you how to get your foot in the door with topics like: The education you need to succeed The range of big data career path options An overview of major big data employers A plan to develop your job-landing strategy Your analytic inclinations may be your ticket to long-lasting success. In a highly competitive job market, developing your data skills can create a situation where you pick your employer rather than the other way around. If you're ready to get in on the ground floor of the next big thing, Getting a Big Data Job For Dummies will teach you everything you need to know to get started today. COMPUTERS,General

Writing for Computer Science All researchers need to write or speak about their work, and to have research that is worth presenting. Based on the author's decades of experience as a researcher and advisor, this third edition provides detailed guidance on writing and presentations and a comprehensive introduction to research methods, the how-to of being a successful scientist. Topics include: · Development of ideas into research questions; · How to find, read, evaluate and referee other research; · Design and evaluation of experiments and appropriate use of statistics; · Ethics, the principles of science and examples of science gone wrong. Much of the book is a step-by-step guide to effective communication, with advice on: · Writing style and editing; · Figures, graphs and tables; · Mathematics and algorithms; · Literature reviews and referees’ reports; · Structuring of arguments and results into papers and theses; · Writing of other professional documents; · Presentation of talks and posters. Written in an accessible style and including handy checklists and exercises, Writing for Computer Science is not only an introduction to the doing and describing of research, but is a valuable reference for working scientists in the computing and mathematical sciences. COMPUTERS,General

A Guide to Algorithm Design Presenting a complementary perspective to standard books on algorithms, A Guide to Algorithm Design: Paradigms, Methods, and Complexity Analysis provides a roadmap for readers to determine the difficulty of an algorithmic problem by finding an optimal solution or proving complexity results. It gives a practical treatment of algorithmic complexity and guides readers in solving algorithmic problems. Divided into three parts, the book offers a comprehensive set of problems with solutions as well as in-depth case studies that demonstrate how to assess the complexity of a new problem. Part I helps readers understand the main design principles and design efficient algorithms. Part II covers polynomial reductions from NP-complete problems and approaches that go beyond NP-completeness. Part III supplies readers with tools and techniques to evaluate problem complexity, including how to determine which instances are polynomial and which are NP-hard. Drawing on the authors’ classroom-tested material, this text takes readers step by step through the concepts and methods for analyzing algorithmic complexity. Through many problems and detailed examples, readers can investigate polynomial-time algorithms and NP-completeness and beyond. COMPUTERS,General

Machine Learning For Dummies Your no-nonsense guide to making sense of machine learning Machine learning can be a mind-boggling concept for the masses, but those who are in the trenches of computer programming know just how invaluable it is. Without machine learning, fraud detection, web search results, real-time ads on web pages, credit scoring, automation, and email spam filtering wouldn't be possible, and this is only showcasing just a few of its capabilities. Written by two data science experts, Machine Learning For Dummies offers a much-needed entry point for anyone looking to use machine learning to accomplish practical tasks. Covering the entry-level topics needed to get you familiar with the basic concepts of machine learning, this guide quickly helps you make sense of the programming languages and tools you need to turn machine learning-based tasks into a reality. Whether you're maddened by the math behind machine learning, apprehensive about AI, perplexed by preprocessing data—or anything in between—this guide makes it easier to understand and implement machine learning seamlessly. Grasp how day-to-day activities are powered by machine learning Learn to 'speak' certain languages, such as Python and R, to teach machines to perform pattern-oriented tasks and data analysis Learn to code in R using R Studio Find out how to code in Python using Anaconda Dive into this complete beginner's guide so you are armed with all you need to know about machine learning! COMPUTERS,General

Women into Computing This book contains the majority of the papers presented at the 1990 Women into Computing Conference, together with selected papers from the 1989 and 1988 Conferences. In 1988, the main theme running through the Conference was that of dismay at the low number of women taking computing courses or following computing careers. The 1989 Conference was concerned solely with workshops for schoolgirls and the 1990 Conference concentrated on strategies rather than an assessment of the situation. As editors, we set as our task to make a selection of papers presenting the overall picture in 1990. We found that many of the issues discussed in 1988 are still a cause for concern in 1990, but that strategies to improve the situation are many and varied. Section I contains speeches from the invited speakers and needs little introduction. Section II contains papers covering so me attitudes and issues of concern, ranging from the specific (Gill Russell on child care and Laurie Keller on hacker mentality) through to broader aspects of gender inequality (the papers of Flis Henwood, Margaret Bruce and Alison Adam, and Lyn Bryant). Susan Jones takes a look at the reasons why we should want to see more women in computing, whilst Gillian Lovegrove and Wendy Hall present a more general paper on school and higher education. COMPUTERS,General

Cyber Security Cyber security involves protecting organisations from cyber risks, the threats to organisations caused by digital technology. These risks can cause direct damage to revenues and profits as well as indirect damage through reduced efficiency, lower employee morale, and reputational damage. Cyber security is often thought to be the domain of specialist IT professionals however, cyber risks are found across and within organisations. Unfortunately, many managers outside IT feel they are ill equipped to deal with cyber risks and the use of jargon makes the subject especially hard to understand. For this reason cyber threats are worse than they really need to be. The reality is that the threat from cyber risks is constantly growing, thus non-technical managers need to understand and manage it. As well as offering practical advice, the author guides readers through the processes that will enable them to manage and mitigate such threats and protect their organisations. COMPUTERS,General

ISO 9001 With a quality management system (QMS) based on ISO 9001 you can ensure the quality of the products and services your company provides, thereby enhancing customer satisfaction and increasing profitability. ISO 9001:2015 – A Pocket Guide provides a useful introduction to ISO 9001 and the principles of quality management. COMPUTERS,General

Big-Data Analytics for Cloud, IoT and Cognitive Computing The definitive guide to successfully integrating social, mobile, Big-Data analytics, cloud and IoT principles and technologies The main goal of this book is to spur the development of effective big-data computing operations on smart clouds that are fully supported by IoT sensing, machine learning and analytics systems. To that end, the authors draw upon their original research and proven track record in the field to describe a practical approach integrating big-data theories, cloud design principles, Internet of Things (IoT) sensing, machine learning, data analytics and Hadoop and Spark programming. Part 1 focuses on data science, the roles of clouds and IoT devices and frameworks for big-data computing. Big data analytics and cognitive machine learning, as well as cloud architecture, IoT and cognitive systems are explored, and mobile cloud-IoT-interaction frameworks are illustrated with concrete system design examples. Part 2 is devoted to the principles of and algorithms for machine learning, data analytics and deep learning in big data applications. Part 3 concentrates on cloud programming software libraries from MapReduce to Hadoop, Spark and TensorFlow and describes business, educational, healthcare and social media applications for those tools. The first book describing a practical approach to integrating social, mobile, analytics, cloud and IoT (SMACT) principles and technologies Covers theory and computing techniques and technologies, making it suitable for use in both computer science and electrical engineering programs Offers an extremely well-informed vision of future intelligent and cognitive computing environments integrating SMACT technologies Fully illustrated throughout with examples, figures and approximately 150 problems to support and reinforce learning Features a companion website with an instructor manual and PowerPoint slides www.wiley.com/go/hwangIOT Big-Data Analytics for Cloud, IoT and Cognitive Computing satisfies the demand among university faculty and students for cutting-edge information on emerging intelligent and cognitive computing systems and technologies. Professionals working in data science, cloud computing and IoT applications will also find this book to be an extremely useful working resource. COMPUTERS,General

Learn CentOS Linux Network Services Learn to set up the latest CentOS Linux network services including DNS, DHCP, SSH and VNC, Web, FTP, Mail, Firewall, and LDAP, enabling you to provide these services on your own network. CentOS continues to be a popular Linux distribution choice, and setting up your own services is a key skill for anyone maintaining a CentOS network. You will learn how to install CentOS, and manage basic administration. You’ll then move onto understanding networking, and how to set up your required services. Each chapter is written in an easy-to-digest format and teaches you how set up, manage, and troubleshoot each service. You’ll be running your own network in no time at all. What You Will Learn Install and set up the latest version of CentOS Configure and manage a wide range of network services Solve problems remotely and manage your network efficiently Who This Book Is For Anyone who wants to learn how to set up and manage CentOS Linux network services. Some previous Linux experience is beneficial, but this book is designed to be used by beginners. COMPUTERS,General

Pragmatic Application of Service Management Completely updated by service management gurus Suzanne D. Van Hove and Mark Thomas, the second edition of Pragmatic Application of Service Management – The Five Anchor Approach provides comprehensive guidance, instructive illustrations, and helpful tables to create an integrated system based on COBIT, ISO 20000, ITIL, and CMMI-SVC. COMPUTERS,General

Machining For Dummies Start a successful career in machining Metalworking is an exciting field that's currently experiencing a shortage of qualified machinists—and there's no time like the present to capitalize on the recent surge in manufacturing and production opportunities. Covering everything from lathe operation to actual CNC programming, Machining For Dummies provides you with everything it takes to make a career for yourself as a skilled machinist. Written by an expert offering real-world advice based on experience in the industry, this hands-on guide begins with basic topics like tools, work holding, and ancillary equipment, then goes into drilling, milling, turning, and other necessary metalworking processes. You'll also learn about robotics and new developments in machining technology that are driving the future of manufacturing and the machining market. Be profitable in today's competitive manufacturing environment Set up and operate a variety of computer-controlled and mechanically controlled machines Produce precision metal parts, instruments, and tools Become a part of an industry that's experiencing steady growth Manufacturing is the backbone of America, and this no-nonsense guide will provide you with valuable information to help you get a foot in the door as a machinist. COMPUTERS,General

Computer Science Named a Notable Book in the 21st Annual Best of Computing list by the ACM! Robert Sedgewick and Kevin Wayne’s Computer Science: An Interdisciplinary Approach is the ideal modern introduction to computer science with Java programming for both students and professionals. Taking a broad, applications-based approach, Sedgewick and Wayne teach through important examples from science, mathematics, engineering, finance, and commercial computing. The book demystifies computation, explains its intellectual underpinnings, and covers the essential elements of programming and computational problem solving in today’s environments. The authors begin by introducing basic programming elements such as variables, conditionals, loops, arrays, and I/O. Next, they turn to functions, introducing key modular programming concepts, including components and reuse. They present a modern introduction to object-oriented programming, covering current programming paradigms and approaches to data abstraction. Building on this foundation, Sedgewick and Wayne widen their focus to the broader discipline of computer science. They introduce classical sorting and searching algorithms, fundamental data structures and their application, and scientific techniques for assessing an implementation’s performance. Using abstract models, readers learn to answer basic questions about computation, gaining insight for practical application. Finally, the authors show how machine architecture links the theory of computing to real computers, and to the field’s history and evolution. For each concept, the authors present all the information readers need to build confidence, together with examples that solve intriguing problems. Each chapter contains question-and-answer sections, self-study drills, and challenging problems that demand creative solutions. Companion web site (introcs.cs.princeton.edu/java) contains Extensive supplementary information, including suggested approaches to programming assignments, checklists, and FAQs Graphics and sound libraries Links to program code and test data Solutions to selected exercises Chapter summaries Detailed instructions for installing a Java programming environment Detailed problem sets and projects Companion 20-part series of video lectures is available at informit.com/title/9780134493831 COMPUTERS,General

How Software Works We use software every day to perform all kinds of magical, powerful tasks. It's the force behind stunning CGI graphics, safe online shopping, and speedy Google searches. Software drives the modern world, but its inner workings remain a mystery to many. How Software Works explains how computers perform common-yet-amazing tasks that we take for granted every day. Inside you'll learn:–How data is encrypted–How passwords are used and protected–How computer graphics are created–How video is compressed for streaming and storage–How data is searched (and found) in huge databases–How programs can work together on the same problem without conflict–How data travels over the Internet How Software Works breaks down these processes with patient explanations and intuitive diagrams so that anyone can understand—no technical background is required, and you won't be reading through any code. In plain English, you'll examine the intricate logic behind the technologies you constantly use but never understood. If you've ever wondered what really goes on behind your computer screen, How Software Works will give you fascinating look into the software all around you. COMPUTERS,General

Maschinelles Lernen mit Python und R für Dummies Maschinelles Lernen ist aufregend: Mit schnellen Prozessoren und großen Speichern können Computer aus Erfahrungen lernen, künstliche Intelligenz kommt wieder in Reichweite. Mit diesem Buch verstehen Sie, was maschinelles Lernen bedeutet, für welche Probleme es sich eignet, welche neuen Herangehensweisen damit möglich sind und wie Sie mit Python, R und speziellen Werkzeugen maschinelles Lernen implementieren. Sie brauchen dafür keine jahrelange Erfahrung als Programmierer und kein Mathematikstudium. Die praktische Anwendung maschinellen Lernens steht in diesem Buch im Vordergrund. Spielen Sie mit den Tools und haben Sie Spaß dabei! Lernen Sie Fakten und Mythen zum maschinellen Lernen zu unterscheiden. COMPUTERS,General

Game Engine Architecture, Third Edition In this new and improved third edition of the highly popular Game Engine Architecture, Jason Gregory draws on his nearly two decades of experience at Midway, Electronic Arts and Naughty Dog to present both the theory and practice of game engine software development. In this book, the broad range of technologies and techniques used by AAA game studios are each explained in detail, and their roles within a real industrial-strength game engine are illustrated. New to the Third Edition This third edition offers the same comprehensive coverage of game engine architecture provided by previous editions, along with updated coverage of: computer and CPU hardware and memory caches, compiler optimizations, C++ language standardization, the IEEE-754 floating-point representation, 2D user interfaces, plus an entirely new chapter on hardware parallelism and concurrent programming. This book is intended to serve as an introductory text, but it also offers the experienced game programmer a useful perspective on aspects of game development technology with which they may not have deep experience. As always, copious references and citations are provided in this edition, making it an excellent jumping off point for those who wish to dig deeper into any particular aspect of the game development process. Key Features Covers both the theory and practice of game engine software development Examples are grounded in specific technologies, but discussion extends beyond any particular engine or API. Includes all mathematical background needed. Comprehensive text for beginners and also has content for senior engineers. COMPUTERS,General

CompTIA IT Fundamentals (ITF+) Study Guide NOTE: The name of the exam has changed from IT Fundamentals to IT Fundamentals+ (ITF+). However, the FC0-U61 exam objectives are exactly the same. After the book was printed with IT Fundamentals in the title, CompTIA changed the name to IT Fundamentals+ (ITF+). We have corrected the title to IT Fundamentals+ (ITF+) in subsequent book printings, but earlier printings that were sold may still show IT Fundamentals in the title. Please rest assured that the book content is 100% the same. The ultimate study guide for the essential entry-level IT cert! The CompTIA IT Fundamentals Study Guide: Exam FC0-U61, Second Edition is your ideal companion for comprehensive exam preparation. Covering 100 percent of the latest exam objectives, this book contains everything you need to know to pass with flying colors—the first time! Clear, concise language breaks down fundamental IT concepts to help you truly grasp important concepts, and practical examples illustrate how each new skill is applied in real-world situations. You’ll learn your way around hardware and software, conduct installations, and connect to networks to get a workstation up and running smoothly; you’ll also develop the knowledge base needed to identify compatibility and security issues, mitigate risks, and conduct all-important preventative maintenance that keeps the end-user problem-free. The CompTIA IT Fundamentals certification validates your skills as a systems support specialist, and gets your foot in the door to a successful IT career. This book is your ultimate preparation resource, with expert guidance backed by online tools to take your preparation to the next level! Master 100 percent of Exam FC0-U61 objectives Learn real-world applications and practical on-the-job skills Know what to expect with exam highlights and review questions Access online study tools including flashcards, chapter tests, a practice exam, and more! The IT department is instrumental in keeping any organization on its feet. As support staff, you will be called upon to assess and repair common problems, set up and configure workstations, address individual issues, and much more. If you decide to continue on to more advanced IT positions, the CompTIA IT Fundamentals certification is a great springboard; if you’re ready to launch your career, the CompTIA IT Fundamentals Study Guide offers complete, practical prep to help you face the exam with confidence. COMPUTERS,General

Workflow A pro isn’t just a person who can do it well. It’s a person who can do it well every time, on demand and on deadline; which is why the key to being a professional creative is having a great creative process. Whether it’s writing a book, animating a shot, designing a game level or composing a soundtrack—ultimately, we’re all facing similar challenges. Since we share challenges, we can also share solutions. This book is a practical guide, featuring a universal creative process that can streamline any serious creative work, on any scale. Key Features Universal approach: applies to any process that starts with an idea and ends with a refined product. Profound and light: combines conceptual ideas with practical tips and fun anecdotes. Caricatures and samples: helps visually clarify ideas and processes. Variety of creative fields: draws on examples from writing, animation, game design, 3D modeling, music, sculpting and more Printable summaries: provides visual outlines that can be used as cheat-sheets. COMPUTERS,General

Spring Unlock the power of Spring Boot to build and deploy production-ready microservices About This Book Get to know the advanced features of Spring Boot in order to develop and monitor applications Use Spring cloud to deploy and manage microservices on the cloud Look at embedded servers and deploy a test application to a PaaS Cloud platform Embedded with assessments that will help you revise the concepts you have learned in this book Who This Book Is For This book is aimed at Java developers who knows the basics of Spring programming and want to build microservices with Spring Boot. What You Will Learn Use Spring Initializr to create a basic spring project Build a basic microservice with Spring Boot Implement caching and exception handling Secure your microservice with Spring security and OAuth2 Deploy microservices using self-contained HTTP server Monitor your microservices with Spring Boot actuator Learn to develop more effectively with developer tools In Detail Microservices helps in decomposing applications into small services and move away from a single monolithic artifact. It helps in building systems that are scalable, flexible, and high resilient. Spring Boot helps in building REST-oriented, production-grade microservices. This book is a quick learning guide on how to build, monitor, and deploy microservices with Spring Boot. You'll be first familiarized with Spring Boot before delving into building microservices. You will learn how to document your microservice with the help of Spring REST docs and Swagger documentation. You will then learn how to secure your microservice with Spring Security and OAuth2. You will deploy your app using a self-contained HTTP server and also learn to monitor a microservice with the help of Spring Boot actuator. This book is ideal for Java developers who knows the basics of Spring programming and want to build microservices with Spring Boot. This book is embedded with useful assessments that will help you revise the concepts you have learned in this book. Style and approach This book follows a practical approach to teach you how to build, monitor, and deploy microservices with Spring Boot. Note: This book is a blend of text and quizzes, all packaged up keeping your journey in mind. It includes content from the following Packt product: Mastering Spring 5.0 by Ranga Rao Karanam COMPUTERS,General

Introduction to Proteins Introduction to Proteins provides a comprehensive and state-of-the-art introduction to the structure, function, and motion of proteins for students, faculty, and researchers at all levels. The book covers proteins and enzymes across a wide range of contexts and applications, including medical disorders, drugs, toxins, chemical warfare, and animal behavior. Each chapter includes a Summary, Exercies, and References. New features in the thoroughly-updated second edition include: A brand-new chapter on enzymatic catalysis, describing enzyme biochemistry, classification, kinetics, thermodynamics, mechanisms, and applications in medicine and other industries. These are accompanied by multiple animations of biochemical reactions and mechanisms, accessible via embedded QR codes (which can be viewed by smartphones) An in-depth discussion of G-protein-coupled receptors (GPCRs) A wider-scale description of biochemical and biophysical methods for studying proteins, including fully accessible internet-based resources, such as databases and algorithms Animations of protein dynamics and conformational changes, accessible via embedded QR codes Additional features Extensive discussion of the energetics of protein folding, stability and interactions A comprehensive view of membrane proteins, with emphasis on structure-function relationship Coverage of intrinsically unstructured proteins, providing a complete, realistic view of the proteome and its underlying functions Exploration of industrial applications of protein engineering and rational drug design Each chapter includes a Summary, Exercies, and References Approximately 300 color images Downloadable solutions manual available at www.crcpress.com For more information, including all presentations, tables, animations, and exercises, as well as a complete teaching course on proteins' structure and function, please visit the author's website: http://ibis.tau.ac.il/wiki/nir_bental/index.php/Introduction_to_Proteins_Book . Praise for the first edition "This book captures, in a very accessible way, a growing body of literature on the structure, function and motion of proteins. This is a superb publication that would be very useful to undergraduates, graduate students, postdoctoral researchers, and instructors involved in structural biology or biophysics courses or in research on protein structure-function relationships." --David Sheehan, ChemBioChem, 2011 "Introduction to Proteins is an excellent, state-of-the-art choice for students, faculty, or researchers needing a monograph on protein structure. This is an immensely informative, thoroughly researched, up-to-date text, with broad coverage and remarkable depth. Introduction to Proteins would provide an excellent basis for an upper-level or graduate course on protein structure, and a valuable addition to the libraries of professionals interested in this centrally important field." --Eric Martz, Biochemistry and Molecular Biology Education, 2012 COMPUTERS,General

The Importance of Being Fuzzy How has computer science changed mathematical thinking? In this first ever comprehensive survey of the subject for popular science readers, Arturo Sangalli explains how computers have brought a new practicality to mathematics and mathematical applications. By using fuzzy logic and related concepts, programmers have been able to sidestep the traditional and often cumbersome search for perfect mathematical solutions to embrace instead solutions that are "good enough." If mathematicians want their work to be relevant to the problems of the modern world, Sangalli shows, they must increasingly recognize "the importance of being fuzzy." As Sangalli explains, fuzzy logic is a technique that allows computers to work with imprecise terms--to answer questions with "maybe" rather than just "yes" and "no." The practical implications of this flexible type of mathematical thinking are remarkable. Japanese programmers have used fuzzy logic to develop the city of Sendai's unusually energy-efficient and smooth-running subway system--one that does not even require drivers. Similar techniques have been used in fields as diverse as medical diagnosis, image understanding by robots, the engineering of automatic transmissions, and the forecasting of currency exchange rates. Sangalli also explores in his characteristically clear and engaging manner the limits of classical computing, reviewing many of the central ideas of Turing and Godel. He shows us how "genetic algorithms" can solve problems by an evolutionary process in which chance plays a fundamental role. He introduces us to "neural networks," which recognize ill-defined patterns without an explicit set of rules--much as a dog can be trained to scent drugs without ever having an exact definition of "drug." Sangalli argues that even though "fuzziness" and related concepts are often compared to human thinking, they can be understood only through mathematics--but the math he uses in the book is straightforward and easy to grasp. Of equal appeal to specialists and the general reader, The Importance of Being Fuzzy reveals how computer science is changing both the nature of mathematical practice and the shape of the world around us. COMPUTERS,General

A Brief History of Everything Wireless Since the discovery of electromagnetic waves less than 150 years ago, the application of wireless communications technology has not only revolutionized our daily lives, but also fundamentally changed the course of world history. A Brief History of Everything Wireless charts the fascinating story of wireless communications. The book leads the reader on an intriguing journey of personal triumphs and stinging defeats, relating the prominent events, individuals and companies involved in each progressive leap in technology, with a particular focus on the phenomenal impact of each new invention on society. Beginning at the early days of spark-gap transmitters, this tale touches on the emergence of radio and television broadcasting, as well as radio navigation and radar, before moving on to the rise of satellite, near-field and light-based communications. Finally, the development of wireless home networks and the explosive growth of modern cellular technologies are revealed, complete with a captivating account of their corresponding company histories and behind-the-scenes battles over standards. For those wishing to peek behind the magic curtain of friendly user interfaces and clever engineering, and delve further into various processes underlying the ubiquitous technology we depend upon yet take for granted, the book also contains special “TechTalk†chapters that explain the theoretical basics in an intuitive way. COMPUTERS,General

Computational Thinking In diesem Buch lernen Sie die Grundzüge und Vorteile des Computational Thinking kennen, also des analytischen, von Algorithmen geprägten Denkens. Die Autoren behandeln dabei unterhaltsam und anwendungsbezogen die Grundelemente dieser Denkweise - darunter Denken in Algorithmen, Zerlegung, Abstraktion und Mustererkennung. Diese Prinzipien werden anschaulich an Hand von Zaubertricks, Spielen und Rätseln, aber auch an echten, anspruchsvollen Problemen erklärt. Sie erkunden dabei auch die Verbindungen zwischen Computational Thinking und wissenschaftlichem, aber auch kreativem Denken - und wie daraus Innovationen entstehen können. Computational Thinking hat die Art und Weise, wie wir alle leben, arbeiten und spielen, verändert. Es hat Auswirkungen darauf, wie Wissenschaft betrieben wird, Kriege gewonnen, ganz neue Industrien geschaffen und Leben gerettet werden. Es ist das Herzstück der Programmierung und ein leistungsfähiger Ansatz zur Problemlösung, mit oder ohne Computer. In einigen Ländern werden bereits Kindern in der Grundschule diese Fertigkeiten beigebracht. Ob Sie also einfach wissen wollen, um was es beim Computational Thinking geht oder ob Sie neue Möglichkeiten finden wollen, auch im Alltag effektiver zu werden, ob Sie (Informatik-)Lehrer oder Schüler sind oder einfach Spaß an Spielen und Rätseln haben – in diesem Buch finden Sie die nötigen Grundlagen. COMPUTERS,General

Computer Graphics Through OpenGL® COMPREHENSIVE COVERAGE OF SHADERS AND THE PROGRAMMABLE PIPELINE From geometric primitives to animation to 3D modeling to lighting, shading and texturing, Computer Graphics Through OpenGL®: From Theory to Experiments is a comprehensive introduction to computer graphics which uses an active learning style to teach key concepts. Equally emphasizing theory and practice, the book provides an understanding not only of the principles of 3D computer graphics, but also the use of the OpenGL® Application Programming Interface (API) to code 3D scenes and animation, including games and movies. The undergraduate core of the book takes the student from zero knowledge of computer graphics to a mastery of the fundamental concepts with the ability to code applications using fourth-generation OpenGL®. The remaining chapters explore more advanced topics, including the structure of curves and surfaces, applications of projective spaces and transformations and the implementation of graphics pipelines. This book can be used for introductory undergraduate computer graphics courses over one to two semesters. The careful exposition style attempting to explain each concept in the simplest terms possible should appeal to the self-study student as well. Features • Covers the foundations of 3D computer graphics, including animation, visual techniques and 3D modeling• Comprehensive coverage of OpenGL® 4.x, including the GLSL and vertex, fragment, tessellation and geometry shaders• Includes 180 programs with 270 experiments based on them• Contains 750 exercises, 110 worked examples, and 700 four-color illustrations• Requires no previous knowledge of computer graphics• Balances theory with programming practice using a hands-on interactive approach to explain the underlying concepts COMPUTERS,General

Architects of Intelligence Financial Times Best Books of the Year 2018 TechRepublic Top Books Every Techie Should Read Book Description How will AI evolve and what major innovations are on the horizon? What will its impact be on the job market, economy, and society? What is the path toward human-level machine intelligence? What should we be concerned about as artificial intelligence advances? Architects of Intelligence contains a series of in-depth, one-to-one interviews where New York Times bestselling author, Martin Ford, uncovers the truth behind these questions from some of the brightest minds in the Artificial Intelligence community. Martin has wide-ranging conversations with twenty-three of the world's foremost researchers and entrepreneurs working in AI and robotics: Demis Hassabis (DeepMind), Ray Kurzweil (Google), Geoffrey Hinton (Univ. of Toronto and Google), Rodney Brooks (Rethink Robotics), Yann LeCun (Facebook) , Fei-Fei Li (Stanford and Google), Yoshua Bengio (Univ. of Montreal), Andrew Ng (AI Fund), Daphne Koller (Stanford), Stuart Russell (UC Berkeley), Nick Bostrom (Univ. of Oxford), Barbara Grosz (Harvard), David Ferrucci (Elemental Cognition), James Manyika (McKinsey), Judea Pearl (UCLA), Josh Tenenbaum (MIT), Rana el Kaliouby (Affectiva), Daniela Rus (MIT), Jeff Dean (Google), Cynthia Breazeal (MIT), Oren Etzioni (Allen Institute for AI), Gary Marcus (NYU), and Bryan Johnson (Kernel). Martin Ford is a prominent futurist, and author of Financial Times Business Book of the Year, Rise of the Robots. He speaks at conferences and companies around the world on what AI and automation might mean for the future. Meet the minds behind the AI superpowers as they discuss the science, business and ethics of modern artificial intelligence. Read James Manyika's thoughts on AI analytics, Geoffrey Hinton's breakthroughs in AI programming and development, and Rana el Kaliouby's insights into AI marketing. This AI book collects the opinions of the luminaries of the AI business, such as Stuart Russell (coauthor of the leading AI textbook), Rodney Brooks (a leader in AI robotics), Demis Hassabis (chess prodigy and mind behind AlphaGo), and Yoshua Bengio (leader in deep learning) to complete your AI education and give you an AI advantage in 2019 and the future. COMPUTERS,General

Mastering Vim Mastering Vim, reviewed by Bram Moolenaar, the creator of Vim, covers usage of Vim and Neovim, showcases relevant plugins, and teaches Vimscript Key Features Expert Vim and Vimscript techniques to work with Python and other development environment Accomplish end-to-end software development tasks with Neovim and Vim plugins Understand best practices for various facets of projects like version control, building, and testing Book Description Vim is a ubiquitous text editor that can be used for all programming languages. It has an extensive plugin system and integrates with many tools. Vim offers an extensible and customizable development environment for programmers, making it one of the most popular text editors in the world. Mastering Vim begins with explaining how the Vim editor will help you build applications efficiently. With the fundamentals of Vim, you will be taken through the Vim philosophy. As you make your way through the chapters, you will learn about advanced movement, text operations, and how Vim can be used as a Python (or any other language for that matter) IDE. The book will then cover essential tasks, such as refactoring, debugging, building, testing, and working with a version control system, as well as plugin configuration and management. In the concluding chapters, you will be introduced to additional mindset guidelines, learn to personalize your Vim experience, and go above and beyond with Vimscript. By the end of this book, you will be sufficiently confident to make Vim (or its fork, Neovim) your first choice when writing applications in Python and other programming languages. What you will learn Get the most recent Vim, GVim, and Neovim versions installed Become efficient at navigating and editing text Uncover niche Vim plugins and pick the best ones Discover multiple ways of organizing plugins Explore and tailor Vim UI to fit your needs Organize and maintain Vim configuration across environments Write scripts to complement your workflow using Vimscript Who this book is for Mastering Vim is written for beginner, intermediate, and expert developers.The book will teach you to effectively embed Vim in your daily workflow. No prior experience with Python or Vim is required. COMPUTERS,General

Microsoft Dynamics NAV Development Quick Start Guide Learn development skills and improve productivity when programming in Microsoft Dynamics NAV 2018 - the popular Enterprise Resourse Planning management system used across a variety of industries for business process management Key Features Solve common business problems with the valuable features and flexibility of Dynamics NAV Understand the structure of NAV database - how documents and business entities are mapped to DB tables Design user interface and bind the presentation layer with the data storage Book Description Microsoft Dynamics NAV is an enterprise resource planning (ERP) software suite for organizations. The system offers specialized functionality for manufacturing, distribution, government, retail, and other industries. This book gets you started with its integrated development environment for solving problems by customizing business processes. This book introduces the NAV development environment – C/SIDE. It gives an overview of the internal system language and the most essential development tools. The book will enable the reader to customize and extend NAV functionality with C/AL code, design a user interface through pages, create role centers, and build advanced reports in Microsoft Visual Studio. By the end of the book, you will have learned how to extend the NAV data model, how to write and debug custom code, and how to exchange data with external applications. What you will learn Manage NAV Server configuration with Microsoft Management Console Manage NAV installation with the NAV Administration Shell Create integration events and extend functionality via the NAV event model Run XML Ports from C/AL code Design reports and write client code in RDLC expressions Who this book is for This book is for experienced NAV users who have an understanding of basic programming concepts. Familiarity with NAV development environment or its internal development language-C/AL is not expected. COMPUTERS,General

Hands-On High Performance Programming with Qt 5 Build efficient and fast Qt applications, target performance problems, and discover solutions to refine your code Key Features Build efficient and concurrent applications in Qt to create cross-platform applications Identify performance bottlenecks and apply the correct algorithm to improve application performance Delve into parallel programming and memory management to optimize your code Book Description Achieving efficient code through performance tuning is one of the key challenges faced by many programmers. This book looks at Qt programming from a performance perspective. You'll explore the performance problems encountered when using the Qt framework and means and ways to resolve them and optimize performance. The book highlights performance improvements and new features released in Qt 5.9, Qt 5.11, and 5.12 (LTE). You'll master general computer performance best practices and tools, which can help you identify the reasons behind low performance, and the most common performance pitfalls experienced when using the Qt framework. In the following chapters, you'll explore multithreading and asynchronous programming with C++ and Qt and learn the importance and efficient use of data structures. You'll also get the opportunity to work through techniques such as memory management and design guidelines, which are essential to improve application performance. Comprehensive sections that cover all these concepts will prepare you for gaining hands-on experience of some of Qt's most exciting application fields - the mobile and embedded development domains. By the end of this book, you'll be ready to build Qt applications that are more efficient, concurrent, and performance-oriented in nature What you will learn Understand classic performance best practices Get to grips with modern hardware architecture and its performance impact Implement tools and procedures used in performance optimization Grasp Qt-specific work techniques for graphical user interface (GUI) and platform programming Make Transmission Control Protocol (TCP) and Hypertext Transfer Protocol (HTTP) performant and use the relevant Qt classes Discover the improvements Qt 5.9 (and the upcoming versions) holds in store Explore Qt's graphic engine architecture, strengths, and weaknesses Who this book is for This book is designed for Qt developers who wish to build highly performance applications for desktop and embedded devices. Programming Experience with C++ is required. COMPUTERS,General

Hands-On Test Management with Jira Learn best practices for testing with Jira and model industry workflows that can be used during the software development lifecycle Key Features Integrate Jira with test management tools such as Zephyr, Test Management, and SynapseRT Understand test case management, traceability, and test execution with reports Implement continuous integration using Jira, Jenkins, and automated testing tools Book Description Hands-On Test Management with Jira begins by introducing you to the basic concepts of Jira and takes you through real-world software testing processes followed by various organizations. As you progress through the chapters, the book explores and compares the three most popular Jira plugins—Zephyr, Test Management, and synapseRT. With this book, you'll gain a practical understanding of test management processes using Jira. You'll learn how to create and manage projects, create Jira tickets to manage customer requirements, and track Jira tickets. You'll also understand how to develop test plans, test cases, and test suites, and create defects and requirement traceability matrices, as well as generating reports in Jira. Toward the end, you'll understand how Jira can help the SQA teams to use the DevOps pipeline for automating execution and managing test cases. You'll get to grips with configuring Jira with Jenkins to execute automated test cases in Selenium. By the end of this book, you'll have gained a clear understanding of how to model and implement test management processes using Jira. What you will learn Understand QMS to effectively implement quality systems in your organization Explore a business-driven structured approach to Test Management using TMap NEXT Implement different aspects of test planning, test strategy, and test execution Organize and manage Agile projects in Scrum and Kanban Uncover Jira plugins available in the Atlassian Marketplace for testing and project management Configure a DevOps pipeline for continuous integration using Jira with Jenkins Who this book is for If you're a quality assurance professional, software project manager, or test manager interested in learning test management best practices in your team or organization, this book is for you. Prior knowledge of test management and Jenkins will be beneficial in understanding the concepts covered in this book. COMPUTERS,General

Python Machine Learning Cookbook Discover powerful ways to effectively solve real-world machine learning problems using key libraries including scikit-learn, TensorFlow, and PyTorch Key Features Learn and implement machine learning algorithms in a variety of real-life scenarios Cover a range of tasks catering to supervised, unsupervised and reinforcement learning techniques Find easy-to-follow code solutions for tackling common and not-so-common challenges Book Description This eagerly anticipated second edition of the popular Python Machine Learning Cookbook will enable you to adopt a fresh approach to dealing with real-world machine learning and deep learning tasks. With the help of over 100 recipes, you will learn to build powerful machine learning applications using modern libraries from the Python ecosystem. The book will also guide you on how to implement various machine learning algorithms for classification, clustering, and recommendation engines, using a recipe-based approach. With emphasis on practical solutions, dedicated sections in the book will help you to apply supervised and unsupervised learning techniques to real-world problems. Toward the concluding chapters, you will get to grips with recipes that teach you advanced techniques including reinforcement learning, deep neural networks, and automated machine learning. By the end of this book, you will be equipped with the skills you need to apply machine learning techniques and leverage the full capabilities of the Python ecosystem through real-world examples. What you will learn Use predictive modeling and apply it to real-world problems Explore data visualization techniques to interact with your data Learn how to build a recommendation engine Understand how to interact with text data and build models to analyze it Work with speech data and recognize spoken words using Hidden Markov Models Get well versed with reinforcement learning, automated ML, and transfer learning Work with image data and build systems for image recognition and biometric face recognition Use deep neural networks to build an optical character recognition system Who this book is for This book is for data scientists, machine learning developers, deep learning enthusiasts and Python programmers who want to solve real-world challenges using machine-learning techniques and algorithms. If you are facing challenges at work and want ready-to-use code solutions to cover key tasks in machine learning and the deep learning domain, then this book is what you need. Familiarity with Python programming and machine learning concepts will be useful. COMPUTERS,General

Building Serverless Microservices in Python A practical guide for developing end-to-end serverless microservices in Python for developers, DevOps, and architects. Key Features Create a secure, cost-effective, and scalable serverless data API Use identity management and authentication for a user-specific and secure web application Go beyond traditional web hosting to explore the full range of cloud hosting options Book Description Over the last few years, there has been a massive shift from monolithic architecture to microservices, thanks to their small and independent deployments that allow increased flexibility and agile delivery. Traditionally, virtual machines and containers were the principal mediums for deploying microservices, but they involved a lot of operational effort, configuration, and maintenance. More recently, serverless computing has gained popularity due to its built-in autoscaling abilities, reduced operational costs, and increased productivity. Building Serverless Microservices in Python begins by introducing you to serverless microservice structures. You will then learn how to create your first serverless data API and test your microservice. Moving on, you'll delve into data management and work with serverless patterns. Finally, the book introduces you to the importance of securing microservices. By the end of the book, you will have gained the skills you need to combine microservices with serverless computing, making their deployment much easier thanks to the cloud provider managing the servers and capacity planning. What you will learn Discover what microservices offer above and beyond other architectures Create a serverless application with AWS Gain secure access to data and resources Run tests on your configuration and code Create a highly available serverless microservice data API Build, deploy, and run your serverless configuration and code Who this book is for If you are a developer with basic knowledge of Python and want to learn how to build, test, deploy, and secure microservices, then this book is for you. No prior knowledge of building microservices is required. COMPUTERS,General

Dungeons and Desktops Computer role-playing games (CRPGs) are a special genre of computer games that bring the tabletop role-playing experience of games such as Dungeons & Dragons to the computer screen. Thisnew edition inlcudes two new chapters: The Modern Age, and a chapter on Indies and Mobile CRPGs. The new modern age chapter will cover, among other topics, Kickstarter/FIG crowdfunded projects such as Torment: Tides of Numenera and Pillars of Eternity. It'll also bring the book up to date with major games such as Dragon Age, Witcher, Skyrim. Expanded info in first chapter about educational potential of CRPGs. Color figures will be introduced for the first time. Key Features gives reviews of hundreds of games across many platforms. comprehensive book covering the history of computer RPGs. comprehensive index at the back, letting you quickly look up your favourite titles COMPUTERS,General

Salesforce CRM - The Definitive Admin Handbook A definitive guide covering all the core concepts necessary to pass the Salesforce Administrator Certification exam Key Features Understand critical design considerations for setting up Salesforce CRM Facilitate and manage the transition from Salesforce Classic to Lightning Experience Learn key functions of application security to manage user profiles and data Book Description Salesforce's winter '19 release offers a host of new features for CRM designed to meet your sales and marketing requirements. With this comprehensive guide to implementing Salesforce CRM, administrators of all levels can easily get a thorough understanding of the platform. This Salesforce handbook begins by guiding you in setting up users and security and then progresses to configuration, data management, and data analytics. You'll discover process automation and approval mechanisms, while also exploring the functional areas of Sales Cloud, Service Cloud, Marketing Cloud, and Salesforce Chatter. This book covers Salesforce CRM system administration in a practical way, and it'll serve as an invaluable reference for both new administrators and experienced professionals. Furthermore, you'll also delve into Salesforce mobile apps and mobile administration, along with Salesforce Adoption Manager. You'll gain insights into Lightning Experience, Salesforce's new app, and learn how its modern design and sleek interface helps you to build customizable components. Finally, we'll see how the two versions compare and help manage the transition from Salesforce Classic to Lightning Experience. By the end of the book, you will have mastered the techniques to configure and control various user interface features in Salesforce CRM. What you will learn Configure a variety of user interface features in Salesforce CRM Understand the capabilities of the Salesforce CRM sharing model Explore Einstein Analytics - Salesforce's new wave of advanced reporting Get to grips with the Lightning Process Builder workflow Set up user profiles, security, and login access mechanisms Find out how Apex and Visualforce coding can be used in Salesforce CRM Manage the transition from Salesforce Classic to Lightning Experience Implement data manipulation features to apply best practices in data management Who this book is for This book is for administrators who want to develop and strengthen their Salesforce CRM skills in the areas of configuration and system management. Whether you are a new or experienced professional, this book will enhance your knowledge and understanding of Salesforce CRM features. COMPUTERS,General

Mastering Python for Finance Take your financial skills to the next level by mastering cutting-edge mathematical and statistical financial applications Key Features Explore advanced financial models used by the industry and ways of solving them using Python Build state-of-the-art infrastructure for modeling, visualization, trading, and more Empower your financial applications by applying machine learning and deep learning Book Description The second edition of Mastering Python for Finance will guide you through carrying out complex financial calculations practiced in the industry of finance by using next-generation methodologies. You will master the Python ecosystem by leveraging publicly available tools to successfully perform research studies and modeling, and learn to manage risks with the help of advanced examples. You will start by setting up your Jupyter notebook to implement the tasks throughout the book. You will learn to make efficient and powerful data-driven financial decisions using popular libraries such as TensorFlow, Keras, Numpy, SciPy, and sklearn. You will also learn how to build financial applications by mastering concepts such as stocks, options, interest rates and their derivatives, and risk analytics using computational methods. With these foundations, you will learn to apply statistical analysis to time series data, and understand how time series data is useful for implementing an event-driven backtesting system and for working with high-frequency data in building an algorithmic trading platform. Finally, you will explore machine learning and deep learning techniques that are applied in finance. By the end of this book, you will be able to apply Python to different paradigms in the financial industry and perform efficient data analysis. What you will learn Solve linear and nonlinear models representing various financial problems Perform principal component analysis on the DOW index and its components Analyze, predict, and forecast stationary and non-stationary time series processes Create an event-driven backtesting tool and measure your strategies Build a high-frequency algorithmic trading platform with Python Replicate the CBOT VIX index with SPX options for studying VIX-based strategies Perform regression-based and classification-based machine learning tasks for prediction Use TensorFlow and Keras in deep learning neural network architecture Who this book is for If you are a financial or data analyst or a software developer in the financial industry who is interested in using advanced Python techniques for quantitative methods in finance, this is the book you need! You will also find this book useful if you want to extend the functionalities of your existing financial applications by using smart machine learning techniques. Prior experience in Python is required. COMPUTERS,General

Building Blocks of Tabletop Game Design Building Blocks of Tabletop Game Design: An Encyclopedia of Mechanisms compiles hundreds of different mechanisms, organized by category. Each has a description of how it works, discussion of its pros and cons, how it can be implemented, and examples of specific games that use it. Building Blocks can be read cover to cover, used as a reference when looking for inspiration for a new design, help solving a specific problem, or assist in getting unstuck in the midst of a project. This book, the first to collect mechanisms like this in the tabletop game design field, aims to be a practical guide that will be a great starting point for beginning designers, a handy guidebook for the experienced, and an ideal classroom textbook. Key Features The first compendium of its kind in the tabletop game field. Covers the nuts and bolts of design to resolve specific challenges. Serves as a practical guide, a great starting point for beginning designers, and a reference for seasoned professionals. Contains discussion of a series of standalone mechanisms, in a standard format and style, with cross-links to related mechanics and specific examples. Includes hundreds of mechanism entries with accompanying diagrams and sample games to study. Ideal for professional or classroom use. COMPUTERS,General

The Signal Computers are the foundation of the information age, but communication technology is the foundation of the foundation. Without the theories and practical applications of theory brought to us by the pioneers of communication, the computer age would perhaps have remained in the back office, hidden away as infrastructure like electricity or running water – critical to modern life, but not as transforming as the combination of communications and computing. The information age exploded once machines were endowed with the ability to talk among themselves. The Signal connects everything to everything else, in both communication, and in the metaphorical sense as the link between and among people. Features Identifies the key ideas underlying modern communications technology, and documents the contributions of its inventors Explores the signal in communication, and also in the metaphorical sense as the link between and among people Leads the reader through a journey from ancient number systems to Voyager II to radio and MP3s to quantum cryptography Includes coverage of "Signals from Hell," including memes and "fake news" on the Internet Looks to the future of communication, with emergent 5G COMPUTERS,General

Hands-On Mobile Development with .NET Core Develop native applications for multiple mobile and desktop platforms including but not limited to iOS, Android, and UWP with the Xamarin framework and Xamarin.Forms Key Features Understand .NET Core and its cross-platform development philosophy Build Android, iOS, and Windows mobile applications with C#, .NET Core, and Azure Cloud Services Bring Artificial Intelligence capabilities into your mobile applications with Azure AI Book Description .NET Core is the general umbrella term used for Microsoft's cross-platform toolset. Xamarin used for developing mobile applications, is one of the app model implementations for .NET Core infrastructure. In this book, you will learn how to design, architect, and develop highly attractive, maintainable, efficient, and robust mobile applications for multiple platforms, including iOS, Android, and UWP, with the toolset provided by Microsoft using Xamarin, .NET Core, and Azure Cloud Services. This book will take you through various phases of application development with Xamarin, from environment setup, design, and architecture to publishing, using real-world scenarios. Throughout the book, you will learn how to develop mobile apps using Xamarin, Xamarin.Forms and .NET Standard; implement a webbased backend composed of microservices with .NET Core using various Azure services including but not limited to Azure App Services, Azure Active Directory, Notification Hub, Logic Apps, and Azure Functions, Cognitive Services; create data stores using popular database technologies such as Cosmos DB, SQL and Realm. Towards the end, the book will help developers to set up an efficient and maintainable development pipeline to manage the application life cycle using Visual Studio App Center and Visual Studio Services. What you will learn Implement native applications for multiple mobile and desktop platforms Understand and use various Azure Services with .NET Core Make use of architectural patterns designed for mobile and web applications Understand the basic Cosmos DB concepts Understand how different app models can be used to create an app service Explore the Xamarin and Xamarin.Forms UI suite with .NET Core for building mobile applications Who this book is for This book is for mobile developers who wish to develop cross-platform mobile applications. Programming experience with C# is required. Some knowledge and understanding of core elements and cross-platform application development with .NET is required. COMPUTERS,General

Probability and Statistics for Computer Scientists Praise for the Second Edition: "The author has done his homework on the statistical tools needed for the particular challenges computer scientists encounter... [He] has taken great care to select examples that are interesting and practical for computer scientists. ... The content is illustrated with numerous figures, and concludes with appendices and an index. The book is erudite and … could work well as a required text for an advanced undergraduate or graduate course." ---Computing Reviews Probability and Statistics for Computer Scientists, Third Edition helps students understand fundamental concepts of Probability and Statistics, general methods of stochastic modeling, simulation, queuing, and statistical data analysis; make optimal decisions under uncertainty; model and evaluate computer systems; and prepare for advanced probability-based courses. Written in a lively style with simple language and now including R as well as MATLAB, this classroom-tested book can be used for one- or two-semester courses. Features: Axiomatic introduction of probability Expanded coverage of statistical inference and data analysis, including estimation and testing, Bayesian approach, multivariate regression, chi-square tests for independence and goodness of fit, nonparametric statistics, and bootstrap Numerous motivating examples and exercises including computer projects Fully annotated R codes in parallel to MATLAB Applications in computer science, software engineering, telecommunications, and related areas In-Depth yet Accessible Treatment of Computer Science-Related Topics Starting with the fundamentals of probability, the text takes students through topics heavily featured in modern computer science, computer engineering, software engineering, and associated fields, such as computer simulations, Monte Carlo methods, stochastic processes, Markov chains, queuing theory, statistical inference, and regression. It also meets the requirements of the Accreditation Board for Engineering and Technology (ABET). About the Author Michael Baron is David Carroll Professor of Mathematics and Statistics at American University in Washington D. C. He conducts research in sequential analysis and optimal stopping, change-point detection, Bayesian inference, and applications of statistics in epidemiology, clinical trials, semiconductor manufacturing, and other fields. M. Baron is a Fellow of the American Statistical Association and a recipient of the Abraham Wald Prize for the best paper in Sequential Analysis and the Regents Outstanding Teaching Award. M. Baron holds a Ph.D. in statistics from the University of Maryland. In his turn, he supervised twelve doctoral students, mostly employed on academic and research positions. COMPUTERS,General

Hands-On System Programming with Go Explore the fundamentals of systems programming starting from kernel API and filesystem to network programming and process communications Key Features Learn how to write Unix and Linux system code in Golang v1.12 Perform inter-process communication using pipes, message queues, shared memory, and semaphores Explore modern Go features such as goroutines and channels that facilitate systems programming Book Description System software and applications were largely created using low-level languages such as C or C++. Go is a modern language that combines simplicity, concurrency, and performance, making it a good alternative for building system applications for Linux and macOS. This Go book introduces Unix and systems programming to help you understand the components the OS has to offer, ranging from the kernel API to the filesystem, and familiarize yourself with Go and its specifications. You'll also learn how to optimize input and output operations with files and streams of data, which are useful tools in building pseudo terminal applications. You'll gain insights into how processes communicate with each other, and learn about processes and daemon control using signals, pipes, and exit codes. This book will also enable you to understand how to use network communication using various protocols, including TCP and HTTP. As you advance, you'll focus on Go's best feature-concurrency helping you handle communication with channels and goroutines, other concurrency tools to synchronize shared resources, and the context package to write elegant applications. By the end of this book, you will have learned how to build concurrent system applications using Go What you will learn Explore concepts of system programming using Go and concurrency Gain insights into Golang's internals, memory models and allocation Familiarize yourself with the filesystem and IO streams in general Handle and control processes and daemons' lifetime via signals and pipes Communicate with other applications effectively using a network Use various encoding formats to serialize complex data structures Become well-versed in concurrency with channels, goroutines, and sync Use concurrency patterns to build robust and performant system applications Who this book is for If you are a developer who wants to learn system programming with Go, this book is for you. Although no knowledge of Unix and Linux system programming is necessary, intermediate knowledge of Go will help you understand the concepts covered in the book COMPUTERS,General

Mastering Windows PowerShell Scripting Grasp advanced PowerShell Core 6.0 functionalities to automate your environment Key Features Keep up with changes introduced in PowerShell Core 6.0 Easily maintain appropriate compatibility with older versions Automate complex tasks, manipulate data, and secure your environment with PowerShell Core 6.0 Book Description PowerShell scripts offer a handy way to automate various chores, however working effectively with these scripts can be a difficult task. This comprehensive guide starts with the fundamentals before moving on to advanced-level topics to help you become a PowerShell Core 6.0 expert. The first module, PowerShell Core 6.0 Fundamentals, begins with the new features of PowerShell Core 6.0, installing it on Linux, and working with parameters, objects and .NET classes from within PowerShell Core 6.0. As you make your way through the chapters, you'll see how to efficiently manage large amounts of data and interact with other services using PowerShell Core 6.0. You'll be able to make the most of PowerShell Core 6.0's powerful automation feature, where you will have different methods available to parse data and manipulate regular expressions and Windows Management Instrumentation (WMI). After having explored automation, you will enter the extending PowerShell Core 6.0 module, covering asynchronous processing and desired state configuration. In the last module, you will learn to extend PowerShell Core 6.0 using advanced scripts and filters, and also debug issues along with working on error handling techniques. By the end of this book, you will be an expert in scripting with PowerShell Core 6.0. What you will learn Optimize code through the use of functions, switches, and looping structures Work with objects and operators to test and manipulate data Parse and manipulate different data types Create scripts and functions using PowerShell Use jobs, events, and popular public modules which assist with implementing multithreading Write .NET classes with ease within the PowerShell Create and implement regular expressions in PowerShell scripts Make use of advanced techniques to define and restrict the behavior of parameters Who this book is for If you are a system administrator who wants to become an expert in controlling and automating your Windows environment, then Mastering Windows PowerShell Scripting is for you. It is also ideal for those new to the PowerShell language. COMPUTERS,General

Jira 8 Essentials Explore the new and improved Jira 8 features such as agile board and advanced search for efficient project management Key Features Work on agile projects in Jira from both the administrator and end user's perspective Explore the improved Scrum and Kanban board and backlog Work through exercises at the end of each chapter to reinforce your skills Book Description Atlassian Jira enables effective bug tracking for your software and mobile applications and provides tools to track and manage tasks for your projects. Jira Essentials is a comprehensive guide, now updated to Jira 8 to include enhanced features such as updates to Scrum and Kanban UI, additional search capabilities, and changes to Jira Service Desk. The book starts by explaining how to plan and set up a new Jira 8 instance from scratch before getting you acquainted with key features such as emails, workflows, business processes, and much more. You'll then understand Jira's data hierarchy and how to design and work with projects. Since Jira is used for issue management, this book delves into the different issues that can arise in your projects. You'll explore fields, including custom fields, and learn to use them for more effective data collection. You'll create new screens from scratch and customize them to suit your requirements. The book also covers workflows and business processes, and guides you in setting up incoming and outgoing mail servers. Toward the end, you'll study Jira's security model and Jira Service Desk, which allows you to run Jira as a support portal. By the end of this Jira book, you will be able to implement Jira 8 in your projects with ease. What you will learn Understand Jira's data hierarchy and how to design and work with projects in Jira Use Jira for agile software projects, business process management, customer service support, and more Understand issues and work with them Design both system and custom fields to behave differently under different contexts Create and design your own screens and apply them to different project and issue types Gain an understanding of the workflow and its various components Set up both incoming and outgoing mail servers to work with e-mails Who this book is for This book will be especially useful for project managers but it's also intended for other Jira users, including developers, and any other industry besides software development, who would like to leverage Jira's powerful task management and workflow features to better manage their business processes. COMPUTERS,General

Hands-On Embedded Programming with Qt A comprehensive guide that will get you up and running with embedded software development using Qt5 Key Features Learn to create fluid, cross-platform applications for embedded devices Achieve optimum performance in your applications with QT Lite project Explore the implementation of Qt with IoT using QtMqtt, QtKNX, and QtWebSockets Book Description Qt is an open-source toolkit suitable for cross-platform and embedded application development. This book uses inductive teaching to help you learn how to create applications for embedded and Internet of Things (IoT) devices with Qt 5. You'll start by learning to develop your very first application with Qt. Next, you'll build on the first application by understanding new concepts through hands-on projects and written text. Each project will introduce new features that will help you transform your basic first project into a connected IoT application running on embedded hardware. In addition to practical experience in developing an embedded Qt project, you will also gain valuable insights into best practices for Qt development, along with exploring advanced techniques for testing, debugging, and monitoring the performance of Qt applications. Through the course of the book, the examples and projects are demonstrated in a way so that they can be run both locally and on an embedded platform. By the end of this book, you will have the skills you need to use Qt 5 to confidently develop modern embedded applications. What you will learn Understand how to develop Qt applications using Qt Creator under Linux Explore various Qt GUI technologies to build resourceful and interactive applications Understand Qt's threading model to maintain a responsive UI Get to grips with remote target load and debug under Qt Creator Become adept at writing IoT code using Qt Learn a variety of software best practices to ensure that your code is efficient Who this book is for This book is for software and hardware professionals with experience in different domains who are seeking new career opportunities in embedded systems and IoT. Working knowledge of the C++ Linux command line will be useful to get the most out of this book. COMPUTERS,General

Hidden Markov Models This book presents, in an integrated form, both the analysis and synthesis of three different types of hidden Markov models. Unlike other books on the subject, it is generic and does not focus on a specific theme, e.g. speech processing. Moreover, it presents the translation of hidden Markov models’ concepts from the domain of formal mathematics into computer codes using MATLAB®. The unique feature of this book is that the theoretical concepts are first presented using an intuition-based approach followed by the description of the fundamental algorithms behind hidden Markov models using MATLAB®. This approach, by means of analysis followed by synthesis, is suitable for those who want to study the subject using a more empirical approach. Key Selling Points: Presents a broad range of concepts related to Hidden Markov Models (HMM), from simple problems to advanced theory Covers the analysis of both continuous and discrete Markov chains Discusses the translation of HMM concepts from the realm of formal mathematics into computer code Offers many examples to supplement mathematical notation when explaining new concepts COMPUTERS,General

Quantum Computing This book integrates the foundations of quantum computing with a hands-on coding approach to this emerging field; it is the first work to bring these strands together in an updated manner. This work is suitable for both academic coursework and corporate technical training. This volume comprises three books under one cover: Part I outlines the necessary foundations of quantum computing and quantum circuits. Part II walks through the canon of quantum computing algorithms and provides code on a range of quantum computing methods in current use. Part III covers the mathematical toolkit required to master quantum computing. Additional resources include a table of operators and circuit elements and a companion GitHub site providing code and updates. Jack D. Hidary is a research scientist in quantum computing and in AI at Alphabet X, formerly Google X. “Quantum Computing will change our world in unexpected ways. Everything technology leaders, engineers and graduate students need is in this book including the methods and hands-on code to program on this novel platform.†—Eric Schmidt, PhD, Former Chairman and CEO of Google; Founder, Innovation Endeavors COMPUTERS,General

VMware vSphere 6.7 Cookbook Proven, actionable ways to install, manage, secure and monitor your vSphere 6.7 environments Key Features Get up to speed with the installation and life cycle management of a vSphere 6.7 environment, using a task-based approach Secure your vSphere environment using SSL Certificates Get introduced to the tools that are used to monitor the performance of the vSphere Environment Book Description VMware vSphere is the most comprehensive core suite of SDDC solutions on the market. It helps transform data centers into simplified on-premises private cloud infrastructures. This edition of the book focuses on the latest version, vSphere 6.7. The books starts with chapters covering the greenfield deployment of vSphere 6.7 components and the upgrade of existing vSphere components to 6.7. You will then learn how to configure storage and network access for a vSphere environment. Get to grips with optimizing your vSphere environment for resource distribution and utilization using features such as DRS and DPM, along with enabling high availability for vSphere components using vSphere HA, VMware FT, and VCHA. Then, you will learn how to facilitate large-scale deployment of stateless/stateful ESXi hosts using Auto Deploy. Finally, you will explore how to upgrade/patch a vSphere environment using vSphere Update Manager, secure it using SSL certificates, and then monitor its performance with tools such as vSphere Performance Charts and esxtop. By the end of this book, you'll be well versed in the core functionalities of vSphere 6.7 and be able to effectively deploy, manage, secure, and monitor your environment. What you will learn Deploy a new vSphere 6.7 environment or upgrade an existing vSphere environment to version 6.7 Learn how to configure and manage storage and network access for a vSphere environment Enable high availability for Hosts, VMs and vCenter Server Optimize your vSphere environment for resource distribution/utilization Patch or upgrade a vSphere environment using vSphere Update Manager Secure vSphere infrastructure components using SSL certificates Effectively monitor the performance of your vSphere environment Who this book is for If you are a systems administrator, support engineer, or anyone who wants to learn how to install, configure, and manage a vSphere environment in a quick, hands-on manner, then this book is for you. Consultants and infrastructure architects who wish to design and deploy vSphere 6.7 environments will also find this book helpful. COMPUTERS,General

Python Parallel Programming Cookbook Implement effective programming techniques in Python to build scalable software that saves time and memory Key Features Design distributed computing systems and massive computational tasks coherently Learn practical recipes with concise explanations that address development pain points encountered while coding parallel programs Understand how to host your parallelized applications on the cloud Book Description Nowadays, it has become extremely important for programmers to understand the link between the software and the parallel nature of their hardware so that their programs run efficiently on computer architectures. Applications based on parallel programming are fast, robust, and easily scalable. This updated edition features cutting-edge techniques for building effective concurrent applications in Python 3.7. The book introduces parallel programming architectures and covers the fundamental recipes for thread-based and process-based parallelism. You'll learn about mutex, semaphores, locks, queues exploiting the threading, and multiprocessing modules, all of which are basic tools to build parallel applications. Recipes on MPI programming will help you to synchronize processes using the fundamental message passing techniques with mpi4py. Furthermore, you'll get to grips with asynchronous programming and how to use the power of the GPU with PyCUDA and PyOpenCL frameworks. Finally, you'll explore how to design distributed computing systems with Celery and architect Python apps on the cloud using PythonAnywhere, Docker, and serverless applications. By the end of this book, you will be confident in building concurrent and high-performing applications in Python. What you will learn Synchronize multiple threads and processes to manage parallel tasks Use message passing techniques to establish communication between processes to build parallel applications Program your own GPU cards to address complex problems Manage computing entities to execute distributed computational task Write efficient programs by adopting the event-driven programming model Explore cloud technology with Django and Google App Engine Apply parallel programming techniques that can lead to performance improvements Who this book is for The Python Parallel Programming Cookbook is for software developers who are well-versed with Python and want to use parallel programming techniques to write powerful and efficient code. This book will help you master the basics and the advanced of parallel computing. COMPUTERS,General

Learning Geospatial Analysis with Python Learn the core concepts of geospatial data analysis for building actionable and insightful GIS applications Key Features Create GIS solutions using the new features introduced in Python 3.7 Explore a range of GIS tools and libraries such as PostGIS, QGIS, and PROJ Learn to automate geospatial analysis workflows using Python and Jupyter Book Description Geospatial analysis is used in almost every domain you can think of, including defense, farming, and even medicine. With this systematic guide, you'll get started with geographic information system (GIS) and remote sensing analysis using the latest features in Python. This book will take you through GIS techniques, geodatabases, geospatial raster data, and much more using the latest built-in tools and libraries in Python 3.7. You'll learn everything you need to know about using software packages or APIs and generic algorithms that can be used for different situations. Furthermore, you'll learn how to apply simple Python GIS geospatial processes to a variety of problems, and work with remote sensing data. By the end of the book, you'll be able to build a generic corporate system, which can be implemented in any organization to manage customer support requests and field support personnel. What you will learn Automate geospatial analysis workflows using Python Code the simplest possible GIS in just 60 lines of Python Create thematic maps with Python tools such as PyShp, OGR, and the Python Imaging Library Understand the different formats that geospatial data comes in Produce elevation contours using Python tools Create flood inundation models Apply geospatial analysis to real-time data tracking and storm chasing Who this book is for This book is for Python developers, researchers, or analysts who want to perform geospatial modeling and GIS analysis with Python. Basic knowledge of digital mapping and analysis using Python or other scripting languages will be helpful. COMPUTERS,General

Computer Basics Absolute Beginner's Guide, Windows 10 Edition (includes Content Update Program) Updated for the Latest Windows 10 2019 This is today’s best beginner’s guide to using your computer or tablet with the Windows 10 operating system. Make the most of your Windows 10 notebook or desktop computer—without becoming a technical expert! This is the fastest way to get comfortable, get productive, get online, get started with social networking, make more connections, and have more fun! Even if you’ve never used a Windows computer before, this book shows you how to do what you want, one incredibly clear and easy step at a time. Here’s a small sample of what you’ll learn: Set up your computer and use the Windows 10 Start menu and desktop Connect to the Internet and browse the Web with Microsoft Edge Get started with social networking on Facebook, Twitter, Pinterest, and LinkedIn Use Windows 10’s built-in apps—and find great new apps in the Windows Store Connect printers and external storage, and set up automatic file backup Connect to a home wireless network or public Wi-Fi hotspot Go online to shop and sell—and smart search with Microsoft Cortana® Get work done quickly with Microsoft Office Organize, view, and share photos Listen to streaming music with Pandora and Spotify Watch streaming movies and TV shows with Amazon Prime Video, Hulu, Netflix, and more Protect yourself against viruses, spyware, and spam Keep your system running reliably at top speed COMPUTERS,General

AI Crash Course Unlock the power of artificial intelligence with top Udemy AI instructor Hadelin de Ponteves. Key Features Learn from friendly, plain English explanations and practical activities Put ideas into action with 5 hands-on projects that show step-by-step how to build intelligent software Use AI to win classic video games and construct a virtual self-driving car Book Description Welcome to the Robot World ... and start building intelligent software now! Through his best-selling video courses, Hadelin de Ponteves has taught hundreds of thousands of people to write AI software. Now, for the first time, his hands-on, energetic approach is available as a book. Starting with the basics before easing you into more complicated formulas and notation, AI Crash Course gives you everything you need to build AI systems with reinforcement learning and deep learning. Five full working projects put the ideas into action, showing step-by-step how to build intelligent software using the best and easiest tools for AI programming, including Python, TensorFlow, Keras, and PyTorch. AI Crash Course teaches everyone to build an AI to work in their applications. Once you've read this book, you're only limited by your imagination. What you will learn Master the basics of AI without any previous experience Build fun projects, including a virtual-self-driving car and a robot warehouse worker Use AI to solve real-world business problems Learn how to code in Python Discover the 5 principles of reinforcement learning Create your own AI toolkit Who this book is for If you want to add AI to your skillset, this book is for you. It doesn't require data science or machine learning knowledge. Just maths basics (high school level). COMPUTERS,General

Must Know High School Computer Programming The new Must Know series is like a lightning bolt to the brain Every school subject has must know ideas, or essential concepts, that lie behind it. This book will use that fact to help you learn in a unique way. Most study guides start a chapter with a set of goals, often leaving the starting point unclear. In Must Know High School Computer Programming, however, each chapter will immediately introduce you to the must know idea, or ideas, that lie behind the new programming topic. As you learn these must know ideas, the book will show you how to apply that knowledge to solving computer programming problems. Focused on the essential concepts of computer programming, this accessible guide will help you develop a solid understanding of the subject quickly and painlessly. Clear explanations are accompanied by numerous examples and followed with more challenging aspects of computer programming. Practical exercises close each chapter and will instill you with confidence in your growing programming skills. Must Know High School Computer Programming features: • Each chapter begins with the must know ideas behind the new topic• Extensive examples illustrate these must know ideas• Students learn how to apply this new knowledge to problem solving• Skills that can be applied to a number of courses, including Object Oriented Programming, Game Design, Robotics, AP Computer Science Principles, and AP Computer Science A• A robotics project that will bring computer programming to (electronic!) life• 250 practical review questions instill confidence• IRL (In Real Life) sidebars present real-life examples of the subject at work in culture, science, and history• Special BTW (By the Way) sidebars provide study tips, exceptions to the rule, and issues students should pay extra attention to• Bonus app includes 100 flashcards to reinforce what students have learned COMPUTERS,General

Cyber Minds Cyber Minds brings together an unrivalled panel of international experts who offer their insights into current cybersecurity issues in the military, business, and government. Key Features Explore the latest developments in cybersecurity Hear expert insight from the industry's top practitioners Dive deep into cyber threats in business, government, and military Book Description Shira Rubinoff's Cyber Minds brings together the top authorities in cybersecurity to discuss the emergent threats that face industries, societies, militaries, and governments today. With new technology threats, rising international tensions, and state-sponsored cyber attacks, cybersecurity is more important than ever. Cyber Minds serves as a strategic briefing on cybersecurity and data safety, collecting expert insights from sector security leaders, including: General Gregory Touhill, former Federal Chief Information Security Officer of the United States Kevin L. Jackson, CEO and Founder, GovCloud Mark Lynd, Digital Business Leader, NETSYNC Joseph Steinberg, Internet Security advisor and thought leader Jim Reavis, Co-Founder and CEO, Cloud Security Alliance Dr. Tom Kellerman, Chief Cybersecurity Officer for Carbon Black Inc and Vice Chair of Strategic Cyber Ventures Board Mary Ann Davidson, Chief Security Officer, Oracle Dr. Sally Eaves, Emergent Technology CTO, Global Strategy Advisor – Blockchain AI FinTech, Social Impact award winner, keynote speaker and author Dr. Guenther Dobrauz, Partner with PwC in Zurich and Leader of PwC Legal Switzerland Barmak Meftah, President, AT&T Cybersecurity Cleve Adams, CEO, Site 1001 (AI and big data based smart building company) Ann Johnson, Corporate Vice President – Cybersecurity Solutions Group, Microsoft Barbara Humpton, CEO, Siemens USA Businesses and states depend on effective cybersecurity. This book will help you to arm and inform yourself on what you need to know to keep your business – or your country – safe. What you will learn The threats and opportunities presented by AI How to mitigate social engineering and other human threats Developing cybersecurity strategies for the cloud Major data breaches, their causes, consequences, and key takeaways Blockchain applications for cybersecurity Implications of IoT and how to secure IoT services The role of security in cyberterrorism and state-sponsored cyber attacks Who this book is for This book is essential reading for business leaders, the C-Suite, board members, IT decision makers within an organization, and anyone with a responsibility for cybersecurity. COMPUTERS,General

Full Stack Development with JHipster Written by the core development team of JHipster and fully updated for JHipster 6, Java 11, and Spring Boot 2.1, this book will show you how to build modern web applications with real-world examples and best practices Key Features Build full stack applications with modern JavaScript frameworks such as Angular, React, and Vue.js Explore the JHipster microservices stack, which includes Spring Cloud, Netflix OSS, and the Elastic Stack Learn advanced local and cloud deployment strategies using Docker and Kubernetes Book Description JHipster is an open source development platform that allows you to easily create web apps and microservices from scratch without spending time on wiring and integrating different technologies. Updated to include JHipster 6, Java 11, Spring Boot 2.1, Vue.js, and Istio, this second edition of Full Stack Development with JHipster will help you build full stack applications and microservices seamlessly. You'll start by understanding JHipster and its associated tools, along with the essentials of full stack development, before building a monolithic web app. You'll then learn the JHipster Domain Language (JDL) with entity modeling using JDL-Studio. With this book, you'll create production-ready web apps using Spring Boot, Spring Framework, Angular, and Bootstrap, and run tests and set up continuous integration pipelines with Jenkins. As you advance, you'll learn how to convert your monoliths to microservices and how to package your application for production with various deployment options, including Heroku and Google Cloud. You'll also learn about Docker and Kubernetes, along with an introduction to the Istio service mesh. Finally, you'll build your client-side with React and Vue.js and discover JHipster's best practices. By the end of the book, you'll be able to leverage the best tools available to build modern web apps. What you will learn Create full stack apps from scratch using the latest features of JHipster 6 and Spring Boot 2.1 Build business logic by creating and developing entity models using JDL Understand how to convert a monolithic architecture into a full-fledged microservices architecture Build and package your apps for production using Docker Deploy your application to Google Cloud with Kubernetes Create continuous integration/continuous delivery pipelines with Jenkins Create applications using Angular, React, and Vue.js client-side frameworks Who this book is for This book is for full stack developers who want to build web applications and microservices speedily without writing a lot of boilerplate code. If you're a backend developer looking to learn full stack development with JavaScript frameworks and libraries such as Angular, React, and Vue.js, you'll find this book useful. Experience in building Java web applications is required. Some exposure to the Spring Framework would be beneficial but not necessary to get the most out of this book. COMPUTERS,General

Mastering Service Mesh Understand how to use service mesh architecture to efficiently manage and safeguard microservices-based applications with the help of examples Key Features Manage your cloud-native applications easily using service mesh architecture Learn about Istio, Linkerd, and Consul – the three primary open source service mesh providers Explore tips, techniques, and best practices for building secure, high-performance microservices Book Description Although microservices-based applications support DevOps and continuous delivery, they can also add to the complexity of testing and observability. The implementation of a service mesh architecture, however, allows you to secure, manage, and scale your microservices more efficiently. With the help of practical examples, this book demonstrates how to install, configure, and deploy an efficient service mesh for microservices in a Kubernetes environment. You'll get started with a hands-on introduction to the concepts of cloud-native application management and service mesh architecture, before learning how to build your own Kubernetes environment. While exploring later chapters, you'll get to grips with the three major service mesh providers: Istio, Linkerd, and Consul. You'll be able to identify their specific functionalities, from traffic management, security, and certificate authority through to sidecar injections and observability. By the end of this book, you will have developed the skills you need to effectively manage modern microservices-based applications. What you will learn Compare the functionalities of Istio, Linkerd, and Consul Become well-versed with service mesh control and data plane concepts Understand service mesh architecture with the help of hands-on examples Work through hands-on exercises in traffic management, security, policy, and observability Set up secure communication for microservices using a service mesh Explore service mesh features such as traffic management, service discovery, and resiliency Who this book is for This book is for solution architects and network administrators, as well as DevOps and site reliability engineers who are new to the cloud-native framework. You will also find this book useful if you're looking to build a career in DevOps, particularly in operations. Working knowledge of Kubernetes and building microservices that are cloud-native is necessary to get the most out of this book. COMPUTERS,General

The Universal Service Desk (USD) The Universal Service Desk (USD) – Implementing, controlling and improving service delivery defines what a USD is, why it is valuable to an organisation and how to build and implement one. It also discusses the evolution of the USD as part of integrated workplace management. Understand the essentials of any USD – buy this book today! COMPUTERS,General

ITIL® 4 Essentials ITIL® 4 Essentials contains everything you need to know to pass the ITIL 4 Foundation Certificate, plus more. It covers practices and concepts that are not addressed as part of the Foundation syllabus, making it ideal for newly qualified practitioners. This second edition has been updated to align with amendments to the ITIL ® 4 Foundation syllabus. COMPUTERS,General

Computational Advertising This book introduces computational advertising, and Internet monetization. It provides a macroscopic understanding of how consumer products in the Internet era push user experience and monetization to the limit. Part One of the book focuses on the basic problems and background knowledge of online advertising. Part Two targets the product, operations, and sales staff, as well as high-level decision makers of the Internet products. It explains the market structure, trading models, and the main products in computational advertising. Part Three targets systems, algorithms, and architects, and focuses on the key technical challenges of different advertising products. Features · Introduces computational advertising and Internet monetization · Covers data processing, utilization, and trading · Uses business logic as the driving force to explain online advertising products and technology advancement · Explores the products and the technologies of computational advertising, to provide insights on the realization of personalization systems, constrained optimization, data monetization and trading, and other practical industry problems · Includes case studies and code snippets COMPUTERS,General

Law 3.0 Putting technology front and centre in our thinking about law, this book introduces Law 3.0: the future of the legal landscape. Technology not only disrupts the traditional idea of what it is ‘to think like a lawyer,’ as per Law 1.0; it presents major challenges to regulators who are reasoning in a Law 2.0 mode. As this book demonstrates, the latest developments in technology offer regulators the possibility of employing a technical fix rather than just relying on rules – thus, we are introducing Law 3.0. Law 3.0 represents, so to speak, the state we are in and the conversation that we now need to have, and this book identifies some of the key points for discussion in that conversation. Thinking like a lawyer might continue to be associated with Law 1.0, but from 2020 onward, Law 3.0 is the conversation that we all need to join. And, as this book argues, law and the evolution of legal reasoning cannot be adequately understood unless we grasp the significance of technology in shaping both legal doctrine and our regulatory thinking. This is a book for those studying, or about to study, law – as well as others with interests in the legal, political, and social impact of technology. COMPUTERS,General

A Practical Approach to Metaheuristics using LabVIEW and MATLAB® Metaheuristic optimization has become a prime alternative for solving complex optimization problems in several areas. Hence, practitioners and researchers have been paying extensive attention to those metaheuristic algorithms that are mainly based on natural phenomena. However, when those algorithms are implemented, there are not enough books that deal with theoretical and experimental problems in a friendly manner so this book presents a novel structure that includes a complete description of the most important metaheuristic optimization algorithms as well as a new proposal of a new metaheuristic optimization named earthquake optimization. This book also has several practical exercises and a toolbox for MATLAB® and a toolkit for LabVIEW are integrated as complementary material for this book. These toolkits allow readers to move from a simulation environment to an experimentation one very fast. This book is suitable for researchers, students, and professionals in several areas, such as economics, architecture, computer science, electrical engineering, and control systems. The unique features of this book are as follows: Developed for researchers, undergraduate and graduate students, and practitioners A friendly description of the main metaheuristic optimization algorithms Theoretical and practical optimization examples A new earthquake optimization algorithm Updated state-of-the-art and research optimization projects The authors are multidisciplinary/interdisciplinary lecturers and researchers who have written a structure-friendly learning methodology to understand each metaheuristic optimization algorithm presented in this book. COMPUTERS,General

Mastering Metasploit Discover the next level of network defense and penetration testing with the Metasploit 5.0 framework Key Features Make your network robust and resilient with this updated edition covering the latest pentesting techniques Explore a variety of entry points to compromise a system while remaining undetected Enhance your ethical hacking skills by performing penetration tests in highly secure environments Book Description Updated for the latest version of Metasploit, this book will prepare you to face everyday cyberattacks by simulating real-world scenarios. Complete with step-by-step explanations of essential concepts and practical examples, Mastering Metasploit will help you gain insights into programming Metasploit modules and carrying out exploitation, as well as building and porting various kinds of exploits in Metasploit. Giving you the ability to perform tests on different services, including databases, IoT, and mobile, this Metasploit book will help you get to grips with real-world, sophisticated scenarios where performing penetration tests is a challenge. You'll then learn a variety of methods and techniques to evade security controls deployed at a target's endpoint. As you advance, you'll script automated attacks using CORTANA and Armitage to aid penetration testing by developing virtual bots and discover how you can add custom functionalities in Armitage. Following real-world case studies, this book will take you on a journey through client-side attacks using Metasploit and various scripts built on the Metasploit 5.0 framework. By the end of the book, you'll have developed the skills you need to work confidently with efficient exploitation techniques What you will learn Develop advanced and sophisticated auxiliary, exploitation, and post-exploitation modules Learn to script automated attacks using CORTANA Test services such as databases, SCADA, VoIP, and mobile devices Attack the client side with highly advanced pentesting techniques Bypass modern protection mechanisms, such as antivirus, IDS, and firewalls Import public exploits to the Metasploit Framework Leverage C and Python programming to effectively evade endpoint protection Who this book is for If you are a professional penetration tester, security engineer, or law enforcement analyst with basic knowledge of Metasploit, this book will help you to master the Metasploit framework and guide you in developing your exploit and module development skills. Researchers looking to add their custom functionalities to Metasploit will find this book useful. As Mastering Metasploit covers Ruby programming and attack scripting using Cortana, practical knowledge of Ruby and Cortana is required. COMPUTERS,General

ISO 22301 Understand the basics of business continuity and ISO 22301:2019 with this concise pocket guide, which will help you ensure your organisation can continue to operate in the event of a disruption. COMPUTERS,General

Being a Researcher This book explores research from the researchers’ perspective: why to engage in research, what methods to follow, how to operate in daily life, what the responsibilities are, how to engage with society, and the ethical issues confronting professionals in their day-to-day research. The book systematically discusses what every student should be told when entering academic or industrial research so that they can avoid going through the painful process of learning by personal experience and lots of errors. Rather than being technical, it is philosophical and sometimes even anecdotal, combining factual information and commonly accepted knowledge on research and its methods, while at the same time clearly distinguishing between objective and factual concepts and data, and subjective considerations. The book is about scientific research in general and as such holds true for any scientific field. However, it is fair to say that the different fields differ in their research cultures and in their eco-systems. The book reflects the author’s experience accumulated over almost 50 years of teaching graduate courses and lecturing in doctoral symposia at Politecnico di Milano, University of Zurich, TU Wien, Peking University, and at various conferences, and of academic research in informatics (also known as computer science). This book is mainly intended for students who are considering research as a possible career option; for in-progress researchers who have entered doctoral programs; and for junior postdoctoral researchers. It will also appeal to senior researchers involved in mentoring students and junior researchers. COMPUTERS,General

Intuitive Understanding of Kalman Filtering with MATLAB® The emergence of affordable micro sensors, such as MEMS Inertial Measurement Systems, are applied in embedded systems and Internet-of-Things devices. This has brought techniques such as Kalman Filtering, which are capable of combining information from multiple sensors or sources, to the interest of students and hobbyists. This book will explore the necessary background concepts, helping a much wider audience of readers develop an understanding and intuition that will enable them to follow the explanation for the Kalman Filtering algorithm. Key Features: Provides intuitive understanding of Kalman Filtering approach Succinct overview of concepts to enhance accessibility and appeal to a wide audience Interactive learning techniques with code examples Malek Adjouadi, PhD, is Ware Professor with the Department of Electrical and Computer Engineering at Florida International University, Miami. He received his PhD from the Electrical Engineering Department at the University of Florida, Gainesville. He is the Founding Director of the Center for Advanced Technology and Education funded by the National Science Foundation. His earlier work on computer vision to help persons with blindness led to his testimony to the U.S. Senate on the committee of Veterans Affairs on the subject of technology to help persons with disabilities. His research interests are in imaging, signal processing and machine learning, with applications in brain research and assistive technology. Armando Barreto, PhD, is Professor of the Electrical and Computer Engineering Department at Florida International University, Miami, as well as the Director of FIU’s Digital Signal Processing Laboratory, with more than 25 years of experience teaching DSP to undergraduate and graduate students. He earned his PhD in electrical engineering from the University of Florida, Gainesville. His work has focused on applying DSP techniques to the facilitation of human-computer interactions, particularly for the benefit of individuals with disabilities. He has developed human-computer interfaces based on the processing of signals and has developed a system that adds spatialized sounds to the icons in a computer interface to facilitate access by individuals with "low vision." With his research team, he has explored the use of Magnetic, Angular-Rate and Gravity (MARG) sensor modules and Inertial Measurement Units (IMUs) for human-computer interaction applications. He is a senior member of the Institute of Electrical and Electronics Engineers (IEEE) and the Association for Computing Machinery (ACM). Francisco R. Ortega, PhD, is an Assistant Professor at Colorado State University and Director of the Natural User Interaction Lab (NUILAB). Dr. Ortega earned his PhD in Computer Science (CS) in the field of Human-Computer Interaction (HCI) and 3D User Interfaces (3DUI) from Florida International University (FIU). He also held a position of Post-Doc and Visiting Assistant Professor at FIU. His main research area focuses on improving user interaction in 3DUI by (a) eliciting (hand and full-body) gesture and multimodal interactions, (b) developing techniques for multimodal interaction, and (c) developing interactive multimodal recognition systems. His secondary research aims to discover how to increase interest for CS in non-CS entry-level college students via virtual and augmented reality games. His research has resulted in multiple peer-reviewed publications in venues such as ACM ISS, ACM SUI, and IEEE 3DUI, among others. He is the first-author of the CRC Press book Interaction Design for 3D User Interfaces: The World of Modern Input Devices for Research, Applications and Game Development. Nonnarit O-larnnithipong, PhD, is an Instructor at Florida International University. Dr. O-larnnithipong earned his PhD in Electrical Engineering, majoring in Digital Signal Processing from Florida International University (FIU). He also held a position of Post-Doctoral Associate at FIU in 2019. His research has focused on (1) implementing the sensor fusion algorithm to improve orientation measurement using MEMS inertial and magnetic sensors and (2) developing a 3D hand motion tracking system using Inertial Measurement Units (IMUs) and infrared cameras. His research has resulted in multiple peer-reviewed publications in venues such as HCI-International and IEEE Sensors. COMPUTERS,General

The Digital Gaming Handbook The Digital Gaming Handbook covers the state-of-the-art in video and digital game research and development, from traditional to emerging elements of gaming across multiple disciplines. Chapters are presented with applicability across all gaming platforms over a broad range of topics, from game content creation through gameplay at a level accessible for the professional game developer while being deep enough to provide a valuable reference of the state-of-the-art research in this field. Key Features: International experts share their research and experience in game development and design Provides readers with inside perspectives on the cross-disciplinary aspects of the industry Includes retrospective and forward-looking examinations of gaming Editor: Dr. Roberto Dillon is a leading game studies educator with more than 15 years of experience in the field of game design and development. COMPUTERS,General

Haptics An accessible, nontechnical overview of active touch sensing, from sensory receptors in the skin to tactile surfaces on flat screen displays. Haptics, or haptic sensing, refers to the ability to identify and perceive objects through touch. This is active touch, involving exploration of an object with the hand rather than the passive sensing of a vibration or force on the skin. The development of new technologies, including prosthetic hands and tactile surfaces for flat screen displays, depends on our knowledge of haptics. In this volume in the MIT Press Essential Knowledge series, Lynette Jones offers an accessible overview of haptics, or active touch sensing, and its applications. Jones explains that haptics involves integrating information from touch and kinesthesia—that is, information both from sensors in the skin and from sensors in muscles, tendons, and joints. The challenge for technology is to reproduce in a virtual world some of the sensations associated with physical interactions with the environment. Jones maps the building blocks of the tactile system, the receptors in the skin and the skin itself, and how information is processed at this interface with the external world. She describes haptic perception, the processing of haptic information in the brain; haptic illusions, or distorted perceptions of objects and the body itself; tactile and haptic displays, from braille to robotic systems; tactile compensation for other sensory impairments; surface haptics, which creates virtual haptic effects on physical surfaces such as touch screens; and the development of robotic and prosthetic hands that mimic the properties of human hands. COMPUTERS,General

Bits to Bitcoin An accessible guide to our digital infrastructure, explaining the basics of operating systems, networks, security, and other topics for the general reader. Most of us feel at home in front of a computer; we own smartphones, tablets, and laptops; we look things up online and check social media to see what our friends are doing. But we may be a bit fuzzy about how any of this really works. In Bits to Bitcoin, Mark Stuart Day offers an accessible guide to our digital infrastructure, explaining the basics of operating systems, networks, security, and related topics for the general reader. He takes the reader from a single process to multiple processes that interact with each other; he explores processes that fail and processes that overcome failures; and he examines processes that attack each other or defend themselves against attacks. Day tells us that steps are digital but ramps are analog; that computation is about “doing something with stuff” and that both the “stuff” and the “doing” can be digital. He explains timesharing, deadlock, and thrashing; virtual memory and virtual machines; packets and networks; resources and servers; secret keys and public keys; Moore's law and Thompson's hack. He describes how building in redundancy guards against failure and how endpoints communicate across the Internet. He explains why programs crash or have other bugs, why they are attacked by viruses, and why those problems are hard to fix. Finally, after examining secrets, trust, and cheating, he explains the mechanisms that allow the Bitcoin system to record money transfers accurately while fending off attacks. COMPUTERS,General

Data Science A concise introduction to the emerging field of data science, explaining its evolution, relation to machine learning, current uses, data infrastructure issues, and ethical challenges. The goal of data science is to improve decision making through the analysis of data. Today data science determines the ads we see online, the books and movies that are recommended to us online, which emails are filtered into our spam folders, and even how much we pay for health insurance. This volume in the MIT Press Essential Knowledge series offers a concise introduction to the emerging field of data science, explaining its evolution, current uses, data infrastructure issues, and ethical challenges. It has never been easier for organizations to gather, store, and process data. Use of data science is driven by the rise of big data and social media, the development of high-performance computing, and the emergence of such powerful methods for data analysis and modeling as deep learning. Data science encompasses a set of principles, problem definitions, algorithms, and processes for extracting non-obvious and useful patterns from large datasets. It is closely related to the fields of data mining and machine learning, but broader in scope. This book offers a brief history of the field, introduces fundamental data concepts, and describes the stages in a data science project. It considers data infrastructure and the challenges posed by integrating data from multiple sources, introduces the basics of machine learning, and discusses how to link machine learning expertise with real-world problems. The book also reviews ethical and legal issues, developments in data regulation, and computational approaches to preserving privacy. Finally, it considers the future impact of data science and offers principles for success in data science projects. COMPUTERS,General

Practical R 4 Get started with an accelerated introduction to the R ecosystem, programming language, and tools including R script and RStudio. Utilizing many examples and projects, this book teaches you how to get data into R and how to work with that data using R. Once grounded in the fundamentals, the rest of Practical R 4 dives into specific projects and examples starting with running and analyzing a survey using R and LimeSurvey. Next, you'll carry out advanced statistical analysis using R and MouselabWeb. Then, you’ll see how R can work for you without statistics, including how R can be used to automate data formatting, manipulation, reporting, and custom functions. The final part of this book discusses using R on a server; you’ll build a script with R that can run an RStudio Server and monitor a report source for changes to alert the user when something has changed. This project includes both regular email alerting and push notification. And, finally, you’ll use R to create a customized daily rundown report of a person's most important information such as a weather report, daily calendar, to-do's and more. This demonstrates how to automate such a process so that every morning, the user navigates to the same web page and gets the updated report. What You Will Learn Set up and run an R script, including installation on a new machine and downloading and configuring R Turn any machine into a powerful data analytics platform accessible from anywhere with RStudio Server Write basic R scripts and modify existing scripts to suit your own needs Create basic HTML reports in R, inserting information as needed Build a basic R package and distribute it Who This Book Is For Some prior exposure to statistics, programming, and maybe SAS is recommended but not required. COMPUTERS,General

Computational Models for Cognitive Vision Learn how to apply cognitive principles to the problems of computer vision Computational Models for Cognitive Vision formulates the computational models for the cognitive principles found in biological vision, and applies those models to computer vision tasks. Such principles include perceptual grouping, attention, visual quality and aesthetics, knowledge-based interpretation and learning, to name a few. The author’s ultimate goal is to provide a framework for creation of a machine vision system with the capability and versatility of the human vision. Written by Dr. Hiranmay Ghosh, the book takes readers through the basic principles and the computational models for cognitive vision, Bayesian reasoning for perception and cognition, and other related topics, before establishing the relationship of cognitive vision with the multi-disciplinary field broadly referred to as “artificial intelligenceâ€. The principles are illustrated with diverse application examples in computer vision, such as computational photography, digital heritage and social robots. The author concludes with suggestions for future research and salient observations about the state of the field of cognitive vision. Other topics covered in the book include: · knowledge representation techniques · evolution of cognitive architectures · deep learning approaches for visual cognition Undergraduate students, graduate students, engineers, and researchers interested in cognitive vision will consider this an indispensable and practical resource in the development and study of computer vision. COMPUTERS,General

The Service Desk Handbook – A guide to service desk implementation, management and support The Service Desk Handbook - A guide to service desk implementation, management and support provides operational guidance for implementing, managing and supporting service desks in the enterprise. It will help service desk teams in adopting ITIL® to accomplish their tasks while making the necessary adaptations as per their organisation’s needs. COMPUTERS,General

Guerrilla Capacity Planning In these days of shortened fiscal horizons and contracted time-to-market schedules, traditional approaches to capacity planning are often seen by management as tending to inflate their production schedules. Rather than giving up in the face of this kind of relentless pressure to get things done faster, Guerrilla Capacity Planning facilitates rapid forecasting of capacity requirements based on the opportunistic use of whatever performance data and tools are available in such a way that management insight is expanded but their schedules are not. A key Guerrilla concept is tactical planning whereby short-range planning questions and projects are brought up in team meetings such that management is compelled to know the answer, and therefore buys into capacity planning without recognizing it as such. Once you have your "foot in the door", capacity planning methods can be refined in an iterative cycle of improvement called "The Wheel of Capacity Planning". Another unique Guerrilla tool is Virtual Load Testing, based on Dr. Gunther's "Universal Law of Computational Scaling", which provides a highly cost-effective method for assessing application scalability. COMPUTERS,Hardware,Cell Phones & Devices

Mobile Design and Development Mobile devices outnumber desktop and laptop computers three to one worldwide, yet little information is available for designing and developing mobile applications. Mobile Design and Development fills that void with practical guidelines, standards, techniques, and best practices for building mobile products from start to finish. With this book, you'll learn basic design and development principles for all mobile devices and platforms. You'll also explore the more advanced capabilities of the mobile web, including markup, advanced styling techniques, and mobile Ajax. If you're a web designer, web developer, information architect, product manager, usability professional, content publisher, or an entrepreneur new to the mobile web, Mobile Design and Development provides you with the knowledge you need to work with this rapidly developing technology. Mobile Design and Development will help you: Understand how the mobile ecosystem works, how it differs from other mediums, and how to design products for the mobile context Learn the pros and cons of building native applications sold through operators or app stores versus mobile websites or web apps Work with flows, prototypes, usability practices, and screen-size-independent visual designs Use and test cross-platform mobile web standards for older devices, as well as devices that may be available in the future Learn how to justify a mobile product by building it on a budget COMPUTERS,Hardware,Cell Phones & Devices

Probabilistic Safety Assessment and Management ’96 IE-2 > FV 5E-3 > FV IE-3 > FV IE-4 > FV Trun- Total IST and IST Components Total IST FV> IE-2 Type >5E-3 > IE-3 > IE-4 >0 cated IPE Components Not Modeled in PRA Components 11 3 6 5 27 73 100 AOV 2 CV 4 21 24 16 12 77 94 171 4 6 10 HOV 4 34 158 MOV 2 5 35 33 24 25 124 43 43 MV 2 PORV 1 1 2 PUMP 12 5 6 1 3 27 9 36 54 54 SOV SRV 20 3 23 23 Total 39 17 73 61 49 45 284 313 597 ------- --- Table 2. Levell IPEEE Basic Event Importance - Risk Achievement Worth Total IST and (PE IST Components Not Total IST 2>RAW>0 Truncated Type RAW>2 Components Modeled in PRA Components 100 AOV 13 9 5 27 73 CV 52 16 9 77 94 171 4 4 6 10 HOV MOV 60 54 10 124 34 158 43 43 MV PORV 2 2 2 PUMP 24 3 27 9 36 SOV 54 54 SRV 23 23 23 597 Total 155 102 27 284 313 ~~--- -. . j S 702 and 2 includes the following IST component types: pumps, air-operated valves (AOV), check valves (CV), hydraulically-operated valves (HOV), motor-operated valves (MOV), manual valves (MV), pressurizer power-operated relief valves (PORV), solenoid operated valves (SOV), and safety reliefvalves (SRV). COMPUTERS,Hardware,Cell Phones & Devices

MacBook Pro Portable Genius Learn the skills, tools and shortcuts you need in order to make the most of your MacBook Pro This easy-to-use, compact guide skips the fluff and gets right to the essentials so that you can maximize all the latest features of the MacBook Pro. Packed with savvy insights and tips on key tools and shortcuts, this handy book aims to help you increase your productivity and save you time and hassle. From desktop sharing and wireless networking to running Windows applications and more, this book shows you what you want to know. Includes the latest version of OS X, iCloud, FaceTime, and more Covers all the essential tools, topics, and shortcuts on things like running Windows applications, using the Intel Ivy Bridge processor, and more Features Genius icons throughout the book that provide smart and innovative ways to handle tasks and save yourself time MacBook Pro Portable Genius, 5th Edition puts you well on the way to being a pro at using your MacBook Pro! COMPUTERS,Hardware,Cell Phones & Devices

Getting Started with Bluetooth Low Energy With Bluetooth Low Energy (BLE), smart devices are about to become even smarter. This practical guide demonstrates how this exciting wireless technology helps developers build mobile apps that share data with external hardware, and how hardware engineers can gain easy and reliable access to mobile operating systems. This book provides a solid, high-level overview of how devices use BLE to communicate with each other. You’ll learn useful low-cost tools for developing and testing BLE-enabled mobile apps and embedded firmware and get examples using various development platforms—including iOS and Android for app developers and embedded platforms for product designers and hardware engineers. Understand how data is organized and transferred by BLE devices Explore BLE’s concepts, key limitations, and network topology Dig into the protocol stack to grasp how and why BLE operates Learn how BLE devices discover each other and establish secure connections Set up the tools and infrastructure for BLE application development Get examples for connecting BLE to iPhones, iPads, Android devices, and sensors Develop code for a simple device that transmits heart rate data to a mobile device COMPUTERS,Hardware,Cell Phones & Devices

7th UK Computer and Telecommunications Performance Engineering Workshop Performance engineering is a fast-moving field where advances in technology mean that new issues constantly need to be addressed. In response to this, the UK Computer and Telecommunications Performance Engineering workshops were set up in 1985 to provide a valuable opportunity for the discussion and exchange of ideas. They have subsequently become well established as the focus for academic and industrial practitioners from the UK and Europe with an interest in performance and modelling and analysis. This volume contains the 16 papers which were presented at the 7th annual workshop, held in Edinburgh in July 1991. The workshop highlighted various aspects of parallel computing - an area which is attracting an increasing amount of interest - and the work presented in these papers is of particular interest as the contributors used real analysis to evaluate their models. The papers cover an unusually wide range of topics, both practical and theoretical, including advances in queueing theory, common performance problems and their solutions, assessments of available tools and presentations of new theoretical results. The result is an extremely comprehensive coverage of this important and challenging field. This volume provides an up-to-date assessment of work being carried out by performance engineers in the UK and Europe and will be an invaluable reference book for researchers and practitioners wishing to familiarise themselves with the benefits of performance and analysis. COMPUTERS,Hardware,Cell Phones & Devices

iPhone X For Dummies Get the most out of your iPhone X Apple's iPhone X represents such a radical departure from all previous models of the globally known iPhone that it needs its own book to help users navigate the new features. Luckily, iPhone X For Dummies is here to provide the guidance you need to figure out the features of your new iPhone and the software that powers it. Written by the experts who've created all previous editions of iPhone For Dummies, this book takes a deep dive into this fabulous new phone and its unique controls. It then delves into iOS 11 and how it works on the iPhone X. It leaves no stone unturned and offers all the in-depth coverage you need to make your iPhone X work for you—right out of the box! Control your iPhone X with iOS 11 gestures Explore advanced camera tools that produce stunning photos Set up face recognition to access your phone with a smile Charge your iPhone wirelessly If you’ve invested in this awesome new device, you deserve to get the very most out of it. And this book shows you how! COMPUTERS,Hardware,Cell Phones & Devices

iPhone The iPhone XS, XS Max, and XR aren’t just faster and more powerful than ever—they’re also better at all of the things you use an iPhone for. With the latest edition of this bestselling guide, you get a funny, gorgeously illustrated guide to the tips, shortcuts, and workarounds that will turn you into an iPhone master. This easy-to-use book will also get you up to speed on all iOS 12 features, including new Siri shortcuts, Group FaceTime, and improved parental controls. Missing Manual series creator and former New York Times columnist David Pogue helps you accomplish everything from web browsing to watching videos. You’ll get up to speed on features such as Dual SIM Support that lets you use two lines on one phone and True Tone technology that adjusts the display to your environment. Pick up this beautiful full-color book and learn how to get the most out of your iPhone. COMPUTERS,Hardware,Cell Phones & Devices

Apple Watch For Dummies Get connected with Apple Watch The new and improved Apple Watch does it all—tells time, tracks your fitness, monitors your health, keeps you connected, and so much more! Apple Watch for Dummies covers the latest series and version of Apple Watch, giving you the lowdown on the new WatchOS. You’ll learn how to use all the exciting new features, watch faces, improvements to Siri, and how to customize your Apple Watch to suit your needs! From picking the right watch model and learning the “newbie†basics to must-have apps, troubleshooting, and beyond, this book will help you wrap your head around the Apple Watch! Send and receive text message and e-mails Use Siri to control Apple Watch with your voice Taking advantage of advanced health and fitness features Adjust Apple Watch settings to meet your needs Push Apple Watch to its limits with advanced techniques Whether you’re a beginner or already an Apple Watch veteran, read this book to get a handle on all the features and tools of the latest and greatest Apple Watch. COMPUTERS,Hardware,Cell Phones & Devices

iPhone The iPhone 11, 11 Pro, 11R, and 11Max are faster than ever and have more powerful cameras. With the latest edition of this bestselling guide, you get a funny, gorgeously illustrated guide to the tips, shortcuts, and workarounds that will turn you into an iPhone master. Written by David Pogue—Missing Manual series creator, New York Times columnist, and Emmy-winning tech correspondent for CNBC, CBS, and NPR—this update shows you everything you need to know about new iPhone features and the iOS 13 user interface. Pick up this beautiful full-color book and learn how to get the most out of your iPhone. COMPUTERS,Hardware,Cell Phones & Devices

Teach Yourself VISUALLY iPhone 11, 11Pro, and 11 Pro Max Know your new iPhone 11, 11 Pro, and 11 Pro Max from the inside-out with 900 color screen shots! Teach Yourself VISUALLY iPhone is your ultimate guide to getting the most out of your iPhone! Apple's graphics-driven iOS is perfect for visual learners, so this book uses a visual approach to show you everything you need to know to get up and running—and much more. Full-color screen shots walk you step-by-step through setup, customization, and everything your iPhone can do. Whether you are new to the iPhone or have just upgraded to the 11, 11 Pro, or 11 Pro Max, this book helps you discover your phone's full functionality and newest capabilities. Stay in touch by phone, text, email, FaceTime Audio or FaceTime Video calls, or social media; download and enjoy books, music, movies, and more; take, edit, and manage photos; track your health, fitness, and habits; organize your schedule, your contacts, and your commitments; and much more! The iPhone is designed to be user-friendly, attractive, and functional. But it is capable of so much more than you think—don't you want to explore the possibilities? This book walks you through iOS 13 visually to help you stay in touch, get things done, and have some fun while you're at it! Get to know iOS 13 with 900 full-color screen shots Master the iPhone's basic functions and learn the latest features Customize your iPhone to suit your needs and get optimal performance Find the apps and services that can make your life easier The iPhone you hold in your hand represents the pinnacle of mobile technology and is a masterpiece of industrial design. Once you get to know it, you'll never be without it. Teach Yourself VISUALLY iPhone is your personal map for exploring your new tech companion. COMPUTERS,Hardware,Cell Phones & Devices

iPad For Seniors For Dummies Get to know the exciting features of your new iPad! The iPad can do almost anything: entertain you, help you stay in touch with the world, boost your productivity, and more. If you have lots of life experience but are a little less tech savvy, iPad For Seniors For Dummies is here to help you make the most of your wireless device. Learn the essentials of any model of iPad with this friendly, easy-to-follow guide. You’ll learn to connect to the Internet, play games, watch movies, listen to music, use video chat, update your social media accounts, read the news, and just about anything else you might want to do. Set up your Apple ID and navigate the iPad screens Connect to the internet, check your e-mail, and update social media Cue up music, TV, or a movie to stay entertained Take photos, chat with family and friends, and more! In this edition, you’ll also learn to teach your iPad to answer your voice commands, making life with your new iPad easier and more convenient than ever! COMPUTERS,Hardware,Cell Phones & Devices

iPad and iPad Pro For Dummies The A to Z guide to getting the most from your iPad Your iPad is a magical piece of technology connecting you to the rest of the world pretty much anytime and anywhere. Super thin and (well, almost) light as a feather, it allows you to keep up with your day to day duties, stay in touch with family and friends, catch up with work, relax with books and movies, or even create your own works of art! Given all it’s capable of, it’s essential to have a guide to help you make the most of your device. The latest edition of iPad and iPad Pro for Dummies helps users of all experience levels navigate this amazing looking glass. Assuming no prior knowledge, it takes you from the basics—including getting to know the iPad and adding useful accessories such as keyboards and pencils—to setting up email, connecting with other devices, maintaining files, and researching and installing the best apps for you. Discover the simple steps to get up and running Make your iPad work better and faster for you Explore the features of the brand new iPadOS Get easy fixes to common problems Pick up your copy today and find out just how sweet life in Apple tablet form can be! COMPUTERS,Hardware,Cell Phones & Devices

Practical Mobile Forensics Become well-versed with forensics for the Android, iOS, and Windows 10 mobile platforms by learning essential techniques and exploring real-life scenarios Key Features Apply advanced forensic techniques to recover deleted data from mobile devices Retrieve and analyze data stored not only on mobile devices but also on the cloud and other connected mediums Use the power of mobile forensics on popular mobile platforms by exploring different tips, tricks, and techniques Book Description Mobile phone forensics is the science of retrieving data from a mobile phone under forensically sound conditions. This updated fourth edition of Practical Mobile Forensics delves into the concepts of mobile forensics and its importance in today's world. The book focuses on teaching you the latest forensic techniques to investigate mobile devices across various mobile platforms. You will learn forensic techniques for multiple OS versions, including iOS 11 to iOS 13, Android 8 to Android 10, and Windows 10. The book then takes you through the latest open source and commercial mobile forensic tools, enabling you to analyze and retrieve data effectively. From inspecting the device and retrieving data from the cloud, through to successfully documenting reports of your investigations, you'll explore new techniques while building on your practical knowledge. Toward the end, you will understand the reverse engineering of applications and ways to identify malware. Finally, the book guides you through parsing popular third-party applications, including Facebook and WhatsApp. By the end of this book, you will be proficient in various mobile forensic techniques to analyze and extract data from mobile devices with the help of open source solutions. What you will learn Discover new data extraction, data recovery, and reverse engineering techniques in mobile forensics Understand iOS, Windows, and Android security mechanisms Identify sensitive files on every mobile platform Extract data from iOS, Android, and Windows platforms Understand malware analysis, reverse engineering, and data analysis of mobile devices Explore various data recovery techniques on all three mobile platforms Who this book is for This book is for forensic examiners with basic experience in mobile forensics or open source solutions for mobile forensics. Computer security professionals, researchers or anyone looking to gain a deeper understanding of mobile internals will also find this book useful. Some understanding of digital forensic practices will be helpful to grasp the concepts covered in the book more effectively. COMPUTERS,Hardware,Cell Phones & Devices

Modern Computer Architecture and Organization A no-nonsense, practical guide to current and future processor and computer architectures, enabling you to design computer systems and develop better software applications across a variety of domains Key Features Understand digital circuitry with the help of transistors, logic gates, and sequential logic Examine the architecture and instruction sets of x86, x64, ARM, and RISC-V processors Explore the architecture of modern devices such as the iPhone X and high-performance gaming PCs Book Description Are you a software developer, systems designer, or computer architecture student looking for a methodical introduction to digital device architectures but overwhelmed by their complexity? This book will help you to learn how modern computer systems work, from the lowest level of transistor switching to the macro view of collaborating multiprocessor servers. You'll gain unique insights into the internal behavior of processors that execute the code developed in high-level languages and enable you to design more efficient and scalable software systems. The book will teach you the fundamentals of computer systems including transistors, logic gates, sequential logic, and instruction operations. You will learn details of modern processor architectures and instruction sets including x86, x64, ARM, and RISC-V. You will see how to implement a RISC-V processor in a low-cost FPGA board and how to write a quantum computing program and run it on an actual quantum computer. By the end of this book, you will have a thorough understanding of modern processor and computer architectures and the future directions these architectures are likely to take. What you will learn Get to grips with transistor technology and digital circuit principles Discover the functional elements of computer processors Understand pipelining and superscalar execution Work with floating-point data formats Understand the purpose and operation of the supervisor mode Implement a complete RISC-V processor in a low-cost FPGA Explore the techniques used in virtual machine implementation Write a quantum computing program and run it on a quantum computer Who this book is for This book is for software developers, computer engineering students, system designers, reverse engineers, and anyone looking to understand the architecture and design principles underlying modern computer systems from tiny embedded devices to warehouse-size cloud server farms. A general understanding of computer processors is helpful but not required. COMPUTERS,Hardware,Cell Phones & Devices

Exploring Chromebook 2020 Edition Updated to cover the new features, Exploring Chromebook is the perfect companion for your Chromebook. Written by best-selling technology author, lecturer, and computer trainer Kevin Wilson, Exploring Chromebook is packed with step-by-step instructions, full color photos, illustrations, helpful tips and video demos. Updated for 2020, Exploring Chromebook will help you : Setting up your Chromebook Configuring your Chromebook Transferring data from your old machine Setting up email and social media accounts Bluetooth devices and printers Connecting to Wifi and the internet Chromebook navigation with touch gestures Using Gmail, Chrome browser, calendar, contacts Using Google Drive, Docs, Sheets and Slides Video chat with Hangouts Editing photos Downloading music, films, and TV programs Installing and Using Android Apps Installing and Using Linux Apps and more... In addition, you will learn how to make the most of the new features of Chrome OS on the Chromebook with clear explanations and video demos to help you along the way. Finally, maintenance tips to help you keep your device running smoothly complete this invaluable guide. You'll want to keep this edition handy as you make your way around your new Chromebook. COMPUTERS,Hardware,Cell Phones & Devices

Embedded Systems Design using the Rabbit 3000 Microprocessor The Rabbit 3000 is a popular high-performance microprocessor specifically designed for embedded control, communications, and Ethernet connectivity. This new technical reference book will help designers get the most out of the Rabbit's powerful feature set. The first book on the market to focus exclusively on the Rabbit 3000, it provides detailed coverage of: Rabbit architecture and development environment, interfacing to the external world, networking, Rabbit assembly language, multitasking, debugging, Dynamic C and much more! Authors Kamal Hyder and Bob Perrin are embedded engineers with years of experience and they offer a wealth of design details and "insider" tips and techniques. Extensive embedded design examples are supported by fully tested source code. Whether you're already working with the Rabbit or considering it for a future design, this is one reference you can't be without! Let the experts teach you how to design embedded systems that efficiently hook up to the Internet using networked core modules Provides a number of projects and source code using RabbitCore, which will make it easy for the system designer and programmer to get hands-on experience developing networked devices COMPUTERS,Hardware,Chips & Processors

The Art of Designing Embedded Systems Jack Ganssle has been forming the careers of embedded engineers for 20+ years. He has done this with four books, over 500 articles, a weekly column, and continuous lecturing. Technology moves fast and since the first edition of this best-selling classic much has changed. The new edition will reflect the author's new and ever evolving philosophy in the face of new technology and realities. Now more than ever an overarching philosophy of development is needed before just sitting down to build an application. Practicing embedded engineers will find that Jack provides a high-level strategic plan of attack to the often times chaotic and ad hoc design and development process. He helps frame and solve the issues an engineer confronts with real-time code and applications, hardware and software coexistences, and streamlines detail management. CONTENTS: Chapter 1 - IntroductionChapter 2 – The ProjectChapter 3 – The CodeChapter 4 – Real TimeChapter 5 – The Real WorldChapter 6 – Disciplined DevelopmentAppendix A – A Firmware StandardAppendix B - A Simple Drawing SystemAppendix C – A Boss’s Guide to Process *Authored by Jack Ganssle, Tech Editor of Embedded Systems Programming and weekly column on embedded.com*Keep schedules in check as projects and codes grow by taking time to understand the project beforehand*Understand how cost/benefit coexists with design and development COMPUTERS,Hardware,Chips & Processors

Embedded Systems Security The ultimate resource for making embedded systems reliable, safe, and secure Embedded Systems Security provides: A broad understanding of security principles, concerns, and technologies Proven techniques for the efficient development of safe and secure embedded software A study of the system architectures, operating systems and hypervisors, networking, storage, and cryptographic issues that must be considered when designing secure embedded systems Nuggets of practical advice and numerous case studies throughout Written by leading authorities in the field with 65 years of embedded security experience: one of the original developers of the world’s only Common Criteria EAL 6+ security certified software product and a lead designer of NSA certified cryptographic systems. This book is indispensable for embedded systems and security professionals, new and experienced. An important contribution to the understanding of the security of embedded systems. The Kleidermachers are experts in their field. As the Internet of things becomes reality, this book helps business and technology management as well as engineers understand the importance of "security from scratch." This book, with its examples and key points, can help bring more secure, robust systems to the market. Dr. Joerg Borchert, Vice President, Chip Card & Security, Infineon Technologies North America Corp.; President and Chairman, Trusted Computing Group Embedded Systems Security provides real-world examples of risk and exploitation; most importantly the book offers clear insight into methods used to counter vulnerabilities to build true, native security into technology. Adriel Desautels, President and CTO, Netragard, LLC. Security of embedded systems is more important than ever. The growth in networking is just one reason. However, many embedded systems developers have insufficient knowledge of how to achieve security in their systems. David Kleidermacher, a world-renowned expert in this field, shares in this book his knowledge and long experience with other engineers. A very important book at the right time. Prof. Dr.-Ing. Matthias Sturm, Leipzig University of Applied Sciences; Chairman, Embedded World Conference steering board Gain an understanding of the operating systems, microprocessors, and network security critical issues that must be considered when designing secure embedded systems Contains nuggets of practical and simple advice on critical issues highlighted throughout the text Short and to –the- point real case studies included to demonstrate embedded systems security in practice COMPUTERS,Hardware,Chips & Processors

Embedded C Programming This book provides a hands-on introductory course on concepts of C programming using a PIC® microcontroller and CCS C compiler. Through a project-based approach, this book provides an easy to understand method of learning the correct and efficient practices to program a PIC® microcontroller in C language. Principles of C programming are introduced gradually, building on skill sets and knowledge. Early chapters emphasize the understanding of C language through experience and exercises, while the latter half of the book covers the PIC® microcontroller, its peripherals, and how to use those peripherals from within C in great detail. This book demonstrates the programming methodology and tools used by most professionals in embedded design, and will enable you to apply your knowledge and programming skills for any real-life application. Providing a step-by-step guide to the subject matter, this book will encourage you to alter, expand, and customize code for use in your own projects. A complete introduction to C programming using PIC microcontrollers, with a focus on real-world applications, programming methodology and tools Each chapter includes C code project examples, tables, graphs, charts, references, photographs, schematic diagrams, flow charts and compiler compatibility notes to channel your knowledge into real-world examples Online materials include presentation slides, extended tests, exercises, quizzes and answers, real-world case studies, videos and weblinks COMPUTERS,Hardware,Chips & Processors

The Manga Guide to Microprocessors Ayumi is a world-class shogi (Japanese chess) player who can’t be beaten—that is, until she loses to a powerful computer called the Shooting Star. Ayumi vows to find out everything she can about her new nemesis. Lucky for her, Yuu Kano, the genius programmer behind the Shooting Star, is willing to teach her all about the inner workings of the microprocessor—the “brain” inside all computers, phones, and gadgets. Follow along with Ayumi in The Manga Guide to Microprocessors and you’ll learn about: -How the CPU processes information and makes decision-How computers perform arithmetic operations and store information-logic gates and how they’re used in integrated circuits-the Key components of modern computers, including registers, GPUs, and RAM-Assembly language and how it differs from high-level programming languages Whether you’re a computer science student or just want to understand the power of microprocessors, you’ll find what you need to know in The Manga Guide to Microprocessors. COMPUTERS,Hardware,Chips & Processors

Intel Edison Projects Build powerful Robots and IoT solutions using Intel Edison About This Book Learn to build advanced level robots with Intel Edison and Arduino Efficiently build and program home automation and IoT projects with Intel Edison Master the skills of creating enticing projects with Intel Edison. Who This Book Is For If you are a hobbyist, robot engineer, IoT enthusiast, programmer, or developer who wants to create autonomous projects with Intel Edison, then this book is for you. Prior programming knowledge would be beneficial. What You Will Learn Program your device using the Arduino processor language, Python, and Node.js Interface different sensors with the Intel Edison Build a home automation system using MQTT, Android, and WPF Perform face detection using Intel Edison Develop a high-speed line follower robot Control a robot using a PC application and an custom controller In Detail Change the way you look at embedded electronics with Intel Edison. It is a small computing platform packed with a set of robust features to deliver hands-on performance, durability, and software support. This book is a perfect place to kickstart development and rapid prototyping using Intel Edison. It will start by introducing readers to the Intel Edison board and explaining how to get started with it. You will learn how to build a mini weather station, which will help you to acquire temperature and smoke level and push it to the IoT platform. Then you will see how to build a home automation device and control your appliances using an Android app. Furthermore, we will build a security system using a webcam to detect faces and perform voice recognition. Toward the end, the book will demonstrate how you can build two robots, which will be based on different line sensing sensors and can be controlled by a PC. The book will guide the readers through each and every step of execution of a project, using Intel Edison. Style and approach A project-based guide that will take the readers through various domains of projects like robotics, IoT and so on. COMPUTERS,Hardware,Chips & Processors

Hands-On RTOS with Microcontrollers Build a strong foundation in designing and implementing real-time systems with the help of practical examples Key Features Get up and running with the fundamentals of RTOS and apply them on STM32 Enhance your programming skills to design and build real-world embedded systems Get to grips with advanced techniques for implementing embedded systems Book Description A real-time operating system (RTOS) is used to develop systems that respond to events within strict timelines. Real-time embedded systems have applications in various industries, from automotive and aerospace through to laboratory test equipment and consumer electronics. These systems provide consistent and reliable timing and are designed to run without intervention for years. This microcontrollers book starts by introducing you to the concept of RTOS and compares some other alternative methods for achieving real-time performance. Once you've understood the fundamentals, such as tasks, queues, mutexes, and semaphores, you'll learn what to look for when selecting a microcontroller and development environment. By working through examples that use an STM32F7 Nucleo board, the STM32CubeIDE, and SEGGER debug tools, including SEGGER J-Link, Ozone, and SystemView, you'll gain an understanding of preemptive scheduling policies and task communication. The book will then help you develop highly efficient low-level drivers and analyze their real-time performance and CPU utilization. Finally, you'll cover tips for troubleshooting and be able to take your new-found skills to the next level. By the end of this book, you'll have built on your embedded system skills and will be able to create real-time systems using microcontrollers and FreeRTOS. What you will learn Understand when to use an RTOS for a project Explore RTOS concepts such as tasks, mutexes, semaphores, and queues Discover different microcontroller units (MCUs) and choose the best one for your project Evaluate and select the best IDE and middleware stack for your project Use professional-grade tools for analyzing and debugging your application Get FreeRTOS-based applications up and running on an STM32 board Who this book is for This book is for embedded engineers, students, or anyone interested in learning the complete RTOS feature set with embedded devices. A basic understanding of the C programming language and embedded systems or microcontrollers will be helpful. COMPUTERS,Hardware,Chips & Processors

Serial Port Complete PC COM ports, USB virtual COM ports, and ports in embedded systems are all addressed in this updated guide to programming, interfacing, and using serial ports. Topics include using .NET's SerialPort class for COM-port communications on PCs; upgrading existing RS-232 designs to USB or wireless networks; and creating serial networks of embedded systems and PCs. Example circuits and code provide a quick start to projects. Installation and maintenance staff will also find tips for ensuring reliable operation and problem tracking. COMPUTERS,Hardware,General

Creating Cool MINDSTORMS NXT Robots Build and program MINDSTORM NXT robots with Daniele Benedettelli, one of the world’s most respected NXT robot builders. He shows you how to build and program them from scratch, starting with the simplest robots and progressing in difficulty to a total of seven award–winning robots! You can download all the code, along with low–resolution videos that show how your robot works when it’s finished. You don’t need to be a programmer to develop these cool robots, because all the code is provided, but advanced developers will enjoy seeing the secrets of Benedettelli’s code and techniques revealed. COMPUTERS,Hardware,General

Designing Embedded Hardware Embedded computer systems literally surround us: they're in our cell phones, PDAs, cars, TVs, refrigerators, heating systems, and more. In fact, embedded systems are one of the most rapidly growing segments of the computer industry today.Along with the growing list of devices for which embedded computer systems are appropriate, interest is growing among programmers, hobbyists, and engineers of all types in how to design and build devices of their own. Furthermore, the knowledge offered by this book into the fundamentals of these computer systems can benefit anyone who has to evaluate and apply the systems.The second edition of Designing Embedded Hardware has been updated to include information on the latest generation of processors and microcontrollers, including the new MAXQ processor. If you're new to this and don't know what a MAXQ is, don't worry--the book spells out the basics of embedded design for beginners while providing material useful for advanced systems designers.Designing Embedded Hardware steers a course between those books dedicated to writing code for particular microprocessors, and those that stress the philosophy of embedded system design without providing any practical information. Having designed 40 embedded computer systems of his own, author John Catsoulis brings a wealth of real-world experience to show readers how to design and create entirely new embedded devices and computerized gadgets, as well as how to customize and extend off-the-shelf systems.Loaded with real examples, this book also provides a roadmap to the pitfalls and traps to avoid. Designing Embedded Hardware includes: The theory and practice of embedded systems Understanding schematics and data sheets Powering an embedded system Producing and debugging an embedded system Processors such as the PIC, Atmel AVR, and Motorola 68000-series Digital Signal Processing (DSP) architectures Protocols (SPI and I2C) used to add peripherals RS-232C, RS-422, infrared communication, and USB CAN and Ethernet networking Pulse Width Monitoring and motor control If you want to build your own embedded system, or tweak an existing one, this invaluable book gives you the understanding and practical skills you need. COMPUTERS,Hardware,General

Beginning Arduino In Beginning Arduino, you will learn all about the popular Arduino microcontroller by working your way through an amazing set of 50 cool projects. You'll progress from a complete beginner regarding Arduino programming and electronics knowledge to intermediate skills and the confidence to create your own amazing Arduino projects. Absolutely no experience in programming or electronics required! Rather than requiring you to wade through pages of theory before you start making things, this book has a hands-on approach. You will dive into making projects right from the start, learning how to use various electronic components and how to program the Arduino to control or communicate with those components. Each project is designed to build upon the knowledge learned in earlier projects and to further your knowledge in programming as well as skills with electronics. By the end of the book you will be able create your own projects confidently and with creativity. Please note: the print version of this title is black & white; the eBook is full color. You can download the color diagrams in the book from http://www.apress.com/9781430232407 COMPUTERS,Hardware,General

Building Your Own Electronics Lab What should an electronics hackerspace look like? Is it in your bedroom, garage, a classroom, or even a suitcase? And where do you start? What parts are essential, and which are just nice to have? And how do you organize it all? Dale Wheat, the author of Arduino Internals, will show you how to build your own electronics lab complete with tools, parts, and power sources. You'll learn how to create a portable lab, a small lab to save space, and even a lab for small groups and classrooms. You'll learn which parts and tools are indispensable no matter what type projects you're working on: which soldering irons are best, which tools, cables, and testing equipment you'll need. You'll also learn about different chips, boards, sensors, power sources, and which ones you'll want to keep on hand. Finally, you'll learn how to assemble everything for the type of lab best suited to your needs. If you need to carry everything to your local makerspace, you can build the Portable Lab. If you plan to tinker at home or in the garage, there is the Corner Lab. If you're going to run your own local makerspace or you need to set up a lab to teach others, there is the Small-Group Lab. No matter what your gadgeteering needs may be, Building Your Own Electronics Lab will show you exactly how to put it all together so you have what you need to get started. COMPUTERS,Hardware,General

The Ergonomics of Computer Pointing Devices We first began looking at pointing devices and human performance in 1990 when the senior author, Sarah Douglas, was asked to evaluate the human performance ofa rather novel device: a finger-controlled isometric joystick placed under a key on the keyboard. Since 1990 we have been involved in the development and evaluation ofother isometric joysticks, a foot-controlled mouse, a trackball, and a wearable computer with head mounted display. We unabashedly believe that design and evaluation of pointing devices should evolve from a broad spectrum of values which place the human being at the center. These values include performance iss ues such as pointing-time and errors, physical issues such as comfort and health, and contextual issues such as task usabilityand user acceptance. This book chronicles this six-year history of our relationship as teacher (Douglas) and student (Mithal), as we moved from more traditional evalu ation using Fitts' law as the paradigm, to understanding the basic research literature on psychomotor behavior. During that process we became pro foundly aware that many designers of pointing devices fail to understand the constraints of human performance, and often do not even consider experimental evaluation critical to usability decisions before marketing a device. We also became aware ofthe fact that, contraryto popularbeliefin the human-computer interaction community, the problem of predicting pointing device performance has not been solved by Fitts' law. Similarly, our expectations were biased by the cognitive revolution of the past 15 years with the beliefpointing device research was 'low-level' and uninter esting. COMPUTERS,Hardware,General

Data Compression in Digital Systems Data compression is now indispensable to products and services of many industries including computers, communications, healthcare, publishing and entertainment. This invaluable resource introduces this area to information system managers and others who need to understand how it is changing the world of digital systems. For those who know the technology well, it reveals what happens when data compression is used in real-world applications and provides guidance for future technology development. COMPUTERS,Hardware,General

The Information Revolution J.-E. Dubois and N. Gershon This book was inspired by the Symposium on "Communications and Computer Aided Systems" held at the 14th International CODATA Conference in September 1994 in Chambery, France. It was conceived and influenced by the discussions at the symposium and most of the contributions were written following the Conference. This is the first comprehensive book, published in one volume, of issues concerning the challenges and the vital impact of the information revolution (including the Internet and the World Wide Web) on science and technology. Topics concerning the impact of the information revolution on science and technology include: • Dramatic improvement in sharing of data and information among scientists and engineers around the world • Collaborations (on-line and off-line) of scientists and engineers separated by distance . • Availability of visual tools and methods to view, understand, search, and share information contained in data • Improvements in data and information browsing, search and access and • New ways of publishing scientific and technological data and information. These changes have dramatically modified the way research and development in science and technology are being carried out. However, to facilitate this information flow nationally and internationally, the science and technology communities need to develop and put in place new standards and policies and resolve some legal issues. COMPUTERS,Hardware,General

Industrial Applications of Fuzzy Technology The application of fuzzy technology is widely known as a technological revolution. Shortly after it appeared, its value has rapidly become appreciated. It is absolutely indispensable for introducing the latest developments not only domestically but also internationally. This book is arranged to introduce easy to understand explanations mainly centered on concrete applications. It consists of twelve chapters in total which are all independently readable and provide different approaches on various projects. The minimum of Fuzzy Theory that is needed to understand its practical applications is given in Chapter 1. Chapters 2 to 5 discuss hardware, including chips, and software tools used in constructing system. Chapters 6 to 12 cover a series of practical applications. These in clude applications for industrial processes and plants, transportation systems, which were among the first applications, and applications for consumer products such as household electrical appliances. These elements together finally produced the worldwide "Fuzzy Boom". This book can be read by a wide variety of people, from undergraduate and graduate students in universities to practical engineers and project managers working in plants. The information contained in this book is a first step to this field of interest. COMPUTERS,Hardware,General

Three-Dimensional Object Recognition from Range Images Computer Science Workbench is a monograph series which will provide you with an in-depth working knowledge of current developments in computer technology. Every volume in this series will deal with a topic of importance in computer science and elaborate on how you yourself can build systems related to the main theme. You will be able to develop a variety of systems, including computer software tools, computer graphics, computer animation, database management systems, and computer-aided design and manufacturing systems. Computer Science Workbench represents an important new contribution in the field of practical computer technology. T08iyasu L. Kunii PREFACE The primary aim of this book is to present a coherent and self-contained de scription of recent advances in three-dimensional object recognition from range images. Three-dimensional object recognition concerns recognition and localiza tion of objects of interest in a scene from input images. This problem is one of both theoretical and practical importance. On the theoretical side, it is an ideal vehicle for the study of the general area of computer vision since it deals with several important issues encountered in computer vision-for example, issues such as feature extraction, acquisition, representation and proper use of knowl edge, employment of efficient control strategies, coupling numerical and symbolic computations, and parallel implementation of algorithms. On the practical side, it has a wide range of applications in areas such as robot vision, autonomous navigation, automated inspection of industrial parts, and automated assembly. COMPUTERS,Hardware,General

Advances in Computer Graphics Hardware V This volume contains papers representing a comprehensive record of the contributions to the fifth workshop at EG '90 in Lausanne. The Eurographics hardware workshops have now become an established forum for the exchange of information about the latest developments in this field of growing importance. The first workshop took place during EG '86 in Lisbon. All participants considered this to be a very rewarding event to be repeated at future EG conferences. This view was reinforced at the EG '87 Hardware Workshop in Amsterdam and firmly established the need for such a colloquium in this specialist area within the annual EG conference. The third EG Hardware Workshop took place in Nice in 1988 and the fourth in Hamburg at EG '89. The first part of the book is devoted to rendering machines. The papers in this part address techniques for accelerating the rendering of images and efficient ways of improv ing their quality. The second part on ray tracing describes algorithms and architectures for producing photorealistic images, with emphasis on ways of reducing the time for this computationally intensive task. The third part on visualization systems covers a num ber of topics, including voxel-based systems, radiosity, animation and special rendering techniques. The contributions show that there is flourishing activity in the development of new algorithmic and architectural ideas and, in particular, in absorbing the impact of VLSI technology. The increasing diversity of applications encourage new solutions, and graphics hardware has become a research area of high activity and importance. COMPUTERS,Hardware,General

SBus Workstation and computer users have an ever increasing need for solutions that offer high performance, low cost, small footprints (space requirements), and ease of use. Also, the availability of a wide range of software and hardware options (from a variety of independent vendors) is important because it simplifies the task of expanding existing applications and stretching into new ones. The SBus has been designed and optimized within this framework, and it represents a next-generation approach to a system's I/O intercon nect needs. This book is a collection of information intended to ease the task of developing and integrating new SBus-based products. The focus is primarily on hardware, due to the author's particular expertise, but firmware and software concepts are also included where appropriate. This book is based on revision B.O of the SBus Specification. This revision has been a driving force in the SBus market longer than any other, and is likely to remain a strong influence for some time to come. As of this writing there is currently an effort (desig nated P1496) within the IEEE to produce a new version of the SBus specification that conforms to that group's policies and requirements. This might result in some changes to the specifica tion, but in most cases these will be minor. Most of the information this book contains will remain timely and applicable. To help ensure this, the author has included key information about pro posed or planned changes. COMPUTERS,Hardware,General

Testing and Diagnosis of Analog Circuits and Systems IS THE TOPIC ANALOG TESTING AND DIAGNOSIS TIMELY? Yes, indeed it is. Testing and Diagnosis is an important topic and fulfills a vital need for the electronic industry. The testing and diagnosis of digital electronic circuits has been successfuIly developed to the point that it can be automated. Unfortu nately, its development for analog electronic circuits is still in its Stone Age. The engineer's intuition is still the most powerful tool used in the industry! There are two reasons for this. One is that there has been no pressing need from the industry. Analog circuits are usuaIly small in size. Sometimes, the engineer's experience and intuition are sufficient to fulfill the need. The other reason is that there are no breakthrough results from academic re search to provide the industry with critical ideas to develop tools. This is not because of a lack of effort. Both academic and industrial research groups have made major efforts to look into this problem. Unfortunately, the prob lem for analog circuits is fundamentally different from and much more diffi cult than its counterpart for digital circuits. These efforts have led to some important findings, but are still not at the point of being practicaIly useful. However, these situations are now changing. The current trend for the design of VLSI chips is to use analog/digital hybrid circuits, instead of digital circuits from the past. Therefore, even Ix x Preface though the analog circuit may be small, the total circuit under testing is large. COMPUTERS,Hardware,General

Make What if your clothing could change color to complement your skin tone, respond to your racing heartbeat, or connect you with a loved one from afar? Welcome to the world of shoes that can dynamically shift your height, jackets that display when the next bus is coming, and neckties that can nudge your business partner from across the room. Whether it be for fashion, function, or human connectedness, wearable electronics can be used to design interactive systems that are intimate and engaging. Make: Wearable Electronics is intended for those with an interest in physical computing who are looking to create interfaces or systems that live on the body. Perfect for makers new to wearable tech, this book introduces you to the tools, materials, and techniques for creating interactive electronic circuits and embedding them in clothing and other things you can wear. Each chapter features experiments to get you comfortable with the technology and then invites you to build upon that knowledge with your own projects. Fully illustrated with step-by-step instructions and images of amazing creations made by artists and professional designers, this book offers a concrete understanding of electronic circuits and how you can use them to bring your wearable projects from concept to prototype. COMPUTERS,Hardware,General

Drones For Dummies The fast and easy way to pick out, set up, and learn to fly your drone Ready to soar into the world of unmanned aircraft? Drones For Dummies introduces you to the fascinating world of UAVs. Written in plain English and brimming with friendly instruction, Drones For Dummies provides you with the information you need to find and purchase the right drone for your needs, examples of ways to use a drone, and even drone etiquette and the laws and regulations governing consumer drone usage. Plus, you'll discover the basics of flight, including how to use a drone to capture photos and video. Originally designed to assist in military and special operations applications, the use of drones has expanded into the public service sector and the consumer market for people looking to have a good time flying an aircraft remotely. Drones For Dummies covers everything you need to know to have fun with your UAV, and is packed with cool ways to expand your drone's use beyond simply flying. Pick the perfect drone to suit your needs Properly set up and fly a drone Use a drone to capture images and footage with a camera Tips for maintaining your drone If you're interested in the exciting new technology of unmanned aircraft vehicles, Drones For Dummies helps you take flight. COMPUTERS,Hardware,General

Arduino Sketches Master programming Arduino with this hands-on guide Arduino Sketches is a practical guide to programming the increasingly popular microcontroller that brings gadgets to life. Accessible to tech-lovers at any level, this book provides expert instruction on Arduino programming and hands-on practice to test your skills. You'll find coverage of the various Arduino boards, detailed explanations of each standard library, and guidance on creating libraries from scratch – plus practical examples that demonstrate the everyday use of the skills you're learning. Work on increasingly advanced programming projects, and gain more control as you learn about hardware-specific libraries and how to build your own. Take full advantage of the Arduino API, and learn the tips and tricks that will broaden your skillset. The Arduino development board comes with an embedded processor and sockets that allow you to quickly attach peripherals without tools or solders. It's easy to build, easy to program, and requires no specialized hardware. For the hobbyist, it's a dream come true – especially as the popularity of this open-source project inspires even the major tech companies to develop compatible products. Arduino Sketches is a practical, comprehensive guide to getting the most out of your Arduino setup. You'll learn to: Communicate through Ethernet, WiFi, USB, Firmata, and Xbee Find, import, and update user libraries, and learn to create your own Master the Arduino Due, Esplora, Yun, and Robot boards for enhanced communication, signal-sending, and peripherals Play audio files, send keystrokes to a computer, control LED and cursor movement, and more This book presents the Arduino fundamentals in a way that helps you apply future additions to the Arduino language, providing a great foundation in this rapidly-growing project. If you're looking to explore Arduino programming, Arduino Sketches is the toolbox you need to get started. COMPUTERS,Hardware,General

Multichip Module Technologies and Alternatives Far from being the passive containers for semiconductor devices of the past, the packages in today's high performance computers pose numerous challenges in interconnecting, powering, cooling and protecting devices. While semiconductor circuit performance measured in picoseconds continues to improve, computer performance is expected to be in nanoseconds for the rest of this century -a factor of 1000 difference between on-chip and off-chip performance which is attributable to losses associated with the package. Thus the package, which interconnects all the chips to form a particular function such as a central processor, is likely to set the limits on how far computers can evolve. Multichip packaging, which can relax these limits and also improve the reliability and cost at the systems level, is expected to be the basis of all advanced computers in the future. In addition, since this technology allows chips to be spaced more closely, in less space and with less weight, it has the added advantage of being useful in portable consumer electronics as well as in medical, aerospace, automotive and telecommunications products. The multichip technologies with which these applications can be addressed are many. They range from ceramics to polymer-metal thin films to printed wiring boards for interconnections; flip chip, TAB or wire bond for chip-to-substrate connections; and air or water cooling for the removal of heat. COMPUTERS,Hardware,General

Microelectronics Packaging Handbook Electronics has become the largest industry, surpassing agriculture, auto, and heavy metal industries. It has become the industry of choice for a country to prosper, already having given rise to the phenomenal prosperity of Japan, Korea, Singapore, Hong Kong, and Ireland among others. At the current growth rate, total worldwide semiconductor sales will reach $300B by the year 2000. The key electronic technologies responsible for the growth of the industry include semiconductors, the packaging of semiconductors for systems use in auto, telecom, computer, consumer, aerospace, and medical industries, displays, magnetic, and optical storage as well as software and system technologies. There has been a paradigm shift, however, in these technologies, from mainframe and supercomputer applications at any cost, to consumer applications at approximately one-tenth the cost and size. Personal computers are a good example, going from $500IMIP when products were first introduced in 1981, to a projected $IIMIP within 10 years. Thin, light portable, user friendly and very low-cost are, therefore, the attributes of tomorrow's computing and communications systems. Electronic packaging is defined as interconnection, powering, cool ing, and protecting semiconductor chips for reliable systems. It is a key enabling technology achieving the requirements for reducing the size and cost at the system and product level. COMPUTERS,Hardware,General

Getting Started with the Photon The Photon is an open source, inexpensive, programmable, WiFi-enabled module for building connected projects and prototypes. Powered by an ARM Cortex-M3 microcontroller and a Broadcom WiFi chip, the Photon is just as happy plugged into a hobbyist's breadboard as it is into a product rolling off of an assembly line. While the Photon--and its accompanying cloud platform--is designed as a ready-to-go foundation for product developers and manufacturers, it's great for Maker projects, as you'll see in this book. You'll learn how to get started with the free development tools, deploy your sketches over WiFi, and build electronic projects that take advantage of the Photon's processing power, cloud platform, and input/output pins. What's more, the Photon is backward-compatible with its predecessor, the Spark Core. COMPUTERS,Hardware,General

Exploring Raspberry Pi Expand Raspberry Pi capabilities with fundamental engineering principles Exploring Raspberry Pi is the innovators guide to bringing Raspberry Pi to life. This book favors engineering principles over a 'recipe' approach to give you the skills you need to design and build your own projects. You'll understand the fundamental principles in a way that transfers to any type of electronics, electronic modules, or external peripherals, using a "learning by doing" approach that caters to both beginners and experts. The book begins with basic Linux and programming skills, and helps you stock your inventory with common parts and supplies. Next, you'll learn how to make parts work together to achieve the goals of your project, no matter what type of components you use. The companion website provides a full repository that structures all of the code and scripts, along with links to video tutorials and supplementary content that takes you deeper into your project. The Raspberry Pi's most famous feature is its adaptability. It can be used for thousands of electronic applications, and using the Linux OS expands the functionality even more. This book helps you get the most from your Raspberry Pi, but it also gives you the fundamental engineering skills you need to incorporate any electronics into any project. Develop the Linux and programming skills you need to build basic applications Build your inventory of parts so you can always "make it work" Understand interfacing, controlling, and communicating with almost any component Explore advanced applications with video, audio, real-world interactions, and more Be free to adapt and create with Exploring Raspberry Pi. COMPUTERS,Hardware,General

Beginning C for Arduino, Second Edition Beginning C for Arduino, Second Edition is written for those who have no prior experience with microcontrollers or programming but would like to experiment and learn both. Updated with new projects and new boards, this book introduces you to the C programming language, reinforcing each programming structure with a simple demonstration of how you can use C to control the Arduino family of microcontrollers. Author Jack Purdum uses an engaging style to teach good programming techniques using examples that have been honed during his 25 years of university teaching. Beginning C for Arduino, Second Edition will teach you: The C programming language How to use C to control a microcontroller and related hardware How to extend C by creating your own libraries, including an introduction to object-oriented programming During the course of the book, you will learn the basics of programming, such as working with data types, making decisions, and writing control loops. You'll then progress onto some of the trickier aspects of C programming, such as using pointers effectively, working with the C preprocessor, and tackling file I/O. Each chapter ends with a series of exercises and review questions to test your knowledge and reinforce what you have learned. COMPUTERS,Hardware,General

Getting Started With Raspberry Pi The Raspberry Pi is a credit card-sized computer that plugs into your TV and a keyboard. It is a capable little computer which can be used in electronics projects, and for many of the things that your desktop PC does, like spreadsheets, word processing, browsing the internet, and playing games. It also plays high-definition video. This book takes you step-by-step through many fun and educational possibilities. Take advantage of several preloaded programming languages. Use the Raspberry Pi with Arduino. Create Internet-connected projects. Play with multimedia. With Raspberry Pi, you can do all of this and more. COMPUTERS,Hardware,General

Building a Virtual Assistant for Raspberry Pi Build a voice-controlled virtual assistant using speech-to-text engines, text-to-speech engines, and conversation modules. This book shows you how to program the virtual assistant to gather data from the internet (weather data, data from Wikipedia, data mining); play music; and take notes. Each chapter covers building a mini project/module to make the virtual assistant better. You'll develop the software on Linux or OS X before transferring it to your Raspberry Pi, ready for deploying in your own home-automation or Internet of Things applications. Building a Virtual Assistant for Raspberry Pi walks you through various STTs and TTSs and the implementation of these components with the help of Python. After that you will start implementing logic for handling user queries and commands, so that the user can have conversations with Melissa. You will then work to improve logic handling to detect what the user wants Melissa to do. You will also work on building some useful applications/modules for Melissa, which will allow you to gain interesting information from Melissa such as the time, weather information, and data from Wikipedia. You will develop a music playing application as well as a note taking application for Melissa, laying the foundations for how Melissa can be further extended. Finally, you will learn how to deploy this software to your Raspberry Pi and how you can further scale Melissa to make her more intelligent, interactive and how you can use her in other projects such as home automation as well. What You'll Learn Design the workflow and discover the concepts of building a voice controlled assistant Develop modules for having conversations with the assistant Enable the assistant to retrieve information from the internet Build utilities like a music player and a note taking application for the virtual assistant Integrate this software with a Raspberry Pi Who This Book Is For Anyone who has built a home automation project with Raspberry Pi and now want to enhance it by making it voice-controlled. The book would also interest students from computer science or related disciplines. COMPUTERS,Hardware,General

Raspberry Pi IoT Projects Build your own Internet of Things (IoT) projects for prototyping and proof-of-concept purposes. This book contains the tools needed to build a prototype of your design, sense the environment, communicate with the Internet (over the Internet and Machine to Machine communications) and display the results. Raspberry Pi IoT Projects provides several IoT projects and designs are shown from the start to the finish including an IoT Heartbeat Monitor, an IoT Swarm, IoT Solar Powered Weather Station, an IoT iBeacon Application and a RFID (Radio Frequency Identification) IoT Inventory Tracking System. The software is presented as reusable libraries, primarily in Python and C with full source code available. Raspberry Pi IoT Projects: Prototyping Experiments for Makers is also a valuable learning resource for classrooms and learning labs. What You'll Learn build IOT projects with the Raspberry Pi Talk to sensors with the Raspberry Pi Use iBeacons with the IOT Raspberry Pi Communicate your IOT data to the Internet Build security into your IOT device Who This Book Is For Primary audience are those with some technical background, but not necessarily engineers. It will also appeal to technical people wanting to learn about the Raspberry Pi in a project-oriented method. COMPUTERS,Hardware,General

Raspberry Pi For Dummies Get your slice of Raspberry Pi With the invention of the unique credit card-sized single-board computer comes a new wave of hardware geeks, hackers, and hobbyists who are excited about the possibilities with the Raspberry Pi—and this is the perfect guide to get you started. With this down-to-earth book, you'll quickly discover why the Raspberry Pi is in high demand! There's a reason the Raspberry Pi sold a million units in its first year, and you're about to find out why! In Raspberry Pi For Dummies, 3rd Edition veteran tech authors Sean McManus and Mike Cook make it easier than ever to get you up and running on your Raspberry Pi, from setting it up, downloading the operating system, and using the desktop environment to editing photos, playing music and videos, and programming with Scratch—and everything in between. Covers connecting the Pi to other devices such as a keyboard, mouse, monitor, and more Teaches you basic Linux System Admin Explores creating simple hardware projects Shows you how to create web pages Raspberry Pi For Dummies, 3rd Edition makes computing as easy as pie! COMPUTERS,Hardware,General

Electronics Cookbook If you’re among the many hobbyists and designers who came to electronics through Arduino and Raspberry Pi, this cookbook will help you learn and apply the basics of electrical engineering without the need for an EE degree. Through a series of practical recipes, you’ll learn how to solve specific problems while diving into as much or as little theory as you’re comfortable with. Author Simon Monk (Raspberry Pi Cookbook) breaks down this complex subject into several topics, from using the right transistor to building and testing projects and prototypes. With this book, you can quickly search electronics topics and go straight to the recipe you need. It also serves as an ideal reference for experienced electronics makers. This cookbook includes: Theoretical concepts such as Ohm’s law and the relationship between power, voltage, and current The fundamental use of resistors, capacitors and inductors, diodes, transistors and integrated circuits, and switches and relays Recipes on power, sensors and motors, integrated circuits, and radio frequency for designing electronic circuits and devices Advice on using Arduino and Raspberry Pi in electronics projects How to build and use tools, including multimeters, oscilloscopes, simulations software, and unsoldered prototypes COMPUTERS,Hardware,General

Exploring Arduino The bestselling beginner Arduino guide, updated with new projects! Exploring Arduino makes electrical engineering and embedded software accessible. Learn step by step everything you need to know about electrical engineering, programming, and human-computer interaction through a series of increasingly complex projects. Arduino guru Jeremy Blum walks you through each build, providing code snippets and schematics that will remain useful for future projects. Projects are accompanied by downloadable source code, tips and tricks, and video tutorials to help you master Arduino. You'll gain the skills you need to develop your own microcontroller projects! This new 2nd edition has been updated to cover the rapidly-expanding Arduino ecosystem, and includes new full-color graphics for easier reference. Servo motors and stepper motors are covered in richer detail, and you'll find more excerpts about technical details behind the topics covered in the book. Wireless connectivity and the Internet-of-Things are now more prominently featured in the advanced projects to reflect Arduino's growing capabilities. You'll learn how Arduino compares to its competition, and how to determine which board is right for your project. If you're ready to start creating, this book is your ultimate guide! Get up to date on the evolving Arduino hardware, software, and capabilities Build projects that interface with other devices—wirelessly! Learn the basics of electrical engineering and programming Access downloadable materials and source code for every project Whether you're a first-timer just starting out in electronics, or a pro looking to mock-up more complex builds, Arduino is a fantastic tool for building a variety of devices. This book offers a comprehensive tour of the hardware itself, plus in-depth introduction to the various peripherals, tools, and techniques used to turn your little Arduino device into something useful, artistic, and educational. Exploring Arduino is your roadmap to adventure—start your journey today! COMPUTERS,Hardware,General

Samsung Galaxy Tabs For Dummies Welcome to the Galaxy Popular for both work and play, Android tablets fill a useful niche between smartphone and computer. Samsung’s Galaxy Tab kicks it up a notch, offering both hardware and software technology beyond its competitors. Samsung enhances the basics—web, email, eReader, navigation, music, video, camera—and offers unique tools such as the Bixby assistant and the high-tech S-Pen. Coupled with an envious design, Galaxy Tab is a formidable contender to other devices, offering features you won’t find anywhere else. Samsung Galaxy Tab For Dummies helps you take full advantage of everything this sweet device has to offer. Whether you’re looking to keep in touch with friends and family on social media, want a portable way to stay connected to your work, or desire to read the latest potboiler or catch-up with the latest streaming TV drama, the Galaxy Tab makes it possible—and this book shows you how. Set up and start using your new tablet Connect with email, video chat, and explore social media Play games, enjoy music, watch movies and streaming TV Browse digital magazines and enjoy ebooks A whole new galaxy awaits! Get ready to soak it all in! COMPUTERS,Hardware,General

Jumpstarting the Raspberry Pi Zero W Get up and running quickly with the new Jumpstarting ebook series from Make:. The super-small $10 Raspberry Pi Zero W includes wireless LAN and Bluetooth connectivity and is 40% faster than the original Raspberry Pi. COMPUTERS,Hardware,General

Learn Autodesk Inventor 2018 Basics Get started with the basics of part modeling, assembly modeling, presentations, and drawings in this step-by-step tutorial on Autodesk Inventor fundamentals. Next, this book teaches you some intermediate-level topics such as additional part modeling tools, sheet metal modeling, top-down assembly features, assembly joints, and dimension and annotations. Engaging explanations, practical examples, and step-by-step instructions make this tutorial book complete. Once you have read Learn Autodesk Inventor 2018 Basics you will be able to use Autodesk Inventor for 3D modeling, 2D drawings, finite element analysis, mold design, and other purposes, just like a design professional. You will gain all the basic information and essential skills you need to work in Autodesk Inventor immediately. What You'll Learn Carry out virtual 3D modeling for your next 3D printing projects Design molds for 3D printing and other projects Generate 2D drawings Who This Book Is For Novice users of Autodesk Inventor. COMPUTERS,Hardware,General

Beginning STM32 Using FreeRTOS and libopencm3 instead of the Arduino software environment, this book will help you develop multi-tasking applications that go beyond Arduino norms. In addition to the usual peripherals found in the typical Arduino device, the STM32 device includes a USB controller, RTC (Real Time Clock), DMA (Direct Memory Access controller), CAN bus and more. Each chapter contains clear explanations of the STM32 hardware capabilities to help get you started with the device, including GPIO and several other ST Microelectronics peripherals like USB and CAN bus controller. You’ll learn how to download and set up the libopencm3 + FreeRTOS development environment, using GCC. With everything set up, you’ll leverage FreeRTOS to create tasks, queues, and mutexes. You’ll also learn to work with the I2C bus to add GPIO using the PCF8574 chip. And how to create PWM output for RC control using hardware timers.You'll be introduced to new concepts that are necessary to master the STM32, such as how to extend code with GCC overlays using an external Winbond ​W25Q32 flash chip. Your knowledge is tested at the end of each chapter with exercises. Upon completing this book, you’ll be ready to work with any of the devices in the STM32 family. Beginning STM32 provides the professional, student, or hobbyist a way to learn about ARM without costing an arm! What You'll Learn Initialize and use the libopencm3 drivers and handle interrupts Use DMA to drive a SPI based OLED displaying an analog meter Read PWM from an RC control using hardware timers Who This Book Is For Experienced embedded engineers, students, hobbyists and makers wishing to explore the ARM architecture, going beyond Arduino limits. COMPUTERS,Hardware,General

Samsung Galaxy S9 For Dummies The bestselling guide to getting the most out of your Android Samsung Galaxy S9 Samsung Galaxy S9 For Dummies documents all the features and capabilities of this popular smartphone, approaching them from the point of view of a user who is perhaps a bit baffled by the documentation and online support that comes with the phone. All aspects of the device are covered, from setup and configuration, to extensive use of the new features and capabilities. Whether you’re looking for approachable guidance on the basics like texting, e-mailing, and accessing the internet, or more advanced topics like downloading apps, synching with a PC, and expanding the phone’s potential with new software releases, this trusted resource covers it all. Take pictures, watch movies, and record videos Use maps and navigation Stay connected on social networking sites Make sense of software updates You’ll want to keep this book close by, referring to it often as you explore the features and functions of your new Samsung Galaxy S9 smartphone. COMPUTERS,Hardware,General

Artificial Intelligence for Robotics Bring a new degree of interconnectivity to your world by building your own intelligent robots Key Features Leverage fundamentals of AI and robotics Work through use cases to implement various machine learning algorithms Explore Natural Language Processing (NLP) concepts for efficient decision making in robots Book Description Artificial Intelligence for Robotics starts with an introduction to Robot Operating Systems (ROS), Python, robotic fundamentals, and the software and tools that are required to start out with robotics. You will learn robotics concepts that will be useful for making decisions, along with basic navigation skills. As you make your way through the chapters, you will learn about object recognition and genetic algorithms, which will teach your robot to identify and pick up an irregular object. With plenty of use cases throughout, you will explore natural language processing (NLP) and machine learning techniques to further enhance your robot. In the concluding chapters, you will learn about path planning and goal-oriented programming, which will help your robot prioritize tasks. By the end of this book, you will have learned to give your robot an artificial personality using simulated intelligence. What you will learn Get started with robotics and artificial intelligence Apply simulation techniques to give your robot an artificial personality Understand object recognition using neural networks and supervised learning techniques Pick up objects using genetic algorithms for manipulation Teach your robot to listen using NLP via an expert system Use machine learning and computer vision to teach your robot how to avoid obstacles Understand path planning, decision trees, and search algorithms in order to enhance your robot Who this book is for If you have basic knowledge about robotics and want to build or enhance your existing robot's intelligence, then Artificial Intelligence for Robotics is for you. This book is also for enthusiasts who want to gain knowledge of AI and robotics. COMPUTERS,Hardware,General

Practical Tinker Board Get started with the ASUS Tinker Board and begin building and expanding your own projects. This book covers the basic operating systems offered by ASUS for the Tinker Board and Tinker Board S, TinkerOS and Android, and then dives deeper into its capabilities for projects; such as a music streamer or a weather display with internet connectivity. Beginners will find the resources necessary to follow along and more seasoned makers can review additional information to engage with this new single-board computer platform. The projects are broad enough to show off the capability of the Tinker Board’s hardware and they can be used as is or you can add to them based on your skill level. The ASUS Tinker Board offers an increase in hardware specs and, as a result, is more powerful compared to other single-board computers on the market, making it a great option for projects that would have previously been a challenge to run on other boards, such as the Raspberry Pi. Single-board computers in general are also gaining in popularity as solutions for many DIY tech projects, ranging from gaming to file storage to being a small form factor desktop Linux computer. Practical Tinker Board is a great resource to the maker community, enabling people to begin truly exploring the Tinker Board. What You’ll Learn: Review ASUS Tinker Board's capabilities and functions Gain a deeper understanding of different Linux distributions Build useful projects with a range of hardware and software Take an in-depth look at how to install, configure and use ASUS Tinker Board in projects Who This Book Is For: Those who have previously worked on some beginner maker projects, such as basic Arduino and Raspberry Pi projects, and are looking to expand their skills and knowledge of Linux, single board computers, programming and project builds. COMPUTERS,Hardware,General

Developing Games on the Raspberry Pi Learn to set up a Pi-based game development environment, and then develop a game with Lua, a popular scripting language used in major game frameworks like Unreal Engine (BioShock Infinite), CryEngine (Far Cry series), Diesel (Payday: The Heist), Silent Storm Engine (Heroes of Might and Magic V) and many others. More importantly, learn how to dig deeper into programming languages to find and understand new functions, frameworks, and languages to utilize in your games.You’ll start by learning your way around the Raspberry Pi. Then you’ll quickly dive into learning game development with an industry-standard and scalable language. After reading this book, you'll have the ability to write your own games on a Raspberry Pi, and deliver those games to Linux, Mac, Windows, iOS, and Android. And you’ll learn how to publish your games to popular marketplaces for those desktop and mobile platforms. Whether you're new to programming or whether you've already published to markets like Itch.io or Steam, this book showcases compelling reasons to use the Raspberry Pi for game development. Use Developing Games on the Raspberry Pi as your guide to ensure that your game plays on computers both old and new, desktop or mobile. What You'll Learn Confidently write programs in Lua and the LOVE game engine on the Raspberry Pi Research and learn new libraries, methods, and frameworks for more advanced programming Write, package, and sell apps for mobile platforms Deliver your games on multiple platforms Who This Book Is For Software engineers, teachers, hobbyists, and development professionals looking to up-skill and develop games for mobile platforms, this book eases them into a parallel universe of lightweight, POSIX, ARM-based development. COMPUTERS,Hardware,General

Exploring BeagleBone In-depth instruction and practical techniques for building with the BeagleBone embedded Linux platform Exploring BeagleBone is a hands-on guide to bringing gadgets, gizmos, and robots to life using the popular BeagleBone embedded Linux platform. Comprehensive content and deep detail provide more than just a BeagleBone instruction manual-you'll also learn the underlying engineering techniques that will allow you to create your own projects. The book begins with a foundational primer on essential skills, and then gradually moves into communication, control, and advanced applications using C/C++, allowing you to learn at your own pace. In addition, the book's companion website features instructional videos, source code, discussion forums, and more, to ensure that you have everything you need. The BeagleBone's small size, high performance, low cost, and extreme adaptability have made it a favorite development platform, and the Linux software base allows for complex yet flexible functionality. The BeagleBone has applications in smart buildings, robot control, environmental sensing, to name a few; and, expansion boards and peripherals dramatically increase the possibilities. Exploring BeagleBone provides a reader-friendly guide to the device, including a crash course in computer engineering. While following step by step, you can: Get up to speed on embedded Linux, electronics, and programming Master interfacing electronic circuits, buses and modules, with practical examples Explore the Internet-connected BeagleBone and the BeagleBone with a display Apply the BeagleBone to sensing applications, including video and sound Explore the BeagleBone's Programmable Real-Time Controllers Updated to cover the latest Beagle boards, Linux kernel versions, and Linux software releases. Includes new content on Linux kernel development, the Linux Remote Processor Framework, CAN bus, IoT frameworks, and much more! Hands-on learning helps ensure that your new skills stay with you, allowing you to design with electronics, modules, or peripherals even beyond the BeagleBone. Insightful guidance and online peer support help you transition from beginner to expert as you master the techniques presented in Exploring BeagleBone, the practical handbook for the popular computing platform. COMPUTERS,Hardware,General

Massive MIMO Detection Algorithm and VLSI Architecture This book introduces readers to a reconfigurable chip architecture for future wireless communication systems, such as 5G and beyond. The proposed architecture perfectly meets the demands for future mobile communication solutions to support different standards, algorithms, and antenna sizes, and to accommodate the evolution of standards and algorithms. It employs massive MIMO detection algorithms, which combine the advantages of low complexity and high parallelism, and can fully meet the requirements for detection accuracy. Further, the architecture is implemented using ASIC, which offers high energy efficiency, high area efficiency and low detection error. After introducing massive MIMO detection algorithms and circuit architectures, the book describes the ASIC implementation for verifying the massive MIMO detection. In turn, it provides detailed information on the proposed reconfigurable architecture: the data path and configuration path for massive MIMO detection algorithms, including the processing unit, interconnections, storage mechanism, configuration information format, and configuration method. COMPUTERS,Hardware,General

Game Boy Modding Complete beginner's guide to all aspects of modifying the classic Nintendo Game Boy. Game Boy Modding teaches you how to purchase, refurbish, mod, and customize Nintendo handheld consoles. The consoles are widely available and the customizations are affordable, requiring only limited tools and know-how. Retro consoles are seeing a resurgence of popularity worldwide, and king among these throwback devices is the Nintendo Game Boy, which sold over 100 million units in its lifetime and introduced gamers to Mario and Pokemon. These consoles emanate pixelated 8-bit retro charm, but lack the modern technological enhancements that we take for granted in 2020. You'll learn basic soldering and hardware modification techniques; how to change speakers, buttons, and screen lenses; how to fix dead speakers and sticky buttons; and how to personalize your Game Boy to your heart's content. COMPUTERS,Hardware,General

Build Your Own IoT Platform Discover how every solution in some way related to the IoT needs a platform and how to create that platform. This book is about being agile and reducing time to market without breaking the bank. It is about designing something that you can scale incrementally without having to do a lot of rework and potentially disrupting your current state of the work. So the key questions are: what does it take, how long does it take, and how much does it take to build your own IoT platform? Build Your Own IoT Platform answers these questions and provides you with step-by-step guidance on how to build your own IoT platform. The author bursts the bubble of IoT platforms and highlights what the core of an IoT platform looks like. There are must-haves and there are nice-to-haves; this book will distinguish the two and focus on how to build the must-haves. Building your own IoT platform is not only the biggest cost saver, but also can be a satisfying learning experience, giving you control over your project. What You Will Learn Architect an interconnected system Develop a flexible architecture Create a redundant communication platform Prioritize system requirements with a bottom-up approach Who This Book Is For IoT developers and development teams in small- to medium-sized companies. Basic to intermediate programming skills are required. COMPUTERS,Hardware,General

Hands-On Internet of Things with MQTT Develop a variety of projects and connect them to microcontrollers and web servers using the lightweight messaging protocol MQTT Key Features Leverage the power of MQTT to build a pet food dispenser, e-ink to-do list, and a productivity cube Learn about technologies like laser cutting, 3D printing, and PCB production for building robust prototypes Explore practical uses cases to gain an in-depth understanding of MQTT Book Description MQ Telemetry Transport (MQTT) is a lightweight messaging protocol for smart devices that can be used to build exciting, highly scalable Internet of Things (IoT) projects. This book will get you started with a quick introduction to the concepts of IoT and MQTT and explain how the latter can help you build your own internet-connected prototypes. As you advance, you'll gain insights into how microcontrollers communicate, and you'll get to grips with the different messaging protocols and techniques involved. Once you are well-versed with the essential concepts, you'll be able to put what you've learned into practice by building three projects from scratch, including an automatic pet food dispenser and a smart e-ink to-do display. You'll also discover how to present your own prototypes professionally. In addition to this, you'll learn how to use technologies from third-party web service providers, along with other rapid prototyping technologies, such as laser cutting, 3D printing, and PCB production. By the end of this book, you'll have gained hands-on experience in using MQTT to build your own IoT prototypes. What you will learn Explore MQTT programming with Arduino Discover how to make your prototypes talk to each other Send MQTT messages from your smartphone to your prototypes Discover how you can make websites interact with your prototypes Learn about MQTT servers, libraries, and apps Explore tools such as laser cutting and 3D printing in order to build robust prototype cases Who this book is for If you are an IoT developer or enthusiast who wants to start building IoT prototypes using MQTT, this book is for you. Basic knowledge of programming with Arduino will be useful. COMPUTERS,Hardware,General

Beginner's Guide to Interfacing the B. B. C. Microcomputer COMPUTERS,Hardware,General

IoT and Edge Computing for Architects Learn to design, implement, and secure your IoT infrastructure. Revised and expanded for edge computing. Key Features Build a complete IoT system that's the best fit for your organization Learn about different concepts, tech, and trade-offs in the IoT architectural stack Understand the theory and implementation of each element that comprises IoT design Book Description Industries are embracing IoT technologies to improve operational expenses, product life, and people's well-being. An architectural guide is needed if you want to traverse the spectrum of technologies needed to build a successful IoT system, whether that's a single device or millions of IoT devices. IoT and Edge Computing for Architects, Second Edition encompasses the entire spectrum of IoT solutions, from IoT sensors to the cloud. It examines modern sensor systems, focusing on their power and functionality. It also looks at communication theory, paying close attention to near-range PAN, including the new Bluetooth® 5.0 specification and mesh networks. Then, the book explores IP-based communication in LAN and WAN, including 802.11ah, 5G LTE cellular, Sigfox, and LoRaWAN. It also explains edge computing, routing and gateways, and their role in fog computing, as well as the messaging protocols of MQTT 5.0 and CoAP. With the data now in internet form, you'll get an understanding of cloud and fog architectures, including the OpenFog standards. The book wraps up the analytics portion with the application of statistical analysis, complex event processing, and deep learning models. The book then concludes by providing a holistic view of IoT security, cryptography, and shell security in addition to software-defined perimeters and blockchains. What you will learn Understand the role and scope of architecting a successful IoT deployment Scan the landscape of IoT technologies, from sensors to the cloud and more See the trade-offs in choices of protocols and communications in IoT deployments Become familiar with the terminology needed to work in the IoT space Broaden your skills in the multiple engineering domains necessary for the IoT architect Implement best practices to ensure reliability, scalability, and security in your IoT infrastructure Who this book is for This book is for architects, system designers, technologists, and technology managers who want to understand the IoT ecosphere, technologies, and trade-offs, and develop a 50,000-foot view of IoT architecture. An understanding of the architectural side of IoT is necessary. COMPUTERS,Hardware,General

Programming with 64-Bit ARM Assembly Language Mastering ARM hardware architecture opens a world of programming for nearly all phones and tablets including the iPhone/iPad and most Android phones. It’s also the heart of many single board computers like the Raspberry Pi. Gain the skills required to dive into the fundamentals of the ARM hardware architecture with this book and start your own projects while you develop a working knowledge of assembly language for the ARM 64-bit processor. You'll review assembly language programming for the ARM Processor in 64-bit mode and write programs for a number of single board computers, including the Nvidia Jetson Nano and the Raspberry Pi (running 64-bit Linux). The book also discusses how to target assembly language programs for Apple iPhones and iPads along with 64-Bit ARM based Android phones and tablets. It covers all the tools you require, the basics of the ARM hardware architecture, all the groups of ARM 64-Bit Assembly instructions, and how data is stored in the computer’s memory. In addition, interface apps to hardware such as the Raspberry Pi’s GPIO ports. The book covers code optimization, as well as how to inter-operate with C and Python code. Readers will develop enough background to use the official ARM reference documentation for their own projects.With Programming with 64-Bit ARM Assembly Language as your guide you’ll study how to read, reverse engineer and hack machine code, then be able to apply these new skills to study code examples and take control of both your ARM devices’ hardware and software. What You'll Learn Make operating system calls from assembly language and include other software libraries in your projects Interface apps to hardware devices such as the Raspberry Pi GPIO ports Reverse engineer and hack code Use the official ARM reference documentation for your own projects Who This Book Is For Software developers who have already learned to program in a higher-level language like Python, Java, C#, or even C and now wish to learn Assembly programming. COMPUTERS,Hardware,General

Mastering 3D Printing Get the most out of your printer, including how to design models, choose materials, work with different printers, and integrate 3D printing with traditional prototyping to make techniques like sand casting more efficient.This book is for new 3D printer owners, makers of all kinds, entrepreneurs, technology educators, and anyone curious about what you can do with a 3D printer. In this revised and expanded new edition of Mastering 3D Printing, which has been a trusted resource through five years of evolution in the 3D printing industry, you’ll gain a comprehensive understanding of 3D printing. This book presumes no foreknowledge and describes what you need to know about how printers work, how to decide which type of printer (filament, resin, or powder) makes the most sense for you, and then how to go forward in the case of filament and resin printers. This new edition now includes material about consumer resin printing, the evolution of lower-cost metal printing, and the plethora of both materials and applications. What You’ll Learn Choose among the different 3D printing technologies Create or find 3D models to print Make both easy and challenging prints come out as you imagined Assess whether your business, factory, home or classroom will benefit from 3D printing Work with applications that are good candidates for first projects in home and industrial applications Who This Book Is For People who are encountering 3D printing for the first time, or for those who want to level up their skills. It is designed for the nontechnical adult and minimizes jargon. However more sophisticated users will still find tips and insights of value. COMPUTERS,Hardware,General

Science and Engineering Projects Using the Arduino and Raspberry Pi Hone your understanding of science and engineering concepts with the versatile Arduino microcontroller and powerful Raspberry Pi mini-computer. The simple, straightforward, fun projects in this book use the Arduino and Raspberry Pi to build systems that explore key scientific concepts and develop engineering skills. Areas explored include force/acceleration, heat transfer, light, and astronomy. You'll work with advanced tools, such as data logging, advanced design, manufacturing, and assembly techniques that will take you beyond practical application of the projects you'll be creating. Technology is ever evolving and changing. This book goes beyond simple how-tos to teach you the concepts behind these projects and sciences. You'll gain the skills to observe and adapt to changes in technology as you work through fun and easy projects that explore fundamental concepts of engineering and science. What You'll Learn Measure the acceleration of a car you're riding in Simulate zero gravity Calculate the heat transfer in and out of your house Photography the moon and planets Who This Book Is For Hobbyists, students, and instructors interested in practical applications and methods to measure and learn about the physical world using inexpensive Maker technologies. COMPUTERS,Hardware,General

Beginning Sensor Networks with XBee, Raspberry Pi, and Arduino Build sensor networks with Python and MicroPython using XBee radio modules, Raspberry Pi, and Arduino boards. This revised and updated edition will put all of these together to form a sensor network, and show you how to turn your Raspberry Pi into a MySQL database server to store your sensor data! You'll review the different types of sensors and sensor networks, along with new technology, including how to build a simple XBee network. You'll then walk through building an sensor nodes on the XBee, Raspberry Pi, and Arduino, and also learn how to collect data from multiple sensor nodes. The book also explores different ways to store sensor data, including writing to an SD card, sending data to the cloud, and setting up a Raspberry Pi MySQL server to host your data. You'll even learn how to connect to and interact with a MySQL database server directly from an Arduino! Finally you'll see how to put it all together by connecting your sensor nodes to your new Raspberry Pi database server. If you want to see how well XBee, Raspberry Pi, and Arduino can get along, especially to create a sensor network, then Beginning Sensor Networks with XBee, Raspberry Pi, and Arduino is just the book you need. What You'll Learn Code your sensor nodes with Python and MicroPython Work with new XBee 3 modules Host your data on Raspberry Pi Get started with MySQL Create sophisticated sensor networks Who This Book Is For Those interested in building or experimenting with sensor networks and IoT solutions, including those with little or no programming experience. A secondary target includes readers interested in using XBee modules with Raspberry Pi and Arduino, those interested in controlling XBee modules with MicroPython. COMPUTERS,Hardware,General

Beginning Data Science, IoT, and AI on Single Board Computers Learn to use technology to undertake data science and to leverage the Internet of Things (IoT) in your experimentation. Designed to take you on a fascinating journey, this book introduces the core concepts of modern data science. You'll start with simple applications that you can undertake on a BBC micro:bit and move to more complex experiments with additional hardware. The skills and narrative are as generic as possible and can be implemented with a range of hardware options. One of the most exciting and fastest growing topics in education is data science. Understanding how data works, and how to work with data, is a key life skill in the 21st century. In a world driven by information it is essential that students are equipped with the tools they need to make sense of it all. For instance, consider how data science was the key factor that identified the dangers of climate change -- and continues to help us identify and react to the threats it presents. This book explores the power of data and how you can apply it using hardware you have at hand. You'll learn the core concepts of data science, how to apply them in the real world and how to utilize the vast potential of IoT. By the end, you'll be able to execute sophisticated and meaningful data science experiments - why not become a citizen scientist and make a real contribution to the fight against climate change. There is something of a digital revolution going these days, especially in the classroom. With increasing access to microprocessors, classrooms are are incorporating them more and more into lessons. Close to 5 million BBC micro:bits will be in the hands of young learners by the end of the year and millions of other devices are also being used by educators to teach a range of topics and subjects. This presents an opportunity: microprocessors such as micro:bit provide the perfect tool to use to build 21st century data science skills. Beginning Data Science and IoT on the BBC micro:bit provides you with a solid foundation in applied data science. What You'll Learn · Use sensors with a microprocessor to gather or "create" data · Extract, tabulate, and utilize data it from the microprocessor · Connect a microprocessor to an IoT platform to share and then use the data we collect · Analyze and convert data into information Who This Book Is For Educators, citizen scientists, and tinkerers interested in an introduction to the concepts of IoT and data on a broad scale. COMPUTERS,Hardware,General

Designing and Programming CICS Applications CICS is an application server that delivers industrial-strength, online transaction management for critical enterprise applications. Proven in the market for over 30 years with many of the world's leading businesses, CICS enables today's customers to modernize and extend their applications to take advantage of the opportunities provided by e-business while maximizing the benefits of their existing investments.Designing and Programming CICS Applications will benefit a diverse audience. It introduces new users of IBM's mainframe (OS/390) to CICS features. It shows experienced users how to integrate existing mainframe systems with newer technologies, including the Web, CORBA, Java, CICS clients, and Visual Basic; as well as how to link MQSeries and CICS.Each part of Designing and Programming CICS Applications addresses the design requirements for specific components and gives a step-by-step approach to developing a simple application. The book reviews the basic concepts of a business application and the way CICS meets these requirements. It then covers a wide range of application development technologies, including VisualAge for Java, WebSphere Studio, and Visual Basic. Users learn not only how to design and write their programs but also how to deploy their applications.Designing and Programming CICS Applications shows how to: Develop and modify existing COBOL applications Become familiar with the CICS Java environment and write a simple Java wrapper for a COBOL application Develop a web front end using servlets, JSP and JavaBeans. Link the web front end to an existing COBOL application using CORBA Write a Visual Basic application to develop a customer GUI Link an existing COBOL application using a CICS Client ECI call Develop a Java application using Swing as an MQSeries Client Use the MQSeries-CICS bridge to access an existing COBOL application Whether for working with thousands of terminals or for a client/server environment with workstations and LANs exploiting modern technology such as graphical interfaces or multimedia, Designing and Programming CICS Applications delivers the power to create, modernize and extend CICS applications. COMPUTERS,Hardware,Mainframes & Minicomputers

"Is This Thing On?" Now updated and revised, the user-friendliest, most reassuring, jargon-free, smartest, and most comprehensive nuts-and-bolts guide to all things technology (computers, tablets, smartphones, and more) for seniors. COMPUTERS,Hardware,Personal Computers,General

iPhone Hacks With iPhone Hacks, you can make your iPhone do all you'd expect of a mobile smartphone -- and more. Learn tips and techniques to unleash little-known features, find and create innovative applications for both the iPhone and iPod touch, and unshackle these devices to run everything from network utilities to video game emulators. This book will teach you how to: Import your entire movie collection, sync with multiple computers, and save YouTube videos Remotely access your home network, audio, and video, and even control your desktop Develop native applications for the iPhone and iPod touch on Linux, Windows, or Mac Check email, receive MMS messages, use IRC, and record full-motion video Run any application in the iPhone's background, and mirror its display on a TV Make your iPhone emulate old-school video game platforms, and play classic console and arcade games Integrate your iPhone with your car stereo Build your own electronic bridges to connect keyboards, serial devices, and more to your iPhone without "jailbreaking" iPhone Hacks explains how to set up your iPhone the way you want it, and helps you give it capabilities that will rival your desktop computer. This cunning little handbook is exactly what you need to make the most of your iPhone. COMPUTERS,Hardware,Personal Computers,Macintosh

The Cult of Mac, 2nd Edition It's been nearly fifteen years since Apple fans raved over the first edition of the critically-acclaimed The Cult of Mac. This long-awaited second edition brings the reader into the world of Apple today while also filling in the missing history since the 2004 edition, including the creation of Apple brand loyalty, the introduction of the iPhone, and the death of Steve Jobs. Apple is a global luxury brand whose products range from mobile phones and tablets to streaming TVs and smart home speakers. Yet despite this dominance, a distinct subculture persists, which celebrates the ways in which Apple products seem to encourage self-expression, identity, and innovation. The beautifully designed second edition of The Cult of Mac takes you inside today's Apple fandom to explore how devotions--new and old--keep the fire burning. Join journalists Leander Kahney and David Pierini as they explore how enthusiastic fans line up for the latest product releases, and how artists pay tribute to Steve Jobs' legacy in sculpture and opera. Learn why some photographers and filmmakers have eschewed traditional gear in favor of iPhone cameras. Discover a community of collectors around the world who spend tens of thousands of dollars to buy, restore, and enshrine Apple artifacts, like the Newton MessagePad and Apple II. Whether you're an Apple fan or just a casual observer, this second edition of The Cult of Mac is sure to reveal more than a few surprises, offering an intimate look at some of the most dedicated members in the Apple community. COMPUTERS,Hardware,Personal Computers,Macintosh

Upgrading and Fixing Laptops For Dummies Keep your laptop on top of its game! Find out how to care for your laptop, what can go wrong, and what you can fix A laptop is much more than a PC that shrank. It has unique needs, and this book shows you how to meet them. You'll discover how to diagnose and fix common problems, replace parts, add external upgrades, and develop workarounds. You'll even get the lowdown on networks, and find out when to repair and when to replace your laptop. Discover how to * Treat your laptop properly * Identify common problems * Know when repair may not make economic sense * Install a new operating system * Troubleshoot CD and DVD drives * Add cool peripherals COMPUTERS,Hardware,Personal Computers,PCs

Build It. Fix It. Own It BUILD IT. FIX it. OWN IT. A Beginner’s Guide to Building and Upgrading a PC Build It. Fix It. Own It. is the ultimate beginner’s guide to building and fixing your own PC. With a friendly, knowledgeable tone, this book shows the beginning PC builder everything he or she needs to know to build a computer or upgrade an existing one. We step you through the parts that lurk inside a PC, from the motherboard and power supply to the CPU, memory, hard drive, video card, sound card, and networking hardware. In each case, you will learn how the hardware works, what it does, what types of hardware are available, and what to look for when buying the hardware. Then we walk you step-by-step though a series of PC building projects. We show you how to build five different types of PC: a basic business PC, a home theater PC, a high-performance PC, a killer gaming PC, and a budget PC. And if building a new PC from scratch isn’t in your budget, we show you how to resurrect an old PC by swapping out a few key components. When you have your PC built and running, we show you how to set up a wireless network and the BIOS and maintain your new rig. Build It. Fix It. Own It. is the ultimate PC builder’s guide, even if you’ve never ventured inside a PC case before! Author Bio Paul McFedries is one of the industry’s most well known and respected technical writers and is a passionate computer tinkerer. He is the author of more than 70 computer books that have sold more than three million copies worldwide. His recent titles include the Sams Publishing books Windows Vista Unleashed and Windows Home Server Unleashed and the Que Publishing books Networking with Microsoft Windows Vista, Formulas and Functions with Microsoft Excel 2007, Tricks of the Microsoft Office 2007 Gurus, and Microsoft Access 2007 Forms, Reports, and Queries. Paul also is the proprietor of Word Spy (www.wordspy.com), a website devoted to tracking new words and phrases as they enter the English language. Category Hardware Covers PC Hardware User Level Beginner—Intermediate COMPUTERS,Hardware,Personal Computers,PCs

How Computers Work The Evolution of Technology Having sold more than 2 million copies over its lifetime, How Computers Work is the definitive illustrated guide to the world of PCs and technology. In this new edition, you’ll find detailed information not just about PCs, but about how changes in technology have evolved the giant, expensive computer dinosaurs of last century into the smaller but more powerful smartphones, tablets, and wearable computing of today. Whether your interest is in business, gaming, digital photography, entertainment, communications, or security, you’ll learn how computing is evolving the way you live. A full-color, illustrated adventure into the wonders of TECHNOLOOGY This full-color, fully illustrated guide to the world of technology assumes nothing and explains everything. Only the accomplished and award-winning team of writer Ron White and artist Tim Downs has the unique ability to meld descriptive text with one-of-a-kind visuals to fully explain how the electronic gear we depend on every day is made possible. In addition to all the content you’ve come to expect from prior editions, this newly revised edition includes all-new coverage of topics such as: • How smartphones and tablet PCs put the power of a desktop computer in your hands–literally • How computing technology is linking our homes, work place, entertainment, and daily communications • How advances such as Facebook, Twitter, Google, eBay, and smartphones are expanding our universe of friends, knowledge, and opportunity • How increased miniaturization leads to new products, such as smartphone, smartwatches, and Google Glass • How computing technology takes advantages of quantum physics and innovations no one even imagined a few years ago For two decades, How Computers Work has helped newbies understand new technology, while hackers and IT pros have treasured it for the depth of knowledge it contains. This is the perfect book about computing to capture your imagination, delight your eyes, and expand your mind, no matter what your technical level! Beautifully detailed illustrations and jargon-free explanations walk you through the technology that is shaping our lives. See the hidden workings inside computers, smartphones, tablets, Google Glass, and the latest tech inventions. COMPUTERS,Hardware,Personal Computers,PCs

Upgrading and Repairing PCs Access to 3 hours of troubleshooting videos as well as PDFs of previous editions are available through product registration—see instructions in back pages of your eBook. For more than 25 years, Upgrading and Repairing PCs has been the world’s #1 guide to PC hardware: The single source for reliable information on how PCs work, troubleshooting and fixing problems, adding hardware, optimizing performance, and building new PCs. This 22nd edition offers beefed-up coverage of the newest hardware innovations and maintenance techniques, plus more than two hours of new video. Scott Mueller delivers practical answers about PC processors, mother-boards, buses, BIOSes, memory, SSD and HDD storage, video, audio, networks, Internet connectivity, power, and much more. You’ll find the industry’s best coverage of diagnostics, testing, and repair—plus cutting-edge discussions of improving PC performance via overclocking and other techniques. Mueller has taught thousands of professionals in person and millions more through his books and videos—nobody knows more about keeping PCs running perfectly. Whether you’re a professional technician, a small business owner trying to save money, or a home PC enthusiast, this is the only PC hardware book you need! NEW IN THIS EDITION The newest processors, including Intel’s latest Core i Haswell processors and AMD’s Kaveri core processors. Everything you need to know about the latest GPU technology from NVIDIA and AMD, including developments in OpenGL, DirectX, and Mantle. New firmware innovations like the InSyde BIOS, Back to BIOS buttons, and all the updated settings available for the newest processors and chipsets. The latest in updated home networking standards, from blazing fast 802.11ac Wi-Fi to HomeGrid and G.hn powerline networking. Ever larger storage, thanks to new technologies like helium-filled hard disks, shingled magnetic recording, and Cfast and XQD for flash memory. Emerging interfaces such as mSATA, USB 3.1, and M.2 Updated coverage of building PCs from scratch—from choosing and assembling hardware through BIOS setup and troubleshooting COMPUTERS,Hardware,Personal Computers,PCs

Troubleshooting & Maintaining Your PC All-in-One For Dummies Stop being a prisoner to your PC! Need a PC problem fixed in a pinch? Presto! Troubleshooting & Maintaining Your PC All-in-One For Dummies offers 5 books in 1 and takes the pain out of wading through those incomprehensible manuals, or waiting for a high-priced geek to show up days or weeks after you need them. Arming you with everything you need to get that pesky PC working for you ASAP, this handy guide walks you through all the steps to restoring whatever's making your PC go rogue —so you can get back to making it work for you. There's nothing worse than firing up your PC only to discover it's inexplicably unresponsive. With this guide, you'll gain all the skills and insight you need to need to bring it back to life —and to prevent it from ever leaving you in the lurch again. Find out what's behind common PC problems Solve email and web woes, both big and small Perform regular maintenance and get serious about backups Troubleshoot to find solutions to your issues and learn proper maintenance to head off future headaches! Your PC problems aren't as big as you think! Take matters into your own hands with the helpful instruction provided inside this book! COMPUTERS,Hardware,Personal Computers,PCs

Arduino For Dummies The quick, easy way to leap into the fascinating world of physical computing This is no ordinary circuit board. Arduino allows anyone, whether you're an artist, designer, programmer or hobbyist, to learn about and play with electronics. Through this book you learn how to build a variety of circuits that can sense or control things in the real world. Maybe you'll prototype your own product or create a piece of interactive artwork? This book equips you with everything you'll need to build your own Arduino project, but what you make is up to you! If you're ready to bring your ideas into the real world or are curious about the possibilities, this book is for you. ? Learn by doing ? start building circuits and programming your Arduino with a few easy to follow examples - right away! ? Easy does it ? work through Arduino sketches line by line in plain English, to learn of how a they work and how to write your own ? Solder on! ? Only ever used a breadboard in the kitchen? Don't know your soldering iron from a curling iron? No problem, you'll be prototyping in no time ? Kitted out ? discover new and interesting hardware to make your Arduino into anything from a mobile phone to a geiger counter! ? Become an Arduino savant ? learn all about functions, arrays, libraries, shields and other tools of the trade to take your Arduino project to the next level. ? Get social ? teach your Arduino to communicate with software running on a computer to link the physical world with the virtual world It's hardware, it's software, it's fun! Start building the next cool gizmo with Arduino and Arduino For Dummies. COMPUTERS,Hardware,Printers,Scanners & External Accessories

USB Complete Now in its fifth edition, bridges the gap between the technical specifications and the real world of designing and programming devices that connect over the Universal Serial Bus (USB). Readers will learn how to select the appropriate USB speed, device class, and hardware for a device; communicate with devices using Visual C#; use standard host drivers to access devices, including devices that perform vendor-defined tasks; save power with USB's built-in power-conserving protocols; and create robust designs using testing and debugging tools. This fully revised edition also includes instruction on how to increase bus speed with SuperSpeed and SuperSpeedPlus, implement wireless communications, and develop for USB On-The-Go and embedded hosts COMPUTERS,Hardware,Printers,Scanners & External Accessories

The Soul of A New Machine Tracy Kidder's "riveting" (Washington Post) story of one company's efforts to bring a new microcomputer to market won both the Pulitzer Prize and the National Book Award and has become essential reading for understanding the history of the American tech industry. Computers have changed since 1981, when The Soul of a New Machine first examined the culture of the computer revolution. What has not changed is the feverish pace of the high-tech industry, the go-for-broke approach to business that has caused so many computer companies to win big (or go belly up), and the cult of pursuing mind-bending technological innovations. The Soul of a New Machine is an essential chapter in the history of the machine that revolutionized the world in the twentieth century. "Fascinating...A surprisingly gripping account of people at work." --Wall Street Journal COMPUTERS,History

The New Kingmakers The New Kingmakers documents the rise of the developer class, and provides strategies for companies to adapt to the new technology landscape. From recruiting to retention, it provides a playbook to work more efficiently and effectively with the most important members of your organization. COMPUTERS,History

Fire in the Valley In the 1970s, while their contemporaries were protesting the computer as a tool of dehumanization and oppression, a motley collection of college dropouts, hippies, and electronics fanatics were engaged in something much more subversive. Obsessed with the idea of getting computer power into their own hands, they launched from their garages a hobbyist movement that grew into an industry, and ultimately a social and technological revolution. What they did was invent the personal computer: not just a new device, but a watershed in the relationship between man and machine. This is their story. Fire in the Valley is the definitive history of the personal computer, drawn from interviews with the people who made it happen, written by two veteran computer writers who were there from the start. Working at InfoWorld in the early 1980s, Swaine and Freiberger daily rubbed elbows with people like Steve Jobs and Bill Gates when they were creating the personal computer revolution. A rich story of colorful individuals, Fire in the Valley profiles these unlikely revolutionaries and entrepreneurs, such as Ed Roberts of MITS, Lee Felsenstein at Processor Technology, and Jack Tramiel of Commodore, as well as Jobs and Gates in all the innocence of their formative years. This completely revised and expanded third edition brings the story to its completion, chronicling the end of the personal computer revolution and the beginning of the post-PC era. It covers the departure from the stage of major players with the deaths of Steve Jobs and Douglas Engelbart and the retirements of Bill Gates and Steve Ballmer; the shift away from the PC to the cloud and portable devices; and what the end of the PC era means for issues such as personal freedom and power, and open source vs. proprietary software. COMPUTERS,History

Cult of the Dead Cow The shocking untold story of the elite secret society of hackers fighting to protect our privacy, our freedom, and even democracy itself. Cult of the Dead Cow is the tale of the oldest, most respected, and most famous American hacking group of all time. Though until now it has remained mostly anonymous, its members invented the concept of hacktivism, released the top tool for testing password security, and created what was for years the best technique for controlling computers from afar, forcing giant companies to work harder to protect customers. They contributed to the development of Tor, the most important privacy tool on the net, and helped build cyberweapons that advanced US security without injuring anyone. With its origins in the earliest days of the Internet, the cDc is full of oddball characters -- activists, artists, even future politicians. Many of these hackers have become top executives and advisors walking the corridors of power in Washington and Silicon Valley. The most famous is former Texas Congressman and current presidential candidate Beto O'Rourke, whose time in the cDc set him up to found a tech business, launch an alternative publication in El Paso, and make long-shot bets on unconventional campaigns. Today, the group and its followers are battling electoral misinformation, making personal data safer, and battling to keep technology a force for good instead of for surveillance and oppression. Cult of the Dead Cow shows how governments, corporations, and criminals came to hold immense power over individuals and how we can fight back against them. COMPUTERS,History

The Hacker Crackdown The bestselling cyberpunk author “has produced by far the most stylish report from the computer outlaw culture since Steven Levy’s Hackers†(Publishers Weekly). Bruce Sterling delves into the world of high-tech crime and punishment in one of the first books to explore the cyberspace breaches that threaten national security. From the crash of AT&T’s long-distance switching system to corporate cyberattacks, he investigates government and law enforcement efforts to break the back of America’s electronic underground in the 1990s. In this modern classic, “Sterling makes the hackers—who live in the ether between terminals under noms de net such as VaxCat—as vivid as Wyatt Earp and Doc Holliday. His book goes a long way towards explaining the emerging digital world and its ethos†(Publishers Weekly). This edition features a new preface by the author that analyzes the sobering increase in computer crime over the twenty-five years since The Hacker Crackdown was first published. “Offbeat and brilliant.†—Booklist “Thoroughly researched, this account of the government’s crackdown on the nebulous but growing computer-underground provides a thoughtful report on the laws and rights being defined on the virtual frontier of cyberspace. . . . An enjoyable, informative, and (as the first mainstream treatment of the subject) potentially important book . . . Sterling is a fine and knowledgeable guide to this strange new world.†—Kirkus Reviews “A well-balanced look at this new group of civil libertarians. Written with humor and intelligence, this book is highly recommended.†—Library Journal COMPUTERS,History

Programmed Inequality How Britain lost its early dominance in computing by systematically discriminating against its most qualified workers: women. In 1944, Britain led the world in electronic computing. By 1974, the British computer industry was all but extinct. What happened in the intervening thirty years holds lessons for all postindustrial superpowers. As Britain struggled to use technology to retain its global power, the nation's inability to manage its technical labor force hobbled its transition into the information age. In Programmed Inequality, Mar Hicks explores the story of labor feminization and gendered technocracy that undercut British efforts to computerize. That failure sprang from the government's systematic neglect of its largest trained technical workforce simply because they were women. Women were a hidden engine of growth in high technology from World War II to the 1960s. As computing experienced a gender flip, becoming male-identified in the 1960s and 1970s, labor problems grew into structural ones and gender discrimination caused the nation's largest computer user—the civil service and sprawling public sector—to make decisions that were disastrous for the British computer industry and the nation as a whole. Drawing on recently opened government files, personal interviews, and the archives of major British computer companies, Programmed Inequality takes aim at the fiction of technological meritocracy. Hicks explains why, even today, possessing technical skill is not enough to ensure that women will rise to the top in science and technology fields. Programmed Inequality shows how the disappearance of women from the field had grave macroeconomic consequences for Britain, and why the United States risks repeating those errors in the twenty-first century. COMPUTERS,History

IBM A history of one of the most influential American companies of the last century. For decades, IBM shaped the way the world did business. IBM products were in every large organization, and IBM corporate culture established a management style that was imitated by companies around the globe. It was “Big Blue, ” an icon. And yet over the years, IBM has gone through both failure and success, surviving flatlining revenue and forced reinvention. The company almost went out of business in the early 1990s, then came back strong with new business strategies and an emphasis on artificial intelligence. In this authoritative, monumental history, James Cortada tells the story of one of the most influential American companies of the last century. Cortada, a historian who worked at IBM for many years, describes IBM's technology breakthroughs, including the development of the punch card (used for automatic tabulation in the 1890 census), the calculation and printing of the first Social Security checks in the 1930s, the introduction of the PC to a mass audience in the 1980s, and the company's shift in focus from hardware to software. He discusses IBM's business culture and its orientation toward employees and customers; its global expansion; regulatory and legal issues, including antitrust litigation; and the track records of its CEOs. The secret to IBM's unequalled longevity in the information technology market, Cortada shows, is its capacity to adapt to changing circumstances and technologies. COMPUTERS,History

Peripheral Vision How the S-C 4020—a mainframe peripheral intended to produce scientific visualizations—shaped a series of early computer art projects that emerged from Bell Labs. In 1959, the electronics manufacturer Stromberg-Carlson produced the S-C 4020, a device that allowed mainframe computers to present and preserve images. In the mainframe era, the output of text and image was quite literally peripheral; the S-C 4020—a strange and elaborate apparatus, with a cathode ray screen, a tape deck, a buffer unit, a film camera, and a photo-paper camera—produced most of the computer graphics of the late 1950s and early 1960s. At Bell Laboratories in Murray Hill, New Jersey, the S-C 4020 became a crucial part of ongoing encounters among art, science, and technology. In this book, Zabet Patterson examines the extraordinary uses to which the Bell Labs SC-2040 was put between 1961 and 1972, exploring a series of early computer art projects shaped by the special computational affordances of the S-C 4020. The S-C 4020 produced tabular data, graph plotting and design drawings, grid projections, and drawings of axes and vectors; it made previously impossible visualizations possible. Among the works Patterson describes are E. E. Zajac's short film of an orbiting satellite, which drew on the machine's graphic capacities as well as the mainframe's calculations; a groundbreaking exhibit of “computer generated pictures” by Béla Julesz and Michael Noll, two scientists interested in visualization; animations by Kenneth Knowlton and the Bell Labs artist-in-residence Stan VanDerBeek; and Lillian Schwartz's “cybernetic” film Pixillation. Arguing for the centrality of a peripheral, Patterson makes a case for considering computational systems not simply as machines but in their cultural and historical context. COMPUTERS,History

For Fun and Profit The free and open source software movement, from its origins in hacker culture, through the development of GNU and Linux, to its commercial use today. In the 1980s, there was a revolution with far-reaching consequences—a revolution to restore software freedom. In the early 1980s, after decades of making source code available with programs, most programmers ceased sharing code freely. A band of revolutionaries, self-described “hackers,” challenged this new norm by building operating systems with source code that could be freely shared. In For Fun and Profit, Christopher Tozzi offers an account of the free and open source software (FOSS) revolution, from its origins as an obscure, marginal effort by a small group of programmers to the widespread commercial use of open source software today. Tozzi explains FOSS's historical trajectory, shaped by eccentric personalities—including Richard Stallman and Linus Torvalds—and driven both by ideology and pragmatism, by fun and profit. Tozzi examines hacker culture and its influence on the Unix operating system, the reaction to Unix's commercialization, and the history of early Linux development. He describes the commercial boom that followed, when companies invested billions of dollars in products using FOSS operating systems; the subsequent tensions within the FOSS movement; and the battles with closed source software companies (especially Microsoft) that saw FOSS as a threat. Finally, Tozzi describes FOSS's current dominance in embedded computing, mobile devices, and the cloud, as well as its cultural and intellectual influence. COMPUTERS,History

The Computer Boys Take Over The contentious history of the computer programmers who developed the software that made the computer revolution possible. This is a book about the computer revolution of the mid-twentieth century and the people who made it possible. Unlike most histories of computing, it is not a book about machines, inventors, or entrepreneurs. Instead, it tells the story of the vast but largely anonymous legions of computer specialists—programmers, systems analysts, and other software developers—who transformed the electronic computer from a scientific curiosity into the defining technology of the modern era. As the systems that they built became increasingly powerful and ubiquitous, these specialists became the focus of a series of critiques of the social and organizational impact of electronic computing. To many of their contemporaries, it seemed the “computer boys” were taking over, not just in the corporate setting, but also in government, politics, and society in general. In The Computer Boys Take Over, Nathan Ensmenger traces the rise to power of the computer expert in modern American society. His rich and nuanced portrayal of the men and women (a surprising number of the “computer boys” were, in fact, female) who built their careers around the novel technology of electronic computing explores issues of power, identity, and expertise that have only become more significant in our increasingly computerized society. In his recasting of the drama of the computer revolution through the eyes of its principle revolutionaries, Ensmenger reminds us that the computerization of modern society was not an inevitable process driven by impersonal technological or economic imperatives, but was rather a creative, contentious, and above all, fundamentally human development. COMPUTERS,History

Recoding Gender The untold history of women and computing: how pioneering women succeeded in a field shaped by gender biases. Today, women earn a relatively low percentage of computer science degrees and hold proportionately few technical computing jobs. Meanwhile, the stereotype of the male “computer geek” seems to be everywhere in popular culture. Few people know that women were a significant presence in the early decades of computing in both the United States and Britain. Indeed, programming in postwar years was considered woman's work (perhaps in contrast to the more manly task of building the computers themselves). In Recoding Gender, Janet Abbate explores the untold history of women in computer science and programming from the Second World War to the late twentieth century. Demonstrating how gender has shaped the culture of computing, she offers a valuable historical perspective on today's concerns over women's underrepresentation in the field. Abbate describes the experiences of women who worked with the earliest electronic digital computers: Colossus, the wartime codebreaking computer at Bletchley Park outside London, and the American ENIAC, developed to calculate ballistics. She examines postwar methods for recruiting programmers, and the 1960s redefinition of programming as the more masculine “software engineering.” She describes the social and business innovations of two early software entrepreneurs, Elsie Shutt and Stephanie Shirley; and she examines the career paths of women in academic computer science. Abbate's account of the bold and creative strategies of women who loved computing work, excelled at it, and forged successful careers will provide inspiration for those working to change gendered computing culture. COMPUTERS,History

ENIAC in Action The history of the first programmable electronic computer, from its conception, construction, and use to its afterlife as a part of computing folklore. Conceived in 1943, completed in 1945, and decommissioned in 1955, ENIAC (the Electronic Numerical Integrator and Computer) was the first general-purpose programmable electronic computer. But ENIAC was more than just a milestone on the road to the modern computer. During its decade of operational life, ENIAC calculated sines and cosines and tested for statistical outliers, plotted the trajectories of bombs and shells, and ran the first numerical weather simulations. ENIAC in Action tells the whole story for the first time, from ENIAC's design, construction, testing, and use to its afterlife as part of computing folklore. It highlights the complex relationship of ENIAC and its designers to the revolutionary approaches to computer architecture and coding first documented by John von Neumann in 1945. Within this broad sweep, the authors emphasize the crucial but previously neglected years of 1947 to 1948, when ENIAC was reconfigured to run what the authors claim was the first modern computer program to be executed: a simulation of atomic fission for Los Alamos researchers. The authors view ENIAC from diverse perspectives—as a machine of war, as the “first computer,” as a material artifact constantly remade by its users, and as a subject of (contradictory) historical narratives. They integrate the history of the machine and its applications, describing the mathematicians, scientists, and engineers who proposed and designed ENIAC as well as the men—and particularly the women who—built, programmed, and operated it. COMPUTERS,History

Spam What spam is, how it works, and how it has shaped online communities and the Internet itself. The vast majority of all email sent every day is spam, a variety of idiosyncratically spelled requests to provide account information, invitations to spend money on dubious products, and pleas to send cash overseas. Most of it is caught by filters before ever reaching an in-box. Where does it come from? As Finn Brunton explains in Spam, it is produced and shaped by many different populations around the world: programmers, con artists, bots and their botmasters, pharmaceutical merchants, marketers, identity thieves, crooked bankers and their victims, cops, lawyers, network security professionals, vigilantes, and hackers. Every time we go online, we participate in the system of spam, with choices, refusals, and purchases the consequences of which we may not understand. This is a book about what spam is, how it works, and what it means. Brunton provides a cultural history that stretches from pranks on early computer networks to the construction of a global criminal infrastructure. The history of spam, Brunton shows us, is a shadow history of the Internet itself, with spam emerging as the mirror image of the online communities it targets. Brunton traces spam through three epochs: the 1970s to 1995, and the early, noncommercial computer networks that became the Internet; 1995 to 2003, with the dot-com boom, the rise of spam's entrepreneurs, and the first efforts at regulating spam; and 2003 to the present, with the war of algorithms—spam versus anti-spam. Spam shows us how technologies, from email to search engines, are transformed by unintended consequences and adaptations, and how online communities develop and invent governance for themselves. COMPUTERS,History

Now the Chips Are Down The story of a pioneering microcomputer: its beginnings as part of a national Computer Literary Project, its innovative hardware, and its creative uses. In 1982, the British Broadcasting Corporation launched its Computer Literacy Project, intended “to introduce interested adults to the world of computers and computing.” The BBC accompanied this initiative with television programs, courses, books, and software—an early experiment in multi-platform education. The BBC, along with Acorn Computers, also introduced the BBC Microcomputer, which would be at the forefront of the campaign. The BBC Micro was designed to meet the needs of users in homes and schools, to demystify computing, and to counter the general pessimism among the media in Britain about technology. In this book, Alison Gazzard looks at the BBC Micro, examining the early capabilities of multi-platform content generation and consumption and the multiple literacies this approach enabled—not only in programming and software creation, but also in accessing information across a range of media, and in “do-it-yourself” computing. She links many of these early developments to current new-media practices. Gazzard looks at games developed for the BBC Micro, including Granny's Garden, an educational game for primary schools, and Elite, the seminal space-trading game. She considers the shift in focus from hardware to peripherals, describing the Teletext Adapter as an early model for software distribution and the Domesday Project (which combined texts, video, and still photographs) as a hypermedia-like experience. Gazzard's account shows the BBC Micro not only as a vehicle for various literacies but also as a user-oriented machine that pushed the boundaries of what could be achieved in order to produce something completely new. COMPUTERS,History

Computing A compact and accessible history, from punch cards and calculators to UNIVAC and ENIAC, the personal computer, Silicon Valley, and the Internet. The history of computing could be told as the story of hardware and software, or the story of the Internet, or the story of “smart” hand-held devices, with subplots involving IBM, Microsoft, Apple, Facebook, and Twitter. In this concise and accessible account of the invention and development of digital technology, computer historian Paul Ceruzzi offers a broader and more useful perspective. He identifies four major threads that run throughout all of computing's technological development: digitization—the coding of information, computation, and control in binary form, ones and zeros; the convergence of multiple streams of techniques, devices, and machines, yielding more than the sum of their parts; the steady advance of electronic technology, as characterized famously by “Moore's Law”; and the human-machine interface. Ceruzzi guides us through computing history, telling how a Bell Labs mathematician coined the word “digital” in 1942 (to describe a high-speed method of calculating used in anti-aircraft devices), and recounting the development of the punch card (for use in the 1890 U.S. Census). He describes the ENIAC, built for scientific and military applications; the UNIVAC, the first general purpose computer; and ARPANET, the Internet's precursor. Ceruzzi's account traces the world-changing evolution of the computer from a room-size ensemble of machinery to a “minicomputer” to a desktop computer to a pocket-sized smart phone. He describes the development of the silicon chip, which could store ever-increasing amounts of data and enabled ever-decreasing device size. He visits that hotbed of innovation, Silicon Valley, and brings the story up to the present with the Internet, the World Wide Web, and social networking. COMPUTERS,History

CRACK99 The utterly gripping story of the most outrageous case of cyber piracy prosecuted by the U.S. Department of Justice. A former U.S. Navy intelligence officer, David Locke Hall was a federal prosecutor when a bizarre-sounding website, CRACK99, came to his attention. It looked like Craigslist on acid, but what it sold was anything but amateurish: thousands of high-tech software products used largely by the military, and for mere pennies on the dollar. Want to purchase satellite tracking software? No problem. Aerospace and aviation simulations? No problem. Communications systems designs? No problem. Software for Marine One, the presidential helicopter? No problem. With delivery times and customer service to rival the world’s most successful e-tailers, anybody, anywhere—including rogue regimes, terrorists, and countries forbidden from doing business with the United States—had access to these goods for any purpose whatsoever. But who was behind CRACK99, and where were they? The Justice Department discouraged potentially costly, risky cases like this, preferring the low-hanging fruit that scored points from politicians and the public. But Hall and his colleagues were determined to find the culprit. They bought CRACK99's products for delivery in the United States, buying more and more to appeal to the budding entrepreneur in the man they identified as Xiang Li. After winning his confidence, they lured him to Saipan—a U.S. commonwealth territory where Hall’s own father had stormed the beaches with the marines during World War II. There they set up an audacious sting that culminated in Xiang Li's capture and imprisonment. The value of the goods offered by CRACK99? A cool $100 million. An eye-opening look at cybercrime and its chilling consequences for national security, CRACK99 reads like a caper that resonates with every amazing detail. COMPUTERS,History

Managing Risk The human element is the principle cause of incidents and accidents in all technology industries; hence it is evident that an understanding of the interaction between humans and technology is crucial to the effective management of risk. Despite this, no tested model that explicitly and quantitatively includes the human element in risk prediction is currently available. Managing Risk: the Human Element combines descriptive and explanatory text with theoretical and mathematical analysis, offering important new concepts that can be used to improve the management of risk, trend analysis and prediction, and hence affect the accident rate in technological industries. It uses examples of major accidents to identify common causal factors, or “echoesâ€, and argues that the use of specific experience parameters for each particular industry is vital to achieving a minimum error rate as defined by mathematical prediction. New ideas for the perception, calculation and prediction of risk are introduced, and safety management is covered in depth, including for rare events and “unknown†outcomes Discusses applications to multiple industries including nuclear, aviation, medical, shipping, chemical, industrial, railway, offshore oil and gas; Shows consistency between learning for large systems and technologies with the psychological models of learning from error correction at the personal level; Offers the expertise of key leading industry figures involved in safety work in the civil aviation and nuclear engineering industries; Incorporates numerous fascinating case studies of key technological accidents. Managing Risk: the Human Element is an essential read for professional safety experts, human reliability experts and engineers in all technological industries, as well as risk analysts, corporate managers and statistical analysts. It is also of interest to professors, researchers and postgraduate students of reliability and safety engineering, and to experts in human performance. “…congratulations on what appears to be, at a high level of review, a significant contribution to the literature…I have found much to be admired in (your) research†Mr. Joseph Fragola – Vice President of Valador Inc. “The book is not only technically informative, but also attractive to all concerned readers and easy to be comprehended at various level of educational background. It is truly an excellent book ever written for the safety risk managers and analysis professionals in the engineering community, especially in the high reliability organizations…†Dr Feng Hsu, Head of Risk Assessment and Management, NASA Goddard Space Flight Center “I admire your courage in confronting your theoretical ideas with such diverse, ecologically valid data, and your success in capturing a major trend in them….I should add that I find all this quite inspiring . …The idea that you need to find the right measure of accumulated experience and not just routinely used calendar time makes so much sense that it comes as a shock to realize that this is a new ideaâ€, Professor Stellan Ohlsson, Professor of Psychology, University of Illinois at Chicago COMPUTERS,Human-Computer Interaction (HCI)

The Cathedral & the Bazaar Open source provides the competitive advantage in the Internet Age. According to the August Forrester Report, 56 percent of IT managers interviewed at Global 2,500 companies are already using some type of open source software in their infrastructure and another 6 percent will install it in the next two years. This revolutionary model for collaborative software development is being embraced and studied by many of the biggest players in the high-tech industry, from Sun Microsystems to IBM to Intel.The Cathedral & the Bazaar is a must for anyone who cares about the future of the computer industry or the dynamics of the information economy. Already, billions of dollars have been made and lost based on the ideas in this book. Its conclusions will be studied, debated, and implemented for years to come. According to Bob Young, "This is Eric Raymond's great contribution to the success of the open source revolution, to the adoption of Linux-based operating systems, and to the success of open source users and the companies that supply them."The interest in open source software development has grown enormously in the past year. This revised and expanded paperback edition includes new material on open source developments in 1999 and 2000. Raymond's clear and effective writing style accurately describing the benefits of open source software has been key to its success. With major vendors creating acceptance for open source within companies, independent vendors will become the open source story in 2001. COMPUTERS,Human-Computer Interaction (HCI)

Usability Testing Essentials Usability Testing Essentials provides readers with the tools and techniques needed to begin usability testing or to advance their knowledge in this area. The book begins by presenting the essentials of usability testing, which include focusing on the user and not the product; knowing when to conduct small or large studies; and thinking of usability as hill climbing. It then reviews testing options and places usability testing into the context of a user-centered design (UCD). It goes on to discuss the planning, preparation, and implementation of a usability test. The remaining chapters cover the analysis and reporting of usability test findings, and the unique aspects of international usability testing. This book will be useful to anyone else involved in the development or support of any type of product, such as software or web developers, engineers, interaction designers, information architects, technical communicators, visual or graphic designers, trainers, user-assistance specialists, and instructional technologists. Provides a comprehensive, step-by-step guide to usability testing, a crucial part of every product’s development The fully updated four-color edition now features important usability issues such as international testing, persona creation, remote testing, and accessibility Follow-up to Usability Testing and Research (9780205315192, Longman, 2001), winner of the highest-level award from the Society for Technical Communication COMPUTERS,Human-Computer Interaction (HCI)

Sketching User Experiences Sketching Working Experience: The Workbook provides information about the step-by-step process of the different sketching techniques. It offers methods called design thinking, as a way to think as a user, and sketching, a way to think as a designer. User-experience designers are designers who sketch based on their actions, interactions, and experiences. The book discusses the differences between the normal ways to sketch and sketching used by user-experience designers. It also describes some motivation on why a person should sketch and introduces the sketchbook. The book reviews the different sketching methods and the modules that contain a particular sketching method. It also explains how the sketching methods are used. Readers who are interested in learning, understanding, practicing, and teaching experience design, information design, interface design, and information architecture will find this book relevant. Features standalone modules detailing methods and exercises for practitioners who want to learn and develop their sketching skills Extremely practical, with illustrated examples detailing all steps on how to do a method Excellent for individual learning, for classrooms, and for a team that wants to develop a culture of design practice Perfect complement to Buxton’s Sketching User Experience or any UX text Author-maintained companion website at http://grouplab.cpsc.ucalgary.ca/sketchbook/ COMPUTERS,Human-Computer Interaction (HCI)

Human-Computer Interaction Human-Computer Interaction: An Empirical Research Perspective is the definitive guide to empirical research in HCI. The book begins with foundational topics including historical context, the human factor, interaction elements, and the fundamentals of science and research. From there, you'll progress to learning about the methods for conducting an experiment to evaluate a new computer interface or interaction technique. There are detailed discussions and how-to analyses on models of interaction, focusing on descriptive models and predictive models. Writing and publishing a research paper is explored with helpful tips for success. Throughout the book, you'll find hands-on exercises, checklists, and real-world examples. This is your must-have, comprehensive guide to empirical and experimental research in HCI—an essential addition to your HCI library. Master empirical and experimental research with this comprehensive, A-to-Z guide in a concise, hands-on reference Discover the practical and theoretical ins-and-outs of user studies Find exercises, takeaway points, and case studies throughout COMPUTERS,Human-Computer Interaction (HCI)

Designing with the Mind in Mind In this completely updated and revised edition of Designing with the Mind in Mind, Jeff Johnson provides you with just enough background in perceptual and cognitive psychology that user interface (UI) design guidelines make intuitive sense rather than being just a list or rules to follow. Early UI practitioners were trained in cognitive psychology, and developed UI design rules based on it. But as the field has evolved since the first edition of this book, designers enter the field from many disciplines. Practitioners today have enough experience in UI design that they have been exposed to design rules, but it is essential that they understand the psychology behind the rules in order to effectively apply them. In this new edition, you'll find new chapters on human choice and decision making, hand-eye coordination and attention, as well as new examples, figures, and explanations throughout. Provides an essential source for user interface design rules and how, when, and why to apply them Arms designers with the science behind each design rule, allowing them to make informed decisions in projects, and to explain those decisions to others Equips readers with the knowledge to make educated tradeoffs between competing rules, project deadlines, and budget pressures Completely updated and revised, including additional coverage on human choice and decision making, hand-eye coordination and attention, and new mobile and touch-screen examples throughout COMPUTERS,Human-Computer Interaction (HCI)

Multiscreen UX Design People today use technology on different devices in different locations. Users expect to access information on all relevant screens and across multiple channels through smartphones, tablets, laptops/desktops, smart (internet-connected) TVs, and other devices, such as smartwatches for example. Multiscreen is no longer a nice add-on, it’s a requirement. In this environment, user experience needs to cater to multiple devices. This book provides a holistic approach that will help UX professionals to offer a hands-on guide for UX design across multiple screens. It presents an opportunity to learn how to cater designs for customers. Readers will find patterns, strategies, examples and case studies, methodologies, and insights to help inspire them to develop a viable strategy for their own digital products and services. UX professionals will walk through important elements of multiscreen UX: Investigating the devices and their capabilities Understanding the users and their capabilities Considering the context in which users use these devices Navigating next generation information experiences and the future of content management Designing content and UI architecture for multiscreen projects A hands-on, practical guide to UX design for how users approach content – across more than one screen at a time Discusses devices, users, and their practices Includes best practices, real-world examples, and tips and tricks A preface written by Scott Jenson COMPUTERS,Human-Computer Interaction (HCI)

Contextual Design Contextual Design: Design for Life, Second Edition, describes the core techniques needed to deliberately produce a compelling user experience. Contextual design was first invented in 1988 to drive a deep understanding of the user into the design process. It has been used in a wide variety of industries and taught in universities all over the world. Until now, the basic CD approach has needed little revision, but with the wide adoption of handheld devices, especially smartphones, the way technology is integrated into people’s lives has fundamentally changed. Contextual Design V2.0 introduces both the classic CD techniques and the new techniques needed to "design for life", fulfilling core human motives while supporting activities. This completely updated and revised edition is written in a clear, informal style without excessive jargon, and is the must-have book for any UX Design library. Users will find coverage of mobile devices and consumer and business products, all illustrated with new examples, case studies, and discussions on how to use CD with the agile development and other project requirements methods. Provides tactics on how to gather detailed data on how people live, work, and use products Helps develop a coherent picture of a whole user population Presents tactics on how to use the seven "Cool Concepts" to support core human motives and generate new product concepts guided by user data, ideation techniques, and principles key to producing a compelling user experience Explains how to structure the system and user interface to best support the user across place, time, and platform COMPUTERS,Human-Computer Interaction (HCI)

Voice User Interface Projects Develop intelligent voice-empowered applications and Chatbots that not only understand voice commands but also respond to it Key Features Target multiple platforms by creating voice interactions for your applications Explore real-world examples of how to produce smart and practical virtual assistants Build a virtual assistant for cars using Android Auto in Xamarin Book Description From touchscreen and mouse-click, we are moving to voice- and conversation-based user interfaces. By adopting Voice User Interfaces (VUIs), you can create a more compelling and engaging experience for your users. Voice User Interface Projects teaches you how to develop voice-enabled applications for desktop, mobile, and Internet of Things (IoT) devices. This book explains in detail VUI and its importance, basic design principles of VUI, fundamentals of conversation, and the different voice-enabled applications available in the market. You will learn how to build your first voice-enabled application by utilizing DialogFlow and Alexa's natural language processing (NLP) platform. Once you are comfortable with building voice-enabled applications, you will understand how to dynamically process and respond to the questions by using NodeJS server deployed to the cloud. You will then move on to securing NodeJS RESTful API for DialogFlow and Alexa webhooks, creating unit tests and building voice-enabled podcasts for cars. Last but not the least you will discover advanced topics such as handling sessions, creating custom intents, and extending built-in intents in order to build conversational VUIs that will help engage the users. By the end of the book, you will have grasped a thorough knowledge of how to design and develop interactive VUIs. What you will learn Understand NLP platforms with machine learning Exploit best practices and user experiences in creating VUI Build voice-enabled chatbots Host, secure, and test in a cloud platform Create voice-enabled applications for personal digital assistant devices Develop a virtual assistant for cars Who this book is for Voice User Interface Projects is for you if you are a software engineer who wants to develop voice-enabled applications for your personal digital assistant devices such as Amazon Echo and Google Home, along with your car's virtual assistant systems. Some experience with JavaScript is required. COMPUTERS,Human-Computer Interaction (HCI)

From Gutenberg to Google Network revolutions of the past have shaped the present and set the stage for the revolution we are experiencing today In an era of seemingly instant change, it's easy to think that today's revolutions—in communications, business, and many areas of daily life—are unprecedented. Today's changes may be new and may be happening faster than ever before. But our ancestors at times were just as bewildered by rapid upheavals in what we now call “networksâ€â€”the physical links that bind any society together. In this fascinating book, former FCC chairman Tom Wheeler brings to life the two great network revolutions of the past and uses them to help put in perspective the confusion, uncertainty, and even excitement most people face today. The first big network revolution was the invention of movable-type printing in the fifteenth century. This book, its millions of predecessors, and even such broad trends as the Reformation, the Renaissance, and the multiple scientific revolutions of the past 500 years would not have been possible without that one invention. The second revolution came with the invention of the telegraph early in the nineteenth century. Never before had people been able to communicate over long distances faster than a horse could travel. Along with the development of the world's first high-speed network—the railroad—the telegraph upended centuries of stability and literally redrew the map of the world. Wheeler puts these past revolutions into the perspective of today, when rapid-fire changes in networking are upending the nature of work, personal privacy, education, the media, and nearly every other aspect of modern life. But he doesn't leave it there. Outlining “What's Next,†he describes how artificial intelligence, virtual reality, blockchain, and the need for cybersecurity are laying the foundation for a third network revolution. COMPUTERS,Human-Computer Interaction (HCI)

Living in Information Websites and apps are places where critical parts of our lives happen. We shop, bank, learn, gossip, and select our leaders there. But many of these places weren’t intended to support these activities. Instead, they're designed to capture your attention and sell it to the highest bidder. Living in Information draws upon architecture as a way to design information environments that serve our humanity. COMPUTERS,Human-Computer Interaction (HCI)

Handbook of Automotive Human Factors Thanks to advances in computer technology in the last twenty years, navigation system, cabin environment control, ACC, advanced driver assistance system (ADAS) and automated driving have become a part of the automobile experience. Improvement in technology enables us to design these with greater flexibility and provide greater value to the driver (human centered design). To achieve this, research is required by laboratories, automobile and auto parts manufacturers. Although there has been a lot of effort in human factors research and development, starting from basic research to product development, the knowledge and experience has not been integrated optimally. The aim of this book is to collect and review the information for researchers, designers and developers to learn and apply them for further research and development of human centered design of future automotive technologies. Automotive human factors include psychological, physiological, mathematical, engineering and even sociological aspects. This book offers valuable insights to applying the right approach in the right place. COMPUTERS,Human-Computer Interaction (HCI)

Designing Interfaces Designing good application interfaces isn’t easy now that companies need to create compelling, seamless user experiences across an exploding number of channels, screens, and contexts. In this updated third edition, you’ll learn how to navigate through the maze of design options. By capturing UI best practices as design patterns, this best-selling book provides solutions to common design problems. You’ll learn patterns for mobile apps, web applications, and desktop software. Each pattern contains full-color examples and practical design advice you can apply immediately. Experienced designers can use this guide as an idea sourcebook, and novices will find a road map to the world of interface and interaction design. Understand your users before you start designing Build your software’s structure so it makes sense to users Design components to help users complete tasks on any device Learn how to promote wayfinding in your software Place elements to guide users to information and functions Learn how visual design can make or break product usability Display complex data with artful visualizations COMPUTERS,Human-Computer Interaction (HCI)

Designing Displays for Older Adults, Second Edition This book focuses on the design of displays and user interfaces for the older user. Aging is related to complex mental, physical, and social changes. While conventional wisdom says getting older leads to a decline, the reality is that some capabilities decline with age while others remain stable or increase. This book distills decades of aging research into practical advice on the design of displays. Technology has changed dramatically since the publication of the first edition. This new edition covers cutting-edge technology design such as ubiquitous touchscreens, smart speakers, and augmented reality interfaces, among others. COMPUTERS,Human-Computer Interaction (HCI)

The Infinite Retina A compelling and insightful look at the future of Spatial Computing, and how this cutting-edge technology is changing the way we do business across seven primary industries, and what it means for humanity as a whole.Key FeaturesDiscover how Spatial Computing is changing the face of technologyGet a roadmap for the disruptions caused by Spatial Computing and how it will affect seven major industriesGain insights about the past, present, and future of technology from the world's leading experts and innovatorsBook DescriptionWhat is Spatial Computing and why is everyone from Tesla, Apple, and Facebook investing heavily in it?In The Infinite Retina, authors Irena Cronin and Robert Scoble attempt to answer that question by helping you understand where Spatial Computing?an augmented reality where humans and machines can interact in a physical space?came from, where it's going, and why it's so fundamentally different from the computers or mobile phones that came before.They present seven visions of the future and the industry verticals in which Spatial Computing has the most influence?Transportation; Technology, Media, and Telecommunications; Manufacturing; Retail; Healthcare; Finance; and Education.The book also shares insights about the past, present, and future from leading experts an other industry veterans and innovators, including Sebastian Thrun, Ken Bretschneider, and Hugo Swart. They dive into what they think will happen in Spatial Computing in the near and medium term, and also explore what it could mean for humanity in the long term.The Infinite Retina then leaves it up to you to decide whether Spatial Computing is truly where the future of technology is heading or whether it's just an exciting, but passing, phase.What you will learnLook back at historical paradigms that changed the face of technologyConsider how Spatial Computing could be the new technology that changes our livesSee how Virtual and Augmented Reality will change the way we do healthcareLearn how Spatial Computing technology will lead to fully automated transportationThink about how Spatial Computing will change the manufacturing industryExplore how finance and retail are going to be impacted through Spatial Computing devicesHear accounts from industry experts on what they expect Spatial Computing to bring to their sectorsWho this book is forThe Infinite Retina is for anyone interested in the future of technology and how Augmented Reality and Spatial Computing (among other developments) will affect both businesses and the individual. COMPUTERS,Human-Computer Interaction (HCI)

Handbook of Human Factors for Automated, Connected, and Intelligent Vehicles Handbook of Human Factors for Automated, Connected, and Intelligent Vehicles Subject Guide: Ergonomics & Human Factors Automobile crashes are the seventh leading cause of death worldwide, resulting in over 1.25 million deaths yearly. Automated, connected, and intelligent vehicles have the potential to reduce crashes significantly, while also reducing congestion, carbon emissions, and increasing accessibility. However, the transition could take decades. This new handbook serves a diverse community of stakeholders, including human factors researchers, transportation engineers, regulatory agencies, automobile manufacturers, fleet operators, driving instructors, vulnerable road users, and special populations. It provides information about the human driver, other road users, and human–automation interaction in a single, integrated compendium in order to ensure that automated, connected, and intelligent vehicles reach their full potential. Features Addresses four major transportation challenges—crashes, congestion, carbon emissions, and accessibility—from a human factors perspective Discusses the role of the human operator relevant to the design, regulation, and evaluation of automated, connected, and intelligent vehicles Offers a broad treatment of the critical issues and technological advances for the designing of transportation systems with the driver in mind Presents an understanding of the human factors issues that are central to the public acceptance of these automated, connected, and intelligent vehicles Leverages lessons from other domains in understanding human interactions with automation Sets the stage for future research by defining the space of unexplored questions COMPUTERS,Human-Computer Interaction (HCI)

Post Normal Accident Post Normal Accident revisits Perrow’s classic Normal Accident published in 1984 and provides additional insights to our sociological view of safety-critical organisations. The operating landscape of high-risk systems has indeed profoundly changed in the past 20 to 30 years but the core sociological models of safety remain associated with classics of the 1980s and 1990s. This book examines the conceptual and empirical evolutions of the past two to three decades to explore their implications for safety management based on several strands of works in various research traditions in safety (e.g. cognitive engineering and system safety, high-reliability organisation, sociology of safety, regulatory studies) and other interdisciplinary fields (e.g. international business, globalisation studies, strategy management, ecology). It offers a new and insightful interpretation to the challenges of today. It investigates how globalisation has reconfigured the operating landscape of high-risk systems and emphasises the importance of thinking safety through a strategic angle. This book serves as an ideal resource for the safety professionals and safety researchers from any established disciplines such as sociology, engineering, psychology, political science or management. Features: Introduces an original analysis of popular safety writings, including Normal Accident, by Perrow Identifies the importance of thinking safety from a sociological angle with the help of key writers Stresses the need for greater sensitivity to strategy and "errors from the top" when it comes to the safety of high-risk systems Explains how globalisation has reconfigured the operating landscape of high-risk systems Renews our understanding of the current safety management challenges in an increasingly global risk picture COMPUTERS,Human-Computer Interaction (HCI)

Transparency for Robots and Autonomous Systems Based on scientific understanding and empirical evidence of how humans understand and interact with robotic and autonomous systems, this book reviews the concerns that have been raised around the deployment of AI and robots in human society, and the potential for disruption and harm. COMPUTERS,Human-Computer Interaction (HCI)

Acting with Technology A systematic presentation of activity theory, its application to interaction design, and an argument for the development of activity theory as a basis for understanding how people interact with technology. Activity theory holds that the human mind is the product of our interaction with people and artifacts in the context of everyday activity. Acting with Technology makes the case for activity theory as a basis for understanding our relationship with technology. Victor Kaptelinin and Bonnie Nardi describe activity theory's principles, history, relationship to other theoretical approaches, and application to the analysis and design of technologies. The book provides the first systematic entry-level introduction to the major principles of activity theory. It describes the accumulating body of work in interaction design informed by activity theory, drawing on work from an international community of scholars and designers. Kaptelinin and Nardi examine the notion of the object of activity, describe its use in an empirical study, and discuss key debates in the development of activity theory. Finally, they outline current and future issues in activity theory, providing a comparative analysis of the theory and its leading theoretical competitors within interaction design: distributed cognition, actor-network theory, and phenomenologically inspired approaches. COMPUTERS,Human-Computer Interaction (HCI)

Mood and Mobility An argument that as we engage with social media on our digital devices we receive, modify, intensify, and transmit moods. We are active with our mobile devices; we play games, watch films, listen to music, check social media, and tap screens and keyboards while we are on the move. In Mood and Mobility, Richard Coyne argues that not only do we communicate, process information, and entertain ourselves through devices and social media; we also receive, modify, intensify, and transmit moods. Designers, practitioners, educators, researchers, and users should pay more attention to the moods created around our smartphones, tablets, and laptops. Drawing on research from a range of disciplines, including experimental psychology, phenomenology, cultural theory, and architecture, Coyne shows that users of social media are not simply passive receivers of moods; they are complicit in making moods. Devoting each chapter to a particular mood—from curiosity and pleasure to anxiety and melancholy—Coyne shows that devices and technologies do affect people's moods, although not always directly. He shows that mood effects are transitional; different moods suit different occasions, and derive character from emotional shifts. Furthermore, moods are active; we enlist all the resources of human sociability to create moods. And finally, the discourse about mood is deeply reflexive; in a kind of meta-moodiness, we talk about our moods and have feelings about them. Mood, in Coyne's distinctive telling, provides a new way to look at the ever-changing world of ubiquitous digital technologies. COMPUTERS,Human-Computer Interaction (HCI)

Reality Mining A look at how Big Data can be put to positive use, from helping users break bad habits to tracking the global spread of disease. Big Data is made up of lots of little data: numbers entered into cell phones, addresses entered into GPS devices, visits to websites, online purchases, ATM transactions, and any other activity that leaves a digital trail. Although the abuse of Big Data—surveillance, spying, hacking—has made headlines, it shouldn't overshadow the abundant positive applications of Big Data. In Reality Mining, Nathan Eagle and Kate Greene cut through the hype and the headlines to explore the positive potential of Big Data, showing the ways in which the analysis of Big Data (“Reality Mining”) can be used to improve human systems as varied as political polling and disease tracking, while considering user privacy. Eagle, a recognized expert in the field, and Greene, an experienced technology journalist, describe Reality Mining at five different levels: the individual, the neighborhood and organization, the city, the nation, and the world. For each level, they first offer a nontechnical explanation of data collection methods and then describe applications and systems that have been or could be built. These include a mobile app that helps smokers quit smoking; a workplace “knowledge system”; the use of GPS, Wi-Fi, and mobile phone data to manage and predict traffic flows; and the analysis of social media to track the spread of disease. Eagle and Greene argue that Big Data, used respectfully and responsibly, can help people live better, healthier, and happier lives. COMPUTERS,Human-Computer Interaction (HCI)

The Stuff of Bits An argument that the material arrangements of information—how it is represented and interpreted—matter significantly for our experience of information and information systems. Virtual entities that populate our digital experience, like e-books, virtual worlds, and online stores, are backed by the large-scale physical infrastructures of server farms, fiber optic cables, power plants, and microwave links. But another domain of material constraints also shapes digital living: the digital representations sketched on whiteboards, encoded into software, stored in databases, loaded into computer memory, and transmitted on networks. These digital representations encode aspects of our everyday world and make them available for digital processing. The limits and capacities of those representations carry significant consequences for digital society. In The Stuff of Bits, Paul Dourish examines the specific materialities that certain digital objects exhibit. He presents four case studies: emulation, the creation of a “virtual” computer inside another; digital spreadsheets and their role in organizational practice; relational databases and the issue of “the databaseable”; and the evolution of digital networking and the representational entailments of network protocols. These case studies demonstrate how a materialist account can offer an entry point to broader concerns—questions of power, policy, and polity in the realm of the digital. COMPUTERS,Human-Computer Interaction (HCI)

Embodied Computing Practitioners and scholars explore ethical, social, and conceptual issues arising in relation to such devices as fitness monitors, neural implants, and a toe-controlled computer mouse. Body-centered computing now goes beyond the “wearable” to encompass implants, bionic technology, and ingestible sensors—technologies that point to hybrid bodies and blurred boundaries between human, computer, and artificial intelligence platforms. Such technologies promise to reconfigure the relationship between bodies and their environment, enabling new kinds of physiological interfacing, embodiment, and productivity. Using the term embodied computing to describe these devices, this book offers essays by practitioners and scholars from a variety of disciplines that explore the accompanying ethical, social, and conceptual issues. The contributors examine technologies that range from fitness monitors to neural implants to a toe-controlled mouse. They discuss topics that include the policy implications of ingestibles; the invasive potential of body area networks, which transmit data from bodily devices to the internet; cyborg experiments, linking a human brain directly to a computer; the evolution of the ankle monitor and other intrusive electronic monitoring devices; fashiontech, which offers users an aura of “cool” in exchange for their data; and the “final frontier” of technosupremacism: technologies that seek to read our minds. Taken together, the essays show the importance of considering embodied technologies in their social and political contexts rather than in isolated subjectivity or in purely quantitative terms. Contributors Roba Abbas, Andrew Iliadis, Gary Genosko, Suneel Jethani, Deborah Lupton, Katina Michael, M. G. Michael, Marcel O'Gorman, Maggie Orth, Isabel Pedersen, Christine Perakslis, Kevin Warwick, Elizabeth Wissinger COMPUTERS,Human-Computer Interaction (HCI)

The Tuning of Place How pervasive digital devices—smartphones, iPods, GPS navigation systems, and their networks—us formulate a sense of place and refine social relationships How do pervasive digital devices—smartphones, iPods, GPS navigation systems, and cameras, among others—influence the way we use spaces? In The Tuning of Place, Richard Coyne argues that these ubiquitous devices and the networks that support them become the means of making incremental adjustments within spaces—of tuning place. Pervasive media help us formulate a sense of place, writes Coyne, through their capacity to introduce small changes, in the same way that tuning a musical instrument invokes the subtle process of recalibration. Places are inhabited spaces, populated by people, their concerns, memories, stories, conversations, encounters, and artifacts. The tuning of place—whereby people use their devices in their interactions with one another—is also a tuning of social relations. The range of ubiquity is vast—from the familiar phones and hand-held devices through RFID tags, smart badges, dynamic signage, microprocessors in cars and kitchen appliances, wearable computing, and prosthetics, to devices still in development. Rather than catalog achievements and predictions, Coyne offers a theoretical framework for discussing pervasive media that can inform developers, designers, and users as they contemplate interventions into the environment. Processes of tuning can lead to consideration of themes highly relevant to pervasive computing: intervention, calibration, wedges, habits, rhythm, tags, taps, tactics, thresholds, aggregation, noise, and interference. COMPUTERS,Human-Computer Interaction (HCI)

Taking [A]part A critical inquiry into the value and experience of participation in design research. In Taking [A]part, John McCarthy and Peter Wright consider a series of boundary-pushing research projects in human-computer interaction (HCI) in which the design of digital technology is used to inquire into participative experience. McCarthy and Wright view all of these projects—which range from the public and performative to the private and interpersonal—through the critical lens of participation. Taking participation, in all its variety, as the generative and critical concept allows them to examine the projects as a part of a coherent, responsive movement, allied with other emerging movements in DIY culture and participatory art. Their investigation leads them to rethink such traditional HCI categories as designer and user, maker and developer, researcher and participant, characterizing these relationships instead as mutually responsive and dialogical. McCarthy and Wright explore four genres of participation—understanding the other, building relationships, belonging in community, and participating in publics—and they examine participatory projects that exemplify each genre. These include the Humanaquarium, a participatory musical performance; the Personhood project, in which a researcher and a couple explored the experience of living with dementia; the Prayer Companion project, which developed a technology to inform the prayer life of cloistered nuns; and the development of social media to support participatory publics in settings that range from reality game show fans to on-line deliberative democracies. COMPUTERS,Human-Computer Interaction (HCI)

Heteromation, and Other Stories of Computing and Capitalism An exploration of a new division of labor between machines and humans, in which people provide value to the economy with little or no compensation. The computerization of the economy—and everyday life—has transformed the division of labor between humans and machines, shifting many people into work that is hidden, poorly compensated, or accepted as part of being a “user” of digital technology. Through our clicks and swipes, logins and profiles, emails and posts, we are, more or less willingly, participating in digital activities that yield economic value to others but little or no return to us. Hamid Ekbia and Bonnie Nardi call this kind of participation—the extraction of economic value from low-cost or free labor in computer-mediated networks—“heteromation.” In this book, they explore the social and technological processes through which economic value is extracted from digitally mediated work, the nature of the value created, and what prompts people to participate in the process. Arguing that heteromation is a new logic of capital accumulation, Ekbia and Nardi consider different kinds of heteromated labor: communicative labor, seen in user-generated content on social media; cognitive labor, including microwork and self-service; creative labor, from gaming environments to literary productions; emotional labor, often hidden within paid jobs; and organizing labor, made up of collaborative groups such as citizen scientists. Ekbia and Nardi then offer a utopian vision: heteromation refigured to bring end users more fully into the prosperity of capitalism. COMPUTERS,Human-Computer Interaction (HCI)

Where the Action Is Computer science as an engineering discipline has been spectacularly successful. Yet it is also a philosophical enterprise in the way it represents the world and creates and manipulates models of reality, people, and action. In this book, Paul Dourish addresses the philosophical bases of human-computer interaction. He looks at how what he calls "embodied interaction"—an approach to interacting with software systems that emphasizes skilled, engaged practice rather than disembodied rationality—reflects the phenomenological approaches of Martin Heidegger, Ludwig Wittgenstein, and other twentieth-century philosophers. The phenomenological tradition emphasizes the primacy of natural practice over abstract cognition in everyday activity. Dourish shows how this perspective can shed light on the foundational underpinnings of current research on embodied interaction. He looks in particular at how tangible and social approaches to interaction are related, how they can be used to analyze and understand embodied interaction, and how they could affect the design of future interactive systems. COMPUTERS,Human-Computer Interaction (HCI)

Ambient Commons On rediscovering surroundings when information goes everywhere. The world is filling with ever more kinds of media, in ever more contexts and formats. Glowing rectangles have become part of the scene; screens, large and small, appear everywhere. Physical locations are increasingly tagged and digitally augmented. Amid this flood, your attention practices matter more than ever. You might not be able to tune this world out. So it is worth remembering that underneath all these augmentations and data flows, fixed forms persist, and that to notice them can improve other sensibilities. In Ambient Commons, Malcolm McCullough explores the workings of attention through a rediscovery of surroundings. McCullough describes what he calls the Ambient: an increasing tendency to perceive information superabundance whole, where individual signals matter less and at least some mediation assumes inhabitable form. He explores how the fixed forms of architecture and the city play a cognitive role in the flow of ambient information. As a persistently inhabited world, can the Ambient be understood as a shared cultural resource, to be socially curated, voluntarily limited, and self-governed as if a commons? Ambient Commons invites you to look past current obsessions with smart phones to rethink attention itself, to care for more situated, often inescapable forms of information. COMPUTERS,Human-Computer Interaction (HCI)

Thoughtful Interaction Design The authors of Thoughtful Interaction Design go beyond the usual technical concerns of usability and usefulness to consider interaction design from a design perspective. The shaping of digital artifacts is a design process that influences the form and functions of workplaces, schools, communication, and culture; the successful interaction designer must use both ethical and aesthetic judgment to create designs that are appropriate to a given environment. This book is not a how-to manual, but a collection of tools for thought about interaction design.Working with information technology—called by the authors "the material without qualities"—interaction designers create not a static object but a dynamic pattern of interactivity. The design vision is closely linked to context and not simply focused on the technology. The authors' action-oriented and context-dependent design theory, drawing on design theorist Donald Schön's concept of the reflective practitioner, helps designers deal with complex design challenges created by new technology and new knowledge. Their approach, based on a foundation of thoughtfulness that acknowledges the designer's responsibility not only for the functional qualities of the design product but for the ethical and aesthetic qualities as well, fills the need for a theory of interaction design that can increase and nurture design knowledge. From this perspective they address the fundamental question of what kind of knowledge an aspiring designer needs, discussing the process of design, the designer, design methods and techniques, the design product and its qualities, and conditions for interaction design. COMPUTERS,Human-Computer Interaction (HCI)

Quantified What is at stake socially, culturally, politically, and economically when we routinely use technology to gather information about our bodies and environments? Today anyone can purchase technology that can track, quantify, and measure the body and its environment. Wearable or portable sensors detect heart rates, glucose levels, steps taken, water quality, genomes, and microbiomes, and turn them into electronic data. Is this phenomenon empowering, or a new form of social control? Who volunteers to enumerate bodily experiences, and who is forced to do so? Who interprets the resulting data? How does all this affect the relationship between medical practice and self care, between scientific and lay knowledge? Quantified examines these and other issues that arise when biosensing technologies become part of everyday life. The book offers a range of perspectives, with views from the social sciences, cultural studies, journalism, industry, and the nonprofit world. The contributors consider data, personhood, and the urge to self-quantify; legal, commercial, and medical issues, including privacy, the outsourcing of medical advice, and self-tracking as a “paraclinical” practice; and technical concerns, including interoperability, sociotechnical calibration, alternative views of data, and new space for design. Contributors Marc Böhlen, Geoffrey C. Bowker, Sophie Day, Anna de Paula Hanika, Deborah Estrin, Brittany Fiore-Gartland, Dana Greenfield, Judith Gregory, Mette Kragh-Furbo, Celia Lury, Adrian Mackenzie, Rajiv Mehta, Maggie Mort, Dawn Nafus, Gina Neff, Helen Nissenbaum, Heather Patterson, Celia Roberts, Jamie Sherman, Alex Taylor, Gary Wolf COMPUTERS,Human-Computer Interaction (HCI)

The Systemic Image A new conceptualization of the relationship between the systemic and the iconic in real-time simulations that distinguishes among four levels of forming. Computer simulations conceive objects and situations dynamically, in their changes and progressions. In The Systemic Image, Inge Hinterwaldner considers not only the technical components of dynamic computer simulations but also the sensory aspects of the realization. Examining the optic, the acoustic, the tactile, and the sensorimotor impressions that interactive real-time simulations provide, she finds that iconicity plays a dominant yet unexpected role. Based on this, and close readings of a series of example works, Hinterwaldner offers a new conceptualization of the relationship between systemic configuration and the iconic aspects in these calculated complexes. Hinterwaldner discusses specifications of sensorialization, necessary to make the simulation dynamic perceivable. Interweaving iconicity with simulation, she explores the expressive possibilities that can be achieved under the condition of continuously calculated explicit changes. She distinguishes among four levels of forming: the systems perspective, as a process and schema that establishes the most general framework of simulations; the mathematical model, which marks off the boundaries of the simulation's actualization; the iconization and its orientation toward the user; and interaction design, necessary for the full unfolding of the simulation. The user makes manifest what is initially latent. Viewing the simulation as an interface, Hinterwaldner argues that not only does the sensorially designed aspect of the simulation seduce the user but the user also makes an impact on the simulation—on the dynamic and perhaps on the iconization, although not on the perspectivation. The influence is reciprocal. COMPUTERS,Human-Computer Interaction (HCI)

Human Information Interaction A fresh research approach that bridges the study of human information interaction and the design of information systems. Human information interaction (HII) is an emerging area of study that investigates how people interact with information; its subfield human information behavior (HIB) is a flourishing, active discipline. Yet despite their obvious relevance to the design of information systems, these research areas have had almost no impact on systems design. One issue may be the contextual complexity of human interaction with information; another may be the difficulty in translating real-life and unstructured HII complexity into formal, linear structures necessary for systems design. In this book, Raya Fidel proposes a research approach that bridges the study of human information interaction and the design of information systems: cognitive work analysis (CWA). Developed by Jens Rasmussen and his colleagues, CWA embraces complexity and provides a conceptual framework and analytical tools that can harness it to create design requirements. CWA offers an ecological approach to design, analyzing the forces in the environment that shape human interaction with information. Fidel reviews research in HIB, focusing on its contribution to systems design, and then presents the CWA framework. She shows that CWA, with its ecological approach, can be used to overcome design challenges and lead to the development of effective systems. Researchers and designers who use CWA can increase the diversity of their analytical tools, providing them with an alternative approach when they plan research and design projects. The CWA framework enables a collaboration between design and HII that can create information systems tailored to fit human lives. COMPUTERS,Human-Computer Interaction (HCI)

Collaborative Media A thorough analysis of contemporary digital media practices, showing how people increasingly not only consume but also produce and even design media. With many new forms of digital media–including such popular social media as Facebook, Twitter, and Flickr—the people formerly known as the audience no longer only consume but also produce and even design media. Jonas Löwgren and Bo Reimer term this phenomenon collaborative media, and in this book they investigate the qualities and characteristics of these forms of media in terms of what they enable people to do. They do so through an interdisciplinary research approach that combines the social sciences and humanities traditions of empirical and theoretical work with practice-based, design-oriented interventions. Löwgren and Reimer offer analysis and a series of illuminating case studies—examples of projects in collaborative media that range from small multidisciplinary research experiments to commercial projects used by millions of people. Löwgren and Reimer discuss the case studies at three levels of analysis: society and the role of collaborative media in societal change; institutions and the relationship of collaborative media with established media structures; and tribes, the nurturing of small communities within a large technical infrastructure. They conclude by advocating an interventionist turn within social analysis and media design. COMPUTERS,Human-Computer Interaction (HCI)

Positive Computing A case for building a digital environment that can make us happier and healthier, not just more productive, and a theoretical framework for doing so. On the eve of Google's IPO in 2004, Larry Page and Sergey Brin vowed not to be evil. Today, a growing number of technologists would go further, trying to ensure that their work actively improves people's lives. Technology, so pervasive and ubiquitous, has the capacity to increase stress and suffering; but it also has the less-heralded potential to improve the well-being of individuals, society, and the planet. In this book, Rafael Calvo and Dorian Peters investigate what they term “positive computing”—the design and development of technology to support psychological well-being and human potential. Calvo and Peters explain that technologists' growing interest in social good is part of a larger public concern about how our digital experience affects our emotions and our quality of life—which itself reflects an emerging focus on humanistic values in many different disciplines. Synthesizing theory, knowledge, and empirical methodologies from a variety of fields, they offer a rigorous and coherent foundational framework for positive computing. Sidebars by experts from psychology, neuroscience, human–computer interaction, and other disciplines supply essential context. Calvo and Peters examine specific well-being factors, including positive emotions, self-awareness, mindfulness, empathy, and compassion, and explore how technology can support these factors. Finally, they offer suggestions for future research and funding. Sidebars Timothy N. Bickmore, Jeremy Bailenson, danah boyd, Jane Burns, David R. Caruso, Mihaly Csikszentmihalyi, Felicia Huppert, Mary-Helen Immordino-Yang, Adele Krusche and J. Mark G. Williams, Jane McGonigal, Jonathan Nicholas, Don Norman, Yvonne Rogers COMPUTERS,Human-Computer Interaction (HCI)

Introduction to Non-Invasive EEG-Based Brain-Computer Interfaces for Assistive Technologies This book aims to bring to the reader an overview of different applications of brain-computer interfaces (BCIs) based on more than 20 years of experience working on these interfaces. The author provides a review of the human brain and EEG signals, describing the human brain, anatomically and physiologically, with the objective of showing some of the patterns of EEG (electroencephalogram) signals used to control BCIs. It then introduces BCIs and different applications, such as a BCI based on ERD/ERS Patterns in α rhythms (used to command a robotic wheelchair with an augmentative and alternative communication (AAC) system onboard it); a BCI based on dependent-SSVEP to command the same robotic wheelchair; a BCI based on SSVEP to command a telepresence robot and its onboard AAC system; a BCI based on SSVEP to command an autonomous car; a BCI based on independent-SSVEP (using Depth-of-Field) to command the same robotic wheelchair; the use of compressive technique in SSVEP-based BCI; a BCI based on motor imagery (using different techniques) to command a robotic monocycle and a robotic exoskeleton; and the first steps to build a neurorehabilitation system based on motor imagery of pedalling together an in immersive virtual environment. This book is intended for researchers, professionals and students working on assistive technology. COMPUTERS,Human-Computer Interaction (HCI)

GIMP Bible The ultimate reference and guide to the GNU image manipulation program GIMP is a free, Photoshop-like image manipulation program, and as its use grows, so does the demand for detailed instruction on how to get the very most out of it. GIMP Bible is the most comprehensive and current independent GIMP reference available that goes beyond official documentation. If you're a digital artist or photographer, the step-by-step explanations in this authoritative guide show you how to power-use GIMP throughout a production pipeline. Topics include understanding the GIMP interface and how to work with it, how to use all of GIMP's tools to create high-quality images, GIMP's default filters and plug-ins, advanced techniques for customization with Python and Scheme scripting, and much more. GIMP (GNU Image Manipulation Program) is a free graphics editor that runs on Linux, Windows, or Macs; it is used to process digital graphics and photographs including creating graphics and logos, resizing and cropping photos, altering colors, combining images, creating basic GIF animated images, and more Whether you're a digital artist, professional photographer, or beginner, this detailed how-to shows you best practices, valuable techniques, and helpful tips for getting the most out of GIMP for your projects Topics include the GIMP interface and how to work with it, in-depth description of GIMP's tools and how to use them to create high-quality images, a comprehensive reference for all of GIMP's default filters and common plug-ins, and advanced customization with Python and Scheme scripting Get the most out of this free image editing tool for your production pipeline with the GIMP Bible. Note: CD-ROM/DVD and other supplementary materials are not included as part of eBook file. COMPUTERS,Image Processing

Google SketchUp 8 For Dummies Go 3D with Google's exciting architectural design software for Mac and Windows Whether you need to learn 3D modeling for business or you're just eager to see what you can create, Google SketchUp and Google SketchUp 8 For Dummies are for you. Available in both a free hobbyist version and a full-featured professional version, SketchUp explodes the myth that 3D modeling software must be complicated to learn and use. This book will take you step by step through downloading and using both versions on both Mac and Windows. There are even video walkthroughs on the companion Web site. Google's exciting 3D modeling software offers hobbyists as well as architects, engineers, and industrial designers a less complicated tool for architectural rendering, urban planning, set design, game design, and other uses This guide explains both the free and professional versions for both Windows and Mac Covers the basic concepts of 3D modeling and how to build a 3D model, print or share your work online, export your drawing to another design package or Google Earth, and create a detailed set of plans Companion Web site features video walkthroughs Google SketchUp 8 For Dummies gets you up and running with 3D modeling quickly and easily. COMPUTERS,Image Processing

Photoshop CS6 For Dummies The bestselling guide to the leading image-editing software, Photoshop CS6, fully updated! Want picture-perfect photos, every time? Get up to speed on the most popular professional photo-editing software on the market: Photoshop. In this new edition of Photoshop CS6 For Dummies, expert Peter Bauer shows you how to use the latest Photoshop tools to change a background, adjust brightness, improve color, or fix flaws. Richly illustrated in full color, this edition covers all the updates in Photoshop CS6, the gold standard for image-editing programs. Used by professional photographers, graphic designers, Web designers, and serious hobbyists, Photoshop has more than four million users worldwide. Photoshop is the image-editing software preferred by professional photographers and designers around the world; the latest version includes new functionality and enhanced tools Teaches all the basics for first-time users and advanced techniques for more experienced digital imaging professionals, including how to work with the menus, panels, tools, options, and essential shortcuts Covers how to fix red-eye, remove blemishes and wrinkles, remove people or objects from a photo, adjust brightness, improve color, add shadows and highlights, work with Camera Raw, decrease digital noise, create composite images, use channels and masks, work with HDR tools, and optimize images for the web Photoshop CS6 For Dummies helps both amateur and professional Photoshop users take advantage of all the program has to offer. COMPUTERS,Image Processing

AutoCAD 2018 and AutoCAD LT 2018 Essentials The step-by-step, full-color AutoCAD 2018 guide with real-world practicality AutoCAD 2018 and AutoCAD LT 2018 Essentials provides a full-color, task-based approach to mastering this powerful software. Straightforward, easy-to-follow instruction pairs with real-world, hands-on exercises to help you quickly get up to speed with core features and functions; screenshots illustrate tutorial steps to help you follow along, and each chapter concludes with a more open-ended project so you can dive in and explore a specific topic in-depth. From 2D drawing and organization to 3D modeling, dimensioning, presenting, and more, this helpful guide walks you through everything you need to know to become productive with AutoCAD 2018 and AutoCAD LT 2018. The companion website features downloadable starting and ending files for each exercise, so you can jump in at any point and compare your work to the pros, as well as additional tutorials to help you go as deep as you need to go. Exercises walk you through the real-world process of drafting while teaching you critical skills along the way. Understand the AutoCAD interface and foundational concepts Master essential drawing and visualization tools Stay organized with layers, groups, and blocks Experiment with 3D modeling, add text and dimensions, and much more AutoCAD is the industry-leading technical drawing software, and complete mastery is a vital skill for any design and drafting professional. AutoCAD 2018 and AutoCAD LT 2018 Essentials is a smart, quick resource that will help you get up to speed with real-world practical instruction. COMPUTERS,Image Processing

Mastering Autodesk Revit 2018 The best-selling Revit guide, now more complete than ever with all-new coverage on the 2018 release Mastering Autodesk Revit 2018 for Architecture is packed with focused discussions, detailed exercises, and real-world examples to help you get up to speed quickly on the latest version of Autodesk Revit for Architecture. Organized according to how you learn and implement the software, this book provides expert guidance for all skill levels. Hands-on tutorials allow you to dive right in and start accomplishing vital tasks, while compelling examples illustrate how Revit for Architecture is used in every project. Available online downloads include before-and-after tutorial files and additional advanced content to help you quickly master this powerful software. From basic interface topics to advanced visualization techniques and documentation, this invaluable guide is your ideal companion through the Revit Architecture workflow. Whether you're preparing for Autodesk certification exams or just want to become more productive with the architectural design software, practical exercises and expert instruction will get you where you need to be. Understand key BIM and Revit concepts and master the Revit interface Delve into templates, work-sharing, and managing Revit projects Master modeling and massing, the Family Editor, and visualization techniques Explore documentation, including annotation, detailing, and complex structures BIM software has become a mandatory asset in today's architecture field; automated documentation updates reduce errors while saving time and money, and Autodesk's Revit is the industry leader in the BIM software space. COMPUTERS,Image Processing

Mastering AutoCAD 2018 and AutoCAD LT 2018 30th Anniversary of the bestselling AutoCAD reference - fully updated for the 2018 release Mastering AutoCAD 2018 and AutoCAD LT 2018 is the complete tutorial and reference every design and drafting professional needs. Step-by-step instructions coupled with concise explanation walk you through everything you need to know about the latest AutoCAD tools and techniques; read through from beginning to end for complete training, or dip in as needed to for quick reference—it's all here. Hands-on projects teach you practical skills that apply directly to real-world projects, and the companion website features the accompanying project files and other bonus content to help you master every crucial technique. This new edition has been updated to include the latest AutoCAD and AutoCAD LT capabilities, so your skills will transfer directly to real-world projects. With expert guidance and a practical focus, this complete reference is your ultimate resource for mastering this powerful software. AutoCAD is a critical skill in the design fields; whether you're preparing for a certification exam, or just want to become more productive with the software, this book will help you: Master the basic drafting tools that you'll use in every project Work with hatches, fields, tables, attributes, dynamic blocks, and other intermediate tools Turn your 2D drawing into a 3D model with advanced modeling and imaging techniques Customize AutoCAD to fit the way you work, integrate outside data, and much more If you're new to AutoCAD, this book will be your "bible;" if you're an experienced user, this book will introduce you to unfamiliar tools and techniques, and show you tips and tricks that streamline your workflow. COMPUTERS,Image Processing

Adobe Photoshop CC For Dummies The fast and easy way to grasp Photoshop CC essentials Photoshop is the gold standard when it comes to photo and image editing tools. But unless you've ever taken a class or gotten help from a Photoshop guru, you may find yourself a bit confused on where to start and how to get things done. Photoshop CC For Dummies, 2nd Edition is the book for those of us who don't know a layer from a level and just want to learn how to make photos look better. This update to Photoshop CC For Dummies, the first since the product launched, packs an even more powerful punch to help you manage and enhance your images. In Photoshop CC For Dummies, 2nd Edition you'll find clear explanations of the menus, panels, tools, options, and shortcuts you'll use the most. Plus, you'll discover invaluable tips for fixing common photo flaws, improving color quality, adjusting brightness, removing unwanted background elements, and more. Whether you want to improve how your family photos look or need to add a new skillset to your resume, this friendly guide gives you all the steps to navigating the software and getting top-notch results. Get a handle on the most common tools Improve focus and color in photos Add text and illustrations to create stunning graphics Find insider tips and tricks the pros use The sky's the limit for stunning photos and innovative images when you have Photoshop CC For Dummies, 2nd Edition in your design toolbox! COMPUTERS,Image Processing

Mastering AutoCAD 2019 and AutoCAD LT 2019 The world’s favorite guide to everything AutoCAD and AutoCAD LT—updated for 2019! Mastering AutoCAD 2019 and AutoCAD LT 2019 is the world’s all-time best-selling guide to the world’s most popular drafting software. Packed with tips, tricks, techniques, and tutorials, this guide covers every inch of AutoCAD and AutoCAD LT—including certification. This new edition has been fully updated to align with the software’s 2019 update, featuring the same expert instruction augmented by videos of crucial techniques. Step-by-step walk-throughs, concise explanations, specific examples and plenty of hands-on projects help you learn essential AutoCAD skills by working directly with the necessary tools—giving you a skill set that translates directly to on-the-job use. AutoCAD is the dominant design and drafting software for 2D and 3D technical drawings, while AutoCAD LT is the more affordable version often used by students and hobbyists. Professional designers need complete command of the software’s tools and functions, but a deeper exploration of more complex capabilities can help even hobbyists produce work at a higher level of technical proficiency. This book is your ultimate guide to AutoCAD and AutoCAD LT, whether you’re seeking certification or just looking to draw. Get acquainted with the workspace and basic drafting tools Gain greater control of your drawings with hatches, fields, fills, dynamic blocks, and curves Explore the 3D modeling and imaging tools that bring your drawing to life Customize AutoCAD to the way you work, integrate it with other software, and more As certification preparation material, this book is Autodesk-endorsed; as a self-study guide to AutoCAD and AutoCAD LT mastery, this book is the gold-standard, having led over a half million people on the journey to better design. If you’re ready to learn quickly so you can get down to work, Mastering AutoCAD 2019 and AutoCAD LT 2019 is your ideal resource. COMPUTERS,Image Processing

Image Processing And Analysis This textbook guides readers through their first steps into the challenging world of mimicking human vision with computational tools and techniques pertaining to the field of image processing and analysis. While today's theoretical and applied processing and analysis of images meet with challenging and complex problems, this primer is confined to a much simpler, albeit critical, collection of image-to-image transformations, including image normalisation, enhancement, and filtering.It serves as an introduction to beginners, a refresher for undergraduate and graduate students, as well as engineers and computer scientists confronted with a problem to solve in computer vision. The book covers basic image processing/computer vision pipeline techniques, which are widely used in today's computer vision, computer graphics, and image processing, giving the readers enough knowledge to successfully tackle a wide range of applied problems. COMPUTERS,Image Processing

Mastering SolidWorks The complete SolidWorks reference-tutorial for beginner to advanced techniques Mastering SolidWorks is the reference-tutorial for all users. Packed with step-by-step instructions, video tutorials for over 40 chapters, and coverage of little-known techniques, this book takes you from novice to power user with clear instruction that goes beyond the basics. Fundamental techniques are detailed with real-world examples for hands-on learning, and the companion website provides tutorial files for all exercises. Even veteran users will find value in new techniques that make familiar tasks faster, easier, and more organized, including advanced file management tools that simplify and streamline pre-flight checks. SolidWorks is the leading 3D CAD program, and is an essential tool for engineers, mechanical designers, industrial designers, and drafters around the world. User friendly features such as drag-and-drop, point-and-click, and cut-and-paste tools belie the software’s powerful capabilities that can help you create cleaner, more precise, more polished designs in a fraction of the time. This book is the comprehensive reference every SolidWorks user needs, with tutorials, background, and more for beginner to advanced techniques. Get a grasp on fundamental SolidWorks 2D and 3D tasks using realistic examples with text-based tutorials Delve into advanced functionality and capabilities not commonly covered by how-to guides Incorporate improved search, Pack-and-Go and other file management tools into your workflow Adopt best practices and exclusive techniques you won’t find anywhere else Work through this book beginning-to-end as a complete SolidWorks course, or dip in as needed to learn new techniques and time-saving tricks on-demand. Organized for efficiency and designed for practicality, these tips will remain useful at any stage of expertise. With exclusive coverage and informative detail, Mastering SolidWorks is the tutorial-reference for users at every level of expertise. COMPUTERS,Image Processing

Mastering Autodesk Revit 2020 The best-selling Revit guide, now more complete than ever with all-new coverage on the 2020 release Mastering Autodesk Revit 2020 is packed with focused discussions, detailed exercises, and real-world examples to help you get up to speed quickly on the latest version of Autodesk Revit. Organized according to how you learn and implement the software, this book provides expert guidance for all skill levels. Hands-on tutorials allow you to dive right in and start accomplishing vital tasks, while compelling examples illustrate how Revit for Architecture is used in every project. Available online downloads include before-and-after tutorial files and additional advanced content to help you quickly master this powerful software. From basic interface topics to advanced visualization techniques and documentation, this invaluable guide is your ideal companion through the Revit workflow. Whether you're preparing for Autodesk certification exams or just want to become more productive with the architectural design software, practical exercises and expert instruction will get you where you need to be. Understand key BIM and Revit concepts and master the Revit interface Delve into templates, work-sharing, and managing Revit projects Master modeling and massing, the Family Editor, and visualization techniques Explore documentation, including annotation, detailing, and complex structures BIM software has become a mandatory asset in today's architecture field; automated documentation updates reduce errors while saving time and money, and Autodesk's Revit is the industry leader in the BIM software space. COMPUTERS,Image Processing

Machine Learning Machine Learning: A Bayesian and Optimization Perspective, 2nd edition, gives a unified perspective on machine learning by covering both pillars of supervised learning, namely regression and classification. The book starts with the basics, including mean square, least squares and maximum likelihood methods, ridge regression, Bayesian decision theory classification, logistic regression, and decision trees. It then progresses to more recent techniques, covering sparse modelling methods, learning in reproducing kernel Hilbert spaces and support vector machines, Bayesian inference with a focus on the EM algorithm and its approximate inference variational versions, Monte Carlo methods, probabilistic graphical models focusing on Bayesian networks, hidden Markov models and particle filtering. Dimensionality reduction and latent variables modelling are also considered in depth. This palette of techniques concludes with an extended chapter on neural networks and deep learning architectures. The book also covers the fundamentals of statistical parameter estimation, Wiener and Kalman filtering, convexity and convex optimization, including a chapter on stochastic approximation and the gradient descent family of algorithms, presenting related online learning techniques as well as concepts and algorithmic versions for distributed optimization. Focusing on the physical reasoning behind the mathematics, without sacrificing rigor, all the various methods and techniques are explained in depth, supported by examples and problems, giving an invaluable resource to the student and researcher for understanding and applying machine learning concepts. Most of the chapters include typical case studies and computer exercises, both in MATLAB and Python. The chapters are written to be as self-contained as possible, making the text suitable for different courses: pattern recognition, statistical/adaptive signal processing, statistical/Bayesian learning, as well as courses on sparse modeling, deep learning, and probabilistic graphical models. New to this edition: Complete re-write of the chapter on Neural Networks and Deep Learning to reflect the latest advances since the 1st edition. The chapter, starting from the basic perceptron and feed-forward neural networks concepts, now presents an in depth treatment of deep networks, including recent optimization algorithms, batch normalization, regularization techniques such as the dropout method, convolutional neural networks, recurrent neural networks, attention mechanisms, adversarial examples and training, capsule networks and generative architectures, such as restricted Boltzman machines (RBMs), variational autoencoders and generative adversarial networks (GANs). Expanded treatment of Bayesian learning to include nonparametric Bayesian methods, with a focus on the Chinese restaurant and the Indian buffet processes. Presents the physical reasoning, mathematical modeling and algorithmic implementation of each method Updates on the latest trends, including sparsity, convex analysis and optimization, online distributed algorithms, learning in RKH spaces, Bayesian inference, graphical and hidden Markov models, particle filtering, deep learning, dictionary learning and latent variables modeling Provides case studies on a variety of topics, including protein folding prediction, optical character recognition, text authorship identification, fMRI data analysis, change point detection, hyperspectral image unmixing, target localization, and more COMPUTERS,Image Processing

Python Image Processing Cookbook Explore Keras, scikit-image, open source computer vision (OpenCV), Matplotlib, and a wide range of other Python tools and frameworks to solve real-world image processing problems Key Features Discover solutions to complex image processing tasks using Python tools such as scikit-image and Keras Learn popular concepts such as machine learning, deep learning, and neural networks for image processing Explore common and not-so-common challenges faced in image processing Book Description With the advancements in wireless devices and mobile technology, there's increasing demand for people with digital image processing skills in order to extract useful information from the ever-growing volume of images. This book provides comprehensive coverage of the relevant tools and algorithms, and guides you through analysis and visualization for image processing. With the help of over 60 cutting-edge recipes, you'll address common challenges in image processing and learn how to perform complex tasks such as object detection, image segmentation, and image reconstruction using large hybrid datasets. Dedicated sections will also take you through implementing various image enhancement and image restoration techniques, such as cartooning, gradient blending, and sparse dictionary learning. As you advance, you'll get to grips with face morphing and image segmentation techniques. With an emphasis on practical solutions, this book will help you apply deep learning techniques such as transfer learning and fine-tuning to solve real-world problems. By the end of this book, you'll be proficient in utilizing the capabilities of the Python ecosystem to implement various image processing techniques effectively. What you will learn Implement supervised and unsupervised machine learning algorithms for image processing Use deep neural network models for advanced image processing tasks Perform image classification, object detection, and face recognition Apply image segmentation and registration techniques on medical images to assist doctors Use classical image processing and deep learning methods for image restoration Implement text detection in images using Tesseract, the optical character recognition (OCR) engine Understand image enhancement techniques such as gradient blending Who this book is for This book is for image processing engineers, computer vision engineers, software developers, machine learning engineers, or anyone who wants to become well-versed with image processing techniques and methods using a recipe-based approach. Although no image processing knowledge is expected, prior Python coding experience is necessary to understand key concepts covered in the book. COMPUTERS,Image Processing

Advances in Computational Techniques for Biomedical Image Analysis Advances in Computational Techniques for Biomedical Image Analysis: Methods and Applications focuses on post-acquisition challenges such as image enhancement, detection of edges and objects, analysis of shape, quantification of texture and sharpness, and pattern analysis. It discusses the archiving and transfer of images, presents a selection of techniques for the enhancement of contrast and edges, for noise reduction and for edge-preserving smoothing. It examines various feature detection and segmentation techniques, together with methods for computing a registration or normalization transformation. Advances in Computational Techniques for Biomedical Image Analysis: Method and Applications is ideal for researchers and post graduate students developing systems and tools for health-care systems. Covers various challenges and common research issues related to biomedical image analysis Describes advanced computational approaches for biomedical image analysis Shows how algorithms are applied to a broad range of application areas, including Chest X-ray, breast CAD, lung and chest, microscopy and pathology, etc. Explores a range of computational algorithms and techniques, such as neural networks, fuzzy sets, and evolutionary optimization Explores cloud based medical imaging together with medical imaging security and forensics COMPUTERS,Image Processing

Intravascular Ultrasound Intravascular Ultrasound: From Acquisition to Advanced Quantitative Analysis covers topics of the whole imaging pipeline, ranging from the definition of the clinical problem and image acquisition systems to image processing and analysis, including the assisted clinical-decision making procedures and treatment planning (stent deployment and follow up). Atherosclerosis, a disease of the vessel wall that produces vessel narrowing and obstruction, is the major cause of cardiovascular diseases, such as heart attack or stroke. This book covers all aspects of this imaging tool that allows for the visualization of internal vessel structures and the quantification and characterization of coronary plaque. Provides an introduction to the clinical workflow and current challenges in endovascular interventions Presents a review of the state-of-the-art methodologies in IVUS imaging and their applications Includes a rich analysis of the current and potential future connections between the academic, clinical and industrial fields COMPUTERS,Image Processing

Raspberry Pi Computer Vision Programming Perform a wide variety of computer vision tasks such as image processing and manipulation, feature and object detection, and image restoration to build real-life computer vision applications Key Features Explore the potential of computer vision with Raspberry Pi and Python programming Perform computer vision tasks such as image processing and manipulation using OpenCV and Raspberry Pi Discover easy-to-follow examples and screenshots to implement popular computer vision techniques and applications Book Description Raspberry Pi is one of the popular single-board computers of our generation. All the major image processing and computer vision algorithms and operations can be implemented easily with OpenCV on Raspberry Pi. This updated second edition is packed with cutting-edge examples and new topics, and covers the latest versions of key technologies such as Python 3, Raspberry Pi, and OpenCV. This book will equip you with the skills required to successfully design and implement your own OpenCV, Raspberry Pi, and Python-based computer vision projects. At the start, you'll learn the basics of Python 3, and the fundamentals of single-board computers and NumPy. Next, you'll discover how to install OpenCV 4 for Python 3 on Raspberry Pi, before covering major techniques and algorithms in image processing, manipulation, and computer vision. By working through the steps in each chapter, you'll understand essential OpenCV features. Later sections will take you through creating graphical user interface (GUI) apps with GPIO and OpenCV. You'll also learn to use the new computer vision library, Mahotas, to perform various image processing operations. Finally, you'll explore the Jupyter Notebook and how to set up a Windows computer and Ubuntu for computer vision. By the end of this book, you'll be able to confidently build and deploy computer vision apps. What you will learn Set up a Raspberry Pi for computer vision applications Perform basic image processing with libraries such as NumPy, Matplotlib, and OpenCV Demonstrate arithmetical, logical, and other operations on images Work with a USB webcam and the Raspberry Pi Camera Module Implement low-pass and high-pass filters and understand their applications in image processing Cover advanced techniques such as histogram equalization and morphological transformations Create GUI apps with Python 3 and OpenCV Perform machine learning with K-means clustering and image quantization Who this book is for This book is for beginners as well as experienced Raspberry Pi and Python 3 enthusiasts who are looking to explore the amazing world of computer vision. Working knowledge of the Python 3 programming language is assumed. COMPUTERS,Image Processing

Guide to the Successful Thesis and Dissertation Augmented with a new bibliography and streamlined appendices, the Guide to the Successful Thesis and Dissertation, Fifth Edition views the valuable addition of references to university research libraries and advanced information on websites, online searches, electronic literature, and other modern computer methods as crucial for the successful comp COMPUTERS,Information Technology

Understanding Broadband over Power Line Understanding Broadband over Power Line explores all aspects of the emerging technology that enables electric utilities to provide support for high-speed data communications via their power infrastructure. This book examines the two methods used to connect consumers and businesses to the Internet through the utility infrastructure: the existing ele COMPUTERS,Information Technology

Elements of Information Theory The latest edition of this classic is updated with new problem sets and material The Second Edition of this fundamental textbook maintains the book's tradition of clear, thought-provoking instruction. Readers are provided once again with an instructive mix of mathematics, physics, statistics, and information theory. All the essential topics in information theory are covered in detail, including entropy, data compression, channel capacity, rate distortion, network information theory, and hypothesis testing. The authors provide readers with a solid understanding of the underlying theory and applications. Problem sets and a telegraphic summary at the end of each chapter further assist readers. The historical notes that follow each chapter recap the main points. The Second Edition features: * Chapters reorganized to improve teaching * 200 new problems * New material on source coding, portfolio theory, and feedback capacity * Updated references Now current and enhanced, the Second Edition of Elements of Information Theory remains the ideal textbook for upper-level undergraduate and graduate courses in electrical engineering, statistics, and telecommunications. COMPUTERS,Information Technology

Official (ISC)2® Guide to the CISSP®-ISSEP® CBK® The Official (ISC)2 Guide to the CISSP-ISSEP CBK provides an inclusive analysis of all of the topics covered on the newly created CISSP-ISSEP Common Body of Knowledge. The first fully comprehensive guide to the CISSP-ISSEP CBK, this book promotes understanding of the four ISSEP domains: Information Systems Security Engineering (ISSE); Certifica COMPUTERS,Information Technology

Video Communications Case studies document how, in businesses all across this country, people are communicating via videoconferences with broadcast quality reception. The authors detail how the proliferation of IP networks has driven quality improvements and cost savings in COMPUTERS,Information Technology

Practical UML Statecharts in C/C++ Practical UML Statecharts in C/C++ Second Edition bridges the gap between high-level abstract concepts of the Unified Modeling Language (UML) and the actual programming aspects of modern hierarchical state machines (UML statecharts). The book describes a lightweight, open source, event-driven infrastructure, called QP that enables direct manual cod COMPUTERS,Information Technology

Making Things Happen In the updated edition of this critically acclaimed and bestselling book, Microsoft project veteran Scott Berkun offers a collection of essays on field-tested philosophies and strategies for defining, leading, and managing projects. Each essay distills complex concepts and challenges into practical nuggets of useful advice, and the new edition now adds more value for leaders and managers of projects everywhere. Based on his nine years of experience as a program manager for Internet Explorer, and lead program manager for Windows and MSN, Berkun explains to technical and non-technical readers alike what it takes to get through a large software or web development project. Making Things Happen doesn't cite specific methods, but focuses on philosophy and strategy. Unlike other project management books, Berkun offers personal essays in a comfortable style and easy tone that emulate the relationship of a wise project manager who gives good, entertaining and passionate advice to those who ask. Topics in this new edition include: How to make things happen Making good decisions Specifications and requirements Ideas and what to do with them How not to annoy people Leadership and trust The truth about making dates What to do when things go wrong Complete with a new forward from the author and a discussion guide for forming reading groups/teams, Making Things Happen offers in-depth exercises to help you apply lessons from the book to your job. It is inspiring, funny, honest, and compelling, and definitely the one book that you and your team need to have within arm's reach throughout the life of your project. Coming from the rare perspective of someone who fought difficult battles on Microsoft's biggest projects and taught project design and management for MSTE, Microsoft's internal best practices group, this is valuable advice indeed. It will serve you well with your current work, and on future projects to come. COMPUTERS,Information Technology

Using Microsoft Dynamics AX 2009 When looking for a business management solution supporting business processes in mid sized and large companies, Microsoft Dynamics AX is likelyto be your favorite. Because of its deep functional and technological integration, it is as well a good choice for universities teaching ERP systems. Reading This Book Theprimary purpose of this book is to provide you with a good knowledge of thestandard application concept and functionality, which is required to run business processes in Mi crosoft Dynamics AX 2009. This book therefore is for you, if you arean enduser, student or consultant, interested in learning how to use Dynamics AX. Going beyond the operations on the user interface, you will also learn how thedifferent parts of the application tie together. As a result, you will as well take advantage learning the end to endapplication concept, if you are a system administrator, developer, IT execu tive or experienced consultant not knowing the complete application already. Actually working in an application is the best way to learn it. Therefore, the chapters of this book include exercises that build up on each other in a comprehensive case study. If you need support to solve the exercises, you may access a free download of sample solutions. This book is the English version of the successful book “Grundkurs Microsoft Dynam ics AXâ€, recommended by Microsoft in Germany. Based on the second edition of the Ger man volume, it includes the core improvements of Dynamics AX in version AX 2009. COMPUTERS,Information Technology

Hacking Healthcare Ready to take your IT skills to the healthcare industry? This concise book provides a candid assessment of the US healthcare system as it ramps up its use of electronic health records (EHRs) and other forms of IT to comply with the government’s Meaningful Use requirements. It’s a tremendous opportunity for tens of thousands of IT professionals, but it’s also a huge challenge: the program requires a complete makeover of archaic records systems, workflows, and other practices now in place. This book points out how hospitals and doctors’ offices differ from other organizations that use IT, and explains what’s necessary to bridge the gap between clinicians and IT staff. Get an overview of EHRs and the differences among medical settings Learn the variety of ways institutions deal with patients and medical staff, and how workflows vary Discover healthcare’s dependence on paper records, and the problems involved in migrating them to digital documents Understand how providers charge for care, and how they get paid Explore how patients can use EHRs to participate in their own care Examine healthcare’s most pressing problem—avoidable errors—and how EHRs can both help and exacerbate it COMPUTERS,Information Technology

Big Data Governance Written by a leading expert in the field, this guide focuses on the convergence of two major trends in information management—big data and information governance—by taking a strategic approach oriented around business cases and industry imperatives. With the advent of new technologies, enterprises are expanding and handling very large volumes of data; this book, nontechnical in nature and geared toward business audiences, encourages the practice of establishing appropriate governance over big data initiatives and addresses how to manage and govern big data, highlighting the relevant processes, procedures, and policies. It teaches readers to understand how big data fits within an overall information governance program; quantify the business value of big data; apply information governance concepts such as stewardship, metadata, and organization structures to big data; appreciate the wide-ranging business benefits for various industries and job functions; sell the value of big data governance to businesses; and establish step-by-step processes to implement big data governance. COMPUTERS,Information Technology

The Definitive Guide to Complying with the HIPAA/HITECH Privacy and Security Rules The Definitive Guide to Complying with the HIPAA/HITECH Privacy and Security Rules is a comprehensive manual to ensuring compliance with the implementation standards of the Privacy and Security Rules of HIPAA and provides recommendations based on other related regulations and industry best practices. The book is designed to assist you in reviewing the accessibility of electronic protected health information (EPHI) to make certain that it is not altered or destroyed in an unauthorized manner, and that it is available as needed only by authorized individuals for authorized use. It can also help those entities that may not be covered by HIPAA regulations but want to assure their customers they are doing their due diligence to protect their personal and private information. Since HIPAA/HITECH rules generally apply to covered entities, business associates, and their subcontractors, these rules may soon become de facto standards for all companies to follow. Even if you aren't required to comply at this time, you may soon fall within the HIPAA/HITECH purview. So, it is best to move your procedures in the right direction now. The book covers administrative, physical, and technical safeguards; organizational requirements; and policies, procedures, and documentation requirements. It provides sample documents and directions on using the policies and procedures to establish proof of compliance. This is critical to help prepare entities for a HIPAA assessment or in the event of an HHS audit. Chief information officers and security officers who master the principles in this book can be confident they have taken the proper steps to protect their clients' information and strengthen their security posture. This can provide a strategic advantage to their organization, demonstrating to clients that they not only care about their health and well-being, but are also vigilant about protecting their clients' privacy. COMPUTERS,Information Technology

B 102 Informationstechnologien bewerten - Theoriebuch In Unternehmen steht bei Technologieentscheiden viel auf dem Spiel. Es lohnt sich deshalb, sich mit den Methoden der Technologiebewertung vertraut zu machen. Die strategische Technologiebewertung behandelt Vorgehensweisen, die aufzeigen, wie ein Technologieeinsatz erwogen und beurteilt werden kann. Die Zielsetzung der strategischen Technologiebewertung ist, die technologische Marschrichtung des Unternehmens zu erarbeiten, ohne sich bereits auf technische Lösungen festzulegen. COMPUTERS,Information Technology

Information and Communication Technologies in Tourism 1997 For the fourth time now, experts in tourism from various countries come to attend the ENTER conference in order to inform themselves and others about the current devel opments in the usage of information and communication technologies. The ENTER conference is thought as a platform for the exchange of ideas, experi ences, opinions, and visions among scientists and practitioners. The visions presented at the last three ENTER conferences have triggered many requirements of important on-going and planned projects in the application of communication and information technologies in tourism. The scope of the papers of this proceedings covers the most recent and relevant to pics in our area of interest. The sessions are primarily devoted to intelligent agents and systems, the future role of global (reservation) systems, the new. chances of data base applications due to the most recent technological developments. and above all the role of the Internet (and Intranet). I would like to express my cordial thanks to all institutions actively supporting this event, namely: • The Edinburgh & Lothian Tourist Board • The International Federation of Information Technology in Tourism (IFITT) Several people spent numerous hours organizing the scientific programme of EN TER. The names of most of them will appear in the following pages. COMPUTERS,Information Technology

Practical Formal Methods for Hardware Design Formal methods for hardware design still find limited use in industry. Yet current practice has to change to cope with decreasing design times and increasing quality requirements. This research report presents results from the Esprit project FORMAT (formal methods in hardware verification) which involved the collaboration of the enterprises Siemens, Italtel, Telefonica I+D, TGI, and AHL, the research institute OFFIS, and the universities of Madrid and Passau. The work presented involves advanced specification languages for hardware design that are intuitive to the designer, like timing diagrams and state based languages, as well as their relation to VHDL and formal languages like temporal logic and a process-algebraic calculus. The results of experimental tests of the tools are also presented. COMPUTERS,Information Technology

Adaptive Analog VLSI Neural Systems amplitude ~---. -----. -----. -----,-----. -----,-,~ VfT:j·" 4. 50 4. 00 3. 50 q . 3. 00 /'\. ~ -'" : ! . 2. 50 ,: \ . . . 1! -. i "'" " 2. 00 1. 50 ··GO··O_O_ ,-. . . . &. , . ; D Q . " . . . / 1. 00 0. 50 0. 00 L. -----1. . ---. . l. -----:-:::''"::-::--::-::-'-:::-::------=--::-'-::-:=---=-=""=_:' 5. 00 10. 00 15. 00 Figure 7. 1 The morphology of ST and VT retrograde 1:1. © 1995 IEEE [Coggins, labri, Flower and Pickard {1995}]. ing to the analog domain. Additionally, the use of differential pair multipliers and current node summing in the network allows a min imum of devices in the network itself and hence associated savings in power and area. However, in the last few decades analog signal processing has been used sparingly due to the effects of device off sets, noise and drift*. The neural network architecture alleviates these problems to a large extent due to the fact that it is both highly parallel and adaptive. The fact that the network is trained to recognize morphologies with the analog circuits in-loop means that the synaptic weights can be adapted to cancel device offsets [Castro, Tam and Holler (1993); Castro and Sweet (1993)]. The impact of local un correlated noise is reduced by the parallelism of * Most fabrication processes have been optimised for digital design techniques which results in poor analog performance. COMPUTERS,Information Technology

Information and Communication Technologies in Tourism For the third time now, experts in tourism from all over the world come to Innsbruck in order to exchange ideas, inform themselves and others about current developments and build a network of personal relations. The main topics of ENTER 96 are business engineering and standardisation, covering a wide area of subjects like the redesign of touristic products and the processes of their production. This covers, however, not only single business processes but also the entire value chain in tourism, ending up in redesign of distribution channel and changing relations among principals, tour operators, travel agents and customers. Standardisation increasingly becomes a prerequisite for interorganisational coordination and cooperation, EDI is slowly being introduced in tourism and Internet related standards like HTML and VRML. will have a major impact on the future development of electronic distribution platforms for services in tourism. As the proceedings underscore, ENTER has been established as an international platform for scientific and practical discourse on Information and Communication Technologies in Tourism. The close interdisciplinary link between technological and economic questions in tourism opens up new, promising threads for applied research and development likewise. COMPUTERS,Information Technology

Multimedia ’96 In the last few years multimedia hardware and applications have become widely available on PC and workstations. Moreover, through the tremendous development and the wide usage of the World Wide Web multimedia applications have been brought over the network to many people. This book presents the results of the fourth in a well established series of international workshops on Multimedia organized by the EUROGRAPHICS Association, and held from May 28 to 30, 1996, in Rostock, Germany. The workshop had the special topic Multimedia on the Net and was the follow up of the EUROGRAPHICS Symposium and Workshop on Multimedia held in Graz in June 1994. The workshop program consisted of an invited keynote speech and five technical sessions. The fifteen contributions selected for this volume treat topics of particular interest in current research and address actual problems of the use of multimedia in distributed applications over the network. According to the technical sessions they can be roughly structured in the parts concepts for handling multimedia data, still and motion pictures on the net, WWW and multimedia, collaborative multimedia, and multimedia and education. Concepts for handling multimedia data are addressed in two contributions. The first treats a frame based presentation model for distributed information systems (Kirste), the other one presents a temporal logic formalism for specifying navigational transformation in hypermedia applications (Mere et al.). COMPUTERS,Information Technology

Spinning the Web This book is written for: • anyone who wants to serve information on the WWW. The book contains detailed instructions on how to fetch, configure, and administer the most popular WWW server programs. The server chapter is separated into sections that discuss how to set up common configurations and sections that serve as references for all the directives that control server behavior. • anyone who wants to maintain a secure WWW site. The book discusses how to create a secure site. It covers inse cure configurations of servers, browsers, and scripts, and it gives a list of measures that reduce the likelihood of a security breach. • anyone who wants to create information to be served on the WWW. HTML is the language used to create WWW pages, and almost all the variations, extensions, and fla~ vors of HTML are discussed in the book. Two chapters, introductory and advanced, teach HTML by example, and an extensive reference chapter contains all ofHTML 2, all the HTML 3 that is implemented or proposed as of the writ ing of this book, and Netscape Navigator 2 and Spyglass Enhanced Mosaic extensions. It's comprehensive. • anyone who wants to create state-of-the art WWW docu ments. The book discusses how to include images, sounds, and video in documents; how to store and manipulate im ages for optimal effect - for example, rapid transmission vii ~ii ________________________________________________ P_~_rn_c_e over the network; and how to use scripts, both simple and sophisticated. COMPUTERS,Information Technology

Mosaic™ for Windows® Mosaic for Windows is an informative book on how to use the most popular Internet navigation tool ever developed. By focussing on the PC Windows version of Mosaic (NCSA, AIR Mosaic, and Spyglass), including Web browsers like NetScape, WinWeb and WebSurfer, this book will provide an easy-to-follow guide to using a PC and Mosaic to browse, collect, and discover information and resources across the entire electronic world. COMPUTERS,Information Technology

Parallel Language and Compiler Research in Japan Parallel Language and Compiler Research in Japan offers the international community an opportunity to learn in-depth about key Japanese research efforts in the particular software domains of parallel programming and parallelizing compilers. These are important topics that strongly bear on the effectiveness and affordability of high performance computing systems. The chapters of this book convey a comprehensive and current depiction of leading edge research efforts in Japan that focus on parallel software design, development, and optimization that could be obtained only through direct and personal interaction with the researchers themselves. COMPUTERS,Information Technology

Information and Communications Technologies in Tourism The conference ENTER • International Conference on However, the tourist market has several specific characteristics Information and Communications Technologies in Tourism with regard to the use of technological infrastructure: represents a fll'St attempt • On the demand side computerized reservation and general • to provide an international forum for the discussion of the distribution systems (eRS and GDS), managed by big role of telecommunication and information systems in airlines, are well organized and technological pioneers. In tourism, the past they typically focused on the business traveller, • to inform potential users and people concerned with the nowadays they also try to cover the vacation sector. These importance of such technologies and to explain their systems work on a world-wide level and are highly functioning sophisticated. However, it should be added that the • to give an opportunity to the research community, nowadays information provided is rather poor and also selective, scattered into different areas of research, to discuss their which may restrict its usefulness for the promotion of an results on a common platform, and, fmally, entire tourist region. • to intensify the contact and the communication between • Similar to CRSlGDS several tour operators have begun to develop their own systems, although with varying success. researchers, system developers and users. COMPUTERS,Information Technology

Parallel Computing on Distributed Memory Multiprocessors Proceedings of the NATO Advanced Study Institute on Parallel Computing on Distributed Memory Multiprocessors, held at Bilkent University, Ankara, Turkey, July 1-13, 1991 COMPUTERS,Information Technology

Computer Systems and Software Engineering Computer Systems and Software Engineering is a compilation of sixteen state-of-the-art lectures and keynote speeches given at the COMPEURO '92 conference. The contributions are from leading researchers, each of whom gives a new insight into subjects ranging from hardware design through parallelism to computer applications. The pragmatic flavour of the contributions makes the book a valuable asset for both researchers and designers alike. The book covers the following subjects: Hardware Design: memory technology, logic design, algorithms and architecture; Parallel Processing: programming, cellular neural networks and load balancing; Software Engineering: machine learning, logic programming and program correctness; Visualization: the graphical computer interface. COMPUTERS,Information Technology

Parallel Computing and Mathematical Optimization This special volume contains the Proceedings of a Workshop on "Parallel Algorithms and Transputers for Optimization" which was held at the University of Siegen, on November 9, 1990. The purpose of the Workshop was to bring together those doing research on 2.lgorithms for parallel and distributed optimization and those representatives from industry and business who have an increasing demand for computing power and who may be the potential users of nonsequential approaches. In contrast to many other conferences, especially North-American, on parallel processing and supercomputers the main focus of the contributions and discussion was "problem oriented". This view reflects the following philosophy: How can the existing computing infrastructure (PC's, workstations, local area networks) of an institution or a company be used for parallel and/or distributed problem solution in optimization. This volume of the LECfURE NOTES ON ECONOMICS AND MA THEMA TICAL SYSTEMS contains most of the papers presented at the workshop, plus some additional invited papers covering other important topics related to this workshop. The papers appear here grouped according to four general areas. (1) Solution of optimization problems using massive parallel systems (data parallelism). The authors of these papers are: Lootsma; Gehne. (II) Solution of optimization problems using coarse-grained parallel approaches on multiprocessor systems (control parallelism). The authors of these papers are: Bierwirth, Mattfeld, and Stoppler; Schwartz; Boden, Gehne, and Grauer; and Taudes and Netousek. COMPUTERS,Information Technology

Advances in Computer Technology and Applications in Japan This book contains chapters written by eminent scientists on the latest de velopment in computer technology and applications in Japan. The material contained in this book is an edited version of the presenta tion at a seminar arranged by the Computational Mechanics Institute of the Wessex Institute of Technology at Southampton during 1989. The objective of the Seminar was to provide an awareness of the considerable advances being made by Japanese scientists in the general area of information tech nology and in the so-called Fifth Generation Computer Systems. In the first chapter, Watanabe of the NEC Corporation, describes advanced architecture and technology of supercomputing systems. This theme is fol lowed by Nakamura of Tohoku University in the next chapter. Another type of supercomputer for vector processing, the FACOM VP 2000 Series is then described by Uchida of Fujitsu Ltd in Chapter Three. Expert systems are presented in the next two chapters by Ueno and Oomari of Tokyo Denki University and by Koseki and Goto of the NEC Corpora tion. Important applications in computer graphics are described in Chapter Six by Ishii and Murakami of Fujitsu Laboratories. Hayashi from the same Laboratory then discusses neurocomputers in Japan. The final chapter by Noguchi of Tohoku University illustrates an important application in com munications. The Editors acknowledge the help of Computational Mechanics Publica tions in the preparation and sub-editing of the manuscript and are grateful for the high standards of presentation. COMPUTERS,Information Technology

Designing Hypermedia for Learning Proceedings of the NATO Advanced Research Workshop on Designing Hypertext/Hypermedia for Learning, held in Rottenburg/Neckar, FRG, July 3-8, 1989 COMPUTERS,Information Technology

PDCA/Test Most manuals assume software testing is being performed as part of a well-defined, structured development cycle based on clearly stated requirements and standards. Unfortunately, this is not often the case in the real world. Indeed, the one true constant in software development is change. PDCA/TEST presents a continuous quality framework bas COMPUTERS,Information Technology

Secure and Resilient Software Development Although many software books highlight open problems in secure software development, few provide easily actionable, ground-level solutions. Breaking the mold, Secure and Resilient Software Development teaches you how to apply best practices and standards for consistent and secure software development. It details specific quality software developmen COMPUTERS,Information Technology

Software Testing This updated and reorganized fourth edition of Software Testing: A Craftsman's Approach applies the strong mathematics content of previous editions to a coherent treatment of Model-Based Testing for both code-based (structural) and specification-based (functional) testing. These techniques are extended from the usual unit testing discussions to full coverage of less understood levels integration and system testing. The Fourth Edition: Emphasizes technical inspections and is supplemented by an appendix with a full package of documents required for a sample Use Case technical inspection Introduces an innovative approach that merges the Event-Driven Petri Nets from the earlier editions with the "Swim Lane" concept from the Unified Modeling Language (UML) that permits model-based testing for four levels of interaction among constituents in a System of Systems Introduces model-based development and provides an explanation of how to conduct testing within model-based development environments Presents a new section on methods for testing software in an Agile programming environment Explores test-driven development, reexamines all-pairs testing, and explains the four contexts of software testing Thoroughly revised and updated, Software Testing: A Craftsman’s Approach, Fourth Edition is sure to become a standard reference for those who need to stay up to date with evolving technologies in software testing. Carrying on the tradition of previous editions, it will continue to serve as a valuable reference for software testers, developers, and engineers. COMPUTERS,Information Technology

Programming Languages for MIS Programming Languages for MIS: Concepts and Practice supplies a synopsis of the major computer programming languages, including C++, HTML, JavaScript, CSS, VB.NET, C#.NET, ASP.NET, PHP (with MySQL), XML (with XSLT, DTD, and XML Schema), and SQL. Ideal for undergraduate students in IS and IT programs, this textbook and its previous versions have bee COMPUTERS,Information Technology

Official (ISC)2® Guide to the ISSAP® CBK Candidates for the CISSP-ISSAP professional certification need to not only demonstrate a thorough understanding of the six domains of the ISSAP CBK, but also need to have the ability to apply this in-depth knowledge to develop a detailed security architecture. Supplying an authoritative review of the key concepts and requirements of the ISSAP CBK, the Official (ISC)2® Guide to the ISSAP® CBK®, Second Edition provides the practical understanding required to implement the latest security protocols to improve productivity, profitability, security, and efficiency. Encompassing all of the knowledge elements needed to create secure architectures, the text covers the six domains: Access Control Systems and Methodology, Communications and Network Security, Cryptology, Security Architecture Analysis, BCP/DRP, and Physical Security Considerations. Newly Enhanced Design – This Guide Has It All! Only guide endorsed by (ISC)2 Most up-to-date CISSP-ISSAP CBK Evolving terminology and changing requirements for security professionals Practical examples that illustrate how to apply concepts in real-life situations Chapter outlines and objectives Review questions and answers References to free study resources Read It. Study It. Refer to It Often. Build your knowledge and improve your chance of achieving certification the first time around. Endorsed by (ISC)2 and compiled and reviewed by CISSP-ISSAPs and (ISC)2 members, this book provides unrivaled preparation for the certification exam and is a reference that will serve you well into your career. Earning your ISSAP is a deserving achievement that gives you a competitive advantage and makes you a member of an elite network of professionals worldwide. COMPUTERS,Information Technology

Official (ISC)2 Guide to the CISSP-ISSMP CBK The Certified Information Systems Security Professional-Information Systems Security Management Professional (CISSP-ISSMP) certification was developed for CISSPs who are seeking to further their careers and validate their expertise in information systems security management. Candidates for the ISSMP need to demonstrate a thorough understanding of t COMPUTERS,Information Technology

Breakthrough Strategic It And Process Planning This book is the first publication that combines the principles of business process management with strategic IT planning; the result being a groundbreaking work on strategic IT and process planning. While Breakthrough Strategic IT and Process Planning focuses on the real world of organizations, extensive treatment is also devoted to the politics of strategic planning. As such, a project management approach that combines process improvement, IT, and change management is employed. Other important aspects of process planning are discussed in detail: the strategic allocation of resources, short and long term implementation of the strategic plan, marketing of the plan to gain support for implementation, and development of strategic IT and process plans for business units and departments. COMPUTERS,Information Technology

Model Free Adaptive Control Model Free Adaptive Control: Theory and Applications summarizes theory and applications of model-free adaptive control (MFAC). MFAC is a novel adaptive control method for the unknown discrete-time nonlinear systems with time-varying parameters and time-varying structure, and the design and analysis of MFAC merely depend on the measured input and ou COMPUTERS,Information Technology

Official (ISC)2 Guide to the CISSP CBK As a result of a rigorous, methodical process that (ISC) follows to routinely update its credential exams, it has announced that enhancements will be made to both the Certified Information Systems Security Professional (CISSP) credential, beginning April 15, 2015. (ISC) conducts this process on a regular basis to ensure that the examinations and COMPUTERS,Information Technology

Enterprise Security Architecture Security is too important to be left in the hands of just one department or employee-it's a concern of an entire enterprise. Enterprise Security Architecture shows that having a comprehensive plan requires more than the purchase of security software-it requires a framework for developing and maintaining a system that is proactive. The book is based COMPUTERS,Information Technology

VLSI for Neural Networks and Artificial Intelligence Neural network and artificial intelligence algorithrns and computing have increased not only in complexity but also in the number of applications. This in turn has posed a tremendous need for a larger computational power that conventional scalar processors may not be able to deliver efficiently. These processors are oriented towards numeric and data manipulations. Due to the neurocomputing requirements (such as non-programming and learning) and the artificial intelligence requirements (such as symbolic manipulation and knowledge representation) a different set of constraints and demands are imposed on the computer architectures/organizations for these applications. Research and development of new computer architectures and VLSI circuits for neural networks and artificial intelligence have been increased in order to meet the new performance requirements. This book presents novel approaches and trends on VLSI implementations of machines for these applications. Papers have been drawn from a number of research communities; the subjects span analog and digital VLSI design, computer design, computer architectures, neurocomputing and artificial intelligence techniques. This book has been organized into four subject areas that cover the two major categories of this book; the areas are: analog circuits for neural networks, digital implementations of neural networks, neural networks on multiprocessor systems and applications, and VLSI machines for artificial intelligence. The topics that are covered in each area are briefly introduced below. COMPUTERS,Information Technology

Managing A Network Vulnerability Assessment The instant access that hackers have to the latest tools and techniques demands that companies become more aggressive in defending the security of their networks. Conducting a network vulnerability assessment, a self-induced hack attack, identifies the network components and faults in policies, and procedures that expose a company to the damage caused by malicious network intruders. Managing a Network Vulnerability Assessment provides a formal framework for finding and eliminating network security threats, ensuring that no vulnerabilities are overlooked. This thorough overview focuses on the steps necessary to successfully manage an assessment, including the development of a scope statement, the understanding and proper use of assessment methodology, the creation of an expert assessment team, and the production of a valuable response report. The book also details what commercial, freeware, and shareware tools are available, how they work, and how to use them. By following the procedures outlined in this guide, a company can pinpoint what individual parts of their network need to be hardened, and avoid expensive and unnecessary purchases. COMPUTERS,Information Technology

Mathematical Foundations of Public Key Cryptography In Mathematical Foundations of Public Key Cryptography, the authors integrate the results of more than 20 years of research and teaching experience to help students bridge the gap between math theory and crypto practice. The book provides a theoretical structure of fundamental number theory and algebra knowledge supporting public-key cryptography.R COMPUTERS,Information Technology

Advances in Human-Computer Interaction "User is king" is not a new concept, but it is certainly one that has gathered considerable momentum in the recent years. The driving force are the increasing and relentless pace of competition and the consequent attempts by many companies to keep and improve their marketshare. Since the beginning of ESPRIT Programme in 1984, the Human Computer Interface has been the subject of attention, in terms of technology development and utilisation of those technologies in various applications in the fields of Information Processing Systems, Computer Integrated Manufacturing, and Office and Business Systems. This topic area had been addressed in a number of different perspectives: user modelling, task analysis, cognitive aspects of interaction and assimilation of information, natural language speech and graphics, processing of multisensor information and its presentation, and a wide range of applications in which these technologies are used. In addition to the previous ESPRIT programmes, the specific programme for Information Technology of the European Framework Programme for 1994-1999 has recognised the ever increasing importance of "ease of use" in computer applications. The work programme on Human Comfort and Security is an attempt to address these issues. Its primary objectives are the exploitation of existing knowledge and expertise in usability engineering by integrating methods and tools into coherent toolsets, the generation of improved human computer interface components, demonstrating their application in practice, and widely disseminating the results and promoting the take-up of these technologies. COMPUTERS,Information Technology

Enterprise Architecture at Work Lankhorst and his co‑authors present ArchiMate® 3.0, enterprise modelling language that captures the complexity of architectural domains and their relations and allows the construction of integrated enterprise architecture models. They provide architects with concrete instruments that improve their architectural practice. As this is not enough, they additionally present techniques and heuristics for communicating with all relevant stakeholders about these architectures. Since an architecture model is useful not only for providing insight into the current or future situation but can also be used to evaluate the transition from ‘as‑is’ to ‘to‑be’, the authors also describe analysis methods for assessing both the qualitative impact of changes to an architecture and the quantitative aspects of architectures, such as performance and cost issues. The modelling language presented has been proven in practice in many real‑life case studies and has been adopted by The Open Group as an international standard. So this book is an ideal companion for enterprise IT or business architects in industry as well as for computer or management science students studying the field of enterprise architecture. This fourth edition of the book has been completely reworked to be compatible with ArchiMate® 3.0, and it includes a new chapter relating this new version to other standards. New sections on capability analysis, risk analysis, and business architecture in general have also been introduced. COMPUTERS,Information Technology

Implementing Cybersecurity The book provides the complete strategic understanding requisite to allow a person to create and use the RMF process recommendations for risk management. This will be the case both for applications of the RMF in corporate training situations, as well as for any individual who wants to obtain specialized knowledge in organizational risk management. It is an all-purpose roadmap of sorts aimed at the practical understanding and implementation of the risk management process as a standard entity. It will enable an "application" of the risk management process as well as the fundamental elements of control formulation within an applied context. COMPUTERS,Information Technology

The Discipline of Organizing We organize things. We organize information, information about things, and information about information. Organizing is a fundamental issue in many professional fields, but these fields have only limited agreement in how they approach problems of organizing and in what they seek as their solutions. The Discipline of Organizing synthesizes insights from library science, information science, computer science, cognitive science, systems analysis, business, and other disciplines to create an Organizing System for understanding organizing. This framework is robust and forward-looking, enabling effective sharing of insights and design patterns between disciplines that weren't possible before. The 4th edition of this award-winning and widely adopted text adds content to bridge between the foundations of organizing systems and the new statistical and computational techniques of data science because at its core, data science is about how resources are described and organized. The 4th edition reframes descriptive statistics as organizing techniques, expands the treatment of classification to include computational methods, and incorporates many new examples of data-driven resource selection, organization, maintenance, and personalization. The Informatics edition contains all the new content related to data science, but omits the discipline-specific content about library science, museums, and document archives. COMPUTERS,Information Technology

The Discipline of Organizing We organize things. We organize information, information about things, and information about information. Organizing is a fundamental issue in many professional fields, but these fields have only limited agreement in how they approach problems of organizing and in what they seek as their solutions. The Discipline of Organizing synthesizes insights from library science, information science, computer science, cognitive science, systems analysis, business, and other disciplines to create an Organizing System for understanding organizing. This framework is robust and forward-looking, enabling effective sharing of insights and design patterns between disciplines that weren't possible before. The 4th edition of this award-winning and widely adopted text adds content to bridge between the foundations of organizing systems and the new statistical and computational techniques of data science because at its core, data science is about how resources are described and organized. The 4th edition reframes descriptive statistics as organizing techniques, expands the treatment of classification to include computational methods, and incorporates many new examples of data-driven resource selection, organization, maintenance, and personalization. The Core Concepts edition is an abridged version that is simpler to read because it does not tempt the reader with the deep scholarly web of endnotes contained in the Professional edition. Instead, it seeks to reinforce the concepts and design patterns with numerous "Stop and Think" exercises, and omits some of the theoretical nuance of the Professional edition to put more emphasis on concrete examples. COMPUTERS,Information Technology

Cognitive Sensors and IoT This book presents the Cognitive Information Centric Sensor Network (CICSN) framework for the IoT. This framework is built on top of cognitive nodes, capable of knowledge representation, learning, and reasoning, along with an information-centric approach for data delivery. It also discusses the most appropriate deployment strategy for these cognitive nodes under realistic assumptions that cares about the Quality of Information (QoI). In addition, it uses a QoI aware data delivery strategy, with Analytic Hierarchy Process (AHP) as the reasoning technique to identify data delivery paths that dynamically adapt to changing network conditions and user requirements. COMPUTERS,Information Technology

5G LTE Narrowband Internet of Things (NB-IoT) This book explains the 3GPP technical specifications for the upcoming 5G Internet of Things (IoT) technology based on latest release which is Release 15. It details the LTE protocol stack of an IoT device, architecture and framework, how they are functioning and communicate with cellular infrastructure, and supported features and capability. NB-IoT is designed to connect a large number of devices in a wide range of application domains forming so-called Internet of Things (IoT). Connected devices are to communicate through cellular infrastructure. This technology is new within the 3GPP specifications and is part of upcoming new wireless technology known as 5G. Table of Contents Preface. Acknowledgments. Author. List of Abbreviations. 1. Internet of Things. 2. 4G and 5G Systems. 3. Radio Resource Control Sublayer. 4. Packet Data Convergence Protocol Sublayer. 5. Radio Link Control Sublayer. 6. Medium Access Control Sublayer. 7. Physical Sublayer. 8. Quality of Service Architecture. 9. Use Cases and Deployment. References. Index. COMPUTERS,Information Technology

The Esri Guide to GIS Analysis, Volume 3 The third volume in a popular series about geographic information systems (GIS) covers spatial interaction, site selection, routing, and scheduling. COMPUTERS,Information Technology

Bring Your Own Device (BYOD) The increasing use of personal devices such as smartphones and tablets at work is offering an opportunity as well as a challenge for organisations, in particular the IT department. This ebook looks at ways to embrace the benefits of BYOD while offering advice on how to minimise the risks. COMPUTERS,Information Technology

CompTIA Security+ Certification Guide This is a practical certification guide covering all the exam topics in an easy-to-follow manner backed with mock tests and self-assesment scenarios for better preparation. Key Features Learn cryptography and various cryptography algorithms for real-world implementations Discover security policies, plans, and procedures to protect your security infrastructure Written by Ian Neil, one of the world's top CompTIA Security+ (SY0-501) trainer Book Description CompTIA Security+ is a worldwide certification that establishes the fundamental knowledge required to perform core security functions and pursue an IT security career. CompTIA Security+ Certification Guide is a best-in-class exam study guide that covers all of CompTIA Security+ 501 exam objectives. It is authored by Ian Neil, who is a world-class trainer of CompTIA Security+ 501. Packed with self-assessment scenarios and realistic exam questions, this guide will help you master the core concepts to succeed in the exam the first time you take it. Using relevant examples, you will learn all the important security fundamentals from Certificates and Encryption to Identity and Access Management concepts. You will then dive into the important domains of the exam; namely, threats, attacks and vulnerabilities, technologies and tools, architecture and design, risk management, and cryptography and Public Key Infrastructure (PKI). This book comes with over 600 practice questions with detailed explanation that is at the exam level and also includes two mock exams to help you with your study plan. This guide will ensure that encryption and certificates are made easy for you. What you will learn Get to grips with security fundamentals from Certificates and Encryption to Identity and Access Management Secure devices and applications that are used by your company Identify the different types of malware and virus and take appropriate actions to protect against them Protect your environment against social engineering and advanced attacks Implement PKI concepts Learn about secure coding techniques, quality control, and testing Troubleshoot common security issues Who this book is for This book is designed for anyone who is seeking to pass the CompTIA Security+ SY0-501 exam. It is a stepping stone for anyone who wants to become a security professional or move into cyber security. This certification guide assumes no prior knowledge of the product. COMPUTERS,Information Technology

Software Defined-WAN for the Digital Age SD-WAN is an advanced networking approach that creates hybrid networks to integrate broadband or other network services into the corporate WAN, not only just handling general business workloads and traffic, but also being capable of maintaining the performance and security of real-time and sensitive applications. This book posits that Software Defined (SD) WAN is the answer to questions such as what changes can be made to the networking sector? What innovations can make WAN, which plays a vital integrated part of the cloud ecosystem, more cost effective, performance robust, provisioning efficient, and operation intelligent? COMPUTERS,Information Technology

Cloud Computing Using Oracle Application Express Get the domain knowledge you need to develop real-world business apps for and in the cloud. You’ll see how Oracle APEX has made the life of web developers much easier and how it helps you create web-based data-centric applications easily and instantly without writing screeds of code. In Cloud Computing Using Oracle Application Express, you will develop a complete general ledger accounting system named the Cloud Accountant which will be accessible through a variety of devices including desktops, laptops, and the latest smartphones. This new edition also incorporates the new application page creation process, which differs from the previous version. You’ll cover other new areas, such as the updated UI elements and properties, and the interactive grid. Besides the development of a full application that you can deploy in your organization, the book teaches many new techniques to further enhance your APEX development skills. What You Will Learn Discover new development techniques for APEX developers Develop cloud-based ERP applications Build a cloud-based application on Oracle APEX Integrate the free JasperReports server and report designing tool with Oracle APEX Who This Book Is For Web developers who possess some working knowledge of Oracle Application Express, and developers who have been using Oracle Forms and now wish to use their existing SQL and PL/SQL expertise. COMPUTERS,Information Technology

Inside the Dark Web Inside the Dark Web provides a broad overview of emerging digital threats and computer crimes, with an emphasis on cyberstalking, hacktivism, fraud and identity theft, and attacks on critical infrastructure. The book also analyzes the online underground economy and digital currencies and cybercrime on the dark web. The book further explores how dark web crimes are conducted on the surface web in new mediums, such as the Internet of Things (IoT) and peer-to-peer file sharing systems as well as dark web forensics and mitigating techniques. This book starts with the fundamentals of the dark web along with explaining its threat landscape. The book then introduces the Tor browser, which is used to access the dark web ecosystem. The book continues to take a deep dive into cybersecurity criminal activities in the dark net and analyzes the malpractices used to secure your system. Furthermore, the book digs deeper into the forensics of dark web, web content analysis, threat intelligence, IoT, crypto market, and cryptocurrencies. This book is a comprehensive guide for those who want to understand the dark web quickly. After reading Inside the Dark Web, you’ll understand The core concepts of the dark web. The different theoretical and cross-disciplinary approaches of the dark web and its evolution in the context of emerging crime threats. The forms of cybercriminal activity through the dark web and the technological and "social engineering" methods used to undertake such crimes. The behavior and role of offenders and victims in the dark web and analyze and assess the impact of cybercrime and the effectiveness of their mitigating techniques on the various domains. How to mitigate cyberattacks happening through the dark web. The dark web ecosystem with cutting edge areas like IoT, forensics, and threat intelligence and so on. The dark web-related research and applications and up-to-date on the latest technologies and research findings in this area. For all present and aspiring cybersecurity professionals who want to upgrade their skills by understanding the concepts of the dark web, Inside the Dark Web is their one-stop guide to understanding the dark web and building a cybersecurity plan. COMPUTERS,Information Technology

Mastering Azure Machine Learning Master expert techniques for building automated and highly scalable end-to-end machine learning models and pipelines in Azure using TensorFlow, Spark, and Kubernetes Key Features Make sense of data on the cloud by implementing advanced analytics Train and optimize advanced deep learning models efficiently on Spark using Azure Databricks Deploy machine learning models for batch and real-time scoring with Azure Kubernetes Service (AKS) Book Description The increase being seen in data volume today requires distributed systems, powerful algorithms, and scalable cloud infrastructure to compute insights and train and deploy machine learning (ML) models. This book will help you improve your knowledge of building ML models using Azure and end-to-end ML pipelines on the cloud. The book starts with an overview of an end-to-end ML project and a guide on how to choose the right Azure service for different ML tasks. It then focuses on Azure ML and takes you through the process of data experimentation, data preparation, and feature engineering using Azure ML and Python. You'll learn advanced feature extraction techniques using natural language processing (NLP), classical ML techniques, and the secrets of both a great recommendation engine and a performant computer vision model using deep learning methods. You'll also explore how to train, optimize, and tune models using Azure AutoML and HyperDrive, and perform distributed training on Azure ML. Then, you'll learn different deployment and monitoring techniques using Azure Kubernetes Services with Azure ML, along with the basics of MLOps—DevOps for ML to automate your ML process as CI/CD pipeline. By the end of this book, you'll have mastered Azure ML and be able to confidently design, build and operate scalable ML pipelines in Azure. What you will learn Setup your Azure ML workspace for data experimentation and visualization Perform ETL, data preparation, and feature extraction using Azure best practices Implement advanced feature extraction using NLP and word embeddings Train gradient boosted tree-ensembles, recommendation engines and deep neural networks on Azure ML Use hyperparameter tuning and AutoML to optimize your ML models Employ distributed ML on GPU clusters using Horovod in Azure ML Deploy, operate and manage your ML models at scale Automated your end-to-end ML process as CI/CD pipelines for MLOps Who this book is for This machine learning book is for data professionals, data analysts, data engineers, data scientists, or machine learning developers who want to master scalable cloud-based machine learning architectures in Azure. This book will help you use advanced Azure services to build intelligent machine learning applications. A basic understanding of Python and working knowledge of machine learning are mandatory. COMPUTERS,Information Technology

Convergence of Artificial Intelligence and the Internet of Things This book gathers recent research work on emerging Artificial Intelligence (AI) methods for processing and storing data generated by cloud-based Internet of Things (IoT) infrastructures. Major topics covered include the analysis and development of AI-powered mechanisms in future IoT applications and architectures. Further, the book addresses new technological developments, current research trends, and industry needs. Presenting case studies, experience and evaluation reports, and best practices in utilizing AI applications in IoT networks, it strikes a good balance between theoretical and practical issues. It also provides technical/scientific information on various aspects of AI technologies, ranging from basic concepts to research grade material, including future directions. The book is intended for researchers, practitioners, engineers and scientists involved in the design and development of protocols and AI applications for IoT-related devices. As the book covers a wide range of mobile applications and scenarios where IoT technologies can be applied, it also offers an essential introduction to the field. COMPUTERS,Information Technology

17th International Conference on Information Technology–New Generations (ITNG 2020) This volume presents the 17th International Conference on Information Technology—New Generations (ITNG), and chronicles an annual event on state of the art technologies for digital information and communications. The application of advanced information technology to such domains as astronomy, biology, education, geosciences, security, and healthcare are among the themes explored by the ITNG proceedings. Visionary ideas, theoretical and experimental results, as well as prototypes, designs, and tools that help information flow to end users are of special interest. Specific topics include Machine Learning, Robotics, High Performance Computing, and Innovative Methods of Computing. The conference features keynote speakers; a best student contribution award, poster award, and service award; a technical open panel, and workshops/exhibits from industry, government, and academia. COMPUTERS,Information Technology

Advanced Information Systems Engineering Workshops This book constitutes the thoroughly refereed proceedings of the international workshops associated with the 32nd International Conference on Advanced Information Systems Engineering, CAiSE 2020, which was planned to take place in Grenoble, France, during June 8-12, 2020. Due to the Coronavirus pandemic the conference was held virtually. The workshops included in this book are: KET4DF, The Second International Workshop on Key Enabling Technologies for Digital Factories ISESL, The First International Workshop on Information Systems Engineering for Smarter Life The total of 8 full and 3 short papers presented in this volume were carefully reviewed and selected from 20 submissions. The book also contains one invited talk. COMPUTERS,Information Technology

Internet of Things (IoT) This books objective is to explore the concepts and applications related to Internet of Things with the vision to identify and address existing challenges. Additionally, the book provides future research directions in this domain, and explores the different applications of IoT and its associated technologies. Studies investigate applications for crowd sensing and sourcing, as well as smart applications to healthcare solutions, agriculture and intelligent disaster management. This book will appeal to students, practitioners, industry professionals and researchers working in the field of IoT and its integration with other technologies to develop comprehensive solutions to real-life problems COMPUTERS,Information Technology

Enterprise, Business-Process and Information Systems Modeling This book contains the proceedings of two long-running events held along with the CAiSE conference relating to the areas of enterprise, business-process and information systems modeling: * the 21st International Conference on Business Process Modeling, Development and Support, BPMDS 2020, and * the 25th International Conference on Exploring Modeling Methods for Systems Analysis and Development, EMMSAD 2020. The conferences were planned to take place in Grenoble, France, during June 8–9, 2020. They were held virtually due to the COVID-19 pandemic. For BPMDS 13 full papers and 1 short paper were carefully reviewed and selected for publication from a total of 30 submissions; for EMMSAD 11 full papers and 4 short papers were accepted from 29 submissions. The papers were organized in topical sections named as follows: BPMDS: Business process execution and monitoring, BPM applications in industry and practice, planning and scheduling in business processes, process mining, process models and visualizations EMMSAD: Requirements and method engineering, enterprise and business modeling, software-related modeling, domain-speciï¬c modeling, evaluation-related research. COMPUTERS,Information Technology

Advanced Information Systems Engineering This book constitutes the refereed proceedings of the 32nd International Conference on Advanced Information Systems Engineering, CAiSE 2020, held in Grenoble, France, in June 2020.* The 33 full papers presented in this volume were carefully reviewed and selected from 185 submissions. The book also contains one invited talk in full paper length. The papers were organized in topical sections named: distributed applications; AI and big data in IS; process mining and analysis; requirements and modeling; and information systems engineering. Abstracts on the CAiSE 2020 tutorials can be found in the back matter of the volume. *The conference was held virtually due to the COVID-19 pandemic. COMPUTERS,Information Technology

Information Technology in Disaster Risk Reduction This volume constitutes the refereed and revised post-conference proceedings of the 4th IFIP TC 5 DCITDRR International Conference on Information Technology in Disaster Risk Reduction, ITDRR 2019, in Kyiv, Ukraine, in October 2019. The 17 full papers and 2 short papers presented were carefully reviewed and selected from 53 submissions. The papers focus on various aspects and challenges of coping with disaster risk reduction. The main topics include areas such as natural disasters, big data, cloud computing, Internet of Things, mobile computing, emergency management, disaster information processing, and disaster risk assessment and management. COMPUTERS,Information Technology

Benchmarking, Measuring, and Optimizing This book constitutes the refereed proceedings of the Second International Symposium on Benchmarking, Measuring, and Optimization, Bench 2019, held in Denver, CO, USA, in November 2019. The 20 full papers and 11 short papers presented were carefully reviewed and selected from 79 submissions. The papers are organized in topical sections named: Best Paper Session; AI Challenges on Cambircon using AIBenc; AI Challenges on RISC-V using AIBench; AI Challenges on X86 using AIBench; AI Challenges on 3D Face Recognition using AIBench; Benchmark; AI and Edge; Big Data; Datacenter; Performance Analysis; Scientific Computing. COMPUTERS,Information Technology

Web Engineering This book constitutes the proceedings of the 20th International Conference on Web Engineering, ICWE 2020, which was planned to take place in Helsinki, Finland, during June 9-12, 2020. Due to the corona pandemic the conference changed to a virtual format. The total of 24 full and 10 short contributions presented in this volume were carefully reviewed and selected from 78 submissions. The book also contains 4 PhD and 7 demo papers. The papers were organized in topical sections named: User interface technologies; performance of Web technologies; machine learning; testing of Web applications; emotion detection; location-aware applications; sentiment analysis; open data; liquid Web applications; Web-based learning; PhD symposium; demos and posters. COMPUTERS,Information Technology

Cybersecurity for Information Professionals Information professionals have been paying more attention and putting a greater focus on privacy over cybersecurity. However, the number of both cybersecurity and privacy breach incidents are soaring, which indicates that cybersecurity risks are high and growing. Utilizing cybersecurity awareness training in organizations has been an effective tool to promote a cybersecurity-conscious culture, making individuals more cybersecurity-conscious as well. However, it is unknown if employees’ security behavior at work can be extended to their security behavior at home and personal life. On the one hand, information professionals need to inherit their role as data and information gatekeepers to safeguard data and information assets. On the other hand, information professionals can aid in enabling effective information access and dissemination of cybersecurity knowledge to make users conscious about the cybersecurity and privacy risks that are often hidden in the cyber universe. Cybersecurity for Information Professionals: Concepts and Applications introduces fundamental concepts in cybersecurity and addresses some of the challenges faced by information professionals, librarians, archivists, record managers, students, and professionals in related disciplines. This book is written especially for educators preparing courses in information security, cybersecurity, and the integration of privacy and cybersecurity. The chapters contained in this book present multiple and diverse perspectives from professionals in the field of cybersecurity. They cover such topics as: Information governance and cybersecurity User privacy and security online and the role of information professionals Cybersecurity and social media Healthcare regulations, threats, and their impact on cybersecurity A socio-technical perspective on mobile cybersecurity Cybersecurity in the software development life cycle Data security and privacy Above all, the book addresses the ongoing challenges of cybersecurity. In particular, it explains how information professionals can contribute to long-term workforce development by designing and leading cybersecurity awareness campaigns or cybersecurity hygiene programs to change people’s security behavior. COMPUTERS,Information Technology

Cybercrime Investigations Cybercrime continues to skyrocket but we are not combatting it effectively yet. We need more cybercrime investigators from all backgrounds and working in every sector to conduct effective investigations. This book is a comprehensive resource for everyone who encounters and investigates cybercrime, no matter their title, including those working on behalf of law enforcement, private organizations, regulatory agencies, or individual victims. It provides helpful background material about cybercrime's technological and legal underpinnings, plus in-depth detail about the legal and practical aspects of conducting cybercrime investigations. Key features of this book include: Understanding cybercrime, computers, forensics, and cybersecurity Law for the cybercrime investigator, including cybercrime offenses; cyber evidence-gathering; criminal, private and regulatory law, and nation-state implications Cybercrime investigation from three key perspectives: law enforcement, private sector, and regulatory Financial investigation Identification (attribution) of cyber-conduct Apprehension Litigation in the criminal and civil arenas. This far-reaching book is an essential reference for prosecutors and law enforcement officers, agents and analysts; as well as for private sector lawyers, consultants, information security professionals, digital forensic examiners, and more. It also functions as an excellent course book for educators and trainers. We need more investigators who know how to fight cybercrime, and this book was written to achieve that goal. Authored by two former cybercrime prosecutors with a diverse array of expertise in criminal justice and the private sector, this book is informative, practical, and readable, with innovative methods and fascinating anecdotes throughout. COMPUTERS,Information Technology

Research Challenges in Information Science This book constitutes the proceedings of the 14th International Conference on Research Challenges in Information Sciences, RCIS 2020, held in Limassol, Cyprus, during September 23-25, 2020. The conference was originally scheduled for May 2020, but the organizing committee was forced to postpone the conference due to the outbreak of the COVID-19 pandemic. The scope of RCIS 2020 is summarized by the thematic areas of information systems and their engineering; user-oriented approaches; data and information management; business process management; domain-specific information systems engineering; data science; information infrastructures, and reflective research and practice. The 26 full papers and 3 work in progress papers presented in this volume were carefully reviewed and selected from 106 submissions. They were organized in topical sections named: Data Analytics and Business Intelligence; Digital Enterprise and Technologies; Human Factors in Information Systems; Information Systems Development and Testing; Machine Learning and Text Processing; and Security and Privacy. The volume also contains 12 poster and demo-papers, and 4 Doctoral Consortium papers. COMPUTERS,Information Technology

Quantum Error Correction This text presents an algebraic approach to the construction of several important families of quantum codes derived from classical codes by applying the well-known Calderbank-Shor-Steane (CSS), Hermitian, and Steane enlargement constructions to certain classes of classical codes. In addition, the book presents families of asymmetric quantum codes with good parameters and provides a detailed description of the procedures adopted to construct families of asymmetric quantum convolutional codes. Featuring accessible language and clear explanations, the book is suitable for use in advanced undergraduate and graduate courses as well as for self-guided study and reference. It provides an expert introduction to algebraic techniques of code construction and, because all of the constructions are performed algebraically, it enables the reader to construct families of codes, rather than only codes with specific parameters. The text offers an abundance of worked examples, exercises, and open-ended problems to motivate the reader to further investigate this rich area of inquiry. End-of-chapter summaries and a glossary of key terms allow for easy review and reference. COMPUTERS,Information Technology

Current Trends in Web Engineering This book constitutes the thoroughly refereed post-workshop proceedings of the 19th International Conference on Web Engineering, ICWE 2019, held in Daejeon, South Korea, in June 2019. The 11 revised full papers were selected from 25 submissions. The workshops complement the main conference and explore new trends on core topics of Web engineering and provide an open discussion space combining solid theory work with practical on-the-field experience. The workshop committee accepted three workshops for publication in this volume: 5th International Workshop on Knowledge Discovery on the Web (KDWEB 2019), Second International Workshop on Maturity of Web Engineering Practices (MATWEP 2019), International Workshop on Data Science and Knowledge Graph (DSKG 2019). COMPUTERS,Information Technology

Media Technologies Scholars from communication and media studies join those from science and technology studies to examine media technologies as complex, sociomaterial phenomena. In recent years, scholarship around media technologies has finally shed the assumption that these technologies are separate from and powerfully determining of social life, looking at them instead as produced by and embedded in distinct social, cultural, and political practices. Communication and media scholars have increasingly taken theoretical perspectives originating in science and technology studies (STS), while some STS scholars interested in information technologies have linked their research to media studies inquiries into the symbolic dimensions of these tools. In this volume, scholars from both fields come together to advance this view of media technologies as complex sociomaterial phenomena. The contributors first address the relationship between materiality and mediation, considering such topics as the lived realities of network infrastructure. The contributors then highlight media technologies as always in motion, held together through the minute, unobserved work of many, including efforts to keep these technologies alive. Contributors Pablo J. Boczkowski, Geoffrey C. Bowker, Finn Brunton, Gabriella Coleman, Gregory J. Downey, Kirsten A. Foot, Tarleton Gillespie, Steven J. Jackson, Christopher M. Kelty, Leah A. Lievrouw, Sonia Livingstone, Ignacio Siles, Jonathan Sterne, Lucy Suchman, Fred Turner COMPUTERS,Information Technology

Scholarship in the Digital Age An exploration of the technical, social, legal, and economic aspects of the scholarly infrastructure needed to support research activities in all fields in the twenty-first century. Scholars in all fields now have access to an unprecedented wealth of online information, tools, and services. The Internet lies at the core of an information infrastructure for distributed, data-intensive, and collaborative research. Although much attention has been paid to the new technologies making this possible, from digitized books to sensor networks, it is the underlying social and policy changes that will have the most lasting effect on the scholarly enterprise. In Scholarship in the Digital Age, Christine Borgman explores the technical, social, legal, and economic aspects of the kind of infrastructure that we should be building for scholarly research in the twenty-first century. Borgman describes the roles that information technology plays at every stage in the life cycle of a research project and contrasts these new capabilities with the relatively stable system of scholarly communication, which remains based on publishing in journals, books, and conference proceedings. No framework for the impending “data deluge” exists comparable to that for publishing. Analyzing scholarly practices in the sciences, social sciences, and humanities, Borgman compares each discipline's approach to infrastructure issues. In the process, she challenges the many stakeholders in the scholarly infrastructure—scholars, publishers, libraries, funding agencies, and others—to look beyond their own domains to address the interaction of technical, legal, economic, social, political, and disciplinary concerns. Scholarship in the Digital Age will provoke a stimulating conversation among all who depend on a rich and robust scholarly environment. COMPUTERS,Information Technology

Transforming Global Information and Communication Markets Innovation in information and communication technology (ICT) fuels the growth of the global economy. How ICT markets evolve depends on politics and policy, and since the 1950s periodic overhauls of ICT policy have transformed competition and innovation. For example, in the 1980s and the 1990s a revolution in communication policy (the introduction of sweeping competition) also transformed the information market. Today, the diffusion of Internet, wireless, and broadband technology, growing modularity in the design of technologies, distributed computing infrastructures, and rapidly changing business models signal another shift. This pathbreaking examination of ICT from a political economy perspective argues that continued rapid innovation and economic growth require new approaches in global governance that will reconcile diverse interests and enable competition to flourish. The authors (two of whom were architects of international ICT policy reforms in the 1990s) discuss this crucial turning point in both theoretical and practical terms. COMPUTERS,Information Technology

Human Information Retrieval An overview of information retrieval rooted in the humanities and social sciences but informed by an understanding of information technology and information theory. Information retrieval in the age of Internet search engines has become part of ordinary discourse and everyday practice: “Google” is a verb in common usage. Thus far, more attention has been given to practical understanding of information retrieval than to a full theoretical account. In Human Information Retrieval, Julian Warner offers a comprehensive overview of information retrieval, synthesizing theories from different disciplines (information and computer science, librarianship and indexing, and information society discourse) and incorporating such disparate systems as WorldCat and Google into a single, robust theoretical framework. There is a need for such a theoretical treatment, he argues, one that reveals the structure and underlying patterns of this complex field while remaining congruent with everyday practice. Warner presents a labor theoretic approach to information retrieval, building on his previously formulated distinction between semantic and syntactic mental labor, arguing that the description and search labor of information retrieval can be understood as both semantic and syntactic in character. Warner's information science approach is rooted in the humanities and the social sciences but informed by an understanding of information technology and information theory. The chapters offer a progressive exposition of the topic, with illustrative examples to explain the concepts presented. Neither narrowly practical nor largely speculative, Human Information Retrieval meets the contemporary need for a broader treatment of information and information systems. COMPUTERS,Information Technology

Subversion, Conversion, Development Explorations of design, use, and reuse of information technology in diverse historical and cultural contexts. This book explores alternative cultural encounters with and around information technologies. These encounters are alternative because they counter dominant, Western-oriented notions of media consumption; they include media practices as forms of cultural resistance and subversion, “DIY cultures,” and other nonmainstream models of technology production. The contributors—leading thinkers in science and technology studies, anthropology, and software design—pay special attention to the specific inflections that different cultures and communities give to the value of knowledge. The richly detailed accounts presented here challenge the dominant view of knowledge as a neutral good—information available for representation and encoding but separated from all social relations. The chapters examine specific cases in which the forms of knowledge and cross-cultural encounters are shaping technology use and development. They consider design, use, and reuse of technological tools, including databases, GPS devices, books, and computers, in locations that range from Australia and New Guinea to Germany and the United States. Contributors Poline Bala, Alan Blackwell, Wade Chambers, Michael Christie, Hildegard Diemberger, Stephen Hugh-Jones, James Leach, Jerome Lewis, Dawn Nafus, Gregers Petersen, Marilyn Strathern, David Turnbull, Helen Verran, Laura Watts, Lee Wilson COMPUTERS,Information Technology

Library Information Technology and Networks Offers an historical perspective of the past 25 years of computers in libraries, profileing currently available processing systems according to their size and platform. The short- and long-term future of information technology in libraries.;College or university bookstores may order five or more copies at a special student price which is available from Marcel Dekker upon request. COMPUTERS,Information Technology

Business Modeling and Software Design This book constitutes the refereed proceedings of the 10th International Symposium on Business Modeling and Software Design, BMSD 2020, which took place in Berlin, Germany, in July 2020. BMSD is a leading international forum that brings together researchers and practitioners interested in business modeling and its relation to software design. Particular areas of interest are: Business Processes and Enterprise Engineering; Business Models and Requirements; Business Models and Services; Business Models and Software; Information Systems Architectures and Paradigms; Data Aspects in Business Modeling and Software Development; Blockchain-Based Business Models and Information Systems; IoT and Implications for Enterprise Information Systems. The theme of BMSD 2020 was: Towards Knowledge-Driven Enterprise Information Systems. COMPUTERS,Information Technology

Design, Operation and Evaluation of Mobile Communications This LNCS 12216 constitutes the refereed proceedings of the First International Conference on Design, Operation and Evaluation of Mobile Communications, MOBILE 2020, held as part of HCI International 2020 in Copenhagen, Denmark in July 2020. The conference was held virtually due to the corona pandemic. The total of 1439 papers and 238 posters included in the 40 HCII 2020 proceedings volumes was carefully reviewed and selected from 6326 submissions. The regular papers of Design, Operation and Evaluation of Mobile Communications, MOBILE 2020, presented in this volume were organized in topical section around the subject: Design, Operation and Evaluation of Mobile Communications. COMPUTERS,Information Technology

HCI in Games This book constitutes the refereed proceedings of the Second International Conference on HCI in Games, HCI-Games 2020, held in July 2020 as part of HCI International 2020 in Copenhagen, Denmark.* HCII 2020 received a total of 6326 submissions, of which 1439 papers and 238 posters were accepted for publication after a careful reviewing process. The 38 papers presented in this volume are organized in topical sections named: designing games and gamified interactions; user engagement and game impact; and serious games. *The conference was held virtually due to the COVID-19 pandemic. COMPUTERS,Information Technology

Distributed, Ambient and Pervasive Interactions This conference proceeding LNCS 12203 constitutes the refereed proceedings of the 12th International Conference on Cross-Cultural Design, CCD 2020, held as part of HCI International 2020 in Copenhagen, Denmark in July 2020. The conference was held virtually due to the corona pandemic. The total of 1439 papers and 238 posters included in the 40 HCII 2020 proceedings volumes was carefully reviewed and selected from 6326 submissions. The regular papers of DAPI 2020, Distributed, Ambient and Pervasive Interactions, presented in this volume were organized in topical sections named: Design Approaches, Methods and Tools, Smart Cities and Landscapes, Well-being, Learning and Culture in Intelligent Environments and much more. COMPUTERS,Information Technology

The First Generation of Electronic Records Archivists in the United States This book helps readers understand the current status of archivists in the United States. It addresses issues of professionalization by re-examining two major aspects of the archival community: institutional forms and structures, and the basic educational foundations that are important to any profession. While United States archivists now seem poised to develop new approaches to the management of electronic records, including research and education venues, this profession?s long journey to reach this point is an interesting step on the continuing road to professionalization. The First Generation of Electronic Records Archivists in the United States represents the first major study of how and why American archivists have struggled to contend with the management of electronic records. The book provides a framework for studying this issue, includes suggestions for additional research, and serves as a basis for discussion about the continued strengthening of the archival profession. Despite more than thirty years of striving to manage electronic records, American archivists have not developed an effective infrastructure for this purpose. The First Generation of Electronic Records Archivists in the United States considers the evidence for this failure by evaluating archival literature on the topic of electronic records management. It examines how position descriptions in state government archives and job advertisements across the discipline have reflected a bias toward paper-based formats, and the failure of graduate and continuing archival education programs to deal effectively with electronic records. The book details: state government archives and position descriptions trends and practices in the Information Age, 1976--1990 graduate archival education and electronic records: an analysis of current approaches and their strengths and weaknesses the effectiveness of the NAGARA Institute as a form of advanced archival education problems, challenges, opportunities, and needs for additional research The First Generation of Electronic Records Archivists in the United States is an enlightening study for library and information science educators, archival graduate students, and archivists themselves as they work toward the professionalization of their field. COMPUTERS,Information Technology

Multimedia and Megachange The use of multimedia strikes at the very heart of traditional teaching and learning methods, and is changing the way educators think about the whole process of teaching and learning. Multimedia and Megachange spurs ideas for the use of interactive technology to revolutionize teaching and learning. It describes and analyzes issues and trends that are currently setting a research and development agenda for educators. Contributors to this volume explore all fronts on which computer technology are changing the educational process: concept and theory research application design Multimedia and Megachange opens up the exciting world of how technology is dramatically changing how teachers teach and students learn. It also highlights spin-off changes for classroom management, greater sources of information, and improved evaluation and grading techniques. COMPUTERS,Information Technology

Scientific and Technical Information Resources This book focuses on current practices in scientific and technical communication, historical aspects, and characteristics and biblioÂgraphic control of various forms of scientific and technical literature. It integrates the inventory approach for scientific and technical communication. COMPUTERS,Information Technology

Acronyms and Abbreviations of Computer Technology and Telecommunications Catalogues approximately 7000 acronyms and abbreviations used in computer technology, telecommunications and related fields. The entries are organized in tabular form to enable readers to locate any specific acronym easily. COMPUTERS,Information Technology

Effective Methods for Software Engineering Software is important because it is used by a great many people in companies and institutions. This book presents engineering methods for designing and building software. Based on the author’s experience in software engineering as a programmer in the defense and aerospace industries, this book explains how to ensure a software that is programmed operates according to its requirements. It also shows how to develop, operate, and maintain software engineering capabilities by instilling an engineering discipline to support programming, design, builds, and delivery to customers. This book helps software engineers to: Understand the basic concepts, standards, and requirements of software engineering. Select the appropriate programming and design techniques. Effectively use software engineering tools and applications. Create specifications to comply with the software standards and requirements. Utilize various methods and techniques to identify defects. Manage changes to standards and requirements. Besides providing a technical view, this book discusses the moral and ethical responsibility of software engineers to ensure that the software they design and program does not cause serious problems. Software engineers tend to be concerned with the technical elegance of their software products and tools, whereas customers tend to be concerned only with whether a software product meets their needs and is easy and ready to use. This book looks at these two sides of software development and the challenges they present for software engineering. A critical understanding of software engineering empowers developers to choose the right methods for achieving effective results. Effective Methods for Software Engineering guides software programmers and developers to develop this critical understanding that is so crucial in today’s software-dependent society. COMPUTERS,Information Technology

Databases and Mobile Computing Database and Mobile Computing brings together in one place important contributions and up-to-date research results in this important area. Databases and Mobile Computing serves as an excellent reference, providing insight into some of the most important research issues in the field. COMPUTERS,Information Theory

Video Database Systems Great advances have been made in the database field. Relational and object- oriented databases, distributed and client/server databases, and large-scale data warehousing are among the more notable. However, none of these advances promises to have as great and direct an effect on the daily lives of ordinary citizens as video databases. Video databases will provide a quantum jump in our ability to deal with visual data, and in allowing people to access and manipulate visual information in ways hitherto thought impossible. Video Database Systems: Issues, Products and Applications gives practical information on academic research issues, commercial products that have already been developed, and the applications of the future driving this research and development. This book can also be considered a reference text for those entering the field of video or multimedia databases, as well as a reference for practitioners who want to identify the kinds of products needed in order to utilize video databases. Video Database Systems: Issues, Products and Applications covers concepts, products and applications. It is written at a level which is less detailed than that normally found in textbooks but more in-depth than that normally written in trade press or professional reference books. Thus, it seeks to serve both an academic and industrial audience by providing a single source of information about the research issues in the field, and the state-of-the-art of practice. COMPUTERS,Information Theory

Model Theory Since the second edition of this book (1977), Model Theory has changed radically, and is now concerned with fields such as classification (or stability) theory, nonstandard analysis, model-theoretic algebra, recursive model theory, abstract model theory, and model theories for a host of nonfirst order logics. Model theoretic methods have also had a major impact on set theory, recursion theory, and proof theory.This new edition has been updated to take account of these changes, while preserving its usefulness as a first textbook in model theory. Whole new sections have been added, as well as new exercises and references. A number of updates, improvements and corrections have been made to the main text. COMPUTERS,Information Theory

Entropy and Information Theory 1 Information Sources.- 2 Entropy and Information.- 3 The Entropy Ergodic Theorem.- 4 Information Rates I.- 5 Relative Entropy.- 6 Information Rates II.- 7 Relative Entropy Rates.- 8 Ergodic Theorems for Densities.- 9 Channels and Codes.- 10 Distortion.- 11 Source Coding Theorems.- 12 Coding for noisy channels. COMPUTERS,Information Theory

Climate and Environmental Database Systems Climate and Environmental Database Systems contains the papers presented at the Second International Workshop on Climate and Environmental Database Systems, held November 21-23, 1995, in Hamburg, Germany. Climate and environmental data may be separated into two classes, large amounts of well structured data and smaller amounts of less structured data. The large amounts are produced by numerical climate models and by satellites, handling data in the order of magnitude of 100 Tbytes for the climate modelling sites and 1000 Tbytes for the recording and processing of satellite data. Smaller amounts of poorly structured data are the environmental data, which come mainly from observations and measurements. Present-day problems in data management are connected with a variety of data types. Climate and Environmental Database Systems addresses the state of the art, practical experience, and future perspectives for climate and environmental database systems, and may be used as a text for a graduate level course on the subject or as a reference for researchers or practitioners in industry. COMPUTERS,Information Theory

Flexible Query Answering Systems Flexible Query Answering Systems is an edited collection of contributed chapters. It focuses on developing computer systems capable of transforming a query into an answer with useful information. The emphasis is on problems associated with high-level intelligent answering systems. The coverage is multidisciplinary with chapters by authors from information science, logic, fuzzy systems, databases, artificial intelligence and knowledge representation. Each contribution represents a theory involving flexibility in query-answering, and each addresses specific answering problems. Coverage includes topics such as fuzzy sets in flexible querying, non-standard database interactions, metareasoning and agents, and many others. Contributions for this volume were written by leading researchers from their respective subject areas, including Patrick Bosc, Bernadette Bouchon-Meunier, Amihai Motro, Henri Prade and Ron Yager, among others. Flexible Query Answering Systems is a timely contribution for researchers working on high-level query mechanism systems. COMPUTERS,Information Theory

Index Data Structures in Object-Oriented Databases Object-oriented database management systems (OODBMS) are used to imple ment and maintain large object databases on persistent storage. Regardless whether the underlying database model follows the object-oriented, the rela tional or the object-relational paradigm, a key feature of any DBMS product is content based access to data sets. On the one hand this feature provides user-friendly query interfaces based on predicates to describe the desired data. On the other hand it poses challenging questions regarding DBMS design and implementation as well as the application development process on top of the DBMS. The reason for the latter is that the actual query performance depends on a technically meaningful use of access support mechanisms. In particular, if chosen and applied properly, such a mechanism speeds up the execution of predicate based queries. In the object-oriented world, such queries may involve arbitrarily complex terms referring to inheritance hierarchies and aggregation paths. These features are attractive at the application level, however, they increase the complexity of appropriate access support mechanisms which are known to be technically non-trivial in the relational world. COMPUTERS,Information Theory

Information and Meaning Information and Meaning is the third book in a trilogy exploring the nature of information, intelligence and meaning. It begins by providing an overview of the first two works of the trilogy, then goes on to consider the meaning of meaning. This explorat ion leads to a theory of how the brain works. This book differs from others in the field, in that it is written from the perspective of a theoretical biologist looking at the evolution of information systems as a basis for studying the phenomena of information, intelligence and meaning. It describes how neurons create a brain which understands information inputs and then is able to operate on such information. COMPUTERS,Information Theory

Indexing Techniques for Advanced Database Systems Recent years have seen an explosive growth in the use of new database applications such as CAD/CAM systems, spatial information systems, and multimedia information systems. The needs of these applications are far more complex than traditional business applications. They call for support of objects with complex data types, such as images and spatial objects, and for support of objects with wildly varying numbers of index terms, such as documents. Traditional indexing techniques such as the B-tree and its variants do not efficiently support these applications, and so new indexing mechanisms have been developed. As a result of the demand for database support for new applications, there has been a proliferation of new indexing techniques. The need for a book addressing indexing problems in advanced applications is evident. For practitioners and database and application developers, this book explains best practice, guiding the selection of appropriate indexes for each application. For researchers, this book provides a foundation for the development of new and more robust indexes. For newcomers, this book is an overview of the wide range of advanced indexing techniques. Indexing Techniques for Advanced Database Systems is suitable as a secondary text for a graduate level course on indexing techniques, and as a reference for researchers and practitioners in industry. COMPUTERS,Information Theory

Groupware and the World Wide Web The advent of the World Wide Web has changed the perspectives of groupware systems. The interest and deployment of Internet and intranet groupware solutions is growing rapidly, not just in academic circles but also in the commercial arena. The first generation of Web-based groupware tools has already started to emerge, and leading groupware vendors are urgently adapting their products for compatibility and integration with Web technologies. The focus of Groupware and the World Wide Web is to explore the potential for Web-based groupware. This book includes an analysis of the key characteristics of the Web, presenting reasons for its success, and describes developments of a diverse range of Web-based groupware systems. An emphasis on the technical obstacles and challenges is implemented by more analytical discussions and perspectives, including that of Information Technology managers looking to deploy groupware solutions within their organizations. Written by experts from different backgrounds - academic and commercial, technical and organizational - this book provides a unique overview of and insight into current issues and future possibilities concerning extension of the World Wide Web for group working. COMPUTERS,Information Theory

Intelligent Data Analysis in Medicine and Pharmacology Intelligent data analysis, data mining and knowledge discovery in databases have recently gained the attention of a large number of researchers and practitioners. This is witnessed by the rapidly increasing number of submissions and participants at related conferences and workshops, by the emergence of new journals in this area (e.g., Data Mining and Knowledge Discovery, Intelligent Data Analysis, etc.), and by the increasing number of new applications in this field. In our view, the awareness of these challenging research fields and emerging technologies has been much larger in industry than in medicine and pharmacology. The main purpose of this book is to present the various techniques and methods that are available for intelligent data analysis in medicine and pharmacology, and to present case studies of their application. Intelligent Data Analysis in Medicine and Pharmacology consists of selected (and thoroughly revised) papers presented at the First International Workshop on Intelligent Data Analysis in Medicine and Pharmacology (IDAMAP-96) held in Budapest in August 1996 as part of the 12th European Conference on Artificial Intelligence (ECAI-96), IDAMAP-96 was organized with the motivation to gather scientists and practitioners interested in computational data analysis methods applied to medicine and pharmacology, aimed at narrowing the increasing gap between excessive amounts of data stored in medical and pharmacological databases on the one hand, and the interpretation, understanding and effective use of stored data on the other hand. Besides the revised Workshop papers, the book contains a selection of contributions by invited authors. The expected readership of the book is researchers and practitioners interested in intelligent data analysis, data mining, and knowledge discovery in databases, particularly those who are interested in using these technologies in medicine and pharmacology. Researchers and students in artificial intelligence and statistics should find this book of interest as well. Finally, much of the presented material will be interesting to physicians and pharmacologists challenged by new computational technologies, or simply in need of effectively utilizing the overwhelming volumes of data collected as a result of improved computer support in their daily professional practice. COMPUTERS,Information Theory

Database Issues in Geographic Information Systems Geographic Information Systems (GIS) have been experiencing a steady and unprecedented growth in terms of general interest, theory development, and new applications in the last decade or so. GIS is an inter-disciplinary field that brings together many diverse areas such as computer science, geography, cartography, engineering, and urban planning. Database Issues in Geographic Information Systems approaches several important topics in GIS from a database perspective. Database management has a central role to play in most computer-based information systems, and is expected to have an equally important role to play in managing information in GIS as well. Existing database technology, however, focuses on the alphanumeric data that are required in business applications. GIS, like many other application areas, requires the ability to handle spatial as well as alphanumeric data. This requires new innovations in data management, which is the central theme of this monograph. The monograph begins with an overview of different application areas and their data and functional requirements. Next it addresses the following topics in the context of GIS: representation and manipulation of spatial data, data modeling, indexing, and query processing. Future research directions are outlined in each of the above topics. The last chapter discusses issues that are emerging as important areas of technological innovations in GIS. Database Issues in Geographic Information Systems is suitable as a secondary text for a graduate level course on Geographic Information Systems, Database Systems or Cartography, and as a reference for researchers and practitioners in industry. COMPUTERS,Information Theory

Advanced Transaction Models and Architectures Motivation Modem enterprises rely on database management systems (DBMS) to collect, store and manage corporate data, which is considered a strategic corporate re source. Recently, with the proliferation of personal computers and departmen tal computing, the trend has been towards the decentralization and distribution of the computing infrastructure, with autonomy and responsibility for data now residing at the departmental and workgroup level of the organization. Users want their data delivered to their desktops, allowing them to incor porate data into their personal databases, spreadsheets, word processing doc uments, and most importantly, into their daily tasks and activities. They want to be able to share their information while retaining control over its access and distribution. There are also pressures from corporate leaders who wish to use information technology as a strategic resource in offering specialized value-added services to customers. Database technology is being used to manage the data associated with corporate processes and activities. Increasingly, the data being managed are not simply formatted tables in relational databases, but all types of ob jects, including unstructured text, images, audio, and video. Thus, the database management providers are being asked to extend the capabilities of DBMS to include object-relational models as well as full object-oriented database man agement systems. COMPUTERS,Information Theory

Real-Time Database and Information Systems Real-time systems are defined as those for which correctness depends not only on the logical properties of the produced results, but also on the temporal properties of these results. In a database, real-time means that in addition to typical logical consistency constraints, such as a constraint on a data item's value, there are constraints on when transactions execute and on the `freshness' of the data transactions access. The challenges and tradeoffs faced by the designers of real-time database systems are quite different from those faced by the designers of general-purpose database systems. To achieve the fundamental requirements of timeliness and predictability, not only do conventional methods for scheduling and transaction management have to be redesigned, but also new concepts that have not been considered in conventional database systems or in real-time systems need to be added. Real-Time Database and Information Systems: Research Advances is devoted to new techniques for scheduling of transactions, concurrency management, transaction logging, database languages, and new distributed database architectures. Real-Time Database and Information Systems: Research Advances is primarily intended for practicing engineers and researchers working in the growing area of real-time database and information retrieval systems. For practitioners, the book will provide a much needed bridge for technology transfer and continued education. For researchers, the book will provide a comprehensive reference for well-established results. The book can also be used in a senior or graduate level course on real-time systems, real-time database systems, and database systems, or closely related courses. COMPUTERS,Information Theory

Client Data Caching Despite the significant ongoing work in the development of new database systems, many of the basic architectural and performance tradeoffs involved in their design have not previously been explored in a systematic manner. The designers of the various systems have adopted a wide range of strategies in areas such as process structure, client-server interaction, concurrency control, transaction management, and memory management. This monograph investigates several fundamental aspects of the emerging generation of database systems. It describes and investigates implementation techniques to provide high performance and scalability while maintaining the transaction semantics, reliability, and availability associated with more traditional database architectures. The common theme of the techniques developed here is the exploitation of client resources through caching-based data replication. Client Data Caching: A Foundation for High Performance Object Database Systems should be a value to anyone interested in the performance and architecture of distributed information systems in general and Object-based Database Management Systems in particular. It provides useful information for designers of such systems, as well as for practitioners who need to understand the inherent tradeoffs among the architectural alternatives in order to evaluate existing systems. Furthermore, many of the issues addressed in this book are relevant to other systems beyond the ODBMS domain. Such systems include shared-disk parallel database systems, distributed file systems, and distributed virtual memory systems. The presentation is suitable for practitioners and advanced students in all of these areas, although a basic understanding of database transaction semantics and techniques is assumed. COMPUTERS,Information Theory

Implementing Practical DB2 Applications Implementing Practical DB2 Applications provides a concise source of information for the development and implication of applications using IBM's DB2 relational database package in the MVS environment. The book describes the flagship DB2 version, namely that implemented for the MVS operating system environment where DB2 operates with the MVS transaction processing subsystems: CICS, IMS and TSO. The book is intended for both beginners and experts. It describes how the various components of SQL are used to provide practical applications. Containing tips and notes that were discovered the hard way - through hands on experience - this book will be welcomed by all those looking to implement applications in DB2. COMPUTERS,Information Theory

Database Concurrency Control Database Concurrency Control: Methods, Performance and Analysis is a review of developments in concurrency control methods for centralized database systems, with a quick digression into distributed databases and multicomputers, the emphasis being on performance. The main goals of Database Concurrency Control: Methods, Performance and Analysis are to succinctly specify various concurrency control methods; to describe models for evaluating the relative performance of concurrency control methods; to point out problem areas in earlier performance analyses; to introduce queuing network models to evaluate the baseline performance of transaction processing systems; to provide insights into the relative performance of transaction processing systems; to illustrate the application of basic analytic methods to the performance analysis of various concurrency control methods; to review transaction models which are intended to relieve the effect of lock contention; to provide guidelines for improving the performance of transaction processing systems due to concurrency control; and to point out areas for further investigation. This monograph should be of direct interest to computer scientists doing research on concurrency control methods for high performance transaction processing systems, designers of such systems, and professionals concerned with improving (tuning) the performance of transaction processing systems. COMPUTERS,Information Theory

Theoretical Advances in Neural Computation and Learning For any research field to have a lasting impact, there must be a firm theoretical foundation. Neural networks research is no exception. Some of the founda tional concepts, established several decades ago, led to the early promise of developing machines exhibiting intelligence. The motivation for studying such machines comes from the fact that the brain is far more efficient in visual processing and speech recognition than existing computers. Undoubtedly, neu robiological systems employ very different computational principles. The study of artificial neural networks aims at understanding these computational prin ciples and applying them in the solutions of engineering problems. Due to the recent advances in both device technology and computational science, we are currently witnessing an explosive growth in the studies of neural networks and their applications. It may take many years before we have a complete understanding about the mechanisms of neural systems. Before this ultimate goal can be achieved, an swers are needed to important fundamental questions such as (a) what can neu ral networks do that traditional computing techniques cannot, (b) how does the complexity of the network for an application relate to the complexity of that problem, and (c) how much training data are required for the resulting network to learn properly? Everyone working in the field has attempted to answer these questions, but general solutions remain elusive. However, encouraging progress in studying specific neural models has been made by researchers from various disciplines. COMPUTERS,Information Theory

Universal Compression and Retrieval Objectives Computer and communication practice relies on data compression and dictionary search methods. They lean on a rapidly developing theory. Its exposition from a new viewpoint is the purpose of the book. We start from the very beginning and finish with the latest achievements of the theory, some of them in print for the first time. The book is intended for serving as both a monograph and a self-contained textbook. Information retrieval is the subject of the treatises by D. Knuth (1973) and K. Mehlhorn (1987). Data compression is the subject of source coding. It is a chapter of information theory. Its up-to-date state is presented in the books of Storer (1988), Lynch (1985), T. Bell et al. (1990). The difference between them and the present book is as follows. First. We include information retrieval into source coding instead of discussing it separately. Information-theoretic methods proved to be very effective in information search. Second. For many years the target of the source coding theory was the estimation of the maximal degree of the data compression. This target is practically bit today. The sought degree is now known for most of the sources. We believe that the next target must be the estimation of the price of approaching that degree. So, we are concerned with trade-off between complexity and quality of coding. Third. We pay special attention to universal families that contain a good com pressing map for every source in a set. COMPUTERS,Information Theory

Automatic Parallelization Distributed-memory multiprocessing systems (DMS), such as Intel's hypercubes, the Paragon, Thinking Machine's CM-5, and the Meiko Computing Surface, have rapidly gained user acceptance and promise to deliver the computing power required to solve the grand challenge problems of Science and Engineering. These machines are relatively inexpensive to build, and are potentially scalable to large numbers of processors. However, they are difficult to program: the non-uniformity of the memory which makes local accesses much faster than the transfer of non-local data via message-passing operations implies that the locality of algorithms must be exploited in order to achieve acceptable performance. The management of data, with the twin goals of both spreading the computational workload and minimizing the delays caused when a processor has to wait for non-local data, becomes of paramount importance. When a code is parallelized by hand, the programmer must distribute the program's work and data to the processors which will execute it. One of the common approaches to do so makes use of the regularity of most numerical computations. This is the so-called Single Program Multiple Data (SPMD) or data parallel model of computation. With this method, the data arrays in the original program are each distributed to the processors, establishing an ownership relation, and computations defining a data item are performed by the processors owning the data. COMPUTERS,Information Theory

Interfaces to Database Systems (IDS92) Despite the volume of research carried out into the design of database systems and the design of user interfaces, there is little cross-fertilization between the two areas. The control of user interfaces to database systems is, therefore, significantly less advanced than other aspects of DBMS design. As database functionality is used in a wider range of areas, such as design applications, the suitability of the user interface is becoming increasingly important. It is, therefore, necessary to begin applying the knowledge developed by HCI researchers to the specialised domain of database systems. This volume contains revised papers from the International Workshop on Interfaces to Database Systems, held in Glasgow, 1-3 July 1992. The workshop aimed to develop an interaction between the design of database systems and user interfaces. It discussed both the production of interfaces tailored to particular applications, and also more general systems within which interfaces can be developed. Some of the papers concentrate on usability aspects, some discuss different interface metaphors, whilst others tackle the question of designing a general conceptual model. The latter topic is of particular importance, as it is only by achieving an abstract model of what the user understands to be in the database that the data can be associated with appropriate interface facilities. Among the contents of the volume are: integrated interfaces to publicly available databases; database query interface for medical information systems; an integrated approach to task oriented database retrieval interfaces; GRADI: a graphical database interface for a multimedia DBMS; cognitive view mechanism for multimedia information systems; a graphical schema representation for object oriented databases; a conceptual framework for error analysis in SQL interfaces; a browser for a version entity relationship database. Interfaces to Database Systems (IDS92) is unique in that it brings together a variety of approaches from the database and HCI research communities. It will provide essential reading for researchers of database systems and also industrial developers of DBMS. COMPUTERS,Information Theory

Research Directions in Database Security Many commercial and defense applications require a database system that protects data of different sensitivities while still allowing users of different clearances to access the system. This book is a collection of papers covering aspects of the emerging security technology for multilevel database systems. It contains reports on such landmark systems as SeaView, LDV, ASD, Secure Sybase, the UNISYS secure distributed system, and the secure entity-relationship system GTERM. Much of the research is concerned with the relational model, although security for the entity-relationship and object-oriented models of data are also discussed. Because the field is so new, it has been extremely difficult to learn about the research going on in this area, until now. This book will be invaluable to researchers and system designers in database systems and computer security. It will also be of interest to data users and custodians who are concerned with the security of their information. This book can also be used as a text for an advanced topics course on computer security in a computer science curriculum. COMPUTERS,Information Theory

Understanding Compression If you want to attract and retain users in the booming mobile services market, you need a quick-loading app that won’t churn through their data plans. The key is to compress multimedia and other data into smaller files, but finding the right method is tricky. This witty book helps you understand how data compression algorithms work—in theory and practice—so you can choose the best solution among all the available compression tools. With tables, diagrams, games, and as little math as possible, authors Colt McAnlis and Aleks Haecky neatly explain the fundamentals. Learn how compressed files are better, cheaper, and faster to distribute and consume, and how they’ll give you a competitive edge. Learn why compression has become crucial as data production continues to skyrocket Know your data, circumstances, and algorithm options when choosing compression tools Explore variable-length codes, statistical compression, arithmetic numerical coding, dictionary encodings, and context modeling Examine tradeoffs between file size and quality when choosing image compressors Learn ways to compress client- and server-generated data objects Meet the inventors and visionaries who created data compression algorithms COMPUTERS,Information Theory

Quantum Random Number Generation This book provides an overview of state-of-the-art implementations of quantum random number generators (QRNGs), and especially examines their relation to classical statistical randomness models and numerical techniques for computing random numbers. The reader – who ideally has a background in classical statistics, computer science, or cryptography – is introduced to the world of quantum bits step by step, and explicit relations between QRNGs and their classical counterparts are identified along the way. Random number generation is a major pillar of cryptography. Capitalizing on the randomness inherent in quantum phenomena is a rapidly evolving branch of quantum cryptography with countless applications for the future. The value of quantum randomness for cryptographic purposes is empirically demonstrated in statistical evaluations of QRNGs’ performance compared to classical techniques for true and pseudorandom number generation. The book then provides an overview of technical implementations of QRNGs, before a concluding discussion of major achievements and remaining obstacles in the field rounds out the coverage, while also opening the door for future research directions. COMPUTERS,Information Theory

Algorithmic Information Theory for Physicists and Natural Scientists This book has been written in the hope that readers will be able to absorb the key ideas behind algorithmic information theory so that they are in a better position to access the mathematical developments and to apply the ideas to their own areas of interest. COMPUTERS,Information Theory

Search Foundations A call to redirect the intellectual focus of information retrieval and science (IR&S) toward the phenomenon of technology-mediated experience. In this book, Sachi Arafat and Elham Ashoori issue a call to reorient the intellectual focus of information retrieval and science (IR&S) away from search and related processes toward the more general phenomenon of technology-mediated experience. Technology-mediated experience accounts for an increasing proportion of human lived experience; the phenomenon of mediation gets at the heart of the human-machine relationship. Framing IR&S more broadly in this way generalizes its problems and perspectives, dovetailing them with those shared across disciplines dealing with socio-technical phenomena. This reorientation of IR&S requires imagining it as a new kind of science: a science of technology-mediated experience (STME). Arafat and Ashoori not only offer detailed analysis of the foundational concepts underlying IR&S and other technical disciplines but also boldly call for a radical, systematic appropriation of the sciences and humanities to create a better understanding of the human-technology relationship. Arafat and Ashoori discuss the notion of progress in IR&S and consider ideas of progress from the history and philosophy of science. They argue that progress in IR&S requires explicit linking between technical and nontechnical aspects of discourse. They develop a network of basic questions and present a discursive framework for addressing these questions. With this book, Arafat and Ashoori provide both a manifesto for the reimagining of their field and the foundations on which a reframed IR&S would rest. COMPUTERS,Information Theory

Advances in Computing and Data Sciences This book constitutes the post-conference proceedings of the 4th International Conference on Advances in Computing and Data Sciences, ICACDS 2020, held in Valletta, Malta, in April 2020.* The 46 full papers were carefully reviewed and selected from 354 submissions. The papers are centered around topics like advanced computing, data sciences, distributed systems organizing principles, development frameworks and environments, software verification and validation, computational complexity and cryptography, machine learning theory, database theory, probabilistic representations. * The conference was held virtually due to the COVID-19 pandemic. COMPUTERS,Information Theory

Multimedia Information Systems Multimedia Information Systems explores the technical, human, organizational and socio-economic issues which underpin the implementation and use of multimedia information systems. This unique book comprehensively defines multimedia information systems and its emerging architecture. Today's important issues of networked multimedia information systems and multimedia trafficking on the information superhighway are thoroughly investigated. Multimedia information systems applications and organizational implications are also discussed along with multimedia authoring systems. Multimedia Information Systems is essential reading for all students and professionals faced with the challenges of multimedia information systems management and development. Multimedia Information Systems develops an awareness of the problems associated with multimedia information systems management, and the ability to understand and address these emerging challenges on an organizational and technical level. The book explores the limitations of multimedia on the information superhighway, and offers solutions for present and future development on the Internet. This book also scrutinizes the current applications of multimedia information systems, and examines how they can be developed. Multimedia Information Systems serves as an excellent text for courses on the subject, and as an invaluable reference for multimedia information systems professionals. COMPUTERS,Interactive & Multimedia

Representation and Retrieval of Video Data in Multimedia Systems Representation and Retrieval of Video Data in Multimedia Systems brings together in one place important contributions and up-to-date research results in this important area. Representation and Retrieval of Video Data in Multimedia Systems serves as an excellent reference, providing insight into some of the most important research issues in the field. COMPUTERS,Interactive & Multimedia

Representation and Retrieval of Visual Media in Multimedia Systems Representation and Retrieval of Visual Media in Multimedia Systems brings together in one place important contributions and up-to-date researcg results in this important area. Representation and Retrieval of Visual Media in Multimedia Systems serves as an excellent reference, providing insight into some of the most important research issues in the field. COMPUTERS,Interactive & Multimedia

Buffering Techniques for Delivery of Compressed Video in Video-on-Demand Systems Many emerging technologies such as video conferencing, video-on-demand, and digital libraries require the efficient delivery of compressed video streams. For applications that require the delivery of compressed stored multimedia streams, the a priori knowledge available about these compressed streams can aid in the allocation of server and network resources. By using a client-side buffer, the resource requirements from the server and network can be minimized. Buffering Techniques for Delivery of Compressed Video in Video-on-Demand Systems presents a comprehensive description of buffering techniques for the delivery of compressed, prerecorded multimedia data. While these techniques can be applied to any compressed data streams, this book focusses primarily on the delivery of video streams because of the large resource requirements that they can consume. The book first describes buffering techniques for the continuous playback of stored video sources. In particular, several bandwidth smoothing (or buffering) algorithms that are provably optimal under certain conditions are presented. To provide a well-rounded discussion, the book then describes extensions that aid in the ability to provide interactive delivery of video across networks. Specifically, reservation techniques that take into account interactive functions such as fast-forward and rewind are described. In addition, extensions to the bandwidth smoothing algorithms presented in the first few chapters are described. These algorithms are designed with interactive, continuous playback of stored video in mind and are also provably optimal under certain constraints. Buffering Techniques for Delivery of Compressed Video in Video-on-Demand Systems serves as an excellent resource for multimedia systems, networking and video-on-demand designers, and may be used as a text for advanced courses on the topic. COMPUTERS,Interactive & Multimedia

Video on Demand Systems Video on Demand Systems brings together in one place important contributions and up-to-date research results in this fast moving area. Video on Demand Systems serves as an excellent reference, providing insight into some of the most challenging research issues in the field. COMPUTERS,Interactive & Multimedia

Adobe Premiere Pro CS5 Classroom in a Book Those creative professionals seeking the fastest, easiest, most comprehensive way to learn Adobe Premiere Pro CS5 choose Adobe Premiere Pro CS5 Classroom in a Book from the Adobe Creative Team at Adobe Press. The 22 project-based lessons in this book show readers step-by-step the key techniques for working in Premiere Pro CS5. Readers learn the basics on things like using audio, creating transitions, producing titles, and adding effects. Once they have the basics down, they'll learn how to take their projects further by sweetening and mixing sound, compositing the footage, adjusting color, authoring DVDs, and much more. This completely revised CS5 edition covers new features such as Ultra, the new high-performance keyer. New workflows for creative collaboration are also explored, from the script all the way to the screen using Adobe Story, OnLocation, Speech Search, and other Adobe tools that are right at users' fingertips. Best of all, the companion DVD includes lesson files so readers can work step-by-step along with the book. All of Peachpit's eBooks contain the same content as the print edition. You will find a link in the last few pages of your eBook that directs you to the media files. Helpful tips: If you are able to search the book, search for "Where are the lesson files?" Go to the very last page of the book and scroll backwards. You will need a web-enabled device or computer in order to access the media files that accompany this ebook. Entering the URL supplied into a computer with web access will allow you to get to the files. Depending on your device, it is possible that your display settings will cut off part of the URL. To make sure this is not the case, try reducing your font size and turning your device to a landscape view. This should cause the full URL to appear. Note from the publisher: FREE Adobe Premiere Pro CS5.5 updates are available for this title. Simply register your product at www.peachpit.com/register and you will receive the updates when they become available. COMPUTERS,Interactive & Multimedia

Moodle For Dummies The fun and friendly guide to the world's most popular online learning management system Modular Object Oriented Dynamic Learning Environment, also known as Moodle, is an online learning management system that creates opportunities for rich interaction between educators and their audience. However, the market has been lacking a simple, easy-to-understand guide that covers all the essentials of Moodle?until now. Using straightforward language and an entertaining tone to decipher the intricate world of Moodle, this book provides you with the resources you need to take advantage of all the eLearning and eTraining possibilities that Moodle offers. Offers a hands-on approach to learning Moodle, the revolutionary online learning management system Uses simple language peppered with good humor to break down the complexities of Moodle into easily digested pieces of information Caters to the specific needs of teachers and business trainers by providing the resources they need Moodle For Dummies provides you with the tools you need to acquire a solid understanding of Moodle and start implementing it in your courses. COMPUTERS,Interactive & Multimedia

The Ultimate Digital Music Guide Everything You Need to Know about Digital Music! Your hard-core, up-to-the-minute, how-to guide Download, rip, store, organize, play, stream–anything, anywhere Seriously into digital music? Best-selling how-to author, serious audiophile, and eclectic music-lover Michael Miller will help you get all the digital tunes you want, whenever and wherever you want them! Miller guides you through today’s best new options, from iTunes to Spotify…helps you make the most of social music, Internet radio, and cloud music services…even shows how to transform your home into a digital music paradise. This book is packed with practical answers, easy step-by-step instructions, insider tips, great ideas, and new music sources you never knew existed! For everyone who’s passionate about music! • Discover brand-new digital music services, sites, and devices that fit your lifestyle • Find great new music on iTunes, Amazon, and sites you’ve never heard of • Get the truth about piracy, file sharing, and copyright • Find huge amounts of legally free music • Rip, store, and organize: Build your perfect music library • Determine the best audio file format and compression rate for your collection • Create simply amazing playlists • Stream songs anywhere, with Spotify, Pandora, Internet radio, and the cloud • Get great sound from your iPod or iPhone on your home audio system • Build a whole-house digital audio system, the easy way • Choose your best next media player (Apple or otherwise) • Find and share tunes on Facebook, Twitter, Google+, and beyond COMPUTERS,Interactive & Multimedia

Adobe Premiere Pro CC Classroom in a Book The fastest, easiest, most comprehensive way to learn Adobe Premiere Pro CC Classroom in a Book®, the best-selling series of hands-on software training workbooks, offers what no other book or training program does–an official training series from Adobe Systems Incorporated, developed with the support of Adobe product experts. Adobe Premiere Pro CC Classroom in a Book contains 19 lessons that cover the basics, providing countless tips and techniques to help you become more productive with the program. You can follow the book from start to finish or choose only those lessons that interest you. Purchasing this book gives you access to the same lesson files that appear on the included DVD in addition to electronic book updates covering new features that Adobe releases for Creative Cloud customers. For access, go to www.peachpit.com/redeem and redeem the code provided inside this book. “The Classroom in a Book series is by far the best training material on the market. Everything you need to master the software is included: clear explanations of each lesson, step-by-step instructions, and the project files for the students.†Barbara Binder, Adobe Certified Instructor, Rocky Mountain Training COMPUTERS,Interactive & Multimedia

Searching Multimedia Databases by Content Searching Multimedia Databases by Content bridges the gap between the database and signal processing communities by providing the necessary background information for the reader and presenting it along with the intuition and mechanics of the best existing tools in each area. The first half of Searching Multimedia Databases by Content reviews the most successful database access methods, in increasing complexity, reaching up to spatial access methods and text retrieval. In all cases, the emphasis is on practical approaches that have been incorporated in commercial systems, or that seem very promising. The second half of the book uses the above access methods to achieve fast searching in a database of signals. A general methodology is presented, which suggests extracting a few good features from each multimedia object, thus mapping objects into points in a metric space. Finally, the book concludes by presenting some recent successful applications of the methodology on time series and color images. Searching Multimedia Databases by Content is targeted towards researchers and developers of multimedia systems. The book can also serve as a textbook for a graduate course on multimedia searching, covering both access methods as well as the basics of signal processing. COMPUTERS,Interactive & Multimedia

Human Face Recognition Using Third-Order Synthetic Neural Networks Human Face Recognition Using Third-Order Synthetic Neural Networks explores the viability of the application of High-order synthetic neural network technology to transformation-invariant recognition of complex visual patterns. High-order networks require little training data (hence, short training times) and have been used to perform transformation-invariant recognition of relatively simple visual patterns, achieving very high recognition rates. The successful results of these methods provided inspiration to address more practical problems which have grayscale as opposed to binary patterns (e.g., alphanumeric characters, aircraft silhouettes) and are also more complex in nature as opposed to purely edge-extracted images - human face recognition is such a problem. Human Face Recognition Using Third-Order Synthetic Neural Networks serves as an excellent reference for researchers and professionals working on applying neural network technology to the recognition of complex visual patterns. COMPUTERS,Interactive & Multimedia

The Web Publisher’s Illustrated Quick Reference HTML, or hypertext mark-up language, is the standard for all world wide web pages throughout the world. With HTML 3.0 new features have been added and in addition VRML, the virtual reality mark-up language, is also attracting attention to enable browsers to move through "virtual reality" web sites. This book provides a reference guide to both HTML and VRML modelled on the author's previous successful reference guides to AutoCad. Each HTML and VRMl command is given a description, its syntax, and examples of its use. - Visual snapshots of each markup in use.- Each HTML tag is marked with its version number to highlight the new 3.0 features.- Covers all the known VRML tags for 2.0.- Examples cover related and optional attributes. COMPUTERS,Interactive & Multimedia

Multimedia Database Management Systems Multimedia Database Management Systems presents the issues and the techniques used in building multimedia database management systems. Chapter 1 provides an overview of multimedia databases and underlines the new requirements for these applications. Chapter 2 discusses the techniques used for storing and retrieving multimedia objects. Chapter 3 presents the techniques used for generating metadata for various media objects. Chapter 4 examines the mechanisms used for storing the index information needed for accessing different media objects. Chapter 5 analyzes the approaches for modeling media objects, both their temporal and spatial characteristics. Object-oriented approach, with some additional features, has been widely used to model multimedia information. The book discusses two systems that use object-oriented models: OVID (Object Video Information Database) and Jasmine. The models for representing temporal and spatial requirements of media objects are then studied. The book also describes authoring techniques used for specifying temporal and spatial characteristics of multimedia databases. Chapter 6 explains different types of multimedia queries, the methodologies for processing them and the language features for describing them. The features offered by query languages such as SQL/MM (Structured Query Language for Multimedia), PICQUERY+, and Video SQL are also studied. Chapter 7 deals with the communication requirements for multimedia databases. A client accessing multimedia data over computer networks needs to identify a schedule for retrieving various media objects composing the database. The book identifies possible ways for generating a retrieval schedule. Chapter 8 ties together the techniques discussed in the previous chapters by providing a simple architecture of a distributed multimedia database management system. Multimedia Database Management Systems can be used as a text for graduate students and researchers working in the area of multimedia databases. In addition, the book serves as essential reading material for computer professionals who are in (or moving to) the area of multimedia databases. COMPUTERS,Interactive & Multimedia

Video Data Compression for Multimedia Computing During the past few years, we have been witnessing the rapid growth of the ap plications of Interactive Digital Video, Multimedia Computing, Desktop Video Teleconferencing, Virtual Reality, and High Definition Television (HDTV). An other information revolution which is tied to Cyberspace is almost within reach. The information, data, text, graphics, video, sound, etc. , in the form of multi media, can be requested, accessed, distributed, and transmitted to potentially every household. This is changing and will continue to change the way of people doing business, functioning in the society, and entertaining. In the foreseeable future, many personalized, portable information terminals, which can be car ried while traveling, will provide the link to central computer network to allow information exchange including videos from a node to node, from a center to a node, or nodes. Facing this opportunity, the question is what are the major significant technical challenges that people have to solve to push the-state-of-the-art for the realiza tion of the above mentioned technology advancement? From our professional judgement We feel that one of the major technical challenges is in Video Data Compression. Video communications in the form of desktop teleconferencing, videophone, network video delivery on demand, even games, are going to be major media traveling in the information super highway, hopping from one node in the Cyberspace to the other. COMPUTERS,Interactive & Multimedia

Multimedia Database Management Systems Multimedia Database Management Systems brings together in one place important contributions and up-to-date research results in this important area. Multimedia Database Management Systems serves as an excellent reference, providing insight into some of the most important research issues in the field. COMPUTERS,Interactive & Multimedia

Multimedia Information Retrieval Multimedia Information Retrieval: Content-Based Information Retrieval from Large Text and Audio Databases addresses the future need for sophisticated search techniques that will be required to find relevant information in large digital data repositories, such as digital libraries and other multimedia databases. Because of the dramatically increasing amount of multimedia data available, there is a growing need for new search techniques that provide not only fewer bits, but also the most relevant bits, to those searching for multimedia digital data. This book serves to bridge the gap between classic ranking of text documents and modern information retrieval where composite multimedia documents are searched for relevant information. Multimedia Information Retrieval: Content-Based Information Retrieval from Large Text and Audio Databases begins to pave the way for speech retrieval; only recently has the search for information in speech recordings become feasible. This book provides the necessary introduction to speech recognition while discussing probabilistic retrieval and text retrieval, key topics in classic information retrieval. The book then discusses speech retrieval, which is even more challenging than retrieving text documents because word boundaries are difficult to detect, and recognition errors affect the retrieval effectiveness. This book also addresses the problem of integrating information retrieval and database functions, since there is an increasing need for retrieving information from frequently changing data collections which are organized and managed by a database system. Multimedia Information Retrieval: Content-Based Information Retrieval from Large Text and Audio Databases serves as an excellent reference source and may be used as a text for advanced courses on the topic. COMPUTERS,Interactive & Multimedia

Color Correction Handbook The colorist is responsible for the critical final stage of refinement of the film and broadcast image. Using all of the controls modern color correction software provides, colorists refine the mood, create style, add polish to scenes, and breathe life into the visuals. The craft of color correction can take considerable trial and error to learn, while the art of color grading takes years to perfect. Alexis Van Hurkman draws on his wealth of industry experience to provide a thoroughly updated edition of what has become the standard guide to color correction. Using a friendly, clear teaching style and a slew of real-world examples and anecdotes, Alexis demonstrates how to achieve professional results for any project, using any number of dedicated grading applications, or even an editing program’s built-in color correction tools. From the most basic methods for evaluating and correcting an overall image to the most advanced targeted corrections and creative stylizations, Color Correction Handbook, Second Edition, is your one-stop guide. Among many valuable concepts and techniques, you’ll learn to: • Set up a professional color correction environment using the latest technologies and adhere to the most up-to-date standards • Work with log-encoded media and LUTs • Analyze shots quickly and correct errors of color and exposure • Create idealized adjustments for key features such as skin tone, skies, and product shots • Develop strategies for balancing clips in a scene to match one another for continuity, and grading greenscreen clips destined for visual effects • Master a variety of stylistic techniques used to set a scene’s mood • Apply principles of color and contrast to add depth and visual interest • Browse valuable research about memory colors, audience preferences, and critical corrections for achieving appealing skin tones and controlled environments • Follow along with the downloadable files that accompany this book, including HD footage, cross-platform exercises, and project files. COMPUTERS,Interactive & Multimedia

Color Correction Look Book The digital colorist’s job is no longer to simply balance, fix, and optimize. Today’s filmmakers often want to recreate the idiosyncrasies of older recording methods, or are looking for something completely new, to differentiate the look of a given project. Furthermore, end-to-end digital shooting, postproduction, and distribution means that stylizations and effects once created by the film lab are no longer photochemically available. The color grading suite has become the lab, and these sorts of stylizations are now part of the colorist’s job description. In this follow-up volume to the bestseller Color Correction Handbook, Alexis Van Hurkman walks you through twenty-one categories of creative grading techniques, designed to give you an arsenal of stylizations you can pull out of your hat when the client asks for something special, unexpected, and unique. Each chapter presents an in-depth examination and step-by-step, cross-platform breakdown of stylistic techniques used in music videos, commercial spots, and cinema. These customizable techniques can be mixed and matched for your own unique effects and include: • bleach bypass looks • cross-processing simulation • day-for-night treatments • emulating film stocks • flat looks • glows, blooms, and gauze looks • grain, noise, and texture • greenscreen compositing workflows • lens flaring and veiling glare • light leaks and color bleeds • monitor and screen glow • monochrome looks • sharpening • tints and color washes • undertones • vibrance and targeted saturation • and many more! COMPUTERS,Interactive & Multimedia

Writing Interactive Music for Video Games “This book is a must read for newcomers and experienced composers wanting to learn more about the art of video game composition.†—Chuck Doud, Director of Music, Sony Computer Entertainment Worldwide Studios All You Need to Know to Create Great Video Game Music Written by the developer of Berklee School of Music’s pioneering game scoring program, this guide covers everything professional composers and music students need to know about composing interactive music for video games, and contains exclusive tools for interactive scoring—tools that were previously available only at Berklee. Drawing on twenty years of professional experience in the game industry, Michael Sweet helps you master the unique language of music storytelling in games. Next, he walks you through the entire music composition process, from initial conceptualization and creative direction through implementation. Inside, you’ll find dozens of examples that illustrate adaptive compositional techniques, from small downloadable games to multimillion dollar console titles. In addition, this guide covers the business side of video game composition, sharing crucial advice about contracts, pricing, sales, and marketing. Coverage includes Overcoming the unique challenges of writing for games Composing music that can adapt in real time to player actions Developing thematic ideas Using audio middleware to create advanced interactive scores Working effectively with game development teams Understanding the life of a video game composer Managing contracts, rights, estimating, and negotiation Finding work The companion website contains software tools to help you master interactive music concepts explored in this book, with additional resources and links to learn more about scoring for games. See Appendix A for details. COMPUTERS,Interactive & Multimedia

Digital Audio Essentials Join the digital audio revolution! Tens of millions of users are embracing digital music, and with Digital Audio Essentials, you can, too. Nearly every personal computer built in the last few years contains a CD-burning drive; MP3 and other portable player sales dominate the consumer electronics industry; and new networkable stereo equipment lets you use your digital music collection to power your home entertainment system.Whether it's downloading music, ripping CDs, organizing, finding, and creating higher quality music files, buying music players and accessories, or constructing a home stereo system, Digital Audio Essentials helps you do get it done.An indispensable reference for music enthusiasts, digital archivists, amateur musicians, and anyone who likes a good groove, Digital Audio Essentials helps you avoid time-consuming, costly trial and error in downloading audio files, burning CDs, converting analog music to digital form, publishing music to and streaming from the Web, setting up home stereo configurations, and creating your own MP3 and other audio files. The book--for both Mac and PC users--includes reliable hardware and software recommendations, tutorials, resources, and file sharing, and it even explains the basics of the DMCA and intellectual property law.You may (or may not) already know the basics of ripping CDs or downloading music, but Fries will show you so much more--including advice on the multitude of MP3 players on the market, stereo options, file formats, quality determinations, and the legalities of it all. Both a timely, entertaining guide and an enduring reference, this is the digital audio handbook you need to make the most of your expanding digital music collection. COMPUTERS,Interactive & Multimedia

Adobe Premiere Pro CC Classroom in a Book (2017 release) This is the eBook of the printed book and may not include any media, website access codes, or print supplements that may come packaged with the bound book. Creative professionals seeking the fastest, easiest, most comprehensive way to learn Adobe Premiere Pro CC (2017 release) choose Adobe Premiere Pro CC Classroom in a Book (2017 release) from Adobe Press. The 18 project-based lessons in this book show users step-by-step the key techniques for working in Premiere Pro. Learn to edit video in Adobe Premiere Pro CC 2017 and get the most out of your workflow. Take a project from beginning to end and learn to organize media, add audio, create transitions, produce titles, and add effects. Take your projects further by sweetening and mixing sound, compositing footage, adjusting color, using advanced editing techniques, managing projects, working with 360 video for VR headsets, exporting, and much more. The online companion files include all the necessary assets for readers to complete the projects featured in each chapter as well as ebook updates when Adobe releases new features for Creative Cloud customers. All buyers of the book get full access to the Web Edition: a Web-based version of the complete ebook enhanced with video and interactive multiple-choice quizzes. As always with the Classroom in a Book, Instructor Notes are available for teachers to download. COMPUTERS,Interactive & Multimedia

Adobe After Effects CC Classroom in a Book (2017 release) This is the eBook of the printed book and may not include any media, website access codes, or print supplements that may come packaged with the bound book. Creative professionals seeking the fastest, easiest, most comprehensive way to learn Adobe After Effects CC (2017 release) choose Adobe After Effects CC Classroom in a Book (2017 release) from Adobe Press. The 14 project-based lessons in this book show users step-by-step the key techniques for working in After Effects. Learn how to create, manipulate, and optimize motion graphics for film, video, DVD, the web, and mobile devices. Gain hands-on experience animating text and images, customizing a wide range of effects, tracking and syncing content, rotoscoping, and correcting color. Learn to create 3D content with both After Effects and Maxon Cinema 4D Lite (included with the software). The online companion files include all the necessary assets for readers to complete the projects featured in each chapter as well as ebook updates when Adobe releases new features for Creative Cloud customers. All buyers of the book get full access to the Web Edition: a Web-based version of the complete ebook enhanced with video and interactive multiple-choice quizzes. As always with the Classroom in a Book, Instructor Notes are available for teachers to download. COMPUTERS,Interactive & Multimedia

Adobe Premiere Pro CC Classroom in a Book (2018 release) Creative professionals seeking the fastest, easiest, most comprehensive way to learn Adobe Premiere Pro CC (2018 release) choose Adobe Premiere Pro CC Classroom in a Book (2018 release) from Adobe Press. The 18 project-based lessons in this book show users step-by-step the key techniques for working in Premiere Pro. Learn to edit video in Adobe Premiere Pro CC 2018 and get the most out of your workflow. Take a project from beginning to end and learn to organize media, add audio, create transitions, produce titles, and add effects. Take your projects further by sweetening and mixing sound, compositing footage, adjusting color, using advanced editing techniques, managing projects, working with 360 video for VR headsets, animating graphics, exporting, and much more. The online companion files include all the necessary assets for readers to complete the projects featured in each chapter as well as ebook updates when Adobe releases relevant new features for Creative Cloud customers. All buyers of the book get full access to the Web Edition: a Web-based version of the complete ebook enhanced with video and multiple-choice quizzes. COMPUTERS,Interactive & Multimedia

Final Cut Pro X 10.4 - Apple Pro Training Series The Apple-Certified Way to Learn This fully updated Apple-certified guide presents a real-world workflow from raw media to finished project to demonstrate the features of Final Cut Pro X 10.4 and the practical techniques you will use in editing projects. Using professionally acquired media, you’ll utilize the same tools and editing techniques used by editors worldwide in this revolutionary editing software. Renowned editor and master trainer Brendan Boykin starts with basic video editing techniques and takes you all the way through Final Cut Pro’s powerful features. The lessons start as real world as it gets—with an empty application. After downloading the media files, you will be guided through creating a project from scratch to finished draft. The basic workflow and tools are covered in Lessons 1 through 4 where you create a rough cut. The real-world workflow continues through the remaining lessons as you take the basic project and enhance it with a dive into more robust features including the newest Final Cut Pro X 10.4 tools for 360° editing, precision color grading, and more. • Downloadable lesson and media files to work sequentially through exercises for hours of hands-on training. • Focused lessons teach concepts and take students step by step through professional, real-world editing scenarios to create a final project. • Chapter review questions summarize what students learn to prepare them for the Apple certification exam. • Web Edition provides full text of the book available online with revised content for significant software updates. The Apple Pro Training Series is both a self-paced learning tool and the official curriculum of the Apple Training and Certification program. Upon completing the course material in this guide, you can become Apple Certified by passing the certification exam at an Apple Authorized Training Center. To find an Apple Authorized Training Center near you, please visit training.apple.com. COMPUTERS,Interactive & Multimedia

Adobe Audition CC Classroom in a Book The fastest, easiest, most comprehensive way to learn Adobe Audition CC Classroom in a Book®, the best-selling series of hands-on so ware training workbooks, offers what no other book or training program does–an official training series from Adobe, developed with the support of Adobe product experts. Adobe Audition CC Classroom in a Book contains 17 lessons that cover the basics and beyond, providing countless tips and techniques to help you become more productive with the program. You can follow the book from start to finish or choose only those lessons that interest you. Purchasing this book includes valuable online extras. Follow the instructions in the book’s “Getting Started†section to unlock access to: • Downloadable lesson files you need to work through the projects in the book • Web Edition containing the complete text of the book, interactive quizzes, videos that walk you through the lessons step by step, and updated material covering new feature releases from Adobe What you need to use this book: Adobe Audition CC software, for either Windows or macOS. (Software not included.) Note: Classroom in a Book does not replace the documentation, support, updates, or any other benefits of being a registered owner of Adobe Audition CC software. COMPUTERS,Interactive & Multimedia

Adobe Premiere Pro CC Classroom in a Book Creative professionals seeking the fastest, easiest, most comprehensive way to learn Adobe Premiere Pro CC (2018 release) choose Adobe Premiere Pro CC Classroom in a Book (2019 release) from Adobe Press. The 18 project-based lessons in this book show users step-by-step the key techniques for working in Premiere Pro. Learn to edit video in Adobe Premiere Pro CC 2019 and get the most out of your workflow. Learn how to take a project from beginning to end, organize media, add audio, create transitions, produce titles and captions, and add effects. Take your projects further by sweetening and mixing sound, compositing footage, adjusting color, using advanced editing techniques, managing projects, working with 360 video for VR headsets, animating graphics and video, exporting, and much more. Workflows incorporating Adobe Photoshop, Adobe After Effects, and Adobe Audition expand your creative options. The online companion files include all the necessary assets for readers to complete the projects featured in each chapter as well as ebook updates when Adobe releases relevant new features for Creative Cloud customers. All buyers of the book get full access to the Web Edition: a Web-based version of the complete ebook enhanced with video and multiple-choice quizzes. COMPUTERS,Interactive & Multimedia

Adobe Premiere Pro Classroom in a Book (2020 release) Creative professionals seeking the fastest, easiest, most comprehensive way to learn Adobe Premiere Pro choose Adobe Premiere Pro Classroom in a Book (2020 release ) from Adobe Press. The 17 project-based lessons in this book show students step-by-step the key techniques for working in Premiere Pro. Students learn skills to take a project from beginning to end, including the basics on things like organising media, using audio, creating transitions, producing titles, and adding effects. Once they have the basics down, they'll learn how to take their projects further by sweetening and mixing audio, compositing layered footage, adjusting colour, customising motion graphics, exporting files, and much more. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Interactive & Multimedia

Discord For Dummies Connect with the newest and most vibrant online community Though it was originally a virtual meeting place primarily for gamers, Discord’s userbase has quintupled in size in just two years and branched to include discussions on a multitude of topics. Discord For Dummies shows readers how to connect with the massive Discord audience, both within and well beyond the gaming niche. Celebrated writer, broadcaster, gamer, and technologist Tee Morris teaches readers how to set up a profile, establish channels, and join other conversations. Along the way, he’ll show you how to grow your audience and utilize Discord in your business. You’ll also learn to: · Play by the rules of Discord, both written and unwritten · Build a Discord studio · Create a community · Acquire must-have accessories With an audience of over 250,000,000 active users, you can’t afford to ignore the Discord community. Discord For Dummies is perfect for businesses seeking a larger audience, established media looking for a presence in private chat, and groups looking to organize their communication. COMPUTERS,Interactive & Multimedia

Flash How Flash rose and fell as the world's most ubiquitous yet divisive software platform, enabling the development and distribution of a world of creative content. Adobe Flash began as a simple animation tool and grew into a multimedia platform that offered a generation of creators and innovators an astonishing range of opportunities to develop and distribute new kinds of digital content. For the better part of a decade, Flash was the de facto standard for dynamic online media, empowering amateur and professional developers to shape the future of the interactive Web. In this book, Anastasia Salter and John Murray trace the evolution of Flash into one of the engines of participatory culture. Salter and Murray investigate Flash as both a fundamental force that shaped perceptions of the web and a key technology that enabled innovative interactive experiences and new forms of gaming. They examine a series of works that exemplify Flash's role in shaping the experience and expectations of web multimedia. Topics include Flash as a platform for developing animation (and the “Flashimation” aesthetic); its capacities for scripting and interactive design; games and genres enabled by the reconstruction of the browser as a games portal; forms and genres of media art that use Flash; and Flash's stance on openness and standards—including its platform-defining battle over the ability to participate in Apple's own proprietary platforms. Flash's exit from the mobile environment in 2011 led some to declare that Flash was dead. But, as Salter and Murray show, not only does Flash live, but its role as a definitive cross-platform tool continues to influence web experience. COMPUTERS,Interactive & Multimedia

Hands-On GUI Programming with C++ and Qt5 Create visually appealing and feature-rich applications by using Qt 5 and the C++ language About This Book Explore Qt 5's powerful features to easily design your GUI application Leverage Qt 5 to build attractive cross-platform applications Work with Qt modules for multimedia, networking, and location, to customize your Qt applications Who This Book Is For This book will appeal to developers and programmers who would like to build GUI-based applications. Basic knowledge of C++ is necessary and the basics of Qt would be helpful. What You Will Learn Implement tools provided by Qt 5 to design a beautiful GUI Understand different types of graphs and charts supported by Qt 5 Create a web browser using the Qt 5 WebEngine module and web view widget Connect to the MySQL database and display data obtained from it onto the Qt 5 GUI Incorporate the Qt 5 multimedia and networking module in your application Develop Google Map-like applications using Qt 5's location module Discover cross-platform development by exporting the Qt 5 application to different platforms Uncover the secrets behind debugging Qt 5 and C++ applications In Detail Qt 5, the latest version of Qt, enables you to develop applications with complex user interfaces for multiple targets. It provides you with faster and smarter ways to create modern UIs and applications for multiple platforms. This book will teach you to design and build graphical user interfaces that are functional, appealing, and user-friendly. In the initial part of the book, you will learn what Qt 5 is and what you can do with it. You will explore the Qt Designer, discover the different types of widgets generally used in Qt 5, and then connect your application to the database to perform dynamic operations. Next, you will be introduced to Qt 5 chart which allows you to easily render different types of graphs and charts and incorporate List View Widgets in your application. You will also work with various Qt modules, like QtLocation, QtWebEngine, and the networking module through the course of the book. Finally, we will focus on cross-platform development with QT 5 that enables you to code once and run it everywhere, including mobile platforms. By the end of this book, you will have successfully learned about high-end GUI applications and will be capable of building many more powerful, cross-platform applications. Style and approach This is a comprehensive guide that explores the essential Qt features and implement them in building real-world cross-platform GUI applications COMPUTERS,Internet,Application Development

Industrial IoT Application Architectures and Use Cases As the number of Internet of Things (IoT) elements grows exponentially, their interactions can generate a massive amount of raw and multi-structured data. The challenge with this data explosion is to transform any raw data into information and knowledge, which can be used by people and systems to make intelligent decisions. Industrial IoT Application Architectures and Use Cases explores how artificial intelligence (AI), data analytics, and IoT technology combine to promote intelligent decision-making and automation in a range of industries. With faster, more stable AI algorithms and approaches, knowledge discovery and dissemination from IoT-device data can be simplified and streamlined. An era of powerful cognitive technology is beginning due to cloud-based cognitive systems that are forming the foundation of game-changing intelligent applications. This book presents next-generation use cases of IoT and IoT data analytics for a variety of industrial verticals as given below: An Intelligent IoT framework for smart water management An IoT-enabled smart traffic control system for congestion control and smart traffic management An intelligent airport system for airport management and security surveillance An IoT framework for healthcare to integrate and report patient information Fuzzy scheduling with IoT for tracking and monitoring hotel assets An IoT system for designing drainage systems and monitoring drainage pipes Predictive maintenance of plant equipment to decide the actual mean time to malfunction Integrated neural networks and IoT systems for predictive equipment maintenance IoT integration in blockchain for smart waste management This book also includes a chapter on the IoT paradigm and an overview of uses cases for personal, social, and industrial applications. COMPUTERS,Internet,Application Development

Flutter For Dummies Create awesome iOS and Android apps with a single tool! Flutter is an app developer’s dream come true. With Google’s open source toolkit, you can easily build beautiful apps that work across platforms using a single codebase. This flexibility allows you to get your work out to the widest possible audience. Flutter is already being used by thousands of developers worldwide in a market where billions of apps are downloaded every year. Now is the right time to get ahead of the curve with this incredible tool. Flutter for Dummies is your friendly, ground-up route to creating multi-platform apps. From how to construct your initial frameworks to writing code in Dart, you’ll find the essentials you need to ride the Flutter revolutionary wave to success. This book includes guidance on how to create an intuitive and stunning UI, add interactivity, and easily pull in data. You’ll also see how Flutter features like Hot Reload—providing sub-second refreshes as you refine your work—help you make sure your app is a delight to use. · Start simple: follow steps to build a basic app · It’s alive! Keep connected to online data · It moves! Make things fun with animated features · Get the word out: use tips to expand your audience Whether you’re a fledgling developer or an expert wanting to add a slick feather to your programming cap, join the Flutter revolution now and soar above the rest! COMPUTERS,Internet,Application Development

Blogging to Drive Business BLOGGING TO DRIVE BUSINESS USE BLOGGING TO SUPERCHARGE SALES, CUSTOMER LOYALTY, INNOVATION, AND PROFITS Blogging can help you deepen customer loyalty, reach new customers, gain indispensable feedback, and drive more sales. This no-nonsense guide shows how to craft a business blog that does all that, and more—building your business and increasing your profits. Top e-marketers and business bloggers Eric Butow and Rebecca Bollwitt help you define clear goals, generate the right content with the right tools, attract visitors, build communities, and avoid costly mistakes. They draw on their own extensive experience, as well as the work of innovators from companies such as Intel, Starbucks, ING Direct, Procter & Gamble, and Tumblr. WHATEVER YOUR ROLE IN THE BUSINESS, YOU’LL LEARN HOW TO: Launch a blog that truly represents the best of your business Create a comprehensive, long-term blogging strategy to maximize the return on investment (ROI) from your blog Staff your blogging initiative Integrate blogs with other offline and online marketing programs, including social networking websites Use your blog to drive customers and prospects to the business Push up-to-the-minute information to customers via RSS Build a thriving online community—and learn from what it tells you Manage comments (and decide whether to have them) Operate successful contests and sweepstakes campaigns on your blog Utilize podcasts, vlogs, microblogging, and other new techniques Gain business value from hot new Web 3.0 technologies, including widgets, mashups, personal agents, and the Semantic Web Track your blog performance, spot and respond to trends, and translate and report data you receive from your blog COMPUTERS,Internet,Blogging

WordPress For Dummies The bestselling guide to WordPress—fully updated Updated to capture all the changes expected to come with the latest release of WordPress, the brand-new edition of this bestselling guide gives you an all-access pass to using this powerful publishing platform to get your very own blog or website up and running—in no time. In WordPress For Dummies, you'll find out how to choose and customize a theme, pick the perfect web host, manage multiple websites with multiple authors, and tons more. Due in large part to its state-of-the-art features, WordPress has become the go-to platform for website owners and bloggers who want to be noticed. Whether you're new to the web/blogging community or want to maximize your site, this hands-on guide is packed with everything you need to navigate the wonderful world of WordPress—and ensure the fruit of your labors gets the attention and traffic it deserves. Get set up with a new WordPress.org account Leverage the power of WordPress as a CMS tool Forget one website—manage as many as you want Optimize aesthetics, web standards, and usability Not a WordPress guru? No worries! Everything you need to become a pro is a page—and a click—away! COMPUTERS,Internet,Blogging

Triumphant Are you thinking about starting a blog? Do you already have a blog but you’re just not quite sure what to do with it? If the answer is yes, then this book is for you. What exactly will you find in this book? Well, how about I start by telling you what you won’t find. In this book you’re not going to find cheap blogging philosophy. You know, the kinds of tips and tricks people try to sell you even when they themselves have never had any blogging success. In this book you’re not going to find a “Blogging 101†type of course on the technical details of how to start a blog. In today’s world, blog creation platforms are so intuitive and easy to use that it wouldn’t even be worth your time to read a book like that. So if that’s the kind of thing you’re looking for, I’d recommend you check out one of the many “How to create a blog†tutorials that you can find on YouTube, among other places.Another thing you won’t find in this book is a magic formula for “how to become a blogging millionaire in two weeks.†Believe me, if anyone offers you anything that sounds like that, run away...immediately.What you will find in this book is a short summary of what I’ve written in my personal blog (El Último Blog) over the last ten years. In these ten years I have not only maintained my own personal blog, but I have also directed a blogging network with over 50 other writers, I’ve given conferences and taught classes on blogging, I’ve contributed to various book publications, etc.What I hope to share with you in this book, as a summary of these past ten years of blogging, is a selection of 15 articles which I believe reflect, in a clear and concise way, everything you’ll need in order to write a winning blog .These articles will be just 15 out of the 2,000 plus articles that I have published over the years. I’ve taken the original versions and touched them up a bit, so that while the COMPUTERS,Internet,Blogging

Django 2 Web Development Cookbook Create unbelievably fast, robust and secure web apps with Django Web Framework and Python 3.6 Key Features Discover solutions to a variety of web application scenarios, leveraging the power of the Django framework Understand URL routing, models, forms, templates, and RESTful services with Django 2.14 Test, deploy, and scale your web applications efficiently with Amazon Web Services Book Description Django is a framework designed to balance rapid web development with high performance. It handles high levels of user traffic and interaction, integrates with a variety of databases, and collects and processes data in real time. This book follows a task-based approach to guide you through developing with the Django 2.1 framework, starting with setting up and configuring Docker containers and a virtual environment for your project. You'll learn how to write reusable pieces of code for your models and manage database changes. You'll work with forms and views to enter and list data, applying practical examples using templates and JavaScript together for the optimum user experience. This cookbook helps you to adjust the built-in Django administration to fit your needs and sharpen security and performance to make your web applications as robust, scalable, and dependable as possible. You'll also explore integration with Django CMS, the popular content management suite. In the final chapters, you'll learn programming and debugging tricks and discover how collecting data from different sources and providing it to others in various formats can be a breeze. By the end of the book, you'll learn how to test and deploy projects to a remote dedicated server and scale your application to meet user demands. What you will learn Get started with the basic configuration necessary to start any Django project Build a database structure out of reusable model mixins Secure web applications against malicious usage and address common performance bottlenecks Integrate with, and extend, the Django CMS Construct and manage complex and deep hierarchies Import data from local sources and external web services and export it to third parties Who this book is for This book is designed for Python developers working on fast and secure web apps that can scale over time. You'll also find this book useful if you want to upgrade to latest Django framework. A background in Python 3 along with basic knowledge of the Django framework will be useful. COMPUTERS,Internet,Blogging

Blog for Bucks Proven Advice for Running a Successful, Profitable Blog—from Writing and Organizing to Promoting and Monetizing Millions of people would love to make money from blogging, but they have no clue where to start and how to make it happen. It takes more than simply starting the blog, and this book will show you what you need to know. Jacqueline Bodnar, a professional writer and blogger shares her experience and knowledge, covering everything from how to generate blog post ideas to tracking your blog’s success to connecting with other bloggers. Blog for Bucks includes chapters on topics such as: Blogging Basics Keeping It Active All About Writing Ways to Promote Your Blog Monetizing Your Blog Ways to Enhance Your Blog Where Your Blog Can Take You Whether you are a new or seasoned blogger, there is information in this book that will help you take your blog to the next level. The invaluable information, advice, and insight will inspire you to get started, launch another blog, or get serious about making money from your current one. Don’t miss out on the tried-and-true tips and methods in this book that will help you blog for bucks! COMPUTERS,Internet,Blogging

Web Content Management Looking to select a web content management system (CMS), but confused about the promises, terminology, and buzzwords? Do you want to understand content management without having to dive into the underlying programming? This book provides a clear, unbiased overview of the entire CMS ecosystem—from platforms to implementations—in a language- and platform-agnostic manner for project managers, executives, and new developers alike. Author Deane Barker, a CMS consultant with almost two decades of experience, helps you explore many different systems, technologies, and platforms. By the end of the book, you’ll have the knowledge necessary to make decisions about features, architectures, and implementation methods to ensure that your project solves the right problems. Learn what content is, how to compare different systems, and what the roles of a CMS team are Understand how a modern CMS models and aggregates content, coordinates workflow, and manages assets Explore the scope and structure of a CMS implementation project Learn the process and best practices for successfully running your CMS implementation Examine the practice of migrating web content, and learn how to work with an external CMS integrator COMPUTERS,Internet,Content Management Systems

Building Business Websites with Squarespace 7 Discover the best way to build, design and launch professional websites with Squarespace quickly, without needing to learn any code About This Book Discover time-saving tricks and best practices, and avoid common pitfalls while creating a website Create visually stunning Responsive Design templates for your website with Squarespace 7 Understand how to monitor, measure, and manage your website after launching it Who This Book Is For This book is ideal for anyone who wants to learn how to use the latest version of Squarespace to create a website from scratch and take it through to go-live. You don't need any prior experience with Squarespace, HTML, or CSS, or building websites in general as everything is done using Squarespace's simple, browser-based interface. What You Will Learn Develop an essential Website Toolkit that will act as reference and materials for your entire project, ensuring you stay on-target to meet your objectives Set up your Squarespace account, learn how the interface works, and select the correct template for your website's purpose and goals Create your website framework, fill it with content, and arrange your pages using Squarespace's easy drag-and-drop tools Customize your site's look and feel to match your brand, and create a stunning visual impact for your website on all types of devices, including mobiles and tablets Configure the core functions your business needs, whether connecting to social media, promoting events, showcasing your work, or selling goods and services online Learn time-saving tricks and how to avoid common pitfalls from an experienced professional with years of Squarespace experience Gain valuable insights about search engine optimization, communicating effectively online, and other e-marketing advice How to monitor, measure, and manage your website post-launch In Detail Squarespace is a web-based tool that allows non-technical people to create and manage professional-looking websites quickly, without needing to write any code. It empowers business owners to take total control of their own websites, without needing to pay someone to design or maintain it. This book covers much more than just how to use Squarespace. It covers all aspects of creating a successful business website, from developing your brand identity, to writing and structuring content to match your target audience's needs, and dozens of other other valuable tips that will help your website shine. Most importantly, you'll learn the correct steps to follow in order to ensure your project is smooth and stress-free. The book starts by helping you plan your website project and gather all the raw materials you'll need. Next, you'll set up your account and become familiar with the terminology and tools that you'll be using. Once you've learned the basics of how the Squarespace interface, templates, and different page types operate, you will create the framework of your website, ready for you to insert content and functionality. Then, once all the core elements are in place, you'll apply the aesthetic fine-tuning needed to bring your website in line with your brand. After the aesthetics have been honed and all functions tested, you will launch your website and drive traffic to it, monitor it, and improve it. Style and approach This easy-to-follow guide will teach you to build websites the easiest way in the latest version of Squarespace. COMPUTERS,Internet,Content Management Systems

Magento 2 Development Quick Start Guide Create an interactive online store and customize it further using Magento Key Features Straightforward guide to developing with Magento Examples of different types of extension Customize the Magento storefront and admin areas Book Description Magento is an open source, enterprise-level e-commerce platform with unlimited scope for customization. This makes it a great choice not only for vendors, but for developers as well. This book guides you through Magento development, teaching you how to develop modules that extend or change its functionality, leading to more flexible and proftable Magento stores. You start with a structural overview of the key Magento development components. You will learn where things such as plugins, events, models, controllers, layouts, and UI components ft into the development landscape. You will go through examples of using these components to extend Magento. As you progress, you will be building a diverse series of small but practical Magento modules. By the end of this book, you will not only have a solid foundation in the Magento development architecture; you will also have practical experience of developing modules to customize and extend Magento stores. What you will learn Develop a simple shipping module Build admin interfaces with the built-in form and listing UI components Implement JavaScript components for improved customer experience Accommodate vendor needs by adding new catalog-related features Develop your way to a better checkout Improve customer interaction with new customer-related extensions Create new web APIs to make your modules more extensible Who this book is for This book is for competent PHP developers, with only basic knowledge of the Magento platform required. COMPUTERS,Internet,Content Management Systems

Drupal 8 Module Development Learn to create and customize impressive Drupal 8 modules to extend your website's functionalities Key Features Explore a plethora of Drupal 8 APIs and get the best out of them using the power of PHP coding Learn to implement efficient data management and data security by creating dedicated modules for it. Stay up to date with the changes introduced in the new Drupal 8 releases Book Description Drupal 8 comes with a release cycle that allows for new functionality to be added at a much faster pace. However, this also means code deprecations and changing architecture that you need to stay on top of. This book updates the first edition and includes the new functionality introduced in versions up to, and including 8.7. The book will first introduce you to the Drupal 8 architecture and its subsystems before diving into creating your first module with basic functionality. You will work with the Drupal logging and mailing systems, learn how to output data using the theme layer and work with menus and links programmatically. Then, you will learn how to work with different kinds of data storages, create custom entities, field types and leverage the Database API for lower level database queries. You will further see how to introduce JavaScript into your module, work with the various file systems and ensure the code you write works on multilingual sites. Finally, you will learn how to programmatically work with Views, write automated tests for your functionality and also write secure code in general. By the end, you will have learned how to develop your own custom module that can provide complex business solutions. And who knows, maybe you'll even contribute it back to the Drupal community. Foreword by Dries Buytaert, founder of Drupal. What you will learn Develop Drupal 8 modules that do all the things you want Master numerous Drupal 8 sub-systems and APIs in the process Model, store, manipulate and process data to serve your purposes Display data and content in a clean and secure way using the Drupal 8 theme system Test your business logic to prevent regressions Stay ahead of the curve and write code following the current best practices Who this book is for The primary target of this book is Drupal developers who want to learn how to write modules and develop in Drupal 8. It is also intended for Drupal site builders and PHP developers who have basic Object Oriented Programming skills. A little bit of Symfony experience is helpful but not mandatory. COMPUTERS,Internet,Content Management Systems

WordPress 5 Complete An in-depth and comprehensive take on WordPress, covering everything about the platform such as WordPress posts, pages, themes, plugins, and more. Key Features Get up to date with the latest WordPress 5.0 (Bebo) and all its new features Beginner-friendly layout and advice you can apply from day one with loads of screenshots and examples Enrich your development experience with the new block-based editor Gutenberg Book Description Back in the day, when you wanted to launch a new website, you either had to learn web programming yourself or hire a professional who would take care of the whole process for you. Nowadays, with WordPress, anyone can build an optimized site with the least amount of effort possible and then make it available to the world in no time. Here, in the seventh edition of the book, we are going to show you how to build great looking and functional websites using WordPress. The new version of WordPress – 5.0 – comes with a few important changes, and we tell you all about how to use them effectively. From crafting content pages using the block editor, and customizing the design of your site, through to making sure it's secure, we go through it all. The book starts by introducing WordPress and teaching you how to set it up. You are then shown how to create a blog site, start writing content, and even use plugins and themes to customize the design of the site and add some unique elements to set it apart. If you want to get more in-depth, we also show you how to get started creating your own themes and plugins. Finally, we teach you how to use WordPress for building non-blog websites. By the end of the book, you will be sufficiently skilled to design high-quality websites and will be fully familiar with the ins and outs of WordPress. What you will learn Learn to adapt your plugin with the Gutenberg editor Create content that is optimized for publication on the web Craft great looking pages and posts with the use of block editor Structure your web pages in an accessible and clear way Install and work with plugins and themes Customize the design of your website Upload multimedia content, such as images, audio, and video easily and effectively Develop your own WordPress plugins and themes Use WordPress to build websites that serve purposes other than blogs Who this book is for The ideal target audience for this book would be PHP developers who have some basic knowledge of working with WordPress and who want to get a comprehensive practical understanding of working with WordPress and create production-ready websites with it. COMPUTERS,Internet,Content Management Systems

Web Analytics 2.0 Adeptly address today’s business challenges with this powerful new book from web analytics thought leader Avinash Kaushik. Web Analytics 2.0 presents a new framework that will permanently change how you think about analytics. It provides specific recommendations for creating an actionable strategy, applying analytical techniques correctly, solving challenges such as measuring social media and multichannel campaigns, achieving optimal success by leveraging experimentation, and employing tactics for truly listening to your customers. The book will help your organization become more data driven while you become a super analysis ninja! Note: CD-ROM/DVD and other supplementary materials are not included as part of eBook file. COMPUTERS,Internet,General

The Social Media Marketing Book Are you looking to take advantage of social media for your business or organization? With easy-to-understand introductions to blogging, forums, opinion and review sites, and social networks such as Twitter, Facebook, and LinkedIn, this book will help you choose the best -- and avoid the worst -- of the social web's unique marketing opportunities. The Social Media Marketing Book guides you through the maze of communities, platforms, and social media tools so you can decide which ones to use, and how to use them most effectively. With an objective approach and clear, straightforward language, Dan Zarrella, aka "The Social Media & Marketing Scientist," shows you how to plan and implement campaigns intelligently, and then measure results and track return on investment. Whether you're a seasoned pro or new to the social web, this book will take you beyond the jargon to social media marketing mastery. Make sense of this complicated environment with the help of screenshots, graphs, and visual explanations Understand the history and culture of each social media type, including features, functionality, and protocols Get clear-cut explanations of the methods you need to trigger viral marketing successes Choose the technologies and marketing tactics most relevant to your campaign goals Learn how to set specific goals for your campaigns and evaluate them according to key performance indicators Praise for The Social Media Marketing Book: "Let Zarrella take you to social-media marketing school. You'll learn more from reading this book than a month of research on the Internet."--Guy Kawasaki, co-founder of Alltop.com "If I could be any other person for a day, it would be Dan Zarella. Either him or Brad Pitt. But Dan's smarter. This book is why I say that."--Chris Brogan, President of New Marketing Labs "This book demonstrates a beginning to the endless possibilities of the Social Web."-- Brian Solis, publisher of leading marketing blog PR 2.0 COMPUTERS,Internet,General

Tackling Tumblr A comprehensive guide to the popular web publishing site Tumblr The popularity of Tumblr is growing by leaps and bounds, as it continues to make a name for itself as a reliable, accessible blogging platform. Yet, there is very little documentation on Tumblr, leaving newcomers confused as to where to start. That's where this helpful book comes in. Written by well-respected author Thord Hedengren, this step-by-step guide is an ideal starting point for Tumblr newcomers as well as web designers who want to take their Tumblblogs to the next level. You'll learn how to maximize the full potential of this amazing blogging and lifestreaming platform as you create your first post, make your Tumblr blog unique, create your own custom themes, and more. Introduces you to the exciting world of Tumblr, the popular web publishing platform Walks you through posting quotes, links, photos, audio, and more Addresses finding and installing themes, using a comment system on your Tumblr site, and integrating third-party content Demonstrates how to create your own custom theme, network in the Tumblr community, and modify your Tumblr themes with HTML and CSS Explains ways to integrate Tumblr with other services, including Facebook, Twitter, and Flickr There's no need to grumble about learning Tumblr—this book is all you need! COMPUTERS,Internet,General

Tubes “Andrew Blum plunges into the unseen but real ether of the Internet in a journey both compelling and profound….You will never open an email in quite the same way again.â€â€”Tom Vanderbilt, New York Times bestselling author of Traffic In Tubes, Andrew Blum, a correspondent at Wired magazine, takes us on an engaging, utterly fascinating tour behind the scenes of our everyday lives and reveals the dark beating heart of the Internet itself. A remarkable journey through the brave new technological world we live in, Tubes is to the early twenty-first century what Soul of a New Machine—Tracy Kidder’s classic story of the creation of a new computer—was to the late twentieth. COMPUTERS,Internet,General

APIs Programmers used to be the only people excited about APIs, but now a growing number of companies see them as a hot new product channel. This concise guide describes the tremendous business potential of APIs, and demonstrates how you can use them to provide valuable services to clients, partners, or the public via the Internet. You’ll learn all the steps necessary for building a cohesive API business strategy from experts in the trenches. Facebook and Twitter APIs continue to be extremely successful, and many other companies find that API demand greatly exceeds website traffic. This book offers executives, business development teams, and other key players a complete roadmap for creating a viable API product. Learn about the rise of APIs and why your business might need one Understand the roles of asset owners, providers, and developers in the API value chain Build strategies for designing, implementing, and marketing your product Devise an effective process for security and user management Address legal issues, such as rights management and terms of use Manage traffic and user experience with a reliable operating model Determine the metrics you need to measure your API’s success COMPUTERS,Internet,General

Virtual Unreality The bestselling author of Proofiness and Zero explains how to separate fact from fantasy in the digital world Digital information is a powerful tool that spreads unbelievably rapidly, infects all corners of society, and is all but impossible to control—even when that information is actually a lie. In Virtual Unreality, Charles Seife uses the skepticism, wit, and sharp facility for analysis that captivated readers in Proofiness and Zero to take us deep into the Internet information jungle and cut a path through the trickery, fakery, and cyber skullduggery that the online world enables. Taking on everything from breaking news coverage and online dating to program trading and that eccentric and unreliable source that is Wikipedia, Seife arms his readers with actual tools—or weapons—for discerning truth from fiction online. COMPUTERS,Internet,General

Twitter For Dummies A fully updated new edition of the fun and easy guide to getting up and running on Twitter With more than half a billion registered users, Twitter continues to grow by leaps and bounds. This handy guide, from one of the first marketers to discover the power of Twitter, covers all the new features. It explains all the nuts and bolts, how to make good connections, and why and how Twitter can benefit you and your business. Fully updated to cover all the latest features and changes to Twitter Written by a Twitter pioneer who was one of the first marketers to fully tap into Twitter's business applications Ideal for beginners, whether they want to use Twitter to stay in touch with friends or to market their products and services Explains how to incorporate Twitter into other social media and how to use third-party tools to improve and simplify Twitter COMPUTERS,Internet,General

Misunderstanding the Internet The growth of the internet has been spectacular. There are now more than 3 billion internet users across the globe, some 40 per cent of the world’s population. The internet’s meteoric rise is a phenomenon of enormous significance for the economic, political and social life of contemporary societies. However, much popular and academic writing about the internet continues to take a celebratory view, assuming that the internet’s potential will be realised in essentially positive and transformative ways. This was especially true in the euphoric moment of the mid-1990s, when many commentators wrote about the internet with awe and wonderment. While this moment may be over, its underlying technocentrism – the belief that technology determines outcomes – lingers on and, with it, a failure to understand the internet in its social, economic and political contexts. Misunderstanding the Internet is a short introduction, encompassing the history, sociology, politics and economics of the internet and its impact on society. This expanded and updated second edition is a polemical, sociologically and historically informed guide to the key claims that have been made about the online world. It aims to challenge both popular myths and existing academic orthodoxies that surround the internet. COMPUTERS,Internet,General

The Ambivalent Internet This book explores the weird and mean and in-between that characterize everyday expression online, from absurdist photoshops to antagonistic Twitter hashtags to deceptive identity play. Whitney Phillips and Ryan M. Milner focus especially on the ambivalence of this expression: the fact that it is too unwieldy, too variable across cases, to be essentialized as old or new, vernacular or institutional, generative or destructive. Online expression is, instead, all of the above. This ambivalence, the authors argue, hinges on available digital tools. That said, there is nothing unexpected or surprising about even the strangest online behavior. Ours is a brave new world, and there is nothing new under the sun – a point necessary to understanding not just that online spaces are rife with oddity, mischief, and antagonism, but why these behaviors matter. The Ambivalent Internet is essential reading for students and scholars of digital media and related fields across the humanities, as well as anyone interested in mediated culture and expression. COMPUTERS,Internet,General

To Save Everything, Click Here A New York Times Notable Book of the Year In the very near future, "smart" technologies and "big data" will allow us to make large-scale and sophisticated interventions in politics, culture, and everyday life. Technology will allow us to solve problems in highly original ways and create new incentives to get more people to do the right thing. But how will such "solutionism" affect our society, once deeply political, moral, and irresolvable dilemmas are recast as uncontroversial and easily manageable matters of technological efficiency? What if some such problems are simply vices in disguise? What if some friction in communication is productive and some hypocrisy in politics necessary? The temptation of the digital age is to fix everything -- from crime to corruption to pollution to obesity -- by digitally quantifying, tracking, or gamifying behavior. But when we change the motivations for our moral, ethical, and civic behavior we may also change the very nature of that behavior. Technology, Evgeny Morozov proposes, can be a force for improvement -- but only if we keep solutionism in check and learn to appreciate the imperfections of liberal democracy. Some of those imperfections are not accidental but by design. Arguing that we badly need a new, post-Internet way to debate the moral consequences of digital technologies, To Save Everything, Click Here warns against a world of seamless efficiency, where everyone is forced to wear Silicon Valley's digital straitjacket. COMPUTERS,Internet,General

Consent of the Networked The Internet was going to liberate us, but in truth it has not. For every story about the web's empowering role in events such as the Arab Spring, there are many more about the quiet corrosion of civil liberties by companies and governments using the same digital technologies we have come to depend upon. In Consent of the Networked, journalist and Internet policy specialist Rebecca MacKinnon argues that it is time to fight for our rights before they are sold, legislated, programmed, and engineered away. Every day, the corporate sovereigns of cyberspace (Google and Facebook, among others) make decisions that affect our physical freedom -- but without our consent. Yet the traditional solution to unaccountable corporate behavior -- government regulation -- cannot stop the abuse of digital power on its own, and sometimes even contributes to it. A clarion call to action, Consent of the Networked shows that it is time to stop arguing over whether the Internet empowers people, and address the urgent question of how technology should be governed to support the rights and liberties of users around the world. COMPUTERS,Internet,General

Tubes An engaging, narrative tour behind the scenes of our everyday lives to see the dark beating heart of the Internet itself. We are all connected now. But connected to what, exactly? In Tubes, journalist Andrew Blum takes readers on a fascinating journey to find out. When former Senator Ted Stevens of Alaska famously described the Internet as “a series of tubes,†he seemed hopelessly, foolishly trapped in an old way of knowing the world. But he wasn’t wrong. After all, as Blum writes, the Internet exists: for all the talk of the “placelessness†of our digital age, the Internet is as fixed in real, physical places as any railroad or telephone ever was. It fills enormous buildings, converges in some places and avoids others, and it flows through tubes under ground, up in the air, and under the oceans all over the world. You can map it, you can smell it, and you can even visit it—and that’s just what Blum does in Tubes. From the room in Berkeley where the Internet flickered to life to the busiest streets in Manhattan as new fiber optic cable is laid down; from the coast of Portugal as a 10,000-mile undersea cable just two thumbs’ wide is laid down to connect Europe and West Africa to the wilds of the Pacific Northwest, where Google, Microsoft and Facebook have built monumental data centers—Blum visits them all to chronicle the dramatic story of the Internet’s development, explain how it all works, and capture the spirit of the place/ Like Tracy Kidder’s classic The Soul of a New Machine or Tom Vanderbilt’s recent bestseller Traffic, Tubes combines deep reporting and lucid explanation into an engaging quest to understand the everyday world we live in. COMPUTERS,Internet,General

Driving Digital Strategy Digital transformation is no longer news--it's a necessity. Despite the widespread threat of disruption, many large companies in traditional industries have succeeded at digitizing their businesses in truly transformative ways. The New York Times, formerly a bastion of traditional media, has created a thriving digital product behind a carefully designed paywall. Best Buy has transformed its business in the face of Amazon's threat. John Deere has formed a data-analysis arm to complement its farm-equipment business. And Goldman Sachs and many others are using digital technologies to reimagine their businesses. In Driving Digital Strategy, Harvard Business School professor Sunil Gupta provides an actionable framework for following their lead. For over a decade, Gupta has studied digital transformation at Fortune 500 companies. He knows what works and what doesn't. Merely dabbling in digital or launching a small independent unit, which many companies do, will not bring success. Instead you need to fundamentally change the core of your business and ensure that your digital strategy touches all aspects of your organization: your business model, value chain, customer relationships, and company culture. Gupta covers each aspect in vivid detail while providing navigation tips and best practices along the way. Filled with rich and illuminating case studies of companies at the forefront of digital transformation, Driving Digital Strategy is the comprehensive guide you need to take full advantage of the limitless opportunities the digital age provides. COMPUTERS,Internet,General

Digital Disconnect Celebrants and skeptics alike have produced valuable analyses of the Internet’s effect on us and our world, oscillating between utopian bliss and dystopian hell. But according to Robert W. McChesney, arguments on both sides fail to address the relationship between economic power and the digital world. McChesney’s award-winning Rich Media, Poor Democracy skewered the assumption that a society drenched in commercial information is a democratic one. In Digital Disconnect McChesney returns to this provocative thesis in light of the advances of the digital age, incorporating capitalism into the heart of his analysis. He argues that the sharp decline in the enforcement of antitrust violations, the increase in patents on digital technology and proprietary systems, and other policies and massive indirect subsidies have made the Internet a place of numbing commercialism. A small handful of monopolies now dominate the political economy, from Google, which garners an astonishing 97 percent share of the mobile search market, to Microsoft, whose operating system is used by over 90 percent of the world’s computers. This capitalistic colonization of the Internet has spurred the collapse of credible journalism, and made the Internet an unparalleled apparatus for government and corporate surveillance, and a disturbingly anti-democratic force. In Digital Disconnect Robert McChesney offers a groundbreaking analysis and critique of the Internet, urging us to reclaim the democratizing potential of the digital revolution while we still can. COMPUTERS,Internet,General

Practical Internet of Things Security A practical, indispensable security guide that will navigate you through the complex realm of securely building and deploying systems in our IoT-connected world Key Features Learn best practices to secure your data from the device to the cloud Use systems security engineering and privacy-by-design principles to design a secure IoT ecosystem A practical guide that will help you design and implement cyber security strategies for your organization Book Description With the advent of the Internet of Things (IoT), businesses have to defend against new types of threat. The business ecosystem now includes the cloud computing infrastructure, mobile and fixed endpoints that open up new attack surfaces. It therefore becomes critical to ensure that cybersecurity threats are contained to a minimum when implementing new IoT services and solutions. This book shows you how to implement cybersecurity solutions, IoT design best practices, and risk mitigation methodologies to address device and infrastructure threats to IoT solutions. In this second edition, you will go through some typical and unique vulnerabilities seen within various layers of the IoT technology stack and also learn new ways in which IT and physical threats interact. You will then explore the different engineering approaches a developer/manufacturer might take to securely design and deploy IoT devices. Furthermore, you will securely develop your own custom additions for an enterprise IoT implementation. You will also be provided with actionable guidance through setting up a cryptographic infrastructure for your IoT implementations. You will then be guided on the selection and configuration of Identity and Access Management solutions for an IoT implementation. In conclusion, you will explore cloud security architectures and security best practices for operating and managing cross-organizational, multi-domain IoT deployments. What you will learn Discuss the need for separate security requirements and apply security engineering principles on IoT devices Master the operational aspects of planning, deploying, managing, monitoring, and detecting the remediation and disposal of IoT systems Use Blockchain solutions for IoT authenticity and integrity Explore additional privacy features emerging in the IoT industry, such as anonymity, tracking issues, and countermeasures Design a fog computing architecture to support IoT edge analytics Detect and respond to IoT security incidents and compromises Who this book is for This book targets IT Security Professionals and Security Engineers (including pentesters, security architects and ethical hackers) who would like to ensure the security of their organization's data when connected through the IoT. Business analysts and managers will also find this book useful. COMPUTERS,Internet,General

Lurking A concise but wide-ranging personal history of the internet from—for the first time—the point of view of the user In a shockingly short amount of time, the internet has bound people around the world together and torn us apart and changed not just the way we communicate but who we are and who we can be. It has created a new, unprecedented cultural space that we are all a part of—even if we don’t participate, that is how we participate—but by which we’re continually surprised, betrayed, enriched, befuddled. We have churned through platforms and technologies and in turn been churned by them. And yet, the internet is us and always has been. In Lurking, Joanne McNeil digs deep and identifies the primary (if sometimes contradictory) concerns of people online: searching, safety, privacy, identity, community, anonymity, and visibility. She charts what it is that brought people online and what keeps us here even as the social equations of digital life—what we’re made to trade, knowingly or otherwise, for the benefits of the internet—have shifted radically beneath us. It is a story we are accustomed to hearing as tales of entrepreneurs and visionaries and dynamic and powerful corporations, but there is a more profound, intimate story that hasn’t yet been told. Long one of the most incisive, ferociously intelligent, and widely respected cultural critics online, McNeil here establishes a singular vision of who we are now, tells the stories of how we became us, and helps us start to figure out what we do now. COMPUTERS,Internet,General

The Tangled Web We Weave We all see what the internet does and increasingly don't like it, but do we know how and more importantly who makes it work that way? That's where the real power lays... The internet was supposed to be a thing of revolutions. As that dream curdles, there is no shortage of villains to blame--from tech giants to Russian bot farms. But what if the problem is not an issue of bad actors ruining a good thing? What if the hazards of the internet are built into the system itself? That's what journalist James Ball argues as he takes us to the root of the problem, from the very establishment of the internet's earliest protocols to the cables that wire it together. He shows us how the seemingly abstract and pervasive phenomenon is built on a very real set of materials and rules that are owned, financed, designed and regulated by very real people. In this urgent and necessary book, Ball reveals that the internet is not a neutral force but a massive infrastructure that reflects the society that created it. And making it work for--and not against--us must be an endeavor of the people as well. COMPUTERS,Internet,General

Wireless Internet Of Things This textbook metamorphosed from notes that the author has been using to teach at four universities in Australia and New Zealand. The book treats the physical principles and design of wireless Internet of Things (IoT) systems from engineering perspective. IoT enables communication between people, between people and things, and between things. The book highlights the wide scope of sensors used in IoT - including RFIDs, smart mobile phones, home consumer devices, autonomous cars, utility meters, car park meters, robots, satellites, radars and wireless positioning systems. Three features render the book practically accessible. First, each chapter is organised in sections, each of which ends with a set of authentic review questions to motivate reflection. This is complemented by numerous worked examples in each section. Third, the book introduces two popular industry software packages for hands-on practice — MATLAB® and CelPlanner™. With the growing popularity of softwarisation and cloudification, possessing expertise in these packages makes one useful to the industry. Parts of this book are taught in undergraduate curriculum, while the rest is taught in graduate courses. Both traditional and modern topics including C-RAN, network slicing, NFV, NB-IoT and 5G use cases in IoT are covered.Instructor's resources are provided for free to instructors who adopt the book as textbook for a unit/ course/subject/paper. Please send your request to sales@wspc.com. COMPUTERS,Internet,General

Product Lifecycle Management (PLM) Product Lifecycle Management (PLM): A Digital Journey Using Industrial Internet of Things (IIot) provides a summary of the essential topics of Product Lifecycle Management (PLM) and the Industrial Internet of Things (IIoT) in the era of Industry 4.0. The book discusses emerging technologies, their contribution towards enhancing product design, development, and manufacturing. It also presents the integration of PLM, Enterprise Resource Planning (ERP), and Manufacturing Execution System (MES) along with IIoT as well the integration of mechanical, electronic components, embedded systems, firmware and software focusing on smart design, development, and manufacturing in the digital transformation journey. The book provides a high-level overview of how the smart product development through smart manufacturing materializes within the smart ecosystem. Manufacturing professionals, designers, mechanical, electrical, electronics, instrumentation and industrial engineers, information and communication technology consultants and those working in production planning, process control, and operations will find this book invaluable. COMPUTERS,Internet,General

Framing Internet Safety An examination of youth Internet safety as a technology of governance, seen in panics over online pornography, predators, bullying, and reputation management. Since the beginning of the Internet era, it has become almost impossible to discuss youth and technology without mentioning online danger—pornography that is just a click away, lurking sexual predators, and inescapable cyberbullies. In this book, Nathan Fisk takes an innovative approach to the subject, examining youth Internet safety as a technology of governance—for information technologies and, by extension, for the forms of sociality and society they make possible. He argues that it is through the mobilization of various discourses of online risk that the everyday lives of youth are increasingly monitored and policed and the governing potentials of information technologies are explored. Fisk relates particular panics over youth Internet safety to patterns of technological adoption by young people, focusing on the policy response at the federal level aimed at producing future cybercitizens. He describes pedagogies of surveillance, which position parents as agents of surveillance; the evolution of the youth Internet safety curricula, as seen through materials on cyberbullying and online reputation management; and, drawing on survey results and focus groups, parent and child everyday practice. Finally, Fisk offers recommendations for a “cybersafety of everyday life,” connecting youth Internet safety to trends in national infrastructure protection and corporate information assurance. COMPUTERS,Internet,General

Designing an Internet Why the Internet was designed to be the way it is, and how it could be different, now and in the future. How do you design an internet? The architecture of the current Internet is the product of basic design decisions made early in its history. What would an internet look like if it were designed, today, from the ground up? In this book, MIT computer scientist David Clark explains how the Internet is actually put together, what requirements it was designed to meet, and why different design decisions would create different internets. He does not take today's Internet as a given but tries to learn from it, and from alternative proposals for what an internet might be, in order to draw some general conclusions about network architecture. Clark discusses the history of the Internet, and how a range of potentially conflicting requirements—including longevity, security, availability, economic viability, management, and meeting the needs of society—shaped its character. He addresses both the technical aspects of the Internet and its broader social and economic contexts. He describes basic design approaches and explains, in terms accessible to nonspecialists, how networks are designed to carry out their functions. (An appendix offers a more technical discussion of network functions for readers who want the details.) He considers a range of alternative proposals for how to design an internet, examines in detail the key requirements a successful design must meet, and then imagines how to design a future internet from scratch. It's not that we should expect anyone to do this; but, perhaps, by conceiving a better future, we can push toward it. COMPUTERS,Internet,General

Weaving the Dark Web An exploration of the Dark Web—websites accessible only with special routing software—that examines the history of three anonymizing networks, Freenet, Tor, and I2P. The term “Dark Web” conjures up drug markets, unregulated gun sales, stolen credit cards. But, as Robert Gehl points out in Weaving the Dark Web, for each of these illegitimate uses, there are other, legitimate ones: the New York Times's anonymous whistleblowing system, for example, and the use of encryption by political dissidents. Defining the Dark Web straightforwardly as websites that can be accessed only with special routing software, and noting the frequent use of “legitimate” and its variations by users, journalists, and law enforcement to describe Dark Web practices (judging them “legit” or “sh!t”), Gehl uses the concept of legitimacy as a window into the Dark Web. He does so by examining the history of three Dark Web systems: Freenet, Tor, and I2P. Gehl presents three distinct meanings of legitimate: legitimate force, or the state's claim to a monopoly on violence; organizational propriety; and authenticity. He explores how Freenet, Tor, and I2P grappled with these different meanings, and then discusses each form of legitimacy in detail by examining Dark Web markets, search engines, and social networking sites. Finally, taking a broader view of the Dark Web, Gehl argues for the value of anonymous political speech in a time of ubiquitous surveillance. If we shut down the Dark Web, he argues, we lose a valuable channel for dissent. COMPUTERS,Internet,General

Protocol How Control Exists after Decentralization Is the Internet a vast arena of unrestricted communication and freely exchanged information or a regulated, highly structured virtual bureaucracy? In Protocol, Alexander Galloway argues that the founding principle of the Net is control, not freedom, and that the controlling power lies in the technical protocols that make network connections (and disconnections) possible. He does this by treating the computer as a textual medium that is based on a technological language, code. Code, he argues, can be subject to the same kind of cultural and literary analysis as any natural language; computer languages have their own syntax, grammar, communities, and cultures. Instead of relying on established theoretical approaches, Galloway finds a new way to write about digital media, drawing on his backgrounds in computer programming and critical theory. "Discipline-hopping is a necessity when it comes to complicated socio-technical topics like protocol," he writes in the preface. Galloway begins by examining the types of protocols that exist, including TCP/IP, DNS, and HTML. He then looks at examples of resistance and subversion—hackers, viruses, cyberfeminism, Internet art—which he views as emblematic of the larger transformations now taking place within digital culture. Written for a nontechnical audience, Protocol serves as a necessary counterpoint to the wildly utopian visions of the Net that were so widespread in earlier days. COMPUTERS,Internet,General

Hacker States How hackers and hacking moved from being a target of the state to a key resource for the expression and deployment of state power. In this book, Luca Follis and Adam Fish examine the entanglements between hackers and the state, showing how hackers and hacking moved from being a target of state law enforcement to a key resource for the expression and deployment of state power. Follis and Fish trace government efforts to control the power of the internet; the prosecution of hackers and leakers (including such well-known cases as Chelsea Manning, Edward Snowden, and Anonymous); and the eventual rehabilitation of hackers who undertake “ethical hacking” for the state. Analyzing the evolution of the state's relationship to hacking, they argue that state-sponsored hacking ultimately corrodes the rule of law and offers unchecked advantage to those in power, clearing the way for more authoritarian rule. Follis and Fish draw on a range of methodologies and disciplines, including ethnographic and digital archive methods from fields as diverse as anthropology, STS, and criminology. They propose a novel “boundary work” theoretical framework to articulate the relational approach to understanding state and hacker interactions advanced by the book. In the context of Russian bot armies, the rise of fake news, and algorithmic opacity, they describe the political impact of leaks and hacks, hacker partnerships with journalists in pursuit of transparency and accountability, the increasingly prominent use of extradition in hacking-related cases, and the privatization of hackers for hire. COMPUTERS,Internet,General

Keep Calm and Log On How to survive the digital revolution without getting trampled: your guide to online mindfulness, digital self-empowerment, cybersecurity, creepy ads, trustworthy information, and more. Feeling overwhelmed by an avalanche of online content? Anxious about identity theft? Unsettled by the proliferation of fake news? Welcome to the digital revolution. Wait—wasn't the digital revolution supposed to make our lives better? It was going to be fun and put the world at our fingertips. What happened? Keep Calm and Log On is a survival handbook that will help you achieve online mindfulness and overcome online helplessness—the feeling that tech is out of your control—with tips for handling cybersecurity, creepy ads, untrustworthy information, and much more. Taking a cue from the famous World War II morale-boosting slogan (“Keep Calm and Carry On”), Gus Andrews shows us how to adapt the techniques our ancestors used to survive hard times, so we can live our best lives online. She explains why media and technology stress us out, and offers empowering tools for coping. Mindfulness practices can help us stay calm and conserve our attention purposefully. Andrews shares the secret of understanding our own opinions'' “family trees” in order to identify misleading “fake news.” She provides tools for unplugging occasionally, overcoming feelings that we are “bad at technology,” and taking charge of our security and privacy. Andrews explains how social media algorithms keep us from information we need and why “creepy ads” seem to follow us online. Most importantly, she urges us to work to rebuild the trust in our communities that the internet has broken. COMPUTERS,Internet,General

Access Controlled Reports on a new generation of Internet controls that establish a new normative terrain in which surveillance and censorship are routine. Internet filtering, censorship of Web content, and online surveillance are increasing in scale, scope, and sophistication around the world, in democratic countries as well as in authoritarian states. The first generation of Internet controls consisted largely of building firewalls at key Internet gateways; China's famous “Great Firewall of China” is one of the first national Internet filtering systems. Today the new tools for Internet controls that are emerging go beyond mere denial of information. These new techniques, which aim to normalize (or even legalize) Internet control, include targeted viruses and the strategically timed deployment of distributed denial-of-service (DDoS) attacks, surveillance at key points of the Internet's infrastructure, take-down notices, stringent terms of usage policies, and national information shaping strategies. Access Controlled reports on this new normative terrain. The book, a project from the OpenNet Initiative (ONI), a collaboration of the Citizen Lab at the University of Toronto's Munk Centre for International Studies, Harvard's Berkman Center for Internet and Society, and the SecDev Group, offers six substantial chapters that analyze Internet control in both Western and Eastern Europe and a section of shorter regional reports and country profiles drawn from material gathered by the ONI around the world through a combination of technical interrogation and field research methods. COMPUTERS,Internet,General

Networked Affect Investigations of affective experiences that emerge in online settings that range from Facebook discussion forums to “smart” classrooms. Our encounters with websites, avatars, videos, mobile apps, discussion forums, GIFs, and nonhuman intelligent agents allow us to experience sensations of connectivity, interest, desire, and attachment—as well as detachment, boredom, fear, and shame. Some affective online encounters may arouse complex, contradictory feelings that resist dualistic distinctions. In this book, leading scholars examine the fluctuating and altering dynamics of affect that give shape to online connections and disconnections. Doing so, they tie issues of circulation and connectivity to theorizations of networked affect. Their diverse investigations—considering subjects that range from online sexual dynamics to the liveliness of computer code—demonstrate the value of affect theories for Internet studies. The contributors investigate networked affect in terms of intensity, sensation, and value. They explore online intensities that range from Tumblr practices in LGBTQ communities to visceral reactions to animated avatars; examine the affective materiality of software in such platforms as steampunk culture and nonprofit altporn; and analyze the ascription of value to online activities including the GTD (“getting things done”) movement and the accumulation of personal digital materials. Contributors James Ash, Alex Cho, Jodi Dean, Melissa Gregg, Ken Hillis, Kylie Jarrett, Tero Karppi, Stephen Maddison, Susanna Paasonen, Jussi Parikka, Michael Petit, Jennifer Pybus, Jenny Sundén, Veronika Tzankova COMPUTERS,Internet,General

Digital Methods A proposal to repurpose Web-native techniques for use in social and cultural scholarly research. In Digital Methods, Richard Rogers proposes a methodological outlook for social and cultural scholarly research on the Web that seeks to move Internet research beyond the study of online culture. It is not a toolkit for Internet research, or operating instructions for a software package; it deals with broader questions. How can we study social media to learn something about society rather than about social media use? Rogers proposes repurposing Web-native techniques for research into cultural change and societal conditions. We can learn to reapply such “methods of the medium” as crawling and crowd sourcing, PageRank and similar algorithms, tag clouds and other visualizations; we can learn how they handle hits, likes, tags, date stamps, and other Web-native objects. By “thinking along” with devices and the objects they handle, digital research methods can follow the evolving methods of the medium. Rogers uses this new methodological outlook to examine such topics as the findings of inquiries into 9/11 search results, the recognition of climate change skeptics by climate-change-related Web sites, and the censorship of the Iranian Web. With Digital Methods, Rogers introduces a new vision and method for Internet research and at the same time applies them to the Web's objects of study, from tiny particles (hyperlinks) to large masses (social media). COMPUTERS,Internet,General

Minitel The first scholarly book in English on Minitel, the pioneering French computer network, offers a history of a technical system and a cultural phenomenon. A decade before the Internet became a medium for the masses in the United States, tens of millions of users in France had access to a network for e-mail, e-commerce, chat, research, game playing, blogging, and even an early form of online porn. In 1983, the French government rolled out Minitel, a computer network that achieved widespread adoption in just a few years as the government distributed free terminals to every French telephone subscriber. With this volume, Julien Mailland and Kevin Driscoll offer the first scholarly book in English on Minitel, examining it as both a technical system and a cultural phenomenon. Mailland and Driscoll argue that Minitel was a technical marvel, a commercial success, and an ambitious social experiment. Other early networks may have introduced protocols and software standards that continue to be used today, but Minitel foretold the social effects of widespread telecomputing. They examine the unique balance of forces that enabled the growth of Minitel: public and private, open and closed, centralized and decentralized. Mailland and Driscoll describe Minitel's key technological components, novel online services, and thriving virtual communities. Despite the seemingly tight grip of the state, however, a lively Minitel culture emerged, characterized by spontaneity, imagination, and creativity. After three decades of continuous service, Minitel was shut down in 2012, but the history of Minitel should continue to inform our thinking about Internet policy, today and into the future. COMPUTERS,Internet,General

Beyond the Valley How to repair the disconnect between designers and users, producers and consumers, and tech elites and the rest of us: toward a more democratic internet. In this provocative book, Ramesh Srinivasan describes the internet as both an enabler of frictionless efficiency and a dirty tangle of politics, economics, and other inefficient, inharmonious human activities. We may love the immediacy of Google search results, the convenience of buying from Amazon, and the elegance and power of our Apple devices, but it's a one-way, top-down process. We're not asked for our input, or our opinions—only for our data. The internet is brought to us by wealthy technologists in Silicon Valley and China. It's time, Srinivasan argues, that we think in terms beyond the Valley. Srinivasan focuses on the disconnection he sees between designers and users, producers and consumers, and tech elites and the rest of us. The recent Cambridge Analytica and Russian misinformation scandals exemplify the imbalance of a digital world that puts profits before inclusivity and democracy. In search of a more democratic internet, Srinivasan takes us to the mountains of Oaxaca, East and West Africa, China, Scandinavia, North America, and elsewhere, visiting the “design labs” of rural, low-income, and indigenous people around the world. He talks to a range of high-profile public figures—including Elizabeth Warren, David Axelrod, Eric Holder, Noam Chomsky, Lawrence Lessig, and the founders of Reddit, as well as community organizers, labor leaders, and human rights activists.. To make a better internet, Srinivasan says, we need a new ethic of diversity, openness, and inclusivity, empowering those now excluded from decisions about how technologies are designed, who profits from them, and who are surveilled and exploited by them. COMPUTERS,Internet,General

Internet for Scientists This book provides a straightforward manual and review handbook for accessing and using the resources of the Internet in the day to day labours of the working scientist. It addresses the problem of how to cope with an army who have discovered a whole new toy shop full of goodies. COMPUTERS,Internet,General

The Guide to Complementary and Alternative Medicine on the Internet Learn to identify Internet-based complementary/alternative medicine resources you can trust! This well-organized book takes a commonsense approach to getting the most out of the Internet when it comes to finding reliable information on complementary and alternative medicine. Author Lillian Brazin teaches classes on finding and evaluating health information on the Internet. In this book, she shares her years of experience in using and evaluating medical Internet sites to teach you to spot authoritative resources and avoid misinformation, sales pitches, and out-and-out quackery. In addition to showing you where to find the information you need, this book stresses the importance (the how and why) of working closely with your physician to get the best results from your complementary/alternative medical experience. More than 20 screen shot illustrations give you a preview of what to look for on various sites! The Guide to Complementary and Alternative Medicine on the Internet will show you how to separate the wheat from the chaff when confronted with hundreds of Web sites purporting to provide reliable information. This jargon-free book addresses vital questions, such as: How can I be certain that the information I find is correct? How can I locate a Web site that was recommended to me? How do I start out to research a particular health problem? What do Internet terms like .com, .edu, .gov, listservs, :), BTW, LOL, flames, netiquette, etc. mean? This book will also help you understand controversial hot topics that include: the Pilates exercise method that Jacqueline Kennedy Onassis helped popularize in the 1960s is trendy again, with Pilates studios in most major cities supermarket supplements, such as St. John's wort, gingko biloba, and vitamins A-Z: how can I find out which, if any of them, are for me? the validity of celebrity endorsements for supplements and alternative therapies While providing you with the skills to find the information you seek, this book reflects the author’s cautious perspective. The Internet can be frightening and overwhelming because there is so much information to sift through, digest, and evaluate. The Guide to Complementary and Alternative Medicine on the Internet (first in the new Internet Guides to Consumer Health Care series from The Haworth Information Press) will help you identify Internet resources for complementary and alternative medicine that you can trust. COMPUTERS,Internet,General

Surviving Cyberwar This book examines in depth the major recent cyber attacks that have taken place around the world, discusses the implications of such attacks, and offers solutions to the vulnerabilities that made these attacks possible. Through investigations of the most significant and damaging cyber attacks, the author introduces the reader to cyberwar, outlines an effective defense against cyber threats, and explains how to prepare for future attacks. COMPUTERS,Internet,Online Safety & Privacy

How to Be Invisible "Fascinating... a regular field manual... meticulously researched and very entertaining." --G. Gordon Liddy A thoroughly revised and updated edition of the essential guide to preserving your personal security From cyberspace to crawl spaces, new innovations in information gathering have left the private life of the average person open to scrutiny, and worse, exploitation. In this thoroughly updated third edition of his immensely popular guide How to Be Invisible, J.J. Luna shows you how to protect your home address, hide your ownership of vehicles and real estate, use pagers with dumbphones, switch to low-profile banking and invisible money transfers, use alternate signatures, and how to secretly run a home-based business. J.J. Luna is an expert and highly trained security consultant with years of experience protecting himself, his family, and his clients. Using real life stories and his own consulting experience, J.J. Luna divulges legal methods to attain the privacy you crave and deserve, whether you want to shield yourself from casual scrutiny or take your life savings with you and disappear without a trace. Whatever your needs, Luna reveals the shocking secrets that private detectives and other seekers of personal information use to uncover information and then shows how to make a serious commitment to safeguarding yourself. There is a prevailing sense in our society that true privacy is a thing of the past. In a world where privacy concerns that only continue to grow in magnitude, How to Be Invisible, Third Edition is a critical antidote to the spread of new and more efficient ways of undermining our personal security. Privacy is a commonly-lamented casualty of the Information Age and of the world's changing climate--but that doesn't mean you have to stand for it. This new edition of J. J. Luna's classic manual contains step-by-step advice on building and maintaining your personal security, including brand new chapters on:- The dangers from Facebook, smartphones, and facial recognition- How to locate a nominee (or proxy) you can trust- The art of pretexting, aka social engineering- Moving to Baja California Sur; San Miguel de Allende, Guanajuato; Cuenca, Ecuador; or Spain's Canary Islands- The secrets of international privacy, and much more! COMPUTERS,Internet,Online Safety & Privacy

Social Media Investigation for Law Enforcement Social media is becoming an increasingly important—and controversial—investigative source for law enforcement. Social Media Investigation for Law Enforcement provides an overview of the current state of digital forensic investigation of Facebook and other social media networks and the state of the law, touches on hacktivism, and discusses the implications for privacy and other controversial areas. The authors also point to future trends. COMPUTERS,Internet,Online Safety & Privacy

The Art of Invisibility Real-world advice on how to be invisible online from "the FBI's most wanted hacker" (Wired). Be online without leaving a trace. Your every step online is being tracked and stored, and your identity literally stolen. Big companies and big governments want to know and exploit what you do, and privacy is a luxury few can afford or understand. In this explosive yet practical book, Kevin Mitnick uses true-life stories to show exactly what is happening without your knowledge, teaching you "the art of invisibility" -- online and real-world tactics to protect you and your family, using easy step-by-step instructions. Reading this book, you will learn everything from password protection and smart Wi-Fi usage to advanced techniques designed to maximize your anonymity. Kevin Mitnick knows exactly how vulnerabilities can be exploited and just what to do to prevent that from happening. The world's most famous -- and formerly the US government's most wanted -- computer hacker, he has hacked into some of the country's most powerful and seemingly impenetrable agencies and companies, and at one point was on a three-year run from the FBI. Now Mitnick is reformed and widely regarded as the expert on the subject of computer security. Invisibility isn't just for superheroes; privacy is a power you deserve and need in the age of Big Brother and Big Data. "Who better than Mitnick -- internationally wanted hacker turned Fortune 500 security consultant -- to teach you how to keep your data safe?" --Esquire COMPUTERS,Internet,Online Safety & Privacy

Cyberpower and National Security The cyber domain is undergoing extraordinary changes that present both exceptional opportunities to and major challenges for users of cyberspace. The challenges arise from the malevolent actors who use cyberspace and the many security vulnerabilities that plague this sphere. Exploiting opportunities and overcoming challenges will require a balanced body of knowledge on the cyber domain. Cyberpower and National Security assembles a group of experts and discusses pertinent issues in five areas. The first section provides a broad foundation and overview of the subject by identifying key policy issues, establishing a common vocabulary, and proposing an initial version of a theory of cyberpower. The second section identifies and explores possible changes in cyberspace over the next fifteen years by assessing cyber infrastructure and security challenges. The third section analyzes the potential impact of changes in cyberspace on the military and informational levers of power. The fourth section addresses the extent to which changes in cyberspace serve to empower key entities such as transnational criminals, terrorists, and nation-states. The final section examines key institutional factors, which include issues concerning governance, legal dimensions, critical infrastructure protection, and organization. Cyberpower and National Security frames the key issues concerned and identifies the important questions involved in building the human capacity to address cyber issues, balancing civil liberties with national security considerations, and developing the international partnerships needed to address cyber challenges. With more than two dozen contributors, Cyberpower and National Security covers it all. COMPUTERS,Internet,Online Safety & Privacy

The Smart Girl's Guide to Privacy The whirlwind of social media, online dating, and mobile apps can make life a dream—or a nightmare. For every trustworthy website, there are countless jerks, bullies, and scam artists who want to harvest your personal information for their own purposes. But you can fight back, right now. In The Smart Girl’s Guide to Privacy, award-winning author and investigative journalist Violet Blue shows you how women are targeted online and how to keep yourself safe. Blue’s practical, user-friendly advice will teach you how to:–Delete personal content from websites–Use website and browser privacy controls effectively–Recover from and prevent identity theft–Figure out where the law protects you—and where it doesn’t–Set up safe online profiles–Remove yourself from people-finder websites Even if your privacy has already been compromised, don’t panic. It’s not too late to take control. Let The Smart Girl’s Guide to Privacy help you cut through the confusion and start protecting your online life. COMPUTERS,Internet,Online Safety & Privacy

Penetration Testing Penetration testers simulate cyber attacks to find security weaknesses in networks, operating systems, and applications. Information security experts worldwide use penetration techniques to evaluate enterprise defenses. In Penetration Testing, security expert, researcher, and trainer Georgia Weidman introduces you to the core skills and techniques that every pentester needs. Using a virtual machine–based lab that includes Kali Linux and vulnerable operating systems, you’ll run through a series of practical lessons with tools like Wireshark, Nmap, and Burp Suite. As you follow along with the labs and launch attacks, you’ll experience the key stages of an actual assessment—including information gathering, finding exploitable vulnerabilities, gaining access to systems, post exploitation, and more. Learn how to:–Crack passwords and wireless network keys with brute-forcing and wordlists–Test web applications for vulnerabilities–Use the Metasploit Framework to launch exploits and write your own Metasploit modules–Automate social-engineering attacks–Bypass antivirus software–Turn access to one machine into total control of the enterprise in the post exploitation phase You’ll even explore writing your own exploits. Then it’s on to mobile hacking—Weidman’s particular area of research—with her tool, the Smartphone Pentest Framework. With its collection of hands-on lessons that cover key tools and strategies, Penetration Testing is the introduction that every aspiring hacker needs. COMPUTERS,Internet,Online Safety & Privacy

Dawn of the Code War The inside story of how America's enemies launched a cyber war against us-and how we've learned to fight back With each passing year, the internet-linked attacks on America's interests have grown in both frequency and severity. Overmatched by our military, countries like North Korea, China, Iran, and Russia have found us vulnerable in cyberspace. The "Code War" is upon us. In this dramatic book, former Assistant Attorney General John P. Carlin takes readers to the front lines of a global but little-understood fight as the Justice Department and the FBI chases down hackers, online terrorist recruiters, and spies. Today, as our entire economy goes digital, from banking to manufacturing to transportation, the potential targets for our enemies multiply. This firsthand account is both a remarkable untold story and a warning of dangers yet to come. COMPUTERS,Internet,Online Safety & Privacy

Raising Humans in a Digital World Digital literacy advocate Diana Graber demystifies the complicated digital landscape facing today’s kids and provides answers for parents and teachers eager to show them how to use technology as an empowering force in their lives and in their role as future leaders. COMPUTERS,Internet,Online Safety & Privacy

Transformational Security Awareness Expert guidance on the art and science of driving secure behaviors Transformational Security Awareness empowers security leaders with the information and resources they need to assemble and deliver effective world-class security awareness programs that drive secure behaviors and culture change. When all other processes, controls, and technologies fail, humans are your last line of defense. But, how can you prepare them? Frustrated with ineffective training paradigms, most security leaders know that there must be a better way. A way that engages users, shapes behaviors, and fosters an organizational culture that encourages and reinforces security-related values. The good news is that there is hope. That’s what Transformational Security Awareness is all about. Author Perry Carpenter weaves together insights and best practices from experts in communication, persuasion, psychology, behavioral economics, organizational culture management, employee engagement, and storytelling to create a multidisciplinary masterpiece that transcends traditional security education and sets you on the path to make a lasting impact in your organization. Find out what you need to know about marketing, communication, behavior science, and culture management Overcome the knowledge-intention-behavior gap Optimize your program to work with the realities of human nature Use simulations, games, surveys, and leverage new trends like escape rooms to teach security awareness Put effective training together into a well-crafted campaign with ambassadors Understand the keys to sustained success and ongoing culture change Measure your success and establish continuous improvements Do you care more about what your employees know or what they do? It's time to transform the way we think about security awareness. If your organization is stuck in a security awareness rut, using the same ineffective strategies, materials, and information that might check a compliance box but still leaves your organization wide open to phishing, social engineering, and security-related employee mistakes and oversights, then you NEED this book. COMPUTERS,Internet,Online Safety & Privacy

Cyberpower and National Security The cyber domain is undergoing extraordinary changes that present both exceptional opportunities to and major challenges for users of cyberspace. The challenges arise from the malevolent actors who use cyberspace and the many security vulnerabilities that plague this sphere. Exploiting opportunities and overcoming challenges will require a balanced body of knowledge on the cyber domain. Cyberpower and National Security assembles a group of experts and discusses pertinent issues in five areas. The first section provides a broad foundation and overview of the subject by identifying key policy issues, establishing a common vocabulary, and proposing an initial version of a theory of cyberpower. The second section identifies and explores possible changes in cyberspace over the next fifteen years by assessing cyber infrastructure and security challenges. The third section analyzes the potential impact of changes in cyberspace on the military and informational levers of power. The fourth section addresses the extent to which changes in cyberspace serve to empower key entities such as transnational criminals, terrorists, and nation-states. The final section examines key institutional factors, which include issues concerning governance, legal dimensions, critical infrastructure protection, and organization. Cyberpower and National Security frames the key issues concerned and identifies the important questions involved in building the human capacity to address cyber issues, balancing civil liberties with national security considerations, and developing the international partnerships needed to address cyber challenges. With more than two dozen contributors, Cyberpower and National Security covers it all. COMPUTERS,Internet,Online Safety & Privacy

We Have Root A collection of popular essays from security guru Bruce Schneier In his latest collection of essays, security expert Bruce Schneier tackles a range of cybersecurity, privacy, and real-world security issues ripped from the headlines. Essays cover the ever-expanding role of technology in national security, war, transportation, the Internet of Things, elections, and more. Throughout, he challenges the status quo with a call for leaders, voters, and consumers to make better security and privacy decisions and investments. Bruce’s writing has previously appeared in some of the world's best-known and most-respected publications, including The Atlantic, the Wall Street Journal, CNN, the New York Times, the Washington Post, Wired, and many others. And now you can enjoy his essays in one place—at your own speed and convenience. • Timely security and privacy topics • The impact of security and privacy on our world • Perfect for fans of Bruce’s blog and newsletter • Lower price than his previous essay collections The essays are written for anyone who cares about the future and implications of security and privacy for society. COMPUTERS,Internet,Online Safety & Privacy

Learn Azure Sentinel Understand how to set up, configure, and use Azure Sentinel to provide security incident and event management services for your environment Key Features Secure your network, infrastructure, data, and applications on Microsoft Azure effectively Integrate artificial intelligence, threat analysis, and automation for optimal security solutions Investigate possible security breaches and gather forensic evidence to prevent modern cyber threats Book Description Azure Sentinel is a Security Information and Event Management (SIEM) tool developed by Microsoft to integrate cloud security and artificial intelligence (AI). Azure Sentinel not only helps clients identify security issues in their environment, but also uses automation to help resolve these issues. With this book, you'll implement Azure Sentinel and understand how it can help find security incidents in your environment with integrated artificial intelligence, threat analysis, and built-in and community-driven logic. This book starts with an introduction to Azure Sentinel and Log Analytics. You'll get to grips with data collection and management, before learning how to create effective Azure Sentinel queries to detect anomalous behaviors and patterns of activity. As you make progress, you'll understand how to develop solutions that automate the responses required to handle security incidents. Finally, you'll grasp the latest developments in security, discover techniques to enhance your cloud security architecture, and explore how you can contribute to the security community. By the end of this book, you'll have learned how to implement Azure Sentinel to fit your needs and be able to protect your environment from cyber threats and other security issues. What you will learn Understand how to design and build a security operations center Discover the key components of a cloud security architecture Manage and investigate Azure Sentinel incidents Use playbooks to automate incident responses Understand how to set up Azure Monitor Log Analytics and Azure Sentinel Ingest data into Azure Sentinel from the cloud and on-premises devices Perform threat hunting in Azure Sentinel Who this book is for This book is for solution architects and system administrators who are responsible for implementing new solutions in their infrastructure. Security analysts who need to monitor and provide immediate security solutions or threat hunters looking to learn how to use Azure Sentinel to investigate possible security breaches and gather forensic evidence will also benefit from this book. Prior experience with cloud security, particularly Azure, is necessary. COMPUTERS,Internet,Online Safety & Privacy

Learn Computer Forensics Get up and running with collecting evidence using forensics best practices to present your findings in judicial or administrative proceedings Key Features Learn the core techniques of computer forensics to acquire and secure digital evidence skillfully Conduct a digital forensic examination and document the digital evidence collected Analyze security systems and overcome complex challenges with a variety of forensic investigations Book Description A computer forensics investigator must possess a variety of skills, including the ability to answer legal questions, gather and document evidence, and prepare for an investigation. This book will help you get up and running with using digital forensic tools and techniques to investigate cybercrimes successfully. Starting with an overview of forensics and all the open source and commercial tools needed to get the job done, you'll learn core forensic practices for searching databases and analyzing data over networks, personal devices, and web applications. You'll then learn how to acquire valuable information from different places, such as filesystems, e-mails, browser histories, and search queries, and capture data remotely. As you advance, this book will guide you through implementing forensic techniques on multiple platforms, such as Windows, Linux, and macOS, to demonstrate how to recover valuable information as evidence. Finally, you'll get to grips with presenting your findings efficiently in judicial or administrative proceedings. By the end of this book, you'll have developed a clear understanding of how to acquire, analyze, and present digital evidence like a proficient computer forensics investigator. What you will learn Understand investigative processes, the rules of evidence, and ethical guidelines Recognize and document different types of computer hardware Understand the boot process covering BIOS, UEFI, and the boot sequence Validate forensic hardware and software Discover the locations of common Windows artifacts Document your findings using technically correct terminology Who this book is for If you're an IT beginner, student, or an investigator in the public or private sector this book is for you.This book will also help professionals and investigators who are new to incident response and digital forensics and interested in making a career in the cybersecurity domain. COMPUTERS,Internet,Online Safety & Privacy

Access Contested Experts examine censorship, surveillance, and resistance across Asia, from China and India to Malaysia and the Philippines. A daily battle for rights and freedoms in cyberspace is being waged in Asia. At the epicenter of this contest is China—home to the world's largest Internet population and what is perhaps the world's most advanced Internet censorship and surveillance regime in cyberspace. Resistance to China's Internet controls comes from both grassroots activists and corporate giants such as Google. Meanwhile, similar struggles play out across the rest of the region, from India and Singapore to Thailand and Burma, although each national dynamic is unique. Access Contested, the third volume from the OpenNet Initiative (a collaborative partnership of the Citizen Lab at the University of Toronto's Munk School of Global Affairs, the Berkman Center for Internet and Society at Harvard University, and the SecDev Group in Ottawa), examines the interplay of national security, social and ethnic identity, and resistance in Asian cyberspace, offering in-depth accounts of national struggles against Internet controls as well as updated country reports by ONI researchers. The contributors examine such topics as Internet censorship in Thailand, the Malaysian blogosphere, surveillance and censorship around gender and sexuality in Malaysia, Internet governance in China, corporate social responsibility and freedom of expression in South Korea and India, cyber attacks on independent Burmese media, and distributed-denial-of-service attacks and other digital control measures across Asia. COMPUTERS,Internet,Online Safety & Privacy

Obfuscation How we can evade, protest, and sabotage today's pervasive digital surveillance by deploying more data, not less—and why we should. With Obfuscation, Finn Brunton and Helen Nissenbaum mean to start a revolution. They are calling us not to the barricades but to our computers, offering us ways to fight today's pervasive digital surveillance—the collection of our data by governments, corporations, advertisers, and hackers. To the toolkit of privacy protecting techniques and projects, they propose adding obfuscation: the deliberate use of ambiguous, confusing, or misleading information to interfere with surveillance and data collection projects. Brunton and Nissenbaum provide tools and a rationale for evasion, noncompliance, refusal, even sabotage—especially for average users, those of us not in a position to opt out or exert control over data about ourselves. Obfuscation will teach users to push back, software developers to keep their user data safe, and policy makers to gather data without misusing it. Brunton and Nissenbaum present a guide to the forms and formats that obfuscation has taken and explain how to craft its implementation to suit the goal and the adversary. They describe a series of historical and contemporary examples, including radar chaff deployed by World War II pilots, Twitter bots that hobbled the social media strategy of popular protest movements, and software that can camouflage users' search queries and stymie online advertising. They go on to consider obfuscation in more general terms, discussing why obfuscation is necessary, whether it is justified, how it works, and how it can be integrated with other privacy practices and technologies. COMPUTERS,Internet,Online Safety & Privacy

The Internet Police Chaos and order clash in this riveting exploration of crime and punishment on the Internet. Once considered a borderless and chaotic virtual landscape, the Internet is now home to the forces of international law and order. It’s not just computer hackers and cyber crooks who lurk in the dark corners of the Web—the cops are there, too. In The Internet Police, Ars Technica deputy editor Nate Anderson takes readers on a behind-the-screens tour of landmark cybercrime cases, revealing how criminals continue to find digital and legal loopholes even as police hurry to cinch them closed. From the Cleveland man whose "natural male enhancement" pill inadvertently protected the privacy of your e-mail to the Russian spam king who ended up in a Milwaukee jail to the Australian arrest that ultimately led to the breakup of the largest child pornography ring in the United States, Anderson draws on interviews, court documents, and law-enforcement reports to reconstruct accounts of how online policing actually works. Questions of online crime are as complex and interconnected as the Internet itself. With each episode in The Internet Police, Anderson shows the dark side of online spaces—but also how dystopian a fully "ordered" alternative would be. Includes an afterword that details law enforcement's dramatic seizure of the online black market Silk Road. COMPUTERS,Internet,Online Safety & Privacy

Click Here to Kill Everybody “Sober, lucid and often wise.†—Nature The Internet is powerful, but it is not safe. As “smart†devices proliferate the risks will get worse, unless we act now. From driverless cars to smart thermostats, from autonomous stock-trading systems to drones equipped with their own behavioral algorithms, the Internet now has direct effects on the physical world. Forget data theft: cutting-edge digital attackers can now literally crash your car, pacemaker, and home security system, as well as everyone else’s. In Click Here to Kill Everybody, best-selling author Bruce Schneier explores the risks and security implications of our new, hyper-connected era, and lays out common-sense policies that will allow us to enjoy the benefits of this omnipotent age without falling prey to the consequences of its insecurity. COMPUTERS,Internet,Online Safety & Privacy

Testing and Securing Web Applications Web applications occupy a large space within the IT infrastructure of a business or a corporation. They simply just don’t touch a front end or a back end; today’s web apps impact just about every corner of it. Today’s web apps have become complex, which has made them a prime target for sophisticated cyberattacks. As a result, web apps must be literally tested from the inside and out in terms of security before they can be deployed and launched to the public for business transactions to occur. The primary objective of this book is to address those specific areas that require testing before a web app can be considered to be completely secure. The book specifically examines five key areas: Network security: This encompasses the various network components that are involved in order for the end user to access the particular web app from the server where it is stored at to where it is being transmitted to, whether it is a physical computer itself or a wireless device (such as a smartphone). Cryptography: This area includes not only securing the lines of network communications between the server upon which the web app is stored at and from where it is accessed from but also ensuring that all personally identifiable information (PII) that is stored remains in a ciphertext format and that its integrity remains intact while in transmission. Penetration testing: This involves literally breaking apart a Web app from the external environment and going inside of it, in order to discover all weaknesses and vulnerabilities and making sure that they are patched before the actual Web app is launched into a production state of operation. Threat hunting: This uses both skilled analysts and tools on the Web app and supporting infrastructure to continuously monitor the environment to find all security holes and gaps. The Dark Web: This is that part of the Internet that is not openly visible to the public. As its name implies, this is the "sinister" part of the Internet, and in fact, where much of the PII that is hijacked from a web app cyberattack is sold to other cyberattackers in order to launch more covert and damaging threats to a potential victim. Testing and Securing Web Applications breaks down the complexity of web application security testing so this critical part of IT and corporate infrastructure remains safe and in operation. COMPUTERS,Internet,Online Safety & Privacy

Podcasting For Dummies Produce a podcast like the pros More people than ever are turning to podcasts for on-demand, mobile entertainment and information. Podcasting For Dummies offers a fast and easy way to get the know-how you need to produce and distribute one of your very own. Written by a pair of podcasting pioneers, this book shares insight on the technology behind recording, editing, and sharing podcasts, along with tips and tricks on how to produce a pro-level podcast. Podcasting has enjoyed a recent boom thanks to a new crop of hit podcasts catching the ears of the public and media along with the continued growth of mobile and streaming devices as a source for entertainment. If you want to jump on the podcasting bandwagon, you've come to the right place! In this fully updated edition, would-be and experienced podcasters alike will get all the tech information, production insight, and promotional tips they need to either get a podcast off the ground or improve on an existing one. Get the gear you need Find your podcasting voice Find and build an audience Plan your podcast New tools have made it easier than ever to create a podcast—and this book shows you how. COMPUTERS,Internet,Podcasting & Webcasting

So You Want to Start a Podcast An inspiring, comprehensive, step-by-step guide to creating a hit show, So You Want to Start a Podcast covers everything from hosting and guest booking to editing and marketing - while offering plenty of encouragement and insider stories along the way. Though they are the fastest-growing form of media, podcasts can actually be tricky to create—and even harder to sustain. Few know the secrets of successfully creating a knockout podcast better than Kristen Meinzer. An award-winning commentator, producer, and former director of nonfiction programming for Slate’s sister company, Panoply, Meinzer has also hosted three successful podcasts, reaching more than ten million listeners. Now, she shares her expertise, providing aspiring podcasters with crucial information and guidance to work smarter, not harder as they start their own audio forum. Meinzer believes that we each have a unique voice that deserves to be heard. But many of us may need some help transforming our ideas into reality. So You Want to Start a Podcast asks the tough but important questions to help budding podcasters define and achieve their goals, including: Why do you want to start a podcast? Think about specifically why you want to start a podcast versus a blog, zine, YouTube channel, Instagram feed, or other media outlet. Find out if a podcast is really the best way to tell your story—and what you really need (and don’t need!) in order to get started. What is your show about? For any advertiser, corporate partner, or press outlet, you need a snappy pitch. How would you describe what you want to do in two to three sentences? Who is your podcast for? Who are you trying to reach? How will your content and tone appeal to those listeners? How is your show going to be structured? Create a step-by-step map planning the show out. Think about length, segments, interviews, advice, news reads, and other aspects of successful podcasts you can adapt for your own. With this motivational how-to guide—the only one on the subject available—you’ll find the smart, bottom-line advice and inspiration you need to produce an entertaining and informative podcast and promote it to an audience that will love it. So You Want to Start a Podcast gives you the tools you need to start a podcast—and the insight to keep it thriving! COMPUTERS,Internet,Podcasting & Webcasting

Social Media Livestreaming Social Media Livestreaming: Design for Disruption? addresses a host of emerging issues concerning social media livestreaming, exploring this technology as a disruption and its potential to shape journalism practice and influence society. Live visual images increasingly inundate our digital screens. While once restricted to broadcast news organizations, "going live" is becoming ubiquitous, fueled by smartphones and social networks. As livestreams and eyewitness video permeate our social media feeds, a wide range of possibilities for journalism and society are unfolding. Using international case studies, interviews with journalists, and survey research with citizens, this book explores major themes including livestreaming’s implications for journalism practice and news content production; citizen activism and participation in democracy; ethical, legal, safety and privacy considerations; and the role of livestreaming in shaping public perception. Social Media Livestreaming: Design for Disruption? is ideal for multiple audiences, from academic researchers to professional journalists and social media practitioners as well as policy-makers and organizations. COMPUTERS,Internet,Podcasting & Webcasting

Profit from Your Podcast Methods and Advice for Making the Most of Your Podcast—Pricing, Sponsors, Crowdfunding, and More Pick up any book on podcast monetization, and you will find 90 percent of it only covers how to launch a podcast. If you already have a podcast, you have that information; you’re ready for the next step. Profit from Your Podcast provides top strategies and real-life examples of podcast monetization. This book is more than what to do. It also tells you how to do it. Chapters cover such topics as: How to Grow Your Audience How to Set Your Pricing Understanding Advertising Jargon How to Find Sponsors Best Strategies for Making Money as an Affiliate Master Strategies for Crowdfunding Harnessing the Power of Webinars and Events The Top Tools to Make Your Job Easy Built on the author’s fifteen years of experience in podcasting, this action-packed guide will benefit new and veteran podcasters. Get clear on who your audience is and what they want, deliver value, and build an engaged audience that wants to give you money. Leverage your relationships and the integrity you have built through your podcast to create multiple streams of income. Profit from Your Podcast gives you the tools to do it all. COMPUTERS,Internet,Podcasting & Webcasting

Google Power Search Behind Google's deceptively simple interface is immense power for both market and competitive research—if you know how to use it well. Sure, basic searches are easy, but complex searches require specialized skills. This concise book takes you through the full range of Google's powerful search-refinement features, so you can quickly find the specific information you need. Learn techniques ranging from simple Boolean logic to URL parameters and other advanced tools, and see how they're applied to real-world market research examples. Incorporate advanced search operators such as filetype:, intitle:, daterange:, and others into your queries Use Google filtering tools, including Search Within Results, Similar Pages, and SafeSearch, among others Explore the breadth of Google through auxiliary search services like Google News, Google Books, Google Blog Search, and Google Scholar Acquire advanced Google skills that result in more effective search engine optimization (SEO) COMPUTERS,Internet,Search Engines

The Extreme Searcher's Internet Handbook An essential guide for anyone who conducts research on the internet—including librarians, teachers, students, business professionals, and writers—this fully revised handbook details what users must know to take full advantage of internet search tools and resources. From the latest online tools to the new and enhanced services offered by standbys such as Google, the major search engines and their myriad of possibilities are thoroughly discussed. This revamped fourth edition also features chapters on fact-checking sites and popular social networking sites as well as a collection of up-to-date screenshots for visual reference. For those with little to moderate searching experience, friendly, easy-to-follow guidelines to the world of Web research are provided, while experienced searchers will discover new perspectives on content and techniques. COMPUTERS,Internet,Search Engines

The Art of SEO Three acknowledged experts in search engine optimization share guidelines and innovative techniques that will help you plan and execute a comprehensive SEO strategy. Complete with an array of effective tactics from basic to advanced, this third edition prepares digital marketers for 2016 with updates on SEO tools and new search engine optimization methods that have reshaped the SEO landscape Novices will receive a thorough SEO education, while experienced SEO practitioners get an extensive reference to support ongoing engagements. Comprehend SEO’s many intricacies and complexities Explore the underlying theory and inner workings of search engines Understand the role of social media, user data, and links Discover tools to track results and measure success Examine the effects of Google’s Panda and Penguin algorithms Consider opportunities in mobile, local, and vertical SEO Build a competent SEO team with defined roles Glimpse the future of search and the SEO industry Visit the book website (http://www.artofseobook.com) for FAQs and to post your own burning questions. You’ll have access to special offers and discounts on various SEO tools and services. You can also get exclusive access to instructional videos related to the concepts in the book by sending an email to bonuses@artofseobook.com. COMPUTERS,Internet,Search Engines

The SEO Battlefield Welcome to the battlefield. Every day, companies ranging from startups to enterprises fight to achieve high search rankings, knowing that previous success can quickly vanish. With this practical guide, you’ll learn how to put search engine optimization (SEO) methodology into practice, including the research, data analysis, and constant experimentation required to build an SEO program specific to your organization that can help you improve search results. Running a successful SEO program requires a team with a mix of skills, including marketing, analytics, website development, and automation. Author Anne Ahola Ward walks marketers and developers through SEO essentials and provides real-world case studies of successful and not-so-successful SEO programs. You’ll quickly understand why this is both an exciting and critical time to adopt SEO in your organization. Perform keyword goals and research, and spot search trends Understand the motivation and creativity of the SEO mindset Run a campaign to generate traffic and measure the results Use mobile and platform-agnostic strategies for search growth Demonstrate the value of your search marketing efforts Include web development in your SEO program—everything from quick updates to UX/UI strategy Learn the sweetest way to run and report on an search program COMPUTERS,Internet,Search Engines

The Joy of Search How to be a great online searcher, demonstrated with step-by-step searches for answers to a series of intriguing questions (for example, “Is that plant poisonous?”). We all know how to look up something online by typing words into a search engine. We do this so often that we have made the most famous search engine a verb: we Google it—“Japan population” or “Nobel Peace Prize” or “poison ivy” or whatever we want to know. But knowing how to Google something doesn't make us search experts; there's much more we can do to access the massive collective knowledge available online. In The Joy of Search, Daniel Russell shows us how to be great online researchers. We don't have to be computer geeks or a scholar searching out obscure facts; we just need to know some basic methods. Russell demonstrates these methods with step-by-step searches for answers to a series of intriguing questions—from “what is the wrong side of a towel?” to “what is the most likely way you will die?” Along the way, readers will discover essential tools for effective online searches—and learn some fascinating facts and interesting stories. Russell explains how to frame search queries so they will yield information and describes the best ways to use such resources as Google Earth, Google Scholar, Wikipedia, and Wikimedia. He shows when to put search terms in double quotes, how to use the operator (*), why metadata is important, and how to triangulate information from multiple sources. By the end of this engaging journey of discovering, readers will have the definitive answer to why the best online searches involve more than typing a few words into Google. COMPUTERS,Internet,Search Engines

Social Media ROI Use Social and Viral Technologies to Supercharge Your Customer Service! Use this book to bring true business discipline to your social media program and align with your organization’s goals. Top branding and marketing expert Olivier Blanchard brings together new best practices for strategy, planning, execution, measurement, analysis, and optimization. You will learn how to define the financial and nonfinancial business impacts you are aiming for--and achieve them. Social Media ROI delivers practical solutions for everything from structuring programs to attracting followers, defining metrics to managing crises. Whether you are in a startup or a global enterprise, this book will help you gain more value from every dime you invest in social media. You’ll learn how to: Align social communications with broader business goals and functions Plan for effective performance measurement Establish clarity of vision, purpose, and execution Implement guidelines and operations for effectively managing social media Get started by “listening before talking†Integrate social media into long-term marketing programs, short-term campaigns, and brand initiatives Use social media to deliver real-time, optimized customer support Leverage mobility and the “on-the-fly†social media culture Measure FRY (Frequency, Reach, and Yield) Includes a foreword by Brian Solis. COMPUTERS,Internet,Social Media

Online Community Management For Dummies Learn to manage, grow, and communicate with your online community Online community management is a growing profession and companies are investing in online communities in order to gain consumer insights into products and to test new products. An effective and dedicated community manager is essential to engage and manage a successful online consumer community. This straightforward-but-fun guide shows you how to effectively manage, grow, and communicate with your online community. Clear coverage shares tips for dealing with customers and fans through Twitter, Facebook, forums, and blogs. A practical approach shows you how to ensure that visitors to your site are satisfied, kept happy, and return. You'll explore the various types of online communities and benefit from learning an assortment of tips and tools that will help you stand out above the competition, attract more visitors and gain the attention of potential advertisers and investors. Aims at providing community managers the information they need to get a handle on their online communities and make them successful Addresses the role of the community manager, the core community management tasks, and how to create an online community Highlights ways to build relationships within your community, evaluate return on investment, and handle and respond to criticism Offers advice for establishing policies and transparency and encouraging community interaction Online Community Management For Dummies is the ideal introductory guide for making sure that visitors to your site have a good experience and return for more. COMPUTERS,Internet,Social Media

LinkedIn Marketing A step-by-step guide for succeeding on the for ''business'' social media network LinkedIn Marketing: An Hour a Day helps you create, customize, and optimize a presence on LinkedIn, the world's largest social network for professionals. In this detailed, step-by-step book, LinkedIn expert Viveka von Rosen reveals how to use this powerful platform to ensure that you or your company get noticed by the right audience. Discover previously undocumented tips and tricks for community growth and management, including how to best use Groups, events, and other LinkedIn features and applications. Offers a complete resource for anyone who wants to market and recruit on the world's largest professional network Features hands-on tutorials, case studies, examples, tips, and tactics Reveals how to monitor and maintain a vibrant LinkedIn presence Includes effective tactics for recruiters, job seekers, and entrepreneurs, as well as legal, real estate, and nonprofit professionals Incorporates an exploration of the LinkedIn advertising platform, API, and mobile platform This soup-to-nuts guidebook for tackling every stage of the LinkedIn process ensures your online presence will get noticed. COMPUTERS,Internet,Social Media

Everything You Need to Know about Social Media A simple, step-by-step guide to the major social media platforms—Facebook, Twitter, LinkedIn, Instagram, Snapchat, and more—by former news anchor and media maven Greta Van Susteren. COMPUTERS,Internet,Social Media

Facebook For Dummies Take control of your Facebook profile When you join Facebook, you're joining a community with over two billion people spread around the globe. It helps to have the insight on not only how to set up your profile and add content, but also how to make sure you control who sees—and doesn't see—your posts. Facebook For Dummies provides the trusted guidance you need to set up a profile, add content, and apply the many tools Facebook provides to give you control of your content. Primarily known as a way for individuals to share information, photos and videos, and calendar invitations, Facebook has gained prominence as a means to spread news, market products, and serve as a business platform. Whatever you’re looking to use it for, this book shows you how to use all the features available to make it a more satisfying experience. Build your profile and start adding friends Use Facebook to send private messages and instant notes Discover ways to set privacy and avoid online nuisances Launch a promotion page Get ready to have a whole lot of fun on the largest social network in the world. COMPUTERS,Internet,Social Media

Ten Arguments for Deleting Your Social Media Accounts Right Now A timely call-to-arms from a Silicon Valley pioneer. You might have trouble imagining life without your social media accounts, but virtual reality pioneer Jaron Lanier insists that we’re better off without them. In Ten Arguments for Deleting Your Social Media Accounts Right Now, Lanier, who participates in no social media, offers powerful and personal reasons for all of us to leave these dangerous online platforms. Lanier’s reasons for freeing ourselves from social media’s poisonous grip include its tendency to bring out the worst in us, to make politics terrifying, to trick us with illusions of popularity and success, to twist our relationship with the truth, to disconnect us from other people even as we are more “connected†than ever, to rob us of our free will with relentless targeted ads. How can we remain autonomous in a world where we are under continual surveillance and are constantly being prodded by algorithms run by some of the richest corporations in history that have no way of making money other than being paid to manipulate our behavior? How could the benefits of social media possibly outweigh the catastrophic losses to our personal dignity, happiness, and freedom? Lanier remains a tech optimist, so while demonstrating the evil that rules social media business models today, he also envisions a humanistic setting for social networking that can direct us toward a richer and fuller way of living and connecting with our world. COMPUTERS,Internet,Social Media

The Breakup 2.0 A few generations ago, college students showed their romantic commitments by exchanging special objects: rings, pins, varsity letter jackets. Pins and rings were handy, telling everyone in local communities that you were spoken for, and when you broke... COMPUTERS,Internet,Social Media

InstaStyle Gain Instagram followers, grow your personal brand, and influence others with beautiful photography, fabulous content ideas, the best filters, and the right hashtags. You have unbeatable taste and killer style that just needs to be unleashed to the world. You're a creative force who wants to connect with others who will appreciate and be inspired. Learn how to tell compelling visual stories for every aspect of your charmingly curated life - from a cozy snap of your shabby chic bed, to a candid of your day trip with hubs, to an attractive flat lay of your covetable afternoon-in-the-park outfit. How do people take those aerial shots of breakfast in bed, why do her selfies look so flattering, and how does she have time to capture all those beautiful photos while raising a family? Learn from successful Instagram influencers as they teach you all the exclusive tricks of the trade. InstaStyle is your visual guide for transforming your feed and showcasing your life, while remaining true to your brand. From the moment you create your handle to get started, this book provides content inspiration, advice on curating shots, and editing instructions to keep your grid captivating and professional. Whether you prefer vintage and moody, or soft and blush pink, specific guidelines explain how to create an immediately recognizable photo aesthetic with presets and editing. You'll learn precisely how to drive people to your feed and win a follow so that you ultimately grow your business, and earn money by becoming #sponsored. COMPUTERS,Internet,Social Media

Mining the Social Web Mine the rich data tucked away in popular social websites such as Twitter, Facebook, LinkedIn, and Instagram. With the third edition of this popular guide, data scientists, analysts, and programmers will learn how to glean insights from social media—including who’s connecting with whom, what they’re talking about, and where they’re located—using Python code examples, Jupyter notebooks, or Docker containers. In part one, each standalone chapter focuses on one aspect of the social landscape, including each of the major social sites, as well as web pages, blogs and feeds, mailboxes, GitHub, and a newly added chapter covering Instagram. Part two provides a cookbook with two dozen bite-size recipes for solving particular issues with Twitter. Get a straightforward synopsis of the social web landscape Use Docker to easily run each chapter’s example code, packaged as a Jupyter notebook Adapt and contribute to the code’s open source GitHub repository Learn how to employ best-in-class Python 3 tools to slice and dice the data you collect Apply advanced mining techniques such as TFIDF, cosine similarity, collocation analysis, clique detection, and image recognition Build beautiful data visualizations with Python and JavaScript toolkits COMPUTERS,Internet,Social Media

Instagram For Dummies Go from Instagram newbie to star! Instagram is the fastest-growing social network in the world, soaring from 500 million to 1 billion active users in just two years. Users flock to the site thanks to its simplicity and use of the most popular social media features—image and video sharing, community, and personal insight. Instagram For Dummies is here if you're ready to get acquainted with the platform or want to find ways to do more with your Instagram account. Written by an team led by top Instagram trainer Jenn Herman, this book gives you tips for creating great Instagram images, personalizing your posts, connecting with the Instagram community, and working with Stories and IGTV. Access Instagram on a computer or mobile device Set up your profile Connect with others Share your stories Shoot better Instagram images From handling core functions to connecting with the Instagram community, this book shares the secrets you need to shine on social media like no other! COMPUTERS,Internet,Social Media

Social Media Communication This updated third edition presents a wide-scale, interdisciplinary guide to social media. Examining platforms like Facebook, Instagram, LinkedIn, Snapchat, TikTok, Twitter and YouTube, the book analyzes social media's use in journalism, broadcasting, public relations, advertising and marketing. Lipschultz focuses on key concepts, best practices, data analyses, law and ethics – all promoting the critical thinking that is needed to use new, evolving and maturing networking tools effectively within social and mobile media spaces. Featuring historical markers and contemporary case studies, essays from some of the industry’s leading social media innovators and a comprehensive glossary, this practical, multipurpose textbook gives readers the resources they will need to both evaluate and utilize current and future forms of social media communication. Among other changes, updates to the third edition include a deep dive into new approaches to analytics, as well as greater discussion of law and ethics in light of the Facebook Cambridge Analytica scandal, the roll-out of GDPR and new case law relating to social media. Social Media Communication is the perfect social media primer for students and professionals, and, with a dedicated teaching guide, ideal for instructors, too. COMPUTERS,Internet,Social Media

Reading the Comments What we can learn about human nature from the informative, manipulative, confusing, and amusing messages at the bottom of the web. Online comment can be informative or misleading, entertaining or maddening. Haters and manipulators often seem to monopolize the conversation. Some comments are off-topic, or even topic-less. In this book, Joseph Reagle urges us to read the comments. Conversations “on the bottom half of the Internet,” he argues, can tell us much about human nature and social behavior. Reagle visits communities of Amazon reviewers, fan fiction authors, online learners, scammers, freethinkers, and mean kids. He shows how comment can inform us (through reviews), improve us (through feedback), manipulate us (through fakery), alienate us (through hate), shape us (through social comparison), and perplex us. He finds pre-Internet historical antecedents of online comment in Michelin stars, professional criticism, and the wisdom of crowds. He discusses the techniques of online fakery (distinguishing makers, fakers, and takers), describes the emotional work of receiving and giving feedback, and examines the culture of trolls and haters, bullying, and misogyny. He considers the way comment—a nonstop stream of social quantification and ranking—affects our self-esteem and well-being. And he examines how comment is puzzling—short and asynchronous, these messages can be slap-dash, confusing, amusing, revealing, and weird, shedding context in their passage through the Internet, prompting readers to comment in turn, “WTF?!?” COMPUTERS,Internet,Social Media

Digital Countercultures and the Struggle for Community How countercultural communities have made the Internet meet their needs, subverting established norms of digital technology use. Whether by accidental keystroke or deliberate tinkering, technology is often used in ways that are unintended and unimagined by its designers and inventors. In this book, Jessa Lingel offers an account of digital technology use that looks beyond Silicon Valley and college dropouts-turned-entrepreneurs. Instead, Lingel tells stories from the margins of countercultural communities that have made the Internet meet their needs, subverting established norms of how digital technologies should be used. Lingel presents three case studies that contrast the imagined uses of the web to its lived and often messy practicalities. She examines a social media platform (developed long before Facebook) for body modification enthusiasts, with early web experiments in blogging, community, wikis, online dating, and podcasts; a network of communication technologies (both analog and digital) developed by a local community of punk rockers to manage information about underground shows; and the use of Facebook and Instagram for both promotional and community purposes by Brooklyn drag queens. Drawing on years of fieldwork, Lingel explores issues of alterity and community, inclusivity and exclusivity, secrecy and surveillance, and anonymity and self-promotion. By examining online life in terms of countercultural communities, Lingel argues that looking at outsider experiences helps us to imagine new uses and possibilities for the tools and platforms we use in everyday life. COMPUTERS,Internet,Social Media

The World Made Meme How memetic media—aggregate texts that are collectively created, circulated, and transformed—become a part of public conversations that shape broader cultural debates. Internet memes—digital snippets that can make a joke, make a point, or make a connection—are now a lingua franca of online life. They are collectively created, circulated, and transformed by countless users across vast networks. Most of us have seen the cat playing the piano, Kanye interrupting, Kanye interrupting the cat playing the piano. In The World Made Meme, Ryan Milner argues that memes, and the memetic process, are shaping public conversation. It's hard to imagine a major pop cultural or political moment that doesn't generate a constellation of memetic texts. Memetic media, Milner writes, offer participation by reappropriation, balancing the familiar and the foreign as new iterations intertwine with established ideas. New commentary is crafted by the mediated circulation and transformation of old ideas. Through memetic media, small strands weave together big conversations. Milner considers the formal and social dimensions of memetic media, and outlines five basic logics that structure them: multimodality, reappropriation, resonance, collectivism, and spread. He examines how memetic media both empower and exclude during public conversations, exploring the potential for public voice despite everyday antagonisms. Milner argues that memetic media enable the participation of many voices even in the midst of persistent inequality. This new kind of participatory conversation, he contends, complicates the traditional culture industries. When age-old gatekeepers intertwine with new ways of sharing information, the relationship between collective participation and individual expression becomes ambivalent. For better or worse—and Milner offers examples of both—memetic media have changed the nature of public conversations. COMPUTERS,Internet,User-Generated Content

Rogue Archives An examination of how nonprofessional archivists, especially media fans, practice cultural preservation on the Internet and how “digital cultural memory” differs radically from print-era archiving. The task of archiving was once entrusted only to museums, libraries, and other institutions that acted as repositories of culture in material form. But with the rise of digital networked media, a multitude of self-designated archivists—fans, pirates, hackers—have become practitioners of cultural preservation on the Internet. These nonprofessional archivists have democratized cultural memory, building freely accessible online archives of whatever content they consider suitable for digital preservation. In Rogue Archives, Abigail De Kosnik examines the practice of archiving in the transition from print to digital media, looking in particular at Internet fan fiction archives. De Kosnik explains that media users today regard all of mass culture as an archive, from which they can redeploy content for their own creations. Hence, “remix culture” and fan fiction are core genres of digital cultural production. De Kosnik explores, among other things, the anticanonical archiving styles of Internet preservationists; the volunteer labor of online archiving; how fan archives serve women and queer users as cultural resources; archivists' efforts to attract racially and sexually diverse content; and how digital archives adhere to the logics of performance more than the logics of print. She also considers the similarities and differences among free culture, free software, and fan communities, and uses digital humanities tools to quantify and visualize the size, user base, and rate of growth of several online fan archives. COMPUTERS,Internet,User-Generated Content

React and React Native Get up to speed with React, React Native, GraphQL and Apollo for building cross-platform native apps with the help of practical examples Key Features Covers the latest features of React such as Hooks, Suspense, NativeBase, and Apollo in this updated third edition Get to grips with the React architecture for writing easy-to-manage web and mobile applications Understand GraphQL and Apollo for building a scalable backend for your cross-platform apps Book Description React and React Native, Facebook's innovative User Interface (UI) libraries, are designed to help you build robust cross-platform web and mobile applications. This updated third edition is improved and updated to cover the latest version of React. The book particularly focuses on the latest developments in the React ecosystem, such as modern Hook implementations, code splitting using lazy components and Suspense, user interface framework components using Material-UI, and Apollo. In terms of React Native, the book has been updated to version 0.62 and demonstrates how to apply native UI components for your existing mobile apps using NativeBase. You will begin by learning about the essential building blocks of React components. Next, you'll progress to working with higher-level functionalities in application development, before putting this knowledge to use by developing user interface components for the web and for native platforms. In the concluding chapters, you'll learn how to bring your application together with a robust data architecture. By the end of this book, you'll be able to build React applications for the web and React Native applications for multiple mobile platforms. What you will learn Delve into the React architecture, component properties, state, and context Get to grips with React Hooks for handling functions and components Implement code splitting in React using lazy components and Suspense Build robust user interfaces for mobile and desktop apps using Material-UI Write shared components for Android and iOS mobile apps using React Native Simplify layout design for React Native apps using NativeBase Write GraphQL schemas to power web and mobile apps Implement web and mobile components that are driven by Apollo Who this book is for This book is for any JavaScript developer who wants to start learning how to use Facebook's UI libraries, React and React Native, for mobile and web application development. Although no prior knowledge of React is needed, working knowledge of JavaScript programming will help you understand the concepts covered in the book more effectively. COMPUTERS,Internet,Web Browsers

Hands-On Python Deep Learning for the Web Use the power of deep learning with Python to build and deploy intelligent web applications Key Features Create next-generation intelligent web applications using Python libraries such as Flask and Django Implement deep learning algorithms and techniques for performing smart web automation Integrate neural network architectures to create powerful full-stack web applications Book Description When used effectively, deep learning techniques can help you develop intelligent web apps. In this book, you'll cover the latest tools and technological practices that are being used to implement deep learning in web development using Python. Starting with the fundamentals of machine learning, you'll focus on DL and the basics of neural networks, including common variants such as convolutional neural networks (CNNs). You'll learn how to integrate them into websites with the frontends of different standard web tech stacks. The book then helps you gain practical experience of developing a deep learning-enabled web app using Python libraries such as Django and Flask by creating RESTful APIs for custom models. Later, you'll explore how to set up a cloud environment for deep learning-based web deployments on Google Cloud and Amazon Web Services (AWS). Next, you'll learn how to use Microsoft's intelligent Emotion API, which can detect a person's emotions through a picture of their face. You'll also get to grips with deploying real-world websites, in addition to learning how to secure websites using reCAPTCHA and Cloudflare. Finally, you'll use NLP to integrate a voice UX through Dialogflow on your web pages. By the end of this book, you'll have learned how to deploy intelligent web apps and websites with the help of effective tools and practices. What you will learn Explore deep learning models and implement them in your browser Design a smart web-based client using Django and Flask Work with different Python-based APIs for performing deep learning tasks Implement popular neural network models with TensorFlow.js Design and build deep web services on the cloud using deep learning Get familiar with the standard workflow of taking deep learning models into production Who this book is for This deep learning book is for data scientists, machine learning practitioners, and deep learning engineers who are looking to perform deep learning techniques and methodologies on the web. You will also find this book useful if you're a web developer who wants to implement smart techniques in the browser to make it more interactive. Working knowledge of the Python programming language and basic machine learning techniques will be beneficial. COMPUTERS,Internet,Web Browsers

User is Always Right, The How do we ensure that our Web sites actually give users what they need? What are the best ways to understand our users' goals, behaviors, and attitudes, and then turn that understanding into business results? Personas bring user research to life and make it actionable, ensuring we're making the right decisions based on the right information. This practical guide explains how to create and use personas to make your site more successful. The User Is Always Right: A Practical Guide to Creating and Using Personas takes you through each step of persona creation, including tips for conducting qualitative user research, new ways to apply quantitative research (such as surveys) to persona creation, various methods for generating persona segmentation, and proven techniques for making personas realistic. You'll also learn how to use personas effectively, from directing overall business strategy and prioritizing features and content to making detailed decisions about information architecture, content, and design. COMPUTERS,Internet,Web Design

Designing for Interaction Explore the new design discipline that is behind such products as the iPod and innovative Web sites like Flickr. While other books on this subject are either aimed at more seasoned practitioners or else are too focused on a particular medium like software, this guide will take a more holistic approach to the discipline, looking at interaction design for the Web, software, and devices. It is the only interaction design book that is coming from a designers point of view rather than that of an engineer. This much-needed guide is more than just a how-to manual. It covers interaction design fundamentals, approaches to designing, design research, and more, and spans all mediums—Internet, software, and devices. Even robots! Filled with tips, real-world projects, and interviews, you’ll get a solid grounding in everything you need to successfully tackle interaction design. Designing for Interaction is an AIGA Design Press book, published under Peachpit's New Riders imprint in partnership with AIGA. COMPUTERS,Internet,Web Design

The Complete Idiot's Guide to Creating a Web Page and Blog, 6th Edition Spin your own web! Free CD-ROM included. More people are overcoming their digital fears and producing Internet content rather than just absorbing it. Whether their product is a collection of essays, stories, reviews, jokes, or shopping lists, they want to share it with everyone-from family and friends to strangers across the globe. How do they do it? By starting right here. The Complete Idiot's Guide® to Creating a Web Page and Blog-the only book of its kind- will help anyone build and maintain an Internet website or blog. Coverage includes:*Step-by-step instructions for building a site from the ground up*Important HTML tags*Tips on using fonts, colors, and images*Incorporating tables, forms, style sheets, and JavaScripts*The new blog technology*Plus! A "Webmaster's Toolkit" on a companion CD-ROM, providing files used in this book. COMPUTERS,Internet,Web Design

Learning ActionScript 3.0 In this book, authors Rich Shupe and Zevan Rosser share the knowledge they've gained from their years as multimedia developers/designers and teachers. Learning ActionScript 3.0 gives you a solid foundation in the language of Flash and demonstrates how you can use it for practical, everyday projects. The authors do more than just give you a collection of sample scripts. Written for those of you new to ActionScript 3.0, the book describes how ActionScript and Flash work, giving you a clear look into essential topics such as logic, event handling, displaying content, migrating legacy projects to ActionScript 3.0, classes, and much more. You will learn important techniques through hands-on exercises, and then build on those skills as chapters progress. ActionScript 3.0 represents a significant change for many Flash users, and a steeper learning curve for the uninitiated. This book will help guide you through a variety of scripting scenarios. Rather than relying heavily on prior knowledge of object-oriented programming (OOP), topics are explained in focused examples that originate in the timeline, with optional companion classes for those already comfortable with their use. As chapters progress, the book introduces more and more OOP techniques, allowing you to choose which scripting approach you prefer. Learning ActionScript 3.0 reveals: New ways to harness the power and performance of AS3 Common mistakes that people make with the language Essential coverage of text, sound, video, XML, drawing with code, and more Migration issues from AS1 and AS2 to AS3 Simultaneous development of procedural and object-oriented techniques Tips that go beyond simple script collections, including how to approach a project and which resources can help you along the way The companion web site contains material for all the exercises in the book, as well as short quizzes to make sure you're up to speed with key concepts. ActionScript 3.0 is a different animal from previous versions, and Learning ActionScript 3.0 teaches everything that web designers, GUI-based Flash developers, and those new to ActionScript need to start using the language. COMPUTERS,Internet,Web Design

Rocket Surgery Made Easy In this how-to companion to Don't Make Me Think: A Common Sense Approach to Web Usability, Steve Krug spells out an approach to usability testing that anyone can easily apply to their own web site, application, or other product. In this new book, Steve explains how to: Test any design, from a sketch on a napkin to a fully-functioning web site or application Keep your focus on finding the most important problems (because no one has the time or resources to fix them all) Fix the problems that you find, using his "The least you can do" approach By paring the process of testing and fixing products down to its essentials (A morning a month, that's all we ask ), Rocket Surgery makes it realistic for teams to test early and often, catching problems while it's still easy to fix them. Rocket Surgery Made Easy adds demonstration videos to the proven mix of clear writing, before-and-after examples, witty illustrations, and practical advice that made Don't Make Me Think so popular. COMPUTERS,Internet,Web Design

C# 2010 All-in-One For Dummies A logical, straightforward approach to learning the C# language C# is a complicated programming language for building .NET-connected software for Microsoft Windows, the Web, and a wide range of devices. The friendly All-in-One For Dummies format is a perfect way to present it. Each minibook is a self-contained package of necessary information, making it easy to find what you're looking for. Upgrades in C# 2010 include the ability to build Windows 7 applications and compatibility with Python and Ruby. C# is a somewhat complex programming language for building .NET-connected software for Microsoft Windows, the Web, and other devices Beginning C# programmers will appreciate how the All-in-One format breaks the topic into minibooks, each one addressing a key body of information Minibooks include creating your first C# program, Windows 7 programming, basic C# programming, object-based programming, object-oriented programming, Windows programming with C# and Visual Studio, and debugging Companion Web site includes all sample code Beginning C# programmers will find C# 2010 All-in-One For Dummies explains a complicated topic in an easy, understandable way. Note: CD-ROM/DVD and other supplementary materials are not included as part of eBook file. COMPUTERS,Internet,Web Design

Programming the Semantic Web With this book, the promise of the Semantic Web -- in which machines can find, share, and combine data on the Web -- is not just a technical possibility, but a practical reality Programming the Semantic Web demonstrates several ways to implement semantic web applications, using current and emerging standards and technologies. You'll learn how to incorporate existing data sources into semantically aware applications and publish rich semantic data. Each chapter walks you through a single piece of semantic technology and explains how you can use it to solve real problems. Whether you're writing a simple mashup or maintaining a high-performance enterprise solution,Programming the Semantic Web provides a standard, flexible approach for integrating and future-proofing systems and data. This book will help you: Learn how the Semantic Web allows new and unexpected uses of data to emerge Understand how semantic technologies promote data portability with a simple, abstract model for knowledge representation Become familiar with semantic standards, such as the Resource Description Framework (RDF) and the Web Ontology Language (OWL) Make use of semantic programming techniques to both enrich and simplify current web applications COMPUTERS,Internet,Web Design

High Performance Web Sites Want your web site to display more quickly? This book presents 14 specific rules that will cut 25% to 50% off response time when users request a page. Author Steve Souders, in his job as Chief Performance Yahoo!, collected these best practices while optimizing some of the most-visited pages on the Web. Even sites that had already been highly optimized, such as Yahoo! Search and the Yahoo! Front Page, were able to benefit from these surprisingly simple performance guidelines. The rules in High Performance Web Sites explain how you can optimize the performance of the Ajax, CSS, JavaScript, Flash, and images that you've already built into your site -- adjustments that are critical for any rich web application. Other sources of information pay a lot of attention to tuning web servers, databases, and hardware, but the bulk of display time is taken up on the browser side and by the communication between server and browser. High Performance Web Sites covers every aspect of that process. Each performance rule is supported by specific examples, and code snippets are available on the book's companion web site. The rules include how to: Make Fewer HTTP Requests Use a Content Delivery Network Add an Expires Header Gzip Components Put Stylesheets at the Top Put Scripts at the Bottom Avoid CSS Expressions Make JavaScript and CSS External Reduce DNS Lookups Minify JavaScript Avoid Redirects Remove Duplicates Scripts Configure ETags Make Ajax Cacheable If you're building pages for high traffic destinations and want to optimize the experience of users visiting your site, this book is indispensable. "If everyone would implement just 20% of Steve's guidelines, the Web would be adramatically better place. Between this book and Steve's YSlow extension, there's reallyno excuse for having a sluggish web site anymore." -Joe Hewitt, Developer of Firebug debugger and Mozilla's DOM Inspector "Steve Souders has done a fantastic job of distilling a massive, semi-arcane art down to a set of concise, actionable, pragmatic engineering steps that will change the world of web performance." -Eric Lawrence, Developer of the Fiddler Web Debugger, Microsoft Corporation COMPUTERS,Internet,Web Design

HTTP Behind every web transaction lies the Hypertext Transfer Protocol (HTTP) --- the language of web browsers and servers, of portals and search engines, of e-commerce and web services. Understanding HTTP is essential for practically all web-based programming, design, analysis, and administration.While the basics of HTTP are elegantly simple, the protocol's advanced features are notoriously confusing, because they knit together complex technologies and terminology from many disciplines. This book clearly explains HTTP and these interrelated core technologies, in twenty-one logically organized chapters, backed up by hundreds of detailed illustrations and examples, and convenient reference appendices. HTTP: The Definitive Guide explains everything people need to use HTTP efficiently -- including the "black arts" and "tricks of the trade" -- in a concise and readable manner.In addition to explaining the basic HTTP features, syntax and guidelines, this book clarifies related, but often misunderstood topics, such as: TCP connection management, web proxy and cache architectures, web robots and robots.txt files, Basic and Digest authentication, secure HTTP transactions, entity body processing, internationalized content, and traffic redirection.Many technical professionals will benefit from this book. Internet architects and developers who need to design and develop software, IT professionals who need to understand Internet architectural components and interactions, multimedia designers who need to publish and host multimedia, performance engineers who need to optimize web performance, technical marketing professionals who need a clear picture of core web architectures and protocols, as well as untold numbers of students and hobbyists will all benefit from the knowledge packed in this volume.There are many books that explain how to use the Web, but this is the one that explains how the Web works. Written by experts with years of design and implementation experience, this book is the definitive technical bible that describes the "why" and the "how" of HTTP and web core technologies. HTTP: The Definitive Guide is an essential reference that no technically-inclined member of the Internet community should be without. COMPUTERS,Internet,Web Design

HTTP Pocket Reference The HyperText Transfer Protocol, or HTTP, is the backbone of the World Wide Web. HTTP is the language that each web browser (or other web client) uses to communicate with servers around the world. All web programmers, administrators, and application developers need to be familiar with HTTP in order to work effectively.The HTTP Pocket Reference not only provides a solid conceptual foundation of HTTP, it also serves as a quick reference to each of the headers and status codes that comprise an HTTP transaction. The book starts with a tutorial of HTTP, but then explains the client request and server responses in more detail, and gives a thorough technical explanation of more advanced features of HTTP (such as persistent connections and caching).Most people use the Web every day without knowing anything about HTTP, but for those who need to get "beyond the browser," this book is the place to start. COMPUTERS,Internet,Web Design

Universal Design for Web Applications Universal Design for Web Applications teaches you how to build websites that are more accessible to people with disabilities and explains why doing so is good business. It takes more work up front, but the potential payoff is huge -- especially when mobile users need to access your sites. You'll discover how to use standards-based web technologies -- such as XHTML, CSS, and Ajax, along with video and Flash -- to develop applications for a wide range of users and a variety of devices, including the mobile Web. You'll also learn specifics about this target audience, especially the key over-50 age group, whose use of the Web is rapidly growing. With this book, you will: Learn the importance of metadata and how it affects images, headings, and other design elements Build forms that accommodate cell phones, screen readers, word prediction, and more Create designs using color and text that are effective in a variety of situations Construct tables that present information without spatial cues Design Ajax-driven social networking applications that people with disabilities can access Provide audio with transcriptions and video that includes captions and audio descriptions Discover assistive technology support for Rich Internet Application technologies such as Flash, Flex, and Silverlight Universal Design for Web Applications provides you with a roadmap to help you design easy-to-maintain web applications that benefit a larger audience. COMPUTERS,Internet,Web Design

Add Audio and Video to Your Site Nothing spices up websites like cool sound effects (think ker-thunk as visitors press a button) or embedded videos. Think you need a programmer to add sizzle to your site? Think again. This hands-on guide gives you the techniques you need to add video, music, animated GIFs, and sound effects to your site. This Mini Missing Manual is excerpted from Creating a Web Site: The Missing Manual. COMPUTERS,Internet,Web Design

Mobile Web Design For Dummies The perfect place to learn how to design Web sites for mobile devices! With the popularity of Internet access via cell phones and other mobile devices, Web designers now have to consider as many as eight operating systems, several browsers, and a slew of new devices as they plan a new site, a new interface, or a new sub-site. This easy-to-follow friendly book guides you through this brave new world with a clear look at the fundamentals and offers practical techniques and tricks you may not have considered. Explores all issues to consider in planning a mobile site Covers the tools needed for mobile design, in particular XHTML and CSS Shows you how to plan for multimedia, e-commerce, and marketing your site, including adding audio, video, and social networking Provides real-world examples and tips to help you avoid common pitfalls If you're contemplating Web design in a mobile world, start first with this practical guide. COMPUTERS,Internet,Web Design

Undercover User Experience Design Once you catch the user experience bug, the world changes. Doors open the wrong way, websites don't work, and companies don't seem to care. And while anyone can learn the UX remedies usability testing, personas, prototyping and so on unless your organization 'gets it', putting them into practice is trickier. Undercover User Experience is a pragmatic guide from the front lines, giving frank advice on making UX work in real companies with real problems. Readers will learn how to fit research, ideation, prototyping and testing into their daily workflow, and how to design good user experiences under the all-too-common constraints of time, budget and culture. COMPUTERS,Internet,Web Design

CSS Pocket Guide, The CSS is a language for describing the presentation of elements in a document marked up in HTML. It enables you to rapidly create Web designs that can be shared by multiple pages, accelerates development time, and is the essential tool for building standards-compliant sites. This low-priced pocket guide works as a concise introduction to CSS3 and serves as a handy reference. In it readers will learn The core concepts of CSS How to format text with CSS How to apply CSS style rules to markup How to build multicolumn layouts without using tables And much more This pocket guide along with the HTML Pocket Guide and the JavaScript Pocket Guide make creating standard-compliant websites a breeze. Learn core concepts or skip to the parts you need to solve an immediate problem. They're exactly the resource that every Web designer needs. COMPUTERS,Internet,Web Design

Elements of User Experience,The From the moment it was published almost ten years ago, Elements of User Experience became a vital reference for web and interaction designers the world over, and has come to define the core principles of the practice. Now, in this updated, expanded, and full-color new edition, Jesse James Garrett has refined his thinking about the Web, going beyond the desktop to include information that also applies to the sudden proliferation of mobile devices and applications. Successful interaction design requires more than just creating clean code and sharp graphics. You must also fulfill your strategic objectives while meeting the needs of your users. Even the best content and the most sophisticated technology won't help you balance those goals without a cohesive, consistent user experience to support it. With so many issues involved—usability, brand identity, information architecture, interaction design— creating the user experience can be overwhelmingly complex. This new edition of The Elements of User Experience cuts through that complexity with clear explanations and vivid illustrations that focus on ideas rather than tools or techniques. Garrett gives readers the big picture of user experience development, from strategy and requirements to information architecture and visual design. COMPUTERS,Internet,Web Design

WordPress Bible Get the latest word on the biggest self-hosted blogging tool on the market Within a week of the announcement of WordPress 3.0, it had been downloaded over a million times. Now you can get on the bandwagon of this popular open-source blogging tool with WordPress Bible, 2nd Edition. Whether you're a casual blogger or programming pro, this comprehensive guide covers the latest version of WordPress, from the basics through advanced application development. If you want to thoroughly learn WordPress, this is the book you need to succeed. Explores the principles of blogging, marketing, and social media interaction Shows you how to install and maintain WordPress Thoroughly covers WordPress basics, then ramps up to advanced topics Guides you through best security practices as both a user and a developer Helps you enhance your blog?s findability in major search engines and create customizable and dynamic themes Author maintains a high-profile blog in the WordPress community, Technosailor.com Tech edited by Mark Jaquith, one of the lead developers of WordPress The WordPress Bible is the only resource you need to learn WordPress from beginning to end. COMPUTERS,Internet,Web Design

Web Design For Dummies Get up to speed on the newest technologies, tools, and possibilities in web design Have a great idea for a web site but don't know where or how to begin? Web Design For Dummies, 3rd Edition is an ideal starting point! Fully updated to cover the latest and the greatest in the world of web design, this fun-but-straightforward guide gets you caught up with everything you need to know to organize your ideas, create a template, start development, test to make sure everything is working properly, and launch your finished site. Packed with invaluable advice on incorporating social media aspects, linking content with social sites, and designing for mobile devices, this book will have you web designing like a pro in no time. Highlights the many significant changes in the world of web design since the previous edition, including the introduction of HTML5, new technologies for sharing media, mobile web design, and more Zeroes in on effectively using color, text, and navigation Reveals helpful advice for avoiding common pitfalls Details ways to connect with social sites like Twitter and Facebook Web Design For Dummies, 3rd Edition goes beyond just making a basic web site and instead encourages you to create a site that is appealing, practical, and useful. COMPUTERS,Internet,Web Design

Building Websites All-in-One For Dummies Ten minibooks in one! The perfect reference for beginning web builders This hefty, 800+ page book is your start-to-finish roadmap for building a web site for personal or professional use. Even if you're completely new to the process, this book is packed with everything you need to know to build an attractive, usable, and working site. In addition to being a thorough reference on the basics, this updated new edition also covers the very latest trends and tools, such as HTML5, mobile site planning for smartphones and tablets, connecting with social media, and more. Packs ten minibooks into one hefty reference: Preparation, Site Design, Site Construction, Web Graphics, Multimedia, Interactive Elements, Form Management, Social Media Integration, Site Management, and Case Studies Covers the newest trends and tools, including HTML5, the new Adobe Create Suite, and connecting with social media Offers in-depth reviews and case studies of existing sites created for a variety of purposes and audiences, such as blog sites and non-profit sites Walks you through essential technologies, including Dreamweaver, HTML, CSS, JavaScript, PHP, and more Plan, build, and maintain a site that does exactly what you need, with Building Web Sites All-In-One For Dummies, 3rd Edition. COMPUTERS,Internet,Web Design

Content Strategy for the Web When it was first published in 2009, Content Strategy for the Web was an instant classic. It was the catalyst for the global content strategy conversation, helping organisations understand and implement content strategy as part of their larger business strategies. Much more than a simple introduction, this edition builds upon those foundational ideas and gives you what you need to transform your content into a valuable business asset. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Internet,Web Design

Managing Enterprise Content Smartphones, eBook readers, and tablet computers like the Apple iPad have forever changed the way people access and interact with content. Your customers expect the content you provide them to be adaptive --responding to the device, their location, their situation, and their personalized needs. Authors Ann Rockley and Charles Cooper provide insights and guidelines that will help you develop a unified content strategy—a repeatable, systematic plan that can help you reach your customers, anytime, anywhere, on any device. This up-to-date new edition of Managing Enterprise Content helps you: Determine business requirements Build your vision Design content that adapts to any device Develop content models, metadata, and workflow Put content governance in place Adapt to new and changed roles Identify tools requirements With this book you’ll learn to design adaptable content that frees you from the tyranny of an ever increasing array of devices. COMPUTERS,Internet,Web Design

A Project Guide to UX Design User experience design is the discipline of creating a useful and usable Web site or application that’s easily navigated and meets the needs of the site owner and its users. There’s a lot more to successful UX design than knowing the latest Web technologies or design trends: It takes diplomacy, management skills, and business savvy. That’s where the updated edition of this important book comes in. With new information on design principles, mobile and gestural interactions, content strategy, remote research tools and more, you’ll learn to: Recognize the various roles in UX design, identify stakeholders, and enlist their support Obtain consensus from your team on project objectives Understand approaches such as Waterfall, Agile, and Lean UX Define the scope of your project and avoid mission creep Conduct user research in person or remotely, and document your findings Understand and communicate user behavior with personas Design and prototype your application or site Plan for development, product rollout, and ongoing quality assurance COMPUTERS,Internet,Web Design

Professional WebGL Programming Everything you need to know about developing hardware-accelerated 3D graphics with WebGL! As the newest technology for creating 3D graphics on the web, in both games, applications, and on regular websites, WebGL gives web developers the capability to produce eye-popping graphics. This book teaches you how to use WebGL to create stunning cross-platform apps. The book features several detailed examples that show you how to develop 3D graphics with WebGL, including explanations of code snippets that help you understand the why behind the how. You will also develop a stronger understanding of WebGL development from coverage that: •Provides a comprehensive overview of WebGL and shows how it relates to other graphics-related technologies •Addresses important topics such as the WebGL graphics pipeline, 3D transformations, texturing and lighting •Teaches you how to write vertex shaders and fragment shaders for WebGL •Includes a lot of useful guidelines, tips, and tricks for WebGL performance optimizations Professional WebGL Programming is the first book on the market to delve into this fascinating topic and it puts you on your way to mastering the possibilities that exist with WebGL. COMPUTERS,Internet,Web Design

Microsoft Expression Web 4 In Depth Do more with Microsoft Expression Web 4 SP2—in less time! This is the world’s most expert, complete, and practical guide to succeeding with Expression Web 4 SP2! Microsoft insider Jim Cheshire presents today’s best solutions for everything you need to do with Expression Web 4 SP2 and its brand-new HTML5, CSS3, and jQuery tools!. Create, edit, and manage content… implement leading-edge designs… integrate dynamic content… add powerful features with no custom coding… leverage SP2’s latest time-saving features…do the job right, and do it fast! “In the trenches†solutions, big-picture insights, real examples, time-saving shortcuts Boost productivity with custom workspaces, Snapshot & Snippet panels, Universal Commenting, and other SP2 improvements Optimize every phase of development, from site creation through reporting Use Expression Web 4 features together to solve real web design problems and achieve real business goals Build HTML5/CSS3 standards-compliant sites that work properly in any modern browser Learn high-efficiency techniques for using tables, forms, and QuickTags Add more dynamic, interactive content with Behaviors and Layers Differentiate your site with dynamic components and client-side JavaScript Use ASP.NET’s simple tools to display, edit, and manage data without custom code Develop accessible, Section 508- or WCAG-compliant sites Efficiently test sites and apps with SP2’s enhanced SuperPreview and remote browsing Easily password-protect content with ASP.NET Login controls and membership features Leverage Expression Web’s updated PHP 5.3 support, including module IntelliSense and “Open as PHP†Efficiently troubleshoot any site development problem Register your book at www.quepublishing.com/title/9780789749192 to get the entire book in searchable PDF format, including all examples and sample files, plus a bonus four-chapter mini book on creating add-ins with JavaScript and HTML! COMPUTERS,Internet,Web Design

Learning Web Design Do you want to build web pages, but have no previous experience? This friendly guide is the perfect place to start. You’ll begin at square one, learning how the Web and web pages work, and then steadily build from there. By the end of the book, you’ll have the skills to create a simple site with multi-column pages that adapt for mobile devices. Learn how to use the latest techniques, best practices, and current web standards—including HTML5 and CSS3. Each chapter provides exercises to help you to learn various techniques, and short quizzes to make sure you understand key concepts. This thoroughly revised edition is ideal for students and professionals of all backgrounds and skill levels, whether you’re a beginner or brushing up on existing skills. Build HTML pages with text, links, images, tables, and forms Use style sheets (CSS) for colors, backgrounds, formatting text, page layout, and even simple animation effects Learn about the new HTML5 elements, APIs, and CSS3 properties that are changing what you can do with web pages Make your pages display well on mobile devices by creating a responsive web design Learn how JavaScript works—and why the language is so important in web design Create and optimize web graphics so they’ll download as quickly as possible COMPUTERS,Internet,Web Design

Adobe Dreamweaver CC Classroom in a Book Creative professionals seeking the fastest, easiest, most comprehensive way to learn Adobe Dreamweaver CC choose Adobe Dreamweaver CC: Classroom in a Book from the Adobe Creative Team at Adobe Press. The 15 project-based lessons in this book show you step by step everything you need to know to work in Dreamweaver. You’ll learn to create a professional website without having to write code by hand. This completely revised Creative Cloud edition also covers HTML5, CSS3, and media queries for responsive web design. The book also shows how to create HTML-based headings, paragraphs, lists, and tables; insert graphics and Photoshop Smart Objects; add links to text and images; apply cascading styles sheets; and customize the Dreamweaver workspace. You’ll also learn to add interactive elements to your sites, such as HTML5-compatible video and animation, get guidance for working with code, and finally publish a finished site to the Web. The online companion files include all lesson files so you can work along with the book. “The Classroom in a Book series is by far the best training material on the market. Everything you need to master the software is included: clear explanations of each lesson, step-by-step instructions, and the project files for the students.†–Barbara Binder, Adobe Certified Instructor, Rocky Mountain Training Classroom in a Book®, the best-selling series of hands-on software training workbooks, helps you learn the features of Adobe software quickly and easily. Classroom in a Book offers what no other book or training program does–an official training series from Adobe Systems Incorporated, developed with the support of Adobe product experts. COMPUTERS,Internet,Web Design

CSS Fonts From custom fonts to ad-hoc font families you assemble out of a variety of individual faces, CSS 3 gives you more typographic options than ever before. This concise guide shows you how to use CSS properties to gain a fine-grained and wide-ranging influence over how you display fonts on the Web. Short and sweet, this book is an excerpt from the upcoming fourth edition of CSS: The Definitive Guide. When you purchase either the print or the ebook edition of Fonts, you’ll receive a discount on the entire Definitive Guide once it’s released. Why wait? Learn how to choose and manipulate fonts right away. Specify font families and their generic alternatives Use @font-face to specify customized downloadable fonts Size your fonts with absolute or relative scales, percentages, or length units Understand the difference between italic and oblique styles Learn how to specify or suppress a font’s kerning data and other font features Synthesize your own variants for fonts that lack bold or italic text COMPUTERS,Internet,Web Design

HTML5 Pocket Reference Need help finding the right HTML5 element or attribute for your web page or application? HTML5 Pocket Reference is the classic reference that web designers and developers have been keeping close at hand for more than thirteen years. This fifth edition has been updated to reflect the current state of HTML5, including the HTML5 Candidate Recommendation, the emerging HTML5.1 Working Draft, and the living WHATWG standard. Features include: An alphabetical listing of every element and attribute in HTML5, HTML5.1, and the WHATWG living standard Descriptions, markup examples, content categories, content models, and start- and end-tag requirements for every element At-a-glance notes indicating the differences between the HTML5 specifications and HTML 4.01 Useful charts of special characters An overview of HTML5 APIs If you’re an experienced web designer or developer who needs a quick resource for working with established web standards, this handy book is indispensable. COMPUTERS,Internet,Web Design

Dreamweaver CC With the release of Adobe Creative Suite CC, Dreamweaver again solidifies its role as the de facto tool of choice for anyone designing for the Web. Adobe Dreamweaver CC: Visual QuickStart Guide uses a combination of task-based instruction and strong visuals to teach beginning and intermediate users how to create, design, and publish powerful, innovative Web sites with Dreamweaver. Leading technology authors Tom Negrino and Dori Smith take you step-by-step through the new features in Adobe Dreamweaver CC, with completely revised sections on critical tools like styling pages with CSS, managing styles, and inserting tables. You'll also learn to take advantage of Dreamweaver's ability to simultaneously design sites for a variety of screen sizes, including desktops, tablets, and mobile phones. If you're new to Dreamweaver and web design, you'll learn to create your first Web site, add text, style and lay out page content, manage styles, work with links, incorporate images, media, tables, forms, design site navigation, and so much more. If you're an experienced user, you'll find this a convenient reference to the new features of Dreamweaver CC. COMPUTERS,Internet,Web Design

Developing with PDF PDF is becoming the standard for digital documents worldwide, but it’s not easy to learn on your own. With capabilities that let you use a variety of images and text, embed audio and video, and provide links and navigation, there’s a lot to explore. This practical guide helps you understand how to work with PDF to construct your own documents, troubleshoot problems, and even build your own tools. You’ll also find best practices for producing, manipulating, and consuming PDF documents. In addition, this highly approachable reference will help you navigate the official (and complex) ISO documentation. Learn how to combine PDF objects into a cohesive whole Use PDF’s imaging model to create vector and raster graphics Integrate text, and become familiar with fonts and glyphs Provide navigation within and between documents Use annotations to overlay or incorporate additional content Build interactive forms with the Widget annotation Embed related files such as multimedia, 3D content, and XML files Use optional content to enable non-printing graphics Tag content with HTML-like structures, including paragraphs and tables COMPUTERS,Internet,Web Design

Interface Design for Learning In offices, colleges, and living rooms across the globe, learners of all ages are logging into virtual laboratories, online classrooms, and 3D worlds. Kids from kindergarten to high school are honing math and literacy skills on their phones and iPads. If that weren’t enough, people worldwide are aggregating internet services (from social networks to media content) to learn from each other in “Personal Learning Environments.†Strange as it sounds, the future of education is now as much in the hands of digital designers and programmers as it is in the hands of teachers. And yet, as interface designers, how much do we really know about how people learn? How does interface design actually impact learning? And how do we design environments that support both the cognitive and emotional sides of learning experiences? The answers have been hidden away in the research on education, psychology, and human computer interaction, until now. Packed with over 100 evidence-based strategies, in this book you’ll learn how to: Design educational games, apps, and multimedia interfaces in ways that enhance learning Support creativity, problem-solving, and collaboration through interface design Design effective visual layouts, navigation, and multimedia for online and mobile learning Improve educational outcomes through interface design. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Internet,Web Design

Don't Make Me Think, Revisited Since Don’t Make Me Think was first published in 2000, hundreds of thousands of Web designers and developers have relied on usability guru Steve Krug’s guide to help them understand the principles of intuitive navigation and information design. Witty, commonsensical, and eminently practical, it’s one of the best-loved and most recommended books on the subject. Now Steve returns with fresh perspective to reexamine the principles that made Don’t Make Me Think a classic–with updated examples and a new chapter on mobile usability. And it’s still short, profusely illustrated…and best of all–fun to read. If you’ve read it before, you’ll rediscover what made Don’t Make Me Think so essential to Web designers and developers around the world. If you’ve never read it, you’ll see why so many people have said it should be required reading for anyone working on Web sites. “After reading it over a couple of hours and putting its ideas to work for the past five years, I can say it has done more to improve my abilities as a Web designer than any other book.†–Jeffrey Zeldman, author of Designing with Web Standards COMPUTERS,Internet,Web Design

Microsoft Expression Web 4 Step by Step The smart way to learn Microsoft Expression Web 4 -- one step at a time! Experience learning made easy -- and quickly teach yourself how to create dynamic, standards-based Web sites. With Step by Step, you set the pace -- building and practicing the skills you need, just when you need them! Build your site with customizable templates -- or create your own Adjust settings in Expression Web 4 to create different sites Add Photoshop files, Microsoft Silverlight video, and .wmv files Use CSS, HTML, and XHTML to manage site style and accessibility Connect to servers using Microsoft ASP.NET and PHP Choose the right publishing method for your scenario Your Step by Step digital content includes: All the books practice files -- ready to download and put to work. Fully searchable online edition of this book -- with unlimited access on the Web. Video tutorials illustrating important procedures and concepts COMPUTERS,Internet,Web Design

UX For Dummies Get up to speed quickly on the latest in user experience strategy and design UX For Dummies is a hands-on guide to developing and implementing user experience strategy. Written by globally-recognized UX consultants, this essential resource provides expert insight and guidance on using the tools and techniques that create a great user experience, along with practical advice on implementing a UX strategy that aligns with your organisation's business goals and philosophy. You'll learn how to integrate web design, user research, business planning and data analysis to focus your company's web presence on the needs of your customers, gaining the skills you need to be effective in the field of user experience design. Whether it's the interface, graphics, industrial design, physical interaction or a user manual, being anything less than on point can negatively affect customer satisfaction and retention. User experience design fully encompasses traditional human-computer interaction design, and extends it to address all aspects of a product or service as perceived by users. UX For Dummies provides comprehensive guidance to professionals looking to understand and apply effective UX strategies. Defines UX and offers assistance with determining users and modelling the user experience Provides details on creating a content strategy and building information architectures Explores visual design and designing for specific channels Delves into UX testing and methods for keeping your site relevant The UX field is growing rapidly as companies realise that meeting your business goals requires a web presence aligned with customer needs. This alignment demands smart strategy and even smarter design. Consultants, designers and practitioners must all be on board if the result is to be cohesive and effective. UX For Dummies provides the information and expert advice you need to get up to speed quickly. COMPUTERS,Internet,Web Design

Nicely Said Nicely Said: Writing for the Web with Style and Purpose is a practical guide to writing for digital products and websites. This book will help students develop clear digital communications and improve them over time. This book answers questions like: How do we get people to care about our products? What’s the business value of empathetic communications? Why do we need to worry about voice, tone, and wording? How can we create better web content as our audiences grow? The book walks students through making a framework for great communications—with stories, recipes, and brief examples to learn from. When they finish this book, they’ll see their content in a more meaningful light. They’ll understand how to manage a communication process, find their company’s brand voice, and adjust their tone for different situations. They’ll know how to build trust with customers and show empathy in their writing. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Internet,Web Design

Return on Engagement In the world of web design, if one wants to create a successful web site, one needs an effective content strategy. Return on Engagement shows web designers and developers how to implement an effective content strategy and how to stay ahead in the rapidly changing industry of web design. It presents best practices in terms of web design through a marketing function: content strategy, SEO, social media marketing, and success measurement to help web designers implement a strategy that ensures success for the site they are building. Return on Engagement shows web designers and developers how to not just design an aesthetically pleasing, functional website. This book shows those professionals how to implement marketing strategies and analysis into their website, thus ensuring its success. Nearly 3 years since the previous edition published, new best practices have been formed. Tools in which web developers use to analyze website metrics have advanced. New social media networks and communities have cropped up. New research in how audiences read and receive content has been done, subsequently refining best digital marketing practices. Return on Engagement features a step-by-step breakdown of how to use new tools, techniques, and technologies. The new edition also includes updated case studies of industry leaders who implement best practices on projects. Return on Engagement also features a regularly updated companion site that offers readers sample content, easy sharing tools, and web-based resources to help measure marketing viability of web properties. COMPUTERS,Internet,Web Design

Getting a Web Development Job For Dummies Craving a career in web dev? Chart your path with this helpful guide Getting a Web Development Job For Dummies provides a roadmap to one of the "hot jobs" in the booming world of tech. The web development field is large, and it encompasses many actual functions. This book helps you understand the web development career opportunities and determine the path you should take, based on your own personal needs and preferences, to launch your career. You'll learn about various career options, the skills you'll need to become an attractive candidate, how to go about learning the ropes, and proving your abilities to a potential employer or client. With so many possible goals and no one right way to get there, this book cuts through the confusion to put you on the path to a career you want. The web development industry is expected to grow for the foreseeable future, and there is already a shortage of trained workers to fill the jobs. Whether you lean technical or aesthetic, you can find your place in the industry with right skills—both hard and soft—and with the right plan. Getting a Web Development Job For Dummies is your guide to formulating that plan and getting started right. Find formal or informal ways to build the tech skills you'll need Discover where you fit, whether as a freelancer or within an organization Learn how to build a resume, develop a portfolio, and impress interviewers Get expert tips on finding resources, building a reputation, and more If your pet peeves include malfunctioning forms, flashing banners, and sites that take way too long to load, the web development world needs you. But before you begin your journey, you need a destination and a route in mind. Getting a Web Development Job For Dummies is your roadmap, so you can set out today. COMPUTERS,Internet,Web Design

WordPress Web Design For Dummies Your full-color guide to creating dynamic websites with WordPress Are you familiar with the fundamentals of WordPress, but want to take your skills to the next level? From bestselling author and WordPress expert Lisa Sabin-Wilson, this new edition of WordPress Web Design For Dummies quickly gets you up to speed on the latest release of the software and shows you how to use it as a tool to create a customized, compelling, and cost-effective website—without losing your cool. WordPress can be used to create a custom design for your website using complimentary technologies such as graphic design, CSS, HTML coding, PHP programming, and MySQL administration. With the help of this hands-on, friendly guide, you'll discover how to create an effective navigation system, choose the right color palette and fonts, and select different layouts. Plus, you'll find out how to tweak existing website designs with available themes, both free and premium, and gain the confidence to translate your design skills into paid work. Create dynamic, custom websites with the self-hosted version of WordPress Use free themes and enhance them with CSS and HTML Create a responsive design for mobile devices and tablet users Get to grips with the newest release of WordPress Whether you want to use WordPress to spruce up your existing website or create a brand-new one from scratch, this do-it-yourself guide has you covered. COMPUTERS,Internet,Web Design

Art of Scalability, The The Comprehensive, Proven Approach to IT Scalability–Updated with New Strategies, Technologies, and Case Studies In The Art of Scalability, Second Edition, leading scalability consultants Martin L. Abbott and Michael T. Fisher cover everything you need to know to smoothly scale products and services for any requirement. This extensively revised edition reflects new technologies, strategies, and lessons, as well as new case studies from the authors’ pioneering consulting practice, AKF Partners. Writing for technical and nontechnical decision-makers, Abbott and Fisher cover everything that impacts scalability, including architecture, process, people, organization, and technology. Their insights and recommendations reflect more than thirty years of experience at companies ranging from eBay to Visa, and Salesforce.com to Apple. You’ll find updated strategies for structuring organizations to maximize agility and scalability, as well as new insights into the cloud (IaaS/PaaS) transition, NoSQL, DevOps, business metrics, and more. Using this guide’s tools and advice, you can systematically clear away obstacles to scalability–and achieve unprecedented IT and business performance. Coverage includes • Why scalability problems start with organizations and people, not technology, and what to do about it • Actionable lessons from real successes and failures • Staffing, structuring, and leading the agile, scalable organization • Scaling processes for hyper-growth environments • Architecting scalability: proprietary models for clarifying needs and making choices–including 15 key success principles • Emerging technologies and challenges: data cost, datacenter planning, cloud evolution, and customer-aligned monitoring • Measuring availability, capacity, load, and performance COMPUTERS,Internet,Web Design

Content Strategy Toolkit, The In this essential guide, Meghan Casey outlines a step-by-step approach for doing content strategy, from planning and creating your content to delivering and managing it. Armed with this book, you can confidently tackle difficult activities like telling your boss or client what’s wrong with their content, getting the budget to do content work, and aligning stakeholders on a common vision. Reading The Content Strategy Toolkit is like having your own personal consulting firm on retainer with a complete array of tools and tips for every challenge you’ll face. In this practical and relevant guide, you’ll learn how to: Identify problems with your content and persuade your bosses it’s worth the time and resources to do it right Make sense of your business environment and understand your audience Get stakeholders aligned on business goals and user needs Set your content strategy and decide how to measure success Create, maintain, and govern on-strategy content You’ll learn to control your content—and not have it control you. COMPUTERS,Internet,Web Design

Discussing Design Real critique has become a lost skill among collaborative teams today. Critique is intended to help teams strengthen their designs, products, and services, rather than be used to assert authority or push agendas under the guise of "feedback." In this practical guide, authors Adam Connor and Aaron Irizarry teach you techniques, tools, and a framework for helping members of your design team give and receive critique. Using firsthand stories and lessons from prominent figures in the design community, this book examines the good, the bad, and the ugly of feedback. You’ll come away with tips, actionable insights, activities, and a cheat sheet for practicing critique as a part of your collaborative process. This book covers: Best practices (and anti-patterns) for giving and receiving critique Cultural aspects that influence your ability to critique constructively When, how much, and how often to use critique in the creative process Facilitation techniques for making critiques timely and more effective Strategies for dealing with difficult people and challenging situations COMPUTERS,Internet,Web Design

Creating a Website You can easily create a professional-looking website with nothing more than an ordinary computer and some raw ambition. Want to build a blog, sell products, create forums, or promote an event? No problem! This friendly, jargon-free book gives you the techniques, tools, and advice you need to build a site and get it up on the Web. The important stuff you need to know: Master the basics. Learn HTML5, the language of the Web. Design good-looking pages. Use styles to build polished layouts. Get it online. Find a reliable web host and pick a good web address. Use time-saving tools. Learn free tools for creating web pages and tracking your visitors. Attract visitors. Make sure people can find your site through popular search engines like Google. Build a community. Encourage repeat visits with social media. Bring in the cash. Host Google ads, sell Amazon’s wares, or push your own products that people can buy via PayPal. Add pizzazz. Include audio, video, interactive menus, and a pinch of JavaScript. COMPUTERS,Internet,Web Design

CSS Secrets In this practical guide, CSS expert Lea Verou provides 47 undocumented techniques and tips to help intermediate-to advanced CSS developers devise elegant solutions to a wide range of everyday web design problems. Rather than focus on design, CSS Secrets shows you how to solve problems with code. You'll learn how to apply Lea's analytical approach to practically every CSS problem you face to attain DRY, maintainable, flexible, lightweight, and standards-compliant results. Inspired by her popular talks at over 60 international web development conferences, Lea Verou provides a wealth of information for topics including: Backgrounds and Borders Shapes Visual Effects Typography User Experience Structure and Layout Transitions and Animations COMPUTERS,Internet,Web Design

CSS CSS lets you create professional-looking websites, but learning its finer points can be tricky—even for seasoned web developers. This fully updated edition provides the most modern and effective tips, tricks, and tutorial-based instruction on CSS available today. Learn how to use new tools such as Flexbox and Sass to build web pages that look great and run fast on any desktop or mobile device. Ideal for casual and experienced designers alike. The important stuff you need to know: Start with the basics. Write CSS-friendly HTML, including the HTML5 tags recognized by today’s browsers. Design for mobile devices. Create web pages that look great when visitors use them on the go. Make your pages work for you. Add animations that capture the imagination, and forms that get the job done. Take control of page layouts. Use professional design techniques such as floats and positioning. Make your layouts more flexible. Design websites with Flexbox that adjust to different devices and screen sizes. Work more efficiently. Write less CSS code and work with smaller files, using Syntactically Awesome Stylesheets (Sass). COMPUTERS,Internet,Web Design

Information Architecture Information architecture (IA) is far more challenging—and necessary—than ever. With the glut of information available today, anything your organization wants to share should be easy to find, navigate, and understand. But the experience you provide has to be familiar and coherent across multiple interaction channels, from the Web to smartphones, smartwatches, and beyond. To guide you through this broad ecosystem, this popular guide—now in its fourth edition—provides essential concepts, methods, and techniques for digital design that have withstood the test of time. UX designers, product managers, developers, and anyone involved in digital design will learn how to create semantic structures that will help people engage with your message. This book includes: An overview of IA and the problems it solves for creating effective digital products and services A deep dive into IA components, including organization, labeling, navigation, search, and metadata Processes and methods that take you from research to strategy, design, and IA implementation COMPUTERS,Internet,Web Design

Design Sprint With more than 500 new apps entering the market every day, what does it take to build a successful digital product? You can greatly reduce your risk of failure with design sprints, a process that enables your team to prototype and test a digital product idea within a week. This practical guide shows you exactly what a design sprint involves and how you can incorporate the process into your organization. Design sprints not only let you test digital product ideas before you pour too many resources into a project, they also help everyone get on board—whether they’re team members, decision makers, or potential users. You’ll know within days whether a particular product idea is worth pursuing. Design sprints enable you to: Clarify the problem at hand, and identify the needs of potential users Explore solutions through brainstorming and sketching exercises Distill your ideas into one or two solutions that you can test Prototype your solution and bring it to life Test the prototype with people who would use it COMPUTERS,Internet,Web Design

SVG Colors, Patterns & Gradients As a vector graphics format, SVG uses precisely-defined geometric shapes to build an image. But that doesn't mean that SVG graphics have to look like technical drawings. SVG graphics can be shaded, textured, built from partially-transparent overlapping layers, or even filled with photographic images. SVG Colors, Patterns, and Gradients takes an in-depth look at the different ways SVG text and shapes can be painted on the screen or page. You’ll start with an overview of how color is defined, including the various ways you can control the transparency of SVG content. You’ll then dive deep into the concept of an SVG paint server: gradients, patterns, and other complex graphical content that can be used to fill-in or outline other SVG shapes and text. COMPUTERS,Internet,Web Design

Coding For Dummies Coding For Dummies, (9781119293323) was previously published as Coding For Dummies, (9781118951309). While this version features a new Dummies cover and design, the content is the same as the prior release and should not be considered a new or updated product. Hands-on exercises help you learn to code like a pro No coding experience is required for Coding For Dummies, your one-stop guide to building a foundation of knowledge in writing computer code for web, application, and software development. It doesn't matter if you've dabbled in coding or never written a line of code, this book guides you through the basics. Using foundational web development languages like HTML, CSS, and JavaScript, it explains in plain English how coding works and why it's needed. Online exercises developed by Codecademy, a leading online code training site, help hone coding skills and demonstrate results as you practice. The site provides an environment where you can try out tutorials built into the text and see the actual output from your coding. You'll also gain access to end-of-chapter challenges to apply newly acquired skills to a less-defined assignment. So what are you waiting for? The current demand for workers with coding and computer science skills far exceeds the supply Teaches the foundations of web development languages in an easy-to-understand format Offers unprecedented opportunities to practice basic coding languages Readers can access online hands-on exercises and end-of-chapter assessments that develop and test their new-found skills If you're a student looking for an introduction to the basic concepts of coding or a professional looking to add new skills, Coding For Dummies has you covered. COMPUTERS,Internet,Web Design

Jump Start Sketch Get a Jump Start on the up and coming power tool on the design scene, Sketch! Sketch is fast becoming a favorite tool of modern web designers. With a simple, clean UI, and a raft of powerful features, such as intuitive grids, unlimited artboards, and granular export, Sketch is a great tool for web design; it's easy to see why so many top designers are adding it to their toolbox. This book provides a rapid and practical introduction to using Sketch for web design. If you're currently a Photoshop user, you'll quickly understand how Sketch can supercharge your design process. See how Sketch compares to Photoshop, and when to use one over the other Get to grips with Sketch's UI Use Sketch's built-in layout grid Add plugins to Sketch to boost functionality Export your designs into ready-to-use HTML and CSS And much more! COMPUTERS,Internet,Web Design

Org Design for Design Orgs Design has become the key link between users and today’s complex and rapidly evolving digital experiences, and designers are starting to be included in strategic conversations about the products and services that enterprises ultimately deliver. This has led to companies building in-house digital/experience design teams at unprecedented rates, but many of them don’t understand how to get the most out of their investment. This practical guide provides guidelines for creating and leading design teams within your organization, and explores ways to use design as part of broader strategic planning. You’ll discover: Why design’s role has evolved in the digital age How to infuse design into every product and service experience The 12 qualities of effective design organizations How to structure your design team through a Centralized Partnership Design team roles and evolution The process of recruiting and hiring designers How to manage your design team and promote professional growth COMPUTERS,Internet,Web Design

Designing for Sustainability Pixels use electricity, and a lot of it. If the Internet were a country, it would be the sixth largest in terms of electricity use. That’s because today’s average web page has surpassed two megabytes in size, leading to slow load times, frustrated users, and a lot of wasted energy. With this practical guide, your web design team will learn how to apply sustainability principles for creating speedy, user-friendly, and energy-efficient digital products and services. Author Tim Frick introduces a web design framework that focuses on four key areas where these principles can make a difference: content strategy, performance optimization, design and user experience, and green hosting. You’ll discover how to provide users with a streamlined experience, while reducing the environmental impact of your products and services. Learn why 90% of the data that ever existed was created in the last year Use sustainability principles to innovate, reduce waste, and function more efficiently Explore green hosting, sustainable business practices, and lean/agile workflows Put the right things in front of users at precisely the moment they need them—and nothing more Increase site search engine visibility, streamline user experience, and make streaming video more efficient Use Action Items to explore concepts outlined in each chapter COMPUTERS,Internet,Web Design

Designing UX A recent study found that on average, designing a form to have a great user experience almost doubled the rate of successful first-time completions. For example, Ebay made an additional $USD 500 million annually from redesigning just the button on one of their mobile form screens. More conversions, fewer dissatisfied users, better return on investment. Can you afford not to improve your forms' user experiences? This book will walk you through every part of designing a great forms user experience. From the words, to how the form looks, and on to interactivity, you'll learn how to design a web form that works beautifully on mobiles, laptops and desktops. Filled with practical and engaging insights, and plenty of real-world examples, both good and bad. You'll learn answers to common queries like: Where should field labels go? What makes a question easy to understand? How do you design forms to work on small screens? How does touch impact on form design? How long can a form be? What look and feel should the form have: skeumorphic, flat, or something else? What's best practice for error messaging? COMPUTERS,Internet,Web Design

UX Research One key responsibility of product designers and UX practitioners is to conduct formal and informal research to clarify design decisions and business needs. But there’s often mystery around product research, with the feeling that you need to be a research Zen master to gather anything useful. Fact is, anyone can conduct product research. With this quick reference guide, you’ll learn a common language and set of tools to help you carry out research in an informed and productive manner. This book contains four sections, including a brief introduction to UX research, planning and preparation, facilitating research, and analysis and reporting. Each chapter includes a short exercise so you can quickly apply what you’ve learned. Learn what it takes to ask good research questions Know when to use quantitative and qualitative research methods Explore the logistics and details of coordinating a research session Use softer skills to make research seem natural to participants Learn tools and approaches to uncover meaning in your raw data Communicate your findings with a framework and structure COMPUTERS,Internet,Web Design

Prototyping for Designers Prototyping and user testing is the best way to create successful products, but many designers skip this important step and use gut instinct instead. By explaining the goals and methodologies behind prototyping—and demonstrating how to prototype for both physical and digital products—this practical guide helps beginning and intermediate designers become more comfortable with creating and testing prototypes early and often in the process. Author Kathryn McElroy explains various prototyping methods, from fast and dirty to high fidelity and refined, and reveals ways to test your prototypes with users. You’ll gain valuable insights for improving your product, whether it’s a smartphone app or a new electronic gadget. Learn similarities and differences between prototyping for physical and digital products Know what fidelity level is needed for different prototypes Get best practices for prototyping in a variety of mediums, and choose which prototyping software or components to use Learn electronics prototyping basics and resources for getting started Write basic pseudocode and translate it into usable code for Arduino Conduct user tests to gain insights from prototypes COMPUTERS,Internet,Web Design

The Web Designer's Idea Book, Volume 3 Quick Inspiration for Web Designers Featuring more than 650 examples, this third volume of The Web Designer's Idea Book is packed with visual inspiration for creating top-notch web design. Web design expert Patrick McNeil, author of the popular Web Designer's Idea Book series, is back with the latest examples of the best design on the web today. Arranged thematically, this guide puts important topics like technology, design styles, elements, site types and site structure at your fingertips. This new volume also includes a detailed discussion of the various content management systems available to help you find the best platform for your project. An indispensable reference, this book provides you with the latest in themes, styles and trends you need to keep your projects relevant in the fast-paced and every-changing world of web design. COMPUTERS,Internet,Web Design

Above the Fold This is a different kind of web design book. Above the Fold is not about timely design or technology trends; instead, this book is about the timeless fundamentals of effective communication within the context of web design. It is intended to help you, the reader, understand the considerations that web designers make when developing successful websites. Above the Fold is divided into three sections: Design & Typography Planning & Usability Business Value Each section represents a phase in the continuous cycle of web design. It's the balance among design, usability, and return on investment that makes a website truly great. Topics covered in Above the Fold include: What makes web design unique The history of web design Anatomy of a web page White space and grid use in web design The elements of web design: color, texture, imagery, scale, depth, animation, and variability Web typography, including web-safe type, images of type, and font replacement and embedding Web project planning Information architecture, including site maps, wireframes, and user flow diagrams The elements of usability: navigation, breadcrumbs, links, search, submission forms, and error messaging Search engine optimization Online marketing, including banner ads, viral and social marketing, on-site marketing, and email marketing Web statistics and analysis COMPUTERS,Internet,Web Design

Researching UX Good UX is based on evidence. Qualitative evidence, such as user testing and field research, can only get you so far. To get the full picture of how users are engaging with your website or app, you'll need to use quantitative evidence in the form of analytics. This book will show you, step by step, how you can use website and app analytics data to inform design choices and definitively improve user experience. Offering practical guidelines, with plenty of detailed examples, this book covers: why you need to gather analytics data for your UX projects getting set up with analytics tools analyzing data how to find problems in your analytics using analytics to aid user research, measure and report on outcomes By the end of this book, you'll have a strong understanding of the important role analytics plays in the UX process. It will inspire you to take an "analytics first" approach to your UX projects. COMPUTERS,Internet,Web Design

White Space Is Not Your Enemy White Space Is Not Your Enemy is a practical graphic design and layout guide that introduces concepts and practices necessary for producing effective visual communication across a variety of formats—from web to print. Sections on Gestalt theory, color theory, and WET layout are expanded to offer more in-depth content on those topics. This new edition features new covering current trends in web design—Mobile-first, UI/UX design, and web typography—and how they affect a designer’s approach to a project. The entire book will receive an update using new examples and images that show a more diverse set of graphics that go beyond print and web and focus on tablet, mobile and advertising designs. COMPUTERS,Internet,Web Design

Tragic Design Bad design is everywhere, and its cost is much higher than we think. In this thought-provoking book, authors Jonathan Shariat and Cynthia Savard Saucier explain how poorly designed products can anger, sadden, exclude, and even kill people who use them. The designers responsible certainly didn’t intend harm, so what can you do to avoid making similar mistakes? Tragic Design examines real case studies that show how certain design choices adversely affected users, and includes in-depth interviews with authorities in the design industry. Pick up this book and learn how you can be an agent of change in the design community and at your company. You’ll explore: Designs that can kill, including the bad interface that doomed a young cancer patient Designs that anger, through impolite technology and dark patterns How design can inadvertently cause emotional pain Designs that exclude people through lack of accessibility, diversity, and justice How to advocate for ethical design when it isn’t easy to do so Tools and techniques that can help you avoid harmful design decisions Inspiring professionals who use design to improve our world COMPUTERS,Internet,Web Design

Designing Bots From Facebook Messenger to Kik, and from Slack bots to Google Assistant, Amazon Alexa, and email bots, the new conversational apps are revolutionizing the way we interact with software. This practical guide shows you how to design and build great conversational experiences and delightful bots that help people be more productive, whether it’s for a new consumer service or an enterprise efficiency product. Ideal for designers, product managers, and entrepreneurs, this book explores what works and what doesn’t in real-world bot examples, and provides practical design patterns for your bot-building toolbox. You’ll learn how to use an effective onboarding process, outline different flows, define a bot personality, and choose the right balance of rich control and text. Explore different bot use-cases and design best practices Understand bot anatomy—such as brand and personality, conversations, advanced UI controls—and their associated design patterns Learn steps for building a Facebook Messenger consumer bot and a Slack business bot Explore the lessons learned and shared experiences of designers and entrepreneurs who have built bots Design and prototype your first bot, and experiment with user feedback COMPUTERS,Internet,Web Design

Scalability Rules Scalability Rules , is the easy-to-use scalability primer and reference for every architect, developer, network/software engineer, web professional, and manager. Authors Martin L. Abbott and Michael T. Fisher have helped scale hundreds of high-growth companies and thousands of systems. Drawing on their immense experience, they present 50 up-to-the-minute technical best practices for supporting hyper growth practically anywhere. Fully updated to reflect new technical trends and experiences, this edition is even easier to read, understand, and apply. Abbott and Fisher have also added powerful “stories behind the rulesâ€: actual experiences and case studies from CTOs and technology executives at Etsy, NASDAQ, Salesforce, Shutterfly, Chegg, Warby Parker, Twitter, and other scalability pioneers. Architects will find powerful technology-agnostic insights for creating and evaluating designs. Developers will discover specific techniques for handling everything from databases to state. Managers will get invaluable help in setting goals, making decisions, and interacting with technical teams. Whatever your role, you’ll find practical risk/benefit guidance for setting priorities, translating plans into action, and gaining maximum scalability at minimum cost. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Internet,Web Design

Designing with CSS Grid Layout Layout in CSS has always been a tricky task: hacking solutions using positioning, floats, and the one-dimensional flexbox has never been very satisfactory. Fortunately, there is a new tool to add to our arsenal: CSS Grid Layout. It is an incredibly powerful layout system that allows us to design pages using a two-dimensional grid - offering the kind of fine-grained layout control that print designers take for granted! Grid Layout has been in development for a while, but has recently been made a W3C candidate recommendation and has been added to most of the major browsers, so is ready for prime time. This short selection of tutorials, hand-picked from SitePoint's HTML & CSS channel, will get you up and running with Grid Layout and using it on your own sites in no time. This collection includes: An Introduction to the CSS Grid Layout Module by Ahmad Ajmi Seven Ways You Can Place Elements Using CSS Grid Layout by Nitish Kumar How to Order and Align Items in Grid Layout by Nitish Kumar A Step by Step Guide to the Auto- Placement Algorithm in CSS Grid by Nitish Kumar How I Built a Pure CSS Crossword Puzzle by Adrian Roworth This book is suitable for front end developers and web designers with some CSS experience. COMPUTERS,Internet,Web Design

Presto Sketching Do you feel like your thoughts, ideas, and plans are being suffocated by a constant onslaught of information? Do you want to get those great ideas out of your head, onto the whiteboard and into everyone else’s heads, but find it hard to start? No matter what level of sketching you think you have, Presto Sketching will help you lift your game in visual thinking and visual communication. In this practical workbook, Ben Crothers provides loads of tips, templates, and exercises that help you develop your visual vocabulary and sketching skills to clearly express and communicate your ideas. Learn techniques like product sketching, storyboarding, journey mapping, and conceptual illustration. Dive into how to use a visual metaphor (with a library of 101 visual metaphors), as well as tips for capturing and sharing your sketches digitally, and developing your own style. Designers, product managers, trainers, and entrepreneurs will learn better ways to explore problems, explain concepts, and come up with well-defined ideas - and have fun doing it. COMPUTERS,Internet,Web Design

Adobe Dreamweaver CC Classroom in a Book (2018 release) Creative professionals seeking the fastest, easiest, most comprehensive way to learn Adobe Dreamweaver CC (2018 release) choose Adobe Dreamweaver CC Classroom in a Book (2018 release) from the best-selling series of hands-on software training workbooks from Adobe Press. The 12 project-based step-by-step lessons in this book show users the key techniques for working in Dreamweaver. Learn how to create webpages for the modern web with a minimum of hand coding; incorporate graphics, and text; add links to text and images; add interactive elements to your sites, such as HTML5-compatible interactivity; work with the latest HTML5 and CSS3 code and structures; and publish a finished site to the web. Four additional online lessons provide valuable hands-on experience in working with code and how to use and customize web frameworks to build a fully responsive site design to support a wide variety of desktop computers and mobile devices. The online assets also include three bonus exercises for HTML and Cascading Style Sheets, and creating web assets, essential to your understanding of web design and website development. That’s 16 total lessons chock full of invaluable information and real world examples. The online companion files include all the necessary assets for readers to complete the projects featured in each lesson as well as ebook updates when Adobe releases relevant new features for Creative Cloud customers. All buyers of the book get full access to the Web Edition: a Web-based version of the complete ebook enhanced with video and multiple-choice quizzes. COMPUTERS,Internet,Web Design

Designing Across Senses Today we have the ability to connect speech, touch, haptic, and gestural interfaces into products that engage several human senses at once. This practical book explores examples from current designers and devices to describe how these products blend multiple interface modes together into a cohesive user experience. Authors Christine Park and John Alderman explain the basic principles behind multimodal interaction and introduce the tools you need to root your design in the ways our senses shape experience. This book also includes guides on process, design, and deliverables to help your team get started. The book covers several topics within multimodal design, including: New Human Factors: learn how human sensory abilities allow us to interact with technology and the physical world New Technologies: explore some of the technologies that enable multimodal interactions, products, and capabilities Multimodal Products: examine different categories of products and learn how they deliver sensory-rich experiences Multimodal Design: learn processes and methodologies for multimodal product design, development, and release COMPUTERS,Internet,Web Design

Learning Web Design Do you want to build web pages but have no prior experience? This friendly guide is the perfect place to start. You’ll begin at square one, learning how the web and web pages work, and then steadily build from there. By the end of the book, you’ll have the skills to create a simple site with multicolumn pages that adapt for mobile devices. Each chapter provides exercises to help you learn various techniques and short quizzes to make sure you understand key concepts. This thoroughly revised edition is ideal for students and professionals of all backgrounds and skill levels. It is simple and clear enough for beginners, yet thorough enough to be a useful reference for experienced developers keeping their skills up to date. Build HTML pages with text, links, images, tables, and forms Use style sheets (CSS) for colors, backgrounds, formatting text, page layout, and even simple animation effects Learn how JavaScript works and why the language is so important in web design Create and optimize web images so they’ll download as quickly as possible NEW! Use CSS Flexbox and Grid for sophisticated and flexible page layout NEW! Learn the ins and outs of Responsive Web Design to make web pages look great on all devices NEW! Become familiar with the command line, Git, and other tools in the modern web developer’s toolkit NEW! Get to know the super-powers of SVG graphics COMPUTERS,Internet,Web Design

CSS Master CSS Master is tailor-made for the web designer or front-end devleoper who's really serious about taking their skills to the next level. Discover how to keep ahead of the game by adhering to best practice and employing the most effective, cutting-edge CSS techniques. Now thoroughly updated in its second edition, this book covers how to: Organize your CSS to create the most efficient and most maintainable code Employ advanced approaches to achieve complex layouts: flexbox, grid layouts, multi-column, and more Use next-level effects: transitions, transforms, filters, animations, and more Combine CSS and SVG to create seriously powerful visuals Use efficient debugging techniques And much more! COMPUTERS,Internet,Web Design

CSS Grid Layout CSS has grown from a language for formatting documents into a robust language for designing web applications. Its syntax is easy to learn, making CSS a great entry point for those new to programming. Indeed, it's often the second language that developers learn, right behind HTML. One of CSS's new features is the Grid Layout Module, which enables complex layout designs that previously would have been very difficult to achieve. In this book, we'll examine five projects that use grid layout. It contains: Redesigning a Site to Use CSS Grid Layout by Ilya Bodrov Redesigning a Card-based Tumblr Layout with CSS Grid by Giulio Mainardi Easy and Responsive Modern CSS Grid Layout by Ahmed Bouchefra Progressively Enhanced CSS Layouts from Floats to Flexbox to Grid by Diogo Souza Make Forms Great with CSS Grid by Craig Buckler This book is suitable for developers with some CSS experience. COMPUTERS,Internet,Web Design

The Advanced CSS Collection CSS has grown from a language for formatting documents into a robust language for designing web applications. Its syntax is easy to learn, making CSS a great entry point for those new to programming. Indeed, it's often the second language that developers learn, right behind HTML. As CSS's feature set and abilities have grown, so has its depth. In this collection of books, we'll be exploring some of the amazing things that developers can do with CSS today; tasks that in the past might only have been achievable with some pretty complex JavaScript, if at all. This collection contains: Modern CSS, which explores topics like variable fonts and transforms, and shows how they might be used in the real world CSS Grid Layout: 5 Practical Projects, which shows five complete projects that utilize the Grid Layout Layout module CSS Tools & Skills which looks at essential CSS tools and skills for modern front-end developers COMPUTERS,Internet,Web Design

Learn React with TypeScript 3 Start developing modern day component based web apps using React 16, Redux and TypeScript 3 with this easy to follow guide filled with practical examples. Key Features Learn the latest and core features of React such as components, React Router, and suspense Dive into TypeScript 3 and it`s core components such as interfaces, types aliases, tuples, generics and much more. Build small-to-large scale single page applications with React, Redux, GraphQL and TypeScript Book Description React today is one of the most preferred choices for frontend development. Using React with TypeScript enhances development experience and offers a powerful combination to develop high performing web apps. In this book, you'll learn how to create well structured and reusable react components that are easy to read and maintain by leveraging modern web development techniques. We will start with learning core TypeScript programming concepts before moving on to building reusable React components. You'll learn how to ensure all your components are type-safe by leveraging TypeScript's capabilities, including the latest on Project references, Tuples in rest parameters, and much more. You'll then be introduced to core features of React such as React Router, managing state with Redux and applying logic in lifecycle methods. Further on, you'll discover the latest features of React such as hooks and suspense which will enable you to create powerful function-based components. You'll get to grips with GraphQL web API using Apollo client to make your app more interactive. Finally, you'll learn how to write robust unit tests for React components using Jest. By the end of the book, you'll be well versed with all you need to develop fully featured web apps with React and TypeScript. What you will learn Gain a first-hand experience of TypeScript and its productivity features Transpile your TypeScript code into JavaScript for it to run in a browser Learn relevant advanced types in TypeScript for creating strongly typed and reusable components. Create stateful function-based components that handle lifecycle events using hooks Get to know what GraphQL is and how to work with it by executing basic queries to get familiar with the syntax Become confident in getting good unit testing coverage on your components using Jest Who this book is for The ideal target audience for this book are web developers who want to get started with creating modern day web apps with React and TypeScript.You are expected to have a basic understanding of JavaScript and HTML programming. No prior knowledge of TypeScript and React is needed. COMPUTERS,Internet,Web Design

Adobe Dreamweaver CC Classroom in a Book Creative professionals seeking the fastest, easiest, most comprehensive way to learn Adobe Dreamweaver CC (2019 release) choose Adobe Dreamweaver CC Classroom in a Book (2019 release) from the best-selling series of hands-on software training workbooks from Adobe Press. The 15 project-based step-by-step lessons in this book show users the key techniques for working in Dreamweaver while editing and creating HTML and Cascading Style Sheets (CSS). Learn how to create webpages for the modern web; use and customize popular web frameworks to build webpages for a wide variety of desktop computers and mobile devices with a minimum of hand coding; incorporate graphics and text; add links to text and images; add interactive elements to your pages, such as HTML5-compatible interactivity; work with the latest HTML5 and CSS3 code and structures; and publish a finished site to the web. A 16th lesson (online) provides valuable hands-on experience in writing and working with code using shorthand and various productivity enhancements. The online assets also include bonus exercises for HTML and CSS, essential to a full understanding of web design and website development. The online companion files include all the necessary assets for readers to complete the projects featured in each lesson as well as ebook updates when Adobe releases relevant new features for Creative Cloud customers. All buyers of the book get full access to the Web Edition: a Web-based version of the complete ebook enhanced with video and multiple-choice quizzes. COMPUTERS,Internet,Web Design

React Material-UI Cookbook Develop modern-day applications by implementing Material Design principles in React using Material-UI Key Features Use React components to build intuitive UI elements Explore a variety of styles and themes in the Material-UI framework using React components Learn practical React recipes and best practices for building modern web applications Book Description Material-UI is a component library for rendering UI elements, using modern best practices from React and Material Design. This book will show you how you can create impressive and captivating modern-day web apps by implementing Material Design considerations. The book is designed to help you use a variety of Material-UI components to enhance UI functionality, along with guiding you through React best practices, and using state, context, and other new React 16.8 features. You will start with layout and navigation, exploring the Grid component and understanding how it's used to build layouts for your Material-UI apps. Using Material-UI components, you'll then explore the technique of effectively presenting information. In later sections, you will also learn about the different components for user interactions such as the text input component and buttons. Finally, the book will get you up to speed with customizing the look and feel of your app, right from creating a Material-UI theme through to styling icons and text. By the end of this book, you will have developed the skills you need to improve the look and feel of your applications using Material-UI components. What you will learn Build the overall structure and navigation for your Material-UI app Present simple and complex information in a variety of ways Develop interactive and intuitive controls Group content into sections using tabs and expansion panels Create a general page layout with Material-UI grids Use lists for complex data, and cards for detailed information Who this book is for This book is for React developers who want to implement Material Design principles in their applications. You will also find this book helpful if you are a developer who wants to build a UI using React components without having to build your own UX framework. COMPUTERS,Internet,Web Design

Graphic Design Graphic Design: Learn It, Do It is an introduction to the fundamentals of graphic design and the Adobe Creative Cloud applications used to put these concepts into practice. This book is intended for production-oriented audiences, those interested in the what, why and how of graphic design. The "what" is effective graphic design, a visual solution created using the design principles that stands out in a crowded marketplace. This discussion includes color theory, typography and page layout. Focus on the "why" of design begins with the reasons why we communicate. Attention is paid to the purpose of the visual solution and to its audiences. The conversation highlights output options (print vs. onscreen) and their related file properties. The "how" of design addresses the stages of production and use of Adobe Photoshop CC, Illustrator CC and InDesign CC to translate an idea into a visual solution. Following an overview of each application and its uses, step-by-step exercises are provided to foster familiarity with each application’s workspace and its tools. These exercises provide opportunities to implement the design principles and to produce examples of work for a design portfolio. Key Features: Content based on over a decade’s worth of experience teaching graphic design Contemporary examples and online references Guided exercises for working in the Adobe Creative Cloud applications, Photoshop CC, Illustrator CC and InDesign CC Accompanying exercise files and supporting materials available for download from the book’s companion website Discussion questions and activities included at the end of chapters to expand the presented topics COMPUTERS,Internet,Web Design

Getting Started with Web Components Explore modern Web Component design and integrate them with a variety of web frameworks to build encapsulated reusable UI components for your web apps Key Features Learn Web Components with more than 50 web component examples for both beginners and advanced users Create responsive and highly customizable web pages using HTML, CSS, and JavaScript Extend the potential of Web Components by integrating them with standard web frameworks Book Description Web Components are a set of APIs that help you build reusable UI modules that can operate in any modern browser using just Vanilla JavaScript. The power of Web Components lies in their ability to build frontend web applications with or without web frameworks. With this practical guide, you will understand how Web Components can help you build reusable UI components for your modern web apps. The book starts by explaining the fundamentals of Web Components' design and strategies for using them in your existing frontend web projects. You will also learn how to use JavaScript libraries such as Polymer.js and Stencil.js for building practical components. As you progress, you will build a single-page application using only Web Components to fully realize their potential. This practical guide demonstrates how to work with Shadow DOM and custom elements to build the standard components of a web application. Toward the end of the book, you will learn how to integrate Web Components with standard web frameworks to help you manage large-scale web applications. By the end of this book, you will have learned about the capabilities of Web Components in building custom elements and have the necessary skills for building a reusable UI for your web applications. What you will learn Understand Web Component design, specifications, and life cycle Create single-page applications using Web Components Enable reusability and customization for your UI components Implement Web Components in your web apps using Polymer and Stencil libraries Build powerful frontend components from scratch and deploy them on the web Design patterns and best practices to integrate Web Components into your existing web application Who this book is for This book is for developers who have heard about web components, but don't really know where to start. This book is also for intermediate and advanced developers who know what web components are, but are still afraid to use them in production. This book is also for frontend engineers who are simply looking into web components in order to increase their knowledge and skills. COMPUTERS,Internet,Web Design

Practical Web Design A step by step guide for beginners to create interactive and dynamic websites from scratch. About This Book A fun-filled book with incrementing projects that would help you learn and adapt the fundamentals of web development Bring your web design to life with the help of HTML, CSS, JQuery, and learn to kick-start your future projects with Bootstrap Explore popular web development techniques such as responsive, adaptive, and material design and initiate yourself with Vue.js Who This Book Is For This book is for anyone who wants to learn about web development regardless of previous experience. It's perfect for complete beginners with zero experience; it's also great for anyone who does have some experience in a few technologies (such as HTML and CSS) but not all of them. What You Will Learn Understand the importance of web design and the basic design components Learn HTML5 and CSS3 Difference between adaptive and responsive web design Learn how to create your first website Add interaction and dynamic content to your website with JavaScript and JQuery Implement Bootstrap Framework in your project Get familiar with server-side rendering In Detail Web design is the process of creating websites. It encompasses several different aspects, including webpage layout, content production, and graphic design. This book offers you everything you need to know to build your websites. The book starts off by explaining the importance of web design and the basic design components used in website development. It'll show you insider tips to work quickly and efficiently with web technologies such as HTML5, CSS3, and JavaScript, concluding with a project on creating a static site with good layout. Once you've got that locked down, we'll get our hands dirty by diving straight into learning JavaScript and JQuery, ending with a project on creating dynamic content for your website. After getting our basic website up and running with the dynamic functionalities you'll move on to building your own responsive websites using more advanced techniques such as Bootstrap. Later you will learn smart ways to add dynamic content, and modern UI techniques such as Adaptive UI and Material Design. This will help you understand important concepts such as server-side rendering and UI components. Finally we take a look at various developer tools to ease your web development process. Style and approach This is a fun-filled book with conversational and engaging content ; with each incrementing project, you'll would easily learn and adapt the fundamentals of web development. Each project showcases a different use case and incrementally teaches the web development basics. COMPUTERS,Internet,Web Design

Adobe Dreamweaver Classroom in a Book (2020 release) Adobe Dreamweaver CC Classroom in a Book (2020 release) is the best-selling guide to Adobe’s powerful web design application, fully updated. The 12 project-based lessons in this book show students step-by-step everything they need to know in order to create a professional website without having to write code by hand. Because it’s often useful to understand the code underlying a web site, the book starts with primers on HTML and CSS (the building blocks of website code) and shows students how to plan a web site. They then learn to design individual web pages, adding styled text, images, and interactive elements to make their designs attractive and engaging. Along the way, the book provides guidance and best practices for working with code, and in the end shows how to publish a finished site to the Web. The online companion files include all the necessary assets for students to complete the projects featured in each chapter as well as eBook updates when Adobe releases new features for Creative Cloud customers. And all buyers of the book get full access to the Web Edition: a Web-based version of the complete eBook enhanced with video and interactive multiple-choice quizzes. COMPUTERS,Internet,Web Design

Adobe XD Classroom in a Book (2020 release) Creative professionals, web designers, and UX professionals seeking the fastest, easiest, most comprehensive way to learn Adobe XD (2020 release) choose Adobe XD Classroom in a Book (2020 release) from the best-selling series of hands-on software training workbooks from Adobe Press. The 11 project-based lessons in this book guide users step-by-step through key techniques in XD for designing and prototyping cutting edge content for websites, mobile apps, and presentations. You’ll set up a project, create graphics, add images and text, organize content, and work with components and Libraries. You’ll learn how to add effects and work more efficiently with repeat grid. You’ll also create fully functioning prototypes, and explore how to preview, share, comment, and export production-ready assets. The online companion files include all the necessary assets for readers to complete the projects featured in each chapter. All buyers of the book get full access to the Web Edition: a Web-based version of the complete ebook enhanced with video and multiple-choice quizzes. COMPUTERS,Internet,Web Design

Laws of UX An understanding of psychology—specifically the psychology behind how users behave and interact with digital interfaces—is perhaps the single most valuable nondesign skill a designer can have. The most elegant design can fail if it forces users to conform to the design rather than working within the “blueprint†of how humans perceive and process the world around them. This practical guide explains how you can apply key principles in psychology to build products and experiences that are more intuitive and human-centered. Author Jon Yablonski deconstructs familiar apps and experiences to provide clear examples of how UX designers can build experiences that adapt to how users perceive and process digital interfaces. You’ll learn: How aesthetically pleasing design creates positive responses The principles from psychology most useful for designers How these psychology principles relate to UX heuristics Predictive models including Fitts’s law, Jakob’s law, and Hick’s law Ethical implications of using psychology in design A framework for applying these principles COMPUTERS,Internet,Web Design

Responsive Web Design with HTML5 and CSS Harness the latest capabilities of HTML5 and CSS to create a single UI that works flawlessly on mobile phones, tablets, and desktops — plus everything in-between Key Features Understand what responsive web design is and its significance for modern web development Explore the latest developments in responsive web design including variable fonts, CSS Scroll Snap, and more Get to grips with the uses and benefits of the new CSS Grid layout Book Description Responsive Web Design with HTML5 and CSS, Third Edition is a renewed and extended version of one of the most comprehensive and bestselling books on the latest HTML5 and CSS tools and techniques for responsive web design. Written in the author's signature friendly and informal style, this edition covers all the newest developments and improvements in responsive web design including better user accessibility, variable fonts and font loading, CSS Scroll Snap, and much, much more. With a new chapter dedicated to CSS Grid, you will understand how it differs from the Flexbox layout mechanism and when you should use one over the other. Furthermore, you will acquire practical knowledge of SVG, writing accessible HTML markup, creating stunning aesthetics and effects with CSS, applying transitions, transformations, and animations, integrating media queries, and more. The book concludes by exploring some exclusive tips and approaches for front-end development from the author. By the end of this book, you will not only have a comprehensive understanding of responsive web design and what is possible with the latest HTML5 and CSS, but also the knowledge of how to best implement each technique. What you will learn Integrate CSS media queries into your designs; apply different styles to different devices Load different sets of images depending upon screen size or resolution Leverage the speed, semantics, and clean markup of accessible HTML patterns Implement SVGs into your designs to provide resolution-independent images Apply the latest features of CSS like custom properties, variable fonts, and CSS Grid Add validation and interface elements like date and color pickers to HTML forms Understand the multitude of ways to enhance interface elements with filters, shadows, animations, and more Who this book is for Are you a full-stack developer who needs to gem up on their front-end skills? Perhaps you work on the front-end and you need a definitive overview of all modern HTML and CSS has to offer? Maybe you have done a little website building but you need a deep understanding of responsive web designs and how to achieve them? This is a book for you! All you need to take advantage of this book is a working understanding of HTML and CSS. No JavaScript knowledge is needed. COMPUTERS,Internet,Web Design

Professional WordPress Plugin Development Extend WordPress with plugins using this advanced WordPress development book, updated for the current version This significantly updated edition of Professional WordPress Plugin Development addresses modern plugin development for WordPress, the highly popular content management system (CMS). If you’re using WordPress to create and manage websites, WordPress plugins are the software that can extend or enhance CMS functionality. This book offers guidance on writing plugins for WordPress sites to share or sell to other users. The second edition of Professional WordPress Plugin Development covers the building of advanced plugin development scenarios. It discusses the plugin framework and coding standards as well as dashboards, settings, menus, and related application programming interfaces (APIs). Additional topics include security, performance, data validation, and SQL statements. • Learn about the power of hooks in WordPress • Discover how JavaScript and Ajax will work in your site • Understand key technologies: Block Editor/Gutenberg, JS/React, PHP, and the REST API • Create and use custom post types and taxonomies. • Creating custom dashboard menus and plugin settings • Work with users and user data • Schedule tasks and utilizing Cron • Performance and security considerations Written by experienced plugin developers, Professional WordPress Plugin Development also helps you internationalize and localize your WordPress website. Find out about debugging systems and optimizing your site for speed. As WordPress use continues to increase, you can elevate your professional knowledge of how to extend WordPress through plugins. COMPUTERS,Internet,Web Design

Designing for Behavior Change Designers and managers hope their products become essential for users—integrated into their lives like Instagram, Lyft, and others have become. Such deep integration isn’t accidental: it’s a process of careful design and iterative learning, especially for technology companies. This guide shows you how to apply behavioral science—research that supports many products—to help your users achieve their goals using your product. In this updated edition, Stephen Wendel, head of behavioral science at Morningstar, takes you step-by-step through the process of incorporating behavioral science into product design and development. Product managers, UX and interaction designers, and data analysts will learn a simple and effective approach for identifying target users and behaviors, building the product, and gauging its effectiveness. Learn the three main strategies to help people change behavior Identify behaviors your target audience seeks to change—and obstacles that stand in their way Develop effective designs that are enjoyable to use Measure your product’s impact and learn ways to improve it Combine behavioral science with data science to pinpoint problems and test potential solutions COMPUTERS,Internet,Web Design

JavaScript Demystified Even if you have no programming experience, you'll learn to create dynamic, interactive Web pages with help from this easy-to-use, self-teaching guide. Author and programming instructor Jim Keogh covers the basics of this leading Web development language and explains how to write cross-browser JavaScript programs in no time. COMPUTERS,Internet,Web Programming

SQL Demystified There’s no easier, faster, or more practical way to learn the really tough subjects SQL Demystified explains how to use SQL (Structured Query Language)--the ubiquitous programming language for databases. Readers will learn to create database objects, add and retrieve data from a database, and modify existing data. This self-teaching guide comes complete with key points, background information, quizzes at the end of each chapter, and even a final exam. Simple enough for beginners but challenging enough for advanced students, this is a lively and entertaining brush-up, introductory text, or classroom supplement. COMPUTERS,Internet,Web Programming

Pro JavaScript Design Patterns As a web developer, you’ll already know that JavaScript is a powerful language, allowing you to add an impressive array of dynamic functionality to otherwise static web sites. But there is more power waiting to be unlocked—JavaScript is capable of full object–oriented capabilities, and by applying object-oriented principles, best practices, and design patterns to your code, you can make it more powerful, more efficient, and easier to work with alone or as part of a team. With Pro JavaScript Design Patterns, you’ll start with the basics of object–oriented programming in JavaScript applicable to design patterns, including making JavaScript more expressive, inheritance, encapsulation, information hiding, and more. With that covered, you can kick–start your JavaScript development in the second part of the book, where you’ll find detail on how to implement and take advantage of several design patterns in JavaScript, including composites, decorators, façades, adapters, and many more. Each chapter is packed with real–world examples of how the design patterns are best used and expert advice on writing better code, as well as what to watch out for. Along the way you’ll discover how to create your own libraries and APIs for even more efficient coding. Master the basics of object–oriented programming in JavaScript, as they apply to design patterns Apply design patterns to your kick–start your JavaScript development Work through several real–world examples COMPUTERS,Internet,Web Programming

LINQ Programming Take your LINQ programming skills to the top tier Resolve data format impedance mismatch with guidance from a C# expert and Microsoft MVP. LINQ Programming details cutting-edge techniques to effectively assimilate XML, SQL, ADO.NET, and unstructured data sources. Build powerful LINQ queries, handle hierarchical and relational data, use lambdas and expression trees, and develop multi-threaded applications. Get proven strategies for handling conflicts and exceptions and creating custom extension methods. Additionally, you'll learn how to create your own LINQ provider through a working example, LINQ to Twitter. Filter, order, and group code using LINQ to Objects Query relational and unstructured data with LINQ to SQL and LINQ to XML Work with ADO.NET through LINQ to DataSet Deploy object-oriented programming techniques and LINQ to Entities Read, manipulate, and create C#-based XML documents Generate DBML and external mapping files with SqlMetal Create custom lambdas, expressions, providers, and extensions Support concurrent processing and multi-threading using PLINQ Build a custom LINQ provider for working with any data source COMPUTERS,Internet,Web Programming

Excel 2007 VBA Macro Programming Develop custom Excel VBA macros Perfect for power users, this practical resource reveals how to maximize the features and functionality of Excel 2007. You'll get in-depth details on Excel VBA programming and application development followed by 21 real-world projects--complete with source code--that show you how to set up specific subroutines and functions. The book then explains how to include the subroutines in the Excel menu system and transform a set of interrelated VBA macros into an Excel add-in package. Create your own Excel 2007 VBA macros right away with help from this hands-on guide. Excel 2007 VBA Macro Programming shows you how to: Write and debug VBA code Create custom dialog boxes and buttons Maximize the Excel object model Write code to interact with a database Add functionality to your programs with API calls Insert class modules Develop custom menus for the Ribbon Animate objects in Excel Create and manipulate Pivot Tables in VBA Expand calculation and search functions Create full-fledged Excel add-ins Use VBA to work with XML files COMPUTERS,Internet,Web Programming

Programming in Python 3 Python 3 is the best version of the language yet: It is more powerful, convenient, consistent, and expressive than ever before. Now, leading Python programmer Mark Summerfield demonstrates how to write code that takes full advantage of Python 3’s features and idioms. Programming in Python 3, Second Edition, brings together all the knowledge you need to write any program, use any standard or third-party Python 3 library, and create new library modules of your own. Summerfield draws on his many years of Python experience to share deep insights into Python 3 development you won’t find anywhere else. He begins by illuminating Python’s “beautiful heartâ€: the eight key elements of Python you need to write robust, high-performance programs. Building on these core elements, he introduces new topics designed to strengthen your practical expertise–one concept and hands-on example at a time. Coverage includes: Developing in Python using procedural, objectoriented, and functional programming paradigms Creating custom packages and modules Writing and reading binary, text, and XML files, including optional compression, random access, and text and XML parsing Leveraging advanced data types, collections, control structures, and functions Spreading program workloads across multiple processes and threads Programming SQL databases and key—value DBM files Debugging techniques–and using Test Driven Development to avoid bugs in the first place Utilising Python’s regular expression mini-language and module Parsing techniques, including how to use the third-party PyParsing and PLY modules Building usable, efficient, GUI-based applications Advanced programming techniques, including generators, function and class decorators, context managers, descriptors, abstract base classes, metaclasses, coroutines, and more The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Internet,Web Programming

RESTful Web Services Cookbook While the REST design philosophy has captured the imagination of web and enterprise developers alike, using this approach to develop real web services is no picnic. This cookbook includes more than 100 recipes to help you take advantage of REST, HTTP, and the infrastructure of the Web. You'll learn ways to design RESTful web services for client and server applications that meet performance, scalability, reliability, and security goals, no matter what programming language and development framework you use. Each recipe includes one or two problem statements, with easy-to-follow, step-by-step instructions for solving them, as well as examples using HTTP requests and responses, and XML, JSON, and Atom snippets. You'll also get implementation guidelines, and a discussion of the pros, cons, and trade-offs that come with each solution. Learn how to design resources to meet various application scenarios Successfully design representations and URIs Implement the hypertext constraint using links and link headers Understand when and how to use Atom and AtomPub Know what and what not to do to support caching Learn how to implement concurrency control Deal with advanced use cases involving copying, merging, transactions, batch processing, and partial updates Secure web services and support OAuth COMPUTERS,Internet,Web Programming

Web Design DeMYSTiFieD Website DESIGN just got a whole lot EASIER! Learn the latest website development tools, techniques, and best practices. Web Design Demystified provides the hands-on help you need to get started. Written in a step-by-step format, this practical guide begins by covering website planning and designing for screens. Then, you'll learn how to build pages, use and integrate HTML and CSS, work with JavaScript, PHP, and XML, and use templates. Get tips for testing and going live as well as information on e-mail design and search engine optimization. Clear examples and concise explanations make it easy to understand the material, and end-of-chapter quizzes and a final exam help reinforce key concepts. It's a no-brainer! You'll learn how to: Create design mockups that meet the project goals Add images and multimedia with HTML Style text, lists, links, and forms with CSS Integrate HTML and CSS for layout Improve your site's search engine ranking Code HTML for e-mail Simple enough for a beginner, but challenging enough for an intermediate user, Web Design Demystified gives you the tools you need to create successful websites. COMPUTERS,Internet,Web Programming

Podcasting with Audacity Audacity is universally recognized as the number one software program for creating podcasts. Hundreds of thousands of amateurs and professionals alike have created podcasts using Audacity. This Short Cut is designed to get you podcasting as quickly as possible. The first few chapters show you how to install Audacity, plug in your microphone, record your first podcast, and get it online as quickly as possible. The following chapters cover podcasting-specific topics, such as adding background music or conducting interviews. Finally, the remaining chapters focus on how Audacity works, with lots of tips and tricks to make complicated editing even easier. COMPUTERS,Internet,Web Programming

UML Essential skills for first-time programmers! This easy-to-use book explains the fundamentals of UML. You'll learn to read, draw, and use this visual modeling language to create clear and effective blueprints for software development projects. The modular approach of this series--including drills, sample projects, and mastery checks--makes it easy to learn to use this powerful programming language at your own pace. COMPUTERS,Internet,Web Programming

Excel VBA Macro Programming Make Excel work harder and faster for you. This unique book presents sample code for more than twenty practical, high-powered Excel VBA macro applications. You’ll get all the essentials of VBA, and then explore ways to power Excel with VBA. Automate tasks, convert numbers to labels, transpose cells, add formula details, globally changes values, and much, much more. COMPUTERS,Internet,Web Programming

Estimating Software Costs Deliver bug-free software projects on schedule and within budget Get a clear, complete understanding of how to estimate software costs, schedules, and quality using the real-world information contained in this comprehensive volume. Find out how to choose the correct hardware and software tools, develop an appraisal strategy, deploy tests and prototypes, and produce accurate software cost estimates. Plus, you'll get full coverage of cutting-edge estimating approaches using Java, object-oriented methods, and reusable components. Plan for and execute project-, phase-, and activity-level cost estimations Estimate regression, component, integration, and stress tests Compensate for inaccuracies in data collection, calculation, and analysis Assess software deliverables and data complexity Test design principles and operational characteristics using software prototyping Handle configuration change, research, quality control, and documentation costs "Capers Jones' work offers a unique contribution to the understanding of the economics of software production. It provides deep insights into why our advances in computing are not matched with corresponding improvements in the software that drives it. This book is absolutely required reading for an understanding of the limitations of our technological advances." --Paul A. Strassmann, former CIO of Xerox, the Department of Defense, and NASA COMPUTERS,Internet,Web Programming

Swing From the world’s bestselling programming author Using the practical pedagogy that has made his other Beginner’s Guides so successful, Herb Schildt provides new Swing programmers with a completely integrated learning package. Perfect for the classroom or self-study, Swing: A Beginner’s Guide delivers the appropriate mix of theory and practical coding. You will be programming as early as Chapter 1. COMPUTERS,Internet,Web Programming

DOM Scripting With this second edition of the popular DOM Scripting: Web Design with JavaScript and the Document Object Model comes a modern revision to update best practices and guidelines. It includes full coverage of HTML5 in a new, dedicated chapter, and details on JavaScript libraries and how they can help your scripting. The book provides everything you'll need to start using JavaScript and the Document Object Model to enhance your web pages with client-side dynamic effects and user-controlled animation. It shows how JavaScript, HTML5, and Cascading Style Sheets (CSS) work together to create usable, standards-compliant web designs. We'll also cover cross-browser compatibility with DOM scripts and how to make sure they degrade gracefully when JavaScript isn't available. DOM Scripting: Web Design with JavaScript and the Document Object Model focuses on JavaScript for adding dynamic effects and manipulating page structure on the fly using the Document Object Model. You'll start with a crash course in JavaScript and the DOM, then move on to several real-world examples that you'll build from scratch, including dynamic image galleries and dynamic menus. You'll also learn how to manipulate web page styles using the CSS DOM, and create markup on the fly. If you want to create websites that are beautiful, dynamic, accessible, and standards-compliant, this is the book for you! COMPUTERS,Internet,Web Programming

Professional ASP.NET 4.5 in C# and VB The all-new approach for experienced ASP.NET professionals! ASP.NET is Microsoft's technology for building dynamically generated web pages from database content. Originally introduced in 2002, ASP.NET has undergone many changes in multiple versions and iterations as developers have gained a decade of experience with this popular technology. With that decade of experience, this edition of the book presents a fresh, new overhauled approach. A new focus on how to build ASP.NET sites and applications relying on field-tested reliable methods Integration of "One ASP.NET" philosophy treating ASP.NET Web Forms and ASP.NET MVC as equal tools each with their proper time and place Coverage of hot new ASP.NET 4.5 additions such as the Web API, Websockets and HTML5 & CSS3 use in layout but only to the extent that the tools themselves are practical and useful for working ASP.NET developers Professional ASP.NET 4.5 in C# and VB is an essential tool for programmers who need to be productive and build reliably performing sites with the latest ASP.NET Framework and Visual Studio. COMPUTERS,Internet,Web Programming

JavaScript The Complete Reference 3rd Edition The essential JavaScript resource—fully updated Design, debug, and publish high-performance web pages and applications using tested techniques and best practices from expert developers. The all-new edition of this comprehensive guide has been thoroughly revised and expanded to cover the latest JavaScript features, tools, and programming methods. JavaScript: The Complete Reference, Third Edition provides illustrative examples, line-by-line code samples, and practical development advice—from the core of the language to the various standard and emerging APIs supported by modern web browsers. This in-depth resource covers everything you need to know, whether you’re trying to understand the fundamentals of weak typing in JavaScript, reduce your confusion over closures, or perform common tasks like form validation or Ajax calls. Explore core JavaScript syntax and data types Investigate often confusing concepts such as weak typing and closures Use object-oriented programming the JavaScript way See what changes come from ECMAScript 5 Perform dynamic content updates using DOM methods Handle user-generated events with modern event models Modernize form handling with HTML5 and JavaScript Use the XMLHttpRequest object to create Ajax applications Control animation and multimedia content with JavaScript Generate bitmap graphics with the Canvas API Learn methods to handle the challenges of cross-browser coding Discover defensive development and error handling COMPUTERS,Internet,Web Programming

Testable JavaScript One skill that’s essential for any professional JavaScript developer is the ability to write testable code. This book shows you what writing and maintaining testable JavaScript for the client- or server-side actually entails, whether you’re creating a new application or rewriting legacy code. From methods to reduce code complexity to unit testing, code coverage, debugging, and automation, you’ll learn a holistic approach for writing JavaScript code that you and your colleagues can easily fix and maintain going forward. Testing JavaScript code is complicated. This book helps experienced JavaScript developers simply the process considerably. Get an overview of Agile, test-driven development, and behavior-driven development Use patterns from static languages and standards-based JavaScript to reduce code complexity Learn the advantages of event-based architectures, including modularity, loose coupling, and reusability Explore tools for writing and running unit tests at the functional and application level Generate code coverage to measure the scope and effectiveness of your tests Conduct integration, performance, and load testing, using Selenium or CasperJS Use tools for in-browser, Node.js, mobile, and production debugging Understand what, when, and how to automate your development processes COMPUTERS,Internet,Web Programming

Java The Definitive Java Programming Guide Fully updated for Java SE 8, Java: The Complete Reference, Ninth Edition explains how to develop, compile, debug, and run Java programs. Bestselling programming author Herb Schildt covers the entire Java language, including its syntax, keywords, and fundamental programming principles, as well as significant portions of the Java API library. JavaBeans, servlets, applets, and Swing are examined and real-world examples demonstrate Java in action. New Java SE 8 features such as lambda expressions, the stream library, and the default interface method are discussed in detail. This Oracle Press resource also offers a solid introduction to JavaFX. Coverage includes: Data types, variables, arrays, and operators Control statements Classes, objects, and methods Method overloading and overriding Inheritance Interfaces and packages Exception handling Multithreaded programming Enumerations, autoboxing, and annotations The I/O classes Generics Lambda expressions String handling The Collections Framework Networking Event handling AWT and Swing The Concurrent API The Stream API Regular expressions JavaFX JavaBeans Applets and servlets Much, much more COMPUTERS,Internet,Web Programming

HTML5 Canvas Flash is fading fast as Canvas continues to climb. The second edition of this popular book gets you started with HTML5 Canvas by showing you how to build interactive multimedia applications. You’ll learn how to draw, render text, manipulate images, and create animation—all in the course of building an interactive web game throughout the book. Updated for the latest implementations of Canvas and related HTML5 technologies, this edition includes clear and reusable code examples to help you quickly pick up the basics—whether you currently use Flash, Silverlight, or just HTML and JavaScript. Discover why HTML5 is the future of innovative web development. Create and modify 2D drawings, text, and bitmap images Use algorithms for math-based movement and physics interactions Incorporate and manipulate video, and add audio Build a basic framework for creating a variety of games Use bitmaps and tile sheets to develop animated game graphics Go mobile: build web apps and then modify them for iOS devices Explore ways to use Canvas for 3D and multiplayer game applications COMPUTERS,Internet,Web Programming

Building Database Driven Flash Applications Building Database Driven Flash Applications demonstrates how the capabilities of Flash programming can be combined with Web back-end databases directly, without an intermediate layer of programming. Techniques for utilizing Flash presentation capabilities with the power of back-end databases are covered in step-by-step detail. Techniques and complete out-of-the-box solutions that are ready to be utilized immediately are presented. Provides complete application solutions, out-of-the-box, that are ready for use by the reader Examples on multiple technology platforms, including ASP, ASP .NET, SQL Server, and Access COMPUTERS,Internet,Web Programming

High Performance Browser Networking How prepared are you to build fast and efficient web applications? This eloquent book provides what every web developer should know about the network, from fundamental limitations that affect performance to major innovations for building even more powerful browser applications—including HTTP 2.0 and XHR improvements, Server-Sent Events (SSE), WebSocket, and WebRTC. Author Ilya Grigorik, a web performance engineer at Google, demonstrates performance optimization best practices for TCP, UDP, and TLS protocols, and explains unique wireless and mobile network optimization requirements. You’ll then dive into performance characteristics of technologies such as HTTP 2.0, client-side network scripting with XHR, real-time streaming with SSE and WebSocket, and P2P communication with WebRTC. Deliver superlative TCP, UDP, and TLS performance Speed up network performance over 3G/4G mobile networks Develop fast and energy-efficient mobile applications Address bottlenecks in HTTP 1.x and other browser protocols Plan for and deliver the best HTTP 2.0 performance Enable efficient real-time streaming in the browser Create efficient peer-to-peer videoconferencing and low-latency applications with real-time WebRTC transports COMPUTERS,Internet,Web Programming

RESTful Web APIs The popularity of REST in recent years has led to tremendous growth in almost-RESTful APIs that don’t include many of the architecture’s benefits. With this practical guide, you’ll learn what it takes to design usable REST APIs that evolve over time. By focusing on solutions that cross a variety of domains, this book shows you how to create powerful and secure applications, using the tools designed for the world’s most successful distributed computing system: the World Wide Web. You’ll explore the concepts behind REST, learn different strategies for creating hypermedia-based APIs, and then put everything together with a step-by-step guide to designing a RESTful Web API. Examine API design strategies, including the collection pattern and pure hypermedia Understand how hypermedia ties representations together into a coherent API Discover how XMDP and ALPS profile formats can help you meet the Web API "semantic challenge" Learn close to two-dozen standardized hypermedia data formats Apply best practices for using HTTP in API implementations Create Web APIs with the JSON-LD standard and other the Linked Data approaches Understand the CoAP protocol for using REST in embedded systems COMPUTERS,Internet,Web Programming

Designing Evolvable Web APIs with ASP.NET Design and build Web APIs for a broad range of clients—including browsers and mobile devices—that can adapt to change over time. This practical, hands-on guide takes you through the theory and tools you need to build evolvable HTTP services with Microsoft’s ASP.NET Web API framework. In the process, you’ll learn how design and implement a real-world Web API. Ideal for experienced .NET developers, this book’s sections on basic Web API theory and design also apply to developers who work with other development stacks such as Java, Ruby, PHP, and Node. Dig into HTTP essentials, as well as API development concepts and styles Learn ASP.NET Web API fundamentals, including the lifecycle of a request as it travels through the framework Design the Issue Tracker API example, exploring topics such as hypermedia support with collection+json Use behavioral-driven development with ASP.NET Web API to implement and enhance the application Explore techniques for building clients that are resilient to change, and make it easy to consume hypermedia APIs Get a comprehensive reference on how ASP.NET Web API works under the hood, including security and testability COMPUTERS,Internet,Web Programming

Getting Started with OpenShift Intrigued by the possibilities of developing web applications in the cloud? With this concise book, you get a quick hands-on introduction to OpenShift, the open source Platform as a Service (PaaS) offering from Red Hat. You’ll learn the steps necessary to build, deploy, and host a complete real-world application on OpenShift, without having to read long, detailed explanations of the technologies involved. Though the book uses Python, application examples in other languages are available on GitHub. If you can build web applications, use a command line, and program in Java, Python, Ruby, Node.js, PHP, or Perl, you’re ready to get started. Dive in and create your first example application with OpenShift Modify the example with your own code and hot-deploy the changes Add components such as a database, task scheduling, and monitoring Use external libraries and dependencies in your application Delve into networking, persistent storage, and backup options Explore ways to adapt your team processes to use OpenShift Learn OpenShift terms, technologies, and commands Get a list of resources to learn more about OpenShift and PaaS COMPUTERS,Internet,Web Programming

Web Scalability for Startup Engineers This invaluable roadmap for startup engineers reveals how to successfully handle web application scalability challenges to meet increasing product and traffic demands. Web Scalability for Startup Engineers shows engineers working at startups and small companies how to plan and implement a comprehensive scalability strategy. It presents broad and holistic view of infrastructure and architecture of a scalable web application. Successful startups often face the challenge of scalability, and the core concepts driving a scalable architecture are language and platform agnostic. The book covers scalability of HTTP-based systems (websites, REST APIs, SaaS, and mobile application backends), starting with a high-level perspective before taking a deep dive into common challenges and issues. This approach builds a holistic view of the problem, helping you see the big picture, and then introduces different technologies and best practices for solving the problem at hand. The book is enriched with the author's real-world experience and expert advice, saving you precious time and effort by learning from others' mistakes and successes. Language-agnostic approach addresses universally challenging concepts in Web development/scalability—does not require knowledge of a particular language Fills the gap for engineers in startups and smaller companies who have limited means for getting to the next level in terms of accomplishing scalability Strategies presented help to decrease time to market and increase the efficiency of web applications COMPUTERS,Internet,Web Programming

Building Microservices Distributed systems have become more fine-grained in the past 10 years, shifting from code-heavy monolithic applications to smaller, self-contained microservices. But developing these systems brings its own set of headaches. With lots of examples and practical advice, this book takes a holistic view of the topics that system architects and administrators must consider when building, managing, and evolving microservice architectures. Microservice technologies are moving quickly. Author Sam Newman provides you with a firm grounding in the concepts while diving into current solutions for modeling, integrating, testing, deploying, and monitoring your own autonomous services. You’ll follow a fictional company throughout the book to learn how building a microservice architecture affects a single domain. Discover how microservices allow you to align your system design with your organization’s goals Learn options for integrating a service with the rest of your system Take an incremental approach when splitting monolithic codebases Deploy individual microservices through continuous integration Examine the complexities of testing and monitoring distributed services Manage security with user-to-service and service-to-service models Understand the challenges of scaling microservice architectures COMPUTERS,Internet,Web Programming

ASP.NET MVC 5 with Bootstrap and Knockout.js Bring dynamic server-side web content and responsive web design together to build websites that work and display well on any resolution, desktop or mobile. With this practical book, you’ll learn how by combining the ASP.NET MVC server-side language, the Bootstrap front-end framework, and Knockout.js—the JavaScript implementation of the Model-View-ViewModel pattern. Author Jamie Munro introduces these and other related technologies by having you work with sophisticated web forms. At the end of the book, experienced and aspiring web developers alike will learn how to build a complete shopping cart that demonstrates how these technologies interact with each other in a sleek, dynamic, and responsive web application. Build well-organized, easy-to-maintain web applications by letting ASP.NET MVC 5, Bootstrap, and Knockout.js do the heavy lifting Use ASP.NET MVC 5 to build server-side web applications, interact with a database, and dynamically render HTML Create responsive views with Bootstrap that render on a variety of modern devices; you may never code with CSS again Add Knockout.js to enhance responsive web design with snappy client-side interactions driven by your server-side web application COMPUTERS,Internet,Web Programming

Introducing JavaFX 8 Programming Develop cross-platform, feature-rich JavaFX GUI applications with expert instruction from Java guru Herb Schildt Introducing JavaFX 8 Programming provides a fast-paced introduction to JavaFX, Java’s next-generation GUI programming tool In this easy-to-read guide from Oracle Press, Java guru Herb Schildt presents the key topics and concepts that all Java developers will need to begin developing modern, dynamic JavaFX GUI applications. Of course, it’s written in the cohesive, yet concise format that has made Schildt an international best-selling programming author. Designed expressly for Java programmers, the book’s focus is on the new JavaFX API. As a result, all examples are written entirely in Java. The book begins with the fundamentals, including the general form of a JavaFX program. Readers then advance to event handling, controls, images, fonts, layers, effects, transforms, animation s (including 3D animations), menus, and more. Numerous complete examples are included that put key topics and techniques into action. Presents a cohesive, fast-paced overview of key facets of JavaFX 8 programming Sample code used in the text is available for download from the McGraw-Hill/Oracle Press Web site Written in Herb Schildt’s clear, crisp, uncompromising style that has made him the choice of millions worldwide COMPUTERS,Internet,Web Programming

Joomla! 3 SEO and Performance J oomla 3 SEO and Performance is a concise, 150-page book that helps you to build websites that dominate search engine rankings and have super-fast load times, giving your sites an increased audience. The book takes a very practical approach full of real-world examples. It does not just provide instructions, but also teaches you the logic behind what you are doing. It will make you breathe SEO while building your websites, which is the only way to success. Joomla 3 SEO and Performance starts with the Joomla core SEO possibilities. It shows how even if you are a relative newcomer to Joomla you will be able to build sites that rank high in Google without having to install complicated plugins. The remaining chapters dig much deeper, both into Joomla, and into the use of SEO plugins and extensions with a full chapter dedicated to SH404SEF, probably the best SEO extension for Joomla. In order to keep the visitors that you acquire, Joomla 3 SEO and Performance also shows you how to make your website load faster. This is achieved using Joomla core features as well as plugins. You will be stunned how easy it is to achieve massive improvements! Joomla 3 SEO & Performance: • Walks you through the Joomla SEO options, both basic and advanced • Teaches you to breathe SEO while building your websites • Teaches you how to make your websites screaming fast COMPUTERS,Internet,Web Programming

SQL This fully revised, self-paced learning tool lays out all the necessary steps to quickly and easily start writing SQL programs Thoroughly updated to reflect the most recent ANSI/ISO standard, SQL: A Beginner's Guide, Fourth Edition will get you up-and-running with SQL programming right away. Clear tutorials, annotated code, and proven instructional tools guide you to easily performing queries and modifications, building databases, creating and reviewing embedded statements, troubleshooting system- and data-related problems, and much more. You will learn how to retrieve, insert, update, and delete database data, and perform management and administrative functions. The book also covers new features, including SQL/XML and the long-awaited temporal support. Code examples are provided throughout along with notes on using them with the latest RDBMS software versions such as MySQL 5.7, SQL Server 2014, and Oracle Database 12c. Platform-neutral coverage; all skills can be applied to any database product, and any SQL version Features hands-on exercises and self-tests that reinforce basic knowledge â€Ask the Expert†sections throughout are filled with bonus information and useful tips COMPUTERS,Internet,Web Programming

Front-end Development with ASP.NET Core, Angular, and Bootstrap Stay ahead of the web evolution with elegant combination front-end development Front-End Development with ASP.NET Core, Angular, and Bootstrap is the professional's guide to fast, responsive web development. Utilizing the most popular combination of web technologies for Microsoft developers, this guide provides the latest best practices and ASP.NET MVP guidance to get you up to speed quickly. The newest ASP.NET - now called ASP.NET Core - is leaner, easier to use, and less bound to the operating system and IDE.colle, giving you the perfect opportunity to leverage third-party frameworks and libraries that provide functionalities not native to ASP.NET Core and Visual Studio. This book shows you how to integrate ASP.NET Core with Angular, Bootstrap, and similar frameworks, with a bit of jQuery Mobile, Nuget, continuous deployment, Bower dependencies, and Gulp/Grunt build systems, including development beyond Windows on Mac and Linux. With clear, concise instruction and expert insight, this guide is an invaluable resource for meeting the demands of modern web development. Combine ASP.NET Core with different tools, frameworks, and libraries Utilize third-party libraries with non-native functionalities Adopt the most up-to-date best practices for front-end development Develop flexible, responsive design sites The world of web development is evolving faster than ever before, and the trend is toward small, focused frameworks with modular capabilities. Microsoft has noticed, and upgraded ASP.NET Core to align with the latest industry expectations. Front-End Development with ASP.NET Core, Angular, and Bootstrap helps you elegantly integrate these technologies to develop the sites that the industry demands. COMPUTERS,Internet,Web Programming

Bootstrap in 24 Hours, Sams Teach Yourself Learn to create great-looking responsive web sites with Bootstrap In just 24 lessons of one hour or less, Sams Teach Yourself Bootstrap in 24 Hours helps you use the free and open source Bootstrap framework to quickly build websites that automatically reflect each user’s device and experience, without complex hand crafting. This book’s straightforward, step-by-step approach shows you how to install Bootstrap and quickly build basic sites; extend them with styles, components, and JavaScript plug-ins, and even create sophisticated designs with advanced features. In just a few hours, you’ll be using Bootstrap to bring responsive design to virtually any site. Every lesson builds on what you’ve already learned, giving you a rock-solid foundation for real-world success. Step-by-step instructions carefully walk you through the most common Bootstrap development tasks Practical, hands-on examples show you how to apply what you learn Quizzes and exercises help you test your knowledge and stretch your skills Notes and tips point out shortcuts and solution Learn how to… Download Bootstrap and integrate it into your project Quickly build your first Bootstrap site with the basic template Create beautiful and responsive site layouts with Bootstrap’s built-in grids Display more interesting text with labels, badges, panels, and wells Style tables and forms so they’re attractive, readable, and responsive Use images, media, and icons, including free Glyphicons Quickly create navigation and buttons, including dropdowns and search fields Add alignment, color, and visibility with Bootstrap’s CSS utilities Extend your site with alerts, image carousels, and other JavaScript plugins Rapidly create appealing functional prototypes Customize Bootstrap with CSS, Less, and Sass Lighten Bootstrap downloads by stripping out unnecessary features Build accessible sites Create complex designs that don’t look generic Who This Book is For Those who already have an understanding of the basics of HTML and CSS Having an understanding of JavaScript will make this book a bit easier to absorb, but it is not required because the basics of JavaScript are covered COMPUTERS,Internet,Web Programming

Learn PHP 7 This new book on PHP 7 introduces writing solid, secure, object-oriented code in the new PHP 7: you will create a complete three-tier application using a natural process of building and testing modules within each tier. This practical approach teaches you about app development and introduces PHP features when they are actually needed rather than providing you with abstract theory and contrived examples. In Learn PHP 7, programming examples take advantage of the newest PHP features, including enhanced password encryption using password_hash. This book takes a learn-by-doing approach, providing you with complete coding examples. "Do It" exercises in each chapter provide the opportunity to make adjustments to the example code. The end of chapter programming exercises allow you to develop your own applications using the algorithms demonstrated in the chapter. Each tier is logically and physically separated using object-oriented and dependency injection techniques, thus allowing independent tiers that can be updated with little or no effect on the other tiers. In addition to teaching good programming practices through OOP, there is a strong emphasis on creating secure code. As each chapter is completed, the reader is provide the opportunity to design and create an application reinforcing the concepts learned. COMPUTERS,Internet,Web Programming

Learning Ratpack Build robust, highly scalable reactive web applications with Ratpack, the lightweight JVM framework. With this practical guide, you’ll discover how asynchronous applications differ from more traditional thread-per-request systems—and how you can reap the benefits of complex non-blocking through an API that makes the effort easy to understand and adopt. Author Dan Woods—a member of the Ratpack core team—provides a progressively in-depth tour of Ratpack and its capabilities, from basic concepts to tools and strategies to help you construct fast, test-driven applications in a semantic and expressive way. Ideal for Java web developers familiar with Grails or Spring, this book is applicable to all versions of Ratpack 1.x. Configure your applications and servers to accommodate the cloud Use Ratpack testing structures on both new and legacy applications Add advanced capabilities, such as component binding, with modules Explore Ratpack’s static content generation and serving mechanisms Provide a guaranteed execution order to asynchronous processing Model data and the data access layer to build high-performance, data-driven applications Work with reactive and functional programming strategies Use distribution techniques that support continuous delivery and other deployment tactics COMPUTERS,Internet,Web Programming

Practical D3.js Your indispensable guide to mastering the efficient use of D3.js in professional-standard data visualization projects. You will learn what data visualization is, how to work with it, and how to think like a D3.js expert, both practically and theoretically. Practical D3.js does not just show you how to use D3.js, it teaches you how to think like a data scientist and work with the data in the real world. In Part One, you will learn about theories behind data visualization. In Part Two, you will learn how to use D3.js to create the best charts and layouts. Uniquely, this book intertwines the technical details of D3.js with practical topics such as data journalism and the use of open government data. Written by leading data scientists Tarek Amr and Rayna Stamboliyska, this book is your guide to using D3.js in the real world – add it to your library today. You Will Learn: How to think like a data scientist and present data in the best way What structure and design strategies you can use for compelling data visualization How to use data binding, animations and events, scales, and color pickers How to use shapes, path generators, arcs and polygons Who This Book is For: This book is for anyone who wants to learn to master the use of D3.js in a practical manner, while still learning the important theoretical aspects needed to enable them to work with their data in the best possible way. COMPUTERS,Internet,Web Programming

OpenShift for Developers Keen to build web applications for the cloud? Get a quick hands-on introduction to OpenShift, the open source Platform as a Service (PaaS) offering from Red Hat. With this practical guide, you’ll learn the steps necessary to build, deploy, and host a complete real-world application on OpenShift without having to slog through long, detailed explanations of the technologies involved. OpenShift enables you to use Docker application containers and the Kubernetes cluster manager to automate the way you create, ship, and run applications. Through the course of the book, you’ll learn how to use OpenShift and the Wildfly application server to build and then immediately deploy a Java application online. Learn about OpenShift’s core technology, including Docker-based containers and Kubernetes Use a virtual machine with OpenShift installed and configured on your local environment Create and deploy your first application on the OpenShift platform Add language runtime dependencies and connect to a database Trigger an automatic rebuild and redeployment when you push changes to the repository Get a working environment up in minutes with application templates Use commands to check and debug your application Create and build Docker-based images for your application COMPUTERS,Internet,Web Programming

Learning Rails 5 If you’re a web developer or designer ready to learn Ruby on Rails, this hands-on guide is the ideal way to get started. Rather than toss you into the middle of the framework’s Model-View-Controller architecture, as many books do, Learning Rails 5 begins with the foundations of the Web you already know. You’ll learn how to create something visible with Rails’ view layer before diving into the more difficult inner layers: the database models and controller code. All you need to begin your Rails journey is HTML experience. Each chapter includes exercises and review questions to test your understanding as you go. Present content by building an application with a basic view and a simple controller Build forms and process their results, progressing from simple to more complex Use Rails scaffolding and REST to build effective applications quickly Connect forms to models and create code that maps directly to database structures Build applications that combine data from multiple tables Use migrations to track changes to your database over time Add common elements such as sessions, cookies, and authentication COMPUTERS,Internet,Web Programming

Beginning Laravel Learn about dependency injection, interfaces, service providers, SOLID design, and more with practical and real-world code examples. This book covers everything you need to get started in application development with Laravel 5.3. Beginning Laravel covers features such as method injection, contracts, and authentication. After reading this book, you can develop any application using Laravel 5. It details all you need to know, including the model-view-controller pattern, SQLite databases, routing, authorization, and building CRUD applications. What You Will Learn Work with the new Laravel framework and its new features Develop web applications with Laravel Absorb the concepts of authentication and database migration Manage databases with Eloquent ORM Use middleware, contracts, and facades Who This Book Is For Readers who are new to Laravel development. COMPUTERS,Internet,Web Programming

Pro MERN Stack Assemble the complete stack required to build a modern web app using React: MongoDB (a NoSQL database) and Express (a framework for web application servers), which runs on Node (JavaScript on the server side), complement React very nicely. This book will also cover many other tools that go into building a complete web application: React Router, React-Bootstrap, Redux, Babel, and webpack. Though the primary focus of Pro MERN Stack is to equip you with all that is required to build a full-fledged web application, a large portion of the book will be devoted to React. The popular MEAN (MongoDB, Express, AngularJS, Node) stack introduced Single Page Apps (SPAs) and front-end Model-View-Controller (MVC) as new and efficient paradigms. But it has its shortcomings such as lack of support for SEO friendly server-side rendering and being too prescriptive by being a framework. Facebook's React is a technology that competes indirectly with AngularJS. It is not a full-fledged MVC framework. It is a JavaScript library for building user interfaces (in some sense the View part). Yet, it is possible to build a web app by replacing AngularJS with React – hence the term MERN stack. What You Will Learn Discover the details of React, the React Way, and how to get the maximum out of this library See the basics of MongoDB, Express, and Node, enough to build a web app Work with other tools complementary to React, including React-Bootstrap and React Router Use the tools required to build JavaScript based SPAs Tie all the components together to build a complete web app. Who This Book Is For Developers and architects who have prior experience in any web app stack other than the MERN stack will find the book useful to learn about this modern stack. Prior knowledge of JavaScript, HTML, and CSS is required. COMPUTERS,Internet,Web Programming

Getting Started with Varnish Cache How long does it take for your website to load? Web performance is just as critical for small and medium-sized websites as it is for massive websites that receive tons of hits. Before you pour money and time into rewriting your code or replacing your infrastructure, first consider a reverse-caching proxy server like Varnish. With this practical book, you’ll learn how Varnish can give your website or API an immediate performance boost. Varnish mimicks the behavior of your webserver, caches its output in memory, and serves the result directly to clients without having to access your webserver. If you’re a web developer familiar with HTTP, this book helps you master Varnish basics, so you can get up and running in no time. You’ll learn how to use the Varnish Configuration Language and HTTP best practices to achieve faster performance and a higher hit rate. Understand how Varnish helps you gain optimum web performance Use HTTP to improve the cache-ability of your websites, web applications, and APIs Properly invalidate your cache when the origin data changes Optimize access to your backend servers Avoid common mistakes when using Varnish in the wild Use logging and debugging tools to examine the behavior of Varnish COMPUTERS,Internet,Web Programming

Pro HTML5 with CSS, JavaScript, and Multimedia Get ahead in HTML5, including markup, styling, and scripting, with many practical examples and best practice insights. You’ll quickly understand HTML5 markup elements and when to use them, and then apply the latest CSS3 features to create amazing web pages. Pro HTML5 with CSS, JavaScript, and Multimedia teaches the fundamentals of client-side scripting and covers the immense functionality available with HTML5. Learn to use JavaScript to create web applications that are dynamic and interactive, and add advanced features, including audio, video, SVG, and drag and drop capabilities. Using practical hands-on demonstrations you will access a larger set of technologies to create more diverse and powerful websites and applications. What You'll Learn How, and when, to use all the HTML5 markup tags Use CSS3 features to simplify website design Master JavaScript fundamentals and advanced features Leverage the native browser support for Geolocation, IndexedDB, and drag and drop capabilities Who This Book Is For Web developers and designers who want to increase their HTML5 skills to create modern interactive websites COMPUTERS,Internet,Web Programming

Front-End Web Development Front-end development targets the browser, putting your applications in front of the widest range of users regardless of device or operating system. This guide will give you a solid foundation for creating rich web experiences across platforms. Focusing on JavaScript, CSS3, and HTML5, this book is for programmers with a background in other platforms and developers with previous web experience who need to get up to speed quickly on current tools and best practices. Each chapter of this book will guide you through essential concepts and APIs as you build a series of applications. You will implement responsive UIs, access remote web services, build applications with Ember.js, and more. You will also debug and test your code with cutting-edge development tools and harness the power of Node.js and the wealth of open-source modules in the npm registry. After working through the step-by-step example projects, you will understand how to build modern websites and web applications. COMPUTERS,Internet,Web Programming

Ruby on Rails Tutorial This is the eBook of the printed book and may not include any media, website access codes, or print supplements that may come packaged with the bound book. Used by sites as varied as Twitter, GitHub, Disney, and Airbnb, Ruby on Rails is one of the most popular frameworks for developing web applications, but it can be challenging to learn and use. Whether you’re new to web development or new only to Rails, Ruby on Rails™ Tutorial, Fourth Edition, is the solution. Best-selling author and leading Rails developer Michael Hartl teaches Rails by guiding you through the development of three example applications of increasing sophistication. The tutorial’s examples focus on the general principles of web development needed for virtually any kind of website. The updates to this edition include full compatibility with Rails 5, a division of the largest chapters into more manageable units, and a huge number of new exercises interspersed in each chapter for maximum reinforcement of the material. This indispensable guide provides integrated tutorials not only for Rails, but also for the essential Ruby, HTML, CSS, and SQL skills you need when developing web applications. Hartl explains how each new technique solves a real-world problem, and then he demonstrates it with bite-sized code that’s simple enough to understand, yet novel enough to be useful. Whatever your previous web development experience, this book will guide you to true Rails mastery. This book will help you Install and set up your Rails development environment, including pre-installed integrated development environment (IDE) in the cloud Go beyond generated code to truly understand how to build Rails applications from scratch Learn testing and test-driven development (TDD) Effectively use the Model-View-Controller (MVC) pattern Structure applications using the REST architecture Build static pages and transform them into dynamic ones Master the Ruby programming skills all Rails developers need Create high-quality site layouts and data models Implement registration and authentication systems, including validation and secure passwords Update, display, and delete users Upload images in production using a cloud storage service Implement account activation and password reset, including sending email with Rails Add social features and microblogging, including an introduction to Ajax Record version changes with Git and create a secure remote repository at Bitbucket Deploy your applications early and often with Heroku COMPUTERS,Internet,Web Programming

JavaScript Absolute Beginner's Guide This book is the fastest way to learn JavaScript and use it together with CSS3 and HTML5 to create powerful web and mobile experiences. Students will learn how to do what they want, the way they want, one incredibly easy step at a time. JavaScript has never been this simple! The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Internet,Web Programming

Building Progressive Web Apps Move over native apps. New progressive web apps have capabilities that will soon make you obsolete. With this hands-on guide, web developers and business execs will learn how—and why—to develop web apps that take advantage of features that have so far been exclusive to native apps. Features that include fast load times, push notifications, offline access, homescreen shortcuts, and an entirely app-like experience. By leveraging the latest browser APIs, progressive web apps combine all of the benefits of native apps, while avoiding their issues. Throughout the book, author Tal Ater shows you how to improve a simple website for the fictional Gotham Imperial Hotel into a modern progressive web app. Plus: Understand how service workers work, and use them to create sites that launch in an instant, regardless of the user’s internet connection Create full-screen web apps that launch from the phone's homescreen just like native apps Re-engage users with push notifications, even days after they have left your site Embrace offline-first and build web apps that gracefully handle loss of connectivity Explore new UX opportunities and challenges presented by progressive web apps COMPUTERS,Internet,Web Programming

Java Up-to-Date, Essential Java Programming Skills—Made Easy! Supplement for key JDK 10 new features available from book's Downloads & Resources page at OraclePressBooks.com. Fully updated for Java Platform, Standard Edition 9 (Java SE 9), Java: A Beginner’s Guide, Seventh Edition, gets you started programming in Java right away. Bestselling programming author Herb Schildt begins with the basics, such as how to create, compile, and run a Java program. He then moves on to the keywords, syntax, and constructs that form the core of the Java language. The book also covers some of Java’s more advanced features, including multithreaded programming, generics, lambda expressions, Swing, and JavaFX. This practical Oracle Press guide features details on Java SE 9’s innovative new module system, and, as an added bonus, it includes an introduction to JShell, Java’s new interactive programming tool. Designed for Easy Learning: • Key Skills and Concepts—Chapter-opening lists of specific skills covered in the chapter• Ask the Expert—Q&A sections filled with bonus information and helpful tips• Try This—Hands-on exercises that show you how to apply your skills• Self Tests—End-of-chapter quizzes to reinforce your skills• Annotated Syntax—Example code with commentary that describes the programming techniques being illustrated COMPUTERS,Internet,Web Programming

Beginning Adobe Experience Design Render high quality designs and interactive prototypes of web sites and mobile apps using Adobe XD's powerful drawing and layout tools. This book provides an in-depth look at XD and shows you how to quickly get up-to-speed to simplify these processes with intuitive design tools and a powerful prototyping function. Since the advent of the web, designers have struggled with the need to create functioning demo prototypes of their layouts and designs without an extensive amount of code for their clients. The dawn of mobile apps, which are exponentially more difficult to mock-up and demonstrate, has only intensified this problem. Beginning Adobe Experience Design resolves this for you with it's easy-to-use approach to leveraging XD. What You'll Learn Create links and interactivity to see just how your site or app will function Preview your site or prototype live in a web browser or your mobile device Use Adobe XD on both Mac and Windows Who This Book Is For Web front-end designers and user experience professionals and educators interested in teaching the tool COMPUTERS,Internet,Web Programming

Web Coding & Development All-in-One For Dummies Speak the languages that power the web With more high-paying web development jobs opening every day, people with coding and web/app building skills are having no problems finding employment. If you’re a would-be developer looking to gain the know-how to build the interfaces, databases, and other features that run modern websites, web apps, and mobile apps, look no further. Web Coding & Development All-in-One For Dummies is your go-to interpreter for speaking the languages that handle those tasks. Get started with a refresher on the rules of coding before diving into the languages that build interfaces, add interactivity to the web, or store and deliver data to sites. When you're ready, jump into guidance on how to put it all together to build a site or create an app. Get the lowdown on coding basics Review HTML and CSS Make sense of JavaScript, jQuery, PHP, and MySQL Create code for web and mobile apps There’s a whole world of opportunity out there for developers—and this fast-track boot camp is here to help you acquire the skills you need to take your career to new heights! COMPUTERS,Internet,Web Programming

Java The Definitive Java Programming Guide Supplement for key JDK 10 new features available from book's Downloads & Resources page at OraclePressBooks.com. Fully updated for Java SE 9, Java: The Complete Reference, Tenth Edition explains how to develop, compile, debug, and run Java programs. Bestselling programming author Herb Schildt covers the entire Java language, including its syntax, keywords, and fundamental programming principles. You'll also find information on key portions of the Java API library, such as I/O, the Collections Framework, the stream library, and the concurrency utilities. Swing, JavaFX, JavaBeans, and servlets are examined and numerous examples demonstrate Java in action. Of course, the new module system added by Java SE 9 is discussed in detail. This Oracle Press resource also offers an introduction to JShell, Java’s new interactive programming tool. Coverage includes: • Data types, variables, arrays, and operators • Control statements • Classes, objects, and methods • Method overloading and overriding • Inheritance • Interfaces and packages • Exception handling • Multithreaded programming • Enumerations, autoboxing, and annotations • The I/O classes • Generics • Lambda expressions • Modules • String handling • The Collections Framework • Networking • Event handling • AWT • Swing and JavaFX • The Concurrent API • The Stream API • Regular expressions • JavaBeans • Servlets • Much, much more Code examples in the book are available for download at www.OraclePressBooks.com. TAG: For a complete list of Oracle Press titles, visit www.OraclePressBooks.com. COMPUTERS,Internet,Web Programming

PHP 7 Zend Certification Study Guide Improve your programming knowledge and become Zend Certified. This book closely follows the ZCE2017-PHP exam syllabus and adds important details that help candidates to prepare for the test. Zend Certification is an industry recognized standard for PHP engineers. It is very difficult to pass the examination without extensive preparation. Unlike other books on PHP, this book is very focused on reaching industry standards.The Zend examination syllabus is comprised of three focus areas and a number of additional topics. This book explains the structure of the examination and then addresses each of the topics for PHP 7. A short quiz follows each chapter to help identify gaps in your knowledge. PHP 7 Zend Certification Study Guide also contains a practice test containing 70 questions from the entire syllabus to use when reviewing for your exams. The book provides original code examples throughout and every php featured is explained clearly with examples and uses an efficient way to describe the most important details of the particular feature. What You'll Learn Brush up your knowledge of PHP programming Explore new features of the PHP v7.1 Build a secure configuration of your server Review strategies and tips to get Zend Certified Who this Book Is For Intermediate PHP programmers with two or three years of experience who are appearing for the Zend certification exams and programmers who are proficient in other languages, but want a quick reference book to dive into PHP. COMPUTERS,Internet,Web Programming

ASP.NET Core 2 and Angular 5 Develop a simple, yet fully-functional modern web application using ASP.NET Core MVC, Entity Framework and Angular 5. About This Book Based on the best-selling book ASP.NET Core and Angular 2 Easily build a complete single page application with two of the most impressive frameworks in modern development, ASP.NET Core and Angular Bring together the capabilities and features of both Angular 5 and ASP.NET Core 2 for full stack development Discover a comprehensive approach to building your next web project-From managing data, to application design, through to SEO optimization and security Who This Book Is For This book is for seasoned ASP.NET developers who already know about ASP.NET Core and Angular in general, but want to know more about them and/or understand how to blend them together to craft a production-ready SPA. What You Will Learn Use ASP.NET Core to its full extent to create a versatile backend layer based on RESTful APIs Consume backend APIs with the brand new Angular 5 HttpClient and use RxJS Observers to feed the frontend UI asynchronously Implement an authentication and authorization layer using ASP.NET Identity to support user login with integrated and third-party OAuth 2 providers Configure a web application in order to accept user-defined data and persist it into the database using server-side APIs Secure your application against threats and vulnerabilities in a time efficient way Connect different aspects of the ASP. NET Core framework ecosystem and make them interact with each other for a Full-Stack web development experience In Detail Become fluent in both frontend and backend web development by combining the impressive capabilities of ASP.NET Core 2 and Angular 5 from project setup right through the deployment phase. Full-stack web development means being able to work on both the frontend and backend portions of an application. The frontend is the part that users will see or interact with, while the backend is the underlying engine, that handles the logical flow: server configuration, data storage and retrieval, database interactions, user authentication, and more. Use the ASP.NET Core MVC framework to implement the backend with API calls and server-side routing. Learn how to put the frontend together using top-notch Angular 5 features such as two-way binding, Observables, and Dependency Injection, build the Data Model with Entity Framework Core, style the frontend with CSS/LESS for a responsive and mobile-friendly UI, handle user input with Forms and Validators, explore different authentication techniques, including the support for third-party OAuth2 providers such as Facebook, and deploy the application using Windows Server, SQL Server, and the IIS/Kestrel reverse proxy. Style and approach More than just a technical manual, this guide takes you through the most important technical facets of developing with these two hugely popular frameworks and then demonstrates how to put those skills into practice. It's a book that recognizes that what's really important is the end product. COMPUTERS,Internet,Web Programming

Introducing JavaScript Game Development Learn to build a fully-functional 2D game inspired by the 1979 Atari classic, Asteroids, using just HTML5, CSS and JavaScript. Developing games has never been easier than it is now. New web technology allows even beginner developers to turn their hand to game development. Developed from an undergraduate course module, Introducing JavaScript Game Development teaches each new technology as it is introduced so can be followed by enthusiastic beginners as well as intermediate coders. You will learn how to work with HTML5 and the canvas element, how to understand paths, how to draw to a design and create your spaceship and asteroids. You’ll then move on to animating your game, and finally building. You will work step-by-step through the game design process, starting with only what is necessary to complete each step, and refactoring the code as necessary along the way, reflecting the natural progression that code follows in the real world. Each chapter is designed to take your code base to the next level and to add to your skills. After completing the examples in this book you will have the tools necessary to build your own, high-quality games. Make the process of creating object-oriented 2D games more fun and more productive and get started on your game development journey. COMPUTERS,Internet,Web Programming

Web Scraping with Python If programming is magic then web scraping is surely a form of wizardry. By writing a simple automated program, you can query web servers, request data, and parse it to extract the information you need. The expanded edition of this practical book not only introduces you web scraping, but also serves as a comprehensive guide to scraping almost every type of data from the modern web. Part I focuses on web scraping mechanics: using Python to request information from a web server, performing basic handling of the server’s response, and interacting with sites in an automated fashion. Part II explores a variety of more specific tools and applications to fit any web scraping scenario you’re likely to encounter. Parse complicated HTML pages Develop crawlers with the Scrapy framework Learn methods to store data you scrape Read and extract data from documents Clean and normalize badly formatted data Read and write natural languages Crawl through forms and logins Scrape JavaScript and crawl through APIs Use and write image-to-text software Avoid scraping traps and bot blockers Use scrapers to test your website COMPUTERS,Internet,Web Programming

Mastering Blockchain Learn about cryptography and cryptocurrencies, so you can build highly secure, decentralized applications and conduct trusted in-app transactions. About This Book Get to grips with the underlying technical principles and implementations of blockchain Build powerful applications using Ethereum to secure transactions and create smart contracts Explore cryptography, mine cryptocurrencies, and solve scalability issues with this comprehensive guide Who This Book Is For This book will appeal to those who wish to build fast, highly secure, transactional applications. It targets people who are familiar with the concept of blockchain and are comfortable with a programming language. What You Will Learn Master the theoretical and technical foundations of the blockchain technology Understand the concept of decentralization, its impact, and its relationship with blockchain technology Master how cryptography is used to secure data - with practical examples Grasp the inner workings of blockchain and the mechanisms behind bitcoin and alternative cryptocurrencies Understand the theoretical foundations of smart contracts Learn how Ethereum blockchain works and how to develop decentralized applications using Solidity and relevant development frameworks Identify and examine applications of the blockchain technology - beyond currencies Investigate alternative blockchain solutions including Hyperledger, Corda, and many more Explore research topics and the future scope of blockchain technology In Detail A blockchain is a distributed ledger that is replicated across multiple nodes and enables immutable, transparent and cryptographically secure record-keeping of transactions. The blockchain technology is the backbone of cryptocurrencies, and it has applications in finance, government, media and almost all other industries. Mastering Blockchain, Second Edition has been thoroughly updated and revised to provide a detailed description of this leading technology and its implementation in the real world. This book begins with the technical foundations of blockchain technology, teaching you the fundamentals of distributed systems, cryptography and how it keeps data secure. You will learn about the mechanisms behind cryptocurrencies and how to develop applications using Ethereum, a decentralized virtual machine. You will also explore different other blockchain solutions and get an introduction to business blockchain frameworks under Hyperledger, a collaborative effort for the advancement of blockchain technologies hosted by the Linux Foundation. You will also be shown how to implement blockchain solutions beyond currencies, Internet of Things with blockchain, blockchain scalability, and the future scope of this fascinating and powerful technology. Style and approach This comprehensive guide allows you to build smart blockchain applications and explore the power of this database. The book will let you quickly brush up on the basics of the blockchain database, followed by advanced implementations of blockchain in currency, smart contracts, decentralization, and so on. COMPUTERS,Internet,Web Programming

Learn Node.js by Building 6 Projects. This is an advanced, practical guide to harnessing the power of Node.js by creating 6 full-scale real-world projects, from creating a chat application to an eLearning system. About This Book Develop scalable and lightweight applications using Node.js Learn how to interface Node.js with other popular technologies such as MongoDB, MySQL, and more Your companion to master the Node ecosystem through six real-world projects Who This Book Is For If you are a web developer or a student who wants to learn about Node.js in a hands-on manner, this book will be perfect for you. A basic understanding of HTML, JavaScript, and some front-end programming experience is required. What You Will Learn Create powerful applications using Node.js Build scalable and lightweight web applications Use the Express Framework to build web applications Understand the coding principles behind practical web applications Understand the concepts of network programming Use Node.js with other technologies including Kickstart and Heroku Use Node with database technologies Cassandra and MongoDB In Detail With its event-driven architecture and efficient web services capabilities, more and more companies are building their entire infrastructure around Node.js. Node has become a de facto part of web development that any serious developer needs to master. This book includes six Node.js projects that gradually increase in complexity. You'll start by building a simple web server and create a basic website. You will then move to create the login system, blog system, chat system, and e-learning system. By creating and following the example projects in this book, you'll improve your Node.js skills through practical working projects, and you'll learn how to use Node.js with many other useful technologies, such as ExpressJS, Kickstart, and Heroku. Style and approach This book adopts a unique, learn-as-you-do approach as you build on your understanding of Node.js progressively with each project. It contains six advanced Node.js projects. This book is designed so that implementing each project will empower you with a unique skillset, and enable you to implement the next project more confidently. COMPUTERS,Internet,Web Programming

CSS Pocket Reference When you’re working with CSS and need an answer now, this concise yet comprehensive quick reference provides the essential information you need. Revised and updated for CSS3, this fifth edition is ideal for intermediate to advanced web designers and developers. You’ll find a short introduction to the key concepts of CSS and alphabetical summaries of CSS selectors and properties. You’ll also discover information on new properties, including grid, flexbox, clipping, masking, and compositing. Quickly find the information you need Explore CSS concepts, values, selectors and queries, and properties Learn how new features complement and extend your CSS practices Discover new properties including animations, grid, flexbox, masking, filtering, and compositing in this new edition COMPUTERS,Internet,Web Programming

Learning PHP, MySQL & JavaScript Build interactive, data-driven websites with the potent combination of open source technologies and web standards, even if you have only basic HTML knowledge. In this update to this popular hands-on guide, you’ll tackle dynamic web programming with the latest versions of today’s core technologies: PHP, MySQL, JavaScript, CSS, HTML5, and key jQuery libraries. Web designers will learn how to use these technologies together and pick up valuable web programming practices along the way—including how to optimize websites for mobile devices. At the end of the book, you’ll put everything together to build a fully functional social networking site suitable for both desktop and mobile browsers. Explore MySQL, from database structure to complex queries Use the MySQLi extension, PHP’s improved MySQL interface Create dynamic PHP web pages that tailor themselves to the user Manage cookies and sessions and maintain a high level of security Enhance the JavaScript language with jQuery and jQuery mobile libraries Use Ajax calls for background browser-server communication Style your web pages by acquiring CSS2 and CSS3 skills Implement HTML5 features, including geolocation, audio, video, and the canvas element Reformat your websites into mobile web apps COMPUTERS,Internet,Web Programming

Angular This book will demystify Angular as a framework, as well as provide clear instructions and examples on how to get started with writing scalable Angular applications. Angular: Up & Running covers most of the major pieces of Angular, but in a structured manner that is generally used in hands-on training. Each chapter takes one concept, and use examples to cover how it works. Problems to work on (with solutions) at the end of each chapter reinforce the learnings of each chapter and allow readers to really get hands-on with Angular. COMPUTERS,Internet,Web Programming

REST API Development with Node.js Manage and understand the full capabilities of successful REST development. REST API development is a hot topic in the programming world, but not many resources exist for developers to really understand how you can leverage the advantages. This completely updated second edition provides a brief background on REST and the tools it provides (well known and not so well known), then explains how there is more to REST than just JSON and URLs. You will learn about the maintained modules currently available in the npm community, including Express, Restify, Vatican, and Swagger. Finally you will code an example API from start to finish, using a subset of the tools covered. The Node community is currently flooded with modules; some of them are published once and never updated again - cluttering the entire universe of packages. Pro REST API Development with Node.js shines light into that black hole of modules for the developers trying to create an API. Understand REST API development with Node.js using this book today. What You'll Learn Understand how REST and API development mix up with Node.js Create a scalable, technology agnostic, and uniform interface Prepare your services to be consumed by your clients Test and deploy your API Review troubleshooting techniques Who This Book Is For Any Node.js developer who wants to fully understand REST API development. Beginner and Intermediate Node.js developers who are looking to fully understand how to create RESTful microservices. COMPUTERS,Internet,Web Programming

Getting to Know Vue.js Learn how to render lists of items without repeating your code structure and how to work with conditional rendering items and event handling. Containing all you need to know to get started with Vue.js, this book will take you through using build tools (transpile to ES5), creating custom components, state management, and routers. With Getting to Know Vue.js, you'll see how to combine reusable code with custom components, allowing you to create snippets of reusable code to suit your specific business needs. You'll also explore how to use Single File Components and the Vue.js Command Line Interface (CLI) to build components in a single file and add in build tools as you see fit. Getting started with a new Single Page Application (SPA) JavaScript framework can be an overwhelming task, but Vue.js makes this daunting task simple and easy to learn, allowing you to start implementing business needs with just a script reference to the library and the custom JavaScript required for your use case. Starting with a little reference and a handful of lines of custom JavaScript, you will have a complete Single Page Application before you know it. What You'll Learn Examine Vue.js templating syntax Work with binding methods Manage the state of your app by comparing your options of building a data store Adapt the more robust options compatible with Vue.js Review different router options, including creating your own router, using the Vue-router and using Page.js. Who This Book Is For Software developers with an understanding of HTML, CSS and JavaScript; prior understanding of a Single Page Application framework would be useful but not essential. COMPUTERS,Internet,Web Programming

Pro Vue.js 2 Explore Vue.js to take advantage of the capabilities of modern browsers and devices using the fastest-growing framework for building dynamic JavaScript applications. You will work with the power of the Model-View-Controller (MVC) pattern on the client, creating a strong foundation for complex and rich web apps. Best-selling author Adam Freeman explains how to get the most from Vue.js 2. He begins by describing the MVC pattern and the benefits it can offer. He then shows you how to use Vue.js in your projects, starting from the nuts and bolts and building up to the most advanced and sophisticated features, going in-depth to give you the knowledge you need. Chapters include common problems and how to avoid them. What You'll Learn Gain a solid architectural understanding of the MVC pattern Create rich and dynamic web app clients using Vue.js 2 Extend and customize Vue.js Test your Vue.js projects Who This Book Is For JavaScript developers who want to use Vue.js to create dynamic client-side applications COMPUTERS,Internet,Web Programming

Java A practical introduction to Java programming—fully revised for long-term support release Java SE 11 Thoroughly updated for Java Platform Standard Edition 11, this hands-on resource shows, step by step, how to get started programming in Java from the very first chapter. Written by Java guru Herbert Schildt, the book starts with the basics, such as how to create, compile, and run a Java program. From there, you will learn essential Java keywords, syntax, and commands. Java: A Beginner's Guide, Eighth Edition covers the basics and touches on advanced features, including multithreaded programming, generics, Lambda expressions, and Swing. Enumeration, modules, and interface methods are also clearly explained. This Oracle Press guide delivers the appropriate mix of theory and practical coding necessary to get you up and running developing Java applications in no time. • Clearly explains all of the new Java SE 11 features • Features self-tests, exercises, and downloadable code samples • Written by bestselling author and leading Java authority Herbert Schildt COMPUTERS,Internet,Web Programming

Building Your Online Store With WordPress and WooCommerce Teaches you all about e-commerce and how to create your own online shop using WordPress and WooCommerce. Regardless of a business’s size, e-commerce helps level the playing field, increases a business’s exposure, allows companies to reach customers globally, and streamlines the fulfillment process. In the past, e-commerce websites were expensive, technically difficult, and time-consuming to create but not anymore.WordPress and WooCommerce together are a complete e-commerce solution that can be used to sell both physical and digital products online. You'll learn how to install WordPress and how to plan your e-commerce solution with WooCommerce as well as install, create, secure, test, and market a sample online store. Save time and money by planning your own e-commerce strategy without paying expensive consultants. Increase your brand and products’ or services’ exposure to your target customers, and increase sales by offering target customers the ability to purchase products online as well as reach potential customers globally. What You'll Learn Plan an effective ecommerce strategy Choose a payment merchant and which products or services to sell online Secure your store and add products, descriptions, categories, images, and prices Maintain and expand your online store with WooCommerce extensions Who This Book Is For Ideal for entrepreneurs and small business owners who know their products (physical or digital), but lack the technical background and skills to setup an online store to sell their products and services. COMPUTERS,Internet,Web Programming

Practical Node.js Learn how to build a wide range of scalable real-world web applications using a professional development toolkit. If you already know the basics of Node.js, now is the time to discover how to bring it to production level by leveraging its vast ecosystem of packages.With this book, you'll work with a varied collection of standards and frameworks and see how all those pieces fit together. Practical Node.js takes you from installing all the necessary modules to writing full-stack web applications. You'll harness the power of the Express.js and Hapi frameworks, the MongoDB database with Mongoskin and Mongoose. You'll also work with Pug and Handlebars template engines, Stylus and LESS CSS lanaguages, OAuth and Everyauth libraries, and the Socket.IO and Derby libraries, and everything in between. This exciting second edition is fully updated for ES6/ES2015 and also covers how to deploy to Heroku and AWS, daemonize apps, and write REST APIs. You’ll build full-stack real-world Node.js apps from scratch, and also discover how to write your own Node.js modules and publish them on NPM. Fully supported by a continuously updated source code repository on GitHub and with full-color code examples, learn what you can do with Node.js and how far you can take it! What You'll Learn Manipulate data from the mongo console Use the Mongoskin and Mongoose MongoDB libraries Build REST API servers with Express and Hapi Deploy apps to Heroku and AWS Test services with Mocha, Expect and TravisCI Implement a third-party OAuth strategy with Everyauth Web developers who have some familiarity with the basics of Node.js and want to learn how to use it to build apps in a professional environment. COMPUTERS,Internet,Web Programming

Java The Definitive Java Programming Guide Fully updated for Java SE 11, Java: The Complete Reference, Eleventh Edition explains how to develop, compile, debug, and run Java programs. Best-selling programming author Herb Schildt covers the entire Java language, including its syntax, keywords, and fundamental programming principles. You’ll also find information on key portions of the Java API library, such as I/O, the Collections Framework, the stream library, and the concurrency utilities. Swing, JavaBeans, and servlets are examined and numerous examples demonstrate Java in action. Of course, the very important module system is discussed in detail. This Oracle Press resource also offers an introduction to JShell, Java’s interactive programming tool. Best of all, the book is written in the clear, crisp, uncompromising style that has made Schildt the choice of millions worldwide. Coverage includes: • Data types, variables, arrays, and operators • Control statements • Classes, objects, and methods • Method overloading and overriding • Inheritance • Local variable type inference • Interfaces and packages • Exception handling • Multithreaded programming • Enumerations, autoboxing, and annotations • The I/O classes • Generics • Lambda expressions • Modules • String handling • The Collections Framework • Networking • Event handling • AWT • Swing • The Concurrent API • The Stream API • Regular expressions • JavaBeans • Servlets • Much, much more Code examples in the book are available for download at www.OraclePressBooks.com. COMPUTERS,Internet,Web Programming

Decoupled Drupal in Practice Gain a clear understanding of the most important concepts in the decoupled CMS landscape. You will learn how to architect and implement decoupled Drupal architectures across the stack—from building the back end and designing APIs to integrating with front-end technologies. You'll also review presenting data through consumer applications in widely adopted technologies such as Angular, Ember, React, and Vue.js. Featuring a foreword by Drupal founder and project lead Dries Buytaert, the first part of this book chronicles the history of the CMS and the server–client divide, analyzes the risks and rewards of decoupled CMS architectures, and presents architectural patterns. From there, the book explores the core and contributed landscape for decoupled Drupal, authentication mechanisms, and the surrounding tooling ecosystem before delving into consumer implementations in a variety of technologies. Finally, a series of chapters on advanced topics feature the Drupal REST plugin system, schemas and generated documentation, and caching. Several projects point to a decoupled future for Drupal, including the Contenta CMS and work to modernize Drupal's JavaScript using React. Begin learning about these and other exciting developments with Decoupled Drupal today. What You’ll Learn Evaluate the risks and rewards of decoupled Drupal and classify its architectures Authenticate requests to Drupal using OAuth, JWT, and Basic Authentication Consume and manipulate Drupal content via API through HTTP requests Integrate with other consumer applications for native mobile and desktop as well as set-top boxes (Roku, Apple TV, Samsung TV) Add new resources to Drupal's REST API using the REST plugin system Generate API documentation that complies with the OpenAPI (Swagger) standard Who This Book Is For Those with some exposure to CMSes like WordPress and Drupal and those who wish to follow along with JavaScript application development will benefit. A familiarity with API-first or services-oriented architectures is helpful but not presumed. COMPUTERS,Internet,Web Programming

Pro React 16 Use the enormously popular React framework to build dynamic JavaScript applications that take advantage of the capabilities of modern browsers and devices. You will learn how React brings the power of strong architecture and responsive data to the client, providing the foundation for complex and rich user interfaces. Best-selling author Adam Freeman explains how to get the most from React. He begins by describing the React architecture and the benefits it offers and then shows you how to use React and its associated tools and libraries in your projects, starting from the nuts and bolts and building up to the most advanced and sophisticated features, going in-depth to give you the knowledge you need. Each topic is presented clearly and concisely. Chapters include common problems and how to avoid them. What You’ll Learn Gain a solid understanding of the React design Create rich and dynamic web app clients using React Create data stores using Redux Consume data using REST and GraphQL Test your React projects Who This Book Is For JavaScript developers who want to use React to create dynamic client-side applications COMPUTERS,Internet,Web Programming

Programming WebAssembly with Rust WebAssembly fulfills the long-awaited promise of web technologies: fast code, type-safe at compile time, execution in the browser, on embedded devices, or anywhere else. Rust delivers the power of C in a language that strictly enforces type safety. Combine both languages and you can write for the web like never before! Learn how to integrate with JavaScript, run code on platforms other than the browser, and take a step into IoT. Discover the easy way to build cross-platform applications without sacrificing power, and change the way you write code for the web. WebAssembly is more than just a revolutionary new technology. It's reshaping how we build applications for the web and beyond. Where technologies like ActiveX and Flash have failed, you can now write code in whatever language you prefer and compile to WebAssembly for fast, type-safe code that runs in the browser, on mobile devices, embedded devices, and more. Combining WebAssembly's portable, high-performance modules with Rust's safety and power is a perfect development combination. Learn how WebAssembly's stack machine architecture works, install low-level wasm tools, and discover the dark art of writing raw wast code. Build on that foundation and learn how to compile WebAssembly modules from Rust by implementing the logic for a checkers game. Create wasm modules in Rust to interoperate with JavaScript in many compelling ways. Apply your new skills to the world of non-web hosts, and create everything from an app running on a Raspberry Pi that controls a lighting system, to a fully-functioning online multiplayer game engine where developers upload their own arena-bound WebAssembly combat modules. Get started with WebAssembly today, and change the way you think about the web. What You Need: You'll need a Linux, Mac, or Windows workstation with an Internet connection. You'll need an up-to-date web browser that supports WebAssembly. To work with the sample code, you can use your favorite text editor or IDE. The book will guide you through installing the Rust and WebAssembly tools needed for each chapter. COMPUTERS,Internet,Web Programming

Beginning JavaScript Discover everything you need to know to get up-to-speed with JavaScript development and add dynamic enhancements to web pages. This completely updated third edition reveals how the code works and when to use closures, constants, and execution content. Starting with the basics, you’ll see how to employ prototypical inheritance, as well as memory management, variable hoisting and event bubbling. Also covered is an introduction to Node.js and package managers, key to understanding the tools necessary in front-end development and how they are used with current JavaScript frameworks. JavaScript is one of the most important technologies on the web, providing the means to add dynamic functionality to your web pages and serving as the backbone of working with frameworks like Angular and React. Beginning JavaScript, Third Edition will take you from being a JavaScript novice to working freely with this important technology - begin your JavaScript journey today! What You'll Learn Construct good JavaScript syntax following modern coding practices Use JavaScript to communicate with the server and retrieve data Dynamically manipulate markup, validate forms and deal with images Debug applications using features inside the browser Use TypeScript to bring strong typing to the language Who This Book Is For Beginner to intermediate developers with a basic knowledge of front-end programming who are looking for a deeper understanding of how JavaScript works in the browser and how to answer questions in an interview. COMPUTERS,Internet,Web Programming

React Native for Mobile Development Develop native iOS and Android apps with ease using React Native. Learn by doing through an example-driven approach, and have a substantial running app at the end of each chapter. This second edition is fully updated to include ES7 (ECMAScript 7), the latest version of React Native (including Redux), and development on Android. You will start by setting up React Native and exploring the anatomy of React Native apps. You'll then move on to Redux data flow, how it differs from flux, and how you can include it in your React Native project to solve state management differently and efficiently. You will also learn how to boost your development by including popular packages developed by the React Native community that will help you write less; do more. Finally, you'll learn to how write test cases using Jest and submit your application to the App Store. React Native challenges the status quo of native iOS and Android development with revolutionary components, asynchronous execution, unique methods for touch handling, and much more. This book reveals the the path-breaking concepts of React.js and acquaints you with the React way of thinking so you can learn to create stunning user interfaces. What You'll Learn Build stunning iOS and Android applications Understand the Redux design pattern and use it in your project Interact with iOS and android device capabilities such as addressbook, camera, GPS and more with your apps Test and launch your application to the App Store Who This Book Is For Anyone with JavaScript experience who wants to build native mobile applications but dreads the thought of programming in Objective-C or Java. Developers who have experience with JavaScript but are new or not acquainted to React Native or ReactJS. COMPUTERS,Internet,Web Programming

PHP 7 Solutions Make your websites more dynamic by adding a feedback form, creating a private area where members can upload images that are automatically resized, or perhaps storing all your content in a database. David Powers has updated his definitive book to incorporate the latest techniques and changes to PHP, including the arrival of PHP 7. New features include the spaceship and null coalesce operators, generators, using array shorthand syntax for list(), array dereferencing, and array unpacking with the splat operator.The problem is, you're not a programmer and the thought of writing code sends a chill up your spine. Or maybe you've dabbled a bit in PHP and MySQL, but you can't get past baby steps. If this describes you, then you've just found the right book. PHP and the MySQL database are deservedly the most popular combination for creating dynamic websites. They're free, easy to use, and provided by many web hosting companies in their standard packages. This book also covers MariaDB, a seamless replacement for MySQL that has been adopted on many web servers. Unfortunately, most PHP books either expect you to be an expert already or force you to go through endless exercises of little practical value. In contrast, this book gives you real value right away through a series of practical examples that you can incorporate directly into your sites, optimizing performance and adding functionality such as file uploading, email feedback forms, image galleries, content management systems, and much more. Each solution is created with not only functionality in mind, but also visual design. But this book doesn't just provide a collection of ready-made scripts: each PHP solution builds on what's gone before, teaching you the basics of PHP and database design quickly and painlessly. By the end of the book, you'll have the confidence to start writing your own scripts or—if you prefer to leave that task to others—to adapt existing scripts to your own requirements. Right from the start, you're shown how easy it is to protect your sites by adopting secure coding practices. What You Will Learn Design and build dynamic PHP-based web sites and applications Get started right away through practical examples that you can reuse Incorporate PHP 7 elements including new ways of handling arrays Work with the latest PHP 7 techniques, innovations, and best practices Who This Book Is For Readers should have at least some prior exposure to web development using PHP. COMPUTERS,Internet,Web Programming

Test-Driven React You work in a loop: write code, get feedback, iterate. The faster you get feedback, the faster you can learn and become a more effective developer. Test-Driven React helps you refine your React workflow to give you the feedback you need as quickly as possible. Write strong tests and run them continuously as you work, split complex code up into manageable pieces, and stay focused on what's important by automating away mundane, trivial tasks. Adopt these techniques and you'll be able to avoid productivity traps and start building React components at a stunning pace! React has revolutionized web development by abstracting away the details of DOM manipulation. That conceptual elegance has opened the door to a new generation of web testing: clear, expressive, and lightning-fast. That makes React a perfect fit for test-driven development (TDD), a methodology in which tests are a blueprint instead of an afterthought. Each chapter will present new projects to challenge you and new tools to help you. Write fast, portable tests with Jest. Keep your code tidy with ESLint and Prettier. Perform every task you need from a single window with VS Code. See your test output directly in your code with Wallaby. Use the JavaScript features of the future with Babel. Make assertions about React component behavior with Enzyme. And style components in a testable way with styled-components. By understanding every piece of your project's stack, you'll feel more confident and able to focus on what matters: writing reliable and maintainable code. Discover a more joyful React development experience. Let your tests lead the way! What You Need: You'll need a working knowledge of JavaScript and a computer running macOS, Windows, or Linux. COMPUTERS,Internet,Web Programming

Flask Framework Cookbook Build state-of-the-art web applications quickly and efficiently using Flask and related technologies with Python 3 Key Features Updated to Flask 1.0.3 and Python 3.7 with coverage of Microservices Get the most out of the powerful Flask framework and maintain the flexibility of your design choices Write cleaner and maintainable code with the help of sample apps Book Description Flask, the lightweight Python web framework, is popular due to its powerful modular design that lets you build scalable web apps. With this recipe-based guide, you'll explore modern solutions and best practices for Flask web development. Updated to the latest version of Flask and Python 3, this second edition of Flask Framework Cookbook moves away from some of the old and obsolete libraries and introduces recipes on bleeding edge technologies. You'll discover different ways of using Flask to create, deploy, and manage microservices. This Flask Python book starts by covering the different configurations that a Flask application can make use of, and then helps you work with templates and learn about the ORM and view layers. You'll also be able to write an admin interface and get to grips with debugging and logging errors. Finally, you'll grasp a variety of deployment and post-deployment techniques for platforms such as Apache, Tornado, and Heroku. By the end of this book, you'll have gained all the knowledge you need to write Flask applications in the best possible way and scale them using standard industry practices. What you will learn Explore web application development in Flask, right from installation to post-deployment stages Make use of advanced templating and data modeling techniques Discover effective debugging, logging, and error handling techniques in Flask Integrate Flask with different technologies such as Redis, Sentry, and MongoDB Deploy and package Flask applications with Docker and Kubernetes Design scalable microservice architecture using AWS LambdaContinuous integration and Continuous deployment Who this book is for If you are a web developer who wants to learn more about developing scalable and production-ready applications in Flask, this is the book for you. You'll also find this book useful if you are already aware of Flask's major extensions and want to use them for better application development. Basic Python programming experience along with basic understanding of Flask is assumed. COMPUTERS,Internet,Web Programming

Master Apache JMeter - From Load Testing to DevOps Learn how to get the most out of JMeter, improve the productivity of your apps, and integrate JMeter with your Agile and DevOps processes. Key Features Gain insights into preparing test environments and selecting the correct use cases to load test Learn to analyze a load test with Backend Listener, HTML Report Dashboard, and View Results Tree Explore how to integrate JMeter in the software factory Book Description Load tests help identify the maximum number of requests a software system can handle. One popular open source tool for load testing is JMeter. By leveraging the features and capabilities of JMeter, you can perform extensive load testing and fix issues in your application before they become problematic. This book is written by JMeter developers and begins by discussing the whole process, including recording a script, setting it up, and launching it, enabling you to almost immediately start load testing. You'll learn the best practices that you must follow while designing test cases. You'll also explore the different protocols offered by JMeter through various real-world examples. Finally, you'll see how to integrate JMeter into the DevOps approach and create professional reports. You'll discover ways to use the eco-system of JMeter to integrate new protocols, enrich its monitoring, and leverage its power through the use of the cloud. By the end of this book, you'll know all that's needed to perform comprehensive load testing on your applications by using all the best practices and features of JMeter. What you will learn Explore various JMeter concepts, including Timers scope and Assertions scope Discover the types of test protocols and load tests that JMeter supports Design a realistic test scenario using various tips and best practices Prepare your test environment with injectors and the system under test Learn and apply good practices when recording a script Integrate JMeter with Jenkins using Maven Who this book is for This book contains all the valuable information you need in one place and is a must for everybody who is seriously working with JMeter. It might be a little condensed for absolute beginners, but this book is the best you can find if you already have some performance testing experience and want to get further. In particular, it would be invaluable to developers who want to expand their JMeter knowledge into advanced topics or switch to JMeter from other load testing tools. COMPUTERS,Internet,Web Programming

JavaScript Get up and running on the latest JavaScript standard using this fully updated beginner’s guide This hands-on, fast-paced guide shows, from start to finish, how to create dynamic Web pages complete with special effects using JavaScript. This edition contains updates for all major new features and the latest Web development techniques and practices. You will discover how to extend JavaScript’s capabilities to the server side using Node.js. JavaScript: A Beginner's Guide, Fifth Edition begins by clearly explaining the fundamentals, including variables, functions, operators, event handlers, objects, arrays, strings, and forms. From there, the book moves on to more advanced techniques, such as debugging, accessibility, and security. Throughout, “Ask the Expert,†“Try This,†notes, tips, and self tests highlight salient points and aid in learning. Teaches, step by step, how to get started developing Web applications Features detailed examples and downloadable project files Written by an experienced Web developer and JavaScript expert COMPUTERS,Internet,Web Programming

Web Development with Node and Express Build dynamic web applications with Express, a key component of the Node/JavaScript development stack. In this updated edition, author Ethan Brown teaches you Express fundamentals by walking you through the development of an example application. This hands-on guide covers everything from server-side rendering to API development suitable for usein single-page apps (SPAs). Express strikes a balance between a robust framework and no framework at all, allowing you a free hand in your architecture choices. Frontend and backend engineers familiar with JavaScript will also learn best practices for building multipage and hybrid web apps with Express. Pick up this book anddiscover new ways to look at web development. Create a templating system for rendering dynamic data Dive into request and response objects, middleware, and URL routing Simulate a production environment for testing Persist data in document databases with MongoDB and relational databases with PostgreSQL Make your resources available to other programs with APIs Build secure apps with authentication, authorization, and HTTPS Integrate with social media, geolocation, and more Implement a plan for launching and maintaining your app Learn critical debugging skills COMPUTERS,Internet,Web Programming

Monolith to Microservices How do you detangle a monolithic system and migrate it to a microservice architecture? How do you do it while maintaining business-as-usual? As a companion to Sam Newman’s extremely popular Building Microservices, this new book details a proven method for transitioning an existing monolithic system to a microservice architecture. With many illustrative examples, insightful migration patterns, and a bevy of practical advice to transition your monolith enterprise into a microservice operation, this practical guide covers multiple scenarios and strategies for a successful migration, from initial planning all the way through application and database decomposition. You’ll learn several tried and tested patterns and techniques that you can use as you migrate your existing architecture. Ideal for organizations looking to transition to microservices, rather than rebuild Helps companies determine whether to migrate, when to migrate, and where to begin Addresses communication, integration, and the migration of legacy systems Discusses multiple migration patterns and where they apply Provides database migration examples, along with synchronization strategies Explores application decomposition, including several architectural refactoring patterns Delves into details of database decomposition, including the impact of breaking referential and transactional integrity, new failure modes, and more COMPUTERS,Internet,Web Programming

Building Scalable PHP Web Applications Using the Cloud Eliminate the guesswork involved in writing and deploying a cloud application. This step-by-step guide uses PHP to minimize the complexity of the code and setup, but the tools and techniques can be applied on any platform using any language. Everything that you need to jumpstart your application on the cloud is right here. Clear diagrams, step-by-step configuration information, and complete code listings tell you everything you need to get off the ground and start developing your cloud application today. This book introduces several cloud architectures and technologies that will help you accelerate your application in the cloud. Chapters cover load-balanced clusters, database replication, caching configuration, content delivery networks, infinite-scale file storage, and cloud system administration. Cloud computing has dramatically changed the landscape of web hosting. Instead of spending weeks negotiating contracts for servers, new servers can be deployed with the push of a button, and your application can be resized almost instantly to meet today's needs. No matter what size of web application you are developing, you can benefit from modern cloud servers, and this is the guide to tell you how. What You'll Learn Use the cloud and its various platforms with Docker management tools Build a simple PHP-based scalable web application Create a basic cloud cluster Work with Amazon and Google Cloud Platform in your PHP web application development Who This Book Is For Developers who have some prior programming experience, including PHP, and who are new to building applications COMPUTERS,Internet,Web Programming

Beginning Git and GitHub Learn the fundamentals of version control through step-by-step tutorials that will teach you the ins-and-outs of Git. This book is your complete guide to how Git and GitHub work in a professional team environment. Divided into three parts – Version Control, Project Management and Teamwork – this book reveals what waits for you in the real world and how to resolve the problems you may run into. Once past the basics of Git, you'll see how to manage a software project, and finally how to utilize Git and GithHub to work effectively as a team. You'll examine how to plan, follow and execute a project with GitHub, and then apply those concepts to real-world situations. Workaround the pitfalls that most programmers fall into when driving a project with Git by using proven tactics to avoid them. You will also be taught the easiest and quickest ways to resolve merge conflicts. A lot of modern books on Git don’t go into depth about non-technical topics. Beginning Git and GitHub will help you cover all the bases right at the start of your career. What You'll Learn Review basic and advanced concepts of Git Apply Project Management skills using GitHub Solve conflicts or, ideally, avoid them altogether Use advanced concepts for a more boosted workflow Who This book Is For New developers, developers that have never worked in a team environment before, developers with basic knowledge of Git or GitHub, or anyone who works with text documents. COMPUTERS,Internet,Web Programming

Building Web Apps with WordPress WordPress is much more than a blogging platform. If you have basic PHP, HTML, CSS, and JavaScript experience you can use WordPress to develop fast, scalable, secure, and highly customized web apps, mobile apps, web services, and multisite networks of websites. Along with core WordPress functions and database schema, you’ll learn how to build custom plugins, themes, and services for just about any kind of web or mobile application. In this updated second edition, Brian Messenlehner and Jason Coleman cover new features and functionality added to WordPress up to version 5.4. All code examples in the book are available on GitHub. Compare WordPress with traditional app development frameworks Use themes for views and plugins for backend functionality Get suggestions for choosing or building WordPress plugins Register custom post types (CPTs) and taxonomies Manage user accounts and roles, and access user data Build asynchronous behaviors with jQuery Use WordPress to develop mobile apps for iOS and Android Integrate PHP libraries, external APIs, and web service plugins Collect payments through ecommerce and membership plugins Learn how to speed up and scale your WordPress app Extend the WordPress REST API and create custom endpoints Learn about WordPress Gutenberg blocks development COMPUTERS,Internet,Web Programming

ASP.NET Core 3 and React Build modern, scalable, and cloud-ready single-page applications using ASP.NET Core, React, TypeScript, and Azure Key Features Explore the full potential and latest features of .NET Core 3.0, TypeScript 3, and React Learn how to manage data, application design, and packaging, and secure your web apps Discover best practices for using React and TypeScript to build a scalable frontend that interacts with REST APIs Book Description Microsoft's ASP.NET Core is a robust and high-performing cross-platform web API framework, and Facebook's React uses declarative JavaScript to drive a rich, interactive user experience on the client-side web. Together, they can be used to build full stack apps with enhanced security and scalability at each layer. This book will start by taking you through React and TypeScript components to build an intuitive single-page application. You'll understand how to design scalable REST APIs that can integrate with a React-based frontend. You'll get to grips with the latest features, popular patterns, and tools available in the React ecosystem, including function-based components, React Router, and Redux. The book shows how you can use TypeScript along with React to make the frontend robust and maintainable. You'll then cover important .NET Core features such as API controllers, attribute routing, and model binding to help you build a sturdy backend. Additionally, you'll explore API security with ASP.NET Core identity and authorization policies, and write reliable unit tests using both .NET Core and React before you deploy your app to the Azure cloud. By the end of the book, you'll have gained all the knowledge you need to enhance your C# and JavaScript skills and build full stack, production-ready applications with ASP.NET Core and React. What you will learn Build RESTful APIs with .NET Core using API controllers Create strongly typed, interactive, and function-based React components using Hooks Build forms efficiently using reusable React components Perform client-side state management with Redux and the React Context API Secure REST APIs with ASP.NET identity and authorization policies Run a range of automated tests on the frontend and backend Implement continuous integration (CI) and continuous delivery (CD) processes into Azure using Azure DevOps Who this book is for If you're a web developer looking to build solid full-stack web applications with .NET Core and React, this book is for you. Although this book does not assume any knowledge of React, you're expected to have a basic understanding of .NET Core. COMPUTERS,Internet,Web Programming

Building Progressive Web Applications with Vue.js Obtain all the necessary tools for developing a progressive web application (PWA) with Vue.js, a modern JavaScript framework. You’ll see how PWAs behave like a regular responsive website and have a similar structure to that of a web application, but feel like a native mobile app. Along the way you’ll take advantage of Vue.js features to build fast, high-performing progressive web apps that work offline. Building Progressive Web Applications with Vue.js starts by explaining the basic concepts and structure of PWAs, and moves on to designing the app shell and other features that distinguish a PWA from simple web pages. In the following chapters, the book talks about the improved web technologies, such as service workers, caching strategies, background sync, and push notifications, that make PWAs powerful. What You Will Learn Harness the power of Vue.js to build PWAs Understand the function and relevance of a manifest file Discover service workers and why they are revolutionary Work with the Cache API and caching strategies Use IndexedDB, background sync, and push notifications Enhance your apps with Firebase Implement the Workbox library in your apps Who This Book Is For Web developers who want to venture into building PWAs would find the book useful. COMPUTERS,Internet,Web Programming

Jump Start Web Performance Despite working on the web every day, few developers have a good word to say about the monster they've created. Achingly slow sites with annoying overlays, cookie agreements, instant notifications, and obtrusive ads litter the web landscape. While there may be some excuses for complex web applications, there's little justification for sluggish content-based and ecommerce sites. People are notoriously impatient, and an unresponsive site receives fewer visitors and conversions. This practical, short book provides advice, tips, and best practice for improving website performance, ranging from quick, five-minute configuration changes to major website overhauls. We primarily concentrate on front-end activities and server configurations to optimize the code delivered to a browser. Some back-end tips are provided, but this is often specific to your application, framework, database, and usage patterns. Server-side performance can often be improved with additional or more powerful computing resources. Ideally, everyone involved in a project would consider performance from the start. Somewhat understandably, that rarely occurs, because no one can appreciate the speed of a website or application before it's been created. Many of the tips contained in this book can therefore be applied after your project has been delivered. COMPUTERS,Internet,Web Programming

Web Application Security While many resources for network and IT security are available, detailed knowledge regarding modern web application security has been lacking—until now. This practical guide provides both offensive and defensive security concepts that software engineers can easily learn and apply. Andrew Hoffman, a senior security engineer at Salesforce, introduces three pillars of web application security: recon, offense, and defense. You’ll learn methods for effectively researching and analyzing modern web applications—including those you don’t have direct access to. You’ll also learn how to break into web applications using the latest hacking techniques. Finally, you’ll learn how to develop mitigations for use in your own web applications to protect against hackers. Explore common vulnerabilities plaguing today's web applications Learn essential hacking techniques attackers use to exploit applications Map and document web applications for which you don’t have direct access Develop and deploy customized exploits that can bypass common defenses Develop and deploy mitigations to protect your applications against hackers Integrate secure coding best practices into your development lifecycle Get practical tips to help you improve the overall security of your web applications COMPUTERS,Internet,Web Programming

Architecting CSS ​Leverage various CSS features in combination with popular architectures in order to bring your style sheets back under your control. While CSS is the primary technology used for building beautiful web user interfaces, the style sheet files themselves are often quite ugly; left chaotic and unstructured through lack of a consistent architectural approach. By addressing the structure of your style sheets in the same way that you do with code, see how it is possible to create style rules that are clean and easy to read. Dig deep into CSS fundamentals and learn how to use the available selectors to build powerful rules. You will learn how to use cascading, inheritance, pseudo-classes, pre-processors, and components to produce cleaner, DRY-er style sheets, and how to let these features work for you instead of leading you down the road of rule duplication and design inconsistencies. Embrace the clean, semantic HTML to make your code easier to read, while supporting accessibility and assistive technologies. Separate the concerns of layout and style to simplify dynamic theming and white labeling, making you a marketing hero. Once you've finished this book you will have an advanced knowledge of CSS structures and architectural patterns that will take the pain out of style sheets for you (and your coworkers), and help you implement designs faster and easier than ever before. What You'll Learn Understand the core CSS fundamentals of Inheritance, Cascading, and Specificity Work with architecture and design patterns for better organization and maintenance Maximize code reuse with CSS precompilers Review the strengths and weaknesses of popular architecture patterns Who This Book Is For Primarily for front-end web developers and UI designers and anyone who works with CSS, particularly if they find it cumbersome and inelegant. It’s also suitable for software architects and tech leads who are responsible for the maintainability of their code base. COMPUTERS,Internet,Web Programming

Real-Time Phoenix Give users the real-time experience they expect, by using Elixir and Phoenix Channels to build applications that instantly react to changes and reflect the application's true state. Learn how Elixir and Phoenix make it easy and enjoyable to create real-time applications that scale to a large number of users. Apply system design and development best practices to create applications that are easy to maintain. Gain confidence by learning how to break your applications before your users do. Deploy applications with minimized resource use and maximized performance. Real-time applications come with real challenges - persistent connections, multi-server deployment, and strict performance requirements are just a few. Don't try to solve these challenges by yourself - use a framework that handles them for you. Elixir and Phoenix Channels provide a solid foundation on which to build stable and scalable real-time applications. Build applications that thrive for years to come with the best-practices found in this book. Understand the magic of real-time communication by inspecting the WebSocket protocol in action. Avoid performance pitfalls early in the development lifecycle with a catalog of common problems and their solutions. Leverage GenStage to build a data pipeline that improves scalability. Break your application before your users do and confidently deploy them. Build a real-world project using solid application design and testing practices that help make future changes a breeze. Create distributed apps that can scale to many users with tools like Phoenix Tracker. Deploy and monitor your application with confidence and reduce outages. Deliver an exceptional real-time experience to your users, with easy maintenance, reduced operational costs, and maximized performance, using Elixir and Phoenix Channels. What You Need: You'll need Elixir 1.9+ and Erlang/OTP 22+ installed on a Mac OS X, Linux, or Windows machine. COMPUTERS,Internet,Web Programming

The Definitive Guide to Masonite Build fast and effective applications using Masonite, a Python-based framework. This book covers creating a digital home assistant application, but it’s certainly not the only kind of application you could build. By working on this kind of project, you’ll cover the broad range of topics and requirements you’re likely to find as you establish your own web empire. You’ll see how Masonite is a developer-centric Python framework, which provides all the tools you’ll need to build powerful and maintainable web applications. After reading and using this book, you'll have the tools to make and deploy your own web ecommerce application from scratch using the Masonite framework. What You Will Learn Customize your request and response cycle with middleware, route groups, and headers Add security into your application and protect against possible vulnerabilities Create and control your application’s maintenance features from a terminal Manage a database, so your teammates and environments will always be in sync Represent relational database data with object-oriented programming techniques Read and write from the file system Process large datasets and slow operations in the background Add real-time features and recurring tasks to your application Who This Book Is For Web developers new to the Masonite framework. Some prior Python experience is helpful but is not required. COMPUTERS,Internet,Web Programming

Modern JavaScript for the Impatient Exploit the Power of Modern JavaScript and Avoid the Pitfalls JavaScript was originally designed for small-scale programming in web browsers, but modern JavaScript is radically different. Nowadays, JavaScript programmers actively embrace functional, object-oriented, and asynchronous programming, while deprecating error-prone concepts from the past. Modern JavaScript for the Impatient is a complete yet concise guide to JavaScript E6 and beyond. Rather than first requiring you to learn and transition from older versions, it helps you quickly get productive with today’s far more powerful versions and rapidly move from languages such as Java, C#, C, or C++. Bestselling programming author Cay S. Horstmann covers all you need to know, provided in small chunks organized for quick access and easy understanding. Horstmann’s practical insights and sample code help you take advantage of all that’s new, avoid common pitfalls and obsolete features, and make the most of modern JavaScript’s robust toolchains and frameworks. Quickly master modern JavaScript’s implementation of fundamental programming constructs Avoid legacy techniques that create unnecessary complexity and risk Make the most of functional, object-oriented, and asynchronous techniques Use modules to efficiently organize and run complex programs Write more powerful, flexible, and concise programs with metaprogramming Extend JavaScript’s power via JavaScript libraries, frameworks, and platforms Whether you’re just getting started with JavaScript or you’re an experienced developer, this guide will help you write tomorrow’s most robust, efficient, and secure JavaScript code. Register your book for convenient access to downloads, updates, and/or corrections as they become available. See inside book for details. COMPUTERS,Internet,Web Programming

Ruby on Rails Tutorial “Ruby on Rails™ Tutorial by Michael Hartl has become a must-read for developers learning how to build Rails apps.†—Peter Cooper, Editor of Ruby Inside Used by sites as varied as Disney, GitHub, Shopify, and Airbnb, Ruby on Rails is one of the most popular frameworks for developing web applications, but it can be challenging to learn and use. Whether you’re new to web development or new only to Rails, Ruby on Rails™ Tutorial, Sixth Edition , is the solution. Best-selling author and leading Rails developer Michael Hartl teaches Rails by guiding you through the development of three example applications of increasing sophistication. The tutorial’s examples focus on the general principles of web development needed for virtually any kind of website. The updates to this edition include full compatibility with Rails 6. This indispensable guide provides integrated tutorials not only for Rails, but also for the essential Ruby, HTML, CSS, and SQL skills you need when developing web applications. Hartl explains how each new technique solves a real-world problem, and then he demonstrates it with bite-sized code that’s simple enough to understand while still being useful. Whatever your previous web development experience, this book will guide you to true Rails mastery. This book will help you Install and set up your Rails development environment, including a pre-installed integrated development environment (IDE) in the cloud Go beyond generated code to truly understand how to build Rails applications from scratch Learn testing and test-driven development (TDD) Effectively use the Model-View-Controller (MVC) pattern Structure applications using the REST architecture Build static pages and transform them into dynamic ones Master the Ruby programming skills all Rails developers need Create high-quality site layouts and data models Implement registration and authentication systems, including validation and secure passwords Update, display, and delete users Upload images in production using a cloud storage service Implement account activation and password reset, including sending email with Rails Add social features and microblogging, including an introduction to Ajax Record version changes with Git and create a secure remote repository at GitHub Deploy your applications early and often with Heroku Register your book for convenient access to downloads, updates, and/or corrections as they become available. See inside book for details. COMPUTERS,Internet,Web Programming

Build Your Own Website Build Your Own Website is a fun, illustrated introduction to the basics of creating a website. Join Kim and her little dog Tofu as she learns HTML, the language of web pages, and CSS, the language used to style web pages, from the Web Guru and Glinda, the Good Witch of CSS. Once she figures out the basics, Kim travels to WordPress City to build her first website, with Wendy, the WordPress Maven, at her side. They take control of WordPress® themes, install useful plugins, and more. As you follow along, you’ll learn how to:–Use HTML tags–Make your site shine with CSS–Customize WordPress to fit your needs–Choose a company to host your site and get advice on picking a good domain name The patient, step-by-step advice you’ll find in Build Your Own Website will help you get your website up and running in no time. Stop dreaming of your perfect website and start making it! COMPUTERS,Internet,Web Programming

The HTML and CSS Workshop Cut through the noise and get real results with a step-by-step approach to learning HTML and CSS programming Key Features An HTML and CSS tutorial with step-by-step exercises and activities Structured to let you progress at your own pace, on your own terms Use your physical print copy to redeem free access to the online interactive edition Book Description You already know you want to learn HTML and CSS, and a smarter way to learn HTML and CSS is to learn by doing. The HTML and CSS Workshop focuses on building up your practical skills so that you can build your own static web pages from scratch, or work with existing themes on modern platforms like WordPress and Shopify. It's the perfect way to get started with web development. You'll learn from real examples that lead to real results. Throughout The HTML and CSS Workshop, you'll take an engaging step-by-step approach to beginning HTML and CSS development. You won't have to sit through any unnecessary theory. If you're short on time you can jump into a single exercise each day or spend an entire weekend learning about CSS pre-processors. It's your choice. Learning on your terms, you'll build up and reinforce key skills in a way that feels rewarding. Every physical print copy of The HTML and CSS Workshop unlocks access to the interactive edition. With videos detailing all exercises and activities, you'll always have a guided solution. You can also benchmark yourself against assessments, track progress, and receive free content updates. You'll even earn a secure credential that you can share and verify online upon completion. It's a premium learning experience that's included with your printed copy. To redeem, follow the instructions located at the start of your HTML CSS book. Fast-paced and direct, The HTML and CSS Workshop is the ideal companion for a HTML and CSS beginner. You'll build and iterate on your code like a software developer, learning along the way. This process means that you'll find that your new skills stick, embedded as best practice. A solid foundation for the years ahead. What you will learn Get to grips with the key features of HTML5 and CSS3 Learn how to integrate animation, media, and custom themes Understand how you can easily customize and maintain CSS Develop your own mobile-first approach while designing websites Learn how to diagnose and resolve common style and structural problems Who this book is for Our goal at Packt is to help you be successful, in whatever it is you choose to do. The HTML and CSS Workshop is an ideal HTML and CSS tutorial for the HTML and CSS beginner who is just getting started. Pick up a Workshop today, and let Packt help you develop skills that stick with you for life. COMPUTERS,Internet,Web Programming

Practical hapi Understand the core concepts of hapi and learn to build RESTful APIs that are quick, useful, and productive. Created by the mobile team at Walmart Labs, hapi is a light Node.js framework that is perfect for building API servers, websites, and HTTP proxy applications. With this quick guide, you'll learn the basics of hapi and use those skills to build an application and a REST API with MySQL. You'll then wrap up with a Capstone project of industry relevance, understanding solution design, and how hapi fits into industry relevant projects for data driven apps. Used by companies such as PayPal and Mozilla, hapi is a key framework for anyone serious about enterprise web development. Practical hapi will ensure you focus your time on critical project tasks instead of building infrastructure. What You'll Learn Utilize the power of RESTful APIs and Node.js Build your first hapi application based on its core concepts Work with promises and asynchronous programming effectively Use Sequelize for database connectivity Who This Book Is For Anyone with basic knowledge of JavaScript or Node.js who wants to learn to work with hapi. A primer for the relevant Node.js and JavaScript is provided so those with general programming experience can also use this book. COMPUTERS,Internet,Web Programming

Webpack for Beginners Learn how to use Webpack from installation to configuration without the hassle of complex examples. Webpack has become one of the most popular module bundlers in recent years; it’s widely used by developers, companies, and organizations of all sizes, and many web frameworks use it for the management of their assets. If you are serious about web development these days then you must learn and understand Webpack. You will begin by installing and configuring Webpack, and learn how to write modular code. You’ll then move onto understanding the usage of loaders and plugins with practical use cases, how to make aliases and resolve folders, cache busting, and installing third-party libraries such as jQuery, Bootstrap, QuillJS, and more. By the end of this book you will feel confident and ready to start using Webpack in your projects. Free from complex examples and intended to be as easy-to-follow as possible, this book is ideal for anyone who knows basic HTML, JavaScript, and how to work on the command line. Upgrade your developer skillset using Webpack for Beginners today. What You Will Learn Install and configure Webpack beyond the default settings Efficiently work with plugins and loaders Optimize Webpack for production Use instant refreshing with the Webpack dev server and hot module replacement Explore how to install some common JavaScript libraries Who This Book Is For This book is conceived for beginners and newcomers to Webpack, and assumes you have some very basic knowledge in JavaScript, HTML and working on the command line. This step-by-step guide will help you understand and clarify everything you need to know to bundle your JavaScript hassle-free. COMPUTERS,Internet,Web Programming

Building Event-Driven Microservices Organizations today often struggle to balance business requirements with ever-increasing volumes of data. Additionally, the demand for leveraging large-scale, real-time data is growing rapidly among the most competitive digital industries. Conventional system architectures may not be up to the task. With this practical guide, you’ll learn how to leverage large-scale data usage across the business units in your organization using the principles of event-driven microservices. Author Adam Bellemare takes you through the process of building an event-driven microservice-powered organization. You’ll reconsider how data is produced, accessed, and propagated across your organization. Learn powerful yet simple patterns for unlocking the value of this data. Incorporate event-driven design and architectural principles into your own systems. And completely rethink how your organization delivers value by unlocking near-real-time access to data at scale. You’ll learn: How to leverage event-driven architectures to deliver exceptional business value The role of microservices in supporting event-driven designs Architectural patterns to ensure success both within and between teams in your organization Application patterns for developing powerful event-driven microservices Components and tooling required to get your microservice ecosystem off the ground COMPUTERS,Internet,Web Programming

REST API Design Rulebook In today’s market, where rival web services compete for attention, a well-designed REST API is a must-have feature. This concise book presents a set of API design rules, drawn primarily from best practices that stick close to the Web’s REST architectural style. Along with rules for URI design and HTTP use, you’ll learn guidelines for media types and representational forms. REST APIs are ubiquitous, but few of them follow a consistent design methodology. Using these simple rules, you will design web service APIs that adhere to recognized web standards. To assist you, author Mark Massé introduces the Web Resource Modeling Language (WRML), a conceptual framework he created for the design and implementation of REST APIs. Learn design rules for addressing resources with URIs Apply design principles to HTTP’s request methods and response status codes Work with guidelines for conveying metadata through HTTP headers and media types Get design tips to address the needs of client programs, including the special needs of browser-based JavaScript clients Understand why REST APIs should be designed and configured, not coded COMPUTERS,Internet,Web Services & APIs

Building RESTful Web Services with PHP 7 Learn how to build RESTful API and web services in PHP 7 About This Book Leverage the Lumen framework to build RESTful API endpoints for your applications Understand how to increase efficiency and security of your web service. Learn to apply the concepts by implementing the examples covered in the book Who This Book Is For This book is for PHP developers who wish to learn about the REST architecture to be able to build and consume REST APIs in their applications. What You Will Learn Understand the REST API architecture and its benefits Write RESTful API web services in PHP 7 Address security-elated issues in a REST API Leverage the importance of automated testing and write tests for API endpoints Identify security flaws in our current API endpoints and tackle them effectively Observe the working of Lumen microframeworks and write RESTful web services in it In Detail REST is the most wide spread and effective standard to develop APIs for internet services. With the way PHP and its eco-system has modernized the way code is written by simplifying various operations, it is useful to develop RESTful APIs with PHP 7 and modern tools. This book explains in detail how to create your own RESTful API in PHP 7 that can be consumed by other users in your organization. Starting with a brief introduction to the fundamentals of REST architecture and the new features in PHP 7, you will learn to implement basic RESTful API endpoints using vanilla PHP. The book explains how to identify flaws in security and design and teach you how to tackle them. You will learn about composer, Lumen framework and how to make your RESTful API cleaner, secure and efficient. The book emphasizes on automated tests, teaches about different testing types and give a brief introduction to microservices which is the natural way forward. After reading this book, you will have a clear understanding of the REST architecture and you can build a web service from scratch. Style and approach This book will get you started with REST architecture and will also teach you different methods to build web services from scratch. COMPUTERS,Internet,Web Services & APIs

Architecting Modern Java EE Applications Find out how to craft effective, business-oriented Java EE 8 applications that target customer's demands in the age of Cloud platforms and container technology. About This Book Understand the principles of modern Java EE and how to realize effective architectures Gain knowledge of how to design enterprise software in the age of automation, Continuous Delivery and Cloud platforms Learn about the reasoning and motivations behind state-of-the-art enterprise Java technology, that focuses on business Who This Book Is For This book is for experienced Java EE developers who are aspiring to become the architects of enterprise-grade applications, or software architects who would like to leverage Java EE to create effective blueprints of applications. What You Will Learn What enterprise software engineers should focus on Implement applications, packages, and components in a modern way Design and structure application architectures Discover how to realize technical and cross-cutting aspects Get to grips with containers and container orchestration technology Realize zero-dependency, 12-factor, and Cloud-native applications Implement automated, fast, reliable, and maintainable software tests Discover distributed system architectures and their requirements In Detail Java EE 8 brings with it a load of features, mainly targeting newer architectures such as microservices, modernized security APIs, and cloud deployments. This book will teach you to design and develop modern, business-oriented applications using Java EE 8. It shows how to structure systems and applications, and how design patterns and Domain Driven Design aspects are realized in the age of Java EE 8. You will learn about the concepts and principles behind Java EE applications, and how to effect communication, persistence, technical and cross-cutting concerns, and asynchronous behavior. This book covers Continuous Delivery, DevOps, infrastructure-as-code, containers, container orchestration technologies, such as Docker and Kubernetes, and why and especially how Java EE fits into this world. It also covers the requirements behind containerized, zero-dependency applications and how modern Java EE application servers support these approaches. You will also learn about automated, fast, and reliable software tests, in different test levels, scopes, and test technologies. This book covers the prerequisites and challenges of distributed systems that lead to microservice, shared-nothing architectures. The challenges and solutions of consistency versus scalability will further lead us to event sourcing, event-driven architectures, and the CQRS principle. This book also includes the nuts and bolts of application performance as well as how to realize resilience, logging, monitoring and tracing in a modern enterprise world. Last but not least the demands of securing enterprise systems are covered. By the end, you will understand the ins and outs of Java EE so that you can make critical design decisions that not only live up to, but also surpass your clients' expectations. Style and approach This book focuses on solving business problems and meeting customer demands in the enterprise world. It covers how to create enterprise applications with reasonable technology choices, free of cargo-cult and over-engineering. The aspects shown in this book not only demonstrate how to realize a certain solution, but also explain its motivations and reasoning. COMPUTERS,Internet,Web Services & APIs

Mastering Node.js Expert techniques for building fast servers and scalable, real-time network applications with minimal effort; rewritten for Node.js 8 and Node.js 9 About This Book Packed with practical examples and explanations, Mastering Node.js contains everything you need to take your applications to the next level. Unleash the full potential of Node.js 9 to build real-time and scalable applications. Gain in-depth knowledge of asynchronous programming, event loops, and parallel data processing. Explore Node's innovative event-non-blocking design, and build professional applications with the help of detailed examples. Who This Book Is For This book is targeted at JavaScript developers who want to take an in-depth look at the latest Node.js framework to create faster, scalable, real-time backend applications. Basic JavaScript programming knowledge—and also some previous Node.js development experience—are mandatory to get the best out of this book What You Will Learn Build an Electron desktop app using Node that manages a filesystem Explore Streams and understand how they apply to building networked services Develop and deploy an SMS-driven customer service application Use WebSockets for rapid bi-directional communication Construct serverless applications with Amazon Lambda Test and debug with headless browsers, CPU profiling, Mocha, Sinon, and more Scale applications vertically and horizontally across multiple cores and web services In Detail Node.js, a modern development environment that enables developers to write server- and client-side code with JavaScript, thus becoming a popular choice among developers. This book covers the features of Node that are especially helpful to developers creating highly concurrent real-time applications. It takes you on a tour of Node's innovative event non-blocking design, showing you how to build professional applications. This edition has been updated to cover the latest features of Node 9 and ES6. All code examples and demo applications have been completely rewritten using the latest techniques, introducing Promises, functional programming, async/await, and other cutting-edge patterns for writing JavaScript code. Learn how to use microservices to simplify the design and composition of distributed systems. From building serverless cloud functions to native C++ plugins, from chatbots to massively scalable SMS-driven applications, you'll be prepared for building the next generation of distributed software. By the end of this book, you'll be building better Node applications more quickly, with less code and more power, and know how to run them at scale in production environments. Style and approach Mastering Node.js contains all of the examples and explanations you'll need to build applications in a short amount of time and at a low cost, running rapidly and at scale. COMPUTERS,Internet,Web Services & APIs

Dynamics 365 Application Development Learn, develop, and design applications using the new features in Microsoft Dynamics CRM About This Book Implement business logic using processes, plugins, and client-side scripts with MS Dynamics 365 Develop custom CRM solutions to improve your business applications A comprehensive guide that covers the new features of Microsoft Dynamics 365 and increasingly advanced topics. Who This Book Is For This book targets skilled developers who are looking to build business-solution software and are new to application development in Microsoft Dynamics 365, especially for CRM. What You Will Learn Discover new designers tools included in Dynamics 365 CRM Develop apps using the platform-agnostic Web API Leverage Azure Extensions to design cloud-aware applications Learn how to implement CRUD operation Create integrated real-world apps using Microsoft PowerApps and Flow by combining services such as Twitter, Facebook, and SharePoint Configure and use Artificial Intelligence Azure Cognitive Services for Recommendation and Text Analytic services In Detail Microsoft Dynamics 365 CRM is the most trusted name in enterprise-level customer relationship management. Thelatest version of Dynamics CRM comes with the important addition of exciting features guaranteed to make your life easier. It comes straight off the shelf with a whole new frontier of updated business rules, process enhancements, SDK methods, and other enhancements. This book will introduce you to the components of the new designer tools, such as SiteMap, App Module, and Visual Designer for Business Processes. Going deeper, this book teaches you how to develop custom SaaS applications leveraging the features of PowerApps available in Dynamics 365.Further, you will learn how to automate business processes using Microsoft Flow, and then we explore Web API, the most important platform update in Dynamics 365 CRM. Here, you'll also learn how to implement Web API in custom applications. You will learn how to write an Azure-aware plugin to design and integrate cloud-aware solutions. The book concludes with configuring services using newly released features such as Editable grids, Data Export Service, LinkedIn Integration, Relationship Insights, and Live Assist. Style and approach The book takes a pragmatic approach, exploring Dynamics 365 and its CRM features with the help of real-world scenarios. COMPUTERS,Internet,Web Services & APIs

Learning GraphQL Why is GraphQL the most innovative technology for fetching data since Ajax? By providing a query language for your APIs and a runtime for fulfilling queries with your data, GraphQL presents a clear alternative to REST and ad hoc web service architectures. With this practical guide, Alex Banks and Eve Porcello deliver a clear learning path for frontend web developers, backend engineers, and project and product managers looking to get started with GraphQL. You’ll explore graph theory, the graph data structure, and GraphQL types before learning hands-on how to build a schema for a photo-sharing application. This book also introduces you to Apollo Client, a popular framework you can use to connect GraphQL to your user interface. Explore graph theory and review popular graph examples in use today Learn how GraphQL applies database querying methods to the internet Create a schema for a PhotoShare application that serves as a roadmap and a contract between the frontend and backend teams Use JavaScript to build a fully functioning GraphQL service and Apollo to implement a client Learn how to prepare GraphQL APIs and clients for production COMPUTERS,Internet,Web Services & APIs

Hands-On RESTful API Design Patterns and Best Practices Build effective RESTful APIs for enterprise with design patterns and REST framework's out-of-the-box capabilities Key Features Understand advanced topics such as API gateways, API securities, and cloud Implement patterns programmatically with easy-to-follow examples Modernize legacy codebase using API connectors, layers, and microservices Book Description This book deals with the Representational State Transfer (REST) paradigm, which is an architectural style that allows networked devices to communicate with each other over the internet. With the help of this book, you'll explore the concepts of service-oriented architecture (SOA), event-driven architecture (EDA), and resource-oriented architecture (ROA). This book covers why there is an insistence for high-quality APIs toward enterprise integration. It also covers how to optimize and explore endpoints for microservices with API gateways and touches upon integrated platforms and Hubs for RESTful APIs. You'll also understand how application delivery and deployments can be simplified and streamlined in the REST world. The book will help you dig deeper into the distinct contributions of RESTful services for IoT analytics and applications. Besides detailing the API design and development aspects, this book will assist you in designing and developing production-ready, testable, sustainable, and enterprise-grade APIs. By the end of the book, you'll be empowered with all that you need to create highly flexible APIs for next-generation RESTful services and applications. What you will learn Explore RESTful concepts, including URI, HATEOAS, and Code on Demand Study core patterns like Statelessness, Pagination, and Discoverability Optimize endpoints for linked microservices with API gateways Delve into API authentication, authorization, and API security implementations Work with Service Orchestration to craft composite and process-aware services Expose RESTful protocol-based APIs for cloud computing Who this book is for This book is primarily for web, mobile, and cloud services developers, architects, and consultants who want to build well-designed APIs for creating and sustaining enterprise-class applications. You'll also benefit from this book if you want to understand the finer details of RESTful APIs and their design techniques along with some tricks and tips. COMPUTERS,Internet,Web Services & APIs

Mastering Microservices with Java Master the art of implementing scalable and reactive microservices in your production environment with Java 11 Key Features Use domain-driven designs to build microservices Explore various microservices design patterns such as service discovery, registration, and API Gateway Use Kafka, Avro, and Spring Streams to implement event-based microservices Book Description Microservices are key to designing scalable, easy-to-maintain applications. This latest edition of Mastering Microservices with Java, works on Java 11. It covers a wide range of exciting new developments in the world of microservices, including microservices patterns, interprocess communication with gRPC, and service orchestration. This book will help you understand how to implement microservice-based systems from scratch. You'll start off by understanding the core concepts and framework, before focusing on the high-level design of large software projects. You'll then use Spring Security to secure microservices and test them effectively using REST Java clients and other tools. You will also gain experience of using the Netflix OSS suite, comprising the API Gateway, service discovery and registration, and Circuit Breaker. Additionally, you'll be introduced to the best patterns, practices, and common principles of microservice design that will help you to understand how to troubleshoot and debug the issues faced during development. By the end of this book, you'll have learned how to build smaller, lighter, and faster services that can be implemented easily in a production environment. What you will learn Use domain-driven designs to develop and implement microservices Understand how to implement microservices using Spring Boot Explore service orchestration and distributed transactions using the Sagas Discover interprocess communication using REpresentational State Transfer (REST) and events Gain knowledge of how to implement and design reactive microservices Deploy and test various microservices Who this book is for This book is designed for Java developers who are familiar with microservices architecture and now want to effectively implement microservices at an enterprise level. Basic knowledge and understanding of core microservice elements and applications is necessary. COMPUTERS,Internet,Web Services & APIs

React Projects Build cross-platform applications of varying complexity for the web, mobile, and VR devices using React tooling Key Features Build React applications at scale using effective React patterns and best practices Explore React features such as Hooks, the Context API, and the Suspense API Extend React's integration with React Native for building cross-platform mobile apps and games Book Description Developed by Facebook, React is a popular library for building impressive user interfaces. React extends its capabilities to the mobile platform using the React Native framework and integrates with popular web and mobile tools to build scalable applications. React Projects is your guide to learning React development by using modern development patterns and integrating React with powerful web tools such as GraphQL, Expo, and React 360. You'll start building a real-world project right from the first chapter and get hands on with developing scalable applications as you advance to building more complex projects. Throughout the book, you'll use the latest versions of React and React Native to explore features such as Higher Order Components (HOC), Context, and Hooks on multiple platforms, which will help you build full stack web and mobile applications efficiently. Finally, you'll delve into unit testing with Jest to build test-driven apps. By the end of this React book, you'll have developed the skills necessary to start building scalable React apps across web and mobile platforms. What you will learn Create a wide range of applications using various modern React tools and frameworks Discover how React Hooks modernize state management for React apps Develop progressive web applications using React components Build test-driven React applications using the Jest and Enzyme frameworks Understand full stack development using React, Apollo, and GraphQL Perform server-side rendering using React and React Router Design gestures and animations for a cross-platform game using React Native Who this book is for The book is for JavaScript developers who want to explore React tooling and frameworks for building cross-platform applications. Basic knowledge of web development, ECMAScript, and React will assist with understanding key concepts covered in this book. COMPUTERS,Internet,Web Services & APIs

Django 3 Web Development Cookbook Practical recipes for building fast, robust, and secure web apps using Django 3 and Python Key Features Explore the latest version of Django, and learn effectively with the help of practical examples Follow a task-based approach to develop professional web apps using Django and Python Discover recipes to enhance the security and performance of your apps Book Description Django is a web framework for perfectionists with deadlines, designed to help you build manageable medium and large web projects in a short time span. This fourth edition of the Django Web Development Cookbook is updated with Django 3's latest features to guide you effectively through the development process. This Django book starts by helping you create a virtual environment and project structure for building Python web apps. You'll learn how to build models, views, forms, and templates for your web apps and then integrate JavaScript in your Django apps to add more features. As you advance, you'll create responsive multilingual websites, ready to be shared on social networks. The book will take you through uploading and processing images, rendering data in HTML5, PDF, and Excel, using and creating APIs, and navigating different data types in Django. You'll become well-versed in security best practices and caching techniques to enhance your website's security and speed. This edition not only helps you work with the PostgreSQL database but also the MySQL database. You'll also discover advanced recipes for using Django with Docker and Ansible in development, staging, and production environments. By the end of this book, you will have become proficient in using Django's powerful features and will be equipped to create robust websites. What you will learn Discover how to set the basic configurations to start any Django project Understand full-stack web application development using Django Build a database structure using reusable model mixins Implement security, performance, and deployment features in your web apps Import data from local sources and external web services and export it to your app Secure web applications against malicious usage and find and fix common performance bottlenecks Who this book is for This Django book is for Python web developers who want to build fast and secure web apps that can scale over time. You'll also find this book useful if you are looking to upgrade to the latest Django 3 framework. Prior experience of working with the Django framework is required. COMPUTERS,Internet,Web Services & APIs

Full-Stack React Projects A practical, project-based guide to full-stack JavaScript web development combining the power of React with industry-tested server-side technologies Key Features Build your career as a full-stack developer with this practical guide Understand how the different aspects of a MERN application come together through a series of practical projects Master the MERN stack by building robust social media, E-commerce store, and web-based VR game apps Book Description Facebook's React combined with industry-tested, server-side technologies, such as Node, Express, and MongoDB, enables you to develop and deploy robust real-world full-stack web apps. This updated second edition focuses on the latest versions and conventions of the technologies in this stack, along with their new features such as Hooks in React and async/await in JavaScript. The book also explores advanced topics such as implementing real-time bidding, a web-based classroom app, and data visualization in an expense tracking app. Full-Stack React Projects will take you through the process of preparing the development environment for MERN stack-based web development, creating a basic skeleton app, and extending it to build six different web apps. You'll build apps for social media, classrooms, media streaming, online marketplaces with real-time bidding, and web-based games with virtual reality features. Throughout the book, you'll learn how MERN stack web development works, extend its capabilities for complex features, and gain actionable insights into creating MERN-based apps, along with exploring industry best practices to meet the ever-increasing demands of the real world. By the end of this React book, you'll be able to build production-ready MERN full-stack apps using advanced tools and techniques in modern web development. What you will learn Extend a basic MERN-based application to build a variety of applications Add real-time communication capabilities with Socket.IO Implement data visualization features for React applications using Victory Develop media streaming applications using MongoDB GridFS Improve SEO for your MERN apps by implementing server-side rendering with data Implement user authentication and authorization using JSON web tokens Set up and use React 360 to develop user interfaces with VR capabilities Make your MERN stack applications reliable and scalable with industry best practices Who this book is for This is one of the most useful web development books for JavaScript developers who may have worked with React but have minimal experience in full-stack development with Node, Express, and MongoDB. COMPUTERS,Internet,Web Services & APIs

Jakarta EE Cookbook An enterprise Java developer's guide to learning JAX-RS, context and dependency injection, JavaServer Faces (JSF), and microservices with Eclipse MicroProfile using the latest features of Jakarta EE Key Features Explore Jakarta EE's latest features and API specifications and discover their benefits Build and deploy microservices using Jakarta EE 8 and Eclipse MicroProfile Build robust RESTful web services for various enterprise scenarios using the JAX-RS, JSON-P, and JSON-B APIs Book Description Jakarta EE is widely used around the world for developing enterprise applications for a variety of domains. With this book, Java professionals will be able to enhance their skills to deliver powerful enterprise solutions using practical recipes. This second edition of the Jakarta EE Cookbook takes you through the improvements introduced in its latest version and helps you get hands-on with its significant APIs and features used for server-side development. You'll use Jakarta EE for creating RESTful web services and web applications with the JAX-RS, JSON-P, and JSON-B APIs and learn how you can improve the security of your enterprise solutions. Not only will you learn how to use the most important servers on the market, but you'll also learn to make the best of what they have to offer for your project. From an architectural point of view, this Jakarta book covers microservices, cloud computing, and containers. It allows you to explore all the tools for building reactive applications using Jakarta EE and core Java features such as lambdas. Finally, you'll discover how professionals can improve their projects by engaging with and contributing to the community. By the end of this book, you'll have become proficient in developing and deploying enterprise applications using Jakarta EE. What you will learn Work with Jakarta EE's most commonly used APIs and features for server-side development Enable fast and secure communication in web applications with the help of HTTP2 Build enterprise applications with reusable components Break down monoliths into microservices using Jakarta EE and Eclipse MicroProfile Improve your enterprise applications with multithreading and concurrency Run applications in the cloud with the help of containers Get to grips with continuous delivery and deployment for shipping your applications effectively Who this book is for This book is for Java EE developers who want to build enterprise applications or update their legacy apps with Jakarta EE's latest features and specifications. Some experience of working with Java EE and knowledge of web and cloud computing will assist with understanding the concepts covered in this book. COMPUTERS,Internet,Web Services & APIs

ASP.NET in a Nutshell ASP.NET in a Nutshell is a concise, one-volume reference to everything you need to make effective use of ASP.NET. An invaluable resource that goes beyond the published documentation to highlight little-known details, stress practical uses for particular features, and provide real-world examples that show how features can be used in a working application, ASP.NET in a Nutshell is the definitive guide for developers of both applications and web services.Updated for Visual Studio .NET 2003, the 2nd edition of this book includes fresh information on application and web service development, custom controls, data access, security, deployment, and error handling, new material on web application development for mobile devices, plus an overview of the class libraries. For developers who still use Microsoft's older ASP technology, this book also provides information for migrating to ASP.NET.The material in ASP.NET in a Nutshell is presented in three sections: A fast-paced introduction to ASP.NET that examines topics such as building ASP.NET applications, developing web services, creating custom controls and user controls for maximum code reuse, debugging and handling errors, understanding ASP.NET security, and configuring and deploying an ASP.NET application A detailed reference to the properties, methods, and events of the most frequently used ASP.NET classes which include the Page class and the new .NET classes, such as HttpApplicationState and HttpSessionState, which correspond to the intrinsic objects in classic ASP. Configuration settings in web.config are also documented A Quick Reference to the types (the classes, structures, interfaces, delegates, events, and enumerations) found in web-related namespaces to the .NET Framework Class Library. Like other books in the "In a Nutshell" series, ASP.NET in a Nutshell, 2nd Edition, offers the facts, including critical background information, in a no-nonsense manner that users will refer to again and again. With its wealth of up-to-date information, ASP.NET in a Nutshell is a book that web developers will refer to again and again. COMPUTERS,Languages,.NET

Professional ASP.NET MVC 5 ASP.NET MVC insiders cover the latest updates to the technology in this popular Wrox reference MVC 5 is the newest update to the popular Microsoft technology that enables you to build dynamic, data-driven websites. Like previous versions, this guide shows you step-by-step techniques on using MVC to best advantage, with plenty of practical tutorials to illustrate the concepts. It covers controllers, views, and models; forms and HTML helpers; data annotation and validation; membership, authorization, and security. MVC 5, the latest version of MVC, adds sophisticated features such as single page applications, mobile optimization, and adaptive rendering A team of top Microsoft MVP experts, along with visionaries in the field, provide practical advice on basic and advanced MVC topics Covers controllers, views, models, forms, data annotations, authorization and security, Ajax, routing, ASP.NET web API, dependency injection, unit testing, real-world application, and much more Professional ASP.NET MVC 5 is the comprehensive resource you need to make the best use of the updated Model-View-Controller technology. COMPUTERS,Languages,.NET

Modern Web Development In Modern Web Development , internationally renowned software developer Dino Esposito introduces a pragmatic, problem-driven, and user-focused approach to designing and building dynamic web solutions. Esposito shows experienced developers and solution architects how to drive more value from Microsoft technologies such as ASP.NET 5, MVC, SignalR, Entity Framework, and Web Forms, by using them in conjunction with other technologies, including Bootstrap, JavaScript, AngularJS, Ajax, JSON, and JQuery. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Languages,.NET

ASP.NET Core Create fast, scalable, and high-performance applications with C# and ASP.NET Core About This Book Get first-principle coverage of the latest ASP.NET Core MVC Find out how to bring together the capabilities and features of both Angular 2 and ASP.NET Core Discover common areas you might encounter performance problems with and areas you don't need to worry about Who This Book Is For This book is for developers who want to learn to build web applications using ASP.NET Core, those who want to make a career building web applications using Microsoft technology, and those who are working on other web frameworks and want to learn ASP.NET Core. What You Will Learn Get to know the concepts of ASP.NET MVC Create a Controller with action methods Build a view using several features of the Razor View engine Construct a Model for ASP.NET Core MVC application Find out how the features of ASP.NET Core and Angular 2 perfectly complement each other Handle requests and actions using server-side and client-side Routing Create a Data Model using Entity Framework Core Learn how to use Angular 2 components and master directives Improve performance at the network level and I/O level, and how to optimize the application as a whole Monitor performance as part of Continuous Integration and regression testing In Detail ASP.NET Core is the new, open source, and cross-platform, web-application framework from Microsoft. ASP.NET Core MVC helps you build robust web applications using the Model-View-Controller design. This guide will help you in building applications that can be deployed on non-Windows platforms such as Linux. Starting with an overview of the MVC pattern, you will quickly dive into the aspects that you need to know to get started with ASP.NET. You will learn about the core architecture of model, view, and control. Integrating your application with Bootstrap, validating user input, interacting with databases, and deploying your application are some of the things that you will learn to execute with this fast-paced guide. You will test your knowledge as you build a fully working sample application using the skills you've learned throughout the book. Moving forward, this guide will teach you to combine the impressive capabilities of ASP.NET Core and Angular 2. Not only will you learn how Angular 2 can complement your .NET skills and toolkit, you'll also learn everything you need to build a complete, dynamic single-page application. Find out how to get your data model in place and manage an API, before styling and designing your frontend for an exceptional user experience. You will find out how to optimize your application for SEO, identify and secure vulnerabilities, and how to successfully deploy and maintain your application. From here, you will delve into the latest frameworks and software design patterns to improve your application performance. The course offers premium, highly practical content on the recently released ASP.NET Core, and includes material from the following Packt books: Learning ASP.NET Core MVC Programming, ASP.NET Core and Angular 2, and ASP.NET Core 1.0 High Performance. Style and approach This learning path takes a first-principles approach to help you understand and implement ASP.NET MVC solutions. COMPUTERS,Languages,.NET

Building Microservices with ASP.NET Core At a time when nearly every vertical, regardless of domain, seems to need software running in the cloud to make money, microservices provide the agility and drastically reduced time to market you require. This hands-on guide shows you how to create, test, compile, and deploy microservices, using the ASP.NET Core free and open-source framework. Along the way, you’ll pick up good, practical habits for building powerful and robust services. Building microservices isn’t about learning a specific framework or programming language; it’s about building applications that thrive in elastically scaling environments that don't have host affinity, and that can start and stop at a moment’s notice. This practical book guides you through the process. Learn test-driven and API-first development concepts Communicate with other services by creating and consuming backing services such as databases and queues Build a microservice that depends on an external data source Learn about event sourcing, the event-centric approach to persistence Use ASP.NET Core to build web applications designed to thrive in the cloud Build a service that consumes, or is consumed by, other services Create services and applications that accept external configuration Explore ways to secure ASP.NET Core microservices and applications COMPUTERS,Languages,.NET

Mastering ASP.NET Core 2.0 Become an expert in the shiny new version of ASP.NET About This Book Grasp the advanced concepts of MVC Core and start making professional-grade applications Migrate from previous versions of ASP.NET MVC to ASP.NET Core This book will take you on a journey through all the aspects of ASP.NET Core 2.0 Who This Book Is For If you are a developer who knows the basics of ASP.NET MVC and wants to build powerful applications, this book is for you. Basic C# experience and an understanding of HTML and CSS is assumed. What You Will Learn Get to know the new features of ASP.NET Core 2.0 Find out how to configure ASP.NET Core Configure routes to access ASP.NET Core resources Create controllers and action methods and see how to maintain the state Create views to display contents Implement and validate forms and retrieve information from them Write reusable modules for ASP.NET Core Deploy ASP.NET Core to other environments In Detail ASP.NET is an open source web framework that builds modern web apps and services. This book is your one-stop guide to the new features of ASP.NET Core 2.0, including web APIs and MVC. We begin with a brief overview of the basics, taking you through the MVC pattern, platforms, dependencies, and frameworks. We then move on to setting up and configuring the MVC environment before talking about routing and advanced routing options. Next, we'll look at model binding, controllers and actions, filters, user authentication, and testing. Moving on, you'll learn about all the aspects of syntax and processes when working with Razor. You'll be introduced to client-side development and will get to know about the security aspects of ASP.NET Core. We will also look at microservices with ASP.NET Core. Finally, you'll find out how to deploy ASP.NET Core to new environments such as Azure, AWS, and Docker. By the end of the book, you will be well versed with development in ASP.NET Core and will have a deep understanding of how to interact with the framework and work cross-platform. Style and approach Find out how to design modern, cross-platform, business oriented web applications that serve the client needs in the age of emerging .NET framework COMPUTERS,Languages,.NET

Learning ASP.NET Core 2.0 Learn how web applications can be built efficiently using ASP.NET Core 2.0 and related frameworks About This Book Get to grips with the new features and APIs introduced in ASP.NET Core 2.0 Leverage the MVC framework and Entity Framework Core 2 to build efficient applications Learn to deploy your web applications in new environments such as the cloud and Docker Who This Book Is For This book is for developers who would like to build modern web applications with ASP.NET Core 2.0. No prior knowledge of ASP.NET or .NET Core is required. However, basic programming knowledge is assumed. Additionally, previous Visual Studio experience will be helpful but is not required, since detailed instructions will guide through the samples of the book.This book can also help people, who work in infrastructure engineering and operations, to monitor and diagnose problems during the runtime of ASP.NET Core 2.0 web applications. What You Will Learn Set up your development environment using Visual Studio 2017 and Visual Studio Code Create a fully automated continuous delivery pipeline using Visual Studio Team Services Get to know the basic and advanced concepts of ASP.NET Core 2.0 with detailed examples Build an MVC web application and use Entity Framework Core 2 to access data Add Web APIs to your web applications using RPC, REST, and HATEOAS Authenticate and authorize users with built-in ASP.NET Core 2.0 features Use Azure, Amazon Web Services, and Docker to deploy and monitor your applications In Detail The ability to develop web applications that are highly efficient but also easy to maintain has become imperative to many businesses. ASP.NET Core 2.0 is an open source framework from Microsoft, which makes it easy to build cross-platform web applications that are modern and dynamic. This book will take you through all of the essential concepts in ASP.NET Core 2.0, so you can learn how to build powerful web applications. The book starts with a brief introduction to the ASP.NET Core framework and the improvements made in the latest release, ASP.NET Core 2.0. You will then build, test, and debug your first web application very quickly. Once you understand the basic structure of ASP.NET Core 2.0 web applications, you'll dive deeper into more complex concepts and scenarios. Moving on, we'll explain how to take advantage of widely used frameworks such as Model View Controller and Entity Framework Core 2 and you'll learn how to secure your applications. Finally, we'll show you how to deploy and monitor your applications using Azure, AWS, and Docker. After reading the book, you'll be able to develop efficient and robust web applications in ASP.NET Core 2.0 that have high levels of customer satisfaction and adoption. Style and approach Start an exciting journey to building high performance web applications using ASP.NET Core 2.0 and MVC COMPUTERS,Languages,.NET

Windows Presentation Foundation Development Cookbook Gain comprehensive insight into WPF mechanics and capabilities. About This Book Gain a strong foundation in WPF features and patterns Leverage the MVVM pattern to build decoupled, maintainable apps Increase efficiency through Performance tuning and UI automation Who This Book Is For The book is intended for developers who are relatively new to WPF (Windows Presentation Foundation), or those who have been working with WPF for some time, but want to get a deeper understanding of its foundation and concepts to gain practical knowledge. Basic knowledge of C# and Visual Studio is assumed. What You Will Learn Understand the fundamentals of WPF Explore the major controls and manage element layout Implement data binding Create custom elements that lead to a particular implementation path Customize controls, styles, and templates in XAML Leverage the MVVM pattern to maintain a clean and reusable structure in your code Master practical animations Integrate WCF services in a WPF application Implement WPFs support for debugging and asynchronous operations In Detail Windows Presentation Foundation (WPF) is Microsoft's development tool for building rich Windows client user experiences that incorporate UIs, media, and documents. With the updates in .NET 4.7, Visual Studio 2017, C# 7, and .NET Standard 2.0, WPF has taken giant strides and is now easier than ever for developers to use. If you want to get an in-depth view of WPF mechanics and capabilities, then this book is for you. The book begins by teaching you about the fundamentals of WPF and then quickly shows you the standard controls and the layout options. It teaches you about data bindings and how to utilize resources and the MVVM pattern to maintain a clean and reusable structure in your code. After this, you will explore the animation capabilities of WPF and see how they integrate with other mechanisms. Towards the end of the book, you will learn about WCF services and explore WPF's support for debugging and asynchronous operations. By the end of the book, you will have a deep understanding of WPF and will know how to build resilient applications. Style and approach This book takes a recipe-based approach to teaching you how to create fault-tolerant WPF applications. COMPUTERS,Languages,.NET

Hands-On Parallel Programming with C# 8 and .NET Core 3 Enhance your enterprise application development skills by mastering parallel programming techniques in .NET and C# Key Features Write efficient, fine-grained, and scalable parallel code with C# and .NET Core Experience how parallel programming works by building a powerful application Learn the fundamentals of multithreading by working with IIS and Kestrel Book Description In today's world, every CPU has a multi-core processor. However, unless your application has implemented parallel programming, it will fail to utilize the hardware's full processing capacity. This book will show you how to write modern software on the optimized and high-performing .NET Core 3 framework using C# 8. Hands-On Parallel Programming with C# 8 and .NET Core 3 covers how to build multithreaded, concurrent, and optimized applications that harness the power of multi-core processors. Once you've understood the fundamentals of threading and concurrency, you'll gain insights into the data structure in .NET Core that supports parallelism. The book will then help you perform asynchronous programming in C# and diagnose and debug parallel code effectively. You'll also get to grips with the new Kestrel server and understand the difference between the IIS and Kestrel operating models. Finally, you'll learn best practices such as test-driven development, and run unit tests on your parallel code. By the end of the book, you'll have developed a deep understanding of the core concepts of concurrency and asynchrony to create responsive applications that are not CPU-intensive. What you will learn Analyze and break down a problem statement for parallelism Explore the APM and EAP patterns and how to move legacy code to Task Apply reduction techniques to get aggregated results Create PLINQ queries and study the factors that impact their performance Solve concurrency problems caused by producer-consumer race conditions Discover the synchronization primitives available in .NET Core Understand how the threading model works with IIS and Kestrel Find out how you can make the most of server resources Who this book is for If you want to learn how task parallelism is used to build robust and scalable enterprise architecture, this book is for you. Whether you are a beginner to parallelism in C# or an experienced architect, you'll find this book useful to gain insights into the different threading models supported in .NET Standard and .NET Core. Prior knowledge of C# is required to understand the concepts covered in this book. COMPUTERS,Languages,.NET

Professional Assembly Language Unlike high-level languages such as Java and C++, assembly language is much closer to the machine code that actually runs computers; it's used to create programs or modules that are very fast and efficient, as well as in hacking exploits and reverse engineering Covering assembly language in the Pentium microprocessor environment, this code-intensive guide shows programmers how to create stand-alone assembly language programs as well as how to incorporate assembly language libraries or routines into existing high-level applications Demonstrates how to manipulate data, incorporate advanced functions and libraries, and maximize application performance Examples use C as a high-level language, Linux as the development environment, and GNU tools for assembling, compiling, linking, and debugging COMPUTERS,Languages,Assembly Language

Write Great Code, Volume 2, 2nd Edition Explains how compilers translate high-level language source code (like code written in Python) into low-level machine code (code that the computer can understand) to help readers understand how to produce the best low-level, computer readable machine code. In the beginning, most software was written in assembly, the CPU's low-level language, in order to achieve acceptable performance on relatively slow hardware. Early programmers were sparing in their use of high-level language code, knowing that a high-level language compiler would generate crummy, low-level machine code for their software. Today, however, many programmers write in high-level languages like Python, C/C++/C#, Java, Swift. The result is often sloppy, inefficient code. But you don't need to give up the productivity and portability of high-level languages in order to produce more efficient software. In this second volume of the Write Great Code series, you'll learn: • How to analyze the output of a compiler to verify that your code does, indeed, generate good machine code • The types of machine code statements that compilers typically generate for common control structures, so you can choose the best statements when writing HLL code • Just enough 80x86 and PowerPC assembly language to read compiler output • How compilers convert various constant and variable objects into machine data, and how to use these objects to write faster and shorter programs NEW TO THIS EDITION, COVERAGE OF: • Programming languages like Swift and Java • Code generation on modern 64-bit CPUs • ARM processors on mobile phones and tablets • Stack-based architectures like the Java Virtual Machine • Modern language systems like the Microsoft Common Language Runtime With an understanding of how compilers work, you'll be able to write source code that they can translate into elegant machine code. That understanding starts right here, with Write Great Code, Volume 2: Thinking Low-Level, Writing High-Level. COMPUTERS,Languages,Assembly Language

Mastering Algorithms with C There are many books on data structures and algorithms, including some with useful libraries of C functions. Mastering Algorithms with C offers you a unique combination of theoretical background and working code. With robust solutions for everyday programming tasks, this book avoids the abstract style of most classic data structures and algorithms texts, but still provides all of the information you need to understand the purpose and use of common programming techniques. Implementations, as well as interesting, real-world examples of each data structure and algorithm, are included. Using both a programming style and a writing style that are exceptionally clean, Kyle Loudon shows you how to use such essential data structures as lists, stacks, queues, sets, trees, heaps, priority queues, and graphs. He explains how to use algorithms for sorting, searching, numerical analysis, data compression, data encryption, common graph problems, and computational geometry. And he describes the relative efficiency of all implementations. The compression and encryption chapters not only give you working code for reasonably efficient solutions, they offer explanations of concepts in an approachable manner for people who never have had the time or expertise to study them in depth. Anyone with a basic understanding of the C language can use this book. In order to provide maintainable and extendible code, an extra level of abstraction (such as pointers to functions) is used in examples where appropriate. Understanding that these techniques may be unfamiliar to some programmers, Loudon explains them clearly in the introductory chapters. Contents include: Pointers Recursion Analysis of algorithms Data structures (lists, stacks, queues, sets, hash tables, trees, heaps, priority queues, graphs) Sorting and searching Numerical methods Data compression Data encryption Graph algorithms Geometric algorithms COMPUTERS,Languages,C

GDB Pocket Reference Many Linux and Unix developers are familiar with the GNU debugger (GBD), the invaluable open source tool for testing, fixing, and retesting software. And since GDB can be ported to Windows, Microsoft developers and others who use this platform can also take advantage of this amazing free software that allows you to see exactly what's going on inside of a program as it's executing. This new pocket guide gives you a convenient quick reference for using the debugger with several different programming languages, including C, C++, Java, Fortran and Assembly.The GNU debugger is the most useful tool during the testing phase of the software development cycle because it helps you catch bugs in the act. You can see what a program was doing at the moment it crashed, and then readily pinpoint and correct problem code. With the GDB Pocket Reference on hand, the process is quick and painless. The book covers the essentials of using GBD is a testing environment, including how to specify a target for debugging and how to make a program stop on specified conditions.This handy guide also provides details on using the debugger to examine the stack, source files and data to find the cause of program failure-and then explains ways to use GBD to make quick changes to the program for further testing and debugging.The ability to spot a bug in real time with GDB can save you hours of frustration, and having a quick way to refer to GBD's essential functions is key to making the process work. Once you get your hands on the GDB Pocket Reference, you'll never let go! COMPUTERS,Languages,C

C Pocket Reference C is one of the oldest programming languages and still one of the most widely used. Whether you're an experienced C programmer or you're new to the language, you know how frustrating it can be to hunt through hundreds of pages in your reference books to find that bit of information on a certain function, type or other syntax element. Or even worse, you may not have your books with you. Your answer is the C Pocket Reference. Concise and easy to use, this handy pocket guide to C is a must-have quick reference for any C programmer. It's the only C reference that fits in your pocket and is an excellent companion to O'Reilly's other C books.Ideal as an introduction for beginners and a quick reference for advanced programmers, the C Pocket Reference consists of two parts: a compact description of the C language and a thematically structured reference to the standard library. The representation of the language is based on the ANSI standard and includes extensions introduced in 1999. An index is included to help you quickly find the information you need.This small book covers the following: C language fundamentals Data types Expressions and operators C statements Declarations Functions Preprocessor directives The standard library O'Reilly's Pocket References have become a favorite among programmers everywhere. By providing a wealth of important details in a concise, well-organized format, these handy books deliver just what you need to complete the task at hand. When you've reached a sticking point in your work and need to get to a solution quickly, the new C Pocket Reference is the book you'll want to have. COMPUTERS,Languages,C

Linux Kernel Development Linux Kernel Development details the design and implementation of the Linux kernel, presenting the content in a manner that is beneficial to those writing and developing kernel code, as well as to programmers seeking to better understand the operating system and become more efficient and productive in their coding. The book details the major subsystems and features of the Linux kernel, including its design, implementation, and interfaces. It covers the Linux kernel with both a practical and theoretical eye, which should appeal to readers with a variety of interests and needs. The author, a core kernel developer, shares valuable knowledge and experience on the 2.6 Linux kernel. Specific topics covered include process management, scheduling, time management and timers, the system call interface, memory addressing, memory management, the page cache, the VFS, kernel synchronization, portability concerns, and debugging techniques. This book covers the most interesting features of the Linux 2.6 kernel, including the CFS scheduler, preemptive kernel, block I/O layer, and I/O schedulers. The third edition of Linux Kernel Development includes new and updated material throughout the book: An all-new chapter on kernel data structures Details on interrupt handlers and bottom halves Extended coverage of virtual memory and memory allocation Tips on debugging the Linux kernel In-depth coverage of kernel synchronization and locking Useful insight into submitting kernel patches and working with the Linux kernel community COMPUTERS,Languages,C

Practical C Programming There are lots of introductory C books, but this is the first one that has the no-nonsense, practical approach that has made Nutshell Handbooks® famous.C programming is more than just getting the syntax right. Style and debugging also play a tremendous part in creating programs that run well and are easy to maintain. This book teaches you not only the mechanics of programming, but also describes how to create programs that are easy to read, debug, and update.Practical rules are stressed. For example, there are fifteen precedence rules in C (&& comes before || comes before ?:). The practical programmer reduces these to two: Multiplication and division come before addition and subtraction. Contrary to popular belief, most programmers do not spend most of their time creating code. Most of their time is spent modifying someone else's code. This books shows you how to avoid the all-too-common obfuscated uses of C (and also to recognize these uses when you encounter them in existing programs) and thereby to leave code that the programmer responsible for maintenance does not have to struggle with. Electronic Archaeology, the art of going through someone else's code, is described.This third edition introduces popular Integrated Development Environments on Windows systems, as well as UNIX programming utilities, and features a large statistics-generating program to pull together the concepts and features in the language. COMPUTERS,Languages,C

Head First C Ever wished you could learn C from a book? Head First C provides a complete learning experience for C and structured imperative programming. With a unique method that goes beyond syntax and how-to manuals, this guide not only teaches you the language, it helps you understand how to be a great programmer. You'll learn key areas such as language basics, pointers and pointer arithmetic, and dynamic memory management. Advanced topics include multi-threading and network programming—topics typically covered on a college-level course. This book also features labs: in-depth projects intended to stretch your abilities, test your new skills, and build confidence. Head First C mimics the style of college-level C courses, making it ideal as an accessible textbook for students. We think your time is too valuable to waste struggling with new concepts. Using the latest research in cognitive science and learning theory to craft a multi-sensory learning experience, Head First C uses a visually rich format designed for the way your brain works, not a text-heavy approach that puts you to sleep. COMPUTERS,Languages,C

ZeroMQ Dive into ØMQ (aka ZeroMQ), the smart socket library that gives you fast, easy, message-based concurrency for your applications. With this quick-paced guide, you’ll learn hands-on how to use this scalable, lightweight, and highly flexible networking tool for exchanging messages among clusters, the cloud, and other multi-system environments. ØMQ maintainer Pieter Hintjens takes you on a tour of real-world applications, using extended examples in C to help you work with ØMQ’s API, sockets, and patterns. Learn how to use specific ØMQ programming techniques, build multithreaded applications, and create your own messaging architectures. You’ll discover how ØMQ works with several programming languages and most operating systems—with little or no cost. Learn ØMQ’s main patterns: request-reply, publish-subscribe, and pipeline Work with ØMQ sockets and patterns by building several small applications Explore advanced uses of ØMQ’s request-reply pattern through working examples Build reliable request-reply patterns that keep working when code or hardware fails Extend ØMQ’s core pub-sub patterns for performance, reliability, state distribution, and monitoring Learn techniques for building a distributed architecture with ØMQ Discover what’s required to build a general-purpose framework for distributed applications COMPUTERS,Languages,C

Understanding and Using C Pointers Improve your programming through a solid understanding of C pointers and memory management. With this practical book, you’ll learn how pointers provide the mechanism to dynamically manipulate memory, enhance support for data structures, and enable access to hardware. Author Richard Reese shows you how to use pointers with arrays, strings, structures, and functions, using memory models throughout the book. Difficult to master, pointers provide C with much flexibility and power—yet few resources are dedicated to this data type. This comprehensive book has the information you need, whether you’re a beginner or an experienced C or C++ programmer or developer. Get an introduction to pointers, including the declaration of different pointer types Learn about dynamic memory allocation, de-allocation, and alternative memory management techniques Use techniques for passing or returning data to and from functions Understand the fundamental aspects of arrays as they relate to pointers Explore the basics of strings and how pointers are used to support them Examine why pointers can be the source of security problems, such as buffer overflow Learn several pointer techniques, such as the use of opaque pointers, bounded pointers and, the restrict keyword COMPUTERS,Languages,C

C Programming Absolute Beginner's Guide Updated for C11 Write powerful C programs…without becoming a technical expert! This book is the fastest way to get comfortable with C, one incredibly clear and easy step at a time. You’ll learn all the basics: how to organize programs, store and display data, work with variables, operators, I/O, pointers, arrays, functions, and much more. C programming has neverbeen this simple! Who knew how simple C programming could be? This is today’s best beginner’s guide to writing C programs–and to learning skills you can use with practically any language. Its simple, practical instructions will help you start creating useful, reliable C code, from games to mobile apps. Plus, it’s fully updated for the new C11 standard and today’s free, open source tools! Here’s a small sample of what you’ll learn: • Discover free C programming tools for Windows, OS X, or Linux • Understand the parts of a C program and how they fit together • Generate output and display it on the screen • Interact with users and respond to their input • Make the most of variables by using assignments and expressions • Control programs by testing data and using logical operators • Save time and effort by using loops and other techniques • Build powerful data-entry routines with simple built-in functions • Manipulate text with strings • Store information, so it’s easy to access and use • Manage your data with arrays, pointers, and data structures • Use functions to make programs easier to write and maintain • Let C handle all your program’s math for you • Handle your computer’s memory as efficiently as possible • Make programs more powerful with preprocessing directives COMPUTERS,Languages,C

C Programming Language This ebook is the first authorized digital version of Kernighan and Ritchie’s 1988 classic, The C Programming Language (2nd Ed.). One of the best-selling programming books published in the last fifty years, "K&R" has been called everything from the "bible" to "a landmark in computer science" and it has influenced generations of programmers. Available now for all leading ebook platforms, this concise and beautifully written text is a "must-have" reference for every serious programmer’s digital library. As modestly described by the authors in the Preface to the First Edition, this "is not an introductory programming manual; it assumes some familiarity with basic programming concepts like variables, assignment statements, loops, and functions. Nonetheless, a novice programmer should be able to read along and pick up the language, although access to a more knowledgeable colleague will help." COMPUTERS,Languages,C

Expert C Programming This book is for the knowledgeable C programmer, this is a second book that gives the C programmers advanced tips and tricks. This book will help the C programmer reach new heights as a professional. Organized to make it easy for the reader to scan to sections that are relevant to their immediate needs. COMPUTERS,Languages,C

C Programming in One Hour a Day, Sams Teach Yourself Sams Teach Yourself C Programming in One Hour a Day, Seventh Edition is the newest version of the worldwide best-seller Sams Teach Yourself C in 21 Days. Fully revised for the new C11 standard and libraries, it now emphasizes platform-independent C programming using free, open-source C compilers. This edition strengthens its focus on C programming fundamentals, and adds new material on popular C-based object-oriented programming languages such as Objective-C. Filled with carefully explained code, clear syntax examples, and well-crafted exercises, this is the broadest and deepest introductory C tutorial available. It’s ideal for anyone who’s serious about truly mastering C – including thousands of developers who want to leverage its speed and performance in modern mobile and gaming apps. Friendly and accessible, it delivers step-by-step, hands-on experience that starts with simple tasks and gradually builds to professional-quality techniques. Each lesson is designed to be completed in hour or less, introducing and clearly explaining essential concepts, providing practical examples, and encouraging you to build simple programs on your own. Coverage includes: Understanding C program components and structure Mastering essential C syntax and program control Using core language features, including numeric arrays, pointers, characters, strings, structures, and variable scope Interacting with the screen, printer, and keyboard Using functions and exploring the C Function Library Working with memory and the compiler Contents at a Glance PART I: FUNDAMENTALS OF C 1 Getting Started with C 2 The Components of a C Program 3 Storing Information: Variables and Constants 4 The Pieces of a C Program: Statements, Expressions, and Operators 5 Packaging Code in Functions 6 Basic Program Control 7 Fundamentals of Reading and Writing Information PART II: PUTTING C TO WORK 8 Using Numeric Arrays 9 Understanding Pointers 10 Working with Characters and Strings 11 Implementing Structures, Unions, and TypeDefs 12 Understanding Variable Scope 13 Advanced Program Control 14 Working with the Screen, Printer, and Keyboard PART III: ADVANCED C 15 Pointers to Pointers and Arrays of Pointers 16 Pointers to Functions and Linked Lists 17 Using Disk Files 18 Manipulating Strings 19 Getting More from Functions 20 Exploring the C Function Library 21 Working with Memory 22 Advanced Compiler Use PART IV: APPENDIXES A ASCII Chart B C/C++ Reserved Words C Common C Functions D Answers COMPUTERS,Languages,C

AVR Programming Atmel's AVR microcontrollers are the chips that power Arduino, and are the go-to chip for many hobbyist and hardware hacking projects. In this book you'll set aside the layers of abstraction provided by the Arduino environment and learn how to program AVR microcontrollers directly. In doing so, you'll get closer to the chip and you'll be able to squeeze more power and features out of it. Each chapter of this book is centered around projects that incorporate that particular microcontroller topic. Each project includes schematics, code, and illustrations of a working project. Program a range of AVR chips Extend and re-use other people’s code and circuits Interface with USB, I2C, and SPI peripheral devices Learn to access the full range of power and speed of the microcontroller Build projects including Cylon Eyes, a Square-Wave Organ, an AM Radio, a Passive Light-Sensor Alarm, Temperature Logger, and more Understand what's happening behind the scenes even when using the Arduino IDE COMPUTERS,Languages,C

Ivor Horton's Beginning Visual C++ 2013 Learn C++ with the best tutorial on the market! Horton's unique tutorial approach and step-by-step guidance have helped over 100,000 novice programmers learn C++. In Ivor Horton's Beginning Visual C++ 2013, Horton not only guides you through the fundamentals of the standard C++ language, but also teaches you how C++ is used in the latest Visual Studio 2013 environment. Visual Studio 2013 includes major changes to the IDE and expanded options for C++ coding. Ivor Horton's Beginning Visual C++ 2013 will teach you the latest techniques to take your Visual C++ coding to an all-new level. C++ language and library changes supported under Visual Studio 2013 IDE-specific changes for code formatting and debugging Changes to the C++ Standard Language for both C++ 11 and the new C++ 14 And more Horton introduces you to both Standard C++ and Visual C++ so you can build any component your app requires. Ivor Horton's Beginning Visual C++ 2013 is an indispensable guidebook for any new programmer, and contains plenty of exercises and solutions to help programmers of any level master the important concepts quickly and easily. COMPUTERS,Languages,C

C++ For Dummies The best-selling C++ For Dummies book makes C++ easier! C++ For Dummies, 7th Edition is the best-selling C++ guide on the market, fully revised for the 2014 update. With over 60% new content, this updated guide reflects the new standards, and includes a new Big Data focus that highlights the use of C++ among popular Big Data software solutions. The book provides step-by-step instruction from the ground up, helping beginners become programmers and allowing intermediate programmers to sharpen their skills. The companion website provides all code mentioned in the text, an updated GNU_C++, the new C++ compiler, and other applications. By the end of the first chapter, you will have programmed your first C++ application! As one of the most commonly used programming languages, C++ is a must-have skill for programmers who wish to remain versatile and marketable. C++ For Dummies, 7th Edition provides clear, concise, expert instruction, which is organized for easy navigation and designed for hands-on learning. Whether you're new to programming, familiar with other languages, or just getting up to speed on the new libraries, features, and generics, this guide provides the information you need. Provides you with an introduction to C++ programming Helps you become a functional programmer Features information on classes, inheritance, and optional features Teaches you 10 ways to avoid adding bugs The book incorporates the newest C++ features into the fundamental instruction, allowing beginners to learn the update as they learn the language. Staying current on the latest developments is a crucial part of being a programmer, and C++ For Dummies, 7th Edition gets you started off on the right foot. COMPUTERS,Languages,C

Arduino Programming in 24 Hours, Sams Teach Yourself In just 24 sessions of one hour or less, Sams Teach Yourself Arduino Programming in 24 Hours teaches you C programmingon Arduino, so you can start creating inspired “DIY†hardwareprojects of your own! Using this book’s straightforward, step-by-stepapproach, you’ll walk through everything from setting up yourprogramming environment to mastering C syntax and features, interfacing your Arduino to performing full-fledged prototyping.Every hands-on lesson and example builds on what you’ve alreadylearned, giving you a rock-solid foundation for real-world success! Step-by-step instructions carefully walk you through the most common Arduino programming tasks. Quizzes at the end of each chapter help you test your knowledge. By the Way notes present interesting information related to the discussion. Did You Know? tips offer advice or show you easier ways to perform tasks. Watch Out! cautions alert you to possible problems and give you advice on how to avoid them. Learn how to... Get the right Arduino hardware and accessories for your needs Download the Arduino IDE, install it, and link it to your Arduino Quickly create, compile, upload, and run your first Arduino program Master C syntax, decision control, strings, data structures, and functions Use pointers to work with memory—and avoid common mistakes Store data on your Arduino’s EEPROM or an external SD card Use existing hardware libraries, or create your own Send output and read input from analog devices or digital interfaces Create and handle interrupts in software and hardware Communicate with devices via the SPI interface and I2C protocol Work with analog and digital sensors Write Arduino C programs that control motors Connect an LCD to your Arduino, and code the output Install an Ethernet shield, configure an Ethernet connection, and write networking programs Create prototyping environments, use prototyping shields, and interface electronics to your Arduino COMPUTERS,Languages,C

Programming in C Programming in C will teach you how to write programs in the C programming language. Whether you’re a novice or experienced programmer, this book will provide you with a clear understanding of this language, which is the foundation for many object-oriented programming languages such as C++, Objective-C, C#, and Java. This book teaches C by example, with complete C programs used to illustrate each new concept along the way. Stephen Kochan provides step-by-step explanations for all C functions. You will learn both the language fundamentals and good programming practices. Exercises at the end of each chapter make the book ideally suited for classroom use or for self-instruction. All the features of the C language are covered in this book, including the latest additions added with the C11 standard. Appendixes provide a detailed summary of the language and the standard C library, both organized for quick reference. “Absolutely the best book for anyone starting out programming in C. This is an excellent introductory text with frequent examples and good text.…This is the book I used to learn C–it’s a great book.†–Vinit S. Carpenter, Learn C/C++ Today COMPUTERS,Languages,C

21st Century C Throw out your old ideas about C and get to know a programming language that’s substantially outgrown its origins. With this revised edition of 21st Century C, you’ll discover up-to-date techniques missing from other C tutorials, whether you’re new to the language or just getting reacquainted. C isn’t just the foundation of modern programming languages; it is a modern language, ideal for writing efficient, state-of-the-art applications. Get past idioms that made sense on mainframes and learn the tools you need to work with this evolved and aggressively simple language. No matter what programming language you currently favor, you’ll quickly see that 21st century C rocks. Set up a C programming environment with shell facilities, makefiles, text editors, debuggers, and memory checkers Use Autotools, C’s de facto cross-platform package manager Learn about the problematic C concepts too useful to discard Solve C’s string-building problems with C-standard functions Use modern syntactic features for functions that take structured inputs Build high-level, object-based libraries and programs Perform advanced math, talk to internet servers, and run databases with existing C libraries This edition also includes new material on concurrent threads, virtual tables, C99 numeric types, and other features. COMPUTERS,Languages,C

Beginning Programming with C++ For Dummies Learn to program with C++ quickly with this helpful For Dummies guide Beginning Programming with C++ For Dummies, 2nd Edition gives you plain-English explanations of the fundamental principles of C++, arming you with the skills and know-how to expertly use one of the world's most popular programming languages. You'll explore what goes into creating a program, how to put the pieces together, learn how to deal with standard programming challenges, and much more. Written by the bestselling author of C++ For Dummies, this updated guide explores the basic development concepts and techniques of C++ from a beginner's point of view, and helps make sense of the how and why of C++ programming from the ground up. Beginning with an introduction to how programming languages function, the book goes on to explore how to work with integer expressions and character expressions, keep errors out of your code, use loops and functions, divide your code into modules, and become a functional programmer. Grasp C++ programming like a pro, even if you've never written a line of code Master basic development concepts and techniques in C++ Get rid of bugs and write programs that work Find all the code from the book and an updated C++ compiler on the companion website If you're a student or first-time programmer looking to master this object-oriented programming language, Beginning Programming with C++ For Dummies, 2nd Edition has you covered. COMPUTERS,Languages,C

Learn C the Hard Way You Will Learn C! Zed Shaw has crafted the perfect course for the beginning C programmer eager to advance their skills in any language. Follow it and you will learn the many skills early and junior programmers need to succeed–just like the hundreds of thousands of programmers Zed has taught to date! You bring discipline, commitment, persistence, and experience with any programming language; the author supplies everything else. In Learn C the Hard Way , you’ll learn C by working through 52 brilliantly crafted exercises. Watch Zed Shaw’s teaching video and read the exercise. Type his code precisely. (No copying and pasting!) Fix your mistakes. Watch the programs run. As you do, you’ll learn what good, modern C programs look like; how to think more effectively about code; and how to find and fix mistakes far more efficiently. Most importantly, you’ll master rigorous defensive programming techniques, so you can use any language to create software that protects itself from malicious activity and defects. Through practical projects you’ll apply what you learn to build confidence in your new skills. Shaw teaches the key skills you need to start writing excellent C software, including Setting up a C environment Basic syntax and idioms Compilation, make files, and linkers Operators, variables, and data types Program control Arrays and strings Functions, pointers, and structs Memory allocation I/O and files Libraries Data structures, including linked lists, sort, and search Stacks and queues Debugging, defensive coding, and automated testing Fixing stack overflows, illegal memory access, and more Breaking and hacking your own C code It’ll Be Hard at First. But Soon, You’ll Just Get It–And That Will Feel Great! This tutorial will reward you for every minute you put into it. Soon, you’ll know one of the world’s most powerful programming languages. You’ll be a C programmer. COMPUTERS,Languages,C

C in a Nutshell The new edition of this classic O’Reilly reference provides clear, detailed explanations of every feature in the C language and runtime library, including multithreading, type-generic macros, and library functions that are new in the 2011 C standard (C11). If you want to understand the effects of an unfamiliar function, and how the standard library requires it to behave, you’ll find it here, along with a typical example. Ideal for experienced C and C++ programmers, this book also includes popular tools in the GNU software collection. You’ll learn how to build C programs with GNU Make, compile executable programs from C source code, and test and debug your programs with the GNU debugger. In three sections, this authoritative book covers: C language concepts and language elements, with separate chapters on types, statements, pointers, memory management, I/O, and more The C standard library, including an overview of standard headers and a detailed function reference Basic C programming tools in the GNU software collection, with instructions on how use them with the Eclipse IDE COMPUTERS,Languages,C

Introducing Go Perfect for beginners familiar with programming basics, this hands-on guide provides an easy introduction to Go, the general-purpose programming language from Google. Author Caleb Doxsey covers the language’s core features with step-by-step instructions and exercises in each chapter to help you practice what you learn. Go is a general-purpose programming language with a clean syntax and advanced features, including concurrency. This book provides the one-on-one support you need to get started with the language, with short, easily digestible chapters that build on one another. By the time you finish this book, not only will you be able to write real Go programs, you'll be ready to tackle advanced techniques. Jump into Go basics, including data types, variables, and control structures Learn complex types, such as slices, functions, structs, and interfaces Explore Go’s core library and learn how to create your own package Write tests for your code by using the language’s go test program Learn how to run programs concurrently with goroutines and channels Get suggestions to help you master the craft of programming COMPUTERS,Languages,C

Professional Visual Studio 2017 Skip the basics and delve right into Visual Studio 2017 advanced features and tools Professional Visual Studio 2017 is the industry-favorite guide to getting the most out of Microsoft's primary programming technology. From touring the new UI to exploiting advanced functionality, this book is designed to help professional developers become more productive. A unique IDE-centric approach provides a clear path through the typical workflow while exploring the nooks and crannies that can make your job easier. Visual Studio 2017 includes a host of features aimed at improving developer productivity and UI, and this book covers them all with clear explanation, new figures, and expert insight. Whether you're new to VS or just upgrading, this all-inclusive guide is an essential resource to keep within arm's reach. Visual Studio 2017 fixes the crucial issues that kept professionals from adopting VS 2015, and includes new features and tools that streamline the developer's job. This book provides the straightforward answers you need so you can get up to speed quickly and get back to work. Master the core functionality of Visual Studio 2017 Dig into the tools that make writing code easier Tailor the environment to your workflow, not the other way around Work your way through configuration, debugging, building, deployment, customizing, and more Microsoft is changing their release cadence—it's only been about two years since the last release—so developers need to quickly get a handle on new tools and features if they hope to remain productive. The 2017 release is designed specifically to help you get more done, in less time, with greater accuracy and attention to detail. If you're ready to get acquainted, Professional Visual Studio 2017 is your ideal guide. COMPUTERS,Languages,C

Professional C++ Get up to date quickly on the new changes coming with C++17 Professional C++ is the advanced manual for C++ programming. Designed to help experienced developers get more out of the latest release, this book skims over the basics and dives right in to exploiting the full capabilities of C++17. Each feature is explained by example, each including actual code snippets that you can plug into your own applications. Case studies include extensive, working code that has been tested on Windows and Linux, and the author's expert tips, tricks, and workarounds can dramatically enhance your workflow. Even many experienced developers have never fully explored the boundaries of the language's capabilities; this book reveals the advanced features you never knew about, and drills down to show you how to turn these features into real-world solutions. The C++17 release includes changes that impact the way you work with C++; this new fourth edition covers them all, including nested namespaces, structured bindings, string_view, template argument deduction for constructors, parallel algorithms, generalized sum algorithms, Boyer-Moore string searching, string conversion primitives, a filesystem API, clamping values, optional values, the variant type, the any type, and more. Clear explanations and professional-level depth make this book an invaluable resource for any professional needing to get up to date quickly. Maximize C++ capabilities with effective design solutions Master little-known elements and learn what to avoid Adopt new workarounds and testing/debugging best practices Utilize real-world program segments in your own applications C++ is notoriously complex, and whether you use it for gaming or business, maximizing its functionality means keeping up to date with the latest changes. Whether these changes enhance your work or make it harder depends on how well-versed you are in the newest C++ features. Professional C++ gets you up to date quickly, and provides the answers you need for everyday solutions. COMPUTERS,Languages,C

Jumpstarting C All Make Jumpstart books provide a quick way for makers to "jumpstart" their knowledge of a certain topic.Jumpstarting C takes the reader on a 50-page journey, from installing C on a Raspberry Pi, to creating their first "Hello World" program in C, to building and programming a handheld 4-color memory game using C, pushbuttons and LEDs. COMPUTERS,Languages,C

Test Driven Development for Embedded C Another day without Test-Driven Development means more time wasted chasing bugs and watching your code deteriorate. You thought TDD was for someone else, but it's not! It's for you, the embedded C programmer. TDD helps you prevent defects and build software with a long useful life. This is the first book to teach the hows and whys of TDD for C programmers. TDD is a modern programming practice C developers need to know. It's a different way to program---unit tests are written in a tight feedback loop with the production code, assuring your code does what you think. You get valuable feedback every few minutes. You find mistakes before they become bugs. You get early warning of design problems. You get immediate notification of side effect defects. You get to spend more time adding valuable features to your product. James is one of the few experts in applying TDD to embedded C. With his 1.5 decades of training,coaching, and practicing TDD in C, C++, Java, and C# he will lead you from being a novice in TDD to using the techniques that few have mastered. This book is full of code written for embedded C programmers. You don't just see the end product, you see code and tests evolve. James leads you through the thought process and decisions made each step of the way. You'll learn techniques for test-driving code right nextto the hardware, and you'll learn design principles and how to apply them to C to keep your code clean and flexible. To run the examples in this book, you will need a C/C++ development environment on your machine, and the GNU GCC tool chain or Microsoft Visual Studio for C++ (some project conversion may be needed). COMPUTERS,Languages,C

Access 2019 Bible Master database creation and management Access 2019 Bible is your, comprehensive reference to the world's most popular database management tool. With clear guidance toward everything from the basics to the advanced, this go-to reference helps you take advantage of everything Access 2019 has to offer. Whether you're new to Access or getting started with Access 2019, you'll find everything you need to know to create the database solution perfectly tailored to your needs, with expert guidance every step of the way. The companion website features all examples and databases used in the book, plus trial software and a special offer from Database Creations. Start from the beginning for a complete tutorial, or dip in and grab what you need when you need it. Access enables database novices and programmers to store, organize, view, analyze, and share data, as well as build powerful, integrable, custom database solutions — but databases can be complex, and difficult to navigate. This book helps you harness the power of the database with a solid understanding of their purpose, construction, and application. Understand database objects and design systems objects Build forms, create tables, manipulate datasheets, and add data validation Use Visual Basic automation and XML Data Access Page design Exchange data with other Office applications, including Word, Excel, and more From database fundamentals and terminology to XML and Web services, this book has everything you need to maximize Access 2019 and build the database you need. COMPUTERS,Languages,C

Extreme C Push the limits of what C - and you - can do, with this high-intensity guide to the most advanced capabilities of C Key Features Make the most of C's low-level control, flexibility, and high performance A comprehensive guide to C's most powerful and challenging features A thought-provoking guide packed with hands-on exercises and examples Book Description There's a lot more to C than knowing the language syntax. The industry looks for developers with a rigorous, scientific understanding of the principles and practices. Extreme C will teach you to use C's advanced low-level power to write effective, efficient systems. This intensive, practical guide will help you become an expert C programmer. Building on your existing C knowledge, you will master preprocessor directives, macros, conditional compilation, pointers, and much more. You will gain new insight into algorithm design, functions, and structures. You will discover how C helps you squeeze maximum performance out of critical, resource-constrained applications. C still plays a critical role in 21st-century programming, remaining the core language for precision engineering, aviations, space research, and more. This book shows how C works with Unix, how to implement OO principles in C, and fully covers multi-processing. In Extreme C, Amini encourages you to think, question, apply, and experiment for yourself. The book is essential for anybody who wants to take their C to the next level. What you will learn Build advanced C knowledge on strong foundations, rooted in first principles Understand memory structures and compilation pipeline and how they work, and how to make most out of them Apply object-oriented design principles to your procedural C code Write low-level code that's close to the hardware and squeezes maximum performance out of a computer system Master concurrency, multithreading, multi-processing, and integration with other languages Unit Testing and debugging, build systems, and inter-process communication for C programming Who this book is for Extreme C is for C programmers who want to dig deep into the language and its capabilities. It will help you make the most of the low-level control C gives you. COMPUTERS,Languages,C

Effective C A detailed introduction to the C programming language for experienced programmers. The world runs on code written in the C programming language, yet most schools begin the curriculum with Python or Java. Effective C bridges this gap and brings C into the modern era--covering the modern C17 Standard as well as potential C2x features. With the aid of this instant classic, you'll soon be writing professional, portable, and secure C programs to power robust systems and solve real-world problems. Robert C. Seacord introduces C and the C Standard Library while addressing best practices, common errors, and open debates in the C community. Developed together with other C Standards committee experts, Effective C will teach you how to debug, test, and analyze C programs. You'll benefit from Seacord's concise explanations of C language constructs and behaviors, and from his 40 years of coding experience. You'll learn: • How to identify and handle undefined behavior in a C program • The range and representations of integers and floating-point values • How dynamic memory allocation works and how to use nonstandard functions • How to use character encodings and types • How to perform I/O with terminals and filesystems using C Standard streams and POSIX file descriptors • How to understand the C compiler's translation phases and the role of the preprocessor • How to test, debug, and analyze C programs Effective C will teach you how to write professional, secure, and portable C code that will stand the test of time and help strengthen the foundation of the computing world. COMPUTERS,Languages,C

Learn C Programming Get started with writing simple programs in C while learning the skills that will help you work with practically any programming language Key Features Learn essential C concepts such as variables, data structures, functions, loops, and pointers Get to grips with the core programming aspects that form the base of many modern programming languages Explore the expressiveness and versatility of the C language with the help of sample programs Book Description C is a powerful general-purpose programming language that is excellent for beginners to learn. This book will introduce you to computer programming and software development using C. If you're an experienced developer, this book will help you to become familiar with the C programming language. This C programming book takes you through basic programming concepts and shows you how to implement them in C. Throughout the book, you'll create and run programs that make use of one or more C concepts, such as program structure with functions, data types, and conditional statements. You'll also see how to use looping and iteration, arrays, pointers, and strings. As you make progress, you'll cover code documentation, testing and validation methods, basic input/output, and how to write complete programs in C. By the end of the book, you'll have developed basic programming skills in C, that you can apply to other programming languages and will develop a solid foundation for you to advance as a programmer. What you will learn Understand fundamental programming concepts and implement them in C Write working programs with an emphasis on code indentation and readability Break existing programs intentionally and learn how to debug code Adopt good coding practices and develop a clean coding style Explore general programming concepts that are applicable to more advanced projects Discover how you can use building blocks to make more complex and interesting programs Use C Standard Library functions and understand why doing this is desirable Who this book is for This book is written for two very diverse audiences. If you're an absolute beginner who only has basic familiarity with operating a computer, this book will help you learn the most fundamental concepts and practices you need to know to become a successful C programmer. If you're an experienced programmer, you'll find the full range of C syntax as well as common C idioms. You can skim through the explanations and focus primarily on the source code provided. COMPUTERS,Languages,C

C# Language Pocket Reference C# programmers all have one thing in common -- they're learning a new language. That fact alone brings challenges, frustrations, and constant demands on your patience. And, no matter how good your reference books are, you can't always stop to thumb through hundreds of pages to find the piece of information you need. Your answer is the C# Language Pocket Reference. Concise and easy to use, this handy pocket guide to C# comes from the authors of C# in a Nutshell, and is a must-have quick reference for anyone implementing this new object-oriented language.The C# Language Pocket Reference offers the convenience of a quick reference in a format that will actually fit in your pocket. The book includes a guide to C# language elements, a brief overview of the Framework Class library, a cross-reference for namespaces and assemblies, a list of compiler syntax and switches, a regular expressions reference guide, and more. You'll be surprised at how much information can fit into this slim volume.O'Reilly's Pocket References have become a favorite among programmers everywhere. By providing a wealth of important details in a concise, well-organized format, these handy books deliver just what you need to complete the task at hand. When you've reached a sticking point in your work and need to get to a solution quickly, the new C# Language Pocket Reference is the book you'll want to have. COMPUTERS,Languages,C#

C# & VB.NET Conversion Pocket Reference Though most programmers use two or more languages, they usually have a mastery of one. Although Microsoft has advertised that the .NET runtime is language agnostic and that C# and Visual Basic .NET are so close that switching between the two is really quite easy, that?s only true up to a point. Some of the differences are obvious, but others are very subtle. C# & VB.NET Conversion Pocket Reference helps you easily make the switch from one language to another.The differences occur in three main areas: syntax, object-oriented principles, and the Visual Studio .NET IDE. Syntax concerns the statements and language elements. Object oriented differences are less obvious, and concern differences in implementation and feature sets between the two languages. IDE differences include things like compiler settings or attributes. There is also a fourth area of difference: language features that are present in one language but have no equivalent in the other. These unique language features are also covered in this book.C# & VB.NET Conversion Pocket Reference is a perfect companion for documents and books that don?t have examples using your mastered language. Author Jose Mojica expects that you know one of the two languages, but does not make anassumption about which one. He presents the information in alanguage-neutral point of view so that programmers from either background can read a section and feel that it is targeted to them. COMPUTERS,Languages,C#

C# 4.0 Pocket Reference When you're programming C# 4.0 and need a little help, this tightly focused and practical book tells you exactly what you need to know -- without long introductions or bloated examples. It's ideal as a succinct quick reference or as a guide to get you rapidly up to speed if you already know Java, C++, or an earlier version of C#. Written by the authors of the acclaimed C# 4.0 in a Nutshell (O’Reilly), this book covers the entire C# 4.0 language -- without skimping on the details -- including: Features new to C# 4.0, such as dynamic binding, optional and named parameters, and type parameter variance All of C#'s fundamentals Advanced topics, including operator overloading, custom conversions, type constraints, covariance and contravariance, lambda expressions and closures, iterators, nullable types, and operator lifting LINQ, starting with sequences, lazy execution, and standard query operators; finishing with a complete reference to query expressions Unsafe code and pointers, custom attributes, preprocessor directives, and XML documentation COMPUTERS,Languages,C#

C# Database Basics Working with data and databases in C# certainly can be daunting if you’re coming from VB6, VBA, or Access. With this hands-on guide, you’ll shorten the learning curve considerably as you master accessing, adding, updating, and deleting data with C#—basic skills you need if you intend to program with this language. No previous knowledge of C# is necessary. By following the examples in this book, you’ll learn how to tackle several database tasks in C#, such as working with SQL Server, building data entry forms, and using data in a web service. The book’s code samples will help you get started on your own projects. Create a Windows Forms application with a datagrid Connect to multiple data sources, including Access and SQL Server Add, edit, and update data in a database you choose and design Enable users to choose their data source at runtime Learn the roles of DataTable, DataView, BindingSource, Filters, and other objects Understand where variables are declared and how they impact the code Build a simple web service that connects to a database COMPUTERS,Languages,C#

Programming Entity Framework The DbContext API captures Entity Framework’s (EF) most commonly used features and tasks, simplifying development with EF. This concise book shows you how to use the API to perform set operations with the DbSet class, handle change tracking and resolve concurrency conflicts with the Change Tracker API, and validate changes to your data with the Validation API. With DbContext, you’ll be able to query and update data, whether you’re working with individual objects or graphs of objects and their related data. You’ll find numerous C# code samples to help you get started. All you need is experience with Visual Studio and database management basics. Use EF’s query capabilities to retrieve data, and use LINQ to sort and filter data Learn how to add new data, and change and delete existing data Use the Change Tracker API to access information EF keeps about the state of entity instances Control change tracking information of entities in disconnected scenarios, including NTier applications Validate data changes before they’re sent to the database, and set up validation rules Bypass EF’s query pipeline and interact directly with the database COMPUTERS,Languages,C#

Async in C# 5.0 If you’re writing one of several applications that call for asynchronous programming, this concise hands-on guide shows you how the async feature in C# 5.0 can make the process much simpler. Along with a clear introduction to asynchronous programming, you get an in-depth look at how the async feature works and why you might want to use it in your application. Written for experienced C# programmers—yet approachable for beginners—this book is packed with code examples that you can extend for your own projects. Write your own asynchronous code, and learn how async saves you from this messy chore Discover new performance possibilities in ASP.NET web server code Explore how async and WinRT work together in Windows 8 applications Learn the importance of the await keyword in async methods Understand which .NET thread is running your code—and at what points in the program Use the Task-based Asynchronous Pattern (TAP) to write asynchronous APIs in .NET Take advantage of parallel computing in modern machines Measure async code performance by comparing it with alternatives COMPUTERS,Languages,C#

Head First C# Head First C# is a complete learning experience for learning how to program with C#, XAML, the .NET Framework, and Visual Studio. Fun and highly visual, this introduction to C# is designed to keep you engaged and entertained from first page to last. Updated for Windows 8.1 and Visual Studio 2013, and includes projects for all previous versions of Windows (included in the book, no additional downloading or printing required). You’ll build a fully functional video game in the opening chapter, and then learn how to use classes and object-oriented programming, draw graphics and animation, and query data with LINQ and serialize it to files. And you'll do it all by creating games, solving puzzles, and doing hands-on projects. By the time you're done, you'll be a solid C# programmer—and you'll have a great time along the way! Create a fun arcade game in the first chapter, and build games and other projects throughout the book Learn how to use XAML to design attractive and interactive pages and windows Build modern Windows Store apps using the latest Microsoft technology Learn WPF (Windows Presentation Foundation) using the downloadable WPF Learner's Guide Using the Model-View-ViewModel (MVVM) pattern to create robust architecture Build a bonus Windows Phone project and run it in the Visual Studio Windows Phone emulator Projects in the book work with all editions of Visual Studio, including the free Express editions. COMPUTERS,Languages,C#

CLR via C# Dig deep and master the intricacies of the common language runtime, C#, and .NET development. Led by programming expert Jeffrey Richter, a longtime consultant to the Microsoft .NET team - you’ll gain pragmatic insights for building robust, reliable, and responsive apps and components. Fully updated for .NET Framework 4.5 and Visual Studio 2012 Delivers a thorough grounding in the .NET Framework architecture, runtime environment, and other key topics, including asynchronous programming and the new Windows Runtime Provides extensive code samples in Visual C# 2012 Features authoritative, pragmatic guidance on difficult development concepts such as generics and threading COMPUTERS,Languages,C#

Learning C# 2005 If you're a novice programmer and you want to learn C#, there aren't many books that will guide you. Most C# books are written for experienced C++ and Java programmers.That's why Jesse Liberty, author of the best-selling books Programming C# and Programming ASP.NET, has written an entry-level guide to C#. Written in a warm and friendly manner, Learning C# assumes no prior programming experience, and provides a thorough introduction to Microsoft's premier .NET language. The book helps you build a solid foundation in .NET, and shows you how to apply your skills through the use of dozens of tested examples. You'll learn about the syntax and structure of the C# language, including operators, classes and interfaces, structs, arrays, and strings. Better yet, this updated edition of Learning C# has been completely revised to include the latest additions to the C# language plus a variety of learning aids to help lock-in new knowledge and skills. Here's what's new: Extensive revisions to the text and examples to reflect C# 2005 and .NET 2.0 changes An introduction to Visual Studio 2005, the most popular tool for building Windows and web applications More than 200 questions and fully debugged programming exercises with solutions A greater emphasis on event handling New coverage of generics, generic collections, partial classes, anonymous methods and more. By the time you've finished Learning C#, you'll be ready to move on to a more advanced programming guide that will help you create large-scale web and Windows applications. Whether you have a little object-oriented programming experience or you are new to programming altogether, Learning C# will set you firmly on your way to mastering the essentials of the C# language. COMPUTERS,Languages,C#

Beginning C# 6 Programming with Visual Studio 2015 Get started with Visual C# programming with this great beginner's guide Beginning C# 6 Programming with Visual Studio 2015 provides step-by-step directions for programming with C# in the .NET framework. Beginning with programming essentials, such as variables, flow control, and object-oriented programming, this authoritative text moves into more complicated topics, such as web and Windows programming and data access within both database and XML environments. After your introduction to each of the chapters, you are invited to apply your newfound knowledge in Try it Out sections, which reinforce learning and help you understand the practical applications of the new concepts you have explored. Through this approach, you can write useful programming code following each of the steps that you explore in this essential text. Discover the basics of programming with C#, such as variables, expressions, flow control, and functions Discuss how to keep your program running smoothly through debugging and error handling Understand how to navigate your way through key programming elements, such as classes, class members, collections, comparisons, and conversions Explore object-oriented programming, web programming, and Windows programming Beginning C# 6 Programming with Visual Studio 2015 is a fundamental resource for any programmers who are new to the C# language. COMPUTERS,Languages,C#

C# 6.0 Cookbook Completely updated for C# 6.0, the new edition of this bestseller offers more than 150 code recipes to common and not-so-common problems that C# programmers face every day. More than a third of the recipes have been rewritten to take advantage of new C# 6.0 features. If you prefer solutions to general C# language instruction and quick answers to theory, this is your book.C# 6.0 Cookbook offers new recipes for asynchronous methods, dynamic objects, enhanced error handling, the Rosyln compiler, and more. Here are some of topics covered: Classes and generics Collections, enumerators, and iterators Data types LINQ and Lambda expressions Exception handling Reflection and dynamic programming Regular expressions Filesystem interactions Networking and the Web XML usage Threading, Synchronization, and Concurrency Each recipe in the book includes tested code that you can download from oreilly.com and reuse in your own applications, and each one includes a detailed discussion of how and why the underlying technology works. You don't have to be an experienced C# or .NET developer to use C# 6.0 Cookbook. You just have to be someone who wants to solve a problem now, without having to learn all the related theory first. COMPUTERS,Languages,C#

Professional C# 6 and .NET Core 1.0 A true professional's guide to C# 6 Professional C# 6 and .NET Core 1.0 provides complete coverage of the latest updates, features, and capabilities, giving you everything you need for C#. Get expert instruction on the latest changes to Visual Studio 2015, Windows Runtime, ADO.NET, ASP.NET, Windows Store Apps, Windows Workflow Foundation, and more, with clear explanations, no-nonsense pacing, and valuable expert insight. This incredibly useful guide serves as both tutorial and desk reference, providing a professional-level review of C# architecture and its application in a number of areas. You'll gain a solid background in managed code and .NET constructs within the context of the 2015 release, so you can get acclimated quickly and get back to work. The new updates can actively streamline your workflow, with major changes including reimagined C# refactoring support, a new .NET Web app stack, and the .NET compiler platform that makes C# and Visual Basic compilers available as APIs. This book walks you through the changes with a comprehensive C# review. Explore the new Visual Studio templates for ASP.NET Core 1.0, Web Forms, and MVC Learn about the networking switch to HttpClient and ASP.NET Web API's replacement of WCF Data Services Work with the latest updates to the event log, Windows Runtime 2.0, and Windows 8.1 deployment and localization Dig deep into the new .NET 5.0 GC behaviors and the Migrations addition to ADO.NET Microsoft has stepped up both the cadence and magnitude of their software releases. Professional C# 6 and .NET Core 1.0 shows you everything you need to know about working with C# in a real-world context. COMPUTERS,Languages,C#

C# 7.0 All-in-One For Dummies Sharpen your knowledge of C# C# know-how is a must if you want to be a professional Microsoft developer. It's also good to know a little C# if you're building tools for the web, mobile apps, or other development tasks. C# 7.0 All-in-One For Dummies offers a deep dive into C# for coders still learning the nuances of the valuable programming language. Pop it open to get an intro into coding with C#, how to design secure apps and databases, and even pointers on building web and mobile apps with C#. C# remains one of the most in-demand programming language skills. The language regularly ranks in the top five among "most in-demand" languages, typically along with Java/JavaScript, C++, and Python. A December 2016 ZDNet article noted 'If your employer is a Microsoft developer, you better know C#." Lucky for you, this approachable, all-in-one guide is here to help you do just that—without ever breaking a sweat! Includes coverage of the latest changes to C# Shows you exactly what the language can (and can't) do Presents familiar tasks that you can accomplish with C# Provides insight into developing applications that provide protection against hackers If you have a basic understanding of coding and need to learn C#—or need a reference on the language in order to launch or further your career—look no further. COMPUTERS,Languages,C#

Adaptive Code Write code that can adapt to changes. By applying this book’s principles, you can create code that accommodates new requirements and unforeseen scenarios without significant rewrites. Gary McLean Hall describes Agile best practices, principles, and patterns for designing and writing code that can evolve more quickly and easily, with fewer errors, because it doesn’t impede change. Now revised, updated, and expanded, Adaptive Code, Second Edition adds indispensable practical insights on Kanban, dependency inversion, and creating reusable abstractions. Drawing on over a decade of Agile consulting and development experience, McLean Hall has updated his best-seller with deeper coverage of unit testing, refactoring, pure dependency injection, and more. Master powerful new ways to: • Write code that enables and complements Scrum, Kanban, or any other Agile framework • Develop code that can survive major changes in requirements • Plan for adaptability by using dependencies, layering, interfaces, and design patterns • Perform unit testing and refactoring in tandem, gaining more value from both • Use the “golden master†technique to make legacy code adaptive • Build SOLID code with single-responsibility, open/closed, and Liskov substitution principles • Create smaller interfaces to support more-diverse client and architectural needs • Leverage dependency injection best practices to improve code adaptability • Apply dependency inversion with the Stairway pattern, and avoid related anti-patterns About You This book is for programmers of all skill levels seeking more-practical insight into design patterns, SOLID principles, unit testing, refactoring, and related topics. Most readers will have programmed in C#, Java, C++, or similar object-oriented languages, and will be familiar with core procedural programming techniques. COMPUTERS,Languages,C#

C# 7.1 and .NET Core 2.0 – Modern Cross-Platform Development C# 7.1 and .NET Core 2.0 – Modern Cross-Platform Development, Third Edition is a practical guide to creating powerful cross-platform applications with C# 7 and .NET Core 2.0. About This Book Build modern, cross-platform applications with .NET Core 2.0 Get up to speed with C#, and up to date with all the latest features of C# 7.1 Start creating professional web applications with ASP.NET Core 2.0 Who This Book Is For This book is targeted towards readers who have some prior programming experience or have a science, technology, engineering, or mathematics (STEM) background, and want to gain a solid foundation with C# and to be introduced to the types of applications they could build and will work cross-platform on Windows, Linux, and macOS. What You Will Learn Build cross-platform applications using C# 7.1 and .NET Core 2.0 Explore ASP.NET Core 2.0 and learn how to create professional websites, services, and applications Improve your application's performance using multitasking Use Entity Framework Core and LINQ to query and manipulate data Master object-oriented programming with C# to increase code reuse and efficiency Familiarize yourself with cross-device app development using the Universal Windows Platform Protect and manage your files and data with encryption, streams, and serialization Get started with mobile app development using Xamarin.Forms Preview the nullable reference type feature of C# 8 In Detail C# 7.1 and .NET Core 2.0 – Modern Cross-Platform Development, Third Edition, is a practical guide to creating powerful cross-platform applications with C# 7.1 and .NET Core 2.0. It gives readers of any experience level a solid foundation in C# and .NET. The first part of the book runs you through the basics of C#, as well as debugging functions and object-oriented programming, before taking a quick tour through the latest features of C# 7.1 such as default literals, tuples, inferred tuple names, pattern matching, out variables, and more. After quickly taking you through C# and how .NET works, this book dives into the .NET Standard 2.0 class libraries, covering topics such as packaging and deploying your own libraries, and using common libraries for working with collections, performance, monitoring, serialization, files, databases, and encryption. The final section of the book demonstrates the major types of application that you can build and deploy cross-device and cross-platform. In this section, you'll learn about websites, web applications, web services, Universal Windows Platform (UWP) apps, and mobile apps. By the end of the book, you'll be armed with all the knowledge you need to build modern, cross-platform applications using C# and .NET. Style and approach This book takes a step-by-step approach and is filled with exciting projects and fascinating theory. It uses three high-impact sections to equip you with all the tools you'll need to build modern, cross-platform applications using C# and .NET Core 2.0. COMPUTERS,Languages,C#

Professional C# 7 and .NET Core 2.0 The professional’s guide to C# 7, with expert guidance on the newest features Professional C# 7 and .NET Core 2.0 provides experienced programmers with the information they need to work effectively with the world’s leading programming language. The latest C# update added many new features that help you get more done in less time, and this book is your ideal guide for getting up to speed quickly. C# 7 focuses on data consumption, code simplification, and performance, with new support for local functions, tuple types, record types, pattern matching, non-nullable reference types, immutable types, and better support for variables. Improvements to Visual Studio will bring significant changes to the way C# developers interact with the space, bringing .NET to non-Microsoft platforms and incorporating tools from other platforms like Docker, Gulp, and NPM. Guided by a leading .NET expert and steeped in real-world practicality, this guide is designed to get you up to date and back to work. With Microsoft speeding up its release cadence while offering more significant improvement with each update, it has never been more important to get a handle on new tools and features quickly. This book is designed to do just that, and more—everything you need to know about C# is right here, in the single-volume resource on every developer’s shelf. Tour the many new and enhanced features packed into C# 7 and .NET Core 2.0 Learn how the latest Visual Studio update makes developers’ jobs easier Streamline your workflow with a new focus on code simplification and performance enhancement Delve into improvements made for localization, networking, diagnostics, deployments, and more Whether you’re entirely new to C# or just transitioning to C# 7, having a solid grasp of the latest features allows you to exploit the language’s full functionality to create robust, high -quality apps. Professional C# 7 and .NET Core 2.0 is the one-stop guide to everything you need to know. COMPUTERS,Languages,C#

Beginning C# 7 Programming with Visual Studio 2017 Easily get started programming using the ultra-versatile C# 7 and Visual Studio 2017 Beginning C# 7 Programming with Visual Studio 2017 is the beginner’s ultimate guide to the world’s most popular programming language. Whether you’re new to programming entirely, or just new to C#, there has never been a better time to get started. The new C# 7 and Visual Studio 2017 updates feature a number of new tools and features that streamline the workflow, simplify the code, and make it easier than ever to build high-quality apps. This book walks you through everything you need to know, starting from the very basics, to have you programming in no time. You’ll learn about variables, flow control, and object oriented programming, then move into Web and Windows programming as well as databases and XML. The companion website provides downloadable code examples, and practical Try It Out sections provide explicit, step-by-step instructions for writing your own useful, customizable code. C# 7 can be used to build Windows applications, program Windows 10, and write Web apps when used alongside ASP.NET. With programming skills becoming de rigueur in fields far beyond the tech world, C# 7 is a great place to start building versatile, helpful skills. This book gets you started quickly and easily with instruction from a master-team of C# programmers. Learn how to program using the world’s leading programming language Build smarter, faster apps using the latest features in C# 7 and Visual Studio 2017 Find and fix bugs sooner, saving headaches down the line Integrate with all .NET Core, Azure applications, cloud services, Docker containers, and more The world of programming can seem intimidating to a beginner, and the prospect of learning a whole new “language†can seem daunting. Beginning C# 7 Programming with Visual Studio 2017 demystifies the process and shows you how to bring your ideas to life. COMPUTERS,Languages,C#

Mastering Xamarin.Forms Create high-quality multi-platform native apps with Xamarin.Forms About This Book Packed with real-world scenarios and solutions to help you build professional-grade mobile apps with Xamarin.Forms Build an effective mobile app architecture with the Xamarin.Forms toolkit Find out how, when, and why you should use architectural patterns and get best practices with Xamarin.Forms Who This Book Is For This book is intended for C# developers who are familiar with the Xamarin platform and the Xamarin.Forms toolkit. If you have already started working with Xamarin.Forms and want to take your app to the next level with higher quality, maintainability, testability, and flexibility, then this book is for you. What You Will Learn Implement the Model-View-View-Model (MVVM) pattern and data-binding in Xamarin.Forms mobile apps Extend the Xamarin.Forms navigation API with a custom ViewModel-centric navigation service Leverage the inversion of control and dependency injection patterns in Xamarin.Forms mobile apps Work with online and offline data in Xamarin.Forms mobile apps Test business logic in Xamarin.Forms mobile apps Use platform-specific APIs to build rich custom user interfaces in Xamarin.Forms mobile apps Explore how to improve mobile app quality using Visual Studio AppCenter In Detail Discover how to extend and build upon the components of the Xamarin.Forms toolkit to develop an effective, robust mobile app architecture. Starting with an app built with the basics of the Xamarin.Forms toolkit, you'll go step by step through several advanced topics to create a solution architecture rich with the benefits of good design patterns and best practices. You'll start by introducing a core separation between the app's user interface and its business logic by applying the MVVM pattern and data-binding. Then you focus on building out a layer of plugin-like services that handle platform-specific utilities such as navigation and geo-location, and on how to loosely use these services in the app with inversion of control and dependency injection. Next you connect the app to a live web-based API and set up offline synchronization. Then, you delve into testing the app logic through unit tests. Finally, you set up Visual Studio App Center for monitoring usage and bugs to gain a proactive edge on app quality. Style and approach This easy-to-follow, code-rich guide will walk you through building a real-world Xamarin.Forms mobile app from start to finish. Each chapter builds on the app by applying new advanced capabilities, design patterns, and best practices. Packed with real-world scenarios, this step-by-step guide will help you quickly build professional-grade apps with Xamarin.Forms. COMPUTERS,Languages,C#

Essential C# 7.0 The Comprehensive, Expert Guide to C# Language Programming “This book has been a classic for years, and remains one of the most venerable and trusted titles in the world of C# content, and probably far beyond! . . . Mark is super smart, insists on understanding everything to the core, and has phenomenal insight into how things affect real developers. . . . He goes right to the essence and communicates with great integrity—no sugarcoating—and has a keen eye for practical value and real-world problems.†–Mads Torgersen, C# Program Manager, Microsoft Essential C# 7.0 is a well-organized, no-fluff guide to C# 7.0 for programmers at all levels of experience. Reflecting the most important C# features from 3.0 through 7.0 and including modern programming patterns, it will help you write code that’s simple, powerful, robust, secure, and maintainable. Author Mark Michaelis is a world-class C# expert: a long-time Microsoft MVP and Regional Director who also has served on Microsoft’s C# design review team. He presents a comprehensive tutorial and reference for the entire language, including expert coverage of key C# 7.0 enhancements, C# 7.0’s use with .NET Core/.NET Standard, and cross-platform compilation. He illustrates key C# constructs with succinct examples, and presents best-practice coding guidelines. To help you maintain existing code, separate indexes provide version-specific answers for C# 5.0, 6.0, and 7.0, and visual icons show when each language innovation was introduced. Make the most of C# 7.0 enhancements, including tuples, deconstructors, pattern matching, local functions, and ref returns Work efficiently with C# data types, operators, control flow, methods, and parameters Write more robust code with C# object-oriented constructs Implement reliable, effective exception handling Reduce code complexity with generics, delegates, lambda expressions, and events Leverage advanced dynamic and declarative programming techniques Query diverse data collections using LINQ with query expressions Create custom collections that operate against business objects Access .NET collections via collection interfaces and standard query operators Master multithreading and synchronization, including the async/await paradigm Optimize performance and interoperability with P/Invoke and unsafe code Run your code on Linux or macOS with C# 7.0 cross-platform compilation Includes C# 7.1, 7.2, and 7.3 language enhancements This guide offers you a complete foundation for successful development with modern versions of the C# language in any project or environment. COMPUTERS,Languages,C#

C# and .NET Core Test Driven Development Learn how to apply a test-driven development process by building ready C# 7 and .NET Core applications. About This Book Create tests to quickly detect and resolve issues when writing portable code Uncover code integration issues that improve code quality using continuous integration Set up and use data-driven unit testing to verify your code Who This Book Is For This book is for .NET developers who would like to build efficient applications by implementing principles of test-driven development. C# programming and working knowledge of VS is assumed. What You Will Learn Write flexible, maintainable, and verifiable code for .NET Core Write testable code using SOLID principles and dependency injections Recognize the characteristics of a good unit test Structure and group your unit test Use mock objects to handle dependencies Set up an end-to-end continuous integration process In Detail This book guides developers to create robust, production-ready C# 7 and .NET Core applications through the practice of test-driven development process. In C# and .NET Core Test-Driven Development, you will learn the different stages of the TDD life cycle, basics of TDD, best practices, and anti-patterns. It will teach you how to create an ASP.NET Core MVC sample application, write testable code with SOLID principles and set up a dependency injection for your sample application. Next, you will learn the xUnit testing framework and learn how to use its attributes and assertions. You'll see how to create data-driven unit tests and mock dependencies in your code. You will understand the difference between running and debugging your tests on .NET Core on LINUX versus Windows and Visual Studio. As you move forward, you will be able to create a healthy continuous integration process for your sample application using GitHub, TeamCity, Cake, and Microsoft VSTS. By the end of this book, you will have learned how to write clean and robust code through the effective practice of TDD, set up CI build steps to test and build applications as well as how to package application for deployment on NuGet. Style and approach The book explores the concepts of test driven development in depth so readers can apply these proven techniques to build sophisticated software with C# and .NET. COMPUTERS,Languages,C#

Unity 2018 By Example Build exciting 2D/3D games and virtual reality applications with the help of hands-on examples Key Features Create five different types of games from scratch with Unity 2018 Import custom content into Unity from third-party tools such as Maya and Blender Learn to build NPCs with artificial intelligent behavior. Book Description Unity is the most exciting and popular engine used for developing games. With its 2018 release, Unity has become the primary source of both game development and virtual reality content. In Unity 2018 By Example, you'll learn how to use Unity in order to make amazing games from popular genres - from action shooters to mind-bending puzzle games to adventure and Virtual Reality (VR) games. Even if you have no previous experience of using Unity, this book will help you understand the toolsets it provides in depth. In addition to this, you'll understand how to create time-critical collection games, twin-stick space shooters, platformers, and action-fest games with intelligent enemies. Finally, you'll get to grips with creating VR games with the new toolsets introduced by Unity to help you develop amazing VR experiences. To make things easier, you will be provided with step-by-step tutorials for making five great games in Unity 2018, along with a detailed explanation of all the fundamental concepts. By the end of this book, you'll have established a strong foundation in making games with Unity 2018. What you will learn Understand core Unity concepts, such as game objects, components, and scenes Study level-design techniques for building immersive and interesting worlds Make functional games with C# scripting Use the toolset creatively to build games with different themes and styles Handle player controls and input functionality Work with terrains and world-creation tools Get to grips with making both 2D and 3D games Who this book is for You don't need to have any previous experience with Unity to enjoy Unity 2018 By Example, although you need to have basic knowledge of C#. COMPUTERS,Languages,C#

Hands-On Network Programming with C# and .NET Core A comprehensive guide to understanding network architecture, communication protocols, and network analysis to build secure applications compatible with the latest versions of C# 8 and .NET Core 3.0 Key Features Explore various network architectures that make distributed programming possible Learn how to make reliable software by writing secure interactions between clients and servers Use .NET Core for network device automation, DevOps, and software-defined networking Book Description The C# language and the .NET Core application framework provide the tools and patterns required to make the discipline of network programming as intuitive and enjoyable as any other aspect of C# programming. With the help of this book, you will discover how the C# language and the .NET Core framework make this possible. The book begins by introducing the core concepts of network programming, and what distinguishes this field of programming from other disciplines. After this, you will gain insights into concepts such as transport protocols, sockets and ports, and remote data streams, which will provide you with a holistic understanding of how network software fits into larger distributed systems. The book will also explore the intricacies of how network software is implemented in a more explicit context, by covering sockets, connection strategies such as Transmission Control Protocol (TCP) and User Datagram Protocol (UDP), asynchronous processing, and threads. You will then be able to work through code examples for TCP servers, web APIs served over HTTP, and a Secure Shell (SSH) client. By the end of this book, you will have a good understanding of the Open Systems Interconnection (OSI) network stack, the various communication protocols for that stack, and the skills that are essential to implement those protocols using the C# programming language and the .NET Core framework. What you will learn Understand the breadth of C#'s network programming utility classes Utilize network-layer architecture and organizational strategies Implement various communication and transport protocols within C# Discover hands-on examples of distributed application development Gain hands-on experience with asynchronous socket programming and streams Learn how C# and the .NET Core runtime interact with a hosting network Understand a full suite of network programming tools and features Who this book is for If you're a .NET developer or a system administrator with .NET experience and are looking to get started with network programming, then this book is for you. Basic knowledge of C# and .NET is assumed, in addition to a basic understanding of common web protocols and some high-level distributed system designs. COMPUTERS,Languages,C#

Visual Studio Code Expert guidance on using Visual Studio Code for editing and debugging your web development projects Visual Studio Code, a free, open source, cross-compatible source code editor, is one of the most popular choices for web developers. It is fast, lightweight, customizable, and contains built-in support for JavaScript, Typescript, and Node.js extensions for other languages, including C++, Python, and PHP. Features such as debugging capability, embedded Git control, syntax highlighting, code snippets, and IntelliSense intelligent code completion support—several of which set it apart from the competition—help make Visual Studio Code an impressive, out-of-the-box solution. Visual Studio Code: End-to-End Editing and Debugging Tools for Web Developers helps readers to become familiar with and productive in Visual Studio Code. This up-to-date guide covers all of the essential components of the software, including the editing features of the workspace, advanced functionality such as code refactoring and key binding, and integration with Grunt, Gulp, NPM, and other external tools. New users, experienced developers, and those considering moving from another developer tool will benefit from this book’s detailed, yet easy-to-follow information on Visual Studio Code. This book: Teaches readers how to use Visual Studio Code to do full-stack development Explains the steps to install Visual Studio Code on Windows, Mac and Linux platforms Provides a foundation for non-users considering moving to Visual Studio Code Helps current users expand their knowledge of the tool and its available extensions Describes how to open a .NET Core project and get end-to-end execution and debugging functionality Visual Studio Code: End-to-End Editing and Debugging Tools for Web Developers is an invaluable guide for both professional and hobbyist web developers seeking immediately-useful information on Visual Studio Code. COMPUTERS,Languages,C#

Concurrency in C# Cookbook If you’re one of many developers still uncertain about concurrent and multithreaded development, this practical cookbook will change your mind. With more than 85 code-rich recipes in this updated second edition, author Stephen Cleary demonstrates parallel processing and asynchronous programming techniques using libraries and language features in .NET and C# 8.0. Concurrency is now more common in responsive and scalable application development, but it’s still extremely difficult to code. The detailed solutions in this cookbook show you how modern tools raise the level of abstraction, making concurrency much easier than before. Complete with ready-to-use code and discussions about how and why solutions work, these recipes help you: Get up to speed on concurrency and async and parallel programming Use async and await for asynchronous operations Enhance your code with asynchronous streams Explore parallel programming with .NET’s Task Parallel Library Create dataflow pipelines with .NET’s TPL Dataflow library Understand the capabilities that System.Reactive builds on top of LINQ Utilize threadsafe and immutable collections Learn how to conduct unit testing with concurrent code Make the thread pool work for you Enable clean, cooperative cancellation Examine scenarios for combining concurrent approaches Dive into asynchronous-friendly object-oriented programming Recognize and write adapters for code using older asynchronous styles COMPUTERS,Languages,C#

C# 8.0 Pocket Reference When you need answers about using C# 8.0, this tightly focused and practical book tells you exactly what you need to know without long intros or bloated samples. Easy to browse, C# 8.0 Pocket Reference is ideal as a quick source of information or as a guide to get you rapidly up to speed if you already know Java, C++, or an earlier C# version. All programs and code snippets are available as interactive samples in LINQPad. You can edit these samples and instantly see the results without needing to set up projects in Visual Studio. Written by the author of C# 7.0 in a Nutshell, this pocket reference covers C# 8.0 without skimping on detail, including: C# fundamentals and features new to C# 8.0 Advanced topics like operator overloading, type constraints, iterators, nullable types, operator lifting, lambda expressions, and closures LINQ: sequences, lazy execution, standard query operators, and query expressions Unsafe code and pointers, custom attributes, preprocessor directives, and XML documentation COMPUTERS,Languages,C#

C# 8.0 and .NET Core 3.0 – Modern Cross-Platform Development Learn the fundamentals, practical applications, and latest features of C# 8.0 and .NET Core 3.0 from expert teacher Mark J. Price. Key Features Build modern, cross-platform applications with .NET Core 3.0 Get up to speed with C#, and up to date with all the latest features of C# 8.0 Start creating professional web applications with ASP.NET Core 3.0 Book Description In C# 8.0 and .NET Core 3.0 – Modern Cross-Platform Development, Fourth Edition, expert teacher Mark J. Price gives you everything you need to start programming C# applications. This latest edition uses the popular Visual Studio Code editor to work across all major operating systems. It is fully updated and expanded with new chapters on Content Management Systems (CMS) and machine learning with ML.NET. The book covers all the topics you need. Part 1 teaches the fundamentals of C#, including object-oriented programming, and new C# 8.0 features such as nullable reference types, simplified switch pattern matching, and default interface methods. Part 2 covers the .NET Standard APIs, such as managing and querying data, monitoring and improving performance, working with the filesystem, async streams, serialization, and encryption. Part 3 provides examples of cross-platform applications you can build and deploy, such as web apps using ASP.NET Core or mobile apps using Xamarin.Forms. The book introduces three technologies for building Windows desktop applications including Windows Forms, Windows Presentation Foundation (WPF), and Universal Windows Platform (UWP) apps, as well as web applications, web services, and mobile apps. What you will learn Build cross-platform applications for Windows, macOS, Linux, iOS, and Android Explore application development with C# 8.0 and .NET Core 3.0 Explore ASP.NET Core 3.0 and create professional web applications Learn object-oriented programming and C# multitasking Query and manipulate data using LINQ Use Entity Framework Core and work with relational databases Discover Windows app development using the Universal Windows Platform and XAML Build mobile applications for iOS and Android using Xamarin.Forms Who this book is for Readers with some prior programming experience or with a science, technology, engineering, or mathematics (STEM) background, who want to gain a solid foundation with C# 8.0 and .NET Core 3.0. COMPUTERS,Languages,C#

Programming C# 8.0 C# is undeniably one of the most versatile programming languages available to engineers today. With this comprehensive guide, you’ll learn just how powerful the combination of C# and .NET can be. Author Ian Griffiths guides you through C# 8.0 fundamentals and techniques for building cloud, web, and desktop applications. Designed for experienced programmers, this book provides many code examples to help you work with the nuts and bolts of C#, such as generics, LINQ, and asynchronous programming features. You’ll get up to speed on .NET Core and the latest C# 8.0 additions, including asynchronous streams, nullable references, pattern matching, default interface implementation, ranges and new indexing syntax, and changes in the .NET tool chain. Discover how C# supports fundamental coding features, such as classes, other custom types, collections, and error handling Learn how to write high-performance memory-efficient code with .NET Core’s Span and Memory types Query and process diverse data sources, such as in-memory object models, databases, data streams, and XML documents with LINQ Use .NET’s multithreading features to exploit your computer’s parallel processing capabilities Learn how asynchronous language features can help improve application responsiveness and scalability COMPUTERS,Languages,C#

Hands-On Software Architecture with C# 8 and .NET Core 3 Design scalable and high-performance enterprise applications using the latest features of C# 8 and .NET Core 3 Key Features Become a software architect capable of creating modular apps for specific business needs Design high-performance software systems using the latest features of C# 8 and .NET Core 3 Solve scalability problems in web apps using enterprise architectural patterns Book Description Software architecture is the practice of implementing structures and systems that streamline the software development process and improve the quality of an app. With this software architecture book, you'll follow a hands-on approach to learning various architectural methods that will help you develop and deliver high-quality products. You'll begin by understanding how to transform user requirements into architectural needs and exploring the differences between functional and non-functional requirements. Next, you'll explore how to carefully choose a cloud solution for your infrastructure, along with covering dos and don'ts that will help you manage your app in a cloud-based environment. Later chapters will cover techniques and processes such as DevOps, microservices, and continuous integration, along with providing insights into implementing them using Microsoft technologies such as ASP.NET Core, the Entity Framework, Cosmos DB, and Azure DevOps. You will also learn about testing frameworks and automation tools that will help you through the development process. Finally, you'll discover design patterns and various software approaches that will allow you to solve common problems faced during development. By the end of this book, you'll be able to develop and deliver highly scalable enterprise-ready apps that meet customers' business needs. What you will learn Overcome real-world architectural challenges and solve design consideration issues Apply architectural approaches like Layered Architecture, service-oriented architecture (SOA), and microservices Learn to use tools like containers, Docker, and Kubernetes to manage microservices Get up to speed with Azure Cosmos DB for delivering multi-continental solutions Learn how to program and maintain Azure Functions using C# Understand when to use test-driven development (TDD) as an approach for software development Write automated functional test cases for your projects Who this book is for This book is for engineers and senior developers aspiring to become architects or looking to build enterprise applications with the .NET Stack. Experience with C# and .NET is required to understand this book. COMPUTERS,Languages,C#

Hands-On RESTful Web Services with ASP.NET Core 3 Get up to speed with the latest features of C# 8, ASP.NET Core 3 and .NET Core 3.1 LTS to create robust and maintainable web services Key Features Apply design patterns and techniques to achieve a reactive, scalable web service Document your web services using the OpenAPI standard and test them using Postman Explore mechanisms to implement a secure web service using client-side SSL and token authentication Book Description In recent times, web services have evolved to play a prominent role in web development. Applications are now designed to be compatible with any device and platform, and web services help us keep their logic and UI separate. Given its simplicity and effectiveness in creating web services, the RESTful approach has gained popularity, and this book will help you build RESTful web services using ASP.NET Core. This REST book begins by introducing you to the basics of the REST philosophy, where you'll study the different stages of designing and implementing enterprise-grade RESTful web services. You'll also gain a thorough understanding of ASP.NET Core's middleware approach and learn how to customize it. The book will later guide you through improving API resilience, securing your service, and applying different design patterns and techniques to achieve a scalable web service. In addition to this, you'll learn advanced techniques for caching, monitoring, and logging, along with implementing unit and integration testing strategies. In later chapters, you will deploy your REST web services on Azure and document APIs using Swagger and external tools such as Postman. By the end of this book, you will have learned how to design RESTful web services confidently using ASP.NET Core with a focus on code testability and maintainability. What you will learn Gain a comprehensive working knowledge of ASP.NET Core Integrate third-party tools and frameworks to build maintainable and efficient services Implement patterns using dependency injection to reduce boilerplate code and improve flexibility Use ASP.NET Core's out-of-the-box tools to test your applications Use Docker to run your ASP.NET Core web service in an isolated and self-contained environment Secure your information using HTTPS and token-based authentication Integrate multiple web services using resiliency patterns and messaging techniques Who this book is for This book is for anyone who wants to learn how to build RESTful web services with the ASP.NET Core framework to improve the scalability and performance of their applications. Basic knowledge of C# and .NET Core will help you make the best use of the code samples included in the book. COMPUTERS,Languages,C#

ASP.NET Core 3 and Angular 9 Build a simple, yet fully-functional modern web application using .NET Core 3.1, Entity Framework Core and Angular 9 Key Features Explore the latest edition of the bestselling book ASP.NET Core 2 and Angular 5 Design, build and deploy a Single Page Application or Progressive Web App with ASP.NET Core and Angular Adopt a full stack approach to handle data management, Web APIs, application design, testing, SEO, security and deployment Book Description Learning full stack development calls for knowledge of both frontend and backend web development. By covering the impressive capabilities of ASP.NET Core 3.1 and Angular 9, right from project setup through to the deployment phase, this book will help you to develop your skills effectively. The book will get you started with using the .NET Core framework and Web API Controllers to implement API calls and server-side routing in the backend. Next, you will learn to build a data model with Entity Framework Core and configure it using either a local SQL Server instance or cloud-based data stores such as Microsoft Azure. The book will also help you handle user input with Angular reactive forms and frontend and backend validators for maximum effect. You will later explore the advanced debugging and unit testing features provided by xUnit.net (.NET Core) and Jasmine, as well as Karma for Angular. Finally, you will implement various authentication and authorization techniques with the ASP.NET Core Identity system and the new IdentityServer, as well as deploy your apps on Windows and Linux servers using IIS, Kestrel, and Nginx. By the end of this book, you will be equipped with the skills you need to create efficient web applications using ASP.NET Core and Angular. What you will learn Implement a Web API interface with ASP.NET Core and consume it with Angular using RxJS Observables Create a data model using Entity Framework Core with code-first approach and migrations support Set up and configure a SQL database server using a local instance or a cloud data store on Azure Perform C# and JavaScript debugging using Visual Studio 2019 Create TDD and BDD unit test using xUnit, Jasmine, and Karma Implement authentication and authorization using ASP.NET Identity, IdentityServer4, and Angular API Build Progressive Web Apps and explore Service Workers Who this book is for This book is for experienced ASP.NET developers who already know about ASP.NET Core and Angular and are looking to learn more about them and understand how to use them together to create production-ready Single Page Applications (SPAs) or Progressive Web Applications (PWAs). However, the fully-documented code samples (also available on GitHub) and the step-by-step implementation tutorials make this book easy-to-understand - even for beginners and developers who are just getting started. COMPUTERS,Languages,C#

Mastering Xamarin.Forms New edition of the bestselling guide to building an effective mobile app architecture with Xamarin.Forms 4 that maximizes the overall quality of apps. Key Features Updated for Xamarin.Forms 4 Packed with real-world scenarios and solutions to help you build professional grade mobile apps with Xamarin.Forms Includes design patterns and best practice techniques that every mobile developer should know Book Description Discover how to extend and build upon the components of the most recent version of Xamarin.Forms to develop an effective, robust mobile app architecture. This new edition features Xamarin.Forms 4 updates, including CollectionView and RefreshView, new coverage of client-side validation, and updates on how to implement user authentication. Mastering Xamarin.Forms, Third Edition is one of the few Xamarin books structured around the development of a simple app from start to finish, beginning with a basic Xamarin.Forms app and going step by step through several advanced topics to create a solution architecture rich with the benefits of good design patterns and best practices. This book introduces a core separation between the app's user interface and the app's business logic by applying the MVVM pattern and data binding, and then focuses on building a layer of plugin-like services that handle platform-specific utilities such as navigation and geo-location, as well as how to loosely use these services in the app with inversion of control and dependency injection. You'll connect the app to a live web-based API and set up offline synchronization before testing the app logic through unit testing. Finally, you will learn how to add monitoring to your Xamarin.Forms projects to track crashes and analytics and gain a proactive edge on quality. What you will learn Find out how, when, and why to use architecture patterns and best practices with Xamarin.Forms Implement the Model-View-ViewModel (MVVM) pattern and data binding in Xamarin.Forms mobile apps Incorporate client-side validation in Xamarin.Forms mobile apps Extend the Xamarin.Forms navigation API with a custom ViewModel-centric navigation service Leverage the inversion of control and dependency injection patterns in Xamarin.Forms mobile apps Work with online and offline data in Xamarin.Forms mobile apps Use platform-specific APIs to build rich custom user interfaces in Xamarin.Forms mobile apps Explore how to monitor mobile app quality using Visual Studio App Center Who this book is for This book is intended for .NET developers who are familiar with Xamarin mobile application development and the open source Xamarin.Forms toolkit. If you have already started working with Xamarin.Forms and want to take your app to the next level, making it more maintainable, testable and flexible, then this book is for you. COMPUTERS,Languages,C#

Hands-On Microservices with C# 8 and .NET Core 3 Learn the essential concepts, techniques, and design patterns that will help you build scalable and maintainable distributed systems Key Features Learn to design, implement, test, and deploy your microservices Understand the challenges and complexities of testing and monitoring distributed services Build modular and robust microservice architectures with the latest features of C# 8 and .NET Core 3.1 Book Description The microservice architectural style promotes the development of complex applications as a suite of small services based on specific business capabilities. With this book, you'll take a hands-on approach to build microservices and deploy them using ASP .NET Core and Microsoft Azure. You'll start by understanding the concept of microservices and their fundamental characteristics. This microservices book will then introduce a real-world app built as a monolith, currently struggling under increased demand and complexity, and guide you in its transition to microservices using the latest features of C# 8 and .NET Core 3. You'll identify service boundaries, split the application into multiple microservices, and define service contracts. You'll also explore how to configure, deploy, and monitor microservices using Docker and Kubernetes, and implement autoscaling in a microservices architecture for enhanced productivity. Once you've got to grips with reactive microservices, you'll discover how keeping your code base simple enables you to focus on what's important rather than on messy asynchronous calls. Finally, you'll delve into various design patterns and best practices for creating enterprise-ready microservice applications. By the end of this book, you'll be able to deconstruct a monolith successfully to create well-defined microservices. What you will learn Package, deploy, and manage microservices and containers with Azure Service Fabric Use REST APIs to integrate services using a synchronous approach Protect public APIs using Azure Active Directory and OAuth 2.0 Understand the operation and scaling of microservices using Docker and Kubernetes Implement reactive microservices with Reactive Extensions Discover design patterns and best practices for building enterprise-ready apps Who this book is for This book is for C# and .NET Core developers who want to understand microservices architecture and implement it in their .NET Core applications. If you're new to building microservices or have theoretical knowledge of the architectural approach, this book will help you gain a practical perspective to manage application complexity efficiently. COMPUTERS,Languages,C#

C# 8.0 in a Nutshell When you have questions about C# 8.0 or .NET Core, this best-selling guide has the answers you need. C# is a language of unusual flexibility and breadth, but with its continual growth there’s so much more to learn. In the tradition of the O’Reilly Nutshell guides, this thoroughly updated edition is simply the best one-volume reference to the C# language available today. Organized around concepts and use cases, C# 8.0 in a Nutshell provides intermediate and advanced programmers with a concise map of C# and .NET knowledge that also plumbs significant depths. Get up to speed on C#, from syntax and variables to advanced topics such as pointers, closures, and patterns Dig deep into LINQ with three chapters dedicated to the topic Explore concurrency and asynchrony, advanced threading, and parallel programming Work with .NET features, including regular expressions, networking, serialization, spans, reflection, and cryptography Delve into Roslyn, the modular C# compiler as a service COMPUTERS,Languages,C#

Learn C# Programming Get started with C# and strengthen your knowledge of core programming concepts such as procedural, object-oriented, generic, functional, and asynchronous programming along with the latest features of C# 8 Key Features Learn the fundamentals of C# with the help of easy-to-follow examples and explanations Leverage the latest features of C# 8, including nullable reference types, pattern matching enhancements, and asynchronous streams Explore object-oriented programming, functional programming, and multithreading concepts Book Description The C# programming language is often developers' primary choice for creating a wide range of applications for desktop, cloud, and mobile. In nearly two decades of its existence, C# has evolved from a general-purpose, object-oriented language to a multi-paradigm language with impressive features. This book will take you through C# from the ground up in a step-by-step manner. You'll start with the building blocks of C#, which include basic data types, variables, strings, arrays, operators, control statements, and loops. Once comfortable with the basics, you'll then progress to learning object-oriented programming concepts such as classes and structures, objects, interfaces, and abstraction. Generics, functional programming, dynamic, and asynchronous programming are covered in detail. This book also takes you through regular expressions, reflection, memory management, pattern matching, exceptions, and many other advanced topics. As you advance, you'll explore the .NET Core 3 framework and learn how to use the dotnet command-line interface (CLI), consume NuGet packages, develop for Linux, and migrate apps built with .NET Framework. Finally, you'll understand how to run unit tests with the Microsoft unit testing frameworks available in Visual Studio. By the end of this book, you'll be well-versed with the essentials of the C# language and be ready to start creating apps with it. What you will learn Get to grips with all the new features of C# 8 Discover how to use attributes and reflection to build extendable applications Utilize LINQ to uniformly query various sources of data Use files and streams and serialize data to JSON and XML Write asynchronous code with the async-await pattern Employ .NET Core tools to create, compile, and publish your applications Create unit tests with Visual Studio and the Microsoft unit testing frameworks Who this book is for If you have little experience in coding or C# and want to learn the essentials of C# programming to develop powerful programming techniques, this book is for you. It will also help aspiring programmers to write scripts or programs to accomplish specific tasks. COMPUTERS,Languages,C#

Modern Web Development with ASP.NET Core 3 Explore the tools and techniques to build scalable and secured RESTful web services and web applications using C# 8 and ASP. NET Core 3.1 Key Features Delve into MVC patterns, configuration, routing, and deployment to build professional-grade applications Learn how to integrate ASP applications with the JavaScript frameworks React, Vue, and Angular Improve the performance of applications and the development team by implementing advanced ASP.NET Core concepts Book Description ASP.NET has been the preferred choice of web developers for a long time. With ASP.NET Core 3, Microsoft has made internal changes to the framework along with introducing new additions that will change the way you approach web development. This second edition has been thoroughly updated to help you make the most of the latest features in the framework, right from gRPC and conventions to Blazor, which has a new chapter dedicated to it. You'll begin with an overview of the essential topics, exploring the Model-View-Controller (MVC) pattern, various platforms, dependencies, and frameworks. Next, you'll learn how to set up and configure the MVC environment, before delving into advanced routing options. As you advance, you'll get to grips with controllers and actions to process requests, and later understand how to create HTML inputs for models. Moving on, you'll discover the essential aspects of syntax and processes when working with Razor. You'll also get up to speed with client-side development and explore the testing, logging, scalability, and security aspects of ASP.NET Core. Finally, you'll learn how to deploy ASP.NET Core to several environments, such as Azure, Amazon Web Services (AWS), and Docker. By the end of the book, you'll be well versed in development in ASP.NET Core and will have a deep understanding of how to interact with the framework and work cross-platform. What you will learn Understand the new capabilities of ASP.NET Core 3.1 Become well versed in how to configure ASP.NET Core to use it to its full potential Create controllers and action methods, and understand how to maintain state Implement and validate forms and retrieve information from them Improve productivity by enforcing reuse, process forms, and effective security measures Delve into the new Blazor development model Deploy ASP.NET Core applications to new environments, such as Microsoft Azure, AWS, and Docker Who this book is for If you are a developer with basic knowledge of ASP.NET MVC and want to build powerful applications, then this book is for you. Developers who want to explore the latest changes in ASP.NET Core 3.1 to build professional-level applications will also find this book useful. Familiarity with C#, ASP.NET Core, HTML, and CSS is expected to get the most out of this book. COMPUTERS,Languages,C#

Clean Code in C# Develop your programming skills by exploring essential topics such as code reviews, implementing TDD and BDD, and designing APIs to overcome code inefficiency, redundancy, and other problems arising from bad code Key Features Write code that cleanly integrates with other systems while maintaining well-defined software boundaries Understand how coding principles and standards enhance software quality Learn how to avoid common errors while implementing concurrency or threading Book Description Traditionally associated with developing Windows desktop applications and games, C# is now used in a wide variety of domains, such as web and cloud apps, and has become increasingly popular for mobile development. Despite its extensive coding features, professionals experience problems related to efficiency, scalability, and maintainability because of bad code. Clean Code in C# will help you identify these problems and solve them using coding best practices. The book starts with a comparison of good and bad code, helping you understand the importance of coding standards, principles, and methodologies. You'll then get to grips with code reviews and their role in improving your code while ensuring that you adhere to industry-recognized coding standards. This C# book covers unit testing, delves into test-driven development, and addresses cross-cutting concerns. You'll explore good programming practices for objects, data structures, exception handling, and other aspects of writing C# computer programs. Once you've studied API design and discovered tools for improving code quality, you'll look at examples of bad code and understand which coding practices you should avoid. By the end of this clean code book, you'll have the developed skills you need in order to apply industry-approved coding practices to write clean, readable, extendable, and maintainable C# code. What you will learn Write code that allows software to be modified and adapted over time Implement the fail-pass-refactor methodology using a sample C# console application Address cross-cutting concerns with the help of software design patterns Write custom C# exceptions that provide meaningful information Identify poor quality C# code that needs to be refactored Secure APIs with API keys and protect data using Azure Key Vault Improve your code's performance by using tools for profiling and refactoring Who this book is for This coding book is for C# developers, team leads, senior software engineers, and software architects who want to improve the efficiency of their legacy systems. A strong understanding of C# programming is required. COMPUTERS,Languages,C#

Creating Your First C++ Program Need to know C++ right now, but don’t want a 1,000-page tome? Check out the Peachpit’s new Short Cuts! Quick PDF guides that are...Smart...Handy...Concise. This mini guide covers exactly what you need to know about programming and creating a simple application, and nothing more. Never programmed before? No problem. You’ll get all the techniques and information you need to program, compile, and run a C++ application and quickly build your C++ foundation. You’ll learn: • Basic syntax and instructions for creating a quick C++ source • How to compile and execute this application • How to print messages using C++ • How to momentarily pause the execution of an application • How to use blank spaces and comments in your code • How to create basic C++ programs using two free and popular development applications • And more! COMPUTERS,Languages,C++

C++ Cookbook Despite its highly adaptable and flexible nature, C++ is also one of the more complex programming languages to learn. Once mastered, however, it can help you organize and process information with amazing efficiency and quickness. The C++ Cookbook will make your path to mastery much shorter. This practical, problem-solving guide is ideal if you're an engineer, programmer, or researcher writing an application for one of the legions of platforms on which C++ runs. The algorithms provided in C++ Cookbook will jump-start your development by giving you some basic building blocks that you don't have to develop on your own. Less a tutorial than a problem-solver, the book addresses many of the most common problems you're likely encounter--whether you've been programming in C++ for years or you're relatively new to the language. Here are just some of the time-consuming tasks this book contains practical solutions for: Reading the contents of a directory Creating a singleton class Date and time parsing/arithmetic String and text manipulation Working with files Parsing XML Using the standard containers Typical of O'Reilly's "Cookbook" series, C++ Cookbook is written in a straightforward format, featuring recipes that contain problem statements and code solutions, and apply not to hypothetical situations, but those that you're likely to encounter. A detailed explanation then follows each recipe in order to show you how and why the solution works. This question-solution-discussion format is a proven teaching method, as any fan of the "Cookbook" series can attest to. This book will move quickly to the top of your list of essential C++ references. COMPUTERS,Languages,C++

C++ Pocket Reference C++ is a complex language with many subtle facets. This is especially true when it comes to object-oriented and template programming. The C++ Pocket Reference is a memory aid for C++ programmers, enabling them to quickly look up usage and syntax for unfamiliar and infrequently used aspects of the language. The book's small size makes it easy to carry about, ensuring that it will always be at-hand when needed. Programmers will also appreciate the book's brevity; as much information as possible has been crammed into its small pages.In the C++ Pocket Reference, you will find: Information on C++ types and type conversions Syntax for C++ statements and preprocessor directives Help declaring and defining classes, and managing inheritance Information on declarations, storage classes, arrays, pointers, strings, and expressions Refreshers on key concepts of C++ such as namespaces and scope More! C++ Pocket Reference is useful to Java and C programmers making the transition to C++, or who find themselves occasionally programming in C++. The three languages are often confusingly similar. This book enables programmers familiar with C or Java to quickly come up to speed on how a particular construct or concept is implemented in C++.Together with its companion STL Pocket Reference, the C++ Pocket Reference forms one of the most concise, easily-carried, quick-references to the C++ language available. COMPUTERS,Languages,C++

STL Pocket Reference The STL Pocket Reference describes the functions, classes, and templates in that part of the C++ standard library often referred to as the Standard Template Library (STL). The STL encompasses containers, iterators, algorithms, and function objects, which collectively represent one of the most important and widely used subsets of standard library functionality.The C++ standard library, even the subset known as the STL, is vast. It's next to impossible to work with the STL without some sort of reference at your side to remind you of template parameters, function invocations, return types--indeed, the entire myriad of details you need to know in order to use the STL effectively and get work done. You need a memory-aid.Books that cover the standard library and the STL tend to be quite heavy and large, describing each aspect of the STL in detail. Such books are great when you're not familiar with the library, but get in the way when you simply need to remind yourself of a function name, or the order in which you pass arguments to a function. Programmers familiar with the STL need a small, lightweight memory-aid. That's what the STL Pocket Reference is. It's small, lightweight, and chock-full of information that you can take in at a glance, so you can get on with your work. COMPUTERS,Languages,C++

C++ Coding Standards Consistent, high-quality coding standards improve software quality, reduce time-to-market, promote teamwork, eliminate time wasted on inconsequential matters, and simplify maintenance. Now, two of the world's most respected C++ experts distill the rich collective experience of the global C++ community into a set of coding standards that every developer and development team can understand and use as a basis for their own coding standards. The authors cover virtually every facet of C++ programming: design and coding style, functions, operators, class design, inheritance, construction/destruction, copying, assignment, namespaces, modules, templates, genericity, exceptions, STL containers and algorithms, and more. Each standard is described concisely, with practical examples. From type definition to error handling, this book presents C++ best practices, including some that have only recently been identified and standardized-techniques you may not know even if you've used C++ for years. Along the way, you'll find answers to questions like What's worth standardizing--and what isn't? What are the best ways to code for scalability? What are the elements of a rational error handling policy? How (and why) do you avoid unnecessary initialization, cyclic, and definitional dependencies? When (and how) should you use static and dynamic polymorphism together? How do you practice "safe" overriding? When should you provide a no-fail swap? Why and how should you prevent exceptions from propagating across module boundaries? Why shouldn't you write namespace declarations or directives in a header file? Why should you use STL vector and string instead of arrays? How do you choose the right STL search or sort algorithm? What rules should you follow to ensure type-safe code? Whether you're working alone or with others, C++ Coding Standards will help you write cleaner code--and write it faster, with fewer hassles and less frustration. COMPUTERS,Languages,C++

Effective C++ The first two editions of Effective C++ were embraced by hundreds of thousands of programmers worldwide. The reason is clear: Scott Meyers’ practical approach to C++ describes the rules of thumb used by the experts — the things they almost always do or almost always avoid doing — to produce clear, correct, efficient code. The book is organised around 55 specific guidelines, each of which describes a way to write better C++. Each is backed by concrete examples. For this third edition, more than half the content is new, including added chapters on managing resources and using templates. Topics from the second edition have been extensively revised to reflect modern design considerations, including exceptions, design patterns, and multithreading. Important features of Effective C++ include: Expert guidance on the design of effective classes, functions, templates, and inheritance hierarchies. Applications of new “TR1†standard library functionality, along with comparisons to existing standard library components. Insights into differences between C++ and other languages (e.g., Java, C#, C) that help developers from those languages assimilate “the C++ way†of doing things. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Languages,C++

More Effective C++ More than 150,000 copies in print! Praise for Scott Meyers’ first book, Effective C++: “I heartily recommend Effective C++ to anyone who aspires to mastery of C++ at the intermediate level or above.†– The C/C++ User’s Journal From the author of the indispensable Effective C++, here are 35 new ways to improve your programs and designs. Drawing on years of experience, Meyers explains how to write software that is more effective: more efficient, more robust, more consistent, more portable, and more reusable. In short, how to write C++ software that’s just plain better. More Effective C++ includes: Proven methods for improving program efficiency, including incisive examinations of the time/space costs of C++ language features Comprehensive descriptions of advanced techniques used by C++ experts, including placement new, virtual constructors, smart pointers, reference counting, proxy classes, and double-dispatching Examples of the profound impact of exception handling on the structure and behavior of C++ classes and functions Practical treatments of new language features, including bool, mutable, explicit, namespaces, member templates, the Standard Template Library, and more. If your compilers don’t yet support these features, Meyers shows you how to get the job done without them. More Effective C++ is filled with pragmatic, down-to-earth advice you’ll use every day. Like Effective C++ before it, More Effective C++ is essential reading for anyone working with C++. COMPUTERS,Languages,C++

C++ Gotchas C++ Gotchas is the professional programmer's guide to avoiding and correcting ninety-nine of the most common, destructive, and interesting C++ design and programming errors. It also serves as an inside look at the more subtle C++ features and programming techniques. This book discusses basic errors present in almost all C++ code, as well as complex mistakes in syntax, preprocessing, conversions, initialization, memory and resource management, polymorphism, class design, and hierarchy design. Each error and its repercussions are explained in context, and the resolution of each problem is detailed and demonstrated. Author Stephen Dewhurst supplies readers with idioms and design patterns that can be used to generate customized solutions for common problems. Readers will also learn more about commonly misunderstood features of C++ used in advanced programming and design. A companion Web site, located at http://www.semantics.org, includes detailed code samples from the book. Readers will discover: How to escape both common and complex traps associated with C++ How to produce more reusable, maintainable code Advanced C++ programming techniques Nuances of the C++ language C++ Gotchas shows how to navigate through the greatest dangers in C++ programming, and gives programmers the practical know-how they need to gain expert status. COMPUTERS,Languages,C++

C++ Primer Plus C++ Primer Plus, Sixth Edition New C++11 Coverage C++ Primer Plus is a carefully crafted, complete tutorial on one of the most significant and widely used programming languages today. An accessible and easy-to-use self-study guide, this book is appropriate for both serious students of programming as well as developers already proficient in other languages. The sixth edition of C++ Primer Plus has been updated and expanded to cover the latest developments in C++, including a detailed look at the new C++11 standard. Author and educator Stephen Prata has created an introduction to C++ that is instructive, clear, and insightful. Fundamental programming concepts are explained along with details of the C++ language. Many short, practical examples illustrate just one or two concepts at a time, encouraging readers to master new topics by immediately putting them to use. Review questions and programming exercises at the end of each chapter help readers zero in on the most critical information and digest the most difficult concepts. In C++ Primer Plus, you’ll find depth, breadth, and a variety of teaching techniques and tools to enhance your learning: A new detailed chapter on the changes and additional capabilities introduced in the C++11 standard Complete, integrated discussion of both basic C language and additional C++ features Clear guidance about when and why to use a feature Hands-on learning with concise and simple examples that develop your understanding a concept or two at a time Hundreds of practical sample programs Review questions and programming exercises at the end of each chapter to test your understanding Coverage of generic C++ gives you the greatest possible flexibility Teaches the ISO standard, including discussions of templates, the Standard Template Library, the string class, exceptions, RTTI, and namespaces Table of Contents 1: Getting Started with C++ 2: Setting Out to C++ 3: Dealing with Data 4: Compound Types 5: Loops and Relational Expressions 6: Branching Statements and Logical Operators 7: Functions: C++’s Programming Modules 8: Adventures in Functions 9: Memory Models and Namespaces 10: Objects and Classes 11: Working with Classes 12: Classes and Dynamic Memory Allocation 13: Class Inheritance 14: Reusing Code in C++ 15: Friends, Exceptions, and More 16: The string Class and the Standard Template Library 17: Input, Output, and Files 18: The New C++11 Standard A Number Bases B C++ Reserved Words C The ASCII Character Set D Operator Precedence E Other Operators F The stringTemplate Class G The Standard Template Library Methods and Functions H Selected Readings and Internet Resources I Converting to ISO Standard C++ J Answers to Chapter Reviews COMPUTERS,Languages,C++

C++ Standard Library, The The Best-Selling C++ Resource Now Updated for C++11 The C++ standard library provides a set of common classes and interfaces that greatly extend the core C++ language. The library, however, is not self-explanatory. To make full use of its components–and to benefit from their power–you need a resource that does far more than list the classes and their functions. The C++ Standard Library: A Tutorial and Reference, Second Edition, describes this library as now incorporated into the new ANSI/ISO C++ language standard (C++11). The book provides comprehensive documentation of each library component, including an introduction to its purpose and design; clearly written explanations of complex concepts; the practical programming details needed for effective use; traps and pitfalls; the exact signature and definition of the most important classes and functions; and numerous examples of working code. The book focuses in particular on the Standard Template Library (STL), examining containers, iterators, function objects, and STL algorithms. The book covers all the new C++11 library components, including Concurrency Fractional arithmetic Clocks and timers Tuples New STL containers New STL algorithms New smart pointers New locale facets Random numbers and distributions Type traits and utilities Regular expressions The book also examines the new C++ programming style and its effect on the standard library, including lambdas, range-based for loops, move semantics, and variadic templates. An accompanying Web site, including source code, can be found at www.cppstdlib.com. COMPUTERS,Languages,C++

C++ Primer Bestselling Programming Tutorial and Reference Completely Rewritten for the New C++11 Standard Fully updated and recast for the newly released C++11 standard, this authoritative and comprehensive introduction to C++ will help you to learn the language fast, and to use it in modern, highly effective ways. Highlighting today’s best practices, the authors show how to use both the core language and its standard library to write efficient, readable, and powerful code. C++ Primer, Fifth Edition, introduces the C++ standard library from the outset, drawing on its common functions and facilities to help you write useful programs without first having to master every language detail. The book’s many examples have been revised to use the new language features and demonstrate how to make the best use of them. This book is a proven tutorial for those new to C++, an authoritative discussion of core C++ concepts and techniques, and a valuable resource for experienced programmers, especially those eager to see C++11 enhancements illuminated. Start Fast and Achieve More Learn how to use the new C++11 language features and the standard library to build robust programs quickly, and get comfortable with high-level programming Learn through examples that illuminate today’s best coding styles and program design techniques Understand the “rationale behind the rulesâ€: why C++11 works as it does Use the extensive crossreferences to help you connect related concepts and insights Benefit from up-to-date learning aids and exercises that emphasize key points, help you to avoid pitfalls, promote good practices, and reinforce what you’ve learned Access the source code for the extended examples from informit.com/title/0321714113 C++ Primer, Fifth Edition, features an enhanced, layflat binding, which allows the book to stay open more easily when placed on a flat surface. This special binding method—notable by a small space inside the spine—also increases durability. COMPUTERS,Languages,C++

C++ for the Impatient A Ready Reference for C++ C++ for the Impatient offers both the quickest way for busy programmers to learn the latest features of the C++ language and a handy resource for quickly finding answers to specific language questions. Designed to give you the most accurate and up-to-date information you require fast and to the point, this book is also an essential guide to the new C++11 standard, including advanced uses of the C++ standard library. Features include · Concise descriptions of nearly every function, object, and operator in the C++ core language and standard library, with clear, well-chosen examples for each of them · Information provided “at a glance†through syntax displays, tables, and summaries of important functions · Content organized for quick look-up of needed information · Simple explanations of advanced concepts, using helpful illustrations · Complete program examples that are both useful and intriguing, including puzzles, games, and challenging exercises C++11 features, all covered in the book, include: · Lambdas · rvalue references · Regular-expression library · Randomization library · Hash-table containers · Smart pointers C++ for the Impatient is an ideal resource for anyone who needs to come up to speed quickly on C++11. Whether or not it’s your first C++ book, it will be one you come back to often for reliable answers. COMPUTERS,Languages,C++

Modern C++ Design Modern C++ Design, Andrei Alexandrescu opens new vistas for C++ programmers. Displaying extraordinary creativity and programming virtuosity, Alexandrescu offers a cutting-edge approach to design that unites design patterns, generic programming, and C++, enabling programmers to achieve expressive, flexible, and highly reusable code. This book introduces the concept of generic components–reusable design templates that produce boilerplate code for compiler consumption–all within C++. Generic components enable an easier and more seamless transition from design to application code, generate code that better expresses the original design intention, and support the reuse of design structures with minimal recoding. The author describes the specific C++ techniques and features that are used in building generic components and goes on to implement industrial strength generic components for real-world applications. Recurring issues that C++ developers face in their day-to-day activity are discussed in depth and implemented in a generic way. These include: Policy-based design for flexibility Partial template specialization Typelists–powerful type manipulation structures Patterns such as Visitor, Singleton, Command, and Factories Multi-method engines For each generic component, the book presents the fundamental problems and design options, and finally implements a generic solution. In addition, an accompanying Web site, http://www.awl.com/cseng/titles/0-201-70431-5, makes the code implementations available for the generic components in the book and provides a free, downloadable C++ library, called Loki, created by the author. Loki provides out-of-the-box functionality for virtually any C++ project. Get a value-added service! Try out all the examples from this book at www.codesaw.com. CodeSaw is a free online learning tool that allows you to experiment with live code from your book right in your browser. COMPUTERS,Languages,C++

C++ Programming Language, The The new C++11 standard allows programmers to express ideas more clearly, simply, and directly, and to write faster, more efficient code. Bjarne Stroustrup, the designer and original implementer of C++, has reorganized, extended, and completely rewritten his definitive reference and tutorial for programmers who want to use C++ most effectively. The C++ Programming Language, Fourth Edition, delivers meticulous, richly explained, and integrated coverage of the entire language—its facilities, abstraction mechanisms, standard libraries, and key design techniques. Throughout, Stroustrup presents concise, “pure C++11†examples, which have been carefully crafted to clarify both usage and program design. To promote deeper understanding, the author provides extensive cross-references, both within the book and to the ISO standard. New C++11 coverage includes Support for concurrency Regular expressions, resource management pointers, random numbers, and improved containers General and uniform initialization, simplified for-statements, move semantics, and Unicode support Lambdas, general constant expressions, control over class defaults, variadic templates, template aliases, and user-defined literals Compatibility issues Topics addressed in this comprehensive book include Basic facilities: type, object, scope, storage, computation fundamentals, and more Modularity, as supported by namespaces, source files, and exception handling C++ abstraction, including classes, class hierarchies, and templates in support of a synthesis of traditional programming, object-oriented programming, and generic programming Standard Library: containers, algorithms, iterators, utilities, strings, stream I/O, locales, numerics, and more The C++ basic memory model, in depth This fourth edition makes C++11 thoroughly accessible to programmers moving from C++98 or other languages, while introducing insights and techniques that even cutting-edge C++11 programmers will find indispensable. This book features an enhanced, layflat binding, which allows the book to stay open more easily when placed on a flat surface. This special binding method—noticeable by a small space inside the spine—also increases durability. COMPUTERS,Languages,C++

Tour of C++, A The C++11 standard allows programmers to express ideas more clearly, simply, and directly, and to write faster, more efficient code. Bjarne Stroustrup, the designer and original implementer of C++, thoroughly covers the details of this language and its use in his definitive reference, The C++ Programming Language, Fourth Edition. In A Tour of C++ , Stroustrup excerpts the overview chapters from that complete reference, expanding and enhancing them to give an experienced programmer–in just a few hours–a clear idea of what constitutes modern C++. In this concise, self-contained guide, Stroustrup covers most major language features and the major standard-library components–not, of course, in great depth, but to a level that gives programmers a meaningful overview of the language, some key examples, and practical help in getting started. Stroustrup presents the C++ features in the context of the programming styles they support, such as object-oriented and generic programming. His tour is remarkably comprehensive. Coverage begins with the basics, then ranges widely through more advanced topics, including many that are new in C++11, such as move semantics, uniform initialization, lambda expressions, improved containers, random numbers, and concurrency. The tour ends with a discussion of the design and evolution of C++ and the extensions added for C++11. This guide does not aim to teach you how to program (see Stroustrup’s Programming: Principles and Practice Using C++ for that); nor will it be the only resource you’ll need for C++ mastery (see Stroustrup’s The C++ Programming Language, Fourth Edition, for that). If, however, you are a C or C++ programmer wanting greater familiarity with the current C++ language, or a programmer versed in another language wishing to gain an accurate picture of the nature and benefits of modern C++, you can’t find a shorter or simpler introduction than this tour provides. COMPUTERS,Languages,C++

Programming An introduction to programming by the inventor of C++, Programming prepares students for programming in the real world. This book assumes that they aim eventually to write non-trivial programs, whether for work in software development or in some other technical field. It explains fundamental concepts and techniques in greater depth than traditional introductions. This approach gives students a solid foundation for writing useful, correct, maintainable, and efficient code. This book is an introduction to programming in general, including object-oriented programming and generic programming. It is also a solid introduction to the C++ programming language, one of the most widely used languages for real-world software. It presents modern C++ programming techniques from the start, introducing the C++ standard library to simplify programming tasks. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Languages,C++

C++ All-in-One For Dummies Get ahead of the C++ curve to stay in the game C++ is the workhorse of programming languages and remains one of the most widely used programming languages today. It's cross-platform, multi-functional, and updates are typically open-source. The language itself is object-oriented, offering you the utmost control over data usage, interface, and resource allocation. If your job involves data, C++ proficiency makes you indispensable. C++ All-in-One For Dummies, 3rd Edition is your number-one handbook to C++ mastery. Author John Paul Mueller is a recognized authority in the computer industry, and your ultimate guide to C++. Mueller takes you through all things C++, including information relevant to the 2014 update. Learn how to work with objects and classes Conquer advanced programming and troubleshooting Discover how lambda expressions can make your code more concise and readable See Standard Library features, such as dynamic arrays, in action Online resources include source code from examples in the book as well as a C++ GNU compiler. If you need to learn C++, this is the fastest, most effective way to do it. C++ All-in-One For Dummies, 3rd Edition will get you up and running quickly, so you can get to work producing code faster and better than ever. COMPUTERS,Languages,C++

Effective Modern C++ Coming to grips with C++11 and C++14 is more than a matter of familiarizing yourself with the features they introduce (e.g., auto type declarations, move semantics, lambda expressions, and concurrency support). The challenge is learning to use those features effectively—so that your software is correct, efficient, maintainable, and portable. That’s where this practical book comes in. It describes how to write truly great software using C++11 and C++14—i.e. using modern C++. Topics include: The pros and cons of braced initialization, noexcept specifications, perfect forwarding, and smart pointer make functions The relationships among std::move, std::forward, rvalue references, and universal references Techniques for writing clear, correct, effective lambda expressions How std::atomic differs from volatile, how each should be used, and how they relate to C++'s concurrency API How best practices in "old" C++ programming (i.e., C++98) require revision for software development in modern C++ Effective Modern C++ follows the proven guideline-based, example-driven format of Scott Meyers' earlier books, but covers entirely new material. "After I learned the C++ basics, I then learned how to use C++ in production code from Meyer's series of Effective C++ books. Effective Modern C++ is the most important how-to book for advice on key guidelines, styles, and idioms to use modern C++ effectively and well. Don't own it yet? Buy this one. Now". -- Herb Sutter, Chair of ISO C++ Standards Committee and C++ Software Architect at Microsoft COMPUTERS,Languages,C++

Getting Started with Arduino Arduino is the open source electronics prototyping platform that has taken the Maker Movement by storm. This thorough introduction, updated for the latest Arduino release, helps you start prototyping right away. From obtaining the required components to putting the final touches on your project, all the information you need is here! Getting started with Arduino is a snap. To use the introductory examples in this guide, all you need is an Arduino Uno or Leonardo, along with a USB cable and an LED. The easy-to-use, free Arduino development environment runs on Mac, Windows, and Linux. In Getting Started with Arduino, you'll learn about: Interaction design and physical computing The Arduino board and its software environment Basics of electricity and electronics Prototyping on a solderless breadboard Drawing a schematic diagram Talking to a computer--and the cloud--from Arduino Building a custom plant-watering system COMPUTERS,Languages,C++

C++ Without Fear Learning C++ Doesn’t Have to Be Difficult! Have you ever wanted to learn programming? Have you ever wanted to learn the C++ language behind many of today’s hottest games, business programs, and even advanced spacecraft? C++ Without Fear, Third Edition, is the ideal way to get started. Now updated for the newest C++14 standard and the free Microsoft Visual C++ Community Edition, it will quickly make you productive with C++ even if you’ve never written a line of code! Brian Overland has earned rave reviews for this book’s approach to teaching C++. He starts with short, simple examples you can easily enter and run. Within a couple of chapters, you’ll be creating useful utilities, playing games, and solving puzzles. Everything’s simplified to its essentials, patiently explained, and clearly illustrated with practical examples and exercises that help you make progress quickly. Overland reveals the “whys†and “tricks†behind each C++ language feature. And you’ll never get bogged down in complex or pointless examples: He keeps you 100% focused on learning what works and what matters—while having fun! This new and improved edition Covers installing and using the free Microsoft Visual C++ Community Edition— but you can use any version of C++ Explains valuable improvements in the new C++14 standard Modularizes C++14 coverage so it’s easy to write code that works with older versions Teaches with even more puzzles, games, and relevant exercises Offers more “why†and “how-to†coverage of object orientation, today’s #1 approach to programming Presents more ways to use Standard Template Library (STL) code to save time and get more done Contains an expanded reference section for all your day-to-day programming Whether you want to learn C++ programming for pleasure or you’re considering a career in programming, this book is an outstanding choice. COMPUTERS,Languages,C++

C++ Templates Templates are among the most powerful features of C++, but they remain misunderstood and underutilized, even as the C++ language and development community have advanced. In C++ Templates, Second Edition, three pioneering C++ experts show why, when, and how to use modern templates to build software that’s cleaner, faster, more efficient, and easier to maintain. Now extensively updated for the C++11, C++14, and C++17 standards, this new edition presents state-of-the-art techniques for a wider spectrum of applications. The authors provide authoritative explanations of all new language features that either improve templates or interact with them, including variadic templates, generic lambdas, class template argument deduction, compile-time if, forwarding references, and user-defined literals. They also deeply delve into fundamental language concepts (like value categories) and fully cover all standard type traits. The book starts with an insightful tutorial on basic concepts and relevant language features. The remainder of the book serves as a comprehensive reference, focusing first on language details and then on coding techniques, advanced applications, and sophisticated idioms. Throughout, examples clearly illustrate abstract concepts and demonstrate best practices for exploiting all that C++ templates can do. Understand exactly how templates behave, and avoid common pitfalls Use templates to write more efficient, flexible, and maintainable software Master today’s most effective idioms and techniques Reuse source code without compromising performance or safety Benefit from utilities for generic programming in the C++ Standard Library Preview the upcoming concepts feature The companion website, tmplbook.com, contains sample code and additional updates. COMPUTERS,Languages,C++

Mastering the C++17 STL This book breaks down the C++ STL, teaching you how to extract its gems and apply them to your programming. About This Book Boost your productivity as a C++ developer with the latest features of C++17 Develop high-quality, fast, and portable applications with the varied features of the STL Migrate from older versions (C++11, C++14) to C++17 Who This Book Is For This book is for developers who would like to master the C++ STL and make full use of its components. Prior C++ knowledge is assumed. What You Will Learn Make your own iterator types, allocators, and thread pools. Master every standard container and every standard algorithm. Improve your code by replacing new/delete with smart pointers. Understand the difference between monomorphic algorithms, polymorphic algorithms, and generic algorithms. Learn the meaning and applications of vocabulary type, product type and sum type. In Detail Modern C++ has come a long way since 2011. The latest update, C++17, has just been ratified and several implementations are on the way. This book is your guide to the C++ standard library, including the very latest C++17 features. The book starts by exploring the C++ Standard Template Library in depth. You will learn the key differences between classical polymorphism and generic programming, the foundation of the STL. You will also learn how to use the various algorithms and containers in the STL to suit your programming needs. The next module delves into the tools of modern C++. Here you will learn about algebraic types such as std::optional, vocabulary types such as std::function, smart pointers, and synchronization primitives such as std::atomic and std::mutex. In the final module, you will learn about C++'s support for regular expressions and file I/O. By the end of the book you will be proficient in using the C++17 standard library to implement real programs, and you'll have gained a solid understanding of the library's own internals. Style and approach This book takes a concise but comprehensive approach to explaining and applying the C++ STL, one feature at a time. COMPUTERS,Languages,C++

C++ High Performance Write code that scales across CPU registers, multi-core, and machine clusters About This Book Explore concurrent programming in C++ Identify memory management problems Use SIMD and STL containers for performance improvement Who This Book Is For If you're a C++ developer looking to improve the speed of your code or simply wanting to take your skills up to the next level, then this book is perfect for you. What You Will Learn Find out how to use exciting new tools that will help you improve your code Identify bottlenecks to optimize your code Develop applications that utilize GPU computation Reap the benefits of concurrent programming Write code that can protect against application errors using error handling Use STL containers and algorithms effciently Extend your toolbox with Boost containers Achieve effcient memory management by using custom memory allocators In Detail C++ is a highly portable language and can be used to write complex applications and performance-critical code. It has evolved over the last few years to become a modern and expressive language. This book will guide you through optimizing the performance of your C++ apps by allowing them to run faster and consume fewer resources on the device they're running on. The book begins by helping you to identify the bottlenecks in C++. It then moves on to measuring performance, and you'll see how this affects the way you write code. Next, you'll see the importance of data structure optimization and how it can be used efficiently. After that, you'll see which algorithm should be used to achieve faster execution, followed by how to use STL containers. Moving on, you'll learn how to improve memory management in C++. You'll get hands on experience making use of multiple cores to enable more efficient and faster execution. The book ends with a brief overview of utilizing the capabilities of your GPU by using Boost Compute and OpenCL. Style and approach This easy-to-follow guide is full of examples and self-sufficient code snippets that help you with high performance programming with C++. You'll get your hands dirty with this all-inclusive guide that uncovers hidden performance improvement areas for any C++ code. COMPUTERS,Languages,C++

Learn Qt 5 Learn the fundamentals of QT 5 framework to develop interactive cross-platform applications About This Book A practical guide on the fundamentals of application development with QT 5 Learn to write scalable, robust and adaptable C++ code with QT Deploy your application on different platforms such as Windows, Mac OS, and Linux Who This Book Is For This book is for application developers who want a powerful and flexible framework to create modern, responsive applications on Microsoft Windows, Apple Mac OS X, and Linux desktop platforms. You should be comfortable with C++ but no prior knowledge of Qt or QML is required. What You Will Learn Install and configure the Qt Framework and Qt Creator IDE Create a new multi-project solution from scratch and control every aspect of it with QMake Implement a rich user interface with QML Learn the fundamentals of QtTest and how to integrate unit testing Build self-aware data entities that can serialize themselves to and from JSON Manage data persistence with SQLite and CRUD operations Reach out to the internet and consume an RSS feed Produce application packages for distribution to other users In Detail Qt is a mature and powerful framework for delivering sophisticated applications across a multitude of platforms. It has a rich history in the Linux world, is widely used in embedded devices, and has made great strides in the Mobile arena over the past few years. However, in the Microsoft Windows and Apple Mac OS X worlds, the dominance of C#/.NET and Objective-C/Cocoa means that Qt is often overlooked. This book demonstrates the power and flexibility of the Qt framework for desktop application development and shows how you can write your application once and deploy it to multiple operating systems. Build a complete real-world line of business (LOB) solution from scratch, with distinct C++ library, QML user interface, and QtTest-driven unit-test projects. This is a suite of essential techniques that cover the core requirements for most LOB applications and will empower you to progress from a blank page to shipped application. Style and approach This book takes a hands-on approach to app development that emphasizes the key concepts while you're doing the project work. COMPUTERS,Languages,C++

Modern C++ Programming with Test-Driven Development If you program in C++ you've been neglected. Test-driven development (TDD) is a modern software development practice that can dramatically reduce the number of defects in systems, produce more maintainable code, and give you the confidence to change your software to meet changing needs. But C++ programmers have been ignored by those promoting TDD--until now. In this book, Jeff Langr gives you hands-on lessons in the challenges and rewards of doing TDD in C++. Modern C++ Programming With Test-Driven Development, the only comprehensive treatment on TDD in C++ provides you with everything you need to know about TDD, and the challenges and benefits of implementing it in your C++ systems. Its many detailed code examples take you step-by-step from TDD basics to advanced concepts. As a veteran C++ programmer, you're already writing high-quality code, and you work hard to maintain code quality. It doesn't have to be that hard. In this book, you'll learn: how to use TDD to improve legacy C++ systems how to identify and deal with troublesome system dependencies how to do dependency injection, which is particularly tricky in C++ how to use testing tools for C++ that aid TDD new C++11 features that facilitate TDD As you grow in TDD mastery, you'll discover how to keep a massive C++ system from becoming a design mess over time, as well as particular C++ trouble spots to avoid. You'll find out how to prevent your tests from being a maintenance burden and how to think in TDD without giving up your hard-won C++ skills. Finally, you'll see how to grow and sustain TDD in your team. Whether you're a complete unit-testing novice or an experienced tester, this book will lead you to mastery of test-driven development in C++. What You Need A C++ compiler running under Windows or Linux, preferably one that supports C++11. Examples presented in the book were built under gcc 4.7.2. Google Mock 1.6 (downloadable for free; it contains Google Test as well) or an alternate C++ unit testing tool. Most examples in the book are written for Google Mock, but it isn't difficult to translate them to your tool of choice. A good programmer's editor or IDE. cmake, preferably. Of course, you can use your own preferred make too. CMakeLists.txt files are provided for each project. Examples provided were built using cmake version 2.8.9. Various freely-available third-party libraries are used as the basis for examples in the book. These include: cURL JsonCpp Boost (filesystem, date_time/gregorian, algorithm, assign) Several examples use the boost headers/libraries. Only one example uses cURL and JsonCpp. COMPUTERS,Languages,C++

Game Programming in C++ Program 3D Games in C++: The #1 Language at Top Game Studios Worldwide C++ remains the key language at many leading game development studios. Since it’s used throughout their enormous code bases, studios use it to maintain and improve their games, and look for it constantly when hiring new developers. Game Programming in C++ is a practical, hands-on approach to programming 3D video games in C++. Modeled on Sanjay Madhav’s game programming courses at USC, it’s fun, easy, practical, hands-on, and complete. Step by step, you’ll learn to use C++ in all facets of real-world game programming, including 2D and 3D graphics, physics, AI, audio, user interfaces, and much more. You’ll hone real-world skills through practical exercises, and deepen your expertise through start-to-finish projects that grow in complexity as you build your skills. Throughout, Madhav pays special attention to demystifying the math that all professional game developers need to know. Set up your C++ development tools quickly, and get started Implement basic 2D graphics, game updates, vectors, and game physics Build more intelligent games with widely used AI algorithms Implement 3D graphics with OpenGL, shaders, matrices, and transformations Integrate and mix audio, including 3D positional audio Detect collisions of objects in a 3D environment Efficiently respond to player input Build user interfaces, including Head-Up Displays (HUDs) Improve graphics quality with anisotropic filtering and deferred shading Load and save levels and binary game data Whether you’re a working developer or a student with prior knowledge of C++ and data structures, Game Programming in C++ will prepare you to solve real problems with C++ in roles throughout the game development lifecycle. You’ll master the language that top studios are hiring for—and that’s a proven route to success. COMPUTERS,Languages,C++

The Modern C++ Challenge Test your C++ programming skills by solving real-world programming problems covered in the book About This Book Solve a variety of real-world programming and logic problems by leveraging the power of C++17 Test your skills in using language features, algorithms, data structures, design patterns, and more Explore areas such as cryptography, communication, and image handling in C++ Who This Book Is For This book will appeal to C++ developers of all levels. There's a challenge inside for everyone. What You Will Learn Serialize and deserialize JSON and XML data Perform encryption and signing to facilitate secure communication between parties Embed and use SQLite databases in your applications Use threads and asynchronous functions to implement generic purpose parallel algorithms Compress and decompress files to/from a ZIP archive Implement data structures such as circular buffer and priority queue Implement general purpose algorithms as well as algorithms that solve specific problems Create client-server applications that communicate over TCP/IP Consume HTTP REST services Use design patterns to solve real-world problems In Detail C++ is one of the most widely-used programming languages and has applications in a variety of fields, such as gaming, GUI programming, and operating systems, to name a few. Through the years, C++ has evolved into (and remains) one of the top choices for software developers worldwide. This book will show you some notable C++ features and how to implement them to meet your application needs. Each problem is unique and doesn't just test your knowledge of the language; it tests your ability to think out of the box and come up with the best solutions. With varying levels of difficulty, you'll be faced with a wide variety of challenges. And in case you're stumped, you don't have to worry: we've got the best solutions to the problems in the book. So are you up for the challenge? Style and approach A recipe-based approach where each problem is solved with the help of step by step instructions. COMPUTERS,Languages,C++

Hands-On Concurrency with Rust Get to grips with modern software demands by learning the effective uses of Rust's powerful memory safety. About This Book Learn and improve the sequential performance characteristics of your software Understand the use of operating system processes in a high-scale concurrent system Learn of the various coordination methods available in the Standard library Who This Book Is For This book is aimed at software engineers with a basic understanding of Rust who want to exploit the parallel and concurrent nature of modern computing environments, safely. What You Will Learn Probe your programs for performance and accuracy issues Create your own threading and multi-processing environment in Rust Use coarse locks from Rust's Standard library Solve common synchronization problems or avoid synchronization using atomic programming Build lock-free/wait-free structures in Rust and understand their implementations in the crates ecosystem Leverage Rust's memory model and type system to build safety properties into your parallel programs Understand the new features of the Rust programming language to ease the writing of parallel programs In Detail Most programming languages can really complicate things, especially with regard to unsafe memory access. The burden on you, the programmer, lies across two domains: understanding the modern machine and your language's pain-points. This book will teach you to how to manage program performance on modern machines and build fast, memory-safe, and concurrent software in Rust. It starts with the fundamentals of Rust and discusses machine architecture concepts. You will be taken through ways to measure and improve the performance of Rust code systematically and how to write collections with confidence. You will learn about the Sync and Send traits applied to threads, and coordinate thread execution with locks, atomic primitives, data-parallelism, and more. The book will show you how to efficiently embed Rust in C++ code and explore the functionalities of various crates for multithreaded applications. It explores implementations in depth. You will know how a mutex works and build several yourself. You will master radically different approaches that exist in the ecosystem for structuring and managing high-scale systems. By the end of the book, you will feel comfortable with designing safe, consistent, parallel, and high-performance applications in Rust. Style and approach Readers will be taken through various ways to improve the performance of their Rust code. COMPUTERS,Languages,C++

A Tour of C++ In A Tour of C++, Second Edition, Bjarne Stroustrup, the creator of C++, describes what constitutes modern C++. This concise, self-contained guide covers most major language features and the major standard-library components—not, of course, in great depth, but to a level that gives programmers a meaningful overview of the language, some key examples, and practical help in getting started. Stroustrup presents the C++ features in the context of the programming styles they support, such as object-oriented and generic programming. His tour is remarkably comprehensive. Coverage begins with the basics, then ranges widely through more advanced topics, including many that are new in C++17, such as move semantics, uniform initialization, lambda expressions, improved containers, random numbers, and concurrency. The tour even covers some extensions being made for C++20, such as concepts and modules, and ends with a discussion of the design and evolution of C++. This guide does not aim to teach you how to program (for that, see Stroustrup’s Programming: Principles and Practice Using C++, Second Edition), nor will it be the only resource you’ll need for C++ mastery (for that, see Stroustrup’s The C++ Programming Language, Fourth Edition, and recommended online sources). If, however, you are a C or C++ programmer wanting greater familiarity with the current C++ language, or a programmer versed in another language wishing to gain an accurate picture of the nature and benefits of modern C++, you can’t find a shorter or simpler introduction than this tour provides. COMPUTERS,Languages,C++

Modern C++ Create apps in C++ and leverage its latest features using modern programming techniques. Key Features Develop strong C++ skills to build a variety of applications Explore features of C++17, such as containers, algorithms, and threads Grasp the standard support for threading and concurrency and use them in basic daily tasks Book Description C++ is one of the most widely used programming languages. It is fast, flexible, and used to solve many programming problems. This Learning Path gives you an in-depth and hands-on experience of working with C++, using the latest recipes and understanding most recent developments. You will explore C++ programming constructs by learning about language structures, functions, and classes, which will help you identify the execution flow through code. You will also understand the importance of the C++ standard library as well as memory allocation for writing better and faster programs. Modern C++: Efficient and Scalable Application Development deals with the challenges faced with advanced C++ programming. You will work through advanced topics such as multithreading, networking, concurrency, lambda expressions, and many more recipes. By the end of this Learning Path, you will have all the skills to become a master C++ programmer. This Learning Path includes content from the following Packt products: Beginning C++ Programming by Richard Grimes Modern C++ Programming Cookbook by Marius Bancila The Modern C++ Challenge by Marius Bancila What you will learn Become familiar with the structure of C++ projects Identify the main structures in the language: functions and classes Learn to debug your programs Leverage C++ features to obtain increased robustness and performance Explore functions and callable objects with a focus on modern features Serialize and deserialize JSON and XML data Create client-server applications that communicate over TCP/IP Use design patterns to solve real-world problems Who this book is for This Learning Path is designed for developers who want to gain a solid foundation in C++. The desire to learn how to code in C++ is all you need to get started with this Learning Path COMPUTERS,Languages,C++

Hands-On Design Patterns with C++ A comprehensive guide with extensive coverage on concepts such as OOP, functional programming, generic programming, and STL along with the latest features of C++ Key Features Delve into the core patterns and components of C++ in order to master application design Learn tricks, techniques, and best practices to solve common design and architectural challenges Understand the limitation imposed by C++ and how to solve them using design patterns Book Description C++ is a general-purpose programming language designed with the goals of efficiency, performance, and flexibility in mind. Design patterns are commonly accepted solutions to well-recognized design problems. In essence, they are a library of reusable components, only for software architecture, and not for a concrete implementation. The focus of this book is on the design patterns that naturally lend themselves to the needs of a C++ programmer, and on the patterns that uniquely benefit from the features of C++, in particular, the generic programming. Armed with the knowledge of these patterns, you will spend less time searching for a solution to a common problem and be familiar with the solutions developed from experience, as well as their advantages and drawbacks. The other use of design patterns is as a concise and an efficient way to communicate. A pattern is a familiar and instantly recognizable solution to specific problem; through its use, sometimes with a single line of code, we can convey a considerable amount of information. The code conveys: "This is the problem we are facing, these are additional considerations that are most important in our case; hence, the following well-known solution was chosen." By the end of this book, you will have gained a comprehensive understanding of design patterns to create robust, reusable, and maintainable code. What you will learn Recognize the most common design patterns used in C++ Understand how to use C++ generic programming to solve common design problems Explore the most powerful C++ idioms, their strengths, and drawbacks Rediscover how to use popular C++ idioms with generic programming Understand the impact of design patterns on the program's performance Who this book is for This book is for experienced C++ developers and programmers who wish to learn about software design patterns and principles and apply them to create robust, reusable, and easily maintainable apps. COMPUTERS,Languages,C++

Hands-On Microservices with Rust A comprehensive guide in developing and deploying high performance microservices with Rust Key Features Start your microservices journey and get a broader perspective on microservices development using RUST 2018, Build, deploy, and test microservices using AWS Explore advanced techniques for developing microservices such as actor model, Requests Routing, and threads Book Description Microservice architecture is sweeping the world as the de facto pattern for building web-based applications. Rust is a language particularly well-suited for building microservices. It is a new system programming language that offers a practical and safe alternative to C. This book describes web development using the Rust programming language and will get you up and running with modern web frameworks and crates with examples of RESTful microservices creation. You will deep dive into Reactive programming, and asynchronous programming, and split your web application into a set of concurrent actors. The book provides several HTTP-handling examples with manageable memory allocations. You will walk through stateless high-performance microservices, which are ideally suitable for computation or caching tasks, and look at stateful microservices, which are filled with persistent data and database interactions. As we move along, you will learn how to use Rust macros to describe business or protocol entities of our application and compile them into native structs, which will be performed at full speed with the help of the server's CPU. Finally, you will be taken through examples of how to test and debug microservices and pack them into a tiny monolithic binary or put them into a container and deploy them to modern cloud platforms such as AWS. What you will learn Get acquainted with leveraging Rust web programming Get to grips with various Rust crates, such as hyper, Tokio, and Actix Explore RESTful microservices with Rust Understand how to pack Rust code to a container using Docker Familiarize yourself with Reactive microservices Deploy your microservices to modern cloud platforms such as AWS Who this book is for This book is for developers who have basic knowledge of RUST, and want to learn how to build, test, scale, and manage RUST microservices. No prior experience of writing microservices in RUST is assumed. COMPUTERS,Languages,C++

Hands-On Embedded Programming with C++17 Build safety-critical and memory-safe stand-alone and networked embedded systems Key Features Know how C++ works and compares to other languages used for embedded development Create advanced GUIs for embedded devices to design an attractive and functional UI Integrate proven strategies into your design for optimum hardware performance Book Description C++ is a great choice for embedded development, most notably, because it does not add any bloat, extends maintainability, and offers many advantages over different programming languages. Hands-On Embedded Programming with C++17 will show you how C++ can be used to build robust and concurrent systems that leverage the available hardware resources. Starting with a primer on embedded programming and the latest features of C++17, the book takes you through various facets of good programming. You'll learn how to use the concurrency, memory management, and functional programming features of C++ to build embedded systems. You will understand how to integrate your systems with external peripherals and efficient ways of working with drivers. This book will also guide you in testing and optimizing code for better performance and implementing useful design patterns. As an additional benefit, you will see how to work with Qt, the popular GUI library used for building embedded systems. By the end of the book, you will have gained the confidence to use C++ for embedded programming. What you will learn Choose the correct type of embedded platform to use for a project Develop drivers for OS-based embedded systems Use concurrency and memory management with various microcontroller units (MCUs) Debug and test cross-platform code with Linux Implement an infotainment system using a Linux-based single board computer Extend an existing embedded system with a Qt-based GUI Communicate with the FPGA side of a hybrid FPGA/SoC system Who this book is for If you want to start developing effective embedded programs in C++, then this book is for you. Good knowledge of C++ language constructs is required to understand the topics covered in the book. No knowledge of embedded systems is assumed. COMPUTERS,Languages,C++

Unreal Engine 4 Virtual Reality Projects Learn to design and build Virtual Reality experiences, applications, and games in Unreal Engine 4 through a series of practical, hands-on projects that teach you to create controllable avatars, user interfaces, and more. Key Features Learn about effective VR design and develop virtual reality games and applications for every VR platform Build essential features for VR such as player locomotion and interaction, 3D user interfaces, and 360 media players Learn about multiplayer networking and how to extend the engine using plugins and asset packs Book Description Unreal Engine 4 (UE4) is a powerful tool for developing VR games and applications. With its visual scripting language, Blueprint, and built-in support for all major VR headsets, it's a perfect tool for designers, artists, and engineers to realize their visions in VR. This book will guide you step-by-step through a series of projects that teach essential concepts and techniques for VR development in UE4. You will begin by learning how to think about (and design for) VR and then proceed to set up a development environment. A series of practical projects follows, taking you through essential VR concepts. Through these exercises, you'll learn how to set up UE4 projects that run effectively in VR, how to build player locomotion schemes, and how to use hand controllers to interact with the world. You'll then move on to create user interfaces in 3D space, use the editor's VR mode to build environments directly in VR, and profile/optimize worlds you've built. Finally, you'll explore more advanced topics, such as displaying stereo media in VR, networking in Unreal, and using plugins to extend the engine. Throughout, this book focuses on creating a deeper understanding of why the relevant tools and techniques work as they do, so you can use the techniques and concepts learned here as a springboard for further learning and exploration in VR. What you will learn Understand design principles and concepts for building VR applications Set up your development environment with Unreal Blueprints and C++ Create a player character with several locomotion schemes Evaluate and solve performance problems in VR to maintain high frame rates Display mono and stereo videos in VR Extend Unreal Engine's capabilities using various plugins Who this book is for This book is for anyone interested in learning to develop Virtual Reality games and applications using UE4. Developers new to UE4 will benefit from hands-on projects that guide readers through clearly-explained steps, while both new and experienced developers will learn crucial principles and techniques for VR development in UE4. COMPUTERS,Languages,C++

Hands-On Data Structures and Algorithms with Rust Design and implement professional level programs by exploring modern data structures and algorithms in Rust. Key Features Use data structures such as arrays, stacks, trees, lists and graphs with real-world examples Learn the functional and reactive implementations of the traditional data structures Explore illustrations to present data structures and algorithms, as well as their analysis, in a clear, visual manner. Book Description Rust has come a long way and is now utilized in several contexts. Its key strengths are its software infrastructure and resource-constrained applications, including desktop applications, servers, and performance-critical applications, not forgetting its importance in systems' programming. This book will be your guide as it takes you through implementing classic data structures and algorithms in Rust, helping you to get up and running as a confident Rust programmer. The book begins with an introduction to Rust data structures and algorithms, while also covering essential language constructs. You will learn how to store data using linked lists, arrays, stacks, and queues. You will also learn how to implement sorting and searching algorithms. You will learn how to attain high performance by implementing algorithms to string data types and implement hash structures in algorithm design. The book will examine algorithm analysis, including Brute Force algorithms, Greedy algorithms, Divide and Conquer algorithms, Dynamic Programming, and Backtracking. By the end of the book, you will have learned how to build components that are easy to understand, debug, and use in different applications. What you will learn Design and implement complex data structures in Rust Analyze, implement, and improve searching and sorting algorithms in Rust Create and use well-tested and reusable components with Rust Understand the basics of multithreaded programming and advanced algorithm design Become familiar with application profiling based on benchmarking and testing Explore the borrowing complexity of implementing algorithms Who this book is for This book is for developers seeking to use Rust solutions in a practical/professional setting; who wants to learn essential Data Structures and Algorithms in Rust. It is for developers with basic Rust language knowledge, some experience in other programming languages is required. COMPUTERS,Languages,C++

OpenCV 4 for Secret Agents Turn futuristic ideas about computer vision and machine learning into demonstrations that are both functional and entertaining Key Features Build OpenCV 4 apps with Python 2 and 3 on desktops and Raspberry Pi, Java on Android, and C# in Unity Detect, classify, recognize, and measure real-world objects in real-time Work with images from diverse sources, including the web, research datasets, and various cameras Book Description OpenCV 4 is a collection of image processing functions and computer vision algorithms. It is open source, supports many programming languages and platforms, and is fast enough for many real-time applications. With this handy library, you'll be able to build a variety of impressive gadgets. OpenCV 4 for Secret Agents features a broad selection of projects based on computer vision, machine learning, and several application frameworks. To enable you to build apps for diverse desktop systems and Raspberry Pi, the book supports multiple Python versions, from 2.7 to 3.7. For Android app development, the book also supports Java in Android Studio, and C# in the Unity game engine. Taking inspiration from the world of James Bond, this book will add a touch of adventure and computer vision to your daily routine. You'll be able to protect your home and car with intelligent camera systems that analyze obstacles, people, and even cats. In addition to this, you'll also learn how to train a search engine to praise or criticize the images that it finds, and build a mobile app that speaks to you and responds to your body language. By the end of this book, you will be equipped with the knowledge you need to advance your skills as an app developer and a computer vision specialist. What you will learn Detect motion and recognize gestures to control a smartphone game Detect car headlights and estimate their distance Detect and recognize human and cat faces to trigger an alarm Amplify motion in a real-time video to show heartbeats and breaths Make a physics simulation that detects shapes in a real-world drawing Build OpenCV 4 projects in Python 3 for desktops and Raspberry Pi Develop OpenCV 4 Android applications in Android Studio and Unity Who this book is for If you are an experienced software developer who is new to computer vision or machine learning, and wants to study these topics through creative projects, then this book is for you. The book will also help existing OpenCV users who want upgrade their projects to OpenCV 4 and new versions of other libraries, languages, tools, and operating systems. General familiarity with object-oriented programming, application development, and usage of operating systems (OS), developer tools, and the command line is required. COMPUTERS,Languages,C++

C++ Game Development By Example Explore modern game programming and rendering techniques to build games using C++ programming language and its popular libraries Key Features Learn how you can build basic 2D and complex 3D games with C++ Understand shadows, texturing, lighting, and rendering in 3D game development using OpenGL Uncover modern graphics programming techniques and GPU compute methods using the Vulkan API Book Description Although numerous languages are currently being used to develop games, C++ remains the standard for fabricating expert libraries and tool chains for game development. This book introduces you to the world of game development with C++. C++ Game Development By Example starts by touching upon the basic concepts of math, programming, and computer graphics and creating a simple side-scrolling action 2D game. You'll build a solid foundation by studying basic game concepts such as creating game loops, rendering 2D game scenes using SFML, 2D sprite creation and animation, and collision detection. The book will help you advance to creating a 3D physics puzzle game using modern OpenGL and the Bullet physics engine. You'll understand the graphics pipeline, which entails creating 3D objects using vertex and index buffers and rendering them to the scene using vertex and fragment shaders. Finally, you'll create a basic project using the Vulkan library that'll help you get to grips with creating swap chains, image views, render passes, and frame buffers for building high-performance graphics in your games. By the end of this book, you'll be ready with 3 compelling projects created with SFML, the Vulkan API, and OpenGL, and you'll be able take your game and graphics programming skills to the next level. What you will learn Understand shaders and how to write a basic vertex and fragment shader Build a Visual Studio project and add SFML to it Discover how to create sprite animations and a game character class Add sound effects and background music to your game Grasp how to integrate Vulkan into Visual Studio Create shaders and convert them to the SPIR-V binary format Who this book is for If you're a developer keen to learn game development with C++ or get up to date with game development, this book is for you. Some knowledge of C++ programming is assumed. COMPUTERS,Languages,C++

Learn CUDA Programming Explore different GPU programming methods using libraries and directives, such as OpenACC, with extension to languages such as C, C++, and Python Key Features Learn parallel programming principles and practices and performance analysis in GPU computing Get to grips with distributed multi GPU programming and other approaches to GPU programming Understand how GPU acceleration in deep learning models can improve their performance Book Description Compute Unified Device Architecture (CUDA) is NVIDIA's GPU computing platform and application programming interface. It's designed to work with programming languages such as C, C++, and Python. With CUDA, you can leverage a GPU's parallel computing power for a range of high-performance computing applications in the fields of science, healthcare, and deep learning. Learn CUDA Programming will help you learn GPU parallel programming and understand its modern applications. In this book, you'll discover CUDA programming approaches for modern GPU architectures. You'll not only be guided through GPU features, tools, and APIs, you'll also learn how to analyze performance with sample parallel programming algorithms. This book will help you optimize the performance of your apps by giving insights into CUDA programming platforms with various libraries, compiler directives (OpenACC), and other languages. As you progress, you'll learn how additional computing power can be generated using multiple GPUs in a box or in multiple boxes. Finally, you'll explore how CUDA accelerates deep learning algorithms, including convolutional neural networks (CNNs) and recurrent neural networks (RNNs). By the end of this CUDA book, you'll be equipped with the skills you need to integrate the power of GPU computing in your applications. What you will learn Understand general GPU operations and programming patterns in CUDA Uncover the difference between GPU programming and CPU programming Analyze GPU application performance and implement optimization strategies Explore GPU programming, profiling, and debugging tools Grasp parallel programming algorithms and how to implement them Scale GPU-accelerated applications with multi-GPU and multi-nodes Delve into GPU programming platforms with accelerated libraries, Python, and OpenACC Gain insights into deep learning accelerators in CNNs and RNNs using GPUs Who this book is for This beginner-level book is for programmers who want to delve into parallel computing, become part of the high-performance computing community and build modern applications. Basic C and C++ programming experience is assumed. For deep learning enthusiasts, this book covers Python InterOps, DL libraries, and practical examples on performance estimation. COMPUTERS,Languages,C++

Large-Scale C++ Volume I Writing reliable and maintainable C++ software is hard. Designing such software at scale adds a new set of challenges. Creating large-scale systems requires a practical understanding of logical design – beyond the theoretical concepts addressed in most popular texts. To be successful on an enterprise scale, developers must also address physical design, a dimension of software engineering that may be unfamiliar even to expert developers. Drawing on over 30 years of hands-on experience building massive, mission-critical enterprise systems, John Lakos shows how to create and grow Software Capital. This groundbreaking volume lays the foundation for projects of all sizes and demonstrates the processes, methods, techniques, and tools needed for successful real-world, large-scale development. Up to date and with a solid engineering focus, Large-Scale C++, Volume I: Process and Architecture, demonstrates fundamental design concepts with concrete examples. Professional developers of all experience levels will gain insights that transform their approach to design and development by understanding how to Raise productivity by leveraging differences between infrastructure and application development Achieve exponential productivity gains through feedback and hierarchical reuse Embrace the component’s role as the fundamental unit of both logical and physical design Analyze how fundamental properties of compiling and linking affect component design Discover effective partitioning of logical content in appropriately sized physical aggregates Internalize the important differences among sufficient, complete, minimal, and primitive software Deliver solutions that simultaneously optimize encapsulation, stability, and performance Exploit the nine established levelization techniques to avoid cyclic physical dependencies Use lateral designs judiciously to avoid the “heaviness†of conventional layered architectures Employ appropriate architectural insulation techniques for eliminating compile-time coupling Master the multidimensional process of designing large systems using component-based methods This is the first of John Lakos’s three authoritative volumes on developing large-scale systems using C++. This book, written for fellow software practitioners, uses familiar C++ constructs to solve real-world problems while identifying (and motivating) modern C++ alternatives. Together with the forthcoming Volume II: Design and Implementation and Volume III: Verification and Testing, Large-Scale C++ offers comprehensive guidance for all aspects of large-scale C++ software development. If you are an architect or project leader, this book will empower you to solve critically important problems right now – and serve as your go-to reference for years to come. Register your book for convenient access to downloads, updates, and/or corrections as they become available. See inside book for details. COMPUTERS,Languages,C++

Application Development with Qt Creator Explore Qt Creator, Qt Quick, and QML to design and develop applications that work on desktop, mobile, embedded, and IoT platforms Key Features Build a solid foundation in Qt by learning about its core classes, multithreading, File I/O, and networking Learn GUI programming and build custom interfaces using Qt Widgets, Qt Designer, and QML Use the latest features of C++17 for improving the performance of your Qt applications Book Description Qt is a powerful development framework that serves as a complete toolset for building cross-platform applications, helping you reduce development time and improve productivity. Completely revised and updated to cover C++17 and the latest developments in Qt 5.12, this comprehensive guide is the third edition of Application Development with Qt Creator. You'll start by designing a user interface using Qt Designer and learn how to instantiate custom messages, forms, and dialogues. You'll then understand Qt's support for multithreading, a key tool for making applications responsive, and the use of Qt's Model-View-Controller (MVC) to display data and content. As you advance, you'll learn to draw images on screen using Graphics View Framework and create custom widgets that interoperate with Qt Widgets. This Qt programming book takes you through Qt Creator's latest features, such as Qt Quick Controls 2, enhanced CMake support, a new graphical editor for SCXML, and a model editor. You'll even work with multimedia and sensors using Qt Quick, and finally develop applications for mobile, IoT, and embedded devices using Qt Creator. By the end of this Qt book, you'll be able to create your own cross-platform applications from scratch using Qt Creator and the C++ programming language. What you will learn Create programs from scratch using the Qt framework and C++ language Compile and debug your Qt Quick and C++ applications using Qt Creator Implement map view with your Qt application and display device location on the map Understand how to call Android and iOS native functions from Qt C++ code Localize your application with Qt Linguist Explore various Qt Quick components that provide access to audio and video playbacks Develop GUI applications using both Qt and Qt Quick Who this book is for If you are a beginner looking to harness the power of Qt and the Qt Creator framework for cross-platform development, this book is for you. Although no prior knowledge of Qt and Qt Creator is required, basic knowledge of C++ programming is assumed. COMPUTERS,Languages,C++

Embedded Programming with Modern C++ Cookbook Explore various constraints and challenges that embedded developers encounter in their daily tasks and learn how to build effective programs using the latest standards of C++ Key Features Get hands-on experience in developing a sample application for an embedded Linux-based system Explore advanced topics such as concurrency, real-time operating system (RTOS), and C++ utilities Learn how to test and debug your embedded applications using logs and profiling tools Book Description Developing applications for embedded systems may seem like a daunting task as developers face challenges related to limited memory, high power consumption, and maintaining real-time responses. This book is a collection of practical examples to explain how to develop applications for embedded boards and overcome the challenges that you may encounter while developing. The book will start with an introduction to embedded systems and how to set up the development environment. By teaching you to build your first embedded application, the book will help you progress from the basics to more complex concepts, such as debugging, logging, and profiling. Moving ahead, you will learn how to use specialized memory and custom allocators. From here, you will delve into recipes that will teach you how to work with the C++ memory model, atomic variables, and synchronization. The book will then take you through recipes on inter-process communication, data serialization, and timers. Finally, you will cover topics such as error handling and guidelines for real-time systems and safety-critical systems. By the end of this book, you will have become proficient in building robust and secure embedded applications with C++. What you will learn Get to grips with the fundamentals of an embedded system Understand how to optimize code for the targeted hardware platforms Explore cross-compilation, build types, and remote debugging Discover the importance of logging for debugging and root cause analysis of failures Uncover concepts such as interrupt service routine, memory model, and ring buffer Recognize the need for custom memory management in embedded systems Delve into static code analyzers and tools to improve code quality Who this book is for This book is for developers, electronic hardware professionals, and software and system-on-chip engineers who want to build effective embedded programs in C++. Familiarity with the C++ programming language is expected, but no previous knowledge of embedded systems is required. COMPUTERS,Languages,C++

Sams Teach Yourself Regular Expressions in 10 Minutes RegEx is supported in all major development environments (for use in editing and working with code) and will thus appeal to anyone using these tools. In addition, every JavaScript developer should be using RegEx, but most don't as it has never been taught to them properly before. Developers using ASP, C#, ColdFusion, Java JSP, PHP, Perl, Python, and more can (and should) be using RegEx, and so every one of them is a potential reader too. The reader of this book will learn how to: Match characters sets Match repeating characters (using minimums and maximums if needed) Match (or ignore) based on case Build sub-expressions Use all of the special characters Work with excape sequences Use POSIX classes to simplify complex expressions Use back-references Use look-behind operators Sams Teach Yourself Regular Expressions in 10 Minutes is a tutorial book organized into a series of easy-to-follow 10-minute lessons. These well targeted lessons teach you in 10 minutes what other books might take hundreds of pages to cover. Instead of dwelling on syntax, terminology, and arcane examples and scenarios, this book takes a very hands-on approach to solving the needs of the majority of RegEx users who simply need to manipulate data. COMPUTERS,Languages,General

SQL SQL is a solid guide and reference to the key elements of SQL and how to use it effectively. Developed by authors who needed a good resource for students in their database class, this is an ideal supplement for database courses — no matter what main text you use or what flavor of SQL is required. It features a short and inexpensive introduction to SQL for students who have some programming experience and need to learn the main features of SQL; and suggested shortcuts for learning and practice, depending on the experience of the user. This book is recommended for novice developers, programmers, and database administrators as well as students in database courses, business courses, and IT-related courses. Provides tutorial-based instruction for the main features of SQL for programmers and other technical professionals in need of a brief but really good introduction to SQL. The approach is vendor-neutral—so very adaptable and flexible The focus is on teaching concepts by walking through concrete examples and explanations, and self-review exercises are included at the end of each chapter. Coverage is on the key features of the language that are required to understand SQL and begin using it effectively. SQL 2003-compliant. COMPUTERS,Languages,General

Creating Web Applications with PHP Need to know PHP right now, but don’t want a 1,000-page tome? Check out the Peachpit’s new Short Cuts! Quick PDF guides that are...Smart...Handy...Concise. This mini guide covers exactly what you need to know about programming and creating a simple Web application with PHP, and nothing more. Never programmed before? No problem. You’ll get all the information, functions, and techniques you need to make your Web sites more professional, feature-rich, and easier to maintain. You’ll learn: • How to use external files to break your Web pages into individual pieces • About constants, a special data type in PHP • Using date- and time-related functions built into PHP • Useful programming methods • How to easily send email from PHP • About output buffering and using HTTP headers • And more! COMPUTERS,Languages,General

Creating Basic PHP Functions Want to write your own PHP functions, but don’t want a 1,000-page tome? Peachpit’s new Short Cuts! Quick PDF guides that are...Smart...Handy...Concise. This mini guide covers exactly what you need to know about writing your own functions to perform specific tasks and save you programming time. Functions are a strong step in creating Web applications and building a solid library of PHP code to use in future projects. Why create functions? As you program, you’ll discover that you use certain sections of code frequently, either within a single script or over the course of several scripts. Placing these routines into a self-defined function can save you time and make your programming easier, especially as your Web sites become more complex. You’ll learn: • How to write your own functions • Pass information to the function • Use default values in a function • Have your function return a value • How functions and variables work together • And more! COMPUTERS,Languages,General

Writing Basic PHP Scripts Need to know PHP scripting right now, but don’t want a 1,000-page tome? Check out the Peachpit’s new Short Cuts! Quick PDF guides that are...Smart...Handy...Concise. This mini guide covers exactly what you need to know about writing basic PHP scripts, and nothing more. Never programmed before? No problem. You’ll get all the fundamentals, techniques, and information you need to master standard terms and language syntax so you can build on the basics and truly start PHP programming. You’ll learn about: • Creating and handling an HTML form • Managing magic quotes • Conditionals and operators • Validating form data • Using, creating, accessing, and sorting arrays • Loops and other language constructs • And more! COMPUTERS,Languages,General

Java If you're an experienced programmer, you already have a rock-solid foundation for learning Java. All you need is a resource that takes your experience into account and explains Java's key principles and techniques in an intelligent, efficient way. Java: Practical Guide for Programmers is precisely that resource. Here, you won't have to wade through hundreds of pages of overly simplistic material to learn the basics of Java programming. Instead, you get highly focused instruction in the core elements of Java 1.4, accompanied by carefully chosen examples and line-by-line analyses that are right to the point. You'll be astonished at how soon you can begin productive coding in Java, and how quickly your skills will progress. Written expressly for people who already know a procedural or object-oriented programming language. Takes a concise approach designed to make the most of the experience you already have. Covers the core elements of Java 1.4, including language syntax, OO features, collections, exception handling, input/output, threads, event handling, and Swing components. Filled with incisive coding examples and line-by-line analyses. COMPUTERS,Languages,General

Multi-Tier Application Programming with PHP While many architects use PHP for projects, they are often not aware of the power of PHP in creating enterprise-level applications. This book covers the latest version of PHP – version 5 -- and focuses on its capabilities within a multi-tier application framework. It contains numerous coding samples and commentaries on them. A chapter discusses object orientation in PHP as it applies to the multi-tier architecture and other chapters discuss HTTP and SOAP, the two communication protocols most useful in tying together multiple layers. There is also coverage of database design and query construction as well as information about tricks you can use in generating user interfaces. Covers PHP as it relates to developing software in a multi-tier environment—a crucial aspect of developing robust software with low cost and ease of use as design goals. Makes extensive use of Simple Object Access Protocol (SOAP) and Web Services as implemented in PHP and NuSOAP. Shows precisely how to make use of the InnoDB table type newly available in MySQL. InnoDB supports true referential integrity and row-level locking. An application example (a multi-currency bookkeeping application) runs throughout the book, showing various PHP capabilities as well as the database interaction. COMPUTERS,Languages,General

Cryptography in C and C++ CRYPTOGRAPHY IS AN ANCIENT ART, well over two thousand years old. The need to keep certain information secret has always existed, and attempts to preserve secrets have therefore existed as well. But it is only in the last thirty years that cryptography has developed into a science that has offered us needed security in our daily lives. Whether we are talking about automated teller machines, cellular telephones, Internet commerce, or computerized ignition locks on automobiles, there is cryptography hidden within. And what is more, none of these applications would work without cryptography! The historyofcryptographyoverthepastthirtyyearsisauniquesuccessstory. The most important event was surely the discovery of public key cryptography in the mid 1970s. It was truly a revolution: We know today that things are possible that previously we hadn’t even dared to think about. Dif?e and Hellman were the ?rst to formulate publicly the vision that secure communication must be able to take place spontaneously. Earlier, it was the case that sender and receiver had ?rst to engage in secret communication to establish a common key. Dif?e and Hellman asked, with the naivety of youth, whether one could communicate secretly without sharing a common secret. Their idea was that one could encrypt information without a secret key, that is, one that no one else could know. This idea signaled the birth of public key cryptography. That this vision was more than just wild surmise was shown a few years later with the advent of the RSA algorithm. COMPUTERS,Languages,General

Practical Common Lisp Lisp is often thought of as an academic language, but it need not be. This is the first book that introduces Lisp as a language for the real world. Practical Common Lisp presents a thorough introduction to Common Lisp, providing you with an overall understanding of the language features and how they work. Over a third of the book is devoted to practical examples, such as the core of a spam filter and a web application for browsing MP3s and streaming them via the Shoutcast protocol to any standard MP3 client software (e.g., iTunes, XMMS, or WinAmp). In other "practical" chapters, author Peter Seibel demonstrates how to build a simple but flexible in-memory database, how to parse binary files, and how to build a unit test framework in 26 lines of code. COMPUTERS,Languages,General

Beginning Programming All-in-One Desk Reference For Dummies So you want to be a programmer? Or maybe you just want to be able to make your computer do what YOU want for a change? Maybe you enjoy the challenge of identifying a problem and solving it. If programming intrigues you for whatever reason, Beginning Programming All-In-One Desk Reference For Dummies is like having a starter programming library all in one handy, if beefy, book. In this practical guide, you’ll find out about compiling, algorithms, best practices, debugging your programs, and much more. The concepts are illustrated in several different programming languages, so you’ll get a feel for the variety of languages and the needs they fill. Seven minibooks cover: Getting started Programming basics Data structures Algorithms Web programming Programming language syntax Applications Beginning Programming All-In-One Desk Reference For Dummies shows you how to decide what you want your program to do, turn your instructions into “machine language†that the computer understands, use programming best practices, explore the “how†and “why†of data structuring, and more. You’ll even get a look into various applications like database management, bioinformatics, computer security, and artificial intelligence. Soon you’ll realize that — wow! You’re a programmer! Note: CD-ROM/DVD and other supplementary materials are not included as part of eBook file. COMPUTERS,Languages,General

Getting Started with Arduino This valuable little book offers a thorough introduction to the open-source electronics prototyping platform that's taking the design and hobbyist world by storm. Getting Started with Arduino gives you lots of ideas for Arduino projects and helps you get going on them right away. From getting organized to putting the final touches on your prototype, all the information you need is right in the book. Inside, you'll learn about: Interaction design and physical computing The Arduino hardware and software development environment Basics of electricity and electronics Prototyping on a solderless breadboard Drawing a schematic diagram And more. With inexpensive hardware and open-source software components that you can download free, getting started with Arduino is a snap. To use the introductory examples in this book, all you need is a USB Arduino, USB A-B cable, and an LED. Join the tens of thousands of hobbyists who have discovered this incredible (and educational) platform. Written by the co-founder of the Arduino project, with illustrations by Elisa Canducci, Getting Started with Arduino gets you in on the fun! This 128-page book is a greatly expanded follow-up to the author's original short PDF that's available on the Arduino website. COMPUTERS,Languages,General

Maven For too long, developers have worked on disorganized application projects, where every part seemed to have its own build system, and no common repository existed for information about the state of the project. Now there's help. The long-awaited official documentation to Maven is here. Written by Maven creator Jason Van Zyl and his team at Sonatype, Maven: The Definitive Guide clearly explains how this tool can bring order to your software development projects. Maven is largely replacing Ant as the build tool of choice for large open source Java projects because, unlike Ant, Maven is also a project management tool that can run reports, generate a project website, and facilitate communication among members of a working team. To use Maven, everything you need to know is in this guide. The first part demonstrates the tool's capabilities through the development, from ideation to deployment, of several sample applications -- a simple software development project, a simple web application, a multi-module project, and a multi-module enterprise project. The second part offers a complete reference guide that includes: The POM and Project Relationships The Build Lifecycle Plugins Project website generation Advanced site generation Reporting Properties Build Profiles The Maven Repository Team Collaboration Writing Plugins IDEs such as Eclipse, IntelliJ, ands NetBeans Using and creating assemblies Developing with Maven Archetypes Several sources for Maven have appeared online for some time, but nothing served as an introduction and comprehensive reference guide to this tool -- until now. Maven: The Definitive Guide is the ideal book to help you manage development projects for software, web applications, and enterprise applications. And it comes straight from the source. COMPUTERS,Languages,General

Programming WPF If you want to build applications that take full advantage of Windows Vista's new user interface capabilities, you need to learn Microsoft's Windows Presentation Foundation (WPF). This new edition, fully updated for the official release of .NET 3.0, is designed to get you up to speed on this technology quickly. By page 2, you'll be writing a simple WPF application. By the end of Chapter 1, you'll have taken a complete tour of WPF and its major elements. WPF is the new presentation framework for Windows Vista that also works with Windows XP. It's a cornucopia of new technologies, which includes a new graphics engine that supports 3-D graphics, animation, and more; an XML-based markup language, called XAML, for declaring the structure of your Windows UI; and a radical new model for controls. This second edition includes new chapters on printing, XPS, 3-D, navigation, text and documents, along with a new appendix that covers Microsoft's new WPF/E platform for delivering richer UI through standard web browsers -- much like Adobe Flash. Content from the first edition has been significantly expanded and modified. Programming WPF includes: Scores of C# and XAML examples that show you what it takes to get a WPF application up and running, from a simple "Hello, Avalon" program to a tic-tac-toe game Insightful discussions of the powerful new programming styles that WPF brings to Windows development, especially its new model for controls A color insert to better illustrate WPF support for 3-D, color, and other graphics effects A tutorial on XAML, the new HTML-like markup language for declaring Windows UI An explanation and comparison of the features that support interoperability with Windows Forms and other Windows legacy applications WPF represents the best of the control-based Windows world and the content-based web world. Programming WPF helps you bring it all together. COMPUTERS,Languages,General

Python Pocket Reference Python is optimized for quality, productivity, portability, and integration. Hundreds of thousands of Python developers around the world rely on Python for general-purpose tasks, Internet scripting, systems programming, user interfaces, and product customization. Available on all major computing platforms, including commercial versions of Unix, Linux, Windows, and Mac OS X, Python is portable, powerful and remarkable easy to use.With its convenient, quick-reference format, Python Pocket Reference, 3rd Edition is the perfect on-the-job reference. More importantly, it's now been refreshed to cover the language's latest release, Python 2.4. For experienced Python developers, this book is a compact toolbox that delivers need-to-know information at the flip of a page. This third edition also includes an easy-lookup index to help developers find answers fast!Python 2.4 is more than just optimization and library enhancements; it's also chock full of bug fixes and upgrades. And these changes are addressed in the Python Pocket Reference, 3rd Edition. New language features, new and upgraded built-ins, and new and upgraded modules and packages--they're all clarified in detail.The Python Pocket Reference, 3rd Edition serves as the perfect companion to Learning Python and Programming Python. COMPUTERS,Languages,General

Mastering Regular Expressions Regular expressions are an extremely powerful tool for manipulating text and data. They are now standard features in a wide range of languages and popular tools, including Perl, Python, Ruby, Java, VB.NET and C# (and any language using the .NET Framework), PHP, and MySQL. If you don't use regular expressions yet, you will discover in this book a whole new world of mastery over your data. If you already use them, you'll appreciate this book's unprecedented detail and breadth of coverage. If you think you know all you need to know about regularexpressions, this book is a stunning eye-opener. As this book shows, a command of regular expressions is an invaluable skill. Regular expressions allow you to code complex and subtle text processing that you never imagined could be automated. Regular expressions can save you time and aggravation. They can be used to craft elegant solutions to a wide range of problems. Once you've mastered regular expressions, they'll become an invaluable part of your toolkit. You will wonder how you ever got by without them. Yet despite their wide availability, flexibility, and unparalleled power, regular expressions are frequently underutilized. Yet what is power in the hands of an expert can be fraught with peril for the unwary. Mastering Regular Expressions will help you navigate the minefield to becoming an expert and help you optimize your use of regular expressions. Mastering Regular Expressions, Third Edition, now includes a full chapter devoted to PHP and its powerful and expressive suite of regular expression functions, in addition to enhanced PHP coverage in the central "core" chapters. Furthermore, this edition has been updated throughout to reflect advances in other languages, including expanded in-depth coverage of Sun's java.util.regex package, which has emerged as the standard Java regex implementation.Topics include: A comparison of features among different versions of many languages and tools How the regular expression engine works Optimization (major savings available here!) Matching just what you want, but not what you don't want Sections and chapters on individual languages Written in the lucid, entertaining tone that makes a complex, dry topic become crystal-clear to programmers, and sprinkled with solutions to complex real-world problems, Mastering Regular Expressions, Third Edition offers a wealth information that you can put to immediateuse. Reviews of this new edition and the second edition: "There isn't a better (or more useful) book available on regular expressions." --Zak Greant, Managing Director, eZ Systems "A real tour-de-force of a book which not only covers the mechanics of regexes in extraordinary detail but also talks about efficiency and the use of regexes in Perl, Java, and .NET...If you use regular expressions as part of your professional work (even if you already have a good book on whatever language you're programming in) I would strongly recommend this book to you." --Dr. Chris Brown, Linux Format "The author does an outstanding job leading the reader from regexnovice to master. The book is extremely easy to read and chock full ofuseful and relevant examples...Regular expressions are valuable toolsthat every developer should have in their toolbox. Mastering RegularExpressions is the definitive guide to the subject, and an outstandingresource that belongs on every programmer's bookshelf. Ten out of TenHorseshoes." --Jason Menard, Java Ranch COMPUTERS,Languages,General

Domain-Specific Languages When carefully selected and used, Domain-Specific Languages (DSLs) may simplify complex code, promote effective communication with customers, improve productivity, and unclog development bottlenecks. In Domain-Specific Languages , noted software development expert Martin Fowler first provides the information software professionals need to decide if and when to utilize DSLs. Then, where DSLs prove suitable, Fowler presents effective techniques for building them, and guides software engineers in choosing the right approaches for their applications. This book’s techniques may be utilized with most modern object-oriented languages; the author provides numerous examples in Java and C#, as well as selected examples in Ruby. Wherever possible, chapters are organized to be self-standing, and most reference topics are presented in a familiar patterns format. Armed with this wide-ranging book, developers will have the knowledge they need to make important decisions about DSLs—and, where appropriate, gain the significant technical and business benefits they offer. The topics covered include: How DSLs compare to frameworks and libraries, and when those alternatives are sufficient Using parsers and parser generators, and parsing external DSLs Understanding, comparing, and choosing DSL language constructs Determining whether to use code generation, and comparing code generation strategies Previewing new language workbench tools for creating DSLs COMPUTERS,Languages,General

Tcl and the Tk Toolkit John K. Ousterhout’s Definitive Introduction to Tcl/Tk–Now Fully Updated for Tcl/Tk 8.5 Tcl and the Tk Toolkit, Second Edition, is the fastest way for newcomers to master Tcl/Tk and is the most authoritative resource for experienced programmers seeking to gain from Tcl/Tk 8.5’s powerful enhancements. Written by Tcl/Tk creator John K. Ousterhout and top Tcl/Tk trainer Ken Jones, this updated volume provides the same extraordinary clarity and careful organization that made the first edition the world’s number one Tcl/Tk tutorial. Part I introduces Tcl/Tk through simple scripts that demonstrate its value and offer a flavor of the Tcl/Tk scripting experience. The authors then present detailed, practical guidance on every feature necessary to build effective, efficient production applications–including variables, expressions, strings, lists, dictionaries, control flow, procedures, namespaces, file and directory management, interprocess communication, error and exception handling, creating and using libraries, and more. Part II turns to the Tk extension and Tk 8.5’s new themed widgets, showing how to organize sophisticated user interface elements into modern GUI applications for Tcl. Part III presents incomparable coverage of Tcl’s C functions, which are used to create new commands and packages and to integrate Tcl with existing C software–thereby leveraging Tcl’s simplicity while accessing C libraries or executing performance-intensive tasks. Throughout, the authors illuminate all of Tcl/Tk 8.5’s newest, most powerful improvements. You’ll learn how to use new Starkits and Starpacks to distribute run-time environments and applications through a single file; how to take full advantage of the new virtual file system support to treat entities such as zip archives and HTTP sites as mountable file systems; and more. From basic syntax to simple Tcl commands, user interface development to C integration, this fully updated classic covers it all. Whether you’re using Tcl/Tk to automate system/network administration, streamline testing, control hardware, or even build desktop or Web applications, this is the one Tcl/Tk book you’ll always turn to for answers. COMPUTERS,Languages,General

PHP and MySQL for Dynamic Web Sites, Fourth Edition It hasn't taken Web developers long to discover that when it comes to creating dynamic, database-driven Web sites, MySQL and PHP provide a winning open-source combination. Add this book to the mix, and there's no limit to the powerful, interactive Web sites that developers can create. With step-by-step instructions, complete scripts, and expert tips to guide readers, veteran author and database designer Larry Ullman gets right down to business: After grounding readers with separate discussions of first the scripting language (PHP) and then the database program (MySQL), he goes on to cover security, sessions and cookies, and using additional Web tools, with several sections devoted to creating sample applications. This guide is indispensable for beginning to intermediate level Web designers who want to replace their static sites with something dynamic. In this edition, the bulk of the new material covers the latest features and techniques with PHP and MySQL. Also new to this edition are chapters introducing jQuery and object-oriented programming techniques. COMPUTERS,Languages,General

Tcl/Tk Newly updated with over 150 pages of material on the latest Tcl extensions, Tcl/Tk: A Developer’s Guide is a unique practical tutorial for professional programmers and beginners alike. Starting with a clear picture of the basics, Tcl/Tk covers the variety of tools in this "Swiss army knife" of programming languages, giving you the ability to enhance your programs, extend your application's capabilities, and become a more effective programmer. This updated edition covers all of the new features of version 8.6, including object-oriented programming and the creation of megawidgets, existing data structure implementations, themed widgets and virtual events. Extensive code snippets and online tutorials in various languages will give you a firm grasp on how to use the Tcl/Tk libraries and interpreters and, most importantly, on what constitutes an effective strategy for using Tcl/Tk. Includes the latest features of Tcl/Tk 8.6 Covers Tcl development tools, popular extensions, and packages to allow developers to solve real-world problems with Tcl/Tk immediately Provides straightforward explanations for beginners and offers tips, style guidelines, and debugging techniques for advanced users COMPUTERS,Languages,General

Python Programming Fundamentals Computer programming is a skill that can bring great enjoyment from the creativity involved in designing and implementing a solution to a problem. This classroom-tested and easy-to-follow textbook teaches the reader how to program using Python, an accessible language which can be learned incrementally. Through an extensive use of examples and practical exercises, students will learn to recognize and apply abstract patterns in programming, as well as how to inspect the state of a program using a debugger tool. Features: contains numerous examples and solved practice exercises designed for an interactive classroom environment; highlights several patterns which commonly appear in programs, and presents exercises that reinforce recognition and application of these patterns; introduces the use of a debugger, and includes supporting material that reveals how programs work; presents the Tkinter framework for building graphical user interface applications and event-driven programs; provides helpful additional resources for instructors at the associated website: http://cs.luther.edu/~leekent/CS1. This hands-on textbook for active learning in the classroom will enable undergraduates in computer science to develop the necessary skills to begin developing their own programs. It employs Python as the introductory language due to the wealth of support available for programmers. COMPUTERS,Languages,General

Regular Expressions Cookbook Take the guesswork out of using regular expressions. With more than 140 practical recipes, this cookbook provides everything you need to solve a wide range of real-world problems. Novices will learn basic skills and tools, and programmers and experienced users will find a wealth of detail. Each recipe provides samples you can use right away. This revised edition covers the regular expression flavors used by C#, Java, JavaScript, Perl, PHP, Python, Ruby, and VB.NET. You’ll learn powerful new tricks, avoid flavor-specific gotchas, and save valuable time with this huge library of practical solutions. Learn regular expressions basics through a detailed tutorial Use code listings to implement regular expressions with your language of choice Understand how regular expressions differ from language to language Handle common user input with recipes for validation and formatting Find and manipulate words, special characters, and lines of text Detect integers, floating-point numbers, and other numerical formats Parse source code and process log files Use regular expressions in URLs, paths, and IP addresses Manipulate HTML, XML, and data exchange formats Discover little-known regular expression tricks and techniques COMPUTERS,Languages,General

The F Language Guide Fortran is currently the world's most powerful numeric language and F is a subset of this. F is a programming language which is nearly as powerful as its parent language, containing the modern language features of Fortran, yet smaller and easier to use, debug and teach than Fortran. As with his previous Fortran books, Wilhelm Gehrke has provided a clear and comprehensive guide to the F language in this book which will be welcomed by practitioners and students alike. The F Language Guide will serve as a language reference manual for the novice as well as for the experienced programmer, as teaching material for courses in F programming, and in programming methodology. The guide concentrates on the description of the language as a programmers' tool. A representation of the F Syntax using railroad diagrams will be available on the Springer server at http://www.springer.co.uk/ COMPUTERS,Languages,General

Compiler Technology Compiler technology is fundamental to computer science since it provides the means to implement many other tools. It is interesting that, in fact, many tools have a compiler framework - they accept input in a particular format, perform some processing and present output in another format. Such tools support the abstraction process and are crucial to productive systems development. The focus of Compiler Technology: Tools, Translators and Language Implementation is to enable quick development of analysis tools. Both lexical scanner and parser generator tools are provided as supplements to this book, since a hands-on approach to experimentation with a toy implementation aids in understanding abstract topics such as parse-trees and parse conflicts. Furthermore, it is through hands-on exercises that one discovers the particular intricacies of language implementation. Compiler Technology: Tools, Translators and Language Implementation is suitable as a textbook for an undergraduate or graduate level course on compiler technology, and as a reference for researchers and practitioners interested in compilers and language implementation. COMPUTERS,Languages,General

Essential Visual Basic 5.0 Fast Anyone developing software today is likely to be doing so in a Windows environment and is likely to be using Visual Basic as the development language. This Essential guide focuses on the basics of the language instead of burdening the eager user with small details contained in the manuals. Providing a clear and precise explanation of the most important features of VB5, the book allows readers to develop programs with the same heavyweight feel as the best programs from Microsoft and others. COMPUTERS,Languages,General

Analog and Mixed-Signal Hardware Description Language Hardware description languages (HDL) such as VHDL and Verilog have found their way into almost every aspect of the design of digital hardware systems. Since their inception they gradually proved to be an essential part of modern design methodologies and design automation tools, ever exceeding their original goals of being description and simulation languages. Their use for automatic synthesis, formal proof, and testing are good examples. So far, HDLs have been mainly dealing with digital systems. However, integrated systems designed today require more and more analog parts such as A/D and D/A converters, phase locked loops, current mirrors, etc. The verification of the complete system therefore asks for the use of a single language. Using VHDL or Verilog to handle analog descriptions is possible, as it is shown in this book, but the real power is coming from true mixed-signal HDLs that integrate discrete and continuous semantics into a unified framework. Analog HDLs (AHDL) are considered here a subset of mixed-signal HDLs as they intend to provide the same level of features as HDLs do but with a scope limited to analog systems, possibly with limited support of discrete semantics. Analog and Mixed-Signal Hardware Description Languages covers several aspects related to analog and mixed-signal hardware description languages including: The use of a digital HDL for the description and the simulation of analog systems The emergence of extensions of existing standard HDLs that provide true analog and mixed-signal HDLs. The use of analog and mixed-signal HDLs for the development of behavioral models of analog (electronic) building blocks (operational amplifier, PLL) and for the design of microsystems that do not only involve electronic parts. The use of a front-end tool that eases the description task with the help of a graphical paradigm, yet generating AHDL descriptions automatically. Analog and Mixed-Signal Hardware Description Languages is the first book to show how to use these new hardware description languages in the design of electronic components and systems. It is necessary reading for researchers and designers working in electronic design. COMPUTERS,Languages,General

Essential Visual Basic 4.0 Fast If you are developing software either as a professional programmer, a student, or simply for fun then it is very likely that you will be working in a Windows environment. If you are, and you are looking to build your own Windows applications, you will find Visual Basic provides an easy and effective means of doing so. This book is written specifically to help users get up and running fast on Visual Basic and focusses on how to develop useful programs quickly and effectively. If you are an undergraduate wanting a simple way to program applications, a professional programmer who needs a broad introduction to Visual Basic 3, or even an amateur programmer interested in building Windows applications, then this book will tell you all you need to know. COMPUTERS,Languages,General

Practical Usage of MVS REXX Practical Usage of MVS REXX provides a concise and complete source of information for the development of applications using the REXX language - IBM's systems application architecture procedural language. The book adopts a highly practical approach and includes many lists and diagrams to make finding the relevant information as easy to find and use as possible. It particularly emphasises the interfacing capabilities of REXX. Both beginners and experts will find the book useful. Beginners are led through the steps required to develop REXX applications via a series of worked examples, and experts will find a complete and easy reference to the language. COMPUTERS,Languages,General

Prolog From the viewpoint of an "industrial" this book is most welcome, as one of the most significant demonstrations of the maturity of Prolog. Logic programming is a fascinating area in computer science, which held for years - and still does - the promise of freeing ourselves from programming based on the "Von Neumann" machine. In addition computer programming has long been for solid theoretical foundations. While conventional engineering, dealing mainly with "analogical complexity", developed over some hundred years a complete body of mathematical tools, no such toolset was available for "digital complexity". The only mathematical discipline which deals with digital complexity is logic and Prolog is certainly the operational tool which comes closest to the logical programming ideal. So, why does Prolog, despite nearly twenty years of development, still appear to many today to be more of a research or academic tool, rather than an industrial programming language? A few reasons may explain this: First, I think Prolog suffers from having been largely assimilated into - and thus followed the fate of - Artificial Intelligence. Much hype in the late 1980 created overexpectations and failed to deliver, and the counterreaction threw both AI and Prolog into relative obscurity. In a way, maybe this is a new chance for the Prolog community: the ability to carry out real work and progress without the disturbance of limelights and the unrealistic claims of various gurus. Second, programming in Prolog is a new experience for computer professionals. COMPUTERS,Languages,General

Practical Usage of ISPF Dialog Manager Practical Usage of ISPF Dialog Manager is a concise and comprehensive source of information for the development of applications using IBM's Dialog Management package. Dialog Manager is a vehicle for implementing dialogue applications (such as PDF - Program Development Facility) and is very well suited to the implementation of individual dialogue systems and those systems which are required to run from the TSO/ISPF environment. It is also ideally suited for prototyping. This book is intended for both beginners and experts. With its carefully chosen blend of theory and practice, and extensive use of examples and case studies, this book will provide an invaluable guide to all those needing to learn about or using the ISPF Dialog Manager. COMPUTERS,Languages,General

Pattern Recognition and Image Processing in C++ Parts of this text were used for several years by students in a one~term under graduate course in computer science. The students had to prepare projects in small groups (2~4 students).1 This book emphasizes practical experience with image processing. It offers a comprehensive study of • image processing and image analysis, • basics of speech processing, • object~oriented programming, • software design, • and programming in C++. The book is divided into four parts. In the first part we introduce image processing, image analysis, programming tools, and the basics of C++. In the second part we describe object~oriented programming in general and the possible applications of object~oriented concepts in C++. Several appli cations of object~oriented programming for image processing are discussed as well. The new features of C++ are introduced entirely through the use of examples. We cover the proper representation of the data that is a result of pattern analysis as well. The third part describes a complete system for image segmentation. Some of the material covered refers to the exercises found in the first and second parts: this verifies our belief that an image segmentation system of programs can be developed while simultaneously acquainting others to C++. We combine the data representation described in the second part with the algorithms that use and manipulate them here in the third part. COMPUTERS,Languages,General

Upgrading to Fortran 90 In 1991, a new international standard for Fortran was released which contained specifications for a new version of the language known as Fortran 90. It provides for dramatic extensions to previous Fortran versions. This book is a comprehensive tutorial to Fortran 90 that relies mainly on a large number of short, but complete programming examples to illustrate the differences between the new language and traditional Fortran. The author gives thorough explanations of terminology and concepts which were not in general use before the release of the new standard. Readers are assumed to have a working knowledge of one of the earlier versions of Fortran, but otherwise no prior knowledge of Fortran 90 is assumed. COMPUTERS,Languages,General

LOTOSphere LOTOS (Language Of Temporal Ordering Specification) became an international standard in 1989, although application of preliminary versions of the language to communication services and protocols of the ISO/OSI family dates back to 1984. This history of the use of LOTOS made it apparent that more advantages than the pure production of standard reference documents were to be expected from the use of such formal description techniques. LOTOSphere: Software Development with LOTOS describes in depth a five year project that moved LOTOS out of the ISO tower into software engineering practice. LOTOS became a vehicle for efficient, yet formally based industrial software specification, design, verification, implementation and testing. LOTOSphere: Software Development with LOTOS is divided into six parts. The first introduces the reader to LOTOS and the project LOTOSphere. The five remaining each treat an important part of the software development life cycle using LOTOS. This is the first book to give a comprehensive treatment of the use of these formal description techniques in a software engineering environment. It will thus be a valuable reference for researchers and software developers and can also be used as a text for an advanced course on the subject. COMPUTERS,Languages,General

Z User Workshop, Cambridge 1994 This volume contains papers from the Eighth Z User Meeting, to be held at the University of Cambridge from 29 - 30 June 1994. The papers cover a wide range of issues associated with Z and formal methods, with particular reference to practical application. These issues include education, standards, tool support, and interaction with other design paradigms such as consideration of real-time and object-oriented approaches to development. Among the actual topics covered are: the formal specification in Z of Defence Standard 00-56; formal specification of telephone features; specifying and interpreting class hierarchies in Z; and software quality assurance using the SAZ method. Z User Workshop, Cambridge 1994 provides an important overview of current research into industrial applications of Z, and will provide invaluable reading for researchers, postgraduate students and also potential industrial users of Z. COMPUTERS,Languages,General

Programming in Prolog The continued popularity of Prolog and oflogic programming in general has called for a new edition in which we have corrected a few minor errors found in the previous edition. Since the previous edition of this book, the development of Prolog has proceeded with much vigour and creativity on the part of hundreds of researchers around the world. For example, the International Conference on Logic Programming will meet in 1995 for the twelfth time; the Internet newsgroup comp . 1 ang . pro log exchanges many messages daily; and there are numerous World-Wide Web resources of interest to Prolog users. It is no longer posssible to track the many books on Prolog and implementations of Prolog that are now available. The Prolog idea has been extended to new languages for manipulating sets of constraints, functional expressions, type hierarchies, and object-oriented programs. And yet throughout this time the Edinburgh Prolog syntax and semantics have served as a standard and as a base of stability. In tum, we hope that this book can continue to serve as an introduction to the language and its use. Cambridge, England W. F. C. July 1994 C. S. M. PREFACE TO THE THIRD EDITION We have added new material to Chapter 3 to give an account of up-to-date programming techniques using accumulators and difference structures. Chapter 8 contains some new information on syntax errors. Operator precedences are now compatible with the most widely-used implementations. COMPUTERS,Languages,General

Implementations of Logic Programming Systems SelfLog: Language and Implementation; M. Bugliesi, G. Nardiello. I.C. Prolog II: a Multi-Threaded Prolog System; D. Chu. Memory Management in Quintus Prolog; J. Crammond, T. Lindholm. How Concurrent Logic Programming could Benefit from Using Linda-like Operations; G. Czajkowski, K. Zielinski. Implementing Logic Programming Systems: the Quiche-Eating Approach; S.K. Debray. Call Forwarding: a Simple Low-Level Code Optimization Technique; S.K. Debray, K. De Bosschere, D. Gudeman. Moving Prolog Toward Objects; E. Denti, A. Natali, A. Omicini. MProlog: an Implementation Overview; Z. Farkas, P. Köves, P. Szeredi. Turbo Erlang: Approaching the Speed of C; B. Hausman. A Framework for Sharing Analysis; A. King. Better Late than Never; M. Meier. To Trim or not to Trim? J. Noyé. Divided we Stand: Parallel Distributed Stack Memory Management; K. Shen, M. Hermenegildo. Or-Parallel Prolog on Distributed Shared Memory Architectures; F.M.A. Silva. Implementing Sets with Hash Tables in Declarative Languages; G. Succi, G. Marino, C. Dondina, A. Bergamini. Concurrent Logic Programs à la mode; E. Tick, B. Massey, F. Radkoczi, P. Tulayathun. Index. COMPUTERS,Languages,General

Functional Programming, Glasgow 1992 The Glasgow Functional Programming Group is widely recognised for its research in lazy functional languages. Once again this year, for the fifth time, we retreated to a Scottish seaside town to discuss our latest work, this time spending three days in Ayr. We were joined by a number of colleagues from other universities and from industry, with whom we have been enjoying fruitful collaboration. The workshop serves the dual purpose of ensuring that the whole group remains informed of each other's work, and of providing workshop experience for research students. Most participants presented a short talk about their work, supplemented by papers which appeared in a draft proceedings distributed at the workshop. Since then the papers have been reviewed and the majority are now published here following revision. The workshop also contained a lively discussion session on functional language applications, to which the industrial participants made very helpful contributions. One interesting feature of this volume is the number of papers addressing practical issues of realistic use of functional languages, from benchmarking and profiling, to user interfaces and file handling. It is perhaps indicative that at last lazy functional languages are being used for significantly larger applications than has been typical in the past. This type of paper is likely to feature prominently in relevant conference proceedings for the next few years. Other papers here continue to address more theoretical topics, such as program logic, semantics of non determinism, program analysis, and loop detection. COMPUTERS,Languages,General

Case-Based Learning Case-based reasoning means reasoning based on remembering previous experiences. A reasoner using old experiences (cases) might use those cases to suggest solutions to problems, to point out potential problems with a solution being computed, to interpret a new situation and make predictions about what might happen, or to create arguments justifying some conclusion. A case-based reasoner solves new problems by remembering old situations and adapting their solutions. It interprets new situations by remembering old similar situations and comparing and contrasting the new one to old ones to see where it fits best. Case-based reasoning combines reasoning with learning. It spans the whole reasoning cycle. A situation is experienced. Old situations are used to understand it. Old situations are used to solve a problem (if there is one to be solved). Then the new situation is inserted into memory alongside the cases it used for reasoning, to be used another time. The key to this reasoning method, then, is remembering. Remembering has two parts: integrating cases or experiences into memory when they happen and recalling them in appropriate situations later on. The case-based reasoning community calls this related set of issues the i ndexing problem. In broad terms, it means finding in memory the experience closest to a new situation. In narrower terms, it can be described as a two-part problem: assigning indexes or labels to experiences when they are put into memory that describe the situations to which they are applicable, so that they can be recalled later; and at recall time, elaborating the new situation in enough detail so that the indexes it would have if it were in the memory are identified. Case-Based Learning is an edited volume of original research comprising invited contributions by leading workers. This work has also been published as a special issues of MACHINE LEARNING, Volume 10, No. 3. COMPUTERS,Languages,General

Code Generation — Concepts, Tools, Techniques Code Generation - Concepts, Tools, Techniques is based upon the proceedings of the Dagstuhl workshop on code generation which took place from 20-24 May 1991. The aim of the workshop was to evaluate current methods of code generation and to indicate the main directions which future research is likely to take. It provided an excellent forum for the exchange of ideas and had the added advantage of bringing together European and American experts who were unlikely to meet at less specialised gatherings. This volume contains 14 of the 30 papers presented at the Dagstuhl workshop. The papers deal mainly with the following four topics: tools and techniques for code generation, code generation for parallel architectures, register allocation and phase ordering problems, and formal methods and validations. Most of the papers assess the progress of on-going research work, much of which is published here for the first time, while others provide a review of recently completed projects. The volume also contains summaries of two discussion groups which looked at code generation tools and parallel architectures. As a direct result of one of these discussions, a group of the participants have collaborated to make a pure BURS system available for public distribution. This system, named BURG, is currently being beta-tested. Code Generation - Concepts, Tools, Techniques provides a representative summary of state-of-the-art code generation techniques and an important assessment of possible future innovations. It will be an invaluable reference work for researchers and practitioners in this important area. COMPUTERS,Languages,General

Lancelot LANCELOT is a software package for solving large-scale nonlinear optimization problems. This book is our attempt to provide a coherent overview of the package and its use. This includes details of how one might present examples to the package, how the algorithm tries to solve these examples and various technical issues which may be useful to implementors of the software. We hope this book will be of use to both researchers and practitioners in nonlinear programming. Although the book is primarily concerned with a specific optimization package, the issues discussed have much wider implications for the design and im plementation of large-scale optimization algorithms. In particular, the book contains a proposal for a standard input format for large-scale optimization problems. This proposal is at the heart of the interface between a user's problem and the LANCE LOT optimization package. Furthermore, a large collection of over five hundred test ex amples has already been written in this format and will shortly be available to those who wish to use them. We would like to thank the many people and organizations who supported us in our enterprise. We first acknowledge the support provided by our employers, namely the the Facultes Universitaires Notre-Dame de la Paix (Namur, Belgium), Harwell Laboratory (UK), IBM Corporation (USA), Rutherford Appleton Laboratory (UK) and the University of Waterloo (Canada). We are grateful for the support we obtained from NSERC (Canada), NATO and AMOCO (UK). COMPUTERS,Languages,General

Practical Smalltalk Object-Oriented Programming (OOP) is recognized as one of the most powerful programming techniques to come along in many years. Its power lies in the ability it gives the designer to manage the complex, rapidly changing applications that have become the watchword of modern software. Smalltalk is the most extensively used OOP environment. Now Practical Smalltalk helps you to focus on those aspects of the language that you need to know to be a successful programmer. You'll learn all about the important classes to master, the essential theories to grasp, and then put these ideas to work in constructing everything from a simple counter object all the way through a data graphing application and the core of a functional outliner. The book culmi- nates with the creation of a factory process simulation that takes advantage of Smalltalk's ability to create multi-window, multiprocessing applications. Designed for programmers and managers who must understand the operation and uses of the Smalltalk environment, this book assumes only an elementary working knowledge of OOP and the language. The book uses Smalltalk/V 286, Digitalk's widely used implementation of Smalltalk, but most of the concepts and techniques it teaches can be transferred easily to other versions of the language. COMPUTERS,Languages,General

Organization of Programming Languages Beside the computers itself, programming languages are the most important tools of a computer scientist, because they allow the formulation of algorithms in a way that a computer can perform the desired actions. Without the availability of (high level) languages it would simply be impossible to solve complex problems by using computers. Therefore, high level programming languages form a central topic in Computer Science. It should be a must for every student of Computer Science to take a course on the organization and structure of programming languages, since the knowledge about the design of the various programming languages as well as the understanding of certain compilation techniques can support the decision to choose the right language for a particular problem or application. This book is about high level programming languages. It deals with all the major aspects of programming languages (including a lot of examples and exercises). Therefore, the book does not give an detailed introduction to a certain program ming language (for this it is referred to the original language reports), but it explains the most important features of certain programming languages using those pro gramming languages to exemplify the problems. The book was outlined for a one session course on programming languages. It can be used both as a teacher's ref erence as well as a student text book. COMPUTERS,Languages,General

Real-Time UNIX® Systems A growing concern of mine has been the unrealistic expectations for new computer-related technologies introduced into all kinds of organizations. Unrealistic expectations lead to disappointment, and a schizophrenic approach to the introduction of new technologies. The UNIX and real-time UNIX operating system technologies are major examples of emerging technologies with great potential benefits but unrealistic expectations. Users want to use UNIX as a common operating system throughout large segments of their organizations. A common operating system would decrease software costs by helping to provide portability and interoperability between computer systems in today's multivendor environments. Users would be able to more easily purchase new equipment and technologies and cost-effectively reuse their applications. And they could more easily connect heterogeneous equipment in different departments without having to constantly write and rewrite interfaces. On the other hand, many users in various organizations do not understand the ramifications of general-purpose versus real-time UNIX. Users tend to think of "real-time" as a way to handle exotic heart-monitoring or robotics systems. Then these users use UNIX for transaction processing and office applications and complain about its performance, robustness, and reliability. Unfortunately, the users don't realize that real-time capabilities added to UNIX can provide better performance, robustness and reliability for these non-real-time applications. Many other vendors and users do realize this, however. There are indications even now that general-purpose UNIX will go away as a separate entity. It will be replaced by a real-time UNIX. General-purpose UNIX will exist only as a subset of real-time UNIX. COMPUTERS,Languages,General

Practical SGML Many times there are subjects which demand further explanations and guid ance written about them. Such is the case with SGML, the Standard Generalized Markup Language; and ISO Standard published in October, 1986 under the number 8879. There have been many conferences given on this topic, world-wide, as the interest in SGML exists in Europe, the US, Australia and Japan. This book is the first which contains information not only on ISO 8879 itself, but many helpful hints and ideas on developing SGML, applications and discussions of the current software written to be conforming to the ISO standard. 'Ibis book is critical for any end-user and application developer to understand the many issues neccessary to develop SGML implementations (software selection is one of the topics discussed) and SGML applications. A number of examples of the applications of SGML in various situations are discussed and one can expect that the book will stimulate further discussion of these. This book is a practical guide to various components of the language and the author's experience in development and worldng with SGML in his position as leader of the text processing section at CERN ensures that the guidance is based on practical first-hand experience at an installation with a large number of end-users of very varied experience. COMPUTERS,Languages,General

The Art of Lisp Programming Many of us already have at least a passing acquaintance with procedural languages such as BASIC or Pascal, but may not have met a functional language like Lisp before. Using the same enjoyable and sometimes quirky style that they employed so successfully in "The Art of C-Programming", Robin Jones and his team explain the fundamentals of Lisp in a way that students from school to postgraduates will find lucid and stimulating. The book is unique in illustrating the use of Lisp through the development of a realistic project: the design and implementation of a Lisp-based interpreter for the language ABC. COMPUTERS,Languages,General

Parallel and Concurrent Programming in Haskell If you have a working knowledge of Haskell, this hands-on book shows you how to use the language’s many APIs and frameworks for writing both parallel and concurrent programs. You’ll learn how parallelism exploits multicore processors to speed up computation-heavy programs, and how concurrency enables you to write programs with threads for multiple interactions. Author Simon Marlow walks you through the process with lots of code examples that you can run, experiment with, and extend. Divided into separate sections on Parallel and Concurrent Haskell, this book also includes exercises to help you become familiar with the concepts presented: Express parallelism in Haskell with the Eval monad and Evaluation Strategies Parallelize ordinary Haskell code with the Par monad Build parallel array-based computations, using the Repa library Use the Accelerate library to run computations directly on the GPU Work with basic interfaces for writing concurrent code Build trees of threads for larger and more complex programs Learn how to build high-speed concurrent network servers Write distributed programs that run on multiple machines in a network COMPUTERS,Languages,General

C for Programmers with an Introduction to C11 The professional programmer’s Deitel® guide to procedural programming in C through 130 working code examples Written for programmers with a background in high-level language programming, this book applies the Deitel signature live-code approach to teaching the C language and the C Standard Library. The book presents the concepts in the context of fully tested programs, complete with syntax shading, code highlighting, code walkthroughs and program outputs. The book features approximately 5,000 lines of proven C code and hundreds of savvy tips that will help you build robust applications. Start with an introduction to C, then rapidly move on to more advanced topics, including building custom data structures, the Standard Library, select features of the new C11 standard such as multithreading to help you write high-performance applications for today’s multicore systems, and secure C programming sections that show you how to write software that is more robust and less vulnerable. You’ll enjoy the Deitels’ classic treatment of procedural programming. When you’re finished, you’ll have everything you need to start building industrial-strength C applications. Practical, example-rich coverage of: C programming fundamentals Compiling and debugging with GNU gcc and gdb, and Visual C++® Key new C11 standard features: Type generic expressions, anonymous structures and unions, memory alignment, enhanced Unicode® support, _Static_assert, quick_exit and at_quick_exit, _Noreturn function specifier, C11 headers C11 multithreading for enhanced performance on today’s multicore systems Secure C Programming sections Data structures, searching and sorting Order of evaluation issues, preprocessor Designated initializers, compound literals, bool type, complex numbers, variable-length arrays, restricted pointers, type generic math, inline functions, and more. Visit www.deitel.com For information on Deitel’s Dive Into® Series programming training courses delivered at organizations worldwide visit www.deitel.com/training or write to deitel@deitel.com Download code examples To receive updates for this book, subscribe to the free DEITEL® BUZZ ONLINE e-mail newsletter at www.deitel.com/newsletter/subscribe.html Join the Deitel social networking communities on Facebook® at facebook.com/DeitelFan , Twitter® @deitel, LinkedIn® at bit.ly/DeitelLinkedIn and Google+™ at gplus.to/Deitel COMPUTERS,Languages,General

Mastering VBA for Microsoft Office 2013 A unique, comprehensive guide to creating custom apps with VBA Automating computing tasks to increase productivity is a goal for businesses of all sizes. Visual Basic for Applications (VBA) is a version of Visual Basic designed to be easily understandable for novice programmers, but still powerful enough for IT professionals who need to create specialized business applications. With this invaluable book, you'll learn how to extend the capabilities of Office 2013 applications with VBA programming and use it for writing macros, automating Office applications, and creating custom applications in Word, Excel, PowerPoint, Outlook, and Access. Covers the basics of VBA in clear, systematic tutorials and includes intermediate and advanced content for experienced VB developers Explores recording macros and getting started with VBA; learning how to work with VBA; using loops and functions; using message boxes, input boxes, and dialog boxes; creating effective code; XML-based files, ActiveX, the developer tab, content controls, add-ins, embedded macros, and security Anchors the content with solid, real-world projects in Word, Excel, Outlook, PowerPoint, and Access Covering VBA for the entire suite of Office 2013 applications, Mastering VBA for Microsoft Office 2013 is mandatory reading. COMPUTERS,Languages,General

Practice of Programming, The With the same insight and authority that made their book The Unix Programming Environment a classic, Brian Kernighan and Rob Pike have written The Practice of Programming to help make individual programmers more effective and productive. This book is full of practical advice and real-world examples in C, C++, Java, and a variety of special-purpose languages. Kernighan and Pike have distilled years of experience writing programs, teaching, and working with other programmers to create this book. Anyone who writes software will profit from its principles and guidance. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Languages,General

Beginning iOS Programming For Dummies The ultimate beginner's guide to programming in the iOS environment The Apple App Store is a gold mine for developers, but with more apps for the iPhone, iPad, and iPod touch being added every day, it?s essential to have a solid programming foundation to create the best apps possible. If you're eager to learn the ins and outs of iOS programming, this is your book. It teaches object-oriented programming within the iOS framework from the ground up, preparing you to create the next super iPhone or iPad app. Get a handle on the iOS framework, object-oriented best practices, and the Xcode programming environment, then discover how to create simple interfaces, use libraries, create and extend objects, and more. Whether you're just starting out in programming or only new to iOS, For Dummies is the perfect beginning. Focuses on teaching object-oriented programming within the iOS framework and includes best practices for building apps that are easy to debug, evolve, and maintain Uses simple examples to demonstrate object-oriented programming output in the iPhone environment while teaching real-world programming concepts and applications Provides a thorough understanding of the framework and object-oriented principles to help beginning programmers make optimum use of iOS Covers working with the Xcode environment and storyboards; creating simple interfaces; using libraries, functions, structures, arrays, and pointers; and creating and extending objects Beginning iOS Programming For Dummies is your straightforward guide to getting started with iOS programming. COMPUTERS,Languages,General

Code What do flashlights, the British invasion, black cats, and seesaws have to do with computers? In CODE, they show us the ingenious ways we manipulate language and invent new means of communicating with each other. And through CODE, we see how this ingenuity and our very human compulsion to communicate have driven the technological innovations of the past two centuries. Using everyday objects and familiar language systems such as Braille and Morse code, author Charles Petzold weaves an illuminating narrative for anyone who’s ever wondered about the secret inner life of computers and other smart machines. It’s a cleverly illustrated and eminently comprehensible story—and along the way, you’ll discover you’ve gained a real context for understanding today’s world of PCs, digital media, and the Internet. No matter what your level of technical savvy, CODE will charm you—and perhaps even awaken the technophile within. COMPUTERS,Languages,General

Effective Ruby If you’re an experienced Ruby programmer, Effective Ruby will help you harness Ruby’s full power to write more robust, efficient, maintainable, and well-performing code. Drawing on nearly a decade of Ruby experience, Peter J. Jones brings together 48 Ruby best practices, expert tips, and shortcuts—all supported by realistic code examples. Jones offers practical advice for each major area of Ruby development, from modules to memory to metaprogramming. Throughout, he uncovers little-known idioms, quirks, pitfalls, and intricacies that powerfully impact code behavior and performance. Each item contains specific, actionable, clearly organized guidelines; careful advice; detailed technical arguments; and illuminating code examples. When multiple options exist, Jones shows you how to choose the one that will work best in your situation. Effective Ruby will help you systematically improve your code—not by blindly following rules, but by thoroughly understanding Ruby programming techniques. Key features of this concise guide include How to avoid pitfalls associated with Ruby’s sometimes surprising idiosyncrasies What you should know about inheritance hierarchies to successfully use Rails (and other large frameworks) How to use misunderstood methods to do amazingly useful things with collections Better ways to use exceptions to improve code reliability Powerful metaprogramming approaches (and techniques to avoid) Practical, efficient testing solutions, including MiniTest Unit and Spec Testing How to reliably manage RubyGem dependencies How to make the most of Ruby’s memory management and profiling tools How to improve code efficiency by understanding the Ruby interpreter’s internals COMPUTERS,Languages,General

A Practical Guide to SysML A Practical Guide to SysML, Third Edition, fully updated for SysML version 1.4, provides a comprehensive and practical guide for modeling systems with SysML. With their unique perspective as leading contributors to the language, Friedenthal, Moore, and Steiner provide a full description of the language along with a quick reference guide and practical examples to help you use SysML. The book begins with guidance on the most commonly used features to help you get started quickly. Part 1 explains the benefits of a model-based approach, providing an overview of the language and how to apply SysML to model systems. Part 2 includes a comprehensive description of SysML that provides a detailed understanding that can serve as a foundation for modeling with SysML, and as a reference for practitioners. Part 3 includes methods for applying model-based systems engineering using SysML to specify and design systems, and how these methods can help manage complexity. Part 4 deals with topics related to transitioning MBSE practice into your organization, including integration of the system model with other engineering models, and strategies for adoption of MBSE. Learn how and why to deploy MBSE in your organization with an introduction to systems and model-based systems engineering Use SysML to describe systems with this general overview and a detailed description of the Systems Modeling Language Review practical examples of MBSE methodologies to understand their application to specifying and designing a system Includes comprehensive modeling notation tables as an appendix that can be used as a standalone reference COMPUTERS,Languages,General

Joe Celko's SQL for Smarties SQL for Smarties was hailed as the first book devoted explicitly to the advanced techniques needed to transform an experienced SQL programmer into an expert. Now, 20 years later and in its fifth edition, this classic reference still reigns supreme as the only book written by a SQL master that teaches programmers and practitioners to become SQL masters themselves! These are not just tips and techniques; also offered are the best solutions to old and new challenges. Joe Celko conveys the way you need to think in order to get the most out of SQL programming efforts for both correctness and performance. New to the fifth edition, Joe features new examples to reflect the ANSI/ISO Standards so anyone can use it. He also updates data element names to meet new ISO-11179 rules with the same experience-based teaching style that made the previous editions the classics they are today. You will learn new ways to write common queries, such as finding coverings, partitions, runs in data, auctions and inventory, relational divisions and so forth. SQL for Smarties explains some of the principles of SQL programming as well as the code. A new chapter discusses design flaws in DDL, such as attribute splitting, non-normal forum redundancies and tibbling. There is a look at the traditional acid versus base transaction models, now popular in NoSQL products. You’ll learn about computed columns and the DEFERRABLE options in constraints. An overview of the bi-temporal model is new to this edition and there is a longer discussion about descriptive statistic aggregate functions. The book finishes with an overview of SQL/PSM that is applicable to proprietary 4GL vendor extensions. New to the 5th Edition: Overview of the bitemporal model Extended coverage of descriptive statistic aggregate functions New chapter covers flaws in DDL Examination of traditional acid versus base transaction models Reorganized to help you navigate related topics with ease Expert advice from a noted SQL authority and award-winning columnist Joe Celko, who served on the ANSI SQL standards committee for over a decade Teaches scores of advanced techniques that can be used with any product, in any SQL environment, whether it is SQL 92 or SQL 2011 Offers tips for working around deficiencies and gives insight into real-world challenges COMPUTERS,Languages,General

Developing Web Apps with Haskell and Yesod This fast-moving guide introduces web application development with Haskell and Yesod, a potent language/framework combination that supports high-performing applications that are modular, type-safe, and concise. Fully updated for Yesod 1.4, this second edition shows you how Yesod handles widgets, forms, persistence, and RESTful content. Author Michael Snoyman also introduces various Haskell tools to supplement your basic knowledge of the language. By the time you finish this book, you’ll create a production-quality web application with Yesod’s ready-to-use scaffolding. You’ll also examine several real-world examples, including a blog, a wiki, a JSON web service, and a Sphinx search server. Build a simple application to learn Yesod’s foundation datatype and Web Application Interface (WAI) Output HTML, CSS, and Javascript with Shakespearean template languages Get an indepth look at Yesod’s core monads for producing cleaner, more modular code Probe Yesod’s internal workings: learn the request handling process for a typical application Build forms on top of widgets by implementing the yesod-form declarative API Learn how Yesod and Haskell handle persistence and session data Serve an HTML page and a machine-friendly JSON page from the same URL COMPUTERS,Languages,General

MATLAB Optimization Techniques MATLAB is a high-level language and environment for numerical computation, visualization, and programming. Using MATLAB, you can analyze data, develop algorithms, and create models and applications. The language, tools, and built-in math functions enable you to explore multiple approaches and reach a solution faster than with spreadsheets or traditional programming languages, such as C/C++ or Java. MATLAB Optimization Techniques introduces you to the MATLAB language with practical hands-on instructions and results, allowing you to quickly achieve your goals. It begins by introducing the MATLAB environment and the structure of MATLAB programming before moving on to the mathematics of optimization. The central part of the book is dedicated to MATLAB’s Optimization Toolbox, which implements state-of-the-art algorithms for solving multiobjective problems, non-linear minimization with boundary conditions and restrictions, minimax optimization, semi-infinitely constrained minimization and linear and quadratic programming. A wide range of exercises and examples are included, illustrating the most widely used optimization methods. COMPUTERS,Languages,General

Essential AutoLISP® AutoCAD is the most widely used computer-aided design package in the world. Underneath AutoCAD is a powerful computing language called AutoLISP. This language is designed to automate many functions of AutoCAD. This book is a hands-on introduction to AutoLISP and its applications. AutoLISP is a unique and powerful language that allows you to write, debug, and modify programs extremely quickly, once you understand how the language itself works. Part I contains an easy-to-learn pictorial representation for data and code, a tool used to easily solve problems otherwise approached through trial and error method. Essential AutoLISP is the only book in its field that uses the pictorial representation. Part II is devoted to learning how AutoLISP processes the code entered. Part V not only explains the causes of most common error messages and how to solve them, but examines many other errors that don't necessarily give messages. COMPUTERS,Languages,General

Prolog and its Applications COMPUTERS,Languages,General

Introduction to JavaScript Object Notation What is JavaScript Object Notation (JSON) and how can you put it to work? This concise guide helps busy IT professionals get up and running quickly with this popular data interchange format, and provides a deep understanding of how JSON works. Author Lindsay Bassett begins with an overview of JSON syntax, data types, formatting, and security concerns before exploring the many ways you can apply JSON today. From Web APIs and server-side language libraries to NoSQL databases and client-side frameworks, JSON has emerged as a viable alternative to XML for exchanging data between different platforms. If you have some programming experience and understand HTML and JavaScript, this is your book. Learn why JSON syntax represents data in name-value pairs Explore JSON data types, including object, string, number, and array Find out how you can combat common security concerns Learn how the JSON schema verifies that data is formatted correctly Examine the relationship between browsers, web APIs, and JSON Understand how web servers can both request and create data Discover how jQuery and other client-side frameworks use JSON Learn why the CouchDB NoSQL database uses JSON to store data COMPUTERS,Languages,General

Mastering VBA for Microsoft Office 2016 Enhance productivity in any Office application with zero programming experience Mastering VBA for Microsoft Office 2016 helps you extend the capabilities of the entire Office suite using Visual Basic for Applications (VBA). Even if you have no programming experience , you'll be automating routine computing processes quickly using the simple, yet powerful VBA programming language. Clear, systematic tutorials walk beginners through the basics, while intermediate and advanced content guides more experienced users toward efficient solutions. This comprehensive guide starts at the beginning to get you acquainted with VBA so you can start recording macros right away. You'll then build upon that foundation to utilize the full capabilities of the language as you use loops and functions, message boxes, input boxes, and dialog boxes to design your own Office automation program. Add-ins, embedded macros, content controls, and more give you advanced tools to enhance productivity, and all instruction is backed by real-world practice projects in Word, Excel, Outlook, and PowerPoint. Productivity is the name of the game, and automating certain computing tasks is an easy solution with significant impact for any business. This book shows you how, with step-by-step guidance and expert insight. Expand Office 2016 functionality with macros Learn how to work with VBA and the entire Office suite Create effective code, even with no programing experience Understand ActiveX, XML-based files, the developer tab, and more VBA is designed to be understandable and accessible to beginners, but powerful enough to create specialized business applications. If you're ready to begin exploring the possibilities, Mastering VBA for Microsoft Office 2016 gets you started right away. COMPUTERS,Languages,General

Go Programming Language, The The Go Programming Language is the authoritative resource for any programmer who wants to learn Go. It shows how to write clear and idiomatic Go to solve real-world problems. The book does not assume prior knowledge of Go nor experience with any specific language, so you’ll find it accessible whether you’re most comfortable with JavaScript, Ruby, Python, Java, or C++. The first chapter is a tutorial on the basic concepts of Go, introduced through programs for file I/O and text processing, simple graphics, and web clients and servers. Early chapters cover the structural elements of Go programs: syntax, control flow, data types, and the organization of a program into packages, files, and functions. The examples illustrate many packages from the standard library and show how to create new ones of your own. Later chapters explain the package mechanism in more detail, and how to build, test, and maintain projects using the go tool. The chapters on methods and interfaces introduce Go’s unconventional approach to object-oriented programming, in which methods can be declared on any type and interfaces are implicitly satisfied. They explain the key principles of encapsulation, composition, and substitutability using realistic examples. Two chapters on concurrency present in-depth approaches to this increasingly important topic. The first, which covers the basic mechanisms of goroutines and channels, illustrates the style known as communicating sequential processes for which Go is renowned. The second covers more traditional aspects of concurrency with shared variables. These chapters provide a solid foundation for programmers encountering concurrency for the first time. The final two chapters explore lower-level features of Go. One covers the art of metaprogramming using reflection. The other shows how to use the unsafe package to step outside the type system for special situations, and how to use the cgo tool to create Go bindings for C libraries. The book features hundreds of interesting and practical examples of well-written Go code that cover the whole language, its most important packages, and a wide range of applications. Each chapter has exercises to test your understanding and explore extensions and alternatives. Source code is freely available for download from http://gopl.io/ and may be conveniently fetched, built, and installed using the go get command. COMPUTERS,Languages,General

Dart Programming Language, The Dart is a class-based, object-oriented language that simplifies the development of structured modern apps, scales from small scripts to large applications, and can be compiled to JavaScript for use in any modern browser. In this rigorous but readable introductory text, Dart specification lead Gilad Bracha fully explains both the language and the ideas that have shaped it. The Dart Programming Language offers an authoritative description of Dart for programmers, computer science students, and other well-qualified professionals. The text illuminates key programming constructs with significant examples, focusing on principles of the language, such as optional typing and pure object-orientation. Bracha thoroughly explains reflection in Dart, showing how it is evolving into a form that programmers can easily apply without creating excessively large programs. He also shares valuable insights into Dart’s actor-style model for concurrency and asynchronous programming. Throughout, he covers both language semantics and the rationale for key features, helping you understand not just what Dart does, but why it works the way it does. You will learn about Dart’s object model, in which everything is an object, even numbers and Boolean values How Dart programs are organized into modular libraries How Dart functions are structured, stored in variables, passed as parameters, and returned as results Dart’s innovative approach to optional typing How Dart handles expressions and statements How to use Dart’s implementation of reflection to introspect on libraries, classes, functions, and objects Isolates and other Dart features that support concurrency and distribution Register your product at informit.com/register for convenient access to downloads, updates, and corrections as they become available. COMPUTERS,Languages,General

INNC 90 PARIS International Neural Network Conference, July 9-13, 1990, Palais des Congrès, Paris, France COMPUTERS,Languages,General

Python Programming Fundamentals This easy-to-follow and classroom-tested textbook guides the reader through the fundamentals of programming with Python, an accessible language which can be learned incrementally. This revised and updated new edition will teach students how to recognize and apply abstract patterns in programming through the extensive use of illustrative examples and practical exercises. The book also demonstrates the benefit of using a debugger to inspect the state of a program while it is executing. Topics and features: incudes numerous examples and practice exercises throughout the text, with additional exercises, solutions and review questions at the end of each chapter; highlights the patterns which frequently appear when writing programs, reinforcing the application of these patterns for problem-solving through practice exercises; introduces the use of a debugger tool to inspect a program, enabling students to discover for themselves how programs work and enhance their understanding; presents the Tkinter framework for building graphical user interface applications and event-driven programs; provides instructional videos and additional information for students, as well as support materials for instructors, at an associated website. Ideal for introductory programming courses for undergraduates in computer science, this hands-on textbook for interactive classroom learning will help students to develop the necessary skills to begin writing their own programs. Due to the wealth of support material available, Python is selected as a good first language with little “overhead†in learning to write simple programs. COMPUTERS,Languages,General

Guide to Fortran 2008 Programming This concise and easy-to read textbook provides an accessible introduction to the most important features of Fortran 2008 (also known as Fortran 08), the latest standard version of Fortran. Both the style of the many example programs and the selection of topics discussed in detail guide the reader toward acquiring programming skills to produce Fortran programs that are readable, maintainable, and efficient. The text is organized for instruction from beginning to end, but also so that particular topics may be studied and read independently—making the work eminently suitable as a reference for professionals. Topics and features: presents a complete discussion of all the basic features needed to write complete Fortran programs; makes extensive use of examples and case studies to illustrate the practical use of features of Fortran 08, and supplies simple problems for the reader to test their knowledge; provides a detailed exploration of control constructs, modules, procedures, arrays, character strings, data structures and derived types, pointer variables, and object-oriented programming; includes coverage of such major new features in Fortran 08 as coarrays, submodules, parameterized derived types, and derived-type input and output; highlights the topic of modules as the framework for organizing data and procedures for a Fortran program; investigates the excellent input/output facilities available in Fortran; contains appendices listing the many intrinsic procedures and providing a brief informal syntax specification for the language. This indispensable guide provides a tutorial for anyone who wants to learn Fortran 08, including those familiar with programming language concepts but unfamiliar with Fortran. Experienced Fortran 90/95 programmers will be able to use this volume to assimilate quickly those features in Fortran 03 and 08 that are not in Fortran 90 or 95. COMPUTERS,Languages,General

Common Lisp Recipes Findsolutions to problems and answers to questions you are likely to encounter whenwriting real-world applications in Common Lisp. This book covers areas asdiverse as web programming, databases, graphical user interfaces, integrationwith other programming languages, multi-threading, and mobile devices as wellas debugging techniques and optimization, to name just a few. Written by anauthor who has used Common Lisp in many successful commercial projects overmore than a decade, Common Lisp Recipes is also the first Common Lispbook to tackle such advanced topics as environment access, logical pathnames,Gray streams, delivery of executables, pretty printing, setf expansions, orchanging the syntax of Common Lisp. Thebook is organized around specific problems or questions each followed byready-to-use example solutions and clear explanations of the concepts involved,plus pointers to alternatives and more information. Each recipe can be readindependently of the others and thus the book will earn a special place on yourbookshelf as a reference work you always want to have within reach. Common Lisp Recipes is aimed atprogrammers who are already familiar with Common Lisp to a certain extent butdo not yet have the experience you typically only get from years of hacking ina specific computer language. It is written in a style that mixes hands-onno-frills pragmatism with precise information and prudent mentorship. If you feel attractedto Common Lisp's mix of breathtaking features and down-to-earth utilitarianism,you'll also like this book. COMPUTERS,Languages,General

Harley Hahn's Emacs Field Guide In this book, Harley Hahn demystifies Emacs for programmers, students, and everyday users. The first part of the book carefully creates a context for your work with Emacs. What exactly is Emacs? How does it relate to your personal need to work quickly and to solve problems? Hahn then explains the technical details you need to understand to work with your operating system, the various interfaces, and your file system. In the second part of the book, Hahn provides an authoritative guide to the fundamentals of thinking and creating within the Emacs environment. You start by learning how to install and use Emacs with Linux, BSD-based Unix, Mac OS X, or Microsoft Windows. Written with Hahn's clear, comfortable, and engaging style, Harley Hahn's Emacs Field Guide will surprise you: an engaging book to enjoy now, a comprehensive reference to treasure for years to come. What You Will Learn Special Emacs keys Emacs commands Buffers and windows Cursor, point, and region Kill/delete, move/copy, correcting, spell checking, and filling Searching, including regular expressions Emacs major modes and minor modes Customizing using your .emacs file Built-in tools, including Dired Games and diversions Who This Book Is For Programmers, students, and everyday users, who want an engaging and authoritative introduction to the complex and powerful Emacs working environment. COMPUTERS,Languages,General

Automated Trading with R Learn to trade algorithmically with your existing brokerage, from data management, to strategy optimization, to order execution, using free and publicly available data. Connect to your brokerage’s API, and the source code is plug-and-play. Automated Trading with R explains automated trading, starting with its mathematics and moving to its computation and execution. You will gain a unique insight into the mechanics and computational considerations taken in building a back-tester, strategy optimizer, and fully functional trading platform. The platform built in this book can serve as a complete replacement for commercially available platforms used by retail traders and small funds. Software components are strictly decoupled and easily scalable, providing opportunity to substitute any data source, trading algorithm, or brokerage. This book will: Provide a flexible alternative to common strategy automation frameworks, like Tradestation, Metatrader, and CQG, to small funds and retail traders Offer an understanding of the internal mechanisms of an automated trading system Standardize discussion and notation of real-world strategy optimization problems What You Will Learn Understand machine-learning criteria for statistical validity in the context of time-series Optimize strategies, generate real-time trading decisions, and minimize computation time while programming an automated strategy in R and using its package library Best simulate strategy performance in its specific use case to derive accurate performance estimates Understand critical real-world variables pertaining to portfolio management and performance assessment, including latency, drawdowns, varying trade size, portfolio growth, and penalization of unused capital Who This Book Is For Traders/practitioners at the retail or small fund level with at least an undergraduate background in finance or computer science; graduate level finance or data science students COMPUTERS,Languages,General

Introducing Elixir Smooth, powerful, and small, Elixir is an excellent language for learning functional programming, and with this hands-on introduction, you’ll discover just how powerful Elixir can be. Authors Simon St. Laurent and J. David Eisenberg show you how Elixir combines the robust functional programming of Erlang with an approach that looks more like Ruby, and includes powerful macro features for metaprogramming. Updated to cover Elixir 1.4, the second edition of this practical book helps you write simple Elixir programs by teaching one skill at a time. Once you pick up pattern matching, process-oriented programming, and other concepts, you’ll understand why Elixir makes it easier to build concurrent and resilient programs that scale up and down with ease. Get comfortable with IEx, Elixir’s command line interface Learn Elixir’s basic structures by working with numbers Discover atoms, pattern matching, and guards: the foundations of your program structure Delve into the heart of Elixir processing with recursion, strings, lists, and higher-order functions Create Elixir processes and send messages among them Store and manipulate structured data with Erlang Term Storage and the Mnesia database Build resilient applications with the Open Telecom Platform COMPUTERS,Languages,General

Introducing Erlang If you’re new to Erlang, its functional style can seem difficult, but with help from this hands-on introduction, you’ll scale the learning curve and discover how enjoyable, powerful, and fun this language can be. In this updated second edition, author Simon St.Laurent shows you how to write simple Erlang programs by teaching you one skill at a time. You’ll learn about pattern matching, recursion, message passing, process-oriented programming, and establishing pathways for data rather than telling it where to go. By the end of your journey, you’ll understand why Erlang is ideal for concurrency and resilience. Get cozy with Erlang’s shell, its command line interface Define functions, using the fun tool, to represent repeated calculations Discover atoms, pattern matching, and guards: the foundations of your program structure Delve into the heart of Erlang processing with recursion, strings, lists, and higher-order functions Create processes, send messages among them, and apply pattern matching to incoming messages Store and manipulate structured data with Erlang Term Storage and the Mnesia database Learn about Open Telecom Platform, Erlang’s open source libraries and tools COMPUTERS,Languages,General

Modern C++ Programming Cookbook Over 100 recipes to help you overcome your difficulties with C++ programming and gain a deeper understanding of the working of modern C++ About This Book Explore the most important language and library features of C++17, including containers, algorithms, regular expressions, threads, and more, Get going with unit testing frameworks Boost.Test, Google Test and Catch, Extend your C++ knowledge and take your development skills to new heights by making your applications fast, robust, and scalable. Who This Book Is For If you want to overcome difficult phases of development with C++ and leverage its features using modern programming practices, then this book is for you. The book is designed for both experienced C++ programmers as well as people with strong knowledge of OOP concepts. What You Will Learn Get to know about the new core language features and the problems they were intended to solve Understand the standard support for threading and concurrency and know how to put them on work for daily basic tasks Leverage C++'s features to get increased robustness and performance Explore the widely-used testing frameworks for C++ and implement various useful patterns and idioms Work with various types of strings and look at the various aspects of compilation Explore functions and callable objects with a focus on modern features Leverage the standard library and work with containers, algorithms, and iterators Use regular expressions for find and replace string operations Take advantage of the new filesystem library to work with files and directories Use the new utility additions to the standard library to solve common problems developers encounter including string_view, any , optional and variant types In Detail C++ is one of the most widely used programming languages. Fast, efficient, and flexible, it is used to solve many problems. The latest versions of C++ have seen programmers change the way they code, giving up on the old-fashioned C-style programming and adopting modern C++ instead. Beginning with the modern language features, each recipe addresses a specific problem, with a discussion that explains the solution and offers insight into how it works. You will learn major concepts about the core programming language as well as common tasks faced while building a wide variety of software. You will learn about concepts such as concurrency, performance, meta-programming, lambda expressions, regular expressions, testing, and many more in the form of recipes. These recipes will ensure you can make your applications robust and fast. By the end of the book, you will understand the newer aspects of C++11/14/17 and will be able to overcome tasks that are time-consuming or would break your stride while developing. Style and approach This book follows a recipe-based approach, with examples that will empower you to implement the core programming language features and explore the newer aspects of C++. COMPUTERS,Languages,General

JSON at Work JSON is becoming the backbone for meaningful data interchange over the internet. This format is now supported by an entire ecosystem of standards, tools, and technologies for building truly elegant, useful, and efficient applications. With this hands-on guide, author and architect Tom Marrs shows you how to build enterprise-class applications and services by leveraging JSON tooling and message/document design. JSON at Work provides application architects and developers with guidelines, best practices, and use cases, along with lots of real-world examples and code samples. You’ll start with a comprehensive JSON overview, explore the JSON ecosystem, and then dive into JSON’s use in the enterprise. Get acquainted with JSON basics and learn how to model JSON data Learn how to use JSON with Node.js, Ruby on Rails, and Java Structure JSON documents with JSON Schema to design and test APIs Search the contents of JSON documents with JSON Search tools Convert JSON documents to other data formats with JSON Transform tools Compare JSON-based hypermedia formats, including HAL and jsonapi Leverage MongoDB to store and access JSON documents Use Apache Kafka to exchange JSON-based messages between services COMPUTERS,Languages,General

Vorkurs Informatik Ausgehend von Beispielen vermittelt dieses Lehrbuch grundlegende Paradigmen der Informatik. Die Schwerpunkte liegen auf dem Algorithmenbegriff, einer Einführung in die Programmierung auf Grundlage der Programmiersprache Java und objektorientierten Konzepten. Ferner führt das Buch an die Aufwandsanalyse von Algorithmen und die Funktionsweise von Rechnern heran. Die 5. Auflage enthält ein neues Kapitel, das erweiterten Programmierkonzepten gewidmet ist. Es geht auf Klassenbibliotheken und die Graphikprogrammierung ein, erklärt die Strukturierung von Programmiersprachen sowie die modellgestützte Softwareentwicklung anhand von UML und gibt ausgehend von den vermittelten Java-Kenntnissen eine Einführung in die Programmiersprache C++. So gelingt der Einstieg in das Informatikstudium! COMPUTERS,Languages,General

Low-Level Programming Learn Intel 64 assembly language and architecture, become proficient in C, and understand how the programs are compiled and executed down to machine instructions, enabling you to write robust, high-performance code. Low-Level Programming explains Intel 64 architecture as the result of von Neumann architecture evolution. The book teaches the latest version of the C language (C11) and assembly language from scratch. It covers the entire path from source code to program execution, including generation of ELF object files, and static and dynamic linking. Code examples and exercises are included along with the best code practices. Optimization capabilities and limits of modern compilers are examined, enabling you to balance between program readability and performance. The use of various performance-gain techniques is demonstrated, such as SSE instructions and pre-fetching. Relevant Computer Science topics such as models of computation and formal grammars are addressed, and their practical value explained. What You'll Learn Low-Level Programming teaches programmers to: Freely write in assembly language Understand the programming model of Intel 64 Write maintainable and robust code in C11 Follow the compilation process and decipher assembly listings Debug errors in compiled assembly code Use appropriate models of computation to greatly reduce program complexity Write performance-critical code Comprehend the impact of a weak memory model in multi-threaded applications Who This Book Is For Intermediate to advanced programmers and programming students COMPUTERS,Languages,General

Concurrency in Go Concurrency can be notoriously difficult to get right, but fortunately, the Go open source programming language makes working with concurrency tractable and even easy. If you’re a developer familiar with Go, this practical book demonstrates best practices and patterns to help you incorporate concurrency into your systems. Author Katherine Cox-Buday takes you step-by-step through the process. You’ll understand how Go chooses to model concurrency, what issues arise from this model, and how you can compose primitives within this model to solve problems. Learn the skills and tooling you need to confidently write and implement concurrent systems of any size. Understand how Go addresses fundamental problems that make concurrency difficult to do correctly Learn the key differences between concurrency and parallelism Dig into the syntax of Go’s memory synchronization primitives Form patterns with these primitives to write maintainable concurrent code Compose patterns into a series of practices that enable you to write large, distributed systems that scale Learn the sophistication behind goroutines and how Go’s runtime stitches everything together COMPUTERS,Languages,General

PHP and MySQL Web Development PHP and MySQL Web Development, Fifth Edition The definitive guide to building database-driven Web applications with PHP and MySQL PHP and MySQL are popular open-source technologies that are ideal for quickly developing database-driven Web applications. PHP is a powerful scripting language designed to enable developers to create highly featured Web applications quickly, and MySQL is a fast, reliable database that integrates well with PHP and is suited for dynamic Internet-based applications. PHP and MySQL Web Development shows how to use these tools together to produce effective, interactive Web applications. It clearly describes the basics of the PHP language, explains how to set up and work with a MySQL database, and then shows how to use PHP to interact with the database and the server. This practical, hands-on book consistently focuses on real-world applications, even in the introductory chapters. The authors cover important aspects of security and authentication as they relate to building a real-world website and show you how to implement these aspects in PHP and MySQL. They also introduce you to the integration of front-end and back-end technologies by using JavaScript in your application development. The final part of this book describes how to approach real-world projects and takes the reader through the design, planning, and building of several projects, including: User authentication and personalization Web-based email Social media integration Shopping cart The fifth edition of PHP and MySQL Web Development has been thoroughly updated, revised, and expanded to cover developments in PHP through versions 5.6 and 7, as well as features introduced in recent stable releases of MySQL. Free Access to Web Edition Purchase of this book in any format, electronic or print, includes free access to the corresponding Web Edition, which provides several special features: The complete text of the book online Exercises and interactive quizzes to test your understanding of the material Bonus chapters not included in the print or e-book editions Updates and corrections as they become available The Web Edition can be viewed on all types of computers and mobile devices with any modern web browser that supports HTML5. Contents at a Glance Part I: Using PHP 1 PHP Crash Course 2 Storing and Retrieving Data 3 Using Arrays 4 String Manipulation and Regular Expressions 5 Reusing Code and Writing Functions 6 Object-Oriented PHP 7 Error and Exception Handling Part II: Using MySQL 8 Designing Your Web Database 9 Creating Your Web Database 10 Working with Your MySQL Database 11 Accessing Your MySQL Database from the Web with PHP 12 Advanced MySQL Administration 13 Advanced MySQL Programming Part III: Web Application Security 14 Web Application Security Risks 15 Building a Secure Web Application 16 Implementing Authentication Methods with PHP Part IV: Advanced PHP Techniques 17 Interacting with the File System and the Server 18 Using Network and Protocol Functions 19 Managing the Date and Time 20 Internationalization and Localization 21 Generating Images 22 Using Session Control in PHP 23 Integrating JavaScript and PHP 24 Other Useful Features Part V: Building Practical PHP and MySQL Projects 25 Using PHP and MySQL for Large Projects 26 Debugging and Logging 27 Building User Authentication and Personalization 28 (Web Edition) Building a Web-Based Email Client with Laravel Part I 29 (Web Edition) Building a Web-Based Email Client with Laravel Part II 30 (Web Edition) Social Media Integration Sharing and Authentication 31 (Web Edition) Building a Shopping Cart Part VI: Appendix A Installing Apache, PHP, and MySQL COMPUTERS,Languages,General

Learn You a Haskell for Great Good! It's all in the name: Learn You a Haskell for Great Good! is a hilarious, illustrated guide to this complex functional language. Packed with the author's original artwork, pop culture references, and most importantly, useful example code, this book teaches functional fundamentals in a way you never thought possible. You'll start with the kid stuff: basic syntax, recursion, types and type classes. Then once you've got the basics down, the real black belt master-class begins: you'll learn to use applicative functors, monads, zippers, and all the other mythical Haskell constructs you've only read about in storybooks. As you work your way through the author's imaginative (and occasionally insane) examples, you'll learn to:–Laugh in the face of side effects as you wield purely functional programming techniques–Use the magic of Haskell's "laziness" to play with infinite sets of data–Organize your programs by creating your own types, type classes, and modules–Use Haskell's elegant input/output system to share the genius of your programs with the outside world Short of eating the author's brain, you will not find a better way to learn this powerful language than reading Learn You a Haskell for Great Good! COMPUTERS,Languages,General

The Book of R The Book of R is a comprehensive, beginner-friendly guide to R, the world’s most popular programming language for statistical analysis. Even if you have no programming experience and little more than a grounding in the basics of mathematics, you’ll find everything you need to begin using R effectively for statistical analysis. You’ll start with the basics, like how to handle data and write simple programs, before moving on to more advanced topics, like producing statistical summaries of your data and performing statistical tests and modeling. You’ll even learn how to create impressive data visualizations with R’s basic graphics tools and contributed packages, like ggplot2 and ggvis, as well as interactive 3D visualizations using the rgl package. Dozens of hands-on exercises (with downloadable solutions) take you from theory to practice, as you learn:–The fundamentals of programming in R, including how to write data frames, create functions, and use variables, statements, and loops–Statistical concepts like exploratory data analysis, probabilities, hypothesis tests, and regression modeling, and how to execute them in R–How to access R’s thousands of functions, libraries, and data sets–How to draw valid and useful conclusions from your data–How to create publication-quality graphics of your results Combining detailed explanations with real-world examples and exercises, this book will provide you with a solid understanding of both statistics and the depth of R’s functionality. Make The Book of R your doorway into the growing world of data analysis. COMPUTERS,Languages,General

Scratch Programming Playground Scratch, the colorful drag-and-drop programming language, is used by millions of first-time learners, and in Scratch Programming Playground, you’ll learn to program by making cool games. Get ready to destroy asteroids, shoot hoops, and slice and dice fruit! Each game includes easy-to-follow instructions, review questions, and creative coding challenges to make the game your own. Want to add more levels or a cheat code? No problem, just write some code. You’ll learn to make games like:–Maze Runner: escape the maze!–Snaaaaaake: gobble apples and avoid your own tail–Asteroid Breaker: smash space rocks–Fruit Slicer: a Fruit Ninja clone–Brick Breaker: a remake of Breakout, the brick-breaking classic–Platformer: a game inspired by Super Mario Bros. Learning how to program shouldn’t be dry and dreary. With Scratch Programming Playground, you’ll make a game of it! Uses Scratch 2 COMPUTERS,Languages,General

Clean C++ Write maintainable, extensible, and durable software with modern C++. This book is a must for every developer, software architect, or team leader who is interested in good C++ code, and thus also wants to save development costs. If you want to teach yourself about writing clean C++, Clean C++ is exactly what you need. It is written to help C++ developers of all skill levels and shows by example how to write understandable, flexible, maintainable, and efficient C++ code. Even if you are a seasoned C++ developer, there are nuggets and data points in this book that you will find useful in your work. If you don't take care with your code, you can produce a large, messy, and unmaintainable beast in any programming language. However, C++ projects in particular are prone to be messy and tend to slip into bad habits. Lots of C++ code that is written today looks as if it was written in the 1980s. It seems that C++ developers have been forg otten by those who preach Software Craftsmanship and Clean Code principles. The Web is full of bad, but apparently very fast and highly optimized C++ code examples, with cruel syntax that completely ignores elementary principles of good design and well-written code. This book will explain how to avoid this scenario and how to get the most out of your C++ code. You'll find your coding becomes more efficient and, importantly, more fun. What You'll Learn Gain sound principles and rules for clean coding in C++ Carry out test driven development (TDD) Discover C++ design patterns and idioms Apply these design patterns Who This Book Is For Any C++ developer and software engineer with an interest in producing better code. COMPUTERS,Languages,General

PHP and MySQL for Dynamic Web Sites Learn PHP and MySQL programming— the quick and easy way! Easy visual approach uses demonstrations and real-world examples to guide you step by step through advanced techniques for dynamic Web development using PHP and MySQL. • Concise steps and explanations let you get up and running in no time. • Essential reference guide keeps you coming back again and again. • Whether you’re new to programming or an experienced veteran just needing to get up to speed on PHP and MySQL, this book will teach you all you need to know, including the latest changes in the languages, and much more! COMPUTERS,Languages,General

Software Testing Automation Tips Quickly access 50 tips for software test engineers using automated methods. The tips point to practices that save time and increase the accuracy and reliability of automated test techniques. Techniques that play well during demos of testing tools often are not the optimal techniques to apply on a running project. This book highlights those differences, helping you apply techniques that are repeatable and callable in professionally run software development projects. Emphasis is placed on creating tests that, while automated, are easily adapted as the software under construction evolves toward its final form. Techniques in the book are arranged into five categories: scripting, testing, the environment, running and logging of tests, and reviewing of the results. Every automation engineer sooner or later will face similar issues to the ones covered in these categories, and you will benefit from the simple and clear answers provided in this book. While the focus of the book is on the use of automated tools, the tips are not specific to any one vendor solution. The tips cover general issues that are faced no matter the specific tool, and are broadly applicable, often even to manual testing efforts. What You'll Learn Employ best-practices in automated test design Write test scripts that will easily be understood by others Choose the proper environment for running automated tests Avoid techniques that demo well, but do not scale in practice Manage tests effectively, including testing of test scripts themselves Know when to go beyond automation to employ manual methods instead Who This Book Is For Software test engineers working with automated testing tools, and for developers working alongside testing teams to create software products. The book will aid test engineers, team leads, project managers, software testers, and developers in producing quality software more easily, and in less time. COMPUTERS,Languages,General

Programming Rust Rust is a new systems programming language that combines the performance and low-level control of C and C++ with memory safety and thread safety. Rust’s modern, flexible types ensure your program is free of null pointer dereferences, double frees, dangling pointers, and similar bugs, all at compile time, without runtime overhead. In multi-threaded code, Rust catches data races at compile time, making concurrency much easier to use. Written by two experienced systems programmers, this book explains how Rust manages to bridge the gap between performance and safety, and how you can take advantage of it. Topics include: How Rust represents values in memory (with diagrams) Complete explanations of ownership, moves, borrows, and lifetimes Cargo, rustdoc, unit tests, and how to publish your code on crates.io, Rust’s public package repository High-level features like generic code, closures, collections, and iterators that make Rust productive and flexible Concurrency in Rust: threads, mutexes, channels, and atomics, all much safer to use than in C or C++ Unsafe code, and how to preserve the integrity of ordinary code that uses it Extended examples illustrating how pieces of the language fit together COMPUTERS,Languages,General

Begin to Code with Python Become a Python programmer–and have fun doing it! Start writing software that solves real problems, even if you have absolutely no programming experience! This friendly, easy, full-color book puts you in total control of your own learning, empowering you to build unique and useful programs. Microsoft has completely reinvented the beginning programmer’s tutorial, reflecting deep research into how today’s beginners learn, and why other books fall short. Begin to Code with Python is packed with innovations, from its “Snaps†prebuilt operations to its “Make Something Happen†projects. Whether you’re a total beginner or you’ve tried before, this guide will put the power, excitement, and fun of programming where it belongs: in your hands! Easy, friendly, and you’re in control! Learn how to… Get, install, and use powerful free tools to create modern Python programs Learn key concepts from 170 sample programs, and use them to jumpstart your own Discover exactly what happens when a program runs Approach program development with a professional perspective Learn the core elements of the Python language Build more complex software with classes, methods, and objects Organize programs so they’re easy to build and improve Capture and respond to user input Store and manipulate many types of real-world data Define custom data types to solve specific problems Create interactive games that are fun to play Build modern web and cloud-based applications Use pre-built libraries to quickly create powerful software Get code samples, including complete apps, at: https://aka.ms/BegintoCodePython/downloads About This Book For absolute beginners who’ve never written a line of code For anyone who’s been frustrated with other beginning programming books or courses For people who’ve started out with other languages and now want to learn Python Works with Windows PC, Apple Mac, Linux PC, or Raspberry Pi Includes mapping of MTA exam objectives that are covered in this book, as well as an appendix with further explanation of some of the topics on the exam COMPUTERS,Languages,General

Go in 24 Hours, Sams Teach Yourself In just 24 sessions of one hour or less, Sams Teach Yourself Go in 24 Hours will help new and experienced programmers build software that’s simpler, more reliable, and far more scalable. This book’s straightforward, step-by-step approach guides you from setting up your environment through testing and deploying powerful solutions. Using practical examples, expert Go developer George Ornbo walks you through Go’s fundamental constructs, demonstrates its breakthrough features for concurrent and network programming, and illuminates Go’s powerful new idioms. Every lesson builds on what you’ve already learned, giving you a rock-solid foundation for real-world success. Step-by-step instructions carefully walk you through the most common Go programming tasks and techniques Quizzes and exercises help you test your knowledge and stretch your skills Practical, hands-on examples show you how to apply what you learn Notes and Tips point out shortcuts, solutions, and problems to avoid Two bonus chapters available online: Hour 25, “Creating a RESTful JSON API,†and Hour 26 “Creating a TCP Chat Server†Learn how to… · Get productive quickly with Go development tools and web servers · Master core features, including strings, functions, structs, and methods · Work with types, variables, functions, and control structures · Make the most of Go’s arrays, slices, and maps · Write powerful concurrent software with Goroutines and channels · Handle program errors smoothly · Promote code reuse with packages · Master Go’s unique idioms for highly effective coding · Use regular expressions and time/date functions · Test and benchmark Go code · Write basic command-line programs, HTTP servers, and HTTP clients · Efficiently move Go code into production · Build basic TCP chat servers and JSON APIs Register your book at informit.com/register for convenient access to the two bonus chapters online, downloads, updates, and/or corrections as they become available. COMPUTERS,Languages,General

Microservice Patterns and Best Practices Explore the concepts and tools you need to discover the world of microservices with various design patterns About This Book Get to grips with the microservice architecture and build enterprise-ready microservice applications Learn design patterns and the best practices while building a microservice application Obtain hands-on techniques and tools to create high-performing microservices resilient to possible fails Who This Book Is For This book is for architects and senior developers who would like implement microservice design patterns in their enterprise application development. The book assumes some prior programming knowledge. What You Will Learn How to break monolithic application into microservices Implement caching strategies, CQRS and event sourcing, and circuit breaker patterns Incorporate different microservice design patterns, such as shared data, aggregator, proxy, and chained Utilize consolidate testing patterns such as integration, signature, and monkey tests Secure microservices with JWT, API gateway, and single sign on Deploy microservices with continuous integration or delivery, Blue-Green deployment In Detail Microservices are a hot trend in the development world right now. Many enterprises have adopted this approach to achieve agility and the continuous delivery of applications to gain a competitive advantage. This book will take you through different design patterns at different stages of the microservice application development along with their best practices. Microservice Patterns and Best Practices starts with the learning of microservices key concepts and showing how to make the right choices while designing microservices. You will then move onto internal microservices application patterns, such as caching strategy, asynchronism, CQRS and event sourcing, circuit breaker, and bulkheads. As you progress, you'll learn the design patterns of microservices. The book will guide you on where to use the perfect design pattern at the application development stage and how to break monolithic application into microservices. You will also be taken through the best practices and patterns involved while testing, securing, and deploying your microservice application. At the end of the book, you will easily be able to create interoperable microservices, which are testable and prepared for optimum performance. Style and approach Comprehensive guide that uses architectural patterns with the best choices involved in application development COMPUTERS,Languages,General

Python Testing with pytest Do less work when testing your Python code, but be just as expressive, just as elegant, and just as readable. The pytest testing framework helps you write tests quickly and keep them readable and maintainable - with no boilerplate code. Using a robust yet simple fixture model, it's just as easy to write small tests with pytest as it is to scale up to complex functional testing for applications, packages, and libraries. This book shows you how. For Python-based projects, pytest is the undeniable choice to test your code if you're looking for a full-featured, API-independent, flexible, and extensible testing framework. With a full-bodied fixture model that is unmatched in any other tool, the pytest framework gives you powerful features such as assert rewriting and plug-in capability - with no boilerplate code. With simple step-by-step instructions and sample code, this book gets you up to speed quickly on this easy-to-learn and robust tool. Write short, maintainable tests that elegantly express what you're testing. Add powerful testing features and still speed up test times by distributing tests across multiple processors and running tests in parallel. Use the built-in assert statements to reduce false test failures by separating setup and test failures. Test error conditions and corner cases with expected exception testing, and use one test to run many test cases with parameterized testing. Extend pytest with plugins, connect it to continuous integration systems, and use it in tandem with tox, mock, coverage, unittest, and doctest. Write simple, maintainable tests that elegantly express what you're testing and why. What You Need: The examples in this book are written using Python 3.6 and pytest 3.0. However, pytest 3.0 supports Python 2.6, 2.7, and Python 3.3-3.6. COMPUTERS,Languages,General

Design Patterns in Modern C++ Apply modern C++17 to the implementations of classic design patterns. As well as covering traditional design patterns, this book fleshes out new patterns and approaches that will be useful to C++ developers. The author presents concepts as a fun investigation of how problems can be solved in different ways, along the way using varying degrees of technical sophistication and explaining different sorts of trade-offs. Design Patterns in Modern C++ also provides a technology demo for modern C++, showcasing how some of its latest features (e.g., coroutines) make difficult problems a lot easier to solve. The examples in this book are all suitable for putting into production, with only a few simplifications made in order to aid readability. What You Will Learn Apply design patterns to modern C++ programming Use creational patterns of builder, factories, prototype and singleton Implement structural patterns such as adapter, bridge, decorator, facade and more Work with the behavioral patterns such as chain of responsibility, command, iterator, mediator and more Apply functional design patterns such as Monad and more Who This Book Is For Those with at least some prior programming experience, especially in C++. COMPUTERS,Languages,General

PowerShell for Sysadmins Learn to use PowerShell, Microsoft's scripting language, to automate real-world tasks that IT professionals and system administrators deal with every day. Save Time. Automate. PowerShell® is both a scripting language and an administrative shell that lets you control and automate nearly every aspect of IT. In PowerShell for Sysadmins, five-time Microsoft® MVP "Adam the Automator" Bertram shows you how to use PowerShell to manage and automate your desktop and server environments so that you can head out for an early lunch. You'll learn how to: • Combine commands, control flow, handle errors, write scripts, run scripts remotely, and test scripts with the PowerShell testing framework, Pester • Parse structured data like XML and JSON, work with common domains (like Active Directory, Azure, and Amazon Web Services), and create a real-world server inventory script • Design and build a PowerShell module to demonstrate PowerShell isn't just about ad-hoc scripts • Use PowerShell to create a hands-off, completely automated Windows deployment • Build an entire Active Directory forest from nothing but a Hyper-V host and a few ISO files • Create endless Web and SQL servers with just a few lines of code! Real-world examples throughout help bridge the gap between theory and actual system, and the author's anecdotes keep things lively. Stop with the expensive software and fancy consultants. Learn how to manage your own environment with PowerShell for Sysadmins and make everyone happy. Covers Windows PowerShell v5.1 COMPUTERS,Languages,General

Getting Clojure Behind every programming language lies a vision of how programs should be built. The vision behind Clojure is of a radically simple language framework holding together a sophisticated collection of programming features. Learning Clojure involves much more than just learning the mechanics of the language. To really get Clojure you need to understand the ideas underlying this structure of framework and features. You need this book: an accessible introduction to Clojure that focuses on the ideas behind the language as well as the practical details of writing code. Clojure attracts developers on the cutting edge and is arguably the best language for learning to program in the functional style without compromise. But this comes with a steep learning curve. Getting Clojure directly addresses this by teaching you how to think functionally as it teaches you the language. You'll learn about Clojure's powerful data structures and high-level functions, but you'll also learn what it means for a language to be functional, and how to think in Clojure's functional way. Each chapter of Getting Clojure takes a feature or two or three from the language, explains the syntax and the mechanics behind that feature so that you can make it work before digging into the deeper questions: What is the thinking behind the feature? And how does it fit in with the rest of the language? In Getting Clojure you'll learn Clojure's very simple syntax, but you'll also learn why that syntax is integral the way the language is constructed. You'll discover that most data structures in Clojure are immutable, but also why that leads to more reliable programs. And you'll see how easy it is to write Clojure functions and also how you can use those functions to build complex and capable systems. With real-world examples of how working Clojure programmers use the language, Getting Clojure will help you see the challenges of programming through the eye of experienced Clojure developers. What You Need: You will need to some background in programming. To follow along with the examples in the book, you will need Java 6 or new, Clojure 1.8 or 1.9, and Leiningen 2. COMPUTERS,Languages,General

Practical Object-Oriented Design The Complete Guide to Writing Maintainable, Manageable, Pleasing, and Powerful Object-Oriented Applications Object-oriented programming languages exist to help you create beautiful, straightforward applications that are easy to change and simple to extend. Unfortunately, the world is awash with object-oriented (OO) applications that are difficult to understand and expensive to change. Practical Object-Oriented Design, Second Edition, immerses you in an OO mindset and teaches you powerful, real-world, object-oriented design techniques with simple and practical examples. Sandi Metz demonstrates how to build new applications that can “survive success†and repair existing applications that have become impossible to change. Each technique is illustrated with extended examples in the easy-to-understand Ruby programming language, all downloadable from the companion website, poodr.com. Fully updated for Ruby 2.5, this guide shows how to Decide what belongs in a single class Avoid entangling objects that should be kept separate Define flexible interfaces among objects Reduce programming overhead costs with duck typing Successfully apply inheritance Build objects via composition Whatever your previous object-oriented experience, this concise guide will help you achieve the superior outcomes you’re looking for. Register your book for convenient access to downloads, updates, and/or corrections as they become available. See inside book for details. COMPUTERS,Languages,General

Lua Quick Start Guide The easiest way to learn Lua programming Key Features The easiest way to learn Lua coding Use the Lua standard libraries and debug Lua code Embed Lua as a scripting language using the Lua C API Book Description Lua is a small, powerful and extendable scripting/programming language that can be used for learning to program, and writing games and applications, or as an embedded scripting language. There are many popular commercial projects that allow you to modify or extend them through Lua scripting, and this book will get you ready for that. This book is the easiest way to learn Lua. It introduces you to the basics of Lua and helps you to understand the problems it solves. You will work with the basic language features, the libraries Lua provides, and powerful topics such as object-oriented programming. Every aspect of programming in Lua, variables, data types, functions, tables, arrays and objects, is covered in sufficient detail for you to get started. You will also find out about Lua's module system and how to interface with the operating system. After reading this book, you will be ready to use Lua as a programming language to write code that can interface with the operating system, automate tasks, make playable games, and much more. This book is a solid starting point for those who want to learn Lua in order to move onto other technologies such as Love2D or Roblox. A quick start guide is a focused, shorter title that provides a faster paced introduction to a technology. It is designed for people who don't need all the details at this point in their learning curve. This presentation has been streamlined to concentrate on the things you really need to know. What you will learn Understand the basics of programming the Lua language Understand how to use tables, the data structure that makes Lua so powerful Understand object-oriented programming in Lua using metatables Understand standard LUA libraries for math, file io, and more Manipulate string data using Lua Understand how to debug Lua applications quickly and effciently Understand how to embed Lua into applications with the Lua C API Who this book is for This book is for developers who want to get up and running with Lua. This book is ideal for programmers who want to learn to embed Lua in their own applications, as well as for beginner programmers who have never coded before. COMPUTERS,Languages,General

Julia 1.0 Programming Enter the exciting world of Julia, a high-performance language for technical computing Key Features Leverage Julia's high speed and efficiency for your applications Work with Julia in a multi-core, distributed, and networked environment Apply Julia to tackle problems concurrently and in a distributed environment Book Description The release of Julia 1.0 is now ready to change the technical world by combining the high productivity and ease of use of Python and R with the lightning-fast speed of C++. Julia 1.0 programming gives you a head start in tackling your numerical and data problems. You will begin by learning how to set up a running Julia platform, before exploring its various built-in types. With the help of practical examples, this book walks you through two important collection types: arrays and matrices. In addition to this, you will be taken through how type conversions and promotions work. In the course of the book, you will be introduced to the homo-iconicity and metaprogramming concepts in Julia. You will understand how Julia provides different ways to interact with an operating system, as well as other languages, and then you'll discover what macros are. Once you have grasped the basics, you'll study what makes Julia suitable for numerical and scientific computing, and learn about the features provided by Julia. By the end of this book, you will also have learned how to run external programs. This book covers all you need to know about Julia in order to leverage its high speed and efficiency for your applications. What you will learn Set up your Julia environment to achieve high productivity Create your own types to extend the built-in type system Visualize your data in Julia with plotting packages Explore the use of built-in macros for testing and debugging, among other uses Apply Julia to tackle problems concurrently Integrate Julia with other languages such as C, Python, and MATLAB Who this book is for Julia 1.0 Programming is for you if you are a statistician or data scientist who wants a crash course in the Julia programming language while building big data applications. A basic knowledge of mathematics is needed to understand the various methods that are used or created during the course of the book to exploit the capabilities that Julia is designed with. COMPUTERS,Languages,General

Mastering Java 11 Update your Java knowledge with the latest features of Java 11, such as the low-Overhead Garbage Collector, Local-Variable Syntax for Lambda Parameters, and Dynamic Class-File Constants Key Features Explore the latest features in Java 9,Java 10, and Java 11 Enhance your Java application development and migration approaches Full coverage of modular Java applications, G1 Garbage Collector, JMH Book Description Java 11 is a long-term release and its new features add to the richness of the language. It emphasizes variable-type inference, performance improvements, along with simplified multithreading. The Java platform has a special emphasis on modularity, making this the programming platform of choice for millions of developers. The modern Java platform can be used to build robust software applications, including enterprise-level and mobile applications. Fully updated for Java 11, this book stands to help any Java developer enjoy the richness of the Java programming language. Mastering Java 11 is your one-stop guide to fully understanding recent Java platform updates. It contains detailed explanations of the recent features introduced in Java 9, Java 10, and Java 11 along with obtaining practical guidance on how to apply the new features. As you make your way through the chapters, you'll discover further information on the developments of the Java platform and learn about the changes introduced by the variable handles and Project Coin, along with several enhancements in relation to import statements processing. In the concluding chapters, you'll learn to improve your development productivity, making your applications more efficient. You'll also be able to get to grips with the command-line flags with respect to various utilities and the command-line utility changes featured in the current Java platform. By the end of the book, you'll have obtained an advanced level understanding of the Java platform and its recent changes. What you will learn Write modular Java applications Migrate existing Java applications to modular ones Understand how the default G1 garbage collector works Leverage the possibilities provided by the newly introduced Java Shell Performance test your application effectively with the JVM harness Learn how Java supports the HTTP 2.0 standard Find out how to use the new Process API Explore the additional enhancements and features of Java 9, 10, and 11 Who this book is for Mastering Java 11 is for experienced Java developers with a solid understanding of the Java language and want to progress to an advanced level. COMPUTERS,Languages,General

Practical TLA+ Learn how to design complex, correct programs and fix problems before writing a single line of code. This book is a practical, comprehensive resource on TLA+ programming with rich, complex examples. Practical TLA+ shows you how to use TLA+ to specify a complex system and test the design itself for bugs. You’ll learn how even a short TLA+ spec can find critical bugs. Start by getting your feet wet with an example of TLA+ used in a bank transfer system, to see how it helps you design, test, and build a better application. Then, get some fundamentals of TLA+ operators, logic, functions, PlusCal, models, and concurrency. Along the way you will discover how to organize your blueprints and how to specify distributed systems and eventual consistency. Finally, you’ll put what you learn into practice with some working case study applications, applying TLA+ to a wide variety of practical problems: from algorithm performance and data structures to business code and MapReduce. After reading and using this book, you'll have what you need to get started with TLA+ and how to use it in your mission-critical applications. What You'll Learn Read and write TLA+ specs Check specs for broken invariants, race conditions, and liveness bugs Design concurrency and distributed systems Learn how TLA+ can help you with your day-to-day production work Who This Book Is For Those with programming experience who are new to design and to TLA+. COMPUTERS,Languages,General

Testing and Tuning Market Trading Systems Build, test, and tune financial, insurance or other market trading systems using C++ algorithms and statistics. You’ve had an idea and have done some preliminary experiments, and it looks promising. Where do you go from here? Well, this book discusses and dissects this case study approach. Seemingly good backtest performance isn't enough to justify trading real money. You need to perform rigorous statistical tests of the system's validity. Then, if basic tests confirm the quality of your idea, you need to tune your system, not just for best performance, but also for robust behavior in the face of inevitable market changes. Next, you need to quantify its expected future behavior, assessing how bad its real-life performance might actually be, and whether you can live with that. Finally, you need to find its theoretical performance limits so you know if its actual trades conform to this theoretical expectation, enabling you to dump the system if it does not live up to expectations. This book does not contain any sure-fire, guaranteed-riches trading systems. Those are a dime a dozen... But if you have a trading system, this book will provide you with a set of tools that will help you evaluate the potential value of your system, tweak it to improve its profitability, and monitor its on-going performance to detect deterioration before it fails catastrophically. Any serious market trader would do well to employ the methods described in this book. What You Will Learn See how the 'spaghetti-on-the-wall' approach to trading system development can be done legitimately Detect overfitting early in development Estimate the probability that your system's backtest results could have been due to just good luck Regularize a predictive model so it automatically selects an optimal subset of indicator candidates Rapidly find the global optimum for any type of parameterized trading system Assess the ruggedness of your trading system against market changes Enhance the stationarity and information content of your proprietary indicators Nest one layer of walkforward analysis inside another layer to account for selection bias in complex trading systems Compute a lower bound on your system's mean future performance Bound expected periodic returns to detect on-going system deterioration before it becomes severe Estimate the probability of catastrophic drawdown Who This Book Is For Experienced C++ programmers, developers, and software engineers. Prior experience with rigorous statistical procedures to evaluate and maximize the quality of systems is recommended as well. COMPUTERS,Languages,General

Julia 1.0 Programming Cookbook Discover the new features and widely used packages in Julia to solve complex computational problems in your statistical applications. Key Features Address the core problems of programming in Julia with the most popular packages for common tasks Tackle issues while working with Databases and Parallel data processing with Julia Explore advanced features such as metaprogramming, functional programming, and user defined types Book Description Julia, with its dynamic nature and high-performance, provides comparatively minimal time for the development of computational models with easy-to-maintain computational code. This book will be your solution-based guide as it will take you through different programming aspects with Julia. Starting with the new features of Julia 1.0, each recipe addresses a specific problem, providing a solution and explaining how it works. You will work with the powerful Julia tools and data structures along with the most popular Julia packages. You will learn to create vectors, handle variables, and work with functions. You will be introduced to various recipes for numerical computing, distributed computing, and achieving high performance. You will see how to optimize data science programs with parallel computing and memory allocation. We will look into more advanced concepts such as metaprogramming and functional programming. Finally, you will learn how to tackle issues while working with databases and data processing, and will learn about on data science problems, data modeling, data analysis, data manipulation, parallel processing, and cloud computing with Julia. By the end of the book, you will have acquired the skills to work more effectively with your data What you will learn Boost your code's performance using Julia's unique features Organize data in to fundamental types of collections: arrays and dictionaries Organize data science processes within Julia and solve related problems Scale Julia computations with cloud computing Write data to IO streams with Julia and handle web transfer Define your own immutable and mutable types Speed up the development process using metaprogramming Who this book is for This book is for developers who would like to enhance their Julia programming skills and would like to get some quick solutions to their common programming problems. Basic Julia programming knowledge is assumed. COMPUTERS,Languages,General

Introduction to Python for Science and Engineering Series in Computational Physics Steven A. Gottlieb and Rubin H. Landau, Series Editors Introduction to Python for Science and Engineering This guide offers a quick and incisive introduction to Python programming for anyone. The author has carefully developed a concise approach to using Python in any discipline of science and engineering, with plenty of examples, practical hints, and insider tips. Readers will see why Python is such a widely appealing program, and learn the basics of syntax, data structures, input and output, plotting, conditionals and loops, user-defined functions, curve fitting, numerical routines, animation, and visualization. The author teaches by example and assumes no programming background for the reader. David J. Pine is the Silver Professor and Professor of Physics at New York University, and Chair of the Department of Chemical and Biomolecular Engineering at the NYU Tandon School of Engineering. He is an elected fellow of the American Physical Society and American Association for the Advancement of Science (AAAS), and is a Guggenheim Fellow. COMPUTERS,Languages,General

Mastering Go Exploring the major features and packages of Go, along with its types and data-structures, enabling the reader to write threadsafe, concurrent cloud, and network applications About This Book Not your typical introduction to the Golang programming language Exploring Golang cradle to grave, completes the developer's Golang education A thorough exploration into the core libraries and Golang features, that usually are taken for granted In depth explanation, detailing the rationale behind composite data types, Golang concurrency, and the Golang networking library Who This Book Is For This book is for Golang programmers. You should have previously read an introductory book on Go, or to have worked through the Tour of Go or an equivalent online course. This book will definitely help to remember the basic concepts of concurrency, but network programming will be explained. A certain amount of previous coding and production experience would be helpful. What You Will Learn Understand the design choices of Golang syntax Know enough Go internals to be able to optimize Golang code Appreciate concurrency models available in Golang Understand the interplay of systems and networking code Write server-level code that plays well in all environments Understand the context and appropriate use of Go data types and data structures In Detail The Go programming language, often referred to as Golang (albeit wrongly), is really making strides, with some masterclass developments, architected by the greatest programming minds. Tobias Lutke, CEO of Shopify, recently quoted as saying “Go will be the server language of the futureâ€, powerful words, with much ambition. Go programmers are in high demand, but more controversially, Go takes the stage, where C and Unix programmers previously led the way. The growth of the Go language has seen it become the means by which systems, networking, web, and cloud applications are implemented. Comfortable with syntax, you'll benefit by mastering the use of the libraries and utilise its features, speed, and efficiency, for which the Go ecology is justly famous. You already know a little Go syntax and you've written some small projects, most Go programmers face the difficulty of having to integrate their Golang skills with production code. Typical introductions to Go programming, often stop short of this transition, the author continue on, showing you just how to tackle this. Offering a compendium of Go, the book begins with an account of how Go has been implemented, also, the reader will benefit from a dedicated chapter, an in-depth account of concurrency, systems and network programming, imperative for modern-day native cloud development. Style and approach The approach is a practical one, very much hands-on, and a bit more demanding and in-depth than your average programming language introduction. The aim is to enable a Golang programmer to write and put in production a complete Golang application, regardless of the environment, which will be achieved by a masterclass of well- formed exercises. COMPUTERS,Languages,General

Julia Programming Projects A step-by-step guide that demonstrates how to build simple-to-advanced applications through examples in Julia Lang 1.x using modern tools Key Features Work with powerful open-source libraries for data wrangling, analysis, and visualization Develop full-featured, full-stack web applications Learn to perform supervised and unsupervised machine learning and time series analysis with Julia Book Description Julia is a new programming language that offers a unique combination of performance and productivity. Its powerful features, friendly syntax, and speed are attracting a growing number of adopters from Python, R, and Matlab, effectively raising the bar for modern general and scientific computing. After six years in the making, Julia has reached version 1.0. Now is the perfect time to learn it, due to its large-scale adoption across a wide range of domains, including fintech, biotech, education, and AI. Beginning with an introduction to the language, Julia Programming Projects goes on to illustrate how to analyze the Iris dataset using DataFrames. You will explore functions and the type system, methods, and multiple dispatch while building a web scraper and a web app. Next, you'll delve into machine learning, where you'll build a books recommender system. You will also see how to apply unsupervised machine learning to perform clustering on the San Francisco business database. After metaprogramming, the final chapters will discuss dates and time, time series analysis, visualization, and forecasting. We'll close with package development, documenting, testing and benchmarking. By the end of the book, you will have gained the practical knowledge to build real-world applications in Julia. What you will learn Leverage Julia's strengths, its top packages, and main IDE options Analyze and manipulate datasets using Julia and DataFrames Write complex code while building real-life Julia applications Develop and run a web app using Julia and the HTTP package Build a recommender system using supervised machine learning Perform exploratory data analysis Apply unsupervised machine learning algorithms Perform time series data analysis, visualization, and forecasting Who this book is for Data scientists, statisticians, business analysts, and developers who are interested in learning how to use Julia to crunch numbers, analyze data and build apps will find this book useful. A basic knowledge of programming is assumed. COMPUTERS,Languages,General

AWS Certified Cloud Practitioner (CLF-C01) Cert Guide This is the eBook version of the print title. Note that the eBook does not provide access to the practice test software that accompanies the print book. Learn, prepare, and practice for AWS Certified Cloud Practitioner (CLF-C01) exam success with this Cert Guide from Pearson IT Certification, a leader in IT Certification learning. Master AWS Certified Cloud Practitioner (CLF-C01) exam topics Assess your knowledge with chapter-ending quizzes Review key concepts with exam preparation tasks AWS Certified Cloud Practitioner (CLF-C01) Cert Guide is a best-of-breed exam study guide. Best-selling author and expert instructor Anthony Sequeira shares preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. Material is presented in a concise manner, focusing on increasing your understanding and retention of exam topics. The book presents you with an organized test preparation routine through the use of proven series elements and techniques. Exam topic lists make referencing easy. Chapter-ending Exam Preparation Tasks help you drill on key concepts you must know thoroughly. Review questions help you assess your knowledge, and a final preparation chapter guides you through tools and resources to help you craft your final study plan. Well-regarded for its level of detail, assessment features, and challenging review questions and exercises, this study guide helps you master the concepts and techniques that will enable you to succeed on the exam the first time. The study guide helps you master all the topics on the AWS Certified Cloud Practitioner exam, including how to: Define the AWS Cloud and its value proposition, and discuss its economics Define the AWS Shared Responsibility model, and key AWS security and compliance concepts Identify AWS access management capabilities Define methods of deploying the AWS Cloud and operating within Define the AWS global infrastructure and identify core AWS services Recognize and compare AWS pricing models and account structures Identify support resources for security, AWS cloud technology, and billing COMPUTERS,Languages,General

Head First Go What will you learn from this book? Go makes it easy to build software that’s simple, reliable, and efficient. Andthis book makes it easy for programmers like you to get started. Googledesigned Go for high-performance networking and multiprocessing, but—like Python and JavaScript—the language is easy to read and use. With thispractical hands-on guide, you’ll learn how to write Go code using clearexamples that demonstrate the language in action. Best of all, you’ll understandthe conventions and techniques that employers want entry-level Godevelopers to know. Why does this book look so different? Based on the latest research in cognitive science and learning theory, HeadFirst Go uses a visually rich format to engage your mind rather than a textheavyapproach that puts you to sleep. Why waste your time struggling withnew concepts? This multisensory learning experience is designed for theway your brain really works. COMPUTERS,Languages,General

Think Julia If you’re just learning how to program, Julia is an excellent JIT-compiled, dynamically typed language with a clean syntax. This hands-on guide uses Julia 1.0 to walk you through programming one step at a time, beginning with basic programming concepts before moving on to more advanced capabilities, such as creating new types and multiple dispatch. Designed from the beginning for high performance, Julia is a general-purpose language ideal for not only numerical analysis and computational science but also web programming and scripting. Through exercises in each chapter, you’ll try out programming concepts as you learn them. Think Julia is perfect for students at the high school or college level as well as self-learners and professionals who need to learn programming basics. Start with the basics, including language syntax and semantics Get a clear definition of each programming concept Learn about values, variables, statements, functions, and data structures in a logical progression Discover how to work with files and databases Understand types, methods, and multiple dispatch Use debugging techniques to fix syntax, runtime, and semantic errors Explore interface design and data structures through case studies COMPUTERS,Languages,General

Mastering VBA for Microsoft Office 365 Customize and ramp-up Office 365 applications NOTE: Please click Downloads (located in the menu on the left) to download “Full Code Download.†The revised 2019 edition of Mastering VBA Microsoft Office 365 offers an accessible guide that shows how to extend the capabilities of Office 365 applications with VBA programming. Written in clear terms and understandable language, the book includes systematic tutorials and contains both intermediate and advanced content for experienced VB developers. Designed to be comprehensive, the book addresses not just one Office application, but the entire Office suite. To enhance understanding, the content is explored in real-world projects in Word, Excel, Outlook, and PowerPoint. Since the technical programming methods in the Office applications continue to evolve, the updated 2019 edition reviews the changes to the program. Code libraries, the API, and the object model for each Office program have been modified during the three years since the last version of this book. Various elements within VBA have been deprecated or replaced, and the surface UI changed as well. The updated 2019 edition covers topics such as: • Recording macros and getting started with VBA • Learning how to work with VBA • Using loops and functions • Using message boxes, input boxes, and dialog boxes • Creating effective code • XML-based files, ActiveX, the developer tab, content controls, add-ins, embedded macros, and security Written for all levels of Microsoft Office 365 users, Mastering VBA Microsoft Office 365: 2019 Edition explains how to customize and automate the Office suite of applications. COMPUTERS,Languages,General

The Python Workbook While other textbooks devote their pages to explaining introductory programming concepts, The Python Workbook focuses exclusively on exercises, following the philosophy that computer programming is a skill best learned through experience and practice. Designed to support and encourage hands-on learning about programming, this student-friendly work contains 174 exercises, spanning a variety of academic disciplines and everyday situations. Solutions to selected exercises are also provided, supported by brief annotations that explain the technique used to solve the problem, or highlight specific points of Python syntax. No background knowledge is required to solve the exercises, beyond the material covered in a typical introductory Python programming course. Features: uses an accessible writing style and easy-to-follow structure; includes a mixture of classic exercises from the fields of computer science and mathematics, along with exercises that connect to other academic disciplines; presents the solutions to approximately half of the exercises; provides annotations alongside the solutions, which explain the approach taken to solve the problem and relevant aspects of Python syntax; offers a variety of exercises of different lengths and difficulties; contains exercises that help the development of programming skills using if statements, loops, basic functions, lists, dictionaries, files, and recursive functions. Undergraduate students undergoing their first programming course and wishing to enhance their programming abilities will find the exercises and solutions provided in this book to be ideal for their needs. COMPUTERS,Languages,General

A Beginners Guide to Python 3 Programming This textbook on Python 3 explains concepts such as variables and what they represent, how data is held in memory, how a for loop works and what a string is. It also introduces key concepts such as functions, modules and packages as well as object orientation and functional programming. Each section is prefaced with an introductory chapter, before continuing with how these ideas work in Python. Topics such as generators and coroutines are often misunderstood and these are explained in detail, whilst topics such as Referential Transparency, multiple inheritance and exception handling are presented using examples. A Beginners Guide to Python 3 Programming provides all you need to know about Python, with numerous examples provided throughout including several larger worked case studies illustrating the ideas presented in the previous chapters. COMPUTERS,Languages,General

Introducing Markdown and Pandoc Discover how to write manuscripts in Markdown and translate them with Pandoc into different output formats. You’ll use Markdown to annotate text formatting information with a strong focus on semantic information: you can annotate your text with information about where chapters and sections start, but not how chapter and heading captions should be formatted. As a result, you’ll decouple the structure of a text from how it is visualized and make it easier for you to produce different kinds of output. The same text can easily be formatted as HTML, PDF, or Word documents, with various visual styles, by tools that understand the markup annotations. Finally, you’ll learn to use Pandoc, a tool for translating between different markup languages, such as LaTeX, HTML, and Markdown. This book will not describe all the functionality that Pandoc provides, but will teach you how to translate Markdown documents, how to customize your documents using templates, and how to extend Pandoc’s functionality using filters. If that is something you are interested in, Introducing Markdown and Pandoc will get you started. With this set of skills you’ll be able to write more efficiently without worrying about needless formatting and other distractions. What You Will Learn Why and how to use Markdown and Pandoc Write Markdown Use extensions available in Pandoc and Markdown Write math and code blocks Use templates and produce documents Who This Book Is For Programmers and problem solvers looking for technical documentation solutions. COMPUTERS,Languages,General

Mastering Go Dive deep into the Go language and become an expert Go developer Key Features Second edition of the bestselling guide to advanced Go programming, expanded to cover machine learning, more Go packages and a range of modern development techniques Completes the Go developer's education with real-world guides to building high-performance production systems Packed with practical examples and patterns to apply to your own development work Clearly explains Go nuances and features to remove the frustration from Go development Book Description Often referred to (incorrectly) as Golang, Go is the high-performance systems language of the future. Mastering Go, Second Edition helps you become a productive expert Go programmer, building and improving on the groundbreaking first edition. Mastering Go, Second Edition shows how to put Go to work on real production systems. For programmers who already know the Go language basics, this book provides examples, patterns, and clear explanations to help you deeply understand Go's capabilities and apply them in your programming work. The book covers the nuances of Go, with in-depth guides on types and structures, packages, concurrency, network programming, compiler design, optimization, and more. Each chapter ends with exercises and resources to fully embed your new knowledge. This second edition includes a completely new chapter on machine learning in Go, guiding you from the foundation statistics techniques through simple regression and clustering to classification, neural networks, and anomaly detection. Other chapters are expanded to cover using Go with Docker and Kubernetes, Git, WebAssembly, JSON, and more. If you take the Go programming language seriously, the second edition of this book is an essential guide on expert techniques. What you will learn Clear guidance on using Go for production systems Detailed explanations of how Go internals work, the design choices behind the language, and how to optimize your Go code A full guide to all Go data types, composite types, and data structures Master packages, reflection, and interfaces for effective Go programming Build high-performance systems networking code, including server and client-side applications Interface with other systems using WebAssembly, JSON, and gRPC Write reliable, high-performance concurrent code Build machine learning systems in Go, from simple statistical regression to complex neural networks Who this book is for Mastering Go, Second Edition is for Go programmers who already know the language basics, and want to become expert Go practitioners. COMPUTERS,Languages,General

Professional JavaScript Develop your JavaScript programming skills by learning strategies and techniques commonly used in modern full-stack application development Key Features Write and deploy full-stack applications efficiently with JavaScript Delve into JavaScript's multiple programming paradigms Get up to speed with core concepts such as modularity and functional programming to write efficient code Book Description In depth knowledge of JavaScript makes it easier to learn a variety of other frameworks, including React, Angular, and related tools and libraries. This book is designed to help you cover the core JavaScript concepts you need to build modern applications. You'll start by learning how to represent an HTML document in the Document Object Model (DOM). Then, you'll combine your knowledge of the DOM and Node.js to create a web scraper for practical situations. As you read through further lessons, you'll create a Node.js-based RESTful API using the Express library for Node.js. You'll also understand how modular designs can be used for better reusability and collaboration with multiple developers on a single project. Later lessons will guide you through building unit tests, which ensure that the core functionality of your program is not affected over time. The book will also demonstrate how constructors, async/await, and events can load your applications quickly and efficiently. Finally, you'll gain useful insights into functional programming concepts such as immutability, pure functions, and higher-order functions. By the end of this book, you'll have the skills you need to tackle any real-world JavaScript development problem using a modern JavaScript approach, both for the client and server sides. What you will learn Apply the core concepts of functional programming Build a Node.js project that uses the Express.js library to host an API Create unit tests for a Node.js project to validate it Use the Cheerio library with Node.js to create a basic web scraper Develop a React interface to build processing flows Use callbacks as a basic way to bring control back Who this book is for If you want to advance from being a frontend developer to a full-stack developer and learn how Node.js can be used for hosting full-stack applications, this is an ideal book for you. After reading this book, you'll be able to write better JavaScript code and learn about the latest trends in the language. To easily grasp the concepts explained here, you should know the basic syntax of JavaScript and should've worked with popular frontend libraries such as jQuery. You should have also used JavaScript with HTML and CSS but not necessarily Node.js. COMPUTERS,Languages,General

Refactoring TypeScript Discover various techniques to develop maintainable code and keep it in shape. Key Features Learn all about refactoring - why it is important and how to do it Discover easy ways to refactor code with examples Explore techniques that can be applied to most other programming languages Book Description Refactoring improves your code without changing its behavior. With refactoring, the best approach is to apply small targeted changes to a codebase. Instead of doing a huge sweeping change to your code, refactoring is better as a long-term and continuous enterprise. Refactoring TypeScript explains how to spot bugs and remove them from your code. You'll start by seeing how wordy conditionals, methods, and null checks make code unhealthy and unstable. Whether it is identifying messy nested conditionals or removing unnecessary methods, this book will show various techniques to avoid these pitfalls and write code that is easier to understand, maintain, and test. By the end of the book, you'll have learned some of the main causes of unhealthy code, tips to identify them and techniques to address them. What you will learn Spot and fix common code smells to create code that is easier to read and understand Discover ways to identify long methods and refactor them Create objects that keep your code flexible, maintainable, and testable Apply the Single Responsibility Principle to develop less-coupled code Discover how to combine different refactoring techniques Learn ways to solve the issues caused by overusing primitives Who this book is for This book is designed for programmers who are looking to explore various refactoring techniques to develop healthy and maintainable code. Some experience in JavaScript and TypeScript can help you easily grasp the concepts explained in this book. COMPUTERS,Languages,General

Julia Quick Syntax Reference This quick Julia programming language guide is a condensed code and syntax reference to the Julia 1.x programming language, updated with the latest features of the Julia APIs, libraries, and packages. It presents the essential Julia syntax in a well-organized format that can be used as a handy reference. This book provides an introduction that reveals basic Julia structures and syntax; discusses data types, control flow, functions, input/output, exceptions, metaprogramming, performance, and more. Additionally, you'll learn to interface Julia with other programming languages such as R for statistics or Python. You will learn how to use Julia packages for data analysis, numerical optimization and symbolic computation, and how to disseminate your results in dynamic documents or interactive web pages. In this book, the focus is on providing important information as quickly as possible. It is packed with useful information and is a must-have for any Julia programmer. What You Will Learn Set up the software needed to run Julia and your first Hello World example Work with types and the different containers that Julia makes available for rapid application development Use vectorized, classical loop-based code, logical operators, and blocks Explore Julia functions by looking at arguments, return values, polymorphism, parameters, anonymous functions, and broadcasts Build custom structures in Julia Interface Julia with other languages such as C/C++, Python, and R Program a richer API, modifying the code before it is executed using expressions, symbols, macros, quote blocks, and more Maximize your code’s performance Who This Book Is For Experienced programmers new to Julia, as well as existing Julia coders new to the now stable Julia version 1.0 release. COMPUTERS,Languages,General

Quick Start Guide to Dart Programming Get started with Dart and learn to program with this language suitable for high-performing, modern applications. You'll gain the basics and be ready to move to the next level: web and mobile apps. While you won't learn the specifics of programming web and mobile apps, you will have the foundation to take your Dart skills in that direction. This book starts with an introduction to the Dart IDE, after which you will take a look at the various components of the Dart programming language. You will look at types and variables, and get to know the significance of collections and arrays in Dart. Once you've familiarized yourself with the initial components of Dart, you will see how flow of control and looping can be achieved by using if, else, and conditional expressions. Moving on to functions and objects, you will dig deeper into the concepts of object oriented programming to gauge the importance of constructors in Dart. You will then discover more about inheritance and mixins, seeing how they contain methods for use by other classes. After gauging the importance of abstract classes and methods, you will learn more about anonymous functions such as lambdas and closures. You will then take a look at key data structures including lists and maps to aid you in organizing your information for storage and retrieval. After all this you’ll move on to managing exceptions arising from executing your program. Finally, Dart programming relies heavily on libraries to perform a variety of functions. You will cover some of these packages and libraries, including dart:core and dart:math, and also build a backend server with the help of the Dart core libraries. What You Will Learn Use variables and conditionals in Dart Work with arrays and collections Apply flow control and looping Explore data structures and their use Handle exceptions Use Dart packages and libraries to build a backend server Who This Book Is For Those new to Dart programming who aim to get a quick introduction to its concepts and programming principles. Readers with no coding experience can also take advantage of this book. COMPUTERS,Languages,General

Practical MATLAB Deep Learning Harness the power of MATLAB for deep-learning challenges. This book provides an introduction to deep learning and using MATLAB's deep-learning toolboxes. You’ll see how these toolboxes provide the complete set of functions needed to implement all aspects of deep learning. Along the way, you'll learn to model complex systems, including the stock market, natural language, and angles-only orbit determination. You’ll cover dynamics and control, and integrate deep-learning algorithms and approaches using MATLAB. You'll also apply deep learning to aircraft navigation using images. Finally, you'll carry out classification of ballet pirouettes using an inertial measurement unit to experiment with MATLAB's hardware capabilities. What You Will Learn Explore deep learning using MATLAB and compare it to algorithms Write a deep learning function in MATLAB and train it with examples Use MATLAB toolboxes related to deep learning Implement tokamak disruption prediction Who This Book Is For Engineers, data scientists, and students wanting a book rich in examples on deep learning using MATLAB. COMPUTERS,Languages,General

Learning by Doing with National Instruments Development Boards Learning by Doing with National Instruments Development Boards starts with a brief introduction to LabVIEW programming, which is required to explore the National Instrument platform, an introduction that includes detailed installation and licensing setup. Further, it gives the features and configuration setup of NI SPEEDY-33, NI ELVIS and myRIO boards. The focus of the book is on worked-out case studies for students working in different areas of electronics such as basic digital design, biomedical instrumentation, sensors and measurement. Data acquisition using SPEEDY-33, NI –ELVIS and myRIO kits is also odiscussed. The book also examines the myRIO platform. COMPUTERS,Languages,General

Beginning Ring Programming Gain a gentle introduction to the world of Ring programming with clarity as a first concern using a lot of practical examples. The first part lays the foundations of the language and its basic features (data types, control structures, functions, and classes). The unique way to rigorously structure Ring programs is also explained. Then, in the second part you’ll discover Ring inputs, outputs, and what is in between. You’ll use the basic constructs of computer logic (sequence, selection, and iteration) to build simple and complex logic flows. You’ll go over the common mistakes that lead to code complexity, by example, and cover several strategies to solve them (refactoring, code cleansing, and good variable naming). Then, you’ll see a visual illustration of how Ring deals with scopes at the local, object, and global levels. In part three, you’ll play with two artifacts vital to Ring programming: functions and objects. You’ll learn how they can be composed to solve a problem and how advanced programming paradigms, such as declarative and natural, are beautifully implemented on top of them. As part of the discussion, you’ll also work on game programming. You’ll learn how you design your game declaratively, in Ring code, just as if you were designing it in visual software. Finally, the author lays out how programming can be understood in a gamified context. You will be told the truth about how gaming can be a better metaphor to achieve mastery of Ring programming. This book is for those who are passionate about writing beautiful, expressive, and learnable code. It has been designed so you can enjoy a beginner-friendly set of knowledge about Ring, and benefit from a one-stop collection of lessons learned from real-world, customer-facing programming projects. What You Will Learn Get started with Ring and master its data types, I/O, functions, and classes Carry out structural, object-oriented, functional, declarative, natural, and meta programming in Ring Use the full power of Ring to refactor program code and develop clean program architectures Quickly design professional-grade video games on top of the Ring game engine Who This Book Is For Beginners looking for a consistent and hackable programming environment with a strong flavor of learnability and expressiveness. COMPUTERS,Languages,General

Advanced Perl Programming William "Bo" Rothwell's Advanced Perl Programming continues where his previous book left off, more or less, as it guides you through advanced techniques of the Perl programming language starting with command-line options, references, and arrays and hashes from advanced data types. Next, you'll learn about typeglobs for symbolic entries. Additionally, you'll see advanced subroutine handling, then packages and namespaces. Furthermore, you'll build advanced modules and install CPAN modules. Unlike Java and C++, modules have been around in Perl for a long time now. Along the way, you'll learn and use POD mark up language for Perl documentation. Moreover, you'll get a survey of the many advanced features and data structures of the current Perl programming language. You'll also get a survey of the new features of the latest Perl 5.x release. After reading and using this book, you'll have the tools, techniques, and source code to be an expert Perl programmer. What You Will Learn Carry out command-line parsing and extract scripts Create references; return values from a reference; work with the ref Function and strict refs Work with advanced Perl data types using arrays, hashes, and hash of hashes Use Typeglobs for symbol table entries Build modules and install CPAN modules Write documentation for Perl using POD Work with the newest features in Perl, including the smartmatch operator, yada yada, automated regex modifiers, the CORE namespace and more Who This Book Is For Those with experience with Perl or who have read Rothwell's prior books, Beginning Perl Programming and Pro Perl Programming. COMPUTERS,Languages,General

Swift Programming Through this guide's carefully constructed explanations and examples, you will develop an understanding of Swift grammar and the elements of effective Swift style - all thoroughly revised for Swift 5.3 and Xcode 12. Based on Big Nerd Ranch’s popular Swift training and its well-tested materials and methodology, this guide teaches concepts and coding through hands-on exercises. You will explore Swift features in Xcode playgrounds, and you will end by building sample apps for the command line and for macOS and iOS. After working through the book, you will have the skills to confidently dive into learning app development for Apple platforms like iOS and macOS. COMPUTERS,Languages,General

Super Scratch Programming Adventure! (Covers Version 2) Scratch is the wildly popular educational programming language used by millions of first-time learners in classrooms and homes worldwide. By dragging together colorful blocks of code, kids can learn computer programming concepts and make cool games and animations. The latest version, Scratch 2, brings the language right into your web browser, with no need to download software. In Super Scratch Programming Adventure!, kids learn programming fundamentals as they make their very own playable video games. They’ll create projects inspired by classic arcade games that can be programmed (and played!) in an afternoon. Patient, step-by-step explanations of the code and fun programming challenges will have kids creating their own games in no time. This full-color comic book makes programming concepts like variables, flow control, and subroutines effortless to absorb. Packed with ideas for games that kids will be proud to show off, Super Scratch Programming Adventure! is the perfect first step for the budding programmer. Now Updated for Scratch 2 The free Super Scratch Educator's Guide provides commentary and advice on the book's games suitable for teachers and parents. For Ages 8 and Up COMPUTERS,Languages,General

Functional Programming in Python Learn functional programming concepts and techniques to build Python applications Key Features Study in detail all aspects of functional programming, including immutability, generators, and more Reinforce your learning through elaborate examples Learn how to implement advanced topics like closures, memoization, and monads in your applications Book Description Python supports four programming paradigms – imperative, procedural, object-oriented, and functional. Of these, functional programming is probably the least understood and the least used. This book covers several topics that are directly and indirectly related to functional programming. After a quick overview of functional programming and its characteristics, Functional Programming in Python explains the various concepts of Python, starting with functions. You'll learn how to change the value of an object by using mutability. You'll then look at recursion as a more functional alternative to looping for certain algorithms, and learn how memoization alleviates the limitations of recursion in certain situations. The book further explains how to use closures as function factories and how to handle errors and exceptions with functors and monads. By the end of this book, you'll have all the knowledge you need for developing your applications with functional programming in Python. What you will learn Understand the advantages and disadvantages of functional programming Use closures in your code to dynamically create functions Create your own iterators Use the general-purpose functools to create your own specialized reducing functions Study and implement list and generator comprehensions to create lists Create customized iterators with generators Who this book is for If you are a developer looking to create applications in Python using functional programming, this book is ideal for you. You will only need a basic knowledge of Python. Prior knowledge or experience of functional programming is not required. COMPUTERS,Languages,General

Code-It Workbook 3 Code IT Primary Programming SeriesBasic computer coding is now among the most important skills a child can have for their future. There are many programming languages designed specifically for children to begin their studies, but the Scratch programming language, already recognised in schools around the world, is widely considered as the ideal place to begin programming in early education.The highly successful Code-It series is a comprehensive guide to teaching Scratch to children in a classroom setting. It is designed for the UK-based KS2 curriculum but can easily be used to supplement other programming courses for children between the ages of 7 and 11.There are four pupil workbooks designed to work in conjunction with the Code-It teacher handbook. They provide structure and resources for the children, including optional homework activities to extend to learning outside the classroom. Workbook 3 explains how to think, program and debug exciting programming projects such as Counting Machine, Music Abstraction, Random Word, Coin Sorter, Crab Maze, Toilet Fan, Car Park Barrier and Angle Menu. It also explains how to use analytical computational thinking skills for algorithm design, algorithm evaluation, decomposition, generalisation and abstraction; extend resilience and problem solving through the computational doing skills of converting algorithm into code and debugging; expand pupils’ knowledge of sequence, repetition, selection and variable use; introduce the basic use of a list; and program Lego models using Lego Wedo and Scratch. COMPUTERS,Languages,General

Code-It Workbook 2 Code IT Primary Programming SeriesBasic computer coding is now among the most important skills a child can have for their future. There are many programming languages designed specifically for children to begin their studies, but the Scratch programming language, already recognised in schools around the world, is widely considered as the ideal place to begin programming in early education. The highly successful Code-It series is a comprehensive guide to teaching Scratch to children in a classroom setting. It is designed for the UK-based KS2 curriculum but can easily be used to supplement other programming courses for children between the ages of 7 and 11. There are four pupil workbooks designed to work in conjunction with the Code-It teacher handbook. They provide structure and resources for the children, including optional homework activities to extend to learning outside the classroom. Workbook 2 explains how to think, program and debug exciting programming projects such as Maths Quiz, Music Algorithm to Music Code, Slug Trail Game, Selection Investigation and Teach Your Computer To Do Maths . It also outlines how to use analytical computational thinking skills for algorithm design, algorithm evaluation, decomposition and generalisation; extend resilience and problem solving through the computational doing skills of converting algorithm into code and debugging; and consolidate sequence and repetition in programming whilst introducing selection and variable use. COMPUTERS,Languages,General

Code-It Workbook 1 Code IT Primary Programming SeriesBasic computer coding is now among the most important skills a child can have for their future. There are many programming languages designed specifically for children to begin their studies, but the Scratch programming language, already recognised in schools around the world, is widely considered as the ideal place to begin programming in early education. The highly successful Code-It series is a comprehensive guide to teaching Scratch to children in a classroom setting. It is designed for the UK-based KS2 curriculum but can easily be used to supplement other programming courses for children between the ages of 7 and 11. There are four pupil workbooks designed to work in conjunction with the Code-It teacher handbook. They provide structure and resources for the children, including optional homework activities to extend to learning outside the classroom. Workbook 1 provides all the pupil resources to accompany Year 3, Chapter 2 of the teacher resource book How to Teach Primary Programming Using Scratch, including optional homework activities to extend learning outside the classroom. It explains how to think, program and debug exciting programming projects such as Smoking Car Game, Music Machine, Conversation, Interactive Display and Dressing up Game. It also outlines how to use analytical computational thinking skills for algorithm design, algorithm evaluation, decomposition and generalisation. COMPUTERS,Languages,General

Agile Artificial Intelligence in Pharo Cover classical algorithms commonly used as artificial intelligence techniques and program agile artificial intelligence applications using Pharo. This book takes a practical approach by presenting the implementation details to illustrate the numerous concepts it explains. Along the way, you’ll learn neural net fundamentals to set you up for practical examples such as the traveling salesman problem and cover genetic algorithms including a fun zoomorphic creature example. Furthermore, Practical Agile AI with Pharo finishes with a data classification application and two game applications including a Pong-like game and a Flappy Bird-like game. This book is informative and fun, giving you source code to play along with. You’ll be able to take this source code and apply it to your own projects. What You Will Learn Use neurons, neural networks, learning theory, and more Work with genetic algorithms Incorporate neural network principles when working towards neuroevolution Include neural network fundamentals when building three Pharo-based applications Who This Book Is For Coders and data scientists who are experienced programmers and have at least some prior experience with AI or deep learning. They may be new to Pharo programming, but some prior experience with it would be helpful. COMPUTERS,Languages,General

Creative Projects for Rust Programmers A practical guide to understanding the latest features of the Rust programming language, useful libraries, and frameworks that will help you design and develop interesting projects Key Features Work through projects that will help you build high-performance applications with Rust Delve into concepts such as error handling, memory management, concurrency, generics, and macros with Rust Improve business productivity by choosing the right libraries and frameworks for your applications Book Description Rust is a community-built language that solves pain points present in many other languages, thus improving performance and safety. In this book, you will explore the latest features of Rust by building robust applications across different domains and platforms. The book gets you up and running with high-quality open source libraries and frameworks available in the Rust ecosystem that can help you to develop efficient applications with Rust. You'll learn how to build projects in domains such as data access, RESTful web services, web applications, 2D games for web and desktop, interpreters and compilers, emulators, and Linux Kernel modules. For each of these application types, you'll use frameworks such as Actix, Tera, Yew, Quicksilver, ggez, and nom. This book will not only help you to build on your knowledge of Rust but also help you to choose an appropriate framework for building your project. By the end of this Rust book, you will have learned how to build fast and safe applications with Rust and have the real-world experience you need to advance in your career. What you will learn Access TOML, JSON, and XML files and SQLite, PostgreSQL, and Redis databases Develop a RESTful web service using JSON payloads Create a web application using HTML templates and JavaScript and a frontend web application or web game using WebAssembly Build desktop 2D games Develop an interpreter and a compiler for a programming language Create a machine language emulator Extend the Linux Kernel with loadable modules Who this book is for This Rust programming book is for developers who want to get hands-on experience with implementing their knowledge of Rust programming, and are looking for expert advice on which libraries and frameworks they can adopt to develop software that typically uses the Rust language. COMPUTERS,Languages,General

Accelerator Programming Using Directives This book constitutes the refereed post-conference proceedings of the 6th International Workshop on Accelerator Programming Using Directives, WACCPD 2019, held in Denver, CO, USA, in November 2019.The 7 full papers presented have been carefully reviewed and selected from 13 submissions. The papers share knowledge and experiences to program emerging complex parallel computing systems. They are organized in the following three sections: porting scientific applications to heterogeneous architectures using directives; directive-based programming for math libraries; and performance portability for heterogeneous architectures. COMPUTERS,Languages,General

Code-It Workbook 4 Code IT Primary Programming SeriesBasic computer coding is now among the most important skills a child can have for their future. There are many programming languages designed specifically for children to begin their studies, but the Scratch programming language, already recognised in schools around the world, is widely considered as the ideal place to begin programming in early education. The highly successful Code-It series is a comprehensive guide to teaching Scratch to children in a classroom setting. It is designed for the UK-based KS2 curriculum but can easily be used to supplement other programming courses for children between the ages of 7 and 11. There are four pupil workbooks designed to work in conjunction with the Code-It teacher handbook. They provide structure and resources for the children, including optional homework activities to extend to learning outside the classroom. Workbook 4 explains how to think, program and debug exciting programming projects such as Times Tables Game, Perimeter, Clock, Cartesian Coordinates, Translation, Enlargement & Rotation, Primary Games Maker, Tilt Switch and Chat Bot. It also outlines how to use analytical computational thinking skills of algorithm design, algorithm evaluation, decomposition and generalisation; extend resilience and problem solving through the computational doing skills of converting algorithm into code and debugging; develop pupils' knowledge of sequence, repetition, selection and variable use; and program Lego models using Lego Wedo and Scratch. COMPUTERS,Languages,General

10 PRINT CHR$(205.5+RND(1)); A single line of code offers a way to understand the cultural context of computing. This book takes a single line of code—the extremely concise BASIC program for the Commodore 64 inscribed in the title—and uses it as a lens through which to consider the phenomenon of creative computing and the way computer programs exist in culture. The authors of this collaboratively written book treat code not as merely functional but as a text—in the case of 10 PRINT, a text that appeared in many different printed sources—that yields a story about its making, its purpose, its assumptions, and more. They consider randomness and regularity in computing and art, the maze in culture, the popular BASIC programming language, and the highly influential Commodore 64 computer. COMPUTERS,Languages,General

Advanced R 4 Data Programming and the Cloud Program for data analysis using R and learn practical skills to make your work more efficient. This revised book explores how to automate running code and the creation of reports to share your results, as well as writing functions and packages. It includes key R 4 features such as a new color palette for charts, an enhanced reference counting system, and normalization of matrix and array types where matrix objects now formally inherit from the array class, eliminating inconsistencies. Advanced R 4 Data Programming and the Cloud is not designed to teach advanced R programming nor to teach the theory behind statistical procedures. Rather, it is designed to be a practical guide moving beyond merely using R; it shows you how to program in R to automate tasks. This book will teach you how to manipulate data in modern R structures and includes connecting R to databases such as PostgreSQL, cloud services such as Amazon Web Services (AWS), and digital dashboards such as Shiny. Each chapter also includes a detailed bibliography with references to research articles and other resources that cover relevant conceptual and theoretical topics. What You Will Learn Write and document R functions using R 4 Make an R package and share it via GitHub or privately Add tests to R code to ensure it works as intended Use R to talk directly to databases and do complex data management Run R in the Amazon cloud Deploy a Shiny digital dashboard Generate presentation-ready tables and reports using R Who This Book Is For Working professionals, researchers, and students who are familiar with R and basic statistical techniques such as linear regression and who want to learn how to take their R coding and programming to the next level. COMPUTERS,Languages,General

HTML, XHTML, and CSS, Sixth Edition COMPUTERS,Languages,HTML

HTML Pocket Guide, The This handy low-priced book is packed with HTML/XHTML definitions and tips, including those for HTML5 elements in depth. Snappy writing and illustrative code samples walk readers through HTML uses and element definitions. Handy pocket size provides a convenient reference for HTML coders. A true companion to standards-compliant design. The HTML Pocket Guide is for both beginning users, who want an introduction to HTML, and more advanced users, who are looking for a convenient reference. While HTML5 is still under development, browser manufacturers are already supporting many of its features in Google Chrome, Firefox, Opera, Safari, and the upcoming Internet Explorer 9. So, now is the time to start learning about it. The HTML Pocket Guide is a valuable companion to creating standards-compliant markup that will help Web designers and developers quickly define content and meaning. Accessible, convenient, and inexpensive, this pocket guide is exactly what web designers and developers need. COMPUTERS,Languages,HTML

CSS Cookbook As the industry standard method for enriching the presentation of HTML-based web pages, Cascading Style Sheets (CSS) allow you to give web pages more structure and a more sophisticated look. But first, you have to get past CSS theory and resolve real-world problems. For those all-too-common dilemmas that crop up with each project, CSS Cookbook provides hundreds of practical examples with CSS code recipes that you can use immediately to format your web pages. Arranged in a quick-lookup format for easy reference, the second edition has been updated to explain the unique behavior of the latest browsers: Microsoft's IE 7 and Mozilla's Firefox 1.5. Also, the book has been expanded to cover the interaction of CSS and images and now includes more recipes for beginning CSS users. The explanation that accompanies each recipe enables you to customize the formatting for your specific needs. With topics that range from basic web typography and page layout to techniques for formatting lists, forms, and tables, this book is a must-have companion, regardless of your experience with Cascading Style Sheets. COMPUTERS,Languages,HTML

HTML5 If you don't know about the new features available in HTML5, now's the time to find out. This book provides practical information about how and why the latest version of this markup language will significantly change the way you develop for the Web. HTML5 is still evolving, yet browsers such as Safari, Mozilla, Opera, and Chrome already support many of its features -- and mobile browsers are even farther ahead. HTML5: Up & Running carefully guides you though the important changes in this version with lots of hands-on examples, including markup, graphics, and screenshots. You'll learn how to use HTML5 markup to add video, offline capabilities, and more -- and you’ll be able to put that functionality to work right away. Learn new semantic elements, such as , , and Meet Canvas, a 2D drawing surface you can program with JavaScript Embed video in your web pages without third-party plugins Use Geolocation to let web application visitors share their physical location Take advantage of local storage capacity that goes way beyond cookies Build offline web applications that work after network access is disconnected Learn about several new input types for web forms Create your own custom vocabularies in HTML5 with microdata COMPUTERS,Languages,HTML

Sams Teach Yourself HTML, CSS, and JavaScript All in One Sams Teach Yourself HTML, CSS and JavaScript All in One The all-in-one HTML, CSS and JavaScript beginner's guide: covering the three most important languages for web development. Covers everything beginners need to know about the HTML and CSS standards and today's JavaScript and Ajax libraries - all in one book, for the first time Integrated, well-organized coverage expertly shows how to use all these key technologies together Short, simple lessons teach hands-on skills readers can apply immediately By best-selling author Julie Meloni Mastering HTML, CSS, and JavaScript is vital for any beginning web developer - and the importance of these technologies is growing as web development moves away from proprietary alternatives such as Flash. Sams Teach Yourself HTML, CSS, and JavaScript All in One brings together everything beginners need to build powerful web applications with the HTML and CSS standards and the latest JavaScript and Ajax libraries. With this book, beginners can get all the modern web development knowledge you need from one expert source. Bestselling author Julie Meloni (Sams Teach Yourself PHP, MySQL and Apache All in One) teaches simply and clearly, through brief, hands-on lessons focused on knowledge you can apply immediately. Meloni covers all the building blocks of practical web design and development, integrating new techniques and features into every chapter. Each lesson builds on what's come before, showing you exactly how to use HTML, CSS, and JavaScript together to create great web sites. COMPUTERS,Languages,HTML

HTML and CSS A full-color introduction to the basics of HTML and CSS from the publishers of Wrox! Every day, more and more people want to learn some HTML and CSS. Joining the professional web designers and programmers are new audiences who need to know a little bit of code at work (update a content management system or e-commerce store) and those who want to make their personal blogs more attractive. Many books teaching HTML and CSS are dry and only written for those who want to become programmers, which is why this book takes an entirely new approach. Introduces HTML and CSS in a way that makes them accessible to everyone—hobbyists, students, and professionals—and it’s full-color throughout Utilizes information graphics and lifestyle photography to explain the topics in a simple way that is engaging Boasts a unique structure that allows you to progress through the chapters from beginning to end or just dip into topics of particular interest at your leisure This educational book is one that you will enjoy picking up, reading, then referring back to. It will make you wish other technical topics were presented in such a simple, attractive and engaging way! This book is also available as part of a set in hardcover - Web Design with HTML, CSS, JavaScript and jQuery, 9781119038634; and in softcover - Web Design with HTML, CSS, JavaScript and jQuery, 9781118907443. COMPUTERS,Languages,HTML

HTML5 Want to learn how to build Web sites fast? This best-selling guide’s visual format and step-by-step, task-based instructions will have you up and running with HTML5 and CSS3 in no time. This Seventh Edition is a major revision, with approximately 125 pages added and substantial updates to (or complete rewrites of) nearly every page from the preceding edition. Authors Elizabeth Castro and Bruce Hyslop use clear instructions, friendly prose, and real-world code samples to teach you HTML and CSS from the ground up. Over the course of 21 chapters you will learn how to: Write semantic HTML, both with elements that have been around for years and ones that are new in HTML5. Prepare images for the Web and add them to your pages. Use CSS to style text, add background colors and images, and implement a multicolumn layout. Build a single site for all users—whether they are using a mobile phone, tablet, laptop, desktop computer, or other Web-enabled device—based on many of the components of responsive Web design, including CSS3 media queries. Leverage new selectors in CSS3, add Web fonts to your pages with @font-face, and use CSS3 effects such as opacity, background alpha transparency, gradients, rounded corners, drop shadows, shadows inside elements, text shadows, and multiple background images. Improve your site’s accessibility with ARIA landmark roles and other good coding practices. Build forms to solicit input from your visitors. Include media in your pages with the HTML5 audio and video elements. Test and debug your Web pages. Secure a domain name and publish your site. And much more! All book code samples and more are available on the companion web site. COMPUTERS,Languages,HTML

Head First HTML and CSS Tired of reading HTML books that only make sense after you're an expert? Then it's about time you picked up Head First HTML and really learned HTML. You want to learn HTML so you can finally create those web pages you've always wanted, so you can communicate more effectively with friends, family, fans, and fanatic customers. You also want to do it right so you can actually maintain and expand your web pages over time so they work in all browsers and mobile devices. Oh, and if you've never heard of CSS, that's okay--we won't tell anyone you're still partying like it's 1999--but if you're going to create web pages in the 21st century then you'll want to know and understand CSS. Learn the real secrets of creating web pages, and why everything your boss told you about HTML tables is probably wrong (and what to do instead). Most importantly, hold your own with your co-worker (and impress cocktail party guests) when he casually mentions how his HTML is now strict, and his CSS is in an external style sheet. With Head First HTML, you'll avoid the embarrassment of thinking web-safe colors still matter, and the foolishness of slipping a font tag into your pages. Best of all, you'll learn HTML and CSS in a way that won't put you to sleep. If you've read a Head First book, you know what to expect: a visually-rich format designed for the way your brain works. Using the latest research in neurobiology, cognitive science, and learning theory, this book will load HTML and CSS into your brain in a way that sticks. So what are you waiting for? Leave those other dusty books behind and come join us in Webville. Your tour is about to begin. COMPUTERS,Languages,HTML

HTML and CSS Need to learn HTML and CSS fast? This best-selling reference's visual format and step-by-step, task-based instructions will have you up and running with HTML in no time. In this updated edition author Bruce Hyslop uses crystal-clear instructions and friendly prose to introduce you to all of today's HTML and CSS essentials. The book has been refreshed to feature current web design best practices. You'll learn how to design, structure, and format your website. You'll learn about the new elements and form input types in HTML5. You'll create and use images, links, styles, and forms; and you'll add video, audio, and other multimedia to your site. You'll learn how to add visual effects with CSS3. You'll understand web standards and learn from code examples that reflect today's best practices. Finally, you will test and debug your site, and publish it to the web. Throughout the book, the author covers all of HTML and offers essential coverage of HTML5 and CSS techniques. COMPUTERS,Languages,HTML

Mobile HTML5 Build kickass websites and applications for all mobile (and non-mobile) platforms by adding HTML5 and CSS3 to your web development toolkit. With this hands-on book, you’ll learn how to develop web apps that not only work on iOS, Android, Blackberry, and Windows Phone, but also perform well and provide good user experience. With lots of code and markup examples, you’ll learn best practices for using HTML5 features, including new web forms, SVG, Canvas, localStorage, and related APIs. You’ll also get an in-depth look at CSS3, and discover how to design apps for large monitors and tiny screens alike. Learn HTML5’s elements, syntax, and semantics Build forms that provide enhanced usability with less JavaScript Explore HTML5 media APIs for graphics, video, and audio Enable your applications to work offline, using AppCache, localStorage, and other APIs Learn what you need to know about CSS3 selectors and syntax Dive into CSS3 features such as multiple backgrounds, gradients, border-images, transitions, transforms, and animations Make your web applications usable, responsive, and accessible. Design for performance, user experience, and reliability on all platforms COMPUTERS,Languages,HTML

HTML and CSS in 24 Hours, Sams Teach Yourself Learn HTML5 and CSS3 in 24 one-hour lessons! Sams Teach Yourself HTML and CSS in 24 Hours is a well-organized, clearly written, and generously illustrated tutorial that teaches beginners how to quickly create great-looking web pages using HTML5 and CSS3. With a practical, jargon-free focus on quickly getting web pages created and published to the web, the book's 24 one-hour lessons carefully guide the reader through each step involved in creating, enhancing, and maintaining web sites of all types and sizes. The ninth edition of Sams Teach Yourself HTML and CSS in 24 Hours brings the entire book in line with the HTML5 and CSS3 specifications and capabilities and includes fresh material and examples that take full advantage of the book's full-color layout and design. Anyone who completes the lessons in this book can have his or her web pages be among those that appear on the Internet. In fact, within the first two lessons in this book, someone with no previous HTML experience at all can have a web page ready to go online. If you like learning by doing, this is the book for you. It organizes lessons in the basics of HTML5 and CSS3 into simple steps and then shows you exactly how to tackle each step. Many of these HTML code examples are accompanied by pictures of the output produced by the code. You see how it's done, you read a clear, concise explanation of how it works, and then you immediately do the same thing with your own page. A few minutes later, you're on to the next step. Learn how to… Build your own web page and get it online in an instant Format text for maximum clarity and readability Create links to other pages and to other sites Add graphics, color, and visual pizzazz to your web pages Work with transparent images and background graphics Design your site’s layout and typography using CSS Get user input with web-based forms Publicize your site and make it search-engine friendly Test a website for compatibility with different browsers Make your site easy to maintain and update as it grows Use HTML5 semantic tags to better structure your pages Create columns with CSS Add HTML5-based video and audio to your site Use CSS3 transforms, transitions, and animations to create great visual effects Use HTML5’s powerful form validation capability Contents at a Glance Part I: Getting Started on the Web 1 Understanding How the Web Works 2 Structuring an HTML Document 3 Understanding Cascading Style Sheets Part II: Building Blocks of HTML 4 A Closer Look at HTML5 Page Structure5 Working with Text Blocks and Lists6 Working with Fonts7 Working with Colors and Borders8 Using External and Internal Links 9 Using Tables and Columns10 Creating Images for Use on the Web 11 Using Images in Your Web Site 12 Using Multimedia in Your Web Site Part III: Advanced Web Page Design with CSS 13 Working with Margins, Padding, Alignment, and Floating14 Understanding the CSS Box Model and Positioning 15 Creating Fixed or Liquid Layouts16 Using CSS to Do More with Lists 17 Using CSS to Design Navigation 18 Using Mouse Actions to Modify Text Display 19 Implementing CSS3 Transforms, Transitions, and Animations PART IV: Advanced Web Site Functionality and Management 20 Creating Print-Friendly Web Pages 21 Understanding Dynamic Web Sites and HTML5 Applications 22 Working with Web-Based Forms 23 Organizing and Managing a Web Site24 Helping People Find Your Web Pages COMPUTERS,Languages,HTML

HTML5 HTML5 is more than a markup language—it’s a collection of several independent web standards. Fortunately, this expanded guide covers everything you need in one convenient place. With step-by-step tutorials and real-world examples, HTML5: The Missing Manual shows you how to build web apps that include video tools, dynamic graphics, geolocation, offline features, and responsive layouts for mobile devices. The important stuff you need to know: Structure web pages more effectively. Learn how HTML5 helps web design tools and search engines work smarter. Add audio and video without plugins. Build playback pages that work in every browser. Create stunning visuals with Canvas. Draw shapes, pictures, and text; play animations; and run interactive games. Jazz up your pages with CSS3. Add fancy fonts and eye-catching effects with transitions and animation. Design better web forms. Collect information from visitors more efficiently with HTML5 form elements. Build it once, run it everywhere. Use responsive design to make your site look good on desktops, tablets, and smartphones. Include rich desktop features. Build self-sufficient web apps that work offline and store the data users need. COMPUTERS,Languages,HTML

HTML5 Games HTML5 Games shows you how to combine HTML5, CSS3 and JavaScript to make games for the web and mobiles - games that were previously only possible with plugin technologies like Flash. Using the latest open web technologies, you are guided through the process of creating a game from scratch using Canvas, HTML5 Audio, WebGL and WebSockets. Inside, Jacob Seidelin shows you how features available in HTML5 can be used to create games. First, you will build a framework on which you will create your HTML5 game. Then each chapter covers a new aspect of the game including user input, sound, multiplayer functionality, 2D and 3D graphics and more. By the end of the book, you will have created a fully functional game that can be played in any compatible browser, or on any mobile device that supports HTML5. Topics include: Dealing with backwards compatibility Generating level data Making iOS and Android web apps Taking your game offline Using Web Workers Persistent Game Data Drawing with Canvas Capturing player input Creating 3D graphics with WebGL Textures and lighting Sound with HTML5 Audio And more… COMPUTERS,Languages,HTML

Learn to Code HTML and CSS HTML and CSS can be a little daunting at first but fear not. This book, based on Shay Howe's popular workshop covers the basics and breaks down the barrier to entry, showing readers how they can start using HTML and CSS through practical techniques today. They'll find accompanying code examples online, while they explore topics such as the different structures of HTML and CSS, and common terms. After establishing a basic understanding of HTML and CSS a deeper dive is taken into the box model and how to work with floats. The book includes an exercise focused on cleaning up a web page by improving the user interface and design, solely using HTML and CSS. With a few quick changes the web page changes shape and comes to life. Interactive, technically up-to-the-minute and easy-to-understand, this book will advance a student's skills to a professional level. COMPUTERS,Languages,HTML

Flexbox in CSS Layout designers rejoice: CSS finally has an update that will make your lives easier. Flexible box layout, often called Flexbox, frees you from the challenges of creating layouts with floats and padding? and lets you specify containers and their contents instead. The new model means you can specify the directions in which material flows, how content wraps, and the ways components can expand to fill a space. Whether you've been creating large sites or small, fixed sites or responsive sites, flexbox will simplify your work. COMPUTERS,Languages,HTML

Mastering CSS Rich Finelli's modern CSS training course, based on his bestselling Mastering CSS video, now available in a book. Master CSS from best practices to practical CSS coding. About This Book Learn CSS directly from Rich Finelli, author of the bestselling Mastering CSS training course From best practices to deep coding, Rich Finelli shares his CSS knowledge with you Rich Finelli covers the latest CSS updates with flexbox and works with retina devices Who This Book Is For This book is for web designers who wish to master the best practices of CSS in their web projects. You already know how to work with a web page, and want to use CSS to master website presentation. What You Will Learn Master fundamental CSS concepts like the anatomy of a rule set, the box model, and the differences between block and inline elements Employ flexbox to layout and align elements simply and cleanly Become proficient with CSS3 properties such as transitions, transforms, gradients, and animations Delve into modular, reusable, and scalable CSS for more organized and maintainable style sheets Understand media queries and other pillars of responsive web design Get creative with the @font-face property, Google Web Fonts, font services such as Typekit, as well as, icon fonts Understand the workflow for HiDPI (retina) devices using 2x images, SVG, and the srcset attribute In Detail Rich Finelli trains you in CSS deep learning and shows you the techniques you need to work in the world of responsive, feature-rich web applications. Based on his bestselling Mastering CSS training video, you can now learn with Rich in this book! Rich shares with you his skills in creating advanced layouts, and the critical CSS insights you need for responsive web designs, fonts, transitions, animations, and using flexbox. Rich begins your CSS training with a review of CSS best practices, such as using a good text editor to automate your authoring and setting up a CSS baseline. You then move on to create a responsive layout making use of floats and stylable drop-down menus, with Rich guiding you toward a modular-organized approach to CSS. Your training with Rich Finelli then dives into detail about working with CSS and the best solutions to make your websites work. You'll go with him into CSS3 properties, transforms, transitions, and animations. You'll gain his understanding of responsive web designs, web fonts, icon fonts, and the techniques used to support retina devices. Rich expands your knowledge of CSS so you can master one of the most valuable tools in modern web design. Style and approach Let Rich Finelli train you in CSS! This book has a direct training style because it is based on Rich's bestselling Mastering CSS training course. COMPUTERS,Languages,HTML

Using SVG with CSS3 and HTML5 Using Scalable Vector Graphics (SVG) for illustrations only scratches the surface of this format’s potential on the web. With this practical guide, you’ll learn how to use SVG not only for illustrations but also as graphical documents that you can integrate into complex HTML5 web pages, and style with custom CSS. Web developers will discover ways to adapt designs by adding data based graphics, dynamic styles, interaction, or animation. Divided into five parts, this book includes: SVG on the web: Understand how SVG works with HTML, CSS, and JavaScript to define graphics Drawing with markup: Learn the vector language of x and y coordinates that let SVG create basic and custom shapes Putting graphics in their place: Use the coordinate system to draw SVG shapes and text at different scales and positions Artistic touches: Explore how color is used, how strokes are created and manipulated, and how graphical effects like filters, clipping, and masking are applied SVG as an application: Make your graphic more accessible to humans and computers, and learn how to make it interactive or animated COMPUTERS,Languages,HTML

CSS If you’re a web designer or app developer interested in sophisticated page styling, improved accessibility, and saving time and effort, this book is for you. This revised edition provides a comprehensive guide to CSS implementation, along with a thorough review of the latest CSS specifications. CSS is a constantly evolving language for describing the presentation of web content on screen, printers, speech synthesizers, screen readers, and chat windows. It is used by all browsers on all screen sizes on all types of IoT devices, including phones, computers, video games, televisions, watches, kiosks, and auto consoles. Authors Eric Meyer and Estelle Weyl show you how to improve user experience, speed development, avoid potential bugs, and add life and depth to your applications through layout, transitions and animations, borders, backgrounds, text properties, and many other tools and techniques. This guide covers: Selectors, specificity, and the cascade Values, units, fonts, and text properties Padding, borders, outlines, and margins Colors, backgrounds, and gradients Floats and positioning tricks Flexible box layout The new Grid layout system 2D and 3D transforms, transitions, and animation Filters, blending, clipping, and masking Media and feature queries COMPUTERS,Languages,HTML

HTML, CSS, and JavaScript All in One Teach Yourself HTML, CSS, and JavaScript All in One combines these three fundamental web development technologies into one clearly written, carefully organized, step-by-step tutorial that expertly guides the beginner through these three interconnected technologies. In just a short time, you can learn how to use HTML, Cascading Style Sheets (CSS), and JavaScript together to design, create, and maintain world-class websites. Each lesson in this book builds on the previous ones, enabling you to learn the essentials from the ground up. Clear instructions and practical, hands-on examples show you how to use HTML to create the framework of your website, design your site’s layout and typography with CSS, and then add interactivity with JavaScript and jQuery. Step-by-step instructions carefully walk you through the most common web development tasks.Practical, hands-on examples show you how to apply what you learn.Quizzes and exercises help you test your knowledge and stretch your skills. Learn how to… Build your own web page and get it online in an instant Format text for maximum clarity and readability Create links to other pages and to other sites Add graphics, color, and visual pizzazz to your web pages Work with transparent images and background graphics Design your site’s layout and typography using CSS Make elements move on your page with CSS transformations and transitions Animate with CSS and the HTML5 Canvas element Write HTML that’s responsive web design-ready Design a site for mobile devices Use CSS media queries and breakpoints Get user input with web-based forms Use JavaScript to build dynamic, interactive web pages Add AJAX effects to your web pages Leverage JavaScript libraries such as jQuery Make your site easy to maintain and update as it grows COMPUTERS,Languages,HTML

HTML and CSS HTML and CSS remain the linchpin of the Web. Every beginning web developer needs to understand them thoroughly — including the latest advances in these standards, and the newest techniques based on them. For decades, web professionals have turned to HTML and CSS: Visual QuickStart Guide as the fastest and most practical way to gain that understanding. Now, this full-color guide has been thoroughly updated by a new author who’s taught thousands of beginning web developers. Joe Casabona combines expert introductions to the latest HTML and CSS technologies, new examples and projects, and extensive online video content for a true multi-modal learning experience. Combining definitive reference information with hands-on tutorials, Casabona helps aspiring and current web professionals gain deep mastery of HTML and CSS separately, together, and in the broader context of the overall web project and lifecycle. Drawing on his extensive teaching experience, Casabona offers well-honed explanations that learners will understand, whether they’re working on their own or in classroom environments. From the basics to advanced techniques, he guides you through: Designing, structuring, and formatting sites Using images, links, styles, tables, forms Adding media, visual effects, and animations Using CSS to gain full control over elements, fonts, colors, and layouts Making the most of sophisticated HTML5 and CSS3 capabilities Applying modern best practices for ensuring accessibility and responsiveness, and building high-performance progressive web apps Effectively testing, debugging, and publishing sites and applications Exploring leading JavaScript libraries and build tools for more advanced web development COMPUTERS,Languages,HTML

MySQL and Java Developer's Guide Shows Java developers everything they need to know to build Java database applications with MySQL. Takes a hands-on, code-intensive approach in which readers will learn how to build a sophisticated Web database management application. Begins with a review of the fundamentals of MySQL. Explains using Java's JDBC with MySQL, as well as servlet and JSP programming with MySQL. Provides a code-rich tutorial on how to build the sample Java database application using EJBs. The companion Web site provides the full code examples plus links to useful sites. COMPUTERS,Languages,Java

Java and XML Java and XML, 3rd Edition, shows you how to cut through all the hype about XML and put it to work. It teaches you how to use the APIs, tools, and tricks of XML to build real-world applications. The result is a new approach to managing information that touches everything from configuration files to web sites. After two chapters on XML basics, including XPath, XSL, DTDs, and XML Schema, the rest of the book focuses on using XML from your Java applications. This third edition of Java and XML covers all major Java XML processing libraries, including full coverage of the SAX, DOM, StAX, JDOM, and dom4j APIs as well as the latest version of the Java API for XML Processing (JAXP) and Java Architecture for XML Binding (JAXB). The chapters on web technology have been entirely rewritten to focus on the today's most relevant topics: syndicating content with RSS and creating Web 2.0 applications. You'll learn how to create, read, and modify RSS feeds for syndicated content and use XML to power the next generation of websites with Ajax and Adobe Flash. Topics include: The basics of XML, including DTDs, namespaces, XML Schema, XPath, and Transformations The SAX API, including all handlers, filters, and writers The DOM API, including DOM Level 2, Level 3, and the DOM HTML module The JDOM API, including the core and a look at XPath support The StAX API, including StAX factories, producing documents and XMLPull Data Binding with JAXB, using the new JAXB 2.0 annotations Web syndication and podcasting with RSS XML on the Presentation Layer, paying attention to Ajax and Flash applications If you are developing with Java and need to use XML, or think that you will be in the future; if you're involved in the new peer-to-peer movement, messaging, or web services; or if you're developing software for electronic commerce, Java and XML will be an indispensable companion. COMPUTERS,Languages,Java

Java Generics and Collections This comprehensive guide shows you how to master the most importantchanges to Java since it was first released. Generics and the greatlyexpanded collection libraries have tremendously increased the power ofJava 5 and Java 6. But they have also confused many developers whohaven't known how to take advantage of these new features. Java Generics and Collections covers everything from the mostbasic uses of generics to the strangest corner cases. It teaches youeverything you need to know about the collections libraries, so you'llalways know which collection is appropriate for any given task, andhow to use it. Topics covered include: Fundamentals of generics: type parameters and generic methods Other new features: boxing and unboxing, foreach loops, varargs Subtyping and wildcards Evolution not revolution: generic libraries with legacy clients andgeneric clients with legacy libraries Generics and reflection Design patterns for generics Sets, Queues, Lists, Maps, and their implementations Concurrent programming and thread safety with collections Performance implications of different collections Generics and the new collection libraries they inspired take Java to anew level. If you want to take your software development practice toa new level, this book is essential reading. Philip Wadler is Professor of Theoretical Computer Science at theUniversity of Edinburgh, where his research focuses on the design ofprogramming languages. He is a co-designer of GJ, work thatbecame the basis for generics in Sun's Java 5.0. Maurice Naftalin is Technical Director at Morningside Light Ltd., a software consultancy in the United Kingdom. He has most recently served as an architect and mentor at NSB Retail Systems plc, and as the leader of the client development team of a major UK government social service system. "A brilliant exposition of generics. By far the best book on thetopic, it provides a crystal clear tutorial that starts with thebasics and ends leaving the reader with a deep understanding of boththe use and design of generics." Gilad Bracha, Java Generics Lead, Sun Microsystems COMPUTERS,Languages,Java

Eclipse IDE Pocket Guide Eclipse is the world's most popular IDE for Java development. And although there are plenty of large tomes that cover all the nooks and crannies of Eclipse, what you really need is a quick, handy guide to the features that are used over and over again in Java programming. You need answers to basic questions such as: Where was that menu? What does that command do again? And how can I set my classpath on a per-project basis? This practical pocket guide gets you up to speed quickly with Eclipse. It covers basic concepts, including Views and editors, as well as features that are not commonly understood, such as Perspectives and Launch Configurations. You'll learn how to write and debug your Java code--and how to integrate that code with tools such as Ant and JUnit. You'll also get a toolbox full of tips and tricks to handle common--and sometimes unexpected--tasks that you'll run across in your Java development cycle. Additionally, the Eclipse IDE Pocket Guide has a thorough appendix detailing all of Eclipse's important views, menus, and commands. The Eclipse IDE Pocket Guide is just the resource you need for using Eclipse, whether it's on a daily, weekly, or monthly basis. Put it in your back pocket, or just throw it in your backpack. With this guide in hand, you're ready to tackle the Eclipse programming environment. COMPUTERS,Languages,Java

Java Cryptography Cryptography, the science of secret writing, is the biggest, baddest security tool in the application programmer's arsenal. Cryptography provides three services that are crucial in secure programming. These include a cryptographic cipher that protects the secrecy of your data; cryptographic certificates, which prove identity (authentication); and digital signatures, which ensure your data has not been damaged or tampered with.This book covers cryptographic programming in Java. Java 1.1 and Java 1.2 provide extensive support for cryptography with an elegant architecture, the Java Cryptography Architecture (JCA). Another set of classes, the Java Cryptography Extension (JCE), provides additional cryptographic functionality. This book covers the JCA and the JCE from top to bottom, describing the use of the cryptographic classes as well as their innards.The book is designed for moderately experienced Java programmers who want to learn how to build cryptography into their applications. No prior knowledge of cryptography is assumed. The book is peppered with useful examples, ranging from simple demonstrations in the first chapter to full-blown applications in later chapters.Topics include: The Java Cryptography Architecture (JCA) The Java Cryptography Extension (JCE) Cryptographic providers The Sun key management tools Message digests, digital signatures, and certificates (X509v3) Block and stream ciphers Implementations of the ElGamal signature and cipher algorithms A network talk application that encrypts all data sent over the network An email application that encrypts its messages Covers JDK 1.2 and JCE 1.2. COMPUTERS,Languages,Java

Java NIO Many serious Java programmers, especially enterprise Java programmers, consider the new I/O API--called NIO for New Input/Output--the most important feature in the 1.4 version of the Java 2 Standard Edition. The NIO package includes many things that have been missing from previous editions of Java that are critical to writing high-performance, large-scale applications: improvements in the areas of buffer management, scalable network and file I/O, character-set support, and regular expression matching. Most of all, it boosts performance and speed dramatically.Java NIO explores the new I/O capabilities of version 1.4 in detail and shows you how to put these features to work to greatly improve the efficiency of the Java code you write. This compact volume examines the typical challenges that Java programmers face with I/O and shows you how to take advantage of the capabilities of the new I/O features. You?ll learn how to put these tools to work using examples of common, real-world I/O problems and see how the new features have a direct impact on responsiveness, scalability, and reliability. The book includes: A rundown of the new features in NIO Basic and advanced I/O Concepts Binary I/O and the new buffer classes Memory mapped files and file locking Character I/O: encoding, decoding and transforming character data Regular Expressions and the new java.util.regex package Muliplexing with java.nio Because the NIO APIs supplement the I/O features of version 1.3, rather than replace them, you'll also learn when to use new APIs and when the older 1.3 I/O APIs are better suited to your particular application.Java NIO is for any Java programmer who is interested in learning how to boost I/O performance, but if you're developing applications where performance is critical, such as game computing or large-scale enterprise applications, you'll want to give this book a permanent spot on your bookshelf. With the NIO APIs, Java no longer takes a backseat to any language when it comes to performance. Java NIO will help you realize the benefits of these exciting new features. COMPUTERS,Languages,Java

Tomcat It takes a book as versatile as its subject to cover Apache Tomcat, the popular open source Servlet and JSP container and high performance web server. Tomcat: The Definitive Guide is a valuable reference for administrators and webmasters, a useful guide for programmers who want to use Tomcat as their web application server during development or in production, and an excellent introduction for anyone interested in Tomcat. Updated for the latest version of Tomcat, this new edition offers a complete guide to installing, configuring, maintaining and securing this servlet container. In fact, with such a wealth of new information, this is essentially a new book rather than a simple revision. You will find details for using Tomcat on all major platforms, including Windows, Linux, OS X, Solaris, and FreeBSD, along with specifics on Tomcat configuration files, and step-by-step advice for deploying and running web applications. This book offers complete information for: Installation and startup procedures Configuring Tomcat-including realms, roles, users, servlet sessions, and JNDI resources including JDBC DataSources Deploying web applications-individual servlets and JSP pages, and web application archive files Tuning Tomcat to measure and improve performance Integrating Tomcat with Apache Web Server Securing Tomcat to keep online thugs at bay Tomcat configuration files-server.xml and web.xml, and more Debugging and Troubleshooting-diagnosing problems with Tomcat or a web application Compiling your own Tomcat, rather than using the pre-built release Running two or more Tomcat servlet containers in parallel This book also offers an overview of the Tomcat open source project's community resources, including docs, mailing lists, and more. Community interest fueled a strong demand for a Tomcat guide from O'Reilly. The result clearly exceeds expectations. COMPUTERS,Languages,Java

JBoss at Work Consisting of a number of well-known open source products, JBoss is more a family of interrelated services than a single monolithic application. But, as with any tool that's as feature-rich as JBoss, there are number of pitfalls and complexities, too. Most developers struggle with the same issues when deploying J2EE applications on JBoss: they have trouble getting the many J2EE and JBoss deployment descriptors to work together; they have difficulty finding out how to get started; their projects don't have a packaging and deployment strategy that grows with the application; or, they find the Class Loaders confusing and don't know how to use them, which can cause problems. JBoss at Work: A Practical Guide helps developers overcome these challenges. As you work through the book, you'll build a project using extensive code examples. You'll delve into all the major facets of J2EE application deployment on JBoss, including JSPs, Servlets, EJBs, JMS, JNDI, web services, JavaMail, JDBC, and Hibernate. With the help of this book, you'll: Implement a full J2EE application and deploy it on JBoss Discover how to use the latest features of JBoss 4 and J2EE 1.4, including J2EE-compliant web services Master J2EE application deployment on JBoss with EARs, WARs, and EJB JARs Understand the core J2EE deployment descriptors and how they integrate with JBoss-specific descriptors Base your security strategy on JAAS Written for Java developers who want to use JBoss on their projects, the book covers the gamut of deploying J2EE technologies on JBoss, providing a brief survey of each subject aimed at the working professional with limited time. If you're one of the legions of developers who have decided to give JBoss a try, then JBoss at Work: A Practical Guide is your next logical purchase. It'll show you in plain language how to use the fastest growing open source tool in the industry today. If you've worked with JBoss before, this book will get you up to speed on JBoss 4, JBoss WS (web services), and Hibernate 3. COMPUTERS,Languages,Java

JDBC Pocket Reference JDBC--the Java Database Connectivity specification--is a complex set of application programming interfaces (APIs) that developers need to understand if they want their Java applications to work with databases. JDBC is so complex that even the most experienced developers need to refresh their memories from time to time on specific methods and details. But, practically speaking, who wants to stop and thumb through a weighty tutorial volume each time a question arises? The answer is the JDBC Pocket Reference, a data-packed quick reference that is both a time-saver and a lifesaver.The JDBC Pocket Reference offers quick look-ups for all methods of the standard JDBC classes. These include concise reviews of the procedures for common JDBC tasks such as connecting to a database, executing stored procedures, executing DDL and the like. You'll find documentation of the connect string formats for the most common databases, including Oracle, SQL-Server, and PostgreSQL. You'll even find information on working with large objects, and on using SQL99 user defined datatypes to work with object-relational data. Searching for this sort of material through large tutorials is frustrating and a waste of time, but this pocket-sized book is easy to take anywhere and makes finding the information you need a snap.O'Reilly's Pocket References have become a favorite among developers everywhere. By providing a wealth of important details in a concise, well-organized format, these handy books deliver just what you need to complete the task at hand. When you've reached a sticking point and need to get to the answer quickly, the new JDBC Pocket Reference is the book you'll want close at hand. COMPUTERS,Languages,Java

Head First Java Learning a complex new language is no easy task especially when it s an object-oriented computer programming language like Java. You might think the problem is your brain. It seems to have a mind of its own, a mind that doesn't always want to take in the dry, technical stuff you're forced to study. The fact is your brain craves novelty. It's constantly searching, scanning, waiting for something unusual to happen. After all, that's the way it was built to help you stay alive. It takes all the routine, ordinary, dull stuff and filters it to the background so it won't interfere with your brain's real work--recording things that matter. How does your brain know what matters? It's like the creators of the Head First approach say, suppose you're out for a hike and a tiger jumps in front of you, what happens in your brain? Neurons fire. Emotions crank up. Chemicals surge. That's how your brain knows. And that's how your brain will learn Java. Head First Java combines puzzles, strong visuals, mysteries, and soul-searching interviews with famous Java objects to engage you in many different ways. It's fast, it's fun, and it's effective. And, despite its playful appearance, Head First Java is serious stuff: a complete introduction to object-oriented programming and Java. You'll learn everything from the fundamentals to advanced topics, including threads, network sockets, and distributed programming with RMI. And the new. second edition focuses on Java 5.0, the latest version of the Java language and development platform. Because Java 5.0 is a major update to the platform, with deep, code-level changes, even more careful study and implementation is required. So learning the Head First way is more important than ever. If you've read a Head First book, you know what to expect--a visually rich format designed for the way your brain works. If you haven't, you're in for a treat. You'll see why people say it's unlike any other Java book you've ever read. By exploiting how your brain works, Head First Java compresses the time it takes to learn and retain--complex information. Its unique approach not only shows you what you need to know about Java syntax, it teaches you to think like a Java programmer. If you want to be bored, buy some other book. But if you want to understand Java, this book's for you. COMPUTERS,Languages,Java

Enterprise JavaBeans 3.1 Learn how to code, package, deploy, and test functional Enterprise JavaBeans with the latest edition of this bestselling guide. Written by the developers of JBoss EJB 3.1, this book not only brings you up to speed on each component type and container service in this implementation, it also provides a workbook with several hands-on examples to help you gain immediate experience with these components. With version 3.1, EJB's server-side component model for building distributed business applications is simpler than ever. But it's still a complex technology that requires study and lots of practice to master. Enterprise JavaBeans 3.1 is the most complete reference on this specification. You'll find a straightforward, no-nonsense explanation of the underlying technology, including Java classes and interfaces, the component model, and the runtime behavior of EJB. Develop your first EJBs with a hands-on walkthrough of EJB 3.1 concepts Learn how to encapsulate business logic with Session Beans and Message-Driven Beans Discover how to handle persistence through Entity Beans, the EntityManager, and the Java Persistence API Understand EJB's container services such as dependency injection, concurrency, and interceptors Integrate EJB with other technologies in the Java Enterprise Edition platform Use examples with either the JBossAS, OpenEJB, or GlassFish v3 EJB Containers COMPUTERS,Languages,Java

Building and Testing with Gradle Build and test software written in Java and many other languages with Gradle, the open source project automation tool that’s getting a lot of attention. This concise introduction provides numerous code examples to help you explore Gradle, both as a build tool and as a complete solution for automating the compilation, test, and release process of simple and enterprise-level applications. Discover how Gradle improves on the best ideas of Ant, Maven, and other build tools, with standards for developers who want them and lots of flexibility for those who prefer less structure. Use Gradle with Groovy, Clojure, Scala, and languages beyond the JVM, such as Flex and C Get started building a simple Java program using Gradle's command line tooling and a small build script Learn how to configure and construct tasks, Gradle's fundamental unit of build activity Take advantage of Gradle's integration with Ant Use Gradle to integrate with or transition from Maven, and to build software more cleanly Perform application unit and integration tests using JUnit, TestNG, Spock, and Geb COMPUTERS,Languages,Java

Programming Hive Need to move a relational database application to Hadoop? This comprehensive guide introduces you to Apache Hive, Hadoop’s data warehouse infrastructure. You’ll quickly learn how to use Hive’s SQL dialect—HiveQL—to summarize, query, and analyze large datasets stored in Hadoop’s distributed filesystem. This example-driven guide shows you how to set up and configure Hive in your environment, provides a detailed overview of Hadoop and MapReduce, and demonstrates how Hive works within the Hadoop ecosystem. You’ll also find real-world case studies that describe how companies have used Hive to solve unique problems involving petabytes of data. Use Hive to create, alter, and drop databases, tables, views, functions, and indexes Customize data formats and storage options, from files to external databases Load and extract data from tables—and use queries, grouping, filtering, joining, and other conventional query methods Gain best practices for creating user defined functions (UDFs) Learn Hive patterns you should use and anti-patterns you should avoid Integrate Hive with other data processing programs Use storage handlers for NoSQL databases and other datastores Learn the pros and cons of running Hive on Amazon’s Elastic MapReduce COMPUTERS,Languages,Java

Java Security One of Java's most striking claims is that it provides a secure programming environment. Yet despite endless discussion, few people understand precisely what Java's claims mean and how it backs up those claims. If you're a developer, network administrator or anyone else who must understand or work with Java's security mechanisms, Java Security is the in-depth exploration you need.Java Security, 2nd Edition, focuses on the basic platform features of Java that provide security--the class loader, the bytecode verifier, and the security manager--and recent additions to Java that enhance this security model: digital signatures, security providers, and the access controller. The book covers the security model of Java 2, Version 1.3, which is significantly different from that of Java 1.1. It has extensive coverage of the two new important security APIs: JAAS (Java Authentication and Authorization Service) and JSSE (Java Secure Sockets Extension). Java Security, 2nd Edition, will give you a clear understanding of the architecture of Java's security model and how to use that model in both programming and administration.The book is intended primarily for programmers who want to write secure Java applications. However, it is also an excellent resource for system and network administrators who are interested in Java security, particularly those who are interested in assessing the risk of using Java and need to understand how the security model works in order to assess whether or not Java meets their security needs. COMPUTERS,Languages,Java

JavaMail API Send and receive email from Java applications by using the JavaMail API. With this concise book, you’ll learn how to communicate with existing SMTP, POP, and IMAP servers, and how to write your own. Whether you need to build an email-centric application like a mailing list manager or simply add email notification to a larger product, JavaMail is the answer. Packed with code examples, this book shows you how JavaMail enables you to avoid low-level protocol details, so you can focus on what you actually want to say in a message. Send, receive, and store email with POP3 and IMAP Add password authentication to your programs Manage mailboxes and accounts Download mail attachments Respond to asynchronous email events Design protocol-independent email programs COMPUTERS,Languages,Java

Scala Cookbook Save time and trouble when using Scala to build object-oriented, functional, and concurrent applications. With more than 250 ready-to-use recipes and 700 code examples, this comprehensive cookbook covers the most common problems you’ll encounter when using the Scala language, libraries, and tools. It’s ideal not only for experienced Scala developers, but also for programmers learning to use this JVM language. Author Alvin Alexander (creator of DevDaily.com) provides solutions based on his experience using Scala for highly scalable, component-based applications that support concurrency and distribution. Packed with real-world scenarios, this book provides recipes for: Strings, numeric types, and control structures Classes, methods, objects, traits, and packaging Functional programming in a variety of situations Collections covering Scala's wealth of classes and methods Concurrency, using the Akka Actors library Using the Scala REPL and the Simple Build Tool (SBT) Web services on both the client and server sides Interacting with SQL and NoSQL databases Best practices in Scala development COMPUTERS,Languages,Java

Java Web Services Learn how to develop REST-style and SOAP-based web services and clients with this quick and thorough introduction. This hands-on book delivers a clear, pragmatic approach to web services by providing an architectural overview, complete working code examples, and short yet precise instructions for compiling, deploying, and executing them. You’ll learn how to write services from scratch and integrate existing services into your Java applications. With greater emphasis on REST-style services, this second edition covers HttpServlet, Restlet, and JAX-RS APIs; jQuery clients against REST-style services; and JAX-WS for SOAP-based services. Code samples include an Apache Ant script that compiles, packages, and deploys web services. Learn differences and similarities between REST-style and SOAP-based services Program and deliver RESTful web services, using Java APIs and implementations Explore RESTful web service clients written in Java, JavaScript, and Perl Write SOAP-based web services with an emphasis on the application level Examine the handler and transport levels in SOAP-based messaging Learn wire-level security in HTTP(S), users/roles security, and WS-Security Use a Java Application Server (JAS) as an alternative to a standalone web server COMPUTERS,Languages,Java

Efficient Android Threading Multithreading is essential if you want to create an Android app with a great user experience, but how do you know which techniques can help solve your problem? This practical book describes many asynchronous mechanisms available in the Android SDK, and provides guidelines for selecting the ones most appropriate for the app you’re building. Author Anders Goransson demonstrates the advantages and disadvantages of each technique, with sample code and detailed explanations for using it efficiently. The first part of the book describes the building blocks of asynchronous processing, and the second part covers Android libraries and constructs for developing fast, responsive, and well-structured apps. Understand multithreading basics in Java and on the Android platform Learn how threads communicate within and between processes Use strategies to reduce the risk of memory leaks Manage the lifecycle of a basic thread Run tasks sequentially in the background with HandlerThread Use Java’s Executor Framework to control or cancel threads Handle background task execution with AsyncTask and IntentService Access content providers with AsyncQueryHandler Use loaders to update the UI with new data COMPUTERS,Languages,Java

JavaFX For Dummies Unleash the power of JavaFX for a wide range of devices JavaFX For Dummies gives you access to an innovative software platform that allows you to create and deliver rich Internet applications that can run across a wide variety of connected devices. This accessible book highlights the most important features of this powerful graphics platform, giving you the tools to understand it quickly and easily! No experience with JavaFX? No problem. JavaFX For Dummies has been written especially for newbies and it also serves as a great reference resource for more experienced Java developers. Author Doug Lowe has been writing programming books for decades, and he brings his experience and passion to this guide, sharing his expert approach to coding using JavaFX. The book shows you how to work with JavaFX controls, how to enhance your scenic design, and also offers advice on how to make a splash with your programs. Then, the author wraps it all up with extra recommendations and resources to guide you as you move forward. Helps developers quickly learn to take advantage of JavaFX's lightweight, high-performance platform Highlights essential JavaFX features for simple coding that can be rolled out across multiple devices Instructs readers on methods for creating compelling, visually appealing applications Includes recommendations and resources for honing your JavaFX skills With JavaFX For Dummies, you'll be on your way to easier, more efficient coding for a variety of connected devices. COMPUTERS,Languages,Java

Programming Scala Get up to speed on Scala, the JVM language that offers all the benefits of a modern object model, functional programming, and an advanced type system. Packed with code examples, this comprehensive book shows you how to be productive with the language and ecosystem right away, and explains why Scala is ideal for today's highly scalable, data-centric applications that support concurrency and distribution. This second edition covers recent language features, with new chapters on pattern matching, comprehensions, and advanced functional programming. You’ll also learn about Scala’s command-line tools, third-party tools, libraries, and language-aware plugins for editors and IDEs. This book is ideal for beginning and advanced Scala developers alike. Program faster with Scala’s succinct and flexible syntax Dive into basic and advanced functional programming (FP) techniques Build killer big-data apps, using Scala’s functional combinators Use traits for mixin composition and pattern matching for data extraction Learn the sophisticated type system that combines FP and object-oriented programming concepts Explore Scala-specific concurrency tools, including Akka Understand how to develop rich domain-specific languages Learn good design techniques for building scalable and robust Scala applications COMPUTERS,Languages,Java

OCA Full coverage of functional programming and all OCA Java Programmer exam objectives OCA, Oracle Certified Associate Java SE 8 Programmer I Study Guide, Exam 1Z0-808 is a comprehensive study guide for those taking the Oracle Certified Associate Java SE 8 Programmer I exam (1Z0-808). With complete coverage of 100% of the exam objectives, this book provides everything you need to know to confidently take the exam. The release of Java 8 brought the language's biggest changes to date, and for the first time, candidates are required to learn functional programming to pass the exam. This study guide has you covered, with thorough functional programming explanation and information on all key topic areas Java programmers need to know. You'll cover Java inside and out, and learn how to apply it efficiently and effectively to create solutions applicable to real-world scenarios. Work confidently with operators, conditionals, and loops Understand object-oriented design principles and patterns Master functional programming fundamentals COMPUTERS,Languages,Java

Learning Scala Why learn Scala? You don’t need to be a data scientist or distributed computing expert to appreciate this object-oriented functional programming language. This practical book provides a comprehensive yet approachable introduction to the language, complete with syntax diagrams, examples, and exercises. You’ll start with Scala's core types and syntax before diving into higher-order functions and immutable data structures. Author Jason Swartz demonstrates why Scala’s concise and expressive syntax make it an ideal language for Ruby or Python developers who want to improve their craft, while its type safety and performance ensures that it’s stable and fast enough for any application. Learn about the core data types, literals, values, and variables Discover how to think and write in expressions, the foundation for Scala's syntax Write higher-order functions that accept or return other functions Become familiar with immutable data structures and easily transform them with type-safe and declarative operations Create custom infix operators to simplify existing operations or even to start your own domain-specific language Build classes that compose one or more traits for full reusability, or create new functionality by mixing them in at instantiation COMPUTERS,Languages,Java

Living Clojure If you’re an experienced programmer who has not worked with Clojure before, this guide is the perfect thorough but gentle introduction for you. Author Carin Meier not only provides a practical overview of this JVM language and its functional programming concepts, but also includes a complete hands-on training course to help you learn Clojure in a structured way. The first half of the book takes you through Clojure’s unique design and lets you try your hand at two Clojure projects, including a web app. The holistic course in second half provides you with critical tools and resources, including ways to plug into the Clojure community. Understand the basic structure of a Clojure expression Learn how to shape and control code in a functional way Discover how Clojure handles real-world state and concurrency Take advantage of Java classes and learn how Clojure handles polymorphism Manage and use libraries in a Clojure project Use the core.async library for asynchronous and concurrent communication Explore the power of macros in Clojure programming Learn how to think in Clojure by following the book’s seven-week training course COMPUTERS,Languages,Java

OCP Complete, trusted preparation for the Java Programmer II exam OCP: Oracle Certified Professional Java SE 8 Programmer II Study Guide is your comprehensive companion for preparing for Exam 1Z0-809 as well as upgrade Exam 1Z0-810 and Exam 1Z0-813. With full coverage of 100% of exam objectives, this invaluable guide reinforces what you know, teaches you what you don't know, and gives you the hands-on practice you need to boost your skills. Written by expert Java developers, this book goes beyond mere exam prep with the insight, explanations and perspectives that come from years of experience. You'll review the basics of object-oriented programming, understand functional programming, apply your knowledge to database work, and much more. From the basic to the advanced, this guide walks you through everything you need to know to confidently take the OCP 1Z0-809 Exam and upgrade exams 1Z0-810 and 1Z0-813. Java 8 represents the biggest changes to the language to date, and the latest exam now requires that you demonstrate functional programming competence in order to pass. This guide has you covered, with clear explanations and expert advice. Understand abstract classes, interfaces, and class design Learn object-oriented design principles and patterns Delve into functional programming, advanced strings, and localization Master IO, NIO, and JDBC with expert-led database practice If you're ready to take the next step in your IT career, OCP: Oracle Certified Professional Java SE 8 Programmer II Study Guide is your ideal companion on the road to certification. COMPUTERS,Languages,Java

Core Java Volume I--Fundamentals Core Java® has long been recognized as the leading, no-nonsense tutorial and reference for experienced programmers who want to write robust Java code for real-world applications. Now, Core Java®, Volume I–Fundamentals, Tenth Edition, has been extensively updated to reflect the most eagerly awaited and innovative version of Java in years: Java SE 8. Rewritten and reorganized to illuminate new Java SE 8 features, idioms, and best practices, it contains hundreds of example programs–all carefully crafted for easy understanding and practical applicability. Writing for serious programmers solving real-world problems, Cay Horstmann helps you achieve a deep understanding of the Java language and library. In this first volume of the two-volume work, Horstmann focuses on fundamental language concepts and the foundations of modern user interface programming. You’ll find in-depth coverage of topics ranging from Java object-oriented programming to generics, collections, lambda expressions, Swing UI design, and the latest approaches to concurrency and functional programming. This guide will help you Leverage your existing programming knowledge to quickly master core Java syntax Understand how encapsulation, classes, and inheritance work in Java Master interfaces, inner classes, and lambda expressions for functional programming Improve program robustness with exception handling and effective debugging Write safer, more readable programs with generics and strong typing Use pre-built collections to collect multiple objects for later retrieval Master concurrent programming techniques from the ground up Build modern cross-platform GUIs with standard Swing components Deploy configurable applications and applets, and deliver them across the Internet Simplify concurrency and enhance performance with new functional techniques If you’re an experienced programmer moving to Java SE 8, Core Java®, Tenth Edition, will be your reliable, practical companion–now and for many years to come. Look for the companion volume, Core Java®, Volume II–Advanced Features, Tenth Edition (ISBN-13: 978-0-13-417729-8), for coverage of Java 8 streams, input and output, XML, databases, annotations, and other advanced topics. Register your product or convenient access to downloads, updates, and corrections as they become available. See inside the book for information. COMPUTERS,Languages,Java

Java I/O, NIO and NIO.2 Java I/O, NIO and NIO.2 is a power-packed book that is an accelerated guide and reference on buffers, files, sockets, datagrams, and pipe channels as found in the Java I/O, NIO, and NIO.2 reference implementations. In this book, you'll also learn how and when to use selectors, regular expressions, including patterns, matchers and more. You'll learn how to work with Charsets, formatters and scanners. You'll - all in all - learn how to use and apply NIO, NIO.2 and the enhancements available. After reading and using this book, you'll gain the accelerated knowledge and skill level to really build applications with efficient data access, especially for today's cloud computing streaming data needs. COMPUTERS,Languages,Java

Java For Dummies A new edition of the bestselling guide to Java If you want to learn to speak the world’s most popular programming language like a native, Java For Dummies is your ideal companion. With a focus on reusing existing code, it quickly and easily shows you how to create basic Java objects, work with Java classes and methods, understand the value of variables, learn to control program flow with loops or decision-making statements, and so much more! Java is everywhere, runs on almost any computer, and is the engine that drives the coolest applications. Written for anyone who’s ever wanted to tackle programming with Java but never knew quite where to begin, this bestselling guide is your ticket to success! Featuring updates on everything you’ll encounter in Java 9—and brimming with tons of step-by-step instruction—it’s the perfect resource to get you up and running with Java in a jiffy! Discover the latest features and tools in Java 9 Learn to combine several smaller programs to create a bigger program Create basic Java objects and reuse code Confidently handle exceptions and events If you’re ready to jump into Java, this bestselling guide will help keep your head above water! COMPUTERS,Languages,Java

OCA / OCP Java SE 8 Programmer Practice Tests Test your knowledge and prepare for the OCA/OCP exams OCA/OCP Java SE 8 Programmer Practice Tests complements the Sybex OCA: Oracle Certified Associate Java SE 8 Programmer I Certification Study Guide and the OCP: Oracle Certified Professional Java SE 8 Programmer II Study Guide for exams 1Z0-808 and 1ZO-809 by providing last minute review of 100% of exam objectives. Get the advantage of over 1,000 expert crafted questions that not only provide the answer, but also give detailed explanations. You will have access to unique practice questions that cover all 21 objective domains in the OCA/OCP exams in the format you desire--test questions can also be accessed via the Sybex interactive learning environment. Two additional practice exams will ensure that you are ready for exam day. Whether you have studied with Sybex study guides for your OCA/OCP or have used another brand, this is your chance to test your skills. Access to all practice questions online with the Sybex interactive learning environment Over 1,000 unique practice questions and 2 practice exams include expert explanations Covers 100% of all 21 OCA/OCP objective domains for Exams 1Z0-809 and 1Z0-809 Studying the objectives are one thing, but diving deeper and uncovering areas where further attention is needed can increase your chance of exam day success. Full coverage of all domains shows you what to expect on exam day, and accompanying explanations help you pinpoint which objectives deserve another look. COMPUTERS,Languages,Java

Reactive Programming with RxJava In today’s app-driven era, when programs are asynchronous and responsiveness is so vital, reactive programming can help you write code that’s more reliable, easier to scale, and better-performing. With this practical book, Java developers will first learn how to view problems in the reactive way, and then build programs that leverage the best features of this exciting new programming paradigm. Authors Tomasz Nurkiewicz and Ben Christensen include concrete examples that use the RxJava library to solve real-world performance issues on Android devices as well as the server. You’ll learn how RxJava leverages parallelism and concurrency to help you solve today’s problems. This book also provides a preview of the upcoming 2.0 release. Write programs that react to multiple asynchronous sources of input without descending into "callback hell" Get to that aha! moment when you understand how to solve problems in the reactive way Cope with Observables that produce data too quickly to be consumed Explore strategies to debug and to test programs written in the reactive style Efficiently exploit parallelism and concurrency in your programs Learn about the transition to RxJava version 2 COMPUTERS,Languages,Java

Beginning Programming with Java For Dummies Learn to speak the Java language like the pros Are you new to programming and have decided that Java is your language of choice? Are you a wanna-be programmer looking to learn the hottest lingo around? Look no further! Beginning Programming with Java For Dummies, 5th Edition is the easy-to-follow guide you'll want to keep in your back pocket as you work your way toward Java mastery! In plain English, it quickly and easily shows you what goes into creating a program, how to put the pieces together, ways to deal with standard programming challenges, and so much more. Whether you're just tooling around or embarking on a career, this is the ideal resource you'll turn to again and again as you perfect your understanding of the nuances of this popular programming language. Packed with tons of step-by-step instruction, this is the only guide you need to start programming with Java like a pro. Updated for Java 9, learn the language with samples and the Java toolkit Familiarize yourself with decisions, conditions, statements, and information overload Differentiate between loops and arrays, objects and classes, methods, and variables Find links to additional resources Once you discover the joys of Java programming, you might just find you're hooked. Sound like fun? Here's the place to start. COMPUTERS,Languages,Java

Spock Most developers would agree that writing automated tests is a good idea, but writing good, well-structured tests is still an elusive skill for many. For Java and Groovy developers, however, there’s good news. This practical guide shows you how to write concise and highly readable tests with Spock, the most innovative testing and specification framework for the JVM since JUnit. Author Rob Fletcher takes you from Spock basics to advanced topics, using fully worked integration examples. Through the course of this book, you’ll build a simple web application—Squawker—that allows users to post short messages. You’ll discover how much easier it is to write automated tests with Spock’s straightforward and expressive language. Start by learning how to write simple unit tests Understand the lifecycle of Spock specifications and feature methods Dive into interaction testing, using Spock’s intuitive syntax for dealing with mocks and stubs Learn about parameterized tests—writing feature methods that run for multiple sets of data Move into advanced topics, such as writing idiomatic Spock code and driving parameterized tests with file or database input Learn how everything works together in a standalone, fully-worked, test-driven development example COMPUTERS,Languages,Java

Data Science with Java Data Science is booming thanks to R and Python, but Java brings the robustness, convenience, and ability to scale critical to today’s data science applications. With this practical book, Java software engineers looking to add data science skills will take a logical journey through the data science pipeline. Author Michael Brzustowicz explains the basic math theory behind each step of the data science process, as well as how to apply these concepts with Java. You’ll learn the critical roles that data IO, linear algebra, statistics, data operations, learning and prediction, and Hadoop MapReduce play in the process. Throughout this book, you’ll find code examples you can use in your applications. Examine methods for obtaining, cleaning, and arranging data into its purest form Understand the matrix structure that your data should take Learn basic concepts for testing the origin and validity of data Transform your data into stable and usable numerical values Understand supervised and unsupervised learning algorithms, and methods for evaluating their success Get up and running with MapReduce, using customized components suitable for data science algorithms COMPUTERS,Languages,Java

Learning RxJava Reactive Programming with Java and ReactiveX About This Book Explore the essential tools and operators RxJava provides, and know which situations to use them in Delve into Observables and Subscribers, the core components of RxJava used for building scalable and performant reactive applications Delve into the practical implementation of tools to effectively take on complex tasks such as concurrency and backpressure Who This Book Is For The primary audience for this book is developers with at least a fundamental mastery of Java. Some readers will likely be interested in RxJava to make programs more resilient, concurrent, and scalable. Others may be checking out reactive programming just to see what it is all about, and to judge whether it can solve any problems they may have. What You Will Learn Learn the features of RxJava 2 that bring about many significant changes, including new reactive types such as Flowable, Single, Maybe, and Completable Understand how reactive programming works and the mindset to "think reactively" Demystify the Observable and how it quickly expresses data and events as sequences Learn the various Rx operators that transform, filter, and combine data and event sequences Leverage multicasting to push data to multiple destinations, and cache and replay them Discover how concurrency and parallelization work in RxJava, and how it makes these traditionally complex tasks trivial to implement Apply RxJava and Retrolambda to the Android domain to create responsive Android apps with better user experiences Use RxJava with the Kotlin language to express RxJava more idiomatically with extension functions, data classes, and other Kotlin features In Detail RxJava is a library for composing asynchronous and event-based programs using Observable sequences for the JVM, allowing developers to build robust applications in less time. Learning RxJava addresses all the fundamentals of reactive programming to help readers write reactive code, as well as teach them an effective approach to designing and implementing reactive libraries and applications. Starting with a brief introduction to reactive programming concepts, there is an overview of Observables and Observers, the core components of RxJava, and how to combine different streams of data and events together. You will also learn simpler ways to achieve concurrency and remain highly performant, with no need for synchronization. Later on, we will leverage backpressure and other strategies to cope with rapidly-producing sources to prevent bottlenecks in your application. After covering custom operators, testing, and debugging, the book dives into hands-on examples using RxJava on Android as well as Kotlin. Style and approach This book will be different from other Rx books, taking an approach that comprehensively covers Rx concepts and practical applications. COMPUTERS,Languages,Java

Spring Boot Messaging Build messaging applications using the power of Spring Boot; use Spring application events over the Web; use WebSocket, SockJS, and STOMP messaging with Spring MVC; and use Spring JMS, Redis Pub/Sub and Spring AMQP for reliable messaging solutions. This book covers all the Spring Messaging APIs using Spring Boot. Written by a Pivotal engineer, Spring Boot Messaging is an authoritative guide to the many messaging APIs and how to use these for creating enterprise and integration solutions. You will learn and integrate these messaging APIs with more complex enterprise and cloud applications: for example, you will see how to use Spring Cloud Stream for creating message-driven and cloud native microservices. In addition, you’ll discover the new Spring Integration DSL and use it with Spring Cloud Stream to build integration solutions using every enterprise integration pattern. Finally, you’ll see Spring Reactor and Spring Cloud to take your application to the next level. After reading this book, you will come away with a case study application walk-through and will be able to use it as a template for building your own Spring messaging applications or messaging features within your enterprise or cloud application. What You'll Learn Use the main Spring messaging APIs with Spring Framework 5 Build messaging applications over the Web Use WebSocket, SockJS, and STOMP messaging Integrate Spring JMS and Spring AMQP into your applications Work with Spring Cloud Stream and microservices Who This Book Is For Enterprise Java developers who have at least some previous experience with the Spring Framework and/or the Spring platform. COMPUTERS,Languages,Java

Think Data Structures If you’re a student studying computer science or a software developer preparing for technical interviews, this practical book will help you learn and review some of the most important ideas in software engineering—data structures and algorithms—in a way that’s clearer, more concise, and more engaging than other materials. By emphasizing practical knowledge and skills over theory, author Allen Downey shows you how to use data structures to implement efficient algorithms, and then analyze and measure their performance. You’ll explore the important classes in the Java collections framework (JCF), how they’re implemented, and how they’re expected to perform. Each chapter presents hands-on exercises supported by test code online. Use data structures such as lists and maps, and understand how they work Build an application that reads Wikipedia pages, parses the contents, and navigates the resulting data tree Analyze code to predict how fast it will run and how much memory it will require Write classes that implement the Map interface, using a hash table and binary search tree Build a simple web search engine with a crawler, an indexer that stores web page contents, and a retriever that returns user query results Other books by Allen Downey include Think Java, Think Python, Think Stats, and Think Bayes. COMPUTERS,Languages,Java

Programmer's Guide to Java SE 8 Oracle Certified Associate (OCA), A Unique among Java tutorials, A Programmer’s Guide to Java® SE 8 Oracle Certified Associate (OCA): A Comprehensive Primer combines an integrated, expert introduction to Java SE 8 with comprehensive coverage of Oracle’s new Java SE 8 OCA exam 1Z0-808. Based on Mughal and Rasmussen’s highly regarded guide to the original SCJP Certification, this streamlined volume has been thoroughly revised to reflect major changes in the new Java SE 8 OCA exam. It features an increased focus on analyzing code scenarios and not just individual language constructs, and each exam objective is thoroughly addressed, reflecting the latest Java SE 8 features, API classes, and best practices for effective programming. Other features include Summaries that clearly state what topics to read for each objective of the Java SE 8 OCA exam Dozens of exam-relevant review questions with annotated answers Programming exercises and solutions to put theory into practice A mock exam with realistic questions to find out if you are ready to take the official exam An introduction to essential concepts in object-oriented programming (OOP) and functional-style programming In-depth coverage of declarations, access control, operators, flow control, OOP techniques, lambda expressions, key API classes, and more Program output demonstrating expected results from complete Java programs Advice on avoiding common pitfalls in writing Java code and on taking the certification exam Extensive use of UML (Unified Modeling Language) for illustration purposes COMPUTERS,Languages,Java

Introduction to Programming in Java This is the eBook of the printed book and may not include any media, website access codes, or print supplements that may come packaged with the bound book. Programming skills are indispensable in today’s world, not just for computer science students, but also for anyone in any scientific or technical discipline. Introduction to Programming in Java, Second Edition, by Robert Sedgewick and Kevin Wayne is an accessible, interdisciplinary treatment that emphasizes important and engaging applications, not toy problems. The authors supply the tools needed for students and professionals to learn that programming is a natural, satisfying, and creative experience, and to become conversant with one of the world’s most widely used languages. This example-driven guide focuses on Java’s most useful features and brings programming to life for every student in the sciences, engineering, and computer science. Coverage includes Basic elements of programming: variables, assignment statements, built-in data types, conditionals, loops, arrays, and I/O, including graphics and sound Functions, modules, and libraries: organizing programs into components that can be independently debugged, maintained, and reused Algorithms and data structures: sort/search algorithms, stacks, queues, and symbol tables Applications from applied math, physics, chemistry, biology, and computer science Drawing on their extensive classroom experience, throughout the text the authors provide Q&As, exercises, and opportunities for creative engagement with the material. Together with the companion materials described below, this book empowers people to pursue a modern approach to teaching and learning programming. Companion web site (introcs.cs.princeton.edu/java) contains Chapter summaries Supplementary exercises, some with solutions Detailed instructions for installing a Java programming environment Program code and test data suitable for easy download Detailed creative exercises, projects, and other supplementary materials Companion studio-produced online videos (informit.com/sedgewick) are available for purchase and provide students and professionals with the opportunity to engage with the material at their own pace and give instructors the opportunity to spend their time with students helping them to succeed on assignments and exams. Register your product at informit.com/register for convenient access to downloads, updates, and corrections as they become available. COMPUTERS,Languages,Java

Scala for the Impatient This is the eBook of the printed book and may not include any media, website access codes, or print supplements that may come packaged with the bound book. Interest in the Scala programming language continues to grow for many reasons. Scala embraces the functional programming style without abandoning the object-oriented paradigm, and it allows you to write programs more concisely than in Java. Because Scala runs on the JVM, it can access any Java library and is interoperable with familiar Java frameworks. Scala also makes it easier to leverage the full power of concurrency. Written for experienced Java, C++, or C# programmers who are new to Scala or functional programming, Scala for the Impatient, Second Edition, introduces the key Scala concepts and techniques you need in order to be productive quickly. It is the perfect introduction to the language, particularly for impatient readers who want to learn the fundamentals of Scala so they can start coding quickly. It doesn’t attempt to exhaustively list all the features of the language or make you suffer through long and contrived examples. Instead, carefully crafted examples and hands-on activities guide you through well-defined stages of competency, from basic to expert. This revised edition has been thoroughly updated for Scala 2.12 and reflects current Scala usage. It includes added coverage of recent Scala features, including string interpolation, dynamic invocation, implicit classes, and futures. Scala is a big language, but you can use it effectively without knowing all of its details intimately. This title provides precisely the information that you need to get started in compact, easy-to-understand chunks. Get started quickly with Scala’s interpreter, syntax, tools, and unique idioms Master core language features: functions, arrays, maps, tuples, packages, imports, exception handling, and more Become familiar with object-oriented programming in Scala: classes, inheritance, and traits Use Scala for real-world programming tasks: working with files, regular expressions, and XML Work with higher-order functions and the powerful Scala collections library Leverage Scala’s powerful pattern matching and case classes Create concurrent programs with Scala futures Implement domain-specific languages Understand the Scala type system Apply advanced “power tools,†such as annotations, implicits, and type classes COMPUTERS,Languages,Java

Building Microservices with Go Your one-stop guide to the common patterns and practices, showing you how to apply these using the Go programming language About This Book This short, concise, and practical guide is packed with real-world examples of building microservices with Go It is easy to read and will benefit smaller teams who want to extend the functionality of their existing systems Using this practical approach will save your money in terms of maintaining a monolithic architecture and demonstrate capabilities in ease of use Who This Book Is For You should have a working knowledge of programming in Go, including writing and compiling basic applications. However, no knowledge of RESTful architecture, microservices, or web services is expected. If you are looking to apply techniques to your own projects, taking your first steps into microservice architecture, this book is for you. What You Will Learn Plan a microservice architecture and design a microservice Write a microservice with a RESTful API and a database Understand the common idioms and common patterns in microservices architecture Leverage tools and automation that helps microservices become horizontally scalable Get a grounding in containerization with Docker and Docker-Compose, which will greatly accelerate your development lifecycle Manage and secure Microservices at scale with monitoring, logging, service discovery, and automation Test microservices and integrate API tests in Go In Detail Microservice architecture is sweeping the world as the de facto pattern to build web-based applications. Golang is a language particularly well suited to building them. Its strong community, encouragement of idiomatic style, and statically-linked binary artifacts make integrating it with other technologies and managing microservices at scale consistent and intuitive. This book will teach you the common patterns and practices, showing you how to apply these using the Go programming language. It will teach you the fundamental concepts of architectural design and RESTful communication, and show you patterns that provide manageable code that is supportable in development and at scale in production. We will provide you with examples on how to put these concepts and patterns into practice with Go. Whether you are planning a new application or working in an existing monolith, this book will explain and illustrate with practical examples how teams of all sizes can start solving problems with microservices. It will help you understand Docker and Docker-Compose and how it can be used to isolate microservice dependencies and build environments. We finish off by showing you various techniques to monitor, test, and secure your microservices. By the end, you will know the benefits of system resilience of a microservice and the advantages of Go stack. Style and approach The step-by-step tutorial focuses on building microservices. Each chapter expands upon the previous one, teaching you the main skills and techniques required to be a successful microservice practitioner. COMPUTERS,Languages,Java

Modern Java Recipes The introduction of functional programming concepts in Java SE 8 was a drastic change for this venerable object-oriented language. Lambda expressions, method references, and streams fundamentally changed the idioms of the language, and many developers have been trying to catch up ever since. This cookbook will help. With more than 70 detailed recipes, author Ken Kousen shows you how to use the newest features of Java to solve a wide range of problems. For developers comfortable with previous Java versions, this guide covers nearly all of Java SE 8, and includes a chapter focused on changes coming in Java 9. Need to understand how functional idioms will change the way you write code? This cookbook—chock full of use cases—is for you. Recipes cover: The basics of lambda expressions and method references Interfaces in the java.util.function package Stream operations for transforming and filtering data Comparators and Collectors for sorting and converting streaming data Combining lambdas, method references, and streams Creating instances and extract values from Java’s Optional type New I/O capabilities that support functional streams The Date-Time API that replaces the legacy Date and Calendar classes Mechanisms for experimenting with concurrency and parallelism COMPUTERS,Languages,Java

Pro Java Clustering and Scalability Build clustered and scalable Java-based, real-time applications using Spring Framework, Boot, WebSocket, Cassandra, Redis and RabbitMQ. In this book, you'll tie all this together with a dive-in case study, a real-time scalable chat application under differing scenarios. Pro Java Clustering and Scalability also discusses how to horizontally scale the WebSocket chat application using a full STOMP broker such as RabbitMQ. Although this is a programming book, it also discusses many interesting infrastructure topics and tips about continuous delivery, Docker, NoSQL (Cassandra and Redis) and other related technologies. What You Will Learn Handle clustering and scalability using various open source Java, microservices, and web services tools and technologies Use Spring Framework, Boot, and other Spring technologies Integrate with Redis, RabbitMQ, Cassandra, NoSQL, and much more Test the case study code under various scenarios and stresses Who This Book Is For Experienced Java developers with at least some prior experience with Java, especially Spring Framework, Boot and other tools, and some web services. COMPUTERS,Languages,Java

Java Pocket Guide Any time you need quick answers for developing or debugging Java programs, this pocket guide is the ideal reference to standard features of the Java programming language and its platform. You’ll find helpful programming examples, tables, figures, and lists fast—including Java 9 features such as modular source code and the new JShell interactive command-line REPL. It’s a handy companion, whether you’re in the office, in the lab, or on the road. This book also provides material to help you prepare for the Oracle Certified Associate Java Programmer exam. Quickly find Java language details, such as naming conventions, types, statements and blocks, and object-oriented programming Get details on the Java SE platform, including development basics, memory management, concurrency, and generics Use new features in Java 9, including modular source code and JShell Browse through information on basic input/output, NIO 2.0, the Java collections framework, and the Java Scripting API Get supplemental references to fluent APIs, third-party tools, and basics of the Unified Modeling Language (UML) COMPUTERS,Languages,Java

Modular Programming in Java 9 Kick-start your modular programming journey and gear up for the future of Java development About This Book Master design patterns and best practices to build truly modular applications in Java 9 Upgrade your old Java code to Java 9 with ease Build and run a smooth functioning multi-module application. Who This Book Is For This book is written for Java developers who are interested in learning and understanding the techniques and best practices to build modular applications in Java. The book assumes some previous programming experience in Java 8 or earlier, familiarity with the basic Java types such as classes and interfaces, as well as experience in compiling and executing Java programs. What You Will Learn Get introduced to the concept of modules and modular programming by working on a fully modular Java application Build and configure your own Java 9 modules Work with multiple modules and establish inter-module dependencies Understand and use the principles of encapsulation, readability, and accessibility Use jlink to generate fully loaded custom runtime images like a pro Discover the best practices to help you write awesome modules that are a joy to use and maintain Upgrade your old Java code to use the new Java 9 module system In Detail The Java 9 module system is an important addition to the language that affects the way we design, write, and organize code and libraries in Java. It provides a new way to achieve maintainable code by the encapsulation of Java types, as well as a way to write better libraries that have clear interfaces. Effectively using the module system requires an understanding of how modules work and what the best practices of creating modules are. This book will give you step-by-step instructions to create new modules as well as migrate code from earlier versions of Java to the Java 9 module system. You'll be working on a fully modular sample application and add features to it as you learn about Java modules. You'll learn how to create module definitions, setup inter-module dependencies, and use the built-in modules from the modular JDK. You will also learn about module resolution and how to use jlink to generate custom runtime images. We will end our journey by taking a look at the road ahead. You will learn some powerful best practices that will help you as you start building modular applications. You will also learn how to upgrade an existing Java 8 codebase to Java 9, handle issues with libraries, and how to test Java 9 applications. Style and Approach The book is a step-by-step guide to understanding Modularity and building a complete application using a modular design. COMPUTERS,Languages,Java

Java 9 Modularity The upcoming Java 9 module system will affect existing applications and offer new ways of creating modular and maintainable applications. With this hands-on book, Java developers will learn not only about the joys of modularity, but also about the patterns needed to create truly modular and reliable applications. Authors Sander Mak and Paul Bakker teach you the concepts behind the Java 9 module system, along with the new tools it offers. You’ll also learn how to modularize existing code and how to build new Java applications in a modular way. Understand Java 9 module system concepts Master the patterns and practices for building truly modular applications Migrate existing applications and libraries to Java 9 modules Use JDK 9 tools for modular development and migration COMPUTERS,Languages,Java

Haskell Cookbook Save time and build fast, functional, and concurrent application using Haskell About This Book Comprehensive guide for establishing a strong foundation in Haskell and developing pragmatic code Create a full fledged web application using Haskell Work with Lens, Haskell Extensions, and write code for concurrent and distributed applications Who This Book Is For This book is targeted at readers who wish to learn the Haskell language. If you are a beginner, Haskell Cookbook will get you started. If you are experienced, it will expand your knowledge base. A basic knowledge of programming will be helpful. What You Will Learn Use functional data structures and algorithms to solve problems Understand the intricacies of the type system Create a simple parser for integer expressions with additions Build high-performance web services with Haskell Master mechanisms for concurrency and parallelism in Haskell Perform parsing and handle scarce resources such as filesystem handles Organize your programs by creating your own types and type classes In Detail Haskell is a purely functional language that has the great ability to develop large and difficult, but easily maintainable software. Haskell Cookbook provides recipes that start by illustrating the principles of functional programming in Haskell, and then gradually build up your expertise in creating industrial-strength programs to accomplish any goal. The book covers topics such as Functors, Applicatives, Monads, and Transformers. You will learn various ways to handle state in your application and explore advanced topics such as Generalized Algebraic Data Types, higher kind types, existential types, and type families. The book will discuss the association of lenses with type classes such as Functor, Foldable, and Traversable to help you manage deep data structures. With the help of the wide selection of examples in this book, you will be able to upgrade your Haskell programming skills and develop scalable software idiomatically. Style and approach The book follows a recipe-based approach. Each recipe addresses specific problems and issues. The recipes provide discussions and insights to explain these problems. COMPUTERS,Languages,Java

Beginning Spring Boot 2 Learn Spring Boot and how to build Java-based enterprise, web, and microservice applications with it. In this book, you'll see how to work with relational and NoSQL databases, build your first microservice, enterprise, or web application, and enhance that application with REST APIs. You'll also learn how to build reactive web applications using Spring Boot along with Spring Web Reactive. Then you’ll secure your Spring Boot-created application or service before testing and deploying it. After reading and learning with Beginning Spring Boot 2, you'll have the skills and techniques to start building your first Spring Boot applications and microservices with confidence to take the next steps in your career journey. What You'll Learn Use Spring Boot autoconfiguration Work with relational and NoSQL databases Build web applications with Spring Boot Apply REST APIs using Spring Boot Create reactive web applications using Spring Web Reactive Secure your Spring Boot applications or web services Test and deploy your Spring Boot applications Who This Book Is For Experienced Java and Spring Framework developers who are new to the new Spring Boot micro-framework. COMPUTERS,Languages,Java

Troubleshooting Java Performance Troubleshoot the most widespread and pernicious Java performance problems using a set of open-source and freely-available tools that will make you dramatically more productive in finding the root causes of slow performance. This is a brief book that focuses on a small number of performance anti-patterns, and you’ll find that most problems you encounter fit into one of these anti-patterns. The book provides a specific method in a series of steps referred to as the “P.A.t.h. Checklist†that encompasses persistence, alien systems, threads, and heap management. These steps guide you through a troubleshooting process that is repeatable, that you can apply to any performance problem in a Java application. This technique is especially helpful in 'dark' environments with little monitoring. Performance problems are not always localized to Java, but often fall into the realms of database access and server load. This book gives attention to both of these issues through examples showing how to identify repetitive SQL, and identify architecture-wide performance problems ahead of production rollout. Learn how to apply load like an expert, and determine how much load to apply to determine whether your system scales. Included are walk-throughs of a dozen server-side performance puzzles that are ready to run on your own machine. Following these examples helps you learn to: Assess the performance health of four main problems areas in a Java system: The P.A.t.h. Checklist presents each area with its own set of plug-it-in-now tools Pinpoint the code at fault for CPU and other bottlenecks without a Java profiler Find memory leaks in just minutes using heapSpank, the author's open-source leak detector utility that is freely available from heapSpank.org The repeatable method provided in this book is an antidote to lackluster average response times that are multi-second throughout the industry. This book provides a long absent, easy-to-follow, performance training regimen that will benefit anyone programming in Java. What You'll Learn Avoid the 6 most common ways to mess up a load test Determine the exact number of threads to dial into the load generator to test your system's scalability Detect the three most common SQL performance anti-patterns Measure network response times of calls to back-end systems ('alien systems') Identify whether garbage collection performance is healthy or unhealthy and whether delays are caused by problems in the old or new generation, so you know which generation needs to be adjusted Who This Book Is For Intermediate and expert Java developers and architects. Java experts will be able to update their skill set with the latest and most productive, open-source Java performance tools. Intermediate Java developers are exposed to the most common performance defects that repeatedly show up in Java applications, ones that account for the bulk of slow-performing systems. Experts and intermediates alike will benefit from the chapters on load generation. COMPUTERS,Languages,Java

Spring 5 Recipes Solve all your Spring 5 problems using complete and real-world code examples. When you start a new project, you’ll be able to copy the code and configuration files from this book, and then modify them for your needs. This can save you a great deal of work over creating a project from scratch. The recipes in Spring 5 Recipes cover Spring fundamentals such as Spring IoC container, Spring AOP/ AspectJ, and more. Other recipes include Spring enterprise solutions for topics such as Spring Java EE integration, Spring Integration, Spring Batch, Spring Remoting, messaging, transactions, and working with big data and the cloud using Hadoop and MongoDB. Finally, Spring web recipes cover Spring MVC, other dynamic scripting, integration with the popular Grails Framework (and Groovy), REST/web services, and more. You’ll also see recipes on new topics such as Spring Framework 5, reactive Spring, Spring 5 microservices, the functional web framework and much more. This book builds upon the best-selling success of the previous editions and focuses on the latest Spring Framework features for building enterprise Java applications. What You'll Learn Get re-usable code recipes and snippets for core Spring, annotations and other development tools Access Spring MVC for web development Work with Spring REST and microservices for web services development and integration into your enterprise Java applications Use Spring Batch, NoSQL and big data for building and integrating various cloud computing services and resources Integrate Java Enterprise Edition and other Java APIs for use in Spring Use Grails code and much more Who This Book Is For Experienced Java and Spring programmers. COMPUTERS,Languages,Java

Java Programming for Beginners Java Programming for Beginners is an introduction to Java programming, taking you through the Java syntax and the fundamentals of object-oriented programming. About This Book Learn the basics of Java programming in a step-by-step manner Simple, yet thorough steps that beginners can follow Teaches you transferable skills, such as flow control and object-oriented programming Who This Book Is For This book is for anyone wanting to start learning the Java language, whether you're a student, casual learner, or existing programmer looking to add a new language to your skillset. No previous experience of Java or programming in general is required. What You Will Learn Learn the core Java language for both Java 8 and Java 9 Set up your Java programming environment in the most efficient way Get to know the basic syntax of Java Understand object-oriented programming and the benefits that it can bring Familiarize yourself with the workings of some of Java's core classes Design and develop a basic GUI Use industry-standard XML for passing data between applications In Detail Java is an object-oriented programming language, and is one of the most widely accepted languages because of its design and programming features, particularly in its promise that you can write a program once and run it anywhere. Java Programming for Beginners is an excellent introduction to the world of Java programming, taking you through the basics of Java syntax and the complexities of object-oriented programming. You'll gain a full understanding of Java SE programming and will be able to write Java programs with graphical user interfaces that run on PC, Mac, or Linux machines. This book is full of informative and entertaining content, challenging exercises, and dozens of code examples you can run and learn from. By reading this book, you'll move from understanding the data types in Java, through loops and conditionals, and on to functions, classes, and file handling. The book finishes with a look at GUI development and training on how to work with XML. The book takes an efficient route through the Java landscape, covering all of the core topics that a Java developer needs. Whether you're an absolute beginner to programming, or a seasoned programmer approaching an object-oriented language for the first time, Java Programming for Beginners delivers the focused training you need to become a Java developer. Style and approach This book takes a very hands-on approach, carefully building on lessons learned with snippets and tutorials to build real projects. COMPUTERS,Languages,Java

Spring Security Learn how to secure your Java applications from hackers using Spring Security 4.2 About This Book Architect solutions that leverage the full power of Spring Security while remaining loosely coupled. Implement various scenarios such as supporting existing user stores, user sign up, authentication, and supporting AJAX requests, Integrate with popular Microservice and Cloud services such as Zookeeper, Eureka, and Consul, along with advanced techniques, including OAuth, JSON Web Token's (JWS), Hashing, and encryption algorithms Who This Book Is For This book is intended for Java Web and/or RESTful webservice developers and assumes a basic understanding of creating Java 8, Java Web and/or RESTful webservice applications, XML, and the Spring Framework. You are not expected to have any previous experience with Spring Security. What You Will Learn Understand common security vulnerabilities and how to resolve them Learn to perform initial penetration testing to uncover common security vulnerabilities Implement authentication and authorization Learn to utilize existing corporate infrastructure such as LDAP, Active Directory, Kerberos, CAS, OpenID, and OAuth Integrate with popular frameworks such as Spring, Spring-Boot, Spring-Data, JSF, Vaaden, jQuery, and AngularJS. Gain deep understanding of the security challenges with RESTful webservices and microservice architectures Integrate Spring with other security infrastructure components like LDAP, Apache Directory server and SAML In Detail Knowing that experienced hackers are itching to test your skills makes security one of the most difficult and high-pressured concerns of creating an application. The complexity of properly securing an application is compounded when you must also integrate this factor with existing code, new technologies, and other frameworks. Use this book to easily secure your Java application with the tried and trusted Spring Security framework, a powerful and highly customizable authentication and access-control framework. The book starts by integrating a variety of authentication mechanisms. It then demonstrates how to properly restrict access to your application. It also covers tips on integrating with some of the more popular web frameworks. An example of how Spring Security defends against session fixation, moves into concurrency control, and how you can utilize session management for administrative functions is also included. It concludes with advanced security scenarios for RESTful webservices and microservices, detailing the issues surrounding stateless authentication, and demonstrates a concise, step-by-step approach to solving those issues. And, by the end of the book, readers can rest assured that integrating version 4.2 of Spring Security will be a seamless endeavor from start to finish. Style and approach This practical step-by-step tutorial has plenty of example code coupled with the necessary screenshots and clear narration so that grasping content is made easier and quicker. COMPUTERS,Languages,Java

Effective Java The Definitive Guide to Java Platform Best Practices–Updated for Java 7, 8, and 9 Java has changed dramatically since the previous edition of Effective Java was published shortly after the release of Java 6. This Jolt award-winning classic has now been thoroughly updated to take full advantage of the latest language and library features. The support in modern Java for multiple paradigms increases the need for specific best-practices advice, and this book delivers. As in previous editions, each chapter of Effective Java, Third Edition, consists of several “items,†each presented in the form of a short, stand-alone essay that provides specific advice, insight into Java platform subtleties, and updated code examples. The comprehensive descriptions and explanations for each item illuminate what to do, what not to do, and why. The third edition covers language and library features added in Java 7, 8, and 9, including the functional programming constructs that were added to its object-oriented roots. Many new items have been added, including a chapter devoted to lambdas and streams. New coverage includes Functional interfaces, lambda expressions, method references, and streams Default and static methods in interfaces Type inference, including the diamond operator for generic types The @SafeVarargs annotation The try-with-resources statement New library features such as the Optional interface, java.time, and the convenience factory methods for collections COMPUTERS,Languages,Java

Java EE 8 Application Development Develop Enterprise Java applications compliant with the latest version of the Java EE specification About This Book This book covers all of the major Java EE 8 APIs and includes new additions such as enhanced Security, JSON-B Processing, and more Learn additional Java EE APIs, such as the Java API for Websocket and the Java Message Service (JMS) Develop applications by taking advantage of the latest versions of CDI, Security, Servlets, and JSF and other Java EE specifications Who This Book Is For If you are a Java developer who wants to become proficient with Java EE 8, this book is ideal for you. You are expected to have some experience with Java and to have developed and deployed applications in the past, but you don't need any previous knowledge of Java EE. What You Will Learn Develop and deploy Java EE applications Embrace the latest additions to the Contexts and Dependency Injection (CDI) specification to develop Java EE applications Develop web-based applications by utilizing the latest version of JavaServer Faces, JSF 2.3. Understand the steps needed to process JSON data with JSON-P and the new JSON-B Java EE API Implement RESTful web services using the new JAX-RS 2.1 API, which also includes support for Server-Sent Events (SSE) and the new reactive client API In Detail Java EE is an Enterprise Java standard. Applications written to comply with the Java EE specification do not tie developers to a specific vendor; instead they can be deployed to any Java EE compliant application server. With this book, you'll get all the tools and techniques you need to build robust and scalable applications in Java EE 8. This book covers all the major Java EE 8 APIs including JSF 2.3, Enterprise JavaBeans (EJB) 3.2, Contexts and Dependency Injection (CDI) 2.0, the Java API for WebSockets, JAX-RS 2.1, Servlet 4.0, and more. The book begins by introducing you to Java EE 8 application development and goes on to cover all the major Java EE 8 APIs. It goes beyond the basics to develop Java EE applications that can be deployed to any Java EE 8 compliant application server. It also introduces advanced topics such as JSON-P and JSON-B, the Java APIs for JSON processing, and the Java API for JSON binding. These topics dive deep, explaining how the two APIs (the Model API and the Streaming API) are used to process JSON data. Moving on, we cover additional Java EE APIs, such as the Java API for Websocket and the Java Message Service (JMS), which allows loosely coupled, asynchronous communication. Further on, you'll discover ways to secure Java EE applications by taking advantage of the new Java EE Security API. Finally, you'll learn more about the RESTful web service development using the latest JAX-RS 2.1 specification. You'll also get to know techniques to develop cloud-ready microservices in Java EE. Style and approach The book takes a pragmatic approach, showing you various techniques to utilize new features of Java EE 8 specification. It is packed with clear, step-by-step instructions, practical examples, and straightforward explanations. COMPUTERS,Languages,Java

Kotlin Blueprints Get to know the building blocks of Kotlin and best practices when using quality world-class applications About This Book Learn to build exciting and scalable Android and web applications (both the server-side and client-side parts) with your Kotlin skills Dive into the great ecosystem of Kotlin frameworks and libraries through projects that you'll build using this book This project-based guide contains clear instructions to help you extend your applications across a wide domain Who This Book Is For This practical guide is for programmers who are already familiar with Kotlin. If you are familiar with Kotlin and want to put your knowledge to work, then this is the book for you. Kotlin programming knowledge is a must. What You Will Learn See how Kotlin's power and versatility make it a great choice to create applications across various platforms, and how it delivers business and technology benefits Write a robust web applications using Kotlin with Spring Boot Write Android applications with ease using Kotlin Write rich desktop applications in Kotlin Learn how Kotlin can generate Javascript and how this can be used on client side and server side development Understand how native applications can be written with Kotlin/Native Learn the practical aspects of programming in each of the applications In Detail Kotlin is a powerful language that has applications in a wide variety of fields. It is a concise, safe, interoperable, and tool-friendly language. The Android team has also announced first-class support for Kotlin, which is an added boost to the language. Kotlin's growth is fueled through carefully designed business and technology benefits. The collection of projects demonstrates the versatility of the language and enables you to build standalone applications on your own. You'll build comprehensive applications using the various features of Kotlin. Scale, performance, and high availability lie at the heart of the projects, and the lessons learned throughout this book. You'll learn how to build a social media aggregator app that will help you efficiently track various feeds, develop a geospatial webservice with Kotlin and Spring Boot, build responsive web applications with Kotlin, build a REST API for a news feed reader, and build a server-side chat application with Kotlin. It also covers the various libraries and frameworks used in the projects. Through the course of building applications, you'll not only get to grips with the various features of Kotlin, but you'll also discover how to design and prototype professional-grade applications. Style and approach Each chapter is independent and focuses on a unique technology, where Kotlin is used to build an example application. Together the chapters cover a full spectrum. COMPUTERS,Languages,Java

Pro JPA 2 in Java EE 8 Learn to use the Java Persistence API (JPA) and other related APIs as found in the Java EE 8 platform from the perspective of one of the specification creators. A one-of-a-kind resource, this in-depth book provides both theoretical and practical coverage of JPA usage for experienced Java developers. Authors Mike Keith, Merrick Schincariol and Massimo Nardone take a hands-on approach, based on their wealth of experience and expertise, by giving examples to illustrate each concept of the API and showing how it is used in practice. The examples use a common model from an overarching sample application, giving you a context from which to start and helping you to understand the examples within an already familiar domain. After completing Pro JPA 2 in Java EE 8, you will have a full understanding of JPA and be able to successfully code applications using its annotations and APIs. The book also serves as an excellent reference guide. What You Will Learn Use the JPA in the context of enterprise applications Work with object relational mappings (ORMs), collection mappings and more Build complex enterprise Java applications that persist data long after the process terminates Connect to and persist data with a variety of databases, file formats, and more Use queries, including the Java Persistence Query Language (JPQL) Carry out advanced ORM, queries and XML mappings Package, deploy and test your Java persistence-enabled enterprise applications Who This Book Is For Experienced Java programmers and developers with at least some prior experience with J2EE or Java EE platform APIs. COMPUTERS,Languages,Java

Functional Programming in Java Intermediate level, for programmers fairly familiar with Java, but new to the functional style of programming and lambda expressions. Get ready to program in a whole new way. Functional Programming in Java will help you quickly get on top of the new, essential Java 8 language features and the functional style that will change and improve your code. This short, targeted book will help you make the paradigm shift from the old imperative way to a less error-prone, more elegant, and concise coding style that's also a breeze to parallelize. You'll explore the syntax and semantics of lambda expressions, method and constructor references, and functional interfaces. You'll design and write applications better using the new standards in Java 8 and the JDK. Lambda expressions are lightweight, highly concise anonymous methods backed by functional interfaces in Java 8. You can use them to leap forward into a whole new world of programming in Java. With functional programming capabilities, which have been around for decades in other languages, you can now write elegant, concise, less error-prone code using standard Java. This book will guide you though the paradigm change, offer the essential details about the new features, and show you how to transition from your old way of coding to an improved style. In this book you'll see popular design patterns, such as decorator, builder, and strategy, come to life to solve common design problems, but with little ceremony and effort. With these new capabilities in hand, Functional Programming in Java will help you pick up techniques to implement designs that were beyond easy reach in earlier versions of Java. You'll see how you can reap the benefits of tail call optimization, memoization, and effortless parallelization techniques. Java 8 will change the way you write applications. If you're eager to take advantage of the new features in the language, this is the book for you. What you need: Java 8 with support for lambda expressions and the JDK is required to make use of the concepts and the examples in this book. COMPUTERS,Languages,Java

Java EE 8 Cookbook A practical guide for building effective enterprise solutions with Java EE 8 About This Book Recipes to get you up-and-running with Java EE 8 application development Learn how to apply the major Java EE 8 APIs and specifications Implement microservices and Reactive programming with Java EE 8 Who This Book Is For This book is for developers who want to become proficient with Java EE 8 for their enterprise application development. Basic knowledge of Java is assumed What You Will Learn Actionable information on the new features of Java EE 8 Using the most important APIs with real and working code Building server side applications, web services, and web applications Deploying and managing your application using the most important Java EE servers Building and deploying microservices using Java EE 8 Building Reactive application by joining Java EE APIs and core Java features Moving your application to the cloud using containers Practical ways to improve your projects and career through community involvement In Detail Java EE is a collection of technologies and APIs to support Enterprise Application development. The choice of what to use and when can be dauntingly complex for any developer. This book will help you master this. Packed with easy to follow recipes, this is your guide to becoming productive with Java EE 8. You will begin by seeing the latest features of Java EE 8, including major Java EE 8 APIs and specifications such as JSF 2.3, and CDI 2.0, and what they mean for you. You will use the new features of Java EE 8 to implement web-based services for your client applications. You will then learn to process the Model and Streaming APIs using JSON-P and JSON-B and will learn to use the Java Lambdas support offered in JSON-P. There are more recipes to fine-tune your RESTful development, and you will learn about the Reactive enhancements offered by the JAX-RS 2.1 specification. Later on, you will learn about the role of multithreading in your enterprise applications and how to integrate them for transaction handling. This is followed by implementing microservices with Java EE and the advancements made by Java EE for cloud computing. The final set of recipes shows you how take advantage of the latest security features and authenticate your enterprise application. At the end of the book, the Appendix shows you how knowledge sharing can change your career and your life. Style and approach Task based learning guide to help ease application development with Java EE. COMPUTERS,Languages,Java

Scala Design Patterns Learn how to write efficient, clean, and reusable code with Scala About This Book Unleash the power of Scala and apply it in the real world to build scalable and robust applications. Learn about using and implementing Creational, Structural, Behavioral, and Functional design patterns in Scala Learn how to build scalable and extendable applications efficiently Who This Book Is For If you want to increase your understanding of Scala and apply design patterns to real-life application development, then this book is for you.Prior knowledge of Scala language is assumed/ expected. What You Will Learn Immerse yourself in industry-standard design patterns—structural, creational, and behavioral—to create extraordinary applications See the power of traits and their application in Scala Implement abstract and self types and build clean design patterns Build complex entity relationships using structural design patterns Create applications faster by applying functional design patterns In Detail Design patterns make developers' lives easier by helping them write great software that is easy to maintain, runs efficiently, and is valuable to the company or people concerned. You'll learn about the various features of Scala and will be able to apply well-known, industry-proven design patterns in your work. The book starts off by focusing on some of the most interesting and latest features of Scala while using practical real-world examples. We will be learning about IDE's and Aspect Oriented Programming. We will be looking into different components in Scala. We will also cover the popular "Gang of Four" design patterns and show you how to incorporate functional patterns effectively. The book ends with a practical example that demonstrates how the presented material can be combined in real-life applications. You'll learn the necessary concepts to build enterprise-grade applications. By the end of this book, you'll have enough knowledge and understanding to quickly assess problems and come up with elegant solutions. Style and approach The design patterns in the book are explained using real-world, step-by-step examples. For each design pattern, there are tips on when to use it and when to look for something more suitable. This book can also be used as a practical guide, showing you how to leverage design patterns effectively. We've designed the book to be used as a quick reference guide while creating applications. COMPUTERS,Languages,Java

Optimizing Java Performance tuning is an experimental science, but that doesn’t mean engineers should resort to guesswork and folklore to get the job done. Yet that’s often the case. With this practical book, intermediate to advanced Java technologists working with complex technology stacks will learn how to tune Java applications for performance using a quantitative, verifiable approach. Most resources on performance tend to discuss the theory and internals of Java virtual machines, but this book focuses on the practicalities of performance tuning by examining a wide range of aspects. There are no simple recipes, tips and tricks, or algorithms to learn. Performance tuning is a process of defining and determining desired outcomes. And it requires diligence. Learn how Java principles and technology make the best use of modern hardware and operating systems Explore several performance tests and common anti-patterns that can vex your team Understand the pitfalls of measuring Java performance numbers and the drawbacks of microbenchmarking Dive into JVM garbage collection logging, monitoring, tuning, and tools Explore JIT compilation and Java language performance techniques Learn performance aspects of the Java Collections API and get an overview of Java concurrency COMPUTERS,Languages,Java

Mastering Spring Cloud Learn how to build, test, secure, deploy, and efficiently consume services across distributed systems. About This Book Explore the wealth of options provided by Spring Cloud for wiring service dependencies in microservice systems. Create microservices utilizing Spring Cloud's Netflix OSS Architect your cloud-native data using Spring Cloud. Who This Book Is For This book appeals to developers keen to take advantage of Spring cloud, an open source library which helps developers quickly build distributed systems. Knowledge of Java and Spring Framework will be helpful, but no prior exposure to Spring Cloud is required. What You Will Learn Abstract Spring Cloud's feature set Create microservices utilizing Spring Cloud's Netflix OSS Create synchronous API microservices based on a message-driven architecture. Explore advanced topics such as distributed tracing, security, and contract testing. Manage and deploy applications on the production environment In Detail Developing, deploying, and operating cloud applications should be as easy as local applications. This should be the governing principle behind any cloud platform, library, or tool. Spring Cloud–an open-source library–makes it easy to develop JVM applications for the cloud. In this book, you will be introduced to Spring Cloud and will master its features from the application developer's point of view. This book begins by introducing you to microservices for Spring and the available feature set in Spring Cloud. You will learn to configure the Spring Cloud server and run the Eureka server to enable service registration and discovery. Then you will learn about techniques related to load balancing and circuit breaking and utilize all features of the Feign client. The book now delves into advanced topics where you will learn to implement distributed tracing solutions for Spring Cloud and build message-driven microservice architectures. Before running an application on Docker container s, you will master testing and securing techniques with Spring Cloud. Style and approach This comprehensive guide covers the advanced features of Spring Cloud and communicates them through a practical approach to explore the underlying concepts of how, when, and why to use them. COMPUTERS,Languages,Java

Building Applications with Spring 5 and Kotlin Learn to build a full-fledged application in Spring and Kotlin taking a reactive, microservice-based approach for scalability and robustness in the cloud About This Book Build a full-fledged application in Spring and Kotlin Architect your application to take a microservice-based approach in the cloud Integrate your application with a variety of Spring components Who This Book Is For Developers comfortable using Spring who have basic knowledge of Kotlin and want to take their development skills to the next level and build enterprise-grade applications will benefit from this book. What You Will Learn Explore Spring 5 concepts with Kotlin Learn both dependency injections and complex configurations Utilize Spring Data, Spring Cloud, and Spring Security in your applications Create efficient reactive systems with Project Reactor Write unit tests for your Spring/Kotlin applications Deploy applications on cloud platforms like AWS In Detail Kotlin is being used widely by developers because of its light weight, built-in null safety, and functional and reactive programming aspects. Kotlin shares the same pragmatic, innovative and opinionated mindset as Spring, so they work well together. Spring when combined with Kotlin helps you to reach a new level of productivity. This combination has helped developers to create Functional Applications using both the tools together. This book will teach you how to take advantage of these developments and build robust, scalable and reactive applications with ease. In this book, you will begin with an introduction to Spring and its setup with Kotlin. You will then dive into assessing the design considerations of your application. Then you will learn to use Spring (with Spring Boot) along with Kotlin to build a robust backend in a microservice architecture with a REST based collaboration, and leverage Project Reactor in your application. You'll then learn how to integrate Spring Data and Spring Cloud to manage configurations for database interaction and cloud deployment. You'll also learn to use Spring Security to beef up security of your application before testing it with the JUnit framework and then deploying it on a cloud platform like AWS. Style and approach Everything you learn will be demonstrated on real-world Spring project. In each chapter we will cover some of Spring features and apply it on our project. We will guide you from the project initialization till the project deployment. COMPUTERS,Languages,Java

Beginning EJB in Java EE 8 Build powerful back-end business logic and complex Enterprise JavaBeans (EJB)-based applications using Java EE 8, Eclipse Enterprise for Java (EE4J), Web Tools Project (WTP), and the Microprofile platform. Targeted at Java and Java EE developers, with or without prior EJB experience, this book is packed with practical insights, strategy tips, and code examples. As each chapter unfolds, you'll see how you can apply the new EJB spec to your own applications through specific examples. Beginning EJB in Java EE 8 serves not only as a reference, but also as a how-to guide and repository of practical examples to which you can refer as you build your own applications. It will help you harness the power of EJBs and take your Java EE 8 development to the next level. You'll gain the knowledge and skills you’ll need to create the complex enterprise applications that run today's transactions and more. What You'll Learn Build applications with Enterprise JavaBeans (EJBs) in the new Java EE 8 platform Discover when to use EJBs over contexts and dependency injection Use message-driven beans to do tasks asynchronously Integrate EJBs with microservices using the new Eclipse Microprofile project Manage complex enterprise transactions and much more Who This Book Is For Java programmers new to enterprise development and for those who may have experience with EJBs but are new to Java EE 8, EE4J, and related Eclipse projects. COMPUTERS,Languages,Java

Practical JSF in Java EE 8 Master the Java EE 8 and JSF (JavaServer Faces) APIs and web framework with this practical, projects-driven guide to web development. This book combines theoretical background with a practical approach by building four real-world applications. By developing these JSF web applications, you'll take a tour through the other Java EE technologies such as JPA, CDI, Security, WebSockets, and more. In Practical JSF in Java EE 8, you will learn to use the JavaServer Faces web framework in Java EE 8 to easily construct a web-based user interface from a set of reusable components. Next, you add JSF event handling and then link to a database, persist data, and add security and the other bells and whistles that the Java EE 8 platform has to offer. After reading this book you will have a good foundation in Java-based web development and will have increased your proficiency in sophisticated Java EE 8 web development using the JSF framework. What You Will Learn Use the Java EE 8 and the JavaServer Faces APIs to build Java-based web applications through four practical real-world case studies Process user input with JSF and the expression language by building a calculator application Persist data using JSF templating and Java Persistence to manage an inventory of books Create and manage an alumni database using JSF, Ajax, web services and Java EE 8's security features. Who This Book Is For Those new to Java EE 8 and JSF. Some prior experience with Java is recommended. COMPUTERS,Languages,Java

The Definitive Guide to JSF in Java EE 8 Learn and master the new features in the JSF 2.3 MVC web framework in this definitive guide written by two of the JavaServer Faces (JSF) specification leads. The authors take you through real-world examples that demonstrate how these new features are used with other APIs in Java EE 8. You’ll see the new and exciting ways JSF applications can use to communicate between a client and a server, such as using WebSockets, invoking bean methods directly from Ajax, executing client-side JavaScript when Ajax calls complete, and more Along the way you’ll broaden your knowledge of JSF components and web APIs best practices, and learn a great deal about the internals of JSF and the design decisions that have been made when building the JSF API. For example, you’ll see what artefacts are now CDI injectable, how CDI changed JSF internally, and what some of the caveats are when working with the CDI versions of a JSF artefact. Furthermore, you'll build an example application from scratch. After reading The Definitive Guide to JSF in Java EE 8, you'll be ready to build your own efficient and secure web applications. What You Will Learn Leverage the new features in JSF 2.3 in your existing applications Integrate JSF and CDI Use the brand new Component Search Expression framework, which enables you to more easily locate components from your template Extend the Component Search Expression framework with your own search operators Work with the different ways of mapping requests to JSF, make your application use extensionless URLs, and programmatically inspect which resources are present in your application Master the best practices for web application development and see which are obsolete Who This Book Is For Existing JSF or Java developers who need to create a web UI. No prior knowledge of JSF is required, but the book does skew towards the more experienced developer. Concepts such as dependency injection and MVC are assumed to be known, as is a general knowledge about HTML, HTTP and other web standards. COMPUTERS,Languages,Java

Mastering JavaFX 10 Design modern, rich interfaces for Java apps using JavaFX 10 About This Book Become a pro with the latest JavaFX 10 framework Create dynamic content using the animation API Create and customize plugins and use them efficiently in different applications Who This Book Is For If you're a Java developer who wants to upgrade to the latest version of JavaFX to create stunning, feature-rich graphical applications, this book is for you. What You Will Learn Construct and customize JavaFX windows Manage UI elements and arrange them on the Scene Explore the Bindings API and use it to coordinate various UI elements Use FXML to design amazing FX applications Write and manage CSS to style your applications Add audio and video to your projects Prepare your application to be launched on the target platform In Detail JavaFX 10 is used to create media-rich client applications. This book takes you on a journey to use JavaFX 10 to build applications that display information in a high-performance, modern user interface featuring audio, video, graphics, and animation. Mastering JavaFX 10 begins by introducing you to the JavaFX API. You will understand the steps involved in setting up your development environment and build the necessary dependencies. This is followed by exploring how to work with the assets, modules, and APIs of JavaFX. This book is filled with practical examples to guide you through the major features of JavaFX 10. In addition to this, you will acquire a practical understanding of JavaFX custom animations, merging different application layers smoothly, and creating a user-friendly GUI with ease. By the end of the book, you will be able to create a complete, feature-rich Java graphical application using JavaFX. Style and approach The book adopts a practical, step-by-step approach. COMPUTERS,Languages,Java

Java EE 8 Development with Eclipse Develop and deploy fully functional applications and microservices utilising Tomcat, Glassfish servers, Cloud and docker in Java EE 8 About This Book Explore the complete workflow of developing enterprise Java applications Develop microservices with Docker Container and deploy it in cloud Simplify Java EE application development Who This Book Is For If you are a Java developer with little or no experience in Java EE application development, or if you have experience in Java EE technology but are looking for tips to simplify and accelerate your development process, then this book is for you. What You Will Learn Set up Eclipse, Tomcat, and Glassfish servers for Java EE application development Use JSP, Servlet, JSF, and EJBs to create a user interface and write business logic Create Java EE database applications using JDBC and JPA Handle asynchronous messages using MDBs for better scalability Deploy and debug Java EE applications and create SOAP and REST web services Write unit tests and calculate code coverage Use Eclipse MAT (Memory Analysis Tool) to debug memory issues Create and deploy microservices In Detail Java EE is one of the most popular tools for enterprise application design and development. With recent changes to Java EE 8 specifications, Java EE application development has become a lot simpler with the new specifications, some of which compete with the existing specifications. This guide provides a complete overview of developing highly performant, robust and secure enterprise applications with Java EE with Eclipse. The book begins by exploring different Java EE technologies and how to use them (JSP, JSF, JPA, JDBC, EJB, and more), along with suitable technologies for different scenarios. You will learn how to set up the development environment for Java EE applications and understand Java EE specifications in detail, with an emphasis on examples. The book takes you through deployment of an application in Tomcat, GlassFish Servers, and also in the cloud. It goes beyond the basics and covers topics like debugging, testing, deployment, and securing your Java EE applications. You'll also get to know techniques to develop cloud-ready microservices in Java EE. Style and approach This guide takes a step-by-step approach to developing, testing, debugging, and troubleshooting Java EE applications, complete with examples and tips. COMPUTERS,Languages,Java

Learning Concurrency in Kotlin Take advantage of Kotlin's concurrency primitives to write efficient multithreaded applications Key Features Learn Kotlin's unique approach to multithreading Work through practical examples that will help you write concurrent non-blocking code Improve the overall execution speed in multiprocessor and multicore systems Book Description The primary requirements of modern-day applications are scalability, speed, and making the most use of hardware. Kotlin meets these requirements with its immense support for concurrency. Many concurrent primitives of Kotlin, such as channels and suspending functions, are designed to be non-blocking and efficient. This allows for new approaches to concurrency and creates unique challenges for the design and implementation of concurrent code. Learning Concurrency in Kotlin addresses those challenges with real-life examples and exercises that take advantage of Kotlin's primitives. Beginning with an introduction to Kotlin's coroutines, you will learn how to write concurrent code and understand the fundamental concepts needed to be able to write multithreaded software in Kotlin. You'll explore how to communicate between and synchronize your threads and coroutines to write asynchronous applications that are collaborative. You'll also learn how to handle errors and exceptions, as well as how to leverage multi-core processing. In addition to this, you'll delve into how coroutines work internally, allowing you to see the bigger picture. Throughout the book you'll build an Android application – an RSS reader – designed and implemented according to the different topics covered in the book What you will learn Understand Kotlin's approach to concurrency Implement sequential and asynchronous suspending functions Create suspending data sources that are resumed on demand Explore the best practices for error handling Use channels to communicate between coroutines Uncover how coroutines work under the hood Who this book is for If you're a Kotlin or Android developer interested in learning how to program concurrently to enhance the performance of your applications, this is the book for you. COMPUTERS,Languages,Java

Natural Language Processing with Java Explore various approaches to organize and extract useful text from unstructured data using Java Key Features Use deep learning and NLP techniques in Java to discover hidden insights in text Work with popular Java libraries such as CoreNLP, OpenNLP, and Mallet Explore machine translation, identifying parts of speech, and topic modeling Book Description Natural Language Processing (NLP) allows you to take any sentence and identify patterns, special names, company names, and more. The second edition of Natural Language Processing with Java teaches you how to perform language analysis with the help of Java libraries, while constantly gaining insights from the outcomes. You'll start by understanding how NLP and its various concepts work. Having got to grips with the basics, you'll explore important tools and libraries in Java for NLP, such as CoreNLP, OpenNLP, Neuroph, and Mallet. You'll then start performing NLP on different inputs and tasks, such as tokenization, model training, parts-of-speech and parsing trees. You'll learn about statistical machine translation, summarization, dialog systems, complex searches, supervised and unsupervised NLP, and more. By the end of this book, you'll have learned more about NLP, neural networks, and various other trained models in Java for enhancing the performance of NLP applications. What you will learn Understand basic NLP tasks and how they relate to one another Discover and use the available tokenization engines Apply search techniques to find people, as well as things, within a document Construct solutions to identify parts of speech within sentences Use parsers to extract relationships between elements of a document Identify topics in a set of documents Explore topic modeling from a document Who this book is for Natural Language Processing with Java is for you if you are a data analyst, data scientist, or machine learning engineer who wants to extract information from a language using Java. Knowledge of Java programming is needed, while a basic understanding of statistics will be useful but not mandatory. COMPUTERS,Languages,Java

Core Java Volume I--Fundamentals, 1 The #1 Guide for Serious Programmers: Fully Updated for Java SE 9, 10 & 11 Cay Horstmann’s Core Java, Volume I—Fundamentals, Eleventh Edition, is the definitive guide to writing robust, maintainable code with the Java SE 9, 10, and 11 language and libraries. Horstmann writes for serious programmers who use Java in production projects, and need a deep, practical understanding of the language and API. Throughout, he delivers what you need most: hundreds of real (non-toy) examples revealing the most powerful, effective ways to get the job done. Updated examples reflect the new var keyword and take advantage of improvements in the Java API. You’ll learn how to use JShell’s new Read-Eval-Print Loop (REPL) for more rapid and exploratory development, and apply new features of the APIs for streams, input/output, processes, and concurrency. In this first of two volumes, Horstmann offers in-depth coverage of fundamental Java and UI programming, including object-oriented programming, generics, collections, lambda expressions, Swing design, concurrency, and functional programming. If you’re an experienced programmer moving to Java SE 9, 10, or 11, there’s no better source for expert insight, solutions, and code. Master foundational techniques, idioms, and best practices for writing superior Java code Efficiently implement encapsulation and inheritance Use sound principles of object-oriented design Leverage the full power of objects with interfaces, lambda expressions, and inner classes Harden programs through effective exception handling and debugging Write safer, more reusable code with generic programming Improve performance and efficiency with Java’s standard collections Build cross-platform GUIs with the Swing toolkit Fully utilize multicore processors with Java’s improved concurrency See Core Java, Volume II—Advanced Features, Eleventh Edition (ISBN-13: 978-0-13-516631-4), for expert coverage of Java 9, 10, and 11 enterprise features, the module system, annotations, networking, security, and advanced UI programming. Register your book for convenient access to downloads, updates, and/or corrections as they become available. See inside book for details. COMPUTERS,Languages,Java

Developing Java Applications with Spring and Spring Boot An end-to-end software development guide for the Java eco-system using the most advanced frameworks: Spring and Spring Boot. Learn the complete workflow by building projects and solving problems. About This Book Learn reactive programming by implementing a reactive application with Spring WebFlux Create a robust and scalable messaging application with Spring messaging support Get up-to-date with the defining characteristics of Spring Boot 2.0 in Spring Framework 5 Learn about developer tools, AMQP messaging, WebSockets, security, MongoDB data access, REST, and more This collection of effective recipes serves as guidelines for Spring Boot application development Who This Book Is For Java developers wanting to build production-grade applications using the newest popular Spring tools for a rich end-to-end application development experience. What You Will Learn Get to know the Spring Boot and understand how it makes creating robust applications extremely simple Understand how Spring Data helps us add persistence in MongoDB and SQL databases Implement a websocket to add interactive behaviors in your applications Create powerful, production-grade applications and services with minimal fuss Use custom metrics to track the number of messages published and consumed Build anything from lightweight unit tests to fully running embedded web container integration tests Learn effective testing techniques by integrating Cucumber and Spock Use Hashicorp Consul and Netflix Eureka for dynamic Service Discovery In Detail Spring Framework has become the most popular framework for Java development. It not only simplifies software development but also improves developer productivity. This book covers effective ways to develop robust applications in Java using Spring. The course is up made of three modules, each one having a take-away relating to building end-to-end java applications. The first module takes the approach of learning Spring frameworks by building applications.You will learn to build APIs and integrate them with popular fraemworks suh as AngularJS, Spring WebFlux, and Spring Data. You will also learn to build microservices using Spring's support for Kotlin. You will learn about the Reactive paradigm in the Spring architecture using Project Reactor. In the second module, after getting hands-on with Spring, you will learn about the most popular tool in the Spring ecosystem-Spring Boot. You will learn to build applications with Spring Boot, bundle them, and deploy them on the cloud. After learning to build applications with Spring Boot, you will be able to use various tests that are an important part of application development. We also cover the important developer tools such as AMQP messaging, websockets, security, and more. This will give you a good functional understanding of scalable development in the Spring ecosystem with Spring Boot. In the third and final module, you will tackle the most important challenges in Java application development with Spring Boot using practical recipes. Including recipes for testing, deployment, monitoring, and securing your applications. This module will also address the functional and technical requirements for building enterprise applications. By the end of the course you will be comfortable with using Spring and Spring Boot to develop Java applications and will have mastered the intricacies of production-grade applications. Style and approach A simple step-by-step guide with practical examples to help you develop and deploy Spring and Spring Boot applications in the real-world. COMPUTERS,Languages,Java

Scala Programming Projects Discover unique features and powerful capabilities of Scala Programming as you build projects in a wide range of domains Key Features Develop a range of Scala projects from web applications to big data analysis Leverage full power of modern web programming using Play Framework Build real-time data pipelines in Scala with a Bitcoin transaction analysis app Book Description Scala is a type-safe JVM language that incorporates object-oriented and functional programming (OOP and FP) aspects. This book gets you started with essentials of software development by guiding you through various aspects of Scala programming, helping you bridge the gap between learning and implementing. You will learn about the unique features of Scala through diverse applications and experience simple yet powerful approaches for software development. Scala Programming Projects will help you build a number of applications, beginning with simple projects, such as a financial independence calculator, and advancing to other projects, such as a shopping application and a Bitcoin transaction analyzer. You will be able to use various Scala features, such as its OOP and FP capabilities, and learn how to write concise, reactive, and concurrent applications in a type-safe manner. You will also learn how to use top-notch libraries such as Akka and Play and integrate Scala apps with Kafka, Spark, and Zeppelin, along with deploying applications on a cloud platform. By the end of the book, you will not only know the ins and outs of Scala, but you will also be able to apply it to solve a variety of real-world problems What you will learn Build, test, and package code using Scala Build Tool Decompose code into functions, classes, and packages for maintainability Implement the functional programming capabilities of Scala Develop a simple CRUD REST API using the Play framework Access a relational database using Slick Develop a dynamic web UI using Scala.js Source streaming data using Spark Streaming and write a Kafka producer Use Spark and Zeppelin to analyze data Who this book is for If you are an amateur programmer who wishes to learn how to use Scala, this book is for you. Knowledge of Java will be beneficial, but not necessary, to understand the concepts covered in this book. COMPUTERS,Languages,Java

Hands-On Reactive Programming with Reactor Discover how project Reactor enhances the reactive programming paradigm and allows you to build scalable asynchronous applications Key Features Use reactive APIs, Flux, and Mono to implement reactive extensions Create concurrent applications without the complexity of Java's concurrent API Understand techniques to implement event-driven and reactive applications Book Description Reactor is an implementation of the Java 9 Reactive Streams specification, an API for asynchronous data processing. This specification is based on a reactive programming paradigm, enabling developers to build enterprise-grade, robust applications with reduced complexity and in less time. Hands-On Reactive Programming with Reactor shows you how Reactor works, as well as how to use it to develop reactive applications in Java. The book begins with the fundamentals of Reactor and the role it plays in building effective applications. You will learn how to build fully non-blocking applications and will later be guided by the Publisher and Subscriber APIs. You will gain an understanding how to use two reactive composable APIs, Flux and Mono, which are used extensively to implement Reactive Extensions. All of these components are combined using various operations to build a complete solution. In addition to this, you will get to grips with the Flow API and understand backpressure in order to control overruns. You will also study the use of Spring WebFlux, an extension of the Reactor framework for building microservices. By the end of the book, you will have gained enough confidence to build reactive and scalable microservices. What you will learn Explore benefits of the Reactive paradigm and the Reactive Streams API Discover the impact of Flux and Mono implications in Reactor Expand and repeat data in stream processing Get to grips with various types of processors and choose the best one Understand how to map errors to make corrections easier Create robust tests using testing utilities offered by Reactor Find the best way to schedule the execution of code Who this book is for If you're looking to develop event- and data-driven applications easily with Reactor, this book is for you. Sound knowledge of Java fundamentals is necessary to understand the concepts covered in the book. COMPUTERS,Languages,Java

Learn Scala Programming A step-by-step guide in building high-performance scalable applications with the latest features of Scala. Key Features Develop a strong foundation in functional programming and Scala's Standard Library (STL) Get a detailed coverage of Lightbend Lagom—the latest microservices framework from Lightbend Understand the Akka framework and learn event-based Programming with Scala Book Description The second version of Scala has undergone multiple changes to support features and library implementations. Scala 2.13, with its main focus on modularizing the standard library and simplifying collections, brings with it a host of updates. Learn Scala Programming addresses both technical and architectural changes to the redesigned standard library and collections, along with covering in-depth type systems and first-level support for functions. You will discover how to leverage implicits as a primary mechanism for building type classes and look at different ways to test Scala code. You will also learn about abstract building blocks used in functional programming, giving you sufficient understanding to pick and use any existing functional programming library out there. In the concluding chapters, you will explore reactive programming by covering the Akka framework and reactive streams. By the end of this book, you will have built microservices and learned to implement them with the Scala and Lagom framework. What you will learn Acquaint yourself with the new standard library of Scala 2.13 Get to grips with the Grok functional paradigms Get familiar with type system to express domain constraints Understand the actor model and different Akka libraries Grasp the concept of building microservices using Lagom framework Deep dive into property-based testing and its practical applications Who this book is for This book is for beginner to intermediate level Scala developers who would like to advance and gain knowledge of the intricacies of the Scala language, expand their functional programming tools, and explore actor-based concurrency models. COMPUTERS,Languages,Java

Continuous Delivery in Java Continuous delivery adds enormous value to the business and the entire software delivery lifecycle, but adopting this practice means mastering new skills typically outside of a developer’s comfort zone. In this practical book, Daniel Bryant and Abraham MarÃn-Pérez provide guidance to help experienced Java developers master skills such as architectural design, automated quality assurance, and application packaging and deployment on a variety of platforms. Not only will you learn how to create a comprehensive build pipeline for continually delivering effective software, but you’ll also explore how Java application architecture and deployment platforms have affected the way we rapidly and safely deliver new software to production environments. Get advice for beginning or completing your migration to continuous delivery Design architecture to enable the continuous delivery of Java applications Build application artifacts including fat JARs, virtual machine images, and operating system container (Docker) images Use continuous integration tooling like Jenkins, PMD, and find-sec-bugs to automate code quality checks Create a comprehensive build pipeline and design software to separate the deploy and release processes Explore why functional and system quality attribute testing is vital from development to delivery Learn how to effectively build and test applications locally and observe your system while it runs in production COMPUTERS,Languages,Java

Microservices for the Enterprise Understand the key challenges and solutions around building microservices in the enterprise application environment. This book provides a comprehensive understanding of microservices architectural principles and how to use microservices in real-world scenarios. Architectural challenges using microservices with service integration and API management are presented and you learn how to eliminate the use of centralized integration products such as the enterprise service bus (ESB) through the use of composite/integration microservices. Concepts in the book are supported with use cases, and emphasis is put on the reality that most of you are implementing in a “brownfield†environment in which you must implement microservices alongside legacy applications with minimal disruption to your business. Microservices for the Enterprise covers state-of-the-art techniques around microservices messaging, service development and description, service discovery, governance, and data management technologies and guides you through the microservices design process. Also included is the importance of organizing services as core versus atomic, composite versus integration, and API versus edge, and how such organization helps to eliminate the use of a central ESB and expose services through an API gateway. What You'll Learn Design and develop microservices architectures with confidence Put into practice the most modern techniques around messaging technologies Apply the Service Mesh pattern to overcome inter-service communication challenges Apply battle-tested microservices security patterns to address real-world scenarios Handle API management, decentralized data management, and observability Who This Book Is For Developers and DevOps engineers responsible for implementing applications around a microservices architecture, and architects and analysts who are designing such systems COMPUTERS,Languages,Java

Spring Boot 2 Recipes Solve all your Spring Boot 2 problems using complete and real-world code examples. When you start a new project, you’ll be able to copy the code and configuration files from this book, and then modify them for your needs. This can save you a great deal of work over creating a project from scratch. Using a problem-solution approach, Spring Boot 2 Recipes quickly introduces you to Pivotal's Spring Boot 2 micro-framework, then dives into code snippets on how to apply and integrate Spring Boot 2 with the Spring MVC web framework, Spring Web Sockets, and microservices. You'll also get solutions to common problems with persistence, integrating Spring Boot with batch processing, algorithmic programming via Spring Batch, and much more. Other recipes cover topics such as using and integrating Boot with Spring's enterprise services, Spring Integration, testing, monitoring and more. What You'll Learn Get reusable code recipes and snippets for the Spring Boot 2 micro-framework Discover how Spring Boot 2 integrates with other Spring APIs, tools, and frameworks Access Spring MVC and the new Spring Web Sockets for simpler web development Work with microservices for web services development and integration with your Spring Boot applications Add persistence and a data tier seamlessly to make your Spring Boot web application do more Integrate enterprise services to create a more complex Java application using Spring Boot Who This Book Is For Experienced Java and Spring programmers. COMPUTERS,Languages,Java

Reactive Streams in Java Get an easy introduction to reactive streams in Java to handle concurrency, data streams, and the propagation of change in today's applications. This compact book includes in-depth introductions to RxJava, Akka Streams, and Reactor, and integrates the latest related features from Java 9 and 11, as well as reactive streams programming with the Android SDK. Reactive Streams in Java explains how to manage the exchange of stream data across an asynchronous boundary—passing elements on to another thread or thread-pool—while ensuring that the receiving side is not forced to buffer arbitrary amounts of data which can reduce application efficiency. After reading and using this book, you'll be proficient in programming reactive streams for Java in order to optimize application performance, and improve memory management and data exchanges. What You Will Learn Discover reactive streams and how to use them Work with the latest features in Java 9 and Java 11 Apply reactive streams using RxJava Program using Akka Streams Carry out reactive streams programming in Android Who This Book Is For Experienced Java programmers. COMPUTERS,Languages,Java

Java in a Nutshell This updated edition of Java in a Nutshell not only helps experienced Java programmers get the most out of Java versions 9 through 11, it’s also a learning path for new developers. Chock full of examples that demonstrate how to take complete advantage of modern Java APIs and development best practices, this thoroughly revised book includes new material on Java Concurrency Utilities. The book’s first section provides a fast-paced, no-fluff introduction to the Java programming language and the core runtime aspects of the Java platform. The second section is a reference to core concepts and APIs that explains how to perform real programming work in the Java environment. Get up to speed on language details, including Java 9-11 changes Learn object-oriented programming, using basic Java syntax Explore generics, enumerations, annotations, and lambda expressions Understand basic techniques used in object-oriented design Examine concurrency and memory, and how they’re intertwined Work with Java collections and handle common data formats Delve into Java’s latest I/O APIs, including asynchronous channels Use Nashorn to execute JavaScript on the Java Virtual Machine Become familiar with development tools in OpenJDK COMPUTERS,Languages,Java

Java Design Patterns Get hands-on experience implementing 26 of the most common design patterns using Java and Eclipse. In addition to Gang of Four (GoF) design patterns, you will also learn about alternative design patterns, and understand the criticisms of design patterns with an overview of anti-patterns. For each pattern you will see at least one real-world scenario, a computer-world example, and a complete implementation including output. This book has three parts. The first part covers 23 Gang of Four (GoF) design patterns. The second part includes three alternative design patterns. The third part presents criticisms of design patterns with an overview of anti-patterns. You will work through easy-to-follow examples to understand the concepts in depth and you will have a collection of programs to port over to your own projects. A Q&A session is included in each chapter and covers the pros and cons of each pattern. The last chapter presents FAQs about the design patterns. The step-by-step approach of the book helps you apply your skills to learn other patterns on your own, and to be familiar with the latest version of Java and Eclipse. What You'll Learn Work with each of the design patterns Implement design patterns in real-world applications Choose from alternative design patterns by comparing their pros and cons Use the Eclipse IDE to write code and generate output Read the in-depth Q&A session in each chapter with pros and cons for each design pattern Who This Book Is For Software developers, architects, and programmers COMPUTERS,Languages,Java

Pro Spring Boot 2 Quickly and productively develop complex Spring applications and microservices out of the box, with minimal concern over things like configurations. This revised book will show you how to fully leverage the Spring Boot 2 technology and how to apply it to create enterprise ready applications that just work. It will also cover what's been added to the new Spring Boot 2 release, including Spring Framework 5 features like WebFlux, Security, Actuator and the new way to expose Metrics through Micrometer framework, and more. This book is your authoritative hands-on practical guide for increasing your enterprise Java and cloud application productivity while decreasing development time. It's a no nonsense guide with case studies of increasing complexity throughout the book. The author, a senior solutions architect and Principal Technical instructor with Pivotal, the company behind the Spring Framework, shares his experience, insights and first-hand knowledge about how Spring Boot technology works and best practices. Pro Spring Boot 2 is an essential book for your Spring learning and reference library. What You Will Learn Configure and use Spring Boot Use non-functional requirements with Spring Boot Actuator Carry out web development with Spring Boot Persistence with JDBC, JPA and NoSQL Databases Messaging with JMS, RabbitMQ and WebSockets Test and deploy with Spring Boot A quick look at the Spring Cloud projects Microservices and deployment to the Cloud Extend Spring Boot by creating your own Spring Boot Starter and @Enable feature Who This Book Is For Experienced Spring and Java developers seeking increased productivity gains and decreased complexity and development time in their applications and software services. COMPUTERS,Languages,Java

Core Java, Volume II--Advanced Features The #1 Guide to Advanced Java Programming, Fully Updated for Java 11 Core Java has long been recognized as the leading, no-nonsense tutorial and reference for experienced programmers who want to write robust Java code for real-world applications. Now, Core Java, Volume II—Advanced Features, Eleventh Edition, has been updated for Java 11, with up-to-date coverage of advanced UI and enterprise programming, networking, security, and Java’s powerful new module system. Cay S. Horstmann explores sophisticated new language and library features with the depth and completeness that readers expect from Core Java. He demonstrates how to use these features to build professional-quality applications, using thoroughly tested examples that reflect modern Java style and best practices, including modularization. Horstmann’s examples are carefully crafted for easy understanding and maximum practical value, so you can consistently use them to jump-start your own code. Master advanced techniques, idioms, and best practices for writing superior Java code Take full advantage of modern Java I/O APIs, object serialization, and regular expressions Efficiently connect to network services, implement network clients and servers, and harvest web data Query databases and manage database connections with the latest version of JDBC Simplify all aspects of date and time programming with the Java Date and Time API Write internationalized programs that localize dates, times, numbers, text, and GUIs Process code in three powerful ways: the scripting API, compiler API, and annotation processing Learn how to migrate legacy code to the Java Platform Module System Leverage the modern Java security features most valuable to application programmers Program advanced client-side user interfaces, and generate images on the server Use JNI to interoperate with native C code See Core Java, Volume I—Fundamentals, Eleventh Edition (ISBN-13: 978-0-13-516630-7), for expert coverage of fundamental Java and UI programming, including objects, generics, collections, lambda expressions, Swing design, concurrency, and functional programming. Register your book for convenient access to downloads, updates, and/or corrections as they become available. See inside book for details. COMPUTERS,Languages,Java

Head First Kotlin What will you learn from this book? Head First Kotlin is a complete introduction to coding in Kotlin. This hands-on book helps you learn the Kotlin language with a unique method that goes beyond syntax and how-to manuals and teaches you how to think like a great Kotlin developer. You’ll learn everything from language fundamentals to collections, generics, lambdas, and higher-order functions. Along the way, you’ll get to play with both object-oriented and functional programming. If you want to really understand Kotlin, this is the book for you. Why does this book look so different? Based on the latest research in cognitive science and learning theory, Head First Kotlin uses a visually rich format to engage your mind rather than a text-heavy approach that puts you to sleep. Why waste your time struggling with new concepts? This multisensory learning experience is designed for the way your brain really works. COMPUTERS,Languages,Java

Java XML and JSON Use this guide to master the XML metalanguage and JSON data format along with significant Java APIs for parsing and creating XML and JSON documents from the Java language. New in this edition is coverage of Jackson (a JSON processor for Java) and Oracle’s own Java API for JSON processing (JSON-P), which is a JSON processing API for Java EE that also can be used with Java SE. This new edition of Java XML and JSON also expands coverage of DOM and XSLT to include additional API content and useful examples. All examples in this book have been tested under Java 11. In some cases, source code has been simplified to use Java 11’s var language feature. The first six chapters focus on XML along with the SAX, DOM, StAX, XPath, and XSLT APIs. The remaining six chapters focus on JSON along with the mJson, GSON, JsonPath, Jackson, and JSON-P APIs. Each chapter ends with select exercises designed to challenge your grasp of the chapter's content. An appendix provides the answers to these exercises. What You'll Learn Master the XML language Create, validate, parse, and transform XML documents Apply Java’s SAX, DOM, StAX, XPath, and XSLT APIs Master the JSON format for serializing and transmitting data Code against third-party APIs such as Jackson, mJson, Gson, JsonPath Master Oracle’s JSON-P API in a Java SE context Who This Book Is For Intermediate and advanced Java programmers who are developing applications that must access data stored in XML or JSON documents. The book also targets developers wanting to understand the XML language and JSON data format. COMPUTERS,Languages,Java

Functional Interfaces in Java Reduce development time by organizing your programs as chains of functional interfaces and see that the advantages of using functional interfaces include the flexibility and power of inlined functional chains and reuse of functional methods utilized throughout the Java API. You’ll see how complex logical expressions can be reduced to chains of predicates and how chains of comparators can be used to sort data by several criteria in order. Other examples include streams that utilize functional interfaces to filter, sort, transform, and perform calculations on data; CompletableFutures that use functional interfaces to create cascading and parallel execution threads; and JavaFX programs that use functional interfaces to monitor the data backed by their graphical components. Each chapter contains a complete programming project: the Discount Dave project shows you how to qualify car customers by organizing questions as a list of predicates; the Real Estate Broker project shows you how to use chains of comparators to filter and sort homes according to customer priorities; the Dave's Part Inventory project shows you how to query and write reports from an inventory database using stream operations; and the Sentence Builder project shows you how to correct a sentence by implementing each grammar rule as a separate link in a future chain. Functional Interfaces in Java will help you quickly develop powerful and reliable programs that utilize functional interfaces to implement logic and calculations. What You Will Learn Use the functional interfaces in the java.util.function package to perform conditional logic, transform and generate data, and perform calculations Filter and sort data by several criteria using comparators Process collections and filter, sort, transform, and reduce stream elements with functional interfaces Write cascading and parallel execution threads Who This Book Is For Computer science student or a professional Java programmer. This work is a rigorous discussion of the application of functional interfaces, so prerequisites for this text include basic Java programming and object-oriented Java programming. COMPUTERS,Languages,Java

Rapid Java Persistence and Microservices Gain all the essentials you need to create scalable microservices, which will help you solve real challenges when deploying services into production. This book will take you through creating a scalable data layer with polygot persistence. You’ll cover data access and query patterns in Spring and JPA in high-performance environments. As part of this topic, you’ll see the advantages of multiple persistence frameworks in Java and especially the easy persistence offered by NoSQL databases and reactive web solutions. The last few chapters present advanced concepts that are useful for very high-performance real-time applications: you’ll implement applications using Spring’s good support for Web sockets in their raw form as well as for connecting to message brokers such as RabbitMQ. This can be useful for applications such as navigation systems and gaming platforms. What You Will Learn Build end-to-end modern applications using microservices, persistence essentials, reactive web, and other high-performance concepts Master Spring’s configuration options Secure microservices efficiently Monitor your services post deployment Who This Book Is For Java developers and architects interested in microservices. COMPUTERS,Languages,Java

Practical Microservices Architectural Patterns Take your distributed applications to the next level and see what the reference architectures associated with microservices can do for you. This book begins by showing you the distributed computing architecture landscape and provides an in-depth view of microservices architecture. Following this, you will work with CQRS, an essential pattern for microservices, and get a view of how distributed messaging works. Moving on, you will take a deep dive into Spring Boot and Spring Cloud. Coming back to CQRS, you will learn how event-driven microservices work with this pattern, using the Axon 2 framework. This takes you on to how transactions work with microservices followed by advanced architectures to address non-functional aspects such as high availability and scalability. In the concluding part of the book you develop your own enterprise-grade microservices application using the Axon framework and true BASE transactions, while making it as secure as possible. What You Will Learn Shift from monolith architecture to microservices Work with distributed and ACID transactions Build solid architectures without two-phase commit transactions Discover the high availability principles in microservices Who This Book Is For Java developers with basic knowledge of distributed and multi-threaded application architecture, and no knowledge of Spring Boot or Spring Cloud. Knowledge of CQRS and event-driven architecture is not mandatory as this book will cover these in depth. COMPUTERS,Languages,Java

The Definitive Guide to Spring Batch Work with all aspects of batch processing in a modern Java environment using a selection of Spring frameworks. This book provides up-to-date examples using the latest configuration techniques based on Java configuration and Spring Boot. The Definitive Guide to Spring Batch takes you from the “Hello, World!†of batch processing to complex scenarios demonstrating cloud native techniques for developing batch applications to be run on modern platforms. Finally this book demonstrates how you can use areas of the Spring portfolio beyond just Spring Batch 4 to collaboratively develop mission-critical batch processes. You’ll see how a new class of use cases and platforms has evolved to have an impact on batch-processing. Data science and big data have become prominent in modern IT and the use of batch processing to orchestrate workloads has become commonplace. The Definitive Guide to Spring Batch covers how running finite tasks on cloud infrastructure in a standardized way has changed where batch applications are run. Additionally, you’ll discover how Spring Batch 4 takes advantage of Java 9, Spring Framework 5, and the new Spring Boot 2 micro-framework. After reading this book, you’ll be able to use Spring Boot to simplify the development of your own Spring projects, as well as take advantage of Spring Cloud Task and Spring Cloud Data Flow for added cloud native functionality. Includes a foreword by Dave Syer, Spring Batch project founder. What You'll Learn Discover what is new in Spring Batch 4 Carry out finite batch processing in the cloud using the Spring Batch project Understand the newest configuration techniques based on Java configuration and Spring Boot using practical examples Master batch processing in complex scenarios including in the cloud Develop batch applications to be run on modern platforms Use areas of the Spring portfolio beyond Spring Batch to develop mission-critical batch processes Who This Book Is For Experienced Java and Spring coders new to the Spring Batch platform. This definitive book will be useful in allowing even experienced Spring Batch users and developers to maximize the Spring Batch tool. COMPUTERS,Languages,Java

Learning Groovy 3 Start building powerful apps that take advantage of the dynamic scripting capabilities of the Groovy language, including what's new in Groovy version 3.0. This book covers Groovy fundamentals, such as installing Groovy, using Groovy tools, and working with the Groovy Development Kit (GDK). You'll also learn more advanced aspects of Groovy, such as using Groovy design patterns, writing DSLs in Groovy, and taking advantage of Groovy's functional programming features. Also, Learning Groovy 3 has been updated to Groovy 3.0 to include the new Parrot parser which was extended to support additional syntax options and language features. It also includes coverage of Groovydoc, which allows you to embed Groovydoc comments in various ways. And, this book covers how Groovy supports Java type annotations and more. There is more to Groovy than the core language, so Learning Groovy 3, Second Edition covers the extended Groovy ecosystem. You'll see how to harness Gradle (Groovy's build system), Grails (Groovy's web application framework), Spock (Groovy's testing framework), and Ratpack (Groovy's reactive web library). What You Will Learn Grasp Groovy fundamentals, including the GDK Master advanced Groovy, such as writing Groovy DSLs Discover functional programming in Groovy Work with GPars, the built-in concurrency library Use Gradle, the build system Master Grails, the web application framework Work with Spock, the testing framework Harness Ratpack, the reactive web library Who This Book Is For Those with a Java background, though anyone with basic programming skills can benefit from it. This book is a data-filled, yet easy-to-digest tour of the Groovy language and ecosystem. COMPUTERS,Languages,Java

Practical Domain-Driven Design in Enterprise Java See how Domain-Driven Design (DDD) combines with Jakarta EE MicroProfile or Spring Boot to offer a complete suite for building enterprise-grade applications. In this book you will see how these all come together in one of the most efficient ways to develop complex software, with a particular focus on the DDD process. Practical Domain-Driven Design in Enterprise Java starts by building out the Cargo Tracker reference application as a monolithic application using the Jakarta EE platform. By doing so, you will map concepts of DDD (bounded contexts, language, and aggregates) to the corresponding available tools (CDI, JAX-RS, and JPA) within the Jakarta EE platform. Once you have completed the monolithic application, you will walk through the complete conversion of the monolith to a microservices-based architecture, again mapping the concepts of DDD and the corresponding available tools within the MicroProfile platform (config, discovery, and fault tolerance). To finish this section, you will examine the same microservices architecture on the Spring Boot platform. The final set of chapters looks at what the application would be like if you used the CQRS and event sourcing patterns. Here you’ll use the Axon framework as the base framework. What You Will Learn Discover the DDD architectural principles and use the DDD design patterns Use the new Eclipse Jakarta EE platform Work with the Spring Boot framework Implement microservices design patterns, including context mapping, logic design, entities, integration, testing, and security Carry out event sourcing Apply CQRS Who This Book Is For Junior developers intending to start working on enterprise Java; senior developers transitioning from monolithic- to microservices-based architectures; and architects transitioning to a DDD philosophy of building applications. COMPUTERS,Languages,Java

Pro CDI 2 in Java EE 8 In Pro CDI 2 in Java EE 8, use CDI and the CDI 2.0 to automatically manage the life cycle of your enterprise Java, Java EE, or Jakarta EE application’s beans using predefined scopes and define custom life cycles using scopes. In this book, you will see how you can implement dynamic and asynchronous communication between separate beans in your application with CDI events. The authors explain how to add new capabilities to the CDI platform by implementing these capabilities as extensions. They show you how to use CDI in a Java SE environment with the new CDI initialization and configuration API, and how to dynamically modify the configuration of beans at application startup by using dynamic bean building. This book is compatible with the new open source Eclipse Jakarta EE platform and tools. What You Will Learn Use qualifier annotations to inject specific bean implementations Programmatically retrieve bean instances from the CDI container in both Java SE and Java EE when injecting them into an object isn’t possible Dynamically replace beans using the @Alternative annotation to, for example, replace a bean with a mock version for testing Work with annotation literals to get instances of annotations to use with the CDI API Discover how scopes and events interact Who This Book Is For Those who have some experience with CDI, but may not have experience with some of the more advanced features in CDI. COMPUTERS,Languages,Java

Hands-On Microservices with Spring Boot and Spring Cloud Apply microservices patterns to build resilient and scalable distributed systems Key Features Understand the challenges of building large-scale microservice landscapes Build cloud-native production-ready microservices with this comprehensive guide Discover how to get the best out of Spring Cloud, Kubernetes, and Istio when used together Book Description Microservices architecture allows developers to build and maintain applications with ease, and enterprises are rapidly adopting it to build software using Spring Boot as their default framework. With this book, you'll learn how to efficiently build and deploy microservices using Spring Boot. This microservices book will take you through tried and tested approaches to building distributed systems and implementing microservices architecture in your organization. Starting with a set of simple cooperating microservices developed using Spring Boot, you'll learn how you can add functionalities such as persistence, make your microservices reactive, and describe their APIs using Swagger/OpenAPI. As you advance, you'll understand how to add different services from Spring Cloud to your microservice system. The book also demonstrates how to deploy your microservices using Kubernetes and manage them with Istio for improved security and traffic management. Finally, you'll explore centralized log management using the EFK stack and monitor microservices using Prometheus and Grafana. By the end of this book, you'll be able to build microservices that are scalable and robust using Spring Boot and Spring Cloud. What you will learn Build reactive microservices using Spring Boot Develop resilient and scalable microservices using Spring Cloud Use OAuth 2.0/OIDC and Spring Security to protect public APIs Implement Docker to bridge the gap between development, testing, and production Deploy and manage microservices using Kubernetes Apply Istio for improved security, observability, and traffic management Who this book is for This book is for Java and Spring developers and architects who want to learn how to break up their existing monoliths into microservices and deploy them either on-premises or in the cloud using Kubernetes as a container orchestrator and Istio as a service Mesh. No familiarity with microservices architecture is required to get started with this book. COMPUTERS,Languages,Java

Java Coding Problems Develop your coding skills by exploring Java concepts and techniques such as Strings, Objects and Types, Data Structures and Algorithms, Concurrency, and Functional programming Key Features Solve Java programming challenges and get interview-ready by using the power of modern Java 11 Test your Java skills using language features, algorithms, data structures, and design patterns Explore areas such as web development, mobile development, and GUI programming Book Description The super-fast evolution of the JDK between versions 8 and 12 has increased the learning curve of modern Java, therefore has increased the time needed for placing developers in the Plateau of Productivity. Its new features and concepts can be adopted to solve a variety of modern-day problems. This book enables you to adopt an objective approach to common problems by explaining the correct practices and decisions with respect to complexity, performance, readability, and more. Java Coding Problems will help you complete your daily tasks and meet deadlines. You can count on the 300+ applications containing 1,000+ examples in this book to cover the common and fundamental areas of interest: strings, numbers, arrays, collections, data structures, date and time, immutability, type inference, Optional, Java I/O, Java Reflection, functional programming, concurrency and the HTTP Client API. Put your skills on steroids with problems that have been carefully crafted to highlight and cover the core knowledge that is accessed in daily work. In other words (no matter if your task is easy, medium or complex) having this knowledge under your tool belt is a must, not an option. By the end of this book, you will have gained a strong understanding of Java concepts and have the confidence to develop and choose the right solutions to your problems. What you will learn Adopt the latest JDK 11 and JDK 12 features in your applications Solve cutting-edge problems relating to collections and data structures Get to grips with functional-style programming using lambdas Perform asynchronous communication and parallel data processing Solve strings and number problems using the latest Java APIs Become familiar with different aspects of object immutability in Java Implement the correct practices and clean code techniques Who this book is for If you are a Java developer who wants to level-up by solving real-world problems, then this book is for you. Working knowledge of Java is required to get the most out of this book. COMPUTERS,Languages,Java

Introducing Maven Gain an understanding of Maven’s dependency management and use it to organize basic and multi-module Maven projects. This short book is your quick-start tutorial for learning to use Maven. It includes inconsistently immutable collections, better array construction, and more from the latest Maven version 3.6. This second edition covers the newest in today's most popular build tool for Java development and programming. You'll learn all about Maven and how to set it up. Firstly, you’ll cover the Maven life cycle and how to effectively leverage it. Also, you'll see the basics of site plugins, generating Javadocs, test coverage/FindBugs reports, and version/release notes. Furthermore, you'll take advantage of Maven's archetypes to bootstrap new projects easily. Finally, you will learn how to integrate the Nexus repository manager with Maven release phases. What You Will Learn Set up your basic project in Maven Create more advanced projects Apply the Maven life cycle to your build Work with Maven archetypes and manage Maven releases Integrate with Jenkins, Eclipse, and other IDEs Carry out debugging and password encryption Who This Book Is For Those new to Maven or those who are familiar with Maven, but maybe not with the latest Maven 3.6 release. COMPUTERS,Languages,Java

Kotlin Cookbook Use Kotlin to build Android apps, web applications, and more—while you learn the nuances of this popular language. With this unique cookbook, developers will learn how to apply thisJava-based language to their own projects. Both experienced programmers and those new to Kotlin will benefit from the practical recipes in this book. Author Ken Kousen (Modern Java Recipes) shows you how to solve problems with Kotlin by concentrating on your own use cases rather than on basic syntax. You provide the contextand this book supplies the answers. Already big in Android development, Kotlin can be used anywhere Java is applied, as well as for iOS development, native applications, JavaScriptgeneration, and more. Jump in and build meaningful projects with Kotlin today. Apply functional programming concepts, including lambdas, sequences, and concurrency See how to use delegates, late initialization, and scope functions Explore Java interoperability and access Java libraries using Kotlin Add your own extension functions Use helpful libraries such as JUnit 5 Get practical advice for working with specific frameworks, like Android and Spring COMPUTERS,Languages,Java

Pro Spring Security Build and deploy secure Spring Framework and Spring Boot-based enterprise Java applications with the Spring Security Framework. This book explores a comprehensive set of functionalities to implement industry-standard authentication and authorization mechanisms for Java applications. Pro Spring Security, Second Edition has been updated to incorporate the changes in Spring Framework 5 and Spring Boot 2. It is an advanced tutorial and reference that guides you through the implementation of the security features for a Java web application by presenting consistent examples built from the ground up. This book also provides you with a broader look into Spring security by including up-to-date use cases such as building a security layer for RESTful web services and Grails applications. What You Will Learn Explore the scope of security and how to use the Spring Security Framework Master Spring security architecture and design Secure the web tier in Spring Work with alternative authentication providers Take advantage of business objects and logic security Extend Spring security with other frameworks and languages Secure the service layer Who This Book Is For Experienced Spring and Java developers with prior experience in building Spring Framework or Boot-based applications. COMPUTERS,Languages,Java

OCP Oracle Certified Professional Java SE 11 Programmer I Study Guide This OCP Oracle Certified Professional Java SE 11 Programmer I Study Guide: Exam 1Z0-815 and the Programmer II Study Guide: Exam 1Z0-816 were published before Oracle announced major changes to its OCP certification program and the release of the new Developer 1Z0-819 exam. No matter the changes, rest assured both of the Programmer I and II Study Guides cover everything you need to prepare for and take Exam 1Z0-819. If you’ve purchased one of the Programmer Study Guides, purchase the other one and you’ll be all set. NOTE: The OCP Java SE 11 Programmer I Exam 1Z0-815 and Programmer II Exam 1Z0-816 have been retired (as of October 1, 2020), and Oracle has released a new Developer Exam 1Z0-819 to replace the previous exams. The Upgrade Exam 1Z0-817 remains the same. The comprehensive study aide for those preparing for the new Oracle Certified Professional Java SE Programmer I Exam 1Z0-815 Used primarily in mobile and desktop application development, Java is a platform-independent, object-oriented programming language. It is the principal language used in Android application development as well as a popular language for client-side cloud applications. Oracle has updated its Java Programmer certification tracks for Oracle Certified Professional. OCP Oracle Certified Professional Java SE 11 Programmer I Study Guide covers 100% of the exam objectives, ensuring that you are thoroughly prepared for this challenging certification exam. This comprehensive, in-depth study guide helps you develop the functional-programming knowledge required to pass the exam and earn certification. All vital topics are covered, including Java building blocks, operators and loops, String and StringBuilder, Array and ArrayList, and more. Included is access to Sybex's superior online interactive learning environment and test bank—containing self-assessment tests, chapter tests, bonus practice exam questions, electronic flashcards, and a searchable glossary of important terms. This indispensable guide: Clarifies complex material and strengthens your comprehension and retention of key topics Covers all exam objectives such as methods and encapsulation, exceptions, inheriting abstract classes and interfaces, and Java 8 Dates and Lambda Expressions Explains object-oriented design principles and patterns Helps you master the fundamentals of functional programming Enables you to create Java solutions applicable to real-world scenarios There are over 9 millions developers using Java around the world, yet hiring managers face challenges filling open positions with qualified candidates. The OCP Oracle Certified Professional Java SE 11 Programmer I Study Guide will help you take the next step in your career. COMPUTERS,Languages,Java

Think Java Currently used at many colleges, universities, and high schools, this hands-on introduction to computer science is ideal for people with little or no programming experience. The goal of this concise book is not just to teach you Java, but to help you think like a computer scientist. You’ll learn how to program—a useful skill by itself—but you’ll also discover how to use programming as a means to an end. Authors Allen Downey and Chris Mayfield start with the most basic concepts and gradually move into topics that are more complex, such as recursion and object-oriented programming. Each brief chapter covers the material for one week of a college course and includes exercises to help you practice what you’ve learned. Learn one concept at a time: tackle complex topics in a series of small steps with examples Understand how to formulate problems, think creatively about solutions, and write programs clearly and accurately Determine which development techniques work best for you, and practice the important skill of debugging Learn relationships among input and output, decisions and loops, classes and methods, strings and arrays Work on exercises involving word games, graphics, puzzles, and playing cards The updated second edition of Think Java also features new chapters on polymorphism and data processing, as well as content covering changes through Java 12. COMPUTERS,Languages,Java

Pivotal Certified Professional Core Spring 5 Developer Exam Pass the Pivotal Certified Professional exam for Core Spring, based on the latest Spring Framework 5, using source code examples, study summaries, and mock exams. This book now includes WebFlux, reactive programming, and more found in Spring 5. You'll find a descriptive overview of certification-related Spring modules and a single example application demonstrating the use of all required Spring modules. Furthermore, in Pivotal Certified Professional Core Spring 5 Developer Exam, Second Edition, each chapter contains a brief study summary and question set, and the book’s free downloadable source code package includes one mock exam (50 questions – like a real exam). After using this study guide, you will be ready to take and pass the Pivotal Certified Professional exam. When you become Pivotal Certified, you will have one of the most valuable credentials in Java. Pivotal certification helps you advance your skills and your career, and get the maximum benefit from Spring. Passing the exam demonstrates your understanding of Spring and validates your familiarity with: container-basics, aspect oriented programming (AOP), data access and transactions, Spring Security, Spring Boot, microservices, and Spring model-view-controller (MVC). Good luck! What You Will Learn Understand the core principles of Spring Framework 5 Use dependency injection Work with aspects in Spring and do AOP (aspect oriented programming) Control transactional behavior and work with SQL and NoSQL databases Create and secure web applications based on Spring MVC Get to know the format of the exam and the type of questions in it Create Spring microservices applications Who This Book Is For Spring developers who have taken the Pivotal Core Spring class are eligible to take the Pivotal Certified Professional exam. COMPUTERS,Languages,Java

Java Performance Coding and testing are generally considered separate areas of expertise. In this practical book, Java expert Scott Oaks takes the approach that anyone who works with Java should be adept at understanding how code behaves in the Java Virtual Machine—including the tunings likely to help performance. This updated second edition helps you gain in-depth knowledge of Java application performance using both the JVM and the Java platform. Developers and performance engineers alike will learn a variety of features, tools, and processes for improving the way the Java 8 and 11 LTS releases perform. While the emphasis is on production-supported releases and features, this book also features previews of exciting new technologies such as ahead-of-time compilation and experimental garbage collections. Understand how various Java platforms and compilers affect performance Learn how Java garbage collection works Apply four principles to obtain best results from performance testing Use the JDK and other tools to learn how a Java application is performing Minimize the garbage collector’s impact through tuning and programming practices Tackle performance issues in Java APIs Improve Java-driven database application performance COMPUTERS,Languages,Java

Interactive Object-Oriented Programming in Java Gain the fundamental concepts of object-oriented programming with examples in Java. This second edition comes with detailed coverage and enhanced discussion on fundamental topics such as inheritance, polymorphism, abstract classes, interfaces, and packages. This edition also includes discussions on multithread programming, generic programming, database programming, and exception handling mechanisms in Java. Finally, you will get a quick overview of design patterns including the full implementation of some important patterns. Interactive Object-Oriented Programming in Java begins with the fundamental concepts of object-oriented programming alongside Q&A sessions to further explore the topic. The book concludes with FAQs from all chapters. It also contains a section to test your skills in the language basics with examples to understand Java fundamentals including loops, arrays, and strings. You’ll use the Eclipse IDE to demonstrate the code examples in the book. After reading the book, you will have enhanced your skills in object-oriented programming in Java and you will be able to extend them in interesting ways. What You Will Learn Discover object-oriented programming with Java Test your programming skills Crack Java-based interviews with confidence Use the Eclipse IDE to write code and generate output Who This Book Is For Novice to intermediate programmers, software developers, and software testers. COMPUTERS,Languages,Java

Java Cookbook Java continues to grow and evolve, and this cookbook continues to evolve in tandem. With this guide, you’ll get up to speed right away with hundreds of hands-on recipes across a broad range of Java topics. You’ll learn useful techniques for everything from string handling and functional programming to network communication. Each recipe includes self-contained code solutions that you can freely use, along with a discussion of how and why they work. If you’re familiar with Java basics, this cookbook will bolster your knowledge of the language and its many recent changes, including how to apply them in your day-to-day development. This updated edition covers changes through Java 12 and parts of 13 and 14. Recipes include: Methods for compiling, running, and debugging Packaging Java classes and building applications Manipulating, comparing, and rearranging text Regular expressions for string and pattern matching Handling numbers, dates, and times Structuring data with collections, arrays, and other types Object-oriented and functional programming techniques Input/output, directory, and filesystem operations Network programming on both client and server Processing JSON for data interchange Multithreading and concurrency Using Java in big data applications Interfacing Java with other languages COMPUTERS,Languages,Java

Learning Java If you’re new to Java—or new to programming—this best-selling book will guide you through the language features and APIs of Java 11. With fun, compelling, and realistic examples, authors Marc Loy, Patrick Niemeyer, and Daniel Leuck introduce you to Java fundamentals—including its class libraries, programming techniques, and idioms—with an eye toward building real applications. You’ll learn powerful new ways to manage resources and exceptions in your applications—along with core language features included in recent Java versions. Develop with Java, using the compiler, interpreter, and other tools Explore Java’s built-in thread facilities and concurrency package Learn text processing and the powerful regular expressions API Write advanced networked or web-based applications and services COMPUTERS,Languages,Java

Spring Boot Persistence Best Practices This book is a collection of developer code recipes and best practices for persisting data using Spring, particularly Spring Boot. The book is structured around practical recipes, where each recipe discusses a performance case or performance-related case, and almost every recipe has one or more applications. Mainly, when we try to accomplish something (e.g., read some data from the database), there are several approaches to do it, and, in order to choose the best way, you have to know the implied trades-off from a performance perspective. You’ll see that in the end, all these penalties slow down the application. Besides presenting the arguments that favor a certain choice, the application is written in Spring Boot style which is quite different than plain Hibernate. Persistence is an important set of techniques and technologies for accessing and using data, and this book demonstrates that data is mobile regardless of specific applications and contexts. In Java development, persistence is a key factor in enterprise, ecommerce, cloud and other transaction-oriented applications. After reading and using this book, you'll have the fundamentals to apply these persistence solutions into your own mission-critical enterprise Java applications that you build using Spring. What You Will Learn Shape *-to-many associations for best performances Effectively exploit Spring Projections (DTO) Learn best practices for batching inserts, updates and deletes Effectively fetch parent and association in a single SELECT Learn how to inspect Persistent Context content Dissect pagination techniques (offset and keyset) Handle queries, locking, schemas, Hibernate types, and more Who This Book Is For Any Spring and Spring Boot developer that wants to squeeze the persistence layer performances. COMPUTERS,Languages,Java

Quarkus Cookbook Optimized for Kubernetes, Quarkus is designed to help you create Java applications that are cloud first, container native, and serverless capable. With this cookbook, authors Alex Soto Bueno and Jason Porter from Red Hat provide detailed solutions for installing, interacting with, and using Quarkus in the development and production of microservices. The recipes in this book show midlevel to senior developers familiar with Java enterprise application development how to get started with Quarkus quickly. You’ll become familiar with how Quarkus works within the wider Java ecosystem and discover ways to adapt this framework to your particular needs. You’ll learn how to: Shorten the development cycle by enabling live reloading in dev mode Connect to and communicate with Kafka Develop with the reactive programming model Easily add fault tolerance to your services Build your application as a Kubernetes-ready container Ease development with OpenAPI and test a native Quarkus application COMPUTERS,Languages,Java

Erlang Programming This book is an in-depth introduction to Erlang, a programming language ideal for any situation where concurrency, fault tolerance, and fast response is essential. Erlang is gaining widespread adoption with the advent of multi-core processors and their new scalable approach to concurrency. With this guide you'll learn how to write complex concurrent programs in Erlang, regardless of your programming background or experience. Written by leaders of the international Erlang community -- and based on their training material -- Erlang Programming focuses on the language's syntax and semantics, and explains pattern matching, proper lists, recursion, debugging, networking, and concurrency. This book helps you: Understand the strengths of Erlang and why its designers included specific features Learn the concepts behind concurrency and Erlang's way of handling it Write efficient Erlang programs while keeping code neat and readable Discover how Erlang fills the requirements for distributed systems Add simple graphical user interfaces with little effort Learn Erlang's tracing mechanisms for debugging concurrent and distributed systems Use the built-in Mnesia database and other table storage features Erlang Programming provides exercises at the end of each chapter and simple examples throughout the book. COMPUTERS,Languages,JavaScript

Mastering Perl/Tk Perl/Tk is the marriage of the Tk graphical toolkit with Perl, the powerful programming language used primarily for system administration, web programming, and database manipulation. With Perl/Tk, you can build Perl programs with an attractive, intuitive GUI interface with all the power of Perl behind it.Mastering Perl/Tk is the "bible" of Perl/Tk: It's not only a great book for getting started, but the best reference for learning the techniques of experienced Perl/Tk programmers. The first half of the book contains the basics on how to use Perl/Tk, and then branches out into advanced applications with a series of extensive program examples. The result is a book accessible for novices, and invaluable for experienced programmers ready to learn the next step in the elegant and effective use of Perl/Tk. The book includes: An introduction to each of the basic Perl/Tk widgets and geometry managers A dissection of the MainLoop, including how to use callbacks and bindings effectively Coverage of the Tix widgets, an extended set of widgets that are a part of the standard Perl/Tk distribution Working with images in Perl/Tk, including bitmaps, pixmaps, photos, and how to compose a compound image type How to create custom mega-widgets in Perl/Tk, both composite and derived Handling interprocess communication with Perl/Tk, both with standard Unix utilities (pipes and sockets) and with the send command designed for direct communication between Tk applications Developing your own Tk widget in the C language Examples of web applications written with Perl/Tk and the LWP library The book also includes appendices on installing Perl/Tk, a complete quick-reference for each standard widget, and listings of all the extended examples in the book.Nancy Walsh is the author of Learning Perl/Tk, and Steve Lidie wrote the Perl/Tk Pocket Reference as well as a series of Perl/Tk articles in The Perl Journal. Together, they have written Mastering Perl/Tk to be the definitive guide to Perl/Tk. COMPUTERS,Languages,JavaScript

JavaScript Most programming languages contain good and bad parts, but JavaScript has more than its share of the bad, having been developed and released in a hurry before it could be refined. This authoritative book scrapes away these bad features to reveal a subset of JavaScript that's more reliable, readable, and maintainable than the language as a whole—a subset you can use to create truly extensible and efficient code. Considered the JavaScript expert by many people in the development community, author Douglas Crockford identifies the abundance of good ideas that make JavaScript an outstanding object-oriented programming language-ideas such as functions, loose typing, dynamic objects, and an expressive object literal notation. Unfortunately, these good ideas are mixed in with bad and downright awful ideas, like a programming model based on global variables. When Java applets failed, JavaScript became the language of the Web by default, making its popularity almost completely independent of its qualities as a programming language. In JavaScript: The Good Parts, Crockford finally digs through the steaming pile of good intentions and blunders to give you a detailed look at all the genuinely elegant parts of JavaScript, including: Syntax Objects Functions Inheritance Arrays Regular expressions Methods Style Beautiful features The real beauty? As you move ahead with the subset of JavaScript that this book presents, you'll also sidestep the need to unlearn all the bad parts. Of course, if you want to find out more about the bad parts and how to use them badly, simply consult any other JavaScript book. With JavaScript: The Good Parts, you'll discover a beautiful, elegant, lightweight and highly expressive language that lets you create effective code, whether you're managing object libraries or just trying to get Ajax to run fast. If you develop sites or applications for the Web, this book is an absolute must. COMPUTERS,Languages,JavaScript

Effective Perl Programming The Classic Guide to Solving Real-World Problems with Perl—Now Fully Updated for Today’s Best Idioms! For years, experienced programmers have relied on Effective Perl Programming to discover better ways to solve problems with perl. Now, in this long-awaited second edition, three renowned Perl programmers bring together today’s best idioms, techniques, and examples: everything you need to write more powerful, fluent, expressive, and succinct code with Perl. Nearly twice the size of the first edition, Effective Perl Programming, Second Edition, offers everything from rules of thumb to avoid common pitfalls to the latest wisdom for using Perl modules. You won’t just learn the right ways to use Perl: You’ll learn why these approaches work so well. New coverage in this edition includes Reorganized and expanded material spanning twelve years of Perl evolution Eight new chapters on CPAN, databases, distributions, files and filehandles, production Perl, testing, Unicode, and warnings Updates for Perl 5.12, the latest version of Perl Systematically updated examples reflecting today’s best idioms You’ll learn how to work with strings, numbers, lists, arrays, strictures, namespaces, regular expressions, subroutines, references, distributions, inline code, warnings, Perl::Tidy, data munging, Perl one-liners, and a whole lot more. Every technique is organized in the same Items format that helped make the first edition so convenient and popular. COMPUTERS,Languages,JavaScript

JavaScript Pocket Guide, The JavaScript is an object-oriented scripting language that enables you to modify a document's structure, styling, and content in response to user actions. This handy pocket serves as both a quick introduction to the language and acts a valuable reference. It's packed with tips as well as JavaScript syntax, methods, and properties. Concise and inexpensive, it's exactly the guide many web designers and developers need. COMPUTERS,Languages,JavaScript

Perl Best Practices Many programmers code by instinct, relying on convenient habits or a "style" they picked up early on. They aren't conscious of all the choices they make, like how they format their source, the names they use for variables, or the kinds of loops they use. They're focused entirely on problems they're solving, solutions they're creating, and algorithms they're implementing. So they write code in the way that seems natural, that happens intuitively, and that feels good. But if you're serious about your profession, intuition isn't enough. Perl Best Practices author Damian Conway explains that rules, conventions, standards, and practices not only help programmers communicate and coordinate with one another, they also provide a reliable framework for thinking about problems, and a common language for expressing solutions. This is especially critical in Perl, because the language is designed to offer many ways to accomplish the same task, and consequently it supports many incompatible dialects. With a good dose of Aussie humor, Dr. Conway (familiar to many in the Perl community) offers 256 guidelines on the art of coding to help you write better Perl code--in fact, the best Perl code you possibly can. The guidelines cover code layout, naming conventions, choice of data and control structures, program decomposition, interface design and implementation, modularity, object orientation, error handling, testing, and debugging. They're designed to work together to produce code that is clear, robust, efficient, maintainable, and concise, but Dr. Conway doesn't pretend that this is the one true universal and unequivocal set of best practices. Instead, Perl Best Practices offers coherent and widely applicable suggestions based on real-world experience of how code is actually written, rather than on someone's ivory-tower theories on howsoftware ought to be created. Most of all, Perl Best Practices offers guidelines that actually work, and that many developers around the world are already using. Much like Perl itself, these guidelines are about helping you to get your job done, without getting in the way. Praise for Perl Best Practices from Perl community members: "As a manager of a large Perl project, I'd ensure that every member of my team has a copy of Perl Best Practices on their desk, and use it as the basis for an in-house style guide."-- Randal Schwartz "There are no more excuses for writing bad Perl programs. All levels of Perl programmer will be more productive after reading this book."-- Peter Scott "Perl Best Practices will be the next big important book in the evolution of Perl. The ideas and practices Damian lays down will help bring Perl out from under the embarrassing heading of "scripting languages". Many of us have known Perl is a real programming language, worthy of all the tasks normally delegated to Java and C++. With Perl Best Practices, Damian shows specifically how and why, so everyone else can see, too."-- Andy Lester "Damian's done what many thought impossible: show how to build large, maintainable Perl applications, while still letting Perl be the powerful, expressive language that programmers have loved for years."-- Bill Odom "Finally, a means to bring lasting order to the process and product of real Perl development teams."-- Andrew Sundstrom"Perl Best Practices provides a valuable education in how to write robust, maintainable Perl, and is a definitive citation source when coaching other programmers."-- Bennett Todd"I've been teaching Perl for years, and find the same question keeps being asked: Where can I find a reference for writing reusable, maintainable Perl code? Finally I have a decent answer."-- Paul Fenwick"At last a well researched, well thought-out, comprehensive guide to Perl style. Instead of each of us developing our own, we can learn good practices from one of Perl's most prolific and experienced authors. I recommend this book to anyone who prefers getting on with the job rather than going back and fixing errors caused by syntax and poor style issues."-- Jacinta Richardson"If you care about programming in any language read this book. Even if you don't intend to follow all of the practices, thinking through your style will improve it."-- Steven Lembark"The Perl community's best author is back with another outstanding book. There has never been a comprehensive reference on high quality Perl coding and style until Perl Best Practices. This book fills a large gap in every Perl bookshelf."-- Uri Guttman COMPUTERS,Languages,JavaScript

Perl & LWP Perl soared to popularity as a language for creating and managing web content, but with LWP (Library for WWW in Perl), Perl is equally adept at consuming information on the Web. LWP is a suite of modules for fetching and processing web pages.The Web is a vast data source that contains everything from stock prices to movie credits, and with LWP all that data is just a few lines of code away. Anything you do on the Web, whether it's buying or selling, reading or writing, uploading or downloading, news to e-commerce, can be controlled with Perl and LWP. You can automate Web-based purchase orders as easily as you can set up a program to download MP3 files from a web site.Perl & LWP covers: Understanding LWP and its design Fetching and analyzing URLs Extracting information from HTML using regular expressions and tokens Working with the structure of HTML documents using trees Setting and inspecting HTTP headers and response codes Managing cookies Accessing information that requires authentication Extracting links Cooperating with proxy caches Writing web spiders (also known as robots) in a safe fashion Perl & LWP includes many step-by-step examples that show how to apply the various techniques. Programs to extract information from the web sites of BBC News, Altavista, ABEBooks.com, and the Weather Underground, to name just a few, are explained in detail, so that you understand how and why they work.Perl programmers who want to automate and mine the web can pick up this book and be immediately productive. Written by a contributor to LWP, and with a foreword by one of LWP's creators, Perl & LWP is the authoritative guide to this powerful and popular toolkit. COMPUTERS,Languages,JavaScript

Perl Cookbook Find a Perl programmer, and you'll find a copy of Perl Cookbook nearby. Perl Cookbook is a comprehensive collection of problems, solutions, and practical examples for anyone programming in Perl. The book contains hundreds of rigorously reviewed Perl "recipes" and thousands of examples ranging from brief one-liners to complete applications.The second edition of Perl Cookbook has been fully updated for Perl 5.8, with extensive changes for Unicode support, I/O layers, mod_perl, and new technologies that have emerged since the previous edition of the book. Recipes have been updated to include the latest modules. New recipes have been added to every chapter of the book, and some chapters have almost doubled in size.Covered topic areas include: Manipulating strings, numbers, dates, arrays, and hashes Pattern matching and text substitutions References, data structures, objects, and classes Signals and exceptions Screen addressing, menus, and graphical applications Managing other processes Writing secure scripts Client-server programming Internet applications programming with mail, news, ftp, and telnet CGI and mod_perl programming Web programming Since its first release in 1998, Perl Cookbook has earned its place in the libraries of serious Perl users of all levels of expertise by providing practical answers, code examples, and mini-tutorials addressing the challenges that programmers face. Now the second edition of this bestselling book is ready to earn its place among the ranks of favorite Perl books as well.Whether you're a novice or veteran Perl programmer, you'll find Perl Cookbook, 2nd Edition to be one of the most useful books on Perl available. Its comfortable discussion style and accurate attention to detail cover just about any topic you'd want to know about. You can get by without having this book in your library, but once you've tried a few of the recipes, you won't want to. COMPUTERS,Languages,JavaScript

Tcl/Tk Pocket Reference The Tcl/Tk combination is increasingly popular because it lets you produce sophisticated graphical interfaces with a few easy commands, develop and change scripts quickly, and conveniently tie together existing utilities or programming libraries.The Tcl/Tk Pocket Reference,a handy reference guide to the basic Tcl language elements, Tcl and Tk commands, and Tk widgets, is a companion volume to Tcl/Tk in a Nutshell. COMPUTERS,Languages,JavaScript

Test-Driven JavaScript Development For JavaScript developers working on increasingly large and complex projects, effective automated testing is crucial to success. Test-Driven JavaScript Development is a complete, best-practice guide to agile JavaScript testing and quality assurance with the test-driven development (TDD) methodology. Leading agile JavaScript developer Christian Johansen covers all aspects of applying state-of-the-art automated testing in JavaScript environments, walking readers through the entire development lifecycle, from project launch to application deployment, and beyond. Using real-life examples driven by unit tests, Johansen shows how to use TDD to gain greater confidence in your code base, so you can fearlessly refactor and build more robust, maintainable, and reliable JavaScript code at lower cost. Throughout, he addresses crucial issues ranging from code design to performance optimization, offering realistic solutions for developers, QA specialists, and testers. Coverage includes • Understanding automated testing and TDD • Building effective automated testing workflows • Testing code for both browsers and servers (using Node.js) • Using TDD to build cleaner APIs, better modularized code, and more robust software • Writing testable code • Using test stubs and mocks to test units in isolation • Continuously improving code through refactoring • Walking through the construction and automated testing of fully functional software The accompanying Web site, tddjs.com, contains all of the book’s code listings and additional resources. COMPUTERS,Languages,JavaScript

JavaScript Patterns What's the best approach for developing an application with JavaScript? This book helps you answer that question with numerous JavaScript coding patterns and best practices. If you're an experienced developer looking to solve problems related to objects, functions, inheritance, and other language-specific categories, the abstractions and code templates in this guide are ideal—whether you're using JavaScript to write a client-side, server-side, or desktop application. Written by JavaScript expert Stoyan Stefanov—Senior Yahoo! Technical and architect of YSlow 2.0, the web page performance optimization tool—JavaScript Patterns includes practical advice for implementing each pattern discussed, along with several hands-on examples. You'll also learn about anti-patterns: common programming approaches that cause more problems than they solve. Explore useful habits for writing high-quality JavaScript code, such as avoiding globals, using single var declarations, and more Learn why literal notation patterns are simpler alternatives to constructor functions Discover different ways to define a function in JavaScript Create objects that go beyond the basic patterns of using object literals and constructor functions Learn the options available for code reuse and inheritance in JavaScript Study sample JavaScript approaches to common design patterns such as Singleton, Factory, Decorator, and more Examine patterns that apply specifically to the client-side browser environment COMPUTERS,Languages,JavaScript

Building Hypermedia APIs with HTML5 and Node With this concise book, you’ll learn the art of building hypermedia APIs that don’t simply run on the Web, but that actually exist in the Web. You’ll start with the general principles and technologies behind this architectural approach, and then dive hands-on into three fully-functional API examples. Too many APIs rely on concepts rooted in desktop and local area network patterns that don’t scale well—costly solutions that are difficult to maintain over time. This book shows system architects and web developers how to design and implement human- and machine-readable web services that remain stable and flexible as they scale. Learn the H-Factors for representing application metadata across all media types and formats Understand the four basic design elements for authoring hypermedia types Convert a simple read-only XML-based media type into a successful API design Examine the challenges and advantages of designing a hypermedia type with JSON Use HTML5’s rich set of hypermedia controls in the API design process Learn the details of documenting, publishing, and registering media type designs and link-relation types COMPUTERS,Languages,JavaScript

JavaScript Pocket Reference JavaScript is the ubiquitous programming language of the Web, and for more than 15 years, JavaScript: The Definitive Guide has been the bible of JavaScript programmers around the world. Ideal for JavaScript developers at any level, this book is an all-new excerpt of The Definitive Guide, collecting the essential parts of that hefty volume into this slim yet dense pocket reference. The first 9 chapters document the latest version (ECMAScript 5) of the core JavaScript language, covering: Types, values, and variables Operators, expressions, and statements Objects and arrays Functions and classes The next 5 chapters document the fundamental APIs for using JavaScript with HTML5 and explain how to: Interact with web browser windows Script HTML documents and document elements Modify and apply CSS styles and classes Respond to user input events Communicate with web servers Store data locally on the user's computer This book is a perfect companion to jQuery Pocket Reference. COMPUTERS,Languages,JavaScript

Learning JavaScript Design Patterns With Learning JavaScript Design Patterns, you’ll learn how to write beautiful, structured, and maintainable JavaScript by applying classical and modern design patterns to the language. If you want to keep your code efficient, more manageable, and up-to-date with the latest best practices, this book is for you. Explore many popular design patterns, including Modules, Observers, Facades, and Mediators. Learn how modern architectural patterns—such as MVC, MVP, and MVVM—are useful from the perspective of a modern web application developer. This book also walks experienced JavaScript developers through modern module formats, how to namespace code effectively, and other essential topics. Learn the structure of design patterns and how they are written Understand different pattern categories, including creational, structural, and behavioral Walk through more than 20 classical and modern design patterns in JavaScript Use several options for writing modular code—including the Module pattern, Asyncronous Module Definition (AMD), and CommonJS Discover design patterns implemented in the jQuery library Learn popular design patterns for writing maintainable jQuery plug-ins "This book should be in every JavaScript developer’s hands. It’s the go-to book on JavaScript patterns that will be read and referenced many times in the future."—Andrée Hansson, Lead Front-End Developer, presis! COMPUTERS,Languages,JavaScript

Perl Graphics Programming Graphics programmers aren't the only ones who need to be proficient with graphics. Web and applications programmers know that a dull web page can be quickly transformed into one that's interesting and lively with the use of well-planned graphics. And fortunately, you don't need the skills of a fulltime graphics programmer to use graphics effectively. From access counters and log report graphs to scientific plots and on-the-fly animated GIFs, graphics scripting is within the grasp of most web programmers. Using open source software, like Perl, you have the power to dynamically generate graphics based on user input and activity, easily manipulate graphics content, and optimize graphics for compression and quality.Geared toward Perl users and webmasters, Perl Graphics Programming focuses on open-source scripting programs that manipulate graphics files for use on the Web. The book demystifies the manipulation of graphics formats for newcomers to the Web with a practical, resource-like approach. With this book you'll learn to: Generate dynamic web graphics with charts, tables, and buttons Automate graphics tasks (thumbnails and borders) Create dynamics web documents (PDF, Postscript) Produce rich Internet experiences with Flash and SVG You'll begin with a tour of the most common web graphic file formats--PNG, JPEG, GIF, SWF, SVG, Postscript and PDF--then you'll explore the most powerful tools and Perl modules available for manipulating these graphics, such as GD, PerlMagick, and GIMP. Included in this part of the book is a thorough description of the Ming module for creating on-the-fly Flash files. Next, a "cookbook" section includes practical, all purpose recipes: GIF animation, generating images within a dynamic application, communicating between SWF front-end and Perl back-end, XSLT transformations, compression, and much more.Perl programmers naturally turn to Perl to tackle whatever challenge they have at hand, and graphics programming is no exception. Perl Graphics Programming provides all the tools you need to begin programming and designing graphics for the Web immediately. This book will change how you think about generating and manipulating graphics for the Web. COMPUTERS,Languages,JavaScript

DOM Enlightenment With DOM Enlightenment, you’ll learn how to manipulate HTML more efficiently by scripting the Document Object Model (DOM) without a DOM library. Using code examples in cookbook style, author Cody Lindley (jQuery Cookbook) walks you through modern DOM concepts to demonstrate how various node objects work. Over the past decade, developers have buried the DOM under frameworks that simplify its use. This book brings these tools back into focus, using concepts and code native to modern browsers. If you have JavaScript experience, you’ll understand the role jQuery plays in DOM scripting, and learn how to use the DOM directly in applications for mobile devices and specific browsers that require low overhead. Understand JavaScript node objects and their relationship to the DOM Learn the properties and methods of document, element, text, and DocumentFragment objects Delve into element node selecting, geometry, and inline styles Add CSS style sheets to an HTML document and use CSSStyleRule objects Set up DOM events by using different code patterns Learn the author’s vision for dom.js, a jQuery-inspired DOM Library for modern browsers COMPUTERS,Languages,JavaScript

JavaScript Testing with Jasmine Get a concise introduction to Jasmine, the popular behavior-driven testing framework for JavaScript. This practical guide shows you how to write unit tests with Jasmine that automatically check for bugs in your application. If you have JavaScript experience—with knowledge of some advanced features—you’ll learn how to write specifications for individual components, and then use those specs to test the code you write. Throughout the book, author Evan Hahn focuses primarily on methods for testing browser-based JavaScript applications, but you’ll also discover how to use Jasmine with CoffeeScript, Node.js, Ruby on Rails, and Ruby without Rails. You won’t find a more in-depth source for Jasmine anywhere. Get an overview of both test-driven and behavior-driven development Write useful specs by determining what you need to test—and what you don’t Test the behavior of new and existing code against the specs you create Apply Jasmine matchers and discover how to build your own Organize code suites into groups and subgroups as your code becomes more complex Use a Jasmine spy in place of a function or an object—and learn why it’s valuable COMPUTERS,Languages,JavaScript

Functional JavaScript How can you overcome JavaScript language oddities and unsafe features? With this book, you’ll learn how to create code that’s beautiful, safe, and simple to understand and test by using JavaScript’s functional programming support. Author Michael Fogus shows you how to apply functional-style concepts with Underscore.js, a JavaScript library that facilitates functional programming techniques. Sample code is available on GitHub at https://github.com/funjs/book-source. Fogus helps you think in a functional way to help you minimize complexity in the programs you build. If you’re a JavaScript programmer hoping to learn functional programming techniques, or a functional programmer looking to learn JavaScript, this book is the ideal introduction. Use applicative programming techniques with first-class functions Understand how and why you might leverage variable scoping and closures Delve into higher-order functions—and learn how they take other functions as arguments for maximum advantage Explore ways to compose new functions from existing functions Get around JavaScript’s limitations for using recursive functions Reduce, hide, or eliminate the footprint of state change in your programs Practice flow-based programming with chains and functional pipelines Discover how to code without using classes COMPUTERS,Languages,JavaScript

RaphaelJS Create beautiful, interactive images on the Web with RaphaëlJS, the JavaScript library that lets you draw Scalable Vector Graphics (SVG) right in the browser. With this concise guide, you’ll quickly learn how to paint the screen with shapes and colors that you can turn into lively, animated graphics and visualizations. Author Chris Wilson (Time.com) shows you how to create Raphaël objects and manipulate them with animation, transformations, and other techniques, using just a few lines of code. Packed with working examples, sample code, and cool hands-on projects, RaphaëlJS is ideal for new and experienced JavaScript programmers alike. Create images that work on browsers new and old, as well as mobile devices Start with the basics—shapes, colors, transformations, sets, and text Learn how to build custom curves and shapes with paths Code animations that move through space, follow paths, or change direction Make your artwork come alive through user interaction Bind a dataset to a collection of visual objects—the basis of data visualization Learn techniques to make your detailed visuals stand out on screens of any size COMPUTERS,Languages,JavaScript

Learning Web App Development Grasp the fundamentals of web application development by building a simple database-backed app from scratch, using HTML, JavaScript, and other open source tools. Through hands-on tutorials, this practical guide shows inexperienced web app developers how to create a user interface, write a server, build client-server communication, and use a cloud-based service to deploy the application. Each chapter includes practice problems, full examples, and mental models of the development workflow. Ideal for a college-level course, this book helps you get started with web app development by providing you with a solid grounding in the process. Set up a basic workflow with a text editor, version control system, and web browser Structure a user interface with HTML, and include styles with CSS Use JQuery and JavaScript to add interactivity to your application Link the client to the server with AJAX, JavaScript objects, and JSON Learn the basics of server-side programming with Node.js Store data outside your application with Redis and MongoDB Share your application by uploading it to the cloud with CloudFoundry Get basic tips for writing maintainable code on both client and server COMPUTERS,Languages,JavaScript

Speaking JavaScript Like it or not, JavaScript is everywhere these days—from browser to server to mobile—and now you, too, need to learn the language or dive deeper than you have. This concise book guides you into and through JavaScript, written by a veteran programmer who once found himself in the same position. Speaking JavaScript helps you approach the language with four standalone sections. First, a quick-start guide teaches you just enough of the language to help you be productive right away. More experienced JavaScript programmers will find a complete and easy-to-read reference that covers each language feature in depth. Complete contents include: JavaScript quick start: Familiar with object-oriented programming? This part helps you learn JavaScript quickly and properly. JavaScript in depth: Learn details of ECMAScript 5, from syntax, variables, functions, and object-oriented programming to regular expressions and JSON with lots of examples. Pick a topic and jump in. Background: Understand JavaScript’s history and its relationship with other programming languages. Tips, tools, and libraries: Survey existing style guides, best practices, advanced techniques, module systems, package managers, build tools, and learning resources. COMPUTERS,Languages,JavaScript

Head First JavaScript Programming What will you learn from this book? This brain-friendly guide teaches you everything from JavaScript language fundamentals to advanced topics, including objects, functions, and the browser’s document object model. You won’t just be reading—you’ll be playing games, solving puzzles, pondering mysteries, and interacting with JavaScript in ways you never imagined. And you’ll write real code, lots of it, so you can start building your own web applications. Prepare to open your mind as you learn (and nail) key topics including: The inner details of JavaScript How JavaScript works with the browser The secrets of JavaScript types Using arrays The power of functions How to work with objects Making use of prototypes Understanding closures Writing and testing applications What’s so special about this book? We think your time is too valuable to waste struggling with new concepts. Using the latest research in cognitive science and learning theory to craft a multi-sensory learning experience, Head First JavaScript Programming uses a visually rich format designed for the way your brain works, not a text-heavy approach that puts you to sleep. This book replaces Head First JavaScript, which is now out of print. COMPUTERS,Languages,JavaScript

Programming JavaScript Applications Take advantage of JavaScript’s power to build robust web-scale or enterprise applications that are easy to extend and maintain. By applying the design patterns outlined in this practical book, experienced JavaScript developers will learn how to write flexible and resilient code that’s easier—yes, easier—to work with as your code base grows. JavaScript may be the most essential web programming language, but in the real world, JavaScript applications often break when you make changes. With this book, author Eric Elliott shows you how to add client- and server-side features to a large JavaScript application without negatively affecting the rest of your code. Examine the anatomy of a large-scale JavaScript application Build modern web apps with the capabilities of desktop applications Learn best practices for code organization, modularity, and reuse Separate your application into different layers of responsibility Build efficient, self-describing hypermedia APIs with Node.js Test, integrate, and deploy software updates in rapid cycles Control resource access with user authentication and authorization Expand your application’s reach through internationalization COMPUTERS,Languages,JavaScript

HTML, CSS and JavaScript All in One, Sams Teach Yourself In just a short time, you can learn how to use HTML5, Cascading Style Sheets (CSS3), and JavaScript together to design, create, and maintain world-class websites. Using a straightforward, step-by-step approach, each lesson in this book builds on the previous ones, enabling you to learn the essentials from the ground up. Clear instructions and practical, hands-on examples show you how to use HTML to create the framework of your website, design your site's layout and typography with CSS, and then add interactivity with JavaScript and jQuery. Step-by-step instructions carefully walk you through the most common web development tasks Practical, hands-on examples show you how to apply what you learn Quizzes and exercises help you test your knowledge and stretch your skills Learn how to... Build your own web page and get it online in an instant Format text for maximum clarity and readability Create links to other pages and to other sites Add graphics, color, and visual pizzazz to your web pages Work with transparent images and background graphics Design your site’s layout and typography using CSS Get user input with web-based forms Use JavaScript to build dynamic, interactive web pages Add AJAX effects to your web pages Leverage JavaScript libraries such as jQuery Make your site easy to maintain and update as it grows Contents at a Glance Part I Getting Started on the Web 1 Understanding How the Web Works 2 Structuring an HTML Document 3 Understanding Cascading Style Sheets 4 Understanding JavaScript 5 Validating and Debugging Your Code Part II Building Blocks of Practical Web Design 6 Working with Fonts, Text Blocks, Lists, and Tables 7 Using External and Internal Links 8 Working with Colors, Images, and Multimedia Part III Advanced Web Page Design with CSS 9 Working with Margins, Padding, Alignment, and Floating 10 Understanding the CSS Box Model and Positioning 11 Using CSS to Do More with Lists, Text, and Navigation 12 Creating Fixed or Liquid Layouts Part IV Getting Started with Dynamic Sites 13 Understanding Dynamic Websites and HTML5 Applications 14 Getting Started with JavaScript Programming 15 Working with the Document Object Model (DOM) 16 Using JavaScript Variables, Strings, and Arrays 17 Using JavaScript Functions and Objects 18 Controlling Flow with Conditions and Loops 19 Responding to Events 20 Using Windows Part V Advanced JavaScript Programming 21 JavaScript Best Practices 22 Using Third-Party JavaScript Libraries and Frameworks 23 A Closer Look at jQuery 24 First Steps Toward Creating Rich Interactions with jQuery UI 25 AJAX: Remote Scripting Part VI Advanced Website Functionality and Management 26 Working with Web-Based Forms 27 Organizing and Managing a Website COMPUTERS,Languages,JavaScript

Coding with JavaScript For Dummies Go from beginner to builder quickly with this hands-on JavaScript guide Coding with JavaScript For Dummies provides easy, hands-on instruction for anyone looking to learn this popular client-side language. No experience? No problem! This friendly guide starts from the very beginning and walks you through the basics, then shows you how to apply what you've learned to real projects. You'll start building right away, including web page elements and simple applications, so you can immediately see how JavaScript is used in the real world. Online exercises allow you to test your code and expand your skills, and the easy-to-follow instruction provides step-by-step guidance toward understanding the JavaScript syntax, applications, and language. JavaScript enhances static web pages by providing dynamic elements that can adapt and react to user action. It's a need-to-know tool for aspiring web designers, but anyone can benefit from understanding this core development language. Coding with JavaScript For Dummies takes you from beginner to builder quickly as you: Learn what JavaScript does, how it works, and where to use it Master the core elements of JavaScript and immediately put it to work Build interactive web elements and try out your code online Create basic applications as you apply JavaScript to the app development workflow Anytime a website responds to your movement around the screen, that's JavaScript. It makes websites more functional, more beautiful, and more engaging, and your site visitors will demand nothing less. If you want to build a better website, you need JavaScript. If you need JavaScript, Coding with JavaScript For Dummies gets you started off quickly and painlessly, with plenty of hands-on practice. COMPUTERS,Languages,JavaScript

JavaScript Cookbook Problem solving with JavaScript is a lot trickier now that its use has expanded considerably in size, scope, and complexity. This cookbook has your back, with recipes for common tasks across the JavaScript world, whether you’re working in the browser, the server, or a mobile environment. Each recipe includes reusable code and practical advice for tackling JavaScript objects, Node, Ajax, JSON, data persistence, graphical and media applications, complex frameworks, modular JavaScript, APIs, and many related technologies. Aimed at people who have some experience with JavaScript, the first part covers traditional uses of JavaScript, along with new ideas and improved functionality. The second part dives into the server, mobile development, and a plethora of leading-edge tools. You’ll save time—and learn more about JavaScript in the process. Topics include: Classic JavaScript: Arrays, functions, and the JavaScript Object Accessing the user interface Testing and accessibility Creating and using JavaScript libraries Client-server communication with Ajax Rich, interactive web effects JavaScript, All Blown Up: New ECMAScript standard objects Using Node on the server Modularizing and managing JavaScript Complex JavaScript frameworks Advanced client-server communications Visualizations and client-server graphics Mobile application development COMPUTERS,Languages,JavaScript

jQuery jQuery: Novice to Ninja, 2nd Edition is the perfect book to jump-start your journey into jQuery. You’ll learn all the basics, so you’ll be able to truly appreciate the power of this JavaScript framework. Then you’ll move on to more advanced techniques, such as plugin development and the creation of almost every conceivable UI widget. A practical, hands-on guide to using jQuery Ready-to-use best practice solutions Includes complete working code Fully updated for jQuery 1.6 COMPUTERS,Languages,JavaScript

Learning AngularJS With AngularJS, you can quickly build client-side applications that run well on any desktop or mobile platform, using REST web services for backend processes. You may have heard that the learning curve for this JavaScript MVC framework is too steep, but that’s not the case. This practical guide provides a hands-on approach to learning AngularJS that will have you building high-quality applications and websites in no time. Along with a conceptual understanding of the framework, you’ll also gain direct experience with AngularJS by building a sample application throughout the book. If you’re familiar with JavaScript, web development, and software design concepts and patterns, this book is the perfect way to get started. Understand how AngularJS differs from other MVC frameworks Learn about AngularJS controllers, views, and models by diving into the book’s sample project Connect your working application to public REST services Build the application’s security layer with non-REST AngularJS services Explore the basics of building and testing AngularJS directives Use AngularJS as part of the MEAN stack (MongoDB, ExpressJS, AngularJS, and Node.js) Discover how search engine optimization relates to AngularJS applications and sites COMPUTERS,Languages,JavaScript

JavaScript with Promises Asynchronous JavaScript is everywhere, whether you’re using Ajax, AngularJS, Node.js, or WebRTC. This practical guide shows intermediate to advanced JavaScript developers how Promises can help you manage asynchronous code effectively—including the inevitable flood of callbacks as your codebase grows. You’ll learn the inner workings of Promises and ways to avoid difficulties and missteps when using them. The ability to asynchronously fetch data and load scripts in the browser broadens the capabilities of JavaScript applications. But if you don’t understand how the async part works, you’ll wind up with unpredictable code that’s difficult to maintain. This book is ideal whether you’re new to Promises or want to expand your knowledge of this technology. Understand how async JavaScript works by delving into callbacks, the event loop, and threading Learn how Promises organize callbacks into discrete steps that are easier to read and maintain Examine scenarios you’ll encounter and techniques you can use when writing real-world applications Use features in the Bluebird library and jQuery to work with Promises Learn how the Promise API handles asynchronous errors Explore ECMAScript 6 language features that simplify Promise-related code COMPUTERS,Languages,JavaScript

Beautiful JavaScript JavaScript is arguably the most polarizing and misunderstood programming language in the world. Many have attempted to replace it as the language of the Web, but JavaScript has survived, evolved, and thrived. Why did a language created in such hurry succeed where others failed? This guide gives you a rare glimpse into JavaScript from people intimately familiar with it. Chapters contributed by domain experts such as Jacob Thornton, Ariya Hidayat, and Sara Chipps show what they love about their favorite language—whether it’s turning the most feared features into useful tools, or how JavaScript can be used for self-expression. Contributors include: Angus Croll Jonathan Barronville Sara Chipps Marijn Haverbeke Ariya Hidayat Daryl Koopersmith Anton Kovalyov Rebecca Murphey Daniel Pupius Graeme Roberts Jenn Schiffer Jacob Thornton Ben Vinegar Rick Waldron Nicholas Zakas COMPUTERS,Languages,JavaScript

WebSocket Until recently, creating desktop-like applications in the browser meant using inefficient Ajax or Comet technologies to communicate with the server. With this practical guide, you’ll learn how to use WebSocket, a protocol that enables the client and server to communicate with each other on a single connection simultaneously. No more asynchronous communication or long polling! For developers with a good grasp of JavaScript (and perhaps Node.js), author Andrew Lombardi provides useful hands-on examples throughout the book to help you get up to speed with the WebSocket API. You’ll also learn how to use WebSocket with Transport Layer Security (TLS). Learn how to use WebSocket API events, messages, attributes, and methods within your client application Build bi-directional chat applications on the client and server with WebSocket as the communication layer Create a subprotocol over WebSocket for STOMP 1.0, the Simple Text Oriented Messaging Protocol Use options for older browsers that don’t natively support WebSocket Protect your WebSocket application against various attack vectors with TLS and other tools Debug applications by learning aspects of the WebSocket lifecycle COMPUTERS,Languages,JavaScript

Getting Started with p5.js With p5.js, you can think of your entire Web browser as your canvas for sketching with code! Learn programming the fun way--by sketching with interactive computer graphics! Getting Started with p5.js contains techniques that can be applied to creating games, animations, and interfaces. p5.js is a new interpretation of Processing written in JavaScript that makes it easy to interact with HTML5 objects, including text, input, video, webcam, and sound. Like its older sibling Processing, p5.js makes coding accessible for artists, designers, educators, and beginners. Written by the lead p5.js developer and the founders of Processing, this book provides an introduction to the creative possibilities of today's Web, using JavaScript and HTML. With Getting Started with p5.js, you'll: Quickly learn programming basics, from variables to objects Understand the fundamentals of computer graphics Create interactive graphics with easy-to-follow projects Learn to apply data visualization techniques Capture and manipulate webcam audio and video feeds in the browser COMPUTERS,Languages,JavaScript

Going GAS Whether you’re moving from Microsoft Office to Google Docs or simply want to learn how to automate Docs with Google Apps Script, this practical guide shows you by example how to work with each of the major Apps Script services. Office still supports VBA, but it’s not likely to do so for much longer. If you’re a VBA or .NET developer, you’ll learn how to port existing VBA code and structure to their JavaScript-based Apps Script equivalents with minimal effort. Author Bruce Mcpherson introduces JavaScript basics for experienced developers unfamiliar with the language, and demonstrates ways to build real-world apps using all of the Apps Script services previously covered. Use App Script’s equivalent of Excel’s object model Target the most commonly used parts of Microsoft Word Automate processes in Gmail, Calendar, and Contacts Access the local client filesystem with Google Drive Build and run applications in a browser Store persistent data conveniently Render HTML content in response to HTTP requests Automate the maintenance and creation of pages and content Interact with a REST service or NoSQL database Access Apps Script capabilities from other platforms COMPUTERS,Languages,JavaScript

Learning JavaScript This is an exciting time to learn JavaScript. Now that the latest JavaScript specification—ECMAScript 6.0 (ES6)—has been finalized, learning how to develop high-quality applications with this language is easier and more satisfying than ever. This practical book takes programmers (amateurs and pros alike) on a no-nonsense tour of ES6, along with some related tools and techniques. Author Ethan Brown (Web Development with Node and Express) not only guides you through simple and straightforward topics (variables, control flow, arrays), but also covers complex concepts such as functional and asynchronous programming. You’ll learn how to create powerful and responsive web applications on the client, or with Node.js on the server. Use ES6 today and transcompile code to portable ES5 Translate data into a format that JavaScript can use Understand the basic usage and mechanics of JavaScript functions Explore objects and object-oriented programming Tackle new concepts such as iterators, generators, and proxies Grasp the complexities of asynchronous programming Work with the Document Object Model for browser-based apps Learn Node.js fundamentals for developing server-side applications COMPUTERS,Languages,JavaScript

Designing for Scalability with Erlang/OTP If you need to build a scalable, fault tolerant system with requirements for high availability, discover why the Erlang/OTP platform stands out for the breadth, depth, and consistency of its features. This hands-on guide demonstrates how to use the Erlang programming language and its OTP framework of reusable libraries, tools, and design principles to develop complex commercial-grade systems that simply cannot fail. In the first part of the book, you’ll learn how to design and implement process behaviors and supervision trees with Erlang/OTP, and bundle them into standalone nodes. The second part addresses reliability, scalability, and high availability in your overall system design. If you’re familiar with Erlang, this book will help you understand the design choices and trade-offs necessary to keep your system running. Explore OTP’s building blocks: the Erlang language, tools and libraries collection, and its abstract principles and design rules Dive into the fundamentals of OTP reusable frameworks: the Erlang process structures OTP uses for behaviors Understand how OTP behaviors support client-server structures, finite state machine patterns, event handling, and runtime/code integration Write your own behaviors and special processes Use OTP’s tools, techniques, and architectures to handle deployment, monitoring, and operations COMPUTERS,Languages,JavaScript

Learning Node Take your web development skills from browser to server with Node—and learn how to write fast, highly scalable network applications on this JavaScript-based platform. Updated for the latest Node Long Term Support (LTS) and Node Current (6.0) releases, this hands-on edition helps you master Node’s core fundamentals and gain experience with several built-in and contributed modules. Get up to speed on Node’s event-driven, asynchronous I/O model for developing data-intensive applications that are frequently accessed but computationally simple. If you’re comfortable working with JavaScript, this book provides many programming and deployment examples to help you take advantage of server-side development with Node. Explore the frameworks and functionality for full-stack Node development Dive into Node’s module system and package management support Test your application or module code on the fly with Node’s REPL console Use core Node modules to build web applications and an HTTP server Learn Node’s support for networks, security, and sockets Access operating system functionality with child processes Learn tools and techniques for Node development and production Use Node in microcontrollers, microcomputers, and the Internet of Things COMPUTERS,Languages,JavaScript

JavaScript All of JavaScript's newest features, in depth, made easy to understand. JavaScript is a rapidly changing language and it can be challenging to keep up with all the new toys being added. JavaScript: The New Toys explores the newest features of the world's most popular programming language while also showing readers how to track what's coming next. After setting the stage by covering who manages the process of improving JavaScript, how new features get introduced, terminology, and a high-level overview of new features, it details each new or updated item in depth, with example uses, possible pitfalls, and expert recommendations for updating old habits in light of new features. JavaScript: The New Toys: Covers all the additions to JavaScript in ES2015-ES2020 plus a preview of what's coming next Explores the latest syntax: nullish coalescing, optional chaining, let and const, class syntax, private methods, private fields, new.target, numeric separators, BigInt, destructuring, default parameters, arrow functions, async functions, await, generator functions, ... (rest and spread), template literals, binary and octal literals, ** (exponentiation), computed property/method names, for-of, for-await-of, shorthand properties, and others Details the new features and patterns including modules, promises, iteration, generators, Symbol, Proxy, reflection, typed arrays, Atomics, shared memory, WeakMap, WeakSet, and more Highlights common pitfalls and explains how to avoid them Shows how to follow the improvements process and even participate in the process yourself Explains how to use new features even before they're widely supported With its comprehensive coverage and friendly, accessible style, JavaScript: The New Toys provides an invaluable resource for programmers everywhere, whether they work in web development, Node.js, Electron, Windows Universal Apps, or another JavaScript environment. COMPUTERS,Languages,JavaScript

Refactoring JavaScript How often do you hear people say things like this? "Our JavaScript is a mess, but we’re thinking about using [framework of the month]." Like it or not, JavaScript is not going away. No matter what framework or â€compiles-to-js†language or library you use, bugs and performance concerns will always be an issue if the underlying quality of your JavaScript is poor. Rewrites, including porting to the framework of the month, are terribly expensive and unpredictable. The bugs won’t magically go away, and can happily reproduce themselves in a new context. To complicate things further, features will get dropped, at least temporarily. The other popular method of fixing your JS is playing “JavaScript Jenga,†where each developer slowly and carefully takes their best guess at how the out-of-control system can be altered to allow for new features, hoping that this doesn’t bring the whole stack of blocks down. This book provides clear guidance on how best to avoid these pathological approaches to writing JavaScript: Recognize you have a problem with your JavaScript quality. Forgive the code you have now, and the developers who made it. Learn repeatable, memorable, and time-saving refactoring techniques. Apply these techniques as you work, fixing things along the way. Internalize these techniques, and avoid writing as much problematic code to begin with. Bad code doesn’t have to stay that way. And making it better doesn’t have to be intimidating or unreasonably expensive. COMPUTERS,Languages,JavaScript

Professional JavaScript for Web Developers Update your skill set for ES 6 and 7 with the ultimate JavaScript guide for pros Professional JavaScript for Web Developers is the essential guide to next-level JavaScript development. Written for intermediate-to-advanced programmers, this book jumps right into the technical details to help you clean up your code and become a more sophisticated JavaScript developer. From JavaScript-specific object-oriented programming and inheritance, to combining JavaScript with HTML and other markup languages, expert instruction walks you through the fundamentals and beyond. This new fourth edition has been updated to cover ECMAScript 6 and 7 (also known as ES2015 and ES2016) and the major re-imagination and departure from ES 5.1; new frameworks and libraries, new techniques, new testing tools, and more are explained in detail for the professional developer, with a practical focus that helps you put your new skills to work on real-world projects. The latest—and most dramatic—ES release is already being incorporated into JavaScript engines in major browsers; this, coupled with the rise in mobile web traffic increasing demand for responsive, dynamic web design, means that all web developers need to update their skills—and this book is your ideal resource for quick, relevant guidance. Get up to date with ECMAScript 6 and 7, new frameworks, and new libraries Delve into web animation, emerging APIs, and build systems Test more effectively with mocks, unit tests, functional tests, and other tools Plan your builds for future ES releases Even if you think you know JavaScript, new ES releases bring big changes that will affect the way you work. For a professional-level update that doesn't waste time on coding fundamentals, Professional JavaScript for Web Developers is the ultimate resource to bring you up to speed. COMPUTERS,Languages,JavaScript

React and React Native Use React and React Native to build applications for desktop browsers, mobile browsers, and even as native mobile apps About This Book Build React and React Native applications using familiar component concepts Dive deep into each platform, from routing in React to creating native mobile applications that can run offline Use Facebook's Relay, React and GraphQL technologies, to create a unified architecture that powers both web and native applications Who This Book Is For This book is written for any JavaScript developer—beginner or expert—who wants to start learning how to put both of Facebook's UI libraries to work. No knowledge of React is needed, though a working knowledge of ES2015 will help you follow along better. What You Will Learn Craft reusable React components Control navigation using the React Router to help keep your UI in sync with URLs Build isomorphic web applications using Node.js Use the Flexbox layout model to create responsive mobile designs Leverage the native APIs of Android and iOS to build engaging applications with React Native Respond to gestures in a way that's intuitive for the user Use Relay to build a unified data architecture for your React UIs In Detail React and React Native allow you to build cross-platform desktop and mobile applications using Facebook's innovative UI libraries. Combined with the Flux data architecture and Relay, you can now create powerful and feature-complete applications from just one code base! This book is split into three parts. The first part shows you how to start crafting composable UIs using React, from rendering with JSX and creating reusable components through to routing and creating isomorphic applications that run on Node. We then move on to showing you how to take the concepts of React and apply them to building Native UIs using React Native. You'll find out how to build responsive and streamlined UIs that can properly handle user interactions in a mobile environment. You'll also learn how to access device-specific APIs such as the geolocation API, and how to handle offline development with React Native. Finally, we'll tie all of these skills together and shows you how you can create React applications that run on every major platform. As well as understanding application state in depth, you'll learn how to leverage Relay to make feature-complete, data-driven web and native mobile applications. Style and approach Split into three major sections to help organize your learning, this hands-on, code-first book will help you get up to speed with React and React Native—the UI framework that powers Netflix, Yahoo, and Facebook. COMPUTERS,Languages,JavaScript

Practical Modern JavaScript To get the most out of modern JavaScript, you need learn the latest features of its parent specification, ECMAScript 6 (ES6). This book provides a highly practical look at ES6, without getting lost in the specification or its implementation details. Armed with practical examples, author Nicolas Bevacqua shows you new ways to deal with asynchronous flow control, declare objects or functions, and create proxies or unique sets, among many other features. The first title in Bevacqua’s Modular JavaScript series, Practical Modern JavaScript prepares JavaScript and Node.js developers for applied lessons in modular design, testing, and deployment in subsequent books. This book explains: How JavaScript and its standards development process have evolved Essential ES6 changes, including arrow functions, destructuring, let and const Class syntax for declaring object prototypes, and the new Symbol primitive How to handle flow control with Promises, iterators, generators, and async functions ES6 collection built-in types for creating object maps and unique sets How and when to use the new Proxy and Reflect built-ins Changes to Array, Math, numbers, strings, Unicode, and regular expressions, and other improvements since ES5 COMPUTERS,Languages,JavaScript

Learning Node.js This is the eBook of the printed book and may not include any media, website access codes, or print supplements that may come packaged with the bound book. Learning Node.js brings together the knowledge and JavaScript code needed to build master the Node.js platform and build server-side applications with extraordinary speed and scalability. You’ll start by installing and running Node.js, understanding the extensions it uses, and quickly writing your first app. Next, building on the basics, you’ll write more capable application servers and extend them with today’s most powerful Node.js tools and modules. Finally, you’ll discover today’s best practices for testing, running Node.js code on production servers, and writing command-line utilities. Throughout the book, author Marc Wandschneider teaches by walking the reader line-by-line through carefully crafted examples, demonstrating proven techniques for creating highly efficient applications and servers. The second edition updates coverage of Node.js to reflect changes in the technology and how it is used in the three years since the first edition was published: Explanation of Node's new versioning scheme Updated coverage of Streams New coverage of installation using pre-build installers rather than from source code New coverage of Mongoose in the section on MongoDB New information about deploying Node on Heroku and Azure Expansion of coverage on testing If you're a developer who wants to build server-side web applications with Node.js, Learning Node.js is your fatest route to success. Build Node.js solutions that leverage current JavaScript skills Master Node.js nonblocking IO and async programming Handle more requests and increase an application’s flexibility Use and write modules Perform common JSON/web server tasks Use browsers to generate pages on the fly via Ajax calls and template libraries Simplify development with the Express framework Create database back-ends using popular NoSQL and relational databases Deploy and run Node.js apps on Unix/macOS or Windows servers Deploy apps to Heroku and Microsoft Azure Support virtual hosts and SSL/HTTPS security Test Node.js programs that mix synchronous, async, and RESTful server API functionality COMPUTERS,Languages,JavaScript

JavaScript for Kids JavaScript is the programming language of the Internet, the secret sauce that makes the Web awesome, your favorite sites interactive, and online games fun! JavaScript for Kids is a lighthearted introduction that teaches programming essentials through patient, step-by-step examples paired with funny illustrations. You’ll begin with the basics, like working with strings, arrays, and loops, and then move on to more advanced topics, like building interactivity with jQuery and drawing graphics with Canvas. Along the way, you’ll write games such as Find the Buried Treasure, Hangman, and Snake. You’ll also learn how to:–Create functions to organize and reuse your code–Write and modify HTML to create dynamic web pages–Use the DOM and jQuery to make your web pages react to user input–Use the Canvas element to draw and animate graphics–Program real user-controlled games with collision detection and score keeping With visual examples like bouncing balls, animated bees, and racing cars, you can really see what you’re programming. Each chapter builds on the last, and programming challenges at the end of each chapter will stretch your brain and inspire your own amazing programs. Make something cool with JavaScript today! Ages 10+ (and their parents!) COMPUTERS,Languages,JavaScript

JavaScript JavaScript is a must-have skill for all web developers. JavaScript: Novice to Ninja is a fun, practical, and comprehensive guide to the modern usage of this deceptively powerful language. Comprehensively updated to cover ECMAScript 6 and modern JavaScript development, the second edition of this step-by-step introduction to coding in JavaScript will show you how to to solve real-world problems, design eye-catching animations, build smarter forms, and develop richer applications. Learn the basics of JavaScript programming: functions, methods, properties, loops and logic Use events to track user interactions Build smarter web forms that improve the user experience Work with the document object model (DOM) and Ajax to dynamicall update your pages Add functionality to your apps using HTML5's powerful APIs Use Test Driven Development methodology to write more robust code Build a complete, working JavaScript quiz app from scratch COMPUTERS,Languages,JavaScript

Learning React Native Get a practical introduction to React Native, the JavaScript framework for writing and deploying fully featured mobile apps that render natively. The second edition of this hands-on guide shows you how to build applications that target iOS, Android, and other mobile platforms instead of browsers—apps that can access platform features such as the camera, user location, and local storage. Through code examples and step-by-step instructions, web developers and frontend engineers familiar with React will learn how to build and style interfaces, use mobile components, and debug and deploy apps. You’ll learn how to extend React Native using third-party libraries or your own Java and Objective-C libraries. Understand how React Native works under the hood with native UI components Examine how React Native’s mobile-based components compare to basic HTML elements Create and style your own React Native components and applications Take advantage of platform-specific APIs, as well as modules from the framework’s community Incorporate platform-specific components into cross-platform apps Learn common pitfalls of React Native development, and tools for dealing with them Combine a large application’s many screens into a cohesive UX Handle state management in a large app with the Redux library COMPUTERS,Languages,JavaScript

React Native Cookbook Tackling an app development project on multiple platforms is no simple task. When time is in short supply and customers need access from the tap of a home screen, React Native can provide a lean development team with the tools needed to deliver a multi-platform native experience without juggling multiple programming languages and shifting code bases. React Native is an emerging technology and best practices are only beginning to bubble up. Fortunately, a growing user community—from tech giants such as Facebook, Yahoo, and Airbnb to the independent developers—is hard at work codifying patterns and best practices for how to use React Native. This cookbook is another milestone on that journey. Aimed at people with some JavaScript and web development experience, the first part of this cookbook covers some simple tips for getting started with React Native. Part 2 will cover some emerging patterns that are commonly found in most native applications. COMPUTERS,Languages,JavaScript

Node.js 8 the Right Way Node.js is the platform of choice for creating modern web services. This fast-paced book gets you up to speed on server-side programming with Node.js 8, as you develop real programs that are small, fast, low-profile, and useful. Take JavaScript beyond the browser, explore dynamic language features, and embrace evented programming.Harness the power of the event loop and non-blocking I/O to create highly parallel microservices and applications. This expanded and updated second edition showcases the latest ECMAScript features, current best practices, and modern development techniques. JavaScript is the backbone of the modern web, powering nearly every web app's user interface. Node.js is JavaScript for the server. This greatly expanded second edition introduces new language features while dramatically increasing coverage of core topics. Each hands-on chapter offers progressively more challenging topics and techniques, broadening your skill set and enabling you to think in Node.js. Write asynchronous, non-blocking code using Node.js's style and patterns. Cluster and load balance services with Node.js core features and third-party tools. Harness the power of databases such as Elasticsearch and Redis. Work with many protocols, create RESTful web services, TCP socket clients and servers, and more. Test your code's functionality with Mocha, and manage its life cycle with npm. Discover how Node.js pairs a server-side event loop with a JavaScript runtime to produce screaming fast, non-blocking concurrency. Through a series of practical programming domains, use the latest available ECMAScript features and harness key Node.js classes and popular modules. Create rich command-line tools and a web-based UI using modern web development techniques. Join the smart and diverse community that's rapidly advancing the state of the art in JavaScript development. What You Need: Node.js 8.x Operating system with bash-like shell OMQ (pronounced "Zero-M-Q") library, version 3.2 or higher Elasticsearch version 5.0 or higher jq version 1.5 or higher Redis version 3.2 or higher COMPUTERS,Languages,JavaScript

Vue.js Get a brisk introduction to building fast, interactive single-page web applications with Vue.js, the popular JavaScript framework that organizes and simplifies web development. With this practical guide, you’ll quickly move from basics to custom components and advanced features—including JSX, the JavaScript syntax extension. Author Callum Macrae shows you how to use the most useful libraries in the Vue ecosystem, such as vue-router for routing, vuex for state management, and vue-test-utils for testing. If you’re a frontend developer familiar with JavaScript, HTML, and CSS, this book will show you how to develop a fully featured web application using Vue. Learn Vue.js basics, including its use of templates to display data on a page Set up Vue projects from scratch, or use vue-cli to set up from a template Create a maintainable codebase by splitting code into self-contained components Discover how Vue.js works with CSS to style your websites and applications Use render functions and JSX, rather than templates, to determine what Vue displays Control how code is executed and displayed with vue-router Manage state in one centralized place with the Vuex library Write unit tests to ensure your Vue components don’t break in the future COMPUTERS,Languages,JavaScript

Eloquent JavaScript, 3rd Edition Completely revised and updated, this best-selling introduction to programming in JavaScript focuses on writing real applications. JavaScript lies at the heart of almost every modern web application, from social apps like Twitter to browser-based game frameworks like Phaser and Babylon. Though simple for beginners to pick up and play with, JavaScript is a flexible, complex language that you can use to build full-scale applications. This much anticipated and thoroughly revised third edition of Eloquent JavaScript dives deep into the JavaScript language to show you how to write beautiful, effective code. It has been updated to reflect the current state of Java¬Script and web browsers and includes brand-new material on features like class notation, arrow functions, iterators, async functions, template strings, and block scope. A host of new exercises have also been added to test your skills and keep you on track. As with previous editions, Haverbeke continues to teach through extensive examples and immerses you in code from the start, while exercises and full-chapter projects give you hands-on experience with writing your own programs. You start by learning the basic structure of the JavaScript language as well as control structures, functions, and data structures to help you write basic programs. Then you'll learn about error handling and bug fixing, modularity, and asynchronous programming before moving on to web browsers and how JavaScript is used to program them. As you build projects such as an artificial life simulation, a simple programming language, and a paint program, you'll learn how to: - Understand the essential elements of programming, including syntax, control, and data- Organize and clarify your code with object-oriented and functional programming techniques- Script the browser and make basic web applications- Use the DOM effectively to interact with browsers- Harness Node.js to build servers and utilities Isn't it time you became fluent in the language of the Web? * All source code is available online in an inter¬active sandbox, where you can edit the code, run it, and see its output instantly. COMPUTERS,Languages,JavaScript

Learning Regular Expressions Regular expression experts have long been armed with an incredibly powerful tool, one that can be used to perform all sorts of sophisticated text processing and manipulation in just about every language and on every platform. That’s the good news. The bad news is that for too long, regular expressions have been the exclusive property of only the most tech savvy. Until now. Ben Forta's Learning Regular Expressions teaches you the regular expressions that you really need to know, starting with simple text matches and working up to more complex topics, including the use of backreferences, conditional evaluation, and look-ahead processing. You’ll learn what you can use, and you’ll learn it methodically, systematically, and simply. Regular expressions are nowhere near as complex as they appear to be at first glance. All it takes is a clear understanding of the problem being solved and how to leverage regular expressions to solve them. Read and understand regular expressions Use literal text and metacharacters to build powerful search patterns Take advantage of advanced regular expression features, including lookahead and backreferences Perform powerful search-and-replace operations in all major professional editing tools Add sophisticated form and text processing to web applications Search for files using command-line tools like grep and egrep Use regular expressions in programming languages like JavaScript, Java, PHP, Python, Microsoft .NET, and C#, as well as in DBMSs including MySQL and Oracle Work with phone numbers, postal codes, social security numbers, IP addresses, URLs, email addresses, and credit card numbers The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Languages,JavaScript

Learning React Learning React A hands-on guide to building web applications using React and Redux As far as new web frameworks and libraries go, React is quite the runaway success. It not only deals with the most common problems developers face when building complex apps, it throws in a few additional tricks that make building the visuals for such apps much, much easier. What React isn’t, though, is beginner-friendly and approachable. Until now. In Learning React , author Kirupa Chinnathambi brings his fresh, clear, and very personable writing style to help web developers new to React understand its fundamentals and how to use it to build really performant (and awesome) apps. The only book on the market that helps you get your first React app up and running in just minutes, Learning React is chock-full of colorful illustrations to help you visualize difficult concepts and practical step-by-step examples to show you how to apply what you learn. Build your first React app Create components to define parts of your UI Combine components into other components to build more complex UIs Use JSX to specify visuals without writing full-fledged JavaScript Deal with maintaining state Work with React’s way of styling content Make sense of the mysterious component lifecycle Build multi-page apps using routing and views Optimize your React workflow using tools such as Node, Babel, webpack, and others Use Redux to make managing your app data and state easy Contents at a Glance 1 Introducing React 2 Building Your First React App 3 Components in React 4 Styling in React 5 Creating Complex Components 6 Transferring Properties 7 Meet JSX... Again! 8 Dealing with State in React 9 Going from Data to UI in React 10 Events in React 11 The Component Lifecycle 12 Accessing DOM Elements in React 13 Setting Up Your React Dev Environment 14 Working with External Data in React 15 Building an Awesome Todo List App in React 16 Creating a Sliding Menu in React 17 Avoiding Unnecessary Renders in React 18 Creating a Single-Page App in React Using React Router 19 Introduction to Redux 20 Using Redux with React COMPUTERS,Languages,JavaScript

Full-Stack Web Development with Vue.js and Node Bring the frontend and backend together with Vue, Vuex, and Node.js Key Features Construct modern web applications with Node 10, Express.js, MongoDB, and Vue Leverage the latest web standards to increase code performance, readability, and cross-compatibility Harness the power of the JavaScript ecosystem to effectively run, build, and test your full stack applications Book Description Isomorphic JavaScript was the buzzword of the year 2017, allowing developers to utilize a single language throughout their web development stack and build cost-effective and scalable applications. MEVN is a one such modern web development stack consisting of web applications such as MongoDB, Express.js, Vue.js, and Node.js. Hands-On Full-Stack Web Development with Vue.js 2 and Node.js leverages the harmony of these technologies to help you create full-stack web applications. Starting with the core frameworks, this example-based guide explains all the key concepts of frameworks, how to set them up properly, and how to use popular modules to connect them together and make them work cohesively. You will learn all this with the help of real-world examples. In addition to this, you will be able to scaffold web application architecture, add an authentication layer, and develop the MVC structure to support the development of your application. You'll explore how to create data models for your applications and then write REST APIs by exposing your data model to your application. Solely orientated towards building a full, end-to-end application using the MEVN stack, this book will help you understand how your application development grows. What you will learn Build an application with Express.js Create schemas using Mongoose Develop a single-page application using Vue.js and Express.js Create RESTful APIs using Express.js Add test cases to improve the reliability of the application Learn how to deploy apps on Heroku using GitHub Add authorization using passports Who this book is for If you are a web or a full-stack JavaScript developer, and have tried your hand at traditional stacks such as LAMP, MEAN or MERN, or wish to explore a new stack with modern web technologies, then this book is for you. Prior knowledge of HTML, CSS, and JavaScript would be an added advantage. COMPUTERS,Languages,JavaScript

Simplifying JavaScript The best modern JavaScript is simple, readable, and predictable. Learn to write modern JavaScript not by memorizing a list of new syntax, but with practical examples of how syntax changes can make code more expressive. Starting from variable declarations that communicate intention clearly, see how modern principles can improve all parts of code. Incorporate ideas with curried functions, array methods, classes, and more to create code that does more with less while yielding fewer bugs. It's time to write JavaScript code that's clean and exprssive. Modern JavaScript is simpler and more predictable and readable than ever. Discover how to write better code with clear examples using principles that show how updated syntax can make code better with fewer bugs. Starting from the ground up, learn new syntax (or how to reuse older syntax) to transform code from clunky bug-susceptible scripts to clear and elegant programs that are easy to read and easy to extend. Create a foundation for readable code with simple variable declarations that reduce side effects and subtle bugs. Select collections with clear goals instead of defaulting to objects or arrays. See how to simplify iterations from complex loops to single line array methods. Master techniques for writing flexible and solid code ranging from high-order functions, to reusableclasses, to patterns for architecting large applications creating applications that will last while through rounds of refactoring and changing requirements. The best part is there's no need to read this book straight through. Jump around and incorporate new functionality at will. Most importantly, understand not just what the new syntax is, but when and how to use it. Start writing better code from the first page. What You Need: For the best experience, have the latest version of Node installed (at least version 7). You can test most examples in the console of Chrome or other modern web browser. If you'd like to run the tests, you'll also need to install the latest version of Node Package Manager (npm). COMPUTERS,Languages,JavaScript

6 JavaScript Projects There's no doubt that the JavaScript ecosystem changes fast. Not only are new tools and frameworks introduced and developed at a rapid rate, the language itself has undergone big changes with the introduction of ES2015 (aka ES6). Understandably, many articles have been written complaining about how difficult it is to learn modern JavaScript development these days. We're aiming to minimize that confusion with this set of books on modern JavaScript. This book presents six complete JavaScript projects; each taking advantage of modern JavaScript and its ecosystem. You'll learn to build several different apps, and along the way you'll pick up a ton of useful advice, tips, and techniques. It contains: Build a Full-Sphere 3D Image Gallery with React VR by Michaela Lehr Build a WebRTC Video Chat Application with SimpleWebRTC by Michael Wanyoike Build a JavaScript Single Page App Without a Framework by Michael Wanyoike Build a To-do List with Hyperapp, the 1KB JS Micro-framework by Darren Jones Use Parcel to Bundle a Hyperapp App & Deploy to GitHub Pages by Darren Jones Interactive Data Visualization with Modern JavaScript and D3 by Adam Janes This book is for all front-end developers who wish to improve their JavaScript skills. You'll need to be familiar with HTML and CSS and have a reasonable level of understanding of JavaScript in order to follow the discussion. COMPUTERS,Languages,JavaScript

The Modern JavaScript Collection There's no doubt that the JavaScript ecosystem changes fast. Not only are new tools and frameworks introduced and developed at a rapid rate, the language itself has undergone big changes with the introduction of ES2015 (aka ES6) and further revisions. Understandably, many articles have been written complaining about how difficult it is to learn modern JavaScript development these days. We're aiming to minimize that confusion with this set of books on modern JavaScript. This collection contains: Practical ES6 is a collection of articles introducing many of the powerful new JavaScript language features that were introduced in ECMAScript 2015, as well as features introduced in ECMAScript 2016 and 2017. It also takes a look at the features planned for ECMAScript 2018 in this rapidly evolving language. JavaScript: Best Practice presents articles discussing modern JavaScript best practice, enabling you to write more powerful code that is clean, performant, maintainable, and reusable. 6 JavaScript Projects presents six complete JavaScript projects; each taking advantage of modern JavaScript and its ecosystem. You'll learn to build several different apps, and along the way you'll pick up a ton of useful advice, tips, and techniques. Modern JavaScript Tools & Skills contains a collection of articles outlining essential tools and skills that every modern JavaScript developer should know. This book is for all front-end developers who wish to improve their JavaScript skills. You'll need to be familiar with HTML and CSS and have a reasonable level of understanding of JavaScript in order to follow the discussion. COMPUTERS,Languages,JavaScript

Rediscovering JavaScript JavaScript is no longer to be feared or loathed - the world's most popular and ubiquitous language has evolved into a respectable language. Whether you're writing frontend applications or server side code, the phenomenal features from ES6 and beyond - like the rest operator, generators, destructuring, object literals, arrow functions, modern classes, promises, async, and metaprogramming capabilities - will get you excited and eager to program with JavaScript. You've found the right book to get started quickly and dive deep into the essence of modern JavaScript. Learn practical tips to apply the elegant parts of the language and the gotchas to avoid. JavaScript is a black swan that no one, including the author of the language, thought would become a popular and ubiquitous language. Not long ago, it was the most hated and feared language you could use to program the web. JavaScript ES6 and beyond has gone through a significant makeover. Troublesome features have been replaced with better, elegant, more reliable alternatives. This book includes many practical examples and exercises to help you learn in depth. It will not bore you with idiosyncrasies and arcane details intended for bad interview questions. Instead, it takes you into key features that you can readily use in your day-to-day projects. Whether you program the frontend or the server side, you can now write concise, elegant, and expressive JavaScript with newer features like default parameters, template literals, rest and spread operators, destructuring, arrow functions, and generators. Take it up a notch with features like infinite series, promises, async, and metaprogramming to create flexible, powerful, and extensible libraries. While the evolved features of the language will draw you in, the hundreds of examples in this book will pin the concepts down, for you to use on your projects. Take command of modern JavaScript and unlock your potential to create powerful applications. What You Need: To try out the examples in the book you will need a computer with Node.js, a text editor, and a browser like Chrome installed in it. COMPUTERS,Languages,JavaScript

Beginning React Take your web applications to a whole new level with efficient, component-based UIs that deliver cutting-edge interactivity and performance. Key Features Elaborately explains basics before introducing advanced topics Explains creating and managing the state of components across applications Implement over 15 practical activities and exercises across 11 topics to reinforce your learning Book Description Projects like Angular and React are rapidly changing how development teams build and deploy web applications to production. In this book, you'll learn the basics you need to get up and running with React and tackle real-world projects and challenges. It includes helpful guidance on how to consider key user requirements within the development process, and also shows you how to work with advanced concepts such as state management, data-binding, routing, and the popular component markup that is JSX. As you complete the included examples, you'll find yourself well-equipped to move onto a real-world personal or professional frontend project. What you will learn Understand how React works within a wider application stack Analyze how you can break down a standard interface into specific components Successfully create your own increasingly complex React components with HTML or JSX Correctly handle multiple user events and their impact on overall application state Understand the component lifecycle to optimize the UX of your application Configure routing to allow effortless, intuitive navigation through your components Who this book is for If you are a frontend developer who wants to create truly reactive user interfaces in JavaScript, then this is the book for you. For React, you'll need a solid foundation in the essentials of the JavaScript language, including new OOP features that were introduced in ES2015. An understanding of HTML and CSS is assumed, and a basic knowledge of Node.js will be useful in the context of managing a development workflow, but is not essential. COMPUTERS,Languages,JavaScript

MobX Quick Start Guide Apply functional Reactive programming for simple and scalable state management with MobX Key Features The easiest way to learn MobX to enhance your client-side state-management Understand how the concepts and components fit together Work through different state management scenarios with MobX Book Description MobX is a simple and highly scalable state management library in JavaScript. Its abstractions can help you manage state in small to extremely large applications. However, if you are just starting out, it is essential to have a guide that can help you take the first steps. This book aims to be that guide that will equip you with the skills needed to use MobX and effectively handle the state management aspects of your application. You will first learn about observables, actions, and reactions: the core concepts of MobX. To see how MobX really shines and simplifies state management, you'll work through some real-world use cases. Building on these core concepts and use cases, you will learn about advanced MobX, its APIs, and libraries that extend MobX. By the end of this book, you will not only have a solid conceptual understanding of MobX, but also practical experience. You will gain the confidence to tackle many of the common state management problems in your own projects. What you will learn Explore the fundamental concepts of MobX, such as observables, actions, and reactions Use observables to track state and react to its changes with validations and visual feedback (via React Components) Create a MobX observable from different data types Define form data as an observable state and tackle sync and async form validations Use the special APIs to directly manipulate observables, tracking its changes, and discovering the reasons behind a change Tackle any state management issue you may have in your app by combining mobx-utils and mobx-state-tree Explore the internals of the MobX reactive system by diving into its inner workings Who this book is for This book is for web developers who want to implement easy and scalable state management for their apps. Knowledge of HTML, CSS, and JavaScript is assumed COMPUTERS,Languages,JavaScript

Mastering Modular JavaScript If you have a working knowledge of JavaScript and ECMAScript 6 (ES6), this practical guide will help you tackle modular programming to produce code that’s readable, maintainable, and scalable. You’ll learn the fundamentals of modular architecture with JavaScript and the benefits of writing self-contained code at every system level, including the client and server. Nicolás Bevacqua, author of Practical Modern JavaScript, demonstrates how to scale out JavaScript applications by breaking codebases into smaller modules. By following the design practices in this book, senior developers, technical leaders, and software architects will learn how to create modules that are simple and flexible while keeping internal complexity in check. Learn modular design essentials, including how your application will be consumed and what belongs on the interface Design module internals to keep your code readable and its intent clear Reduce complexity by refactoring code and containing and eliminating state Take advantage of modern JavaScript features to write clear programs and reduce complexity Apply Twelve-Factor App principles to frontend and backend JavaScript application development COMPUTERS,Languages,JavaScript

React Cookbook Over 66 hands-on recipes that cover UI development, animations, component architecture, routing, databases, testing, and debugging with React Key Features Use essential hacks and simple techniques to solve React application development challenges Create native mobile applications for iOS and Android using React Native Learn to write robust tests for your applications using Jest and Enzyme Book Description Today's web demands efficient real-time applications and scalability. If you want to learn to build fast, efficient, and high-performing applications using React 16, this is the book for you. We plunge directly into the heart of all the most important React concepts for you to conquer. Along the way, you'll learn how to work with the latest ECMAScript features. You'll see the fundamentals of Redux and find out how to implement animations. Then, you'll learn how to create APIs with Node, Firebase, and GraphQL, and improve the performance of our application with Webpack 4.x. You'll find recipes on implementing server-side rendering, adding unit tests, and debugging. We also cover best practices to deploy a React application to production. Finally, you'll learn how to create native mobile applications for iOS and Android using React Native. By the end of the book, you'll be saved from a lot of trial and error and developmental headaches, and you'll be on the road to becoming a React expert. What you will learn Gain the ability to wield complex topics such as Webpack and server-side rendering Implement an API using Node.js, Firebase, and GraphQL Learn to maximize the performance of React applications Create a mobile application using React Native Deploy a React application on Digital Ocean Get to know the best practices when organizing and testing a large React application Who this book is for If you're a JavaScript developer who wants to build fast, efficient, scalable solutions, then you're in the right place. Knowledge of React will be an advantage but is not required. Experienced users of React will be able to improve their skills. COMPUTERS,Languages,JavaScript

Node.js While there have been quite a few attempts to get JavaScript working as a server-side language, Node.js (frequently just called Node) has been the first environment that's gained any traction. It's now used by companies such as Netflix, Uber and Paypal to power their web apps. Node allows for blazingly fast performance; thanks to its event loop model, common tasks like network connection and database I/O can be executed very quickly indeed. From a beginner's point of view, one of Node's obvious advantages is that it uses JavaScript, a ubiquitous language that many developers are comfortable with. If you can write JavaScript for the client-side, writing server-side applications with Node should not be too much of a stretch for you. This collection contains three books that will help get you up and running with Node. It contains: Your First Week With Node.js, which will get started using Node, covering all of the basics. 9 Practical Node.js Projects, which offers a selection of hand-on practical projects to develop your skills. Node.js: Related Tools & Skills, which outlines essential tools and skills that all Node developers should know. COMPUTERS,Languages,JavaScript

Blockchain Developer's Guide Build real-world projects like a smart contract deployment platform, betting apps, wallet services, and much more using blockchain Key Features Apply blockchain principles and features for making your life and business better Understand Ethereum for smart contracts and DApp deployment Tackle current and future challenges and problems relating to blockchain Book Description Blockchain applications provide a single-shared ledger to eliminate trust issues involving multiple stakeholders. It is the main technical innovation of Bitcoin, where it serves as the public ledger for Bitcoin transactions. Blockchain Developer's Guide takes you through the electrifying world of blockchain technology. It begins with the basic design of a blockchain and elaborates concepts, such as Initial Coin Offerings (ICOs), tokens, smart contracts, and other related terminologies. You will then explore the components of Ethereum, such as Ether tokens, transactions, and smart contracts that you need to build simple DApps. Blockchain Developer's Guide also explains why you must specifically use Solidity for Ethereum-based projects and lets you explore different blockchains with easy-to-follow examples. You will learn a wide range of concepts - beginning with cryptography in cryptocurrencies and including ether security, mining, and smart contracts. You will learn how to use web sockets and various API services for Ethereum. By the end of this Learning Path, you will be able to build efficient decentralized applications. This Learning Path includes content from the following Packt products: Blockchain Quick Reference by Brenn Hill, Samanyu Chopra, Paul Valencourt Building Blockchain Projects by Narayan Prusty What you will learn Understand how various components of the blockchain architecture work Get familiar with cryptography and the mechanics behind blockchain Apply consensus protocol to determine the business sustainability Understand what ICOs and crypto-mining are, and how they work Who this book is for Blockchain Developer's Guide is for you if you want to get to grips with the blockchain technology and develop your own distributed applications. It is also designed for those who want to polish their existing knowledge regarding the various pillars of the blockchain ecosystem. Prior exposure to an object-oriented programming language such as JavaScript is needed. COMPUTERS,Languages,JavaScript

Hands-On Functional Programming with TypeScript Discover the power of functional programming, lazy evaluation, monads, concurrency, and immutability to create succinct and expressive implementations Key Features Get a solid understanding of how to apply functional programming concepts in TypeScript Explore TypeScript runtime features such as event loop, closures, and Prototypes Gain deeper knowledge on the pros and cons of TypeScript Book Description Functional programming is a powerful programming paradigm that can help you to write better code. However, learning functional programming can be complicated, and the existing literature is often too complex for beginners. This book is an approachable introduction to functional programming and reactive programming with TypeScript for readers without previous experience in functional programming with JavaScript, TypeScript , or any other programming language. The book will help you understand the pros, cons, and core principles of functional programming in TypeScript. It will explain higher order functions, referential transparency, functional composition, and monads with the help of effective code examples. Using TypeScript as a functional programming language, you'll also be able to brush up on your knowledge of applying functional programming techniques, including currying, laziness, and immutability, to real-world scenarios. By the end of this book, you will be confident when it comes to using core functional and reactive programming techniques to help you build effective applications with TypeScript. What you will learn Understand the pros and cons of functional programming Delve into the principles, patterns, and best practices of functional and reactive programming Use lazy evaluation to improve the performance of applications Explore functional optics with Ramda Gain insights into category theory functional data structures such as Functors and Monads Use functions as values, so that they can be passed as arguments to other functions Who this book is for This book is designed for readers with no prior experience of functional programming with JavaScript, TypeScript or any other programming language. Some familiarity with TypeScript and web development is a must to grasp the concepts in the book easily. COMPUTERS,Languages,JavaScript

React Design Patterns and Best Practices Build modular React web apps that are scalable, maintainable and powerful using design patterns and insightful practices Key Features Get familiar with design patterns in React like Render props and Controlled/uncontrolled inputs Learn about class/ functional, style and high order components with React Work through examples that can be used to create reusable code and extensible designs Book Description React is an adaptable JavaScript library for building complex UIs from small, detached bits called components. This book is designed to take you through the most valuable design patterns in React, helping you learn how to apply design patterns and best practices in real-life situations. You'll get started by understanding the internals of React, in addition to covering Babel 7 and Create React App 2.0, which will help you write clean and maintainable code. To build on your skills, you will focus on concepts such as class components, stateless components, and pure components. You'll learn about new React features, such as the context API and React Hooks that will enable you to build components, which will be reusable across your applications. The book will then provide insights into the techniques of styling React components and optimizing them to make applications faster and more responsive. In the concluding chapters, you'll discover ways to write tests more effectively and learn how to contribute to React and its ecosystem. By the end of this book, you will be equipped with the skills you need to tackle any developmental setbacks when working with React. You'll be able to make your applications more flexible, efficient, and easy to maintain, thereby giving your workflow a boost when it comes to speed, without reducing quality. What you will learn Get familiar with the new React features,like context API and React Hooks Learn the techniques of styling and optimizing React components Make components communicate with each other by applying consolidate patterns Use server-side rendering to make applications load faster Write a comprehensive set of tests to create robust and maintainable code Build high-performing applications by optimizing components Who this book is for This book is for web developers who want to increase their understanding of React and apply it to real-life application development. Prior experience with React and JavaScript is assumed. COMPUTERS,Languages,JavaScript

Programming TypeScript Any programmer working with a dynamically typed language will tell you how hard it is to scale to more lines of code and more engineers. That’s why Facebook, Google, and Microsoft invented gradual static type layers for their dynamically typed JavaScript and Python code. This practical book shows you how one such type layer, TypeScript, is unique among them: it makes programming fun with its powerful static type system. If you’re a programmer with intermediate JavaScript experience, author Boris Cherny will teach you how to master the TypeScript language. You’ll understand how TypeScript can help you eliminate bugs in your code and enable you to scale your code across more engineers than you could before. In this book, you’ll: Start with the basics: Learn about TypeScript’s different types and type operators, including what they’re for and how they’re used Explore advanced topics: Understand TypeScript’s sophisticated type system, including how to safely handle errors and build asynchronous programs Dive in hands-on: Use TypeScript with your favorite frontend and backend frameworks, migrate your existing JavaScript project to TypeScript, and run your TypeScript application in production COMPUTERS,Languages,JavaScript

Learn Vue.js Since its release in 2014, Vue.js has seen a meteoric rise to popularity and is is now considered one of the primary front-end frameworks, and not without good reason. Its component-based architecture was designed to be flexible and easy to adopt, making it just as easy to integrate into projects and use alongside non-Vue code as it is to build complex client-side applications. This is a collection of three books covering crucial Vue topics. It contains: Working with Vue.js 11 Practical Vue.js Projects Vue.js: Tools & Skills COMPUTERS,Languages,JavaScript

Vue.js Since its release in 2014, Vue.js has seen a meteoric rise to popularity and is is now considered one of the primary front-end frameworks, and not without good reason. Its component-based architecture was designed to be flexible and easy to adopt, making it just as easy to integrate into projects and use alongside non-Vue code as it is to build complex client-side applications. This book contains a selection of 11 practical projects covering different aspects of working with Vue. It contains: Build a Basic CRUD App with Vue.js, Node and MongoDB by James Hibbard Creating Beautiful Charts Using Vue.js Wrappers for Chart.js by Yomi Eluwande Build a Real-time Chat App with Pusher and Vue.js by Michael Wanyoike Building a Vue Front End for a Headless CMS by Michael Wanyoike How to Build a Chrome Extension with Vue by James Hibbard Build Your Own Link-sharing Site with Nuxt.js and vue-kindergarten by Nilson Jacques An Introduction to Data Visualization with Vue and D3.js by Christopher Vundi How to Build a Reusable Component with Vue by Deji Atoyebi How to Build a Game with Vue.js by Ivaylo Gerchev Build a Shopping List App with Vue, Vuex and Bootstrap Vue by Michael Wanyoike How to Develop and Test Vue Components with Storybook by Ivaylo Gerchev COMPUTERS,Languages,JavaScript

Effective TypeScript TypeScript is a typed superset of JavaScript with the potential to solve many of the headaches for which JavaScript is famous. But TypeScript has a learning curve of its own, and understanding how to use it effectively can take time. This book guides you through 62 specific ways to improve your use of TypeScript. Author Dan Vanderkam, a principal software engineer at Sidewalk Labs, shows you how to apply these ideas, following the format popularized by Effective C++ and Effective Java (both from Addison-Wesley). You’ll advance from a beginning or intermediate user familiar with the basics to an advanced user who knows how to use the language well. Effective TypeScript is divided into eight chapters: Getting to Know TypeScript TypeScript’s Type System Type Inference Type Design Working with any Types Declarations and @types Writing and Running Your Code Migrating to TypeScript COMPUTERS,Languages,JavaScript

JavaScript Absolute Beginner's Guide Who knew how simple using JavaScript could be? Make the most of JavaScript—even if you’ve never programmed anything before. JavaScript Absolute Beginner’s Guide is the fastest way to learn JavaScript and use it together with CSS3 and HTML5 to create powerful web and mobile experiences. Learn how to do what you want, the way you want, one incredibly easy step at a time. JavaScript has never been this simple! Here’s a small sample of what you’ll learn: • Organize your code with variables • Understand how functions make your code reusable • Use the popular if/else statement to help make a decision in code • Learn about switch statements and when to use them • Work with for, while, and do...while loops • Learn how to use global and local scope • Understand what closures are • Learn about the various places your code can live • Understand how to write comments and use good commenting practices • Learn about the basic types of objects you’ll run into in JavaScript • Find out that pizza has an educational value beyond just being deliciously awesome • Learn how to perform common string operations • Use arrays to handle lists of data • Learn to create custom objects • Get up to speed on some of the big ES6 changes COMPUTERS,Languages,JavaScript

JavaScript Everywhere JavaScript is the little scripting language that could. Once used chiefly to add interactivity to web browser windows, JavaScript is now a primary building block of powerful and robust applications. In this practical book, new and experienced JavaScript developers will learn how to use this language to create APIs as well as web, mobile, and desktop applications. Author and engineering leader Adam D. Scott covers technologies such as Node.js, GraphQL, React, React Native, and Electron. Ideal for developers who want to build full stack applications and ambitious web development beginners looking to bootstrap a startup, this book shows you how to create a single CRUD-style application that will work across several platforms. Explore GraphQL’s simple process for querying data Learn about shared authentication for APIs, web apps, and native applications Build performant web applications with React and Styled Components Use React Native to write cross-platform applications for iOS and Android that compile to native code Learn how to write desktop applications with Electron COMPUTERS,Languages,JavaScript

Node.js While there have been quite a few attempts to get JavaScript working as a server-side language, Node.js (frequently just called Node) has been the first environment that's gained any traction. It's now used by companies such as Netflix, Uber and Paypal to power their web apps. Node allows for blazingly fast performance; thanks to its event loop model, common tasks like network connection and database I/O can be executed very quickly indeed. In this book, we'll take a look at a selection of the related tools and skills that will make you a much more productive Node developer. It contains: Installing Multiple Versions of Node.js Using nvm A Beginner's Guide to npm Create New Express.js Apps in Minutes with Express Generator An Introduction to AdonisJs, a Laravel-like Node.js Framework Top 5 Developer-friendly Node.js API Frameworks Using MySQL with Node.js and the mysql JavaScript Client Introduction to MongoDB COMPUTERS,Languages,JavaScript

Your First Week With Node.js While there have been quite a few attempts to get JavaScript working as a server-side language, Node.js (frequently just called Node) has been the first environment that's gained any traction. It's now used by companies such as Netflix, Uber and Paypal to power their web apps. Node allows for blazingly fast performance; thanks to its event loop model, common tasks like network connection and database I/O can be executed very quickly indeed. From a beginner's point of view, one of Node's obvious advantages is that it uses JavaScript, a ubiquitous language that many developers are comfortable with. If you can write JavaScript for the client-side, writing server-side applications with Node should not be too much of a stretch for you. This book offers aselection of beginner-level tutorials to privide you with an introduction to Node and its related technologies, and get you under way writing your first Node applications. It contains: What Is Node and When Should I Use It? Build a Simple Page Counter Service with Node.js Understanding module.exports and exports in Node.js Forms, File Uploads and Security with Node.js and Express Working with Databases in Node How to Build and Structure a Node.js MVC Application Local Authentication Using Passport in Node.js How to Debug a Node App Node Testing for Beginners How to Use SSL/TLS with Node.js Configuring NGINX and SSL with Node.js Using Docker for Node.js Development COMPUTERS,Languages,JavaScript

JavaScript For web developers and other programmers interested in using JavaScript, this bestselling book provides the most comprehensive JavaScript material on the market. The seventh edition represents a significant update, with new information for ECMAScript 2020, and new chapters on language-specific features. JavaScript: The Definitive Guide is ideal for experienced programmers who want to learn the programming language of the web, and for current JavaScript programmers who want to master it. COMPUTERS,Languages,JavaScript

Learning React If you want to learn how to build efficient React applications, this is your book. Ideal for web developers and software engineers who understand how JavaScript, CSS, and HTML work in the browser, this updated edition provides best practices and patterns for writing modern React code. No prior knowledge of React or functional JavaScript is necessary. With their learning road map, authors Alex Banks and Eve Porcello show you how to create UIs that can deftly display changes without page reloads on large-scale, data-driven websites. You’ll also discover how to work with functional programming and the latest ECMAScript features. Once you learn how to build React components with this hands-on guide, you’ll understand just how useful React can be in your organization. Understand key functional programming concepts with JavaScriptLook under the hood to learn how React runs in the browserCreate application presentation layers with React componentsManage data and reduce the time you spend debugging applicationsIncorporate React Hooks to manage state and fetch dataUse a routing solution for single-page application featuresLearn how to structure React applications with servers in mind COMPUTERS,Languages,JavaScript

If Hemingway Wrote JavaScript What if William Shakespeare were asked to generate the Fibonacci series or Jane Austen had to write a factorial program? In If Hemingway Wrote JavaScript, author Angus Croll imagines short JavaScript programs as written by famous wordsmiths. The result is a peculiar and charming combination of prose, poetry, and programming. The best authors are those who obsess about language—and the same goes for JavaScript developers. To master either craft, you must experiment with language to develop your own style, your own idioms, and your own expressions. To that end, If Hemingway Wrote JavaScript playfully bridges the worlds of programming and literature for the literary geek in all of us. Featuring original artwork by Miran Lipova?a. COMPUTERS,Languages,JavaScript

Learning Perl If you’re just getting started with Perl, this is the book you want—whether you’re a programmer, system administrator, or web hacker. Nicknamed "the Llama" by two generations of users, this bestseller closely follows the popular introductory Perl course taught by the authors since 1991. This seventh edition covers recent changes to the language up to version 5.24. Perl is suitable for almost any task on almost any platform, from short fixes to complete web applications. Learning Perl teaches you the basics and shows you how to write programs up to 128 lines long—roughly the size of 90% of the Perl programs in use today. Each chapter includes exercises to help you practice what you’ve just learned. Other books may teach you to program in Perl, but this book will turn you into a Perl programmer. Topics include: Perl data and variable types Subroutines File operations Regular expressions String manipulation (including Unicode) Lists and sorting Process management Smart matching Use of third party modules COMPUTERS,Languages,Perl

Learning Perl 6 f you’re ready to get started with Raku (formerly Perl 6), this is the book you want, whether you’re a programmer, system administrator, or web hacker. Raku is a new language—a modern reinvention of Perl suitable for almost any task, from short fixes to complete web applications. This hands-on tutorial gets you started. Author brian d foy (Mastering Perl) provides a sophisticated introduction to this new programming language. Each chapter in this guide contains exercises to help you practice what you learn as you learn it. Other books may teach you to program in Raku, but this book will turn you into a Raku programmer. Learn how to work with: Numbers, strings, blocks, and positionals Files and directories and input/output Associatives, subroutines, classes, and roles Junctions and sets Regular expressions and built-in grammars Concurrency features: Promises, supplies, and channels Controlling external programs and other advanced features COMPUTERS,Languages,Perl

Web Database Applications with PHP and MySQL There are many reasons for serving up dynamic content from a web site: to offer an online shopping site, create customized information pages for users, or just manage a large volume of content through a database. Anyone with a modest knowledge of HTML and web site management can learn to create dynamic content through the PHP programming language and the MySQL database. This book gives you the background and tools to do the job safely and reliably.Web Database Applications with PHP and MySQL, Second Edition thoroughly reflects the needs of real-world applications. It goes into detail on such practical issues as validating input (do you know what a proper credit card number looks like?), logging in users, and using templatesto give your dynamic web pages a standard look.But this book goes even further. It shows how JavaScript and PHP can be used in tandem to make a user's experience faster and more pleasant. It shows the correct way to handle errors in user input so that a site looks professional. It introduces the vast collection of powerful tools available in the PEAR repository and shows how to use some of the most popular tools.Even while it serves as an introduction to new programmers, the book does not omit critical tasks that web sites require. For instance, every site that allows updates must handle the possibility of multiple users accessing data at the same time. This book explains how to solve the problem in detail with locking.Through a sophisticated sample application--Hugh and Dave's Wine Store--all the important techniques of dynamic content are introduced. Good design is emphasized, such as dividing logic from presentation. The book introduces PHP 5 and MySQL 4.1 features, while providing techniques that can be used on older versions of the software that are still in widespread use.This new edition has been redesigned around the rich offerings of PEAR. Several of these, including the Template package and the database-independent query API, are fully integrated into examples and thoroughly described in the text. Topics include: Installation and configuration of Apache, MySQL, and PHP on Unix®, Windows®, and Mac OS® X systems Introductions to PHP, SQL, and MySQL administration Session management, including the use of a custom database for improved efficiency User input validation, security, and authentication The PEAR repository, plus details on the use of PEAR DB and Template classes Production of PDF reports COMPUTERS,Languages,PHP

Modern PHP PHP is experiencing a renaissance, though it may be difficult to tell with all of the outdated PHP tutorials online. With this practical guide, you’ll learn how PHP has become a full-featured, mature language with object-orientation, namespaces, and a growing collection of reusable component libraries. Author Josh Lockhart—creator of PHP The Right Way, a popular initiative to encourage PHP best practices—reveals these new language features in action. You’ll learn best practices for application architecture and planning, databases, security, testing, debugging, and deployment. If you have a basic understanding of PHP and want to bolster your skills, this is your book. Learn modern PHP features, such as namespaces, traits, generators, and closures Discover how to find, use, and create PHP components Follow best practices for application security, working with databases, errors and exceptions, and more Learn tools and techniques for deploying, tuning, testing, and profiling your PHP applications Explore Facebook’s HVVM and Hack language implementations—and how they affect modern PHP Build a local development environment that closely matches your production server COMPUTERS,Languages,PHP

PHP Master PHP Master is tailor-made for the PHP developer who's serious about taking their server-side applications to the next level and who wants to really keep ahead of the game by adhering to best practice, employing the most effective object-oriented programming techniques, wrapping projects in layers of security and ensuring their code is doing its job perfectly. Create professional, dynamic applications according to an object-oriented programming blueprint Learn advanced performance evaluation techniques for maximum site efficiency Brush up on the best testing methods to refine your code and keep your applications watertight Protect your site against attacks and vulnerabilities with the latest security systems Plug in to some serious functionality with PHP's APIs and libraries COMPUTERS,Languages,PHP

Learning PHP If you want to get started with PHP, this book is essential. Author David Sklar (PHP Cookbook) guides you through aspects of the language you need to build dynamic server-side websites. By exploring features of PHP 5.x and the exciting enhancements in the latest release, PHP 7, you’ll learn how to work with web servers, browsers, databases, and web services. End-of-chapter exercises help you make the lessons stick. Whether you’re a hobbyist looking to build dynamic websites, a frontend developer ready to add server-side programs, or an experienced programmer who wants to get up to speed with this language, this gentle introduction also covers aspects of modern PHP, such as internationalization, using PHP from the command line, and package management. Learn how PHP interacts with browsers and servers Understand data types, variables, logic, looping, and other language basics Explore how to use arrays, functions, and objects Build and validate web forms Work with databases and session management Access APIs to interact with web services and other websites Jumpstart your project with popular PHP web application frameworks COMPUTERS,Languages,PHP

PHP Microservices Transit from monolithic architectures to highly available, scalable, and fault-tolerant microservices About This Book Build your own applications based on event-driven microservices and set them up on a production server. Successfully transform any monolithic application into a microservice. Monitor the health of your application, prevent downtime, and reduce costs. Who This Book Is For PHP developers who want to build scalable, highly available, and secure applications will find this book useful. No knowledge of microservices is assumed. What You Will Learn Set up a development environment using the right strategies and tools. Learn about application design and structure to start implementing your application. Transform a monolithic application into microservices. Explore the best way to start implementing your application using testing. Understand how to monitor your microservices, handle errors, and debug the application. Deploy your finished application into a production environment and learn how to solve common problems. Know how to scale your application based on microservices once it is up–and-running. In Detail The world is moving away from bulky, unreliable, and high-maintenance PHP applications, to small, easy-to-maintain and highly available microservices and the pressing need is for PHP developers to understand the criticalities in building effective microservices that scale at large. This book will be a reliable resource, and one that will help you to develop your skills and teach you techniques for building reliable microservices in PHP. The book begins with an introduction to the world of microservices, and quickly shows you how to set up a development environment and build a basic platform using Docker and Vagrant. You will then get into the different design aspects to be considered while building microservices in your favorite framework and you will explore topics such as testing, securing, and deploying microservices. You will also understand how to migrate a monolithic application to the microservice architecture while keeping scalability and best practices in mind. Furthermore you will get into a few important DevOps techniques that will help you progress on to more complex domains such as native cloud development, as well as some interesting design patterns. By the end of this book you will be able to develop applications based on microservices in an organized and efficient way. You will also gain the knowledge to transform any monolithic applications into microservices. Style and approach Filled with code that you can start typing straightaway, this book will take you through building, testing, securing, and deploying microservices in the most practical way possible. The focus of the book is more inclined towards showing you how it's done, rather than with what to do, although you will get a good idea of those tools most widely used to build microservices. COMPUTERS,Languages,PHP

Domain-Driven Design in PHP Real examples written in PHP showcasing DDD Architectural Styles, Tactical Design, and Bounded Context Integration About This Book Focuses on practical code rather than theory Full of real-world examples that you can apply to your own projects Shows how to build PHP apps using DDD principles Who This Book Is For This book is for PHP developers who want to apply a DDD mindset to their code. You should have a good understanding of PHP and some knowledge of DDD. This book doesn't dwell on the theory, but instead gives you the code that you need. What You Will Learn Correctly design all design elements of Domain-Driven Design with PHP Learn all tactical patterns to achieve a fully worked-out Domain-Driven Design Apply hexagonal architecture within your application Integrate bounded contexts in your applications Use REST and Messaging approaches In Detail Domain-Driven Design (DDD) has arrived in the PHP community, but for all the talk, there is very little real code. Without being in a training session and with no PHP real examples, learning DDD can be challenging. This book changes all that. It details how to implement tactical DDD patterns and gives full examples of topics such as integrating Bounded Contexts with REST, and DDD messaging strategies. In this book, the authors show you, with tons of details and examples, how to properly design Entities, Value Objects, Services, Domain Events, Aggregates, Factories, Repositories, Services, and Application Services with PHP. They show how to apply Hexagonal Architecture within your application whether you use an open source framework or your own. Style and approach This highly practical book shows developers how to apply domain-driven design principles to PHP. It is full of solid code examples to work through. COMPUTERS,Languages,PHP

Mastering PHP 7 Effective, readable, and robust codes in PHP About This Book Leverage the newest tools available in PHP 7 to build scalable applications Embrace serverless architecture and the reactive programming paradigm, which are the latest additions to the PHP ecosystem Explore dependency injection and implement design patterns to write elegant code Who This Book Is For This book is for intermediate level developers who want to become a master of PHP. Basic knowledge of PHP is required across areas such as basic syntax, types, variables, constants, expressions, operators, control structures, and functions. What You Will Learn Grasp the current state of PHP language and the PHP standards Effectively implement logging and error handling during development Build services through SOAP and REST and Apache Trift Get to know the benefits of serverless architecture Understand the basic principles of reactive programming to write asynchronous code Practically implement several important design patterns Write efficient code by executing dependency injection See the working of all magic methods Handle the command-line area tools and processes Control the development process with proper debugging and profiling In Detail PHP is a server-side scripting language that is widely used for web development. With this book, you will get a deep understanding of the advanced programming concepts in PHP and how to apply it practically The book starts by unveiling the new features of PHP 7 and walks you through several important standards set by PHP Framework Interop Group (PHP-FIG). You'll see, in detail, the working of all magic methods, and the importance of effective PHP OOP concepts, which will enable you to write effective PHP code. You will find out how to implement design patterns and resolve dependencies to make your code base more elegant and readable. You will also build web services alongside microservices architecture, interact with databases, and work around third-party packages to enrich applications. This book delves into the details of PHP performance optimization. You will learn about serverless architecture and the reactive programming paradigm that found its way in the PHP ecosystem. The book also explores the best ways of testing your code, debugging, tracing, profiling, and deploying your PHP application. By the end of the book, you will be able to create readable, reliable, and robust applications in PHP to meet modern day requirements in the software industry. Style and approach This is a comprehensive, step-by-step practical guide to developing scalable applications using PHP 7.1 COMPUTERS,Languages,PHP

PHP, MySQL, & JavaScript All-in-One For Dummies Explore the engine that drives the internet It takes a powerful suite of technologies to drive the most-visited websites in the world. PHP, mySQL, JavaScript, and other web-building languages serve as the foundation for application development and programming projects at all levels of the web. Dig into this all-in-one book to get a grasp on these in-demand skills, and figure out how to apply them to become a professional web builder. You’ll get valuable information from seven handy books covering the pieces of web programming, HTML5 & CSS3, JavaScript, PHP, MySQL, creating object-oriented programs, and using PHP frameworks. Helps you grasp the technologies that power web applications Covers PHP version 7.2 Includes coverage of the latest updates in web development Perfect for developers to use to solve problems This book is ideal for the inexperienced programmer interested in adding these skills to their toolbox. New coders who've made it through an online course or boot camp will also find great value in how this book builds on what you already know. COMPUTERS,Languages,PHP

PHP & MySQL PHP & MySQL: Novice to Ninja, 6th Edition is a hands-on guide to learning all the tools, principles, and techniques needed to build a fully functional application using PHP & MySQL. Comprehensively updated to cover PHP 7 and modern best practice, this practical and fun book covers everything from installing PHP and MySQL through to creating a complete online content management system. You'll learn how to: Install PHP & MySQL on Windows, Mac OS X, or Linux Gain a thorough understanding of PHP syntax Use object oriented programming techniques Master database design principles and SQL Develop robust websites that can handle high levels of traffic Build a working content management system (CMS) And much more! COMPUTERS,Languages,PHP

Laravel What sets Laravel apart from other PHP web frameworks? Speed and simplicity, for starters. This rapid application development framework and its ecosystem of tools let you quickly build new sites and applications with clean, readable code. Fully updated to cover Laravel 5.8, the second edition of this practical guide provides the definitive introduction to one of today’s mostpopular web frameworks. Matt Stauffer, a leading teacher and developer in the Laravel community, delivers a high-level overview and concrete examples to help experienced PHP web developers get started with this framework right away. This updated edition also covers Laravel Dusk and Horizon and provides information about community resources and other noncore Laravel packages. Dive into features, including: Blade, Laravel’s powerful custom templating tool Tools for gathering, validating, normalizing, and filtering user-provideddata The Eloquent ORM for working with application databases The role of the Illuminate request object in the application lifecycle PHPUnit, Mockery, and Dusk for testing your PHP code Tools for writing JSON and RESTful APIs Interfaces for filesystem access, sessions, cookies, caches, and search Tools for implementing queues, jobs, events, and WebSocket event publishing COMPUTERS,Languages,PHP

Programming PHP Why is PHP the most widely used programming language on the web? This updated edition teaches everything you need to know to create effective web applications using the latest features in PHP 7.4. You’ll start with the big picture and then dive into language syntax, programming techniques, and other details, using examples that illustrate both correct usage and common idioms. If you have a working knowledge of HTML, authors Kevin Tatroe and Peter MacIntyre provide many style tips and practical programming advice in a clear and concise manner to help you become a top-notch PHP programmer. Understand what’s possible when you use PHP programs Learn language fundamentals, including data types, variables, operators, and flow control statements Explore functions, strings, arrays, and objects Apply common web application techniques, such as form processing, data validation, session tracking, and cookies Interact with relational databases like MySQL or NoSQL databases such as MongoDB Generate dynamic images, create PDF files, and parse XML files Learn secure scripts, error handling, performance tuning, and other advanced topics Get a quick reference to PHP core functions and standard extensions COMPUTERS,Languages,PHP

Python Phrasebook This is the eBook version of the printed book. If the print book includes a CD-ROM, this content is not included within the eBook version. Python Phrasebook Brad Dayley Essential Code and Commands Python Phrasebook gives you the code phrases you need to quickly and effectively complete your programming projects in Python. Concise and Accessible Easy to carry and easy to use—lets you ditch all those bulky books for one portable guide Flexible and Functional Packed with more than 100 customizable code snippets—so you can readily code functional Python in just about any situation Brad Dayley is a software engineer at Novell, Inc. He has been a system administrator and software developer on the Unix, Windows, Linux, and NetWare platforms for the past 14 years. Brad co-developed an advanced debugging course used to train engineers and customers and is the co-author of several Novell Press books. Programming / Python $16.99 USA / $20.99 CAN / £11.99 Net UK COMPUTERS,Languages,Python

Python Python is a remarkably powerful dynamic programming language that is used in a wide variety of application domains such as Web, database access, desktop GUIs, game and software development, and network programming. Fans of Python use the phrase "batteries included" to describe the standard library, which covers everything from asynchronous processing to zip files. The language itself is a flexible powerhouse that can handle practically any application domain. This task-based tutorial is for students with no programming experience as well as those programmers who have some experience with the programming language and now want to take their skills to the next level. The book walks a reader through all the fundamentals and then moves on to more advanced topics. It's a complete end-to-end tutorial and reference. COMPUTERS,Languages,Python

Natural Language Processing with Python This book offers a highly accessible introduction to natural language processing, the field that supports a variety of language technologies, from predictive text and email filtering to automatic summarization and translation. With it, you'll learn how to write Python programs that work with large collections of unstructured text. You'll access richly annotated datasets using a comprehensive range of linguistic data structures, and you'll understand the main algorithms for analyzing the content and structure of written communication. Packed with examples and exercises, Natural Language Processing with Python will help you: Extract information from unstructured text, either to guess the topic or identify "named entities" Analyze linguistic structure in text, including parsing and semantic analysis Access popular linguistic databases, including WordNet and treebanks Integrate techniques drawn from fields as diverse as linguistics and artificial intelligence This book will help you gain practical skills in natural language processing using the Python programming language and the Natural Language Toolkit (NLTK) open source library. If you're interested in developing web applications, analyzing multilingual news sources, or documenting endangered languages -- or if you're simply curious to have a programmer's perspective on how human language works -- you'll find Natural Language Processing with Python both fascinating and immensely useful. COMPUTERS,Languages,Python

Python Essential Reference Python Essential Reference is the definitive reference guide to the Python programming language — the one authoritative handbook that reliably untangles and explains both the core Python language and the most essential parts of the Python library. Designed for the professional programmer, the book is concise, to the point, and highly accessible. It also includes detailed information on the Python library and many advanced subjects that is not available in either the official Python documentation or any other single reference source. Thoroughly updated to reflect the significant new programming language features and library modules that have been introduced in Python 2.6 and Python 3, the fourth edition of Python Essential Reference is the definitive guide for programmers who need to modernize existing Python code or who are planning an eventual migration to Python 3. Programmers starting a new Python project will find detailed coverage of contemporary Python programming idioms. This fourth edition of Python Essential Reference features numerous improvements, additions, and updates: Coverage of new language features, libraries, and modules Practical coverage of Python's more advanced features including generators, coroutines, closures, metaclasses, and decorators Expanded coverage of library modules related to concurrent programming including threads, subprocesses, and the new multiprocessing module Up-to-the-minute coverage of how to use Python 2.6’s forward compatibility mode to evaluate code for Python 3 compatibility Improved organization for even faster answers and better usability Updates to reflect modern Python programming style and idioms Updated and improved example code Deep coverage of low-level system and networking library modules — including options not covered in the standard documentation COMPUTERS,Languages,Python

Dive Into Python 3 Mark Pilgrim's Dive Into Python 3 is a hands-on guide to Python 3 and its differences from Python 2. As in the original book, Dive Into Python, each chapter starts with a real, complete code sample, proceeds to pick it apart and explain the pieces, and then puts it all back together in a summary at the end. This book includes: Example programs completely rewritten to illustrate powerful new concepts now available in Python 3: sets, iterators, generators, closures, comprehensions, and much more A detailed case study of porting a major library from Python 2 to Python 3 A comprehensive appendix of all the syntactic and semantic changes in Python 3 This is the perfect resource for you if you need to port applications to Python 3, or if you like to jump into languages fast and get going right away. COMPUTERS,Languages,Python

Real World Instrumentation with Python Learn how to develop your own applications to monitor or control instrumentation hardware. Whether you need to acquire data from a device or automate its functions, this practical book shows you how to use Python's rapid development capabilities to build interfaces that include everything from software to wiring. You get step-by-step instructions, clear examples, and hands-on tips for interfacing a PC to a variety of devices. Use the book's hardware survey to identify the interface type for your particular device, and then follow detailed examples to develop an interface with Python and C. Organized by interface type, data processing activities, and user interface implementations, this book is for anyone who works with instrumentation, robotics, data acquisition, or process control. Understand how to define the scope of an application and determine the algorithms necessary, and why it's important Learn how to use industry-standard interfaces such as RS-232, RS-485, and GPIB Create low-level extension modules in C to interface Python with a variety of hardware and test instruments Explore the console, curses, TkInter, and wxPython for graphical and text-based user interfaces Use open source software tools and libraries to reduce costs and avoid implementing functionality from scratch COMPUTERS,Languages,Python

Programming Python If you've mastered Python's fundamentals, you're ready to start using it to get real work done. Programming Python will show you how, with in-depth tutorials on the language's primary application domains: system administration, GUIs, and the Web. You'll also explore how Python is used in databases, networking, front-end scripting layers, text processing, and more. This book focuses on commonly used tools and libraries to give you a comprehensive understanding of Python’s many roles in practical, real-world programming. You'll learn language syntax and programming techniques in a clear and concise manner, with lots of examples that illustrate both correct usage and common idioms. Completely updated for version 3.x, Programming Python also delves into the language as a software development tool, with many code examples scaled specifically for that purpose. Topics include: Quick Python tour: Build a simple demo that includes data representation, object-oriented programming, object persistence, GUIs, and website basics System programming: Explore system interface tools and techniques for command-line scripting, processing files and folders, running programs in parallel, and more GUI programming: Learn to use Python’s tkinter widget library Internet programming: Access client-side network protocols and email tools, use CGI scripts, and learn website implementation techniques More ways to apply Python: Implement data structures, parse text-based information, interface with databases, and extend and embed Python COMPUTERS,Languages,Python

Python Algorithms Python Algorithms explains the Python approach to algorithm analysis and design. Written by Magnus Lie Hetland, author of Beginning Python, this book is sharply focused on classical algorithms, but it also gives a solid understanding of fundamental algorithmic problem-solving techniques. The book deals with some of the most important and challenging areas of programming and computer science, but in a highly pedagogic and readable manner. The book covers both algorithmic theory and programming practice, demonstrating how theory is reflected in real Python programs. Well-known algorithms and data structures that are built into the Python language are explained, and the user is shown how to implement and evaluate others himself. COMPUTERS,Languages,Python

Getting Started with RStudio Dive into the RStudio Integrated Development Environment (IDE) for using and programming R, the popular open source software for statistical computing and graphics. This concise book provides new and experienced users with an overview of RStudio, as well as hands-on instructions for analyzing data, generating reports, and developing R software packages. The open source RStudio IDE brings many powerful coding tools together into an intuitive, easy-to-learn interface. With this guide, you’ll learn how to use its main components—including the console, source code editor, and data viewer—through descriptions and case studies. Getting Started with RStudio serves as both a reference and introduction to this unique IDE. Use RStudio to provide enhanced support for interactive R sessions Clean and format raw data quickly with several RStudio components Edit R commands with RStudio’s code editor, and combine them into functions Easily locate and use more than 3,000 add-on packages in R’s CRAN service Develop and document your own R packages with the code editor and related components Create one-click PDF reports in RStudio with a mix of text and R output COMPUTERS,Languages,Python

Python and AWS Cookbook If you intend to use Amazon Web Services (AWS) for remote computing and storage, Python is an ideal programming language for developing applications and controlling your cloud-based infrastructure. This cookbook gets you started with more than two dozen recipes for using Python with AWS, based on the author’s boto library. You’ll find detailed recipes for working with the S3 storage service as well as EC2, the service that lets you design and build cloud applications. Each recipe includes a code solution you can use immediately, along with a discussion of why and how the recipe works. You also get detailed advice for using boto with AWS and other cloud services. This book’s recipes include methods to help you: Launch instances on EC2, and keep track of them with tags Associate an Elastic IP address with an instance Restore a failed Elastic Block Store volume from a snapshot Store and monitor your own custom metrics in CloudWatch Create a bucket in S3 to contain your data objects Reduce the cost of storing noncritical data Prevent accidental deletion of data in S3 COMPUTERS,Languages,Python

Python Cookbook If you need help writing programs in Python 3, or want to update older Python 2 code, this book is just the ticket. Packed with practical recipes written and tested with Python 3.3, this unique cookbook is for experienced Python programmers who want to focus on modern tools and idioms. Inside, you’ll find complete recipes for more than a dozen topics, covering the core Python language as well as tasks common to a wide variety of application domains. Each recipe contains code samples you can use in your projects right away, along with a discussion about how and why the solution works. Topics include: Data Structures and Algorithms Strings and Text Numbers, Dates, and Times Iterators and Generators Files and I/O Data Encoding and Processing Functions Classes and Objects Metaprogramming Modules and Packages Network and Web Programming Concurrency Utility Scripting and System Administration Testing, Debugging, and Exceptions C Extensions COMPUTERS,Languages,Python

Python This task-based tutorial on Python is for students new to the language and walks them through the fundamentals. They'll learn about arithmetic, strings, and variables; writing programs; flow of control, functions; strings; data structures; input and output; and exception handling. At the end of the book, a special section walks them through a longer, realistic application, tying the concepts of the book together. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Languages,Python

Learning Python Get a comprehensive, in-depth introduction to the core Python language with this hands-on book. Based on author Mark Lutz’s popular training course, this updated fifth edition will help you quickly write efficient, high-quality code with Python. It’s an ideal way to begin, whether you’re new to programming or a professional developer versed in other languages. Complete with quizzes, exercises, and helpful illustrations, this easy-to-follow, self-paced tutorial gets you started with both Python 2.7 and 3.3— the latest releases in the 3.X and 2.X lines—plus all other releases in common use today. You’ll also learn some advanced language features that recently have become more common in Python code. Explore Python’s major built-in object types such as numbers, lists, and dictionaries Create and process objects with Python statements, and learn Python’s general syntax model Use functions to avoid code redundancy and package code for reuse Organize statements, functions, and other tools into larger components with modules Dive into classes: Python’s object-oriented programming tool for structuring code Write large programs with Python’s exception-handling model and development tools Learn advanced Python tools, including decorators, descriptors, metaclasses, and Unicode processing COMPUTERS,Languages,Python

Dive Into Python Whether you're an experienced programmer looking to get into Python or grizzled Python veteran who remembers the days when you had to import the string module, Dive Into Python is your 'desert island' Python book. — Joey deVilla, Slashdot contributor As a complete newbie to the language...I constantly had those little thoughts like, 'this is the way a programming language should be taught.' — Lasse Koskela , JavaRanch Apress has been profuse in both its quantity and quality of releasesand (this book is) surely worth adding to your technical reading budget for skills development. — Blane Warrene, Technology Notes I am reading this ... because the language seems like a good way to accomplish programming tasks that don't require the low-level bit handling power of C. — Richard Bejtlich, TaoSecurity Python is a new and innovative scripting language. It is set to replace Perl as the programming language of choice for shell scripters, and for serious application developers who want a feature-rich, yet simple language to deploy their products. Dive Into Python is a hands-on guide to the Python language. Each chapter starts with a real, complete code sample, proceeds to pick it apart and explain the pieces, and then puts it all back together in a summary at the end. This is the perfect resource for you if you like to jump into languages fast and get going right away. If you're just starting to learn Python, first pick up a copy of Magnus Lie Hetland's Practical Python. COMPUTERS,Languages,Python

Learn Python the Hard Way You Will Learn Python! Zed Shaw has perfected the world's best system for learning Python. Follow it and you will succeed-just like the hundreds of thousands of beginners Zed has taught to date! You bring the discipline, commitment, and persistence; the author supplies everything else. In Learn Python the Hard Way, Third Edition, you'll learn Python by working through 52 brilliantly crafted exercises. Read them. Type their code precisely. (No copying and pasting!) Fix your mistakes. Watch the programs run. As you do, you'll learn how software works; what good programs look like; how to read, write, and think about code; and how to find and fix your mistakes using tricks professional programmers use. Most importantly, you'll learn the following, which you need to start writing excellent Python software of your own: Installing a complete Python environment Organizing and writing code Basic mathematics Variables Strings and text Interacting with users Working with files Looping and logic Data structures using lists and dictionaries Program design Object-oriented programming Inheritance and composition Modules, classes, and objects Python packaging Debugging Automated testing Basic game development Basic web development It'll be hard at first. But soon, you'll just get it-and that will feel great! This tutorial will reward you for every minute you put into it. Soon, you'll know one of the world's most powerful, popular programming languages. You'll be a Python programmer. Watch Zed, too! The accompanying DVD contains 5+ hours of passionate, powerful teaching: a complete Python video course! COMPUTERS,Languages,Python

Python Pocket Reference Updated for both Python 3.4 and 2.7, this convenient pocket guide is the perfect on-the-job quick reference. You’ll find concise, need-to-know information on Python types and statements, special method names, built-in functions and exceptions, commonly used standard library modules, and other prominent Python tools. The handy index lets you pinpoint exactly what you need. Written by Mark Lutz—widely recognized as the world’s leading Python trainer—Python Pocket Reference is an ideal companion to O’Reilly’s classic Python tutorials, Learning Python and Programming Python, also written by Mark. This fifth edition covers: Built-in object types, including numbers, lists, dictionaries, and more Statements and syntax for creating and processing objects Functions and modules for structuring and reusing code Python’s object-oriented programming tools Built-in functions, exceptions, and attributes Special operator overloading methods Widely used standard library modules and extensions Command-line options and development tools Python idioms and hints The Python SQL Database API COMPUTERS,Languages,Python

Lightweight Django How can you take advantage of the Django framework to integrate complex client-side interactions and real-time features into your web applications? Through a series of rapid application development projects, this hands-on book shows experienced Django developers how to include REST APIs, WebSockets, and client-side MVC frameworks such as Backbone.js into new or existing projects. Learn how to make the most of Django’s decoupled design by choosing the components you need to build the lightweight applications you want. Once you finish this book, you’ll know how to build single-page applications that respond to interactions in real time. If you’re familiar with Python and JavaScript, you’re good to go. Learn a lightweight approach for starting a new Django project Break reusable applications into smaller services that communicate with one another Create a static, rapid prototyping site as a scaffold for websites and applications Build a REST API with django-rest-framework Learn how to use Django with the Backbone.js MVC framework Create a single-page web application on top of your REST API Integrate real-time features with WebSockets and the Tornado networking library Use the book’s code-driven examples in your own projects COMPUTERS,Languages,Python

Cython Build software that combines Python’s expressivity with the performance and control of C (and C++). It’s possible with Cython, the compiler and hybrid programming language used by foundational packages such as NumPy, and prominent in projects including Pandas, h5py, and scikits-learn. In this practical guide, you’ll learn how to use Cython to improve Python’s performance—up to 3000x— and to wrap C and C++ libraries in Python with ease. Author Kurt Smith takes you through Cython’s capabilities, with sample code and in-depth practice exercises. If you’re just starting with Cython, or want to go deeper, you’ll learn how this language is an essential part of any performance-oriented Python programmer’s arsenal. Use Cython’s static typing to speed up Python code Gain hands-on experience using Cython features to boost your numeric-heavy Python Create new types with Cython—and see how fast object-oriented programming in Python can be Effectively organize Cython code into separate modules and packages without sacrificing performance Use Cython to give Pythonic interfaces to C and C++ libraries Optimize code with Cython’s runtime and compile-time profiling tools Use Cython’s prange function to parallelize loops transparently with OpenMP COMPUTERS,Languages,Python

Effective Python “Each item in Slatkin’s Effective Python teaches a self-contained lesson with its own source code. This makes the book random-access: Items are easy to browse and study in whatever order the reader needs. I will be recommending Effective Python to students as an admirably compact source of mainstream advice on a very broad range of topics for the intermediate Python programmer.†—Brandon Rhodes, software engineer at Dropbox and chair of PyCon 2016-2017 It’s easy to start coding with Python, which is why the language is so popular. However, Python’s unique strengths, charms, and expressiveness can be hard to grasp, and there are hidden pitfalls that can easily trip you up. Effective Python will help you master a truly “Pythonic†approach to programming, harnessing Python’s full power to write exceptionally robust and well-performing code. Using the concise, scenario-driven style pioneered in Scott Meyers’ best-selling Effective C++, Brett Slatkin brings together 59 Python best practices, tips, and shortcuts, and explains them with realistic code examples. Drawing on years of experience building Python infrastructure at Google, Slatkin uncovers little-known quirks and idioms that powerfully impact code behavior and performance. You’ll learn the best way to accomplish key tasks, so you can write code that’s easier to understand, maintain, and improve. Key features include Actionable guidelines for all major areas of Python 3.x and 2.x development, with detailed explanations and examples Best practices for writing functions that clarify intention, promote reuse, and avoid bugs Coverage of how to accurately express behaviors with classes and objects Guidance on how to avoid pitfalls with metaclasses and dynamic attributes More efficient approaches to concurrency and parallelism Better techniques and idioms for using Python’s built-in modules Tools and best practices for collaborative development Solutions for debugging, testing, and optimization in order to improve quality and performance COMPUTERS,Languages,Python

Python Algorithms Python Algorithms, Second Edition explains the Python approach to algorithm analysis and design. Written by Magnus Lie Hetland, author of Beginning Python, this book is sharply focused on classical algorithms, but it also gives a solid understanding of fundamental algorithmic problem-solving techniques. The book deals with some of the most important and challenging areas of programming and computer science in a highly readable manner. It covers both algorithmic theory and programming practice, demonstrating how theory is reflected in real Python programs. Well-known algorithms and data structures that are built into the Python language are explained, and the user is shown how to implement and evaluate others. COMPUTERS,Languages,Python

Introduction to Programming in Python Today, anyone in a scientific or technical discipline needs programming skills. Python is an ideal first programming language, and Introduction to Programming in Python is the best guide to learning it. Princeton University’s Robert Sedgewick, Kevin Wayne, and Robert Dondero have crafted an accessible, interdisciplinary introduction to programming in Python that emphasizes important and engaging applications, not toy problems. The authors supply the tools needed for students to learn that programming is a natural, satisfying, and creative experience. This example-driven guide focuses on Python’s most useful features and brings programming to life for every student in the sciences, engineering, and computer science. Coverage includes Basic elements of programming: variables, assignment statements, built-in data types, conditionals, loops, arrays, and I/O, including graphics and sound Functions, modules, and libraries: organizing programs into components that can be independently debugged, maintained, and reused Object-oriented programming and data abstraction: objects, modularity, encapsulation, and more Algorithms and data structures: sort/search algorithms, stacks, queues, and symbol tables Examples from applied math, physics, chemistry, biology, and computer science—all compatible with Python 2 and 3 Drawing on their extensive classroom experience, the authors provide Q&As, exercises, and opportunities for creative practice throughout. An extensive amount of supplementary information is available at introcs.cs.princeton.edu/python. With source code, I/O libraries, solutions to selected exercises, and much more, this companion website empowers people to use their own computers to teach and learn the material. COMPUTERS,Languages,Python

Fluent Python Python’s simplicity lets you become productive quickly, but this often means you aren’t using everything it has to offer. With this hands-on guide, you’ll learn how to write effective, idiomatic Python code by leveraging its best—and possibly most neglected—features. Author Luciano Ramalho takes you through Python’s core language features and libraries, and shows you how to make your code shorter, faster, and more readable at the same time. Many experienced programmers try to bend Python to fit patterns they learned from other languages, and never discover Python features outside of their experience. With this book, those Python programmers will thoroughly learn how to become proficient in Python 3. This book covers: Python data model: understand how special methods are the key to the consistent behavior of objects Data structures: take full advantage of built-in types, and understand the text vs bytes duality in the Unicode age Functions as objects: view Python functions as first-class objects, and understand how this affects popular design patterns Object-oriented idioms: build classes by learning about references, mutability, interfaces, operator overloading, and multiple inheritance Control flow: leverage context managers, generators, coroutines, and concurrency with the concurrent.futures and asyncio packages Metaprogramming: understand how properties, attribute descriptors, class decorators, and metaclasses work COMPUTERS,Languages,Python

Essential SQLAlchemy Dive into SQLAlchemy, the popular, open-source code library that helps Python programmers work with relational databases such as Oracle, MySQL, PostgresSQL, and SQLite. Using real-world examples, this practical guide shows you how to build a simple database application with SQLAlchemy, and how to connect to multiple databases simultaneously with the same metadata. SQL is a powerful language for querying and manipulating data, but it’s tough to integrate it with your application. SQLAlchemy helps you map Python objects to database tables without substantially changing your existing Python code. If you’re an intermediate Python developer with knowledge of basic SQL syntax and relational theory, this book serves as both a learning tool and a handy reference. Essential SQLAlchemy includes several sections: SQLAlchemy Core: Provide database services to your applications in a Pythonic way with the SQL Expression Language SQLAlchemy ORM: Use the object relational mapper to bind database schema and operations to data objects in your application Alembic: Use this lightweight database migration tool to handle changes to the database as your application evolves Cookbook: Learn how to use SQLAlchemy with web frameworks like Flask and libraries like SQLAcodegen COMPUTERS,Languages,Python

Think Python If you want to learn how to program, working with Python is an excellent way to start. This hands-on guide takes you through the language a step at a time, beginning with basic programming concepts before moving on to functions, recursion, data structures, and object-oriented design. This second edition and its supporting code have been updated for Python 3. Through exercises in each chapter, you’ll try out programming concepts as you learn them. Think Python is ideal for students at the high school or college level, as well as self-learners, home-schooled students, and professionals who need to learn programming basics. Beginners just getting their feet wet will learn how to start with Python in a browser. Start with the basics, including language syntax and semantics Get a clear definition of each programming concept Learn about values, variables, statements, functions, and data structures in a logical progression Discover how to work with files and databases Understand objects, methods, and object-oriented programming Use debugging techniques to fix syntax, runtime, and semantic errors Explore interface design, data structures, and GUI-based programs through case studies COMPUTERS,Languages,Python

Numerical Python Numerical Python by Robert Johansson shows you how to leverage the numerical and mathematical modules in Python and its Standard Library as well as popular open source numerical Python packages like NumPy, FiPy, matplotlib and more to numerically compute solutions and mathematically model applications in a number of areas like big data, cloud computing, financial engineering, business management and more. After reading and using this book, you'll get some takeaway case study examples of applications that can be found in areas like business management, big data/cloud computing, financial engineering (i.e., options trading investment alternatives), and even games. Up until very recently, Python was mostly regarded as just a web scripting language. Well, computational scientists and engineers have recently discovered the flexibility and power of Python to do more. Big data analytics and cloud computing programmers are seeing Python's immense use. Financial engineers are also now employing Python in their work. Python seems to be evolving as a language that can even rival C++, Fortran, and Pascal/Delphi for numerical and mathematical computations. COMPUTERS,Languages,Python

Foundations for Analytics with Python If you’re like many of Excel’s 750 million users, you want to do more with your data—like repeating similar analyses over hundreds of files, or combining data in many files for analysis at one time. This practical guide shows ambitious non-programmers how to automate and scale the processing and analysis of data in different formats—by using Python. After author Clinton Brownley takes you through Python basics, you’ll be able to write simple scripts for processing data in spreadsheets as well as databases. You’ll also learn how to use several Python modules for parsing files, grouping data, and producing statistics. No programming experience is necessary. Create and run your own Python scripts by learning basic syntax Use Python’s csv module to read and parse CSV files Read multiple Excel worksheets and workbooks with the xlrd module Perform database operations in MySQL or with the mysqlclient module Create Python applications to find specific records, group data, and parse text files Build statistical graphs and plots with matplotlib, pandas, ggplot, and seaborn Produce summary statistics, and estimate regression and classification models Schedule your scripts to run automatically in both Windows and Mac environments COMPUTERS,Languages,Python

The Hitchhiker's Guide to Python The Hitchhiker's Guide to Python takes the journeyman Pythonista to true expertise. More than any other language, Python was created with the philosophy of simplicity and parsimony. Now 25 years old, Python has become the primary or secondary language (after SQL) for many business users. With popularity comes diversity—and possibly dilution. This guide, collaboratively written by over a hundred members of the Python community, describes best practices currently used by package and application developers. Unlike other books for this audience, The Hitchhiker’s Guide is light on reusable code and heavier on design philosophy, directing the reader to excellent sources that already exist. COMPUTERS,Languages,Python

Introduction to Machine Learning with Python Machine learning has become an integral part of many commercial applications and research projects, but this field is not exclusive to large companies with extensive research teams. If you use Python, even as a beginner, this book will teach you practical ways to build your own machine learning solutions. With all the data available today, machine learning applications are limited only by your imagination. You’ll learn the steps necessary to create a successful machine-learning application with Python and the scikit-learn library. Authors Andreas Müller and Sarah Guido focus on the practical aspects of using machine learning algorithms, rather than the math behind them. Familiarity with the NumPy and matplotlib libraries will help you get even more from this book. With this book, you’ll learn: Fundamental concepts and applications of machine learning Advantages and shortcomings of widely used machine learning algorithms How to represent data processed by machine learning, including which data aspects to focus on Advanced methods for model evaluation and parameter tuning The concept of pipelines for chaining models and encapsulating your workflow Methods for working with text data, including text-specific processing techniques Suggestions for improving your machine learning and data science skills COMPUTERS,Languages,Python

Lean Python Learn only the essential aspects of Python without cluttering up your mind with features you may never use. This compact book is not a "best way to write code" type of book; rather, the author goes over his most-used functions, which are all you need to know as a beginner and some way beyond. Lean Python takes 58 Python methods and functions and whittles them down to 15: as author Paul Gerrard says, "I haven't found a need for the rest." What You'll Learn Discover lean Python and how to learn just enough to build useful tools Use Python objects, program structure, I/O, modules and more Handle errors and exceptions Test your code Access the Web; do searching; and persist data Who This Book Is For This book is aimed at three categories of reader: The experienced programmer – if you already know a programming language, this book gives you a shortcut to understanding the Python language and some of its design philosophy. You work in IT and need a programming primer – you might be a tester who needs to have more informed technical discussions with programmers. Working through the examples will help you to appreciate the challenge of good programming. First-timer – you want a first book on programming that you can assimilate quickly to help you decide whether programming is for you. COMPUTERS,Languages,Python

Python Data Science Handbook For many researchers, Python is a first-class tool mainly because of its libraries for storing, manipulating, and gaining insight from data. Several resources exist for individual pieces of this data science stack, but only with the Python Data Science Handbook do you get them all—IPython, NumPy, Pandas, Matplotlib, Scikit-Learn, and other related tools. Working scientists and data crunchers familiar with reading and writing Python code will find this comprehensive desk reference ideal for tackling day-to-day issues: manipulating, transforming, and cleaning data; visualizing different types of data; and using data to build statistical or machine learning models. Quite simply, this is the must-have reference for scientific computing in Python. With this handbook, you’ll learn how to use: IPython and Jupyter: provide computational environments for data scientists using Python NumPy: includes the ndarray for efficient storage and manipulation of dense data arrays in Python Pandas: features the DataFrame for efficient storage and manipulation of labeled/columnar data in Python Matplotlib: includes capabilities for a flexible range of data visualizations in Python Scikit-Learn: for efficient and clean Python implementations of the most important and established machine learning algorithms COMPUTERS,Languages,Python

Head First Python Want to learn the Python language without slogging your way through how-to manuals? With Head First Python, you’ll quickly grasp Python’s fundamentals, working with the built-in data structures and functions. Then you’ll move on to building your very own webapp, exploring database management, exception handling, and data wrangling. If you’re intrigued by what you can do with context managers, decorators, comprehensions, and generators, it’s all here. This second edition is a complete learning experience that will help you become a bonafide Python programmer in no time. Why does this book look so different? Based on the latest research in cognitive science and learning theory, Head First Pythonuses a visually rich format to engage your mind, rather than a text-heavy approach that puts you to sleep. Why waste your time struggling with new concepts? This multi-sensory learning experience is designed for the way your brain really works. COMPUTERS,Languages,Python

Beginning Python Gain a fundamental understanding of Python’s syntax and features with this up–to–date introduction and practical reference. Covering a wide array of Python–related programming topics, including addressing language internals, database integration, network programming, and web services, you’ll be guided by sound development principles. Ten accompanying projects will ensure you can get your hands dirty in no time.Updated to reflect the latest in Python programming paradigms and several of the most crucial features found in Python 3, Beginning Python also covers advanced topics such as extending Python and packaging/distributing Python applications. What You'll Learn Become a proficient Python programmer by following along with a friendly, practical guide to the language’s key features Write code faster by learning how to take advantage of advanced features such as magic methods, exceptions, and abstraction Gain insight into modern Python programming paradigms including testing, documentation, packaging, and distribution Learn by following along with ten interesting projects, including a P2P file–sharing application, chat client, video game, remote text editor, and more Who This Book Is For Programmers, novice and otherwise, seeking a comprehensive introduction to the Python programming language. COMPUTERS,Languages,Python

Pro Python Best Practices Learn software engineering and coding best practices to write Python code right and error free. In this book you’ll see how to properly debug, organize, test, and maintain your code, all of which leads to better, more efficient coding. Software engineering is difficult. Programs of any substantial length are inherently prone to errors of all kinds. The development cycle is full of traps unknown to the apprentice developer. Yet, in Python textbooks little attention is paid to this aspect of getting your code to run. At most, there is a chapter on debugging or unit testing in your average basic Python book. However, the proportion of time spent on getting your code to run is much higher in the real world. Pro Python Best Practices aims to solve this problem. What You'll Learn Learn common debugging techniques that help you find and eliminate errors Gain techniques to detect bugs more easily Who This Book Is For Experienced Python coders from web development, big data, and more. COMPUTERS,Languages,Python

Python This book is an introduction to programming concepts that uses Python 3 as the target language. It follows a practical just-in-time presentation – material is given to the student when it is needed. Many examples will be based on games, because Python has become the language of choice for basic game development. Designed as a Year One textbook for introduction to programming classes or for the hobbyist who wants to learn the fundamentals of programming, the text assumes no programming experience. Features: * Introduces programming concepts that use Python 3* Includes many examples based on video game development* 4-color throughout with game demos on the companion files COMPUTERS,Languages,Python

Python in a Nutshell Useful in many roles, from design and prototyping to testing, deployment, and maintenance, Python is consistently ranked among today’s most popular programming languages. The third edition of this practical book provides a quick reference to the language—including Python 3.5, 2.7, and highlights of 3.6—commonly used areas of its vast standard library, and some of the most useful third-party modules and packages. Ideal for programmers with some Python experience, and those coming to Python from other programming languages, this book covers a wide range of application areas, including web and network programming, XML handling, database interactions, and high-speed numeric computing. Discover how Python provides a unique mix of elegance, simplicity, practicality, and sheer power. This edition covers: Python syntax, Object-Oriented Python, standard library modules, and third-party Python packages Python’s support for file and text operations, persistence and databases, concurrent execution, and numeric computations Networking basics, event-driven programming, and client-side network protocol modules Python extension modules, and tools for packaging and distributing extensions, modules, and applications COMPUTERS,Languages,Python

Cracking Codes with Python Learn how to program in Python while making and breaking ciphers—algorithms used to create and send secret messages! After a crash course in Python programming basics, you’ll learn to make, test, and hack programs that encrypt text with classical ciphers like the transposition cipher and Vigenère cipher. You’ll begin with simple programs for the reverse and Caesar ciphers and then work your way up to public key cryptography, the type of encryption used to secure today’s online transactions, including digital signatures, email, and Bitcoin. Each program includes the full code and a line-by-line explanation of how things work. By the end of the book, you’ll have learned how to code in Python and you’ll have the clever programs to prove it! You’ll also learn how to: - Combine loops, variables, and flow control statements into real working programs- Use dictionary files to instantly detect whether decrypted messages are valid English or gibberish- Create test programs to make sure that your code encrypts and decrypts correctly- Code (and hack!) a working example of the affine cipher, which uses modular arithmetic to encrypt a message- Break ciphers with techniques such as brute-force and frequency analysis There’s no better way to learn to code than to play with real programs. Cracking Codes with Python makes the learning fun! COMPUTERS,Languages,Python

Python Machine Learning By Example Take tiny steps to enter the big world of data science through this interesting guide About This Book Learn the fundamentals of machine learning and build your own intelligent applications Master the art of building your own machine learning systems with this example-based practical guide Work with important classification and regression algorithms and other machine learning techniques Who This Book Is For This book is for anyone interested in entering the data science stream with machine learning. Basic familiarity with Python is assumed. What You Will Learn Exploit the power of Python to handle data extraction, manipulation, and exploration techniques Use Python to visualize data spread across multiple dimensions and extract useful features Dive deep into the world of analytics to predict situations correctly Implement machine learning classification and regression algorithms from scratch in Python Be amazed to see the algorithms in action Evaluate the performance of a machine learning model and optimize it Solve interesting real-world problems using machine learning and Python as the journey unfolds In Detail Data science and machine learning are some of the top buzzwords in the technical world today. A resurging interest in machine learning is due to the same factors that have made data mining and Bayesian analysis more popular than ever. This book is your entry point to machine learning. This book starts with an introduction to machine learning and the Python language and shows you how to complete the setup. Moving ahead, you will learn all the important concepts such as, exploratory data analysis, data preprocessing, feature extraction, data visualization and clustering, classification, regression and model performance evaluation. With the help of various projects included, you will find it intriguing to acquire the mechanics of several important machine learning algorithms – they are no more obscure as they thought. Also, you will be guided step by step to build your own models from scratch. Toward the end, you will gather a broad picture of the machine learning ecosystem and best practices of applying machine learning techniques. Through this book, you will learn to tackle data-driven problems and implement your solutions with the powerful yet simple language, Python. Interesting and easy-to-follow examples, to name some, news topic classification, spam email detection, online ad click-through prediction, stock prices forecast, will keep you glued till you reach your goal. Style and approach This book is an enticing journey that starts from the very basics and gradually picks up pace as the story unfolds. Each concept is first succinctly defined in the larger context of things, followed by a detailed explanation of their application. Every concept is explained with the help of a project that solves a real-world problem, and involves hands-on work—giving you a deep insight into the world of machine learning. With simple yet rich language—Python—you will understand and be able to implement the examples with ease. COMPUTERS,Languages,Python

Mission Python Program a graphical adventure game in this hands-on, beginner-friendly introduction to coding in the Python language. Launch into coding with Mission Python, a space-themed guide to building a complete computer game in Python. You'll learn programming fundamentals like loops, strings, and lists as you build Escape!, an exciting game with a map to explore, items to collect, and tricky logic puzzles to solve. As you work through the book, you'll build exercises and mini-projects, like making a spacewalk simulator and creating an astronaut's safety checklist that will put your new Python skills to the test. You'll learn how to use Pygame Zero, a free resource that lets you add graphics and sound effects to your creations, and you'll get useful game-making tips, such as how to design fun puzzles and intriguing maps. Before you know it, you'll have a working, awesome game to stump your friends with (and some nifty coding skills, too!). You can follow this book using a Raspberry Pi or a Microsoft Windows PC, and the 3D graphics and sound effects you need are provided as a download. COMPUTERS,Languages,Python

The Blender Python API Understand Blender's Python API to allow for precision 3D modeling and add-on development. Follow detailed guidance on how to create precise geometries, complex texture mappings, optimized renderings, and much more. This book is a detailed, user-friendly guide to understanding and using Blender’s Python API for programmers and 3D artists. Blender is a popular open source 3D modeling software used in advertising, animation, data visualization, physics simulation, photorealistic rendering, and more. Programmers can produce extremely complex and precise models that would be impossible to replicate by hand, while artists enjoy numerous new community-built add-ons. The Blender Python API is an unparalleled programmable visualization environment. Using the API is made difficult due to its complex object hierarchy and vast documentation. Understanding the Blender Python API clearly explains the interface. You will become familiar with data structures and low-level concepts in both modeling and rendering with special attention given to optimizing procedurally generated models. In addition, the book: Discusses modules of the API as analogs to human input modes in Blender Reviews low-level and data-level manipulation of 3D objects in Blender Python Details how to deploy and extend projects with external libraries Provides organized utilities of novel and mature API abstractions for general use in add-on development What You’ll Learn Generate 3D data visualizations in Blender to better understand multivariate data and mathematical patterns. Create precision object models in Blender of architectural models, procedurally generated landscapes, atomic models, etc. Develop and distribute a Blender add-on, with special consideration given to careful development practices Pick apart Blender’s 3D viewport and Python source code to learn about API behaviors Develop a practical knowledge of 3D modeling and rendering concepts Have a practical reference to an already powerful and vast API Who This Book Is For Python programmers with an interest in data science, game development, procedural generation, and open-source programming as well as programmers of all types with a need to generate precise 3D models. Also for 3D artists with an interest in programming or with programming experience and Blender artists regardless of programming experience. COMPUTERS,Languages,Python

The Python Apprentice Learn the Python skills and culture you need to become a productive member of any Python project. About This Book Taking a practical approach to studying Python A clear appreciation of the sequence-oriented parts of Python Emphasis on the way in which Python code is structured Learn how to produce bug-free code by using testing tools Who This Book Is For The Python Apprentice is for anyone who wants to start building, creating and contributing towards a Python project. No previous knowledge of Python is required, although at least some familiarity with programming in another language is helpful. What You Will Learn Learn the language of Python itself Get a start on the Python standard library Learn how to integrate 3rd party libraries Develop libraries on your own Become familiar with the basics of Python testing In Detail Experienced programmers want to know how to enhance their craft and we want to help them start as apprentices with Python. We know that before mastering Python you need to learn the culture and the tools to become a productive member of any Python project. Our goal with this book is to give you a practical and thorough introduction to Python programming, providing you with the insight and technical craftsmanship you need to be a productive member of any Python project. Python is a big language, and it's not our intention with this book to cover everything there is to know. We just want to make sure that you, as the developer, know the tools, basic idioms and of course the ins and outs of the language, the standard library and other modules to be able to jump into most projects. Style and approach We introduce topics gently and then revisit them on multiple occasions to add the depth required to support your progression as a Python developer. We've worked hard to structure the syllabus to avoid forward references. On only a few occasions do we require you to accept techniques on trust, before explaining them later; where we do, it's to deliberately establish good habits. COMPUTERS,Languages,Python

Learn Python 3 the Hard Way You Will Learn Python 3! Zed Shaw has perfected the world’s best system for learning Python 3. Follow it and you will succeed—just like the millions of beginners Zed has taught to date! You bring the discipline, commitment, and persistence; the author supplies everything else. In Learn Python 3 the Hard Way, you’ll learn Python by working through 52 brilliantly crafted exercises. Read them. Type their code precisely. (No copying and pasting!) Fix your mistakes. Watch the programs run. As you do, you’ll learn how a computer works; what good programs look like; and how to read, write, and think about code. Zed then teaches you even more in 5+ hours of video where he shows you how to break, fix, and debug your code—live, as he’s doing the exercises. Install a complete Python environment Organize and write code Fix and break code Basic mathematics Variables Strings and text Interact with users Work with files Looping and logic Data structures using lists and dictionaries Program design Object-oriented programming Inheritance and composition Modules, classes, and objects Python packaging Automated testing Basic game development Basic web development It’ll be hard at first. But soon, you’ll just get it—and that will feel great! This course will reward you for every minute you put into it. Soon, you’ll know one of the world’s most powerful, popular programming languages. You’ll be a Python programmer. This Book Is Perfect For Total beginners with zero programming experience Junior developers who know one or two languages Returning professionals who haven’t written code in years Seasoned professionals looking for a fast, simple, crash course in Python 3 COMPUTERS,Languages,Python

Python 3 Standard Library by Example, The Master the Powerful Python 3 Standard Library through Real Code Examples “The genius of Doug’s approach is that with 15 minutes per week, any motivated programmer can learn the Python Standard Library. Doug’s guided tour will help you flip the switch to fully power-up Python’s batteries.†–Raymond Hettinger, Distinguished Python Core Developer The Python 3 Standard Library contains hundreds of modules for interacting with the operating system, interpreter, and Internet–all extensively tested and ready to jump-start application development. Now, Python expert Doug Hellmann introduces every major area of the Python 3.x library through concise source code and output examples. Hellmann’s examples fully demonstrate each feature and are designed for easy learning and reuse. You’ll find practical code for working with text, data structures, algorithms, dates/times, math, the file system, persistence, data exchange, compression, archiving, crypto, processes/threads, networking, Internet capabilities, email, developer and language tools, the runtime, packages, and more. Each section fully covers one module, with links to additional resources, making this book an ideal tutorial and reference. The Python 3 Standard Library by Example introduces Python 3.x’s new libraries, significant functionality changes, and new layout and naming conventions. Hellmann also provides expert porting guidance for moving code from 2.x Python standard library modules to their Python 3.x equivalents. Manipulate text with string, textwrap, re (regular expressions), and difflib Use data structures: enum, collections, array, heapq, queue, struct, copy, and more Implement algorithms elegantly and concisely with functools, itertools, and contextlib Handle dates/times and advanced mathematical tasks Archive and data compression Understand data exchange and persistence, including json, dbm, and sqlite Sign and verify messages cryptographically Manage concurrent operations with processes and threads Test, debug, compile, profile, language, import, and package tools Control interaction at runtime with interpreters or the environment COMPUTERS,Languages,Python

Invent Your Own Computer Games with Python, 4E Invent Your Own Computer Games with Python will teach you how to make computer games using the popular Python programming language—even if you’ve never programmed before! Begin by building classic games like Hangman, Guess the Number, and Tic-Tac-Toe, and then work your way up to more advanced games, like a text-based treasure hunting game and an animated collision-dodging game with sound effects. Along the way, you’ll learn key programming and math concepts that will help you take your game programming to the next level. Learn how to:–Combine loops, variables, and flow control statements into real working programs–Choose the right data structures for the job, such as lists, dictionaries, and tuples–Add graphics and animation to your games with the pygame module–Handle keyboard and mouse input–Program simple artificial intelligence so you can play against the computer–Use cryptography to convert text messages into secret code–Debug your programs and find common errors As you work through each game, you’ll build a solid foundation in Python and an understanding of computer science fundamentals. What new game will you create with the power of Python? The projects in this book are compatible with Python 3. COMPUTERS,Languages,Python

Doing Math with Python Doing Math with Python shows you how to use Python to delve into high school–level math topics like statistics, geometry, probability, and calculus. You’ll start with simple projects, like a factoring program and a quadratic-equation solver, and then create more complex projects once you’ve gotten the hang of things. Along the way, you’ll discover new ways to explore math and gain valuable programming skills that you’ll use throughout your study of math and computer science. Learn how to:–Describe your data with statistics, and visualize it with line graphs, bar charts, and scatter plots–Explore set theory and probability with programs for coin flips, dicing, and other games of chance–Solve algebra problems using Python’s symbolic math functions–Draw geometric shapes and explore fractals like the Barnsley fern, the Sierpinski triangle, and the Mandelbrot set–Write programs to find derivatives and integrate functions Creative coding challenges and applied examples help you see how you can put your new math and coding skills into practice. You’ll write an inequality solver, plot gravity’s effect on how far a bullet will travel, shuffle a deck of cards, estimate the area of a circle by throwing 100,000 "darts" at a board, explore the relationship between the Fibonacci sequence and the golden ratio, and more. Whether you’re interested in math but have yet to dip into programming or you’re a teacher looking to bring programming into the classroom, you’ll find that Python makes programming easy and practical. Let Python handle the grunt work while you focus on the math. Uses Python 3 COMPUTERS,Languages,Python

Test-Driven Development with Python By taking you through the development of a real web application from beginning to end, the second edition of this hands-on guide demonstrates the practical advantages of test-driven development (TDD) with Python. You’ll learn how to write and run tests before building each part of your app, and then develop the minimum amount of code required to pass those tests. The result? Clean code that works. In the process, you’ll learn the basics of Django, Selenium, Git, jQuery, and Mock, along with current web development techniques. If you’re ready to take your Python skills to the next level, this book—updated for Python 3.6—clearly demonstrates how TDD encourages simple designs and inspires confidence. Dive into the TDD workflow, including the unit test/code cycle and refactoring Use unit tests for classes and functions, and functional tests for user interactions within the browser Learn when and how to use mock objects, and the pros and cons of isolated vs. integrated tests Test and automate your deployments with a staging server Apply tests to the third-party plugins you integrate into your site Run tests automatically by using a Continuous Integration environment Use TDD to build a REST API with a front-end Ajax interface COMPUTERS,Languages,Python

Elegant SciPy Welcome to Scientific Python and its community. If you’re a scientist who programs with Python, this practical guide not only teaches you the fundamental parts of SciPy and libraries related to it, but also gives you a taste for beautiful, easy-to-read code that you can use in practice. You’ll learn how to write elegant code that’s clear, concise, and efficient at executing the task at hand. Throughout the book, you’ll work with examples from the wider scientific Python ecosystem, using code that illustrates principles outlined in the book. Using actual scientific data, you’ll work on real-world problems with SciPy, NumPy, Pandas, scikit-image, and other Python libraries. Explore the NumPy array, the data structure that underlies numerical scientific computation Use quantile normalization to ensure that measurements fit a specific distribution Represent separate regions in an image with a Region Adjacency Graph Convert temporal or spatial data into frequency domain data with the Fast Fourier Transform Solve sparse matrix problems, including image segmentations, with SciPy’s sparse module Perform linear algebra by using SciPy packages Explore image alignment (registration) with SciPy’s optimize module Process large datasets with Python data streaming primitives and the Toolz library COMPUTERS,Languages,Python

Serious Python An indispensable collection of practical tips and real-world advice for tackling common Python problems and taking your code to the next level. Features interviews with high-profile Python developers who share their tips, tricks, best practices, and real-world advice gleaned from years of experience. Sharpen your Python skills as you dive deep into the Python programming language with Serious Python. You'll cover a range of advanced topics like multithreading and memorization, get advice from experts on things like designing APIs and dealing with databases, and learn Python internals to help you gain a deeper understanding of the language itself. Written for developers and experienced programmers, Serious Python brings together over 15 years of Python experience to teach you how to avoid common mistakes, write code more efficiently, and build better programs in less time. As you make your way through the book's extensive tutorials, you'll learn how to start a project and tackle topics like versioning, layouts, coding style, and automated checks. You'll learn how to package your software for distribution, optimize performance, use the right data structures, define functions efficiently, pick the right libraries, build future-proof programs, and optimize your programs down to the bytecode. You'll also learn how to: - Make and use effective decorators and methods, including abstract, static, and class methods- Employ Python for functional programming using generators, pure functions, and functional functions- Extend flake8 to work with the abstract syntax tree (AST) to introduce more sophisticated automatic checks into your programs- Apply dynamic performance analysis to identify bottlenecks in your code- Work with relational databases and effectively manage and stream data with PostgreSQL If you've been looking for a way to take your Python skills from good to great, Serious Python will help you get there. Learn from the experts and get seriously good at Python with Serious Python! COMPUTERS,Languages,Python

Learning Concurrency in Python Practically and deeply understand concurrency in Python to write efficient programs About This Book Build highly efficient, robust, and concurrent applications Work through practical examples that will help you address the challenges of writing concurrent code Improve the overall speed of execution in multiprocessor and multicore systems and keep them highly available Who This Book Is For This book is for Python developers who would like to get started with concurrent programming. Readers are expected to have a working knowledge of the Python language, as this book will build on these fundamentals concepts. What You Will Learn Explore the concept of threading and multiprocessing in Python Understand concurrency with threads Manage exceptions in child threads Handle the hardest part in a concurrent system — shared resources Build concurrent systems with Communicating Sequential Processes (CSP) Maintain all concurrent systems and master them Apply reactive programming to build concurrent systems Use GPU to solve specific problems In Detail Python is a very high level, general purpose language that is utilized heavily in fields such as data science and research, as well as being one of the top choices for general purpose programming for programmers around the world. It features a wide number of powerful, high and low-level libraries and frameworks that complement its delightful syntax and enable Python programmers to create. This book introduces some of the most popular libraries and frameworks and goes in-depth into how you can leverage these libraries for your own high-concurrent, highly-performant Python programs. We'll cover the fundamental concepts of concurrency needed to be able to write your own concurrent and parallel software systems in Python. The book will guide you down the path to mastering Python concurrency, giving you all the necessary hardware and theoretical knowledge. We'll cover concepts such as debugging and exception handling as well as some of the most popular libraries and frameworks that allow you to create event-driven and reactive systems. By the end of the book, you'll have learned the techniques to write incredibly efficient concurrent systems that follow best practices. Style and approach This easy-to-follow guide teaches you new practices and techniques to optimize your code, and then moves toward more advanced ways to effectively write efficient Python code. Small and simple practical examples will help you test the concepts yourself, and you will be able to easily adapt them for any application. COMPUTERS,Languages,Python

Learn More Python 3 the Hard Way Transform Your Ideas into High-Quality Python Code! Zed Shaw has perfected the world’s best system for becoming a truly effective Python 3.x developer. Follow it and you will succeed—just like the tens of millions of programmers he’s already taught. You bring the discipline, commitment, and persistence; the author supplies everything else. In Learn Python 3 the Hard Way, Zed Shaw taught you the basics of Programming with Python 3. Now, in Learn More Python 3 the Hard Way, you’ll go far beyond the basics by working through 52 brilliantly crafted projects. Each one helps you build a key practical skill, combining demos to get you started and challenges to deepen your understanding. Zed then teaches you even more in 12 hours of online videos, where he shows you how to break, fix, and debug your code. First, you’ll discover how to analyze a concept, idea, or problem to implement in software. Then, step by step, you’ll learn to design solutions based on your analyses and implement them as simply and elegantly as possible. Throughout, Shaw stresses process so you can get started and build momentum, creativity to solve new problems, and quality so you’ll build code people can rely on. Manage complex projects with a programmer’s text editor Leverage the immense power of data structures Apply algorithms to process your data structures Master indispensable text parsing and processing techniques Use SQL to efficiently and logically model stored data Learn powerful command-line tools and skills Combine multiple practices in complete projects It’ll be hard at first. But soon, you’ll just get it—and that will feel great! This course will reward you for every minute you put into it. Soon, you’ll go beyond merely writing code that runs: you’ll craft high-quality Python code that solves real problems. You’ll be a serious Python programmer. Perfect for Everyone Who’s Already Started Working with Python, including Junior Developers and Seasoned Python Programmers Upgrading to Python 3.6+ Register your product at informit.com/register for convenient access to downloads, updates, and/or corrections as they become available. COMPUTERS,Languages,Python

Python Without Fear Praise for this book, Python Without Fear “This is really a great book. I wish I’d had it when I was learning Python.†–John M. Wargo, author of Apache Cordova 4 Programming Praise for the previous book in the series, C++ Without Fear “I’m in love with your C++ Without Fear book. It keeps me awake for hours during the night. Thanks to you, I got most of the idea in just a few hours.†–Laura Viral, graduate physics student at CERN and Istanbul, Turkey “It’s hard to tell where I began and ended with your book. I felt like I woke up and literally knew how to write C++ code. I can’t overstate the confidence you gave me.†– Danny Grady, senior programmer/analyst at a Fortune 500 Company Whether you’re new to programming or moving from another language, Python Without Fear will quickly make you productive! Brian Overland’s unique approach to Python includes: Taking you by the hand while teaching topics from the very basics to intermediate and advanced features of Python Teaching by examples that are explained line by line Heavy emphasis on examples that are fun and useful, including games, graphics, database applications, file storage, puzzles, and more! How to think “Pythonically†and avoid common “gotchas†Register your product at informit.com/register for convenient access to downloads, updates, and/or corrections as they become available. COMPUTERS,Languages,Python

Programming with MicroPython It’s an exciting time to get involved with MicroPython, the re-implementation of Python 3 for microcontrollers and embedded systems. This practical guide delivers the knowledge you need to roll up your sleeves and create exceptional embedded projects with this lean and efficient programming language. If you’re familiar with Python as a programmer, educator, or maker, you’re ready to learn—and have fun along the way. Author Nicholas Tollervey takes you on a journey from first steps to advanced projects. You’ll explore the types of devices that run MicroPython, and examine how the language uses and interacts with hardware to process input, connect to the outside world, communicate wirelessly, make sounds and music, and drive robotics projects. Work with MicroPython on four typical devices: PyBoard, the micro:bit, Adafruit’s Circuit Playground Express, and ESP8266/ESP32 boards Explore a framework that helps you generate, evaluate, and evolve embedded projects that solve real problems Dive into practical MicroPython examples: visual feedback, input and sensing, GPIO, networking, sound and music, and robotics Learn how idiomatic MicroPython helps you express a lot with the minimum of resources Take the next step by getting involved with the Python community COMPUTERS,Languages,Python

Pandas for Everyone The Hands-On, Example-Rich Introduction to Pandas Data Analysis in Python Today, analysts must manage data characterized by extraordinary variety, velocity, and volume. Using the open source Pandas library, you can use Python to rapidly automate and perform virtually any data analysis task, no matter how large or complex. Pandas can help you ensure the veracity of your data, visualize it for effective decision-making, and reliably reproduce analyses across multiple datasets. Pandas for Everyone brings together practical knowledge and insight for solving real problems with Pandas, even if you’re new to Python data analysis. Daniel Y. Chen introduces key concepts through simple but practical examples, incrementally building on them to solve more difficult, real-world problems. Chen gives you a jumpstart on using Pandas with a realistic dataset and covers combining datasets, handling missing data, and structuring datasets for easier analysis and visualization. He demonstrates powerful data cleaning techniques, from basic string manipulation to applying functions simultaneously across dataframes. Once your data is ready, Chen guides you through fitting models for prediction, clustering, inference, and exploration. He provides tips on performance and scalability, and introduces you to the wider Python data analysis ecosystem. Work with DataFrames and Series, and import or export data Create plots with matplotlib, seaborn, and pandas Combine datasets and handle missing data Reshape, tidy, and clean datasets so they’re easier to work with Convert data types and manipulate text strings Apply functions to scale data manipulations Aggregate, transform, and filter large datasets with groupby Leverage Pandas’ advanced date and time capabilities Fit linear models using statsmodels and scikit-learn libraries Use generalized linear modeling to fit models with different response variables Compare multiple models to select the “best†Regularize to overcome overfitting and improve performance Use clustering in unsupervised machine learning COMPUTERS,Languages,Python

Impractical Python Projects Impractical Python Projects is a collection of fun and educational projects designed to entertain programmers while enhancing their Python skills. It picks up where the complete beginner books leave off, expanding on existing concepts and introducing new tools that you'll use every day. And to keep things interesting, each project includes a zany twist featuring historical incidents, pop culture references, and literary allusions. You'll flex your problem-solving skills and employ Python's many useful libraries to do things like:- Help James Bond crack a high-tech safe with a hill-climbing algorithm - Write haiku poems using Markov Chain Analysis- Use genetic algorithms to breed a race of gigantic rats- Crack the world's most successful military cipher using cryptanalysis- Derive the anagram, "I am Lord Voldemort" using linguistical sieves - Plan your parents' secure retirement with Monte Carlo simulation- Save the sorceress Zatanna from a stabby death using palingrams- Model the Milky Way and calculate our odds of detecting alien civilizations- Help the world's smartest woman win the Monty Hall problem argument- Reveal Jupiter's Great Red Spot using optical stacking- Save the head of Mary, Queen of Scots with steganography- Foil corporate security with invisible electronic ink Simulate volcanoes, map Mars, and more, all while gaining valuable experience using free modules like Tkinter, matplotlib, Cprofile, Pylint, Pygame, Pillow, and Python-Docx. Whether you're looking to pick up some new Python skills or just need a pick-me-up, you'll find endless educational, geeky fun with Impractical Python Projects. COMPUTERS,Languages,Python

Introduction to Python for Engineers and Scientists Familiarize yourself with the basics of Python for engineering and scientific computations using this concise, practical tutorial that is focused on writing code to learn concepts. Introduction to Python is useful for industry engineers, researchers, and students who are looking for open-source solutions for numerical computation. In this book you will learn by doing, avoiding technical jargon, which makes the concepts easy to learn. First you’ll see how to run basic calculations, absorbing technical complexities incrementally as you progress toward advanced topics. Throughout, the language is kept simple to ensure that readers at all levels can grasp the concepts. What You'll Learn Understand the fundamentals of the Python programming language Apply Python to numerical computational programming projects in engineering and science Discover the Pythonic way of life Apply data types, operators, and arrays Carry out plotting for visualization Work with functions and loops Who This Book Is For Engineers, scientists, researchers, and students who are new to Python. Some prior programming experience would be helpful but not required. COMPUTERS,Languages,Python

Head First Learn to Code What will you learn from this book? It’s no secret the world around you is becoming more connected, more configurable, more programmable, more computational. You can remain a passive participant, or you can learn to code. With Head First Learn to Code you’ll learn how to think computationally and how to write code to make your computer, mobile device, or anything with a CPU do things for you. Using the Python programming language, you’ll learn step by step the core concepts of programming as well as many fundamental topics from computer science, such as data structures, storage, abstraction, recursion, and modularity. Why does this book look so different? Based on the latest research in cognitive science and learning theory, Head First Learn to Code uses a visually rich format to engage your mind, rather than a text-heavy approach that puts you to sleep. Why waste your time struggling with new concepts? This multi-sensory learning experience is designed for the way your brain really works. COMPUTERS,Languages,Python

Practical Programming Classroom-tested by tens of thousands of students, this new edition of the bestselling intro to programming book is for anyone who wants to understand computer science. Learn about design, algorithms, testing, and debugging. Discover the fundamentals of programming with Python 3.6--a language that's used in millions of devices. Write programs to solve real-world problems, and come away with everything you need to produce quality code. This edition has been updated to use the new language features in Python 3.6. COMPUTERS,Languages,Python

Learn Data Analysis with Python Get started using Python in data analysis with this compact practical guide. This book includes three exercises and a case study on getting data in and out of Python code in the right format. Learn Data Analysis with Python also helps you discover meaning in the data using analysis and shows you how to visualize it. Each lesson is, as much as possible, self-contained to allow you to dip in and out of the examples as your needs dictate. If you are already using Python for data analysis, you will find a number of things that you wish you knew how to do in Python. You can then take these techniques and apply them directly to your own projects. If you aren’t using Python for data analysis, this book takes you through the basics at the beginning to give you a solid foundation in the topic. As you work your way through the book you will have a better of idea of how to use Python for data analysis when you are finished. What You Will Learn Get data into and out of Python code Prepare the data and its format Find the meaning of the data Visualize the data using iPython Who This Book Is For Those who want to learn data analysis using Python. Some experience with Python is recommended but not required, as is some prior experience with data analysis or data science. COMPUTERS,Languages,Python

Flask Web Development Take full creative control of your web applications with Flask, the Python-based microframework. With the second edition of this hands-on book, you’ll learn the framework from the ground up by developing, step-by-step, a real-world project created by author Miguel Grinberg. This refreshed edition accounts for important technology changes that have occurred in the past three years. You’ll learn the framework’s core functionality, as well as how to extend applications with advanced web techniques such as database migration and web service communication. The first part of each chapter provides you with reference and background for the topic in question, while the second part guides you though a hands-on implementation of the topic. If you have Python experience, this book shows you how to take advantage of the creative freedom Flask provides. COMPUTERS,Languages,Python

Python GUI Programming with Tkinter Find out how to create visually stunning and feature-rich applications by empowering Python's built-in Tkinter GUI toolkit About This Book Explore Tkinter's powerful features to easily design and customize your GUI application Learn the basics of 2D and 3D animation in GUI applications. Learn to integrate stunning Data Visualizations using Tkinter Canvas and Matplotlib. Who This Book Is For This book will appeal to developers and programmers who would like to build GUI-based applications. Knowledge of Python is a prerequisite. What You Will Learn Implement the tools provided by Tkinter to design beautiful GUIs Discover cross-platform development through minor customizations in your existing application Visualize graphs in real time as data comes in using Tkinter's animation capabilities Use PostgreSQL authentication to ensure data security for your application Write unit tests to avoid regressions when updating code In Detail Tkinter is a lightweight, portable, and easy-to-use graphical toolkit available in the Python Standard Library, widely used to build Python GUIs due to its simplicity and availability. This book teaches you to design and build graphical user interfaces that are functional, appealing, and user-friendly using the powerful combination of Python and Tkinter. After being introduced to Tkinter, you will be guided step-by-step through the application development process. Over the course of the book, your application will evolve from a simple data-entry form to a complex data management and visualization tool while maintaining a clean and robust design. In addition to building the GUI, you'll learn how to connect to external databases and network resources, test your code to avoid errors, and maximize performance using asynchronous programming. You'll make the most of Tkinter's cross-platform availability by learning how to maintain compatibility, mimic platform-native look and feel, and build executables for deployment across popular computing platforms. By the end of this book, you will have the skills and confidence to design and build powerful high-end GUI applications to solve real-world problems. Style and approach This is a comprehensive guide that explores the essential Tkinter features and modules and implements them in building real-world cross-platform GUI applications COMPUTERS,Languages,Python

Python Penetration Testing Essentials This book gives you the skills you need to use Python for penetration testing, with the help of detailed code examples. This book has been updated for Python 3.6.3 and Kali Linux 2018.1. About This Book Detect and avoid various attack types that put the privacy of a system at risk Leverage Python to build efficient code and eventually build a robust environment Learn about securing wireless applications and information gathering on a web server Who This Book Is For If you are a Python programmer, a security researcher, or an ethical hacker and are interested in penetration testing with the help of Python, then this book is for you. Even if you are new to the field of ethical hacking, this book can help you find the vulnerabilities in your system so that you are ready to tackle any kind of attack or intrusion. What You Will Learn The basics of network pentesting including network scanning and sniffing Wireless, wired attacks, and building traps for attack and torrent detection Web server footprinting and web application attacks, including the XSS and SQL injection attack Wireless frames and how to obtain information such as SSID, BSSID, and the channel number from a wireless frame using a Python script The importance of web server signatures, email gathering, and why knowing the server signature is the first step in hacking In Detail This book gives you the skills you need to use Python for penetration testing (pentesting), with the help of detailed code examples. We start by exploring the basics of networking with Python and then proceed to network hacking. Then, you will delve into exploring Python libraries to perform various types of pentesting and ethical hacking techniques. Next, we delve into hacking the application layer, where we start by gathering information from a website. We then move on to concepts related to website hacking—such as parameter tampering, DDoS, XSS, and SQL injection. By reading this book, you will learn different techniques and methodologies that will familiarize you with Python pentesting techniques, how to protect yourself, and how to create automated programs to find the admin console, SQL injection, and XSS attacks. Style and approach The book starts at a basic level and moves to a higher level of network and web security. The execution and performance of code are both taken into account. COMPUTERS,Languages,Python

Django 2 by Example Learn Django 2.0 with four end-to-end projects About This Book Learn Django by building real-world web applications from scratch Develop powerful web applications quickly using the best coding practices Integrate other technologies into your application with clear, step-by-step explanations and comprehensive example code Who This Book Is For If you are a web developer who wants to see how to build professional sites with Django, this book is for you. You will need a basic knowledge of Python, HTML, and JavaScript, but you don't need to have worked with Django before. What You Will Learn Build practical, real-world web applications with Django Use Django with other technologies, such as Redis and Celery Develop pluggable Django applications Create advanced features, optimize your code, and use the cache framework Add internationalization to your Django projects Enhance your user experience using JavaScript and AJAX Add social features to your projects Build RESTful APIs for your applications In Detail If you want to learn about the entire process of developing professional web applications with Django, then this book is for you. This book will walk you through the creation of four professional Django projects, teaching you how to solve common problems and implement best practices. You will learn how to build a blog application, a social image-bookmarking website, an online shop, and an e-learning platform. The book will teach you how to enhance your applications with AJAX, create RESTful APIs, and set up a production environment for your Django projects. The book walks you through the creation of real-world applications, while solving common problems and implementing best practices. By the end of this book, you will have a deep understanding of Django and how to build advanced web applications Style and approach This easy-to-follow guide takes you through the process of building four different production-ready Django projects with a simple step-by-step approach. COMPUTERS,Languages,Python

Learn Python Programming Learn the fundamentals of Python (3.7) and how to apply it to data science, programming, and web development. Fully updated to include hands-on tutorials and projects. Key Features Learn the fundamentals of Python programming with interactive projects Apply Python to data science with tools such as IPython and Jupyter Utilize Python for web development and build a real-world app using Django Book Description Learn Python Programming is a quick, thorough, and practical introduction to Python - an extremely flexible and powerful programming language that can be applied to many disciplines. Unlike other books, it doesn't bore you with elaborate explanations of the basics but gets you up-and-running, using the language. You will begin by learning the fundamentals of Python so that you have a rock-solid foundation to build upon. You will explore the foundations of Python programming and learn how Python can be manipulated to achieve results. Explore different programming paradigms and find the best approach to a situation; understand how to carry out performance optimization and effective debugging; control the flow of a program; and utilize an interchange format to exchange data. You'll also walk through cryptographic services in Python and understand secure tokens. Learn Python Programming will give you a thorough understanding of the Python language. You'll learn how to write programs, build websites, and work with data by harnessing Python's renowned data science libraries. Filled with real-world examples and projects, the book covers various types of applications, and concludes by building real-world projects based on the concepts you have learned. What you will learn Get Python up and running on Windows, Mac, and Linux Explore fundamental concepts of coding using data structures and control flow Write elegant, reusable, and efficient code in any situation Understand when to use the functional or OOP approach Cover the basics of security and concurrent/asynchronous programming Create bulletproof, reliable software by writing tests Build a simple website in Django Fetch, clean, and manipulate data Who this book is for Learn Python Programming is for individuals with relatively little experience in coding or Python. It's also ideal for aspiring programmers who need to write scripts or programs to accomplish tasks. The book shows you how to create a full-fledged application. COMPUTERS,Languages,Python

Think Complexity Complexity science uses computation to explore the physical and social sciences. In Think Complexity, you’ll use graphs, cellular automata, and agent-based models to study topics in physics, biology, and economics. Whether you’re an intermediate-level Python programmer or a student of computational modeling, you’ll delve into examples of complex systems through a series of worked examples, exercises, case studies, and easy-to-understand explanations. In this updated second edition, you will: Work with NumPy arrays and SciPy methods, including basic signal processing and Fast Fourier Transform Study abstract models of complex physical systems, including power laws, fractals and pink noise, and Turing machines Get Jupyter notebooks filled with starter code and solutions to help you re-implement and extend original experiments in complexity; and models of computation like Turmites, Turing machines, and cellular automata Explore the philosophy of science, including the nature of scientific laws, theory choice, and realism and instrumentalism Ideal as a text for a course on computational modeling in Python, Think Complexity also helps self-learners gain valuable experience with topics and ideas they might not encounter otherwise. COMPUTERS,Languages,Python

Qt5 Python GUI Programming Cookbook Over 60 recipes to help you design interactive, smart, and cross-platform GUI applications Key Features Get succinct QT solutions to pressing GUI programming problems in Python Learn how to effectively implement reactive programming Build customized applications that are robust and reliable Book Description PyQt is one of the best cross-platform interface toolkits currently available; it's stable, mature, and completely native. If you want control over all aspects of UI elements, PyQt is what you need. This book will guide you through every concept necessary to create fully functional GUI applications using PyQt, with only a few lines of code. As you expand your GUI using more widgets, you will cover networks, databases, and graphical libraries that greatly enhance its functionality. Next, the book guides you in using Qt Designer to design user interfaces and implementing and testing dialogs, events, the clipboard, and drag and drop functionality to customize your GUI. You will learn a variety of topics, such as look and feel customization, GUI animation, graphics rendering, implementing Google Maps, and more. Lastly, the book takes you through how Qt5 can help you to create cross-platform apps that are compatible with Android and iOS. You will be able to develop functional and appealing software using PyQt through interesting and fun recipes that will expand your knowledge of GUIs What you will learn Use basic Qt components, such as a radio button, combo box, and sliders Use QSpinBox and sliders to handle different signals generated on mouse clicks Work with different Qt layouts to meet user interface requirements Create custom widgets and set up customizations in your GUI Perform asynchronous I/O operations and thread handling in the Python GUI Employ network concepts, internet browsing, and Google Maps in UI Use graphics rendering and implement animation in your GUI Make your GUI application compatible with Android and iOS devices Who this book is for If you're an intermediate Python programmer wishing to enhance your coding skills by writing powerful GUIs in Python using PyQT, this is the book for you. COMPUTERS,Languages,Python

Clean Code in Python Getting the most out of Python to improve your codebase Key Features Save maintenance costs by learning to fix your legacy codebase Learn the principles and techniques of refactoring Apply microservices to your legacy systems by implementing practical techniques Book Description Python is currently used in many different areas such as software construction, systems administration, and data processing. In all of these areas, experienced professionals can find examples of inefficiency, problems, and other perils, as a result of bad code. After reading this book, readers will understand these problems, and more importantly, how to correct them. The book begins by describing the basic elements of writing clean code and how it plays an important role in Python programming. You will learn about writing efficient and readable code using the Python standard library and best practices for software design. You will learn to implement the SOLID principles in Python and use decorators to improve your code. The book delves more deeply into object oriented programming in Python and shows you how to use objects with descriptors and generators. It will also show you the design principles of software testing and how to resolve software problems by implementing design patterns in your code. In the final chapter we break down a monolithic application to a microservice one, starting from the code as the basis for a solid platform. By the end of the book, you will be proficient in applying industry approved coding practices to design clean, sustainable and readable Python code. What you will learn Set up tools to effectively work in a development environment Explore how the magic methods of Python can help us write better code Examine the traits of Python to create advanced object-oriented design Understand removal of duplicated code using decorators and descriptors Effectively refactor code with the help of unit tests Learn to implement the SOLID principles in Python Who this book is for This book will appeal to team leads, software architects and senior software engineers who would like to work on their legacy systems to save cost and improve efficiency. A strong understanding of Programming is assumed. COMPUTERS,Languages,Python

Python Crash Course, 2nd Edition Second edition of the best-selling Python book in the world. A fast-paced, no-nonsense guide to programming in Python. Updated and thoroughly revised to reflect the latest in Python code and practices. Python Crash Course is the world's best-selling guide to the Python programming language. This fast-paced, thorough introduction to programming with Python will have you writing programs, solving problems, and making things that work in no time. In the first half of the book, you'll learn basic programming concepts, such as variables, lists, classes, and loops, and practice writing clean code with exercises for each topic. You'll also learn how to make your programs interactive and test your code safely before adding it to a project. In the second half, you'll put your new knowledge into practice with three substantial projects: a Space Invaders-inspired arcade game, a set of data visualizations with Python's handy libraries, and a simple web app you can deploy online. As you work through the book, you'll learn how to: • Use powerful Python libraries and tools, including Pygame, Matplotlib, Plotly, and Django • Make 2D games that respond to keypresses and mouse clicks, and that increase in difficulty • Use data to generate interactive visualizations • Create and customize web apps and deploy them safely online • Deal with mistakes and errors so you can solve your own programming problems If you've been thinking about digging into programming, Python Crash Course will get you writing real programs fast. Why wait any longer? Start your engines and code! COMPUTERS,Languages,Python

Mastering Exploratory Analysis with pandas Explore Python frameworks like pandas, Jupyter notebooks, and Matplotlib to build data pipelines and data visualization Key Features Learn to set up data analysis pipelines with pandas and Jupyter notebooks Effective techniques for data selection, manipulation, and visualization Introduction to Matplotlib for interactive data visualization using charts and plots Book Description The pandas is a Python library that lets you manipulate, transform, and analyze data. It is a popular framework for exploratory data visualization and analyzing datasets and data pipelines based on their properties. This book will be your practical guide to exploring datasets using pandas. You will start by setting up Python, pandas, and Jupyter Notebooks. You will learn how to use Jupyter Notebooks to run Python code. We then show you how to get data into pandas and do some exploratory analysis, before learning how to manipulate and reshape data using pandas methods. You will also learn how to deal with missing data from your datasets, how to draw charts and plots using pandas and Matplotlib, and how to create some effective visualizations for your audience. Finally, you will wrapup your newly gained pandas knowledge by learning how to import data out of pandas into some popular file formats. By the end of this book, you will have a better understanding of exploratory analysis and how to build exploratory data pipelines with Python. What you will learn Learn how to read different kinds of data into pandas DataFrames for data analysis Manipulate, transform, and apply formulas to data imported into pandas DataFrames Use pandas to analyze and visualize different kinds of data to gain real-world insights Extract transformed data form pandas DataFrames and convert it into the formats your application expects Manipulate model time-series data, perform algorithmic trading, derive results on fixed and moving windows, and more Effective data visualization using Matplotlib Who this book is for If you are a budding data scientist looking to learn the popular pandas library, or a Python developer looking to step into the world of data analysis, this book is the ideal resource you need to get started. Some programming experience in Python will be helpful to get the most out of this course COMPUTERS,Languages,Python

Hands-On GPU Programming with Python and CUDA Build real-world applications with Python 2.7, CUDA 9, and CUDA 10. We suggest the use of Python 2.7 over Python 3.x, since Python 2.7 has stable support across all the libraries we use in this book. Key Features Expand your background in GPU programming—PyCUDA, scikit-cuda, and Nsight Effectively use CUDA libraries such as cuBLAS, cuFFT, and cuSolver Apply GPU programming to modern data science applications Book Description Hands-On GPU Programming with Python and CUDA hits the ground running: you'll start by learning how to apply Amdahl's Law, use a code profiler to identify bottlenecks in your Python code, and set up an appropriate GPU programming environment. You'll then see how to “query†the GPU's features and copy arrays of data to and from the GPU's own memory. As you make your way through the book, you'll launch code directly onto the GPU and write full blown GPU kernels and device functions in CUDA C. You'll get to grips with profiling GPU code effectively and fully test and debug your code using Nsight IDE. Next, you'll explore some of the more well-known NVIDIA libraries, such as cuFFT and cuBLAS. With a solid background in place, you will now apply your new-found knowledge to develop your very own GPU-based deep neural network from scratch. You'll then explore advanced topics, such as warp shuffling, dynamic parallelism, and PTX assembly. In the final chapter, you'll see some topics and applications related to GPU programming that you may wish to pursue, including AI, graphics, and blockchain. By the end of this book, you will be able to apply GPU programming to problems related to data science and high-performance computing. What you will learn Launch GPU code directly from Python Write effective and efficient GPU kernels and device functions Use libraries such as cuFFT, cuBLAS, and cuSolver Debug and profile your code with Nsight and Visual Profiler Apply GPU programming to datascience problems Build a GPU-based deep neuralnetwork from scratch Explore advanced GPU hardware features, such as warp shuffling Who this book is for Hands-On GPU Programming with Python and CUDA is for developers and data scientists who want to learn the basics of effective GPU programming to improve performance using Python code. You should have an understanding of first-year college or university-level engineering mathematics and physics, and have some experience with Python as well as in any C-based programming language such as C, C++, Go, or Java. COMPUTERS,Languages,Python

Python for Finance The financial industry has recently adopted Python at a tremendous rate, with some of the largest investment banks and hedge funds using it to build core trading and risk management systems. Updated for Python 3, the second edition of this hands-on book helps you get started with the language, guiding developers and quantitative analysts through Python libraries and tools for building financial applications and interactive financial analytics. Using practical examples throughout the book, author Yves Hilpisch also shows you how to develop a full-fledged framework for Monte Carlo simulation-based derivatives and risk analytics, based on a large, realistic case study. Much of the book uses interactive IPython Notebooks. COMPUTERS,Languages,Python

Bayesian Analysis with Python Bayesian modeling with PyMC3 and exploratory analysis of Bayesian models with ArviZ Key Features A step-by-step guide to conduct Bayesian data analyses using PyMC3 and ArviZ A modern, practical and computational approach to Bayesian statistical modeling A tutorial for Bayesian analysis and best practices with the help of sample problems and practice exercises. Book Description The second edition of Bayesian Analysis with Python is an introduction to the main concepts of applied Bayesian inference and its practical implementation in Python using PyMC3, a state-of-the-art probabilistic programming library, and ArviZ, a new library for exploratory analysis of Bayesian models. The main concepts of Bayesian statistics are covered using a practical and computational approach. Synthetic and real data sets are used to introduce several types of models, such as generalized linear models for regression and classification, mixture models, hierarchical models, and Gaussian processes, among others. By the end of the book, you will have a working knowledge of probabilistic modeling and you will be able to design and implement Bayesian models for your own data science problems. After reading the book you will be better prepared to delve into more advanced material or specialized statistical modeling if you need to. What you will learn Build probabilistic models using the Python library PyMC3 Analyze probabilistic models with the help of ArviZ Acquire the skills required to sanity check models and modify them if necessary Understand the advantages and caveats of hierarchical models Find out how different models can be used to answer different data analysis questions Compare models and choose between alternative ones Discover how different models are unified from a probabilistic perspective Think probabilistically and benefit from the flexibility of the Bayesian framework Who this book is for If you are a student, data scientist, researcher, or a developer looking to get started with Bayesian data analysis and probabilistic programming, this book is for you. The book is introductory so no previous statistical knowledge is required, although some experience in using Python and NumPy is expected. COMPUTERS,Languages,Python

Hands-On Predictive Analytics with Python Step-by-step guide to build high performing predictive applications Key Features Use the Python data analytics ecosystem to implement end-to-end predictive analytics projects Explore advanced predictive modeling algorithms with an emphasis on theory with intuitive explanations Learn to deploy a predictive model's results as an interactive application Book Description Predictive analytics is an applied field that employs a variety of quantitative methods using data to make predictions. It involves much more than just throwing data onto a computer to build a model. This book provides practical coverage to help you understand the most important concepts of predictive analytics. Using practical, step-by-step examples, we build predictive analytics solutions while using cutting-edge Python tools and packages. The book's step-by-step approach starts by defining the problem and moves on to identifying relevant data. We will also be performing data preparation, exploring and visualizing relationships, building models, tuning, evaluating, and deploying model. Each stage has relevant practical examples and efficient Python code. You will work with models such as KNN, Random Forests, and neural networks using the most important libraries in Python's data science stack: NumPy, Pandas, Matplotlib, Seaborn, Keras, Dash, and so on. In addition to hands-on code examples, you will find intuitive explanations of the inner workings of the main techniques and algorithms used in predictive analytics. By the end of this book, you will be all set to build high-performance predictive analytics solutions using Python programming. What you will learn Get to grips with the main concepts and principles of predictive analytics Learn about the stages involved in producing complete predictive analytics solutions Understand how to define a problem, propose a solution, and prepare a dataset Use visualizations to explore relationships and gain insights into the dataset Learn to build regression and classification models using scikit-learn Use Keras to build powerful neural network models that produce accurate predictions Learn to serve a model's predictions as a web application Who this book is for This book is for data analysts, data scientists, data engineers, and Python developers who want to learn about predictive modeling and would like to implement predictive analytics solutions using Python's data stack. People from other backgrounds who would like to enter this exciting field will greatly benefit from reading this book. All you need is to be proficient in Python programming and have a basic understanding of statistics and college-level algebra. COMPUTERS,Languages,Python

Mastering Ansible Design, develop, and solve real-world automation and orchestration problems by unlocking the automation capabilities of Ansible. Key Features Tackle complex automation challenges with the newly added features in Ansible 2.7 Book Description Automation is essential for success in the modern world of DevOps. Ansible provides a simple, yet powerful, automation engine for tackling complex automation challenges. This book will take you on a journey that will help you exploit the latest version's advanced features to help you increase efficiency and accomplish complex orchestrations. This book will help you understand how Ansible 2.7 works at a fundamental level and will also teach you to leverage its advanced capabilities. Throughout this book, you will learn how to encrypt Ansible content at rest and decrypt data at runtime. Next, this book will act as an ideal resource to help you master the advanced features and capabilities required to tackle complex automation challenges. Later, it will walk you through workflows, use cases, orchestrations, troubleshooting, and Ansible extensions. Lastly, you will examine and debug Ansible operations, helping you to understand and resolve issues. By the end of the book, you will be able to unlock the true power of the Ansible automation engine and tackle complex, real- world actions with ease. What you will learn Gain an in-depth understanding of how Ansible works under the hood Fully automate Ansible playbook executions with encrypted data Access and manipulate variable data within playbooks Use blocks to perform failure recovery or cleanup Explore the Playbook debugger and the Ansible Console Troubleshoot unexpected behavior effectively Work with cloud infrastructure providers and container systems Develop custom modules, plugins, and dynamic inventory sources Who this book is for This book is for Ansible developers and operators who have an understanding of its core elements and applications but are now looking to enhance their skills in applying automation using Ansible. COMPUTERS,Languages,Python

Data Science for Marketing Analytics Explore new and more sophisticated tools that reduce your marketing analytics efforts and give you precise results Key Features Study new techniques for marketing analytics Explore uses of machine learning to power your marketing analyses Work through each stage of data analytics with the help of multiple examples and exercises Book Description Data Science for Marketing Analytics covers every stage of data analytics, from working with a raw dataset to segmenting a population and modeling different parts of the population based on the segments. The book starts by teaching you how to use Python libraries, such as pandas and Matplotlib, to read data from Python, manipulate it, and create plots, using both categorical and continuous variables. Then, you'll learn how to segment a population into groups and use different clustering techniques to evaluate customer segmentation. As you make your way through the chapters, you'll explore ways to evaluate and select the best segmentation approach, and go on to create a linear regression model on customer value data to predict lifetime value. In the concluding chapters, you'll gain an understanding of regression techniques and tools for evaluating regression models, and explore ways to predict customer choice using classification algorithms. Finally, you'll apply these techniques to create a churn model for modeling customer product choices. By the end of this book, you will be able to build your own marketing reporting and interactive dashboard solutions. What you will learn Analyze and visualize data in Python using pandas and Matplotlib Study clustering techniques, such as hierarchical and k-means clustering Create customer segments based on manipulated data Predict customer lifetime value using linear regression Use classification algorithms to understand customer choice Optimize classification algorithms to extract maximal information Who this book is for Data Science for Marketing Analytics is designed for developers and marketing analysts looking to use new, more sophisticated tools in their marketing analytics efforts. It'll help if you have prior experience of coding in Python and knowledge of high school level mathematics. Some experience with databases, Excel, statistics, or Tableau is useful but not necessary. COMPUTERS,Languages,Python

Big Data Analysis with Python Get to grips with processing large volumes of data and presenting it as engaging, interactive insights using Spark and Python. Key Features Get a hands-on, fast-paced introduction to the Python data science stack Explore ways to create useful metrics and statistics from large datasets Create detailed analysis reports with real-world data Book Description Processing big data in real time is challenging due to scalability, information inconsistency, and fault tolerance. Big Data Analysis with Python teaches you how to use tools that can control this data avalanche for you. With this book, you'll learn practical techniques to aggregate data into useful dimensions for posterior analysis, extract statistical measurements, and transform datasets into features for other systems. The book begins with an introduction to data manipulation in Python using pandas. You'll then get familiar with statistical analysis and plotting techniques. With multiple hands-on activities in store, you'll be able to analyze data that is distributed on several computers by using Dask. As you progress, you'll study how to aggregate data for plots when the entire data cannot be accommodated in memory. You'll also explore Hadoop (HDFS and YARN), which will help you tackle larger datasets. The book also covers Spark and explains how it interacts with other tools. By the end of this book, you'll be able to bootstrap your own Python environment, process large files, and manipulate data to generate statistics, metrics, and graphs. What you will learn Use Python to read and transform data into different formats Generate basic statistics and metrics using data on disk Work with computing tasks distributed over a cluster Convert data from various sources into storage or querying formats Prepare data for statistical analysis, visualization, and machine learning Present data in the form of effective visuals Who this book is for Big Data Analysis with Python is designed for Python developers, data analysts, and data scientists who want to get hands-on with methods to control data and transform it into impactful insights. Basic knowledge of statistical measurements and relational databases will help you to understand various concepts explained in this book. COMPUTERS,Languages,Python

Python All-in-One For Dummies Your one-stop resource on all things Python Thanks to its flexibility, Python has grown to become one of the most popular programming languages in the world. Developers use Python in app development, web development, data science, machine learning, and even in coding education classes. There's almost no type of project that Python can't make better. From creating apps to building complex websites to sorting big data, Python provides a way to get the work done. Python All-in-One For Dummies offers a starting point for those new to coding by explaining the basics of Python and demonstrating how it’s used in a variety of applications. Covers the basics of the language Explains its syntax through application in high-profile industries Shows how Python can be applied to projects in enterprise Delves into major undertakings including artificial intelligence, physical computing, machine learning, robotics and data analysis This book is perfect for anyone new to coding as well as experienced coders interested in adding Python to their toolbox. COMPUTERS,Languages,Python

Odoo 12 Development Cookbook Build customized solutions for your business using the latest features of Odoo 12 and Python Key Features Get up to speed with Odoo 12 to create custom and reusable modules Interconnect your application with other systems by implementing web APIs Understand the mechanisms powering the Odoo framework and Odoo.sh to build robust enterprises Book Description Odoo is a powerful framework known for rapid application development. Its latest release, Odoo 12, introduces tons of new features. With this book, you'll learn how to develop powerful Odoo applications from scratch, using all the latest features. This Odoo cookbook starts by covering Odoo installation and deployment on the server. Next, you'll explore the Odoo framework with real-world examples. You'll create a new Odoo module from the ground up and progress to advanced framework concepts. You'll also learn how to modify existing applications, including Point of Sale (POS). This book is not just limited to backend development; the advanced JavaScript recipes for creating new views and widgets will help you build beautiful UI elements. As you move forward, you'll gain insights into website development and become a quality Odoo developer by studying performance optimization, debugging, and automated tests. Finally, you'll learn the latest concepts like multi-website, In-App Purchasing (IAP), Odoo.sh, and IoT Box. By the end of the book, you'll have all the knowledge you need to build powerful Odoo applications. The development best practices used in this book will undoubtedly come handy when you are working with the Odoo framework. What you will learn Develop a module in the Odoo framework and modify the existing flow of any application Build dynamic websites with Odoo CMS Create and modify backend JavaScript components in Odoo and POS Connect and access any object in Odoo via Remote Procedure Calls (RPC) Illustrate the different tools available in Odoo to implement business processes for your records Implement in-app purchase services Manage, deploy, and test an Odoo instance with the PaaS Odoo.sh Configure IoT Box to add and upgrade Point of Sale (POS) hardware Who this book is for If you're a Python developer who wants to develop highly efficient business applications with the latest Odoo framework, or if you just want a solution guide for all your Odoo development issues, this book is for you. Some JavaScript programming and web development experience is necessary to get the most out of this book. COMPUTERS,Languages,Python

Data Science Projects with Python Gain hands-on experience with industry-standard data analysis and machine learning tools in Python Key Features Tackle data science problems by identifying the problem to be solved Illustrate patterns in data using appropriate visualizations Implement suitable machine learning algorithms to gain insights from data Book Description Data Science Projects with Python is designed to give you practical guidance on industry-standard data analysis and machine learning tools, by applying them to realistic data problems. You will learn how to use pandas and Matplotlib to critically examine datasets with summary statistics and graphs, and extract the insights you seek to derive. You will build your knowledge as you prepare data using the scikit-learn package and feed it to machine learning algorithms such as regularized logistic regression and random forest. You'll discover how to tune algorithms to provide the most accurate predictions on new and unseen data. As you progress, you'll gain insights into the working and output of these algorithms, building your understanding of both the predictive capabilities of the models and why they make these predictions. By then end of this book, you will have the necessary skills to confidently use machine learning algorithms to perform detailed data analysis and extract meaningful insights from unstructured data. What you will learn Install the required packages to set up a data science coding environment Load data into a Jupyter notebook running Python Use Matplotlib to create data visualizations Fit machine learning models using scikit-learn Use lasso and ridge regression to regularize your models Compare performance between models to find the best outcomes Use k-fold cross-validation to select model hyperparameters Who this book is for If you are a data analyst, data scientist, or business analyst who wants to get started using Python and machine learning techniques to analyze data and predict outcomes, this book is for you. Basic knowledge of Python and data analytics will help you get the most from this book. Familiarity with mathematical concepts such as algebra and basic statistics will also be useful. COMPUTERS,Languages,Python

MicroPython Cookbook Learn how you can control LEDs, make music, and read sensor data using popular microcontrollers such as Adafruit Circuit Playground, ESP8266, and the BBC micro:bit Key Features Load and execute your first program with MicroPython Program an IoT device to retrieve weather data using a RESTful API Get to grips with integrating hardware, programming, and networking concepts with MicroPython Book Description MicroPython is an open source implementation of Python 3 that runs in embedded environments. With MicroPython, you can write clean and simple Python code to control hardware instead of using complex low-level languages like C and C++. This book guides you through all the major applications of the MicroPython platform to build and program projects that use microcontrollers. The MicroPython book covers recipes that'll help you experiment with the programming environment and hardware programmed in MicroPython. You'll find tips and techniques for building a variety of objects and prototypes that can sense and respond to touch, sound, position, heat, and light. This book will take you through the uses of MicroPython with a variety of popular input devices and sensors. You'll learn techniques for handling time delays and sensor readings, and apply advanced coding techniques to create complex projects. As you advance, you'll get to deal with Internet of Things (IoT) devices and integration with other online web services. Furthermore, you'll also use MicroPython to make music with bananas and create portable multiplayer video games that incorporate sound and light animations into the game play. By the end of the book, you'll have mastered tips and tricks to troubleshoot your development problems and push your MicroPython project to the next level! What you will learn Execute code without any need for compiling or uploading using REPL (read-evaluate-print-loop) Program and control LED matrix and NeoPixel drivers to display patterns and colors Build projects that make use of light, temperature, and touch sensors Configure devices to create Wi-Fi access points and use network modules to scan and connect to existing networks Use Pulse Width Modulation to control DC motors and servos Build an IoT device to display live weather data from the Internet at the touch of a button Who this book is for If you want to build and program projects that use microcontrollers, this book will offer you dozens of recipes to guide you through all the major applications of the MicroPython platform. Although no knowledge of MicroPython or microcontrollers is expected, a general understanding of Python is necessary to get started with this book. COMPUTERS,Languages,Python

DevOps in Python Explore and apply best practices for efficient application deployment. This book draws upon author Moshe Zadka's years of Dev Ops experience and focuses on the parts of Python, and the Python ecosystem, that are relevant for DevOps engineers. You'll start by writing command-line scripts and automating simple DevOps-style tasks. You'll then move on to more advanced cases, like using Jupyter as an auditable remote-control panel, and writing Ansible and Salt extensions. This work also covers how to use the AWS API to manage cloud infrastructure, and how to manage Python programs and environments on remote machines. Python was invented as a systems management language for distributed operating systems, which makes it an ideal tool for DevOps. ​Assuming a basic understanding of Python concepts, this book is perfect for engineers who want to move from operations/system administration into coding. What You'll Learn Use third party packages and create new packages Create operating system management and automation code in Python Write testable code, and testing best practices Work with REST APIs for web clients Who This Book Is For Junior or intermediate sysadmin who has picked up some bash and Python basics. COMPUTERS,Languages,Python

Data Wrangling with Python Simplify your ETL processes with these hands-on data hygiene tips, tricks, and best practices. Key Features Focus on the basics of data wrangling Study various ways to extract the most out of your data in less time Boost your learning curve with bonus topics like random data generation and data integrity checks Book Description For data to be useful and meaningful, it must be curated and refined. Data Wrangling with Python teaches you the core ideas behind these processes and equips you with knowledge of the most popular tools and techniques in the domain. The book starts with the absolute basics of Python, focusing mainly on data structures. It then delves into the fundamental tools of data wrangling like NumPy and Pandas libraries. You'll explore useful insights into why you should stay away from traditional ways of data cleaning, as done in other languages, and take advantage of the specialized pre-built routines in Python. This combination of Python tips and tricks will also demonstrate how to use the same Python backend and extract/transform data from an array of sources including the Internet, large database vaults, and Excel financial tables. To help you prepare for more challenging scenarios, you'll cover how to handle missing or wrong data, and reformat it based on the requirements from the downstream analytics tool. The book will further help you grasp concepts through real-world examples and datasets. By the end of this book, you will be confident in using a diverse array of sources to extract, clean, transform, and format your data efficiently. What you will learn Use and manipulate complex and simple data structures Harness the full potential of DataFrames and numpy.array at run time Perform web scraping with BeautifulSoup4 and html5lib Execute advanced string search and manipulation with RegEX Handle outliers and perform data imputation with Pandas Use descriptive statistics and plotting techniques Practice data wrangling and modeling using data generation techniques Who this book is for Data Wrangling with Python is designed for developers, data analysts, and business analysts who are keen to pursue a career as a full-fledged data scientist or analytics expert. Although, this book is for beginners, prior working knowledge of Python is necessary to easily grasp the concepts covered here. It will also help to have rudimentary knowledge of relational database and SQL. COMPUTERS,Languages,Python

Python Network Programming Power up your network applications with Python programming Key Features Master Python skills to develop powerful network applications Grasp the fundamentals and functionalities of SDN Design multi-threaded, event-driven architectures for echo and chat servers Book Description This Learning Path highlights major aspects of Python network programming such as writing simple networking clients, creating and deploying SDN and NFV systems, and extending your network with Mininet. You'll also learn how to automate legacy and the latest network devices. As you progress through the chapters, you'll use Python for DevOps and open source tools to test, secure, and analyze your network. Toward the end, you'll develop client-side applications, such as web API clients, email clients, SSH, and FTP, using socket programming. By the end of this Learning Path, you will have learned how to analyze a network's security vulnerabilities using advanced network packet capture and analysis techniques. This Learning Path includes content from the following Packt products: Practical Network Automation by Abhishek Ratan Mastering Python Networking by Eric Chou Python Network Programming Cookbook, Second Edition by Pradeeban Kathiravelu, Dr. M. O. Faruque Sarker What you will learn Create socket-based networks with asynchronous models Develop client apps for web APIs, including S3 Amazon and Twitter Talk to email and remote network servers with different protocols Integrate Python with Cisco, Juniper, and Arista eAPI for automation Use Telnet and SSH connections for remote system monitoring Interact with websites via XML-RPC, SOAP, and REST APIs Build networks with Ryu, OpenDaylight, Floodlight, ONOS, and POX Configure virtual networks in different deployment environments Who this book is for If you are a Python developer or a system administrator who wants to start network programming, this Learning Path gets you a step closer to your goal. IT professionals and DevOps engineers who are new to managing network devices or those with minimal experience looking to expand their knowledge and skills in Python will also find this Learning Path useful. Although prior knowledge of networking is not required, some experience in Python programming will be helpful for a better understanding of the concepts in the Learning Path. COMPUTERS,Languages,Python

Automate the Boring Stuff with Python, 2nd Edition The second edition of this best-selling Python book (100,000+ copies sold in print alone) uses Python 3 to teach even the technically uninclined how to write programs that do in minutes what would take hours to do by hand. There is no prior programming experience required and the book is loved by liberal arts majors and geeks alike. If you've ever spent hours renaming files or updating hundreds of spreadsheet cells, you know how tedious tasks like these can be. But what if you could have your computer do them for you? In this fully revised second edition of the best-selling classic Automate the Boring Stuff with Python, you'll learn how to use Python to write programs that do in minutes what would take you hours to do by hand--no prior programming experience required. You'll learn the basics of Python and explore Python's rich library of modules for performing specific tasks, like scraping data off websites, reading PDF and Word documents, and automating clicking and typing tasks. The second edition of this international fan favorite includes a brand-new chapter on input validation, as well as tutorials on automating Gmail and Google Sheets, plus tips on automatically updating CSV files. You'll learn how to create programs that effortlessly perform useful feats of automation to: • Search for text in a file or across multiple files • Create, update, move, and rename files and folders • Search the Web and download online content • Update and format data in Excel spreadsheets of any size • Split, merge, watermark, and encrypt PDFs • Send email responses and text notifications • Fill out online forms Step-by-step instructions walk you through each program, and updated practice projects at the end of each chapter challenge you to improve those programs and use your newfound skills to automate similar tasks. Don't spend your time doing work a well-trained monkey could do. Even if you've never written a line of code, you can make your computer do the grunt work. Learn how in Automate the Boring Stuff with Python, 2nd Edition. COMPUTERS,Languages,Python

Effective Python Updated and Expanded for Python 3 It’s easy to start developing programs with Python, which is why the language is so popular. However, Python’s unique strengths, charms, and expressiveness can be hard to grasp, and there are hidden pitfalls that can easily trip you up. This second edition of Effective Python will help you master a truly “Pythonic†approach to programming, harnessing Python’s full power to write exceptionally robust and well-performing code. Using the concise, scenario-driven style pioneered in Scott Meyers’ best-selling Effective C++, Brett Slatkin brings together 90 Python best practices, tips, and shortcuts, and explains them with realistic code examples so that you can embrace Python with confidence. Drawing on years of experience building Python infrastructure at Google, Slatkin uncovers little-known quirks and idioms that powerfully impact code behavior and performance. You’ll understand the best way to accomplish key tasks so you can write code that’s easier to understand, maintain, and improve. In addition to even more advice, this new edition substantially revises all items from the first edition to reflect how best practices have evolved. Key features include 30 new actionable guidelines for all major areas of Python Detailed explanations and examples of statements, expressions, and built-in types Best practices for writing functions that clarify intention, promote reuse, and avoid bugs Better techniques and idioms for using comprehensions and generator functions Coverage of how to accurately express behaviors with classes and interfaces Guidance on how to avoid pitfalls with metaclasses and dynamic attributes More efficient and clear approaches to concurrency and parallelism Solutions for optimizing and hardening to maximize performance and quality Techniques and built-in modules that aid in debugging and testing Tools and best practices for collaborative development Effective Python will prepare growing programmers to make a big impact using Python. COMPUTERS,Languages,Python

Python One-Liners Python programmers will improve their computer science skills with these useful one-liners. Python One-Liners will teach you how to read and write "one-liners": concise statements of useful functionality packed into a single line of code. You'll learn how to systematically unpack and understand any line of Python code, and write eloquent, powerfully compressed Python like an expert. The book's five chapters cover tips and tricks, regular expressions, machine learning, core data science topics, and useful algorithms. Detailed explanations of one-liners introduce key computer science concepts and boost your coding and analytical skills. You'll learn about advanced Python features such as list comprehension, slicing, lambda functions, regular expressions, map and reduce functions, and slice assignments. You'll also learn how to: • Leverage data structures to solve real-world problems, like using Boolean indexing to find cities with above-average pollution • Use NumPy basics such as array, shape, axis, type, broadcasting, advanced indexing, slicing, sorting, searching, aggregating, and statistics • Calculate basic statistics of multidimensional data arrays and the K-Means algorithms for unsupervised learning • Create more advanced regular expressions using grouping and named groups, negative lookaheads, escaped characters, whitespaces, character sets (and negative characters sets), and greedy/nongreedy operators • Understand a wide range of computer science topics, including anagrams, palindromes, supersets, permutations, factorials, prime numbers, Fibonacci numbers, obfuscation, searching, and algorithmic sorting By the end of the book, you'll know how to write Python at its most refined, and create concise, beautiful pieces of "Python art" in merely a single line. COMPUTERS,Languages,Python

The Python Workshop Cut through the noise and get real results with a step-by-step approach to learning Python 3.X programming Key Features Ideal for the Python beginner who is getting started for the first time A step-by-step Python tutorial with exercises and activities that help build key skills Structured to let you progress at your own pace, on your own terms Use your physical print copy to redeem free access to the online interactive edition Book Description You already know you want to learn Python, and a smarter way to learn Python 3 is to learn by doing. The Python Workshop focuses on building up your practical skills so that you can work towards building up your machine learning skills as a data scientist, write scripts that help automate your life and save you time, or even create your own games and desktop applications. You'll learn from real examples that lead to real results. Throughout The Python Workshop, you'll take an engaging step-by-step approach to understanding Python. You won't have to sit through any unnecessary theory. If you're short on time you can jump into a single exercise each day or spend an entire weekend learning about Python scripting. It's your choice. Learning on your terms, you'll build up and reinforce key skills in a way that feels rewarding. Every physical print copy of The Python Workshop unlocks access to the interactive edition. With videos detailing all exercises and activities, you'll always have a guided solution. You can also benchmark yourself against assessments, track progress, and receive free content updates. You'll even earn a secure credential that you can share and verify online upon completion. It's a premium learning experience that's included with your printed copy. To redeem, follow the instructions located at the start of your Python book. Fast-paced and direct, The Python Workshop is the ideal companion for Python beginners. You'll build and iterate on your code like a software developer, learning along the way. This process means that you'll find that your new skills stick, embedded as best practice. A solid foundation for the years ahead. What you will learn Learn how to write clean and concise code with Python 3 Understand classes and object-oriented programming Tackle entry-level data science and create engaging visualizations Use Python to create responsive, modern web applications Automate essential day-to-day tasks with Python scripts Get started with predictive Python machine learning Who this book is for This book is designed for professionals, students, and hobbyists who want to learn Python and apply it to solve challenging real-world problems. Although this is a beginner's book, it will help if you already know standard programming topics, such as variables, if-else statements, and functions. Experience with another object-oriented program is beneficial, but not mandatory. COMPUTERS,Languages,Python

PyTorch 1.x Reinforcement Learning Cookbook Implement reinforcement learning techniques and algorithms with the help of real-world examples and recipes Key Features Use PyTorch 1.x to design and build self-learning artificial intelligence (AI) models Implement RL algorithms to solve control and optimization challenges faced by data scientists today Apply modern RL libraries to simulate a controlled environment for your projects Book Description Reinforcement learning (RL) is a branch of machine learning that has gained popularity in recent times. It allows you to train AI models that learn from their own actions and optimize their behavior. PyTorch has also emerged as the preferred tool for training RL models because of its efficiency and ease of use. With this book, you'll explore the important RL concepts and the implementation of algorithms in PyTorch 1.x. The recipes in the book, along with real-world examples, will help you master various RL techniques, such as dynamic programming, Monte Carlo simulations, temporal difference, and Q-learning. You'll also gain insights into industry-specific applications of these techniques. Later chapters will guide you through solving problems such as the multi-armed bandit problem and the cartpole problem using the multi-armed bandit algorithm and function approximation. You'll also learn how to use Deep Q-Networks to complete Atari games, along with how to effectively implement policy gradients. Finally, you'll discover how RL techniques are applied to Blackjack, Gridworld environments, internet advertising, and the Flappy Bird game. By the end of this book, you'll have developed the skills you need to implement popular RL algorithms and use RL techniques to solve real-world problems. What you will learn Use Q-learning and the state–action–reward–state–action (SARSA) algorithm to solve various Gridworld problems Develop a multi-armed bandit algorithm to optimize display advertising Scale up learning and control processes using Deep Q-Networks Simulate Markov Decision Processes, OpenAI Gym environments, and other common control problems Select and build RL models, evaluate their performance, and optimize and deploy them Use policy gradient methods to solve continuous RL problems Who this book is for Machine learning engineers, data scientists and AI researchers looking for quick solutions to different reinforcement learning problems will find this book useful. Although prior knowledge of machine learning concepts is required, experience with PyTorch will be useful but not necessary. COMPUTERS,Languages,Python

Introducing Python Easy to understand and fun to read, this updated edition of Introducing Python is ideal for beginning programmers as well as those new to the language. Author Bill Lubanovic takes you from the basics to more involved and varied topics, mixing tutorials with cookbook-style code recipes to explain concepts in Python 3. End-of-chapter exercises help you practice what you’ve learned. You’ll gain a strong foundation in the language, including best practices for testing, debugging, code reuse, and other development tips. This book also shows you how to use Python for applications in business, science, and the arts, using various Python tools and open source packages. COMPUTERS,Languages,Python

Python Projects for Beginners Immerse yourself in learning Python and introductory data analytics with this book’s project-based approach. Through the structure of a ten-week coding bootcamp course, you’ll learn key concepts and gain hands-on experience through weekly projects. Each chapter in this book is presented as a full week of topics, with Monday through Thursday covering specific concepts, leading up to Friday, when you are challenged to create a project using the skills learned throughout the week. Topics include Python basics and essential intermediate concepts such as list comprehension, generators and iterators, understanding algorithmic complexity, and data analysis with pandas. From beginning to end, this book builds up your abilities through exercises and challenges, culminating in your solid understanding of Python.Challenge yourself with the intensity of a coding bootcamp experience or learn at your own pace. With this hands-on learning approach, you will gain the skills you need to jumpstart a new career in programming or further your current one as a software developer. What You Will Learn Understand beginning and more advanced concepts of the Python language Be introduced to data analysis using pandas, the Python Data Analysis library Walk through the process of interviewing and answering technical questions Create real-world applications with the Python language Learn how to use Anaconda, Jupyter Notebooks, and the Python Shell Who This Book Is For Those trying to jumpstart a new career into programming, and those already in the software development industry and would like to learn Python programming. COMPUTERS,Languages,Python

Python Machine Learning Applied machine learning with a solid foundation in theory. Revised and expanded for TensorFlow 2, GANs, and reinforcement learning. Key Features Third edition of the bestselling, widely acclaimed Python machine learning book Clear and intuitive explanations take you deep into the theory and practice of Python machine learning Fully updated and expanded to cover TensorFlow 2, Generative Adversarial Network models, reinforcement learning, and best practices Book Description Python Machine Learning, Third Edition is a comprehensive guide to machine learning and deep learning with Python. It acts as both a step-by-step tutorial, and a reference you'll keep coming back to as you build your machine learning systems. Packed with clear explanations, visualizations, and working examples, the book covers all the essential machine learning techniques in depth. While some books teach you only to follow instructions, with this machine learning book, Raschka and Mirjalili teach the principles behind machine learning, allowing you to build models and applications for yourself. Updated for TensorFlow 2.0, this new third edition introduces readers to its new Keras API features, as well as the latest additions to scikit-learn. It's also expanded to cover cutting-edge reinforcement learning techniques based on deep learning, as well as an introduction to GANs. Finally, this book also explores a subfield of natural language processing (NLP) called sentiment analysis, helping you learn how to use machine learning algorithms to classify documents. This book is your companion to machine learning with Python, whether you're a Python developer new to machine learning or want to deepen your knowledge of the latest developments. What you will learn Master the frameworks, models, and techniques that enable machines to 'learn' from data Use scikit-learn for machine learning and TensorFlow for deep learning Apply machine learning to image classification, sentiment analysis, intelligent web applications, and more Build and train neural networks, GANs, and other models Discover best practices for evaluating and tuning models Predict continuous target outcomes using regression analysis Dig deeper into textual and social media data using sentiment analysis Who This Book Is For If you know some Python and you want to use machine learning and deep learning, pick up this book. Whether you want to start from scratch or extend your machine learning knowledge, this is an essential resource. Written for developers and data scientists who want to create practical machine learning and deep learning code, this book is ideal for anyone who wants to teach computers how to learn from data. COMPUTERS,Languages,Python

Python for DevOps Much has changed in technology over the past decade. Data is hot, the cloud is ubiquitous, and many organizations need some form of automation. Throughout these transformations, Python has become one of the most popular languages in the world. This practical resource shows you how to use Python for everyday Linux systems administration tasks with today’s most useful DevOps tools, including Docker, Kubernetes, and Terraform. Learning how to interact and automate with Linux is essential for millions of professionals. Python makes it much easier. With this book, you’ll learn how to develop software and solve problems using containers, as well as how to monitor, instrument, load-test, and operationalize your software. Looking for effective ways to "get stuff done" in Python? This is your guide. Python foundations, including a brief introduction to the language How to automate text, write command-line tools, and automate the filesystem Linux utilities, package management, build systems, monitoring and instrumentation, and automated testing Cloud computing, infrastructure as code, Kubernetes, and serverless Machine learning operations and data engineering from a DevOps perspective Building, deploying, and operationalizing a machine learning project COMPUTERS,Languages,Python

The Data Science Workshop Cut through the noise and get real results with a step-by-step approach to data science Key Features Ideal for the data science beginner who is getting started for the first time A data science tutorial with step-by-step exercises and activities that help build key skills Structured to let you progress at your own pace, on your own terms Use your physical print copy to redeem free access to the online interactive edition Book Description You already know you want to learn data science, and a smarter way to learn data science is to learn by doing. The Data Science Workshop focuses on building up your practical skills so that you can understand how to develop simple machine learning models in Python or even build an advanced model for detecting potential bank frauds with effective modern data science. You'll learn from real examples that lead to real results. Throughout The Data Science Workshop, you'll take an engaging step-by-step approach to understanding data science. You won't have to sit through any unnecessary theory. If you're short on time you can jump into a single exercise each day or spend an entire weekend training a model using sci-kit learn. It's your choice. Learning on your terms, you'll build up and reinforce key skills in a way that feels rewarding. Every physical print copy of The Data Science Workshop unlocks access to the interactive edition. With videos detailing all exercises and activities, you'll always have a guided solution. You can also benchmark yourself against assessments, track progress, and receive content updates. You'll even earn a secure credential that you can share and verify online upon completion. It's a premium learning experience that's included with your printed copy. To redeem, follow the instructions located at the start of your data science book. Fast-paced and direct, The Data Science Workshop is the ideal companion for data science beginners. You'll learn about machine learning algorithms like a data scientist, learning along the way. This process means that you'll find that your new skills stick, embedded as best practice. A solid foundation for the years ahead. What you will learn Find out the key differences between supervised and unsupervised learning Manipulate and analyze data using scikit-learn and pandas libraries Learn about different algorithms such as regression, classification, and clustering Discover advanced techniques to improve model ensembling and accuracy Speed up the process of creating new features with automated feature tool Simplify machine learning using open source Python packages Who this book is for Our goal at Packt is to help you be successful, in whatever it is you choose to do. The Data Science Workshop is an ideal data science tutorial for the data science beginner who is just getting started. Pick up a Workshop today and let Packt help you develop skills that stick with you for life. COMPUTERS,Languages,Python

Using Asyncio in Python If you’re among the Python developers put off by asyncio’s complexity, it’s time to take another look. Asyncio is complicated because it aims to solve problems in concurrent network programming for both framework and end-user developers. The features you need to consider are a small subset of the whole asyncio API, but picking out the right features is the tricky part. That’s where this practical book comes in. Veteran Python developer Caleb Hattingh helps you gain a basic understanding of asyncio’s building blocks—enough to get started writing simple event-based programs. You’ll learn why asyncio offers a safer alternative to preemptive multitasking (threading) and how this API provides a simpleway to support thousands of simultaneous socket connections. Get a critical comparison of asyncio and threading for concurrent network programming Take an asyncio walk-through, including a quickstart guidefor hitting the ground looping with event-based programming Learn the difference between asyncio features for end-user developers and those for framework developers Understand asyncio’s new async/await language syntax, including coroutines and task and future APIs Get detailed case studies (with code) of some popular asyncio-compatible third-party libraries COMPUTERS,Languages,Python

Artificial Intelligence with Python New edition of the bestselling guide to artificial intelligence with Python, updated to Python 3.x, with seven new chapters that cover RNNs, AI and Big Data, fundamental use cases, chatbots, and more. Key Features Completely updated and revised to Python 3.x New chapters for AI on the cloud, recurrent neural networks, deep learning models, and feature selection and engineering Learn more about deep learning algorithms, machine learning data pipelines, and chatbots Book Description Artificial Intelligence with Python, Second Edition is an updated and expanded version of the bestselling guide to artificial intelligence using the latest version of Python 3.x. Not only does it provide you an introduction to artificial intelligence, this new edition goes further by giving you the tools you need to explore the amazing world of intelligent apps and create your own applications. This edition also includes seven new chapters on more advanced concepts of Artificial Intelligence, including fundamental use cases of AI; machine learning data pipelines; feature selection and feature engineering; AI on the cloud; the basics of chatbots; RNNs and DL models; and AI and Big Data. Finally, this new edition explores various real-world scenarios and teaches you how to apply relevant AI algorithms to a wide swath of problems, starting with the most basic AI concepts and progressively building from there to solve more difficult challenges so that by the end, you will have gained a solid understanding of, and when best to use, these many artificial intelligence techniques. What you will learn Understand what artificial intelligence, machine learning, and data science are Explore the most common artificial intelligence use cases Learn how to build a machine learning pipeline Assimilate the basics of feature selection and feature engineering Identify the differences between supervised and unsupervised learning Discover the most recent advances and tools offered for AI development in the cloud Develop automatic speech recognition systems and chatbots Apply AI algorithms to time series data Who this book is for The intended audience for this book is Python developers who want to build real-world Artificial Intelligence applications. Basic Python programming experience and awareness of machine learning concepts and techniques is mandatory. COMPUTERS,Languages,Python

Python 3 for Machine Learning This book is designed to provide the reader with basic Python 3 programming concepts related to machine learning. The first four chapters provide a fast-paced introduction to Python 3, NumPy, and Pandas. The fifth chapter introduces the fundamentalconcepts of machine learning. The sixth chapter is devoted to machine learningclassifiers, such as logistic regression, k-NN, decision trees, random forests, and SVMs. The final chapter includes material on NLP and RL. Keras-based code samples are included to supplement the theoretical discussion. The book also contains separate appendices for regular expressions, Keras, and TensorFlow 2. Features: Provides the reader withbasic Python 3 programming concepts related to machine learning Includes separate appendices forregular expressions, Keras, and TensorFlow 2 COMPUTERS,Languages,Python

Applied Machine Learning with Python If you are looking for an engaging book, rich in learning features, which will guide you through the field of Machine Learning, this is it. This book is a modern, concise guide of the topic. It focuses on current ensemble and boosting methods, highlighting contemporray techniques such as XGBoost (2016), Shap (2017) and CatBoost (2018), which are considered novel and cutting edge models for dealing with supervised learning methods. The author goes beyond the simple bag-of-words schema in Natural Language Processing, and describes the modern embedding framework, starting from the Word2Vec, in details. Finally the volume is uniquely identified by the book-specific software egeaML, which is a good companion to implement the proposed Machine Learning methodologies in Python. COMPUTERS,Languages,Python

Hands-On ROS for Robotics Programming Take your ROS skills to the next level by implementing complex robot structures in a ROS simulation Key Features Learn fundamental ROS concepts and apply them to solve navigation tasks Work with single board computers to program smart behavior in mobile robots Understand how specific characteristics of the physical environment influence your robot's performance Book Description Connecting a physical robot to a robot simulation using the Robot Operating System (ROS) infrastructure is one of the most common challenges faced by ROS engineers. With this book, you'll learn how to simulate a robot in a virtual environment and achieve desired behavior in equivalent real-world scenarios. This book starts with an introduction to GoPiGo3 and the sensors and actuators with which it is equipped. You'll then work with GoPiGo3's digital twin by creating a 3D model from scratch and running a simulation in ROS using Gazebo. Next, the book will show you how to use GoPiGo3 to build and run an autonomous mobile robot that is aware of its surroundings. Finally, you'll find out how a robot can learn tasks that have not been programmed in the code but are acquired by observing its environment. You'll even cover topics such as deep learning and reinforcement learning. By the end of this robot programming book, you'll be well-versed with the basics of building specific-purpose applications in robotics and developing highly intelligent autonomous robots from scratch. What you will learn Get to grips with developing environment-aware robots Gain insights into how your robots will react in physical environments Break down a desired behavior into a chain of robot actions Relate data from sensors with context to produce adaptive responses Apply reinforcement learning to allow your robot to learn by trial and error Implement deep learning to enable your robot to recognize its surroundings Who this book is for If you are an engineer looking to build AI-powered robots using the ROS framework, this book is for you. Robotics enthusiasts and hobbyists who want to develop their own ROS robotics projects will also find this book useful. Knowledge of Python and/or C++ programming and familiarity with single board computers such as Raspberry Pi is necessary to get the most out of this book. COMPUTERS,Languages,Python

Architecture Patterns with Python As Python continues to grow in popularity, projects are becoming larger and more complex. Many Python developers are taking an interest in high-level software design patterns such as hexagonal/clean architecture, event-driven architecture, and the strategic patterns prescribed by domain-driven design (DDD). But translating those patterns into Python isn’t always straightforward. With this hands-on guide, Harry Percival and Bob Gregory from MADE.com introduce proven architectural design patterns to help Python developers manage application complexity—and get the most value out of their test suites. Each pattern is illustrated with concrete examples in beautiful, idiomatic Python, avoiding some of the verbosity of Java and C# syntax. Patterns include: Dependency inversion and its links to ports and adapters (hexagonal/clean architecture) Domain-driven design’s distinction between Entities, Value Objects, and Aggregates Repository and Unit of Work patterns for persistent storage Events, commands, and the message bus Command-query responsibility segregation (CQRS) Event-driven architecture and reactive microservices COMPUTERS,Languages,Python

Mastering Python Networking New edition of the bestselling guide to mastering Python Networking, updated to Python 3 and including the latest on network data analysis, Cloud Networking, Ansible 2.8, and new libraries Key Features Explore the power of Python libraries to tackle difficult network problems efficiently and effectively, including pyATS, Nornir, and Ansible 2.8 Use Python and Ansible for DevOps, network device automation, DevOps, and software-defined networking Become an expert in implementing advanced network-related tasks with Python 3 Book Description Networks in your infrastructure set the foundation for how your application can be deployed, maintained, and serviced. Python is the ideal language for network engineers to explore tools that were previously available to systems engineers and application developers. In Mastering Python Networking, Third edition, you'll embark on a Python-based journey to transition from traditional network engineers to network developers ready for the next-generation of networks. This new edition is completely revised and updated to work with Python 3. In addition to new chapters on network data analysis with ELK stack (Elasticsearch, Logstash, Kibana, and Beats) and Azure Cloud Networking, it includes updates on using newer libraries such as pyATS and Nornir, as well as Ansible 2.8. Each chapter is updated with the latest libraries with working examples to ensure compatibility and understanding of the concepts. Starting with a basic overview of Python, the book teaches you how it can interact with both legacy and API-enabled network devices. You will learn to leverage high-level Python packages and frameworks to perform network automation tasks, monitoring, management, and enhanced network security followed by Azure and AWS Cloud networking. Finally, you will use Jenkins for continuous integration as well as testing tools to verify your network. What you will learn Use Python libraries to interact with your network Integrate Ansible 2.8 using Python to control Cisco, Juniper, and Arista network devices Leverage existing Flask web frameworks to construct high-level APIs Learn how to build virtual networks in the AWS & Azure Cloud Learn how to use Elastic Stack for network data analysis Understand how Jenkins can be used to automatically deploy changes in your network Use PyTest and Unittest for Test-Driven Network Development in networking engineering with Python Who this book is for Mastering Python Networking, Third edition is for network engineers, developers, and SREs who want to use Python for network automation, programmability, and data analysis. Basic familiarity with Python programming and networking-related concepts such as Transmission Control Protocol/Internet Protocol (TCP/IP) will be useful. COMPUTERS,Languages,Python

Django 3 By Example Learn Django 3 with four end-to-end web projects Key Features Learn Django 3 by building real-world web applications from scratch in Python, using coding best practices Integrate other technologies into your application with clear, step-by-step explanations and comprehensive example code Implement advanced functionalities like a full-text search engine, a user activity stream, or a recommendation engine Add real-time features with Django Channels and WebSockets Book Description If you want to learn the entire process of developing professional web applications with Python and Django, then this book is for you. In the process of building four professional Django projects, you will learn about Django 3 features, how to solve common web development problems, how to implement best practices, and how to successfully deploy your applications. In this book, you will build a blog application, a social image bookmarking website, an online shop, and an e-learning platform. Step-by-step guidance will teach you how to integrate popular technologies, enhance your applications with AJAX, create RESTful APIs, and set up a production environment for your Django projects. By the end of this book, you will have mastered Django 3 by building advanced web applications. What you will learn Build real-world web applications Learn Django essentials, including models, views, ORM, templates, URLs, forms, and authentication Implement advanced features such as custom model fields, custom template tags, cache, middleware, localization, and more Create complex functionalities, such as AJAX interactions, social authentication, a full-text search engine, a payment system, a CMS, a RESTful API, and more Integrate other technologies, including Redis, Celery, RabbitMQ, PostgreSQL, and Channels, into your projects Deploy Django projects in production using NGINX, uWSGI, and Daphne Who this book is for This book is intended for developers with Python knowledge who wish to learn Django in a pragmatic way. Perhaps you are completely new to Django, or you already know a little but you want to get the most out of it. This book will help you to master the most relevant areas of the framework by building practical projects from scratch. You need to have familiarity with programming concepts in order to read this book. Some previous knowledge of HTML and JavaScript is assumed. COMPUTERS,Languages,Python

Network Automation Cookbook Take your network automation skills to the next level with practical recipes on managing network devices from a variety of vendors like Cisco, Juniper, and Arista Key Features Use Ansible to automate network infrastructure with the help of step-by-step instructions Implement network automation best practices to save cost, avoid critical errors, and reduce downtime Deliver a robust automation framework by integrating Ansible with NAPALM, NetBox, and Batfish Book Description Network Automation Cookbook is designed to help system administrators, network engineers, and infrastructure automation engineers to centrally manage switches, routers, and other devices in their organization's network. This book will help you gain hands-on experience in automating enterprise networks and take you through core network automation techniques using the latest version of Ansible and Python. With the help of practical recipes, you'll learn how to build a network infrastructure that can be easily managed and updated as it scales through a large number of devices. You'll also cover topics related to security automation and get to grips with essential techniques to maintain network robustness. As you make progress, the book will show you how to automate networks on public cloud providers such as AWS, Google Cloud Platform, and Azure. Finally, you will get up and running with Ansible 2.9 and discover troubleshooting techniques and network automation best practices. By the end of this book, you'll be able to use Ansible to automate modern network devices and integrate third-party tools such as NAPALM, NetBox, and Batfish easily to build robust network automation solutions. What you will learn Understand the various components of Ansible Automate network resources in AWS, GCP, and Azure cloud solutions Use IaC concepts to design and build network solutions Automate network devices such as Cisco, Juniper, Arista, and F5 Use NetBox to build network inventory and integrate it with Ansible Validate networks using Ansible and Batfish Who this book is for This Ansible network automation book is for network and DevOps engineers interested in automating complex network tasks. Prior understanding of networking and basic Linux knowledge is required. COMPUTERS,Languages,Python

High Performance Python Your Python code may run correctly, but you need it to run faster. Updated for Python 3, this expanded edition shows you how to locate performance bottlenecks and significantly speed up your code in high-data-volume programs. By exploring the fundamental theory behind design choices, High Performance Python helps you gain a deeper understanding of Python’s implementation. How do you take advantage of multicore architectures or clusters? Or build a system that scales up and down without losing reliability? Experienced Python programmers will learn concrete solutions to many issues, along with war stories from companies that use high-performance Python for social media analytics, productionized machine learning, and more. Get a better grasp of NumPy, Cython, and profilers Learn how Python abstracts the underlying computer architecture Use profiling to find bottlenecks in CPU time and memory usage Write efficient programs by choosing appropriate data structures Speed up matrix and vector computations Use tools to compile Python down to machine code Manage multiple I/O and computational operations concurrently Convert multiprocessing code to run on local or remote clusters Deploy code faster using tools like Docker COMPUTERS,Languages,Python

Beginning PyQt Learn GUI application development from the ground up, taking a practical approach by building simple projects that teach the fundamentals of using PyQt. Each chapter gradually moves on to teach more advanced and diverse concepts to aid you in designing interesting applications using the latest version of PyQt. You’ll start by reviewing the beginning steps of GUI development from, using different projects in every chapter to teach new widgets or concepts that will help you to build better UIs. As you follow along, you will construct more elaborate GUIs, covering topics that include storing data using the clipboard, graphics and animation, support for SQL databases, and multithreading applications. Using this knowledge, you’ll be able to build a photo editor, games, a text editor, a working web browser and an assortment of other GUIs. Beginning PyQt will guide you through the process of creating UIs to help you bring your own ideas to life. Learn what is necessary to begin making your own applications and more with PyQt! What You'll Learn Create your own cross-platform GUIs with PyQt and Python Use PyQt’s many widgets and apply them to building real applications Build larger applications and break the steps into smaller parts for deeper understanding Work with complex applications in PyQt, from animation to databases and more Who This Book Is For Individuals who already have a fundamental understanding of the Python programming language and are looking to either expand their skills in Python or have a project where they need to create a UI, but may have no prior experience or no idea how to begin. COMPUTERS,Languages,Python

Python Automation Cookbook Get a firm grip on the core processes including browser automation, web scraping, Word, Excel, and GUI automation with Python 3.8 and higher Key Features Automate integral business processes such as report generation, email marketing, and lead generation Explore automated code testing and Python's growth in data science and AI automation in three new chapters Understand techniques to extract information and generate appealing graphs, and reports with Matplotlib Book Description In this updated and extended version of Python Automation Cookbook, each chapter now comprises the newest recipes and is revised to align with Python 3.8 and higher. The book includes three new chapters that focus on using Python for test automation, machine learning projects, and for working with messy data. This edition will enable you to develop a sharp understanding of the fundamentals required to automate business processes through real-world tasks, such as developing your first web scraping application, analyzing information to generate spreadsheet reports with graphs, and communicating with automatically generated emails. Once you grasp the basics, you will acquire the practical knowledge to create stunning graphs and charts using Matplotlib, generate rich graphics with relevant information, automate marketing campaigns, build machine learning projects, and execute debugging techniques. By the end of this book, you will be proficient in identifying monotonous tasks and resolving process inefficiencies to produce superior and reliable systems. What you will learn Learn data wrangling with Python and Pandas for your data science and AI projects Automate tasks such as text classification, email filtering, and web scraping with Python Use Matplotlib to generate a variety of stunning graphs, charts, and maps Automate a range of report generation tasks, from sending SMS and email campaigns to creating templates, adding images in Word, and even encrypting PDFs Master web scraping and web crawling of popular file formats and directories with tools like Beautiful Soup Build cool projects such as a Telegram bot for your marketing campaign, a reader from a news RSS feed, and a machine learning model to classify emails to the correct department based on their content Create fire-and-forget automation tasks by writing cron jobs, log files, and regexes with Python scripting Who this book is for Python Automation Cookbook - Second Edition is for developers, data enthusiasts or anyone who wants to automate monotonous manual tasks related to business processes such as finance, sales, and HR, among others. Working knowledge of Python is all you need to get started with this book. COMPUTERS,Languages,Python

Thinking in Pandas Understand and implement big data analysis solutions in pandas with an emphasis on performance. This book strengthens your intuition for working with pandas, the Python data analysis library, by exploring its underlying implementation and data structures. Thinking in Pandas introduces the topic of big data and demonstrates concepts by looking at exciting and impactful projects that pandas helped to solve. From there, you will learn to assess your own projects by size and type to see if pandas is the appropriate library for your needs. Author Hannah Stepanek explains how to load and normalize data in pandas efficiently, and reviews some of the most commonly used loaders and several of their most powerful options. You will then learn how to access and transform data efficiently, what methods to avoid, and when to employ more advanced performance techniques. You will also go over basic data access and munging in pandas and the intuitive dictionary syntax. Choosing the right DataFrame format, working with multi-level DataFrames, and how pandas might be improved upon in the future are also covered. By the end of the book, you will have a solid understanding of how the pandas library works under the hood. Get ready to make confident decisions in your own projects by utilizing pandas—the right way. What You Will Learn Understand the underlying data structure of pandas and why it performs the way it does under certain circumstances Discover how to use pandas to extract, transform, and load data correctly with an emphasis on performance Choose the right DataFrame so that the data analysis is simple and efficient. Improve performance of pandas operations with other Python libraries Who This Book Is For Software engineers with basic programming skills in Python keen on using pandas for a big data analysis project. Python software developers interested in big data. COMPUTERS,Languages,Python

Django Standalone Apps Develop standalone Django apps to serve as the reusable building blocks for larger Django projects. This book explores best practices for publishing these apps, with special considerations for testing Django apps, and strategies for extracting existing functionality into a separate package. This jumpstart reference is divided into four distinct and sequential sections, all containing short, engaging chapters that can be read in a modular fashion, depending on your level of experience. The first section covers the structure and scope of standalone Django apps. The second section digs into questions about pulling code out of existing projects and into new standalone apps for reuse. The third section details additional, advanced technical best practices toward making standalone apps as broadly useful as possible. The fourth and final section covers strategies for managing a published Django app. Django Standalone Apps is the perfect resource for developers who have at least some prior experience working with Django web applications and want to simplify their deployments and share their knowledge as open source packages. What You'll Learn Scope a standalone Django app project for optimum usefulness Extract code from existing projects to reuse Test a standalone app outside of your Django project Reuse your own code for increased delivery cadence and code quality Review best practices for maintaining a Django app package Who This Book Is For Professional developers who work with Django. Deep expertise is not required or expected, but readers should have working familiarity with Django. COMPUTERS,Languages,Python

Introduction to Computation and Programming Using Python, revised and expanded edition An introductory text that teaches students the art of computational problem solving, covering topics that range from simple algorithms to information visualization. This book introduces students with little or no prior programming experience to the art of computational problem solving using Python and various Python libraries, including PyLab. It provides students with skills that will enable them to make productive use of computational techniques, including some of the tools and techniques of “data science” for using computation to model and interpret data. The book is based on an MIT course (which became the most popular course offered through MIT's OpenCourseWare) and was developed for use not only in a conventional classroom but in a massive open online course (or MOOC) offered by the pioneering MIT-Harvard collaboration edX. Students are introduced to Python and the basics of programming in the context of such computational concepts and techniques as exhaustive enumeration, bisection search, and efficient approximation algorithms. The book does not require knowledge of mathematics beyond high school algebra, but does assume that readers are comfortable with rigorous thinking and not intimidated by mathematical concepts. Although it covers such traditional topics as computational complexity and simple algorithms, the book focuses on a wide range of topics not found in most introductory texts, including information visualization, simulations to model randomness, computational techniques to understand data, and statistical techniques that inform (and misinform) as well as two related but relatively advanced topics: optimization problems and dynamic programming. Introduction to Computation and Programming Using Python can serve as a stepping-stone to more advanced computer science courses, or as a basic grounding in computational problem solving for students in other disciplines. COMPUTERS,Languages,Python

Introduction to Computation and Programming Using Python, second edition The new edition of an introductory text that teaches students the art of computational problem solving, covering topics ranging from simple algorithms to information visualization. This book introduces students with little or no prior programming experience to the art of computational problem solving using Python and various Python libraries, including PyLab. It provides students with skills that will enable them to make productive use of computational techniques, including some of the tools and techniques of data science for using computation to model and interpret data. The book is based on an MIT course (which became the most popular course offered through MIT's OpenCourseWare) and was developed for use not only in a conventional classroom but in in a massive open online course (MOOC). This new edition has been updated for Python 3, reorganized to make it easier to use for courses that cover only a subset of the material, and offers additional material including five new chapters. Students are introduced to Python and the basics of programming in the context of such computational concepts and techniques as exhaustive enumeration, bisection search, and efficient approximation algorithms. Although it covers such traditional topics as computational complexity and simple algorithms, the book focuses on a wide range of topics not found in most introductory texts, including information visualization, simulations to model randomness, computational techniques to understand data, and statistical techniques that inform (and misinform) as well as two related but relatively advanced topics: optimization problems and dynamic programming. This edition offers expanded material on statistics and machine learning and new chapters on Frequentist and Bayesian statistics. COMPUTERS,Languages,Python

Exploring Everyday Things with R and Ruby If you’re curious about how things work, this fun and intriguing guide will help you find real answers to everyday problems. By using fundamental math and doing simple programming with the Ruby and R languages, you’ll learn how to model a problem and work toward a solution. All you need is a basic understanding of programming. After a quick introduction to Ruby and R, you’ll explore a wide range of questions by learning how to assemble, process, simulate, and analyze the available data. You’ll learn to see everyday things in a different perspective through simple programs and common sense logic. Once you finish this book, you can begin your own journey of exploration and discovery. Here are some of the questions you’ll explore: Determine how many restroom stalls can accommodate an office with 70 employees Mine your email to understand your particular emailing habits Use simple audio and video recording devices to calculate your heart rate Create an artificial society—and analyze its behavioral patterns to learn how specific factors affect our real society COMPUTERS,Languages,Ruby

Computer Science Programming Basics in Ruby If you know basic high-school math, you can quickly learn and apply the core concepts of computer science with this concise, hands-on book. Led by a team of experts, you’ll quickly understand the difference between computer science and computer programming, and you’ll learn how algorithms help you solve computing problems. Each chapter builds on material introduced earlier in the book, so you can master one core building block before moving on to the next. You’ll explore fundamental topics such as loops, arrays, objects, and classes, using the easy-to-learn Ruby programming language. Then you’ll put everything together in the last chapter by programming a simple game of tic-tac-toe. Learn how to write algorithms to solve real-world problems Understand the basics of computer architecture Examine the basic tools of a programming language Explore sequential, conditional, and loop programming structures Understand how the array data structure organizes storage Use searching techniques and comparison-based sorting algorithms Learn about objects, including how to build your own Discover how objects can be created from other objects Manipulate files and use their data in your software COMPUTERS,Languages,Ruby

Ruby Cookbook Why spend time on coding problems that others have already solved when you could be making real progress on your Ruby project? This updated cookbook provides more than 350 recipes for solving common problems, on topics ranging from basic data structures, classes, and objects, to web development, distributed programming, and multithreading. Revised for Ruby 2.1, each recipe includes a discussion on why and how the solution works. You’ll find recipes suitable for all skill levels, from Ruby newbies to experts who need an occasional reference. With Ruby Cookbook, you’ll not only save time, but keep your brain percolating with new ideas as well. Recipes cover: Data structures including strings, numbers, date and time, arrays, hashes, files and directories Using Ruby’s code blocks, also known as closures OOP features such as classes, methods, objects, and modules XML and HTML, databases and persistence, and graphics and other formats Web development with Rails and Sinatra Internet services, web services, and distributed programming Software testing, debugging, packaging, and distributing Multitasking, multithreading, and extending Ruby with other languages COMPUTERS,Languages,Ruby

Ruby Pocket Reference Updated for Ruby 2.2, this handy reference offers brief yet clear explanations of Ruby’s core elements—from operators to blocks to documentation creation—and highlights the key features you may work with every day. Need to know the correct syntax for a conditional? Forgot the name of that String method? This book is organized to help you find the facts fast. Ruby Pocket Reference, 2nd Edition is ideal for experienced programmers who are new to Ruby. Whether you’ve come to Ruby because of Rails, or you want to take advantage of this clean, powerful, and expressive language for other applications, this reference will help you easily pinpoint the information you need. You’ll find detailed reference material for: Keywords, operators, comments, numbers, and symbols Variables, pre-defined global variables, and regular expressions Conditional statements, method use, classes, and exception handling Methods for the BasicObject, Object, Kernel, String, Array, and Hash classes Time formatting directives New syntax since Ruby 1.9 COMPUTERS,Languages,Ruby

Head First Ruby What will you learn from this book? What’s all the buzz about this Ruby language? Is it right for you? Well, ask yourself: are you tired of all those extra declarations, keywords, and compilation steps in your other language? Do you want to be a more productive programmer? Then you’ll love Ruby. With this unique hands-on learning experience, you’ll discover how Ruby takes care of all the details for you, so you can simply have fun and get more done with less code. Why does this book look so different? Based on the latest research in cognitive science and learning theory, Head First Ruby uses a visually rich format to engage your mind, rather than a text-heavy approach to put you to sleep. Why waste your time struggling with new concepts? This multi-sensory learning experience is designed for the way your brain really works. COMPUTERS,Languages,Ruby

Agile Web Development with Rails 5.1 Learn Rails the way the Rails core team recommends it, along with the tens of thousands of developers who have used this broad, far-reaching tutorial and reference. If you're new to Rails, you'll get step-by-step guidance. If you're an experienced developer, get the comprehensive, insider information you need for the latest version of Ruby on Rails. The new edition of this award-winning classic is completely updated for Rails 5.1 and Ruby 2.4, with information on system testing, Webpack, and advanced JavaScript. Ruby on Rails helps you produce high-quality, beautiful-looking web applications quickly---you concentrate on creating the application, and Rails takes care of the details. Rails 5.1 brings many improvements, and this edition is updated to cover the new features and changes in best practices. We start with a step-by-step walkthrough of building a real application, and in-depth chapters look at the built-in Rails features. Follow along with an extended tutorial as you write a web-based store application. Eliminate tedious configuration and housekeeping; seamlessly incorporate Ajax and JavaScript; send emails and manage background jobs with ActiveJob; build real-time features using WebSockets and ActionCable. Test your applications as you write them using the built-in unit, integration, and system testing frameworks; internationalize your applications; and deploy your applications easily and securely. New in this edition is support for Webpack and advanced JavaScript, as well as Rails' new browser-based system testing. Rails 1.0 was released in December 2005. This book was there from the start, and didn't just evolve alongside Rails, it evolved with Rails. It has been developed in consultation with the Rails core team. In fact, Rails itself is tested against the code in this book. What You Need: All you need is a Windows, Mac OS X, or Linux machine to do development on. This book will take you through the steps to install Rails and its dependencies. If you aren't familiar with the Ruby programming language, this book contains a chapter that covers the basics necessary to understand the material in the book. COMPUTERS,Languages,Ruby

Sams Teach Yourself Microsoft SQL Server T-SQL in 10 Minutes This is the eBook version of the printed book. If the print book includes a CD-ROM, this content is not included within the eBook version. Sams Teach Yourself Microsoft SQL Server T-SQL in 10 Minutes offers straightforward, practical answers when you need fast results. By working through 10-minute lessons, you’ll learn everything you need to know to take advantage of Microsoft SQL Server’s T-SQL language. This handy pocket guide starts with simple data retrieval and moves on to more complex topics, including the use of joins, subqueries, full text-based searches, functions and stored procedures, cursors, triggers, table constraints, XML, and much more. You’ll learn what you need to know methodically, systematically, and simply–in highly focused lessons designed to make you immediately and effortlessly productive. Tips point out shortcuts and solutions Cautions help you avoid common pitfalls Notes explain additional concepts, and provide additional information 10 minutes is all you need to learn how to… Use T-SQL in the Microsoft SQL Server environment Construct complex T-SQL statements using multiple clauses and operators Filter data so you get the information you need quickly Retrieve, sort, and format database contents Join two or more related tables Make SQL Server work for you with globalization and localization Create subqueries to pinpoint your data Automate your workload with triggers Create and alter database tables Work with views, stored procedures, and more Register your book at www.samspublishing.com/register to download examples and source code from this book. COMPUTERS,Languages,SQL

SQL This is the eBook version of the printed book. If the print book includes a CD-ROM, this content is not included within the eBook version.SQL is a standard interactive and programming language for querying and modifying data and managing databases. This task-based tutorial and reference guide takes the mystery out learning and applying SQL. After going over the relational database model and SQL syntax in the first few chapters, veteran author Chris Fehily immediately launches into the tasks that will get readers comfortable with SQL. In addition to covering all the SQL basics, this thoroughly updated reference contains a wealth of in-depth SQL knowledge and serves as an excellent reference for more experienced users. COMPUTERS,Languages,SQL

Mastering Oracle SQL The vast majority of Oracle SQL books discuss some syntax, provide the barest rudiments of using Oracle SQL, and perhaps include a few simple examples. It might be enough to pass a survey course, or give you some buzz words to drop in conversation with real Oracle DBAs. But if you use Oracle SQL on a regular basis, you want much more. You want to access the full power of SQL to write queries in an Oracle environment. You want a solid understanding of what's possible with Oracle SQL, creative techniques for writing effective and accurate queries, and the practical, hands-on information that leads to true mastery of the language. Simply put, you want useful, expert best practices that can be put to work immediately, not just non-vendor specific overview or theory.Updated to cover the latest version of Oracle, Oracle 10g, this edition of the highly regarded Mastering Oracle SQL has a stronger focus on technique and on Oracle's implementation of SQL than any other book on the market. It covers Oracle s vast library of built-in functions, the full range of Oracle SQL query-writing features, regular expression support, new aggregate and analytic functions, subqueries in the SELECT and WITH clauses, multiset union operators, enhanced support for hierarchical queries: leaf and loop detection, and the CONNECT_BY_ROOT operator, new partitioning methods (some introduced in Oracle9i Release 2), and the native XML datatype, XMLType.Mastering Oracle SQL, 2nd Edition fills the gap between the sometimes spotty vendor documentation, and other books on SQL that just don't explore the full depth of what is possible with Oracle-specific SQL. For those who want to harness the untapped (and often overlooked) power of Oracle SQL, this essential guide for putting Oracle SQL to work will prove invaluable. COMPUTERS,Languages,SQL

Transact-SQL Cookbook This unique cookbook contains a wealth of solutions to problems that SQL programmers face all the time. The recipes inside range from how to perform simple tasks, like importing external data, to ways of handling issues that are more complicated, like set algebra. Authors Ales Spetic and Jonathan Gennick, two authorities with extensive database and SQL programming experience, include a discussion with each recipe to explain the logic and concepts underlying the solution.SQL (Structured Query Language) is the closest thing to a standard query language that currently exists, and Transact-SQL -- a full-featured programming language that dramatically extends the power of SQL -- is the procedural language of choice for both Microsoft SQL Server and Sybase SQL Server systems. The Transact-SQL Cookbook is designed so you can use the recipes directly, as a source of ideas, or as a way to learn a little more about SQL and what you can do with it. Topics covered include: Audit logging. In addition to recipes for implementing an audit log, this chapter also includes recipes for: improving performance where large log tables are involved; supporting multiple-languages; and simulating server push. Hierarchies. Recipes show you how to manipulate hierarchical data using Transact-SQL. Importing data. This chapter introduces concepts like normalization and recipes useful for working with imported data tables. Sets. Recipes demonstrate different operations, such as how to find common elements, summarize the data in a set, and find the element in a set that represents an extreme. Statistics. This chapter?s recipes show you how to effectively use SQL for common statistical operations from means and standard deviations to weighted moving averages. Temporal data. Recipes demonstrate how to construct queries against time-based data. Data Structures. This chapter shows how to manipulate data structures like stacks, queues, matrices, and arrays. With an abundance of recipes to help you get your job done more efficiently, the Transact-SQL Cookbook is sure to become an essential part of your library. COMPUTERS,Languages,SQL

The Art of SQL For all the buzz about trendy IT techniques, data processing is still at the core of our systems, especially now that enterprises all over the world are confronted with exploding volumes of data. Database performance has become a major headache, and most IT departments believe that developers should provide simple SQL code to solve immediate problems and let DBAs tune any "bad SQL" later. In The Art of SQL, author and SQL expert Stephane Faroult argues that this "safe approach" only leads to disaster. His insightful book, named after Art of War by Sun Tzu, contends that writing quick inefficient code is sweeping the dirt under the rug. SQL code may run for 5 to 10 years, surviving several major releases of the database management system and on several generations of hardware. The code must be fast and sound from the start, and that requires a firm understanding of SQL and relational theory. The Art of SQL offers best practices that teach experienced SQL users to focus on strategy rather than specifics. Faroult's approach takes a page from Sun Tzu's classic treatise by viewing database design as a military campaign. You need knowledge, skills, and talent. Talent can't be taught, but every strategist from Sun Tzu to modern-day generals believed that it can be nurtured through the experience of others. They passed on their experience acquired in the field through basic principles that served as guiding stars amid the sound and fury of battle. This is what Faroult does with SQL. Like a successful battle plan, good architectural choices are based on contingencies. What if the volume of this or that table increases unexpectedly? What if, following a merger, the number of users doubles? What if you want to keep several years of data online? Faroult's way of looking at SQL performance may be unconventional and unique, but he's deadly serious about writing good SQL and using SQL well. The Art of SQL is not a cookbook, listing problems and giving recipes. The aim is to get you-and your manager-to raise good questions. COMPUTERS,Languages,SQL

Oracle PL/SQL Best Practices In this compact book, Steven Feuerstein, widely recognized as one of the world's leading experts on the Oracle PL/SQL language, distills his many years of programming, teaching, and writing about PL/SQL into a set of best practices-recommendations for developing successful applications. Covering the latest Oracle release, Oracle Database 11gR2, Feuerstein has rewritten this new edition in the style of his bestselling Oracle PL/SQL Programming. The text is organized in a problem/solution format, and chronicles the programming exploits of developers at a mythical company called My Flimsy Excuse, Inc., as they write code, make mistakes, and learn from those mistakes-and each other. This book offers practical answers to some of the hardest questions faced by PL/SQL developers, including: What is the best way to write the SQL logic in my application code? How should I write my packages so they can be leveraged by my entire team of developers? How can I make sure that all my team's programs handle and record errors consistently? Oracle PL/SQL Best Practices summarizes PL/SQL best practices in nine major categories: overall PL/SQL application development; programming standards; program testing, tracing, and debugging; variables and data structures; control logic; error handling; the use of SQL in PL/SQL; building procedures, functions, packages, and triggers; and overall program performance. This book is a concise and entertaining guide that PL/SQL developers will turn to again and again as they seek out ways to write higher quality code and more successful applications. "This book presents ideas that make the difference between a successful project and one that never gets off the ground. It goes beyond just listing a set of rules, and provides realistic scenarios that help the reader understand where the rules come from. This book should be required reading for any team of Oracle database professionals." --Dwayne King, President, KRIDAN Consulting COMPUTERS,Languages,SQL

SQL Pocket Guide SQL is the language of databases. It's used to create and maintain database objects, place data into those objects, query the data, modify the data, and, finally, delete data that is no longer needed. Databases lie at the heart of many, if not most business applications. Chances are very good that if you're involved with software development, you're using SQL to some degree. And if you're using SQL, you should own a good reference or two. Now available in an updated second edition, our very popular SQL Pocket Guide is a major help to programmers, database administrators, and everyone who uses SQL in their day-to-day work. The SQL Pocket Guide is a concise reference to frequently used SQL statements and commonly used SQL functions. Not just an endless collection of syntax diagrams, this portable guide addresses the language's complexity head on and leads by example. The information in this edition has been updated to reflect the latest versions of the most commonly used SQL variants including: Oracle Database 10g, Release 2 (includingthe free Oracle Database 10g Express Edition (XE)) Microsoft SQL Server 2005 MySQL 5 IBM DB2 8.2 PostreSQL 8.1 database COMPUTERS,Languages,SQL

SQL Cookbook You know the rudiments of the SQL query language, yet you feel you aren't taking full advantage of SQL's expressive power. You'd like to learn how to do more work with SQL inside the database before pushing data across the network to your applications. You'd like to take your SQL skills to the next level. Let's face it, SQL is a deceptively simple language to learn, and many database developers never go far beyond the simple statement: SELECT columns FROM table WHERE conditions. But there is so much more you can do with the language. In the SQL Cookbook, experienced SQL developer Anthony Molinaro shares his favorite SQL techniques and features. You'll learn about: Window functions, arguably the most significant enhancement to SQL in the past decade. If you're not using these, you're missing out Powerful, database-specific features such as SQL Server's PIVOT and UNPIVOT operators, Oracle's MODEL clause, and PostgreSQL's very useful GENERATE_SERIES function Pivoting rows into columns, reverse-pivoting columns into rows, using pivoting to facilitate inter-row calculations, and double-pivoting a result set Bucketization, and why you should never use that term in Brooklyn. How to create histograms, summarize data into buckets, perform aggregations over a moving range of values, generate running-totals and subtotals, and other advanced, data warehousing techniques The technique of walking a string, which allows you to use SQL to parse through the characters, words, or delimited elements of a string Written in O'Reilly's popular Problem/Solution/Discussion style, the SQL Cookbook is sure to please. Anthony's credo is: "When it comes down to it, we all go to work, we all have bills to pay, and we all want to go home at a reasonable time and enjoy what's still available of our days." The SQL Cookbook moves quickly from problem to solution, saving you time each step of the way. COMPUTERS,Languages,SQL

SQL Tuning A poorly performing database application not only costs users time, but also has an impact on other applications running on the same computer or the same network. SQL Tuning provides an essential next step for SQL developers and database administrators who want to extend their SQL tuning expertise and get the most from their database applications.There are two basic issues to focus on when tuning SQL: how to find and interpret the execution plan of an SQL statement and how to change SQL to get a specific alternate execution plan. SQL Tuning provides answers to these questions and addresses a third issue that's even more important: how to find the optimal execution plan for the query to use.Author Dan Tow outlines a timesaving method he's developed for finding the optimum execution plan--rapidly and systematically--regardless of the complexity of the SQL or the database platform being used. You'll learn how to understand and control SQL execution plans and how to diagram SQL queries to deduce the best execution plan for a query. Key chapters in the book include exercises to reinforce the concepts you've learned. SQL Tuning concludes by addressing special concerns and unique solutions to "unsolvable problems."Whether you are a programmer who develops SQL-based applications or a database administrator or other who troubleshoots poorly tuned applications, SQL Tuning will arm you with a reliable and deterministic method for tuning your SQL queries to gain optimal performance. COMPUTERS,Languages,SQL

Learning Oracle PL/SQL PL/SQL, Oracle's programming language for stored procedures, delivers a world of possibilities for your database programs. PL/SQL supplements the standard relational database language, SQL, with a wide range of procedural features, including loops, IF-THEN statements, advanced data structures, and rich transactional control--all closely integrated with the Oracle database server.Knowing where to start with Oracle's procedural language is not always obvious to a newcomer, especially considering the language's feature set and the sheer size of the official documentation (not to mention Oracle's ever-increasing number of pre-built PL/SQL programs). But Learning Oracle PL/SQL offers the signposts and guidance you need to come up to speed on the language, delivered in a manageable number of pages while covering all the essentials.Topics include: PL/SQL--what is it, and why use it? Why use PL/SQL instead of Java? Syntax and examples of all core language constructs Creating, using, and reusing stored procedures, functions, and packages Building web-based applications using PL/SQL features available "out of the box" (such as PL/SQL Server Pages) Securing PL/SQL programs against attack Benefits of third-party developer tools and integrated development environments Connecting PL/SQL to email, Java, and the Internet Meticulously crafted with all-new examples downloadable from examples.oreilly.com/learnoracle, the book addresses language features available in all versions of Oracle, from Oracle7 to Oracle8i to Oracle9i.Learning Oracle PL/SQL was written by PL/SQL experts Bill Pribyl and Steven Feuerstein, whose easy-to-read style and attention to detail has made other O'Reilly books (such as the bestselling Oracle PL/SQL Programming) very popular among Oracle developers worldwide. Learning Oracle PL/SQL is meant for a wide range of target audiences, including both beginning programmers and those already experienced with other programming languages. Whether you are a new developer, a crossover programmer from another database system, or a new database administrator who needs to learn PL/SQL, this book will get you well on your way. It is the perfect introduction to Oracle PL/SQL Programming, also by Pribyl and Feuerstein. COMPUTERS,Languages,SQL

Oracle PL/SQL for DBAs PL/SQL, Oracle's powerful procedural language, has been the cornerstone of Oracle application development for nearly 15 years. Although primarily a tool for developers, PL/SQL has also become an essential tool for database administration, as DBAs take increasing responsibility for site performance and as the lines between developers and DBAs blur. Until now, there has not been a book focused squarely on the language topics of special concern to DBAs Oracle PL/SQL for DBAs fills the gap. Covering the latest Oracle version, Oracle Database 10g Release 2 and packed with code and usage examples, it contains: A quick tour of the PL/SQL language, providing enough basic information about language fundamentals to get DBAs up and running Extensive coverage of security topics for DBAs: Encryption (including both traditional methods and Oracle's new Transparent Data Encryption, TDE); Row-Level Security(RLS), Fine-Grained Auditing (FGA); and random value generation Methods for DBAs to improve query and database performance with cursors and table functions Coverage of Oracle scheduling, which allows jobs such as database monitoring andstatistics gathering to be scheduled for regular execution Using Oracle's built-in packages (DBMS_CRYPTO, DBMS_RLS, DBMS_FGA, DBMS_RANDOM,DBMS_SCHEDULING) as a base, the book describes ways of building on top of these packages to suit particular organizational needs. Authors are Arup Nanda, Oracle Magazine 2003 DBA of the Year, and Steven Feuerstein, the world's foremost PL/SQL expert and coauthor of the classic reference, Oracle PL/SQL Programming. DBAs who have not yet discovered how helpful PL/SQL can be will find this book a superb introduction to the language and its special database administration features. Even if you have used PL/SQL for years, you'll find the detailed coverage in this book to be an invaluable resource. COMPUTERS,Languages,SQL

SQL in a Nutshell For programmers, analysts, and database administrators, SQL in a Nutshell is the essential reference for the SQL language used in today's most popular database products. This new edition clearly documents every SQL command according to the latest ANSI standard, and details how those commands are implemented in Microsoft SQL Server 2008, Oracle 11g, and the MySQL 5.1 and PostgreSQL 8.3 open source database products. You'll also get a concise overview of the Relational Database Management System (RDBMS) model, and a clear-cut explanation of foundational RDBMS concepts -- all packed into a succinct, comprehensive, and easy-to-use format. This book provides: Background on the Relational Database Model, including current and previous SQL standards Fundamental concepts necessary for understanding relational databases and SQL commands An alphabetical command reference to SQL statements, according to the SQL2003 ANSI standard The implementation of each command by MySQL, Oracle, PostgreSQL, and SQL Server An alphabetical reference of the ANSI SQL2003 functions, as well as the vendor implementations Platform-specific functions unique to each implementation Beginning where vendor documentation ends, SQL in a Nutshell distills the experiences of professional database administrators and developers who have used SQL variants to support complex enterprise applications. Whether SQL is new to you, or you've been using SQL since its earliest days, you'll get lots of new tips and techniques in this book. COMPUTERS,Languages,SQL

SQL Pocket Guide If you're a programmer or database administrator who uses SQL in your day-to-day work, this popular pocket guide is the ideal on-the-job reference. You'll find many examples that address the language's complexity, along with key aspects of SQL used in IBM DB2 Release 9.7, MySQL 5.1, Oracle Database 11g Release 2, PostgreSQL 9.0, and Microsoft SQL Server 2008 Release 2. SQL Pocket Guide describes how these database systems implement SQL syntax for querying, managing transactions, and making changes to data. It also shows how the systems use SQL functions, regular expression syntax, and type conversion functions and formats. All example SQL statements in this book execute against a set of tables, with data that you can quickly download. The third edition covers important database changes, including: Oracle's support of the recursive WITH syntax, and addition of PIVOT and UNPIVOT operators Functions new to Oracle, such as LISTAGG, NTH_VALUE, and more PostgreSQL’s support of recursive WITH and some window functions DB2 syntax and datatypes, some compatible with Oracle MySQL features such as the TIMESTAMP type and the TO_SECONDS function COMPUTERS,Languages,SQL

Sams Teach Yourself SQL in 24 Hours In just 24 sessions of one hour or less, you’ll learn how to use SQL to build effective databases, efficiently retrieve your data, and manage everything from performance to security! Using this book’s straightforward, step-by-step approach, you’ll learn hands-on through practical examples. Each lesson builds on what you’ve already learned, giving you a strong real-world foundation for success. The authors guide you from the absolute basics to advanced techniques—including views, transactions, Web data publishing, and even powerful SQL extensions for Oracle and Microsoft SQL Server! Step-by-step instructions carefully walk you through the most common SQL tasks. Quizzes and Exercises at the end of each chapter help you test your knowledge. By the Way notes present interesting information related to the discussion. Did You Know? tips offer advice or show you easier ways to perform tasks. Watch Out! cautions alert you to possible problems and give you advice on how to avoid them. Learn how to… Understand what SQL is, how it works, and what it does Define efficient database structures and objects “Normalize†raw databases into logically organized tables Edit relational data and tables with DML Manage database transactions Write effective, well-performing queries Categorize, summarize, sort, group, and restructure data Work with dates and times Join tables in queries, use subqueries, and combine multiple queries Master powerful query optimization techniques Administer databases and manage users Implement effective database security Use views, synonyms, and the system catalog Extend SQL to the enterprise and Internet Master important Oracle and Microsoft SQL Server extensions to ANSI SQL COMPUTERS,Languages,SQL

Oracle SQL by Example The World’s #1 Hands-On Oracle SQL Workbook–Fully Updated for Oracle 11g Crafted for hands-on learning and tested in classrooms worldwide, this book illuminates in-depth every Oracle SQL technique you’ll need. From the simplest query fundamentals to regular expressions and with newly added coverage of Oracle’s powerful new SQL Developer tool, you will focus on the tasks that matter most. Hundreds of step-by-step, guided lab exercises will systematically strengthen your expertise in writing effective, high-performance SQL. Along the way, you’ll acquire a powerful arsenal of useful skills–and an extraordinary library of solutions for your real-world challenges with Oracle SQL. Coverage includes 100% focused on Oracle SQL for Oracle 11 g, today’s #1 database platform–not “generic†SQL! Master all core SQL techniques including every type of join such as equijoins, self joins, and outer joins Understand Oracle functions in depth, especially character, number, date, timestamp, interval, conversion, aggregate, regular expressions, analytical, and more Practice all types of subqueries, such as correlated and scalar subqueries, and learn about set operators and hierarchical queries Build effective queries and learn fundamental Oracle SQL Developer and SQL*Plus skills Make the most of the Data Dictionary and create tables, views, indexes, and sequences Secure databases using Oracle privileges, roles, and synonyms Explore Oracle 11 g’s advanced data warehousing features Learn many practical tips about performance optimization, security, and architectural solutions Avoid common pitfalls and understand and solve common mistakes For every database developer, administrator, designer, or architect, regardless of experience! COMPUTERS,Languages,SQL

SQL in 10 Minutes, Sams Teach Yourself Sams Teach Yourself SQL in 10 Minutes, Fourth Edition New full-color code examples help you see how SQL statements are structured Whether you're an application developer, database administrator, web application designer, mobile app developer, or Microsoft Office users, a good working knowledge of SQL is an important part of interacting with databases. And Sams Teach Yourself SQL in 10 Minutes offers the straightforward, practical answers you need to help you do your job. Expert trainer and popular author Ben Forta teaches you just the parts of SQL you need to know–starting with simple data retrieval and quickly going on to more complex topics including the use of joins, subqueries, stored procedures, cursors, triggers, and table constraints. You'll learn methodically, systematically, and simply–in 22 short, quick lessons that will each take only 10 minutes or less to complete. With the Fourth Edition of this worldwide bestseller, the book has been thoroughly updated, expanded, and improved. Lessons now cover the latest versions of IBM DB2, Microsoft Access, Microsoft SQL Server, MySQL, Oracle, PostgreSQL, SQLite, MariaDB, and Apache Open Office Base. And new full-color SQL code listings help the beginner clearly see the elements and structure of the language. 10 minutes is all you need to learn how to... Use the major SQL statements Construct complex SQL statements using multiple clauses and operators Retrieve, sort, and format database contents Pinpoint the data you need using a variety of filtering techniques Use aggregate functions to summarize data Join two or more related tables Insert, update, and delete data Create and alter database tables Work with views, stored procedures, and more Table of Contents 1 Understanding SQL 2 Retrieving Data 3 Sorting Retrieved Data 4 Filtering Data 5 Advanced Data Filtering 6 Using Wildcard Filtering 7 Creating Calculated Fields 8 Using Data Manipulation Functions 9 Summarizing Data 10 Grouping Data 11 Working with Subqueries 12 Joining Tables 13 Creating Advanced Joins 14 Combining Queries 15 Inserting Data 16 Updating and Deleting Data 17 Creating and Manipulating Tables 18 Using Views 19 Working with Stored Procedures 20 Managing Transaction Processing 21 Using Cursors 22 Understanding Advanced SQL Features Appendix A: Sample Table Scripts Appendix B: Working in Popular Applications Appendix C : SQL Statement Syntax Appendix D: Using SQL Datatypes Appendix E: SQL Reserved Words COMPUTERS,Languages,SQL

Oracle PL/SQL Programming Considered the best Oracle PL/SQL programming guide by the Oracle community, this definitive guide is precisely what you need to make the most of Oracle’s powerful procedural language. The sixth edition describes the features and capabilities of PL/SQL up through Oracle Database 12c Release 1. Hundreds of thousands of PL/SQL developers have benefited from this book over the last twenty years; this edition continues that tradition. With extensive code examples and a lively sense of humor, this book explains language fundamentals, explores advanced coding techniques, and offers best practices to help you solve real-world problems. Get PL/SQL programs up and running quickly, with clear instructions for executing, tracing, testing, debugging, and managing code Understand new 12.1 features, including the ACCESSIBLE_BY clause, WITH FUNCTION and UDF pragma, BEQUEATH CURRENT_USER for views, and new conditional compilation directives Take advantage of extensive code samples, from easy-to-follow examples to reusable packaged utilities Optimize PL/SQL performance with features like the function result cache and Oracle utilities such as PL/Scope and the PL/SQL hierarchical profiler Build modular, easy-to-maintain PL/SQL applications using packages, procedures, functions, and triggers COMPUTERS,Languages,SQL

Learning MySQL and MariaDB If you’re a programmer new to databases—or just new to MySQL and its community-driven variant, MariaDB—you’ve found the perfect introduction. This hands-on guide provides an easy, step-by-step approach to installing, using, and maintaining these popular relational database engines. Author Russell Dyer, Curriculum Manager at MariaDB and former editor of the MySQL Knowledge Base, takes you through database design and the basics of data management and manipulation, using real-world examples and many practical tips. Exercises and review questions help you practice what you’ve just learned. Create and alter MySQL tables and specify fields and columns within them Learn how to insert, select, update, delete, join, and subquery data, using practical examples Use built-in string functions to find, extract, format, and convert text from columns Learn functions for mathematical or statistical calculations, and for formatting date and time values Perform administrative duties such as managing user accounts, backing up databases, and importing large amounts of data Use APIs to connect and query MySQL and MariaDB with PHP and other languages COMPUTERS,Languages,SQL

Practical SQL Practical SQL is an approachable and fast-paced guide to SQL (Structured Query Language), the standard programming language for defining, organizing, and exploring data in relational databases. The book focuses on using SQL to find the story your data tells, with the popular open-source database PostgreSQL and the pgAdmin interface as its primary tools. You’ll first cover the fundamentals of databases and the SQL language, then build skills by analyzing data from the U.S. Census and other federal and state government agencies. With exercises and real-world examples in each chapter, this book will teach even those who have never programmed before all the tools necessary to build powerful databases and access information quickly and efficiently. You’ll learn how to: - Create databases and related tables using your own data - Define the right data types for your information - Aggregate, sort, and filter data to find patterns - Use basic math and advanced statistical functions - Identify errors in data and clean them up - Import and export data using delimited text files - Write queries for geographic information systems (GIS) - Create advanced queries and automate tasks Learning SQL doesn’t have to be dry and complicated. Practical SQL delivers clear examples with an easy-to-follow approach to teach you the tools you need to build and manage your own databases. This book uses PostgreSQL, but the SQL syntax is applicable to many database applications, including Microsoft SQL Server and MySQL. COMPUTERS,Languages,SQL

T-SQL Fundamentals Effectively query and modify data using Transact-SQL Master T-SQL fundamentals and write robust code for Microsoft SQL Server and Azure SQL Database. Itzik Ben-Gan explains key T-SQL concepts and helps you apply your knowledge with hands-on exercises. The book first introduces T-SQL’s roots and underlying logic. Next, it walks you through core topics such as single-table queries, joins, subqueries, table expressions, and set operators. Then the book covers more-advanced data-query topics such as window functions, pivoting, and grouping sets. The book also explains how to modify data, work with temporal tables, and handle transactions, and provides an overview of programmable objects. Microsoft Data Platform MVP Itzik Ben-Gan shows you how to: Review core SQL concepts and its mathematical roots Create tables and enforce data integrity Perform effective single-table queries by using the SELECT statement Query multiple tables by using joins, subqueries, table expressions, and set operators Use advanced query techniques such as window functions, pivoting, and grouping sets Insert, update, delete, and merge data Use transactions in a concurrent environment Get started with programmable objects–from variables and batches to user-defined functions, stored procedures, triggers, and dynamic SQL COMPUTERS,Languages,SQL

SQL Antipatterns Bill Karwin has helped thousands of people write better SQL and build stronger relational databases. Now he's sharing his collection of antipatterns--the most common errors he's identified in those thousands of requests for help. Most developers aren't SQL experts, and most of the SQL that gets used is inefficient, hard to maintain, and sometimes just plain wrong. This book shows you all the common mistakes, and then leads you through the best fixes. What's more, it shows you what's behind these fixes, so you'll learn a lot about relational databases along the way. Each chapter in this book helps you identify, explain, and correct a unique and dangerous antipattern. The four parts of the book group the anti​patterns in terms of logical database design, physical database design, queries, and application development. The chances are good that your application's database layer already contains problems such as Index Shotgun, Keyless Entry, Fear of the Unknown, and Spaghetti Query. This book will help you and your team find them. Even better, it will also show you how to fix them, and how to avoid these and other problems in the future. SQL Antipatterns gives you a rare glimpse into an SQL expert's playbook. Now you can stamp out these common database errors once and for all. Whatever platform or programming language you use, whether you're a junior programmer or a Ph.D., SQL Antipatterns will show you how to design and build databases, how to write better database queries, and how to integrate SQL programming with your application like an expert. You'll also learn the best and most current technology for full-text search, how to design code that is resistant to SQL injection attacks, and other techniques for success. COMPUTERS,Languages,SQL

SQL Server 2017 Developer's Guide Build smarter and efficient database application systems for your organization with SQL Server 2017 About This Book Build database applications by using the development features of SQL Server 2017 Work with temporal tables to get information stored in a table at any time Use adaptive querying to enhance the performance of your queries Who This Book Is For Database developers and solution architects looking to design efficient database applications using SQL Server 2017 will find this book very useful. In addition, this book will be valuable to advanced analysis practitioners and business intelligence developers. Database consultants dealing with performance tuning will get a lot of useful information from this book as well.Some basic understanding of database concepts and T-SQL is required to get the best out of this book.What You Will Learn Explore the new development features introduced in SQL Server 2017 Identify opportunities for In-Memory OLTP technology Use columnstore indexes to get storage and performance improvements Exchange JSON data between applications and SQL Server Use the new security features to encrypt or mask the data Control the access to the data on the row levels Discover the potential of R and Python integration Model complex relationships with the graph databases in SQL Server 2017 In Detail Microsoft SQL Server 2017 is the next big step in the data platform history of Microsoft as it brings in the power of R and Python for machine learning and containerization-based deployment on Windows and Linux. Compared to its predecessor, SQL Server 2017 has evolved into Machine Learning with R services for statistical analysis and Python packages for analytical processing. This book prepares you for more advanced topics by starting with a quick introduction to SQL Server 2017's new features and a recapitulation of the possibilities you may have already explored with previous versions of SQL Server. The next part introduces you to enhancements in the Transact-SQL language and new database engine capabilities and then switches to a completely new technology inside SQL Server: JSON support. We also take a look at the Stretch database, security enhancements, and temporal tables. Furthermore, the book focuses on implementing advanced topics, including Query Store, columnstore indexes, and In-Memory OLTP. Towards the end of the book, you'll be introduced to R and how to use the R language with Transact-SQL for data exploration and analysis. You'll also learn to integrate Python code in SQL Server and graph database implementations along with deployment options on Linux and SQL Server in containers for development and testing. By the end of this book, you will have the required information to design efficient, high-performance database applications without any hassle. Style and approach This book is a detailed guide to mastering the development features offered by SQL Server 2017, with a unique learn-as-you-do approach. All the concepts are explained in a very easy-to-understand manner and are supplemented with examples to ensure that you—the developer—are able to take that next step in building more powerful, robust applications for your organization with ease. COMPUTERS,Languages,SQL

SQL by Example SQL by Example uses one case study to teach the reader basic structured query language (SQL) skills. The author has tested the case study in the classroom with thousands of students. While other SQL texts tend to use examples from many different data sets, the author has found that once students get used to one case study, they learn the material at a much faster rate. The text begins with an introduction to the case study and trains the reader to think like the query processing engine for a relational database management system. Once the reader has a grasp of the case study then SQL programming constructs are introduced with examples from the case study. In order to reinforce concepts, each chapter has several exercises with solutions provided on the book’s website. SQL by Example is designed both for those who have never worked with SQL as well as those with some experience. It is modular in that each chapter can be approached individually or as part of a sequence, giving the reader flexibility in the way that they learn or refresh concepts. This also makes the book a great reference to refer back to once the reader is honing his or her SQL skills on the job. COMPUTERS,Languages,SQL

SQL in 10 Minutes a Day, Sams Teach Yourself Sams Teach Yourself SQL in 10 Minutes offers straightforward, practical answers when you need fast results. By working through the book’s 22 lessons of 10 minutes or less, you’ll learn what you need to know to take advantage of the SQL language. Lessons cover IBM DB2, Microsoft SQL Server and SQL Server Express, MariaDB, MySQL, Oracle and Oracle express, PostgreSQL, and SQLite. Full-color code examples help you understand how SQL statements are structured Tips point out shortcuts and solutions Cautions help you avoid common pitfalls Notes explain additional concepts, and provide additional information 10 minutes is all you need to learn how to… Use the major SQL statements Construct complex SQL statements using multiple clauses and operators Retrieve, sort, and format database contents Pinpoint the data you need using a variety of filtering techniques Use aggregate functions to summarize data Join two or more related tables Insert, update, and delete data Create and alter database tables Work with views, stored procedures, and more COMPUTERS,Languages,SQL

Learning SQL As data floods into your company, you need to put it to work right away—and SQL is the best tool for the job. With the latest edition of this introductory guide, author Alan Beaulieu helps developers get up to speed with SQL fundamentals for writing database applications, performing administrative tasks, and generating reports. You’ll find new chapters on SQL and big data, analytic functions, and working with very large databases. Each chapter presents a self-contained lesson on a key SQL concept or technique using numerous illustrations and annotated examples. Exercises let you practice the skills you learn. Knowledge of SQL is a must for interacting with data. With Learning SQL, you’ll quickly discover how to put the power and flexibility of this language to work. Move quickly through SQL basics and several advanced features Use SQL data statements to generate, manipulate, and retrieve data Create database objects, such as tables, indexes, and constraints with SQL schema statements Learn how datasets interact with queries; understand the importance of subqueries Convert and manipulate data with SQL’s built-in functions and use conditional logic in data statements COMPUTERS,Languages,SQL

Presto Perform fast interactive analytics against different data sources using the Presto high-performance, distributed SQL query engine. With this practical guide, you’ll learn how to conduct analytics on data where it lives, whether it’s Hive, Cassandra, a relational database, or a proprietary data store. Analysts, software engineers, and production engineers will learn how to manage, use, and even develop with Presto. Initially developed by Facebook, open source Presto is now used by Netflix, Airbnb, LinkedIn, Twitter, Uber, and many other companies. Matt Fuller, Manfred Moser, and Martin Traverso from Starburst show you how a single Presto query can combine data from multiple sources to allow for analytics across your entire organization. Get started: Explore Presto’s use cases and learn about tools that will help you connect to Presto and query data Go deeper: Learn Presto’s internal workings, including how to connect to and query data sources with support for SQL statements, operators, functions, and more Put Presto in production: Use this query engine for security and monitoring and with other applications; learn how other organizations apply Presto COMPUTERS,Languages,SQL

Learn SQL Database Programming Learn everything you need to know to build efficient SQL queries using this easy-to-follow beginner's guide Key Features Explore all SQL statements in depth using a variety of examples Get to grips with database querying, data aggregate, manipulation, and much more Understand how to explore and process data of varying complexity to tell a story Book Description SQL is a powerful querying language that's used to store, manipulate, and retrieve data, and it is one of the most popular languages used by developers to query and analyze data efficiently. If you're looking for a comprehensive introduction to SQL, Learn SQL Database Programming will help you to get up to speed with using SQL to streamline your work in no time. Starting with an overview of relational database management systems, this book will show you how to set up and use MySQL Workbench and design a database using practical examples. You'll also discover how to query and manipulate data with SQL programming using MySQL Workbench. As you advance, you'll create a database, query single and multiple tables, and modify data using SQL querying. This SQL book covers advanced SQL techniques, including aggregate functions, flow control statements, error handling, and subqueries, and helps you process your data to present your findings. Finally, you'll implement best practices for writing SQL and designing indexes and tables. By the end of this SQL programming book, you'll have gained the confidence to use SQL queries to retrieve and manipulate data. What you will learn Install, configure, and use MySQL Workbench to restore a database Explore different data types such as string, numeric, and date and time Query a single table using the basic SQL SELECT statement and the FROM, WHERE, and ORDER BY clauses Query multiple tables by understanding various types of table relationships Modify data in tables using the INSERT, UPDATE, and DELETE statements Use aggregate functions to group and summarize data Detect bad data, duplicates, and irrelevant values while processing data Who this book is for This book is for business analysts, SQL developers, database administrators, and students learning SQL. If you want to learn how to query and manipulate SQL data for database administration tasks or simply extract and organize relevant data for analysis, you'll find this book useful. No prior SQL experience is required. COMPUTERS,Languages,SQL

Product Analytics Use Product Analytics to Understand and Change Consumer Behavior at Scale Product Analytics is a complete, hands-on guide to generating actionable business insights from customer data. Experienced data scientist and enterprise manager Joanne Rodrigues introduces practical statistical techniques for determining why things happen and how to change, at scale, what people do. She complements these with powerful social science techniques for creating better theories, designing better metrics, and driving more rapid and sustained behavior change. This book fills the gaps that many other data science book leave behind: how to start a new data science project; how to conceptualize complex ideas; building metrics from the statistic and demographic fundamentals; projecting consumer populations and material needs for a business; and causal inference beyond simple A/B testing techniques, such as difference-in-difference, regression discontinuity, propensity score matching, and uplift modelling. Writing for entrepreneurs, product managers, marketers, and other business analytics professionals, Rodrigues teaches through intuitive examples from both web and offline environments. Avoiding math-heavy explanations, she guides you step by step through choosing the right techniques and algorithms for each application, running analyses in the R programming language, and getting answers you can trust. Whatever your product or service, this guide can help you create precision-targeted marketing campaigns, improve consumer satisfaction and engagement, and grow revenue and profits. Develop core metrics and effective KPIs for user analytics in any web product Truly understand statistical inference, and the differences between correlation and causation Build intuitive predictive models to capture user behavior in products Tease out causal effects from observational data using modern, quasi-experimental designs and statistical matching Improve response through uplift modeling and other sophisticated targeting methods Project business costs and product population changes via advanced demographic techniques Register your book for convenient access to downloads, updates, and/or corrections as they become available. See inside the book for details. COMPUTERS,Languages,SQL

UML in Practice Offers comprehensive coverage of all major modeling viewpoints Provides details of collaboration and class diagrams for filling in the design-level models COMPUTERS,Languages,UML

Absolute Beginner's Guide to VBA Visual Basic for Applications (VBA) is a set of tools based on the Visual Basic language. The great thing about using it to enhance Office applications is that it's easier to learn than Visual Basic and it comes with your Office license. After reading this book, the reader will be proficient in the VBA language and will have extensive knowledge of the Office 2003 Object Model. This book will cover all features of the VBA editor and show how to program some of the more useful new features in the Office 2003 applications. This book assumes no prior programming experience, so even programming novices can get up to speed quickly on the basics of the VBA language. It is very practical and offers the reader tested programs and projects that he or she can implement right away. This book reinforces the reader's learning by presenting useful, end-of-chapter pedagogical resources, including question-and-answer sessions and quizzes, as well as practical exercises that cement and extend the reader's knowledge. It explorers not only the object models of Word and Excel, but also other members of the Office 2003 suite, including PowerPoint, Access, and Outlook. COMPUTERS,Languages,Visual BASIC

VBScript in a Nutshell Lightweight yet powerful, VBScript from Microsoft® is used in four main areas: server-side web applications using Active Server Pages (ASP), client-side web scripts using Internet Explorer, code behind Outlook forms, and automating repetitive tasks using Windows Script Host (WSH). VBScript in a Nutshell, Second Edition delivers current and complete documentation for programmers and system administrators who want to develop effective scripts.Completely updated for VBScript 5.6, WSH 5.6 and ASP 3.0, VBScript In a Nutshell, Second Edition includes updated introductory chapters that will help you keep current with the significant changes since the first edition was published. New chapters introduce the Windows Script Component for creating binary COM components, and the Script Encoder.The main part of the book is a comprehensive reference focusing on VBScript essentials with an alphabetical reference to all statements, keywords and objects, and a section of notes and solutions to real-world gotchas--various undocumented behaviors and aspects of the language--to help you avoid potential problems. Each entry in the reference section details the following: The keyword's syntax, using standard code conventions A list of arguments accepted by the function or procedure, if any exist A discussion of how and where the keyword should be used within the scripting environment A discussion of the differences between the operation of the keyword in Visual Basic or VBA and in VBScript Regardless of your level of experience programming with VBScript, VBScript in a Nutshell, Second Edition is the book you'll want by your side--the most complete, up-to-date, and easy-to-use language reference available. COMPUTERS,Languages,Visual BASIC

Visual Basic 2005 Cookbook This book will help you solve more than 300 of the most common and not-so-common tasks that working Visual Basic 2005 programmers face every day. If you're a seasoned .NET developer, beginning Visual Basic programmer, or a developer seeking a simple and clear migration path from VB6 to Visual Basic 2005, the Visual Basic 2005 Cookbook delivers a practical collection of problem-solving recipes for a broad range of Visual Basic programming tasks. The concise solutions and examples in the Visual Basic 2005 Cookbook range from simple tasks to the more complex, organized by the types of problems you need to solve. Nearly every recipe contains a complete, documented code sample showing you how to solve the specific problem, as well as a discussion of how the underlying technology works and that outlines alternatives, limitations, and other considerations. As with all O'Reilly Cookbooks, each recipe helps you quickly understand a problem, learn how to solve it, and anticipate potential tradeoffs or ramifications. Useful features of the book include: Over 300 recipes written in the familiar O'Reilly Problem-Solution-Discussion format Hundreds of code snippets, examples, and complete solutions available for download VB6 updates to alert VB6 programmers to code-breaking changes in Visual Basic 2005 Recipes that target Visual Basic 2005 features not included in previous releases Code examples covering everyday data manipulation techniques and language fundamentals Advanced projects focusing on multimedia and mathematical transformations using linear algebraic methods Specialized topics covering files and file systems, printing, and databases In addition, you'll find chapters on cryptography and compression, graphics, and special programming techniques. Whether you're a beginner or an expert, the Visual Basic 2005 Cookbook is sure to save you time, serving up the code you need, when you need it. COMPUTERS,Languages,Visual BASIC

ADO.NET in a Nutshell Written by experts on the Microsoft® .NET programming platform, ADO.NET in a Nutshell delivers everything .NET programmers will need to get a jump-start on ADO.NET technology or to sharpen their skills even further. In the tradition of O'Reilly's In a Nutshell Series, ADO.NET in a Nutshell is the most complete and concise source of ADO.NET information available.ADO.NET is the suite of data access technologies in the .NET Framework that developers use to build applications services accessing relational data and XML. Connecting to databases is a fundamental part of most applications, whether they are web, Windows®, distributed, client/server, XML Web Services, or something entirely different. But ADO.NET is substantially different from Microsoft's previous data access technologies--including the previous version of ADO--so even experienced developers need to understand the basics of the new disconnected model before they start programming with it.Current with the .NET Framework 1.1, ADO.NET in a Nutshell offers one place to look when you need help with anything related to this essential technology, including a reference to the ADO.NET namespaces and object model. In addition to being a valuable reference, this book provides a concise foundation for programming with ADO.NET and covers a variety of issues that programmers face when developing web applications or Web Services that rely on database access. Using C#, this book presents real world, practical examples that will help you put ADO.NET to work immediately.Topics covered in the book include: An Introduction to ADO.NET Connections, Commands and DataReaders Disconnected Data Advanced DataSets Transactions DataViews and Data Binding XML and the DataSet Included with the book is a Visual Studio .NET add-in that integrates the entire reference directly into your help files. When combining ADO.NET in a Nutshell with other books from O'Reilly's .NET In a Nutshell series, you'll have a comprehensive, detailed and independent reference collection that will help you become more productive. COMPUTERS,Languages,Visual BASIC

Beginning Visual Basic 2015 Learn Visual Basic step by step and start programming right away Beginning Visual Basic 2015 is the ideal guide for new programmers, especially those learning their first language. This new edition has been updated to align with Visual Studio 2015, and also refocused to concentrate on key beginner topics. Precise, step-by-step instructions walk you through important tasks, and clear explanations targeted to beginners will have you writing your first Visual Basic application quickly. You'll start from the absolute beginning, assuming no prior programming experience, and then gradually build your skills to write Visual Basic applications for Windows and the Web. Coverage includes objects, class libraries, graphics, databases, and much more, with explicit instructions on using ASP.NET, SQL Server, ADO.NET, and XML. Visual Studio is the usual environment for Visual Basic programming, and the latest upgrade has made Visual Basic more feature compatible with C# to allow programmers to move fluidly between the two languages. Don't know C#? Don't worry! This book starts from the very beginning of Visual Basic programming to help you build your skills from the ground-up. Understand flow control and data structure Debug Windows applications, dialog boxes, and menus Master objects and object-oriented techniques Access databases, program graphics, and program for the Web Over three million programmers use Visual Basic, and many of them learned it as their first language. It's beginner-friendly, versatile, and visually oriented, making it an ideal introduction to the programming mindset, workflow, and hard skills. Beginning Visual Basic 2015 gets you started on the right foot, with clear, patient instruction and plenty of hands-on practice. COMPUTERS,Languages,Visual BASIC

Securing Web Services with WS-Security Comprehensive coverage is given in this up-to-date and practical guide to Web services security--the first to cover the final release of new standards SAML 1.1 and WS-Security. Rosenberg and Remy are security experts who co-founded GeoTrust, the #2 Web site certificate authority. COMPUTERS,Languages,XML

XML What is XML? XML, or eXtensible Markup Language, is a specification for storing information. It is also a specification for describing the structure of that information. And while XML is a markup language (just like HTML), XML has no tags of its own. It allows the person writing the XML to create whatever tags they need. The only condition is that these newly created tags adhere to the rules of the XML specification. In the seven years since the first edition of “XML: Visual QuickStart Guide†was published, XML has taken its place next to HTML as a foundational language on the Internet. XML has become a very popular method for storing data and the most popular method for transmitting data between all sorts of systems and applications. The reason being, where HTML was designed to display information, XML was designed to manage it. “XML: Visual QuickStart Guide, 2nd Edition†is divided into seven parts. Each part contains one or more chapters with step-by-step instructions that explain how to perform XML-related tasks. Wherever possible, examples of the concepts being discussed are displayed, and the parts of the examples on which to focus are highlighted. The order of the book is intentionally designed to be an introduction to the fundamentals of XML, followed by discussions of related XML technologies. COMPUTERS,Languages,XML

XSLT 2.0 and XPath 2.0 Programmer's Reference Combining coverage of both XSLT 2.0 and XPath 2.0, this book is the definitive reference to the final recommendation status versions of both specifications. The authors start by covering the concepts in XSLT and XPath, and then delve into elements, operators, expressions with syntax, usage, and examples. Some of the specific topics covered include XSLT processing model, stylesheet structure, serialization, extensibility, and many others. In addition to online content that includes error codes, the book also has case studies you'll find applicable to your own challenges. COMPUTERS,Languages,XML

DocBook 5 If you need a reliable tool for technical documentation, this clear and concise reference will help you take advantage of DocBook, the popular XML schema originally developed to document computer and hardware projects. DocBook 5.0 has been expanded and simplified to address documentation needs in other fields, and it's quickly becoming the tool of choice for many content providers. DocBook 5: The Definitive Guide is the complete, official documentation of DocBook 5.0. You'll find everything you need to know to use DocBook 5.0's features-including its improved content model-whether you're new to DocBook or an experienced user of previous versions. Learn how to write DocBook XML documents Understand DocBook 5.0's elements and attributes, and how they fit together Determine whether your documents conform to the DocBook schema Learn about options for publishing DocBook to various output formats Customize the DocBook schema to meet your needs Get additional information about DocBook editing and processing COMPUTERS,Languages,XML

XSLT After years of anticipation and delay, the W3C finally released the XSLT 2.0 standard in January 2007. The revised edition of this classic book offers practical, real-world examples that demonstrate how you can apply XSLT stylesheets to XML data using either the new specification, or the older XSLT 1.0 standard. XSLT is a critical language for converting XML documents into other formats, such as HTML code or a PDF file. With XSLT, you get a thorough understanding of XSLT and XPath and their relationship to other web standards, along with recommendations for a honed toolkit in an open platform-neutral, standards-based environment. This book: Covers the XSLT basics, including simple stylesheets and methods for setting up transformation engines Walks you through the many parts of XSLT, particularly XSLT's template-based approach to transformations Applies both XSLT 1.0 and 2.0 solutions to the same problems, helping you decide which version of XSLT is more appropriate for your project Includes profuse examples that complement both the tutorial and the reference material The new edition of XSLT has been updated thoroughly to explain XSLT 2.0's many dependencies, notably XML Schema and XPath 2.0. Want to find out how the 2.0 specification improves on the old? This book will explain. COMPUTERS,Languages,XML

Programming Web Services with SOAP The web services architecture provides a new way to think about and implement application-to-application integration and interoperability that makes the development platform irrelevant. Two applications, regardless of operating system, programming language, or any other technical implementation detail, communicate using XML messages over open Internet protocols such as HTTP or SMTP. The Simple Open Access Protocol (SOAP) is a specification that details how to encode that information and has become the messaging protocol of choice for Web services.Programming Web Services with SOAP is a detailed guide to using SOAP and other leading web services standards--WSDL (Web Service Description Language), and UDDI (Universal Description, Discovery, and Integration protocol). You'll learn the concepts of the web services architecture and get practical advice on building and deploying web services in the enterprise.This authoritative book decodes the standards, explaining the concepts and implementation in a clear, concise style. You'll also learn about the major toolkits for building and deploying web services. Examples in Java, Perl, C#, and Visual Basic illustrate the principles. Significant applications developed using Java and Perl on the Apache Tomcat web platform address real issues such as security, debugging, and interoperability.Covered topic areas include: The Web Services Architecture SOAP envelopes, headers, and encodings WSDL and UDDI Writing web services with Apache SOAP and Java Writing web services with Perl's SOAP::Lite Peer-to-peer (P2P) web services Enterprise issues such as authentication, security, and identity Up-and-coming standards projects for web services Programming Web Services with SOAP provides you with all the information on the standards, protocols, and toolkits you'll need to integrate information services with SOAP. You'll find a solid core of information that will help you develop individual Web services or discover new ways to integrate core business processes across an enterprise. COMPUTERS,Languages,XML

XPath and XPointer Referring to specific information inside an XML document is a little like finding a needle in a haystack: how do you differentiate the information you need from everything else? XPath and XPointer are two closely related languages that play a key role in XML processing by allowing developers to find these needles and manipulate embedded information. XPath describes a route for finding specific items by defining a path through the hierarchy of an XML document, abstracting only the information that's relevant for identifying the data. XPointer extends XPath to identify more complex parts of documents. The two technologies are critical for developers seeking needles in haystacks in various types of processing.XPath and XPointer fills an essential need for XML developers by focusing directly on a critical topic that has been covered only briefly. Written by John Simpson, an author with considerable XML experience, the book offers practical knowledge of the two languages that underpin XML, XSLT and XLink. XPath and XPointer cuts through basic theory and provides real-world examples that you can use right away.Written for XML and XSLT developers and anyone else who needs to address information in XML documents, the book assumes a working knowledge of XML and XSLT. It begins with an introduction to XPath basics. You'll learn about location steps and paths, XPath functions and numeric operators. Once you've covered XPath in depth, you'll move on to XPointer--its background, syntax, and forms of addressing. By the time you've finished the book, you'll know how to construct a full XPointer (one that uses an XPath location path to address document content) and completely understand both the XPath and XPointer features it uses.XPath and XPointer contains material on the forthcoming XPath 2.0 spec and EXSLT extensions, as well as versions 1.0 of both XPath and XPointer. A succinct but thorough hands-on guide, no other book on the market provides comprehensive information on these two key XML technologies in one place. COMPUTERS,Languages,XML

Learning XML This second edition of the bestselling Learning XML provides web developers with a concise but grounded understanding of XML (the Extensible Markup Language) and its potential-- not just a whirlwind tour of XML.The author explains the important and relevant XML technologies and their capabilities clearly and succinctly with plenty of real-life projects and useful examples. He outlines the elements of markup--demystifying concepts such as attributes, entities, and namespaces--and provides enough depth and examples to get started. Learning XML is a reliable source for anyone who needs to know XML, but doesn't want to waste time wading through hundreds of web sites or 800 pages of bloated text.For writers producing XML documents, this book clarifies files and the process of creating them with the appropriate structure and format. Designers will learn what parts of XML are most helpful to their team and will get started on creating Document Type Definitions. For programmers, the book makes syntax and structures clear. Learning XML also discusses the stylesheets needed for viewing documents in the next generation of browsers, databases, and other devices.Learning XML illustrates the core XML concepts and language syntax, in addition to important related tools such as the CSS and XSL styling languages and the XLink and XPointer specifications for creating rich link structures. It includes information about three schema languages for validation: W3C Schema, Schematron, and RELAX-NG, which are gaining widespread support from people who need to validate documents but aren't satisfied with DTDs. Also new in this edition is a chapter on XSL-FO, a powerful formatting language for XML. If you need to wade through the acronym soup of XML and start to really use this powerful tool, Learning XML, will give you the roadmap you need. COMPUTERS,Languages,XML

Learning XSLT XSLT is a powerful language for transforming XML documents into something else. That something else can be an HTML document, another XML document, a Portable Document Format (PDF) file, a Scalable Vector Graphics (SVG) file, a Virtual Reality Modeling Language (VRML) file, Java code, or a number of other things. You write an XSLT stylesheet to define the rules for transforming an XML document, and the XSLT processor does the work.As useful as XSLT is, its peculiar characteristics make it a difficult language in which to get started. In fact, newcomers are often a little dazed on first contact. Learning XSLT offers a hands-on introduction to help them get up to speed with XSLT quickly. The book will help web developers and designers understand this powerful but often mystifying template-driven and functional-styled language, getting them over the many differences between XSLT and the more conventional programming languages.Learning XSLT moves smoothly from the simple to complex, illustrating all aspects of XSLT 1.0 through step-by-step examples that you'll practice as you work through the book. Thorough in its coverage of the language, the book makes few assumptions about what you may already know. You'll learn about XSLT's template-based syntax, how XSLT templates work with each other, and gain an understanding of XSLT variables. Learning XSLT also explains how the XML Path Language (XPath) is used by XSLT and provides a glimpse of what the future holds for XSLT 2.0 and XPath 2.0.The ability to transform one XML vocabulary to another is fundamental to exploiting the power of XML. Learning XSLT is a carefully paced, example-rich introduction to XSLT that will have you understanding and using XSLT on your own in no time. COMPUTERS,Languages,XML

XSL-FO No matter how flexible and convenient digital information has become, we haven't done away with the need to see information in print. Extensible Style Language-Formatting Objects, or XSL-FO, is a set of tools developers and web designers use to describe page printouts of their XML (including XHTML) documents. If you need to produce high quality printed material from your XML documents, then XSL-FO provides the bridge.XSL-FO is one of the few books to go beyond a basic introduction to the technology. While many books touch on XSL-FO in their treatment of XSLT, this book offers in-depth coverage of XSL-FO's features and strengths. Author Dave Pawson is well known in the XSLT and XSL-FO communities, and maintains the XSLT FAQ. An online version of this book has helped many developers master this technology. XSL-FO is the first time this reference is available in print.The first part of the book provides an overview of the technology and introduces the XSL-FO vocabulary. The author discusses how to choose among today's implementations, explains how to describe pages, and shows you what is going on in the processor in terms of layout. You'll learn about the basics of formatting and layout as well as readability.The second part focuses on smaller pieces: blocks, inline structures, graphics, color and character level formatting, concluding by showing how to integrate these parts into a coherent whole. XSL-FO also explores organizational aspects you'll need to consider?how to design your stylesheets strategically rather than letting them evolve on their own.XSL-FO is more than just a guide to the technology; the book teaches you how to think about the formatting of your documents and guides you through the questions you'll need to ask to ensure that your printed documents meet the same high standards as your computer-generated content. Written for experienced XML developers and web designers, no other book contains as much useful information on this practical technology. COMPUTERS,Languages,XML

XML in a Nutshell If you're a developer working with XML, you know there's a lot to know about XML, and the XML space is evolving almost moment by moment. But you don't need to commit every XML syntax, API, or XSLT transformation to memory; you only need to know where to find it. And if it's a detail that has to do with XML or its companion standards, you'll find it--clear, concise, useful, and well-organized--in the updated third edition of XML in a Nutshell.With XML in a Nutshell beside your keyboard, you'll be able to: Quick-reference syntax rules and usage examples for the core XML technologies, including XML, DTDs, Xpath, XSLT, SAX, and DOM Develop an understanding of well-formed XML, DTDs, namespaces, Unicode, and W3C XML Schema Gain a working knowledge of key technologies used for narrative XML documents such as web pages, books, and articles technologies like XSLT, Xpath, Xlink, Xpointer, CSS, and XSL-FO Build data-intensive XML applications Understand the tools and APIs necessary to build data-intensive XML applications and process XML documents, including the event-based Simple API for XML (SAX2) and the tree-oriented Document Object Model (DOM) This powerful new edition is the comprehensive XML reference. Serious users of XML will find coverage on just about everything they need, from fundamental syntax rules, to details of DTD and XML Schema creation, to XSLT transformations, to APIs used for processing XML documents. XML in a Nutshell also covers XML 1.1, as well as updates to SAX2 and DOM Level 3 coverage. If you need explanation of how a technology works, or just need to quickly find the precise syntax for a particular piece, XML in a Nutshell puts the information at your fingertips.Simply put, XML in a Nutshell is the critical, must-have reference for any XML developer. COMPUTERS,Languages,XML

Fonts & Encodings This reference is a fascinating and complete guide to using fonts and typography on the Web and across a variety of operating systems and application software. Fonts & Encodings shows you how to take full advantage of the incredible number of typographic options available, with advanced material that covers everything from designing glyphs to developing software that creates and processes fonts. The era of ASCII characters on green screens is long gone, and industry leaders such as Apple, HP, IBM, Microsoft, and Oracle have adopted the Unicode Worldwide Character Standard. Yet, many software applications and web sites still use a host of standards, including PostScript, TrueType, TeX/Omega, SVG, Fontlab, FontForge, Metafont, Panose, and OpenType. This book explores each option in depth, and provides background behind the processes that comprise today's "digital space for writing": Part I introduces Unicode, with a brief history of codes and encodings including ASCII. Learn about the morass of the data that accompanies each Unicode character, and how Unicode deals with normalization, the bidirectional algorithm, and the handling of East Asian characters. Part II discusses font management, including installation, tools for activation/deactivation, and font choices for three different systems: Windows, the Mac OS, and the X Window System (Unix). Part III deals with the technical use of fonts in two specific cases: the TeX typesetting system (and its successor, W, which the author co-developed) and web pages. Part IV describes methods for classifying fonts: Vox, Alessandrini, and Panose-1, which is used by Windows and the CSS standard. Learn about existing tools for creating (or modifying) fonts, including FontLab and FontForge, and become familiar with OpenType properties and AAT fonts. Nowhere else will you find the valuable technical information on fonts and typography that software developers, web developers, and graphic artists need to know to get typography and fonts to work properly. COMPUTERS,Languages,XML

XSLT Cookbook Forget those funky robot toys that were all the rage in the '80s, XSLT (Extensible Stylesheet Transformations) is the ultimate transformer. This powerful language is expert at transforming XML documents into PDF files, HTML documents, JPEG files--virtually anything your heart desires. As useful as XSLT is, though, most people have a difficult time learning its many peculiarities. And now Version 2.0, while elegant and powerful, has only added to the confusion. XSLT Cookbook, Second Edition wants to set the record straight. It helps you sharpen your programming skills and overall understanding of XSLT through a collection of detailed recipes. Each recipe breaks down a specific problem into manageable chunks, giving you an easy-to-grasp roadmap for integrating XSLT with your data and applications. No other XSLT book around employs this practical problem-solution-discussion format. In addition to offering code recipes for solving everyday problems with XSLT 1.0, this new edition shows you how to leverage the improvements found in XSLT 2.0, such as how to simplify the string manipulation and date/time conversion processes. The book also covers XPath 2.0, a critical companion standard, as well as topics ranging from basic transformations to complex sorting and linking. It even explores extension functions on a variety of different XSLT processors and shows ways to combine multiple documents using XSLT. Code examples add a real-world dimension to each technique. Whether you're just starting out in XSLT or looking for advanced techniques, you'll find the level of information you need in XSLT Cookbook, Second Edition. COMPUTERS,Languages,XML

XSLT 1.0 Pocket Reference XSLT is an essential tool for converting XML into other kinds of documents: HTML, PDF file, and many others. It's a critical technology for XML-based platforms such as Microsoft .NET, Sun Microsystems' Sun One, as well as for most web browsers and authoring tools. As useful as XSLT is, however, most people have a difficult time getting used to its peculiar characteristics. The ability to use advanced techniques depends on a clear and exact understanding of how XSLT templates work and interact. The XSLT 1.0 Pocket Reference from O'Reilly wants to make sure you achieve that level of understanding. With its concise approach, this handy pocket guide quickly gets you up to speed on XSLT 1.0 so you can covert XML like a seasoned pro. In addition to covering the basics of stylesheet structure, it also explains how to: use template rules create a result tree apply conditional processing transform multiple source documents employ number formatting Thanks to their convenient, quick-reference format, O'Reilly's Pocket References spare you from having to hunt through larger books for answers. They deliver just what you need to get the job done in a timely fashion. And the XSLT 1.0 Pocket Reference is no different--it's the ideal companion to have at your desk when you need an answer fast. COMPUTERS,Languages,XML

XML Pocket Reference XML, the Extensible Markup Language, is everywhere: the syntax of choice for newly designed document formats across almost all computer applications. Now used daily by developers, XML is living up to its reputation as one of the most important developments in document interchange in the history of computing. A perennial bestseller, the handy XML Pocket Reference from O'Reilly has been revised once again to give you quick access to the latest goods. In addition to its comprehensive look at XML, this third edition has been updated with new material on Namespaces and XML Schema--considered among the most important elements in current XML use--along with RELAX NG and Schematron, additional powerful tools for describing XML document structures. Like other titles in O'Reilly's Pocket Reference series, the XML Pocket Reference, 3rd Edition features a well-organized format that gets right to the point. As a result, it's already won over the allegiance of developers everywhere. If you need XML answers quick and on the fly, this compact book is most definitely the book for you. COMPUTERS,Languages,XML

Definitive XML Schema “XML Schema 1.1 has gone from strong data typing to positively stalwart—so powerful it can enforce database level constraints and business rules, so your data transfer code won’t have to. This book covers the 1.1 changes—and more—in its 500 revisions to Priscilla Walmsley’s 10-year best-selling classic. It’s the guide you need to navigate XML Schema’s complexity—and master its power!†—Charles F. Goldfarb For Ten Years the World’s Favorite Guide to XML Schema—Now Extensively Revised for Version 1.1 and Today’s Best Practices! To leverage XML’s full power, organizations need shared vocabularies based on XML Schema. For a full decade, Definitive XML Schema has been the most practical, accessible, and usable guide to working with XML Schema. Now, author Priscilla Walmsley has thoroughly updated her classic to fully reflect XML Schema 1.1, and to present new best practices for designing successful schemas. Priscilla helped create XML Schema as a member of the W3C XML Schema Working Group, so she is well qualified to explain the W3C recommendation with insight and clarity. Her book teaches practical techniques for writing schemas to support any application, including many new use cases. You’ll discover how XML Schema 1.1 provides a rigorous, complete specification for modeling XML document structure, content, and datatypes; and walk through the many aspects of designing and applying schemas, including composition, instance validation, documentation, and namespaces. Then, building on the fundamentals, Priscilla introduces powerful advanced techniques ranging from type derivation to identity constraints. This edition’s extensive new coverage includes Many new design hints, tips, and tricks – plus a full chapter on creating an enterprise strategy for schema development and maintenance Design considerations in creating schemas for relational and object-oriented models, narrative content, and Web services An all-new chapter on assertions Coverage of new 1.1 features, including overrides, conditional type assignment, open content and more Modernized rules for naming and design Substantially updated coverage of extensibility, reuse, and versioning And much more If you’re an XML developer, architect, or content specialist, with this Second Edition you can join the tens of thousands who rely on Definitive XML Schema for practical insights, deeper understanding, and solutions that work. COMPUTERS,Languages,XML

SVG Essentials Learn the essentials of Scalable Vector Graphics, the mark-up language used by most vector drawing programs and interactive web graphics tools. SVG Essentials takes you through SVG’s capabilities, beginning with simple line drawings and moving through complicated features such as filters, transformations, gradients, and patterns. This thoroughly updated edition includes expanded coverage of animation, interactive graphics, and scripting SVG. Interactive examples online make it easy for you to experiment with SVG features in your web browser. Geared toward experienced designers, this book also includes appendices that explain basic concepts such as XML markup and CSS styling, so even if you have no web design experience, you can start learning SVG. Create and style graphics to match your web design in a way that looks great when printed or displayed on high-resolution screens Make your charts and decorative headings accessible to search engines and assistive technologies Add artistic effects to your graphics, text, and photographs using SVG masks, filters, and transformations Animate graphics with SVG markup, or add interactivity with CSS and JavaScript Create SVG from existing vector data or XML data, using programming languages and XSLT COMPUTERS,Languages,XML

SVG Animations SVG is extremely powerful, with its reduced HTTP requests and crispness on any display. It becomes increasingly more interesting as you explore its capabilities for responsive animation and performance boons. When you animate SVG, you must be aware of normal image traits like composition, color, implementation, and optimization. But when you animate, it increases the complexity of each of these factors exponentially. This practical book takes a deep dive into how you can to solve these problems with stability, performance, and creativity in mind. Learn how to make SVG cross-browser compatible, backwards compatible, optimized, and responsive Plan and debug animation Make a complex animation responsive, as many sites are responsive Profile each animation technique in terms of performance so that you know what you're getting in to with each library or native technology COMPUTERS,Languages,XML

Relational Methods in Computer Science The calculus of relations has been an important component of the development of logic and algebra since the middle of the nineteenth century, when Augustus De Morgan observed that since a horse is an animal we should be able to infer that the head of a horse is the head of an animal. For this, Aristotelian syllogistic does not suffice: We require relational reasoning. George Boole, in his Mathematical Analysis of Logic of 1847, initiated the treatment of logic as part of mathematics, specifically as part of algebra. Quite the opposite conviction was put forward early this century by Bertrand Russell and Alfred North Whitehead in their Principia Mathematica (1910 - 1913): that mathematics was essentially grounded in logic. Logic thus developed in two streams. On the one hand algebraic logic, in which the calculus of relations played a particularly prominent part, was taken up from Boole by Charles Sanders Peirce, who wished to do for the "calculus of relatives" what Boole had done for the calculus of sets. Peirce's work was in turn taken up by Schroder in his Algebra und Logik der Relative of 1895 (the third part of a massive work on the algebra of logic). Schroder's work, however, lay dormant for more than 40 years, until revived by Alfred Tarski in his seminal paper "On the calculus of binary relations" of 1941 (actually his presidential address to the Association for Symbolic Logic). COMPUTERS,Logic Design

Proof and Computation Proceedings of the NATO Advanced Study Institute on Proof and Computation, held in Marktoberdorf, Germany, July 20 - August 1, 1993 COMPUTERS,Logic Design

VLSI Chip Design with the Hardware Description Language VERILOG The art of transforming a circuit idea into a chip has changed permanently. Formerly, the electrical, physical and geometrical tasks were predominant. Later, mainly net lists of gates had to be constructed. Nowadays, hardware description languages (HDL) similar to programming languages are central to digital circuit design. HDL-based design is the main subject of this book.After emphasizing the economic importance of chip design as a key technology, the book deals with VLSI design (Very Large Scale Integration), the design of modern RISC processors, the hardware description language VERILOG, and typical modeling techniques. Numerous examples as well as a VERILOG training simulator are included on a disk. COMPUTERS,Logic Design

Learning FPGAs Learn how to design digital circuits with FPGAs (field-programmable gate arrays), the devices that reconfigure themselves to become the very hardware circuits you set out to program. With this practical guide, author Justin Rajewski shows you hands-on how to create FPGA projects, whether you’re a programmer, engineer, product designer, or maker. You’ll quickly go from the basics to designing your own processor. Designing digital circuits used to be a long and costly endeavor that only big companies could pursue. FPGAs make the process much easier, and now they’re affordable enough even for hobbyists. If you’re familiar with electricity and basic electrical components, this book starts simply and progresses through increasingly complex projects. Set up your environment by installing Xilinx ISE and the author’s Mojo IDE Learn how hardware designs are broken into modules, comparable to functions in a software program Create digital hardware designs and learn the basics on how they’ll be implemented by the FPGA Build your projects with Lucid, a beginner-friendly hardware description language, based on Verilog, with syntax similar to C/C++ and Java COMPUTERS,Logic Design

Reversible Computation This book constitutes the refereed proceedings of the 12th International Conference on Reversible Computation, RC 2020, held in Oslo, Norway, in July 2020. The 17 full papers included in this volume were carefully reviewed and selected from 22 submissions. The papers are organized in the following topical sections: theory and foundation; programming languages; circuit synthesis; evaluation of circuit synthesis; and applications and implementations. COMPUTERS,Logic Design

Automata and Computability The aim of this textbook is to provide undergraduate students with an introduction to the basic theoretical models of computability, and to develop some of the model's rich and varied structure. Students who have already some experience with elementary discrete mathematics will find this a well-paced first course, and a number of supplementary chapters introduce more advanced concepts. The first part of the book is devoted to finite automata and their properties. Pushdown automata provide a broader class of models and enable the analysis of context-free languages. In the remaining chapters, Turing machines are introduced and the book culminates in discussions of effective computability, decidability, and Gödel's incompleteness theorems. Plenty of exercises are provided, ranging from the easy to the challenging. As a result, this text will make an ideal first course for students of computer science. COMPUTERS,Machine Theory

Bayesian Networks Understand the Foundations of Bayesian Networks—Core Properties and Definitions Explained Bayesian Networks: With Examples in R introduces Bayesian networks using a hands-on approach. Simple yet meaningful examples in R illustrate each step of the modeling process. The examples start from the simplest notions and gradually increase in complexity. The authors also distinguish the probabilistic models from their estimation with data sets. The first three chapters explain the whole process of Bayesian network modeling, from structure learning to parameter learning to inference. These chapters cover discrete Bayesian, Gaussian Bayesian, and hybrid networks, including arbitrary random variables. The book then gives a concise but rigorous treatment of the fundamentals of Bayesian networks and offers an introduction to causal Bayesian networks. It also presents an overview of R and other software packages appropriate for Bayesian networks. The final chapter evaluates two real-world examples: a landmark causal protein signaling network paper and graphical modeling approaches for predicting the composition of different body parts. Suitable for graduate students and non-statisticians, this text provides an introductory overview of Bayesian networks. It gives readers a clear, practical understanding of the general approach and steps involved. COMPUTERS,Machine Theory

Automata and Computability These are my lecture notes from CS381/481: Automata and Computability Theory, a one-semester senior-level course I have taught at Cornell Uni versity for many years. I took this course myself in thc fall of 1974 as a first-year Ph.D. student at Cornell from Juris Hartmanis and have been in love with the subject ever sin,:e. The course is required for computer science majors at Cornell. It exists in two forms: CS481, an honors version; and CS381, a somewhat gentler paced version. The syllabus is roughly the same, but CS481 go es deeper into thc subject, covers more material, and is taught at a more abstract level. Students are encouraged to start off in one or the other, then switch within the first few weeks if they find the other version more suitaLle to their level of mathematical skill. The purpose of t.hc course is twofold: to introduce computer science students to the rieh heritage of models and abstractions that have arisen over the years; and to dew!c'p the capacity to form abstractions of their own and reason in terms of them. COMPUTERS,Machine Theory

Brain–Computer Interfaces Handbook Brain–Computer Interfaces Handbook: Technological and Theoretical Advances provides a tutorial and an overview of the rich and multi-faceted world of Brain–Computer Interfaces (BCIs). The authors supply readers with a contemporary presentation of fundamentals, theories, and diverse applications of BCI, creating a valuable resource for anyone involved with the improvement of people’s lives by replacing, restoring, improving, supplementing or enhancing natural output from the central nervous system. It is a useful guide for readers interested in understanding how neural bases for cognitive and sensory functions, such as seeing, hearing, and remembering, relate to real-world technologies. More precisely, this handbook details clinical, therapeutic and human-computer interfaces applications of BCI and various aspects of human cognition and behavior such as perception, affect, and action. It overviews the different methods and techniques used in acquiring and pre-processing brain signals, extracting features, and classifying users’ mental states and intentions. Various theories, models, and empirical findings regarding the ways in which the human brain interfaces with external systems and environments using BCI are also explored. The handbook concludes by engaging ethical considerations, open questions, and challenges that continue to face brain–computer interface research. Features an in-depth look at the different methods and techniques used in acquiring and pre-processing brain signals, extracting features, and classifying the user's intention Covers various theories, models, and empirical findings regarding ways in which the human brain can interface with the systems or external environments Presents applications of BCI technology to understand various aspects of human cognition and behavior such as perception, affect, action, and more Includes clinical trials and individual case studies of the experimental therapeutic applications of BCI Provides human factors and human-computer interface concerns in the design, development, and evaluation of BCIs Overall, this handbook provides a synopsis of key technological and theoretical advances that are directly applicable to brain–computer interfacing technologies and can be readily understood and applied by individuals with no formal training in BCI research and development. COMPUTERS,Machine Theory

R Deep Learning Projects 5 real-world projects to help you master deep learning concepts About This Book Master the different deep learning paradigms and build real-world projects related to text generation, sentiment analysis, fraud detection, and more Get to grips with R's impressive range of Deep Learning libraries and frameworks such as deepnet, MXNetR, Tensorflow, H2O, Keras, and text2vec Practical projects that show you how to implement different neural networks with helpful tips, tricks, and best practices Who This Book Is For Machine learning professionals and data scientists looking to master deep learning by implementing practical projects in R will find this book a useful resource. A knowledge of R programming and the basic concepts of deep learning is required to get the best out of this book. What You Will Learn Instrument Deep Learning models with packages such as deepnet, MXNetR, Tensorflow, H2O, Keras, and text2vec Apply neural networks to perform handwritten digit recognition using MXNet Get the knack of CNN models, Neural Network API, Keras, and TensorFlow for traffic sign classification Implement credit card fraud detection with Autoencoders Master reconstructing images using variational autoencoders Wade through sentiment analysis from movie reviews Run from past to future and vice versa with bidirectional Long Short-Term Memory (LSTM) networks Understand the applications of Autoencoder Neural Networks in clustering and dimensionality reduction In Detail R is a popular programming language used by statisticians and mathematicians for statistical analysis, and is popularly used for deep learning. Deep Learning, as we all know, is one of the trending topics today, and is finding practical applications in a lot of domains. This book demonstrates end-to-end implementations of five real-world projects on popular topics in deep learning such as handwritten digit recognition, traffic light detection, fraud detection, text generation, and sentiment analysis. You'll learn how to train effective neural networks in R—including convolutional neural networks, recurrent neural networks, and LSTMs—and apply them in practical scenarios. The book also highlights how neural networks can be trained using GPU capabilities. You will use popular R libraries and packages—such as MXNetR, H2O, deepnet, and more—to implement the projects. By the end of this book, you will have a better understanding of deep learning concepts and techniques and how to use them in a practical setting. Style and approach This book's unique, learn-as-you-do approach ensures the reader builds on his understanding of deep learning progressively with each project. This book is designed in such a way that implementing each project will empower you with a unique skillset and enable you to implement the next project more confidently. COMPUTERS,Machine Theory

Machine Learning and IoT This book discusses some of the innumerable ways in which computational methods can be used to facilitate research in biology and medicine - from storing enormous amounts of biological data to solving complex biological problems and enhancing treatment of various grave diseases. COMPUTERS,Machine Theory

Handbook of Mixture Analysis Mixture models have been around for over 150 years, and they are found in many branches of statistical modelling, as a versatile and multifaceted tool. They can be applied to a wide range of data: univariate or multivariate, continuous or categorical, cross-sectional, time series, networks, and much more. Mixture analysis is a very active research topic in statistics and machine learning, with new developments in methodology and applications taking place all the time. The Handbook of Mixture Analysis is a very timely publication, presenting a broad overview of the methods and applications of this important field of research. It covers a wide array of topics, including the EM algorithm, Bayesian mixture models, model-based clustering, high-dimensional data, hidden Markov models, and applications in finance, genomics, and astronomy. Features: Provides a comprehensive overview of the methods and applications of mixture modelling and analysis Divided into three parts: Foundations and Methods; Mixture Modelling and Extensions; and Selected Applications Contains many worked examples using real data, together with computational implementation, to illustrate the methods described Includes contributions from the leading researchers in the field The Handbook of Mixture Analysis is targeted at graduate students and young researchers new to the field. It will also be an important reference for anyone working in this field, whether they are developing new methodology, or applying the models to real scientific problems. COMPUTERS,Machine Theory

Machines Who Think This book is a history of artificial intelligence, that audacious effort to duplicate in an artifact what we consider to be our most important property—our intelligence. It is an invitation for anybody with an interest in the future of the human race to participate in the inquiry. COMPUTERS,Machine Theory

Machine Learning for iOS Developers Harness the power of Apple iOS machine learning (ML) capabilities and learn the concepts and techniques necessary to be a successful Apple iOS machine learning practitioner! Machine earning (ML) is the science of getting computers to act without being explicitly programmed. A branch of Artificial Intelligence (AI), machine learning techniques offer ways to identify trends, forecast behavior, and make recommendations. The Apple iOS Software Development Kit (SDK) allows developers to integrate ML services, such as speech recognition and language translation, into mobile devices, most of which can be used in multi-cloud settings. Focusing on Apple’s ML services, Machine Learning for iOS Developers is an up-to-date introduction to the field, instructing readers to implement machine learning in iOS applications. Assuming no prior experience with machine learning, this reader-friendly guide offers expert instruction and practical examples of ML integration in iOS. Organized into two sections, the book’s clearly-written chapters first cover fundamental ML concepts, the different types of ML systems, their practical uses, and the potential challenges of ML solutions. The second section teaches readers to use models—both pre-trained and user-built—with Apple’s CoreML framework. Source code examples are provided for readers to download and use in their own projects. This book helps readers: Understand the theoretical concepts and practical applications of machine learning used in predictive data analytics Build, deploy, and maintain ML systems for tasks such as model validation, optimization, scalability, and real-time streaming Develop skills in data acquisition and modeling, classification, and regression. Compare traditional vs. ML approaches, and machine learning on handsets vs. machine learning as a service (MLaaS) Implement decision tree based models, an instance-based machine learning system, and integrate Scikit-learn & Keras models with CoreML Machine Learning for iOS Developers is a must-have resource software engineers and mobile solutions architects wishing to learn ML concepts and implement machine learning on iOS Apps. COMPUTERS,Machine Theory

Handbook of Automated Scoring "Automated scoring engines […] require a careful balancing of the contributions of technology, NLP, psychometrics, artificial intelligence, and the learning sciences. The present handbook is evidence that the theories, methodologies, and underlying technology that surround automated scoring have reached maturity, and that there is a growing acceptance of these technologies among experts and the public." From the Foreword by Alina von Davier, ACTNext Senior Vice President Handbook of Automated Scoring: Theory into Practice provides a scientifically grounded overview of the key research efforts required to move automated scoring systems into operational practice. It examines the field of automated scoring from the viewpoint of related scientific fields serving as its foundation, the latest developments of computational methodologies utilized in automated scoring, and several large-scale real-world applications of automated scoring for complex learning and assessment systems. The book is organized into three parts that cover (1) theoretical foundations, (2) operational methodologies, and (3) practical illustrations, each with a commentary. In addition, the handbook includes an introduction and synthesis chapter as well as a cross-chapter glossary. COMPUTERS,Machine Theory

Handbook Of Machine Learning - Volume 2 Building on Handbook of Machine Learning - Volume 1: Foundation of Artificial Intelligence, this volume on Optimization and Decision Making covers a range of algorithms and their applications. Like the first volume, it provides a starting point for machine learning enthusiasts as a comprehensive guide on classical optimization methods. It also provides an in-depth overview on how artificial intelligence can be used to define, disprove or validate economic modeling and decision making concepts. COMPUTERS,Machine Theory

Statistical Machine Learning The recent rapid growth in the variety and complexity of new machine learning architectures requires the development of improved methods for designing, analyzing, evaluating, and communicating machine learning technologies. Statistical Machine Learning: A Unified Framework provides students, engineers, and scientists with tools from mathematical statistics and nonlinear optimization theory to become experts in the field of machine learning. In particular, the material in this text directly supports the mathematical analysis and design of old, new, and not-yet-invented nonlinear high-dimensional machine learning algorithms. Features: Unified empirical risk minimization framework supports rigorous mathematical analyses of widely used supervised, unsupervised, and reinforcement machine learning algorithms Matrix calculus methods for supporting machine learning analysis and design applications Explicit conditions for ensuring convergence of adaptive, batch, minibatch, MCEM, and MCMC learning algorithms that minimize both unimodal and multimodal objective functions Explicit conditions for characterizing asymptotic properties of M-estimators and model selection criteria such as AIC and BIC in the presence of possible model misspecification This advanced text is suitable for graduate students or highly motivated undergraduate students in statistics, computer science, electrical engineering, and applied mathematics. The text is self-contained and only assumes knowledge of lower-division linear algebra and upper-division probability theory. Students, professional engineers, and multidisciplinary scientists possessing these minimal prerequisites will find this text challenging yet accessible. About the Author: Richard M. Golden (Ph.D., M.S.E.E., B.S.E.E.) is Professor of Cognitive Science and Participating Faculty Member in Electrical Engineering at the University of Texas at Dallas. Dr. Golden has published articles and given talks at scientific conferences on a wide range of topics in the fields of both statistics and machine learning over the past three decades. His long-term research interests include identifying conditions for the convergence of deterministic and stochastic machine learning algorithms and investigating estimation and inference in the presence of possibly misspecified probability models. COMPUTERS,Machine Theory

Fuzzy Machine Learning Algorithms for Remote Sensing Image Classification This book covers the state-of-art image classification methods for discrimination of earth objects from remote sensing satellite data with an emphasis on fuzzy machine learning and deep learning algorithms. Both types of algorithms are described in such details that these can be implemented directly for thematic mapping of multiple-class or specific-class landcover from multispectral optical remote sensing data. These algorithms along with multi-date, multi-sensor remote sensing are capable to monitor specific stage (for e.g., phenology of growing crop) of a particular class also included. With these capabilities fuzzy machine learning algorithms have strong applications in areas like crop insurance, forest fire mapping, stubble burning, post disaster damage mapping etc. It also provides details about the temporal indices database using proposed Class Based Sensor Independent (CBSI) approach supported by practical examples. As well, this book addresses other related algorithms based on distance, kernel based as well as spatial information through Markov Random Field (MRF)/Local convolution methods to handle mixed pixels, non-linearity and noisy pixels. Further, this book covers about techniques for quantiative assessment of soft classified fraction outputs from soft classification and supported by in-house developed tool called sub-pixel multi-spectral image classifier (SMIC). It is aimed at graduate, postgraduate, research scholars and working professionals of different branches such as Geoinformation sciences, Geography, Electrical, Electronics and Computer Sciences etc., working in the fields of earth observation and satellite image processing. Learning algorithms discussed in this book may also be useful in other related fields, for example, in medical imaging. Overall, this book aims to: exclusive focus on using large range of fuzzy classification algorithms for remote sensing images; discuss ANN, CNN, RNN, and hybrid learning classifiers application on remote sensing images; describe sub-pixel multi-spectral image classifier tool (SMIC) to support discussed fuzzy and learning algorithms; explain how to assess soft classified outputs as fraction images using fuzzy error matrix (FERM) and its advance versions with FERM tool, Entropy, Correlation Coefficient, Root Mean Square Error and Receiver Operating Characteristic (ROC) methods and; combines explanation of the algorithms with case studies and practical applications. COMPUTERS,Machine Theory

The IT Manager's Survival Guide Accessible, refreshingly candid, but above all helpful, this pragmatic guide addresses a real need by dealing with the problems that face the new IT manager. By providing a number of practical recommendations and approaches including how to make the transition from technical professional to manager and dealing with people, to giving advice and guidance on organization structure, architecture and planning approaches, this book covers a whole raft of issues essential to managing an IT unit. If you have chosen to move from the safe haven of technology to the unpredictable world of management, this book could make the difference between success and failure. "The IT Manager's Survival Guide is well named. Aimed at the techie becoming an IT Manager it covers the many alligators of IT management - from legacy systems to managing vendors - in easy chunks with checklists. It also provides the new manager with help to get ahead of the game by including articles from experts on what is wrong with IT management and a set of short reviews of management theorists from Strassman to Mayo. I recommend this book for those who would like to buck the trend - the average tenure of an IT Manager is about 900 days - and run an IT outfit appreciated by customers and staff." Gill Ringland, Fellow of the British Computer Society and Member of the BCS Management Forum. Author of Scenario Planning: Managing for the Future. COMPUTERS,Management Information Systems

Systems Thinking Systems Thinking, Third Edition combines systems theory and interactive design to provide an operational methodology for defining problems and designing solutions in an environment increasingly characterized by chaos and complexity. This new edition has been updated to include all new chapters on self-organizing systems as well as holistic, operational, and design thinking. The book covers recent crises in financial systems and job markets, the housing bubble, and environment, assessing their impact on systems thinking. A companion website is available at interactdesign.com. This volume is ideal for senior executives as well as for chief information/operating officers and other executives charged with systems management and process improvement. It may also be a helpful resource for IT/MBA students and academics. Four NEW chapters on self-organizing systems, holistic thinking, operational thinking, and design thinking Covers the recent crises in financial systems and job markets globally, the housing bubble, and the environment, assessing their impact on systems thinking Companion website to accompany the book is available at interactdesign.com COMPUTERS,Management Information Systems

Business Intelligence Business Intelligence: The Savvy Managers Guide, Second Edition, discusses the objectives and practices for designing and deploying a business intelligence (BI) program. It looks at the basics of a BI program, from the value of information and the mechanics of planning for success to data model infrastructure, data preparation, data analysis, integration, knowledge discovery, and the actual use of discovered knowledge. Organized into 21 chapters, this book begins with an overview of the kind of knowledge that can be exposed and exploited through the use of BI. It then proceeds with a discussion of information use in the context of how value is created within an organization, how BI can improve the ways of doing business, and organizational preparedness for exploiting the results of a BI program. It also looks at some of the critical factors to be taken into account in the planning and execution of a successful BI program. In addition, the reader is introduced to considerations for developing the BI roadmap, the platforms for analysis such as data warehouses, and the concepts of business metadata. Other chapters focus on data preparation and data discovery, the business rules approach, and data mining techniques and predictive analytics. Finally, emerging technologies such as text analytics and sentiment analysis are considered. This book will be valuable to data management and BI professionals, including senior and middle-level managers, Chief Information Officers and Chief Data Officers, senior business executives and business staff members, database or software engineers, and business analysts. Guides managers through developing, administering, or simply understanding business intelligence technology Keeps pace with the changes in best practices, tools, methods and processes used to transform an organization’s data into actionable knowledge Contains a handy, quick-reference to technologies and terminology COMPUTERS,Management Information Systems

Management of Organizational Culture as a Stabilizer of Changes No enterprise today is proud of being unchanged. Stability is understood more as a sign of stagnation than reliability, and enterprises that do not change and do not evolve are commonly regarded as fossilized. Increasing globalization processes often force today’s enterprises to make organizational changes, but the effectiveness of these processes relies on its organizational culture. This book argues that the problem behind organizational culture is its multilevel structure, including the visible and hidden levels. It addresses difficult questions, such as: Is it better to make thorough, but more painful changes, or to gradually introduce small improvements? It also demonstrates that organizational culture is not a fixed phenomenon: its shaping takes place in stages, and it is essential to take such stages into account in the process of implementing the strategy of an enterprise. Providing a comprehensive insight into "organizational culture" and its relationship to change, this book will be essential reading for professionals involved in business management and IT management throughout the world. Its analyses and suggestions will allow for improved organizational culture and change management in business environments. COMPUTERS,Management Information Systems

Algorithms for Computer Algebra Algorithms for Computer Algebra is the first comprehensive textbook to be published on the topic of computational symbolic mathematics. The book first develops the foundational material from modern algebra that is required for subsequent topics. It then presents a thorough development of modern computational algorithms for such problems as multivariate polynomial arithmetic and greatest common divisor calculations, factorization of multivariate polynomials, symbolic solution of linear and polynomial systems of equations, and analytic integration of elementary functions. Numerous examples are integrated into the text as an aid to understanding the mathematical development. The algorithms developed for each topic are presented in a Pascal-like computer language. An extensive set of exercises is presented at the end of each chapter. Algorithms for Computer Algebra is suitable for use as a textbook for a course on algebraic algorithms at the third-year, fourth-year, or graduate level. Although the mathematical development uses concepts from modern algebra, the book is self-contained in the sense that a one-term undergraduate course introducing students to rings and fields is the only prerequisite assumed. The book also serves well as a supplementary textbook for a traditional modern algebra course, by presenting concrete applications to motivate the understanding of the theory of rings and fields. COMPUTERS,Mathematical & Statistical Software

Excel Scientific and Engineering Cookbook Given the improved analytical capabilities of Excel, scientists and engineers everywhere are using it--instead of FORTRAN--to solve problems. And why not? Excel is installed on millions of computers, features a rich set of built-in analyses tools, and includes an integrated Visual Basic for Applications (VBA) programming language. No wonder it's today's computing tool of choice. Chances are you already use Excel to perform some fairly routine calculations. Now the Excel Scientific and Engineering Cookbook shows you how to leverage Excel to perform more complex calculations, too, calculations that once fell in the domain of specialized tools. It does so by putting a smorgasbord of data analysis techniques right at your fingertips. The book shows how to perform these useful tasks and others: Use Excel and VBA in general Import data from a variety of sources Analyze data Perform calculations Visualize the results for interpretation and presentation Use Excel to solve specific science and engineering problems Wherever possible, the Excel Scientific and Engineering Cookbook draws on real-world examples from a range of scientific disciplines such as biology, chemistry, and physics. This way, you'll be better prepared to solve the problems you face in your everyday scientific or engineering tasks. High on practicality and low on theory, this quick, look-up reference provides instant solutions, or "recipes," to problems both basic and advanced. And like other books in O'Reilly's popular Cookbook format, each recipe also includes a discussion on how and why it works. As a result, you can take comfort in knowing that complete, practical answers are a mere page-flip away. COMPUTERS,Mathematical & Statistical Software

Data Analysis with Open Source Tools Collecting data is relatively easy, but turning raw information into something useful requires that you know how to extract precisely what you need. With this insightful book, intermediate to experienced programmers interested in data analysis will learn techniques for working with data in a business environment. You'll learn how to look at data to discover what it contains, how to capture those ideas in conceptual models, and then feed your understanding back into the organization through business plans, metrics dashboards, and other applications. Along the way, you'll experiment with concepts through hands-on workshops at the end of each chapter. Above all, you'll learn how to think about the results you want to achieve -- rather than rely on tools to think for you. Use graphics to describe data with one, two, or dozens of variables Develop conceptual models using back-of-the-envelope calculations, as well asscaling and probability arguments Mine data with computationally intensive methods such as simulation and clustering Make your conclusions understandable through reports, dashboards, and other metrics programs Understand financial calculations, including the time-value of money Use dimensionality reduction techniques or predictive analytics to conquer challenging data analysis situations Become familiar with different open source programming environments for data analysis "Finally, a concise reference for understanding how to conquer piles of data."--Austin King, Senior Web Developer, Mozilla "An indispensable text for aspiring data scientists."--Michael E. Driscoll, CEO/Founder, Dataspora COMPUTERS,Mathematical & Statistical Software

R in a Nutshell If you’re considering R for statistical computing and data visualization, this book provides a quick and practical guide to just about everything you can do with the open source R language and software environment. You’ll learn how to write R functions and use R packages to help you prepare, visualize, and analyze data. Author Joseph Adler illustrates each process with a wealth of examples from medicine, business, and sports. Updated for R 2.14 and 2.15, this second edition includes new and expanded chapters on R performance, the ggplot2 data visualization package, and parallel R computing with Hadoop. Get started quickly with an R tutorial and hundreds of examples Explore R syntax, objects, and other language details Find thousands of user-contributed R packages online, including Bioconductor Learn how to use R to prepare data for analysis Visualize your data with R’s graphics, lattice, and ggplot2 packages Use R to calculate statistical fests, fit models, and compute probability distributions Speed up intensive computations by writing parallel R programs for Hadoop Get a complete desktop reference to R COMPUTERS,Mathematical & Statistical Software

The Essential R Reference An essential library of basic commands you can copy and paste into R The powerful and open-source statistical programming language R is rapidly growing in popularity, but it requires that you type in commands at the keyboard rather than use a mouse, so you have to learn the language of R. But there is a shortcut, and that's where this unique book comes in. A companion book to Visualize This: The FlowingData Guide to Design, Visualization, and Statistics, this practical reference is a library of basic R commands that you can copy and paste into R to perform many types of statistical analyses. Whether you're in technology, science, medicine, business, or engineering, you can quickly turn to your topic in this handy book and find the commands you need. Comprehensive command reference for the R programming language and a companion book to Visualize This: The FlowingData Guide to Design, Visualization, and Statistics Combines elements of a dictionary, glossary, and thesaurus for the R language Provides easy accessibility to the commands you need, by topic, which you can cut and paste into R as needed Covers getting, saving, examining, and manipulating data; statistical test and math; and all the things you can do with graphs Also includes a collection of utilities that you'll find useful Simplify the complex statistical R programming language with The Essential R Reference. . COMPUTERS,Mathematical & Statistical Software

R Graphics Cookbook This practical guide provides more than 150 recipes to help you generate high-quality graphs quickly, without having to comb through all the details of R’s graphing systems. Each recipe tackles a specific problem with a solution you can apply to your own project, and includes a discussion of how and why the recipe works. Most of the recipes use the ggplot2 package, a powerful and flexible way to make graphs in R. If you have a basic understanding of the R language, you’re ready to get started. Use R’s default graphics for quick exploration of data Create a variety of bar graphs, line graphs, and scatter plots Summarize data distributions with histograms, density curves, box plots, and other examples Provide annotations to help viewers interpret data Control the overall appearance of graphics Render data groups alongside each other for easy comparison Use colors in plots Create network graphs, heat maps, and 3D scatter plots Structure data for graphing COMPUTERS,Mathematical & Statistical Software

Data Points A fresh look at visualization from the author of Visualize This Whether it's statistical charts, geographic maps, or the snappy graphical statistics you see on your favorite news sites, the art of data graphics or visualization is fast becoming a movement of its own. In Data Points: Visualization That Means Something, author Nathan Yau presents an intriguing complement to his bestseller Visualize This, this time focusing on the graphics side of data analysis. Using examples from art, design, business, statistics, cartography, and online media, he explores both standard-and not so standard-concepts and ideas about illustrating data. Shares intriguing ideas from Nathan Yau, author of Visualize This and creator of flowingdata.com, with over 66,000 subscribers Focuses on visualization, data graphics that help viewers see trends and patterns they might not otherwise see in a table Includes examples from the author's own illustrations, as well as from professionals in statistics, art, design, business, computer science, cartography, and more Examines standard rules across all visualization applications, then explores when and where you can break those rules Create visualizations that register at all levels, with Data Points: Visualization That Means Something. COMPUTERS,Mathematical & Statistical Software

Mathematica as a Tool More than ten years ago, I wanted to carry out coordinate transformations for Hamiltonian systems, in order to discuss the stability of certain equilibrium posi tions. Basically, the calculations only involved rational expressions, but they turned out to be extremely complicated, because the third and fourth order terms had to be included. After several months of filling whole blocks of paper with for mulas, I was close to resignation. But, by a lucky incident, I met a colleague who showed me the computer algebra package Reduce. It still required a lot of patience and tricks, but Reduce finally did produce the desired results. After this experience, I wondered, why only a few engineers and scientists were aware of the strengths of such computer algebra programs. The mathematical treatment of scientific problems often leads to calculations which can only be solved "by hand" with a considerable investment of time, while a suitable com puter algebra program produces the solution within a couple of seconds or min utes. Even if a closed symbolic solution is not possible, such programs can often simplify a problem, before the cruder tool of numerical simulations is applied. COMPUTERS,Mathematical & Statistical Software

ITSM for Windows The analysis of time series data is an important aspect of data analysis across a wide range of disciplines, including statistics, mathematics, business, engineering, and the natural and social sciences. This package provides both an introduction to time series analysis and an easy-to-use version of a well-known time series computing package called Interactive Time Series Modelling. The programs in the package are intended as a supplement to the text Time Series: Theory and Methods, 2nd edition, also by Peter J. Brockwell and Richard A. Davis. Many researchers and professionals will appreciate this straightforward approach enabling them to run desk-top analyses of their time series data. Amongst the many facilities available are tools for: ARIMA modelling, smoothing, spectral estimation, multivariate autoregressive modelling, transfer-function modelling, forecasting, and long-memory modelling. This version is designed to run under Microsoft Windows 3.1 or later. It comes with two diskettes: one suitable for less powerful machines (IBM PC 286 or later with 540K available RAM and 1.1 MB of hard disk space) and one for more powerful machines (IBM PC 386 or later with 8MB of RAM and 2.6 MB of hard disk space available). COMPUTERS,Mathematical & Statistical Software

Tableau Your Data! Transform your organization's data into actionable insights with Tableau Tableau is designed specifically to provide fast and easy visual analytics. The intuitive drag-and-drop interface helps you create interactive reports, dashboards, and visualizations, all without any special or advanced training. This all new edition of Tableau Your Data! is your Tableau companion, helping you get the most out of this invaluable business toolset. Tableau Your Data! shows you how to build dynamic, best of breed visualizations using the Tableau Software toolset. This comprehensive guide covers the core feature set for data analytics, and provides clear step-by-step guidance toward best practices and advanced techniques that go way beyond the user manual. You'll learn how Tableau is different from traditional business information analysis tools, and how to navigate your way around the Tableau 9.0 desktop before delving into functions and calculations, as well as sharing with the Tableau Server. Analyze data more effectively with Tableau Desktop Customize Tableau's settings for your organization's needs with detailed real-world examples on data security, scaling, syntax, and more Deploy visualizations to consumers throughout the enterprise - from sales to marketing, operations to finance, and beyond Understand Tableau functions and calculations and leverage Tableau across every link in the value chain Learn from actual working models of the book's visualizations and other web-based resources via a companion website Tableau helps you unlock the stories within the numbers, and Tableau Your Data! puts the software's full functionality right at your fingertips. COMPUTERS,Mathematical & Statistical Software

A Course in Statistics with R Integrates the theory and applications of statistics using R A Course in Statistics with R has been written to bridge the gap between theory and applications and explain how mathematical expressions are converted into R programs. The book has been primarily designed as a useful companion for a Masters student during each semester of the course, but will also help applied statisticians in revisiting the underpinnings of the subject. With this dual goal in mind, the book begins with R basics and quickly covers visualization and exploratory analysis. Probability and statistical inference, inclusive of classical, nonparametric, and Bayesian schools, is developed with definitions, motivations, mathematical expression and R programs in a way which will help the reader to understand the mathematical development as well as R implementation. Linear regression models, experimental designs, multivariate analysis, and categorical data analysis are treated in a way which makes effective use of visualization techniques and the related statistical techniques underlying them through practical applications, and hence helps the reader to achieve a clear understanding of the associated statistical models. Key features: Integrates R basics with statistical concepts Provides graphical presentations inclusive of mathematical expressions Aids understanding of limit theorems of probability with and without the simulation approach Presents detailed algorithmic development of statistical models from scratch Includes practical applications with over 50 data sets COMPUTERS,Mathematical & Statistical Software

Parle ’91 Parallel Architectures and Languages Europe The innovative progress in the development oflarge-and small-scale parallel computing systems and their increasing availability have caused a sharp rise in interest in the scientific principles that underlie parallel computation and parallel programming. The biannual "Parallel Architectures and Languages Europe" (PARLE) conferences aim at presenting current research material on all aspects of the theory, design, and application of parallel computing systems and parallel processing. At the same time, the goal of the PARLE conferences is to provide a forum for researchers and practitioners to ex change ideas on recent developments and trends in the field of parallel com puting and parallel programming. The first ~wo conferences, PARLE '87 and PARLE '89, have succeeded in meeting this goal and made PARLE a conference that is recognized worldwide in the field of parallel computation. PARLE '91 again offers a wealth of high-quality research material for the benefit of the scientific community. Compared to its predecessors, the scope of PARLE '91 has been broadened so as to cover the area of parallel algo rithms and complexity, in addition to the central themes of parallel archi tectures and languages. The proceedings of the PARLE '91 conference contain the text of all con tributed papers that were selected for the programme and of the invited papers by leading experts in the field. COMPUTERS,Mathematical & Statistical Software

ggplot2 This new edition to the classic book by ggplot2 creator Hadley Wickham highlights compatibility with knitr and RStudio. ggplot2 is a data visualization package for R that helps users create data graphics, including those that are multi-layered, with ease. With ggplot2, it's easy to: produce handsome, publication-quality plots with automatic legends created from the plot specification superimpose multiple layers (points, lines, maps, tiles, box plots) from different data sources with automatically adjusted common scales add customizable smoothers that use powerful modeling capabilities of R, such as loess, linear models, generalized additive models, and robust regression save any ggplot2 plot (or part thereof) for later modification or reuse create custom themes that capture in-house or journal style requirements and that can easily be applied to multiple plots approach a graph from a visual perspective, thinking about how each component of the data is represented on the final plot This book will be useful to everyone who has struggled with displaying data in an informative and attractive way. Some basic knowledge of R is necessary (e.g., importing data into R). ggplot2 is a mini-language specifically tailored for producing graphics, and you'll learn everything you need in the book. After reading this book you'll be able to produce graphics customized precisely for your problems, and you'll find it easy to get graphics out of your head and on to the screen or page. COMPUTERS,Mathematical & Statistical Software

Statistical Analysis of Noise in MRI This unique text presents a comprehensive review of methods for modeling signal and noise in magnetic resonance imaging (MRI), providing a systematic study, classifying and comparing the numerous and varied estimation and filtering techniques. Features: provides a complete framework for the modeling and analysis of noise in MRI, considering different modalities and acquisition techniques; describes noise and signal estimation for MRI from a statistical signal processing perspective; surveys the different methods to remove noise in MRI acquisitions from a practical point of view; reviews different techniques for estimating noise from MRI data in single- and multiple-coil systems for fully sampled acquisitions; examines the issue of noise estimation when accelerated acquisitions are considered, and parallel imaging methods are used to reconstruct the signal; includes appendices covering probability density functions, combinations of random variables used to derive estimators, and useful MRI datasets. COMPUTERS,Mathematical & Statistical Software

Corpus Linguistics and Statistics with R This textbook examines empirical linguistics from a theoretical linguist’s perspective. It provides both a theoretical discussion of what quantitative corpus linguistics entails and detailed, hands-on, step-by-step instructions to implement the techniques in the field. The statistical methodology and R-based coding from this book teach readers the basic and then more advanced skills to work with large data sets in their linguistics research and studies. Massive data sets are now more than ever the basis for work that ranges from usage-based linguistics to the far reaches of applied linguistics. This book presents much of the methodology in a corpus-based approach. However, the corpus-based methods in this book are also essential components of recent developments in sociolinguistics, historical linguistics, computational linguistics, and psycholinguistics. Material from the book will also be appealing to researchers in digital humanities and the many non-linguistic fields that use textual data analysis and text-based sensorimetrics. Chapters cover topics including corpus processing, frequencing data, and clustering methods. Case studies illustrate each chapter with accompanying data sets, R code, and exercises for use by readers. This book may be used in advanced undergraduate courses, graduate courses, and self-study. COMPUTERS,Mathematical & Statistical Software

Probability and Statistics for Computer Science This textbook is aimed at computer science undergraduates late in sophomore or early in junior year, supplying a comprehensive background in qualitative and quantitative data analysis, probability, random variables, and statistical methods, including machine learning. With careful treatment of topics that fill the curricular needs for the course, Probability and Statistics for Computer Science features: • A treatment of random variables and expectations dealing primarily with the discrete case. • A practical treatment of simulation, showing how many interesting probabilities and expectations can be extracted, with particular emphasis on Markov chains. • A clear but crisp account of simple point inference strategies (maximum likelihood; Bayesian inference) in simple contexts. This is extended to cover some confidence intervals, samples and populations for random sampling with replacement, and the simplest hypothesis testing. • A chapter dealing with classification, explaining why it’s useful; how to train SVM classifiers with stochastic gradient descent; and how to use implementations of more advanced methods such as random forests and nearest neighbors.• A chapter dealing with regression, explaining how to set up, use and understand linear regression and nearest neighbors regression in practical problems. • A chapter dealing with principal components analysis, developing intuition carefully, and including numerous practical examples. There is a brief description of multivariate scaling via principal coordinate analysis. • A chapter dealing with clustering via agglomerative methods and k-means, showing how to build vector quantized features for complex signals. Illustrated throughout, each main chapter includes many worked examples and other pedagogical elements such as boxed Procedures, Definitions, Useful Facts, and Remember This (short tips). Problems and Programming Exercises are at the end of each chapter, with a summary of what the reader should know. Instructor resources include a full set of model solutions for all problems, and an Instructor's Manual with accompanying presentation slides. COMPUTERS,Mathematical & Statistical Software

R Projects For Dummies Make the most of R’s extensive toolset R Projects For Dummies offers a unique learn-by-doing approach. You will increase the depth and breadth of your R skillset by completing a wide variety of projects. By using R’s graphics, interactive, and machine learning tools, you’ll learn to apply R’s extensive capabilities in an array of scenarios. The depth of the project experience is unmatched by any other content online or in print. And you just might increase your statistics knowledge along the way, too! R is a free tool, and it’s the basis of a huge amount of work in data science. It's taking the place of costly statistical software that sometimes takes a long time to learn. One reason is that you can use just a few R commands to create sophisticated analyses. Another is that easy-to-learn R graphics enable you make the results of those analyses available to a wide audience. This book will help you sharpen your skills by applying them in the context of projects with R, including dashboards, image processing, data reduction, mapping, and more. Appropriate for R users at all levels Helps R programmers plan and complete their own projects Focuses on R functions and packages Shows how to carry out complex analyses by just entering a few commands If you’re brand new to R or just want to brush up on your skills, R Projects For Dummies will help you complete your projects with ease. COMPUTERS,Mathematical & Statistical Software

JMP 14 Predictive and Specialized Modeling JMP 14 Predictive and Specialized Modeling provides details about modeling techniques such as partitioning, neural networks, nonlinear regression, and time series analysis. Topics include the Gaussian platform, which is useful in analyzing computer simulation experiments. The book also covers the Response Screening platform, which is useful in testing the effect of a predictor when you have many responses. COMPUTERS,Mathematical & Statistical Software

JMP 14 Essential Graphing Start with JMP 14 Essential Graphing to find the ideal graph for your data. The book begins with Graph Builder, a quick way to create graphs in a drag-and-drop window. Line charts, ellipses, box plots, and maps are just a few of the graphs available in Graph Builder. Find information about creating other types of plots: bubble plots, scatterplots, parallel plots, and more. COMPUTERS,Mathematical & Statistical Software

Statistical Methods in Psychiatry Research and SPSS This volume, Statistical Methods in Psychiatry Research and SPSS, now going into its second edition, has been helping psychiatrists expand their knowledge of statistical methods and fills the gaps in their applications as well as introduces data analysis software. It addresses the statistical needs of physicians and presents a simplified approach. The book emphasizes the classification of fundamental statistical methods in psychiatry research that are precise and simple. Professionals in the field of mental health and allied subjects without any mathematical background will easily understand all the relevant statistical methods and carry out the analysis and interpret the results in their respective field without consulting any statistician. This new volume has over 100 pages of new material, including several new appendixes. The sequence of the chapters, the sections within the chapters, the subsections within the sections, and the points within the subsections have all been arranged to help professionals in classification refine their knowledge in statistical methods and fills the gaps. COMPUTERS,Mathematical & Statistical Software

R Cookbook Perform data analysis with R quickly and efficiently with more than 275 practical recipes in this expanded second edition. The R language provides everything you need to do statistical work, but its structure can be difficult to master. These task-oriented recipes make you productive with R immediately. Solutions range from basic tasks to input and output, general statistics, graphics, and linear regression. Each recipe addresses a specific problem and includes a discussion that explains the solution and provides insight into how it works. If you’re a beginner, R Cookbook will help get you started. If you’re an intermediate user, this book will jog your memory and expand your horizons. You’ll get the job done faster and learn more about R in the process. Create vectors, handle variables, and perform basic functions Simplify data input and output Tackle data structures such as matrices, lists, factors, and data frames Work with probability, probability distributions, and random variables Calculate statistics and confidence intervals and perform statistical tests Create a variety of graphic displays Build statistical models with linear regressions and analysis of variance (ANOVA) Explore advanced statistical techniques, such as finding clusters in your data COMPUTERS,Mathematical & Statistical Software

The Little SAS Book A classic that just keeps getting better, The Little SAS Book is essential for anyone learning SAS programming. Lora Delwiche and Susan Slaughter offer a user-friendly approach so that readers can quickly and easily learn the most commonly used features of the SAS language. Each topic is presented in a self-contained, two-page layout complete with examples and graphics.Nearly every section has been revised to ensure that the sixth edition is fully up-to-date. This edition is also interface-independent, written for all SAS programmers whether they use SAS Studio, SAS Enterprise Guide, or the SAS windowing environment. New sections have been added covering PROC SQL, iterative DO loops, DO WHILE and DO UNTIL statements, %DO statements, using variable names with special characters, the ODS EXCEL destination, and the XLSX LIBNAME engine.This title belongs on every SAS programmer's bookshelf. It's a resource not just to get you started, but one you will return to as you continue to improve your programming skills. COMPUTERS,Mathematical & Statistical Software

Practical Data Analysis with JMP, Third Edition Master the concepts and techniques of statistical analysis using JMP Practical Data Analysis with JMP, Third Edition, highlights the powerful interactive and visual approach of JMP to introduce readers to statistical thinking and data analysis. It helps you choose the best technique for the problem at hand by using real-world cases. It also illustrates best-practice workflow throughout the entire investigative cycle, from asking valuable questions through data acquisition, preparation, analysis, interpretation, and communication of findings. The book can stand on its own as a learning resource for professionals, or it can be used to supplement a college-level textbook for an introductory statistics course. It includes varied examples and problems using real sets of data. Each chapter typically starts with an important or interesting research question that an investigator has pursued. Reflecting the broad applicability of statistical reasoning, the problems come from a wide variety of disciplines, including engineering, life sciences, business, and economics, as well as international and historical examples. Application Scenarios at the end of each chapter challenge you to use your knowledge and skills with data sets that go beyond mere repetition of chapter examples. New in the third edition, chapters have been updated to demonstrate the enhanced capabilities of JMP, including projects, Graph Builder, Query Builder, and Formula Depot. COMPUTERS,Mathematical & Statistical Software

Exercises and Projects for The Little SAS Book, Sixth Edition Hone your SAS skills with Exercises and Projects for The Little SAS Book, Sixth Edition! Now in its sixth edition, the best-selling The Little SAS Book just keeps getting better. Readers worldwide study this easy-to-follow book to help them learn the basics of SAS programming. Rebecca Ottesen has once again teamed up with the authors of The Little SAS Book, Lora Delwiche and Susan Slaughter, to provide a way to challenge and improve your SAS skills through thought-provoking questions, exercises, and projects. Each chapter has been updated to match The Little SAS Book, Sixth Edition. The book contains a mixture of multiple-choice questions, open-ended discussion topics, and programming exercises with selected answers and hints. It also includes comprehensive programming projects that are designed to encourage self-study and to test the skills developed by The Little SAS Book. Exercises and Projects for The Little SAS Book, Sixth Edition is a hands-on workbook that is designed to improve your SAS skills whether you are a student or a professional. COMPUTERS,Mathematical & Statistical Software

Text Analysis with R Now in its second edition, Text Analysis with R provides a practical introduction to computational text analysis using the open source programming language R. R is an extremely popular programming language, used throughout the sciences; due to its accessibility, R is now used increasingly in other research areas. In this volume, readers immediately begin working with text, and each chapter examines a new technique or process, allowing readers to obtain a broad exposure to core R procedures and a fundamental understanding of the possibilities of computational text analysis at both the micro and the macro scale. Each chapter builds on its predecessor as readers move from small scale “microanalysis†of single texts to large scale “macroanalysis†of text corpora, and each concludes with a set of practice exercises that reinforce and expand upon the chapter lessons. The book’s focus is on making the technical palatable and making the technical useful and immediately gratifying. Text Analysis with R is written with students and scholars of literature in mind but will be applicable to other humanists and social scientists wishing to extend their methodological toolkit to include quantitative and computational approaches to the study of text. Computation provides access to information in text that readers simply cannot gather using traditional qualitative methods of close reading and human synthesis. This new edition features two new chapters: one that introduces dplyr and tidyr in the context of parsing and analyzing dramatic texts to extract speaker and receiver data, and one on sentiment analysis using the syuzhet package. It is also filled with updated material in every chapter to integrate new developments in the field, current practices in R style, and the use of more efficient algorithms. COMPUTERS,Mathematical & Statistical Software

Development of Readability Formula The readability formula developed in the present study has direct application in the field of education, mass communication, journalism and agricultural extension. The developed formula can be used by the communicators, writers and authors to know the grade level of the writing. Hence, it would be possible to modify the level of difficulty to suit to the required literacy level of the readers. The formula will be particularly helpful for prior testing of material before publishing it for the benefit of readers in general and farmers in particular. By using the present readability formula, it is also possible to analyze the already published extension literature and other publications to determine their suitability to the intended readers. This work will provide the required feedback for communicators and writers to appropriately modify the written material for the benefit of readers. COMPUTERS,Mathematical & Statistical Software

SAS Viya Learn how to access analytics from SAS Cloud Analytic Services (CAS) using Python and the SAS Viya platform. SAS Viya : The Python Perspective is an introduction to using the Python client on the SAS Viya platform. SAS Viya is a high-performance, fault-tolerant analytics architecture that can be deployed on both public and private cloud infrastructures. While SAS Viya can be used by various SAS applications, it also enables you to access analytic methods from SAS, Python, Lua, and Java, as well as through a REST interface using HTTP or HTTPS. This book focuses on the perspective of SAS Viya from Python. SAS Viya is made up of multiple components. The central piece of this ecosystem is SAS Cloud Analytic Services (CAS). CAS is the cloud-based server that all clients communicate with to run analytical methods. The Python client is used to drive the CAS component directly using objects and constructs that are familiar to Python programmers.Some knowledge of Python would be helpful before using this book; however, there is an appendix that covers the features of Python that are used in the CAS Python client. Knowledge of CAS is not required to use this book. However, you will need to have a CAS server set up and running to execute the examples in this book. With this book, you will learn how to: Install the required components for accessing CAS from PythonConnect to CAS, load data, and run simple analysesWork with CAS using APIs familiar to Python usersGrasp general CAS workflows and advanced features of the CAS Python client SAS Viya : The Python Perspective covers topics that will be useful to beginners as well as experienced CAS users. It includes examples from creating connections to CAS all the way to simple statistics and machine learning, but it is also useful as a desktop reference. COMPUTERS,Mathematical & Statistical Software

Statistical Analysis of Network Data with R The new edition of this book provides an easily accessible introduction to the statistical analysis of network data using R. It has been fully revised and can be used as a stand-alone resource in which multiple R packages are used to illustrate how to conduct a wide range of network analyses, from basic manipulation and visualization, to summary and characterization, to modeling of network data. The central package is igraph, which provides extensive capabilities for studying network graphs in R. The new edition of this book includes an overhaul to recent changes in igraph. The material in this book is organized to flow from descriptive statistical methods to topics centered on modeling and inference with networks, with the latter separated into two sub-areas, corresponding first to the modeling and inference of networks themselves, and then, to processes on networks. The book begins by covering tools for the manipulation of network data. Next, it addresses visualization and characterization of networks. The book then examines mathematical and statistical network modeling. This is followed by a special case of network modeling wherein the network topology must be inferred. Network processes, both static and dynamic are addressed in the subsequent chapters. The book concludes by featuring chapters on network flows, dynamic networks, and networked experiments. Statistical Analysis of Network Data with R, 2nd Ed. has been written at a level aimed at graduate students and researchers in quantitative disciplines engaged in the statistical analysis of network data, although advanced undergraduates already comfortable with R should find the book fairly accessible as well. COMPUTERS,Mathematical & Statistical Software

High-Speed Networking Leading authorities deliver the commandments for designing high-speed networks There are no end of books touting the virtues of one or another high-speed networking technology, but until now, there were none offering networking professionals a framework for choosing and integrating the best ones for their organization's networking needs. Written by two world-renowned experts in the field of high-speed network design, this book outlines a total strategy for designing high-bandwidth, low-latency systems. Using real-world implementation examples to illustrate their points, the authors cover all aspects of network design, including network components, network architectures, topologies, protocols, application interactions, and more. COMPUTERS,Networking,General

Computer Networking First-Step This is the eBook version of the printed book. If the print book includes a CD-ROM, this content is not included within the eBook version. Your first step into the world of computer networking No experience required Includes clear and easily understood explanations Makes learning easy Your first step to computer networking begins here! Learn basic networking terminology Understand how information is routed from place to place Explore Internet connectivity secrets Protect your computer from intrusion Build local-area networks (LANs) Welcome to the world of networking! Networking and the Internet touch our lives in untold ways every day. From connecting our computers together at home and surfing the net at high speeds to editing and sharing digital music and video, computer networking has become both ubiquitous and indispensable. No experience needed! Computer Networking First-Step explains the basics of computer networking in easy-to-grasp language that all of us can understand. This book takes you on a guided tour of the core technologies that make up network and Internet traffic. Whether you are looking to take your first step into a career in networking or are interested in just gaining a conversational knowledge of the technology, this book is for you! COMPUTERS,Networking,General

Road to IP Telephony, The This is the eBook version of the printed book. If the print book includes a CD-ROM, this content is not included within the eBook version. A complete IP Telephony migration planning guide Includes Steps to Success Poster It's everyone's "must have." This is a reference book for the entire project team who works on the deployment of an IP Telephony solution. Take advantage of best practices. Includes more than 200 best practices, lessons learned, and tips for getting you through your IP Telephony deployment successfully. Minimize risk and learn from the mistakes of others. Read the list of the top 10 things that can go wrong during an IP Telephony deployment. Ask the right questions. Get the project team thinking and collaborating together with Stephanie's "Checklist of Questions to Ask the Project Team." Use proven planning tools. Work from sample checklists, templates, project plans, and workflow documents to guide your planning process. Keep the Steps to Success on the minds of your project team. Use the enclosed poster, which illustrates every major step associated with an IP Telephony deployment. There is no better path to the successful implementation of a new technology than to follow in the experienced footsteps of an organization that has already been there. The Road to IP Telephony tells you how Cisco Systems successfully moved its own organization to a converged, enterprise-wide network. You will learn the implementation and operational processes, what worked, what didn't work, and how to develop your own successful methodology. After presenting this topic to hundreds of Cisco customers, including Fortune 500 companies, Stephanie Carhee consistently encountered the same question, "If I decide to move to IP Telephony, where do I begin and what can I do to ensure that I do it right the first time?" Although the needs of every enterprise are different, some things are universal; planning, communication, teamwork, and understanding your user's requirements are as important as technical expertise. The Road to IP Telephony shares with you everything you need to know about managing your deployment. It starts with where to begin, including what needs to be addressed before you even begin the planning process, to building your project team. Key best practices are also offered to help you set the project's pace and schedule, get your users on board, identify a migration strategy, develop a services and support strategy, and work toward the final PBX decommission. "Cisco IT wants to share its implementation experience with Cisco customers and partners to aide in the deployment practices of new Cisco technologies. While conducting our own company-wide cutover, we learned a great deal about what to do and what not to do. This book shares our experiences."-Brad Boston, Senior Vice President and Chief Information Officer, Cisco Systems, Inc. This volume is in the Network Business Series offered by Cisco Press. Books in this series provide IT executives, decision makers, and networking professionals with pertinent information on today's most important technologies and business strategies. COMPUTERS,Networking,General

Multicast Sockets Multicast Sockets: Practical Guide for Programmers is a hands-on, application-centric approach to multicasting (as opposed to a network-centric one) that is filled with examples, ideas, and experimentation. Each example builds on the last to introduce multicast concepts, frameworks, and APIs in an engaging manner that does not burden the reader with lots of theory and jargon. The book is an introduction to multicasting but assumes that the reader has a background in network programming and is proficient in C or Java. After reading the book, you will have a firm grasp on how to write a multicast program. Author team of instructor and application programmer is reflected in this rich instructional and practical approach to the subject material Only book available that provides a clear, concise, application-centric approach to programming multicast applications and covers several languages—C, Java, and C# on the .NET platform Covers important topics like service models, testing reachability, and addressing and scoping Includes numerous examples and exercises for programmers and students to test what they have learned COMPUTERS,Networking,General

Hacking Exposed Web 2.0 Lock down next-generation Web services "This book concisely identifies the types of attacks which are faced daily by Web 2.0 sites, and the authors give solid, practical advice on how to identify and mitigate these threats." --Max Kelly, CISSP, CIPP, CFCE, Senior Director of Security, Facebook Protect your Web 2.0 architecture against the latest wave of cybercrime using expert tactics from Internet security professionals. Hacking Exposed Web 2.0 shows how hackers perform reconnaissance, choose their entry point, and attack Web 2.0-based services, and reveals detailed countermeasures and defense techniques. You'll learn how to avoid injection and buffer overflow attacks, fix browser and plug-in flaws, and secure AJAX, Flash, and XML-driven applications. Real-world case studies illustrate social networking site weaknesses, cross-site attack methods, migration vulnerabilities, and IE7 shortcomings. Plug security holes in Web 2.0 implementations the proven Hacking Exposed way Learn how hackers target and abuse vulnerable Web 2.0 applications, browsers, plug-ins, online databases, user inputs, and HTML forms Prevent Web 2.0-based SQL, XPath, XQuery, LDAP, and command injection attacks Circumvent XXE, directory traversal, and buffer overflow exploits Learn XSS and Cross-Site Request Forgery methods attackers use to bypass browser security controls Fix vulnerabilities in Outlook Express and Acrobat Reader add-ons Use input validators and XML classes to reinforce ASP and .NET security Eliminate unintentional exposures in ASP.NET AJAX (Atlas), Direct Web Remoting, Sajax, and GWT Web applications Mitigate ActiveX security exposures using SiteLock, code signing, and secure controls Find and fix Adobe Flash vulnerabilities and DNS rebinding attacks COMPUTERS,Networking,General

IT Disaster Recovery Planning For Dummies If you have a business or a nonprofit organization, or if you’re the one responsible for information systems at such an operation, you know that disaster recovery planning is pretty vital. But it’s easy to put it off. After all, where do you start? IT Disaster Recovery Planning For Dummies shows you how to get started by creating a safety net while you work out the details of your major plan. The right plan will get your business back on track quickly, whether you're hit by a tornado or a disgruntled employee with super hacking powers. Here's how to assess the situation, develop both short-term and long-term plans, and keep your plans updated. This easy-to-understand guide will help you Prepare your systems, processes, and people for an organized response to disaster when it strikes Identify critical IT systems and develop a long-range strategy Select and train your disaster recovery team Conduct a Business Impact Analysis Determine risks to your business from natural or human-made causes Get management support Create appropriate plan documents Test your plan Some disasters get coverage on CNN, and some just create headaches for the affected organization. With IT Disaster Recovery Planning For Dummies, you’ll be prepared for anything from hackers to hurricanes! COMPUTERS,Networking,General

Hacking Exposed Linux The Latest Linux Security Solutions This authoritative guide will help you secure your Linux network--whether you use Linux as a desktop OS, for Internet services, for telecommunications, or for wireless services. Completely rewritten the ISECOM way, Hacking Exposed Linux, Third Edition provides the most up-to-date coverage available from a large team of topic-focused experts. The book is based on the latest ISECOM security research and shows you, in full detail, how to lock out intruders and defend your Linux systems against catastrophic attacks. Secure Linux by using attacks and countermeasures from the latest OSSTMM research Follow attack techniques of PSTN, ISDN, and PSDN over Linux Harden VoIP, Bluetooth, RF, RFID, and IR devices on Linux Block Linux signal jamming, cloning, and eavesdropping attacks Apply Trusted Computing and cryptography tools for your best defense Fix vulnerabilities in DNS, SMTP, and Web 2.0 services Prevent SPAM, Trojan, phishing, DoS, and DDoS exploits Find and repair errors in C code with static analysis and Hoare Logic COMPUTERS,Networking,General

The Illustrated Network In 1994, W. Richard Stevens and Addison-Wesley published a networking classic: TCP/IP Illustrated. The model for that book was a brilliant, unfettered approach to networking concepts that has proven itself over time to be popular with readers of beginning to intermediate networking knowledge. The Illustrated Network takes this time-honored approach and modernizes it by creating not only a much larger and more complicated network, but also by incorporating all the networking advancements that have taken place since the mid-1990s, which are many. This book takes the popular Stevens approach and modernizes it, employing 2008 equipment, operating systems, and router vendors. It presents an ?illustrated? explanation of how TCP/IP works with consistent examples from a real, working network configuration that includes servers, routers, and workstations. Diagnostic traces allow the reader to follow the discussion with unprecedented clarity and precision. True to the title of the book, there are 330+ diagrams and screen shots, as well as topology diagrams and a unique repeating chapter opening diagram. Illustrations are also used as end-of-chapter questions. A complete and modern network was assembled to write this book, with all the material coming from real objects connected and running on the network, not assumptions. Presents a real world networking scenario the way the reader sees them in a device-agnostic world. Doesn't preach one platform or the other. Here are ten key differences between the two:StevensGoralski's Older operating systems (AIX,svr4,etc.)Newer OSs (XP, Linux, FreeBSD, etc.)Two routers (Cisco, Telebit (obsolete))Two routers (M-series, J-series)Slow Ethernet and SLIP linkFast Ethernet, Gigabit Ethernet, and SONET/SDH links (modern)Tcpdump for tracesNewer, better utility to capture traces (Ethereal, now has a new name!)No IPSecIPSecNo multicastMulticastNo router security discussedFirewall routers detailedNo WebFull Web browser HTML considerationNo IPv6IPv6 overviewFew configuration details More configuration details (ie, SSH, SSL, MPLS, ATM/FR consideration, wireless LANS, OSPF and BGP routing protocols New Modern Approach to Popular Topic Adopts the popular Stevens approach and modernizes it, giving the reader insights into the most up-to-date network equipment, operating systems, and router vendors. Shows and Tells Presents an illustrated explanation of how TCP/IP works with consistent examples from a real, working network configuration that includes servers, routers, and workstations, allowing the reader to follow the discussion with unprecedented clarity and precision. Over 330 Illustrations True to the title, there are 330 diagrams, screen shots, topology diagrams, and a unique repeating chapter opening diagram to reinforce concepts Based on Actual Networks A complete and modern network was assembled to write this book, with all the material coming from real objects connected and running on the network, bringing the real world, not theory, into sharp focus. COMPUTERS,Networking,General

Storage Area Networks For Dummies If you’ve been charged with setting up storage area networks for your company, learning how SANs work and managing data storage problems might seem challenging. Storage Area Networks For Dummies, 2nd Edition comes to the rescue with just what you need to know. Whether you already a bit SAN savvy or you’re a complete novice, here’s the scoop on how SANs save money, how to implement new technologies like data de-duplication, iScsi, and Fibre Channel over Ethernet, how to develop SANs that will aid your company’s disaster recovery plan, and much more. For example, you can: Understand what SANs are, whether you need one, and what you need to build one Learn to use loops, switches, and fabric, and design your SAN for peak performance Create a disaster recovery plan with the appropriate guidelines, remote site, and data copy techniques Discover how to connect or extend SANs and how compression can reduce costs Compare tape and disk backups and network vs. SAN backup to choose the solution you need Find out how data de-duplication makes sense for backup, replication, and retention Follow great troubleshooting tips to help you find and fix a problem Benefit from a glossary of all those pesky acronyms From the basics for beginners to advanced features like snapshot copies, storage virtualization, and heading off problems before they happen, here’s what you need to do the job with confidence! COMPUTERS,Networking,General

A Research Primer for Technical Communication This practical volume provides a thorough introduction to conducting and critically reading research in technical communication, complete with exemplars of research articles for study. Offering a solid grounding in the research underpinnings of the technical communication field, this resource has been developed for use in master’s level and upper-division undergraduate research methods courses in technical and professional communication. COMPUTERS,Networking,General

DNS and BIND DNS and BIND tells you everything you need to work with one of the Internet's fundamental building blocks: the distributed host information database that's responsible for translating names into addresses, routing mail to its proper destination, and even listing phone numbers with the new ENUM standard. This book brings you up-to-date with the latest changes in this crucial service. The fifth edition covers BIND 9.3.2, the most recent release of the BIND 9 series, as well as BIND 8.4.7. BIND 9.3.2 contains further improvements in security and IPv6 support, and important new features such as internationalized domain names, ENUM (electronic numbering), and SPF (the Sender Policy Framework). Whether you're an administrator involved with DNS on a daily basis or a user who wants to be more informed about the Internet and how it works, you'll find that this book is essential reading. Topics include: What DNS does, how it works, and when you need to use it How to find your own place in the Internet's namespace Setting up name servers Using MX records to route mail Configuring hosts to use DNS name servers Subdividing domains (parenting) Securing your name server: restricting who can query your server, preventing unauthorized zone transfers, avoiding bogus servers, etc. The DNS Security Extensions (DNSSEC) and Transaction Signatures (TSIG) Mapping one name to several servers for load sharing Dynamic updates, asynchronous notification of change to a zone, and incremental zone transfers Troubleshooting: using nslookup and dig, reading debugging output, common problems DNS programming using the resolver library and Perl's Net::DNS module COMPUTERS,Networking,General

Essential SNMP Simple Network Management Protocol (SNMP) provides a "simple" set of operations that allows you to more easily monitor and manage network devices like routers, switches, servers, printers, and more. The information you can monitor with SNMP is wide-ranging--from standard items, like the amount of traffic flowing into an interface, to far more esoteric items, like the air temperature inside a router. In spite of its name, though, SNMP is not especially simple to learn. O'Reilly has answered the call for help with a practical introduction that shows how to install, configure, and manage SNMP. Written for network and system administrators, the book introduces the basics of SNMP and then offers a technical background on how to use it effectively. Essential SNMP explores both commercial and open source packages, and elements like OIDs, MIBs, community strings, and traps are covered in depth. The book contains five new chapters and various updates throughout. Other new topics include: Expanded coverage of SNMPv1, SNMPv2, and SNMPv3 Expanded coverage of SNMPc The concepts behind network management and change management RRDTool and Cricket The use of scripts for a variety of tasks How Java can be used to create SNMP applications Net-SNMP's Perl module The bulk of the book is devoted to discussing, with real examples, how to use SNMP for system and network administration tasks. Administrators will come away with ideas for writing scripts to help them manage their networks, create managed objects, and extend the operation of SNMP agents. Once demystified, SNMP is much more accessible. If you're looking for a way to more easily manage your network, look no further than Essential SNMP, 2nd Edition. COMPUTERS,Networking,General

LDAP System Administration Be more productive and make your life easier. That's what LDAP System Administration is all about.System administrators often spend a great deal of time managing configuration information located on many different machines: usernames, passwords, printer configurations, email client configurations, and network filesystem configurations, to name a few. LDAPv3 provides tools for centralizing all of the configuration information and placing it under your control. Rather than maintaining several administrative databases (NIS, Active Directory, Samba, and NFS configuration files), you can make changes in only one place and have all your systems immediately "see" the updated information.Practically platform independent, this book uses the widely available, open source OpenLDAP 2 directory server as a premise for examples, showing you how to use it to help you manage your configuration information effectively and securely. OpenLDAP 2 ships with most Linux® distributions and Mac OS® X, and can be easily downloaded for most Unix-based systems. After introducing the workings of a directory service and the LDAP protocol, all aspects of building and installing OpenLDAP, plus key ancillary packages like SASL and OpenSSL, this book discusses: Configuration and access control Distributed directories; replication and referral Using OpenLDAP to replace NIS Using OpenLDAP to manage email configurations Using LDAP for abstraction with FTP and HTTP servers, Samba, and Radius Interoperating with different LDAP servers, including Active Directory Programming using Net::LDAP If you want to be a master of your domain, LDAP System Administration will help you get up and running quickly regardless of which LDAP version you use. After reading this book, even with no previous LDAP experience, you'll be able to integrate a directory server into essential network services such as mail, DNS, HTTP, and SMB/CIFS. COMPUTERS,Networking,General

Time Management for System Administrators Time is a precious commodity, especially if you're a system administrator. No other job pulls people in so many directions at once. Users interrupt you constantly with requests, preventing you from getting anything done. Your managers want you to get long-term projects done but flood you with requests for quick-fixes that prevent you from ever getting to those long-term projects. But the pressure is on you to produce and it only increases with time. What do you do? The answer is time management. And not just any time management theory--you want Time Management for System Administrators, to be exact. With keen insights into the challenges you face as a sys admin, bestselling author Thomas Limoncelli has put together a collection of tips and techniques that will help you cultivate the time management skills you need to flourish as a system administrator. Time Management for System Administrators understands that an Sys Admin often has competing goals: the concurrent responsibilities of working on large projects and taking care of a user's needs. That's why it focuses on strategies that help you work through daily tasks, yet still allow you to handle critical situations that inevitably arise. Among other skills, you'll learn how to: Manage interruptions Eliminate timewasters Keep an effective calendar Develop routines for things that occur regularly Use your brain only for what you're currently working on Prioritize based on customer expectations Document and automate processes for faster execution What's more, the book doesn't confine itself to just the work environment, either. It also offers tips on how to apply these time management tools to your social life. It's the first step to a more productive, happier you. COMPUTERS,Networking,General

Designing and Implementing IP/MPLS-Based Ethernet Layer 2 VPN Services A guide to designing and implementing VPLS services over an IP/MPLS switched service provider backbone Today's communication providers are looking for convenience, simplicity, and flexible bandwidth across wide area networks-but with the quality of service and control that is critical for business networking applications like video, voice and data. Carrier Ethernet VPN services based on VPLS makes this a reality. Virtual Private LAN Service (VPLS) is a pseudowire (PW) based, multipoint-to-multipoint layer 2 Ethernet VPN service provided by services providers By deploying a VPLS service to customers, the operator can focus on providing high throughput, highly available Ethernet bridging services and leave the layer 3 routing decision up to the customer. Virtual Private LAN Services (VPLS) is quickly becoming the number one choice for many enterprises and service providers to deploy data communication networks. Alcatel-Lucent VPLS solution enables service providers to offer enterprise customers the operational cost benefits of Ethernet with the predictable QoS characteristics of MPLS. Items Covered: Building Converged Service Networks with IP/MPLS VPN Technology IP/MPLS VPN Multi-Service Network Overview Using MPLS Label Switched Paths as Service Transport Tunnels Routing Protocol Traffi c Engineering and CSPF RSVP-TE Protocol MPLS Resiliency — Secondary LSP MPLS Resiliency — RSVP-TE LSP Fast Reroute Label Distribution Protocol IP/MPLS VPN Service Routing Architecture Virtual Leased Line Services Virtual Private LAN Service Hierarchical VPLS High Availability in an IP/MPLS VPN Network VLL Service Resiliency VPLS Service Resiliency VPLS BGP Auto-Discovery PBB-VPLS OAM in a VPLS Service Network COMPUTERS,Networking,General

Zero Configuration Networking It used to be that two laptops, sitting side by side, couldn't communicate with each other; they may as well have been a thousand miles apart. But that was then, before the advent of Zero Configuration Networking technology. This amazing cross-platform open source technology automatically connects electronic devices on a network, allowing them to interoperate seamlessly-without any user configuration. So now you don't have to lift a finger! Needless to say, it has completely changed the way people connect to devices and programs for printing, file sharing, and other activities. Zero Configuration Networking: The Definitive Guide walks you through this groundbreaking network technology, with a complete description of the protocols and ways to implement network-aware applications and devices. Written by two Zero Configuration Networking experts, including one of Apple's own computer scientists, the book covers more than just file sharing and printing. Zero Configuration Networking also enables activities such as music and photo sharing and automatic buddy discovery on Instant Messaging applications. In fact, Zero Configuration Networking can be used for virtually any device that can be controlled by a computer. And this handy guide has the inside scoop on all of its capabilities-and how you can easily apply them in your own environment. For the technically advanced, Zero Configuration Networking: The Definitive Guide examines the three core technologies that make up Zero Configuration Networking: Link-Local Addressing, Multicast DNS, and DNS Service Discovery. It also reviews a series of APIs, including C-API, Java API, CFNetServices, and Cocoa's NSNetServices. Whether you want to understand how iTunes works, or you want to network a series of laptops and other devices at your office for maximum efficiency, you'll find all the answers in this authoritative guide. COMPUTERS,Networking,General

Managing NFS and NIS A modern computer system that's not part of a network is even more of an anomaly today than it was when we published the first edition of this book in 1991. But however widespread networks have become, managing a network and getting it to perform well can still be a problem.Managing NFS and NIS, in a new edition based on Solaris 8, is a guide to two tools that are absolutely essential to distributed computing environments: the Network Filesystem (NFS) and the Network Information System (formerly called the "yellow pages" or YP).The Network Filesystem, developed by Sun Microsystems, is fundamental to most Unix networks. It lets systems ranging from PCs and Unix workstations to large mainframes access each other's files transparently, and is the standard method for sharing files between different computer systems.As popular as NFS is, it's a "black box" for most users and administrators. Updated for NFS Version 3, Managing NFS and NIS offers detailed access to what's inside, including: How to plan, set up, and debug an NFS network Using the NFS automounter Diskless workstations PC/NFS A new transport protocol for NFS (TCP/IP) New security options (IPSec and Kerberos V5) Diagnostic tools and utilities NFS client and server tuning NFS isn't really complete without its companion, NIS, a distributed database service for managing the most important administrative files, such as the passwd file and the hosts file. NIS centralizes administration of commonly replicated files, allowing a single change to the database rather than requiring changes on every system on the network.If you are managing a network of Unix systems, or are thinking of setting up a Unix network, you can't afford to overlook this book. COMPUTERS,Networking,General

Internet Networks In the not too distant future, internet access will be dominated by wireless networks. With that, wireless edge using optical core next-generation networks will become as ubiquitous as traditional telephone networks. This means that telecom engineers, chip designers, and engineering students must prepare to meet the challenges and opportunities that the development and deployment of these technologies will bring. Bringing together cutting-edge coverage of wireless and optical networks in a single volume, Internet Networks Wired, Wireless, and Optical Technologies provides a concise yet complete introduction to these dynamic technologies. Filled with case studies, illustrations, and practical examples from industry, the text explains how wireless, wireline, and optical networks work together. It also: Covers WLAN, WPAN, wireless access, 3G/4G cellular, RF transmission Details optical networks involving long-haul and metropolitan networks, optical fiber, photonic devices, and VLSI chips Provides clear instruction on the application of wireless and optical networks Taking into account recent advances in storage, processing, sensors, displays, statistical data analyses, and autonomic systems, this reference provides forward thinking engineers and students with a realistic vision of how the continued evolution of the technologies that touch wireless communication will soon reshape markets and business models around the world. COMPUTERS,Networking,General

Windows Command Line Administration Instant Reference The perfect companion to any book on Windows Server 2008 or Windows 7, and the quickest way to access critical information Focusing just on the essentials of command-line interface (CLI), Windows Command-Line Administration Instant Reference easily shows how to quickly perform day-to-day tasks of Windows administration without ever touching the graphical user interface (GUI). Specifically designed for busy administrators, Windows Command-Line Administration Instant Reference replaces many tedious GUI steps with just one command at the command-line, while concise, easy to access answers provide solutions on the spot. Provides practical examples, step-by-step instructions, and contextual information Quick-reference style delivers the commands needed for managing data and the network; working with Active Directory; performing diagnostics and maintenance; and, creating batch files and scripts Covers administration for Windows Server 2008 Server Core, Windows Server 2008 (including R2), and Windows 7 Administrators can get more done in less time with CLI than they can with the standard GUI. Compact enough to keep on hand at all times, Windows Command-Line Administration Instant Reference provides administrators with a convenient, fast and simple way to use CLI. COMPUTERS,Networking,General

Hacking Exposed Web Applications, Third Edition The latest Web app attacks and countermeasures from world-renowned practitioners Protect your Web applications from malicious attacks by mastering the weapons and thought processes of today's hacker. Written by recognized security practitioners and thought leaders, Hacking Exposed Web Applications, Third Edition is fully updated to cover new infiltration methods and countermeasures. Find out how to reinforce authentication and authorization, plug holes in Firefox and IE, reinforce against injection attacks, and secure Web 2.0 features. Integrating security into the Web development lifecycle (SDL) and into the broader enterprise information security program is also covered in this comprehensive resource. Get full details on the hacker's footprinting, scanning, and profiling tools, including SHODAN, Maltego, and OWASP DirBuster See new exploits of popular platforms like Sun Java System Web Server and Oracle WebLogic in operation Understand how attackers defeat commonly used Web authentication technologies See how real-world session attacks leak sensitive data and how to fortify your applications Learn the most devastating methods used in today's hacks, including SQL injection, XSS, XSRF, phishing, and XML injection techniques Find and fix vulnerabilities in ASP.NET, PHP, and J2EE execution environments Safety deploy XML, social networking, cloud computing, and Web 2.0 services Defend against RIA, Ajax, UGC, and browser-based, client-side exploits Implement scalable threat modeling, code review, application scanning, fuzzing, and security testing procedures COMPUTERS,Networking,General

IT Auditing Using Controls to Protect Information Assets, 2nd Edition Secure Your Systems Using the Latest IT Auditing Techniques Fully updated to cover leading-edge tools and technologies, IT Auditing: Using Controls to Protect Information Assets, Second Edition, explains, step by step, how to implement a successful, enterprise-wide IT audit program. New chapters on auditing cloud computing, outsourced operations, virtualization, and storage are included. This comprehensive guide describes how to assemble an effective IT audit team and maximize the value of the IT audit function. In-depth details on performing specific audits are accompanied by real-world examples, ready-to-use checklists, and valuable templates. Standards, frameworks, regulations, and risk management techniques are also covered in this definitive resource. Build and maintain an internal IT audit function with maximum effectiveness and value Audit entity-level controls, data centers, and disaster recovery Examine switches, routers, and firewalls Evaluate Windows, UNIX, and Linux operating systems Audit Web servers and applications Analyze databases and storage solutions Assess WLAN and mobile devices Audit virtualized environments Evaluate risks associated with cloud computing and outsourced operations Drill down into applications to find potential control weaknesses Use standards and frameworks, such as COBIT, ITIL, and ISO Understand regulations, including Sarbanes-Oxley, HIPAA, and PCI Implement proven risk management practices COMPUTERS,Networking,General

Mastering Algorithms with Perl Many programmers would love to use Perl for projects that involve heavy lifting, but miss the many traditional algorithms that textbooks teach for other languages. Computer scientists have identified many techniques that a wide range of programs need, such as: Fuzzy pattern matching for text (identify misspellings!) Finding correlations in data Game-playing algorithms Predicting phenomena such as Web traffic Polynomial and spline fitting Using algorithms explained in this book, you too can carry out traditional programming tasks in a high-powered, efficient, easy-to-maintain manner with Perl.This book assumes a basic understanding of Perl syntax and functions, but not necessarily any background in computer science. The authors explain in a readable fashion the reasons for using various classic programming techniques, the kind of applications that use them, and -- most important -- how to code these algorithms in Perl.If you are an amateur programmer, this book will fill you in on the essential algorithms you need to solve problems like an expert. If you have already learned algorithms in other languages, you will be surprised at how much different (and often easier) it is to implement them in Perl. And yes, the book even has the obligatory fractal display program.There have been dozens of books on programming algorithms, some of them excellent, but never before has there been one that uses Perl.The authors include the editor of The Perl Journal and master librarian of CPAN; all are contributors to CPAN and have archived much of the code in this book there."This book was so exciting I lost sleep reading it." Tom Christiansen COMPUTERS,Networking,General

Microsoft Windows Networking Essentials The core concepts and technologies of Windows networking Networking can be a complex topic, especially for those new to the field of IT. This focused, full-color book takes a unique approach to teaching Windows networking to beginners by stripping down a network to its bare basics, thereby making each topic clear and easy to understand. Focusing on the new Microsoft Technology Associate (MTA) program, this book pares down to just the essentials, showing beginners how to gain a solid foundation for understanding networking concepts upon which more advanced topics and technologies can be built. This straightforward guide begins each chapter by laying out a list of topics to be discussed, followed by a concise discussion of the core networking skills you need to have to gain a strong handle on the subject matter. Chapters conclude with review questions and suggested labs so you can measure your level of understanding of the chapter's content. Serves as an ideal resource for gaining a solid understanding of fundamental networking concepts and skills Offers a straightforward and direct approach to networking basics and covers network management tools, TCP/IP, the name resolution process, and network protocols and topologies Reviews all the topics you need to know for taking the MTA 98-366 exam Provides an overview of networking components, discusses connecting computers to a network, and looks at connecting networks with routers If you're new to IT and interested in entering the IT workforce, then Microsoft Windows Networking Essentials is essential reading. COMPUTERS,Networking,General

Network Warrior Pick up where certification exams leave off. With this practical, in-depth guide to the entire network infrastructure, you’ll learn how to deal with real Cisco networks, rather than the hypothetical situations presented on exams like the CCNA. Network Warrior takes you step by step through the world of routers, switches, firewalls, and other technologies based on the author's extensive field experience. You'll find new content for MPLS, IPv6, VoIP, and wireless in this completely revised second edition, along with examples of Cisco Nexus 5000 and 7000 switches throughout. Topics include: An in-depth view of routers and routing Switching, using Cisco Catalyst and Nexus switches as examples SOHO VoIP and SOHO wireless access point design and configuration Introduction to IPv6 with configuration examples Telecom technologies in the data-networking world, including T1, DS3, frame relay, and MPLS Security, firewall theory, and configuration, as well as ACL and authentication Quality of Service (QoS), with an emphasis on low-latency queuing (LLQ) IP address allocation, Network Time Protocol (NTP), and device failures COMPUTERS,Networking,General

Microsoft Windows Server Administration Essentials The core concepts and technologies you need to administer a Windows Server OS Administering a Windows operating system (OS) can be a difficult topic to grasp, particularly if you are new to the field of IT. This full-color resource serves as an approachable introduction to understanding how to install a server, the various roles of a server, and how server performance and maintenance impacts a network. With a special focus placed on the new Microsoft Technology Associate (MTA) certificate, the straightforward, easy-to-understand tone is ideal for anyone new to computer administration looking to enter the IT field. Each chapter offers a clear and concise look at the core Windows administration concepts you need to know to gain an understanding of these difficult topics. Offers a clear, no-nonsense approach to administering a Windows operating system and presents it in such a way that IT beginners will confidently comprehend the subject matter Targets the MTA 98-365 exam by covering Windows Server installation, server roles, storage, and active directory infrastructure Provides you with a solid foundation of various networking topics so that you can gain a strong understanding of Windows Server administration concepts Includes review questions and suggested labs to further enhance your learning process With this book by your side, you will be armed with the core concepts and technologies needed to administer a Windows Server operating system. COMPUTERS,Networking,General

Hacking Exposed Mobile Proven security tactics for today's mobile apps, devices, and networks "A great overview of the new threats created by mobile devices. ...The authors have heaps of experience in the topics and bring that to every chapter." -- Slashdot Hacking Exposed Mobile continues in the great tradition of the Hacking Exposed series, arming business leaders and technology practitioners with an in-depth understanding of the latest attacks and countermeasures--so they can leverage the power of mobile platforms while ensuring that security risks are contained." -- Jamil Farshchi, Senior Business Leader of Strategic Planning and Initiatives, VISA Identify and evade key threats across the expanding mobile risk landscape. Hacking Exposed Mobile: Security Secrets & Solutions covers the wide range of attacks to your mobile deployment alongside ready-to-use countermeasures. Find out how attackers compromise networks and devices, attack mobile services, and subvert mobile apps. Learn how to encrypt mobile data, fortify mobile platforms, and eradicate malware. This cutting-edge guide reveals secure mobile development guidelines, how to leverage mobile OS features and MDM to isolate apps and data, and the techniques the pros use to secure mobile payment systems. Tour the mobile risk ecosystem with expert guides to both attack and defense Learn how cellular network attacks compromise devices over-the-air See the latest Android and iOS attacks in action, and learn how to stop them Delve into mobile malware at the code level to understand how to write resilient apps Defend against server-side mobile attacks, including SQL and XML injection Discover mobile web attacks, including abuse of custom URI schemes and JavaScript bridges Develop stronger mobile authentication routines using OAuth and SAML Get comprehensive mobile app development security guidance covering everything from threat modeling to iOS- and Android-specific tips Get started quickly using our mobile pen testing and consumer security checklists COMPUTERS,Networking,General

WPF 4.5 Unleashed The #1 WPF Book--Now Updated for WPF 4.5! Thorough, authoritative coverage, practical examples, clear writing, and full-color presentation make this one of the most widely acclaimed programming books of the last decade. Windows Presentation Foundation (WPF) is the recommended technology for creating modern Windows desktop apps. Whether you want to develop traditional user interfaces or integrate 3D graphics, audio/video, animation, dynamic skinning, touch, rich document support, speech recognition, or more, WPF enables you to do so in a seamless, resolution-independent manner that scales from small tablets to large TVs. WPF 4.5 Unleashed is the authoritative book that covers it all, in a practical and approachable fashion, authored by WPF guru and Microsoft architect Adam Nathan. Covers everything you need to know about Extensible Application Markup Language (XAML) Examines the WPF feature areas in incredible depth: controls, layout, resources, data binding, styling, graphics, animation, and more Delves into topics that aren’t covered by most books: 3D, speech, audio/video, documents, effects Shows how to create popular UI elements and leverage built-in controls such as the new Office-style Ribbon Demonstrates how to create sophisticated UI mechanisms, such as Visual Studio-like collapsible/dockable panes Explains how to create first-class custom controls for WPF Demonstrates how to create hybrid WPF software that leverages Windows Forms, DirectX, ActiveX, or other non-WPF technologies Explains how to exploit desktop features, such as Jump Lists and taskbar customizations, and the same toast notifications used by Windows Store apps COMPUTERS,Networking,General

The SIMD Model of Parallel Computation 1.1 Background There are many paradigmatic statements in the literature claiming that this is the decade of parallel computation. A great deal of research is being de voted to developing architectures and algorithms for parallel machines with thousands, or even millions, of processors. Such massively parallel computers have been made feasible by advances in VLSI (very large scale integration) technology. In fact, a number of computers having over one thousand pro cessors are commercially available. Furthermore, it is reasonable to expect that as VLSI technology continues to improve, massively parallel computers will become increasingly affordable and common. However, despite the significant progress made in the field, many funda mental issues still remain unresolved. One of the most significant of these is the issue of a general purpose parallel architecture. There is currently a huge variety of parallel architectures that are either being built or proposed. The problem is whether a single parallel computer can perform efficiently on all computing applications. COMPUTERS,Networking,General

Responsive Computer Systems For the second time the International Workshop on Responsive Com puter Systems has brought together a group of international experts from the fields of real-time computing, distributed computing, and fault tolerant systems. The two day workshop met at the splendid facilities at the KDD Research and Development Laboratories at Kamifukuoka, Saitama, in Japan on October 1 and 2, 1992. The program included a keynote address, a panel discussion and, in addition to the opening and closing session, six sessions of submitted presentations. The keynote address "The Concepts and Technologies of Depend able and Real-time Computer Systems for Shinkansen Train Control" covered the architecture of the computer control system behind a very responsive, i. e. , timely and reliable, transport system-the Shinkansen Train. It has been fascinating to listen to the operational experience with a large fault-tolerant computer application. "What are the Key Paradigms in the Integration of Timeliness and Reliability?" was the topic of the lively panel discussion. Once again the pro's and con's of the time-triggered versus the event-triggered paradigm in the design of a real-time systems were discussed. The eighteen submitted presentations covered diverse topics about important issues in the design of responsive systems and a session on progress reports about leading edge research projects. Lively discussions characterized both days of the meeting. This volume contains the revised presentations that incorporate some of the discussions that occurred during the meeting. COMPUTERS,Networking,General

Associative Computing Integrating associative processing concepts with massively parallel SIMD technology, this volume explores a model for accessing data by content rather than abstract address mapping. COMPUTERS,Networking,General

Frontiers of Computing Systems Research Intended for an interdisciplinary audience involved in computer systems research, this second volume presents technical information on emerging topics in the field. COMPUTERS,Networking,General

VLSI for Artificial Intelligence and Neural Networks This book is an edited selection of the papers presented at the International Workshop on VLSI for Artifidal Intelligence and Neural Networks which was held at the University of Oxford in September 1990. Our thanks go to all the contributors and especially to the programme committee for all their hard work. Thanks are also due to the ACM-SIGARCH, the IEEE Computer Society, and the lEE for publicizing the event and to the University of Oxford and SUNY-Binghamton for their active support. We are particularly grateful to Anna Morris, Maureen Doherty and Laura Duffy for coping with the administrative problems. Jose Delgado-Frias Will Moore April 1991 vii PROLOGUE Artificial intelligence and neural network algorithms/computing have increased in complexity as well as in the number of applications. This in tum has posed a tremendous need for a larger computational power than can be provided by conventional scalar processors which are oriented towards numeric and data manipulations. Due to the artificial intelligence requirements (symbolic manipulation, knowledge representation, non-deterministic computations and dynamic resource allocation) and neural network computing approach (non-programming and learning), a different set of constraints and demands are imposed on the computer architectures for these applications. COMPUTERS,Networking,General

Frontiers of Computing Systems Research Computing systems researchers confront two serious problems. (1) The increasingly monolithic, or pseudo-monolithic, integration of complex com puting functions and systems imposes an environment which integrates ad vanced principles and techniques from a broad variety of fields. Researchers not only must confront the increased complexity of topics in their specialty field but also must develop a deeper general understanding of a broadening number of fields. (2) There has been a proliferation of journals, books, workshops and conferences through which research results are reported. Remaining familiar with recent advances in our specific fields is a major challenge. Casually browsing through journals and conference proceedings to remain aware of developments in areas outside our specialization has become an even greater challenge. Frontiers of Computing Systems Research has been established to ad dress these two issues. With the assistance of an advisory board of experts from a wide variety of specialized areas, we hope to provide roughly annual volumes of invited chapters on a broad range of topics and designed for an interdisciplinary research audience. No single volume can cover all the rel evant topics and no single article can convey the full set of directions being pursued within a given topic. For this reason, a chapter listing technical reports available from universities is also included. Often, such unpub lished reports are designed for a general research audience and provide a good, informal look at trends in specialized research topics. COMPUTERS,Networking,General

Visualization in Supercomputing Massive amounts of numeric data are far more comprehensible when converted into graphical form. Hence visualization is becoming an integral part of many areas of research. The idea of visualization is not new, but techniques for visualization are still being developed, and visualization research is just beginning to be recognized as a cornerstone of future computer science. As scientists handle increasingly complex problems with computers, visualization will become an even more essential tool for extracting sense from numbers. This volume is a collection of the best papers selected from those presented at the August 1988 Visualization in Supercomputing Conference in Tokyo, Japan. It is divided into three parts: visualization applications, hardware and performance, and visualization theory. Subjects covered include visualization methods used in computational fluid dynamics research, time-to-solution aspects of visualization, the use of parallel/vector computers with finite element method systems, basic computational performance of two graphics supercomputers, and the applicability of the volume imaging concept in various fields. COMPUTERS,Networking,General

Information Assurance Handbook Best practices for protecting critical data and systems Information Assurance Handbook: Effective Computer Security and Risk Management Strategies discusses the tools and techniques required to prevent, detect, contain, correct, and recover from security breaches and other information assurance failures. This practical resource explains how to integrate information assurance into your enterprise planning in a non-technical manner. It leads you through building an IT strategy and offers an organizational approach to identifying, implementing, and controlling information assurance initiatives for small businesses and global enterprises alike. Common threats and vulnerabilities are described and applicable controls based on risk profiles are provided. Practical information assurance application examples are presented for select industries, including healthcare, retail, and industrial control systems. Chapter-ending critical thinking exercises reinforce the material covered. An extensive list of scholarly works and international government standards is also provided in this detailed guide. Comprehensive coverage includes: Basic information assurance principles and concepts Information assurance management system Current practices, regulations, and plans Impact of organizational structure Asset management Risk management and mitigation Human resource assurance Advantages of certification, accreditation, and assurance Information assurance in system development and acquisition Physical and environmental security controls Information assurance awareness, training, and education Access control Information security monitoring tools and methods Information assurance measurements and metrics Incident handling and computer forensics Business continuity management Backup and restoration Cloud computing and outsourcing strategies Information assurance big data concerns COMPUTERS,Networking,General

Art of the Data Center, The Today, data centers are the beating hearts of the companies they serve. Data centers process billions of Internet transactions every day. It's therefore critical for companies and IT organizations to understand the state-of-the-art in data center design. Narrow aspects - such as cooling, wiring, or power usage - are often the subject of technical documents. But it's rare to find a holistic view of how a great data center was designed - until now. In The Art of the Data Center, Cisco's Douglas Alger takes you behind the scenes at eighteen of the world's most innovative data centers. Through interviews with their designers, Alger reveals why key decisions were made, and shows how construction and other challenges were overcome. He goes behind the scenes with pioneering companies like Cisco, eBay, Facebook, and Yahoo! presenting design lessons that can be applied in widely diverse environments. Readers will encounter amazing data centers like these: A data center built into a 1920s chapel A data center built in an underground military bunker, with artificial daylight, manmade waterfalls, and submarine engines providing standby power A data center inspired by a chicken coop The world's first all solar data center Data center professionals directly involved in planning, design, or operations will find this book remarkably useful - and a much broader audience of IT executives and practitioners will find it utterly fascinating. Do you have a Safari Books Online account? Have a look and a listen, too! The Safari edition of this book includes 8 audio recordings from the author describing lessons learned, industry trends and general insights as well as more detailed explanations of certain Data Center topics raised within the profiles. Links to these recordings appear throughout the book, wherever the topic is discussed. COMPUTERS,Networking,General

Probability and Random Processes for Electrical and Computer Engineers With updates and enhancements to the incredibly successful first edition, Probability and Random Processes for Electrical and Computer Engineers, Second Edition retains the best aspects of the original but offers an even more potent introduction to probability and random variables and processes. Written in a clear, concise style that illustrates the subject’s relevance to a wide range of areas in engineering and physical and computer sciences, this text is organized into two parts. The first focuses on the probability model, random variables and transformations, and inequalities and limit theorems. The second deals with several types of random processes and queuing theory. New or Updated for the Second Edition: A short new chapter on random vectors that adds some advanced new material and supports topics associated with discrete random processes Reorganized chapters that further clarify topics such as random processes (including Markov and Poisson) and analysis in the time and frequency domain A large collection of new MATLAB®-based problems and computer projects/assignments Each Chapter Contains at Least Two Computer Assignments Maintaining the simplified, intuitive style that proved effective the first time, this edition integrates corrections and improvements based on feedback from students and teachers. Focused on strengthening the reader’s grasp of underlying mathematical concepts, the book combines an abundance of practical applications, examples, and other tools to simplify unnecessarily difficult solutions to varying engineering problems in communications, signal processing, networks, and associated fields. COMPUTERS,Networking,General

Healthcare Information Security and Privacy Secure and protect sensitive personal patient healthcare information Written by a healthcare information security and privacy expert, this definitive resource fully addresses security and privacy controls for patient healthcare information. Healthcare Information Security and Privacy introduces you to the realm of healthcare and patient health records with a complete overview of healthcare organization, technology, data, occupations, roles, and third parties. Learn best practices for healthcare information security and privacy with coverage of information governance, risk assessment and management, and incident response. Written for a global audience, this comprehensive guide covers U.S. laws and regulations as well as those within the European Union, Switzerland, and Canada. Healthcare Information and Security and Privacy covers: Healthcare industry Regulatory environment Privacy and security in healthcare Information governance Risk assessment and management COMPUTERS,Networking,General

End-to-End QoS Network Design End-to-End QoS Network Design Quality of Service for Rich-Media & Cloud Networks Second Edition New best practices, technical strategies, and proven designs for maximizing QoS in complex networks This authoritative guide to deploying, managing, and optimizing QoS with Cisco technologies has been thoroughly revamped to reflect the newest applications, best practices, hardware, software, and tools for modern networks. This new edition focuses on complex traffic mixes with increased usage of mobile devices, wireless network access, advanced communications, and video. It reflects the growing heterogeneity of video traffic, including passive streaming video, interactive video, and immersive videoconferences. It also addresses shifting bandwidth constraints and congestion points; improved hardware, software, and tools; and emerging QoS applications in network security. The authors first introduce QoS technologies in high-to-mid-level technical detail, including protocols, tools, and relevant standards. They examine new QoS demands and requirements, identify reasons to reevaluate current QoS designs, and present new strategic design recommendations. Next, drawing on extensive experience, they offer deep technical detail on campus wired and wireless QoS design; next-generation wiring closets; QoS design for data centers, Internet edge, WAN edge, and branches; QoS for IPsec VPNs, and more. Tim Szigeti, CCIE No. 9794 is a Senior Technical Leader in the Cisco System Design Unit. He has specialized in QoS for the past 15 years and authored Cisco TelePresence Fundamentals. Robert Barton, CCIE No. 6660 (R&S and Security), CCDE No. 2013::6 is a Senior Systems Engineer in the Cisco Canada Public Sector Operation. A registered Professional Engineer (P. Eng), he has 15 years of IT experience and is primarily focused on wireless and security architectures. Christina Hattingh spent 13 years as Senior Member of Technical Staff in Unified Communications (UC) in Cisco’s Services Routing Technology Group (SRTG). There, she spoke at Cisco conferences, trained sales staff and partners, authored books, and advised customers. Kenneth Briley, Jr., CCIE No. 9754, is a Technical Lead in the Cisco Network Operating Systems Technology Group. With more than a decade of QoS design/implementation experience, he is currently focused on converging wired and wireless QoS. n Master a proven, step-by-step best-practice approach to successful QoS deployment n Implement Cisco-validated designs related to new and emerging applications n Apply best practices for classification, marking, policing, shaping, markdown, and congestion management/avoidance n Leverage the new Cisco Application Visibility and Control feature-set to perform deep-packet inspection to recognize more than 1000 different applications n Use Medianet architecture elements specific to QoS configuration, monitoring, and control n Optimize QoS in rich-media campus networks using the Cisco Catalyst 3750, Catalyst 4500, and Catalyst 6500 n Design wireless networks to support voice and video using a Cisco centralized or converged access WLAN n Achieve zero packet loss in GE/10GE/40GE/100GE data center networks n Implement QoS virtual access data center designs with the Cisco Nexus 1000V n Optimize QoS at the enterprise customer edge n Achieve extraordinary levels of QoS in service provider edge networks n Utilize new industry standards and QoS technologies, including IETF RFC 4594, IEEE 802.1Q-2005, HQF, and NBAR2 This book is part of the Networking Technology Series from Cisco Press®, which offers networking professionals valuable information for constructing efficient networks, understanding new technologies, and building successful careers. COMPUTERS,Networking,General

UNIX The Definitive UNIX Resource--Fully Updated Get cutting-edge coverage of the newest releases of UNIX-- including Solaris 10, all Linux distributions, HP-UX, AIX, and FreeBSD-- from this thoroughly revised, one-stop resource for users at all experience levels. Written by UNIX experts with many years of experience starting with Bell Laboratories, UNIX: The Complete Reference, Second Edition provides step-by-step instructions on how to use UNIX and take advantage of its powerful tools and utilities. Get up-and-running on UNIX quickly, use the command shell and desktop, and access the Internet and e-mail. You'll also learn to administer systems and networks, develop applications, and secure your UNIX environment. Up-to-date chapters on UNIX desktops, Samba, Python, Java Apache, and UNIX Web development are included. Install, configure, and maintain UNIX on your PC or workstation Work with files, directories, commands, and the UNIX shell Create and modify text files using powerful text editors Use UNIX desktops, including GNOME, CDE, and KDE, as an end user or system administrator Use and manage e-mail, TCP/IP networking, and Internet services Protect and maintain the security of your UNIX system and network Share devices, printers, and files between Windows and UNIX systems Use powerful UNIX tools, including awk, sed, and grep Develop your own shell, Python, and Perl scripts, and Java, C, and C++ programs under UNIX Set up Apache Web servers and develop browser-independent Web sites and applications COMPUTERS,Networking,General

Cloud Networking Cloud Networking: Understanding Cloud-Based Data Center Networks explains the evolution of established networking technologies into distributed, cloud-based networks. Starting with an overview of cloud technologies, the book explains how cloud data center networks leverage distributed systems for network virtualization, storage networking, and software-defined networking. The author offers insider perspective to key components that make a cloud network possible such as switch fabric technology and data center networking standards. The final chapters look ahead to developments in architectures, fabric technology, interconnections, and more. By the end of the book, readers will understand core networking technologies and how they’re used in a cloud data center. Understand existing and emerging networking technologies that combine to form cloud data center networks Explains the evolution of data centers from enterprise to private and public cloud networks Reviews network virtualization standards for multi-tenant data center environments Includes cutting-edge detail on the latest switch fabric technologies from the networking team in Intel COMPUTERS,Networking,General

Hacking Exposed Malware & Rootkits Arm yourself for the escalating war against malware and rootkits Thwart debilitating cyber-attacks and dramatically improve your organization’s security posture using the proven defense strategies in this thoroughly updated guide. Hacking Exposed™ Malware and Rootkits: Security Secrets & Solutions, Second Edition fully explains the hacker’s latest methods alongside ready-to-deploy countermeasures. Discover how to block pop-up and phishing exploits, terminate embedded code, and identify and eliminate rootkits. You will get up-to-date coverage of intrusion detection, firewall, honeynet, antivirus, and anti-rootkit technology. • Learn how malware infects, survives, and propagates across an enterprise• See how hackers develop malicious code and target vulnerable systems• Detect, neutralize, and remove user-mode and kernel-mode rootkits• Use hypervisors and honeypots to uncover and kill virtual rootkits• Defend against keylogging, redirect, click fraud, and identity theft• Block spear phishing, client-side, and embedded-code exploits• Effectively deploy the latest antivirus, pop-up blocker, and firewall software• Identify and stop malicious processes using IPS solutions COMPUTERS,Networking,General

Hacking Exposed Wireless, Third Edition Exploit and defend against the latest wireless network attacks Learn to exploit weaknesses in wireless network environments using the innovative techniques in this thoroughly updated guide. Inside, you’ll find concise technical overviews, the latest attack methods, and ready-to-deploy countermeasures. Find out how to leverage wireless eavesdropping, break encryption systems, deliver remote exploits, and manipulate 802.11 clients, and learn how attackers impersonate cellular networks. Hacking Exposed Wireless, Third Edition features expert coverage of ever-expanding threats that affect leading-edge technologies, including Bluetooth Low Energy, Software Defined Radio (SDR), ZigBee, and Z-Wave. Assemble a wireless attack toolkit and master the hacker’s weapons Effectively scan and enumerate WiFi networks and client devices Leverage advanced wireless attack tools, including Wifite, Scapy, Pyrit, Metasploit, KillerBee, and the Aircrack-ng suite Develop and launch client-side attacks using Ettercap and the WiFi Pineapple Hack cellular networks with Airprobe, Kraken, Pytacle, and YateBTS Exploit holes in WPA and WPA2 personal and enterprise security schemes Leverage rogue hotspots to deliver remote access software through fraudulent software updates Eavesdrop on Bluetooth Classic and Bluetooth Low Energy traffic Capture and evaluate proprietary wireless technology with Software Defined Radio tools Explore vulnerabilities in ZigBee and Z-Wave-connected smart homes and offices Attack remote wireless networks using compromised Windows systems and built-in tools COMPUTERS,Networking,General

Alcatel-Lucent Service Routing Architect (SRA) Self-Study Guide A comprehensive resource for professionals preparing for Alcatel-Lucent Service Routing Architect (SRA) certification Networking professionals are taking note of Alcatel-Lucent and its quick ascent in the networking and telecom industries. IP networking professionals looking for a comprehensive guide to obtaining the Alcatel-Lucent Service Routing Architect (SRA) certification will be pleased to learn of this new publication, Alcatel-Lucent Service Routing Architect (SRA) Self-Study Guide: Preparing for the BGP, VPRN and Multicast Exams. The book comprises approximately 2,100 pages of print and additional online content, making it the foremost resource for those looking to make themselves IP subject matter experts. In this impressive resource, readers will find detailed information to prepare them for various sections of the Service Routing Architect certification, and to familiarize them with topics and learning material for three of the SRA written exams. Pre- and post-chapter assessment questions, sample written exam questions, and valuable lab exercises ensure that readers will gain knowledge and develop strategies for successfully obtaining certification. Other highlights of the book include: Offers a comprehensive look at certification topics through 1,200 pages of printed content and an additional 900 pages of authoritative online information Provides strategies for troubleshooting complex network problems Serves as the premier resource for Service Routing Architect certification—similar books do not offer this level of detail Alcatel-Lucent Service Routing Architect (SRA) Self-Study Guide: Preparing for the BGP, VPRN and Multicast Exams has been developed for industry professionals working in network environments where Alcatel-Lucent products are deployed, and for industry professionals with Cisco and Juniper certifications looking to expand their knowledge and skill base. Engineers and networking professionals with an SRA certification from Alcatel-Lucent will be in high demand. Let this must-have learning resource prepare you for success! COMPUTERS,Networking,General

Group Policy Get up to speed on the latest Group Policy tools, features, and best practices Group Policy, Fundamentals, Security, and the Managed Desktop, 3rd Edition helps you streamline Windows and Windows Server management using the latest Group Policy tools and techniques. This updated edition covers Windows 10 and Windows Server vNext, bringing you up to speed on all the newest settings, features, and best practices. Microsoft Group Policy MVP Jeremy Moskowitz teaches you the major categories of Group Policy, essential troubleshooting techniques, and how to manage your Windows desktops. This is your complete guide to the latest Group Policy features and functions for all modern Windows clients and servers, helping you manage more efficiently and effectively. Perform true desktop and server management with the Group Policy Preferences, ADMX files, and additional add-ons Use every feature of the GPMC and become a top-notch administrator Troubleshoot Group Policy using tools, enhanced logs, Resource Kit utilities, and third-party tools Manage printers, drive maps, restrict hardware, and configure Internet Explorer Deploy software to your desktops, set up roaming profiles, and configure Offline Files for all your Windows clients—and manage it all with Group Policy settings Secure your desktops and servers with AppLocker, Windows Firewall with Advanced Security, and the Security Configuration Manager This is your comprehensive resource to staying current, with expert tips, techniques, and insight. COMPUTERS,Networking,General

XAML Unleashed Full Color: Figures and code appear as they do in Visual Studio. If you want to write Windows apps with XAML, one person can help you more than anyone else: Adam Nathan. He has built a well-deserved reputation as the world’s #1 expert on putting it to work. Now, he’s written the definitive, practical XAML tutorial and reference: XAML Unleashed. Nathan answers the questions you’re most likely to ask, walks through the tasks you’re sure to perform, and helps you avoid problems as you use XAML. You’ll learn how to create effective user interfaces for line-of-business apps, consumer apps, reusable controls, or anything else. These techniques will be invaluable whether you’re creating universal Windows apps or working with Silverlight or WPF. XAML Unleashed is packed with C# and XAML code examples that are fully color-coded to match their appearance in Visual Studio--the same approach that has made Nathan’s previous Unleashed books so popular. Detailed information on how to... Understand and apply XAML’s syntax, namespaces, and keywords Organize controls and other elements in a smooth and intuitive user interface Make the most of XAML’s rich controls for content, items, images, text, and media Build exceptionally powerful user and custom controls Master reliable and efficient ways to mix XAML with procedural code Extend XAML with type converters, markup extensions, and other third-party desktop classes Use data binding to link and synchronize controls with in-memory representations of data Leverage XAML’s support for binary and logical resources Use styles, templates, and visual states to radically redesign controls without sacrificing their built-in functionality Access the Windows animation library to create stunning theme transitions and animations Build custom panels to enforce consistency in unusual user interfaces Understand subtle changes in XAML’s behavior across different Microsoft UI frameworks COMPUTERS,Networking,General

VPNs Illustrated Virtual private networks (VPNs) based on the Internet instead of the traditional leased lines offer organizations of all sizes the promise of a low-cost, secure electronic network. However, using the Internet to carry sensitive information can present serious privacy and security problems. By explaining how VPNs actually work, networking expert Jon Snader shows software engineers and network administrators how to use tunneling, authentication, and encryption to create safe, effective VPNs for any environment. Using an example-driven approach, VPNs Illustrated explores how tunnels and VPNs function by observing their behavior "on the wire." By learning to read and interpret various network traces, such as those produced by tcpdump, readers will be able to better understand and troubleshoot VPN and network behavior. Specific topics covered include: Block and stream symmetric ciphers, such as AES and RC4; and asymmetric ciphers, such as RSA and EIGamal Message authentication codes, including HMACs Tunneling technologies based on gtunnel SSL protocol for building network-to-network VPNs SSH protocols as drop-in replacements for telnet, ftp, and the BSD r-commands Lightweight VPNs, including VTun, CIPE, tinc, and OpenVPN IPsec, including its Authentication Header (AH) protocol, Encapsulating Security Payload (ESP), and IKE (the key management protocol) Packed with details, the text can be used as a handbook describing the functions of the protocols and the message formats that they use. Source code is available for download, and an appendix covers publicly available software that can be used to build tunnels and analyze traffic flow. VPNs Illustrated gives you the knowledge of tunneling and VPN technology you need to understand existing VPN implementations and successfully create your own. COMPUTERS,Networking,General

Foundations of Modern Networking Foundations of Modern Networking is a comprehensive, unified survey of modern networking technology and applications for today’s professionals, managers, and students. Dr. William Stallings offers clear and well-organized coverage of five key technologies that are transforming networks: Software-Defined Networks (SDN), Network Functions Virtualization (NFV), Quality of Experience (QoE), the Internet of Things (IoT), and cloudbased services. Dr. Stallings reviews current network ecosystems and the challenges they face–from Big Data and mobility to security and complexity. Next, he offers complete, self-contained coverage of each new set of technologies: how they work, how they are architected, and how they can be applied to solve real problems. Dr. Stallings presents a chapter-length analysis of emerging security issues in modern networks. He concludes with an up-to date discussion of networking careers, including important recent changes in roles and skill requirements. Coverage: Elements of the modern networking ecosystem: technologies, architecture, services, and applications Evolving requirements of current network environments SDN: concepts, rationale, applications, and standards across data, control, and application planes OpenFlow, OpenDaylight, and other key SDN technologies Network functions virtualization: concepts, technology, applications, and software defined infrastructure Ensuring customer Quality of Experience (QoE) with interactive video and multimedia network traffic Cloud networking: services, deployment models, architecture, and linkages to SDN and NFV IoT and fog computing in depth: key components of IoT-enabled devices, model architectures, and example implementations Securing SDN, NFV, cloud, and IoT environments Career preparation and ongoing education for tomorrow’s networking careers Key Features: Strong coverage of unifying principles and practical techniques More than a hundred figures that clarify key concepts Web support at williamstallings.com/Network/ QR codes throughout, linking to the website and other resources Keyword/acronym lists, recommended readings, and glossary Margin note definitions of key words throughout the text COMPUTERS,Networking,General

Color in Electronic Displays This book is the product of Research Study Group (RSG) 13 on "Human Engineering Evaluation on the Use of Colour in Electronic Displays," of Panel 8, "Defence Applications of Human and Biomedical Sciences," of the NATO Defence Research Group. RSG 13 was chaired by Heino Widdel (Germany) and consisted of Jeffrey Grossman (United States), Jean-Pierre Menu (France), Giampaolo Noja (Italy, point of contact), David Post (United States), and Jan Walraven (Netherlands). Initially, Christopher Gibson (United Kingdom) and Sharon McFaddon (Canada) participated also. Most of these representatives served previously on the NATO program committee that produced Proceedings of a Workshop on Colour Coded vs. Monochrome Displays (edited by Christopher Gibson and published by the Royal Aircraft Establishment, Farnborough, England) in 1984. RSG 13 can be regarded as a descendent of that program committee. RSG 13 was formed in 1987 for the purpose of developing and distributing guidance regarding the use of color on electronic displays. During our first meeting, we discussed the fact that, although there is a tremendous amount of information available concerning color vision, color perception, colorimetry, and color displays-much of it relevant to display design-it is scattered across numerous texts, journals, conference proceedings, and technical reports. We decided that we could fulfill the RSG's purpose best by producing a book that consolidates and summarizes this information, emphasizing those aspects that are most applicable to display design. COMPUTERS,Networking,General

Learning without Boundaries Proceedings of the NATO Defense Research Group, Panel 8 Workshop on Distance/Distributed Learning held in Neubiberg, Munich, Germany, September 28-October 1, 1993. COMPUTERS,Networking,General

MPLS in the SDN Era How can you make multivendor services work smoothly on today’s complex networks? This practical book shows you how to deploy a large portfolio of multivendor Multiprotocol Label Switching (MPLS) services on networks, down to the configuration level. You’ll learn where Juniper Network's Junos, Cisco's IOS XR, and OpenContrail, interoperate and where they don’t. Two network and cloud professionals from Juniper describe how MPLS technologies and applications have rapidly evolved through services and architectures such as Ethernet VPNs, Network Function Virtualization, Seamless MPLS, Egress Protection, External Path Computation, and more. This book contains no vendor bias or corporate messages, just solid information on how to get a multivendor network to function optimally. Topics include: Introduction to MPLS and Software-Defined Networking (SDN) The four MPLS Builders (LDP, RSVP-TE, IGP SPRING, and BGP) Layer 3 unicast and multicast MPLS services, Layer 2 VPN, VPLS, and Ethernet VPN Inter-domain MPLS Services Underlay and overlay architectures: data centers, NVO, and NFV Centralized Traffic Engineering and TE bandwidth reservations Scaling MPLS transport and services Transit fast restoration based on the IGP and RSVP-TE FIB optimization and egress service for fast restoration COMPUTERS,Networking,General

Automating Junos Administration How can you grow and maintain a reliable, flexible, and cost-efficient network in the face of ever-increasing demands? With this practical guide, network engineers will learn how to program Juniper network devices to perform day-to-day tasks, using the automation features of the Junos OS. Junos supports several automation tools that provide powerful solutions to common network automation tasks. Authors Jonathan Looney and Stacy Smith, senior testing engineers at Juniper, will help you determine which tools work best for your particular network requirements. If you have experience with Junos, this book will show you how automation can make a big difference in the operation of your existing network. Manage Junos software with remote procedure calls and a RESTful API Represent devices as Python objects and manage them with Python’s PyEZ package Customize Junos software to detect and block commits that violate your network standards Develop custom CLI commands to present information the way you want Program Junos software to automatically respond to network events Rapidly deploy new Junos devices into your network with ZTP and Netconify tools Learn how to use Ansible or Puppet to manage Junos software COMPUTERS,Networking,General

Hacking Exposed Industrial Control Systems Learn to defend crucial ICS/SCADA infrastructure from devastating attacks the tried-and-true Hacking Exposed way This practical guide reveals the powerful weapons and devious methods cyber-terrorists use to compromise the devices, applications, and systems vital to oil and gas pipelines, electrical grids, and nuclear refineries. Written in the battle-tested Hacking Exposed style, the book arms you with the skills and tools necessary to defend against attacks that are debilitating—and potentially deadly. Hacking Exposed Industrial Control Systems: ICS and SCADA Security Secrets & Solutions explains vulnerabilities and attack vectors specific to ICS/SCADA protocols, applications, hardware, servers, and workstations. You will learn how hackers and malware, such as the infamous Stuxnet worm, can exploit them and disrupt critical processes, compromise safety, and bring production to a halt. The authors fully explain defense strategies and offer ready-to-deploy countermeasures. Each chapter features a real-world case study as well as notes, tips, and cautions. Features examples, code samples, and screenshots of ICS/SCADA-specific attacks Offers step-by-step vulnerability assessment and penetration test instruction Written by a team of ICS/SCADA security experts and edited by Hacking Exposed veteran Joel Scambray COMPUTERS,Networking,General

The Illustrated Network The Illustrated Network: How TCP/IP Works in a Modern Network, Second Edition presents an illustrated explanation on how TCP/IP works, using consistent examples from a working network configuration that includes servers, routers and workstations. Diagnostic traces allow the reader to follow the discussion with unprecedented clarity and precision. True to its title, there are 330+ diagrams and screenshots, as well as topology diagrams and a unique repeating chapter opening diagram. Illustrations are also used as end-of-chapter questions. Based on examples of a complete and modern network, all the material comes from real objects connected and running on the network. The book emphasizes the similarities across all networks, since all share similar components, from the smallest LAN to the global internet. Layered protocols are the rule, and all hosts attached to the Internet run certain core protocols to enable their applications to function properly. This second edition includes updates throughout, along with four completely new chapters that introduce developments that have occurred since the publication of the first edition, including optical networking, cloud concepts and VXLAN. Gives the reader insights into the most up-to-date network equipment, operating systems and router vendors Presents an illustrated explanation on how TCP/IP works with consistent examples from a working network configuration that includes servers, routers, and workstations Contains over 330 Illustrations, screen shots, topology diagrams, and a unique repeating chapter opening diagram to reinforce concepts COMPUTERS,Networking,General

Ansible Among the many configuration management tools available, Ansible has some distinct advantages—it’s minimal in nature, you don’t need to install anything on your nodes, and it has an easy learning curve. With this updated second edition, you’ll learn how to be productive with this tool quickly, whether you’re a developer deploying code to production or a system administrator looking for a better automation solution. Authors Lorin Hochstein and René Moser show you how to write playbooks (Ansible’s configuration management scripts), manage remote servers, and explore the tool’s real power: built-in declarative modules. You’ll discover that Ansible has the functionality you need—and the simplicity you desire. Manage Windows machines, and automate network device configuration Manage your fleet from your web browser with Ansible Tower Understand how Ansible differs from other configuration management systems Use the YAML file format to write your own playbooks Work with a complete example to deploy a non-trivial application Deploy applications to Amazon EC2 and other cloud platforms Create Docker images and deploy Docker containers with Ansible This book is best read start to finish, with later chapters building on earlier ones. Because it’s written in a tutorial style, you can follow along on your own machine. Most examples focus on web applications. COMPUTERS,Networking,General

IP Multicast, Volume I IP Multicast Volume I: Cisco IP Multicast Networking Design, deploy, and operate modern Cisco IP multicast networks IP Multicast, Volume I thoroughly covers basic IP multicast principles and routing techniques for building and operating enterprise and service provider networks to support applications ranging from videoconferencing to data replication. After briefly reviewing data communication in IP networks, the authors thoroughly explain network access, Layer 2 and Layer 3 multicast, and protocol independent multicast (PIM). Building on these essentials, they introduce multicast scoping, explain IPv6 multicast, and offer practical guidance for IP multicast design, operation, and troubleshooting. Key concepts and techniques are illuminated through real-world network examples and detailed diagrams. Reflecting extensive experience working with Cisco customers, the authors offer pragmatic discussions of common features, design approaches, deployment models, and field practices. You’ll find everything from specific commands to start-to-finish methodologies: all you need to deliver and optimize any IP multicast solution. IP Multicast, Volume I is a valuable resource for network engineers, architects, operations technicians, consultants, security professionals, and collaboration specialists. Network managers and administrators will find the implementation case study and feature explanations especially useful. · Review IP multicasting applications and what makes multicast unique · Understand IP multicast at the access layer, from layered encapsulation to switching multicast frames · Work with Layer 2 switching domains, IPv4 group addresses, and MAC address maps · Utilize Layer 3 multicast hosts and understand each PIM mode · Implement basic forwarding trees and rendezvous points · Compare multicast forwarding modes: ASM, SSM, and PIM Bidir · Plan and properly scope basic multicast networks · Choose your best approach to forwarding replication · Apply best practices for security and resiliency · Understand unique IPv6 deployment issues · Efficiently administer and troubleshoot your IP multicast network This book is part of the Networking Technology Series from Cisco Press®, which offers networking professionals valuable information for constructing efficient networks, understanding new technologies, and building successful careers. Category: Networking Covers: IP Multicast COMPUTERS,Networking,General

Designing for Cisco Network Service Architectures (ARCH) Foundation Learning Guide Designing for Cisco Network Service Architectures (ARCH) Foundation Learning Guide, Fourth Edition · Learn about the Cisco modular enterprise architecture · Create highly available enterprise network designs · Develop optimum Layer 3 designs · Examine advanced WAN services design considerations · Evaluate data center design considerations · Design effective modern WAN and data center designs · Develop effective migration approaches to IPv6 · Design resilient IP multicast networks · Create effective network security designs Designing for Cisco Network Service Architectures (ARCH) Foundation Learning Guide , Fourth Edition, is a Cisco-authorized, self-paced learning tool for CCDP foundation learning. This book provides you with the knowledge needed to perform the conceptual, intermediate, and detailed design of a network infrastructure that supports desired network solutions over intelligent network services to achieve effective performance, scalability, and availability. This book presents concepts and examples necessary to design converged enterprise networks. You learn additional aspects of modular campus design, advanced routing designs, WAN service designs, enterprise data center design, IP multicast design, and security design. Advanced and modern network infrastructure solutions, such as virtual private networks (VPN), Cisco Intelligent WAN (IWAN), and Cisco Application-Centric Infrastructure (ACI), are also covered. Chapter-ending review questions illustrate and help solidify the concepts presented in the book. Whether you are preparing for CCDP certification or CCDE certification, or simply want to gain a better understanding of designing scalable and reliable network architectures, you will benefit from the foundation information presented in this book. Designing for Cisco Network Service Architectures (ARCH) Foundation Learning Guide, Fourth Edition, is part of a recommended learning path from Cisco that includes simulation and hands-on training from authorized Cisco Learning Partners and self-study products from Cisco Press. To find out more about instructor-led training, e-learning, and hands-on instruction offered by authorized Cisco Learning Partners worldwide, please visit https://learningnetwork.cisco.com. Category: Cisco Certification Covers: CCDP ARCH 300-320 COMPUTERS,Networking,General

IoT Fundamentals Today, billions of devices are Internet-connected, IoT standards and protocols are stabilizing, and technical professionals must increasingly solve real problems with IoT technologies. Now, five leading Cisco IoT experts present the first comprehensive, practical reference for making IoT work. IoT Fundamentals brings together knowledge previously available only in white papers, standards documents, and other hard-to-find sources—or nowhere at all. The authors begin with a high-level overview of IoT and introduce key concepts needed to successfully design IoT solutions. Next, they walk through each key technology, protocol, and technical building block that combine into complete IoT solutions. Building on these essentials, they present several detailed use cases, including manufacturing, energy, utilities, smart+connected cities, transportation, mining, and public safety. Whatever your role or existing infrastructure, you’ll gain deep insight what IoT applications can do, and what it takes to deliver them. Fully covers the principles and components of next-generation wireless networks built with Cisco IOT solutions such as IEEE 802.11 (Wi-Fi), IEEE 802.15.4-2015 (Mesh), and LoRaWAN Brings together real-world tips, insights, and best practices for designing and implementing next-generation wireless networks Presents start-to-finish configuration examples for common deployment scenarios Reflects the extensive first-hand experience of Cisco experts COMPUTERS,Networking,General

Python Network Programming Cookbook Discover practical solutions for a wide range of real-world network programming tasks About This Book Solve real-world tasks in the area of network programming, system/networking administration, network monitoring, and more. Familiarize yourself with the fundamentals and functionalities of SDN Improve your skills to become the next-gen network engineer by learning the various facets of Python programming Who This Book Is For This book is for network engineers, system/network administrators, network programmers, and even web application developers who want to solve everyday network-related problems. If you are a novice, you will develop an understanding of the concepts as you progress with this book. What You Will Learn Develop TCP/IP networking client/server applications Administer local machines' IPv4/IPv6 network interfaces Write multi-purpose efficient web clients for HTTP and HTTPS protocols Perform remote system administration tasks over Telnet and SSH connections Interact with popular websites via web services such as XML-RPC, SOAP, and REST APIs Monitor and analyze major common network security vulnerabilities Develop Software-Defined Networks with Ryu, OpenDaylight, Floodlight, ONOS, and POX Controllers Emulate simple and complex networks with Mininet and its extensions for network and systems emulations Learn to configure and build network systems and Virtual Network Functions (VNF) in heterogeneous deployment environments Explore various Python modules to program the Internet In Detail Python Network Programming Cookbook - Second Edition highlights the major aspects of network programming in Python, starting from writing simple networking clients to developing and deploying complex Software-Defined Networking (SDN) and Network Functions Virtualization (NFV) systems. It creates the building blocks for many practical web and networking applications that rely on various networking protocols. It presents the power and beauty of Python to solve numerous real-world tasks in the area of network programming, network and system administration, network monitoring, and web-application development. In this edition, you will also be introduced to network modelling to build your own cloud network. You will learn about the concepts and fundamentals of SDN and then extend your network with Mininet. Next, you'll find recipes on Authentication, Authorization, and Accounting (AAA) and open and proprietary SDN approaches and frameworks. You will also learn to configure the Linux Foundation networking ecosystem and deploy and automate your networks with Python in the cloud and the Internet scale. By the end of this book, you will be able to analyze your network security vulnerabilities using advanced network packet capture and analysis techniques. Style and approach This book follows a practical approach and covers major aspects of network programming in Python. It provides hands-on recipes combined with short and concise explanations on code snippets. This book will serve as a supplementary material to develop hands-on skills in any academic course on network programming. This book further elaborates network softwarization, including Software-Defined Networking (SDN), Network Functions Virtualization (NFV), and orchestration. We learn to configure and deploy enterprise network platforms, develop applications on top of them with Python. COMPUTERS,Networking,General

Networking All-in-One For Dummies Becoming a master of networking has never been easier Whether you're in charge of a small network or a large network, Networking All-in-One is full of the information you’ll need to set up a network and keep it functioning. Fully updated to capture the latest Windows 10 releases through Spring 2018, this is the comprehensive guide to setting up, managing, and securing a successful network. Inside, nine minibooks cover essential, up-to-date information for networking in systems such as Windows 10 and Linux, as well as best practices for security, mobile and cloud-based networking, and much more. Serves as a single source for the most-often needed network administration information Covers the latest trends in networking Get nine detailed and easy-to-understand networking minibooks in one affordable package Networking All-in-One For Dummies is the perfect beginner’s guide as well as the professional’s ideal reference book. COMPUTERS,Networking,General

Network Programmability and Automation Like sysadmins before them, network engineers are finding that they cannot do their work manually anymore. As the field faces new protocols, technologies, delivery models, and a pressing need for businesses to be more agile and flexible, network automation is becoming essential. This practical guide shows network engineers how to use a range of technologies and tools—including Linux, Python, JSON, and XML—to automate their systems through code. Network programming and automation will help you simplify tasks involved in configuring, managing, and operating network equipment, topologies, services, and connectivity. Through the course of the book, you’ll learn the basic skills and tools you need to make this critical transition. This book covers: Python programming basics: data types, conditionals, loops, functions, classes, and modules Linux fundamentals to provide the foundation you need on your network automation journey Data formats and models: JSON, XML, YAML, and YANG for networking Jinja templating and its applicability for creating network device configurations The role of application programming interfaces (APIs) in network automation Source control with Git to manage code changes during the automation process How Ansible, Salt, and StackStorm open source automation tools can be used to automate network devices Key tools and technologies required for a Continuous Integration (CI) pipeline in network operations COMPUTERS,Networking,General

Networking Essentials Thoroughly updated to reflect the CompTIA Network+ N10-007 exam, Networking Essentials, Fifth Edition is a practical, up-to-date, and hands-on guide to the basics of networking. Written from the viewpoint of a working network administrator, it requires absolutely no experience with either network concepts or day-to-day network management. Networking Essentials, Fifth Edition guides readers from an entry-level knowledge in computer networks to advanced concepts in Ethernet and TCP/IP networks; routing protocols and router configuration; local, campus, and wide area network configuration; network security; wireless networking; optical networks; Voice over IP; the network server; and Linux networking. This edition contains additional coverage of switch security, troubleshooting IP networks, authorization and access control, best practices for disaster recovery, network infrastructure configuration and management, data traffic network analysis, network security, and VoIP. It also covers approximately 250 new terms now addressed by CompTIA’s N10-007 exam. Clear goals are outlined for each chapter, and every concept is introduced in easy-to-understand language that explains how and why networking technologies are used. Each chapter is packed with real-world examples and practical exercises that reinforce all concepts and guide you through using them to configure, analyze, and fix networks. The companion web site features labs, Wireshark captures, and chapter quizzes. KEY PEDAGOGICAL FEATURES NET-CHALLENGE SIMULATION SOFTWARE provides hands-on experience with entering router and switch commands, setting up functions, and configuring interfaces and protocols WIRESHARK NETWORK PROTOCOL ANALYZER presents techniques and examples of data traffic analysis throughout PROVEN TOOLS FOR MORE EFFECTIVE LEARNING AND NETWORK+ PREP, including chapter outlines, summaries, and Network+ objectives WORKING EXAMPLES IN EVERY CHAPTER to reinforce key concepts and promote mastery KEY TERM DEFINITIONS, LISTINGS, AND EXTENSIVE GLOSSARY to help you master the language of networking QUESTIONS, PROBLEMS, AND CRITICAL THINKING QUESTIONS to help you deepen your understanding COMPUTERS,Networking,General

AWS Certified Advanced Networking Official Study Guide The official study guide for the AWS certification specialty exam The AWS Certified Advanced Networking Official Study Guide – Specialty Exam helps to ensure your preparation for the AWS Certified Advanced Networking – Specialty Exam. Expert review of AWS fundamentals align with the exam objectives, and detailed explanations of key exam topics merge with real-world scenarios to help you build the robust knowledge base you need to succeed on the exam—and in the field as an AWS Certified Networking specialist. Coverage includes the design, implementation, and deployment of cloud-based solutions; core AWS services implementation and knowledge of architectural best practices; AWS service architecture design and maintenance; networking automation; and more. You also get one year of free access to Sybex’s online interactive learning environment and study tools, which features flashcards, a glossary, chapter tests, practice exams, and a test bank to help you track your progress and gauge your readiness as exam day grows near. The AWS credential validates your skills surrounding AWS and hybrid IT network architectures at scale. The exam assumes existing competency with advanced networking tasks, and assesses your ability to apply deep technical knowledge to the design and implementation of AWS services. This book provides comprehensive review and extensive opportunities for practice, so you can polish your skills and approach exam day with confidence. Study key exam essentials with expert insight Understand how AWS skills translate to real-world solutions Test your knowledge with challenging review questions Access online study tools, chapter tests, practice exams, and more Technical expertise in cloud computing, using AWS, is in high demand, and the AWS certification shows employers that you have the knowledge and skills needed to deliver practical, forward-looking cloud-based solutions. The AWS Certified Advanced Networking Official Study Guide – Specialty Exam helps you learn what you need to take this next big step for your career. COMPUTERS,Networking,General

IP Multicast, Volume II Design, operate, and troubleshoot advanced Cisco IP multicast in enterprise, data center, and service provider networks IP Multicast, Volume II thoroughly covers advanced IP multicast designs and protocols specific to Cisco routers and switches. It offers a pragmatic discussion of common features, deployment models, and field practices for advanced Cisco IP multicast networks, culminating with commands and methodologies for implementation and advanced troubleshooting. After fully discussing inter-domain routing and Internet multicast, the authors thoroughly explain multicast scalability, transport diversification, and multicast MPLS VPNs. They share in-depth insights into multicast for the data center, a full chapter of best-practice design solutions, and a start-to-finish troubleshooting methodology designed for complex environments. Reflecting the authors’ extensive experience with service provider and enterprise networks, IP Multicast, Volume II will be indispensable to IP multicast engineers, architects, operations technicians, consultants, security professionals, and collaboration specialists. Network managers and administrators will find its case studies and feature explanations especially valuable. Understand the fundamental requirements for inter-domain multicast Design control planes for identifying source and receiver, as well as the downstream control plane Support multicast transport where cloud service providers don’t support native multicast Use multicast VPNs to logically separate traffic on the same physical infrastructure Explore the unique nuances of multicast in the data center Implement Virtual Port Channel (vPC), Virtual Extensible LAN (VXLAN), and Cisco’s Application Centric Infrastructure (ACI) Design multicast solutions for specific industries or applications Walk through examples of best-practice multicast deployments Master an advanced methodology for troubleshooting large IP multicast networks COMPUTERS,Networking,General

5G Mobile Communications This book will help readers comprehend technical and policy elements of telecommunication particularly in the context of 5G. It first presents an overview of the current research and standardization practices and lays down the global frequency spectrum allocation process. It further lists solutions to accommodate 5G spectrum requirements. The readers will find a considerable amount of information on 4G (LTE-Advanced), LTE-Advance Pro, 5G NR (New Radio); transport network technologies, 5G NGC (Next Generation Core), OSS (Operations Support Systems), network deployment and end-to-end 5G network architecture. Some details on multiple network elements (end products) such as 5G base station/small cells and the role of semiconductors in telecommunication are also provided. Keeping trends in mind, service delivery mechanisms along with state-of-the-art services such as MFS (mobile financial services), mHealth (mobile health) and IoT (Internet-of-Things) are covered at length. At the end, telecom sector’s burning challenges and best practices are explained which may be looked into for today’s and tomorrow’s networks. The book concludes with certain high level suggestions for the growth of telecommunication, particularly on the importance of basic research, departure from ten-year evolution cycle and having a 20–30 year plan. Explains the conceivable six phases of mobile telecommunication’s ecosystem that includes R&D, standardization, product/network/device & application development, and burning challenges and best practices Provides an overview of research and standardization on 5G Discusses solutions to address 5G spectrum requirements while describing the global frequency spectrum allocation process Presents various case studies and policies Provides details on multiple network elements and the role of semiconductors in telecommunication Presents service delivery mechanisms with special focus on IoT COMPUTERS,Networking,General

Troubleshooting Cisco Nexus Switches and NX-OS The definitive deep-dive guide to hardware and software troubleshooting on Cisco Nexus switches The Cisco Nexus platform and NX-OS switch operating system combine to deliver unprecedented speed, capacity, resilience, and flexibility in today's data center networks. Troubleshooting Cisco Nexus Switches and NX-OS is your single reference for quickly identifying and solving problems with these business-critical technologies. Three expert authors draw on deep experience with large Cisco customers, emphasizing the most common issues in real-world deployments, including problems that have caused major data center outages. Their authoritative, hands-on guidance addresses both features and architecture, helping you troubleshoot both control plane forwarding and data plane/data path problems and use NX-OS APIs to automate and simplify troubleshooting. Throughout, you'll find real-world configurations, intuitive illustrations, and practical insights into key platform-specific behaviors. This is an indispensable technical resource for all Cisco network consultants, system/support engineers, network operations professionals, and CCNP/CCIE certification candidates working in the data center domain. · Understand the NX-OS operating system and its powerful troubleshooting tools · Solve problems with cards, hardware drops, fabrics, and CoPP policies · Troubleshoot network packet switching and forwarding · Properly design, implement, and troubleshoot issues related to Virtual Port Channels (VPC and VPC+) · Optimize routing through filtering or path manipulation · Optimize IP/IPv6 services and FHRP protocols (including HSRP, VRRP, and Anycast HSRP) · Troubleshoot EIGRP, OSPF, and IS-IS neighbor relationships and routing paths · Identify and resolve issues with Nexus route maps · Locate problems with BGP neighbor adjacencies and enhance path selection · Troubleshoot high availability components (BFD, SSO, ISSU, and GIR) · Understand multicast protocols and troubleshooting techniques · Identify and solve problems with OTV · Use NX-OS APIs to automate troubleshooting and administrative tasks COMPUTERS,Networking,General

Engineering Trustworthy Systems Cutting-edge cybersecurity solutions to defend against the most sophisticated attacks This professional guide shows, step by step, how to design and deploy highly secure systems on time and within budget. The book offers comprehensive examples, objectives, and best practices and shows how to build and maintain powerful, cost-effective cybersecurity systems. Readers will learn to think strategically, identify the highest priority risks, and apply advanced countermeasures that address the entire attack space. Engineering Trustworthy Systems: Get Cybersecurity Design Right the First Time showcases 35 years of practical engineering experience from an expert whose persuasive vision has advanced national cybersecurity policy and practices. Readers of this book will be prepared to navigate the tumultuous and uncertain future of cyberspace and move the cybersecurity discipline forward by adopting timeless engineering principles, including: • Defining the fundamental nature and full breadth of the cybersecurity problem • Adopting an essential perspective that considers attacks, failures, and attacker mindsets • Developing and implementing risk-mitigating, systems-based solutions • Transforming sound cybersecurity principles into effective architecture and evaluation strategies that holistically address the entire complex attack space COMPUTERS,Networking,General

Managing Mission - Critical Domains and DNS This book will give you an all encompassing view of the domain name ecosystem combined with a comprehensive set of operations strategies. About This Book Manage infrastructure, risk, and management of DNS name servers. Get hands-on with factors like types of name servers, DNS queries and and so on. Practical guide for system administrators to manage mission-critical servers Based on real-world experience - Written by an industry veteran who has made every possible mistake within this field. Who This Book Is For Ideal for sysadmins, webmasters, IT consultants, and developers-anyone responsible for maintaining your organization's core DNS What You Will Learn Anatomy of a domain - how a domain is the sum of both its DNS zone and its registration data, and why that matters. The domain name ecosystem - the role of registries, registrars and oversight bodies and their effect on your names. How DNS queries work - queries and responses are examined including debugging techniques to zero in on problems. Nameserver considerations - alternative nameserver daemons, numbering considerations, and deployment architectures. DNS use cases - the right way for basic operations such as domain transfers, large scale migrations, GeoDNS, Anycast DNS. Securing your domains - All aspects of security from registrar vendor selection, to DNSSEC and DDOS mitigation strategies. In Detail Managing your organization's naming architecture and mitigating risks within complex naming environments is very important. This book will go beyond looking at “how to run a name server†or “how to DNSSEC sign a domainâ€, Managing Mission Critical Domains & DNS looks across the entire spectrum of naming; from external factors that exert influence on your domains to all the internal factors to consider when operating your DNS. The readers are taken on a comprehensive guided tour through the world of naming: from understanding the role of registrars and how they interact with registries, to what exactly is it that ICANN does anyway? Once the prerequisite knowledge of the domain name ecosystem is acquired, the readers are taken through all aspects of DNS operations. Whether your organization operates its own nameservers or utilizes an outsourced vendor, or both, we examine the complex web of interlocking factors that must be taken into account but are too frequently overlooked. By the end of this book, our readers will have an end to end to understanding of all the aspects covered in DNS name servers. Style and approach The book is divided into two parts, the first part looks at the wider domain name ecosystem: registries, registrars and oversight policies. The second and larger part goes into operations. Every aspect of naming is considered from the viewpoint of how this affects ones domains, what are the ramifications of different operating methods as portfolios scale. COMPUTERS,Networking,General

Microsoft Visual C# Step by Step Your hands-on guide to Microsoft Visual C# fundamentals with Visual Studio 2017 Expand your expertise--and teach yourself the fundamentals of programming with the latest version of Visual C# with Visual Studio 2017. If you are an experienced software developer, you’ll get all the guidance, exercises, and code you need to start building responsive, scalable, cloud-connected applications that can run almost anywhere. . Discover how to: Quickly start creating Visual C# code and projects with Visual Studio 2017 Work with variables, operators, expressions, methods, and program flow Build more robust apps with error, exception, and resource management Spot problems fast with the Visual Studio debugger Make the most of improvements to C# methods, parameters, and switch statements Master the C# object model, and create your own functional data structures Leverage advanced properties, indexers, generics, and collection classes Create Windows 10 apps that share data, collaborate, and use cloud services Integrate Cortana to voice-enable your applications Perform complex queries over object collections with LINQ Improve application throughput and response time with asynchronous methods Use delegates and decoupling to construct highly extensible systems Customize C# operator behavior over your own classes and structures Streamline development with app templates Implement the powerful Model-View-ViewModel (MVVM) pattern Develop cloud-connected applications that seamlessly follow users across devices Build UWP applications that retrieve complex data via REST and present it intuitively COMPUTERS,Networking,General

5G NR 5G NR: The Next Generation Wireless Access Technology follows the authors' highly celebrated books on 3G and 4G by providing a new level of insight into 5G NR. After an initial discussion of the background to 5G, including requirements, spectrum aspects and the standardization timeline, all technology features of the first phase of NR are described in detail. Included is a detailed description of the NR physical-layer structure and higher-layer protocols, RF and spectrum aspects and co-existence and interworking with LTE. The book provides a good understanding of NR and the different NR technology components, giving insight into why a certain solution was selected. Content includes: Key radio-related requirements of NR, design principles, technical features Details of basic NR transmission structure, showing where it has been inherited from LTE and where it deviates from it, and the reasons why NR Multi-antenna transmission functionality Detailed description of the signals and functionality of the initial NR access, including signals for synchronization and system information, random access and paging LTE/NR co-existence in the same spectrum, the benefits of their interworking as one system The different aspects of mobility in NR RF requirements for NR will be described both for BS and UE, both for the legacy bands and for the new mm-wave bands Gives a concise and accessible explanation of the underlying technology and standards for 5G NR radio-access technology Provides detailed description of the NR physical-layer structure and higher-layer protocols, RF and spectrum aspects and co-existence and interworking with LTE Gives insight not only into the details of the NR specification but also an understanding of why certain solutions look like they do COMPUTERS,Networking,General

Mastering Python Networking Master the art of using Python for a diverse range of network engineering tasks Key Features Explore the power of Python libraries to tackle difficult network problems efficiently and effectively Use Python for network device automation, DevOps, and software-defined networking Become an expert in implementing advanced network-related tasks with Python Book Description Networks in your infrastructure set the foundation for how your application can be deployed, maintained, and serviced. Python is the ideal language for network engineers to explore tools that were previously available to systems engineers and application developers. In this second edition of Mastering Python Networking, you'll embark on a Python-based journey to transition from traditional network engineers to network developers ready for the next-generation of networks. This book begins by reviewing the basics of Python and teaches you how Python can interact with both legacy and API-enabled network devices. As you make your way through the chapters, you will then learn to leverage high-level Python packages and frameworks to perform network engineering tasks for automation, monitoring, management, and enhanced security. In the concluding chapters, you will use Jenkins for continuous network integration as well as testing tools to verify your network. By the end of this book, you will be able to perform all networking tasks with ease using Python. What you will learn Use Python libraries to interact with your network Integrate Ansible 2.5 using Python to control Cisco, Juniper, and Arista eAPI network devices Leverage existing frameworks to construct high-level APIs Learn how to build virtual networks in the AWS Cloud Understand how Jenkins can be used to automatically deploy changes in your network Use PyTest and Unittest for Test-Driven Network Development Who this book is for Mastering Python Networking is for network engineers and programmers who want to use Python for networking. Basic familiarity with Python programming and networking-related concepts such as Transmission Control Protocol/Internet Protocol (TCP/IP) will be useful. COMPUTERS,Networking,General

Regulating Blockchain As the distributed architecture underpinning the initial Bitcoin anarcho-capitalist, libertarian project, 'blockchain' entered wider public imagination and vocabulary only very recently. Yet in a short space of time it has become more mainstream and synonymous with a spectacular variety of commercial and civic 'problem'/'solution' concepts and ideals. From commodity provenance, to electoral fraud prevention, to a wholesale decentralisation of power and the banishing of the exploitative practices of 'middlemen', blockchain stakeholders are nothing short of evangelical in their belief that it is a force for good. For these reasons and more the technology has captured the attention of entrepreneurs, venture capitalists, global corporations and governments the world over. Blockchain may indeed offer a unique technical opportunity to change cultures of transparency and trust within cyberspace, and as ‘revolutionary’ and ‘disruptive’ has the potential to shift global socioeconomic and political conventions. But as a yet largely unregulated, solutionist-driven phenomenon, blockchain exists squarely within the boundaries of capitalist logic and reason, fast becoming central to the business models of many sources of financial and political power the technology was specifically designed to undo, and increasingly allied to neoliberal strategies with scant regard for collective, political or democratic accountability in the public interest. Regulating Blockchain casts a critical eye over the technology, its ‘ecosystem’ of stakeholders, and offers a challenge to the prevailing discourse proclaiming it to be the great techno-social enabler of our times. COMPUTERS,Networking,General

Network Scanning Cookbook Discover network vulnerabilities and threats to design effective network security strategies Key Features Plunge into scanning techniques using the most popular tools Effective vulnerability assessment techniques to safeguard network infrastructure Explore the Nmap Scripting Engine (NSE) and the features used for port and vulnerability scanning Book Description Network scanning is a discipline of network security that identifies active hosts on networks and determining whether there are any vulnerabilities that could be exploited. Nessus and Nmap are among the top tools that enable you to scan your network for vulnerabilities and open ports, which can be used as back doors into a network. Network Scanning Cookbook contains recipes for configuring these tools in your infrastructure that get you started with scanning ports, services, and devices in your network. As you progress through the chapters, you will learn how to carry out various key scanning tasks, such as firewall detection, OS detection, and access management, and will look at problems related to vulnerability scanning and exploitation in the network. The book also contains recipes for assessing remote services and the security risks that they bring to a network infrastructure. By the end of the book, you will be familiar with industry-grade tools for network scanning, and techniques for vulnerability scanning and network protection. What you will learn Install and configure Nmap and Nessus in your network infrastructure Perform host discovery to identify network devices Explore best practices for vulnerability scanning and risk assessment Understand network enumeration with Nessus and Nmap Carry out configuration audit using Nessus for various platforms Write custom Nessus and Nmap scripts on your own Who this book is for If you're a network engineer or information security professional wanting to protect your networks and perform advanced scanning and remediation for your network infrastructure, this book is for you. COMPUTERS,Networking,General

Mobile Forensic Investigations Master the tools and techniques of mobile forensic investigations Conduct mobile forensic investigations that are legal, ethical, and highly effective using the detailed information contained in this practical guide. Mobile Forensic Investigations: A Guide to Evidence Collection, Analysis, and Presentation, Second Edition fully explains the latest tools and methods along with features, examples, and real-world case studies. Find out how to assemble a mobile forensics lab, collect prosecutable evidence, uncover hidden files, and lock down the chain of custody. This comprehensive resource shows not only how to collect and analyze mobile device data but also how to accurately document your investigations to deliver court-ready documents. • Legally seize mobile devices, USB drives, SD cards, and SIM cards • Uncover sensitive data through both physical and logical techniques • Properly package, document, transport, and store evidence • Work with free, open source, and commercial forensic software • Perform a deep dive analysis of iOS, Android, and Windows Phone file systems • Extract evidence from application, cache, and user storage files • Extract and analyze data from IoT devices, drones, wearables, and infotainment systems • Build SQLite queries and Python scripts for mobile device file interrogation • Prepare reports that will hold up to judicial and defense scrutiny COMPUTERS,Networking,General

Hands-On Dark Web Analysis Understanding the concept Dark Web and Dark Net to utilize it for effective cybersecurity Key Features Understand the concept of Dark Net and Deep Web Use Tor to extract data and maintain anonymity Develop a security framework using Deep web evidences Book Description The overall world wide web is divided into three main areas - the Surface Web, the Deep Web, and the Dark Web. The Deep Web and Dark Web are the two areas which are not accessible through standard search engines or browsers. It becomes extremely important for security professionals to have control over these areas to analyze the security of your organization. This book will initially introduce you to the concept of the Deep Web and the Dark Web and their significance in the security sector. Then we will deep dive into installing operating systems and Tor Browser for privacy, security and anonymity while accessing them. During the course of the book, we will also share some best practices which will be useful in using the tools for best effect. By the end of this book, you will have hands-on experience working with the Deep Web and the Dark Web for security analysis What you will learn Access the Deep Web and the Dark Web Learn to search and find information in the Dark Web Protect yourself while browsing the Dark Web Understand what the Deep Web and Dark Web are Learn what information you can gather, and how Who this book is for This book is targeted towards security professionals, security analyst, or any stakeholder interested in learning the concept of deep web and dark net. No prior knowledge on Deep Web and Dark Net is required COMPUTERS,Networking,General

Zabbix 4 Network Monitoring Gather detailed statistics and deploy impressive business solutions with Zabbix 4.0 Key Features Experience the full impact of Zabbix 4.0, a useful and increasingly popular tool Enhance your network's performance and manage hosts and systems A step-by-step guide to smarter network monitoring Book Description Zabbix 4 Network Monitoring is the perfect starting point for monitoring the performance of your network devices and applications with Zabbix. Even if you've never used a monitoring solution before, this book will get you up and running quickly. You'll learn to monitor more sophisticated operations with ease and soon feel in complete control of your network, ready to meet any challenges you might face. Starting with the installation, you will discover the new features in Zabbix 4.0. You will then get to grips with native Zabbix agents and Simple Network Management Protocol (SNMP) devices. You will also explore Zabbix's integrated functionality for monitoring Java application servers and VMware. This book also covers notifications, permission management, system maintenance, and troubleshooting, so you can be confident that every potential challenge and task is under your control. If you're working with larger environments, you'll also be able to find out more about distributed data collection using Zabbix proxies. Once you're confident and ready to put these concepts into practice, you will understand how to optimize and improve performance. Troubleshooting network issues is vital for anyone working with Zabbix, so the book also helps you work through any technical snags and glitches you might face. By the end of this book, you will have learned more advanced techniques to fine-tune your system and make sure it is in a healthy state. What you will learn Install Zabbix server and an agent from source Manage hosts, users, and permissions while acting upon monitored conditions Visualize data with the help of ad hoc graphs, custom graphs, and maps Simplify complex configurations and learn to automate them Monitor everything from web pages to IPMI devices and Java applications to VMware stats Configure Zabbix to send alerts including problem severity and time periods Troubleshoot any network issue Who this book is for If you're new to Zabbix look no further than this book. Zabbix 4 Network Monitoring is for system and network administrators who are looking to put their knowledge to work with Zabbix 4.0. COMPUTERS,Networking,General

LISP Network, The The complete guide to seamless anytime/anywhere networking with LISP In an era of ubiquitous clouds, virtualization, mobility, and the Internet of Things, information and resources must be accessible anytime, from anywhere. Connectivity to devices and workloads must be seamless even when people move, and their location must be fully independent of device identity. The Locator/ID Separation Protocol (LISP) makes all this possible. The LISP Network is the first comprehensive, in-depth guide to LISP concepts, architecture, techniques, behavior, and applications. Co-authored by LISP co-creator Dino Farinacci and Victor Moreno–co-developer of the Cisco LISP implementation–it will help you identify the opportunities and benefits of deploying LISP in any data center, campus and branch access, WAN edge, or service provider core network. This largely implementation-agnostic guide will be valuable to architects, engineers, consultants, technical sales professionals, and senior IT professionals in any largescale network environment. The authors show how LISP overcomes key problems in large-scale networking, thoroughly introduce its key applications, guide you through designing real-world solutions, and present detailed deployment case studies based on their pioneering experience. · Understand LISP’s core principles, history, motivation, and applications · Explore LISP’s technical architecture, components, mechanisms, and workflows · Use LISP to seamlessly deliver diverse network services and enable major advances in data center connectivity · Improve mobility, network segmentation, and policy management · Leverage software-defined WANs (SD-WANs) to efficiently move traffic from access to data center · Evolve access networks to provide pervasive, mega-scale, high-density modern connectivity · Integrate comprehensive security into the networking control and data plane, and learn how LISP infrastructure is protected against attacks · Enforce access control policies, connection integrity, confidentiality for data in flight, and end-point anonymity · Discover how LISP mobility mechanisms anticipate tomorrow’s application use cases COMPUTERS,Networking,General

AWS Certified Solutions Architect Study Guide The AWS Certified Solutions Architect Study Guide: Associate (SAA-C01) Exam is your complete and fully updated resource to the AWS Solutions Architect - Associate certification. This invaluable Sybex study guide covers all relevant aspects of the AWS Solutions Architect job role, including mapping multi-tier architectures to AWS services, loose coupling and stateless systems, applying AWS security features, deploying and managing services, designing large scale distributed systems, and many more. Written by two AWS subject-matter experts, this self-study guide and reference provides all the tools and information necessary to master the exam, earn your certification, and gain insights into the job of an AWS Solutions Architect. Efficient and logical presentation of exam objectives allows for flexible study of topics, and powerful learning tools increase comprehension and retention of key exam elements. Practice questions, chapter reviews, and detailed examination of essential concepts fully prepare you for the AWS Solutions Architect – Associate certification. The certification is highly valued in IT and cloud computing professionals. Now in a new edition—reflecting the latest changes, additions, and updates to the AWS Solutions Architect – Associate certification exam guide—this book is your complete, one-stop resource: Access the Sybex interactive learning environment and test bank, including chapter tests, practice exams, electronic flashcards, and a searchable glossary of key terms. Learn all the components of the AWS exam and know what to expect on exam day Review challenging exam topics and focus on the areas that need improvement Expand your AWS skillset and keep pace with current cloud computing technologies The AWS Certified Solutions Architect Study Guide: Associate (SAA-C01) Exam enables you to validate your skills, increase your competitive advantage, and take the next step on your career path. Comprehensive and up-to-date content and superior study tools make this guide a must-have resource for those seeking AWS Solutions Architect – Associate certification. COMPUTERS,Networking,General

Essential Guide to Telecommunications, The “Annabel Dodd has cogently untangled the wires and switches and technobabble of the telecommunications revolution and explained how the introduction of the word ‘digital’ into our legislative and regulatory lexicon will affect consumers, companies and society into the next millennium.†– United States Senator Edward J. Markey of Massachusetts; Member, U.S. Senate Subcommittee on Communications, Technology, Innovation, and the Internet “Annabel Dodd has a unique knack for explaining complex technologies in understandable ways. This latest revision of her book covers the rapid changes in the fields of broadband, cellular, and streaming technologies; newly developing 5G networks; and the constant changes happening in both wired and wireless networks. This book is a must-read for anyone who wants to understand the rapidly evolving world of telecommunications in the 21st century!†– David Mash, Retired Senior Vice President for Innovation, Strategy, and Technology, Berklee College of Music Completely updated for current trends and technologies, The Essential Guide to Telecommunications, Sixth Edition, is the world’s top-selling, accessible guide to the fast-changing global telecommunications industry. Writing in easy-to-understand language, Dodd demystifies today’s most significant technologies, standards, architectures, and trends. She introduces leading providers worldwide, explains where they fit in the marketplace, and reveals their key strategies. New topics covered in this edition include: LTE Advanced and 5G wireless, modern security threats and countermeasures, emerging applications, and breakthrough techniques for building more scalable, manageable networks. Gain a practical understanding of modern cellular, Wi-Fi, Internet, cloud, and carrier technologies Discover how key technical, business, and regulatory innovations are changing the industry See how streaming video, social media, cloud computing, smartphones, and the Internet of Things are transforming networks Explore growing concerns about security and privacy, and review modern strategies for detecting and mitigating network breaches Learn how Software Defined Networks (SDN) and Network Function Virtualization (NFV) add intelligence to networks, enabling automation, flexible configurations, and advanced networks Preview cutting-edge, telecom-enabled applications and gear–from mobile payments to drones Whether you’re an aspiring network engineer looking for a broad understanding of the industry, or a salesperson, marketer, investor, or customer, this indispensable guide provides everything you need to know about telecommunications right now. This new edition is ideal for both self-study and classroom instruction. Register your product for convenient access to downloads, updates, and/or corrections as they become available. COMPUTERS,Networking,General

Network Programmability with YANG Today, networks must evolve and scale faster than ever. You can’t manage everything by hand anymore: You need to automate relentlessly. YANG, along with the NETCONF, RESTCONF, or gRPC/gNMI protocols, is the most practical solution, but most implementers have had to learn by trial and error. Now, Network Programmability with YANG gives you complete and reliable guidance for unlocking the full power of network automation using model-driven APIs and protocols. Authored by three YANG pioneers, this plain-spoken book guides you through successfully applying software practices based on YANG data models. The authors focus on the network operations layer, emphasizing model-driven APIs, and underlying transports. Whether you’re a network operator, DevOps engineer, software developer, orchestration engineer, NMS/OSS architect, service engineer, or manager, this guide can help you dramatically improve value, agility, and manageability throughout your network. Discover the value of implementing YANG and Data Model-Driven Management in your network Explore the layers and components of a complete working solution Build a business case where value increases as your solution grows Drill down into transport protocols: NETCONF, RESTCONF, and gNMI/gRPC See how telemetry can establish a valuable automated feedback loop Find data models you can build on, and evaluate models with similar functionality Understand models, metadata, and tools from several viewpoints: architect, operator, module author, and application developer Walk through a complete automation journey: business case, service model, service implementation, device integration, and operation Leverage the authors’ experience to design successful YANG models and avoid pitfalls COMPUTERS,Networking,General

Internet of Things (IoT) The Internet of Things (IoT) is one of the core technologies of current and future information and communications technology (ICT) sectors. IoT technologies will be deployed in numerous industries, including health, transport, smart cities, utility sectors, environment, security, and many other areas. In a manner suitable to a broad range of readers, this book introduces various key IoT technologies focusing on algorithms, process algebra, network architecture, energy harvesting, wireless communications, and network security. It presents IoT system design techniques, international IoT standards, and recent research outcomes relevant to the IoT system developments and provides existing and emerging solutions to the design and development of IoT platforms for multi-sector industries, particularly for Industry 4.0. The book also addresses some of the regulatory issues and design challenges related to IoT system deployments and proposes guidelines for possible future applications. COMPUTERS,Networking,General

AWS Certified Cloud Practitioner Study Guide Set yourself apart by becoming an AWS Certified Cloud Practitioner Take the next step in your career by expanding and validating your skills on the Amazon Web Services (AWS) Cloud. The AWS Certified Cloud Practitioner Study Guide: Exam CLF-C01 provides a solid introduction to this industry-leading technology, relied upon by thousands of businesses across the globe, as well as the resources you need to prove your knowledge in the AWS Certification Exam. This guide offers complete and thorough treatment of all topics included in the exam, beginning with a discussion of what the AWS cloud is and its basic global infrastructure and architectural principles. Other chapters dive into the technical, exploring core characteristics of deploying and operating in the AWS Cloud Platform, as well as basic security and compliance aspects and the shared security model. In addition, the text identifies sources of documentation or technical assistance, such as white papers or support tickets. To complete their coverage, the authors discuss the AWS Cloud value proposition and define billing, account management, and pricing models. This includes describing the key services AWS can provide and their common use cases (e.g., compute, analytics, etc.). Distinguish yourself as an expert by obtaining a highly desirable certification in a widely used platform Hone your skills and gain new insights on AWS whether you work in a technical, managerial, sales, purchasing, or financial field Fully prepare for this new exam using expert content and real-world knowledge, key exam essentials, chapter review questions, and other textual resources Benefit from access to the Sybex online interactive learning environment and test bank, including chapter tests, practice exams, key term glossary, and electronic flashcards The AWS Certified Cloud Practitioner Study Guide is essential reading for any professional in IT or other fields that work directly with AWS, soon-to-be graduates studying in those areas, or anyone hoping to prove themselves as an AWS Certified Cloud Practitioner. COMPUTERS,Networking,General

Networking Fundamentals A clear and concise resource on Windows networking, perfect for IT beginners Did you know that nearly 85% of IT support roles require a good understanding of networking concepts? If you are looking to advance your IT career, you will need a foundational understanding of Windows networking. Network Fundamentals covers everything you need to know about network infrastructures, hardware, protocols, and services. You will learn everything you need to gain the highly in-demand Networking Fundamentals MTA Certification. This entry-level credential could be your first step into a rewarding, stable and lucrative IT career. This new Sybex guide covers the basics of networking starting from the “ground level,†so no previous IT knowledge is required. Each chapter features approachable discussion of the latest networking technologies and concepts, closing with a quiz so you can test your knowledge before moving to the next section. Even if you are brand new to computers, Network Fundamentals will guide you to confidence and mastery. Understand wired and wireless networks in every detail Learn everything you need to attain the Networking Fundamentals MTA Certification Test your knowledge with end-of-chapter quiz questions Understand internet protocol (IP) and categorize IPv4 addresses Work with networking services and area networks Define network infrastructures and network security, including intranets, extranets, and VPNs Beginning and established IT professionals looking to understand more about networking will gain the knowledge to create a network diagram and confidently explain basic networking concepts. Thanks to the features in this book, you will be able to apply your new networking skills in real world situations and feel confident when taking the certification test. COMPUTERS,Networking,General

Build Your Own Cybersecurity Testing Lab Publisher's Note: Products purchased from Third Party sellers are not guaranteed by the publisher for quality, authenticity, or access to any online entitlements included with the product. Manage your own robust, inexpensive cybersecurity testing environment This hands-on guide shows clearly how to administer an effective cybersecurity testing lab using affordable technologies and cloud resources. Build Your Own Cybersecurity Testing Lab: Low-cost Solutions for Testing in Virtual and Cloud-based Environments fully explains multiple techniques for developing lab systems, including the use of Infrastructure-as-Code, meaning you can write programs to create your labs quickly, without manual steps that could lead to costly and frustrating mistakes. Written by a seasoned IT security professional and academic, this book offers complete coverage of cloud and virtual environments as well as physical networks and automation. Included with the book is access to videos that demystify difficult concepts. Inside, you will discover how to: • Gather network requirements and build your cybersecurity testing lab• Set up virtual machines and physical systems from inexpensive components• Select and configure the necessary operating systems• Gain remote access through SSH, RDP, and other remote access protocols• Efficiently isolate subnets with physical switches, routers, and VLANs• Analyze the vulnerabilities and challenges of cloud-based infrastructures• Handle implementation of systems on Amazon Web Services, Microsoft Azure, and Google Cloud Engine• Maximize consistency and repeatability using the latest automation tools COMPUTERS,Networking,General

Building a Future-Proof Cloud Infrastructure Prepare for the future of cloud infrastructure: Distributed Services Platforms By moving service modules closer to applications, Distributed Services (DS) Platforms will future-proof cloud architectures—improving performance, responsiveness, observability, and troubleshooting. Network pioneer Silvano Gai demonstrates DS Platforms’ remarkable capabilities and guides you through implementing them in diverse hardware. Focusing on business benefits throughout, Gai shows how to provide essential shared services such as segment routing, NAT, firewall, micro-segmentation, load balancing, SSL/TLS termination, VPNs, RDMA, and storage—including storage compression and encryption. He also compares three leading hardware-based approaches—Sea of Processors, FPGAs, and ASICs—preparing you to evaluate solutions, ask the right questions, and plan strategies for your environment. Understand the business drivers behind DS Platforms, and the value they offer See how modern network design and virtualization create a foundation for DS Platforms Achieve unprecedented scale through domain-specific hardware, standardized functionalities, and granular distribution Compare advantages and disadvantages of each leading hardware approach to DS Platforms Learn how P4 Domain-Specific Language and architecture enable high-performance, low-power ASICs that are data-plane-programmable at runtime Distribute cloud security services, including firewalls, encryption, key management, and VPNs Implement distributed storage and RDMA services in large-scale cloud networks Utilize Distributed Services Cards to offload networking processing from host CPUs Explore the newest DS Platform management architectures Building a Future-Proof Cloud Architecture is for network, cloud, application, and storage engineers, security experts, and every technology professional who wants to succeed with tomorrow’s most advanced service architectures. COMPUTERS,Networking,General

Linux Administration Publisher's Note: Products purchased from Third Party sellers are not guaranteed by the publisher for quality, authenticity, or access to any online entitlements included with the product. Gain Essential Linux Administration Skills Easily Effectively set up and manage popular Linux distributions on individual servers and build entire network infrastructures using this practical resource. Fully updated to cover the latest tools and techniques, Linux Administration: A Beginner’s Guide, Eighth Edition features clear explanations, step-by-step instructions, and real-world examples. Find out how to configure hardware and software, work from the command line or GUI, maintain Internet and network services, and secure your data. Performance tuning, virtualization, containers, software management, security, and backup solutions are covered in detail. Install and configure Linux, including the latest distributions from Fedora, Ubuntu, CentOS, openSUSE, Debian, and RHEL. Set up and administer core system services, daemons, users, and groups. Manage software applications from source code or binary packages. Customize, build, or patch the Linux kernel. Understand and manage the Linux network stack and networking protocols, including TCP/IP, ARP, IPv4, and IPv6. Minimize security threats and build reliable firewalls and routers with Netfilter (iptables and nftables) and Linux. Create and maintain DNS, FTP, web, e-mail, print, LDAP, VoIP, and SSH servers and services. Share resources using GlusterFS, NFS, and Samba. Spin-up and manage Linux-based servers in popular cloud environments, such as OpenStack, AWS, Azure, Linode, and GCE. Explore virtualization and container technologies using KVM, Docker, Kubernetes, and Open Container Initiative (OCI) tooling. Download specially curated Virtual Machine image and containers that replicate various exercises, software, servers, commands, and concepts covered in the book. Wale Soyinka is a father, system administrator, a DevOps/SecOps aficionado, an open source evangelist, a hacker, and a well-respected world-renowned chef (in his mind). He is the author of Advanced Linux Administration as well as other Linux, Network, and Windows administration training materials. COMPUTERS,Networking,General

Networking For Dummies Set up a secure network at home or the office Fully revised to cover Windows 10 and Windows Server 2019, this new edition of the trusted Networking For Dummies helps both beginning network administrators and home users to set up and maintain a network. Updated coverage of broadband and wireless technologies, as well as storage and back-up procedures, ensures that you’ll learn how to build a wired or wireless network, secure and optimize it, troubleshoot problems, and much more. From connecting to the Internet and setting up a wireless network to solving networking problems and backing up your data—this #1 bestselling guide covers it all. Build a wired or wireless network Secure and optimize your network Set up a server and manage Windows user accounts Use the cloud—safely Written by a seasoned technology author—and jam-packed with tons of helpful step-by-step instructions—this is the book network administrators and everyday computer users will turn to again and again. COMPUTERS,Networking,General

Computing in Communication Networks Computing in Communication Networks: From Theory to Practice provides comprehensive details and practical implementation tactics on the novel concepts and enabling technologies at the core of the paradigm shift from store and forward (dumb) to compute and forward (intelligent) in future communication networks and systems. The book explains how to create virtualized large scale testbeds using well-established open source software, such as Mininet and Docker. It shows how and where to place disruptive techniques, such as machine learning, compressed sensing, or network coding in a newly built testbed. In addition, it presents a comprehensive overview of current standardization activities. Specific chapters explore upcoming communication networks that support verticals in transportation, industry, construction, agriculture, health care and energy grids, underlying concepts, such as network slicing and mobile edge cloud, enabling technologies, such as SDN/NFV/ ICN, disruptive innovations, such as network coding, compressed sensing and machine learning, how to build a virtualized network infrastructure testbed on one’s own computer, and more. Provides a uniquely comprehensive overview on the individual building blocks that comprise the concept of computing in future networks Gives practical hands-on activities to bridge theory and implementation Includes software and examples that are not only employed throughout the book, but also hosted on a dedicated website COMPUTERS,Networking,General

Euro-Par 2019 This book constitutes revised selected papers from the workshops held at 25th International Conference on Parallel and Distributed Computing, Euro-Par 2019, which took place in Göttingen, Germany, in August 2019. The 53 full papers and 10 poster papers presented in this volume were carefully reviewed and selected from 77 submissions. Euro-Par is an annual, international conference in Europe, covering all aspects of parallel and distributed processing. These range from theory to practice, from small to the largest parallel and distributed systems and infrastructures, from fundamental computational problems to full-edged applications, from architecture, compiler, language and interface design and implementation to tools, support infrastructures, and application performance aspects. Chapter "In Situ Visualization of Performance-Related Data in Parallel CFD Applications" is available open access under a Creative Commons Attribution 4.0 International License via link.springer.com. COMPUTERS,Networking,General

Cisco Software-Defined Access The definitive Cisco SD-Access resource, from the architects who train Cisco’s own engineers and partners This comprehensive book guides you through all aspects of planning, implementing, and operating Cisco Software-Defined Access (SD-Access). Through practical use cases, you’ll learn how to use intent-based networking, Cisco ISE, and Cisco DNA Center to improve any campus network’s security and simplify its management. Drawing on their unsurpassed experience architecting solutions and training technical professionals inside and outside Cisco, the authors explain when and where to leverage Cisco SD-Access instead of a traditional legacy design. They illuminate the fundamental building blocks of a modern campus fabric architecture, show how to design a software-defined campus that delivers the most value in your environment, and introduce best practices for administration, support, and troubleshooting. Case studies show how to use Cisco SD-Access to address secure segmentation, plug and play, software image management (SWIM), host mobility, and more. The authors also present full chapters on advanced Cisco SD-Access and Cisco DNA Center topics, plus detailed coverage of Cisco DNA monitoring and analytics. * Learn how Cisco SD-Access addresses key drivers for network change, including automation and security * Explore how Cisco DNA Center improves network planning, deployment, evolution, and agility * Master Cisco SD-Access essentials: design, components, best practices, and fabric construction * Integrate Cisco DNA Center and Cisco ISE, and smoothly onboard diverse endpoints * Efficiently operate Cisco SD-Access and troubleshoot common fabric problems, step by step * Master advanced topics, including multicast flows, Layer 2 flooding, and the integration of IoT devices * Extend campus network policies to WANs and data center networks * Choose the right deployment options for Cisco DNA Center in your environment * Master Cisco DNA Assurance analytics and tests for optimizing the health of clients, network devices, and applications COMPUTERS,Networking,General

Randomly Deployed Wireless Sensor Networks Wireless sensor networks have a range of applications, including military uses and in environmental monitoring. When an area of interest is inaccessible by conventional means, such a network can be deployed in ways resulting in a random distribution of the sensors. Randomly Deployed Wireless Sensor Networks offers a probabilistic method to model and analyze these networks. The book considers the network design, coverage, target detection, localization and tracking of sensors in randomly deployed wireless networks, and proposes a stochastic model. It quantifies the relationship between parameters of the network and its performance, and puts forward a communication protocol. The title provides analyses and formulas, giving engineering insight into randomly deployed wireless sensor networks. Five chapters consider the analysis of coverage performance; working modes and scheduling mechanisms; the relationship between sensor behavior and network performance properties; probabilistic forwarding routing protocols; localization methods for multiple targets and target number estimation; and experiments on target localization and tracking with a Mica sensor system. Details a probabilistic method to model and analyze randomly deployed wireless sensor networks Gives working modes and scheduling mechanisms for sensor nodes, allowing high-probability of target detection Considers the relationship between sensor behaviour and network performance and lifetime Offers probabilistic forwarding routing protocols for randomly deployed wireless sensor networks Describes a method for localizing multiple targets and estimating their number COMPUTERS,Networking,General

Advances in Optical Networks and Components This book is intended as a graduate/post graduate level textbook for courses on high-speed optical networks as well as computer networks. The ten chapters cover basic principles of the technology as well as latest developments and further discuss network security, survivability, and reliability of optical networks and priority schemes used in wavelength routing. This book also goes on to examine Fiber To The Home (FTTH) standards and their deployment and research issues and includes examples in all the chapters to aid the understanding of problems and solutions. Presents advanced concepts of optical network devices Includes examples and exercises inall the chapters of the book to aid the understanding of basic problems and solutions for undergraduate and postgraduate students Discusses optical ring metropolitan area networks and queuing system and its interconnection with other networks Discusses routing and wavelength assignment Examines restoration schemes in the survivability of optical networks COMPUTERS,Networking,General

Fundamentals of Optical Networks and Components This book is intended as an undergraduate/postgraduate level textbook for courses on high-speed optical networks as well as computer networks. Nine chapters cover the basic principles of the technology and different devices for optical networks, as well as processing of integrated waveguide devices of optical networks using different technologies. It provides students, researchers and practicing engineers with an expert guide to the fundamental concepts, issues and state-of-the-art developments in optical networks. It includes examples throughout all the chapters of the book to aid understanding of basic problems and solutions. Presents basics of the optical network devices and discusses latest developments Includes examples and exercises throughout all the chapters of the book to aid understanding of basic problems and solutions for undergraduate and postgraduate students Discusses different optical network node architectures and their components Includes basic theories and latest developments of hardware devices with their fabrication technologies (such as optical switch, wavelength router, wavelength division multiplexer/demultiplexer and add/drop multiplexer), helpful for researchers to initiate research on this field and to develop research problem-solving capability Reviews fiber-optic networks without WDM and single-hop and multi-hop WDM optical networks P. P. Sahu received his M.Tech. degree from the Indian Institute of Technology Delhi and his Ph.D. degree in engineering from Jadavpur University, India. In 1991, he joined Haryana State Electronics Development Corporation Limited, where he has been engaged in R&D works related to optical fiber components and telecommunication instruments. In 1996, he joined Northeastern Regional Institute of Science and Technology as a faculty member. At present, he is working as a professor in the Department of Electronics and Communication Engineering, Tezpur Central University, India. His field of interest is integrated optic and electronic circuits, wireless and optical communication, clinical instrumentation, green energy, etc. He has received an INSA teacher award (instituted by the highest academic body Indian National Science Academy) for high level of teaching and research. He has published more than 90 papers in peer-reviewed international journals, 60 papers in international conference, and has written five books published by Springer Nature, McGraw-Hill. Dr Sahu is a Fellow of the Optical Society of India, Life Member of Indian Society for Technical Education and Senior Member of the IEEE. COMPUTERS,Networking,General

Mobile Service Computing This book introduces readers to the background and principles of mobile service computing. It discusses various aspects of service computing in mobile environments, including key methods and techniques for service selection, recommendation, composition, offloading, execution, deployment, and provision. COMPUTERS,Networking,General

Advanced Antenna Systems for 5G Network Deployments Advanced Antenna Systems for 5G Network Deployments: Bridging the Gap between Theory and Practice provides a comprehensive understanding of the field of advanced antenna systems (AAS) and how they can be deployed in 5G networks. The book gives a thorough understanding of the basic technology components, the state-of-the-art multi-antenna solutions, what support 3GPP has standardized together with the reasoning, AAS performance in real networks, and how AAS can be used to enhance network deployments. Explains how AAS features impact network performance and how AAS can be effectively used in a 5G network, based on either NR and/or LTE Shows what AAS configurations and features to use in different network deployment scenarios, focusing on mobile broadband, but also including fixed wireless access Presents the latest developments in multi-antenna technologies, including Beamforming, MIMO and cell shaping, along with the potential of different technologies in a commercial network context Provides a deep understanding of the differences between mid-band and mm-Wave solutions COMPUTERS,Networking,General

Metropolitan Area WDM Networks Metropolitan Area WDM Networks: An AWG Based Approach provides a comprehensive and technically detailed overview of the latest metropolitan area WDM network experimental systems, architectures, and access protocols. Its main focus is on the novel star WDM networks based on a wavelength-selective Arrayed-Waveguide Grating (AWG). Network researchers, engineers, professionals, and graduate students will benefit from the thorough overview and gain an in-depth understanding of current and next-generation metro WDM networks. The AWG based metro star WDM network is discussed at length and extensively investigated by means of stochastic analyses and simulations. The book provides: *an up-to-date overview of ring and star metro WDM networks and access protocols, *in-depth performance comparison studies of AWG based multihop vs. single-hop WDM networks and AWG vs. Passive Star Coupler based single-hop WDM networks, *a thorough description of the AWG based network and node architectures and access protocols, *a novel highly-efficient approach to provide survivability for star WDM networks, *extensive analytical results for both unicast and multicast variable-size packet traffic and bandwidth on demand, *supplementary simulation results, including packet header trace files. COMPUTERS,Networking,Hardware

Wireless ATM and Ad-Hoc Networks ATM is regarded as the next high speed multimedia networking paradigm. Mobile computing, which is a confluence of mobile communications, computing and networks, is changing the way people work. Wireless ATM combines wireless and ATM technologies to provide mobility support and multimedia services to mobile users. Wireless ATM and Ad-Hoc Networks: Protocols and Architectures, a consolidated reference work, presents the state of the art in wireless ATM technology. It encompasses the protocol and architectural aspects of Wireless ATM networks. The topics covered in this book include: mobile communications and computing, fundamentals of ATM and Wireless ATM, mobile routing and switch discovery, handover protocol design and implementation, mobile quality of service, unifying handover strategy for both unicast and multicast mobile connections, and roaming between Wireless ATM LANs. A novel routing protocol for ad-hoc mobile networks (also known as Cambridge Ad-hoc) is also presented in this book along with information about ETSI HIPERLAN, the RACE Mobile Broadband System, and SUPERNET. This timely book is a valuable reference source for researchers, scientists, consultants, engineers, professors and graduate students working in this new and exciting field. COMPUTERS,Networking,Hardware

Networking Security and Standards Security is the science and technology of secure communications and resource protection from security violation such as unauthorized access and modification. Putting proper security in place gives us many advantages. It lets us exchange confidential information and keep it confidential. We can be sure that a piece of information received has not been changed. Nobody can deny sending or receiving a piece of information. We can control which piece of information can be accessed, and by whom. We can know when a piece of information was accessed, and by whom. Networks and databases are guarded against unauthorized access. We have seen the rapid development of the Internet and also increasing security requirements in information networks, databases, systems, and other information resources. This comprehensive book responds to increasing security needs in the marketplace, and covers networking security and standards. There are three types of readers who are interested in security: non-technical readers, general technical readers who do not implement security, and technical readers who actually implement security. This book serves all three by providing a comprehensive explanation of fundamental issues of networking security, concept and principle of security standards, and a description of some emerging security technologies. The approach is to answer the following questions: 1. What are common security problems and how can we address them? 2. What are the algorithms, standards, and technologies that can solve common security problems? 3. COMPUTERS,Networking,Hardware

Intelligent Broadband Multimedia Networks Intelligent Broadband Multimedia Networks is a non-mathematical, but highly systems oriented, coverage of modern intelligent information networks. This volume focuses on the convergence of computers and communications technologies. Most of the concepts that are generic to all intelligent networks, and their microscopic and macroscopic functions, are presented. This book includes specific architectures that can be used by network designers and planners, telecommunications managers, computer scientists, and telecommunications professionals. The breadth of this coverage and the systems orientation of this work make the text suitable for use in advanced level courses on intelligent communications networks. The material in this volume ranges from defining intelligent networks to more specific coverage of educational, medical, and knowledge-based networks. Each of the 20 chapters address issues that can help make the transition from computer design, to the underlying concepts of modern telecommunications systems, to considerations necessary for the implementation of intelligent network services. Special and timely coverage of emerging technologies, such as HDSL, ADSL, BISDN, wireless, broadband access, ATM, and other topics, are given expanded treatment. The authors have included design methodologies for installing intelligence into almost any communications systems, and procedures for using such intelligence according to the type of function expected from these networks. Unique features of the book are: a 64-page glossary of key terms (with expanded explanations) used in the field, a 23-page index that makes it easy to search for important information, running headers on each page to help the busy professional use the book as a reference/design tool, complete references including additional reading for more detailed information, and accurate and concise information to help telecommunications professionals understand the intricacies of the field. COMPUTERS,Networking,Hardware

Hypermedia Systems and Applications It is a pleasure and an honor to write a foreword for Jennifer Lennon's book Hypermedia Systems and Applications: World Wide Web and Beyond. I am fortunate to have been able to follow the development of this book from an excellent Ph.D. thesis to what I would consider one of the best and most comprehensive books in the area. It has a good chance to become a must for teachers, researchers, and practitioners. For the sake ofthis foreword let us combine the phenomena hypermedia, the Internet, and the WWW by just calling them the Web. Well, this Web surely has become one of the "super hot topics", from both a scholarly and a commercial point ofview! We have a saying that the Web is like a dog: one year's development of the Web corresponds to seven human years. You will be familiar with Murphy's law: "Anything that can go wrong will go wrong", and with a plethora of derivatives or specializations thereof like: "If you are in an otherwise empty locker room, the only other person there is bound to have a locker just on top ofyours"; or: "If traffic is moving slowly, you are always going to be in the slowest moving lane", and so on. Well, I have coined a version that applies to the Web: "Whenever you have understood an important new development concerning the Web you can be sure that it is obsolete". COMPUTERS,Networking,Hardware

Design and Engineering of Intelligent Communication Systems FIGURE 18.13e. Detector Output. ..................................................................... 618 FIGURE 18.14a. WDM Energy Distrubution into the Fiber ........................... 619 FIGURE 18.14b. Fiber Loss for the WDM Band .............................................. 619 FIGURE 18.14c. Fiber Group Delay Distribution ............................................ 619 FIGURE 18.14d. Receive Energy Distribution ................................................. 619 FIGURE 18.15a. Channell Eye Diagram at PIN Diode ................................. 621 FIGURE 18.15b. Channel 2 Eye Diagram at PIN Diode ................................. 621 FIGURE 18.15c. Channell System Output at Detector ................................. 621 FIGURE 18.15d. Channel 2 System Output at Detector ................................. 621 PREFACE The emerging networks in our society will touch upon the life of everyone. These networks have started to bring about an immense information revolution. The revolution within our intellectual life will be similar to the materialistic revolution that followed the invention of the steam and the internal combustion engines. From the perspective of the 1980s, the information networks are indeed evolving and their influence can only be gradual. However, the strides of progress are accelerating in the 1990s. Networks in our society offer the most candid area of convergence for the computer and the communication technologies. The two technologies are mature in their own right. However, there are a few major factors that prevent network engineers from constructing modern communication systems from components borrowed from each of these two technologies: • Major innovations are happening. • Specialized components evolve in synergistic patterns. • New technologies emerge. • Inquisitive minds cross disciplinary barriers. COMPUTERS,Networking,Hardware

Semantics of Parallelism Semantics of Parallelism is the only book which provides a unified treatment of the non-interleaving approach to process semantics (as opposed to the interleaving approach of the process algebraists). Many results found in this book are collected for the first time outside conference and journal articles on the mathematics of non-interleaving semantics. It gives the reader a unified view of various attempts to model parallelism within one conceptual frame work. It is aimed at postgraduates in theoretical computer science and academics who are teaching and researching in the modelling of discrete, concurrent/distributed systems. Workers in the information technology industry who are interested in available theoretical studies on parallelism will also be interested in this book. COMPUTERS,Networking,Hardware

Linguistic Concepts and Methods in CSCW Linguistic Concepts and Methods in CSCW is the first book devoted to the innovative new area of research in CSCW. It concentrates on the use of language in context - the area most widely researched in conjunction with CSCW - but also examines grammatical construction, semantics and the significance of the spoken, written and graphic mediums. A variety of other related topics, such as sociolinguistics, stylistics, psycholinguistics, computational linguistics, and applied linguistics are also covered. This book will be of interest to researchers in CSCW, linguistics and computational linguistics. It will also provide invaluable reading for industrial and commercial researchers who are interested in the implications of such research for the design of marketable systems. COMPUTERS,Networking,Hardware

The Information Superhighway and Private Households Wolfgang Glatthaar International Business Machines (IBM), Gennany The rapid developments in infonnation technology (IT) will continue through the coming years. New application areas will be added. Whereas the use of infonnation technology in the past decade has been concentrated primarily on business and public administration, in future the suppliers of infonnation technology will develop an increasing number of applications for the private household (see fig. 1). Traditional perspective: New perspective: 'IT-solutions for the "IT-solutions for the company' private household" ~ . . . . . . \ . . . . . . . . . . . . \ . . . . . . . . . . . . \ . . . . . . . . . . . . \ . . . . . . . . . . . . \ . . . . . . . . . . . . \ \ \ \ \ Fig. 1. New perspective on information technology This development has already generated considerable market dynamics. Latest forecasts for the USA suggest that by 1996 at the latest the private household will present greater sales potential for home computers than business and public administration. VI Preface Up to now the use of infonnation technology in the private household has not been regarded as highly significant by either business or science, even though PCs have become widespread in the private sphere. In the ESPRIT framework there have been individual projects dealing with home networks, and in a number of Asian and European countries, as well as America, experiments with interactive television are taking place. Internet and commercial online services are experiencing rapid growth. This application area for infonnation technology in the private household, which is generating increasing business attention, must also be the subject of appropriate research activities. COMPUTERS,Networking,Hardware

Resource Management for Distributed Multimedia Systems Resource Management for Distributed Multimedia Systems addresses the problems and challenges of handling several continuous- media data streams in networked multimedia environments. The work demonstrates how resource management mechanisms can be integrated into a stream handling system. The resulting system includes functions for Quality of Service (QoS) calculations, scheduling, determination of resource requirements, and methods to reduce resource requirements. The work explains the following: a suitable system architecture and resource management scheme that allows for the provision and enforcement of QoS guarantee, resource scheduling mechanisms for CPU and buffer space, mechanisms to measure and collect resource requirements, methods to extend resource management to future scenarios by allowing the reservation of resources in advance and offering sealing mechanisms. . Resource Management for Distributed Multimedia Systems is a comprehensive view of resource management for a broad technical audience that includes computer scientists and engineers involved in developing multimedia applications. COMPUTERS,Networking,Hardware

ATM Network Performance ATM Network Performance describes a unified approach to ATM network management. The focus is on satisfying quality-of-service requirements for individual B-ISDN connections. For an ATM network of output-buffer switches, the author describes how the basic network resources (switch buffer memory and link transmission bandwidth) should be allocated to achieve the required quality-of-service connections. The performance of proposed bandwidth scheduling policies is evaluated. Both single node and end-to-end performance results are given. In particular, these results are applied to resource provisioning problems for prerecorded (stored) video and video teleconferencing. The flow control problem for available bit rate traffic is also described. This book is intended for a one-term course in performance of Broadband Integrated-Services Digital Networks (B-ISDNs) based on a type of packet-switched communication network called Asynchronous Transfer Mode (ATM). The level of presentation is at the first year of graduate studies and for professionals working in the field, but it may be accessible to senior undergraduates as well. Some familiarity with ATM standards is assumed as such standards are only briefly outlined. All of the required background in discrete-time queueing theory is supplied. Exercises are given at the end of chapters. Solutions and/or hints to selected exercises are given in an Appendix. COMPUTERS,Networking,Hardware

High-Speed Networking for Multimedia Applications High-Speed Networking for Multimedia Applications presents the latest research on the architecture and protocols for high-speed networks, focusing on communication support for distributed multimedia applications. This includes the two major issues of ATM Networking and quality of service for multimedia applications. It is to be expected that most of the bandwidth in future high-speed networks will be taken up by multimedia applications, transmitting digital audio and video. Traditional networking protocols are not suitable for this as they do not provide guaranteed bandwidth, end-to-end delay or delay jitter, nor do they have addressing schemes or routing algorithms for multicast connections. High-Speed Networking for Multimedia Applications is a collection of high quality research papers which address these issues, providing interesting and innovative solutions. It is an essential reference for engineers and computer scientists working in this area. It is also a comprehensive text for graduate students of high-speed networking and multimedia applications. COMPUTERS,Networking,Hardware

Building Interactive Systems Architectures and tools are two important considerations in the construction of interactive computer systems. The former is concerned with the optimal structural organisation of systems and the latter with the effective support of the design and management of user interfaces. They are regarded as the areas of research most likely to contribute to the development of existing interactive systems, in particular by providing improved architectures capable of supporting new styles of interaction and more sophisticated software tools to improve productivity. This volume combines the proceedings of two workshops held in York and Glasgow which concentrated on architectures and tools respectively. In doing so it addresses the problems of user interface construction from two complementary viewpoints and provides alternative perspectives on many of the central issues. Some of the papers are published in expanded form to provide a more comprehensive coverage of the topics and two additional papers have been included which offer a useful insight into issues raised by the workshops. The papers address formal and theoretical concerns as well as academic and commercial ones. Specific topics covered include novel-input models, architectures for real-time systems and object-oriented user interface tools for X-widgets, NeWS- and Smalltalk-based applications. The papers also include presentations of new tools and architectural designs. Building Interactive Systems: Architectures and Tools provides the most extensive recent account of research into the relationship between architectures and tools in the construction of interactive computer systems and will be of interest to researchers, postgraduate students and software developers. COMPUTERS,Networking,Hardware

Collaborative Learning Through Computer Conferencing The idea for the Workshop on which this book is based arose from discussions which we had when we both attended an earlier - and more broadly based - NATO Advanced Research Workshop on Computer Supported Collaborative Learning, directed by Claire O'Malley in Maratea, Italy, in 1989. We both felt that it would be interesting to organise a second Workshop in this area, but specifically concerned with the use of computers and networking (telematics) as communication tools for collaborative learning outside the formal school setting. We were particularly interested in examining the ways in which computer conferencing can be used for collaboration and group learning in the contexts of distance education, adult learning, professional training, and organisational networking. And we wanted to ensure that we included, in the scope of the Workshop, situations in which learning is a primary, explicit goal (e.g. an online training programme) as well as situations where learning occurs as a secondary, even incidental, outcome of a collaborative activity whose explicit purpose might be different (e.g. the activities of networked product teams or task groups). Another goal was to try to bring together for a few days people with three different perspectives on the use of computer conferencing: users, researchers, and software designers. We hoped that, if we could assemble a group of people from these three different constituencies, we might, collectively, be able to make a small contribution to real progress in the field. COMPUTERS,Networking,Hardware

High-Speed Communication Networks TriComm '92 was the fifth in the series of Research Triangle conferences on Computer Communications. This series emerged from a need to provide a forum for the people who are actively involved in Research and Development in the Research Triangle area in which they could present and discuss new ideas in Computer Communications. TriComm '92 was dedicated to High Speed networks. In particular, the program was developed around the following themes: local ATM, preventive and reactive congestion control. routing. transport protocols. traffic measurements, software engineering for telecommunication systems. and standards. I would like to thank all the speakers who agreed to present a paper. and the members of the program committee who patiently refereed the papers despite their busy schedules. I would also like to thank Mr. Ed Bowen, IBM, Research Triangle Park, for covering the expenses for the preparation of the pre-conference proceedings. and Dr. Raif Onvural. IBM, Research Triangle Park, for overseeing the photocopying of the proceedings. I would also like to thank my "Guardian Angel" Ms. Margaret Hudacko. Center for Communications and Signal Processing. State University, who made all the local arrangements. North Carolina Without her help, this conference would have been a complete disaster. Many thanks also go to Norene Miller. Center for Communications and Signal Processing. North Carolina State University. Finally. I would like to thank Mr. Charles Lord, Eastern NC Chapter of the IEEE Communications SOCiety. for providing us with mailing lists. COMPUTERS,Networking,Hardware

Distributed Environments Nowadays, with an increase in requests from users for easily used and personalized workstations, it is necessary to promote basic research into software development techniques, including new languages and communication software, in the network environment. This book contains the results of a joint research project between IBM Japan and twelve universities, the purpose of which was to implement prototypes of some of the technologies that are feasible at current research levels. The project was organized into three groups: 1) paradigms for software development, processing, and communication, 2) natural-language interfaces, and 3) software development environments with related operating systems. The results may be implemented as research tools, possibly for business use, in the field of software development techniques. COMPUTERS,Networking,Hardware

High-Capacity Local and Metropolitan Area Networks Proceedings of the NATO Advanced Research Workshop on Architecture and Performance Issues of High-Capacity Local and Metropolitan Area Networks, held in Sophia Antipolis, France, June 25-27, 1990 COMPUTERS,Networking,Hardware

Document Architecture in Open Systems In 1989, the ISO Standard 8613 "Office Document Architecture(ODA) and Interchange Format" was published. The Standard isintended for the interchange of documents in an Open Systemsenvironment. ISO 8613 is technically identical to the CCITTRecommendations of the T.410 series called "Open DocumentArchitecture (ODA) and Interchange Format" published in1988. Almost all major companies in the office automationand telecommunication area are currently developing productsbased on this Standard.In this book, all important aspects of the presentlypublishedeight parts of the Standard are discussed. Thebook provides a comprehensiveand detailed introduction tothe technical specifications of ISO 8613 and the concepts onwhich these specifications are based, including theextensions which were added to the ODA Standard in 1991.The book isprimarily addressed to readers who want toinvestigate the applicability of the Standard for theirdocument interchange problems, plan to acquire productsbased on the Standard, or intend to develop documentprocessingsystems conforming to the Standard. COMPUTERS,Networking,Hardware

Delta-4 Delta-4 is a 5-nation, 13-partner project that has been investigating the achievement of dependability in open distributed systems, including real-time systems. This book describes the design and validation of the distributed fault-tolerant architecture developed within this project. The key features of the Delta-4 architecture are: (a) a distributed object-oriented application support environment; (b) built-in support for user-transparent fault tolerance; (c) use of multicast or group communication protocols; and (d) use of standard off the-shelf processors and standard local area network technology with minimum specialized hardware. The book is organized as follows: The first 3 chapters give an overview of the architecture's objectives and of the architecture itself, and compare the proposed solutions with other approaches. Chapters 4 to 12 give a more detailed insight into the Delta-4 architectural concepts. Chapters 4 and 5 are devoted to providing a firm set of general concepts and terminology regarding dependable and real-time computing. Chapter 6 is centred on fault-tolerance techniques based on distribution. The description of the architecture itself commences with a description of the Delta-4 application support environment (Deltase) in chapter 7. Two variants of the architecture - the Delta-4 Open System Architecture (OSA) and the Delta-4 Extra Performance Architecture (XPA) - are described respectively in chapters 8 and 9. Both variants of the architecture have a common underlying basis for dependable multicasting, i. e. COMPUTERS,Networking,Hardware

Wireless Communications Networks for the Smart Grid This brief presents a comprehensive review of the network architecture and communication technologies of the smart grid communication network (SGCN). It then studies the strengths, weaknesses and applications of two promising wireless mesh routing protocols that could be used to implement the SGCN. Packet transmission reliability, latency and robustness of these two protocols are evaluated and compared by simulations in various practical SGCN scenarios. Finally, technical challenges and open research opportunities of the SGCN are addressed. Wireless Communications Networks for Smart Grid provides communication network architects and engineers with valuable proven suggestions to successfully implement the SGCN. Advanced-level students studying computer science or electrical engineering will also find the content helpful. COMPUTERS,Networking,Hardware

Architecture and Protocols for High-Speed Networks Multimedia data streams will form a major part of the new generation of applications in high-speed networks. Continuous media streams, however, require transmission with guaranteed performance. In addition, many multimedia applications will require peer-to-multipeer communication. Guaranteed performance can only be provided with resource reservation in the network, and efficient multipeer communication must be based on multicast support in the lower layers of the network. Architecture and Protocols for High-Speed Networks focuses on techniques for building the networks that will meet the needs of these multimedia applications. In particular two areas of current research interest in such communication systems are covered in depth. These are the protocol related aspects, such as switched networks, ATM, MAC layer, network and transport layer; and the services and applications. Architecture and Protocols for High-Speed Networks contains contributions from leading world experts, giving the most up-to-date research available. It is an essential reference for all professionals, engineers and researchers working in the area of high-speed networks. COMPUTERS,Networking,Hardware

Beginning FPGA Use Arrow's affordable and breadboard-friendly FPGA development board (BeMicro MAX 10) to create a light sensor, temperature sensor, motion sensor, and the KITT car display from Knight Rider. You don't need an electronics engineering degree or even any programming experience to get the most out of Beginning FPGA: Programming Metal. Just bring your curiosity and your Field-Programmable Gate Array. This book is for those who have tinkered with Arduino or Raspberry Pi, and want to get more hands-on experience with hardware or for those new to electronics who just want to dive in. You'll learn the theory behind FPGAs and electronics, including the math and logic you need to understand what's happening - all explained in a fun, friendly, and accessible way. It also doesn't hurt that you'll be learning VHDL, a hardware description language that is also an extremely marketable skill. What You'll Learn: Learn what an FPGA is and how it's different from a microcontroller or ASIC Set up your toolchain Use VHDL, a popular hardware description language, to tell your FPGA what to be Explore the theory behind FPGA and electronics Use your FPGA with a variety of sensors and to talk to a Raspberry Pi Who This Book is For: Arduino, Raspberry Pi, and other electronics enthusiasts who want a clear and practical introduction to FPGA. COMPUTERS,Networking,Hardware

IoT Projects with Bluetooth Low Energy Use the power of BLE to create exciting IoT applications About This Book Build hands-on IoT projects using Bluetooth Low Energy and learn about Bluetooth 5 and its features. Build a health tracking system, and indoor navigation and warehouse weather monitoring projects using smart devices. Build on a theoretical foundation and create a practice-based understanding of Bluetooth Low Energy. Who This Book Is For If you're an application developer, a hardware enthusiast, or just curious about the Internet of Things and how to convert it into hands-on projects, then this book is for you. Having some knowledge of writing mobile applications will be advantageous. What You Will Learn Learn about the architecture and IoT uses of BLE, and in which domains it is being used the most Set up and learn about various development platforms (Android, iOS, Firebase, Raspberry Pi, Beacons, and GitHub) Create an Explorer App (Android/iOS) to diagnose a Fitness Tracker Design a Beacon with the Raspberry Pi and write an app to detect the Beacon Write a mobile app to periodically poll the BLE tracking sensor Compose an app to read data periodically from temperature and humidity sensors Explore more applications of BLE with IoT Design projects for both Android and iOS mobile platforms In Detail Bluetooth Low Energy, or Bluetooth Smart, is Wireless Personal Area networking aimed at smart devices and IoT applications. BLE has been increasingly adopted by application developers and IoT enthusiasts to establish connections between smart devices. This book initially covers all the required aspects of BLE, before you start working on IoT projects. In the initial stages of the book, you will learn about the basic aspects of Bluetooth Low Energy—such as discovering devices, services, and characteristics—that will be helpful for advanced-level projects. This book will guide you through building hands-on projects using BLE and IoT. These projects include tracking health data, using a mobile App, and making this data available for health practitioners; Indoor navigation; creating beacons using the Raspberry Pi; and warehouse weather Monitoring. This book also covers aspects of Bluetooth 5 (the latest release) and its effect on each of these projects. By the end of this book, you will have hands-on experience of using Bluetooth Low Energy to integrate with smart devices and IoT projects. Style and Approach A practical guide that will help you promote yourself into an expert by building and exploring practical applications of Bluetooth Low Energy. COMPUTERS,Networking,Hardware

Guide to Security in SDN and NFV This book highlights the importance of security in the design, development and deployment of systems based on Software-Defined Networking (SDN) and Network Functions Virtualization (NFV), together referred to as SDNFV. Presenting a comprehensive guide to the application of security mechanisms in the context of SDNFV, the content spans fundamental theory, practical solutions, and potential applications in future networks.Topics and features: introduces the key security challenges of SDN, NFV and Cloud Computing, providing a detailed tutorial on NFV security; discusses the issue of trust in SDN/NFV environments, covering roots of trust services, and proposing a technique to evaluate trust by exploiting remote attestation; reviews a range of specific SDNFV security solutions, including a DDoS detection and remediation framework, and a security policy transition framework for SDN; describes the implementation of a virtual home gateway, and a project that combines dynamic security monitoring with big-data analytics to detect network-wide threats; examines the security implications of SDNFV in evolving and future networks, from network-based threats to Industry 4.0 machines, to the security requirements for 5G; investigates security in the Observe, Orient, Decide and Act (OODA) paradigm, and proposes a monitoring solution for a Named Data Networking (NDN) architecture; includes review questions in each chapter, to test the reader’s understanding of each of the key concepts described. This informative and practical volume is an essential resource for researchers interested in the potential of SDNFV systems to address a broad range of network security challenges. The work will also be of great benefit to practitioners wishing to design secure next-generation communication networks, or to develop new security-related mechanisms for SDNFV systems. COMPUTERS,Networking,Hardware

Design, Launch, and Scale IoT Services The Internet of Things is causing major industry disruption, so companies need to plan and manage their “IoT journey†to maximize all business opportunities. In this book companies can learn how to successfully create, launch and manage Internet of Things services. It takes the reader through the process of specifying, implementing, and deploying IoT services; detailing how to scale and manage an IoT business. It introduces the fundamentals of IoT services, explaining IoT service building blocks and the key factors to be considered in the design of IoT services. Moving into the IoT field requires speed. This book provides a fast track approach to IoT; summarizing the global experiences of the author, detailing the discussions, mistakes, successes, learnings and conclusions. Building an Internet of Things Service enables readers to accelerate their own on-boarding in their IoT journey. What You'll Learn Create new IoT Services Review the basic IoT concepts and business implications you need to know as you embark on your IoT journey Solve the major challenges presented by the IoT disruption. Accelerate your own on-boarding in their IoT journey. Who This Book Is For The primary audience is made up of business executives and IoT startups. The secondary audience is students studying IoT in universities and those interested in understanding the fundamentals of an IoT business. No technical background is required. COMPUTERS,Networking,Hardware

The IoT Hacker's Handbook Take a practioner’s approach in analyzing the Internet of Things (IoT) devices and the security issues facing an IoT architecture. You’ll review the architecture's central components, from hardware communication interfaces, such as UARTand SPI, to radio protocols, such as BLE or ZigBee. You'll also learn to assess a device physically by opening it, looking at the PCB, and identifying the chipsets and interfaces. You'll then use that information to gain entry to the device or to perform other actions, such as dumping encryption keys and firmware. As the IoT rises to one of the most popular tech trends, manufactures need to take necessary steps to secure devices and protect them from attackers. The IoT Hacker's Handbook breaks down the Internet of Things, exploits it, and reveals how these devices can be built securely. What You’ll Learn Perform a threat model of a real-world IoT device and locate all possible attacker entry points Use reverse engineering of firmware binaries to identify security issues Analyze,assess, and identify security issues in exploited ARM and MIPS based binaries Sniff, capture, and exploit radio communication protocols, such as Bluetooth Low Energy (BLE), and ZigBee Who This Book is For Those interested in learning about IoT security, such as pentesters working in different domains, embedded device developers, or IT people wanting to move to an Internet of Things security role. COMPUTERS,Networking,Hardware

Internet of Things Projects with ESP32 Create and program Internet of Things projects using the Espressif ESP32. Key Features Getting to know the all new powerful EPS32 boards and build interesting Internet of Things projects Configure your ESP32 to the cloud technologies and explore the networkable modules that will be utilised in your IoT projects A step-by-step guide that teaches you the basic to advanced IoT concepts with ESP32 Book Description ESP32 is a low-cost MCU with integrated Wi-Fi and BLE. Various modules and development boards-based on ESP32 are available for building IoT applications easily. Wi-Fi and BLE are a common network stack in the Internet of Things application. These network modules can leverage your business and projects needs for cost-effective benefits. This book will serve as a fundamental guide for developing an ESP32 program. We will start with GPIO programming involving some sensor devices. Then we will study ESP32 development by building a number of IoT projects, such as weather stations, sensor loggers, smart homes, Wi-Fi cams and Wi-Fi wardriving. Lastly, we will enable ESP32 boards to execute interactions with mobile applications and cloud servers such as AWS. By the end of this book, you will be up and running with various IoT project-based ESP32 chip. What you will learn Understand how to build a sensor monitoring logger Create a weather station to sense temperature and humidity using ESP32 Build your own W-iFi wardriving with ESP32. Use BLE to make interactions between ESP32 and Android Understand how to create connections to interact between ESP32 and mobile applications Learn how to interact between ESP32 boards and cloud servers Build an IoT Application-based ESP32 board Who this book is for This book is for those who want to build a powerful and inexpensive IoT projects using the ESP32.Also for those who are new to IoT, or those who already have experience with other platforms such as Arduino, ESP8266, and Raspberry Pi. COMPUTERS,Networking,Hardware

Guide to Automotive Connectivity and Cybersecurity This comprehensive text/reference presents an in-depth review of the state of the art of automotive connectivity and cybersecurity with regard to trends, technologies, innovations, and applications. The text describes the challenges of the global automotive market, clearly showing where the multitude of innovative activities fit within the overall effort of cutting-edge automotive innovations, and provides an ideal framework for understanding the complexity of automotive connectivity and cybersecurity.Topics and features: discusses the automotive market, automotive research and development, and automotive electrical/electronic and software technology; examines connected cars and autonomous vehicles, and methodological approaches to cybersecurity to avoid cyber-attacks against vehicles; provides an overview on the automotive industry that introduces the trends driving the automotive industry towards smart mobility and autonomous driving; reviews automotive research and development, offering background on the complexity involved in developing new vehicle models; describes the technologies essential for the evolution of connected cars, such as cyber-physical systems and the Internet of Things; presents case studies on Car2Go and car sharing, car hailing and ridesharing, connected parking, and advanced driver assistance systems; includes review questions and exercises at the end of each chapter. The insights offered by this practical guide will be of great value to graduate students, academic researchers and professionals in industry seeking to learn about the advanced methodologies in automotive connectivity and cybersecurity. COMPUTERS,Networking,Hardware

Computational Science and Its Applications – ICCSA 2019 The six volumes LNCS 11619-11624 constitute the refereed proceedings of the 19th International Conference on Computational Science and Its Applications, ICCSA 2019, held in Saint Petersburg, Russia, in July 2019. The 64 full papers, 10 short papers and 259 workshop papers presented were carefully reviewed and selected form numerous submissions. The 64 full papers are organized in the following five general tracks: computational methods, algorithms and scientific applications; high performance computing and networks; geometric modeling, graphics and visualization; advanced and emerging applications; and information systems and technologies. The 259 workshop papers were presented at 33 workshops in various areas of computational sciences, ranging from computational science technologies to specific areas of computational sciences, such as software engineering, security, artificial intelligence and blockchain technologies. COMPUTERS,Networking,Hardware

Pro PowerShell for Amazon Web Services Amazon Web Services (AWS) is the leading public cloud platform. In this book you will learn to use Microsoft PowerShell to create, host, manage, and administer workloads using Amazon Web Services. You will learn how to create virtual machines, provision storage, configure networks, and more—all using your preferred Windows scripting language. CIOs everywhere are leading their organizations to the cloud, but there are few books available to help. This book focuses on moving Microsoft Windows workloads to the cloud using technologies familiar to enterprise Microsoft-based professionals. The completely revised and expanded Pro PowerShell for Amazon Web Services is written specifically for Windows professionals who already know PowerShell and want to learn to host Windows workloads on Amazon Web Services. The cloud offers information technology workers significant cost savings and agility unimaginable even just a few years ago. Tasks that traditionally took weeks of work, costing thousands of dollars, can be completed in minutes for a fraction of a penny. New chapters in this second edition cover: AWS Lambda, Amazon WorkSpaces, Amazon AppStream 2.0, AWS Directory Service, Amazon WorkDocs, and AWS System Manager. What You'll Learn Create and manage Windows servers on Elastic Compute Cloud (EC2) Configure and secure networks with Virtual Private Cloud (VPC) Leverage autoscaling to adjust resources as load changes Deploy and manage SQL Server using the Relational Database Service (RDS) Manage virtual desktops using WorkSpaces and AppStream Leverage AWS Systems Manager to manage Windows at scale Who This Book Is For Windows professionals who want to learn more about Amazon Web Services, with a focus on running Windows workloads and automated management at scale using PowerShell tools for AWS. The book assumes you have knowledge of Windows and PowerShell, but are new to AWS. COMPUTERS,Networking,Hardware

Demystifying Smart Cities The concept of Smart Cities is accurately regarded as a potentially transformative power all over the world. Bustling metropolises infused with the right combination of the Internet of Things, artificial intelligence, big data, and blockchain promise to improve both our daily lives and larger structural operations at a city government level. The practical realities pose challenges that a significant sector of the tech industry now revolves around solving. Cut through the hype with Demystifying Smart Cities. In this book, the real-world implementations of successful Smart City technology in places like New York, Amsterdam, Copenhagen, and more are analyzed, and insights are gained from recorded attempts in similar urban centers that have not reached their full Smart City potential. From the logistical complications of securing thousands of devices to collect millions of pieces of data daily, to the complicated governmental processes that are required to install Smart City tech, Demystifying Smart Cities covers every aspect of this revolutionary modern technology. This book is the essential guide for anybody who touches a step of the Smart City process—from salespeople representing product vendors to city government officials to data scientists—and provides a more well-rounded understanding of the full positive and negative impacts of Smart City technology deployment. Demystifying Smart Cities evaluates how our cities can behave in a more intelligent way, and how producing novel solutions can pose equally novel challenges. The future of the metropolis is here, and the expert knowledge in the book is your greatest asset. What You'll Learn Practical issues and challenges of managing thousands and millions of IoT devices in a city The different types of city data and how to manage and secure it The possibilities of utilizing AI into a city (and how it differs from working with the private sector) Examples of how to make cities smarter with technology Who This Book Is For Primarily for those already familiar with the hype of smart city technologies but not the details of its implementation, along with technologists interested in learning how city government works when integrating technology. Also, people working for smart city vendors, especially sales people and product managers who need to understand their target market. COMPUTERS,Networking,Hardware

Intelligent Technologies and Applications This book constitutes the refereed proceedings of the Second International Conference on Intelligent Technologies and Applications, INTAP 2019, held in Bahawalpur, Pakistan, in November 2019. The 60 revised full papers and 6 revised short papers presented were carefully reviewed and selected from 224 submissions. Additionally, the volume presents 1 invited paper. The papers of this volume are organized in topical sections on AI and health; sentiment analysis; intelligent applications; social media analytics; business intelligence;Natural Language Processing; information extraction; machine learning; smart systems; semantic web; decision support systems; image analysis; automated software engineering. COMPUTERS,Networking,Hardware

Internet of Things This comprehensive overview of IoT systems architecture includes in-depth treatment of all key components: edge, communications, cloud, data processing, security, management, and uses. Internet of Things: Concepts and System Design provides a reference and foundation for students and practitioners that they can build upon to design IoT systems and to understand how the specific parts they are working on fit into and interact with the rest of the system. This is especially important since IoT is a multidisciplinary area that requires diverse skills and knowledge including: sensors, embedded systems, real-time systems, control systems, communications, protocols, Internet, cloud computing, large-scale distributed processing and storage systems, AI and ML, (preferably) coupled with domain experience in the area where it is to be applied, such as building or manufacturing automation. Written in a reader-minded approach that starts by describing the problem (why should I care?), placing it in context (what does this do and where/how does it fit in the great scheme of things?) and then describing salient features of solutions (how does it work?), this book covers the existing body of knowledge and design practices, but also offers the author’s insights and articulation of common attributes and salient features of solutions such as IoT information modeling and platform characteristics. COMPUTERS,Networking,Hardware

Cloud Computing, Smart Grid and Innovative Frontiers in Telecommunications This book constitutes the refereed proceedings of the 9thInternational Conference on Cloud Computing, CloudComp 2019, and the 4th International Conference on Smart Grid and Innovative Frontiers in Telecommunications, SmartGIFT 2019, both held in Beijing, China, in December 2019. The55 full papers of both conferences were selected from 113 submissions. CloudComp 2019 presents recent advances and experiences in clouds, cloud computing and related ecosystems and business support. The papers are grouped thematically in tracks on cloud architecture and scheduling; cloud-based data analytics; cloud applications; and cloud security and privacy. SmartGIFT 2019 focus on all aspects of smart grids and telecommunications, broadly understood as the renewable generation and distributed energy resources integration, computational intelligence applications, information and communication technologies. COMPUTERS,Networking,Hardware

Smart Grid and Internet of Things This book constitutes the refereed proceedings of the Third EAI International Conference on Smart Grid and Internet of Things, SGIoT 2019, held in TaiChung, Taiwan, in November 2019. The 10 papers presented were carefully reviewed and selected from 22 submissions and present results on how to achieve more efficient use of resources based largely on the IoT-based machine-to-machine (M2M) interactions of millions of smart meters and sensors in the smart grid specific communication networks such as home area networks, building area networks, and neighborhood area networks. The smart grid also encompasses IoT technologies, which monitor transmission lines, manage substations, integrate renewable energy generation. Through these technologies, the authorities can smartly identify outage problems, and intelligently schedule the power generation and delivery to the customers. Furthermore, the smart grid should teach us a valuable lesson that security must be designed in from the start of any IoT deployment. COMPUTERS,Networking,Hardware

Distributed Applications and Interoperable Systems This book constitutes the proceedings of the 20th IFIP International Conference on Distributed Applications and Interoperable Systems, DAIS 2020, which was supposed to be held in Valletta, Malta, in June 2020, as part of the 15th International Federated Conference on Distributed Computing Techniques, DisCoTec 2020. The conference was held virtually due to the COVID-19 pandemic. The 10 full papers presented together with 1 short paper and 1 invited paper were carefully reviewed and selected from 17 submissions. The papers addressed challenges in multiple application areas, such as privacy and security, cloud and systems, fault-tolerance and reproducibility, machine learning for systems, and distributed algorithms. COMPUTERS,Networking,Hardware

Computer Networks This book constitutes the thoroughly refereed proceedings of the 27th International Conference on Computer Networks, CN 2020, held in June 2020. Due to the COVID-19 pandemic the conference was held virtually. The 14 full papers presented were carefully reviewed and selected from 34 submissions. They are organized according to the topical sections on computer networks; cybersecurity and quality of service; queueing theory and queueing networks. COMPUTERS,Networking,Hardware

IoT Development for ESP32 and ESP8266 with JavaScript This book introduces a new approach to embedded development, grounded in modern, industry-standard JavaScript. Using the same language that powers web browsers and Node.js, the Moddable SDK empowers IoT developers to apply many of the same tools and techniques used to build sophisticated websites and mobile apps.The Moddable SDK enables you to unlock the full potential of inexpensive microcontrollers like the ESP32 and ESP8266. Coding for these microcontrollers in C or C++ with the ESP-IDF and Arduino SDKs works for building basic products but doesn't scale to handle the increasingly complex IoT products that customers expect. The Moddable SDK adds the lightweight XS JavaScript engine to those traditional environments, accelerating development with JavaScript while keeping the performance benefits of a native SDK. Building user interfaces and communicating over the network are two areas where JavaScript really shines. IoT Development for ESP32 and ESP8266 with JavaScript shows you how to build responsive touch screen user interfaces using the Piu framework. You'll learn how easy it is to securely send and receive JSON data over Wi-Fi with elegant JavaScript APIs for common IoT protocols, including HTTP/HTTPS, WebSocket, MQTT, and mDNS. You'll also learn how to integrate common sensors and actuators, Bluetooth Low Energy (BLE), file systems, and more into your projects, and you'll see firsthand how JavaScript makes it easier to combine these diverse technologies.If you're an embedded C or C++ developer who has never worked in JavaScript, don't worry. This book includes an introduction to the JavaScript language just for embedded developers experienced with C or C++. What You'll Learn Building, installing, and debugging JavaScript projects on the ESP32 and ESP8266 Using modern JavaScript for all aspects of embedded development with the Moddable SDK Developing IoT products with animated user interfaces, touch input, networking, BLE, sensors, actuators, and more Who This Book Is For Professional embedded developers who want the speed, flexibility, and power of web development in their embedded software work Makers who want a faster, easier way to build their hobby projects Web developers working in JavaScript who want to extend their skills to hardware products COMPUTERS,Networking,Hardware

Industrial IoT Proliferation of Internet of Things (IoT) enabled rapid enhancements for the applications not only in home and environment scenarios, but also in factory automation. Now, Industrial Internet of Things (IIoT) offers all the advantages of IoT to the industrial scenarios, applications ranging from remote sensing and actuating to de-centralization and autonomy. In this book, the editor aims at presenting the IIoT and its place during the industrial revolution (Industry 4.0), while they are taking us to a better, sustainable, automated and safer world. The book covers the cross relations and implications of IIoT with existing wired/wireless communication/networking and safety technologies of the Industrial Networks. Moreover, practical use-case scenarios from the industry, for the application of IIoT on smart factories, smart cities and smart grid are presented. Especially, IoT-driven advances in commercial and industrial building lighting and in street lighting are presented as a specific example to shed light on the application domain of IIoT. The state of the art in Industrial Automation is also presented not only to give a better understanding of the enabling technologies, potential advantages and challenges of the Industry 4.0 and IIoT but also to foster interest on exploring this promising area. Finally yet importantly, the security section of the book covers the cyber-security related needs of the IIoT users and the services that might address these needs. First, user privacy, data ownership, proprietary information handling related to IIoT networks are investigated. Then, the intrusion prevention, detection and mitigation part conclude the book. COMPUTERS,Networking,Hardware

Architecture of Computing Systems – ARCS 2020 This book constitutes the proceedings of the 33rd International Conference on Architecture of Computing Systems, ARCS 2020, held in Aachen, Germany, in May 2020.* The 12 full papers in this volume were carefully reviewed and selected from 33 submissions. 6 workshop papers are also included. ARCS has always been a conference attracting leading-edge research outcomes in Computer Architecture and Operating Systems, including a wide spectrum of topics ranging from embedded and real-time systems all the way to large-scale and parallel systems. The selected papers focus on concepts and tools for incorporating self-adaptation and self-organization mechanisms in high-performance computing systems. This includes upcoming approaches for runtime modifications at various abstraction levels, ranging from hardware changes to goal changes and their impact on architectures, technologies, and languages. *The conference was canceled due to the COVID-19 pandemic. COMPUTERS,Networking,Hardware

Fractal Dimensions of Networks Current interest in fractal dimensions of networks is the result of more than a century of previous research on dimensions. Fractal Dimensions of Networks ties the theory and methods for computing fractal dimensions of networks to the “classic†theory of dimensions of geometric objects. The goal of the book is to provide a unified treatment of fractal dimensions of sets and networks. Since almost all of the major concepts in fractal dimensions originated in the study of sets, the book achieves this goal by first clearly presenting, with an abundance of examples and illustrations, the theory and algorithms for sets, and then showing how the theory and algorithms have been applied to networks. Thus, the book presents the classical theory and algorithms for the box counting dimension for sets, and then presents the box counting dimension for networks. All the major fractal dimensions are studied, e.g., the correlation dimension, the information dimension, the Hausdorff dimension, the multifractal spectrum, as well as many lesser known dimensions. Algorithm descriptions are accompanied by worked examples, many applications of the methods are presented, and many exercises, ranging in difficulty from easy to research level, are included. COMPUTERS,Networking,Hardware

E-Business and Telecommunications This book constitutes the refereed proceedings of the 16th International Joint Conference on E-Business and Telecommunications, ICETE 2019, held in Prague, Czech Republic, in July 2019. ICETE is a joint international conference integrating four major areas of knowledge that are divided into six corresponding conferences: International Conference on Data Communication Networking, DCNET; International Conference on E-Business, ICE-B; International Conference on Optical Communication Systems, OPTICS; International Conference on Security and Cryptography, SECRYPT; International Conference on Signal Processing and Multimedia, SIGMAP; International Conference on Wireless Information Systems, WINSYS. The 11 full papers presented in the volume were carefully reviewed and selected from the 166 submissions. The papers cover the following key areas of data communication networking, e-business, security and cryptography, signal processing and multimedia applications. COMPUTERS,Networking,Hardware

Blockchain With the development of big data, data sharing has become increasingly popular and important in optimizing resource allocation and improving information utilization. However, the expansion of data sharing means there is an urgent need to address the issue of the privacy protection – an area where the emerging blockchain technology offers considerable advantages. Although there are a large number of research papers on data sharing modeling and analysis of network security, there are few books dedicated to blockchain-based secure data sharing.Filing this gap in the literature, the book proposes a new data-sharing model based on the blockchain system, which is being increasingly used in medical and credit reporting contexts. It describes in detail various aspects of the model, including its role, transaction structure design, secure multi-party computing and homomorphic encryption services, and incentive mechanisms, and presents corresponding case studies. The book explains the security architecture model and the practice of building data sharing from the blockchain infrastructure, allowing readers to understand the importance of data sharing security based on the blockchain framework, as well as the threats to security and privacy. Further, by presenting specific data sharing case studies, it offers insights into solving data security sharing problems in more practical fields. The book is intended for readers with a basic understanding of the blockchain infrastructure, consensus mechanisms, smart contracts, secure multiparty computing, homomorphic encryption and image retrieval technologies. COMPUTERS,Networking,Hardware

The Internet of Things and Big Data Analytics This book comprehensively conveys the theoretical and practical aspects of IoT and big data analytics with the solid contributions from practitioners as well as academicians. This book examines and expounds the unique capabilities of the big data analytics platforms in capturing, cleansing and crunching IoT device/sensor data in order to extricate actionable insights. A number of experimental case studies and real-world scenarios are incorporated in this book in order to instigate our book readers. This book Analyzes current research and development in the domains of IoT and big data analytics Gives an overview of latest trends and transitions happening in the IoT data analytics space Illustrates the various platforms, processes, patterns, and practices for simplifying and streamlining IoT data analytics The Internet of Things and Big Data Analytics: Integrated Platforms and Industry Use Cases examines and accentuates how the multiple challenges at the cusp of IoT and big data can be fully met. The device ecosystem is growing steadily. It is forecast that there will be billions of connected devices in the years to come. When these IoT devices, resource-constrained as well as resource-intensive, interact with one another locally and remotely, the amount of multi-structured data generated, collected, and stored is bound to grow exponentially. Another prominent trend is the integration of IoT devices with cloud-based applications, services, infrastructures, middleware solutions, and databases. This book examines the pioneering technologies and tools emerging and evolving in order to collect, pre-process, store, process and analyze data heaps in order to disentangle actionable insights. COMPUTERS,Networking,Intranets & Extranets

802.11 Wireless Networks As we all know by now, wireless networks offer many advantages over fixed (or wired) networks. Foremost on that list is mobility, since going wireless frees you from the tether of an Ethernet cable at a desk. But that's just the tip of the cable-free iceberg. Wireless networks are also more flexible, faster and easier for you to use, and more affordable to deploy and maintain.The de facto standard for wireless networking is the 802.11 protocol, which includes Wi-Fi (the wireless standard known as 802.11b) and its faster cousin, 802.11g. With easy-to-install 802.11 network hardware available everywhere you turn, the choice seems simple, and many people dive into wireless computing with less thought and planning than they'd give to a wired network. But it's wise to be familiar with both the capabilities and risks associated with the 802.11 protocols. And 802.11 Wireless Networks: The Definitive Guide, 2nd Edition is the perfect place to start.This updated edition covers everything you'll ever need to know about wireless technology. Designed with the system administrator or serious home user in mind, it's a no-nonsense guide for setting up 802.11 on Windows and Linux. Among the wide range of topics covered are discussions on: deployment considerations network monitoring and performance tuning wireless security issues how to use and select access points network monitoring essentials wireless card configuration security issues unique to wireless networks With wireless technology, the advantages to its users are indeed plentiful. Companies no longer have to deal with the hassle and expense of wiring buildings, and households with several computers can avoid fights over who's online. And now, with 802.11 Wireless Networks: The Definitive Guide, 2nd Edition, you can integrate wireless technology into your current infrastructure with the utmost confidence. COMPUTERS,Networking,Local Area Networks (LANs)

Ethernet Switches If you’re ready to build a large network system, this handy excerpt from Ethernet: The Definitive Guide, Second Edition gets you up to speed on a basic building block: Ethernet switches. Whether you’re working on an enterprise or campus network, data center, or Internet service provider network, you’ll learn how Ethernet switches function and how they’re used in network designs. This brief tutorial also provides an overview of the most important features found in switches, from the basics to more advanced features found in higher-cost and specialized switches. Get an overview of basic switch operation, the spanning tree protocol, and switch performance issues Learn about switch management and some of the most widely used switch features Discover how a hierarchical design can help maintain stable network operations Delve into special-purpose switches, such as multi-layer, access, stacking, and wireless access-point switches Learn about advanced switch features designed for specific networking environments Dive deeper into switches, with a list of protocol and package documentation COMPUTERS,Networking,Local Area Networks (LANs)

Ethernet Get up to speed on the latest Ethernet capabilities for building and maintaining networks for everything from homes and offices to data centers and server machine rooms. This thoroughly revised, comprehensive guide covers a wide range of Ethernet technologies, from basic operation to network management, based on the authors’ many years of field experience. When should you upgrade to higher speed Ethernet? How do you use switches to build larger networks? How do you troubleshoot the system? This book provides the answers. If you’re looking to build a scalable network with Ethernet to satisfy greater bandwidth and market requirements, this book is indeed the definitive guide. Examine the most widely used media systems, as well as advanced 40 and 100 gigabit Ethernet Learn about Ethernet’s four basic elements and the IEEE standards Explore full-duplex Ethernet, Power over Ethernet, and Energy Efficient Ethernet Understand structured cabling systems and the components you need to build your Ethernet system Use Ethernet switches to expand and improve network design Delve into Ethernet performance, from specific channels to the entire network Get troubleshooting techniques for problems common to twisted-pair and fiber optic systems COMPUTERS,Networking,Local Area Networks (LANs)

Alcatel-Lucent Scalable IP Networks Self-Study Guide By offering the new Service Routing Certification Program, Alcatel-Lucent is extending their reach and knowledge to networking professionals with a comprehensive demonstration of how to build smart, scalable networks. Serving as a course in a book from Alcatel-Lucent—the world leader in designing and developing scalable systems—this resource pinpoints the pitfalls to avoid when building scalable networks, examines the most successful techniques available for engineers who are building and operating IP networks, and provides overviews of the Internet, IP routing and the IP layer, and the practice of opening the shortest path first. COMPUTERS,Networking,Network Protocols

TCP/IP Network Administration This complete guide to setting up and running a TCP/IP network is essential for network administrators, and invaluable for users of home systems that access the Internet. The book starts with the fundamentals -- what protocols do and how they work, how addresses and routing are used to move data through the network, how to set up your network connection -- and then covers, in detail, everything you need to know to exchange information via the Internet.Included are discussions on advanced routing protocols (RIPv2, OSPF, and BGP) and the gated software package that implements them, a tutorial on configuring important network services -- including DNS, Apache, sendmail, Samba, PPP, and DHCP -- as well as expanded chapters on troubleshooting and security. TCP/IP Network Administration is also a command and syntax reference for important packages such as gated, pppd, named, dhcpd, and sendmail.With coverage that includes Linux, Solaris, BSD, and System V TCP/IP implementations, the third edition contains: Overview of TCP/IP Delivering the data Network services Getting startedM Basic configuration Configuring the interface Configuring routing Configuring DNS Configuring network servers Configuring sendmail Configuring Apache Network security Troubleshooting Appendices include dip, ppd, and chat reference, a gated reference, a dhcpd reference, and a sendmail reference This new edition includes ways of configuring Samba to provide file and print sharing on networks that integrate Unix and Windows, and a new chapter is dedicated to the important task of configuring the Apache web server. Coverage of network security now includes details on OpenSSH, stunnel, gpg, iptables, and the access control mechanism in xinetd. Plus, the book offers updated information about DNS, including details on BIND 8 and BIND 9, the role of classless IP addressing and network prefixes, and the changing role of registrars.Without a doubt, TCP/IP Network Administration, 3rd Edition is a must-have for all network administrators and anyone who deals with a network that transmits data over the Internet. COMPUTERS,Networking,Network Protocols

BGP Border Gateway Protocol (BGP) is the routing protocol used to exchange routing information across the Internet. It makes it possible for ISPs to connect to each other and for end-users to connect to more than one ISP. BGP is the only protocol that is designed to deal with a network of the Internet's size, and the only protocol that can deal well with having multiple connections to unrelated routing domains.This book is a guide to all aspects of BGP: the protocol, its configuration and operation in an Internet environment, and how to troubleshooting it. The book also describes how to secure BGP, and how BGP can be used as a tool in combating Distributed Denial of Service (DDoS) attacks. Although the examples throughout this book are for Cisco routers, the techniques discussed can be applied to any BGP-capable router.The topics include: Requesting an AS number and IP addresses Route filtering by remote ISPs and how to avoid this Configuring the initial BGP setup Balancing the available incoming or outgoing traffic over the available connections Securing and troubleshooting BGP BGP in larger networks: interaction with internal routing protocols, scalability issues BGP in Internet Service Provider networks The book is filled with numerous configuration examples with more complex case studies at the end of the book to strengthen your understanding. BGP is for anyone interested in creating reliable connectivity to the Internet. COMPUTERS,Networking,Network Protocols

DNS and BIND on IPv6 If you're preparing to roll out IPv6 on your network, this concise book provides the essentials you need to support this protocol with DNS. You'll learn how DNS was extended to accommodate IPv6 addresses, and how you can configure a BIND name server to run on the network. This book also features methods for troubleshooting problems with IPv6 forward- and reverse-mapping, and techniques for helping islands of IPv6 clients communicate with IPv4 resources. Topics include: DNS and IPv6—Learn the structure and representation of IPv6 addresses, and the syntaxes of AAAA and PTR records in the ip6.arpa IPv6 reverse-mapping zone BIND on IPv6—Use IPv6 addresses and networks in ACLs, and register and delegate to IPv6-speaking name servers Resolver Configuration—Configure popular stub resolvers (Linux/Unix, MacOS X, and Windows) to query IPv6-speaking name servers DNS64—Learn about the transition technology that allows clients with IPv6-only network stacks to communicate with IPv4 servers Troubleshooting—Use the nslookup and dig troubleshooting tools to look up the IPv6 addresses of a domain name, or reverse-map an IPv6 address to a domain name COMPUTERS,Networking,Network Protocols

Patterns in Network Architecture Groundbreaking Patterns for Building Simpler, More Powerful Networks In Patterns in Network Architecture, pioneer John Day takes a unique approach to solving the problem of network architecture. Piercing the fog of history, he bridges the gap between our experience from the original ARPANET and today’s Internet to a new perspective on networking. Along the way, he shows how socioeconomic forces derailed progress and led to the current crisis. Beginning with the seven fundamental, and still unanswered, questions identified during the ARPANET’s development, Patterns in Network Architecture returns to bedrock and traces our experience both good and bad. Along the way, he uncovers overlooked patterns in protocols that simplify design and implementation and resolves the classic conflict between connection and connectionless while retaining the best of both. He finds deep new insights into the core challenges of naming and addressing, along with results from upper-layer architecture. All of this in Day’s deft hands comes together in a tour de force of elegance and simplicity with the annoying turn of events that the answer has been staring us in the face: Operating systems tell us even more about networking than we thought. The result is, in essence, the first “unified theory of networking,†and leads to a simpler, more powerful—and above all—more scalable network infrastructure. The book then lays the groundwork for how to exploit the result in the design, development, and management as we move beyond the limitations of the Internet. Using this new model, Day shows how many complex mechanisms in the Internet today (multihoming, mobility, and multicast) are, with this collapse in complexity, now simply a consequence of the structure. The problems of router table growth of such concern today disappear. The inescapable conclusion is that the Internet is an unfinished demo, more in the tradition of DOS than Unix, that has been living on Moore’s Law and 30 years of band-aids. It is long past time to get networking back on track. • Patterns in network protocols that synthesize “contradictory†approaches and simplify design and implementation • “Deriving†that networking is interprocess communication (IPC) yielding • A distributed IPC model that repeats with different scope and range of operation • Making network addresses topological makes routing purely a local matter • That in fact, private addresses are the norm—not the exception—with the consequence that the global public addresses required today are unnecessary • That mobility is dynamic multihoming and unicast is a subset of multicast, but multicast devolves into unicast and facilitates mobility • That the Internet today is more like DOS, but what we need should be more like Unix • For networking researchers, architects, designers, engineers Provocative, elegant, and profound, Patterns in Network Architecture transforms the way you envision, architect, and implement networks. Preface: The Seven Unanswered Questions xiii Chapter 1: Foundations for Network Architecture 1 Chapter 2: Protocol Elements 23 Chapter 3: Patterns in Protocols 57 Chapter 4: Stalking the Upper-Layer Architecture 97 Chapter 5: Naming and Addressing 141 Chapter 6: Divining Layers 185 Chapter 7: The Network IPC Model 235 Chapter 8: Making Addresses Topological 283 Chapter 9: Multihoming, Multicast, and Mobility 317 Chapter 10: Backing Out of a Blind Alley 351 Appendix A: Outline for Gedanken Experiment on Separating Mechanism and Policy 385 Bibliography 389 Index 399 COMPUTERS,Networking,Network Protocols

TCP/IP Illustrated, Volume 2 TCP/IP Illustrated, an ongoing series covering the many facets of TCP/IP, brings a highly-effective visual approach to learning about this networking protocol suite. TCP/IP Illustrated, Volume 2 contains a thorough explanation of how TCP/IP protocols are implemented. There isn't a more practical or up-to-date bookothis volume is the only one to cover the de facto standard implementation from the 4.4BSD-Lite release, the foundation for TCP/IP implementations run daily on hundreds of thousands of systems worldwide. Combining 500 illustrations with 15,000 lines of real, working code, TCP/IP Illustrated, Volume 2 uses a teach-by-example approach to help you master TCP/IP implementation. You will learn about such topics as the relationship between the sockets API and the protocol suite, and the differences between a host implementation and a router. In addition, the book covers the newest features of the 4.4BSD-Lite release, including multicasting, long fat pipe support, window scale, timestamp options, and protection against wrapped sequence numbers, and many other topics. Comprehensive in scope, based on a working standard, and thoroughly illustrated, this book is an indispensable resource for anyone working with TCP/IP. COMPUTERS,Networking,Network Protocols

Packet Guide to Core Network Protocols Take an in-depth tour of core Internet protocols and learn how they work together to move data packets from one network to another. With this updated edition, you’ll dive into the aspects of each protocol, including operation basics and security risks, and learn the function of network hardware such as switches and routers. New chapters examine the transmission control protocol (TCP) and user datagram protocol in detail. Ideal for beginning network engineers, each chapter in this book includes a set of review questions, as well as practical, hands-on lab exercises. You’ll explore topics including: Basic network architecture: how protocols and functions fit together The structure and operation of the Ethernet protocol TCP/IP protocol fields, operations, and addressing used for networks The address resolution process in a typical IPv4 network Switches, access points, routers, and components that process packets TCP details, including packet content and client-server packet flow How the Internet Control Message Protocol provides error messages during network operations How network mask (subnetting) helps determine the network The operation, structure, and common uses of the user datagram protocol COMPUTERS,Networking,Network Protocols

Alcatel-Lucent Network Routing Specialist II (NRS II) Self-Study Guide The definitive resource for the NRS II exams—three complete courses in a book Alcatel-Lucent is a world leader in designing and developing scalable systems for service providers. If you are a network designer or operator who uses Alcatel-Lucent's 7750 family of service routers, prepare for certification as an A-L network routing specialist with this complete self-study course. You'll get thorough preparation for the NRS II exams while you learn to build state-of-the-art, scalable IP/MPLS-based service networks. The book provides you with an in-depth understanding of the protocols and technologies involved in building an IP/MPLS network while teaching you how to avoid pitfalls and employ the most successful techniques available. Topics covered include interior routing protocols, multiprotocol label switching (MPLS), Layer2/Layer3 services and IPv6. The included CD features practice exam questions, sample lab exercises, and more. Prepares network professionals for Alcatel-Lucent Service Routing Certification (SRC) exams 4A0-101, 4A0-103, 4A0-104 and NRSII4A0 Covers content from Alcatel-Lucent's SRC courses on Interior Routing Protocols, Multiprotocol Label Switching, and Services Architecture Specific topics include MPLS (RSVP-TE and LDP), services architecture, Layer2/Layer 3 services (VPWS/VPLS/VPRN/IES/service inter-working/IPv6 tunneling), and OSPF and IS-IS for traffic engineering and IPv6. CD includes practice exam questions, lab exercises and solutions. This Self-Study Guide is the authoritative resource for network professionals preparing for the Alcatel-Lucent NRS II certification exams. COMPUTERS,Networking,Network Protocols

Advanced QoS for Multi-Service IP/MPLS Networks Advanced QoS for Multi-Service IP/MPLS Networks is the definitive guide to Quality of Service (QoS), with comprehensive information about its features and benefits. Find a solid theoretical and practical overview of how QoS can be implemented to reach the business objectives defined for an IP/MPLS network. Topics include standard QoS models for IP/MPLS networks, essential QoS features, forwarding classes and queuing priorities, buffer management, multipoint shared queuing, hierarchical scheduling, and rate limiting. This book will enable you to create a solid QoS architecture/design, which is mandatory for prioritizing services throughout the network. COMPUTERS,Networking,Network Protocols

TCP/IP Illustrated, Volume 1 “For an engineer determined to refine and secure Internet operation or to explore alternative solutions to persistent problems, the insights provided by this book will be invaluable.†—Vint Cerf, Internet pioneer TCP/IP Illustrated, Volume 1, Second Edition, is a detailed and visual guide to today’s TCP/IP protocol suite. Fully updated for the newest innovations, it demonstrates each protocol in action through realistic examples from modern Linux, Windows, and Mac OS environments. There’s no better way to discover why TCP/IP works as it does, how it reacts to common conditions, and how to apply it in your own applications and networks. Building on the late W. Richard Stevens’ classic first edition, author Kevin R. Fall adds his cutting-edge experience as a leader in TCP/IP protocol research, updating the book to fully reflect the latest protocols and best practices. He first introduces TCP/IP’s core goals and architectural concepts, showing how they can robustly connect diverse networks and support multiple services running concurrently. Next, he carefully explains Internet addressing in both IPv4 and IPv6 networks. Then, he walks through TCP/IP’s structure and function from the bottom up: from link layer protocols–such as Ethernet and Wi-Fi–through network, transport, and application layers. Fall thoroughly introduces ARP, DHCP, NAT, firewalls, ICMPv4/ICMPv6, broadcasting, multicasting, UDP, DNS, and much more. He offers extensive coverage of reliable transport and TCP, including connection management, timeout, retransmission, interactive data flow, and congestion control. Finally, he introduces the basics of security and cryptography, and illuminates the crucial modern protocols for protecting security and privacy, including EAP, IPsec, TLS, DNSSEC, and DKIM. Whatever your TCP/IP experience, this book will help you gain a deeper, more intuitive understanding of the entire protocol suite so you can build better applications and run more reliable, efficient networks. COMPUTERS,Networking,Network Protocols

NFS Illustrated The Network File System (NFS) protocol that enables remote access to files is now a key element of any LAN. It is also currently and increasingly used as a key technology with the Web and wide area networks. Written for programmers creating NFS-based applications, network engineers creating new implementations of NFS, and network managers, NFS Illustrated promotes a thorough understanding of that protocol through extensive diagrams and real protocol traces that show NFS in action. Covering NFS versions 2 and 3, the book also looks into WebNFS and the new NFS version 4, with Internet support. Detailed and authoritative, the book not only examines NFS in depth, but also describes the protocols that underlie and support it, including External Data Representation (XDR), Remote Procedure Call (RPC), the NFS MOUNT protocol, and the NFS Lock Manager protocol. It discusses several NFS variants and compares NFS to a number of alternative file systems. You will find a detailed discussion on the NFS filesystem model and a procedure-by-procedure description of NFS versions 2 and 3, illustrated through the use of snoop traces that capture and display protocol packets from the network. In addition, the book addresses real-world implementation issues faced by those building an NFS client or server, factors that affect NFS performance, and critical performance benchmarks. Specific topics of interest include: NFS version 4, highlighting performance improvements, security features, and cross-platform interoperability for Internet operation RPC authentication and security Differences between NFS versions 2 and 3 Implementation issues for clients and servers Read-ahead and write-behind Caching policies The Lock Manager protocol Automounting NFS variants, including Spritely NFS, NQNFS, Trusted NFS, and NASD NFS NFS competitors: RFS, AFS, DCE/DFS, and CIFS The PCNFS protocol for implementing NFS on PC operating systems SPEC SFS benchmarks, WebNFS, and firewalls Comprehensive and current, NFS Illustrated is an essential resource for network professionals who want to use this widespread and evolving technology to its fullest. COMPUTERS,Networking,Network Protocols

Versatile Routing and Services with BGP Design a robust BGP control plane within a secure, scalable network for smoother services A robust Border Gateway Protocol setup is vital to ensuring reliable connectivity, an essential capability for any organization. The Internet has become a necessary, always-on service in homes and businesses, and BGP is the protocol that keeps communication flowing. But BGP also has become crucial to delivery of intra-domain business services. But the network is only as reliable as BGP, so service enablement depends upon making BGP more stable, reliable, and service-rich. Alcatel-Lucent Service Router Operating System is engineered to bear the load of the most demanding networks. The system features support for Symmetric Multiprocessing and unprecedented depth of advanced routing features, all within a single OS that's supported across the entire Alcatel-Lucent IP/MPLS router portfolio. Versatile Routing and Services with BGP provides guidance toward implementation of BGP within SR-OS, and details the use and control of each feature. The book provides in-depth coverage of topics such as: BGP/MPLS IP-VPN, VPLS, VPWS Labeled Unicast IPv4, reconvergence, and multicast Security, graceful restart and error handling IPv6 PE (6PE) and IPv6 extensions to BGP/MPLS IP-VPN A look at forthcoming features such as Ethernet VPN Basic BGP competency is assumed, but the book is accessible even to those with zero familiarity with Alcatel-Lucent's SR-OS. It underscores the idea that BGP is more than just service enablement, and can also be used for infrastructure layer transport - but both layers must be solid, scalable, and able to quickly reconverge. Versatile Routing and Services with BGP demonstrates the creation of a robust BGP control plane within a, secure network, allowing the delivery of flawless, uninterrupted service. COMPUTERS,Networking,Network Protocols

IPv6 Essentials If your organization is gearing up for IPv6, this in-depth book provides the practical information and guidance you need to plan for, design, and implement this vastly improved protocol. Author Silvia Hagen takes system and network administrators, engineers, and network designers through the technical details of IPv6 features and functions, and provides options for those who need to integrate IPv6 with their current IPv4 infrastructure. The flood of Internet-enabled devices has made migrating to IPv6 a paramount concern worldwide. In this updated edition, Hagen distills more than ten years of studying, working with, and consulting with enterprises on IPv6. It’s the only book of its kind. IPv6 Essentials covers: Address architecture, header structure, and the ICMPv6 message format IPv6 mechanisms such as Neighbor Discovery, Stateless Address autoconfiguration, and Duplicate Address detection Network-related aspects and services: Layer 2 support, Upper Layer Protocols, and Checksums IPv6 security: general practices, IPSec basics, IPv6 security elements, and enterprise security models Transitioning to IPv6: dual-stack operation, tunneling, and translation techniques Mobile IPv6: technology for a new generation of mobile services Planning options, integration scenarios, address plan, best practices, and dos and don’ts COMPUTERS,Networking,Network Protocols

MQTT Essentials - A Lightweight IoT Protocol Send and receive messages with the MQTT protocol for your IoT solutions. About This Book Make your connected devices less prone to attackers by understanding practical security mechanisms Dive deep into one of IoT's extremely lightweight machines to enable connectivity protocol with some real-world examples Learn to take advantage of the features included in MQTT for IoT and Machine-to-Machine communications with complete real-life examples Who This Book Is For This book is a great resource for developers who want to learn more about the MQTT protocol to apply it to their individual IoT projects. Prior knowledge of working with IoT devices is essential. What You Will Learn Understand how MQTTv3.1 and v3.1.1 works in detail Install and secure a Mosquitto MQTT broker by following best practices Design and develop IoT solutions combined with mobile and web apps that use MQTT messages to communicate Explore the features included in MQTT for IoT and Machine-to-Machine communications Publish and receive MQTT messages with Python, Java, Swift, JavaScript, and Node.js Implement the security best practices while setting up the MQTT Mosquitto broker In Detail This step-by-step guide will help you gain a deep understanding of the lightweight MQTT protocol. We'll begin with the specific vocabulary of MQTT and its working modes, followed by installing a Mosquitto MQTT broker. Then, you will use best practices to secure the MQTT Mosquitto broker to ensure that only authorized clients are able to publish and receive messages. Once you have secured the broker with the appropriate configuration, you will develop a solution that controls a drone with Python. Further on, you will use Python on a Raspberry Pi 3 board to process commands and Python on Intel Boards (Joule, Edison and Galileo). You will then connect to the MQTT broker, subscribe to topics, send messages, and receive messages in Python. You will also develop a solution that interacts with sensors in Java by working with MQTT messages. Moving forward, you will work with an asynchronous API with callbacks to make the sensors interact with MQTT messages. Following the same process, you will develop an iOS app with Swift 3, build a website that uses WebSockets to connect to the MQTT broker, and control home automation devices with HTML5, JavaScript code, Node.js and MQTT messages Style and approach This step-by-step guide describes the MQTT protocol for your IoT projects COMPUTERS,Networking,Network Protocols

Learning HTTP/2 What can your organization gain by adopting HTTP/2? How about faster, simpler, and more robust websites and applications? This practical guide demonstrates how the latest version of the Hypertext Transfer Protocol can dramatically improve website and application performance. You’ll take a deep dive into HTTP/2 details, and learn how this updated protocol is changing the web landscape. HTTP/1.1 has been the primary means of communicating data across the web for the past 20 years, but the level of interaction today has gone well beyond what people envisioned in 1997. With this book, authors Stephen Ludin and Javier Garza show you how HTTP/2 will help speed the execution of modern sites and applications. With this book, you’ll explore: Performance challenges that led to the HTTP upgrade HTTP/2 in a nutshell, including benefits and transition methods Existing best practices and hacks to improve web performance HTTP/2 support for browsers, servers, proxies, and content delivery networks How the performance of sites using HTTP/2 compares to their HTTP/1.1 experience HTTP/2’s effect on specific issues such as latency, packet loss, and Time to First Byte (TTFB) HTTP/2’s effect on specific issues such as latency, packet loss, and Time to First Byte (TTFB) COMPUTERS,Networking,Network Protocols

TCP/IP in 24 Hours, Sams Teach Yourself Sams Teach Yourself TCP/IP in 24 Hours, Sixth Edition is a practical guide to the simple yet illusive protocol system that powers the Internet. A step-by-step approach reveals how the protocols of the TCP/IP stack really work and explores the rich array of services available on the Internet today. You’ll learn about configuring and managing real-world networks, and you’ll gain the deep understanding you’ll need to troubleshoot new problems when they arise. Sams Teach Yourself TCP/IP in 24 Hours is the only single-volume introduction to TCP/IP that receives regular updates to incorporate new technologies of the ever-changing Internet. This latest edition includes up-to-date material on recent topics such as tracking and privacy, cloud computing, mobile networks, and the Internet of Things. Each chapter also comes with: Practical, hands-on examples, showing you how to apply what you learnQuizzes and exercises that test your knowledge and stretch your skillsNotes and tips with shortcuts, solutions, and workarounds If you're looking for a smart, concise introduction to the TCP/IP protocols,start your clock and look inside. Learn how to... Understand TCP/IP’s role, how it works, and how it continues to evolve Work with TCP/IP’s Network Access, Internet, Transport, and Application layers Design modern networks that will scale and resist attack Address security and privacy issues with encryption, digital signatures, VPNs, Kerberos, web tracking, cookies, anonymity networks, and firewalls Discover how IPv6 differs from IPv4, and how to migrate or coexist with IPv6 Configure dynamic addressing, DHCP, NAT, and Zeroconf Establish efficient and reliable routing, subnetting, and name resolution Use TCP/IP in modern cloud-based environments Integrate IoT devices into your TCP/IP network Improve your efficiency with the latest TCP/IP tools and utilities Support high-performance media streaming and webcasting Troubleshoot problems with connectivity, protocols, name resolution, and performance Walk through TCP/IP network implementation, from start to finish COMPUTERS,Networking,Network Protocols

Learning CoreDNS Until recently, learning CoreDNS required reading the code or combing through the skimpy documentation on the website. No longer. With this practical book, developers and operators working with Docker or Linux containers will learn how to use this standard DNS server with Kubernetes. John Belamaric, senior staff software engineer at Google, and Cricket Liu, chief DNS architect at Infoblox, show you how to configure CoreDNS using real-world configuration examples to achieve specific purposes. You’ll learn the basics of DNS, including how it functions as a location broker in container environments and how it ties into Kubernetes. Dive into DNS theory: the DNS namespace, domain names, domains, and zones Learn how to configure your CoreDNS server Manage and serve basic and advanced zone data with CoreDNS Configure CoreDNS service discovery with etcd and Kubernetes Learn one of the most common use cases for CoreDNS: the integration with Kubernetes Manipulate queries and responses as they flow through the plug-in chain Monitor and troubleshoot the availability and performance of your DNS service Build custom versions of CoreDNS and write your own plug-ins COMPUTERS,Networking,Network Protocols

Networking Fundamentals Become well-versed with basic networking concepts such as routing, switching, and subnetting, and prepare for the Microsoft 98-366 exam Key Features Build a strong foundation in networking concepts Explore both the hardware and software aspects of networking Prepare by taking mock tests with up-to-date exam questions Book Description A network is a collection of computers, servers, mobile devices, or other computing devices connected for sharing data. This book will help you become well versed in basic networking concepts and prepare to pass Microsoft's MTA Networking Fundamentals Exam 98-366. Following Microsoft's official syllabus, the book starts by covering network infrastructures to help you differentiate intranets, internets, and extranets, and learn about network topologies. You'll then get up to date with common network hardware devices such as routers and switches and the media types used to connect them together. As you advance, the book will take you through different protocols and services and the requirements to follow a standardized approach to networking. You'll get to grips with the OSI and TCP/IP models as well as IPv4 and IPv6. The book also shows you how to recall IP addresses through name resolution. Finally, you'll be able to practice everything you've learned and take the exam confidently with the help of mock tests. By the end of this networking book, you'll have developed a strong foundation in the essential networking concepts needed to pass Exam 98-366. What you will learn Things you will learn: Become well versed in networking topologies and concepts Understand network infrastructures such as intranets, extranets, and more Explore network switches, routers, and other network hardware devices Get to grips with different network protocols and models such as OSI and TCP/IP Work with a variety of network services such as DHCP, NAT, firewalls, and remote access Apply networking concepts in different real-world scenarios Who this book is for If you're new to the IT industry or simply want to gain a thorough understanding of networking, this book is for you. A basic understanding of the Windows operating system and your network environment will be helpful. COMPUTERS,Networking,Network Protocols

Art of Computer Virus Research and Defense, The, Portable Documents Symantec's chief antivirus researcher has written the definitive guide to contemporary virus threats, defense techniques, and analysis tools. Unlike most books on computer viruses, The Art of Computer Virus Research and Defense is a reference written strictly for white hats: IT and security professionals responsible for protecting their organizations against malware. Peter Szor systematically covers everything you need to know, including virus behavior and classification, protection strategies, antivirus and worm-blocking techniques, and much more. Szor presents the state-of-the-art in both malware and protection, providing the full technical detail that professionals need to handle increasingly complex attacks. Along the way, he provides extensive information on code metamorphism and other emerging techniques, so you can anticipate and prepare for future threats. Szor also offers the most thorough and practical primer on virus analysis ever published—addressing everything from creating your own personal laboratory to automating the analysis process. This book's coverage includes Discovering how malicious code attacks on a variety of platforms Classifying malware strategies for infection, in-memory operation, self-protection, payload delivery, exploitation, and more Identifying and responding to code obfuscation threats: encrypted, polymorphic, and metamorphic Mastering empirical methods for analyzing malicious code—and what to do with what you learn Reverse-engineering malicious code with disassemblers, debuggers, emulators, and virtual machines Implementing technical defenses: scanning, code emulation, disinfection, inoculation, integrity checking, sandboxing, honeypots, behavior blocking, and much more Using worm blocking, host-based intrusion prevention, and network-level defense strategies COMPUTERS,Networking,Vendor Specific

Security Metrics This is the eBook version of the printed book. If the print book includes a CD-ROM, this content is not included within the eBook version. <> The Definitive Guide to Quantifying, Classifying, and Measuring Enterprise IT Security Operations Security Metrics is the first comprehensive best-practice guide to defining, creating, and utilizing security metrics in the enterprise. Using sample charts, graphics, case studies, and war stories, Yankee Group Security Expert Andrew Jaquith demonstrates exactly how to establish effective metrics based on your organization’s unique requirements. You’ll discover how to quantify hard-to-measure security activities, compile and analyze all relevant data, identify strengths and weaknesses, set cost-effective priorities for improvement, and craft compelling messages for senior management. Security Metrics successfully bridges management’s quantitative viewpoint with the nuts-and-bolts approach typically taken by security professionals. It brings together expert solutions drawn from Jaquith’s extensive consulting work in the software, aerospace, and financial services industries, including new metrics presented nowhere else. You’ll learn how to: • Replace nonstop crisis response with a systematic approach to security improvement • Understand the differences between “good†and “bad†metrics • Measure coverage and control, vulnerability management, password quality, patch latency, benchmark scoring, and business-adjusted risk • Quantify the effectiveness of security acquisition, implementation, and other program activities • Organize, aggregate, and analyze your data to bring out key insights • Use visualization to understand and communicate security issues more clearly • Capture valuable data from firewalls and antivirus logs, third-party auditor reports, and other resources • Implement balanced scorecards that present compact, holistic views of organizational security effectiveness Whether you’re an engineer or consultant responsible for security and reporting to management–or an executive who needs better information for decision-making–Security Metrics is the resource you have been searching for. Andrew Jaquith, program manager for Yankee Group’s Security Solutions and Services Decision Service, advises enterprise clients on prioritizing and managing security resources. He also helps security vendors develop product, service, and go-to-market strategies for reaching enterprise customers. He co-founded @stake, Inc., a security consulting pioneer acquired by Symantec Corporation in 2004. His application security and metrics research has been featured in CIO, CSO, InformationWeek, IEEE Security and Privacy, and The Economist. Foreword Preface Acknowledgments About the Author Chapter 1 Introduction: Escaping the Hamster Wheel of Pain Chapter 2 Defining Security Metrics Chapter 3 Diagnosing Problems and Measuring Technical Security Chapter 4 Measuring Program Effectiveness Chapter 5 Analysis Techniques Chapter 6 Visualization Chapter 7 Automating Metrics Calculations Chapter 8 Designing Security Scorecards Index COMPUTERS,Networking,Vendor Specific

Counter Hack Reloaded For years, Counter Hack has been the primary resource for every network/system administrator and security professional who needs a deep, hands-on understanding of hacker attacks and countermeasures. Now, leading network security expert Ed Skoudis, with Tom Liston, has thoroughly updated this best-selling guide, showing how to defeat today’s newest, most sophisticated, and most destructive attacks. For this second edition, more than half the content is new and updated, including coverage of the latest hacker techniques for scanning networks, gaining and maintaining access, and preventing detection. The authors walk you through each attack and demystify every tool and tactic. You’ll learn exactly how to establish effective defenses, recognize attacks in progress, and respond quickly and effectively in both UNIX/Linux and Windows environments. Important features of this new edition include All-new “anatomy-of-an-attack†scenarios and tools An all-new section on wireless hacking: war driving, wireless sniffing attacks, and more Fully updated coverage of reconnaissance tools, including Nmap port scanning and “Google hacking†New coverage of tools for gaining access, including uncovering Windows and Linux vulnerabilities with Metasploit New information on dangerous, hard-to-detect, kernel-mode rootkits COMPUTERS,Networking,Vendor Specific

Is It Safe? Protecting Your Computer, Your Business, and Yourself Online Is It Safe? PROTECTING YOUR COMPUTER, YOUR BUSINESS, AND YOURSELF ONLINE IDENTITY THEFT. DATA THEFT. INTERNET FRAUD. ONLINE SURVEILLANCE. EMAIL SCAMS. Hacks, attacks, and viruses. The Internet is a dangerous place. In years past, you could protect your computer from malicious activity by installing an antivirus program and activating a firewall utility. Unfortunately, that’s no longer good enough; the Internet has become a much darker place, plagued not only by rogue software but also by dangerous criminals and shadowy government agencies. Is It Safe? addresses the new generation of security threat. It presents information about each type of threat and then discusses ways to minimize and recover from those threats. Is It Safe? differs from other security books by focusing more on the social aspects of online security than purely the technical aspects. Yes, this book still covers topics such as antivirus programs and spam blockers, but it recognizes that today’s online security issues are more behavioral in nature–phishing schemes, email scams, and the like. Are you being scammed? Learn how to spot the newest and most insidious computer security threats–fraudulent retailers, eBay scammers, online con artists, and the like. Is your identity safe? Avoid being one of the nine million Americans each year who have their identities stolen. Today’s real Internet threats aren’t viruses and spam. Today’s real threat are thieves who steal your identity, rack up thousands on your credit card, open businesses under your name, commit crimes, and forever damage your reputation! Is Big Brother watching? Get the scoop on online tracking and surveillance. We examine just who might be tracking your online activities and why. Is your employer watching you? How to tell when you’re being monitored; and how to determine what is acceptable and what isn’t. Michael Miller has written more than 80 nonfiction books over the past two decades. His best-selling books include Que’s YouTube 4 You, Googlepedia: The Ultimate Google Resource, iPodpedia: The Ultimate iPod and iTunes Resource, and Absolute Beginner’s Guide to Computer Basics. He has established a reputation for clearly explaining technical topics to nontechnical readers and for offering useful real-world advice about complicated topics. COMPUTERS,Networking,Vendor Specific

Tao of Network Security Monitoring, The "The book you are about to read will arm you with the knowledge you need to defend your network from attackers—both the obvious and the not so obvious.... If you are new to network security, don't put this book back on the shelf! This is a great book for beginners and I wish I had access to it many years ago. If you've learned the basics of TCP/IP protocols and run an open source or commercial IDS, you may be asking 'What's next?' If so, this book is for you." —Ron Gula, founder and CTO, Tenable Network Security, from the Foreword "Richard Bejtlich has a good perspective on Internet security—one that is orderly and practical at the same time. He keeps readers grounded and addresses the fundamentals in an accessible way." —Marcus Ranum, TruSecure "This book is not about security or network monitoring: It's about both, and in reality these are two aspects of the same problem. You can easily find people who are security experts or network monitors, but this book explains how to master both topics." —Luca Deri, ntop.org "This book will enable security professionals of all skill sets to improve their understanding of what it takes to set up, maintain, and utilize a successful network intrusion detection strategy." —Kirby Kuehl, Cisco Systems Every network can be compromised. There are too many systems, offering too many services, running too many flawed applications. No amount of careful coding, patch management, or access control can keep out every attacker. If prevention eventually fails, how do you prepare for the intrusions that will eventually happen? Network security monitoring (NSM) equips security staff to deal with the inevitable consequences of too few resources and too many responsibilities. NSM collects the data needed to generate better assessment, detection, and response processes—resulting in decreased impact from unauthorized activities. In The Tao of Network Security Monitoring , Richard Bejtlich explores the products, people, and processes that implement the NSM model. By focusing on case studies and the application of open source tools, he helps you gain hands-on knowledge of how to better defend networks and how to mitigate damage from security incidents. Inside, you will find in-depth information on the following areas. The NSM operational framework and deployment considerations. How to use a variety of open-source tools—including Sguil, Argus, and Ethereal—to mine network traffic for full content, session, statistical, and alert data. Best practices for conducting emergency NSM in an incident response scenario, evaluating monitoring vendors, and deploying an NSM architecture. Developing and applying knowledge of weapons, tactics, telecommunications, system administration, scripting, and programming for NSM. The best tools for generating arbitrary packets, exploiting flaws, manipulating traffic, and conducting reconnaissance. Whether you are new to network intrusion detection and incident response, or a computer-security veteran, this book will enable you to quickly develop and apply the skills needed to detect, prevent, and respond to new and emerging threats. COMPUTERS,Networking,Vendor Specific

Art of Software Security Assessment, The “There are a number of secure programming books on the market, but none that go as deep as this one. The depth and detail exceeds all books that I know about by an order of magnitude.†—Halvar Flake, CEO and head of research, SABRE Security GmbH The Definitive Insider’s Guide to Auditing Software Security This is one of the most detailed, sophisticated, and useful guides to software security auditing ever written. The authors are leading security consultants and researchers who have personally uncovered vulnerabilities in applications ranging from sendmail to Microsoft Exchange, Check Point VPN to Internet Explorer. Drawing on their extraordinary experience, they introduce a start-to-finish methodology for “ripping apart†applications to reveal even the most subtle and well-hidden security flaws. The Art of Software Security Assessment covers the full spectrum of software vulnerabilities in both UNIX/Linux and Windows environments. It demonstrates how to audit security in applications of all sizes and functions, including network and Web software. Moreover, it teaches using extensive examples of real code drawn from past flaws in many of the industry's highest-profile applications. Coverage includes • Code auditing: theory, practice, proven methodologies, and secrets of the trade • Bridging the gap between secure software design and post-implementation review • Performing architectural assessment: design review, threat modeling, and operational review • Identifying vulnerabilities related to memory management, data types, and malformed data • UNIX/Linux assessment: privileges, files, and processes • Windows-specific issues, including objects and the filesystem • Auditing interprocess communication, synchronization, and state • Evaluating network software: IP stacks, firewalls, and common application protocols • Auditing Web applications and technologies This book is an unprecedented resource for everyone who must deliver secure software or assure the safety of existing software: consultants, security specialists, developers, QA staff, testers, and administrators alike. Contents ABOUT THE AUTHORS xv PREFACE xvii ACKNOWLEDGMENTS xxi I Introduction to Software Security Assessment 1 SOFTWARE VULNERABILITY FUNDAMENTALS 3 2 DESIGN REVIEW 25 3 OPERATIONAL REVIEW 67 4 APPLICATION REVIEW PROCESS 91 II Software Vulnerabilities 5 MEMORY CORRUPTION 167 6 C LANGUAGE ISSUES 203 7 PROGRAM BUILDING BLOCKS 297 8 STRINGS ANDMETACHARACTERS 387 9 UNIX I: PRIVILEGES AND FILES 459 10 UNIX II: PROCESSES 559 11 WINDOWS I: OBJECTS AND THE FILE SYSTEM 625 12 WINDOWS II: INTERPROCESS COMMUNICATION 685 13 SYNCHRONIZATION AND STATE 755 III Software Vulnerabilities in Practice 14 NETWORK PROTOCOLS 829 15 FIREWALLS 891 16 NETWORK APPLICATION PROTOCOLS 921 17 WEB APPLICATIONS 1007 18 WEB TECHNOLOGIES 1083 BIBLIOGRAPHY 1125 INDEX 1129 COMPUTERS,Networking,Vendor Specific

Network Security The classic guide to network security—now fully updated!"Bob and Alice are back!" Widely regarded as the most comprehensive yet comprehensible guide to network security, the first edition of Network Security received critical acclaim for its lucid and witty explanations of the inner workings of network security protocols. In the second edition, this most distinguished of author teams draws on hard-won experience to explain the latest developments in this field that has become so critical to our global network-dependent society. Network Security, Second Edition brings together clear, insightful, and clever explanations of every key facet of information security, from the basics to advanced cryptography and authentication, secure Web and email services, and emerging security standards. Coverage includes: All-new discussions of the Advanced Encryption Standard (AES), IPsec, SSL, and Web security Cryptography: In-depth, exceptionally clear introductions to secret and public keys, hashes, message digests, and other crucial concepts Authentication: Proving identity across networks, common attacks against authentication systems, authenticating people, and avoiding the pitfalls of authentication handshakes Core Internet security standards: Kerberos 4/5, IPsec, SSL, PKIX, and X.509 Email security: Key elements of a secure email system-plus detailed coverage of PEM, S/MIME, and PGP Web security: Security issues associated with URLs, HTTP, HTML, and cookies Security implementations in diverse platforms, including Windows, NetWare, and Lotus Notes The authors go far beyond documenting standards and technology: They contrast competing schemes, explain strengths and weaknesses, and identify the crucial errors most likely to compromise secure systems. Network Security will appeal to a wide range of professionals, from those who design or evaluate security systems to system administrators and programmers who want a better understanding of this important field. It can also be used as a textbook at the graduate or advanced undergraduate level. COMPUTERS,Networking,Vendor Specific

Analyzing Computer Security In this book, the authors of the 20-year best-selling classic Security in Computing take a fresh, contemporary, and powerfully relevant new approach to introducing computer security. Organised around attacks and mitigations, the Pfleegers' new Analyzing Computer Security will attract students' attention by building on the high-profile security failures they may have already encountered in the popular media. Each section starts with an attack description. Next, the authors explain the vulnerabilities that have allowed this attack to occur. With this foundation in place, they systematically present today's most effective countermeasures for blocking or weakening the attack. One step at a time, students progress from attack/problem/harm to solution/protection/mitigation, building the powerful real-world problem solving skills they need to succeed as information security professionals. Analyzing Computer Security addresses crucial contemporary computer security themes throughout, including effective security management and risk analysis; economics and quantitative study; privacy, ethics, and laws; and the use of overlapping controls. The authors also present significant new material on computer forensics, insiders, human factors, and trust. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Networking,Vendor Specific

Network Security First-Step Network Security first-step Second Edition Tom Thomas and Donald Stoddard Your first step into the world of network security No security experience required Includes clear and easily understood explanations Makes learning easy Your first step to network security begins here! Learn how hacker attacks work, from start to finish Choose the right security solution for each type of risk Create clear and enforceable security policies, and keep them up to date Establish reliable processes for responding to security advisories Use encryption effectively, and recognize its limitations Secure your network with firewalls, routers, and other devices Prevent attacks aimed at wireless networks No security experience required! Computer networks are indispensible, but they also are not secure. With the proliferation of security threats, many people and companies are looking for ways to increase the security of their networks and data. Before you can effectively implement security technologies and techniques, you need to make sense of this complex and quickly evolving world of hackers and malware, as well as the tools to combat them. Network Security First-Step, Second Edition explains the basics of network security in easy-to-grasp language that all of us can understand. This book takes you on a guided tour of the core technologies that make up and control network security. Whether you are looking to take your first step into a career in network security or simply are interested in gaining knowledge of the technology, this book is for you! COMPUTERS,Networking,Vendor Specific

Digital Archaeology The Definitive, Up-to-Date Guide to Digital Forensics The rapid proliferation of cyber crime is increasing the demand for digital forensics experts in both law enforcement and in the private sector. In Digital Archaeology, expert practitioner Michael Graves has written the most thorough, realistic, and up-to-date guide to the principles and techniques of modern digital forensics. Graves begins by providing a solid understanding of the legal underpinnings of and critical laws affecting computer forensics, including key principles of evidence and case law. Next, he explains how to systematically and thoroughly investigate computer systems to unearth crimes or other misbehavior, and back it up with evidence that will stand up in court. Drawing on the analogy of archaeological research, Graves explains each key tool and method investigators use to reliably uncover hidden information in digital systems. His detailed demonstrations often include the actual syntax of command-line utilities. Along the way, he presents exclusive coverage of facilities management, a full chapter on the crucial topic of first response to a digital crime scene, and up-to-the-minute coverage of investigating evidence in the cloud. Graves concludes by presenting coverage of important professional and business issues associated with building a career in digital forensics, including current licensing and certification requirements. Topics Covered Include Acquiring and analyzing data in ways consistent with forensic procedure Recovering and examining e-mail, Web, and networking activity Investigating users’ behavior on mobile devices Overcoming anti-forensics measures that seek to prevent data capture and analysis Performing comprehensive electronic discovery in connection with lawsuits Effectively managing cases and documenting the evidence you find Planning and building your career in digital forensics Digital Archaeology is a key resource for anyone preparing for a career as a professional investigator; for IT professionals who are sometimes called upon to assist in investigations; and for those seeking an explanation of the processes involved in preparing an effective defense, including how to avoid the legally indefensible destruction of digital evidence. COMPUTERS,Networking,Vendor Specific

CCENT Practice and Study Guide CCENT Practice and Study Guide is designed with dozens of exercises to help you learn the concepts and configurations crucial to your success with the Interconnecting Cisco Networking Devices Part 1 (ICND1 100-101) exam. The author has mapped the chapters of this book to the first two Cisco Networking Academy courses in the CCNA Routing and Switching curricula, Introduction to Networks and Routing and Switching Essentials. These courses cover the objectives of the Cisco Certified Networking Entry Technician (CCENT) certification. Getting your CCENT certification means that you have the knowledge and skills required to successfully install, operate, and troubleshoot a small branch office network. As a Cisco Networking Academy student or someone taking CCENT-related classes from professional training organizations, or college- and university-level networking courses, you will gain a detailed understanding of routing by successfully completing all the exercises in this book. Each chapter is designed with a variety of exercises, activities, and scenarios to help you: · Review vocabulary · Strengthen troubleshooting skills · Boost configuration skills · Reinforce concepts · Research and analyze topics COMPUTERS,Networking,Vendor Specific

Security Program and Policies Everything you need to know about information security programs and policies, in one book Clearly explains all facets of InfoSec program and policy planning, development, deployment, and management Thoroughly updated for today’s challenges, laws, regulations, and best practices The perfect resource for anyone pursuing an information security management career ¿ In today’s dangerous world, failures in information security can be catastrophic. Organizations must protect themselves. Protection begins with comprehensive, realistic policies. This up-to-date guide will help you create, deploy, and manage them. Complete and easy to understand, it explains key concepts and techniques through real-life examples. You’ll master modern information security regulations and frameworks, and learn specific best-practice policies for key industry sectors, including finance, healthcare, online commerce, and small business. ¿ If you understand basic information security, you’re ready to succeed with this book. You’ll find projects, questions, exercises, examples, links to valuable easy-to-adapt information security policies...everything you need to implement a successful information security program. ¿ Learn how to ·¿¿¿¿¿¿¿¿ Establish program objectives, elements, domains, and governance ·¿¿¿¿¿¿¿¿ Understand policies, standards, procedures, guidelines, and plans—and the differences among them ·¿¿¿¿¿¿¿¿ Write policies in “plain language,†with the right level of detail ·¿¿¿¿¿¿¿¿ Apply the Confidentiality, Integrity & Availability (CIA) security model ·¿¿¿¿¿¿¿¿ Use NIST resources and ISO/IEC 27000-series standards ·¿¿¿¿¿¿¿¿ Align security with business strategy ·¿¿¿¿¿¿¿¿ Define, inventory, and classify your information and systems ·¿¿¿¿¿¿¿¿ Systematically identify, prioritize, and manage InfoSec risks ·¿¿¿¿¿¿¿¿ Reduce “people-related†risks with role-based Security Education, Awareness, and Training (SETA) ·¿¿¿¿¿¿¿¿ Implement effective physical, environmental, communications, and operational security ·¿¿¿¿¿¿¿¿ Effectively manage access control ·¿¿¿¿¿¿¿¿ Secure the entire system development lifecycle ·¿¿¿¿¿¿¿¿ Respond to incidents and ensure continuity of operations ·¿¿¿¿¿¿¿¿ Comply with laws and regulations, including GLBA, HIPAA/HITECH, FISMA, state data security and notification rules, and PCI DSS ¿ COMPUTERS,Networking,Vendor Specific

Information Security Information Security: Principles and Practices covers all 10 domains of today's Information Security Common Body of Knowledge. Written by two of the world's most experienced IT security practitioners, it brings together foundational knowledge that prepares readers for real-world environments, making it ideal for introductory courses in information security, and for anyone interested in entering the field. This edition addresses today's newest trends, from cloud and mobile security to BYOD and the latest compliance requirements. The authors present updated real-life case studies, review questions, and exercises throughout. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Networking,Vendor Specific

Practical Guide to Computer Forensics Investigations, A All you need to know to succeed in digital forensics: technical and investigative skills, in one book Complete, practical, and up-to-date Thoroughly covers digital forensics for Windows, Mac, mobile, hardware, and networks Addresses online and lab investigations, documentation, admissibility, and more By Dr. Darren Hayes, founder of Pace University’s Code Detectives forensics lab–one of America’s “Top 10 Computer Forensics Professors†Perfect for anyone pursuing a digital forensics career or working with examiners Criminals go where the money is. Today, trillions of dollars of assets are digital, and digital crime is growing fast. In response, demand for digital forensics experts is soaring. To succeed in this exciting field, you need strong technical and investigative skills. In this guide, one of the world’s leading computer orensics experts teaches you all the skills you’ll need. Writing for students and professionals at all levels, Dr. Darren Hayes presents complete best practices for capturing and analyzing evidence, protecting the chain of custody, documenting investigations, and scrupulously adhering to the law, so your evidence can always be used. Hayes introduces today’s latest technologies and technical challenges, offering detailed coverage of crucial topics such as mobile forensics, Mac forensics, cyberbullying, and child endangerment. This guide’s practical activities and case studies give you hands-on mastery of modern digital forensics tools and techniques. Its many realistic examples reflect the author’s extensive and pioneering work as a forensics examiner in both criminal and civil investigations. Understand what computer forensics examiners do, and the types of digital evidence they work with Explore Windows and Mac computers, understand how their features affect evidence gathering, and use free tools to investigate their contents Extract data from diverse storage devices Establish a certified forensics lab and implement good practices for managing and processing evidence Gather data and perform investigations online Capture Internet communications, video, images, and other content Write comprehensive reports that withstand defense objections and enable successful prosecution Follow strict search and surveillance rules to make your evidence admissible Investigate network breaches, including dangerous Advanced Persistent Threats (APTs) Retrieve immense amounts of evidence from smartphones, even without seizing them Successfully investigate financial fraud performed with digital devices Use digital photographic evidence, including metadata and social media images COMPUTERS,Networking,Vendor Specific

Thinking Security If you’re a security or network professional, you already know the “do’s and don’tsâ€: run AV software and firewalls, lock down your systems, use encryption, watch network traffic, follow best practices, hire expensive consultants . . . but it isn’t working. You’re at greater risk than ever, and even the world’s most security-focused organizations are being victimized by massive attacks. In Thinking Security, author Steven M. Bellovin provides a new way to think about security. As one of the world’s most respected security experts, Bellovin helps you gain new clarity about what you’re doing and why you’re doing it. He helps you understand security as a systems problem, including the role of the all-important human element, and shows you how to match your countermeasures to actual threats. You’ll learn how to move beyond last year’s checklists at a time when technology is changing so rapidly. You’ll also understand how to design security architectures that don’t just prevent attacks wherever possible, but also deal with the consequences of failures. And, within the context of your coherent architecture, you’ll learn how to decide when to invest in a new security product and when not to. Bellovin, co-author of the best-selling Firewalls and Internet Security, caught his first hackers in 1971. Drawing on his deep experience, he shares actionable, up-to-date guidance on issues ranging from SSO and federated authentication to BYOD, virtualization, and cloud security. Perfect security is impossible. Nevertheless, it’s possible to build and operate security systems far more effectively. Thinking Security will help you do just that. COMPUTERS,Networking,Vendor Specific

Security Operations Center Security Operations Center Building, Operating, and Maintaining Your SOC The complete, practical guide to planning, building, and operating an effective Security Operations Center (SOC) Security Operations Center is the complete guide to building, operating, and managing Security Operations Centers in any environment. Drawing on experience with hundreds of customers ranging from Fortune 500 enterprises to large military organizations, three leading experts thoroughly review each SOC model, including virtual SOCs. You’ll learn how to select the right strategic option for your organization, and then plan and execute the strategy you’ve chosen. Security Operations Center walks you through every phase required to establish and run an effective SOC, including all significant people, process, and technology capabilities. The authors assess SOC technologies, strategy, infrastructure, governance, planning, implementation, and more. They take a holistic approach considering various commercial and open-source tools found in modern SOCs. This best-practice guide is written for anybody interested in learning how to develop, manage, or improve a SOC. A background in network security, management, and operations will be helpful but is not required. It is also an indispensable resource for anyone preparing for the Cisco SCYBER exam. · Review high-level issues, such as vulnerability and risk management, threat intelligence, digital investigation, and data collection/analysis · Understand the technical components of a modern SOC · Assess the current state of your SOC and identify areas of improvement · Plan SOC strategy, mission, functions, and services · Design and build out SOC infrastructure, from facilities and networks to systems, storage, and physical security · Collect and successfully analyze security data · Establish an effective vulnerability management practice · Organize incident response teams and measure their performance · Define an optimal governance and staffing model · Develop a practical SOC handbook that people can actually use · Prepare SOC to go live, with comprehensive transition plans · React quickly and collaboratively to security incidents · Implement best practice security operations, including continuous enhancement and improvement COMPUTERS,Networking,Vendor Specific

IT Essentials Companion Guide v6 IT Essentials v6 Companion Guide supports the Cisco Networking Academy IT Essentials version 6 course. The course is designed for Cisco Networking Academy students who want to pursue careers in IT and learn how computers work, how to assemble computers, and how to safely and securely troubleshoot hardware and software issues. As CompTIA Approved Quality Content, the course also helps you prepare for the CompTIA A+ certification exams 220-901 and 220-902. Students must pass both exams to earn the CompTIA A+ certification. The features of the Companion Guide are designed to help you study and succeed in this course: Chapter objectives–Review core concepts by answering the focus questions listed at the beginning of each chapter. Key terms–Refer to the updated lists of networking vocabulary introduced, and turn to the highlighted terms in context. Course section numbering–Follow along with the course heading numbers to easily jump online to complete labs, activities, and quizzes referred to within the text. Check Your Understanding Questions and Answer Key–Evaluate your readiness with the updated end-of-chapter questions that match the style of questions you see on the online course quizzes. This icon in the Companion Guide indicates when there is a hands-on Lab to do. All the Labs from the course are compiled and published in the separate book, IT Essentials v6 Lab Manual. Practicing and performing all these tasks will reinforce the concepts and help you become a successful PC technician. COMPUTERS,Networking,Vendor Specific

Introduction to Networks v6 Companion Guide This is the eBook of the printed book and may not include any media, website access codes, or print supplements that may come packaged with the bound book. Introduction to Networks Companion Guide v6 is the official supplemental textbook for the Introduction to Networks course in the Cisco® Networking Academy® CCNA® Routing and Switching curriculum. The course introduces the architecture, structure, functions, components, and models of the Internet and computer networks. The principles of IP addressing and fundamentals of Ethernet concepts, media, and operations are introduced to provide a foundation for the curriculum. By the end of the course, you will be able to build simple LANs, perform basic configurations for routers and switches, and implement IP addressing schemes. The Companion Guide is designed as a portable desk reference to use anytime, anywhere to reinforce the material from the course and organize your time. The book’s features help you focus on important concepts to succeed in this course: Chapter Objectives—Review core concepts by answering the focus questions listed at the beginning of each chapter Key Terms—Refer to the lists of networking vocabulary introduced and highlighted in context in each chapter. Glossary—Consult the comprehensive Glossary with more than 250 terms. Summary of Activities and Labs—Maximize your study time with this complete list of all associated practice exercises at the end of each chapter. Check Your Understanding—Evaluate your readiness with the end-ofchapter questions that match the style of questions you see in the online course quizzes. The answer key explains each answer. COMPUTERS,Networking,Vendor Specific

Computer Security Fundamentals ONE-VOLUME INTRODUCTION TO COMPUTER SECURITY Clearly explains core concepts, terminology, challenges, technologies, and skills Covers today’s latest attacks and countermeasures The perfect beginner’s guide for anyone interested in a computer security career Chuck Easttom brings together complete coverage of all basic concepts, terminology, and issues, along with all the skills you need to get started. Drawing on 20+ years of experience as a security instructor, consultant, and researcher, Easttom helps you take a proactive, realistic approach to assessing threats and implementing countermeasures. Writing clearly and simply, he addresses crucial issues that many introductory security books ignore, while addressing the realities of a world where billions of new devices are Internet-connected. This guide covers web attacks, hacking, spyware, network defense, security appliances, VPNs, password use, and much more. Its many tips and examples reflect new industry trends and the state-of-the-art in both attacks and defense. Exercises, projects, and review questions in every chapter help you deepen your understanding and apply all you’ve learned. Whether you’re a student, a professional, or a manager, this guide will help you protect your assets—and expand your career options. Learn how to · Identify and prioritize potential threats to your network · Use basic networking knowledge to improve security · Get inside the minds of hackers, so you can deter their attacks · Implement a proven layered approach to network security · Resist modern social engineering attacks · Defend against today’s most common Denial of Service (DoS) attacks · Halt viruses, spyware, worms, Trojans, and other malware · Prevent problems arising from malfeasance or ignorance · Choose the best encryption methods for your organization · Compare security technologies, including the latest security appliances · Implement security policies that will work in your environment · Scan your network for vulnerabilities · Evaluate potential security consultants · Master basic computer forensics and know what to do if you’re attacked · Learn how cyberterrorism and information warfare are evolving COMPUTERS,Networking,Vendor Specific

Network Defense and Countermeasures All you need to know about defending networks, in one book · Clearly explains concepts, terminology, challenges, tools, and skills · Covers key security standards and models for business and government · The perfect introduction for all network/computer security professionals and students Welcome to today’s most useful and practical introduction to defending modern networks. Drawing on decades of experience, Chuck Easttom brings together updated coverage of all the concepts, terminology, techniques, and solutions you’ll need to be effective. Easttom thoroughly introduces the core technologies of modern network security, including firewalls, intrusion-detection systems, and VPNs. Next, he shows how encryption can be used to safeguard data as it moves across networks. You’ll learn how to harden operating systems, defend against malware and network attacks, establish robust security policies, and assess network security using industry-leading standards and models. You’ll also find thorough coverage of key issues such as physical security, forensics, and cyberterrorism. Throughout, Easttom blends theory and application, helping you understand both what to do and why. In every chapter, quizzes, exercises, projects, and web resources deepen your understanding and help you use what you’ve learned–in the classroom and in your career. Learn How To · Evaluate key network risks and dangers · Choose the right network security approach for your organization · Anticipate and counter widespread network attacks, including those based on “social engineering†· Successfully deploy and apply firewalls and intrusion detection systems · Secure network communication with virtual private networks · Protect data with cryptographic public/private key systems, digital signatures, and certificates · Defend against malware, including ransomware, Trojan horses, and spyware · Harden operating systems and keep their security up to date · Define and implement security policies that reduce risk · Explore leading security standards and models, including ISO and NIST standards · Prepare for an investigation if your network has been attacked · Understand the growing risks of espionage and cyberterrorism COMPUTERS,Networking,Vendor Specific

CCNA Cybersecurity Operations Companion Guide CCNA Cybersecurity Operations Companion Guide is the official supplemental textbook for the Cisco Networking Academy CCNA Cybersecurity Operations course. The course emphasizes real-world practical application, while providing opportunities for you to gain the skills needed to successfully handle the tasks, duties, and responsibilities of an associate-level security analyst working in a security operations center (SOC). The Companion Guide is designed as a portable desk reference to use anytime, anywhere to reinforce the material from the course and organize your time. The book’s features help you focus on important concepts to succeed in this course: · Chapter Objectives—Review core concepts by answering the focus questions listed at the beginning of each chapter. · Key Terms—Refer to the lists of networking vocabulary introduced and highlighted in context in each chapter. · Glossary—Consult the comprehensive Glossary with more than 360 terms. · Summary of Activities and Labs—Maximize your study time with this complete list of all associated practice exercises at the end of each chapter. · Check Your Understanding—Evaluate your readiness with the end-of-chapter questions that match the style of questions you see in the online course quizzes. The answer key explains each answer. How To—Look for this icon to study the steps you need to learn to perform certain tasks. Interactive Activities—Reinforce your understanding of topics with dozens of exercises from the online course identified throughout the book with this icon. Packet Tracer Activities—Explore and visualize networking concepts using Packet Tracer. There are exercises interspersed throughout the chapters and provided in the accompanying Lab Manual book. Videos—Watch the videos embedded within the online course. Hands-on Labs—Develop critical thinking and complex problem-solving skills by completing the labs and activities included in the course and published in the separate Lab Manual. COMPUTERS,Networking,Vendor Specific

Orchestrating and Automating Security for the Internet of Things Master powerful techniques and approaches for securing IoT systems of all kinds–current and emerging Internet of Things (IoT) technology adoption is accelerating, but IoT presents complex new security challenges. Fortunately, IoT standards and standardized architectures are emerging to help technical professionals systematically harden their IoT environments. In Orchestrating and Automating Security for the Internet of Things, three Cisco experts show how to safeguard current and future IoT systems by delivering security through new NFV and SDN architectures and related IoT security standards. The authors first review the current state of IoT networks and architectures, identifying key security risks associated with nonstandardized early deployments and showing how early adopters have attempted to respond. Next, they introduce more mature architectures built around NFV and SDN. You’ll discover why these lend themselves well to IoT and IoT security, and master advanced approaches for protecting them. Finally, the authors preview future approaches to improving IoT security and present real-world use case examples. This is an indispensable resource for all technical and security professionals, business security and risk managers, and consultants who are responsible for systems that incorporate or utilize IoT devices, or expect to be responsible for them. · Understand the challenges involved in securing current IoT networks and architectures · Master IoT security fundamentals, standards, and modern best practices · Systematically plan for IoT security · Leverage Software-Defined Networking (SDN) and Network Function Virtualization (NFV) to harden IoT networks · Deploy the advanced IoT platform, and use MANO to manage and orchestrate virtualized network functions · Implement platform security services including identity, authentication, authorization, and accounting · Detect threats and protect data in IoT environments · Secure IoT in the context of remote access and VPNs · Safeguard the IoT platform itself · Explore use cases ranging from smart cities and advanced energy systems to the connected car · Preview evolving concepts that will shape the future of IoT security COMPUTERS,Networking,Vendor Specific

Developing Cybersecurity Programs and Policies All the Knowledge You Need to Build Cybersecurity Programs and Policies That Work Clearly presents best practices, governance frameworks, and key standards Includes focused coverage of healthcare, finance, and PCI DSS compliance An essential and invaluable guide for leaders, managers, and technical professionals Today, cyberattacks can place entire organizations at risk. Cybersecurity can no longer be delegated to specialists: success requires everyone to work together, from leaders on down. Developing Cybersecurity Programs and Policies offers start-to-finish guidance for establishing effective cybersecurity in any organization. Drawing on more than 20 years of real-world experience, Omar Santos presents realistic best practices for defining policy and governance, ensuring compliance, and collaborating to harden the entire organization. First, Santos shows how to develop workable cybersecurity policies and an effective framework for governing them. Next, he addresses risk management, asset management, and data loss prevention, showing how to align functions from HR to physical security. You’ll discover best practices for securing communications, operations, and access; acquiring, developing, and maintaining technology; and responding to incidents. Santos concludes with detailed coverage of compliance in finance and healthcare, the crucial Payment Card Industry Data Security Standard (PCI DSS) standard, and the NIST Cybersecurity Framework. Whatever your current responsibilities, this guide will help you plan, manage, and lead cybersecurity–and safeguard all the assets that matter. Learn How To · Establish cybersecurity policies and governance that serve your organization’s needs · Integrate cybersecurity program components into a coherent framework for action · Assess, prioritize, and manage security risk throughout the organization · Manage assets and prevent data loss · Work with HR to address human factors in cybersecurity · Harden your facilities and physical environment · Design effective policies for securing communications, operations, and access · Strengthen security throughout the information systems lifecycle · Plan for quick, effective incident response and ensure business continuity · Comply with rigorous regulations in finance and healthcare · Plan for PCI compliance to safely process payments · Explore and apply the guidance provided by the NIST Cybersecurity Framework COMPUTERS,Networking,Vendor Specific

Computer Security Fundamentals Clearly explains core concepts, terminology, challenges, technologies, and skills Covers today’s latest attacks and countermeasures The perfect beginner’s guide for anyone interested in a computer security career Dr. Chuck Easttom brings together complete coverage of all basic concepts, terminology, and issues, along with all the skills you need to get started. Drawing on 30 years of experience as a security instructor, consultant, and researcher, Easttom helps you take a proactive, realistic approach to assessing threats and implementing countermeasures. Writing clearly and simply, he addresses crucial issues that many introductory security books ignore, while addressing the realities of a world where billions of new devices are Internet-connected. This guide covers web attacks, hacking, spyware, network defense, security appliances, VPNs, password use, and much more. Its many tips and examples reflect new industry trends and the state-of-the-art in both attacks and defense. Exercises, projects, and review questions in every chapter help you deepen your understanding and apply all you’ve learned. Whether you’re a student, a professional, or a manager, this guide will help you protect your assets—and expand your career options. LEARN HOW TO Identify and prioritize potential threats to your network Use basic networking knowledge to improve security Get inside the minds of hackers, so you can deter their attacks Implement a proven layered approach to network security Resist modern social engineering attacks Defend against today’s most common Denial of Service (DoS) attacks Halt viruses, spyware, worms, Trojans, and other malware Prevent problems arising from malfeasance or ignorance Choose the best encryption methods for your organization Compare security technologies, including the latest security appliances Implement security policies that will work in your environment Scan your network for vulnerabilities Evaluate potential security consultants Master basic computer forensics and know what to do if you’re attacked Learn how cyberterrorism and information warfare are evolving COMPUTERS,Networking,Vendor Specific

IT Essentials Companion Guide v7 IT Essentials v7 Companion Guide supports the Cisco Networking Academy IT Essentials version 7 course. The course is designed for Cisco Networking Academy students who want to pursue careers in IT and learn how computers work, how to assemble computers, and how to safely and securely troubleshoot hardware and software issues. The features of the Companion Guide are designed to help you study and succeed in this course: Chapter objectives–Review core concepts by answering the focus questions listed at the beginning of each chapter. Key terms–Refer to the updated lists of networking vocabulary introduced, and turn to the highlighted terms in context. Course section numbering–Follow along with the course heading numbers to easily jump online to complete labs, activities, and quizzes referred to within the text. Check Your Understanding Questions and Answer Key–Evaluate your readiness with the updated end-of-chapter questions that match the style of questions you see on the online course quizzes. This book is part of the Cisco Networking Academy Series from Cisco Press®. Books in this series support and complement the Cisco Networking Academy. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Networking,Vendor Specific

Practical Guide to Digital Forensics Investigations, A THE DEFINITIVE GUIDE TO DIGITAL FORENSICS—NOW THOROUGHLY UPDATED WITH NEW TECHNIQUES, TOOLS, AND SOLUTIONS Complete, practical coverage of both technical and investigative skills Thoroughly covers modern devices, networks, and the Internet Addresses online and lab investigations, documentation, admissibility, and more Aligns closely with the NSA Knowledge Units and the NICE Cybersecurity Workforce Framework As digital crime soars, so does the need for experts who can recover and evaluate evidence for successful prosecution. Now, Dr. Darren Hayes has thoroughly updated his definitive guide to digital forensics investigations, reflecting current best practices for securely seizing, extracting and analyzing digital evidence, protecting the integrity of the chain of custody, effectively documenting investigations, and scrupulously adhering to the law, so that your evidence is admissible in court. Every chapter of this new Second Edition is revised to reflect newer technologies, the latest challenges, technical solutions, and recent court decisions. Hayes has added detailed coverage of wearable technologies, IoT forensics, 5G communications, vehicle forensics, and mobile app examinations; advances in incident response; and new iPhone and Android device examination techniques. Through practical activities, realistic examples, and fascinating case studies, you’ll build hands-on mastery—and prepare to succeed in one of today’s fastest-growing fields. LEARN HOW TO Understand what digital forensics examiners do, the evidence they work with, and the opportunities available to them Explore how modern device features affect evidence gathering, and use diverse tools to investigate them Establish a certified forensics lab and implement best practices for managing and processing evidence Gather data online to investigate today’s complex crimes Uncover indicators of compromise and master best practices for incident response Investigate financial fraud with digital evidence Use digital photographic evidence, including metadata and social media images Investigate wearable technologies and other “Internet of Things†devices Learn new ways to extract a full fi le system image from many iPhones Capture extensive data and real-time intelligence from popular apps Follow strict rules to make evidence admissible, even after recent Supreme Court decisions COMPUTERS,Networking,Vendor Specific

Introduction to Networks Companion Guide (CCNAv7) Introduction to Networks Companion Guide is the official supplemental textbook for the Introduction to Networks course in the Cisco Networking Academy CCNA curriculum. The course introduces the architecture, protocols, functions, components, and models of the internet and computer networks. The principles of IP addressing and fundamentals of Ethernet concepts, media, and operations are introduced to provide a foundation for the curriculum. By the end of the course, you will be able to build simple LANs, perform basic configurations for routers and switches, understand the fundamentals of network security, and implement IP addressing schemes. The Companion Guide is designed as a portable desk reference to use anytime, anywhere to reinforce the material from the course and organize your time. The book’s features help you focus on important concepts to succeed in this course: * Chapter objectives: Review core concepts by answering the focus questions listed at the beginning of each chapter. * Key terms: Refer to the lists of networking vocabulary introduced and highlighted in context in each chapter. * Glossary: Consult the comprehensive Glossary with more than 300 terms. * Summary of Activities and Labs: Maximize your study time with this complete list of all associated practice exercises at the end of each chapter. * Check Your Understanding: Evaluate your readiness with the end-of-chapter questions that match the style of questions you see in the online course quizzes. The answer key explains each answer. * How To: Look for this icon to study the steps you need to learn to perform certain tasks. * Interactive Activities: Reinforce your understanding of topics with dozens of exercises from the online course identified throughout the book with this icon. * Videos: Watch the videos embedded within the online course. * Packet Tracer Activities: Explore and visualize networking concepts using Packet Tracer. There are multiple exercises interspersed throughout the chapters and provided in the accompanying Labs & Study Guide book. * Hands-on Labs: Work through all the labs and other activities that are included in the course and published in the separate Labs & Study Guide. This book is offered exclusively for students enrolled in Cisco Networking Academy courses. It is not designed for independent study or professional certification preparation. Visit netacad.com to learn more about program options and requirements. Related titles: CCNA 200-301 Portable Command Guide Book: 9780135937822 eBook: 9780135937709 31 Days Before Your CCNA Exam Book: 9780135964088 eBook: 9780135964231 CCNA 200-301 Official Cert Guide, Volume 1 Book: 9780135792735 Premium Edition: 9780135792728 CCNA 200-301 Official Cert Guide, Volume 2 Book: 9781587147135 Premium Edition: 9780135262719 COMPUTERS,Networking,Vendor Specific

Enterprise Networking, Security, and Automation Companion Guide (CCNAv7) Enterprise Networking, Security, and Automation Companion Guide is the official supplemental textbook for the Enterprise Networking, Security, and Automation v7 course in the Cisco Networking Academy CCNA curriculum. This course describes the architectures and considerations related to designing, securing, operating, and troubleshooting enterprise networks. You will implement the OSPF dynamic routing protocol, identify and protect against cybersecurity threats, configure access control lists (ACLs), implement Network Address Translation (NAT), and learn about WANs and IPsec VPNs. You will also learn about QoS mechanisms, network management tools, network virtualisation, and network automation. The books features help you focus on important concepts to succeed in this course: Chapter objectives: Review core concepts by answering the focus questions listed at the beginning of each chapter. Key terms: Refer to the lists of networking vocabulary introduced and highlighted in context in each chapter. Glossary: Consult the comprehensive Glossary with more than 500 terms. Summary of Activities and Labs: Maximise your study time with this complete list of all associated practice exercises at the end of each chapter. Check Your Understanding: Evaluate your readiness with the end-of-chapter questions that match the style of questions you see in the online course quizzes. The answer key explains each answer. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Networking,Vendor Specific

Switching, Routing, and Wireless Essentials Companion Guide (CCNAv7) Switching, Routing, and Wireless Essentials Companion Guide (CCNAv7) is the official supplemental textbook for the Switching, Routing, and Wireless Essentials course in the Cisco Networking Academy CCNA curriculum. This course describes the architecture, components, and operations of routers and switches in a small network. The Companion Guide is designed as a portable desk reference to use anytime, anywhere to reinforce the material from the course and organize your time. The book’s features help you focus on important concepts to succeed in this course: * Chapter objectives: Review core concepts by answering the focus questions listed at the beginning of each chapter. * Key terms: Refer to the lists of networking vocabulary introduced and highlighted in context in each chapter. * Glossary: Consult the comprehensive Glossary with more than 300 terms. * Summary of Activities and Labs: Maximize your study time with this complete list of all associated practice exercises at the end of each chapter. * Check Your Understanding: Evaluate your readiness with the end-of-chapter questions that match the style of questions you see in the online course quizzes. The answer key explains each answer. How To: Look for this icon to study the steps you need to learn to perform certain tasks. Interactive Activities: Reinforce your understanding of topics with dozens of exercises from the online course identified throughout the book with this icon. Videos: Watch the videos embedded within the online course. Packet Tracer Activities: Explore and visualize networking concepts using Packet Tracer exercises interspersed throughout the chapters and provided in the accompanying Labs & Study Guide book. Hands-on Labs: Work through all the course labs and additional Class Activities that are included in the course and published in the separate Labs & Study Guide. This book is offered exclusively for students enrolled in Cisco Networking Academy courses. It is not designed for independent study or professional certification preparation. Visit netacad.com to learn more about program options and requirements. Related titles: CCNA 200-301 Portable Command Guide Book: 9780135937822 eBook: 9780135937709 31 Days Before Your CCNA Exam Book: 9780135964088 eBook: 9780135964231 CCNA 200-301 Official Cert Guide, Volume 1 Book: 9780135792735 Premium Edition: 9780135792728 CCNA 200-301 Official Cert Guide, Volume 2 Book: 9781587147135 Premium Edition: 9780135262719 COMPUTERS,Networking,Vendor Specific

Cisco Certified DevNet Associate DEVASC 200-901 Official Cert Guide This is the eBook edition of the Cisco Certified DevNet Associate DEVASC 200-901 Official Cert Guide. This eBook does not include access to the companion website with practice exam that comes with the print edition. Access to the video mentoring is available through product registration at Cisco Press; or see the instructions in the back pages of your eBook. Trust the best-selling Official Cert Guide series from Cisco Press to help you learn, prepare, and practice for exam success. They are built with the objective of providing assessment, review, and practice to help ensure you are fully prepared for your certification exam. Master Cisco Certified DevNet Associate DEVASC 200-901 exam topics Assess your knowledge with chapter-opening quizzes Review key concepts with exam preparation tasks Learn from more than two hours of video mentoring Cisco Certified DevNet Associate DEVASC 200-901 Official Cert Guide presents you with an organized test preparation routine through the use of proven series elements and techniques. “Do I Know This Already?†quizzes open each chapter and enable you to decide how much time you need to spend on each section. Exam topic lists make referencing easy. Chapter-ending Exam Preparation Tasks help you drill on key concepts you must know thoroughly. Cisco Certified DevNet Associate DEVASC 200-901 Official Cert Guide focuses specifically on the objectives for the Cisco Certified DevNet Associate DEVASC exam. Four leading Cisco technology experts share preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. Material is presented in a concise manner, focusing on increasing your understanding and retention of exam topics. Well regarded for its level of detail, assessment features, comprehensive design scenarios, this official study guide helps you master the concepts and techniques that will enable you to succeed on the exam the first time. The official study guide helps you master all the topics on the Cisco Certified DevNet Associate DEVASC 200-901 exam, including: Software Development and Design Understanding and Using APIs Cisco Platforms and Development Application Deployment and Security Infrastructure and Automation Network Fundamentals COMPUTERS,Networking,Vendor Specific

Multimedia Database Systems With the rapid growth in the use of computers to manipulate, process, and reason about multimedia data, the problem of how to store and retrieve such data is becoming increasingly important. Thus, although the field of multimedia database systems is only about 5 years old, it is rapidly becoming a focus for much excitement and research effort. Multimedia database systems are intended to provide unified frameworks for requesting and integrating information in a wide variety of formats, such as audio and video data, document data, and image data. Such data often have special storage requirements that are closely coupled to the various kinds of devices that are used for recording and presenting the data, and for each form of data there are often multiple representations and multiple standards - all of which make the database integration task quite complex. Some of the problems include: - what a multimedia database query means - what kinds of languages to use for posing queries - how to develop compilers for such languages - how to develop indexing structures for storing media on ancillary devices - data compression techniques - how to present and author presentations based on user queries. Although approaches are being developed for a number of these problems, they have often been ad hoc in nature, and there is a need to provide a princi pled theoretical foundation. COMPUTERS,Online Services

Executive Guide to Business Success through Human-Centred Systems This book is about people and skilled work. There has been much turmoil in the business environment about how to best manage the balance between people and technology, at a time when pressures for cost reduction are ever greater. Our argument is that people are central to business success, and the appropriate use of technology should support their needs. This is not always easy in practice. We work in a period when change occurs in ever-shortening cycles. Black-and-white solutions may seem attractive, but the long-term consequences are rarely advantageous. A new system is required, build ing on lessons from the past. Human-centred systems build upon core skills of the workforce within a rich, emancipatory environment, utilising the benefits of tech nology. Change can be embraced to achieve competitive advantage and mutual benefit. The three authors are, respectively, engineering director of an inno vative international manufacturing company; analyst for an inter national merchant bank; and university business school professor. The book is intended to offer a new synthesis of theory and practical experience, derived from recent British and European collaborative pro grammes. We are grateful to our colleagues and families for their tolerance during the writing of this book. Even human-centred books impose pressures on busy people. Old Windsor, Brighton and Kingston, June 1995 A.A. R.K. COMPUTERS,Online Services

OOIS’94 This volume contains the papers presented at the Intemational Conference on Object Oriented Information Systems 00lS'94, held at South Bank University, London, December 19 - 21, 1994. In response to our call for papers, a total 85 papers from 24 different countries were submitted. Each paper was evaluated by at least two Program Committee members and an additional reviewer. Together, we selected 41 papers for presentation at the conference and inclusion in the Proceedings. Also included are the keynote addresses by Peter Gray and Michael Jackson. The other submissions were recommended for presentation in the poster sessions. Peter Gray, our invited speaker, evaluates the problems of object-oriented systems and data independence by looking at how object oriented database applications are failing to perceive its benefits, and instead rely too much on encapsulation. He suggests alternative kinds of object storage to preserve data independence. The second invited speaker, Michael Jackson describes a way of solving problems, by focusing directly on the problems themselves, their components and structures and on the relationships between the problem and the solution method. He discusses a particular view of the role of object-orientation in software development. COMPUTERS,Online Services

Incompleteness and Uncertainty in Information Systems The Software Engineering and Knowledgebase Systems (SOFfEKS) Research Group of the Department of Computer Science, Concordia University, Canada, organized a workshop on Incompleteness and Uncertainty in Information Systems from October 8-9, 1993 in Montreal. A major aim of the workshop was to bring together researchers who share a concern for issues of incompleteness and uncertainty. The workshop attracted people doing fundamental research and industry oriented research in databases, software engineering and AI from North America, Europe and Asia. The workshop program featured six invited talks and twenty other presentations. The invited speakers were: Martin Feather (University of Southern CalifornialInformation Systems Institute) Laks V. S. Lakshmanan (Concordia University) Ewa Orlowska (Polish Academy of Sciences) z. Pawlak (Warsaw Technical University and Academy of Sciences) F. Sadri (Concordia University) A. Skowron (Warsaw University) The papers can be classified into four groups: rough sets and logic, concept analysis, databases and information retrieval, and software engineering. The workshop opened with a warm welcome speech from Dr. Dan Taddeo, Dean, Faculty of Engineering and Computer Science. The first day's presentations were in rough sets, databases and information retrieval. Papers given on the second day centered around software engineering and concept analysis. Sufficient time was given in between presentations to promote active interactions and numerous lively discussions. At the end of two days, the participants expressed their hope that this workshop would be continued. COMPUTERS,Online Services

Information Systems Engineering This book presents a selection of subjects which the authors deem to be important for information systems engineers. The book is intended for introductory teaching. We have tried to write the book in such a way that students with only fragmented knowledge of computers are able to read the book without too many difficulties. Students who have had only an intro ductory course in computer programming should be able to read most of the book. We have tried to achieve simplicity without compromising on depth in our discussions of the various aspects of information systems engineering. So it is our hope that also those who have deeper knowledge in computing may find pleasure in reading parts of the book. The writing of a textbook is a major undertaking for its authors. One is quite often forced to reexamine truisms in the subject area, and must be prepared to reevaluate one's opinions and priorities as one learns more. In particular this is so in new fields, where formalisms have been scarcely used, and where consensus has not yet emerged either on what constitutes the subject area or on how practical problems within the field shall be approached. Contemporary practice in computer applications is confronted with an increasingly complex world, both in a technical sense and in the complexity of problems that are solved by computer. COMPUTERS,Online Services

Interactive Computer Systems Focusing on the business aspects of interactive systems, this book pays particular attention to applications involving videotex and multimedia. The author describes the technology of these systems, presents case studies detailing their applications, and offers a methodology for planning and producing such systems. Managers, planners, and academics who wish to apply information technology for operational and strategic ends will find no other book more practical, readable, or comprehensive. COMPUTERS,Online Services

Cooperation Among Organizations This book reports research conducted in the ESPRIT project PECOS, which investigated the requirements for effective CSCW (Computer Supported Cooperative Work) with special reference to cooperation among organisations in large projects. It indicates commercial areas where CSCW technology can be applied, and examines such methodological issues as enterprise modelling, system architecture, and the incorporation of artificial intelligence techniques. PECOS studied two practical contexts. The first was the management of a complex industrial project, the construction of a high-speed train for the Italian railway, which required cooperation among four private companies. The second was the design of an information system for water management in the Lombardy region, which required cooperation among several different branches of public administration.fhese contexts were analysed, applying techniques of enterprise modelling, in order to identify requirements for CSCW systems. The composition of the book is as follows. Chapter 1 presents some highlights of the vast literature on cooperation, including results from psycholOgy, sociology, management science, linguistics, and artificial intelligence. Chapter 2 reviews the much shorter history of CSCW, with reference to a catalogue of existing systems given in an appendix at the end of the book. The next four chapters contain our original findings. COMPUTERS,Online Services

Evolution of Information Processing Systems An interdisciplinary team of scientists is presenting a newparadigm: all existing structures on earth are theconsequence of information processing. Since thesestructures have been evolved over the last five billionyears, information processing and its systems have anevolution.This is under consideration in the book. Startingwith a basic paper which summarizes the essential hypothesesabout the evolution of informaion processing systems,sixteen international scientists have tried to verify orfalsify these hypothesises. This has been done at thephysical, the chemical, the genetic, the neural, the social,the societal and the socio-technical level. Thus, the readergets an insight into the recent status of research on theevolution of information processing systems. The papers arethe result of an interdisciplinary project in whichscientists of the classical disciplines have been invited tocollaborate. Their inputs have been intensively discussed ina workshop. The book is the output of the workshop. Thefirst goal of the bookis to give the reader an insight intobasic principles about the evolution of informationprocessing systems. This, however, leads directly to a veryold and essential question: who is controlling the world,"matter" or an "immaterial intelligence"? Several authors ofthe papers are arguing that there is a basic concept ofinformation processing in nature. This is the crucialprocess, which, however, needs a material basis. The readerhas a chance to understand this paradigm as an approachwhich is valid for all levels of inorganic, organic andsocietal structures. This provocative concept is open todebate. COMPUTERS,Online Services

ESPRIT ’90 Proceedings of the Annual ESPRIT Conference, Brussels, November 12-15, 1990 and Additional Synopses and Technical Factsheets COMPUTERS,Online Services

Accountable Governance Public accountability is a hallmark of modern democratic governance and the foundation of the popular performance management movement. Democracy is just an empty exercise if those in power cannot be held accountable in public for their acts and omissions, for their decisions, their policies, and their expenditures. This book offers a finely detailed and richly informed consideration of accountability in both government and the contemporary world of governance. Twenty-five leading experts cover varying aspects of the accountability movement, including multiple and competing accountabilities, measuring accountability, accountability and democratic legitimacy, and accountability and information technology, and apply them to governments, quasi-governments, non-government organizations, governance organizations, and voluntary organizations. Together they provide the most comprehensive consideration of accountability currently available, with a blend of theoretical, empirical, and applied approaches. COMPUTERS,Online Services

Building Tools with GitHub For your next project on GitHub, take advantage of the service’s powerful API to meet your unique development requirements. This practical guide shows you how to build your own software tools for customizing the GitHub workflow. Each hands-on chapter is a compelling story that walks you through the tradeoffs and considerations for building applications on top of various GitHub technologies. If you’re an experienced programmer familiar with GitHub, you’ll learn how to build tools with the GitHub API and related open source technologies such as Jekyll (site builder), Hubot (NodeJS chat robot), and Gollum (wiki). Build a simple Ruby server with Gist API command-line tools and Ruby’s "Octokit" API client Use the Gollum command-line tool to build an image management application Build a GUI tool to search GitHub with Python Document interactions between third-party tools and your code Use Jekyll to create a fully-featured blog from material in your GitHub repository Create an Android mobile application that reads and writes information into a Jekyll repository Host an entire single-page JavaScript application on GitHub Use Hubot to automate pull request reviews COMPUTERS,Online Services

Introducing GitHub If you’re new to GitHub, this concise book shows you just what you need to get started and no more. It’s perfect for project and product managers, stakeholders, and other team members who want to collaborate on a development project—whether it’s to review and comment on work in progress or to contribute specific changes. It’s also great for developers just learning GitHub. GitHub has rapidly become the default platform for software development, but it’s also ideal for other text-based documents, from contracts to screenplays. This hands-on book shows you how to use GitHub’s web interface to view projects and collaborate effectively with your team. The updated second edition covers code review, and includes updates to the desktop application, the Atom text editor, protected branches, and project management features. Keep track of, and work with, developers more effectively Learn the basics so you can contribute to your software projects Understand foundational Git knowledge, including commits and cloning Get tips on positive interaction with developers COMPUTERS,Online Services

Modern Data Strategy This book contains practical steps business users can take to implement data management in a number of ways, including data governance, data architecture, master data management, business intelligence, and others. It defines data strategy, and covers chapters that illustrate how to align a data strategy with the business strategy, a discussion on valuing data as an asset, the evolution of data management, and who should oversee a data strategy. This provides the user with a good understanding of what a data strategy is and its limits. Critical to a data strategy is the incorporation of one or more data management domains. Chapters on key data management domains—data governance, data architecture, master data management and analytics, offer the user a practical approach to data management execution within a data strategy. The intent is to enable the user to identify how execution on one or more data management domains can help solve business issues. This book is intended for business users who work with data, who need to manage one or more aspects of the organization’s data, and who want to foster an integrated approach for how enterprise data is managed. This book is also an excellent reference for students studying computer science and business management or simply for someone who has been tasked with starting or improving existing data management. COMPUTERS,Online Services

Technology-Inspired Smart Learning for Future Education This book constitutes the refereed proceedings of the 29th National Conference on Computer Science Technology and Education, NCCSTE 2019, held in Kaifeng, China, in October 2019. The 12 full papers presented were thoroughly reviewed and selected from 50 submissions. The papers focus on the diverse environments of smart learning, including massive open online courses with AI assistants, intelligent tutoring systems, interactive learning courseware, learning games, collaborative programming communities, community tutorial systems, personalized exercise programs, tutoring robotics, etc. The papers are organized in the following topical sections: ​smart learning; information technologies. COMPUTERS,Online Services

Computer Science – CACIC 2019 This book constitutes revised selected papers from the 25th Argentine Congress on Computer Science, CACIC 2019, held in RÃo Cuarto, Argentina, in October 2019.The 27 full papers presented in this volume were carefully reviewed and selected from a total of 185 submissions. They were organized in topical sections named: intelligent agents and systems; distributed and parallel processing; computer technology applied to education; graphic computation, images and visualization; software engineering; databases and data mining; hardware architectures, networks, and operating systems; innovation in software systems; signal processing and real-time systems; computer security; innovation in computer science education; and digital governance and smart cities. COMPUTERS,Online Services

Data Science and Analytics This two-volume set (CCIS 1229 and CCIS 1230) constitutes the refereed proceedings of the 5th International Conference on Recent Developments in Science, Engineering and Technology, REDSET 2019, held in Gurugram, India, in November 2019. The 74 revised full papers presented were carefully reviewed and selected from total 353 submissions. The papers are organized in topical sections on data centric programming; next generation computing; social and web analytics; security in data science analytics; big data analytics. COMPUTERS,Online Services

Data Science and Analytics This two-volume set (CCIS 1229 and CCIS 1230) constitutes the refereed proceedings of the 5th International Conference on Recent Developments in Science, Engineering and Technology, REDSET 2019, held in Gurugram, India, in November 2019. The 74 revised full papers presented were carefully reviewed and selected from total 353 submissions. The papers are organized in topical sections on data centric programming; next generation computing; social and web analytics; security in data science analytics; big data analytics. COMPUTERS,Online Services

Smart Applications and Data Analysis This volume constitutes refereed proceedings of the Third International Conference on Smart Applications and Data Analysis, SADASC 2020, held in Marrakesh, Morocco. Due to the COVID-19 pandemic the conference has been postponed to June 2020. The 24 full papers and 3 short papers presented were thoroughly reviewed and selected from 44 submissions. The papers are organized according to the following topics: ontologies and meta modeling; cyber physical systems and block-chains; recommender systems; machine learning based applications; combinatorial optimization; simulations and deep learning. COMPUTERS,Online Services

Image Analysis and Recognition This two-volume set LNCS 12131 and LNCS 12132 constitutes the refereed proceedings of the 17th International Conference on Image Analysis and Recognition, ICIAR 2020, held in Póvoa de Varzim, Portugal, in June 2020.The 54 full papers presented together with 15 short papers were carefully reviewed and selected from 123 submissions. The papers are organized in the following topical sections: image processing and analysis; video analysis; computer vision; 3D computer vision; machine learning; medical image and analysis; analysis of histopathology images; diagnosis and screening of ophthalmic diseases; and grand challenge on automatic lung cancer patient management. Due to the corona pandemic, ICIAR 2020 was held virtually only. COMPUTERS,Online Services

Cognitive Cities This book constitutes refereed proceeding of the Second International Cognitive Cities Conference, IC3 2019, held in Kyoto, Japan, in September 2019. The 37 full papers and 46 short papers were thoroughly reviewed and selected from 206 submissions. The papers are organized according to the topical sections on cognitive city for special needs; cognitive city theory, modeling and simulation; XR and educational innovations for cognitive city; educational technology and strategy in cognitive city; safety, security and privacy in cognitive city; artificial intelligence theory and technology related to cognitive city; Internet of Things for cognitive city; business application and management for cognitive city; big data for cognitive city; engineering technology and applied science for cognitive city; maker, CT and STEAM education for cognitive city. COMPUTERS,Online Services

Big Data Analytics for Cyber-Physical Systems This book highlights research and survey articles dedicated to big data techniques for cyber-physical system (CPS), which addresses the close interactions and feedback controls between cyber components and physical components. The book first discusses some fundamental big data problems and solutions in large scale distributed CPSs. The book then addresses the design and control challenges in multiple CPS domains such as vehicular system, smart city, smart building, and digital microfluidic biochips. This book also presents the recent advances and trends in the maritime simulation system and the flood defence system. COMPUTERS,Online Services

Bias and Social Aspects in Search and Recommendation This book constitutes refereed proceedings of the First International Workshop on Algorithmic Bias in Search and Recommendation, BIAS 2020, held in April, 2020. Due to the COVID-19 pandemic BIAS 2020 was held virtually. The 10 full papers and 7 short papers were carefully reviewed and seleced from 44 submissions. The papers cover topics that go from search and recommendation in online dating, education, and social media, over the impact ofgender bias in word embeddings, to tools that allow to explore bias and fairnesson the Web. COMPUTERS,Online Services

Finite Automata Interest in finite automata theory continues to grow, not only because of its applications in computer science, but also because of more recent applications in mathematics, particularly group theory and symbolic dynamics. The subject itself lies on the boundaries of mathematics and computer science, and with a balanced approach that does justice to COMPUTERS,Operating Systems,General

RSA and Public-Key Cryptography Although much literature exists on the subject of RSA and public-key cryptography, until now there has been no single source that reveals recent developments in the area at an accessible level. Acclaimed author Richard A. Mollin brings together all of the relevant information available on public-key cryptography (PKC), from RSA to the latest applic COMPUTERS,Operating Systems,General

Solaris 10 ZFS Essentials The ZFS file system offers a dramatic advance in data management with an innovative approach to data integrity, tremendous performance improvements, and a welcome integration of file system and volume management capabilities. The centerpiece of this new architecture is the concept of a virtual storage pool, which decouples the file system from physical storage in the same way that virtual memory abstracts the address space from physical memory, allowing for much more efficient use of storage devices. In ZFS, space is shared dynamically between multiple file systems from a single storage pool and is parceled out from the pool as file systems request it. Physical storage can therefore be added to storage pools dynamically, without interrupting services. This provides new levels of flexibility, availability, and performance. Because ZFS is a 128-bit file system, its theoretical limits are truly mind-boggling–2128 bytes of storage and 264 for everything else, including file systems, snapshots, directory entries, devices, and more. Solaris ™ 10 ZFS Essentials is the perfect guide for learning how to deploy and manage ZFS file systems. If you are new to Solaris or are using ZFS for the first time, you will find it very easy to get ZFS up and running on your home system or your business IT infrastructure by following the simple instructions in this book. Then you too will understand all the benefits ZFS offers: Rock-solid data integrity No silent data corruption–ever Mind-boggling scalability Breathtaking speed Near-zero administration Solaris ™ 10 ZFS Essentials is part of the Solaris System Administration Series and is intended for use as a full introduction and hands-on guide to Solaris ZFS. COMPUTERS,Operating Systems,General

Shell Scripting A compendium of shell scripting recipes that can immediately be used, adjusted, and applied The shell is the primary way of communicating with the Unix and Linux systems, providing a direct way to program by automating simple-to-intermediate tasks. With this book, Linux expert Steve Parker shares a collection of shell scripting recipes that can be used as is or easily modified for a variety of environments or situations. The book covers shell programming, with a focus on Linux and the Bash shell; it provides credible, real-world relevance, as well as providing the flexible tools to get started immediately. Shares a collection of helpful shell scripting recipes that can immediately be used for various of real-world challenges Features recipes for system tools, shell features, and systems administration Provides a host of plug and play recipes for to immediately apply and easily modify so the wheel doesn't have to be reinvented with each challenge faced Come out of your shell and dive into this collection of tried and tested shell scripting recipes that you can start using right away! COMPUTERS,Operating Systems,General

Linux Universe I ntrod uction or some time 32-bit machines have been a hot topic in the world F ofPCs. It seems that more powerful operating systems will soon be displacing DOS. Meanwhile, at least in the professional literature, lively discussion has been raging about what the future standard will be. Two alternatives seem to be emerging for the domain of server operating systems: Windows NT, and UNIX variants such as UNIX VS. Windows NT Solaris 2, UnixWare, and NextStep 486. In this context OS/2 plays no significant role since it is seen more as a competitor to Windows in its current version and future 32-bit versions. We cannot yet predict which system will finally predominate. However, the significant rise in the power of hardware in recent years has unleashed the demand for a modern operating system that makes use of these developments. Under a modern server operating system, the borderline between classical UNIX workstations and high-end workstations PCs will tend to become more fluid. 1.1 Historical perspectives on Linux An extremely powerful alternative to the above proprietary systems has evolved far from all the big debates on strategy. The system is Linux, a UNIX system for Intel processors that is available for free. COMPUTERS,Operating Systems,General

LINUX Start-up Guide Preface The Linux Start-Up Guide has been written for both private and professional Linux users. Its purpose is to give a solid under standing of the Unix-like operating system kernel and its-system commands. This book is intended for beginners, system administrators, and people who have worked with other systems. Experienced Unix and Linux users will still find it useful, as all main Linux features have been treated extensive, reducing the need to study other documentation. Without a doubt, it is not possible to give a comprehensive description of every typical Linux tool in just 300 pages. There fore, I have concentrated on providing detailed and well struc tured explanations of the fundamental Unix commands, the most important editors, network applications, and the X Window System. I also thought it important to give a general idea of the concepts underlying each topic and to mention the historic milestones that influenced the current state of development. COMPUTERS,Operating Systems,General

Linux Unleashing the Workstation in Your PC NIX achieved its widespread propagation, its penetration of the UNIX history U university domain, and its reach into research and industry due to its early dissemination by AT&T to all interested parties at almost no cost and as source code. UNIX's present functionality emanated not just from AT&T developers but also from many external developers who used the product and contributed their own further developments, which they then put at AT&T's disposal. (Consider the contributions of the University of California at Berkeley, for example. ) With the rising commercialization of UNIX by AT&T (and the current owner, Novell) since 1983, and with the philosophical wars between the large UNIX vendors such as Sun, HP, Digital, IBM, SCQ and the UNIX laboratory, as well the more rhetorical than factual discussions between QSF and UNIX International , such creative and cooperative continuing development became increasingly restricted, and UNIX source code today has become unaffordably expensive and de facto inaccessible. Linux has changed the situation. Linux provides interested computer scientists and users with a system that revives the old UNIX tradition: Linux is available for free, and everyone is heartily free & participatory invited (but not obliged) to contribute to its continuing development. When I wrote the foreword to the first edition of this book in 1994, Linux, because it ran on PC systems, had begun to penetrate the workrooms of many computer science students and computer freaks. COMPUTERS,Operating Systems,General

The Craft of Windows 95â„¢ Interface Design Good software interface design is as crucial to a product's success as is its functionality. With the availability of visual development tools such as Visual Basic and Visual C++, more and more developers of applications will need to understand and use principles of good interface design. This book will help guide the reader to a better understanding of how to make Windows software simple to navigate and a pleasure to use. The author concentrates on the development of user-interfaces for Windows 95 and NT software and introduces some important design techniques such as prototyping, UI bulking, Rapid Layout Comparison, and the Side-by-Side Design Approach. Readers are assumed to have a working knowledge of development tools such as Visual C++ and to be working with the Microsoft Guidelines for Interface Design. COMPUTERS,Operating Systems,General

LINUX UNIX achieved its widespread propagation, its penetration of the UNIX history university domain, and its reach into research and industry due to its early dissemination by AT&T to all interested parties at almost no cost and as source code. UNIX's present functionality emanated not just from AT&T developers but also from external developers who used the product and contributed their own further developments, which they then put at AT&T's disposal. (Consider the contributions of the University of California at Berkeley, for example.) With the rising commercialization of UNIX by AT&T (now by Novell) since 1983, such creative and cooperative further development became increasingly restricted, and UNIX source code today has become unaffordably expensive and scarcely accessible. Linux provides interested computer scientists and us"ers with a system that revives the old UNIX tradition: Linux is available for free, and everyone is heartily invited (but not obliged) to free & participatory contribute to its further development. Since Linux runs on PC systems, it has begun to penetrate the workrooms of many computer science students and computer freaks. COMPUTERS,Operating Systems,General

Programming with Motifâ„¢ About this Book This book is a detailed introduction to programming with the OSF /MotifI'M graphical user interface. It is an introduction in that it does not require the reader to have experience programming in the X Window environment. It is detailed in that it teaches you how to use the interface components provided by Motif in a complex application. Although it contains a great deal of reference material, it is not meant as an authoritative reference - that is the job of the OSF/Motif Programmer's Reference, which uses over 900 pages in the process. Instead, this book provides its reference material in a practical, "how to" manner and allows the reader to use the Programmer's Reference effectively. The target reader is an experienced C programmer and user of the X Window System under the UNIX operating system. 'the reader should be familiar with the tools provided by UNIX for the compilation and testing of programs; while this book does examine the process by which a Motif program is compiled, it does not explain that process. It also assumes that the reader is familiar with "x" terms such as 'pointer' and 'display'. COMPUTERS,Operating Systems,General

Catalogue of Distributed File/Operating Systems In general, distributed systems can be classified into Distributed File Systems (DFS) and Distributed Operating Systems (DOS). The survey which follows distinguishes be tween DFS approaches in Chapters 2-3, and DOS approaches in Chapters 4-5. Within DFS and DOS, I further distinguish "traditional" and object-oriented approaches. A traditional approach is one where processes are the active components in the systems and where the name space is hierarchically organized. In a centralized environment, UNIX would be a good example of a traditional approach. On the other hand, an object-oriented approach deals with objects in which all information is encapsulated. Some systems of importance do not fit into the DFS/DOS classification. I call these systems "closely related" and put them into Chapter 6. Chapter 7 contains a table of comparison. This table gives a lucid overview summarizing the information provided and allowing for quick access. The last chapter is added for the sake of completeness. It contains very brief descriptions of other related systems. These systems are of minor interest or do not provide transparency at all. Sometimes I had to assign a system to this chapter simply for lack of adequate information about it. COMPUTERS,Operating Systems,General

PC Viruses PC viruses are not necessarily a major disaster despite what is sometimes written about them. But a virus infection is at the very least a nuisance, and potentially can lead to loss of data. Quite often it is the user's panic reaction to discovering a virus infection that does more than the virus itself. This book demystifies PC viruses, providing clear, accurate information about this relatively new PC problem. It enables managers and PC users to formulate an appropriate response; adequate for prevention and cure, but not `over the top'. Over 100 PC viruses and variants are documented in detail. You are told how to recognise each one, what it does, how it copies itself, and how to get rid of it. Other useful and relevant technical information is also provided. Strategies for dealing with potential and actual virus outbreaks are described for business, academic and other environments, with the emphasis on sensible but not unreasonable precautions. All users of IBM PC or compatible computers - from single machines to major LAN's - will find this book invaluable. All that is required is a working knowledge of DOS. Dr. Alan Solomon has been conducting primary research into PC viruses since they first appeared, and has developed the best-selling virus protection software Dr. Solomon's Anti-Virus Toolkit. COMPUTERS,Operating Systems,General

A System V Guide to UNIX and XENIX A System V Guide to UNIX and XENIX takes the novice reader through the features of the UNIX system step-by-step without jargon and assumptions about the reader's technical knowledge found in similar books. With its clear explanations, numerous examles, and straightforward organization, this book appeals to many non-technical people just beginning to work with UNIX, as well as engineers and programmers with prior experience. Anyone who reads this book will learn how to use the features of UNIX, and how to modify and customize those features. It is organized in such a way that it leads the reader from the UNIX basics to the more complex and powerful concepts such as shell-programming and networking. Although the book is written as introduction and reference for the UNIX user, it can very well be used as a textbook in undergraduate computer science or computer engineering courses. COMPUTERS,Operating Systems,General

Handbook of Graph Theory In the ten years since the publication of the best-selling first edition, more than 1,000 graph theory papers have been published each year. Reflecting these advances, Handbook of Graph Theory, Second Edition provides comprehensive coverage of the main topics in pure and applied graph theory. This second edition-over 400 pages longer than its prede COMPUTERS,Operating Systems,General

Introduction to Modern Cryptography Cryptography is ubiquitous and plays a key role in ensuring data secrecy and integrity as well as in securing computer systems more broadly. Introduction to Modern Cryptography provides a rigorous yet accessible treatment of this fascinating subject. The authors introduce the core principles of modern cryptography, with an emphasis on formal defini COMPUTERS,Operating Systems,General

Applied Combinatorics Now with solutions to selected problems, Applied Combinatorics, Second Edition presents the tools of combinatorics from an applied point of view. This bestselling textbook offers numerous references to the literature of combinatorics and its applications that enable readers to delve more deeply into the topics. After introducing fundamental counting rules and the tools of graph theory and relations, the authors focus on three basic problems of combinatorics: counting, existence, and optimization problems. They discuss advanced tools for dealing with the counting problem, including generating functions, recurrences, inclusion/exclusion, and Pólya theory. The text then covers combinatorial design, coding theory, and special problems in graph theory. It also illustrates the basic ideas of combinatorial optimization through a study of graphs and networks. COMPUTERS,Operating Systems,General

Linux - Unleashing the Workstation in Your PC NIX achieved its widespread propagation, its penetration of UNIX history U the university domain, and its reach into research and industry due to its early dissemination by AT&T to all interested parties at almost no cost and as source code. UNIX's present functionality emanated not just from AT&T developers but also from many external developers who used the product and contributed their own further developments, which they then put at AT&T's disposal. (Consider the contributions of the University of California at Berkeley, for example.) With the rising commercialization of UNIX by AT&T (and the current owner, Novell) since 1983, and with the philosophical wars between the large UNIX vendors such as Sun, HP, Digital, IBM, SCQ, and the UNIX laboratory, as well the more rhetorical than factual discussions between QSF and UNIX International, such creative and cooperative continuing development became increasingly restricted, and UNIX source code today has become unaffordably expensive and de facto inaccessible. Linux has changed the situation. Linux provides interested computer scientists and users with a system that revives the old UNIX tradition: Linux is available for free, and everyone is heartily free & participatory invited (but not obliged) to contribute to its continuing development. When I wrote the foreword to the first edition of this book in 1994, Linux, because it ran on PC systems, had begun to penetrate the workrooms of many computer science students and computer freaks. COMPUTERS,Operating Systems,General

Linux Universe Linux is a relatively new shareware Unix system for PCs (386 to Pentium) which was developed by an international community on the Internet. It is a viable alternative to commercial Unix workstations with characteristics comparable to a RISC workstation. This CD contains a complete Linux system and comes with a complete installation guide. The graphical administration tools make it easy to use even for novices. COMPUTERS,Operating Systems,General

Introduction to Enumerative and Analytic Combinatorics Introduction to Enumerative and Analytic Combinatorics fills the gap between introductory texts in discrete mathematics and advanced graduate texts in enumerative combinatorics. The book first deals with basic counting principles, compositions and partitions, and generating functions. It then focuses on the structure of permutations, graph enumerat COMPUTERS,Operating Systems,General

Discrete Mathematics and Applications Discrete Mathematics and Applications, Second Edition is intended for a one-semester course in discrete mathematics. Such a course is typically taken by mathematics, mathematics education, and computer science majors, usually in their sophomore year. Calculus is not a prerequisite to use this book. Part one focuses on how to write proofs, then moves on to topics in number theory, employing set theory in the process. Part two focuses on computations, combinatorics, graph theory, trees, and algorithms. Emphasizes proofs, which will appeal to a subset of this course market Links examples to exercise sets Offers edition that has been heavily reviewed and developed Focuses on graph theory Covers trees and algorithms COMPUTERS,Operating Systems,General

JUNOS Automation Cookbook Administer, configure, and monitor Junos in your organization About This Book Get well acquainted with security and routing policies to identify the use of firewall filters. Learn to provide end-user authentication and protect each layer in an enterprise network. A recipe-based guide that will help you configure and monitor Junos OS and basic device operations. Who This Book Is For This book targets network engineers, developers, support personals, and administrators who are working on devices running Junos OS and are looking at automating their organisation's operations. Some understanding about Junos would be necessary What You Will Learn Start using NETCONF RPC standard and understand its usefulness in programming JUNOS Write SLAX scripts to respond to events in the JUNOS environment Automate JUNOS with PyEZ Deal with events in the JUNOS environment, and writing response handlers to deal with them Make the most of automation technologies to help with maintenance and monitoring of JUNOS Use the Ansible framework to extend the automation functionality of Junos In Detail The JUNOS Automation Cookbook is a companion guide for the complex field of automating tasks on JUNOS devices. With a foundation in industry-standrd XML, JUNOS provides an ideal environment for programmatic interation, allowing you to build upon the capabilities provided by Juniper, with your own original code. You will begin by learning about, and setting up, the industry-standard NETCONF remote procedure call mechanisms on your device. After initial setup, you'll walk through SLAX - Juniper's foundation scripting language - for manipulating XML representations of JUNOS concepts and elements. You'll learn how to write your own SLAX scripts to customise the operating environment, and also how to write proactive event handlers that deal with situations as they happen. You'll then delve into PyEZ - Juniper's bridging framework to make automation accessible to Python code - allowing you to build automation applications in the popular scripting language. You'll witness some examples of how to write applications that can monitor configuration changes, implement BGP security policies and implement ad-hoc routing protocols, for those really tricky situations. You'll also leaarn how asynchronous I/O frameworks like Node.js can be used to implement automation applications that present an acceptable web interface. Along with way, you'll explore how to make use of the latest RESTful APIs that JUNOS provides, how to visualize aspects of your JUNOS network, and how to integrate your automation capabilities with enterprise-wide orchestration systems like Ansible. By the end of the book, you'll be able to tackle JUNOS automation challenges with confidence and understanding, and without hassle. Style and Approach A guide that will cover all the automation tools along with steps on leveraging these tools COMPUTERS,Operating Systems,General

Introduction to Radar Analysis Introduction to Radar Analysis, Second Edition is a major revision of the popular textbook. It is written within the context of communication theory as well as the theory of signals and noise. By emphasizing principles and fundamentals, the textbook serves as a vital source for students and engineers. Part I bridges the gap between communication, signal analysis, and radar. Topics include modulation techniques and associated Continuous Wave (CW) and pulsed radar systems. Part II is devoted to radar signal processing and pulse compression techniques. Part III presents special topics in radar systems including radar detection, radar clutter, target tracking, phased arrays, and Synthetic Aperture Radar (SAR). Many new exercise are included and the author provides comprehensive easy-to-follow mathematical derivations of all key equations and formulas. The author has worked extensively for the U.S. Army, the U.S. Space and Missile Command, and other military agencies. This is not just a textbook for senior level and graduates students, but a valuable tool for practicing radar engineers. Features Authored by a leading industry radar professional. Comprehensive up-to-date coverage of radar systems analysis issues. Easy to follow mathematical derivations of all equations and formulas Numerous graphical plots and table format outputs. One part of the book is dedicated to radar waveforms and radar signal processing. COMPUTERS,Operating Systems,General

Windows Server 2016 Administration Fundamentals Manage and administer your environment with ease About This Book Get your hands on learning the fundamentals to managing and administering Windows Server 2016. A step-by-step guide that will help you develop necessary skills and knowledge to manage an enterprise environment. Learn to implement strong networking and security practices into your Windows Server environment. Who This Book Is For If you are a System administrator or an IT professional interested in configuring and deploying Windows Server 2016 then, this book is for you. This book will also help readers clear the MTA: Windows Server Administration Fundamentals: 98-365 exam. What You Will Learn Become familiar with Windows Server OS concepts Learn how to install Windows Server 2016 Learn how to install device drivers and run services in Windows Server 2016 Learn how to add and install roles in Windows Server 2016 Learn how to apply GPO to your Windows Server 2016 environment Learn how to tune, maintain, update, and troubleshoot Windows Server 2016 Prepare for the MTA 98-365 exam In Detail Windows Server 2016 is the server operating system developed by Microsoft as part of the Windows NT family of operating systems, developed concurrently with Windows 10. This book is designed to get you started with Windows Server 2016. It will prepare you for your MTA 98-365 exam. With step-by-step instructions driven by targeted, easy-to-understand graphics, you will be able to understand the roles, features, functions, and quirks of Windows Server 2016. The book begins with the basics of Windows Server 2016, which includes the installation process and basic configuration. You will then move on to roles and features such as Active Directory, Hyper-V, Remote Access, Storage, and Printer. With the help of real-world examples, you will get to grips with the fundamentals of Windows Server 2016, which will help you solve difficult tasks the easy way. Later, the book also shows you maintenance and troubleshooting tasks, where with the help of best practices you will be able to manage Windows Server 2016 with ease. Each chapter ends with a questionnaire to ensure you make the best use of the content provided. By the end of this book, you will have the knowledge required to administer and manage Windows Server environments. Style and approach With step-by-step instructions driven by targeted, easy-to-understand graphics, this book explains and shows you how to use the roles and features, functions, and quirks of the Windows Server 2016. The chapters are presented in a step by step format accompanied by graphics wherever applicable. COMPUTERS,Operating Systems,General

Mastering Ubuntu Server Get up-to-date with the finer points of Ubuntu Server using this comprehensive guide About This Book A practical easy-to-understand book that will teach you how to deploy, maintain and troubleshoot Ubuntu Server Get well-versed with newly-added features in Ubuntu 18.04. Learn to manage cutting-edge technologies such as virtualization, containers, Nextcloud and more Who This Book Is For This book is intended for readers with intermediate or advanced-beginner skills with Linux, who would like to learn all about setting up servers with Ubuntu Server. This book assumes that the reader knows the basics of Linux, such as editing configuration files and running basic commands. What You Will Learn Manage users, groups, and permissions Encrypt and decrypt disks with Linux Unified Key Setup (LUKS) Set up SSH for remote access, and connect it to other nodes Add, remove, and search for packages Use NFS and Samba to share directories with other users Get to know techniques for managing Apache and MariaDB Explore best practices and troubleshooting techniques Get familiar with scripting Automate server deployments with Ansible In Detail Ubuntu Server has taken the data centers by storm. Whether you're deploying Ubuntu for a large-scale project or for a small office, it is a stable, customizable, and powerful Linux distribution that leads the way with innovative and cutting-edge features. For both simple and complex server deployments, Ubuntu's flexible nature can be easily adapted to meet to the needs of your organization. With this book as your guide, you will learn all about Ubuntu Server, from initial deployment to creating production-ready resources for your network. The book begins with the concept of user management, group management, and filesystem permissions. Continuing into managing storage volumes, you will learn how to format storage devices, utilize logical volume management, and monitor disk usage. Later, you will learn how to virtualize hosts and applications, which will cover setting up KVM/QEMU, as well as containerization with both Docker and LXD. As the book continues, you will learn how to automate configuration with Ansible, as well as take a look at writing scripts. Lastly, you will explore best practices and troubleshooting techniques when working with Ubuntu Server that are applicable to real-world scenarios. By the end of the book, you will be an expert Ubuntu Server administrator who is well-versed in its advanced concepts. Style and approach This book is an advanced guide that will show readers how to administer, manage, and deploy Ubuntu server and will also provide expert-level knowledge on advanced security and backup techniques. COMPUTERS,Operating Systems,General

Graph Theory and Its Applications Graph Theory and Its Applications, Third Edition is the latest edition of the international, bestselling textbook for undergraduate courses in graph theory, yet it is expansive enough to be used for graduate courses as well. The textbook takes a comprehensive, accessible approach to graph theory, integrating careful exposition of classical developments with emerging methods, models, and practical needs. The authors’ unparalleled treatment is an ideal text for a two-semester course and a variety of one-semester classes, from an introductory one-semester course to courses slanted toward classical graph theory, operations research, data structures and algorithms, or algebra and topology. Features of the Third Edition Expanded coverage on several topics (e.g., applications of graph coloring and tree-decompositions) Provides better coverage of algorithms and algebraic and topological graph theory than any other text Incorporates several levels of carefully designed exercises that promote student retention and develop and sharpen problem-solving skills Includes supplementary exercises to develop problem-solving skills, solutions and hints, and a detailed appendix, which reviews the textbook’s topics About the Authors Jonathan L. Gross is a professor of computer science at Columbia University. His research interests include topology and graph theory. Jay Yellen is a professor of mathematics at Rollins College. His current areas of research include graph theory, combinatorics, and algorithms. Mark Anderson is also a mathematics professor at Rollins College. His research interest in graph theory centers on the topological or algebraic side. COMPUTERS,Operating Systems,General

Discrete Mathematical Structures This book contains fundamental concepts on discrete mathematical structures in an easy to understand style so that the reader can grasp the contents and explanation easily. The concepts of discrete mathematical structures have application to computer science, engineering and information technology including in coding techniques, switching circuits, pointers and linked allocation, error corrections, as well as in data networking, Chemistry, Biology and many other scientific areas. The book is for undergraduate and graduate levels learners and educators associated with various courses and progammes in Mathematics, Computer Science, Engineering and Information Technology. The book should serve as a text and reference guide to many undergraduate and graduate programmes offered by many institutions including colleges and universities. Readers will find solved examples and end of chapter exercises to enhance reader comprehension. Features Offers comprehensive coverage of basic ideas of Logic, Mathematical Induction, Graph Theory, Algebraic Structures and Lattices and Boolean Algebra Provides end of chapter solved examples and practice problems Delivers materials on valid arguments and rules of inference with illustrations Focuses on algebraic structures to enable the reader to work with discrete structures COMPUTERS,Operating Systems,General

Operating Systems Interview Questions You'll Most Likely Be Asked 225 Operating Systems Interview Questions 77 HR Interview Questions Real life scenario-based questions Strategies to respond to interview questions 2 Aptitude Tests Operating Systems Interview Questions You'll Most Likely Be Asked is a perfect companion to stand ahead above the rest in today’s competitive job market. Rather than going through comprehensive, textbook-sized reference guides, this book includes only the information required immediately for job search to build an IT career. This book puts the interviewee in the driver's seat and helps them steer their way to impress the interviewer. Includes: a) 225 Operating Systems Interview Questions, Answers and proven Strategies for getting hired as an IT professional b) Dozens of examples to respond to interview questions c) 77 HR Questions with Answers and proven strategies to give specific, impressive, answers that help nail the interviews d) 2 Aptitude Tests download available on www.vibrantpublishers.com COMPUTERS,Operating Systems,General

Fedora 31 Essentials Gain access to all the information you need to get started with this exciting, cutting-edge operating system Key Features Start with installation and explore advanced topics, such as file sharing using both Samba and NFS Gain insight into using logical volume management and firewall configuration on a Fedora 31 system Get an overview of network management, including using the NetworkManager service Book Description Linux kernel development is perhaps the world's largest collaborative project to date. With Fedora 31 Essentials, you'll be given easily accessible information to install, use, and administer the Fedora 31 distribution. The book begins with a concise history of the Linux operating system and the Fedora project. You'll learn how to install Fedora 31 using the dual boot configuration so that it can coexist with Windows on the same drive. After installing Fedora 31, you'll learn how to use GNOME 3 — the desktop environment included with Fedora 31 that helps you navigate through the distribution. As you progress, you'll explore the Cockpit web interface that enables you to perform tasks via a web browser instead of using the command-line. You'll also learn how to manage user access and roles on the Fedora 31 system by adding, removing, and managing users and groups. While learning advanced topics, you'll discover how to use Fedora Modularity to list, install, and remove the software packages that make up a functioning Fedora 31 system. By the end of the book, you'll have all the information you need to confidently start working with Fedora 31. What you will learn Manage swap space efficiently to maintain the performance of the Fedora 31 system Perform systemd unit configuration tasks using the systemctl command-line tool Add new disk space to increase the capacity of the root file system Configure a basic Linux-based email environment Configure a Fedora 31 system to act as a web server using Apache Create and manage containers on Fedora 31 Who this book is for Fedora 31 Essentials is the ideal book if you're looking for essential information on getting started using the Fedora 31 distribution. Whether you are a developer, a system administrator, or a tech lover with no previous Linux administration background, you'll be able to start your adventure with this book. COMPUTERS,Operating Systems,General

CentOS 8 Essentials Learn how to install, use, and administer CentOS 8 with the help of expert guidance and engaging examples Key Features Become familiar with a popular and stable Red Hat Enterprise Linux distribution Gain a thorough overview of the operating system by learning concepts such as disk partitioning, KVM virtualization, and more Explore advanced topics such as logical volume management and firewall configuration Book Description Linux kernel development is perhaps the world's largest collaborative project to date. With CentOS 8 Essentials, you'll be given easily accessible information to install, use, and administer the CentOS 8 distribution. The book begins with a concise history of the Linux operating system and CentOS. You'll then learn how to install CentOS 8 using the dual boot configuration so that it can coexist with Windows on the same drive. After installing CentOS, you'll learn GNOME 3 — the desktop environment included with CentOS 8 that helps you navigate through the distribution. As you progress, you'll explore the Cockpit web interface that enables you to perform tasks via a web browser instead of using the command-line. You'll then take a brief tour of the Bash shell environment and learn ways to administer a system that doesn't have a desktop or a Cockpit interface. While learning advanced concepts, you'll see how to manage swap space efficiently and control the performance of CentOS 8. By the end of the book, you'll have all the essential information you need to comfortably start using the CentOS 8 distribution. What you will learn Work in dual boot environments Install and manage packages with App Streams Perform systemd unit configuration tasks using the systemctl command-line tool Configure the RHEL 8 firewall Share files with Linux and Windows systems using Samba and NFS Deploy KVM-based virtual machines Who this book is for CentOS 8 Essentials is an ideal book for you if you want essential information to start using the CentOS 8 distribution. Whether you are a developer, a system administrator, or a tech lover with no previous Linux administration background, you'll be able to start your adventure with this book. COMPUTERS,Operating Systems,General

Cross-Platform GUI Programming with wxWidgets "This book is the best way for beginning developers to learn wxWidgets programming in C++. It is a must-have for programmers thinking of using wxWidgets and those already using it." –Mitch Kapor, founder of Lotus Software and the Open Source Applications Foundation Build advanced cross-platform applications that support native look-and-feel on Windows, Linux, Unix, Mac OS X, and even Pocket PC Master wxWidgets from start to finish–even if you've never built GUI applications before Leverage advanced wxWidgets capabilities: networking, multithreading, streaming, and more CD-ROM: library of development tools, source code, and sample applications Foreword by Mitch Kapor, founder, Lotus Development and Open Source Application Foundation wxWidgets is an easy-to-use, open source C++ API for writing GUI applications that run on Windows, Linux, Unix, Mac OS X, and even Pocket PC–supporting each platform's native look and feel with virtually no additional coding. Now, its creator and two leading developers teach you all you need to know to write robust cross-platform software with wxWidgets. This book covers everything from dialog boxes to drag-and-drop, from networking to multithreading. It includes all the tools and code you need to get great results, fast. From AMD to AOL, Lockheed Martin to Xerox, world-class developers are using wxWidgets to save money, increase efficiency, and reach new markets. With this book, you can, too. wxWidgets quickstart: event/input handling, window layouts, drawing, printing, dialogs, and more Working with window classes, from simple to advanced Memory management, debugging, error checking, internationalization, and other advanced topics Includes extensive code samples for Windows, Linux (GTK+), and Mac OS X About the CD-ROM The CD-ROM contains all of the source code from the book; wxWidgets distributions for Windows, Linux, Unix, Mac OS X, and other platforms; the wxWidgets reference guide; and development tools including the OpenWatcom C++ compiler, the poEdit translation helper, and the DialogBlocks user interface builder. © Copyright Pearson Education. All rights reserved. COMPUTERS,Operating Systems,Linux

Linux Device Drivers Device drivers literally drive everything you're interested in--disks, monitors, keyboards, modems--everything outside the computer chip and memory. And writing device drivers is one of the few areas of programming for the Linux operating system that calls for unique, Linux-specific knowledge. For years now, programmers have relied on the classic Linux Device Drivers from O'Reilly to master this critical subject. Now in its third edition, this bestselling guide provides all the information you'll need to write drivers for a wide range of devices.Over the years the book has helped countless programmers learn: how to support computer peripherals under the Linux operating system how to develop and write software for new hardware under Linux the basics of Linux operation even if they are not expecting to write a driver The new edition of Linux Device Drivers is better than ever. The book covers all the significant changes to Version 2.6 of the Linux kernel, which simplifies many activities, and contains subtle new features that can make a driver both more efficient and more flexible. Readers will find new chapters on important types of drivers not covered previously, such as consoles, USB drivers, and more.Best of all, you don't have to be a kernel hacker to understand and enjoy this book. All you need is an understanding of the C programming language and some background in Unix system calls. And for maximum ease-of-use, the book uses full-featured examples that you can compile and run without special hardware.Today Linux holds fast as the most rapidly growing segment of the computer market and continues to win over enthusiastic adherents in many application areas. With this increasing support, Linux is now absolutely mainstream, and viewed as a solid platform for embedded systems. If you're writing device drivers, you'll want this book. In fact, you'll wonder how drivers are ever written without it. COMPUTERS,Operating Systems,Linux

Understanding the Linux Kernel In order to thoroughly understand what makes Linux tick and why it works so well on a wide variety of systems, you need to delve deep into the heart of the kernel. The kernel handles all interactions between the CPU and the external world, and determines which programs will share processor time, in what order. It manages limited memory so well that hundreds of processes can share the system efficiently, and expertly organizes data transfers so that the CPU isn't kept waiting any longer than necessary for the relatively slow disks. The third edition of Understanding the Linux Kernel takes you on a guided tour of the most significant data structures, algorithms, and programming tricks used in the kernel. Probing beyond superficial features, the authors offer valuable insights to people who want to know how things really work inside their machine. Important Intel-specific features are discussed. Relevant segments of code are dissected line by line. But the book covers more than just the functioning of the code; it explains the theoretical underpinnings of why Linux does things the way it does. This edition of the book covers Version 2.6, which has seen significant changes to nearly every kernel subsystem, particularly in the areas of memory management and block devices. The book focuses on the following topics: Memory management, including file buffering, process swapping, and Direct memory Access (DMA) The Virtual Filesystem layer and the Second and Third Extended Filesystems Process creation and scheduling Signals, interrupts, and the essential interfaces to device drivers Timing Synchronization within the kernel Interprocess Communication (IPC) Program execution Understanding the Linux Kernel will acquaint you with all the inner workings of Linux, but it's more than just an academic exercise. You'll learn what conditions bring out Linux's best performance, and you'll see how it meets the challenge of providing good system response during process scheduling, file access, and memory management in a wide variety of environments. This book will help you make the most of your Linux system. COMPUTERS,Operating Systems,Linux

Managing RAID on Linux Redundant Array of Independent Disks (RAID) technology is becoming a standard feature of computer systems that support mission-critical services like file sharing, mail exchange, or Web servers. RAID offers two benefits to these essential systems: improved I/O performance and fail-safe data storage.Although bandwidth problems on networks are well documented, the internal data transfer bottleneck that exists at the hardware level in each system can also leave you with perplexing performance issues. RAID is a cost-effective and easy-to-manage way to alleviate this bandwidth problem by distributing the I/O load seamlessly across multiple disks and controllers.RAID also provides uninterrupted data access through disk mirroring and parity algorithms. That means systems can remain online even during a disk or controller failure. RAID is scalable, making it robust enough for large, high-traffic sites and small, critical systems. By using RAID, system administrators can combine single disks into terabytes worth of data storage.Managing RAID on Linux covers everything system administrators need to know to put together a system that can support RAID. You will learn about the different types of RAID, along with associated technologies and issues, and how to choose the best RAID system for your needs. With a step-by-step, hands-on approach, the author guides you through the installation of either Linux software RAID or a hardware RAID card. The book shows how to build an array and optionally install a high-performance file system. Contents include: An introduction to RAID and Linux Planning and architecture of your RAID system Building a software RAID Software RAID tools and references Building a hardware RAID Performance and tuning of your RAID system RAID has become the low-cost solution of choice to deal with the ever-increasing demand for data storage space. Written for system administrators, power users, tech managers, and anyone who wants to learn about RAID technology, Managing RAID on Linux sidesteps the often-confusing vendor-specific approach you'll find elsewhere to give you the straight story on RAID. Even non-Linux users will find this book full of valuable material. COMPUTERS,Operating Systems,Linux

Linux in a Nutshell Everything you need to know about Linux is in this book. Written by Stephen Figgins, Ellen Siever, Robert Love, and Arnold Robbins -- people with years of active participation in the Linux community -- Linux in a Nutshell, Sixth Edition, thoroughly covers programming tools, system and network administration tools, the shell, editors, and LILO and GRUB boot loaders. This updated edition offers a tighter focus on Linux system essentials, as well as more coverage of new capabilities such as virtualization, wireless network management, and revision control with git. It also highlights the most important options for using the vast number of Linux commands. You'll find many helpful new tips and techniques in this reference, whether you're new to this operating system or have been using it for years. Get the Linux commands for system administration and network management Use hundreds of the most important shell commands available on Linux Understand the Bash shell command-line interpreter Search and process text with regular expressions Manage your servers via virtualization with Xen and VMware Use the Emacs text editor and development environment, as well as the vi, ex, and vim text-manipulation tools Process text files with the sed editor and the gawk programming language Manage source code with Subversion and git COMPUTERS,Operating Systems,Linux

Ubuntu Ubuntu for everyone! This popular Linux-based operating system is perfect for people with little technical background. It's simple to install, and easy to use -- with a strong focus on security. Ubuntu: Up and Running shows you the ins and outs of this system with a complete hands-on tour. You'll learn how Ubuntu works, how to quickly configure and maintain Ubuntu 10.04, and how to use this unique operating system for networking, business, and home entertainment. This book includes a DVD with the complete Ubuntu system and several specialized editions -- including the Mythbuntu multimedia release. Choose among three desktop environments: GNOME, KDE, or XFCE Connect printers, sound cards, cameras, webcams, and iPhones Use the Linux filesystem with either the desktop or the command line Learn networking functions, such as file and folder sharing and Internet access Get an in-depth introduction to the OpenOffice.org business productivity suite Learn how to use WINE to run Windows programs Implement upgrades quickly and easily Find out where to get, and how to install, other great software for Linux COMPUTERS,Operating Systems,Linux

Understanding Linux Network Internals If you've ever wondered how Linux carries out the complicated tasks assigned to it by the IP protocols -- or if you just want to learn about modern networking through real-life examples -- Understanding Linux Network Internals is for you. Like the popular O'Reilly book, Understanding the Linux Kernel, this book clearly explains the underlying concepts and teaches you how to follow the actual C code that implements it. Although some background in the TCP/IP protocols is helpful, you can learn a great deal from this text about the protocols themselves and their uses. And if you already have a base knowledge of C, you can use the book's code walkthroughs to figure out exactly what this sophisticated part of the Linux kernel is doing. Part of the difficulty in understanding networks -- and implementing them -- is that the tasks are broken up and performed at many different times by different pieces of code. One of the strengths of this book is to integrate the pieces and reveal the relationships between far-flung functions and data structures. Understanding Linux Network Internals is both a big-picture discussion and a no-nonsense guide to the details of Linux networking. Topics include: Key problems with networking Network interface card (NIC) device drivers System initialization Layer 2 (link-layer) tasks and implementation Layer 3 (IPv4) tasks and implementation Neighbor infrastructure and protocols (ARP) Bridging Routing ICMP Author Christian Benvenuti, an operating system designer specializing in networking, explains much more than how Linux code works. He shows the purposes of major networking features and the trade-offs involved in choosing one solution over another. A large number of flowcharts and other diagrams enhance the book's understandability. COMPUTERS,Operating Systems,Linux

Linux Multimedia Hacks The fact that Linux has more multimedia application choices than Mac OS X and Windows combined may come as a surprise to many, but not to those who know Linux well. In Linux Multimedia Hacks, author Kyle Rankin showcases the best available multimedia tools so you can maximize the entertainment capabilities of your favorite OS. Included are tips and tricks for connecting to iPods, creating MP3s and Oggs, watching and making DVDs, turning your Linux box into a Tivo ala MythTV, and much more. You don't have to be a Linux server guru to make use of this book. Linux Multimedia Hacks takes the best of Linux's multimedia tools and with step-by-step instructions shows even novice users how to do cool and useful things with images, audio, and video. It includes entry level hacks that nearly all Linux users will want, such as installing codecs for audio and video playback and managing thousands of photographs. Later, you'll find hacks that cover a variety of advanced projects, from ripping and organizing media files with metatags, to editing video and audio tracks, to creating your own DVDs. Basic or advanced, each hack stands on its own, so you can feel free to jump around to only the sections that interest you. The book is divided into five easy-to-understand chapters: Images: tips range from basic image edits to automated image manipulation Audio: hacks include audio format conversion and tweaking metadata within audio files Video: learn how to covert between video formats, plus how to create your own VCDs and DVDs Broadcast Media: tips include how to access and create you own web broadcasts as well as watch and record TV Web: learn how to make your multimedia creations available to the world As one of the most powerful multimedia platforms around, Linux has far more capabilities and features than meets the eye. This latest Hacks book gives you the technical chops to enjoy them all. COMPUTERS,Operating Systems,Linux

Official Ubuntu Server Book, Portable Documents, The Ubuntu Server is a complete, free server operating system that just works, with the extra Ubuntu polish, innovation, and simplicity that administrators love. Now, there’s a definitive, authoritative guide to getting up-and-running quickly with the newest, most powerful versions of Ubuntu Server. Written by leading members of the Ubuntu community, The Official Ubuntu Server Book, Second Edition, covers all you need to know to make the most of Ubuntu Server, whether you’re a beginner or a battle-hardened senior system administrator. The authors cover Ubuntu Server from start to finish: installation, basic administration and monitoring, security, backup, troubleshooting, system rescue, and much more. They walk through deploying each of the most common server applications, from file and print services to state-of-the-art, cost-saving virtualization and cloud computing. In addition, you’ll learn how to Make the most of Ubuntu Server’s latest, most powerful technologies Discover easy, fast ways to perform key administration tasks Automate Ubuntu installs, no matter how many servers you’re installing Quickly set up low-cost Web servers and e-mail Protect your server with Ubuntu’s built-in and optional security tools Minimize downtime with fault tolerance and clustering Master proven, step-by-step server and network troubleshooting techniques Walk through rescuing an Ubuntu server that won’t boot Create your own private cloud computing infrastructure COMPUTERS,Operating Systems,Linux

Essential Linux Device Drivers This is the eBook version of the printed book. If the print book includes a CD-ROM, this content is not included within the eBook version. “Probably the most wide ranging and complete Linux device driver book I’ve read.†--Alan Cox, Linux Guru and Key Kernel Developer “Very comprehensive and detailed, covering almost every single Linux device driver type.†--Theodore Ts’o, First Linux Kernel Developer in North America and Chief Platform Strategist of the Linux Foundation The Most Practical Guide to Writing Linux Device Drivers Linux now offers an exceptionally robust environment for driver development: with today’s kernels, what once required years of development time can be accomplished in days. In this practical, example-driven book, one of the world’s most experienced Linux driver developers systematically demonstrates how to develop reliable Linux drivers for virtually any device. Essential Linux Device Drivers is for any programmer with a working knowledge of operating systems and C, including programmers who have never written drivers before. Sreekrishnan Venkateswaran focuses on the essentials, bringing together all the concepts and techniques you need, while avoiding topics that only matter in highly specialized situations. Venkateswaran begins by reviewing the Linux 2.6 kernel capabilities that are most relevant to driver developers. He introduces simple device classes; then turns to serial buses such as I2C and SPI; external buses such as PCMCIA, PCI, and USB; video, audio, block, network, and wireless device drivers; user-space drivers; and drivers for embedded Linux–one of today’s fastest growing areas of Linux development. For each, Venkateswaran explains the technology, inspects relevant kernel source files, and walks through developing a complete example. • Addresses drivers discussed in no other book, including drivers for I2C, video, sound, PCMCIA, and different types of flash memory • Demystifies essential kernel services and facilities, including kernel threads and helper interfaces • Teaches polling, asynchronous notification, and I/O control • Introduces the Inter-Integrated Circuit Protocol for embedded Linux drivers • Covers multimedia device drivers using the Linux-Video subsystem and Linux-Audio framework • Shows how Linux implements support for wireless technologies such as Bluetooth, Infrared, WiFi, and cellular networking • Describes the entire driver development lifecycle, through debugging and maintenance • Includes reference appendixes covering Linux assembly, BIOS calls, and Seq files COMPUTERS,Operating Systems,Linux

Embedded Linux Primer Up-to-the-Minute, Complete Guidance for Developing Embedded Solutions with Linux Linux has emerged as today’s #1 operating system for embedded products. Christopher Hallinan’s Embedded Linux Primer has proven itself as the definitive real-world guide to building efficient, high-value, embedded systems with Linux. Now, Hallinan has thoroughly updated this highly praised book for the newest Linux kernels, capabilities, tools, and hardware support, including advanced multicore processors. Drawing on more than a decade of embedded Linux experience, Hallinan helps you rapidly climb the learning curve, whether you’re moving from legacy environments or you’re new to embedded programming. Hallinan addresses today’s most important development challenges and demonstrates how to solve the problems you’re most likely to encounter. You’ll learn how to build a modern, efficient embedded Linux development environment, and then utilize it as productively as possible. Hallinan offers up-to-date guidance on everything from kernel configuration and initialization to bootloaders, device drivers to file systems, and BusyBox utilities to real-time configuration and system analysis. This edition adds entirely new chapters on UDEV, USB, and open source build systems. Tour the typical embedded system and development environment and understand its concepts and components. Understand the Linux kernel and userspace initialization processes. Preview bootloaders, with specific emphasis on U-Boot. Configure the Memory Technology Devices (MTD) subsystem to interface with flash (and other) memory devices. Make the most of BusyBox and latest open source development tools. Learn from expanded and updated coverage of kernel debugging. Build and analyze real-time systems with Linux. Learn to configure device files and driver loading with UDEV. Walk through detailed coverage of the USB subsystem. Introduces the latest open source embedded Linux build systems. Reference appendices include U-Boot and BusyBox commands. COMPUTERS,Operating Systems,Linux

Practical Guide to Fedora and Red Hat Enterprise Linux, A “I have found this book to be a very useful classroom text, as well as a great Linux resource. It teaches Linux using a ground-up approach that gives students the chance to progress with their skills and grow into the Linux world. I have often pointed to this book when asked to recommend a solid Linux reference.†—Eric Hartwell, Chair, School of Information Technology, ITT Technical Institute The #1 Fedora and RHEL resource–a tutorial AND on-the-job reference Master Linux administration and security using GUI-based tools, the command line, and Perl scripts Set up key Internet servers, step by step, including Samba, Apache, sendmail, DNS, LDAP, FTP, and more Master All the Techniques You Need to Succeed with Fedora™ and Red Hat® Enterprise Linux® In this book, one of the world’s leading Linux experts brings together all the knowledge you need to master Fedora or Red Hat Enterprise Linux and succeed with it in the real world. Best-selling author Mark Sobell explains Linux clearly and effectively, focusing on skills you’ll actually use as a user, programmer, or administrator. Now an even more versatile learning resource, this edition adds skill objectives at the beginning of each chapter. Sobell assumes no prior Linux knowledge. He starts at the beginning and walks you through every topic and task that matters, using easy-to-understand examples. Step by step, you’ll learn how to install and configure Linux, navigate its graphical user interface, provide file/print sharing, configure network servers, secure Linux desktops and networks, work with the command line, administer Linux efficiently, and even automate administration with Perl scripts. Mark Sobell has taught hundreds of thousands of Linux and UNIX professionals. He knows every Linux nook and cranny–and he never forgets what it’s like to be new to Linux. Whatever you want to do with Linux–now or in the future–you’ll find it here. Compared with the other Linux books out there, A Practical Guide to Fedora™ and Red Hat® Enterprise Linux®, Sixth Edition, delivers Complete, up-to-the-minute coverage of Fedora 15 and RHEL 6 State-of-the-art security techniques, including up-to-date firewall setup techniques using system-config-firewall and iptables, and a full chapter on OpenSSH (ssh) Coverage of crucial topics such as using su and sudo, and working with the new systemd init daemon Comprehensive coverage of the command line and key system GUI tools More practical coverage of file sharing using Samba, NFS, and FTP Superior coverage of automating administration with Perl More usable, realistic coverage of Internet server configuration, including Apache (Web), sendmail, NFSv4, DNS/BIND, and LDAP, plus new coverage of IPv6 More and better coverage of system/network administration tasks, including network monitoring with Cacti Deeper coverage of essential administration tasks–from managing users to CUPS printing, configuring LANs to building a kernel Complete instructions on keeping Linux systems up-to-date using yum And much more, including a 500+ term glossary and comprehensive indexes COMPUTERS,Operating Systems,Linux

Red Hat Enterprise Linux 6 Administration The definitive guide to administering a Red Hat Enterprise Linux 6 network Linux professionals who need a go-to guide on version 6 of Red Hat Enterprise Linux (RHEL) will find what they need in this comprehensive Sybex book. It covers RHEL administration in detail, including how to set up and manage web and mail services, use RHEL in enterprise environments, secure it, optimize storage, configure for virtualization and high availability, and much more. It also provides a great study aid for those preparing for either the RHCSA or RHCE certification exam. Red Hat is the Linux market leader, and Red Hat administrators are in demand This Sybex guide is a comprehensive resource on Red Hat Enterprise Linux administration and useful for those preparing for one of the Red Hat certification exams Covers setting up and managing web and mail services, using RHEL in enterprise environments, securing RHEL, and optimizing storage to fit your environment Explores advanced RHEL configurations, including virtualization and high availability Red Hat Enterprise Linux 6 Administration is the guide Linux professionals and Red Hat administrators need to stay current on the newest version. COMPUTERS,Operating Systems,Linux

Linux System Programming Write software that draws directly on services offered by the Linux kernel and core system libraries. With this comprehensive book, Linux kernel contributor Robert Love provides you with a tutorial on Linux system programming, a reference manual on Linux system calls, and an insider’s guide to writing smarter, faster code. Love clearly distinguishes between POSIX standard functions and special services offered only by Linux. With a new chapter on multithreading, this updated and expanded edition provides an in-depth look at Linux from both a theoretical and applied perspective over a wide range of programming topics, including: A Linux kernel, C library, and C compiler overview Basic I/O operations, such as reading from and writing to files Advanced I/O interfaces, memory mappings, and optimization techniques The family of system calls for basic process management Advanced process management, including real-time processes Thread concepts, multithreaded programming, and Pthreads File and directory management Interfaces for allocating memory and optimizing memory access Basic and advanced signal interfaces, and their role on the system Clock management, including POSIX clocks and high-resolution timers COMPUTERS,Operating Systems,Linux

Linux Command Line and Shell Scripting Bible Talk directly to your system for a faster workflow with automation capability Linux Command Line and Shell Scripting Bible is your essential Linux guide. With detailed instruction and abundant examples, this book teaches you how to bypass the graphical interface and communicate directly with your computer, saving time and expanding capability. This third edition incorporates thirty pages of new functional examples that are fully updated to align with the latest Linux features. Beginning with command line fundamentals, the book moves into shell scripting and shows you the practical application of commands in automating frequently performed functions. This guide includes useful tutorials, and a desk reference value of numerous examples. The Linux command line allows you to type specific shell commands directly into the system to manipulate files and query system resources. Command line statements can be combined into short programs called shell scripts, a practice increasing in popularity due to its usefulness in automation. This book is a complete guide providing detailed instruction and expert advice working within this aspect of Linux. Write simple script utilities to automate tasks Understand the shell, and create shell scripts Produce database, e-mail, and web scripts Study scripting examples ranging from basic to advanced Whether used as a tutorial or as a quick reference, this book contains information that every Linux user should know. Why not learn to use the system to its utmost capability? Linux is a robust system with tremendous potential, and Linux Command Line and Shell Scripting Bible opens the door to new possibilities. COMPUTERS,Operating Systems,Linux

Linux Firewalls The Definitive Guide to Building Firewalls with Linux As the security challenges facing Linux system and network administrators have grown, the security tools and techniques available to them have improved dramatically. In Linux® Firewalls, Fourth Edition, long-time Linux security expert Steve Suehring has revamped his definitive Linux firewall guide to cover the important advances in Linux security. An indispensable working resource for every Linux administrator concerned with security, this guide presents comprehensive coverage of both iptables and nftables. Building on the solid networking and firewalling foundation in previous editions, it also adds coverage of modern tools and techniques for detecting exploits and intrusions, and much more. Distribution neutral throughout, this edition is fully updated for today’s Linux kernels, and includes current code examples and support scripts for Red Hat/Fedora, Ubuntu, and Debian implementations. If you’re a Linux professional, it will help you establish an understanding of security for any Linux system, and for networks of all sizes, from home to enterprise. Inside, you’ll find just what you need to Install, configure, and update a Linux firewall running either iptables or nftables Migrate to nftables, or take advantage of the latest iptables enhancements Manage complex multiple firewall configurations Create, debug, and optimize firewall rules Use Samhain and other tools to protect filesystem integrity, monitor networks, and detect intrusions Harden systems against port scanning and other attacks Uncover exploits such as rootkits and backdoors with chkrootkit COMPUTERS,Operating Systems,Linux

Linux Pocket Guide If you use Linux in your day-to-day work, this popular pocket guide is the perfect on-the-job reference. The third edition features new commands for processing image files and audio files, running and killing programs, reading and modifying the system clipboard, and manipulating PDF files, as well as other commands requested by readers. You’ll also find powerful command-line idioms you might not be familiar with, such as process substitution and piping into bash. Linux Pocket Guide provides an organized learning path to help you gain mastery of the most useful and important commands. Whether you’re a novice who needs to get up to speed on Linux or an experienced user who wants a concise and functional reference, this guide provides quick answers. Selected topics include: The filesystem and shell File creation and editing Text manipulation and pipelines Backups and remote storage Viewing and controlling processes User account management Becoming the superuser Network connections Audio and video Installing software Programming with shell scripts COMPUTERS,Operating Systems,Linux

Mastering Embedded Linux Programming Master the techniques needed to build great, efficient embedded devices on Linux About This Book Discover how to build and configure reliable embedded Linux devices This book has been updated to include Linux 4.9 and Yocto Project 2.2 (Morty) This comprehensive guide covers the remote update of devices in the field and power management Who This Book Is For If you are an engineer who wishes to understand and use Linux in embedded devices, this book is for you. It is also for Linux developers and system programmers who are familiar with embedded systems and want to learn and program the best in class devices. It is appropriate for students studying embedded techniques, for developers implementing embedded Linux devices, and engineers supporting existing Linux devices. What You Will Learn Evaluate the Board Support Packages offered by most manufacturers of a system on chip or embedded module Use Buildroot and the Yocto Project to create embedded Linux systems quickly and efficiently Update IoT devices in the field without compromising security Reduce the power budget of devices to make batteries last longer Interact with the hardware without having to write kernel device drivers Debug devices remotely using GDB, and see how to measure the performance of the systems using powerful tools such as perk, ftrace, and valgrind Find out how to configure Linux as a real-time operating system In Detail Embedded Linux runs many of the devices we use every day, from smart TVs to WiFi routers, test equipment to industrial controllers - all of them have Linux at their heart. Linux is a core technology in the implementation of the inter-connected world of the Internet of Things. The comprehensive guide shows you the technologies and techniques required to build Linux into embedded systems. You will begin by learning about the fundamental elements that underpin all embedded Linux projects: the toolchain, the bootloader, the kernel, and the root filesystem. You'll see how to create each of these elements from scratch, and how to automate the process using Buildroot and the Yocto Project. Moving on, you'll find out how to implement an effective storage strategy for flash memory chips, and how to install updates to the device remotely once it is deployed. You'll also get to know the key aspects of writing code for embedded Linux, such as how to access hardware from applications, the implications of writing multi-threaded code, and techniques to manage memory in an efficient way. The final chapters show you how to debug your code, both in applications and in the Linux kernel, and how to profile the system so that you can look out for performance bottlenecks. By the end of the book, you will have a complete overview of the steps required to create a successful embedded Linux system. Style and approach This book is an easy-to-follow and pragmatic guide with in-depth analysis of the implementation of embedded devices. It follows the life cycle of a project from inception through to completion, at each stage giving both the theory that underlies the topic and practical step-by-step walkthroughs of an example implementation. COMPUTERS,Operating Systems,Linux

Embedded Linux Systems with the Yocto Project Build Complete Embedded Linux Systems Quickly and Reliably Developers are increasingly integrating Linux into their embedded systems: It supports virtually all hardware architectures and many peripherals, scales well, offers full source code, and requires no royalties. The Yocto Project makes it much easier to customize Linux for embedded systems. If you’re a developer with working knowledge of Linux, Embedded Linux Systems with the Yocto Project™ will help you make the most of it. An indispensable companion to the official documentation, this guide starts by offering a solid grounding in the embedded Linux landscape and the challenges of creating custom distributions for embedded systems. You’ll master the Yocto Project’s toolbox hands-on, by working through the entire development lifecycle with a variety of real-life examples that you can incorporate into your own projects. Author Rudolf Streif offers deep insight into Yocto Project’s build system and engine, and addresses advanced topics ranging from board support to compliance management. You’ll learn how to Overcome key challenges of creating custom embedded distributions Jumpstart and iterate OS stack builds with the OpenEmbedded Build System Master build workflow, architecture, and the BitBake Build Engine Quickly troubleshoot build problems Customize new distros with built-in blueprints or from scratch Use BitBake recipes to create new software packages Build kernels, set configurations, and apply patches Support diverse CPU architectures and systems Create Board Support Packages (BSP) for hardware-specific adaptations Provide Application Development Toolkits (ADT) for round-trip development Remotely run and debug applications on actual hardware targets Ensure open-source license compliance Scale team-based projects with Toaster, Build History, Source Mirrors, and Autobuilder COMPUTERS,Operating Systems,Linux

Getting Started with Terraform Build, Manage and Improve your infrastructure effortlessly. About This Book An up-to-date and comprehensive resource on Terraform that lets you quickly and efficiently launch your infrastructure Learn how to implement your infrastructure as code and make secure, effective changes to your infrastructure Learn to build multi-cloud fault-tolerant systems and simplify the management and orchestration of even the largest scale and most complex cloud infrastructures Who This Book Is For This book is for developers and operators who already have some exposure to working with infrastructure but want to improve their workflow and introduce infrastructure as a code practice. Knowledge of essential Amazon Web Services components (EC2, VPC, IAM) would help contextualize the examples provided. Basic understanding of Jenkins and Shell scripts will be helpful for the chapters on the production usage of Terraform. What You Will Learn Understand what Infrastructure as Code (IaC) means and why it matters Install, configure, and deploy Terraform Take full control of your infrastructure in the form of code Manage complete infrastructure, starting with a single server and scaling beyond any limits Discover a great set of production-ready practices to manage infrastructure Set up CI/CD pipelines to test and deliver Terraform stacks Construct templates to simplify more complex provisioning tasks In Detail Terraform is a tool used to efficiently build, configure, and improve the production infrastructure. It can manage the existing infrastructure as well as create custom in-house solutions. This book shows you when and how to implement infrastructure as a code practices with Terraform. It covers everything necessary to set up the complete management of infrastructure with Terraform, starting with the basics of using providers and resources. It is a comprehensive guide that begins with very small infrastructure templates and takes you all the way to managing complex systems, all using concrete examples that evolve over the course of the book. The book ends with the complete workflow of managing a production infrastructure as code—this is achieved with the help of version control and continuous integration. The readers will also learn how to combine multiple providers in a single template and manage different code bases with many complex modules. It focuses on how to set up continuous integration for the infrastructure code. The readers will be able to use Terraform to build, change, and combine infrastructure safely and efficiently. Style and approach This book will help and guide you to implement Terraform in your infrastructure. The readers will start by working on very small infrastructure templates and then slowly move on to manage complex systems, all by using concrete examples that will evolve during the course of the book. COMPUTERS,Operating Systems,Linux

How Linux Works, 2nd Edition Unlike some operating systems, Linux doesn’t try to hide the important bits from you—it gives you full control of your computer. But to truly master Linux, you need to understand its internals, like how the system boots, how networking works, and what the kernel actually does. In this completely revised second edition of the perennial best seller How Linux Works, author Brian Ward makes the concepts behind Linux internals accessible to anyone curious about the inner workings of the operating system. Inside, you’ll find the kind of knowledge that normally comes from years of experience doing things the hard way. You’ll learn:–How Linux boots, from boot loaders to init implementations (systemd, Upstart, and System V)–How the kernel manages devices, device drivers, and processes–How networking, interfaces, firewalls, and servers work–How development tools work and relate to shared libraries–How to write effective shell scripts You’ll also explore the kernel and examine key system tasks inside user space, including system calls, input and output, and filesystems. With its combination of background, theory, real-world examples, and patient explanations, How Linux Works will teach you what you need to know to solve pesky problems and take control of your operating system. COMPUTERS,Operating Systems,Linux

Wicked Cool Shell Scripts, 2nd Edition Shell scripts are an efficient way to interact with your machine and manage your files and system operations. With just a few lines of code, your computer will do exactly what you want it to do. But you can also use shell scripts for many other essential (and not-so-essential) tasks. This second edition of Wicked Cool Shell Scripts offers a collection of useful, customizable, and fun shell scripts for solving common problems and personalizing your computing environment. Each chapter contains ready-to-use scripts and explanations of how they work, why you’d want to use them, and suggestions for changing and expanding them. You'll find a mix of classic favorites, like a disk backup utility that keeps your files safe when your system crashes, a password manager, a weather tracker, and several games, as well as 23 brand-new scripts, including: – ZIP code lookup tool that reports the city and state – Bitcoin address information retriever – suite of tools for working with cloud services like Dropbox and iCloud – for renaming and applying commands to files in bulk – processing and editing tools Whether you want to save time managing your system or just find new ways to goof off, these scripts are wicked cool! COMPUTERS,Operating Systems,Linux

Linux Device Drivers Development Learn to develop customized device drivers for your embedded Linux system About This Book Learn to develop customized Linux device drivers Learn the core concepts of device drivers such as memory management, kernel caching, advanced IRQ management, and so on. Practical experience on the embedded side of Linux Who This Book Is For This book will help anyone who wants to get started with developing their own Linux device drivers for embedded systems. Embedded Linux users will benefit highly from this book. This book covers all about device driver development, from char drivers to network device drivers to memory management. What You Will Learn Use kernel facilities to develop powerful drivers Develop drivers for widely used I2C and SPI devices and use the regmap API Write and support devicetree from within your drivers Program advanced drivers for network and frame buffer devices Delve into the Linux irqdomain API and write interrupt controller drivers Enhance your skills with regulator and PWM frameworks Develop measurement system drivers with IIO framework Get the best from memory management and the DMA subsystem Access and manage GPIO subsystems and develop GPIO controller drivers In Detail Linux kernel is a complex, portable, modular and widely used piece of software, running on around 80% of servers and embedded systems in more than half of devices throughout the World. Device drivers play a critical role in how well a Linux system performs. As Linux has turned out to be one of the most popular operating systems used, the interest in developing proprietary device drivers is also increasing steadily. This book will initially help you understand the basics of drivers as well as prepare for the long journey through the Linux Kernel. This book then covers drivers development based on various Linux subsystems such as memory management, PWM, RTC, IIO, IRQ management, and so on. The book also offers a practical approach on direct memory access and network device drivers. By the end of this book, you will be comfortable with the concept of device driver development and will be in a position to write any device driver from scratch using the latest kernel version (v4.13 at the time of writing this book). Style and approach A set of engaging examples to develop Linux device drivers COMPUTERS,Operating Systems,Linux

A Practical Guide to Linux Commands, Editors, and Shell Programming The Most Useful Tutorial and Reference, with Hundreds of High-Quality Examples for Every Popular Linux Distribution “First Sobell taught people how to use Linux . . . now he teaches you the power of Linux. A must-have book for anyone who wants to take Linux to the next level.†–Jon “maddog†Hall, Executive Director, Linux International Discover the Power of Linux—Covers macOS, too! Learn from hundreds of realistic, high-quality examples, and become a true command-line guru Covers MariaDB, DNF, and Python 3 300+ page reference section covers 102 utilities, including macOS commands For use with all popular versions of Linux, including Ubuntu,™ Fedora,™ openSUSE,™ Red Hat,® Debian, Mageia, Mint, Arch, CentOS, and macOS Linux is today’s dominant Internet server platform. System administrators and Web developers need deep Linux fluency, including expert knowledge of shells and the command line. This is the only guide with everything you need to achieve that level of Linux mastery. Renowned Linux expert Mark Sobell has brought together comprehensive, insightful guidance on the tools sysadmins, developers, and power users need most, and has created an outstanding day-to-day reference, updated with assistance from new coauthor Matthew Helmke. This title is 100 percent distribution and release agnostic. Packed with hundreds of high-quality, realistic examples, it presents Linux from the ground up: the clearest explanations and most useful information about everything from filesystems to shells, editors to utilities, and programming tools to regular expressions. Use a Mac? You’ll find coverage of the macOS command line, including macOS-only tools and utilities that other Linux/UNIX titles ignore. A Practical Guide to Linux® Commands, Editors, and Shell Programming, Fourth Edition, is the only guide to deliver A MariaDB chapter to get you started with this ubiquitous relational database management system (RDBMS) A masterful introduction to Python for system administrators and power users In-depth coverage of the bash and tcsh shells, including a complete discussion of environment, inheritance, and process locality, plus coverage of basic and advanced shell programming Practical explanations of core utilities, from aspell to xargs, including printf and sshfs/curlftpfs, PLUS macOS–specific utilities from ditto to SetFile Expert guidance on automating remote backups using rsync Dozens of system security tips, including step-by-step walkthroughs of implementing secure communications using ssh and scp Tips and tricks for customizing the shell, including step values, sequence expressions, the eval builtin, and implicit command-line continuation High-productivity editing techniques using vim and emacs A comprehensive, 300-plus-page command reference section covering 102 utilities, including find, grep, sort, and tar Instructions for updating systems using apt-get and dnf And much more, including coverage of BitTorrent, gawk, sed, find, sort, bzip2, and regular expressions COMPUTERS,Operating Systems,Linux

Linux All-in-One For Dummies 8 mini books chock full of Linux! Inside, over 800 pages of Linux topics are organized into eight task-oriented mini books that help you understand all aspects of the latest OS distributions of the most popular open-source operating system in use today. Topics include getting up and running with basics, desktops, networking, internet services, administration, security, scripting, Linux certification, and more. This new edition of Linux All-in-One For Dummies has a unique focus on Ubuntu, while still including coverage of Debian, Red Hat, SuSE, and others. The market is looking for administrators, and part of the qualifications needed for job openings is the authentication of skills by vendor-neutral third parties (CompTIA/Linux Professional Institute)—and that’s something other books out there don’t address. Install and configure peripherals, software packages, and keep everything current Connect to the internet, set up a local area network (including a primer on TCP/IP, and managing a local area network using configuration tools and files) Browse the web securely and anonymously Get everything you need to pass your entry-level Linux certification exams This book is for anyone getting familiar with the Linux OS, and those looking for test-prep content as they study for the level-1 Linux certification! COMPUTERS,Operating Systems,Linux

Linux Basics for Hackers This practical, tutorial-style book uses the Kali Linux distribution to teach Linux basics with a focus on how hackers would use them. Topics include Linux command line basics, filesystems, networking, BASH basics, package management, logging, and the Linux kernel and drivers. If you're getting started along the exciting path of hacking, cybersecurity, and pentesting, Linux Basics for Hackers is an excellent first step. Using Kali Linux, an advanced penetration testing distribution of Linux, you'll learn the basics of using the Linux operating system and acquire the tools and techniques you'll need to take control of a Linux environment. First, you'll learn how to install Kali on a virtual machine and get an introduction to basic Linux concepts. Next, you'll tackle broader Linux topics like manipulating text, controlling file and directory permissions, and managing user environment variables. You'll then focus in on foundational hacking concepts like security and anonymity and learn scripting skills with bash and Python. Practical tutorials and exercises throughout will reinforce and test your skills as you learn how to: - Cover your tracks by changing your network information and manipulating the rsyslog logging utility- Write a tool to scan for network connections, and connect and listen to wireless networks- Keep your internet activity stealthy using Tor, proxy servers, VPNs, and encrypted email- Write a bash script to scan open ports for potential targets- Use and abuse services like MySQL, Apache web server, and OpenSSH- Build your own hacking tools, such as a remote video spy camera and a password cracker Hacking is complex, and there is no single way in. Why not start at the beginning with Linux Basics for Hackers? COMPUTERS,Operating Systems,Linux

Ubuntu Unleashed 2019 Edition Covers 18.04, 18.10, 19.04, and 19.10 Ubuntu Unleashed 2019 Edition is filled with unique and advanced information for everyone who wants to make the most of the Ubuntu Linux operating system. This new edition has been thoroughly updated, including two new chapters, by a long-time Ubuntu community leader to reflect the exciting new Ubuntu 18.04 LTS release, with forthcoming online updates for 18.10, 19.04, and 19.10 when they are released. Linux writer Matthew Helmke covers all you need to know about Ubuntu 18.04 LTS installation, configuration, productivity, multimedia, development, system administration, server operations, networking, virtualization, security, DevOps, and more—including intermediate-to-advanced techniques you won’t find in any other book. Helmke presents up-to-the-minute introductions to Ubuntu’s key productivity and web development tools, programming languages, hardware support, and more. You’ll find new or improved coverage of the Ubuntu desktop experience, common web servers and software stacks, containers like Docker and Kubernetes, as well as a wealth of systems administration information that is stable and valuable over many years. Configure and use the Ubuntu desktop Get started with multimedia and productivity applications, including LibreOffice Manage Linux services, users, and software packages Administer and run Ubuntu from the command line Automate tasks and use shell scripting Provide secure remote access and configure a secure VPN Manage kernels and modules Administer file, print, email, proxy, LDAP, DNS, and HTTP servers (Apache, Nginx, or alternatives) Learn about new options for managing large numbers of servers Work with databases (both SQL and the newest NoSQL alternatives) Get started with virtualization and cloud deployment, including information about containers Learn the basics about popular programming languages including Python, PHP, Perl, and gain an introduction to new alternatives such as Go and Rust COMPUTERS,Operating Systems,Linux

Learning Kali Linux With more than 600 security tools in its arsenal, the Kali Linux distribution can be overwhelming. Experienced and aspiring security professionals alike may find it challenging to select the most appropriate tool for conducting a given test. This practical book covers Kali’s expansive security capabilities and helps you identify the tools you need to conduct a wide range of security tests and penetration tests. You’ll also explore the vulnerabilities that make those tests necessary. Author Ric Messier takes you through the foundations of Kali Linux and explains methods for conducting tests on networks, web applications, wireless security, password vulnerability, and more. You’ll discover different techniques for extending Kali tools and creating your own toolset. Learn tools for stress testing network stacks and applications Perform network reconnaissance to determine what’s available to attackers Execute penetration tests using automated exploit tools such as Metasploit Use cracking tools to see if passwords meet complexity requirements Test wireless capabilities by injecting frames and cracking passwords Assess web application vulnerabilities with automated or proxy-based tools Create advanced attack techniques by extending Kali tools or developing your own Use Kali Linux to generate reports once testing is complete COMPUTERS,Operating Systems,Linux

Linux Essentials for Cybersecurity ALL YOU NEED TO KNOW TO SECURE LINUX SYSTEMS, NETWORKS, APPLICATIONS, AND DATA–IN ONE BOOK From the basics to advanced techniques: no Linux security experience necessaryRealistic examples & step-by-step activities: practice hands-on without costly equipmentThe perfect introduction to Linux-based security for all students and IT professionals Linux distributions are widely used to support mission-critical applications and manage crucial data. But safeguarding modern Linux systems is complex, and many Linux books have inadequate or outdated security coverage. Linux Essentials for Cybersecurity is your complete solution. Leading Linux certification and security experts William “Bo†Rothwell and Dr. Denise Kinsey introduce Linux with the primary goal of enforcing and troubleshooting security. Their practical approach will help you protect systems, even if one or more layers are penetrated. First, you’ll learn how to install Linux to achieve optimal security upfront, even if you have no Linux experience. Next, you’ll master best practices for securely administering accounts, devices, services, processes, data, and networks. Then, you’ll master powerful tools and automated scripting techniques for footprinting, penetration testing, threat detection, logging, auditing, software management, and more. To help you earn certification and demonstrate skills, this guide covers many key topics on CompTIA Linux+ and LPIC-1 exams. Everything is organized clearly and logically for easy understanding, effective classroom use, and rapid on-the-job training. LEARN HOW TO: Review Linux operating system components from the standpoint of security Master key commands, tools, and skills for securing Linux systems Troubleshoot common Linux security problems, one step at a time Protect user and group accounts with Pluggable Authentication Modules (PAM), SELinux, passwords, and policies Safeguard files and directories with permissions and attributes Create, manage, and protect storage devices: both local and networked Automate system security 24/7 by writing and scheduling scripts Maintain network services, encrypt network connections, and secure network-accessible processes Examine which processes are running–and which may represent a threat Use system logs to pinpoint potential vulnerabilities Keep Linux up-to-date with Red Hat or Debian software management tools Modify boot processes to harden security Master advanced techniques for gathering system information COMPUTERS,Operating Systems,Linux

The Linux Command Line, 2nd Edition You've experienced the shiny, point-and-click surface of your Linux computer--now dive below and explore its depths with the power of the command line. The Linux Command Line takes you from your very first terminal keystrokes to writing full programs in Bash, the most popular Linux shell (or command line). Along the way you'll learn the timeless skills handed down by generations of experienced, mouse-shunning gurus: file navigation, environment configuration, command chaining, pattern matching with regular expressions, and more. In addition to that practical knowledge, author William Shotts reveals the philosophy behind these tools and the rich heritage that your desktop Linux machine has inherited from Unix supercomputers of yore. As you make your way through the book's short, easily-digestible chapters, you'll learn how to: • Create and delete files, directories, and symlinks • Administer your system, including networking, package installation, and process management • Use standard input and output, redirection, and pipelines • Edit files with Vi, the world's most popular text editor • Write shell scripts to automate common or boring tasks • Slice and dice text files with cut, paste, grep, patch, and sed Once you overcome your initial "shell shock," you'll find that the command line is a natural and expressive way to communicate with your computer. Just don't be surprised if your mouse starts to gather dust. COMPUTERS,Operating Systems,Linux

LPIC-1 Linux Professional Institute Certification Study Guide The bestselling study guide for the popular Linux Professional Institute Certification Level 1 (LPIC-1). The updated fifth edition of LPIC-1: Linux Professional Institute Certification Study Guide is a comprehensive, one-volume resource that covers 100% of all exam objectives. Building on the proven Sybex Study Guide approach, this essential resource offers a comprehensive suite of study and learning tools such as assessment tests, hands-on exercises, chapter review questions, and practical, real-world examples. This book, completely updated to reflect the latest 101-500 and 102-500 exams, contains clear, concise, and user-friendly information on all of the Linux administration topics you will encounter on test day. Key exam topics include system architecture, Linux installation and package management, GNU and UNIX commands, user interfaces and desktops, essential system services, network and server security, and many more. Linux Servers currently have a 20% market share which continues to grow. The Linux OS market saw a 75% increase from last year and is the third leading OS, behind Windows and MacOS. There has never been a better time to expand your skills, broaden your knowledge, and earn certification from the Linux Professional Institute. A must-have guide for anyone preparing for the 101-500 and 102-500 exams, this study guide enables you to: Assess your performance on practice exams to determine what areas need extra study Understand and retain vital exam topics such as administrative tasks, network configuration, booting Linux, working with filesystems, writing scripts, and using databases Gain insights and tips from two of the industry’s most highly respected instructors, consultants, and authors Access Sybex interactive tools that include electronic flashcards, an online test bank, customizable practice exams, bonus chapter review questions, and a searchable PDF glossary of key terms LPIC-1: Linux Professional Institute Certification Study Guide is ideal for network and system administrators studying for the LPIC-1 exams, either for the first time or for the purpose of renewing their certifications. COMPUTERS,Operating Systems,Linux

Red Hat RHCSA 8 Cert Guide Learn, prepare, and practice for Red Hat RHCSA 8 (EX200) exam success with this Cert Guide from Pearson IT Certification, a leader in IT Certification learning. Master Red Hat RHCSA 8 EX200 exam topics Assess your knowledge with chapter-ending quizzes Review key concepts with exam-preparation tasks Practice with four unique... COMPUTERS,Operating Systems,Linux

BPF Performance Tools Use BPF Tools to Optimize Performance, Fix Problems, and See Inside Running Systems BPF-based performance tools give you unprecedented visibility into systems and applications, so you can optimize performance, troubleshoot code, strengthen security, and reduce costs. BPF Performance Tools: Linux System and Application Observability is the definitive guide to using these tools for observability. Pioneering BPF expert Brendan Gregg presents more than 150 ready-to-run analysis and debugging tools, expert guidance on applying them, and step-by-step tutorials on developing your own. You’ll learn how to analyze CPUs, memory, disks, file systems, networking, languages, applications, containers, hypervisors, security, and the kernel. Gregg guides you from basic to advanced tools, helping you generate deeper, more useful technical insights for improving virtually any Linux system or application. • Learn essential tracing concepts and both core BPF front-ends: BCC and bpftrace • Master 150+ powerful BPF tools, including dozens created just for this book, and available for download • Discover practical strategies, tips, and tricks for more effective analysis • Analyze compiled, JIT-compiled, and interpreted code in multiple languages: C, Java, bash shell, and more • Generate metrics, stack traces, and custom latency histograms • Use complementary tools when they offer quick, easy wins • Explore advanced tools built on BPF: PCP and Grafana for remote monitoring, eBPF Exporter, and kubectl-trace for tracing Kubernetes • Foreword by Alexei Starovoitov, creator of the new BPF BPF Performance Tools will be an indispensable resource for all administrators, developers, support staff, and other IT professionals working with any recent Linux distribution in any enterprise or cloud environment. COMPUTERS,Operating Systems,Linux

Mastering Linux Security and Hardening A comprehensive guide to securing your Linux system against cyberattacks and intruders Key Features Deliver a system that reduces the risk of being hacked Explore a variety of advanced Linux security techniques with the help of hands-on labs Master the art of securing a Linux environment with this end-to-end practical guide Book Description From creating networks and servers to automating the entire working environment, Linux has been extremely popular with system administrators for the last couple of decades. However, security has always been a major concern. With limited resources available in the Linux security domain, this book will be an invaluable guide in helping you get your Linux systems properly secured. Complete with in-depth explanations of essential concepts, practical examples, and self-assessment questions, this book begins by helping you set up a practice lab environment and takes you through the core functionalities of securing Linux. You'll practice various Linux hardening techniques and advance to setting up a locked-down Linux server. As you progress, you will also learn how to create user accounts with appropriate privilege levels, protect sensitive data by setting permissions and encryption, and configure a firewall. The book will help you set up mandatory access control, system auditing, security profiles, and kernel hardening, and finally cover best practices and troubleshooting techniques to secure your Linux environment efficiently. By the end of this Linux security book, you will be able to confidently set up a Linux server that will be much harder for malicious actors to compromise. What you will learn Create locked-down user accounts with strong passwords Configure firewalls with iptables, UFW, nftables, and firewalld Protect your data with different encryption technologies Harden the secure shell service to prevent security break-ins Use mandatory access control to protect against system exploits Harden kernel parameters and set up a kernel-level auditing system Apply OpenSCAP security profiles and set up intrusion detection Configure securely the GRUB 2 bootloader and BIOS/UEFI Who this book is for This book is for Linux administrators, system administrators, and network engineers interested in securing moderate to complex Linux environments. Security consultants looking to enhance their Linux security skills will also find this book useful. Working experience with the Linux command line and package management is necessary to understand the concepts covered in this book. COMPUTERS,Operating Systems,Linux

Learn Docker – Fundamentals of Docker 19.x Explore the core functionality of containerizing your applications and making them production-ready Key Features Grasp basic to advanced Docker concepts with this comprehensive guide Get acquainted with Docker containers, Docker images, orchestrators, cloud integration, and networking Learn to simplify dependencies and deploy and test containers in production Book Description Containers enable you to package an application with all the components it needs, such as libraries and other dependencies, and ship it as one package. Docker containers have revolutionized the software supply chain in both small and large enterprises. Starting with an introduction to Docker fundamentals and setting up an environment to work with it, you'll delve into concepts such as Docker containers, Docker images, and Docker Compose. As you progress, the book will help you explore deployment, orchestration, networking, and security. Finally, you'll get to grips with Docker functionalities on public clouds such as Amazon Web Services (AWS), Azure, and Google Cloud Platform (GCP), and learn about Docker Enterprise Edition features. Additionally, you'll also discover the benefits of increased security with the use of containers. By the end of this Docker book, you'll be able to build, ship, and run a containerized, highly distributed application on Docker Swarm or Kubernetes, running on-premises or in the cloud. What you will learn Containerize your traditional or microservice-based applications Develop, modify, debug, and test an application running inside a container Share or ship your application as an immutable container image Build a Docker Swarm and a Kubernetes cluster in the cloud Run a highly distributed application using Docker Swarm or Kubernetes Update or rollback a distributed application with zero downtime Secure your applications with encapsulation, networks, and secrets Troubleshoot a containerized, highly distributed application in the cloud Who this book is for This book is for Linux professionals, system administrators, operations engineers, DevOps engineers, and developers or stakeholders who are interested in getting started with Docker from scratch. No prior experience with Docker containers is required. Users with a Linux system would be able to take full advantage of this book. COMPUTERS,Operating Systems,Linux

Linux Bible The industry favorite Linux guide Linux Bible, 10th Edition is the ultimate hands-on Linux user guide, whether you're a true beginner or a more advanced user navigating recent changes. this updated tenth edition covers the latest versions of Red Hat Enterprise Linux (RHEL 8), Fedora 30, and Ubuntu 18.04 LTS. It includes information on cloud computing, with new guidance on containerization, Ansible automation, and Kubernetes and OpenShift. With a focus on RHEL 8, this new edition teaches techniques for managing storage, users, and security, while emphasizing simplified administrative techniques with Cockpit. Written by a Red Hat expert, this book provides the clear explanations and step-by-step instructions that demystify Linux and bring the new features seamlessly into your workflow. This useful guide assumes a base of little or no Linux knowledge, and takes you step by step through what you need to know to get the job done. Get Linux up and running quickly Master basic operations and tackle more advanced tasks Get up to date on the recent changes to Linux server system management Bring Linux to the cloud using Openstack and Cloudforms Simplified Linux administration through the Cockpit Web Interface Automated Linux Deployment with Ansible Learn to navigate Linux with Amazon (AWS), Google (GCE), and Microsofr Azure Cloud services Linux Bible, 10th Edition is the one resource you need, and provides the hands-on training that gets you on track in a flash. COMPUTERS,Operating Systems,Linux

Ubuntu Linux Unleashed 2021 Edition Covers 20.04, 20.10, and 21.04 Ubuntu Linux Unleashed 2021 Edition is filled with unique and advanced information for everyone who wants to make the most of the Ubuntu Linux operating system. This new edition has been thoroughly updated by a long-time Ubuntu user and early community leader to reflect the exciting new Ubuntu 20.04 LTS release, with a forthcoming online update mid-2021, at the halfway mark before the next LTS release comes out. Linux writer Matthew Helmke covers all you need to know about Ubuntu 20.04 LTS installation, configuration, productivity, command-line usage, development, systems administration, server operations, networking, virtualization, cloud computing, DevOps, and more—including intermediate-to-advanced techniques you won’t find in any other book. Helmke presents up-to-the-minute introductions to Ubuntu’s key productivity and web development tools, programming languages, hardware support, and more. You’ll find new or improved coverage of the Ubuntu desktop experience, common web servers and software stacks, an introduction to containers like Docker and Kubernetes, as well as a wealth of systems administration information that is stable and valuable over many years. Configure and use the Ubuntu desktop Get started with multimedia and productivity applications Manage Linux services, users, and software packages Administer and run Ubuntu from the command line Automate tasks and use shell scripting Provide secure remote access and configure a secure VPN Manage kernels and modules Administer file, print, email, proxy, LDAP, DNS, and HTTP servers (Apache, Nginx, or alternatives) Work with databases (SQL) and learn about NoSQL alternatives Get started with virtualization and cloud deployment, including information about containers Learn about options for managing large numbers of servers, including in the cloud Learn the basics about popular programming languages including Python, PHP, Perl, and gain an introduction to new alternatives such as Go and Rust COMPUTERS,Operating Systems,Linux

AppleScript From newspapers to NASA, Mac users around the world use AppleScript to automate their daily computing routines. Famed for its similarity to English and its ease of integration with other programs, AppleScript is the perfect programming language for time-squeezed Mac fans. As beginners quickly realize, however, AppleScript has one major shortcoming: it comes without a manual.No more. You don't need a degree in computer science, a fancy system administrator title, or even a pocket protector and pair of nerdy glasses to learn the Mac's most popular scripting language; you just need the proper guide at your side. AppleScript: The Missing Manual is that guide.Brilliantly compiled by author Adam Goldstein, AppleScript: The Missing Manual is brimming with useful examples. You'll learn how to clean up your Desktop with a single click, for example, and how to automatically optimize pictures for a website. Along the way, you ll learn the overall grammar of AppleScript, so you can write your own customized scripts when you feel the need.Naturally, AppleScript: The Missing Manual isn't merely for the uninitiated scripter. While its hands-on approach certainly keeps novices from feeling intimidated, this comprehensive guide is also suited for system administrators, web and graphics professionals, musicians, scientists, mathematicians, engineers, and others who need to learn the ins and outs of AppleScript for their daily work.Thanks to AppleScript: The Missing Manual, the path from consumer to seasoned script has never been clearer. Now you, too, can automate your Macintosh in no time. COMPUTERS,Operating Systems,Mac OS

AppleScript in a Nutshell AppleScript in a Nutshell is the first complete reference to AppleScript, the popular programming language that gives both power users and sophisticated enterprise customers the important ability to automate repetitive tasks and customize applications. As the Macintosh continues to expand and solidify its base in the multimedia and publishing industries, AppleScript is the tool of choice on this platform for creating sophisticated time- and money-saving workflow applications (applets). These applets automate the processing and management of digital video, imaging, print, and web-based material. AppleScript is also gaining a foothold in scientific programming, as technical organizations adopt G4 CPU-based systems for advanced computing and scientific analysis. Finally, "power users" and script novices will find that AppleScript is a great everyday Mac programming tool, similar to Perl on Windows NT or Unix.In this well-organized and concise reference, AppleScript programmers will find: Detailed coverage of AppleScript Version 1.4 and beyond on Mac OS 9 and Mac OS X. Complete descriptions of AppleScript language features, such as data types, flow-control statements, functions, object-oriented features (script objects and libraries), and other syntactical elements. Descriptions and hundreds of code samples on programming the various "scriptable" system components, such as the Finder, File Sharing, File Exchange, Network scripting, Web scripting, Apple System Profiler, the ColorSync program, and the numerous powerful language extensions called "osax" or scripting additions.Most other AppleScript books are hopelessly out of date. AppleScript in a Nutshell covers the latest updates and improvements with practical, easy to understand tips, including: Using AppleScript as a tool for distributed computing, an exciting development that Apple Computer calls "program linking over IP." Programmers can now do distributed computing with Macs over TCP/IP networks, including controlling remote applications with AppleScript and calling AppleScript methods on code libraries that are located on other machines. Using the Sherlock find application to automate web and network searching. Insights on scripting new Apple technologies such as Apple Data Detectors, Folder Actions, Keychain Access, and Apple Verifier.AppleScript in a Nutshell is a high-end handbook at a low-end price--an essential desktop reference that puts the full power of this user-friendly programming language into every AppleScript user's hands. COMPUTERS,Operating Systems,Mac OS

OS X Yosemite With Yosemite, Apple has unleashed the most innovative version of OS X yet—and once again, David Pogue brings his expertise and humor to the #1 bestselling Mac book. Mac OS X 10.10 includes more innovations from the iPad and adds a variety of new features throughout the operating system. This updated edition covers it all with something new on practically every page. Get the scoop on Yosemite’s big-ticket changes Learn enhancements to existing applications, such as Safari and Mail Take advantage of shortcuts and undocumented tricks Use power user tips for networking, file sharing, and building your own services COMPUTERS,Operating Systems,Mac OS

OS X El Capitan With El Capitan, Apple brings never-before-seen features to OS X—like a split-screen desktop, improved window controls, and amazing graphics. The new edition of David Pogue's #1 bestselling Mac book shows you how to use key new features such as swiping gestures, Notes, a new Spotlight search system, the Safari pinning feature, and Split View. Missing Manuals creator David Pogue is one of the most widely recognized technology authors in the world. A former New York Times technology columnist, he founded and now produces videos for Yahoo Tech. COMPUTERS,Operating Systems,Mac OS

Learning Unix for OS X Think your Mac is powerful now? This practical guide shows you how to get much more from your system by tapping into Unix, the robust operating system concealed beneath OS X’s beautiful user interface. OS X puts more than a thousand Unix commands at your fingertips—for finding and managing files, remotely accessing your Mac from other computers, and using freely downloadable open source applications. If you’re an experienced Mac user, this updated edition teaches you all the basic commands you need to get started with Unix. You’ll soon learn how to gain real control over your system. Get your Mac to do exactly what you want, when you want Make changes to your Mac’s filesystem and directories Use Unix’s find, locate, and grep commands to locate files containing specific information Create unique "super commands" to perform tasks that you specify Run multiple Unix programs and processes at the same time Access remote servers and interact with remote filesystems Install the X Window system and learn the best X11 applications Take advantage of command-line features that let you shorten repetitive tasks COMPUTERS,Operating Systems,Mac OS

macOS High Sierra With High Sierra, Apple has taken its macOS operating system to new heights. From Apple’s efficient new file system to improved video streaming and support for virtual reality, this latest macOS version provides features improve your experience. And once again, David Pogue brings his humor and expertise to the #1 bestselling Mac book. Whether you’re a developer or a home-user, this guide offers a wealth of detail on Apple’s macOS 10.13 operating system, this new edition covers everything High Sierra has to offer. Perfect for newcomers. Get crystal-clear, jargon-free introductions to the best and brightest macOS apps, including Siri, Safari, iCloud, FaceTime, and AirDrop. Get the whole picture. Learn more efficient ways to navigate, organize, and edit your photos with new features in the Photos app. Go in-depth. Take advantage of Apple’s new graphics technology, and its support for virtual reality. Gain real insight. David Pogue doesn't just tell you how to use macOS features. You’ll also learn why to use them—and how to avoid common pitfalls.i COMPUTERS,Operating Systems,Mac OS

Logic Pro X 10.4 - Apple Pro Training Series Record, arrange, mix, produce, and polish your audio files with this best-selling, Apple-certified guide to Logic Pro X 10.4. Veteran producer and composer David Nahmani uses step-bystep, project-based instructions and straightforward explanations to teach everything from basic music creation to sophisticated production techniques. Using the book’s downloadable lesson files and Logic Pro X, you’ll begin making music in the first lesson. From there, learn to record audio and MIDI data, create and edit sequences, and master mixing and automation techniques such as submixing with track stacks. Create both acoustic and electronic virtual drum performances using Drummer tracks with Drum Kit Designer and Drum Machine Designer. Use Logic Pro X MIDI FX and Smart Controls to control software synthesizers from a MIDI controller or an iPad. Harness the power of Smart Tempo to make sure all recordings, imported audio files, and samples play in time. Flex Time allows you to precisely edit the timing of notes inside an audio recording, and you’ll explore Flex Pitch to correct the pitch of a vocal recording. Finally, you mix, automate, and master the song, using plug-ins to process only selected sections or entire tracks, giving your audio creations the final polish needed to achieve a professional sound. Downloadable lesson and media files allow you to perform the hands-on exercises. Focused lessons take you step by step through practical, real-world tasks. Accessible writing style puts an expert instructor at your side Ample illustrations help you master techniques fast. Lesson goals and time estimates help you plan your time. Chapter review questions summarize what you’ve learned and help you prepare for the Apple certification exam. COMPUTERS,Operating Systems,Mac OS

macOS Mojave For Dummies Pro tips for macOS from “Dr. Mac†Your shiny new iMac or trusty old MacBook both rely on macOS to help you get things done. It helps to have an equally reliable guidebook to steer you through the tasks and steps that make macOS run efficiently. This fun and friendly guide provides the direction you need to easily navigate macOS. Longtime expert Bob "Dr. Mac" LeVitus shares his years of experience to help you better understand macOS and make it a timesaving tool in your life. Take a tour of the macOS interface Get organized and save time with macOS applications Get pro tips on speeding up your Mac Back up your data with ease Covering the fundamentals of the OS and offering insight into the most common functions of macOS, this is indispensable reading for new or inexperienced macOS users. COMPUTERS,Operating Systems,Mac OS

macOS Mojave Answers found here! Apple’s latest Mac software, macOS Mojave, is a glorious boxcar full of new features and refinements. What’s still not included, though, is a single page of printed instructions. Fortunately, David Pogue is back, delivering the expertise and humor that have made this the #1 bestselling Mac book for 18 years straight. The important stuff you need to know Big-ticket changes. The stunning new Dark Mode. Self-tidying desktop stacks. FaceTime video calls with up to 32 people. New screen-recording tools. If Apple has it, this book covers it. Apps. This book also demystifies the 50 programs that come with the Mac, including the four new ones in Mojave: News, Stocks, Home, and Voice Memos. Shortcuts. This must be the tippiest, trickiest Mac book ever written. Undocumented surprises await on every page. Power users. Security, networking, remote access, file sharing with Windows—this one witty, expert guide makes it all crystal clear. MacOS Mojave gives the Mac more polish, power, and pep— and in your hands, you hold the ultimate guide to unlocking its potential. COMPUTERS,Operating Systems,Mac OS

macOS Support Essentials 10.14 - Apple Pro Training Series This is the official curriculum of the Apple Mojave 101: OS X Support Essentials 10.14 course and preparation for Apple Certified Support Professional (ACSP) 10.14 certification–as well as a top-notch primer for anyone who needs to support, troubleshoot, or optimize macOS Mojave. This guide provides comprehensive coverage of Mojave and is part of the Apple Pro Training series–the only Apple-certified books on the market. Designed for support technicians, help desk specialists, and ardent Mac users, this guide takes you deep inside macOS Mojave. Readers will find in-depth, step-by-step instruction on everything from installing and configuring High Sierra to managing networks and system administration. Whether you run a computer lab or an IT department, you’ll learn to set up users, configure system preferences, manage security and permissions, use diagnostic and repair tools, troubleshoot peripheral devices, and more–all on your way to preparing for the industry-standard ACSP certification. This is a step-by-step guide that works through lessons designed to teach practical, real-world tasks, with lesson files let you practice as you learn. COMPUTERS,Operating Systems,Mac OS

Mastering Swift 5 Harness the power of the latest edition with this in-depth and comprehensive guide to the Swift language Key Features Fifth edition of this bestselling book, improved and updated to cover the latest version of the Swift 5 programming language Get to grips with popular and modern design techniques to write easy-to-manage Swift code Learn how to use core Swift features such as concurrency, generics, and copy-on-write in your code Book Description Over the years, the Mastering Swift book has established itself amongst developers as a popular choice as an in-depth and practical guide to the Swift programming language. The latest edition is fully updated and revised to cover the new version: Swift 5. Inside this book, you'll find the key features of Swift 5 easily explained with complete sets of examples. From the basics of the language to popular features such as concurrency, generics, and memory management, this definitive guide will help you develop your expertise and mastery of the Swift language. Mastering Swift 5, Fifth Edition will give you an in-depth knowledge of some of the most sophisticated elements in Swift development, including protocol extensions, error handling, and closures. It will guide you on how to use and apply them in your own projects. Later, you'll see how to leverage the power of protocol-oriented programming to write flexible and easier-to-manage code. You will also see how to add the copy-on-write feature to your custom value types and how to avoid memory management issues caused by strong reference cycles. What you will learn Understand core Swift components, including operators, collections, control flows, and functions Learn how and when to use classes, structures, and enumerations Understand how to use protocol-oriented design with extensions to write easier-to-manage code Use design patterns with Swift, to solve commonly occurring design problems Implement copy-on-write for you custom value types to improve performance Add concurrency to your applications using Grand Central Dispatch and Operation Queues Implement generics to write flexible and reusable code Who this book is for This book is for developers who want to delve into the newest version of Swift. If you are a developer and learn best by looking at and working with code, then this book is for you. A basic understanding of Apple's tools would be beneficial but not mandatory. All examples should work on the Linux platform as well. COMPUTERS,Operating Systems,Mac OS

macOS Catalina For Dummies Get a handle on macOS Catalina It doesn't matter if you're doing your computing on an old reliable Macbook or a brand-new Mac desktop, both rely on macOS to help you get things done. It helps to have an equally reliable guidebook to steer you through the tasks and steps that make macOS run efficiently. This fun and friendly guide provides the direction you need to easily navigate the classic and brand new features in macOS Catalina. Longtime expert Bob "Dr. Mac" LeVitus shares his years of experience to help you better understand Catalina and make it a timesaving tool in your life. Take a tour of the macOS Catalina interface Get organized and save time with macOS applications Find pro tips on speeding up your Mac Back up your data macOS Catalina For Dummies is perfect for new and inexperienced macOS users looking to grasp the fundamentals of the operating system. COMPUTERS,Operating Systems,Mac OS

MacBook Pro with MacOS Catalina NOTE: This book is based off of "MacOS Catalina: Getting Started with MacOS 10.15 for Macbooks and iMacs" and contains additional content on the MacBook Pros specs. In 2008, Apple released something revolutionary: a notebook so thin it could fit in an envelope! The newest MacBook Pro did something equally revolutionary—it’s nearly as thin and slim, but it packs the power of many desktop computers. For many people, however, one thing really stands out: it does not have Windows! MacOS is something completely different—but that’s not a bad thing. Once you start using it, you’ll probably prefer it to Windows and never want to go back. If you are a Windows user coming to Mac, then this book will help you out! It will show you all the tricks to making the switch as quickly and easily as possible. If you’ve been using MacOS for a while and just want to know your way around OS Catalina (10.15), then this book will show you what you need to know. It’s intended for newer users who just want the basics. If you’re the type of person who wants to know every single tiny detail and feature about the operating system, then this book is not for you. The goal is to teach you what you need to know, so you can start using your computer. Are you ready to start enjoying the new MacOS? Then let’s get started! COMPUTERS,Operating Systems,Mac OS

macOS Catalina Apple gives macOS new features and improvements right on your desktop and under the hood with Catalina—aka OS X 10.15. With this updated guide, you’ll learn how to use your iPad as a second screen, work with iPad apps on your Mac, and use Screen Time on your Mac. This new edition of the #1 bestselling Mac book shows you how to use the revamped apps for Music, Podcasts, and TV. Loaded with illustrations, step-by-step instructions, tips, and tricks, this book from David Pogue—Missing Manual series creator, New York Times columnist, and Emmy-winning tech correspondent for CNBC, CBS, and NPR—covers everything Catalina has to offer with lots of humor and technical insight. COMPUTERS,Operating Systems,Mac OS

macOS Support Essentials 10.15 - Apple Pro Training Series macOS Support Essentials 10.15 - Apple Pro Training Series The Apple-Certified Way to Learn This is the official book for the macOS Support Essentials 10.15course and you can use it to prepare for the Apple Certified Support Professional (ACSP) 10.15 exam. It’s a top-notch primer for anyone who needs to support, troubleshoot, or optimize macOS Catalina, such as IT professionals, technicians, help desk specialists, and ardent Mac users. This is the only Apple Pro Training Series book that covers macOS Catalina. You’ll find in-depth, step-by-step instructions on everything from upgrading, updating, reinstalling and configuring macOS Catalina to configuring network services like the Content Caching service. This book covers updated system utilities and new features in macOS Catalina, including Voice Control and other accessibility features, user privacy settings, notarized apps, Startup Security Utility, and the separation of the startup disk into a read-only APFS System volume and a read write APFS Data volume. This book includes the following content: Authoritative explanations of underlying technologies, troubleshooting, system administration, and much more Focused lessons that take you step by step through practical, real-world tasks A Web Edition that provides the full text of the book online The Apple Pro Training Series includes self-paced learning tools and is the official curriculum of the Apple Training and Certification program. After you complete this book, take the macOS Support Essentials 10.15 exam as a step towards becoming an Apple Certified Support Professional. Work through this book independently or attend a class at an Apple Authorized Training Provider or both to prepare for the exam. To learn more, visit training.apple.com. Also in the Apple Pro Training Series: Final Cut Pro X Logic Pro X COMPUTERS,Operating Systems,Mac OS

Unix Shell Programming Unix Shell Programming is a tutorial aimed at helping Unix and Linux users get optimal performance out of their operating out of their operating system. It shows them how to take control of their systems and work efficiently by harnessing the power of the shell to solve common problems. The reader learns everything he or she needs to know to customize the way a Unix system responds. The vast majority of Unix users utilize the Korn shell or some variant of the Bourne shell, such as bash. Three are covered in the third edition of Unix Shell Programming. It begins with a generalized tutorial of Unix and tools and then moves into detailed coverage of shell programming. Topics covered include: regular expressions, the kernel and the utilities, command files, parameters, manipulating text filters, understanding and debugging shell scripts, creating and utilizing variables, tools, processes, and customizing the shell. COMPUTERS,Operating Systems,UNIX

Classic Shell Scripting Shell scripting skills never go out of style. It's the shell that unlocks the real potential of Unix. Shell scripting is essential for Unix users and system administrators-a way to quickly harness and customize the full power of any Unix system. With shell scripts, you can combine the fundamental Unix text and file processing commands to crunch data and automate repetitive tasks. But beneath this simple promise lies a treacherous ocean of variations in Unix commands and standards. Classic Shell Scripting is written to help you reliably navigate these tricky waters.Writing shell scripts requires more than just a knowledge of the shell language, it also requires familiarity with the individual Unix programs: why each one is there, how to use them by themselves, and in combination with the other programs. The authors are intimately familiar with the tips and tricks that can be used to create excellent scripts, as well as the traps that can make your best effort a bad shell script. With Classic Shell Scripting you'll avoid hours of wasted effort. You'll learn not only write useful shell scripts, but how to do it properly and portably.The ability to program and customize the shell quickly, reliably, and portably to get the best out of any individual system is an important skill for anyone operating and maintaining Unix or Linux systems. Classic Shell Scripting gives you everything you need to master these essential skills. COMPUTERS,Operating Systems,UNIX

grep Pocket Reference grep Pocket Reference is the first guide devoted to grep, the powerful Unix content-location utility. This handy book is ideal for system administrators, security professionals, developers, and others who want to learn more about grep and take new approaches with it -- for everything from mail filtering and system log management to malware analysis. With grep Pocket Reference, you will: Learn methods for filtering large files for specific content Acquire information not included in the current grep documentation Get several tricks for using variants such as egrep Keep key information about grep right at your fingertips Find the answers you need about grep quickly and easily. If you're familiar with this utility, grep Pocket Reference will help you refresh your basic knowledge, understand rare situations, and work more efficiently. If you're new to grep, this book is the best way to get started. COMPUTERS,Operating Systems,UNIX

Tcl/Tk in a Nutshell The Tcl language and Tk graphical toolkit are simple and powerful building blocks for custom applications. The Tcl/Tk combination is increasingly popular because it lets you produce sophisticated graphical interfaces with a few easy commands, develop and change scripts quickly, and conveniently tie together existing utilities or programming libraries.One of the attractive features of Tcl/Tk is the wide variety of commands, many offering a wealth of options. Most of the things you'd like to do have been anticipated by the language's creator, John Ousterhout, or one of the developers of Tcl/Tk's many powerful extensions. Thus, you'll find that a command or option probably exists to provide just what you need.And that's why it's valuable to have a quick reference that briefly describes every command and option in the core Tcl/Tk distribution as well as the most popular extensions. Keep this book on your desk as you write scripts, and you'll be able to find almost instantly the particular option you need.Most chapters consist of alphabetical listings. Since Tk and mega-widget packages break down commands by widget, the chapters on these topics are organized by widget along with a section of core commands where appropriate. Contents include: Core Tcl and Tk commands and Tk widgets C interface (prototypes) Expect [incr Tcl] and [incr Tk] Tix TclX BLT Oratcl, SybTcl, and Tclodbc COMPUTERS,Operating Systems,UNIX

Essential System Administration Essential System Administration,3rd Edition is the definitive guide for Unix system administration, covering all the fundamental and essential tasks required to run such divergent Unix systems as AIX, FreeBSD, HP-UX, Linux, Solaris, Tru64 and more. Essential System Administration provides a clear, concise, practical guide to the real-world issues that anyone responsible for a Unix system faces daily.The new edition of this indispensable reference has been fully updated for all the latest operating systems. Even more importantly, it has been extensively revised and expanded to consider the current system administrative topics that administrators need most. Essential System Administration,3rd Edition covers: DHCP, USB devices, the latest automation tools, SNMP and network management, LDAP, PAM, and recent security tools and techniques.Essential System Administration is comprehensive. But what has made this book the guide system administrators turn to over and over again is not just the sheer volume of valuable information it provides, but the clear, useful way the information is presented. It discusses the underlying higher-level concepts, but it also provides the details of the procedures needed to carry them out. It is not organized around the features of the Unix operating system, but around the various facets of a system administrator's job. It describes all the usual administrative tools that Unix provides, but it also shows how to use them intelligently and efficiently.Whether you use a standalone Unix system, routinely provide administrative support for a larger shared system, or just want an understanding of basic administrative functions, Essential System Administration is for you. This comprehensive and invaluable book combines the author's years of practical experience with technical expertise to help you manage Unix systems as productively and painlessly as possible. COMPUTERS,Operating Systems,UNIX

Learning the bash Shell O'Reilly's bestselling book on Linux's bash shell is at it again. Now that Linux is an established player both as a server and on the desktop Learning the bash Shell has been updated and refreshed to account for all the latest changes. Indeed, this third edition serves as the most valuable guide yet to the bash shell.As any good programmer knows, the first thing users of the Linux operating system come face to face with is the shell the UNIX term for a user interface to the system. In other words, it's what lets you communicate with the computer via the keyboard and display. Mastering the bash shell might sound fairly simple but it isn't. In truth, there are many complexities that need careful explanation, which is just what Learning the bash Shell provides.If you are new to shell programming, the book provides an excellent introduction, covering everything from the most basic to the most advanced features. And if you've been writing shell scripts for years, it offers a great way to find out what the new shell offers. Learning the bash Shell is also full of practical examples of shell commands and programs that will make everyday use of Linux that much easier. With this book, programmers will learn: How to install bash as your login shell The basics of interactive shell use, including UNIX file and directory structures, standard I/O, and background jobs Command line editing, history substitution, and key bindings How to customize your shell environment without programming The nuts and bolts of basic shell programming, flow control structures, command-line options and typed variables Process handling, from job control to processes, coroutines and subshells Debugging techniques, such as trace and verbose modes Techniques for implementing system-wide shell customization and features related to system security COMPUTERS,Operating Systems,UNIX

sed and awk Pocket Reference For people who create and modify text files, sed and awk are power tools for editing. sed, awk, and regular expressions allow programmers and system administrators to automate editing tasks that need to be performed on one or more files, to simplify the task of performing the same edits on multiple files, and to write conversion programs.The sed & awk Pocket Reference is a companion volume to sed & awk, Second Edition, Unix in a Nutshell, Third Edition, and Effective awk Programming, Third Edition. This new edition has expanded coverage of gawk (GNU awk), and includes sections on: An overview of sed and awk?s command line syntax Alphabetical summaries of commands, including nawk and gawk Profiling with pgawk Coprocesses and sockets with gawk Internationalization with gawk A listing of resources for sed and awk users This small book is a handy reference guide to the information presented in the larger volumes. It presents a concise summary of regular expressions and pattern matching, and summaries of sed and awk.Arnold Robbins, an Atlanta native now happily living in Israel, is a professional programmer and technical author and coauthor of various O'Reilly Unix titles. He has been working with Unix systems since 1980, and currently maintains gawk and its documentation. COMPUTERS,Operating Systems,UNIX

vi Editor Pocket Reference For many users, working in the UNIX environment means using vi, a full-screen text editor available on most UNIX systems. Even those who know vi often make use of only a small number of its features.The vi Editor Pocket Reference is a companion volume to O'Reilly's updated sixth edition of Learning the vi Editor, a complete guide to text editing with vi. New topics in Learning the vi Editor include multi-screen editing and coverage of four vi clones: vim,elvis, nvi, and vile.This small book is a handy reference guide to the information in the larger volume, presenting movement and editing commands, the command-line options, and other elements of the vi editor in an easy-to-use tabular format. COMPUTERS,Operating Systems,UNIX

Using csh & tcsh If you use UNIX, you probably use csh to type commands even if you've never heard of it. It's the standard shell (command line) on most UNIX systems. tcsh is an enhanced version that's freely available and highly recommended.Using csh & tcsh describes from the beginning how to use these shells interactively. More important, it shows how to get your work done faster with less typing. Even if you've used UNIX for years, techniques described in this book can make you more efficient.You'll learn how to: Make your prompt tell you where you are (no more pwd) Use what you've typed before (history) Type long command lines with very few keystrokes (command and filename completion) Remind yourself of filenames when in the middle of typing a command Edit a botched command instead of retyping it This book does not cover programming or script writing in csh ortcsh because the tasks are better done with a different shell, such as sh (the Bourne shell) or a language like Perl. COMPUTERS,Operating Systems,UNIX

flex & bison If you need to parse or process text data in Linux or Unix, this useful book explains how to use flex and bison to solve your problems quickly. flex & bison is the long-awaited sequel to the classic O'Reilly book, lex & yacc. In the nearly two decades since the original book was published, the flex and bison utilities have proven to be more reliable and more powerful than the original Unix tools. flex & bison covers the same core functionality vital to Linux and Unix program development, along with several important new topics. You'll find revised tutorials for novices and references for advanced users, as well as an explanation of each utility's basic usage and simple, standalone applications you can create with them. With flex & bison, you'll discover the wide range of uses these flexible tools offer. Address syntax crunching that regular expressions tools can't handle Build compilers and interpreters, and handle a wide range of text processing functions Interpret code, configuration files, or any other structured format Learn key programming techniques, including abstract syntax trees and symbol tables Implement a full SQL grammar-with complete sample code Use new features such as pure (reentrant) lexers and parsers, powerful GLR parsers, and interfaces to C++ COMPUTERS,Operating Systems,UNIX

Learning the vi and Vim Editors There's nothing that hard-core Unix and Linux users are more fanatical about than their text editor. Editors are the subject of adoration and worship, or of scorn and ridicule, depending upon whether the topic of discussion is your editor or someone else's. vi has been the standard editor for close to 30 years. Popular on Unix and Linux, it has a growing following on Windows systems, too. Most experienced system administrators cite vi as their tool of choice. And since 1986, this book has been the guide for vi. However, Unix systems are not what they were 30 years ago, and neither is this book. While retaining all the valuable features of previous editions, the 7th edition of Learning the vi and vim Editors has been expanded to include detailed information on vim, the leading vi clone. vim is the default version of vi on most Linux systems and on Mac OS X, and is available for many other operating systems too. With this guide, you learn text editing basics and advanced tools for both editors, such as multi-window editing, how to write both interactive macros and scripts to extend the editor, and power tools for programmers -- all in the easy-to-follow style that has made this book a classic. Learning the vi and vim Editors includes: A complete introduction to text editing with vi: How to move around vi in a hurry Beyond the basics, such as using buffers vi's global search and replacement Advanced editing, including customizing vi and executing Unix commands How to make full use of vim: Extended text objects and more powerful regular expressions Multi-window editing and powerful vim scripts How to make full use of the GUI version of vim, called gvim vim's enhancements for programmers, such as syntax highlighting, folding and extended tags Coverage of three other popular vi clones -- nvi, elvis, and vile -- is also included. You'll find several valuable appendixes, including an alphabetical quick reference to both vi and ex mode commands for regular vi and for vim, plus an updated appendix on vi and the Internet. Learning either vi or vim is required knowledge if you use Linux or Unix, and in either case, reading this book is essential. After reading this book, the choice of editor will be obvious for you too. COMPUTERS,Operating Systems,UNIX

Unix Power Tools With the growing popularity of Linux and the advent of Darwin, Unix has metamorphosed into something new and exciting. No longer perceived as a difficult operating system, more and more users are discovering the advantages of Unix for the first time. But whether you are a newcomer or a Unix power user, you'll find yourself thumbing through the goldmine of information in the new edition of Unix Power Tools to add to your store of knowledge. Want to try something new? Check this book first, and you're sure to find a tip or trick that will prevent you from learning things the hard way.The latest edition of this best-selling favorite is loaded with advice about almost every aspect of Unix, covering all the new technologies that users need to know. In addition to vital information on Linux, Darwin, and BSD, Unix Power Tools 3rd Edition now offers more coverage of bash, zsh, and other new shells, along with discussions about modern utilities and applications. Several sections focus on security and Internet access. And there is a new chapter on access to Unix from Windows, addressing the heterogeneous nature of systems today. You'll also find expanded coverage of software installation and packaging, as well as basic information on Perl and Python.Unix Power Tools 3rd Edition is a browser's book...like a magazine that you don't read from start to finish, but leaf through repeatedly until you realize that you've read it all. Bursting with cross-references, interesting sidebars explore syntax or point out other directions for exploration, including relevant technical details that might not be immediately apparent. The book includes articles abstracted from other O'Reilly books, new information that highlights program tricks and gotchas, tips posted to the Net over the years, and other accumulated wisdom.Affectionately referred to by readers as "the" Unix book, UNIX Power Tools provides access to information every Unix user is going to need to know. It will help you think creatively about UNIX, and will help you get to the point where you can analyze your own problems. Your own solutions won't be far behind. COMPUTERS,Operating Systems,UNIX

Unix in a Nutshell As an open operating system, Unix can be improved on by anyone and everyone: individuals, companies, universities, and more. As a result, the very nature of Unix has been altered over the years by numerous extensions formulated in an assortment of versions. Today, Unix encompasses everything from Sun's Solaris to Apple's Mac OS X and more varieties of Linux than you can easily name. The latest edition of this bestselling reference brings Unix into the 21st century. It's been reworked to keep current with the broader state of Unix in today's world and highlight the strengths of this operating system in all its various flavors. Detailing all Unix commands and options, the informative guide provides generous descriptions and examples that put those commands in context. Here are some of the new features you'll find in Unix in a Nutshell, Fourth Edition: Solaris 10, the latest version of the SVR4-based operating system, GNU/Linux, and Mac OS X Bash shell (along with the 1988 and 1993 versions of ksh) tsch shell (instead of the original Berkeley csh) Package management programs, used for program installation on popular GNU/Linux systems, Solaris and Mac OS X GNU Emacs Version 21 Introduction to source code management systems Concurrent versions system Subversion version control system GDB debugger As Unix has progressed, certain commands that were once critical have fallen into disuse. To that end, the book has also dropped material that is no longer relevant, keeping it taut and current. If you're a Unix user or programmer, you'll recognize the value of this complete, up-to-date Unix reference. With chapter overviews, specific examples, and detailed command. COMPUTERS,Operating Systems,UNIX

Exploring Expect Expect is quickly becoming a part of every UNIX user's toolbox. It allows you to automate Telnet, FTP, passwd, rlogin, and hundreds of other applications that normally require human interaction. Using Expect to automate these applications will allow you to speed up tasks and, in many cases, solve new problems that you never would have even considered before.For example, you can use Expect to test interactive programs with no changes to their interfaces. Or wrap interactive programs with Motif-like front-ends to control applications by buttons, scrollbars, and other graphic elements with no recompilation of the original programs. You don't even need the source code! Expect works with remote applications, too. Use it to tie together Internet applications including Telnet, Archie, FTP, Gopher, and Mosaic.Don Libes is the creator of Expect as well as the author of this book. In Exploring Expect, he provides a comprehensive tutorial on all of Expect's features, allowing you to put it immediately to work on your problems. In a down-to-earth and humorous style, he provides numerous examples of challenging real-world applications and how they can be automated using Expect to save you time and money.Expect is the first of a new breed of programs based on Tcl, the Tool Command Language that is rocking the computer science community. This book provides an introduction to Tcl and describes how Expect applies Tcl's power to the new field of interaction automation. Whether your interest is in Expect or interaction automation or you simply want to learn about Tcl and see how it has been used in real software, you will find Exploring Expect a treasure trove of easy-to-understand and valuable information. COMPUTERS,Operating Systems,UNIX

sed & awk sed & awk describes two text processing programs that are mainstays of the UNIX programmer's toolbox.sed is a "stream editor" for editing streams of text that might be too large to edit as a single file, or that might be generated on the fly as part of a larger data processing step. The most common operation done with sed is substitution, replacing one block of text with another.awk is a complete programming language. Unlike many conventional languages, awk is "data driven" -- you specify what kind of data you are interested in and the operations to be performed when that data is found. awk does many things for you, including automatically opening and closing data files, reading records, breaking the records up into fields, and counting the records. While awk provides the features of most conventional programming languages, it also includes some unconventional features, such as extended regular expression matching and associative arrays. sed & awk describes both programs in detail and includes a chapter of example sed and awk scripts.This edition covers features of sed and awk that are mandated by the POSIX standard. This most notably affects awk, where POSIX standardized a new variable, CONVFMT, and new functions, toupper() and tolower(). The CONVFMT variable specifies the conversion format to use when converting numbers to strings (awk used to use OFMT for this purpose). The toupper() and tolower() functions each take a (presumably mixed case) string argument and return a new version of the string with all letters translated to the corresponding case.In addition, this edition covers GNU sed, newly available since the first edition. It also updates the first edition coverage of Bell Labs nawk and GNU awk (gawk), covers mawk, an additional freely available implementation of awk, and briefly discusses three commercial versions of awk, MKS awk, Thompson Automation awk (tawk), and Videosoft (VSAwk). COMPUTERS,Operating Systems,UNIX

Practice of System and Network Administration, The The first edition of The Practice of System and Network Administration introduced a generation of system and network administrators to a modern IT methodology. Whether you use Linux, Unix, or Windows, this newly revised edition describes the essential practices previously handed down only from mentor to protégé. This wonderfully lucid, often funny cornucopia of information introduces beginners to advanced frameworks valuable for their entire career, yet is structured to help even the most advanced experts through difficult projects. The book's four major sections build your knowledge with the foundational elements of system administration. These sections guide you through better techniques for upgrades and change management, catalog best practices for IT services, and explore various management topics. Chapters are divided into The Basics and The Icing. When you get the Basics right it makes every other aspect of the job easier--such as automating the right things first. The Icing sections contain all the powerful things that can be done on top of the basics to wow customers and managers. Inside, you'll find advice on topics such as The key elements your networks and systems need in order to make all other services run better Building and running reliable, scalable services, including web, storage, email, printing, and remote access Creating and enforcing security policies Upgrading multiple hosts at one time without creating havoc Planning for and performing flawless scheduled maintenance windows Managing superior helpdesks and customer care Avoiding the "temporary fix" trap Building data centers that improve server uptime Designing networks for speed and reliability Web scaling and security issues Why building a backup system isn't about backups Monitoring what you have and predicting what you will need How technically oriented workers can maintain their job's technical focus (and avoid an unwanted management role) Technical management issues, including morale, organization building, coaching, and maintaining positive visibility Personal skill techniques, including secrets for getting more done each day, ethical dilemmas, managing your boss, and loving your job System administration salary negotiation It's no wonder the first edition received Usenix SAGE's 2005 Outstanding Achievement Award! This eagerly anticipated second edition updates this time-proven classic: Chapters reordered for easier navigation Thousands of updates and clarifications based on reader feedback Plus three entirely new chapters: Web Services, Data Storage, and Documentation COMPUTERS,Operating Systems,UNIX

Learning the Korn Shell The Korn shell is an interactive command and scripting language for accessing Unix® and other computer systems. As a complete and high-level programming language in itself, it's been a favorite since it was developed in the mid 1980s by David G. Korn at AT&T Bell Laboratories. Knowing how to use it is an essential skill for serious Unix users. Learning the Korn Shell shows you how to use the Korn shell as a user interface and as a programming environment.Writing applications is often easier and quicker with Korn than with other high-level languages. Because of this, the Korn shell is the most often used shell in commercial environments and among inexperienced users. There are two other widely used shells, the Bourne shell and the C shell. The Korn shell, or ksh, has the best features of both, plus many new features of its own. ksh can do much to enhance productivity and the quality of a user's work, both in interacting with the system, and in programming. The new version, ksh93, has the functionality of other scripting languages such as awk, icon, Perl, rexx, and tcl.Learning the Korn Shell is the key to gaining control of the Korn shell and becoming adept at using it as an interactive command and scripting language. Prior programming experience is not required in order to understand the chapters on basic shell programming. Readers will learn how to write many applications more easily and quickly than with other high-level languages. In addition, readers will also learn about Unix utilities and the way the Unix operating system works in general. The authors maintain that you shouldn't have to be an internals expert to use and program the shell effectively.The second edition covers all the features of the current version of the Korn shell, including many new features not in earlier versions of ksh93, making it the most up-to-date reference available on the Korn shell. It compares the current version of the Korn shell to several other Bourne-compatible shells, including several Unix emulation environments for MS-DOS and Windows. In addition, it describes how to download and build ksh93 from source code.A solid offering for many years, this newly revised title inherits a long tradition of trust among computer professionals who want to learn or refine an essential skill. COMPUTERS,Operating Systems,UNIX

Advanced Programming in the UNIX Environment For more than twenty years, serious C programmers have relied on one book for practical, in-depth knowledge of the programming interfaces that drive the UNIX and Linux kernels: W. Richard Stevens’ Advanced Programming in the UNIX® Environment . Now, once again, Rich’s colleague Steve Rago has thoroughly updated this classic work. The new third edition supports today’s leading platforms, reflects new technical advances and best practices, and aligns with Version 4 of the Single UNIX Specification. Steve carefully retains the spirit and approach that have made this book so valuable. Building on Rich’s pioneering work, he begins with files, directories, and processes, carefully laying the groundwork for more advanced techniques, such as signal handling and terminal I/O. He also thoroughly covers threads and multithreaded programming, and socket-based IPC. This edition covers more than seventy new interfaces, including POSIX asynchronous I/O, spin locks, barriers, and POSIX semaphores. Most obsolete interfaces have been removed, except for a few that are ubiquitous. Nearly all examples have been tested on four modern platforms: Solaris 10, Mac OS X version 10.6.8 (Darwin 10.8.0), FreeBSD 8.0, and Ubuntu version 12.04 (based on Linux 3.2). As in previous editions, you’ll learn through examples, including more than ten thousand lines of downloadable, ISO C source code. More than four hundred system calls and functions are demonstrated with concise, complete programs that clearly illustrate their usage, arguments, and return values. To tie together what you’ve learned, the book presents several chapter-length case studies, each reflecting contemporary environments. Advanced Programming in the UNIX® Environment has helped generations of programmers write code with exceptional power, performance, and reliability. Now updated for today’s systems, this third edition will be even more valuable. COMPUTERS,Operating Systems,UNIX

Systems Performance The Complete Guide to Optimizing Systems Performance Written by the winner of the 2013 LISA Award for Outstanding Achievement in System Administration Large-scale enterprise, cloud, and virtualized computing systems have introduced serious performance challenges. Now, internationally renowned performance expert Brendan Gregg has brought together proven methodologies, tools, and metrics for analyzing and tuning even the most complex environments. Systems Performance: Enterprise and the Cloud focuses on Linux® and Unix® performance, while illuminating performance issues that are relevant to all operating systems. You’ll gain deep insight into how systems work and perform, and learn methodologies for analyzing and improving system and application performance. Gregg presents examples from bare-metal systems and virtualized cloud tenants running Linux-based Ubuntu®, Fedora®, CentOS, and the illumos-based Joyent® SmartOS™ and OmniTI OmniOS®. He systematically covers modern systems performance, including the “traditional†analysis of CPUs, memory, disks, and networks, and new areas including cloud computing and dynamic tracing. This book also helps you identify and fix the “unknown unknowns†of complex performance: bottlenecks that emerge from elements and interactions you were not aware of. The text concludes with a detailed case study, showing how a real cloud customer issue was analyzed from start to finish. Coverage includes • Modern performance analysis and tuning: terminology, concepts, models, methods, and techniques • Dynamic tracing techniques and tools, including examples of DTrace, SystemTap, and perf • Kernel internals: uncovering what the OS is doing • Using system observability tools, interfaces, and frameworks • Understanding and monitoring application performance • Optimizing CPUs: processors, cores, hardware threads, caches, interconnects, and kernel scheduling • Memory optimization: virtual memory, paging, swapping, memory architectures, busses, address spaces, and allocators • File system I/O, including caching • Storage devices/controllers, disk I/O workloads, RAID, and kernel I/O • Network-related performance issues: protocols, sockets, interfaces, and physical connections • Performance implications of OS and hardware-based virtualization, and new issues encountered with cloud computing • Benchmarking: getting accurate results and avoiding common mistakes This guide is indispensable for anyone who operates enterprise or cloud environments: system, network, database, and web admins; developers; and other professionals. For students and others new to optimization, it also provides exercises reflecting Gregg’s extensive instructional experience. COMPUTERS,Operating Systems,UNIX

Learning the Unix Operating System If you are new to Unix, this concise book will tell you just what you need to get started and no more. Unix was one of the first operating systems written in C, a high-level programming language, and its natural portability and low price made it a popular choice among universities. Initially, two main dialects of Unix existed: one produced by AT&T known as System V, and one developed at UC Berkeley and known as BSD. In recent years, many other dialects have been created, including the highly popular Linux operating system and the new Mac OS X (a derivative of BSD).Learning the Unix Operating System is a handy book for someone just starting with Unix or Linux, and it's an ideal primer for Mac and PC users of the Internet who need to know a little about Unix on the systems they visit. The fifth edition is the most effective introduction to Unix in print, covering Internet usage for email, file transfers, web browsing, and many major and minor updates to help the reader navigate the ever-expanding capabilities of the operating system: In response to the popularity of Linux, the book now focuses on the popular bash shell preferred by most Linux users. Since the release of the fourth edition, the Internet and its many functions has become part of most computer user's lives. A new chapter explains how to use ftp, pine for mail, and offers useful knowledge on how to surf the web. Today everyone is concerned about security. With this in mind, the author has included tips throughout the text on security basics, especially in the Internet and networking sections. The book includes a completely updated quick reference card to make it easier for the reader to access the key functions of the command line. COMPUTERS,Operating Systems,UNIX

Design and Implementation of the FreeBSD Operating System, The The most complete, authoritative technical guide to the FreeBSD kernel’s internal structure has now been extensively updated to cover all major improvements between Versions 5 and 11. Approximately one-third of this edition’s content is completely new, and another one-third has been extensively rewritten. Three long-time FreeBSD project leaders begin with a concise overview of the FreeBSD kernel’s current design and implementation. Next, they cover the FreeBSD kernel from the system-call level down–from the interface to the kernel to the hardware. Explaining key design decisions, they detail the concepts, data structures, and algorithms used in implementing each significant system facility, including process management, security, virtual memory, the I/O system, filesystems, socket IPC, and networking. This Second Edition • Explains highly scalable and lightweight virtualization using FreeBSD jails, and virtual-machine acceleration with Xen and Virtio device paravirtualization • Describes new security features such as Capsicum sandboxing and GELI cryptographic disk protection • Fully covers NFSv4 and Open Solaris ZFS support • Introduces FreeBSD’s enhanced volume management and new journaled soft updates • Explains DTrace’s fine-grained process debugging/profiling • Reflects major improvements to networking, wireless, and USB support Readers can use this guide as both a working reference and an in-depth study of a leading contemporary, portable, open source operating system. Technical and sales support professionals will discover both FreeBSD’s capabilities and its limitations. Applications developers will learn how to effectively and efficiently interface with it; system administrators will learn how to maintain, tune, and configure it; and systems programmers will learn how to extend, enhance, and interface with it. Marshall Kirk McKusick writes, consults, and teaches classes on UNIX- and BSD-related subjects. While at the University of California, Berkeley, he implemented the 4.2BSD fast filesystem. He was research computer scientist at the Berkeley Computer Systems Research Group (CSRG), overseeing development and release of 4.3BSD and 4.4BSD. He is a FreeBSD Foundation board member and a long-time FreeBSD committer. Twice president of the Usenix Association, he is also a member of ACM, IEEE, and AAAS. George V. Neville-Neil hacks, writes, teaches, and consults on security, networking, and operating systems. A FreeBSD Foundation board member, he served on the FreeBSD Core Team for four years. Since 2004, he has written the “Kode Vicious†column for Queue and Communications of the ACM. He is vice chair of ACM’s Practitioner Board and a member of Usenix Association, ACM, IEEE, and AAAS. Robert N.M. Watson is a University Lecturer in systems, security, and architecture in the Security Research Group at the University of Cambridge Computer Laboratory. He supervises advanced research in computer architecture, compilers, program analysis, operating systems, networking, and security. A FreeBSD Foundation board member, he served on the Core Team for ten years and has been a committer for fifteen years. He is a member of Usenix Association and ACM. COMPUTERS,Operating Systems,UNIX

Effective awk Programming When processing text files, the awk language is ideal for handling data extraction, reporting, and data-reformatting jobs. This practical guide serves as both a reference and tutorial for POSIX-standard awk and for the GNU implementation, called gawk. This book is useful for novices and awk experts alike. In this thoroughly revised edition, author and gawk lead developer Arnold Robbins describes the awk language and gawk program in detail, shows you how to use awk and gawk for problem solving, and then dives into specific features of gawk. System administrators, programmers, webmasters, and other power users will find everything they need to know about awk and gawk. You will learn how to: Format text and use regular expressions in awk and gawk Process data using awk's operators and built-in functions Manage data relationships using associative arrays Define your own functions "Think in awk" with two full chapters of sample functions and programs Take advantage of gawk's many advanced features Debug awk programs with the gawk built-in debugger Extend gawk by writing new functions in C or C++ This book is published under the terms of the GNU Free Documentation License. You have the freedom to copy and modify this GNU manual. Royalties from the sales of this book go to the Free Software Foundation and to the author. COMPUTERS,Operating Systems,UNIX

Practice of System and Network Administration, The With 28 new chapters, the third edition of The Practice of System and Network Administration innovates yet again! Revised with thousands of updates and clarifications based on reader feedback, this new edition also incorporates DevOps strategies even for non-DevOps environments. Whether you use Linux, Unix, or Windows, this new edition describes the essential practices previously handed down only from mentor to protégé. This wonderfully lucid, often funny cornucopia of information introduces beginners to advanced frameworks valuable for their entire career, yet is structured to help even experts through difficult projects. Other books tell you what commands to type. This book teaches you the cross-platform strategies that are timeless! DevOps techniques: Apply DevOps principles to enterprise IT infrastructure, even in environments without developers Game-changing strategies: New ways to deliver results faster with less stress Fleet management: A comprehensive guide to managing your fleet of desktops, laptops, servers and mobile devices Service management: How to design, launch, upgrade and migrate services Measurable improvement: Assess your operational effectiveness; a forty-page, pain-free assessment system you can start using today to raise the quality of all services Design guides: Best practices for networks, data centers, email, storage, monitoring, backups and more Management skills: Organization design, communication, negotiation, ethics, hiring and firing, and more Have you ever had any of these problems? Have you been surprised to discover your backup tapes are blank? Ever spent a year launching a new service only to be told the users hate it? Do you have more incoming support requests than you can handle? Do you spend more time fixing problems than building the next awesome thing? Have you suffered from a botched migration of thousands of users to a new service? Does your company rely on a computer that, if it died, can’t be rebuilt? Is your network a fragile mess that breaks any time you try to improve it? Is there a periodic “hell month†that happens twice a year? Twelve times a year? Do you find out about problems when your users call you to complain? Does your corporate “Change Review Board†terrify you? Does each division of your company have their own broken way of doing things? Do you fear that automation will replace you, or break more than it fixes? Are you underpaid and overworked? No vague “management speak†or empty platitudes. This comprehensive guide provides real solutions that prevent these problems and more! COMPUTERS,Operating Systems,UNIX

Shell Programming in Unix, Linux and OS X Shell Programming in Unix, Linux and OS X is a thoroughly updated revision of Kochan and Wood’s classic Unix Shell Programming tutorial. Following the methodology of the original text, the book focuses on the POSIX standard shell, and teaches you how to develop programs in this useful programming environment, taking full advantage of the underlying power of Unix and Unix-like operating systems. After a quick review of Unix utilities, the book’s authors take you step-by-step through the process of building shell scripts, debugging them, and understanding how they work within the shell’s environment. All major features of the shell are covered, and the large number of practical examples make it easy for you to build shell scripts for your particular applications. The book also describes the major features of the Korn and Bash shells. Learn how to… Take advantage of the many utilities provided in the Unix system Write powerful shell scripts Use the shell’s built-in decision-making and looping constructs Use the shell’s powerful quoting mechanisms Make the most of the shell’s built-in history and command editing capabilities Use regular expressions with Unix commands Take advantage of the special features of the Korn and Bash shells Identify the major differences between versions of the shell language Customize the way your Unix system responds to you Set up your shell environment Make use of functions Debug scripts Contents at a Glance 1 A Quick Review of the Basics 2 What Is the Shell? 3 Tools of the Trade 4 And Away We Go 5 Can I Quote You on That? 6 Passing Arguments 7 Decisions, Decisions 8 ‘Round and ‘Round She Goes 9 Reading and Printing Data 10 Your Environment 11 More on Parameters 12 Loose Ends 13 Rolo Revisited 14 Interactive and Nonstandard Shell Features A Shell Summary B For More Information COMPUTERS,Operating Systems,UNIX

Absolute OpenBSD, 2nd Edition OpenBSD, the elegant, highly secure Unix-like operating system, is widely used as the basis for critical DNS servers, routers, firewalls, and more. This long-awaited second edition of Absolute OpenBSD maintains author Michael Lucas's trademark straightforward and practical approach that readers have enjoyed for years. You'll learn the intricacies of the platform, the technical details behind certain design decisions, and best practices, with bits of humor sprinkled throughout. This edition has been completely updated for OpenBSD 5.3, including new coverage of OpenBSD's boot system, security features like W^X and ProPolice, and advanced networking techniques. You'll learn how to: –Manage network traffic with VLANs, trunks, IPv6, and the PF packet filter–Make software management quick and effective using the ports and packages system–Give users only the access they need with groups, sudo, and chroots–Configure OpenBSD's secure implementations of SNMP, DHCP, NTP, hardware sensors, and more–Customize the installation and upgrade processes for your network and hardware, or build a custom OpenBSD release Whether you're a new user looking for a complete introduction to OpenBSD or an experienced sysadmin looking for a refresher, Absolute OpenBSD, 2nd Edition will give you everything you need to master the intricacies of the world's most secure operating system. COMPUTERS,Operating Systems,UNIX

UNIX and Linux System Administration Handbook UNIX and Linux System Administration Handbook is today’s definitive guide to installing, configuring, and maintaining any UNIX or Linux system, including systems that supply core Internet and cloud infrastructure. Updated for new distributions and cloud environments, this comprehensive guide covers best practices for every facet of system administration, including storage management, network design and administration, security, web hosting, automation, configuration management, performance analysis, virtualisation, DNS, security, and the management of IT service organisations. The authors—world-class, hands-on technologists—offer indispensable new coverage of cloud platforms, the DevOps philosophy, continuous deployment, containerisation, monitoring, and many other essential topics. Whatever your role in running systems and networks built on UNIX or Linux, this conversational, well-written guide will improve your efficiency and help solve your knottiest problems. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Operating Systems,UNIX

bash Cookbook For system administrators, programmers, and end users, shell command or carefully crafted shell script can save you time and effort, or facilitate consistency and repeatability for a variety of common tasks. This cookbook provides more than 300 practical recipes for using bash, the popular Unix shell that enables you to harness and customize the power of any Unix or Linux system. Ideal for new and experienced users alike—including proficient Windows users and sysadmins—this updated second edition helps you solve a wide range of problems. You’ll learn ways to handle input/output, file manipulation, program execution, administrative tasks, and many other challenges. Each recipe includes one or more scripting examples and a discussion of why the solution works. You’ll find recipes for problems including: Standard output and input, and executing commands Shell variables, shell logic, and arithmetic Intermediate shell tools and advanced scripting Searching for files with find, locate, and slocate Working with dates and times Creating shell scripts for various end-user tasks Working with tasks that require parsing Writing secure shell scripts Configuring and customizing bash COMPUTERS,Operating Systems,UNIX

Digital Forensics with Kali Linux Learn the skills you need to take advantage of Kali Linux for digital forensics investigations using this comprehensive guide About This Book Master powerful Kali Linux tools for digital investigation and analysis Perform evidence acquisition, preservation, and analysis using various tools within Kali Linux Implement the concept of cryptographic hashing and imaging using Kali Linux Perform memory forensics with Volatility and internet forensics with Xplico. Discover the capabilities of professional forensic tools such as Autopsy and DFF (Digital Forensic Framework) used by law enforcement and military personnel alike Who This Book Is For This book is targeted at forensics and digital investigators, security analysts, or any stakeholder interested in learning digital forensics using Kali Linux. Basic knowledge of Kali Linux will be an advantage. What You Will Learn Get to grips with the fundamentals of digital forensics and explore best practices Understand the workings of file systems, storage, and data fundamentals Discover incident response procedures and best practices Use DC3DD and Guymager for acquisition and preservation techniques Recover deleted data with Foremost and Scalpel Find evidence of accessed programs and malicious programs using Volatility. Perform network and internet capture analysis with Xplico Carry out professional digital forensics investigations using the DFF and Autopsy automated forensic suites In Detail Kali Linux is a Linux-based distribution used mainly for penetration testing and digital forensics. It has a wide range of tools to help in forensics investigations and incident response mechanisms. You will start by understanding the fundamentals of digital forensics and setting up your Kali Linux environment to perform different investigation practices. The book will delve into the realm of operating systems and the various formats for file storage, including secret hiding places unseen by the end user or even the operating system. The book will also teach you to create forensic images of data and maintain integrity using hashing tools. Next, you will also master some advanced topics such as autopsies and acquiring investigation data from the network, operating system memory, and so on. The book introduces you to powerful tools that will take your forensic abilities and investigations to a professional level, catering for all aspects of full digital forensic investigations from hashing to reporting. By the end of this book, you will have had hands-on experience in implementing all the pillars of digital forensics—acquisition, extraction, analysis, and presentation using Kali Linux tools. Style and approach While covering the best practices of digital forensics investigations, evidence acquisition, preservation, and analysis, this book delivers easy-to-follow practical examples and detailed labs for an easy approach to learning forensics. Following the guidelines within each lab, you can easily practice all readily available forensic tools in Kali Linux, within either a dedicated physical or virtual machine. COMPUTERS,Operating Systems,UNIX

XAML in a Nutshell When Microsoft releases Windows Vista, the new operating system will support applications that employ graphics now used by computer games--clear, stunning, and active. The cornerstone for building these new user interfaces is XAML ("Zammel"), the XML-based markup language that works with Windows Presentation Foundation (WPF), Vista's new graphics subsystem. An acronym for Extensible Application Markup Language, XAML offers a wealth of new controls and elements with exciting capabilities, including animation and rendering of 3D graphics. Windows developers are already jazzed by the possibilities of using XAML for fixed and flow format documents like PDF and HTML, 2D and 3D vector-based graphics, form development, animation, audio and video, transparent layering, and a lot more. Many feel that XAML will eliminate the need for multiple file formats or plug-ins (read: Flash), while lowering development costs and reducing time to market. The problem is, most developers don't know XAML. While it is fairly easy to understand, you still need a quick guide to bring you up to speed before Vista's release, and that's where this book's simple, no nonsense approach comes in. XAML in a Nutshell covers everything necessary to design user interfaces and .NET applications that take advantage of WPF. Prerequisites such as Microsoft's new unified build system, MSBuild, and core XAML constructs and syntax--including shortcuts--are all presented with plenty of examples to get you started. The Core XAML Reference section lets you dig even deeper into syntax rules and attributes for all XAML elements with a series of quick-reference chapters. This section divides XAML elements into logical categories of elements, controls, shapes and geometry, layout, animations, and transformations for easy reference. XAML in a Nutshell helps you learn, firsthand, how to use this XML-based markup language to implement the new generation of user interface graphics. As one reviewer noted, "Strong code examples and an efficient, conversational style take the tedium out of learning XAML and make the subject understandable--even interesting." COMPUTERS,Operating Systems,Windows Desktop

DNS & Bind Cookbook The DNS & BIND Cookbook presents solutions to the many problems faced by network administrators responsible for a name server. Following O'Reilly's popular problem-and-solution cookbook format, this title is an indispensable companion to DNS & BIND, 4th Edition, the definitive guide to the critical task of name server administration. The cookbook contains dozens of code recipes showing solutions to everyday problems, ranging from simple questions, like, "How do I get BIND?" to more advanced topics like providing name service for IPv6 addresses. It's full of BIND configuration files that you can adapt to your sites requirements.With the wide range of recipes in this book, you'll be able to Check whether a name is registered Register your domain name and name servers Create zone files for your domains Protect your name server from abuse Set up back-up mail servers and virtual email addresses Delegate subdomains and check delegation Use incremental transfer Secure zone transfers Restrict which queries a server will answer Upgrade to BIND 9 from earlier version Perform logging and troubleshooting Use IPv6 and much more.These recipes encompass all the day-to-day tasks you're faced with when managing a name server, and many other tasks you'll face as your site grows. Written by Cricket Liu, a noted authority on DNS, and the author of the bestselling DNS & BIND and DNS on Windows 2000, the DNS & BIND Cookbook belongs in every system or network administrator's library. COMPUTERS,Operating Systems,Windows Desktop

Windows Internals, Part 1 Delve inside Windows architecture and internals—and see how core components work behind the scenes. Led by three renowned internals experts, this classic guide is fully updated for Windows 7 and Windows Server 2008 R2—and now presents its coverage in two volumes. As always, you get critical insider perspectives on how Windows operates. And through hands-on experiments, you’ll experience its internal behavior firsthand—knowledge you can apply to improve application design, debugging, system performance, and support. In Part 1, you will: Understand how core system and management mechanisms work—including the object manager, synchronization, Wow64, Hyper-V, and the registry Examine the data structures and activities behind processes, threads, and jobs Go inside the Windows security model to see how it manages access, auditing, and authorization Explore the Windows networking stack from top to bottom—including APIs, BranchCache, protocol and NDIS drivers, and layered services Dig into internals hands-on using the kernel debugger, performance monitor, and other tools COMPUTERS,Operating Systems,Windows Desktop

Windows Internals, Part 2 Delve inside Windows architecture and internals—and see how core components work behind the scenes. Led by three renowned internals experts, this classic guide is fully updated for Windows 7 and Windows Server 2008 R2—and now presents its coverage in two volumes. As always, you get critical insider perspectives on how Windows operates. And through hands-on experiments, you’ll experience its internal behavior firsthand—knowledge you can apply to improve application design, debugging, system performance, and support. In Part 2, you’ll examine: Core subsystems for I/O, storage, memory management, cache manager, and file systems Startup and shutdown processes Crash-dump analysis, including troubleshooting tools and techniques COMPUTERS,Operating Systems,Windows Desktop

Windows 10 Simplified Learn Windows 10 quickly and painlessly with this beginner's guide Windows 10 Simplified is your absolute beginner's guide to the ins and outs of Windows. Fully updated to cover Windows 10, this highly visual guide covers all the new features in addition to the basics, giving you a one-stop resource for complete Windows 10 mastery. Every page features step-by-step screen shots and plain-English instructions that walk you through everything you need to know, no matter how new you are to Windows. You'll master the basics as you learn how to navigate the user interface, work with files, create user accounts, and practice using the tools that make Windows 10 the most efficient Windows upgrade yet. This guide gets you up to speed quickly, with step-by-step screen shots that help you follow along with the clear, patient instruction. Shed your beginner status with easy-to-follow instructions Master the basics of the interface, files, and accounts Browse the web, use media features, and send and receive email Customize Windows to look and work the way you want Learning new computer skills can be intimidating, but it doesn't have to be. Even if you have no Windows experience at all, this visually rich guide demonstrates everything you need to know, starting from the very beginning. If you're ready to become fluent in Windows, Windows 10 Simplified is the easiest, fastest way to learn. COMPUTERS,Operating Systems,Windows Desktop

Windows 10 At Work For Dummies The fast and easy way to get up and running with Windows 10 at work If you want to spend less time figuring out Windows and more time getting things accomplished, you've come to the right place. Covering Windows 10 and packed with time-saving tips to help you get the most out of the software, Windows 10 At Work For Dummies offers everything you need to get back precious hours of your work day and make Windows work for you, rather than against you. This full-color, all-encompassing guide breaks down the most common Windows tasks into easily digestible parts, providing you with illustrated, step-by-step instructions on everything you'll encounter in Windows 10. From setting up your desktop with your favorite apps to finding the files and applications you need—and everything in between—this hands-on, friendly guide takes the headache out of working with Windows. Provides over 300 tasks broken into core steps Provides easy-to-follow answers to all of your Windows questions Illustrates the new features of Windows 10 If you're a time-pressed professional looking to find answers to all of your Windows-related questions, this is the one-stop resource you'll turn to again and again. COMPUTERS,Operating Systems,Windows Desktop

Windows PowerShell in 24 Hours, Sams Teach Yourself In just 24 lessons of one hour or less, Sams Teach Yourself Windows PowerShell in 24 Hours helps you streamline all facets of Windows administration, supercharging your effectiveness as an IT professional or power user. This book’s straightforward, step-by-step approach shows you how to build and run scripts, extend Windows PowerShell reach, manage computers remotely, and automate a wide variety of tasks on any modern Windows server or client. Every lesson builds on what you’ve already learned, giving you a rock-solid foundation for real-world success! Step-by-step instructions carefully walk you through the most common PowerShell scripting tasks. Practical, hands-on examples show you how to apply what you learn. Quizzes and exercises help you test your knowledge and stretch your skills. Notes, tips, and cautions point out shortcuts, pitfalls, and solutions. Learn how to... Install, configure, and explore Windows PowerShell (including updates for PowerShell 5) Leverage .NET’s remarkable power and scope with easy-to-use cmdlets Build new scripts with the console, ISE visual tools, and other popular hosts Apply best practices for writing more reliable, flexible, team-friendly scripts Work effectively with the pipeline, objects, and data Extend Windows PowerShell reach via providers, drives, and output Run external tools like ping, ipconfig, and tracert from within PowerShell Remotely manage computers with basic and advanced remoting (WinRM), WMI, and Regex Configure Windows devices across the web with PSWA Sort, filter, measure, format, export, and convert script output Run Windows PowerShell flexibly, using background and scheduled jobs Customize your environment with profile scripts, alternate credentials, thirdparty tools, and packages Strengthen your control over Windows systems and services with Desired State Configuration Administer key tasks on SQL Server, SharePoint, and other Windows servers Master PowerShell skills needed to earn many Microsoft certifications COMPUTERS,Operating Systems,Windows Desktop

Windows 10 Bible A complete, detailed Windows 10 reference for beginners and power users alike Windows 10 Bible is one of the most thorough references on the market with complete coverage of Windows 10. Whether you're a beginner seeking guidance or a power-user looking for fresh tips and tricks, this book contains everything you could ever hope to know about the Windows operating system. You will get the insider guidance of a Microsoft support manager as you discover everything there is to know about Windows customization, content management, networking, hardware, performance, security, and more. Step-by-step instructions walk you through new and important procedures, and screen shots help you stay on track every step of the way. Whether you're starting from scratch or just looking to become more proficient, this guide is your ideal solution. You'll learn just what Windows can do, and how to take full advantage so you can get more done faster. Go beyond the desktop to personalize the system Manage your content, media, software, and security Eliminate issues related to printing, faxing, and scanning Fine-tune performance, connect to a network, work with the cloud, and more Whether you want a complete basic introduction or the nitty-gritty detail, Windows 10 Bible has you covered. COMPUTERS,Operating Systems,Windows Desktop

Troubleshooting with the Windows Sysinternals Tools Optimize Windows system reliability and performance with Sysinternals IT pros and power users consider the free Windows Sysinternals tools indispensable for diagnosing, troubleshooting, and deeply understanding the Windows platform. In this extensively updated guide, Sysinternals creator Mark Russinovich and Windows expert Aaron Margosis help you use these powerful tools to optimize any Windows system’s reliability, efficiency, performance, and security. The authors first explain Sysinternals’ capabilities and help you get started fast. Next, they offer in-depth coverage of each major tool, from Process Explorer and Process Monitor to Sysinternals’ security and file utilities. Then, building on this knowledge, they show the tools being used to solve real-world cases involving error messages, hangs, sluggishness, malware infections, and much more. Windows Sysinternals creator Mark Russinovich and Aaron Margosis show you how to: Use Process Explorer to display detailed process and system information Use Process Monitor to capture low-level system events, and quickly filter the output to narrow down root causes List, categorize, and manage software that starts when you start or sign in to your computer, or when you run Microsoft Office or Internet Explorer Verify digital signatures of files, of running programs, and of the modules loaded in those programs Use Autoruns, Process Explorer, Sigcheck, and Process Monitor features that can identify and clean malware infestations Inspect permissions on files, keys, services, shares, and other objects Use Sysmon to monitor security-relevant events across your network Generate memory dumps when a process meets specified criteria Execute processes remotely, and close files that were opened remotely Manage Active Directory objects and trace LDAP API calls Capture detailed data about processors, memory, and clocks Troubleshoot unbootable devices, file-in-use errors, unexplained communication, and many other problems Understand Windows core concepts that aren’t well-documented elsewhere COMPUTERS,Operating Systems,Windows Desktop

Windows Internals, Part 1 The definitive guide–fully updated for Windows 10 and Windows Server 2016 Delve inside Windows architecture and internals, and see how core components work behind the scenes. Led by a team of internals experts, this classic guide has been fully updated for Windows 10 and Windows Server 2016. Whether you are a developer or an IT professional, you’ll get critical, insider perspectives on how Windows operates. And through hands-on experiments, you’ll experience its internal behavior firsthand–knowledge you can apply to improve application design, debugging, system performance, and support. This book will help you: · Understand the Window system architecture and its most important entities, such as processes and threads · Examine how processes manage resources and threads scheduled for execution inside processes · Observe how Windows manages virtual and physical memory · Dig into the Windows I/O system and see how device drivers work and integrate with the rest of the system · Go inside the Windows security model to see how it manages access, auditing, and authorization, and learn about the new mechanisms in Windows 10 and Server 2016 COMPUTERS,Operating Systems,Windows Desktop

Windows 10 All-in-One For Dummies Welcome to the world of Windows 10! Are you ready to become the resident Windows 10 expert in your office? Look no further! This book is your one-stop shop for everything related to the latest updates to this popular operating system. With the help of this comprehensive resource, you'll be able to back up your data and ensure the security of your network, use Universal Apps to make your computer work smarter, and personalize your Windows 10 experience. Windows 10 powers more than 400 million devices worldwide—and now you can know how to make it work better for you with Windows 10 All-in-One For Dummies. You’ll find out how to personalize Windows, use the universal apps, control your system, secure Windows 10, and so much more. Covers the most recent updates to this globally renowned operating system Shows you how to start out with Windows 10 Walks you through maintaining and enhancing the system Makes it easy to connect with universal and social apps If you’re a businessperson or Windows power-user looking to make this popular software program work for you, the buck stops here! COMPUTERS,Operating Systems,Windows Desktop

My Windows 10 Computer for Seniors The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. My Microsoft® Windows® 10 Computer for Seniors is an easy, full-colour tutorial on the latest operating system from Microsoft. Veteran author Michael Miller is known for his ability to explain complex topics to everyday readers. Michael wrote this book from the 50+ point of view, using step-by-step instructions and large, full-colour photos to cover all the most popular tasks. Miller will help you learn to: Get started with Windows 10, whether you’re experienced with computers or not Configure Windows 10 to work better for those with vision and physical challenges Explore the web with Microsoft’s Edge browser and Google Search Find, install, and use the best new Windows apps Reliably connect to the Internet, both at home and away Find online bargains, shop safely, and avoid online scams Make and receive video and voice calls with Skype Stay connected with friends and family on Facebook and Pinterest Capture, touch up, organise, and share your pictures Read eBooks on your PC—even enlarge text for greater comfort Send and receive email with Windows 10’s Email app Keep track of all your files, and back them up safely Discover great new music with Spotify and Pandora Fix common PC and Internet problems Search your computer and the Internet—and send and receive text messages—with the Cortana virtual assistant COMPUTERS,Operating Systems,Windows Desktop

Easy Windows 10 Visual, step-by-step hands-on tutorials for the most common tasks a user needs to perform. Updated for the 2017 Spring and Fall Creator releases of Windows 10. See it done. Do it yourself. It’s that Easy! Easy Windows 10 teaches you the fundamentals to help you get the most from Windows 10. Fully illustrated steps with simple instructions guide you through each task, building the skills you need to perform the most common tasks with Windows. No need to feel intimidated; we’ll hold your hand every step of the way. Learn how to… • Use the improved Windows 10 Fall Creators Update Start menu in Desktop and Tablet mode versions • Discover exciting new 3D and mixed reality apps • Share your wireless Internet connection with smartphones, tablets, and PCs • Use Cortana with more apps and new Cortana-enabled speakers • Use the new OneDrive Files on Demand feature for easy access to files stored in the cloud • Use Windows Ink to enhance your photos and make map directions more powerful • Touchscreen, keyboard, or mouse—use Windows 10 your way! COMPUTERS,Operating Systems,Windows Desktop

Exam Ref 70-697 Configuring Windows Devices Prepare for Microsoft Exam 70-697–and help demonstrate your real-world mastery of configuring Windows 10 devices in the enterprise. Designed for experienced IT professionals ready to advance their status, this Exam Ref focuses on the critical-thinking and decision-making acumen needed for success at the MCSA level. Focus on the expertise measured by these objectives: • Manage identity • Plan desktop and device deployment • Plan and implement a Microsoft 365 Solution • Configure networking • Configure storage • Manage data access and protection • Manage remote access • Manage apps • Manage updates and recovery This Microsoft Exam Ref: • Organizes its coverage by exam objectives • Features strategic, what-if scenarios to challenge you • Assumes you have experience with Windows desktop administration, maintenance, and troubleshooting; Windows 10 security, and integrated Azure features; as well as a basic understanding of Windows networking, Active Directory, and Microsoft Intune For details on requirements for taking Exam 70-697, go to https://www.microsoft.com/en-us/learning/exam-70-697.aspx COMPUTERS,Operating Systems,Windows Desktop

System Center Configuration Manager Current Branch Unleashed (includes Content Update Program) System Center Configuration Manager Current Branch provides a total systems management solution for a people-centric world. It can deploy applications to individuals using virtually any device or platform, centralizing and automating management across on-premise, service provider, and Microsoft Azure environments. In System Center Configuration Manager Current Branch Unleashed, a team of world-renowned System Center experts shows you how to make the most of this powerful toolset. The authors begin by introducing modern systems management and offering practical strategies for coherently managing today’s IT infrastructures. Drawing on their immense consulting experience, they offer expert guidance for ConfigMgr planning, architecture, and implementation. You’ll walk through efficiently performing a wide spectrum of ConfigMgr operations, from managing clients, updates, and compliance to reporting. Finally, you’ll find current best practices for administering ConfigMgr, from security to backups. Detailed information on how to: Successfully manage distributed, people-centric, cloud-focused IT environments Optimize ConfigMgr architecture, design, and deployment plans to reflect your environment Smoothly install ConfigMgr Current Branch and migrate from Configuration Manager 2012 Save time and improve efficiency by automating system management Use the console to centralize control over infrastructure, software, users, and devices Discover and manage clients running Windows, macOS, Linux, and UNIX Define, monitor, enforce, remediate, and report on all aspects of configuration compliance Deliver the right software to the right people with ConfigMgr applications and deployment types Reliably manage patches and updates, including Office 365 client updates Integrate Intune to manage on-premise and mobile devices through a single console Secure access to corporate resources from mobile devices Manage Microsoft’s enterprise antimalware platform with System Center Endpoint Protection Using this guide’s proven techniques and comprehensive reference information, you can maximize the value of ConfigMgr in your environment–no matter how complex it is or how quickly it’s changing. COMPUTERS,Operating Systems,Windows Desktop

Exam Ref 70-698 Installing and Configuring Windows 10 Prepare for Microsoft Exam 70-698—and help demonstrate your real-world mastery of installing, configuring, managing, and maintaining Windows 10 core services. Designed for experienced IT professionals ready to advance their status, this Exam Ref focuses on the critical-thinking and decision-making acumen needed for success at the MCSA level. Focus on the expertise measured by these objectives: • Implement Windows • Configure and support core services • Manage and maintain Windows This Microsoft Exam Ref: • Organizes its coverage by exam objectives • Features strategic, what-if scenarios to challenge you • Assumes you have experience with installing, configuring, and locally managing and maintaining Windows 10 core services COMPUTERS,Operating Systems,Windows Desktop

Windows 10 Inside Out Conquer today’s Windows 10—from the inside out! Dive into Windows 10—and really put your Windows expertise to work. Focusing on Windows 10’s newest, most powerful, and most innovative features, this supremely organized reference packs hundreds of timesaving solutions, up-to-date tips, and workarounds. From the new Timeline to key improvements in Microsoft Edge, Cortana, security, and virtualization, you’ll discover how experts tackle today’s essential tasks. Adapt to faster change in today’s era of “Windows as a service,†as you challenge yourself to new levels of mastery. • Install, configure, and personalize the latest versions of Windows 10 • Manage Windows reliability, security, and feature updates in any environment • Maximize your productivity with Windows 10’s growing library of built-in apps • Pinpoint information fast with advanced Windows Search and Cortana techniques • Discover major Microsoft Edge enhancements, from extensions to accessibility • Use Cortana to perform tasks, set reminders, retrieve data, and get instant answers to pressing questions • Secure devices, data, and identities, and block malware and intruders • Safeguard your business with BYOD work accounts, Windows Hello, biometrics, and Azure AD • Deploy, use, and manage Universal Windows Platform (UWP) apps • Store, sync, and share content with OneDrive and OneDrive for Business • Collaborate more efficiently with the Windows 10 Mail, Calendar, and Skype apps • Seamlessly manage both physical and virtual storage • Optimize performance and battery life and troubleshoot crashes COMPUTERS,Operating Systems,Windows Desktop

Windows 10 May 2019 Update The Windows 10 May 2019 Update adds a host of new and improved features to Microsoft’s flagship operating system—and this jargon-free guide helps you get the most out of every component. This in-depth Missing Manual covers the entire system and introduces you to the latest features in the Windows Professional, Enterprise, Education, and Home editions. You’ll learn how to take advantage of improvements to the Game Bar, Edge browser, Windows Online, smartphone features, and a lot more. Written by David Pogue—tech critic for Yahoo Finance and former columnist for The New York Times—this updated edition illuminates its subject with technical insight, plenty of wit, and hardnosed objectivity. COMPUTERS,Operating Systems,Windows Desktop

Microsoft Exam MD-100 Windows 10 Certification Guide An administrator's guide to deploying, configuring, securing, managing, and monitoring devices and client applications in an enterprise environment and passing Exam MD-100: Windows 10 easily Key Features Equip yourself to earn the Microsoft 365 Certified: Modern Desktop Administrator Associate certification Develop the skills needed to pass the Exam MD-100 and advance in your organization Learn to install Windows 10 operating systems and deploy and manage modern desktops and devices Book Description Microsoft Exam MD-100 Windows 10 Certification Guide offers complete, up-to-date coverage of the MD-100 exam, helping you take the exam with confidence, fully equipped to pass on the first attempt. Complete with a clear, succinct explanation of key concepts, self-assessment questions, tips, and mock exams with detailed answers, this MD-100 study guide covers different facets of upgrading and deploying Windows 10. You'll learn how to manage devices and data, configure connectivity, troubleshoot OS and app problems, and secure and maintain Windows 10 with updates and recovery. You'll also explore different Windows 10 editions and learn how to choose the best fit for your organization. This book will guide you in installing and configuring Windows 10 using different approaches. As you advance, you'll get to grips with managing local users and groups in Windows 10 and learn how to establish connections via different networks, such as a LAN and WLAN/Wi-Fi. By the end of this book, you'll have covered everything you need to pass the MD-100 certification exam and become a Microsoft 365 Certified: Modern Desktop Administrator Associate. What you will learn Deploy Windows 10 in a variety of ways Manage local users, groups, and devices Configure networking and remote connectivity Gain insights into Windows 10 maintenance Customize different Windows 10 features Become an expert at troubleshooting and recovery Get to grips with managing log files Monitor and manage Windows security Who this book is for This book is for both experienced and novice IT administrators who work with deploying, configuring, securing, and monitoring devices. Anyone with a working knowledge of managing identity, access, policies, updates, and apps can take this exam. Although not necessary, experience with Microsoft 365 workloads, Windows 10 devices, and non-Windows devices will be helpful. COMPUTERS,Operating Systems,Windows Desktop

Teach Yourself VISUALLY Windows 10 Master Windows 10 by reading only one book Teach Yourself Visually Windows 10, 3 rd Edition brings together all of the necessary resources to make you an expert in the use of the latest version of Windows. Using highly visual techniques to maximize learner retention and memory, Teach Yourself Visually Windows 10 will have you breezing through the most popular operating system in the world in no time. The book includes hundreds of step-by-step and illustrated sets of instructions to teach you both the basics and the complexities of Windows 10 operation. Lessons include: · Installing and repairing applications · System maintenance · Setting up password-protection · Downloading photos · Managing media files · And more Teach Yourself Visually Windows 10 combines the best of visual learning techniques with comprehensive source material about the interface and substance of Windows 10 to leave you with encyclopedic knowledge of the operating system. Perfect for beginners and intermediate users alike, this book will turn your Windows-using experience from a slow slog into a lighting-fast masterclass of efficiency. COMPUTERS,Operating Systems,Windows Desktop

My Windows 10 Computer for Seniors My Microsoft Windows 10 Computer for Seniors is an easy, full-color tutorial on the latest operating system from Microsoft. Veteran author Michael Miller is known for his ability to explain complex topics to everyday readers. Michael wrote this book from the 50+ point of view, using step-by-step instructions and large, full-color photos to cover all the most popular tasks. Miller will help you learn to: • Get started with Windows 10, whether you’re experienced with computers or not • Configure Windows 10 to work better for those with vision and physical challenges • Explore the web with Microsoft’s Edge browser and Google Search • Find, install, and use the best Windows apps • Reliably connect to the Internet, both at home and away • Shop safely online and avoid online scams • Make and receive video and voice calls with Skype • Connect your phone to your PC to text and make calls • Stay connected with friends and family on Facebook, Pinterest, and Twitter • Store, touch up, and share your pictures • Send and receive email with Windows 10’s Email app • Keep track of all your files, and back them up safely • Watch streaming video on your PC with Disney+, Netflix, YouTube, and more • Discover great new music with Spotify and Pandora • Fix common PC problems, and manage Windows updates COMPUTERS,Operating Systems,Windows Desktop

Active Directory For Dummies Whether you’re new to Active Directory (AD) or a savvy system administrator looking to brush up on your skills, Active Directory for Dummies, 2nd Edition will steer you in the right direction! Since its original release, Microsoft’s implementation of the lightweight directory access protocol (LDAP) for the Windows Server line of networking software has become one of the most popular directory service products in the world. If you are involved with the design and support of Microsoft directory services and/or solutions, you really need this book! You’ll understand the basics of AD and utilize its structures to simplify your life and secure your digital environment. You’ll discover how to exert fine-grained control over groups, assets, security, permissions, and policies on a Windows network and efficiently configure, manage, and update the network. You’ll find new and updated material on security improvements, significant user interface changes, and updates to the AD scripting engine, password policies, accidental object deletion protection, and more. You will learn how to: Navigate the functions and structures of AD Understand business and technical requirements and determine goals Become familiar with physical components like site links, network services, and site topology Manage and monitor new features, AD replication, and schema management Maintain AD databases Avoid common AD mistakes that can undermine network security Complete with lists of the ten most important points about AD, and ten cool Web resources, and ten troubleshooting tips, Active Directory For Dummies, 2nd Edition is your one-stop guide to setting up, working with, and making the most of Active Directory. Note: CD-ROM/DVD and other supplementary materials are not included as part of eBook file. COMPUTERS,Operating Systems,Windows Server

The Best of Windows 7 Secrets The Best of Windows 7 Secrets delivers a concise and value-packed punch that includes the most important Windows 7 features that all Windows 7 users need to know. This e-book delivers the most important content on this major Microsoft upgrade to value-minded e-book buyers. Written by well-known Windows experts and excerpted from best-selling Windows 7 Secrets, this book is the go-to guide for every Windows 7 user. The lead author Paul Thurrott runs the SuperSite for Windows (WinSuperSite.com), which has been described by Microsoft as the most influential Windows-oriented Web site in the world. Paul is joined by Rafael Rivera the blogger and programmer behind Within Windows (WithinWindows.com), a blog devoted to the technical internals of Microsoft's Windows operating systems. COMPUTERS,Operating Systems,Windows Server

Microsoft Windows Server 2012 Administration Instant Reference Fast, accurate answers for common Windows Server questions Serving as a perfect companion to all Windows Server books, this reference provides you with quick and easily searchable solutions to day-to-day challenges of Microsoft's newest version of Windows Server. Using helpful design features such as thumb tabs, tables of contents, and special heading treatments, this resource boasts a smooth and seamless approach to finding information. Plus, quick-reference tables and lists provide additional on-the-spot answers. Covers such key topics as server roles and functionality, user and group maintenance, directory management and replication, and backup and recovery Addresses automating administrative tasks and managing server remote access Helps you with disk management and storage, folder security, and performance tuning Walks you through common troubleshooting issues as well as maintaining and controlling the centralized desktop Microsoft Windows Server 2012 Administration Instant Reference is a must-have resource for finding quick answers quickly! COMPUTERS,Operating Systems,Windows Server

Windows Server 2012 R2 Pocket Consultant Volume 1 Portable and precise, this pocket-sized guide delivers ready answers for core configuration and administrative tasks in Windows Server 2012 R2. Zero in on the essentials through quick-reference tables, instructions, and lists. You'll get the focused information you need to save time and get the job done - whether at your desk or in the field. Coverage includes: Administration overview Managing servers running Windows Server 2012 R2 Monitoring services, processes, and events Automating administrative tasks, policies, and procedures Enhancing computer security Using Active Directory Core Active Directory administration Creating user and group accounts Managing existing user and group accounts COMPUTERS,Operating Systems,Windows Server

Windows Server 2012 R2 Pocket Consultant Volume 2 Portable and precise, this pocket-sized guide delivers ready answers for administering storage, security, and networking features in Windows Server 2012 R2. Zero in on core tasks through quick-reference tables, instructions, and lists. You'll get the focused information you need to save time and get the job done - whether at your desk or in the field. Coverage includes: Managing file systems and drives Configuring storage Data sharing Managing TCP/IP networking Running DHCP clients and servers Optimizing DNS Administering network printers and print services Security, compliance, and auditing Backup and recovery COMPUTERS,Operating Systems,Windows Server

Virtualization Essentials Learn virtualization skills by building your own virtual machine Virtualization Essentials, Second Edition provides new and aspiring IT professionals with immersive training in working with virtualization environments. Clear, straightforward discussion simplifies complex concepts, and the hands-on tutorial approach helps you quickly get up to speed on the fundamentals. You'll begin by learning what virtualization is and how it works within the computing environment, then you'll dive right into building your own virtual machine. You'll learn how to set up the CPU, memory, storage, networking, and more as you master the skills that put you in-demand on the job market. Each chapter focuses on a specific goal, and concludes with review questions that test your understanding as well as suggested exercises that help you reinforce what you've learned. As more and more companies are leveraging virtualization, it's imperative that IT professionals have the skills and knowledge to interface with virtualization-centric infrastructures. This book takes a learning-by-doing approach to give you hands-on training and a core understanding of virtualization. Understand how virtualization works Create a virtual machine by scratch and migration Configure and manage basic components and supporting devices Develop the necessary skill set to work in today's virtual world Virtualization was initially used to build test labs, but its use has expanded to become best practice for a tremendous variety of IT solutions including high availability, business continuity, dynamic IT, and more. Cloud computing and DevOps rely on virtualization technologies, and the exponential spread of these and similar applications make virtualization proficiency a major value-add for any IT professional. Virtualization Essentials, Second Edition provides accessible, user-friendly, informative virtualization training for the forward-looking pro. COMPUTERS,Operating Systems,Windows Server

PowerShell Learn PowerShell from the inside out, right from basic scripting all the way to becoming a master at automating, managing, and maintaining your Windows environment About This Book Use proven best practices to optimize code and automate redundant tasks Get to grips with PowerShell's advanced functions and effectively administer your system Create a variety of PowerShell scripts to automate your environment Who This Book Is For If you are a system administrator who wants to become an expert in automating and managing your Windows environment, then this course is for you. Some basic understanding of PowerShell would be helpful. What You Will Learn Discover PowerShell commands and cmdlets and understand PowerShell formatting Solve common problems using basic file input/output functions Use .NET classes in Windows PowerShell and C# and manage Exchange Online Use PowerShell in C# to manage Exchange Online and work with .NET classes in PowerShell Automate LYNC clients, consuming client-side object models to administrate SharePoint Online Optimize code through the use of functions, switches, and looping structures Manage files, folders, and registries through the use of PowerShell Discover best practices to manage Microsoft systems In Detail Are you tired of managing Windows administrative tasks manually and are looking to automate the entire process? If yes, then this is the right course for you. This learning path starts your PowerShell journey and will help you automate the administration of the Windows operating system and applications that run on Windows. It will get you up and running with PowerShell, taking you from the basics of installation to writing scripts and performing web server automation. You will explore the PowerShell environment and discover how to use cmdlets, functions, and scripts to automate Windows systems. The next installment of the course focuses on gaining concrete knowledge of Windows PowerShell scripting to perform professional-level scripting. The techniques here are packed with PowerShell scripts and sample C# code to automate tasks. You will use .NET classes in PowerShell and C# to manage Exchange Online. In the final section, you will delve into real-world examples to learn how to simplify the management of your Windows environment. You will get to grips with PowerShell's advanced functions and how to most effectively administer your system. This Learning Path combines some of the best that Packt has to offer in one complete, curated package. It includes content from the following Packt products: Getting Started with PowerShell by Michael Shepard Windows PowerShell for .Net Developers Second Edition by Chendrayan Venkatesan and Sherif Talaat Mastering Windows PowerShell Scripting by Brenton J.W. Blawat Style and approach This is a step-by-step course to help you effectively administer and maintain your development environment with PowerShell. COMPUTERS,Operating Systems,Windows Server

Mastering Windows Server 2016 The IT pro's must-have guide to Windows Server 2016 Mastering Windows Server 2016 is a complete resource for IT professionals needing to get quickly up to date on the latest release. Designed to provide comprehensive information in the context of real-world usage, this book offers expert guidance through the new tools and features to help you get Windows Server 2016 up and running quickly. Straightforward discussion covers all aspects, including virtualization products, identity and access, automation, networking, security, storage and more, with clear explanations and immediately-applicable instruction. Find the answers you need, and explore new solutions as Microsoft increases their focus on security, software-defined infrastructure, and the cloud; new capabilities including containers and Nano Server, Shielded VMs, Failover Clustering, PowerShell, and more give you plenty of tools to become more efficient, more effective, and more productive. Windows Server 2016 is the ideal server for Windows 10 clients, and is loaded with new features that IT professionals need to know. This book provides a comprehensive resource grounded in real-world application to help you get up to speed quickly. Master the latest features of Windows Server 2016 Apply new tools in real-world scenarios Explore new capabilities in security, networking, and the cloud Gain expert guidance on all aspect of Windows Server 2016 migration and management System administrators tasked with upgrading, migrating, or managing Windows Server 2016 need a one-stop resource to help them get the job done. Mastering Windows Server 2016 has the answers you need, the practicality you seek, and the latest information to get you up to speed quickly. COMPUTERS,Operating Systems,Windows Server

Exam Ref 70-743 Upgrading Your Skills to MCSA About the Book: Prepare for Microsoft Exam 70-743—and demonstrate that your skills are upgraded for Windows Server 2016. Designed for experienced IT pros ready to advance their status, this Exam Ref focuses on the critical-thinking and decision-making acumen needed for success at the MCSA level. Focus on the skills measured on the exam: • Install Windows servers in host and compute environments • Implement storage solutions • Implement Hyper-V • Implement Windows containers• Implement high availability• Implement Domain Name System (DNS)• Implement IP Address Management (IPAM)• Implement network connectivity and remote access solutions• Implement an advanced network infrastructure• Install and configure Active Directory Domain Services (AD DS)• Implement identity federation and access solutions This Microsoft Exam Ref: • Organizes its coverage by the “Skills measured†posted on the exam webpage • Features strategic, what-if scenarios to challenge you • Points to in-depth material by topic for exam candidates needing additional review • Assumes you are an IT pro looking to validate your skills in and knowledge of installing and configuring Windows Server 2016 COMPUTERS,Operating Systems,Windows Server

Exam Ref 70-741 Networking with Windows Server 2016 Microsoft Exam 70-741 is for IT Pros interested in enhancing their skills for the latest version of Windows Server. This exam validates skills and knowledge for configuring advanced tasks required to deploy, manage, and maintain a Windows Server 2016 infrastructure, such as fault tolerance, certificate services, and identity federation. Passing this exam along with two other exams is required for MCSA and MCSE certifications. The Exam Ref is the official study guide for Microsoft certification exam 70-741. Featuring concise, objective-by-objective reviews and strategic case scenarios and Thought Experiments, exam candidates get professional-level preparation for the exam. The Exam Ref helps candidates maximize their performance on the exam and sharpen their job-role skills. It organizes material by the exam's objective domains Focus is on the skills measured on the exam: • Implement Domain Name System (DNS) • Implement DHCP • Implement IP Address Management (IPAM) • Implement network connectivity and remote access solutions • Implement core and distributed network solutions • Implement an advanced network infrastructure This Microsoft Exam Ref: • Organizes its coverage by the “Skills measured†posted on the exam webpage • Features strategic, what-if scenarios to challenge you • Points to in-depth material by topic for exam candidates needing additional review • Assumes you are an IT pro looking to validate your skills in and knowledge of installing and configuring Windows Server 2016 COMPUTERS,Operating Systems,Windows Server

Windows Server 2016 Automation with PowerShell Cookbook Over 100 recipes to help you leverage PowerShell to automate Windows Server 2016 manual tasks About This Book Automate Windows server tasks with the powerful features of the PowerShell Language Master new features such as DevOps, containers, and Nano servers, and speed up their performance using PowerShell Improve PowerShell's usability, and control and manage Windows-based environments by working through inviting recipes Who This Book Is For If you are a systems administrator, engineer, or an architect working with Windows Server 2016 and want to automate tasks with PowerShell, then this book is for you. A basic knowledge of PowerShell is expected. What You Will Learn Streamline routine administration processes Improve the performance and storage of your Windows server with enhanced large-scale PowerShell scripts Use DSC to leverage Windows server features Generate automatic reports that highlight unexpected changes in your environment Monitor performance and report on system utilization using detailed graphs and analysis Create and manage a reliable and redundant Hyper-V environment Manage your enterprise's patch level Utilize multiple tools and protocols to manage your environment In Detail This book showcases several ways that Windows administrators can use to automate and streamline their job. You'll start with the PowerShell and Windows Server fundamentals, where you'll become well versed with PowerShell and Windows Server features. In the next module, Core Windows Server 2016, you'll implement Nano Server, manage Windows updates, and implement troubleshooting and server inventories. You'll then move on to the Networking module, where you'll manage Windows network services and network shares. The last module covers Azure and DSC, where you will use Azure on PowerShell and DSC to easily maintain Windows servers. Style and approach This is a practical guide packed with attractive recipes to help you effectively use PowerShell to accelerate your daily administrative tasks with Windows server. COMPUTERS,Operating Systems,Windows Server

Microsoft Hybrid Cloud Unleashed with Azure Stack and Azure Microsoft Hybrid Cloud Unleashed brings together comprehensive and practical insights into hybrid cloud technologies, complete CloudOps and DevOps implementation strategies, and detailed guidance for deploying Microsoft Azure Stack in your environment. Written by five Microsoft Cloud and Datacenter Management MVPs, this book is built on real-world scenarios and the authors’ extraordinary hands-on experiences as early adopters. Step by step, the authors help you integrate your optimal mix of private and public cloud, with a unified management experience that lets you move workloads at will, achieving unprecedented flexibility. The authors also guide you through all aspects of building your own secure, high-performance hybrid cloud infrastructure. You’ll discover how Azure Stack enables you to run data centers with the same scalability, redundancy, and reliability as Microsoft’s Azure data centers; how to integrate Azure infrastructure and platform services with internal operations; and how to manage crucial external dependencies. The book concludes with a deep dive into automating and customizing Azure Stack for maximum reliability, productivity, and cost savings. Detailed information on how to Run a private/hybrid cloud on your hardware in your data center, using APIs and code identical to public Azure Apply ITIL and DevOps lifecycles to your hybrid cloud implementation Gain a deep understanding of Azure Stack architecture, components, and internals Install and configure Azure Stack and master the Azure Stack Portal Integrate and utilize infrastructure, core, and custom resource providers Effectively provision, secure, and manage tenants Manage, monitor, troubleshoot, and back up Azure Stack with CloudOps Automate resource provisioning with PowerShell, the Azure CLI, templates, and Azure Stack’s API Write your own Azure Resource Manager templates Centrally automate cloud management and complex tasks connected to external systems Develop customized, production-ready Azure Stack marketplace items COMPUTERS,Operating Systems,Windows Server

MCSA SQL 2016 BI Development Exam Ref 2-pack Direct from Microsoft, these Exam Refs are the official study guides for the new Microsoft 70-767 Implementing a SQL Data Warehouse and the new Microsoft 70-768 Developing SQL Data Models certification exams. Exam Ref 70-767 Implementing a SQL Data Warehouse , the first book in this bundle (ISBN 978150936473), offers professional-level preparation that helps candidates maximize their exam performance and sharpen their skills on the job. It focuses on the specific areas of expertise modern IT professionals need to successfully build modern data warehouses to support advanced business intelligence solutions. Written by Microsoft Data Platform MVP Stacia Varga, Exam Ref 70-768 Developing SQL Data Models , the second book in this bundle (ISBN 9781509305155), offers professional-level preparation that helps candidates maximize their exam performance and sharpen their skills on the job. It focuses on the specific areas of expertise modern database and business intelligence professionals need to succeed with SQL Server 2016 Analysis Services. COMPUTERS,Operating Systems,Windows Server

Programming Microsoft Azure Service Fabric Build, operate, and orchestrate scalable microservices applications in the cloud This book combines a comprehensive guide to success with Microsoft Azure Service Fabric and a practical catalog of design patterns and best practices for microservices design, implementation, and operation. Haishi Bai brings together all the information you’ll need to deliver scalable and reliable distributed microservices applications on Service Fabric. He thoroughly covers the crucial DevOps aspects of utilizing Service Fabric, reviews its interactions with key cloud-based services, and introduces essential service integration mechanisms such as messaging systems and reactive systems. Leading Microsoft Azure expert Haishi Bai shows how to: Set up your Service Fabric development environment Program and deploy Service Fabric applications to a local or a cloud-based cluster Compare and use stateful services, stateless services, and the actor model Design Service Fabric applications to maximize availability, reliability, and scalability Improve management efficiency via scripting Configure network security and other advanced cluster settings Collect diagnostic data, and use Azure Operational Management Suite to interpret it Integrate microservices components developed in parallel Use containers to mobilize applications for failover, replication, scaling, and load balancing Streamline containerization with Docker in Linux and Windows environments Orchestrate containers to schedule workloads and maintain services at desired states Implement proven design patterns for common cloud application workloads Balance throughput, latency, scalability, and cost COMPUTERS,Operating Systems,Windows Server

Windows Server 2019 Automation with PowerShell Cookbook Automate Windows server tasks with the powerful features of the PowerShell Language Key Features Leverage PowerShell to automate complex Windows server tasks Master new features such as DevOps, and containers, and speed up their performance using PowerShell Improve PowerShell's usability, and control and manage Windows-based environments by working through exciting recipes Book Description Windows Server 2019 represents the latest version of Microsoft's flagship server operating system. It also comes with PowerShell Version 5.1 and has a number of additional features that IT pros find useful. The book helps the reader learn how to use PowerShell and manage core roles, features, and services of Windows Server 2019. You will begin with creating a PowerShell Administrative Environment that has updated versions of PowerShell and the Windows Management Framework, updated versions of the .NET Framework, and third-party modules. Next, you will learn to use PowerShell to set up and configure Windows Server 2019 networking and also managing objects in the AD environment. You will also learn to set up a host to utilize containers and how to deploy containers. You will also be implementing different mechanisms for achieving desired state configuration along with getting well versed with Azure infrastructure and how to setup Virtual Machines, web sites, and shared files on Azure. Finally, you will be using some powerful tools you can use to diagnose and resolve issues with Windows Server 2019. By the end of the book, you will learn a lot of trips and tricks to automate your windows environment with PowerShell What you will learn Perform key admin tasks on Windows Server 2019 Employing best practices for writing PowerShell scripts and configuring Windows Server 2019 Use the .NET Framework to achieve administrative scripting Set up VMs, websites, and shared files on Azure Report system performance using built-in cmdlets and WMI to obtain single measurements Know the tools you can use to diagnose and resolve issues with Windows Server Who this book is for If you are a systems administrator, engineer, or an architect working with Windows Server 2016 interested in upgrading to Windows Server 2019 and automating tasks with PowerShell, then this book is for you. A basic knowledge of PowerShell is expected. COMPUTERS,Operating Systems,Windows Server

Windows Server 2019 Administration Fundamentals Deploy, set up, and deliver network services with Windows Server 2019, and prepare for the MTA 98-365 exam Key Features Get started with server installation, performance monitoring, and server maintenance Develop the skills necessary to manage an enterprise environment Implement networking and security best practices in your Windows Server environment Book Description Windows Server 2019 is the server operating system introduced by Microsoft as part of the Windows NT family of operating systems, developed concurrently with Windows 10. This book will not only get you started with Windows Server 2019, but will also help you prepare for the MTA 98-365 exam. With step-by-step instructions and easy-to-understand graphics, you will become well-versed with the roles, features, and functions of Windows Server 2019. Starting with the installation process, upgrades, and basic configuration, you will move on to explore roles and features such as Active Directory, Hyper-V, remote access, storage, and printers. The book then takes you through maintenance and troubleshooting tasks to guide you in efficiently managing Windows Server 2019. In addition, it covers Windows Server 2019 best practices using real-world examples. Complete with questionnaires, and detailed answers at the end of the book, you can test your understanding of the concepts covered in each chapter. By the end of this book, you will be equipped with the knowledge you need to troubleshoot, update, and maintain servers so as to ensure business continuity. What you will learn Grasp the fundamentals of Windows Server 2019 Understand how to deploy Windows Server 2019 Discover Windows Server post-installation tasks Add roles to your Windows Server environment Apply Windows Server 2019 GPOs to your network Delve into virtualization and Hyper-V concepts Explore ways to tune, maintain, update, and troubleshoot Windows Server 2019 Study relevant concepts in preparation for the MTA 98-365 exam Who this book is for If you are a system administrator or an IT professional who wants to deploy and configure Windows Server 2019, this book is for you. You can also use this as a reference guide for the MTA: Windows Server Administration Fundamentals: 98-365 exam. COMPUTERS,Operating Systems,Windows Server

Windows Server Administration Fundamentals Did you know, 91% of hiring managers consider certification as part of their hiring requirements? IT Professionals who are new to the industry need a strong foundational understanding of the fundamentals before moving on towards more challenging technology certifications. This book covers everything you need to know about understanding how to manage windows servers and storage along with monitoring and troubleshooting servers as well. Written to the Windows Server Administration Fundamentals MTA Certification, it is a recommended entry point into IT certification. This book covers the basics of Windows Server Administration. Each chapter closes with a quiz to make sure you can practice exam questions and test your knowledge begore moving to the next section. We start by discussing what a server is and does by providing an in-depth overview including installation of Windows Server 2016. There are sections dedicated to the following: Preforming configurations and managing your Windows Server, by configuring your IP address settings and managing devices and device drivers. Managing your storage, by identifying storage technologies, understanding disk structure, and using disk management tools. Monitoring and troubleshooting servers, by managing information technology, and understanding performance, backups and preforming server repair. Overview of popular Windows network services and applications, like understanding remote access, server virtualization, and introducing remote administration. IT Professionals looking to understand more about Windows Server Administration will gain he knowledge to effectively install and manage a Windows Server including basic troubleshooting. Thanks to some troubleshooting tools and tops it will be easier to apply the skills in real world situations and feel confident when taking the certification. COMPUTERS,Operating Systems,Windows Server

Exam Ref AZ-900 Microsoft Azure Fundamentals Prepare for Microsoft Exam AZ-900—and help demonstrate your real-world mastery of cloud services and how they can be provided with Microsoft Azure. Designed for professionals in any non-technical or technical role, Exam Ref focuses on the critical thinking and decision-making acumen needed for success at the Microsoft Certified Fundamentals level. Focus on the expertise measured by these objectives: Understand cloud concepts Understand core Azure services Understand security, privacy, compliance, and trust Understand Azure pricing and support This Microsoft Exam Ref: Organizes its coverage by exam objectives Features strategic, what-if scenarios to challenge you Assumes you want to show foundational knowledge of cloud services and their delivery with Microsoft Azure; no technical background or IT experience is required About the Exam Exam AZ-900 focuses on knowledge needed to evaluate cloud service’s value; explain IaaS, PaaS, and SaaS; compare public, private, and hybrid cloud models; understand core Azure architectural components, products, and management tools; describe the Azure Marketplace, its usage, and key solutions; understand Azure security, identity services, and monitoring; manage privacy, compliance, and data protection; price subscriptions and manage costs; choose support options; use Service Level Agreements; and understand the Azure service lifecycle. About Microsoft Certification Passing this exam fulfills your requirements for the Microsoft Certified Azure Fundamentals credential, demonstrating that you understand cloud concepts, core Azure Services, Azure pricing and support, and the fundamentals of cloud security, privacy, compliance, and trust. See full details at: www.microsoft.com/learn COMPUTERS,Operating Systems,Windows Server

Exam Ref AZ-204 Developing Solutions for Microsoft Azure Prepare for Microsoft Exam AZ-204–and help demonstrate your real-world mastery of Microsoft Azure solutions development. Designed for working Azure developers, this Exam Ref focuses on the critical thinking and decision-making acumen needed for success at the Microsoft Certified Azure Developer Associate level. Focus on the expertise measured by these objectives: Develop for cloud storage Create Platform as a Service (PaaS) Solutions Secure cloud solutions Develop for an Azure cloud model Implement cloud integration solutions Develop Azure Cognitive Services, Bot, and IoT solutions Develop Azure Infrastructure as a Service compute solutions Develop Azure Platform as a Service compute solutions Develop for Azure storage Implement Azure security Monitor, troubleshoot, and optimize solutions Connect to and consume Azure services and third-party services This Microsoft Exam Ref: Organizes its coverage by exam objectives Features strategic, what-if scenarios to challenge you Assumes you want to show your ability to design and build diverse Microsoft Azure cloud solutions, and successfully participate in all phases of their development About the Exam Exam AZ-204 focuses on knowledge needed to develop Azure compute solutions; develop for Azure storage; implement Azure security; monitor, troubleshoot, and optimize Azure solutions; connect to and consume Azure services and third-party services. About Microsoft Certification Passing this exam fulfills your requirements for the Microsoft Certified: Azure Developer Associate credential, demonstrating your readiness to design, build, test, and maintain Microsoft Azure cloud solutions, and partner with other cloud professionals and clients to implement them. This exam is also a prerequisite for the Microsoft Certified: Azure DevOps Engineer Expert credential. See full details at: microsoft.com/learn COMPUTERS,Operating Systems,Windows Server

Implementation Patterns Software Expert Kent Beck Presents a Catalog of Patterns Infinitely Useful for Everyday Programming Great code doesn’t just function: it clearly and consistently communicates your intentions, allowing other programmers to understand your code, rely on it, and modify it with confidence. But great code doesn’t just happen. It is the outcome of hundreds of small but critical decisions programmers make every single day. Now, legendary software innovator Kent Beck—known worldwide for creating Extreme Programming and pioneering software patterns and test-driven development—focuses on these critical decisions, unearthing powerful “implementation patterns†for writing programs that are simpler, clearer, better organized, and more cost effective. Beck collects 77 patterns for handling everyday programming tasks and writing more readable code. This new collection of patterns addresses many aspects of development, including class, state, behavior, method, collections, frameworks, and more. He uses diagrams, stories, examples, and essays to engage the reader as he illuminates the patterns. You’ll find proven solutions for handling everything from naming variables to checking exceptions. COMPUTERS,Programming Languages,BASIC

Delphi Cookbook Quickly learn and employ practical recipes for developing real-world, cross-platform applications using Delphi. Key Features Get to grips with Delphi to build and deploy various cross-platform applications Design and deploy real-world apps by implementing a single source codebase Build robust and optimized GUI applications with ease Book Description Delphi is a cross-platform integrated development environment (IDE) that supports rapid application development on different platforms, saving you the pain of wandering amid GUI widget details or having to tackle inter-platform incompatibilities. Delphi Cookbook begins with the basics of Delphi and gets you acquainted with JSON format strings, XSLT transformations, Unicode encodings, and various types of streams. You'll then move on to more advanced topics such as developing higher-order functions and using enumerators and run-time type information (RTTI). As you make your way through the chapters, you'll understand Delphi RTL functions, use FireMonkey in a VCL application, and cover topics such as multithreading, using aparallel programming library and deploying Delphi on a server. You'll take a look at the new feature of WebBroker Apache modules, join the mobile revolution with FireMonkey, and learn to build data-driven mobile user interfaces using the FireDAC database access framework. This book will also show you how to integrate your apps with Internet of Things (IoT). By the end of the book, you will have become proficient in Delphi by exploring its different aspects such as building cross-platforms and mobile applications, designing server-side programs, and integrating these programs with IoT. What you will learn Develop visually stunning applications using FireMonkey Deploy LiveBinding effectively with the right object-oriented programming (OOP) approach Create RESTful web services that run on Linux or Windows Build mobile apps that read data from a remote server efficiently Call platform native API on Android and iOS for an unpublished API Manage software customization by making better use of an extended RTTI Integrate your application with IOT Who this book is for Delphi Cookbook is for intermediate developers with a basic knowledge of Delphi who want to discover and understand all the development possibilities offered by it. COMPUTERS,Programming Languages,Pascal

Mastering GUI Programming with Python An advanced guide to creating powerful high-performance GUIs for modern, media-rich applications in various domains such as business and game development Key Features Gain comprehensive knowledge of Python GUI development using PyQt 5.12 Explore advanced topics including multithreaded programming, 3D animation, and SQL databases Build cross-platform GUIs for Windows, macOS, Linux, and Raspberry Pi Book Description PyQt5 has long been the most powerful and comprehensive GUI framework available for Python, yet there is a lack of cohesive resources available to teach Python programmers how to use it. This book aims to remedy the problem by providing comprehensive coverage of GUI development with PyQt5. You will get started with an introduction to PyQt5, before going on to develop stunning GUIs with modern features. You will then learn how to build forms using QWidgets and learn about important aspects of GUI development such as layouts, size policies, and event-driven programming. Moving ahead, you'll discover PyQt5's most powerful features through chapters on audio-visual programming with QtMultimedia, database-driven software with QtSQL, and web browsing with QtWebEngine. Next, in-depth coverage of multithreading and asynchronous programming will help you run tasks asynchronously and build high-concurrency processes with ease. In later chapters, you'll gain insights into QOpenGLWidget, along with mastering techniques for creating 2D graphics with QPainter. You'll also explore PyQt on a Raspberry Pi and interface it with remote systems using QtNetwork. Finally, you will learn how to distribute your applications using setuptools and PyInstaller. By the end of this book, you will have the skills you need to develop robust GUI applications using PyQt. What you will learn Get to grips with the inner workings of PyQt5 Learn how elements in a GUI application communicate with signals and slots Learn techniques for styling an application Explore database-driven applications with the QtSQL module Create 2D graphics with QPainter Delve into 3D graphics with QOpenGLWidget Build network and web-aware applications with QtNetwork and QtWebEngine Who this book is for This book is for programmers who want to create attractive, functional, and powerful GUIs using the Python language. You'll also find this book useful if you are a student, professional, or anyone who wants to start exploring GUIs or take your skills to the next level. Although prior knowledge of the Python language is assumed, experience with PyQt, Qt, or GUI programming is not required. COMPUTERS,Programming Languages,Prolog

Database Design for Mere Mortals “This book takes the somewhat daunting process of database design and breaks it into completely manageable and understandable components. Mike’s approach whilst simple is completely professional, and I can recommend this book to any novice database designer.†– Sandra Barker, Lecturer, University of South Australia, Australia “Databases are a critical infrastructure technology for information systems and today’s business. Mike Hernandez has written a literate explanation of database technology–a topic that is intricate and often obscure. If you design databases yourself, this book will educate you about pitfalls and show you what to do. If you purchase products that use a database, the book explains the technology so that you can understand what the vendor is doing and assess their products better.†– Michael Blaha, consultant and trainer, author of A Manager’s Guide to Database Technology “If you told me that Mike Hernandez could improve on the first edition of Database Design for Mere Mortals I wouldn’t have believed you, but he did! The second edition is packed with more real-world examples, detailed explanations, and even includes database-design tools on the CD-ROM! This is a must-read for anyone who is even remotely interested in relational database design, from the individual who is called upon occasionally to create a useful tool at work, to the seasoned professional who wants to brush up on the fundamentals. Simply put, if you want to do it right, read this book!†– Matt Greer, Process Control Development, The Dow Chemical Company “Mike’s approach to database design is totally common-sense based, yet he’s adhered to all the rules of good relational database design. I use Mike’s books in my starter database-design class, and I recommend his books to anyone who’s interested in learning how to design databases or how to write SQL queries.†– Michelle Poolet, President, MVDS, Inc. “Slapping together sophisticated applications with poorly designed data will hurt you just as much now as when Mike wrote his first edition, perhaps even more. Whether you’re just getting started developing with data or are a seasoned pro; whether you've read Mike’s previous book or this is your first; whether you're happier letting someone else design your data or you love doing it yourself–this is the book for you. Mike’s ability to explain these concepts in a way that’s not only clear, but fun, continues to amaze me.†–From the Foreword by Ken Getz, MCW Technologies, coauthor ASP.NET Developer's JumpStart “The first edition of Mike Hernandez’s book Database Design for Mere Mortals was one of the few books that survived the cut when I moved my office to smaller quarters. The second edition expands and improves on the original in so many ways. It is not only a good, clear read, but contains a remarkable quantity of clear, concise thinking on a very complex subject. It’s a must for anyone interested in the subject of database design.†– Malcolm C. Rubel, Performance Dynamics Associates “Mike’s excellent guide to relational database design deserves a second edition. His book is an essential tool for fledgling Microsoft Access and other desktop database developers, as well as for client/server pros. I recommend it highly to all my readers.†– Roger Jennings, author of Special Edition Using Access 2002 “There are no silver bullets! Database technology has advanced dramatically, the newest crop of database servers perform operations faster than anyone could have imagined six years ago, but none of these technological advances will help fix a bad database design, or capture data that you forgot to include! Database Design for Mere Mortals™, Second Edition, helps you design your database right in the first place!†– Matt Nunn, Product Manager, SQL Server, Microsoft Corporation “When my brother started his professional career as a developer, I gave him Mike’s book to help him understand database concepts and make real-world application of database technology. When I need a refresher on the finer points of database design, this is the book I pick up. I do not think that there is a better testimony to the value of a book than that it gets used. For this reason I have wholeheartedly recommended to my peers and students that they utilize this book in their day-to-day development tasks.†– Chris Kunicki, Senior Consultant, OfficeZealot.com “Mike has always had an incredible knack for taking the most complex topics, breaking them down, and explaining them so that anyone can ‘get it.’ He has honed and polished his first very, very good edition and made it even better. If you're just starting out building database applications, this book is a must-read cover to cover COMPUTERS,Programming,Algorithms

Algorithms This fourth edition of Robert Sedgewick and Kevin Wayne’s Algorithms is the leading textbook on algorithms today and is widely used in colleges and universities worldwide. This book surveys the most important computer algorithms currently in use and provides a full treatment of data structures and algorithms for sorting, searching, graph processing, and string processing--including fifty algorithms every programmer should know. In this edition, new Java implementations are written in an accessible modular programming style, where all of the code is exposed to the reader and ready to use. The algorithms in this book represent a body of knowledge developed over the last 50 years that has become indispensable, not just for professional programmers and computer science students but for any student with interests in science, mathematics, and engineering, not to mention students who use computation in the liberal arts. The companion web site, algs4.cs.princeton.edu, contains An online synopsis Full Java implementations Test data Exercises and answers Dynamic visualizations Lecture slides Programming assignments with checklists Links to related material The MOOC related to this book is accessible via the "Online Course" link at algs4.cs.princeton.edu. The course offers more than 100 video lecture segments that are integrated with the text, extensive online assessments, and the large-scale discussion forums that have proven so valuable. Offered each fall and spring, this course regularly attracts tens of thousands of registrants. Robert Sedgewick and Kevin Wayne are developing a modern approach to disseminating knowledge that fully embraces technology, enabling people all around the world to discover new ways of learning and teaching. By integrating their textbook, online content, and MOOC, all at the state of the art, they have built a unique resource that greatly expands the breadth and depth of the educational experience. COMPUTERS,Programming,Algorithms

Algorithms in C, Part 5 Once again, Robert Sedgewick provides a current and comprehensive introduction to important algorithms. The focus this time is on graph algorithms, which are increasingly critical for a wide range of applications, such as network connectivity, circuit design, scheduling, transaction processing, and resource allocation. In this book, Sedgewick offers the same successful blend of theory and practice with concise implementations that can be tested on real applications, which has made his work popular with programmers for many years. Algorithms in C, Third Edition, Part 5: Graph Algorithms is the second book in Sedgewick's thoroughly revised and rewritten series. The first book, Parts 1-4, addresses fundamental algorithms, data structures, sorting, and searching. A forthcoming third book will focus on strings, geometry, and a range of advanced algorithms. Each book's expanded coverage features new algorithms and implementations, enhanced descriptions and diagrams, and a wealth of new exercises for polishing skills. A focus on abstract data types makes the programs more broadly useful and relevant for the modern object-oriented programming environment. Coverage includes: A complete overview of graph properties and types Diagraphs and DAGs Minimum spanning trees Shortest paths Network flows Diagrams, sample C code, and detailed algorithm descriptions The Web site for this book (http://www.cs.princeton.edu/~rs/) provides additional source code for programmers along with numerous support materials for educators. A landmark revision, Algorithms in C, Third Edition, Part 5 provides a complete tool set for programmers to implement, debug, and use graph algorithms across a wide range of computer applications. COMPUTERS,Programming,Algorithms

Algorithms in C++ Part 5 Once again, Robert Sedgewick provides a current and comprehensive introduction to important algorithms. The focus this time is on graph algorithms, which are increasingly critical for a wide range of applications, such as network connectivity, circuit design, scheduling, transaction processing, and resource allocation. In this book, Sedgewick offers the same successful blend of theory and practice that has made his work popular with programmers for many years. Christopher van Wyk and Sedgewick have developed concise new C++ implementations that both express the methods in a natural and direct manner and also can be used in real applications. Algorithms in C++, Third Edition, Part 5: Graph Algorithms is the second book in Sedgewick's thoroughly revised and rewritten series. The first book, Parts 1-4, addresses fundamental algorithms, data structures, sorting, and searching. A forthcoming third book will focus on strings, geometry, and a range of advanced algorithms. Each book's expanded coverage features new algorithms and implementations, enhanced descriptions and diagrams, and a wealth of new exercises for polishing skills. A focus on abstract data types makes the programs more broadly useful and relevant for the modern object-oriented programming environment. Coverage includes: A complete overview of graph properties and types Diagraphs and DAGs Minimum spanning trees Shortest paths Network flows Diagrams, sample C++ code, and detailed algorithm descriptions The Web site for this book (http://www.cs.princeton.edu/~rs/) provides additional source code for programmers along with a wide range of academic support materials for educators. A landmark revision, Algorithms in C++, Third Edition, Part 5 provides a complete tool set for programmers to implement, debug, and use graph algorithms across a wide range of computer applications. COMPUTERS,Programming,Algorithms

Introduction to Reliable and Secure Distributed Programming In modern computing a program is usually distributed among several processes. The fundamental challenge when developing reliable and secure distributed programs is to support the cooperation of processes required to execute a common task, even when some of these processes fail. Failures may range from crashes to adversarial attacks by malicious processes. Cachin, Guerraoui, and Rodrigues present an introductory description of fundamental distributed programming abstractions together with algorithms to implement them in distributed systems, where processes are subject to crashes and malicious attacks. The authors follow an incremental approach by first introducing basic abstractions in simple distributed environments, before moving to more sophisticated abstractions and more challenging environments. Each core chapter is devoted to one topic, covering reliable broadcast, shared memory, consensus, and extensions of consensus. For every topic, many exercises and their solutions enhance the understanding This book represents the second edition of "Introduction to Reliable Distributed Programming". Its scope has been extended to include security against malicious actions by non-cooperating processes. This important domain has become widely known under the name "Byzantine fault-tolerance". COMPUTERS,Programming,Algorithms

Bandit Algorithms for Website Optimization When looking for ways to improve your website, how do you decide which changes to make? And which changes to keep? This concise book shows you how to use Multiarmed Bandit algorithms to measure the real-world value of any modifications you make to your site. Author John Myles White shows you how this powerful class of algorithms can help you boost website traffic, convert visitors to customers, and increase many other measures of success. This is the first developer-focused book on bandit algorithms, which were previously described only in research papers. You’ll quickly learn the benefits of several simple algorithms—including the epsilon-Greedy, Softmax, and Upper Confidence Bound (UCB) algorithms—by working through code examples written in Python, which you can easily adapt for deployment on your own website. Learn the basics of A/B testing—and recognize when it’s better to use bandit algorithms Develop a unit testing framework for debugging bandit algorithms Get additional code examples written in Julia, Ruby, and JavaScript with supplemental online materials COMPUTERS,Programming,Algorithms

The Golden Ticket The P-NP problem is the most important open problem in computer science, if not all of mathematics. Simply stated, it asks whether every problem whose solution can be quickly checked by computer can also be quickly solved by computer. The Golden Ticket provides a nontechnical introduction to P-NP, its rich history, and its algorithmic implications for everything we do with computers and beyond. Lance Fortnow traces the history and development of P-NP, giving examples from a variety of disciplines, including economics, physics, and biology. He explores problems that capture the full difficulty of the P-NP dilemma, from discovering the shortest route through all the rides at Disney World to finding large groups of friends on Facebook. The Golden Ticket explores what we truly can and cannot achieve computationally, describing the benefits and unexpected challenges of this compelling problem. COMPUTERS,Programming,Algorithms

The Maple Handbook How to Use This Handbook The Maple Handbook is a complete reference tool for the Maple lan guage, and is written for all Maple users, regardless of their discipline or field(s) of interest. All the built-in mathematical, graphic, and system based commands available in Maple V Release 4 are detailed herein. Please note that The Maple Handbook does not teach the mathematics behind Maple commands. If you do not know the meaning of such concepts as definite integral, identity matrix, or prime integer, do not expect to learn them here. As well, while the introductory sections to each chapter taken together provide a basic overview of the capabil ities of Maple, it is highly recommended that you also read a more thorough tutorial such as Introduction to Maple by Andre Heck, or one of standard manuals shipped with Maple V Release 4. Overall Organization One of the main premises of The Maple Handbook is that most Maple users approach the system to solve a particular problem (or set of prob lems) in a specific subject area. Therefore, all commands are organized in logical subsets that reflect these different categories, e.g., calculus, algebra, data manipulation, etc.; the commands within a subset are ex plained in a similar language, creating a tool that allows you quick and confident access to the information necessary to complete the problem you have brought to the system. COMPUTERS,Programming,Algorithms

The Maple Handbook How to Use This Handbook The Maple Handbook is a complete reference tool for the Maple language, and is written for all Maple users, regardless of their dis cipline or field(s) of interest. All the built-in mathematical, graphic, and system-based commands available in Maple V Release 3 are detailed herein. Please note that The Maple Handbook does not teach about the mathematics behind Maple commands. If you do not know the meaning of such concepts as definite integral, identity matrix, or prime integer, do not expect to learn them here. As well, while the introductory sections to each chapter taken together do provide a basic overview of the capabilities of Maple, it is highly recom mended that you also read a more thorough tutorial such as In troduction to Maple by Andre Heck or First Leaves: A Tutorial Introduction to Maple V. Overall Organization One of the main premises of The Maple Handbook is that most Maple users approach the system to solve a particular problem (or set of problems) in a specific subject area. Therefore, all commands are organized in logical subsets that reflect these different cate gories (e.g., calculus, algebra, data manipulation, etc.) and the com mands within a subset are explained in a similar language, creating a tool that allows you quick and confident access to the information necessary to complete the problem you have brought to the system. COMPUTERS,Programming,Algorithms

Guaranteed Accuracy in Numerical Linear Algebra There exists a vast literature on numerical methods of linear algebra. In our bibliography list, which is by far not complete, we included some monographs on the subject [46], [15], [32], [39], [11], [21]. The present book is devoted to the theory of algorithms for a single problem of linear algebra, namely, for the problem of solving systems of linear equations with non-full-rank matrix of coefficients. The solution of this problem splits into many steps, the detailed discussion of which are interest ing problems on their own (bidiagonalization of matrices, computation of singular values and eigenvalues, procedures of deflation of singular values, etc. ). Moreover, the theory of algorithms for solutions of the symmetric eigenvalues problem is closely related to the theory of solv ing linear systems (Householder's algorithms of bidiagonalization and tridiagonalization, eigenvalues and singular values, etc. ). It should be stressed that in this book we discuss algorithms which to computer programs having the virtue that the accuracy of com lead putations is guaranteed. As far as the final program product is con cerned, this means that the user always finds an unambiguous solution of his problem. This solution might be of two kinds: 1. Solution of the problem with an estimate of errors, where abso lutely all errors of input data and machine round-offs are taken into account. 2. COMPUTERS,Programming,Algorithms

Combinatorial Optimization There have been significant developments in the theory and practice of combinatorial optimization in the last 15 years. This progress has been evidenced by a continuously increasing number of international and local conferences, books and papers in this area. This book is also another contribution to this burgeoning area of operations research and optimization. This volume contains the contributions of the participants of the recent NATO Ad vanced Study Institute, New Frontiers in the Theory and Practice of Combinatorial Op timization, which was held at the campus of Bilkent University, in Ankara, Turkey, July 16-29, 1990. In this conference, we brought many prominent researchers and young and promising scientists together to discuss current and future trends in the theory and prac tice of combinatorial optimization. The Bilkent campus was an excellent environment for such an undertaking. Being outside of Ankara, the capital of Turkey, Bilkent University gave the participants a great opportunity for exchanging ideas and discussing new theories and applications without much distraction. One of the primary goals of NATO ASIs is to bring together a group of scientists and research scientists primarily from the NATO countries for the dissemination of ad vanced scientific knowledge and the promotion of international contacts among scientists. We believe that we accomplished this mission very successfully by bringing together 15 prominent lecturers and 45 promising young scientists from 12 countries, in a university environment for 14 days of intense lectures, presentations and discussions. COMPUTERS,Programming,Algorithms

Numerical Linear Algebra, Digital Signal Processing and Parallel Algorithms Proceedings of the NATO Advanced Study Institute on Numerical Linear Algebra, Digital Signal Processing and Parallel Algorithms, held in Leuven, Belgium, August 1-12, 1988 COMPUTERS,Programming,Algorithms

Computational Methods for General Sparse Matrices 'Et moi, ...• si j'avait su comment en revenir, One service mathematics has rendered the je n 'y serais point aile.' human race. It has put common sense back where it belongs, on the topmost shelf next Jules Verne to the dusty canister labelled 'discarded non- The series is divergent; therefore we may be sense'. able to do something with it. Eric T. Bell 0. Heaviside Mathematics is a tool for thought. A highly necessary tool in a world where both feedback and non linearities abound. Similarly, all kinds of parts of mathematics serve as tools for other parts and for other sciences. Applying a simple rewriting rule to the quote on the right above one finds such statements as: 'One service topology has rendered mathematical physics .. .'; 'One service logic has rendered com puter science .. .'; 'One service category theory has rendered mathematics .. .'. All arguably true. And all statements obtainable this way form part of the raison d'elre of this series. COMPUTERS,Programming,Algorithms

High-Speed Range Estimation Based on Intensity Gradient Analysis A fast and reasonably accurate perception of the environment is essential for successful navigation of an autonomous agent. Although many modes of sensing are applicable to this task and have been used, vision remains the most appealing due to its passive nature, good range, and resolution. Most vision techniques to recover depth for navigation use stereo. In the last few years, researchers have started studying techniques to combine stereo with the motion of the camera. Skifstad's dissertation proposes a new approach to recover depth information using known camera motion. This approach results in a robust technique for fast estimation of distances to objects in an image using only one translating camera. A very interesting aspect of the approach pursued by Skifstad is the method used to bypass the most difficult and computationally expensive step in using stereo or similar approaches for the vision-based depth esti mation. The correspondence problem has been the focus of research in most stereo approaches. Skifstad trades the correspondence problem for the known translational motion by using the fact that it is easier to detect single pixel disparities in a sequence of images rather than arbitrary disparities after two frames. A very attractive feature of this approach is that the computations required to detect single pixel disparities are local and hence can be easily parallelized. Another useful feature of the approach, particularly in naviga tion applications, is that the closer objects are detected earlier. COMPUTERS,Programming,Algorithms

Computer Algorithms for Solving Linear Algebraic Equations Proceedings of the NATO Advanced Study Institute on Computer Algorithms for Solving Linear Equations: The State of the Art, held at Il Ciocco, Barga, Italy, September 9-21, 1990 COMPUTERS,Programming,Algorithms

Complexity Theory Retrospective In 1965 Juris Hartmanis and Richard E. Stearns published a paper "On the Computational Complexity of Algorithms". The field of complexity theory takes its name from this seminal paper and many of the major concepts and issues of complexity theory were introduced by Hartmanis in subsequent work. In honor of the contribution of Juris Hartmanis to the field of complexity theory, a special session of invited talks by Richard E. Stearns, Allan Borodin and Paul Young was held at the third annual meeting of the Structure in Complexity conference, and the first three chapters of this book are the final versions of these talks. They recall intellectual and professional trends in Hartmanis' contributions. All but one of the remainder of the chapters in this volume originated as a presentation at one of the recent meetings of the Structure in Complexity Theory Conference and appeared in preliminary form in the conference proceedings. In all, these expositions form an excellent description of much of contemporary complexity theory. COMPUTERS,Programming,Algorithms

Hacker's Delight "This is the first book that promises to tell the deep, dark secrets of computer arithmetic, and it delivers in spades. It contains every trick I knew plus many, many more. A godsend for library developers, compiler writers, and lovers of elegant hacks, it deserves a spot on your shelf right next to Knuth." --Josh Bloch (Praise for the first edition) In Hacker’s Delight, Second Edition, Hank Warren once again compiles an irresistible collection of programming hacks: timesaving techniques, algorithms, and tricks that help programmers build more elegant and efficient software, while also gaining deeper insights into their craft. Warren’s hacks are eminently practical, but they’re also intrinsically interesting, and sometimes unexpected, much like the solution to a great puzzle. They are, in a word, a delight to any programmer who is excited by the opportunity to improve. Extensive additions in this edition include A new chapter on cyclic redundancy checking (CRC), including routines for the commonly used CRC-32 code A new chapter on error correcting codes (ECC), including routines for the Hamming code More coverage of integer division by constants, including methods using only shifts and adds Computing remainders without computing a quotient More coverage of population count and counting leading zeros Array population count New algorithms for compress and expand An LRU algorithm Floating-point to/from integer conversions Approximate floating-point reciprocal square root routine A gallery of graphs of discrete functions Now with exercises and answers COMPUTERS,Programming,Algorithms

Art of Computer Programming, Volume 1, Fascicle 1, The Finally, after a wait of more than thirty-five years, the first part of Volume 4 is at last ready for publication. Check out the boxed set that brings together Volumes 1 - 4A in one elegant case, and offers the purchaser a $50 discount off the price of buying the four volumes individually. The Art of Computer Programming, Volumes 1-4A Boxed Set, 3/e ISBN: 0321751043 Art of Computer Programming, Volume 1, Fascicle 1, The: MMIX -- A RISC Computer for the New Millennium This multivolume work on the analysis of algorithms has long been recognized as the definitive description of classical computer science. The three complete volumes published to date already comprise a unique and invaluable resource in programming theory and practice. Countless readers have spoken about the profound personal influence of Knuth's writings. Scientists have marveled at the beauty and elegance of his analysis, while practicing programmers have successfully applied his "cookbook" solutions to their day-to-day problems. All have admired Knuth for the breadth, clarity, accuracy, and good humor found in his books. To begin the fourth and later volumes of the set, and to update parts of the existing three, Knuth has created a series of small books called fascicles, which will be published t regular intervals. Each fascicle will encompass a section or more of wholly new or evised material. Ultimately, the content of these fascicles will be rolled up into the comprehensive, final versions of each volume, and the enormous undertaking that began in 1962 will be complete. Volume 1, Fascicle 1 This first fascicle updates The Art of Computer Programming, Volume 1, Third Edition: Fundamental Algorithms, and ultimately will become part of the fourth edition of that book. Specifically, it provides a programmer's introduction to the long-awaited MMIX, a RISC-based computer that replaces the original MIX, and describes the MMIX assembly language. The fascicle also presents new material on subroutines, coroutines, and interpretive routines. Ebook (PDF version) produced by Mathematical Sciences Publishers (MSP),http://msp.org COMPUTERS,Programming,Algorithms

Combinatory Logic Combinatory logic is one of the most versatile areas within logic that is tied to parts of philosophical, mathematical, and computational logic. Functioning as a comprehensive source for current developments of combinatory logic, this book is the only one of its kind to cover results of the last four decades. Using a reader-friendly style, the author presents the most up-to-date research studies. She includes an introduction to combinatory logic before progressing to its central theorems and proofs. The text makes intelligent and well-researched connections between combinatory logic and lambda calculi and presents models and applications to illustrate these connections. COMPUTERS,Programming,Algorithms

Advances in Algorithms, Languages, and Complexity This book contains a collection of survey papers in the areas of algorithms, lan guages and complexity, the three areas in which Professor Ronald V. Book has made significant contributions. As a fonner student and a co-author who have been influenced by him directly, we would like to dedicate this book to Professor Ronald V. Book to honor and celebrate his sixtieth birthday. Professor Book initiated his brilliant academic career in 1958, graduating from Grinnell College with a Bachelor of Arts degree. He obtained a Master of Arts in Teaching degree in 1960 and a Master of Arts degree in 1964 both from Wesleyan University, and a Doctor of Philosophy degree from Harvard University in 1969, under the guidance of Professor Sheila A. Greibach. Professor Book's research in discrete mathematics and theoretical com puter science is reflected in more than 150 scientific publications. These works have made a strong impact on the development of several areas of theoretical computer science. A more detailed summary of his scientific research appears in this volume separately. COMPUTERS,Programming,Algorithms

Adaptive Methods — Algorithms, Theory and Applications The GAMM Committee for "Efficient Numerical Methods for Partial Differential Equations" organizes workshops on subjects concerning the algorithmical treat ment of partial differential equations. The topics are discretization methods like the finite element and finite volume method for various types of applications in structural and fluid mechanics. Particular attention is devoted to advanced solu tion techniques. th The series of such workshops was continued in 1993, January 22-24, with the 9 Kiel-Seminar on the special topic "Adaptive Methods Algorithms, Theory and Applications" at the Christian-Albrechts-University of Kiel. The seminar was attended by 76 scientists from 7 countries and 23 lectures were given. The list of topics contained general lectures on adaptivity, special discretization schemes, error estimators, space-time adaptivity, adaptive solvers, multi-grid me thods, wavelets, and parallelization. Special thanks are due to Michael Heisig, who carefully compiled the contribu tions to this volume. November 1993 Wolfgang Hackbusch Gabriel Wittum v Contents Page A. AUGE, G. LUBE, D. WEISS: Galerkin/Least-Squares-FEM and Ani- tropic Mesh Refinement. 1 P. BASTIAN, G. WmUM : Adaptive Multigrid Methods: The UG Concept. 17 R. BEINERT, D. KRONER: Finite Volume Methods with Local Mesh Alignment in 2-D. 38 T. BONK: A New Algorithm for Multi-Dimensional Adaptive Nume- cal Quadrature. 54 F. A. BORNEMANN: Adaptive Solution of One-Dimensional Scalar Conservation Laws with Convex Flux. 69 J. CANU, H. RITZDORF : Adaptive, Block-Structured Multigrid on Local Memory Machines. 84 S. DAHLKE, A. KUNaTH: Biorthogonal Wavelets and Multigrid. 99 B. ERDMANN, R. H. W. HOPPE, R. COMPUTERS,Programming,Algorithms

Adjoint Equations and Analysis of Complex Systems New statements of problems arose recently demanding thorough ana lysis. Notice, first of all, the statements of problems using adjoint equations which gradually became part of our life. Adjoint equations are capable to bring fresh ideas to various problems of new technology based on linear and nonlinear processes. They became part of golden fund of science through quantum mechanics, theory of nuclear reactors, optimal control, and finally helped in solving many problems on the basis of perturbation method and sensitivity theory. To emphasize the important role of adjoint problems in science one should mention four-dimensional analysis problem and solution of inverse problems. This range of problems includes first of all problems of global climate changes on our planet, state of environment and protection of environ ment against pollution, preservation of the biosphere in conditions of vigorous growth of population, intensive development of industry, and many others. All this required complex study of large systems: interac tion between the atmosphere and oceans and continents in the theory of climate, cenoses in the biosphere affected by pollution of natural and anthropogenic origin. Problems of local and global perturbations and models sensitivity to input data join into common complex system. COMPUTERS,Programming,Algorithms

Minimax and Applications Techniques and principles of minimax theory play a key role in many areas of research, including game theory, optimization, and computational complexity. In general, a minimax problem can be formulated as min max f(x, y) (1) ",EX !lEY where f(x, y) is a function defined on the product of X and Y spaces. There are two basic issues regarding minimax problems: The first issue concerns the establishment of sufficient and necessary conditions for equality minmaxf(x,y) = maxminf(x,y). (2) "'EX !lEY !lEY "'EX The classical minimax theorem of von Neumann is a result of this type. Duality theory in linear and convex quadratic programming interprets minimax theory in a different way. The second issue concerns the establishment of sufficient and necessary conditions for values of the variables x and y that achieve the global minimax function value f(x*, y*) = minmaxf(x, y). (3) "'EX !lEY There are two developments in minimax theory that we would like to mention. COMPUTERS,Programming,Algorithms

Parameterized Algorithms This comprehensive textbook presents a clean and coherent account of most fundamental tools and techniques in Parameterized Algorithms and is a self-contained guide to the area. The book covers many of the recent developments of the field, including application of important separators, branching based on linear programming, Cut & Count to obtain faster algorithms on tree decompositions, algorithms based on representative families of matroids, and use of the Strong Exponential Time Hypothesis. A number of older results are revisited and explained in a modern and didactic way. The book provides a toolbox of algorithmic techniques. Part I is an overview of basic techniques, each chapter discussing a certain algorithmic paradigm. The material covered in this part can be used for an introductory course on fixed-parameter tractability. Part II discusses more advanced and specialized algorithmic ideas, bringing the reader to the cutting edge of current research. Part III presents complexity results and lower bounds, giving negative evidence by way of W[1]-hardness, the Exponential Time Hypothesis, and kernelization lower bounds. All the results and concepts are introduced at a level accessible to graduate students and advanced undergraduate students. Every chapter is accompanied by exercises, many with hints, while the bibliographic notes point to original publications and related work. COMPUTERS,Programming,Algorithms

Algorithms in a Nutshell Creating robust software requires the use of efficient algorithms, but programmers seldom think about them until a problem occurs. This updated edition of Algorithms in a Nutshell describes a large number of existing algorithms for solving a variety of problems, and helps you select and implement the right algorithm for your needs—with just enough math to let you understand and analyze algorithm performance. With its focus on application, rather than theory, this book provides efficient code solutions in several programming languages that you can easily adapt to a specific project. Each major algorithm is presented in the style of a design pattern that includes information to help you understand why and when the algorithm is appropriate. With this book, you will: Solve a particular coding problem or improve on the performance of an existing solution Quickly locate algorithms that relate to the problems you want to solve, and determine why a particular algorithm is the right one to use Get algorithmic solutions in C, C++, Java, and Ruby with implementation tips Learn the expected performance of an algorithm, and the conditions it needs to perform at its best Discover the impact that similar design decisions have on different algorithms Learn advanced data structures to improve the efficiency of algorithms COMPUTERS,Programming,Algorithms

Algorithms For Dummies Discover how algorithms shape and impact our digital world All data, big or small, starts with algorithms. Algorithms are mathematical equations that determine what we see—based on our likes, dislikes, queries, views, interests, relationships, and more—online. They are, in a sense, the electronic gatekeepers to our digital, as well as our physical, world. This book demystifies the subject of algorithms so you can understand how important they are business and scientific decision making. Algorithms for Dummies is a clear and concise primer for everyday people who are interested in algorithms and how they impact our digital lives. Based on the fact that we already live in a world where algorithms are behind most of the technology we use, this book offers eye-opening information on the pervasiveness and importance of this mathematical science—how it plays out in our everyday digestion of news and entertainment, as well as in its influence on our social interactions and consumerism. Readers even learn how to program an algorithm using Python! Become well-versed in the major areas comprising algorithms Examine the incredible history behind algorithms Get familiar with real-world applications of problem-solving procedures Experience hands-on development of an algorithm from start to finish with Python If you have a nagging curiosity about why an ad for that hammock you checked out on Amazon is appearing on your Facebook page, you'll find Algorithm for Dummies to be an enlightening introduction to this integral realm of math, science, and business. COMPUTERS,Programming,Algorithms

Concrete Mathematics This book introduces the mathematics that supports advanced computer programming and the analysis of algorithms. The primary aim of its well-known authors is to provide a solid and relevant base of mathematical skills - the skills needed to solve complex problems, to evaluate horrendous sums, and to discover subtle patterns in data. It is an indispensable text and reference not only for computer scientists - the authors themselves rely heavily on it! - but for serious users of mathematics in virtually every discipline. Concrete Mathematics is a blending of CONtinuous and disCRETE mathematics. "More concretely," the authors explain, "it is the controlled manipulation of mathematical formulas, using a collection of techniques for solving problems." The subject matter is primarily an expansion of the Mathematical Preliminaries section in Knuth's classic Art of Computer Programming, but the style of presentation is more leisurely, and individual topics are covered more deeply. Several new topics have been added, and the most significant ideas have been traced to their historical roots. The book includes more than 500 exercises, divided into six categories. Complete answers are provided for all exercises, except research problems, making the book particularly valuable for self-study. Major topics include: Sums Recurrences Integer functions Elementary number theory Binomial coefficients Generating functions Discrete probability Asymptotic methods This second edition includes important new material about mechanical summation. In response to the widespread use of the first edition as a reference book, the bibliography and index have also been expanded, and additional nontrivial improvements can be found on almost every page. Readers will appreciate the informal style of Concrete Mathematics. Particularly enjoyable are the marginal graffiti contributed by students who have taken courses based on this material. The authors want to convey not only the importance of the techniques presented, but some of the fun in learning and using them. COMPUTERS,Programming,Algorithms

Exercises for Programmers When you write software, you need to be at the top of your game. Great programmers practice to keep their skills sharp. Get sharp and stay sharp with more than fifty practice exercises rooted in real-world scenarios. If you're a new programmer, these challenges will help you learn what you need to break into the field, and if you're a seasoned pro, you can use these exercises to learn that hot new language for your next gig. One of the best ways to learn a programming language is to use it to solve problems. That's what this book is all about. Instead of questions rooted in theory, this book presents problems you'll encounter in everyday software development. These problems are designed for people learning their first programming language, and they also provide a learning path for experienced developers to learn a new language quickly. Start with simple input and output programs. Do some currency conversion and figure out how many months it takes to pay off a credit card. Calculate blood alcohol content and determine if it's safe to drive. Replace words in files and filter records, and use web services to display the weather, store data, and show how many people are in space right now. At the end you'll tackle a few larger programs that will help you bring everything together. Each problem includes constraints and challenges to push you further, but it's up to you to come up with the solutions. And next year, when you want to learn a new programming language or style of programming (perhaps OOP vs. functional), you can work through this book again, using new approaches to solve familiar problems. What You Need: You need access to a computer, a programming language reference, and the programming language you want to use. COMPUTERS,Programming,Algorithms

Applied Scientific Computing This book is a gentle and sympathetic introduction to many of the problems of scientific computing, and the wide variety of methods used for their solutions. It is ideal for students taking a first course in numerical mathematics who need a low level entry to the subject. It gives an appreciation of the need for numerical methods for the solution of different types of problem, and discusses basic approaches. For each of the problems, at least some mathematical justification and examples provide both practical evidence and motivations for the reader to follow. Practical justification of the methods is presented through computer examples and exercises. The book also includes an introduction to MATLAB, but the code used is not intended to exemplify sophisticated or robust pieces of software; it is purely illustrative of the methods under discussion. COMPUTERS,Programming,Algorithms

Unity 2018 Artificial Intelligence Cookbook Explore various recipes to build games using popular artificial intelligence techniques and algorithms such as Navmesh navigation A*, DFS, and UCB1 Key Features Explore different algorithms for creating decision-making agents that go beyond simple behaviors and movement Discover the latest features of the NavMesh API for scripting intelligent behaviour in your game characters Create games that are non-predictable and dynamic and have a high replayability factor Book Description Interactive and engaging games come with intelligent enemies, and this intellectual behavior is combined with a variety of techniques collectively referred to as Artificial Intelligence. Exploring Unity's API, or its built-in features, allows limitless possibilities when it comes to creating your game's worlds and characters. This cookbook covers both essential and niche techniques to help you take your AI programming to the next level. To start with, you'll quickly run through the essential building blocks of working with an agent, programming movement, and navigation in a game environment, followed by improving your agent's decision-making and coordination mechanisms – all through hands-on examples using easily customizable techniques. You'll then discover how to emulate the vision and hearing capabilities of your agent for natural and humanlike AI behavior, and later improve the agents with the help of graphs. This book also covers the new navigational mesh with improved AI and pathfinding tools introduced in the Unity 2018 update. You'll empower your AI with decision-making functions by programming simple board games, such as tic-tac-toe and checkers, and orchestrate agent coordination to get your AIs working together as one. By the end of this book, you'll have gained expertise in AI programming and developed creative and interactive games. What you will learn Create intelligent pathfinding agents with popular AI techniques such as A* and A*mbush Implement different algorithms for adding coordination between agents and tactical algorithms for different purposes Simulate senses so agents can make better decisions, taking account of the environment Explore different algorithms for creating decision-making agents that go beyond simple behaviors and movement Create coordination between agents and orchestrate tactics when dealing with a graph or terrain Implement waypoints by making a manual selector Who this book is for The Unity 2018 Artificial Intelligence Cookbook is for you if you are eager to get more tools under your belt to solve AI- and gameplay-related problems. Basic knowledge of Unity and prior knowledge of C# is an advantage. COMPUTERS,Programming,Algorithms

First Course in Algorithms Through Puzzles This textbook introduces basic algorithms and explains their analytical methods. All algorithms and methods introduced in this book are well known and frequently used in real programs. Intended to be self-contained, the contents start with the basic models, and no prerequisite knowledge is required. This book is appropriate for undergraduate students in computer science, mathematics, and engineering as a textbook, and is also appropriate for self-study by beginners who are interested in the fascinating field of algorithms. More than 40 exercises are distributed throughout the text, and their difficulty levels are indicated. Solutions and comments for all the exercises are provided in the last chapter. These detailed solutions will enable readers to follow the author’s steps to solve problems and to gain a better understanding of the contents. Although details of the proofs and the analyses of algorithms are also provided, the mathematical descriptions in this book are not beyond the range of high school mathematics. Some famous real puzzles are also used to describe the algorithms. These puzzles are quite suitable for explaining the basic techniques of algorithms, which show how to solve these puzzles. COMPUTERS,Programming,Algorithms

Graph Algorithms Discover how graph algorithms can help you leverage the relationships within your data to develop more intelligent solutions and enhance your machine learning models. You’ll learn how graph analytics are uniquely suited to unfold complex structures and reveal difficult-to-find patterns lurking in your data. Whether you are trying to build dynamic network models or forecast real-world behavior, this book illustrates how graph algorithms deliver value—from finding vulnerabilities and bottlenecks to detecting communities and improving machine learning predictions. This practical book walks you through hands-on examples of how to use graph algorithms in Apache Spark and Neo4j—two of the most common choices for graph analytics. Also included: sample code and tips for over 20 practical graph algorithms that cover optimal pathfinding, importance through centrality, and community detection. Learn how graph analytics vary from conventional statistical analysis Understand how classic graph algorithms work, and how they are applied Get guidance on which algorithms to use for different types of questions Explore algorithm examples with working code and sample datasets from Spark and Neo4j See how connected feature extraction can increase machine learning accuracy and precision Walk through creating an ML workflow for link prediction combining Neo4j and Spark COMPUTERS,Programming,Algorithms

Sequential and Parallel Algorithms and Data Structures This textbook is a concise introduction to the basic toolbox of structures that allow efficient organization and retrieval of data, key algorithms for problems on graphs, and generic techniques for modeling, understanding, and solving algorithmic problems. The authors aim for a balance between simplicity and efficiency, between theory and practice, and between classical results and the forefront of research. Individual chapters cover arrays and linked lists, hash tables and associative arrays, sorting and selection, priority queues, sorted sequences, graph representation, graph traversal, shortest paths, minimum spanning trees, optimization, collective communication and computation, and load balancing. The authors also discuss important issues such as algorithm engineering, memory hierarchies, algorithm libraries, and certifying algorithms. Moving beyond the sequential algorithms and data structures of the earlier related title, this book takes into account the paradigm shift towards the parallel processing required to solve modern performance-critical applications and how this impacts on the teaching of algorithms. The book is suitable for undergraduate and graduate students and professionals familiar with programming and basic mathematical language. Most chapters have the same basic structure: the authors discuss a problem as it occurs in a real-life situation, they illustrate the most important applications, and then they introduce simple solutions as informally as possible and as formally as necessary so the reader really understands the issues at hand. As they move to more advanced and optional issues, their approach gradually leads to a more mathematical treatment, including theorems and proofs. The book includes many examples, pictures, informal explanations, and exercises, and the implementation notes introduce clean, efficient implementations in languages such as C++ and Java. COMPUTERS,Programming,Algorithms

Hands-On Design Patterns and Best Practices with Julia Design and develop high-performance, reusable, and maintainable applications using traditional and modern Julia patterns with this comprehensive guide Key Features Explore useful design patterns along with object-oriented programming in Julia 1.0 Implement macros and metaprogramming techniques to make your code faster, concise, and efficient Develop the skills necessary to implement design patterns for creating robust and maintainable applications Book Description Design patterns are fundamental techniques for developing reusable and maintainable code. They provide a set of proven solutions that allow developers to solve problems in software development quickly. This book will demonstrate how to leverage design patterns with real-world applications. Starting with an overview of design patterns and best practices in application design, you'll learn about some of the most fundamental Julia features such as modules, data types, functions/interfaces, and metaprogramming. You'll then get to grips with the modern Julia design patterns for building large-scale applications with a focus on performance, reusability, robustness, and maintainability. The book also covers anti-patterns and how to avoid common mistakes and pitfalls in development. You'll see how traditional object-oriented patterns can be implemented differently and more effectively in Julia. Finally, you'll explore various use cases and examples, such as how expert Julia developers use design patterns in their open source packages. By the end of this Julia programming book, you'll have learned methods to improve software design, extensibility, and reusability, and be able to use design patterns efficiently to overcome common challenges in software development. What you will learn Master the Julia language features that are key to developing large-scale software applications Discover design patterns to improve overall application architecture and design Develop reusable programs that are modular, extendable, performant, and easy to maintain Weigh up the pros and cons of using different design patterns for use cases Explore methods for transitioning from object-oriented programming to using equivalent or more advanced Julia techniques Who this book is for This book is for beginner to intermediate-level Julia programmers who want to enhance their skills in designing and developing large-scale applications. COMPUTERS,Programming,Algorithms

Nine Algorithms That Changed the Future Nine revolutionary algorithms that power our computers and smartphones Every day, we use our computers to perform remarkable feats. A simple web search picks out a handful of relevant needles from the world's biggest haystack. Uploading a photo to Facebook transmits millions of pieces of information over numerous error-prone network links, yet somehow a perfect copy of the photo arrives intact. Without even knowing it, we use public-key cryptography to transmit secret information like credit card numbers, and we use digital signatures to verify the identity of the websites we visit. How do our computers perform these tasks with such ease? John MacCormick answers this question in language anyone can understand, using vivid examples to explain the fundamental tricks behind nine computer algorithms that power our PCs, tablets, and smartphones. COMPUTERS,Programming,Algorithms

Recent Advances in Hybrid Metaheuristics for Data Clustering An authoritative guide to an in-depth analysis of various state-of-the-art data clustering approaches using a range of computational intelligence techniques Recent Advances in Hybrid Metaheuristics for Data Clustering offers a guide to the fundamentals of various metaheuristics and their application to data clustering. Metaheuristics are designed to tackle complex clustering problems where classical clustering algorithms have failed to be either effective or efficient. The authors—noted experts on the topic—provide a text that can aid in the design and development of hybrid metaheuristics to be applied to data clustering. The book includes performance analysis of the hybrid metaheuristics in relationship to their conventional counterparts. In addition to providing a review of data clustering, the authors include in-depth analysis of different optimization algorithms. The text offers a step-by-step guide in the build-up of hybrid metaheuristics and to enhance comprehension. In addition, the book contains a range of real-life case studies and their applications. This important text: Includes performance analysis of the hybrid metaheuristics as related to their conventional counterparts Offers an in-depth analysis of a range of optimization algorithms Highlights a review of data clustering Contains a detailed overview of different standard metaheuristics in current use Presents a step-by-step guide to the build-up of hybrid metaheuristics Offers real-life case studies and applications Written for researchers, students and academics in computer science, mathematics, and engineering, Recent Advances in Hybrid Metaheuristics for Data Clustering provides a text that explores the current data clustering approaches using a range of computational intelligence techniques. COMPUTERS,Programming,Algorithms

Algorithms For Analysis, Inference, And Control Of Boolean Networks The Boolean network (BN) is a mathematical model of genetic networks and other biological networks. Although extensive studies have been done on BNs from a viewpoint of complex systems, not so many studies have been undertaken from a computational viewpoint. This book presents rigorous algorithmic results on important computational problems on BNs, which include inference of a BN, detection of singleton and periodic attractors in a BN, and control of a BN. This book also presents algorithmic results on fundamental computational problems on probabilistic Boolean networks and a Boolean model of metabolic networks. Although most contents of the book are based on the work by the author and collaborators, other important computational results and techniques are also reviewed or explained. COMPUTERS,Programming,Algorithms

Introduction To The Analysis Of Algorithms, An (3rd Edition) A successor to the first and second editions, this updated and revised book is a leading companion guide for students and engineers alike, specifically software engineers who design algorithms. While succinct, this edition is mathematically rigorous, covering the foundations for both computer scientists and mathematicians with interest in the algorithmic foundations of Computer Science.Besides expositions on traditional algorithms such as Greedy, Dynamic Programming and Divide & Conquer, the book explores two classes of algorithms that are often overlooked in introductory textbooks: Randomised and Online algorithms — with emphasis placed on the algorithm itself. The book also covers algorithms in Linear Algebra, and the foundations of Computation.The coverage of Randomized and Online algorithms is timely: the former have become ubiquitous due to the emergence of cryptography, while the latter are essential in numerous fields as diverse as operating systems and stock market predictions.While being relatively short to ensure the essentiality of content, a strong focus has been placed on self-containment, introducing the idea of pre/post-conditions and loop invariants to readers of all backgrounds, as well as all the necessary mathematical foundations. The programming exercises in Python will be available on the web (see www.msoltys.com/book for the companion web site). COMPUTERS,Programming,Algorithms

Collaborative Recommendations Recommender systems are very popular nowadays, as both an academic research field and services provided by numerous companies for e-commerce, multimedia and Web content. Collaborative-based methods have been the focus of recommender systems research for more than two decades.The unique feature of the compendium is the technical details of collaborative recommenders. The book chapters include algorithm implementations, elaborate on practical issues faced when deploying these algorithms in large-scale systems, describe various optimizations and decisions made, and list parameters of the algorithms.This must-have title is a useful reference materials for researchers, IT professionals and those keen to incorporate recommendation technologies into their systems and services. COMPUTERS,Programming,Algorithms

40 Algorithms Every Programmer Should Know Learn algorithms for solving classic computer science problems with this concise guide covering everything from fundamental algorithms, such as sorting and searching, to modern algorithms used in machine learning and cryptography Key Features Learn the techniques you need to know to design algorithms for solving complex problems Become familiar with neural networks and deep learning techniques Explore different types of algorithms and choose the right data structures for their optimal implementation Book Description Algorithms have always played an important role in both the science and practice of computing. Beyond traditional computing, the ability to use algorithms to solve real-world problems is an important skill that any developer or programmer must have. This book will help you not only to develop the skills to select and use an algorithm to solve real-world problems but also to understand how it works. You'll start with an introduction to algorithms and discover various algorithm design techniques, before exploring how to implement different types of algorithms, such as searching and sorting, with the help of practical examples. As you advance to a more complex set of algorithms, you'll learn about linear programming, page ranking, and graphs, and even work with machine learning algorithms, understanding the math and logic behind them. Further on, case studies such as weather prediction, tweet clustering, and movie recommendation engines will show you how to apply these algorithms optimally. Finally, you'll become well versed in techniques that enable parallel processing, giving you the ability to use these algorithms for compute-intensive tasks. By the end of this book, you'll have become adept at solving real-world computational problems by using a wide range of algorithms. What you will learn Explore existing data structures and algorithms found in Python libraries Implement graph algorithms for fraud detection using network analysis Work with machine learning algorithms to cluster similar tweets and process Twitter data in real time Predict the weather using supervised learning algorithms Use neural networks for object detection Create a recommendation engine that suggests relevant movies to subscribers Implement foolproof security using symmetric and asymmetric encryption on Google Cloud Platform (GCP) Who this book is for This book is for the serious programmer! Whether you are an experienced programmer looking to gain a deeper understanding of the math behind the algorithms or have limited programming or data science knowledge and want to learn more about how you can take advantage of these battle-tested algorithms to improve the way you design and write code, you'll find this book useful. Experience with Python programming is a must, although knowledge of data science is helpful but not necessary. COMPUTERS,Programming,Algorithms

Introduction to Computational Origami This book focuses on origami from the point of view of computer science. Ranging from basic theorems to the latest research results, the book introduces the considerably new and fertile research field of computational origami as computer science. Part I introduces basic knowledge of the geometry of development, also called a net, of a solid. Part II further details the topic of nets. In the science of nets, there are numerous unresolved issues, and mathematical characterization and the development of efficient algorithms by computer are closely connected with each other. Part III discusses folding models and their computational complexity. When a folding model is fixed, to find efficient ways of folding is to propose efficient algorithms. If this is difficult, it is intractable in terms of computational complexity. This is, precisely, an area for computer science research. Part IV presents some of the latest research topics as advanced problems. Commentaries on all exercises included in the last chapter. The contents are organized in a self-contained way, and no previous knowledge is required. This book is suitable for undergraduate, graduate, and even high school students, as well as researchers and engineers interested in origami. COMPUTERS,Programming,Algorithms

What Algorithms Want The gap between theoretical ideas and messy reality, as seen in Neal Stephenson, Adam Smith, and Star Trek. We depend on—we believe in—algorithms to help us get a ride, choose which book to buy, execute a mathematical proof. It's as if we think of code as a magic spell, an incantation to reveal what we need to know and even what we want. Humans have always believed that certain invocations—the marriage vow, the shaman's curse—do not merely describe the world but make it. Computation casts a cultural shadow that is shaped by this long tradition of magical thinking. In this book, Ed Finn considers how the algorithm—in practical terms, “a method for solving a problem”—has its roots not only in mathematical logic but also in cybernetics, philosophy, and magical thinking. Finn argues that the algorithm deploys concepts from the idealized space of computation in a messy reality, with unpredictable and sometimes fascinating results. Drawing on sources that range from Neal Stephenson's Snow Crash to Diderot's Encyclopédie, from Adam Smith to the Star Trek computer, Finn explores the gap between theoretical ideas and pragmatic instructions. He examines the development of intelligent assistants like Siri, the rise of algorithmic aesthetics at Netflix, Ian Bogost's satiric Facebook game Cow Clicker, and the revolutionary economics of Bitcoin. He describes Google's goal of anticipating our questions, Uber's cartoon maps and black box accounting, and what Facebook tells us about programmable value, among other things. If we want to understand the gap between abstraction and messy reality, Finn argues, we need to build a model of “algorithmic reading” and scholarship that attends to process, spearheading a new experimental humanities. COMPUTERS,Programming,Algorithms

Algorithms Unlocked For anyone who has ever wondered how computers solve problems, an engagingly written guide for nonexperts to the basics of computer algorithms. Have you ever wondered how your GPS can find the fastest way to your destination, selecting one route from seemingly countless possibilities in mere seconds? How your credit card account number is protected when you make a purchase over the Internet? The answer is algorithms. And how do these mathematical formulations translate themselves into your GPS, your laptop, or your smart phone? This book offers an engagingly written guide to the basics of computer algorithms. In Algorithms Unlocked, Thomas Cormen—coauthor of the leading college textbook on the subject—provides a general explanation, with limited mathematics, of how algorithms enable computers to solve problems. Readers will learn what computer algorithms are, how to describe them, and how to evaluate them. They will discover simple ways to search for information in a computer; methods for rearranging information in a computer into a prescribed order (“sorting”); how to solve basic problems that can be modeled in a computer with a mathematical structure called a “graph” (useful for modeling road networks, dependencies among tasks, and financial relationships); how to solve problems that ask questions about strings of characters such as DNA structures; the basic principles behind cryptography; fundamentals of data compression; and even that there are some problems that no one has figured out how to solve on a computer in a reasonable amount of time. COMPUTERS,Programming,Algorithms

Distributed Algorithms A comprehensive guide to distributed algorithms that emphasizes examples and exercises rather than mathematical argumentation. This book offers students and researchers a guide to distributed algorithms that emphasizes examples and exercises rather than the intricacies of mathematical models. It avoids mathematical argumentation, often a stumbling block for students, teaching algorithmic thought rather than proofs and logic. This approach allows the student to learn a large number of algorithms within a relatively short span of time. Algorithms are explained through brief, informal descriptions, illuminating examples, and practical exercises. The examples and exercises allow readers to understand algorithms intuitively and from different perspectives. Proof sketches, arguing the correctness of an algorithm or explaining the idea behind fundamental results, are also included. An appendix offers pseudocode descriptions of many algorithms. Distributed algorithms are performed by a collection of computers that send messages to each other or by multiple software threads that use the same shared memory. The algorithms presented in the book are for the most part “classics,” selected because they shed light on the algorithmic design of distributed systems or on key issues in distributed computing and concurrent programming. Distributed Algorithms can be used in courses for upper-level undergraduates or graduate students in computer science, or as a reference for researchers in the field. COMPUTERS,Programming,Algorithms

Distributed Algorithms, second edition The new edition of a guide to distributed algorithms that emphasizes examples and exercises rather than the intricacies of mathematical models. This book offers students and researchers a guide to distributed algorithms that emphasizes examples and exercises rather than the intricacies of mathematical models. It avoids mathematical argumentation, often a stumbling block for students, teaching algorithmic thought rather than proofs and logic. This approach allows the student to learn a large number of algorithms within a relatively short span of time. Algorithms are explained through brief, informal descriptions, illuminating examples, and practical exercises. The examples and exercises allow readers to understand algorithms intuitively and from different perspectives. Proof sketches, arguing the correctness of an algorithm or explaining the idea behind fundamental results, are also included. The algorithms presented in the book are for the most part “classics,” selected because they shed light on the algorithmic design of distributed systems or on key issues in distributed computing and concurrent programming. This second edition has been substantially revised. A new chapter on distributed transaction offers up-to-date treatment of database transactions and the important evolving area of transactional memory. A new chapter on security discusses two exciting new topics: blockchains and quantum cryptography. Sections have been added that cover such subjects as rollback recovery, fault-tolerant termination detection, and consensus for shared memory. An appendix offers pseudocode descriptions of many algorithms. Solutions and slides are available for instructors. Distributed Algorithms can be used in courses for upper-level undergraduates or graduate students in computer science, or as a reference for researchers in the field. COMPUTERS,Programming,Algorithms

Decomposition-based Evolutionary Optimization In Complex Environments Multi-objective optimization problems (MOPs) and uncertain optimization problems (UOPs) which widely exist in real life are challengeable problems in the fields of decision making, system designing, and scheduling, amongst others. Decomposition exploits the ideas of ‘making things simple’ and ‘divide and conquer’ to transform a complex problem into a series of simple ones with the aim of reducing the computational complexity. In order to tackle the abovementioned two types of complicated optimization problems, this book introduces the decomposition strategy and conducts a systematic study to perfect the usage of decomposition in the field of multi-objective optimization, and extend the usage of decomposition in the field of uncertain optimization. COMPUTERS,Programming,Algorithms

Role of Edge Analytics in Sustainable Smart City Development Efficient Single Board Computers (SBCs) and advanced VLSI systems have resulted in edge analytics and faster decision making. The QoS parameters like energy, delay, reliability, security, and throughput should be improved on seeking better intelligent expert systems. The resource constraints in the Edge devices, challenges the researchers to meet the required QoS. Since these devices and components work in a remote unattended environment, an optimum methodology to improve its lifetime has become mandatory. Continuous monitoring of events is mandatory to avoid tragic situations; it can only be enabled by providing high QoS. The applications of IoT in digital twin development, health care, traffic analysis, home surveillance, intelligent agriculture monitoring, defense and all common day to day activities have resulted in pioneering embedded devices, which can offer high computational facility without much latency and delay. The book address industrial problems in designing expert system and IoT applications. It provides novel survey and case study report on recent industrial approach towards Smart City development. COMPUTERS,Programming,Algorithms

Writing Compilers and Interpreters Long-awaited revision to a unique guide that covers both compilers and interpreters Revised, updated, and now focusing on Java instead of C++, this long-awaited, latest edition of this popular book teaches programmers and software engineering students how to write compilers and interpreters using Java. You?ll write compilers and interpreters as case studies, generating general assembly code for a Java Virtual Machine that takes advantage of the Java Collections Framework to shorten and simplify the code. In addition, coverage includes Java Collections Framework, UML modeling, object-oriented programming with design patterns, working with XML intermediate code, and more. COMPUTERS,Programming,Compilers

Language Implementation Patterns Learn to build configuration file readers, data readers, model-driven code generators, source-to-source translators, source analyzers, and interpreters. You don't need a background in computer science--ANTLR creator Terence Parr demystifies language implementation by breaking it down into the most common design patterns. Pattern by pattern, you'll learn the key skills you need to implement your own computer languages. Knowing how to create domain-specific languages (DSLs) can give you a huge productivity boost. Instead of writing code in a general-purpose programming language, you can first build a custom language tailored to make you efficient in a particular domain. The key is understanding the common patterns found across language implementations. Language Design Patterns identifies and condenses the most common design patterns, providing sample implementations of each. The pattern implementations use Java, but the patterns themselves are completely general. Some of the implementations use the well-known ANTLR parser generator, so readers will find this book an excellent source of ANTLR examples as well. But this book will benefit anyone interested in implementing languages, regardless of their tool of choice. Other language implementation books focus on compilers, which you rarely need in your daily life. Instead, Language Design Patterns shows you patterns you can use for all kinds of language applications. You'll learn to create configuration file readers, data readers, model-driven code generators, source-to-source translators, source analyzers, and interpreters. Each chapter groups related design patterns and, in each pattern, you'll get hands-on experience by building a complete sample implementation. By the time you finish the book, you'll know how to solve most common language implementation problems. COMPUTERS,Programming,Compilers

Programming Sudoku Sudoku is a wildly popular puzzle game. Sudoku puzzles are 9x9 grids, and each square in the grid consists of a 3x3 subgrid called a region. Your goal is to fill in the squares so that each column, row, and region contains the numbers 1 through 9 exactly once. And some squares already contain numbers or symbols, which lend clues toward the solution. Programming Sudoku provides you with great approaches to building and solving Sudoku and other similar puzzles. Using ingenious artificial intelligence and game theory techniques, you’ll learn how to get a computer to solve these puzzles for you. This is a fun, intriguing read, whether you're a novice or advanced programmer. It acknowledges the .NET platform as a base, but you’ll find this book interesting whatever your programming background. The core techniques in the book enable you to solve Sudoku on any programming platform. COMPUTERS,Programming,Games

Drawn to Life - Volume 2 Discover the lessons that helped bring about a new golden age of Disney animation! Published for the first time ever, Drawn to Life is a two volume collection of the legendary lectures from long-time Disney animator Walt Stanchfield. For over twenty years, Walt helped breathe life into the new golden age of animation with these teachings at the Walt Disney Animation Studios and influenced such talented artists as Tim Burton, Brad Bird, Glen Keane, and John Lasseter. These writings represent the quintessential refresher for fine artists and film professionals, and it is a vital tutorial for students who are now poised to be part of another new generation in the art form. Written by Walt Stanchfield (1919-2000), who began work for the Walt Disney Studios in the 1950s. His work can be seen in films like Sleeping Beauty, The Jungle Book, 101 Dalmatians, and Peter Pan. Edited by Academy Award®-nominated producer Don Hahn, who has produced such classic Disney films as Beauty and the Beast and The Lion King. COMPUTERS,Programming,Games

3D Math Primer for Graphics and Game Development This engaging book presents the essential mathematics needed to describe, simulate, and render a 3D world. Reflecting both academic and in-the-trenches practical experience, the authors teach you how to describe objects and their positions, orientations, and trajectories in 3D using mathematics. The text provides an introduction to mathematics for COMPUTERS,Programming,Games

Computer Security Literacy Computer users have a significant impact on the security of their computer and personal information as a result of the actions they perform (or do not perform). Helping the average user of computers, or more broadly information technology, make sound security decisions, Computer Security Literacy: Staying Safe in a Digital World focuses on practica COMPUTERS,Programming,Games

Ideas for the Animated Short Follow from start to finish the creation of an animated short from the pre-production thought process to story development and character design. Explore the best practices and avoid the common pitfalls of creating two to five minute shorts. Watch a specially created animated short, demonstrating the core techniques and principles at the companion website! Packed with illustrated examples of idea generation, character and story development, acting, dialogue and storyboarding practice this is your conceptual toolkit proven to meet the challenges of this unique art form. The companion website includes in-depth interviews with industry insiders, 18 short animations (many with accompanying animatics, character designs and environment designs) and an acting workshop to get your animated short off to a flying start! With all NEW content on script writing, acting, sound design and visual storytelling as well as stereoscopic 3D storytelling, further enhance your animated shorts and apply the industry best practices to your own projects and workflows. COMPUTERS,Programming,Games

Introduction to Game Physics with Box2D Written by a pioneer of game development in academia, Introduction to Game Physics with Box2D covers the theory and practice of 2D game physics in a relaxed and entertaining yet instructional style. It offers a cohesive treatment of the topics and code involved in programming the physics for 2D video games. Focusing on writing elementary game physics code, the first half of the book helps you grasp the challenges of programming game physics from scratch, without libraries or outside help. It examines the mathematical foundation of game physics and illustrates how it is applied in practice through coding examples. The second half of the book shows you how to use Box2D, a popular open source 2D game physics engine. A companion website provides supplementary material, including source code and videos. This book helps you become a capable 2D game physics programmer through its presentation of both the theory and applications of 2D game physics. After reading the book and experimenting with the code samples, you will understand the basics of 2D game physics and know how to use Box2D to make a 2D physics-based game. COMPUTERS,Programming,Games

Hardware Security Beginning with an introduction to cryptography, Hardware Security: Design, Threats, and Safeguards explains the underlying mathematical principles needed to design complex cryptographic algorithms. It then presents efficient cryptographic algorithm implementation methods, along with state-of-the-art research and strategies for the design of very la COMPUTERS,Programming,Games

HTML5 Game Development from the Ground Up with Construct 2 Written for the new generation of hobbyists and aspiring game developers, HTML5 Game Development from the Ground Up with Construct 2 shows you how to use the sophisticated yet user-friendly HTML5-based game engine Construct 2 to develop and release polished, two-dimensional games on a multitude of different platforms. The book also covers the found COMPUTERS,Programming,Games

Computational and Visualization Techniques for Structural Bioinformatics Using Chimera A Step-by-Step Guide to Describing Biomolecular StructureComputational and Visualization Techniques for Structural Bioinformatics Using Chimera shows how to perform computations with Python scripts in the Chimera environment. It focuses on the three core areas needed to study structural bioinformatics: biochemistry, mathematics, and computation.Und COMPUTERS,Programming,Games

Exercises in Programming Style Using a simple computational task (term frequency) to illustrate different programming styles, Exercises in Programming Style helps readers understand the various ways of writing programs and designing systems. It is designed to be used in conjunction with code provided on an online repository. The book complements and explains the raw code in a way that is accessible to anyone who regularly practices the art of programming. The book can also be used in advanced programming courses in computer science and software engineering programs. The book contains 33 different styles for writing the term frequency task. The styles are grouped into nine categories: historical, basic, function composition, objects and object interactions, reflection and metaprogramming, adversity, data-centric, concurrency, and interactivity. The author verbalizes the constraints in each style and explains the example programs. Each chapter first presents the constraints of the style, next shows an example program, and then gives a detailed explanation of the code. Most chapters also have sections focusing on the use of the style in systems design as well as sections describing the historical context in which the programming style emerged. COMPUTERS,Programming,Games

Theory of Fun for Game Design Now in full color, the 10th anniversary edition of this classic book takes you deep into the influences that underlie modern video games, and examines the elements they share with traditional games such as checkers. At the heart of his exploration, veteran game designer Raph Koster takes a close look at the concept of fun and why it’s the most vital element in any game. Why do some games become boring quickly, while others remain fun for years? How do games serve as fundamental and powerful learning tools? Whether you’re a game developer, dedicated gamer, or curious observer, this illustrated, fully updated edition helps you understand what drives this major cultural force, and inspires you to take it further. You’ll discover that: Games play into our innate ability to seek patterns and solve puzzles Most successful games are built upon the same elements Slightly more females than males now play games Many games still teach primitive survival skills Fictional dressing for modern games is more developed than the conceptual elements Truly creative designers seldom use other games for inspiration Games are beginning to evolve beyond their prehistoric origins COMPUTERS,Programming,Games

C# and Game Programming The second edition of C# and Game Programming offers the same practical, hands-on approach as the first edition to learning the C# language through classic arcade game applications. Complete source code for games like Battle Bit, Asteroid Miner, and Battle Tennis, included on the CD-ROM, demonstrates programming strategies and complements the comprehensive treatment of C# in the text. From the basics of adding graphics and sound to games, to advanced concepts such as the .Net framework and object-oriented programming, this book provides the foundations for a beginner to become a full-fledged programmer. New in this edition: - Supports DirectX 9.0 - Revised programs and examples - Improved frame rate for game examples COMPUTERS,Programming,Games

Sensors for Mobile Robots The author compiles everything a student or experienced developmental engineer needs to know about the supporting technologies associated with the rapidly evolving field of robotics.From the table of contents: Design Considerations * Dead Reckoning * Odometry Sensors * Doppler and Inertial Navigation * Typical Mobility Configurations * Tactile and COMPUTERS,Programming,Games

Service Robots The copious photographs in this book lavishly illustrate the current and future applications for robots in a wide scope of fields such as entertainment, medicine, space exploration, underwater navigation, and many more. Everyone from professional roboticists to amateur robot and technology enthusiasts will find this book fascinating. COMPUTERS,Programming,Games

Game Development Tools This book brings the insights of game professionals, DCC creators, hardware vendors, and current researchers together into a collection that focuses on the most underrepresented and critical part of game production: tools development. The first gems-type book dedicated to game tools, this volume focuses on practical, implementable tools for game de COMPUTERS,Programming,Games

Mobile Robots Revised and updated, the second edition includes several new chapters with projects and applications. The authors keep pace with the ever-growing and rapidly expanding field of robotics. The new edition reflects technological developments and includes programs and activities for robot enthusiasts. Using photographs, illustrations, and informative t COMPUTERS,Programming,Games

Clustering in Bioinformatics and Drug Discovery With a DVD of color figures, Clustering in Bioinformatics and Drug Discovery provides an expert guide on extracting the most pertinent information from pharmaceutical and biomedical data. It offers a concise overview of common and recent clustering methods used in bioinformatics and drug discovery.Setting the stage for subsequent material, the firs COMPUTERS,Programming,Games

Vintage Game Consoles Vintage Game Consoles tells the story of the most influential videogame platforms of all time, including the Apple II, Commodore 64, Nintendo Entertainment System, Game Boy, Sega Genesis, Sony PlayStation, and many more. It uncovers the details behind the consoles, computers, handhelds, and arcade machines that made videogames possible. Drawing on extensive research and the authors’ own lifelong experience with videogames, Vintage Game Consoles explores each system’s development, history, fan community, its most important games, and information for collectors and emulation enthusiasts. It also features hundreds of exclusive full-color screenshots and images that help bring each system’s unique story to life. Vintage Game Consoles is the ideal book for gamers, students, and professionals who want to know the story behind their favorite computers, handhelds, and consoles, without forgetting about why they play in the first place – the fun! Bill Loguidice is a critically acclaimed technology author who has worked on over a dozen books, including CoCo: The Colorful History of Tandy’s Underdog Computer, written with Boisy G. Pitre. He’s also the co-founder and Managing Director for the popular Website, Armchair Arcade. A noted videogame and computer historian and subject matter expert, Bill personally owns and maintains well over 400 different systems from the 1970s to the present day, including a large volume of associated materials. Matt Barton is an associate professor of English at Saint Cloud State University in Saint Cloud, Minnesota, where he lives with his wife Elizabeth. He’s the producer of the "Matt Chat," a weekly YouTube series featuring in-depth interviews with notable game developers. In addition to the original Vintage Games, which he co-authored with Bill, he’s author of Dungeons & Desktops: The History of Computer Role-Playing Games and Honoring the Code: Conversations with Great Game Designers. COMPUTERS,Programming,Games

Creative Web Design with Adobe Muse You’ve found your Muse; now learn how to create with it Creative Web Design with Adobe Muse is a step-by-step guide to creating fully-featured websites using Adobe Muse. Adobe Muse can be a complicated program, and web design itself is no easy task, although your clients might think so. This book takes you from the initial design and layout stage right up to helping you publish your beautifully designed and richly developed site. Each chapter covers a different section of the website and, in turn, introduces the tools and features of the program, accompanied by useful tips and tricks that help you speed up your workflow. Follow along as a website is created from concept to execution and rich content such as slideshows, galleries, and social media are incorporated. See how each aspect of a website is created with Muse; watch as it’s published; and visit the final version after learning how it was made. If seeing a website created start to finish wasn’t enough, this book also features: Tips on how to incorporate Photoshop into Muse A companion website that was created with Muse where you can get up-to-the-minute coverage on Muse and other tutorials to help you design the perfect website Through this perfect blend of instruction and inspiration, you’ll be up and running with Adobe Muse in no time. COMPUTERS,Programming,Games

Intermediate C Programming Teach Your Students How to Program WellIntermediate C Programming provides a stepping-stone for intermediate-level students to go from writing short programs to writing real programs well. It shows students how to identify and eliminate bugs, write clean code, share code with others, and use standard Linux-based tools, such as ddd and valgrind.The COMPUTERS,Programming,Games

From Computing to Computational Thinking Computational Thinking (CT) involves fundamental concepts and reasoning, distilled from computer science and other computational sciences, which become powerful general mental tools for solving problems, increasing efficiency, reducing complexity, designing procedures, or interacting with humans and machines. An easy-to-understand guidebook, From Computing to Computational Thinking gives you the tools for understanding and using CT. It does not assume experience or knowledge of programming or of a programming language, but explains concepts and methods for CT with clarity and depth. Successful applications in diverse disciplines have shown the power of CT in problem solving. The book uses puzzles, games, and everyday examples as starting points for discussion and for connecting abstract thinking patterns to real-life situations. It provides an interesting and thought-provoking way to gain general knowledge about modern computing and the concepts and thinking processes underlying modern digital technologies. COMPUTERS,Programming,Games

Multiplayer Game Programming The Practical Guide to Building Reliable Networked Multiplayer Games Networked multiplayer games are a multibillion dollar business: some games now attract tens of millions of players. In this practical, code-rich guide, Joshua Glazer and Sanjay Madhav guide you through every aspect of engineering them. Drawing on their immense experience as both game developers and instructors, the authors lead you through building a robust multiplayer architecture, and creating every engine-level system. You’ll learn through in-depth working code examples for two complete games: an action game and a real time strategy (RTS) game. First, Madhav and Glazer review the essentials of networking and network programming from the standpoint of game developers. Next, they walk through managing game data transmission, updating game objects across the network, and organizing the devices that join your game. You’ll learn how to ensure reliable performance despite the Internet’s inherent inconsistencies, and how to design game code for maximum security and scalability. The authors conclude by addressing two increasingly crucial issues: incorporating gamer services and hosting your games in the cloud. This guide’s content has been extensively tested through the authors’ multiplayer game programming courses at USC. It is equally valuable both to students and to working game programmers moving into networked games. Coverage includes How games have evolved to meet the challenges of networked environments Using Internet communication protocols and standards in game development Working with Berkeley Socket, the most widely used networking construct in multiplayer gaming Formatting game data for efficient Internet transmission Synchronizing states so all players share the same world Organizing networking topologies for large-scale games Overcoming latency and jitter problems that cause delays or lost data Scaling games without compromising performance Combating security vulnerabilities and software cheats Leveraging the networking functionality of the popular Unreal 4 and Unity game engines Integrating gamer services such as matchmaking, achievements, and leaderboards Running game servers in the cloud About the Website C++ source code for all examples is available at github.com/MultiplayerBook . Instructors will also find a full set of PowerPoint slides and a sample syllabus. COMPUTERS,Programming,Games

Unity Game Development in 24 Hours, Sams Teach Yourself In just 24 lessons of one hour or less, Sams Teach Yourself Unity Game Development in 24 Hours will help you master the Unity 5 game engine at the heart of Hearthstone: Heroes of Warcraft, Kerbal Space Program, and many other sizzling-hot games! This book’s straightforward, step-by-step approach teaches you everything from the absolute basics through sophisticated game physics, animation, and mobile device deployment techniques. Every lesson builds on what you’ve already learned, giving you a rock-solid foundation for real-world success. Step-by-step instructions carefully walk you through the most common Unity game development tasks. Practical, hands-on examples show you how to apply what you learn. Quizzes and exercises help you test your knowledge and stretch your skills. Notes and tips point out shortcuts and solutions. COMPUTERS,Programming,Games

Android Studio Game Development This short book walks you through the process of creating mobile games using the new Android Studio IDE. Android Studio Game Development introduces you to the key tools in Android Studio and gives you the knowledge you need to develop games in Android Studio. This book takes you from installing Android Studio, through exploring the IDE to creating a new project and setting up GitHub as a VCS. You'll then be well equipped to tackle the game-development topics that make up the rest of the book. You'll learn about OpenGL ES and how to deal with polygons, before mastering image loading and sprite sheets. The final three chapters cover topics vital to successful game development: interactivity. You'll gain skills in reading user input, responding to that input with in-game movement, and detecting collisions. You'll learn: How to create projects in Android Studio How to use the SDK manager to keep your Android SDK current How to commit to and get projects from GitHub How to use OpenGL ES to load images How to react to player input How to debug your games using Android Studio Audience This book is for those who may be new to game development who have some experience with Android Studio IDE and Android. To learn about Android Studio, check out Learn Android Studio IDE by Gerber and Craig (Apress). COMPUTERS,Programming,Games

Story Structure and Development Professor Craig Caldwell’s Story Structure and Development offers a clear approach to the essentials of story. It lays out the fundamental elements, principles, and structure for animators, designers, and artists so they can incorporate these concepts in their work. As a practical guide it includes extensive insights and advice from industry professionals. Readers will learn the universal patterns of story and narrative used in today’s movies, animation, games, and VR. With over 200 colorful images, this book has been designed for visual learners, and is organized to provide access to story concepts for the screen media professional and student. Readers will discover the story fundamentals referred to by every director and producer when they say "It’s all about story". Key Features Consolidates into one text universal story structure used across the digital media industry Includes enormous visuals that illustrate and reinforce concepts for visual learners Organizes content for faculty to use sections in a non-linear manner Includes chapter objectives, review questions, and key terms to guide the reader COMPUTERS,Programming,Games

Introduction to Middleware "A stereotype of computer science textbooks is that they are dry, boring, and sometimes even intimidating. As a result, they turn students’ interests off from the subject matter instead of enticing them into it. This textbook is the opposite of such a stereotype. The author presents the subject matter in a refreshing story-telling style and aims to bring the Internet-generation of students closer to her stories." --Yingcai Xiao, The University of Akron Introduction to Middleware: Web Services, Object Components, and Cloud Computing provides a comparison of different middleware technologies and the overarching middleware concepts they are based on. The various major paradigms of middleware are introduced and their pros and cons are discussed. This includes modern cloud interfaces, including the utility of Service Oriented Architectures. The text discusses pros and cons of RESTful vs. non-RESTful web services, and also compares these to older but still heavily used distributed object/component middleware. The text guides readers to select an appropriate middleware technology to use for any given task, and to learn new middleware technologies as they appear over time without being greatly overwhelmed by any new concept. The book begins with an introduction to different distributed computing paradigms, and a review of the different kinds of architectures, architectural styles/patterns, and properties that various researchers have used in the past to examine distributed applications and determine the quality of distributed applications. Then it includes appropriate background material in networking and the web, security, and encoding necessary to understand detailed discussion in this area. The major middleware paradigms are compared, and a comparison methodology is developed. Readers will learn how to select a paradigm and technology for a particular task, after reading this text. Detailed middleware technology review sections allow students or industry practitioners working to expand their knowledge to achieve practical skills based on real projects so as to become well-functional in that technology in industry. Major technologies examined include: RESTful web services (RESTful cloud interfaces such as OpenStack, AWS EC2 interface, CloudStack; AJAX, JAX-RS, ASP.NET MVC and ASP.NET Core), non-RESTful (SOAP and WSDL-based) web services (JAX-WS, Windows Communication Foundation), distributed objects/ components (Enterprise Java Beans, .NET Remoting, CORBA). The book presents two projects that can be used to illustrate the practical use of middleware, and provides implementations of these projects over different technologies. This versatile and class-tested textbook is suitable (depending on chapters selected) for undergraduate or first-year graduate courses on client server architectures, middleware, and cloud computing, web services, and web programming. COMPUTERS,Programming,Games

Building the Network of the Future From the Foreword: "This book lays out much of what we’ve learned at AT&T about SDN and NFV. Some of the smartest network experts in the industry have drawn a map to help you navigate this journey. Their goal isn’t to predict the future but to help you design and build a network that will be ready for whatever that future holds. Because if there’s one thing the last decade has taught us, it’s that network demand will always exceed expectations. This book will help you get ready."—Randall Stephenson, Chairman, CEO, and President of AT&T "Software is changing the world, and networks too. In this in-depth book, AT&T's top networking experts discuss how they're moving software-defined networking from concept to practice, and why it's a business imperative to do this rapidly."—Urs Hölzle, SVP Cloud Infrastructure, Google "Telecom operators face a continuous challenge for more agility to serve their customers with a better customer experience and a lower cost. This book is a very inspiring and vivid testimony of the huge transformation this means, not only for the networks but for the entire companies, and how AT&T is leading it. It provides a lot of very deep insights about the technical challenges telecom engineers are facing today. Beyond AT&T, I’m sure this book will be extremely helpful to the whole industry."—Alain Maloberti, Group Chief Network Officer, Orange Labs Networks "This new book should be read by any organization faced with a future driven by a "shift to software." It is a holistic view of how AT&T has transformed its core infrastructure from hardware based to largely software based to lower costs and speed innovation. To do so, AT&T had to redefine their technology supply chain, retrain their workforce, and move toward open source user-driven innovation; all while managing one of the biggest networks in the world. It is an amazing feat that will put AT&T in a leading position for years to come."—Jim Zemlin, Executive Director, The Linux Foundation This book is based on the lessons learned from AT&T’s software transformation journey starting in 2012 when rampant traffic growth necessitated a change in network architecture and design. Using new technologies such as NFV, SDN, Cloud, and Big Data, AT&T’s engineers outlined and implemented a radical network transformation program that dramatically reduced capital and operating expenditures. This book describes the transformation in substantial detail. The subject matter is of great interest to telecom professionals worldwide, as well as academic researchers looking to apply the latest techniques in computer science to solving telecom’s big problems around scalability, resilience, and survivability. COMPUTERS,Programming,Games

Evolutionary Multi-Objective System Design Real-world engineering problems often require concurrent optimization of several design objectives, which are conflicting in cases. This type of optimization is generally called multi-objective or multi-criterion optimization. The area of research that applies evolutionary methodologies to multi-objective optimization is of special and growing interest. It brings a viable computational solution to many real-world problems. Generally, multi-objective engineering problems do not have a straightforward optimal design. These kinds of problems usually inspire several solutions of equal efficiency, which achieve different trade-offs. Decision makers’ preferences are normally used to select the most adequate design. Such preferences may be dictated before or after the optimization takes place. They may also be introduced interactively at different levels of the optimization process. Multi-objective optimization methods can be subdivided into classical and evolutionary. The classical methods usually aim at a single solution while the evolutionary methods provide a whole set of so-called Pareto-optimal solutions. Evolutionary Multi-Objective System Design: Theory and Applications provides a representation of the state-of-the-art in evolutionary multi-objective optimization research area and related new trends. It reports many innovative designs yielded by the application of such optimization methods. It also presents the application of multi-objective optimization to the following problems: Embrittlement of stainless steel coated electrodes Learning fuzzy rules from imbalanced datasets Combining multi-objective evolutionary algorithms with collective intelligence Fuzzy gain scheduling control Smart placement of roadside units in vehicular networks Combining multi-objective evolutionary algorithms with quasi-simplex local search Design of robust substitution boxes Protein structure prediction problem Core assignment for efficient network-on-chip-based system design COMPUTERS,Programming,Games

Writing Interactive Fiction with Twine Writing Interactive Fiction with Twine: Play Inside a Story If you’ve ever dreamed about walking through the pages of a book, fighting dragons, or exploring planets then Twine is for you. This interactive fiction program enables you to create computer games where worlds are constructed out of words and simple scripts can allow the player to pick up or drop objects, use items collected in the game to solve puzzles, or track injury in battle by reducing hit points. If you’ve clicked your way through 80 Days, trekked through the underground Zork kingdom, or attempted to save an astronaut with Lifeline, you’re already familiar with interactive fiction. If not, get ready to have your imagination stretched as you learn how to direct a story path. The best part about interactive fiction stories is that they are simple to make and can serve as a gateway into the world of coding for the nonprogrammer or new programmer. You’ll find expert advice on everything from creating vivid characters to building settings that come alive. Ford’s easy writing prompts help you get started, so you’ll never face a blank screen. Her “Try It Out†exercises go way beyond the basics, helping you bring personal creativity and passion to every story you create! Get familiar with the popular Twine scripting program Learn how to design puzzles Build your own role-playing game with stat systems Maintain an inventory of objects Learn game design and writing basics Change the look of your story using CSS and HTML Discover where you can upload your finished games and find players COMPUTERS,Programming,Games

Games, Design and Play The play-focused, step-by-step guide to creating great game designs This book offers a play-focused, process-oriented approach for designing games people will love to play. Drawing on a combined 35 years of design and teaching experience, Colleen Macklin and John Sharp link the concepts and elements of play to the practical tasks of game design. Using full-color examples, they reveal how real game designers think and work, and illuminate the amazing expressive potential of great game design. Focusing on practical details, this book guides you from idea to prototype to playtest and fully realized design. You’ll walk through conceiving and creating a game’s inner workings, including its core actions, themes, and especially its play experience. Step by step, you’ll assemble every component of your “videogame,†creating practically every kind of play: from cooperative to competitive, from chance-based to role-playing, and everything in between. Macklin and Sharp believe that games are for everyone, and game design is an exciting art form with a nearly unlimited array of styles, forms, and messages. Cutting across traditional platform and genre boundaries, they help you find inspiration wherever it exists. Games, Design and Play is for all game design students, and for beginning-to-intermediate-level game professionals, especially independent game designers. Bridging the gaps between imagination and production, it will help you craft outstanding designs for incredible play experiences! Coverage includes: Understanding core elements of play design: actions, goals, rules, objects, playspace, and players Mastering “tools†such as constraint, interaction, goals, challenges, strategy, chance, decision, storytelling, and context Comparing types of play and player experiences Considering the demands videogames make on players Establishing a game’s design values Creating design documents, schematics, and tracking spreadsheets Collaborating in teams on a shared design vision Brainstorming and conceptualizing designs Using prototypes to realize and playtest designs Improving designs by making the most of playtesting feedback Knowing when a design is ready for production Learning the rules so you can break them! COMPUTERS,Programming,Games

Large-Scale Machine Learning in the Earth Sciences From the Foreword: "While large-scale machine learning and data mining have greatly impacted a range of commercial applications, their use in the field of Earth sciences is still in the early stages. This book, edited by Ashok Srivastava, Ramakrishna Nemani, and Karsten Steinhaeuser, serves as an outstanding resource for anyone interested in the opportunities and challenges for the machine learning community in analyzing these data sets to answer questions of urgent societal interest…I hope that this book will inspire more computer scientists to focus on environmental applications, and Earth scientists to seek collaborations with researchers in machine learning and data mining to advance the frontiers in Earth sciences." --Vipin Kumar, University of Minnesota Large-Scale Machine Learning in the Earth Sciences provides researchers and practitioners with a broad overview of some of the key challenges in the intersection of Earth science, computer science, statistics, and related fields. It explores a wide range of topics and provides a compilation of recent research in the application of machine learning in the field of Earth Science. Making predictions based on observational data is a theme of the book, and the book includes chapters on the use of network science to understand and discover teleconnections in extreme climate and weather events, as well as using structured estimation in high dimensions. The use of ensemble machine learning models to combine predictions of global climate models using information from spatial and temporal patterns is also explored. The second part of the book features a discussion on statistical downscaling in climate with state-of-the-art scalable machine learning, as well as an overview of methods to understand and predict the proliferation of biological species due to changes in environmental conditions. The problem of using large-scale machine learning to study the formation of tornadoes is also explored in depth. The last part of the book covers the use of deep learning algorithms to classify images that have very high resolution, as well as the unmixing of spectral signals in remote sensing images of land cover. The authors also apply long-tail distributions to geoscience resources, in the final chapter of the book. COMPUTERS,Programming,Games

Build an HTML5 Game If you already have even basic familiarity with HTML, CSS, and JavaScript, you’re ready to learn how to build a browser-based game. In Build an HTML5 Game, you’ll use your skills to create a truly cross-platform bubble-shooter game—playable in both desktop and mobile browsers. As you follow along with this in-depth, hands-on tutorial, you’ll learn how to:–Send sprites zooming around the screen with JavaScript animations–Make things explode with a jQuery plug-in–Use hitboxes and geometry to detect collisions–Implement game logic to display levels and respond to player input–Convey changes in game state with animation and sound–Add flair to a game interface with CSS transitions and transformations–Gain pixel-level control over your game display with the HTML canvas The programming starts right away in Chapter 1—no hemming and hawing, history, or throat clearing. Exercises at the end of each chapter challenge you to dig in to the bubble shooter’s code and modify the game. Go ahead. Take the plunge. Learn to create a complete HTML5 game right now and then use your newfound skills to build your own mega-popular, addictive game. COMPUTERS,Programming,Games

Mobile Game Development with Unity Do you want to build mobile games, but lack game development experience? No problem. This practical guide shows you how to create beautiful, interactive content for iOS and Android devices with the Unity game engine. Authors Jon Manning and Paris Buttfield-Addison (iOS Swift Game Development Cookbook) provide a top-to-bottom overview of Unity’s features with specific, project-oriented guidance on how to use them in real game situations. Over the course of this book, you’ll learn hands-on how to build 2D and 3D games from scratch that will hook and delight players. If you have basic programming skills, you’re ready to get started. Explore the basics of Unity, and learn how to structure games, graphics, scripting, sounds, physics, and particle systems Use 2D graphics and physics features to build a side-scrolling action game Create a 3D space combat simulator with projectile shooting and respawning objects, and learn how to manage the appearance of 3D models Dive into Unity’s advanced features, such as precomputed lighting, shading, customizing the editor, and deployment COMPUTERS,Programming,Games

Introduction to Game Design, Prototyping, and Development Master the Unity Game Engine to Design and Develop Games for Web, Mobile, Windows, macOS, and More! If you want to design and develop games, there’s no substitute for strong hands-on experience with modern techniques and tools—and that is exactly what this book provides. The first edition was frequently the top-selling game design book on Amazon, with more than 70% of the reviews being 5 stars. In a testament to the iterative process of design, this new edition includes hundreds of improvements throughout the text, all designed to make the book easier to understand and even more useful. This book was written with Unity 2017; the book.prototools.net website will cover changes for later versions of the software. Award-winning game designer and professor Jeremy Gibson Bond has spent more than a decade teaching game design and building great games. In that time, his most successful students have been those who combine knowledge of three critical disciplines: game design theory, rapid iterative prototyping, and practical programming. In this book, Bond distills the most important aspects of all three disciplines into one place. Part I: Game Design and Paper Prototyping • The Layered Tetrad framework: a synthesis of 50 years of game design theory • Proven practices for brainstorming and refining game designs through the iterative process of design • Methods and tools to manage game projects and small teams • Processes to make playtesting and feedback easier Part II: Digital Prototyping with Unity and C# • Chapters that guide you through learning C# the right way • Instruction that takes you from no prior programming knowledge through object-oriented programming • Deep exploration of Unity, today’s most popular game engine on both macOS and Windows • Methods for understanding and debugging code issues you encounter Part III: Game Prototype Examples and Tutorials • In-depth tutorials for seven different game prototypes, including a simple action game, a space shooter, a solitaire card game, a word game, and a top-down adventure • Instructions to compile these games for PC, web, or any of the dozens of other release platforms supported by Unity • Improved structure and layout that makes the steps of each tutorial easier to follow • A completely new Dungeon Delver prototype not present in the first edition COMPUTERS,Programming,Games

Java in 24 Hours, Sams Teach Yourself (Covering Java 9) Computer programming with Java is easier than it looks. In just 24 lessons of one hour or less, you can learn to write computer programs in Java. Using a straightforward, step-by-step approach, popular author Rogers Cadenhead helps you master the skills and technology you need to create desktop and web programs, web services, an Android app, and even Minecraft mods in Java. Each lesson builds on what you’ve already learned, giving you a rock-solid foundation for real-world success. Full-color figures and clear step-by-step instructions visually show you how to program with Java. Quizzes and Exercises at the end of each chapter help you test your knowledge. Notes, Tips, and Cautions provide related information, advice, and warnings. Learn how to… • Set up your Java programming environment • Write your first working program in just minutes • Control program decisions and behavior • Store and work with information • Build straightforward user interfaces • Create interactive web programs • Use threading to build more responsive programs • Read and write files and XML data • Master best practices for object-oriented programming • Use Java 9’s new HTTP client • Use Java to create an Android app • Expand your skills with closures • Create Minecraft mods with Java Contents at a Glance Part I Getting Started 1 Becoming a Programmer 2 Writing Your First Program 3 Vacationing in Java 4 Understanding How Java Programs Work Part II Learning the Basics of Programming 5 Storing and Changing Information in a Program 6 Using Strings to Communicate 7 Using Conditional Tests to Make Decisions 8 Repeating an Action with Loops Part III Working with Information in New Ways 9 Storing Information with Arrays 10 Creating Your First Object 11 Describing What Your Object is Like 12 Making the Most of Existing Objects Part IV Moving into Advanced Topics 13 Storing Objects in Data Structures 14 Handling Errors in a Program 15 Creating a Threaded Program 16 Using Inner Classes and Closures Part V Programming a Graphical User Interface 17 Building a Simple User Interface in Swing 18 Laying Out a User Interface 19 Responding to User Input Part VI Writing Internet Applications 20 Reading and Writing Files 21 Using Java 9's New HTTP Client 22 Creating Java2D Graphics 23 Creating Minecraft Mods with Java 24 Writing Android Apps Appendixes A Using the NetBeans Integrated Development Environment B Where to Go from Here Java Resources C This Book's Web Site D Fixing a Problem with the Android Studio Emulator COMPUTERS,Programming,Games

A Systematic Approach to Learning Robot Programming with ROS A Systematic Approach to Learning Robot Programming with ROS provides a comprehensive, introduction to the essential components of ROS through detailed explanations of simple code examples along with the corresponding theory of operation. The book explores the organization of ROS, how to understand ROS packages, how to use ROS tools, how to incorporate existing ROS packages into new applications, and how to develop new packages for robotics and automation. It also facilitates continuing education by preparing the reader to better understand the existing on-line documentation. The book is organized into six parts. It begins with an introduction to ROS foundations, including writing ROS nodes and ROS tools. Messages, Classes, and Servers are also covered. The second part of the book features simulation and visualization with ROS, including coordinate transforms. The next part of the book discusses perceptual processing in ROS. It includes coverage of using cameras in ROS, depth imaging and point clouds, and point cloud processing. Mobile robot control and navigation in ROS is featured in the fourth part of the book The fifth section of the book contains coverage of robot arms in ROS. This section explores robot arm kinematics, arm motion planning, arm control with the Baxter Simulator, and an object-grabber package. The last part of the book focuses on system integration and higher-level control, including perception-based and mobile manipulation. This accessible text includes examples throughout and C++ code examples are also provided at https://github.com/wsnewman/learning_ros COMPUTERS,Programming,Games

Internet Infrastructure Internet Infrastructure: Networking, Web Services, and Cloud Computing provides a comprehensive introduction to networks and the Internet from several perspectives: the underlying media, the protocols, the hardware, the servers, and their uses. The material in the text is divided into concept chapters that are followed up with case study chapters that examine how to install, configure, and secure a server that offers the given service discussed. The book covers in detail the Bind DNS name server, the Apache web server, and the Squid proxy server. It also provides background on those servers by discussing DNS, DHCP, HTTP, HTTPS, digital certificates and encryption, web caches, and the variety of protocols that support web caching. Introductory networking content, as well as advanced Internet content, is also included in chapters on networks, LANs and WANs, TCP/IP, TCP/IP tools, cloud computing, and an examination of the Amazon Cloud Service. Online resources include supplementary content that is available via the textbook’s companion website, as well useful resources for faculty and students alike, including: a complete lab manual; power point notes, for installing, configuring, securing and experimenting with many of the servers discussed in the text; power point notes; animation tutorials to illustrate some of the concepts; two appendices; and complete input/output listings for the example Amazon cloud operations covered in the book. COMPUTERS,Programming,Games

How to Cheat in Adobe Animate CC Would you rather take months to learn every tool, every feature, and every concept in Adobe Animate or start right now making your own creations with just a few steps? Myra Ferguson is teaming up with Chris Georgenes to help you create great animation, bring objects to life with cool motion effects, and enhance your productivity in Animate CC! How to Cheat in Adobe Animate CC is a goldmine of artistic inspiration, time-saving practical tips, and step-by-step walkthroughs. Let your sasquatch sunbathe, your coyote howl, and your lint spider see the light of day. With real-world projects and project source files, you can follow along and try for yourself. This book includes all NEW content and cheats for Animate CC, such as making cinemagraphs, creating a double exposure effect, speeding up the process of making real life doodles, simulating a bokeh effect, converting your documents to HTML5, and more. Key Features • Glimpse into the workflow of digital media and animation experts and apply practical techniques and tips to your own projects with source files, examples, and tutorials. • Learn a myriad of tricks based on real-life working methods to help you work faster and more efficiently with new features in Adobe Animate CC and the Creative Cloud. • Work from the problem to the solution to gain the best possible results from Animate. COMPUTERS,Programming,Games

Digital Type Design for Branding The approach will be to give visual aid (illustrated) and written reference to young designers who are either launching their careers or taking their first stab at designing letterforms for a logo, lettermark, signage, advertising or an alphabet. The book will focus on the roots of each letterform and give the designers the knowledge of why weight variations (stress) exist and how to correctly apply them to their designs. Key Features A how-to resource for designers to referencee while designing letterforms. The designer will be left with a clear understanding of why letterforms look the way they do, and the moethod and order of letterform development, enabling the designer to draw on history when developing their glyphs. How-to illustrations will highlight the process and downloadable vectors will give the designer templates to begin their project. This book gives designers a solid footing when designing a series of characters without developing a complete alphabet. Custom typography is a growing trend and every newly minted designer should have a practical knowledge of the origins of letters and the method of building letterforms. COMPUTERS,Programming,Games

Artificial Intelligence The first edition of this popular textbook, Contemporary Artificial Intelligence , provided an accessible and student friendly introduction to AI. This fully revised and expanded update, Artificial Intelligence: With an Introduction to Machine Learning, Second Edition, retains the same accessibility and problem-solving approach, while providing new material and methods. The book is divided into five sections that focus on the most useful techniques that have emerged from AI. The first section of the book covers logic-based methods, while the second section focuses on probability-based methods. Emergent intelligence is featured in the third section and explores evolutionary computation and methods based on swarm intelligence. The newest section comes next and provides a detailed overview of neural networks and deep learning. The final section of the book focuses on natural language understanding. Suitable for undergraduate and beginning graduate students, this class-tested textbook provides students and other readers with key AI methods and algorithms for solving challenging problems involving systems that behave intelligently in specialized domains such as medical and software diagnostics, financial decision making, speech and text recognition, genetic analysis, and more. COMPUTERS,Programming,Games

A Concise Introduction to Programming in Python A Concise Introduction to Programming in Python, Second Edition provides a hands-on and accessible introduction to writing software in Python, with no prior programming experience required. The Second Edition was thoroughly reorganized and rewritten based on classroom experience to incorporate: A spiral approach, starting with turtle graphics, and then revisiting concepts in greater depth using numeric, textual, and image data Clear, concise explanations written for beginning students, emphasizing core principles A variety of accessible examples, focusing on key concepts Diagrams to help visualize new concepts New sections on recursion and exception handling, as well as an earlier introduction of lists, based on instructor feedback The text offers sections designed for approximately one class period each, and proceeds gradually from procedural to object-oriented design. Examples, exercises, and projects are included from diverse application domains, including finance, biology, image processing, and textual analysis. It also includes a brief "How-To" sections that introduce optional topics students may be interested in exploring. The text is written to be read, making it a good fit in flipped classrooms. Designed for either classroom use or self-study, all example programs and solutions to odd-numbered exercises (except for projects) are available at: http://www.central.edu/go/conciseintro/. COMPUTERS,Programming,Games

Unity 2018 Game Development in 24 Hours, Sams Teach Yourself In just 24 lessons of one hour or less, Sams Teach Yourself Unity Game Development in 24 Hours will help you master the Unity 2018 game engine at the heart of Ori and the Blind Forest, Firewatch, Monument Valley, and many other sizzling-hot games! This book’s straightforward, step-by-step approach teaches you everything from the absolute basics through sophisticated game physics, animation, and mobile device deploymenttechniques. Every lesson builds on what you’ve already learned, giving you a rock-solid foundation for real-world success. Step-by-step instructions carefully walk you through the most common Unity game development tasks. Practical, hands-on examples show you how to apply what you learn. Quizzes and exercises help you test your knowledge and stretch your skills. Notes and Tips point out shortcuts and solutions Learn how to… Get up and running fast with the Unity 2018 game engine and editor Work efficiently with Unity’s graphical asset pipeline Make the most of lights and cameras Sculpt stunning worlds with Unity’s terrain and environmental tools Script tasks ranging from capturing input to building complex behaviors Quickly create repeatable, reusable game objects with prefabs Implement easy, intuitive game user interfaces Control players through built-in and custom character controllers Build realistic physical and trigger collisions Leverage the full power of Unity’s Animation and new Timeline systems Integrate complex audio into your games Use mobile device accelerometers and multi-touch displays Build engaging 2D games with Unity’s 2D tools and Tilemap Apply the “finishing touches†and deploy your games COMPUTERS,Programming,Games

Video Game Law Video Game Law is aimed at game developers and industry professionals who want to better understand the industry or are in need of expert legal guidance. Given the rise in international competition, the increasing complexity of video game features, and the explosive growth of the industry in general, game developers can quickly find themselves in serious trouble, becoming vulnerable to copyright infringement claims, piracy, and even security breaches. Not every video game company has the financial resources to retain in-house counsel–which Video Game Law seeks to address by discussing many of the common pitfalls, legal questions, and scenarios facing the industry. S. Gregory Boyd, Brian Pyne, and Sean F. Kane, the most prominent, sought after, and respected video game attorneys in the country, break down the laws and legal concepts that every game developer and industry professional needs to know in order to better protect their game and grow their company. KEY FEATURES:• Provides a solid understanding of intellectual property (IP) concepts and laws, includingcopyright, trademark, trade secret, and other protections that apply to video games andhow each can be employed to protect a company’s unique and valuable IP• Explores cutting edge legal issues that affect the gaming industry, including gambling,virtual currency, privacy laws, the Digital Millennium Copyright Act, tax incentives, andrelevant piracy laws• Provides an overview of legal and privacy vocabulary and concepts needed to navigateand succeed in an industry that is constantly growing and evolving• Provides illustrative examples and legal concepts from the video game industry in everychapter COMPUTERS,Programming,Games

How to Cheat in Maya 2017 This is not a book about Maya software with a few animation pointers thrown in here and there. This is a guide to Maya software written by professional animators. This book provides you with complete, set-by-step walkthroughs of essential animation techniques that increase your speed and efficiency while using Maya 2017 for character animation. From curves to constraints, this book covers all of the methods available in the latest version of Maya. Featuring gold-mine coverage this book teaches you new techniques for working with characters in animation tests and short films. Accompanied by a companion site, this is the one and only guide to get you up to speed. Key Features Complete step-by-step, walkthroughs of essential techniques every animator needs to know. Features interviews with leading experts and experienced animation leads. Companion web site including all exercise/example scene files and extras such as video tutorials and animation files. Interlude articles covering everything from Reference Video to Resumes. COMPUTERS,Programming,Games

Behavior Trees in Robotics and AI Behavior Trees (BTs) provide a way to structure the behavior of an artificial agent such as a robot or a non-player character in a computer game. Traditional design methods, such as finite state machines, are known to produce brittle behaviors when complexity increases, making it very hard to add features without breaking existing functionality. BTs were created to address this very problem, and enables the creation of systems that are both modular and reactive. Behavior Trees in Robotics and AI: An Introduction provides a broad introduction as well as an in-depth exploration of the topic, and is the first comprehensive book on the use of BTs. This book introduces the subject of BTs from simple topics, such as semantics and design principles, to complex topics, such as learning and task planning. For each topic, the authors provide a set of examples, ranging from simple illustrations to realistic complex behaviors, to enable the reader to successfully combine theory with practice. Starting with an introduction to BTs, the book then describes how BTs relate to, and in many cases, generalize earlier switching structures, or control architectures. These ideas are then used as a foundation for a set of efficient and easy to use design principles. The book then presents a set of important extensions and provides a set of tools for formally analyzing these extensions using a state space formulation of BTs. With the new analysis tools, the book then formalizes the descriptions of how BTs generalize earlier approaches and shows how BTs can be automatically generated using planning and learning. The final part of the book provides an extended set of tools to capture the behavior of Stochastic BTs, where the outcomes of actions are described by probabilities. These tools enable the computation of both success probabilities and time to completion. This book targets a broad audience, including both students and professionals interested in modeling complex behaviors for robots, game characters, or other AI agents. Readers can choose at which depth and pace they want to learn the subject, depending on their needs and background. COMPUTERS,Programming,Games

Game Design Workshop Game Design Workshop is a truly great book, and has become, in my opinion, the de facto standard text for beginner- to intermediate-level game design education. This updated new edition is extremely relevant, useful and inspiring to all kinds of game designers. — Richard Lemarchand, Interactive Media & Games Division, School of Cinematic Arts, University of Southern California———————————————————————————————————————————————————This is the perfect time for a new edition. The updates refresh elements of the book that are important as examples, but don't radically alter the thing about the book that is great: a playcentric approach to game design. — Colleen Macklin, Associate Professor, Parsons The New School for Design———————————————————————————————————————————————————Tracy Fullerton’s Game Design Workshop covers pretty much everything a working or wannabe game designer needs to know. She covers game theory, concepting, prototyping, testing and tuning, with stops along the way to discuss what it means to a professional game designer and how to land a job. When I started thinking about my game studies course at the University of Texas at Austin, this was one book I knew I had to use.— Warren Spector, Studio Director, OtherSide Entertainment———————————————————————————————————————————————————"Create the digital games you love to play." Discover an exercise-driven, non-technical approach to game design, without the need for programming or artistic expertise with Game Design Workshop, Fourth Edition. Tracy Fullerton demystifies the creative process with clear and accessible analysis of the formal and dramatic systems of game design. Using examples of popular games, illustrations of design techniques, and refined exercises to strengthen your understanding of how game systems function and give you the skills and tools necessary to create a compelling and engaging game. Game Design Workshop puts you to work prototyping, playtesting, and revising your own games with time-tested methods and tools. These skills will provide the foundation for your career in any facet of the game industry including design, producing, programming, and visual design. Tracy Fullerton is an award-winning game designer and educator with over 20 years of professional experience, most recently winning the Games for Change Game of the Year Award for her independent game Walden, a game. She has also been awarded the 2016 GDC Ambassador Award, the 2015 Games for Change Game Changer Award, and the IndieCade 2013 Trailblazer award for her pioneering work in the independent games community. Tracy is a Professor of Interactive Media & Games at the USC School of Cinematic Arts and the Director of the USC Games Program, the #1 game design program in North America as ranked by the Princeton Review. Key Features Provides step-by-step introduction to the art of game designing, prototyping and playtesting innovative games A design methodology used in the USC Interactive Media program, a cutting edge program with hands-on exercises that demonstrate key concepts and the design methodology Insights from top industry game designers presented through interview format COMPUTERS,Programming,Games

Artificial Intelligence Safety and Security The history of robotics and artificial intelligence in many ways is also the history of humanity’s attempts to control such technologies. From the Golem of Prague to the military robots of modernity, the debate continues as to what degree of independence such entities should have and how to make sure that they do not turn on us, its inventors. Numerous recent advancements in all aspects of research, development and deployment of intelligent systems are well publicized but safety and security issues related to AI are rarely addressed. This book is proposed to mitigate this fundamental problem. It is comprised of chapters from leading AI Safety researchers addressing different aspects of the AI control problem as it relates to the development of safe and secure artificial intelligence. The book is the first edited volume dedicated to addressing challenges of constructing safe and secure advanced machine intelligence. The chapters vary in length and technical content from broad interest opinion essays to highly formalized algorithmic approaches to specific problems. All chapters are self-contained and could be read in any order or skipped without a loss of comprehension. COMPUTERS,Programming,Games

The Internet Book The Internet Book, Fifth Edition explains how computers communicate, what the Internet is, how the Internet works, and what services the Internet offers. It is designed for readers who do not have a strong technical background — early chapters clearly explain the terminology and concepts needed to understand all the services. It helps the reader to understand the technology behind the Internet, appreciate how the Internet can be used, and discover why people find it so exciting. In addition, it explains the origins of the Internet and shows the reader how rapidly it has grown. It also provides information on how to avoid scams and exaggerated marketing claims. The first section of the book introduces communication system concepts and terminology. The second section reviews the history of the Internet and its incredible growth. It documents the rate at which the digital revolution occurred, and provides background that will help readers appreciate the significance of the underlying design. The third section describes basic Internet technology and capabilities. It examines how Internet hardware is organized and how software provides communication. This section provides the foundation for later chapters, and will help readers ask good questions and make better decisions when salespeople offer Internet products and services. The final section describes application services currently available on the Internet. For each service, the book explains both what the service offers and how the service works. About the Author Dr. Douglas Comer is a Distinguished Professor at Purdue University in the departments of Computer Science and Electrical and Computer Engineering. He has created and enjoys teaching undergraduate and graduate courses on computer networks and Internets, operating systems, computer architecture, and computer software. One of the researchers who contributed to the Internet as it was being formed in the late 1970s and 1980s, he has served as a member of the Internet Architecture Board, the group responsible for guiding the Internet’s development. Prof. Comer is an internationally recognized expert on computer networking, the TCP/IP protocols, and the Internet, who presents lectures to a wide range of audiences. In addition to research articles, he has written a series of textbooks that describe the technical details of the Internet. Prof. Comer’s books have been translated into many languages, and are used in industry as well as computer science, engineering, and business departments around the world. Prof. Comer joined the Internet project in the late 1970s, and has had a high-speed Internet connection to his home since 1981. He wrote this book as a response to everyone who has asked him for an explanation of the Internet that is both technically correct and easily understood by anyone. An Internet enthusiast, Comer displays INTRNET on the license plate of his car. COMPUTERS,Programming,Games

Unity 2018 Cookbook Develop quality game components and solve common gameplay problems with various game design patterns Key Features Become proficient at traditional 2D and 3D game development Build amazing interactive interfaces with Unity's UI system Develop professional games with realistic animation and graphics, materials and cameras, and AI with Unity 2018 Book Description With the help of the Unity 2018 Cookbook, you'll discover how to make the most of the UI system and understand how to animate both 2D and 3D characters and game scene objects using Unity's Mecanim animation toolsets. Once you've got to grips with the basics, you will familiarize yourself with shaders and Shader Graphs, followed by understanding the animation features to enhance your skills in building fantastic games. In addition to this, you will discover AI and navigation techniques for nonplayer character control and later explore Unity 2018's newly added features to improve your 2D and 3D game development skills. This book provides many Unity C# gameplay scripting techniques. By the end of this book, you'll have gained comprehensive knowledge in game development with Unity 2018. What you will learn Get creative with Unity's shaders and learn to build your own shaders with the new Shader Graph tool Create a text and image character dialog with the free Fungus Unity plugin Explore new features integrated into Unity 2018, including TextMesh Pro and ProBuilder Master Unity audio, including ducking, reverbing, and matching pitch to animation speeds Work with the new Cinemachine and timeline to intelligently control camera movements Improve ambiance through the use of lights and effects, including reflection and light probes Create stylish user interfaces with the UI system, including power bars and clock displays Who this book is for Unity 2018 Cookbook is for you if you want to explore a wide range of Unity scripting and multimedia features and find ready-to-use solutions for many game features. This book also helps programmers explore multimedia features. It is assumed that you already know basics of Unity and have some programming knowledge of C#. COMPUTERS,Programming,Games

Artificial Intelligence for Autonomous Networks Artificial Intelligence for Autonomous Networks introduces the autonomous network by juxtaposing two unique technologies and communities: Networking and AI. The book reviews the technologies behind AI and software-defined network/network function virtualization, highlighting the exciting opportunities to integrate those two worlds. Outlining the new frontiers for autonomous networks, this book highlights their impact and benefits to consumers and enterprise customers. It also explores the potential of the autonomous network for transforming network operation, cyber security, enterprise services, 5G and IoT, infrastructure monitoring and traffic optimization, and finally, customer experience and care. With contributions from leading experts, this book will provide an invaluable resource for network engineers, software engineers, artificial intelligence, and machine learning researchers. COMPUTERS,Programming,Games

iOS Swift Game Development Cookbook Ready to make amazing games for the iPhone and iPad? With Apple’s Swift programming language, it’s never been easier. This updated cookbook provides detailed recipes for managing a wide range of common iOS game-development issues, ranging from 2D and 3D math, SpriteKit, and OpenGL to augmented reality with ARKit. You get simple, direct solutions to common problems found in iOS game programming. Need to figure out how to give objects physical motion, or want a refresher on gaming-related math problems? This book provides sample projects and straightforward answers. All you need to get started is some familiarity with iOS development in Swift. COMPUTERS,Programming,Games

Swift Game Development Embrace the mobile gaming revolution by creating popular iOS games with Swift 4.2 Key Features Learn to create games for iPhone and iPad with the latest Swift Programming language Understand the fundamental concepts of game development like game physics, camera action, sprites, controls, among others Build Augmented reality games using ARKit for true performance Book Description Swift is the perfect choice for game development. Developers are intrigued by Swift and want to make use of new features to develop their best games yet. Packed with best practices and easy-to-use examples, this book leads you step by step through the development of your first Swift game. The book starts by introducing Swift's best features – including its new ones for game development. Using SpriteKit, you will learn how to animate sprites and textures. Along the way, you will master physics, animations, and collision effects and how to build the UI aspects of a game. You will then work on creating a 3D game using the SceneKit framework. Further, we will look at how to add monetization and integrate Game Center. With iOS 12, we see the introduction of ARKit 2.0. This new version allows us to integrate shared experiences such as multiplayer augmented reality and persistent AR that is tied to a specific location so that the same information can be replicated on all connected devices. In the next section, we will dive into creating Augmented Reality games using SpriteKit and SceneKit. Then, finally, we will see how to create a Multipeer AR project to connect two devices, and send and receive data back and forth between those devices in real time. By the end of this book, you will be able to create your own iOS games using Swift and publish them on the iOS App Store. What you will learn Deliver powerful graphics, physics, and sound in your game by using SpriteKit and SceneKit Set up a scene using the new capabilities of the scene editor and custom classes Maximize gameplay with little-known tips and strategies for fun, repeatable action Make use of animations, graphics, and particles to polish your game Understand the current mobile monetization landscape Integrate your game with Game Center Develop 2D and 3D Augmented Reality games using Apple's new ARKit framework Publish your game to the App Store Who this book is for If you wish to create and publish iOS games using Swift, then this book is for you. No prior game development or experience with Apple ecosystem is needed. COMPUTERS,Programming,Games

Practical Guide to ChIP-seq Data Analysis Chromatin immunoprecipitation sequencing (ChIP-seq), which maps the genome-wide localization patterns of transcription factors and epigenetic marks, is among the most widely used methods in molecular biology. Practical Guide to ChIP-seq Data Analysis will guide readers through the steps of ChIP-seq analysis: from quality control, through peak calling, to downstream analyses. It will help experimental biologists to design their ChIP-seq experiments with the analysis in mind, and to perform the basic analysis steps themselves. It also aims to support bioinformaticians to understand how the data is generated, what the sources of biases are, and which methods are appropriate for different analyses. COMPUTERS,Programming,Games

Mechanical Creations in 3D Cogs, cranks, wheels, plates, chains, springs and pistons - a nightmare for animators. This book shows 3D artists how to create, setup, control and automate movements for complex and technically challenging mechanical structures all while working on a super-detailed steampunk train! This book will specifically implement current industry trends and techniques for animated mechanical structures. We will be using Autodesk 3ds Max only, with no plugins and no additional software required. Readers will close out this book with a completed steampunk train for their portfolios and practical knowledge to combat other tricky hard-surface rigging and animation challenges. Key Features This is the only book available for mechanical setups in Autodesk 3ds Max. Although 3ds Max specific, the techniques and foundations will work for any 3D application. By following the step-by-step guides in this book, you can finish and complete a portfolio-ready steampunk train. Each chapter will include an introduction and a summary, giving significance to the start and end of each section where readers can rest! Boxed step-by-step guides will be used for the creation of technical setups in 3ds Max. A "Memory Refresh" section is included in each chapter, this gives short and quick reminders for the stages needed to complete the chapter setup - helpful as a reference guide for those that have already read the book and just need a reminder, saving them time as they won’t have to re-read the whole thing! COMPUTERS,Programming,Games

Let’s Build a Multiplayer Phaser Game Create a fully working multiplayer game from scratch using TypeScript, Socket.IO, and the community edition of Phaser.js. You will achieve amazing feats in the browser without having to install any software. This book teaches you how to use the Phaser game engine APIs to tap into physics, and how to utilize HUD information and fire lasers. Let’s Build a Multiplayer Phaser Game dives into the details to show you how to create a multiplayer game from beginning to end. Once you have finished this book, you will be well versed in creating not only a game, but also an application that you can extend with new functionality to enjoy with your friends. What You'll Learn Discover the ins and outs of Socket.IO for real-time web communication Use TypeScript to allow your project to be typed and self-documenting See how gaming mechanics work to make a game entertaining Get a deeper understanding of how to structure your working directory and your code Scale what you have created Who This Book Is For Developers who want to know how to create and structure a complex online game COMPUTERS,Programming,Games

Think Like a UX Researcher Think Like a UX Researcher will challenge your preconceptions about user experience (UX) research and encourage you to think beyond the obvious. You’ll discover how to plan and conduct UX research, analyze data, persuade teams to take action on the results and build a career in UX. The book will help you take a more strategic view of product design so you can focus on optimizing the user’s experience. UX Researchers, Designers, Project Managers, Scrum Masters, Business Analysts and Marketing Managers will find tools, inspiration and ideas to rejuvenate their thinking, inspire their team and improve their craft. Key Features A dive-in-anywhere book that offers practical advice and topical examples. Thought triggers, exercises and scenarios to test your knowledge of UX research. Workshop ideas to build a development team’s UX maturity. War stories from seasoned researchers to show you how UX research methods can be tailored to your own organization. COMPUTERS,Programming,Games

Google Daydream VR Cookbook The Complete, Up-to-Date Guide to Building AR and VR Games Google’s new ARCore and Daydream VR platforms enable you to deliver advanced augmented and virtual reality games and apps on a wide spectrum of modern Android devices. Now for the first time, there’s a comprehensive deep dive into both ARCore and Daydream for every Android developer and designer. Multi-award-winning AR/VR developer Sam Keene takes a hands-on approach, leading you through all aspects of the ARCore and Daydream frameworks and SDKs, with step-by-step tutorials and advice for building pro-quality AR/VR games and apps. Keene presents his material as a cookbook of recipes to get you up and running with VR/AR development as fast and as painlessly as possible. The recipes in most chapters start by assembling the essential building blocks, which are pieced together to create something larger. You are then free to take these building blocks and turn them into your own creation. Keene also provides an extensive library of downloadable, up-to-the-minute ARCore and Daydream code to jumpstart your project. In addition, he takes you through crucial UX design principles and best practices learned from building large scale VR and AR apps at Google. Google Daydream VR Cookbook shows you how to: Install and explore the Google Daydream development tools Master basic and advanced Daydream Controller techniques Implement intuitive VR user interfaces Integrate audio, video, and realistic physics into your VR games Install and explore the ARCore SDK and development tools Learn how to build AR apps that solve real user needs Master AR game development using ARCore Optimize VR and AR game performance Whether you are a software developer, UX professional, visual designer, beginner, or you come from a different design field, this book is a great practical introduction to VR and AR. COMPUTERS,Programming,Games

Procedural Storytelling in Game Design This edited collection of chapters concerns the evolving discipline of procedural storytelling in video games. Games are an interactive medium, and this interplay between author, player and machine provides new and exciting ways to create and tell stories. In each essay, practitioners of this artform demonstrate how traditional storytelling tools such as characterization, world-building, theme, momentum and atmosphere can be adapted to full effect, using specific examples from their games. The reader will learn to construct narrative systems, write procedural dialog, and generate compelling characters with unique personalities and backstories. Key Features Introduces the differences between static/traditional game design and procedural game design Demonstrates how to solve or avoid common problems with procedural game design in a variety of concrete ways World’s finest guide for how to begin thinking about procedural design COMPUTERS,Programming,Games

Learning C# by Developing Games with Unity 2019 Understand the fundamentals of C# programming and get started with coding from ground up in an engaging and practical manner Key Features Beginner's guide to getting started with software development concepts from a macro level Leverage the power of the latest C# in solving the complex programming problems Learn to script and customize your 3D games and implement animation techniques to make them engaging Book Description Learning to program in today's technical landscape can be a daunting task, especially when faced with the sheer number of languages you have to choose from. Luckily, Learning C# with Unity 2019 removes the guesswork and starts you off on the path to becoming a confident, and competent, programmer using game development with Unity. You'll start off small by learning the building blocks of programming, from variables, methods, and conditional statements to classes and object-oriented systems. After you have the basics under your belt you'll explore the Unity interface, creating C# scripts, and translating your newfound knowledge into simple game mechanics. Throughout this journey, you'll get hands-on experience with programming best practices and macro-level topics such as manager classes and flexible application architecture. By the end of the book, you'll be familiar with intermediate C# topics like generics, delegates, and events, setting you up to take on projects of your own. What you will learn Understand programming fundamentals with practice examples in C# Explore the interface and features of Unity 2019 Learn C# programming syntax from scratch Create a game design document and prototype level Explore intermediate programming topics and best practices Implement game mechanics, interactions, and UI elements with C# Who this book is for The book caters to developers and programmers who want to get started with C# programming in a fun and engaging manner. Anyone who wants to build games and script in C# language and Unity can take this book up. No prior programming or Unity experience is required. COMPUTERS,Programming,Games

Python, PyGame, and Raspberry Pi Game Development Expand your basic knowledge of Python and use PyGame to create fast-paced video games with great graphics and sounds. This second edition shows how you can integrate electronic components with your games using the build-in general purpose input/output (GPIO) pins and some Python code to create two new games. You'll learn about object-oriented programming (OOP) as well as design patterns, such as model-view-controller (MVC) and finite-state machines (FSMs). Whether using Windows, macOS, Linux, or a Raspberry Pi, you can unleash the power of Python and PyGame to create great looking games. The book also includes complete code listings and explanations for "Bricks," "Snake," and "Invaders"—three fully working games. These allow you to get started in making your own great games and then modify them or build your own exciting titles. The concepts are further explained using games such as “Copycat,†where the player must concentrate and repeat the sequence of lights and sounds, and “Couch Quiz,†in which PyGame and electronic components create a quiz game for 2–4 players. What You’ll Learn Gain basic knowledge of Python and employ it for game development Study game projects you can use as templates, such as Bricks, Snake, and Invaders Work with user-defined functions, inheritance, composition, and aggregation Implement finite state machines Integrate your game with electronics using the GPIO pins Who This Book Is For Experienced coders or game developers new to Python, PyGame and Raspberry Pi would find this book helpful. It is also for beginners interested in getting into game development. COMPUTERS,Programming,Games

Hands-On Game Development with WebAssembly Make your WebAssembly journey fun while making a game with it Key Features Create a WebAssembly game that implements sprites, animations, physics, particle systems, and other game development fundamentals Get to grips with advanced game mechanics in WebAssembly Learn to use WebAssembly and WebGL to render to the HTML5 canvas element Book Description Within the next few years, WebAssembly will change the web as we know it. It promises a world where you can write an application for the web in any language, and compile it for native platforms as well as the web. This book is designed to introduce web developers and game developers to the world of WebAssembly by walking through the development of a retro arcade game. You will learn how to build a WebAssembly application using C++, Emscripten, JavaScript, WebGL, SDL, and HTML5. This book covers a lot of ground in both game development and web application development. When creating a game or application that targets WebAssembly, developers need to learn a plethora of skills and tools. This book is a sample platter of those tools and skills. It covers topics including Emscripten, C/C++, WebGL, OpenGL, JavaScript, HTML5, and CSS. The reader will also learn basic techniques for game development, including 2D sprite animation, particle systems, 2D camera design, sound effects, 2D game physics, user interface design, shaders, debugging, and optimization. By the end of the book, you will be able to create simple web games and web applications targeting WebAssembly. What you will learn Build web applications with near-native performance using WebAssembly Become familiar with how web applications can be used to create games using HTML5 Canvas, WebGL, and SDL Become well versed with game development concepts such as sprites, animation, particle systems, AI, physics, camera design, sound effects, and shaders Deploy C/C++ applications to the browser using WebAssembly and Emscripten Understand how Emscripten HTML shell templates, JavaScript glue code, and a WebAssembly module interact Debug and performance tune your WebAssembly application Who this book is for Web developers and game developers interested in creating applications for the web using WebAssembly. Game developers interested in deploying their games to the web Web developers interested in creating applications that are potentially orders of magnitude faster than their existing JavaScript web apps C/C++ developers interested in using their existing skills to deploy applications to the web COMPUTERS,Programming,Games

The Art of Game Design Presents over 100 sets of questions, or different lenses, for viewing a game’s design. Written by one of the world's top game designers, this book describes the deepest and most fundamental principles of game design, demonstrating how tactics used in board, card, and athletic games also work in video games. It provides practical instruction on creating world-class games that will be played again and again. New to this edition: many great examples from new VR and AR platforms as well as examples from modern games such as Uncharted 4 and The Last of Us, Free to Play games, hybrid games, transformational games, and more. COMPUTERS,Programming,Games

Learning Python by Building Games Explore modern game development and programming techniques to build games using Python and its popular libraries such as Pygame and PyOpenGL Key Features Learn game development and Python through a practical, example-driven approach Discover a variety of game development techniques to build games that gradually increase in complexity Leverage popular Python gaming libraries such as Pygame, PyOpenGL, Pymunk, and Pyglet Book Description A fun and interactive way to get started with the Python language and its libraries is by getting hands-on with game development. Learning Python by Building Games brings you the best of both worlds. The book will first introduce you to Python fundamentals, which you will then use to develop a basic game. You'll gradually explore the different Python libraries best suited for game development such as Pygame, Pyglet, and PyOpenGL. From building game characters through to using 3D animation techniques, you'll discover how to create an aesthetic game environment. In addition to this, you'll focus on game physics to give your effects a realistic feel, complete with movements and collisions. The book will also cover how you can use particle systems to simulate phenomena such as an explosion or smoke. In later chapters, you will gain insights into object-oriented programming by modifying a snake game, along with exploring GUI programming to build a user interface with Python's turtle module. By the end of this book, you'll be well-versed with Python programming concepts and popular libraries, and have the confidence to build your own games What you will learn Explore core Python concepts by understanding Python libraries Build your first 2D game using Python scripting Understand concepts such as decorators and properties in the Python ecosystem Create animations and movements by building a Flappy Bird-like game Design game objects and characters using Pygame, PyOpenGL, and Pymunk Add intelligence to your gameplay by incorporating game artificial intelligence (AI) techniques using Python Who this book is for If you are completely new to Python or game programming and want to develop your programming skills, then this book is for you. The book also acts as a refresher for those who already have experience of using Python and want to learn how to build exciting games. COMPUTERS,Programming,Games

Actionable Gamification Learn all about implementing a good gamification design into your products, workplace, and lifestyle Key Features Explore what makes a game fun and engaging Gain insight into the Octalysis Framework and its applications Discover the potential of the Core Drives of gamification through real-world scenarios Book Description Effective gamification is a combination of game design, game dynamics, user experience, and ROI-driving business implementations. This book explores the interplay between these disciplines and captures the core principles that contribute to a good gamification design. The book starts with an overview of the Octalysis Framework and the 8 Core Drives that can be used to build strategies around the various systems that make games engaging. As the book progresses, each chapter delves deep into a Core Drive, explaining its design and how it should be used. Finally, to apply all the concepts and techniques that you learn throughout, the book contains a brief showcase of using the Octalysis Framework to design a project experience from scratch. After reading this book, you'll have the knowledge and skills to enable the widespread adoption of good gamification and human-focused design in all types of industries. What you will learn Discover ways to use gamification techniques in real-world situations Design fun, engaging, and rewarding experiences with Octalysis Understand what gamification means and how to categorize it Leverage the power of different Core Drives in your applications Explore how Left Brain and Right Brain Core Drives differ in motivation and design methodologies Examine the fascinating intricacies of White Hat and Black Hat Core Drives Who this book is for Anyone who wants to implement gamification principles and techniques into their products, workplace, and lifestyle will find this book useful. COMPUTERS,Programming,Games

Virtual Reality with VRTK4 Virtual reality is quickly becoming the next medium to communicate your ideas. Once siloed in make-believe world of science fiction, virtual reality can now touch any aspect of your life. This book shows you how to create original virtual reality content using the Unity game engine and the Virtual Reality Tool Kit. By the end of the book you'll be creating your own virtual reality experience using the fundamental building blocks within. You'll start by reviewing spatial computing, an emerging field that encompasses self-driving cars to space exploration. You'll also create your own virtual reality environments for use on headsets such as those from Oculus and HTC. Using the Unity3D game engine and the Virtual Reality Toolkit on a computer or laptop, you will walk through the fundamentals of virtual reality with as little code as possible. That is the beauty of Unity and the Virtual Reality Toolkit. You will discover how to use buttons in a virtual space, gaze-tracking for user input, and physics for enabling interaction between a human and a virtual space. From game design to education to healthcare to human resources, virtual reality offers new and creative ways to engage users, students, patients, customers, and more. Not a coding book, Virtual Reality with VRTK4 shows that you don't need to be a computer or graphics whiz to begin creating your own virtual reality experiences. What You'll Learn Grasp Virtual Reality Toolkit and its interaction with Unity3D Explore the fundamental science of virtual reality Review the inner workings of Unity3D and its integration with VRTK Understand the big picture of C# coding in Unity3D Incorporate head and hand movement into virtual experiences Who This Book Is For Creative professionals or students who are familiar with computer design programs and want to begin prototyping their own original virtual reality work as quickly as possible. COMPUTERS,Programming,Games

Modeling and Animation Using Blender Discover the 3D-modeling and animation power of Blender 3D. This book starts with a brief introduction to Blender 3D including installation and the user interface. The following two chapters then introduce you to the upgraded tools in Blender 2.80 for 3D modeling, texturing, shading, and animation. The last chapter discusses the Blender game engine and all its core features. Along the way you’ll see why Blender 3D has proved its competency in UV unwrapping, texturing, raster graphic editing, rigging, sculpting, animating, motion graphics, and video editing through the years. Modeling and Animation Using Blender gives a thorough tour of Blender Eevee, covering its new features and how to make best use of them. After reading this book you will have the confidence to choose Blender for your next project. What You Will Learn Master the features of Blender Eevee Work with modeling, animation, and much more using the updated software Understand important concepts such as physics and particles Who This Book Is For Art enthusiasts and professionals who want to learn Blender 3D. Blender 3D professionals who want to learn about the latest version would find the book useful. COMPUTERS,Programming,Games

Elements of Game Design An introduction to the basic concepts of game design, focusing on techniques used in commercial game production. This textbook by a well-known game designer introduces the basics of game design, covering tools and techniques used by practitioners in commercial game production. It presents a model for analyzing game design in terms of three interconnected levels--mechanics and systems, gameplay, and player experience--and explains how novice game designers can use these three levels as a framework to guide their design process. The text is notable for emphasizing models and vocabulary used in industry practice and focusing on the design of games as dynamic systems of gameplay. COMPUTERS,Programming,Games

Beginning PBR Texturing Delve into the concepts of physically based rendering (PBR) using Allegorithmic’s Substance Painter. This book covers the integration of PBR textures with various 3D modeling and rendering packages as well as with the Unreal Engine 4 game engine. Beginning PBR Texturing covers all aspects of the software and guides you in implementing its incredible possibilities, including using materials, masks, and baking. Integration with both internal and popular external rendering engines is covered. This book teaches you the skills you need to use the texturing tool that is recognized by studios worldwide. You will know tips and tricks to implement the pipeline and speed up your workflow. What You Will Learn Know the fundamentals of PBR-based texturing from the ground up Create production-ready textured models from scratch Integrate PBR textures with standard 3D modeling and rendering applications Create portfolio-ready renders using offline renderers Who This Book Is For Beginners in the fields of 3D animation, computer graphics, and game technology COMPUTERS,Programming,Games

For the Love of Cybernetics For the Love of Cybernetics: Personal Narratives by Cyberneticians is a collection of personal accounts that offer unique insights into cybernetics via the personal journeys of nine individuals. For the authors in this collection, cybernetics is not their "area of interest"–it is how they think about what they do, and it is their practice. Ray Ison, Bruce Clarke, Frank Galuzska, Paul Pangaro, Klaus Krippendorff, Peter Tuddenham, Lucas Pawlik, Bernard Scott, and Jocelyn Chapman differ in their lineage, emphasis, and engagement with cybernetics. What they have in common is that they share the belief that cybernetics is not a tool to apply here and there, but a unifying way of seeing the world that transforms how we behave, thus increasing possibilities for positive systemic change. This book was originally published as a special issue of the journal, World Futures. COMPUTERS,Programming,Games

Handbook of Energy-Aware and Green Computing, Volume 1 Implementing energy-efficient CPUs and peripherals as well as reducing resource consumption have become emerging trends in computing. As computers increase in speed and power, their energy issues become more and more prevalent. The need to develop and promote environmentally friendly computer technologies and systems has also come to the forefront COMPUTERS,Programming,Games

Nature-Inspired Optimization Algorithms Nature-Inspired Optimization Algorithms, a comprehensive work on the most popular optimization algorithms based on nature, starts with an overview of optimization going from the classical to the latest swarm intelligence algorithm. Nature has a rich abundance of flora and fauna that inspired the development of optimization techniques, providing us with simple solutions to complex problems in an effective and adaptive manner. The study of the intelligent survival strategies of animals, birds, and insects in a hostile and ever-changing environment has led to the development of techniques emulating their behavior. This book is a lucid description of fifteen important existing optimization algorithms based on swarm intelligence and superior in performance. It is a valuable resource for engineers, researchers, faculty, and students who are devising optimum solutions to any type of problem ranging from computer science to economics and covering diverse areas that require maximizing output and minimizing resources. This is the crux of all optimization algorithms. Features: Detailed description of the algorithms along with pseudocode and flowchart Easy translation to program code that is also readily available in Mathworks website for some of the algorithms Simple examples demonstrating the optimization strategies are provided to enhance understanding Standard applications and benchmark datasets for testing and validating the algorithms are included This book is a reference for undergraduate and post-graduate students. It will be useful to faculty members teaching optimization. It is also a comprehensive guide for researchers who are looking for optimizing resources in attaining the best solution to a problem. The nature-inspired optimization algorithms are unconventional, and this makes them more efficient than their traditional counterparts. COMPUTERS,Programming,Games

Multilingual Text Analysis Text analytics (TA) covers a very wide research area. Its overarching goal is to discover and present knowledge — facts, rules, and relationships — that is otherwise hidden in the textual content. The authors of this book guide us in a quest to attain this knowledge automatically, by applying various machine learning techniques.This book describes recent development in multilingual text analysis. It covers several specific examples of practical TA applications, including their problem statements, theoretical background, and implementation of the proposed solution. The reader can see which preprocessing techniques and text representation models were used, how the evaluation process was designed and implemented, and how these approaches can be adapted to multilingual domains. COMPUTERS,Programming,Games

Game Programming with Unity and C# ​Designed for beginners with no knowledge or experience in game development or programming, this book teaches the essentials of the Unity game engine, the C# programming language, and the art of object-oriented programming. New concepts are not only explained, but thoroughly demonstrated. Starting with an introduction to Unity, you'll learn about scenes, GameObjects, prefabs, components, and how to use the various windows to interact with the engine. You'll then dive into the fundamentals of programming by reviewing syntax rules, formatting, methods, variables, objects and types, classes, and inheritance, all while getting your hands dirty writing and testing code yourself. Later, the book explains how to expose script data in the Inspector and the basics of Unity’s serialization system. This carefully crafted work guides you through the planning and development of bare bones, simple game projects designed to exercise programming concepts while keeping less relevant interruptions out of the way, allowing you to focus on the implementation of game mechanics first and foremost. Through these example projects, the book teaches input handling, rigidbodies, colliders, cameras, prefab instantiation, scene loading, user interface design and coding, and more. By the end, you'll have built a solid foundation in programming that will pave your way forward in understanding core C# syntax and fundamentals of object-oriented programming—not just what to type but why it's typed and what it’s really doing. Game Programming with Unity and C# will send you on your way to becoming comfortable with the Unity game engine and its documentation and how to independently seek further information on yet-untouched concepts and challenges. What You'll Learn Understand the fundamentals of object-oriented computer programming, including topics specifically relevant for games. Leverage beginner-to-intermediate-level skills of the C# programming language and its syntax. Review all major component types of the Unity game engine: colliders and rigidbodies, lights, cameras, scripts, etc. Use essential knowledge of the Unity game engine and its features to balance gameplay mechanics for making interesting experiences. Who This Book Is For Beginners who have no prior experience in programming or game development who would like to learn with a solid foundation that prepares them to further develop their skills. COMPUTERS,Programming,Games

Moving from Unity to Godot Are you a Unity developer looking to switch to the Godot engine quickly? If so, this no-nonsense book is your guide to mastering the most popular open-source game engine. Godot is a completely free game engine for creating high-quality 2D and 3D games that can be launched on multiple platforms. You'll see how to transition seamlessly from Unity to Godot, getting up and running quickly and effectively, using practical case studies. In addition to building functional worlds from meshes and physical interactions, you'll work with reusable assets, such as textures. The book then moves on to lighting and rendering 2D and 3D scenes with baked and real-time lighting. You'll also work with navigation and path-finding for NPCs, and see how to create save-game states with JSON. With Moving from Unity to Godot you’ll be ready to create amazing 2D and 3D games that will supercharge your business. What You Will Learn Explore the similarities and differences between Unity and Godot Maximize the benefits from Unity and Godot Create believable game world and characters with Godot Master the unique aspects of C# coding in Godot Who This Book is For Developers familiar with Unity who want to master another game engine, such as Godot. COMPUTERS,Programming,Games

Hands-On C++ Game Animation Programming Learn animation programming from first principles and implement modern animation techniques that can be integrated into any game development workflow Key Features Build a functional and production-ready modern animation system with complete features using C++ Learn basic, advanced, and skinned animation programming with this step-by-step guide Discover the math required to implement cutting edge animation techniques such as inverse kinematics and dual quaternions Book Description Animation is one of the most important parts of any game. Modern animation systems work directly with track-driven animation and provide support for advanced techniques such as inverse kinematics (IK), blend trees, and dual quaternion skinning. This book will walk you through everything you need to get an optimized, production-ready animation system up and running, and contains all the code required to build the animation system. You'll start by learning the basic principles, and then delve into the core topics of animation programming by building a curve-based skinned animation system. You'll implement different skinning techniques and explore advanced animation topics such as IK, animation blending, dual quaternion skinning, and crowd rendering. The animation system you will build following this book can be easily integrated into your next game development project. The book is intended to be read from start to finish, although each chapter is self-contained and can be read independently as well. By the end of this book, you'll have implemented a modern animation system and got to grips with optimization concepts and advanced animation techniques. What you will learn Get the hang of 3D vectors, matrices, and transforms, and their use in game development Discover various techniques to smoothly blend animations Get to grips with GLTF file format and its design decisions and data structures Design an animation system by using animation tracks and implementing skinning Optimize various aspects of animation systems such as skinned meshes, clip sampling, and pose palettes Implement the IK technique for your game characters using CCD and FABRIK solvers Understand dual quaternion skinning and how to render large instanced crowds Who this book is for This book is for professional, independent, and hobbyist developers interested in building a robust animation system from the ground up. Some knowledge of the C++ programming language will be helpful. COMPUTERS,Programming,Games

Recent Advances in Computer Based Systems, Processes and Applications This was the first conference organized by the school of Computer Science Engineering in VIT-AP University campus withthe cumulative efforts of all the faculty members. The proceedings discusses recent advancements and novel ideas in areas of interest. It covers topics such as advances in computer based systems, processes and applications COMPUTERS,Programming,Games

Cooperative Gaming Description Cooperative Gaming provides context and practical advice regarding diversity in the games industry. The book begins with a deep dive into research literature and the history of diversity in the games industry to provide context around what diversity is and why it is a topic worth considering. The book looks at the different facets of diversity and games, exploring the issues and solutions within game development, studio management, event planning, and more. It provides people with practical advice about being a marginalized person in the games industry and how to be heard, how studios can support inclusive practices, and events can actively become more accessible to a diverse audience. Key Features • Explores the history of diversity in games • Provides important information around what it is like to be a marginalized person in the industry • Gives practical steps to improve the inclusivity of the industry that are designed to aid in contextualizing and upskilling new developers Author Bios Alayna Cole is the managing director of Queerly Represent Me, a not-for-profit championing queer representation in games. Alayna is also a producer at Sledgehammer Games, co-chair of the IGDA LGBTQ+ special interest group, and an award-winning games journalist and game developer. She was featured on the 2016 and 2017 Develop Pacific 30 Under 30 lists and the 2017 and 2019 Develop Pacific Women in Games lists, and she has received several other accolades in the industry. Jessica Zammit started writing in 2013 for Start Select Media, and for the next five years she followed her interest in writing about representations of mental health, diversity, and particularly, sexuality in video games. Jessica has been speaking about diversity in games at conventions such as PAX Australia since 2016 and has been featured on several other discussions in and around the topic of representation in games and games criticism. Along with her co-author, she is co-chair of the IGDA LGBTQ+ special interest group, and she was featured on the 2018 Develop Pacific 30 Under 30 and Women in Games lists. COMPUTERS,Programming,Games

Swarm Intelligence for Cloud Computing Swarm Intelligence in Cloud Computing is an invaluable treatise for researchers involved in delivering intelligent optimized solutions for reliable deployment, infrastructural stability, and security issues of cloud-based resources. Starting with a bird’s eye view on the prevalent state-of-the-art techniques, this book enriches the readers with the knowledge of evolving swarm intelligent optimized techniques for addressing different cloud computing issues including task scheduling, virtual machine allocation, load balancing and optimization, deadline handling, power-aware profiling, fault resilience, cost-effective design, and energy efficiency. The book offers comprehensive coverage of the most essential topics, including: Role of swarm intelligence on cloud computing services Cloud resource sharing strategies Cloud service provider selection Dynamic task and resource scheduling Data center resource management. Indrajit Pan is an Associate Professor in Information Technology of RCC Institute of Information Technology, India. He received his PhD from Indian Institute of Engineering Science and Technology, Shibpur, India. With an academic experience of 14 years, he has published around 40 research publications in different international journals, edited books, and conference proceedings. Mohamed Abd Elaziz is a Lecturer in the Mathematical Department of Zagazig University, Egypt. He received his PhD from the same university. He is the author of more than 100 articles. His research interests include machine learning, signal processing, image processing, cloud computing, and evolutionary algorithms. Siddhartha Bhattacharyya is a Professor in Computer Science and Engineering of Christ University, Bangalore. He received his PhD from Jadavpur University, India. He has published more than 230 research publications in international journals and conference proceedings in his 20 years of academic experience. COMPUTERS,Programming,Games

Beginning Unity Android Game Development Master the art of programming games for Android using the Unity3D game engine. This book will help you understand basic concepts of game development in Unity. By the end of Beginning Unity Android Game Development, you will have the knowledge to confidently build an Android game. The book starts by explaining simple programming concepts to make beginners comfortable with the jargon. You will then learn to navigate around the Unity interface and use basic tools (hand, move, rotate, scale, and rect). You will also be acquainted with the creation of basic 3D objects in the game while understanding the purpose of several of Unity’s windows. In the last chapters, you will learn to create a simple game for Android using the concepts studied in the previous chapters. Scripts will be written to handle the behaviors of the player and enemies as well as to handle other aspects of the game. The author shares tips along the way to help improve in-game performance, such as switching to the universal rendering pipeline when targeting mobile platforms. At the end of the book, you will have a solid knowledge in making basic Android games that can be upgraded later to make more complex games. What You Will Learn Explore basic Unity and C# programming concepts and scripting for Android games Navigate around the Unity interface and use its basic tools Make the most of popular components and features of Unity Write an Android game with optimizations Who This Book Is For Absolute beginners learning to program games for the Android platform using Unity3D. Basic knowledge of programming would be beneficial for the reader but is not required. COMPUTERS,Programming,Games

Rules of Play An impassioned look at games and game design that offers the most ambitious framework for understanding them to date. As pop culture, games are as important as film or television—but game design has yet to develop a theoretical framework or critical vocabulary. In Rules of Play Katie Salen and Eric Zimmerman present a much-needed primer for this emerging field. They offer a unified model for looking at all kinds of games, from board games and sports to computer and video games. As active participants in game culture, the authors have written Rules of Play as a catalyst for innovation, filled with new concepts, strategies, and methodologies for creating and understanding games. Building an aesthetics of interactive systems, Salen and Zimmerman define core concepts like "play," "design," and "interactivity." They look at games through a series of eighteen "game design schemas," or conceptual frameworks, including games as systems of emergence and information, as contexts for social play, as a storytelling medium, and as sites of cultural resistance. Written for game scholars, game developers, and interactive designers, Rules of Play is a textbook, reference book, and theoretical guide. It is the first comprehensive attempt to establish a solid theoretical framework for the emerging discipline of game design. COMPUTERS,Programming,Games

Introduction to IoT with Machine Learning and Image Processing using Raspberry Pi Machine Learning a branch of Artificial Intelligence is influencing the society, industry and academia at large. The adaptability of Python programming language to Machine Learning has increased its popularity further. Another technology on the horizon is Internet of Things (IoT). The present book tries to address IoT, Python and Machine Learning along with a small introduction to Image Processing. If you are a novice programmer or have just started exploring IoT or Machine Learning with Python, then this book is for you. Features: Raspberry Pi as IoT is described along with the procedure for installation and configuration. A simple introduction to Python Programming Language along with its popular library packages like NumPy, Pandas, SciPy and Matplotlib are dealt in an exhaustive manner along with relevant examples. Machine Learning along with Python Scikit-Learn library is explained to audience with an emphasis on supervised learning and classification. Image processing on IoT is introduced to the audience who love to apply Machine Learning algorithms to Images The book follows hands-on approach and provide a huge collection of Python programs. COMPUTERS,Programming,Games

Exercises in Programming Style Using a simple computational task (term frequency) to illustrate different programming styles, Exercises in Programming Style helps readers understand the various ways of writing programs and designing systems. It is designed to be used in conjunction with code provided on an online repository. The book complements and explains the raw code in a way that is accessible to anyone who regularly practices the art of programming. The first edition was honored as an ACM Notable Book and praised as "The best programming book of the decade." This new edition will retain the same presentation, but the entire book will be upgraded to Python 3, and a new section will be added on neural network styles. The book contains 33 different styles for writing the term frequency task. The styles are grouped into nine categories: historical, basic, function composition, objects and object interactions, reflection and metaprogramming, adversity, data-centric, concurrency, and interactivity. The author verbalizes the constraints in each style and explains the example programs. Each chapter first presents the constraints of the style, next shows an example program, and then gives a detailed explanation of the code. Most chapters also have sections focusing on the use of the style in systems design as well as sections describing the historical context in which the programming style emerged. COMPUTERS,Programming,Games

Exploring Roguelike Games Since 1980, in-the-know computer gamers have been enthralled by the unpredictable, random, and incredibly deep gameplay of Rogue and those games inspired by it, known to fans as "roguelikes." For decades, this venerable genre was off the radar of most players and developers for a variety of reasons: deceptively simple graphics (often just text characters), high difficulty, and their demand that a player brings more of themselves to the game than your typical AAA title asks. This book covers many of the most prominent titles and explains in great detail what makes them interesting, the ways to get started playing them, the history of the genre, and more. It includes interviews, playthroughs, and hundreds of screenshots. It is a labor of love: if even a fraction of the author’s enthusiasm for these games gets through these pages to you, then you will enjoy it a great deal. Key Features: Playing tips and strategy for newcomers to the genre Core roguelikes Rogue, Angband, NetHack, Dungeon Crawl Stone Soup, ADOM, and Brogue The "lost roguelikes" Super Rogue and XRogue, and the early RPG dnd for PLATO systems The Japanese console roguelikes Taloon’s Mystery Dungeon and Shiren the Wanderer Lesser-known but extremely interesting games like Larn, DoomRL, HyperRogue, Incursion, and Dungeon Hack "Rogue-ish" games that blur the edges of the genre, including Spelunky, HyperRogue, ToeJam & Earl, Defense of the Oasis, Out There, and Zelda Randomizer Interviews with such developers as Keith Burgun (100 Rogues and Auro), Rodain Joubert (Desktop Dungeons), Josh Ge (Cogmind), Dr. Thomas Biskup (ADOM), and Robin Bandy (devnull public NetHack tournament) An interview regarding Strange Adventures in Infinite Space Design issues of interest to developers and enthusiasts Author Bio: John Harris has bumped around the Internet for more than 20 years. In addition to writing the columns @Play and Pixel Journeys for GameSetWatch and developer interviews for Gamasutra, he has spoken at Roguelike Celebration. John Harris has a MA in English Literature from Georgia Southern University. COMPUTERS,Programming,Games

Agile Game Development The definitive guide to more effective and personally fulfilling game development with Agile Methods—now revamped to reflect ten more years of experience and improvements Game development is in crisis—facing bloated budgets, impossible schedules, unmanageable complexity, and death-march overtime. It’s no wonder so many development studios are struggling to survive. Fortunately, there is a solution. Agile and Lean methods have revolutionized development in the game development industry. In Agile Game Development, long-time game developer and consultant Clinton Keith shows exactly how these methods have been successfully applied to the unique challenges of modern game development. Clint has spent more than 25 years developing games and training and coaching hundreds of game development teams. Drawing on this unparalleled expertise, he shows how teams can use the practices of Scrum and Kanban, customized to game development, to deliver games more efficiently, rapidly, and cost-effectively; craft games that offer more entertainment value; and make life more fulfilling for development teams at the same time. Contains several new chapters on live games, leadership, and coaching, including an all-new section on Agile for large teams of up to 1000 developers Updates to all chapters to reflect a decade of experience with more than 200 studios Now covering Kanban and other Agile approaches alongside Scrum Understanding Agile goals, roles, and practices in the context of game development Discovering how Agile benefits every specialty in game development from art to QA Communicating and planning your game’s vision, features, and progress Game developers and leaders are recognizing the modern challenges of gaming. Game development organizations need a far better way to work. Agile Game Development gives them that—and brings the profitability, creativity, and fun back to game development. COMPUTERS,Programming,Games

C++ Best-selling genius Herb Schildt covers everything from keywords, syntax, and libraries, to advanced features such as overloading, inheritance, virtual functions, namespaces, templates, and RTTI—plus, a complete description of the Standard Template Library (STL). COMPUTERS,Programming,General

Computer Organization and Design This best selling text on computer organization has been thoroughly updated to reflect the newest technologies. Examples highlight the latest processor designs, benchmarking standards, languages and tools. As with previous editions, a MIPs processor is the core used to present the fundamentals of hardware technologies at work in a computer system. The book presents an entire MIPS instruction set—instruction by instruction—the fundamentals of assembly language, computer arithmetic, pipelining, memory hierarchies and I/O. A new aspect of the third edition is the explicit connection between program performance and CPU performance. The authors show how hardware and software components--such as the specific algorithm, programming language, compiler, ISA and processor implementation--impact program performance. Throughout the book a new feature focusing on program performance describes how to search for bottlenecks and improve performance in various parts of the system. The book digs deeper into the hardware/software interface, presenting a complete view of the function of the programming language and compiler--crucial for understanding computer organization. A CD provides a toolkit of simulators and compilers along with tutorials for using them. For instructor resources click on the grey "companion site" button found on the right side of this page. This new edition represents a major revision. New to this edition: * Entire Text has been updated to reflect new technology* 70% new exercises.* Includes a CD loaded with software, projects and exercises to support courses using a number of tools * A new interior design presents defined terms in the margin for quick reference * A new feature, "Understanding Program Performance" focuses on performance from the programmer's perspective * Two sets of exercises and solutions, "For More Practice" and "In More Depth," are included on the CD * "Check Yourself" questions help students check their understanding of major concepts * "Computers In the Real World" feature illustrates the diversity of uses for information technology *More detail below... COMPUTERS,Programming,General

Real World Haskell This easy-to-use, fast-moving tutorial introduces you to functional programming with Haskell. You'll learn how to use Haskell in a variety of practical ways, from short scripts to large and demanding applications. Real World Haskell takes you through the basics of functional programming at a brisk pace, and then helps you increase your understanding of Haskell in real-world issues like I/O, performance, dealing with data, concurrency, and more as you move through each chapter. COMPUTERS,Programming,General

The Productive Programmer Anyone who develops software for a living needs a proven way to produce it better, faster, and cheaper. The Productive Programmer offers critical timesaving and productivity tools that you can adopt right away, no matter what platform you use. Master developer Neal Ford not only offers advice on the mechanics of productivity-how to work smarter, spurn interruptions, get the most out your computer, and avoid repetition-he also details valuable practices that will help you elude common traps, improve your code, and become more valuable to your team. You'll learn to: Write the test before you write the code Manage the lifecycle of your objects fastidiously Build only what you need now, not what you might need later Apply ancient philosophies to software development Question authority, rather than blindly adhere to standards Make hard things easier and impossible things possible through meta-programming Be sure all code within a method is at the same level of abstraction Pick the right editor and assemble the best tools for the job This isn't theory, but the fruits of Ford's real-world experience as an Application Architect at the global IT consultancy ThoughtWorks. Whether you're a beginner or a pro with years of experience, you'll improve your work and your career with the simple and straightforward principles in The Productive Programmer. COMPUTERS,Programming,General

Managing Projects with GNU Make The utility simply known as make is one of the most enduring features of both Unix and other operating systems. First invented in the 1970s, make still turns up to this day as the central engine in most programming projects; it even builds the Linux kernel. In the third edition of the classic Managing Projects with GNU make, readers will learn why this utility continues to hold its top position in project build software, despite many younger competitors.The premise behind make is simple: after you change source files and want to rebuild your program or other output files, make checks timestamps to see what has changed and rebuilds just what you need, without wasting time rebuilding other files. But on top of this simple principle, make layers a rich collection of options that lets you manipulate multiple directories, build different versions of programs for different platforms, and customize your builds in other ways.This edition focuses on the GNU version of make, which has deservedly become the industry standard. GNU make contains powerful extensions that are explored in this book. It is also popular because it is free software and provides a version for almost every platform, including a version for Microsoft Windows as part of the free Cygwin project. Managing Projects with GNU make, 3rd Edition provides guidelines on meeting the needs of large, modern projects. Also added are a number of interesting advanced topics such as portability, parallelism, and use with Java.Robert Mecklenburg, author of the third edition, has used make for decades with a variety of platforms and languages. In this book he zealously lays forth how to get your builds to be as efficient as possible, reduce maintenance, avoid errors, and thoroughly understand what make is doing. Chapters on C++ and Java provide makefile entries optimized for projects in those languages. The author even includes a discussion of the makefile used to build the book. COMPUTERS,Programming,General

Coders at Work Peter Seibel interviews 15 of the most interesting computer programmers alive today in Coders at Work, offering a companion volume to Apress’s highly acclaimed best-seller Founders at Work by Jessica Livingston. As the words “at work” suggest, Peter Seibel focuses on how his interviewees tackle the day-to-day work of programming, while revealing much more, like how they became great programmers, how they recognize programming talent in others, and what kinds of problems they find most interesting. Hundreds of people have suggested names of programmers to interview on the Coders at Work web site: www.codersatwork.com. The complete list was 284 names. Having digested everyone’s feedback, we selected 15 folks who’ve been kind enough to agree to be interviewed: Frances Allen: Pioneer in optimizing compilers, first woman to win the Turing Award (2006) and first female IBM fellow Joe Armstrong: Inventor of Erlang Joshua Bloch: Author of the Java collections framework, now at Google Bernie Cosell: One of the main software guys behind the original ARPANET IMPs and a master debugger Douglas Crockford: JSON founder, JavaScript architect at Yahoo! L. Peter Deutsch: Author of Ghostscript, implementer of Smalltalk-80 at Xerox PARC and Lisp 1.5 on PDP-1 Brendan Eich: Inventor of JavaScript, CTO of the Mozilla Corporation Brad Fitzpatrick: Writer of LiveJournal, OpenID, memcached, and Perlbal Dan Ingalls: Smalltalk implementor and designer Simon Peyton Jones: Coinventor of Haskell and lead designer of Glasgow Haskell Compiler Donald Knuth: Author of The Art of Computer Programming and creator of TeX Peter Norvig: Director of Research at Google and author of the standard text on AI Guy Steele: Coinventor of Scheme and part of the Common Lisp Gang of Five, currently working on Fortress Ken Thompson: Inventor of UNIX Jamie Zawinski: Author of XEmacs and early Netscape/Mozilla hacker COMPUTERS,Programming,General

97 Things Every Programmer Should Know Tap into the wisdom of experts to learn what every programmer should know, no matter what language you use. With the 97 short and extremely useful tips for programmers in this book, you'll expand your skills by adopting new approaches to old problems, learning appropriate best practices, and honing your craft through sound advice. With contributions from some of the most experienced and respected practitioners in the industry--including Michael Feathers, Pete Goodliffe, Diomidis Spinellis, Cay Horstmann, Verity Stob, and many more--this book contains practical knowledge and principles that you can apply to all kinds of projects. A few of the 97 things you should know: "Code in the Language of the Domain" by Dan North "Write Tests for People" by Gerard Meszaros "Convenience Is Not an -ility" by Gregor Hohpe "Know Your IDE" by Heinz Kabutz "A Message to the Future" by Linda Rising "The Boy Scout Rule" by Robert C. Martin (Uncle Bob) "Beware the Share" by Udi Dahan COMPUTERS,Programming,General

Cocoa in a Nutshell Cocoa® is more than just a collection of classes, and is certainly more than a simple framework. Cocoa is a complete API set, class library, framework, and development environment for building applications and tools to run on Mac OS® X. With over 240 classes, Cocoa is divided into two essential frameworks: Foundation and Application Kit. Above all else, Cocoa is a toolkit for creating Mac OS X application interfaces, and it provides access to all of the standard Aqua® interface components such as menus, toolbars, windows, buttons, to name a few. Cocoa in a Nutshell begins with a complete overview of Cocoa's object classes. It provides developers who may be experienced with other application toolkits the grounding they'll need to start developing Cocoa applications. Common programming tasks are described, and many chapters focus on the larger patterns in the frameworks so developers can understand the larger relationships between the classes in Cocoa, which is essential to using the framework effectively. Cocoa in a Nutshell is divided into two parts, with the first part providing a series of overview chapters that describe specific features of the Cocoa frameworks. Information you'll find in Part I includes: An overview of the Objective-C language Coverage of the Foundation and Application Kit frameworks Overviews of Cocoa's drawing and text handling classes Network services such as hosts, Rendezvous URL services, sockets, and file handling Distributed notifications and distributed objects for interapplication communication Extending Cocoa applications with other frameworks, including the AddressBook, DiscRecording, and Messaging frameworks The second half of the book is a detailed quick reference to Cocoa's Foundation and Application Kit (AppKit) classes. A complement to Apple's documentation, Cocoa in a Nutshell is the only reference to the classes, functions, types, constants, protocols, and methods that make up Cocoa's Foundation and Application Kit frameworks, based on the Jaguar release (Mac OS X 10.2). Peer-reviewed and approved by Apple's engineers to be part of the Apple Developer Connection (ADC) Series, Cocoa in a Nutshell is the book developers will want close at hand as they work. It's the desktop quick reference they can keep by their side to look something up quickly without leaving their work. Cocoa in a Nutshell is the book developers will want close at hand as they work. It's the desktop quick reference they can keep by their side to look something up quickly without leaving their work. COMPUTERS,Programming,General

Regular Expression Pocket Reference This handy little book offers programmers a complete overview of the syntax and semantics of regular expressions that are at the heart of every text-processing application. Ideal as a quick reference, Regular Expression Pocket Reference covers the regular expression APIs for Perl 5.8, Ruby (including some upcoming 1.9 features), Java, PHP, .NET and C#, Python, vi, JavaScript, and the PCRE regular expression libraries. This concise and easy-to-use reference puts a very powerful tool for manipulating text and data right at your fingertips. Composed of a mixture of symbols and text, regular expressions can be an outlet for creativity, for brilliant programming, and for the elegant solution. Regular Expression Pocket Reference offers an introduction to regular expressions, pattern matching, metacharacters, modes and constructs, and then provides separate sections for each of the language APIs, with complete regex listings including: Supported metacharacters for each language API Regular expression classes and interfaces for Ruby, Java, .NET, and C# Regular expression operators for Perl 5.8 Regular expression module objects and functions for Python Pattern-matching functions for PHP and the vi editor Pattern-matching methods and objects for JavaScript Unicode Support for each of the languages With plenty of examples and other resources, Regular Expression Pocket Reference summarizes the complex rules for performing this critical text-processing function, and presents this often-confusing topic in a friendly and well-organized format. This guide makes an ideal on-the-job companion. COMPUTERS,Programming,General

An Introduction to Parallel Programming An Introduction to Parallel Programming is the first undergraduate text to directly address compiling and running parallel programs on the new multi-core and cluster architecture. It explains how to design, debug, and evaluate the performance of distributed and shared-memory programs. The author Peter Pacheco uses a tutorial approach to show students how to develop effective parallel programs with MPI, Pthreads, and OpenMP, starting with small programming examples and building progressively to more challenging ones. The text is written for students in undergraduate parallel programming or parallel computing courses designed for the computer science major or as a service course to other departments; professionals with no background in parallel computing. Takes a tutorial approach, starting with small programming examples and building progressively to more challenging examples Focuses on designing, debugging and evaluating the performance of distributed and shared-memory programs Explains how to develop parallel programs using MPI, Pthreads, and OpenMP programming models COMPUTERS,Programming,General

vi and Vim Editors Pocket Reference Many Unix, Linux, and Mac OS X geeks enjoy using the powerful, platform-agnostic text editors vi and Vim, but there are far too many commands for anyone to remember. Author Arnold Robbins has chosen the most valuable commands for vi, Vim, and vi's main clones—vile, elvis, and nvi—and packed them into this easy-to-browse pocket reference. You'll find commands for all kinds of editing tasks, such as programming, modifying system files, and writing and marking up articles. This second edition includes: Command-line options vi commands and set options Input mode shortcuts Substitution and regular expressions ex commands and options Initialization and recovery Enhanced tags and tag stacks A greatly expanded section on Vim commands and options Additional features in vile, elvis, and nvi Internet resources for vi A full index COMPUTERS,Programming,General

Pragmatic Programmer, The What others in the trenches say about The Pragmatic Programmer... “The cool thing about this book is that it’s great for keeping the programming process fresh. The book helps you to continue to grow and clearly comes from people who have been there.†— Kent Beck, author of Extreme Programming Explained: Embrace Change “I found this book to be a great mix of solid advice and wonderful analogies!†— Martin Fowler, author of Refactoring and UML Distilled “I would buy a copy, read it twice, then tell all my colleagues to run out and grab a copy. This is a book I would never loan because I would worry about it being lost.†— Kevin Ruland, Management Science, MSG-Logistics “The wisdom and practical experience of the authors is obvious. The topics presented are relevant and useful.... By far its greatest strength for me has been the outstanding analogies—tracer bullets, broken windows, and the fabulous helicopter-based explanation of the need for orthogonality, especially in a crisis situation. I have little doubt that this book will eventually become an excellent source of useful information for journeymen programmers and expert mentors alike.†— John Lakos, author of Large-Scale C++ Software Design “This is the sort of book I will buy a dozen copies of when it comes out so I can give it to my clients.†— Eric Vought, Software Engineer “Most modern books on software development fail to cover the basics of what makes a great software developer, instead spending their time on syntax or technology where in reality the greatest leverage possible for any software team is in having talented developers who really know their craft well. An excellent book.†— Pete McBreen, Independent Consultant “Since reading this book, I have implemented many of the practical suggestions and tips it contains. Across the board, they have saved my company time and money while helping me get my job done quicker! This should be a desktop reference for everyone who works with code for a living.†— Jared Richardson, Senior Software Developer, iRenaissance, Inc. “I would like to see this issued to every new employee at my company....†— Chris Cleeland, Senior Software Engineer, Object Computing, Inc. “If I’m putting together a project, it’s the authors of this book that I want. . . . And failing that I’d settle for people who’ve read their book.†— Ward Cunningham Straight from the programming trenches, The Pragmatic Programmer cuts through the increasing specialization and technicalities of modern software development to examine the core process--taking a requirement and producing working, maintainable code that delights its users. It covers topics ranging from personal responsibility and career development to architectural techniques for keeping your code flexible and easy to adapt and reuse. Read this book, and you'll learn how to Fight software rot; Avoid the trap of duplicating knowledge; Write flexible, dynamic, and adaptable code; Avoid programming by coincidence; Bullet-proof your code with contracts, assertions, and exceptions; Capture real requirements; Test ruthlessly and effectively; Delight your users; Build teams of pragmatic programmers; and Make your developments more precise with automation. Written as a series of self-contained sections and filled with entertaining anecdotes, thoughtful examples, and interesting analogies, The Pragmatic Programmer illustrates the best practices and major pitfalls of many different aspects of software development. Whether you're a new coder, an experienced programmer, or a manager responsible for software projects, use these lessons daily, and you'll quickly see improvements in personal productivity, accuracy, and job satisfaction. You'll learn skills and develop habits and attitudes that form the foundation for long-term success in your career. You'll become a Pragmatic Programmer. COMPUTERS,Programming,General

USB Embedded Hosts A guide for designing and programming small, embedded systems that access USB devices, this book includes topics such as how embedded USB hosts differ from USB hosts in PCs, choosing a hardware and programming platform for a project, understanding USB host programming in embedded Linux systems, how host applications can access USB devices of all types, and designing a system that can communicate with both USB hosts and USB devices. Example code explains how to read and write to files on drives, get user input from keyboards, communicate over virtual serial ports and Ethernet bridges, record and play audio and video, print documents, use a USB display monitor, and access vendor-defined devices of any type. The example code runs on embedded Linux systems, including the popular BeagleBoard-xM open development board. This book is a companion to USB Complete. COMPUTERS,Programming,General

Making Embedded Systems Interested in developing embedded systems? Since they don’t tolerate inefficiency, these systems require a disciplined approach to programming. This easy-to-read guide helps you cultivate a host of good development practices, based on classic software design patterns and new patterns unique to embedded programming. Learn how to build system architecture for processors, not operating systems, and discover specific techniques for dealing with hardware difficulties and manufacturing requirements. Written by an expert who’s created embedded systems ranging from urban surveillance and DNA scanners to children’s toys, this book is ideal for intermediate and experienced programmers, no matter what platform you use. Optimize your system to reduce cost and increase performance Develop an architecture that makes your software robust in resource-constrained environments Explore sensors, motors, and other I/O devices Do more with less: reduce RAM consumption, code space, processor cycles, and power consumption Learn how to update embedded code directly in the processor Discover how to implement complex mathematics on small processors Understand what interviewers look for when you apply for an embedded systems job "Making Embedded Systems is the book for a C programmer who wants to enter the fun (and lucrative) world of embedded systems. It’s very well written—entertaining, even—and filled with clear illustrations."—Jack Ganssle, author and embedded system expert. COMPUTERS,Programming,General

Introducing Regular Expressions If you’re a programmer new to regular expressions, this easy-to-follow guide is a great place to start. You’ll learn the fundamentals step-by-step with the help of numerous examples, discovering first-hand how to match, extract, and transform text by matching specific words, characters, and patterns. Regular expressions are an essential part of a programmer’s toolkit, available in various Unix utlilities as well as programming languages such as Perl, Java, JavaScript, and C#. When you’ve finished this book, you’ll be familiar with the most commonly used syntax in regular expressions, and you’ll understand how using them will save you considerable time. Discover what regular expressions are and how they work Learn many of the differences between regular expressions used with command-line tools and in various programming languages Apply simple methods for finding patterns in text, including digits, letters, Unicode characters, and string literals Learn how to use zero-width assertions and lookarounds Work with groups, backreferences, character classes, and quantifiers Use regular expressions to mark up plain text with HTML5 COMPUTERS,Programming,General

Version Control with Git Get up to speed on Git for tracking, branching, merging, and managing code revisions. Through a series of step-by-step tutorials, this practical guide takes you quickly from Git fundamentals to advanced techniques, and provides friendly yet rigorous advice for navigating the many functions of this open source version control system. This thoroughly revised edition also includes tips for manipulating trees, extended coverage of the reflog and stash, and a complete introduction to the GitHub repository. Git lets you manage code development in a virtually endless variety of ways, once you understand how to harness the system’s flexibility. This book shows you how. Learn how to use Git for several real-world development scenarios Gain insight into Git’s common-use cases, initial tasks, and basic functions Use the system for both centralized and distributed version control Learn how to manage merges, conflicts, patches, and diffs Apply advanced techniques such as rebasing, hooks, and ways to handle submodules Interact with Subversion (SVN) repositories—including SVN to Git conversions Navigate, use, and contribute to open source projects though GitHub COMPUTERS,Programming,General

Cloud Architecture Patterns If your team is investigating ways to design applications for the cloud, this concise book introduces 11 architecture patterns that can help you take advantage of cloud-platform services. You’ll learn how each of these platform-agnostic patterns work, when they might be useful in the cloud, and what impact they’ll have on your application architecture. You’ll also see an example of each pattern applied to an application built with Windows Azure. The patterns are organized into four major topics, such as scalability and handling failure, and primer chapters provide background on each topic. With the information in this book, you’ll be able to make informed decisions for designing effective cloud-native applications that maximize the value of cloud services, while also paying attention to user experience and operational efficiency. Learn about architectural patterns for: Scalability. Discover the advantages of horizontal scaling. Patterns covered include Horizontally Scaling Compute, Queue-Centric Workflow, and Auto-Scaling. Big data. Learn how to handle large amounts of data across a distributed system. Eventual consistency is explained, along with the MapReduce and Database Sharding patterns. Handling failure. Understand how multitenant cloud services and commodity hardware influence your applications. Patterns covered include Busy Signal and Node Failure. Distributed users. Learn how to overcome delays due to network latency when building applications for a geographically distributed user base. Patterns covered include Colocation, Valet Key, CDN, and Multi-Site Deployment. COMPUTERS,Programming,General

Understanding Computation Finally, you can learn computation theory and programming language design in an engaging, practical way. Understanding Computation explains theoretical computer science in a context you’ll recognize, helping you appreciate why these ideas matter and how they can inform your day-to-day programming. Rather than use mathematical notation or an unfamiliar academic programming language like Haskell or Lisp, this book uses Ruby in a reductionist manner to present formal semantics, automata theory, and functional programming with the lambda calculus. It’s ideal for programmers versed in modern languages, with little or no formal training in computer science. Understand fundamental computing concepts, such as Turing completeness in languages Discover how programs use dynamic semantics to communicate ideas to machines Explore what a computer can do when reduced to its bare essentials Learn how universal Turing machines led to today’s general-purpose computers Perform complex calculations, using simple languages and cellular automata Determine which programming language features are essential for computation Examine how halting and self-referencing make some computing problems unsolvable Analyze programs by using abstract interpretation and type systems COMPUTERS,Programming,General

Object-Oriented Programming Without a doubt the idea of object-oriented programming has brought some motion into the field of programming methodology and enlarged the set of programming languages. Object-oriented programming is nothing new-it first arose in the sixties. The motivation came from the simulation of discrete event systems. The concept first manifested itself in the language Simula 67. It took nearly two decades for the method to gain impetus, and today object-oriented programming is an important concept and a powerful technique. Meanwhile, we can even speak of an over reaction, for the concept has become a buzzword. But buzzwords always appear where there is the hope of exploiting ill-informed clients because they see the new approach as the solution to all their problems. Thus object-oriented programming is often hailed as a panacea. And so the question is justified: What is really behind it? To let the cat out of the bag: There is more to object-oriented programming than merely putting data as objects in the fore ground, instead of algorithms to which the data are subject. It is more than purely an alternative view of programmed systems. To identify the essence of object-oriented programming, is the subject of this book. This is a textbook that shows in a didactically skillful way which concepts and constructs are new, where they can be employed reasonably, and what advantages they offer. For, not all programs are automatically improved by merely recasting them in an object-oriented style. COMPUTERS,Programming,General

How to Solve It No pleasure lasts long unless there is variety in it. Publilius Syrus, Moral Sayings We've been very fortunate to receive fantastic feedback from our readers during the last four years, since the first edition of How to Solve It: Modern Heuristics was published in 1999. It's heartening to know that so many people appreciated the book and, even more importantly, were using the book to help them solve their problems. One professor, who published a review of the book, said that his students had given the best course reviews he'd seen in 15 years when using our text. There can be hardly any better praise, except to add that one of the book reviews published in a SIAM journal received the best review award as well. We greatly appreciate your kind words and personal comments that you sent, including the few cases where you found some typographical or other errors. Thank you all for this wonderful support. COMPUTERS,Programming,General

OOIS’96 This volume contains the papers presented at the Third International Conference on Object Oriented Information Systems (00lS'96) which was held at South Bank University, London. The keynote addresses, by Professor Colette Roland and Mr Ian Graham, are also included. The acceptance rate for papers was around 47%. The papers for the Industry Day were invited papers. The keynote paper by Professor Roland analyses the challenges in object modelling, particularly the impact of requirements engineering for conceptual modelling. She suggests innovative research perspectives to enhance and extend object oriented approaches in order to deal with the emerging area of requirements engineering. The keynote paper presented by Mr. Graham focuses on the problems and solutions for adopting use cases. In his paper, Graham illustrates the theoretical issues and practical problems of use cases, and highlights them using examples. The papers included in this volume cover different aspects of object modelling, object oriented software development, object databases, and interoperability. In the modelling session, Ram, et al. outline an extended object model to tackle the problems of capturing complex requirements of office information systems. Simons' paper concentrates on core object modelling concepts and presents a mathematical theory of class. COMPUTERS,Programming,General

Clause and Effect This book is for people who have done some programming, either in Prolog or in a language other than Prolog, and who can find their way around a reference manual. The emphasis of this book is on a simplified and disciplined methodology for discerning the mathematical structures related to a problem, and then turning these structures into Prolog programs. This book is therefore not concerned about the particular features of the language nor about Prolog programming skills or techniques in general. A relatively pure subset of Prolog is used, which includes the 'cut', but no input/output, no assert/retract, no syntactic extensions such as if then-else and grammar rules, and hardly any built-in predicates apart from arithmetic operations. I trust that practitioners of Prolog program ming who have a particular interest in the finer details of syntactic style and language features will understand my purposes in not discussing these matters. The presentation, which I believe is novel for a Prolog programming text, is in terms of an outline of basic concepts interleaved with worksheets. The idea is that worksheets are rather like musical exercises. Carefully graduated in scope, each worksheet introduces only a limited number of new ideas, and gives some guidance for practising them. The principles introduced in the worksheets are then applied to extended examples in the form of case studies. COMPUTERS,Programming,General

Programming in Dylan Programming in Dylan is aimed at programmers who are already familiar with languages such as Pascal or C but who, as yet, have no knowledge of object-oriented languages. The author takes the reader through the development of Dylan by Apple and introduces the concept of object oriented languages, comparing Dylan to other languages such as CLOS, Smalltalk and C++. The author looks at fundamental concepts of the Dylan language before moving on to present the basic types (Boolean, vectors, strings etc.). Variables, expressions and assignment, and functions (both named and anonymous) are covered in detail. The Dylan class is introduced in its simple form and generic functions and library classes are discussed in depth. The author shows how modularisation needs to be used if large applications are to be developed and illustrates how to construct program libraries. A simulation and modelling example runs through the book. COMPUTERS,Programming,General

Essential Java Fast Java is a new and exciting object-oriented programming language which is set to transform the world wide web. Java allows users to write applications which can be accessed across different platforms and provides an effective means of building small but powerful programs that enable a huge range of new applications - such as animation, live updating, two-way interactions etc. - to be quickly and easily implemented. As with all the 'Essential Series' books Essential Java Fast provides a highly readable and accessible introduction to the Java programming language allowing the reader to get up and running fast when developing their own programs. Software developers producing software for the Internet, those writing substantial commercial applications in a Windows environment, as well as individuals wanting to produce single versions of an application to run on any platform, should read this book from cover to cover. COMPUTERS,Programming,General

Object-Oriented Programming A Unified Foundation by Luea Cardelli Ever since Strachey's work in the 1960's, polymorphism has been classified into the parametric and overloading varieties. Parametric polymorphism has been the subject of extensive study for over two decades. Overloading, on the other hand, has often been considered too ad hoc to deserve much attention even though it has been, in some form, an ingredient of virtually every programming lan guage (much more so than parametric polymorphism). With the introduction of object-oriented languages, and in particular with multiple-dispatch object-oriented languages, overloading has become less of a programming convenience and more of a fundamental feature in need of proper explanation. This book provides a compelling framework for the study of run-time over loading and of its interactions with subtyping and with parametric polymorphism. The book also describes applications to object-oriented programming. This new framework is motivated by the relatively recent spread of programming languages that are entirely based on run-time overloading; this fact probably explains why this subject was not investigated earlier. Once properly understood, overloading reveals itself relevant also to the study of older and more conventional (single dispatch) object-oriented languages, clarifying delicate issues of covariance and contravariance of method types, and of run-time type analysis. In the final chapters, a synthesis is made between parametric and overloading polymorphism. COMPUTERS,Programming,General

Programming in Modula-3 by Joseph Weizenbaum Since the dawn of the age of computers, people have cursed the difficulty of programming. Over and over again we encounter the suggestion that we should be able to communicate to a computer in natural language what we want it to do. Unfortunately, such advice rests upon a misconception of both the computer and its task. The computer might not be stupid, but it is stubborn. That is, the computer does what all the details of its pro gram command it to do, i. e. , what the programmer "tells" it to do. And this can be quite different from what the programmer intended. The misun derstanding with respect to tasks posed to the computer arises from the failure to recognize that such tasks can scarcely be expressed in natural language, if indeed at all. For example, can we practice music, chemistry or mathematics without their respective special symbolic languages? Yet books about computers and programming languages can be written more or less reasonably, even if they are not quite poetic or lyrical. This book can serve as an example of this art and as a model for anyone at tempting to teach inherently difficult subject matters to others. Klagenfurt, April 1995 Preface Striving to make learning to program easier, this book addresses primarily students beginning a computer science major. For our program examples, we employ a new, elegant programming language, Modula-3. COMPUTERS,Programming,General

OOIS’ 95 OOIS'95 (Object-Oriented Information Systems '95) contains contributions from leading researchers and practitioners working on object oriented technology and its application in information systems design and development. The book has a strong practical focus and contains much technical insight of particular relevance to professionals working in the field. The papers cover two main areas of the field: academic research trends into object oriented concepts and principles, and state of the art applications in industry. Among the specific topics covered are modelling, knowledgebases, software development, interface design, object databases, distributed databases, and emerging object technologies. All those working in the field of information technology will find the book a useful source of reference. COMPUTERS,Programming,General

Programming in SCHEME Scheme provides a flexible and powerful language for programming embodying many of the best features of logical and functional programming. This enjoyable book provides readers with an introduction to programming in Scheme by constructing a series of interesting and re-usable programs. The book includes two diskettes containing MIT Scheme to run on Windows PCs. COMPUTERS,Programming,General

Essential Delphi 2.0 Fast Delphi is a new Windows software development environment from Borland. Released in 1995, it has quickly built up an excellent reputation as one of the best Windows software development tools.John Cowell shows how to program in Delphi using various tools. He provides lots of examples and illustrations and describes various database specific tools included with the Delphi package. The book shows how to use the Borland database engine along with other database formats (including Microsoft's Access). There are a number of chapters which cover the object-oriented aspects of Pascal, and advanced programming techniques such as drag-and-drop, DDE, OLE, and the creation of on-line help systems are also looked at. New users, as well as current Visual Basic users wanting to get up to speed on Delphi, will find this clear and informative book provides all the information they need to develop Windows applications quickly, competently, and easily. COMPUTERS,Programming,General

Object-Oriented Programming in Oberon-2 Without a doubt the idea of object-oriented programming has brought some motion into the field of programming methodology and enlarged the set of programming languages. Object-oriented programming is nothing new-it first arose in the sixties. The motivation came from the simulation of discrete event systems. The concept first manifested itself in the language Simula 67. It took nearly two decades for the method to gain impetus, and today object-oriented programming is an important concept and a powerful technique. Meanwhile, we can even speak of an over reaction, for the concept has become a buzzword. But buzzwords always appear where there is the hope of exploiting ill-informed clients because they see the new approach as the solution to all their problems. Thus object-oriented programming is often hailed as a panacea. And so the question is justified: What is really behind it? To let the cat out of the bag: There is more to object-oriented programming than merely putting data as objects in the fore ground, instead of algorithms to which the data are subject. It is more than purely an alternative view of programmed systems. To identify the essence of object-oriented programming, is the subject of this book. This is a textbook that shows in a didactically skillful way which concepts and constructs are new, where they can be employed reasonably, and what advantages they offer. For, not all programs are automatically improved by merely recasting them in an object-oriented style. COMPUTERS,Programming,General

Functional Programming, Glasgow 1993 The Functional Programming Group at the University of Glasgow was started in 1986 by John Hughes and Mary Sheeran. Since then it has grown in size and strength, becoming one of the largest computing science research groups at Glasgow and earning an international reputation. The first Glasgow Functional Programming Workshop was organised in the summer of 1988. Its purpose was threefold: to provide a snapshot of all the research going on within the group, to share research ideas between Glaswegians and colleagues in the U.K. and abroad, and to introduce research students to the art of writing and presenting papers at a semi-formal (but still local and friendly) conference. The success of the first workshop has led to an annual series: Rothesay (1988), Fraserburgh (1989), Ullapool (1990). Portree (1991), Ayr (1992), and the workshop reported in these proceedings: Ayr (1993). Most participants wrote a paper that appeared in the draft proceedings (distributed at the workshop), and each draft paper was presented by one of the authors. The papers were all refereed by several other participants at the workshop, both internal and external, and the programme committee selected papers for these proceedings. Most papers have been revised twice, based firstly on feedback at the workshop, and secondly using the referee reports. COMPUTERS,Programming,General

Logic Program Synthesis and Transformation This volume contains extended versions of papers presented at the Third International Workshop on Logic Program Synthesis and Transformation (LOPSTR 93) held in Louvain-la-Neuve in July 1993. Much of the success of the workshop is due to Yves Deville who served as Organizer and Chair. Many people believe that machine support for the development and evolution of software will play a critical role in future software engineering environments. Machine support requires the formalization of the artifacts and processes that arise during the software lifecycle. Logic languages are unique in providing a uniform declarative notation for precisely describing application domains, software requirements, and for prescribing behavior via logic programs. Program synthesis and transfonnation techniques formalize the process of developing correct and efficient programs from requirement specifications. The natural intersection of these two fields of research has been the focus of the LOPSTR workshops. The papers in this volume address many aspects of software develop ment including: deductive synthesis, inductive synthesis, transforma tions for optimizing programs and exploiting parallelism, program analysis techniques (particularly via abstract interpretation), meta programming languages and tool support, and various extensions to Prolog-like languages, admitting non-Horn clauses, functions, and constraints. Despite the progress represented in this volume, the transition from laboratory to practice is fraught with difficulties. COMPUTERS,Programming,General

Logic Program Synthesis and Transformation Sponsored by the Association for Logic Programming and ALPUK COMPUTERS,Programming,General

C2 Compiler Concepts Writing a compiler is a very good practice for learning how complex problems could be solved using methods from software engineering. It is extremely important to program rather carefully and exactly, because we have to remember that a compiler is a program which has to handle an input that is usually incorrect. Therefore, the compiler itself must be error-free. Referring to Niklaus Wirth, we postulate that the grammatical structure of a language must be reflected in the structure of the compiler. Thus, the complexity of a language determines the complexity of the compiler (cf. Compilerbau. B. G. Teubner Verlag, Stuttgart, 1986). This book is about the translation of programs written in a high level programming language into machine code. It deals with all the major aspects of compilation systems (including a lot of examples and exercises), and was outlined for a one session course on compilers. The book can be used both as a teacher's reference and as a student's text book. In contrast to some other books on that topic, this text is rather concentrated to the point. However, it treats all aspects which are necessary to understand how compilation systems will work. Chapter One gives an introductory survey of compilers. Different types of compilation systems are explained, a general compiler environment is shown, and the principle phases of a compiler are introduced in an informal way to sensitize the reader for the topic of compilers. COMPUTERS,Programming,General

ALPUK92 Since its conception nearly 20 years ago, logic programming has been developed to the point where it now plays an important role in areas such as database theory, artificial intelligence and software engineering. There are, however, still many outstanding research issues which need to be addressed, and the UK branch of the Association for Logic Programming was set up to provide a forum where the flourishing research community could discuss important issues which were often by- passed at the larger international conferences. This volume contains the invited papers, refereed papers and tutorials presented at the 4th ALPUK Conference, which aimed to broaden the frontiers of logic programming by encouraging interaction between it and other related disciplines. The papers cover a variety of technical areas, including concurrent logic languages and their semantics, applications of logic languages to other (non-classical) logical systems, modules, types and error-handling, and the distributed execution of Prolog programs. The wide scope of the papers refelects the breadth of interest in this important area of computer science. ALPUK 92 provides a comprehensive overview of current progress being made in logic programming research. It will be of interest to all workers in the field, especially researchers, postgraduate students, and research and development workers in industry. COMPUTERS,Programming,General

Logic Program Synthesis and Transformation Logic programming synthesis and transformation are methods of deriving logic programs from their specifications and, where necessary, producing alternative but equivalent forms of a given program. The techniques involved in synthesis and transformation are extremely important as they allow the systematic construction of correct and efficient programs and have the potential to enhance current methods of software production. Transformation strategies are also being widely used in the field of logic program development. LOPSTR 91 was the first workshop to deal exclusively with both logic program synthesis and transformation and, as such, filled an obvious gap in the existing range of logic programming workshops. In attempting to cover the subject as comprehensively as possible, the workshop brought together researchers with an interest in all aspects of logic (including Horn Clause and first order logic) and all approaches to program synthesis and transformation. Logic Program Synthesis and Transformation provides a complete record of the workshop, with all the papers reproduced either in full or as extended abstracts. They cover a wide range of aspects, both practical and theoretical, including the use of mode input-output in program transformation, program specification and synthesis in constructive formal systems and a case study in formal program development in modular Prolog. This volume provides a comprehensive overview of current research and will be invaluable to researchers and postgraduate students who wish to enhance their understanding of logic programming techniques. COMPUTERS,Programming,General

Software Fault Tolerance The first ESPRIT programme contained several ambitious projects. of which REQUEST. with its wide brief covering all issues of assessment of quality and reliability of software process and product. was one. Within REQUEST. the research described in this volume. concerning those special problems of software that is required to have extremely high reliability. was particularly difficult and ambitious. The problems of software reliability are essentially twofold. On the one hand there is a concern with methods for achieving adequate reliability. on the other hand there is a need to evaluate what has actually been achieved in a particular case. Naturally. far more effort has been spent over the years on the former problem; indeed. there is a sense in which all of conventional software engineering can be seen as a response to this problem. However. it is becoming clearer than ever that we can only claim to have a truly sCientific approach. and so justify the description software engineering. when we are able to measure the attributes of process and product. It is still common to find software development methods recommended to users on purely anecdotal grounds. This is not good enough. Rational choices between rival approaches can only be made on the basis of quantified costs and benefits. Even more worrying is the tendency to argue that a software product can be depended upon merely because it has been developed by honest men using such anecdotal 'good practice'. COMPUTERS,Programming,General

Verification of Sequential and Concurrent Programs This book provides a structured introduction to the verification of sequen tial and concurrent programs. It thus belongs to the area of programming languages but at the same time it is firmly based on mathematical logic. In logic one usually studies fixed syntactic or semantic objects. This is not necessarily the case in the area of program verification. The objects studied here, namely programs, do not have a standard syntax, their semantics can be defined in many different ways, and several approaches to their verification can be contemplated. These differences lead to various difficult design decisions. Even though we restrict our attention here to one programming style - imperative pro gramming - we are still confronted with a veritable cornucopia of pro gramming constructs from which an appropriate selection has to be made. Having studied some of these constructs separately does not yet imply that we understand their combined effect. COMPUTERS,Programming,General

Logic, Algebra, and Computation Proceedings of the NATO Advanced Study Institute on Logic, Algebra, and Computation held at Marktoberdorf, Federal Republic of Germany, July 25 - August 6, 1989. COMPUTERS,Programming,General

Functional Programming, Glasgow 1990 The Third Glasgow Workshop on Functional Programming was held in Ullapool, Scotland, 13-15th August 1990. Members of the functional programming groups at Glasgow and Stirling University attended the workshop together with a small number of invited participants from other universities and industry. The workshop was organised by Kei Davis, Jak Deschner, Kevin Hammond, Carsten Kehler Holst, John Hughes, Graham Hutton, and John Launchbury, all from Glasgow University. We are very grateful for the support of our industrial sponsors: British Telecom, Hewlett Packard, ICL and Software AG. Their financial help made the workshop possible. Thanks to Samson Abramsky, Tony Field, and Paul Kelly, all from Imperial College, for their help in refereeing many of the papers. Glasgow University The Programme Committee: December 1990 Simon Peyton Jones (chairman) Chris Hankin Carsten Kehler Holst John Hughes Graham Hutton Philip Wadler Contents Lifetime Analysis Guy Argo . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Compiling Laziness by Partial Evaluation Anders Bondorf . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9 Strictness Analysis in 4D Kei Davis and Philip Wadler . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23 An Algorithmic and Semantic Approach to Debugging Cordelia Hall, Kevin Hammond and John O'Donnell . . . . . . . . . . . . . . . . . . . . 44 Abstract Interpretation of Term Graph Rewriting Systems Chris Hankin . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54 Compile-Time Garbage Collection by Necessity Analysis Geoff W Hamilton and Simon B. Jones. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 66 Improving Full Laziness Carsten Kehler Holst . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 71 Towards Binding-Time Improvement for Free Carsen Kehler Holst and John Hughes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 83 Towards Relating Forwards and Backwards Analyses John Hughes and John Launchbury . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 101 PERs Generalise Projections for Strictness Analysis Sebastian Hunt . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 114 Functional Programming with Relations Graham Hutton . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . COMPUTERS,Programming,General

The Collected Works of J. Richard Büchi J. Richard Biichi is well known for his work in mathematical logic and theoretical computer science. (He himself would have sharply objected to the qualifier "theoretical," because he more or less identified science and theory, using "theory" in a broader sense and "science" in a narrower sense than usual.) We are happy to present here this collection of his papers. I (DS)1 worked with Biichi for many years, on and off, ever since I did my Ph.D. thesis on his Sequential Calculus. His way was to travel locally, not globally: When we met we would try some specific problem, but rarely dis cussed research we had done or might do. After he died in April 1984 I sifted through the manuscripts and notes left behind and was dumbfounded to see what areas he had been in. Essentially I knew about his work in finite au tomata, monadic second-order theories, and computability. But here were at least four layers on his writing desk, and evidently he had been working on them all in parallel. I am sure that many people who knew Biichi would tell an analogous story. COMPUTERS,Programming,General

Strategies for Real-Time System Specification This is the digital version of the printed book (Copyright © 1987). Here is a casebook, a practical reference, and an indispensable guide for creating a systematic, formal methodology for large, real-time, software-based systems. The book introduces the widely implemented Hatley/Pirbhai methods, a major extension of the DeMarco analysis method describing how external events control the system's operating behavior. The techniques are used in major avionics and electronics companies worldwide, and are automated by most major CASE tools, including TurboCASE/Sys by StructSoft, Inc. Large software-based systems, especially those for real-time applications, require multi-mode operation, direct interaction with a rapidly changing physical environment, and fast response times. In the past, the development of such systems was prone to massive cost and schedule overruns, and to inadequate performance and reliability. Strategies for Real-Time System Specification addresses these problems by integrating a finite-state machine structure into classical analysis methods. The book contains nearly 200 diagrams, many of which illustrate the requirements specification of a flight management system for a major avionics developer. COMPUTERS,Programming,General

C Primer Plus C Primer Plus is a carefully tested, well-crafted, and complete tutorial on a subject core to programmers and developers. This computer science classic teaches principles of programming, including structured code and top-down design. Author and educator Stephen Prata has created an introduction to C that is instructive, clear, and insightful. Fundamental programming concepts are explained along with details of the C language. Many short, practical examples illustrate just one or two concepts at a time, encouraging readers to master new topics by immediately putting them to use. Review questions and programming exercises at the end of each chapter bring out the most critical pieces of information and help readers understand and digest the most difficult concepts. A friendly and easy-to-use self-study guide, this book is appropriate for serious students of programming, as well as developers proficient in other languages with a desire to better understand the fundamentals of this core language. The sixth edition of this book has been updated and expanded to cover the latest developments in C as well as to take a detailed look at the new C11 standard. In C Primer Plus you’ll find depth, breadth, and a variety of teaching techniques and tools to enhance your learning: Complete, integrated discussion of both C language fundamentals and additional features Clear guidance about when and why to use different parts of the language Hands-on learning with concise and simple examples that develop your understanding of a concept or two at a time Hundreds of practical sample programs Review questions and programming exercises at the end of each chapter to test your understanding Coverage of generic C to give you the greatest flexibility COMPUTERS,Programming,General

Python. Receptury. Wydanie III Python to j?zyk programowania z ponad 20-letni? histori?. Opracowany na pocz?tku lat 90. ubieg?ego wieku, b?yskawicznie zdoby? sympati? programistów. Jest u?ywany zarówno do pisania przydatnych skryptów czy ma?ych narz?dzi, jak i do pracy nad du?ymi projektami. Korzysta z automatycznego zarz?dzania pami?ci? oraz pozwala na podej?cie obiektowe i funkcyjne do tworzonego programu. Wokó? j?zyka Python skupiona jest bardzo silna spo?eczno?? programistów. Ta ksi??ka to sprawdzone ?ród?o informacji na temat Pythona i jego najcz?stszych zastosowa?. Nale?y ona do cenionej serii „Recepturyâ€, w której znajdziesz najlepsze sposoby rozwi?zywania problemów. Przekonaj si?, jak wydajnie operowa? na strukturach danych, ?a?cuchach znaków, tek?cie i liczbach. Zobacz, jak korzysta? z iteratorów i generatorów. Ponadto naucz si? tworzy? w?asne klasy i funkcje oraz sprawd?, jak uzyska? dost?p do plików i sieci. Te i dziesi?tki innych receptur opisano w tej ksi??ce. To obowi?zkowa pozycja na pó?ce ka?dego programisty pracuj?cego z j?zykiem Python. Dzi?ki tej ksi??ce: poznasz podstawy j?zyka Python rozwi??esz w optymalny sposób najcz?stsze problemy napiszesz program korzystaj?cy z puli w?tków b?dziesz lepszym programist? Pythona! Najlepsze rozwi?zania typowych problemów! COMPUTERS,Programming,General

Art of Computer Programming, The &>The bible of all fundamental algorithms and the work that taught many of today's software developers most of what they know about computer programming. —Byte, September 1995 I can't begin to tell you how many pleasurable hours of study and recreation they have afforded me! I have pored over them in cars, restaurants, at work, at home... and even at a Little League game when my son wasn't in the line-up. —Charles Long If you think you're a really good programmer... read [Knuth's] Art of Computer Programming... You should definitely send me a resume if you can read the whole thing. —Bill Gates It's always a pleasure when a problem is hard enough that you have to get the Knuths off the shelf. I find that merely opening one has a very useful terrorizing effect on computers. —Jonathan Laventhol This first volume in the series begins with basic programming concepts and techniques, then focuses more particularly on information structures—the representation of information inside a computer, the structural relationships between data elements and how to deal with them efficiently. Elementary applications are given to simulation, numerical methods, symbolic computing, software and system design. Dozens of simple and important algorithms and techniques have been added to those of the previous edition. The section on mathematical preliminaries has been extensively revised to match present trends in research. Ebook (PDF version) produced by Mathematical Sciences Publishers (MSP),http://msp.org COMPUTERS,Programming,General

Art of Computer Programming, Volume 2 The bible of all fundamental algorithms and the work that taught many of today's software developers most of what they know about computer programming. –Byte, September 1995 I can't begin to tell you how many pleasurable hours of study and recreation they have afforded me! I have pored over them in cars, restaurants, at work, at home... and even at a Little League game when my son wasn't in the line-up. –Charles Long If you think you're a really good programmer... read [Knuth's] Art of Computer Programming... You should definitely send me a resume if you can read the whole thing. –Bill Gates It's always a pleasure when a problem is hard enough that you have to get the Knuths off the shelf. I find that merely opening one has a very useful terrorizing effect on computers. –Jonathan Laventhol The second volume offers a complete introduction to the field of seminumerical algorithms, with separate chapters on random numbers and arithmetic. The book summarizes the major paradigms and basic theory of such algorithms, thereby providing a comprehensive interface between computer programming and numerical analysis. Particularly noteworthy in this third edition is Knuth's new treatment of random number generators, and his discussion of calculations with formal power series. Ebook (PDF version) produced by Mathematical Sciences Publishers (MSP),http://msp.org COMPUTERS,Programming,General

Beginning Programming Basic computer programming can be intimidating to anyone who has ever attempted to write their first line of code. Idiot's Guides: Basic Programming takes the fear out of learning programming by teaching readers the basics of programming with Python, an open-source (free) environment which is considered one of the easiest languages to learn for beginners, Python has consistent syntax, a solid standardized library, and a simplicity that isn't always present in other languages. Readers will learn not only the "how" of programming but the "why" so that they not only know how to write code, but why that code works, and how it relates to other languages and forms of programming. Readers will learn how to program through simple projects that help them to learn how basic programming works, while encouraging them to be creative and enabling them to see the tangible results of their coding. COMPUTERS,Programming,General

Art of Computer Programming, The The bible of all fundamental algorithms and the work that taught many of today's software developers most of what they know about computer programming. –Byte, September 1995 I can't begin to tell you how many pleasurable hours of study and recreation they have afforded me! I have pored over them in cars, restaurants, at work, at home... and even at a Little League game when my son wasn't in the line-up. –Charles Long If you think you're a really good programmer... read [Knuth's] Art of Computer Programming... You should definitely send me a resume if you can read the whole thing. –Bill Gates It's always a pleasure when a problem is hard enough that you have to get the Knuths off the shelf. I find that merely opening one has a very useful terrorizing effect on computers. –Jonathan Laventhol The first revision of this third volume is the most comprehensive survey of classical computer techniques for sorting and searching. It extends the treatment of data structures in Volume 1 to consider both large and small databases and internal and external memories. The book contains a selection of carefully checked computer methods, with a quantitative analysis of their efficiency. Outstanding features of the second edition include a revised section on optimum sorting and new discussions of the theory of permutations and of universal hashing. Ebook (PDF version) produced by Mathematical Sciences Publishers (MSP),http://msp.org COMPUTERS,Programming,General

Art of Computer Programming, Volume 4A, The The Art of Computer Programming, Volume 4A: Combinatorial Algorithms, Part 1 Knuth’s multivolume analysis of algorithms is widely recognized as the definitive description of classical computer science. The first three volumes of this work have long comprised a unique and invaluable resource in programming theory and practice. Scientists have marveled at the beauty and elegance of Knuth’s analysis, while practicing programmers have successfully applied his “cookbook†solutions to their day-to-day problems. The level of these first three volumes has remained so high, and they have displayed so wide and deep a familiarity with the art of computer programming, that a sufficient “review†of future volumes could almost be: “Knuth, Volume n has been published.†—Data Processing Digest Knuth, Volume n has been published, where n = 4A. In this long-awaited new volume, the old master turns his attention to some of his favorite topics in broadword computation and combinatorial generation (exhaustively listing fundamental combinatorial objects, such as permutations, partitions, and trees), as well as his more recent interests, such as binary decision diagrams. The hallmark qualities that distinguish his previous volumes are manifest here anew: detailed coverage of the basics, illustrated with well-chosen examples; occasional forays into more esoteric topics and problems at the frontiers of research; impeccable writing peppered with occasional bits of humor; extensive collections of exercises, all with solutions or helpful hints; a careful attention to history; implementations of many of the algorithms in his classic step-by-step form. There is an amazing amount of information on each page. Knuth has obviously thought long and hard about which topics and results are most central and important, and then, what are the most intuitive and succinct ways of presenting that material. Since the areas that he covers in this volume have exploded since he first envisioned writing about them, it is wonderful how he has managed to provide such thorough treatment in so few pages. —Frank Ruskey, Department of Computer Science, University of Victoria The book is Volume 4A, because Volume 4 has itself become a multivolume undertaking. Combinatorial searching is a rich and important topic, and Knuth has too much to say about it that is new, interesting, and useful to fit into a single volume, or two, or maybe even three. This book alone includes approximately 1500 exercises, with answers for self-study, plus hundreds of useful facts that cannot be found in any other publication. Volume 4A surely belongs beside the first three volumes of this classic work in every serious programmer’s library. Finally, after a wait of more than thirty-five years, the first part of Volume 4 is at last ready for publication. Check out the boxed set that brings together Volumes 1 - 4A in one elegant case, and offers the purchaser a $50 discount off the price of buying the four volumes individually. Ebook (PDF version) produced by Mathematical Sciences Publishers (MSP), http://msp.org The Art of Computer Programming, Volumes 1-4A Boxed Set, 3/e COMPUTERS,Programming,General

Becoming a Better Programmer If you’re passionate about programming and want to get better at it, you’ve come to the right source. Code Craft author Pete Goodliffe presents a collection of useful techniques and approaches to the art and craft of programming that will help boost your career and your well-being. Goodliffe presents sound advice that he’s learned in 15 years of professional programming. The book’s standalone chapters span the range of a software developer’s life—dealing with code, learning the trade, and improving performance—with no language or industry bias. Whether you’re a seasoned developer, a neophyte professional, or a hobbyist, you’ll find valuable tips in five independent categories: Code-level techniques for crafting lines of code, testing, debugging, and coping with complexity Practices, approaches, and attitudes: keep it simple, collaborate well, reuse, and create malleable code Tactics for learning effectively, behaving ethically, finding challenges, and avoiding stagnation Practical ways to complete things: use the right tools, know what “done†looks like, and seek help from colleagues Habits for working well with others, and pursuing development as a social activity COMPUTERS,Programming,General

R For Dummies Mastering R has never been easier Picking up R can be tough, even for seasoned statisticians and data analysts. R For Dummies, 2nd Edition provides a quick and painless way to master all the R you'll ever need. Requiring no prior programming experience and packed with tons of practical examples, step-by-step exercises, and sample code, this friendly and accessible guide shows you how to know your way around lists, data frames, and other R data structures, while learning to interact with other programs, such as Microsoft Excel. You'll learn how to reshape and manipulate data, merge data sets, split and combine data, perform calculations on vectors and arrays, and so much more. R is an open source statistical environment and programming language that has become very popular in varied fields for the management and analysis of data. R provides a wide array of statistical and graphical techniques, and has become the standard among statisticians for software development and data analysis. R For Dummies, 2nd Edition takes the intimidation out of working with R and arms you with the knowledge and know-how to master the programming language of choice among statisticians and data analysts worldwide. Covers downloading, installing, and configuring R Includes tips for getting data in and out of R Offers advice on fitting regression models and ANOVA Provides helpful hints for working with graphics R For Dummies, 2nd Edition is an ideal introduction to R for complete beginners, as well as an excellent technical reference for experienced R programmers. COMPUTERS,Programming,General

MMIX Supplement, The In the first edition of Volume 1 of The Art of Computer Programming, Donald E. Knuth introduced the MIX computer and its machine language: a teaching tool that powerfully illuminated the inner workings of the algorithms he documents. Later, with the publication of his Fascicle 1, Knuth introduced MMIX: a modern, 64-bit RISC replacement to the now-obsolete MIX. Now, with Knuth’s guidance and approval, Martin Ruckert has rewritten all MIX example programs from Knuth’s Volumes 1-3 for MMIX, thus completing this MMIX update to the original classic. Building on contributions from the international MMIXmasters volunteer group, Ruckert fully addresses MMIX basic concepts, information structures, random numbers, arithmetic, sorting, and searching. In the preparation of this supplement, about 15,000 lines of MMIX code were written and checked for correctness; over a thousand test cases were written and executed to ensure the code is of the highest possible quality. The MMIX Supplement should be read side by side with The Art of Computer Programming, Volumes 1-3, and Knuth’s Fascicle 1, which introduces the MMIX computer, its design, and its machine language. Throughout, this supplement contains convenient page references to corresponding coverage in the original volumes. To further simplify the transition to MMIX, Ruckert stayed as close as possible to the original–preserving programming style, analysis techniques, and even wording, while highlighting differences where appropriate. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Programming,General

Git for Teams You can do more with Git than just build software. This practical guide delivers a unique people-first approach to version control that also explains how using Git as a focal point can help your team work better together. You’ll learn how to plan and pursue a Git workflow that not only ensures that you accomplish project goals, but also fits the immediate needs and future growth of your team. The first part of the book on structuring workflow is useful for project managers, technical team leads, and CTOs. The second part provides hands-on exercises to help developers gain a better understanding of Git commands. Explore the dynamics of team building Walk through the process of creating and deploying software with Git Structure workflow to influence the way your team collaborates Learn a useful process for conducting code reviews Set up a shared repository and identify specific team members as contributors, consumers, or maintainers Know the why behind the Git commands your teammates use Use branching strategies to separate different approaches to your project Examine popular collaboration platforms: GitHub, Bitbucket, and GitLab COMPUTERS,Programming,General

Evolutionary Algorithms in Engineering Applications Evolutionary algorithms are general-purpose search procedures based on the mechanisms of natural selection and population genetics. They are appealing because they are simple, easy to interface, and easy to extend. This volume is concerned with applications of evolutionary algorithms and associated strategies in engineering. It will be useful for engineers, designers, developers, and researchers in any scientific discipline interested in the applications of evolutionary algorithms. The volume consists of five parts, each with four or five chapters. The topics are chosen to emphasize application areas in different fields of engineering. Each chapter can be used for self-study or as a reference by practitioners to help them apply evolutionary algorithms to problems in their engineering domains. COMPUTERS,Programming,General

ALPUK91 Since its conception nearly 20 years ago, Logic Programming - the idea of using logic as a programming language - has been developed to the point where it now plays an important role in areas such as database theory, artificial intelligence and software engineering. However, there are still many challenging research issues to be addressed and the UK branch of the Association for Logic Programming was set up to provide a forum where the flourishing research community could discuss important issues of Logic Programming which were often by-passed at the large international conferences. This volume contains the twelve papers which were presented at the ALPUK's 3rd conference which was held in Edinburgh, 10-12 April 1991. The aim of the conference was to give a broad but detailed technical insight into the work currently being done in this field, both in the UK and by researchers as far afield as Canada and Bulgaria. The breadth of interest in this area of Computer Science is reflected in the range of the papers which cover - amongst other areas - massively parallel implementation, constraint logic programming, circuit modelling, algebraic proof of program properties, deductive databases, specialised editors and standardisation. The resulting volume gives a good overview of the current progress being made in the field and will be of interest to researchers and students of any aspects of logic programming, parallel computing or database techniques and management. COMPUTERS,Programming,General

Declarative Programming, Sasbachwalden 1991 Declarative programming languages are based on sound mathematical foundations which means that they offer many advantages for software development. These advantages include their powerful descriptive capabilities, the availability of program analysis techniques and the potential for parallel execution. This volume contains the proceedings of a seminar and workshop organised by the Esprit Basic Research Action Phoenix in collaboration with the Esprit Basic Research Action Integration. Both these groups have been closely involved in investigating the foundations of declarative programming and the integration of various language paradigms, as well as the developing aspects of related technology. The main aim of the seminar and workshop was to provide a forum for the results of this work, together with contributions from other researchers in the same field. These papers cover a variety of important technical areas such as foundations and languages, program transformation and analysis, integrated approaches, implementation techniques, abstract machines and programming methodology. The resulting volume provides an in-depth picture of current research into declarative programming. It will be of special interest to researchers in programming languages and methodology, students of artificial intelligence and anyone involved in industrial research and development. COMPUTERS,Programming,General

Security for Object-Oriented Systems This volume contains papers from the OOPSLA-93 Conference Workshop on Security for Object-Oriented Systems, held in Washington DC, USA, on 26 September 1993. The workshop addressed the issue of how to introduce an acceptable level of security into object-oriented systems, as the use of such systems becomes increasingly widespread. The topic is approached from two different, but complementary, viewpoints: the incorporation of security into object-oriented systems, and the use of object-oriented design and modelling techniques for designing secure applications. The papers cover a variety of issues, relating to both mandatory and discretionary security, including security facilities of PCTE, information flow control, the design of multilevel secure data models, and secure database interoperation via role translation. The resulting volume provides a comprehensive overview of current work in this important area of research. COMPUTERS,Programming,General

Constraint Programming Proceedings of the NATO Advanced Study Institute on Constraint Programming, held in Pärnu, Estonia, August 13 - 24, 1993 COMPUTERS,Programming,General

CONCUR '94 This volume constitutes the proceedings of the Fifth International Conference on Concurrency Theory, CONCUR '94, held at Uppsala, Sweden in August 1994.In total, 29 refereed research papers selected from 108 submissions for the conference are presented together with full papers or abstracts of the 5 invited talks by prominent speakers. The book contains recent results on all relevant aspects of concurrency research and thus competently documents the progress of the field since the predecessor conference CONCUR '93, the proceedings of which are published as LNCS 715. COMPUTERS,Programming,General

ECOOP '93 - Object-Oriented Programming It is now more than twenty-five years since object-oriented programming was “inve- ed†(actually, more than thirty years since work on Simula started), but, by all accounts, it would appear as if object-oriented technology has only been “discovered†in the past ten years! When the first European Conference on Object-Oriented Programming was held in Paris in 1987, I think it was generally assumed that Object-Oriented Progr- ming, like Structured Programming, would quickly enter the vernacular, and that a c- ference on the subject would rapidly become superfluous. On the contrary, the range and impact of object-oriented approaches and methods continues to expand, and, - spite the inevitable oversell and hype, object-oriented technology has reached a level of scientific maturity that few could have foreseen ten years ago. Object-oriented technology also cuts across scientific cultural boundaries like p- haps no other field of computer science, as object-oriented concepts can be applied to virtually all the other areas and affect virtually all aspects of the software life cycle. (So, in retrospect, emphasizing just Programming in the name of the conference was perhaps somewhat short-sighted, but at least the acronym is pronounceable and easy to rem- ber!) This year’s ECOOP attracted 146 submissions from around the world - making the selection process even tougher than usual. The selected papers range in topic from programming language and database issues to analysis and design and reuse, and from experience reports to theoretical contributions. COMPUTERS,Programming,General

ECOOP '95 - Object-Oriented Programming For the ninth time now, the European Conference on Object-Oriented P- gramming provides a mid-summer gathering place for researchers, practitioners, students and newcomers in the field of object technology. Despite fierce c- petition from an increasing number of attractive conferences on object-related topics, ECOOP has successfully positioned itself as the premier European - ject technology conference. One reason is without doubt the composition of the conference week and the nature of its events. Running in parallel on the first two days, a comprehensive tutorial program and a very selective workshop program are offered to attendees. This is followed by a three-day technical p- gram organized in a single track providing a highly communicative atmosphere of scientific exchange and learning. Overlapping with these events are a two-day industrial exhibition and a two-day opportunity for non-industrial system dev- opers to demonstrate their software. Thus, ECOOP is not just a conference on programming but an event touching on the full spectrum of object technology. This volume constitutes the proceedings of the Ninth European Conference on Object-Oriented Programming, ECOOP, held in Aarhus, Denmark, August 7-11, 1995. Previous ECOOP conferences were held in Paris (France), Oslo (Norway), Nottingham (England), Ottawa (Canada, jointly with OOPSLA) , Geneva (Switzerland), Utrecht (the Netherlands) , Kaiserslautern (Germany) , and Bologna (Italy). Object technology continues to increase its impact on the corporate world. COMPUTERS,Programming,General

Automatic Verification of Sequential Infinite-State Processes A common approach in software engineering is to apply during the design phase a variety of structured techniques like top-down design, decomposition and abstraction, while only subsequently, in the implementation phase, is the design tested to ensure reliability. But this approach neglects that central aspects of software design and program development have a strong formal character which admits tool support for the construction of reliable and correct computer systems based on formal reasoning. This monograph provides much information both for theoreticians interested in algebraic theories, and for software engineers building practically relevant tools. The author presents the theoretical foundations needed for the verification of reactive, sequential infinite-state systems. COMPUTERS,Programming,General

Decentralized Applications Take advantage of Bitcoin’s underlying technology, the blockchain, to build massively scalable, decentralized applications known as dapps. In this practical guide, author Siraj Raval explains why dapps will become more widely used—and profitable—than today’s most popular web apps. You’ll learn how the blockchain’s cryptographically stored ledger, scarce-asset model, and peer-to-peer (P2P) technology provide a more flexible, better-incentivized structure than current software models. Once you understand the theory behind dapps and what a thriving dapp ecosystem looks like, Raval shows you how to use existing tools to create a working dapp. You’ll then take a deep dive into the OpenBazaar decentralized market, and examine two case studies of successful dapps currently in use. Learn advances in distributed-system technology that make distributed data, wealth, identity, computing, and bandwidth possible Build a Twitter clone with the Go language, distributed architecture, decentralized messaging app, and peer-to-peer data store Learn about OpenBazaar’s decentralized market and its structure for supporting transactions Explore Lighthouse, a decentralized crowdfunding project that rivals sites such as Kickstarter and IndieGogo Take an in-depth look at La’Zooz, a P2P ridesharing app that transmits data directly between riders and drivers COMPUTERS,Programming,General

Coding All-in-One For Dummies See all the things coding can accomplish The demand for people with coding know-how exceeds the number of people who understand the languages that power technology. Coding All-in-One For Dummies gives you an ideal place to start when you're ready to add this valuable asset to your professional repertoire. Whether you need to learn how coding works to build a web page or an application or see how coding drives the data revolution, this resource introduces the languages and processes you'll need to know. Peek inside to quickly learn the basics of simple web languages, then move on to start thinking like a professional coder and using languages that power big applications. Take a look inside for the steps to get started with updating a website, creating the next great mobile app, or exploring the world of data science. Whether you're looking for a complete beginner's guide or a trusted resource for when you encounter problems with coding, there's something for you! Create code for the web Get the tools to create a mobile app Discover languages that power data science See the future of coding with machine learning tools With the demand for skilled coders at an all-time high, Coding All-in-One For Dummies is here to propel coding newbies to the ranks of professional programmers. COMPUTERS,Programming,General

Programming Beyond Practices Writing code is the easy part of your work as a software developer. This practical book lets you explore the other 90%—everything from requirements discovery and rapid prototyping to business analysis and designing for maintainability. Instead of providing neatly packaged advice from on high, author Gregory Brown presents detailed examples of the many problems developers encounter, including the thought process it takes to solve them. He does this in an unusual and entertaining fashion by making you the main character in a series of chapter-length stories. As these stories progress, the examples become more complex, and your responsibilities increase. Together, these stories take you on a journey that will make you question and refine the way you think about, and work on, software projects. Steps in this unique journey include: Using prototypes to explore project ideas Spotting hidden dependencies in incremental changes Identifying the pain points of service integrations Developing a rigorous approach towards problem-solving Designing software from the bottom up Data modeling in an imperfect world Gradual process improvement as an antidote for over-commitment The future of software development COMPUTERS,Programming,General

macOS Programming for Absolute Beginners Learn how to code for the iMac, Mac mini, Mac Pro, and MacBook using Swift, Apple's hottest programming language. Fully updated to cover the new MacBook Touch Bar, macOS Programming for Absolute Beginners will not only teach complete programming novices how to write macOS programs, but it can also help experienced programmers moving to the Mac for the first time. You will learn the principles of programming, how to use Swift and Xcode, and how to combine your knowledge into writing macOS programs. If you've always wanted to learn coding but felt stymied by the limitation of simplistic programming languages or intimidated by professional but complicated programming languages, then you'll want to learn Swift. Swift is your gateway to both Mac and iOS app development while being powerful and easy to learn at the same time, and macOS Programming for Absolute Beginners is the perfect place to start - add it to your library today. What You'll Learn Master the basic principles of object-oriented programming Use Xcode, the main programming tool used for both macOS and iOS development See what makes Swift unique and powerful as a programming language and why you should learn it Create macOS programs using Swift and Xcode Apply interface principles that follow Apple's Human Interface Guidelines Take advantage of the new Touch Bar Who This Book Is For People who want to learn programming for the first time and for experienced programmers wanting to learn Xcode and the Mac for the first time. COMPUTERS,Programming,General

Confident Coding Master the essentials of coding and take your career to new heights with this accessible guide that takes the scary out of the subject. COMPUTERS,Programming,General

Advanced Object-Oriented Programming in R Learn how to write object-oriented programs in R and how to construct classes and class hierarchies in the three object-oriented systems available in R. This book gives an introduction to object-oriented programming in the R programming language and shows you how to use and apply R in an object-oriented manner. You will then be able to use this powerful programming style in your own statistical programming projects to write flexible and extendable software. After reading Advanced Object-Oriented Programming in R, you'll come away with a practical project that you can reuse in your own analytics coding endeavors. You’ll then be able to visualize your data as objects that have state and then manipulate those objects with polymorphic or generic methods. Your projects will benefit from the high degree of flexibility provided by polymorphism, where the choice of concrete method to execute depends on the type of data being manipulated. What You'll Learn Define and use classes and generic functions using R Work with the R class hierarchies Benefit from implementation reuse Handle operator overloading Apply the S4 and R6 classes Who This Book Is For Experienced programmers and for those with at least some prior experience with R programming language. COMPUTERS,Programming,General

Programming Pearls When programmers list their favorite books, Jon Bentley’s collection of programming pearls is commonly included among the classics. Just as natural pearls grow from grains of sand that irritate oysters, programming pearls have grown from real problems that have irritated real programmers. With origins beyond solid engineering, in the realm of insight and creativity, Bentley’s pearls offer unique and clever solutions to those nagging problems. Illustrated by programs designed as much for fun as for instruction, the book is filled with lucid and witty descriptions of practical programming techniques and fundamental design principles. It is not at all surprising that Programming Pearls has been so highly valued by programmers at every level of experience. In this revision, the first in 14 years, Bentley has substantially updated his essays to reflect current programming methods and environments. In addition, there are three new essays on testing, debugging, and timing set representations string problems All the original programs have been rewritten, and an equal amount of new code has been generated. Implementations of all the programs, in C or C++, are now available on the Web. What remains the same in this new edition is Bentley’s focus on the hard core of programming problems and his delivery of workable solutions to those problems. Whether you are new to Bentley’s classic or are revisiting his work for some fresh insight, the book is sure to make your own list of favorites. COMPUTERS,Programming,General

Automate the Boring Stuff with Python If you’ve ever spent hours renaming files or updating hundreds of spreadsheet cells, you know how tedious tasks like these can be. But what if you could have your computer do them for you? In Automate the Boring Stuff with Python, you’ll learn how to use Python to write programs that do in minutes what would take you hours to do by hand—no prior programming experience required. Once you’ve mastered the basics of programming, you’ll create Python programs that effortlessly perform useful and impressive feats of automation to:–Search for text in a file or across multiple files–Create, update, move, and rename files and folders–Search the Web and download online content–Update and format data in Excel spreadsheets of any size–Split, merge, watermark, and encrypt PDFs–Send reminder emails and text notifications–Fill out online forms Step-by-step instructions walk you through each program, and practice projects at the end of each chapter challenge you to improve those programs and use your newfound skills to automate similar tasks. Don’t spend your time doing work a well-trained monkey could do. Even if you’ve never written a line of code, you can make your computer do the grunt work. Learn how in Automate the Boring Stuff with Python. Note: The programs in this book are written to run on Python 3. COMPUTERS,Programming,General

Beginning Programming with Python For Dummies The easy way to learn programming fundamentals with Python Python is a remarkably powerful and dynamic programming language that's used in a wide variety of application domains. Some of its key distinguishing features include a very clear, readable syntax, strong introspection capabilities, intuitive object orientation, and natural expression of procedural code. Plus, Python features full modularity, supporting hierarchical packages, exception-based error handling, and modules easily written in C, C++, Java, R, or .NET languages, such as C#. In addition, Python supports a number of coding styles that include: functional, imperative, object-oriented, and procedural. Due to its ease of use and flexibility, Python is constantly growing in popularity—and now you can wear your programming hat with pride and join the ranks of the pros with the help of this guide. Inside, expert author John Paul Mueller gives a complete step-by-step overview of all there is to know about Python. From performing common and advanced tasks, to collecting data, to interacting with package—this book covers it all! Use Python to create and run your first application Find out how to troubleshoot and fix errors Learn to work with Anaconda and use Magic Functions Benefit from completely updated and revised information since the last edition If you've never used Python or are new to programming in general, Beginning Programming with Python For Dummies is a helpful resource that will set you up for success. COMPUTERS,Programming,General

TensorFlow For Dummies Become a machine learning pro! Google TensorFlow has become the darling of financial firms and research organizations, but the technology can be intimidating and the learning curve is steep. Luckily, TensorFlow For Dummies is here to offer you a friendly, easy-to-follow book on the subject. Inside, you’ll find out how to write applications with TensorFlow, while also grasping the concepts underlying machine learning—all without ever losing your cool! Machine learning has become ubiquitous in modern society, and its applications include language translation, robotics, handwriting analysis, financial prediction, and image recognition. TensorFlow is Google's preeminent toolset for machine learning, and this hands-on guide makes it easy to understand, even for those without a background in artificial intelligence. Install TensorFlow on your computer Learn the fundamentals of statistical regression and neural networks Visualize the machine learning process with TensorBoard Perform image recognition with convolutional neural networks (CNNs) Analyze sequential data with recurrent neural networks (RNNs) Execute TensorFlow on mobile devices and the Google Cloud Platform (GCP) If you’re a manager or software developer looking to use TensorFlow for machine learning, this is the book you’ll want to have close by. COMPUTERS,Programming,General

Pro Functional PHP Programming Bring the power of functional programming to your PHP applications. From performance optimizations to concurrency, improved testability to code brevity, functional programming has a host of benefits when compared to traditional imperative programming. Part one of Pro Functional PHP Programming takes you through the basics of functional programming, outlining the key concepts and how they translate into standard PHP functions and code. Part two takes this theory and shows you the strategies for implementing it to solve real problems in your new or existing PHP applications. Functional programming is popular in languages such as Lisp, Scheme and Clojure, but PHP also contains all you need to write functional code. This book will show you how to take advantage of functional programming in your own projects, utilizing the PHP programming language that you already know. What You'll Learn Discover functional programming in PHP Work with functional programming functions Design strategies for high-performance applications Manage business logic with functions Use functional programming in object-oriented and procedural applications Employ helper libraries in your application Process big data with functional PHP Who This Book Is For Programmers and web developers with experience of PHP who are looking to get more out of their PHP coding and be able to do more with PHP. COMPUTERS,Programming,General

Network Programming with Rust Learn to write servers and network clients using Rust's low-level socket classes with this guide About This Book Build a solid foundation in Rust while also mastering important network programming details Leverage the power of a number of available libraries to perform network operations in Rust Develop a fully functional web server to gain the skills you need, fast Who This Book Is For This book is for software developers who want to write networking software with Rust. A basic familiarity with networking concepts is assumed. Beginner-level knowledge of Rust will help but is not necessary. What You Will Learn Appreciate why networking is important in implementing distributed systems Write a non-asynchronous echo server over TCP that talks to a client over a network Parse JSON and binary data using parser combinators such as nom Write an HTTP client that talks to the server using reqwest Modify an existing Rust HTTTP server and add SSL to it Master asynchronous programming support in Rust Use external packages in a Rust project In Detail Rust is low-level enough to provide fine-grained control over memory while providing safety through compile-time validation. This makes it uniquely suitable for writing low-level networking applications. This book is divided into three main parts that will take you on an exciting journey of building a fully functional web server. The book starts with a solid introduction to Rust and essential networking concepts. This will lay a foundation for, and set the tone of, the entire book. In the second part, we will take an in-depth look at using Rust for networking software. From client-server networking using sockets to IPv4/v6, DNS, TCP, UDP, you will also learn about serializing and deserializing data using serde. The book shows how to communicate with REST servers over HTTP. The final part of the book discusses asynchronous network programming using the Tokio stack. Given the importance of security for modern systems, you will see how Rust supports common primitives such as TLS and public-key cryptography. After reading this book, you will be more than confident enough to use Rust to build effective networking software Style and approach This book will get you started with building networking software in Rust by taking you through all the essential concepts. COMPUTERS,Programming,General

A Beginner's Guide to Scala, Object Orientation and Functional Programming Scala is now an established programming language developed by Martin Oderskey and his team at the EPFL. The name Scala is derived from Sca(lable) La(nguage). Scala is a multi-paradigm language, incorporating object oriented approaches with functional programming. Although some familiarity with standard computing concepts is assumed (such as the idea of compiling a program and executing this compiled from etc.) and with basic procedural language concepts (such as variables and allocation of values to these variables) the early chapters of the book do not assume any familiarity with object orientation nor with functional programming These chapters also step through other concepts with which the reader may not be familiar (such as list processing). From this background, the book provides a practical introduction to both object and functional approaches using Scala. These concepts are introduced through practical experience taking the reader beyond the level of the language syntax to the philosophy and practice of object oriented development and functional programming. Students and those actively involved in the software industry will find this comprehensive introduction to Scala invaluable. COMPUTERS,Programming,General

Low Level X Window Programming This is the missing X Window book. While others have shown what the X Window system has available, this book shows how to convert this potential into working tools to fulfil your visualisation needs. It is of the show-me class of books. The majority of the book covers Xlib, although a short coverage of Xcb is also given. Included are: . The relationship between Xlib and the X Window protocol; . All the basic Xlib topics are covered; . Complete working programs with their results; . Exercises to reinforce the material just covered. A 9 part partition to building a complete X program is used throughout. This partitioning fosters the inclusion of all code necessary. All programs are written in C and are one to four pages in length. Open source programs with the occasional Postscript script are shown to provide support as needed. Throughout the examples consideration is given to using colour. The examples produce simple results with the aim of providing building blocks for application oriented codes. The book is directed at graduate students and researchers who create computer code to visualise their data. COMPUTERS,Programming,General

Software Architect's Handbook A comprehensive guide to exploring software architecture concepts and implementing best practices Key Features Enhance your skills to grow your career as a software architect Design efficient software architectures using patterns and best practices Learn how software architecture relates to an organization as well as software development methodology Book Description The Software Architect's Handbook is a comprehensive guide to help developers, architects, and senior programmers advance their career in the software architecture domain. This book takes you through all the important concepts, right from design principles to different considerations at various stages of your career in software architecture. The book begins by covering the fundamentals, benefits, and purpose of software architecture. You will discover how software architecture relates to an organization, followed by identifying its significant quality attributes. Once you have covered the basics, you will explore design patterns, best practices, and paradigms for efficient software development. The book discusses which factors you need to consider for performance and security enhancements. You will learn to write documentation for your architectures and make appropriate decisions when considering DevOps. In addition to this, you will explore how to design legacy applications before understanding how to create software architectures that evolve as the market, business requirements, frameworks, tools, and best practices change over time. By the end of this book, you will not only have studied software architecture concepts but also built the soft skills necessary to grow in this field. What you will learn Design software architectures using patterns and best practices Explore the different considerations for designing software architecture Discover what it takes to continuously improve as a software architect Create loosely coupled systems that can support change Understand DevOps and how it affects software architecture Integrate, refactor, and re-architect legacy applications Who this book is for The Software Architect's Handbook is for you if you are a software architect, chief technical officer (CTO), or senior developer looking to gain a firm grasp of software architecture. COMPUTERS,Programming,General

Fundamentals of Forecasting Using Excel Forecasting is an integral part of almost all business enterprises. This book provides readers with the tools to analyze their data, develop forecasting models and present the results in Excel. Progressing from data collection, data presentation, to a step-by-step development of the forecasting techniques, this essential text covers techniques that include but not limited to time series-moving average, exponential smoothing, trending, simple and multiple regression, and Box-Jenkins. And unlike other products of its kind that require either high-priced statistical software or Excel add-ins, this book does not require such software. It can be used both as a primary text and as a supplementary text. Highlights the use of Excel screen shots, data tables, and graphs. Features Full Scale Use of Excel in Forecasting without the Use of Specialized Forecast Packages Includes Excel templates. Emphasizes the practical application of forecasting. Provides coverage of Special Forecasting, including New Product Forecasting, Network Models Forecasting, Links to Input/Output Modeling, and Combination of Forecasting. COMPUTERS,Programming,General

Microservices Development Cookbook Quickly learn and employ practical methods for developing microservices Key Features Get to grips with microservice architecture to build enterprise-ready applications Adopt the best practices to find solutions to specific problems Monitor and manage your services in production Book Description Microservices have become a popular way to build distributed systems that power modern web and mobile apps. Deploying your application as a suite of independently deployable, modular, and scalable services has many benefits. In this book, you'll learn to employ microservices in order to make your application more fault-tolerant and easier to scale and change. Using an example-driven approach, Microservice Development Cookbook introduces you to the microservice architectural style. You'll learn how to transition from a traditional monolithic application to a suite of small services that interact to provide smooth functionality to your client applications. You'll also learn about the patterns used to organize services, so you can optimize request handling and processing and see how to handle service-to-service interactions. You'll then move on to understanding how to secure microservices and add monitoring in order to debug problems. This book also covers fault-tolerance and reliability patterns that help you use microservices to isolate failures in your applications. By the end of the book, you'll be able to work with a team to break a large, monolithic codebase into independently deployable and scalable microservices. You'll also study how to efficiently and effortlessly manage a microservice-based architecture. What you will learn Learn how to design microservice-based systems Create services that fail without impacting users Monitor your services to perform debugging and create observable systems Manage the security of your services Create fast and reliable deployment pipelines Manage multiple environments for your services Simplify the local development of microservice-based systems Who this book is for Microservice Development Cookbook is for developers who would like to build effective and scalable microservices. Basic knowledge of the microservices architecture is assumed. COMPUTERS,Programming,General

A First Introduction to Quantum Computing and Information This book addresses and introduces new developments in the field of Quantum Information and Computing (QIC) for a primary audience of undergraduate students. Developments over the past few decades have spurred the need for QIC courseware at major research institutions. This book broadens the exposure of QIC science to the undergraduate market. The subject matter is introduced in such a way so that it is accessible to students with only a first-year calculus background. Greater accessibility allows a broader range of academic offerings. Courses, based on this book, could be offered in the Physics, Engineering, Math and Computer Science departments. This textbook incorporates Mathematica-based examples into the book. In this way students are allowed a hands-on experience in which difficult abstract concepts are actualized by simulations. The students can ‘turn knobs" in parameter space and explore how the system under study responds. The incorporation of symbolic manipulation software into course-ware allows a more holistic approach to the teaching of difficult concepts. Mathematica software is used here because it is easy to use and allows a fast learning curve for students who have limited experience with scientific programming. COMPUTERS,Programming,General

Hands-On Microservices – Monitoring and Testing Learn and implement various techniques related to testing, monitoring and optimization for microservices architecture. Key Features Learn different approaches for testing microservices to design and implement, robust and secure applications Become more efficient while working with microservices Explore Testing and Monitoring tools such as JMeter, Ready API,and AppDynamics Book Description Microservices are the latest "right" way of developing web applications. Microservices architecture has been gaining momentum over the past few years, but once you've started down the microservices path, you need to test and optimize the services. This book focuses on exploring various testing, monitoring, and optimization techniques for microservices. The book starts with the evolution of software architecture style, from monolithic to virtualized, to microservices architecture. Then you will explore methods to deploy microservices and various implementation patterns. With the help of a real-world example, you will understand how external APIs help product developers to focus on core competencies. After that, you will learn testing techniques, such as Unit Testing, Integration Testing, Functional Testing, and Load Testing. Next, you will explore performance testing tools, such as JMeter, and Gatling. Then, we deep dive into monitoring techniques and learn performance benchmarking of the various architectural components. For this, you will explore monitoring tools such as Appdynamics, Dynatrace, AWS CloudWatch, and Nagios. Finally, you will learn to identify, address, and report various performance issues related to microservices. What you will learn Understand the architecture of microservices and how to build services Establish how external APIs help to accelerate the development process Understand testing techniques, such as unit testing, integration testing, end-to-end testing, and UI/functional testing Explore various tools related to the performance testing, monitoring, and optimization of microservices Design strategies for performance testing Identify performance issues and fine-tune performance Who this book is for This book is for developers who are involved with microservices architecture to develop robust and secure applications. Basic knowledge of microservices is essential in order to get the most out of this book. COMPUTERS,Programming,General

Python 3 Object-Oriented Programming Uncover modern Python with this guide to Python data structures, design patterns, and effective object-oriented techniques Key Features In-depth analysis of many common object-oriented design patterns that are more suitable to Python's unique style Learn the latest Python syntax and libraries Explore abstract design patterns and implement them in Python 3.8 Book Description Object-oriented programming (OOP) is a popular design paradigm in which data and behaviors are encapsulated in such a way that they can be manipulated together. This third edition of Python 3 Object-Oriented Programming fully explains classes, data encapsulation, and exceptions with an emphasis on when you can use each principle to develop well-designed software. Starting with a detailed analysis of object-oriented programming, you will use the Python programming language to clearly grasp key concepts from the object-oriented paradigm. You will learn how to create maintainable applications by studying higher level design patterns. The book will show you the complexities of string and file manipulation, and how Python distinguishes between binary and textual data. Not one, but two very powerful automated testing systems, unittest and pytest, will be introduced in this book. You'll get a comprehensive introduction to Python's concurrent programming ecosystem. By the end of the book, you will have thoroughly learned object-oriented principles using Python syntax and be able to create robust and reliable programs confidently. What you will learn Implement objects in Python by creating classes and defining methods Grasp common concurrency techniques and pitfalls in Python 3 Extend class functionality using inheritance Understand when to use object-oriented features, and more importantly when not to use them Discover what design patterns are and why they are different in Python Uncover the simplicity of unit testing and why it's so important in Python Explore concurrent object-oriented programming Who this book is for If you're new to object-oriented programming techniques, or if you have basic Python skills and wish to learn in depth how and when to correctly apply OOP in Python, this is the book for you. If you are an object-oriented programmer for other languages or seeking a leg up in the new world of Python 3.8, you too will find this book a useful introduction to Python. Previous experience with Python 3 is not necessary. COMPUTERS,Programming,General

Python Fundamentals With an interesting mix of theory and practicals, explore Python and its features, and progress from beginner to being skilled in this popular scripting language Key Features A comprehensive introduction to the world of Python programming Paves an easy-to-follow path for you to navigate through concepts Filled with over 90 practical exercises and activities to reinforce your learning Book Description After a brief history of Python and key differences between Python 2 and Python 3, you'll understand how Python has been used in applications such as YouTube and Google App Engine. As you work with the language, you'll learn about control statements, delve into controlling program flow and gradually work on more structured programs via functions. As you settle into the Python ecosystem, you'll learn about data structures and study ways to correctly store and represent information. By working through specific examples, you'll learn how Python implements object-oriented programming (OOP) concepts of abstraction, encapsulation of data, inheritance, and polymorphism. You'll be given an overview of how imports, modules, and packages work in Python, how you can handle errors to prevent apps from crashing, as well as file manipulation. By the end of this book, you'll have built up an impressive portfolio of projects and armed yourself with the skills you need to tackle Python projects in the real world. What you will learn Use control statements Manipulate primitive and non-primitive data structures Use loops to iterate over objects or data for accurate results Write encapsulated and succinct Python functions Build Python classes using object-oriented programming Manipulate files on the file system (open, read, write, and delete) Who this book is for Python Fundamentals is great for anyone who wants to start using Python to build anything from simple command-line programs to web applications. Prior knowledge of Python isn't required. COMPUTERS,Programming,General

Python for Data Science For Dummies The fast and easy way to learn Python programming and statistics Python is a general-purpose programming language created in the late 1980s—and named after Monty Python—that's used by thousands of people to do things from testing microchips at Intel, to powering Instagram, to building video games with the PyGame library. Python For Data Science For Dummies is written for people who are new to data analysis, and discusses the basics of Python data analysis programming and statistics. The book also discusses Google Colab, which makes it possible to write Python code in the cloud. Get started with data science and Python Visualize information Wrangle data Learn from data The book provides the statistical background needed to get started in data science programming, including probability, random distributions, hypothesis testing, confidence intervals, and building regression models for prediction. COMPUTERS,Programming,General

How to Speak Tech Things you’ve done online: ordered a pizza, checked the weather, booked a hotel, and reconnected with long-lost friends. Now it’s time to find out how these things work. Vinay Trivedi peels back the mystery of the Internet, explains it all in the simplest terms, and gives you the knowledge you need to speak confidently when the subject turns to technology. This revised second edition of How to Speak Tech employs the strategy of the popular first edition: through the narrative of setting up a fictitious startup, it introduces you to essential tech concepts. New tech topics that were added in this edition include the blockchain, augmented and virtual reality, Internet of Things, and artificial intelligence.The author’s key message is: technology isn’t beyond the understanding of anyone! By breaking down major tech concepts involved with a modern startup into bite-sized chapters, the author’s approach helps you understand topics that aren’t always explained clearly and shows you that they aren’t rocket science. So go ahead, grab this book, start to “speak tech,†and hold your own in any tech-related conversation! What You'll Learn Understand the basics of new and established technologies such as blockchain, artificial intelligence (AI), augmented and virtual reality (AR and VR), Internet of Things (IoT), software development, programming languages, databases, and more Listen intelligently and speak confidently when technologies are brought up in your business Be confident in your grasp of terms and technologies when setting up your own organization's application Who This Book Is For Students who want to understand different technologies relevant to their future careers at startups and established organizations, as well as business and other non-technical professionals who encounter and require an understanding of key technical terms and trends to succeed in their roles Reviews “Finally, a book non-techies can use to understand the technologies that are changing our lives.†Paul Bottino, Executive Director, Technology and Entrepreneurship Center, Harvard University “A great book everyone can use to understand how tech startups work.†Rene Reinsberg, Founder at Celo; Former VP of Emerging Products, GoDaddy “Through the simplicity of his presentation, Vinay shows that the basics of technology can be straightforwardly understood by anyone who puts in the time and effort to learn.†Joseph Lassiter, Professor of Management Science, Harvard Business School and Harvard Innovation Lab COMPUTERS,Programming,General

Deep Learning For Dummies Take a deep dive into deep learning Deep learning provides the means for discerning patterns in the data that drive online business and social media outlets. Deep Learning for Dummies gives you the information you need to take the mystery out of the topic—and all of the underlying technologies associated with it. In no time, you’ll make sense of those increasingly confusing algorithms, and find a simple and safe environment to experiment with deep learning. The book develops a sense of precisely what deep learning can do at a high level and then provides examples of the major deep learning application types. Includes sample code Provides real-world examples within the approachable text Offers hands-on activities to make learning easier Shows you how to use Deep Learning more effectively with the right tools This book is perfect for those who want to better understand the basis of the underlying technologies that we use each and every day. COMPUTERS,Programming,General

GitHub For Dummies Code collaboratively with GitHub Once you’ve learned the basics of coding the next step is to start sharing your expertise, learning from other coding pros, or working as a collaborative member of development teams. GitHub is the go-to community for facilitating coding collaboration, and GitHub For Dummies is the next step on your journey as a developer. Written by a GitHub engineer, this book is packed with insight on how GitHub works and how you can use it to become a more effective, efficient, and valuable member of any collaborative programming team. Store and share your work online with GitHub Collaborate with others on your team or across the international coding community Embrace open-source values and processes Establish yourself as a valuable member of the GitHub community From setting up GitHub on your desktop and launching your first project to cloning repositories, finding useful apps on the marketplace, and improving workflow, GitHub For Dummies covers the essentials the novice programmer needs to enhance collaboration and teamwork with this industry-standard tool. COMPUTERS,Programming,General

Julia 1.0 Programming Complete Reference Guide Learn dynamic programming with Julia to build apps for data analysis, visualization, machine learning, and the web Key Features Leverage Julia's high speed and efficiency to build fast, efficient applications Perform supervised and unsupervised machine learning and time series analysis Tackle problems concurrently and in a distributed environment Book Description Julia offers the high productivity and ease of use of Python and R with the lightning-fast speed of C++. There's never been a better time to learn this language, thanks to its large-scale adoption across a wide range of domains, including fintech, biotech and artificial intelligence (AI). You will begin by learning how to set up a running Julia platform, before exploring its various built-in types. This Learning Path walks you through two important collection types: arrays and matrices. You'll be taken through how type conversions and promotions work, and in further chapters you'll study how Julia interacts with operating systems and other languages. You'll also learn about the use of macros, what makes Julia suitable for numerical and scientific computing, and how to run external programs. Once you have grasped the basics, this Learning Path goes on to how to analyze the Iris dataset using DataFrames. While building a web scraper and a web app, you'll explore the use of functions, methods, and multiple dispatches. In the final chapters, you'll delve into machine learning, where you'll build a book recommender system. By the end of this Learning Path, you'll be well versed with Julia and have the skills you need to leverage its high speed and efficiency for your applications. This Learning Path includes content from the following Packt products: Julia 1.0 Programming - Second Edition by Ivo Balbaert Julia Programming Projects by Adrian Salceanu What you will learn Create your own types to extend the built-in type system Visualize your data in Julia with plotting packages Explore the use of built-in macros for testing and debugging Integrate Julia with other languages such as C, Python, and MATLAB Analyze and manipulate datasets using Julia and DataFrames Develop and run a web app using Julia and the HTTP package Build a recommendation system using supervised machine learning Who this book is for If you are a statistician or data scientist who wants a quick course in the Julia programming language while building big data applications, this Learning Path is for you. Basic knowledge of mathematics and programming is a must. COMPUTERS,Programming,General

The Complete Rust Programming Reference Guide Design and implement professional-level programs by leveraging modern data structures and algorithms in Rust Key Features Improve your productivity by writing more simple and easy code in Rust Discover the functional and reactive implementations of traditional data structures Delve into new domains of Rust, including WebAssembly, networking, and command-line tools Book Description Rust is a powerful language with a rare combination of safety, speed, and zero-cost abstractions. This Learning Path is filled with clear and simple explanations of its features along with real-world examples, demonstrating how you can build robust, scalable, and reliable programs. You'll get started with an introduction to Rust data structures, algorithms, and essential language constructs. Next, you will understand how to store data using linked lists, arrays, stacks, and queues. You'll also learn to implement sorting and searching algorithms, such as Brute Force algorithms, Greedy algorithms, Dynamic Programming, and Backtracking. As you progress, you'll pick up on using Rust for systems programming, network programming, and the web. You'll then move on to discover a variety of techniques, right from writing memory-safe code, to building idiomatic Rust libraries, and even advanced macros. By the end of this Learning Path, you'll be able to implement Rust for enterprise projects, writing better tests and documentation, designing for performance, and creating idiomatic Rust code. This Learning Path includes content from the following Packt products: Mastering Rust - Second Edition by Rahul Sharma and Vesa Kaihlavirta Hands-On Data Structures and Algorithms with Rust by Claus Matzinger What you will learn Design and implement complex data structures in Rust Create and use well-tested and reusable components with Rust Understand the basics of multithreaded programming and advanced algorithm design Explore application profiling based on benchmarking and testing Study and apply best practices and strategies in error handling Create efficient web applications with the Actix-web framework Use Diesel for type-safe database interactions in your web application Who this book is for If you are already familiar with an imperative language and now want to progress from being a beginner to an intermediate-level Rust programmer, this Learning Path is for you. Developers who are already familiar with Rust and want to delve deeper into the essential data structures and algorithms in Rust will also find this Learning Path useful. COMPUTERS,Programming,General

Learn Kotlin Programming Delve into the world of Kotlin and learn to build powerful Android and web applications Key Features Learn the fundamentals of Kotlin to write high-quality code Test and debug your applications with the different unit testing frameworks in Kotlin Explore Kotlin's interesting features such as null safety, reflection, and annotations Book Description Kotlin is a general-purpose programming language used for developing cross-platform applications. Complete with a comprehensive introduction and projects covering the full set of Kotlin programming features, this book will take you through the fundamentals of Kotlin and get you up to speed in no time. Learn Kotlin Programming covers the installation, tools, and how to write basic programs in Kotlin. You'll learn how to implement object-oriented programming in Kotlin and easily reuse your program or parts of it. The book explains DSL construction, serialization, null safety aspects, and type parameterization to help you build robust apps. You'll learn how to destructure expressions and write your own. You'll then get to grips with building scalable apps by exploring advanced topics such as testing, concurrency, microservices, coroutines, and Kotlin DSL builders. Furthermore, you'll be introduced to the kotlinx.serialization framework, which is used to persist objects in JSON, Protobuf, and other formats. By the end of this book, you'll be well versed with all the new features in Kotlin and will be able to build robust applications skillfully. What you will learn Explore the latest Kotlin features in order to write structured and readable object-oriented code Get to grips with using lambdas and higher-order functions Write unit tests and integrate Kotlin with Java code Create real-world apps in Kotlin in the microservices style Use Kotlin extensions with the Java collections library Uncover destructuring expressions and find out how to write your own Understand how Java-nullable code can be integrated with Kotlin features Who this book is for If you're a beginner or intermediate programmer who wants to learn Kotlin to build applications, this book is for you. You'll also find this book useful if you're a Java developer interested in switching to Kotlin. COMPUTERS,Programming,General

Modern Programming Discover the untapped features of object-oriented programming and use it with other software tools to code fast, efficient applications. Key Features Explore the complexities of object-oriented programming (OOP) Discover what OOP can do for you Learn to use the key tools and software engineering practices to support your own programming needs Book Description Your experience and knowledge always influence the approach you take and the tools you use to write your programs. With a sound understanding of how to approach your goal and what software paradigms to use, you can create high-performing applications quickly and efficiently. In this two-part book, you'll discover the untapped features of object-oriented programming and use it with other software tools to code fast and efficient applications. The first part of the book begins with a discussion on how OOP is used today and moves on to analyze the ideas and problems that OOP doesn't address. It continues by deconstructing the complexity of OOP, showing you its fundamentally simple core. You'll see that, by using the distinctive elements of OOP, you can learn to build your applications more easily. The next part of this book talks about acquiring the skills to become a better programmer. You'll get an overview of how various tools, such as version control and build management, help make your life easier. This book also discusses the pros and cons of other programming paradigms, such as aspect-oriented programming and functional programming, and helps to select the correct approach for your projects. It ends by talking about the philosophy behind designing software and what it means to be a "good" developer. By the end of this two-part book, you will have learned that OOP is not always complex, and you will know how you can evolve into a better programmer by learning about ethics, teamwork, and documentation. What you will learn Untangle the complexity of object-oriented programming by breaking it down to its essential building blocks Realize the full potential of OOP to design efficient, maintainable programs Utilize coding best practices, including TDD, pair programming and code reviews, to improve your work Use tools, such as source control and IDEs, to work more efficiently Learn how to most productively work with other developers Build your own software development philosophy Who this book is for This book is ideal for programmers who want to understand the philosophy behind creating software and what it means to be “good†at designing software. Programmers who want to deconstruct the OOP paradigm and see how it can be reconstructed in a clear, straightforward way will also find this book useful. To understand the ideas expressed in this book, you must be an experienced programmer who wants to evolve their practice. COMPUTERS,Programming,General

Go Programming Cookbook Tackle the trickiest of problems in Go programming with this practical guide Key Features Develop applications for different domains using modern programming techniques Tackle common problems when it comes to parallelism, concurrency, and reactive programming in Go Work with ready-to-execute code based on the latest version of Go Book Description Go (or Golang) is a statically typed programming language developed at Google. Known for its vast standard library, it also provides features such as garbage collection, type safety, dynamic-typing capabilities, and additional built-in types. This book will serve as a reference while implementing Go features to build your own applications. This Go cookbook helps you put into practice the advanced concepts and libraries that Golang offers. The recipes in the book follow best practices such as documentation, testing, and vendoring with Go modules, as well as performing clean abstractions using interfaces. You'll learn how code works and the common pitfalls to watch out for. The book covers basic type and error handling, and then moves on to explore applications, such as websites, command-line tools, and filesystems, that interact with users. You'll even get to grips with parallelism, distributed systems, and performance tuning. By the end of the book, you'll be able to use open source code and concepts in Go programming to build enterprise-class applications without any hassle. What you will learn Work with third-party Go projects and modify them for your use Write Go code using modern best practices Manage your dependencies with the new Go module system Solve common problems encountered when dealing with backend systems or DevOps Explore the Go standard library and its uses Test, profile, and fine-tune Go applications Who this book is for If you're a web developer, programmer, or enterprise developer looking for quick solutions to common and not-so-common problems in Go programming, this book is for you. Basic knowledge of the Go language is assumed. COMPUTERS,Programming,General

Machine Learning with AWS Use artificial intelligence and machine learning on AWS to create engaging applications Key Features Explore popular AI and ML services with their underlying algorithms Use the AWS environment to manage your AI workflow Reinforce key concepts with hands-on exercises using real-world datasets Book Description Machine Learning with AWS is the right place to start if you are a beginner interested in learning useful artificial intelligence (AI) and machine learning skills using Amazon Web Services (AWS), the most popular and powerful cloud platform. You will learn how to use AWS to transform your projects into apps that work at high speed and are highly scalable. From natural language processing (NLP) applications, such as language translation and understanding news articles and other text sources, to creating chatbots with both voice and text interfaces, you will learn all that there is to know about using AWS to your advantage. You will also understand how to process huge numbers of images fast and create machine learning models. By the end of this book, you will have developed the skills you need to efficiently use AWS in your machine learning and artificial intelligence projects. What you will learn Get up and running with machine learning on the AWS platform Analyze unstructured text using AI and Amazon Comprehend Create a chatbot and interact with it using speech and text input Retrieve external data via your chatbot Develop a natural language interface Apply AI to images and videos with Amazon Rekognition Who this book is for Machine Learning with AWS is ideal for data scientists, programmers, and machine learning enthusiasts who want to learn about the artificial intelligence and machine learning capabilities of Amazon Web Services. COMPUTERS,Programming,General

Learning C# by Programming Games Developing computer games is a perfect way to learn how to program in modern programming languages. This book teaches how to program in C# through the creation of computer games – and without requiring any previous programming experience. Contrary to most programming books, van Toll, Egges, and Fokker do not organize the presentation according to programming language constructs, but instead use the structure and elements of computer games as a framework. For instance, there are chapters on dealing with player input, game objects, game worlds, game states, levels, animation, physics, and intelligence. The reader will be guided through the development of four games showing the various aspects of game development. Starting with a simple shooting game, the authors move on to puzzle games consisting of multiple levels, and conclude the book by developing a full-fledged platform game with animation, game physics, and intelligent enemies. They show a number of commonly used techniques in games, such as drawing layers of sprites, rotating, scaling and animating sprites, dealing with physics, handling interaction between game objects, and creating pleasing visual effects. At the same time, they provide a thorough introduction to C# and object-oriented programming, introducing step by step important programming concepts such as loops, methods, classes, collections, and exception handling. This second edition includes a few notable updates. First of all, the book and all example programs are now based on the library MonoGame 3.6, instead of the obsolete XNA Game Studio. Second, instead of explaining how the example programs work, the text now invites readers to write these programs themselves, with clearly marked reference points throughout the text. Third, the book now makes a clearer distinction between general (C#) programming concepts and concepts that are specific to game development. Fourth, the most important programming concepts are now summarized in convenient “Quick Reference†boxes, which replace the syntax diagrams of the first edition. Finally, the updated exercises are now grouped per chapter and can be found at the end of each chapter, allowing readers to test their knowledge more directly. The book is also designed to be used as a basis for a game-oriented programming course. Supplementary materials for organizing such a course are available on an accompanying web site, which also includes all example programs, game sprites, sounds, and the solutions to all exercises. COMPUTERS,Programming,General

Beginning Programming in 24 Hours, Sams Teach Yourself Sams Teach Yourself Beginning Programming in 24 Hours explains the basics of programming in the successful 24 Hours format. The book's examples are easily readable and understandable by even those with no previous exposure to programming. This book covers the absolute basics of programming: Why program? What tools to use? How does a program tell the computer what to do? Readers will learn how to program the computer and will explore some of the most popular programming languages in use. This book will introduce the reader to common programming fundamentals using Python and will provide an overview of other common programming languages and their uses. COMPUTERS,Programming,General

Beginner's Step-by-Step Coding Course With this visual guide to computer programming for beginners, it has never been easier to learn how to code. Coding skills are in high demand and the need for programmers is still growing. Covering three of the most popular languages for new coders, this book uses a graphic method to break complex subjects into user-friendly chunks, bringing essential skills within easy reach. Each chapter contains tutorials on practical projects designed to teach you the main applications of each language, such as building websites, creating games, and designing apps. The book also looks at many of the main coding languages that are out there, outlining the key applications of each language, so you can choose the right language for you. You'll learn to think like a programmer by breaking a problem down into parts, before turning those parts into lines of code. Short, easy-to-follow steps then show you, piece by piece, how to build a complete program. There are challenges for you to tackle to build your confidence before moving on. Written by a team of expert coders and coding teachers, Beginner's Step-by-Step Coding Course is the ideal way to get to set you on the road to code. COMPUTERS,Programming,General

Guide to Competitive Programming Building on what already is the most comprehensive introduction to competitive programming, this enhanced new textbook features new material on advanced topics, such as calculating Fourier transforms, finding minimum cost flows in graphs, and using automata in string problems. Critically, the text accessibly describes and shows how competitive programming is a proven method of implementing and testing algorithms, as well as developing computational thinking and improving both programming and debugging skills. Topics and features: introduces dynamic programming and other fundamental algorithm design techniques, and investigates a wide selection of graph algorithms; compatible with the IOI Syllabus, yet also covering more advanced topics, such as maximum flows, Nim theory, and suffix structures; surveys specialized algorithms for trees, and discusses the mathematical topics that are relevant in competitive programming; reviews the features of the C++ programming language, and describes how to create efficient algorithms that can quickly process large data sets; discusses sorting algorithms and binary search, and examines a selection of data structures of the C++ standard library; covers such advanced algorithm design topics as bit-parallelism and amortized analysis, and presents a focus on efficiently processing array range queries; describes a selection of more advanced topics, including square-root algorithms and dynamic programming optimization. Fully updated, expanded and easy to follow, this core textbook/guide is an ideal reference for all students needing to learn algorithms and to practice for programming contests. Knowledge of programming basics is assumed, but previous background in algorithm design or programming contests is not necessary. With its breadth of topics, examples and references, the book is eminently suitable for both beginners and more experienced readers alike. COMPUTERS,Programming,General

A Pipelined Multi-Core Machine with Operating System Support This work is building on results from the book named “A Pipelined Multi-core MIPS Machine: Hardware Implementation and Correctness†by M. Kovalev, S.M. Müller, and W.J. Paul, published as LNCS 9000 in 2014. It presents, at the gate level, construction and correctness proof of a multi-core machine with pipelined processors and extensive operating system support with the following features: • MIPS instruction set architecture (ISA) for application and for system programming • cache coherent memory system • store buffers in front of the data caches • interrupts and exceptions• memory management units (MMUs) • pipelined processors: the classical five-stage pipeline is extended by two pipeline stages for address translation • local interrupt controller (ICs) supporting inter-processor interrupts (IPIs) • I/O-interrupt controller and a disk COMPUTERS,Programming,General

Trends in Functional Programming This book constitutes the thoroughly refereed revised selected papers of the 20th International Symposium on Trends in Functional Programming, TFP 2019, held in Vancouver, Canada, in June 2019. The 6 revised full papers were selected from 11 submissions and present papers in all aspects of functional programming, taking a broad view of current and future trends in the area. It aspires to be a lively environment for presenting the latest research results, and other contributions, described in draft papers submitted prior to the symposium. COMPUTERS,Programming,General

Fields of Logic and Computation III This Festschrift is published in honor of Yuri Gurevich’s 80th birthday. An associated conference, YuriFest 2020, was planned for May 18–20 in Fontainebleau, France, in combination with the 39th Journées sur les Arithmétiques Faibles also celebrating Yuri’s 80th birthday. Because of the coronavirus situation, the conference had to be postponed, but this Festschrift is being published as originally planned. It addresses a very wide variety of topics, but by no means all of the fields of logic and computation in which Yuri has made important progress. COMPUTERS,Programming,General

Developments in Language Theory This book constitutes the proceedings of the 24th International Conference on Developments in Language Theory, DLT 2020, which was due to be held in Tampa, Florida, USA, in May 2020. The conference was cancelled due to the COVID-19 pandemic. The 24 full papers presented were carefully reviewed and selected from 38 submissions. The papers present current developments in language theory, formal languages, automata theory and related areas, such as algorithmic, combinatorial, and algebraic properties of words and languages, cellular automata, algorithms on words, etc. COMPUTERS,Programming,General

Theory And Practice Of Computation - Proceedings Of Workshop On Computation This is the proceedings of the Seventh Workshop on Computing: Theory and Practice, WCTP 2017 devoted to theoretical and practical approaches to computation. This workshop was organized by four top universities in Japan and the Philippines: Tokyo Institute of Technology, Osaka University, University of the Philippines Diliman, and De La Salle University. The proceedings provides a view of the current movement in computational research in these two countries. The papers included in the proceedings focus on both: theoretical and practical aspects of computation. COMPUTERS,Programming,General

Usability Testing Essentials Usability Testing Essentials presents a practical, step-by-step approach to learning the entire process of planning and conducting a usability test. It explains how to analyze and apply the results and what to do when confronted with budgetary and time restrictions. This is the ideal book for anyone involved in usability or user-centered design—from students to seasoned professionals. Filled with new examples and case studies, Usability Testing Essentials, 2nd Edition is completely updated to reflect the latest approaches, tools and techniques needed to begin usability testing or to advance in this area. Provides a comprehensive, step-by-step guide to usability testing, a crucial part of every product’s development Discusses important usability issues such as international testing, persona creation, remote testing, and accessibility Presents new examples covering mobile devices and apps, websites, web applications, software, and more Includes strategies for using tools for moderated and unmoderated testing, expanded content on task analysis, and on analyzing and reporting results COMPUTERS,Programming,General

Application and Theory of Petri Nets and Concurrency This book constitutes the proceedings of the 41st International Conference on Application and Theory of Petri Nets and Concurrency, PETRI NETS 2020, which was supposed to be held in Paris, France, in June 2020. The conference was held virtually due to the COVID-19 pandemic. The 17 regular and 6 tool papers presented together in this volume were carefully reviewed and selected from 56 submissions. The focus of the conference is on following topics: application of concurrency to system design; languages and synthesis; semantics; process mining and applications; extensions and model checking; tools. COMPUTERS,Programming,General

Coding Literacy How the theoretical tools of literacy help us understand programming in its historical, social and conceptual contexts. The message from educators, the tech community, and even politicians is clear: everyone should learn to code. To emphasize the universality and importance of computer programming, promoters of coding for everyone often invoke the concept of “literacy,” drawing parallels between reading and writing code and reading and writing text. In this book, Annette Vee examines the coding-as-literacy analogy and argues that it can be an apt rhetorical frame. The theoretical tools of literacy help us understand programming beyond a technical level, and in its historical, social, and conceptual contexts. Viewing programming from the perspective of literacy and literacy from the perspective of programming, she argues, shifts our understandings of both. Computer programming becomes part of an array of communication skills important in everyday life, and literacy, augmented by programming, becomes more capacious. Vee examines the ways that programming is linked with literacy in coding literacy campaigns, considering the ideologies that accompany this coupling, and she looks at how both writing and programming encode and distribute information. She explores historical parallels between writing and programming, using the evolution of mass textual literacy to shed light on the trajectory of code from military and government infrastructure to large-scale businesses to personal use. Writing and coding were institutionalized, domesticated, and then established as a basis for literacy. Just as societies demonstrated a “literate mentality” regardless of the literate status of individuals, Vee argues, a “computational mentality” is now emerging even though coding is still a specialized skill. COMPUTERS,Programming,General

The Little Prover An introduction to writing proofs about computer programs, written in an accessible question-and-answer style, complete with step-by-step examples and a simple proof assistant. The Little Prover introduces inductive proofs as a way to determine facts about computer programs. It is written in an approachable, engaging style of question-and-answer, with the characteristic humor of The Little Schemer (fourth edition, MIT Press). Sometimes the best way to learn something is to sit down and do it; the book takes readers through step-by-step examples showing how to write inductive proofs. The Little Prover assumes only knowledge of recursive programs and lists (as presented in the first three chapters of The Little Schemer) and uses only a few terms beyond what novice programmers already know. The book comes with a simple proof assistant to help readers work through the book and complete solutions to every example. COMPUTERS,Programming,General

How to Design Programs, second edition A completely revised edition, offering new design recipes for interactive programs and support for images as plain values, testing, event-driven programming, and even distributed programming. This introduction to programming places computer science at the core of a liberal arts education. Unlike other introductory books, it focuses on the program design process, presenting program design guidelines that show the reader how to analyze a problem statement, how to formulate concise goals, how to make up examples, how to develop an outline of the solution, how to finish the program, and how to test it. Because learning to design programs is about the study of principles and the acquisition of transferable skills, the text does not use an off-the-shelf industrial language but presents a tailor-made teaching language. For the same reason, it offers DrRacket, a programming environment for novices that supports playful, feedback-oriented learning. The environment grows with readers as they master the material in the book until it supports a full-fledged language for the whole spectrum of programming tasks. This second edition has been completely revised. While the book continues to teach a systematic approach to program design, the second edition introduces different design recipes for interactive programs with graphical interfaces and batch programs. It also enriches its design recipes for functions with numerous new hints. Finally, the teaching languages and their IDE now come with support for images as plain values, testing, event-driven programming, and even distributed programming. COMPUTERS,Programming,General

Critical Code Studies An argument that we must read code for more than what it does—we must consider what it means. Computer source code has become part of popular discourse. Code is read not only by programmers but by lawyers, artists, pundits, reporters, political activists, and literary scholars; it is used in political debate, works of art, popular entertainment, and historical accounts. In this book, Mark Marino argues that code means more than merely what it does; we must also consider what it means. We need to learn to read code critically. Marino presents a series of case studies—ranging from the Climategate scandal to a hactivist art project on the US-Mexico border—as lessons in critical code reading. Marino shows how, in the process of its circulation, the meaning of code changes beyond its functional role to include connotations and implications, opening it up to interpretation and inference—and misinterpretation and reappropriation. The Climategate controversy, for example, stemmed from a misreading of a bit of placeholder code as a “smoking gun” that supposedly proved fabrication of climate data. A poetry generator created by Nick Montfort was remixed and reimagined by other poets, and subject to literary interpretation. Each case study begins by presenting a small and self-contained passage of code—by coders as disparate as programming pioneer Grace Hopper and philosopher Friedrich Kittler—and an accessible explanation of its context and functioning. Marino then explores its extra-functional significance, demonstrating a variety of interpretive approaches. COMPUTERS,Programming,General

Exploratory Programming for the Arts and Humanities A book for anyone who wants to learn programming to explore and create, with exercises and projects to help the reader learn by doing. This book introduces programming to readers with a background in the arts and humanities; there are no prerequisites, and no knowledge of computation is assumed. In it, Nick Montfort reveals programming to be not merely a technical exercise within given constraints but a tool for sketching, brainstorming, and inquiring about important topics. He emphasizes programming's exploratory potential—its facility to create new kinds of artworks and to probe data for new ideas. The book is designed to be read alongside the computer, allowing readers to program while making their way through the chapters. It offers practical exercises in writing and modifying code, beginning on a small scale and increasing in substance. In some cases, a specification is given for a program, but the core activities are a series of “free projects,” intentionally underspecified exercises that leave room for readers to determine their own direction and write different sorts of programs. Throughout the book, Montfort also considers how computation and programming are culturally situated—how programming relates to the methods and questions of the arts and humanities. The book uses Python and Processing, both of which are free software, as the primary programming languages. COMPUTERS,Programming,General

Learning RSLogix 5000 Programming Get to grips with the Logix platform, Rockwell Automation terminologies, and the online resources available in the Literature Library Key Features Build real-world solutions using ControlLogix, CompactLogix, and RSLogix 5000/Studio 5000 Understand the different controllers and form factors offered by the ControlLogix and CompactLogix platforms Explore the latest changes in the Studio 5000 Automation Engineering and Design software suite Book Description Understanding programmable logic controller (PLC) programming with Rockwell Software's Logix Designer and the Studio 5000 platform, which includes ControlLogix, CompactLogix, and SoftLogix, is key to building robust PLC solutions. RSLogix 5000/Studio 5000's Logix Designer are user-friendly IEC 61131-3-compliant interfaces for programming the current generation of Rockwell Automation Controllers using Ladder Diagram (LD), Function Block Diagram (FBD), Structured Text (ST), and Sequential Function Chart (SFC). This second edition of Learning RSLogix 5000 Programming guides you through the technicalities and comes packed with the latest features of Studio 5000, industrial networking fundamentals, and industrial cybersecurity best practices. You'll go through the essential hardware and software components of Logix, before learning all about the new L8 processor model and the latest Studio 5000 architecture to build effective integrated solutions. Entirely new for this edition, you'll discover a chapter on cybersecurity concepts with RSLogix 5000. The book even gets you hands-on with building a robot bartender control system from start to finish. By the end of this Logix 5000 book, you'll have a clear understanding of the capabilities of the Logix platform and be able to confidently navigate Rockwell Automation Literature Library resources. What you will learn Gain insights into Rockwell Automation and the evolution of the Logix platform Find out the key platform changes in Studio 5000 and Logix Designer Explore a variety of ControlLogix and CompactLogix controllers Understand the Rockwell Automation industrial networking fundamentals Implement cybersecurity best practices using Rockwell Automation technologies Discover the key considerations for engineering a Rockwell Automation solution Who this book is for If you're a PLC programmer, an electrician, an instrumentation technician, or an automation professional with basic PLC programming knowledge, but no knowledge of RSLogix 5000, this RSLogix 5000 book is for you. You'll also find the book useful if you're already familiar with automation and want to learn about RSLogix 5000 software in a short time span. COMPUTERS,Programming,General

Probabilistic Extensions of Various Logical Systems The contributions in this book survey results on combinations of probabilistic and various other classical, temporal and justification logical systems. Formal languages of these logics are extended with probabilistic operators. The aim is to provide a systematic overview and an accessible presentation of mathematical techniques used to obtain results on formalization, completeness, compactness and decidability. The book will be of value to researchers in logic and it can be used as a supplementary text in graduate courses on non-classical logics. COMPUTERS,Programming,General

Beginning Objective C Objective-C is today's fastest growing programming language, at least in part due to the popularity of Apple's Mac, iPhone and iPad. Beginning Objective-C is for you if you have some programming experience, but you're new to the Objective-C programming language and you want a modern—and fast—way forwards to your own coding projects. Beginning Objective-C offers you a modern programmer's perspective on Objective-C courtesy of two of the best iOS and Mac developers in the field today, and gets you programming to the best of your ability in this important language. It gets you rolling fast into the sound fundamentals and idioms of Objective-C on the Mac and iOS, in order to learn how best to construct your applications and libraries, making the best use of the tools it provides— no matter what projects you plan to build. The book offers thorough introductions to the core tenets of the language itself and its primary toolkits: the Foundation and AppKit frameworks. Within its pages you will encounter a mine of information on many topics, including use of the file system and network APIs, concurrency and multi-core programming, the user interface system architecture, data modeling, and more. You'll soon find yourself building a fairly complex Objective-C based application, and mastering the language ready for your own projects. If you're new to programming altogether, then Apress has other Objective-C books for you such as our Learning and Absolute Beginner titles—otherwise, let your existing skills ramp you fast forwards in Objective-C with Beginning Objective-C so that you can start building your own applications quickly. COMPUTERS,Programming,Macintosh

Objective-C Recipes Objective-C Recipes provides a problem solution approach for dealing with key aspects of Objective-C programming, ensuring you have the indispensable reference you need to successfully execute common programming tasks. You will see how to use the unique features of the Objective-C programming language, the helpful features of the Foundation framework, and the benefits of using Objective-J as an alternative. Solutions are available for a range of problems, including: Application development with Xcode Working with strings, numbers and object collections Using foundation classes like NSArray, NSString, NSData and more Dealing with threads, multi-core processing and asynchronous processing Building applications that take advantage of dates and timers and memory management How to use Objective-C on other platforms Objective-C Recipes is an essential reference for every Objective-C programmer, and offers solutions in a concise and easy-to-follow manner. Matthew Campbell has trained over 800 new iOS developers at the Mobile App Mastery Institute and iOS Code Camp, and here brings his expertise to offer you the ability to use and exploit Objective-C to get the most out of all of your projects. COMPUTERS,Programming,Macintosh

Cocoa Programming for OS X <>Covering the bulk of what you need to know to develop full-featured applications for OS X, this edition is updated for OS X Yosemite (10.10), Xcode 6, and Swift. Written in an engaging tutorial style and class-tested for clarity and accuracy, it is an invaluable resource for any Mac programmer. The authors introduce the two most commonly used Mac developer tools: Xcode and Instruments. They also cover the Swift language, basic application architecture, and the major design patterns of Cocoa. Examples are illustrated with exemplary code, written in the idioms of the Cocoa community, to show you how Mac programs should be written. After reading this book, you will know enough to understand and utilize Apple’s online documentation for your own unique needs. And you will know enough to write your own stylish code. This edition was written for Xcode 6.3 and Swift 1.2. At WWDC 2015, Apple announced Xcode 7 and Swift 2, both of which introduce significant updates that (along with some changes to Cocoa for OS X 10.11) affect some of the exercises in this book. We have prepared a companion guide listing the changes needed to use Xcode 7 to work through the exercises in the book; it is available at https://github.com/bignerdranch/cocoa-programming-for-osx-5e/blob/master/Swift2.md. COMPUTERS,Programming,Macintosh

iOS Programming Updated for Xcode 8, Swift 3, and iOS 10, iOS Programming: The Big Nerd Ranch Guide leads you through the essential concepts, tools, and techniques for developing iOS applications. After completing this book, you will have the know-how and the confidence you need to tackle iOS projects of your own. Based on Big Nerd Ranch's popular iOS training and its well-tested materials and methodology, this bestselling guide teaches iOS concepts and coding in tandem. The result is instruction that is relevant and useful. Throughout the book, the authors explain what's important and share their insights into the larger context of the iOS platform. You get a real understanding of how iOS development works, the many features that are available, and when and where to apply what you've learned. COMPUTERS,Programming,Macintosh

Swift Programming This is the eBook of the printed book and may not include any media, website access codes, or print supplements that may come packaged with the bound book. Through the authors' carefully constructed explanations and examples, you will develop an understanding of Swift grammar and the elements of effective Swift style. This book is written for Swift 3.0 and will also show you how to navigate Xcode 8 and get the most out of Apple's documentation. Throughout the book, the authors share their insights into Swift to ensure that you understand the hows and whys of Swift and can put that understanding to use in different contexts. After working through the book, you will have the knowledge and confidence to develop your own solutions to a wide range of programming challenges using Swift. COMPUTERS,Programming,Macintosh

Learn FileMaker Pro 16 Extend FileMaker's built-in functionality and totally customize your data management environment with specialized functions and menus to super-charge the results and create a truly unique and focused experience. This book includes everything a beginner needs to get started building databases with FileMaker and contains advanced tips and techniques that the most seasoned professionals will appreciate. Written by a long time FileMaker developer, this book contains material for developers of every skill level. FileMaker Pro 16 is a powerful database development application used by millions of people in diverse industries to simplify data management tasks, leverage their business information in new ways and automate many mundane tasks. A custom solution built with FileMaker can quickly tap into a powerful set of capabilities and technologies to offer users an intuitive and pleasing environment in which to achieve new levels of efficiency and professionalism. What You’ll learn Create SQL queries to build fast and efficient formulas Discover new features of version 16 such as JSON functions, Cards, Layout Object window, SortValues, UniqueValues, using variables in Data Sources Write calculations using built-in and creating your own custom functions Discover the importance of a good approach to interface and technical design Apply best practices for naming conventions and usage standards Explore advanced topics about designing professional, open-ended solutions and using advanced techniques Who This Book Is For Casual programmers, full time consultants and IT professionals. COMPUTERS,Programming,Macintosh

Core Data in Swift Core Data is intricate, powerful, and necessary. Discover the powerful capabilities integrated into Core Data, and how to use Core Data in your iOS and OS X projects. All examples are current for OS X El Capitan, iOS 9, and the latest release of Core Data. All the code is written in Swift, including numerous examples of how best to integrate Core Data with Apple's newest programming language. Core Data expert Marcus Zarra walks you through a fully developed application based around the Core Data APIs. You'll build on this application throughout the book, learning key Core Data elements such as NSPredicate, NSFetchRequest, thread management, and memory management. Start with the basics of Core Data and learn how to use it to develop your application. Then delve deep into the API details. Explore how to get Core Data integrated into your application properly, and work with this flexible API to create convenience methods to improve your application's maintainability. Reduce your migration difficulties, integrate your Core Data app with iCloud and Watch Kit, and use Core Data in a queue-based environment. By the end of the book, you'll have built a full-featured application, gained a complete understanding of Core Data, and learned how to integrate your application into the iPhone/iPad platform. This book is based on Core Data in Objective-C, Third Edition. It focuses on Swift and adds an additional chapter on how to integrate Core Data with an efficient network implementation, with best practices on how to load and pre-load data into your Swift application. What You Need: Mac OS X El Capitan and iOS 9 and a basic working knowledge of Swift COMPUTERS,Programming,Macintosh

Objective-C for Absolute Beginners Learn Objective-C and its latest release, and learn how to mix Swift with it. You have a great idea for an app, but how do you bring it to fruition? With Objective-C, the universal language of iPhone, iPad, and Mac apps. Using a hands-on approach, you'll learn how to think in programming terms, how to use Objective-C to construct program logic, and how to synthesize it all into working apps. Gary Bennett, an experienced app developer and trainer, will guide you on your journey to becoming a successful app developer. Along the way you'll discover the flexibility of Apple’s developer tools If you're looking to take the first step towards App Store success, Objective-C for Absolute Beginners, Fourth Edition is the place to start. What You'll Learn Understand the fundamentals of computer programming: variables, design data structures, and working with file systems Examine the logic of object-oriented programming: how to use classes, objects, and methods Install Xcode and write programs in Objective-C Who This Book Is For Anyone who wants to learn to develop apps for the iPhone, iPad, Mac, or Watch using the Objective-C programming language. No previous programming experience is necessary. COMPUTERS,Programming,Macintosh

Learning Swift Get valuable hands-on experience with Swift, the open source programming language developed by Apple. With this practical guide, skilled programmers with little or no knowledge of Apple development will learn how to code with the latest version of Swift by developing a working iOS app from start to finish. You’ll begin with Swift programming basics—including guidelines for making your code "Swifty"—and learn how to work with Xcode and its built-in Interface Builder. Then you’ll dive step-by-step into building and customizing a basic app for taking, editing, and deleting selfies. You’ll also tune and test the app for performance and manage the app’s presence in the App Store. Divided into four parts, this book includes: Swift 4 basics: Learn Swift’s basic building blocks and the features of object-oriented development Building the Selfiegram app: Build model objects and the UI for your selfie app and add location support, user settings, and notifications Polishing Selfiegram: Create a theme and support for sharing and add custom views, image overlays, and localization Beyond app development: Debug and performance test with Xcode, automate chores with Fastlane, and user-test the app with TestFlight COMPUTERS,Programming,Macintosh

Programming iOS 12 If you’re grounded in the basics of Swift, Xcode, and the Cocoa framework, this book provides a structured explanation of all essential real-world iOS app components. Through deep exploration and copious code examples, you’ll learn how to create views, manipulate view controllers, and add features from iOS frameworks. Create, arrange, draw, layer, and animate views that respond to touch Use view controllers to manage multiple screens of interface Master interface classes for scroll views, table views, text, popovers, split views, web views, and controls Dive into frameworks for sound, video, maps, and sensors Access user libraries: music, photos, contacts, and calendar Explore additional topics, including files, networking, and threads Stay up-to-date on iOS 12 innovations, such as User Notification framework improvements, as well as changes in Xcode 10 and Swift 4.2. All example code is available on GitHub for you to download, study, and run. Want to brush up on the basics? Pick up iOS 12 Programming Fundamentals with Swift to learn about Swift, Xcode, and Cocoa. Together with Programming iOS 12, you’ll gain a solid, rigorous, and practical understanding of iOS 12 development. COMPUTERS,Programming,Macintosh

Program the Internet of Things with Swift for iOS Learn how to build apps using Apple’s native APIs for the Internet of Things, including the Apple Watch, HomeKit, and Apple Pay. You'll also see how to interface with popular third-party hardware such as the Raspberry Pi, Arduino, and the FitBit family of devices. Program the Internet of Things with Swift and iOS is an update to the previous version and includes all new Swift 4 code. This book is a detailed tutorial that provides a detailed "how" and "why" for each topic, explaining Apple-specific design patterns as they come up and pulling lessons from other popular apps. To help you getting up and running quickly, each chapter is framed within a working project, allowing you to use the sample code directly in your apps. The Internet of Things is not limited to Apple devices alone, so this book also explains how to interface with popular third-party hardware devices, such as the Fitbit and Raspberry Pi, and generic interfaces, like Restful API’s and HTTPS. You'll also review new API's like Face ID and new design considerations, and look more closely at SSL and how to make IoT connected apps more resistant to hackers. The coverage of Apple Watch has been expanded as well. The Internet of Things is waiting — be a part of it! What You'll Learn Use Apple's native IoT Frameworks, such as HealthKit, HomeKit, and FaceID Interact with popular third-party hardware, such as the Raspberry Pi, Arduino, and FitBit Work with real projects to develop skills based in experience Make a smarter IoT with SiriKit and CoreML Who This Book Is For The primary audience for this book are readers who have a grasp of the basics of iOS development and are looking to improve their Internet of Things-specific skills. Intermediate to Advanced level. The secondary audience would be business decision makers (managers, business analysts, executives) who are looking to gain a rough understanding of what is involved in Internet of Things development for iOS. COMPUTERS,Programming,Macintosh

Beginning iPhone Development with Swift 5 Learn how to integrate all the interface elements iOS users have come to know and love, such as buttons, switches, pickers, toolbars, and sliders. In this edition of the best selling book, you’ll also learn about touch gestures, table views, and collection views for displaying data on a user interface. Assuming little or no working knowledge of the Swift programming language, and written in a friendly, easy-to-follow style, this book offers a comprehensive course in iPhone and iPad programming. The book starts with a gentle introduction to using Xcode and then guides you though the creation of your first simple application.You’ll start with designing basic user interfaces and then explore more sophisticated ones that involve multiple screens such as navigation controllers, tab bars, tool bars, page views, and split views that are particularly useful on the larger screens of the iPad and certain iPhone models. And there’s much more! Beginning iPhone Development with Swift 5 covers the basic information you need to get up and running quickly to turn your great ideas into working iOS apps. Once you’re ready, move on to Pro iPhone Development with Swift 5 to learn more of the really unique aspects of iOS programming and the Swift language. What You Will Learn Discover what data persistence is, and why it’s important Build cool, crisp user interfaces Display data in Table Views Work with all the most commonly used iOS Frameworks Who This Book is For Aspiring iOS app developers new to the Apple Swift programming language and/or the iOS SDK. COMPUTERS,Programming,Macintosh

Pro iPhone Development with Swift 5 If you’ve already learned the basics of Swift and iOS programming, it’s time to take your skills to the next level. In this follow up work to the best-selling Beginning iPhone Development with Swift, you’ll learn tips for organizing and debugging Swift code, using multi-threaded programming with Grand Central Dispatch, passing data between view controllers, and designing apps for multiple languages. You’ll also see how to play audio and video files, access the camera and save pictures to the Photos library, use location services to pinpoint your position on a map, display web pages, and create animation to spice up any user interface. Finally, you’ll learn how to use Apple’s advanced frameworks for machine learning, facial and text recognition, and creating augmented reality apps. Pro iPhone Development with Swift 5 provides insightful instruction on how to improve your existing apps or create powerful new iOS apps using the latest version of the Swift programming language. What You Will Learn Save and retrieve data when apps close or get pushed in the background Recognize speech with Apple’s advanced frameworks Create augmented reality apps Understand spoken commands with Siri Who This Book is For Aspiring iOS app developers familiar with the Apple Swift programming language and/or the iOS SDK, but ready to move to the next level. COMPUTERS,Programming,Macintosh

Swift 5 for Absolute Beginners Stay motivated and overcome obstacles while learning to use Swift Playgrounds and Xcode 10.2 to become a great iOS developer. This book, fully updated for Swift 5, is perfect for those with no programming background, those with some programming experience but no object-oriented experience, or those that have a great idea for an app but haven’t programmed since school.Many people have a difficult time believing they can learn to write iOS apps. Swift 5 for Absolute Beginners will show you how to do so. You'll learn Object-Oriented Programming (OOP) and be introduced to User Interface (UI) design following Apple’s Human Interface Guidelines (HIG) using storyboards and the Model-View-Controller (MVC) pattern before moving on to write your own iPhone and Apple Watch apps from scratch. What You’ll Learn Work with Swift classes, properties, and functions Examine proper User Interface (UI) and User Experience (UX) design Understand Swift data types: integers, floats, strings, and booleans Use Swift data collections: arrays and dictionaries Review Boolean logic, comparing data, and flow control Use the Xcode debugger to troubleshoot problems with your apps Store data in local app preferences and Core Data databases Who This Book Is For Anyone who wants to learn to develop apps for the Mac, iPhone, iPad, and Apple Watch using the Swift programming language. No previous programming experience is necessary. COMPUTERS,Programming,Macintosh

Practical Artificial Intelligence with Swift Create and implement AI-based features in your Swift apps for iOS, macOS, tvOS, and watchOS. With this practical book, programmers and developers of all kinds will find a one-stop shop for AI and machine learning with Swift. Taking a task-based approach, you’ll learn how to build features that use powerful AI features to identify images, make predictions, generate content, recommend things, and more. AI is increasingly essential for every developer—and you don’t need to be a data scientist or mathematician to take advantage of it in your apps. Explore Swift-based AI and ML techniques for building applications. Learn where and how AI-driven features make sense. Inspect tools such as Apple’s Python-powered Turi Create and Google’s Swift for TensorFlow to train and build models. I: Fundamentals and Tools—Learn AI basics, our task-based approach, and discover how to build or find a dataset. II: Task Based AI—Build vision, audio, text, motion, and augmentation-related features; learn how to convert preexisting models. III: Beyond—Discover the theory behind task-based practice, explore AI and ML methods, and learn how you can build it all from scratch... if you want to COMPUTERS,Programming,Macintosh

SwiftUI for Absolute Beginners Dive into the world of developing for all of Apple platforms with SwiftUI, Apple’s new framework that makes writing applications faster and easier with fewer lines of code. This book teaches the basics of SwiftUI to help you write amazing native applications using XCode. For developers already familiar with ReactNative, this book reviews the declarative, state-based DSL that manages the UI and updates it automatically will feel just like what they’re used to. You'll see how SwiftUI reduces the number of lines of code required to achieve the same effects by over 60% and provides a much better experience. Like the announcement of Swift in 2014, SwiftUI is expected to fundamentally change the way developing programmers approach coding iPhone and iPad applications. This book examines how SwiftUI lowers the entry barrier for developers to write amazing cross-platform applications for iOS and iPadOS as well as WatchOS, Mac OS, and TVOS. What You'll Learn Write code in the new SwiftUI syntax Combine views to arrange them for an application Add gestures and controls to an application Who This Book Is For Anyone who wants to learn to develop apps for the Mac, iPhone, iPad, and Apple Watch using the Swift programming language. No previous programming experience is necessary. COMPUTERS,Programming,Macintosh

Programming iOS 13 If you’re grounded in the basics of Swift, Xcode, and the Cocoa framework, this book provides a structured explanation of all essential real-world iOS app components. Through deep exploration and copious code examples, you’ll learn how to create views, manipulate view controllers, and add features from iOS frameworks. Create, arrange, draw, layer, and animate views that respondto touch Use view controllers to manage multiple screens of interface Master interface classes for scroll views, table views, text,popovers, split views, web views, and controls Dive into frameworks for sound, video, maps, and sensors Access user libraries: music, photos, contacts, and calendar Explore files, networking, and threads Stay up-to-date on iOS 13 innovations, such as: Symbol images Light and dark mode Sheet presentation Diffable data sources and compositional layout Context menus and previews Window scene delegates and multiple windows on iPad Want to brush up on the basics? Pick up iOS 13 Programming Fundamentals with Swiftto learn about Swift, Xcode, and Cocoa. Together with Programming iOS 13, you’ll gaina solid, rigorous, and practical understanding of iOS 13 development. COMPUTERS,Programming,Macintosh

iOS 13 Programming for Beginners A step-by-step guide to learning iOS app development and exploring the latest Apple development tools Key Features Explore the latest features of Xcode 11 and the Swift 5 programming language in this updated fourth edition Kick-start your iOS programming career and have fun building your own iOS apps Discover the new features of iOS 13 such as Dark Mode, iPad apps for Mac, SwiftUI, and more Book Description iOS 13 comes with features ranging from Dark Mode and Catalyst through to SwiftUI and Sign In with Apple. If you're a beginner and are looking to experiment and work with these features to create your own apps, then this updated fourth edition gets you off to a strong start. The book offers a comprehensive introduction for programmers who are new to iOS, covering the entire process of learning the Swift language, writing your own apps, and publishing them on the App Store. This edition is updated and revised to cover the new iOS 13 features along with Xcode 11 and Swift 5. The book starts with an introduction to the Swift programming language, and how to accomplish common programming tasks with it. You'll then start building the user interface (UI) of a complete real-world app, using the latest version of Xcode, and also implement the code for views, view controllers, data managers, and other aspects of mobile apps. The book will then help you apply the latest iOS 13 features to existing apps, along with introducing you to SwiftUI, a new way to design UIs. Finally, the book will take you through setting up testers for your app, and what you need to do to publish your app on the App Store. By the end of this book, you'll be well versed with how to write and publish apps, and will be able to apply the skills you've gained to enhance your apps. What you will learn Get to grips with the fundamentals of Xcode 11 and Swift 5, the building blocks of iOS development Understand how to prototype an app using storyboards Discover the Model-View-Controller design pattern, and how to implement the desired functionality within the app Implement the latest iOS features such as Dark Mode and Sign In with Apple Understand how to convert an existing iPad app into a Mac app Design, deploy, and test your iOS applications with industry patterns and practices Who this book is for This book is for anyone who has programming experience but is completely new to Swift and iOS app development. Experienced programmers looking to explore the latest iOS 13 features will also find this book useful. COMPUTERS,Programming,Macintosh

iOS Programming Updated for Xcode 11, Swift 5, and iOS 13, iOS Programming: The Big Nerd Ranch Guide leads you through the essential concepts, tools, and techniques for developing iOS applications. After completing this book, you will have the know-how and the confidence you need to tackle iOS projects of your own. Based on Big Nerd Ranch's popular iOS training and its well-tested materials and methodology, this bestselling guide teaches iOS concepts and coding in tandem. The result is instruction that is relevant and useful. Throughout the book, the authors explain what's important and share their insights into the larger context of the iOS platform. You get a real understanding of how iOS development works, the many features that are available, and when and where to apply what you've learned. COMPUTERS,Programming,Macintosh

Apple macOS and iOS System Administration Effectively manage Apple devices anywhere from a handful of Macs at one location to thousands of iPhones across many locations. This book is a comprehensive guide for supporting Mac and iOS devices in organizations of all sizes. You'll learn how to control a fleet of macOS clients using tools like Profile Manager, Apple Device Enrollment Program (DEP), and Apple Remote Desktop. Then integrate your Mac clients into your existing Microsoft solutions for file sharing, print sharing, Exchange, and Active Directory authentication without having to deploy additional Mac-specific middle-ware or syncing between multiple directory services. Apple macOS and iOS System Administration shows how to automate the software installation and upgrade process using the open source Munki platform and provides a scripted out-of-the box experience for large scale deployments of macOS endpoints in any organization. Finally, you'll see how to provision and manage thousands of iOS devices in a standardized and secure fashion with device restrictions and over-the-air configuration. What You'll Learn Integrate macOS and iOS clients into enterprise Microsoft environments Use Apple’s Volume Purchase Program to manage App installations and share pools of Apps across multiple users Mass deploy iOS devices with standard configurations Remotely manage a fleet of macOS devices using Apple's Remote Desktop Who This Book Is For System or desktop administrators in enterprise organizations who need to integrate macOS or iOS clients into their existing IT infrastructure or set-up a new infrastructure for an Apple environment from scratch. COMPUTERS,Programming,Macintosh

Beginning ASP.NET E-Commerce in C# The book teaches the reader how to build a complete e-commerce web site written in ASP.NET 3.5 by taking them through the entire design and build process. Uniquely, this book shows how to handle payments through PayPal and DataCash; meaning that the reader is left with a fully functional e-commerce site at the end of the book. The previous edition sold 3,269 copies and still sells 80 a month two years after its release. COMPUTERS,Programming,Microsoft

Pro Excel Financial Modeling Learn the business thinking behind financial modeling and execute what you know effectively using Microsoft Excel. Many believe that sales and profitability projections shown in financial models are the keys to success in attracting investors. The truth is that investors will come up with their own projections. The investor wants to understand the assumptions, structure, and relationships within the modeling of a startup. If the investor is satiated, the entrepreneur has successfully demonstrated a complete understanding of the business side of the enterprise. Pro Excel Financial Modeling provides the keys necessary to learn this thinking and to build the models that will illustrate it. Step–by–step approach to developing financial models in Excel Extensive case studies and Excel templates provided COMPUTERS,Programming,Microsoft

Pro LINQ LINQ is the part of the .NET Framework that provides a generic approach to querying data from different data sources. It has quickly become the next must-have skill for .NET developers. Pro LINQ: Language Integrated Query in C# 2010 is all about code. Literally, this book starts with code and ends with code. Most books show the simplest examples of how to use a method, but they so rarely show how to use the more complex prototypes. This book is different. Demonstrating the overwhelming majority of LINQ operators and prototypes, it is a veritable treasury of LINQ examples. Rather than obscure the relevant LINQ principles in code examples by focusing on a demonstration application you have no interest in writing, this book cuts right to the chase of each LINQ operator, method, or class. However, where complexity is necessary to truly demonstrate an issue, the examples are right there in the thick of it. For example, code samples demonstrating how to handle concurrency conflicts actually create concurrency conflicts so you can step through the code and see them unfold. Face it, most technical books, while informative, are dull. LINQ need not be dull. Written with a sense of humor, this book will attempt to entertain you on your journey through the wonderland of LINQ and C# 2010. COMPUTERS,Programming,Microsoft

Beginning Microsoft Excel 2010 Beginning Microsoft Excel 2010 is a practical, step-by-step guide to getting started with the world’s most widely-used spreadsheet application. The book offers a hands-on approach to learning how to create and edit spreadsheets, use various calculation formulas, employ charts/graphs, and get work done efficiently. Microsoft rolled out several new features with Excel 2010—perhaps the most notable was the ability to use Excel 2010 online and collaborate on a project in real time. Beginning Microsoft Office 2010 keeps you up-to-date with all of these features and more. COMPUTERS,Programming,Microsoft

Fluent Visual Basic Based on the principles of cognitive science and instructional design, Fluent Visual Basic, part of the Fluent Learning series, is a true tutorial that will help you build effective working models for understanding a large and complex subject: developing .NET Framework applications in Visual Basic. Most introductory books just talk at you and give you “exercises†that have more to do with taking dictation than actually learning. Fluent Visual Basic is different. It guides you through learning the way your mind likes to learn: by solving puzzles, making connections, and building genuine understanding instead of just memorizing random facts. DETAILED INFORMATION ON HOW TO… Write .NET applications in Visual Basic Leverage the incredible power of the .NET Framework Class Library Apply Object-Oriented principles, Design Patterns, and best practices to your code Develop desktop applications using the powerful Windows Presentation Foundation user interface API COMPUTERS,Programming,Microsoft

Pro WCF 4 Pro WCF 4.0: Practical Microsoft SOA Implementation is a complete guide to Windows Communication Foundation from the service-oriented architecture (SOA) perspective, showing you why WCF is important to service-oriented architecture and development. This book provides deep insight into the functionality of WCF, which shipped with .NET 4.0-like service discovery, routing service, simplified configuration, and other advanced features. Included in this title are informative examples that will aid the reader in understanding and implementing these important additions. This book also covers the unified programming model, reliable messaging, security, and the peer-to-peer programming model. You'll also learn how to move your current .NET remoting and web service applications to WCF, and how to integrate those applications with WCF 4. This book offers genuine insight into solving real enterprise problems using WCF and .NET 4.0. COMPUTERS,Programming,Microsoft

Windows PowerShell for Developers Want to perform programming tasks better, faster, simpler, and make them repeatable? Take a deep dive into Windows PowerShell and discover what this distributed automation platform can do. Whether you’re a .NET developer or IT pro, this concise guide will show you how PowerShell’s scripting language can help you be more productive on everyday tasks. Quickly learn how to create PowerShell scripts and embed them into your existing applications, write "little languages" to solve specific problems, and take charge of your code. This book includes example scripts that you can easily pull apart, tweak, and then use in your own PowerShell and .NET solutions. Slice and dice text, XML, CSV, and JSON with ease Embed PowerShell to provide scripting capabilities for your C# apps Create GUI applications five to ten times faster with less code Leverage PowerShell’s capabilities to work with the Internet Interact with DLLs and create objects, automatically display properties, and call methods in live interactive sessions Build domain-specific languages (DSLs) and vocabularies to express solutions more clearly Work with Microsoft Office via the Component Object Model (COM) Discover PowerShell v3 features included with Windows 8 and Windows Server 2012 COMPUTERS,Programming,Microsoft

Windows PowerShell Pocket Reference This portable reference to Windows PowerShell 3.0 summarizes the command shell and scripting language, and provides a concise reference to the many tasks that make PowerShell so useful. If you’re a busy Windows administrator, and don’t have time to plow through huge books or search online, this is the ideal on-the-job tool. Written by Microsoft PowerShell team member Lee Holmes, and excerpted from his Windows PowerShell Cookbook, this edition offers up-to-date coverage of PowerShell 3.0. You’ll find information on the .NET classes and legacy tools you need to manage your system, along with chapters on how to write scripts, manage errors, and format output. Beginning with a guided tour of Windows PowerShell, this handy guide covers: PowerShell language and environment Regular expression reference XPath quick reference .NET string formatting .NET DateTime formatting Selected .NET classes and their uses WMI reference Selected COM objects and their uses Selected events and their uses Standard PowerShell verbs COMPUTERS,Programming,Microsoft

Windows PowerShell Cookbook How do you use Windows PowerShell to navigate the filesystem, manage files and folders, or retrieve a web page? This introduction to the PowerShell language and scripting environment provides more than 400 task-oriented recipes to help you solve all kinds of problems. Intermediate to advanced system administrators will find more than 100 tried-and-tested scripts they can copy and use immediately. Updated for PowerShell 3.0, this comprehensive cookbook includes hands-on recipes for common tasks and administrative jobs that you can apply whether you’re on the client or server version of Windows. You also get quick references to technologies used in conjunction with PowerShell, including format specifiers and frequently referenced registry keys to selected .NET, COM, and WMI classes. Learn how to use PowerShell on Windows 8 and Windows Server 2012 Tour PowerShell’s core features, including the command model, object-based pipeline, and ubiquitous scripting Master fundamentals such as the interactive shell, pipeline, and object concepts Perform common tasks that involve working with files, Internet-connected scripts, user interaction, and more Solve tasks in systems and enterprise management, such as working with Active Directory and the filesystem COMPUTERS,Programming,Microsoft

Pro SharePoint 2013 Administration Pro SharePoint 2013 Administration is a practical guide to SharePoint 2013 for intermediate to advanced SharePoint administrators and power users, covering the out-of-the-box feature set and capabilities of Microsoft's collaboration and business productivity platform. SharePoint 2013 is an incredibly complex product, with many moving parts, new features, best practices, and "gotchas." Author Rob Garrett distills SharePoint's portfolio of features, capabilities, and utilities into an in-depth professional guide—with no fluff and copious advice—that is designed from scratch to be the manual Microsoft never wrote. Starting with a detailed deployment and initial configuration walkthrough, the book covers all major feature areas, including document management, social computing, metadata management, and administration. You'll also learn about planning for capacity, backup administration and disaster recovery, business intelligence, monitoring, and more. Unlike other books, Pro SharePoint 2013 Administration covers all elements of the product, but has a specific emphasis on features new and enhanced in the 2013 release. Pro SharePoint 2013 Administration is the only book you'll need as you set out to deploy and administer SharePoint 2013. COMPUTERS,Programming,Microsoft

Microsoft Visual C++/CLI Step by Step Your hands-on guide to Visual C++/CLI fundamentals Expand your expertise—and teach yourself the fundamentals of the Microsoft Visual C++/CLI language. If you have previous programming experience but are new to Visual C++, this tutorial delivers the step-by-step guidance and coding exercises you need to master core topics and techniques. Discover how to: Write and debug object-oriented C++ programs in Visual Studio 2012 Utilize the various features of the C++/CLI language Make use of the Microsoft .NET Framework Class Library Create a simple Windows Store app Use .NET features such as properties, delegates and events Access data from disparate sources using ADO.NET Create and consume web services using Windows Communication Foundation Work effectively with legacy code and COM COMPUTERS,Programming,Microsoft

Pro ASP.NET MVC 5 The ASP.NET MVC 5 Framework is the latest evolution of Microsoft’s ASP.NET web platform. It provides a high-productivity programming model that promotes cleaner code architecture, test-driven development, and powerful extensibility, combined with all the benefits of ASP.NET.ASP.NET MVC 5 contains a number of advances over previous versions, including the ability to define routes using C# attributes and the ability to override filters. The user experience of building MVC applications has also been substantially improved. The new, more tightly integrated, Visual Studio 2013 IDE has been created specifically with MVC application development in mind and provides a full suite of tools to improve development times and assist in reporting, debugging and deploying your code. The popular Bootstrap JavaScript library has also now been included natively within MVC 5 providing you, the developer, with a wider range of multi-platform CSS and HTML5 options than ever before without the penalty of having to load-in third party libraries. COMPUTERS,Programming,Microsoft

Using Office 365 Learn Office the easy way, no jargon. Clear, concise and to the point... Using Microsoft Office 365, is the essential step by step guide to getting the most out of the traditional Microsoft Office applications (not SharePoint), providing a complete resource for both the beginner and the enthusiast.Techniques are illustrated step-by-step using photography and screen prints throughout, together with concise, easy to follow text from an established expert in the field, provide a comprehensive guide to office applications. Whether you are new to Microsoft Office, an experienced user or studying a computer skills course this book will provide you with a firm grasp of the underpinning foundations and equip you with the skills needed to use Office like a pro. COMPUTERS,Programming,Microsoft

Microsoft .NET - Architecting Applications for the Enterprise A software architect’s digest of core practices, pragmatically applied Designing effective architecture is your best strategy for managing project complexity–and improving your results. But the principles and practices of software architecting–what the authors call the “science of hard decisionsâ€â€“have been evolving for cloud, mobile, and other shifts. Now fully revised and updated, this book shares the knowledge and real-world perspectives that enable you to design for success–and deliver more successful solutions. In this fully updated Second Edition, you will: Learn how only a deep understanding of domain can lead to appropriate architecture Examine domain-driven design in both theory and implementation Shift your approach to code first, model later–including multilayer architecture Capture the benefits of prioritizing software maintainability See how readability, testability, and extensibility lead to code quality Take a user experience (UX) first approach, rather than designing for data Review patterns for organizing business logic Use event sourcing and CQRS together to model complex business domains more effectively Delve inside the persistence layer, including patterns and implementation. COMPUTERS,Programming,Microsoft

Advanced Excel Essentials Advanced Excel Essentials is the only book for experienced Excel developers who want to channel their skills into building spreadsheet applications and dashboards. This book starts from the assumption that you are well-versed in Excel and builds on your skills to take them to an advanced level. It provides the building blocks of advanced development and then takes you through the development of your own advanced spreadsheet application. For the seasoned analyst, accountant, financial professional, management consultant, or engineer—this is the book you’ve been waiting for! Author Jordan Goldmeier builds on a foundation of industry best practices, bringing his own forward-thinking approach to Excel and rich real-world experience, to distill a unique blend of advanced essentials. Among other topics, he covers advanced formula concepts like array formulas and Boolean logic and provides insight into better code and formulas development. He supports that insight by showing you how to build correctly with hands-on examples. COMPUTERS,Programming,Microsoft

Professional Visual Studio 2015 In-depth coverage of the major Visual Studio 2015 revamp Professional Visual Studio 2015 is the leading pro's guide to new and upgraded features of Microsoft Visual Studio. With a unique IDE-centric approach and deep dive into the software's many nooks and crannies, this book will bring you up to speed quickly on everything Visual Studio 2015 has to offer. Whether you're new to Visual Studio or just upgrading, you'll appreciate in-depth, professional explanation of updates, features, and support. Visual Studio 2015 is packed with improvements that increase productivity, and this book walks you through each one in succession to help you smooth your workflow and get more accomplished. From customization and the interface to code snippets and debugging, the Visual Studio upgrade expands your options — and this book is your fast-track guide to getting on board quickly. The Visual Studios 2015 release fixes a number of issues that deterred many professionals from adopting VS 2013. Old products have been retooled, and new features are aimed at productivity enhancement and fixes to UI. Fully aligned with VS 2015, this guide walks you through the changes and helps you incorporate helpful new features into the way you work. Discover new options for themes, displays, and settings Learn the new workflow and shortcuts to ASP.NET code Master improved debugging and unit testing support capabilities Exploit changes to Windows STORE apps, phone apps, Azure, and SharePoint COMPUTERS,Programming,Microsoft

M Is for (Data) Monkey Power Query is one component of the Power BI (Business Intelligence) product from Microsoft, and "M" is the name of the programming language created by it. As more business intelligence pros begin using Power Pivot, they find that they do not have the Excel skills to clean the data in Excel; Power Query solves this problem. This book shows how to use the Power Query tool to get difficult data sets into both Excel and Power Pivot, and is solely devoted to Power Query dashboarding and reporting. COMPUTERS,Programming,Microsoft

Dashboards for Excel This book takes a hands-on approach to developing dashboards, from instructing users on advanced Excel techniques to addressing dashboard pitfalls common in the real world. Dashboards for Excel is your key to creating informative, actionable, and interactive dashboards and decision support systems. Throughout the book, the reader is challenged to think about Excel and data analytics differently—that is, to think outside the cell. This book shows you how to create dashboards in Excel quickly and effectively. In this book, you learn how to: Apply data visualization principles for more effective dashboards Employ dynamic charts and tables to create dashboards that are constantly up-to-date and providing fresh information Use understated yet powerful formulas for Excel development Apply advanced Excel techniques mixing formulas and Visual Basic for Applications (VBA) to create interactive dashboards Create dynamic systems for decision support in your organization Avoid common problems in Excel development and dashboard creation Get started with the Excel data model, PowerPivot, and Power Query COMPUTERS,Programming,Microsoft

Microsoft Azure Written for IT and business professionals, this book provides the technical and business insight needed to plan, deploy and manage the services provided by the Microsoft Azure cloud. Find out how to integrate the infrastructure-as-a-service (IaaS) and platform-as-a-service (PaaS) models with your existing business infrastructure while maximizing availability, ensuring continuity and safety of your data, and keeping costs to a minimum. The book starts with an introduction to Microsoft Azure and how it differs from Office 365—Microsoft’s ‘other’ cloud. You'll also get a useful overview of the services available. Part II then takes you through setting up your Azure account, and gets you up-and-running on some of the core Azure services, including creating web sites and virtual machines, and choosing between fully cloud-based and hybrid storage solutions, depending on your needs. Part III now takes an in-depth look at how to integrate Azure with your existing infrastructure. The authors, Anthony Puca, Mike Manning, Brent Rush, Marshall Copeland and Julian Soh, bring their depth of experience in cloud technology and customer support to guide you through the whole process, through each layer of your infrastructure from networking to operations. High availability and disaster recovery are the topics on everyone’s minds when considering a move to the cloud, and this book provides key insights and step-by-step guidance to help you set up and manage your resources correctly to optimize for these scenarios. You’ll also get expert advice on migrating your existing VMs to Azure using InMage, mail-in and the best 3rd party tools available, helping you ensure continuity of service with minimum disruption to the business. In the book’s final chapters, you’ll find cutting edge examples of cloud technology in action, from machine learning to business intelligence, for a taste of some exciting ways your business could benefit from your new Microsoft Azure deployment. COMPUTERS,Programming,Microsoft

Extending SSIS with .NET Scripting Extending SSIS with .NET Scripting is a timeless and comprehensive scripting toolkit for SQL Server Integration Services to solve a wide array of everyday problems that SSIS developers encounter. The detailed explanation of the Script Task and Script Component foundations helps you develop your own scripting solutions, but this book also shows a broad arsenal of readymade and well-documented scripting solutions for common problems. All examples are in both C# and VB.NET, and work for all current versions of SSIS. SSIS is one of the leading ETL, Data Consolidation, and Data Transformation tools in today’s market. SSIS is used by ETL Developers, DBAs and Data Analysts to transform data as required for different ETL processes. There are many built-in components and tasks to help developers to perform actions. For example, there are tasks for sending and receiving files through FTP, sending an email, and for accessing a wide range of database management systems. Yet there are times when developers require a task or component that does not exist and it would make their life much easier if they could create that task or component, and that is what this book it is about. It shows how to write .NET scripts and use the powerful Microsoft .NET library to implement new functionality as needed. Provides a timeless scripting toolkit for all current SSIS versions Gives a comprehensive explanation of scripting in SSIS Offers a wide array of readymade examples for everyday problems COMPUTERS,Programming,Microsoft

File Management Made Simple, Windows Edition Managing data is an essential skill that every PC user should have. Surprisingly though, a large number of users--even highly experienced users--exhibit poor file management skills, resulting in frustration and lost data. This brief but invaluable book, File Management Made Simple can resolve this by providing you with the skills and best practices needed for creating, managing and protecting your data. Do any of the following scenarios sound familiar to you? You’ve downloaded an attachment from your e-mail, but aren’t sure where you downloaded it to. You spent an entire evening working on a document only to discover the next morning that you didn’t save it to your flash drive like you thought you had? Maybe you had a guest visiting and wanted to share with them the pictures you took of your kids recital, yet when you went to get them you were unable to recall where you stored them on your PC. Or you scanned your receipts for your expense reports on day and came back the next day and scanned some for another report only to find that the new ones numbered Scan 1, Scan 2,... still exist. Unfortunately, for a vast number of PC users, scenarios like these are all too common. These situations are not only extremely frustrating for the user, but also tend to discourage them from ever wanting to touch a PC again! Why is that? What is the common factor? It’s simple really. Each of these issues can be attributed to poor file management skills. In my experience, the people with the worst file management skills are simply the ones that lack an understanding of how to navigate the Windows operating system. However this situation can be easily rectified. And once you can successfully navigate your computer's drive and folder structure, you'll be hard pressed to misplace anything. Although this process can seem daunting to the uninitiated, this isn’t black magic. In fact, it’s actually quite simple. Keeping your files and folders organized on the computer is no more difficult than keeping them organized in real life. There is a place for everything and everything has its place. We will show you how to navigate Windows correctly and efficiently. Where specific types of files should be stored. We’ll also show you how best to name and manage your files; such as using descriptive folders to identify files, implementing the best naming conventions for files and directories, and how to group various types of data together; ensuring that the data you need is always readily available. Finally we’ll introduce you to some of the best options for transporting and protecting your data. We will show you the skills you need to easily manage your data, using clear and simple English, without the confusing technical jargon. All this and more can be accomplished with File Management Made Simple by your side. COMPUTERS,Programming,Microsoft

Windows 10 Troubleshooting Learn how to troubleshoot Windows 10 the way the experts do, whatever device or form-factor you’re using. Focus on the problems that most commonly plague PC users and fix each one with a step-by-step approach that helps you understand the cause, the solution, and the tools required. Discover the connections between the different hardware and software in your devices, and how their bonds with external hardware, networks, and the Internet are more dependent than you think, and learn how to build resilience into any computer system, network, or device running Windows 10. If you're fed up of those nagging day-to-day issues, want to avoid costly repairs, or just want to learn more about how PCs work, Windows 10 Troubleshooting is your ideal one-stop guide to the Windows 10 operating system. What You Will Learn: Understand your PC’s ecosystem and how to connect the dots, so you can successfully track problems to their source Create resilient backups of your operating system, files, and documents, and enable quick and easy restore Learn your way around Windows' built-in administration tools, to quickly fix the typical problems that come up Diagnose and repair a wide range of common problems with printers and other essential peripherals Solve complex startup problems that can prevent a PC form booting Make your PC safe and secure for the whole family, and for everybody in your workplace Understand the threat from malware and viruses and a range of approaches to dealing with them, depending on the situation Bomb-proof your PC with advanced security, group policy, and firewall policies Learn the top Tips and tricks for researching difficult problems, including third-party tools and useful web resources Work with the registry, file system, and Sysinternals to troubleshooting PCs in the workplace Who This Book Is For: Anyone using Windows 10 on a desktop, laptop, or hybrid device COMPUTERS,Programming,Microsoft

Programming Excel with VBA Learn to harness the power of Visual Basic for Applications (VBA) in Microsoft Excel to develop interesting, useful, and interactive Excel applications. This book will show you how to manipulate Excel with code, allowing you to unlock extra features, accuracy, and efficiency in working with your data. Programming Excel 2016 with VBA is a complete guide to Excel application development, using step-by-step guidance, example applications, and screenshots in Excel 2016. In this book, you will learn: How to interact with key Excel objects, such as the application object, workbook object, and range object Methods for working with ranges in detail using code Usage of Excel as a database repository How to exchange data between Excel applications How to use the Windows API to expand the capabilities of Excel A step-by-step method for producing your own custom Excel ribbon Who This Book Is For: Developers and intermediate-to-advanced Excel users who want to dive deeper into the capabilities of Excel 2016 using code. COMPUTERS,Programming,Microsoft

SharePoint 2016 User's Guide Learn how to make the most of SharePoint 2016 and its wide range of capabilities to support your information management, collaboration, and business process management needs. Whether you are using SharePoint as an intranet or business solution platform, you will learn how to use the resources (such as lists, libraries, and sites) and services (such as search, workflow, and social) that make up these environments. In the fifth edition of this bestselling book, author Tony Smith walks you through the components and capabilities that make up a SharePoint 2016 environment. He provides step-by-step instructions for using and managing these elements, as well as recommendations for how to get the best out of them. What You Wi ll Learn Create and use common SharePoint resources like lists, libraries, sites, pages and web parts Understand when and how workflows and information management policies can be used to automate process Learn how to take advantage of records retention, management, and disposition Make the most of SharePoint search services Take advantage of social capabilities to create social solutions Who This Book Is For Whether you have not yet used SharePoint at all, have used previous versions, have just started using the basic features, or have been using it for a long of time, this book provides the skills you need to work efficiently with the capabilities SharePoint 2016 provides. COMPUTERS,Programming,Microsoft

Mastering Windows Presentation Foundation Master the art of building modern desktop applications on Windows About This Book Learn how to use the MVVM software architectural pattern and see the benefits of using it with Windows Presentation Fountain (WPF) Explore various ways to enhance efficiency through performance tuning and UI automation Obtain a deep understanding of data validation and understand various methods that suit different situations Who This Book Is For This book is for working developers with a moderate level of knowledge about Windows Presentation Foundation. It will also be of special interest to ambitious individuals who want to know more about application architecture. It is also suitable for those who just want to learn how to build visually stunning user interfaces. What You Will Learn Use MVVM to improve workflow Create visually stunning user interfaces Perform data binds proficiently Implement advanced data validation Locate and resolve errors quickly Master practical animations Improve your applications' performance In Detail Windows Presentation Foundation is rich in possibilities when it comes to delivering an excellent user experience. This book will show you how to build professional-grade applications that look great and work smoothly. We start by providing you with a foundation of knowledge to improve your workflow – this includes teaching you how to build the base layer of the application, which will support all that comes after it. We'll also cover the useful details of data binding. Next, we cover the user interface and show you how to get the most out of the built-in and custom WPF controls. The final section of the book demonstrates ways to polish your applications, from adding practical animations and data validation to improving application performance. The book ends with a tutorial on how to deploy your applications and outlines potential ways to apply your new-found knowledge so you can put it to use right away. The book also covers 2D and 3D graphics, UI automation, and performance tuning. Style and approach Filled with intriguing and practical examples, this book delineates concepts that will help you take your WPF skills to the next level. COMPUTERS,Programming,Microsoft

Cyber Security on Azure Prevent destructive attacks to your Azure public cloud infrastructure, remove vulnerabilities, and instantly report cloud security readiness. This book provides comprehensive guidance from a security insider's perspective. Cyber Security on Azure explains how this 'security as a service' (SECaaS) business solution can help you better manage security risk and enable data security control using encryption options such as Advanced Encryption Standard (AES) cryptography. Discover best practices to support network security groups, web application firewalls, and database auditing for threat protection. Configure custom security notifications of potential cyberattack vectors to prevent unauthorized access by hackers, hacktivists, and industrial spies. What You'll Learn This book provides step-by-step guidance on how to: Support enterprise security policies Improve cloud security Configure intrusion detection Identify potential vulnerabilities Prevent enterprise security failures Who This Book Is For IT, cloud, and security administrators; CEOs, CIOs, and other business professionals COMPUTERS,Programming,Microsoft

Essential Angular for ASP.NET Core MVC Angular 5 and .NET Core 2 updates for this book are now available. Follow the Download Source Code link for this book on the Apress website. Discover Angular, the leading client-side web framework, from the point of view of an ASP.NET Core MVC developer. Best-selling author Adam Freeman brings these two key technologies together and explains how to use ASP.NET Core MVC to provide back-end services for Angular applications. This fast-paced, practical guide starts from the nuts and bolt and gives you the knowledge you need to combine Angular (from version 2.0 up) and ASP.NET Core MVC in your projects. What You’ll Learn Gain a solid understanding of how ASP.NET Core MVC and Angular can work together Use Visual Studio 2017 to develop Angular/ASP.NET Core MVC projects Create ASP.NET Core RESTful web services to support Angular applications Expose data from Entity Framework Core to Angular applications Use ASP.NET Core Identity to provide security services to Angular applications Each topic is covered clearly and concisely and is packed with the essential details you need to learn to be truly effective. Who This Book Is For This book is for developers with a knowledge of ASP.NET Core MVC who are introducing Angular into their projects. COMPUTERS,Programming,Microsoft

IoT Solutions in Microsoft's Azure IoT Suite Collect and analyze sensor and usage data from Internet of Things applications with Microsoft Azure IoT Suite. Internet connectivity to everyday devices such as light bulbs, thermostats, and even voice-command devices such as Google Home and Amazon.com's Alexa is exploding. These connected devices and their respective applications generate large amounts of data that can be mined to enhance user-friendliness and make predictions about what a user might be likely to do next. Microsoft's Azure IoT Suite is a cloud-based platform that is ideal for collecting data from connected devices. You'll learn in this book about data acquisition and analysis, including real-time analysis. Real-world examples are provided to teach you to detect anomalous patterns in your data that might lead to business advantage. We live in a time when the amount of data being generated and stored is growing at an exponential rate. Understanding and getting real-time insight into these data is critical to business. IoT Solutions in Microsoft's Azure IoT Suite walks you through a complete, end-to-end journey of how to collect and store data from Internet-connected devices. You'll learn to analyze the data and to apply your results to solving real-world problems. Your customers will benefit from the increasingly capable and reliable applications that you'll be able to deploy to them. You and your business will benefit from the gains in insight and knowledge that can be applied to delight your customers and increase the value from their business. What You'll Learn Go through data generation, collection, and storage from sensors and devices, both relational and non-relational Understand, from end to end, Microsoft’s analytic services and where they fit into the analytical ecosystem Look at the Internet of your things and find ways to discover and draw on the insights your data can provide Understand Microsoft's IoT technologies and services, and stitch them together for business insight and advantage Who This Book Is For Developers and architects who plan on delivering IoT solutions, data scientists who want to understand how to get better insights into their data, and anyone needing or wanting to do real-time analysis of data from the Internet of Things COMPUTERS,Programming,Microsoft

Pro ASP.NET Core MVC 2 Now in its 7th edition, the best selling book on MVC is updated for ASP.NET Core MVC 2. It contains detailed explanations of the Core MVC functionality which enables developers to produce leaner, cloud optimized and mobile-ready applications for the .NET platform. This book puts ASP.NET Core MVC into context and dives deep into the tools and techniques required to build modern, cloud optimized extensible web applications. All the new MVC features are described in detail and the author explains how best to apply them to both new and existing projects. The ASP.NET Core MVC Framework is the latest evolution of Microsoft’s ASP.NET web platform, built on a completely new foundation. It represents a fundamental change to how Microsoft constructs and deploys web frameworks and is free of the legacy of earlier technologies such as Web Forms. ASP.NET Core MVC provides a "host agnostic" framework and a high-productivity programming model that promotes cleaner code architecture, test-driven development, and powerful extensibility. Best-selling author Adam Freeman has thoroughly revised this market-leading book and explains how to get the most from ASP.NET Core MVC. He starts with the nuts-and-bolts and shows you everything through to advanced features, going in-depth to give you the knowledge you need. The book includes a fully worked case study of a functioning web application that readers can use as a template for their own projects. What's New in This Edition Fully updated for Visual Studio 2017, C# 7 and .NET Core 2 Coverage of new features such as view filters Wider platform and tooling coverage than ever before, with more on Visual Studio Code and working with .NET Core on non-Windows platforms Docker-based application deployment What You Will Learn Gain a solid architectural understanding of ASP.NET Core MVC Explore the entire ASP.NET MVC Framework as a cohesive whole See how MVC and test-driven development work in action Learn what's new in ASP.NET Core MVC 2 and how best to apply these new features to your own work See how to create RESTful web services and Single Page Applications Build on your existing knowledge of previous MVC releases to get up and running with the new programming model quickly and effectively Who This Book Is For This book is for web developers with a basic knowledge of ASP.NET and C# who want to incorporate the latest improvements and functionality in the ASP.NET Core MVC 2 Framework. COMPUTERS,Programming,Microsoft

Pro C# 7 This essential classic title provides a comprehensive foundation in the C# programming language and the frameworks it lives in. Now in its 8th edition, you’ll find all the very latest C# 7.1 and .NET 4.7 features here, along with four brand new chapters on Microsoft’s lightweight, cross-platform framework, .NET Core, up to and including .NET Core 2.0. Coverage of ASP.NET Core, Entity Framework (EF) Core, and more, sits alongside the latest updates to .NET, including Windows Presentation Foundation (WPF), Windows Communication Foundation (WCF), and ASP.NET MVC. Dive in and discover why Pro C# has been a favorite of C# developers worldwide for over 15 years. Gain a solid foundation in object-oriented development techniques, attributes and reflection, generics and collections as well as numerous advanced topics not found in other texts (such as CIL opcodes and emitting dynamic assemblies). With the help of this book you’ll have the confidence to put C# into practice and explore the .NET universe on your own terms. What You Will Learn Discover the latest C# 7.1 features, from tuples to pattern matching Hit the ground running with Microsoft’s lightweight, open source .NET Core platform, including ASP.NET Core MVC, ASP.NET Core web services, and Entity Framework Core Find complete coverage of XAML, .NET 4.7, and Visual Studio 2017 Understand the philosophy behind .NET and the new, cross-platform alternative, .NET Core COMPUTERS,Programming,Microsoft

C# Programming for Absolute Beginners Get started using the C# programming language. Based on the author’s 15 years of experience teaching beginners, the book provides you with a step-by-step introduction to the principles of programming, or rather, how to think like a programmer. The task-solution approach will get you immersed, with minimum theory and maximum action. What You Will Learn Understand what programming is all about Write simple, but non-trivial, programs Become familiar with basic programming constructs such as statements, types, variables, conditions, and loops Learn to think like a programmer and combine these programming constructs in new ways Get to know C# as a modern, mainstream programming language, and Visual Studio as one of the world’s most popular programming tools Who This Book Is For Those with very little or no experience in computer programming, who know how to use a computer, install a program, and navigate the web. COMPUTERS,Programming,Microsoft

Pro Entity Framework Core 2 for ASP.NET Core MVC Model, map, and access data effectively with Entity Framework Core 2, the latest evolution of Microsoft’s object-relational mapping framework. You will access data utilizing .NET objects via the most common data access layer used in ASP.NET Core MVC 2 projects. Best-selling author Adam Freeman explains how to get the most from Entity Framework Core 2 in MVC projects. He begins by describing the different ways that Entity Framework Core 2 can model data and the different types of databases that can be used. He then shows you how to use Entity Framework Core 2 in your own MVC projects, starting from the nuts and bolts and building up to the most advanced and sophisticated features, going in-depth to give you the knowledge you need. Chapters include common problems and how to avoid them. What You’ll Learn Gain a solid architectural understanding of Entity Framework Core 2 Create databases using your MVC data model Create MVC models using an existing database Access data in an MVC application using Entity Framework Core 2 Use Entity Framework in RESTful Web Services Who This Book Is For ASP.NET Core MVC 2 developers who want to use Entity Framework Core 2 as the data access layer in their projects COMPUTERS,Programming,Microsoft

Programming ASP.NET Core, Programming ASP.NET Core The complete, pragmatic guide to building high-value solutions with ASP.NET Core Programming ASP.NET Core is the definitive guide to practical web-based application development with Microsoft’s new ASP.NET Core framework. Microsoft MVP Dino Esposito introduces proven techniques and well-crafted example code for solving real problems with ASP.NET Core. Step by step, he guides you through using all key ASP.NET Core technologies, including MVC for HTML generation, .NET Core, EF Core, ASP.NET Identity, dependency injection, and much more. Esposito thoroughly covers ASP.NET Core’s cross-platform capabilities and what’s changed from older ASP.NET versions, but he doesn’t stop there: he offers a complete learning path for every developer who wants to build production solutions, including mobile-specific solutions. Microsoft MVP Dino Esposito shows how to: • Create new projects and understand their structure • Set up and use the familiar MVC application model in ASP.NET Core • Write controller class code to govern all stages of request processing • Serve HTML from controllers, or directly via Razor Pages • Master the Razor language for quickly defining the layout of HTML views • Manage cross-cutting concerns such as global configuration data, error and exception handling, controller class design, and dependency injection • Secure applications with user authentication and ASP.NET Core’s policy-based user authorization API • Design for efficient data access, and choose the right option for reading and writing data • Build ASP.NET Core Web APIs that return JSON, XML, or other data • Use data binding to programmatically update visual components with fresh information • Build device-friendly web views for iOS and Android • Explore the radically new ASP.NET Core runtime environment and Dependency Injection (DI) infrastructure COMPUTERS,Programming,Microsoft

Practical Microsoft Azure IaaS Adopt Azure IaaS and migrate your on-premise infrastructure partially or fully to Azure. This book provides practical solutions by following Microsoft’s design and best practice guidelines for building highly available, scalable, and secure solution stacks using Microsoft Azure IaaS. The author starts by giving an overview of Azure IaaS and its components: you’ll see the new aspects of Azure Resource Manager, storage in IaaS, and Azure networking. As such, you’ll cover design considerations for migration and implementation of infrastructure services, giving you practical skills to apply to your own projects. The next part of the book takes you through the different components of Azure IaaS that need to be included in a resilient architecture and how to set up a highly available infrastructure in Azure. The author focuses on the tools available for Azure IaaS automated provisioning and the different performance monitoring and fine-tuning options available for the platform. Finally, you’ll gain practical skills in Azure security and implementing Azure architectures. After reading Practical Microsoft Azure IaaS, you will have learned how to map the familiar on-premise architecture components to their cloud infrastructure counterparts. This book provides a focused and practical approach to designing solutions to be hosted in Azure IaaS. What You Will Learn Map the key Azure components to familiar concepts in infrastructure, such as virtualization, storage provisioning, switching, and firewalls Implement Azure IaaS deployment architectures Design IaaS environments in line with the Microsoft recommended best practices for scalability, resiliency, availability, performance, and security Manage the operational aspects of hosted environments, leverage automation, and fine tune for optimal performance Who This Book Is For Infrastructure and solution architects with skills in on-premise infrastructure design who want to up-skill in Azure IaaS. COMPUTERS,Programming,Microsoft

Mastering Microsoft Teams Do you need to learn how to use Microsoft Teams? Are you questioning how to drive user adoption, govern content, and manage access for your Teams deployment? Either way, Mastering Microsoft Teams is your one-stop-shop to learning everything you need to know to find success with Microsoft Teams. Microsoft’s new chat-based collaboration software has many rich features that enable teams to be more efficient, and save valuable time and resources. However, as with all software, there is a learning curve and pitfalls that should be avoided. Begin by learning the core components and use cases for Teams. From there the authors guide you through ideas to create governance and adoption plans that make sense for your organization or customer. Wrap up with an understanding of features and services in progress, and a road map to the future of the product. What You'll Learn Implement, use, and manage Microsoft Teams Understand how Teams drives productivity and engagement by combining the functionality of Microsoft Groups, SharePoint, OneDrive, Outlook, and other services in one location Govern, explain, and use Teams in your organization Know the pitfalls to avoid that may create challenges in your usage of Teams Become familiar with the functionality and components of Teams via walkthroughs, including opportunities for automating business processes in Teams Who This Book Is For Anyone who wants to learn Microsoft Teams. To get the most out of the book, a basic understanding of Office 365 and a subscription, including a Microsoft Teams license, is useful. COMPUTERS,Programming,Microsoft

Deep Learning with Azure Get up-to-speed with Microsoft's AI Platform. Learn to innovate and accelerate with open and powerful tools and services that bring artificial intelligence to every data scientist and developer. Artificial Intelligence (AI) is the new normal. Innovations in deep learning algorithms and hardware are happening at a rapid pace. It is no longer a question of should I build AI into my business, but more about where do I begin and how do I get started with AI? Written by expert data scientists at Microsoft, Deep Learning with the Microsoft AI Platform helps you with the how-to of doing deep learning on Azure and leveraging deep learning to create innovative and intelligent solutions. Benefit from guidance on where to begin your AI adventure, and learn how the cloud provides you with all the tools, infrastructure, and services you need to do AI. What You'll Learn Become familiar with the tools, infrastructure, and services available for deep learning on Microsoft Azure such as Azure Machine Learning services and Batch AI Use pre-built AI capabilities (Computer Vision, OCR, gender, emotion, landmark detection, and more) Understand the common deep learning models, including convolutional neural networks (CNNs), recurrent neural networks (RNNs), generative adversarial networks (GANs) with sample code and understand how the field is evolving Discover the options for training and operationalizing deep learning models on Azure Who This Book Is For Professional data scientists who are interested in learning more about deep learning and how to use the Microsoft AI platform. Some experience with Python is helpful. COMPUTERS,Programming,Microsoft

DevOps for SharePoint Deploy a SharePoint farm in a repeatable, predictable, and reliable fashion using Infrastructure as Code (IaC) techniques to automate provisioning. Savvy IT pros will learn how to use DevOps practices and open source tools to greatly reduce costs, and streamline management operations for SharePoint farms deployed via Amazon Web Services (AWS), Azure, or on premise. DevOps for SharePoint will help you navigate the complex challenges of deploying and managing SharePoint Server farms. You will learn how to reduce time-consuming tasks and errors when generating development, testing, or production environments. And you will benefit from learning proven methods to apply Microsoft updates with minimal downtime and productivity loss. Whether you are a SharePoint architect, IT pro, or developer helping customers with the SharePoint platform, this book will teach you the most useful DevOps practices to tackle those issues and broaden your skill set. What You’ll Learn Understand the basics of the most popular open source tools—Vagrant, Packer, Terraform, and Ansible—and how to use them in the context of deploying and scaling a SharePoint farm Use Vagrant to build SharePoint development environments in less than an hour, and add automated testing Use Packer to create a “golden image†with preconfigured settings, and then use it as the base image in your Terraform configuration for both AWS and Azure farms Use Terraform to scale your SharePoint farm topology Use Red Hat’s Ansible Playbooks to perform configuration management on your farm Use Terraform to deploy immutable infrastructure environments using IaC (Infrastructure as Code) Use InSpec 2.0 to stay in compliance by testing your cloud infrastructure Use Ansible to apply Microsoft updates and patches Who This Book Is For IT pros and developers who are looking to expand their knowledge and take a modern approach by using open source technologies to work with Microsoft products. Experience installing SharePoint, and a basic understanding of either Azure or AWS, is helpful. COMPUTERS,Programming,Microsoft

Pro .NET Memory Management Understand .NET memory management internal workings, pitfalls, and techniques in order to effectively avoid a wide range of performance and scalability problems in your software. Despite automatic memory management in .NET, there are many advantages to be found in understanding how .NET memory works and how you can best write software that interacts with it efficiently and effectively. Pro .NET Memory Management is your comprehensive guide to writing better software by understanding and working with memory management in .NET. Thoroughly vetted by the .NET Team at Microsoft, this book contains 25 valuable troubleshooting scenarios designed to help diagnose challenging memory problems. Readers will also benefit from a multitude of .NET memory management “rules†to live by that introduce methods for writing memory-aware code and the means for avoiding common, destructive pitfalls. What You'll Learn Understand the theoretical underpinnings of automatic memory management Take a deep dive into every aspect of .NET memory management, including detailed coverage of garbage collection (GC) implementation, that would otherwise take years of experience to acquire Get practical advice on how this knowledge can be applied in real-world software development Use practical knowledge of tools related to .NET memory management to diagnose various memory-related issues Explore various aspects of advanced memory management, including use of Span and Memory types Who This Book Is For .NET developers, solution architects, and performance engineers COMPUTERS,Programming,Microsoft

Xamarin.Forms Solutions Use the solutions provided in this book to handle common challenges in Xamarin.Forms that are encountered on a daily basis. Working examples and techniques are presented that you can modify and drop directly into your own projects. You will be able to deliver working code faster than ever. Examples are made available through GitHub, maximizing the convenience and value this book provides to Xamarin.Forms developers. Solutions in the book are organized broadly into problem domains such as user interface for applications, data and security, connectivity and external services, and more. Within each domain the book presents specific solutions addressing challenges that are commonly faced. Under data and security, for example, you’ll find specific solutions around storing login credentials, local data caching, and sending authorization tokens in HTTP requests. Not only do the solutions in the book solve specific problems, they also present best practices that can inform and improve the quality of the code that you write. Xamarin.Forms Solutions is chock full of practical advice and code examples that no Xamarin.Forms programmer will want to be without. The basics of Xamarin.Forms are provided for beginning developers. What You'll Learn Know the in-depth basics of Xamarin.Forms and the inner workings Create custom renderers and dependency services Manage the appearance of user interfaces through styling and theming, layout options, rotation, and animation Build sophisticated user interfaces using a variety of controls that allow for PDF viewing, barcode interpretation, searching and finding, and other controls Secure your applications, and communicate securely with services via HTTP requests Sign and deploy your apps and optimize the binary file size Who This Book Is For Those building mobile applications on the Xamarin platform for iOS and Android. By mixing together the solutions and a thorough explanation of the basics of Xamarin.Forms, the book spans the needs of beginning through intermediate Xamarin.Forms developers. Even experts will find a few gems to improve the quality and speed of their application development work. COMPUTERS,Programming,Microsoft

Microsoft 365 Business for Admins For Dummies Learn streamlined management and maintenance capabilities for Microsoft 365 Business If you want to make it easy for your teams to work together using the latest productivity solutions with built-in security—while saving thousands of dollars in implementing the solution—you've picked the right book. Inside, you'll gain an understanding of Microsoft 365 Business, a complete integrated solution for business productivity and security powered by Office 365 and Windows 10. You’ll also learn how this cloud-based solution can help grow your business while protecting company data from potential threats using the same security management tools large enterprises use. Microsoft 365 Business For Admins For Dummies provides business owners, IT teams, and even end users an understanding of the capabilities of Microsoft 365 Business: an integrated platform and security solution built with the latest features to enable today's modern workforce and empower businesses to achieve their goals. De-mystifies the complexities of the bundled solution to help you avoid common deployment pitfalls Includes the latest information about the services included in Microsoft 365 Business Enhance team collaboration with intelligent tools Manage company-owned or bring your own device (BYOD) devices from one portal Step through a guided tour for running a successful deployment Get the guidance you need to deploy Microsoft 365 Business and start driving productivity in your organization while taking advantage of the built-in security features in the solution to grow and protect your business today. COMPUTERS,Programming,Microsoft

Mastering Microsoft Dynamics 365 Customer Engagement A comprehensive guide packed with the latest features of Dynamics 365 for customer relationship management Key Features Create efficient client-side apps and customized plugins that work seamlessly Learn best practices from field experience to use Dynamics 365 efficiently Unleash the power of Dynamics 365 to maximize your organization's profits Book Description Microsoft Dynamics 365 is an all-in-one business management solution that's easy to use and adapt. It helps you connect your finances, sales, service, and operations to streamline business processes, improve customer interactions, and enable growth. This book gives you all the information you need to become an expert in MS Dynamics 365. This book starts with a brief overview of the functional features of Dynamics 365. You will learn how to create Word and Excel templates using CRM data to enable customized data analysis for your organization. This book helps you understand how to use Dynamics 365 as an XRM Framework, gain a deep understanding of client-side scripting in Dynamics 365, and create client-side applications using JavaScript and the Web API. In addition to this, you will discover how to customize Dynamics 365, and quickly move on to grasp the app structure, which helps you customize Dynamics 365 better. You will also learn how Dynamics 365 can be seamlessly embedded into various productivity tools to customize them for machine learning and contextual guidance. By the end of this book, you will have mastered utilizing Dynamics 365 features through real-world scenarios. What you will learn Manage various divisions of your organization using Dynamics 365 customizations Explore the XRM Framework and leverage its features Provide an enhanced mobile and tablet experience Develop client-side applications using JavaScript and the Web API Understand how to develop plugins and workflows using Dynamics 365 Explore solution framework improvements and new field types Who this book is for Mastering Microsoft Dynamics 365 Customer Engagement is for you if you have knowledge of Dynamics CRM and want to utilize the latest features of Dynamics 365. This book is also for you if you're a skilled developer looking to move to the Microsoft stack to build business solution software. Extensive Dynamics CRM development experience will be beneficial to understand the concepts covered in this book. COMPUTERS,Programming,Microsoft

BizTalk Server 2016 Gain an in depth view of optimizing the performance of BizTalk Server. This book provides best practices and techniques for improving development of high mission critical solutions. You'll see how the BizTalk Server engine works and how to proactively detect and remedy potential bottlenecks before they occur. The book starts with an overview of the BizTalk Server internal mechanisms that will help you understand the optimizations detailed throughout the book. You'll then see how the mechanisms can be applied to a BizTalk Server environment to improve low and high latency throughput scenarios. A section on testing BizTalk server solutions will guide you through the most frequently adopted techniques used to develop solutions such as performance and unit testing as part of the development cycle. With BizTalk Server 2016 you'll see how to apply side-by-side versioning to your solutions to reduce the chances of downtime, You'll also review instrumentation techniques using Event Traces for windows and business activity monitoring (BAM). While the book is focused on the latest version of BizTalk Server, most of the topics discussed will also work with BizTalk Server 2013R2. What You'll Learn Review BizTalk Server internals and how the message engine works Understand BizTalk Server architecture Gather and analyze BizTalk Server performance data Develop BizTalk Server performance solutions Use advanced troubleshooting tools to help diagnose your platform Who This Book Is For Those who have strong BizTalk and .NET Framework knowledge and want to get their BizTalk Server knowledge to the next level COMPUTERS,Programming,Microsoft

Blazor Revealed Build web applications in Microsoft .NET that run in any modern browser, helping you to transfer your .NET experience and skills to a new environment and build browser-based applications using a robust and type-safe language and runtime. Developing a web site with rich client-side behavior means most developers need to learn a transpiled language like JavaScript or TypeScript. But today you can also develop rich browser applications using the .NET runtime and C# using Blazor. With Blazor you can use all that experience you have amassed over the years, and can use thousands of already existing libraries, right in the browser. Blazor Revealed will allow you to create a rich web site experience in no time. You will learn how to build user interfaces, and present data to a user for display and modification, capturing the user’s changes via data binding. The book shows you how to access a rich library of .NET functionality such as a component model for building a composable user interface, including how to develop reusable components that can be used across many pages and web sites. Also covered is data exchange with a server, giving you access to microservices and database services. Blazor provides a fresh take on web development by eliminating the need for you to learn different languages and frameworks for client- and server-side development. Blazor allows C# and .NET to be used on all sides, providing a robust feature set that is well suited toward scalable, enterprise-level applications. Blazor Revealed gets you started in using this important new toolkit for web application development. What You'll Learn Build user interfaces and display data for users to edit Capture the user’s changes via data binding Transfer data back and forth between server and client Communicate with microservices and database services Develop reusable components and assemble them into bigger components Use routing to build single page applications (SPAs) Build Blazor libraries that are reusable across applications Who This Book Is For Experienced .NET developers who want to apply their existing skills to building professional quality, client-side web applications that run in any browser. The book is for web developers who want to step away from JavaScript and its complexities, and instead use a proven technology (.NET) that is robust toward creating enterprise-quality applications that scale and are reliable and that provide good user experience. The book is for intermediate to advanced .NET web developers with no experience using Blazor. COMPUTERS,Programming,Microsoft

Learn Microsoft Visual Studio App Center Use Visual Studio App Center with Xamarin Forms to set up a DevOps CI/CD pipeline, set up your mobile builds on either iOS or Android, set up Android and Apple certificates and provisioning profiles, distribute your app to your developers and testers, capture analytics and crashes from your users, communicate to your users with push notifications, and run UI tests on the Microsoft cloud. You will see how to automate and manage the life cycle of your apps through Microsoft's Cloud Service, with a focus on integrating App Center into your Xamarin Forms apps with clear, practical examples. As you follow along with the sample app, you will see how easy it is to configure your builds, to test the sample app on various iOS and Android devices on the App Center cloud, and to distribute your app to real devices. Whether you are a developer on a small team or a startup or an architect in a large organization curious about the benefits of Visual Studio App Center, after finishing this book, you will be confident in setting up App Center on your next mobile project. Come join me on this journey through Visual Studio App Center with Xamarin Forms. What You Will Learn Create a DevOps CI/CD pipeline for your mobile app on both iOS and Android devices Save money without buying multiple iOS and Android devices and instead run cloud UI tests Stay informed about build successes and failures by integrating App Center with Slack Set up groups and add team members to your groups on App Center Distribute your app to your team on either iOS or Android devices Capture important user events in your code and report to App Center Give a friendly user experience by handling crashes gracefully and reporting to App Center Keep and analyze your user’s data on Azure by setting up automatic data export to Azure Communicate with your users using iOS and Android notification services from App Center Give your users a better experience by sending silent push notifications Include custom data in your push notifications Who This Book Is For Xamarin Forms mobile developers with previous experience using the Xamarin framework. COMPUTERS,Programming,Microsoft

Customizing Dynamics 365 Gain an understanding of basic and advanced customizations in Dynamics 365 and learn how they can be effectively used to implement simple business requirements. This is a practical book for developers that explains the use of various Dynamics 365 features as well as use of advanced concepts such as Azure integration and custom development. Customizing Dynamics 365 starts by explaining the business requirements of the example application, which will explain the platform features, and discussing why Dynamics 365 is the ideal platform for the solution. Next, you will set up your development environment and use the different customizations of the platform to implement the basic business requirements of the example application. Further, you will automate the business process and create advanced customizations with plugins and custom workflow activities. Towards the end you will learn more about Azure integration, reports and dashboards, portal development, and data migration techniques, which will help you select the best option for a particular scenario. After reading this book you will be able to develop solutions with Dynamic 365 by understanding the various features and customizations of the platform. What You Will Learn Choose the right customizations and configurations to meet end-user requirements Use Azure features with Dynamics 365 to implement complex business scenarios Understand the importance of using source control for Dynamics 365 customizations Discover new trends with Dynamics 365 mobility Who This Book Is For Dynamics 365 developers, consultants, and architects. COMPUTERS,Programming,Microsoft

Beginning Azure IoT Edge Computing Use a step-by-step process to create and deploy your first Azure IoT Edge solution. Modern day developers and architects in today’s cloud-focused world must understand when it makes sense to leverage the cloud. Computing on the edge is a new paradigm for most people. The Azure IoT Edge platform uses many existing technologies that may be familiar to developers, but understanding how to leverage those technologies in an edge computing scenario can be challenging. Beginning Azure IoT Edge Computing demystifies computing on the edge and explains, through concrete examples and exercises, how and when to leverage the power of intelligent edge computing. It introduces the possibilities of intelligent edge computing using the Azure IoT Edge platform, and guides you through hands-on exercises to make edge computing approachable, understandable, and highly useful. Through user-friendlydiscussion you will not only understand how to build edge solutions, but also when to build them. By explaining some common solution patterns, the decision on when to use the cloud and when to avoid the cloud will become much clearer. What You'll Learn Create and deploy Azure IoT Edge solutions Recognize when to leverage the intelligent edge pattern and when to avoid it Leverage the available developer tooling to develop and debug IoT Edge solutions Know which off-the-shelf edge computing modules are available Become familiar with some of the lesser-known device protocols used in conjunction with edge computing Understand how to securely deploy and bootstrap an IoT Edge device Explore related topics such as containers and secure device provisioning Who This Book Is For Developers or architects who want to understand edge computing and when and where to use it. Readers should be familiar with C# or Python and have a high-level understanding of the Azure IoT platform. COMPUTERS,Programming,Microsoft

Design Patterns in .NET Implement design patterns in .NET using the latest versions of the C# and F# languages. This book provides a comprehensive overview of the field of design patterns as they are used in today’s developer toolbox. Using the C# programming language, Design Patterns in .NET explores the classic design pattern implementation and discusses the applicability and relevance of specific language features for the purpose of implementing patterns. You will learn by example, reviewing scenarios where patterns are applicable. MVP and patterns expert Dmitri Nesteruk demonstrates possible implementations of patterns, discusses alternatives and pattern inter-relationships, and illustrates the way that a dedicated refactoring tool (ReSharper) can be used to implement design patterns with ease. What You'll Learn Know the latest pattern implementations available in C# and F# Refer to researched and proven variations of patterns Study complete, self-contained examples including many that cover advanced scenarios Use the latest implementations of C# and Visual Studio/ReSharper Who This Book Is For Developers who have some experience in the C# language and want to expand their comprehension of the art of programming by leveraging design approaches to solving modern problems COMPUTERS,Programming,Microsoft

Deploying SharePoint 2019 Update to a version of SharePoint that offers the best of both on-premise and the cloud using SharePoint 2019, the latest release of this cornerstone technology from Microsoft. Don your technical learning hat to get up close and confident on the new time-saving modern features of on-premise, and the many new security and hybrid settings. Deploying SharePoint 2019 begins with a general introduction to SharePoint 2019, covering new features and expanding your knowledge and capability with the technology systematically. You will learn about the new world of SharePoint, and how it was “cloud-born†from Office 365. From there you will dive into learning how to design a physical architecture for SharePoint Server 2019 and get familiar with the key concepts of high availability (HA) and disaster recovery (DR) solutions. What You'll Learn Install, configure, and optimize SharePoint 2019 Understand SharePoint 2019 as a hybrid framework Get comfortable with new tools, such as Flow, PowerApps, and Power BI Configure systems connected to SharePoint, such as Office Online Server and Workflow Manager Migrate content and service databases from previous versions of SharePoint to SharePoint 2019 Implement HA and DR topologies with SharePoint 2019 to satisfy business continuity requirements Who This Book Is For Those tasked with installing, configuring, and maintaining SharePoint Server 2019 for their organization. This book assumes some working knowledge of a previous release of SharePoint Server, such as SharePoint 2013 or SharePoint 2016. COMPUTERS,Programming,Microsoft

Integrating Serverless Architecture Design, develop, build, and deliver an end-to-end serverless architecture by leveraging Azure services, frameworks, and tools. This book offers a holistic approach, guiding you through the design and development of a Twitter Bot application, while leveraging Azure Functions. Integrating Serverless Architecture begins with an overview of serverless computing and getting started with Azure Functions. Here, you will create a Twitter bot function which scans Twitter for the latest tweets and makes use of dependency injection. Further, you will learn about Azure Cosmos DB where you will cover its change feed mechanism and the repository pattern. You will create a Cosmos DB trigger-based tweet notifier function, which will broadcast the latest tweets to connected clients. You will explore the basics of Azure Service Bus and create a tweet scheduler function, which will prioritize different keywords for the Twitter bot function. Along the way, you will debug, deliver, and test the functions in the Azure environment. This book shows you how to secure your Azure Function secrets with the help of Azure Key Vault. To further your understanding of the technology, you will learn logging and exception handling in Azure Functions.Later in the book, you will build a Twitter bot web application by using ASP.NET Core and Materialize CSS, which will interact with several HTTP-based Azure Functions. The Twitter bot web application allows users to log in through the Twitter Identity Provider, subscribe to different keywords/hashtags, and browse the latest tweets based on subscriptions. You will get started with SignalR Service and integrate it with Azure Functions and web applications. Towards the end you will go through app service authentication on Azure Functions and discover how to configure continuous integration and delivery to Azure Functions. After reading this book, you will be able to understand the steps involved in design, development, and delivery of a workflow using Azure Functions. What You Will Learn Design and develop a Twitter bot application using Azure Functions with Azure Web App Service as the front end Leverage Azure Cosmos DB as data storage and trigger notifications using its change feed mechanism Store and retrieve secrets from Azure Key Vault Integrate Azure Functions with Azure SignalR Service to broadcast real-time messages Secure Azure Functions by enabling Twitter identity authentication using built-in App Service authentication Build a continuous integration and continuous delivery pipeline for Azure Functions using Visual Studio Team Services (VSTS) Who This Book Is For Developers, software engineers, and architects who design and manage infrastructures and build applications by leveraging Microsoft cloud services. COMPUTERS,Programming,Microsoft

Building Microservices Applications on Microsoft Azure Implement microservices starting with their architecture and moving on to their deployment, manageability, security, and monitoring. This book focuses on the key scenarios where microservices architecture is preferred over a monolithic architecture. Building Microservices Applications on Microsoft Azure begins with a survey of microservices architecture compared to monolithic architecture and covers microservices implementation in detail. You'll see the key scenarios where microservices architecture is preferred over a monolithic approach. From there, you will explore the critical components and various deployment options of microservices on platforms such as Microsoft Azure (public cloud) and Azure Stack (hybrid cloud). This includes in-depth coverage of developing, deploying, and monitoring microservices on containers and orchestrating with Azure Service Fabric and Azure Kubernetes Cluster (AKS). This book includes practical experience from large-scale enterprise deployments, therefore it can be a quick reference for solution architects and developers to understand the critical factors while designing a microservices application. What You Will Learn Explore the use cases of microservices and monolithic architecture Discover the architecture patterns to build scalable, agile, and secure microservices applications Develop and deploy microservices using Azure Service Fabric and Azure Kubernetes Service Secure microservices using the gateway pattern See the deployment options for Microservices on Azure Stack Implement database patterns to handle the complexities introduced by microservices Who This Book Is For Architects and consultants who work on Microsoft Azure and manage large-scale deployments. COMPUTERS,Programming,Microsoft

Exploring the .NET Core 3.0 Runtime Explore advanced .NET APIs and create a basic .NET core library with dynamic code generation and metadata inspection to be used by other libraries or client applications. This book starts with the benefits of .NET including its fundamental tasks and tools where you will learn .NET SDK tools and the ILDasm tool. This is followed by a detailed discussion on code generation in .NET API programming. Along the way, you will learn how to build a programming model through a code-generator tool and metadata inspector tool using .NET version information for .NET assembly and binary code. Exploring the .NET Core 3.0 Runtime covers the features of Microsoft Visual Studio 2019 using a tutorial and shows you how to create a .NET Core 3.0 application. Here you will configure and deploy your .NET projects along with meta packages and see some do's and don'ts. Finally, you will compare the features of .NET Core 3.0 with the .NET Framework library and its GUI frameworks. After reading this book, you will be able to work in a .NET 3.0 environment and program for its two advanced features: code generation and metadata inspection. What You Will Learn Understand the inner workings of an assembly’s structural organization Work with reflection through the .NET Core platform Carry out dynamic code generation using the .NET Core API's code document model (CodeDOM) Use the metadata mechanism of the .NET Core platform Who This Book Is For Software developers and engineers using .NET and/or the .NET Core platform and tools. COMPUTERS,Programming,Microsoft

Developing Applications with Azure Active Directory Explore tools for integrating resources and applications with Azure Active Directory for authentication and authorization. This book starts with an introduction to Azure Active Directory (AAD) where you will learn the core concepts necessary to understand AAD and authentication in general. You will then move on to learn OpenID Connect and OAuth along with its flows, followed by a deep dive into the integration of web applications for user-based authentication. Next, you go through user authentication and how to enable the integration of various native applications with AAD. This is followed by an overview of authenticating applications along with a detailed discussion on collaboration with external users and other AD tenants. Moving forward, Developing Applications with Azure Active Directory covers using schemas of AD objects, such as users, to add custom attributes on top of ADD’s predefined attributes. You will see how multi-tenancy can be supported in Azure AD as well as how to design authorization with Azure AD. After reading this book, you will be able to integrate, design, and develop authentication and authorization techniques in Azure Active Directory. What You Will Learn Integrate applications with Azure AD for authentication Explore various Azure AD authentication scenarios Master core Azure AD concepts Integrate external users and tenants Who is this book for: The book will be useful for architects and developers, planning to use Azure AD for authentication. COMPUTERS,Programming,Microsoft

Essential Angular for ASP.NET Core MVC 3 Combine the strengths of Angular, the leading framework for developing complex client-side applications, and ASP.NET Core MVC 3, the latest evolution of Microsoft’s framework for server-side applications. This new edition offers updated Angular, ASP.NET Core 3, Entity Framework Core 3 examples, an all-new chapter on interoperability with Blazor, and more! Best-selling author Adam Freeman brings together these two key technologies and explains how to use ASP.NET Core MVC 3 to provide back-end services for Angular applications. This fast-paced and practical guide starts from the nuts and bolts and gives you the knowledge you need to combine Angular and ASP.NET Core MVC 3 in your projects.Each topic is covered clearly and concisely and is packed with the essential details you need to learn to be truly effective. What You Will Learn Gain a solid understanding of how ASP.NET Core MVC 3 and Angular can work together Utilize both Visual Studio and Visual Studio Code to develop Angular/ASP.NET Core MVC projects Create ASP.NET Core RESTful web services to support Angular applications Expose data from Entity Framework Core to Angular applications Use ASP.NET Core Identity to provide security services to Angular applications Understand how Angular and Blazor applications can work together Who This Book Is For This book is for developers with knowledge of ASP.NET Core MVC who are introducing Angular into their projects. COMPUTERS,Programming,Microsoft

Creating Business Applications with Office 365 Take your Office 365 and SharePoint projects to a higher level by using PowerApps, Flow, Power BI, JavaScript/jQuery jQuery UI widgets, Cascading Style Sheets (CSS), and more. This book will help you create easier solutions to client-side problems and applications. Additionally, you will be able to effectively visualize your data with Power BI. This book starts with configuration of SharePoint and Office 365 followed by your first example of PowerApps. You will lay the foundation for a help ticket application and see how to update a SharePoint list with PowerApps. You then will work with the jQuery open source library and learn how to use the developer tools within your browser. This allows you to customize data displays in SharePoint. Next, you will add jQuery UI widgets such as buttons and dialogs to SharePoint, learning how to configure and manipulate them via JavaScript. You will use these new skills to convert a normal SharePoint announcement into a visually compelling page of network alerts. You also will use JavaScript and styles to hugely improve native SharePoint calendars by color-coding them by category or location. To prevent overlapping events in calendars, you will work with SharePoint's web services and JavaScript. You will use similar concepts to make appealing accordion SharePoint pages. You then will explore Microsoft Forms, Flow, and Power BI, including building surveys in both Forms and SharePoint and using Power BI to show results over the last week, month, quarter, and year. Using advanced Power BI you will see how to deal with JSON, XML, and Yes/No data. Next, you will look at how to display Office documents as well as interact with them via JavaScript. Switching back to PowerApps, you will build the final help ticketing system before using Power BI to see how to visualize the ticket information. After a quick detour on using iFrames in SharePoint, you will jump into building a power routing application using InfoPath and SharePoint Designer. You will even call SharePoint’s web services from Designer to customize email notifications. You end the InfoPath set of chapters with a highly useful application for signing up for and managing attendance for training and other classes. Finally, you will add Google Analytics to track SharePoint usage. What You Will Learn Build powerful applications with PowerApps Extend SharePoint’s capabilities using JavaScript Create surveys with SharePoint and Microsoft Forms, copy the results to SharePoint using Flow, and visualize the data with Power BI Employ advanced Power BI techniques to include custom columns, pivoting, and dealing with JSON, XML, and Yes/No data Use InfoPath and SharePoint workflows to create routing systems, schedule classes, and other advanced tasks Who This Book Is For Business and application developers COMPUTERS,Programming,Microsoft

Getting Started with Dynamics 365 Portals Use the full range of features of Dynamics 365 Portal to develop and implement end user portals to provide your audience an online location to communicate and collaborate. This book guides you through implementation and highlights the best practices for each feature.Author Sanjaya Yapa begins with an introduction to end user portals in Dynamics 365 and takes you through a practical example that explains the features in detail. He then teaches you how the portal security works and best practices involved while configuring security such as local and federated authentication, web roles, and access rules. Helpful illustrations and directives guide you in setting up your portal with Dynamics 365 Customer Engagement (CE), basic customizations, content management, and web forms. You learn how to configure and manage document storage and learn about liquid templates, which is important when implementing custom web experiences for your end users. After reading this book, you will be able to implement a portal with Dynamics 365 CE and incorporate best practices in your enterprise-scale solutions. What You Will Learn Set up Dynamics 365 Portal within your Dynamics 365 instance Get familiar with Portal Management Interface and its features Know the security models and how to choose the best option Use Entity Forms, lists, displaying charts, and customize Portal Refer to practical examples and case studies for developing and implementing advanced liquid templates Who This Book Is For Developers working in a Dynamics 365 CE environment COMPUTERS,Programming,Microsoft

Getting Started with Visual Studio 2019 Know how to use the features of Visual Studio 2019 and utilize the IDE correctly to become your one-stop solution for creating quality code. Learn what's new in VS 2019 and explore the existing features of Visual Studio so you can use them more efficiently. Getting Started with Visual Studio 2019 begins with an overview of Visual Studio and explores new features such as Visual Studio Live Share, Visual Studio Search, Solution Filters, and Intellicode. Author Dirk Strauss teaches you how to create project templates, write code snippets, and manage NuGet packages. You will learn how to: debug your code using breakpoints and step into specific methods, use data tips, and utilize the DebuggerDisplay attribute. You will then move on to learn unit testing and explore the tools provided by Visual Studio to create and run unit tests. The book also covers source control integration in Visual Studio and how to use GitHub to implement a source control strategy in your code. What You Will Learn Create and use code snippets in Visual Studio 2019 Utilize diagnostic tools and the Immediate window for code debugging Generate unit tests with IntelliTest Use NuGet in applications Create and handle pull requests Who This Book Is For Beginners and software developers working on the .NET stack COMPUTERS,Programming,Microsoft

Exploring Blazor Build and develop web applications with Blazor in C#. This book will cover all three types of Blazor – server-side, client-side, and hosted along with other features of the technology. You’ll see that Blazor is a web UI framework based on C#, Razor, and HTML and how it runs front-end logic using C# either on the server or on the browser using WebAssembly. The author starts by introducing WebAssembly and gives an overview of Blazor along with its various categories. Next, you’ll get started with Blazor where you learn the basics, including Razor syntax implementation. Here you will go over the major differences between Blazor and Razor and how the syntax works. A demo of the layout and navigation for server-side Blazor is followed by usage of Razor syntax to control an application in client-side Blazor. Further, you will go through the project layout, navigation, and routes for the API. Here, you will understand how to access the API from the front end and use the shared library for different models.Moving forward, you will discover how Blazor works with storage, files, and JavaScript. Finally, you will create web applications in Blazor using practical implementations and real-life scenarios for server-side, client-side, and hosted applications. After reading this book you will be able to build web applications with Blazor in C# and .NET Core 3.0. What You Will Learn Bind one-way and two-way data Combine Blazor and JavaScript Understand layout in server-side and client-side applications Execute the general syntax in Razor Who This Book Is For C# and .NET Core developers COMPUTERS,Programming,Microsoft

Introducing Azure Kubernetes Service Go from zero to sixty deploying and running a Kubernetes cluster on Microsoft Azure! This hands-on practical guide to Microsoft’s Azure Kubernetes Service (AKS), a managed container orchestration platform, arms you with the tools and knowledge you need to easily deploy and operate on this complex platform. Take a journey inside Docker containers, container registries, Kubernetes architecture, Kubernetes components, and core Kubectl commands. Drawing on hard-earned experience in the field, the authors provide just enough theory to help you grasp important concepts, teaching the practical straightforward knowledge you need to start running your own AKS cluster. You will dive into topics related to the deployment and operation of AKS, including Rancher for management, security, networking, storage, monitoring, backup, scaling, identity, package management with HELM, and AKS in CI/CD. What You Will Learn Develop core knowledge of Docker containers, registries, and Kubernetes Gain AKS skills for Microsoft’s fastest growing services in the cloud Understand the pros and cons of deploying and operating AKS Deploy and manage applications on the AKS platform Use AKS within a DevOps CI/CD process Who This Book Is For IT professionals who work with DevOps, the cloud, Docker, networking, storage, Linux, or Windows. Experience with cloud, DevOps, Docker, or application development is helpful. COMPUTERS,Programming,Microsoft

Pro DAX with Power BI Learn the intricate workings of DAX and the mechanics that are necessary to solve advanced Power BI challenges. This book is all about DAX (Data Analysis Expressions), the formula language used in Power BI—Microsoft’s leading self-service business intelligence application—and covers other products such as PowerPivot and SQL Server Analysis Services Tabular. You will learn how to leverage the advanced applications of DAX to solve complex tasks. Often a task seems complex due to a lack of understanding, or a misunderstanding of core principles, and how certain components interact with each other. The authors of this book use solutions and examples to teach you how to solve complex problems. They explain the intricate workings of important concepts such as Filter Context and Context Transition. You will learn how Power BI, through combining DAX building blocks (such as measures, table filtering, and data lineage), can yield extraordinary analytical power. Throughout Pro Dax with Power BI these building blocks are used to create and compose solutions for advanced DAX problems, so you can independently build solutions to your own complex problems, and gain valuable insight from your data. What You Will Learn Understand the intricate workings of DAX to solve advanced problems Deconstruct problems into manageable parts in order to create your own recipes Apply predefined solutions for addressing problems, and link back step-by-step to the mechanics of DAX, to know the foundation of this powerful query language Get fully on board with DAX, a new and evolving language, by learning best practices Who This Book Is For Anyone who wants to use Power BI to build advanced and complex models. Some experience writing DAX is helpful, but not essential if you have experience with other data query languages such as MDX or SQL. COMPUTERS,Programming,Microsoft

Beginning Microsoft Power BI Analyze company data quickly and easily using Microsoft’s powerful data tools. Learn to build scalable and robust data models, clean and combine different data sources effectively, and create compelling and professional visuals. Beginning Power BI is a hands-on, activity-based guide that takes you through the process of analyzing your data using the tools that that encompass the core of Microsoft’s self-service BI offering. Starting with Power Query, you will learn how to get data from a variety of sources, and see just how easy it is to clean and shape the data prior to importing it into a data model. Using Power BI tabular and the Data Analysis Expressions (DAX), you will learn to create robust scalable data models which will serve as the foundation of your data analysis. From there you will enter the world of compelling interactive visualizations to analyze and gain insight into your data. You will wrap up your Power BI journey by learning how to package and share your reports and dashboards with your colleagues. Author Dan Clark takes you through each topic using step-by-step activities and plenty of screen shots to help familiarize you with the tools. This third edition covers the new and evolving features in the Power BI platform and new chapters on data flows and composite models. This book is your hands-on guide to quick, reliable, and valuable data insight. What You Will Learn Simplify data discovery, association, and cleansing Build solid analytical data models Create robust interactive data presentations Combine analytical and geographic data in map-based visualizations Publish and share dashboards and reports Who This Book Is For Business analysts, database administrators, developers, and other professionals looking to better understand and communicate with data COMPUTERS,Programming,Microsoft

Getting Started with Containers in Azure Deploy and execute Microsoft Azure container and containerized applications on Azure. This second book in author Shimon Ifrah’s series on containers will help you manage and scale containers along with their applications, tools and services. You’ll start by setting up the Azure environment and quickly work through techniques and methods of managing container images with Azure Container Registry (ACR). As you move forward, deploying containerized applications with Azure container instances and Azure Kubernetes Service is discussed in detail, and in the process, you’ll see how to install Docker container host on Azure Virtual Machine. This is followed by a discussion on security in Azure containers where you’ll learn how to monitor containers and containerized applications backed by illustrative examples. Next, you will review how to scale containers along with methods for backing up and restoring containers and containerized applications on Azure. Towards the end, the book demonstrates troubleshooting applications and Docker container host issues in Azure. Getting Started with Containers in Azure will equip you to deploy, manage and secure containerized applications using Azure tools and services for containers. What You’ll Learn Explore containers on Microsoft Azure. Store Docker images on Azure Container Registry Automate deployment of container services using Azure CLI and Azure Cloud Shell Use Azure Container Instances (ACI) for smaller deployment Who This Book Is For Azure administrators, developers, and architects who want to get started and learn more about containers and containerized applications on Microsoft Azure. COMPUTERS,Programming,Microsoft

Unlocking Blockchain on Azure Design, architect, and build Blockchain applications with Azure in industrial scenarios to revolutionize conventional processes and data security. This book will empower you to build better decentralized applications that have stronger encryption, better architectures, and effective deployment structures over the cloud. You’ll start with an overview of Blockchain, distributed networks, Azure components in Blockchain, such as Azure Workbench, and independent Blockchain-as-a-service solutions. Next, you’ll move on to aspects of Blockchain transactions where the author discusses encryption and distribution along with practical examples. You’ll cover permissioned Blockchains and distributed ledgers with the help of use cases of financial institutions, followed by code and development aspects of smart contracts. Here, you will learn how to utilise the templates provided by Azure Resource Manager to quickly develop an Ethereum-based smart contract. Further, you will go through Blockchain points of integration, where the author demonstrates enterprise integration, automated processing of smart contracts, and lifecycle events. Finally, you will go through every deployment of HyperLedger, Ethereum, and other decentralized ledger examples over Azure, thus understanding the elements of creation, design, development, security, and deployment. After reading Unlocking Blockchain on Azure you will be able to design and develop Blockchain applications in Azure to decentralize social networks, financial organisations, and data. You’ll be able to implement encryption over a Blockchain and have full control over shared instances digitally. You will be able to program smart contracts to digitize rules and trigger timely transactions. What You Will Learn Build decentralized applications Program, design, and deploy dynamic smart contracts Model Blockchains in the form of token economics, hybrid networks, and infrastructure Develop end-to-end encryption and distributed systems Who This Book Is For Developers and solutions architects who want to develop Blockchain applications in Azure and decentralize applications in different scenarios. COMPUTERS,Programming,Microsoft

Microsoft Blazor Build web applications in C# and Microsoft .NET that run in any modern browser. This second edition is updated to work with the release version of Blazor and covers Blazor’s use in creating both server-side and WebAssembly Blazor applications. Developers are able to use all their experience in .NET along with thousands of existing libraries, right in the browser. There is important new coverage in this edition on the new and improved Razor syntax, how to easily validate user input with Blazor validation, and how to build complex interacting components with Cascading Properties and Templated Components. You will learn how to build user interfaces and present data to a user for display and modification, capturing the user’s changes via data binding. The book shows you how to access a rich library of .NET functionality such as a component model for building a composable user interface, including how to develop reusable components that can be used across many pages and websites. Also covered is data exchange with a server, giving you access to microservices and database services. Blazor provides a fresh take on web development by eliminating the need for you to learn different languages and frameworks for client- and server-side development. Blazor allows C# and .NET to be used on all sides, providing a robust feature set that is well suited toward scalable, enterprise-level applications. This book gets you started using this important new toolkit for web application development. What You Will Learn Build user interfaces and display data for users to edit Capture the user’s changes via data binding Transfer data back and forth between server and client Communicate with microservices and database services Develop reusable components and assemble them into bigger components Use routing to build single-page applications (SPAs) Build Blazor libraries that are reusable across applications Who This Book Is For Experienced .NET developers who want to apply their existing skills toward building professional-quality, client-side web applications that run in any browser. The book is for web developers who want to step away from JavaScript and its complexities, and instead use a proven technology (.NET) that is robust toward creating enterprise-quality applications that scale and are reliable, that provide good user experience. COMPUTERS,Programming,Microsoft

The SQL Server DBA’s Guide to Docker Containers Get introduced to the world of Docker containers from a SQL Server DBA’s perspective. This book explains container technology and how it can improve the deployment of your SQL Server databases without infrastructure lock-in. You will be equipped with the right technical skills to guide stakeholders in your business as they adopt and adapt to new technologies to improve time-to-market and competitiveness. You will learn how to build a lab environment at home on which to build skills that transfer directly into your day job. This book teaches you how to install and configure Docker on both Windows Server and Linux operating systems. You will learn the most common Docker commands that you need to know as a DBA to deploy and manage SQL Server on containers. Support for SQL Server on Linux is new, and this book has your back with guidance on creating Docker images specifically for deployment to a Linux platform. Included is coverage of key Linux commands needed to manage SQL Server on that operating system. By the end of the book you will have learned how to create your own custom SQL Server container images with configuration settings that are specific to your organization, that are capable of being deployed to both Windows Server and Linux. What You Will Learn Create Docker containers for agile deployment of SQL Server Run multiple SQL Server instances on a single Linux machine Deploy custom images specific to your organization’s needs Know the benefits and architecture of container technology Install and configure Docker on Windows Server and Linux Manage and persist SQL Server data in Docker containers Who This Book Is For Intermediate to senior SQL Server DBAs who are familiar with SQL Server on Windows and want to build their existing skills to deploy and manage SQL Server on Linux and through Docker containers. Readers should have a grasp of relational database concepts and be comfortable with the Transact-SQL language. COMPUTERS,Programming,Microsoft

Understanding System.IO for .NET Core 3 Take full advantage of the .NET APIs in System.IO to achieve fundamental I/O operations and produce better quality software. You’ll start with the basics of creating a .NET Core custom library for System.IO. You will learn the purpose and benefits of a custom cross-platform .NET Core library along with the implementation architecture of the custom library components. Moving forward, you will learn how to use the .NET APIs of System.IO for getting information about resources. Here, you will go through drives, directories, files, and much more in the .NET API. You’ll discuss manipulation of resources and the environment, where you will learn how to build custom IO actions for resource manipulation followed by its properties and security. Next, you will learn special .NET API operations with System.IO with demonstrations on working with collection of resources, directories, files, and system information. Finally, you will go through the managed and unmanaged streams in the .NET API such as memory stream, file stream, and much more.After reading Understanding System.IO for .NET Core 3, you will be able to work with different features of .System.IO in .NET Core and implement its internal and commercial tools for different I/O scenarios. What You Will Learn Discover the inner workings of the System.IO BCL implementation on the .NET Core platform Work with System.IO mechanisms available through the .NET Core platform Write a custom library that encapsulates .NET APIs from System.IO Design and implement various tools in System.IO Who This Book Is For Developers with prior experience of working in .NET or .NET Core. COMPUTERS,Programming,Microsoft

DevSecOps for .NET Core Automate core security tasks by embedding security controls and processes early in the DevOps workflow through DevSecOps. You will not only learn the various stages in the DevOps pipeline through examples of solutions developed and deployed using .NET Core, but also go through open source SDKs and toolkits that will help you to incorporate automation, security, and compliance. The book starts with an outline of modern software engineering principles and gives you an overview of DevOps in .NET Core. It further explains automation in DevOps for product development along with security principles to improve product quality. Next, you will learn how to improve your product quality and avoid code issues such as SQL injection prevention, cross-site scripting, and many more. Moving forward, you will go through the steps necessary to make security, compliance, audit, and UX automated to increase the efficiency of your organization. You’ll see demonstrations of the CI phase of DevOps, on-premise and hosted, along with code analysis methods to verify product quality. Finally, you will learn network security in Docker and containers followed by compliance and security standards. After reading DevSecOps for .NET Core, you will be able to understand how automation, security, and compliance works in all the stages of the DevOps pipeline while showcasing real-world examples of solutions developed and deployed using .NET Core 3. What You Will Learn Implement security for the .NET Core runtime for cross-functional workloads Work with code style and review guidelines to improve the security, performance, and maintenance of components Add to DevOps pipelines to scan code for security vulnerabilities Deploy software on a secure infrastructure, on Docker, Kubernetes, and cloud environments Who This Book Is For Software engineers and developers who develop and maintain a secure code repository. COMPUTERS,Programming,Microsoft

Pro ASP.NET Core 3 Now in its 8th edition, Pro ASP.NET Core has been thoroughly updated for ASP.NET Core 3. This comprehensive, full-color guide is the only book you need to learn ASP.NET Core development! Professional developers get ready to produce leaner applications for the ASP.NET Core platform. This edition puts ASP.NET Core 3 into context, and takes a deep dive into the tools and techniques required to build modern, extensible web applications. New features and capabilities such as MVC 3, Razor Pages, Blazor Server, and Blazor WebAssembly are covered, along with demonstrations of how they can be applied in practice. Following the same popular format and style found in previous editions, author Adam Freeman explains how to get the most out of ASP.NET Core 3. Starting with the nuts-and-bolts topics, he teaches readers about middleware components, built-in services, request model binding, and more. Moving along, he introduces increasingly more complex topics and advanced features, including endpoint routing and dependency injection. Written for professionals wanting to incorporate the latest functionality of ASP.NET Core 3 into their projects, this book also serves as a complete reference on ASP.NET Core. Beginners with some background in Microsoft web development will also greatly benefit from the in-depth coverage provided throughout. What You Will Learn: Build a solid foundation and skill set for working with the entire ASP.NET Core platform Apply ASP.NET Core 3 features in your developer environment; plentiful reusable templates See how to create RESTful web services, web applications, and client-side applications Leverage existing knowledge to efficiently get up and running with new programming models Adam Freeman is an experienced IT professional who has held senior positions in a range of companies, most recently serving as chief technology officer and chief operating officer of a global bank. Now retired, he spends his time writing and long-distance running. “The Rolls-Royce of ASP.NET books, (or if you’re American, the Cadillac). Very thorough!†Les Jackson, MCSD, DotNet Playbook “The author’s instruction is direct, easy to understand and supplemented with clear code examples... Whether you are a beginner learning ASP.NET Core 3.1 app development, or an experienced professional ready to master advanced concepts, I consider this book a 'must have' for you!" Jeremy Likness, Senior Program Manager, Microsoft “…the best single resource for teaching MVC web apps using ASP.NET. “ Charles Carter, MSCS, MSwE, JD, Cloud Application Development Instructor, Microsoft Software and Systems Academy COMPUTERS,Programming,Microsoft

Building Single Page Applications in .NET Core 3 Attention .NET developers who no longer want to use JavaScript for your front end. Quickly and efficiently learn how to use C# for your single-page application (SPA) thanks to Blazor. Today’s reality is that most modern applications are web-based and if you want the same user experience as a desktop application, you need to be able to create a single-page application. While there are multiple frameworks and libraries to choose from (including Angular, React, and VueJS), you still need to know how to code in JavaScript. But now there is another option from Microsoft. Blazor is an open-source framework that enables developers to create web applications using C# and HTML, and everything you need to get started is covered in this guide. You will learn the steps, through build-along coding examples, that will allow you to use the same language for both the front end and the back end of your application. This book is designed to get you comfortable creating a single-page application in the shortest time possible. Get ready to create a complete business application that teaches and reinforces the skills you need in a Blazor production environment. What You Will Learn Develop the front end of an application using C# and .NET Core Use this quick-start for .NET developers who need to improve their application with a single-page front end Take a code-first approach that models an actual business application Gain insights for developing a high-functioning and maintainable application Study guidance on repurposing your .NET skill set Who This Book Is For C# and .NET developers who have some experience in web development COMPUTERS,Programming,Microsoft

Pro Power BI Desktop Deliver eye-catching and insightful business intelligence with Microsoft Power BI Desktop. This new edition has been updated to cover all the latest features of Microsoft’s continually evolving visualization product. New in this edition is help with storytelling—adapted to PCs, tablets, and smartphones—and the building of a data narrative. You will find coverage of templates and JSON style sheets, data model annotations, and the use of composite data sources. Also provided is an introduction to incorporating Python visuals and the much awaited Decomposition Tree visual. Pro Power BI Desktop shows you how to use source data to produce stunning dashboards and compelling reports that you mold into a data narrative to seize your audience’s attention. Slice and dice the data with remarkable ease and then add metrics and KPIs to project the insights that create your competitive advantage. Convert raw data into clear, accurate, and interactive information with Microsoft’s free self-service BI tool. This book shows you how to choose from a wide range of built-in and third-party visualization types so that your message is always enhanced. You will be able to deliver those results on PCs, tablets, and smartphones, as well as share results via the cloud. The book helps you save time by preparing the underlying data correctly without needing an IT department to prepare it for you. What You Will Learn Deliver attention-grabbing information, turning data into insight Find new insights as you chop and tweak your data as never before Build a data narrative through interactive reports with drill-through and cross-page slicing Mash up data from multiple sources into a cleansed and coherent data model Build interdependent charts, maps, and tables to deliver visually stunning information Create dashboards that help in monitoring key performance indicators of your business Adapt delivery to mobile devices such as phones and tablets Who This Book Is For Power users who are ready to step up to the big leagues by going beyond what Microsoft Excel by itself can offer. The book also is for line-of-business managers who are starved for actionable data needed to make decisions about their business. And the book is for BI analysts looking for an easy-to-use tool to analyze data and share results with C-suite colleagues they support. COMPUTERS,Programming,Microsoft

Essential Visual Studio 2019 Discover how Visual Studio 2019 can improve your development process. Visual Studio is an integral part of the daily life of millions of developers worldwide. Even as this rich integrated development environment approaches two decades, it has never ceased in innovating ways to make developers’ work life more productive. Essential Visual Studio 2019 offers explicit guidance for the developer who is already familiar with Visual Studio, but might feel a little lost when it comes to understanding the more recent features and advances of the IDE. Busy developers simply don’t have the time to digest and distill what the latest and greatest tools are with each version. As a result, useful process and performance features may be overlooked. This book, by simply focusing on the most recent innovations in Visual Studio and its tangential developer market, is the perfect "go to" for bridging that gap. Be ready to plunge headfirst into key features and advances that have been added, expanded, or improved, and topics such as unit testing, refactoring, Git, debugging, containers, and more. You will procure the basic concepts and value first, before diving into hands-on code that is designed to quickly get you up and running. The goal of this book is to bring the developer up to speed on Visual Studio 2019. It does not focus just on functionality added in Visual Studio 2019, but takes a deep dive into the areas where Visual Studio 2019 changed. That way, even if you’re coming from much earlier versions of Visual Studio, you can easily discern how upgrading to Visual Studio 2019 can make you more productive. What You Will Learn Know how the new features and improvements in Visual Studio 2019 can make you more productive Understand the value of modifications and when they can be used to take full advantage of this powerful IDE Review changes to Visual Studio over the last two versions and see where the development process is heading Discover the cloud-based, containerized, dev-ops-aware, and platform-flexible aspects of Visual Studio Gain clarity on the areas that have the greatest impact to you personally Who This Book Is For Developers who use Visual Studio on a daily basis. Familiarity with earlier versions is helpful, as the book is not a soup-to-nuts survey of the IDE and some basic functions will not be covered. COMPUTERS,Programming,Microsoft

Learn Data Mining Through Excel Use popular data mining techniques in Microsoft Excel to better understand machine learning methods. Software tools and programming language packages take data input and deliver data mining results directly, presenting no insight on working mechanics and creating a chasm between input and output. This is where Excel can help. Excel allows you to work with data in a transparent manner. When you open an Excel file, data is visible immediately and you can work with it directly. Intermediate results can be examined while you are conducting your mining task, offering a deeper understanding of how data is manipulated and results are obtained. These are critical aspects of the model construction process that are hidden in software tools and programming language packages. This book teaches you data mining through Excel. You will learn how Excel has an advantage in data mining when the data sets are not too large. It can give you a visual representation of data mining, building confidence in your results. You will go through every step manually, which offers not only an active learning experience, but teaches you how the mining process works and how to find the internal hidden patterns inside the data. What You Will Learn Comprehend data mining using a visual step-by-step approach Build on a theoretical introduction of a data mining method, followed by an Excel implementation Unveil the mystery behind machine learning algorithms, making a complex topic accessible to everyone Become skilled in creative uses of Excel formulas and functions Obtain hands-on experience with data mining and Excel Who This Book Is For Anyone who is interested in learning data mining or machine learning, especially data science visual learners and people skilled in Excel, who would like to explore data science topics and/or expand their Excel skills. A basic or beginner level understanding of Excel is recommended. COMPUTERS,Programming,Microsoft

The Modern Data Warehouse in Azure Build a modern data warehouse on Microsoft's Azure Platform that is flexible, adaptable, and fast—fast to snap together, reconfigure, and fast at delivering results to drive good decision making in your business. Gone are the days when data warehousing projects were lumbering dinosaur-style projects that took forever, drained budgets, and produced business intelligence (BI) just in time to tell you what to do 10 years ago. This book will show you how to assemble a data warehouse solution like a jigsaw puzzle by connecting specific Azure technologies that address your own needs and bring value to your business. You will see how to implement a range of architectural patterns using batches, events, and streams for both data lake technology and SQL databases. You will discover how to manage metadata and automation to accelerate the development of your warehouse while establishing resilience at every level. And you will know how to feed downstream analytic solutions such as Power BI and Azure Analysis Services to empower data-driven decision making that drives your business forward toward a pattern of success. This book teaches you how to employ the Azure platform in a strategy to dramatically improve implementation speed and flexibility of data warehousing systems. You will know how to make correct decisions in design, architecture, and infrastructure such as choosing which type of SQL engine (from at least three options) best meets the needs of your organization. You also will learn about ETL/ELT structure and the vast number of accelerators and patterns that can be used to aid implementation and ensure resilience. Data warehouse developers and architects will find this book a tremendous resource for moving their skills into the future through cloud-based implementations. What You Will Learn Choose the appropriate Azure SQL engine for implementing a given data warehouse Develop smart, reusable ETL/ELT processes that are resilient and easily maintained Automate mundane development tasks through tools such as PowerShell Ensure consistency of data by creating and enforcing data contracts Explore streaming and event-driven architectures for data ingestion Create advanced staging layers using Azure Data Lake Gen 2 to feed your data warehouse Who This Book Is For Data warehouse or ETL/ELT developers who wish to implement a data warehouse project in the Azure cloud, and developers currently working in on-premise environments who want to move to the cloud, and for developers with Azure experience looking to tighten up their implementation and consolidate their knowledge COMPUTERS,Programming,Microsoft

Azure Serverless Computing Cookbook Discover recipes for implementing solutions to real-world business problems through serverless applications Key Features Test, troubleshoot, and monitor Azure functions to deliver high-quality and reliable cloud-centric applications Understand Visual Studio's integrated developer experience for Azure functions Explore best practices for organizing and refactoring code within the Azure functions Book Description This third edition of Azure Serverless Computing Cookbook guides you through the development of a basic back-end web API that performs simple operations, helping you understand how to persist data in Azure Storage services. You'll cover the integration of Azure Functions with other cloud services, such as notifications (SendGrid and Twilio), Cognitive Services (computer vision), and Logic Apps, to build simple workflow-based applications. With the help of this book, you'll be able to leverage Visual Studio tools to develop, build, test, and deploy Azure functions quickly. It also covers a variety of tools and methods for testing the functionality of Azure functions locally in the developer's workstation and in the cloud environment. Once you're familiar with the core features, you'll explore advanced concepts such as durable functions, starting with a "hello world" example, and learn about the scalable bulk upload use case, which uses durable function patterns, function chaining, and fan-out/fan-in. By the end of this Azure book, you'll have gained the knowledge and practical experience needed to be able to create and deploy Azure applications on serverless architectures efficiently. What you will learn Implement continuous integration and continuous deployment (CI/CD) of Azure functions Develop different event-based handlers in a serverless architecture Integrate Azure functions with different Azure services to develop enterprise-level applications Accelerate your cloud application development using Azure function triggers and bindings Automate mundane tasks at various levels, from development to deployment and maintenance Develop stateful serverless applications and self-healing jobs using durable functions Who this book is for If you are a cloud developer or architect who wants to build cloud-native systems and deploy serverless applications with Azure functions, this book is for you. Prior experience with Microsoft Azure core services will help you to make the most out of this book. COMPUTERS,Programming,Microsoft

Introducing Disaster Recovery with Microsoft Azure Explore and learn the key building blocks of Microsoft Azure services and tools for implementing a disaster-recovery solution of any on-premises or cloud-based application. In this book, you will go through various aspects of planning, designing, and configuring a robust recovery solution on Azure. Introducing Disaster Recovery with Microsoft Azure starts by explaining the disaster-recovery landscape and how Azure disaster recovery is different from the traditional approach. You will learn how to leverage Azure site recovery and various Azure-based services to design and implement a recovery solution and much more. Moving forward, you will design and implement various scenarios such as on-premises to Azure, Azure to Azure, and on-premises to on-premises disaster recovery. You will also learn common considerations and technicalities of implementing recovery solutions for various multi-tier, monolithic, and modern micro-services enterprise applications. Finally, you will go through real-life examples, scenarios, and exercises. After reading this book, you will be able to design and implement disaster recovery on Azure in different scenarios. You will also look at a few real-world scenarios that will provide more practical insights. What You Will Learn Discover the fundamental building blocks of disaster recovery on Azure Examine various application-specific considerations for disaster recovery Leverage various PaaS capabilities to achieve maximum benefit Design and implement a multi-regional Azure to Azure disaster recovery plan Who This Book Is For Consultants, architects, and Azure administrators. COMPUTERS,Programming,Microsoft

Getting Started with Advanced C# Understand and work with the most important features of advanced C# in different programming environments. This book teaches you the fundamental features of advanced C# and how to incorporate them in different programming techniques using Visual Studio 2019. The book is divided into two parts. Part I covers the fundamentals and essentials of advanced programming in C#. You will be introduced to delegates and events and then move on to lambda expressions. Part II teaches you how to implement these features in different programming techniques, starting with generic programming. After that, you will learn about thread programming and asynchronous programming, to benefit from a multi-threaded environment. Finally, you will learn database programming using ADO.NET to connect to a MySQL database and you will know how to exercise SQL statements and stored procedures through your C# applications. What You Will Learn Use delegates, events, and lambda expressions in advanced programming Make your application flexible by utilizing generics Create a fast application with multi-threading and asynchronous programming Work in Visual Studio Community Edition, which is the most common IDE for using C# Understand alternative implementations along with their pros and cons Who This Book Is For Developers and programmers who are already working in C# COMPUTERS,Programming,Microsoft

Dynamics 365 Essentials Discover what the Common Data Service is and how Dynamics 365 fits in the Power Platform. Learn how to set up core Dynamics 365 Customer Engagement functionality and build more customized processes using model-driven apps. This book covers the Dynamics 365 Online system for sales, customer service, marketing, field service, and Outlook integration. In this second edition, core platform changes from the Common Data Service are included and you will know what this means for Dynamics 365. Updated features include processes, the latest form and view designer, and Business Process Flows. The book also includes new chapters on portals and power virtual agents. After reading Dynamics 365 Essentials , you will have mastered the core functionality available in Dynamics 365 CE and model-driven applications, and will be able to set it up for a range of different business scenarios. What You Will Learn Set up the core standard features of Dynamics 365 CE Create model-driven apps within Dynamics 365 customized to specific business needs Customize Dynamics 365 CE and leverage process automation functionality through the UI Study the Common Data Service for Apps Who This Book Is For Consultants, business analysts, administrators, and project managers who are looking for more information about Dynamics 365 COMPUTERS,Programming,Microsoft

Visual Studio Extensibility Development Learn the extensibility model of Visual Studio to enhance the Visual Studio integrated development environment (IDE). This book will cover every aspect, starting from developing an extension to publishing it and making it available to the end user. The book begins with an introduction to the basic concepts of Visual Studio including data structures and design patterns and moves forward with the fundamentals of the VS extensibility model. Here you will learn how to work on Roslyn - the .NET compiler platform - and load extensions in VS. Next, you will go through the extensibility model and see how various extensions, such as menus, commands, and tool windows, can be plugged into VS. Moving forward, you’ll cover developing VS extensions and configuring them, along with demonstrations on customizing extension by developing option pages. Further, you will learn to create custom code snippets and use a debugger visualizer. Next, you will go through creation of project and item templates including deployment of VS extensions using continuous integration (CI). Finally, you will learn tips and tricks for Visual Studio and its extensibility and integration with Azure DevOps. After reading Visual Studio Extensibility Development you will be able to develop, deploy, and customize extensions in Visual Studio IDE. What You Will Learn Discover the Visual Studio extensibility and automation model Code Visual Studio extensions from scratch Customize extensions by developing a tools option page for them Create project templates, item templates, and code snippets. Work with code generation using T4 templates Code analysis and refactoring using Roslyn analyzers Create and deploy a private extension gallery and upload the extensions Upload a VS extension using CI Ship your extension to Visual Studio Marketplace Who This Book Is For Developers in Visual Studio IDE covering C#, Visual Basic (VB), JavaScript, and CSS. COMPUTERS,Programming,Microsoft

Understanding Microsoft Teams Administration Explore solutions, best practices, tips, and workarounds to plan, design, customize, implement, and manage Microsoft Teams in any environment. The book starts with an overview of Microsoft Teams where you will go through the teams architecture, teams/channels, audio/video meetings, and the phone system. It further dives into deployment and management of teams, clients, guests and external access, and live events, followed by network assessment and bandwidth planning for Teams. Here, you will learn about deployment of quality of service and how to configure your phone systems using direct routing and calling plans. Moving forward, you will learn Microsoft Teams administration and policy management along with the migration process of Skype for Business on-prem to Microsoft Teams. Towards the end, you will learn troubleshooting techniques in Teams for call quality issues and connectivity challenges. After reading Understanding Microsoft Teams Administration, you will be able to effectively configure, customize, and manage the Teams experience using the Teams admin portal and other tools and techniques. What You Will Learn Understand the Microsoft Teams architecture including the different components involved Enable and manage external and guest access for Teams users Manage Teams and channels with a private channel Implement quality of service for audio/video calls and meetings Establish Office 365 data classifications, loss prevention plans, and governance Manage resource types, licensing, service health reporting, and support Work with Microsoft Teams room and live event management Implement and manage messaging, calling policies, and settings Who This Book Is For Administrators and technical consultants working on Teams. COMPUTERS,Programming,Microsoft

Data Mashup with Microsoft Excel Using Power Query and M Master the art of loading external data into Excel for use in reporting, charting, dashboarding, and business intelligence. This book provides a complete and thorough explanation of Microsoft Excel’s Get and Transform feature set, showing you how to connect to a range of external databases and other data sources to find data and pull that data into your local spreadsheet for further analysis. Leading databases are covered, including Microsoft Azure data sources and web sources, and you will learn how to access those sources from your Microsoft Excel spreadsheets. Getting data into Excel is a prerequisite for using Excel's analytics capabilities. This book takes you beyond copying and pasting by showing you how to connect to your corporate databases that are hosted in the Azure cloud, and how to pull data from Oracle Database and SQL Server, and other sources. Accessing data is only half the problem, and the other half involves cleansing and rearranging your data to make it useful in spreadsheet form. Author Adam Aspin shows you how to create datasets and transformations. For advanced problems, there is help on the M language that is built into Excel, specifically to support mashing up data in support of business intelligence and analysis. If you are an Excel user, you won't want to be without this book that teaches you to extract and prepare external data ready for use in what is arguably the world’s leading analytics tool. What You Will Learn Connect to a range of external data, from databases to Azure sources Ingest data directly into your spreadsheets, or into PowerPivot data models Cleanse and prepare external data so it can be used inside Excel Refresh data quickly and easily to always have the latest information Transform data into ready-to-use structures that fit the spreadsheet format Execute M language functions for complex data transformations Who This Book Is For Excel users who want to access data from external sources—including the Microsoft Azure platform—in order to create business intelligence reporting, dashboards, and visualizations. For Excel users needing to cleanse and rearrange such data to meet their own, specific needs. COMPUTERS,Programming,Microsoft

The Business of Android Apps Development The growing but still evolving success of the Android platform has ushered in a second mobile technology “gold rush†for app developers. Google Play and Amazon Appstore for Android apps has become the second go-to apps eco for today's app developers. While not yet as large in terms of number of apps as iTunes, Google Play and Amazon Appstore have so many apps that it has become increasingly difficult for new apps to stand out in the crowd. Achieving consumer awareness and sales longevity for your Android app requires a lot of organization and some strategic planning. Written for today's Android apps developer or apps development shop, this new and improved book from Apress, The Business of Android Apps Development, Second Edition , tells you today's story on how to make money on Android apps. This book shows you how to take your app from idea to design to development to distribution and marketing your app on Google Play or Amazon Appstore. This book takes you step-by-step through cost-effective marketing, public relations and sales techniques that have proven successful for professional Android app creators and indie shops—perfect for independent developers on shoestring budgets. It even shows you how to get interest from venture capitalists and how they view a successful app vs. the majority of so-so to unsuccessful apps in Android. No prior business knowledge is required. This is the book you wish you had read before you launched your first app! COMPUTERS,Programming,Mobile Devices

Core iOS Developer's Cookbook, The The best place to start iOS application development The Core iOS Developer’s Cookbook provides ready-to-use code solutions for common iOS challenges, providing recipes that help you master the core technology at the heart of iOS. Renowned iOS programming expert Erica Sadun and top iOS developer Rich Wardwell cover the topics you need to create successful mobile applications that take full advantage of iOS graphics, touches, and views. As in all of Sadun’s iOS bestsellers, The Core iOS Developer’s Cookbook translates modern best practices into working code, distilling key concepts into concise recipes you can easily understand and apply to your own projects. This isn’t just cut-and-paste; using examples, Sadun and Wardwell fully explain both the “how†and “why†that underscore effective and successful iOS development. Coverage includes Creating direct touch-based interfaces with multi-touch, gestures, and custom gesture recognizers Building and customizing controls in powerful ways Adding novel motion effects Alerting users via pop-ups, progress bars, local notifications, popovers, audio cues, and more Using Xcode modules to easily integrate system frameworks and headers Assembling views and animation, organizing view hierarchies, and understanding how views work together Supporting multiple screen geometries with the breakthrough Auto Layout constraints system Controlling keyboards, making onscreen elements “text aware,†and efficiently scanning and formatting text Organizing user workspaces with view controllers Managing photos, videos, email, and text messages Leveraging enhanced iOS support for social media activities, including Flickr and Vimeo Implementing VoiceOver accessibility, including text-to-speech Getting started with Core Data-managed data stores Leveraging powerful networking and web services support Using APIs to enhance the user experience COMPUTERS,Programming,Mobile Devices

App Inventor 2 Yes, you can create your own apps for Android devices—and it’s easy to do. This extraordinary book introduces you to App Inventor 2, a powerful visual tool that lets anyone build apps. Learn App Inventor basics hands-on with step-by-step instructions for building more than a dozen fun projects, including a text answering machine app, a quiz app, and an app for finding your parked car! The second half of the book features an Inventor’s Manual to help you understand the fundamentals of app building and computer science. App Inventor 2 makes an excellent textbook for beginners and experienced developers alike. Use programming blocks to build apps—like working on a puzzle Create custom multi-media quizzes and study guides Design games and other apps with 2D graphics and animation Make a custom tour of your city, school, or workplace Control a LEGO® MINDSTORMS® NXT robot with your phone Build location-aware apps by working with your phone’s sensors Explore apps that incorporate information from the Web COMPUTERS,Programming,Mobile Devices

Advanced Android Application Development Advanced Android™ Application Development, Fourth Edition, is the definitive guide to building robust, commercial-grade Android apps. Systematically revised and updated, this guide brings together powerful, advanced techniques for the entire app development cycle, including design, coding, testing, debugging, and distribution. With the addition of quizzes and exercises in every chapter, it is ideal for both professional and classroom use. An outstanding practical reference for the newest Android APIs, this guide provides in-depth explanations of code utilizing key API features and includes downloadable sample apps for nearly every chapter. Together, they provide a solid foundation for any modern app project. Throughout, the authors draw on decades of in-the-trenches experience as professional mobile developers to provide tips and best practices for highly efficient development. They show you how to break through traditional app boundaries with optional features, including the Android NDK, Google Analytics and Android Wear APIs, and Google Play Game Services. New coverage in this edition includes Integrating Google Cloud Messaging into your apps Utilizing the new Google location and Google Maps Android APIs Leveraging in-app billing from Google Play, as well as third-party providers Getting started with the Android Studio IDE Localizing language and using Google Play App Translation services Extending your app’s reach with Lockscreen widgets and DayDreams Leveraging improvements to Notification, Web, SMS, and other APIs Annuzzi has released new source code samples for use with Android Studio. The code updates are posted to the associated blog site: http://advancedandroidbook.blogspot.com/ This title is an indispensable resource for intermediate- to advanced-level Java programmers who are now developing for Android, and for seasoned mobile developers who want to make the most of the new Android platform and hardware. This revamped, newly titled edition is a complete update of Android™ Wireless Application Development, Volume II: Advanced Topics, Third Edition. COMPUTERS,Programming,Mobile Devices

Swift Development with Cocoa Ready to build apps for iPhone, iPad, and Mac now that Swift has landed? If you’re an experienced programmer who’s never touched Apple developer tools, this hands-on book shows you how to use the Swift language to make incredible iOS and OS X apps, using Cocoa and Cocoa Touch. Learn how to use Swift in a wide range of real-world situations, with Cocoa features such as Event Kit and Core Animation. You’ll pick up Swift language features and syntax along the way, and understand why using Swift (instead of Objective-C) makes iOS and Mac app development easier, faster, and safer. You’ll also work with several exercises to help you practice as you learn. Learn the OS X and iOS application lifecycle Use storyboards to design adaptive interfaces Explore graphics systems, including the built-in 2D and 3D game frameworks Display video and audio with AVFoundation Store data locally with the file system, or on the network with iCloud Display lists or collections of data with table views and collection views Build apps that let users create, edit, and work with documents Use MapKit, Core Location, and Core Motion to interact with the world COMPUTERS,Programming,Mobile Devices

Expert Android Studio Take your Android programming skills to the next level by unleashing the potential of Android Studio Expert Android Studio bridges the gap between your Android programing skills with the provided tools including Android Studio, NDK, Gradle and Plugins for IntelliJ Idea Platform. Packed with best practices and advanced tips and techniques on Android tools, development cycle, continuos integration, release management, testing, and performance, this book offers professional guidance to experienced developers who want to push the boundaries of the Android platform with the developer tools. You'll discover how to use the tools and techniques to unleash your true potential as a developer. Discover the basics of working in Android Studio and Gradle, as well as the application architecture of the latest Android platform Understand Native Development Kit and its integration with Android Studio Complete your development lifecycle with automated tests, dependency management, continuos integration and release management Writing your own Gradle plugins to customize build cycle Writing your own plugins for Android Studio to help your development tasks. Expert Android Studio is a tool for expert and experienced developers who want to learn how to make use of the tools while creating Android applications for use on mobile devices. COMPUTERS,Programming,Mobile Devices

Introduction to Android Application Development What Every Android App Developer Should Know Today: Android 6 Tools, App/UI Design, Testing, Publishing, and More Introduction to Android ™ Application Development, Fifth Edition , is the most useful real-world guide to building robust, commercial-grade Android apps with the new Android 6 SDK, Android Studio, and latest development best practices. Bigger, better, and more comprehensive than ever, this book covers everything you need to start developing professional apps for modern Android devices. If you’re serious about Android development, this guide will prepare you to build virtually any app you can imagine! Three well-respected experts guide you through setting up your development environment, designing user interfaces, developing for diverse devices, and optimizing your entire app-development process. Up-to-date code listings support in-depth explanations of key API features, and many chapters contain multiple sample apps. This fifth edition adds brand-new chapters on material design, styling applications, design patterns, and querying with SQLite. You’ll find a treasure trove of Android Studio tips, plus a brand-new appendix on the Gradle build system. This edition also offers Updated coverage of the latest Android 5.1 and 6 APIs, tools, utilities, and best practices New coverage of the Android 6.0 permission model Powerful techniques for integrating material design into your apps An all-new chapter on using styles and reusing common UI components Extensive new coverage of app design, architecture, and backward compatibility A full chapter on using SQLite with persistent database-backed app data Revised quiz questions and exercises to test your knowledge Download this book’s source code at informit.com/title/9780134389455 or introductiontoandroid.blogspot.com. COMPUTERS,Programming,Mobile Devices

High Performance Mobile Web Optimize the performance of your mobile websites and webapps to the extreme. With this hands-on book, veteran mobile and web developer Maximiliano Firtman demonstrates which aspects of your site or app slow down the user’s experience, and what you can do to achieve lightning-fast performance. There’s much at stake: if you want to boost your app’s conversion rate, then tackling performance issues is the best way to start. Learn tools and techniques for working with responsive web design, images, the network layer, and many other ingredients—plus the metrics to check your progress. Ideal for web developers and web designers with HTML, CSS, JavaScript, and HTTP experience, this is your guide to superior mobile web performance. You’ll dive into: Emulators, simulators, and other tools for measuring performance Basic web performance concepts, including metrics, charts, and goals How to get real data from mobile browsers on your real networks APIs and specs for measuring, tracking and improving web performance Insights and tricks for optimizing the first view experience Ways to optimize post-loading experiences and future visits Responsive web design and its performance challenges Tips for extreme performance to achieve best conversion rates How to work with web views inside native apps COMPUTERS,Programming,Mobile Devices

Mobile Test Automation with Appium Automate your mobile app testing About This Book How to automate testing with Appium Apply techniques for creating comprehensive tests How to test on physical devices or emulators Who This Book Is For Are you a mobile developer or a software tester who wishes to use Appium for your test automation? If so, then this is the right book for you .You must have basic Java programming knowledge. You don't need to have prior knowledge of Appium. What You Will Learn Discover Appium and how to set up an automation framework for mobile testing Understand desired capabilities and learn to find element locators Learn to automate gestures and synchronize tests using Appium Take an incremental approach to implement page object pattern Learn to run Appium tests on emulators or physical devices Set up Jenkins to run mobile automation tests by easy to learn steps Discover tips and tricks to record video of test execution, inter app automation concepts Learn to run Appium tests in parallel on multiple devices simultaneously In Detail Appium is an open source test automation framework for mobile applications. It allows you to test all three types of mobile applications: native, hybrid, and mobile web. It allows you to run the automated tests on actual devices, emulators, and simulators. Today, when every mobile app is made on at least two platforms, iOS and Android, you need a tool that allows you to test across platforms. Having two different frameworks for the same app increases the cost of the product and time to maintain it as well. Appium helps save this cost. With mobile app growth exploding, mobile app automation is mainstream now. In this book, author Nishant Verma provides you with a firm grounding in the concepts of Appium while diving into how to set up appium & Cucumber-jvm test automation framework, implement page object design pattern, automate gestures, test execution on emulators and physical devices, and implement continuous integration with Jenkins. The mobile app we have referenced in this book is Quikr because of its relatively lower learning curve to understand the application. It's a local classifieds shopping app. Style and approach This book takes a practical, step-by-step approach to testing and automating individual apps such as native, hybrid, and mobile web apps using different examples. COMPUTERS,Programming,Mobile Devices

Android Programming Android Programming: The Big Nerd Ranch Guide is an introductory Android book for programmers with Java experience. Based on Big Nerd Ranch’s popular Android bootcamps, this guide will lead you through the wilderness using hands-on example apps combined with clear explanations of key concepts and APIs. This book focuses on practical techniques for developing apps compatible with Android 4.4 (KitKat) through Android 7.0 (Nougat) and beyond. Write and run code every step of the way, using Android Studio to create apps that integrate with other apps, download and display pictures from the web, play sounds, and more. Each chapter and app has been designed and tested to provide the knowledge and experience you need to get started in Android development. COMPUTERS,Programming,Mobile Devices

Coding iPhone Apps for Kids Apple’s Swift is a powerful, beginner-friendly programming language that anyone can use to make cool apps for the iPhone or iPad. In Coding iPhone Apps for Kids, you’ll learn how to use Swift to write programs, even if you’ve never programmed before. You’ll work in the Xcode playground, an interactive environment where you can play with your code and see the results of your work immediately! You’ll learn the fundamentals of programming too, like how to store data in arrays, use conditional statements to make decisions, and create functions to organize your code—all with the help of clear and patient explanations. Once you master the basics, you’ll build a birthday tracker app so that you won’t forget anyone’s birthday and a platform game called Schoolhouse Skateboarder with animation, jumps, and more! As you begin your programming adventure, you’ll learn how to:–Build programs to save you time, like one that invites all of your friends to a party with just the click of a button!–Program a number-guessing game with loops to make the computer keep guessing until it gets the right answer–Make a real, playable game with graphics and sound effects using SpriteKit–Challenge players by speeding up your game and adding a high-score systemWhy should serious adults have all the fun? Coding iPhone Apps for Kids is your ticket to the exciting world of computer programming. Covers Swift 3.x and Xcode 8.x. Requires OS X 10.11 or higher. COMPUTERS,Programming,Mobile Devices

Head First Android Development What will you learn from this book? If you have an idea for a killer Android app, this fully revised and updated edition will help you build your first working application in a jiffy. You’ll learn hands-on how to structure your app, design flexible and interactive interfaces, run services in the background, make your app work on various smartphones and tablets, and much more. It’s like having an experienced Android developer sitting right next to you! All you need to get started is some Java know-how. Why does this book look so different? Based on the latest research in cognitive science and learning theory, Head First Android Development uses a visually rich format to engage your mind, rather than a text-heavy approach that puts you to sleep. Why waste your time struggling with new concepts? This multi-sensory learning experience is designed for the way your brain really works. COMPUTERS,Programming,Mobile Devices

Building Android UIs with Custom Views Create engaging user experiences and awesome user interfaces using this guide About This Book Move beyond default UI templates, create and customize amazing UIs with Android Custom View Enable smooth data flow and create futuristic UIs by creating flexible custom views Scale your apps with responsive and data intensive views Who This Book Is For This book is for Android developers who want to create great user interfaces and move beyond the basics of the standard UI elements. They must have basic Android development knowledge along with basic Java programming. What You Will Learn Extend the standard UI widget framework by creating Custom views Add complex rendering, animations, and interactions to your views Optimize performance and decrease battery usage Implement custom views to share between multiple projects, or share it publicly Create 3D custom views using OpenGL ES In Detail To build great user interfaces for your Android apps that go beyond the standard UI elements, you need to use custom Android views. With these, you can give your app a distinctive look and ensure that it functions properly across multiple devices. This book will help you construct a great UI for your apps by teaching you how to create custom Android views. You will start by creating your first Android custom view and go through the design considerations. You will then see how the right choices will enable your custom view to perform seamlessly across multiple platforms and Android versions. You will create custom styleable attributes that work with Android XML layouts, learn to process touch events, define custom attributes, and add properties and events to them. By the end of this book, you will be able to create apps with custom views that are responsive and adaptable to make your app distinctive and an instant hit with its users. Style and approach The approach will be that of a step by step practical tutorial. The book will take you through a complete journey, right from creating your first Android view to customizing it to enable it to support any complex app. COMPUTERS,Programming,Mobile Devices

Beginning PowerApps Build mobile apps that specifically target your company’s unique business needs, with the same ease of writing a simple spreadsheet! With this book, you will build business apps designed to work with your company's systems and databases, without having to enlist the expertise of costly, professionally trained software developers. In Beginning PowerApps, author and business applications expert Tim Leung guides you step-by-step through the process of building your own mobile app. He assumes no technical background, although if you have worked with Excel, you are one step closer. He guides you through scenarios, such as what to do if you have existing databases with complex data structures and how to write screens that can connect to those data. You will come away with an understanding of how to set up screen navigation, manipulate data from within apps, and write solutions to perform specific tasks. What You'll Learn Connect with data Write formulas Visualize your data through charts Work with global positioning systems (GPS) Build flows Import and export data Manage offline scenarios Develop custom application programming interfaces (API) Who This Book Is For Beginners and non-developers, and assumes no prior knowledge of PowerApps COMPUTERS,Programming,Mobile Devices

iOS 11 Swift Programming Cookbook iOS 11, Swift 4, and Xcode 9 provide many new APIs for iOS developers. With this cookbook, you’ll learn more than 170 proven solutions for tackling the latest features in iOS 11 and watchOS 4, including new ways to use Swift and Xcode to make your day-to-day app development life easier. This collection of code-rich recipes also gets you up to speed on continuous delivery and continuous integration systems. Ideal for intermediate and advanced iOS developers looking to work with the newest version of iOS, these recipes include reusable code on GitHub, so you can put them to work in your project right away. Among the topics covered in this book: New features in Swift 4 and Xcode 9 Tools for continuous delivery and continuous integration Snapshot testing and test automation Creating document-based applications Updated Map view and Core Location features iOS 11’s Security and Password Autofill Data storage with Apple’s Core Data Creating lively user interfaces with UI Dynamics Building iMessage applications and sticker packages Integrating Siri into your apps with Siri Kit Creating fascinating apps for Apple Watch COMPUTERS,Programming,Mobile Devices

Hello, Android Google Android dominates the mobile market, and by targeting Android, your apps can run on most of the phones and tablets in the world. This new fourth edition of the #1 book for learning Android covers all modern Android versions from Android 4.1 through Android 5.0. Freshly added material covers new Android features such as Fragments and Google Play Services. Android is a platform you can't afford not to learn, and this book gets you started. Android is a software toolkit for mobile phones and tablets, created by Google. It's inside more than a billion devices, making Android the number one platform for application developers. Your own app could be running on all those devices! Getting started developing with Android is easy. You don't even need access to an Android phone, just a computer where you can install the Android SDK and the emulator that comes with it. Within minutes, Hello, Android gets you creating your first working application: Android's version of "Hello, World." From there, you'll build up a more substantial example: an Ultimate Tic-Tac-Toe game. By gradually adding features to the game, you'll learn about many aspects of Android programming, such as creating animated user interfaces, playing music and sound effects, building location-based services (including GPS and cell-tower triangulation), and accessing web services. You'll also learn how to publish your applications to the Google Play Store. This fourth edition of the bestselling Android classic has been revised for Android 4.1-4.3 (Jelly Bean), 4.4 (KitKat), and Android 5.0 (Lollipop). Topics have been streamlined and simplified based on reader feedback, and every page and example has been reviewed and updated for compatibility with the latest versions of Android. If you'd rather be coding than reading about coding, this book is for you. COMPUTERS,Programming,Mobile Devices

Kotlin Programming Kotlin is a statically typed programming language designed to interoperate with Java and fully supported by Google on the Android operating system. Based on Big Nerd Ranch’s popular Kotlin Essentials course, this guide shows you how to work effectively with the Kotlin programming language through hands-on examples and clear explanations of key Kotlin concepts and foundational APIs. Written for Kotlin 1.2, this book will also introduce you to JetBrains’ IntelliJ IDEA development environment. Whether you are an experienced Android developer looking for modern features beyond what Java offers or a new developer ready to learn your first programming language, the authors will guide you from first principles to advanced usage of Kotlin. By the end of this book, you will be empowered to create reliable, concise applications in Kotlin. COMPUTERS,Programming,Mobile Devices

Pro Android with Kotlin Develop Android apps with Kotlin to create more elegant programs than the Java equivalent. This book covers the various aspects of a modern Android app that professionals are expected to encounter. There are chapters dealing with all the important aspects of the Android platform, including GUI design, file- and data-handling, coping with phone calls, multimedia apps, interaction with location and mapping services, monetizing apps, and much more. Pro Android with Kotlin is an invaluable source for developers wanting to build real-world state-of-the-art apps for modern Android devices. What You Will Learn Integrate activities, such as intents, services, toasts and more, into your Android apps Build UIs in Android using layouts, widgets, lists, menus, and action bars Deal with data in your Android apps using data persistence and cloud access Design for different Android devices Create multimedia apps in Android Secure, deploy, and monetize your Android apps Who This Book Is For Professional Android app developers. COMPUTERS,Programming,Mobile Devices

The Mobile Frontier Mobile user experience is a new frontier. Untethered from a keyboard and mouse, this rich design space is lush with opportunity to invent new and more human ways for people to interact with information. Invention requires casting off many anchors and conventions inherited from the last 50 years of computer science and traditional design and jumping head first into a new and unfamiliar design space. COMPUTERS,Programming,Mobile Devices

Android Programming for Beginners Learn all the Java and Android skills you need to start making powerful mobile applications with practical and actionable steps Key Features Kick-start your Android programming career, or just have fun publishing apps to the Google Play marketplace A first-principles introduction to Java, via Android, which means you'll be able to start building your own applications from scratch Learn by example and build four real-world apps and dozens of mini-apps throughout the book Book Description Are you trying to start a career in programming, but haven't found the right way in? Do you have a great idea for an app, but don't know how to make it a reality? Or maybe you're just frustrated that in order to learn Android, you must know Java. If so, then this book is for you. This new and expanded second edition of Android Programming for Beginners will be your companion to create Android Pie applications from scratch. We will introduce you to all the fundamental concepts of programming in an Android context, from the basics of Java to working with the Android API. All examples use the up-to-date API classes, and are created from within Android Studio, the official Android development environment that helps supercharge your application development process. After this crash course, we'll dive deeper into Android programming and you'll learn how to create applications with a professional-standard UI through fragments and store your user's data with SQLite. In addition, you'll see how to make your apps multilingual, draw to the screen with a finger, and work with graphics, sound, and animations too. By the end of this book, you'll be ready to start building your own custom applications in Android and Java. What you will learn Master the fundamentals of coding Java for Android Pie Install and set up your Android development environment Build functional user interfaces with the Android Studio visual designer Add user interaction, data captures, sound, and animation to your apps Manage your apps' data using the built-in Android SQLite database Find out about the design patterns used by professionals to make top-grade applications Build, deploy, and publish real Android applications to the Google Play marketplace Who this book is for This book is for you if you are completely new to Java, Android, or programming and want to make Android applications. This book also acts as a refresher for those who already have experience of using Java on Android to advance their knowledge and make fast progress through the early projects. COMPUTERS,Programming,Mobile Devices

Mastering iOS 12 Programming Become a professional iOS developer with the most in-depth and advanced guide to Swift, Xcode 10, ARKit, and Core ML Key Features Explore the extensive world of iOS development through practical examples Gain detailed insights into core iOS programming concepts such as app extensions and performance Extend your iOS apps by adding augmented reality and machine learning capabilities Book Description The iOS development environment has significantly matured, and with Apple users spending more money in the App Store, there are plenty of development opportunities for professional iOS developers. However, the journey to mastering iOS development and the new features of iOS 12 is not straightforward. This book will help you make that transition smoothly and easily. With the help of Swift 4.2, you'll not only learn how to program for iOS 12, but also how to write efficient, readable, and maintainable Swift code that maintains industry best practices. Mastering iOS 12 Programming will help you build real-world applications and reflect the real-world development flow. You will also find a mix of thorough background information and practical examples, teaching you how to start implementing your newly gained knowledge. By the end of this book, you will have got to grips with building iOS applications that harness advanced techniques and make best use of the latest and greatest features available in iOS 12. What you will learn Build a professional iOS application using Xcode 10 and Swift 4.2 Use AutoLayout to create complex layouts that look great on every device Delve into advanced animations with UIViewPropertyAnimator and UIKit Dynamics Enhance your app by using instruments and building your own profiling tools Integrate iMessage, Siri, and more in your app through app extensions Train and use machine learning models with Core ML 2 and Create ML Create engaging augmented reality experiences with ARKit 2 Who this book is for If you're a developer with some experience in iOS programming and want to enhance your skills by unlocking the full potential of the latest iOS version with Swift to build great applications, this book is for you. COMPUTERS,Programming,Mobile Devices

Build Mobile Apps with Ionic 4 and Firebase Leverage your existing web development skills to learn the whole cycle of hybrid mobile app development. This edition is fully updated with the changes in Ionic 4, including Stencil, a new framework based on the web components standard. It explains Ionic and Firebase in detail, including how to create hybrid mobile apps using using React and Vue, and run those apps in an internal browser using a wrapper created by Apache Cordova. Build Mobile Apps with Ionic 4 and Firebase shows you how to focus on developing front-end code, without needing to manage any back-end code or servers. You'll learn in the context of building a Hacker News client app, which can view top stories in Hacker News, view comments of a story, and add stories to favorites. Explore how Ionic 4 uses Angular as the JavaScript framework to easily develop apps using an interface similar to native apps, and how to access Firebase, a real-time database, in web apps using JavaScript. What You'll Learn Create content-based Ionic mobile apps Work with new Ionic 4 compnents like gesture, text, and keyboard controller Manage your apps with RxJS & Redux Who This Book Is For Front-end developers and mobile app developers COMPUTERS,Programming,Mobile Devices

iOS 12 Programming for Beginners Begin your iOS 12 app development journey with this practical guide Key Features Kick-start your iOS programming career and have fun building iOS apps of your choice Get to grips with Xcode 10 and Swift 4.2, the building blocks of iOS development Discover the latest features of iOS 12 - SiriKit, notifications, and much more Book Description Want to build iOS 12 applications from scratch with the latest Swift 4.2 language and Xcode 10 by your side? Forget sifting through tutorials and blog posts; this book is a direct route to iOS development, taking you through the basics and showing you how to put principles into practice. Take advantage of this developer-friendly guide and start building applications that may just take the App Store by storm! If you're already an experienced programmer, you can jump right in and learn the latest iOS 12 features. For beginners, this book starts by introducing you to iOS development as you learn Xcode and Swift. You'll also study advanced iOS design topics, such as gestures and animations, to give your app the edge. You'll explore the latest Swift 4.2 and iOS 12 developments by incorporating new features, such as the latest in notifications, custom-UI notifications, maps, and the recent additions in Sirikit. The book will guide you in using TestFlight to quickly get to grips with everything you need to get your project on the App Store. By the end of this book, you'll be ready to start building your own cool iOS applications confidently. What you will learn Explore the distinctive design principles that define the iOS user experience Navigate panels within an Xcode project Use the latest Xcode asset catalogue of Xcode 10 Create a playgrounds project within your projects and understand how Ranges and Control flow work Study operations with integers and work your way through if statements Build a responsive UI and add privacy to your custom-rich notifications Set up Sirikit to add voice for Siri shortcuts Collect valuable feedback with TestFlight before releasing your apps on the App Store Who this book is for This book is for you if you are completely new to Swift, iOS, or programming and want to make iOS applications. However, you'll also find this book useful if you're an experienced programmer looking to explore the latest iOS 12 features. COMPUTERS,Programming,Mobile Devices

Unity Game Development Cookbook Discover how to use the Unity game engine to its full potential for both 3D and 2D game development—from the basics of scripting to useful tricks in gameplay, behavior, and animation. With this problem-solving cookbook, you’ll get started in two ways: First, you’ll learn about the Unity game engine through brief recipes that teach specific features of the software and scripting systems. Second, you’ll apply a collection of snippets to address common gameplay scenarios, such as properly keeping score. Using our cookbook format, we pinpoint the problem, set out the solution, and discuss how to solve your problem in the best and most straightforward way possible. This book is ideal for beginning to intermediate Unity developers. You’ll find solutions for: 2D and 3D graphics Math, physics, and character control Animation and movement Behavior and AI Sound and music Input and gameplay Scripting and user interface COMPUTERS,Programming,Mobile Devices

Android Programming with Kotlin for Beginners Build smart looking Kotlin apps with UI and functionality for the Android platform Key Features Start your Android programming career, or just have fun publishing apps on Google Play marketplace The first-principle introduction to Kotlin through Android, to start building easy-to-use apps Learn by example and build four real-world apps and dozens of mini-apps Book Description Android is the most popular mobile operating system in the world and Kotlin has been declared by Google as a first-class programming language to build Android apps. With the imminent arrival of the most anticipated Android update, Android 10 (Q), this book gets you started building apps compatible with the latest version of Android. It adopts a project-style approach, where we focus on teaching the fundamentals of Android app development and the essentials of Kotlin by building three real-world apps and more than a dozen mini-apps. The book begins by giving you a strong grasp of how Kotlin and Android work together before gradually moving onto exploring the various Android APIs for building stunning apps for Android with ease. You will learn to make your apps more presentable using different layouts. You will dive deep into Kotlin programming concepts such as variables, functions, data structures, Object-Oriented code, and how to connect your Kotlin code to the UI. You will learn to add multilingual text so that your app is accessible to millions of more potential users. You will learn how animation, graphics, and sound effects work and are implemented in your Android app. By the end of the book, you will have sound knowledge about significant Kotlin programming concepts and start building your own fully featured Android apps. What you will learn Learn how Kotlin and Android work together Build a graphical drawing app using Object-Oriented Programming (OOP) principles Build beautiful, practical layouts using ScrollView, RecyclerView, NavigationView, ViewPager and CardView Write Kotlin code to manage an apps' data using different strategies including JSON and the built-in Android SQLite database Add user interaction, data captures, sound, and animation to your apps Implement dialog boxes to capture input from the user Build a simple database app that sorts and stores the user's data Who this book is for This book is for people who are new to Kotlin, Android and want to develop Android apps.It also acts as a refresher for those who have some experience in programming with Android and Kotlin. COMPUTERS,Programming,Mobile Devices

Swift Protocol-Oriented Programming Embrace the Protocol-Oriented Programming paradigm, for better code maintainability and increased performance, with Swift programming. Key Features Leverage the power of Protocol-Oriented Programming in your applications Leverage generics to create very flexible frameworks Learn how to implement common design patterns in a protocol-oriented way Book Description Protocol-oriented programming is an incredibly powerful concept at the heart of Swift's design. Swift's standard library was developed using POP techniques, generics, and first-class value semantics; therefore, it is important for every Swift developer to understand these core concepts and take advantage of them. The fourth edition of this book is improved and updated to the latest version of the Swift programming language. This book will help you understand what protocol-oriented programming is all about and how it is different from other programming paradigms such as object-oriented programming. This book covers topics such as generics, Copy-On-Write, extensions, and of course protocols. It also demonstrates how to use protocol-oriented programming techniques via real-world use cases. By the end of this book, you will know how to use protocol-oriented programming techniques to build powerful and practical applications. What you will learn Learn the differences between object-oriented programming and protocol-oriented programming Understand why value types should be prioritized over reference types Delve into protocols, protocol inheritance, protocol composition, and protocol extensions Learn how to implement COW (Copy-On-Write) within your custom value types Understand how memory management works in Swift and how to avoid common pitfalls Design applications by starting with the protocol rather than the implementation Who this book is for This book is intended for Swift developers who have, at minimum an introductory knowledge of the Swift programming language and would like to understand how they can use Protocol-Oriented Programming techniques in their applications. COMPUTERS,Programming,Mobile Devices

Android Programming Android Programming: The Big Nerd Ranch Guide is an introductory Android book for programmers with Kotlin experience. Based on Big Nerd Ranch’s popular Android Bootcamp, this guide will lead you through the wilderness using hands-on example apps combined with clear explanations of key concepts and APIs. This book focuses on practical techniques for developing apps in Kotlin compatible with Android 5.0 (Lollipop) through Android 8.1 (Oreo) and beyond. Write and run code every step of the way, using Android Studio to create apps that integrate with other apps, download and display pictures from the web, play sounds, and more. Each chapter and app has been designed and tested to provide the knowledge and experience you need to get started in Android development. The Android team is constantly improving and updating Android Studio and other tools. As a result, some of the instructions provided in the book have changed. You can find an addendum addressing breaking changes at: https://github.com/bignerdranch/AndroidCourseResources/raw/master/4thEdition/Errata/4eAddendum.pdf. COMPUTERS,Programming,Mobile Devices

Beginning Flutter Build your first app in Flutter—no experience necessary! Beginning Flutter: A Hands-On Guide to App Development is the essential resource for both experienced and novice developers interested in getting started with Flutter—the powerful new mobile software development kit. With Flutter, you can quickly and easily develop beautiful, powerful apps for both Android and iOS, without the need to learn multiple programming languages or juggle more than one code base. This book walks you through the process step by step. In Flutter, you’ll be working with Dart, the programming language of choice for top app developers. Even if you’re just starting out in your development career, you can learn Dart quickly, eliminating the barrier to entry for building apps. This is a more efficient way to develop and maintain cross-platform mobile apps, and this book makes the process even easier with a teach-by-example approach. Focus on providing quality content by eliminating the need to switch between multiple coding languages Learn the ins and outs of Flutter, including all the frameworks, widgets, and tools available to developers Accelerate your app development pace, keeping all the code for your cross-platform app in a single code base Leapfrog barriers to entry to the mobile software market, creating your first app with no experience necessary The Flutter community is growing rapidly and transforming the way Android and iOS apps get made. Beginning Flutter allows you to get on board with the latest app development technology, giving your mobile development career a big head start. COMPUTERS,Programming,Mobile Devices

Flutter Recipes Take advantage of this comprehensive reference to solving common problems when developing with Flutter. Along with an introduction to the basic concepts of Flutter development, the recipes in this book cover all important aspects of this emerging technology, including development, testing, debugging, performance tuning, app publishing, and continuous integration. Although Flutter presents a rich, cross-platform mobile development framework, helpful documentation is not easily found. Here you’ll review solutions to various scenarios and use creative, tested ways to accomplish everything from simple to complex development tasks. Flutter is developed using Dart and contains a unique technology stack that sets it apart from its competitors. This book takes the mystery out of working with the Dart language and integrating Flutter into your already existing workflows and development projects. With Flutter Recipes, you’ll learn how to build and deploy apps freshly started in Flutter, as well as apps already in progress, while side-stepping any potential roadblocks you may face along the way. What You'll Learn Debug with Dart Observatory Program accessibility and localization features Build and release apps for iOS and Android Incorporate reactive programming Who This Book Is For Mobile developers with some experience in other frameworks who would like to work with the growing and popular Flutter. COMPUTERS,Programming,Mobile Devices

Native Mobile Development Learn how to make mobile native app development easier. If your team frequently works with both iOS and Android—or plans to transition from one to the other—this hands-on guide shows you how to perform the most common development tasks in each platform. Want to learn how to make network connections in iOS? Or how to work with a database in Android? This book has you covered. In the book’s first part, authors Shaun Lewis and Mike Dunn from O’Reilly’s mobile engineering group provide a list of common, platform-agnostic tasks. The second part helps you create a bare-bones app in each platform, using the techniques from part one. Common file and database operations Network communication with remote APIs Application lifecycle Custom views and components Threading and asynchronous work Unit and integration tests Configuring, building, and running an app on a device COMPUTERS,Programming,Mobile Devices

SwiftUI Essentials - iOS Edition The goal of this book is to teach the skills necessary to build iOS 13 applications using SwiftUI, Xcode 11 and the Swift 5 programming language. Beginning with the basics, this book provides an outline of the steps necessary to set up an iOS development environment together with an introduction to the use of Swift Playgrounds to learn and experiment with Swift. The book also includes in depth chapters introducing the Swift 5 programming language including data types, control flow, functions, object-oriented programming, property wrappers and error handling. An introduction to the key concepts of SwiftUI and project architecture is followed by a guided tour of Xcode in SwiftUI development mode. The book also covers the creation of custom SwiftUI views and explains how these views are combined to create user interface layouts including the use of stacks, frames and forms. Other topics covered include data handling using state properties and both observable and environment objects, as are key user interface design concepts such as modifiers, lists, tabbed views, context menus and user interface navigation. The book also includes chapters covering graphics drawing, user interface animation, view transitions and gesture handling. Chapters are also provided explaining how to integrate SwiftUI views into existing UIKit-based projects and explains the integration of UIKit code into SwiftUI. Finally, the book explains how to package up a completed app and upload it to the App Store for publication. Along the way, the topics covered in the book are put into practice through detailed tutorials, the source code for which is also available for download. The aim of this book, therefore, is to teach you the skills necessary to build your own apps for iOS 13 using SwiftUI. Assuming you are ready to download the iOS 13 SDK and Xcode 11 and have an Intel-based Mac you are ready to get started. COMPUTERS,Programming,Mobile Devices

Beginning App Development with Flutter Create iOS and Android apps with Flutter using just one codebase. App development on multiple platforms has historically been difficult and complex. This book breaks down complex concepts and tasks into easily digestible segments with examples, pictures, and hands-on labs with starters and solutions. In doing so, you'll develop a basic understanding of the Dart programming language; the entire Flutter development toolchain; the differences between stateful and stateless widgets; and a working knowledge of the architecture of apps. All the most important parts of app development with Flutter are covered in this book. Work with themes and styles. Develop custom widgets. Teach your app to respond to gestures like taps, swipes, and pinches. Design, create and control the layout of your app. Create tools to handle form data entry from users. And ultimately create killer multiscreen apps with navigation, menus, and tabs. Flutter is Google's new framework for creating mobile apps that run on iOS and Android phones both.You had to be a super-developer to write apps for iOS or Android alone. But writing for both? Forget about it! You had to be familiar with Swift, Java/Kotlin, Xcode, Eclipse, and a bunch of other technologies simultaneously. Beginning App Development with Flutter simplifies the entire process. What You'll Learn Get the most out of great Flutter widgets Create custom widgets, both stateless and stateful Exercise expert control over your Flutter layouts Make your app respond to gestures like swiping, pinching and tapping Initiate async Ajax calls to RESTful APIs — including Google Firebase! Who This Book Is For Developers who have coded in Java, C#, C++, or any similar language. It brings app development within the reach of younger developers, so STEM groups are likely to pick up the technology. Managers, product owners, and business analysts need to understand Flutter's capabilities. COMPUTERS,Programming,Mobile Devices

Flutter Projects Learn Flutter and the Dart programming language by building impressive real-world mobile applications for Android and iOS Key Features Learn cross-platform mobile development with Flutter and Dart by building 11 real-world apps Create wide array of mobile projects such as 2D game, productivity timer, movie browsing app, and more Practical projects demonstrating Flutter development techniques with tips, tricks, and best practices Book Description Flutter is a modern reactive mobile framework that removes a lot of the complexity found in building native mobile apps for iOS and Android. With Flutter, developers can now build fast and native mobile apps from a single codebase. This book is packed with 11 projects that will help you build your own mobile applications using Flutter. It begins with an introduction to Dart programming and explains how it can be used with the Flutter SDK to customize mobile apps. Each chapter contains instructions on how to build an independent app from scratch, and each project focuses on important Flutter features.From building Flutter Widgets and applying animations to using databases (SQLite and sembast) and Firebase, you'll build on your knowledge through the chapters. As you progress, you'll learn how to connect to remote services, integrate maps, and even use Flare to create apps and games in Flutter. Gradually, you'll be able to create apps and games that are ready to be published on the Google Play Store and the App Store. In the concluding chapters, you'll learn how to use the BLoC pattern and various best practices related to creating enterprise apps with Flutter. By the end of this book, you will have the skills you need to write and deliver fully functional mobile apps using Flutter. What you will learn Design reusable mobile architectures that can be applied to apps at any scale Get up to speed with error handling and debugging for mobile application development Apply the principle of ‘composition over inheritance' to break down complex problems into many simple problems Update your code and see the results immediately using Flutter's hot reload Identify and prevent bugs from reappearing with Flutter's developer tools Manage an app's state with Streams and the BLoC pattern Build a simple web application using Flutter Web Who this book is for This book is for mobile developers and software developers who want to learn Flutter to build state-of-the-art mobile apps. Although prior experience with Dart programming or Flutter is not required, knowledge of object-oriented programming (OOP), data structures and software design patterns will be beneficial. COMPUTERS,Programming,Mobile Devices

Programming Flutter Work in Flutter, a framework designed from the ground up for dual platform development, with support for native Java/Kotlin or Objective-C/Swift methods from Flutter apps. Write your next app in one language and build it for both Android and iOS. Deliver the native look, feel, and performance you and your users expect from an app written with each platform's own tools and languages. Deliver apps fast, doing half the work you were doing before and exploiting powerful new features to speed up development. Write once, run anywhere. Learn Flutter, Google's multi-platform mobile development framework. Instantly view the changes you make to an app with stateful hot reload and define a declarative UI in the same language as the app logic, without having to use separate XML UI files. You can also reuse existing platform-specific Android and iOS code and interact with it in an efficient and simple way. Use built-in UI elements - or build your own - to create a simple calculator app. Run native Java/Kotlin or Objective-C/Swift methods from your Flutter apps, and use a Flutter package to make HTTP requests to a Web API or to perform read and write operations on local storage. Apply visual effects to widgets, create transitions and animations, create a chat app using Firebase, and deploy everything on both platforms. Get native look and feel and performance in your Android and iOS apps, and the ability to build for both platforms from a single code base. What You Need: Flutter can be used for Android development on any Linux, Windows or macOS computer, but macOS is needed for iOS development. COMPUTERS,Programming,Mobile Devices

Android Studio 3.6 Development Essentials - Java Edition Update your Android studio skills and build modern Android applications using Java Key Features Develop a comprehensive understanding of Android Jetpack Build your familiarity with Android architecture guidelines Study the design of Android applications and its user interfaces in-depth Book Description To meet the demands of the mobile market and keep its developer community ahead, Android rolls out frequent updates. Focussing on Android Jetpack libraries, this book teaches you how to build reliable Android applications using Java. The book begins with the set-up of Android development and testing environments on Windows, macOS, and Linux. You will create an Android app and test it on an Android virtual device and a physical Android device. Next, you'll explore the features of Android Studio 3.6, Android 10, Android architecture, and Android Jetpack. Moving ahead, you'll cover touch-screen handling, cloud-based file storage, and foldable device support. The book then covers advanced topics such as views and widget implementation, multi-window support integration, and biometric authentication. Finally, you will learn to upload your app to the Google Play Console and handle the build process with Gradle. By the end of this book, you'll have all the knowledge and skills needed to create modern Android applications. What you will learn Design UI for Android applications using Android Studio Editor Build reliable apps with fewer coding errors using Android Jetpack Test Android applications on physical devices and emulators Explore unique ways to handle single- and multi-touch events Use Gesture libraries to implement gesture and pinch recognition systems Increase your app visibility with app links Who this book is for This book is ideal for application developers and programmers who want to leverage their Android skills using Java. A basic understanding of Java and Android SDK will help you to learn the concepts covered in this book more quickly. COMPUTERS,Programming,Mobile Devices

Android Studio 3.6 Development Essentials - Kotlin Edition Update your Android Studio skills and build modern Android applications using Kotlin Key Features Set up Android development and testing environments Gain core knowledge of the Kotlin programming language Study the design of Android applications and its user interfaces in-depth Book Description The popularity of Kotlin as an Android-compatible language keeps growing every day. This book will help you build your own Android applications using Kotlin. Android Studio 3.6 Development Essentials – Kotlin Edition first shows you how to install Android development and test environments on different operating systems. Next, you will create an Android app and a virtual device in Android Studio and install an Android application on an emulator. You will test apps on emulators and on physical Android devices. Next, you'll explore the features of Android Studio 3.6, Android 10, and Android architecture. The focus then shifts to the Kotlin language. You'll be given an overview of Kotlin, and practice converting code from Java to Kotlin. You'll also explore data types, operators, expressions, loops, functions, and the basics of OOP in Kotlin. The book will then cover Android Jetpack and how to create an example app project using the ViewModel component. You'll study advanced topics such as views and widget implementation, multi-window support integration, and biometric authentication. Finally, you will learn to upload your app to the Google Play Console and handle the build process with Gradle. By the end of this book, you will have gained the knowledge and skills required to develop powerful Android applications using Kotlin. What you will learn Build reliable apps with less error-prone code using Kotlin Use Java-based Android libraries in Kotlin Reduce the amount of code using Android Jetpack Explore unique ways to handle single and multi-touch events Use Gesture libraries to implement gesture and pinch recognition systems Increase your app visibility with app links Who this book is for This book is ideal for anyone who wants to learn how to develop powerful Android Applications using Kotlin and Android Studio 3.6. A basic understanding of Kotlin and Android SDK is recommended. COMPUTERS,Programming,Mobile Devices

Xamarin.Forms Projects Learn to build cross-platform mobile apps using the latest features in Xamarin.Forms 4 with the help of a series of projects including apps for real-time chatting, AR games, location-tracking, weather, photo galleries, and much more Key Features Develop mobile apps, AR games, and chatbots of varying complexity with the help of real-world examples Explore the important features of Xamarin.Forms 4 such as Shell, CollectionView, and CarouselView Get to grips with advanced concepts such as AR and VR and machine learning for mobile development Book Description Xamarin.Forms is a lightweight cross-platform development toolkit for building apps with a rich user interface. Improved and updated to cover the latest features of Xamarin.Forms, this second edition covers CollectionView and Shell, along with interesting concepts such as augmented reality (AR) and machine learning. Starting with an introduction to Xamarin and how it works, this book shares tips for choosing the type of development environment you should strive for when planning cross-platform mobile apps. You'll build your first Xamarin.Forms app and learn how to use Shell to implement the app architecture. The book gradually increases the level of complexity of the projects, guiding you through creating apps ranging from a location tracker and weather map to an AR game and face recognition. As you advance, the book will take you through modern mobile development frameworks such as SQLite, .NET Core Mono, ARKit, and ARCore. You'll be able to customize your apps for both Android and iOS platforms to achieve native-like performance and speed. The book is filled with engaging examples, so you can grasp essential concepts by writing code instead of reading through endless theory. By the end of this book, you'll be ready to develop your own native apps with Xamarin.Forms and its associated technologies, such as .NET Core, Visual Studio 2019, and C#. What you will learn Set up Xamarin.Forms to build native apps with code-sharing capabilities Understand the core aspects of developing a mobile app, such as its layout, UX, and rendering Use custom renderers to gain platform-specific access Discover how to create custom layouts for your apps with Xamarin.Forms Shell Use Azure SignalR to implement serverless services in your Xamarin apps Create an augmented reality (AR) game for Android and iOS using ARCore and ARKit, respectively Build and train machine learning models using CoreML, TensorFlow, and Azure Cognitive Services Who this book is for This book is for C# and .NET developers who want to learn Xamarin.Forms and get started with native Xamarin mobile application development from the ground up. Working knowledge of Visual Studio will help you to get the most out of this book. COMPUTERS,Programming,Mobile Devices

Learn Java for Android Development Gain the essential Java language skills necessary for using the Android SDK platform to build Java-based Android apps. This book includes the latest Java SE releases that Android supports, and is geared towards the Android SDK version 10. It includes new content including JSON documents, functional programming, and lambdas as well as other language features important for migrating Java skills to Android development. Android is still the world's most popular mobile platform and because this technology is still mostly based on Java, you should first obtain a solid grasp of the Java language and its APIs in order to improve your chances of succeeding as an effective Android apps developer. Learn Java for Android Development, 4th Edition helps you do that. Each of the book’s chapters provides an exercise section that gives you the opportunity to reinforce your understanding of the chapter’s material. Answers to the book’s more than 500 exercises are provided in an appendix. Once you finish, you will be ready to begin your Android app development journey using Java. What You Will Learn Discover the latest Java programming language features relevant to Android SDK development Apply inheritance, polymorphism, and interfaces to Android development Use Java collections, concurrency, I/O, networks, persistence, functional programming, and data access in Android apps Parse, create, and transform XML and JSON documents Migrate your Java skills for mobile development using the Android platform Who This Book Is For Programmers with at least some prior Java programming experience looking to get into mobile Java development with the Android platform. COMPUTERS,Programming,Mobile Devices

Architecting Enterprise Solutions A practical, nuts-and-bolts guide to architectural solutions that describes step-by-step how to design robustness and flexibility into an Internet-based system Based on real-world problems and systems, and illustrated with a running case study Enables software architects and project managers to ensure that nonfunctional requirements are met so that the system won't fall over, that it can be maintained and upgraded without being switched off, and that it can deal with security, scalability, and performance demands Platform and vendor independence will empower architects to challenge product-dictated limitations COMPUTERS,Programming,Object Oriented

Patterns of Enterprise Application Architecture The practice of enterprise application development has benefited from the emergence of many new enabling technologies. Multi-tiered object-oriented platforms, such as Java and .NET, have become commonplace. These new tools and technologies are capable of building powerful applications, but they are not easily implemented. Common failures in enterprise applications often occur because their developers do not understand the architectural lessons that experienced object developers have learned. Patterns of Enterprise Application Architecture is written in direct response to the stiff challenges that face enterprise application developers. The author, noted object-oriented designer Martin Fowler, noticed that despite changes in technology--from Smalltalk to CORBA to Java to .NET--the same basic design ideas can be adapted and applied to solve common problems. With the help of an expert group of contributors, Martin distills over forty recurring solutions into patterns. The result is an indispensable handbook of solutions that are applicable to any enterprise application platform. This book is actually two books in one. The first section is a short tutorial on developing enterprise applications, which you can read from start to finish to understand the scope of the book's lessons. The next section, the bulk of the book, is a detailed reference to the patterns themselves. Each pattern provides usage and implementation information, as well as detailed code examples in Java or C#. The entire book is also richly illustrated with UML diagrams to further explain the concepts. Armed with this book, you will have the knowledge necessary to make important architectural decisions about building an enterprise application and the proven patterns for use when building them. The topics covered include · Dividing an enterprise application into layers · The major approaches to organizing business logic · An in-depth treatment of mapping between objects and relational databases · Using Model-View-Controller to organize a Web presentation · Handling concurrency for data that spans multiple transactions · Designing distributed object interfaces COMPUTERS,Programming,Object Oriented

Refactoring As the application of object technology--particularly the Java programming language--has become commonplace, a new problem has emerged to confront the software development community. Significant numbers of poorly designed programs have been created by less-experienced developers, resulting in applications that are inefficient and hard to maintain and extend. Increasingly, software system professionals are discovering just how difficult it is to work with these inherited, "non-optimal" applications. For several years, expert-level object programmers have employed a growing collection of techniques to improve the structural integrity and performance of such existing software programs. Referred to as "refactoring," these practices have remained in the domain of experts because no attempt has been made to transcribe the lore into a form that all developers could use. . .until now. In Refactoring: Improving the Design of Existing Code, renowned object technology mentor Martin Fowler breaks new ground, demystifying these master practices and demonstrating how software practitioners can realize the significant benefits of this new process. With proper training a skilled system designer can take a bad design and rework it into well-designed, robust code. In this book, Martin Fowler shows you where opportunities for refactoring typically can be found, and how to go about reworking a bad design into a good one. Each refactoring step is simple--seemingly too simple to be worth doing. Refactoring may involve moving a field from one class to another, or pulling some code out of a method to turn it into its own method, or even pushing some code up or down a hierarchy. While these individual steps may seem elementary, the cumulative effect of such small changes can radically improve the design. Refactoring is a proven way to prevent software decay. In addition to discussing the various techniques of refactoring, the author provides a detailed catalog of more than seventy proven refactorings with helpful pointers that teach you when to apply them; step-by-step instructions for applying each refactoring; and an example illustrating how the refactoring works. The illustrative examples are written in Java, but the ideas are applicable to any object-oriented programming language. COMPUTERS,Programming,Object Oriented

Pattern-Oriented Software Architecture, A Pattern Language for Distributed Computing The eagerly awaited Pattern-Oriented Software Architecture (POSA) Volume 4 is about a pattern language for distributed computing. The authors will guide you through the best practices and introduce you to key areas of building distributed software systems. POSA 4 connects many stand-alone patterns, pattern collections and pattern languages from the existing body of literature found in the POSA series. Such patterns relate to and are useful for distributed computing to a single language. The panel of experts provides you with a consistent and coherent holistic view on the craft of building distributed systems. Includes a foreword by Martin Fowler A must read for practitioners who want practical advice to develop a comprehensive language integrating patterns from key literature. COMPUTERS,Programming,Object Oriented

Domain-Specific Modeling "[The authors] are pioneers. . . . Few in our industry have their breadth of knowledge and experience." —From the Foreword by Dave Thomas, Bedarra Labs Domain-Specific Modeling (DSM) is the latest approach to software development, promising to greatly increase the speed and ease of software creation. Early adopters of DSM have been enjoying productivity increases of 500–1000% in production for over a decade. This book introduces DSM and offers examples from various fields to illustrate to experienced developers how DSM can improve software development in their teams. Two authorities in the field explain what DSM is, why it works, and how to successfully create and use a DSM solution to improve productivity and quality. Divided into four parts, the book covers: background and motivation; fundamentals; in-depth examples; and creating DSM solutions. There is an emphasis throughout the book on practical guidelines for implementing DSM, including how to identify the necessary language constructs, how to generate full code from models, and how to provide tool support for a new DSM language. The example cases described in the book are available the book's Website, www.dsmbook.com, along with, an evaluation copy of the MetaEdit+ tool (for Windows, Mac OS X, and Linux), which allows readers to examine and try out the modeling languages and code generators. Domain-Specific Modeling is an essential reference for lead developers, software engineers, architects, methodologists, and technical managers who want to learn how to create a DSM solution and successfully put it into practice. COMPUTERS,Programming,Object Oriented

UML 2.0 in a Nutshell System developers have used modeling languages for decades to specify, visualize, construct, and document systems. The Unified Modeling Language (UML) is one of those languages. UML makes it possible for team members to collaborate by providing a common language that applies to a multitude of different systems. Essentially, it enables you to communicate solutions in a consistent, tool-supported language.Today, UML has become the standard method for modeling software systems, which means you're probably confronting this rich and expressive language more than ever before. And even though you may not write UML diagrams yourself, you'll still need to interpret diagrams written by others.UML 2.0 in a Nutshell from O'Reilly feels your pain. It's been crafted for professionals like you who must read, create, and understand system artifacts expressed using UML. Furthermore, it's been fully revised to cover version 2.0 of the language.This comprehensive new edition not only provides a quick-reference to all UML 2.0 diagram types, it also explains key concepts in a way that appeals to readers already familiar with UML or object-oriented programming concepts.Topics include: The role and value of UML in projects The object-oriented paradigm and its relation to the UML An integrated approach to UML diagrams Class and Object, Use Case, Sequence, Collaboration, Statechart, Activity, Component, and Deployment Diagrams Extension Mechanisms The Object Constraint Language (OCL) If you're new to UML, a tutorial with realistic examples has even been included to help you quickly familiarize yourself with the system. COMPUTERS,Programming,Object Oriented

Head First Object-Oriented Analysis and Design "Head First Object Oriented Analysis and Design is a refreshing look at subject of OOAD. What sets this book apart is its focus on learning. The authors have made the content of OOAD accessible, usable for the practitioner." Ivar Jacobson, Ivar Jacobson Consulting "I just finished reading HF OOA&D and I loved it! The thing I liked most about this book was its focus on why we do OOA&D-to write great software!" Kyle Brown, Distinguished Engineer, IBM "Hidden behind the funny pictures and crazy fonts is a serious, intelligent, extremely well-crafted presentation of OO Analysis and Design. As I read the book, I felt like I was looking over the shoulder of an expert designer who was explaining to me what issues were important at each step, and why." Edward Sciore,Associate Professor, Computer Science Department, Boston College Tired of reading Object Oriented Analysis and Design books that only makes sense after you're an expert? You've heard OOA&D can help you write great software every time-software that makes your boss happy, your customers satisfied and gives you more time to do what makes you happy. But how? Head First Object-Oriented Analysis & Design shows you how to analyze, design, and write serious object-oriented software: software that's easy to reuse, maintain, and extend; software that doesn't hurt your head; software that lets you add new features without breaking the old ones. Inside you will learn how to: Use OO principles like encapsulation and delegation to build applications that are flexible Apply the Open-Closed Principle (OCP) and the Single Responsibility Principle (SRP) to promote reuse of your code Leverage the power of design patterns to solve your problems more efficiently Use UML, use cases, and diagrams to ensure that all stakeholders arecommunicating clearly to help you deliver the right software that meets everyone's needs. By exploiting how your brain works, Head First Object-Oriented Analysis & Design compresses the time it takes to learn and retain complex information. Expect to have fun, expect to learn, expect to be writing great software consistently by the time you're finished reading this! COMPUTERS,Programming,Object Oriented

Patterns for Fault Tolerant Software Software patterns have revolutionized the way developer’s and architects think about how software is designed, built and documented. This new title in Wiley’s prestigious Series in Software Design Patterns presents proven techniques to achieve patterns for fault tolerant software. This is a key reference for experts seeking to select a technique appropriate for a given system. Readers are guided from concepts and terminology, through common principles and methods, to advanced techniques and practices in the development of software systems. References will provide access points to the key literature, including descriptions of exemplar applications of each technique. Organized into a collection of software techniques, specific techniques can be easily found with sufficient detail to allow appropriate choices for the system being designed. COMPUTERS,Programming,Object Oriented

Enterprise Patterns and MDA Enterprise Patterns and MDA teaches you how to customize any archetype pattern–such as Customer, Product, and Order–to reflect the idiosyncrasies of your own business environment. Because all the patterns work harmoniously together and have clearly documented relationships to each other, you’ll come away with a host of reusable solutions to common problems in business-software design. This book shows you how using a pattern or a fragment of a pattern can save you months of work and help you avoid costly errors. You’ll also discover how–when used in literate modeling–patterns can solve the difficult challenge of communicating UML models to broad audiences. The configurable patterns can be used manually to create executable code. However, the authors draw on their extensive experience to show you how to tap the significant power of MDA and UML for maximum automation. Not surprisingly, the patterns included in this book are highly valuable; a blue-chip company recently valued a similar, but less mature, set of patterns at hundreds of thousands of dollars. Use this practical guide to increase the efficiency of your designs and to create robust business applications that can be applied immediately in a business setting. COMPUTERS,Programming,Object Oriented

Pattern-Oriented Software Architecture For Dummies Implement programming best practices from the ground up Imagine how much easier it would be to solve a programming problem, if you had access to the best practices from all the top experts in the field, and you could follow the best design patterns that have evolved through the years. Well, now you can. This unique book offers development solutions ranging from high-level architectural patterns, to design patterns that apply to specific problems encountered after the overall structure has been designed, to idioms in specific programming languages--all in one, accessible, guide. Not only will you improve your understanding of software design, you'll also improve the programs you create and successfully take your development ideas to the next level. Pulls together the best design patterns and best practices for software design into one accessible guide to help you improve your programming projects Helps you avoid re-creating the wheel and also meet the ever-increasing pace of rev cycles, as well as the ever-increasing number of new platforms and technologies for mobile, web, and enterprise computing Fills a gap in the entry-level POSA market, as well as a need for guidance in implementing best practices from the ground up Save time and avoid headaches with your software development projects with Pattern-Oriented Software Architecture For Dummies. COMPUTERS,Programming,Object Oriented

Object-Oriented Thought Process, The The Object-Oriented Thought Process, Fourth Edition An introduction to object-oriented concepts for developers looking to master modern application practices Object-oriented programming (OOP) is the foundation of modern programming languages, including C++, Java, C#, Visual Basic .NET, Ruby, and Objective-C. Objects also form the basis for many web technologies such as JavaScript, Python, and PHP. It is of vital importance to learn the fundamental concepts of object orientation before starting to use object-oriented development environments. OOP promotes good design practices, code portability, and reuse–but it requires a shift in thinking to be fully understood. Programmers new to OOP should resist the temptation to jump directly into a particular programming language (such as Objective-C, VB .NET, C++, C# .NET, or Java) or a modeling language (such as UML), and instead first take the time to learn what author Matt Weisfeld calls “the object-oriented thought process.†Written by a developer for developers who want to make the leap to object-oriented technologies, The Object-Oriented Thought Process provides a solutions-oriented approach to object-oriented programming. Readers will learn to understand the proper uses of inheritance and composition, the difference between aggregation and association, and the important distinction between interfaces and implementations. While programming technologies have been changing and evolving over the years, object-oriented concepts remain a constant–no matter what the platform. This revised edition focuses on interoperability across programming technologies, whether you are using objects in traditional application design, in XML-based data transactions, in web page development, in mobile apps, or in any modern programming environment. “Programmers who aim to create high quality software–as all programmers should–must learn the varied subtleties of the familiar yet not so familiar beasts called objects and classes. Doing so entails careful study of books such as Matt Weisfeld’s The Object-Oriented Thought Process.†–Bill McCarty, author of Java Distributed Objects, and Object-Oriented Design in Java Contents at a Glance 1 Introduction to Object-Oriented Concepts2 How to Think in Terms of Objects3 Advanced Object-Oriented Concepts4 The Anatomy of a Class5 Class Design Guidelines6 Designing with Objects7 Mastering Inheritance and Composition8 Frameworks and Reuse: Designing with Interfaces and Abstract Classes9 Building Objects and Object-Oriented Design10 Creating Object Models11 Objects and Portable Data: XML and JSON12 Persistent Objects: Serialization, Marshaling, and Relational Databases13 Objects in Web Services, Mobile Apps, and Hybrids14 Objects and Client/Server Applications15 Design Patterns COMPUTERS,Programming,Object Oriented

Writing Effective Use Cases Writing use cases as a means of capturing the behavioral requirements of software systems and business processes is a practice that is quickly gaining popularity. Use cases provide a beneficial means of project planning because they clearly show how people will ultimately use the system being designed. On the surface, use cases appear to be a straightforward and simple concept. Faced with the task of writing a set of use cases, however, practitioners must ask: "How exactly am I supposed to write use cases?" Because use cases are essentially prose essays, this question is not easily answered, and as a result, the task can become formidable. In Writing Effective Use Cases, object technology expert Alistair Cockburn presents an up-to-date, practical guide to use case writing. The author borrows from his extensive experience in this realm, and expands on the classic treatments of use cases to provide software developers with a "nuts-and-bolts" tutorial for writing use cases. The book thoroughly covers introductory, intermediate, and advanced concepts, and is, therefore, appropriate for all knowledge levels. Illustrative writing examples of both good and bad use cases reinforce the author's instructions. In addition, the book contains helpful learning exercises--with answers--to illuminate the most important points. Highlights of the book include: A thorough discussion of the key elements of use cases--actors, stakeholders, design scope, scenarios, and more A use case style guide with action steps and suggested formats An extensive list of time-saving use case writing tips A helpful presentation of use case templates, with commentary on when and where they should be employed A proven methodology for taking advantage of use cases With this book as your guide, you will learn the essential elements of use case writing, improve your use case writing skills, and be well on your way to employing use cases effectively for your next development project. COMPUTERS,Programming,Object Oriented

UML Distilled More than 300,000 developers have benefited from past editions of UML Distilled . This third edition is the best resource for quick, no-nonsense insights into understanding and using UML 2.0 and prior versions of the UML. Some readers will want to quickly get up to speed with the UML 2.0 and learn the essentials of the UML. Others will use this book as a handy, quick reference to the most common parts of the UML. The author delivers on both of these promises in a short, concise, and focused presentation. This book describes all the major UML diagram types, what they're used for, and the basic notation involved in creating and deciphering them. These diagrams include class, sequence, object, package, deployment, use case, state machine, activity, communication, composite structure, component, interaction overview, and timing diagrams. The examples are clear and the explanations cut to the fundamental design logic. Includes a quick reference to the most useful parts of the UML notation and a useful summary of diagram types that were added to the UML 2.0. If you are like most developers, you don't have time to keep up with all the new innovations in software engineering. This new edition of Fowler's classic work gets you acquainted with some of the best thinking about efficient object-oriented software design using the UML--in a convenient format that will be essential to anyone who designs software professionally. COMPUTERS,Programming,Object Oriented

Refactoring "Whenever you read [Refactoring ], it’s time to read it again. And if you haven’t read it yet, please do before writing another line of code." –David Heinemeier Hansson, Creator of Ruby on Rails, Founder & CTO at Basecamp Fully Revised and Updated—Includes New Refactorings and Code Examples “Any fool can write code that a computer can understand. Good programmers write code that humans can understand.†–M. Fowler (1999) For more than twenty years, experienced programmers worldwide have relied on Martin Fowler’s Refactoring to improve the design of existing code and to enhance software maintainability, as well as to make existing code easier to understand. This eagerly awaited new edition has been fully updated to reflect crucial changes in the programming landscape. Refactoring, Second Edition, features an updated catalog of refactorings and includes JavaScript code examples, as well as new functional examples that demonstrate refactoring without classes. Like the original, this edition explains what refactoring is; why you should refactor; how to recognize code that needs refactoring; and how to actually do it successfully, no matter what language you use. Understand the process and general principles of refactoring Quickly apply useful refactorings to make a program easier to comprehend and change Recognize “bad smells†in code that signal opportunities to refactor Explore the refactorings, each with explanations, motivation, mechanics, and simple examples Build solid tests for your refactorings Recognize tradeoffs and obstacles to refactoring Includes free access to the canonical web edition, with even more refactoring resources. (See inside the book for details about how to access the web edition.) COMPUTERS,Programming,Object Oriented

Foundations of GTK+ Development GTK+ is one of the most influential graphical toolkits for the Linux operating system. It is the technology upon which the GNOME and XFCE desktop environments are based, and its crucial to have clear understanding of its complexities to build even a simple Linux desktop application. Foundations of GTK+ Development guides you through these complexities, laying the foundation that will allow you to cross from novice to professional. Foundations of GTK+ Development is aimed at C programmers and presents numerous real-life examples that you can immediately put to use in your projects. Some familiarity with C programming is assumed, as the book delves into new topics from the beginning. Topics like object inheritance are covered early on to allow for complete understanding of code examples later. And the provided examples are real-life situations that can help you get a head start on your own applications. COMPUTERS,Programming,Open Source

Building Android Apps with HTML, CSS, and JavaScript If you know HTML, CSS, and JavaScript, you already have the tools you need to develop Android applications. Now updated for HTML5, the second edition of this hands-on guide shows you how to use open source web standards to design and build apps that can be adapted for any Android device. You’ll learn how to create an Android-friendly web app on the platform of your choice, and then use Adobe’s free PhoneGap framework to convert it to a native Android app. Discover why device-agnostic mobile apps are the wave of the future, and start building apps that offer greater flexibility and a much broader reach. Convert a website into a web application, complete with progress indicators and other features Add animation with JQTouch to make your web app look and feel like a native Android app Make use of client-side data storage with apps that run when the Android device is offline Use PhoneGap to hook into advanced Android features, including the accelerometer, geolocation, and alerts Test and debug your app on the Web with real users, and submit the finished product to the Android Market COMPUTERS,Programming,Open Source

Getting Started with OAuth 2.0 Whether you develop web applications or mobile apps, the OAuth 2.0 protocol will save a lot of headaches. This concise introduction shows you how OAuth provides a single authorization technology across numerous APIs on the Web, so you can securely access users’ data—such as user profiles, photos, videos, and contact lists—to improve their experience of your application. Through code examples, step-by-step instructions, and use-case examples, you’ll learn how to apply OAuth 2.0 to your server-side web application, client-side app, or mobile app. Find out what it takes to access social graphs, store data in a user’s online filesystem, and perform many other tasks. Understand OAuth 2.0’s role in authentication and authorization Learn how OAuth’s Authorization Code flow helps you integrate data from different business applications Discover why native mobile apps use OAuth differently than mobile web apps Use OpenID Connect and eliminate the need to build your own authentication system COMPUTERS,Programming,Open Source

Becoming Functional If you have an imperative (and probably object-oriented) programming background, this hands-on book will guide you through the alien world of functional programming. Author Joshua Backfield begins slowly by showing you how to apply the most useful implementation concepts before taking you further into functional-style concepts and practices. In each chapter, you’ll learn a functional concept and then use it to refactor the fictional XXY company’s imperative-style legacy code, writing and testing the functional code yourself. As you progress through the book, you’ll migrate from Java 7 to Groovy and finally to Scala as the need for better functional language support gradually increases. Learn why today’s finely tuned applications work better with functional code Transform imperative-style patterns into functional code, following basic steps Get up to speed with Groovy and Scala through examples Understand how first-class functions are passed and returned from other functions Convert existing methods into pure functions, and loops into recursive methods Change mutable variables into immutable variables Get hands-on experience with statements and nonstrict evaluations Use functional programming alongside object-oriented design COMPUTERS,Programming,Open Source

The Rust Programming Language The Rust Programming Language is the official book on Rust, an open-source, community-developed systems programming language that runs blazingly fast, prevents segfaults, and guarantees thread safety. This is the undisputed go-to guide to Rust, written by two members of the Rust core team, with feedback and contributions from 42 members of the community. The book assumes that you’ve written code in another programming language but makes no assumptions about which one, meaning the material is accessible and useful to developers from a wide variety of programming backgrounds. Known by the Rust community as “The Book,” The Rust Programming Language includes concept chapters, where you’ll learn about a particular aspect of Rust, and project chapters, where you’ll apply what you’ve learned so far to build small programs. The Book opens with a quick hands-on project to introduce the basics then explores key concepts in depth, such as ownership, the type system, error handling, and fearless concurrency. Next come detailed explanations of Rust-oriented perspectives on topics like pattern matching, iterators, and smart pointers, with concrete examples and exercises--taking you from theory to practice. The Rust Programming Language will also show you how to:- Grasp important concepts unique to Rust, like ownership, borrowing, and lifetimes- Use Cargo, Rust’s built-in package manager, to build and maintain your code, including downloading and building dependencies- Effectively use Rust’s zero-cost abstractions and employ your own You’ll learn to develop reliable code that’s speed and memory efficient, while avoiding the infamous and arcane programming pitfalls common at the systems level. When you need to dive down into lower-level control, this guide will show you how without taking on the customary risk of crashes or security holes and without requiring you to learn the fine points of a fickle toolchain. You’ll also learn how to create command line programs, build single- and multithreaded web servers, and much more. The Rust Programming Language fully embraces Rust’s potential to empower its users. This friendly and approachable guide will help you build not only your knowledge of Rust but also your ability to program with confidence in a wider variety of domains. COMPUTERS,Programming,Open Source

The Linux Programming Interface The Linux Programming Interface (TLPI) is the definitive guide to the Linux and UNIX programming interface—the interface employed by nearly every application that runs on a Linux or UNIX system. In this authoritative work, Linux programming expert Michael Kerrisk provides detailed descriptions of the system calls and library functions that you need in order to master the craft of system programming, and accompanies his explanations with clear, complete example programs. You'll find descriptions of over 500 system calls and library functions, and more than 200 example programs, 88 tables, and 115 diagrams. You'll learn how to:–Read and write files efficiently–Use signals, clocks, and timers–Create processes and execute programs–Write secure programs–Write multithreaded programs using POSIX threads–Build and use shared libraries–Perform interprocess communication using pipes, message queues, shared memory, and semaphores–Write network applications with the sockets API While The Linux Programming Interface covers a wealth of Linux-specific features, including epoll, inotify, and the /proc file system, its emphasis on UNIX standards (POSIX.1-2001/SUSv3 and POSIX.1-2008/SUSv4) makes it equally valuable to programmers working on other UNIX platforms. The Linux Programming Interface is the most comprehensive single-volume work on the Linux and UNIX programming interface, and a book that's destined to become a new classic. COMPUTERS,Programming,Open Source

Introducing ZFS on Linux Learn the basics of do-it-yourself ZFS storage on Linux. This book delivers explanations of key features and provides best practices for planning, creating and sharing your storage. ZFS as a file system simplifies many aspects of the storage administrator's day-to-day job and solves a lot of problems that administrators face, but it can be confusing. Introducing ZFS on Linux addresses some of these issues and shows you how to resolve them. This book explains the technical side of ZFS, through planning the hardware list to planning the physical and logical layout of the storage. What You'll Learn Understand the gains ZFS gives system and storage administrators and utilize its features Install and configure ZFS software Create and maintain ZFS pool Administer ZFS storage, including sharing Who This Book is For This book is ideal for those who already have experience working with Linux systems but want to understand the bare basics of ZFS before moving further. COMPUTERS,Programming,Open Source

Learning Functional Programming in Go Function literals, Monads, Lazy evaluation, Currying, and more About This Book Write concise and maintainable code with streams and high-order functions Understand the benefits of currying your Golang functions Learn the most effective design patterns for functional programming and learn when to apply each of them Build distributed MapReduce solutions using Go Who This Book Is For This book is for Golang developers comfortable with OOP and interested in learning how to apply the functional paradigm to create robust and testable apps. Prior programming experience with Go would be helpful, but not mandatory. What You Will Learn Learn how to compose reliable applications using high-order functions Explore techniques to eliminate side-effects using FP techniques such as currying Use first-class functions to implement pure functions Understand how to implement a lambda expression in Go Compose a working application using the decorator pattern Create faster programs using lazy evaluation Use Go concurrency constructs to compose a functionality pipeline Understand category theory and what it has to do with FP In Detail Functional programming is a popular programming paradigm that is used to simplify many tasks and will help you write flexible and succinct code. It allows you to decompose your programs into smaller, highly reusable components, without applying conceptual restraints on how the software should be modularized. This book bridges the language gap for Golang developers by showing you how to create and consume functional constructs in Golang. The book is divided into four modules. The first module explains the functional style of programming; pure functional programming (FP), manipulating collections, and using high-order functions. In the second module, you will learn design patterns that you can use to build FP-style applications. In the next module, you will learn FP techniques that you can use to improve your API signatures, to increase performance, and to build better Cloud-native applications. The last module delves into the underpinnings of FP with an introduction to category theory for software developers to give you a real understanding of what pure functional programming is all about, along with applicable code examples. By the end of the book, you will be adept at building applications the functional way. Style and approach This book takes a pragmatic approach and shows you techniques to write better functional constructs in Golang. We'll also show you how use these concepts to build robust and testable apps. COMPUTERS,Programming,Open Source

Architecting Data-Intensive Applications Architect and design data-intensive applications and, in the process, learn how to collect, process, store, govern, and expose data for a variety of use cases Key Features Integrate the data-intensive approach into your application architecture Create a robust application layout with effective messaging and data querying architecture Enable smooth data flow and make the data of your application intensive and fast Book Description Are you an architect or a developer who looks at your own applications gingerly while browsing through Facebook and applauding it silently for its data-intensive, yet ?uent and efficient, behaviour? This book is your gateway to build smart data-intensive systems by incorporating the core data-intensive architectural principles, patterns, and techniques directly into your application architecture. This book starts by taking you through the primary design challenges involved with architecting data-intensive applications. You will learn how to implement data curation and data dissemination, depending on the volume of your data. You will then implement your application architecture one step at a time. You will get to grips with implementing the correct message delivery protocols and creating a data layer that doesn't fail when running high traffic. This book will show you how you can divide your application into layers, each of which adheres to the single responsibility principle. By the end of this book, you will learn to streamline your thoughts and make the right choice in terms of technologies and architectural principles based on the problem at hand. What you will learn Understand how to envision a data-intensive system Identify and compare the non-functional requirements of a data collection component Understand patterns involving data processing, as well as technologies that help to speed up the development of data processing systems Understand how to implement Data Governance policies at design time using various Open Source Tools Recognize the anti-patterns to avoid while designing a data store for applications Understand the different data dissemination technologies available to query the data in an efficient manner Implement a simple data governance policy that can be extended using Apache Falcon Who this book is for This book is for developers and data architects who have to code, test, deploy, and/or maintain large-scale, high data volume applications. It is also useful for system architects who need to understand various non-functional aspects revolving around Data Intensive Systems. COMPUTERS,Programming,Open Source

Accelerating Development Velocity Using Docker Discover how a software engineer can leverage Docker in order to expedite development velocity. This book focuses on the fundamental concepts this program is built upon and explores how it can help you get your services up and running inside Docker containers. You'll also review tips on how to debug microservices applications that run inside Docker containers. Tech companies are now developing complex softwares that are comprised of multiple services running on different platforms, and Docker has become an essential part of coordinating the communication between these services and platforms. This book addresses problems caused by drifting microservices, debugging across services, inconsistent environments across machines, and coordinating development of machine learning systems between a team of developers, etc. Accelerating Development Velocity Using Docker puts you on the path to transforming your complex systems into more efficient ones. What You'll Learn Setup Docker and employ quick solutions to road blocks Review challenges associated with debugging microservices that sit behind a complex application Leverage Docker features to seamlessly get multiple microservices up and running Debug inside a Docker container Review advanced use cases of Docker that can help consistency of development environments· Who This Book Is For Ideal for new to mid-level infrastructure engineers who want to learn how to make their development environments efficient across their and cross teams, or for students who aspire to learn basics of how to debug distributed systems and how to develop efficient applications. COMPUTERS,Programming,Open Source

Forge Your Future with Open Source Free and open source is the foundation of software development, and it's built by people just like you. Discover the fundamental tenets that drive the movement. Take control of your career by selecting the right project to meet your professional goals. Master the language and avoid the pitfalls that typically ensnare new contributors. Join a community of like-minded people and change the world. Programmers, writers, designers, and everyone interested in software will make their mark through free and open source software contributions. Free and open source software is the default choice for the programming languages and technologies which run our world today, and it's all built and maintained by people just like you. No matter your skill level or area of expertise, with this book you will contribute to free and open source software projects. Using this practical approach you'll understand not only the mechanics of contributing, but also how doing so helps your career as well as the community. This book doesn't assume that you're a programmer, or even that you have prior experience with free and open source software. Learn what open source is, where it came from, and why it's important. Start on the right foot by mastering the structure and tools you need before you contribute. Choose the right project for you, amplifying the impact of your contribution. Submit your first contribution, whether it's code, writing, design, or community organising. Find out what to do when things don't go the way you expect. Discover how to start your own project and make it friendly and welcoming to contributors. Anyone can contribute! Make your mark today and help others while also helping yourself. COMPUTERS,Programming,Open Source

Practical LPIC-3 300 Gain the essential skills and hands-on expertise required to pass the LPIC-3 300 certification exam. This book provides the insight for you to confidently install, manage and troubleshoot OpenLDAP, Samba, and FreeIPA. Helping you to get started from scratch, this guide is divided into three comprehensive sections covering everything you'll need to prepare for the exam. Part 1 focuses on OpenLDAP and topics including securing the directory, integration with PAM and replication. Part 2 covers Samba and teaches you about Samba architecture, using different back ends, print services, and deploying Samba as a stand-alone server, PDC, and Active Directory Domain Controller. Finally, Part 3 explains how to manage FreeIPA and how to integrate it with Active Directory. Practical LPIC-3 300 is the perfect study guide for anyone interested in the LPIC-3 300 certification exam, OpenLDAP, Samba, or FreeIPA. What You'll Learn Integrate LDAP with PAM and NSS, and with Active Directory and Kerberos Manage OpenLDAP replication and server performance tuning Use Samba as a PDC and BDC Configure Samba as a domain member server in an existing NT domain Use Samba as an AD Compatible Domain Controller Replicate, manage, and integrate FreeIPA Who This Book Is For This book is for anyone who is preparing for the LPIC-3 300 exam, or those interested in learning about OpenLDAP and Samba in general. COMPUTERS,Programming,Open Source

Practical Flutter Explore what Flutter has to offer, where it came from, and where it’s going. Mobile development is progressing at a fast rate and with Flutter – an open-source mobile application development SDK created by Google – you can develop applications for Android and iOS, as well as Google Fuchsia.Learn to create three apps (a personal information manager, a chat system, and a game project) that you can install on your mobile devices and use for real. You will begin by getting a solid foundation of Flutter knowledge, and building on it immediately by constructing two more traditional productivity apps.. You will also learn to create a game, enabling you to see a whole other perspective on what Flutter can do. In addition to building these apps, you'll have the benefit of reviewing real-world issues you might encounter, along with ways to deal with them through tips and tricks, all designed to make your Flutter experience that much more productive and, frankly, fun! Practical Flutter will leave you with a solid grasp of how to build apps with Flutter, and springboard into creating more advanced apps on your own. By the time your journey through this material concludes, another larger one will begin as you springboard, well-prepared, into the larger world of Flutter development, tackling any project that comes your way with aplomb. Practical Flutter is a learning adventure you won't want to miss. What You'll Learn Get a Flutter project started and logically structure it Use the interface elements Flutter provides, such as widgets, controls, and extensions Build layouts using interface elements Use available tooling, specifically Android Studio Leverage server-side development and connect a Flutter app to a server back-end. Who This Book Is For Mobile developers who are looking to build for multiple mobile platforms and trying to do so with a codebase that is largely the same across all. Basic knowledge of iOS and Android generally, and some general programming experience is expected. COMPUTERS,Programming,Open Source

The PHP Workshop Cut through the noise and get real results with a step-by-step approach to learning PHP programming Key Features Ideal for the PHP beginner who is getting started for the first time Complete step-by-step exercises and open-ended activities to help build and reinforce key skills Structured to let you progress at your own pace, on your own terms Use your physical copy to redeem free access to the online interactive edition Book Description You already know you want to learn PHP 7, and a smarter way to learn PHP development is to learn by doing. The PHP Workshop focuses on building up your practical skills so that you can develop cutting-edge, high-performance web applications. It's ideal if you're looking to work with an existing application, or even develop your own side project with a PHP framework like Laravel. You'll learn from real examples that lead to real results. Throughout The PHP Workshop, you'll take an engaging step-by-step approach to understanding PHP development. You won't have to sit through any unnecessary theory. If you're short on time you can jump into a single exercise each day or spend an entire weekend learning about third-party libraries. It's your choice. Learning on your terms, you'll build up and reinforce key skills in a way that feels rewarding. Every physical copy of The PHP Workshop unlocks access to the interactive edition. With videos detailing all exercises and activities, you'll always have a guided solution. You can also benchmark yourself against assessments, track progress, and receive content updates. It's a premium learning experience that's included with your printed copy. To redeem, follow the instructions located at the start of your PHP guide. Fast-paced and direct, The PHP Workshop is the ideal companion for PHP beginners. You'll build and iterate on your code like a software developer, learning along the way. This process means that you'll find that your new skills stick, embedded as best practice. A solid foundation for the years ahead. What you will learn Get to grips with fundamental concepts and conventions of PHP 7 Work with PHP MySQL databases and build dynamic applications Learn how to compile logical errors and handle exceptions in your programs Explore how PHP unit testing can help create a bug-free development process Integrate third-party packages into your applications Connect external web services to your applications with tools like Guzzle Who this book is for Workshops are ideal for foundational, entry-level developers who are learning something new. COMPUTERS,Programming,Open Source

Getting Started with Istio Service Mesh Build an in-depth understanding of the Istio service mesh and see why a service mesh is required for a distributed application. This book covers the Istio architecture and its features using a hands-on approach with language-neutral examples. To get your Istio environment up and running, you will go through its setup and learn the concepts of control plane and data plane. You will become skilled with the new concepts and apply them with best practices to continuously deliver applications. What You Will Learn Discover the Istio architecture components and the Envoy proxy Master traffic management for service routing and application deployment Build application resiliency using timeout, circuit breakers, and connection pools Monitor using Prometheus and Grafana Configure application security Who This Book Is For Developers and project managers who are trying to run their application using Kubernetes. The book is not specific for any programming language even though all examples will be in Java or Python. COMPUTERS,Programming,Open Source

Bash Command Line and Shell Scripts Pocket Primer As part of thebest-selling Pocket Primer series, this book is designed to introducereaders to an assortment of useful command-line utilities that can be combinedto create simple, yet powerful shell scripts. While all examples and scriptsuse the “bash†command set, many of the concepts translate into other commandshells (such as sh, ksh, zsh, and csh), including theconcept of piping data between commands and the highly versatile sed and awk commands. Aimedat a reader relatively new to working in a bash environment, the book iscomprehensive enough to be a good reference and teach a few new techniques tothose who already have some experience with creating shell scripts. It containsa variety of code fragments and shell scripts for data scientists, dataanalysts, and other people who want shell-based solutions to “clean†varioustypes of text files. In addition, the concepts and code samples in this bookare useful for people who want to simplify routine tasks. Includes companion files with all of the source code examples (download from the publisher by writing to info@merclearning.com). Features: Takesintroductory concepts and commands in bash, and then demonstrates their uses insimple, yet powerful shell scripts Contains anassortment of shell scripts for data scientists, data analysts, and otherpeople who want shell-based solutions to “clean†various types of text files Includes companion files with all of thesource code examples (available for download from the publisher) COMPUTERS,Programming,Open Source

Pro Angular 9 This book has accompanying online files for Angular 9 and 10; all examples in the book work without changes in Angular 10. Welcome to this one-stop-shop for learning Angular. Pro Angular is the most concise and comprehensive guide available, giving you the knowledge you need to take full advantage of this popular framework for building your own dynamic JavaScript applications. The fourth edition of this full-color guide explains how to get the most from Angular, starting with an in-depth overview of the MVC pattern and presenting the range of benefits it can offer. From there, you will begin learning how to use Angular in your projects, starting with the nuts-and-bolts concepts, and progressing on to more advanced and sophisticated features. Each topic provides you with precisely enough learning and detail to be effective. In true Adam Freeman style, the most important features are given full court press treatment, while also addressing common problems and how to avoid them. What You Will Learn: Get access to accompanying online files for Angular 9 and 10; book examples work without changes in Angular 10 Gain a solid architectural understanding of the MVC Pattern Create rich and dynamic web app clients using Angular Use the ng tools to create and build an Angular project Extend and customize Angular Acquire skills to unit test your Angular projects Who This Book Is For: This book is for web developers who want to create rich client-side applications. Foundational knowledge of HTML and JavaScript is recommended. "Adam's books provide a finely tuned blend of architectural overview, technical depth, and experience-born wisdom. His clear, concise writing style, coupled with project driven real world examples, make me comfortable recommending his books to a broad audience, ranging from developers working with a technology for the first time to seasoned professionals who need to learn a new skill quickly." Keith Dublin, Solution Principal, Slalom Consulting “Adam’s books are the print version of a chat bot. His investment in learning how developers learn pays off in dividends, making this one of the most comprehensive resources available. Novices and experienced professionals alike will gain knowledge from the accessible and insightful material.†Mark Donile, Software Engineer, MS CS COMPUTERS,Programming,Open Source

Adopting Open Source Software A rich case-study analysis of open source software adoption by public organizations in different countries and settings. Government agencies and public organizations often consider adopting open source software (OSS) for reasons of transparency, cost, citizen access, and greater efficiency in communication and delivering services. Adopting Open Source Software offers five richly detailed real-world case studies of OSS adoption by public organizations. The authors analyze the cases and develop an overarching, conceptual framework to clarify the various enablers and inhibitors of OSS adoption in the public sector. The book provides a useful resource for policymakers, practitioners, and academics.The five cases of OSS adoption include a hospital in Ireland; an IT consortium serving all the municipalities of the province of Bozen-Bolzano, Italy; schools and public offices in the Extremadura region of Spain; the Massachusetts state government's open standards policy in the United States; and the ICT department of the Italian Chamber of Deputies. The book provides a comparative analysis of these cases around the issues of motivation, strategies, technologies, economic and social aspects, and the implications for theory and practice. COMPUTERS,Programming,Open Source

ZooKeeper Building distributed applications is difficult enough without having to coordinate the actions that make them work. This practical guide shows how Apache ZooKeeper helps you manage distributed systems, so you can focus mainly on application logic. Even with ZooKeeper, implementing coordination tasks is not trivial, but this book provides good practices to give you a head start, and points out caveats that developers and administrators alike need to watch for along the way. In three separate sections, ZooKeeper contributors Flavio Junqueira and Benjamin Reed introduce the principles of distributed systems, provide ZooKeeper programming techniques, and include the information you need to administer this service. Learn how ZooKeeper solves common coordination tasks Explore the ZooKeeper API’s Java and C implementations and how they differ Use methods to track and react to ZooKeeper state changes Handle failures of the network, application processes, and ZooKeeper itself Learn about ZooKeeper’s trickier aspects dealing with concurrency, ordering, and configuration Use the Curator high-level interface for connection management Become familiar with ZooKeeper internals and administration tools COMPUTERS,Programming,Parallel

Hadoop Get ready to unlock the power of your data. With the fourth edition of this comprehensive guide, you’ll learn how to build and maintain reliable, scalable, distributed systems with Apache Hadoop. This book is ideal for programmers looking to analyze datasets of any size, and for administrators who want to set up and run Hadoop clusters. Using Hadoop 2 exclusively, author Tom White presents new chapters on YARN and several Hadoop-related projects such as Parquet, Flume, Crunch, and Spark. You’ll learn about recent changes to Hadoop, and explore new case studies on Hadoop’s role in healthcare systems and genomics data processing. Learn fundamental components such as MapReduce, HDFS, and YARN Explore MapReduce in depth, including steps for developing applications with it Set up and maintain a Hadoop cluster running HDFS and MapReduce on YARN Learn two data formats: Avro for data serialization and Parquet for nested data Use data ingestion tools such as Flume (for streaming data) and Sqoop (for bulk data transfer) Understand how high-level data processing tools like Pig, Hive, Crunch, and Spark work with Hadoop Learn the HBase distributed database and the ZooKeeper distributed configuration service COMPUTERS,Programming,Parallel

Hadoop Application Architectures Get expert guidance on architecting end-to-end data management solutions with Apache Hadoop. While many sources explain how to use various components in the Hadoop ecosystem, this practical book takes you through architectural considerations necessary to tie those components together into a complete tailored application, based on your particular use case. To reinforce those lessons, the book’s second section provides detailed examples of architectures used in some of the most commonly found Hadoop applications. Whether you’re designing a new Hadoop application, or planning to integrate Hadoop into your existing data infrastructure, Hadoop Application Architectures will skillfully guide you through the process. This book covers: Factors to consider when using Hadoop to store and model data Best practices for moving data in and out of the system Data processing frameworks, including MapReduce, Spark, and Hive Common Hadoop processing patterns, such as removing duplicate records and using windowing analytics Giraph, GraphX, and other tools for large graph processing on Hadoop Using workflow orchestration and scheduling tools such as Apache Oozie Near-real-time stream processing with Apache Storm, Apache Spark Streaming, and Apache Flume Architecture examples for clickstream analysis, fraud detection, and data warehousing COMPUTERS,Programming,Parallel

Seven Concurrency Models in Seven Weeks Your software needs to leverage multiple cores, handle thousands of users and terabytes of data, and continue working in the face of both hardware and software failure. Concurrency and parallelism are the keys, and Seven Concurrency Models in Seven Weeks equips you for this new world. See how emerging technologies such as actors and functional programming address issues with traditional threads and locks development. Learn how to exploit the parallelism in your computer's GPU and leverage clusters of machines with MapReduce and Stream Processing. And do it all with the confidence that comes from using tools that help you write crystal clear, high-quality code. This book will show you how to exploit different parallel architectures to improve your code's performance, scalability, and resilience. You'll learn about seven concurrency models: threads and locks, functional programming, separating identity and state, actors, sequential processes, data parallelism, and the lambda architecture. Learn about the perils of traditional threads and locks programming and how to overcome them through careful design and by working with the standard library. See how actors enable software running on geographically distributed computers to collaborate, handle failure, and create systems that stay up 24/7/365. Understand why shared mutable state is the enemy of robust concurrent code, and see how functional programming together with technologies such as Software Transactional Memory (STM) and automatic parallelism help you tame it. You'll learn about the untapped potential within every GPU and how GPGPU software can unleash it. You'll see how to use MapReduce to harness massive clusters to solve previously intractable problems, and how, in concert with Stream Processing, big data can be tamed. With an understanding of the strengths and weaknesses of each of the different models and hardware architectures, you'll be empowered to tackle any problem with confidence. What You Need: The example code can be compiled and executed on *nix, OS X, or Windows. Instructions on how to download the supporting build systems are given in each chapter. COMPUTERS,Programming,Parallel

Programming Quantum Computers Quantum computers are set to kick-start a second computing revolution in an exciting and intriguing way. Learning to program a Quantum Processing Unit (QPU) is not only fun and exciting, but it's a way to get your foot in the door. Like learning any kind of programming, the best way to proceed is by getting your hands dirty and diving into code. This practical book uses publicly available quantum computing engines, clever notation, and a programmer’s mindset to get you started. You'll be able to build up the intuition, skills, and tools needed to start writing quantum programs and solve problems that you care about. COMPUTERS,Quantum Computing

Algebraic and Stochastic Coding Theory Using a simple yet rigorous approach, Algebraic and Stochastic Coding Theory makes the subject of coding theory easy to understand for readers with a thorough knowledge of digital arithmetic, Boolean and modern algebra, and probability theory. It explains the underlying principles of coding theory and offers a clear, detailed description of each code. More advanced readers will appreciate its coverage of recent developments in coding theory and stochastic processes. After a brief review of coding history and Boolean algebra, the book introduces linear codes, including Hamming and Golay codes. It then examines codes based on the Galois field theory as well as their application in BCH and especially the Reed–Solomon codes that have been used for error correction of data transmissions in space missions. The major outlook in coding theory seems to be geared toward stochastic processes, and this book takes a bold step in this direction. As research focuses on error correction and recovery of erasures, the book discusses belief propagation and distributions. It examines the low-density parity-check and erasure codes that have opened up new approaches to improve wide-area network data transmission. It also describes modern codes, such as the Luby transform and Raptor codes, that are enabling new directions in high-speed transmission of very large data to multiple users. This robust, self-contained text fully explains coding problems, illustrating them with more than 200 examples. Combining theory and computational techniques, it will appeal not only to students but also to industry professionals, researchers, and academics in areas such as coding theory and signal and image processing. COMPUTERS,Security,Cryptography & Encryption

The Manga Guide to Cryptography Cryptography is hard, but it’s less hard when it’s filled with adorable Japanese manga. The latest addition to the Manga Guide series, The Manga Guide to Cryptography, turns the art of encryption and decryption into plain, comic illustrated English. As you follow Inspector Jun Meguro in his quest to bring a cipher-wielding thief to justice, you’ll learn how cryptographic ciphers work. (Ciphers are the algorithms at the heart of cryptography.) Like all books in the Manga Guide series, The Manga Guide to Cryptography is illustrated throughout with memorable Japanese manga as it dives deep into advanced cryptography topics, such as classic substitution, polyalphabetic, and transposition ciphers; symmetric-key algorithms like block and DES (Data Encryption Standard) ciphers; and how to use public key encryption technology. It also explores practical applications of encryption such as digital signatures, password security, and identity fraud countermeasures. The Manga Guide to Cryptography is the perfect introduction to cryptography for programmers, security professionals, aspiring cryptographers, and anyone who finds cryptography just a little bit hard. COMPUTERS,Security,Cryptography & Encryption

Applied Cryptography From the world's most renowned security technologist, Bruce Schneier, this 20th Anniversary Edition is the most definitive reference on cryptography ever published and is the seminal work on cryptography. Cryptographic techniques have applications far beyond the obvious uses of encoding and decoding information. For developers who need to know about capabilities, such as digital signatures, that depend on cryptographic techniques, there's no better overview than Applied Cryptography, the definitive book on the subject. Bruce Schneier covers general classes of cryptographic protocols and then specific techniques, detailing the inner workings of real-world cryptographic algorithms including the Data Encryption Standard and RSA public-key cryptosystems. The book includes source-code listings and extensive advice on the practical aspects of cryptography implementation, such as the importance of generating truly random numbers and of keeping keys secure. ". . .the best introduction to cryptography I've ever seen. . . .The book the National Security Agency wanted never to be published. . . ." -Wired Magazine ". . .monumental . . . fascinating . . . comprehensive . . . the definitive work on cryptography for computer programmers . . ." -Dr. Dobb's Journal ". . .easily ranks as one of the most authoritative in its field." -PC Magazine The book details how programmers and electronic communications professionals can use cryptography-the technique of enciphering and deciphering messages-to maintain the privacy of computer data. It describes dozens of cryptography algorithms, gives practical advice on how to implement them into cryptographic software, and shows how they can be used to solve security problems. The book shows programmers who design computer applications, networks, and storage systems how they can build security into their software and systems. With a new Introduction by the author, this premium edition will be a keepsake for all those committed to computer and cyber security. COMPUTERS,Security,Cryptography & Encryption

Investigating Cryptocurrencies Investigate crimes involving cryptocurrencies and other blockchain technologies Bitcoin has traditionally been the payment system of choice for a criminal trading on the Dark Web, and now many other blockchain cryptocurrencies are entering the mainstream as traders are accepting them from low-end investors putting their money into the market. Worse still, the blockchain can even be used to hide information and covert messaging, unknown to most investigators. Investigating Cryptocurrencies is the first book to help corporate, law enforcement, and other investigators understand the technical concepts and the techniques for investigating crimes utilizing the blockchain and related digital currencies such as Bitcoin and Ethereum. Understand blockchain and transaction technologies Set up and run cryptocurrency accounts Build information about specific addresses Access raw data on blockchain ledgers Identify users of cryptocurrencies Extracting cryptocurrency data from live and imaged computers Following the money With nearly $150 billion in cryptocurrency circulating and $3 billion changing hands daily, crimes committed with or paid for with digital cash are a serious business. Luckily, Investigating Cryptocurrencies Forensics shows you how to detect it and, more importantly, stop it in its tracks. COMPUTERS,Security,Cryptography & Encryption

An Introduction to Number Theory with Cryptography Building on the success of the first edition, An Introduction to Number Theory with Cryptography, Second Edition, increases coverage of the popular and important topic of cryptography, integrating it with traditional topics in number theory. The authors have written the text in an engaging style to reflect number theory's increasing popularity. The book is designed to be used by sophomore, junior, and senior undergraduates, but it is also accessible to advanced high school students and is appropriate for independent study. It includes a few more advanced topics for students who wish to explore beyond the traditional curriculum. Features of the second edition include Over 800 exercises, projects, and computer explorations Increased coverage of cryptography, including Vigenere, Stream, Transposition,and Block ciphers, along with RSA and discrete log-based systems "Check Your Understanding" questions for instant feedback to students New Appendices on "What is a proof?" and on Matrices Select basic (pre-RSA) cryptography now placed in an earlier chapter so that the topic can be covered right after the basic material on congruences Answers and hints for odd-numbered problems About the Authors: Jim Kraft received his Ph.D. from the University of Maryland in 1987 and has published several research papers in algebraic number theory. His previous teaching positions include the University of Rochester, St. Mary's College of California, and Ithaca College, and he has also worked in communications security. Dr. Kraft currently teaches mathematics at the Gilman School. Larry Washington received his Ph.D. from Princeton University in 1974 and has published extensively in number theory, including books on cryptography (with Wade Trappe), cyclotomic fields, and elliptic curves. Dr. Washington is currently Professor of Mathematics and Distinguished Scholar-Teacher at the University of Maryland. COMPUTERS,Security,Cryptography & Encryption

The Mathematics of Secrets Explaining the mathematics of cryptography The Mathematics of Secrets takes readers on a fascinating tour of the mathematics behind cryptography—the science of sending secret messages. Using a wide range of historical anecdotes and real-world examples, Joshua Holden shows how mathematical principles underpin the ways that different codes and ciphers work. He focuses on both code making and code breaking and discusses most of the ancient and modern ciphers that are currently known. He begins by looking at substitution ciphers, and then discusses how to introduce flexibility and additional notation. Holden goes on to explore polyalphabetic substitution ciphers, transposition ciphers, connections between ciphers and computer encryption, stream ciphers, public-key ciphers, and ciphers involving exponentiation. He concludes by looking at the future of ciphers and where cryptography might be headed. The Mathematics of Secrets reveals the mathematics working stealthily in the science of coded messages. A blog describing new developments and historical discoveries in cryptography related to the material in this book is accessible at http://press.princeton.edu/titles/10826.html. COMPUTERS,Security,Cryptography & Encryption

Mastering Ethereum Ethereum represents the gateway to a worldwide, decentralized computing paradigm. This platform enables you to run decentralized applications (DApps) and smart contracts that have no central points of failure or control, integrate with a payment network, and operate on an open blockchain. With this practical guide, Andreas M. Antonopoulos and Gavin Wood provide everything you need to know about building smart contracts and DApps on Ethereum and other virtual-machine blockchains. Discover why IBM, Microsoft, NASDAQ, and hundreds of other organizations are experimenting with Ethereum. This essential guide shows you how to develop the skills necessary to be an innovator in this growing and exciting new industry. Run an Ethereum client, create and transmit basic transactions, and program smart contracts Learn the essentials of public key cryptography, hashes, and digital signatures Understand how "wallets" hold digital keys that control funds and smart contracts Interact with Ethereum clients programmatically using JavaScript libraries and Remote Procedure Call interfaces Learn security best practices, design patterns, and anti-patterns with real-world examples Create tokens that represent assets, shares, votes, or access control rights Build decentralized applications using multiple peer-to-peer (P2P) components COMPUTERS,Security,Cryptography & Encryption

Cryptology Cryptology: Classical and Modern, Second Edition proficiently introduces readers to the fascinating field of cryptology. The book covers classical methods including substitution, transposition, Alberti, Vigenère, and Hill ciphers. It also includes coverage of the Enigma machine, Turing bombe, and Navajo code. Additionally, the book presents modern methods like RSA, ElGamal, and stream ciphers, as well as the Diffie-Hellman key exchange and Advanced Encryption Standard. When possible, the book details methods for breaking both classical and modern methods. The new edition expands upon the material from the first edition which was oriented for students in non-technical fields. At the same time, the second edition supplements this material with new content that serves students in more technical fields as well. Thus, the second edition can be fully utilized by both technical and non-technical students at all levels of study. The authors include a wealth of material for a one-semester cryptology course, and research exercises that can be used for supplemental projects. Hints and answers to selected exercises are found at the end of the book. Features: Requires no prior programming knowledge or background in college-level mathematics Illustrates the importance of cryptology in cultural and historical contexts, including the Enigma machine, Turing bombe, and Navajo code Gives straightforward explanations of the Advanced Encryption Standard, public-key ciphers, and message authentication Describes the implementation and cryptanalysis of classical ciphers, such as substitution, transposition, shift, affine, Alberti, Vigenère, and Hill COMPUTERS,Security,Cryptography & Encryption

Cybersecurity Blue Team Toolkit A practical handbook to cybersecurity for both tech and non-tech professionals As reports of major data breaches fill the headlines, it has become impossible for any business, large or small, to ignore the importance of cybersecurity. Most books on the subject, however, are either too specialized for the non-technical professional or too general for positions in the IT trenches. Thanks to author Nadean Tanner’s wide array of experience from teaching at a University to working for the Department of Defense, the Cybersecurity Blue Team Toolkit strikes the perfect balance of substantive and accessible, making it equally useful to those in IT or management positions across a variety of industries. This handy guide takes a simple and strategic look at best practices and tools available to both cybersecurity management and hands-on professionals, whether they be new to the field or looking to expand their expertise. Tanner gives comprehensive coverage to such crucial topics as security assessment and configuration, strategies for protection and defense, offensive measures, and remediation while aligning the concept with the right tool using the CIS Controls version 7 as a guide. Readers will learn why and how to use fundamental open source and free tools such as ping, tracert, PuTTY, pathping, sysinternals, NMAP, OpenVAS, Nexpose Community, OSSEC, Hamachi, InSSIDer, Nexpose Community, Wireshark, Solarwinds Kiwi Syslog Server, Metasploit, Burp, Clonezilla and many more. Up-to-date and practical cybersecurity instruction, applicable to both management and technical positions • Straightforward explanations of the theory behind cybersecurity best practices • Designed to be an easily navigated tool for daily use • Includes training appendix on Linux, how to build a virtual lab and glossary of key terms The Cybersecurity Blue Team Toolkit is an excellent resource for anyone working in digital policy as well as IT security professionals, technical analysts, program managers, and Chief Information and Technology Officers. This is one handbook that won’t gather dust on the shelf, but remain a valuable reference at any career level, from student to executive. COMPUTERS,Security,Cryptography & Encryption

Tribe of Hackers Tribe of Hackers: Cybersecurity Advice from the Best Hackers in the World (9781119643371) was previously published as Tribe of Hackers: Cybersecurity Advice from the Best Hackers in the World (9781793464187). While this version features a new cover design and introduction, the remaining content is the same as the prior release and should not be considered a new or updated product. Looking for real-world advice from leading cybersecurity experts? You’ve found your tribe. Tribe of Hackers: Cybersecurity Advice from the Best Hackers in the World is your guide to joining the ranks of hundreds of thousands of cybersecurity professionals around the world. Whether you’re just joining the industry, climbing the corporate ladder, or considering consulting, Tribe of Hackers offers the practical know-how, industry perspectives, and technical insight you need to succeed in the rapidly growing information security market. This unique guide includes inspiring interviews from 70 security experts, including Lesley Carhart, Ming Chow, Bruce Potter, Robert M. Lee, and Jayson E. Street. Get the scoop on the biggest cybersecurity myths and misconceptions about security Learn what qualities and credentials you need to advance in the cybersecurity field Uncover which life hacks are worth your while Understand how social media and the Internet of Things has changed cybersecurity Discover what it takes to make the move from the corporate world to your own cybersecurity venture Find your favorite hackers online and continue the conversation Tribe of Hackers is a must-have resource for security professionals who are looking to advance their careers, gain a fresh perspective, and get serious about cybersecurity with thought-provoking insights from the world’s most noteworthy hackers and influential security specialists. COMPUTERS,Security,Cryptography & Encryption

The Digital Big Bang Cybersecurity experts from across industries and sectors share insights on how to think like scientists to master cybersecurity challenges Humankind’s efforts to explain the origin of the cosmos birthed disciplines such as physics and chemistry. Scientists conceived of the cosmic ‘Big Bang’ as an explosion of particles—everything in the universe centered around core elements and governed by laws of matter and gravity. In the modern era of digital technology, we are experiencing a similar explosion of ones and zeros, an exponentially expanding universe of bits of data centered around the core elements of speed and connectivity. One of the disciplines to emerge from our efforts to make sense of this new universe is the science of cybersecurity. Cybersecurity is as central to the Digital Age as physics and chemistry were to the Scientific Age. The Digital Big Bang explores current and emerging knowledge in the field of cybersecurity, helping readers think like scientists to master cybersecurity principles and overcome cybersecurity challenges. This innovative text adopts a scientific approach to cybersecurity, identifying the science’s fundamental elements and examining how these elements intersect and interact with each other. Author Phil Quade distills his over three decades of cyber intelligence, defense, and attack experience into an accessible, yet detailed, single-volume resource. Designed for non-specialist business leaders and cybersecurity practitioners alike, this authoritative book is packed with real-world examples, techniques, and strategies no organization should be without. Contributions from many of the world’s leading cybersecurity experts and policymakers enable readers to firmly grasp vital cybersecurity concepts, methods, and practices. This important book: Guides readers on both fundamental tactics and advanced strategies Features observations, hypotheses, and conclusions on a wide range of cybersecurity issues Helps readers work with the central elements of cybersecurity, rather than fight or ignore them Includes content by cybersecurity leaders from organizations such as Microsoft, Target, ADP, Capital One, Verisign, AT&T, Samsung, and many others Offers insights from national-level security experts including former Secretary of Homeland Security Michael Chertoff and former Director of National Intelligence Mike McConnell The Digital Big Bang is an invaluable source of information for anyone faced with the challenges of 21st century cybersecurity in all industries and sectors, including business leaders, policy makers, analysts and researchers as well as IT professionals, educators, and students. COMPUTERS,Security,Cryptography & Encryption

Cryptography Apocalypse Will your organization be protected the day a quantum computer breaks encryption on the internet? Computer encryption is vital for protecting users, data, and infrastructure in the digital age. Using traditional computing, even common desktop encryption could take decades for specialized ‘crackers’ to break and government and infrastructure-grade encryption would take billions of times longer. In light of these facts, it may seem that today’s computer cryptography is a rock-solid way to safeguard everything from online passwords to the backbone of the entire internet. Unfortunately, many current cryptographic methods will soon be obsolete. In 2016, the National Institute of Standards and Technology (NIST) predicted that quantum computers will soon be able to break the most popular forms of public key cryptography. The encryption technologies we rely on every day—HTTPS, TLS, WiFi protection, VPNs, cryptocurrencies, PKI, digital certificates, smartcards, and most two-factor authentication—will be virtually useless. . . unless you prepare. Cryptography Apocalypse is a crucial resource for every IT and InfoSec professional for preparing for the coming quantum-computing revolution. Post-quantum crypto algorithms are already a reality, but implementation will take significant time and computing power. This practical guide helps IT leaders and implementers make the appropriate decisions today to meet the challenges of tomorrow. This important book: Gives a simple quantum mechanics primer Explains how quantum computing will break current cryptography Offers practical advice for preparing for a post-quantum world Presents the latest information on new cryptographic methods Describes the appropriate steps leaders must take to implement existing solutions to guard against quantum-computer security threats Cryptography Apocalypse: Preparing for the Day When Quantum Computing Breaks Today's Crypto is a must-have guide for anyone in the InfoSec world who needs to know if their security is ready for the day crypto break and how to fix it. COMPUTERS,Security,Cryptography & Encryption

Transforming Information Security Providing a unique perspective from the center of the debates on end-to-end encryption, Moriarty explores emerging trends in both information security and transport protocol evolution, going beyond simply pointing out today’s problems to providing solutions for the future of our product space. COMPUTERS,Security,Cryptography & Encryption

Cryptology For Engineers Cryptology is increasingly becoming one of the most essential topics of interest in everyday life. Digital communication happens by transferring data between at least two participants — But do we want to disclose private information while executing a sensitive bank transfer? How about allowing third-party entities to eavesdrop on private calls while performing an important secret business discussion? Do we want to allow ambient communication concerning us to be manipulated while control software is driving our autonomous car along a steep slope? Questions like these make it clear why issues of security are a great concern in our increasingly augmented world.Cryptology for Engineers is a study of digital security in communications systems. The book covers the cryptographical functionalities of ciphering, hash generation, digital signature generation, key management and random number generation, with a clear sense of the mathematical background on the one hand and engineers' requirements on the other. Numerous examples computable by hand or with a small additional cost in most cases are provided inside. COMPUTERS,Security,Cryptography & Encryption

Digital Media Steganography The common use of the Internet and cloud services in transmission of large amounts of data over open networks and insecure channels, exposes that private and secret data to serious situations. Ensuring the information transmission over the Internet is safe and secure has become crucial, consequently information security has become one of the most important issues of human communities because of increased data transmission over social networks. Digital Media Steganography: Principles, Algorithms, and Advances covers fundamental theories and algorithms for practical design, while providing a comprehensive overview of the most advanced methodologies and modern techniques in the field of steganography. The topics covered present a collection of high-quality research works written in a simple manner by world-renowned leaders in the field dealing with specific research problems. It presents the state-of-the-art as well as the most recent trends in digital media steganography. Covers fundamental theories and algorithms for practical design which form the basis of modern digital media steganography Provides new theoretical breakthroughs and a number of modern techniques in steganography Presents the latest advances in digital media steganography such as using deep learning and artificial neural network as well as Quantum Steganography COMPUTERS,Security,Cryptography & Encryption

Burdens of Proof An examination of the challenges of establishing the authenticity of electronic documents—in particular the design of a cryptographic equivalent to handwritten signatures. The gradual disappearance of paper and its familiar evidential qualities affects almost every dimension of contemporary life. From health records to ballots, almost all documents are now digitized at some point of their life cycle, easily copied, altered, and distributed. In Burdens of Proof, Jean-François Blanchette examines the challenge of defining a new evidentiary framework for electronic documents, focusing on the design of a digital equivalent to handwritten signatures. From the blackboards of mathematicians to the halls of legislative assemblies, Blanchette traces the path of such an equivalent: digital signatures based on the mathematics of public-key cryptography. In the mid-1990s, cryptographic signatures formed the centerpiece of a worldwide wave of legal reform and of an ambitious cryptographic research agenda that sought to build privacy, anonymity, and accountability into the very infrastructure of the Internet. Yet markets for cryptographic products collapsed in the aftermath of the dot-com boom and bust along with cryptography's social projects. Blanchette describes the trials of French bureaucracies as they wrestled with the application of electronic signatures to real estate contracts, birth certificates, and land titles, and tracks the convoluted paths through which electronic documents acquire moral authority. These paths suggest that the material world need not merely succumb to the virtual but, rather, can usefully inspire it. Indeed, Blanchette argues, in renewing their engagement with the material world, cryptographers might also find the key to broader acceptance of their design goals. COMPUTERS,Security,Cryptography & Encryption

Cryptography A nuts-and-bolts explanation of cryptography from a leading expert in information security. Despite its reputation as a language only of spies and hackers, cryptography plays a critical role in our everyday lives. Though often invisible, it underpins the security of our mobile phone calls, credit card payments, web searches, internet messaging, and cryptocurrencies—in short, everything we do online. Increasingly, it also runs in the background of our smart refrigerators, thermostats, electronic car keys, and even the cars themselves. As our daily devices get smarter, cyberspace—home to all the networks that connect them—grows. Broadly defined as a set of tools for establishing security in this expanding cyberspace, cryptography enables us to protect and share our information. Understanding the basics of cryptography is the key to recognizing the significance of the security technologies we encounter every day, which will then help us respond to them. What are the implications of connecting to an unprotected Wi-Fi network? Is it really so important to have different passwords for different accounts? Is it safe to submit sensitive personal information to a given app, or to convert money to bitcoin? In clear, concise writing, information security expert Keith Martin answers all these questions and more, revealing the many crucial ways we all depend on cryptographic technology. He demystifies its controversial applications and the nuances behind alarming headlines about data breaches at banks, credit bureaus, and online retailers. We learn, for example, how cryptography can hamper criminal investigations and obstruct national security efforts, and how increasingly frequent ransomware attacks put personal information at risk. Yet we also learn why responding to these threats by restricting the use of cryptography can itself be problematic. Essential reading for anyone with a password, Cryptography offers a profound perspective on personal security, online and off. COMPUTERS,Security,Cryptography & Encryption

Implementing Cryptography Using Python Learn to deploy proven cryptographic tools in your applications and services Cryptography is, quite simply, what makes security and privacy in the digital world possible. Tech professionals, including programmers, IT admins, and security analysts, need to understand how cryptography works to protect users, data, and assets. Implementing Cryptography Using Python will teach you the essentials, so you can apply proven cryptographic tools to secure your applications and systems. Because this book uses Python, an easily accessible language that has become one of the standards for cryptography implementation, you’ll be able to quickly learn how to secure applications and data of all kinds. In this easy-to-read guide, well-known cybersecurity expert Shannon Bray walks you through creating secure communications in public channels using public-key cryptography. You’ll also explore methods of authenticating messages to ensure that they haven’t been tampered with in transit. Finally, you’ll learn how to use digital signatures to let others verify the messages sent through your services. Learn how to implement proven cryptographic tools, using easy-to-understand examples written in Python Discover the history of cryptography and understand its critical importance in today’s digital communication systems Work through real-world examples to understand the pros and cons of various authentication methods Protect your end-users and ensure that your applications and systems are using up-to-date cryptography COMPUTERS,Security,Cryptography & Encryption

The Art of Deception The world's most infamous hacker offers an insider's view of the low-tech threats to high-tech security Kevin Mitnick's exploits as a cyber-desperado and fugitive form one of the most exhaustive FBI manhunts in history and have spawned dozens of articles, books, films, and documentaries. Since his release from federal prison, in 1998, Mitnick has turned his life around and established himself as one of the most sought-after computer security experts worldwide. Now, in The Art of Deception, the world's most notorious hacker gives new meaning to the old adage, "It takes a thief to catch a thief." Focusing on the human factors involved with information security, Mitnick explains why all the firewalls and encryption protocols in the world will never be enough to stop a savvy grifter intent on rifling a corporate database or an irate employee determined to crash a system. With the help of many fascinating true stories of successful attacks on business and government, he illustrates just how susceptible even the most locked-down information systems are to a slick con artist impersonating an IRS agent. Narrating from the points of view of both the attacker and the victims, he explains why each attack was so successful and how it could have been prevented in an engaging and highly readable style reminiscent of a true-crime novel. And, perhaps most importantly, Mitnick offers advice for preventing these types of social engineering hacks through security protocols, training programs, and manuals that address the human element of security. COMPUTERS,Security,General

Firewalls For Dummies What an amazing world we live in! Almost anything you can imagine can be researched, compared, admired, studied, and in many cases, bought, with the click of a mouse. The Internet has changed our lives, putting a world of opportunity before us. Unfortunately, it has also put a world of opportunity into the hands of those whose motives are less than honorable. A firewall, a piece of software or hardware that erects a barrier between your computer and those who might like to invade it, is one solution. If you’ve been using the Internet for any length of time, you’ve probably received some unsavory and unsolicited e-mail. If you run a business, you may be worried about the security of your data and your customers’ privacy. At home, you want to protect your personal information from identity thieves and other shady characters. Firewalls For Dummies® will give you the lowdown on firewalls, then guide you through choosing, installing, and configuring one for your personal or bus iness network. Firewalls For Dummies® helps you understand what firewalls are, how they operate on different types of networks, what they can and can’t do, and how to pick a good one (it’s easier than identifying that perfect melon in the supermarket.) You’ll find out about Developing security policies Establishing rules for simple protocols Detecting and responding to system intrusions Setting up firewalls for SOHO or personal use Creating demilitarized zones Using Windows or Linux as a firewall Configuring ZoneAlarm, BlackICE, and Norton personal firewalls Installing and using ISA server and FireWall-1 With the handy tips and hints this book provides, you’ll find that firewalls are nothing to fear – that is, unless you’re a cyber-crook! You’ll soon be able to keep your data safer, protect your family’s privacy, and probably sleep better, too. COMPUTERS,Security,General

Perfect Password User passwords are the keys to the network kingdom, yet most users choose overly simplistic passwords (like password) that anyone could guess, while system administrators demand impossible to remember passwords littered with obscure characters and random numerals. Every computer user must face the problems of password security. According to a recent British study, passwords are usually obvious: around 50 percent of computer users select passwords based on names of a family member, spouse, partner, or a pet. Many users face the problem of selecting strong passwords that meet corporate security requirements. Too often, systems reject user-selected passwords because they are not long enough or otherwise do not meet complexity requirements. This book teaches users how to select passwords that always meet complexity requirements. A typical computer user must remember dozens of passwords and they are told to make them all unique and never write them down. For most users, the solution is easy passwords that follow simple patterns. This book teaches users how to select strong passwords they can easily remember. * Examines the password problem from the perspective of the administrator trying to secure their network* Author Mark Burnett has accumulated and analyzed over 1,000,000 user passwords and through his research has discovered what works, what doesn't work, and how many people probably have dogs named Spot* Throughout the book, Burnett sprinkles interesting and humorous password ranging from the Top 20 dog names to the number of references to the King James Bible in passwords COMPUTERS,Security,General

Hardware Hacking "If I had this book 10 years ago, the FBI would never have found me!" -- Kevin Mitnick This book has something for everyone---from the beginner hobbyist with no electronics or coding experience to the self-proclaimed "gadget geek." Take an ordinary piece of equipment and turn it into a personal work of art. Build upon an existing idea to create something better. Have fun while voiding your warranty! Some of the hardware hacks in this book include: * Don't toss your iPod away when the battery dies! Don't pay Apple the $99 to replace it! Install a new iPod battery yourself without Apple's "help"* An Apple a day! Modify a standard Apple USB Mouse into a glowing UFO Mouse or build a FireWire terabyte hard drive and custom case* Have you played Atari today? Create an arcade-style Atari 5200 paddle controller for your favorite retro videogames or transform the Atari 2600 joystick into one that can be used by left-handed players* Modern game systems, too! Hack your PlayStation 2 to boot code from the memory card or modify your PlayStation 2 for homebrew game development* Videophiles unite! Design, build, and configure your own Windows- or Linux-based Home Theater PC* Ride the airwaves! Modify a wireless PCMCIA NIC to include an external antenna connector or load Linux onto your Access Point* Stick it to The Man! Remove the proprietary barcode encoding from your CueCat and turn it into a regular barcode reader* Hack your Palm! Upgrade the available RAM on your Palm m505 from 8MB to 16MB · Includes hacks of today's most popular gaming systems like Xbox and PS/2.· Teaches readers to unlock the full entertainment potential of their desktop PC.· Frees iMac owners to enhance the features they love and get rid of the ones they hate. COMPUTERS,Security,General

Secure Programming with Static Analysis This is the eBook version of the printed book. If the print book includes a CD-ROM, this content is not included within the eBook version. The First Expert Guide to Static Analysis for Software Security! Creating secure code requires more than just good intentions. Programmers need to know that their code will be safe in an almost infinite number of scenarios and configurations. Static source code analysis gives users the ability to review their work with a fine-toothed comb and uncover the kinds of errors that lead directly to security vulnerabilities. Now, there’s a complete guide to static analysis: how it works, how to integrate it into the software development processes, and how to make the most of it during security code review. Static analysis experts Brian Chess and Jacob West look at the most common types of security defects that occur today. They illustrate main points using Java and C code examples taken from real-world security incidents, showing how coding errors are exploited, how they could have been prevented, and how static analysis can rapidly uncover similar mistakes. This book is for everyone concerned with building more secure software: developers, security engineers, analysts, and testers. Coverage includes: Why conventional bug-catching often misses security problems How static analysis can help programmers get security right The critical attributes and algorithms that make or break a static analysis tool 36 techniques for making static analysis more effective on your code More than 70 types of serious security vulnerabilities, with specific solutions Example vulnerabilities from Firefox, OpenSSH, MySpace, eTrade, Apache httpd, and many more Techniques for handling untrusted input Eliminating buffer overflows: tactical and strategic approaches Avoiding errors specific to Web applications, Web services, and Ajax Security-aware logging, debugging, and error/exception handling Creating, maintaining, and sharing secrets and confidential information Detailed tutorials that walk you through the static analysis process “We designed Java so that it could be analyzed statically. This book shows you how to apply advanced static analysis techniques to create more secure, more reliable software.†–Bill Joy, Co-founder of Sun Microsystems, co-inventor of the Java programming language “'Secure Programming with Static Analysis' is a great primer on static analysis for security-minded developers and security practitioners. Well-written, easy to read, tells you what you need to know.†–David Wagner, Associate Professor, University of California Berkeley “Software developers are the first and best line of defense for the security of their code. This book gives them the security development knowledge and the tools they need in order to eliminate vulnerabilities before they move into the final products that can be exploited.†–Howard A. Schmidt, Former White House Cyber Security Advisor BRIAN CHESS is Founder and Chief Scientist of Fortify Software, where his research focuses on practical methods for creating secure systems. He holds a Ph.D. in Computer Engineering from University of California Santa Cruz, where he studied the application of static analysis to finding security-related code defects. JACOB WEST manages Fortify Software’s Security Research Group, which is responsible for building security knowledge into Fortify’s products. He brings expertise in numerous programming languages, frameworks, and styles together with deep knowledge about how real-world systems fail. CD contains a working demonstration version of Fortify Software’s Source Code Analysis (SCA) product; extensive Java and C code samples; and the tutorial chapters from the book in PDF format COMPUTERS,Security,General

The Best Damn IT Security Management Book Period The security field evolves rapidly becoming broader and more complex each year. The common thread tying the field together is the discipline of management. The Best Damn Security Manager's Handbook Period has comprehensive coverage of all management issues facing IT and security professionals and is an ideal resource for those dealing with a changing daily workload. Coverage includes Business Continuity, Disaster Recovery, Risk Assessment, Protection Assets, Project Management, Security Operations, and Security Management, and Security Design & Integration. Compiled from the best of the Syngress and Butterworth Heinemann libraries and authored by business continuity expert Susan Snedaker, this volume is an indispensable addition to a serious security professional's toolkit. * An all encompassing book, covering general security management issues and providing specific guidelines and checklists* Anyone studying for a security specific certification or ASIS certification will find this a valuable resource* The only book to cover all major IT and security management issues in one place: disaster recovery, project management, operations management, and risk assessment COMPUTERS,Security,General

Hacking Exposed Windows The latest Windows security attack and defense strategies "Securing Windows begins with reading this book." --James Costello (CISSP) IT Security Specialist, Honeywell Meet the challenges of Windows security with the exclusive Hacking Exposed "attack-countermeasure" approach. Learn how real-world malicious hackers conduct reconnaissance of targets and then exploit common misconfigurations and software flaws on both clients and servers. See leading-edge exploitation techniques demonstrated, and learn how the latest countermeasures in Windows XP, Vista, and Server 2003/2008 can mitigate these attacks. Get practical advice based on the authors' and contributors' many years as security professionals hired to break into the world's largest IT infrastructures. Dramatically improve the security of Microsoft technology deployments of all sizes when you learn to: Establish business relevance and context for security by highlighting real-world risks Take a tour of the Windows security architecture from the hacker's perspective, exposing old and new vulnerabilities that can easily be avoided Understand how hackers use reconnaissance techniques such as footprinting, scanning, banner grabbing, DNS queries, and Google searches to locate vulnerable Windows systems Learn how information is extracted anonymously from Windows using simple NetBIOS, SMB, MSRPC, SNMP, and Active Directory enumeration techniques Prevent the latest remote network exploits such as password grinding via WMI and Terminal Server, passive Kerberos logon sniffing, rogue server/man-in-the-middle attacks, and cracking vulnerable services See up close how professional hackers reverse engineer and develop new Windows exploits Identify and eliminate rootkits, malware, and stealth software Fortify SQL Server against external and insider attacks Harden your clients and users against the latest e-mail phishing, spyware, adware, and Internet Explorer threats Deploy and configure the latest Windows security countermeasures, including BitLocker, Integrity Levels, User Account Control, the updated Windows Firewall, Group Policy, Vista Service Refactoring/Hardening, SafeSEH, GS, DEP, Patchguard, and Address Space Layout Randomization COMPUTERS,Security,General

Elliptic Curves Like its bestselling predecessor, Elliptic Curves: Number Theory and Cryptography, Second Edition develops the theory of elliptic curves to provide a basis for both number theoretic and cryptographic applications. With additional exercises, this edition offers more comprehensive coverage of the fundamental theory, techniques, and application COMPUTERS,Security,General

Computer Forensics For Dummies Uncover a digital trail of e-evidence by using the helpful, easy-to-understand information in Computer Forensics For Dummies! Professional and armchair investigators alike can learn the basics of computer forensics, from digging out electronic evidence to solving the case. You won’t need a computer science degree to master e-discovery. Find and filter data in mobile devices, e-mail, and other Web-based technologies. You’ll learn all about e-mail and Web-based forensics, mobile forensics, passwords and encryption, and other e-evidence found through VoIP, voicemail, legacy mainframes, and databases. You’ll discover how to use the latest forensic software, tools, and equipment to find the answers that you’re looking for in record time. When you understand how data is stored, encrypted, and recovered, you’ll be able to protect your personal privacy as well. By the time you finish reading this book, you’ll know how to: Prepare for and conduct computer forensics investigations Find and filter data Protect personal privacy Transfer evidence without contaminating it Anticipate legal loopholes and opponents’ methods Handle passwords and encrypted data Work with the courts and win the case Plus, Computer Forensics for Dummies includes lists of things that everyone interested in computer forensics should know, do, and build. Discover how to get qualified for a career in computer forensics, what to do to be a great investigator and expert witness, and how to build a forensics lab or toolkit. Note: CD-ROM/DVD and other supplementary materials are not included as part of eBook file. COMPUTERS,Security,General

OSSEC Host-Based Intrusion Detection Guide This book is the definitive guide on the OSSEC Host-based Intrusion Detection system and frankly, to really use OSSEC you are going to need a definitive guide. Documentation has been available since the start of the OSSEC project but, due to time constraints, no formal book has been created to outline the various features and functions of the OSSEC product. This has left very important and powerful features of the product undocumented...until now! The book you are holding will show you how to install and configure OSSEC on the operating system of your choice and provide detailed examples to help prevent and mitigate attacks on your systems. -- Stephen Northcutt OSSEC determines if a host has been compromised in this manner by taking the equivalent of a picture of the host machine in its original, unaltered state. This "picture" captures the most relevant information about that machine's configuration. OSSEC saves this "picture" and then constantly compares it to the current state of that machine to identify anything that may have changed from the original configuration. Now, many of these changes are necessary, harmless, and authorized, such as a system administrator installing a new software upgrade, patch, or application. But, then there are the not-so-harmless changes, like the installation of a rootkit, trojan horse, or virus. Differentiating between the harmless and the not-so-harmless changes determines whether the system administrator or security professional is managing a secure, efficient network or a compromised network which might be funneling credit card numbers out to phishing gangs or storing massive amounts of pornography creating significant liability for that organization. Separating the wheat from the chaff is by no means an easy task. Hence the need for this book. The book is co-authored by Daniel Cid, who is the founder and lead developer of the freely available OSSEC host-based IDS. As such, readers can be certain they are reading the most accurate, timely, and insightful information on OSSEC.* Nominee for Best Book Bejtlich read in 2008! * http://taosecurity.blogspot.com/2008/12/best-book-bejtlich-read-in-2008.html • Get Started with OSSECGet an overview of the features of OSSEC including commonly used terminology, pre-install preparation, and deployment considerations. • Follow Steb-by-Step Installation InstructionsWalk through the installation process for the "local, “agent, and "server" install types on some of the most popular operating systems available.• Master ConfigurationLearn the basic configuration options for your install type and learn how to monitor log files, receive remote messages, configure email notification, and configure alert levels.• Work With RulesExtract key information from logs using decoders and how you can leverage rules to alert you of strange occurrences on your network.• Understand System Integrity Check and Rootkit DetectionMonitor binary executable files, system configuration files, and the Microsoft Windows registry.• Configure Active ResponseConfigure the active response actions you want and bind the actions to specific rules and sequence of events.• Use the OSSEC Web User InterfaceInstall, configure, and use the community-developed, open source web interface available for OSSEC.• Play in the OSSEC VMware Environment Sandbox• Dig Deep into Data Log MiningTake the “high art of log analysis to the next level by breaking the dependence on the lists of strings or patterns to look for in the logs. COMPUTERS,Security,General

The IT / Digital Legal Companion The IT/Digital Legal Companion is a comprehensive business and legal guidance covering intellectual property for digital business; digital contract fundamentals; open source rules and strategies; development, consulting and outsourcing; software as a service; business software licensing, partnering, and distribution; web and Internet agreements; privacy on the Internet; digital multimedia content clearance and distribution; IT standards; video game development and content deals; international distribution; and user-created content, mash-ups, MMOGs, and web widgets. Chapters deal with topics such as copyrights on the Internet, for software protection and around the world; trademarks and domain names; patents and digital technology companies; trade secrets and non-disclosure agreements; confidentiality, rights transfer, and non-competition agreements for employees; introduction to digital product and service contracts; a pragmatic guide to open source; IT services - development, outsourcing, and consulting; beta test agreements; commercial end-user agreements; terms of use for web sites and online applications; privacy and use of personal data; digital technology standards - opportunities, risks, and strategies; content for digital media; and deals in the web and mobile value chains. This book is intended for executives, entrepreneurs, finance and business development officers; technology and engineering officers; marketers, licensing professionals, and technology professionals; in-house counsel; and anyone else that deals with software or digital technology in business.Comprehensive Business and Legal Guidance including * Securing Intellectual Property for Digital Business* Digital Contract Fundamentals* Open Source Rules and Strategies* Development, Consulting and Outsourcing* Software as a Service* Business Software Licensing, Partnering, and Distribution* Web and Internet Agreements* Privacy on the Internet* Digital Multimedia Content Clearance and Distribution* IT Standards* Video Game Development and Content Deals* International Distribution* User-Created Content, Mash-Ups, MMOGs, and Web Widgets* And Much More Key Features: * Up-to-the-Moment Legal Guide * In Plain English * Includes 38 Contract and Web Forms in the Book COMPUTERS,Security,General

Digital Identity The rise of network-based, automated services in the past decade has definitely changed the way businesses operate, but not always for the better. Offering services, conducting transactions and moving data on the Web opens new opportunities, but many CTOs and CIOs are more concerned with the risks. Like the rulers of medieval cities, they've adopted a siege mentality, building walls to keep the bad guys out. It makes for a secure perimeter, but hampers the flow of commerce. Fortunately, some corporations are beginning to rethink how they provide security, so that interactions with customers, employees, partners, and suppliers will be richer and more flexible. Digital Identity explains how to go about it. This book details an important concept known as "identity management architecture" (IMA): a method to provide ample protection while giving good guys access to vital information and systems. In today's service-oriented economy, digital identity is everything. IMA is a coherent, enterprise-wide set of standards, policies, certifications and management activities that enable companies like yours to manage digital identity effectively--not just as a security check, but as a way to extend services and pinpoint the needs of customers. Author Phil Windley likens IMA to good city planning. Cities define uses and design standards to ensure that buildings and city services are consistent and workable. Within that context, individual buildings--or system architectures--function as part of the overall plan. With Windley's experience as VP of product development for Excite@Home.com and CIO of Governor Michael Leavitt's administration in Utah, he provides a rich, real-world view of the concepts, issues, and technologies behind identity management architecture. How does digital identity increase business opportunity? Windley's favorite example is the ATM machine. With ATMs, banks can now offer around-the-clock service, serve more customers simultaneously, and do it in a variety of new locations. This fascinating book shows CIOs, other IT professionals, product managers, and programmers how security planning can support business goals and opportunities, rather than holding them at bay. COMPUTERS,Security,General

Kerberos Kerberos, the single sign-on authentication system originally developed at MIT, deserves its name. It's a faithful watchdog that keeps intruders out of your networks. But it has been equally fierce to system administrators, for whom the complexity of Kerberos is legendary.Single sign-on is the holy grail of network administration, and Kerberos is the only game in town. Microsoft, by integrating Kerberos into Active Directory in Windows 2000 and 2003, has extended the reach of Kerberos to all networks large or small. Kerberos makes your network more secure and more convenient for users by providing a single authentication system that works across the entire network. One username; one password; one login is all you need.Fortunately, help for administrators is on the way. Kerberos: The Definitive Guide shows you how to implement Kerberos for secure authentication. In addition to covering the basic principles behind cryptographic authentication, it covers everything from basic installation to advanced topics like cross-realm authentication, defending against attacks on Kerberos, and troubleshooting.In addition to covering Microsoft's Active Directory implementation, Kerberos: The Definitive Guide covers both major implementations of Kerberos for Unix and Linux: MIT and Heimdal. It shows you how to set up Mac OS X as a Kerberos client. The book also covers both versions of the Kerberos protocol that are still in use: Kerberos 4 (now obsolete) and Kerberos 5, paying special attention to the integration between the different protocols, and between Unix and Windows implementations.If you've been avoiding Kerberos because it's confusing and poorly documented, it's time to get on board! This book shows you how to put Kerberos authentication to work on your Windows and Unix systems. COMPUTERS,Security,General

SSH, The Secure Shell Are you serious about network security? Then check out SSH, the Secure Shell, which provides key-based authentication and transparent encryption for your network connections. It's reliable, robust, and reasonably easy to use, and both free and commercial implementations are widely available for most operating systems. While it doesn't solve every privacy and security problem, SSH eliminates several of them very effectively.Everything you want to know about SSH is in our second edition of SSH, The Secure Shell: The Definitive Guide. This updated book thoroughly covers the latest SSH-2 protocol for system administrators and end users interested in using this increasingly popular TCP/IP-based solution.How does it work? Whenever data is sent to the network, SSH automatically encrypts it. When data reaches its intended recipient, SSH decrypts it. The result is "transparent" encryption-users can work normally, unaware that their communications are already encrypted. SSH supports secure file transfer between computers, secure remote logins, and a unique "tunneling" capability that adds encryption to otherwise insecure network applications. With SSH, users can freely navigate the Internet, and system administrators can secure their networks or perform remote administration.Written for a wide, technical audience, SSH, The Secure Shell: The Definitive Guide covers several implementations of SSH for different operating systems and computing environments. Whether you're an individual running Linux machines at home, a corporate network administrator with thousands of users, or a PC/Mac owner who just wants a secure way to telnet or transfer files between machines, our indispensable guide has you covered. It starts with simple installation and use of SSH, and works its way to in-depth case studies on large, sensitive computer networks.No matter where or how you're shipping information, SSH, The Secure Shell: The Definitive Guide will show you how to do it securely. COMPUTERS,Security,General

RADIUS The subject of security never strays far from the minds of IT workers, for good reason. If there is a network with even just one connection to another network, it needs to be secured. RADIUS, or Remote Authentication Dial-In User Service, is a widely deployed protocol that enables companies to authenticate, authorize and account for remote users who want access to a system or service from a central network server. Originally developed for dial-up remote access, RADIUS is now used by virtual private network (VPN) servers, wireless access points, authenticating Ethernet switches, Digital Subscriber Line (DSL) access, and other network access types. Extensible, easy to implement, supported, and actively developed, RADIUS is currently the de facto standard for remote authentication.RADIUS provides a complete, detailed guide to the underpinnings of the RADIUS protocol, with particular emphasis on the utility of user accounting. Author Jonathan Hassell draws from his extensive experience in Internet service provider operations to bring practical suggestions and advice for implementing RADIUS. He also provides instructions for using an open-source variation called FreeRADIUS."RADIUS is an extensible protocol that enjoys the support of a wide range of vendors," says Jonathan Hassell. "Coupled with the amazing efforts of the open source development community to extend RADIUS's capabilities to other applications-Web, calling card security, physical device security, such as RSA's SecureID-RADIUS is possibly the best protocol with which to ensure only the people that need access to a resource indeed gain that access."This unique book covers RADIUS completely, from the history and theory of the architecture around which it was designed, to how the protocol and its ancillaries function on a day-to-day basis, to implementing RADIUS-based security in a variety of corporate and service provider environments. If you are an ISP owner or administrator, corporate IT professional responsible for maintaining mobile user connectivity, or a web presence provider responsible for providing multiple communications resources, you'll want this book to help you master this widely implemented but little understood protocol. COMPUTERS,Security,General

Cyber Attacks Cyber Attacks takes the national debate on protecting critical infrastructure in an entirely new and fruitful direction. It initiates an intelligent national (and international) dialogue amongst the general technical community around proper methods for reducing national risk. This includes controversial themes such as the deliberate use of deception to trap intruders. It also serves as an attractive framework for a new national strategy for cyber security, something that several Presidential administrations have failed in attempting to create. In addition, nations other than the US might choose to adopt the framework as well. This book covers cyber security policy development for massively complex infrastructure using ten principles derived from experiences in U.S. Federal Government settings and a range of global commercial environments. It provides a unique and provocative philosophy of cyber security that directly contradicts conventional wisdom about info sec for small or enterprise-level systems. It illustrates the use of practical, trial-and-error findings derived from 25 years of hands-on experience protecting critical infrastructure on a daily basis at AT&T. Each principle is presented as a separate security strategy, along with pages of compelling examples that demonstrate use of the principle. Cyber Attacks will be of interest to security professionals tasked with protection of critical infrastructure and with cyber security; CSOs and other top managers; government and military security specialists and policymakers; security managers; and students in cybersecurity and international security programs. * Covers cyber security policy development for massively complex infrastructure using ten principles derived from experiences in U.S. Federal Government settings and a range of global commercial environments. * Provides a unique and provocative philosophy of cyber security that directly contradicts conventional wisdom about info sec for small or enterprise-level systems. * Illustrates the use of practical, trial-and-error findings derived from 25 years of hands-on experience protecting critical infrastructure on a daily basis at AT&T. COMPUTERS,Security,General

Malware Analyst's Cookbook and DVD A computer forensics "how-to" for fighting malicious code and analyzing incidents With our ever-increasing reliance on computers comes an ever-growing risk of malware. Security professionals will find plenty of solutions in this book to the problems posed by viruses, Trojan horses, worms, spyware, rootkits, adware, and other invasive software. Written by well-known malware experts, this guide reveals solutions to numerous problems and includes a DVD of custom programs and tools that illustrate the concepts, enhancing your skills. Security professionals face a constant battle against malicious software; this practical manual will improve your analytical capabilities and provide dozens of valuable and innovative solutions Covers classifying malware, packing and unpacking, dynamic malware analysis, decoding and decrypting, rootkit detection, memory forensics, open source malware research, and much more Includes generous amounts of source code in C, Python, and Perl to extend your favorite tools or build new ones, and custom programs on the DVD to demonstrate the solutions Malware Analyst's Cookbook is indispensible to IT security administrators, incident responders, forensic analysts, and malware researchers. COMPUTERS,Security,General

Security Engineering The world has changed radically since the first edition of this book was published in 2001. Spammers, virus writers, phishermen, money launderers, and spies now trade busily with each other in a lively online criminal economy and as they specialize, they get better. In this indispensable, fully updated guide, Ross Anderson reveals how to build systems that stay dependable whether faced with error or malice. Here's straight talk on critical topics such as technical engineering basics, types of attack, specialized protection mechanisms, security psychology, policy, and more. COMPUTERS,Security,General

Eleventh Hour CISSP Eleventh Hour CISSP Study Guide serves as a guide for those who want to be information security professionals. The main job of an information security professional is to evaluate the risks involved in securing assets and to find ways to mitigate those risks. Information security jobs include firewall engineers, penetration testers, auditors, and the like. The book is composed of 10 domains of the Common Body of Knowledge. In each section, it defines each domain. The first domain provides information about risk analysis and mitigation, and it discusses security governance. The second domain discusses techniques of access control, which is the basis for all security disciplines. The third domain explains the concepts behind cryptography, which is a secure way of communicating that is understood only by certain recipients. Domain 5 discusses security system design, which is fundamental in operating the system and software security components. Domain 6 is one of the critical domains in the Common Body of Knowledge, the Business Continuity Planning and Disaster Recovery Planning. It is the final control against extreme events such as injury, loss of life, or failure of an organization. Domain 7, Domain 8 and Domain 9 discuss telecommunications and network security, application development security, and the operations domain, respectively. Domain 10 focuses on the major legal systems that provide a framework for determining laws about information system. The only guide you need for last-minute studying Answers the toughest questions and highlights core topics Can be paired with any other study guide so you are completely prepared COMPUTERS,Security,General

Cryptography Engineering The ultimate guide to cryptography, updated from an author team of the world's top cryptography experts. Cryptography is vital to keeping information safe, in an era when the formula to do so becomes more and more challenging. Written by a team of world-renowned cryptography experts, this essential guide is the definitive introduction to all major areas of cryptography: message security, key negotiation, and key management. You'll learn how to think like a cryptographer. You'll discover techniques for building cryptography into products from the start and you'll examine the many technical changes in the field. After a basic overview of cryptography and what it means today, this indispensable resource covers such topics as block ciphers, block modes, hash functions, encryption modes, message authentication codes, implementation issues, negotiation protocols, and more. Helpful examples and hands-on exercises enhance your understanding of the multi-faceted field of cryptography. An author team of internationally recognized cryptography experts updates you on vital topics in the field of cryptography Shows you how to build cryptography into products from the start Examines updates and changes to cryptography Includes coverage on key servers, message security, authentication codes, new standards, block ciphers, message authentication codes, and more Cryptography Engineering gets you up to speed in the ever-evolving field of cryptography. COMPUTERS,Security,General

Microsoft Windows Security Essentials Windows security concepts and technologies for IT beginners IT security can be a complex topic, especially for those new to the field of IT. This full-color book, with a focus on the Microsoft Technology Associate (MTA) program, offers a clear and easy-to-understand approach to Windows security risks and attacks for newcomers to the world of IT. By paring down to just the essentials, beginners gain a solid foundation of security concepts upon which more advanced topics and technologies can be built. This straightforward guide begins each chapter by laying out a list of topics to be discussed, followed by a concise discussion of the core networking skills you need to have to gain a strong handle on the subject matter. Chapters conclude with review questions and suggested labs so you can measure your level of understanding of the chapter's content. Serves as an ideal resource for gaining a solid understanding of fundamental security concepts and skills Offers a straightforward and direct approach to security basics and covers anti-malware software products, firewalls, network topologies and devices, network ports, and more Reviews all the topics you need to know for taking the MTA 98-367 exam Provides an overview of security components, looks at securing access with permissions, addresses audit policies and network auditing, and examines protecting clients and servers If you're new to IT and interested in entering the IT workforce, then Microsoft Windows Security Essentials is essential reading. COMPUTERS,Security,General

Implementing SSL / TLS Using Cryptography and PKI Hands-on, practical guide to implementing SSL and TLS protocols for Internet security If you are a network professional who knows C programming, this practical book is for you. Focused on how to implement Secure Socket Layer (SSL) and Transport Layer Security (TLS), this book guides you through all necessary steps, whether or not you have a working knowledge of cryptography. The book covers SSLv2, TLS 1.0, and TLS 1.2, including implementations of the relevant cryptographic protocols, secure hashing, certificate parsing, certificate generation, and more. Coverage includes: Understanding Internet Security Protecting against Eavesdroppers with Symmetric Cryptography Secure Key Exchange over an Insecure Medium with Public Key Cryptography Authenticating Communications Using Digital Signatures Creating a Network of Trust Using X.509 Certificates A Usable, Secure Communications Protocol: Client-Side TLS Adding Server-Side TLS 1.0 Support Advanced SSL Topics Adding TLS 1.2 Support to Your TLS Library Other Applications of SSL A Binary Representation of Integers: A Primer Installing TCPDump and OpenSSL Understanding the Pitfalls of SSLv2 Set up and launch a working implementation of SSL with this practical guide. COMPUTERS,Security,General

Cyber Warfare Cyber Warfare Techniques, Tactics and Tools for Security Practitioners provides a comprehensive look at how and why digital warfare is waged. This book explores the participants, battlefields, and the tools and techniques used during today's digital conflicts. The concepts discussed will give students of information security a better idea of how cyber conflicts are carried out now, how they will change in the future, and how to detect and defend against espionage, hacktivism, insider threats and non-state actors such as organized criminals and terrorists. Every one of our systems is under attack from multiple vectors - our defenses must be ready all the time and our alert systems must detect the threats every time. This book provides concrete examples and real-world guidance on how to identify and defend a network against malicious attacks. It considers relevant technical and factual information from an insider's point of view, as well as the ethics, laws and consequences of cyber war and how computer criminal law may change as a result. Starting with a definition of cyber warfare, the book’s 15 chapters discuss the following topics: the cyberspace battlefield; cyber doctrine; cyber warriors; logical, physical, and psychological weapons; computer network exploitation; computer network attack and defense; non-state actors in computer network operations; legal system impacts; ethics in cyber warfare; cyberspace challenges; and the future of cyber war. This book is a valuable resource to those involved in cyber warfare activities, including policymakers, penetration testers, security professionals, network and systems administrators, and college instructors. The information provided on cyber tactics and attacks can also be used to assist in developing improved and more efficient procedures and technical defenses. Managers will find the text useful in improving the overall risk management strategies for their organizations. Provides concrete examples and real-world guidance on how to identify and defend your network against malicious attacks Dives deeply into relevant technical and factual information from an insider's point of view Details the ethics, laws and consequences of cyber war and how computer criminal law may change as a result COMPUTERS,Security,General

Surreptitious Software “This book gives thorough, scholarly coverage of an area of growing importance in computer security and is a ‘must have’ for every researcher, student, and practicing professional in software protection.†—Mikhail Atallah, Distinguished Professor of Computer Science at Purdue University Theory, Techniques, and Tools for Fighting Software Piracy, Tampering, and Malicious Reverse Engineering The last decade has seen significant progress in the development of techniques for resisting software piracy and tampering. These techniques are indispensable for software developers seeking to protect vital intellectual property. Surreptitious Software is the first authoritative, comprehensive resource for researchers, developers, and students who want to understand these approaches, the level of security they afford, and the performance penalty they incur. Christian Collberg and Jasvir Nagra bring together techniques drawn from related areas of computer science, including cryptography, steganography, watermarking, software metrics, reverse engineering, and compiler optimization. Using extensive sample code, they show readers how to implement protection schemes ranging from code obfuscation and software fingerprinting to tamperproofing and birthmarking, and discuss the theoretical and practical limitations of these techniques. Coverage includes Mastering techniques that both attackers and defenders use to analyze programs Using code obfuscation to make software harder to analyze and understand Fingerprinting software to identify its author and to trace software pirates Tamperproofing software using guards that detect and respond to illegal modifications of code and data Strengthening content protection through dynamic watermarking and dynamic obfuscation Detecting code theft via software similarity analysis and birthmarking algorithms Using hardware techniques to defend software and media against piracy and tampering Detecting software tampering in distributed system Understanding the theoretical limits of code obfuscation COMPUTERS,Security,General

The Security Risk Assessment Handbook The Security Risk Assessment Handbook: A Complete Guide for Performing Security Risk Assessments provides detailed insight into precisely how to conduct an information security risk assessment. Designed for security professionals and their customers who want a more in-depth understanding of the risk assessment process, this volume contains real-wor COMPUTERS,Security,General

Information Security Now updated—your expert guide to twenty-first century information security Information security is a rapidly evolving field. As businesses and consumers become increasingly dependent on complex multinational information systems, it is more imperative than ever to protect the confidentiality and integrity of data. Featuring a wide array of new information on the most current security issues, this fully updated and revised edition of Information Security: Principles and Practice provides the skills and knowledge readers need to tackle any information security challenge. Taking a practical approach to information security by focusing on real-world examples, this book is organized around four major themes: Cryptography: classic cryptosystems, symmetric key cryptography, public key cryptography, hash functions, random numbers, information hiding, and cryptanalysis Access control: authentication and authorization, password-based security, ACLs and capabilities, multilevel security and compartments, covert channels and inference control, security models such as BLP and Biba's model, firewalls, and intrusion detection systems Protocols: simple authentication protocols, session keys, perfect forward secrecy, timestamps, SSH, SSL, IPSec, Kerberos, WEP, and GSM Software: flaws and malware, buffer overflows, viruses and worms, malware detection, software reverse engineering, digital rights management, secure software development, and operating systems security This Second Edition features new discussions of relevant security topics such as the SSH and WEP protocols, practical RSA timing attacks, botnets, and security certification. New background material has been added, including a section on the Enigma cipher and coverage of the classic "orange book" view of security. Also featured are a greatly expanded and upgraded set of homework problems and many new figures, tables, and graphs to illustrate and clarify complex topics and problems. A comprehensive solutions manual is available to assist in course development. Minimizing theory while providing clear, accessible content, Information Security remains the premier text for students and instructors in information technology, computer science, and engineering, as well as for professionals working in these fields. COMPUTERS,Security,General

Predicting Malicious Behavior A groundbreaking exploration of how to identify and fight security threats at every level This revolutionary book combines real-world security scenarios with actual tools to predict and prevent incidents of terrorism, network hacking, individual criminal behavior, and more. Written by an expert with intelligence officer experience who invented the technology, it explores the keys to understanding the dark side of human nature, various types of security threats (current and potential), and how to construct a methodology to predict and combat malicious behavior. The companion CD demonstrates available detection and prediction systems and presents a walkthrough on how to conduct a predictive analysis that highlights proactive security measures. Guides you through the process of predicting malicious behavior, using real world examples and how malicious behavior may be prevented in the future Illustrates ways to understand malicious intent, dissect behavior, and apply the available tools and methods for enhancing security Covers the methodology for predicting malicious behavior, how to apply a predictive methodology, and tools for predicting the likelihood of domestic and global threats CD includes a series of walkthroughs demonstrating how to obtain a predictive analysis and how to use various available tools, including Automated Behavior Analysis Predicting Malicious Behavior fuses the behavioral and computer sciences to enlighten anyone concerned with security and to aid professionals in keeping our world safer. COMPUTERS,Security,General

The Web Application Hacker's Handbook The highly successful security book returns with a new edition, completely updated Web applications are the front door to most organizations, exposing them to attacks that may disclose personal information, execute fraudulent transactions, or compromise ordinary users. This practical book has been completely updated and revised to discuss the latest step-by-step techniques for attacking and defending the range of ever-evolving web applications. You'll explore the various new technologies employed in web applications that have appeared since the first edition and review the new attack techniques that have been developed, particularly in relation to the client side. Reveals how to overcome the new technologies and techniques aimed at defending web applications against attacks that have appeared since the previous edition Discusses new remoting frameworks, HTML5, cross-domain integration techniques, UI redress, framebusting, HTTP parameter pollution, hybrid file attacks, and more Features a companion web site hosted by the authors that allows readers to try out the attacks described, gives answers to the questions that are posed at the end of each chapter, and provides a summarized methodology and checklist of tasks Focusing on the areas of web application security where things have changed in recent years, this book is the most current resource on the critical topic of discovering, exploiting, and preventing web application security flaws. COMPUTERS,Security,General

Computer Security A completely up-to-date resource on computer security Assuming no previous experience in the field of computer security, this must-have book walks you through the many essential aspects of this vast topic, from the newest advances in software and technology to the most recent information on Web applications security. This new edition includes sections on Windows NT, CORBA, and Java and discusses cross-site scripting and JavaScript hacking as well as SQL injection. Serving as a helpful introduction, this self-study guide is a wonderful starting point for examining the variety of competing security systems and what makes them different from one another. Unravels the complex topic of computer security and breaks it down in such a way as to serve as an ideal introduction for beginners in the field of computer security Examines the foundations of computer security and its basic principles Addresses username and password, password protection, single sign-on, and more Discusses operating system integrity, hardware security features, and memory Covers Unix security, Windows security, database security, network security, web security, and software security Packed with in-depth coverage, this resource spares no details when it comes to the critical topic of computer security. COMPUTERS,Security,General

A Classical Introduction to Cryptography A Classical Introduction to Cryptography: Applications for Communications Security introduces fundamentals of information and communication security by providing appropriate mathematical concepts to prove or break the security of cryptographic schemes. This advanced-level textbook covers conventional cryptographic primitives and cryptanalysis of these primitives; basic algebra and number theory for cryptologists; public key cryptography and cryptanalysis of these schemes; and other cryptographic protocols, e.g. secret sharing, zero-knowledge proofs and undeniable signature schemes. A Classical Introduction to Cryptography: Applications for Communications Security is designed for upper-level undergraduate and graduate-level students in computer science. This book is also suitable for researchers and practitioners in industry. A separate exercise/solution booklet is available as well, please go to www.springeronline.com under author: Vaudenay for additional details on how to purchase this booklet. COMPUTERS,Security,General

The Basics of Cyber Warfare The Basics of Cyber Warfare provides readers with fundamental knowledge of cyber war in both theoretical and practical aspects. This book explores the principles of cyber warfare, including military and cyber doctrine, social engineering, and offensive and defensive tools, tactics and procedures, including computer network exploitation (CNE), attack (CNA) and defense (CND). Readers learn the basics of how to defend against espionage, hacking, insider threats, state-sponsored attacks, and non-state actors (such as organized criminals and terrorists). Finally, the book looks ahead to emerging aspects of cyber security technology and trends, including cloud computing, mobile devices, biometrics and nanotechnology. The Basics of Cyber Warfare gives readers a concise overview of these threats and outlines the ethics, laws and consequences of cyber warfare. It is a valuable resource for policy makers, CEOs and CIOs, penetration testers, security administrators, and students and instructors in information security. Provides a sound understanding of the tools and tactics used in cyber warfare. Describes both offensive and defensive tactics from an insider's point of view. Presents doctrine and hands-on techniques to understand as cyber warfare evolves with technology. COMPUTERS,Security,General

The Basics of Cloud Computing As part of the Syngress Basics series, The Basics of Cloud Computing provides readers with an overview of the cloud and how to implement cloud computing in their organizations. Cloud computing continues to grow in popularity, and while many people hear the term and use it in conversation, many are confused by it or unaware of what it really means. This book helps readers understand what the cloud is and how to work with it, even if it isn’t a part of their day-to-day responsibility. Authors Derrick Rountree and Ileana Castrillo explains the concepts of cloud computing in practical terms, helping readers understand how to leverage cloud services and provide value to their businesses through moving information to the cloud. The book will be presented as an introduction to the cloud, and reference will be made in the introduction to other Syngress cloud titles for readers who want to delve more deeply into the topic. This book gives readers a conceptual understanding and a framework for moving forward with cloud computing, as opposed to competing and related titles, which seek to be comprehensive guides to the cloud. Provides a sound understanding of the cloud and how it works Describes both cloud deployment models and cloud services models, so you can make the best decisions for deployment Presents tips for selecting the best cloud services providers COMPUTERS,Security,General

Business Continuity and Disaster Recovery Planning for IT Professionals Powerful Earthquake Triggers Tsunami in Pacific. Hurricane Isaac Makes Landfall in the Gulf Coast. Wildfires Burn Hundreds of Houses and Businesses in Colorado. Tornado Touches Down in Missouri. These headlines not only have caught the attention of people around the world, they have had a significant effect on IT professionals as well. The new 2nd Edition of Business Continuity and Disaster Recovery for IT Professionals gives you the most up-to-date planning and risk management techniques for business continuity and disaster recovery (BCDR). With distributed networks, increasing demands for confidentiality, integrity and availability of data, and the widespread risks to the security of personal, confidential and sensitive data, no organization can afford to ignore the need for disaster planning. Author Susan Snedaker shares her expertise with you, including the most current options for disaster recovery and communication, BCDR for mobile devices, and the latest infrastructure considerations including cloud, virtualization, clustering, and more. Snedaker also provides you with new case studies in several business areas, along with a review of high availability and information security in healthcare IT. Don’t be caught off guard—Business Continuity and Disaster Recovery for IT Professionals, 2nd Edition , is required reading for anyone in the IT field charged with keeping information secure and systems up and running. Complete coverage of the 3 categories of disaster: natural hazards, human-caused hazards, and accidental / technical hazards Extensive disaster planning and readiness checklists for IT infrastructure, enterprise applications, servers and desktops Clear guidance on developing alternate work and computing sites and emergency facilities Actionable advice on emergency readiness and response Up-to-date information on the legal implications of data loss following a security breach or disaster COMPUTERS,Security,General

Simple Steps to Data Encryption Everyone wants privacy and security online, something that most computer users have more or less given up on as far as their personal data is concerned. There is no shortage of good encryption software, and no shortage of books, articles and essays that purport to be about how to use it. Yet there is precious little for ordinary users who want just enough information about encryption to use it safely and securely and appropriately--WITHOUT having to become experts in cryptography. Data encryption is a powerful tool, if used properly. Encryption turns ordinary, readable data into what looks like gibberish, but gibberish that only the end user can turn back into readable data again. The difficulty of encryption has much to do with deciding what kinds of threats one needs to protect against and then using the proper tool in the correct way. It's kind of like a manual transmission in a car: learning to drive with one is easy; learning to build one is hard. The goal of this title is to present just enough for an average reader to begin protecting his or her data, immediately. Books and articles currently available about encryption start out with statistics and reports on the costs of data loss, and quickly get bogged down in cryptographic theory and jargon followed by attempts to comprehensively list all the latest and greatest tools and techniques. After step-by-step walkthroughs of the download and install process, there's precious little room left for what most readers really want: how to encrypt a thumb drive or email message, or digitally sign a data file. There are terabytes of content that explain how cryptography works, why it's important, and all the different pieces of software that can be used to do it; there is precious little content available that couples concrete threats to data with explicit responses to those threats. This title fills that niche. By reading this title readers will be provided with a step by step hands-on guide that includes: Simple descriptions of actual threat scenarios Simple, step-by-step instructions for securing data How to use open source, time-proven and peer-reviewed cryptographic software Easy to follow tips for safer computing Unbiased and platform-independent coverage of encryption tools and techniques Simple descriptions of actual threat scenarios Simple, step-by-step instructions for securing data How to use open source, time-proven and peer-reviewed cryptographic software Easy-to-follow tips for safer computing Unbiased and platform-independent coverage of encryption tools and techniques COMPUTERS,Security,General

The Basics of Web Hacking The Basics of Web Hacking introduces you to a tool-driven process to identify the most widespread vulnerabilities in Web applications. No prior experience is needed. Web apps are a "path of least resistance" that can be exploited to cause the most damage to a system, with the lowest hurdles to overcome. This is a perfect storm for beginning hackers. The process set forth in this book introduces not only the theory and practical information related to these vulnerabilities, but also the detailed configuration and usage of widely available tools necessary to exploit these vulnerabilities. The Basics of Web Hacking provides a simple and clean explanation of how to utilize tools such as Burp Suite, sqlmap, and Zed Attack Proxy (ZAP), as well as basic network scanning tools such as nmap, Nikto, Nessus, Metasploit, John the Ripper, web shells, netcat, and more. Dr. Josh Pauli teaches software security at Dakota State University and has presented on this topic to the U.S. Department of Homeland Security, the NSA, BlackHat Briefings, and Defcon. He will lead you through a focused, three-part approach to Web security, including hacking the server, hacking the Web app, and hacking the Web user. With Dr. Pauli’s approach, you will fully understand the what/where/why/how of the most widespread Web vulnerabilities and how easily they can be exploited with the correct tools. You will learn how to set up a safe environment to conduct these attacks, including an attacker Virtual Machine (VM) with all necessary tools and several known-vulnerable Web application VMs that are widely available and maintained for this very purpose. Once you complete the entire process, not only will you be prepared to test for the most damaging Web exploits, you will also be prepared to conduct more advanced Web hacks that mandate a strong base of knowledge. Provides a simple and clean approach to Web hacking, including hands-on examples and exercises that are designed to teach you how to hack the server, hack the Web app, and hack the Web user Covers the most significant new tools such as nmap, Nikto, Nessus, Metasploit, John the Ripper, web shells, netcat, and more! Written by an author who works in the field as a penetration tester and who teaches Web security classes at Dakota State University COMPUTERS,Security,General

The Basics of Hacking and Penetration Testing The Basics of Hacking and Penetration Testing, Second Edition, serves as an introduction to the steps required to complete a penetration test or perform an ethical hack from beginning to end. The book teaches students how to properly utilize and interpret the results of the modern-day hacking tools required to complete a penetration test. It provides a simple and clean explanation of how to effectively utilize these tools, along with a four-step methodology for conducting a penetration test or hack, thus equipping students with the know-how required to jump start their careers and gain a better understanding of offensive security. Each chapter contains hands-on examples and exercises that are designed to teach learners how to interpret results and utilize those results in later phases. Tool coverage includes: Backtrack Linux, Google reconnaissance, MetaGooFil, dig, Nmap, Nessus, Metasploit, Fast Track Autopwn, Netcat, and Hacker Defender rootkit. This is complemented by PowerPoint slides for use in class. This book is an ideal resource for security consultants, beginning InfoSec professionals, and students. Each chapter contains hands-on examples and exercises that are designed to teach you how to interpret the results and utilize those results in later phases. Written by an author who works in the field as a Penetration Tester and who teaches Offensive Security, Penetration Testing, and Ethical Hacking, and Exploitation classes at Dakota State University. Utilizes the Kali Linux distribution and focuses on the seminal tools required to complete a penetration test. COMPUTERS,Security,General

Introduction to Cryptography Due to the rapid growth of digital communication and electronic data exchange, information security has become a crucial issue in industry, business, and administration. Modern cryptography provides essential techniques for securing information and protecting data. In the first part, this book covers the key concepts of cryptography on an undergraduate level, from encryption and digital signatures to cryptographic protocols. Essential techniques are demonstrated in protocols for key exchange, user identification, electronic elections and digital cash. In the second part, more advanced topics are addressed, such as the bit security of one-way functions and computationally perfect pseudorandom bit generators. The security of cryptographic schemes is a central topic. Typical examples of provably secure encryption and signature schemes and their security proofs are given. Though particular attention is given to the mathematical foundations, no special background in mathematics is presumed. The necessary algebra, number theory and probability theory are included in the appendix. Each chapter closes with a collection of exercises. The second edition contains corrections, revisions and new material, including a complete description of the AES, an extended section on cryptographic hash functions, a new section on random oracle proofs, and a new section on public-key encryption schemes that are provably secure against adaptively-chosen-ciphertext attacks. COMPUTERS,Security,General

Personal Medical Information In the last few years, the protection of computerised medical records, and of other personal health information, has become the subject of both technical research and political dispute in a number of countries. In Britain, the issue arose initially as an argument between the British Me dical Association and the Department of Health over whether encryption should be used in a new medical network. In Germany, the focus was the issue to all patients of a smartcard to hold insurance details and facilitate payment; while in the USA, the debate has been whether federal law should preempt state re gulation of computerised medical records, and if so, what technical and legal protection should be afforded the patient. Whatever the origin and evolution of this debate in specific countries, it has become clear that policy and technical matters are closely intertwined. What does 'computer security' mean in the medical context? What are we trying to do? What are the threats that we are trying to forestall? What costs might reasonably be incurred? To what extent is the existing technology - largely developed to meet military and banking requirements - of use? And perhaps hardest of all, what is the right balance between technical and legal controls? As the debate spread, it became clear that there was little serious contact between the people who could state the requirements - clinical professionals, medical ethicists and patients - and the people who could explore how to meet COMPUTERS,Security,General

Guide to Computer Viruses For those who didn't buy the first edition, welcome aboard. For those who did buy the first edition, welcome back, and thanks for making the second edition possible. For those who bought the first edition and are standing in the book store wondering whether to buy the second, what's in it for you? Well, for one thing, it's smaller. (No, no! Don't leave!) I tried to make the first edition a kind of master reference for antiviral protection. That meant I included a lot of stuff that I thought might possibly be helpful, even if I had some doubts about it. This time I've tried to be a little more selective. I've added a little more material to Chapter 4 (Computer Opera tions and Viral Operations) dealing with the question of computer vi ruses infecting data files and the new "macro" viruses. I've added two new sections to Chapter 7 (The Virus and Society). One looks at the increasing problem of false alarms while the other looks at the ethics of virus writing and exchange. COMPUTERS,Security,General

Executive Guide to Preventing Information Technology Disasters Recent and well-publicised disasters have highlighted the fact that organisations of all kinds - from healthcare to aerospace - are critically dependent on Information Technology systems. The prevention of catastrophic I.T. failure is now an essential part of management. In this thought-provoking guide for executives and managers Richard Ennals argues that the critical factor is not technology, but people and communication. COMPUTERS,Security,General

Building in Big Brother The announcement of the Clipper chip by the U.S. Government in April 1993 set off a frenzy of discussions about cryptography policy in the technological community. The shock waves from it ultimately included front page treatment in The New York Times, repeated questions to the Vice President, creation of several new newsgroups on the Internet, and some very productive public discussions about striking the balance between national security, law enforcement, and civil liberties. We still don't have good answers for some of the questions that have been raised. As the Global Information Infrastructure is being built, we are writing portions of the Constitution for Cyberspace. I've been fortunate to have a front row seat and to share much of this with my students. The original reading and selection of materials was made by the first cohort of students* in The George Washington University Accel erated Master of Science Program in Telecommunications and Com puters at the Ashburn, Virginia campus. They worked many long hours-reading, debating, and selecting materials for this book. In addition, Bob Patton spent a great deal of time scanning and editing the material. Nestor Torres prepared the index. And Harish Nalinak shan provided an enormous amount of technical and administrative assistance and kept the project on track as new developments took place in the debate and new papers and legislation reflected these. As with most readings books, some of the selections cover similar material. We have tried to hold this duplication to an acceptable level. COMPUTERS,Security,General

Differential Cryptanalysis of the Data Encryption Standard DES, the Data Encryption Standard, is the best known and most widely used civilian cryptosystem. It was developed by IBM and adopted as a US national standard in the mid 1970`s, and had resisted all attacks in the last 15 years. This book presents the first successful attack which can break the full 16 round DES faster than via exhaustive search. It describes in full detail, the novel technique of Differential Cryptanalysis, and demonstrates its applicability to a wide variety of cryptosystems and hash functions, including FEAL, Khafre, REDOC-II, LOKI, Lucifer, Snefru, N-Hash, and many modified versions of DES. The methodology used offers valuable insights to anyone interested in data security and cryptography, and points out the intricacies of developing, evaluating, testing, and implementing such schemes. This book was written by two of the field`s leading researchers, and describes state-of-the-art research in a clear and completely contained manner. COMPUTERS,Security,General

Cyber Warfare Cyber Warfare, Second Edition, takes a comprehensive look at how and why digital warfare is waged. The book explores the participants, battlefields, and the tools and techniques used in today's digital conflicts. The concepts discussed gives students of information security a better idea of how cyber conflicts are carried out now, how they will change in the future, and how to detect and defend against espionage, hacktivism, insider threats and non-state actors such as organized criminals and terrorists. This book provides concrete examples and real-world guidance on how to identify and defend a network against malicious attacks. It probes relevant technical and factual information from an insider's point of view, as well as the ethics, laws and consequences of cyber war and how computer criminal law may change as a result. Logical, physical, and psychological weapons used in cyber warfare are discussed. This text will appeal to information security practitioners, network security administrators, computer system administrators, and security analysts. Provides concrete examples and real-world guidance on how to identify and defend your network against malicious attacks Dives deeply into relevant technical and factual information from an insider's point of view Details the ethics, laws and consequences of cyber war and how computer criminal law may change as a result COMPUTERS,Security,General

ISO27001/ISO27002 Information security means much more than a technology solution, and requires buy-in from senior managers and the collaboration of all staff in the organisation. By looking at ISO27001 and ISO27002 together, this pocket guide gives a wider view of what it means to implement an ISO27001 ISMS. COMPUTERS,Security,General

Cybersecurity A must-have, hands-on guide for working in the cybersecurity profession Cybersecurity involves preventative methods to protect information from attacks. It requires a thorough understanding of potential threats, such as viruses and other malicious code, as well as system vulnerability and security architecture. This essential book addresses cybersecurity strategies that include identity management, risk management, and incident management, and also serves as a detailed guide for anyone looking to enter the security profession. Doubling as the text for a cybersecurity course, it is also a useful reference for cybersecurity testing, IT test/development, and system/network administration. Covers everything from basic network administration security skills through advanced command line scripting, tool customization, and log analysis skills Dives deeper into such intense topics as wireshark/tcpdump filtering, Google hacks, Windows/Linux scripting, Metasploit command line, and tool customizations Delves into network administration for Windows, Linux, and VMware Examines penetration testing, cyber investigations, firewall configuration, and security tool customization Shares techniques for cybersecurity testing, planning, and reporting Cybersecurity: Managing Systems, Conducting Testing, and Investigating Intrusions is a comprehensive and authoritative look at the critical topic of cybersecurity from start to finish. COMPUTERS,Security,General

The Basics of IT Audit The Basics of IT Audit: Purposes, Processes, and Practical Information provides you with a thorough, yet concise overview of IT auditing. Packed with specific examples, this book gives insight into the auditing process and explains regulations and standards such as the ISO-27000, series program, CoBIT, ITIL, Sarbanes-Oxley, and HIPPA. IT auditing occurs in some form in virtually every organization, private or public, large or small. The large number and wide variety of laws, regulations, policies, and industry standards that call for IT auditing make it hard for organizations to consistently and effectively prepare for, conduct, and respond to the results of audits, or to comply with audit requirements. This guide provides you with all the necessary information if you're preparing for an IT audit, participating in an IT audit or responding to an IT audit. Provides a concise treatment of IT auditing, allowing you to prepare for, participate in, and respond to the results Discusses the pros and cons of doing internal and external IT audits, including the benefits and potential drawbacks of each Covers the basics of complex regulations and standards, such as Sarbanes-Oxley, SEC (public companies), HIPAA, and FFIEC Includes most methods and frameworks, including GAAS, COSO, COBIT, ITIL, ISO (27000), and FISCAM COMPUTERS,Security,General

Advanced Criminal Investigations and Intelligence Operations Tradecraft is a term used within the intelligence community to describe the methods, practices, and techniques used in espionage and clandestine investigations. Whether the practitioner is a covert agent for the government or an identity thief and con man, the methods, practices, tactics, and techniques are often the same and sometimes learned from COMPUTERS,Security,General

IT-Sicherheitsmanagement nach ISO 27001 und Grundschutz Die Normreihe ISO 27000 und der IT-Grundschutz werden immer wichtiger für Unternehmen und Behörden, die ein IT-Sicherheitsmanagement in ihrer Organisation einführen und betreiben wollen. Im internationalen Kontext ist die Anwendung der ISO 27001 für viele Organisationen nahezu unverzichtbar. Das Buch führt den Leser Schritt für Schritt in diese Standards ein und legt verständlich dar, wie man ein adäquates Management-System (ISMS) aufbaut und bestehende Risiken analysiert und bewertet. Die ausführlich kommentierten Controls unterstützen Sicherheitsverantwortliche bei der Auswahl geeigneter Sicherheitsmaßnahmen in allen Bereichen. Die Nutzung von Kennzahlen zur Messung der Sicherheit wird an Beispielen erläutert. Zusätzlich erhält der Leser detaillierte Informationen zu internen und externen Audits sowie der Zertifizierung nach ISO 27001. Diese erweiterte 4. Auflage des Buches berücksichtigt u. a. die aktuelle Weiterentwicklung der ISO 27000 Normenreihe und vertieft Themen wie IT-Revision und Compliance. Viele Abschnitte wurden nach Vorschlägen der Leser früherer Auflagen überarbeitet und ergänzt. Zum Buch wird auch ein Online-Service bereit gestellt, der Checklisten und Vorlagen als Arbeitsmittel für das Sicherheitsmanagement bietet. COMPUTERS,Security,General

Unmasking the Social Engineer Learn to identify the social engineer by non-verbal behavior Unmasking the Social Engineer: The Human Element of Security focuses on combining the science of understanding non-verbal communications with the knowledge of how social engineers, scam artists and con men use these skills to build feelings of trust and rapport in their targets. The author helps readers understand how to identify and detect social engineers and scammers by analyzing their non-verbal behavior. Unmasking the Social Engineer shows how attacks work, explains nonverbal communications, and demonstrates with visuals the connection of non-verbal behavior to social engineering and scamming. Clearly combines both the practical and technical aspects of social engineering security Reveals the various dirty tricks that scammers use Pinpoints what to look for on the nonverbal side to detect the social engineer Sharing proven scientific methodology for reading, understanding, and deciphering non-verbal communications, Unmasking the Social Engineer arms readers with the knowledge needed to help protect their organizations. COMPUTERS,Security,General

Practical Reverse Engineering Analyzing how hacks are done, so as to stop them in the future Reverse engineering is the process of analyzing hardware or software and understanding it, without having access to the source code or design documents. Hackers are able to reverse engineer systems and exploit what they find with scary results. Now the good guys can use the same tools to thwart these threats. Practical Reverse Engineering goes under the hood of reverse engineering for security analysts, security engineers, and system programmers, so they can learn how to use these same processes to stop hackers in their tracks. The book covers x86, x64, and ARM (the first book to cover all three); Windows kernel-mode code rootkits and drivers; virtual machine protection techniques; and much more. Best of all, it offers a systematic approach to the material, with plenty of hands-on exercises and real-world examples. Offers a systematic approach to understanding reverse engineering, with hands-on exercises and real-world examples Covers x86, x64, and advanced RISC machine (ARM) architectures as well as deobfuscation and virtual machine protection techniques Provides special coverage of Windows kernel-mode code (rootkits/drivers), a topic not often covered elsewhere, and explains how to analyze drivers step by step Demystifies topics that have a steep learning curve Includes a bonus chapter on reverse engineering tools Practical Reverse Engineering: Using x86, x64, ARM, Windows Kernel, and Reversing Tools provides crucial, up-to-date guidance for a broad range of IT professionals. COMPUTERS,Security,General

Threat Modeling The only security book to be chosen as a Dr. Dobbs Jolt Award Finalist since Bruce Schneier's Secrets and Lies and Applied Cryptography! Adam Shostack is responsible for security development lifecycle threat modeling at Microsoft and is one of a handful of threat modeling experts in the world. Now, he is sharing his considerable expertise into this unique book. With pages of specific actionable advice, he details how to build better security into the design of systems, software, or services from the outset. You'll explore various threat modeling approaches, find out how to test your designs against threats, and learn effective ways to address threats that have been validated at Microsoft and other top companies. Systems security managers, you'll find tools and a framework for structured thinking about what can go wrong. Software developers, you'll appreciate the jargon-free and accessible introduction to this essential skill. Security professionals, you'll learn to discern changing threats and discover the easiest ways to adopt a structured approach to threat modeling. Provides a unique how-to for security and software developers who need to design secure products and systems and test their designs Explains how to threat model and explores various threat modeling approaches, such as asset-centric, attacker-centric and software-centric Provides effective approaches and techniques that have been proven at Microsoft and elsewhere Offers actionable how-to advice not tied to any specific software, operating system, or programming language Authored by a Microsoft professional who is one of the most prominent threat modeling experts in the world As more software is delivered on the Internet or operates on Internet-connected devices, the design of secure software is absolutely critical. Make sure you're ready with Threat Modeling: Designing for Security. COMPUTERS,Security,General

Introduction to Network Security Unlike data communications of the past, today’s networks consist of numerous devices that handle the data as it passes from the sender to the receiver. However, security concerns are frequently raised in circumstances where interconnected computers use a network not controlled by any one entity or organization. Introduction to Network Security examines various network protocols, focusing on vulnerabilities, exploits, attacks, and methods to mitigate an attack. The book begins with a brief discussion of network architectures and the functions of layers in a typical network. It then examines vulnerabilities and attacks divided into four categories: header-, protocol-, authentication-, and traffic-based. The author next explores the physical, network, and transport layers of each network as well as the security of several common network applications. The last section recommends several network-based security solutions that can be successfully deployed. This book uses a define-attack-defend methodology for network security. The author briefly introduces the relevant protocols and follows up with detailed descriptions of known vulnerabilities and possible attack methods. He delineates the threats against the protocol and presents possible solutions. Sample problems and lab experiments based on the concepts allow readers to experiment with attacks and assess the effectiveness of solutions. Two appendices provide further clarification and a companion website is offered which supplements the material. While most of the books available on this subject focus solely on cryptographic techniques to mitigate attacks, this volume recognizes the limitations of this methodology and considers a wider range of security problems and solutions. By focusing on a practical view of network security and examining actual protocols, readers can better understand the vulnerabilities and develop appropriate countermeasures. COMPUTERS,Security,General

Logical Investigative Methods All too often, professional investigations fail because those involved jump to conclusions and draw faulty premises that leave the trail cold. Correct conclusions are not the result of guessing, but by applying efficient thought processes. Logical Investigative Methods: Critical Thinking and Reasoning for Successful Investigations is designed to he COMPUTERS,Security,General

CERT® C Coding Standard, Second Edition, The “At Cisco, we have adopted the CERT C Coding Standard as the internal secure coding standard for all C developers. It is a core component of our secure development lifecycle. The coding standard described in this book breaks down complex software security topics into easy-to-follow rules with excellent real-world examples. It is an essential reference for any developer who wishes to write secure and resilient software in C and C++.†—Edward D. Paradise, vice president, engineering, threat response, intelligence, and development, Cisco Systems Secure programming in C can be more difficult than even many experienced programmers realize. To help programmers write more secure code, The CERT® C Coding Standard, Second Edition, fully documents the second official release of the CERT standard for secure coding in C. The rules laid forth in this new edition will help ensure that programmers’ code fully complies with the new C11 standard; it also addresses earlier versions, including C99. The new standard itemizes those coding errors that are the root causes of current software vulnerabilities in C, prioritizing them by severity, likelihood of exploitation, and remediation costs. Each of the text’s 98 guidelines includes examples of insecure code as well as secure, C11-conforming, alternative implementations. If uniformly applied, these guidelines will eliminate critical coding errors that lead to buffer overflows, format-string vulnerabilities, integer overflow, and other common vulnerabilities. This book reflects numerous experts’ contributions to the open development and review of the rules and recommendations that comprise this standard. Coverage includes Preprocessor Declarations and Initialization Expressions Integers Floating Point Arrays Characters and Strings Memory Management Input/Output Environment Signals Error Handling Concurrency Miscellaneous Issues COMPUTERS,Security,General

The Basics of Information Security As part of the Syngress Basics series, The Basics of Information Security provides you with fundamental knowledge of information security in both theoretical and practical aspects. Author Jason Andress gives you the basic knowledge needed to understand the key concepts of confidentiality, integrity, and availability, and then dives into practical applications of these ideas in the areas of operational, physical, network, application, and operating system security. The Basics of Information Security gives you clear-non-technical explanations of how infosec works and how to apply these principles whether you're in the IT field or want to understand how it affects your career and business. The new Second Edition has been updated for the latest trends and threats, including new material on many infosec subjects. Learn about information security without wading through a huge textbook Covers both theoretical and practical aspects of information security Provides a broad view of the information security field in a concise manner All-new Second Edition updated for the latest information security trends and threats, including material on incident response, social engineering, security awareness, risk management, and legal/regulatory issues COMPUTERS,Security,General

Informants, Cooperating Witnesses, and Undercover Investigations The use of informants has been described as the "black hole of law enforcement." Failures in the training of police officers and federal agents in the recruitment and operation of informants has undermined costly long-term investigations, destroyed the careers of prosecutors and law enforcement officers, and caused death and serious injuries to inn COMPUTERS,Security,General

Windows Performance Analysis Field Guide Microsoft Windows 8.1 and Windows Server 2012 R2 are designed to be the best performing operating systems to date, but even the best systems can be overwhelmed with load and/or plagued with poorly performing code. Windows Performance Analysis Field Guide gives you a practical field guide approach to performance monitoring and analysis from experts who do this work every day. Think of this book as your own guide to "What would Microsoft support do?" when you have a Windows performance issue. Author Clint Huffman, a Microsoft veteran of over fifteen years, shows you how to identify and alleviate problems with the computer resources of disk, memory, processor, and network. You will learn to use performance counters as the initial indicators, then use various tools to "dig in" to the problem, as well as how to capture and analyze boot performance problems. This field guide gives you the tools and answers you need to improve Microsoft Windows performance Save money on optimizing Windows performance with deep technical troubleshooting that tells you "What would Microsoft do to solve this?" Includes performance counter templates so you can collect the right data the first time. Learn how to solve performance problems using free tools from Microsoft such as the Windows Sysinternals tools and more. In a rush? Chapter 1 Start Here gets you on the quick path to solving the problem. Also covers earlier versions such as Windows 7 and Windows Server 2008 R2. COMPUTERS,Security,General

Measuring and Managing Information Risk Using the factor analysis of information risk (FAIR) methodology developed over ten years and adopted by corporations worldwide, Measuring and Managing Information Risk provides a proven and credible framework for understanding, measuring, and analyzing information risk of any size or complexity. Intended for organizations that need to either build a risk management program from the ground up or strengthen an existing one, this book provides a unique and fresh perspective on how to do a basic quantitative risk analysis. Covering such key areas as risk theory, risk calculation, scenario modeling, and communicating risk within the organization, Measuring and Managing Information Risk helps managers make better business decisions by understanding their organizational risk. Uses factor analysis of information risk (FAIR) as a methodology for measuring and managing risk in any organization. Carefully balances theory with practical applicability and relevant stories of successful implementation. Includes examples from a wide variety of businesses and situations presented in an accessible writing style. COMPUTERS,Security,General

Governance of Enterprise IT based on COBIT 5 Written for IT service managers, consultants and other practitioners in IT governance, risk and compliance, this practical book discusses all the key concepts of COBIT®5, and explains how to direct the governance of enterprise IT (GEIT) using the COBIT®5 framework. COMPUTERS,Security,General

Industrial Network Security As the sophistication of cyber-attacks increases, understanding how to defend critical infrastructure systems—energy production, water, gas, and other vital systems—becomes more important, and heavily mandated. Industrial Network Security, Second Edition arms you with the knowledge you need to understand the vulnerabilities of these distributed supervisory and control systems. The book examines the unique protocols and applications that are the foundation of industrial control systems, and provides clear guidelines for their protection. This how-to guide gives you thorough understanding of the unique challenges facing critical infrastructures, new guidelines and security measures for critical infrastructure protection, knowledge of new and evolving security tools, and pointers on SCADA protocols and security implementation. All-new real-world examples of attacks against control systems, and more diagrams of systems Expanded coverage of protocols such as 61850, Ethernet/IP, CIP, ISA-99, and the evolution to IEC62443 Expanded coverage of Smart Grid security New coverage of signature-based detection, exploit-based vs. vulnerability-based detection, and signature reverse engineering COMPUTERS,Security,General

The Basics of Digital Forensics The Basics of Digital Forensics provides a foundation for people new to the digital forensics field. This book teaches you how to conduct examinations by discussing what digital forensics is, the methodologies used, key tactical concepts, and the tools needed to perform examinations. Details on digital forensics for computers, networks, cell phones, GPS, the cloud and the Internet are discussed. Also, learn how to collect evidence, document the scene, and how deleted data can be recovered. The new Second Edition of this book provides you with completely up-to-date real-world examples and all the key technologies used in digital forensics, as well as new coverage of network intrusion response, how hard drives are organized, and electronic discovery. You'll also learn how to incorporate quality assurance into an investigation, how to prioritize evidence items to examine (triage), case processing, and what goes into making an expert witness. The Second Edition also features expanded resources and references, including online resources that keep you current, sample legal documents, and suggested further reading. Learn what Digital Forensics entails Build a toolkit and prepare an investigative plan Understand the common artifacts to look for in an exam Second Edition features all-new coverage of hard drives, triage, network intrusion response, and electronic discovery; as well as updated case studies, expert interviews, and expanded resources and references COMPUTERS,Security,General

Hacking Web Intelligence Open source intelligence (OSINT) and web reconnaissance are rich topics for infosec professionals looking for the best ways to sift through the abundance of information widely available online. In many cases, the first stage of any security assessment—that is, reconnaissance—is not given enough attention by security professionals, hackers, and penetration testers. Often, the information openly present is as critical as the confidential data. Hacking Web Intelligence shows you how to dig into the Web and uncover the information many don't even know exists. The book takes a holistic approach that is not only about using tools to find information online but also how to link all the information and transform it into presentable and actionable intelligence. You will also learn how to secure your information online to prevent it being discovered by these reconnaissance methods. Hacking Web Intelligence is an in-depth technical reference covering the methods and techniques you need to unearth open source information from the Internet and utilize it for the purpose of targeted attack during a security assessment. This book will introduce you to many new and leading-edge reconnaissance, information gathering, and open source intelligence methods and techniques, including metadata extraction tools, advanced search engines, advanced browsers, power searching methods, online anonymity tools such as TOR and i2p, OSINT tools such as Maltego, Shodan, Creepy, SearchDiggity, Recon-ng, Social Network Analysis (SNA), Darkweb/Deepweb, data visualization, and much more. Provides a holistic approach to OSINT and Web recon, showing you how to fit all the data together into actionable intelligence Focuses on hands-on tools such as TOR, i2p, Maltego, Shodan, Creepy, SearchDiggity, Recon-ng, FOCA, EXIF, Metagoofil, MAT, and many more Covers key technical topics such as metadata searching, advanced browsers and power searching, online anonymity, Darkweb / Deepweb, Social Network Analysis (SNA), and how to manage, analyze, and visualize the data you gather Includes hands-on technical examples and case studies, as well as a Python chapter that shows you how to create your own information-gathering tools and modify existing APIs COMPUTERS,Security,General

Crafting the InfoSec Playbook Any good attacker will tell you that expensive security monitoring and prevention tools aren’t enough to keep you secure. This practical book demonstrates a data-centric approach to distilling complex security monitoring, incident response, and threat analysis ideas into their most basic elements. You’ll learn how to develop your own threat intelligence and incident detection strategy, rather than depend on security tools alone. Written by members of Cisco’s Computer Security Incident Response Team, this book shows IT and information security professionals how to create an InfoSec playbook by developing strategy, technique, and architecture. Learn incident response fundamentals—and the importance of getting back to basics Understand threats you face and what you should be protecting Collect, mine, organize, and analyze as many relevant data sources as possible Build your own playbook of repeatable methods for security monitoring and response Learn how to put your plan into action and keep it running smoothly Select the right monitoring and detection tools for your environment Develop queries to help you sort through data and create valuable reports Know what actions to take during the incident response phase COMPUTERS,Security,General

Critical Infrastructure Protection The present volume aims to provide an overview of the current understanding of the so-called Critical Infrastructure (CI), and particularly the Critical Information Infrastructure (CII), which not only forms one of the constituent sectors of the overall CI, but also is unique in providing an element of interconnectionbetween sectors as well as often also intra-sectoral control mechanisms.The 14 papers of this book present a collection of pieces of scientific work in the areas of critical infrastructure protection. In combining elementary concepts and models with policy-related issues on one hand and placing an emphasis on the timely area of control systems, the book aims to highlight some of the key issues facing the research community. COMPUTERS,Security,General

Advances in Cryptology — CRYPTO ’96 Crypto '96, the Sixteenth Annual Crypto Conference, is sponsored by the International Association for Cryptologic Research (IACR), in cooperation with the IEEE Computer Society Technical Committee on Security and P- vacy and the Computer Science Department of the University of California at Santa Barbara (UCSB). It takes place at UCSB from August 18 to 22, 1996. The General Chair, Richard Graveman, is responsible for local organization and registration. The scientific program was organized by the 16-member Program C- mittee. We considered 115 papers. (An additional 15 submissions had to be summarily rejected because of lateness or major noncompliance with the c- ditions in the Call for Papers.) Of these, 30 were accepted for presentation. In addition, there will be five invited talks by Ernest Brickell. Andrew Clark, Whitfield Diffie, Ronald Rivest, and Cliff Stoll. A Rump Session will be chaired by Stuart Haber. These proceedings contain the revised versions of the 30 contributed talks. least three com- The submitted version of each paper was examined by at mittee members and/or outside experts, and their comments were taken into account in the revisions. However, the authors (and not the committee) bear full responsibility for the content of their papers. COMPUTERS,Security,General

Essential Cybersecurity Science If you’re involved in cybersecurity as a software developer, forensic investigator, or network administrator, this practical guide shows you how to apply the scientific method when assessing techniques for protecting your information systems. You’ll learn how to conduct scientific experiments on everyday tools and procedures, whether you’re evaluating corporate security systems, testing your own security product, or looking for bugs in a mobile game. Once author Josiah Dykstra gets you up to speed on the scientific method, he helps you focus on standalone, domain-specific topics, such as cryptography, malware analysis, and system security engineering. The latter chapters include practical case studies that demonstrate how to use available tools to conduct domain-specific scientific experiments. Learn the steps necessary to conduct scientific experiments in cybersecurity Explore fuzzing to test how your software handles various inputs Measure the performance of the Snort intrusion detection system Locate malicious “needles in a haystack†in your network and IT environment Evaluate cryptography design and application in IoT products Conduct an experiment to identify relationships between similar malware binaries Understand system-level security requirements for enterprise networks and web services COMPUTERS,Security,General

CISSP Study Guide CISSP Study Guide, Third Edition provides readers with information on the CISSP certification, the most prestigious, globally-recognized, vendor-neutral exam for information security professionals. With over 100,000 professionals certified worldwide, and many more joining their ranks, this new third edition presents everything a reader needs to know on the newest version of the exam's Common Body of Knowledge. The eight domains are covered completely and as concisely as possible, allowing users to ace the exam. Each domain has its own chapter that includes a specially-designed pedagogy to help users pass the exam, including clearly-stated exam objectives, unique terms and definitions, exam warnings, "learning by example" modules, hands-on exercises, and chapter ending questions. Provides the most complete and effective study guide to prepare users for passing the CISSP exam, giving them exactly what they need to pass the test Authored by Eric Conrad who has prepared hundreds of professionals for passing the CISSP exam through SANS, a popular and well-known organization for information security professionals Covers all of the new information in the Common Body of Knowledge updated in January 2015, and also provides two exams, tiered end-of-chapter questions for a gradual learning curve, and a complete self-test appendix COMPUTERS,Security,General

Advances in Cryptology - CRYPTO '89 CRYPTO is a conference devoted to all aspects of cryptologic research. It is held each year at the University of California at Santa Barbara. Annual meetings on this topic also take place in Europe and are regularly published in this Lecture Notes series under the name of EUROCRYPT. This volume presents the proceedings of the ninth CRYPTO meeting. The papers are organized into sections with the following themes: Why is cryptography harder than it looks?, pseudo-randomness and sequences, cryptanalysis and implementation, signature and authentication, threshold schemes and key management, key distribution and network security, fast computation, odds and ends, zero-knowledge and oblivious transfer, multiparty computation. COMPUTERS,Security,General

Advances in Cryptology — CRYPTO ’95 The Crypto ’95 conference was sponsored by the International Association for Cryptologic Research (IACR), in cooperation with the IEEE Computer - ciety Technical Committee on Security and Privacy, and the Computer Science Department of the University of California, Santa Barbara. It took place at the University of California, Santa Barbara, from August 27-31, 1995. This was the fifteenth annual Crypto conference; all have been held at UCSB. For the second time, proceedings were available at the conference. The General Chair, Stafford Tavares, was responsible for local organization and registration. The Program Committee considered 151 papers and selected 36 for pres- tation. There were also two invited talks. Robert Morris, Sr. gave a talk on “Ways of Losing Information,†which included some non-cryptographic means of leaking secrets that are often overlooked by cryptographers. The second talk, “Cryptography - Myths and Realities,†was given by Adi Shamir, this year’s IACR Distinguished Lecturer. Shamir is the second person to receive this honor, the first having been Gus Simmons at Crypto ’94. These proceedings contain revised versions of the 36 contributed talks. Each paper was sent to at least three members of the program committee for c- ments. Revisions were not checked on their scientific aspects. Some authors will write final versions of their papers for publication in refereed journals. Of course, the authors bear full responsibility for the contents of their papers. COMPUTERS,Security,General

Advances in Cryptology – EUROCRYPT '91 A series of open workshops devoted to modem cryptology began in Santa Barbara, California in 1981 and was followed in 1982 by a European counterpart in Burg Feurstein, Germany. The series has been maintained with summer meetings in Santa Barbara and spring meetings somewhere in Europe. At the 1983 meeting in Santa Barbara the International Association for Cryptologic Research was launched and it now sponsors all the meetings of the series. Following the tradition of the series, papers were invited in the form of extended abstracts and were reviewed by the programme committee, which selected those to be presented. After the meeting, full papers were produced, in some cases with impro- ments and corrections. These papers form the main part of the present volume. They are placed in the same order that they took at the meeting and under the same headings, for ease of reference by those who attended. The classification under these headings was a little arbitary, needing to fit the timing of the day‘s activities, but it makes a workable method of arrangement. Also following tradition, a “rump session’’ was held during one evening, under the effective chairmanship of John Gordon. These were short presentations and those present found them to have some real interest, therefore we have taken the unusual step of including short papers contributed by the rump session speakers at the end of this volume, with a necessarily simplified review process. COMPUTERS,Security,General

Advances in Cryptology — CRYPTO ’91 Crypto '91 was the eleventh in a series of workshops oncryptology sponsoredby the International Association forCryptologic Research and was held in Santa Barbara,California, in August 1991.This volume contains a full paper or an extended abstractfor each of the 39 talks presented at the workshop. Alltheoretical and practical aspects of cryptology arerepresented, including: protocol design and analysis,combinatorics and authentication, secret sharing andinformation theory, cryptanalysis, complexity theory,cryptographic schemas based on number theory,pseudorandomness, applications and implementations, viruses,public-key cryptosystems, and digital signatures. COMPUTERS,Security,General

Advances in Cryptology – EUROCRYPT '90 Eurocrypt is a conference devoted to all aspects of cryptologic research, both theoretical and practical, sponsored by the International Association for Cryptologic Research (IACR). Eurocrypt 90 took place in Åarhus, Denmark, in May 1990. From the 85 papers submitted, 42 were selected for presentation at the conference and for inclusion in this volume. In addition to the formal contributions, short abstracts of a number of informal talks are included in these proceedings. The proceedings are organized into sessions on protocols, number-theoretic algorithms, boolean functions, binary sequences, implementations, combinatorial schemes, cryptanalysis, new cryptosystems, signatures and authentication, and impromptu talks. COMPUTERS,Security,General

Computer Security - ESORICS 92 This volume presents the proceedings of the second European Symposium on Research in Computer Security (ESORICS 92), held in Toulouse in November 1992. The aim of this symposium is to further the progress of research in computer security by bringing together researchers in this area, by promoting the exchange of ideas with system developers, and by encouraging links with researchers in areas related to computer science, informationtheory, and artificial intelligence. The volume contains 24 papers organizedinto sections on access control, formal methods, authentication, distributed systems, database security, system architectures, and applications. ESORICS 92 was organized by AFCET (Association francaise des sciences et technologies de l'information et des syst mes) in cooperation with a large number of national and international societies and institutes. COMPUTERS,Security,General

Advances in Cryptology – EUROCRYPT ’92 A series of workshops devoted to modern cryptography beganin Santa Barbara,California in 1981 and was followed in1982 by a European counterpart in Burg Feuerstein, Germany.The series has been maintained with summer meetings in SantaBarbara and spring meetings somewhere in Europe. At the 1983meeting in Santa Barbara the International Association forCryptologic Research was launched and it now sponsors allthe meetings of the series. This volume presents theproceedings of Eurocrypt '92, held in Hungary. The papersare organized into the following parts: Secret sharing, Hashfunctions, Block ciphers, Stream ciphers, Public key I,Factoring, Trapdoor primes and moduli (panel report), Publickey II, Pseudo-random permutation generators, Complexitytheory and cryptography I, Zero-knowledge, Digital knowledgeand electronic cash, Complexity theory andcryptography II,Applications, and selected papers from the rump session.Following the tradition of the series, the authors producedfull papers after the meeting, in some cases with revisions. COMPUTERS,Security,General

Advances in Cryptology — CRYPTO ’92 Crypto'92 took place on August 16-20, 1992. It was the twelfth in the series of annual cryptology conferences held on the beautiful campus of the University of California, Santa Barbara. Once again, it was sponsored by the International Association for Cryptologic Research, in cooperation with the IEEE Computer Society Technical Committee on Security and Privacy. The conference ran smoothly, due to the diligent efforts of the g- eral chair, Spyros Magliveras of the University of Nebraska. One of the measures of the success of this series of conferences is represented by the ever increasing number of papers submitted. This year, there were 135 submissions to the c- ference, which represents a new record. Following the practice of recent program comm- tees, the papers received anonymous review. The program committee accepted 38 papers for presentation. In addition, there were two invited presentations, one by Miles Smid on the Digital Signature Standard, and one by Mike Fellows on presenting the concepts of cryptology to elementary-age students. These proceedings contains these 40 papers plus 3 papers that were presented at the Rump Session. I would like to thank all of the authors of the submitted papers and all of the speakers who presented papers. I would like to express my sincere appreciation to the work of the program committee: Ivan Damgard (Aarhus University, Denmark), Odd Goldreich (Technion, Israel), Burt Kaliski (RSA Data Security, USA), Joe Kilian (NEC, USA). COMPUTERS,Security,General

Advances in Cryptology – EUROCRYPT ’93 Eurocrypt is a series of open workshops on the theory andapplication of cryptographic techniques. These meetings havetaken place in Europe every year since 1982 and aresponsored by the International Association for CryptologicResearch.Eurocrypt '93 was held in the village of Lofthus in Norwayin May 1993. The call for papers resulted in 117 submissionswith authors representing 27 different countries. The 36accepted papers were selected by the program committee aftera blind refereeing process. The papers are grouped intoparts on authentication, public key, block ciphers, secretsharing, stream ciphers, digital signatures, protocols, hashfunctions, payment systems, and cryptanalysis. The volumeincludes 6 further rump session papers. COMPUTERS,Security,General

Advances in Cryptology — CRYPTO ’93 The CRYPTO ’93 conference was sponsored by the International Association for Cryptologic Research (IACR) and Bell-Northern Research (a subsidiary of Northern Telecom), in co-operation with the IEEE Computer Society Technical Committee. It took place at the University of California, Santa Barbara, from August 22-26, 1993. This was the thirteenth annual CRYPTO conference, all of which have been held at UCSB. The conference was very enjoyable and ran very of the General Chair, Paul Van Oorschot. smoothly, largely due to the efforts It was a pleasure working with Paul throughout the months leading up to the conference. There were 136 submitted papers which were considered by the Program Committee. Of these, 38 were selected for presentation at the conference. There was also one invited talk at the conference, presented by Miles Smid, the title of which was “A Status Report On the Federal Government Key Escrow System.†The conference also included the customary Rump Session, which was presided over by Whit Diffie in his usual inimitable fashion. Thanks again to Whit for organizing and running the Rump session. This year, the Rump Session included an interesting and lively panel discussion on issues pertaining to key escrowing. Those taking part were W. Diffie, J. Gilmore, S. Goldwasser, M. Hellman, A. Herzberg, S. Micali, R. Rueppel, G. Simmons and D. Weitzner. COMPUTERS,Security,General

Advances in Cryptology — CRYPTO ’94 The CRYPTO ’94 conference is sponsored by the International Association for Cryptologic Research (IACR), in co-operation with the IEEE Computer Society Technical Committee on Security and Privacy. It has taken place at the Univ- sity of California, Santa Barbara, from August 21-25,1994. This is the fourteenth annual CRYPTO conference, all of which have been held at UCSB. This is the first time that proceedings are available at the conference. The General Chair, Jimmy R. Upton has been responsible for local organization, registration, etc. There were 114 submitted papers which were considered by the Program Committee. Of these, 1 was withdrawn and 38 were selected for the proce- ings. There are also 3 invited talks. Two of these are on aspects of cryptog- phy in the commercial world. The one on hardware aspects will be presented by David Maher (AT&T), the one on software aspects by Joseph Pato (Hewlett- Packard). There will also be a panel discussion on “Securing an Electronic World: Are We Ready?†The panel members will be: Ross Anderson, Bob Blakley, Matt Blaze, George Davida, Yvo Desmedt (moderator), Whitfield Diffie, Joan Feig- baum, Blake Greenlee, Martin Hellman, David Maher, Miles Smid. The topic of the panel will be introduced by the invited talk of Whitfield Diffie on â€Securing the Information Highway. †These proceedings contain revised versions of the 38 contributed talks. Each i paper was sent to at least 3 members of the program committee for comments. COMPUTERS,Security,General

Advances in Cryptology – EUROCRYPT ’95 EUROCRYPT '95. Sponsored by the International Association for Cryp- logic Research (IACR), in cooperation with the Centre Commun d'Etudes de T616vision et T61Qcommunications (CCETT), a workshop on the theory and - plications of cryptographic techniques takes place at the Palais du Grand Large, Saint Malo, France, May 21-25, 1995. The General Chair of EUROCRYPT '95 is Franqoise Scarabin. The Or- nization Committee was helped by Maryvonne Lahaie and her communication team. Moreover, the CCETT has generously provided the help of a young - glish lady, Miss Virginia Cooper, for the secretariat of both the Organization arid Program Committees. They all did an excellent job in preparing the conference. It is our pleasure to thank them for their essential work. IACR and EUROCRYPT. According to a very good suggestion expressed during CRYPTO '82, the Association was established at CRYPTO '83. Today, the Association has approximately 600 members and the mailing file managed by its Secretariat consists of more than 2 000 names. The main goal of the Association is the sponsoring of two annual conferences: CRYPTO, every summer at the University of California, Santa Barbara (UCSB), and EUROCRYPT, every spring in a different European country. Moreover, the Association edits quarterly the Journal of Cryptology (JoC). COMPUTERS,Security,General

Advances in Cryptology – EUROCRYPT ’96 The EUROCRYPT ’96 conference was sponsored by the International Asso- ation for Cryptologic Research (IACR)l, in cooperation with the University of Saragossa. It took place at the Palacio de Congresos in Saragossa, Spain, during May 12-16, 1996. This was the fifteenth annual EUROCRYPT conference (this name has been used since the third conference held in 1984), each of which has been held in a different city in Europe. For the second time, proceedings were available at the conference. JosC Pastor Franco, the General Chair, was resp- sible for local organization and registration. His contribution to the snccess of the conference is gratefully acknowledged. The Program Committee considered 126 submitted papers and selected 34 for presentation. Each paper was sent to all members of the Program Committee and was assigned to at least three of them for careful evaluation. There were also two invited talks. James L. Massey, this year’s IACR Distinguished Ltcturer, gave a lecture entitled “The difficulty with difficultyâ€. Massey is the third to receive this honor, the first two being Gustavus Simmons and Adi Shamir. Shafi Goldwasser gave an invited talk entitled “Multi party secure protocols: past and presentâ€. These proceedings contain revised versions of the 34 contributed talks. While the papers were carefully selected, they have not been refereed like submissions to a refereed journal. The authors bear full responsibility for the contents of their papers. Some authors may write final versions of their papers for publication in a refereed journal. COMPUTERS,Security,General

Fundamentals of Information Security Risk Management Auditing An introductory guide to information risk management auditing, giving an interesting and useful insight into the risks and controls/mitigations that you may encounter when performing or managing an audit of information risk. Case studies and chapter summaries impart expert guidance. COMPUTERS,Security,General

Identity and Data Security for Web Development Developers, designers, engineers, and creators can no longer afford to pass responsibility for identity and data security onto others. Web developers who don’t understand how to obscure data in transmission, for instance, can open security flaws on a site without realizing it. With this practical guide, you’ll learn how and why everyone working on a system needs to ensure that users and data are protected. Authors Jonathan LeBlanc and Tim Messerschmidt provide a deep dive into the concepts, technology, and programming methodologies necessary to build a secure interface for data and identity—without compromising usability. You’ll learn how to plug holes in existing systems, protect against viable attack vectors, and work in environments that sometimes are naturally insecure. Understand the state of web and application security today Design security password encryption, and combat password attack vectors Create digital fingerprints to identify users through browser, device, and paired device detection Build secure data transmission systems through OAuth and OpenID Connect Use alternate methods of identification for a second factor of authentication Harden your web applications against attack Create a secure data transmission system using SSL/TLS, and synchronous and asynchronous cryptography COMPUTERS,Security,General

Eleventh Hour CISSP® Eleventh Hour CISSP: Study Guide, Third Edition provides readers with a study guide on the most current version of the Certified Information Systems Security Professional exam. This book is streamlined to include only core certification information, and is presented for ease of last-minute studying. Main objectives of the exam are covered concisely with key concepts highlighted. The CISSP certification is the most prestigious, globally-recognized, vendor neutral exam for information security professionals. Over 100,000 professionals are certified worldwide, with many more joining their ranks. This new third edition is aligned to cover all of the material in the most current version of the exam’s Common Body of Knowledge. All domains are covered as completely and concisely as possible, giving users the best possible chance of acing the exam. Completely updated for the most current version of the exam’s Common Body of Knowledge Provides the only guide you need for last-minute studying Answers the toughest questions and highlights core topics Streamlined for maximum efficiency of study, making it ideal for professionals updating their certification or for those taking the test for the first time COMPUTERS,Security,General

IT Security Risk Control Management Follow step-by-step guidance to craft a successful security program. You will identify with the paradoxes of information security and discover handy tools that hook security controls into business processes. Information security is more than configuring firewalls, removing viruses, hacking machines, or setting passwords. Creating and promoting a successful security program requires skills in organizational consulting, diplomacy, change management, risk analysis, and out-of-the-box thinking. What You Will Learn: Build a security program that will fit neatly into an organization and change dynamically to suit both the needs of the organization and survive constantly changing threats Prepare for and pass such common audits as PCI-DSS, SSAE-16, and ISO 27001 Calibrate the scope, and customize security controls to fit into an organization’s culture Implement the most challenging processes, pointing out common pitfalls and distractions Frame security and risk issues to be clear and actionable so that decision makers, technical personnel, and users will listen and value your advice Who This Book Is For: IT professionals moving into the security field; new security managers, directors, project heads, and would-be CISOs; and security specialists from other disciplines moving into information security (e.g., former military security professionals, law enforcement professionals, and physical security professionals) COMPUTERS,Security,General

Cybersecurity Essentials An accessible introduction to cybersecurity concepts and practices Cybersecurity Essentials provides a comprehensive introduction to the field, with expert coverage of essential topics required for entry-level cybersecurity certifications. An effective defense consists of four distinct challenges: securing the infrastructure, securing devices, securing local networks, and securing the perimeter. Overcoming these challenges requires a detailed understanding of the concepts and practices within each realm. This book covers each challenge individually for greater depth of information, with real-world scenarios that show what vulnerabilities look like in everyday computing scenarios. Each part concludes with a summary of key concepts, review questions, and hands-on exercises, allowing you to test your understanding while exercising your new critical skills. Cybersecurity jobs range from basic configuration to advanced systems analysis and defense assessment. This book provides the foundational information you need to understand the basics of the field, identify your place within it, and start down the security certification path. Learn security and surveillance fundamentals Secure and protect remote access and devices Understand network topologies, protocols, and strategies Identify threats and mount an effective defense Cybersecurity Essentials gives you the building blocks for an entry level security certification and provides a foundation of cybersecurity knowledge COMPUTERS,Security,General

Operational Auditing Internal auditors are expected to perform risk-based audits, but do so partially because they focus on financial and compliance risks at the expense of operational, strategic and technological ones. This limits their ability to evaluate critical risks and processes. This book merges traditional internal audit concepts and practices with contemporary quality control methodologies, tips, tools and techniques. It helps internal auditors perform value-added operational audits that result in meaningful findings and useful recommendations to help organizations meet objectives and improve the perception of internal auditors as high-value contributors, appropriate change agents and trusted advisors. COMPUTERS,Security,General

The Data Protection Officer The EU's General Data Protection Regulation created the position of corporate Data Protection Officer (DPO), who is empowered to ensure the organization is compliant with all aspects of the new data protection regime. Organizations must now appoint and designate a DPO. The specific definitions and building blocks of the data protection regime are enhanced by the new General Data Protection Regulation and therefore the DPO will be very active in passing the message and requirements of the new data protection regime throughout the organization. This book explains the roles and responsiblies of the DPO, as well as highlights the potential cost of getting data protection wrong. COMPUTERS,Security,General

Network Security Assessment How secure is your network? The best way to find out is to attack it, using the same tactics attackers employ to identify and exploit weaknesses. With the third edition of this practical book, you’ll learn how to perform network-based penetration testing in a structured manner. Security expert Chris McNab demonstrates common vulnerabilities, and the steps you can take to identify them in your environment. System complexity and attack surfaces continue to grow. This book provides a process to help you mitigate risks posed to your network. Each chapter includes a checklist summarizing attacker techniques, along with effective countermeasures you can use immediately. Learn how to effectively test system components, including: Common services such as SSH, FTP, Kerberos, SNMP, and LDAP Microsoft services, including NetBIOS, SMB, RPC, and RDP SMTP, POP3, and IMAP email services IPsec and PPTP services that provide secure network access TLS protocols and features providing transport security Web server software, including Microsoft IIS, Apache, and Nginx Frameworks including Rails, Django, Microsoft ASP.NET, and PHP Database servers, storage protocols, and distributed key-value stores COMPUTERS,Security,General

Critical Infrastructure Protection, Risk Management, and Resilience Critical Infrastructure Protection and Risk Management covers the history of risk assessment, crtical infrastructure protection, and the various structures that make up the homeland security enterprise. The authors examine risk assessment in the public and private sectors, the evolution of laws and regulations, and the policy challenges facing the 16 critical infrastructure sectors. The book will take a comprehensive look at the issues surrounding risk assessment and the challenges facing decision makers who must make risk assessment choices. COMPUTERS,Security,General

CompTIA CySA+ Study Guide NOTE: The name of the exam has changed from CSA+ to CySA+. However, the CS0-001 exam objectives are exactly the same. After the book was printed with CSA+ in the title, CompTIA changed the name to CySA+. We have corrected the title to CySA+ in subsequent book printings, but earlier printings that were sold may still show CSA+ in the title. Please rest assured that the book content is 100% the same. Prepare yourself for the newest CompTIA certification The CompTIA Cybersecurity Analyst+ (CySA+) Study Guide provides 100% coverage of all exam objectives for the new CySA+ certification. The CySA+ certification validates a candidate's skills to configure and use threat detection tools, perform data analysis, identify vulnerabilities with a goal of securing and protecting organizations systems. Focus your review for the CySA+ with Sybex and benefit from real-world examples drawn from experts, hands-on labs, insight on how to create your own cybersecurity toolkit, and end-of-chapter review questions help you gauge your understanding each step of the way. You also gain access to the Sybex interactive learning environment that includes electronic flashcards, a searchable glossary, and hundreds of bonus practice questions. This study guide provides the guidance and knowledge you need to demonstrate your skill set in cybersecurity. Key exam topics include: Threat management Vulnerability management Cyber incident response Security architecture and toolsets COMPUTERS,Security,General

Cybersecurity This book examines the legal and policy aspects of cyber-security. It takes a much needed look at cyber-security from a geopolitical perspective. Through this lens, it seeks to broaden the reader's understanding of the legal and political considerations of individuals, corporations, law enforcement and regulatory bodies and management of the complex relationships between them. In drawing on interviews conducted with experts from a wide range of fields, the book presents the reader with dilemmas and paradigms that confront law makers, corporate leaders, law enforcement, and national leaders. The book is structured in a novel format by employing a series of vignettes which have been created as exercises intended to confront the reader with the dilemmas involved in cyber-security. Through the use of vignettes, the work seeks to highlight the constant threat of cyber-security against various audiences, with the overall aim of facilitating discussion and reaction to actual probable events. In this sense, the book seeks to provide recommendations for best practices in response to the complex and numerous threats related to cyber-security. This book will be of interest to students of cyber-security, terrorism, international law, security studies and IR in general, as well as policy makers, professionals and law-enforcement officials. COMPUTERS,Security,General

Data Analytics for Internal Auditors There are many webinars and training courses on Data Analytics for Internal Auditors, but no handbook written from the practitioner’s viewpoint covering not only the need and the theory, but a practical hands-on approach to conducting Data Analytics. The spread of IT systems makes it necessary that auditors as well as management have the ability to examine high volumes of data and transactions to determine patterns and trends. The increasing need to continuously monitor and audit IT systems has created an imperative for the effective use of appropriate data mining tools. This book takes an auditor from a zero base to an ability to professionally analyze corporate data seeking anomalies. COMPUTERS,Security,General

Neun Schritte zum Erfolg Dieses Buch wird Ihnen in jeder Phase Ihres ISO 27001-Projekts helfen, da es die Methode von Beratern in hundert erfolgreichen ISMS-Implementierungen darstellt. COMPUTERS,Security,General

ISO27001/ISO27002 Esta guÃa de bolsillo indispensable da una visión de conjunto útil sobre dos normas importantes de la seguridad de la información. Llena de consejos prácticos para implementar un sistema de gestión de la seguridad de la información, se preguntará como se las arregló sin ella. Consiga su copia hoy. COMPUTERS,Security,General

Black Hat Go Like the best-selling Black Hat Python, Black Hat Go explores the darker side of the popular Go programming language. This collection of short scripts will help you test your systems, build and automate tools to fit your needs, and improve your offensive security skillset. Black Hat Go explores the darker side of Go, the popular programming language revered by hackers for its simplicity, efficiency, and reliability. It provides an arsenal of practical tactics from the perspective of security practitioners and hackers to help you test your systems, build and automate tools to fit your needs, and improve your offensive security skillset, all using the power of Go. You'll begin your journey with a basic overview of Go's syntax and philosophy and then start to explore examples that you can leverage for tool development, including common network protocols like HTTP, DNS, and SMB. You'll then dig into various tactics and problems that penetration testers encounter, addressing things like data pilfering, packet sniffing, and exploit development. You'll create dynamic, pluggable tools before diving into cryptography, attacking Microsoft Windows, and implementing steganography. You'll learn how to: • Make performant tools that can be used for your own security projects • Create usable tools that interact with remote APIs • Scrape arbitrary HTML data • Use Go's standard package, net/http, for building HTTP servers • Write your own DNS server and proxy • Use DNS tunneling to establish a C2 channel out of a restrictive network • Create a vulnerability fuzzer to discover an application's security weaknesses • Use plug-ins and extensions to future-proof productsBuild an RC2 symmetric-key brute-forcer • Implant data within a Portable Network Graphics (PNG) image. Are you ready to add to your arsenal of security tools? Then let's Go! COMPUTERS,Security,General

CompTIA CySA+ Practice Tests 1,000 practice questions for smart CompTIA CySA+ preparation CompTIA CySA+ Practice Tests provides invaluable preparation for the Cybersecurity Analyst exam CS0-001. With 1,000 questions covering 100% of the exam objectives, this book offers a multitude of opportunities for the savvy CySA+ candidate. Prepare more efficiently by working through questions before you begin studying, to find out what you already know—and focus study time only on what you don't. Test yourself periodically to gauge your progress along the way, and finish up with a 'dry-run' of the exam to avoid surprises on the big day. These questions are organized into four full-length tests, plus two bonus practice exams that show you what to expect and help you develop your personal test-taking strategy. Each question includes full explanations to help you understand the reasoning and approach, and reduces the chance of making the same error twice. The CySA+ exam tests your knowledge and skills related to threat management, vulnerability management, cyber incident response, and security architecture and tools. You may think you're prepared, but are you absolutely positive? This book gives you an idea of how you are likely to perform on the actual exam—while there's still time to review. Test your understanding of all CySA+ exam domains Pinpoint weak areas in need of review Assess your level of knowledge before planning your study time Learn what to expect on exam day The CompTIA CySA+ certification validates your skill set in the cybersecurity arena. As security becomes more and more critical, the demand for qualified professionals will only rise. CompTIA CySA+ Practice Tests is an invaluable tool for the comprehensive Cybersecurity Analyst preparation that helps you earn that career-making certification. COMPUTERS,Security,General

Practical Malware Analysis Malware analysis is big business, and attacks can cost a company dearly. When malware breaches your defenses, you need to act quickly to cure current infections and prevent future ones from occurring. For those who want to stay ahead of the latest malware, Practical Malware Analysis will teach you the tools and techniques used by professional analysts. With this book as your guide, you'll be able to safely analyze, debug, and disassemble any malicious software that comes your way. You'll learn how to:–Set up a safe virtual environment to analyze malware–Quickly extract network signatures and host-based indicators–Use key analysis tools like IDA Pro, OllyDbg, and WinDbg–Overcome malware tricks like obfuscation, anti-disassembly, anti-debugging, and anti-virtual machine techniques–Use your newfound knowledge of Windows internals for malware analysis–Develop a methodology for unpacking malware and get practical experience with five of the most popular packers–Analyze special cases of malware with shellcode, C++, and 64-bit code Hands-on labs throughout the book challenge you to practice and synthesize your skills as you dissect real malware samples, and pages of detailed dissections offer an over-the-shoulder look at how the pros do it. You'll learn how to crack open malware to see how it really works, determine what damage it has done, thoroughly clean your network, and ensure that the malware never comes back. Malware analysis is a cat-and-mouse game with rules that are constantly changing, so make sure you have the fundamentals. Whether you're tasked with securing one network or a thousand networks, or you're making a living as a malware analyst, you'll find what you need to succeed in Practical Malware Analysis. COMPUTERS,Security,General

Metasploit The Metasploit Framework makes discovering, exploiting, and sharing vulnerabilities quick and relatively painless. But while Metasploit is used by security professionals everywhere, the tool can be hard to grasp for first-time users. Metasploit: The Penetration Tester's Guide fills this gap by teaching you how to harness the Framework and interact with the vibrant community of Metasploit contributors. Once you've built your foundation for penetration testing, you’ll learn the Framework's conventions, interfaces, and module system as you launch simulated attacks. You’ll move on to advanced penetration testing techniques, including network reconnaissance and enumeration, client-side attacks, wireless attacks, and targeted social-engineering attacks. Learn how to:–Find and exploit unmaintained, misconfigured, and unpatched systems–Perform reconnaissance and find valuable information about your target–Bypass anti-virus technologies and circumvent security controls–Integrate Nmap, NeXpose, and Nessus with Metasploit to automate discovery–Use the Meterpreter shell to launch further attacks from inside the network–Harness standalone Metasploit utilities, third-party tools, and plug-ins–Learn how to write your own Meterpreter post exploitation modules and scripts You'll even touch on exploit discovery for zero-day research, write a fuzzer, port existing exploits into the Framework, and learn how to cover your tracks. Whether your goal is to secure your own networks or to put someone else's to the test, Metasploit: The Penetration Tester's Guide will take you there and beyond. COMPUTERS,Security,General

Black Hat Python When it comes to creating powerful and effective hacking tools, Python is the language of choice for most security analysts. But just how does the magic happen? In Black Hat Python, the latest from Justin Seitz (author of the best-selling Gray Hat Python), you’ll explore the darker side of Python’s capabilities—writing network sniffers, manipulating packets, infecting virtual machines, creating stealthy trojans, and more. You’ll learn how to:–Create a trojan command-and-control using GitHub–Detect sandboxing and automate common malware tasks, like keylogging and screenshotting–Escalate Windows privileges with creative process control–Use offensive memory forensics tricks to retrieve password hashes and inject shellcode into a virtual machine–Extend the popular Burp Suite web-hacking tool–Abuse Windows COM automation to perform a man-in-the-browser attack–Exfiltrate data from a network most sneakily Insider techniques and creative challenges throughout show you how to extend the hacks and how to write your own exploits. When it comes to offensive security, your ability to create powerful tools on the fly is indispensable. Learn how in Black Hat Python. Uses Python 2 COMPUTERS,Security,General

Agile Application Security Agile continues to be the most adopted software development methodology among organizations worldwide, but it generally hasn't integrated well with traditional security management techniques. And most security professionals aren’t up to speed in their understanding and experience of agile development. To help bridge the divide between these two worlds, this practical guide introduces several security tools and techniques adapted specifically to integrate with agile development. Written by security experts and agile veterans, this book begins by introducing security principles to agile practitioners, and agile principles to security practitioners. The authors also reveal problems they encountered in their own experiences with agile security, and how they worked to solve them. You’ll learn how to: Add security practices to each stage of your existing development lifecycle Integrate security with planning, requirements, design, and at the code level Include security testing as part of your team’s effort to deliver working software in each release Implement regulatory compliance in an agile or DevOps environment Build an effective security program through a culture of empathy, openness, transparency, and collaboration COMPUTERS,Security,General

Private Security and the Law Private Security and the Law, Fifth Edition , is a singular resource that provides the most comprehensive analysis of practices in the security industry with respect to law, regulation, licensure, and constitutional questions of case and statutory authority. The book begins with a historical background of the security industry, laws and regulations that walks step-by-step through the analysis of the development of case law over the years as it applies to situations commonly faced by security practitioners. It describes the legal requirements faced by security firms and emphasizes the liability problems common to security operations, including negligence and tortious liability, civil actions frequently litigated, and strategies to avoid legal actions that affect business efficiency. In addition, chapters examine the constitutional and due-process dimensions of private security both domestically and internationally, including recent cases and trends that are likely to intensify in the future. Updated coverage new to this edition includes developments in statutory authority, changes to state and federal processes of oversight and licensure, and special analysis of public-private cooperative relationships in law enforcement. Key features include: Up to date case law analysis provides cutting edge legal treatment of evolving standards Complicated material is presented in a straight-forward, readable style perfect for the student or security professional Includes over 200 tables and figures that illustrate concepts and present critical comparative data on statutes and regulations National scope provides crucial parameters to security practitioners throughout the U.S. Numerous case studies, case readings, and case examples provide real-world examples of security law and litigation in practice Private Security and the Law, Fifth Edition is an authoritative, scholarly treatise that serves as a valuable reference for professionals and an introduction for students in security management and criminal justice programs regarding the legal and ethical standards that shape the industry. COMPUTERS,Security,General

Private Security There are few textbooks available that outline the foundation of security principles while reflecting the modern practices of private security as an industry. Private Security: An Introduction to Principles and Practice takes a new approach to the subject of private sector security that will be welcome addition to the field. The book focuses on the recent history of the industry and the growing dynamic between private sector security and public safety and law enforcement. Coverage will include history and security theory, but emphasis is on current practice, reflecting the technology-driven, fast-paced, global security environment. Such topics covered include a history of the security industry, security law, risk management, physical security, Human Resources and personnel, investigations, institutional and industry-specific security, crisis and emergency planning, critical infrastructure protection, IT and computer security, and more. Rather than being reduced to single chapter coverage, homeland security and terrorism concepts are referenced throughout the book, as appropriate. Currently, it vital that private security entities work with public sector authorities seamlessly—at the state and federal levels—to share information and understand emerging risks and threats. This modern era of security requires an ongoing, holistic focus on the impact and implications of global terror incidents; as such, the book’s coverage of topics consciously takes this approach throughout. Highlights include: Details the myriad changes in security principles, and the practice of private security, particularly since 9/11 Focuses on both foundational theory but also examines current best practices—providing sample forms, documents, job descriptions, and functions—that security professionals must understand to perform and succeed Outlines the distinct, but growing, roles of private sector security companies versus the expansion of federal and state law enforcement security responsibilities Includes key terms, learning objectives, end of chapter questions, Web exercises, and numerous references—throughout the book—to enhance student learning Presents the full range of career options available for those looking entering the field of private security Includes nearly 400 full-color figures, illustrations, and photographs. Private Security: An Introduction to Principles and Practice provides the most comprehensive, up-to-date coverage of modern security issues and practices on the market. Professors will appreciate the new, fresh approach, while students get the most "bang for their buck," insofar as the real-world knowledge and tools needed to tackle their career in the ever-growing field of private industry security. An instructor’s manual with Exam questions, lesson plans, and chapter PowerPoint® slides are available upon qualified course adoption. COMPUTERS,Security,General

Collaborative Cyber Threat Intelligence Threat intelligence is a surprisingly complex topic that goes far beyond the obvious technical challenges of collecting, modelling and sharing technical indicators. Most books in this area focus mainly on technical measures to harden a system based on threat intel data and limit their scope to single organizations only. This book provides a unique angle on the topic of national cyber threat intelligence and security information sharing. It also provides a clear view on ongoing works in research laboratories world-wide in order to address current security concerns at national level. It allows practitioners to learn about upcoming trends, researchers to share current results, and decision makers to prepare for future developments. COMPUTERS,Security,General

Industrial Cybersecurity Your one-step guide to understanding industrial cyber security, its control systems, and its operations. About This Book Learn about endpoint protection such as anti-malware implementation, updating, monitoring, and sanitizing user workloads and mobile devices Filled with practical examples to help you secure critical infrastructure systems efficiently A step-by-step guide that will teach you the techniques and methodologies of building robust infrastructure systems Who This Book Is For If you are a security professional and want to ensure a robust environment for critical infrastructure systems, this book is for you. IT professionals interested in getting into the cyber security domain or who are looking at gaining industrial cyber security certifications will also find this book useful. What You Will Learn Understand industrial cybersecurity, its control systems and operations Design security-oriented architectures, network segmentation, and security support services Configure event monitoring systems, anti-malware applications, and endpoint security Gain knowledge of ICS risks, threat detection, and access management Learn about patch management and life cycle management Secure your industrial control systems from design through retirement In Detail With industries expanding, cyber attacks have increased significantly. Understanding your control system's vulnerabilities and learning techniques to defend critical infrastructure systems from cyber threats is increasingly important. With the help of real-world use cases, this book will teach you the methodologies and security measures necessary to protect critical infrastructure systems and will get you up to speed with identifying unique challenges.Industrial cybersecurity begins by introducing Industrial Control System (ICS) technology, including ICS architectures, communication media, and protocols. This is followed by a presentation on ICS (in) security. After presenting an ICS-related attack scenario, securing of the ICS is discussed, including topics such as network segmentation, defense-in-depth strategies, and protective solutions. Along with practical examples for protecting industrial control systems, this book details security assessments, risk management, and security program development. It also covers essential cybersecurity aspects, such as threat detection and access management. Topics related to endpoint hardening such as monitoring, updating, and anti-malware implementations are also discussed. Style and approach A step-by-step guide to implement Industrial Cyber Security effectively. COMPUTERS,Security,General

Social Engineering Harden the human firewall against the most current threats Social Engineering: The Science of Human Hacking reveals the craftier side of the hacker’s repertoire—why hack into something when you could just ask for access? Undetectable by firewalls and antivirus software, social engineering relies on human fault to gain access to sensitive spaces; in this book, renowned expert Christopher Hadnagy explains the most commonly-used techniques that fool even the most robust security personnel, and shows you how these techniques have been used in the past. The way that we make decisions as humans affects everything from our emotions to our security. Hackers, since the beginning of time, have figured out ways to exploit that decision making process and get you to take an action not in your best interest. This new Second Edition has been updated with the most current methods used by sharing stories, examples, and scientific study behind how those decisions are exploited. Networks and systems can be hacked, but they can also be protected; when the “system†in question is a human being, there is no software to fall back on, no hardware upgrade, no code that can lock information down indefinitely. Human nature and emotion is the secret weapon of the malicious social engineering, and this book shows you how to recognize, predict, and prevent this type of manipulation by taking you inside the social engineer’s bag of tricks. Examine the most common social engineering tricks used to gain access Discover which popular techniques generally don’t work in the real world Examine how our understanding of the science behind emotions and decisions can be used by social engineers Learn how social engineering factors into some of the biggest recent headlines Learn how to use these skills as a professional social engineer and secure your company Adopt effective counter-measures to keep hackers at bay By working from the social engineer’s playbook, you gain the advantage of foresight that can help you protect yourself and others from even their best efforts. Social Engineering gives you the inside information you need to mount an unshakeable defense. COMPUTERS,Security,General

IoT Penetration Testing Cookbook Over 80 recipes to master IoT security techniques. About This Book Identify vulnerabilities in IoT device architectures and firmware using software and hardware pentesting techniques Understand radio communication analysis with concepts such as sniffing the air and capturing radio signals A recipe based guide that will teach you to pentest new and unique set of IoT devices. Who This Book Is For This book targets IoT developers, IoT enthusiasts, pentesters, and security professionals who are interested in learning about IoT security. Prior knowledge of basic pentesting would be beneficial. What You Will Learn Set up an IoT pentesting lab Explore various threat modeling concepts Exhibit the ability to analyze and exploit firmware vulnerabilities Demonstrate the automation of application binary analysis for iOS and Android using MobSF Set up a Burp Suite and use it for web app testing Identify UART and JTAG pinouts, solder headers, and hardware debugging Get solutions to common wireless protocols Explore the mobile security and firmware best practices Master various advanced IoT exploitation techniques and security automation In Detail IoT is an upcoming trend in the IT industry today; there are a lot of IoT devices on the market, but there is a minimal understanding of how to safeguard them. If you are a security enthusiast or pentester, this book will help you understand how to exploit and secure IoT devices. This book follows a recipe-based approach, giving you practical experience in securing upcoming smart devices. It starts with practical recipes on how to analyze IoT device architectures and identify vulnerabilities. Then, it focuses on enhancing your pentesting skill set, teaching you how to exploit a vulnerable IoT device, along with identifying vulnerabilities in IoT device firmware. Next, this book teaches you how to secure embedded devices and exploit smart devices with hardware techniques. Moving forward, this book reveals advanced hardware pentesting techniques, along with software-defined, radio-based IoT pentesting with Zigbee and Z-Wave. Finally, this book also covers how to use new and unique pentesting techniques for different IoT devices, along with smart devices connected to the cloud. By the end of this book, you will have a fair understanding of how to use different pentesting techniques to exploit and secure various IoT devices. Style and approach This recipe-based book will teach you how to use advanced IoT exploitation and security automation. COMPUTERS,Security,General

PoC or GTFO, Volume 2 PoC or GTFO, Volume 2 follows-up the wildly popular first volume with issues 9-13 of the eponymous hacker zine. Contributions range from humorous poems to deeply technical essays. The International Journal of Proof-of-Concept or Get The Fuck Out is a celebrated magazine of reverse engineering, retro-computing, and systems internals. This second collected volume holds all of the articles from releases nine to thirteen. Learn how to patch the firmware of a handheld amateur radio, then emulate that radio's proprietary audio code under Linux. How to slow the Windows kernel when exploiting a race condition and how to make a PDF file that is also an Android app, an audio file, or a Gameboy speedrun. How to hack a Wacom pen table with voltage glitching, then hack it again by pure software to read RDID tags from its surface. How to disassemble every last byte of an Atari game and how to bypass every classic form of copy protection on Apple ][. But above all else, beyond the nifty tricks and silly songs, this book exists to remind you what a clever engineer can build from a box of parts with a bit of free time. Not to show you what others have done, but to show you how they did it so that you can do the same. COMPUTERS,Security,General

Machine Learning and Security Can machine learning techniques solve our computer security problems and finally put an end to the cat-and-mouse game between attackers and defenders? Or is this hope merely hype? Now you can dive into the science and answer this question for yourself! With this practical guide, you’ll explore ways to apply machine learning to security issues such as intrusion detection, malware classification, and network analysis. Machine learning and security specialists Clarence Chio and David Freeman provide a framework for discussing the marriage of these two fields, as well as a toolkit of machine-learning algorithms that you can apply to an array of security problems. This book is ideal for security engineers and data scientists alike. Learn how machine learning has contributed to the success of modern spam filters Quickly detect anomalies, including breaches, fraud, and impending system failure Conduct malware analysis by extracting useful information from computer binaries Uncover attackers within the network by finding patterns inside datasets Examine how attackers exploit consumer-facing websites and app functionality Translate your machine learning algorithms from the lab to production Understand the threat attackers pose to machine learning solutions COMPUTERS,Security,General

Cybersecurity – Attack and Defense Strategies Enhance your organization's secure posture by improving your attack and defense strategies About This Book Gain a clear understanding of the attack methods, and patterns to recognize abnormal behavior within your organization with Blue Team tactics. Learn to unique techniques to gather exploitation intelligence, identify risk and demonstrate impact with Red Team and Blue Team strategies. A practical guide that will give you hands-on experience to mitigate risks and prevent attackers from infiltrating your system. Who This Book Is For This book aims at IT professional who want to venture the IT security domain. IT pentester, Security consultants, and ethical hackers will also find this course useful. Prior knowledge of penetration testing would be beneficial. What You Will Learn Learn the importance of having a solid foundation for your security posture Understand the attack strategy using cyber security kill chain Learn how to enhance your defense strategy by improving your security policies, hardening your network, implementing active sensors, and leveraging threat intelligence Learn how to perform an incident investigation Get an in-depth understanding of the recovery process Understand continuous security monitoring and how to implement a vulnerability management strategy Learn how to perform log analysis to identify suspicious activities In Detail The book will start talking about the security posture before moving to Red Team tactics, where you will learn the basic syntax for the Windows and Linux tools that are commonly used to perform the necessary operations. You will also gain hands-on experience of using new Red Team techniques with powerful tools such as python and PowerShell, which will enable you to discover vulnerabilities in your system and how to exploit them. Moving on, you will learn how a system is usually compromised by adversaries, and how they hack user's identity, and the various tools used by the Red Team to find vulnerabilities in a system. In the next section, you will learn about the defense strategies followed by the Blue Team to enhance the overall security of a system. You will also learn about an in-depth strategy to ensure that there are security controls in each network layer, and how you can carry out the recovery process of a compromised system. Finally, you will learn how to create a vulnerability management strategy and the different techniques for manual log analysis. By the end of this book, you will be well-versed with Red Team and Blue Team techniques and will have learned the techniques used nowadays to attack and defend systems. Style and approach This book uses a practical approach of the cybersecurity kill chain to explain the different phases of the attack, which includes the rationale behind each phase, followed by scenarios and examples that brings the theory into practice. COMPUTERS,Security,General

CASP+ CompTIA Advanced Security Practitioner Study Guide Comprehensive coverage of the new CASP+ exam, with hands-on practice and interactive study tools The CASP+ CompTIA Advanced Security Practitioner Study Guide: Exam CAS-003, Third Edition, offers invaluable preparation for exam CAS-003. Covering 100 percent of the exam objectives, this book provides expert walk-through of essential security concepts and processes to help you tackle this challenging exam with full confidence. Practical examples and real-world insights illustrate critical topics and show what essential practices look like on the ground, while detailed explanations of technical and business concepts give you the background you need to apply identify and implement appropriate security solutions. End-of-chapter reviews help solidify your understanding of each objective, and cutting-edge exam prep software features electronic flashcards, hands-on lab exercises, and hundreds of practice questions to help you test your knowledge in advance of the exam. The next few years will bring a 45-fold increase in digital data, and at least one third of that data will pass through the cloud. The level of risk to data everywhere is growing in parallel, and organizations are in need of qualified data security professionals; the CASP+ certification validates this in-demand skill set, and this book is your ideal resource for passing the exam. Master cryptography, controls, vulnerability analysis, and network security Identify risks and execute mitigation planning, strategies, and controls Analyze security trends and their impact on your organization Integrate business and technical components to achieve a secure enterprise architecture CASP+ meets the ISO 17024 standard, and is approved by U.S. Department of Defense to fulfill Directive 8570.01-M requirements. It is also compliant with government regulations under the Federal Information Security Management Act (FISMA). As such, this career-building credential makes you in demand in the marketplace and shows that you are qualified to address enterprise-level security concerns. The CASP+ CompTIA Advanced Security Practitioner Study Guide: Exam CAS-003, Third Edition, is the preparation resource you need to take the next big step for your career and pass with flying colors. COMPUTERS,Security,General

VMware NSX Cookbook Network virtualization at your fingertips About This Book Over 70 practical recipes created by two VCIX-NV certified NSX experts Explore best practices to deploy, operate, and upgrade VMware NSX for vSphere Leverage NSX REST API using various tools from Python in VMware vRealize Orchestrator Who This Book Is For If you are a security and network administrator and looking to gain an intermediate level for network and security virtualization, then this book is for you. The reader should have a basic knowledge with VMware NSX. What You Will Learn Understand, install, and configure VMware NSX for vSphere solutions Configure logical switching, routing, and Edge Services Gateway in VMware NSX for vSphere Learn how to plan and upgrade VMware NSX for vSphere Learn how to use built-in monitoring tools such as Flow Monitoring, Traceflow, Application Rule Manager, and Endpoint Monitoring Learn how to leverage the NSX REST API for management and automation using various tools from Python to VMware vRealize Orchestrator In Detail This book begins with a brief introduction to VMware's NSX for vSphere Network Virtualization solutions and how to deploy and configure NSX components and features such as Logical Switching, Logical Routing, layer 2 bridging and the Edge Services Gateway. Moving on to security, the book shows you how to enable micro-segmentation through NSX Distributed Firewall and Identity Firewall and how to do service insertion via network and guest introspection. After covering all the feature configurations for single-site deployment, the focus then shifts to multi-site setups using Cross-vCenter NSX. Next, the book covers management, backing up and restoring, upgrading, and monitoring using built-in NSX features such as Flow Monitoring, Traceflow, Application Rule Manager, and Endpoint Monitoring. Towards the end, you will explore how to leverage VMware NSX REST API using various tools from Python to VMware vRealize Orchestrator. Style and approach The book follows a practical, recipe-based approach and teaches readers how to leverage VMware NSX and implement these recipes directly into their enterprise. COMPUTERS,Security,General

Gray Hat Hacking Cutting-edge techniques for finding and fixing critical security flaws Fortify your network and avert digital catastrophe with proven strategies from a team of security experts. Completely updated and featuring 13 new chapters, Gray Hat Hacking, The Ethical Hacker’s Handbook, Fifth Edition explains the enemy’s current weapons, skills, and tactics and offers field-tested remedies, case studies, and ready-to-try testing labs. Find out how hackers gain access, overtake network devices, script and inject malicious code, and plunder Web applications and browsers. Android-based exploits, reverse engineering techniques, and cyber law are thoroughly covered in this state-of-the-art resource. And the new topic of exploiting the Internet of things is introduced in this edition. • Build and launch spoofing exploits with Ettercap • Induce error conditions and crash software using fuzzers • Use advanced reverse engineering to exploit Windows and Linux software • Bypass Windows Access Control and memory protection schemes • Exploit web applications with Padding Oracle Attacks • Learn the use-after-free technique used in recent zero days • Hijack web browsers with advanced XSS attacks • Understand ransomware and how it takes control of your desktop • Dissect Android malware with JEB and DAD decompilers • Find one-day vulnerabilities with binary diffing • Exploit wireless systems with Software Defined Radios (SDR) • Exploit Internet of things devices • Dissect and exploit embedded devices • Understand bug bounty programs • Deploy next-generation honeypots • Dissect ATM malware and analyze common ATM attacks • Learn the business side of ethical hacking COMPUTERS,Security,General

Hands-On Cybersecurity with Blockchain Develop blockchain application with step-by-step instructions, working example and helpful recommendations About This Book Understanding the blockchain technology from the cybersecurity perspective Developing cyber security solutions with Ethereum blockchain technology Understanding real-world deployment of blockchain based applications Who This Book Is For The book is targeted towards security professionals, or any stakeholder dealing with cybersecurity who wants to understand the next-level of securing infrastructure using Blockchain. Basic understanding of Blockchain can be an added advantage. What You Will Learn Understand the cyberthreat landscape Learn about Ethereum and Hyperledger Blockchain Program Blockchain solutions Build Blockchain-based apps for 2FA, and DDoS protection Develop Blockchain-based PKI solutions and apps for storing DNS entries Challenges and the future of cybersecurity and Blockchain In Detail Blockchain technology is being welcomed as one of the most revolutionary and impactful innovations of today. Blockchain technology was first identified in the world's most popular digital currency, Bitcoin, but has now changed the outlook of several organizations and empowered them to use it even for storage and transfer of value. This book will start by introducing you to the common cyberthreat landscape and common attacks such as malware, phishing, insider threats, and DDoS. The next set of chapters will help you to understand the workings of Blockchain technology, Ethereum and Hyperledger architecture and how they fit into the cybersecurity ecosystem. These chapters will also help you to write your first distributed application on Ethereum Blockchain and the Hyperledger Fabric framework. Later, you will learn about the security triad and its adaptation with Blockchain. The last set of chapters will take you through the core concepts of cybersecurity, such as DDoS protection, PKI-based identity, 2FA, and DNS security. You will learn how Blockchain plays a crucial role in transforming cybersecurity solutions. Toward the end of the book, you will also encounter some real-world deployment examples of Blockchain in security cases, and also understand the short-term challenges and future of cybersecurity with Blockchain. Style and approach This book will follow a practical approach to help understand blockchain technology to transform cybersecurity solutions COMPUTERS,Security,General

Open Source Intelligence Methods and Tools Apply Open Source Intelligence (OSINT) techniques, methods, and tools to acquire information from publicly available online sources to support your intelligence analysis. Use the harvested data in different scenarios such as financial, crime, and terrorism investigations as well as performing business competition analysis and acquiring intelligence about individuals and other entities. This book will also improve your skills to acquire information online from both the regular Internet as well as the hidden web through its two sub-layers: the deep web and the dark web. The author includes many OSINT resources that can be used by intelligence agencies as well as by enterprises to monitor trends on a global level, identify risks, and gather competitor intelligence so more effective decisions can be made. You will discover techniques, methods, and tools that are equally used by hackers and penetration testers to gather intelligence about a specific target online. And you will be aware of how OSINT resources can be used in conducting social engineering attacks. Open Source Intelligence Methods and Tools takes a practical approach and lists hundreds of OSINT resources that can be used to gather intelligence from online public sources. The book also covers how to anonymize your digital identity online so you can conduct your searching activities without revealing your identity. What You’ll Learn Identify intelligence needs and leverage a broad range of tools and sources to improve data collection, analysis, and decision making in your organization Use OSINT resources to protect individuals and enterprises by discovering data that is online, exposed, and sensitive and hide the data before it is revealed by outside attackers Gather corporate intelligence about business competitors and predict future market directions Conduct advanced searches to gather intelligence from social media sites such as Facebook and Twitter Understand the different layers that make up the Internet and how to search within the invisible web which contains both the deep and the dark webs Who This Book Is For Penetration testers, digital forensics investigators, intelligence services, military, law enforcement, UN agencies, and for-profit/non-profit enterprises COMPUTERS,Security,General

Information Technology Control and Audit, Fifth Edition The new fifth edition of Information Technology Control and Audit has been significantly revised to include a comprehensive overview of the IT environment, including revolutionizing technologies, legislation, audit process, governance, strategy, and outsourcing, among others. This new edition also outlines common IT audit risks, procedures, and involvement associated with major IT audit areas. It further provides cases featuring practical IT audit scenarios, as well as sample documentation to design and perform actual IT audit work. Filled with up-to-date audit concepts, tools, techniques, and references for further reading, this revised edition promotes the mastery of concepts, as well as the effective implementation and assessment of IT controls by organizations and auditors. For instructors and lecturers there are an instructor’s manual, sample syllabi and course schedules, PowerPoint lecture slides, and test questions. For students there are flashcards to test their knowledge of key terms and recommended further readings. Go to http://routledgetextbooks.com/textbooks/9781498752282/ for more information. COMPUTERS,Security,General

NIST Cybersecurity Framework The NIST CSF is a framework for organizations to manage and mitigate cybersecurity risk based on existing standards, guidelines, and practices. COMPUTERS,Security,General

Cybersecurity Incident Response Create, maintain, and manage a continual cybersecurity incident response program using the practical steps presented in this book. Don't allow your cybersecurity incident responses (IR) to fall short of the mark due to lack of planning, preparation, leadership, and management support. Surviving an incident, or a breach, requires the best response possible. This book provides practical guidance for the containment, eradication, and recovery from cybersecurity events and incidents. The book takes the approach that incident response should be a continual program. Leaders must understand the organizational environment, the strengths and weaknesses of the program and team, and how to strategically respond. Successful behaviors and actions required for each phase of incident response are explored in the book. Straight from NIST 800-61, these actions include: Planning and practicing Detection Containment Eradication Post-incident actions What You’ll Learn Know the sub-categories of the NIST Cybersecurity Framework Understand the components of incident response Go beyond the incident response plan Turn the plan into a program that needs vision, leadership, and culture to make it successful Be effective in your role on the incident response team Who This Book Is For Cybersecurity leaders, executives, consultants, and entry-level professionals responsible for executing the incident response plan when something goes wrong COMPUTERS,Security,General

Hands-On Red Team Tactics Your one-stop guide to learning and implementing Red Team tactics effectively Key Features Target a complex enterprise environment in a Red Team activity Detect threats and respond to them with a real-world cyber-attack simulation Explore advanced penetration testing tools and techniques Book Description Red Teaming is used to enhance security by performing simulated attacks on an organization in order to detect network and system vulnerabilities. Hands-On Red Team Tactics starts with an overview of pentesting and Red Teaming, before giving you an introduction to few of the latest pentesting tools. We will then move on to exploring Metasploit and getting to grips with Armitage. Once you have studied the fundamentals, you will learn how to use Cobalt Strike and how to set up its team server. The book introduces some common lesser known techniques for pivoting and how to pivot over SSH, before using Cobalt Strike to pivot. This comprehensive guide demonstrates advanced methods of post-exploitation using Cobalt Strike and introduces you to Command and Control (C2) servers and redirectors. All this will help you achieve persistence using beacons and data exfiltration, and will also give you the chance to run through the methodology to use Red Team activity tools such as Empire during a Red Team activity on Active Directory and Domain Controller. In addition to this, you will explore maintaining persistent access, staying untraceable, and getting reverse connections over different C2 covert channels. By the end of this book, you will have learned about advanced penetration testing tools, techniques to get reverse shells over encrypted channels, and processes for post-exploitation. What you will learn Get started with red team engagements using lesser-known methods Explore intermediate and advanced levels of post-exploitation techniques Get acquainted with all the tools and frameworks included in the Metasploit framework Discover the art of getting stealthy access to systems via Red Teaming Understand the concept of redirectors to add further anonymity to your C2 Get to grips with different uncommon techniques for data exfiltration Who this book is for Hands-On Red Team Tactics is for you if you are an IT professional, pentester, security consultant, or ethical hacker interested in the IT security domain and wants to go beyond Penetration Testing. Prior knowledge of penetration testing is beneficial. COMPUTERS,Security,General

CompTIA PenTest+ Study Guide World-class preparation for the new PenTest+ exam The CompTIA PenTest+ Study Guide: Exam PT0-001 offers comprehensive preparation for the newest intermediate cybersecurity certification exam. With expert coverage of Exam PT0-001 objectives, this book is your ideal companion throughout all stages of study; whether you’re just embarking on your certification journey or finalizing preparations for the big day, this invaluable resource helps you solidify your understanding of essential skills and concepts. Access to the Sybex online learning environment allows you to study anytime, anywhere with electronic flashcards, a searchable glossary, and more, while hundreds of practice exam questions help you step up your preparations and avoid surprises on exam day. The CompTIA PenTest+ certification validates your skills and knowledge surrounding second-generation penetration testing, vulnerability assessment, and vulnerability management on a variety of systems and devices, making it the latest go-to qualification in an increasingly mobile world. This book contains everything you need to prepare; identify what you already know, learn what you don’t know, and face the exam with full confidence! Perform security assessments on desktops and mobile devices, as well as cloud, IoT, industrial and embedded systems Identify security weaknesses and manage system vulnerabilities Ensure that existing cybersecurity practices, configurations, and policies conform with current best practices Simulate cyberattacks to pinpoint security weaknesses in operating systems, networks, and applications As our information technology advances, so do the threats against it. It’s an arms race for complexity and sophistication, and the expansion of networked devices and the Internet of Things has integrated cybersecurity into nearly every aspect of our lives. The PenTest+ certification equips you with the skills you need to identify potential problems—and fix them—and the CompTIA PenTest+ Study Guide: Exam PT0-001 is the central component of a complete preparation plan. COMPUTERS,Security,General

Data Science For Cyber-security Cyber-security is a matter of rapidly growing importance in industry and government. This book provides insight into a range of data science techniques for addressing these pressing concerns.The application of statistical and broader data science techniques provides an exciting growth area in the design of cyber defences. Networks of connected devices, such as enterprise computer networks or the wider so-called Internet of Things, are all vulnerable to misuse and attack, and data science methods offer the promise to detect such behaviours from the vast collections of cyber traffic data sources that can be obtained. In many cases, this is achieved through anomaly detection of unusual behaviour against understood statistical models of normality.This volume presents contributed papers from an international conference of the same name held at Imperial College. Experts from the field have provided their latest discoveries and review state of the art technologies. COMPUTERS,Security,General

Kali Linux 2018 Become the ethical hacker you need to be to protect your network Key Features Set up, configure, and run a newly installed Kali-Linux 2018.x Footprint, monitor, and audit your network and investigate any ongoing infestations Customize Kali Linux with this professional guide so it becomes your pen testing toolkit Book Description Microsoft Windows is one of the two most common OSes, and managing its security has spawned the discipline of IT security. Kali Linux is the premier platform for testing and maintaining Windows security. Kali is built on the Debian distribution of Linux and shares the legendary stability of that OS. This lets you focus on using the network penetration, password cracking, and forensics tools, and not the OS. This book has the most advanced tools and techniques to reproduce the methods used by sophisticated hackers to make you an expert in Kali Linux penetration testing. You will start by learning about the various desktop environments that now come with Kali. The book covers network sniffers and analysis tools to uncover the Windows protocols in use on the network. You will see several tools designed to improve your average in password acquisition, from hash cracking, online attacks, offline attacks, and rainbow tables to social engineering. It also demonstrates several use cases for Kali Linux tools like Social Engineering Toolkit, and Metasploit, to exploit Windows vulnerabilities. Finally, you will learn how to gain full system-level access to your compromised system and then maintain that access. By the end of this book, you will be able to quickly pen test your system and network using easy-to-follow instructions and support images. What you will learn Learn advanced set up techniques for Kali and the Linux operating system Understand footprinting and reconnaissance of networks Discover new advances and improvements to the Kali operating system Map and enumerate your Windows network Exploit several common Windows network vulnerabilities Attack and defeat password schemes on Windows Debug and reverse engineer Windows programs Recover lost files, investigate successful hacks, and discover hidden data Who this book is for If you are a working ethical hacker who is looking to expand the offensive skillset with a thorough understanding of Kali Linux, then this is the book for you. Prior knowledge about Linux operating systems, BASH terminal, and Windows command line would be highly beneficial. COMPUTERS,Security,General

Computer Security Today, everyone recognises the importance of safeguarding computer systems and networks from vulnerability, attack, and compromise. But computer security is neither an easy art nor a simple science: its methodologies and technologies require rigorous study, and a deep grounding in principles that can be applied even as technologies change. Moreover, practitioners must understand how to align concepts with real policies, and then actually implement those policies -- managing inevitable tradeoffs such as “How secure do our devices really need to be, and how much inconvenience can we accept?†In his extensively updated Computer Security: Art and Science, 2nd Edition, University of California at Davis Computer Security Laboratory co-director Matt Bishop offers a clear, rigorous, and thorough introduction to the entire modern field of computer security. Bishop covers access control; security, confidentiality, integrity, availability, and hybrid policies; policy composition; cryptography; authentication; identity management; information flow; assurance; formal methods; system evaluation; vulnerability analysis; auditing; intrusion detection, and many other topics. This edition adds four new chapters, including a brand-new chapter-length case study on the high-profile issue of electronic voting. Through this case study, Bishop demonstrates how principles, policies, procedures, and technology come together in a crucial real-world application. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Security,General

CISO COMPASS #1 Best Selling 2019 Information Security Book by Taylor & Francis 2020 Cybersecurity CANON Hall of Fame Winner! Todd Fitzgerald, co-author of the ground-breaking (ISC)2 CISO Leadership: Essential Principles for Success, Information Security Governance Simplified: From the Boardroom to the Keyboard, co-author for the E-C Council CISO Body of Knowledge, and contributor to many others including Official (ISC)2 Guide to the CISSP CBK, COBIT 5 for Information Security, and ISACA CSX Cybersecurity Fundamental Certification, is back with this new book incorporating practical experience in leading, building, and sustaining an information security/cybersecurity program. CISO COMPASS includes personal, pragmatic perspectives and lessons learned of over 75 award-winning CISOs, security leaders, professional association leaders, and cybersecurity standard setters who have fought the tough battle. Todd has also, for the first time, adapted the McKinsey 7S framework (strategy, structure, systems, shared values, staff, skills and style) for organizational effectiveness to the practice of leading cybersecurity to structure the content to ensure comprehensive coverage by the CISO and security leaders to key issues impacting the delivery of the cybersecurity strategy and demonstrate to the Board of Directors due diligence. The insights will assist the security leader to create programs appreciated and supported by the organization, capable of industry/ peer award-winning recognition, enhance cybersecurity maturity, gain confidence by senior management, and avoid pitfalls. The book is a comprehensive, soup-to-nuts book enabling security leaders to effectively protect information assets and build award-winning programs by covering topics such as developing cybersecurity strategy, emerging trends and technologies, cybersecurity organization structure and reporting models, leveraging current incidents, security control frameworks, risk management, laws and regulations, data protection and privacy, meaningful policies and procedures, multi-generational workforce team dynamics, soft skills, and communicating with the Board of Directors and executive management. The book is valuable to current and future security leaders as a valuable resource and an integral part of any college program for information/ cybersecurity. COMPUTERS,Security,General

Beginning Ethical Hacking with Kali Linux Get started in white-hat ethical hacking using Kali Linux. This book starts off by giving you an overview of security trends, where you will learn the OSI security architecture. This will form the foundation for the rest of Beginning Ethical Hacking with Kali Linux. With the theory out of the way, you’ll move on to an introduction to VirtualBox, networking, and common Linux commands, followed by the step-by-step procedure to build your own web server and acquire the skill to be anonymous . When you have finished the examples in the first part of your book, you will have all you need to carry out safe and ethical hacking experiments. After an introduction to Kali Linux, you will carry out your first penetration tests with Python and code raw binary packets for use in those tests. You will learn how to find secret directories on a target system, use a TCP client in Python, and scan ports using NMAP. Along the way you will discover effective ways to collect important information, track email, and use important tools such as DMITRY and Maltego, as well as take a look at the five phases of penetration testing. The coverage of vulnerability analysis includes sniffing and spoofing, why ARP poisoning is a threat, how SniffJoke prevents poisoning, how to analyze protocols with Wireshark, and using sniffing packets with Scapy. The next part of the book shows you detecting SQL injection vulnerabilities, using sqlmap, and applying brute force or password attacks. Besides learning these tools, you will see how to use OpenVas, Nikto, Vega, and Burp Suite. The book will explain the information assurance model and the hacking framework Metasploit, taking you through important commands, exploit and payload basics. Moving on to hashes and passwords you will learn password testing and hacking techniques with John the Ripper and Rainbow. You will then dive into classic and modern encryption techniques where you will learn the conventional cryptosystem. In the final chapter you will acquire the skill of exploiting remote Windows and Linux systems and you will learn how to own a target completely. What You Will Learn Master common Linux commands and networking techniques Build your own Kali web server and learn to be anonymous Carry out penetration testing using Python Detect sniffing attacks and SQL injection vulnerabilities Learn tools such as SniffJoke, Wireshark, Scapy, sqlmap, OpenVas, Nikto, and Burp Suite Use Metasploit with Kali Linux Exploit remote Windows and Linux systems Who This Book Is For Developers new to ethical hacking with a basic understanding of Linux programming. COMPUTERS,Security,General

Cyber Security Cyber security is more essential today than ever, not just in the workplace but at home too. This book covers the various types of cyber threat and explains what you can do to mitigate these risks and keep your data secure. COMPUTERS,Security,General

Securing the Perimeter Leverage existing free open source software to build an identity and access management (IAM) platform that can serve your organization for the long term. With the emergence of open standards and open source software, it’s now easier than ever to build and operate your own IAM stack. The most common culprit of the largest hacks has been bad personal identification. In terms of bang for your buck, effective access control is the best investment you can make. Financially, it’s more valuable to prevent than to detect a security breach. That’s why Identity and Access Management (IAM) is a critical component of an organization’s security infrastructure. In the past, IAM software has been available only from large enterprise software vendors. Commercial IAM offerings are bundled as “suites†because IAM is not just one component. It’s a number of components working together, including web, authentication, authorization, cryptographic, and persistence services. Securing the Perimeter documents a recipe to take advantage of open standards to build an enterprise-class IAM service using free open source software. This recipe can be adapted to meet the needs of both small and large organizations. While not a comprehensive guide for every application, this book provides the key concepts and patterns to help administrators and developers leverage a central security infrastructure. Cloud IAM service providers would have you believe that managing an IAM is too hard. Anything unfamiliar is hard, but with the right road map, it can be mastered. You may find SaaS identity solutions too rigid or too expensive. Or perhaps you don’t like the idea of a third party holding the credentials of your users—the keys to your kingdom. Open source IAM provides an alternative. Take control of your IAM infrastructure if digital services are key to your organization’s success. What You’ll Learn Understand why you should deploy a centralized authentication and policy management infrastructure Use the SAML or Open ID Standards for web or single sign-on, and OAuth for API Access Management Synchronize data from existing identity repositories such as Active Directory Deploy two-factor authentication services Who This Book Is For Security architects (CISO, CSO), system engineers/administrators, and software developers COMPUTERS,Security,General

Financial Cybersecurity Risk Management Understand critical cybersecurity and risk perspectives, insights, and tools for the leaders of complex financial systems and markets. This book offers guidance for decision makers and helps establish a framework for communication between cyber leaders and front-line professionals. Information is provided to help in the analysis of cyber challenges and choosing between risk treatment options. Financial cybersecurity is a complex, systemic risk challenge that includes technological and operational elements. The interconnectedness of financial systems and markets creates dynamic, high-risk environments where organizational security is greatly impacted by the level of security effectiveness of partners, counterparties, and other external organizations. The result is a high-risk environment with a growing need for cooperation between enterprises that are otherwise direct competitors. There is a new normal of continuous attack pressures that produce unprecedented enterprise threats that must be met with an array of countermeasures. Financial Cybersecurity Risk Management explores a range of cybersecurity topics impacting financial enterprises. This includes the threat and vulnerability landscape confronting the financial sector, risk assessment practices and methodologies, and cybersecurity data analytics. Governance perspectives, including executive and board considerations, are analyzed as are the appropriate control measures and executive risk reporting. What You’ll Learn Analyze the threat and vulnerability landscape confronting the financial sector Implement effective technology risk assessment practices and methodologies Craft strategies to treat observed risks in financial systems Improve the effectiveness of enterprise cybersecurity capabilities Evaluate critical aspects of cybersecurity governance, including executive and board oversight Identify significant cybersecurity operational challenges Consider the impact of the cybersecurity mission across the enterprise Leverage cybersecurity regulatory and industry standards to help manage financial services risks Use cybersecurity scenarios to measure systemic risks in financial systems environments Apply key experiences from actual cybersecurity events to develop more robust cybersecurity architectures Who This Book Is For Decision makers, cyber leaders, and front-line professionals, including: chief risk officers, operational risk officers, chief information security officers, chief security officers, chief information officers, enterprise risk managers, cybersecurity operations directors, technology and cybersecurity risk analysts, cybersecurity architects and engineers, and compliance officers COMPUTERS,Security,General

Mastering Kali Linux for Advanced Penetration Testing A practical guide to testing your infrastructure security with Kali Linux, the preferred choice of pentesters and hackers Key Features Employ advanced pentesting techniques with Kali Linux to build highly secured systems Discover various stealth techniques to remain undetected and defeat modern infrastructures Explore red teaming techniques to exploit secured environment Book Description This book takes you, as a tester or security practitioner, through the reconnaissance, vulnerability assessment, exploitation, privilege escalation, and post-exploitation activities used by pentesters. To start with, you'll use a laboratory environment to validate tools and techniques, along with an application that supports a collaborative approach for pentesting. You'll then progress to passive reconnaissance with open source intelligence and active reconnaissance of the external and internal infrastructure. You'll also focus on how to select, use, customize, and interpret the results from different vulnerability scanners, followed by examining specific routes to the target, which include bypassing physical security and the exfiltration of data using a variety of techniques. You'll discover concepts such as social engineering, attacking wireless networks, web services, and embedded devices. Once you are confident with these topics, you'll learn the practical aspects of attacking user client systems by backdooring with fileless techniques, followed by focusing on the most vulnerable part of the network – directly attacking the end user. By the end of this book, you'll have explored approaches for carrying out advanced pentesting in tightly secured environments, understood pentesting and hacking techniques employed on embedded peripheral devices. What you will learn Configure the most effective Kali Linux tools to test infrastructure security Employ stealth to avoid detection in the infrastructure being tested Recognize when stealth attacks are being used against your infrastructure Exploit networks and data systems using wired and wireless networks as well as web services Identify and download valuable data from target systems Maintain access to compromised systems Use social engineering to compromise the weakest part of the network - the end users Who this book is for This third edition of Mastering Kali Linux for Advanced Penetration Testing is for you if you are a security analyst, pentester, ethical hacker, IT professional, or security consultant wanting to maximize the success of your infrastructure testing using some of the advanced features of Kali Linux. Prior exposure of penetration testing and ethical hacking basics will be helpful in making the most out of this book. COMPUTERS,Security,General

Hands-On Penetration Testing with Python Implement defensive techniques in your ecosystem successfully with Python Key Features Identify and expose vulnerabilities in your infrastructure with Python Learn custom exploit development . Make robust and powerful cybersecurity tools with Python Book Description With the current technological and infrastructural shift, penetration testing is no longer a process-oriented activity. Modern-day penetration testing demands lots of automation and innovation; the only language that dominates all its peers is Python. Given the huge number of tools written in Python, and its popularity in the penetration testing space, this language has always been the first choice for penetration testers. Hands-On Penetration Testing with Python walks you through advanced Python programming constructs. Once you are familiar with the core concepts, you'll explore the advanced uses of Python in the domain of penetration testing and optimization. You'll then move on to understanding how Python, data science, and the cybersecurity ecosystem communicate with one another. In the concluding chapters, you'll study exploit development, reverse engineering, and cybersecurity use cases that can be automated with Python. By the end of this book, you'll have acquired adequate skills to leverage Python as a helpful tool to pentest and secure infrastructure, while also creating your own custom exploits. What you will learn Get to grips with Custom vulnerability scanner development Familiarize yourself with web application scanning automation and exploit development Walk through day-to-day cybersecurity scenarios that can be automated with Python Discover enterprise-or organization-specific use cases and threat-hunting automation Understand reverse engineering, fuzzing, buffer overflows , key-logger development, and exploit development for buffer overflows. Understand web scraping in Python and use it for processing web responses Explore Security Operations Centre (SOC) use cases Get to understand Data Science, Python, and cybersecurity all under one hood Who this book is for If you are a security consultant , developer or a cyber security enthusiast with little or no knowledge of Python and want in-depth insight into how the pen-testing ecosystem and python combine to create offensive tools , exploits , automate cyber security use-cases and much more then this book is for you. Hands-On Penetration Testing with Python guides you through the advanced uses of Python for cybersecurity and pen-testing, helping you to better understand security loopholes within your infrastructure . COMPUTERS,Security,General

Practical Cloud Security With their rapidly changing architecture and API-driven automation, cloud platforms come with unique security challenges and opportunities. This hands-on book guides you through security best practices for multivendor cloud environments, whether your company plans to move legacy on-premises projects to the cloud or build a new infrastructure from the ground up. Developers, IT architects, and security professionals will learn cloud-specific techniques for securing popular cloud platforms such as Amazon Web Services, Microsoft Azure, and IBM Cloud. Chris Dotson—an IBM senior technical staff member—shows you how to establish data asset management, identity and access management, vulnerability management, network security, and incident response in your cloud environment. COMPUTERS,Security,General

Practical Security Most security professionals don't have the words "security" or "hacker" in their job title. Instead, as a developer or admin you often have to fit in security alongside your official responsibilities - building and maintaining computer systems. Implement the basics of good security now, and you'll have a solid foundation if you bring in a dedicated security staff later. Identify the weaknesses in your system, and defend against the attacks most likely to compromise your organization, without needing to become a trained security professional. Computer security is a complex issue. But you don't have to be an expert in all the esoteric details to prevent many common attacks. Attackers are opportunistic and won't use a complex attack when a simple one will do. You can get a lot of benefit without too much complexity, by putting systems and processes in place that ensure you aren't making the obvious mistakes. Secure your systems better, with simple (though not always easy) practices. Plan to patch often to improve your security posture. Identify the most common software vulnerabilities, so you can avoid them when writing software. Discover cryptography - how it works, how easy it is to get wrong, and how to get it right. Configure your Windows computers securely. Defend your organization against phishing attacks with training and technical defenses. Make simple changes to harden your system against attackers. What You Need: You don't need any particular software to follow along with this book. Examples in the book describe security vulnerabilities and how to look for them. These examples will be more interesting if you have access to a code base you've worked on. Similarly, some examples describe network vulnerabilities and how to detect them. These will be more interesting with access to a network you support. COMPUTERS,Security,General

Nature-Inspired Cyber Security and Resiliency This is a timely review of the fundamentals, the latest developments and the diverse applications of nature-inspired algorithms in cyber security and resiliency. Based on concepts from natural processes, phenomena and organisms, it presents novel methodologies to cope with cyber security challenges. COMPUTERS,Security,General

CompTIA PenTest+ Practice Tests The must-have test prep for the new CompTIA PenTest+ certification CompTIA PenTest+ is an intermediate-level cybersecurity certification that assesses second-generation penetration testing, vulnerability assessment, and vulnerability-management skills. These cognitive and hands-on skills are required worldwide to responsibly perform assessments of IT systems, identify weaknesses, manage the vulnerabilities, and determine if existing cybersecurity practices deviate from accepted practices, configurations and policies. Five unique 160-question practice tests Tests cover the five CompTIA PenTest+ objective domains Two additional 100-question practice exams A total of 1000 practice test questions This book helps you gain the confidence you need for taking the CompTIA PenTest+ Exam PT0-001. The practice test questions prepare you for test success. COMPUTERS,Security,General

Web Security for Developers Website security made easy. This book covers the most common ways websites get hacked and how web developers can defend themselves. The world has changed. Today, every time you make a site live, you're opening it up to attack. A first-time developer can easily be discouraged by the difficulties involved with properly securing a website. But have hope: an army of security researchers is out there discovering, documenting, and fixing security flaws. Thankfully, the tools you'll need to secure your site are freely available and generally easy to use. Web Security for Developers will teach you how your websites are vulnerable to attack and how to protect them. Each chapter breaks down a major security vulnerability and explores a real-world attack, coupled with plenty of code to show you both the vulnerability and the fix. You'll learn how to: • Protect against SQL injection attacks, malicious JavaScript, and cross-site request forgery • Add authentication and shape access control to protect accounts • Lock down user accounts to prevent attacks that rely on guessing passwords, stealing sessions, • or escalating privileges • Implement encryption • Manage vulnerabilities in legacy code • Prevent information leaks that disclose vulnerabilities • Mitigate advanced attacks like malvertising and denial-of-service As you get stronger at identifying and fixing vulnerabilities, you'll learn to deploy disciplined, secure code and become a better programmer along the way. COMPUTERS,Security,General

Practical Cyber Forensics Become an effective cyber forensics investigator and gain a collection of practical, efficient techniques to get the job done. Diving straight into a discussion of anti-forensic techniques, this book shows you the many ways to effectively detect them. Now that you know what you are looking for, you’ll shift your focus to network forensics, where you cover the various tools available to make your network forensics process less complicated. Following this, you will work with cloud and mobile forensic techniques by considering the concept of forensics as a service (FaSS), giving you cutting-edge skills that will future-proof your career. Building on this, you will learn the process of breaking down malware attacks, web attacks, and email scams with case studies to give you a clearer view of the techniques to be followed. Another tricky technique is SSD forensics, so the author covers this in detail to give you the alternative analysis techniques you’ll need. To keep you up to speed on contemporary forensics, Practical Cyber Forensics includes a chapter on Bitcoin forensics, where key crypto-currency forensic techniques will be shared. Finally, you will see how to prepare accurate investigative reports. What You Will Learn Carry out forensic investigation on Windows, Linux, and macOS systems Detect and counter anti-forensic techniques Deploy network, cloud, and mobile forensics Investigate web and malware attacks Write efficient investigative reports Who This Book Is For Intermediate infosec professionals looking for a practical approach to investigative cyber forensics techniques. COMPUTERS,Security,General

Practical Vulnerability Management Practical Vulnerability Management shows you how to weed out system security weaknesses and squash cyber threats in their tracks. Bugs: they're everywhere. Software, firmware, hardware -- they all have them. Bugs even live in the cloud. And when one of these bugs is leveraged to wreak havoc or steal sensitive information, a company's prized technology assets suddenly become serious liabilities. Fortunately, exploitable security weaknesses are entirely preventable; you just have to find them before the bad guys do. Practical Vulnerability Management will help you achieve this goal on a budget, with a proactive process for detecting bugs and squashing the threat they pose. The book starts by introducing the practice of vulnerability management, its tools and components, and detailing the ways it improves an enterprise's overall security posture. Then it's time to get your hands dirty! As the content shifts from conceptual to practical, you're guided through creating a vulnerability-management system from the ground up, using open-source software. Along the way, you'll learn how to: • Generate accurate and usable vulnerability intelligence • Scan your networked systems to identify and assess bugs and vulnerabilities • Prioritize and respond to various security risks • Automate scans, data analysis, reporting, and other repetitive tasks • Customize the provided scripts to adapt them to your own needs Playing whack-a-bug won't cut it against today's advanced adversaries. Use this book to set up, maintain, and enhance an effective vulnerability management system, and ensure your organization is always a step ahead of hacks and attacks. COMPUTERS,Security,General

Learn Social Engineering Improve information security by learning Social Engineering. About This Book Learn to implement information security using social engineering Get hands-on experience of using different tools such as Kali Linux, the Social Engineering toolkit and so on Practical approach towards learning social engineering, for IT security Who This Book Is For This book targets security professionals, security analysts, penetration testers, or any stakeholder working with information security who wants to learn how to use social engineering techniques. Prior knowledge of Kali Linux is an added advantage What You Will Learn Learn to implement information security using social engineering Learn social engineering for IT security Understand the role of social media in social engineering Get acquainted with Practical Human hacking skills Learn to think like a social engineer Learn to beat a social engineer In Detail This book will provide you with a holistic understanding of social engineering. It will help you to avoid and combat social engineering attacks by giving you a detailed insight into how a social engineer operates. Learn Social Engineering starts by giving you a grounding in the different types of social engineering attacks,and the damages they cause. It then sets up the lab environment to use different toolS and then perform social engineering steps such as information gathering. The book covers topics from baiting, phishing, and spear phishing, to pretexting and scareware. By the end of the book, you will be in a position to protect yourself and your systems from social engineering threats and attacks. All in all, the book covers social engineering from A to Z , along with excerpts from many world wide known security experts. Style and approach A step-by-step practical guide that will get you well acquainted with Social Engineering. You'll be able to get started with it in a matter of minutes with the help of different tools such as the Social Engineering toolkit , Kali Linux and so on. COMPUTERS,Security,General

Cybersecurity For Dummies Protect your business and family against cyber attacks Cybersecurity is the protection against the unauthorized or criminal use of electronic data and the practice of ensuring the integrity, confidentiality, and availability of information. Being "cyber-secure" means that a person or organization has both protected itself against attacks by cyber criminals and other online scoundrels, and ensured that it has the ability to recover if it is attacked. If keeping your business or your family safe from cybersecurity threats is on your to-do list, Cybersecurity For Dummies will introduce you to the basics of becoming cyber-secure! You’ll learn what threats exist, and how to identify, protect against, detect, and respond to these threats, as well as how to recover if you have been breached! The who and why of cybersecurity threats Basic cybersecurity concepts What to do to be cyber-secure Cybersecurity careers What to think about to stay cybersecure in the future Now is the time to identify vulnerabilities that may make you a victim of cyber-crime — and to defend yourself before it is too late. COMPUTERS,Security,General

Cybersecurity Law The second edition of the definitive guide to cybersecurity law, updated to reflect recent legal developments The revised and updated second edition of Cybersecurity Law offers an authoritative guide to the key statutes, regulations, and court rulings that pertain to cybersecurity. Written by an experienced cybersecurity lawyer and law professor, the second edition includes new and expanded information that reflects the latest changes in laws and regulations. The book includes material on recent FTC data security consent decrees and data breach litigation. Topics covered reflect new laws, regulations, and court decisions that address financial sector cybersecurity, the law of war as applied to cyberspace, and recently updated guidance for public companies’ disclosure of cybersecurity risks. This important guide: Provides a new appendix, with 15 edited opinions covering a wide range of cybersecurity-related topics, for students learning via the caselaw method Includes new sections that cover topics such as: compelled access to encrypted devices, New York’s financial services cybersecurity regulations, South Carolina’s insurance sector cybersecurity law, the Internet of Things, bug bounty programs, the vulnerability equities process, international enforcement of computer hacking laws, the California Consumer Privacy Act, and the European Union’s Network and Information Security Directive Contains a new chapter on the critical topic of law of cyberwar Presents a comprehensive guide written by a noted expert on the topic Offers a companion Instructor-only website that features discussion questions for each chapter and suggested exam questions for each chapter Written for students and professionals of cybersecurity, cyber operations, management-oriented information technology (IT), and computer science, Cybersecurity Law, Second Edition is the up-to-date guide that covers the basic principles and the most recent information on cybersecurity laws and regulations. JEFF KOSSEFF is Assistant Professor of Cybersecurity Law at the United States Naval Academy in Annapolis, Maryland. He was a finalist for the Pulitzer Prize, and a recipient of the George Polk Award for national reporting. COMPUTERS,Security,General

Building Blockchain Apps A Developer's Guide to Blockchain Programming Fundamentals Blockchain development is entering a period of explosive growth, as real applications gain traction throughout multiple industries and cryptocurrencies earn greater acceptance throughout the financial sector. Blockchain represents one of the most promising opportunities for developers to advance and succeed. Building Blockchain Apps is an accessible guide to today’s most advanced and robust blockchain programming models and architectures. Building on his pioneering experience, Michael Juntao Yuan covers a wide range of blockchain application development paradigms. The book starts with a concise introduction to blockchain and smart contract technologies. It then guides you through application development on Ethereum-compatible smart contract platforms. Ethereum is the largest and most robust blockchain ecosystem in the world. Coverage includes Ethereum topics such as tools, application frameworks, internal data structures, external data interfaces, and future roadmap An introduction to new blockchain data protocol based on ElasticSearch, which provides insights into the current state of smart contracts and enables new application designs How to build an application-specific smart contract protocol by modifying and customizing the open source Ethereum Virtual Machine and its programming language tools How to extend and support language features that are most suitable for particular kinds of smart contracts (e.g., smart contracts for e-commerce marketplaces) with the open source Lity project How to customize and change the blockchain consensus layer beneath the application layer via the popular Tendermint and Cosmos SDK frameworks A survey of cryptocurrency and financial topics from the developers’ point of view, providing an analytical framework for valuating cryptocurrencies and explaining the roles of crypto exchanges Register your book for convenient access to downloads, updates, and/or corrections as they become available. See inside book for details. COMPUTERS,Security,General

Microsoft 365 Mobility and Security – Exam Guide MS-101 Get up to speed with planning, deploying, and managing Microsoft Office 365 services and gain the skills you need to pass the MS-101 exam Key Features Explore everything from mobile device management and compliance,through to data governance and auditing Get to grips with using Azure advanced threat protection and Azure information protection Learn effectively through exam-focused practice exercises and mock tests Book Description Exam MS-101: Microsoft 365 Mobility and Security is a part of the Microsoft 365 Certified: Enterprise Administrator Expert certification path designed to help users validate their skills in evaluating, planning, migrating, deploying, and managing Microsoft 365 services. This book will help you implement modern device services, apply Microsoft 365 security and threat management, and manage Microsoft 365 governance and compliance. Written in a succinct way, you'll explore chapter-wise self-assessment questions, exam tips, and mock exams with answers. You'll start by implementing mobile device management (MDM) and handling device compliance. You'll delve into threat detection and management, learning how to manage security reports and configure Microsoft 365 alerts. Later, you'll discover data loss prevention (DLP) tools to protect data as well as tools for configuring audit logs and policies. The book will also guide you through using Azure Information Protection (AIP) for deploying clients, applying policies, and configuring services and users to enhance data security. Finally, you'll cover best practices for configuring settings across your tenant to ensure compliance and security. By the end of this book, you'll have learned to work with Microsoft 365 services and covered the concepts and techniques you need to know to pass the MS-101 exam. What you will learn Implement modern device services Discover tools for configuring audit logs and policies Plan, deploy, and manage Microsoft 365 services such as MDM and DLP Get up to speed with configuring eDiscovery settings and features to enhance your organization's ability to mitigate and respond to issues Implement Microsoft 365 security and threat management Explore best practices for effectively configuring settings Who this book is for This book is for IT professionals looking to pass the Microsoft 365 Mobility and Security certification exam. System administrators and network engineers interested in mobility, security, compliance, and supporting technologies will also benefit from this book. Some experience with Microsoft 365, Exchange servers, and PowerShell is necessary. COMPUTERS,Security,General

(ISC)2 CCSP Certified Cloud Security Professional Official Study Guide The only official study guide for the new CCSP exam (ISC)2 CCSP Certified Cloud Security Professional Official Study Guide is your ultimate resource for the CCSP exam. As the only official study guide reviewed and endorsed by (ISC)2, this guide helps you prepare faster and smarter with the Sybex study tools that include pre-test assessments that show you what you know, and areas you need further review. Objective maps, exercises, and chapter review questions help you gauge your progress along the way, and the Sybex interactive online learning environment includes access to a PDF glossary, hundreds of flashcards, and two complete practice exams. Covering all CCSP domains, this book walks you through Architectural Concepts and Design Requirements, Cloud Data Security, Cloud Platform and Infrastructure Security, Cloud Application Security, Operations, and Legal and Compliance with real-world scenarios to help you apply your skills along the way. The CCSP is the latest credential from (ISC)2 and the Cloud Security Alliance, designed to show employers that you have what it takes to keep their organization safe in the cloud. Learn the skills you need to be confident on exam day and beyond. Review 100% of all CCSP exam objectives Practice applying essential concepts and skills Access the industry-leading online study tool set Test your knowledge with bonus practice exams and more As organizations become increasingly reliant on cloud-based IT, the threat to data security looms larger. Employers are seeking qualified professionals with a proven cloud security skillset, and the CCSP credential brings your resume to the top of the pile. (ISC)2 CCSP Certified Cloud Security Professional Official Study Guide gives you the tools and information you need to earn that certification, and apply your skills in a real-world setting. COMPUTERS,Security,General

Cybersecurity – Attack and Defense Strategies Updated and revised edition of the bestselling guide to developing defense strategies against the latest threats to cybersecurity Key Features Covers the latest security threats and defense strategies for 2020 Introduces techniques and skillsets required to conduct threat hunting and deal with a system breach Provides new information on Cloud Security Posture Management, Microsoft Azure Threat Protection, Zero Trust Network strategies, Nation State attacks, the use of Azure Sentinel as a cloud-based SIEM for logging and investigation, and much more Book Description Cybersecurity – Attack and Defense Strategies, Second Edition is a completely revised new edition of the bestselling book, covering the very latest security threats and defense mechanisms including a detailed overview of Cloud Security Posture Management (CSPM) and an assessment of the current threat landscape, with additional focus on new IoT threats and cryptomining. Cybersecurity starts with the basics that organizations need to know to maintain a secure posture against outside threat and design a robust cybersecurity program. It takes you into the mindset of a Threat Actor to help you better understand the motivation and the steps of performing an actual attack – the Cybersecurity kill chain. You will gain hands-on experience in implementing cybersecurity using new techniques in reconnaissance and chasing a user's identity that will enable you to discover how a system is compromised, and identify and then exploit the vulnerabilities in your own system. This book also focuses on defense strategies to enhance the security of a system. You will also discover in-depth tools, including Azure Sentinel, to ensure there are security controls in each network layer, and how to carry out the recovery process of a compromised system. What you will learn The importance of having a solid foundation for your security posture Use cyber security kill chain to understand the attack strategy Boost your organization's cyber resilience by improving your security policies, hardening your network, implementing active sensors, and leveraging threat intelligence Utilize the latest defense tools, including Azure Sentinel and Zero Trust Network strategy Identify different types of cyberattacks, such as SQL injection, malware and social engineering threats such as phishing emails Perform an incident investigation using Azure Security Center and Azure Sentinel Get an in-depth understanding of the disaster recovery process Understand how to consistently monitor security and implement a vulnerability management strategy for on-premises and hybrid cloud Learn how to perform log analysis using the cloud to identify suspicious activities, including logs from Amazon Web Services and Azure Who this book is for For the IT professional venturing into the IT security domain, IT pentesters, security consultants, or those looking to perform ethical hacking. Prior knowledge of penetration testing is beneficial. COMPUTERS,Security,General

Advanced API Security Prepare for the next wave of challenges in enterprise security. Learn to better protect, monitor, and manage your public and private APIs. Enterprise APIs have become the common way of exposing business functions to the outside world. Exposing functionality is convenient, but of course comes with a risk of exploitation. This book teaches you about TLS Token Binding, User Managed Access (UMA) 2.0, Cross Origin Resource Sharing (CORS), Incremental Authorization, Proof Key for Code Exchange (PKCE), and Token Exchange. Benefit from lessons learned from analyzing multiple attacks that have taken place by exploiting security vulnerabilities in various OAuth 2.0 implementations. Explore root causes, and improve your security practices to mitigate against similar future exploits. Security must be an integral part of any development project. This book shares best practices in designing APIs for rock-solid security. API security has evolved since the first edition of this book, and the growth of standards has been exponential. OAuth 2.0 is the most widely adopted framework that is used as the foundation for standards, and this book shows you how to apply OAuth 2.0 to your own situation in order to secure and protect your enterprise APIs from exploitation and attack. What You Will Learn Securely design, develop, and deploy enterprise APIs Pick security standards and protocols to match business needs Mitigate security exploits by understanding the OAuth 2.0 threat landscape Federate identities to expand business APIs beyond the corporate firewall Protect microservices at the edge by securing their APIs Develop native mobile applications to access APIs securely Integrate applications with SaaS APIs protected with OAuth 2.0 Who This Book Is For Enterprise security architects who are interested in best practices around designing APIs. The book is also for developers who are building enterprise APIs and integrating with internal and external applications. COMPUTERS,Security,General

Solving Identity Management in Modern Applications Know how to design and use identity management to protect your application and the data it manages. At a time when security breaches result in increasingly onerous penalties, it is paramount that application developers and owners understand identity management and the value it provides when building applications. This book takes you from account provisioning to authentication to authorization, and covers troubleshooting and common problems to avoid. The authors include predictions about why this will be even more important in the future. Application best practices with coding samples are provided. Solving Identity and Access Management in Modern Applications gives you what you need to design identity and access management for your applications and to describe it to stakeholders with confidence. You will be able to explain account creation, session and access management, account termination, and more. What You’ll Learn Understand key identity management concepts Incorporate essential design principles Design authentication and access control for a modern application Know the identity management frameworks and protocols used today (OIDC/ OAuth 2.0, SAML 2.0) Review historical failures and know how to avoid them Who This Book Is For Developers, enterprise or application architects, business application or product owners, and anyone involved in an application's identity management solution COMPUTERS,Security,General

Big Data Analytics and Computing for Digital Forensic Investigations Digital forensics has recently gained a notable development and become the most demanding area in today’s information security requirement. This book investigates the areas of digital forensics, digital investigation and data analysis procedures as they apply to computer fraud and cybercrime, with the main objective of describing a variety of digital crimes and retrieving potential digital evidence. Big Data Analytics and Computing for Digital Forensic Investigations gives a contemporary view on the problems of information security. It presents the idea that protective mechanisms and software must be integrated along with forensic capabilities into existing forensic software using big data computing tools and techniques. Features Describes trends of digital forensics served for big data and the challenges of evidence acquisition Enables digital forensic investigators and law enforcement agencies to enhance their digital investigation capabilities with the application of data science analytics, algorithms and fusion technique This book is focused on helping professionals as well as researchers to get ready with next-generation security systems to mount the rising challenges of computer fraud and cybercrimes as well as with digital forensic investigations. Dr Suneeta Satpathy has more than ten years of teaching experience in different subjects of the Computer Science and Engineering discipline. She is currently working as an associate professor in the Department of Computer Science and Engineering, College of Bhubaneswar, affiliated with Biju Patnaik University and Technology, Odisha. Her research interests include computer forensics, cybersecurity, data fusion, data mining, big data analysis and decision mining. Dr Sachi Nandan Mohanty is an associate professor in the Department of Computer Science and Engineering at ICFAI Tech, ICFAI Foundation for Higher Education, Hyderabad, India. His research interests include data mining, big data analysis, cognitive science, fuzzy decision-making, brain–computer interface, cognition and computational intelligence. COMPUTERS,Security,General

The Cybersecurity Body of Knowledge The Cybersecurity Body of Knowledge explains the content, purpose, and use of eight knowledge areas that define the boundaries of the discipline of cybersecurity. The discussion focuses on, and is driven by, the essential concepts of each knowledge area that collectively capture the cybersecurity body of knowledge to provide a complete picture of the field. This book is based on a brand-new and up to this point unique, global initiative, known as CSEC2017, which was created and endorsed by ACM, IEEE-CS, AIS SIGSEC, and IFIP WG 11.8. This has practical relevance to every educator in the discipline of cybersecurity. Because the specifics of this body of knowledge cannot be imparted in a single text, the authors provide the necessary comprehensive overview. In essence, this is the entry-level survey of the comprehensive field of cybersecurity. It will serve as the roadmap for individuals to later drill down into a specific area of interest. This presentation is also explicitly designed to aid faculty members, administrators, CISOs, policy makers, and stakeholders involved with cybersecurity workforce development initiatives. The book is oriented toward practical application of a computing-based foundation, crosscutting concepts, and essential knowledge and skills of the cybersecurity discipline to meet workforce demands. Dan Shoemaker, PhD, is full professor, senior research scientist, and program director at the University of Detroit Mercy’s Center for Cyber Security and Intelligence Studies. Dan is a former chair of the Cybersecurity & Information Systems Department and has authored numerous books and journal articles focused on cybersecurity. Anne Kohnke, PhD, is an associate professor of cybersecurity and the principle investigator of the Center for Academic Excellence in Cyber Defence at the University of Detroit Mercy. Anne’s research is focused in cybersecurity, risk management, threat modeling, and mitigating attack vectors. Ken Sigler, MS, is a faculty member of the Computer Information Systems (CIS) program at the Auburn Hills campus of Oakland Community College in Michigan. Ken’s research is in the areas of software management, software assurance, and cybersecurity. COMPUTERS,Security,General

PCI DSS Gain a broad understanding of how PCI DSS is structured and obtain a high-level view of the contents and context of each of the 12 top-level requirements. The guidance provided in this book will help you effectively apply PCI DSS in your business environments, enhance your payment card defensive posture, and reduce the opportunities for criminals to compromise your network or steal sensitive data assets. Businesses are seeing an increased volume of data breaches, where an opportunist attacker from outside the business or a disaffected employee successfully exploits poor company practices. Rather than being a regurgitation of the PCI DSS controls, this book aims to help you balance the needs of running your business with the value of implementing PCI DSS for the protection of consumer payment card data. Applying lessons learned from history, military experiences (including multiple deployments into hostile areas), numerous PCI QSA assignments, and corporate cybersecurity and InfoSec roles, author Jim Seaman helps you understand the complexities of the payment card industry data security standard as you protect cardholder data. You will learn how to align the standard with your business IT systems or operations that store, process, and/or transmit sensitive data. This book will help you develop a business cybersecurity and InfoSec strategy through the correct interpretation, implementation, and maintenance of PCI DSS. What You Will Learn Be aware of recent data privacy regulatory changes and the release of PCI DSS v4.0 Improve the defense of consumer payment card data to safeguard the reputation of your business and make it more difficult for criminals to breach security Be familiar with the goals and requirements related to the structure and interdependencies of PCI DSS Know the potential avenues of attack associated with business payment operations Make PCI DSS an integral component of your business operations Understand the benefits of enhancing your security culture See how the implementation of PCI DSS causes a positive ripple effect across your business Who This Book Is For Business leaders, information security (InfoSec) practitioners, chief information security managers, cybersecurity practitioners, risk managers, IT operations managers, business owners, military enthusiasts, and IT auditors COMPUTERS,Security,General

Advances in Cryptology – EUROCRYPT 2020 The three volume-set LNCS 12105, 12106, and 12107 constitute the thoroughly refereed proceedings of the 39th Annual International Conference on the Theory and Applications of Cryptographic Techniques, EUROCRYPT 2020, which was due to be held in Zagreb, Croatia, in May 2020. The conference was held virtually due to the COVID-19 pandemic. The 81 full papers presented were carefully reviewed and selected from 375 submissions. The papers are organized into the following topical sections: invited talk; best paper awards; obfuscation and functional encryption; symmetric cryptanalysis; randomness extraction; symmetric cryptography I; secret sharing; fault-attack security; succinct proofs; generic models; secure computation I; quantum I; foundations; isogeny-based cryptography; lattice-based cryptography; symmetric cryptography II; secure computation II; asymmetric cryptanalysis; verifiable delay functions; signatures; attribute-based encryption; side-channel security; non-interactive zero-knowledge; public-key encryption; zero-knowledge; quantum II. COMPUTERS,Security,General

Advances in Cryptology – EUROCRYPT 2020 The three volume-set LNCS 12105, 12106, and 12107 constitute the thoroughly refereed proceedings of the 39th Annual International Conference on the Theory and Applications of Cryptographic Techniques, EUROCRYPT 2020, which was due to be held in Zagreb, Croatia, in May 2020. The conference was held virtually due to the COVID-19 pandemic. The 81 full papers presented were carefully reviewed and selected from 375 submissions. The papers are organized into the following topical sections: invited talk; best paper awards; obfuscation and functional encryption; symmetric cryptanalysis; randomness extraction; symmetric cryptography I; secret sharing; fault-attack security; succinct proofs; generic models; secure computation I; quantum I; foundations; isogeny-based cryptography; lattice-based cryptography; symmetric cryptography II; secure computation II; asymmetric cryptanalysis; verifiable delay functions; signatures; attribute-based encryption; side-channel security; non-interactive zero-knowledge; public-key encryption; zero-knowledge; quantum II. COMPUTERS,Security,General

Advances in Cryptology – EUROCRYPT 2020 The three volume-set LNCS 12105, 12106, and 12107 constitute the thoroughly refereed proceedings of the 39th Annual International Conference on the Theory and Applications of Cryptographic Techniques, EUROCRYPT 2020, which was due to be held in Zagreb, Croatia, in May 2020. The conference was held virtually due to the COVID-19 pandemic. The 81 full papers presented were carefully reviewed and selected from 375 submissions. The papers are organized into the following topical sections: invited talk; best paper awards; obfuscation and functional encryption; symmetric cryptanalysis; randomness extraction; symmetric cryptography I; secret sharing; fault-attack security; succinct proofs; generic models; secure computation I; quantum I; foundations; isogeny-based cryptography; lattice-based cryptography; symmetric cryptography II; secure computation II; asymmetric cryptanalysis; verifiable delay functions; signatures; attribute-based encryption; side-channel security; non-interactive zero-knowledge; public-key encryption; zero-knowledge; quantum II. COMPUTERS,Security,General

Fundamentals of Digital Forensics This practical and accessible textbook/reference describes the theory and methodology of digital forensic examinations, presenting examples developed in collaboration with police authorities to ensure relevance to real-world practice. The coverage includes discussions on forensic artifacts and constraints, as well as forensic tools used for law enforcement and in the corporate sector. Emphasis is placed on reinforcing sound forensic thinking, and gaining experience in common tasks through hands-on exercises. This enhanced second edition has been expanded with new material on incident response tasks and computer memory analysis. Topics and features: Outlines what computer forensics is, and what it can do, as well as what its limitations are Discusses both the theoretical foundations and the fundamentals of forensic methodology Reviews broad principles that are applicable worldwide Explains how to find and interpret several important artifacts Describes free and open source software tools, along with the AccessData Forensic Toolkit Features exercises and review questions throughout, with solutions provided in the appendices Includes numerous practical examples, and provides supporting video lectures online This easy-to-follow primer is an essential resource for students of computer forensics, and will also serve as a valuable reference for practitioners seeking instruction on performing forensic examinations. Joakim Kävrestad is a lecturer and researcher at the University of Skövde, Sweden, and an AccessData Certified Examiner. He also serves as a forensic consultant, with several years of experience as a forensic expert with the Swedish police. COMPUTERS,Security,General

The Design of Rijndael Rijndael was the surprise winner of the contest for the new Advanced En cryption Standard (AES) for the United States. This contest was organized and run by the National Institute for Standards and Technology (NIST) be ginning in January 1997; Rijndael was announced as the winner in October 2000. It was the "surprise winner" because many observers (and even some participants) expressed scepticism that the D.S. government would adopt as an encryption standard any algorithm that was not designed by D.S. citizens. Yet NIST ran an open, international, selection process that should serve as model for other standards organizations. For example, NIST held their 1999 AES meeting in Rome, Italy. The five finalist algorithms were designed by teams from all over the world. In the end, the elegance, efficiency, security, and principled design of Rijndael won the day for its two Belgian designers, Joan Daemen and Vincent Rijmen, over the competing finalist designs from RSA, IBM, Counterpane Systems, and an EnglishjIsraelijDanish team. This book is the story of the design of Rijndael, as told by the designers themselves. It outlines the foundations of Rijndael in relation to the previous ciphers the authors have designed. It explains the mathematics needed to and the operation of Rijndael, and it provides reference C code and underst test vectors for the cipher. COMPUTERS,Security,General

Hands-On Web Penetration Testing with Metasploit Identify, exploit, and test web application security with ease Key Features Get up to speed with Metasploit and discover how to use it for pentesting Understand how to exploit and protect your web environment effectively Learn how an exploit works and what causes vulnerabilities Book Description Metasploit has been a crucial security tool for many years. However, there are only a few modules that Metasploit has made available to the public for pentesting web applications. In this book, you'll explore another aspect of the framework – web applications – which is not commonly used. You'll also discover how Metasploit, when used with its inbuilt GUI, simplifies web application penetration testing. The book starts by focusing on the Metasploit setup, along with covering the life cycle of the penetration testing process. Then, you will explore Metasploit terminology and the web GUI, which is available in the Metasploit Community Edition. Next, the book will take you through pentesting popular content management systems such as Drupal, WordPress, and Joomla, which will also include studying the latest CVEs and understanding the root cause of vulnerability in detail. Later, you'll gain insights into the vulnerability assessment and exploitation of technological platforms such as JBoss, Jenkins, and Tomcat. Finally, you'll learn how to fuzz web applications to find logical security vulnerabilities using third-party tools. By the end of this book, you'll have a solid understanding of how to exploit and validate vulnerabilities by working with various tools and techniques. What you will learn Get up to speed with setting up and installing the Metasploit framework Gain first-hand experience of the Metasploit web interface Use Metasploit for web-application reconnaissance Understand how to pentest various content management systems Pentest platforms such as JBoss, Tomcat, and Jenkins Become well-versed with fuzzing web applications Write and automate penetration testing reports Who this book is for This book is for web security analysts, bug bounty hunters, security professionals, or any stakeholder in the security sector who wants to delve into web application security testing. Professionals who are not experts with command line tools or Kali Linux and prefer Metasploit's graphical user interface (GUI) will also find this book useful. No experience with Metasploit is required, but basic knowledge of Linux and web application pentesting will be helpful. COMPUTERS,Security,General

Combating Security Challenges in the Age of Big Data This book addresses the key security challenges in the big data centric computing and network systems, and discusses how to tackle them using a mix of conventional and state-of-the-art techniques. The incentive for joining big data and advanced analytics is no longer in doubt for businesses and ordinary users alike. Technology giants like Google, Microsoft, Amazon, Facebook, Apple, and companies like Uber, Airbnb, NVIDIA, Expedia, and so forth are continuing to explore new ways to collect and analyze big data to provide their customers with interactive services and new experiences. With any discussion of big data, security is not, however, far behind. Large scale data breaches and privacy leaks at governmental and financial institutions, social platforms, power grids, and so forth, are on the rise that cost billions of dollars. The book explains how the security needs and implementations are inherently different at different stages of the big data centric system, namely at the point of big data sensing and collection, delivery over existing networks, and analytics at the data centers. Thus, the book sheds light on how conventional security provisioning techniques like authentication and encryption need to scale well with all the stages of the big data centric system to effectively combat security threats and vulnerabilities. The book also uncovers the state-of-the-art technologies like deep learning and blockchain which can dramatically change the security landscape in the big data era. COMPUTERS,Security,General

Cyber Threat Intelligence for the Internet of Things This book reviews IoT-centric vulnerabilities from a multidimensional perspective by elaborating on IoT attack vectors, their impacts on well-known security objectives, attacks which exploit such vulnerabilities, coupled with their corresponding remediation methodologies. This book further highlights the severity of the IoT problem at large, through disclosing incidents of Internet-scale IoT exploitations, while putting forward a preliminary prototype and associated results to aid in the IoT mitigation objective. Moreover, this book summarizes and discloses findings, inferences, and open challenges to inspire future research addressing theoretical and empirical aspects related to the imperative topic of IoT security. At least 20 billion devices will be connected to the Internet in the next few years. Many of these devices transmit critical and sensitive system and personal data in real-time. Collectively known as “the Internet of Things†(IoT), this market represents a $267 billion per year industry. As valuable as this market is, security spending on the sector barely breaks 1%. Indeed, while IoT vendors continue to push more IoT devices to market, the security of these devices has often fallen in priority, making them easier to exploit. This drastically threatens the privacy of the consumers and the safety of mission-critical systems. This book is intended for cybersecurity researchers and advanced-level students in computer science. Developers and operators working in this field, who are eager to comprehend the vulnerabilities of the Internet of Things (IoT) paradigm and understand the severity of accompanied security issues will also be interested in this book. COMPUTERS,Security,General

Cybersecurity Threats, Malware Trends, and Strategies After scrutinizing numerous cybersecurity strategies, Microsoft's former Global Chief Security Advisor provides unique insights on the evolution of the threat landscape and how enterprises can address modern cybersecurity challenges. Key Features Protect your organization from cybersecurity threats with field-tested strategies by the former most senior security advisor at Microsoft Discover the most common ways enterprises initially get compromised Measure the effectiveness of your organization's current cybersecurity program against cyber attacks Book Description Cybersecurity Threats, Malware Trends, and Strategies shares numerous insights about the threats that both public and private sector organizations face and the cybersecurity strategies that can mitigate them. The book provides an unprecedented long-term view of the global threat landscape by examining the twenty-year trend in vulnerability disclosures and exploitation, nearly a decade of regional differences in malware infections, the socio-economic factors that underpin them, and how global malware has evolved. This will give you further perspectives into malware protection for your organization. It also examines internet-based threats that CISOs should be aware of. The book will provide you with an evaluation of the various cybersecurity strategies that have ultimately failed over the past twenty years, along with one or two that have actually worked. It will help executives and security and compliance professionals understand how cloud computing is a game changer for them. By the end of this book, you will know how to measure the effectiveness of your organization's cybersecurity strategy and the efficacy of the vendors you employ to help you protect your organization and yourself. What you will learn Discover cybersecurity strategies and the ingredients critical to their success Improve vulnerability management by reducing risks and costs for your organization Learn how malware and other threats have evolved over the past decade Mitigate internet-based threats, phishing attacks, and malware distribution sites Weigh the pros and cons of popular cybersecurity strategies of the past two decades Implement and then measure the outcome of a cybersecurity strategy Learn how the cloud provides better security capabilities than on-premises IT environments Who this book is for This book is for senior management at commercial sector and public sector organizations, including Chief Information Security Officers (CISOs) and other senior managers of cybersecurity groups, Chief Information Officers (CIOs), Chief Technology Officers (CTOs) and senior IT managers who want to explore the entire spectrum of cybersecurity, from threat hunting and security risk management to malware analysis. Governance, risk, and compliance professionals will also benefit. Cybersecurity experts that pride themselves on their knowledge of the threat landscape will come to use this book as a reference. COMPUTERS,Security,General

Cyber Breach Response That Actually Works You will be breached—the only question is whether you'll be ready A cyber breach could cost your organization millions of dollars—in 2019, the average cost of a cyber breach for companies was $3.9M, a figure that is increasing 20-30% annually. But effective planning can lessen the impact and duration of an inevitable cyberattack. Cyber Breach Response That Actually Works provides a business-focused methodology that will allow you to address the aftermath of a cyber breach and reduce its impact to your enterprise. This book goes beyond step-by-step instructions for technical staff, focusing on big-picture planning and strategy that makes the most business impact. Inside, you’ll learn what drives cyber incident response and how to build effective incident response capabilities. Expert author Andrew Gorecki delivers a vendor-agnostic approach based on his experience with Fortune 500 organizations. Understand the evolving threat landscape and learn how to address tactical and strategic challenges to build a comprehensive and cohesive cyber breach response program Discover how incident response fits within your overall information security program, including a look at risk management Build a capable incident response team and create an actionable incident response plan to prepare for cyberattacks and minimize their impact to your organization Effectively investigate small and large-scale incidents and recover faster by leveraging proven industry practices Navigate legal issues impacting incident response, including laws and regulations, criminal cases and civil litigation, and types of evidence and their admissibility in court In addition to its valuable breadth of discussion on incident response from a business strategy perspective, Cyber Breach Response That Actually Works offers information on key technology considerations to aid you in building an effective capability and accelerating investigations to ensure your organization can continue business operations during significant cyber events. COMPUTERS,Security,General

Professional Security Management Historically, security managers have tended to be sourced from either the armed forces or law enforcement. But the increasing complexity of the organisations employing them, along with the technologies employed by them, is forcing an evolution and expansion of the role, and security managers must meet this challenge in order to succeed in their field and protect the assets of their employers. Risk management, crisis management, continuity management, strategic business operations, data security, IT, and business communications all fall under the purview of the security manager. This book is a guide to meeting those challenges, providing the security manager with the essential skill set and knowledge base to meet the challenges faced in contemporary, international, or tech-oriented businesses. It covers the basics of strategy, risk, and technology from the perspective of the security manager, focussing only on the 'need to know'. The reader will benefit from an understanding of how risk management aligns its functional aims with the strategic goals and operations of the organisation. This essential book supports professional vocational accreditation and qualifications, such as the Chartered Security Professional (CSyP) or Certified Protection Professional (CPP), and advises on pathways to higher education qualifications in the fields of security and risk management. It is ideal for any risk manager looking to further their training and development, as well as being complementary for risk and security management programs with a focus on practice. COMPUTERS,Security,General

Privileged Attack Vectors See how privileges, insecure passwords, administrative rights, and remote access can be combined as an attack vector to breach any organization. Cyber attacks continue to increase in volume and sophistication. It is not a matter of if, but when, your organization will be breached. Threat actors target the path of least resistance: users and their privileges. In decades past, an entire enterprise might be sufficiently managed through just a handful of credentials. Today’s environmental complexity has seen an explosion of privileged credentials for many different account types such as domain and local administrators, operating systems (Windows, Unix, Linux, macOS, etc.), directory services, databases, applications, cloud instances, networking hardware, Internet of Things (IoT), social media, and so many more. When unmanaged, these privileged credentials pose a significant threat from external hackers and insider threats. We are experiencing an expanding universe of privileged accounts almost everywhere. There is no one solution or strategy to provide the protection you need against all vectors and stages of an attack. And while some new and innovative products will help protect against or detect against a privilege attack, they are not guaranteed to stop 100% of malicious activity. The volume and frequency of privilege-based attacks continues to increase and test the limits of existing security controls and solution implementations. Privileged Attack Vectors details the risks associated with poor privilege management, the techniques that threat actors leverage, and the defensive measures that organizations should adopt to protect against an incident, protect against lateral movement, and improve the ability to detect malicious activity due to the inappropriate usage of privileged credentials. This revised and expanded second edition covers new attack vectors, has updated definitions for privileged access management (PAM), new strategies for defense, tested empirical steps for a successful implementation, and includes new disciplines for least privilege endpoint management and privileged remote access. What You Will Learn Know how identities, accounts, credentials, passwords, and exploits can be leveraged to escalate privileges during an attack Implement defensive and monitoring strategies to mitigate privilege threats and risk Understand a 10-step universal privilege management implementation plan to guide you through a successful privilege access management journey Develop a comprehensive model for documenting risk, compliance, and reporting based on privilege session activity Who This Book Is For Security management professionals, new security professionals, and auditors looking to understand and solve privilege access management problems COMPUTERS,Security,General

Data and Applications Security and Privacy XXXIV This book constitutes the refereed proceedings of the 34th Annual IFIP WG 11.3 Conference on Data and Applications Security and Privacy, DBSec 2020, held in Regensburg, Germany, in June 2020.* The 14 full papers and 8 short papers presented were carefully reviewed and selected from 39 submissions. The papers present high-quality original research from academia, industry, and government on theoretical and practical aspects of information security. They are organized in topical sections named network and cyber-physical systems security; information flow and access control; privacy-preserving computation; visualization and analytics for security; spatial systems and crowdsourcing security; and secure outsourcing and privacy. *The conference was held virtually due to the COVID-19 pandemic. COMPUTERS,Security,General

Cyber-Security in Critical Infrastructures This book presents a compendium of selected game- and decision-theoretic models to achieve and assess the security of critical infrastructures. Given contemporary reports on security incidents of various kinds, we can see a paradigm shift to attacks of an increasingly heterogeneous nature, combining different techniques into what we know as an advanced persistent threat. Security precautions must match these diverse threat patterns in an equally diverse manner; in response, this book provides a wealth of techniques for protection and mitigation. Much traditional security research has a narrow focus on specific attack scenarios or applications, and strives to make an attack “practically impossible.†A more recent approach to security views it as a scenario in which the cost of an attack exceeds the potential reward. This does not rule out the possibility of an attack but minimizes its likelihood to the least possible risk. The book follows this economic definition of security, offering a management scientific view that seeks a balance between security investments and their resulting benefits. It focuses on optimization of resources in light of threats such as terrorism and advanced persistent threats. Drawing on the authors’ experience and inspired by real case studies, the book provides a systematic approach to critical infrastructure security and resilience. Presenting a mixture of theoretical work and practical success stories, the book is chiefly intended for students and practitioners seeking an introduction to game- and decision-theoretic techniques for security. The required mathematical concepts are self-contained, rigorously introduced, and illustrated by case studies. The book also provides software tools that help guide readers in the practical use of the scientific models and computational frameworks. COMPUTERS,Security,General

Cyber Security Cryptography and Machine Learning This book constitutes the refereed proceedings of the Fourth International Symposium on Cyber Security Cryptography and Machine Learning, CSCML 2020, held in Beer-Sheva, Israel, in July 2020.The 12 full and 4 short papers presented in this volume were carefully reviewed and selected from 38 submissions. They deal with the theory, design, analysis, implementation, or application of cyber security, cryptography and machine learning systems and networks, and conceptually innovative topics in these research areas. COMPUTERS,Security,General

Cyber Arms This book will raise awareness on emerging challenges of AIempowered cyber arms used in weapon systems and stockpiled in the global cyber arms race. Based on real life events, it provides a comprehensive analysis of cyber offensive and defensive landscape, analyses the cyber arms evolution from prank malicious codes into lethal weapons of mass destruction, reveals the scale of cyber offensive conflicts, explores cyber warfare mutation, warns about cyber arms race escalation and use of Artificial Intelligence (AI) for military purposes. It provides an expert insight into the current and future malicious and destructive use of the evolved cyber arms, AI and robotics, with emphasis on cyber threats to CBRNe and critical infrastructure. The book highlights international efforts in regulating the cyber environment, reviews the best practices of the leading cyber powers and their controversial approaches, recommends responsible state behaviour. It also proposes information security and cyber defence solutions and provides definitions for selected conflicting cyber terms. The disruptive potential of cyber tools merging with military weapons is examined from the technical point of view, as well as legal, ethical, and political perspectives. COMPUTERS,Security,General

Information Systems Security and Privacy This book constitutes the revised selected papers of the 5th International Conference on Information Systems Security and Privacy, ICISSP 2019, held in Prague, Czech Republic, in February 2019. The 19 full papers presented were carefully reviewed and selected from a total of 100 submissions. The papers presented in this volume address various topical research, including new approaches for attack modelling andprevention, incident management and response, and user authentication andaccess control, as well as business and human-oriented aspects such as data pro-tection and privacy, and security awareness. COMPUTERS,Security,General

Trusted Data, revised and expanded edition How to create an Internet of Trusted Data in which insights from data can be extracted without collecting, holding, or revealing the underlying data. Trusted Data describes a data architecture that places humans and their societal values at the center of the discussion. By involving people from all parts of the ecosystem of information, this new approach allows us to realize the benefits of data-driven algorithmic decision making while minimizing the risks and unintended consequences. It proposes a software architecture and legal framework for an Internet of Trusted Data that provides safe, secure access for everyone and protects against bias, unfairness, and other unintended effects. This approach addresses issues of data privacy, security, ownership, and trust by allowing insights to be extracted from data held by different people, companies, or governments without collecting, holding, or revealing the underlying data. The software architecture, called Open Algorithms, or OPAL, sends algorithms to databases rather than copying or sharing data. The data is protected by existing firewalls; only encrypted results are shared. Data never leaves its repository. A higher security architecture, ENIGMA, built on OPAL, is fully encrypted. Contributors Michiel Bakker, Yves-Alexandre de Montjoye, Daniel Greenwood, Thomas Hardjoni, Jake Kendall, Cameron Kerry, Bruno Lepri, Alexander Lipton, Takeo Nishikata, Alejandro Noriega-Campero, Nuria Oliver, Alex Pentland, David L. Shrier, Jacopo Staiano, Guy Zyskind An MIT Connection Science and Engineering Book COMPUTERS,Security,General

You'll See This Message When It Is Too Late What we can learn from the aftermath of cybersecurity breaches and how we can do a better job protecting online data. Cybersecurity incidents make the news with startling regularity. Each breach—the theft of 145.5 million Americans' information from Equifax, for example, or the Russian government's theft of National Security Agency documents, or the Sony Pictures data dump—makes headlines, inspires panic, instigates lawsuits, and is then forgotten. The cycle of alarm and amnesia continues with the next attack, and the one after that. In this book, cybersecurity expert Josephine Wolff argues that we shouldn't forget about these incidents, we should investigate their trajectory, from technology flaws to reparations for harm done to their impact on future security measures. We can learn valuable lessons in the aftermath of cybersecurity breaches. Wolff describes a series of significant cybersecurity incidents between 2005 and 2015, mapping the entire life cycle of each breach in order to identify opportunities for defensive intervention. She outlines three types of motives underlying these attacks—financial gain, espionage, and public humiliation of the victims—that have remained consistent through a decade of cyberattacks, offers examples of each, and analyzes the emergence of different attack patterns. The enormous TJX breach in 2006, for instance, set the pattern for a series of payment card fraud incidents that led to identity fraud and extortion; the Chinese army conducted cyberespionage campaigns directed at U.S.-based companies from 2006 to 2014, sparking debate about the distinction between economic and political espionage; and the 2014 breach of the Ashley Madison website was aimed at reputations rather than bank accounts. COMPUTERS,Security,General

Data and Goliath “Bruce Schneier’s amazing book is the best overview of privacy and security ever written.â€â€”Clay Shirky Your cell phone provider tracks your location and knows who’s with you. Your online and in-store purchasing patterns are recorded, and reveal if you're unemployed, sick, or pregnant. Your e-mails and texts expose your intimate and casual friends. Google knows what you’re thinking because it saves your private searches. Facebook can determine your sexual orientation without you ever mentioning it. The powers that surveil us do more than simply store this information. Corporations use surveillance to manipulate not only the news articles and advertisements we each see, but also the prices we’re offered. Governments use surveillance to discriminate, censor, chill free speech, and put people in danger worldwide. And both sides share this information with each other or, even worse, lose it to cybercriminals in huge data breaches. Much of this is voluntary: we cooperate with corporate surveillance because it promises us convenience, and we submit to government surveillance because it promises us protection. The result is a mass surveillance society of our own making. But have we given up more than we’ve gained? In Data and Goliath, security expert Bruce Schneier offers another path, one that values both security and privacy. He brings his bestseller up-to-date with a new preface covering the latest developments, and then shows us exactly what we can do to reform government surveillance programs, shake up surveillance-based business models, and protect our individual privacy. You'll never look at your phone, your computer, your credit cards, or even your car in the same way again. COMPUTERS,Security,General

Progress in Cryptology - AFRICACRYPT 2020 This book constitutes the refereed proceedings of the 12th International Conference on the Theory and Application of Cryptographic Techniques in Africa, AFRICACRYPT 2020, held in Cairo, Egypt, in July 2020. The 21 papers presented in this book were carefully reviewed and selected from 49 submissions. The papers are organized in topical sections on zero knowledge, symmetric key cryptography, elliptic curves, post quantum cryptography, lattice based cryptography, side channel attacks, cryptanalysis and new algorithms and schemes. AFRICACRYPT is a major scientific event that seeks to advance and promote the field of cryptology on the African continent. The conference has systematically drawn some excellent contributions to the field. The conference has always been organized in cooperation with the International Association for Cryptologic Research (IACR). COMPUTERS,Security,General

Detection of Intrusions and Malware, and Vulnerability Assessment This book constitutes the proceedings of the 17th International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment, DIMVA 2020, held in Lisbon, Portugal, in June 2020.* The 13 full papers presented in this volume were carefully reviewed and selected from 45 submissions. The contributions were organized in topical sections named: vulnerability discovery and analysis; attacks; web security; and detection and containment. ​*The conference was held virtually due to the COVID-19 pandemic. COMPUTERS,Security,General

SQL Injection Strategies Learn to exploit vulnerable database applications using SQL injection tools and techniques, while understanding how to effectively prevent attacks Key Features Understand SQL injection and its effects on websites and other systems Get hands-on with SQL injection using both manual and automated tools Explore practical tips for various attack and defense strategies relating to SQL injection Book Description SQL injection (SQLi) is probably the most infamous attack that can be unleashed against applications on the internet. SQL Injection Strategies is an end-to-end guide for beginners looking to learn how to perform SQL injection and test the security of web applications, websites, or databases, using both manual and automated techniques. The book serves as both a theoretical and practical guide to take you through the important aspects of SQL injection, both from an attack and a defense perspective. You'll start with a thorough introduction to SQL injection and its impact on websites and systems. Later, the book features steps to configure a virtual environment, so you can try SQL injection techniques safely on your own computer. These tests can be performed not only on web applications but also on web services and mobile applications that can be used for managing IoT environments. Tools such as sqlmap and others are then covered, helping you understand how to use them effectively to perform SQL injection attacks. By the end of this book, you will be well-versed with SQL injection, from both the attack and defense perspective. What you will learn Focus on how to defend against SQL injection attacks Understand web application security Get up and running with a variety of SQL injection concepts Become well-versed with different SQL injection scenarios Discover SQL injection manual attack techniques Delve into SQL injection automated techniques Who this book is for This book is ideal for penetration testers, ethical hackers, or anyone who wants to learn about SQL injection and the various attack and defense strategies against this web security vulnerability. No prior knowledge of SQL injection is needed to get started with this book. COMPUTERS,Security,General

Blockchain for Cybersecurity and Privacy Blockchain technology is defined as a decentralized system of distributed registers that are used to record data transactions on multiple computers. The reason this technology has gained popularity is that you can put any digital asset or transaction in the blocking chain, the industry does not matter. Blockchain technology has infiltrated all areas of our lives, from manufacturing to healthcare and beyond. Cybersecurity is an industry that has been significantly affected by this technology and may be more so in the future. Blockchain for Cybersecurity and Privacy: Architectures, Challenges, and Applications is an invaluable resource to discover the blockchain applications for cybersecurity and privacy. The purpose of this book is to improve the awareness of readers about blockchain technology applications for cybersecurity and privacy. This book focuses on the fundamentals, architectures, and challenges of adopting blockchain for cybersecurity. Readers will discover different applications of blockchain for cybersecurity in IoT and healthcare. The book also includes some case studies of the blockchain for e-commerce online payment, retention payment system, and digital forensics. The book offers comprehensive coverage of the most essential topics, including: Blockchain architectures and challenges Blockchain threats and vulnerabilities Blockchain security and potential future use cases Blockchain for securing Internet of Things Blockchain for cybersecurity in healthcare Blockchain in facilitating payment system security and privacy This book comprises a number of state-of-the-art contributions from both scientists and practitioners working in the fields of blockchain technology and cybersecurity. It aspires to provide a relevant reference for students, researchers, engineers, and professionals working in this particular area or those interested in grasping its diverse facets and exploring the latest advances on the blockchain for cybersecurity and privacy. COMPUTERS,Security,General

Financial Cryptography and Data Security This book constitutes the thoroughly refereed post-conference proceedings of the 24th International Conference on Financial Cryptography and Data Security, FC 2020, held in Kota Kinabalu, Malaysia, in February 2020. The 34 revised full papers and 2 short papers were carefully selected and reviewed from 162 submissions. The papers are grouped in the following topical sections: attacks; consensus; cryptoeconomics; layer 2; secure computation; privacy; crypto foundations; empirical studies; and smart contracts. COMPUTERS,Security,General

Cyber Defense Mechanisms This book discusses the evolution of security and privacy issues and brings related technological tools, techniques, and solutions into one single source. The book will take readers on a journey to understanding the security issues and possible solutions involving various threats, attacks, and defense mechanisms, which include IoT, cloud computing, Big Data, lightweight cryptography for blockchain, and data-intensive techniques, and how it can be applied to various applications for general and specific use. Graduate and postgraduate students, researchers, and those working in this industry will find this book easy to understand and use for security applications and privacy issues. COMPUTERS,Security,General

Network Security with OpenSSL Most applications these days are at least somewhat network aware, but how do you protect those applications against common network security threats? Many developers are turning to OpenSSL, an open source version of SSL/TLS, which is the most widely used protocol for secure network communications.The OpenSSL library is seeing widespread adoption for web sites that require cryptographic functions to protect a broad range of sensitive information, such as credit card numbers and other financial transactions. The library is the only free, full-featured SSL implementation for C and C++, and it can be used programmatically or from the command line to secure most TCP-based network protocols.Network Security with OpenSSL enables developers to use this protocol much more effectively. Traditionally, getting something simple done in OpenSSL could easily take weeks. This concise book gives you the guidance you need to avoid pitfalls, while allowing you to take advantage of the library?s advanced features. And, instead of bogging you down in the technical details of how SSL works under the hood, this book provides only the information that is necessary to use OpenSSL safely and effectively. In step-by-step fashion, the book details the challenges in securing network communications, and shows you how to use OpenSSL tools to best meet those challenges.As a system or network administrator, you will benefit from the thorough treatment of the OpenSSL command-line interface, as well as from step-by-step directions for obtaining certificates and setting up your own certification authority. As a developer, you will further benefit from the in-depth discussions and examples of how to use OpenSSL in your own programs. Although OpenSSL is written in C, information on how to use OpenSSL with Perl, Python and PHP is also included.OpenSSL may well answer your need to protect sensitive data. If that?s the case, Network Security with OpenSSL is the only guide available on the subject. COMPUTERS,Security,Network Security

Hacking Exposed Computer Forensics, Second Edition "Provides the right mix of practical how-to knowledge in a straightforward, informative fashion that ties it all the complex pieces together with real-world case studies. ...Delivers the most valuable insight on the market. The authors cut to the chase of what people must understand to effectively perform computer forensic investigations." --Brian H. Karney, COO, AccessData Corporation The latest strategies for investigating cyber-crime Identify and investigate computer criminals of all stripes with help from this fully updated. real-world resource. Hacking Exposed Computer Forensics, Second Edition explains how to construct a high-tech forensic lab, collect prosecutable evidence, discover e-mail and system file clues, track wireless activity, and recover obscured documents. Learn how to re-create an attacker's footsteps, communicate with counsel, prepare court-ready reports, and work through legal and organizational challenges. Case studies straight from today's headlines cover IP theft, mortgage fraud, employee misconduct, securities fraud, embezzlement, organized crime, and consumer fraud cases. Effectively uncover, capture, and prepare evidence for investigation Store and process collected data in a highly secure digital forensic lab Restore deleted documents, partitions, user activities, and file systems Analyze evidence gathered from Windows, Linux, and Macintosh systems Use the latest Web and client-based e-mail tools to extract relevant artifacts Overcome the hacker's anti-forensic, encryption, and obscurity techniques Unlock clues stored in cell phones, PDAs, and Windows Mobile devices Prepare legal documents that will hold up to judicial and defense scrutiny COMPUTERS,Security,Network Security

Ghost in the Wires In this "intriguing, insightful and extremely educational" novel, the world's most famous hacker teaches you easy cloaking and counter-measures for citizens and consumers in the age of Big Brother and Big Data (Frank W. Abagnale). Kevin Mitnick was the most elusive computer break-in artist in history. He accessed computers and networks at the world's biggest companies -- and no matter how fast the authorities were, Mitnick was faster, sprinting through phone switches, computer systems, and cellular networks. As the FBI's net finally began to tighten, Mitnick went on the run, engaging in an increasingly sophisticated game of hide-and-seek that escalated through false identities, a host of cities, and plenty of close shaves, to an ultimate showdown with the Feds, who would stop at nothing to bring him down. Ghost in the Wires is a thrilling true story of intrigue, suspense, and unbelievable escapes -- and a portrait of a visionary who forced the authorities to rethink the way they pursued him, and forced companies to rethink the way they protect their most sensitive information. "Mitnick manages to make breaking computer code sound as action-packed as robbing a bank." -- NPR COMPUTERS,Security,Network Security

Effective Monitoring and Alerting With this practical book, you’ll discover how to catch complications in your distributed system before they develop into costly problems. Based on his extensive experience in systems ops at large technology companies, author Slawek Ligus describes an effective data-driven approach for monitoring and alerting that enables you to maintain high availability and deliver a high quality of service. Learn methods for measuring state changes and data flow in your system, and set up alerts to help you recover quickly from problems when they do arise. If you’re a system operator waging the daily battle to provide the best performance at the lowest cost, this book is for you. Monitor every component of your application stack, from the network to user experience Learn how to draw the right conclusions from the metrics you obtain Develop a robust alerting system that can identify problematic anomalies—without raising false alarms Address system failures by their impact on resource utilization and user experience Plan an alerting configuration that scales with your expanding network Learn how to choose appropriate maintenance times automatically Develop a work environment that fosters flexibility and adaptability COMPUTERS,Security,Network Security

Juniper QFX5100 Series Ideal for network engineers involved in building a data center, this practical guide provides a comprehensive and technical deep-dive into the new Juniper QFX5100 switching family. You’ll learn how the Juniper QFX5100 enables you to create simple-to-use data centers or build some of the largest IP Fabrics in the world. This book is chock-full of helpful technical illustrations and code examples to help you get started on all of the major architectures and features of Juniper QFX5100 switches, whether you’re an enterprise or service provider. With this book, you’ll be well on your way to becoming a Juniper QFX5100 expert. All of the examples and features are based on Junos releases 13.2X51-D20.2 and 14.1X53-D10. Fully understand the hardware and software architecture of the Juniper QFX5100 Design your own IP Fabric architecture Perform in-service software upgrades Be familiar with the performance and scaling maximums Create a data center switching fabric with Virtual Chassis Fabric Automate networking devices with Python, Ruby, Perl, and Go Build an overlay architecture with VMware NSX and Juniper Contrail Export real-time analytics information to graph latency, jitter, bandwidth, and other features COMPUTERS,Security,Network Security

The Network Security Test Lab The ultimate hands-on guide to IT security and proactive defense The Network Security Test Lab is a hands-on, step-by-step guide to ultimate IT security implementation. Covering the full complement of malware, viruses, and other attack technologies, this essential guide walks you through the security assessment and penetration testing process, and provides the set-up guidance you need to build your own security-testing lab. You'll look inside the actual attacks to decode their methods, and learn how to run attacks in an isolated sandbox to better understand how attackers target systems, and how to build the defenses that stop them. You'll be introduced to tools like Wireshark, Networkminer, Nmap, Metasploit, and more as you discover techniques for defending against network attacks, social networking bugs, malware, and the most prevalent malicious traffic. You also get access to open source tools, demo software, and a bootable version of Linux to facilitate hands-on learning and help you implement your new skills. Security technology continues to evolve, and yet not a week goes by without news of a new security breach or a new exploit being released. The Network Security Test Lab is the ultimate guide when you are on the front lines of defense, providing the most up-to-date methods of thwarting would-be attackers. Get acquainted with your hardware, gear, and test platform Learn how attackers penetrate existing security systems Detect malicious activity and build effective defenses Investigate and analyze attacks to inform defense strategy The Network Security Test Lab is your complete, essential guide. COMPUTERS,Security,Network Security

The Official (ISC)2 Guide to the CCSP CBK Globally recognized and backed by the Cloud Security Alliance (CSA) and the (ISC)2 the CCSP credential is the ideal way to match marketability and credibility to your cloud security skill set. The Official (ISC)2 Guide to the CCSPSM CBK Second Edition is your ticket for expert insight through the 6 CCSP domains. You will find step-by-step guidance through real-life scenarios, illustrated examples, tables, best practices, and more. This Second Edition features clearer diagrams as well as refined explanations based on extensive expert feedback. Sample questions help you reinforce what you have learned and prepare smarter. Numerous illustrated examples and tables are included to demonstrate concepts, frameworks and real-life scenarios. The book offers step-by-step guidance through each of CCSP’s domains, including best practices and techniques used by the world's most experienced practitioners. Developed by (ISC)², endorsed by the Cloud Security Alliance® (CSA) and compiled and reviewed by cloud security experts across the world, this book brings together a global, thorough perspective. The Official (ISC)² Guide to the CCSP CBK should be utilized as your fundamental study tool in preparation for the CCSP exam and provides a comprehensive reference that will serve you for years to come. COMPUTERS,Security,Network Security

Juniper MX Series Discover why routers in the Juniper MX Series—with their advanced feature sets and record-breaking scale—are so popular among enterprises and network service providers. This revised and expanded edition shows you step-by-step how to implement high-density, high-speed Layer 2 and Layer 3 Ethernet services, using Router Engine DDoS Protection, Multi-chassis LAG, Inline NAT, IPFLOW, and many other Juniper MX features. This second edition was written by a Senior NOC engineer, whose vast experience with the MX Series is well documented. Each chapter covers a specific Juniper MX vertical and includes review questions to help you test what you’ve learned. This edition includes new chapters on load balancing and vMX—Juniper MX’s virtual instance. Work with Juniper MX’s bridging, VLAN mapping, and support for thousands of virtual switches Examine Juniper MX high-availability features and protocols Use Trio Chipset’s load balancing features for different types of traffic Explore the benefits and typical use cases of vMX Add an extra layer of security with Junos DDoS protection Create a firewall filter framework that applies filters specific to your network Discover the advantages of hierarchical scheduling Combine Juniper MX routers, using a virtual chassis or Multi-chassis LAG Install network services such as Network Address Translation (NAT) COMPUTERS,Security,Network Security

Network Forensics Intensively hands-on training for real-world network forensics Network Forensics provides a uniquely practical guide for IT and law enforcement professionals seeking a deeper understanding of cybersecurity. This book is hands-on all the way—by dissecting packets, you gain fundamental knowledge that only comes from experience. Real packet captures and log files demonstrate network traffic investigation, and the learn-by-doing approach relates the essential skills that traditional forensics investigators may not have. From network packet analysis to host artifacts to log analysis and beyond, this book emphasizes the critical techniques that bring evidence to light. Network forensics is a growing field, and is becoming increasingly central to law enforcement as cybercrime becomes more and more sophisticated. This book provides an unprecedented level of hands-on training to give investigators the skills they need. Investigate packet captures to examine network communications Locate host-based artifacts and analyze network logs Understand intrusion detection systems—and let them do the legwork Have the right architecture and systems in place ahead of an incident Network data is always changing, and is never saved in one place; an investigator must understand how to examine data over time, which involves specialized skills that go above and beyond memory, mobile, or data forensics. Whether you're preparing for a security certification or just seeking deeper training for a law enforcement or IT role, you can only learn so much from concept; to thoroughly understand something, you need to do it. Network Forensics provides intensive hands-on practice with direct translation to real-world application. COMPUTERS,Security,Network Security

Advanced Penetration Testing Build a better defense against motivated, organized, professional attacks Advanced Penetration Testing: Hacking the World's Most Secure Networks takes hacking far beyond Kali linux and Metasploit to provide a more complex attack simulation. Featuring techniques not taught in any certification prep or covered by common defensive scanners, this book integrates social engineering, programming, and vulnerability exploits into a multidisciplinary approach for targeting and compromising high security environments. From discovering and creating attack vectors, and moving unseen through a target enterprise, to establishing command and exfiltrating data—even from organizations without a direct Internet connection—this guide contains the crucial techniques that provide a more accurate picture of your system's defense. Custom coding examples use VBA, Windows Scripting Host, C, Java, JavaScript, Flash, and more, with coverage of standard library applications and the use of scanning tools to bypass common defensive measures. Typical penetration testing consists of low-level hackers attacking a system with a list of known vulnerabilities, and defenders preventing those hacks using an equally well-known list of defensive scans. The professional hackers and nation states on the forefront of today's threats operate at a much more complex level—and this book shows you how to defend your high security network. Use targeted social engineering pretexts to create the initial compromise Leave a command and control structure in place for long-term access Escalate privilege and breach networks, operating systems, and trust structures Infiltrate further using harvested credentials while expanding control Today's threats are organized, professionally-run, and very much for-profit. Financial institutions, health care organizations, law enforcement, government agencies, and other high-value targets need to harden their IT infrastructure and human capital against targeted advanced attacks from motivated professionals. Advanced Penetration Testing goes beyond Kali linux and Metasploit and to provide you advanced pen testing for high security networks. COMPUTERS,Security,Network Security

Kali Linux Intrusion and Exploitation Cookbook Over 70 recipes for system administrators or DevOps to master Kali Linux 2 and perform effective security assessments About This Book Set up a penetration testing lab to conduct a preliminary assessment of attack surfaces and run exploits Improve your testing efficiency with the use of automated vulnerability scanners Work through step-by-step recipes to detect a wide array of vulnerabilities, exploit them to analyze their consequences, and identify security anomalies Who This Book Is For This book is intended for those who want to know more about information security. In particular, it's ideal for system administrators and system architects who want to ensure that the infrastructure and systems they are creating and managing are secure. This book helps both beginners and intermediates by allowing them to use it as a reference book and to gain in-depth knowledge. What You Will Learn Understand the importance of security assessments over merely setting up and managing systems/processes Familiarize yourself with tools such as OPENVAS to locate system and network vulnerabilities Discover multiple solutions to escalate privileges on a compromised machine Identify security anomalies in order to make your infrastructure secure and further strengthen it Acquire the skills to prevent infrastructure and application vulnerabilities Exploit vulnerabilities that require a complex setup with the help of Metasploit In Detail With the increasing threats of breaches and attacks on critical infrastructure, system administrators and architects can use Kali Linux 2.0 to ensure their infrastructure is secure by finding out known vulnerabilities and safeguarding their infrastructure against unknown vulnerabilities. This practical cookbook-style guide contains chapters carefully structured in three phases – information gathering, vulnerability assessment, and penetration testing for the web, and wired and wireless networks. It's an ideal reference guide if you're looking for a solution to a specific problem or learning how to use a tool. We provide hands-on examples of powerful tools/scripts designed for exploitation. In the final section, we cover various tools you can use during testing, and we help you create in-depth reports to impress management. We provide system engineers with steps to reproduce issues and fix them. Style and approach This practical book is full of easy-to-follow recipes with based on real-world problems faced by the authors. Each recipe is divided into three sections, clearly defining what the recipe does, what you need, and how to do it. The carefully structured recipes allow you to go directly to your topic of interest. COMPUTERS,Security,Network Security

Computer and Information Security Handbook Computer and Information Security Handbook, Third Edition, provides the most current and complete reference on computer security available in one volume. The book offers deep coverage of an extremely wide range of issues in computer and cybersecurity theory, applications, and best practices, offering the latest insights into established and emerging technologies and advancements. With new parts devoted to such current topics as Cloud Security, Cyber-Physical Security, and Critical Infrastructure Security, the book now has 100 chapters written by leading experts in their fields, as well as 12 updated appendices and an expanded glossary. It continues its successful format of offering problem-solving techniques that use real-life case studies, checklists, hands-on exercises, question and answers, and summaries. Chapters new to this edition include such timely topics as Cyber Warfare, Endpoint Security, Ethical Hacking, Internet of Things Security, Nanoscale Networking and Communications Security, Social Engineering, System Forensics, Wireless Sensor Network Security, Verifying User and Host Identity, Detecting System Intrusions, Insider Threats, Security Certification and Standards Implementation, Metadata Forensics, Hard Drive Imaging, Context-Aware Multi-Factor Authentication, Cloud Security, Protecting Virtual Infrastructure, Penetration Testing, and much more. Online chapters can also be found on the book companion website: https://www.elsevier.com/books-and-journals/book-companion/9780128038437 Written by leaders in the field Comprehensive and up-to-date coverage of the latest security technologies, issues, and best practices Presents methods for analysis, along with problem-solving techniques for implementing practical solutions COMPUTERS,Security,Network Security

Nmap Over 100 practical recipes related to network and application security auditing using the powerful Nmap About This Book Learn through practical recipes how to use Nmap for a wide range of tasks for system administrators and penetration testers. Learn the latest and most useful features of Nmap and the Nmap Scripting Engine. Learn to audit the security of networks, web applications, databases, mail servers, Microsoft Windows servers/workstations and even ICS systems. Learn to develop your own modules for the Nmap Scripting Engine. Become familiar with Lua programming. 100% practical tasks, relevant and explained step-by-step with exact commands and optional arguments description Who This Book Is For The book is for anyone who wants to master Nmap and its scripting engine to perform real life security auditing checks for system administrators and penetration testers. This book is also recommended to anyone looking to learn about network security auditing. Finally, novice Nmap users will also learn a lot from this book as it covers several advanced internal aspects of Nmap and related tools. What You Will Learn Learn about Nmap and related tools, such as Ncat, Ncrack, Ndiff, Zenmap and the Nmap Scripting Engine Master basic and advanced techniques to perform port scanning and host discovery Detect insecure configurations and vulnerabilities in web servers, databases, and mail servers Learn how to detect insecure Microsoft Windows workstations and scan networks using the Active Directory technology Learn how to safely identify and scan critical ICS/SCADA systems Learn how to optimize the performance and behavior of your scans Learn about advanced reporting Learn the fundamentals of Lua programming Become familiar with the development libraries shipped with the NSE Write your own Nmap Scripting Engine scripts In Detail This is the second edition of 'Nmap 6: Network Exploration and Security Auditing Cookbook'. A book aimed for anyone who wants to master Nmap and its scripting engine through practical tasks for system administrators and penetration testers. Besides introducing the most powerful features of Nmap and related tools, common security auditing tasks for local and remote networks, web applications, databases, mail servers, Microsoft Windows machines and even ICS SCADA systems are explained step by step with exact commands and argument explanations. The book starts with the basic usage of Nmap and related tools like Ncat, Ncrack, Ndiff and Zenmap. The Nmap Scripting Engine is thoroughly covered through security checks used commonly in real-life scenarios applied for different types of systems. New chapters for Microsoft Windows and ICS SCADA systems were added and every recipe was revised. This edition reflects the latest updates and hottest additions to the Nmap project to date. The book will also introduce you to Lua programming and NSE script development allowing you to extend further the power of Nmap. Style and approach This book consists of practical recipes on network exploration and security auditing techniques, enabling you to get hands-on experience through real life scenarios. COMPUTERS,Security,Network Security

Zero Trust Networks The perimeter defenses guarding your network perhaps are not as secure as you think. Hosts behind the firewall have no defenses of their own, so when a host in the "trusted" zone is breached, access to your data center is not far behind. That’s an all-too-familiar scenario today. With this practical book, you’ll learn the principles behind zero trust architecture, along with details necessary to implement it. The Zero Trust Model treats all hosts as if they’re internet-facing, and considers the entire network to be compromised and hostile. By taking this approach, you’ll focus on building strong authentication, authorization, and encryption throughout, while providing compartmentalized access and better operational agility. Understand how perimeter-based defenses have evolved to become the broken model we use today Explore two case studies of zero trust in production networks on the client side (Google) and on the server side (PagerDuty) Get example configuration for open source tools that you can use to build a zero trust network Learn how to migrate from a perimeter-based network to a zero trust network in production COMPUTERS,Security,Network Security

CCNA Cyber Ops SECFND #210-250 Official Cert Guide This is the eBook version of the print title. Note that the eBook does not provide access to the practice test software that accompanies the print book. Learn, prepare, and practice for CCNA Cyber Ops SECFND 210-250 exam success with this Cert Guide from Pearson IT Certification, a leader in IT Certification learning. Master CCNA Cyber Ops SECFND 210-250 exam topics Assess your knowledge with chapter-ending quizzes Review key concepts with exam preparation tasks CCNA Cyber Ops SECFND 210-250 Official Cert Guide is a best-of-breed exam study guide. Cisco enterprise security experts Omar Santos, Joseph Muniz, and Stefano De Crescenzo share preparation hints and test-taking tips, helping you identify areas of weakness and improve both your conceptual knowledge and hands-on skills. Material is presented in a concise manner, focusing on increasing your understanding and retention of exam topics. The book presents you with an organized test preparation routine through the use of proven series elements and techniques. Exam topic lists make referencing easy. Chapter-ending Exam Preparation Tasks help you drill on key concepts you must know thoroughly. Review questions help you assess your knowledge, and a final preparation chapter guides you through tools and resources to help you craft your final study plan. Well-regarded for its level of detail, assessment features, and challenging review questions and exercises, this study guide helps you master the concepts and techniques that will allow you to succeed on the exam the first time. The study guide helps you master all the topics on the CCNA Cyber Ops SECFND exam, including: Fundamentals of networking protocols and networking device types Network security devices and cloud services Security principles Access control models Security management concepts and techniques Fundamentals of cryptography and PKI Essentials of Virtual Private Networks (VPNs) Windows-based Analysis Linux /MAC OS X-based Analysis Endpoint security technologies Network and host telemetry Security monitoring operations and challenges Types of attacks and vulnerabilities Security evasion techniques COMPUTERS,Security,Network Security

Network Security Through Data Analysis Traditional intrusion detection and logfile analysis are no longer enough to protect today’s complex networks. In the updated second edition of this practical guide, security researcher Michael Collins shows InfoSec personnel the latest techniques and tools for collecting and analyzing network traffic datasets. You’ll understand how your network is used, and what actions are necessary to harden and defend the systems within it. In three sections, this book examines the process of collecting and organizing data, various tools for analysis, and several different analytic scenarios and techniques. New chapters focus on active monitoring and traffic manipulation, insider threat detection, data mining, regression and machine learning, and other topics. You’ll learn how to: Use sensors to collect network, service, host, and active domain data Work with the SiLK toolset, Python, and other tools and techniques for manipulating data you collect Detect unusual phenomena through exploratory data analysis (EDA), using visualization and mathematical techniques Analyze text data, traffic behavior, and communications mistakes Identify significant structures in your network with graph analysis Examine insider threat data and acquire threat intelligence Map your network and identify significant hosts within it Work with operations to develop defenses and analysis techniques COMPUTERS,Security,Network Security

Web Penetration Testing with Kali Linux Build your defense against web attacks with Kali Linux, including command injection flaws, crypto implementation layers, and web application security holes About This Book Know how to set up your lab with Kali Linux Discover the core concepts of web penetration testing Get the tools and techniques you need with Kali Linux Who This Book Is For Since this book sets out to cover a large number of tools and security fields, it can work as an introduction to practical security skills for beginners in security. In addition, web programmers and also system administrators would benefit from this rigorous introduction to web penetration testing. Basic system administration skills are necessary, and the ability to read code is a must. What You Will Learn Learn how to set up your lab with Kali Linux Understand the core concepts of web penetration testing Get to know the tools and techniques you need to use with Kali Linux Identify the difference between hacking a web application and network hacking Expose vulnerabilities present in web servers and their applications using server-side attacks Understand the different techniques used to identify the flavor of web applications See standard attacks such as exploiting cross-site request forgery and cross-site scripting flaws Get an overview of the art of client-side attacks Explore automated attacks such as fuzzing web applications In Detail Web Penetration Testing with Kali Linux - Third Edition shows you how to set up a lab, helps you understand the nature and mechanics of attacking websites, and explains classical attacks in great depth. This edition is heavily updated for the latest Kali Linux changes and the most recent attacks. Kali Linux shines when it comes to client-side attacks and fuzzing in particular. From the start of the book, you'll be given a thorough grounding in the concepts of hacking and penetration testing, and you'll see the tools used in Kali Linux that relate to web application hacking. You'll gain a deep understanding of classicalSQL, command-injection flaws, and the many ways to exploit these flaws. Web penetration testing also needs a general overview of client-side attacks, which is rounded out by a long discussion of scripting and input validation flaws. There is also an important chapter on cryptographic implementation flaws, where we discuss the most recent problems with cryptographic layers in the networking stack. The importance of these attacks cannot be overstated, and defending against them is relevant to most internet users and, of course, penetration testers. At the end of the book, you'll use an automated technique called fuzzing to identify flaws in a web application. Finally, you'll gain an understanding of web application vulnerabilities and the ways they can be exploited using the tools in Kali Linux. Style and approach This step-by-step guide covers each topic with detailed practical examples. Every concept is explained with the help of illustrations using the tools available in Kali Linux. COMPUTERS,Security,Network Security

Mastering Python for Networking and Security Master Python scripting to build a network and perform security operations Key Features Learn to handle cyber attacks with modern Python scripting Discover various Python libraries for building and securing your network Understand Python packages and libraries to secure your network infrastructure Book Description It's becoming more and more apparent that security is a critical aspect of IT infrastructure. A data breach is a major security incident, usually carried out by just hacking a simple network line. Increasing your network's security helps step up your defenses against cyber attacks. Meanwhile, Python is being used for increasingly advanced tasks, with the latest update introducing many new packages. This book focuses on leveraging these updated packages to build a secure network with the help of Python scripting. This book covers topics from building a network to the different procedures you need to follow to secure it. You'll first be introduced to different packages and libraries, before moving on to different ways to build a network with the help of Python scripting. Later, you will learn how to check a network's vulnerability using Python security scripting, and understand how to check vulnerabilities in your network. As you progress through the chapters, you will also learn how to achieve endpoint protection by leveraging Python packages along with writing forensic scripts. By the end of this book, you will be able to get the most out of the Python language to build secure and robust networks that are resilient to attacks. What you will learn Develop Python scripts for automating security and pentesting tasks Discover the Python standard library's main modules used for performing security-related tasks Automate analytical tasks and the extraction of information from servers Explore processes for detecting and exploiting vulnerabilities in servers Use network software for Python programming Perform server scripting and port scanning with Python Identify vulnerabilities in web applications with Python Use Python to extract metadata and forensics Who this book is for This book is ideal for network engineers, system administrators, or any security professional looking at tackling networking and security challenges. Programmers with some prior experience in Python will get the most out of this book. Some basic understanding of general programming structures and Python is required. COMPUTERS,Security,Network Security

Securing Network Infrastructure Plug the gaps in your network's infrastructure with resilient network security models Key Features Develop a cost-effective and end-to-end vulnerability management program Explore best practices for vulnerability scanning and risk assessment Understand and implement network enumeration with Nessus and Network Mapper (Nmap) Book Description Digitization drives technology today, which is why it's so important for organizations to design security mechanisms for their network infrastructures. Analyzing vulnerabilities is one of the best ways to secure your network infrastructure. This Learning Path begins by introducing you to the various concepts of network security assessment, workflows, and architectures. You will learn to employ open source tools to perform both active and passive network scanning and use these results to analyze and design a threat model for network security. With a firm understanding of the basics, you will then explore how to use Nessus and Nmap to scan your network for vulnerabilities and open ports and gain back door entry into a network. As you progress through the chapters, you will gain insights into how to carry out various key scanning tasks, including firewall detection, OS detection, and access management to detect vulnerabilities in your network. By the end of this Learning Path, you will be familiar with the tools you need for network scanning and techniques for vulnerability scanning and network protection. This Learning Path includes content from the following Packt books: Network Scanning Cookbook by Sairam Jetty Network Vulnerability Assessment by Sagar Rahalkar What you will learn Explore various standards and frameworks for vulnerability assessments and penetration testing Gain insight into vulnerability scoring and reporting Discover the importance of patching and security hardening Develop metrics to measure the success of a vulnerability management program Perform configuration audits for various platforms using Nessus Write custom Nessus and Nmap scripts on your own Install and configure Nmap and Nessus in your network infrastructure Perform host discovery to identify network devices Who this book is for This Learning Path is designed for security analysts, threat analysts, and security professionals responsible for developing a network threat model for an organization. Professionals who want to be part of a vulnerability management team and implement an end-to-end robust vulnerability management program will also find this Learning Path useful. COMPUTERS,Security,Network Security

The Official (ISC)2 Guide to the CISSP CBK Reference The only official, comprehensive reference guide to the CISSP All new for 2019 and beyond, this is the authoritative common body of knowledge (CBK) from (ISC)2 for information security professionals charged with designing, engineering, implementing, and managing the overall information security program to protect organizations from increasingly sophisticated attacks. Vendor neutral and backed by (ISC)2, the CISSP credential meets the stringent requirements of ISO/IEC Standard 17024. This CBK covers the new eight domains of CISSP with the necessary depth to apply them to the daily practice of information security. Written by a team of subject matter experts, this comprehensive reference covers all of the more than 300 CISSP objectives and sub-objectives in a structured format with: Common and good practices for each objective Common vocabulary and definitions References to widely accepted computing standards Highlights of successful approaches through case studies Whether you've earned your CISSP credential or are looking for a valuable resource to help advance your security career, this comprehensive guide offers everything you need to apply the knowledge of the most recognized body of influence in information security. COMPUTERS,Security,Network Security

(ISC)2 SSCP Systems Security Certified Practitioner Official Study Guide The only SSCP study guide officially approved by (ISC)2 The (ISC)2 Systems Security Certified Practitioner (SSCP) certification is a well-known vendor-neutral global IT security certification. The SSCP is designed to show that holders have the technical skills to implement, monitor, and administer IT infrastructure using information security policies and procedures. This comprehensive Official Study Guide—the only study guide officially approved by (ISC)2—covers all objectives of the seven SSCP domains. Access Controls Security Operations and Administration Risk Identification, Monitoring, and Analysis Incident Response and Recovery Cryptography Network and Communications Security Systems and Application Security If you’re an information security professional or student of cybersecurity looking to tackle one or more of the seven domains of the SSCP, this guide gets you prepared to pass the exam and enter the information security workforce with confidence. COMPUTERS,Security,Network Security

IT Auditing Using Controls to Protect Information Assets, Third Edition Secure Your Systems Using the Latest IT Auditing Techniques Fully updated to cover leading-edge tools and technologies, IT Auditing: Using Controls to Protect Information Assets, Third Edition, explains, step by step, how to implement a successful, enterprise-wide IT audit program. New chapters on auditing cybersecurity programs, big data and data repositories, and new technologies are included. This comprehensive guide describes how to assemble an effective IT audit team and maximize the value of the IT audit function. In-depth details on performing specific audits are accompanied by real-world examples, ready-to-use checklists, and valuable templates. Standards, frameworks, regulations, and risk management techniques are also covered in this definitive resource. • Build and maintain an internal IT audit function with maximum effectiveness and value• Audit entity-level controls and cybersecurity programs• Assess data centers and disaster recovery• Examine switches, routers, and firewalls• Evaluate Windows, UNIX, and Linux operating systems• Audit Web servers and applications• Analyze databases and storage solutions• Review big data and data repositories• Assess end user computer devices, including PCs and mobile devices• Audit virtualized environments• Evaluate risks associated with cloud computing and outsourced operations• Drill down into applications and projects to find potential control weaknesses• Learn best practices for auditing new technologies• Use standards and frameworks, such as COBIT, ITIL, and ISO• Understand regulations, including Sarbanes-Oxley, HIPAA, and PCI• Implement proven risk management practices COMPUTERS,Security,Network Security

Applied Incident Response Incident response is critical for the active defense of any network, and incident responders need up-to-date, immediately applicable techniques with which to engage the adversary. Applied Incident Response details effective ways to respond to advanced attacks against local and remote network resources, providing proven response techniques and a framework through which to apply them. As a starting point for new incident handlers, or as a technical reference for hardened IR veterans, this book details the latest techniques for responding to threats against your network, including: Preparing your environment for effective incident response Leveraging MITRE ATT&CK and threat intelligence for active network defense Local and remote triage of systems using PowerShell, WMIC, and open-source tools Acquiring RAM and disk images locally and remotely Analyzing RAM with Volatility and Rekall Deep-dive forensic analysis of system drives using open-source or commercial tools Leveraging Security Onion and Elastic Stack for network security monitoring Techniques for log analysis and aggregating high-value logs Static and dynamic analysis of malware with YARA rules, FLARE VM, and Cuckoo Sandbox Detecting and responding to lateral movement techniques, including pass-the-hash, pass-the-ticket, Kerberoasting, malicious use of PowerShell, and many more Effective threat hunting techniques Adversary emulation with Atomic Red Team Improving preventive and detective controls COMPUTERS,Security,Network Security

(ISC)2 CCSP Certified Cloud Security Professional Official Practice Tests The only official CCSP practice test product endorsed by (ISC)² With over 1,000 practice questions, this book gives you the opportunity to test your level of understanding and gauge your readiness for the Certified Cloud Security Professional (CCSP) exam long before the big day. These questions cover 100% of the CCSP exam domains, and include answers with full explanations to help you understand the reasoning and approach for each. Logical organization by domain allows you to practice only the areas you need to bring you up to par, without wasting precious time on topics you’ve already mastered. As the only official practice test product for the CCSP exam endorsed by (ISC)², this essential resource is your best bet for gaining a thorough understanding of the topic. It also illustrates the relative importance of each domain, helping you plan your remaining study time so you can go into the exam fully confident in your knowledge. When you’re ready, two practice exams allow you to simulate the exam day experience and apply your own test-taking strategies with domains given in proportion to the real thing. The online learning environment and practice exams are the perfect way to prepare, and make your progress easy to track. COMPUTERS,Security,Network Security

Penetration Testing For Dummies Target, test, analyze, and report on security vulnerabilities with pen testing Pen Testing is necessary for companies looking to target, test, analyze, and patch the security vulnerabilities from hackers attempting to break into and compromise their organizations data. It takes a person with hacking skills to look for the weaknesses that make an organization susceptible to hacking. Pen Testing For Dummies aims to equip IT enthusiasts at various levels with the basic knowledge of pen testing. It is the go-to book for those who have some IT experience but desire more knowledge of how to gather intelligence on a target, learn the steps for mapping out a test, and discover best practices for analyzing, solving, and reporting on vulnerabilities. The different phases of a pen test from pre-engagement to completion Threat modeling and understanding risk When to apply vulnerability management vs penetration testing Ways to keep your pen testing skills sharp, relevant, and at the top of the game Get ready to gather intelligence, discover the steps for mapping out tests, and analyze and report results! COMPUTERS,Security,Network Security

Constructing cybersecurity Constructing cybersecurity adopts a constructivist approach to cybersecurity and problematises the state of contemporary knowledge within this field. Setting out by providing a concise overview of such knowledge this book subsequently adopts Foucauldian positions on power and security to highlight assumptions and limitations found herein. What follows is a detailed analysis of the discourse produced by various internet security companies demonstrating the important role that these security professionals play constituting and entrenching this knowledge by virtue of their specific epistemic authority. As a relatively new source within a broader security dispositif these security professionals have created relationships of mutual recognition and benefit with traditional political and security professionals. COMPUTERS,Security,Network Security

Mastering Azure Security Leverage Azure security services to architect robust cloud solutions in Microsoft Azure Key Features Secure your Azure cloud workloads across applications and networks Protect your Azure infrastructure from cyber attacks Discover tips and techniques for implementing, deploying, and maintaining secure cloud services using best practices Book Description Security is always integrated into cloud platforms, causing users to let their guard down as they take cloud security for granted.Cloud computing brings new security challenges, but you can overcome these with Microsoft Azure's shared responsibility model. Mastering Azure Security covers the latest security features provided by Microsoft to identify different threats and protect your Azure cloud using innovative techniques. The book takes you through the built-in security controls and the multi-layered security features offered by Azure to protect cloud workloads across apps and networks. You'll get to grips with using Azure Security Center for unified security management, building secure application gateways on Azure, protecting the cloud from DDoS attacks, safeguarding with Azure Key Vault, and much more. Additionally, the book covers Azure Sentinel, monitoring and auditing, Azure security and governance best practices, and securing PaaS deployments. By the end of this book, you'll have developed a solid understanding of cybersecurity in the cloud and be able to design secure solutions in Microsoft Azure. What you will learn Understand cloud security concepts Get to grips with managing cloud identities Adopt the Azure security cloud infrastructure Grasp Azure network security concepts Discover how to keep cloud resources secure Implement cloud governance with security policies and rules Who this book is for This book is for Azure cloud professionals, Azure architects, and security professionals looking to implement secure cloud services using Azure Security Centre and other Azure security features. A fundamental understanding of security concepts and prior exposure to the Azure cloud will help you understand the key concepts covered in the book more effectively. COMPUTERS,Security,Network Security

Mastering Windows Security and Hardening Enhance Windows security and protect your systems and servers from various cyber attacks Key Features Protect your device using a zero-trust approach and advanced security techniques Implement efficient security measures using Microsoft Intune, Configuration Manager, and Azure solutions Understand how to create cyber-threat defense solutions effectively Book Description Are you looking for effective ways to protect Windows-based systems from being compromised by unauthorized users? Mastering Windows Security and Hardening is a detailed guide that helps you gain expertise when implementing efficient security measures and creating robust defense solutions. We will begin with an introduction to Windows security fundamentals, baselining, and the importance of building a baseline for an organization. As you advance, you will learn how to effectively secure and harden your Windows-based system, protect identities, and even manage access. In the concluding chapters, the book will take you through testing, monitoring, and security operations. In addition to this, you'll be equipped with the tools you need to ensure compliance and continuous monitoring through security operations. By the end of this book, you'll have developed a full understanding of the processes and tools involved in securing and hardening your Windows environment. What you will learn Understand baselining and learn the best practices for building a baseline Get to grips with identity management and access management on Windows-based systems Delve into the device administration and remote management of Windows-based systems Explore security tips to harden your Windows server and keep clients secure Audit, assess, and test to ensure controls are successfully applied and enforced Monitor and report activities to stay on top of vulnerabilities Who this book is for This book is for system administrators, cybersecurity and technology professionals, solutions architects, or anyone interested in learning how to secure their Windows-based systems. A basic understanding of Windows security concepts, Intune, Configuration Manager, Windows PowerShell, and Microsoft Azure will help you get the best out of this book. COMPUTERS,Security,Network Security

Sandworm From Wired senior writer Andy Greenberg comes the true story of the most devastating cyberattack in history and the desperate hunt to identify and track the elite Russian agents behind it. "Much more than a true-life techno-thriller ... a tour through a realm that is both invisible and critical to the daily lives of every person alive in the 21st century." —Los Angeles Times In 2014, the world witnessed the start of a mysterious series of cyberattacks. Targeting American utility companies, NATO, and electric grids in Eastern Europe, the strikes grew ever more brazen. They culminated in the summer of 2017, when the malware known as NotPetya was unleashed, penetrating, disrupting, and paralyzing some of the world's largest businesses—from drug manufacturers to software developers to shipping companies. At the attack's epicenter in Ukraine, ATMs froze. The railway and postal systems shut down. Hospitals went dark. NotPetya spread around the world, inflicting an unprecedented ten billion dollars in damage—the largest, most destructive cyberattack the world had ever seen. The hackers behind these attacks are quickly gaining a reputation as the most dangerous team of cyberwarriors in history: a group known as Sandworm. Working in the service of Russia's military intelligence agency, they represent a persistent, highly skilled force, one whose talents are matched by their willingness to launch broad, unrestrained attacks on the most critical infrastructure of their adversaries. They target government and private sector, military and civilians alike. A chilling, globe-spanning detective story, Sandworm considers the danger this force poses to our national security and stability. As the Kremlin's role in foreign government manipulation comes into greater focus, Sandworm exposes the realities not just of Russia's global digital offensive, but of an era where warfare ceases to be waged on the battlefield. It reveals how the lines between digital and physical conflict, between wartime and peacetime, have begun to blur—with world-shaking implications. COMPUTERS,Security,Viruses & Malware

Cyber Security This comprehensive work focuses on the current state of play regarding cyber security threats to government and business, which are imposing unprecedented costs and disruption. At the same time, it aggressively takes a forward-looking approach to such emerging industries as automobiles and appliances, the operations of which are becoming more closely tied to the internet. Revolutionary developments will have security implications unforeseen by manufacturers, and the authors explore these in detail, drawing on lessons from overseas as well as the United States to show how nations and businesses can combat these threats. The book's first section describes existing threats and their consequences. The second section identifies newer cyber challenges across an even broader spectrum, including the internet of things. The concluding section looks at policies and practices in the United States, United Kingdom, and elsewhere that offer ways to mitigate threats to cyber security. Written in a nontechnical, accessible manner, the book will appeal to a diverse audience of policymakers, business leaders, cyber security experts, and interested general readers. COMPUTERS,Security,Viruses & Malware

The Complete Metasploit Guide Master the Metasploit Framework and become an expert in penetration testing. Key Features Gain a thorough understanding of the Metasploit Framework Develop the skills to perform penetration testing in complex and highly secure environments Learn techniques to integrate Metasploit with the industry's leading tools Book Description Most businesses today are driven by their IT infrastructure, and the tiniest crack in this IT network can bring down the entire business. Metasploit is a pentesting network that can validate your system by performing elaborate penetration tests using the Metasploit Framework to secure your infrastructure. This Learning Path introduces you to the basic functionalities and applications of Metasploit. Throughout this book, you'll learn different techniques for programming Metasploit modules to validate services such as databases, fingerprinting, and scanning. You'll get to grips with post exploitation and write quick scripts to gather information from exploited systems. As you progress, you'll delve into real-world scenarios where performing penetration tests are a challenge. With the help of these case studies, you'll explore client-side attacks using Metasploit and a variety of scripts built on the Metasploit Framework. By the end of this Learning Path, you'll have the skills required to identify system vulnerabilities by using thorough testing. This Learning Path includes content from the following Packt products: Metasploit for Beginners by Sagar Rahalkar Mastering Metasploit - Third Edition by Nipun Jaswal What you will learn Develop advanced and sophisticated auxiliary modules Port exploits from Perl, Python, and many other programming languages Bypass modern protections such as antivirus and IDS with Metasploit Script attacks in Armitage using the Cortana scripting language Customize Metasploit modules to modify existing exploits Explore the steps involved in post-exploitation on Android and mobile platforms Who this book is for This Learning Path is ideal for security professionals, web programmers, and pentesters who want to master vulnerability exploitation and get the most of the Metasploit Framework. Basic knowledge of Ruby programming and Cortana scripting language is required. COMPUTERS,Security,Viruses & Malware

Digital Forensics and Incident Response Build your organization's cyber defense system by effectively implementing digital forensics and incident management techniques Key Features Create a solid incident response framework and manage cyber incidents effectively Perform malware analysis for effective incident response Explore real-life scenarios that effectively use threat intelligence and modeling techniques Book Description An understanding of how digital forensics integrates with the overall response to cybersecurity incidents is key to securing your organization's infrastructure from attacks. This updated second edition will help you perform cutting-edge digital forensic activities and incident response. After focusing on the fundamentals of incident response that are critical to any information security team, you'll move on to exploring the incident response framework. From understanding its importance to creating a swift and effective response to security incidents, the book will guide you with the help of useful examples. You'll later get up to speed with digital forensic techniques, from acquiring evidence and examining volatile memory through to hard drive examination and network-based evidence. As you progress, you'll discover the role that threat intelligence plays in the incident response process. You'll also learn how to prepare an incident response report that documents the findings of your analysis. Finally, in addition to various incident response activities, the book will address malware analysis, and demonstrate how you can proactively use your digital forensic skills in threat hunting. By the end of this book, you'll have learned how to efficiently investigate and report unwanted security breaches and incidents in your organization. What you will learn Create and deploy an incident response capability within your own organization Perform proper evidence acquisition and handling Analyze the evidence collected and determine the root cause of a security incident Become well-versed with memory and log analysis Integrate digital forensic techniques and procedures into the overall incident response process Understand the different techniques for threat hunting Write effective incident reports that document the key findings of your analysis Who this book is for This book is for cybersecurity and information security professionals who want to implement digital forensics and incident response in their organization. You will also find the book helpful if you are new to the concept of digital forensics and are looking to get started with the fundamentals. A basic understanding of operating systems and some knowledge of networking fundamentals are required to get started with this book. COMPUTERS,Security,Viruses & Malware

The Inmates Are Running the Asylum Imagine, at a terrifyingly aggressive rate, everything you regularly use is being equipped with computer technology. Think about your phone, cameras, cars-everything-being automated and programmed by people who in their rush to accept the many benefits of the silicon chip, have abdicated their responsibility to make these products easy to use. The Inmates Are Running the Asylum argues that the business executives who make the decisions to develop these products are not the ones in control of the technology used to create them. Insightful and entertaining, The Inmates Are Running the Asylum uses the author's experiences in corporate America to illustrate how talented people continuously design bad software-based products and why we need technology to work the way average people think. Somewhere out there is a happy medium that makes these types of products both user and bottom-line friendly; this book discusses why we need to quickly find that medium. COMPUTERS,Social Aspects

Hackers & Painters "The computer world is like an intellectual Wild West, in which you can shoot anyone you wish with your ideas, if you're willing to risk the consequences. " --from Hackers & Painters: Big Ideas from the Computer Age, by Paul Graham We are living in the computer age, in a world increasingly designed and engineered by computer programmers and software designers, by people who call themselves hackers. Who are these people, what motivates them, and why should you care? Consider these facts: Everything around us is turning into computers. Your typewriter is gone, replaced by a computer. Your phone has turned into a computer. So has your camera. Soon your TV will. Your car was not only designed on computers, but has more processing power in it than a room-sized mainframe did in 1970. Letters, encyclopedias, newspapers, and even your local store are being replaced by the Internet. Hackers & Painters: Big Ideas from the Computer Age, by Paul Graham, explains this world and the motivations of the people who occupy it. In clear, thoughtful prose that draws on illuminating historical examples, Graham takes readers on an unflinching exploration into what he calls "an intellectual Wild West." The ideas discussed in this book will have a powerful and lasting impact on how we think, how we work, how we develop technology, and how we live. Topics include the importance of beauty in software design, how to make wealth, heresy and free speech, the programming language renaissance, the open-source movement, digital design, internet startups, and more. COMPUTERS,Social Aspects

Understanding Open Source and Free Software Licensing If you've held back from developing open source or free software projects because you don't understand the implications of the various licenses, you're not alone. Many developers believe in releasing their software freely, but have hesitated to do so because they're concerned about losing control over their software. Licensing issues are complicated, and both the facts and fallacies you hear word-of-mouth can add to the confusion.Understanding Open Source and Free Software Licensing helps you make sense of the different options available to you. This concise guide focuses on annotated licenses, offering an in-depth explanation of how they compare and interoperate, and how license choices affect project possibilities. Written in clear language that you don't have to be a lawyer to understand, the book answers such questions as: What rights am I giving up? How will my use of OS/FS licensing affect future users or future developers? Does a particular use of this software--such as combining it with proprietary software--leave me vulnerable to lawsuits?Following a quick look at copyright law, contracts, and the definition of "open source," the book tackles the spectrum of licensing, including: The MIT (or X), BSD, Apache and Academic Free licenses The GPL, LGPL, and Mozilla licenses The QT, Artistic, and Creative Commons licenses Classic Proprietary licenses Sun Community Source license and Microsoft Shared Source project The book wraps up with a look at the legal effects--both positive and negative--of open source/free software licensing.Licensing is a major part of what open source and free software are all about, but it's still one of the most complicated areas of law. Even the very simple licenses are tricky. Understanding Open Source and Free Software Licensing bridges the gap between the open source vision and the practical implications of its legal underpinnings. If open source and free software licenses interest you, this book will help you understand them. If you're an open source/free software developer, this book is an absolute necessity. COMPUTERS,Social Aspects

Internet and Surveillance The Internet has been transformed in the past years from a system primarily oriented on information provision into a medium for communication and community-building. The notion of “Web 2.0â€, social software, and social networking sites such as Facebook, Twitter and MySpace have emerged in this context. With such platforms comes the massive provision and storage of personal data that are systematically evaluated, marketed, and used for targeting users with advertising. In a world of global economic competition, economic crisis, and fear of terrorism after 9/11, both corporations and state institutions have a growing interest in accessing this personal data. Here, contributors explore this changing landscape by addressing topics such as commercial data collection by advertising, consumer sites and interactive media; self-disclosure in the social web; surveillance of file-sharers; privacy in the age of the internet; civil watch-surveillance on social networking sites; and networked interactive surveillance in transnational space. This book is a result of a research action launched by the intergovernmental network COST (European Cooperation in Science and Technology). COMPUTERS,Social Aspects

CyberLaw CyberLaw provides a comprehensive guide to legal issues which have arisen as a result of the growth of the Internet and World Wide Web. As well as discussing each topic in detail, the book includes extensive coverage of the relevant cases and their implications for the future. The book covers a wide range of legal issues, including copyright and trademark issues, defamation, privacy, liability, electronic contracts, taxes, and ethics. A comprehensive history of the significant legal events is also included. COMPUTERS,Social Aspects

Hello, Startup This book is the "Hello, World" tutorial for building products, technologies, and teams in a startup environment. It's based on the experiences of the author, Yevgeniy (Jim) Brikman, as well as interviews with programmers from some of the most successful startups of the last decade, including Google, Facebook, LinkedIn, Twitter, GitHub, Stripe, Instagram, AdMob, Pinterest, and many others. Hello, Startup is a practical, how-to guide that consists of three parts: Products, Technologies, and Teams. Although at its core, this is a book for programmers, by programmers, only Part II (Technologies) is significantly technical, while the rest should be accessible to technical and non-technical audiences alike. If you’re at all interested in startups—whether you’re a programmer at the beginning of your career, a seasoned developer bored with large company politics, or a manager looking to motivate your engineers—this book is for you. COMPUTERS,Social Aspects

Ethics in Computing This textbook raises thought-provoking questions regarding our rapidly-evolving computing technologies, highlighting the need for a strong ethical framework in our computer science education. Ethics in Computing offers a concise introduction to this topic, distilled from the more expansive Ethical and Social Issues in the Information Age. Features: introduces the philosophical framework for analyzing computer ethics; describes the impact of computer technology on issues of security, privacy and anonymity; examines intellectual property rights in the context of computing; discusses such issues as the digital divide, employee monitoring in the workplace, and health risks; reviews the history of computer crimes and the threat of cyberbullying; provides coverage of the ethics of AI, virtualization technologies, virtual reality, and the Internet; considers the social, moral and ethical challenges arising from social networks and mobile communication technologies; includes discussion questions and exercises. COMPUTERS,Social Aspects

Algorithms of Oppression A revealing look at how negative biases against women of color are embedded in search engine results and algorithms Run a Google search for “black girlsâ€â€”what will you find? “Big Booty†and other sexually explicit terms are likely to come up as top search terms. But, if you type in “white girls,†the results are radically different. The suggested porn sites and un-moderated discussions about “why black women are so sassy†or “why black women are so angry†presents a disturbing portrait of black womanhood in modern society. In Algorithms of Oppression, Safiya Umoja Noble challenges the idea that search engines like Google offer an equal playing field for all forms of ideas, identities, and activities. Data discrimination is a real social problem; Noble argues that the combination of private interests in promoting certain sites, along with the monopoly status of a relatively small number of Internet search engines, leads to a biased set of search algorithms that privilege whiteness and discriminate against people of color, specifically women of color. Through an analysis of textual and media searches as well as extensive research on paid online advertising, Noble exposes a culture of racism and sexism in the way discoverability is created online. As search engines and their related companies grow in importance—operating as a source for email, a major vehicle for primary and secondary school learning, and beyond—understanding and reversing these disquieting trends and discriminatory practices is of utmost importance. An original, surprising and, at times, disturbing account of bias on the internet, Algorithms of Oppression contributes to our understanding of how racism is created, maintained, and disseminated in the 21st century. COMPUTERS,Social Aspects

Cyberbullying Cyberbullying is a modern form of harassment that anyone can suffer, but the situation is especially worrying when dealing with minors.This short guide presents answers to some of the most important questions on this subject that any parent with children of school age should bear in mind, such as: What is cyberbullying? How does cyberbullying affect people? Can cyberbullying be prevented? And, above all, what to do if your child is suffering from cyberbullying? Discover all the facts about cyberbullying, based on results from the latest research in the field of psychology on this matter. COMPUTERS,Social Aspects

Cultural Analytics A book at the intersection of data science and media studies, presenting concepts and methods for computational analysis of cultural data. How can we see a billion images? What analytical methods can we bring to bear on the astonishing scale of digital culture--the billions of photographs shared on social media every day, the hundreds of millions of songs created by twenty million musicians on Soundcloud, the content of four billion Pinterest boards? In Cultural Analytics, Lev Manovich presents concepts and methods for computational analysis of cultural data. Drawing on more than a decade of research and projects from his own lab, Manovich offers a gentle, nontechnical introduction to the core ideas of data analytics and discusses the ways that our society uses data and algorithms. COMPUTERS,Social Aspects

Securing Social Identity in Mobile Platforms The book presents novel research in the areas of social identity and security when using mobile platforms. The topics cover a broad range of applications related to securing social identity as well as the latest advances in the field, including the presentation of novel research methods that are in the service of all citizens using mobile devices. More specifically, academic, industry-related and government (law enforcement, intelligence and defence) organizations, will benefit from the research topics of this book that cover the concept of identity management and security using mobile platforms from various perspectives, i.e. whether a user navigates to social media, accesses their own phone devices, access their bank accounts, uses online shopping service providers, accesses their personal documents or accounts with valuable information, surfs the internet, or even becomes a victim of cyberattacks. In all of the aforementioned cases, there is a need for mobile related technologies that protect the users’ social identity and well-being in the digital world, including the use of biometrics, cybersecurity software and tools, active authentication and identity anti-spoofing algorithms and more. COMPUTERS,Social Aspects

The Blockchain and the New Architecture of Trust How the blockchain—a system built on foundations of mutual mistrust—can become trustworthy. The blockchain entered the world on January 3, 2009, introducing an innovative new trust architecture: an environment in which users trust a system—for example, a shared ledger of information—without necessarily trusting any of its components. The cryptocurrency Bitcoin is the most famous implementation of the blockchain, but hundreds of other companies have been founded and billions of dollars invested in similar applications since Bitcoin's launch. Some see the blockchain as offering more opportunities for criminal behavior than benefits to society. In this book, Kevin Werbach shows how a technology resting on foundations of mutual mistrust can become trustworthy. The blockchain, built on open software and decentralized foundations that allow anyone to participate, seems like a threat to any form of regulation. In fact, Werbach argues, law and the blockchain need each other. Blockchain systems that ignore law and governance are likely to fail, or to become outlaw technologies irrelevant to the mainstream economy. That, Werbach cautions, would be a tragic waste of potential. If, however, we recognize the blockchain as a kind of legal technology that shapes behavior in new ways, it can be harnessed to create tremendous business and social value. COMPUTERS,Social Aspects

The Archived Web An original methodological framework for approaching the archived web, both as a source and as an object of study in its own right. As life continues to move online, the web becomes increasingly important as a source for understanding the past. But historians have yet to formulate a methodology for approaching the archived web as a source of study. How should the history of the present be written? In this book, Niels Brügger offers an original methodological framework for approaching the web of the past, both as a source and as an object of study in its own right. While many studies of the web focus solely on its use and users, Brügger approaches the archived web as a semiotic, textual system in order to offer the first book-length treatment of its scholarly use. While the various forms of the archived web can challenge researchers' interactions with it, they also present a range of possibilities for interpretation. The Archived Web identifies characteristics of the online web that are significant now for scholars, investigates how the online web became the archived web, and explores how the particular digitality of the archived web can affect a historian's research process. Brügger offers suggestions for how to translate traditional historiographic methods for the study of the archived web, focusing on provenance, creating an overview of the archived material, evaluating versions, and citing the material. The Archived Web lays the foundations for doing web history in the digital age, offering important and timely guidance for today's media scholars and tomorrow's historians. COMPUTERS,Social Aspects

This Is Why We Can't Have Nice Things Why the troll problem is actually a culture problem: how online trolling fits comfortably within today's media landscape. Internet trolls live to upset as many people as possible, using all the technical and psychological tools at their disposal. They gleefully whip the media into a frenzy over a fake teen drug crisis; they post offensive messages on Facebook memorial pages, traumatizing grief-stricken friends and family; they use unabashedly racist language and images. They take pleasure in ruining a complete stranger's day and find amusement in their victim's anguish. In short, trolling is the obstacle to a kinder, gentler Internet. To quote a famous Internet meme, trolling is why we can't have nice things online. Or at least that's what we have been led to believe. In this provocative book, Whitney Phillips argues that trolling, widely condemned as obscene and deviant, actually fits comfortably within the contemporary media landscape. Trolling may be obscene, but, Phillips argues, it isn't all that deviant. Trolls' actions are born of and fueled by culturally sanctioned impulses—which are just as damaging as the trolls' most disruptive behaviors. Phillips describes, for example, the relationship between trolling and sensationalist corporate media—pointing out that for trolls, exploitation is a leisure activity; for media, it's a business strategy. She shows how trolls, “the grimacing poster children for a socially networked world,” align with social media. And she documents how trolls, in addition to parroting media tropes, also offer a grotesque pantomime of dominant cultural tropes, including gendered notions of dominance and success and an ideology of entitlement. We don't just have a trolling problem, Phillips argues; we have a culture problem. This Is Why We Can't Have Nice Things isn't only about trolls; it's about a culture in which trolls thrive. COMPUTERS,Social Aspects

Technically Wrong “An entertaining romp that tells us where and why the tech industry, once America’s darling, went wrong, and what it might do to recover its good graces.†—Tim Wu, author of The Master Switch Buying groceries, tracking our health, finding a date: whatever we want to do, odds are that we can now do it online. But few of us realize just how many oversights, biases, and downright ethical nightmares are baked inside the tech products we use every day. It’s time we change that. In Technically Wrong, Sara Wachter-Boettcher demystifies the tech industry, leaving those of us on the other side of the screen better prepared to make informed choices about the services we use—and to demand more from the companies behind them. A Wired Top Tech Book of the YearA Fast Company Best Business and Leadership Book of the Year COMPUTERS,Social Aspects

Color Theory and Modeling for Computer Graphics, Visualization, and Multimedia Applications Color Theory and Modeling for Computer Graphics, Visualization, and Multimedia Applications deals with color vision and visual computing. This book provides an overview of the human visual system with an emphasis on color vision and perception. The book then goes on to discuss how human color vision and perception are applied in several applications using computer-generated displays, such as computer graphics and information and data visualization. Color Theory and Modeling for Computer Graphics, Visualization, and Multimedia Applications is suitable as a secondary text for a graduate-level course on computer graphics, computer imaging, or multimedia computing and as a reference for researchers and practitioners developing computer graphics and multimedia applications. COMPUTERS,Software Development & Engineering,Computer Graphics

Digital Lighting and Rendering Crafting a perfect rendering in 3D software means nailing all the details. And no matter what software you use, your success in creating realistic-looking illumination, shadows and textures depends on your professional lighting and rendering techniques. In this lavishly illustrated new edition, Pixar's Jeremy Birn shows you how to: Master Hollywood lighting techniques to produce professional results in any 3D application Convincingly composite 3D models into real-world environments Apply advanced rendering techniques using subsurface scattering, global illumination, caustics, occlusion, and high dynamic range images Design realistic materials and paint detailed texture maps Mimic real-life camera properties such as f-stops, exposure times, depth-of-field, and natural color temperatures for photorealistic renderings Render in multiple passes for greater efficiency and creative control Understand production pipelines at visual effects and animation studios Develop your lighting reel to get a job in the industry COMPUTERS,Software Development & Engineering,Computer Graphics

ZAG COMPUTERS,Software Development & Engineering,Computer Graphics

Digital Modeling of Material Appearance Computer graphics systems are capable of generating stunningly realistic images of objects that have never physically existed. In order for computers to create these accurately detailed images, digital models of appearance must include robust data to give viewers a credible visual impression of the depicted materials. In particular, digital models demonstrating the nuances of how materials interact with light are essential to this capability. Digital Modeling of Material Appearance is the first comprehensive work on the digital modeling of material appearance: it explains how models from physics and engineering are combined with keen observation skills for use in computer graphics rendering. Written by the foremost experts in appearance modeling and rendering, this book is for practitioners who want a general framework for understanding material modeling tools, and also for researchers pursuing the development of new modeling techniques. The text is not a "how to" guide for a particular software system. Instead, it provides a thorough discussion of foundations and detailed coverage of key advances. Practitioners and researchers in applications such as architecture, theater, product development, cultural heritage documentation, visual simulation and training, as well as traditional digital application areas such as feature film, television, and computer games, will benefit from this much needed resource. ABOUT THE AUTHORS Julie Dorsey and Holly Rushmeier are professors in the Computer Science Department at Yale University and co-directors of the Yale Computer Graphics Group. François Sillion is a senior researcher with INRIA (Institut National de Recherche en Informatique et Automatique), and director of its Grenoble Rhône-Alpes research center. First comprehensive treatment of the digital modeling of material appearance Provides a foundation for modeling appearance, based on the physics of how light interacts with materials, how people perceive appearance, and the implications of rendering appearance on a digital computer An invaluable, one-stop resource for practitioners and researchers in a variety of fields dealing with the digital modeling of material appearance COMPUTERS,Software Development & Engineering,Computer Graphics

Robin Williams Cool Mac Apps This is the eBook version of the printed book. If the print book includes a CD-ROM, this content is not included within the eBook version.This popular book shows readers how to take advantage of the iLife '08 applications that to many are the coolest parts of using a Mac. Through tutorials, tips, and techniques readers will learn how to use each of the powerful applications -- individually and as part of an integrated, interactive suite. Robin and John also cover the features of the immensely popular .Mac Web Gallery, which enables you to share your iPhoto library with family and friends with just a few clicks. Friendly, practical instructions will have new and veteran Mac owners using all that's new in the suite in no time. They'll find everything about getting on the Internet and using email; using the way-cool iChat AV, which adds audio and video to instant messaging; using iTunes, including access to the iTunes Music Store; the new video libary in iMovie; new organization and editing tools in iPhoto; new animated themes in iDVD; and much more! COMPUTERS,Software Development & Engineering,Computer Graphics

Brand Gap, Revised Edition, The THE BRAND GAP is the first book to present a unified theory of brand-building. Whereas most books on branding are weighted toward either a strategic or creative approach, this book shows how both ways of thinking can unite to produce a “charismatic brandâ€â€”a brand that customers feel is essential to their lives. In an entertaining two-hour read you’ll learn: • the new definition of brand • the five essential disciplines of brand-building • how branding is changing the dynamics of competition • the three most powerful questions to ask about any brand • why collaboration is the key to brand-building • how design determines a customer’s experience • how to test brand concepts quickly and cheaply • the importance of managing brands from the inside • 220-word brand glossary From the back cover: Not since McLuhan’s THE MEDIUM IS THE MESSAGE has a book compressed so many ideas into so few pages. Using the visual language of the boardroom, Neumeier presents the first unified theory of branding—a set of five disciplines to help companies bridge the gap between brand strategy and customer experience. Those with a grasp of branding will be inspired by the new perspectives they find here, and those who would like to understand it better will suddenly “get it.†This deceptively simple book offers everyone in the company access to “the most powerful business tool since the spreadsheet.†COMPUTERS,Software Development & Engineering,Computer Graphics

Non-Designer's Photoshop Book, The Many designers and photographers own the entire suite of Adobe creative products, but they manage to learn only one or two of the applications really well. This new addition to the popular Non-Designer’s books from best-selling authors Robin Williams and John Tollett uses a series of individual exercises to teach image-editing tasks in Adobe Photoshop CS5.5 specifically to designers, who need to enhance their photos for use in brochures, advertising, Flickr, Facebook, websites, and so on. In this fun, full-color, straight-forward guide to Photoshop CS5.5, you’ll learn: Basic photo editing, such as how to smooth out wrinkles, remove blemishes, lose a little weight, clean up dust and scratches, brighten and sharpen the image, delete people, remove or add space in the middle of a photo, and more How to further manipulate and enhance images with filters and effects How to draw and paint with customized brushes, and how to colorize a black-and-white image All about layers and how to take advantage of them How and when to use paths, layer masks, and clipping masks to increase your editing capabilities How to merge several photos into one panorama, use the Puppet Warp feature, remove lens distortion, and much more Whether you need to improve or edit your photos for your graphic design work or to upload to your Flickr or Facebook account, this book is the easiest path to mastering basic tasks in Photoshop. COMPUTERS,Software Development & Engineering,Computer Graphics

Beginning Google Sketchup for 3D Printing The age of 3D printing and personal fabrication is upon us! You’ve probably heard of the incredibly sophisticated, yet inexpensive 3D printers that can produce almost any creation you give them. But how do you become part of that revolution? Sandeep Singh takes you through the skills you need to learn and the services and technologies you need to know—explaining what 3D printing is, how it works, and what it can do for you. You’ll find yourself rapidly prototyping and learning to produce complex designs that can be fabricated by online 3D printing services or privately-owned 3D printers—in your hands in no time. Beginning Google SketchUp for 3D Printing starts by explaining how to use SketchUp and its plug-ins to make your design products. You will learn how to present and animate 3D models, and how to use Google Earth and 3D Warehouse to sell and market your 3D models. You'll also catch a glimpse of the 3D printing's future so you can plan ahead while mastering today's tools. Beginning Google SketchUp for 3D Printing is the perfect book for 3D designers, hobbyists, woodworkers, craftspeople, and artists interested in the following: Designing in 3D using SketchUp Using the online 3D printing pipeline Animating SketchUp 3D models Becoming familiar with rapid prototyping technology Navigating new 3D and personal fabrication technologies Working with Google Earth and 3D Warehouse with confidence Welcome to the era of 3D printing and personal fabrication! COMPUTERS,Software Development & Engineering,Computer Graphics

The Non-Designer's Illustrator Book Many designers and photographers own the entire suite of Adobe creative products, but they manage to learn only one or two of the applications really well. This new addition to the popular Non-Designer’s series from best-selling authors Robin Williams and John Tollett includes many individual exercises designed specifically to teach the tools and features in Illustrator CS5.5 that designers (as opposed to illustrators) need to use. Along the way, the book offers many design tips for non-designers. Individual exercises ensure that a reader can jump in at any point and learn a specific tool or technique. In this non-designer’s guide to Illustrator techniques, you’ll learn: How vector images, as in Illustrator, are different from raster images, as in Photoshop, and when to choose which one How to use Illustrator CS5.5’s tools to create and work with lines, shapes, anchor points and control handles, color, etc. How to draw your own shapes and trace others How to enter text and control the design of it How to take advantage of the symbol libraries, clipping masks, variable-width strokes, and much more When and why to rasterize elements of your vector image COMPUTERS,Software Development & Engineering,Computer Graphics

Photoshop CS6 This best-selling guide from authors Elaine Weinmann and Peter Lourekas has been the go-to tutorial and reference book for photography/design professionals and the textbook of choice in college classrooms for decades. This edition includes their trademark features of clear, concise, step-by-step instructions; hundreds of full-color images; screen captures of program features; and supplemental tips and sidebars in every chapter. Among the new CS6 features covered in this extensively updated guide are: Field Blur, Iris Blur and Tilt-Shift filters; Properties panel; Exporting and Importing presets; Content-Aware Move tool and Content-Aware option for the Patch tool; Timeline panel for video editing; Photographic Toning libraries for Gradient Map adjustments; and Open Type options. Improved CS6 features covered: Crop tool options and features, Adjustment Brush tool in Camera Raw, and Vector masks. New and updated Photoshop CS6 features are clearly marked with bright red stars in both the table of contents and main text. COMPUTERS,Software Development & Engineering,Computer Graphics

The NURBS Book Until recently B-spline curves and surfaces (NURBS) were principally of interest to the computer aided design community, where they have become the standard for curve and surface description. Today we are seeing expanded use of NURBS in modeling objects for the visual arts, including the film and entertainment industries, art, and sculpture. NURBS are now also being used for modeling scenes for virtual reality applications. These applications are expected to increase. Consequently, it is quite appropriate for The.N'U'R-BS Book to be part of the Monographs in Visual Communication Series. B-spline curves and surfaces have been an enduring element throughout my pro fessional life. The first edition of Mathematical Elements for Computer Graphics, published in 1972, was the first computer aided design/interactive computer graph ics textbook to contain material on B-splines. That material was obtained through the good graces of Bill Gordon and Louie Knapp while they were at Syracuse University. A paper of mine, presented during the Summer of 1977 at a Society of Naval Architects and Marine Engineers meeting on computer aided ship surface design, was arguably the first to examine the use of B-spline curves for ship design. For many, B-splines, rational B-splines, and NURBS have been a bit mysterious. COMPUTERS,Software Development & Engineering,Computer Graphics
Geometric Modeling The Blaubeuren Conference "Theory and Practice of Geometric Modeling" has become a meeting place for leading experts from industrial and academic research institutions, CAD system developers and experienced users to exchange new ideas and to discuss new concepts and future directions in geometric modeling. The relaxed and calm atmosphere of the Heinrich-Fabri-Institute in Blaubeuren provides the appropriate environment for profound and engaged discussions that are not equally possible on other occasions. Real problems from current industrial projects as well as theoretical issues are addressed on a high scientific level. This book is the result of the lectures and discussions during the conference which took place from October 14th to 18th, 1996. The contents is structured in 4 parts: Mathematical Tools Representations Systems Automated Assembly. The editors express their sincere appreciation to the contributing authors, and to the members of the program committee for their cooperation, the careful reviewing and their active participation that made the conference and this book a success. COMPUTERS,Software Development & Engineering,Computer Graphics

Rate-Distortion Based Video Compression One of the most intriguing problems in video processing is the removal of the redundancy or the compression of a video signal. There are a large number of applications which depend on video compression. Data compression represents the enabling technology behind the multimedia and digital television revolution. In motion compensated lossy video compression the original video sequence is first split into three new sources of information, segmentation, motion and residual error. These three information sources are then quantized, leading to a reduced rate for their representation but also to a distorted reconstructed video sequence. After the decomposition of the original source into segmentation, mo tion and residual error information is decided, the key remaining problem is the allocation of the available bits into these three sources of information. In this monograph a theory is developed which provides a solution to this fundamental bit allocation problem. It can be applied to all quad-tree-based motion com pensated video coders which use a first order differential pulse code modulation (DPCM) scheme for the encoding of the displacement vector field (DVF) and a block-based transform scheme for the encoding of the displaced frame differ ence (DFD). An optimal motion estimator which results in the smallest DFD energy for a given bit rate for the encoding of the DVF is also a result of this theory. Such a motion estimator is used to formulate a motion compensated interpolation scheme which incorporates a global smoothness constraint for the DVF. COMPUTERS,Software Development & Engineering,Computer Graphics

Motion-Based Recognition Motion-based recognition deals with the recognition of an object and/or its motion, based on motion in a series of images. In this approach, a sequence containing a large number of frames is used to extract motion information. The advantage is that a longer sequence leads to recognition of higher level motions, like walking or running, which consist of a complex and coordinated series of events. Unlike much previous research in motion, this approach does not require explicit reconstruction of shape from the images prior to recognition. This book provides the state-of-the-art in this rapidly developing discipline. It consists of a collection of invited chapters by leading researchers in the world covering various aspects of motion-based recognition including lipreading, gesture recognition, facial expression recognition, gait analysis, cyclic motion detection, and activity recognition. Audience: This volume will be of interest to researchers and post- graduate students whose work involves computer vision, robotics and image processing. COMPUTERS,Software Development & Engineering,Computer Graphics

Advances in Computer Vision Computer vision solutions used to be very specific and difficult to adapt to different or even unforeseen situations. The current development is calling for simple to use yet robust applications that could be employed in various situations. This trend requires the reassessment of some theoretical issues in computer vision. A better general understanding of vision processes, new insights and better theories are needed. The papers selected from the conference staged in Dagstuhl in 1996 to gather scientists from the West and the former eastern-block countries address these goals and cover such fields as 2D images (scale space, morphology, segmentation, neural networks, Hough transform, texture, pyramids), recovery of 3-D structure (shape from shading, optical flow, 3-D object recognition) and how vision is integrated into a larger task-driven framework (hand-eye calibration, navigation, perception-action cycle). COMPUTERS,Software Development & Engineering,Computer Graphics

Image and Video Compression Standards New to the Second Edition: offers the latest developments in standards activities (JPEG-LS, MPEG-4, MPEG-7, and H.263) provides a comprehensive review of recent activities on multimedia enhanced processors, multimedia coprocessors, and dedicated processors, including examples from industry. Image and Video Compression Standards: Algorithms and Architectures, Second Edition presents an introduction to the algorithms and architectures that form the underpinnings of the image and video compressions standards, including JPEG (compression of still-images), H.261 and H.263 (video teleconferencing), and MPEG-1 and MPEG-2 (video storage and broadcasting). The next generation of audiovisual coding standards, such as MPEG-4 and MPEG-7, are also briefly described. In addition, the book covers the MPEG and Dolby AC-3 audio coding standards and emerging techniques for image and video compression, such as those based on wavelets and vector quantization. Image and Video Compression Standards: Algorithms and Architectures, Second Edition emphasizes the foundations of these standards; namely, techniques such as predictive coding, transform-based coding such as the discrete cosine transform (DCT), motion estimation, motion compensation, and entropy coding, as well as how they are applied in the standards. The implementation details of each standard are avoided; however, the book provides all the material necessary to understand the workings of each of the compression standards, including information that can be used by the reader to evaluate the efficiency of various software and hardware implementations conforming to these standards. Particular emphasis is placed on those algorithms and architectures that have been found to be useful in practical software or hardware implementations. Image and Video Compression Standards: Algorithms and Architectures, Second Edition uniquely covers all major standards (JPEG, MPEG-1, MPEG-2, MPEG-4, H.261, H.263) in a simple and tutorial manner, while fully addressing the architectural considerations involved when implementing these standards. As such, it serves as a valuable reference for the graduate student, researcher or engineer. The book is also used frequently as a text for courses on the subject, in both academic and professional settings. COMPUTERS,Software Development & Engineering,Computer Graphics

Intelligent Vision Systems for Industry The application of intelligent imaging techniques to industrial vision problems is an evolving aspect of current machine vision research. Machine vision is a relatively new technology, more concerned with systems engineering than with computer science, and with much to offer the manufacturing industry in terms of improving efficiency, safety and product quality. Beginning with an introductory chapter on the basic concepts, the authors develop these ideas to describe intelligent imaging techniques for use in a new generation of industrial imaging systems. Sections cover the application of AI languages such as Prolog, the use of multi-media interfaces and multi-processor systems, external device control, and colour recognition. The text concludes with a discussion of several case studies that illustrate how intelligent machine vision techniques can be used in industrial applications. COMPUTERS,Software Development & Engineering,Computer Graphics

Number by Colors Numbering with colors is tutorial in nature, with many practical examples given throughout the presentation. It is heavily illustrated with gray-scale images, but also included is an 8-page signature of 4-color illustrations to support the presentation. While the organization is somewhat similar to that found in "The Data Handbook," there is little overlap with the content material in that publication. The first section in the book discusses Color Physics, Physiology and Psychology, talking about the details of the eye, the visual pathway, and how the brain converts colors into perceptions of hues. This is followed by the second section, in which Color Technologies are explained, i.e. how we describe colors using the CIE diagram, and how colors can be reproduced using various technologies such as offset printing and video screens. The third section of the book, Using Colors, relates how scientists and engineers can use color to help gain insight into their data sets through true color, false color, and pseudocolor imaging. COMPUTERS,Software Development & Engineering,Computer Graphics

Computer Animation and Simulation ’97 This volume contains the research papers presented at the Eighth Eurographics Workshop on Computer Animation and Simulation which took place in Budapest, Hungary, September 2-3, 1997. The workshop is an international forum for research in human animation, physically-based modeling, motion control, animation systems, and other key aspects of animation and simulation. The problem of realistically and efficiently modeling the motion of people, ob jects, fluids, etc. remains a significant challenge in computer graphics. This workshop is representative of the continuing interest in this field of study. This year, animation and simulation of human shape and motion is of particular interest. In fact, nine of the papers in this volume deal with techniques which are applicable to human animation. Others are concerned with equally interesting dy namic natural phenomena, such as clouds, plant development, and coastal scenes. The call for papers required submission of the full papers for review, and each paper was reviewed by at least 3 members on the international program committee, consisting of: Bruno Arnaldi (IRISA/INRIA Rennes, France) Norman Badler (University of Pennsylvania, U. S. A. ) Ronan Boulic (Swiss Federal Institute of Technology, Switzerland) Michael Cohen (Microsoft, U. S. A. ) Sabine Coquillart (INRIA, France) David Forsey (University of British Columbia, Canada) Marie-Paule Gascuel (iMAGIS-IMAG, France) Gerard Hegron (Ecoles des Mines de Nantes, France) Jessica Hodgins (Georgia Institute of Technology, U. S. A. COMPUTERS,Software Development & Engineering,Computer Graphics

Document Imaging Document imaging is a new discipline in applied computer science. It is building bridges between computer graphics, the world of prepress and press, and the areas of color vision and color reproduction. The focus of this book is of special relevance to people learning how to utilize and integrate such available technology as digital printing or short run color, how to make use of CIM techniques for print products, and how to evaluate related technologies that will become relevant in the next few years. This book is the first to give a comprehensive overview of document imaging, the areas involved, and how they relate. For readers with a background in computer graphics it gives insight into all problems related to putting information in print, a field only very thinly covered in textbooks on computer graphics. COMPUTERS,Software Development & Engineering,Computer Graphics

Seeing Between the Pixels Pictures are at the heart of how we communicate with computers, emblematic of our cur rent fascination with multimedia and web-based computing. Nevertheless, most of us know far less about pictures and the way in which they work than we know about the text that often accompanies them. In an attempt to understand pictures, perhaps the most fundamental question we can ask is, "What is a picture?" What is it that objects as di verse as icons, bar charts, paintings, and photographs have in common that makes us refer to all of them as pictures? And what is it about pictures that convinces us to use them instead of, or in addition to, text? We often talk about how pictures "depict" things. But, even the process of depiction seems to differ from one picture to another. On a computer, we may use a paint system to guide a virtual brush over the screen, a video camera to capture a live image, a spread sheet to automatically generate a corresponding bar chart, or a rendering system that models the interactions of synthetic lights, objects, and cameras. Is there some un derlying property that these processes all share? Computer scientists are used to thinking of pictures in terms of their representation: an array of pixels, a list or hierarchy of graphics primitives, or even a program written in a language such as PostScript. COMPUTERS,Software Development & Engineering,Computer Graphics

Mathematical Morphology and Its Applications to Image and Signal Processing Mathematical morphology (MM) is a powerful methodology for the quantitative analysis of geometrical structures. It consists of a broad and coherent collection of theoretical concepts, nonlinear signal operators, and algorithms aiming at extracting, from images or other geometrical objects, information related to their shape and size. Its mathematical origins stem from set theory, lattice algebra, and integral and stochastic geometry. MM was initiated in the late 1960s by G. Matheron and J. Serra at the Fontainebleau School of Mines in France. Originally it was applied to analyzing images from geological or biological specimens. However, its rich theoretical framework, algorithmic efficiency, easy implementability on special hardware, and suitability for many shape- oriented problems have propelled its widespread diffusion and adoption by many academic and industry groups in many countries as one among the dominant image analysis methodologies. The purpose of Mathematical Morphology and its Applications to Image and Signal Processing is to provide the image analysis community with a sampling from the current developments in the theoretical (deterministic and stochastic) and computational aspects of MM and its applications to image and signal processing. The book consists of the papers presented at the ISMM'96 grouped into the following themes: Theory Connectivity Filtering Nonlinear System Related to Morphology Algorithms/Architectures Granulometries, Texture Segmentation Image Sequence Analysis Learning Document Analysis Applications COMPUTERS,Software Development & Engineering,Computer Graphics

Object-Oriented and Mixed Programming Paradigms The area of computer graphics is characterized by rapid evolution. New techniques in hardware and software developments, e. g. , new rendering methods, have led to new ap plications and broader acceptance of graphics in fields such as scientific visualization, multi-media applications, computer aided design, and virtual reality systems. The evolving functionality and the growing complexity of graphics algorithms and sys tems make it more difficult for the application programmer to take full advantage of these systems. Conventional programming methods are no longer suited to manage the increasing complexity, so new programming paradigms and system architectures are re quired. One important step in this direction is the introduction and use of object-oriented methods. Intuition teils us that visible graphical entities are objects, and experience has indeed shown that object-oriented software techniques are quite useful for graphics. The expressiveness of object-oriented languages compared to pure procedurallanguages gives the graphics application programmer much better support when transforming his mental intentions into computer code. Moreover, object-oriented software development is a, weil founded technology, allowing software to be built from reusable and extensible compo nents. This book contains selected, reviewed and thoroughly revised vers ions of papers submit ted to and presented at the Fourth Eurographies Workshops on Object-Oriented Graphics, held on May 9-11, 1994 in Sintra, Portugal. COMPUTERS,Software Development & Engineering,Computer Graphics

Video Coding In recent years there has been an increasing interest in Second Generation Image and Video Coding Techniques. These techniques introduce new concepts from image analysis that greatly improve the performance of the coding schemes for very high compression. This interest has been further emphasized by the future MPEG 4 standard. Second generation image and video coding techniques are the ensemble of approaches proposing new and more efficient image representations than the conventional canonical form. As a consequence, the human visual system becomes a fundamental part of the encoding/decoding chain. More insight to distinguish between first and second generation can be gained if it is noticed that image and video coding is basically carried out in two steps. First, image data are converted into a sequence of messages and, second, code words are assigned to the messages. Methods of the first generation put the emphasis on the second step, whereas methods of the second generation put it on the first step and use available results for the second step. As a result of including the human visual system, second generation can be also seen as an approach of seeing the image composed by different entities called objects. This implies that the image or sequence of images have first to be analyzed and/or segmented in order to find the entities. It is in this context that we have selected in this book three main approaches as second generation video coding techniques: Segmentation-based schemes Model Based Schemes Fractal Based Schemes £/LIST£ Video Coding: The Second Generation Approach is an important introduction to the new coding techniques for video. As such, all researchers, students and practitioners working in image processing will find this book of interest. COMPUTERS,Software Development & Engineering,Computer Graphics

Exploratory Vision Advances in sensing, signal processing, and computer technology during the past half century have stimulated numerous attempts to design general-purpose ma chines that see. These attempts have met with at best modest success and more typically outright failure. The difficulties encountered in building working com puter vision systems based on state-of-the-art techniques came as a surprise. Perhaps the most frustrating aspect of the problem is that machine vision sys tems cannot deal with numerous visual tasks that humans perform rapidly and effortlessly. In reaction to this perceived discrepancy in performance, various researchers (notably Marr, 1982) suggested that the design of machine-vision systems should be based on principles drawn from the study of biological systems. This "neuro morphic" or "anthropomorphic" approach has proven fruitful: the use of pyramid (multiresolution) image representation methods in image compression is one ex ample of a successful application based on principles primarily derived from the study of biological vision systems. It is still the case, however, that the perfor of computer vision systems falls far short of that of the natural systems mance they are intended to mimic, suggesting that it is time to look even more closely at the remaining differences between artificial and biological vision systems. COMPUTERS,Software Development & Engineering,Computer Graphics

Computer Animation and Simulation ’96 Englischer Kurztext!!!The 14 papers in this volume vividly demonstrate the current state of research in real-time animation of complex articulated structures in particular (humans, legged robots, plants) and of dynamic scenes in general. Special emphasis is given on innovative approaches to the fast design of realistic movements, 2D and 3D deformations, and simulation optimization. COMPUTERS,Software Development & Engineering,Computer Graphics

Theoretical Foundations of Computer Vision Computer Vision is a rapidly growing field of research investigating computational and algorithmic issues associated with image acquisition, processing, and understanding. It serves tasks like manipulation, recognition, mobility, and communication in diverse application areas such as manufacturing, robotics, medicine, security and virtual reality. This volume contains a selection of papers devoted to theoretical foundations of computer vision covering a broad range of fields, e.g. motion analysis, discrete geometry, computational aspects of vision processes, models, morphology, invariance, image compression, 3D reconstruction of shape. Several issues have been identified to be of essential interest to the community: non-linear operators; the transition between continuous to discrete representations; a new calculus of non-orthogonal partially dependent systems. COMPUTERS,Software Development & Engineering,Computer Graphics

High Performance Computing for Computer Graphics and Visualisation This book contains mainly a selection of papers that were presented at the International Workshop on High Performance Computing/or Computer Graphics and Visualisation, held in Swansea, United Kingdom on 3-4 July 1995. The workshop was sponsored by the HEFCWI Initiative on ·Parallel Computing - Foundations and Applications·, and it has provided the international computer graphics community with a platform for: • assessing and reviewing the impact of the development of high performance computing on the progress of computer graphics and visualisation; • presenting the current use of high performance computing architecture and software tools in computer graphics and visualisation, and the development of parallel graphics algorithms; • identifying potential high performance computing applications in computer graphics and visualisation, and encouraging members of the graphics community to think about their problems from the perspective of parallelism. The book is divided into six sections. The first section, which acts as the introduction of the book, gives an overview of the current state of the art It contains a comprehensive survey, by Whitman, of parallel algorithms for computer graphics and visualisation; and a discussion, by Hansen, on the past, present and future high performance computing applications in computer graphics and visualisation. The second section is focused on the design and implementation of high performance architecture, software tools and algorithms for surface rendering. COMPUTERS,Software Development & Engineering,Computer Graphics

Virtual Environments and Scientific Visualization ’96 Englischer Kurztext!!!!The papers in the first part of the book deal with virtual environment system architecture and programming styles, mixed reality and algorithms for virtual environments, synthetic actors, crowd simulations and modeling aspects, application experience in surgery support, geographic information systems, and engineering and virtual housing systems. The main topics treated in the second part of the book are volume rendering, user interfaces and scientific visualization, architecture of scientific visualization systems, and flow visualization. COMPUTERS,Software Development & Engineering,Computer Graphics

Image Processing for Broadcast and Video Production Recent developments in computer visualisation mean that it is now possible to combine computer-generated image sequences with real video, in real time, for broadcast quality production. This will not only revolutionise the broadcast industry, by making "electronic film sets" possible for example, but also has important implications for related fields such as virtual reality, multi-media, industrial vision, and medical image processing. This volume contains papers from the European Workshop on Combined Real and Synthetic Image Processing for Broadcast and Video Production, held in Hamburg, 23-24 November 1994. The papers cover three main aspects of research: hardware, image analysis, and image synthesis, and include several key contributions from the EU RACE II supported MONA LISA (MOdelling NAturaL Images for Synthesis and Animation) project. The resulting volume gives a comprehensive overview of this important area of research, and will be of interest to practitioners, researchers, and postgraduate students. COMPUTERS,Software Development & Engineering,Computer Graphics

Interactive Systems Making systems easier to use implies increasingly complex management of communication between users and applications. An increasing part of the application program is devoted to the user interface. In order to manage this complexity, it is very important to have tools, notations, and methodologies that support the designer's work during the refinement process from specification to implementation. The purpose of this proceedings of the first (1994) Eurographics workshop on this area is to review the state of the art. It compares the different existing approaches in order to identify the principal requirements and the most suitable notations and methods, and indicates the relevant results. COMPUTERS,Software Development & Engineering,Computer Graphics

Object-Oriented Programming for Graphics Object-oriented concepts are particularly applicable to computer graphics in its broadest sense, including interaction, image synthesis, animation, and computer-aided design. The use of object-oriented techniques in computer graphics is a widely acknowledged way of dealing with the complexities encountered in graphics systems. But the field of object-oriented graphics (OOG) is still young and full of problems. This book reports on latest advances in this field and discusses how the discipline of OOG is being explored and developed. The topics covered include object-oriented constraint programming, object-oriented modeling of graphics applications to handle complexity, object-oriented techniques for developing user interfaces, and 3D modeling and rendering. COMPUTERS,Software Development & Engineering,Computer Graphics

Computer Animation and Simulation ’95 This volume contains research papers that were presented at the Sixth Eurographics Workshop on Animation and Simulation which took place at Maastricht, The Nether lands, September 2-3, 1995. A core area within computer graphics, animation is concerned with the computer synthesis of dynamic scenes. The creation of realistic animation based on the simulation of physical and biological phenomena is a unify ing and rapidly evolving research theme. This series of workshops, an activity of the Eurographics Working Group on Animation and Simulation, is an international forum where researchers representing the animation and simulation communities convene to exchange knowledge and experience related to this theme and to physics-based mod elling, human modelling, motion control, visualization, etc. Of keen interest at this sixth workshop were novel animation techniques and animation systems that simulate the dynamics and interactions of physical objects-solid, fluid, and gaseous-as well as the behaviors of living systems such as plants, lower animals, and humans. The workshop continued to promote the confluence of animation and simulation as a leading edge of computer graphics research that is providing animators with sophisticated new algorithms for synthesizing dynamic scenes. The call for extended abstracts for the workshop, issued in February 1995, elicited an enthusiastic response. COMPUTERS,Software Development & Engineering,Computer Graphics

Adobe Photoshop CC on Demand Need answers quickly? Adobe Photoshop CC on Demand provides those answers in a visual step-by-step format. We will show you exactly what to do through lots of full color illustrations and easy-to-follow instructions. Includes • Online Workshops that focus on real-world techniques • Online Adobe certification resources for both ACE and ACA • More than 500 essential Photoshop CC tasks Inside the Book • Improve productivity and efficiency with Adobe Creative Cloud • Use automatic saving options for better efficiency and protection • Use automatic layer alignment and blending to work with objects • Use Adobe Camera Raw to enhance or correct a photo • Use content-aware options for scaling and fill • Create eye-catching images with special effect filters • Select and modify one or more shapes at the same time • Create character and paragraph styles to manage and use text • Transform video in Photoshop just like an image • Create and manipulate 3D models using presets and custom options Numbered Steps guide you through each task See Also points you to related information in the book Did You Know alerts you to tips and techniques Illustrations with matching steps Tasks are presented on one or two pages Bonus Online Content Register your book at queondemand.com to gain access to: • Workshops and related files • Keyboard shortcutsVisit the author site: perspection.com COMPUTERS,Software Development & Engineering,Computer Graphics

Epioptics The study of condensed matter using optical techniques, where photons act as both probe and signal, has a long history. It is only recently, however, that the extraction of surface and interface information, with submonolayer resolution, has been shown to be possible using optical techniques (where "optical" applies to electromagnetic radiation in and around the visible region of the spectrum). This book describes these "epioptic" techniques, which have now been quite widely applied to semiconductor surfaces and interfaces. Particular emphasis in the book is placed on recent studies of submonolayer growth on well-characterised semiconductor surfaces, many of which have arisen from CEC DGJGII ESPRIT Basic Research Action No. 3177 "EPIOPTIC", and CEU DGIII ESPRIT Basic Research Action No. 6878 "EASI". Techniques using other areas of the spectrum such as the infra-red region (IR spectroscopy, in its various surface configurations), and the x-ray region (surface x-ray diffraction, x-ray standing wave), are omitted. The optical techniques described use simple lamp or small laser sources and are thus, in principle, easily accessible. Epioptic probes can provide new information on solid-gas, solid-liquid and liquid-liquid interfaces. They are particularly suited to growth monitoring. Emerging process technologies for fabricating submicron and nanoscale semiconductor devices and novel multilayer materials, whether based on silicon or compound semiconductors, all require extremely precise control of growth at surfaces. In situ, non-destructive, real-time monitoring and characterisation of surfaces under growth conditions is needed for further progress. Both atomic scale resolution, and non-destructive characterisation of buried structures, are required. COMPUTERS,Software Development & Engineering,Computer Graphics

Digital Image Compression Digital image business applications are expanding rapidly, driven by recent advances in the technology and breakthroughs in the price and performance of hardware and firmware. This ever increasing need for the storage and transmission of images has in turn driven the technology of image compression: image data rate reduction to save storage space and reduce transmission rate requirements. Digital image compression offers a solution to a variety of imaging applications that require a vast amount of data to represent the images, such as document imaging management systems, facsimile transmission, image archiving, remote sensing, medical imaging, entertainment, HDTV, broadcasting, education and video teleconferencing. Digital Image Compression: Algorithms and Standards introduces the reader to compression algorithms, including the CCITT facsimile standards T.4 and T.6, JBIG, CCITT H.261 and MPEG standards. The book provides comprehensive explanations of the principles and concepts of the algorithms, helping the readers' understanding and allowing them to use the standards in business, product development and R&D. Audience: A valuable reference for the graduate student, researcher and engineer. May also be used as a text for a course on the subject. COMPUTERS,Software Development & Engineering,Computer Graphics
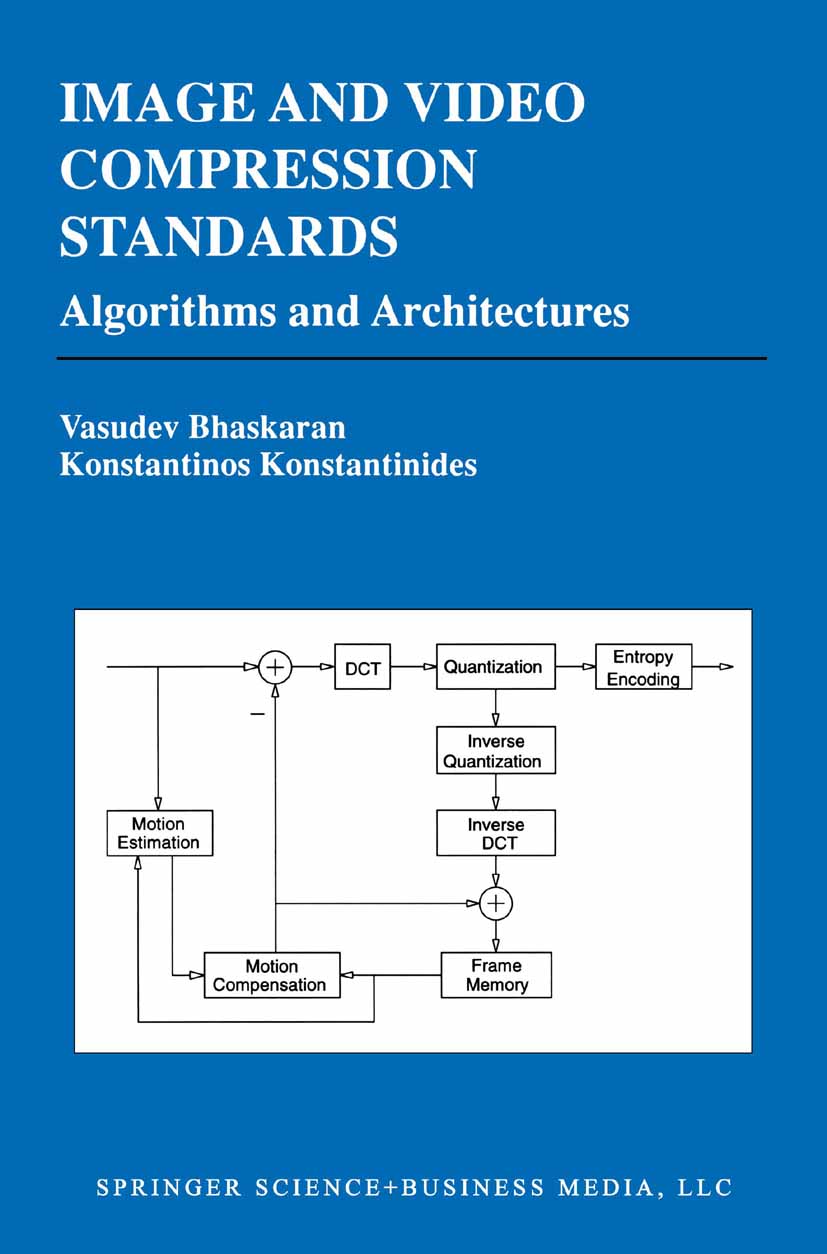
Image and Video Compression Standards Image and Video Compression Standards: Algorithms and Architectures presents an introduction to the algorithms and architectures that underpin the image and video compression standards, including JPEG (compression of still images), H.261 (video teleconferencing), MPEG-1 and MPEG-2 (video storage and broadcasting). In addition, the book covers the MPEG and Dolby AC-3 audio encoding standards, as well as emerging techniques for image and video compression, such as those based on wavelets and vector quantization. The book emphasizes the foundations of these standards, i.e. techniques such as predictive coding, transform-based coding, motion compensation, and entropy coding, as well as how they are applied in the standards. How each standard is implemented is not dealt with, but the book does provide all the material necessary to understand the workings of each of the compression standards, including information that can be used to evaluate the efficiency of various software and hardware implementations conforming to the standards. Particular emphasis is placed on those algorithms and architectures that have been found to be useful in practical software or hardware implementations. Audience: A valuable reference for the graduate student, researcher or engineer. May also be used as a text for a course on the subject. COMPUTERS,Software Development & Engineering,Computer Graphics

Photorealistic Rendering Techniques This book contains the final versions of the proceedings of the fifth EUROGRA PHICS Workshop on Rendering held in Darmstadt, Germany, between 13-15 June 1994. With around 80 participants and 30 papers, the event continued the successful tradition of the previous ones establishing the event as the most im portant meeting for persons working on this area world-wide. After more than 20 years of research, rendering remains an partially unsolved, interesting, and challenging topic. This year 71 (!) papers have been submitted from Europe, North America, and Asia. The average quality in terms of technical merit was impressive, showing that substantial work is achieved on this topic from several groups around the world. In general we all gained the impression that in the mean time the technical quality of the contributions is comparable to that of a specialised high-end, full scale conference. All papers have been reviewed from at least three members of the program committee. In addition, several colleagues helped us in managing the reviewing process in time either by supporting additional reviews, or by assisting the members of the committee. We have been very happy to welcome eminent invited speakers. Holly Rush meier is internationally well known for her excellent work in all areas of rendering and gave us a review of modelling and rendering participating media with em phasis on scientific visualization. In addition, Peter Shirley presented a survey about future rends in rendering techniques. COMPUTERS,Software Development & Engineering,Computer Graphics

Design, Specification and Verification of Interactive Systems ’95 This book is the final outcome of the Eurographics Workshop on Design, Specification and Verification of Interactive Systems, that was held in Bonas, from June 7 to 9, 1995. This workshop was the second of its kind, following the successful first edition in Italy in 1994. The goal of this ongoing series of meetings is to review the state of the art in the domain of tools, notations and methodologies supporting the design of Interactive Systems. This acknowledges the fact that making systems that are friendlier to the user makes the task ever harder to the designers of such systems, and that much research is still needed to provide the appropriate conceptual and practical tools. The workshop was located in the Chateau de Bonas, in the distant countryside of Toulouse, France. Tms location has been selected to preserve the quiet and studious atmosphere that was established in the monastery of Santa Croce at Bocca di Magra for the first edition, and that was much enjoyed by the participants. The conversations initiated during the sessions often lasted till late at night, in the peaceful atmosphere of the Gers landscape. COMPUTERS,Software Development & Engineering,Computer Graphics

The Dictionary of Computer Graphics and Virtual Reality Superblack, superblock, supercase, superquadric, supersampling, superred, supergreen, and superblue are just a few of the words which make up the language of computer graphics. This new edition of a widely acclaimed dictionary provides a guide to this fast-moving subject for both relative novices and professionals working in the field. The main changes have been to add new terminology relating to virtual reality and the related topics of robotics and networked simulation. This dictionary covers the software, hardware, and applications of computer graphics and contains hundreds of terms not found elsewhere. Definitions are clear and concise, with special attention given to alternate spellings and meanings. Acronyms are decoded, and pronunciation of the seemingly unpronounceable is given, from WYSIWYG (whizzy-wig) to NAPLPS (nap-lips). COMPUTERS,Software Development & Engineering,Computer Graphics

Virtual Environments ’95 Virtual Environments -(VE) the new dimension in man-machine-communication -have been developed and experienced in Europe since 1990. In early 1993 the Eurographics Association decided to establish a working group on Virtual Environments with the aim to communicate advances in this fascinating area on a scientific and technical level. In September 1993 the first workshop on VEs was held in Barcelona, Spain, in conjunction with the annual Eurographics conference. The workshop brought together about 35 researchers from Europe and the US. The second workshop was held together with Imagina '95 in Monte Carlo, Monaco. This time, around 40 researchers from Europe, the US, but also from Asia met for a 2-day exchange of experience. Needless to say -as in all Eurographics workshops -we found the atmosphere very open and refreshing. The workshops were sponsored by ONR (Office of Naval Research), UK; US Army Research Institute, UK; University of Catalonia, Spain; EDF France; CAE France, INA France and IGD Germany and locally organized by Daniele Tost and Jaques David. While in the first workshop in 1993 many concepts in VE were presented, the '95 workshop showed up various applications in different areas and demonstrated quite clearly that Virtual Environments are now used in interactive applications. COMPUTERS,Software Development & Engineering,Computer Graphics

Interactive 3D Graphics in Windows® Interactive 3-D Graphics in Windows is a hands-on book which uses a component software approach to help Visual C++ programmers quickly and easily develop windows-integrated, interactive 3-D graphics applications. The book includes JOEY, a 3-D user interface toolkit which addresses interaction issues not dealt with in the Microsoft User Interface Style Guide. JOEY provides a 3-D user interface, 3-D tools OLE Linking and Embedding and OLE automation within the MFC framework so that the application programmer can focus on application functionality. Using this book and JOEY, an experienced Visual C++ programmer can create an interactive 3-D application in a few hours. Roy Hall and Danielle Forsyth are the founders of Crisis in Perspective, Inc. in Portland, Oregon. Crisis in Perspective develops modeling systems for architects and building professionals which facilitate modeling and animation in the same way that word processors facilitate written document design; powerful, flexible, and extensive modeling systems for people that do not yet know exactly what they want to build. COMPUTERS,Software Development & Engineering,Computer Graphics

Multimedia Multimedia computing is a logical next step by which computing technology will become ever more useful and ubiquitous in our everyday lives. From the perspective of technical challenges, multimedia affects nearly every aspect of computer hardware and software. The long-heralded marriage of computing, communications, and information services is now being consummated, and is manifesting itself in literally dozens of new alliances between companies ranging from semiconductors to cable TV, from newspapers and telephone companies to computer hardware and software. COMPUTERS,Software Development & Engineering,Computer Graphics

Multimedia/Hypermedia in Open Distributed Environments Over the last few years, multimedia hardware and applications have become widely available in the personal computer and workstation environments, and multimedia is rapidly becoming an integral part of stand-alone, single-user sy stems. In contrast, the problems encountered when moving to open, distributed environments are only just beginning to be identified. Examples are the trans mission of dynamic data (video, sound) over large distances and cooperative work. Following on from two successful workshops on multimedia, EG-MM '94 concentrates on topics related to multimedia/hypermedia in open, distributed environments. The goal of this symposium was not only to give a comprehensive overview of the current state of research, development, and standardisation in the field, but also to provide an opportunity for live demonstrations to experience directly the presented results. The symposium program consists of two invited keynote speeches, eight tech .nical sessions, one tutorial, and one demonstration session. A workshop following immediately after the symposium provides an opportunity for in-depth discussi ons of open problems among experts. It is intended to fill a gap often experienced at larger meetings and conferences: the lack of time to discuss in detail issues raised during the event, such as the characteristics of different approaches to a certain problem. It is intended that the results of the workshop be published as a Eurographics Technical Report. COMPUTERS,Software Development & Engineering,Computer Graphics

Fast Algorithms for 3D-Graphics The aim of this book is to provide a mathematical background to techniques in computer graphics, to develop a graphics program in C implementing these techniques, and to illustrate the use of C stressing portability and speed. As a result, many students and professionals will find this presentation will give them a thorough understanding of the most fundamental algorithms in graphics programming as well as to provide with them a usable graphics package. Readers are assumed to be moderately familiar with programming though all type definitions, global variables, and macros are described thoroughly before their first applications. Whilst ray-tracing is not covered, the book does cover: hidden surfaces, shadows, reflections, patterns, and modelling curves and surfaces. COMPUTERS,Software Development & Engineering,Computer Graphics

From Object Modelling to Advanced Visual Communication This book is a collection of the best papers originally presented as state-of-the-art reports or tutorials at the EUROGRAPHICS'91 conference in Vienna. A choice has been made giving priority to information of lasting value. Another goal was to cover all aspects of computer graphics -except hardware -as completely as possible from modelling to advanced visualization and communication. The editors consider that the ten contributions by internationally renowned experts fulfil this goal perfectly. Some important problem areas are treated from different viewpoints thus enhancing and deepening the reader's perspective. Sabine Coquillart Wolfgang Strafier Peter Stucki Table of Contents l. Through the Cracks of the Solid Modeling Milestone 1 J arek R. Rossignac 2. Kinematics and Dynamics for Computer Animation 76 H. Ruder, T. Ertl, K. Gruber, M. Gunther, F. Hospach, M. Ruder, J. Subke, K. Widmayer 3. Dynamic Animation of Deformable Bodies 118 Marie-Paul Gascuel, Claude Puech 4. Stochastic Methods and Non-Fractal Applications 140 Huw Jones 5. State of the Art in Volume Visualization 166 Arie Kaufman 6. On the Theorey and Application of Stereolithographics in Scientific Visualization 178 Eric Hibbard, Michael Bauer, Margaret Bradshaw, Glenn Deardorff, Ken Hu, David Whitney 7. User Interface Management Systems: Present and Future 197 Michel Beaudouin-Lafon 8. Trends in Edge Detection Techniques 224 Eduard Antoniu 9. COMPUTERS,Software Development & Engineering,Computer Graphics

Visual Computing Advances in computing and communications have brought about an increasing demand for visual information. Visual Computing addresses the principles behind "visual technology", and provides readers with a good understanding of how the integration of Computer Graphics, Visual Perception and Imaging is achieved. Included in the book is an overview of important research areas within this integration which will be useful for further work in the field. Foundations of visual perception and psychophysics are presented as well as basic methods of imaging and computer vision. This book serves as an excellent reference and textbook for those who wish to apply or study "visual computing technology." COMPUTERS,Software Development & Engineering,Computer Graphics

Mathematical Morphology and Its Applications to Image Processing Mathematical morphology (MM) is a theory for the analysis of spatial structures. It is called morphology since it aims at analysing the shape and form of objects, and it is mathematical in the sense that the analysis is based on set theory, topology, lattice algebra, random functions, etc. MM is not only a theory, but also a powerful image analysis technique. The purpose of the present book is to provide the image analysis community with a snapshot of current theoretical and applied developments of MM. The book consists of forty-five contributions classified by subject. It demonstrates a wide range of topics suited to the morphological approach. COMPUTERS,Software Development & Engineering,Computer Graphics

Visualization in Scientific Computing Visualization in scientific computing is getting more and more attention from many people. Especially in relation with the fast increase of com puting power, graphic tools are required in many cases for interpreting and presenting the results of various simulations, or for analyzing physical phenomena. The Eurographics Working Group on Visualization in Scientific Com puting has therefore organized a first workshop at Electricite de France (Clamart) in cooperation with ONERA (Chatillon). A wide range of pa pers were selected in order to cover most of the topics of interest for the members of the group, for this first edition, and 26 of them were presented in two days. Subsequently 18 papers were selected for this volume. 1'he presentations were organized in eight small sessions, in addition to discussions in small subgroups. The first two sessions were dedicated to the specific needs for visualization in computational sciences: the need for graphics support in large computing centres and high performance net works, needs of research and education in universities and academic cen tres, and the need for effective and efficient ways of integrating numerical computations or experimental data and graphics. Three of those papers are in Part I of this book. The third session discussed the importance and difficulties of using stan dards in visualization software, and was related to the fourth session where some reference models and distributed graphics systems were discussed. Part II has five papers from these sessions. COMPUTERS,Software Development & Engineering,Computer Graphics

State of the Art in Computer Graphics State of the Art in Computer Graphics Aspects of Visualization This is the fourth volume derived from a State of . . . the Art in Computer Graphics Summer Institute. It represents a snapshot of a number of topics in computer graphics, topics which include visualization of scientific data; modeling; some aspects of visualization in virtual reality; and hardware architectures for visu alization. Many papers first present a background introduction to the topic, followed by discussion of current work in the topic. The volume is thus equally suitable for nonspecialists in a particular area, and for the more experienced researcher in the field. It also enables general readers to obtain an acquaintance with a particular topic area sufficient to apply that knowledge in the context of solving current problems. The volume is organized into four chapters - Visualization of Data, Modeling, Virtual Reality Techniques, and Hardware Architectures for Visualization. In the first chapter, Val Watson and Pamela Walatka address the visual aspects of fluid dynamic computations. They discuss algorithms for function-mapped surfaces and cutting planes, isosurfaces, particle traces, and topology extractions. They point out that current visualization systems are limited by low information transfer bandwidth, poor response to viewing and model accuracy modification requests, mismatches between model rendering and human cognitive capabilities, and ineffective interactive tools. However, Watson and Walatka indicate that proposed systems will correct most of these problems. COMPUTERS,Software Development & Engineering,Computer Graphics

Modeling in Computer Graphics In the history of technology, many fields have passed from an initial stage of empirical recipes to a mature stage where work is based on formal theories and procedures. This transition is made possible through a process called "modeling". Also Computer Graphics as a separate field of Computer Science makes extensive use of formal theories and procedures of modeling, often derived from related disciplines such as mathematics and physics. Modeling makes different application results consistent, unifying varieties of techniques and formal approaches into a smaller number of models by generalizing and abstracting the knowledge in Computer Graphics. This volume presents a selection of research papers submitted to the conference "Modeling in Computer Graphics: Methods and Applications" held at the Research Area of the National Research Council in Genoa, Italy, on June 28 -July 1, 1993. This meeting was the ideal continuation of a previous conference organized in Tokyo, Japan, in April 1991. The success and the variety of research themes discussed at that meeting suggested to promote a new working conference on methods and applications of modeling to be held in Italy two years later. COMPUTERS,Software Development & Engineering,Computer Graphics

Motion and Structure from Image Sequences Motion and Structure from Image Sequences is invaluablereading for researchers, graduate students, and practicingengineers dealing with computer vision. It presents abalanced treatment of the theoretical and practical issues,including very recent results - some of which are publishedhere for the first time.The topics covered in detail are:- image matching and optical flow computation- structure from stereo- structure from motion- motion estimation- integration of multiple views- motion modeling and predictionAspects such as uniqueness of the solution, degeneracyconditions, error analysis, stability, optimality, androbustness are also investigated. These details togetherwith the fact that the algorithms are accessible withoutnecessarily studying the rest of the material, make thisbook particularly attractive to practitioners. COMPUTERS,Software Development & Engineering,Computer Graphics

Communicating with Virtual Worlds Proceedings of the 11th International Conference on Computer Graphics, CGI '93 COMPUTERS,Software Development & Engineering,Computer Graphics
Modern Geometric Computing for Visualization This volume is on "modem geometric computing for visualization" which is at the forefront of multi-disciplinary advanced research areas. This area is attracting intensive research interest across many application fields: singularity in cosmology, turbulence in ocean engineering, high energy physics, molecular dynamics, environmental problems, modem mathe matics, computer graphics, and pattern recognition. Visualization re quires the computation of displayable shapes which are becoming more and more complex in proportion to the complexity of the objects and phenomena visualized. Fast computation requires information locality. Attaining information locality is achieved through characterizing the shapes in geometry and topology, and the large amount of computation required through the use of supercomputers. This volume contains the initial results of our efforts to satisfy these re quirements by inviting experts and selecting new research works through review processes. To be more specific, this book presents the proceedings of the International Workshop on Modem Geometric Computing for Visualization held at Kogakuin University, Tokyo, Japan, June 29-30, 1992 organized by the Computer Graphics Society, Japan Personal Com puter Software Association, Kogakuin University, and the Department of Information Science, Faculty of Science, The University of Tokyo. We received extremely high-quality papers for review from five different countries, one from Australia, one from Italy, four from Japan, one from Singapore and three from the United States, and we accepted eight papers and rejected two. COMPUTERS,Software Development & Engineering,Computer Graphics

Interactive Learning Through Visualization This book contains a selection of papers presented at the Computer Graphics and Education '91 Conference, held from 4th to 6th Apri11991, in Begur, Spain. The conference was organised under the auspices of the International Federation for Information Processing (IPIP) Working Group 5.10 on Computer Graphics. The goal of the organisers was to take a forward look at the impact on education of anticipated developments in graphics and related technologies, such as multimedia, in the next five years. We felt that at a time when many educational establishments are facing financial stringency and when major changes are taking place in patterns of education and training, this could be valuable for both educators and companies developing the technology: for educators, because they are often too bogged down in day-to-day problems to undertake adequate forward planning, and for companies, to see some of the problems faced by educators and to see what their future requirements might be. COMPUTERS,Software Development & Engineering,Computer Graphics
Computer Graphics and Mathematics Since its very existence as a separate field within computerscience, computer graphics had to make extensive use ofnon-trivial mathematics, for example, projective geometry,solid modelling, and approximation theory. This interplay ofmathematics and computer science is exciting, but also makesit difficult for students and researchers to assimilate ormaintain a view of the necessary mathematics. Thepossibilities offered by an interdisciplinary approach arestill not fully utilized. This book gives a selection ofcontributions to a workshop held near Genoa, Italy, inOctober 1991, where a group of mathematicians and computerscientists gathered to explore ways of extending thecooperation between mathematics and computer graphics. COMPUTERS,Software Development & Engineering,Computer Graphics

Photorealism in Computer Graphics The goal of this book is to present the most advanced research works in realistic computer generated images. It is made up of the papers presented during a Eurographics workshop that has been held in Rennes (France) on June 1990. Although realism in computer graphics has existed for many years, we have considered that two research directions can now clearly be identified. One makes use of empirical methods to efficiently create images that look real. As opposed to this approach, the other orientation makes use of physics to produce images that are exact representations of the real world (at the expense of additional processing time), hence the term photosimulation which indeed was the subject of this book. The objectives of this workshop were to assemble experts from physics and computer graphics in order to contribute to the introduction of physics-based approaches in the field of computer generated images. The fact that this workshop was the first entirely devoted to this topic was a bet and fortunately it turned out that it was a success. The contents of this book is organized in five chapters: Efficient Ray Tracing Meth ods, Theory of Global Illumination Models, Photometric Algorithms, Form-Factor Cal culations and Physics-Based Methods. COMPUTERS,Software Development & Engineering,Computer Graphics

Multimedia This volume is a record of the first Eurographics Workshop on Multimedia, held at the department of Numerical Analysis and Computing Science (NADA), Royal Institute of Technology, Stockholm, April 18-19, 1991. Eurographics is the European Association for Computer Graphics. It is a non-profit organization, one of whose activities is organizing workshops to provide an interface between academic and industrial research in the field of computer graphics. The idea of holding a Eurographics workshop on multimedia was put forward at the Eurographics conference in 1989. Following the success of this first workshop, a second workshop has been announced, to take place in Darmstadt, May 4-6, 1992. The Stockholm workshop met with great interest and many good contributions were received by the program committee. There were approximately 40 participants and 23 presentations were given - so many indeed that one might characterize the workshop as a working conference - and there were many discussions focusing on the presentations. The presentations dealt with a range of topics, including the clarification of ideas about the different concepts in multimedia, object-oriented methods for multimedia, multimedia from psychological perspectives, synchronization problems in multimedia, cooperative work using multimedia, and building multimedia interfaces. The presentations were the focus for numerous discussions. There was also a small exhibition of four different multimedia systems, representing the spectrum from research prototypes to commercial products. COMPUTERS,Software Development & Engineering,Computer Graphics

Multiresolution Image Shape Description Much of our understanding of the relationships among geometric struc tures in images is based on the shape of these structures and their relative orientations, positions and sizes. Thus, developing quantitative methods for capturing shape information from digital images is an important area for computer vision research. This book describes the theory, implemen tation, and application of two multi resolution image shape description methods. The author begins by motivating the need for quantitative methods for describing both the spatial and intensity variations of struc tures in grey-scale images. Two new methods which capture this informa tion are then developed. The first, the intensity axis of symmetry, is a collection of branching and bending surfaces which correspond to the skeleton of the image. The second method, multiresolution vertex curves, focuses on surface curvature properties as the image is blurred by a sequence of Gaussian filters. Implementation techniques for these image shape descriptions are described in detail. Surface functionals are mini mized subject to symmetry constraints to obtain the intensity axis of symmetry. Robust numerical methods are developed for calculating and following vertex curves through scale space. Finally, the author demon strates how grey-scale images can be segmented into geometrically coher ent regions using these shape description techniques. Building quantita tive analysis applications in terms of these visually sensible image regions promises to be an exciting area of biomedical computer vision research. v Acknowledgments This book is a corrected and revised version of the author's Ph. D. COMPUTERS,Software Development & Engineering,Computer Graphics

Modeling of Curves and Surfaces in CAD/CAM 1 Aims and Features of This Book The contents of t. his book were originally planned t. o be included in a book en titled Geometric lIIodeling and CAD/CAM to be written by M. Hosaka and F. Kimura, but since the draft. of my part of the book was finished much earlier than Kimura's, we decided to publish this part separately at first. In it, geometrically oriented basic methods and tools used for analysis and synthesis of curves and surfaces used in CAD/CAM, various expressions and manipulations of free-form surface patches and their connection, interference as well as their qualit. y eval uation are treated. They are important elements and procedures of geometric models. And construction and utilization of geometric models which include free-form surfaces are explained in the application examples, in which the meth ods and the techniques described in this book were used. In the succeeding book which Kimura is to write, advanced topics such as data structures of geometric models, non-manifold models, geometric inference as well as tolerance problems and product models, process planning and so on are to be included. Conse quently, the title of this book is changed to Modeling of Curves and Surfaces in CAD/CAM. Features of this book are the following. Though there are excellent text books in the same field such as G. Farin's Curves and Surfaces for CAD /CAM[l] and C. M. COMPUTERS,Software Development & Engineering,Computer Graphics

Advances in Scientific Visualization Scientific visualization is a new and rapidly growing areain which efforts from computer graphics research and manyscientific and engineering disciplines are integrated. Itsaim is to enhance interpretation and understanding byscientists of large amounts of data from measurements orcomplex computer simulations, using computer generatedimages and animation sequences. It exploits the power ofhuman visual perception to identify trends and structures,and recognize shapes and patterns. Development of newnumerical simulation methods in many areas increasinglydepends on visualization as an effective way to obtain anintuitive understanding of a problem.This book contains a selection of papers presented at thesecond Eurographics workshop on Visualization in ScientificComputing, held in Delft, the Netherlands, in April 1991.Theissues addressed are visualization tool and systemdesign, new presentation techniques for volume data andvector fields, and numerous case studies in scientificvisualization. Application areas include geology, medicine,fluid dynamics, molecular science, and environmentalprotection.The book will interest researchers and students in computergraphics and scientists from many disciplines interested inrecent results in visual data analysis and presentation. Itreflects the state of the art in visualization researchand shows a wide variety of experimental systems andimaginative applications. COMPUTERS,Software Development & Engineering,Computer Graphics

Visual Computing This volume presents the proceedings of the 10th International Conference of the Computer Graphics Society, CG International '92, Visual Computing - Integrating Computer Graphics with Computer Vision -, held at Kogakuin University, Tokyo in Japan from June 22-26,1992. Since its foundation in 1983, this conference has continued to attract high quality research articles in all aspects of computer graphics and its applications. Previous conferences in this series were held in Japan (1983-1987), in Switzerland (1988), in the United Kingdom (1989), in Singapore (1990), and in the United States of America (1991). Future CG International conferences are planned in Switzerland (1993), in Australia (1994), and in the United Kingdom (1995). It has been the editor's dream to research the integration of computer graphics with computer vision through data structures. The conference the editor put together in Los Angeles in 1975 involving the UCLA and IEEE Computer Societies had to spell out these three areas explicitly in the conference title, "computer graphics," "pattern recognition" and "data structures," as well as in the title of the proceedings published by IEEE Computer Society Press. In 1985, the editor gave the name "visual computer" to machines having all the three functionalities as seen in the journal under that name from Springer. Finally, the research in integrating visual information processing has now reached reality as seen in this proceedings of CG International '92. Chapters on virtual reality, and on tools and environments provide examples. COMPUTERS,Software Development & Engineering,Computer Graphics

Image Synthesis The images produced by means ofcomputers have invaded our daily lives. One has but to see the "identification logos" of most television broadcasts or some advenisement "spots" to be convinced of this. This proves that the synthesis ofimages has reached maturity. The progress that has been made in the last few years allows one to predict the use ofrealistic illustrations in more and more domains ofapplication. It is thus understandable that more and more people seek to understand how these images are produced. Such a person may be an amateur who likes to understand in a general way the processing involved, or he may be a computer scientist who wants to develop some new application using graphics procedures. This book by Michel Bret meets these desires by giving a complete overview of the techniques of image synthesis by computer. The different stages of the creation of a numerical image are explained in detail, and they are accompanied by descriptions of the most modem methods. Thus the geometrical models that are described go from those with plane polygonal facets, via surfaces of all types, to systems of panicles. Visualization is treated in complete detail, and due attention is given to all the various roads that lead to a realistic image: simple projections on the basis of wire-frame models, the elimination of hidden pans, and fmally the modelling oflight and its effects. COMPUTERS,Software Development & Engineering,Computer Graphics
Scientific Visualization Background A group of UKexperts on Scientific Visualization and its associated applications gathered at The Cosener's House in Abingdon, Oxford shire (UK) in February 1991 to consider all aspects of scientific visualization and to produce a number of documents: • a detailed summary of current knowledge, techniques and appli cations in the field (this book); • an Introductory Guide to Visualization that could be widely dis tributed to the UK academic community as an encouragement to use visualization techniques and tools in their work; • a Management Report (to the UK Advisory Group On Computer Graphics - AGOCG) documenting the principal results of the workshop and making recommendations as appropriate. This book proposes a framework through which scientific visualiza tion systems may be understood and their capabilities described. It then provides overviews of the techniques, data facilities and human-computer interface that are required in a scientific visualiza tion system. The ways in which scientific visualization has been applied to a wide range of applications is reviewed and the available products that are scientific visualization systems or contribute to sci entific visualization systems are described. The book is completed by a comprehensive bibliography of literature relevant to scientific visualization and a glossary of terms. VI Scientific Visualization Acknowledgements This book was predominantly written during the workshop in Abingdon. The participants started from an "input document" pro duced by Ken Brodlie, Lesley Ann Carpenter, Rae Earnshaw, Julian Gallop (with Janet Haswell), Chris Osland and Peter Quarendon. COMPUTERS,Software Development & Engineering,Computer Graphics

Workstations for Experiments Powerful new technology has been made available to researchers by an increasingly competitive workstation market. Papers from Canada, Japan, Italy, Germany, and the U.S., to name a few of the countries represented in this volume, discuss how workstations are used in experiments and what impact this new technology will have on experiments. As usual for IFIP workshops, the emphasis in this volume is on the formulation of strategies for future research, the determination of new market areas, and the identification of new areas for workstation research. This is the first volume of a book series reporting the work of IFIP WG 5.10. The mission of this IFIP work- ing group is to promote, develop and encourage advancement of the field of computer graphics as a basic tool, as an enabling technology and as an important part of various application areas. COMPUTERS,Software Development & Engineering,Computer Graphics

Advances in Computer Graphics This book is a collection of several tutorials from the EUROGRAPHICS '90 conference in Montreux. The conference was held under the motto "IMAGES: Synthesis, Analysis and Interaction", and the tutorials, partly presented in this volume, reflect the conference theme. As such, this volume provides a unique collection of advanced texts on 'traditional' com puter graphics as well as of tutorials on image processing and image reconstruction. As with all the volumes of the series "Advances in Computer Graphics", the contributors are leading experts in their respective fields. The chapter Design and Display of Solid Models provides an extended introduction to interactive graphics techniques for design, fast display, and high-quality rendering of solid models. The text focuses on techniques for Constructive Solid Geometry (CSG). The follow ing topics are treated in depth: interactive design techniques (specification of curves, surfaces and solids; graphical user interfaces; procedural languages and direct manipulation) and display techniques (depth-buffer, scan-line and ray-tracing techniques; CSG classification techniques; efficiency-improving methods; software and hardware implementations). COMPUTERS,Software Development & Engineering,Computer Graphics

PHIGS by Example The Programmer's Hierarchical Interactive Graphics System (PHIGS) is a computer-graphics standard defining an interface between an application program and a computer-graphics system. PHIGS has been actively under development since 1980. Much of this development has been performed by Technical Committee X3H3 under the American National Standard Institute (ANSI) procedures. PHIGS is also an international standard sponsored by the United States and developed by the international computer-graphics committee, ISO TC97/SC21/WG2. In addition, PHIGS has been selected as the graphics extension to the X-window standard and as part of the Intel i860 P.A.X. standard. The PHIGS standard has received wide acceptance throughout the computer graphics industry. PHIGS libraries are available on most of the high performance three-dimensional graphics platforms. These include IBM, DEC, HP, Sun, Alliant, Stardent, and Silicon Graphics. Despite this acceptance, there are few texts that provide the software engineer with an overview of the standard. The only currently available PHIGS references are in the form of the ANSI functional description, technical papers, and device-specific PHIGS to the novice PHIGS programmer. COMPUTERS,Software Development & Engineering,Computer Graphics

Modeling in Computer Graphics In order to capture the essential features of computer graphics, fundamental methods, concepts, and techniques have been integrated into generalized models through a process known as modeling. This volume outlines the progress made in computer graphic modeling and presents previously unpublished results and surveys which will help readers better understand the concepts and applications of this fascinating subject. COMPUTERS,Software Development & Engineering,Computer Graphics

Geometric Modeling This book is based on lectures presented at an international workshop on geometric modeling held at Hewlett Packard GmbH in Boblingen, FRG, in June 1990. International experts from academia and industry were selected to speak on the most interesting topics in geometric modeling. The resulting papers, published in this volume, give a state-of-the-art survey of the relevant problems and issues. The following topics are discussed: - Methods for constructing surfaces on surfaces: four different solutions to the multidimen sional problem of constructing an interpolant from surface data are provided. - Surfaces in solid modeling: current results on the implementation of free-fonn solids in three well established solid models are reviewed. - Box splines and applications: an introduction to box spline methods for the representation of surfaces is given. Basic properties of box splines are derived, and refinement and evaluation methods for box splines are presented in detail. Shape preserving properties, the construction of non-rectangular box spline surfaces, applications to surface modeling, and imbedding problems, are discussed. - Advanced computer graphics techniques for volume visualization: the steps to be executed in the visualization process of volume data are described and tools are discussed that assist in handling this data. - Rational B-splines: an introduction to the representation of curves and surfaces using rational B-splines is given, together with a critical evaluation of their potential for industrial application. COMPUTERS,Software Development & Engineering,Computer Graphics

Computer Animation ’91 This book contains invited papers and a selection of research papers submitted to Computer Animation '91, the third international work shop on Computer Animation, which was held in Geneva on May 22-24. This workshop, now an annual event, has been organized by the Computer Graphics Society, the University of Geneva, and the Swiss Federal Institute of Technology in Lausanne. During the international workshop on Computer Animation '91, the fourth Computer-generated Film Festival of Geneva, was held. The book presents original research results and applications experience of the various areas of computer animation. This year most papers are related to character animation, human animation, facial animation, and motion contro!. NA DIA MAGNENAT THALMANN DANIEL THALMANN v Table of Contents Part I: Facial Animation Contral Parameterization for Facial Animation F. I. PARKE . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3 Linguistic Issues in Facial Animation C. PELACHAUD, N. !. BADLER, M. STEEDMAN . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15 Facial Animation by Spatial Mapping E. C. PATTERSON, P. c. LITWINOWICZ, N. GREENE . . . . . . . . . . . . . . . . . . . . . . . . . 31 A Transformation Method for Modeling and Animation of the Human Face fram Photographs T. KURlHARA, K. ARAI . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45 Techniques for Realistic Facial Modeling and Animation D. TERZOPOULOS, K. WATERS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 59 Part ll: Human Modeling and Animation Generation of Human Motion with Emotion M. UNUMA, R. TAKEUCHI . . . . . . . . . . •. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 77 Creating Realistic Three-Dimensional Human Shape Characters for Computer-Generated Films A. PAOURl, N. MAGNENATTHALMANN, D. THALMANN . . . . . . . . . . . . . . . . . . . 89 Design of Realistic Gaits for the Purpose of Animation N. VASlLONIKOLIDAKIS, G. J CLAPWORTHY . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . COMPUTERS,Software Development & Engineering,Computer Graphics

Scientific Visualization of Physical Phenomena Scientific Visualization of Physical Phenomena reflects the special emphasis of the Computer Graphics Society's Ninth International Conference, held at the MIT in Cambridge, Massachusetts, USA in June, 1991. This volume contains the proceedings of the conference, which, since its foundation in 1983, continues to attract high quality research articles in all aspects of Computer Graphics and its applications. Visualization in science and engineering is rapidly developing into a vital area because of its potential for significantly contributing to the understanding of physical processes and the design automation of man-made systems. With the increasing emphasis in handling complicated physical and artificial processes and systems and with continuing advances in specialized graphics hardware and processing software and algorithms, visualization is expected to play an increasingly dominant role in the foreseeable future. COMPUTERS,Software Development & Engineering,Computer Graphics

User Interface Management and Design This volume is a record of the Workshop on User Interface Management Systems and Environments held at INESC, Lisbon, Portugal, between 4 and 6 June 1990. The main impetus for the workshop came from the Graphics and Interaction in ESPRIT Technical Interest Group of the European Community ESPRIT Programme. The Graphics and Interac tion in ESPRIT Technical Interest Group arose from a meeting of researchers held in Brussels in May 1988, which identified a number of technical areas of common interest across a significant number of ESPRIT I and ESPRIT II projects. It was recognized that there was a need to share information on such activities between projects, to disseminate results from the projects to the world at large, and for projects to be aware of related activities elsewhere in the world. The need for a Technical Interest Group was confirmed at a meeting held during ESPRIT Technical Week in November 1989, attended by over 50 representatives from ESPRIT projects and the Commission of the European Communities. Information exchange sessions were organized during the EUROGRAPHICS '89 confer ence, with the intention of disseminating information from ESPRIT projects to the wider research and development community, both in Europe and beyond. COMPUTERS,Software Development & Engineering,Computer Graphics

Advances in Computer Graphics Hardware IV EUROGRAPHICS workshops on Graphics hardware have now become an established forum for an exchange of information con cerning the latest developments in this field of growing importance. The first workshop took place during EG'86 in Lisbon. All parti cipants in this event considered it a very rewarding workshop to be repeated at future EG conferences. This view was reinforced at the EG'87 Hardware Workshop in Amsterdam which firmly esta blished the need for and a high interest in such a colloquium of technical discussion in this specialist area within the annual EG conference. The third EG Hardware Workshop took place in Nice in 1988 and this volume is a record of the fourth workshop at EG'89 in Hamburg. The material in this book contains papers representing a com prehensive record of the contributions to the 1989 workshop. The first part considers Algorithms and Architectures of graphics systems. These papers discuss the broader issues of system design, without necessarily raising issues concerning the details of the implementation. The second part on Systems describes hardware solutions and realisations of machines dedicated to graphics processing. Many of these contributions make important references to algorithmic and architectural issues as well, but there is now a greater emphasis on realisation. Indeed many VLSI designs are described. COMPUTERS,Software Development & Engineering,Computer Graphics

Fundamental Algorithms for Computer Graphics Proceedings of the NATO Advanced Study Institute on Fundamental Algorithms for Computer Graphics Held at Ilkley, Yorkshire, England, March 30 - April 12, 1985 COMPUTERS,Software Development & Engineering,Computer Graphics

Hands In this book a global shape model is developed and applied to the analysis of real pictures acquired with a visible light camera under varying conditions of optical degradation. Computational feasibility of the algorithms derived from this model is achieved by analytical means. The aim is to develop methods for image understanding based on structured restoration, for example automatic detection of abnormalities. We also want to find the limits of applicability of the algorithms. This is done by making the optical degradations more and more severe until the algorithms no longer succeed in their task. This computer experiment in pattern theory is one of several. The others, LEAVES, X-RAYS, and RANGE are described elsewhere. This book is suitable for an advanced undergraduate or graduate seminar in pattern theory, or as an accompanying book for applied probability, computer vision, or pattern recognition. COMPUTERS,Software Development & Engineering,Computer Graphics

Advances in Computer Graphics IV This fourth volume of Advances in Computer Graphics gathers together a selection of the tutorials presented at the EUROGRAPHICS annual conference in Nice, France, Septem ber 1988. The six contributions cover various disciplines in Computer Graphics, giving either an in-depth view of a specific topic or an updated overview of a large area. Chapter 1, Object-oriented Computer Graphics, introduces the concepts of object ori ented programming and shows how they can be applied in different fields of Computer Graphics, such as modelling, animation and user interface design. Finally, it provides an extensive bibliography for those who want to know more about this fast growing subject. Chapter 2, Projective Geometry and Computer Graphics, is a detailed presentation of the mathematics of projective geometry, which serves as the mathematical background for all graphic packages, including GKS, GKS-3D and PRIGS. This useful paper gives in a single document information formerly scattered throughout the literature and can be used as a reference for those who have to implement graphics and CAD systems. Chapter 3, GKS-3D and PHIGS: Theory and Practice, describes both standards for 3D graphics, and shows how each of them is better adapted in different typical applications. It provides answers to those who have to choose a basic 3D graphics library for their developments, or to people who have to define their future policy for graphics. COMPUTERS,Software Development & Engineering,Computer Graphics

Visual Structures and Integrated Functions This volume integrates theory and experiment to place the study of vision within the context of the action systems which use visual information. This theme is developed by stressing: (a) The importance of situating anyone part of the brain in the context of its interactions with other parts of the brain in subserving animal behavior. The title of this volume emphasizes that visual function is to be be viewed in the context of the integrated functions of the organism. (b) Both the intrinsic interest of frog and toad as animals in which to study the neural mechanisms of visuomotor coordination, and the importance of comparative studies with other organisms so that we may learn from an analysis of both similarities and differences. The present volume thus supplements our studies of frog and toad with papers on salamander, bird and reptile, turtle, rat, gerbil, rabbit, and monkey. (c) Perhaps most distinctively, the interaction between theory and experiment. COMPUTERS,Software Development & Engineering,Computer Graphics

Advances in Object-Oriented Graphics I Object-oriented systems have gained a great deal of popularity recently and their application to graphics has been very successful. This book documents a number of recent advances and indicates numerous areas of current research. The purpose of the book is: - to demonstrate the extraordinary practical utility of object-oriented methods in computer graphics (including user interfaces, image synthesis, CAD), - to examine outstanding research issues in the field of object-oriented graphics, and in particular to investi- gate extensions and shortcomings of the methodology when applied to computer graphics. Papers included in the book extend existing object-oriented graphical techniques, such as Smalltalk's "model view controller" or "constraints", introduce the use of complex and persistent objects in graphics, and give approaches to direct manipulation interfaces. The reader is presented with an in-depth treatment of a number of significant existing graphics systems, both for user interfaces and for image synthesis. There are theoretical surveys and chapters pointing to new directions in the broad field of computer graphics. Computer language scientists will find a useful critique of object-oriented language constructs and suggested ways to extend object-oriented theory. COMPUTERS,Software Development & Engineering,Computer Graphics

The Dictionary of Computer Graphics Technology and Applications Using this Dictionary.- Dictionary of Computer Graphics Technology and Applications.- Word List.- Acknowledgments. COMPUTERS,Software Development & Engineering,Computer Graphics

Intelligent Image Processing in Prolog After a slow and somewhat tentative beginning, machine vision systems are now finding widespread use in industry. So far, there have been four clearly discernible phases in their development, based upon the types of images processed and how that processing is performed: (1) Binary (two level) images, processing in software (2) Grey-scale images, processing in software (3) Binary or grey-scale images processed in fast, special-purpose hardware (4) Coloured/multi-spectral images Third-generation vision systems are now commonplace, although a large number of binary and software-based grey-scale processing systems are still being sold. At the moment, colour image processing is commercially much less significant than the other three and this situation may well remain for some time, since many industrial artifacts are nearly monochrome and the use of colour increases the cost of the equipment significantly. A great deal of colour image processing is a straightforward extension of standard grey-scale methods. Industrial applications of machine vision systems can also be sub divided, this time into two main areas, which have largely retained distinct identities: (i) Automated Visual Inspection (A VI) (ii) Robot Vision (RV) This book is about a fifth generation of industrial vision systems, in which this distinction, based on applications, is blurred and the processing is marked by being much smarter (i. e. more "intelligent") than in the other four generations. COMPUTERS,Software Development & Engineering,Computer Graphics

A Taxonomy for Texture Description and Identification A central issue in computer vision is the problem of signal to symbol transformation. In the case of texture, which is an important visual cue, this problem has hitherto received very little attention. This book presents a solution to the signal to symbol transformation problem for texture. The symbolic de- scription scheme consists of a novel taxonomy for textures, and is based on appropriate mathematical models for different kinds of texture. The taxonomy classifies textures into the broad classes of disordered, strongly ordered, weakly ordered and compositional. Disordered textures are described by statistical mea- sures, strongly ordered textures by the placement of primitives, and weakly ordered textures by an orientation field. Compositional textures are created from these three classes of texture by using certain rules of composition. The unifying theme of this book is to provide standardized symbolic descriptions that serve as a descriptive vocabulary for textures. The algorithms developed in the book have been applied to a wide variety of textured images arising in semiconductor wafer inspection, flow visualization and lumber processing. The taxonomy for texture can serve as a scheme for the identification and description of surface flaws and defects occurring in a wide range of practical applications. COMPUTERS,Software Development & Engineering,Computer Graphics

Describing and Recognizing 3-D Objects Using Surface Properties Surface properties play a very important role in many perception tasks. Object recognition, navigation, and inspection use surface properties ex tensively. Characterizing surfaces at different scales in given data is often the first and possibly the most important step. Most early research in ma chine perception relied on only very coarse characterization of surfaces. In the last few years, surface characterization has been receiving due attention. Dr. T. J. Fan is one of the very few researchers who designed and im plemented a complete system for object recognition. He studied issues re lated to characterization of surfaces in the context of object recognition, and then uses the features thus developed for recognizing objects. He uses a multi-view representation of 3-D objects for recognition, and he devel ops techniques for the segmentation of range images to obtain features for recognition. His matching approach also allows him to recognize objects from their partial views in the presence of other occluding objects. The efficacy of his approach is demonstrated in many examples. COMPUTERS,Software Development & Engineering,Computer Graphics

Parallel Algorithms for Machine Intelligence and Vision Recent research results in the area of parallel algorithms for problem solving, search, natural language parsing, and computer vision, are brought together in this book. The research reported demonstrates that substantial parallelism can be exploited in various machine intelligence and vision problems. The chapter authors are prominent researchers actively involved in the study of parallel algorithms for machine intelligence and vision. Extensive experimental studies are presented that will help the reader in assessing the usefulness of an approach to a specific problem. Intended for students and researchers actively involved in parallel algorithms design and in machine intelligence and vision, this book will serve as a valuable reference work as well as an introduction to several research directions in these areas. COMPUTERS,Software Development & Engineering,Computer Graphics

CG International ’90 In recent years, we have witnessed an increasing use of sophisticated graphics in designing and manufacturing complex architectural and engineering systems; in modeling, simulating and visualizing complicated physical processes; in generating, highly realistic images and animation; and, in most man-machine interfaces. These trends are made possible by the improvement in performance and the lowering of cost of hardware since the mid 1970s, and the continuing advances in many areas of computer graphics. The major advances in computer graphics include: greater sophistication and realism of image generation techniques, improved man-machine interaction techniques, superior geometric modeling techniques for the representation and modeling of complex physical and mathematical objects, sophisticated software systems for animation and modeling of incorporating latest AI and software engineering techniques, greater integration of CAD and CAM in CIM, and techniques to represent and visualize complicated physical processes. These advances are reflected in this present volume either as papers dealing with one particular aspect of research, or as multifaceted studies involving several different areas. COMPUTERS,Software Development & Engineering,Computer Graphics

Computational Graph Theory One ofthe most important aspects in research fields where mathematics is "applied is the construction of a formal model of a real system. As for structural relations, graphs have turned out to provide the most appropriate tool for setting up the mathematical model. This is certainly one of the reasons for the rapid expansion in graph theory during the last decades. Furthermore, in recent years it also became clear that the two disciplines of graph theory and computer science have very much in common, and that each one has been capable of assisting significantly in the development of the other. On one hand, graph theorists have found that many of their problems can be solved by the use of com puting techniques, and on the other hand, computer scientists have realized that many of their concepts, with which they have to deal, may be conveniently expressed in the lan guage of graph theory, and that standard results in graph theory are often very relevant to the solution of problems concerning them. As a consequence, a tremendous number of publications has appeared, dealing with graphtheoretical problems from a computational point of view or treating computational problems using graph theoretical concepts. COMPUTERS,Software Development & Engineering,Computer Graphics

Synthetic Actors This book presents the making of computer-generated films using three-dimensional synthetic actors. It is based mainly on the production of the film Rendez-vous a Montreal, an animated film that uses advanced computer techniques to achieve such effects as reincarnating film stars Humphrey Bogart and Marilyn Monroe. The main purpose of Rendez-vous a Montreal is to show that true synthetic actors can be created. This fllm represents a technological breakthrough which opens up new vistas in motion pictures, television, and advertising. With this technique, it will now be possible to produce short fllms or motion pictures featuring any celebrity in any situation. The book explains in detail how such a film can be produced using numerous drawings and color pictures. In particular, the following topics are presented: - Preparation of object construction: documentation search, and plaster models preparation - Object construction: digitizing and modeling - Body animation - Hand animation and object grasping - Facial animation: expressions, phonemes and emotions - Choreography: decors, actors, cameras, and lights - Realism: colors, lights, shading, shadows, and textures - Image recording: special effects Finally, an extensive appendix describes in detail the HUMAN FACTORY system. COMPUTERS,Software Development & Engineering,Computer Graphics

Recursive Block Coding for Image Data Compression Recursive Block Coding, a new image data compression technique that has its roots in noncausal models for 1d and 2d signals, is the subject of this book. The underlying theory provides a multitude of compression algorithms that encompass two course coding, quad tree coding, hybrid coding and so on. Since the noncausal models provide a fundamentally different image representation, they lead to new approaches to many existing algorithms, including useful approaches for asymmetric, progressive, and adaptive coding techniques. On the theoretical front, the basic result shows that a random field (an ensemble of images) can be coded block by block such that the interblock redundancy can be completely removed while the individual blocks are transform coded. On the practical side, the artifact of tiling, a block boundary effect, present in conventional block by block transform coding techniques has been greatly suppressed. This book contains not only a theoretical discussion of the algorithms but also exhaustive simulation and suggested methodologies for ensemble design techniques. Each of the resulting algorithms has been applied to twelve images over a wide range of image data rates and the results are reported using subjective descriptions, photographs, mathematical MSE values, and h-plots, a recently proposed graphical representation showing a high level of agreement with image quality as judged subjectively. COMPUTERS,Software Development & Engineering,Computer Graphics

Computer Aided Design 2 e This book describes principles, methods and tools that are common to computer applications for design tasks. CAD is considered in this book as a discipline that provides the required know-how in computer hardware and software, in systems analysis and in engineering methodology for specifying, designing, implementing, introducing, and using computer based systems for design purposes. The first chapter gives an impression of the book as a whole, and following chapters deal with the history and the components of CAD, the process aspect of CAD, CAD architecture, graphical devices and systems, CAD engineering methods, CAD data transfer, and application examples. The flood of new developments in the field and the success of the first edition of this book have led the authors to prepare this completely revised, updated and extended second edition. Extensive new material is included on computer graphics, implementation methodology and CAD data transfer; the material on graphics standards is updated. The book is aimed primarily at engineers who design or install CAD systems. It is also intended for students who seek a broad fundamental background in CAD. COMPUTERS,Software Development & Engineering,Computer Graphics

Object-Oriented Graphics At present, object-oriented programming is emerging from the research labora tories and invading into the field of industrial applications. More and more products have been implemented with the aid of object-oriented programming techniques and tools, usually as extensions of traditional languages in hybrid development systems. Some of the better known examples are OSF-Motif, News, Objective-C on the NeXT computer, the C extension C++, and CLOS an object oriented extension of LISP. All of these developments incorporate interactive graphics. Effective object-oriented systems in combination with a graphics kernel does it mean that the field of computer graphics has now become merely an aspect of the object-oriented world? We do not think so. In spite of interesting individual developments, there are still no sound object-oriented graphics sys tems available. If it is desired to develop a complex graphics application embed ded in a window-oriented system then it is still necessary to work with elemen tary tools. What is to be displayed and interactively modified inside a window must be specified with a set of graphics primitives at a low level, or has to be written with a standardized graphics kernel system such as GKS or PHIGS, i. e. , by kernels specified and implemented in a non-object-oriented style. With the terms GKS and PHIGS we enter the world of international graphics standards. GKS and PHIGS constitute systems, not mere collections of graphics primitives. COMPUTERS,Software Development & Engineering,Computer Graphics

Analysis and Interpretation of Range Images Computer vision researchers have been frustrated in their attempts to automatically derive depth information from conventional two-dimensional intensity images. Research on "shape from texture", "shape from shading", and "shape from focus" is still in a laboratory stage and had not seen much use in commercial machine vision systems. A range image or a depth map contains explicit information about the distance from the sensor to the object surfaces within the field of view in the scene. Information about "surface geometry" which is important for, say, three-dimensional object recognition is more easily extracted from "2 1/2 D" range images than from "2D" intensity images. As a result, both active sensors such as laser range finders and passive techniques such as multi-camera stereo vision are being increasingly utilized by vision researchers to solve a variety of problems. This book contains chapters written by distinguished computer vision researchers covering the following areas: Overview of 3D Vision Range Sensing Geometric Processing Object Recognition Navigation Inspection Multisensor Fusion A workshop report, written by the editors, also appears in the book. It summarizes the state of the art and proposes future research directions in range image sensing, processing, interpretation, and applications. The book also contains an extensive, up-to-date bibliography on the above topics. This book provides a unique perspective on the problem of three-dimensional sensing and processing; it is the only comprehensive collection of papers devoted to range images. Both academic researchers interested in research issues in 3D vision and industrial engineers in search of solutions to particular problems will find this a useful reference book. COMPUTERS,Software Development & Engineering,Computer Graphics

Computer Animation Computer Science Workbench is a monograph series which will provide you with an in-depth working knowledge of current developments in computer technology. Every volume in this series will deal with a topic of importance in computer science and elaborate on how you yourself can build systems related to the main theme. You will be able to develop a variety of systems, including computer software tools, computer gra phics, computer animation, database management systems, and compu ter-aided design and manufacturing systems. Computer Science Work bench represents an important new contribution in the field of practical computer technology. TOSIYASU L. KUNII Preface to the Second Edition Computer graphics is growing very rapidly; only computer animation grows faster. The first edition of the book Computer Animation: Theory and Practice was released in 1985. Four years later, computer animation has exploded. Conferences on computer animation have appeared and the topic is recognized in well-known journals as a leading theme. Computer-generated film festivals now exist in each country and several thousands of films are produced each year. From a commercial point of view, the computer animation market has grown considerably. TV logos are computer-made and more and more simulations use the technique of computer animation. What is the most fascinating is certainly the development of computer animation from a research point-of-view. COMPUTERS,Software Development & Engineering,Computer Graphics

Illustrator CC For almost two decades, the best-selling Visual QuickStart Guides by Elaine Weinmann and Peter Lourekas have been the textbooks of choice in classrooms and the go-to tutorial and reference for art and design professionals. This edition includes their trademark features: clear, concise, step-by-step instructions; hundreds of full-color illustrations; screen captures of program features; and supplemental tips and sidebars in every chapter. This fully updated edition for Illustrator CC covers the new enhancements and features, including significant upgrades to the interface, new unembed an image, multiple file placement, images in Brushes, and touch type and Free Transform tool. The new and updated Illustrator CC features are clearly marked with bright red stars in both the table of contents and main text. Readers can follow the steps in a tutorial fashion, or use the book as a reference guide to individual program features. Many of the key illustrations used in the book are available via Web download for practice by readers. COMPUTERS,Software Development & Engineering,Computer Graphics

Advanced Global Illumination This book provides a fundamental understanding of global illumination algorithms. It discusses a broad class of algorithms for realistic image synthesis and introduces a theoretical basis for the algorithms presented. Topics include: physics of light transport, Monte Carlo methods, general strategies for solving the rendering equation, stochastic path-tracing algorithms such as ray tracing and light tracing, stochastic radiosity including photon density estimation and hierarchical Monte Carlo radiosity, hybrid algorithms, metropolis light transport, irradiance caching, photon mapping and instant radiosity, beyond the rendering equation, image display and human perception. If you want to design and implement a global illumination rendering system or need to use and modify an existing system for your specific purpose, this book will give you the tools and the understanding to do so. COMPUTERS,Software Development & Engineering,Computer Graphics

Photoshop Down & Dirty Tricks for Designers, Volume 2 Corey Barker–Executive Producer of PlanetPhotoshop.com and one of the Photoshop Guys of Photoshop User TV–brings you this completely new set of techniques, tricks, and tutorials in this second volume of the Down & Dirty Tricks for Designers series. Ever wonder how that movie poster was created, or how they created that cool ad in the magazine, or maybe even how to take a seemingly mundane photo and give it the Hollywood treatment? This is the book for you. Whether you are a designer, artist, or even a photographer, there is something here for everyone. Corey starts out discussing the common techniques and resources you'll use over and over again, such as extracting elements from backgrounds, creating and using brushes, and incorporating textures into your work. He then dives deep into dedicated chapters on typography, design effects, special effects, photography and design, and 3D. As you work through these exercises, you will start to see the potential of some of Photoshop's most powerful features and how, with a little experimentation, you can open up a whole new world of dazzling effects. COMPUTERS,Software Development & Engineering,Computer Graphics

Processing This book demonstrates how Processing is an excellent language for beginners to learn the fundamentals of computer programming. Originally designed to make it simpler for digital artists to learn to program, Processing is a wonderful first language for anyone to learn. Given its origins, Processing enables a multimodal approach to programming instruction, well suited to students with interests in computer science or in the arts and humanities. The book uses Processing’s capabilities for graphics and interactivity in order to create examples that are simple, illustrative, interesting, and fun. It is designed to appeal to a broad range of readers, including those who want to learn to program to create digital art, as well as those who seek to learn to program to process numerical information or data. It can be used by students and instructors in a first course on programming, as well as by anyone eager to teach them self to program. Following a traditional sequence of topics for introducing programming, the book introduces key computer science concepts, without overwhelming readers with extensive detail. The conversational style and pace of the book are based upon the authors’ extensive experience with teaching programming to a wide variety of beginners in a classroom. No prior programming experience is expected. COMPUTERS,Software Development & Engineering,Computer Graphics

Infographics For Dummies Create stunning infographics with this hands-on guide Infographics For Dummies is a comprehensive guide to creating data visualization with viral appeal. Written by the founder of Infographic World, a New York City based infographic agency, and his top designers, the book focuses on the how-to of data, design, and distribution to create stunning, shareable infographics. Step-by-step instruction allows you to handle data like a pro, while creating eye-catching graphics with programs like Adobe Illustrator and Photoshop. The book walks you through the different types of infographics, explaining why they're so effective, and when they're appropriate. Ninety percent of the information transmitted to your brain is visual, so it's important to tickle the optic nerves to get people excited about your data. Infographics do just that. Much more exciting than a spreadsheet, infographics can add humor, interest, and flash while imparting real information. Putting your data in graphic form makes it more likely to be shared via Twitter, Facebook, Pinterest, and other social media sites, and the visual interest makes it less likely to be ignored. Infographics For Dummies provides a tried-and-true method for creating infographics that tell a story and get people excited. Topics include: Talking to clients about the data Discovering trends, outliers, and patterns Designing with mood boards and wireframes Launching and promoting your infographic The book, written by Justin Beegel, MBA, founder of Infographic World, Inc., describes the elements of a successful infographic, and stresses the must-have ingredients that get your data noticed. Humans are visual creatures, telling stories in a visual way. In today's world filled with data and messaging, an infographic is one of the best ways to get your point across. COMPUTERS,Software Development & Engineering,Computer Graphics

Adobe Illustrator WOW! Book for CS6 and CC, The For decades, Sharon Steuer and her international WOW! team have been showcasing the world’s best artists and designers working in Illustrator. In this expanded edition of the best-selling and award-winning Illustrator WOW! Book, you’ll find hundreds of tips, tricks, and techniques derived from actual projects from top Illustrator artists. You’ll learn to use new features, discover exciting ways to create complex effects, and find fresh ways to use venerable old tools and¿speed up your workflow. This edition includes coverage of the 2014 release and is loaded with and lessons with stunning new artwork that feature: Painting and generating objects with raster brushes Harnessing Live Corners, Live Rectangles, and new ways to reshape paths Manipulating live type characters with the Touch Type tool Creating airbrush and neon effects with gradients on strokes Building complex styles with multiple lines, fills, and effects Composing complex repeating patterns Auto-generating corners for pattern brushes Incorporating transparency into mesh and gradients Building and modifying scenes in perspective and 3D Transforming raster art to Illustrator vectors Preparing artwork for animation and the web Integrating Illustrator with Photoshop and other apps Creating photorealism in Illustrator WOW! ONLINE Register the book at peachpit.com/register to access artwork to pick apart and special PDFs from artists to you. Keep up with tips on the latest Illustrator features at WOWartist.com. COMPUTERS,Software Development & Engineering,Computer Graphics

Learning to Program Everyone can benefit from basic programming skills–and after you start, you just might want to go a whole lot further. Author Steven Foote taught himself to program, figuring out the best ways to overcome every obstacle. Now a professional web developer, he’ll help you follow in his footsteps. He teaches concepts you can use with any modern programming language, whether you want to program computers, smartphones, tablets, or even robots. Learning to Program will help you build a solid foundation in programming that can prepare you to achieve just about any programming goal. Whether you want to become a professional software programmer, or you want to learn how to more effectively communicate with programmers, or you are just curious about how programming works, this book is a great first step in helping to get you there. Learning to Program will help you get started even if you aren’t sure where to begin. • Learn how to simplify and automate many programming tasks • Handle different types of data in your programs • Use regular expressions to find and work with patterns • Write programs that can decide what to do, and when to do it • Use functions to write clean, well-organized code • Create programs others can easily understand and improve • Test and debug software to make it reliable • Work as part of a programming team • Learn the next steps to take to build a lifetime of programming skills COMPUTERS,Software Development & Engineering,Computer Graphics

Introduction to Image Processing I. The past. the present . . . and the future It is possible to take the view that ever since it began, the "ancient" branch of physics known as Optics has been concerned with process ing images. But since the Nineteen-Thirties increasingly close ties have been forming between Optics, which until then had been largely based on instruments, and the sciences of communication and infor mation arising out of mathematics and electronics. Such developments follow naturally, since communication systems and image-forming systems are all designed to receive or transmit information. Further more the same mathematical forms are used for describing the beha viour of electrical and optical systems. It is a question of systems theory, particularly linear systems, and of Fourier's analysis methods, which together constitute an important part of Signal Theory. In the case of communication systems carrying signals of an electrical nature, information is time-related or temporal. Transmitted signals are one-dimensional and functions of a single variable, time t. In the case of optical systems information is spatial in nature. Signals are distributions of light intensity in space. In general they are treated as two-dimensional signals, being functions of two spatia! variables written as x and y. In the early Fifties the way forward became clearer still when some scientists at the Institut d'Optique in Paris began using optical filtering techniques in coherent light in order to enhance the quality of photographs. COMPUTERS,Software Development & Engineering,Computer Graphics

Applications of Fractals and Chaos Applications of Fractals and Chaos presents new developmentsin this rapidlydeveloping subject area. The presentation ismore than merely theoretical, it specifically presentsparticular applications in a wide range of applicationsareas. Under the oceans, we consider the ways in whichsponges and corals grow; we look, too, at the stability ofships on their surfaces. Land itself is modelled andapplications to art, medicineand camouflage are presented.Readers should find general interest in the range of areasconsidered and should also be able to discover methods ofvalue for their own specific areas of interest fromstudying the structure of related activities. COMPUTERS,Software Development & Engineering,Computer Graphics

Adobe InDesign CC Classroom in a Book (2015 release) Creative professionals who seek the fastest, easiest, and most comprehensive way to learn Adobe InDesign CC choose Adobe InDesign CC Classroom in a Book (2015 release) from Adobe Press. The 16 project-based lessons in this book show users step-by-step the key techniques for working in Adobe InDesign. Users learn how to create engaging page layouts, flow and edit text, create and use styles, incorporate graphics and tables, and create PDF forms and ebooks. In addition to learning the key elements of the InDesign interface, this completely revised CC (2015 release) edition covers new features, including paragraph shading, easier and more flexible table creation, graphic cells for tables, and sharing styles, swatches, and settings across Creative Cloud applications. This thorough, self-paced guide is ideal for beginning users wanting to get up to speed on the key features of this program. Those who already have some experience with InDesign can improve their skills and learn InDesign’s newest tools. The online companion files include all the necessary assets for readers to complete the projects featured in each chapter as well as ebook updates when Adobe releases new features for Creative Cloud customers. And new to this release, all buyers of the book get full access to the Web Edition: a Web-based version of the complete ebook enhanced with video and interactive multiple-choice quizzes. As always with the Classroom in a Book, Instructor Notes are available for teachers to download. COMPUTERS,Software Development & Engineering,Computer Graphics

Photoshop CC This best-selling guide from authors Elaine Weinmann and Peter Lourekas has been the go-to tutorial and reference book for photography/design professionals and the textbook of choice in college classrooms for decades. This edition includes their trademark features of clear, concise, step-by-step instructions; hundreds of full-color images; screen captures of program features; and supplemental tips and sidebars in every chapter. This new edition includes an all-new material, a bonus chapter, and downloadable assets. New and updated Photoshop CC (2015 release) features—including linked assets, multiple artboards, and new asset export—are clearly marked with bright red stars in both the table of contents and main text. COMPUTERS,Software Development & Engineering,Computer Graphics

Learning Processing Learning Processing, Second Edition, is a friendly start-up guide to Processing, a free, open-source alternative to expensive software and daunting programming languages. Requiring no previous experience, this book is for the true programming beginner. It teaches the basic building blocks of programming needed to create cutting-edge graphics applications including interactive art, live video processing, and data visualization. Step-by-step examples, thorough explanations, hands-on exercises, and sample code, supports your learning curve. A unique lab-style manual, the book gives graphic and web designers, artists, and illustrators of all stripes a jumpstart on working with the Processing programming environment by providing instruction on the basic principles of the language, followed by careful explanations of select advanced techniques. The book has been developed with a supportive learning experience at its core. From algorithms and data mining to rendering and debugging, it teaches object-oriented programming from the ground up within the fascinating context of interactive visual media. This book is ideal for graphic designers and visual artists without programming background who want to learn programming. It will also appeal to students taking college and graduate courses in interactive media or visual computing, and for self-study. A friendly start-up guide to Processing, a free, open-source alternative to expensive software and daunting programming languages No previous experience required—this book is for the true programming beginner! Step-by-step examples, thorough explanations, hands-on exercises, and sample code supports your learning curve COMPUTERS,Software Development & Engineering,Computer Graphics

Vector Basic Training Attention, designers, it’s time to get serious about your creative process. For too long you’ve allowed yourself to go soft, relying on your software to do all of your creative work at the expense of your craftsmanship. This book will NOT show you how to use every tool and feature in Adobe Illustrator. This book WILL, however, teach you the importance of drawing out your ideas, analyzing the shapes, and then methodically building them precisely in vector form using the techniques explained in this book. In Vector Basic Training, Second Edition acclaimed illustrative designer Von Glitschka takes you through his systematic process for creating the kind of precise vector graphics that separate the pros from the mere toolers. Along the way, he’ll whip your drawing skills into shape and show you how to create elegant curves and precise anchor points for your designs. In addition to new illustrative examples throughout the book, this edition includes an all-new chapter on how to apply color and detail to your illustrations using tried-and-true methods that you’ll use over and over again. You’ll also get access to over seven hours of all-new HD video tutorials and source files so you can follow along with Von as he walks you through his entire process. Whether you’re creating illustrations in Adobe Illustrator, Affinity Designer, CorelDRAW, or even Inkscape, you’ll be able to use Von’s techniques to establish a successful creative process for crafting consistently precise illustrations every single time you pick you up your pen, stylus, or mouse. In Vector Basic Training, Second Edition, you’ll learn: The tools and shortcuts that make up a design pro’s creative arsenal How to use “The Clockwork Method†to create accurate curves every time When and where to set just the right number of anchor points for any design How to build shapes quickly using basic Illustrator tools and plug-ins Techniques for art directing yourself to get the results you desire Fundamental methods for applying color and detail to your illustrations COMPUTERS,Software Development & Engineering,Computer Graphics

Best of The Digital Photography Book Series, The What could top the #1 best-selling photography book of all time? We’re talking about the award-winning, worldwide smash hit, written by Scott Kelby, that’s been translated into dozens of different languages, because it’s the one book that really shows you how to take professional-quality shots using the same tricks today’s top digital pros use. Well, what if you took that book, created four more just like it but with even more tips, plucked out only the best tips from all five of THOSE books, updated the images, referenced all-new gear, and added a completely new chapter on how to make the transition from shooting photos with your phone to making photographs with your new DSLR? In The Best of The Digital Photography Book, you’ll find all of Scott’s favorite tips and techniques curated and updated from The Digital Photography Book, Parts 1-5, along with a brand new chapter on transitioning from your phone to a full-fledged DSLR. You’ll find everything that made the first five titles a success: Scott answering questions, giving out advice, and sharing the secrets he’s learned just like he would with a friend–without all the technical explanations and techie photo speak. This book will help you shoot dramatically better-looking, sharper, more colorful, more professional-looking photos every time. COMPUTERS,Software Development & Engineering,Computer Graphics

CUDA for Engineers CUDA for Engineers gives you direct, hands-on engagement with personal, high-performance parallel computing, enabling you to do computations on a gaming-level PC that would have required a supercomputer just a few years ago. The authors introduce the essentials of CUDA C programming clearly and concisely, quickly guiding you from running sample programs to building your own code. Throughout, you’ll learn from complete examples you can build, run, and modify, complemented by additional projects that deepen your understanding. All projects are fully developed, with detailed building instructions for all major platforms. Ideal for any scientist, engineer, or student with at least introductory programming experience, this guide assumes no specialised background in GPU-based or parallel computing. In an appendix, the authors also present a refresher on C programming for those who need it. Coverage includes Preparing your computer to run CUDA programs Understanding CUDA’s parallelism model and C extensions Transferring data between CPU and GPU Managing timing, profiling, error handling, and debugging Creating 2D grids Interoperating with OpenGL to provide real-time user interactivity Performing basic simulations with differential equations Using stencils to manage related computations across threads Exploiting CUDA’s shared memory capability to enhance performance Interacting with 3D data: slicing, volume rendering, and ray casting Using CUDA libraries Finding more CUDA resources and code The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Software Development & Engineering,Computer Graphics

Fundamentals of Computer Graphics Drawing on an impressive roster of experts in the field, Fundamentals of Computer Graphics, Fourth Edition offers an ideal resource for computer course curricula as well as a user-friendly personal or professional reference. Focusing on geometric intuition, the book gives the necessary information for understanding how images get onto the screen by using the complementary approaches of ray tracing and rasterization. It covers topics common to an introductory course, such as sampling theory, texture mapping, spatial data structure, and splines. It also includes a number of contributed chapters from authors known for their expertise and clear way of explaining concepts. Highlights of the Fourth Edition Include: Updated coverage of existing topics Major updates and improvements to several chapters, including texture mapping, graphics hardware, signal processing, and data structures A text now printed entirely in four-color to enhance illustrative figures of concepts The fourth edition of Fundamentals of Computer Graphics continues to provide an outstanding and comprehensive introduction to basic computer graphic technology and theory. It retains an informal and intuitive style while improving precision, consistency, and completeness of material, allowing aspiring and experienced graphics programmers to better understand and apply foundational principles to the development of efficient code in creating film, game, or web designs. Key Features Provides a thorough treatment of basic and advanced topics in current graphics algorithms Explains core principles intuitively, with numerous examples and pseudo-code Gives updated coverage of the graphics pipeline, signal processing, texture mapping, graphics hardware, reflection models, and curves and surfaces Uses color images to give more illustrative power to concepts COMPUTERS,Software Development & Engineering,Computer Graphics

Fast Algorithms for 3D-Graphics In this book, a variety of algoritbms are described that may be of interest to everyone who writes software for 3D-graphics. It is a book that haB been written for programmers at an intermediate level as well aB for experienced software engineers who simply want to have some particular functions at their disposal, without having to think too much about details like special cases or optimization for speed. The programming language we use is C, and that has many advantages, because it makes the code both portable and efficient. Nevertheless, it should be possible to adapt the ideas to other high-level programming languages. The reader should have a reasonable knowledge of C, because sophisticated pro grams with economical storage household and fast sections cannot be written without the use of pointers. You will find that in the long run it is just aB easy to work with pointer variables as with multiple arrays . .Aß the title of the book implies, we will not deal with algorithms that are very computation-intensive such as ray tracing or the radiosity method. Furthermore, objects will always be (closed or not closed) polyhedra, which consist of a certain number of polygons. COMPUTERS,Software Development & Engineering,Computer Graphics

Models and Techniques in Computer Animation This book contains the invited papers and a selection of research papers submitted to Computer Animation '93, the fifth international workshop on Computer Animation, which was held in Geneva on June 16-18, 1993. This workshop, now an annual event, has been organized by the Computer Graphics Society, the University of Geneva, and the Swiss Federal Institute of Technology in Lausanne. During the international workshop on Computer Animation '93, the sixth Computer-generated Film Festival of Geneva, was also held. The volume presents original research results and applications experience to the various areas of computer animation. Most of the contributions are related to motion control, visualization, human animation, and rendering techniques. COMPUTERS,Software Development & Engineering,Computer Graphics

The Algorithmic Beauty of Sea Shells For centuries scientists have tried to understand the growth and development of multicellular organisms. More recently, with the help of mathematical models and computerized simulations, they have discovered algorithmic patterns and models that seem to describe the dynamic processes in which organisms grow, reproduce, and respond to external factors. In this fascinating and beautifully illustrated book, Hans Meinhardt explains and illustrates these structural growth patterns in the case of sea shells. The book delightfully conveys the intuitive appeal and the "touch of magic" in this research. A diskette packaged with the book contains a program that allows the reader to run the simulations on a PC. New patterns can be generated interactively to provide an insight into the process of biological pattern formation. COMPUTERS,Software Development & Engineering,Computer Graphics

Multisensor Fusion for Computer Vision Proceedings of the NATO Advanced Research Workshop on Multisensor Fusion for Computer Vision, held in Grenoble, France, June 26-30, 1989 COMPUTERS,Software Development & Engineering,Computer Graphics

Visualization in Scientific Computing ’97 Visualization is now recognized as a powerful approach to get insight in large datasets produced by scientific experimentations and simulations. The contributions to this book cover technical aspects as well as concreteapplications of visualization in various domains such as finance, physics, astronomy and medicine, providing researchers and engineers with valuable information for setting up new powerful environments. COMPUTERS,Software Development & Engineering,Computer Graphics

The Traveling Salesman Still today I am receiving requests for reprints of the book, but unfortunately it is out of print. Therefore, since the book still seems to receive some attention, I p- posed to Springer Verlag to provide a free online edition. I am very happy that Springer agreed. Except for the correction of some typographical errors, the online edition is just a copy of the printed version, no updates have been made. In particular, Table 13.1 gives the status of TSPLIB at the time of publishing the book. For accessing TSPLIB the link http://www.iwr.uni-heidelberg.de/iwr/comopt/software/TSPLIB95/ should be used instead of following the procedure described in Chapter 13. Heidelberg, January 2001 Gerhard Reinelt Preface More than ?fteen years ago, I was faced with the following problem in an assignment for a class in computer science. A brewery had to deliver beer to ?ve stores, and the task was to write a computer program for determining the shortest route for the truck driver to visit all stores and return to the brewery. All my attemps to ?nd a reasonable algorithm failed, I could not help enumerating all possible routes and then select the best one. COMPUTERS,Software Development & Engineering,Computer Graphics

SIGMA It has long been a dream to realize machines with flexible visual perception capability. Research on digital image processing by computers was initiated about 30 years ago, and since then a wide variety of image processing algorithms have been devised. Using such image processing algorithms and advanced hardware technologies, many practical ma chines with visual recognition capability have been implemented and are used in various fields: optical character readers and design chart readers in offices, position-sensing and inspection systems in factories, computer tomography and medical X-ray and microscope examination systems in hospitals, and so on. Although these machines are useful for specific tasks, their capabilities are limited. That is, they can analyze only simple images which are recorded under very carefully adjusted photographic conditions: objects to be recognized are isolated against a uniform background and under well-controlled artificial lighting. In the late 1970s, many image understanding systems were de veloped to study the automatic interpretation of complex natural scenes. They introduced artificial intelligence techniques to represent the knowl edge about scenes and to realize flexible control structures. The first author developed an automatic aerial photograph interpretation system based on the blackboard model (Naga1980). Although these systems could analyze fairly complex scenes, their capabilities were still limited; the types of recognizable objects were limited and various recognition vii viii Preface errors occurred due to noise and the imperfection of segmentation algorithms. COMPUTERS,Software Development & Engineering,Computer Graphics

Automated Biometrics Biometrics-based authentication and identification are emerging as the most reliable method to authenticate and identify individuals. Biometrics requires that the person to be identified be physically present at the point-of-identification and relies on `something which you are or you do' to provide better security, increased efficiency, and improved accuracy. Automated biometrics deals with physiological or behavioral characteristics such as fingerprints, signature, palmprint, iris, hand, voice and face that can be used to authenticate a person's identity or establish an identity from a database. With rapid progress in electronic and Internet commerce, there is also a growing need to authenticate the identity of a person for secure transaction processing. Designing an automated biometrics system to handle large population identification, accuracy and reliability of authentication are challenging tasks. Currently, there are over ten different biometrics systems that are either widely used or under development. Some automated biometrics, such as fingerprint identification and speaker verification, have received considerable attention over the past 25 years, and some issues like face recognition and iris-based authentication have been studied extensively resulting in successful development of biometrics systems in commercial applications. However, very few books are exclusively devoted to such issues of automated biometrics. Automated Biometrics: Technologies and Systems systematically introduces the technologies and systems, and explores how to design the corresponding systems with in-depth discussion. The issues addressed in this book are highly relevant to many fundamental concerns of both researchers and practitioners of automated biometrics in computer and system security. COMPUTERS,Software Development & Engineering,Computer Graphics

Learn Adobe Illustrator CC for Graphic Design and Illustration This study guide uses text integrated with video to help you gain real-world skills that will get you started in your career in graphics, design, or illustration, and lays the foundation for taking the Illustrator ACA exam. A mix of project-based lessons, practical videos, and regular assessments throughout prepares you for an entry-level position in a competitive job market. Adobe conducted research to identify the foundational skills students need to effectively communicate using digital media tools. Based on feedback from educators, design professionals, businesses, and educational institutions around the world, the objectives cover entry-level skill expectations for each topic. The ACA exams have proved to be highly successful; Adobe reports that the total number of exams taken worldwide has reached one million since 2008. To create this new product, Peachpit and Adobe Press have joined forces with team of outstanding instructors who have a great track record getting students certified: Rob Schwartz and his colleagues at BrainBuffet.com. COMPUTERS,Software Development & Engineering,Computer Graphics

Physically Based Rendering Physically Based Rendering: From Theory to Implementation, Third Edition, describes both the mathematical theory behind a modern photorealistic rendering system and its practical implementation. Through a method known as 'literate programming', the authors combine human-readable documentation and source code into a single reference that is specifically designed to aid comprehension. The result is a stunning achievement in graphics education. Through the ideas and software in this book, users will learn to design and employ a fully-featured rendering system for creating stunning imagery. This completely updated and revised edition includes new coverage on ray-tracing hair and curves primitives, numerical precision issues with ray tracing, LBVHs, realistic camera models, the measurement equation, and much more. It is a must-have, full color resource on physically-based rendering. Presents up-to-date revisions of the seminal reference on rendering, including new sections on bidirectional path tracing, numerical robustness issues in ray tracing, realistic camera models, and subsurface scattering Provides the source code for a complete rendering system allowing readers to get up and running fast Includes a unique indexing feature, literate programming, that lists the locations of each function, variable, and method on the page where they are first described Serves as an essential resource on physically-based rendering COMPUTERS,Software Development & Engineering,Computer Graphics

Simulating Heterogeneous Crowds with Interactive Behaviors This book provides a deep understanding of state-of-art methods for simulation of heterogeneous crowds in computer graphics. It will cover different aspects that are necessary to achieve plausible crowd behaviors. The book will be a review of the most recent literature in this field that can help professionals and graduate students interested in this field to get up to date with the latest contributions, and open problems for their possible future research. The chapter contributors are well known researchers and practitioners in the field and they include their latest contributions in the different topics required to achieve believable heterogeneous crowd simulation. Provides crowd simulation methodology to populate virtual environments, for video games or any kind of applications that requires believable multi-agent behavior Presents the latest contributions on crowd simulation, animation, planning, rendering and evaluation with detailed algorithms for implementation purposes Includes perspectives of both academic researchers and industrial practitioners with reference to open source solutions and commercial applications, where appropriate COMPUTERS,Software Development & Engineering,Computer Graphics

Displays In the extensive fields of optics, holography and virtual reality, technology continues to evolve. Displays: Fundamentals and Applications, Second Edition addresses these updates and discusses how real-time computer graphics and vision enable the application and displays of graphical 2D and 3D content. This book explores in detail these technological developments, as well as the shifting techniques behind projection displays, projector-camera systems, stereoscopic and autostereoscopic displays. This new edition contains many updates and additions reflecting the changes in fast developing areas such as holography and near-eye displays for Augmented and Virtual reality applications. Perfect for the student looking to sharpen their developing skill or the master refining their technique, Rolf Hainich and Oliver Bimber help the reader understand the basics of optics, light modulation, visual perception, display technologies, and computer-generated holography. With almost 500 illustrations Displays will help the reader see the field of augmentation and virtual reality display with new eyes. Features: • Covers physics, technology and techniques behind flat-panel as well as projection displays, projector-camera systems, stereoscopic and autostereoscopic displays, computer-generated holography, and near-eye displays • Discusses how real-time computer graphics and computer vision enable the visualization of graphical 2D and 3D content • Augmented by close to 500 rich illustrations, which give readers a clear understanding of existing and emerging display technology COMPUTERS,Software Development & Engineering,Computer Graphics

Fluid Engine Development From the splash of breaking waves to turbulent swirling smoke, the mathematical dynamics of fluids are varied and continue to be one of the most challenging aspects in animation. Fluid Engine Development demonstrates how to create a working fluid engine through the use of particles and grids, and even a combination of the two. Core algorithms are explained from a developer’s perspective in a practical, approachable way that will not overwhelm readers. The Code Repository offers further opportunity for growth and discussion with continuously changing content and source codes. This book helps to serve as the ultimate guide to navigating complex fluid animation and development. Explains how to create a fluid simulation engine from scratch Offers an approach that is code-oriented rather than math-oriented, allowing readers to learn how fluid dynamics works with code, with downloadable code available Explores various kinds of simulation techniques for fluids using particles and grids Discusses practical issues such as data structure design and optimizations Covers core numerical tools including linear system and level set solvers COMPUTERS,Software Development & Engineering,Computer Graphics

Adobe Illustrator CC Classroom in a Book (2017 release) This is the eBook of the printed book and may not include any media, website access codes, or print supplements that may come packaged with the bound book. Creative professionals seeking the fastest, easiest, most comprehensive way to learn Adobe Illustrator CC (2017 release) choose Adobe Illustrator CC Classroom in a Book (2017 release) from the best-selling series of hands-on software training workbooks from Adobe Press. The 15 project-based lessons in this book show users step-by-step the key techniques for working in Illustrator. Build a strong foundation for working with Adobe Illustrator CC by following hands-on projects for creating logos, illustrations, and posters. Learn how to use the Shaper tool and Live Shapes along with dynamic symbols to streamline graphics creation. Create website assets and export them in multiple formats to support modern responsive web designs. From exacting illustration to more free-form painting, you’ll gain vital Illustrator skills as you progress through the lessons. COMPUTERS,Software Development & Engineering,Computer Graphics

OpenGL Programming Guide The latest version of today’s leading worldwide standard for computer graphics, OpenGL 4.5 delivers significant improvements in application efficiency, flexibility, and performance. OpenGL 4.5 is an exceptionally mature and robust platform for programming high-quality computer-generated images and interactive applications using 2D and 3D objects, color images, and shaders. OpenGL Programming Guide, 9th Edition , presents definitive, comprehensive information on OpenGL 4.5, 4.4, SPIR-V, OpenGL extensions, and the OpenGL Shading Language. It will serve you for as long as you write or maintain OpenGL code. This edition of the best-selling “Red Book†fully integrates shader techniques alongside classic, function-centric approaches, and contains extensive code examples that demonstrate modern techniques. Starting with the fundamentals, its wide-ranging coverage includes drawing, color, pixels, fragments, transformations, textures, framebuffers, light and shadow, and memory techniques for advanced rendering and nongraphical applications. It also offers discussions of all shader stages, including thorough explorations of tessellation, geometric, and compute shaders. New coverage in this edition includes Thorough coverage of OpenGL 4.5 Direct State Access (DSA), which overhauls the OpenGL programming model and how applications access objects Deeper discussions and more examples of shader functionality and GPU processing, reflecting industry trends to move functionality onto graphics processors Demonstrations and examples of key features based on community feedback and suggestions Updated appendixes covering the latest OpenGL libraries, related APIs, functions, variables, formats, and debugging and profiling techniques The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Software Development & Engineering,Computer Graphics

The Adobe Photoshop CC Book for Digital Photographers (2017 release) This is the eBook of the printed book and may not include any media, website access codes, or print supplements that may come packaged with the bound book. AN AMAZING NEW VERSION OF THE PHOTOSHOP BOOK THAT BREAKS ALL THE RULES! Scott Kelby, Editor and Publisher of Photoshop User magazine—and the best-selling photography techniques author in the world today—once again takes this book to a whole new level as he uncovers more of the latest, most important, and most useful Adobe Photoshop techniques for photographers. This update to his award-winning, record-breaking book does something for digital photographers that’s never been done before—it cuts through the bull and shows you exactly “how to do it.†It’s not a bunch of theory; it doesn’t challenge you to come up with your own settings or figure it out on your own. Instead, Scott shows you step by step the exact techniques used by today’s cutting-edge digital photographers, and best of all, he shows you flat-out exactly which settings to use, when to use them, and why. LEARN HOW THE PROS DO IT The photographer’s workflow in Photoshop has evolved greatly over time, and in this current version of book you’ll wind up doing a lot of your processing and editing in Photoshop’s Adobe Camera Raw feature (whether you shoot in RAW, JPEG or TIFF—it works for all three). That’s because for years now, Adobe has been adding most of Photoshop’s new features for photography directly into Camera Raw itself. Since today’s photography workflow in Photoshop is based around Camera Raw, about one third of this book is about mastering Camera Raw like a pro. Plus, you’ll learn: • The sharpening techniques the pros really use. • The pros’ tricks for fixing the most common digital photo problems fast! • The most useful retouching techniques for photographers, and how to make “impossible†selections like wind-blown hair (it’s easy, once you know the secrets), and how to use Layers like a pro. • How to seamlessly remove distracting junk from your images. • How to stitch panoramas, how to process HDR for a realistic look, and tricks for pulling way more out of your images than you ever dreamed possible. • The latest Photoshop special effects for photographers (there’s a whole chapter just on these!). • A host of shortcuts, workarounds, and slick “insider†tricks to send your productivity through the roof! Scott includes a special chapter with his own workflow, from start to finish, plus, each chapter ends with a Photoshop Killer Tips section, packed with time-saving, job-saving tips that make all the difference. He also provides four bonus chapters, along with the images used in the book for download so you can follow right along. If you’re ready to learn all the “tricks of the tradeâ€â€”the same ones that today’s leading pros use to correct, edit, retouch, and sharpen their work—then you’re holding the book that will do just that. COMPUTERS,Software Development & Engineering,Computer Graphics

Adobe Illustrator CC Classroom in a Book (2018 release) Creative professionals seeking the fastest, easiest, most comprehensive way to learn Adobe Illustrator CC (2018 release) choose Adobe Illustrator CC Classroom in a Book (2018 release) from the best-selling series of hands-on software training workbooks from Adobe Press. The 15 project-based lessons show users the key techniques for realizing your creative potential with Adobe Illustrator CC. Following hands-on step-by-step projects, users create logos, illustrations, posters, and more. Explore the new Essentials workspace that makes learning Illustrator even easier. Learn how to use the Shaper tool and Live Shapes along with dynamic symbols to streamline graphics creation. Create website assets and export them in multiple formats to support modern responsive web designs. From exacting illustration to free-form painting, you’ll build a strong foundation in Illustrator as you progress through the lessons. The online companion files include all the necessary assets for readers to complete the projects featured in each chapter as well as ebook updates when Adobe releases relevant new features for Creative Cloud customers. All buyers of the book get full access to the Web Edition: a Web-based version of the complete ebook enhanced with video and multiple-choice quizzes. COMPUTERS,Software Development & Engineering,Computer Graphics

Adobe After Effects CC Classroom in a Book (2018 release) Creative professionals seeking the fastest, easiest, most comprehensive way to learn Adobe After Effects CC (2018 release) choose Adobe After Effects CC Classroom in a Book (2018 release) from Adobe Press. The 15 project-based lessons in this book show users step-by-step the key techniques for working in After Effects. Learn how to create, manipulate, and optimize motion graphics for film, video, DVD, the web, and mobile devices. Gain hands-on experience animating text and images, customizing a wide range of effects, tracking and syncing content, rotoscoping, and correcting color. Create Motion Graphics templates in After Effects so colleagues can make specific edits in Premiere Pro without accidentally changing other critical settings. Learn to create 3D content with both After Effects and Maxon Cinema 4D Lite (included with the software). The online companion files include all the necessary assets for readers to complete the projects featured in each chapter as well as ebook updates when Adobe releases relevant new features for Creative Cloud customers. All buyers of the book get full access to the Web Edition: a Web-based version of the complete ebook enhanced with video and multiple-choice quizzes. COMPUTERS,Software Development & Engineering,Computer Graphics

Essential Skills in Organic Modeling This is a beginner’s guide to learning and implementing the essential aspects of modeling organic objects and using an organic workflow to model anything. This book gives an aspiring modeler all the tools that they need to know in order to begin creating great models that are efficient and laid out properly for rigging and texturing. The reader will be taken through all the primary techniques and methodologies for making “liveable†creatures for video, film, or games. The reader will also learn the basic physical structure that designates something as organic vs artificial, and how these varying structures can be tackled from a modeling perspective.through a practical, hands-on approach. Features Designed to approach organic modeling in a software-independent manner. Builds fundamental knowledge of 3D digital art from the ground up. Each lesson builds on the previous lesson. Has industry standard knowledge, based on simplicity and efficiency that will work for either production rendering or game development. Defines what organic modeling is and how it works, and why each technique was developed and implemented as it currently stands. COMPUTERS,Software Development & Engineering,Computer Graphics

Data-Driven Storytelling This book presents an accessible introduction to data-driven storytelling. Resulting from unique discussions between data visualization researchers and data journalists, it offers an integrated definition of the topic, presents vivid examples and patterns for data storytelling, and calls out key challenges and new opportunities for researchers and practitioners. COMPUTERS,Software Development & Engineering,Computer Graphics

Visual Data Storytelling with Tableau Tell Insightful, Actionable Business Stories with Tableau, the World’s Leading Data Visualization Tool! Visual Data Storytelling with Tableau brings together knowledge, context, and hands-on skills for telling powerful, actionable data stories with Tableau. This full-color guide shows how to organize data and structure analysis with storytelling in mind, embrace exploration and visual discovery, and articulate findings with rich data, carefully curated visualizations, and skillfully crafted narrative. You don’t need any visualization experience. Each chapter illuminates key aspects of design practice and data visualization, and guides you step-by-step through applying them in Tableau. Through realistic examples and classroom-tested exercises, Professor Lindy Ryan helps you use Tableau to analyze data, visualize it, and help people connect more intuitively and emotionally with it. Whether you’re an analyst, executive, student, instructor, or journalist, you won’t just master the tools: you’ll learn to craft data stories that make an immediate impact--and inspire action. Learn how to: • Craft more powerful stories by blending data science, genre, and visual design • Ask the right questions upfront to plan data collection and analysis • Build storyboards and choose charts based on your message and audience • Direct audience attention to the points that matter most • Showcase your data stories in high-impact presentations • Integrate Tableau storytelling throughout your business communication • Explore case studies that show what to do--and what not to do • Discover visualization best practices, tricks, and hacks you can use with any tool • Includes coverage up through Tableau 10 COMPUTERS,Software Development & Engineering,Computer Graphics

Learn Adobe Photoshop CC for Visual Communication The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. This study guide uses text integrated with video to help learners gain real-world skills that will get them started in their career in photography, graphics, or design and lays the foundation for taking the Photoshop Adobe Certified Associate (ACA) exam. A mix of project-based lessons, videos, and quizzes throughout prepares beginning learners for an entry-level position in a competitive job market. Written by an instructor with classroom teaching experience, the book covers all of the objectives of the latest Visual Communication Using Adobe Photoshop CC Adobe Certified Associate Exam. Following are the top level domain objectives for the Visual Communication Using Adobe Photoshop ACA exam: Setting Project Requirements Identifying Design Elements When Preparing Images Understanding Adobe Photoshop Manipulating Images by Using Adobe Photoshop Publishing Digital Images by Using Adobe Photoshop COMPUTERS,Software Development & Engineering,Computer Graphics

Real-Time Rendering, Fourth Edition Thoroughly updated, this fourth edition focuses on modern techniques used to generate synthetic three-dimensional images in a fraction of a second. With the advent of programmable shaders, a wide variety of new algorithms have arisen and evolved over the past few years. This edition discusses current, practical rendering methods used in games and o COMPUTERS,Software Development & Engineering,Computer Graphics

Learn Adobe Illustrator CC for Graphic Design and Illustration This study guide uses text integrated with video to help learners gain real-world skills that will get them started in their career in graphic design and/or illustration and lays the foundation for taking the Illustrator Adobe Certified Associate (ACA) exam. A mix of project-based lessons, videos, and quizzes throughout prepares beginning learners for an entry-level position in a competitive job market. Written by an instructor with classroom teaching experience, the book covers all of the objectives of the latest Graphic Design and Illustration Using Illustrator Adobe Certified Associate Exam. Following are the top level domain objectives for the Graphic Design and Illustration Using Illustrator ACA exam: Setting Project Requirements Identifying Design Elements Used When Preparing Graphics Understanding Adobe Illustrator Create Graphics Using Adobe Illustrator Archive, Export, and Publish Graphics Using Adobe Illustrator The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Software Development & Engineering,Computer Graphics

Adobe Photoshop CC Classroom in a Book Creative professionals seeking the fastest, easiest, most comprehensive way to learn Adobe Photoshop choose Adobe Photoshop CC Classroom in a Book (2019 release) from Adobe Press. The 15 project-based lessons show key step-by-step techniques for working in Photoshop, including how to correct, enhance, and distort digital images, create image composites, and prepare images for print and the web. In addition to learning the essential elements of the Photoshop interface, this revised edition for the 2019 release covers features like the new Frame tool, designing reflected and radial art with Paint Symmetry, correcting mistakes with updated Undo, Navigating the redesigned Home screen, removing objects with upgraded Content-Aware Fill, saving time with simplified editing and transformations, and much more! The online companion files include all the necessary assets for readers to complete the projects featured in each chapter. All buyers of the book get full access to the Web Edition: A Web-based version of the complete ebook enhanced with video and multiple-choice quizzes. COMPUTERS,Software Development & Engineering,Computer Graphics

R Graphics, Third Edition This third edition of Paul Murrell’s classic book on using R for graphics represents a major update, with a complete overhaul in focus and scope. It focuses primarily on the two core graphics packages in R - graphics and grid - and has a new section on integrating graphics. This section includes three new chapters: importing external images in to R; integrating the graphics and grid systems; and advanced SVG graphics. The emphasis in this third edition is on having the ability to produce detailed and customised graphics in a wide variety of formats, on being able to share and reuse those graphics, and on being able to integrate graphics from multiple systems. This book is aimed at all levels of R users. For people who are new to R, this book provides an overview of the graphics facilities, which is useful for understanding what to expect from R's graphics functions and how to modify or add to the output they produce. For intermediate-level R users, this book provides all of the information necessary to perform sophisticated customizations of plots produced in R. For advanced R users, this book contains vital information for producing coherent, reusable, and extensible graphics functions. COMPUTERS,Software Development & Engineering,Computer Graphics
Adobe Illustrator CC Classroom in a Book Creative professionals seeking the fastest, easiest, most comprehensive way to learn Adobe Illustrator CC (2019 release) choose Adobe Illustrator CC Classroom in a Book (2019 release) from the best-selling series of hands-on software training workbooks from Adobe Press. The 15 project-based lessons show users the key techniques for realizing your creative potential with Adobe Illustrator CC. Following hands-on step-by-step projects, users create logos, illustrations, posters, and more. Explore the new streamlined Tools panel and all of the features essential for being creative in Illustrator, including working with the Shaper tool and Live Shapes along with dynamic symbols to streamline graphics creation. Create website assets and export them in multiple formats to support modern responsive web designs. From exacting illustration to free-form painting, you’ll build a strong foundation in Illustrator as you progress through the lessons. The online companion files include all the necessary assets for readers to complete the projects featured in each. All buyers of the book get full access to the Web Edition: A Web-based version of the complete ebook enhanced with video and multiple-choice quizzes. COMPUTERS,Software Development & Engineering,Computer Graphics

Learning C# Programming with Unity 3D, second edition Learning C# Programming with Unity 3D, Second Edition is for the novice game programmer without any prior programming experience. Readers will learn how C# is used to make a game in Unity 3D. Many example projects provide working code to learn from and experiment with. As C# evolves, Unity 3D evolves along with it. Many new features and aspects of C# are included and explained. Common programming tasks are taught by way of making working game mechanics. The reader will understand how to read and apply C# in Unity 3D and apply that knowledge to other development environments that use C#. New to this edition: includes latest C# language features and useful tools included with the .NET library like LINQ, Local Functions Tuples, and more! Key Features Provides a starting point for the first-time programmer C# Code examples are simple short and clear Learn the very basics on up to interesting tricks which C# offers COMPUTERS,Software Development & Engineering,Computer Graphics

Modeling and Simulation Models and simulations of all kinds are tools for dealing with reality. Humans have always used mental models to better understand the world around them: to make plans, to consider different possibilities, to share ideas with others, to test changes, and to determine whether or not the development of an idea is feasible. The book Modeling and Simulation uses exactly the same approach except that the traditional mental model is translated into a computer model, and the simulations of alternative outcomes under varying conditions are programmed on the computer. The advantage of this method is that the computer can track the multitude of implications and consequences in complex relationships much more quickly and reliably than the human mind. This unique interdisciplinary text not only provides a self contained and complete guide to the methods and mathematical background of modeling and simulation software (SIMPAS) and a collection of 50 systems models on an accompanying diskette. Students from fields as diverse as ecology and economics will find this clear interactive package an instructive and engaging guide. COMPUTERS,Software Development & Engineering,Computer Graphics

Advanced Graphics with the Commodore 128 COMPUTERS,Software Development & Engineering,Computer Graphics

Adobe Illustrator Classroom in a Book (2020 release) The fastest, easiest, most comprehensive way to learn. The best-selling series of hands-on software training workbooks, offers what no other book or training program does—an official training series from Adobe, developed with the support of Adobe product experts. Contains 16 lessons that cover the basics and beyond, providing countless tips and techniques to help you become more productive with the program. You can follow the book from start to finish or choose only those lessons that interest you. Build a strong foundation by following hands-on projects for creating logos, illustrations, and posters. Learn how to use the Shaper tool and Live Shapes along with dynamic symbols to streamline graphics creation. Create website assets and export them in multiple formats to support modern responsive web designs. From exacting illustration to more free-form painting, you’ll gain vital skills as you progress through the lessons. The online companion files include all the necessary assets for readers to complete the projects featured in each chapter. All buyers of the book get full access to the Web Edition: A Web-based version of the complete ebook enhanced with video and multiple-choice quizzes. COMPUTERS,Software Development & Engineering,Computer Graphics

Adobe Dimension Classroom in a Book (2020 release) Adobe Dimension empowers graphic designers to create high-quality photorealistic imagery using 2D and 3D assets -- and if you have an Adobe Creative Cloud subscription, it's already included. Adobe Dimension Classroom in a Book (2020 release) offers complete hands-on training in 14 lessons that help you master it quickly and easily. Straight from Adobe Press, this is the latest in our best-selling series of official Adobe software training guides -- packed with self-paced lessons and downloadable files designed by Adobe training experts. Each chapter contains a project that builds on your growing knowledge of the program, and end-of-chapter review questions reinforce each lesson. Long-time Adobe design consultant and educator Keith Gilbert covers all you need to know about building scenes, applying and editing surface materials, customizing lighting, rendering, and much more -- even if you've never worked with 3D tools before! The online companion files include all the necessary assets for students to complete the projects featured in each chapter as well as eBook updates when Adobe releases new features for Creative Cloud customers. And all buyers of the book get full access to the Web Edition: a Web-based version of the complete eBook enhanced with video and interactive multiple-choice quizzes. COMPUTERS,Software Development & Engineering,Computer Graphics

Information Visualization Information Visualization: Perception for Design, Fourth Edition explores the art and science of why we see objects the way we do. Based on the science of perception and vision, the author presents the key principles at work for a wide range of applications--resulting in visualization of improved clarity, utility and persuasiveness. This new edition has been revised and updated to include the latest relevant research findings. Content has been updated in areas such as the cognitive neuroscience of maps and navigation, the neuroscience of pattern perception, and the hierarchy of learned patterns. New changes to the book make it easier to apply perceptual lessons to design decisions. In addition, the book offers practical guidelines that can be applied by anyone, including interaction designers and graphic designers of all kinds. Includes the latest research findings in visualization and perception Provides a new chapter on designing for perception to help bridge the gap between specific perception-based guidelines and common design decisions Presents over 400 informative, full color illustrations that are key to an understanding of the subject COMPUTERS,Software Development & Engineering,Computer Graphics

Brainlesion The two-volume set LNCS 11992 and 11993 constitutes the thoroughly refereed proceedings of the 5th International MICCAI Brainlesion Workshop, BrainLes 2019, the International Multimodal Brain Tumor Segmentation (BraTS) challenge, the Computational Precision Medicine: Radiology-Pathology Challenge on Brain Tumor Classification (CPM-RadPath) challenge, as well as the tutorial session on Tools Allowing Clinical Translation of Image Computing Algorithms (TACTICAL). These were held jointly at the Medical Image Computing for Computer Assisted Intervention Conference, MICCAI, in Shenzhen, China, in October 2019. The revised selected papers presented in these volumes were organized in the following topical sections: brain lesion image analysis (12 selected papers from 32 submissions); brain tumor image segmentation (57 selected papers from 102 submissions); combined MRI and pathology brain tumor classification (4 selected papers from 5 submissions); tools allowing clinical translation of image computing algorithms (2 selected papers from 3 submissions.) COMPUTERS,Software Development & Engineering,Computer Graphics

Brainlesion The two-volume set LNCS 11992 and 11993 constitutes the thoroughly refereed proceedings of the 5th International MICCAI Brainlesion Workshop, BrainLes 2019, the International Multimodal Brain Tumor Segmentation (BraTS) challenge, the Computational Precision Medicine: Radiology-Pathology Challenge on Brain Tumor Classification (CPM-RadPath) challenge, as well as the tutorial session on Tools Allowing Clinical Translation of Image Computing Algorithms (TACTICAL). These were held jointly at the Medical Image Computing for Computer Assisted Intervention Conference, MICCAI, in Shenzhen, China, in October 2019. The revised selected papers presented in these volumes were organized in the following topical sections: brain lesion image analysis (12 selected papers from 32 submissions); brain tumor image segmentation (57 selected papers from 102 submissions); combined MRI and pathology brain tumor classification (4 selected papers from 5 submissions); tools allowing clinical translation of image computing algorithms (2 selected papers from 3 submissions.) COMPUTERS,Software Development & Engineering,Computer Graphics

Introduction to Medical Image Analysis This easy-to-follow textbook presents an engaging introduction to the fascinating world of medical image analysis. Avoiding an overly mathematical treatment, the text focuses on intuitive explanations, illustrating the key algorithms and concepts in a way which will make sense to students from a broad range of different backgrounds. Topics and features: explains what light is, and how it can be captured by a camera and converted into an image, as well as how images can be compressed and stored; describes basic image manipulation methods for understanding and improving image quality, and a useful segmentation algorithm; reviews the basic image processing methods for segmenting or enhancing certain features in an image, with a focus on morphology methods for binary images; examines how to detect, describe, and recognize objects in an image, and how the nature of color can be used for segmenting objects; introduces a statistical method to determine what class of object the pixels in an image represent; describes how to change the geometry within an image, how to align two images so that they are as similar as possible, and how to detect lines and paths in images; provides further exercises and other supplementary material at an associated website. This concise and accessible textbook will be invaluable to undergraduate students of computer science, engineering, medicine, and any multi-disciplinary courses that combine topics on health with data science. Medical practitioners working with medical imaging devices will also appreciate this easy-to-understand explanation of the technology. COMPUTERS,Software Development & Engineering,Computer Graphics

Image Restoration Image Restoration: Fundamentals and Advances responds to the need to update most existing references on the subject, many of which were published decades ago. Providing a broad overview of image restoration, this book explores breakthroughs in related algorithm development and their role in supporting real-world applications associated with various scientific and engineering fields. These include astronomical imaging, photo editing, and medical imaging, to name just a few. The book examines how such advances can also lead to novel insights into the fundamental properties of image sources. Addressing the many advances in imaging, computing, and communications technologies, this reference strikes just the right balance of coverage between core fundamental principles and the latest developments in this area. Its content was designed based on the idea that the reproducibility of published works on algorithms makes it easier for researchers to build on each other’s work, which often benefits the vitality of the technical community as a whole. For that reason, this book is as experimentally reproducible as possible. Topics covered include: Image denoising and deblurring Different image restoration methods and recent advances such as nonlocality and sparsity Blind restoration under space-varying blur Super-resolution restoration Learning-based methods Multi-spectral and color image restoration New possibilities using hybrid imaging systems Many existing references are scattered throughout the literature, and there is a significant gap between the cutting edge in image restoration and what we can learn from standard image processing textbooks. To fill that need but avoid a rehash of the many fine existing books on this subject, this reference focuses on algorithms rather than theories or applications. Giving readers access to a large amount of downloadable source code, the book illustrates fundamental techniques, key ideas developed over the years, and the state of the art in image restoration. It is a valuable resource for readers at all levels of understanding. COMPUTERS,Software Development & Engineering,Computer Graphics

Handbook of Image Processing and Computer Vision Across three volumes, the Handbook of Image Processing and Computer Vision presents a comprehensive review of the full range of topics that comprise the field of computer vision, from the acquisition of signals and formation of images, to learning techniques for scene understanding. The authoritative insights presented within cover all aspects of the sensory subsystem required by an intelligent system to perceive the environment and act autonomously. Volume 1 (From Energy to Image) examines the formation, properties, and enhancement of a digital image. Topics and features: •Describes the fundamental processes in the field of artificial vision that enable the formation of digital images from light energy •Covers light propagation, color perception, optical systems, and the analog-to-digital conversion of the signal •Discusses the information recorded in a digital image, and the image processing algorithms that can improve the visual qualities of the image •Reviews boundary extraction algorithms, key linear and geometric transformations, and techniques for image restoration •Presents a selection of different image segmentation algorithms, and of widely-used algorithms for the automatic detection of points of interest •Examines important algorithms for object recognition, texture analysis, 3D reconstruction, motion analysis, and camera calibration •Provides an introduction to four significant types of neural network, namely RBF, SOM, Hopfield, and deep neural networks This all-encompassing survey offers a complete reference for all students, researchers, and practitioners involved in developing intelligent machine vision systems. The work is also an invaluable resource for professionals within the IT/software and electronics industries involved in machine vision, imaging, and artificial intelligence. Dr. Cosimo Distante is a Research Scientist in Computer Vision and Pattern Recognition in the Institute of Applied Sciences and Intelligent Systems (ISAI) at the Italian National Research Council (CNR). Dr. Arcangelo Distante is a researcher and the former Director of the Institute of Intelligent Systems for Automation (ISSIA) at the CNR. His research interests are in the fields of Computer Vision, Pattern Recognition, Machine Learning, and Neural Computation. COMPUTERS,Software Development & Engineering,Computer Graphics
Deformable Registration Techniques for Thoracic CT Images This book focuses on novel approaches for thoracic computed tomography (CT) image registration and determination of respiratory motion models in a range of patient scenarios. It discusses the use of image registration processes to remove the inconsistencies between medical images acquired using different devices. In the context of comparative research and medical analysis, these methods are of immense value in image registration procedures, not just for thoracic CT images, but for all types of medical images in multiple modalities, and also in establishing a mean respiration motion model. Combined with advanced techniques, the methods proposed have the potential to advance the field of computer vision and help improve existing methods. The book is a valuable resource for those in the scientific community involved in modeling respiratory motion for a large number of people. COMPUTERS,Software Development & Engineering,Computer Graphics

Handbook of Image Processing and Computer Vision Across three volumes, the Handbook of Image Processing and Computer Vision presents a comprehensive review of the full range of topics that comprise the field of computer vision, from the acquisition of signals and formation of images, to learning techniques for scene understanding. The authoritative insights presented within cover all aspects of the sensory subsystem required by an intelligent system to perceive the environment and act autonomously. Volume 2 (From Image to Pattern) examines image transforms, image restoration, and image segmentation. Topics and features: •Describes the fundamental processes in the field of artificial vision that enable the formation of digital images from light energy •Covers light propagation, color perception, optical systems, and the analog-to-digital conversion of the signal •Discusses the information recorded in a digital image, and the image processing algorithms that can improve the visual qualities of the image •Reviews boundary extraction algorithms, key linear and geometric transformations, and techniques for image restoration •Presents a selection of different image segmentation algorithms, and of widely-used algorithms for the automatic detection of points of interest •Examines important algorithms for object recognition, texture analysis, 3D reconstruction, motion analysis, and camera calibration •Provides an introduction to four significant types of neural network, namely RBF, SOM, Hopfield, and deep neural networks This all-encompassing survey offers a complete reference for all students, researchers, and practitioners involved in developing intelligent machine vision systems. The work is also an invaluable resource for professionals within the IT/software and electronics industries involved in machine vision, imaging, and artificial intelligence. Dr. Cosimo Distante is a Research Scientist in Computer Vision and Pattern Recognition in the Institute of Applied Sciences and Intelligent Systems (ISAI) at the Italian National Research Council (CNR). Dr. Arcangelo Distante is a researcher and the former Director of the Institute of Intelligent Systems for Automation (ISSIA) at the CNR. His research interests are in the fields of Computer Vision, Pattern Recognition, Machine Learning, and Neural Computation. COMPUTERS,Software Development & Engineering,Computer Graphics

Robust Methods for Dense Monocular Non-Rigid 3D Reconstruction and Alignment of Point Clouds Vladislav Golyanik proposes several new methods for dense non-rigid structure from motion (NRSfM) as well as alignment of point clouds. The introduced methods improve the state of the art in various aspects, i.e. in the ability to handle inaccurate point tracks and 3D data with contaminations. NRSfM with shape priors obtained on-the-fly from several unoccluded frames of the sequence and the new gravitational class of methods for point set alignment represent the primary contributions of this book. About the Author: Vladislav Golyanik is currently a postdoctoral researcher at the Max Planck Institute for Informatics in Saarbrücken, Germany. The current focus of his research lies on 3D reconstruction and analysis of general deformable scenes, 3D reconstruction of human body and matching problems on point sets and graphs. He is interested in machine learning (both supervised and unsupervised), physics-based methods as well as new hardware and sensors for computer vision and graphics (e.g., quantum computers and event cameras). COMPUTERS,Software Development & Engineering,Computer Graphics

Biomedical Image Registration This book constitutes the refereed proceedings of the 9th International Workshop on Biomedical Image Registration, WBIR 2020, which was supposed to be held in Portorož, Slovenia, in June 2020. The conference was postponed until December 2020 due to the COVID-19 pandemic. The 16 full and poster papers included in this volume were carefully reviewed and selected from 22 submitted papers. The papers are organized in the following topical sections: Registration initialization and acceleration, interventional registration, landmark based registration, multi-channel registration, and sliding motion. COMPUTERS,Software Development & Engineering,Computer Graphics

Handbook of Image Processing and Computer Vision Across three volumes, the Handbook of Image Processing and Computer Vision presents a comprehensive review of the full range of topics that comprise the field of computer vision, from the acquisition of signals and formation of images, to learning techniques for scene understanding. The authoritative insights presented within cover all aspects of the sensory subsystem required by an intelligent system to perceive the environment and act autonomously. Volume 3 (From Pattern to Object) examines object recognition, neural networks, motion analysis, and 3D reconstruction of a scene. Topics and features: •Describes the fundamental processes in the field of artificial vision that enable the formation of digital images from light energy •Covers light propagation, color perception, optical systems, and the analog-to-digital conversion of the signal •Discusses the information recorded in a digital image, and the image processing algorithms that can improve the visual qualities of the image •Reviews boundary extraction algorithms, key linear and geometric transformations, and techniques for image restoration •Presents a selection of different image segmentation algorithms, and of widely-used algorithms for the automatic detection of points of interest •Examines important algorithms for object recognition, texture analysis, 3D reconstruction, motion analysis, and camera calibration •Provides an introduction to four significant types of neural network, namely RBF, SOM, Hopfield, and deep neural networks This all-encompassing survey offers a complete reference for all students, researchers, and practitioners involved in developing intelligent machine vision systems. The work is also an invaluable resource for professionals within the IT/software and electronics industries involved in machine vision, imaging, and artificial intelligence. Dr. Cosimo Distante is a Research Scientist in Computer Vision and Pattern Recognition in the Institute of Applied Sciences and Intelligent Systems (ISAI) at the Italian National Research Council (CNR). Dr. Arcangelo Distante is a researcher and the former Director of the Institute of Intelligent Systems for Automation (ISSIA) at the CNR. His research interests are in the fields of Computer Vision, Pattern Recognition, Machine Learning, and Neural Computation. COMPUTERS,Software Development & Engineering,Computer Graphics

The Hidden Power of Adobe Photoshop The Hidden Power of Adobe Photoshop for Photographers is about mastering your tools as a path towards mastering your art. Renowned Photoshop teacher Scott Valentine combines expert recipes and instructions with insightful technical and philosophical discussions that help you experiment and expand your knowledge, so you’re no longer dependent on specific settings or cookbook-style presentations. Now revamped to focus specifically on digital photography, this edition contains dozens of hands-on examples and projects designed to give you an edge in technical, personal, and commercial projects – as well as indispensable advanced techniques for image enhancement and correction. Valentine offers expert insights and approaches for using blending modes and adjustment layers, and using special effects, compositing, and illustration techniques more creatively. If you crave deeper understanding, greater flexibility, and more effective workflows – and you don’t just want to simulate someone else’s work – this is the Photoshop guide you’ve been searching for. COMPUTERS,Software Development & Engineering,Computer Graphics

Techniques of Visual Persuasion In today’s remote-oriented, work-from-home world, clear, persuasive communication is more important than ever. People don’t read, they skim. Persuasive images that attract, hold, and motivate an audience is essential. Techniques of Visual Persuasion shows how to use images to grab the viewer’s attention long enough to powerfully share a message and move them to action. These techniques help you improve: Persuasive techniques Communication skills Business presentations Photos and images Videos and motion graphics To communicate clearly and effectively today, you need to consider how a message looks, as well as what a message says. This book is essential reading for anyone who wants to create change. COMPUTERS,Software Development & Engineering,Computer Graphics

Image Analysis and Recognition This two-volume set LNCS 12131 and LNCS 12132 constitutes the refereed proceedings of the 17th International Conference on Image Analysis and Recognition, ICIAR 2020, held in Póvoa de Varzim, Portugal, in June 2020.The 54 full papers presented together with 15 short papers were carefully reviewed and selected from 123 submissions. The papers are organized in the following topical sections: image processing and analysis; video analysis; computer vision; 3D computer vision; machine learning; medical image and analysis; analysis of histopathology images; diagnosis and screening of ophthalmic diseases; and grand challenge on automatic lung cancer patient management. Due to the corona pandemic, ICIAR 2020 was held virtually only. COMPUTERS,Software Development & Engineering,Computer Graphics

Heterogeneous Facial Analysis and Synthesis This book presents a comprehensive review of heterogeneous face analysis and synthesis, ranging from the theoretical and technical foundations to various hot and emerging applications, such as cosmetic transfer, cross-spectral hallucination and face rotation. Deep generative models have been at the forefront of research on artificial intelligence in recent years and have enhanced many heterogeneous face analysis tasks. Not only has there been a constantly growing flow of related research papers, but there have also been substantial advances in real-world applications. Bringing these together, this book describes both the fundamentals and applications of heterogeneous face analysis and synthesis. Moreover, it discusses the strengths and weaknesses of related methods and outlines future trends. Offering a rich blend of theory and practice, the book represents a valuable resource for students, researchers and practitioners who need to construct face analysis systems with deep generative networks. COMPUTERS,Software Development & Engineering,Computer Graphics
Combinatorial Image Analysis This book constitutes the refereed proceedings of the 20th International Workshop on Combinatorial Image Analysis, IWCIA 2020, held in Novi Sad, Serbia, in July 2020. The 20 full papers presented were carefully reviewed and selected from 23 submissions. The papers are grouped into two sections. The first one includes twelve papers devoted to theoretical foundations of combinatorial image analysis, including digital geometry and topology, array grammars, picture languages, digital tomography, and other technical tools for image analysis. The second part includes eight papers presenting application-driven research on topics such as image repairing, annotation of images, image reconstruction, forgery detection, and dealing with noise in images. COMPUTERS,Software Development & Engineering,Computer Graphics

Medical Image Understanding and Analysis This book constitutes the refereed proceedings of the 24th Conference on Medical Image Understanding and Analysis, MIUA 2020, held in July 2020. Due to COVID-19 pandemic the conference was held virtually. The 29 full papers and 5 short papers presented were carefully reviewed and selected from 70 submissions. They were organized according to following topical sections: ​image segmentation; image registration, reconstruction and enhancement; radiomics, predictive models, and quantitative imaging biomarkers; ocular imaging analysis; biomedical simulation and modelling. COMPUTERS,Software Development & Engineering,Computer Graphics

Image and Signal Processing This volume constitutes the refereed proceedings of the 9th International Conference on Image and Signal Processing, ICISP 2020, which was due to be held in Marrakesh, Morocco, in June 2020. The conference was cancelled due to the COVID-19 pandemic. The 40 revised full papers were carefully reviewed and selected from 84 submissions. The contributions presented in this volume were organized in the following topical sections: digital cultural heritage & color and spectral imaging; data and image processing for precision agriculture; machine learning application and innovation; biomedical imaging; deep learning and applications; pattern recognition; segmentation and retrieval; mathematical imaging & signal processing. COMPUTERS,Software Development & Engineering,Computer Graphics

Modelling Human Motion The new frontiers of robotics research foresee future scenarios where artificial agents will leave the laboratory to progressively take part in the activities of our daily life. This will require robots to have very sophisticated perceptual and action skills in many intelligence-demanding applications, with particular reference to the ability to seamlessly interact with humans. It will be crucial for the next generation of robots to understand their human partners and at the same time to be intuitively understood by them. In this context, a deep understanding of human motion is essential for robotics applications, where the ability to detect, represent and recognize human dynamics and the capability for generating appropriate movements in response sets the scene for higher-level tasks. This book provides a comprehensive overview of this challenging research field, closing the loop between perception and action, and between human-studies and robotics. The book is organized in three main parts. The first part focuses on human motion perception, with contributions analyzing the neural substrates of human action understanding, how perception is influenced by motor control, and how it develops over time and is exploited in social contexts. The second part considers motion perception from the computational perspective, providing perspectives on cutting-edge solutions available from the Computer Vision and Machine Learning research fields, addressing higher-level perceptual tasks. Finally, the third part takes into account the implications for robotics, with chapters on how motor control is achieved in the latest generation of artificial agents and how such technologies have been exploited to favor human-robot interaction. This book considers the complete human-robot cycle, from an examination of how humans perceive motion and act in the world, to models for motion perception and control in artificial agents. In this respect, the book will provide insights into the perception and action loop in humans and machines, joining together aspects that are often addressed in independent investigations. As a consequence, this book positions itself in a field at the intersection of such different disciplines as Robotics, Neuroscience, Cognitive Science, Psychology, Computer Vision, and Machine Learning. By bridging these different research domains, the book offers a common reference point for researchers interested in human motion for different applications and from different standpoints, spanning Neuroscience, Human Motor Control, Robotics, Human-Robot Interaction, Computer Vision and Machine Learning. Chapter 'The Importance of the Affective Component of Movement in Action Understanding' of this book is available open access under a CC BY 4.0 license at link.springer.com. COMPUTERS,Software Development & Engineering,Computer Graphics

Transactions on Computational Science XXXVII The LNCS journal Transactions on Computational Science reflects recent developments in the field of Computational Science, conceiving the field not as a mere ancillary science but rather as an innovative approach supporting many other scientific disciplines. The journal focuses on original high-quality research in the realm of computational science in parallel and distributed environments, encompassing the facilitating theoretical foundations and the applications of large-scale computations and massive data processing. It addresses researchers and practitioners in areas ranging from aerospace to biochemistry, from electronics to geosciences, from mathematics to software architecture, presenting verifiable computational methods, findings, and solutions, and enabling industrial users to apply techniques of leading-edge, large-scale, high performance computational methods.This, the 37th issue of the Transactions on Computational Science, is devoted to the area of Computer Graphics. The 9 papers included in the volume constitute extended versions of selected papers presented at the 36th Computer Graphics International Conference, CGI 2019. Topics covered include virtual reality, augmented reality, image retrieval, animation of elastoplastic material, and visualization of 360°HDR images. COMPUTERS,Software Development & Engineering,Computer Graphics

3D Rotations 3D rotation analysis is widely encountered in everyday problems thanks to the development of computers. Sensing 3D using cameras and sensors, analyzing and modeling 3D for computer vision and computer graphics, and controlling and simulating robot motion all require 3D rotation computation. This book focuses on the computational analysis of 3D rotation, rather than classical motion analysis. It regards noise as random variables and models their probability distributions. It also pursues statistically optimal computation for maximizing the expected accuracy, as is typical of nonlinear optimization. All concepts are illustrated using computer vision applications as examples. Mathematically, the set of all 3D rotations forms a group denoted by SO(3). Exploiting this group property, we obtain an optimal solution analytical or numerically, depending on the problem. Our numerical scheme, which we call the "Lie algebra method," is based on the Lie group structure of SO(3). This book also proposes computing projects for readers who want to code the theories presented in this book, describing necessary 3D simulation setting as well as providing real GPS 3D measurement data. To help readers not very familiar with abstract mathematics, a brief overview of quaternion algebra, matrix analysis, Lie groups, and Lie algebras is provided as Appendix at the end of the volume. COMPUTERS,Software Development & Engineering,Computer Graphics

The Designer's Guide to Product Vision As organizations increasingly recognize the centrality of design to strategy, designers have an opportunity to shape decisions at the highest level, moving beyond low-level UI/UX decisions to product vision and strategy. In The Designer's Guide to Product Vision , pioneering product design visionary Laura Fish helps you level up your skills and become a modern design leader. Fish shows how to make the hard-won transformation to strategic designer, and harness your new power by championing product visions that make a powerful difference. You’ll learn how to: Lead digital product journeys in an agile world, using product vision as a strategic compass that keeps everyone aligned in the face of change Bind your product to purposeful direction: delivering the best experience that solves for user problems through the lens of business objectives Master the exceptional business communication skills you need to command business endeavors based on product or service vision Secure dedicated resources, assemble your team, and captain your visioneering expedition to success Fish provides practical tools that help you apply her strategies, including product vision proposal document deliverables, storytelling arc templates, vision solution story templates, and more. With her guidance and resources, you can leave pixel-pushing behind -- and change your world. COMPUTERS,Software Development & Engineering,Computer Graphics

Agile Modeling The first book to cover Agile Modeling, a new modeling technique created specifically for XP projects eXtreme Programming (XP) has created a buzz in the software development community-much like Design Patterns did several years ago. Although XP presents a methodology for faster software development, many developers find that XP does not allow for modeling time, which is critical to ensure that a project meets its proposed requirements. They have also found that standard modeling techniques that use the Unified Modeling Language (UML) often do not work with this methodology. In this innovative book, Software Development columnist Scott Ambler presents Agile Modeling (AM)-a technique that he created for modeling XP projects using pieces of the UML and Rational's Unified Process (RUP). Ambler clearly explains AM, and shows readers how to incorporate AM, UML, and RUP into their development projects with the help of numerous case studies integrated throughout the book. AM was created by the author for modeling XP projects-an element lacking in the original XP design The XP community and its creator have embraced AM, which should give this book strong market acceptance Companion Web site at www.agilemodeling.com features updates, links to XP and AM resources, and ongoing case studies about agile modeling. COMPUTERS,Software Development & Engineering,General

Knowledge-Based Software Engineering Knowledge-Based Software Engineering brings together in one place important contributions and up-to-date research results in this important area. Knowledge-Based Software Engineering serves as an excellent reference, providing insight into some of the most important research issues in the field. COMPUTERS,Software Development & Engineering,General

Crystal Clear Carefully researched over ten years and eagerly anticipated by the agile community, Crystal Clear: A Human-Powered Methodology for Small Teams is a lucid and practical introduction to running a successful agile project in your organization. Each chapter illuminates a different important aspect of orchestrating agile projects. Highlights include Attention to the essential human and communication aspects of successful projects Case studies, examples, principles, strategies, techniques, and guiding properties Samples of work products from real-world projects instead of blank templates and toy problems Top strategies used by software teams that excel in delivering quality code in a timely fashion Detailed introduction to emerging best-practice techniques, such as Blitz Planning, Project 360º, and the essential Reflection Workshop Question-and-answer with the author about how he arrived at these recommendations, including where they fit with CMMI, ISO, RUP, XP, and other methodologies A detailed case study, including an ISO auditor's analysis of the project Perhaps the most important contribution this book offers is the Seven Properties of Successful Projects. The author has studied successful agile projects and identified common traits they share. These properties lead your project to success; conversely, their absence endangers your project. COMPUTERS,Software Development & Engineering,General

Reversing Beginning with a basic primer on reverse engineering-including computer internals, operating systems, and assembly language-and then discussing the various applications of reverse engineering, this book provides readers with practical, in-depth techniques for software reverse engineering. The book is broken into two parts, the first deals with security-related reverse engineering and the second explores the more practical aspects of reverse engineering. In addition, the author explains how to reverse engineer a third-party software library to improve interfacing and how to reverse engineer a competitor's software to build a better product. * The first popular book to show how software reverse engineering can help defend against security threats, speed up development, and unlock the secrets of competitive products * Helps developers plug security holes by demonstrating how hackers exploit reverse engineering techniques to crack copy-protection schemes and identify software targets for viruses and other malware * Offers a primer on advanced reverse-engineering, delving into "disassembly"-code-level reverse engineering-and explaining how to decipher assembly language COMPUTERS,Software Development & Engineering,General

Error Correction Coding An unparalleled learning tool and guide to error correction coding Error correction coding techniques allow the detection and correction of errors occurring during the transmission of data in digital communication systems. These techniques are nearly universally employed in modern communication systems, and are thus an important component of the modern information economy. Error Correction Coding: Mathematical Methods and Algorithms provides a comprehensive introduction to both the theoretical and practical aspects of error correction coding, with a presentation suitable for a wide variety of audiences, including graduate students in electrical engineering, mathematics, or computer science. The pedagogy is arranged so that the mathematical concepts are presented incrementally, followed immediately by applications to coding. A large number of exercises expand and deepen students' understanding. A unique feature of the book is a set of programming laboratories, supplemented with over 250 programs and functions on an associated Web site, which provides hands-on experience and a better understanding of the material. These laboratories lead students through the implementation and evaluation of Hamming codes, CRC codes, BCH and R-S codes, convolutional codes, turbo codes, and LDPC codes. This text offers both "classical" coding theory-such as Hamming, BCH, Reed-Solomon, Reed-Muller, and convolutional codes-as well as modern codes and decoding methods, including turbo codes, LDPC codes, repeat-accumulate codes, space time codes, factor graphs, soft-decision decoding, Guruswami-Sudan decoding, EXIT charts, and iterative decoding. Theoretical complements on performance and bounds are presented. Coding is also put into its communications and information theoretic context and connections are drawn to public key cryptosystems. Ideal as a classroom resource and a professional reference, this thorough guide will benefit electrical and computer engineers, mathematicians, students, researchers, and scientists. COMPUTERS,Software Development & Engineering,General

Reverse Engineering of Object Oriented Code During maintenance of a software system, not all questions can be answered directly by resorting to otherwise reliable and accurate source code. Reverse engineering aims at extracting abstract, goal-oriented views of the system, able to summarize relevant properties of the program's computations. Reverse Engineering of Object-Oriented Code provides a comprehensive overview of several techniques that have been recently investigated in the field of reverse engineering. The book describes the algorithms involved in recovering UML diagrams from the code and the techniques that can be adopted for their visualization. This is important because the UML has become the standard for representing design diagrams in object-oriented development. A state-of-the-art exposition on how to design object-oriented code and accompanying algorithms that can be reverse engineered for greater flexibility in future code maintenance and alteration. Essential object-oriented concepts and programming methods for software engineers and researchers. COMPUTERS,Software Development & Engineering,General

Fortran 95 This is the second edition of the first introductory textbook written for the FORTRAN 90 standard. It remains suitable for the novice scientific programmer, drawing on a larger number of examples and exercises in this new edition. COMPUTERS,Software Development & Engineering,General

Extreme Programming Explained Accountability. Transparency. Responsibility. These are not words that are often applied to software development. In this completely revised introduction to Extreme Programming (XP), Kent Beck describes how to improve your software development by integrating these highly desirable concepts into your daily development process. The first edition of Extreme Programming Explained is a classic. It won awards for its then-radical ideas for improving small-team development, such as having developers write automated tests for their own code and having the whole team plan weekly. Much has changed in five years. This completely rewritten second edition expands the scope of XP to teams of any size by suggesting a program of continuous improvement based on: Five core values consistent with excellence in software development Eleven principles for putting those values into action Thirteen primary and eleven corollary practices to help you push development past its current business and technical limitations Whether you have a small team that is already closely aligned with your customers or a large team in a gigantic or multinational organization, you will find in these pages a wealth of ideas to challenge, inspire, and encourage you and your team members to substantially improve your software development. You will discover how to: Involve the whole team–XP style Increase technical collaboration through pair programming and continuous integration Reduce defects through developer testing Align business and technical decisions through weekly and quarterly planning Improve teamwork by setting up an informative, shared workspace You will also find many other concrete ideas for improvement, all based on a philosophy that emphasizes simultaneously increasing the humanity and effectiveness of software development. Every team can improve. Every team can begin improving today. Improvement is possible–beyond what we can currently imagine. Extreme Programming Explained, Second Edition, offers ideas to fuel your improvement for years to come. COMPUTERS,Software Development & Engineering,General

Beginning Cryptography with Java Beginning Cryptography with Java While cryptography can still be a controversial topic in the programming community, Java has weathered that storm and provides a rich set of APIs that allow you, the developer, to effectively include cryptography in applications-if you know how. This book teaches you how. Chapters one through five cover the architecture of the JCE and JCA, symmetric and asymmetric key encryption in Java, message authentication codes, and how to create Java implementations with the API provided by the Bouncy Castle ASN.1 packages, all with plenty of examples. Building on that foundation, the second half of the book takes you into higher-level topics, enabling you to create and implement secure Java applications and make use of standard protocols such as CMS, SSL, and S/MIME. What you will learn from this book How to understand and use JCE, JCA, and the JSSE for encryption and authentication The ways in which padding mechanisms work in ciphers and how to spot and fix typical errors An understanding of how authentication mechanisms are implemented in Java and why they are used Methods for describing cryptographic objects with ASN.1 How to create certificate revocation lists and use the Online Certificate Status Protocol (OCSP) Real-world Web solutions using Bouncy Castle APIs Who this book is for This book is for Java developers who want to use cryptography in their applications or to understand how cryptography is being used in Java applications. Knowledge of the Java language is necessary, but you need not be familiar with any of the APIs discussed. Wrox Beginning guides are crafted to make learning programming languages and technologies easier than you think, providing a structured, tutorial format that will guide you through all the techniques involved. COMPUTERS,Software Development & Engineering,General

What Every Engineer Should Know about Software Engineering Do you Use a computer to perform analysis or simulations in your daily work? Write short scripts or record macros to perform repetitive tasks? Need to integrate off-the-shelf software into your systems or require multiple applications to work together? Find yourself spending too much time working the kink COMPUTERS,Software Development & Engineering,General

Pro PayPal E-Commerce Pro PayPal E-Commerce contains the most comprehensive collection of information on PayPal technologies. It takes the approach of PayPal as a digital money platform, and shows how its a dynamic service that offers far more than just payment processing. With its breadth of technologies and APIs, the PayPal platform is a basis for development and innovation for an unlimited number of possibilities. It offers a wide range of payment technologies, but its not always easy to decipher which technology is the best choice for a web site. This book gets under the hood to show you how the different technologies work, how to choose the right solution, and how to implement the solutioncomplete with real-world PayPal success stories. Youll learn how to integrate PayPal directly into web sites to make use of its payment technologies. This allows you, no matter what language you program in, to build shopping carts or similar channel products with PayPal as a payment option. You can also use this book to learn about the basics of e-commerce, where PayPal fits in, and how you can meet your own e-commerce needs. This book covers How PayPal works Using the PayPal API Website Payments Standard Website Payments Pro Instant Payment Notification Payment Data Transfer Encrypted Website Payments Administration Reporting Fraud protection Payflow Gateway COMPUTERS,Software Development & Engineering,General

Java Methods for Financial Engineering In order to build a successful, Java-based application it is important to have a clear understanding of the principles underlying the various financial models. Those models guide the application designer in choosing the most appropriate Java data structures and implementation strategy. This book describes the principles of model building in financial engineering and explains those models as designs and working implementations for Java-based applications. Throughout the book a series of packaged classes are developed to address a wide range of financial applications. Java methods are designed and implemented based on the most widely used models in financial engineering and investment practice. The classes and methods are explained and designed in a way which allows the financial engineer complete flexibility. The classes can be used as off-the-shelf working solutions or the innovative developer can re-arrange and modify methods to create new products COMPUTERS,Software Development & Engineering,General

Smart and Gets Things Done A guide to attracting, recruiting, interviewing, and hiring the best technical talent. A comprehensive system for hiring top–notch technical employees Packed with useful information and specific advice written in a breezy, humorous style Learn how to find great people—and get them to work for you—in an afternoon! The top software developers are ten times more productive than average developers. Ten times. You can’t afford not to hire them. But if you haven’t been reading Joel Spolsky’s books or blog, you probably don’t know how to find them and make them want to work for you. In this brief book, Joel reveals all his secrets—from his years at Microsoft, and as the co–founder of Fog Creek Software—for recruiting the best developers in the world. If you’ve ever wondered what you should be looking for in a resume, if you’ve ever struggled to decide whether to hire someone at the end of an interview, or if you’re wondering why you can’t find great programmers, stop everything and read this book. COMPUTERS,Software Development & Engineering,General

Managing Humans Managing Humans is a selection of the best essays from Michael Lopp's web site, Rands in Repose. Drawing on Lopp's management experiences at Apple, Netscape, Symantec, and Borland, this book is full of stories based on companies in the Silicon Valley where people have been known to yell at each other. It is a place full of dysfunctional bright people who are in an incredible hurry to find the next big thing so they can strike it rich and then do it all over again. Among these people are managers, a strange breed of people who through a mystical organizational ritual have been given power over your future and your bank account. Whether you're an aspiring manager, a current manager, or just wondering what the heck a manager does all day, there is a story in this book that will speak to you. COMPUTERS,Software Development & Engineering,General

Software Architecture Software architecture has emerged as an important subdiscipline of software engineering encompassing a broad set of languages, styles, models, tools, and processes. The role of software architecture in the engineering of software-intensive applications has become more and more important and widespread. Indeed, component-based and service-oriented architectures have become key to the design, development, and evolution of most software systems. The European Conference on Software Architecture (ECSA) is the premier European conference dedicated to the field of software architecture, covering all architectural features of software and service engineering. It is the follow-up of a successful series of European workshops on software architecture held in the United Kingdom in 2004 (Springer LNCS 3047), Italy in 2005 (Springer LNCS 3527), and France in 2006 (Springer LNCS 4344). Due to its success, it has evolved into a fu- fledged series of European conferences whose first edition was ECSA 2007, held in Madrid, Spain September 24–26, 2007. ECSA 2007 provided an international forum for researchers and practitioners from academia and industry to present innovative research and to discuss a wide range of topics in the area of software architecture. It focused on formalisms, technologies, and processes for describing, verifying, validating, transforming, building, and evolving software systems, in particular founded on component-based and service-oriented architectures. Covered topics included architecture modeling, architectural aspects, architecture analysis, transformation and synthesis, quality attributes, model-driven engineering, and architecture-based support for developing, adapting, reconfiguring, and evolving component-based and service-oriented systems. COMPUTERS,Software Development & Engineering,General

Software Testing and Continuous Quality Improvement It is often assumed that software testing is based on clearly defined requirements and software development standards. However, testing is typically performed against changing, and sometimes inaccurate, requirements. The third edition of a bestseller, Software Testing and Continuous Quality Improvement, Third Edition provides a continuous quality framework for the software testing process within traditionally structured and unstructured environments. This framework aids in creating meaningful test cases for systems with evolving requirements. This completely revised reference provides a comprehensive look at software testing as part of the project management process, emphasizing testing and quality goals early on in development. Building on the success of previous editions, the text explains testing in a Service Orientated Architecture (SOA) environment, the building blocks of a Testing Center of Excellence (COE), and how to test in an agile development. Fully updated, the sections on test effort estimation provide greater emphasis on testing metrics. The book also examines all aspects of functional testing and looks at the relation between changing business strategies and changes to applications in development. Includes New Chapters on Process, Application, and Organizational Metrics All IT organizations face software testing issues, but most are unprepared to manage them. Software Testing and Continuous Quality Improvement, Third Edition is enhanced with an up-to-date listing of free software tools and a question-and-answer checklist for choosing the best tools for your organization. It equips you with everything you need to effectively address testing issues in the most beneficial way for your business. COMPUTERS,Software Development & Engineering,General

Semantic Web Programming The next major advance in the Web-Web 3.0-will be built on semantic Web technologies, which will allow data to be shared and reused across application, enterprise, and community boundaries. Written by a team of highly experienced Web developers, this book explains examines how this powerful new technology can unify and fully leverage the ever-growing data, information, and services that are available on the Internet. Helpful examples demonstrate how to use the semantic Web to solve practical, real-world problems while you take a look at the set of design principles, collaborative working groups, and technologies that form the semantic Web. The companion Web site features full code, as well as a reference section, a FAQ section, a discussion forum, and a semantic blog. COMPUTERS,Software Development & Engineering,General

Discovering Requirements "This book is not only of practical value. It's also a lot of fun to read." Michael Jackson, The Open University. Do you need to know how to create good requirements? Discovering Requirements offers a set of simple, robust, and effective cognitive tools for building requirements. Using worked examples throughout the text, it shows you how to develop an understanding of any problem, leading to questions such as: What are you trying to achieve? Who is involved, and how? What do those people want? Do they agree? How do you envisage this working? What could go wrong? Why are you making these decisions? What are you assuming? The established author team of Ian Alexander and Ljerka Beus-Dukic answer these and related questions, using a set of complementary techniques, including stakeholder analysis, goal modelling, context modelling, storytelling and scenario modelling, identifying risks and threats, describing rationales, defining terms in a project dictionary, and prioritizing. This easy to read guide is full of carefully-checked tips and tricks. Illustrated with worked examples, checklists, summaries, keywords and exercises, this book will encourage you to move closer to the real problems you're trying to solve. Guest boxes from other experts give you additional hints for your projects. Invaluable for anyone specifying requirements including IT practitioners, engineers, developers, business analysts, test engineers, configuration managers, quality engineers and project managers. A practical sourcebook for lecturers as well as students studying software engineering who want to learn about requirements work in industry. Once you've read this book you will be ready to create good requirements! COMPUTERS,Software Development & Engineering,General

The Algorithm Design Manual Most professional programmers that I’ve encountered are not well prepared to tacklealgorithmdesignproblems.Thisisapity,becausethetechniquesofalgorithm design form one of the core practical technologies of computer science. Designing correct, e?cient, and implementable algorithms for real-world problems requires access to two distinct bodies of knowledge: • Techniques – Good algorithm designers understand several fundamental - gorithm design techniques, including data structures, dynamic programming, depth-?rst search, backtracking, and heuristics. Perhaps the single most - portantdesigntechniqueismodeling,theartofabstractingamessyreal-world application into a clean problem suitable for algorithmic attack. • Resources – Good algorithm designers stand on the shoulders of giants. Ratherthanlaboringfromscratchtoproduceanewalgorithmforeverytask, they can ?gure out what is known about a particular problem. Rather than re-implementing popular algorithms from scratch, they seek existing imp- mentations to serve as a starting point. They are familiar with many classic algorithmic problems, which provide su?cient source material to model most any application. This book is intended as a manual on algorithm design, providing access to combinatorial algorithm technology for both students and computer professionals. COMPUTERS,Software Development & Engineering,General

Learning UML 2.0 "Since its original introduction in 1997, the Unified Modeling Language has revolutionized software development. Every integrated software development environment in the world--open-source, standards-based, and proprietary--now supports UML and, more importantly, the model-driven approach to software development. This makes learning the newest UML standard, UML 2.0, critical for all software developers--and there isn't a better choice than this clear, step-by-step guide to learning the language." --Richard Mark Soley, Chairman and CEO, OMG If you're like most software developers, you're building systems that are increasingly complex. Whether you're creating a desktop application or an enterprise system, complexity is the big hairy monster you must manage. The Unified Modeling Language (UML) helps you manage this complexity. Whether you're looking to use UML as a blueprint language, a sketch tool, or as a programming language, this book will give you the need-to-know information on how to apply UML to your project. While there are plenty of books available that describe UML, Learning UML 2.0 will show you how to use it. Topics covered include: Capturing your system's requirements in your model to help you ensure that your designs meet your users' needs Modeling the parts of your system and their relationships Modeling how the parts of your system work together to meet your system's requirements Modeling how your system moves into the real world, capturing how your system will be deployed Engaging and accessible, this book shows you how to use UML to craft and communicate your project's design. Russ Miles and Kim Hamilton have written a pragmatic introduction to UML based on hard-earned practice, not theory. Regardless of the software process or methodology you use, this book is the one source you need to get up and running with UML 2.0. Additional information including exercises can be found at www.learninguml2.com. Russ Miles is a software engineer for General Dynamics UK, where he works with Java and Distributed Systems, although his passion at the moment is Aspect Orientation and, in particular, AspectJ. Kim Hamilton is a senior software engineer at Northrop Grumman, where she's designed and implemented a variety of systems including web applications and distributed systems, with frequent detours into algorithms development. COMPUTERS,Software Development & Engineering,General

The Art of Concurrency If you're looking to take full advantage of multi-core processors with concurrent programming, this practical book provides the knowledge and hands-on experience you need. The Art of Concurrency is one of the few resources to focus on implementing algorithms in the shared-memory model of multi-core processors, rather than just theoretical models or distributed-memory architectures. The book provides detailed explanations and usable samples to help you transform algorithms from serial to parallel code, along with advice and analysis for avoiding mistakes that programmers typically make when first attempting these computations. Written by an Intel engineer with over two decades of parallel and concurrent programming experience, this book will help you: Understand parallelism and concurrency Explore differences between programming for shared-memory and distributed-memory Learn guidelines for designing multithreaded applications, including testing and tuning Discover how to make best use of different threading libraries, including Windows threads, POSIX threads, OpenMP, and Intel Threading Building Blocks Explore how to implement concurrent algorithms that involve sorting, searching, graphs, and other practical computations The Art of Concurrency shows you how to keep algorithms scalable to take advantage of new processors with even more cores. For developing parallel code algorithms for concurrent programming, this book is a must. COMPUTERS,Software Development & Engineering,General

RESTful .NET RESTful .NET is the first book that teaches Windows developers to build RESTful web services using the latest Microsoft tools. Written by Windows Communication Foundation (WFC) expert Jon Flanders, this hands-on tutorial demonstrates how you can use WCF and other components of the .NET 3.5 Framework to build, deploy and use REST-based web services in a variety of application scenarios. RESTful architecture offers a simpler approach to building web services than SOAP, SOA, and the cumbersome WS- stack. And WCF has proven to be a flexible technology for building distributed systems not necessarily tied to WS- standards. RESTful .NET provides you with a complete guide to the WCF REST programming model for building web services consumed either by machines or humans. You'll learn how to: Program Read-Only (GET) services Program READ/WRITE services Host REST services Program REST feeds Program AJAX REST clients Secure REST endpoints Use workflow to deliver REST services Consume RESTful XML services using WCF Work with HTTP Work with ADO.NET Data Services (Astoria) RESTful .NET introduces you to the ideas of REST and RESTful architecture, and includes a detailed discussion of how the Web/REST model plugs into the WCF architecture. If you develop with .NET, it's time to jump on the RESTful bandwagon. This book explains how. "While REST is simple, WCF is not. To really understand and exploit this part of WCF requires a knowledgeable and experienced guide. I don't know anybody who's better suited for this role than Jon Flanders. ...Jon is first-rate at explaining complicated things. This book is the best introduction I've seen to creating and using these services with WCF."--David Chappell, Chappell & Associates COMPUTERS,Software Development & Engineering,General

Eclipse Java programmers know how finicky Java can be to work with. An omitted semi-colon or the slightest typo will cause the Java command-line compiler to spew pages of annoying error messages across your screen. And it doesn't fix them--that's up to you: fix them, compile again, and hope that nothing goes wrong this time.Eclipse, the popular Java integrated development environment (IDE) provides an elegant and powerful remedy for this common, frustrating scenario. It doesn't just catch your errors before you compile, it also suggests solutions. All you need to do is point and click. And it's free--what could be better? Still, if you're like most programmers, mastering a new technology--no matter how productive it will make you in the long run--is going to take a chunk out of your productivity now. You want to get up to speed quickly without sacrificing efficiency.O'Reilly's new guide to the technology, Eclipse, provides exactly what you're looking for: a fast-track approach to mastery of Eclipse. This insightful, hands-on book delivers clear and concise coverage, with no fluff, that gets down to business immediately. The book is tightly focused, covering all aspects of Eclipse: the menus, preferences, views, perspectives, editors, team and debugging techniques, and how they're used every day by thousands of developers. Development of practical skills is emphasized with dozens of examples presented throughout the book.From cover-to-cover, the book is pure Eclipse, covering hundreds of techniques beginning with the most basic Java development through creating your own plug-in editors for the Eclipse environment. Some of the topics you'll learn about include: Using Eclipse to develop Java code Testing and debugging Working in teams using CVS Building Eclipse projects using Ant The Standard Widget Toolkit (SWT) Web development Developing Struts applications with Eclipse From basics to advanced topics, Eclipse takes you through the fundamentals of Eclipse and more. You may be an Eclipse novice when you pick up the book, but you'll be a pro by the time you've finished. COMPUTERS,Software Development & Engineering,General

97 Things Every Software Architect Should Know In this truly unique technical book, today's leading software architects present valuable principles on key development issues that go way beyond technology. More than four dozen architects -- including Neal Ford, Michael Nygard, and Bill de hOra -- offer advice for communicating with stakeholders, eliminating complexity, empowering developers, and many more practical lessons they've learned from years of experience. Among the 97 principles in this book, you'll find useful advice such as: Don't Put Your Resume Ahead of the Requirements (Nitin Borwankar) Chances Are, Your Biggest Problem Isn't Technical (Mark Ramm) Communication Is King; Clarity and Leadership, Its Humble Servants (Mark Richards) Simplicity Before Generality, Use Before Reuse (Kevlin Henney) For the End User, the Interface Is the System (Vinayak Hegde) It's Never Too Early to Think About Performance (Rebecca Parsons) To be successful as a software architect, you need to master both business and technology. This book tells you what top software architects think is important and how they approach a project. If you want to enhance your career, 97 Things Every Software Architect Should Know is essential reading. COMPUTERS,Software Development & Engineering,General

Software Performance and Scalability Praise from the Reviewers: "The practicality of the subject in a real-world situation distinguishes this book from others available on the market." —Professor Behrouz Far, University of Calgary "This book could replace the computer organization texts now in use that every CS and CpE student must take. . . . It is much needed, well written, and thoughtful." —Professor Larry Bernstein, Stevens Institute of Technology A distinctive, educational text onsoftware performance and scalability This is the first book to take a quantitative approach to the subject of software performance and scalability. It brings together three unique perspectives to demonstrate how your products can be optimized and tuned for the best possible performance and scalability: The Basics—introduces the computer hardware and software architectures that predetermine the performance and scalability of a software product as well as the principles of measuring the performance and scalability of a software product Queuing Theory—helps you learn the performance laws and queuing models for interpreting the underlying physics behind software performance and scalability, supplemented with ready-to-apply techniques for improving the performance and scalability of a software system API Profiling—shows you how to design more efficient algorithms and achieve optimized performance and scalability, aided by adopting an API profiling framework (perfBasic) built on the concept of a performance map for drilling down performance root causes at the API level Software Performance and Scalability gives you a specialized skill set that will enable you to design and build performance into your products with immediate, measurable improvements. Complemented with real-world case studies, it is an indispensable resource for software developers, quality and performance assurance engineers, architects, and managers. It is anideal text for university courses related to computer and software performance evaluation and can also be used to supplement a course in computer organization or in queuing theory for upper-division and graduate computer science students. COMPUTERS,Software Development & Engineering,General

Assembly Language Step-by-Step The eagerly anticipated new edition of the bestselling introduction to x86 assembly language The long-awaited third edition of this bestselling introduction to assembly language has been completely rewritten to focus on 32-bit protected-mode Linux and the free NASM assembler. Assembly is the fundamental language bridging human ideas and the pure silicon hearts of computers, and popular author Jeff Dunteman retains his distinctive lighthearted style as he presents a step-by-step approach to this difficult technical discipline. He starts at the very beginning, explaining the basic ideas of programmable computing, the binary and hexadecimal number systems, the Intel x86 computer architecture, and the process of software development under Linux. From that foundation he systematically treats the x86 instruction set, memory addressing, procedures, macros, and interface to the C-language code libraries upon which Linux itself is built. Serves as an ideal introduction to x86 computing concepts, as demonstrated by the only language directly understood by the CPU itself Uses an approachable, conversational style that assumes no prior experience in programming of any kind Presents x86 architecture and assembly concepts through a cumulative tutorial approach that is ideal for self-paced instruction Focuses entirely on free, open-source software, including Ubuntu Linux, the NASM assembler, the Kate editor, and the Gdb/Insight debugger Includes an x86 instruction set reference for the most common machine instructions, specifically tailored for use by programming beginners Woven into the presentation are plenty of assembly code examples, plus practical tips on software design, coding, testing, and debugging, all using free, open-source software that may be downloaded without charge from the Internet. COMPUTERS,Software Development & Engineering,General

Mastering Unix Shell Scripting UNIX expert Randal K. Michael guides you through every detail of writing shell scripts to automate specific tasks. Each chapter begins with a typical, everyday UNIX challenge, then shows you how to take basic syntax and turn it into a shell scripting solution. Covering Bash, Bourne, and Korn shell scripting, this updated edition provides complete shell scripts plus detailed descriptions of each part. UNIX programmers and system administrators can tailor these to build tools that monitor for specific system events and situations, building solid UNIX shell scripting skills to solve real-world system administration problems. COMPUTERS,Software Development & Engineering,General

Beginning Python Beginning Python: Using Python 2.6 and Python 3.1 introduces this open source, portable, interpreted, object-oriented programming language that combines remarkable power with clear syntax. This book enables you to quickly create robust, reliable, and reusable Python applications by teaching the basics so you can quickly develop Web and scientific applications, incorporate databases, and master systems tasks on various operating systems, including Linux, MAC OS, and Windows. You'll get a comprehensive tutorial that guides you from writing simple, basic Python scripts all the way through complex concepts, and also features a reference of the standard modules with examples illustrating how to implement features in the various modules. Plus, the book covers using Python in specific program development domains, such as XML, databases, scientific applications, network programming, and Web development. Note: CD-ROM/DVD and other supplementary materials are not included as part of eBook file. COMPUTERS,Software Development & Engineering,General

World of Warcraft Programming The #1 bestselling programming book is back with updated and expanded coverage of the newest release of WoW! World of Warcraft (WoW) is currently the world's largest massively multiplayer online role-playing game. The newest release, "Wrath of the Lich King," has created a demand for updated information on writing addons. This eagerly anticipated edition answers that request and is an essential reference for creating WoW addons. Written by a duo of authors who have each contributed a number of successful WoW addons, the book offers an overview of Lua and XML (the programming languages used to write addons) and includes coverage of specific pitfalls and common programming mistakes-and how to avoid them. Valuable examples show you detailed aspects of writing addons for WoW and demonstrate how to implement addon concepts such as variables, slash commands, secure templates, and more. World of Warcraft insiders share their techniques for writing addons for both the latest version of WoW as well as the new Wrath of the Lich King expansion set Guides you through the specific nuances of the WoW API with the use of detailed examples Discusses ways to distribute and host your WoW addons so others can download and use them Explains how to respond to events, create frames, and use the WoW API to interact with the game You'll be well on your way to creating exciting WoW addons with this comprehensive reference by your side. Note: CD-ROM/DVD and other supplementary materials are not included as part of eBook file. COMPUTERS,Software Development & Engineering,General

Beginning Ubuntu Linux Beginning Ubuntu Linux, Fourth Edition is the update to the bestselling book on Ubuntu, today’s hottest Linux distribution. Targeting newcomers to Linux and to the Ubuntu distribution alike, readers are presented with an introduction to the world of Linux and open source community, followed by a detailed overview of Ubuntu’s installation and configuration process. From there readers learn how to wield total control over their newly installed operating system, and are guided through common tasks such as writing documents, listening to audio CDs and MP3s, watching movies, using VoIP and chat, and of course general system maintenance matters. Additionally, there’s a series of comprehensive tutorials on Linux internals and the command–line prompt—essential for any Linux user—and the book includes special sections on optimization, security, and system maintenance. The book comes with a DVD containing the complete Ubuntu Linux distribution. All you need to do is insert the DVD and follow the instructions in the book to install this distribution. The ultimate guide to Ubuntu, the hottest Linux distribution on the planet. Forgoes introductions to esoteric Linux topics so commonly found in other books and instead focuses on everyday tasks for everyday users: printer and file sharing configuration, office document management, and listening to MP3s and watching movies among them. COMPUTERS,Software Development & Engineering,General

Apprenticeship Patterns Are you doing all you can to further your career as a software developer? With today's rapidly changing and ever-expanding technologies, being successful requires more than technical expertise. To grow professionally, you also need soft skills and effective learning techniques. Honing those skills is what this book is all about. Authors Dave Hoover and Adewale Oshineye have cataloged dozens of behavior patterns to help you perfect essential aspects of your craft. Compiled from years of research, many interviews, and feedback from O'Reilly's online forum, these patterns address difficult situations that programmers, administrators, and DBAs face every day. And it's not just about financial success. Apprenticeship Patterns also approaches software development as a means to personal fulfillment. Discover how this book can help you make the best of both your life and your career. Solutions to some common obstacles that this book explores in-depth include: Burned out at work? "Nurture Your Passion" by finding a pet project to rediscover the joy of problem solving. Feeling overwhelmed by new information? Re-explore familiar territory by building something you've built before, then use "Retreat into Competence" to move forward again. Stuck in your learning? Seek a team of experienced and talented developers with whom you can "Be the Worst" for a while. "Brilliant stuff! Reading this book was like being in a time machine that pulled me back to those key learning moments in my career as a professional software developer and, instead of having to learn best practices the hard way, I had a guru sitting on my shoulder guiding me every step towards master craftsmanship. I'll certainly be recommending this book to clients. I wish I had this book 14 years ago!"-Russ Miles, CEO, OpenCredo COMPUTERS,Software Development & Engineering,General

Unicode Explained Fundamentally, computers just deal with numbers. They store letters and other characters by assigning a number for each one. There are hundreds of different encoding systems for mapping characters to numbers, but Unicode promises a single mapping. Unicode enables a single software product or website to be targeted across multiple platforms, languages and countries without re-engineering. It's no wonder that industry giants like Apple, Hewlett-Packard, IBM andMicrosoft have all adopted Unicode. Containing everything you need to understand Unicode, this comprehensive reference from O'Reilly takes you on a detailed guide through the complex character world. For starters, it explains how to identify and classify characters - whether they're common, uncommon, or exotic. It then shows you how to type them, utilize their properties, and process character data in a robust manner. The book is broken up into three distinct parts. The first few chapters provide you with a tutorial presentation of Unicode and character data. It gives you a firm grasp of the terminology you need to reference various components, including character sets, fonts and encodings, glyphs and character repertoires. The middle section offers more detailed information about using Unicode and other character codes. It explains the principles and methods of defining character codes, describes some of the widely used codes, and presents code conversion techniques. It also discusses properties of characters, collation and sorting, line breaking rules and Unicode encodings. The final four chapters cover more advanced material, suchas programming to support Unicode. You simply can't afford to be without the nuggets of valuable information detailed in Unicode Explained. COMPUTERS,Software Development & Engineering,General

Beautiful Code How do the experts solve difficult problems in software development? In this unique and insightful book, leading computer scientists offer case studies that reveal how they found unusual, carefully designed solutions to high-profile projects. You will be able to look over the shoulder of major coding and design experts to see problems through their eyes. This is not simply another design patterns book, or another software engineering treatise on the right and wrong way to do things. The authors think aloud as they work through their project's architecture, the tradeoffs made in its construction, and when it was important to break rules.This book contains 33 chapters contributed by Brian Kernighan, KarlFogel, Jon Bentley, Tim Bray, Elliotte Rusty Harold, Michael Feathers,Alberto Savoia, Charles Petzold, Douglas Crockford, Henry S. Warren,Jr., Ashish Gulhati, Lincoln Stein, Jim Kent, Jack Dongarra and PiotrLuszczek, Adam Kolawa, Greg Kroah-Hartman, Diomidis Spinellis, AndrewKuchling, Travis E. Oliphant, Ronald Mak, Rogerio Atem de Carvalho andRafael Monnerat, Bryan Cantrill, Jeff Dean and Sanjay Ghemawat, SimonPeyton Jones, Kent Dybvig, William Otte and Douglas C. Schmidt, AndrewPatzer, Andreas Zeller, Yukihiro Matsumoto, Arun Mehta, TV Raman,Laura Wingerd and Christopher Seiwald, and Brian Hayes. Beautiful Code is an opportunity for master coders to tell their story. All author royalties will be donated to Amnesty International. COMPUTERS,Software Development & Engineering,General

Intel Threading Building Blocks Multi-core chips from Intel and AMD offer a dramatic boost in speed and responsiveness, and plenty of opportunities for multiprocessing on ordinary desktop computers. But they also present a challenge: More than ever, multithreading is a requirement for good performance. This guide explains how to maximize the benefits of these processors through a portable C++ library that works on Windows, Linux, Macintosh, and Unix systems. With it, you'll learn how to use Intel Threading Building Blocks (TBB) effectively for parallel programming -- without having to be a threading expert. Written by James Reinders, Chief Evangelist of Intel Software Products, and based on the experience of Intel's developers and customers, this book explains the key tasks in multithreading and how to accomplish them with TBB in a portable and robust manner. With plenty of examples and full reference material, the book lays out common patterns of uses, reveals the gotchas in TBB, and gives important guidelines for choosing among alternatives in order to get the best performance. You'll learn how Intel Threading Building Blocks: Enables you to specify tasks instead of threads for better portability, easier programming, more understandable source code, and better performance and scalability in general Focuses on the goal of parallelizing computationally intensive work to deliver high-level solutions Is compatible with other threading packages, and doesn't force you to pick one package for your entire program Emphasizes scalable, data-parallel programming, which allows program performance to increase as you add processors Relies on generic programming, which enables you to write the best possible algorithms with the fewest constraints Any C++ programmer who wants to write an application to run on a multi-core system will benefit from this book. TBB is also very approachable for a C programmer or a C++ programmer without much experience with templates. Best of all, you don't need experience with parallel programming or multi-core processors to use this book. COMPUTERS,Software Development & Engineering,General

The Ruby Programming Language The Ruby Programming Language is the authoritative guide to Ruby and provides comprehensive coverage of versions 1.8 and 1.9 of the language. It was written (and illustrated!) by an all-star team: David Flanagan, bestselling author of programming language "bibles" (including JavaScript: The Definitive Guide and Java in a Nutshell) and committer to the Ruby Subversion repository. Yukihiro "Matz" Matsumoto, creator, designer and lead developer of Ruby and author of Ruby in a Nutshell, which has been expanded and revised to become this book. why the lucky stiff, artist and Ruby programmer extraordinaire. This book begins with a quick-start tutorial to the language, and then explains the language in detail from the bottom up: from lexical and syntactic structure to datatypes to expressions and statements and on through methods, blocks, lambdas, closures, classes and modules. The book also includes a long and thorough introduction to the rich API of the Ruby platform, demonstrating -- with heavily-commented example code -- Ruby's facilities for text processing, numeric manipulation, collections, input/output, networking, and concurrency. An entire chapter is devoted to Ruby's metaprogramming capabilities. The Ruby Programming Language documents the Ruby language definitively but without the formality of a language specification. It is written for experienced programmers who are new to Ruby, and for current Ruby programmers who want to challenge their understanding and increase their mastery of the language. COMPUTERS,Software Development & Engineering,General

Head First Design Patterns What’s so special about design patterns? At any given moment, someone struggles with the same software design problems you have. And, chances are, someone else has already solved your problem. This edition of Head First Design Patterns—now updated for Java 8—shows you the tried-and-true, road-tested patterns used by developers to create functional, elegant, reusable, and flexible software. By the time you finish this book, you’ll be able to take advantage of the best design practices and experiences of those who have fought the beast of software design and triumphed. What’s so special about this book? We think your time is too valuable to spend struggling with new concepts. Using the latest research in cognitive science and learning theory to craft a multi-sensory learning experience, Head First Design Patterns uses a visually rich format designed for the way your brain works, not a text-heavy approach that puts you to sleep. COMPUTERS,Software Development & Engineering,General

Head First PMP Media Reviews "I have been doing project management for over 30 years and am considered a subject matter expert in the PMBOK(r) Guide -Third Edition primarily because I am the Project Manager who led the team that developed this edition. As a consultant I was hired to review and evaluate eight of the top selling PMP Exam Preparation books for their accuracy in following the PMBOK® Guide - Third Edition. I have developed and taught a PMP Exam Prep course for a leading R.E.P., and taught PMP Exam preparation classes for PMI Chapters. I can honestly say that Head First PMP is by far the best PMP Exam Preparation book of all I have reviewed in depth. It is the very best basic education and training book that I have read that presents the processes for managing a project, which makes it a great resource for a basic project management class for beginners as well as a tool for practitioners who want to pass the PMP exam. The graphical story format is unique, as project management books go, which makes it both fun and easy to read while driving home the basics that are necessary for preparing someone is just getting started and those who want to take the exam." --Dennis Bolles, PMP DLB Associates, LLC and co-author of The Power of Enterprise-Wide Project Management "This looks like too much fun to be a PMP study guide! Behind the quirky humor and nutty graphics lies an excellent explanation of the project management processes. Not only will this book make it easier to pass the exam, you'll learn a lot of good stuff to use on the job too." --Carol Steuer, PMP and PMBOK(r) Guide, 3rd Edition Leadership Team "This is the best thing to happen to PMP since, well, ever. You'll laugh,learn, pass the exam, and become a better project manager all at the sametime." -- Scott Berkun, author of The Art of Project Management and The Myths of Innovation "Original, fresh, and fun... this is truly the perfect study companion for anyone aiming for PMP certification." --Teresa Simmermacher, PMP and Project Manager at Avanade "I love this format! Head First PMP covers everything you need to know to pass your PMP exam. The sound-bite format combined with the whimsical images turns a dry subject into entertainment. The organization starts with the basics then drills into the details. The in-depth coverage of complex topics like Earned Value and Quality Control are presented in an easy to understand format with descriptions, pictures, and examples. This book will not only help you pass the PMP, it should be used as an daily reference for practicing project managers. I sure wish I had this when I was studying for the exam." --Mike Jenkins, PMP, MBA "I think that under the fonts and formalized goofiness, the book has a good heart (intending to cover basic principles in an honest way rather than just to pass the test). Head First PMP attempts to educate potential project managers instead of being a mere "how to pass the PMP exam" book filled with test taking tips. This is truly something which sets it apart from the other PMP certification exam books." --Jack Dahlgren, Project Management Consultant "Head First PMP is a great tool to help make sense of the Project Management Body of Knowledge for the everyday Project Manager." --Mark Poinelli, PMP About the Book A PMP certification is more than just passing a test. It means that you have the knowledge to solve most common project problems, and proves that you know your stuff. Once you're certified, your projects are more likely to succeed because you have the skills and knowledge to make them successful. Not only that, it can mean a better job, more money, and greater respect from your peers. But studying for a difficult four-hour exam on project management isn't easy, even for experienced project managers. You want to remember everything that you're learning about project management, but your brain is working against you! Your brain craves novelty, and most PMP certification prep books are anything but novel. When you keep putting down a boring book instead of studying, it's because your brain doesn't think the information in it is worth learning. Your brain has more important stuff to think about, like how to keep you alive and out of danger-and it doesn't think that failing the PMP exam qualifies as life-threatening! So how do you trick your brain into thinking that your life does depend on learning everything you need to know to pass the PMP Exam? Head First PMP is the answer! Using the latest research in neurobiology, cognitive science and learning theory, Head First PMP has a visually rich format designed for the way your brain works-a multi-sensory experience that helps the material stick, not a text-heavy approach that puts you to sleep. Head First PMP offers 100% coverage of The PMBOK® Guide principles and certification objectives in a way that's engaging, not tedious COMPUTERS,Software Development & Engineering,General

CJKV Information Processing First published a decade ago, CJKV Information Processing quickly became the unsurpassed source of information on processing text in Chinese, Japanese, Korean, and Vietnamese. It has now been thoroughly updated to provide web and application developers with the latest techniques and tools for disseminating information directly to audiences in East Asia. This second edition reflects the considerable impact that Unicode, XML, OpenType, and newer operating systems such as Windows XP, Vista, Mac OS X, and Linux have had on East Asian text processing in recent years. Written by its original author, Ken Lunde, a Senior Computer Scientist in CJKV Type Development at Adobe Systems, this book will help you: Learn about CJKV writing systems and scripts, and their transliteration methods Explore trends and developments in character sets and encodings, particularly Unicode Examine the world of typography, specifically how CJKV text is laid out on a page Learn information-processing techniques, such as code conversion algorithms and how to apply them using different programming languages Process CJKV text using different platforms, text editors, and word processors Become more informed about CJKV dictionaries, dictionary software, and machine translation software and services Manage CJKV content and presentation when publishing in print or for the Web Internationalizing and localizing applications is paramount in today's global market -- especially for audiences in East Asia, the fastest-growing segment of the computing world. CJKV Information Processing will help you understand how to develop web and other applications effectively in a field that many find difficult to master. COMPUTERS,Software Development & Engineering,General

Making Software Many claims are made about how certain tools, technologies, and practices improve software development. But which claims are verifiable, and which are merely wishful thinking? In this book, leading thinkers such as Steve McConnell, Barry Boehm, and Barbara Kitchenham offer essays that uncover the truth and unmask myths commonly held among the software development community. Their insights may surprise you. Are some programmers really ten times more productive than others? Does writing tests first help you develop better code faster? Can code metrics predict the number of bugs in a piece of software? Do design patterns actually make better software? What effect does personality have on pair programming? What matters more: how far apart people are geographically, or how far apart they are in the org chart? Contributors include: Jorge Aranda Tom Ball Victor R. Basili Andrew Begel Christian Bird Barry Boehm Marcelo Cataldo Steven Clarke Jason Cohen Robert DeLine Madeline Diep Hakan Erdogmus Michael Godfrey Mark Guzdial Jo E. Hannay Ahmed E. Hassan Israel Herraiz Kim Sebastian Herzig Cory Kapser Barbara Kitchenham Andrew Ko Lucas Layman Steve McConnell Tim Menzies Gail Murphy Nachi Nagappan Thomas J. Ostrand Dewayne Perry Marian Petre Lutz Prechelt Rahul Premraj Forrest Shull Beth Simon Diomidis Spinellis Neil Thomas Walter Tichy Burak Turhan Elaine J. Weyuker Michele A. Whitecraft Laurie Williams Wendy M. Williams Andreas Zeller Thomas Zimmermann COMPUTERS,Software Development & Engineering,General

Lean Architecture More and more Agile projects are seeking architectural roots as they struggle with complexity and scale - and they're seeking lightweight ways to do it Still seeking? In this book the authors help you to find your own path Taking cues from Lean development, they can help steer your project toward practices with longstanding track records Up-front architecture? Sure. You can deliver an architecture as code that compiles and that concretely guides development without bogging it down in a mass of documents and guesses about the implementation Documentation? Even a whiteboard diagram, or a CRC card, is documentation: the goal isn't to avoid documentation, but to document just the right things in just the right amount Process? This all works within the frameworks of Scrum, XP, and other Agile approaches COMPUTERS,Software Development & Engineering,General

API Design for C++ API Design for C++ provides a comprehensive discussion of Application Programming Interface (API) development, from initial design through implementation, testing, documentation, release, versioning, maintenance, and deprecation. It is the only book that teaches the strategies of C++ API development, including interface design, versioning, scripting, and plug-in extensibility. Drawing from the author's experience on large scale, collaborative software projects, the text offers practical techniques of API design that produce robust code for the long term. It presents patterns and practices that provide real value to individual developers as well as organizations. API Design for C++ explores often overlooked issues, both technical and non-technical, contributing to successful design decisions that product high quality, robust, and long-lived APIs. It focuses on various API styles and patterns that will allow you to produce elegant and durable libraries. A discussion on testing strategies concentrates on automated API testing techniques rather than attempting to include end-user application testing techniques such as GUI testing, system testing, or manual testing. Each concept is illustrated with extensive C++ code examples, and fully functional examples and working source code for experimentation are available online. This book will be helpful to new programmers who understand the fundamentals of C++ and who want to advance their design skills, as well as to senior engineers and software architects seeking to gain new expertise to complement their existing talents. Three specific groups of readers are targeted: practicing software engineers and architects, technical managers, and students and educators. The only book that teaches the strategies of C++ API development, including design, versioning, documentation, testing, scripting, and extensibility. Extensive code examples illustrate each concept, with fully functional examples and working source code for experimentation available online. Covers various API styles and patterns with a focus on practical and efficient designs for large-scale long-term projects. COMPUTERS,Software Development & Engineering,General

Semantic Web for the Working Ontologist Semantic Web for the Working Ontologist: Effective Modeling in RDFS and OWL, Second Edition, discusses the capabilities of Semantic Web modeling languages, such as RDFS (Resource Description Framework Schema) and OWL (Web Ontology Language). Organized into 16 chapters, the book provides examples to illustrate the use of Semantic Web technologies in solving common modeling problems. It uses the life and works of William Shakespeare to demonstrate some of the most basic capabilities of the Semantic Web. The book first provides an overview of the Semantic Web and aspects of the Web. It then discusses semantic modeling and how it can support the development from chaotic information gathering to one characterized by information sharing, cooperation, and collaboration. It also explains the use of RDF to implement the Semantic Web by allowing information to be distributed over the Web, along with the use of SPARQL to access RDF data. Moreover, the reader is introduced to components that make up a Semantic Web deployment and how they fit together, the concept of inferencing in the Semantic Web, and how RDFS differs from other schema languages. Finally, the book considers the use of SKOS (Simple Knowledge Organization System) to manage vocabularies by taking advantage of the inferencing structure of RDFS-Plus. This book is intended for the working ontologist who is trying to create a domain model on the Semantic Web. Updated with the latest developments and advances in Semantic Web technologies for organizing, querying, and processing information, including SPARQL, RDF and RDFS, OWL 2.0, and SKOS Detailed information on the ontologies used in today's key web applications, including ecommerce, social networking, data mining, using government data, and more Even more illustrative examples and case studies that demonstrate what semantic technologies are and how they work together to solve real-world problems COMPUTERS,Software Development & Engineering,General

Lessons Learned in Software Testing Decades of software testing experience condensed into the most important lessons learned. The world's leading software testing experts lend you their wisdom and years of experience to help you avoid the most common mistakes in testing software. Each lesson is an assertion related to software testing, followed by an explanation or example that shows you the how, when, and why of the testing lesson. More than just tips, tricks, and pitfalls to avoid, Lessons Learned in Software Testing speeds you through the critical testing phase of the software development project without the extensive trial and error it normally takes to do so. The ultimate resource for software testers and developers at every level of expertise, this guidebook features: * Over 200 lessons gleaned from over 30 years of combined testing experience * Tips, tricks, and common pitfalls to avoid by simply reading the book rather than finding out the hard way * Lessons for all key topic areas, including test design, test management, testing strategies, and bug reporting * Explanations and examples of each testing trouble spot help illustrate each lesson's assertion COMPUTERS,Software Development & Engineering,General

Python For Dummies Python is one of the most powerful, easy-to-read programming languages around, but it does have its limitations. This general purpose, high-level language that can be extended and embedded is a smart option for many programming problems, but a poor solution to others. Python For Dummies is the quick-and-easy guide to getting the most out of this robust program. This hands-on book will show you everything you need to know about building programs, debugging code, and simplifying development, as well as defining what actions it can perform. You’ll wrap yourself around all of its advanced features and become an expert Python user in no time. This guide gives you the tools you need to: Master basic elements and syntax Document, design, and debug programs Work with strings like a pro Direct a program with control structures Integrate integers, complex numbers, and modules Build lists, stacks, and queues Create an organized dictionary Handle functions, data, and namespace Construct applications with modules and packages Call, create, extend, and override classes Access the Internet to enhance your library Understand the new features of Python 2.5 Packed with critical idioms and great resources to maximize your productivity, Python For Dummies is the ultimate one-stop information guide. In a matter of minutes you’ll be familiar with Python’s building blocks, strings, dictionaries, and sets; and be on your way to writing the program that you’ve dreamed about! COMPUTERS,Software Development & Engineering,General

Documenting Software Architectures Software architecture—the conceptual glue that holds every phase of a project together for its many stakeholders—is widely recognized as a critical element in modern software development. Practitioners have increasingly discovered that close attention to a software system’s architecture pays valuable dividends. Without an architecture that is appropriate for the problem being solved, a project will stumble along or, most likely, fail. Even with a superb architecture, if that architecture is not well understood or well communicated the project is unlikely to succeed. Documenting Software Architectures, Second Edition, provides the most complete and current guidance, independent of language or notation, on how to capture an architecture in a commonly understandable form. Drawing on their extensive experience, the authors first help you decide what information to document, and then, with guidelines and examples (in various notations, including UML), show you how to express an architecture so that others can successfully build, use, and maintain a system from it. The book features rules for sound documentation, the goals and strategies of documentation, architectural views and styles, documentation for software interfaces and software behavior, and templates for capturing and organizing information to generate a coherent package. New and improved in this second edition: Coverage of architectural styles such as service-oriented architectures, multi-tier architectures, and data models Guidance for documentation in an Agile development environment Deeper treatment of documentation of rationale, reflecting best industrial practices Improved templates, reflecting years of use and feedback, and more documentation layout options A new, comprehensive example (available online), featuring documentation of a Web-based service-oriented system Reference guides for three important architecture documentation languages: UML, AADL, and SySML COMPUTERS,Software Development & Engineering,General

Clean Coder, The Programmers who endure and succeed amidst swirling uncertainty and nonstop pressure share a common attribute: They care deeply about the practice of creating software. They treat it as a craft. They are professionals. In The Clean Coder: A Code of Conduct for Professional Programmers, legendary software expert Robert C. Martin introduces the disciplines, techniques, tools, and practices of true software craftsmanship. This book is packed with practical advice–about everything from estimating and coding to refactoring and testing. It covers much more than technique: It is about attitude. Martin shows how to approach software development with honor, self-respect, and pride; work well and work clean; communicate and estimate faithfully; face difficult decisions with clarity and honesty; and understand that deep knowledge comes with a responsibility to act. Readers will learn What it means to behave as a true software craftsman How to deal with conflict, tight schedules, and unreasonable managers How to get into the flow of coding, and get past writer’s block How to handle unrelenting pressure and avoid burnout How to combine enduring attitudes with new development paradigms How to manage your time, and avoid blind alleys, marshes, bogs, and swamps How to foster environments where programmers and teams can thrive When to say “Noâ€â€“and how to say it When to say “Yesâ€â€“and what yes really means Great software is something to marvel at: powerful, elegant, functional, a pleasure to work with as both a developer and as a user. Great software isn’t written by machines. It is written by professionals with an unshakable commitment to craftsmanship. The Clean Coder will help you become one of them–and earn the pride and fulfillment that they alone possess. COMPUTERS,Software Development & Engineering,General

Emergent Design This is the eBook version of the printed book. If the print book includes a CD-ROM, this content is not included within the eBook version. For software to consistently deliver promised results, software development must mature into a true profession. Emergent Design points the way. As software continues to evolve and mature, software development processes become more complicated, relying on a variety of methodologies and approaches. This book illuminates the path to building the next generation of software. Author Scott L. Bain integrates the best of today’s most important development disciplines into a unified, streamlined, realistic, and fully actionable approach to developing software. Drawing on patterns, refactoring, and test-driven development, Bain offers a blueprint for moving efficiently through the entire software lifecycle, smoothly managing change, and consistently delivering systems that are robust, reliable, and cost-effective. Reflecting a deep understanding of the natural flow of system development, Emergent Design helps developers work with the flow, instead of against it. Bain introduces the principles and practices of emergent design one step at a time, showing how to promote the natural evolution of software systems over time, making systems work better and provide greater value. To illuminate his approach, Bain presents code examples wherever necessary and concludes with a complete project case study. This book provides developers, project leads, and testers powerful new ways to collaborate, achieve immediate goals, and build systems that improve in quality with each iteration. Coverage includes How to design software in a more natural, evolutionary, and professional way How to use the “open-closed†principle to mitigate risks and eliminate waste How and when to test your design throughout the development process How to translate design principles into practices that actually lead to better code How to determine how much design is enough How refactoring can help you reduce over-design and manage change more effectively The book’s companion Web site, www.netobjectives.com/resources, provides updates, links to related materials, and support for discussions of the book’s content. COMPUTERS,Software Development & Engineering,General

User Stories Applied Thoroughly reviewed and eagerly anticipated by the agile community, User Stories Applied offers a requirements process that saves time, eliminates rework, and leads directly to better software. The best way to build software that meets users' needs is to begin with "user stories": simple, clear, brief descriptions of functionality that will be valuable to real users. In User Stories Applied, Mike Cohn provides you with a front-to-back blueprint for writing these user stories and weaving them into your development lifecycle. You'll learn what makes a great user story, and what makes a bad one. You'll discover practical ways to gather user stories, even when you can't speak with your users. Then, once you've compiled your user stories, Cohn shows how to organize them, prioritize them, and use them for planning, management, and testing. User role modeling: understanding what users have in common, and where they differ Gathering stories: user interviewing, questionnaires, observation, and workshops Working with managers, trainers, salespeople and other "proxies" Writing user stories for acceptance testing Using stories to prioritize, set schedules, and estimate release costs Includes end-of-chapter practice questions and exercises User Stories Applied will be invaluable to every software developer, tester, analyst, and manager working with any agile method: XP, Scrum... or even your own home-grown approach. COMPUTERS,Software Development & Engineering,General

Agile Principles, Patterns, and Practices in C# With the award-winning book Agile Software Development: Principles, Patterns, and Practices, Robert C. Martin helped bring Agile principles to tens of thousands of Java and C++ programmers. Now .NET programmers have a definitive guide to agile methods with this completely updated volume from Robert C. Martin and Micah Martin, Agile Principles, Patterns, and Practices in C#. This book presents a series of case studies illustrating the fundamentals of Agile development and Agile design, and moves quickly from UML models to real C# code. The introductory chapters lay out the basics of the agile movement, while the later chapters show proven techniques in action. The book includes many source code examples that are also available for download from the authors’ Web site. Readers will come away from this book understanding Agile principles, and the fourteen practices of Extreme Programming Spiking, splitting, velocity, and planning iterations and releases Test-driven development, test-first design, and acceptance testing Refactoring with unit testing Pair programming Agile design and design smells The five types of UML diagrams and how to use them effectively Object-oriented package design and design patterns How to put all of it together for a real-world project Whether you are a C# programmer or a Visual Basic or Java programmer learning C#, a software development manager, or a business analyst, Agile Principles, Patterns, and Practices in C# is the first book you should read to understand agile software and how it applies to programming in the .NET Framework. COMPUTERS,Software Development & Engineering,General

Clean Code This is the eBook version of the printed book. If the print book includes a CD-ROM, this content is not included within the eBook version.Even bad code can function. But if code isn’t clean, it can bring a development organization to its knees. Every year, countless hours and significant resources are lost because of poorly written code. But it doesn’t have to be that way. Noted software expert Robert C. Martin, presents a revolutionary paradigm with Clean Code: A Handbook of Agile Software Craftsmanship . Martin, who has helped bring agile principles from a practitioner’s point of view to tens of thousands of programmers, has teamed up with his colleagues from Object Mentor to distill their best agile practice of cleaning code “on the fly†into a book that will instill within you the values of software craftsman, and make you a better programmer—but only if you work at it. What kind of work will you be doing? You’ll be reading code—lots of code. And you will be challenged to think about what’s right about that code, and what’s wrong with it. More importantly you will be challenged to reassess your professional values and your commitment to your craft. Clean Code is divided into three parts. The first describes the principles, patterns, and practices of writing clean code. The second part consists of several case studies of increasing complexity. Each case study is an exercise in cleaning up code—of transforming a code base that has some problems into one that is sound and efficient. The third part is the payoff: a single chapter containing a list of heuristics and “smells†gathered while creating the case studies. The result is a knowledge base that describes the way we think when we write, read, and clean code. Readers will come away from this book understanding How to tell the difference between good and bad code How to write good code and how to transform bad code into good code How to create good names, good functions, good objects, and good classes How to format code for maximum readability How to implement complete error handling without obscuring code logic How to unit test and practice test-driven development What “smells†and heuristics can help you identify bad code This book is a must for any developer, software engineer, project manager, team lead, or systems analyst with an interest in producing better code. COMPUTERS,Software Development & Engineering,General

Agile Software Development “Agile Software Development is a highly stimulating and rich book. The author has a deep background and gives us a tour de force of the emerging agile methods.†—Tom Gilb The agile model of software development has taken the world by storm. Now, in Agile Software Development, Second Edition, one of agile’s leading pioneers updates his Jolt Productivity award-winning book to reflect all that’s been learned about agile development since its original introduction. Alistair Cockburn begins by updating his powerful model of software development as a “cooperative game of invention and communication.†Among the new ideas he introduces: harnessing competition without damaging collaboration; learning lessons from lean manufacturing; and balancing strategies for communication. Cockburn also explains how the cooperative game is played in business and on engineering projects, not just software development Next, he systematically illuminates the agile model, shows how it has evolved, and answers the questions developers and project managers ask most often, including · Where does agile development fit in our organization? · How do we blend agile ideas with other ideas? · How do we extend agile ideas more broadly? Cockburn takes on crucial misconceptions that cause agile projects to fail. For example, you’ll learn why encoding project management strategies into fixed processes can lead to ineffective strategy decisions and costly mistakes. You’ll also find a thoughtful discussion of the controversial relationship between agile methods and user experience design. Cockburn turns to the practical challenges of constructing agile methodologies for your own teams. You’ll learn how to tune and continuously reinvent your methodologies, and how to manage incomplete communication. This edition contains important new contributions on these and other topics: · Agile and CMMI · Introducing agile from the top down · Revisiting “custom contracts†· Creating change with “stickers†In addition, Cockburn updates his discussion of the Crystal methodologies, which utilize his “cooperative game†as their central metaphor. If you’re new to agile development, this book will help you succeed the first time out. If you’ve used agile methods before, Cockburn’s techniques will make you even more effective. COMPUTERS,Software Development & Engineering,General

Refactoring Databases Refactoring has proven its value in a wide range of development projects–helping software professionals improve system designs, maintainability, extensibility, and performance. Now, for the first time, leading agile methodologist Scott Ambler and renowned consultant Pramodkumar Sadalage introduce powerful refactoring techniques specifically designed for database systems. Ambler and Sadalage demonstrate how small changes to table structures, data, stored procedures, and triggers can significantly enhance virtually any database design–without changing semantics. You’ll learn how to evolve database schemas in step with source code–and become far more effective in projects relying on iterative, agile methodologies. This comprehensive guide and reference helps you overcome the practical obstacles to refactoring real-world databases by covering every fundamental concept underlying database refactoring. Using start-to-finish examples, the authors walk you through refactoring simple standalone database applications as well as sophisticated multi-application scenarios. You’ll master every task involved in refactoring database schemas, and discover best practices for deploying refactorings in even the most complex production environments. The second half of this book systematically covers five major categories of database refactorings. You’ll learn how to use refactoring to enhance database structure, data quality, and referential integrity; and how to refactor both architectures and methods. This book provides an extensive set of examples built with Oracle and Java and easily adaptable for other languages, such as C#, C++, or VB.NET, and other databases, such as DB2, SQL Server, MySQL, and Sybase. Using this book’s techniques and examples, you can reduce waste, rework, risk, and cost–and build database systems capable of evolving smoothly, far into the future. COMPUTERS,Software Development & Engineering,General

Agile Project Management Best practices for managing projects in agile environments—now updated with new techniques for larger projects Today, the pace of project management moves faster. Project management needs to become more flexible and far more responsive to customers. Using Agile Project Management (APM), project managers can achieve all these goals without compromising value, quality, or business discipline. In Agile Project Management, Second Edition, renowned agile pioneer Jim Highsmith thoroughly updates his classic guide to APM, extending and refining it to support even the largest projects and organizations. Writing for project leaders, managers, and executives at all levels, Highsmith integrates the best project management, product management, and software development practices into an overall framework designed to support unprecedented speed and mobility. The many topics added in this new edition include incorporating agile values, scaling agile projects, release planning, portfolio governance, and enhancing organizational agility. Project and business leaders will especially appreciate Highsmith’s new coverage of promoting agility through performance measurements based on value, quality, and constraints. This edition’s coverage includes: Understanding the agile revolution’s impact on product development Recognizing when agile methods will work in project management, and when they won’t Setting realistic business objectives for Agile Project Management Promoting agile values and principles across the organization Utilizing a proven Agile Enterprise Framework that encompasses governance, project and iteration management, and technical practices Optimizing all five stages of the agile project: Envision, Speculate, Explore, Adapt, and Close Organizational and product-related processes for scaling agile to the largest projects and teams Agile project governance solutions for executives and management The “Agile Triangleâ€: measuring performance in ways that encourage agility instead of discouraging it The changing role of the agile project leader COMPUTERS,Software Development & Engineering,General

Coaching Agile Teams The Provocative and Practical Guide to Coaching Agile Teams As an agile coach, you can help project teams become outstanding at agile, creating products that make them proud and helping organizations reap the powerful benefits of teams that deliver both innovation and excellence. More and more frequently, ScrumMasters and project managers are being asked to coach agile teams. But it’s a challenging role. It requires new skills—as well as a subtle understanding of when to step in and when to step back. Migrating from “command and control†to agile coaching requires a whole new mind-set. In Coaching Agile Teams, Lyssa Adkins gives agile coaches the insights they need to adopt this new mind-set and to guide teams to extraordinary performance in a re-energized work environment. You’ll gain a deep view into the role of the agile coach, discover what works and what doesn’t, and learn how to adapt powerful skills from many allied disciplines, including the fields of professional coaching and mentoring. Coverage includes Understanding what it takes to be a great agile coach Mastering all of the agile coach’s roles: teacher, mentor, problem solver, conflict navigator, and performance coach Creating an environment where self-organized, high-performance teams can emerge Coaching teams past cooperation and into full collaboration Evolving your leadership style as your team grows and changes Staying actively engaged without dominating your team and stunting its growth Recognizing failure, recovery, and success modes in your coaching Getting the most out of your own personal agile coaching journey Whether you’re an agile coach, leader, trainer, mentor, facilitator, ScrumMaster, project manager, product owner, or team member, this book will help you become skilled at helping others become truly great. What could possibly be more rewarding? COMPUTERS,Software Development & Engineering,General

Succeeding with Agile Proven, 100% Practical Guidance for Making Scrum and Agile Work in Any Organization This is the definitive, realistic, actionable guide to starting fast with Scrum and agile–and then succeeding over the long haul. Leading agile consultant and practitioner Mike Cohn presents detailed recommendations, powerful tips, and real-world case studies drawn from his unparalleled experience helping hundreds of software organizations make Scrum and agile work. Succeeding with Agile is for pragmatic software professionals who want real answers to the most difficult challenges they face in implementing Scrum. Cohn covers every facet of the transition: getting started, helping individuals transition to new roles, structuring teams, scaling up, working with a distributed team, and finally, implementing effective metrics and continuous improvement. Throughout, Cohn presents “Things to Try Now†sections based on his most successful advice. Complementary “Objection†sections reproduce typical conversations with those resisting change and offer practical guidance for addressing their concerns. Coverage includes Practical ways to get started immediately–and “get good†fast Overcoming individual resistance to the changes Scrum requires Staffing Scrum projects and building effective teams Establishing “improvement communities†of people who are passionate about driving change Choosing which agile technical practices to use or experiment with Leading self-organizing teams Making the most of Scrum sprints, planning, and quality techniques Scaling Scrum to distributed, multiteam projects Using Scrum on projects with complex sequential processes or challenging compliance and governance requirements Understanding Scrum’s impact on HR, facilities, and project management Whether you've completed a few sprints or multiple agile projects and whatever your role–manager, developer, coach, ScrumMaster, product owner, analyst, team lead, or project lead–this book will help you succeed with your very next project. Then, it will help you go much further: It will help you transform your entire development organization. COMPUTERS,Software Development & Engineering,General

Continuous Delivery Winner of the 2011 Jolt Excellence Award! Getting software released to users is often a painful, risky, and time-consuming process. This groundbreaking new book sets out the principles and technical practices that enable rapid, incremental delivery of high quality, valuable new functionality to users. Through automation of the build, deployment, and testing process, and improved collaboration between developers, testers, and operations, delivery teams can get changes released in a matter of hours— sometimes even minutes–no matter what the size of a project or the complexity of its code base. Jez Humble and David Farley begin by presenting the foundations of a rapid, reliable, low-risk delivery process. Next, they introduce the “deployment pipeline,†an automated process for managing all changes, from check-in to release. Finally, they discuss the “ecosystem†needed to support continuous delivery, from infrastructure, data and configuration management to governance. The authors introduce state-of-the-art techniques, including automated infrastructure management and data migration, and the use of virtualization. For each, they review key issues, identify best practices, and demonstrate how to mitigate risks. Coverage includes • Automating all facets of building, integrating, testing, and deploying software • Implementing deployment pipelines at team and organizational levels • Improving collaboration between developers, testers, and operations • Developing features incrementally on large and distributed teams • Implementing an effective configuration management strategy • Automating acceptance testing, from analysis to implementation • Testing capacity and other non-functional requirements • Implementing continuous deployment and zero-downtime releases • Managing infrastructure, data, components and dependencies • Navigating risk management, compliance, and auditing Whether you’re a developer, systems administrator, tester, or manager, this book will help your organization move from idea to release faster than ever—so you can deliver value to your business rapidly and reliably. COMPUTERS,Software Development & Engineering,General

Agile Product Management with Scrum The First Guide to Scrum-Based Agile Product Management In Agile Product Management with Scrum, leading Scrum consultant Roman Pichler uses real-world examples to demonstrate how product owners can create successful products with Scrum. He describes a broad range of agile product management practices, including making agile product discovery work, taking advantage of emergent requirements, creating the minimal marketable product, leveraging early customer feedback, and working closely with the development team. Benefitting from Pichler’s extensive experience, you’ll learn how Scrum product ownership differs from traditional product management and how to avoid and overcome the common challenges that Scrum product owners face. Coverage includes Understanding the product owner’s role: what product owners do, how they do it, and the surprising implications Envisioning the product: creating a compelling product vision to galvanize and guide the team and stakeholders Grooming the product backlog: managing the product backlog effectively even for the most complex products Planning the release: bringing clarity to scheduling, budgeting, and functionality decisions Collaborating in sprint meetings: understanding the product owner’s role in sprint meetings, including the dos and don’ts Transitioning into product ownership: succeeding as a product owner and establishing the role in the enterprise This book is an indispensable resource for anyone who works as a product owner, or expects to do so, as well as executives and coaches interested in establishing agile product management. COMPUTERS,Software Development & Engineering,General

Agile Software Requirements “We need better approaches to understanding and managing software requirements, and Dean provides them in this book. He draws ideas from three very useful intellectual pools: classical management practices, Agile methods, and lean product development. By combining the strengths of these three approaches, he has produced something that works better than any one in isolation.†–From the Foreword by Don Reinertsen, President of Reinertsen & Associates; author of Managing the Design Factory; and leading expert on rapid product development Effective requirements discovery and analysis is a critical best practice for serious application development. Until now, however, requirements and Agile methods have rarely coexisted peacefully. For many enterprises considering Agile approaches, the absence of effective and scalable Agile requirements processes has been a showstopper for Agile adoption. In Agile Software Requirements, Dean Leffingwell shows exactly how to create effective requirements in Agile environments. Part I presents the “big picture†of Agile requirements in the enterprise, and describes an overall process model for Agile requirements at the project team, program, and portfolio levels Part II describes a simple and lightweight, yet comprehensive model that Agile project teams can use to manage requirements Part III shows how to develop Agile requirements for complex systems that require the cooperation of multiple teams Part IV guides enterprises in developing Agile requirements for ever-larger “systems of systems,†application suites, and product portfolios This book will help you leverage the benefits of Agile without sacrificing the value of effective requirements discovery and analysis. You’ll find proven solutions you can apply right now–whether you’re a software developer or tester, executive, project/program manager, architect, or team leader. COMPUTERS,Software Development & Engineering,General

Growing Object-Oriented Software, Guided by Tests Test-Driven Development (TDD) is now an established technique for delivering better software faster. TDD is based on a simple idea: Write tests for your code before you write the code itself. However, this "simple" idea takes skill and judgment to do well. Now there's a practical guide to TDD that takes you beyond the basic concepts. Drawing on a decade of experience building real-world systems, two TDD pioneers show how to let tests guide your development and “grow†software that is coherent, reliable, and maintainable. Steve Freeman and Nat Pryce describe the processes they use, the design principles they strive to achieve, and some of the tools that help them get the job done. Through an extended worked example, you’ll learn how TDD works at multiple levels, using tests to drive the features and the object-oriented structure of the code, and using Mock Objects to discover and then describe relationships between objects. Along the way, the book systematically addresses challenges that development teams encounter with TDD—from integrating TDD into your processes to testing your most difficult features. Coverage includes Implementing TDD effectively: getting started, and maintaining your momentum throughout the project Creating cleaner, more expressive, more sustainable code Using tests to stay relentlessly focused on sustaining quality Understanding how TDD, Mock Objects, and Object-Oriented Design come together in the context of a real software development project Using Mock Objects to guide object-oriented designs Succeeding where TDD is difficult: managing complex test data, and testing persistence and concurrency COMPUTERS,Software Development & Engineering,General

Measuring the Software Process "While it is usually helpful to launch improvement programs, many such programs soon get bogged down in detail. They either address the wrong problems, or they keep beating on the same solutions, wondering why things don't improve. This is when you need an objective way to look at the problems. This is the time to get some data." Watts S. Humphrey, from the Foreword This book, drawing on work done at the Software Engineering Institute and other organizations, shows how to use measurements to manage and improve software processes. The authors explain specifically how quality characteristics of software products and processes can be quantified, plotted, and analyzed so the performance of software development activities can be predicted, controlled, and guided to achieve both business and technical goals. The measurement methods presented, based on the principles of statistical quality control, are illuminated by application examples taken from industry. Although many of the methods discussed are applicable to individual projects, the book's primary focus is on the steps software development organizations can take toward broad-reaching, long-term success. The book particularly addresses the needs of software managers and practitioners who have already set up some kind of basic measurement process and are ready to take the next step by collecting and analyzing software data as a basis for making process decisions and predicting process performance. Highlights of the book include: Insight into developing a clear framework for measuring process behavior Discussions of process performance, stability, compliance, capability, and improvement Explanations of what you want to measure (and why) and instructions on how to collect your data Step-by-step guidance on how to get started using statistical process control If you have responsibilities for product quality or process performance and you are ready to use measurements to manage, control, and predict your software processes, this book will be an invaluable resource. COMPUTERS,Software Development & Engineering,General

Agile Experience Design Agile development methodologies may have started life in IT, but their widespread and continuing adoption means there are many practitioners outside of IT--including designers--who need to change their thinking and adapt their practices. This is the missing book about agile that shows how designers, product managers, and development teams can integrate experience design into lean and agile product development. It equips you with tools, techniques and a framework for designing great experiences using agile methods so you can deliver timely products that are technically feasible, profitable for the business, and desirable from an end-customer perspective. This book will help you successfully integrate your design process on an agile project and feel like part of the agile team. do good design faster by doing just enough, just in time. use design methods from disciplines such as design thinking, customer-centered design, product design, and service design. create successful digital products by considering the needs of the end-customer, the business, and technology. understand the next wave of thinking about continuous design and continuous delivery. COMPUTERS,Software Development & Engineering,General

Touch of Class From object technology pioneer and ETH Zurich professor Bertrand Meyer, winner of the Jolt award and the ACM Software System Award, a revolutionary textbook that makes learning programming fun and rewarding. Meyer builds his presentation on a rich object-oriented software system supporting graphics and multimedia, which students can use to produce impressive applications from day one, then understand inside out as they learn new programming techniques. Unique to Touch of Class is a combination of a practical, hands-on approach to programming with the introduction of sound theoretical support focused on helping students learn the construction of high quality software. The use of full color brings exciting programming concepts to life. Among the useful features of the book is the use of Design by Contract, critical to software quality and providing a gentle introduction to formal methods. Will give students a major advantage by teaching professional-level techniques in a literate, relaxed and humorous way. COMPUTERS,Software Development & Engineering,General

Git Pocket Guide This pocket guide is the perfect on-the-job companion to Git, the distributed version control system. It provides a compact, readable introduction to Git for new users, as well as a reference to common commands and procedures for those of you with Git experience. Written for Git version 1.8.2, this handy task-oriented guide is organized around the basic version control functions you need, such as making commits, fixing mistakes, merging, and searching history. Examine the state of your project at earlier points in time Learn the basics of creating and making changes to a repository Create branches so many people can work on a project simultaneously Merge branches and reconcile the changes among them Clone an existing repository and share changes with push/pull commands Examine and change your repository’s commit history Access remote repositories, using different network protocols Get recipes for accomplishing a variety of common tasks COMPUTERS,Software Development & Engineering,General

Z User Workshop The mathematical concepts and notational conventions we know of as Z were first proposed around 1981. Its origins were in line with the objectives of the PRG - to establish a mathematical basis for program ming concepts and to verify the work by case studies with industry. Hence among early Z users some were from academic circles, with interests in the mathematical basis of programming; others came from industry and were involved with pilot projects and case studies linked with the Programming Research Group. Four years ago we had the first Z User Meeting, a fairly modest affair with representatives more or less equally divided between academia and industry. At the first meeting there were, as in this meeting, a variety of technical papers, reports of work in progress and discussions. A number of people from industry came along, either because they had begun to use Z or were curious about the new direction. In the discussion sessions at the end of the meeting, there were calls from attendees for the establishment of a more stable base for the notation, including work on its documentation and standards. Many of these requests have now been satisfied and the notation is now being proposed for standards development. COMPUTERS,Software Development & Engineering,General

Visual Basic .NET and the .NET Platform In VB.NET and the .NET Platform (BETA 2), Andrew Troelsen shows readers how to use VB.NET for developing virtually every possible kind of .NET application. From Windows-based to Web-based applications, it's all here. There are detailed discussions of every aspect of .NET development and useful examples with no toy code. Relentlessly practical and complete, VB.NET and the .NET Platform starts with a brief overview of the VB.NET language and then quickly moves to key technical and architectural issues for .NET developers. Not only is there extensive coverage of the .NET framework, but Troelsen also shows readers about such necessary but subtle areas as the proper use of threads. Readers will also learn how to use VB.NET for GUI applications with a complete discussion of Windows Forms and GDI+. There are equally useful discussions of how to use VB.NET and .NET Framework for Web development, Web Services, and data access using ADO.NET. Written in the same five-star style as his previous book, this is the comprehensive book on VB.NET and .NET Framework that developers have been waiting for! COMPUTERS,Software Development & Engineering,General
The Engineer’s Error Coding Handbook Error coding is a fascinating subject as much, if not more so, as it is an indispensable part of modem engineering systems. Unfortunately, in a bid to remain general and to create a solid foundation upon which to build, many books on this subject are out of the reach of those with more engineering-based, or non-mathematical backgrounds. This is a pity because in many cases the maths is tractable with few and simple rules. If we are content to believe that it works, and let others worry about the deeper mysteries of how or why, then with a little practice the design and implementation of practical error coding systems becomes straightforward. In this text I have attempted to reveal the useful kernel of the subject, removing the shell of terms and proofs that usually surrounds it. Being somewhat empirical in nature ( an empiricist), and occasionally heard to quote the adage, 'if it works twice it's a law', my explanations take this form. For many, including myself, abstract ideas are often better grasped by practical illustration than from yards of theory. COMPUTERS,Software Development & Engineering,General

Life Cycle Management For Dependability Dependability has always been an vital attribute of operational systems, regardless of whether they are highly-specialised (like electricity generating plants) or more general-purpose (like domestic appliances). This volume provides a highly-readable overview of the topic, concentrating on dependability as a life-cycle management issue rather than as a technical subject. Specifically avoiding technical language and complex mathematics, it is designed to be accessible to readers at all levels. It will be of particular interest to project managers and software engineers in industries where dependability is of particular importance, such as aerospace, process control, and mining. It will also provide useful reading material for students taking courses with modules in dependability. Felix Redmill and Chris Dale have both worked in industry for over 15 years, and now run successful consultancy businesses. COMPUTERS,Software Development & Engineering,General

Safer Systems The contributions to this book are the invited papers presented at the fifth annual Safety-critical Systems Symposium. They cover a broad spectrum of issues affecting safety, from a philosophical appraisal to technology transfer, from requirements analysis to assessment, from formal methods to artificial intelligence and psychological aspects. They touch on a number of industry sectors, but are restricted to none, for the essence of the event is the transfer of lessons and technologies between sectors. All address practical issues and of fer useful information and advice. Contributions from industrial authors provide evidence of both safety con sciousness and safety professionalism in industry. Smith's on safety analysis in air traffic control and Rivett's on assessment in the automotive industry are informative on current practice; Frith's thoughtful paper on artificial intelli gence in safety-critical systems reflects an understanding of questions which need to be resolved; Tomlinson's, Alvery's and Canning's papers report on collaborative projects, the first on results which emphasise the importance of human factors in system development, the second on the development and trial of a comprehensive tool set, and the third on experience in achieving tech nology transfer - something which is crucial to increasing safety. COMPUTERS,Software Development & Engineering,General

Software Engineering with Reusable Components Software is rarely built completely from scratch. To a great extent, existing software documents (source code, design documents, etc.) are copied and adapted to fit new requirements. Yet we are far from the goal of making reuse the standard approach to software development. Software reuse is the process of creating software systems from existing software rather than building them from scratch. Software reuse is still an emerging discipline. It appears in many different forms from ad-hoc reuse to systematic reuse, and from white-box reuse to black-box reuse. Many different products for reuse range from ideas and algorithms to any documents that are created during the software life cycle. Source code is most commonly reused; thus many people misconceive software reuse as the reuse of source code alone. Recently source code and design reuse have become popular with (object-oriented) class libraries, application frameworks, and design patterns. Software components provide a vehicle for planned and systematic reuse. The software community does not yet agree on what a software component is exactly. Nowadays, the term component is used as a synonym for object most of the time, but it also stands for module or function. Recently the term component-based or component-oriented software development has be come popular. In this context components are defined as objects plus some thing. What something is exactly, or has to be for effective software develop ment, remains yet to be seen. However, systems and models are emerging to support that notion. COMPUTERS,Software Development & Engineering,General

Concepts of Object-Oriented Programming with Visual Basic This book is about object-oriented programming and how it is implemented in Microsoft Visual Basic. Accordingly, the book has two separate, but inter twined, goals. The first is to describe the general concepts of object orientation and the second is to describe how to do object-oriented programming in Visual Basic. I intend this to be a short, no-nonsense book that can be read through once and then easily referred to at later times. (Long stories about a mythical company and its programming problems are seldom interesting the first time through, let alone the second, third or fourth times!) To read this book, you need only a minimal acquaintance with Visual Basic. In particular, I assume you can construct a simple Visual Basic program and have some rudimentary knowledge of fundamental programming tech niques. This book does not teach Visual Basic - it teaches you how to pro gram Visual Basic in an object-oriented way. The issue here is not how much Visual Basic you already know - it is that you want to learn about object oriented programming techniques. With regard to the first goal of the book, it is my feeling that a discussion of the underlying concepts of object orientation Oust what is an object, a class, encapsulation, abstraction, and so on) is essential in order to take full advan tage of any object-oriented language. Simply put, it will help you understand what you are doing if you know why you are doing it. COMPUTERS,Software Development & Engineering,General

Safety and Reliability of Software Based Systems Safety and Reliability of Software Based Systems contains papers, presented at the twelfth annual workshop organised by the Centre for Software Reliability. Contributions come from different industries in many countries, and provide discussion and cross-fertilisation of ideas relevant to systems whose safety and/or reliability are of paramount concern. This book discusses safety cases and their varying roles in different industries; using measurement to improve reliability and safety of software-based systems; latest developments in managing, developing and assessing software intensive systems where reliability and/or safety are important considerations; and practical experiences of others in industry. COMPUTERS,Software Development & Engineering,General

Safe Comp 97 York, UK, September 7 - 10, 1997 COMPUTERS,Software Development & Engineering,General

Developments in Global Optimization In recent years global optimization has found applications in many interesting areas of science and technology including molecular biology, chemical equilibrium problems, medical imaging and networks. The collection of papers in this book indicates the diverse applicability of global optimization. Furthermore, various algorithmic, theoretical developments and computational studies are presented. Audience: All researchers and students working in mathematical programming. COMPUTERS,Software Development & Engineering,General

Modern Software Tools for Scientific Computing Looking back at the years that have passed since the realization of the very first electronic, multi-purpose computers, one observes a tremendous growth in hardware and software performance. Today, researchers and engi neers have access to computing power and software that can solve numerical problems which are not fully understood in terms of existing mathemati cal theory. Thus, computational sciences must in many respects be viewed as experimental disciplines. As a consequence, there is a demand for high quality, flexible software that allows, and even encourages, experimentation with alternative numerical strategies and mathematical models. Extensibil ity is then a key issue; the software must provide an efficient environment for incorporation of new methods and models that will be required in fu ture problem scenarios. The development of such kind of flexible software is a challenging and expensive task. One way to achieve these goals is to in vest much work in the design and implementation of generic software tools which can be used in a wide range of application fields. In order to provide a forum where researchers could present and discuss their contributions to the described development, an International Work shop on Modern Software Tools for Scientific Computing was arranged in Oslo, Norway, September 16-18, 1996. This workshop, informally referred to as Sci Tools '96, was a collaboration between SINTEF Applied Mathe matics and the Departments of Informatics and Mathematics at the Uni versity of Oslo. COMPUTERS,Software Development & Engineering,General

ML with Concurrency Both functional and concurrent programming are relatively new paradigms with great promise. In this book, a survey is provided of extensions to Standard ML, one of the most widely used functional languages, with new primitives for concurrent programming. Computer scientists and graduate students will find this a valuable guide to this topic. COMPUTERS,Software Development & Engineering,General

Developing Business Applications with OpenStepâ„¢ OpenStep is the software development environment co-developed by Sun and Next Computers. This book provides the first introduction to OpenStep and how it is used to build business applications for Next, Sun, and Windows NT systems. As well as covering the basics, it covers WebObjects (for developing world wide web applications) and the Enterprise Objects framework for developing database applications. No serious OpenStep developer will want to be without this book. COMPUTERS,Software Development & Engineering,General

Advances in the Design of Symbolic Computation Systems New methodological aspects related to design and implementation of symbolic computation systems are considered in this volume aiming at integrating such aspects into a homogeneous software environment for scientific computation. The proposed methodology is based on a combination of different techniques: algebraic specification through modular approach and completion algorithms, approximated and exact algebraic computing methods, object-oriented programming paradigm, automated theorem proving through methods à la Hilbert and methods of natural deduction. In particular the proposed treatment of mathematical objects, via techniques for method abstraction, structures classification, and exact representation, the programming methodology which supports the design and implementation issues, and reasoning capabilities supported by the whole framework are described. COMPUTERS,Software Development & Engineering,General

The Responsible Software Engineer You might expect that a person invited to contribute a foreword to a book on the 1 subject of professionalism would himself be a professional of exemplary standing. I am gladdened by that thought, but also disquieted. The disquieting part of it is that if I am a professional, I must be a professional something, but what? As someone who has tried his best for the last thirty years to avoid doing anything twice, I lack one of the most important characteristics of a professional, the dedicated and persistent pursuit of a single direction. For the purposes of this foreword, it would be handy if I could think of myself as a professional abstractor. That would allow me to offer up a few useful abstractions about professionalism, patterns that might illuminate the essays that follow. I shall try to do this by proposing three successively more complex models of professionalism, ending up with one that is discomfortingly soft, but still, the best approximation I can make of what the word means to me. The first of these models I shall designate Model Zero. I intend a pejorative sense to this name, since the attitude represented by Model Zero is retrograde and offensive ... but nonetheless common. In this model, the word "professionalism" is a simple surrogate for compliant uniformity. COMPUTERS,Software Development & Engineering,General

Safe Comp 96 SAFECOMP '96 contains papers presented at the 15th International Conference on Computer Safety, Reliability and Security held in Vienna, Austria, 23-25 October 1996. The conference aimed to provide an opportunity for technical developers and users to discuss and review their experiences, to consider the best technologies currently available, and to identify the skills and technologies required for the future. SAFECOMP '96 focuses on critical computer applications and is intended as a platform for technology transfer between academia, industry and research institutions. SAFECOMP '96 will be of interest to all those in universities, research institutions, industry and business who want to be well-informed about the current international state of the art in computer safety, reliability and security. COMPUTERS,Software Development & Engineering,General

Safety-Critical Systems Leeds, 6 - 8 February 1996 COMPUTERS,Software Development & Engineering,General

Computer Aided Software Engineering Computer Aided Software Engineering brings together in one place important contributions and up-to-date research results in this important area. Computer Aided Software Engineering serves as an excellent reference, providing insight into some of the most important research issues in the field. COMPUTERS,Software Development & Engineering,General

Formal Specification Techniques for Engineering Modular C Programs Software is difficult to develop, maintain, and reuse. Two factors that contribute to this difficulty are the lack of modular design and good program documentation. The first makes software changes more difficult to implement. The second makes programs more difficult to understand and to maintain. Formal Specification Techniques for Engineering Modular C Programs describes a novel approach to promoting program modularity. The book presents a formal specification language that promotes software modularity through the use of abstract data types, even though the underlying programming language may not have such support. This language is structured to allow useful information to be extracted from a specification, which is then used to perform consistency checks between the specification and its implementation. Formal Specification Techniques for Engineering Modular C Programs also describes a specification-driven, software re-engineering process model for improving existing programs. The aim of this process is to make existing programs easier to maintain and reuse while keeping their essential functionalities unchanged. Audience: Suitable as a secondary text for graduate level courses in software engineering, and as a reference for researchers and practitioners in industry. COMPUTERS,Software Development & Engineering,General

Linux Universe ongratulations on the purchase of your new Linux Universe C CD. Welcome to the universe of Linux! This manual is meant to help you install Linux on your computer and work with Linux. Linux Universe is preconfigured and deliv ered on CD-ROM for the utmost in ease of installation. We aim to minimize your installation effort. Since you do not have to copy files to your hard disk, Linux Universe enables you to start working immediately. Nevertheless, all sources and documenta tion are available on-line at any time. These instructions do not replace books on UNIX. This User's Manual only explains the most important operations regarding installation and provides you with necessary information. We assume that you are acquainted with computers and software and that UNIX is not totally new to you. For more information on Linux and a more detailed overview of the system, please refer to our book: Linux - Unleashing the Workstation in your PC Stefan Strobel, Thomas Uhl Springer-Verlag ISBN 0-387-94601-2 Chapter 2 Features inux is a free UNIX-like operating system kernel. Our Linux L Universe Distribution includes this kernel together with many tools from the Free Software Foundation's GNU project and other freely available programs and utilities. They were developed by many volunteers all over the world. Together they build a complete UNIX-like system. To give you a better orientation, we offer the following summary of the most important features of Linux and our distribution: • A full-fledged 32-bit multi-user/multitasking UNIX system. COMPUTERS,Software Development & Engineering,General

Tools and Environments for Parallel and Distributed Systems Developing correct and efficient software is far more complex for parallel and distributed systems than it is for sequential processors. Some of the reasons for this added complexity are: the lack of a universally acceptable parallel and distributed programming paradigm, the criticality of achieving high performance, and the difficulty of writing correct parallel and distributed programs. These factors collectively influence the current status of parallel and distributed software development tools efforts. Tools and Environments for Parallel and Distributed Systems addresses the above issues by describing working tools and environments, and gives a solid overview of some of the fundamental research being done worldwide. Topics covered in this collection are: mainstream program development tools, performance prediction tools and studies; debugging tools and research; and nontraditional tools. Audience: Suitable as a secondary text for graduate level courses in software engineering and parallel and distributed systems, and as a reference for researchers and practitioners in industry. COMPUTERS,Software Development & Engineering,General

Systematic Reuse Based on papers accepted for presentation at the 1996 Workshop on Systematic Reuse: Issues in Initiating and Improving a Reuse Program, Liverpool, UK, this volume provides a comprehensive introduction to the effective management of software reuse. It examines a number of central issues such as: the critical success factors for reuse; the amount of investment required and the expected payback period; the type of training needed; tools; and the impact of reuse on organisation structure. There is a strong emphasis on the industrial application of systematic reuse - an area which is currently expanding at a rapid rate - illustrated by the experiences of leading international companies such as IBM, Hitachi Europe, and AT&T. Overall this volume sets out comprehensive guidelines on the introduction and maintenance of a reuse program. It will provide an invaluable reference book for software development practitioners, systems analysts and architects, and development managers. COMPUTERS,Software Development & Engineering,General

Global Optimization in Engineering Design Mathematical Programming has been of significant interest and relevance in engineering, an area that is very rich in challenging optimization problems. In particular, many design and operational problems give rise to nonlinear and mixed-integer nonlinear optimization problems whose modeling and solu tion is often nontrivial. Furthermore, with the increased computational power and development of advanced analysis (e. g. , process simulators, finite element packages) and modeling systems (e. g. , GAMS, AMPL, SPEEDUP, ASCEND, gPROMS), the size and complexity of engineering optimization models is rapidly increasing. While the application of efficient local solvers (nonlinear program ming algorithms) has become widespread, a major limitation is that there is often no guarantee that the solutions that are generated correspond to global optima. In some cases finding a local solution might be adequate, but in others it might mean incurring a significant cost penalty, or even worse, getting an incorrect solution to a physical problem. Thus, the need for finding global optima in engineering is a very real one. It is the purpose of this monograph to present recent developments of tech niques and applications of deterministic approaches to global optimization in engineering. The present monograph is heavily represented by chemical engi neers; and to a large extent this is no accident. The reason is that mathematical programming is an active and vibrant area of research in chemical engineering. This trend has existed for about 15 years. COMPUTERS,Software Development & Engineering,General

Rapid Application Generation of Business and Finance Software Rapid Application Generation of Business and Finance Software describes a method for developing wide ranging computing applications with emerging software technologies. The pressure of the market place calls for reducing the time to market of new software applications. This book shows how to build such software faster and more reliably. Using an elegant concept of extended tools, the book presents a method for the constructive building of `hybrid' applications. The book includes such application areas as direct marketing, banking insurance and executive information systems. The methods used adopt the latest object-oriented and client-server techniques. Rapid Application Generation of Business and Finance Software is an important book for computer scientists working on rapid application development. It is also of interest to information systems specialists. COMPUTERS,Software Development & Engineering,General

Persistent Object Systems The Sixth International Workshop on Persistent Object Systems was held at Les Mazets des Roches near Tarascon, Provence in southern France from the fifth to the ninth of September 1994. The attractive context and autumn warmth greeted the 53 participants from 12 countries spread over five continents. Persistent object systems continue to grow in importance. Almost all significant uses of computers to support human endeavours depend on long-lived and large-scale systems. As expectations and ambitions rise so the sophistication of the systems we attempt to build also rises. The quality and integrity of the systems and their feasibility for supporting large groups of co-operating people depends on their technical founda tion. Persistent object systems are being developed which provide a more robust and yet simpler foundation for these persistent applications. The workshop followed the tradition of the previous workshops in the series, focusing on the design, implementation and use of persistent object systems in particular and persistent systems in general. There were clear signs that this line of research is maturing, as engineering issues were discussed with the aid of evidence from operational systems. The work presented covered the complete range of database facilities: transactions, concurrency, distribution, integrity and schema modifica tion. There were examples of very large scale use, one involving tens of terabytes of data. Language issues, particularly the provision of reflection, continued to be important. COMPUTERS,Software Development & Engineering,General

VLISP A Verified Implementation of Scheme The VLISP project showed how to produce a comprehensively verified implemen tation for a programming language, namely Scheme [4, 15). Some of the major elements in this verification were: • The proof was based on the Clinger-Rees denotational semantics of Scheme given in [15). Our goal was to produce a "warts-and-all" verification of a real language. With very few exceptions, we constrained ourselves to use the se mantic specification as published. The verification was intended to be rigorous, but. not. complet.ely formal, much in the style of ordinary mathematical discourse. Our goal was to verify the algorithms and data types used in the implementat.ion, not their embodiment. in code. See Section 2 for a more complete discussion ofthese issues. Our decision to be faithful to the published semantic specification led to the most difficult portions ofthe proofs; these are discussed in [13, Section 2.3-2.4). • Our implementation was based on the Scheme48 implementation of Kelsey and Rees [17). This implementation t.ranslates Scheme into an intermediate-level "byte code" language, which is interpreted by a virtual machine. The virtual machine is written in a subset of Scheme called PreScheme. The implementationissufficient.ly complete and efficient to allow it to bootstrap itself. We believe that this is the first. verified language implementation with these properties. COMPUTERS,Software Development & Engineering,General

Achievement and Assurance of Safety Each year there are improvements in safety-critical system technology. These arise both from developments in the contributing technologies, such as safety engineering, software engineering, human factors and risk assessment, and from the adoption or adaptation of appropriate techniques from other domains, such as security. For these improvements to be of real benefit, they need to be applied during the appropriate stage in the life cycle of the system, whether it be development, assessment, or operation. For this to occur, they must be communicated and explained. Each year the Safety-critical Systems Symposium offers a distinguished forum for the presentation of papers on such developments, and also for papers from industry on the lessons learned from the use of technologies and methods. The results of many collaborative research projects, with components from both industry and academia, are reported in a universally understandable form. In 1995 the Symposium was held in Brighton, a venue calculated to stimulate not just the presenters of papers, but all the delegates. Yet, this book of Proceedings is intended not only for the delegates but also for readers not able to attend the event itself. We welcome both categories of reader. Delegates have the benefit of attending the presentations and the opportunity to participate in the discussions; those who take up this book after the event can peruse it attheir leisure and, perhaps, on account of it will resolve to attend subsequent symposia. COMPUTERS,Software Development & Engineering,General

Safe Comp 95 Safety-related computer systems are those which may lead to loss of life, injury or plant and environmental damage. Such systems therefore have to be developed and implemented so that they meet strict require and security because their applications cover ments on safety, reliability nearly all areas of daily life and range from controlling and monitoring industrial processes, through robotics and power generation, to transport systems. Highly reliable electronic systems for safety-related applications represent an area in which industry has been involved for many years and which is now gaining increasing importance in academia. Their relevance also results from an increased perception of safety by society. Therefore, not only are technicians involved in this area, but psycho logical and sociological aspects also play a major role. Dealing with safety-related systems we have to consider the whole lifecycle of these systems, starting from specification up to implementation, assessment and operation. All those issues mentioned above are covered in this book, which represents the proceedings of the 14th International Conference on Computer Safety, Reliability and Security, SAFECOMP '95, held in Belgirate, Italy, 11-13 October 1995. The conference continues the series of SAFECOMP conferences which was originated by the European Workshop on Industrial Computer Systems, Technical Committee 7 on Safety, Security and Reliability (EWICS TC7) and reflects the state of the art, experience and new trends in the area of safety-related computer systems. COMPUTERS,Software Development & Engineering,General

Formal Object-Oriented Development Formal Object-Oriented Development provides a comprehensive overview of the use of formal object-oriented methods; it covers how and where they should be introduced into the development process, how they can be introduced selectively for critical parts of an application, and how to incorporate them effectively into existing deveopmental practices.The text is extensively illustrated, both with tutorial and self-assessment excercises and with examples of industrial applications from the reactive systems domain. This book will be of interest to academic and industrial researchers, software engineering practitioners and consultants, and will also provide invaluable reading material for students learning Z++ and VDM++. COMPUTERS,Software Development & Engineering,General

Multimedia and Groupware for Editing Multimedia techniques enable the production of non-traditional documents containing enourmous amounts of information. The production of such documents by a group, as opposed to an individual, is the main subject of this book. A group needs to communicate, and multimedia technology can be used to enhance group communication. How multimedia documentation and communication and groups of authors fit together are the main questions tackled. The book describes the construction of a conceptual framework and the prototype system, CoMEdiA, as well as how the system was used to conduct a group effectiveness study involving two applications: cooperative software engineering and data production. Thus the work relates to multimedia communication, cooperative editing, and group support and effectiveness. COMPUTERS,Software Development & Engineering,General

Distributed Systems The purpose of this book is to make the reader famliar with software engineering for distributed systems. Software engineering is a valuable discipline in the develop ment of software. The reader has surely heard of software systems completed months or years later than scheduled with huge cost overruns, systems which on completion did not provide the performance promised, and systems so catastrophic that they had to be abandoned without ever doing any useful work. Software engi neering is the discipline of creating and maintaining software; when used in con junction with more general methods for effective management its use does reduce the incidence of horrors mentioned above. The book gives a good impression of software engineering particularly for dis tributed systems. It emphasises the relationship between software life cycles, meth ods, tools and project management, and how these constitute the framework of an open software engineering environment, especially in the development of distrib uted software systems. There is no closed software engineering environment which can encompass the full range of software missions, just as no single flight plan, airplane or pilot can perform all aviation missions. There are some common activities in software engi neering which must be addressed independent of the applied life cycle or methodol ogy. Different life cycles, methods, related tools and project management ap proaches should fit in such a software engineering framework. COMPUTERS,Software Development & Engineering,General

Semantics of Specification Languages (SoSL) SoSL was the first International Workshop on Semantics of Specification Languages, held from 25-27 October 1993 in Utrecht, the Netherlands. The workshop was organized by the Department of Philosophy of Utrecht University with financial support from the Nationale Faciliteit Informatica of the Nederlandse Organisatie voor Wetenschappelijk Onderzoek (NWO), and under the auspices of the British Computer Society'S specialist group in Formal Aspects of Computing Science (BCS FACS). The concern of the workshop was the semantics of specification languages, and the issues closely related to this area, such as type checking and the justification of proof rules and proof obligations. Its aim was the exchange of problems and ideas in this field of formal methods, and the identification of common programs of work for further investigation. The program of SoSL consisted of 3 invited lectures presenting the developments of the semantics of 3 major specification languages. Furthermore, there were 16 presentations of submitted papers. This volume provides a direct account of the workshop. It contains 3 papers that match the invited lectures and the 16 selected papers. The editors want to thank all those who have contributed to the workshop; the Program Committee and the referees for selecting the contributed papers, the invited speakers for their interesting talks, the Organizing Committee for all their efforts, and of course the participants. We have the feeling that the workshop was worthwhile and should be repeated. COMPUTERS,Software Development & Engineering,General

Algebraic Methodology and Software Technology (AMAST’93) The goal of the AMAST conferences is to foster algebraic methodology as a foundation for software technology, and to show that this can lead to practical mathematical alternatives to the ad-hoc approaches commonly used in software engineering and development. The first two AMAST conferences, held in May 1989 and May 1991 at the University of Iowa, were well received and encouraged the regular organization of further AMAST conferences on a biennial schedule. The third Conference on Algebraic Methodology and Software Technology was held in the campus of the University of Twente, The Netherlands, during the first week of Summer 1993. Nearly a hundred people from all continents attended the conference. The largest interest received by the AMAST conference among the professionals extended to include the administration organizations as well. AMAST'93 was opened by the Rector of the University of Twente, followed by the Local Chairman. Their opening addresses open this proceedings, too. The proceedings contains 8 invited papers and 32 selected communica tions. The selection was very strict, for 121 submissions were received. COMPUTERS,Software Development & Engineering,General
Object-Oriented Programming Object-oriented programming is a popular buzzword these days. What is the reason for this popularity? Is object-oriented programming the solution to the software crisis or is it just a fad? Is it a simple evolutionary step or a radical change in software methodology? What is the central idea behind object-orien ted design? Are there special applications for which object-oriented program ming is particularly suited? Which object-oriented language should be used? There is no simple answer to these questions. Although object-oriented programming was invented more than twenty years ago, we still cannot claim that we know everything about this programming technique. Many new con cepts have been developed during the past decade, and new applications and implications of object-oriented programming are constantly being discovered. This book can only try to explain the nature of object-oriented program ming in as much detail as possible. It should serve three purposes. First, it is intended as an introduction to the basic concepts of object-oriented program ming. Second, the book describes the concept of prototypes and explains why and how they can improve the way in which object-oriented programs are developed. Third, it introduces the programming language Omega, an object oriented language that was designed with easy, safe and efficient software development in mind. COMPUTERS,Software Development & Engineering,General

Technology and Assessment of Safety-Critical Systems The programme for the Second Safety-critical Systems Symposium was planned to examine the various aspects of technology currently employed in the design of safety-critical systems, as well as to emphasise the importance of safety and risk management in their design and operation. assessment There is an even balance of contributions from academia and industry. Thus, industry is given the opportunity to express its views of the safety-critical domain and at the same time offered a glimpse of the technologies which are currently under development and which, if successful, will be available in the medium-term future. In the field of technology, a subject whose importance is increasingly being recognised is human factors, and there are papers on this from the University of Hertfordshire and Rolls-Royce. Increasingly, PLCs are being employed in safety-critical applications, and this domain is represented by contributions from Nuclear Electric and August Computers. Then there are papers on maintainability, Ada, reverse engineering, social issues, formal methods, and medical systems, all in the context of safety. And, of course, it is not possible to keep the 'new' technologies out of the safety-critical domain: there are papers on neural networks from the University of Exeter and knowledge-based systems from ERA Technology. COMPUTERS,Software Development & Engineering,General

Studies in Computer Science Proceedings of a conference held in West Lafayette, Indiana, November 1-3, 1989 COMPUTERS,Software Development & Engineering,General

Directions in Safety-Critical Systems 0 e This is the proceedings of the first annual symposium of the Safety-critical Systems Club (The Watershed Media Centre, Bristol, 9-11 February 1993), which provided a forum for exploring and discussing ways of achieving safety in computer systems to be used in safety-critical industrial applications. The book is divided into three parts, which correspond with the themes of the three days of the symposium. The first - Experience from Around Europe - brings together information on developments in safety-critical systems outside the UK. The second - Current Research - consists of papers on large projects within the UK, which involve collaboration between academia and industry, providing techniques and methods to enhance safety. The final part - Achieving and Evaluating Safety - explores how methods already in use in other domains may be applied to safety, and examines the relationships between safety and other attributes such as quality and security. The papers identify the current problems and issues of interest in the field of safety-critical software-based systems, and provide valuable up-to-date material for those in both academia and industry. The academic will benefit from information about current research complimentary to his own, and the industrialist will learn of the technologies which will soon be available and where to find them. COMPUTERS,Software Development & Engineering,General

NAPAW 92 This proceedings contains fourteen papers on process algebras presented at the First North American Process Algebra Workshop, held on 28 August 1992 in Stony Brook, New York. NAPAW was held in conjunc tion with CONCUR 92. It is hoped that NAPAW will be held yearly to bring together researchers from the North American continent interested in process algebras. We would like to thank the program committee members for reading through the abstracts, and Scott Smolka whose encouragement and assistance was critical to the success of the workshop. November 1992 S. Purushothaman University Park, PA Amy Zwarico Baltimore, MD Program Committee Rance Cleaveland, North Carolina State University Richard Gerber, University of Maryland at College Park Faron Moller, University of Edinburgh S. Purushothaman, Pennsylvania State University Amy Zwarico, Johns Hopkins University Contents Session 1 Real-Time Calculi and Expansion Theorems (Extended Abstract) J. C. Godskesen and K. G. Larsen . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3 Modal Logics in Timed Process Algebras L. Brim . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13 Process Communication Environment D. P. Gruska andA. Maggiolo-Schettini . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27 Session 2 A Process Calculus with Incomparable Priorities H. Hansson and F. Orava . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43 CCSR 92: Calculus for Communicating Shared Resources with Dynamic Priorities P. Bremond-Gregoire, S. Davidson and I. Lee . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 65 Exception Handling in Process Algebra F. S. de Boer, J. Coenen and R. Gerth . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 86 Session 3 Observation Trees (Extended Abstract) P. Degano, R. De Nicola and U. Montanari. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 103 Computing Ready Simulations Efficiently B. Bloom and R. Paige . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119 Verification of Value-Passing Systems Z. Schreiber . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . COMPUTERS,Software Development & Engineering,General

Persistent Object Systems The Fifth International Workshop on Persistent Object Systems took place in the historic setting of Centro Studi "I Cappuccini" della Cassa di Risparmio di San Miniato. San Miniato (pisa). Italy from 1-4 September 1992. The workshop continued the tradition of the previous four in concentrating on the design. implementation and use of persistent systems. The other workshops in the series are: Venue Date Organisers Appin POSI 27-30 August Atkinson. Buneman 1985 Scotland and Morrison Appin POS2 25-28 August Atkinson and Morrison 1987 Scotland Newcastle POS3 10-13 January Koch and Rosenberg 1989 Australia POS4 23-27 September Marthas Vineyard DearIe. Mitchell 1990 USA andZdonik The series of Workshops on Database Programming Languages is closely related to the POS workshops. These have been held every other year out of phase with POS. and tend to concentrate on the design and theory of persistent systems. The workshops in the DBPL series are: Date Venue Organisers DBPL 1 7-10 September Roscoff Bancilhon and France 1987 Buneman DBPL2 4-8 June Salishan Hull. Morrison and 1989 USA Stemple 27-30 August Nafplion Kanellakis and DBPL3 Greece Schmidt 1991 Preface vi This book follows the format of the workshop. Of the 39 papers submitted for the workshop, 22 were accepted in order to allow plenty of time for discussion. As at POS 4 in Marthas Vineyard each paper was followed by 5 minutes of questions and each session by a 30 minute discussion. COMPUTERS,Software Development & Engineering,General

Formal Methods in Databases and Software Engineering Logic and object-orientation have come to be recognized as being among the most powerful paradigms for modeling information systems. The term "information systems" is used here in a very general context to denote database systems, software development systems, knowledge base systems, proof support systems, distributed systems and reactive systems. One of the most vigorously researched topics common to all information systems is "formal modeling". An elegant high-level abstraction applicable to both application domain and system domain concepts will always lead to a system design from "outside in"; that is, the aggregation of ideas is around real-life objects about which the system is to be designed. Formal methods \yhen applied with this view in mind, especially during early stages of system development, can lead to a formal reasoning on the intended properties, thus revealing system flaws that might otherwise be discovered much later. Logic in different styles and semantics is being used to model databases and their transactions; it is also used to specify concurrent, distributed, real-time, and reactive systems. ,The notion of "object" is central to the modeling of object oriented databases, as well as object-oriented design and programs in software engineering. Both database and software engineering communities have undoubtedly made important contributions to formalisms based on logic and objects. It is worthwhile bringing together the ideas developed by the two communities in isolation, and focusing on integrating their common strengths. COMPUTERS,Software Development & Engineering,General

A Practical Theory of Programming There are several theories of programming. The first usable theory, often called "Hoare's Logic", is still probably the most widely known. In it, a specification is a pair of predicates: a precondition and postcondition (these and all technical terms will be defined in due course). Another popular and closely related theory by Dijkstra uses the weakest precondition predicate transformer, which is a function from programs and postconditions to preconditions. lones's Vienna Development Method has been used to advantage in some industries; in it, a specification is a pair of predicates (as in Hoare's Logic), but the second predicate is a relation. Temporal Logic is yet another formalism that introduces some special operators and quantifiers to describe some aspects of computation. The theory in this book is simpler than any of those just mentioned. In it, a specification is just a boolean expression. Refinement is just ordinary implication. This theory is also more general than those just mentioned, applying to both terminating and nonterminating computation, to both sequential and parallel computation, to both stand-alone and interactive computation. And it includes time bounds, both for algorithm classification and for tightly constrained real-time applications. COMPUTERS,Software Development & Engineering,General

Software Engineering on Sun Workstations® Software Engineering on Sun Workstations is the most comprehensive volume of technical information about software development available for the Sun Workstation. This book is of great interest to both large and small-scale software developers in all sectors of commercial, scientific and technical applications programming. This book presents an in-depth look at Computer Assisted Software Engineering (CASE) and CASE tools, an important element in building large-scale commercial computer applications and state-of-the-art programs. Topics explored in the book include: ToolTalk interapplication message service; SPAR-Compiler technology; SPARCWorks programming environment; integrating third party applications with SPARCWorks; using DEVGuide to build open windows user interfaces; and integrating X11 applications with the open windows desktop. All Sun Workstation users are potential buyers of this book. More specific users include software developers and computer programmers working on the Sun system, as well as Unix "derivative" developers. Also applicable to users considering switching to a Unix-based system, as the Sun Workstation is true state-of-the-art computing and is the most widely used workstation computing environment in the world. COMPUTERS,Software Development & Engineering,General

Software Development and Reality Construction The present book is based on the conference Software Development and Reality Construction held at SchloB Eringerfeld in Germany, September 25 - 30, 1988. This was organized by the Technical University of Berlin (TUB) in cooperation with the German National Research Center for Computer Science (GMD), Sankt Augustin, and sponsored by the Volkswagen Foundation whose financial support we gratefully acknowledge. The conference was an interdisciplinary scientific and cultural event aimed at promoting discussion on the nature of computer science as a scientific discipline and on the theoretical foundations and systemic practice required for human-oriented system design. In keeping with the conversational style of the conference, the book comprises a series of individual contributions, arranged so as to form a coherent whole. Some authors reflect on their practice in computer science and system design. Others start from approaches developed in the humanities and the social sciences for understanding human learning and creativity, individual and cooperative work, and the interrelation between technology and organizations. Thus, each contribution makes its specific point and can be read on its own merit. But, at the same time, it takes its place as a chapter in the book, along with all the other contributions, to give what seemed to us a meaningful overall line of argumentation. This required careful editorial coordination, and we are grateful to all the authors for bearing with us throughout the slow genesis of the book and for complying with our requests for extensive revision of some of the manuscripts. COMPUTERS,Software Development & Engineering,General

Interactive Multimedia Learning Environments Multimedia environments suggest to us a new perception of the state of changes in and the integration of new technologies that can increase our ability to process information. Moreover, they are obliging us to change our idea of knowledge. These changes are reflected in the obvious synergetic convergence of different types of access, communication and information exchange. The multimedia learning environment should not represent a passive object that only contains or assembles information but should become, on one side, the communication medium of the pedagogical intentions of the professor/designer and, on the other side, the place where the learner reflects and where he or she can play with, test and access information and try to interpret it, manipulate it and build new knowledge. The situation created by such a new learning environments that give new powers to individuals, particularly with regard to accessing and handling diversified dimensions of information, is becoming increasingly prevalent in the field of education. The old static equilibrium, in which fixed roles are played by the teacher (including the teaching environment) and the learner, is shifting to dynamic eqUilibrium where the nature of information and its processing change, depending on the situation, the learning context and the individual's needs. COMPUTERS,Software Development & Engineering,General

Global Software John Sculley In the short history of personal computing, the task of the software programmer has been one of the least recognized-but one of the most significant-in the industry. In addition to defining the prob lems, and presenting the solutions, the software programmer is con fronted with the challenge of having to predict what combination of ideas and technologies will move the industry forward in the most compelling way. Even though we've seen the development of tremendous applications in a surprisingly short period of time, the most difficult problems often surface when we try to elevate a suc cessful local idea to the international arena. In the case of Apple Computer, these challenges become especially profound when you consider that Apple sells Macintosh not just in the United States, but in Japan, China, the Middle East, Africa, East ern Europe, and even to the United Nations itself. Of course, this means that the personal computer must work everywhere around the world. But more significantly, it also means that the software must reflect the uniqueness of a given culture, its language, morals, and even its sense of humor. To step away from a narrowly-defined, nationally-based paradigm for software development, programmers, management, and entire corporations must learn to recognize what elements of an interface, problem solving technique, documentation illustration, package de sign, and advertisement are local, and which elements are appro priate for global markets. COMPUTERS,Software Development & Engineering,General

Functional Programming, Glasgow 1991 Published in collaboration with the British Computer Society COMPUTERS,Software Development & Engineering,General

Case Technology 'I would recommend that you buy the book just for the Humphrey article alone.' The Computer Journal 3:5 1992 COMPUTERS,Software Development & Engineering,General

Software Failure Risk The author here presents a detailed explanation of the methodolgy of software reliablity evaluation, and then demonstrates its applications to a commercial loan system, a funds transfer security system, and a payables processing system. Her well-written, practical text enables users to design original software modules, as well as to critically assess commercial software products. COMPUTERS,Software Development & Engineering,General

Z User Workshop, York 1991 In ordinary mathematics, an equation can be written down which is syntactically correct, but for which no solution exists. For example, consider the equation x = x + 1 defined over the real numbers; there is no value of x which satisfies it. Similarly it is possible to specify objects using the formal specification language Z [3,4], which can not possibly exist. Such specifications are called inconsistent and can arise in a number of ways. Example 1 The following Z specification of a functionf, from integers to integers "f x : ~ 1 x ~ O· fx = x + 1 (i) "f x : ~ 1 x ~ O· fx = x + 2 (ii) is inconsistent, because axiom (i) gives f 0 = 1, while axiom (ii) gives f 0 = 2. This contradicts the fact that f was declared as a function, that is, f must have a unique result when applied to an argument. Hence no suchfexists. Furthermore, iff 0 = 1 andfO = 2 then 1 = 2 can be deduced! From 1 = 2 anything can be deduced, thus showing the danger of an inconsistent specification. Note that all examples and proofs start with the word Example or Proof and end with the symbol.1. COMPUTERS,Software Development & Engineering,General

Shifting Paradigms in Software Engineering Object-orientation and the need for multi-paradigmatic systems constitute a challenge for researchers, practitioners and instructors. Presentations at the OCG/NJSZT joint conference in Klagenfurt, Austria, in September 1992 addressed these issues. The proceedings comprise such topics as: project management, artificial intelligence - modelling aspects, artificial intelligence - tool building aspects, language features, object-orientied software development, the challenge of coping with complexity, methodology, and experience, software engineering education, science policy, etc. COMPUTERS,Software Development & Engineering,General

A Primer in Petri Net Design Petri nets provide a formal framework for system modelingand validation which has proven to be very reliable inpractice. This book presents variousnet models appropriatefor designing specific systems, where systems are understoodvery generally as "organizational systems" in whichregulatedflows of objects and information are significant.The models are interrelated in the sense that they havecommon interpretation patterns: together they can beunderstood as a method for specifying any given system orany section of such a system to any given degree ofrefinement. The simple and immediately understandableprinciples of system modelling with nets makes it possibleto provide an illustrated description of this method withoutgoing into the mathematics behind it. The text is based oncourses the author developed for project engineers andproject managers in the area of embedded computer systems. COMPUTERS,Software Development & Engineering,General

Towards a Software Factory The subject of this book is the control of software engineering. The rapidly increasing demand for software is accompanied by a growth in the number of products on the market, as well as their size and complexity. Our ability to control software engineering is hardly keeping pace with this growth. As a result, software projects are often late, software products sometimes lack the required quality and the productivity improvements achieved by software engineering are insufficient to keep up with the demand This book describes ways to improve software engineering control. It argues that this should be expanded to include control of the development, maintenance and reuse of software, thus making it possible to apply many of the ideas and concepts that originate in production control and quality control. The book is based on research and experience accumulated over a number of years. During this period I had two employers: Eindhoven University of Technology and Philips Electronics. Research is not a one-man activity and I would like to thank the following persons for their contributions to the successful completion of this project. First and foremost my Ph. D. advisers Theo Bemelmans, Hans van Vliet and Fred Heemstra whose insights and experience proved invaluable at every stage. Many thanks are also due to Rob Kusters and Fred Heemstra for their patience in listening to my sometimes wild ideas and for being such excellent colleagues. COMPUTERS,Software Development & Engineering,General

Modeling Design Objects and Processes A little more than a decade ago my colleagues and I faced the necessity for providing a database management system which might commonly serve a number of different types of computer aided design applications at different manufacturing enterprises. We evaluated some wellknown cases of conceptual models and commercially available DBMSs, and found none fuHy meeting the requirements. Yet the analysis of them led us to the development of what we named the Logical Structure Management System (LMS). Syntactically the LMS language is somewhat similar to ALPHA by E. F. Codd. The underly ing conceptual model is entirely different from that of the relational model, however. LMS has been since put into practical use, meanwhile a further ef fort in search of asound theoretical base and a concrete linguistic framework for true product modeling together with comparative studies of various ap proaches has been made. Here, the term product modeling is used to signify the construction of informational models of design objects and design pro cesses in which it must be possible to include not a fixed set of attributes and relations, such as geometry, physical properties, part-of hierarchy, etc. , but whatever aspects of design designers may desire to be included. The purpose of this book is to present the major results of the said effort, which are primarily of a theoretical or conceptual nature. Following the intro duction (Chap. COMPUTERS,Software Development & Engineering,General

High-level Petri Nets High-level Petri nets are now widely used in both theoretical analysis and practical modelling of concurrent systems. The main reason for the success of this class of net models is that they make it possible to obtain much more succinct and manageable de scriptions than can be obtained by means of low-level Petri nets-while, on the other hand, they still offer a wide range of analysis methods and tools. The step from low-level nets to high-level nets can be compared to the step from assembly languages to modem programming languages with an elaborated type concept. In low-level nets there is only one kind of token and this means that the state of a place is described by an integer (and in many cases even by a boolean value). In high-level nets each token can carry complex information which, e. g. , may describe the entire state of a process or a data base. Today most practical applications of Petri nets use one of the different kinds of high-level nets. A considerable body of knowledge exists about high-level Petri nets this includes theoretical foundations, analysis methods and many applications. Unfortunately, the papers on high-level Petri nets have been scattered throughout various journals and collections. As a result, much of this knowledge is not readily available to people who may be interested in using high-level nets. COMPUTERS,Software Development & Engineering,General

Software Reuse Observers in the present usually have an advantage when it comes to interpreting events of the past. In the case of software reuse, how ever, it is unclear why an idea that has gained such universal accep tance was the source of swirling controversy when it began to be taken seriously by the software engineering community in the mid-1980's. From a purely conceptual point of view, the reuse of software de signs and components promises nearly risk-free benefits to the devel oper. Virtually every model of software cost and development effort predicts first-order dependencies on either products size or the num ber of steps carried out in development. Reduce the amount of new product to be developed and the cost of producing the product de creases. Remove development steps, and total effort is reduced. By reusing previously developed engineering products the amount of new product and the number of development steps can be reduced. In this way, reuse clearly has a major influence on reducing total development cost and effort. This, of course, raises the issue of from whence the reused products arise. There has to be a prior investment in creating "libraries of reuse products before reuse can be successfuL . . " How can organizations with a "bottom line" orientation be enticed into contributing to a reuse venture? Fortunately, the economics of reuse l resembles many other financial investment situations . COMPUTERS,Software Development & Engineering,General

The Art of Distributed Applications Powerful networked workstations are adding a new dimension to the world of computing. Programmers are challenged to write applications that exploit the speed and parallelism of such distributed systems, programs that take advantage of the networking and communication features of high-speed workstations. John Corbin, a senior engineer in Sun's networking group, bases his approach on RPC (Remote Procedure Call), a technique for programming communication processes in UNIX environments. A professional reference book as well as a textbook on RPC programming techniques, The Art of Distributed Applications: Programming Techniques for Remote Procedure Call, is for the working programmer who needs to explore the possibilities of designing distributed networked applications under UNIX. The book can also be recommended as a supplemental text in a distributed systems course, providing the basis for lab assignments. COMPUTERS,Software Development & Engineering,General
Fault-Tolerant Computing Systems 5th International GI/ITG/GMA Conference, Nürnberg, September 25-27, 1991. Proceedings COMPUTERS,Software Development & Engineering,General

Chemical Information 2 2nd Proceedings of the International Conference, Montreux, Switzerland, September 1990 COMPUTERS,Software Development & Engineering,General

The NIAM Information Analysis Method About information analysis Everywhere people are working, they are communicating or exchanging informa tion about their work. Unless they come to reasonable agreements about this communication, i.e., agreements describing the "language" of their communica tion so that they can understand each other's information, sooner or later there will be such a "Tower of Babel" that their goal of communication will be doomed to failure. There are a lot of places wh~re some of the communication between people working together is being carried out via an information system. In these cases too, a clear agreement about communication must be made, so that people communi cating via an information system can understand each other at all times. In such an agreement, it is determined which data may be exchanged with the information system and the meaning everyone should assign to that data. For communication taking place via an information system, such an agreement is called a "grammar" or a "conceptual schemea" of this information system. "Information analysis" is that field and also that phase of development of an information system in which the grammar or the conceptual schemea of the information system is determined. The grammar or the conceptual scheme is an essential part of the specifications of present-day information systems. COMPUTERS,Software Development & Engineering,General

Semantics for Concurrency The semantics of concurrent systems is one of the most vigorous areas of research in theoretical computer science, but suffers from disagree ment due to different, and often incompatible, attitudes towards abstracting non-sequential behaviour. When confronted with process algebras, which give rise to very elegant, highly abstract and com positional models, traditionally based on the interleaving abstraction, some argue that the wealth of contribution they have made is partially offset by the difficulty in dealing with topics such as faimess. On the other hand, the non-interleaving approaches, based on causality, although easing problems with fairness and confusion, still lack struc ture, compositionality, and the elegance of the interleaving counter parts. Since both these approaches have undoubtedly provided important contributions towards understanding of concurrent systems, one should concentrate on what they have in common, rather than the way they differ. The Intemational Workshop on Semantics for Concurrency held at the University of Leicester on 23-25 July 1990 was organised to help overcome this problem. Its main objective was not to be divisive, but rather to encourage discussions leading towards the identification of the positive objective features of the main approaches, in the hope of furthering common understanding. The Workshop met with an excel lent response, and attracted contributions from all over the world. The result was an interesting and varied programme, which was a combi nation of invited and refereed papers. The invited speakers were: Prof. dr. E. Best (Hildesheim University) Prof. dr. A. COMPUTERS,Software Development & Engineering,General

Software Engineering for Large Software Systems These proceedings include tutorials and papers presented at the Sixth CSR Confer ence on the topic of Large Software Systems. The aim of the Conference was to identify solutions to the problems of developing and maintaining large software systems, based on approaches which are currently being undertaken by software practitioners. These proceedings are intended to make these solutions more widely available to the software industry. The papers from software practitioners describe: • important working systems, highlighting their problems and successes; • techniques for large system development and maintenance, including project management, quality management, incremental delivery, system security, in dependent V & V, and reverse engineering. In addition, academic and industrial researchers discuss the practical impact of current research in formal methods, object-oriented design and advanced environ ments. The keynote paper is provided by Professor Brian Warboys of ICL and the University of Manchester, who masterminded the development of the ICL VME Operating System, and the production of the first database-driven software en gineering environment (CADES). The proceedings commence with reports of the two tutorial sessions which preceded the conference: • Professor Keith Bennett of the Centre for Software Maintenance at Durham University on Software Maintenance; • Professor John McDermid of the University of York on Systems Engineering Environments for High Integrity Systems. The remaining papers deal with reports on existing systems (starting with Professor Warboys' keynote paper), approaches to large systems development, methods for large systems maintenance and the expected impact of current research. COMPUTERS,Software Development & Engineering,General

Functional Programming Functional Programming is a relatively new area of computer science. These proceedings contain 25 papers representing an excellent snapshot of the current state of functional programming and are written by the leading computer scientists in this aera. In some universities, a functional programming language is used as the introductory teaching language and computer architectures are being designed and investigated to support functional languages. COMPUTERS,Software Development & Engineering,General

Persistent Object Systems Persistent object systems are systems which support the creation and manipulation of objects in a uniform manner, regardless of how long they persist. This is in direct contrast with conventional systems where temporary objects are created and manipulated using one mechanism (typically programming language data structures) and permanent objects are maintained using a different mechanism (usually a filestore). The unification of temporary and permanent objects yields systems which are smaller and more efficient than conventional systems and which provide a powerful and flexible platform for the development of large, data intensive applications. This volume presents the proceedings of a workshop at which latest research in this area was discussed. The papers are grouped into sections on the following topics: type systems and persistence, persistent programming languages, implementing persistence, object stores, measurement of persistent systems, transactions and persistence, and persistent machines. COMPUTERS,Software Development & Engineering,General

Security and Persistence During a short visit to Bremen in December 1989 John Rosenberg had several discussions with me about computer architecture. Although we had previously worked together for more than a decade in Australia we had not seen each other for over a year, following my move to Bremen in 1988. Meanwhile John was spending a year on study leave at the University of St. Andrews in Scotland with Professor Ron Morrison and his persistent programming research group. From our conversations it was quite clear that John was having a most fruitful time in St. Andrews and was gaining valuable new insights into the world of persistent programming. He was very keen to explore the significance of these insights for the MONADS Project, which we had been jOintly directing since the early 1980s. MONADS was not about persistent programming. In fact it had quite different origins, in the areas of software engineering and information protection. In an earlier stage of the project our ideas on these themes had led us into the world of computer architecture and even hardware deSign, in our attempts to provide an efficient base machine for our software ideas. The most important practical result of this phase of the project had been the development of the MONADS-PC, a mini computer which would be better compared with say a V tv COMPUTERS,Software Development & Engineering,General

Formal Methods in Standards 3. 1 What are formal methods? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17 3. 2 A survey of formal methods . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18 3. 2. 1 FDTs and FSLs for sequential software . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18 3. 2. 1. 1 VDM (Vienna Development Method). . . . . . . . . . . . . . . . . . . . . 19 3. 2. 1. 2 Z. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20 3. 2. 1. 3 me too . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20 3. 2. 1. 4 HOS and AXES. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20 3. 2. 1. 5 Gist. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20 3. 2. 1. 6 Clear . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21 3. 2. 1. 7 OBJ. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21 3. 2. 1. 8 ACT ONE and ACT TWO. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21 3. 2. 1. 9 CIP-L. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21 3. 2. 1. 10 LPG. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21 3. 2. 1. 11 Larch. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21 3. 2. 1. 12 Logic languages-the Prolog family. . . . . . . . . . . . . . . . . . . 22 3. 2. 1. 13 Functional languages. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22 3. 2. 2 FDTs and FSLs for concurrent software. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22 3. 2. 2. 1 LOTOS. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23 3. 2. 2. 2 Estelle. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24 3. 2. 2. 3 SDL. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24 3. 2. 2. 4 ASN. l . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24 3. 2. 2. 5 TTCN. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25 3. 2. 2. 6 Gypsy. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25 3. 2. 3 Graphical formalisms . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25 3. 2. 3. 1 Petri nets. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25 3. 2. 3. 2 Higraphs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25 3. 2. 4 Less formal methods and notations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26 3. 2. 4. 1 SADT. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26 3. 2. 4. 2 Structured Design . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26 3. 2. 4. 3 SSADM and LSDM . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26 3. 2. 4. 4 JSPandJSD. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26 3. 2. 4. 5 HDM and the SPECIAL language . . . . . . . . . . . . . . . . . . . . . . . . . . 27 3. 2. 4. 6 Structured analysis and design of real-time systems. . 27 3. 3 Support tools for FDTs. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . COMPUTERS,Software Development & Engineering,General

Process for System Architecture and Requirements Engineering This is the digital version of the printed book (Copyright © 2000). Derek Hatley and Imtiaz Pirbhai—authors of Strategies for Real-Time System Specification—join with influential consultant Peter Hruschka to present a much anticipated update to their widely implemented Hatley/Pirbhai methods. Process for System Architecture and Requirements Engineering introduces a new approach that is particularly useful for multidisciplinary system development: It applies equally well to all technologies and thereby provides a common language for developers in widely differing disciplines. The Hatley-Pirbhai-Hruschka approach (H/H/P) has another important feature: the coexistence of the requirements and architecture methods and of the corresponding models they produce. These two models are kept separate, but the approach fully records their ongoing and changing interrelationships. This feature is missing from virtually all other system and software development methods and from CASE tools that only automate the requirements model. System managers, system architects, system engineers, and managers and engineers in all of the diverse engineering technologies will benefit from this comprehensive, pragmatic text. In addition to its models of requirements and architecture and of the development process itself, the book uses in-depth case studies of a hospital monitoring system and of a multidisciplinary groundwater analysis system to illustrate the principles. Compatibility Between the H/H/P Methods and the UML: The Hatley/Pirbhai architecture and requirements methods—described in Strategies for Real-Time System Specification—have been widely used for almost two decades in system and software development. Now known as the Hatley/Hruschka/Pirbhai (H/H/P) methods, they have always been compatible with object-oriented software techniques, such as the UML, by defining architectural elements as classes, objects, messages, inheritance relationships, and so on. In Process for System Architecture and Requirements Engineering, that compatibility is made more specific through the addition of message diagrams, inheritance diagrams, and new notations that go with them. In addition, state charts, while never excluded, are now specifically included as a representation of sequential machines. These additions make definition of the system/software boundary even more straightforward, while retaining the clear separation of requirements and design at the system levels that is a hallmark of the H/H/P methods—not shared by most OO techniques. Once the transition to software is made, the developer is free to continue using the H/H/P methods, or to use the UML or any other software-specific technique. COMPUTERS,Software Development & Engineering,General

Software Architecture in Practice The award-winning and highly influential Software Architecture in Practice, Third Edition, has been substantially revised to reflect the latest developments in the field. In a real-world setting, the book once again introduces the concepts and best practices of software architecture—how a software system is structured and how that system’s elements are meant to interact. Distinct from the details of implementation, algorithm, and data representation, an architecture holds the key to achieving system quality, is a reusable asset that can be applied to subsequent systems, and is crucial to a software organization’s business strategy. The authors have structured this edition around the concept of architecture influence cycles. Each cycle shows how architecture influences, and is influenced by, a particular context in which architecture plays a critical role. Contexts include technical environment, the life cycle of a project, an organization’s business profile, and the architect’s professional practices. The authors also have greatly expanded their treatment of quality attributes, which remain central to their architecture philosophy—with an entire chapter devoted to each attribute—and broadened their treatment of architectural patterns. If you design, develop, or manage large software systems (or plan to do so), you will find this book to be a valuable resource for getting up to speed on the state of the art. Totally new material covers Contexts of software architecture: technical, project, business, and professional Architecture competence: what this means both for individuals and organizations The origins of business goals and how this affects architecture Architecturally significant requirements, and how to determine them Architecture in the life cycle, including generate-and-test as a design philosophy; architecture conformance during implementation; architecture and testing; and architecture and agile development Architecture and current technologies, such as the cloud, social networks, and end-user devices COMPUTERS,Software Development & Engineering,General

Implementing Domain-Driven Design Implementing Domain-Driven Design presents a top-down approach to understanding domain-driven design (DDD) in a way that fluently connects strategic patterns to fundamental tactical programming tools. Vaughn Vernon couples guided approaches to implementation with modern architectures, highlighting the importance and value of focusing on the business domain while balancing technical considerations. Building on Eric Evans’ seminal book, Domain-Driven Design , the author presents practical DDD techniques through examples from familiar domains. Each principle is backed up by realistic Java examples–all applicable to C# developers–and all content is tied together by a single case study: the delivery of a large-scale Scrum-based SaaS system for a multitenant environment. The author takes you far beyond “DDD-lite†approaches that embrace DDD solely as a technical toolset, and shows you how to fully leverage DDD’s “strategic design patterns†using Bounded Context, Context Maps, and the Ubiquitous Language. Using these techniques and examples, you can reduce time to market and improve quality, as you build software that is more flexible, more scalable, and more tightly aligned to business goals. Coverage includes Getting started the right way with DDD, so you can rapidly gain value from it Using DDD within diverse architectures, including Hexagonal, SOA, REST, CQRS, Event-Driven, and Fabric/Grid-Based Appropriately designing and applying Entities–and learning when to use Value Objects instead Mastering DDD’s powerful new Domain Events technique Designing Repositories for ORM, NoSQL, and other databases The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Software Development & Engineering,General

Essential Scrum A Practical Guide to the Most Popular Agile Process The Single-Source, Comprehensive Guide to Scrum for All Team Members, Managers, and Executives If you want to use Scrum to develop innovative products and services that delight your customers, Essential Scrum is the complete, single-source reference you’ve been searching for. Leading Scrum coach and trainer Kenny Rubin illuminates the values, principles, and practices of Scrum, and describes flexible, proven approaches that can help you implement it far more effectively. Whether you are new to Scrum or years into your use, this book will introduce, clarify, and deepen your Scrum knowledge at the team, product, and portfolio levels. Drawing from Rubin’s experience helping hundreds of organizations succeed with Scrum, this book provides easy-to-digest descriptions enhanced by more than two hundred illustrations based on an entirely new visual icon language for describing Scrum’s roles, artifacts, and activities. Essential Scrum will provide every team member, manager, and executive with a common understanding of Scrum, a shared vocabulary they can use in applying it, and practical knowledge for deriving maximum value from it. COMPUTERS,Software Development & Engineering,General

Adaptive Leadership Lessons from Agile’s First Decade…Leadership for Agile’s Next Decade The agile software movement has now been around for a full decade. As coauthor of the original Agile Manifesto, Jim Highsmith has been at its heart since the beginning. He’s spent the past decade helping hundreds of organizations transition to agile/lean. When it comes to agile, he’s seen it all–in a variety of industries, worldwide. Now, in Adaptive Leadership , he has compiled, updated, and extended his best writings about agile and lean methods for a management audience. Highsmith doesn’t just reveal what’s working and what isn’t; he offers a powerful new vision for extending agility across the enterprise. Drawing on what’s been learned in application development, this guide shows how to use adaptive leadership techniques to transform the way you deliver complete solutions, whatever form they take. You’ll learn how enterprise agility can enable the ambitious organizational missions that matter most; how leaders can deliver a continuous stream of value; how to think disruptively about opportunities, and how to respond quickly by creating more adaptive, innovative organizations. Coverage includes Discovering and executing new business opportunities far more quickly Delivering complete business solutions earlier, and iterating them more often Organizing for innovation, and systematically managing opportunity flow Clarifying the degree of strategic, portfolio, and operational agility you need, and focusing on your highest-value transformations Creating cultures that actually can adapt and learn Reinvigorating the roots of agile value and values Understanding IT’s changing value proposition, and retraining your people accordingly Integrating economics, products, and social responsibility Choosing metrics that guide agility, not counterproductive traditional metrics Understanding the financial implications of technical debt Optimizing business value by doing less–and guiding the process with â€NOT to do“ lists Speculating intelligently when you can’t plan away uncertainty Customizing management to each project’s needs (because not all projects should be equally agile) COMPUTERS,Software Development & Engineering,General

Mastering Visual Studio .NET Mastering Visual Studio .NET provides you, as an experienced programmer, with all the information needed to get the most out of the latest and greatest development tool from Microsoft®. It doesn't matter if you're an MFC, C++, STL, ATL, COM, Win32, Visual Basic, C#, HTML, XML, ASP.NET, database, web application, Web service, NT service, stand-alone client, or component programmer targeting Windows® or one of the Windows variants (i.e. Windows CE or the PocketPC) -- this is the book that will help you master the toolkit.Written by experienced developers and trainers John Flanders, Ian Griffiths, and Chris Sells, Mastering Visual Studio .NET begins with fundamental information about maximizing the power of Visual Studio .NET as it comes out of the box, including the following topics: projects and solutions files and the various file editors debugging web projects database projects setup projects To experience the full spectrum of functionality and extensibility, Mastering Visual Studio .NET provides you with the practical depth and detail needed to best put these features to work. The second section of the book is about extending VS.NET to suit your specific needs: integrating controls and components with VS.NET the VS.NET automation object model macros and add-ins custom wizards the Visual Studio Integration Program (VSIP) If you're serious about using the VS.NET toolkit, you'll want a book of this magnitude close by. Mastering Visual Studio .NET will take you beyond what you'll read in the standard documentation by offering hints and recommendations that the authors and the community at large have found to be useful after many years of experience. COMPUTERS,Software Development & Engineering,General

Code Complete Widely considered one of the best practical guides to programming, Steve McConnell’s original CODE COMPLETE has been helping developers write better software for more than a decade. Now this classic book has been fully updated and revised with leading-edge practices—and hundreds of new code samples—illustrating the art and science of software construction. Capturing the body of knowledge available from research, academia, and everyday commercial practice, McConnell synthesizes the most effective techniques and must-know principles into clear, pragmatic guidance. No matter what your experience level, development environment, or project size, this book will inform and stimulate your thinking—and help you build the highest quality code. Discover the timeless techniques and strategies that help you: Design for minimum complexity and maximum creativity Reap the benefits of collaborative development Apply defensive programming techniques to reduce and flush out errors Exploit opportunities to refactor—or evolve—code, and do it safely Use construction practices that are right-weight for your project Debug problems quickly and effectively Resolve critical construction issues early and correctly Build quality into the beginning, middle, and end of your project COMPUTERS,Software Development & Engineering,General

Level Up! The Guide to Great Video Game Design Want to design your own video games? Let expert Scott Rogers show you how! If you want to design and build cutting-edge video games but aren’t sure where to start, then the SECOND EDITION of the acclaimed Level Up! is for you! Written by leading video game expert Scott Rogers, who has designed the hits Pac Man World, Maximo and SpongeBob Squarepants, this updated edition provides clear and well-thought out examples that forgo theoretical gobbledygook with charmingly illustrated concepts and solutions based on years of professional experience. Level Up! 2nd Edition has been NEWLY EXPANDED to teach you how to develop marketable ideas, learn what perils and pitfalls await during a game’s pre-production, production and post-production stages, and provide even more creative ideas to serve as fuel for your own projects including: Developing your game design from the spark of inspiration all the way to production Learning how to design the most exciting levels, the most precise controls, and the fiercest foes that will keep your players challenged Creating games for mobile and console systems – including detailed rules for touch and motion controls Monetizing your game from the design up Writing effective and professional design documents with the help of brand new examples Level Up! 2nd Edition is includes all-new content, an introduction by David “God of War†Jaffe and even a brand-new chili recipe –making it an even more indispensable guide for video game designers both “in the field†and the classroom. Grab your copy of Level Up! 2nd Edition and let’s make a game! COMPUTERS,Software Development & Engineering,General

Object Thinking In OBJECT THINKING, esteemed object technologist David West contends that the mindset makes the programmer—not the tools and techniques. Delving into the history, philosophy, and even politics of object-oriented programming, West reveals how the best programmers rely on analysis and conceptualization—on thinking—rather than formal process and methods. Both provocative and pragmatic, this book gives form to what’s primarily been an oral tradition among the field’s revolutionary thinkers—and it illustrates specific object-behavior practices that you can adopt for true object design and superior results. Gain an in-depth understanding of: Prerequisites and principles of object thinking. Object knowledge implicit in eXtreme Programming (XP) and Agile software development. Object conceptualization and modeling. Metaphors, vocabulary, and design for object development. Learn viable techniques for: Decomposing complex domains in terms of objects. Identifying object relationships, interactions, and constraints. Relating object behavior to internal structure and implementation design. Incorporating object thinking into XP and Agile practice. COMPUTERS,Software Development & Engineering,General

Rapid Development Corporate and commercial software-development teams all want solutions for one important problem—how to get their high-pressure development schedules under control. In RAPID DEVELOPMENT, author Steve McConnell addresses that concern head-on with overall strategies, specific best practices, and valuable tips that help shrink and control development schedules and keep projects moving. Inside, you’ll find: A rapid-development strategy that can be applied to any project and the best practices to make that strategy work Candid discussions of great and not-so-great rapid-development practices—estimation, prototyping, forced overtime, motivation, teamwork, rapid-development languages, risk management, and many others A list of classic mistakes to avoid for rapid-development projects, including creeping requirements, shortchanged quality, and silver-bullet syndrome Case studies that vividly illustrate what can go wrong, what can go right, and how to tell which direction your project is going RAPID DEVELOPMENT is the real-world guide to more efficient applications development. COMPUTERS,Software Development & Engineering,General

Enterprise and Scrum, The It’s time to extend the benefits of Scrum—greater agility, higher-quality products, and lower costs—from individual teams to your entire enterprise. However, with Scrum’s lack of prescribed rules, the friction of change can be challenging as people struggle to break from old project management habits. In this book, agile-process revolution leader Ken Schwaber takes you through change management—for your organizational and interpersonal processes—explaining how to successfully adopt Scrum across your entire organization. A cofounder of Scrum, Ken draws from decades of experience, answering your questions through case studies of proven practices and processes. With them, you’ll learn how to adopt—and adapt—Scrum in the enterprise. And gain profound levels of transparency into your development processes. Discover how to: Evaluate the benefits of adopting Scrum in any size organization Initiate an enterprise transition project Implement a single, prioritized Product Backlog Organize effective Scrum teams using a top-down approach Adapt and apply solutions for integrating engineering practices across multiple teams Shorten release times by managing high-value increments Refine your Scrum practices and help reduce the length of Sprints COMPUTERS,Software Development & Engineering,General

Incremental Commitment Spiral Model, The “The title makes a huge promise: a way to divide commitment into increments that are both meetable (good news for developers) and meaningful (good news for managers and stakeholders). And the book makes good on that promise.†–Tom DeMarco, Principal, The Atlantic Systems Guild, author of Peopleware, Deadline, and Slack “I am seriously impressed with this ICSM book. Besides being conceptually sound, I was amazed by the sheer number of clear and concise characterizations of issues, relationships, and solutions. I wanted to take a yellow highlighter to it until I realized I’d be highlighting most of the book.†–Curt Hibbs, Chief Agile Evangelist, Boeing Use the ICSM to Generate and Evolve Your Life-Cycle Process Assets to Best Fit Your Organization’s Diverse and Changing Needs Many systems development practitioners find traditional “one-size-fits-all†processes inadequate for the growing complexity, diversity, dynamism, and assurance needs of their products and services. The Incremental Commitment Spiral Model (ICSM) responds with a principle- and risk-based framework for defining and evolving your project and corporate process assets, avoiding pitfalls and disruption, and leveraging opportunities to increase value. This book explains ICSM’s framework of decision criteria and principles, and shows how to apply them through relevant examples. It demonstrates ICSM’s potential for reducing rework and technical debt, improving maintainability, handling emergent requirements, and raising assurance levels. Its coverage includes What makes a system development successful ICSM’s goals, principles, and usage as a process-generation framework Creating and evolving processes to match your risks and opportunities Integrating your current practices and adopting ICSM concepts incrementally, focusing on your greatest needs and opportunities About the Website: Download the evolving ICSM guidelines, subprocesses, templates, tools, white papers, and academic support resources at csse.usc.edu/ICSM. COMPUTERS,Software Development & Engineering,General

Developing Safety-Critical Software The amount of software used in safety-critical systems is increasing at a rapid rate. At the same time, software technology is changing, projects are pressed to develop software faster and more cheaply, and the software is being used in more critical ways. Developing Safety-Critical Software: A Practical Guide for Aviation Software and DO-178C Compliance equips you with the information you need to effectively and efficiently develop safety-critical, life-critical, and mission-critical software for aviation. The principles also apply to software for automotive, medical, nuclear, and other safety-critical domains. An international authority on safety-critical software, the author helped write DO-178C and the U.S. Federal Aviation Administration’s policy and guidance on safety-critical software. In this book, she draws on more than 20 years of experience as a certification authority, an avionics manufacturer, an aircraft integrator, and a software developer to present best practices, real-world examples, and concrete recommendations. The book includes: An overview of how software fits into the systems and safety processes Detailed examination of DO-178C and how to effectively apply the guidance Insight into the DO-178C-related documents on tool qualification (DO-330), model-based development (DO-331), object-oriented technology (DO-332), and formal methods (DO-333) Practical tips for the successful development of safety-critical software and certification Insightful coverage of some of the more challenging topics in safety-critical software development and verification, including real-time operating systems, partitioning, configuration data, software reuse, previously developed software, reverse engineering, and outsourcing and offshoring An invaluable reference for systems and software managers, developers, and quality assurance personnel, this book provides a wealth of information to help you develop, manage, and approve safety-critical software more confidently. COMPUTERS,Software Development & Engineering,General

Functional Thinking If you’re familiar with functional programming basics and want to gain a much deeper understanding, this in-depth guide takes you beyond syntax and demonstrates how you need to think in a new way. Software architect Neal Ford shows intermediate to advanced developers how functional coding allows you to step back a level of abstraction so you can see your programming problem with greater clarity. Each chapter shows you various examples of functional thinking, using numerous code examples from Java 8 and other JVM languages that include functional capabilities. This book may bend your mind, but you’ll come away with a much better grasp of functional programming concepts. Understand why many imperative languages are adding functional capabilities Compare functional and imperative solutions to common problems Examine ways to cede control of routine chores to the runtime Learn how memoization and laziness eliminate hand-crafted solutions Explore functional approaches to design patterns and code reuse View real-world examples of functional thinking with Java 8, and in functional architectures and web frameworks Learn the pros and cons of living in a paradigmatically richer world If you’re new to functional programming, check out Josh Backfield’s book Becoming Functional . COMPUTERS,Software Development & Engineering,General

Mastering Risk and Procurement in Project Management Master the crucial risk management and procurement tasks that are indispensable to project success! In Mastering Risk and Procurement in Project Management, expert project manager and seasoned professor Wilson addresses every stage of the project where risk management and procurement are relevant, especially planning, monitoring, and control. Teaching through relevant examples and case studies, Wilson explains: Why risk management and procurement are so crucial to achieving your project's goals The deep and surprising linkages that exist across risk management and procurement How to avoid common pitfalls How to integrate best-practice risk management and procurement throughout your PMBOK processes. Drawing on his own extensive experience, he offers in-depth coverage of topics ranging from contracting and risk monitoring to project close-out, and gives readers practical knowledge of critical processes and tasks in project management. COMPUTERS,Software Development & Engineering,General

User Story Mapping User story mapping is a valuable tool for software development, once you understand why and how to use it. This insightful book examines how this often misunderstood technique can help your team stay focused on users and their needs without getting lost in the enthusiasm for individual product features. Author Jeff Patton shows you how changeable story maps enable your team to hold better conversations about the project throughout the development process. Your team will learn to come away with a shared understanding of what you’re attempting to build and why. Get a high-level view of story mapping, with an exercise to learn key concepts quickly Understand how stories really work, and how they come to life in Agile and Lean projects Dive into a story’s lifecycle, starting with opportunities and moving deeper into discovery Prepare your stories, pay attention while they’re built, and learn from those you convert to working software COMPUTERS,Software Development & Engineering,General

Rapid Prototyping Software for Avionics Systems The design, implementation and validation of avionics and aeronautical systems have become extremely complex tasks due to the increase of functionalities that are deployed in current avionics systems and the need to be able certify them before putting them into production. This book proposes a methodology to enable the rapid prototyping of such a system by considering from the start the certification aspects of the solution produced. This method takes advantage of the model-based design approaches as well as the use of formal methods for the validation of these systems. Furthermore, the use of automatic software code generation tools using models makes it possible to reduce the development phase as well as the final solution testing. This book presents, firstly, an overview of the model-based design approaches such as those used in the field of aeronautical software engineering. Secondly, an original methodology that is perfectly adapted to the field of aeronautical embedded systems is introduced. Finally, the authors illustrate the use of this method using a case study for the design, implementation and testing of a new generation aeronautical router. COMPUTERS,Software Development & Engineering,General

Learning Agile Learning Agile is a comprehensive guide to the most popular agile methods, written in a light and engaging style that makes it easy for you to learn. Agile has revolutionized the way teams approach software development, but with dozens of agile methodologies to choose from, the decision to "go agile" can be tricky. This practical book helps you sort it out, first by grounding you in agile’s underlying principles, then by describing four specific—and well-used—agile methods: Scrum, extreme programming (XP), Lean, and Kanban. Each method focuses on a different area of development, but they all aim to change your team’s mindset—from individuals who simply follow a plan to a cohesive group that makes decisions together. Whether you’re considering agile for the first time, or trying it again, you’ll learn how to choose a method that best fits your team and your company. Understand the purpose behind agile’s core values and principles Learn Scrum’s emphasis on project management, self-organization, and collective commitment Focus on software design and architecture with XP practices such as test-first and pair programming Use Lean thinking to empower your team, eliminate waste, and deliver software fast Learn how Kanban’s practices help you deliver great software by managing flow Adopt agile practices and principles with an agile coach COMPUTERS,Software Development & Engineering,General

The Art of Application Performance Testing Because performance is paramount today, this thoroughly updated guide shows you how to test mission-critical applications for scalability and performance before you deploy them—whether it’s to the cloud or a mobile device. You’ll learn the complete testing process lifecycle step-by-step, along with best practices to plan, coordinate, and conduct performance tests on your applications. Set realistic performance testing goals Implement an effective application performance testing strategy Interpret performance test results Cope with different application technologies and architectures Understand the importance of End User Monitoring (EUM) Use automated performance testing tools Test traditional local applications, web applications, and web services Recognize and resolves issues often overlooked in performance tests Written by a consultant with over 15 years’ experience with performance testing, The Art of Application Performance Testing thoroughly explains the pitfalls of an inadequate testing strategy and offers a robust, structured approach for ensuring that your applications perform well and scale effectively when the need arises. COMPUTERS,Software Development & Engineering,General

Patterns, Principles, and Practices of Domain-Driven Design Methods for managing complex software construction following the practices, principles and patterns of Domain-Driven Design with code examples in C# This book presents the philosophy of Domain-Driven Design (DDD) in a down-to-earth and practical manner for experienced developers building applications for complex domains. A focus is placed on the principles and practices of decomposing a complex problem space as well as the implementation patterns and best practices for shaping a maintainable solution space. You will learn how to build effective domain models through the use of tactical patterns and how to retain their integrity by applying the strategic patterns of DDD. Full end-to-end coding examples demonstrate techniques for integrating a decomposed and distributed solution space while coding best practices and patterns advise you on how to architect applications for maintenance and scale. Offers a thorough introduction to the philosophy of DDD for professional developers Includes masses of code and examples of concept in action that other books have only covered theoretically Covers the patterns of CQRS, Messaging, REST, Event Sourcing and Event-Driven Architectures Also ideal for Java developers who want to better understand the implementation of DDD COMPUTERS,Software Development & Engineering,General

Android App Development For Dummies The updated edition of the bestselling guide to Android app development If you have ambitions to build an Android app, this hands-on guide gives you everything you need to dig into the development process and turn your great idea into a reality! In this new edition of Android App Development For Dummies, you'll find easy-to-follow access to the latest programming techniques that take advantage of the new features of the Android operating system. Plus, two programs are provided: a simple program to get you started and an intermediate program that uses more advanced aspects of the Android platform. Android mobile devices currently account for nearly 80% of mobile phone market share worldwide, making it the best platform to reach the widest possible audience. With the help of this friendly guide, developers of all stripes will quickly find out how to install the tools they need, design a good user interface, grasp the design differences between phone and tablet applications, handle user input, avoid common pitfalls, and turn a "meh" app into one that garners applause. Create seriously cool apps for the latest Android smartphones and tablets Adapt your existing apps for use on an Android device Start working with programs and tools to create Android apps Publish your apps to the Google Play Store Whether you're a new or veteran programmer, Android App Development For Dummies will have you up and running with the ins and outs of the Android platform in no time. COMPUTERS,Software Development & Engineering,General

Software Craftsman, The Be a Better Developer and Deliver Better Code Despite advanced tools and methodologies, software projects continue to fail. Why? Too many organizations still view software development as just another production line. Too many developers feel that way, too—and they behave accordingly. In The Software Craftsman: Professionalism, Pragmatism, Pride, Sandro Mancuso offers a better and more fulfilling path. If you want to develop software with pride and professionalism; love what you do and do it with excellence; and build a career with autonomy, mastery, and purpose, it starts with the recognition that you are a craftsman. Once you embrace this powerful mindset, you can achieve unprecedented levels of technical excellence and customer satisfaction. Mancuso helped found the world’s largest organization of software craftsmen; now, he shares what he’s learned through inspiring examples and pragmatic advice you can use in your company, your projects, and your career. You will learn Why agile processes aren’t enough and why craftsmanship is crucial to making them work How craftsmanship helps you build software right and helps clients in ways that go beyond code How and when to say “No†and how to provide creative alternatives when you do Why bad code happens to good developers and how to stop creating and justifying it How to make working with legacy code less painful and more productive How to be pragmatic—not dogmatic—about your practices and tools How to lead software craftsmen and attract them to your organization What to avoid when advertising positions, interviewing candidates, and hiring developers How developers and their managers can create a true culture of learning How to drive true technical change and overcome deep patterns of skepticism Sandro Mancuso has coded for startups, software houses, product companies, international consultancies, and investment banks. In October 2013, he cofounded Codurance, a consultancy based on Software Craftsmanship principles and values. His involvement with Software Craftsmanship began in 2010, when he founded the London Software Craftsmanship Community (LSCC), now the world’s largest and most active Software Craftsmanship community, with more than two thousand craftsmen. For the past four years, he has inspired and helped developers to organize Software Craftsmanship communities throughout Europe, the United States, and the rest of the world. COMPUTERS,Software Development & Engineering,General

Swift For Dummies Get up and running with Swift—swiftly Brimming with expert advice and easy-to-follow instructions, Swift For Dummies shows new and existing programmers how to quickly port existing Objective-C applications into Swift and get into the swing of the new language like a pro. Designed from the ground up to be a simpler programming language, it's never been easier to get started creating apps for the iPhone or iPad, or applications for Mac OS X. Inside the book, you'll find out how to set up Xcode for a new Swift application, use operators, objects, and data types, and control program flow with conditional statements. You'll also get the scoop on creating new functions, statements, and declarations, learn useful patterns in an object-oriented environment, and take advantage of frameworks to speed your coding along. Plus, you'll find out how Swift does away with pointer variables and how to reference and dereference variables instead. Set up a playground development environment for Mac, iPhone, iPad, and wearable computers Move an existing Objective-C program to Swift Take advantage of framework components and subcomponents Create an app that uses location, mapping, and social media Whether you're an existing Objective-C programmer looking to port your code to Swift or you've never programmed for Apple in the past, this fun and friendly guide gets you up to speed swiftly. COMPUTERS,Software Development & Engineering,General

Elements of Hypermedia Design The hypermedia authoring process has been vividly described in a special issue of the Economist as a combination of writing a book, a play, a film, and a radio or television show: A hypermedia document combines all these elements and adds some of its own. The author' s first job is to structure and explain all of the infor mation. The author then must distill the information into brief, descriptive nodes. Each node has to contain a Iist of the ingredients, and instructions on how the ingredients are mixed together to the greatest advantage. The structure of the material provided is translated into an architectural metaphor of some kind; much of the designer' s work is the creation of this imaginary space. Then, the designers must chart the details of what to animate, what to film, who to inter view, and how to arrange the information in the space tobe built [Eco95a]. This book presents guidelines, tools, and techniques for prospective authors such that they can design better hypermedia documents and applications. lt surveys the different techniques used to organize, search, and structure infor mation in a large information system. It then describes the algorithms used to locate, reorganize, and link data to enable navigation and retrieval. It Iooks in detail at the creation and presentation of certain types of visual information, namely algorithm animations. It introduces new mechanisms for editing audio and video data streams. COMPUTERS,Software Development & Engineering,General

Fundamentals of Operating Systems An operating system is probably the most important part of the body of soft ware which goes with any modem computer system. Its importance is reflected in the large amount of manpower usually invested in its construction, and in the mystique by which it is often surrounded. To the non-expert, the design and construction of operating systems has often appeared an activity impenetrable to those who do not practise it. I hope this book will go some way toward dispelling the mystique, and encourage a greater general under standing of the principles on which operating systems are constructed. The material in the book is based on a course of lectures I have given for the past few years to undergraduate students of computer science. The book is therefore a suitable introduction to operating systems for students who have a basic grounding in computer science, or for people who have worked with computers for some time. Ideally the reader should have a knowledge of pro gramming and be familiar with general machine architecture, common data structures such as lists and trees, and the functions of system software such as compilers, loaders and editors. It will also be helpful if he or she has had some experience of using a large operating system, seeing it, as it were, from the outside. COMPUTERS,Software Development & Engineering,General

Nonlinear Optimization and Applications This volume contains the edited texts of the lectures presented at the workshop on Nonlinear Optimization: Theory and Applications, held in Erice at the "G. Stampacchia" School of Mathematics of the "E. Majorana" International Centre for Scientific Culture June 13-21, 1995. The meeting was conceived to review and discuss recent advances and promising research trends concerning theory, algorithms, and innovative applications in the field This is a field of mathematics which is providing viable of Nonlinear Optimization. tools in engineering, in economics and in other applied sciences, and which is giving a great contribution also in the solution of the more practiced linear optimization prob lems. The meeting was attended by approximately 70 people from 18 countries. Besides the lectures, several formal and informal discussions took place. The result was a broad exposure providing a wide and deep understanding of the present research achievements in the field. We wish to express our appreciation for the active contributions of all the partici pants in the meeting. Our gratitude is due to the Ettore Majorana Center in Erice, which offered its facilities and stimulating environment: its staff was certainly instrumental for the success of the meeting. Our gratitude is also due to Francisco Facchinei and Massino Roma for the time spent in the organization of the workshop, and to Giuliana Cai for the careful typesetting of this volume. COMPUTERS,Software Development & Engineering,General

Software Design for Real-time Systems WHAT IS THIS BOOKABOUT7 In recent times real-time computer systems have become increasingly complex and sophisticated. It has now become apparent that, to implement such schemes effectively, professional, rigorous software methods must be used. This includes analysis, design and implementation. Unfortunately few textbooks cover this area well. Frequently they are hardware oriented with limited coverage of software, or software texts which ignore the issues of real-time systems. This book aims to fill that gap by describing the total software design and is given development process for real-time systems. Further, special emphasis of microprocessor-based real-time embedded systems. to the needs WHAT ARE REAL-TIME COMPUTER SYSTEMS? Real-time systems are those which must produce correct responses within a definite time limit. Should computer responses exceed these time bounds then performance degradation and/or malfunction results. WHAT ARE REAL-TIME EMBEDDED COMPUTER SYSTEMS? Here the computer is merely one functional element within a real-time system; it is not a computing machine in its own right. WHO SHOULD READ THIS BOOK? Those involved, or who intend to get involved, in the design of software for real-time systems. It is written with both software and hardware engineers in mind, being suitable for students and professional engineers. COMPUTERS,Software Development & Engineering,General

Object-Oriented Software in C++ COMPUTERS,Software Development & Engineering,General

Health Care Computing Most health professionals have to use computers - at least some of the time. Frequently, those computers are personal computers -the generic name for the ones that are variously known as 'IBM compatible' or 'IBM clones' or just PCs. This separates them out from certain other makes such as the Apple Macintosh, the Amstrad dedicated word processor, the Atari, Amiga and a number of others. This book is about PCs. When you need information about your computer when you are busy, you don't want to have to wade through piles of manuals to find what you need. You often need a fairly straightforward piece of information - now. Computers can be infuriating. When they are up and running properly, they can save time and help you to be more productive. When something goes wrong, they can be extremely frustrating. Once you have called in someone else to fix your problem, it is often apparent that the answer to your problem was only a few keystrokes away. This book aims at supplying you with small chunks of information that can aid your productivity, get you out of awkward corners and help you to become more at home with your Pc. It has been my experience - as a health care lecturer and as a regular com puter user - that you need to develop a certain baseline of confidence in working with them. COMPUTERS,Software Development & Engineering,General

Professional Android The comprehensive developer guide to the latest Android features and capabilities Professional Android, 4th Edition shows developers how to leverage the latest features of Android to create robust and compelling mobile apps. This hands-on approach provides in-depth coverage through a series of projects, each introducing a new Android platform feature and highlighting the techniques and best practices that exploit its utmost functionality. The exercises begin simply, and gradually build into advanced Android development. Clear, concise examples show you how to quickly construct real-world mobile applications. This book is your guide to smart, efficient, effective Android development. Learn the best practices that get more out of Android Understand the anatomy, lifecycle, and UI metaphor of Android apps Design for all mobile platforms, including tablets Utilize both the Android framework and Google Play services COMPUTERS,Software Development & Engineering,General

Scrumban [R]Evolution, The Scrumban allows you to use Kanban as a catalyst for increasingly valuable changes to your existing software development processes, amplifying and expanding upon Scrum’s benefits. Now, there’s a definitive guide to Scrumban that explains what it is (and isn’t), how and why it works, and how to use it to improve both team and organisational performance. Comprehensive, coherent, and practical, The Scrumban [R]Evolution will help you incrementally apply proven Lean/Agile principles to get what matters most: pragmatic, bottom-line results. Pioneering Scrumban coach Ajay Reddy clarifies Scrumban’s core concepts and principles, and illuminates their application through real-life examples. He takes you from the absolute basics through sustainable adoption, and from choosing metrics to advanced forecasting and adaptive management. Whatever your role in the organisation, this essential guide liberates you to tailor Kanban systems based on your unique challenges–and to solve delivery problems and improvement stagnation you haven’t been able to solve with Scrum alone. Discover how Scrumban can help you reignite stalled Agile initiatives Clarify crucial relationships between purpose, values, and performance Quickly develop shared understanding in and across teams Use Scrumban to better manage Product Owner/Customer expectations Improve the rollout of Scrum in any team using Scrumban Use Scrumban and let real improvements spread with least resistance Use the right metrics to gain insight, track progress, and improve forecasting Take advantage of Scrumban’s advanced capabilities as you gain experience Develop leaders to successfully guide your Agile initiatives Integrate modeling to reliably refine your forecasting and decision-making The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Software Development & Engineering,General

Managing Agile This book examines agile approaches from a management perspective by focusing on matters of strategy, implementation, organization and people. It examines the turbulence of the marketplace and business environment in order to identify what role agile management has to play in coping with such change and uncertainty. Based on observations, personal experience and extensive research, it clearly identifies the fabric of the agile organization, helping managers to become agile leaders in an uncertain world. The book opens with a broad survey of agile strategies, comparing and contrasting some of the major methodologies selected on the basis of where they lie on a continuum of ceremony and formality, ranging from the minimalist technique-driven and software engineering focused XP, to the pragmatic product-project paradigm that is Scrum and its scaled counterpart SAFe®, to the comparatively project-centric DSDM. Subsequently, the core of the book focuses on DSDM, owing to the method’s comprehensive elaboration of program and project management practices. This work will chiefly be of interest to all those with decision-making authority within their organizations (e.g., senior managers, line managers, program, project and risk managers) and for whom topics such as strategy, finance, quality, governance and risk management constitute a daily aspect of their work. It will, however, also be of interest to those readers in advanced management or business administration courses (e.g., MBA, MSc), who wish to engage in the management of agile organizations and thus need to adapt their skills and knowledge accordingly. COMPUTERS,Software Development & Engineering,General

Analysis Patterns ALERT: Before you purchase, check with your instructor or review your course syllabus to ensure that you select the correct ISBN. Several versions of Pearson's MyLab & Mastering products exist for each title, including customized versions for individual schools, and registrations are not transferable. In addition, you may need a CourseID, provided by your instructor, to register for and use Pearson's MyLab & Mastering products. Student can use the URL and phone number below to help answer questions: http://247pearsoned.custhelp.com/app/home 800-677-6337 Packages Access codes for Pearson's MyLab & Mastering products may not be included when purchasing or renting from companies other than Pearson; check with the seller before completing your purchase. Used or rental books If you rent or purchase a used book with an access code, the access code may have been redeemed previously and you may have to purchase a new access code. Access codes Access codes that are purchased from sellers other than Pearson carry a higher risk of being either the wrong ISBN or a previously redeemed code. Check with the seller prior to purchase. This innovative book recognizes the need within the object-oriented community for a book that goes beyond the tools and techniques of the typical methodology book. In Analysis Patterns: Reusable Object Models, Martin Fowler focuses on the end result of object-oriented analysis and design—the models themselves. He shares with you his wealth of object modeling experience and his keen eye for identifying repeating problems and transforming them into reusable models. Analysis Patterns provides a catalogue of patterns that have emerged in a wide range of domains including trading, measurement, accounting and organizational relationships. Recognizing that conceptual patterns cannot exist in isolation, the author also presents a series of "support patterns" that discuss how to turn conceptual models into software that in turn fits into an architecture for a large information system. Included in each pattern is the reasoning behind their design, rules for when they should and should not be used, and tips for implementation. The examples presented in this book comprise a cookbook of useful models and insight into the skill of reuse that will improve analysis, modeling and implementation. COMPUTERS,Software Development & Engineering,General

ITSM COMPUTERS,Software Development & Engineering,General

The Sun Technology Papers The Technology of Sun M icrosystems Two years ago, Sun Microsystems began publishing a quarterly tech nical journal, Sun Technology: The Journal for Sun Users. Since then, its pages have explored in detail diverse technology and products relating to Sun. The journal's technically sophisticated readers are likely to apply the information published in the journal to their work. Sun Technology has been written by technologists for technologists. In the pages of The Sun Technology Papers, you will find an extensive selection of those articles. No other single volume offers you such a broad view of Sun-related technology and products. Yet this sweeping embrace of subjects does not diminish the level of detail in this collection. Short of Sun's 40 pounds or so of documentation, no other single source provides as deep and broad an understanding of Sun technology as this book does. Because Sun is a key developer in so many areas of computer technology, the book comprises four general sections. The first, "Soft ware," includes chapters on Open Network Computing, Sun's compil ers, SunOS and SPARC, and the Network Software Environment. The "Hardware" section covers SPARC in great detail and includes the most in-depth examination of the popular SPARCstation 1. This sec tion also contains chapters on the Sun386i workstation. COMPUTERS,Software Development & Engineering,General

First International Workshop on Larch The papers in this volume were presented at the First International Workshop on Larch, held at MIT Endicott House near Boston on 13-15 July 1992. Larch is a family of formal specification languages and tools, and this workshop was a forum for those who have designed the Larch languages, built tool support for them, particularly the Larch Prover, and used them to specify and reason about software and hardware systems. The Larch Project started in 1980, led by John Guttag at MIT and James Horning, then at Xerox/Palo Alto Research Center and now at Digital Equipment Corporation/Systems Research Center (DEC/SRC). Major applications have included VLSI circuit synthesis, medical device communications, compiler development and concurrent systems based on Lamport's TLA, as well as several applications to classical theorem proving and algebraic specification. Larch supports a two-tiered approach to specifying software and hardware modules. One tier of a specification is wrillen in the Larch Shared Language (LSL). An LSL specification describes mathematical abstractions such as sets, relations, and algebras; its semantics is defined in terms of first-order theories. The second tier is written in a Larch interface language, one designed for a specific programming language. An interface specification describes the effects of individual modules, e.g. state changes, resource allocation, and exceptions; its semantics is defined in terms of first-order predicates over two states, where state is defined in terms of the programming language's notion of state. Thus, LSL is programming language independent; a Larch interface language is programming language dependent. COMPUTERS,Software Development & Engineering,General

Object Orientation in Z This collection of papers draws together a variety of approaches for adding ob ject orientation to the Z formal specification language. These papers are not a conference proceedings, but have a slightly more complicated his tory. This work has grown and evolved from some work originally done in the ZIP project, under the United Kingdom's Department of Trade and Industry (DTI) IED initiative. ZIP is a three year project which aims to make the use of the Z specification language more widespread. It hopes to achieve this by producing a standard for Zj developing a method for Zj building tool support for Zj and carrying out research into refinement, proof and concurrency in Z. The ZIP methods work includes performing a survey of current Z practitioners (reported in [Barden et al. 1992])j investigating current styles and methods of Z usagej and developing a Z Method handbook (available early in 1993). As part of this work, we carried out a comparative study of the ways in which object orientation has been combined with Z. A summary of that work has been published as [Stepney et al. 1992]. COMPUTERS,Software Development & Engineering,General

Z User Workshop, Oxford 1990 The approach described in [JonSl, JonS3a, JonS3b] set out to extend operation decom position methods for sequential programs - such as are used in VDM [Jon90] - to cover concurrent shared-variable systems. The essential step in [JonSl] was to recognise that 1 inter/erence had to be specified. This is necessary in order to achieve a notion of compo sitionality - contrast [Owi75]. Rather than the many erudite definitions of composition ality (e. g. [ZwiSS]), the view taken here is that, when a development task is decomposed into sub-tasks, these must be simpler than the original 'task. This is easy to achieve for sequential programs: decomposing a specified operation S into (Sl; S2), the specifica tions of the Sj should neither include unnecessary information from each other nor from the context (i. e. S). An interesting discussion of the 'Quest for Compositionality' (in the context of concurrency) is contained in [dRS5, dRS6]. The rely/guarantee idea provided an existence proof that specifications and developments could be made powerful enough to cope with some forms of interference. The work initially attracted little attention but 2 3 there have recently been some critiques and attempts to extend the work • Most notably, Ketil St~len's thesis [St~90] addresses the main shortcomings of [JonSl]: the fact that no attempt had been made to handle synchronization has been remedied by adding a wait condition and other limitations of expressiveness have been shown to succumb to the judicious use of auxiliary variables. COMPUTERS,Software Development & Engineering,General

Formal Methods for Trustworthy Computer Systems (FM89) The 1989 Workshop on the Assessment of Formal Methods for Trustworthy Com puter Systems (FM89} was an invitational workshop that brought together repre sentatives from the research, commercial and governmental spheres of Canada, the United Kingdom, and the United States. The workshop was held in Halifax, Nova Scotia, Canada, from July 23 through July 27, 1989. This document reports the activities, observations, recommendations and conclusions resulting. from FM89. 1. 1 Purpose of Workshop The primary purpose for holding FM89 was to assess the role of formal methods in the development and fielding of trustworthy critical systems. The need for this assessment was predicated upon four observations: 1. Critical systems are increasingly being controlled by computer systems; 2. Existing techniques for developing, assuring and certifying computer-based critical systems are inadequate; 3. Formal methods have the potential for playing the same role in the devel opment of computer-based systems as applied mathematics does for other engineering disciplines; and 4. Formal methods have had limited impact on the development of comput- based systems and supporting technologies. · The goal of the workshop was to complete the following tasks: 1. Assess the problems retarding the development of trustworthy critical systems; 2. Determine the (potential) impact of applying formal methods techniques to the development of trustworthy critical systems; 3. Determine the research and development required to facilitate a broader ap plication of formal methods techniques; 4. COMPUTERS,Software Development & Engineering,General

User-Centred Requirements for Software Engineering Environments The idea for this workshop originated when I came across and read Martin Zelkowitz's book on Requirements for Software Engineering Environments (the proceedings of a small workshop held at the University of Maryland in 1986). Although stimulated by the book I was also disappointed in that it didn't adequately address two important questions - "Whose requirements are these?" and "Will the environment which meets all these requirements be usable by software engineers?". And thus was the decision made to organise this workshop which would explicitly address these two questions. As time went by setting things up, it became clear that our workshop would happen more than five years after the Maryland workshop and thus, at the same time as addressing the two questions above, this workshop would attempt to update the Zelkowitz approach. Hence the workshop acquired two halves, one dominated by discussion of what we already know about usability problems in software engineering and the other by discussion of existing solutions (technical and otherwise) to these problems. This scheme also provided a good format for bringing together those in the HeI community concerned with the human factors of software engineering and those building tools to solve acknowledged, but rarely understood problems. COMPUTERS,Software Development & Engineering,General

UML @ Classroom This textbook mainly addresses beginners and readers with a basic knowledge of object-oriented programming languages like Java or C#, but with little or no modeling or software engineering experience – thus reflecting the majority of students in introductory courses at universities. Using UML, it introduces basic modeling concepts in a highly precise manner, while refraining from the interpretation of rare special cases. After a brief explanation of why modeling is an indispensable part of software development, the authors introduce the individual diagram types of UML (the class and object diagram, the sequence diagram, the state machine diagram, the activity diagram, and the use case diagram), as well as their interrelationships, in a step-by-step manner. The topics covered include not only the syntax and the semantics of the individual language elements, but also pragmatic aspects, i.e., how to use them wisely at various stages in the software development process. To this end, the work is complemented with examples that were carefully selected for their educational and illustrative value. Overall, the book provides a solid foundation and deeper understanding of the most important object-oriented modeling concepts and their application in software development. An additional website offers a complete set of slides to aid in teaching the contents of the book, exercises and further e-learning material. COMPUTERS,Software Development & Engineering,General
The Programming and Proof System ATES Today, people use a large number of "systems" ranging in complexity from washing machines to international airline reservation systems. Computers are used in nearly all such systems: accuracy and security are becoming increasingly essential. The design of such computer systems should make use of development methods as systematic as those used in other engineering disciplines. A systematic development method must provide a way of writing specifications which are both precise and concise; it must also supply a way of relating design to specification. A concise specification can be achieved by restricting attention to what a system has to do: all considerations of implementation details are postponed. With computer systems, this is done by: 1) building an abstract model of the system -operations being specified by pre-and post-conditions; 2) defining languages by mapping program texts onto some collection of objects modelizing the concepts of the system to be dealt with, whose meaning is understood; 3) defining complex data objects in terms of abstractions known from mathematics. This last topic, the use of abstract data types, pervades all work on specifications and is necessary in order to apply ideas to systems of significant complexity. The use of mathematics based notations is the best way to achieve precision. 1.1 ABSTRACT DATA TYPES, PROOF TECHNIQUES From a practical point of view, a solution to these three problems consists to introduce abstract data types in the programming languages, and to consider formal proof methods. COMPUTERS,Software Development & Engineering,General

Database Application Engineering with DAIDA In the early 1980s, a trend towards formal undeIStanding and knowledge-based assistance for the development and maintenance of database-intensive information systems became apparent. The group of John Mylopoulos at the UniveISity of Toronto and their European collaboratoIS moved from semantic models of information systems design (Taxis project) towards earlier stages of the software lifecycle. Joachim Schmidt's group at the University of Hamburg completed their early work on the design and implementation of database programming languages (Pascal/R) and began to consider tools for the development of large database program packages. The Belgian company BIM developed a fast commercial Prolog which turned out to be useful as an implementation language for object oriented knowledge representation schemes and as a prototyping tool for formal design models. Case studies by Vasant Dhar and Matthias Jarke in New York pointed out the need for formally representing process knowledge, and a number of projects in the US and Europe began to consider computer assistance (CASE) as a viable approach to support software engineering. In 1985, the time appeared ripe for an attempt at integrating these experiences in a comprehensive CASE framework relating all phases of an information systems lifecycle. The Commission of the European Communities decided in early 1986 to fund this joint effort by six European software houses and research institutions in the Software Technology section of the ESPRIT I program. The project was given the number 892 and the title DAIDA - Development Assistance for Intelligent Database Applications. COMPUTERS,Software Development & Engineering,General

Algebraic and Coalgebraic Methods in the Mathematics of Program Construction Program construction is about turning specifications of computer software into implementations. Recent research aimed at improving the process of program construction exploits insights from abstract algebraic tools such as lattice theory, fixpoint calculus, universal algebra, category theory, and allegory theory.This textbook-like tutorial presents, besides an introduction, eight coherently written chapters by leading authorities on ordered sets and complete lattices, algebras and coalgebras, Galois connections and fixed point calculus, calculating functional programs, algebra of program termination, exercises in coalgebraic specification, algebraic methods for optimization problems, and temporal algebra. COMPUTERS,Software Development & Engineering,General

Scrum Field Guide, The Thousands of organizations are adopting Scrum to transform the way they execute complex projects, in software and beyond. This guide will give you the skills and confidence needed to deploy Scrum, resulting in high-performing teams and satisfied customers. Drawing on years of hands-on experience helping companies succeed, Certified Scrum Trainer (CST) Mitch Lacey helps you overcome the major challenges of Scrum adoption and the deeper issues that emerge later. Extensively revised to reflect improved Scrum practices and tools, this edition adds an all-new section of tips from the field. Lacey covers many new topics, including immersive interviewing, collaborative estimation, and deepening business alignment. In 35 engaging chapters, you’ll learn how to build support and maximize value across your company. Now part of the renowned Mike Cohn Signature Series on agile development, this pragmatic guide addresses everything from establishing roles and priorities to determining team velocity, setting sprint length, and conducting customer reviews. Coverage includes Bringing teams and new team members on board Creating a workable definition of “done†Planning for short-term wins, and removing impediments to success Balancing predictability and adaptability in release planning Running productive daily scrums Fixing failing sprints Accurately costing projects, and measuring the value they deliver Managing risks in dynamic Scrum projects Prioritizing and estimating backlogs Working with distributed and offshore teams Institutionalizing improvements, and extending agility throughout the organization Packed with real-world examples straight from Lacey’s experience, this book will be invaluable to anyone transitioning to Scrum, seeking to improve their early results, or trying to get back on track. COMPUTERS,Software Development & Engineering,General

Semantic Networks for Understanding Scenes Figure 1.1. An outdoor scene "A bus is passing three cars which are parking between trees at the side of the road. Houses having two storeys are lined up at the street. 3 4 Introduction Figure 1.2. An assembly scene There seems to be a small open place between the group of houses in the foreground and the store in the background". In such or a similar way the content of the natural scene shown above can be described. It is quite easy to give such a short description. The problem is somewhat more complex for the second image. First of all, it can be stated that the image does not show an everyday scene. It appears as a kind of man made surrounding. But everyone can accept the following statements about this image: 1. The image shows a snapshot of an assembly line. 2. The robot in front is screwing. 3. There is no person in the working area of the robots. 4. All objects on the conveyor belt are worked on by robots. There are no free objects on the belt. COMPUTERS,Software Development & Engineering,General

Quasidifferentiability and Nonsmooth Modelling in Mechanics, Engineering and Economics Nonsmooth energy functions govern phenomena which occur frequently in nature and in all areas of life. They constitute a fascinating subject in mathematics and permit the rational understanding of yet unsolved or partially solved questions in mechanics, engineering and economics. This is the first book to provide a complete and rigorous presentation of the quasidifferentiability approach to nonconvex, possibly nonsmooth, energy functions, of the derivation and study of the corresponding variational expressions in mechanics, engineering and economics, and of their numerical treatment. The new variational formulations derived are illustrated by many interesting numerical problems. The techniques presented will permit the reader to check any solution obtained by other heuristic techniques for nonconvex, nonsmooth energy problems. A civil, mechanical or aeronautical engineer can find in the book the only existing mathematically sound technique for the formulation and study of nonconvex, nonsmooth energy problems. Audience: The book will be of interest to pure and applied mathematicians, physicists, researchers in mechanics, civil, mechanical and aeronautical engineers, structural analysts and software developers. It is also suitable for graduate courses in nonlinear mechanics, nonsmooth analysis, applied optimization, control, calculus of variations and computational mechanics. COMPUTERS,Software Development & Engineering,General

Building Maintainable Software, Java Edition Have you ever felt frustrated working with someone else’s code? Difficult-to-maintain source code is a big problem in software development today, leading to costly delays and defects. Be part of the solution. With this practical book, you’ll learn 10 easy-to-follow guidelines for delivering Java software that’s easy to maintain and adapt. These guidelines have been derived from analyzing hundreds of real-world systems. Written by consultants from the Software Improvement Group (SIG), this book provides clear and concise explanations, with advice for turning the guidelines into practice. Examples for this edition are written in Java, while our companion C# book provides workable examples in that language. Write short units of code: limit the length of methods and constructors Write simple units of code: limit the number of branch points per method Write code once, rather than risk copying buggy code Keep unit interfaces small by extracting parameters into objects Separate concerns to avoid building large classes Couple architecture components loosely Balance the number and size of top-level components in your code Keep your codebase as small as possible Automate tests for your codebase Write clean code, avoiding "code smells" that indicate deeper problems COMPUTERS,Software Development & Engineering,General

Java Programming for Android Developers For Dummies Develop the next killer Android App using Java programming! Android is everywhere! It runs more than half the smartphones in the U.S.—and Java makes it go. If you want to cash in on its popularity by learning to build Android apps with Java, all the easy-to-follow guidance you need to get started is at your fingertips. Inside, you'll learn the basics of Java and grasp how it works with Android; then, you'll go on to create your first real, working application. How cool is that? The demand for Android apps isn't showing any signs of slowing, but if you're a mobile developer who wants to get in on the action, it's vital that you get the necessary Java background to be a success. With the help of Java Programming for Android Developers For Dummies, you'll quickly and painlessly discover the ins and outs of using Java to create groundbreaking Android apps—no prior knowledge or experience required! Get the know-how to create an Android program from the ground up Make sense of basic Java development concepts and techniques Develop the skills to handle programming challenges Find out how to debug your app Don't sit back and watch other developers release apps that bring in the bucks! Everything you need to create that next killer Android app is just a page away! COMPUTERS,Software Development & Engineering,General

Effective DevOps Some companies think that adopting devops means bringing in specialists or a host of new tools. With this practical guide, you’ll learn why devops is a professional and cultural movement that calls for change from inside your organization. Authors Ryn Daniels and Jennifer Davis provide several approaches for improving collaboration within teams, creating affinity among teams, promoting efficient tool usage in your company, and scaling up what works throughout your organization’s inflection points. Devops stresses iterative efforts to break down information silos, monitor relationships, and repair misunderstandings that arise between and within teams in your organization. By applying the actionable strategies in this book, you can make sustainable changes in your environment regardless of your level within your organization. Explore the foundations of devops and learn the four pillars of effective devops Encourage collaboration to help individuals work together and build durable and long-lasting relationships Create affinity among teams while balancing differing goals or metrics Accelerate cultural direction by selecting tools and workflows that complement your organization Troubleshoot common problems and misunderstandings that can arise throughout the organizational lifecycle Learn from case studies from organizations and individuals to help inform your own devops journey COMPUTERS,Software Development & Engineering,General

Requirements Writing for System Engineering Learn how to create good requirements when designing hardware and software systems. While this book emphasizes writing traditional “shall†statements, it also provides guidance on use case design and creating user stories in support of agile methodologies. The book surveys modeling techniques and various tools that support requirements collection and analysis. You’ll learn to manage requirements, including discussions of document types and digital approaches using spreadsheets, generic databases, and dedicated requirements tools. Good, clear examples are presented, many related to real-world work the author has done during his career. Requirements Writing for System Engineeringantages of different requirements approaches and implement them correctly as your needs evolve. Unlike most requirements books, Requirements Writing for System Engineering teaches writing both hardware and software requirements because many projects include both areas. To exemplify this approach, two example projects are developed throughout the book, one focusing on hardware and the other on software. This book Presents many techniques for capturing requirements. Demonstrates gap analysis to find missing requirements. Shows how to address both software and hardware, as most projects involve both. Provides extensive examples of “shall†statements, user stories, and use cases. Explains how to supplement or replace traditional requirement statements with user stories and use cases that work well in agile development environments What You Will Learn Understand the 14 techniques for capturing all requirements. Address software and hardware needs; because most projects involve both. Ensure all statements meet the 16 attributes of a good requirement. Differentiate the 19 different functional types of requirement, and the 31 non-functional types. Write requirements properly based on extensive examples of good ‘shall’ statements, user stories, and use cases. Employ modeling techniques to mitigate the imprecision of words. Audience Writing Requirements teaches you to write requirements the correct way. It is targeted at the requirements engineer who wants to improve and master his craft. This is also an excellent book from which to teach requirements engineering at the university level. Government organizations at all levels, from Federal to local levels, can use this book to ensure they begin all development projects correctly. As well, contractor companies supporting government development are also excellent audiences for this book. COMPUTERS,Software Development & Engineering,General

Production-Ready Microservices One of the biggest challenges for organizations that have adopted microservice architecture is the lack of architectural, operational, and organizational standardization. After splitting a monolithic application or building a microservice ecosystem from scratch, many engineers are left wondering what’s next. In this practical book, author Susan Fowler presents a set of microservice standards in depth, drawing from her experience standardizing over a thousand microservices at Uber. You’ll learn how to design microservices that are stable, reliable, scalable, fault tolerant, performant, monitored, documented, and prepared for any catastrophe. Explore production-readiness standards, including: Stability and Reliability: develop, deploy, introduce, and deprecate microservices; protect against dependency failures Scalability and Performance: learn essential components for achieving greater microservice efficiency Fault Tolerance and Catastrophe Preparedness: ensure availability by actively pushing microservices to fail in real time Monitoring: learn how to monitor, log, and display key metrics; establish alerting and on-call procedures Documentation and Understanding: mitigate tradeoffs that come with microservice adoption, including organizational sprawl and technical debt COMPUTERS,Software Development & Engineering,General

3D User Interfaces The Complete, Up-To-Date Guide to Building Great 3D User Interfaces for Any Application 3D interaction is suddenly everywhere. But simply using 3D input or displays isn’t enough: 3D interfaces must be carefully designed for optimal user experience. 3D User Interfaces: Theory and Practice, Second Edition is today’s most comprehensive primary reference to building state-of-the-art 3D user interfaces and interactions. Five pioneering researchers and practitioners cover the full spectrum of emerging applications, techniques, and best practices. The authors combine theoretical foundations, analysis of leading devices, and empirically validated design guidelines. This edition adds two new chapters on human factors and general human-computer interaction—indispensable foundational knowledge for building any 3D user interface. It also demonstrates advanced concepts at work through two running case studies: a first-person VR game and a mobile augmented reality application. Coverage Includes 3D user interfaces: evolution, elements, and roadmaps Key applications: virtual and augmented reality (VR, AR), mobile/wearable devices What 3D UI designers should know about human sensory systems and cognition ergonomics How proven human-computer interaction techniques apply to 3D UIs 3D UI output hardware for visual, auditory, and haptic/ tactile systems Obtaining 3D position, orientation, and motion data for users in physical space 3D object selection and manipulation Navigation and wayfinding techniques for moving through virtual and physical spaces Changing application state with system control techniques, issuing commands, and enabling other forms of user input Strategies for choosing, developing, and evaluating 3D user interfaces Utilizing 2D, “magic,†“natural,†multimodal, and two-handed interaction The future of 3D user interfaces: open research problems and emerging technologies COMPUTERS,Software Development & Engineering,General

Domain-Driven Design Distilled Domain-Driven Design (DDD) software modeling delivers powerful results in practice, not just in theory, which is why developers worldwide are rapidly moving to adopt it. Now, for the first time, there’s an accessible guide to the basics of DDD: What it is, what problems it solves, how it works, and how to quickly gain value from it. Concise, readable, and actionable, Domain-Driven Design Distilled never buries you in detail–it focuses on what you need to know to get results. Vaughn Vernon, author of the best-selling Implementing Domain-Driven Design, draws on his twenty years of experience applying DDD principles to real-world situations. He is uniquely well-qualified to demystify its complexities, illuminate its subtleties, and help you solve the problems you might encounter. Vernon guides you through each core DDD technique for building better software. You’ll learn how to segregate domain models using the powerful Bounded Contexts pattern, to develop a Ubiquitous Language within an explicitly bounded context, and to help domain experts and developers work together to create that language. Vernon shows how to use Subdomains to handle legacy systems and to integrate multiple Bounded Contexts to define both team relationships and technical mechanisms. Domain-Driven Design Distilled brings DDD to life. Whether you’re a developer, architect, analyst, consultant, or customer, Vernon helps you truly understand it so you can benefit from its remarkable power. Coverage includes What DDD can do for you and your organization–and why it’s so important The cornerstones of strategic design with DDD: Bounded Contexts and Ubiquitous Language Strategic design with Subdomains Context Mapping: helping teams work together and integrate software more strategically Tactical design with Aggregates and Domain Events Using project acceleration and management tools to establish and maintain team cadence COMPUTERS,Software Development & Engineering,General

Service-Oriented Architecture The Top-Selling, De Facto Guide to SOA--Now Updated with New Content and Coverage of Microservices! For more than a decade, Thomas Erl’s best-selling Service-Oriented Architecture: Concepts, Technology, and Design has been the definitive end-to-end tutorial on SOA, service-orientation, and service technologies. Now, Erl has thoroughly updated the industry’s de facto guide to SOA to reflect new practices, technologies, and strategies that have emerged through hard-won experience and creative innovation. This Second Edition officially introduces microservices and micro task abstraction as part of service-oriented architecture and its associated service layers. Updated case study examples and illustrations further explain and position the microservice model alongside and in relation to more traditional types of services. Coverage includes: • Easy-to-understand, plain English explanations of SOA and service-orientation fundamentals (as compiled from series titles) • Microservices, micro task abstraction, and containerization • Service delivery lifecycle and associated phases • Analysis and conceptualization of services and microservices • Service API design with REST services, web services, and microservices • Modern service API and contract versioning techniques for web services and REST services • Up-to-date appendices with service-orientation principles, REST constraints, and SOA patterns (including three new patterns) Service-Oriented Architecture: Analysis and Design for Services and Microservices, Second Edition, will be indispensable to application architects, enterprise architects, software developers, and any IT professionals interested in learning about or responsible for designing or implementing modern-day, service-oriented solutions. Chapter 1: Introduction Chapter 2: Case Study Backgrounds Part I: Fundamentals Chapter 3: Understanding Service-Orientation Chapter 4: Understanding SOA Chapter 5: Understanding Layers with Services and Microservices Part II: Service-Oriented Analysis and Design Chapter 6: Analysis and Modeling with Web Services and Microservices Chapter 7: Analysis and Modeling with REST Services and Microservices Chapter 8: Service API and Contract Design with Web Services Chapter 9: Service API and Contract Design with REST Services and Microservices Chapter 10: Service API and Contract Versioning with Web Services and REST Services Part III: Appendices Appendix A: Service-Orientation Principles Reference Appendix B: REST Constraints Reference Appendix C: SOA Design Patterns Reference Appendix D: The Annotated SOA Manifesto COMPUTERS,Software Development & Engineering,General

Designing Software Architectures Designing Software Architectures will teach you how to design any software architecture in a systematic, predictable, repeatable, and cost-effective way. This book introduces a practical methodology for architecture design that any professional software engineer can use, provides structured methods supported by reusable chunks of design knowledge, and includes rich case studies that demonstrate how to use the methods. Using realistic examples, you’ll master the powerful new version of the proven Attribute-Driven Design (ADD) 3.0 method and will learn how to use it to address key drivers, including quality attributes, such as modifiability, usability, and availability, along with functional requirements and architectural concerns. Drawing on their extensive experience, Humberto Cervantes and Rick Kazman guide you through crafting practical designs that support the full software life cycle, from requirements to maintenance and evolution. You’ll learn how to successfully integrate design in your organisational context, and how to design systems that will be built with agile methods. Comprehensive coverage includes Understanding what architecture design involves, and where it fits in the full software development life cycle Mastering core design concepts, principles, and processes Understanding how to perform the steps of the ADD method Scaling design and analysis up or down, including design for pre-sale processes or lightweight architecture reviews Recognising and optimising critical relationships between analysis and design Utilising proven, reusable design primitives and adapting them to specific problems and contexts Solving design problems in new domains, such as cloud, mobile, or big data The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Software Development & Engineering,General

Large-Scale Scrum The Go-To Resource for Large-Scale Organizations to Be Agile Rather than asking, “How can we do agile at scale in our big complex organization?†a different and deeper question is, “How can we have the same simple structure that Scrum offers for the organization, and be agile at scale rather than do agile?†This profound insight is at the heart of LeSS (Large-Scale Scrum). In Large-Scale Scrum: More with LeSS, Craig Larman and Bas Vodde have distilled over a decade of experience in large-scale LeSS adoptions towards a simpler organization that delivers more flexibility with less complexity, more value with less waste, and more purpose with less prescription. Targeted to anyone involved in large-scale development, Large-Scale Scrum: More with LeSS, offers straight-to-the-point guides for how to be agile at scale, with LeSS. It will clearly guide you to Adopt LeSS Structure a large development organization for customer value Clarify the role of management and Scrum Master Define what your product is, and why Be a great Product Owner Work with multiple whole-product focused feature teams in one Sprint that produces a shippable product Coordinate and integrate between teams Work with multi-site teams COMPUTERS,Software Development & Engineering,General

SAFe 4.0 Distilled SAFe®: The World’s Leading Framework for Enterprise Agility “SAFe® 4.0 Distilled is the book we’ve all been waiting for. It breaks down the complexity of the Framework into easily digestible explanations and actionable guidance. A must-have resource for beginners as well as seasoned practitioners.†—Lee Cunningham, Sr. Director, Enterprise Agile Strategy at VersionOne, Inc. To succeed in today’s adapt-or-die marketplace, businesses must be able to rapidly change the way they create and deliver value to their customers. Hundreds of the world’s most successful companies—including Hewlett Packard Enterprise, AstraZeneca, Cisco, and Philips—have turned to the Scaled Agile Framework® (SAFe®) to achieve agility at scale and maintain a competitive edge. SAFe® 4.0 Distilled: Applying the Scaled Agile Framework® for Lean Software and Systems Engineering explains how adopting SAFe can quickly improve time to market and increase productivity, quality, and employee engagement. In this book, you will Understand the business case for SAFe: its benefits, the problems it solves, and how to apply it Get an overview of SAFe across all parts of the business: team, program, value stream, and portfolio Learn why SAFe works: the power of SAFe’s Lean-Agile mindset, values, and principles Discover how systems thinking, Agile development, and Lean product development form the underlying basis for SAFe Learn how to become a Lean-Agile leader and effectively drive an enterprise-wide transformation COMPUTERS,Software Development & Engineering,General

Programming Interviews Exposed Ace technical interviews with smart preparation Programming Interviews Exposed is the programmer’s ideal first choice for technical interview preparation. Updated to reflect changing techniques and trends, this new fourth edition provides insider guidance on the unique interview process that today's programmers face. Online coding contests are being used to screen candidate pools of thousands, take-home projects have become commonplace, and employers are even evaluating a candidate's public code repositories at GitHub—and with competition becoming increasingly fierce, programmers need to shape themselves into the ideal candidate well in advance of the interview. This book doesn't just give you a collection of questions and answers, it walks you through the process of coming up with the solution so you learn the skills and techniques to shine on whatever problems you’re given. This edition combines a thoroughly revised basis in classic questions involving fundamental data structures and algorithms with problems and step-by-step procedures for new topics including probability, data science, statistics, and machine learning which will help you fully prepare for whatever comes your way. Learn what the interviewer needs to hear to move you forward in the process Adopt an effective approach to phone screens with non-technical recruiters Examine common interview problems and tests with expert explanations Be ready to demonstrate your skills verbally, in contests, on GitHub, and more Technical jobs require the skillset, but you won’t get hired unless you are able to effectively and efficiently demonstrate that skillset under pressure, in competition with hundreds of others with the same background. Programming Interviews Exposed teaches you the interview skills you need to stand out as the best applicant to help you get the job you want. COMPUTERS,Software Development & Engineering,General

Clean Architecture Practical Software Architecture Solutions from the Legendary Robert C. Martin (“Uncle Bobâ€) By applying universal rules of software architecture, you can dramatically improve developer productivity throughout the life of any software system. Now, building upon the success of his best-selling books Clean Code and The Clean Coder, legendary software craftsman Robert C. Martin (“Uncle Bobâ€) reveals those rules and helps you apply them. Martin’s Clean Architecture doesn’t merely present options. Drawing on over a half-century of experience in software environments of every imaginable type, Martin tells you what choices to make and why they are critical to your success. As you’ve come to expect from Uncle Bob, this book is packed with direct, no-nonsense solutions for the real challenges you’ll face–the ones that will make or break your projects. Learn what software architects need to achieve–and core disciplines and practices for achieving it Master essential software design principles for addressing function, component separation, and data management See how programming paradigms impose discipline by restricting what developers can do Understand what’s critically important and what’s merely a “detail†Implement optimal, high-level structures for web, database, thick-client, console, and embedded applications Define appropriate boundaries and layers, and organize components and services See why designs and architectures go wrong, and how to prevent (or fix) these failures Clean Architecture is essential reading for every current or aspiring software architect, systems analyst, system designer, and software manager–and for every programmer who must execute someone else’s designs. Register your product for convenient access to downloads, updates, and/or corrections as they become available. COMPUTERS,Software Development & Engineering,General

Arduino For Dummies Bring your ideas to life with the latest Arduino hardware and software Arduino is an affordable and readily available hardware development platform based around an open source, programmable circuit board. You can combine this programmable chip with a variety of sensors and actuators to sense your environment around you and control lights, motors, and sound. This flexible and easy-to-use combination of hardware and software can be used to create interactive robots, product prototypes and electronic artwork, whether you’re an artist, designer or tinkerer. Arduino For Dummies is a great place to start if you want to find out about Arduino and make the most of its incredible capabilities. It helps you become familiar with Arduino and what it involves, and offers inspiration for completing new and exciting projects. • Covers the latest software and hardware currently on the market • Includes updated examples and circuit board diagrams in addition to new resource chapters • Offers simple examples to teach fundamentals needed to move onto more advanced topics • Helps you grasp what’s possible with this fantastic little board Whether you’re a teacher, student, programmer, hobbyist, hacker, engineer, designer, or scientist, get ready to learn the latest this new technology has to offer! COMPUTERS,Software Development & Engineering,General

Learn Computer Science with Swift Master the basics of solving logic puzzles, and creating algorithms using Swift on Apple platforms. This book is based on the curriculum currently being used in common computer classes. You’ll learn to automate algorithmic processes that scale using Swift in the context of iOS, macOS, tvOS, and watchOS. Begin by understanding how to think computationally: to formulate a computational problem and recognize patterns and ways to validate it. Then jump ahead past the abstractions and conceptual work into using code snippets to build frameworks and write code using Xcode and Swift. Once you have frameworks in place, you’ll learn to use algorithms and structure data. Finally, you’ll see how to bring people into what you’ve built through a useable UI and how UI and code relate. What You'll Learn Recognize patterns and use abstractions Build code into reusable frameworks Manage code and share version control Solve logic puzzles Who This Book Is For Young professionals interested in learning computer science from an Apple platform standpoint. COMPUTERS,Software Development & Engineering,General

The Agile Safety Case The safety case (SC) is one of the railway industry’s most important deliverables for creating confidence in their systems. This is the first book on how to write an SC, based on the standard EN 50129:2003. Experience has shown that preparing and understanding an SC is difficult and time consuming, and as such the book provides insights that enhance the training for writing an SC. The book discusses both "regular" safety cases and agile safety cases, which avoid too much documentation, improve communication between the stakeholders, allow quicker approval of the system, and which are important in the light of rapidly changing technology. In addition, it discusses the necessity of frequently updating software due to market requirements, changes in requirements and increased cyber-security threats. After a general introduction to SCs and agile thinking in chapter 1, chapter 2 describes the majority of the roles that are relevant when developing railway-signaling systems. Next, chapter 3 provides information related to the assessment of signaling systems, to certifications based on IEC 61508 and to the authorization of signaling systems. Chapter 4 then explains how an agile safety plan satisfying the requirements given in EN 50126-1:1999 can be developed, while chapter 5 provides a brief introduction to safety case patterns and notations. Lastly, chapter 6 combines all this and describes how an (agile) SC can be developed and what it should include. To ensure that infrastructure managers, suppliers, consultants and others can take full advantage of the agile mind-set, the book includes concrete examples and presents relevant agile practices. Although the scope of the book is limited to signaling systems, the basic foundations for (agile) SCs are clearly described so that they can also be applied in other cases. COMPUTERS,Software Development & Engineering,General

Release It! A single dramatic software failure can cost a company millions of dollars - but can be avoided with simple changes to design and architecture. This new edition of the best-selling industry standard shows you how to create systems that run longer, with fewer failures, and recover better when bad things happen. New coverage includes DevOps, microservices, and cloud-native architecture. Stability antipatterns have grown to include systemic problems in large-scale systems. This is a must-have pragmatic guide to engineering for production systems. If you're a software developer, and you don't want to get alerts every night for the rest of your life, help is here. With a combination of case studies about huge losses - lost revenue, lost reputation, lost time, lost opportunity - and practical, down-to-earth advice that was all gained through painful experience, this book helps you avoid the pitfalls that cost companies millions of dollars in downtime and reputation. Eighty percent of project life-cycle cost is in production, yet few books address this topic. This updated edition deals with the production of today's systems - larger, more complex, and heavily virtualized - and includes information on chaos engineering, the discipline of applying randomness and deliberate stress to reveal systematic problems. Build systems that survive the real world, avoid downtime, implement zero-downtime upgrades and continuous delivery, and make cloud-native applications resilient. Examine ways to architect, design, and build software - particularly distributed systems - that stands up to the typhoon winds of a flash mob, a Slashdotting, or a link on Reddit. Take a hard look at software that failed the test and find ways to make sure your software survives. To skip the pain and get the experience...get this book. COMPUTERS,Software Development & Engineering,General

Pragmatic Thinking and Learning Printed in full color. Software development happens in your head. Not in an editor, IDE, or designtool. You're well educated on how to work with software and hardware, but what about wetware--our own brains? Learning new skills and new technology is critical to your career, and it's all in your head. In this book by Andy Hunt, you'll learn how our brains are wired, and how to take advantage of your brain's architecture. You'll learn new tricks and tipsto learn more, faster, and retain more of what you learn. You need a pragmatic approach to thinking and learning. You need to Refactor Your Wetware. Programmers have to learn constantly; not just the stereotypical new technologies, but also the problem domain of the application, the whims of the user community, the quirks of your teammates, the shifting sands of the industry, and the evolving characteristics of the project itself as it is built. We'll journey together through bits of cognitive and neuroscience, learning and behavioral theory. You'll see some surprising aspects of how our brains work, and how you can take advantage of the system to improve your own learning and thinking skills. In this book you'll learn how to: Use the Dreyfus Model of Skill Acquisition to become more expert Leverage the architecture of the brain to strengthen different thinking modes Avoid common "known bugs" in your mind Learn more deliberately and more effectively Manage knowledge more efficiently COMPUTERS,Software Development & Engineering,General

Programming Erlang A multi-user game, web site, cloud application, or networked database can have thousands of users all interacting at the same time. You need a powerful, industrial-strength tool to handle the really hard problems inherent in parallel, concurrent environments. You need Erlang. In this second edition of the bestselling Programming Erlang, you'll learn how to write parallel programs that scale effortlessly on multicore systems. Using Erlang, you'll be surprised at how easy it becomes to deal with parallel problems, and how much faster and more efficiently your programs run. That's because Erlang uses sets of parallel processes-not a single sequential process, as found in most programming languages. Joe Armstrong, creator of Erlang, introduces this powerful language in small steps, giving you a complete overview of Erlang and how to use it in common scenarios. You'll start with sequential programming, move to parallel programming and handling errors in parallel programs, and learn to work confidently with distributed programming and the standard Erlang/Open Telecom Platform (OTP) frameworks. You need no previous knowledge of functional or parallel programming. The chapters are packed with hands-on, real-world tutorial examples and insider tips and advice, and finish with exercises for both beginning and advanced users. The second edition has been extensively rewritten. New to this edition are seven chapters covering the latest Erlang features: maps, the type system and the Dialyzer, WebSockets, programming idioms, and a new stand-alone execution environment. You'll write programs that dynamically detect and correct errors, and that can be upgraded without stopping the system. There's also coverage of rebar (the de facto Erlang build system), and information on how to share and use Erlang projects on github, illustrated with examples from cowboy and bitcask. Erlang will change your view of the world, and of how you program. What You Need The Erlang/OTP system. Download it from erlang.org. COMPUTERS,Software Development & Engineering,General

tmux 2 Your mouse is slowing you down. The time you spend context switching between your editor and your consoles eats away at your productivity. Take control of your environment with tmux, a terminal multiplexer that you can tailor to your workflow. With this updated second edition for tmux 2.3, you'll customize, script, and leverage tmux's unique abilities to craft a productive terminal environment that lets you keep your fingers on your keyboard's home row. You have a database console, web server, test runner, and text editor running at the same time, but switching between them and trying to find what you need takes up valuable time and breaks your concentration. By using tmux 2.3, you can improve your productivity and regain your focus. This book will show you how. This second edition includes many features requested by readers, including how to integrate plugins into your workflow, how to integrate tmux with Vim for seamless navigation - oh, and how to use tmux on Windows 10. Use tmux to manage multiple terminal sessions in a single window using only your keyboard. Manage and run programs side by side in panes, and create the perfect development environment with custom scripts so that when you're ready to work, your programs are waiting for you. Manipulate text with tmux's copy and paste buffers, so you can move text around freely between applications. Discover how easy it is to use tmux to collaborate remotely with others, and explore more advanced usage as you manage multiple tmux sessions, add custom scripts into the tmux status line, and integrate tmux with your system. Whether you're an application developer or a system administrator, you'll find many useful tricks and techniques to help you take control of your terminal. COMPUTERS,Software Development & Engineering,General

Agile Retrospectives Project retrospectives help teams examine what went right and what went wrong on a project. But traditionally, retrospectives (also known as “post-mortemsâ€) are only held at the end of the project—too late to help. You need agile retrospectives that are iterative and incremental. You need to accurately find and fix problems to help the team today. Now Esther and Diana show you the tools, tricks and tips you need to fix the problems you face on a software development project on an on-going basis. You’ll see how to architect retrospectives in general, how to design them specifically for your team and organization, how to run them effectively, how to make the needed changes and how to scale these techniques up. You’ll learn how to deal with problems, and implement solutions effectively throughout the project—not just at the end. This book will help you: Design and run effective retrospectives Learn how to find and fix problems Find and reinforce team strengths Address people issues as well as technological Use tools and recipes proven in the real world With regular tune-ups, your team will hum like a precise, world-class orchestra. COMPUTERS,Software Development & Engineering,General

Java By Comparison Write code that's clean, concise, and to the point: code that others will read with pleasure and reuse. Comparing your code to that of expert programmers is a great way to improve your coding skills. Get hands-on advice to level up your coding style through small and understandable examples that compare flawed code to an improved solution. Discover handy tips and tricks, as well as common bugs an experienced Java programmer needs to know. Make your way from a Java novice to a master craftsman. This book is a useful companion for anyone learning to write clean Java code. The authors introduce you to the fundamentals of becoming a software craftsman, by comparing pieces of problematic code with an improved version, to help you to develop a sense for clean code. This unique before-and-after approach teaches you to create clean Java code. Learn to keep your booleans in check, dodge formatting bugs, get rid of magic numbers, and use the right style of iteration. Write informative comments when needed, but avoid them when they are not. Improve the understandability of your code for others by following conventions and naming your objects accurately. Make your programs more robust with intelligent exception handling and learn to assert that everything works as expected using JUnit5 as your testing framework. Impress your peers with an elegant functional programming style and clear-cut object-oriented class design. Writing excellent code isn't just about implementing the functionality. It's about the small important details that make your code more readable, maintainable, flexible, robust, and faster. Java by Comparison teaches you to spot these details and trains you to become a better programmer. What You Need: You need a Java 8 compiler, a text editor, and a fresh mind.That's it. COMPUTERS,Software Development & Engineering,General

SAFe 4.5 Reference Guide The Must-have Reference Guide for SAFe® Professionals “There are a lot of methods of scale out there, but the Scaled Agile Framework is the one lighting up the world.†–Steve Elliot, Founder/CEO AgileCraft “Since beginning our Lean-Agile journey with SAFe, Vantiv has focused its strategic efforts and its execution. We have improved the predictability of product delivery while maintaining high quality, and have become even more responsive to customers–resulting in higher customer satisfaction. And just as important, employee engagement went up over the past year.†–Dave Kent, Enterprise Agile Coach, Vantiv Fully updated to include the new innovations in SAFe 4.5, the SAFe® 4.5 Reference Guide is ideal for anyone serious about learning and implementing the world’s leading framework for enterprise agility. Inside, you’ll find complete coverage of the scaledagileframework.com knowledge base, the website that thousands of the world’s largest brands turn to for building better software and systems. SAFe was developed from real-world field experience and provides proven success patterns for implementing Lean-Agile software and systems development at enterprise scale. This book provides comprehensive guidance for work at the enterprise Portfolio, Large Solution, Program, and Team levels, including the various roles, activities, and artifacts that constitute the Framework. Education & Training Key to Success The practice of SAFe is spreading rapidly throughout the world. The majority of Fortune 100 companies have certified SAFe professionals and consultants, as do an increasing percentage of the Global 2000. Case study results–visit scaledagileframework.com/case-studies–typically include: 30 — 75% faster time-to-market 25 — 75% increase in productivity 20 — 50% improvements in quality 10 — 50% increased employee engagement Successful implementations may vary in context but share a common attribute: a workforce well trained and educated in SAFe practices. This book–along with authorized training and certification–will help you understand how to maximize the value of your role within a SAFe organization. The result is greater alignment and visibility, improved performance throughout the enterprise, and ultimately better outcomes for the business. COMPUTERS,Software Development & Engineering,General

Professional Product Owner, The The Professional Product Owner’s Guide to Maximizing Value with Scrum “This book presents a method of communicating our desires, cogently, coherently, and with a minimum of fuss and bother.†—Ken Schwaber, Chairman & Founder, Scrum.org The role of the Product Owner is more crucial than ever. But it’s about much more than mechanics: it’s about taking accountability and refocusing on value as the primary objective of all you do. In The Professional Product Owner, two leading experts in successful Scrum product ownership show exactly how to do this. You’ll learn how to identify where value can be found, measure it, and maximize it throughout your entire product lifecycle. Drawing on their combined 40+ years of experience in using agile and Scrum in product management, Don McGreal and Ralph Jocham guide you through all facets of envisioning, emerging, and maturing a product using the Scrum framework. McGreal and Jocham discuss strategy, showing how to connect Vision, Value, and Validation in ROI-focused agile product management. They lay out Scrum best-practices for managing complexity and continuously delivering value, and they define the concrete practices and tools you can use to manage Product Backlogs and release plans, all with the goal of making you a more successful Product Owner. Throughout, the authors share revealing personal experiences that illuminate obstacles to success and show how they can be overcome. Define success from the “outside in,†using external customer-driven measurements to guide development and maximize value Bring empowerment and entrepreneurship to the Product Owner’s role, and align everyone behind a shared business model Use Evidence-Based Management (EBMgt) to invest in the right places, make smarter decisions, and reduce risk Effectively apply Scrum’s Product Owner role, artifacts, and events Populate and manage Product Backlogs, and use just-in-time specifications Plan and manage releases, improve transparency, and reduce technical debt Scale your product, not your Scrum Use Scrum to inject autonomy, mastery, and purpose into your product team’s work Whatever your role in product management or agile development, this guide will help you deliver products that offer more value, more rapidly, and more often. Register your book for convenient access to downloads, updates, and/or corrections as they become available. See inside book for details. COMPUTERS,Software Development & Engineering,General

SAFe 4.5 Distilled SAFe®: The World’s Leading Framework for Enterprise Agility “Philips is continuously driving to develop high-quality software in a predictable, fast, and Agile way. SAFe addresses this primary goal, and offers these further benefits: reduced time-to-market, improved quality, stronger alignment across geographically distributed multi-disciplinary teams, and collaboration across teams to deliver meaningful value to customers with reduced cycle time.†—Sundaresan Jagadeesan, SW CoE Program Director, Philips To succeed in today’s adapt-or-die marketplace, businesses must be able to rapidly change the way they create and deliver value to their customers. Hundreds of the world’s most successful companies–including Intel, Capital One, AstraZeneca, Cisco, and Philips–have turned to the Scaled Agile Framework® (SAFe®) to achieve agility at scale and maintain a competitive edge. SAFe® 4.5 Distilled: Applying the Scaled Agile Framework® for Lean Enterprises explains how adopting SAFe can quickly improve time to market and increase productivity, quality, and employee engagement. In this book, you will Understand the business case for SAFe: its benefits, the problems it solves, and how to apply it Get an overview of SAFe across all parts of the business: team, program, value stream, and portfolio Learn why SAFe works: the power of SAFe’s Lean-Agile mindset, values, and principles Discover how systems thinking, Agile development, and Lean product development form the underlying basis for SAFe Learn how to become a Lean-Agile leader and effectively drive an enterprise-wide transformation Register your book for convenient access to downloads, updates, and/or corrections as they become available. See inside book for details. COMPUTERS,Software Development & Engineering,General

Python programmieren lernen für Dummies Der Einstieg in die Programmierung kann ganz leicht sein, das beweist Ihnen dieses Buch! Schritt für Schritt führt Sie John Paul Mueller in die Grundlagen der beliebten Programmiersprache Python ein und zeigt Ihnen, wie Sie Ihren Computer dazu bringen, das zu tun, was Sie wollen. Downloaden und installieren Sie die Python-Distribution Anaconda, lernen Sie die Programmiersprache Python kennen und schreiben Sie Ihre ersten eigenen Programme. Erfahren Sie außerdem, wie Sie Informationen managen und modifizieren, Schleifen durchlaufen, Fehler beheben und mit Listen und Strings arbeiten. Erhalten Sie zusätzlich einen Einblick in fortgeschrittene Techniken. Mit den vielen Beispielen zum Herunterladen und Herumexperimentieren können Sie das Gelernte direkt ausprobieren, sodass Sie sich schnell in der Welt der Programmierer zuhause fühlen. COMPUTERS,Software Development & Engineering,General

Advanced Software Testing - Vol. 1, 2nd Edition This book is written for the test analyst who wants to achieve advanced skills in test analysis, design, and execution. With a hands-on, exercise-rich approach, this book teaches you how to define and carry out the tasks required to put a test strategy into action. Learn how to analyze the system, taking into account the user’s quality expectations. Additionally, learn how to evaluate system requirements as part of formal and informal reviews, using an understanding of the business domain to determine requirement validity. You will be able to analyze, design, implement, and execute tests, using risk considerations to determine the appropriate effort and priority for tests. You will also learn how to report on testing progress and provide necessary evidence to support your evaluations of system quality. With a quarter-century of software and systems engineering experience, author Rex Black is President of RBCS, a leader in software, hardware, and systems testing, and is the most prolific author practicing in the field of software testing today. He published several books on testing that sold tens of thousands of copies worldwide. He is President of the International Software Testing Qualifications Board (ISTQB) and is a Director of the American Software Testing Qualifications Board (ASTQB). This book will also help you prepare for the ISTQB Advanced Test Analyst exam. Included are sample exam questions, at the appropriate level of difficulty, for most of the learning objectives covered by the ISTQB Advanced Level syllabus. The ISTQB certification program is the leading software tester certification program in the world. With about 400,000 certificate holders and a global presence in 50 countries, you can be confident in the value and international stature that the Advanced Test Analyst certificate can offer you. The 2nd edition has been thoroughly revised and is aligned with the curriculum. In addition, some minor corrections have been included. COMPUTERS,Software Development & Engineering,General

Web Application Development with R Using Shiny Analyze, communicate, and design your own sophisticated and interactive web applications using the R (v 3.4) Shiny (1.1.0) package Key Features Explore the power of R Shiny to make interactive web applications easily Create engaging user interfaces using elements such as HTML5 shiny tags and Ttabsets Build and deploy your interactive Shiny web application using shinyapps.io Book Description Web Application Development with R Using Shiny helps you become familiar with the complete R Shiny package. The book starts with a quick overview of R and its fundamentals, followed by an exploration of the fundamentals of Shiny and some of the things that it can help you do. You'll learn about the wide range of widgets and functions within Shiny and how they fit together to make an attractive and easy to use application. Once you have understood the basics, you'll move on to studying more advanced UI features, including how to style apps in detail using the Bootstrap framework or and Shiny's inbuilt layout functions. You'll learn about enhancing Shiny with JavaScript, ranging from adding simple interactivity with JavaScript right through to using JavaScript to enhance the reactivity between your app and the UI. You'll learn more advanced Shiny features of Shiny, such as uploading and downloading data and reports, as well as how to interact with tables and link reactive outputs. Lastly, you'll learn how to deploy Shiny applications over the internet, as well as and how to handle storage and data persistence within Shiny applications, including the use of relational databases. By the end of this book, you'll be ready to create responsive, interactive web applications using the complete R (v 3.4) Shiny (1.1.0) suite. What you will learn Harness the power of JavaScript to customize your applications Build dashboards with predefined UI and layouts Engage your users and build better analytics using interactive plots Learn advanced code patterns to make your applications easy to write and maintain. Develop a full understanding of Shiny's UI functions to give you the power to build a wide variety of attractive applications. Store data and interact with databases with Shiny. Learn how to share your Shiny applications Understand reactivity at the conceptual level to build more efficient and robust apps Who this book is for Web Application Development with R Using Shiny is for you if you are interested in creating compelling web applications and interactive data visualization over the web using Shiny. Programming experience with R is required. COMPUTERS,Software Development & Engineering,General

Technology Strategy Patterns Technologists who want their ideas heard, understood, and funded are often told to speak the language of business—without really knowing what that is. This book’s toolkit provides architects, product managers, technology managers, and executives with a shared language—in the form of repeatable, practical patterns and templates—to produce great technology strategies. Author Eben Hewitt developed 39 patterns over the course of a decade in his work as CTO, CIO, and chief architect for several global tech companies. With these proven tools, you can define, create, elaborate, refine, and communicate your architecture goals, plans, and approach in a way that executives can readily understand, approve, and execute. This book covers: Architecture and strategy: Adopt a strategic architectural mindset to make a meaningful material impact Creating your strategy: Define the components of your technology strategy using proven patterns Communicating the strategy: Convey your technology strategy in a compelling way to a variety of audiences Bringing it all together: Employ patterns individually or in clusters for specific problems; use the complete framework for a comprehensive strategy COMPUTERS,Software Development & Engineering,General

A Study Guide to the ISTQB® Foundation Level 2018 Syllabus This book is an excellent, helpful and up-to-date resource for all candidates preparing for the ISTQB Foundation Level certification exam based on the new Foundation Level 2018 Syllabus. Although there are plenty of sample questions and information related to the Foundation Level exam on the web, there are two problems with these: Firstly, most of them will soon be outdated, as the old syllabus and exams are going to be retracted in June 2019. Secondly, much of what is available is of poor quality, since many of the sample questions do not follow the strict ISTQB examination rules. This book stands out from other ISTQB-related works through a number of special features: Topicality: The material complies with the latest version of the Foundation Level syllabus published in 2018. Quality and originality: The exam questions are original, not redundant, of high quality, fully aligned with the ISTQB exam requirements and have not been published before. Huge amount of material: It includes 5 full sample exams (200 questions in total) designed in accordance with the ISTQB exam rules, and with the appropriate distribution of questions regarding the learning objectives and K-levels. Well-thought-out sample questions: The questions not only appropriately cover the corresponding learning objectives (LOs), but also to show the typical pitfalls. Diversity: The questions from various sample exams related to the same LO are diversified, that is, each of them points out different aspects of a given LO. This is an excellent method for better and more effective learning and preparing for the exam. Comprehensive, intelligible explanations: All answers are justified and there are detailed and easy-to-understand explanations not only of why a given answer is correct, but also why all the others are wrong. A lot of bonus material: The book includes a great bonus pack: chapters that explain the white-box and black-box test techniques in a detailed way, a set of exercises on test techniques and the detailed solutions to them, and much more. COMPUTERS,Software Development & Engineering,General

SQL For Dummies Get ready to make SQL easy! Updated for the latest version of SQL, the new edition of this perennial bestseller shows programmers and web developers how to use SQL to build relational databases and get valuable information from them. Covering everything you need to know to make working with SQL easier than ever, topics include how to use SQL to structure a DBMS and implement a database design; secure a database; and retrieve information from a database; and much more. SQL is the international standard database language used to create, access, manipulate, maintain, and store information in relational database management systems (DBMS) such as Access, Oracle, SQL Server, and MySQL. SQL adds powerful data manipulation and retrieval capabilities to conventional languages—and this book shows you how to harness the core element of relational databases with ease. Server platform that gives you choices of development languages, data types, on-premises or cloud, and operating systems Find great examples on the use of temporal data Jump right in—without previous knowledge of database programming or SQL As database-driven websites continue to grow in popularity—and complexity—SQL For Dummies is the easy-to-understand, go-to resource you need to use it seamlessly. COMPUTERS,Software Development & Engineering,General

Using Microsoft Dynamics 365 for Finance and Operations This book provides precise descriptions and instructions which enable users, students and consultants to understand Microsoft Dynamics 365 for Finance and Operations rapidly. Microsoft offers Dynamics 365 as its premium ERP solution, supporting large and mid-sized organizations with a complete business management solution which is easy to use. Going through a simple but comprehensive case study, this book provides the required knowledge to handle all basic business processes in Microsoft Dynamics 365 for Finance and Operations. Exercises are there to train the processes and functionality, also making this book a good choice for self-study. COMPUTERS,Software Development & Engineering,General

Python Machine Learning Python makes machine learning easy for beginners and experienced developers With computing power increasing exponentially and costs decreasing at the same time, there is no better time to learn machine learning using Python. Machine learning tasks that once required enormous processing power are now possible on desktop machines. However, machine learning is not for the faint of heart—it requires a good foundation in statistics, as well as programming knowledge. Python Machine Learning will help coders of all levels master one of the most in-demand programming skillsets in use today. Readers will get started by following fundamental topics such as an introduction to Machine Learning and Data Science. For each learning algorithm, readers will use a real-life scenario to show how Python is used to solve the problem at hand. • Python data science—manipulating data and data visualization • Data cleansing • Understanding Machine learning algorithms • Supervised learning algorithms • Unsupervised learning algorithms • Deploying machine learning models Python Machine Learning is essential reading for students, developers, or anyone with a keen interest in taking their coding skills to the next level. COMPUTERS,Software Development & Engineering,General

Effective Project Management The popular guide to the project management body of knowledge, now fully updated Now in its eighth edition, this comprehensive guide to project management has long been considered the standard for both professionals and academics, with nearly 40,000 copies sold in the last three editions! Well-known expert Robert Wysocki has added four chapters of new content based on instructor feedback, enhancing the coverage of best-of-breed methods and tools for ensuring project management success. With enriched case studies, accompanying exercises and solutions on the companion website, and PowerPoint slides for all figures and tables, the book is ideal for instructors and students as well as active project managers. Serves as a comprehensive guide to project management for both educators and project management professionals Updated to cover the new PMBOK® Sixth Edition Examines traditional, agile, and extreme project management techniques; the Enterprise Project Management Model; and Kanban and Scrumban methodologies Includes a companion website with exercises and solutions and well as PowerPoint slides for all the figures and tables used Written by well-known project management expert Robert Wysocki Effective Project Management, Eighth Edition remains the comprehensive resource for project management practitioners, instructors, and students. (PMBOK is a registered mark of the Project Management Institute, Inc.) COMPUTERS,Software Development & Engineering,General

Behavior-Driven Development with Cucumber Master BDD to deliver higher-value software more quickly To develop high-value products quickly, software development teams need better ways to collaborate. Agile methods like Scrum and Kanban are helpful, but they’re not enough. Teams need better ways to work inside each sprint or work item. Behavior-driven development (BDD) adds just enough structure for product experts, testers, and developers to collaborate more effectively. Drawing on extensive experience helping teams adopt BDD, Richard Lawrence and Paul Rayner show how to explore changes in system behavior with examples through conversations, how to capture your examples in expressive language, and how to flow the results into effective automated testing with Cucumber. Where most BDD resources focus on test automation, this guide goes deep into how BDD changes team collaboration and what that collaboration looks like day to day. Concrete examples and practical advice will prepare you to succeed with BDD, whatever your context or role. · Learn how to collaborate better by using concrete examples of system behavior · Identify your project’s meaningful increment of value so you’re always working on something important · Begin experimenting with BDD slowly and at low risk · Move smoothly from informal examples to automated tests in Cucumber · Use BDD to deliver more frequently with greater visibility · Make Cucumber scenarios more expressive to ensure you’re building the right thing · Grow a Cucumber suite that acts as high-value living documentation · Sustainably work with complex scenario data · Get beyond the “mini-waterfalls†that often arise on Scrum teams COMPUTERS,Software Development & Engineering,General

Essential Algorithms A friendly introduction to the most useful algorithms written in simple, intuitive English The revised and updated second edition of Essential Algorithms, offers an accessible introduction to computer algorithms. The book contains a description of important classical algorithms and explains when each is appropriate. The author shows how to analyze algorithms in order to understand their behavior and teaches techniques that the can be used to create new algorithms to meet future needs. The text includes useful algorithms such as: methods for manipulating common data structures, advanced data structures, network algorithms, and numerical algorithms. It also offers a variety of general problem-solving techniques. In addition to describing algorithms and approaches, the author offers details on how to analyze the performance of algorithms. The book is filled with exercises that can be used to explore ways to modify the algorithms in order to apply them to new situations. This updated edition of Essential Algorithms: Contains explanations of algorithms in simple terms, rather than complicated math Steps through powerful algorithms that can be used to solve difficult programming problems Helps prepare for programming job interviews that typically include algorithmic questions Offers methods can be applied to any programming language Includes exercises and solutions useful to both professionals and students Provides code examples updated and written in Python and C# Essential Algorithms has been updated and revised and offers professionals and students a hands-on guide to analyzing algorithms as well as the techniques and applications. The book also includes a collection of questions that may appear in a job interview. The book’s website will include reference implementations in Python and C# (which can be easily applied to Java and C++). COMPUTERS,Software Development & Engineering,General

NASA Formal Methods This book constitutes the proceedings of the 11th International Symposium on NASA Formal Methods, NFM 2019, held in Houston, TX, USA, in May 2019. The 20 full and 8 short papers presented in this volume were carefully reviewed and selected from 102 submissions. The papers focus on formal verification, including theorem proving, model checking, and static analysis; advances in automated theorem proving including SAT and SMT solving; use of formal methods in software and system testing; run-time verification; techniques and algorithms for scaling formal methods, such as abstraction and symbolic methods, compositional techniques, as well as parallel and/or distributed techniques; code generation from formally verified models; safety cases and system safety; formal approaches to fault tolerance; theoretical advances and empirical evaluations of formal methods techniques for safety-critical systems, including hybrid and embedded systems; formal methods in systems engineering and model-based development; correct-by-design controller synthesis; formal assurance methods to handle adaptive systems. COMPUTERS,Software Development & Engineering,General

Delphi Programming Projects Improve your Delphi programming skills by building robust applications for Android, iOS, and Windows platform Key Features Build responsive user interfaces (UIs) for desktop and mobile with FireMonkey Implement a microservices architecture using the Rapid Application Development(RAD) server Create clones of popular applications like Instagram and Facebook using Delphi 10.3 Book Description Delphi is a cross-platform programming language and software development kit that supports rapid application development for Microsoft Windows, Apple Mac OS X, Android, and iOS. With the help of seven practical projects, this book will guide you through the best practices, Delphi Run-Time Library (RTL) resources, and design patterns. Whether you use the Visual Component Library (VCL) or FireMonkey (FMX) framework, these design patterns will be implemented in the same way in Delphi, using Object Pascal. In the first few chapters, you will explore advanced features that will help you build rich applications using the same code base for both mobile and desktop projects. In addition to this, you'll learn how to implement microservice architecture in Delphi. As you get familiar with the various aspects of Delphi, you will no longer need to maintain source code for similar projects, program business rules on screens, or fill your forms with data access components. By the end of this book, you will have gained an understanding of the principles of clean code and become proficient in building robust and scalable applications in Delphi. What you will learn Get to grips with the advanced features of RTL Understand how to deal with the paradigm change between multiplatform projects Build rich interfaces with Google's Material Design features Understand how to implement design patterns in Delphi Turn a mobile device into a remote controller with app tethering technology Build a multi-database system using VCL Who this book is for This book is for developers, programmers, and IT professionals who want to learn the best market practices by implementing practical projects. Prior knowledge of the Delphi language is a must. COMPUTERS,Software Development & Engineering,General

The Pragmatic Programmer The Pragmatic Programmer is one of those tech books you’ll read, re-read, and read again over the years. Whether you’re new to the field or an experienced practitioner, you’ll come away with fresh insights each and every time. Dave Thomas and Andy Hunt wrote the first edition of this influential book in 1999 to help their clients create better software and rediscover the joy of coding. These lessons have helped a generation of programmers examine the very essence of software development, independent of any particular language, framework, or methodology, and the Pragmatic philosophy has spawned hundreds of books, screencasts, and audio books, as well as thousands of careers and success stories. Now, twenty years later, this new edition re-examines what it means to be a modern programmer. Topics range from personal responsibility and career development to architectural techniques for keeping your code flexible and easy to adapt and reuse. Read this book, and you’ll learn how to: Fight software rot Learn continuously Avoid the trap of duplicating knowledge Write flexible, dynamic, and adaptable code Harness the power of basic tools Avoid programming by coincidence Learn real requirements Solve the underlying problems of concurrent code Guard against security vulnerabilities Build teams of Pragmatic Programmers Take responsibility for your work and career Test ruthlessly and effectively, including property-based testing Implement the Pragmatic Starter Kit Delight your users The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Software Development & Engineering,General
Write Great Code, Volume 1, 2nd Edition Understanding the Machine , the first volume in the landmark Write Great Code series by Randall Hyde, explains the underlying mechanics of how a computer works. This, the first volume in Randall Hyde's Write Great Code series, dives into machine organization without the extra overhead of learning assembly language programming. Written for high-level language programmers, Understanding the Machine fills in the low-level details of machine organization that are often left out of computer science and engineering courses. Learn: • How the machine represents numbers, strings, and high-level data structures, so you'll know the inherent cost of using them. • How to organize your data, so the machine can access it efficiently. • How the CPU operates, so you can write code that works the way the machine does. • How I/O devices operate, so you can maximize your application's performance when accessing those devices. • How to best use the memory hierarchy to produce the fastest possible programs. Great code is efficient code. But before you can write truly efficient code, you must understand how computer systems execute programs and how abstractions in programming languages map to the machine's low-level hardware. After all, compilers don't write the best machine code; programmers do. This book gives you the foundation upon which all great software is built. NEW IN THIS EDITION, COVERAGE OF: • Programming languages like Swift and Java • Code generation on modern 64-bit CPUs • ARM processors on mobile phones and tablets • Newer peripheral devices • Larger memory systems and large-scale SSDs COMPUTERS,Software Development & Engineering,General

DevOps For Dummies Develop faster with DevOps DevOps embraces a culture of unifying the creation and distribution of technology in a way that allows for faster release cycles and more resource-efficient product updating. DevOps For Dummies provides a guidebook for those on the development or operations side in need of a primer on this way of working. Inside, DevOps evangelist Emily Freeman provides a roadmap for adopting the management and technology tools, as well as the culture changes, needed to dive head-first into DevOps. Identify your organization’s needs Create a DevOps framework Change your organizational structure Manage projects in the DevOps world DevOps For Dummies is essential reading for developers and operations professionals in the early stages of DevOps adoption. COMPUTERS,Software Development & Engineering,General

EDGE EDGE: The Agile Operating Model That Will Help You Successfully Execute Your Digital Transformation “[The authors’] passion for technology allows them to recognize that for most enterprises in the 21st century, technology is THE business. This is what really separates the EDGE approach. It is a comprehensive operating model with technology at its core.†—From the Foreword by Heidi Musser, Executive Vice President and Principal Consultant, Leading Agile; retired, Vice President and CIO, USAA Maximum innovation happens at the edge of chaos: the messy, risky, and uncertain threshold between randomness and structure. Operating there is uncomfortable but it’s where organizations “invent the future.†EDGE is a set of fast, iterative, adaptive, lightweight, and value-driven tools to achieve digital transformation, and EDGE: Value-Driven Digital Transformation is your guide to using this operating model for innovation. Jim Highsmith is one of the world’s leading agile pioneers and a coauthor of the Agile Manifesto. He, Linda Luu, and David Robinson know from their vast in-the-trenches experience that sustainable digital transformation requires far more than adopting isolated agile practices or conventional portfolio management. This hard, indispensable work involves changing culture and mindset, and going beyond transforming the IT department. EDGE embraces an adaptive mindset in the face of market uncertainty, a visible, value-centered portfolio approach that encourages continual value linkages from vision to detailed initiatives, incremental funding that shifts as strategies evolve, collaborative decision-making, and better risk mitigation. This guide shows leaders how to use the breakthrough EDGE approach to go beyond incremental improvement in a world of exponential opportunities. Build an organization that adapts fast enough to thrive Clear away unnecessary governance processes, obsolete “command and control†leadership approaches, and slow budgeting/planning cycles Improve collaboration when major, fast-paced responses are necessary Continually optimize investment allocation and monitoring based on your vision and goals Register your product for convenient access to downloads, updates, and/or corrections as they become available. See inside book for details. COMPUTERS,Software Development & Engineering,General

Agile Leadership Toolkit Practical, Proven Tools for Leading and Empowering High-Performing Agile Teams A leader is like a farmer, who doesn’t grow crops by pulling them but instead creates the perfect environment for the crops to grow and thrive. If you lead in organizations that have adopted agile methods, you know it’s crucial to create the right environment for your agile teams. Traditional tools such as Gantt charts, detailed plans, and internal KPIs aren’t adequate for complex and fast-changing markets, but merely trusting employees and teams to self-manage is insufficient as well. In Agile Leadership Toolkit, longtime agile leader Peter Koning provides a practical and invaluable steering wheel for agile leaders and their teams. Drawing on his extensive experience helping leaders drive more value from agile, Koning offers a comprehensive toolkit for continuously improving your environment, including structures, metrics, meeting techniques, and governance for creating thriving teams that build disruptive products and services. Koning thoughtfully explains how to lead agile teams at large scale and how team members fit into both the team and the wider organization. Architect environments that help teams learn, grow, and flourish for the long term Get timely feedback everyone can use to improve Co-create goals focused on the customer, not the internal organization Help teams brainstorm and visualize the value of their work to the customer Facilitate team ownership and accelerate team learning Support culture change, and design healthier team habits Make bigger changes faster This actionable guide is for leaders at all levels—whether you’re supervising your first agile team, responsible for multiple teams, or lead the entire company. Register your book for convenient access to downloads, updates, and/or corrections as they become available. See inside book for details. COMPUTERS,Software Development & Engineering,General

Mastering Professional Scrum “Our job as Scrum professionals is to continually improve our ability to use Scrum to deliver products and services that help customers achieve valuable outcomes. This book will help you to improve your ability to apply Scrum.†–From the Foreword by Ken Schwaber, co-author of Scrum Mastering Professional Scrum is for anyone who wants to deliver increased value by using Scrum more effectively. Leading Scrum practitioners Stephanie Ockerman and Simon Reindl draw on years of Scrum training and coaching to help you return to first principles and apply Scrum with the professionalism required to achieve its transformative potential. The authors aim to help you focus on proven Scrum approaches for improving quality, getting and using fast feedback, and becoming more adaptable, instead of “going through the motions†and settling for only modest improvements. Whether you’re a Scrum Master, Development Team member, or Product Owner, you’ll find practical advice for facing challenges with transparency and courage, overcoming a wide array of common challenges, and continually improving your Scrum practice. Realistically assess your current Scrum practice, and identify areas for improvement Recognize what a great Scrum Team looks like and get there Focus on “Doneâ€â€“not “sort-of-Done†or “almost-Done†Measure and optimize the value delivered by every Product Increment Improve the way you plan, develop, and grow Clear away wider organizational impediments to agility and professionalism Overcome common misconceptions that stand in the way of progress Register your book for convenient access to downloads, updates, and/or corrections as they become available. See inside book for details. COMPUTERS,Software Development & Engineering,General

Eiffel Object-Oriented Programming Eiffel is a pure object-oriented programming language which is attracting growing attention both in education and in industry. It is a high-level language, and is particularly suitable as a starting point for those who wish to learn the fundamentals of object orientation. Eiffel is, however, much more than a teaching language: it incorporates an approach to software development based on ideas of reusability, extendibility and reliability. Uniquely among object-oriented languages, it was created with mechanisms for making formal assertions about software components, based on the 'design by contract' philosophy. This book provides an introduction to object orientation and a practical introduction to virtually all the features provided by the Eiffel programming language. It is suitable for those with some experience of programming who wish to learn about object-oriented programming. It will also appeal to those who already have some knowledge of object orientation, and wish to find out about the Eiffel language. After an introductory chapter on object orientation, several of the early chapters review basic concepts required by readers with little formal knowledge of computer programming. From chapter 6 onwards the author examines more difficult issues of object instantiation, copying and comparison, and the use of class libraries for string and array handling. COMPUTERS,Software Development & Engineering,General

Righting Software Righting Software presents the proven, structured, and highly engineered approach to software design that renowned architect Juval Löwy has practiced and taught around the world. Although companies of every kind have successfully implemented his original design ideas across hundreds of systems, these insights have never before appeared in print. Based on first principles in software engineering and a comprehensive set of matching tools and techniques, Löwy’s methodology integrates system design and project design. First, he describes the primary area where many software architects fail and shows how to decompose a system into smaller building blocks or services, based on volatility. Next, he shows how to flow an effective project design from the system design; how to accurately calculate the project duration, cost, and risk; and how to devise multiple execution options. The method and principles in Righting Software apply regardless of your project and company size, technology, platform, or industry. Löwy starts the reader on a journey that addresses the critical challenges of software development today by righting software systems and projects as well as careers–and possibly the software industry as a whole. Software professionals, architects, project leads, or managers at any stage of their career will benefit greatly from this book, which provides guidance and knowledge that would otherwise take decades and many projects to acquire. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Software Development & Engineering,General

Real-World Software Development Explore the latest Java-based software development techniques and methodologies through the project-based approach in this practical guide. Unlike books that use abstract examples and lots of theory, Real-World Software Development shows you how to develop several relevant projects while learning best practices along the way. With this engaging approach, junior developers capable of writing basic Java code will learn about state-of-the-art software development practices for building modern, robust and maintainable Java software. You’ll work with many different software development topics that are often excluded from software develop how-to references. Featuring real-world examples, this book teaches you techniques and methodologies for functional programming, automated testing, security, architecture, and distributed systems. COMPUTERS,Software Development & Engineering,General

The Ghidra Book A guide to using the Ghidra software reverse engineering tool suite. The result of more than a decade of research and development within the NSA, the Ghidra platform was developed to address some of the agency's most challenging reverse-engineering problems. With the open-source release of this formerly restricted tool suite, one of the world's most capable disassemblers and intuitive decompilers is now in the hands of cybersecurity defenders everywhere -- and The Ghidra Book is the one and only guide you need to master it. In addition to discussing RE techniques useful in analyzing software and malware of all kinds, the book thoroughly introduces Ghidra's components, features, and unique capacity for group collaboration. You'll learn how to: • Navigate a disassembly • Use Ghidra's built-in decompiler to expedite analysis • Analyze obfuscated binaries • Extend Ghidra to recognize new data types • Build new Ghidra analyzers and loaders • Add support for new processors and instruction sets • Script Ghidra tasks to automate workflows • Set up and use a collaborative reverse engineering environment Designed for beginner and advanced users alike, The Ghidra Book will effectively prepare you to meet the needs and challenges of RE, so you can analyze files like a pro. COMPUTERS,Software Development & Engineering,General

Practical Machine Learning in R Guides professionals and students through the rapidly growing field of machine learning with hands-on examples in the popular R programming language Machine learning—a branch of Artificial Intelligence (AI) which enables computers to improve their results and learn new approaches without explicit instructions—allows organizations to reveal patterns in their data and incorporate predictive analytics into their decision-making process. Practical Machine Learning in R provides a hands-on approach to solving business problems with intelligent, self-learning computer algorithms. Bestselling author and data analytics experts Fred Nwanganga and Mike Chapple explain what machine learning is, demonstrate its organizational benefits, and provide hands-on examples created in the R programming language. A perfect guide for professional self-taught learners or students in an introductory machine learning course, this reader-friendly book illustrates the numerous real-world business uses of machine learning approaches. Clear and detailed chapters cover data wrangling, R programming with the popular RStudio tool, classification and regression techniques, performance evaluation, and more. Explores data management techniques, including data collection, exploration and dimensionality reduction Covers unsupervised learning, where readers identify and summarize patterns using approaches such as apriori, eclat and clustering Describes the principles behind the Nearest Neighbor, Decision Tree and Naive Bayes classification techniques Explains how to evaluate and choose the right model, as well as how to improve model performance using ensemble methods such as Random Forest and XGBoost Practical Machine Learning in R is a must-have guide for business analysts, data scientists, and other professionals interested in leveraging the power of AI to solve business problems, as well as students and independent learners seeking to enter the field. COMPUTERS,Software Development & Engineering,General

97 Things Every Scrum Practitioner Should Know Improve your understanding of Scrum through the proven experience and collected wisdom of experts around the world. Based on real-life experiences, the 97 essays in this unique book provide a wealth of knowledge and expertise from established practitioners who have dealt with specific problems and challenges with Scrum. You’ll find out more about the rules and roles of this framework, as well as tactics, strategies, specific patterns to use with Scrum, and stories from the trenches. You’ll also gain insights on how to apply, tune, and tweak Scrum for your work. This guide is an ideal resource for people new to Scrum and those who want to assess and improve their understanding of this framework. "Scrum Is Simple. Just Use It As Is.," Ken Schwaber "The 'Standing Meeting,'" Bob Warfield “Specialization Is for Insects,†James O. Coplien "Scrum Events Are Rituals to Ensure Good Harvest," Jasper Lamers “Servant Leadership Starts from Within,†Bob Galen "Agile Is More than Sprinting," James W. Grenning COMPUTERS,Software Development & Engineering,General

Software Developer This book explains the software developer role, including the relevant skills and competencies you will need. Discussion of popular programming languages is covered, as well as tools and techniques of the trade. Career progression tips and software developer case studies round off the book. COMPUTERS,Software Development & Engineering,General

97 Things Every Java Programmer Should Know If you want to push your Java skills to the next level, this book provides expert advice from Java leaders and practitioners. You’ll be encouraged to look at problems in new ways, take broader responsibility for your work, stretch yourself by learning new techniques, and become as good at the entire craft of development as you possibly can. Edited by Kevlin Henney and Trisha Gee, 97 Things Every Java Programmer Should Know reflects lifetimes of experience writing Java software and living with the process of software development. Great programmers share their collected wisdom to help you rethink Java practices, whether working with legacy code or incorporating changes since Java 8. A few of the 97 things you should know: "Behavior Is Easy, State Is Hard"—Edson Yanaga “Learn Java Idioms and Cache in Your Brainâ€â€”Jeanne Boyarsky “Java Programming from a JVM Performance Perspectiveâ€â€”Monica Beckwith "Garbage Collection Is Your Friend"—Holly K Cummins “Java's Unspeakable Typesâ€â€”Ben Evans "The Rebirth of Java"—Sander Mak “Do You Know What Time It Is?â€â€”Christin Gorman COMPUTERS,Software Development & Engineering,General

Advances in Computers Advances in Computers, Volume 119, presents innovations in computer hardware, software, theory, design, and applications, with this updated volume including new chapters on Fast Execution of RDF Queries Using Apache Hadoop, A Study of DVFS Methodologies for Multicore Systems with Islanding Feature, Effectiveness of State-of-the-art Dynamic Analysis Techniques in Identifying Diverse Android Malware and Future Enhancements, Eyeing the Patterns: Data Visualization Using Doubly-Seriated Color Heatmaps, Eigenvideo for Video Indexing. Contains novel subject matter that is relevant to computer science Includes the expertise of contributing authors Presents an easy to comprehend writing style COMPUTERS,Software Development & Engineering,General

Cloud Computing and Services Science This book constitutes extended, revised and selected papers from the 9th International Conference on Cloud Computing and Services Science, CLOSER 2019, held in Heraklion, Greece, in May 2019.The 11 papers presented in this volume were carefully reviewed and selected from a total of 102 submissions. CLOSER 2019 focuses on the emerging area of Cloud Computing, inspired by some latest advances that concern the infrastructure, operations, and available servicesthrough the global network. COMPUTERS,Software Development & Engineering,General

Formal Techniques for Distributed Objects, Components, and Systems This book constitutes the proceedings of the 40th IFIP WG 6.1 International Conference on Formal Techniques for Distributed Objects, Components, and Systems, FORTE 2020, held in Valletta, Malta, in June 2020, as part of the 15th International Federated Conference on Distributed Computing Techniques, DisCoTec 2020.* The 10 full papers and 1 short paper presented were carefully reviewed and selected from 25 submissions. The conference is dedicated to fundamental research on theory, models, tools, and applications for distributed systems. *The conference was held virtually due to the COVID-19 pandemic. Chapter ‘Conformance-Based Doping Detection for Cyber-Physical Systems’ is available open access under a Creative Commons Attribution 4.0 International License via link.springer.com. COMPUTERS,Software Development & Engineering,General

Coordination Models and Languages This book constitutes the proceedings of the 22nd International Conference on Coordination Models and Languages, COORDINATION 2020, which was due to be held in Valletta, Malta, in June 2020, as part of the 15th International Federated Conference on Distributed Computing Techniques, DisCoTec 2020. The conference was held virtually due to the COVID-19 pandemic. The 12 full papers and 6 short papers included in this volume were carefully reviewed and selected from 30 submissions. They are presented in this volume together with 2 invited tutorials and 4 tool papers. The papers are organized in the following topical sections: tutorials; coordination languages; message-based communication; communications: types & implementations; service-oriented computing; large-scale decentralized systems; smart contracts; modelling; verification & analysis. COMPUTERS,Software Development & Engineering,General

High Performance Computing This book constitutes the refereed proceedings of the 35th International Conference on High Performance Computing, ISC High Performance 2020, held in Frankfurt/Main, Germany, in June 2020.*The 27 revised full papers presented were carefully reviewed and selected from 87 submissions. The papers cover a broad range of topics such as architectures, networks & infrastructure; artificial intelligence and machine learning; data, storage & visualization; emerging technologies; HPC algorithms; HPC applications; performance modeling & measurement; programming models & systems software. *The conference was held virtually due to the COVID-19 pandemic. Chapters "Scalable Hierarchical Aggregation and Reduction Protocol (SHARP) Streaming-Aggregation Hardware Design and Evaluation", "Solving Acoustic Boundary Integral Equations Using High Performance Tile Low-Rank LU Factorization", "Scaling Genomics Data Processing with Memory-Driven Computing to Accelerate Computational Biology", "Footprint-Aware Power Capping for Hybrid Memory Based Systems", and "Pattern-Aware Staging for Hybrid Memory Systems" are available open access under a Creative Commons Attribution 4.0 International License via link.springer.com. COMPUTERS,Software Development & Engineering,General

Tests and Proofs This book constitutes the refereed proceedings of the 14th International Conference on Tests and Proofs, TAP 2020, held as part of the 4th World Congress on Formal Methods 2020, Bergen, Norway, in June 2020.The 7 regular papers, 1 short paper and 2 demonstration papers presented in this volume were carefully reviewed and selected from 209 submissions. The TAP conference promotes research in verification and formal methods that targets the interplay of proofs and testing: the advancement of techniques of each kind and their combination, with the ultimate goal of improving software and system dependability. COMPUTERS,Software Development & Engineering,General

Front-End Developer This book covers the role of front-end developer in terms of typical responsibilities, required skills and relevant tools, methods and techniques. Career progression for front-end developers is also discussed. COMPUTERS,Software Development & Engineering,General

OCP Oracle Certified Professional Java SE 11 Programmer II Study Guide This OCP Oracle Certified Professional Java SE 11 Programmer I Study Guide: Exam 1Z0-815 and the Programmer II Study Guide: Exam 1Z0-816 were published before Oracle announced major changes to its OCP certification program and the release of the new Developer 1Z0-819 exam. No matter the changes, rest assured both of the Programmer I and II Study Guides cover everything you need to prepare for and take Exam 1Z0-819. If you’ve purchased one of the Programmer Study Guides, purchase the other one and you’ll be all set. NOTE: The OCP Java SE 11 Programmer I Exam 1Z0-815 and Programmer II Exam 1Z0-816 have been retired (as of October 1, 2020), and Oracle has released a new Developer Exam 1Z0-819 to replace the previous exams. The Upgrade Exam 1Z0-817 remains the same. The completely-updated preparation guide for the new OCP Oracle Certified Professional Java SE 11 Programmer II exam—covers Exam 1Z0-816 Java, a platform-independent, object-oriented programming language, is used primarily in mobile and desktop application development. It is a popular language for client-side cloud applications and the principal language used to develop Android applications. Oracle has recently updated its Java Programmer certification tracks for Oracle Certified Professional. OCP Oracle Certified Professional Java SE 11 Programmer II Study Guide ensures that you are fully prepared for this difficult certification exam. Covering 100% of exam objectives, this in-depth study guide provides comprehensive coverage of the functional-programming knowledge necessary to succeed. Every exam topic is thoroughly and completely covered including exceptions and assertions, class design, generics and collections, threads, concurrency, IO and NIO, and more. Access to Sybex's superior online interactive learning environment and test bank—including self-assessment tests, chapter tests, bonus practice exam questions, electronic flashcards, and a searchable glossary of important terms—provides everything you need to be fully prepared on exam day. This must-have guide: Covers all exam objectives such as inheriting abstract classes and interfaces, advanced strings and localization, JDBC, and Object-Oriented design principles and patterns Explains complex material and reinforces your comprehension and retention of important topics Helps you master more advanced areas of functional programming Demonstrates practical methods for building Java solutions OCP Oracle Certified Professional Java SE 11 Programmer II Study Guide will prove invaluable for anyone seeking achievement of this challenging exam, as well as junior- to senior-level programmers who uses Java as their primary programming language. COMPUTERS,Software Development & Engineering,General
The Problem with Software An industry insider explains why there is so much bad software—and why academia doesn't teach programmers what industry wants them to know. Why is software so prone to bugs? So vulnerable to viruses? Why are software products so often delayed, or even canceled? Is software development really hard, or are software developers just not that good at it? In The Problem with Software, Adam Barr examines the proliferation of bad software, explains what causes it, and offers some suggestions on how to improve the situation. For one thing, Barr points out, academia doesn't teach programmers what they actually need to know to do their jobs: how to work in a team to create code that works reliably and can be maintained by somebody other than the original authors. As the size and complexity of commercial software have grown, the gap between academic computer science and industry has widened. It's an open secret that there is little engineering in software engineering, which continues to rely not on codified scientific knowledge but on intuition and experience. Barr, who worked as a programmer for more than twenty years, describes how the industry has evolved, from the era of mainframes and Fortran to today's embrace of the cloud. He explains bugs and why software has so many of them, and why today's interconnected computers offer fertile ground for viruses and worms. The difference between good and bad software can be a single line of code, and Barr includes code to illustrate the consequences of seemingly inconsequential choices by programmers. Looking to the future, Barr writes that the best prospect for improving software engineering is the move to the cloud. When software is a service and not a product, companies will have more incentive to make it good rather than “good enough to ship." COMPUTERS,Software Development & Engineering,General

The Software Arts An alternative history of software that places the liberal arts at the very center of software's evolution. In The Software Arts, Warren Sack offers an alternative history of computing that places the arts at the very center of software's evolution. Tracing the origins of software to eighteenth-century French encyclopedists' step-by-step descriptions of how things were made in the workshops of artists and artisans, Sack shows that programming languages are the offspring of an effort to describe the mechanical arts in the language of the liberal arts. Sack offers a reading of the texts of computing—code, algorithms, and technical papers—that emphasizes continuity between prose and programs. He translates concepts and categories from the liberal and mechanical arts—including logic, rhetoric, grammar, learning, algorithm, language, and simulation—into terms of computer science and then considers their further translation into popular culture, where they circulate as forms of digital life. He considers, among other topics, the “arithmetization” of knowledge that presaged digitization; today's multitude of logics; the history of demonstration, from deduction to newer forms of persuasion; and the post-Chomsky absence of meaning in grammar. With The Software Arts, Sack invites artists and humanists to see how their ideas are at the root of software and invites computer scientists to envision themselves as artists and humanists. COMPUTERS,Software Development & Engineering,General

The Stack A comprehensive political and design theory of planetary-scale computation proposing that The Stack—an accidental megastructure—is both a technological apparatus and a model for a new geopolitical architecture. What has planetary-scale computation done to our geopolitical realities? It takes different forms at different scales—from energy and mineral sourcing and subterranean cloud infrastructure to urban software and massive universal addressing systems; from interfaces drawn by the augmentation of the hand and eye to users identified by self—quantification and the arrival of legions of sensors, algorithms, and robots. Together, how do these distort and deform modern political geographies and produce new territories in their own image? In The Stack, Benjamin Bratton proposes that these different genres of computation—smart grids, cloud platforms, mobile apps, smart cities, the Internet of Things, automation—can be seen not as so many species evolving on their own, but as forming a coherent whole: an accidental megastructure called The Stack that is both a computational apparatus and a new governing architecture. We are inside The Stack and it is inside of us. In an account that is both theoretical and technical, drawing on political philosophy, architectural theory, and software studies, Bratton explores six layers of The Stack: Earth, Cloud, City, Address, Interface, User. Each is mapped on its own terms and understood as a component within the larger whole built from hard and soft systems intermingling—not only computational forms but also social, human, and physical forces. This model, informed by the logic of the multilayered structure of protocol “stacks,” in which network technologies operate within a modular and vertical order, offers a comprehensive image of our emerging infrastructure and a platform for its ongoing reinvention. The Stack is an interdisciplinary design brief for a new geopolitics that works with and for planetary-scale computation. Interweaving the continental, urban, and perceptual scales, it shows how we can better build, dwell within, communicate with, and govern our worlds. thestack.org COMPUTERS,Software Development & Engineering,General

Modeling and Simulating Software Architectures A new, quantitative architecture simulation approach to software design that circumvents costly testing cycles by modeling quality of service in early design states. Too often, software designers lack an understanding of the effect of design decisions on such quality attributes as performance and reliability. This necessitates costly trial-and-error testing cycles, delaying or complicating rollout. This book presents a new, quantitative architecture simulation approach to software design, which allows software engineers to model quality of service in early design stages. It presents the first simulator for software architectures, Palladio, and shows students and professionals how to model reusable, parametrized components and configured, deployed systems in order to analyze service attributes. The text details the key concepts of Palladio's domain-specific modeling language for software architecture quality and presents the corresponding development stage. It describes how quality information can be used to calibrate architecture models from which detailed simulation models are automatically derived for quality predictions. Readers will learn how to approach systematically questions about scalability, hardware resources, and efficiency. The text features a running example to illustrate tasks and methods as well as three case studies from industry. Each chapter ends with exercises, suggestions for further reading, and “takeaways” that summarize the key points of the chapter. The simulator can be downloaded from a companion website, which offers additional material. The book can be used in graduate courses on software architecture, quality engineering, or performance engineering. It will also be an essential resource for software architects and software engineers and for practitioners who want to apply Palladio in industrial settings. COMPUTERS,Software Development & Engineering,General

Android Application Development All-in-One For Dummies Conquer the world of Android app development Android has taken over the mobile and TV markets and become unstoppable! Android offers a vast stage for developers to serve millions—and rake in the profits—with diverse and wide-ranging app ideas. Whether you’re a raw recruit or a veteran programmer, you can get in on the action and become a master of the Android programming universe with the new edition of Android Application Development For Dummies All-in-One. In addition to receiving guidance on mobile and TV development, you’ll find overviews of native code, watch, car, Android wear, and other device development. This friendly, easy-to-follow book kicks off by offering a fundamental understanding of Android’s major technical ideas, including functional programming techniques. It moves on to show you how to work effectively in Studio, program cool new features, and test your app to make sure it’s ready to release to a waiting world. You’ll also have an opportunity to brush up on your Kotlin and develop your marketing savvy. There are millions of potential customers out there, and you want to stand out from the crowd! Understand new features and enhancements Get development best-practices Know your Android hardware Access online materials With a market share like Android’s, the stakes couldn’t be higher. Android Application Development For Dummies All-in-One levels the field and gives you the tools you need to take on the world. COMPUTERS,Software Development & Engineering,General

Variable Domain-specific Software Languages with DjDSL This book details the conceptual foundations, design and implementation of the domain-specific language (DSL) development system DjDSL. DjDSL facilitates design-decision-making on and implementation of reusable DSL and DSL-product lines, and represents the state-of-the-art in language-based and composition-based DSL development. As such, it unites elements at the crossroads between software-language engineering, model-driven software engineering, and feature-oriented software engineering. The book is divided into six chapters. Chapter 1 (“DSL as Variable Softwareâ€) explains the notion of DSL as variable software in greater detail and introduces readers to the idea of software-product line engineering for DSL-based software systems. Chapter 2 (“Variability Support in DSL Developmentâ€) sheds light on a number of interrelated dimensions of DSL variability: variable development processes, variable design-decisions, and variability-implementation techniques for DSL. The three subsequent chapters are devoted to the key conceptual and technical contributions of DjDSL: Chapter 3 (“Variable Language Modelsâ€) explains how to design and implement the abstract syntax of a DSL in a variable manner. Chapter 4 (“Variable Context Conditionsâ€) then provides the means to refine an abstract syntax (language model) by using composable context conditions (invariants). Next, Chapter 5 (“Variable Textual Syntaxesâ€) details solutions to implementing variable textual syntaxes for different types of DSL. In closing, Chapter 6 (“A Story of a DSL Familyâ€) shows how to develop a mixed DSL in a step-by-step manner, demonstrating how the previously introduced techniques can be employed in an advanced example of developing a DSL family. The book is intended for readers interested in language-oriented as well as model-driven software development, including software-engineering researchers and advanced software developers alike. An understanding of software-engineering basics (architecture, design, implementation, testing) and software patterns is essential. Readers should especially be familiar with the basics of object-oriented modelling (UML, MOF, Ecore) and programming (e.g., Java). COMPUTERS,Software Development & Engineering,General

User Experience Foundations This book provides a reasoned and authoritative description of what user experience (UX) is, why it works and what tools and techniques are involved, in line with the BCS Foundation Certificate in User Experience, based on ISO 9241-210. COMPUTERS,Software Development & Engineering,General

The Art of Immutable Architecture This book teaches you how to evaluate a distributed system from the perspective of immutable objects. You will understand the problems in existing designs, know how to make small modifications to correct those problems, and learn to apply the principles of immutable architecture to your tools. Most software components focus on the state of objects. They store the current state of a row in a relational database. They track changes to state over time, making several basic assumptions: there is a single latest version of each object, the state of an object changes sequentially, and a system of record exists. This is a challenge when it comes to building distributed systems. Whether dealing with autonomous microservices or disconnected mobile apps, many of the problems we try to solve come down to synchronizing an ever-changing state between isolated components. Distributed systems would be a lot easier to build if objects could not change. After reading The Art of Immutable Architecture , you will come away with an understanding of the benefits of using immutable objects in your own distributed systems. You will learn a set of rules for identifying and exchanging immutable objects, and see a collection of useful theorems that emerges and ensures that the distributed systems we build are eventually consistent. Using patterns, you will find where the truth converges, see how changes are associative, rather than sequential, and come to feel comfortable understanding that there is no longer a single source of truth. Practical hands-on examples reinforce how to build software using the described patterns, techniques, and tools. By the end, you will possess the language and resources needed to analyze and construct distributed systems with confidence. The assumptions of the past were sufficient for building single-user, single-computer systems. But as we expand to multiple devices, shared experiences, and cloud computing, they work against us. It is time for a new set of assumptions. Start with immutable objects, and build better distributed systems. What You Will Learn Evaluate a distributed system from the perspective of immutable objects Recognize the problems in existing designs, and make small modifications to correct them Start a new system from scratch, applying patterns Apply the principles of immutable architecture to your tools, including SQL databases, message queues, and the network protocols that you already use Discover new tools that natively apply these principles Who This Book Is For Software architects and senior developers. It contains examples in SQL and languages such as JavaScript and C#. Past experience with distributed computing, data modeling, or business analysis is helpful. COMPUTERS,Software Development & Engineering,General

OCP Oracle Certified Professional Java SE 11 Developer Complete Study Guide This OCP Oracle Certified Professional Java SE 11 Developer Complete Study Guide was published before Oracle announced major changes to its OCP certification program and the release of the new Developer 1Z0-819 exam. No matter the changes, rest assured this Study Guide covers everything you need to prepare for and take the exam. NOTE: The OCP Java SE 11 Programmer I Exam 1Z0-815 and Programmer II Exam 1Z0-816 have been retired (as of October 1, 2020), and Oracle has released a new Developer Exam 1Z0-819 to replace the previous exams. The Upgrade Exam 1Z0-817 remains the same. This is the most comprehensive prep guide available for the OCP Oracle Certified Professional Java SE 11 Developer certification—it covers Exam 1Z0-819 and the Upgrade Exam 1Z0-817 (as well as the retired Programmer I Exam 1Z0-815 and Programmer II Exam 1Z0-816)! Java is widely-used for backend cloud applications, Software as a Service applications (SAAS), and is the principal language used to develop Android applications. This object-oriented programming language is designed to run on all platforms that support Java without the need for recompilation. Oracle Java Programmer certification is highly valued by employers throughout the technology industry. The OCP Oracle Certified Professional Java SE 11 Developer Complete Study Guide in an indispensable resource for anyone preparing for the certification exam. This fully up-to-date guide covers 100% of exam objectives for Exam 1Z0-819 and Upgrade Exam 1Z0-817 (in addition to the previous Exam 1Z0-815 and Exam 1Z0-816). In-depth chapters present clear, comprehensive coverage of the functional-programming knowledge necessary to succeed. Each chapter clarifies complex material while reinforcing your understanding of vital exam topics. Also included is access to Sybex's superior online interactive learning environment and test bank that includes self-assessment tests, chapter tests, bonus practice exam questions, electronic flashcards, and a searchable glossary of important terms. The ultimate study aid for the challenging OCP exams, this popular guide: Helps you master the changes in depth, difficultly, and new module topics of the latest OCP exams Covers all exam objectives such as Java arrays, primitive data types, string APIs, objects and classes, operators and decision constructs, and applying encapsulation Allows developers to catch up on all of the newest Java material like lambda expressions, streams, concurrency, annotations, generics, and modules Provides practical methods for building Java applications, handling exceptions, programming through interfaces, secure coding in Java SE, and more Enables you to gain the information, understanding, and practice you need to pass the OCP exams The OCP Oracle Certified Professional Java SE 11 Developer Complete Study Guide is a must-have book for certification candidates needing to pass these challenging exams, as well as junior- to senior-level developers who use Java as their primary programming language. COMPUTERS,Software Development & Engineering,General

SAFe 5.0 Distilled SAFe® 5.0: The World's Leading Framework for Business Agility "Those who master large-scale software delivery will define the economic landscape of the twenty-first century. SAFe 5.0 is a monumental release that I am convinced will be key in helping countless enterprise organizations succeed in their shift from project to product."–Dr. Mik Kersten, CEO of Tasktop and author of the book Project to Product Business agility is the ability to compete and thrive in the digital age by quickly responding to unprecedented market changes, threats, and emerging opportunities with innovative business solutions. SAFe® 5.0 Distilled: Achieving Business Agility with Scaled Agile Framework® explains how adopting SAFe helps enterprises use the power of Agile, Lean, and DevOps to outflank the competition and deliver complex, technology-based business solutions in the shortest possible time. This book will help you Understand the business case for SAFe: its benefits, and the problems it solves Learn the technical, organizational and leadership competencies needed for business agility Refocus on customer centricity with design thinking Better align strategy and execution with Lean Portfolio Management Learn the leadership skills needed to thrive in the digital age Increase the flow of value to customers with value stream networks Register your book for convenient access to downloads, updates, and/or corrections as they become available. See inside book for details. COMPUTERS,Software Development & Engineering,General

Mythical Man-Month, Anniversary Edition, The Few books on software project management have been as influential and timeless as The Mythical Man-Month. With a blend of software engineering facts and thought-provoking opinions, Fred Brooks offers insight for anyone managing complex projects. These essays draw from his experience as project manager for the IBM System/360 computer family and then for OS/360, its massive software system. Now, 20 years after the initial publication of his book, Brooks has revisited his original ideas and added new thoughts and advice, both for readers already familiar with his work and for readers discovering it for the first time. The added chapters contain (1) a crisp condensation of all the propositions asserted in the original book, including Brooks' central argument in The Mythical Man-Month: that large programming projects suffer management problems different from small ones due to the division of labor; that the conceptual integrity of the product is therefore critical; and that it is difficult but possible to achieve this unity; (2) Brooks' view of these propositions a generation later; (3) a reprint of his classic 1986 paper "No Silver Bullet"; and (4) today's thoughts on the 1986 assertion, "There will be no silver bullet within ten years." COMPUTERS,Software Development & Engineering,Project Management

Management 3.0 In many organisations, management is the biggest obstacle to successful Agile development. Unfortunately, reliable guidance on Agile management has been scarce indeed. Now, leading Agile manager Jurgen Appelo fills that gap, introducing a realistic approach to leading, managing, and growing your Agile team or organisation. Writing for current managers and developers moving into management, Appelo shares insights that are grounded in modern complex systems theory, reflecting the intense complexity of modern software development. Appelo’s Management 3.0 model recognises that today’s organizations are living, networked systems; and that management is primarily about people and relationships. Management 3.0 doesn’t offer mere checklists or prescriptions to follow slavishly; rather, it deepens your understanding of how organisations and Agile teams work and gives you tools to solve your own problems. Drawing on his extensive experience as an Agile manager, the author identifies the most important practices of Agile management and helps you improve each of them. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Software Development & Engineering,Project Management

Adrenaline Junkies and Template Zombies This is the digital version of the printed book (Copyright © 2008). Adrenaline junkies, dead fish, project sluts, true believers, Lewis and Clark, template zombies . . . Most developers, testers, and managers on IT projects are pretty good at recognizing patterns of behavior and gut-level hunches, as in, “I sense that this project is headed for disaster.†But it has always been more difficult to transform these patterns and hunches into a usable form, something a team can debate, refine, and use. Until now. In Adrenaline Junkies and Template Zombies, the six principal consultants of The Atlantic Systems Guild present the patterns of behavior they most often observe at the dozens of IT firms they transform each year, around the world. The result is a quick-read guide to identifying nearly ninety typical scenarios, drawing on a combined one-hundred-and-fifty years of project management experience. Project by project, you’ll improve the accuracy of your hunches and your ability to act on them. The patterns are presented in an easy-reference format, with names designed to ease communication with your teammates. In just a few words, you can describe what’s happening on your project. Citing the patterns of behavior can help you quickly move those above and below you to the next step on your project. You’ll find classic patterns such as these: News Improvement Management by Mood Ring Piling On Rattle Yer Dags Natural Authority Food++ Fridge Door and more than eighty more! Not every pattern will be evident in your organization, and not every pattern is necessarily good or bad. However, you’ll find many patterns that will apply to your current and future assignments, even in the most ambiguous circumstances. When you assess your situation and follow your next hunch, you'll have the collective wisdom of six world-class consultants at your side. COMPUTERS,Software Development & Engineering,Project Management

Measuring and Managing Performance in Organizations This is the digital version of the printed book (Copyright © 1996). Based on an award-winning doctoral thesis at Carnegie Mellon University, Measuring and Managing Performance in Organizations presents a captivating analysis of the perils of performance measurement systems. In the book’s foreword, Peopleware authors Tom DeMarco and Timothy Lister rave, “We believe this is a book that needs to be on the desk of just about anyone who manages anything.†Because people often react with unanticipated sophistication when they are being measured, measurement-based management systems can become dysfunctional, interfering with achievement of intended results. Fortunately, as the author shows, measurement dysfunction follows a pattern that can be identified and avoided. The author’s findings are bolstered by interviews with eight recognized experts in the use of measurement to manage computer software development: David N. Card, of Software Productivity Solutions; Tom DeMarco, of the Atlantic Systems Guild; Capers Jones, of Software Productivity Research; John Musa, of AT&T Bell Laboratories; Daniel J. Paulish, of Siemens Corporate Research; Lawrence H. Putnam, of Quantitative Software Management; E. O. Tilford, Sr., of Fissure; plus the anonymous Expert X. A practical model for analyzing measurement projects solidifies the text–don’t start without it! COMPUTERS,Software Development & Engineering,Project Management

Implementing Lean Software Development "This remarkable book combines practical advice, ready-to-use techniques, anda deep understanding of why this is the right way to develop software. I haveseen software teams transformed by the ideas in this book." --Mike Cohn, author of Agile Estimating and Planning "As a lean practitioner myself, I have loved and used their first book for years.When this second book came out, I was delighted that it was even better. If youare interested in how lean principles can be useful for software developmentorganizations, this is the book you are looking for. The Poppendiecks offer abeautiful blend of history, theory, and practice." --Alan Shalloway, coauthor of Design Patterns Explained "I've enjoyed reading the book very much. I feel it might even be better than thefirst lean book by Tom and Mary, while that one was already exceptionallygood! Mary especially has a lot of knowledge related to lean techniques inproduct development and manufacturing. It's rare that these techniques areactually translated to software. This is something no other book does well(except their first book)." --Bas Vodde "The new book by Mary and Tom Poppendieck provides a well-written andcomprehensive introduction to lean principles and selected practices for softwaremanagers and engineers. It illustrates the application of the values andpractices with well-suited success stories. I enjoyed reading it." --Roman Pichler "In Implementing Lean Software Development, the Poppendiecks explore moredeeply the themes they introduced in Lean Software Development. They beginwith a compelling history of lean thinking, then move to key areas such asvalue, waste, and people. Each chapter includes exercises to help you apply keypoints. If you want a better understanding of how lean ideas can work withsoftware, this book is for you." --Bill Wake, independent consultant In 2003, Mary and Tom Poppendieck's Lean Software Development introduced breakthrough development techniques that leverage Lean principles to deliver unprecedented agility and value. Now their widely anticipated sequel and companion guide shows exactly how to implement Lean software development, hands-on. This new book draws on the Poppendiecks' unparalleled experience helping development organizations optimize the entire software value stream. You'll discover the right questions to ask, the key issues to focus on, and techniques proven to work. The authors present case studies from leading-edge software organizations, and offer practical exercises for jumpstarting your own Lean initiatives. Managing to extend, nourish, and leverage agile practices Building true development teams, not just groups Driving quality through rapid feedback and detailed discipline Making decisions Just-in-Time, but no later Delivering fast: How PatientKeeper delivers 45 rock-solid releases per year Making tradeoffs that really satisfy customers Implementing Lean Software Development is indispensable to anyone who wants more effective development processes--managers, project leaders, senior developers, and architects in enterprise IT and software companies alike. COMPUTERS,Software Development & Engineering,Project Management

Kanban Change Leadership Explains how and why Kanban offers a new approach to change in 21st Century businesses This book provides an understanding of what is necessary to properly understand change management with Kanban as well as how to apply it optimally in the workplace. The book emphasizes critical aspects, several traps which users repeatedly fall into, and presents some practical guidelines for Kanban change management to help avoid these traps. The authors have organized the book into three sections. The first section focuses on the foundations of Kanban, establishing the technical basis of Kanban and indicating the mechanisms required to enact change. In the second section, the authors explain the context of Kanban change management—the options for change, how they can be set in motion, and their consequences for a business. The third section takes the topics from the previous sections and relates them to the social system of business—the goal is to guide readers in the process of building a culture of continuousimprovement by reviewing real case studies and seeing how Kanban is applied in various situations. Kanban Change Leadership: Explains how to implement sustainable system-wide changes using Kanban principles Addresses the principles and core practices of Kanban including visualization, WIP limits, classes of service, operation and coordination, metrics, and improvement Describes implementation, preparation, assessment, training, feedback, commissioning, and operation processes in order to create a culture of continuous improvement Kanban Change Leadership is an educational and comprehensive text for: software and systems engineers; IT project managers; commercial and industrial executives and managers; as well as anyone interested in Kanban. COMPUTERS,Software Development & Engineering,Project Management

Debugging Teams In the course of their 20+-year engineering careers, authors Brian Fitzpatrick and Ben Collins-Sussman have picked up a treasure trove of wisdom and anecdotes about how successful teams work together. Their conclusion? Even among people who have spent decades learning the technical side of their jobs, most haven’t really focused on the human component. Learning to collaborate is just as important to success. If you invest in the "soft skills" of your job, you can have a much greater impact for the same amount of effort. The authors share their insights on how to lead a team effectively, navigate an organization, and build a healthy relationship with the users of your software. This is valuable information from two respected software engineers whose popular series of talks—including "Working with Poisonous People"—has attracted hundreds of thousands of followers. COMPUTERS,Software Development & Engineering,Project Management

The DevOps Adoption Playbook Achieve streamlined, rapid production with enterprise-level DevOps Awarded DevOps 2017 Book of the Year, The DevOps Adoption Playbook provides practical, actionable, real-world guidance on implementing DevOps at enterprise scale. Author Sanjeev Sharma heads the DevOps practice for IBM; in this book, he provides unique guidance and insight on implementing DevOps at large organizations. Most DevOps literature is aimed at startups, but enterprises have unique needs, capabilities, limitations, and challenges; "DevOps for startups" doesn't work at this scale, but the DevOps paradigm can revolutionize enterprise IT. Deliver high-value applications and systems with velocity and agility by adopting the necessary practices, automation tools, and organizational and cultural changes that lead to innovation through rapid experimentation. Speed is an advantage in the face of competition, but it must never come at the expense of quality; DevOps allows your organization to keep both by intersecting development, quality assurance, and operations. Enterprise-level DevOps comes with its own set of challenges, but this book shows you just how easily they are overcome. With a slight shift in perspective, your organization can stay ahead of the competition while keeping costs, risks, and quality under control. Grasp the full extent of the DevOps impact on IT organizations Achieve high-value innovation and optimization with low cost and risk Exceed traditional business goals with higher product release efficiency Implement DevOps in large-scale enterprise IT environments DevOps has been one of IT's hottest trends for the past decade, and plenty of success stories testify to its effectiveness in organizations of any size, industry, or level of IT maturity, all around the world. The DevOps Adoption Playbook shows you how to get your organization on board so you can slip production into the fast lane and innovate your way to the top. COMPUTERS,Software Development & Engineering,Project Management

Building Software Teams Why does poor software quality continue to plague enterprises of all sizes in all industries? Part of the problem lies with the process, rather than individual developers. This practical guide provides ten best practices to help team leaders create an effective working environment through key adjustments to their process. As a follow-up to their popular book, Building Maintainable Software, consultants with the Software Improvement Group (SIG) offer critical lessons based on their assessment of development processes used by hundreds of software teams. Each practice includes examples of goalsetting to help you choose the right metrics for your team. Achieve development goals by determining meaningful metrics with the Goal-Question-Metric approach Translate those goals to a verifiable Definition of Done Manage code versions for consistent and predictable modification Control separate environments for each stage in the development pipeline Automate tests as much as possible and steer their guidelines and expectations Let the Continuous Integration server do much of the hard work for you Automate the process of pushing code through the pipeline Define development process standards to improve consistency and simplicity Manage dependencies on third party code to keep your software consistent and up to date Document only the most necessary and current knowledge COMPUTERS,Software Development & Engineering,Project Management

Agile Project Management For Dummies Flex your project management muscle Agile project management is a fast and flexible approach to managing all projects, not just software development. By learning the principles and techniques in this book, you'll be able to create a product roadmap, schedule projects, and prepare for product launches with the ease of Agile software developers. You'll discover how to manage scope, time, and cost, as well as team dynamics, quality, and risk of every project. As mobile and web technologies continue to evolve rapidly, there is added pressure to develop and implement software projects in weeks instead of months—and Agile Project Management For Dummies can help you do just that. Providing a simple, step-by-step guide to Agile project management approaches, tools, and techniques, it shows product and project managers how to complete and implement projects more quickly than ever. Complete projects in weeks instead of months Reduce risk and leverage core benefits for projects Turn Agile theory into practice for all industries Effectively create an Agile environment Get ready to grasp and apply Agile principles for faster, more accurate development. COMPUTERS,Software Development & Engineering,Project Management

Head First Agile Head First Agile is a complete guide to learning real-world agile ideas, practices, principles. What will you learn from this book? In Head First Agile, you'll learn all about the ideas behind agile and the straightforward practices that drive it. You'll take deep dives into Scrum, XP, Lean, and Kanban, the most common real-world agile approaches today. You'll learn how to use agile to help your teams plan better, work better together, write better code, and improve as a team—because agile not only leads to great results, but agile teams say they also have a much better time at work. Head First Agile will help you get agile into your brain... and onto your team! Preparing for your PMI-ACP® certification? This book also has everything you need to get certified, with 100% coverage of the PMI-ACP® exam. Luckily, the most effective way to prepare for the exam is to get agile into your brain—so instead of cramming, you're learning. Why does this book look so different? Based on the latest research in cognitive science and learning theory, Head First Agile uses a visually rich format to engage your mind, rather than a text-heavy approach that puts you to sleep. Why waste your time struggling with new concepts? This multi-sensory learning experience is designed for the way your brain really works. COMPUTERS,Software Development & Engineering,Project Management

Product Management in Practice Product management has become a critical connective role for modern organizations, from small technology startups to global corporate enterprises. And yet the day-to-day work of product management remains largely misunderstood. In theory, product management is about building products that people love. The real-world practice of product management is often about difficult conversations, practical compromises, and hard-won incremental gains. In this book, author Matt LeMay focuses on the CORE connective skills— communication, organization, research, execution—that can build a successful product management practice across industries, organizations, teams, andtoolsets. For current and aspiring product managers, this book explores:? On-the-ground tactics for facilitating collaboration and communication? How to talk to users and work with executives? The importance of setting clear and actionable goals? Using roadmaps to connect and align your team? A values-first approach to implementing Agile practices? Common behavioral traps that turn good product managers bad COMPUTERS,Software Development & Engineering,Project Management

The Agile Samurai Printed in full color. Faced with a software project of epic proportions? Tired of over-committing and under-delivering? Enter the dojo of the agile samurai, where agile expert Jonathan Rasmusson shows you how to kick-start, execute, and deliver your agile projects. Combining cutting-edge tools with classic agile practices, The Agile Samurai gives you everything you need to deliver something of value every week and make rolling your software into production a non-event. Get ready to kick some software project butt. By learning the ways of the agile samurai you will discover: how to create plans and schedules your customer and your team can believe in what characteristics make a good agile team and how to form your own how to gather requirements in a fraction of the time using agile user stories what to do when you discover your schedule is wrong, and how to look like a pro correcting it how to execute fiercely by leveraging the power of agile software engineering practices By the end of this book you will know everything you need to set up, execute, and successfully deliver agile projects, and have fun along the way. If you're a project lead, this book gives you the tools to set up and lead your agile project from start to finish. If you are an analyst, programmer, tester, usability designer, or project manager, this book gives you the insight and foundation necessary to become a valuable agile team member. The Agile Samurai slices away the fluff and theory that make other books less-than-agile. It's packed with best practices, war stories, plenty of humor and hands-on tutorial exercises that will get you doing the right things, the right way. This book will make a difference. COMPUTERS,Software Development & Engineering,Project Management

Real-World Kanban Your team is stressed; priorities are unclear. You're not sure what your teammates are working on, and management isn't helping. If your team is struggling with any of these symptoms, these four case studies will guide you to project success. See how Kanban was used to significantly improve time to market and to create a shared focus across marketing, IT, and operations. Each case study comes with illustrations of the Kanban board and diagrams and graphs to help you see behind the scenes. Learn a Lean approach by seeing how Kanban made a difference in four real-world situations. You'll explore how four different teams used Kanban to make paradigm-changing improvements in software development. These teams were struggling with overwork, unclear priorities, and lack of direction. As you discover what worked for them, you'll understand how to make significant changes in real situations. The four case studies in this book explain how to: Improve the full value chain by using Enterprise Kanban Boost engagement, teamwork, and flow in change management and operations Save a derailing project with Kanban Help an office team outside IT keep up with growth using Kanban What seems easy in theory can become tangled in practice. Discover why "improving IT" can make you miss your biggest improvement opportunities, and why you should focus on fixing quality and front-end operations before IT. Discover how to keep long-term focus and improve across department borders while dealing with everyday challenges. Find out what happened when using Kanban to find better ways to do work in a well-established company, including running multi-team development without a project office. You'll inspire your team and engage management to make it easier to develop better products. What You Need: This is a case study book, so there are no software requirements. The book covers the relevant bits of theory before presenting the case studies. COMPUTERS,Software Development & Engineering,Project Management

Liftoff Ready, set, liftoff! Align your team to one purpose: successful delivery. Learn new insights and techniques for starting projects and teams the right way, with expanded concepts for planning, organizing, and conducting liftoff meetings. Real-life stories illustrate how others have effectively started (or restarted) their teams and projects. Master coaches Diana Larsen and Ainsley Nies have successfully "lifted off" numerous agile projects worldwide. Are you ready for success? Every team needs a great start. If you're a business or product leader, team coach or agile practice lead, project or program manager, you'll gain strategic and tactical benefits from liftoffs. Discover new step-by-step instructions and techniques for boosting team performance in this second edition of Liftoft. Concrete examples from our practices show you how to get everyone on the same page from the start as you form the team. You'll find pointers for refocusing an effort that's gone off in the weeds, and practices for working with teams as complex systems. See how to scale liftoffs for multiple teams across the enterprise, address the three key elements for collaborative team chartering, establish the optimal conditions for learning and improvement, and apply the GEFN (Good Enough for Now) rule for efficient liftoffs. Throughout the book are stories from real-life teams lifting off, as seasoned coaches describe their experiences with liftoffs and agile team chartering. Focused conversations help the team align, form, and build enough trust for collaborating. You'll build a common understanding of the teams' context within business goals. Every liftoff is unique, but success is common! COMPUTERS,Software Development & Engineering,Project Management

Building Products for the Enterprise If you’re new to software product management or just want to learn more about it, there’s plenty of advice available—but most of it is geared toward consumer products. Creating high-quality software for the enterprise involves a much different set of challenges. In this practical book, two expert product managers provide straightforward guidance for people looking to join the thriving enterprise market. Authors Blair Reeves and Benjamin Gaines explain critical differences between enterprise and consumer products, and deliver strategies for overcoming challenges when building for the enterprise. You’ll learn how to cultivate knowledge of your organization, the products you build, and the industry you serve. Explore why: Identifying customer vs user problems is an enterprise project manager’s main challenge Effective collaboration requires in-depth knowledge of the organization Analyzing data is key to understanding why users buy and retain your product Having experience in the industry you’re building products for is valuable Product longevity depends on knowing where the industry isheaded COMPUTERS,Software Development & Engineering,Project Management

Working with Odoo 11 Transform and modernize your businesses and upgrade your enterprise management skills with Odoo 11, the most comprehensive management software About This Book Use project management along with analytics for better reporting Build an Odoo module and integrate it with other platforms with this practical guide Explore new design and mobile updates from the Odoo enterprise Who This Book Is For This book is for beginners, and will help you learn advanced-level features with Odoo such as creating your own custom modules. You do not need any prior knowledge of Odoo. What You Will Learn Configure a functioning customer relationship management system Set up a purchasing and receiving system Implement manufacturing operations and processes using real-world examples Discover the capabilities of Odoo's financial accounting and reporting features Integrate powerful human resource applications Utilize Odoo's project management application to organize tasks Customize Odoo without writing a line of code In Detail Odoo is an all-in-one management software that offers an array of business applications, forming a complete suite of enterprise management applications. Odoo 11 comes with advances on usability, speed, and design. Working with Odoo 11 starts with how to set up Odoo, both online and on your own server. You'll then configure the basic company settings required to quickly get your first Odoo system up and running. Later, you'll explore customer relationship management in Odoo and its importance in a modern business environment. You'll then dive into purchasing applications with Odoo, learn some of the primary functionalities of ERP systems for manufacturing operations, and use analytic accounting to provide better reporting. After that, you'll learn how to work with Odoo for mobile, and finally, you will walk through the recent Odoo 11 features with respect to the community and enterprise edition, giving you a complete understanding of what Odoo can do for your business. Style and approach A guide to learning the advanced features of Odoo 11, to enable customization of Odoo modules to suite ones' business needs. COMPUTERS,Software Development & Engineering,Project Management

Head First PMP What will you learn from this book? Head First PMP teaches you the latest principles and certification objectives in The PMBOK® Guide in a unique and inspiring way. This updated fourth edition takes you beyond specific questions and answers with a unique visual format that helps you grasp the big picture of project management. By putting PMP concepts into context, you’ll be able to understand, remember, and apply them—not just on the exam, but on the job. No wonder so many people have used Head First PMP as their sole source for passing the PMP exam. This book will help you: Learn PMP’s underlying concepts to help you understand the PMBOK principles and pass the certification exam with flying colors Get 100% coverage of the latest principles and certification objectives in The PMBOK® Guide, Sixth Edition Make use of a thorough and effective preparation guide with hundreds of practice questions and exam strategies Explore the material through puzzles, games, problems, and exercises that make learning easy and entertaining Why does this book look so different? Based on the latest research in cognitive science and learning theory, Head First PMP uses a visually rich format to engage your mind, rather than a text-heavy approach that puts you to sleep. Why waste your time struggling with new concepts? This multi-sensory learning experience is designed for the way your brain really works. COMPUTERS,Software Development & Engineering,Project Management

Continuous API Management A lot of work is required to release an API, but the effort doesn’t always pay off. Overplanning before an API matures is a wasted investment, while underplanning can lead to disaster. This practical guide provides maturity models for individual APIs and multi-API landscapes to help you invest the right human and company resources for the right maturity level at the right time. How do you balance the desire for agility and speed with the need for robust and scalable operations? Four experts from the API Academy show software architects, program directors, and product owners how to maximize the value of their APIs by managing them as products through a continuous life cycle. Learn which API decisions you need to govern and how and where to do so Design, deploy, and manage APIs using an API-as-a-product (AaaP) approach Examine ten pillars that form the foundation of API product work Learn how the continuous improvement model governs changes throughout an API’s lifetime Explore the five stages of a complete API product life cycle Delve into team roles needed to design, build, and maintain your APIs Learn how to manage your API landscape—the set of APIs published by your organization COMPUTERS,Software Development & Engineering,Project Management

Jira 8 Administration Cookbook Build customized solutions that fulfil your business requirements using the latest features of Jira 8 Key Features Learn how to customize Jira applications to suit your organizational requirements Extend Jira's capabilities for custom integrations with other products and services such as Slack and GitHub Explore practical recipes for troubleshooting and securing your Jira instances with best practices Book Description Jira is a project management tool used widely by organizations to plan, track, and release software. Jira administrators are at the heart of these processes and need to know how to successfully administer and customize Jira offerings. This updated Jira 8 Administration Cookbook demonstrates how to efficiently work with Jira Core and Jira Service Desk. The book starts with a variety of recipes to help you manage users and workflows. You'll learn how to set up custom forms and capture important data with custom fields and screens. Next, you'll gain insights into the latest email capabilities, which assist you with everything from managing outgoing email rules to processing incoming emails for automated issue creation. Later, you'll be guided through running scripts to automate tasks, getting easy access to logs, and even working with tools to troubleshoot problems. The book will also ensure you understand how to integrate Jira with Slack, set up SSO with Google, and delegate administrator permissions. Finally, the chapter on Jira Service Desk will enable you to set up and customize your own support portal, work with internal teams to solve problems, and achieve optimized services with Service Level Agreement (SLA). By the end of this book, you'll have the skills to extend and customize your Jira implementation effectively. What you will learn Learn how to delegate administrator permissions effectively Gain insights into integrating Jira with Bitbucket Cloud and GitHub Explore ways to collaborate with your internal teams on service requests Understand how to add permissions to fields Learn how to set up SSO with Google Discover how to copy over configuration settings between Jira instances Who this book is for This book is for administrators who are looking to customize, support, and maintain Jira for their organizations. A good understanding of Jira's core concepts is a must to make the most out of this book. For certain recipes, some knowledge of HTML, CSS, JavaScript, and basic programming will also be helpful. COMPUTERS,Software Development & Engineering,Project Management

Fixing Your Scrum A Scrum Master's work is never done. The Development team needs your support, the Product Owner is often lost in the complexities of agile product management, and your managers and stakeholders need to know what will be done, by when, and for how much. Learn how experienced Scrum Masters balance the demands of these three levels of servant leadership while removing organizational impediments and helping Scrum Teams deliver real world value. Discover how to visualize your work, resolve impediments, and empower your teams to self-organize and deliver using the Scrum Values, Agile Principles, and advanced coaching and facilitation techniques. A Scrum Master needs to know when their team is in trouble and understand how to help them get back on the path to delivery. Become a better Scrum master so you can find the problems holding your teams back. Has your Daily Scrum turned in to a meeting? Does your team struggle with creating user stories? Are stakeholders disengaged during Sprint Review? These issues are common. Learn to use empiricism as your guide and help your teams create great products. Scrum is so much more than a checklist of practices to follow, yet that's exactly how many organizations practice it. Bring life back to your Scrum events by using advanced facilitation techniques to leverage the full intelligence of your team. Improve your retrospectives with new formats and exercises. Ask powerful questions that spark introspection and improvement. Get support and buy-in from management. Use Scrum as a competitive advantage for your organization. Create a definition of done that improves quality and fix failing sprints. Take the next step on your journey as a Scrum master. Transform your Scrum practices to help your teams enjoy their work again as they deliver high quality products that bring value to the world. What You Need: A moderate level of experience using the Scrum Framework. COMPUTERS,Software Development & Engineering,Project Management

Competing with Unicorns Today's tech unicorns develop software differently. They've developed a way of working that lets them scale like an enterprise while working like a startup. These techniques can be learned. This book takes you behind the scenes and shows you how companies like Google, Facebook, and Spotify do it. Leverage their insights, so your teams can work better together, ship higher-quality product faster, innovate more quickly, and compete with the unicorns. Massively successful tech companies, or Unicorns, have discovered how to take the techniques that made them successful as a startup and scale them to the enterprise level. Amazon, Facebook, Google, and Spotify all work like startups, despite having workforces numbering in the tens of thousands. Ex-Spotify engineer and coach, Jonathan Rasmusson, takes you behind the scenes and shows you how to develop software the way the best companies do it. Learn how to give teams purpose through Missions, empower and trust with Squads, and align large scale efforts through Bets. Create the culture necessary to make it happen. If you're a tech or product lead and you want to ship product better, this is your playbook on how the world's best do it. If you're an engineer, tester, analyst, or project manager, and you suspect there are better ways you could be working, you are correct. This book will show you how. And if you're a manager, Agile coach, or someone just charged with improving how your company ships software, this book will give you the tools, techniques, and practices of the world's most innovative, delivery-focused companies. Don't just admire the top companies - learn from them. COMPUTERS,Software Development & Engineering,Project Management

Software Configuration Management Patterns Stereotypes portray software engineers as a reckless lot, and stereotypes paint software configuration management (SCM) devotees as inflexible. Based on these impressions, it is no wonder that projects can be riddled with tension! The truth probably lies somewhere in between these stereotypes, and this book shows how proven SCM practices can foster a healthy team-oriented culture that produces better software. The authors show that workflow, when properly managed, can avert delays, morale problems, and cost overruns. A patterns approach (proven solutions to recurring problems) is outlined so that SCM can be easily applied and successfully leveraged in small to medium sized organizations. The patterns are presented with an emphasis on practicality. The results speak for themselves: improved processes and a motivated workforce that synergize to produce better quality software. COMPUTERS,Software Development & Engineering,Project Management

SQL Server Database Programming with Visual Basic.NET A guide to the practical issues and applications in database programming with updated Visual Basic.NET SQL Server Database Programming with Visual Basic.NET offers a guide to the fundamental knowledge and practical techniques for the design and creation of professional database programs that can be used for real-world commercial and industrial applications. The author—a noted expert on the topic—uses the most current version of Visual Basic.NET, Visual Basic.NET 2017 with Visual Studio.NET 2017. In addition, he introduces the updated SQL Server database and Microsoft SQL Server 2017 Express. All sample program projects can be run in the most updated version, Visual Basic.NET 2019 with Visual Studio.NET 2019. Written in an accessible, down-to-earth style, the author explains how to build a sample database using the SQL Server management system and Microsoft SQL Server Management Studio 2018. The latest version of ASP.NET, ASP.NET 4.7, is also discussed to provide the most up-to-date Web database programming technologies. This important book: Offers illustrative practical examples and detailed descriptions to aid in comprehension of the material presented Includes both fundamental and advanced database programming techniques Integrates images into associated database tables using a DevExpress UI tools -WindowsUI Written for graduate and senior undergraduate students studying database implementations and programming courses, SQL Server Database Programming with Visual Basic.NET shows how to develop professional and practical database programs in Visual Basic.NET 2017/Visual Basic.NET 2019. COMPUTERS,Software Development & Engineering,Project Management

xUnit Test Patterns This is the eBook version of the printed book. If the print book includes a CD-ROM, this content is not included within the eBook version. Automated testing is a cornerstone of agile development. An effective testing strategy will deliver new functionality more aggressively, accelerate user feedback, and improve quality. However, for many developers, creating effective automated tests is a unique and unfamiliar challenge. xUnit Test Patterns is the definitive guide to writing automated tests using xUnit, the most popular unit testing framework in use today. Agile coach and test automation expert Gerard Meszaros describes 68 proven patterns for making tests easier to write, understand, and maintain. He then shows you how to make them more robust and repeatable--and far more cost-effective. Loaded with information, this book feels like three books in one. The first part is a detailed tutorial on test automation that covers everything from test strategy to in-depth test coding. The second part, a catalog of 18 frequently encountered "test smells," provides trouble-shooting guidelines to help you determine the root cause of problems and the most applicable patterns. The third part contains detailed descriptions of each pattern, including refactoring instructions illustrated by extensive code samples in multiple programming languages. Topics covered include Writing better tests--and writing them faster The four phases of automated tests: fixture setup, exercising the system under test, result verification, and fixture teardown Improving test coverage by isolating software from its environment using Test Stubs and Mock Objects Designing software for greater testability Using test "smells" (including code smells, behavior smells, and project smells) to spot problems and know when and how to eliminate them Refactoring tests for greater simplicity, robustness, and execution speed This book will benefit developers, managers, and testers working with any agile or conventional development process, whether doing test-driven development or writing the tests last. While the patterns and smells are especially applicable to all members of the xUnit family, they also apply to next-generation behavior-driven development frameworks such as RSpec and JBehave and to other kinds of test automation tools, including recorded test tools and data-driven test tools such as Fit and FitNesse. Visual Summary of the Pattern Language Foreword Preface Acknowledgments Introduction Refactoring a Test PART I: The Narratives Chapter 1 A Brief Tour Chapter 2 Test Smells Chapter 3 Goals of Test Automation Chapter 4 Philosophy of Test Automation Chapter 5 Principles of Test Automation Chapter 6 Test Automation Strategy Chapter 7 xUnit Basics Chapter 8 Transient Fixture Management Chapter 9 Persistent Fixture Management Chapter 10 Result Verification Chapter 11 Using Test Doubles Chapter 12 Organizing Our Tests Chapter 13 Testing with Databases Chapter 14 A Roadmap to Effective Test Automation PART II: The Test Smells Chapter 15 Code Smells Chapter 16 Behavior Smells Chapter 17 Project Smells PART III: The Patterns Chapter 18 Test Strategy Patterns Chapter 19 xUnit Basics Patterns Chapter 20 Fixture Setup Patterns Chapter 21 Result Verification Patterns Chapter 22 Fixture Teardown Patterns Chapter 23 Test Double Patterns Chapter 24 Test Organization Patterns Chapter 25 Database Patterns Chapter 26 Design-for-Testability Patterns Chapter 27 Value Patterns PART IV: Appendixes Appendix A Test Refactorings Appendix B xUnit Terminology Appendix C xUnit Family Members Appendix D Tools Appendix E Goals and Principles COMPUTERS,Software Development & Engineering,Quality Assurance & Testing

Agile Testing Testing is a key component of agile development. The widespread adoption of agile methods has brought the need for effective testing into the limelight, and agile projects have transformed the role of testers. Much of a tester’s function, however, remains largely misunderstood. What is the true role of a tester? Do agile teams actually need members with QA backgrounds? What does it really mean to be an “agile tester?†Two of the industry’s most experienced agile testing practitioners and consultants, Lisa Crispin and Janet Gregory, have teamed up to bring you the definitive answers to these questions and many others. In Agile Testing, Crispin and Gregory define agile testing and illustrate the tester’s role with examples from real agile teams. They teach you how to use the agile testing quadrants to identify what testing is needed, who should do it, and what tools might help. The book chronicles an agile software development iteration from the viewpoint of a tester and explains the seven key success factors of agile testing. Readers will come away from this book understanding How to get testers engaged in agile development Where testers and QA managers fit on an agile team What to look for when hiring an agile tester How to transition from a traditional cycle to agile development How to complete testing activities in short iterations How to use tests to successfully guide development How to overcome barriers to test automation This book is a must for agile testers, agile teams, their managers, and their customers. COMPUTERS,Software Development & Engineering,Quality Assurance & Testing

Working Effectively with Legacy Code Get more out of your legacy systems: more performance, functionality, reliability, and manageability Is your code easy to change? Can you get nearly instantaneous feedback when you do change it? Do you understand it? If the answer to any of these questions is no, you have legacy code, and it is draining time and money away from your development efforts. In this book, Michael Feathers offers start-to-finish strategies for working more effectively with large, untested legacy code bases. This book draws on material Michael created for his renowned Object Mentor seminars: techniques Michael has used in mentoring to help hundreds of developers, technical managers, and testers bring their legacy systems under control. The topics covered include Understanding the mechanics of software change: adding features, fixing bugs, improving design, optimizing performance Getting legacy code into a test harness Writing tests that protect you against introducing new problems Techniques that can be used with any language or platform—with examples in Java, C++, C, and C# Accurately identifying where code changes need to be made Coping with legacy systems that aren't object-oriented Handling applications that don't seem to have any structure This book also includes a catalog of twenty-four dependency-breaking techniques that help you work with program elements in isolation and make safer changes. COMPUTERS,Software Development & Engineering,Quality Assurance & Testing

The Robert C. Martin Clean Code Collection (Collection) The Robert C. Martin Clean Code Collection consists of two bestselling eBooks: Clean Code: A Handbook of Agile Software Craftmanship The Clean Coder: A Code of Conduct for Professional Programmers In Clean Code, legendary software expert Robert C. Martin has teamed up with his colleagues from Object Mentor to distill their best agile practice of cleaning code “on the fly†into a book that will instill within you the values of a software craftsman and make you a better programmer--but only if you work at it. You will be challenged to think about what’s right about that code and what’s wrong with it. More important, you will be challenged to reassess your professional values and your commitment to your craft. In The Clean Coder, Martin introduces the disciplines, techniques, tools, and practices of true software craftsmanship. This book is packed with practical advice--about everything from estimating and coding to refactoring and testing. It covers much more than technique: It is about attitude. Martin shows how to approach software development with honor, self-respect, and pride; work well and work clean; communicate and estimate faithfully; face difficult decisions with clarity and honesty; and understand that deep knowledge comes with a responsibility to act. Readers of this collection will come away understanding How to tell the difference between good and bad code How to write good code and how to transform bad code into good code How to create good names, good functions, good objects, and good classes How to format code for maximum readability How to implement complete error handling without obscuring code logic How to unit test and practice test-driven development What it means to behave as a true software craftsman How to deal with conflict, tight schedules, and unreasonable managers How to get into the flow of coding and get past writer’s block How to handle unrelenting pressure and avoid burnout How to combine enduring attitudes with new development paradigms How to manage your time and avoid blind alleys, marshes, bogs, and swamps How to foster environments where programmers and teams can thrive When to say “Noâ€--and how to say it When to say “Yesâ€--and what yes really means COMPUTERS,Software Development & Engineering,Quality Assurance & Testing

Inside Windows Debugging Use Windows debuggers throughout the development cycle—and build better software Rethink your use of Windows debugging and tracing tools—and learn how to make them a key part of test-driven software development. Led by a member of the Windows Fundamentals Team at Microsoft, you’ll apply expert debugging and tracing techniques—and sharpen your C++ and C# code analysis skills—through practical examples and common scenarios. Learn why experienced developers use debuggers in every step of the development process, and not just when bugs appear. Discover how to: Go behind the scenes to examine how powerful Windows debuggers work Catch bugs early in the development cycle with static and runtime analysis tools Gain practical strategies to tackle the most common code defects Apply expert tricks to handle user-mode and kernel-mode debugging tasks Implement postmortem techniques such as JIT and dump debugging Debug the concurrency and security aspects of your software Use debuggers to analyze interactions between your code and the operating system Analyze software behavior with Xperf and the Event Tracing for Windows (ETW) framework COMPUTERS,Software Development & Engineering,Quality Assurance & Testing

Developer Testing How do successful agile teams deliver bug-free, maintainable software—iteration after iteration? The answer is: By seamlessly combining development and testing. On such teams, the developers write testable code that enables them to verify it using various types of automated tests. This approach keeps regressions at bay and prevents “testing crunchesâ€â€”which otherwise may occur near the end of an iteration—from ever happening. Writing testable code, however, is often difficult, because it requires knowledge and skills that cut across multiple disciplines. In Developer Testing, leading test expert and mentor Alexander Tarlinder presents concise, focused guidance for making new and legacy code far more testable. Tarlinder helps you answer questions like: When have I tested this enough? How many tests do I need to write? What should my tests verify? You’ll learn how to design for testability and utilize techniques like refactoring, dependency breaking, unit testing, data-driven testing, and test-driven development to achieve the highest possible confidence in your software. Through practical examples in Java, C#, Groovy, and Ruby, you’ll discover what works—and what doesn’t. You can quickly begin using Tarlinder’s technology-agnostic insights with most languages and toolsets while not getting buried in specialist details. The author helps you adapt your current programming style for testability, make a testing mindset “second nature,†improve your code, and enrich your day-to-day experience as a software professional. With this guide, you will Understand the discipline and vocabulary of testing from the developer’s standpoint Base developer tests on well-established testing techniques and best practices Recognize code constructs that impact testability Effectively name, organize, and execute unit tests Master the essentials of classic and “mockist-style†TDD Leverage test doubles with or without mocking frameworks Capture the benefits of programming by contract, even without runtime support for contracts Take control of dependencies between classes, components, layers, and tiers Handle combinatorial explosions of test cases, or scenarios requiring many similar tests Manage code duplication when it can’t be eliminated Actively maintain and improve your test suites Perform more advanced tests at the integration, system, and end-to-end levels Develop an understanding for how the organizational context influences quality assurance Establish well-balanced and effective testing strategies suitable for agile teams COMPUTERS,Software Development & Engineering,Quality Assurance & Testing

iOS and macOS Performance Tuning This is the eBook of the printed book and may not include any media, website access codes, or print supplements that may come packaged with the bound book. In iOS and macOS™ Performance Tuning, Marcel Weiher drills down to the code level to help you systematically optimize CPU, memory, I/O, graphics, and program responsiveness in any Objective-C, Cocoa, or CocoaTouch program. This up-to-date guide focuses entirely on performance optimization for macOS and iOS. Drawing on 25 years of experience optimizing Apple device software, Weiher identifies concrete performance problems that can be discovered empirically via measurement. Then, based on a deep understanding of fundamental principles, he presents specific techniques for solving them. Weiher presents insights you won’t find anywhere else, most of them applying to both macOS and iOS development. Throughout, he reveals common pitfalls and misconceptions about Apple device performance, explains the realities, and helps you reflect those realities in code that performs beautifully. Understand optimization principles, measurement, tools, pitfalls, and techniques Recognize when to carefully optimize, and when it isn’t worth your time Balance performance and encapsulation to create efficient object representations, communication, data access, and computation Avoid mistakes that slow down Objective-C programs and hinder later optimization Fix leaks and other problems with memory and resource management Address I/O issues associated with drives, networking, serialization, and SQLite Code graphics and UIs that don’t overwhelm limited iOS device resources Learn what all developers need to know about Swift performance COMPUTERS,Software Development & Engineering,Quality Assurance & Testing

Practical Vim Vim is a fast and efficient text editor that will make you a faster and more efficient developer. It's available on almost every OS, and if you master the techniques in this book, you'll never need another text editor. In more than 120 Vim tips, you'll quickly learn the editor's core functionality and tackle your trickiest editing and writing tasks. This beloved bestseller has been revised and updated to Vim 7.4 and includes three brand-new tips and five fully revised tips. A highly configurable, cross-platform text editor, Vim is a serious tool for programmers, web developers, and sysadmins who want to raise their game. No other text editor comes close to Vim for speed and efficiency; it runs on almost every system imaginable and supports most coding and markup languages. Learn how to edit text the "Vim way": complete a series of repetitive changes with The Dot Formula using one keystroke to strike the target, followed by one keystroke to execute the change. Automate complex tasks by recording your keystrokes as a macro. Discover the "very magic" switch that makes Vim's regular expression syntax more like Perl's. Build complex patterns by iterating on your search history. Search inside multiple files, then run Vim's substitute command on the result set for a project-wide search and replace. All without installing a single plugin! Three new tips explain how to run multiple ex commands as a batch, autocomplete sequences of words, and operate on a complete search match. Practical Vim, Second Edition will show you new ways to work with Vim 7.4 more efficiently, whether you're a beginner or an intermediate Vim user. All this, without having to touch the mouse. What You Need: Vim version 7.4 COMPUTERS,Software Development & Engineering,Quality Assurance & Testing

The Way of the Web Tester This book is for everyone who needs to test the web. As a tester, you'll automate your tests. As a developer, you'll build more robust solutions. And as a team, you'll gain a vocabulary and a means to coordinate how to write and organize automated tests for the web. Follow the testing pyramid and level up your skills in user interface testing, integration testing, and unit testing. Your new skills will free you up to do other, more important things while letting the computer do the one thing it's really good at: quickly running thousands of repetitive tasks. This book shows you how to do three things: How to write really good automated tests for the web. How to pick and choose the right ones. * How to explain, coordinate, and share your efforts with others. If you're a traditional software tester who has never written an automated test before, this is the perfect book for getting started. Together, we'll go through everything you'll need to start writing your own tests. If you're a developer, but haven't thought much about testing, this book will show you how to move fast without breaking stuff. You'll test RESTful web services and legacy systems, and see how to organize your tests. And if you're a team lead, this is the Rosetta Stone you've been looking for. This book will help you bridge that testing gap between your developers and your testers by giving your team a model to discuss automated testing, and most importantly, to coordinate their efforts. The Way of the Web Tester is packed with cartoons, graphics, best practices, war stories, plenty of humor, and hands-on tutorial exercises that will get you doing the right things, the right way. COMPUTERS,Software Development & Engineering,Quality Assurance & Testing

Effective Testing with RSpec 3 "Our tests are broken again!" "Why does the suite take so long to run?" "What value are we getting from these tests anyway?" Solve your testing problems by building and maintaining quality software with RSpec - the popular BDD-flavored Ruby testing framework. This definitive guide from RSpec's lead developer shows you how to use RSpec to drive more maintainable designs, specify and document expected behavior, and prevent regressions during refactoring. Build a project using RSpec to design, describe, and test the behavior of your code. Whether you're new to automated tests or have been using them for years, this book will help you write more effective tests. RSpec has been downloaded more than 100 million times and has inspired countless test frameworks in other languages. Use this influential Ruby testing framework to iteratively develop a project with the confidence that comes from well-tested code. This book guides you through creating a Ruby project with RSpec, and explores the individual components in detail. Start by learning the basics of installing and using RSpec. Then build a real-world JSON API, using RSpec throughout the process to drive a BDD-style outside-in workflow. Apply an effective test strategy to write fast, robust tests that support evolutionary design through refactoring. The rest of the book provides the definitive guide to RSpec's components. Use rspec-core's metadata to slice and dice your spec suite. Dig into rspec-expectations' matchers: compose them in flexible ways, specify expected outcomes with precision, and diagnose problems quickly with the help of good failure messages. Write fast, isolated tests with rspec-mocks' test doubles while pushing your code toward simpler interfaces. The authors, with a combined 20 years of automated testing experience, share testing wisdom that will lead to a fun, productive testing experience. What You Need: To follow along with the book, you'll need Ruby 2.2+. The book will guide you through installing RSpec 3 and setting up a new project to use it. COMPUTERS,Software Development & Engineering,Quality Assurance & Testing

Software Testing This practical guide provides insight into software testing, explaining the basics of the testing process and how to perform effective tests. It provides an overview of different techniques and how to apply them. It is the best-selling official textbook of the ISTQB-BCS Certified Tester Foundation Level. COMPUTERS,Software Development & Engineering,Quality Assurance & Testing

Practical Test Design This book presents the key test design techniques, in line with ISTQB, and explains when and how to use them, including in combination, with practical, real-life examples. Automated test design methods are also explored. Tips and exercises are included throughout the book, allowing you to test your knowledge as you progress. COMPUTERS,Software Development & Engineering,Quality Assurance & Testing

Clean Agile Nearly twenty years after the Agile Manifesto was first presented, the legendary Robert C. Martin (“Uncle Bobâ€) reintroduces Agile values and principles for a new generation—programmers and nonprogrammers alike. Martin, author of Clean Code and other highly influential software development guides, was there at Agile’s founding. Now, in Clean Agile: Back to Basics, he strips away misunderstandings and distractions that over the years have made it harder to use Agile than was originally intended. Martin describes what Agile is in no uncertain terms: a small discipline that helps small teams manage small projects . . . with huge implications because every big project is comprised of many small projects. Drawing on his fifty years’ experience with projects of every conceivable type, he shows how Agile can help you bring true professionalism to software development. Get back to the basics—what Agile is, was, and should always be Understand the origins, and proper practice, of SCRUM Master essential business-facing Agile practices, from small releases and acceptance tests to whole-team communication Explore Agile team members’ relationships with each other, and with their product Rediscover indispensable Agile technical practices: TDD, refactoring, simple design, and pair programming Understand the central roles values and craftsmanship play in your Agile team’s success If you want Agile’s true benefits, there are no shortcuts: You need to do Agile right. Clean Agile: Back to Basics will show you how, whether you’re a developer, tester, manager, project manager, or customer. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Software Development & Engineering,Quality Assurance & Testing

Design of Design, The Making Sense of Design Effective design is at the heart of everything from software development to engineering to architecture. But what do we really know about the design process? What leads to effective, elegant designs? The Design of Design addresses these questions. These new essays by Fred Brooks contain extraordinary insights for designers in every discipline. Brooks pinpoints constants inherent in all design projects and uncovers processes and patterns likely to lead to excellence. Drawing on conversations with dozens of exceptional designers, as well as his own experiences in several design domains, Brooks observes that bold design decisions lead to better outcomes. The author tracks the evolution of the design process, treats collaborative and distributed design, and illuminates what makes a truly great designer. He examines the nuts and bolts of design processes, including budget constraints of many kinds, aesthetics, design empiricism, and tools, and grounds this discussion in his own real-world examples—case studies ranging from home construction to IBM’s Operating System/360. Throughout, Brooks reveals keys to success that every designer, design project manager, and design researcher should know. COMPUTERS,Software Development & Engineering,Systems Analysis & Design

Algorithms in C++, Parts 1-4 Robert Sedgewick has thoroughly rewritten and substantially expanded and updated his popular work to provide current and comprehensive coverage of important algorithms and data structures. Christopher Van Wyk and Sedgewick have developed new C++ implementations that both express the methods in a concise and direct manner, and also provide programmers with the practical means to test them on real applications. Many new algorithms are presented, and the explanations of each algorithm are much more detailed than in previous editions. A new text design and detailed, innovative figures, with accompanying commentary, greatly enhance the presentation. The third edition retains the successful blend of theory and practice that has made Sedgewick's work an invaluable resource for more than 250,000 programmers! This particular book, Parts 1n4, represents the essential first half of Sedgewick's complete work. It provides extensive coverage of fundamental data structures and algorithms for sorting, searching, and related applications. Although the substance of the book applies to programming in any language, the implementations by Van Wyk and Sedgewick also exploit the natural match between C++ classes and ADT implementations. Highlights Expanded coverage of arrays, linked lists, strings, trees, and other basic data structures Greater emphasis on abstract data types (ADTs), modular programming, object-oriented programming, and C++ classes than in previous editions Over 100 algorithms for sorting, selection, priority queue ADT implementations, and symbol table ADT (searching) implementations New implementations of binomial queues, multiway radix sorting, randomized BSTs, splay trees, skip lists, multiway tries, B trees, extendible hashing, and much more Increased quantitative information about the algorithms, giving you a basis for comparing them Over 1000 new exercises to help you learn the properties of algorithms Whether you are learning the algorithms for the first time or wish to have up-to-date reference material that incorporates new programming styles with classic and new algorithms, you will find a wealth of useful information in this book. COMPUTERS,Software Development & Engineering,Systems Analysis & Design

Code Simplicity Good software design is simple and easy to understand. Unfortunately, the average computer program today is so complex that no one could possibly comprehend how all the code works. This concise guide helps you understand the fundamentals of good design through scientific laws—principles you can apply to any programming language or project from here to eternity. Whether you’re a junior programmer, senior software engineer, or non-technical manager, you’ll learn how to create a sound plan for your software project, and make better decisions about the pattern and structure of your system. Discover why good software design has become the missing science Understand the ultimate purpose of software and the goals of good design Determine the value of your design now and in the future Examine real-world examples that demonstrate how a system changes over time Create designs that allow for the most change in the environment with the least change in the software Make easier changes in the future by keeping your code simpler now Gain better knowledge of your software’s behavior with more accurate tests COMPUTERS,Software Development & Engineering,Systems Analysis & Design

Domain-Driven Design “Eric Evans has written a fantastic book on how you can make the design of your software match your mental model of the problem domain you are addressing. “His book is very compatible with XP. It is not about drawing pictures of a domain; it is about how you think of it, the language you use to talk about it, and how you organize your software to reflect your improving understanding of it. Eric thinks that learning about your problem domain is as likely to happen at the end of your project as at the beginning, and so refactoring is a big part of his technique. “The book is a fun read. Eric has lots of interesting stories, and he has a way with words. I see this book as essential reading for software developers—it is a future classic.†—Ralph Johnson, author of Design Patterns “If you don’t think you are getting value from your investment in object-oriented programming, this book will tell you what you’ve forgotten to do. “Eric Evans convincingly argues for the importance of domain modeling as the central focus of development and provides a solid framework and set of techniques for accomplishing it. This is timeless wisdom, and will hold up long after the methodologies du jour have gone out of fashion.†—Dave Collins, author of Designing Object-Oriented User Interfaces “Eric weaves real-world experience modeling—and building—business applications into a practical, useful book. Written from the perspective of a trusted practitioner, Eric’s descriptions of ubiquitous language, the benefits of sharing models with users, object life-cycle management, logical and physical application structuring, and the process and results of deep refactoring are major contributions to our field.†—Luke Hohmann, author of Beyond Software Architecture “This book belongs on the shelf of every thoughtful software developer.†—Kent Beck “What Eric has managed to capture is a part of the design process that experienced object designers have always used, but that we have been singularly unsuccessful as a group in conveying to the rest of the industry. We've given away bits and pieces of this knowledge...but we've never organized and systematized the principles of building domain logic. This book is important.†—Kyle Brown, author of Enterprise Java™ Programming with IBM® WebSphere® The software development community widely acknowledges that domain modeling is central to software design. Through domain models, software developers are able to express rich functionality and translate it into a software implementation that truly serves the needs of its users. But despite its obvious importance, there are few practical resources that explain how to incorporate effective domain modeling into the software development process. Domain-Driven Design fills that need. This is not a book about specific technologies. It offers readers a systematic approach to domain-driven design, presenting an extensive set of design best practices, experience-based techniques, and fundamental principles that facilitate the development of software projects facing complex domains. Intertwining design and development practice, this book incorporates numerous examples based on actual projects to illustrate the application of domain-driven design to real-world software development. Readers learn how to use a domain model to make a complex development effort more focused and dynamic. A core of best practices and standard patterns provides a common language for the development team. A shift in emphasis—refactoring not just the code but the model underlying the code—in combination with the frequent iterations of Agile development leads to deeper insight into domains and enhanced communication between domain expert and programmer. Domain-Driven Design then builds on this foundation, and addresses modeling and design for complex systems and larger organizations.Specific topics covered include: Getting all team members to speak the same language Connecting model and implementation more deeply Sharpening key distinctions in a model Managing the lifecycle of a domain object Writing domain code that is safe to combine in elaborate ways Making complex code obvious and predictable Formulating a domain vision statement Distilling the core of a complex domain Digging out implicit concepts needed in the model Applying analysis patterns Relating design patterns to the model Maintaining model integrity in a large system Dealing with coexisting models on the same project Organizing systems with large-scale structures Recognizing and responding to modeling breakthroughs With this book in hand, object-oriented developers, system analysts, and designers will have the guidance they need to organize and focus their work, create rich and useful domain models, and leverage those models into quality, long-lasting software implementations. COMPUTERS,Software Development & Engineering,Systems Analysis & Design

Best Interface Is No Interface, The Our love affair with the digital interface is out of control. We’ve embraced it in the boardroom, the bedroom, and the bathroom. Screens have taken over our lives. Most people spend over eight hours a day staring at a screen, and some “technological innovators†are hoping to grab even more of your eyeball time. You have screens in your pocket, in your car, on your appliances, and maybe even on your face. Average smartphone users check their phones 150 times a day, responding to the addictive buzz of Facebook or emails or Twitter. Are you sick? There’s an app for that! Need to pray? There’s an app for that! Dead? Well, there’s an app for that, too! And most apps are intentionally addictive distractions that end up taking our attention away from things like family, friends, sleep, and oncoming traffic. There’s a better way. In this book, innovator Golden Krishna challenges our world of nagging, screen-based bondage, and shows how we can build a technologically advanced world without digital interfaces. In his insightful, raw, and often hilarious criticism, Golden reveals fascinating ways to think beyond screens using three principles that lead to more meaningful innovation. Whether you’re working in technology, or just wary of a gadget-filled future, you’ll be enlighted and entertained while discovering that the best interface is no interface. COMPUTERS,Software Development & Engineering,Systems Analysis & Design

Algorithms in C, Parts 1-4 Robert Sedgewick has thoroughly rewritten and substantially expanded his popular work to provide current and comprehensive coverage of important algorithms and data structures. Many new algorithms are presented, and the explanations of each algorithm are much more detailed than in previous editions. A new text design and detailed, innovative figures, with accompanying commentary, greatly enhance the presentation. The third edition retains the successful blend of theory and practice that has made Sedgewick's work an invaluable resource for more than 250,000 programmers! This particular book, Parts 1-4, represents the essential first half of Sedgewick's complete work. It provides extensive coverage of fundamental data structures and algorithms for sorting, searching, and related applications. The algorithms and data structures are expressed in concise implementations in C, so that you can both appreciate their fundamental properties and test them on real applications. Of course, the substance of the book applies to programming in any language. Highlights Expanded coverage of arrays, linked lists, strings, trees, and other basic data structures Greater emphasis on abstract data types (ADTs) than in previous editions Over 100 algorithms for sorting, selection, priority queue ADT implementations, and symbol table ADT (searching) implementations New implementations of binomial queues, multiway radix sorting, Batcher's sorting networks, randomized BSTs, splay trees, skip lists, multiway tries, and much more Increased quantitative information about the algorithms, including extensive empirical studies and basic analytic studies, giving you a basis for comparing them Over 1000 new exercises to help you learn the properties of algorithms Whether you are a student learning the algorithms for the first time or a professional interested in having up-to-date reference material, you will find a wealth of useful information in this book. COMPUTERS,Software Development & Engineering,Systems Analysis & Design

Designing the Requirements Too many software applications don’t do what’s needed or they do it clumsily, frustrating their users and owners. The core problem: poorly conceived and poorly crafted requirements. In Designing the Requirements, Chris Britton explains why it’s not enough to simply “gather†requirements—you need to design them. Britton offers powerful techniques for understanding stakeholders’ concerns and working with stakeholders to get the requirements right. Using Britton’s context-driven approach to requirements design, you can detect inconsistencies, incompleteness, poor usability, and misalignment with business goals upstream—long before developers start coding. You can also design outward-looking applications and services that will integrate more effectively in a coherent IT architecture. First, Britton explains what requirements design really means and presents a hierarchy of designs that move step by step from requirements through implementation. Next, he demonstrates how to build on requirements processes you already use and how to overcome their serious limitations in large-scale development. Then, he walks you through designing your application’s relationship with the business, users, data, and other software to ensure superior usability, security, and maximum scalability and resilience. Whether you’re a software designer, architect, project manager, or programmer, Designing the Requirements will help you design software that works—for users, IT, and the entire business. Coverage includes Designing the entire business solution, not just its software component Using engineering-style design analysis to find flaws before implementation Designing services, and splitting large development efforts into smaller, more manageable projects Planning logical user interfaces that lead to superior user experiences Designing databases and data access to reflect the meaning of your data Building application frameworks that simplify life for programmers and project managers Setting reasonable and achievable goals for performance, availability, and security Designing for security at all levels, from strategy to code Identifying new opportunities created by context-driven design COMPUTERS,Software Development & Engineering,Systems Analysis & Design

RESTful Web Clients Powerful web-based REST and hypermedia-style APIs are becoming more common every day, but instead of applying the same techniques and patterns to hypermedia clients, many developers rely on custom client code. With this practical guide, you’ll learn how to move from one-off implementations to general-purpose client apps that are stable, flexible, and reusable. Author Mike Amundsen provides extensive background, easy-to-follow examples, illustrative dialogues, and clear recommendations for building effective hypermedia-based client applications. Along the way, you’ll learn how to harness many of the basic principles that underpin the Web. Convert HTML-only web apps into a JSON API service Overcome the challenges of maintaining plain JSON-style client apps Decouple the output format from the internal object model with the representor pattern Explore client apps built with HAL—Hypertext Application Language Tackle reusable clients with the Request, Parse, Wait Loop (RPW) pattern Learn the pros and cons of building client apps with the Siren content type Deal with API versioning by adopting a change-over-time aesthetic Compare how JSON, HAL, Siren, and Collection+JSON clients handle the Objects/Addresses/Actions Challenge Craft a single client application that can consume multiple services COMPUTERS,Software Development & Engineering,Systems Analysis & Design

Design It! Don't engineer by coincidence-design it like you mean it! Filled with practical techniques, Design It! is the perfect introduction to software architecture for programmers who are ready to grow their design skills. Lead your team as a software architect, ask the right stakeholders the right questions, explore design options, and help your team implement a system that promotes the right -ilities. Share your design decisions, facilitate collaborative design workshops that are fast, effective, and fun-and develop more awesome software! With dozens of design methods, examples, and practical know-how, Design It! shows you how to become a software architect. Walk through the core concepts every architect must know, discover how to apply them, and learn a variety of skills that will make you a better programmer, leader, and designer. Uncover the big ideas behind software architecture and gain confidence working on projects big and small. Plan, design, implement, and evaluate software architectures and collaborate with your team, stakeholders, and other architects. Identify the right stakeholders and understand their needs, dig for architecturally significant requirements, write amazing quality attribute scenarios, and make confident decisions. Choose technologies based on their architectural impact, facilitate architecture-centric design workshops, and evaluate architectures using lightweight, effective methods. Write lean architecture descriptions people love to read. Run an architecture design studio, implement the architecture you've designed, and grow your team's architectural knowledge. Good design requires good communication. Talk about your software architecture with stakeholders using whiteboards, documents, and code, and apply architecture-focused design methods in your day-to-day practice. Hands-on exercises, real-world scenarios, and practical team-based decision-making tools will get everyone on board and give you the experience you need to become a confident software architect. COMPUTERS,Software Development & Engineering,Systems Analysis & Design

The Cucumber Book Your customers want rock-solid, bug-free software that does exactly what they expect it to do. Yet they can't always articulate their ideas clearly enough for you to turn them into code. You need Cucumber: a testing, communication, and requirements tool-all rolled into one. All the code in this book is updated for Cucumber 2.4, Rails 5, and RSpec 3.5. Express your customers' wild ideas as a set of clear, executable specifications that everyone on the team can read. Feed those examples into Cucumber and let it guide your development. Build just the right code to keep your customers happy. You can use Cucumber to test almost any system or any platform. Get started by using the core features of Cucumber and working with Cucumber's Gherkin DSL to describe-in plain language-the behavior your customers want from the system. Then write Ruby code that interprets those plain-language specifications and checks them against your application. Next, consolidate the knowledge you've gained with a worked example, where you'll learn more advanced Cucumber techniques, test asynchronous systems, and test systems that use a database. Recipes highlight some of the most difficult and commonly seen situations the authors have helped teams solve. With these patterns and techniques, test Ajax-heavy web applications with Capybara and Selenium, REST web services, Ruby on Rails applications, command-line applications, legacy applications, and more. Written by the creator of Cucumber and the co-founders of Cucumber Ltd., this authoritative guide will give you and your team all the knowledge you need to start using Cucumber with confidence. What You Need: Windows, Mac OS X (with XCode) or Linux, Ruby 1.9.2 and upwards, Cucumber 2.4, Rails 5, and RSpec 3.5 COMPUTERS,Software Development & Engineering,Systems Analysis & Design

The DevOps 2.2 Toolkit Learn from an expert on how use self-adapting and self-healing systems within Docker. About This Book Viktor Farcic shows you all aspects in the creation of self-adapting and self-healing systems in both a practical and hands-on approach. Learn how to choose a successful solution for metrics storage and query, including InfluxDB, Nagios and Sensu, Prometheus and Graphite. Discover how to integrate Docker Flow Monitor with Docker Flow Proxy. How to apply Docker self-healing and self-adaptive to both services and infrastructure. Who This Book Is For This book is for professionals experienced with Docker looking to create both self-adapting and self-healing systems using the software. What You Will Learn Let Viktor Farcic show you all aspects in the creation of self-adapting and self-healing systems in both a practical and hands-on approach. Learn how to choose a successful solution for metrics storage and query, including InfluxDB, Nagios and Sensu, Prometheus and Graphite. Understand how to integrate Docker Flow Monitor with Docker Flow Proxy. The creation of cluster-wide alerts by creating alerts based on metrics. How to apply self-healing and self-adaptive to both services and infrastructure. In Detail Building on The DevOps 2.0 Toolkit and The DevOps 2.1 Toolkit: Docker Swarm, Viktor Farcic brings his latest exploration of the Docker technology as he records his journey to explore two new programs, self-adaptive and self-healing systems within Docker. The DevOps 2.2 Toolkit: Self-Sufficient Docker Clusters is the latest book in Viktor Farcic's series that helps you build a full DevOps Toolkit. This book in the series looks at Docker, the tool designed to make it easier in the creation and running of applications using containers. In this latest entry, Viktor combines theory with a hands-on approach to guide you through the process of creating self-adaptive and self-healing systems. Within this book, Viktor will cover a wide-range of emerging topics, including what exactly self-adaptive and self-healing systems are, how to choose a solution for metrics storage and query, the creation of cluster-wide alerts and what a successful self-sufficient system blueprint looks like. Work with Viktor and dive into the creation of self-adaptive and self-healing systems within Docker. Style and approach Readers join Viktor Farcic as he continues his exploration of Docker and begins to explore new opportunities with the platform. COMPUTERS,Software Development & Engineering,Systems Analysis & Design

Developing Information Systems Systems development is the process of creating and maintaining information systems. This practical book provides a comprehensive introduction to the topic and can also be used as a handy reference guide by those already working in the field. It is the only textbook that supports the BCS Certificate in Systems Development. COMPUTERS,Software Development & Engineering,Systems Analysis & Design

AWS Certified Developer – Associate Guide Learn from the AWS subject-matter experts, explore real-world scenarios, and pass the AWS Certified Developer – Associate exam Key Features This fast-paced guide will help you clear the AWS Certified Developer – Associate (DVA-C01) exam with confidence Gain valuable insights to design, develop, and deploy cloud-based solutions using AWS Develop expert core AWS skills with practice questions and mock tests Book Description This book will focus on the revised version of AWS Certified Developer Associate exam. The 2019 version of this exam guide includes all the recent services and offerings from Amazon that benefits developers. AWS Certified Developer - Associate Guide starts with a quick introduction to AWS and the prerequisites to get you started. Then, this book will describe about getting familiar with Identity and Access Management (IAM) along with Virtual private cloud (VPC). Next, this book will teach you about microservices, serverless architecture, security best practices, advanced deployment methods and more. Going ahead we will take you through AWS DynamoDB A NoSQL Database Service, Amazon Simple Queue Service (SQS) and CloudFormation Overview. Lastly, this book will help understand Elastic Beanstalk and will also walk you through AWS lambda. At the end of this book, we will cover enough topics, tips and tricks along with mock tests for you to be able to pass the AWS Certified Developer - Associate exam and develop as well as manage your applications on the AWS platform. What you will learn Create and manage users, groups, and permissions using AWS IAM services Create a secured VPC with Public and Private Subnets, NAC, and Security groups Launching your first EC2 instance, and working with it Handle application traffic with ELB and monitor AWS resources with CloudWatch Work with AWS storage services such as S3, Glacier, and CloudFront Get acquainted with AWS DynamoDB a NoSQL database service Use SWS to coordinate work across distributed application components Who this book is for This book is for IT professionals and developers looking to clear the AWS Certified Developer Associate 2019 exam. Developers looking to develop and manage their applications on the AWS platform will also find this book useful. No prior AWS experience is needed. COMPUTERS,Software Development & Engineering,Systems Analysis & Design

Kubernetes Kubernetes radically changes the way applications are built and deployed in the cloud. Since its introduction in 2014, this container orchestrator has become one of the largest and most popular open source projects in the world. The updated edition of this practical book shows developers and ops personnel how Kubernetes and container technology can help you achieve new levels of velocity, agility, reliability, and efficiency. Kelsey Hightower, Brendan Burns, and Joe Beda—who’ve worked on Kubernetes at Google and beyond—explain how this system fits into the lifecycle of a distributed application. You’ll learn how to use tools and APIs to automate scalable distributed systems, whether it’s for online services, machine learning applications, or a cluster of Raspberry Pi computers. Create a simple cluster to learn how Kubernetes works Dive into the details of deploying an application using Kubernetes Learn specialized objects in Kubernetes, such as DaemonSets, jobs, ConfigMaps, and secrets Explore deployments that tie together the lifecycle of a complete application Get practical examples of how to develop and deploy real-world applications in Kubernetes COMPUTERS,Software Development & Engineering,Systems Analysis & Design

Learn Microsoft PowerApps A step-by-step guide that will help you create, share, and deploy applications across your organization using MS PowerApps Key Features Create apps with rich user experiences without paying for costly developers Improve productivity with business process automation using Microsoft Power Automate Build enterprise-grade apps with MS PowerApps' built-in storage space, Common Data Service Book Description Microsoft PowerApps provides a modern approach to building business applications for mobile, tablet, and browser. Learn Microsoft PowerApps will guide you in creating powerful and productive apps that will add value to your organization by helping you transform old and inefficient processes and workflows. Starting with an introduction to PowerApps, this book will help you set up and configure your first application. You'll explore a variety of built-in templates and understand the key difference between types of applications such as canvas and model-driven apps, which are used to create apps for specific business scenarios. In addition to this, you'll learn how to generate and integrate apps directly with SharePoint, and gain an understanding of PowerApps key components such as connectors and formulas. As you advance, you'll be able to use various controls and data sources, including technologies such as GPS, and combine them to create an iterative app. Finally, the book will help you understand how PowerApps can use several Microsoft Power Automate and Azure functionalities to improve your applications. By the end of this PowerApps book, you'll be ready to confidently develop lightweight business applications with minimal code. What you will learn Design an app by simply dragging and dropping elements onto your canvas Understand how to store images within PowerApps Explore the use of GPS and how you can use GPS data in PowerApps Get to grips with using barcodes and QR codes in your apps Share your applications with the help of Microsoft Teams and SharePoint Use connectors to share data between your app and Microsoft's app ecosystem Who this book is for This book is ideal for business analysts, IT professionals, and both developers and non-developers alike. If you want to meet business needs by creating high productivity apps, this book is for you. Don't worry if you have no experience or knowledge of PowerApps, this book simplifies PowerApps for beginners. COMPUTERS,Software Development & Engineering,Systems Analysis & Design

Learn SOLIDWORKS 2020 Explore a practical and example-driven approach to understanding SOLIDWORKS 2020 and achieving CSWA and CSWP certification Key Features Gain comprehensive insights into the core aspects of mechanical part modeling Get up to speed with generating assembly designs with both standard and advanced mates Focus on design practices for both 2D as well as 3D modeling and prepare to achieve CWSP and CWSA certification Book Description SOLIDWORKS is the leading choice for 3D engineering and product design applications across industries such as aviation, automobiles, and consumer product design. This book takes a practical approach to getting you up and running with SOLIDWORKS 2020. You'll start with the basics, exploring the software interface and working with drawing files. The book then guides you through topics such as sketching, building complex 3D models, generating dynamic and static assemblies, and generating 2D engineering drawings to equip you for mechanical design projects. You'll also do practical exercises to get hands-on with creating sketches, 3D part models, assemblies, and drawings. To reinforce your understanding of SOLIDWORKS, the book is supplemented by downloadable files that will help you follow up with the concepts and exercises found in the book. By the end of this book, you'll have gained the skills you need to create professional 3D mechanical models using SOLIDWORKS, and you'll be able to prepare effectively for the Certified SOLIDWORKS Associate (CSWA) and Certified SOLIDWORKS Professional (CSWP) exams. What you will learn Understand the fundamentals of SOLIDWORKS and parametric modeling Create professional 2D sketches as bases for 3D models using simple and advanced modeling techniques Use SOLIDWORKS drawing tools to generate standard engineering drawings Evaluate mass properties and materials for designing parts and assemblies Understand the objectives and the formats of the CSWA and CSWP exams Discover expert tips and tricks to generate different part and assembly configurations for your mechanical designs Who this book is for This book is for aspiring engineers, designers, drafting technicians, or anyone looking to get started with the latest version of SOLIDWORKS. Anyone interested in becoming a Certified SOLIDWORKS Associate (CSWA) or Certified SOLIDWORKS Professional (CSWP) will also find this book useful. COMPUTERS,Software Development & Engineering,Systems Analysis & Design

gRPC Get a comprehensive understanding of gRPC fundamentals through real-world examples. With this practical guide, you’ll learn how this high-performance interprocess communication protocol is capable of connecting polyglot services in microservices architecture, while providing a rich framework for defining service contracts and data types. Complete with hands-on examples written in Go, Java, Node, and Python, this book also covers the essential techniques and best practices to use gRPC in production systems. Authors Kasun Indrasiri and Danesh Kuruppu discuss the importance of gRPC in the context of microservices development. COMPUTERS,Software Development & Engineering,Systems Analysis & Design

Kubernetes Operators Operators are a way of packaging, deploying, and managing Kubernetes applications. A Kubernetes application doesn’t just run on Kubernetes; it’s composed and managed in Kubernetes terms. Operators add application-specific operational knowledge to a Kubernetes cluster, making it easier to automate complex, stateful applications and to augment the platform. Operators can coordinate application upgrades seamlessly, react to failures automatically, and streamline repetitive maintenance like backups. Think of Operators as site reliability engineers in software. They work by extending the Kubernetes control plane and API, helping systems integrators, cluster administrators, and application developers reliably deploy and manage key services and components. Using real-world examples, authors Jason Dobies and Joshua Wood demonstrate how to use Operators today and how to create Operators for your applications with the Operator Framework and SDK. Learn how to establish a Kubernetes cluster and deploy an Operator Examine a range of Operators from usage to implementation Explore the three pillars of the Operator Framework: the Operator SDK, the Operator Lifecycle Manager, and Operator Metering Build Operators from the ground up using the Operator SDK Build, package, and run an Operator in development, testing, and production phases Learn how to distribute your Operator for installation on Kubernetes clusters COMPUTERS,Software Development & Engineering,Systems Analysis & Design

Framework Design Guidelines Master Today’s Best Practices for Building Reusable .NET Frameworks, Libraries, and Components “.NET Core [contains] advances important to cloud application developers: performance, resource utilization, container support, and others. This third edition of Framework Design Guidelines adds guidelines related to changes that the .NET team adopted during transition from the world of client-server application to the world of the Cloud.†—From the Foreword by Scott Guthrie Framework Design Guidelines has long been the definitive guide to best practices for developing components and component libraries in Microsoft .NET. Now, this third edition has been fully revised to reflect game-changing API design innovations introduced by Microsoft through eight recent updates to C#, eleven updates to .NET Framework, and the emergence and evolution of .NET Core. Three leading .NET architects share the same guidance Microsoft teams are using to evolve .NET, so you can design well-performing components that feel like natural extensions to the platform. Building on the book’s proven explanatory style, the authors and expert annotators offer insider guidance on new .NET and C# concepts, including major advances in asynchronous programming and lightweight memory access. Throughout, they clarify and refresh existing content, helping you take full advantage of best practices based on C# 8, .NET Framework 4.8, and .NET Core. Discover which practices should always, generally, rarely, or never be used—including practices that are no longer recommended Learn the general philosophy and fundamental principles of modern framework design Explore common framework design patterns with up-to-date C# examples Apply best practices for naming, types, extensibility, and exceptions Learn how to design libraries that scale in the cloud Master new async programming techniques utilizing Task and ValueTask Make the most of the Memory<T> and Span<T> types for lightweight memory access This guide is an indispensable resource for everyone who builds reusable .NET-based frameworks, libraries, or components at any scale: large system frameworks, medium-size reusable layers of large distributed systems, extensions to system frameworks, or even small shared components. Register your book for convenient access to downloads, updates, and/or corrections as they become available. See inside book for details. COMPUTERS,Software Development & Engineering,Systems Analysis & Design

Software Design Decoded An engaging, illustrated collection of insights revealing the practices and principles that expert software designers use to create great software. What makes an expert software designer? It is more than experience or innate ability. Expert software designers have specific habits, learned practices, and observed principles that they apply deliberately during their design work. This book offers sixty-six insights, distilled from years of studying experts at work, that capture what successful software designers actually do to create great software. The book presents these insights in a series of two-page illustrated spreads, with the principle and a short explanatory text on one page, and a drawing on the facing page. For example, “Experts generate alternatives” is illustrated by the same few balloons turned into a set of very different balloon animals. The text is engaging and accessible; the drawings are thought-provoking and often playful. Organized into such categories as “Experts reflect,” “Experts are not afraid,” and “Experts break the rules,” the insights range from “Experts prefer simple solutions” to “Experts see error as opportunity.” Readers learn that “Experts involve the user”; “Experts take inspiration from wherever they can”; “Experts design throughout the creation of software”; and “Experts draw the problem as much as they draw the solution.” One habit for an aspiring expert software designer to develop would be to read and reread this entertaining but essential little book. The insights described offer a guide for the novice or a reference for the veteran—in software design or any design profession. A companion web site provides an annotated bibliography that compiles key underpinning literature, the opportunity to suggest additional insights, and more. COMPUTERS,Software Development & Engineering,Systems Analysis & Design

bash Quick Reference In this quick reference, you'll find everything you need to know about the bash shell. Whether you print it out or read it on the screen, this PDF gives you the answers to the annoying questions that always come up when you're writing shell scripts: What characters do you need to quote? How do you get variable substitution to do exactly what you want? How do you use arrays? It's also helpful for interactive use. If you're a Unix user or programmer, or if you're using bash on Windows, you'll find this quick reference indispensable. COMPUTERS,Software Development & Engineering,Tools

Jenkins 2 Design, implement, and execute continuous delivery pipelines with a level of flexibility, control, and ease of maintenance that was not possible with Jenkins before. With this practical book, build administrators, developers, testers, and other professionals will learn how the features in Jenkins 2 let you define pipelines as code, leverage integration with other key technologies, and create automated, reliable pipelines to simplify and accelerate your DevOps environments. Author Brent Laster shows you how Jenkins 2 is significantly different from the more traditional, web-only versions of this popular open source automation platform. If you’re familiar with Jenkins and want to take advantage of the new technologies to transform your legacy pipelines or build new modern, automated continuous delivery environments, this is your book. Create continuous delivery pipelines as code with the Jenkins domain-specific language Get practical guidance on how to migrate existing jobs and pipelines Harness best practices and new methods for controlling access and security Explore the structure, implementation, and use of shared pipeline libraries Learn the differences between declarative syntax and scripted syntax Leverage new and existing project types in Jenkins Understand and use the new Blue Ocean graphical interface Take advantage of the capabilities of the underlying OS in your pipeline Integrate analysis tools, artifact management, and containers COMPUTERS,Software Development & Engineering,Tools

Modern Vim Turn Vim into a full-blown development environment using Vim 8's new features and this sequel to the beloved bestseller Practical Vim. Integrate your editor with tools for building, testing, linting, indexing, and searching your codebase. Discover the future of Vim with Neovim: a fork of Vim that includes a built-in terminal emulator that will transform your workflow. Whether you choose to switch to Neovim or stick with Vim 8, you'll be a better developer. A serious tool for programmers and web developers, no other text editor comes close to Vim for speed and efficiency. Make Vim the centerpiece of a Unix-based IDE as you discover new ways to work with Vim 8 and Neovim in more than 20 hands-on tips. Execute tasks asynchronously, allowing you to continue in Vim while linting, grepping, building a project, or running a test suite. Install plugins to be loaded on startup - or on-demand when you need them - with Vim 8's new package support. Save and restore sessions, enabling you to quit Vim and restart again while preserving your window layout and undo history. Use Neovim as a drop-in replacement for Vim - it supports all of the features Vim 8 offers and more, including an integrated terminal that lets you quickly perform interactive commands. And if you enjoy using tmux and Vim together, you'll love Neovim's terminal emulator, which lets you run an interactive shell in a buffer. The terminal buffers fit naturally with Vim's split windows, and you can use Normal mode commands to scroll, search, copy, and paste. On top of all that: Neovim's terminal buffers are scriptable. With Vim at the core of your development environment, you'll become a faster and more efficient developer. What You Need: You'll need a Unix-based environment and an up-to-date release of Vim (8.0 or newer). For the tips about running a terminal emulator, you'll need to install Neovim. COMPUTERS,Software Development & Engineering,Tools

Blender Quick Start Guide Learn the new Blender 2.8 user interface and make 3D models Key Features Find your way round the new user interface and tools of Blender 2.8 Create materials, apply textures and render scenes Use the new cutting-edge real-time render EEVEE in your projects Book Description Blender is open source 3D creation software. With a long history and an enthusiastic community of users, it is the ideal choice for almost any kind of work with 3D modeling or animation. However, for new users, its power and ?exibillity can sometimes be daunting, and that's when you need this book! The book starts by showing you round the all-new Blender 2.8 user interface. You'll look at the most commonly-used options and tools, such as navigating in 3D and selecting objects. You will then use and manipulate one of the most important windows of the interface, the 3D View. You'll learn how to use essential tools for working with 3D modeling. To give your models the feel of real-world objects, you'll learn how to create materials and set up surfaces. You'll see how to use Physically-Based Rendering (PBR), which allows you to craft realistic surfaces such as wood, stone, and metal. You will also work with Eevee, a new real-time render engine in Blender. You will see how to add motion to objects, making use of Blender's impressive 3D animation features. Finally, you'll learn how to create scenes and organize them for rendering, and later add titles and effects using built-in Blender tools. By the end of the book, you will be able to use Blender 2.8 new UI, Create 3D Models with textures, Animations, and Render them in real-time using Eevee. What you will learn Manipulate and visualize your 3D objects in Blender Use polygon modeling tools such as extrude, loop cut, and more Apply precision modeling tools like snapping and the 3D Cursor Render a scene using the real-time engine Eevee Create materials for Eevee and Cycles Render a scene with the Eevee real-time engine Use PBR textures to craft realistic surfaces such as wood with the Shader Editor Add motion and animation using keyframes Create animation loops using curves and modifiers Who this book is for This book is for anyone interested in taking their steps with Blender. If you're an experienced 3D artists or hobbyist, this book will help you with its features. COMPUTERS,Software Development & Engineering,Tools

Docker Quick Start Guide Develop and build your Docker images and deploy your Docker containers securely. Key Features Learn Docker installation on different types of OS Get started with developing Docker images Use Docker with your Jenkins CI/CD system Book Description Docker is an open source software platform that helps you with creating, deploying, and running your applications using containers. This book is your ideal introduction to Docker and containerization. You will learn how to set up a Docker development environment on a Linux, Mac, or Windows workstation, and learn your way around all the commands to run and manage your Docker images and containers. You will explore the Dockerfile and learn how to build your own enterprise-grade Docker images. Then you will learn about Docker networks, Docker swarm, and Docker volumes, and how to use these features with Docker stacks in order to define, deploy, and maintain highly-scalable, fault-tolerant multi-container applications. Finally, you will learn how to leverage Docker with Jenkins to automate the building of Docker images and the deployment of Docker containers. By the end of this book, you will be well prepared when it comes to using Docker for your next project. What you will learn Set up your Docker workstation on various platforms Utilize a number of Docker commands with parameters Create Docker images using Dockerfiles Learn how to create and use Docker volumes Deploy multi-node Docker swarm infrastructure Create and use Docker local and remote networks Deploy multi-container applications that are HA and FT Use Jenkins to build and deploy Docker images Who this book is for This guide is for anyone who needs to make a quick decision about using Docker for their next project. It is for developers who want to get started using Docker right away. COMPUTERS,Software Development & Engineering,Tools

The Rust Programming Language (Covers Rust 2018) The official book on the Rust programming language, written by the Rust development team at the Mozilla Foundation, fully updated for Rust 2018. The Rust Programming Language is the official book on Rust: an open source systems programming language that helps you write faster, more reliable software. Rust offers control over low-level details (such as memory usage) in combination with high-level ergonomics, eliminating the hassle traditionally associated with low-level languages. The authors of The Rust Programming Language, members of the Rust Core Team, share their knowledge and experience to show you how to take full advantage of Rust's features--from installation to creating robust and scalable programs. You'll begin with basics like creating functions, choosing data types, and binding variables and then move on to more advanced concepts, such as: • Ownership and borrowing, lifetimes, and traits • Using Rust's memory safety guarantees to build fast, safe programs • Testing, error handling, and effective refactoring • Generics, smart pointers, multithreading, trait objects, and advanced pattern matching • Using Cargo, Rust's built-in package manager, to build, test, and document your code and manage dependencies • How best to use Rust's advanced compiler with compiler-led programming techniques You'll find plenty of code examples throughout the book, as well as three chapters dedicated to building complete projects to test your learning: a number guessing game, a Rust implementation of a command line tool, and a multithreaded server. New to this edition: An extended section on Rust macros, an expanded chapter on modules, and appendixes on Rust development tools and editions. COMPUTERS,Software Development & Engineering,Tools

Get Your Hands Dirty on Clean Architecture Gain insight into how hexagonal architecture can help to keep the cost of development low over the complete lifetime of an application Key Features Explore ways to make your software flexible, extensible, and adaptable Learn new concepts that you can easily blend with your own software development style Develop the mindset of building maintainable solutions instead of taking shortcuts Book Description We would all like to build software architecture that yields adaptable and flexible software with low development costs. But, unreasonable deadlines and shortcuts make it very hard to create such an architecture. Get Your Hands Dirty on Clean Architecture starts with a discussion about the conventional layered architecture style and its disadvantages. It also talks about the advantages of the domain-centric architecture styles of Robert C. Martin's Clean Architecture and Alistair Cockburn's Hexagonal Architecture. Then, the book dives into hands-on chapters that show you how to manifest a hexagonal architecture in actual code. You'll learn in detail about different mapping strategies between the layers of a hexagonal architecture and see how to assemble the architecture elements into an application. The later chapters demonstrate how to enforce architecture boundaries. You'll also learn what shortcuts produce what types of technical debt and how, sometimes, it is a good idea to willingly take on those debts. After reading this book, you'll have all the knowledge you need to create applications using the hexagonal architecture style of web development. What you will learn Identify potential shortcomings of using a layered architecture Apply methods to enforce architecture boundaries Find out how potential shortcuts can affect the software architecture Produce arguments for when to use which style of architecture Structure your code according to the architecture Apply various types of tests that will cover each element of the architecture Who this book is for This book is for you if you care about the architecture of the software you are building. To get the most out of this book, you must have some experience with web development. The code examples in this book are in Java. If you are not a Java programmer but can read object-oriented code in other languages, you will be fine. In the few places where Java or framework specifics are needed, they are thoroughly explained. COMPUTERS,Software Development & Engineering,Tools

Jump Start Git Get a Jump Start on version control with Git today! If you've worked on a web development project of any size, you've probably used Git, the most broadly adopted distributed version control system available. It enables you to store different versions of project files and directories, so you can roll back to an earlier one if something goes wrong. And since it's distributed, it smoothes the path for dev team collaboration. This short, practical book will help you to: Understand Git's core philosophy. Get started with Git: install it, learn the basic commands, and set up your first project. Work with Git as part of a collaborative team. Use Git's debugging tools for maximum debug efficiency. Master Git workflow Take control with Git's advanced features: reflog, rebase, stash, and more. Use Git with cloud-based Git repository host services like Github and Bitbucket. See how Git's used effectively on large open-source projects. Whether you're a Git newbie or you've been using it for some time but only really scratching the surface of its capabilities, this book will help you to gain a deep understanding of how Git works, and how to use it to streamline your workflow. COMPUTERS,Software Development & Engineering,Tools

Natural Language Generation in Artificial Intelligence and Computational Linguistics One of the aims of Natural Language Processing is to facilitate .the use of computers by allowing their users to communicate in natural language. There are two important aspects to person-machine communication: understanding and generating. While natural language understanding has been a major focus of research, natural language generation is a relatively new and increasingly active field of research. This book presents an overview of the state of the art in natural language generation, describing both new results and directions for new research. The principal emphasis of natural language generation is not only to facili tate the use of computers but also to develop a computational theory of human language ability. In doing so, it is a tool for extending, clarifying and verifying theories that have been put forth in linguistics, psychology and sociology about how people communicate. A natural language generator will typically have access to a large body of knowledge from which to select information to present to users as well as numer of expressing it. Generating a text can thus be seen as a problem of ous ways decision-making under multiple constraints: constraints from the propositional knowledge at hand, from the linguistic tools available, from the communicative goals and intentions to be achieved, from the audience the text is aimed at and from the situation and past discourse. Researchers in generation try to identify the factors involved in this process and determine how best to represent the factors and their dependencies. COMPUTERS,Speech & Audio Processing

Intelligent Integration of Information Intelligent Integration of Information presents a collection of chapters bringing the science of intelligent integration forward. The focus on integration defines tasks that increase the value of information when information from multiple sources is accessed, related, and combined. This contributed volume has also been published as a special double issue of the Journal of Intelligent Information Systems (JIIS), Volume 6:2/3. COMPUTERS,Speech & Audio Processing

Integration of Natural Language and Vision Processing Although there has been much progress in developing theories, models and systems in the areas of Natural Language Processing (NLP) and Vision Processing (VP), there has heretofore been little progress on integrating these two subareas of Artificial Intelligence (AI). This book contains a set of edited papers addressing theoretical issues and the grounding of representations in NLP and VP from philosophical and psychological points of view. The papers focus on site descriptions such as the reasoning work on space at Leeds, UK, the systems work of the ILS (Illinois, U.S.A.) and philosophical work on grounding at Torino, Italy, on Schank's earlier work on pragmatics and meaning incorporated into hypermedia teaching systems, Wilks' visions on metaphor, on experimental data for how people fuse language and vision and theories and computational models, mainly connectionist, for tackling Searle's Chinese Room Problem and Harnad's Symbol Grounding Problem. The Irish Room is introduced as a mechanism through which integration solves the Chinese Room. The U.S.A., China and the EU are well reflected, showing the fact that integration is a truly international issue. There is no doubt that all of this will be necessary for the SuperInformationHighways of the future. COMPUTERS,Speech & Audio Processing

Advanced Relational Programming Databaseprogrammingis the process ofdeveloping data-intensiveapplications which demand the access to large amounts of structured, persistent data. The primary tool required for implementing such applications is a database programming language, namely aformal language which is specialized in the definition and manipulationof relevant large-scale data. As such, a database programming language is expected to provide high-level data modeling capabilitiesas well as avarietyofconstructs which facilitatethehandlingofthespecifieddata. Inthis perspective, the aim of this book is: (i) to present the recent advances in database technologyfrom theviewpointofthe novel database paradigmsproposedfor the developmentofadvanced, non-standard, data-intensive applications, (ii) to focus specificallyon the relational approach, with considerableemphasis on the extensions proposed in the last decade, and (iii) to describe the extended relational database languageAlgres which is primarily the outcome of research work conducted by the authorsincooperationwithalargenumberofothercolleaguesandstudents. Furthermore, in orderto put the concepts presented in the book into practice, the reader is invited to experiment with the Algres system, afree copyofwhich can be requestedfromKluwerAcademicPublishers,ordirectlyfromtheauthors. Dependingonthespecific interest andbackgroundofthereader,thebookcanserve either:(1) to overview recent trends in databases, (2) to introduce in more detail the concepts and theory of the nested relational model, or (3) to present a complete advancedrelationallanguagewhichcanbefreelyusedforexperimentalpurposeswithin academicandresearchframeworks. COMPUTERS,Speech & Audio Processing

Integration of Natural Language and Vision Processing Although there has been much progress in developing theories, models and systems in the areas of natural language processing (NLP) and vision processing (VP), there has hitherto been little progress in integrating these two subareas of artificial intelligence. The papers in Integration of Natural Language and Vision Processing focus on site descriptions, such as the work at Apple Computer, California, and the DFKI, Saarbrücken, on historical surveys and philosophical issues, on systems that have been built, enabling communication through text, speech, sound, touch, video, graphics and icons, and on the automatic presentation of information, whether it be in the form of instruction manuals, statistical data or visualisation of language. There is also a review of Mark Maybury's book Intelligent Multimedia Interfaces. Audience: Vital reading for all interested in the SuperInformationHighways of the future. COMPUTERS,Speech & Audio Processing

The SGML Implementation Guide Foreword------------------------------------- SGML is misunderstood and underestimated. I have always wanted to write this book. I am pleased that two people with whom I have had the pleasure to work were finally able to do so. Since I have always been a bit of an evangelist, I feel pride when my "students" become recognized "teachers". In the early years of SGML we struggled to define a language that would bring the information to its rightful place. We succeeded. Then we had to explain these idea to technical adoptors. Again, I think we have succeeded. We have learned much about SGML in the process of implementing it. These experiences must now also be shared, along with comprehensible information on the lan guage itself. The word must move out of the lab and the computer center and reach the business people, the users, the movers and shakers. The next generation will do things with SGML that we can't even imagine yet- it is that versatile. COMPUTERS,Speech & Audio Processing

Fachwörterbuch Kommunikationsdesign / Dictionary of Communication Design Deutsch-Englisch, Englisch-Deutsch COMPUTERS,Speech & Audio Processing

Cooperative Computer-Aided Authoring and Learning Cooperative Computer-Aided Authoring and Learning: A Systems Approach describes in detail a practical system for computer assisted authoring and learning. Drawing from the experiences gained during the Nestor project, jointly run between the Universities of Karlsruhe, Kaiserslautern and Freiburg and the Digital Equipment Corp. Center for Research and Advanced Development, the book presents a concrete example of new concepts in the domain of computer-aided authoring and learning. The conceptual foundation is laid by a reference architecture for an integrated environment for authoring and learning. This overall architecture represents the nucleus, shell and common denominator for the R&D activities carried out. From its conception, the reference architecture was centered around three major issues: Cooperation among and between authors and learners in an open, multimedia and distributed system as the most important attribute; Authoring/learning as the central topic; Laboratory as the term which evoked the most suitable association with the envisioned authoring/learning environment. Within this framework, the book covers four major topics which denote the most important technical domains, namely: The system kernel, based on object orientation and hypermedia; Distributed multimedia support; Cooperation support, and Reusable instructional design support. Cooperative Computer-Aided Authoring and Learning: A Systems Approach is a major contribution to the emerging field of collaborative computing and is essential reading for researchers and practitioners alike. Its pedagogic flavor also makes it suitable for use as a text for a course on the subject. COMPUTERS,Speech & Audio Processing

Text Encoding Initiative Charles F. Goldfarb Saratoga. California If asked for a sure recipe for chaos I would propose a I am delighted that my invention, the Standard project in which several thousand impassioned special Generalized Markup Language, was able to play a ists in scores of disciplines from a dozen or more role in the TEl's magnificent accomplishment, particu countries would be given five years to produce some larly because almost all of the original applications 1300 pages of guidelines for representing the informa of SGML were in the commercial and technological tion models of their specialties in a rigorous, machine realms. It is reasonable, of course, that organiza verifiable notation. Clearly, it would be sociologically tions with massive economic investments in new and and technologically impossible for such a group even changing information should want the benefits of infor to agree on the subject matter of such guidelines, let mation asset preservation and reuse that SGML offers. alone the coding details. But just as clearly as the It is gratifying that the TEl, representing the guardians bumblebee flies despite the laws of aerodynamics, the of humanity's oldest and most truly valuable informa Text Encoding Initiative has actually succeeded in such tion, chose SGML for those same benefits. an effort. The vaunted "information superhighway" would The TEl Guidelines are extraordinary. COMPUTERS,Speech & Audio Processing

Digital Typefaces Summary his book was written primarily for people who intend or wish to develop new machines for the output of typefaces. It is practical to categorize equipment into three groups for which digital alphabets are required - 1) display devices, 2) typesetting machines and 3) numerically controlled (NC) machines. Until now, development of typefaces has been overly dependent upon the design of the respective machine on which it was to be used. This need not be the case. Digitization of type should be undertaken in two steps: the preparation of a database using hand-digitization, and the subsequent automatic generation of machine formats by soft scanning, through the use of a computer-based program. Digital formats for typefaces are ideally suited to system atic ordering, as are coding techniques. In this volume, various formats are investigated, their properties discussed and rela tive production requirements analyzed. Appendices provide readers additional information, largely on digital formats for typeface storage introduced by the IKARUS system. This book was composed in Latino type, developed by Hermann Zapf from his Melior for URW in 1990. Compo sition was accomplished on a Linotronic 300, as well as on an Agfa 9400 typesetter using PostScript. v Preface Preface his book was brought out by URW Publishers in 1986 with the title «Digital Formats for Typefaces;). It was translated into English in 1987, Japanese in 1989 and French in 1991. COMPUTERS,Speech & Audio Processing

Font Technology Computers have changed typography and prepress as well as printing. Typefaces are manufactured by "digital punch cutters" with a PC, not any more by punch cutters. Typefaces are constructed an output by a new technolgy, the so-called fonttechnology. The book by Peter Karow covers the whole area of it. It offers various chapters about (among others) issues like intelligent font scaling, kerning, quality of type, legibility, and problems of different output devices. It is interesting to read about Gutenberg setting, the font market, optical scaling, and last but not least a "hand on" Kanjhi, the Chinese/Japanese Glyphs. Furthermore, Fonttechnology contains a number of valuable and instructive appendices. Almost everything one has to know about type and computers! COMPUTERS,Speech & Audio Processing

Making Hypermedia Work Making Hypermedia Work: A User's Guide to HyTime discusses how the HyTime standard can be applied to real world problems of navigating from here to there in collections of documents. The HyTime standard itself provides enabling method and templates for various information structures such as links and various kinds of location indicators. A HyTime application specifies how a group applies those templates to their particular requirements. This involves choosing which HyTime structures are needed, setting up conventions for how they are to be used and setting up management and processes for creation, conversion and update of hypermedia documents. A HyTime engine is the last ingredient: actually using an application typically involves choosing software to support one's use of HyTime and customizing it as needed. This may be as simple as setting up hypertextual style sheets that determine how links and other things look and act. More specialized applications may require full-scale design and programming. Making Hypermedia Work: A User's Guide to HyTime presents the first in-depth guide to the HyTime specifications, both describing its key features and providing guidelines on how it is used. The book begins with the more familiar structures of books, graphics and cross-references, detailing the HyTime constructs and models used to identify, locate, and link data. It goes on to introduce some of HyTime's mechanisms for linking multidimensional, multimedia data, and for scheduling it in space and time. The authors help the reader become fluent in HyTime as it applies to the simpler and most widely understood data types. After mastering this level of HyTime, readers will be ready and able to explore the exciting potential of HyTime for more sophisticated multimedia applications. COMPUTERS,Speech & Audio Processing

TEX TEX is the program for printing high quality mathematicaltext to which all others are compared. It is flexible enoughto be used on many different computer architectures andoperating systems ranging from microcomputers to mainframes.In a relatively short period of time it has become thestandard tool for mathematical typesetting at practicallyall major universities. The versality of TEX has allowed itto be used in a wide variety of applications; for example,it is used for publishing scholarly journals which adhere tothe highest typesetting standards, and also to publishstudent papers and theses.This book is designed for the complete newcomer to TEX. Itstarts by showing how to typeset simple text that mostlyuses the defaults predefined by TEX. By use of gradedexercises, the situations covered slowly become more complexand include many different types of mathematicalconstructions and tables. In the end it is possible tohandle almost any standard mathematical situation.The different tables presented in this book allow it to beused as a quick reference. The similar features of TEX aregathered together whenever possible to give an overview thatis a good foundation forbecoming more proficient and fordoing more creative typesetting.This book can be used either as a tool to learn just enoughTEX to write standardmathematical papers of modestcomplexity or as a building block to prepare for moreambitious typesetting projects. COMPUTERS,Speech & Audio Processing

Integrated Management of Technical Documentation Writing documentation is an integral part of any technical product development. A significant amount of time is spent describing the product functionality, giving insights into technical details, providing maintenance instructions, specifying marketing information, writing user manuals, etc. As the creation of such documentation is generally a source of higher production costs, many large companies are realising the need to increase the efficiency of documentation handling. Simple documents consisting of only a few pages can be developed on simple systems. Basic components of such systems are an editor handling text and graphics, file storage, and a printer. Such configurations, however, are not sufficient to handle professional documentation as produced by larger companies. Detailed studies of technical documentation requirements have revealed that in particular the following functionality is not usually provided by such simple documentation systems: Technical documentation is often very large; documents having hundreds or even thousands of pages are not exceptional. Due to size and complexity, technical documentation is developed most often by a team of authors. A system for technical documentation has to provide functionality supporting the organisation of a group of authors. Technical documentation usually consists of many different documents combined into one large documentation for a particular product. The optimum organisation of the storage and retrieval of documents is crucial for the performance and acceptability of the system. The functionality offered by normal file systems is not adequate to organise complex systems. COMPUTERS,Speech & Audio Processing

Hypermedia Courseware This book is based on the NATO Advanced Research Workshop on Structures of Com munication and Intelligent Help for Hypermedia Courseware, which was held at Espinho, Portugal, April 19-24, 1990. The texts included here should not be regarded as untouched proceedings of this meeting, but as the result of the reflections which took place there and which led the authors to revise their texts in that light. The Espinho ARW was itself to some extent the continuation of the ARW on Designing Hypermedia/Hypertext for Learning, held in Germany in 1989 (D. H. Jonassen, H. Mandl (eds.): Designing Hypermedia for Learning. NATO ASI Series F, Vol. 67. Springer 1990). At that meeting an essential conclusion becarne apparent: the importance and interest of hyper media products as potential pedagogical tools. It was then already predictable that the enormous evolution of hypermedia would lead to its association with multimedia technologies, namely for the production of courseware. Parallel to the improvement of the didactic potential and quality which results from this association, it nevertheless brought along a natural array of difficulties, some old, some new, in the con ception and use of hypermedia products. Today there is agreement that one of the most promising technological advances for education is represented by the use of text, sound and images based on nonlinear techniques of information handling and searching of hypermedia architectures. The problem of hypermedia is fundamentally one of communication; this leads to an attempt at defining a language for hypermedia. COMPUTERS,Speech & Audio Processing

De Motu and the Analyst Berkeley's philosophy has been much studied and discussed over the years, and a growing number of scholars have come to the realization that scientific and mathematical writings are an essential part of his philosophical enterprise. The aim of this volume is to present Berkeley's two most important scientific texts in a form which meets contemporary standards of scholarship while rendering them accessible to the modern reader. Although editions of both are contained in the fourth volume of the Works, these lack adequate introductions and do not provide com plete and corrected texts. The present edition contains a complete and critically established text of both De Motu and The Analyst, in addi tion to a new translation of De Motu. The introductions and notes are designed to provide the background necessary for a full understanding of Berkeley's account of science and mathematics. Although these two texts are very different, they are united by a shared a concern with the work of Newton and Leibniz. Berkeley's De Motu deals extensively with Newton's Principia and Leibniz's Specimen Dynamicum, while The Analyst critiques both Leibnizian and Newto nian mathematics. Berkeley is commonly thought of as a successor to Locke or Malebranche, but as these works show he is also a successor to Newton and Leibniz. COMPUTERS,Speech & Audio Processing

Current Issues in Parsing Technology COMPUTERS,Speech & Audio Processing

The Craft of Text Editing Never before has a book been published that describes the techniques and technology used in writing text editors, word processors and other software. Written for the working professional and serious student, this book covers all aspects of the task. The topics range from user psychology to selecting a language to implementing redisplay to designing the command set. More than just facts are involved, however, as this book also promotes insight into an understanding of the issues encountered when designing such software. After reading this book, you should have a clear understanding of how to go about writing text editing or word processing software. In addition, this book introduces the concepts and power of the Emacs-type of text editor. This type of editor can trace its roots to the first computer text editor written and is still by far the most powerful editor available. COMPUTERS,Speech & Audio Processing

Practical LaTeX Practical LaTeX covers the material that is needed for everyday LaTeX documents. This accessible manual is friendly, easy to read, and is designed to be as portable as LaTeX itself. A short chapter, Mission Impossible, introduces LaTeX documents and presentations. Read these 30 pages; you then should be able to compose your own work in LaTeX. The remainder of the book delves deeper into the topics outlined in Mission Impossible while avoiding technical subjects. Chapters on presentations and illustrations are a highlight, as is the introduction of LaTeX on an iPad.Students, faculty, and professionals in the worlds of mathematics and technology will benefit greatly from this new, practical introduction to LaTeX. George Grätzer, author of More Math into LaTeX (now in its 4th edition) and First Steps in LaTeX, has been a LaTeX guru for over a quarter of century.From the reviews of More Math into LaTeX:``There are several LaTeX guides, but this one wins hands down for the elegance of its approach and breadth of coverage.'' —Amazon.com, Best of 2000, Editors Choice ``A very helpful and useful tool for all scientists and engineers.'' —Review of Astronomical Tools ``A novice reader will be able to learn the most essential features of LaTeX sufficient to begin typesetting papers within a few hours of time…An experienced TeX user, on the other hand, will find a systematic and detailed discussion of all LaTeX features, supporting software, and many other advanced technical issues.''—Reports on Mathematical Physics COMPUTERS,Speech & Audio Processing

Math into TeX COMPUTERS,Speech & Audio Processing

DigiScriptâ„¢ DigiScript edits for production all digital manuscripts in the current industry formats PostScript and PDF, including pictures, text, graphics, color, and production parameters, independently of the hardware and software platforms used to prepare the document. Fundamental background information, technical know-how, and application examples from the professional prepress field are combined to help the user solve difficult production problems efficiently. The complete description of the DigiScript production environment allows the book to serve as a self-contained reference work. The accompanying CD-ROM provides all the data you need to test DigiScript on your NEXTSTEP 3.3 system as well as review copies of the examples introduced in the user handbook. COMPUTERS,Speech & Audio Processing

Translator’s Workbench The Translator's Workbench Project was a European Community sponsored research and development project which dealt with issues in multi-lingual communication and docu mentation. This book presents an integrated toolset as a solution to problems in translation and docu mentation. Professional translators and teachers of translation were involved in the proc ess of software development, starting with a detailed study of the user requirements and ending with several evaluation-and-improvement cycles of the resulting toolset. English, German, Greek, and Spanish are addressed in the contributions, however, some of the techniques are inherently language-independent and can thus be extended to cover other languages as well. Translation can be viewed broadly as the execution of three cognitive processes, and this book has been structured along these lines: • First, the translation pre-process, understanding the target language text at a lexico semantic level on the one hand, and making sense of the source language document on the other hand. The tools for the pre-translation process include access to electronic networks, conversion of documents from one format to another, creation of terminol ogy data banks and access to existing data banks, and terminology dictionaries. • Second, the translation process, rendering sentences in the source language into equiva lent target sentences. The translation process refers to the potential of conventional machine translation systems, like METAL, and of the statistically oriented translation memory. COMPUTERS,Speech & Audio Processing

Compositional Translation Franciska de Jong and Jan Landsbergen Jan Landsbergen 2 A compositional definition of the translation relation Jan Odijk 3 M-grammars Jan Landsbergen and Franciska de Jong 4 The translation process Lisette Appelo 5 The Rosetta characteristics Joep Rous and Harm Smit 6 Morphology Jan Odijk, Harm Smit and Petra de Wit 7 Dictionaries Jan Odijk 8 Syntactic rules Modular and controlled Lisette Appelo 9 M-grammars Compositionality and syntactic Jan Odijk 10 generalisations Jan Odijk and Elena Pinillos Bartolome 11 Incorporating theoretical linguistic insights Lisette Appelo 12 Divergences between languages Lisette Appelo 13 Categorial divergences Translation of temporal Lisette Appelo 14 expressions Andre Schenk 15 Idioms and complex predicates Lisette Appelo and Elly van Munster 16 Scope and negation Rene Leermakers and Jan Landsbergen 17 The formal definition of M-grammars Rene Leermakers and Joep Rous 18 An attribute grammar view Theo Janssen 19 An algebraic view Rene Leermakers 20 Software engineering aspects Jan Landsbergen 21 Conclusion Contents 1 1 Introduction 1. 1 Knowledge needed for translation . . . . . . . . . . . 2 1. 1. 1 Knowledge of language and world knowledge 2 1. 1. 2 Formalisation. . . . . . . . . . . . . . . . . 4 1. 1. 3 The underestimation of linguistic problems . 5 1. 1. 4 The notion of possible translation . 5 1. 2 Applications. . . . . . . . . . . 7 1. 3 A linguistic perspective on MT 9 1. 3. 1 Scope of the project 9 1. 3. 2 Scope of the book 11 1. 4 Organisation of the book . . COMPUTERS,Speech & Audio Processing

More Math Into LaTeX For over two decades, this comprehensive manual has been the standard introduction and complete reference for writing articles and books containing mathematical formulas. If the reader requires a streamlined approach to learning LaTeX for composing everyday documents, Grätzer’s © 2014 Practical LaTeX may also be a good choice. In this carefully revised fifth edition, the Short Course has been brought up to date and reflects a modern and practical approach to LaTeX usage. New chapters have been added on illustrations and how to use LaTeX on an iPad. Key features: An example-based, visual approach and a gentle introduction with the Short Course A detailed exposition of multiline math formulas with a Visual Guide A unified approach to TeX, LaTeX, and the AMS enhancements A quick introduction to creating presentations with formulas From earlier reviews: Grätzer’s book is a solution. —European Mathematical Society Newsletter There are several LaTeX guides, but this one wins hands down for the elegance of its approach and breadth of coverage. —Amazon.com, Best of 2000, Editor’s choice A novice reader will be able to learn the most essential features of LaTeX sufficient to begin typesetting papers within a few hours of time… An experienced TeX user, on the other hand, will find a systematic and detailed discussion of LaTeX fea tures. —Report on Mathematical Physics A very helpful and useful tool for all scientists and engineers. —Review of Astronomical Tools COMPUTERS,Speech & Audio Processing

Natural Language Processing and Information Systems This book constitutes the refereed proceedings of the 25th International Conference on Applications of Natural Language to Information Systems, NLDB 2020, held in Saarbrücken, Germany, in June 2020.* The 15 full papers and 10 short papers were carefully reviewed and selected from 68 submissions. The papers are organized in the following topical sections: semantic analysis; question answering and answer generation; classiï¬cation; sentiment analysis; personality, affect and emotion; retrieval, conversational agents and multimodal analysis. *The conference was held virtually due to the COVID-19 pandemic. COMPUTERS,Speech & Audio Processing

Computational Linguistics This book constitutes the refereed proceedings of the 16th International Conference of the Pacific Association for Computational Linguistics, PACLING 2019, held in Hanoi, Vietnam, in October 2019. The 28 full papers and 14 short papers presented were carefully reviewed and selected from 70 submissions. The papers are organized in topical sections on text summarization; relation and word embedding; machine translation; text classification; web analyzing; question and answering, dialog analyzing; speech and emotion analyzing; parsing and segmentation; information extraction; and grammar error and plagiarism detection. COMPUTERS,Speech & Audio Processing

Postfix Postfix is a Mail Transfer Agent (MTA): software that mail servers use to route email. Postfix is highly respected by experts for its secure design and tremendous reliability. And new users like it because it's so simple to configure. In fact, Postfix has been adopted as the default MTA on Mac OS X. It is also compatible with sendmail, so that existing scripts and programs continue to work seamlesslyafter it is installed.Postfix was written by well-known security expert Wietse Venema, who reviewed this book intensively during its entire development. Author Kyle Dent covers a wide range of Postfix tasks, from virtual hosting to controls for unsolicited commercial email.While basic configuration of Postfix is easy, every site has unique needs that call for a certain amount of study. This book, with careful background explanations and generous examples, eases readers from the basic configuration to the full power of Postfix. It discusses the Postfix interfaces to various tools that round out a fully scalable and highly secure email system. These tools include POP, IMAP, LDAP, MySQL, Simple Authentication and Security Layer (SASL), and Transport Layer Security (TLS, an upgrade of SSL). A reference section for Postfix configuration parameters and an installation guide are included.Topics include: Basic installation and configuration DNS configuration for email Working with POP/IMAP servers Hosting multiple domains (virtual hosting) Mailing lists Handling unsolicited email (spam blocking) Security through SASL and TLS From compiling and installing Postfix to troubleshooting, Postfix: The Definitive Guide offers system administrators and anyone who deals with Postfix an all-in-one, comprehensive tutorial and reference to this MTA. COMPUTERS,System Administration,Email Servers

sendmail A classic O'Reilly title since 1993, sendmail now covers Versions 8.10 through 8.14 of this email routing program, including dozens of new features, options, and macros. This edition also takes a more nuts-and-bolts approach than its predecessors. It includes both an administration handbook and a reference guide that provide you with clear options for installing, configuring and managing sendmail's latest versions and companion programs. The sendmail program has withstood the test of time because of its ability to solve the mail-routing needs of all sites large or small, complex or simple. But it's also difficult to configure and even more difficult to understand. That's why this book has proven valuable since the dawn of email. With it, you will be able to configure the program to meet any need, so that you never again have to call in a sendmail guru to bail you out. sendmail includes the following sections: Some Basics is especially useful for people new to the program. It covers the basic concepts underlying mail delivery and the roles sendmail plays in that delivery Administration covers all aspects of handling sendmail, from downloading and installing new releases to managing mailing lists and aliases Configuration Reference contains a heavily cross-referenced guide for configuring and tuning sendmail. Every arcane detail of sendmail is listed alphabetically Appendices contain more detail about sendmail than you may ever need This edition also includes new material on SSL and AUTH and a new chapter on Mitlers. If you're interested in what has changed since the last edition, one appendix categorizes the many improvements of sendmail's intervening versions by chapter, complete with references to the appropriate sections and page numbers in the book. With sendmail, system administrators, programmers, network engineers, and even inexperienced users will be able to match this challenging but necessary utility to the needs of their network. COMPUTERS,System Administration,Email Servers

Microsoft Exchange Server 2013 Unleashed Microsoft Exchange Server 2013 doesn’t just add dozens of new features: It integrates multiple technologies into a common, unified communications system that can add value in many new ways. Now, five leading Exchange Server consultants help you deploy Exchange Server 2013 quickly and smoothly--and then efficiently manage, troubleshoot, and support it for years to come. More than a comprehensive, authoritative reference, Microsoft Exchange Server 2013 Unleashed presents hundreds of helpful tips and tricks based on the authors’ unsurpassed early adopter experience with Exchange Server 2013 in real production environments. Carefully and thoroughly, the authors explain what’s new and different in Microsoft Exchange 2013 and guide you through architecting, planning, implementing, and transitioning to your new Exchange Server environment. They offer best practices for establishing solid Active Directory, DNS, fabric, virtualization, and PKI security environments to support Exchange; implementing high availability and site resilience; and much more. You’ll find expert discussions of security and compliance and uniquely practical and detailed coverage of day-to-day administration, management, maintenance, and optimization. The authors next turn to advanced platform integration, helping you leverage the full benefits of linking Exchange Server, SharePoint, and Unified Messaging. They conclude with a full section on Exchange Server’s dramatically improved support for endpoint clients, including Apple, Android, and Microsoft smartphones and tablets. Detailed information on how to... Use proven best practices to install Exchange Server 2013 from scratch or to upgrade from Exchange Server 2007/2010 Integrate Active Directory, DNS, fabric, and virtualization with Exchange Server 2013 Implement certificate-based Public Key Infrastructure (PKI) Plan, deploy, migrate to, and support public folders Protect your users and organization with both policy-based and content-enforced security Design and implement message archiving, retention, and eDiscovery Administer, optimize, and document your Exchange Server 2013 environment Architect all aspects of an integrated, enterprise-level Exchange Server 2013 environment Integrate Exchange Server with SharePoint Site Mailboxes, Enterprise Search, and more Leverage the robust Outlook client for Windows, Mac, Web, tablet, and mobile phones COMPUTERS,System Administration,Email Servers

Monitoring with Ganglia Written by Ganglia designers and maintainers, this book shows you how to collect and visualize metrics from clusters, grids, and cloud infrastructures at any scale. Want to track CPU utilization from 50,000 hosts every ten seconds? Ganglia is just the tool you need, once you know how its main components work together. This hands-on book helps experienced system administrators take advantage of Ganglia 3.x. Learn how to extend the base set of metrics you collect, fetch current values, see aggregate views of metrics, and observe time-series trends in your data. You’ll also examine real-world case studies of Ganglia installs that feature challenging monitoring requirements. Determine whether Ganglia is a good fit for your environment Learn how Ganglia’s gmond and gmetad daemons build a metric collection overlay Plan for scalability early in your Ganglia deployment, with valuable tips and advice Take data visualization to a new level with gweb, Ganglia’s web frontend Write plugins to extend gmond’s metric-collection capability Troubleshoot issues you may encounter with a Ganglia installation Integrate Ganglia with the sFlow and Nagios monitoring systems Contributors include: Robert Alexander, Jeff Buchbinder, Frederiko Costa, Alex Dean, Dave Josephsen, Peter Phaal, and Daniel Pocock. Case study writers include: John Allspaw, Ramon Bastiaans, Adam Compton, Andrew Dibble, and Jonah Horowitz. COMPUTERS,System Administration,General

Vagrant Discover why Vagrant is a must-have tool for thousands of developers and ops engineers. This hands-on guide shows you how to use this open source software to build a virtual machine for any purpose—including a completely sandboxed, fully provisioned development environment right on your desktop. Vagrant creator Mitchell Hashimoto shows you how to share a virtual machine image with members of your team, set up a separate virtualization for each project, and package virtual machines for use by others. This book covers the V1 (1.0.x) configuration syntax running on top of a V2 (1.1+) core, the most stable configuration format running on the latest core. Build a simple virtual machine with just two commands and no configuration Create a development environment that closely resembles production Automate software installation and management with shell scripts, Chef, or Puppet Set up a network interface to access your virtual machine from any computer Use your own editor and browser to develop and test your applications Test complicated multi-machine clusters with a single Vagrantfile Change Vagrant’s default operating system to match your production OS Extend Vagrant features with plugins, including components you build yourself COMPUTERS,System Administration,General

Docker Updated to cover Docker version 1.10 Docker is quickly changing the way that organizations are deploying software at scale. But understanding how Linux containers fit into your workflow—and getting the integration details right—are not trivial tasks. With this practical guide, you’ll learn how to use Docker to package your applications with all of their dependencies, and then test, ship, scale, and support your containers in production. Two Lead Site Reliability Engineers at New Relic share much of what they have learned from using Docker in production since shortly after its initial release. Their goal is to help you reap the benefits of this technology while avoiding the many setbacks they experienced. Learn how Docker simplifies dependency management and deployment workflow for your applications Start working with Docker images, containers, and command line tools Use practical techniques to deploy and test Docker-based Linux containers in production Debug containers by understanding their composition and internal processes Deploy production containers at scale inside your data center or cloud environment Explore advanced Docker topics, including deployment tools, networking, orchestration, security, and configuration COMPUTERS,System Administration,General

Docker Cookbook Whether you’re deploying applications on premise or in the cloud, this cookbook provides developers, operators, and IT professionals with more than 130 proven recipes for working with Docker. With these practical solutions, experienced developers with no previous knowledge of Docker will be able to package and deploy distributed applications within a couple of chapters. IT professionals will be able to solve everyday problems, as well as create, run, share, and deploy Docker images. Operators will quickly be able to adopt the tools that will change the way they work. The recipes in this book will help you: Manage containers, mount data volumes, and link containers Create and share container images Network containers across single or multiple hosts Tackle advanced topics such as Docker configuration and development Deploy multi-container applications on a distributed cluster with Kubernetes Use a new generation of operating systems optimized for Docker Learn tools for application deployment, continuous integration, service discovery, and orchestration Access a Docker host on Amazon AWS, Google GCE, and Microsoft Azure Monitor containers and explore different application use cases COMPUTERS,System Administration,General

Using Docker Docker containers offer simpler, faster, and more robust methods for developing, distributing, and running software than previously available. With this hands-on guide, you’ll learn why containers are so important, what you’ll gain by adopting Docker, and how to make it part of your development process. Ideal for developers, operations engineers, and system administrators—especially those keen to embrace a DevOps approach—Using Docker will take you from Docker and container basics to running dozens of containers on a multi-host system with networking and scheduling. The core of the book walks you through the steps needed to develop, test, and deploy a web application with Docker. Get started with Docker by building and deploying a simple web application Use Continuous Deployment techniques to push your application to production multiple times a day Learn various options and techniques for logging and monitoring multiple containers Examine networking and service discovery: how do containers find each other and how do you connect them? Orchestrate and cluster containers to address load-balancing, scaling, failover, and scheduling Secure your system by following the principles of defense-in-depth and least privilege COMPUTERS,System Administration,General

Site Reliability Engineering The overwhelming majority of a software system’s lifespan is spent in use, not in design or implementation. So, why does conventional wisdom insist that software engineers focus primarily on the design and development of large-scale computing systems? In this collection of essays and articles, key members of Google’s Site Reliability Team explain how and why their commitment to the entire lifecycle has enabled the company to successfully build, deploy, monitor, and maintain some of the largest software systems in the world. You’ll learn the principles and practices that enable Google engineers to make systems more scalable, reliable, and efficient—lessons directly applicable to your organization. This book is divided into four sections: Introduction—Learn what site reliability engineering is and why it differs from conventional IT industry practices Principles—Examine the patterns, behaviors, and areas of concern that influence the work of a site reliability engineer (SRE) Practices—Understand the theory and practice of an SRE’s day-to-day work: building and operating large distributed computing systems Management—Explore Google's best practices for training, communication, and meetings that your organization can use COMPUTERS,System Administration,General

Infrastructure as Code Virtualization, cloud, containers, server automation, and software-defined networking are meant to simplify IT operations. But many organizations adopting these technologies have found that it only leads to a faster-growing sprawl of unmanageable systems. This is where infrastructure as code can help. With this practical guide, author Kief Morris of ThoughtWorks shows you how to effectively use principles, practices, and patterns pioneered through the DevOps movement to manage cloud age infrastructure. Ideal for system administrators, infrastructure engineers, team leads, and architects, this book demonstrates various tools, techniques, and patterns you can use to implement infrastructure as code. In three parts, you’ll learn about the platforms and tooling involved in creating and configuring infrastructure elements, patterns for using these tools, and practices for making infrastructure as code work in your environment. Examine the pitfalls that organizations fall into when adopting the new generation of infrastructure technologies Understand the capabilities and service models of dynamic infrastructure platforms Learn about tools that provide, provision, and configure core infrastructure resources Explore services and tools for managing a dynamic infrastructure Learn specific patterns and practices for provisioning servers, building server templates, and updating running servers COMPUTERS,System Administration,General

Microsoft System Center 2016 Service Manager Cookbook Discover over 100 practical recipes to help you master the art of IT service management for your organization About This Book Unleash the capabilities of Microsoft System Center 2016 Service Manager Master the skills of configuring, deploying, managing, and troubleshooting your Service Manager 2016 This book contains practical recipes that leverage the key and newly added features and functionalities of Microsoft System Center 2016 Service Manager Who This Book Is For This book will be useful to IT professionals including SCSM administrators who want to configure and administer System Center Service Manager 2016 and understand how to solve specific problems and scenarios that arise. It will also be useful to users of Service Manager 2012 who want to learn about the new features and capabilities of the Service Manager 2016 release. It will be ideal if you have Service Manager experience as well as experience with other System Center products. What You Will Learn See a practical implementation of the ITSM framework and processes based on ITIL Deploy and configure the new Service Manager HTML5 Self-Service Portal along with Service Catalog design and configuration Get to know about Incident, Problem, and Change Management processes and configuration Get to grips with performing advanced personalization in Service Manager Discover how to set up and use automation with and within Service Manager 2016 Work with Service Manager Data Warehouse Find out what Security Roles are and how to implement them Learn how to upgrade from SCSM 2012 R2 to SCSM 2016 In Detail System Center Service Manager (SCSM) is an integrated platform that offers a simplified data center management experience by implementing best practices such as Incident Management, Service Request, and Change Control to achieve efficient service delivery across your organization. This book provides you with real-world recipes that can be used immediately and will show you how to configure and administer SCSM 2016. You'll also find out how to solve particular problems and scenarios to take this tool further. You'll start with recipes on implementing ITSM frameworks and processes and configuring Service Level Agreements (SLAs). Then, you'll work through deploying and configuring the HTML5 Self-Service Portal, configuring Incident and Problem Management, and designing and configuring Change and Release Management. You'll also learn about security roles and overall Microsoft SCSM 2016 administration. Toward the end of the book, we'll look at advanced topics, such as presenting the wealth of information stored within the Service Manager Data Warehouse, standardizing SCSM deployments, and implementing automation. Style and approach This book will enlighten you on Microsoft System Center 2016 Service Manager through recipes that can be implemented directly in any enterprise. You can read the book from start to end if you're a beginner, or just open up any chapter and start following the recipes as a reference for advanced users. This book consists of a pool of step-by-step recipes on how to perform activities in Service Manager. COMPUTERS,System Administration,General

Monitoring with Graphite Graphite has become one of the most powerful monitoring tools available today, due to its ease of use, rapid graph prototyping abilities, and a friendly rendering API. With this practical guide, system administrators and engineers will learn how to use this open source tool to track operational data you need to monitor your systems, as well as application-level metrics for profiling your services. Author Jason Dixon, member of the Graphite project, provides a thorough introduction of Graphite from the basics to the skills and tools you need for troubleshooting and scaling out its software components. If you want to learn more about monitoring systems, services, or applications, this is the book you need. Get an introduction to monitoring, including important concepts and terminology Examine the features and functionality of key Graphite components, including Carbon and Whisper Learn the typical user workflow necessary to create a basic line chart Build complex charts with chained functions and multiple axes that interact directly with the rendering API Understand how to use the native Graphite dashboard, as well as the more popular third-party dashboards Master the art of scaling and troubleshooting high-performance or highly available Graphite clusters COMPUTERS,System Administration,General

Terraform Terraform has emerged as a key player in the DevOps world for defining, launching, and managing infrastructure as code (IAC) across a variety of cloud and virtualization platforms, including AWS, Google Cloud, and Azure. This hands-on book is the fastest way to get up and running with Terraform. Gruntwork co-founder Yevgeniy (Jim) Brikman walks you through dozens of code examples that demonstrate how to use Terraform’s simple, declarative programming language to deploy and manage infrastructure with just a few commands. Whether you’re a novice developer, aspiring DevOps engineer, or veteran sysadmin, this book will take you from Terraform basics to running a full tech stack capable of supporting a massive amount of traffic and a large team of developers. Compare Terraform to other IAC tools, such as Chef, Puppet, Ansible, and Salt Stack Use Terraform to deploy server clusters, load balancers, and databases Learn how Terraform manages the state of your infrastructure and how it impacts file layout, isolation, and locking Create reusable infrastructure with Terraform modules Try out advanced Terraform syntax to implement loops, if-statements, and zero-downtime deployment Use Terraform as a team, including best practices for writing, testing, and versioning Terraform code COMPUTERS,System Administration,General

Mastering Salesforce CRM Administration Learn about the Advanced Administration Certification Examination and build a successful career in Salesforce administration About This Book Build your skills and knowledge to crack the Advanced Admin Certification Examination Leverage the advanced administration capabilities of Salesforce and Salesforce1 Optimize and extend Sales Cloud and Service Cloud applications Who This Book Is For This book is written for Salesforce admins who are looking to gain an in-depth knowledge of the Salesforce platform and grow their value in their organization. It will teach them to implement and design advanced business process automation for the benefit of their organization. What You Will Learn Adopt Lightning Experience to improve the productivity of your organization's sales team Create and maintain service entitlements and entitlement processes Process Builder basic and advanced concepts Different ways to deploy applications between environments Best practices for improving and enriching data quality In Detail The book starts by refreshing your knowledge of common admin tasks. You will go over Lightning Experience and various security aspects. You will be shown how to implement territory management in your organization and make use of custom objects. From here, the book progresses to advanced configuration, data management, and data analytics before swiftly moving on to setting up advanced organization-wide features that affect the look and feel of the application. Extend the capabilities of your organization's Salesforce implementation by optimizing and extending Sales Cloud, Salesforce1, and Service Cloud applications. This guide will equip you with the tools you need to build a successful career in Salesforce. Style and approach The book takes a straightforward, no-nonsense approach to working with the Salesforce CRM platform. It is filled with examples, advanced use cases, and all the resources you need to be a Salesforce Jedi. COMPUTERS,System Administration,General

Learning Docker Docker lets you create, deploy, and manage your applications anywhere at anytime – flexibility is key so you can deploy stable, secure, and scalable app containers across a wide variety of platforms and delve into microservices architecture About This Book This up-to-date edition shows how to leverage Docker's features to deploy your existing applications Learn how to package your applications with Docker and build, ship, and scale your containers Explore real-world examples of securing and managing Docker containers Who This Book Is For This book is ideal for developers, operations managers, and IT professionals who would like to learn about Docker and use it to build and deploy container-based apps. No prior knowledge of Docker is expected. What You Will Learn Develop containerized applications using the Docker version 17.03 Build Docker images from containers and launch them Develop Docker images and containers leveraging Dockerfiles Use Docker volumes to share data Get to know how data is shared between containers Understand Docker Jenkins integration Gain the power of container orchestration Familiarize yourself with the frequently used commands such as docker exec, docker ps, docker top, and docker stats In Detail Docker is an open source containerization engine that offers a simple and faster way for developing and running software. Docker containers wrap software in a complete filesystem that contains everything it needs to run, enabling any application to be run anywhere – this flexibily and portabily means that you can run apps in the cloud, on virtual machines, or on dedicated servers. This book will give you a tour of the new features of Docker and help you get started with Docker by building and deploying a simple application. It will walk you through the commands required to manage Docker images and containers. You'll be shown how to download new images, run containers, list the containers running on the Docker host, and kill them. You'll learn how to leverage Docker's volumes feature to share data between the Docker host and its containers – this data management feature is also useful for persistent data. This book also covers how to orchestrate containers using Docker compose, debug containers, and secure containers using the AppArmor and SELinux security modules. Style and approach This step-by-step guide will walk you through the features and use of Docker, from Docker software installation to the impenetrable security of containers. COMPUTERS,System Administration,General

DevOps with OpenShift For many organizations, a big part of DevOps’ appeal is software automation using infrastructure-as-code techniques. This book presents developers, architects, and infra-ops engineers with a more practical option. You’ll learn how a container-centric approach from OpenShift, Red Hat’s cloud-based PaaS, can help your team deliver quality software through a self-service view of IT infrastructure. Three OpenShift experts at Red Hat explain how to configure Docker application containers and the Kubernetes cluster manager with OpenShift’s developer- and operational-centric tools. Discover how this infrastructure-agnostic container management platform can help companies navigate the murky area where infrastructure-as-code ends and application automation begins. Get an application-centric view of automation—and understand why it’s important Learn patterns and practical examples for managing continuous deployments such as rolling, A/B, blue-green, and canary Implement continuous integration pipelines with OpenShift’s Jenkins capability Explore mechanisms for separating and managing configuration from static runtime software Learn how to use and customize OpenShift’s source-to-image capability Delve into management and operational considerations when working with OpenShift-based application workloads Install a self-contained local version of the OpenShift environment on your computer COMPUTERS,System Administration,General

Mastering AWS Lambda Build cost-effective and highly scalable Serverless applications using AWS Lambda. About This Book Leverage AWS Lambda to significantly lower your infrastructure costs and deploy out massively scalable, event-driven systems and applications Learn how to design and build Lambda functions using real-world examples and implementation scenarios Explore the Serverless ecosystem with a variety of toolsets and AWS services including DynamoDB, API Gateway, and much more! Who This Book Is For If you are a Cloud administrator and/or developer who wishes to explore, learn, and leverage AWS Lambda to design, build, and deploy Serverless applications in the cloud, then this is the book for you! The book assumes you have some prior knowledge and hands-on experience with AWS core services such as EC2, IAM, S3, along with the knowledge to work with any popular programming language such as Node.Js, Java, C#, and so on. What You Will Learn Understand the hype, significance, and business benefits of Serverless computing and applications Plunge into the Serverless world of AWS Lambda and master its core components and how it works Find out how to effectively and efficiently design, develop, and test Lambda functions using Node.js, along with some keen coding insights and best practices Explore best practices to effectively monitor and troubleshoot Serverless applications using AWS CloudWatch and other third-party services in the form of Datadog and Loggly Quickly design and develop Serverless applications by leveraging AWS Lambda, DynamoDB, and API Gateway using the Serverless Application Framework (SAF) and other AWS services such as Step Functions Explore a rich variety of real-world Serverless use cases with Lambda and see how you can apply it to your environments In Detail AWS is recognized as one of the biggest market leaders for cloud computing and why not? It has evolved a lot since the time it started out by providing just basic services such as EC2 and S3 and today; they go all the way from IoT to Machine Learning, Image recognition, Chatbot Frameworks, and much more! One of those recent services that is also gaining a lot of traction is AWS Lambda! Although seemingly simple and easy to use, Lambda is a highly effective and scalable compute service that provides developers with a powerful platform to design and develop Serverless event-driven systems and applications. The book begins with a high-level introduction into the world of Serverless computing and its advantages and use cases, followed by a deep dive into AWS Lambda! You'll learn what services AWS Lambda provides to developers; how to design, write, and test Lambda functions; as well as monitor and troubleshoot them. The book is designed and accompanied with a vast variety of real-world examples, use cases, and code samples that will enable you to get started on your Serverless applications quickly. By the end of the book, you will have gained all the skills required to work with AWS Lambda services! Style and approach This step-by-step guide will help you build Serverless applications and run Serverless workloads using the AWS Lambda service. You'll be able to get started with it in a matter of minutes with easy-to-follow code snippets and examples. COMPUTERS,System Administration,General

Puppet 5 Essentials A Guide to managing servers and automation About This Book Breeze through Puppet's key features and performance improvements to bring real advantages to your IT infrastructure Discover Puppet best practices to help you avoid common mistakes and pitfalls Examples to help you get to grips with Puppet and succeed with everyday IT automation Who This Book Is For This book targets experienced IT professionals and new Puppet uses, who will learn all they need to know to go from installation to advanced automation. Get a rapid introduction to the essential topics and learn how to build best practices for advanced automation with Puppet. What You Will Learn Understand declarative configuration management Make use of GIT-based deployment workflows Extend Factor with secure elements Create modular and reusable Puppet code Extend your code base with publicly available Puppet modules Separate logic from data by using Hiera Understand and develop Puppet Roles and Profiles In Detail Puppet is a configuration management tool that allows you to automate all your IT configurations, giving you control over what you do to each Puppet Agent in a network, and when and how you do it. In this age of digital delivery and ubiquitous Internet presence, it's becoming increasingly important to implement scaleable and portable solutions, not only in terms of software, but also the system that runs it. This book gets you started quickly with Puppet and its tools in the right way. It highlights improvements in Puppet and provides solutions for upgrading. It starts with a quick introduction to Puppet in order to quickly get your IT automation platform in place. Then you learn about the Puppet Agent and its installation and configuration along with Puppet Server and its scaling options. The book adopts an innovative structure and approach, and Puppet is explained with flexible use cases that empower you to manage complex infrastructures easily. Finally, the book will take readers through Puppet and its companion tools such as Facter, Hiera, and R10k and how to make use of tool chains. Style and approach This book aims to impart all the knowledge required to tap into not only the basics of Puppet, but also its core. The basic ideas and principles of Puppet-based designs are explored and explained. Sophisticated tools are presented to enable you to use Puppet efficiently and productively. COMPUTERS,System Administration,General

The Art of Capacity Planning In their early days, Twitter, Flickr, Etsy, and many other companies experienced sudden spikes in activity that took their web services down in minutes. Today, determining how much capacity you need for handling traffic surges is still a common frustration of operations engineers and software developers. This hands-on guide provides the knowledge and tools you need to measure, deploy, and manage your web application infrastructure before you experience explosive growth. In this thoroughly updated edition, authors Arun Kejariwal (MZ) and John Allspaw provide a systematic, robust, and practical approach to capacity planning—rather than theoretical models—based on their own experiences and those of many colleagues in the industry. They address the vast sea change in web operations, especially cloud computing. Understand issues that arise on heavily trafficked websites or mobile apps Explore how capacity fits into web/mobile app availability and performance Use tools for measuring and monitoring computer performance and usage Turn measurement data into robust forecasts and learn how trending fits into the planning process Examine related deployment concepts: installation, configuration, and management automation Learn how cloud autoscaling enables you to scale your app’s capacity up or down COMPUTERS,System Administration,General

Cloud Native Infrastructure Cloud native infrastructure is more than servers, network, and storage in the cloud—it is as much about operational hygiene as it is about elasticity and scalability. In this book, you’ll learn practices, patterns, and requirements for creating infrastructure that meets your needs, capable of managing the full life cycle of cloud native applications. Justin Garrison and Kris Nova reveal hard-earned lessons on architecting infrastructure from companies such as Google, Amazon, and Netflix. They draw inspiration from projects adopted by the Cloud Native Computing Foundation (CNCF), and provide examples of patterns seen in existing tools such as Kubernetes. With this book, you will: Understand why cloud native infrastructure is necessary to effectively run cloud native applications Use guidelines to decide when—and if—your business should adopt cloud native practices Learn patterns for deploying and managing infrastructure and applications Design tests to prove that your infrastructure works as intended, even in a variety of edge cases Learn how to secure infrastructure with policy as code COMPUTERS,System Administration,General

Practical Monitoring Do you have a nagging feeling that your monitoring needs improvement, but you just aren’t sure where to start or how to do it? Are you plagued by constant, meaningless alerts? Does your monitoring system routinely miss real problems? This is the book for you. Mike Julian lays out a practical approach to designing and implementing effective monitoring—from your enterprise application down to the hardware in a datacenter, and everything between. Practical Monitoring provides you with straightforward strategies and tactics for designing and implementing a strong monitoring foundation for your company. This book takes a unique vendor-neutral approach to monitoring. Rather than discuss how to implement specific tools, Mike teaches the principles and underlying mechanics behind monitoring so you can implement the lessons in any tool. Practical Monitoring covers essential topics including: Monitoring antipatterns Principles of monitoring design How to build an effective on-call rotation Getting metrics and logs out of your application COMPUTERS,System Administration,General

Mastering VMware vSphere 6.5 Deliver great business value by adopting the virtualization platform VMware vSphere 6.5, from the design to the deployment About This Book This new edition is based on vSphere 6.5 and has described new features in different areas, including management, security, scalability, availability and so on. Design, deploy and manage VMware datacenters Implement monitoring and security of VMware workloads with ease. Who This Book Is For If you are an administrator, infrastructure engineer, IT architect, or an IT consultant and analyst who has basic knowledge of VMware vSphere and now wants to master it, then this book is for you. What You Will Learn Get a deep understanding of vSphere 6.5 functionalities Design and plan a virtualization environment based on vSphere 6.5 Manage and administer a vSphere 6.5 environment and resources Get tips for the VCP6-DCV and VCIX6-DCV exams (along with use of the vSphere 6 documentation) Implement different migration techniques to move your workload across different environments. Save your configuration, data and workload from your virtual infrastructure. In Detail VMware vSphere 6.5 provides a powerful, flexible and secure foundation for next-generation applications which helps you create an effective digital transformation. This book will be based on VMware vSphere 6.5 which empowers you to virtualize any complex application with ease. You'll begin by getting an overview of all the products, solutions and features of the vSphere 6.5 suite, comparing the evolutions with the previous releases. Next ,you'll design and plan a virtualization infrastructure to drive planning and performance analysis. Following this , you will be proceeding with workflow and installation of components. New network trends are also covered which will help you in optimally designing the vSphere environment. You will also learn the practices and procedures involved in configuring and managing virtual machines in a vSphere infrastructure. With vSphere 6.5, you'll make use of significantly more powerful capabilities for patching, upgrading, and managing the configuration of the virtual environment. Next we'll focus on specific availability and resiliency solutions in vSphere. Towards the end of the book you will get information on how to save your configuration, data and workload from your virtual infrastructure. By the end of the book you'll learn about VMware vSphere 6.5 right from design to deployment and management. Style and Approach This book acts as a reference guide providing real-world scenarios and a possible baseline for each virtualization project based on VMware vSphere. COMPUTERS,System Administration,General

Salesforce CRM Admin Cookbook Extend and unleash the power of Salesforce CRM and the advanced features of the Lightning interface to create techniques for user interaction and derive real-world solutions. About This Book Implement advanced user interface techniques to improve the look and feel of Salesforce CRM. Discover hidden features and hacks that extend standard configuration to provide enhanced functionality and customization. Build real-world process automation using detailed recipes to harness the full power of Salesforce CRM. Who This Book Is For If you are a system administrator interested in developing and enhancing your skills with data management, process automation and security enhancements with SalesforceCRM, then this book is for you. Some basic understanding of SalesforceCRM and system administration knowledge would be needed. What You Will Learn Building home page components and creating custom links to provide additional functionality and improve the Home Tab layout Improving the look and feel of Salesforce CRM with the presentation of graphical elements using advanced user interface techniques Improving the data quality in Salesforce CRM and automatic data capture Implement an approval process to control the way approvals are managed for records in Salesforce CRM Increase productivity using tools and features to provide advanced administration Extend Lightning Experience Record Pages to tailor user interaction experience Create Lightning component to implement Search before Create for customer/person accounts In Detail Salesforce CRM is a market-leading customer relationship management (CRM) application that is accessed over the internet. This application greatly enhances a company's sales performance, improves customer satisfaction, and provides a robust customer relationship management system for an organization. Salesforce CRM Admin Cookbook, Second Edition enables you to instantly extend and unleash the power of Salesforce CRM and its Lightning Experience framework. It provides clear, comprehensive instructions along with detailed screenshots and code. Whether you are looking for solutions to enhance the core features, such as data management, process automation, data validation, and home page administration, or are looking for ideas on advanced customization techniques, this book will provide you with immediate, practical, and exciting real-world recipes. This book guides you through interesting topics spanning a variety of functional areas. Recipes are provided that allow you to configure, build and extend the capability of Salesforce CRM using the Lightning Experience framework. Style and approach We will be discussing recipes about several modules, which will help you gain mastery over different modules, such as data management, security enhancements, and so on, which is expected of an administrator. COMPUTERS,System Administration,General

Kubernetes Cookbook Kubernetes is becoming the de-facto standard for container orchestration and distributed applications management across a microservices framework. With this practical cookbook, you’ll learn hands-on recipes for automating the deployment, scaling, and operations of application containers across clusters of hosts. The book's easy-lookup problem-solution-discussion format helps you find the detailed answers you need—quickly. Kubernetes lets you deploy your applications quickly and predictably, so you can efficiently respond to customer demand. This cookbook, ideal for developers and system administers alike, provides the essential knowledge you need to get there. You’ll find recipes for: Kubernetes installation Kubernetes API, API groups Application primitives Monitoring Troubleshooting COMPUTERS,System Administration,General

Extending OpenStack Discover new opportunities to empower your private cloud by making the most of the OpenStack universe About This Book This practical guide teaches you how to extend the core functionalities of OpenStack Discover OpenStack's flexibility by writing custom applications and network plugins Deploy a containerized environment in OpenStack through a hands-on and example-driven approach Who This Book Is For This book is for system administrators, cloud architects, and developers who have experience working with OpenStack and are ready to step up and extend its functionalities. A good knowledge of basic OpenStack components is required. In addition, familiarity with Linux boxes and a good understanding of network and virtualization jargon is required. What You Will Learn Explore new incubated projects in the OpenStack ecosystem and see how they work Architect your OpenStack private cloud with extended features of the latest versions Consolidate OpenStack authentication in your large infrastructure to avoid complexity Find out how to expand your computing power in OpenStack on a large scale Reduce your OpenStack storage cost management by taking advantage of external tools Provide easy, on-demand, cloud-ready applications to developers using OpenStack in no time Enter the big data world and find out how to launch elastic jobs easily in OpenStack Boost your extended OpenStack private cloud performance through real-world scenarios In Detail OpenStack is a very popular cloud computing platform that has enabled several organizations during the last few years to successfully implement their Infrastructure as a Service (IaaS) platforms. This book will guide you through new features of the latest OpenStack releases and how to bring them into production straightaway in an agile way. It starts by showing you how to expand your current OpenStack setup and how to approach your next OpenStack Data Center generation deployment. You will discover how to extend your storage and network capacity and also take advantage of containerization technology such as Docker and Kubernetes in OpenStack. Additionally, you'll explore the power of big data as a Service terminology implemented in OpenStack by integrating the Sahara project. This book will teach you how to build Hadoop clusters and launch jobs in a very simple way. Then you'll automate and deploy applications on top of OpenStack. You will discover how to write your own plugin in the Murano project. The final part of the book will go through best practices for security such as identity, access management, and authentication exposed by Keystone in OpenStack. By the end of this book, you will be ready to extend and customize your private cloud based on your requirements. Style and approach This guide is filled with practical scenarios on how to extend and enhance OpenStack's functionality. We will be covering various installation and configuration platforms along with a focus on plugins and extending OpenStack's core functionalities. COMPUTERS,System Administration,General

Mastering Kubernetes Exploit design, deployment, and management of large-scale containers About This Book Explore the latest features available in Kubernetes 1.10 Ensure that your clusters are always available, scalable, and up to date Master the skills of designing and deploying large clusters on various cloud platforms Who This Book Is For Mastering Kubernetes is for you if you are a system administrator or a developer who has an intermediate understanding of Kubernetes and wish to master its advanced features. Basic knowledge of networking would also be helpful. In all, this advanced-level book provides a smooth pathway to mastering Kubernetes. What You Will Learn Architect a robust Kubernetes cluster for long-time operation Discover the advantages of running Kubernetes on GCE, AWS, Azure, and bare metal Understand the identity model of Kubernetes, along with the options for cluster federation Monitor and troubleshoot Kubernetes clusters and run a highly available Kubernetes Create and configure custom Kubernetes resources and use third-party resources in your automation workflows Enjoy the art of running complex stateful applications in your container environment Deliver applications as standard packages In Detail Kubernetes is an open source system that is used to automate the deployment, scaling, and management of containerized applications. If you are running more containers or want automated management of your containers, you need Kubernetes at your disposal. To put things into perspective, Mastering Kubernetes walks you through the advanced management of Kubernetes clusters. To start with, you will learn the fundamentals of both Kubernetes architecture and Kubernetes design in detail. You will discover how to run complex stateful microservices on Kubernetes including advanced features such as horizontal pod autoscaling, rolling updates, resource quotas, and persistent storage backend. Using real-world use cases, you will explore the options for network configuration, and understand how to set up, operate, and troubleshoot various Kubernetes networking plugins. In addition to this, you will get to grips with custom resource development and utilization in automation and maintenance workflows. To scale up your knowledge of Kubernetes, you will encounter some additional concepts based on the Kubernetes 1.10 release, such as Promethus, Role-based access control, API aggregation, and more. By the end of this book, you'll know everything you need to graduate from intermediate to advanced level of understanding Kubernetes. Style and approach Delving into the design of the Kubernetes platform, the reader will be exposed to Kubernetes advanced features and best practices. This advanced-level book will provide a pathway to mastering Kubernetes. COMPUTERS,System Administration,General

Deploying to OpenShift Get an in-depth tour of OpenShift, the container-based software deployment and management platform from Red Hat that provides a secure multi-tenant environment for the enterprise. This practical guide describes in detail how OpenShift, building on Kubernetes, enables you to automate the way you create, ship, and run applications in a containerized environment. Author Graham Dumpleton provides the knowledge you need to make the best use of the OpenShift container platform to deploy not only your cloud-native applications, but also more traditional stateful applications. Developers and administrators will learn how to run, access, and manage containers in OpenShift, including how to orchestrate them at scale. Build application container images from source and deploy them Implement and extend application image builders Use incremental and chained builds to accelerate build times Automate builds by using a webhook to link OpenShift to a Git repository Add configuration and secrets to the container as project resources Make an application visible outside the OpenShift cluster Manage persistent storage inside an OpenShift container Monitor application health and manage the application lifecycle This book is a perfect follow-up to OpenShift for Developers: A Guide for Impatient Beginners (O’Reilly). COMPUTERS,System Administration,General

Learn Ansible Run Ansible playbooks to launch complex multi-tier applications hosted in public clouds About This Book Build your learning curve using Ansible Automate cloud, network, and security infrastructures with ease Gain hands-on exposure on Ansible Who This Book Is For Learn Ansible is perfect for system administrators and developers who want to take their current workflows and transform them into repeatable playbooks using Ansible. No prior knowledge of Ansible is required. What You Will Learn Write your own playbooks to configure servers running CentOS, Ubuntu, and Windows Identify repeatable tasks and write playbooks to automate them Define a highly available public cloud infrastructure in code, making it easy to distribute your infrastructure configuration Deploy and configure Ansible Tower and Ansible AWX Learn to use community contributed roles Use Ansible in your day-to-day role and projects In Detail Ansible has grown from a small, open source orchestration tool to a full-blown orchestration and configuration management tool owned by Red Hat. Its powerful core modules cover a wide range of infrastructures, including on-premises systems and public clouds, operating systems, devices, and services—meaning it can be used to manage pretty much your entire end-to-end environment. Trends and surveys say that Ansible is the first choice of tool among system administrators as it is so easy to use. This end-to-end, practical guide will take you on a learning curve from beginner to pro. You'll start by installing and configuring the Ansible to perform various automation tasks. Then, we'll dive deep into the various facets of infrastructure, such as cloud, compute and network infrastructure along with security. By the end of this book, you'll have an end-to-end understanding of Ansible and how you can apply it to your own environments. Style and approach A hands-on approach to give you practical experience of writing playbooks and roles and executing them. At the end of each chapter, you'll find test questions to test your knowledge on Ansible. COMPUTERS,System Administration,General

Prometheus Get up to speed with Prometheus, the metrics-based monitoring system used by tens of thousands of organizations in production. This practical guide provides application developers, sysadmins, and DevOps practitioners with a hands-on introduction to the most important aspects of Prometheus, including dashboarding and alerting, direct code instrumentation, and metric collection from third-party systems with exporters. This open source system has gained popularity over the past few years for good reason. With its simple yet powerful data model and query language, Prometheus does one thing, and it does it well. Author and Prometheus developer Brian Brazil guides you through Prometheus setup, the Node exporter, and the Alertmanager, then demonstrates how to use them for application and infrastructure monitoring. Know where and how much to apply instrumentation to your application code Identify metrics with labels using unique key-value pairs Get an introduction to Grafana, a popular tool for building dashboards Learn how to use the Node Exporter to monitor your infrastructure Use service discovery to provide different views of your machines and services Use Prometheus with Kubernetes and examine exporters you can use with containers Convert data from other monitoring systems into the Prometheus format COMPUTERS,System Administration,General

The Site Reliability Workbook In 2016, Google’s Site Reliability Engineering book ignited an industry discussion on what it means to run production services today—and why reliability considerations are fundamental to service design. Now, Google engineers who worked on that bestseller introduce The Site Reliability Workbook, a hands-on companion that uses concrete examples to show you how to put SRE principles and practices to work in your environment. This new workbook not only combines practical examples from Google’s experiences, but also provides case studies from Google’s Cloud Platform customers who underwent this journey. Evernote, The Home Depot, The New York Times, and other companies outline hard-won experiences of what worked for them and what didn’t. Dive into this workbook and learn how to flesh out your own SRE practice, no matter what size your company is. You’ll learn: How to run reliable services in environments you don’t completely control—like cloud Practical applications of how to create, monitor, and run your services via Service Level Objectives How to convert existing ops teams to SRE—including how to dig out of operational overload Methods for starting SRE from either greenfield or brownfield COMPUTERS,System Administration,General

Puppet Best Practices If you maintain or plan to build Puppet infrastructure, this practical guide will take you a critical step further with best practices for managing the task successfully. Authors Chris Barbour and Jo Rhett present best-in-class design patterns for deploying Puppet environments and discuss the impact of each. The conceptual designs and implementation patterns in this book will help you create solutions that are easy to extend, maintain, and support. Essential for companies upgrading their Puppet deployments, this book teaches you powerful new features and implementation models that weren’t available in the older versions. DevOps engineers will learn how best to deploy Puppet with long-term maintenance and future growth in mind. Explore Puppet’s design philosophy and data structures Get best practices for using Puppet’s declarative language Examine Puppet resources in depth—the building blocks of state management Learn to model and describe business and site-specific logic in Puppet See best-in-class models for multitiered data management with Hiera Explore available options and community experience for node classification Utilize r10k to simplify and accelerate Puppet change management Review the cost benefits of creating your own extensions to Puppet Get detailed advice for extending Puppet in a maintainable manner COMPUTERS,System Administration,General

Hands-On Continuous Integration and Delivery Understand various tools and practices for building a continuous integration and delivery pipeline effectively Key Features Get up and running with the patterns of continuous integration Learn Jenkins UI for developing plugins and build an effective Jenkins pipeline Automate CI/CD with command-line tools and scripts Book Description Hands-On Continuous Integration and Delivery starts with the fundamentals of continuous integration (CI) and continuous delivery (CD) and where it fits in the DevOps ecosystem. You will explore the importance of stakeholder collaboration as part of CI/CD. As you make your way through the chapters, you will get to grips with Jenkins UI, and learn to install Jenkins on different platforms, add plugins, and write freestyle scripts. Next, you will gain hands-on experience of developing plugins with Jenkins UI, building the Jenkins 2.0 pipeline, and performing Docker integration. In the concluding chapters, you will install Travis CI and Circle CI and carry out scripting, logging, and debugging, helping you to acquire a broad knowledge of CI/CD with Travis CI and CircleCI. By the end of this book, you will have a detailed understanding of best practices for CI/CD systems and be able to implement them with confidence. What you will learn Install Jenkins on multiple operating systems Work with Jenkins freestyle scripts, pipeline syntax, and methodology Explore Travis CI build life cycle events and multiple build languages Master the Travis CI CLI (command-line interface) and automate tasks with the CLI Use CircleCI CLI jobs and work with pipelines Automate tasks using CircleCI CLI and learn to debug and troubleshoot Learn open source tooling such as Git and GitHub Install Docker and learn concepts in shell scripting Who this book is for Hands-On Continuous Integration and Delivery is for system administrators, DevOps engineers, and build and release engineers who want to understand the concept of CI and gain hands-on experience working with prominent tools in the CI ecosystem. Basic knowledge of software delivery is an added advantage. COMPUTERS,System Administration,General

Bash Quick Start Guide Learn how to write shell script effectively with Bash, to quickly and easily write powerful scripts to manage processes, automate tasks, and to redirect and filter program input and output in useful and novel ways. Key Features Demystify the Bash command line Write shell scripts safely and effectively Speed up and automate your daily work Book Description Bash and shell script programming is central to using Linux, but it has many peculiar properties that are hard to understand and unfamiliar to many programmers, with a lot of misleading and even risky information online. Bash Quick Start Guide tackles these problems head on, and shows you the best practices of shell script programming. This book teaches effective shell script programming with Bash, and is ideal for people who may have used its command line but never really learned it in depth. This book will show you how even simple programming constructs in the shell can speed up and automate any kind of daily command-line work. For people who need to use the command line regularly in their daily work, this book provides practical advice for using the command-line shell beyond merely typing or copy-pasting commands into the shell. Readers will learn techniques suitable for automating processes and controlling processes, on both servers and workstations, whether for single command lines or long and complex scripts. The book even includes information on configuring your own shell environment to suit your workflow, and provides a running start for interpreting Bash scripts written by others. What you will learn Understand where the Bash shell fits in the system administration and programming worlds Use the interactive Bash command line effectively Get to grips with the structure of a Bash command line Master pattern-matching and transforming text with Bash Filter and redirect program input and output Write shell scripts safely and effectively Who this book is for People who use the command line on Unix and Linux servers already, but don't write primarily in Bash. This book is ideal for people who've been using a scripting language such as Python, JavaScript or PHP, and would like to understand and use Bash more effectively. COMPUTERS,System Administration,General

Hands-On Cloud Administration in Azure Explore Azure services such as networking, virtual machines, web apps, databases, cloud migration, and security Key Features Understand Azure services to build, deploy, and manage workloads on cloud Learn in-depth core Azure services and work through real-world scenarios and case studies A concise and practical guide for learning cloud administration on Azure Book Description Azure continues to dominate the public cloud market and grow rapidly thanks to a number of recent innovations. Azure's wide range of services and support has led to a large number of customers switching to Azure cloud. Hands-On Cloud Administration in Azure starts with the basics of Azure cloud fundamentals and key concepts of the cloud computing ecosystem and services. Then, you will gradually get acquainted with core services provided by Azure, including Azure VNet, types and assignments of IP addresses, and network security groups. You will also work on creating and administering Azure Virtual Machines, types of virtual machines (VMs), and design VM solutions based on computing workloads. As you make your way through the chapters, you will explore Azure App Service, discover how to host your web apps in Azure, and monitor and troubleshoot them. In the concluding chapters, you will learn more complex and abstract services, such as Azure Storage, Azure Backup, and Azure Site Recovery. You will also get to grips with Azure SQL Databases and the SQL on Azure VM concept. By the end of this book, you will have obtained practical experience of working with Azure services and Azure administration, along with maintaining, monitoring, and securing your Azure resources. What you will learn Understand the concepts of IaaS and PaaS Learn design patterns for Azure solutions Design data solutions in Azure Explore concepts of hybrid clouds with Azure Implement Azure Security in cloud Create and manage Azure resources with script-based tools Who this book is for Hands-On Cloud Administration in Azure is for system administrators, cloud admins, cloud engineers, and DevOps engineers who are interested in understanding administration-related services in Azure. Prior experience of working with Azure is an added advantage. COMPUTERS,System Administration,General

Implementing VMware Horizon 7.7 Effectively implement features and components for any computing environment Key Features Explore the latest features of VMware Horizon 7.7 Virtualize your desktop infrastructure using new features introduced in Horizon Implement App Volumes and User Environment Manager in your infrastructure Book Description This third edition of Implementing VMware Horizon 7.7 has been updated to get you up to speed with VMware Horizon 7.7 by showing you how to use its key features and deploying an end-user computing infrastructure for your own organization. The book begins by guiding you on how to deploy all the core requirements for a VMware Horizon infrastructure. It then moves on to show you how to provision and administer end-user computing resources using VMware Horizon. You'll not only be able to deploy the core VMware Horizon features, but you'll also be able to implement new features, such as the Just-in-Time Management Platform (JMP) and the Horizon Console. You'll also focus on the latest features and components of the Horizon platform and learn when and how they are used. By the end of the book, you will have developed a solid understanding of how your organization can benefit from the capabilities VMware Horizon offers and how each of its components is implemented. What you will learn Work with the different products that make up VMware Horizon Implement a multi-site VMware Horizon Pod using the Cloud Pod Architecture feature Deploy and configure VMware Horizon's optional components Implement and maintain Microsoft RDSH, Horizon Linux, and Windows Desktop Pools and RDSH Application Pools Configure and manage Horizon remotely using PowerCLI Learn about the Microsoft Windows Group Policy templates for Horizon Understand how to manage the SSL certificates for each of the VMware Horizon components Who this book is for If you're a system administrator, solutions architect, or desktop engineer looking to level up your skills working with VMware's Horizon ecosystem and want to build a successful deployment strategy for desktops and applications, this book is for you. COMPUTERS,System Administration,General

Identity with Windows Server 2016 Equip yourself with the most complete and comprehensive preparation experience for Identity with Windows Server 2016: Microsoft 70-742 exam. Key Features Helps you demonstrate real-world mastery of Windows Server 2016 identity features and functionality and prepare for 70-742 Acquire skills to reduce IT costs and deliver more business value Enhance your existing skills through practice questions and mock tests Book Description MCSA: Windows Server 2016 certification is one of the most sought-after certifications for IT professionals, which includes working with Windows Server and performing administrative tasks around it. This book is aimed at the 70-742 certification and is part of Packt's three-book series on MCSA Windows Server 2016 certification, which covers Exam 70-740, Exam 70-741, and Exam 70-742. This exam guide covers the exam objectives for the 70-742 Identity with Windows Server 2016 exam. It starts with installing and configuring Active Directory Domain Services (AD DS), managing and maintaining AD DS objects and advanced configurations, configuring Group Policy, Active Directory Certificate Services, and Active Directory Federation Services and Rights Management. At the end of each chapter, convenient test questions will help you in preparing for the certification in a practical manner. By the end of this book, you will be able to develop the knowledge and skills needed to complete MCSA Exam 70-742: Identity with Windows Server 2016 with confidence. What you will learn Install, configure, and maintain Active Directory Domain Services (AD DS) Manage Active Directory Domain Services objects Configure and manage Active Directory Certificate Services Configure and manage Group Policy Design, implement, and configure Active Directory Federation Services Implement and configure Active Directory Rights Management Services Who this book is for This book primarily targets system administrators who are looking to gain knowledge about identity and access technologies with Windows Server 2016 and aiming to pass the 70-742 certification. This will also help infrastructure administrators who are looking to gain advanced knowledge and understanding of identity and access technologies with Windows Server 2016. Familiarity with the concepts such as Active Directory, DNS is assumed. COMPUTERS,System Administration,General

Mastering Windows Server 2019 Enhance and secure your datacenter with the newest Microsoft server platform Key Features Develop necessary skills to design and implement Microsoft Server 2019 in enterprise environment Provide support to your medium to large enterprise and leverage your experience in administering Microsoft Server 2019 Effectively administering Windows server 2019 with the help of practical examples Book Description Mastering Windows Server 2019 – Second Edition covers all of the essential information needed to implement and utilize this latest-and-greatest platform as the core of your data center computing needs. You will begin by installing and managing Windows Server 2019, and by clearing up common points of confusion surrounding the versions and licensing of this new product. Centralized management, monitoring, and configuration of servers is key to an efficient IT department, and you will discover multiple methods for quickly managing all of your servers from a single pane of glass. To this end, you will spend time inside Server Manager, PowerShell, and even the new Windows Admin Center, formerly known as Project Honolulu. Even though this book is focused on Windows Server 2019 LTSC, we will still discuss containers and Nano Server, which are more commonly related to the SAC channel of the server platform, for a well-rounded exposition of all aspects of using Windows Server in your environment. We also discuss the various remote access technologies available in this operating system, as well as guidelines for virtualizing your data center with Hyper-V. By the end of this book, you will have all the ammunition required to start planning for, implementing, and managing Windows. What you will learn Work with the updated Windows Server 2019 interface, including Server Core and Windows Admin Center Secure your network and data with new technologies in Windows Server 2019 Learn about containers and understand the appropriate situations to use Nano Server Discover new ways to integrate your data center with Microsoft Azure Harden your Windows Servers to help keep the bad guys out Virtualize your data center with Hyper-V Who this book is for If you are a System Administrator or an IT professional interested in designing and deploying Windows Server 2019 then this book is for you. Previous experience of Windows Server operating systems and familiarity with networking concepts is required. COMPUTERS,System Administration,General

Cybersecurity Ops with bash If you hope to outmaneuver threat actors, speed and efficiency need to be key components of your cybersecurity operations. Mastery of the standard command-line interface (CLI) is an invaluable skill in times of crisis because no other software application can match the CLI’s availability, flexibility, and agility. This practical guide shows you how to use the CLI with the bash shell to perform tasks such as data collection and analysis, intrusion detection, reverse engineering, and administration. Authors Paul Troncone, founder of Digadel Corporation, and Carl Albing, coauthor of bash Cookbook (O’Reilly), provide insight into command-line tools and techniques to help defensive operators collect data, analyze logs, and monitor networks. Penetration testers will learn how to leverage the enormous amount of functionality built into nearly every version of Linux to enable offensive operations. In four parts, security practitioners, administrators, and students will examine: Foundations: Principles of defense and offense, command-line and bash basics, and regular expressions Defensive security operations: Data collection and analysis, real-time log monitoring, and malware analysis Penetration testing: Script obfuscation and tools for command-line fuzzing and remote access Security administration: Users, groups, and permissions; device and software inventory COMPUTERS,System Administration,General

Kubernetes Patterns The way developers design, build, and run software has changed significantly with the evolution of microservices and containers. These modern architectures use new primitives that require a different set of practices than most developers, tech leads, and architects are accustomed to. With this focused guide, Bilgin Ibryam and Roland Huß from Red Hat provide common reusable elements, patterns, principles, and practices for designing and implementing cloud-native applications on Kubernetes. Each pattern includes a description of the problem and a proposed solution with Kubernetes specifics. Many patterns are also backed by concrete code examples. This book is ideal for developers already familiar with basic Kubernetes concepts who want to learn common cloud native patterns. You’ll learn about the following pattern categories: Foundational patterns cover the core principles and practices for building container-based cloud-native applications. Behavioral patterns explore finer-grained concepts for managing various types of container and platform interactions. Structural patterns help you organize containers within a pod, the atom of the Kubernetes platform. Configuration patterns provide insight into how application configurations can be handled in Kubernetes. Advanced patterns covers more advanced topics such as extending the platform with operators. COMPUTERS,System Administration,General

MCSA Windows Server 2016 Certification Guide A comprehensive certification guide that will help you prepare for the exam from day one of your preparation journey Key Features Get well-versed with the nitty-gritty of Windows server 2016 A practical guide towards installing, upgrading, and migrating to Windows Server 2016 Enhance your skills with practice questions and mock tests Book Description MCSA: Windows Server 2016 is one of the most sought-after certifications for IT professionals which include working with Windows Server and performing administrative tasks around it. It targets Exam 70-740, Exam 70-741, Exam 70-742 and Exam 70-743 certifications and the demand for these certifications is increasingly high. This book will start with installation, upgrade and migration to Windows Server 2016, cover imaging and deployment and proceed with High Availability and Clustering. Then we will deep dive into fundamental concepts like Core networking, DNS, DHCP, Storage and proceed to Hyper-V, Network Access and Distributed File System. It will also explain Advanced Networking topics such as Software Defined Networking and High-Performance Networking. Furthermore, it will also cover advanced Identity topics in Windows Server 2016 such as Active Directory installation and configuration, Group Policy, Active Directory Certificate Services, and Active Directory Federation Services and Rights Management. Towards the end of this book, test questions and mock preparation items will help in preparing for the certifications with more ease. By the end of this book, you will be able to complete MCSA: Windows Server 2016 certification with more confidence. What you will learn Prepare for exam 70-741 Networking with Windows Server 2016 Learn to apply the technology to real-world examples Learn core networking, name resolution and connectivity technologies in Windows Server 2016. Get prepared for exam 70-742 Identity with Windows Server 2016 Get ways to clear the exam 70-743 Upgrading Your Skills to MCSA: Windows Server 2016 Practice critical skills and test your knowledge of the objectives of all three MCSA exams Who this book is for This book is targeted towards system administrators or windows server administrators who are interested in clearing the MCSA certification with ease. COMPUTERS,System Administration,General

The Complete Kubernetes Guide Design, deploy, and manage large-scale containers using Kubernetes Key Features Gain insight into the latest features of Kubernetes, including Prometheus and API aggregation Discover ways to keep your clusters always available, scalable, and up-to-date Master the skills of designing and deploying large clusters on various cloud platforms Book Description If you are running a number of containers and want to be able to automate the way they're managed, it can be helpful to have Kubernetes at your disposal. This Learning Path guides you through core Kubernetes constructs, such as pods, services, replica sets, replication controllers, and labels. You'll get started by learning how to integrate your build pipeline and deployments in a Kubernetes cluster. As you cover more chapters in the Learning Path, you'll get up to speed with orchestrating updates behind the scenes, avoiding downtime on your cluster, and dealing with underlying cloud provider instability in your cluster. With the help of real-world use cases, you'll also explore options for network configuration, and understand how to set up, operate, and troubleshoot various Kubernetes networking plugins. In addition to this, you'll gain insights into custom resource development and utilization in automation and maintenance workflows. By the end of this Learning Path, you'll have the expertise you need to progress from an intermediate to an advanced level of understanding Kubernetes. This Learning Path includes content from the following Packt products: Getting Started with Kubernetes - Third Edition by Jonathan Baier and Jesse White Mastering Kubernetes - Second Edition by Gigi Sayfan What you will learn Download, install, and configure the Kubernetes code base Create and configure custom Kubernetes resources Use third-party resources in your automation workflows Deliver applications as standard packages Set up and access monitoring and logging for Kubernetes clusters Set up external access to applications running in the cluster Manage and scale Kubernetes with hosted platforms on Amazon Web Services (AWS), Azure, and Google Cloud Platform (GCP) Run multiple clusters and manage them from a single control plane Who this book is for If you are a developer or a system administrator with an intermediate understanding of Kubernetes and want to master its advanced features, then this book is for you. Basic knowledge of networking is required to easily understand the concepts explained. COMPUTERS,System Administration,General

Learning Chaos Engineering Most companies work hard to avoid costly failures, but in complex systems a better approach is to embrace and learn from them. Through chaos engineering, you can proactively hunt for evidence of system weaknesses before they trigger a crisis. This practical book shows software developers and system administrators how to plan and run successful chaos engineering experiments. System weaknesses go beyond your infrastructure, platforms, and applications to include policies, practices, playbooks, and people. Author Russ Miles explains why, when, and how to test systems, processes, and team responses using simulated failures on Game Days. You’ll also learn how to work toward continuous chaos through automation with features you can share across your team and organization. Learn to think like a chaos engineer Build a hypothesis backlog to determine what could go wrong in your system Develop your hypotheses into chaos engineering experiment Game Days Write, run, and learn from automated chaos experiments using the open source Chaos Toolkit Turn chaos experiments into tests to confirm that you’ve overcome the weaknesses you discovered Observe and control your automated chaos experiments while they are running COMPUTERS,System Administration,General

Installation, Storage, and Compute with Windows Server 2016 A comprehensive guide for MCSA Exam 70-740, that will help you prepare from day one to earn the valuable Microsoft Certificate Key Features Leverage practice questions and mock tests to pass this certification with confidence Learn to Install Windows Servers,implement high availability, and monitor server environments Gain necessary skills to implement and configure storage and compute features Book Description MCSA: Windows Server 2016 certification is one of the most sought-after certifications for IT professionals, which includes working with Windows Server and performing administrative tasks around it. This book is aimed at the 70-740 certification and is part of Packt's three-book series on MCSA Windows Server 2016 certification, which covers Exam 70-740, Exam 70-741, and Exam 70-742. This book will cover exam objectives for the 70-740 exam, and starting from installing and configuring Windows Server 2016, Windows Server imaging and deployment to configuring and managing disks and volumes, implementing and configuring server storage and implementing Hyper-V. At the end of each chapter you will be provided test questions to revise your learnings which will boost your confidence in preparing for the actual certifications. By the end of this book, you will learn everything needed to pass the, MCSA Exam 70-740: Installation, Storage, and Compute with Windows Server 2016, certification. What you will learn Install Windows Server 2016 Upgrade and Migrate servers and workloads Implement and configure server storage Install and configure Hyper-V Configure the virtual machine (VM) settings Configure Hyper-V storage Configure Hyper-V networking Who this book is for This book is ideal for system administrators interested in installing and configuring storage and compute features with Windows Sever 2016 and aiming to pass the 70-740 certification. Some experience with Windows Server in an enterprise environment is assumed. COMPUTERS,System Administration,General

Terraform Terraform has become a key player in the DevOps world for defining, launching, and managing infrastructure as code (IaC) across a variety of cloud and virtualization platforms, including AWS, Google Cloud, Azure, and more. This hands-on second edition, expanded and thoroughly updated for Terraform version 0.12 and beyond, shows you the fastest way to get up and running. Gruntwork cofounder Yevgeniy (Jim) Brikman walks you through code examples that demonstrate Terraform’s simple, declarative programming language for deploying and managing infrastructure with a few commands. Veteran sysadmins, DevOps engineers, and novice developers will quickly go from Terraform basics to running a full stack that can support a massive amount of traffic and a large team of developers. Explore changes from Terraform 0.9 through 0.12, including backends, workspaces, and first-class expressions Learn how to write production-grade Terraform modules Dive into manual and automated testing for Terraform code Compare Terraform to Chef, Puppet, Ansible, CloudFormation, and Salt Stack Deploy server clusters, load balancers, and databases Use Terraform to manage the state of your infrastructure Create reusable infrastructure with Terraform modules Use advanced Terraform syntax to achieve zero-downtime deployment COMPUTERS,System Administration,General

Istio You did it. You successfully transformed your application into a microservices architecture. But now that you’re running services across different environments—public to public, private to public, virtual machine to container—your cloud native software is beginning to encounter reliability issues. How do you stay on top of this ever-increasing complexity? With the Istio service mesh, you’ll be able to manage traffic, control access, monitor, report, get telemetry data, manage quota, trace, and more with resilience across your microservice. In this book, Lee Calcote and Zack Butcher explain why your services need a service mesh and demonstrate step-by-step how Istio fits into the life cycle of a distributed application. You’ll learn about the tools and APIs for enabling and managing many of the features found in Istio. Explore the observability challenges Istio addresses Use request routing, traffic shifting, fault injection, and other features essential to running a solid service mesh Generate and collect telemetry information Try different deployment patterns, including A/B, blue/green, and canary Get examples of how to develop and deploy real-world applications with Istio support COMPUTERS,System Administration,General

Migrating Applications to the Cloud with Azure Modernize your apps with Microsoft Azure by moving web, desktop, and mobile apps to the cloud Key Features Decide which migration strategy is most suitable for your organization and create a migration roadmap Move existing infrastructure to Azure and learn strategies to reduce cost, increase storage, and improve ROI Design secure, scalable, and cost-effective solutions with the help of practical examples Book Description Whether you are trying to re-architect a legacy app or build a cloud-ready app from scratch, using the Azure ecosystem with .NET and Java technologies helps you to strategize and plan your app modernization process effectively. With this book, you'll learn how to modernize your applications by using Azure for containerization, DevOps, microservices, and serverless solutions to reduce development time and costs, while also making your applications robust, secure, and scalable. You will delve into improving application efficiency by using container services such as Azure Container Service, Azure Kubernetes Service (AKS), and more. Next, you will learn to modernize your application by implementing DevOps throughout your application development life cycle. You will then focus on increasing the scalability and performance of your overall application with microservices, before learning how to add extra functionality to your application with Azure serverless solutions. Finally, you'll get up to speed with monitoring and troubleshooting techniques. By the end of this book, you will have learned how to use the Azure ecosystem to refactor, re-architect, and rebuild your web, mobile, and desktop applications. What you will learn Use DevOps and containerization technologies to modernize your applications and infrastructure Build microservices using Azure Service Fabric Develop scalable applications using Azure Functions Manage and deploy your application code and database connectivity Secure and monitor your applications in Azure effectively Design for high availability and disaster recovery Who this book is for This book is for.NET and Java developers who want to modernize their applications using Azure. Solution architects and experienced developers interested in modernizing legacy applications using Azure will also find this book useful. Some prior understanding of cloud computing concepts will be beneficial. COMPUTERS,System Administration,General

Cloud FinOps Despite many uncertainties in cloud computing, one truth is evident: costs will always tend to go up unless you’re actively engaged in the process. Whether you’re new to managing cloud spend or a seasoned pro, this book will clarify the often misunderstood workings of cloud billing fundamentals and provide expert strategies on creating a culture of cloud cost management in your organization. Drawing on real-world examples of successes and failures of large-scale cloud spenders, this book outlines a road map for building a culture of FinOps in your organization. Beginning with the fundamental concepts required to understand cloud billing concepts, you’ll learn how to enable an efficient and effective FinOps machine. Learn how the cloud works when it comes to financial management Set up a FinOps team and build a framework for making spend efficiency a priority Examine the anatomy of a cloud bill and learn how to manage it Get operational recipes for maximizing cloud efficiency Understand how to motivate engineering teams to take cost-saving actions Explore the FinOps lifecycle: Inform, Optimize, and Operate Learn the DNA of a highly functional cloud FinOps culture COMPUTERS,System Administration,General

Chaos Engineering As more companies move toward microservices and other distributed technologies, the complexity of these systems increases. You can’t remove the complexity, but through Chaos Engineering you can discover vulnerabilities and prevent outages before they impact your customers. This practical guide shows engineers how to navigate complex systems while optimizing to meet business goals. Two of the field’s prominent figures, Casey Rosenthal and Nora Jones, pioneered the discipline while working together at Netflix. In this book, they expound on the what, how, and why of Chaos Engineering while facilitating a conversation from practitioners across industries. Many chapters are written by contributing authors to widen the perspective across verticals within (and beyond) the software industry. Learn how Chaos Engineering enables your organization to navigate complexity Explore a methodology to avoid failures within your application, network, and infrastructure Move from theory to practice through real-world stories from industry experts at Google, Microsoft, Slack, and LinkedIn, among others Establish a framework for thinking about complexity within software systems Design a Chaos Engineering program around game days and move toward highly targeted, automated experiments Learn how to design continuous collaborative chaos experiments COMPUTERS,System Administration,General

Container Security To facilitate scalability and resilience, many organizations now run applications in cloud native environments using containers and orchestration. But how do you know if the deployment is secure? This practical book examines key underlying technologies to help developers, operators, and security professionals assess security risks and determine appropriate solutions. Author Liz Rice, VP of open source engineering at Aqua Security, looks at how the building blocks commonly used in container-based systems are constructed in Linux. You’ll understand what’s happening when you deploy containers and learn how to assess potential security risks that could affect your deployments. If you run container applications with kubectl or docker and use Linux command-line tools such as ps and grep, you’re ready to get started. Explore attack vectors that affect container deployments Dive into the Linux constructs that underpin containers Examine measures for hardening containers Understand how misconfigurations can compromise container isolation Learn best practices for building container images Identify container images that have known software vulnerabilities Leverage secure connections between containers Use security tooling to prevent attacks on your deployment COMPUTERS,System Administration,General

Building Secure and Reliable Systems Can a system be considered truly reliable if it isn't fundamentally secure? Or can it be considered secure if it's unreliable? Security is crucial to the design and operation of scalable systems in production, as it plays an important part in product quality, performance, and availability. In this book, experts from Google share best practices to help your organization design scalable and reliable systems that are fundamentally secure. Two previous O’Reilly books from Google—Site Reliability Engineering and The Site Reliability Workbook—demonstrated how and why a commitment to the entire service lifecycle enables organizations to successfully build, deploy, monitor, and maintain software systems. In this latest guide, the authors offer insights into system design, implementation, and maintenance from practitioners who specialize in security and reliability. They also discuss how building and adopting their recommended best practices requires a culture that’s supportive of such change. You’ll learn about secure and reliable systems through: Design strategies Recommendations for coding, testing, and debugging practices Strategies to prepare for, respond to, and recover from incidents Cultural best practices that help teams across your organization collaborate effectively COMPUTERS,System Administration,General

Salesforce for Beginners Get a 360-degree view of the Salesforce platform and learn how to use it for sales, service, marketing, and automating business processes. Key Features Understand how to use core Salesforce objects for maximum efficiency Build various dashboards and reports to analyze results and improve visibility in your business processes Learn the basics of Salesforce administration and mobile app set up Book Description Salesforce is the world's leading Customer Relationship Management (CRM) software, helping businesses connect with their constituents and partners. This book will give you a comprehensive introduction to managing sales, marketing, customer relationships, and overall administration for your organization. You'll learn how to configure and use Salesforce for maximum efficiency and return on investment. You'll start by learning how to create activities, manage leads, and develop your prospects and sales pipeline using opportunities and accounts, and then understand how you can enhance marketing activities using campaigns. Packed with real-world business use cases, this Salesforce book will show you how to analyze your business information accurately to make productive decisions. As you advance, you'll get to grips with building various reports and dashboards in Salesforce to derive valuable business insights. Finally, you'll explore tools such as process builder, approval processes, and assignment rules to achieve business process automation and set out on the path to becoming a successful Salesforce Administrator. By the end of the book, you'll have learned how to use Salesforce effectively to achieve your business goals. What you will learn Understand the difference between Salesforce Lightning and Salesforce Classic Create and manage leads in Salesforce Explore business development with accounts and contacts in Salesforce Find out how stages and sales processes help you manage your opportunity pipeline Achieve marketing goals using Salesforce campaigns Perform business analysis using reports and dashboards Gain a high-level overview of the items in the administration section Grasp the different aspects needed to build an effective and flexible Salesforce security model Who this book is for If you're new to Salesforce and want to learn it from scratch, this book is for you. No prior knowledge of Salesforce is required to get started with this book. COMPUTERS,System Administration,General

Practical Ansible 2 Leverage the power of Ansible to gain complete control over your systems and automate application deployment Key Features Use Ansible 2.9 to automate and control your infrastructure Delve into advanced functionality such as plugins and custom modules in Ansible Automate and orchestrate major cloud platforms such as OpenStack, AWS, and Azure using Ansible Book Description Ansible enables you to automate software provisioning, configuration management, and application roll-outs, and can be used as a deployment and orchestration tool. While Ansible provides simple yet powerful features to automate multi-layer environments using agentless communication, it can also solve other critical IT challenges, such as ensuring continuous integration and continuous deployment (CI/CD) with zero downtime. In this book, you'll work with Ansible 2.9 and learn to solve complex issues quickly with the help of task-oriented scenarios. You'll start by installing and configuring Ansible on Linux and macOS to automate monotonous and repetitive IT tasks and get to grips with concepts such as playbooks, inventories, and network modules. As you progress, you'll gain insight into the YAML syntax and learn how to port between Ansible versions. In addition to this, you'll also understand how Ansible enables you to orchestrate multi-layer environments such as networks, containers, and the cloud. By the end of this Ansible book, you'll be well - versed in writing playbooks and other related Ansible code to overcome just about all of your IT challenges, from infrastructure-as-code provisioning to application deployments, and even handling the mundane day-to-day maintenance tasks that take up so much valuable time. What you will learn Become familiar with the fundamentals of the Ansible framework Set up role-based variables and dependencies Avoid common mistakes and pitfalls when writing automation code in Ansible Extend Ansible by developing your own modules and plugins Contribute to the Ansible project by submitting your own code Follow best practices for working with cloud environment inventories Troubleshoot issues triggered during Ansible playbook runs Who this book is for If you are a DevOps engineer, administrator, or any IT professional looking to automate IT tasks using Ansible, this book is for you. Prior knowledge of Ansible is not necessary. COMPUTERS,System Administration,General

Bash Pocket Reference It’s simple: if you want to interact deeply with Mac OS X, Linux, and other Unix-like systems, you need to know how to work with the Bash shell. This concise little book puts all of the essential information about Bash right at your fingertips. You’ll quickly find answers to the annoying questions that generally come up when you’re writing shell scripts: What characters do you need to quote? How do you get variable substitution to do exactly what you want? How do you use arrays? Updated for Bash version 4.4, this book has the answers to these and other problems in a format that makes browsing quick and easy. Topics include: Invoking the shell Syntax Functions and variables Arithmetic expressions Command history Programmable completion Job control Shell options Command execution Coprocesses Restricted shells Built-in commands COMPUTERS,System Administration,Linux & UNIX Administration

Docker Docker is rapidly changing the way organizations deploy software at scale. However, understanding how Linux containers fit into your workflow—and getting the integration details right—is not a trivial task. With the updated edition of this practical guide, you’ll learn how to use Docker to package your applications with all of their dependencies and then test, ship, scale, and support your containers in production. This edition includes significant updates to the examples and explanations that reflect the substantial changes that have occurred over the past couple of years. Sean Kane and Karl Matthias have added a complete chapter on Docker Compose, deeper coverage of Docker Swarm mode, introductions to both Kubernetes and AWS Fargate, examples on how to optimize your Docker images, and much more. Learn how Docker simplifies dependency management and deployment workflow for your applications Start working with Docker images, containers, and command line tools Use practical techniques to deploy and test Docker containers in production Debug containers by understanding their composition and internal processes Deploy production containers at scale inside your data center or cloud environment Explore advanced Docker topics, including deployment tools, networking, orchestration, security, and configuration COMPUTERS,System Administration,Linux & UNIX Administration

Linux Observability with BPF Build your expertise in the BPF virtual machine in the Linux kernel with this practical guide for systems engineers. You’ll not only dive into the BPF program lifecycle but also learn to write applications that observe and modify the kernel’s behavior; inject code to monitor, trace, and securely observe events in the kernel; and more. Authors David Calavera and Lorenzo Fontana help you harness the power of BPF to make any computing system more observable. Familiarize yourself with the essential concepts you’ll use on a day-to-day basis and augment your knowledge about performance optimization, networking, and security. Then see how it all comes together with code examples in C, Go, and Python. Write applications that use BPF to observe and modify the Linux kernel’s behavior on demand Inject code to monitor, trace, and observe events in the kernel in a secure way—no need to recompile the kernel or reboot the system Explore code examples in C, Go, and Python Gain a more thorough understanding of the BPF program lifecycle COMPUTERS,System Administration,Linux & UNIX Administration

Kubernetes - A Complete DevOps Cookbook Leverage Kubernetes and container architecture to successfully run production-ready workloads Key Features Implement Kubernetes to orchestrate and scale applications proficiently Leverage the latest features of Kubernetes to resolve common as well as complex problems in a cloud-native environment Gain hands-on experience in securing, monitoring, and troubleshooting your application Book Description Kubernetes is a popular open source orchestration platform for managing containers in a cluster environment. With this Kubernetes cookbook, you'll learn how to implement Kubernetes using a recipe-based approach. The book will prepare you to create highly available Kubernetes clusters on multiple clouds such as Amazon Web Services (AWS), Google Cloud Platform (GCP), Azure, Alibaba, and on-premises data centers. Starting with recipes for installing and configuring Kubernetes instances, you'll discover how to work with Kubernetes clients, services, and key metadata. You'll then learn how to build continuous integration/continuous delivery (CI/CD) pipelines for your applications, and understand various methods to manage containers. As you advance, you'll delve into Kubernetes' integration with Docker and Jenkins, and even perform a batch process and configure data volumes. You'll get to grips with methods for scaling, security, monitoring, logging, and troubleshooting. Additionally, this book will take you through the latest updates in Kubernetes, including volume snapshots, creating high availability clusters with kops, running workload operators, new inclusions around kubectl and more. By the end of this book, you'll have developed the skills required to implement Kubernetes in production and manage containers proficiently. What you will learn Deploy cloud-native applications on Kubernetes Automate testing in the DevOps workflow Discover and troubleshoot common storage issues Dynamically scale containerized services to manage fluctuating traffic needs Understand how to monitor your containerized DevOps environment Build DevSecOps into CI/CD pipelines Who this book is for This Kubernetes book is for developers, IT professionals, and DevOps engineers and teams who want to use Kubernetes to manage, scale, and orchestrate applications in their organization. Basic understanding of Kubernetes and containerization is necessary. COMPUTERS,System Administration,Linux & UNIX Administration

Learn Helm A comprehensive introduction to automated application deployment on Kubernetes for beginners Key Features Effectively manage applications deployed in Kubernetes using Helm Learn to install, upgrade, share, and manage applications deployed in Kubernetes Get up and running with a package manager for Kubernetes Book Description Containerization is currently known to be one of the best ways to implement DevOps. While Docker introduced containers and changed the DevOps era, Google developed an extensive container orchestration system, Kubernetes, which is now considered the frontrunner in container orchestration. With the help of this book, you'll explore the efficiency of managing applications running on Kubernetes using Helm. Starting with a short introduction to Helm and how it can benefit the entire container environment, you'll then delve into the architectural aspects, in addition to learning about Helm charts and its use cases. You'll understand how to write Helm charts in order to automate application deployment on Kubernetes. Focused on providing enterprise-ready patterns relating to Helm and automation, the book covers best practices for application development, delivery, and lifecycle management with Helm. By the end of this Kubernetes book, you will have learned how to leverage Helm to develop an enterprise pattern for application delivery. What you will learn Develop an enterprise automation strategy on Kubernetes using Helm Create easily consumable and configurable Helm charts Use Helm in orchestration tooling and Kubernetes operators Explore best practices for application delivery and life cycle management Leverage Helm in a secure and stable manner that is fit for your enterprise Discover the ins and outs of automation with Helm Who this book is for This book is for Kubernetes developers or administrators who are interested in learning Helm to provide automation for application development on Kubernetes. Although no prior knowledge of Helm is required, basic knowledge of Kubernetes application development will be useful. COMPUTERS,System Administration,Linux & UNIX Administration

Learn Kubernetes Security Secure your container environment against cyberattacks and deliver robust deployments with this practical guide Key Features Explore a variety of Kubernetes components that help you to prevent cyberattacks Perform effective resource management and monitoring with Prometheus and built-in Kubernetes tools Learn techniques to prevent attackers from compromising applications and accessing resources for crypto-coin mining Book Description Kubernetes is an open source orchestration platform for managing containerized applications. Despite widespread adoption of the technology, DevOps engineers might be unaware of the pitfalls of containerized environments. With this comprehensive book, you'll learn how to use the different security integrations available on the Kubernetes platform to safeguard your deployments in a variety of scenarios. Learn Kubernetes Security starts by taking you through the Kubernetes architecture and the networking model. You'll then learn about the Kubernetes threat model and get to grips with securing clusters. Throughout the book, you'll cover various security aspects such as authentication, authorization, image scanning, and resource monitoring. As you advance, you'll learn about securing cluster components (the kube-apiserver, CoreDNS, and kubelet) and pods (hardening image, security context, and PodSecurityPolicy). With the help of hands-on examples, you'll also learn how to use open source tools such as Anchore, Prometheus, OPA, and Falco to protect your deployments. By the end of this Kubernetes book, you'll have gained a solid understanding of container security and be able to protect your clusters from cyberattacks and mitigate cybersecurity threats. What you will learn Understand the basics of Kubernetes architecture and networking Gain insights into different security integrations provided by the Kubernetes platform Delve into Kubernetes' threat modeling and security domains Explore different security configurations from a variety of practical examples Get to grips with using and deploying open source tools to protect your deployments Discover techniques to mitigate or prevent known Kubernetes hacks Who this book is for This book is for security consultants, cloud administrators, system administrators, and DevOps engineers interested in securing their container deployments. If you're looking to secure your Kubernetes clusters and cloud-based deployments, you'll find this book useful. A basic understanding of cloud computing and containerization is necessary to make the most of this book. COMPUTERS,System Administration,Linux & UNIX Administration

Information Retrieval Systems The growth of the Internet and the availability of enormous volumes of data in digital form have necessitated intense interest in techniques to assist the user in locating data of interest. The Internet has over 350 million pages of data and is expected to reach over one billion pages by the year 2000. Buried on the Internet are both valuable nuggets to answer questions as well as a large quantity of information the average person does not care about. The Digital Library effort is also progressing, with the goal of migrating from the traditional book environment to a digital library environment. The challenge to both authors of new publications that will reside on this information domain and developers of systems to locate information is to provide the information and capabilities to sort out the non-relevant items from those desired by the consumer. In effect, as we proceed down this path, it will be the computer that determines what we see versus the human being. The days of going to a library and browsing the new book shelf are being replaced by electronic searching the Internet or the library catalogs. Whatever the search engines return will constrain our knowledge of what information is available. An understanding of Information Retrieval Systems puts this new environment into perspective for both the creator of documents and the consumer trying to locate information. COMPUTERS,System Administration,Storage & Retrieval

Information Systems and Data Compression Information Systems and Data Compression presents a uniform approach and methodology for designing intelligent information systems. A framework for information concepts is introduced for various types of information systems such as communication systems, information storage systems and systems for simplifying structured information. The book introduces several new concepts and presents a novel interpretation of a wide range of topics in communications, information storage, and information compression. Numerous illustrations for designing information systems for compression of digital data and images are used throughout the book. COMPUTERS,System Administration,Storage & Retrieval

Content Management Bible Written by one of the leading experts in content management systems (CMS), this newly revised bestseller guides readers through the confusing-and often intimidating-task of building, implementing, running, and managing a CMS Updated to cover recent developments in online delivery systems, as well as XML and related technologies Reflects valuable input from CMS users who attended the author's workshops, conferences, and courses An essential reference showing anyone involved in information delivery systems how to plan and implement a system that can handle large amounts of information and help achieve an organization's overall goals COMPUTERS,System Administration,Storage & Retrieval

USB Mass Storage This developer's guide for designers and programmers of mass-storage devices that use the Universal Serial Bus (USB) interface provides developers with information on how to choose storage media, interface the media to a microcontroller or other CPU, and write device firmware to access the media and perform USB communications. Comparisons of popular storage-media options to help users choose a media type for a project are included, and the types described cover hard drives and flash-memory cards such as the MultiMediaCard (MMC), Secure Digital (SD) card, and CompactFlash card. Helpful tips on developing an embedded host that can access USB mass-storage devices are also covered. COMPUTERS,System Administration,Storage & Retrieval

Backup & Recovery Packed with practical, freely available backup and recovery solutions for Unix, Linux, Windows, and Mac OS X systems -- as well as various databases -- this new guide is a complete overhaul of Unix Backup & Recovery by the same author, now revised and expanded with over 75% new material. Backup & Recovery starts with a complete overview of backup philosophy and design, including the basic backup utilities of tar, dump, cpio, ntbackup, ditto, and rsync. It then explains several open source backup products that automate backups using those utilities, including AMANDA, Bacula, BackupPC, rdiff-backup, and rsnapshot. Backup & Recovery then explains how to perform bare metal recovery of AIX, HP-UX, Linux, Mac OS, Solaris, VMWare, & Windows systems using freely-available utilities. The book also provides overviews of the current state of the commercial backup software and hardware market, including overviews of CDP, Data De-duplication, D2D2T, and VTL technology. Finally, it covers how to automate the backups of DB2, Exchange, MySQL, Oracle, PostgreSQL, SQL-Server, and Sybase databases - without purchasing a commercial backup product to do so. For environments of all sizes and budgets, this unique book shows you how to ensure data protection without resorting to expensive commercial solutions. You will soon learn to: Automate the backup of popular databases without a commercial utility Perform bare metal recovery of any popular open systems platform, including your PC or laptop Utilize valuable but often unknown open source backup products Understand the state of commercial backup software, including explanations of CDP and data de-duplication software Access the current state of backup hardware, including Virtual Tape Libraries (VTLs) COMPUTERS,System Administration,Storage & Retrieval

Information Assurance When you first hear the term Information Assurance you tend to conjure up an image of a balanced set of reasonable measures that have been taken to protect the information after an assessment has been made of risks that are posed to it. In truth this is the Holy Grail that all organisations that value their information should strive to achieve, but which few even understand. Information Assurance is a term that has recently come into common use. When talking with old timers in IT (or at least those that are over 35 years old), you will hear them talking about information security, a term that has survived since the birth of the computer. In the more recent past, the term Information Warfare was coined to describe the measures that need to be taken to defend and attack information. This term, however, has military connotations - after all, warfare is normally their domain. Shortly after the term came into regular use, it was applied to a variety of situations encapsulated by Winn Schwartau as the three classes of Information Warfare: Class 1- Personal Information Warfare. Class 2 - Corporate Information Warfare. Class 3 - Global Information Warfare. Political sensitivities lead to "warfare" being replaced by "operations", a much more "politically correct" word. Unfortunately, "operations" also has an offensive connotation and is still the terminology of the military and governments. COMPUTERS,System Administration,Storage & Retrieval

Advances in Databases and Information Systems This volume results from the regular sessions of the Second International Workshop of the Moscow ACM SIGMOD Chapter "Advances in Databases and Information Systems" (ADBIS'95) that took place 27th-30th June 1995, in Moscow, Russia. ADBIS'95 continues a series of annual Workshops on Advances in Databases and Information Systems organized by the Moscow ACM SIGMOD Chapter in cooperation with the Russian Founda tion for Basic Research. Past successful ADBIS conferences include the ADBIS'93 and ADBIS'94 Workshops that took place in Moscow. The aims of these workshops are to provide a forum for the presentation and in-depth discussion of advanced research directions that will effectively improve the building and use of future information systems and to increase communication between the Eastern and Western research communities which were formerly separated and still have only rare possibilities to interact. Improving of the contacts and exchange of ideas between researchers from the East and from the West will eventually lead to better collaboration between them. The ADBIS'95 Call for Submissions attracted 60 submissions from 15 countries of which 35 submissions were accepted for presentation at the regular sessions, 9 as posters, and 7 as presentations for a special session for the Information Systems for Science. This volume contains the papers presented in the regular sessions. COMPUTERS,System Administration,Storage & Retrieval

Active and Real-Time Database Systems (ARTDB-95) The areas of active and real-time databases have seen a tremendous growth of interest in the past few years, particularly with regard to their support of time-critical and embedded applications. ARTDB-95 provided, therefore, an important forum for researchers from both communities to discuss research results, and also to chart new directions for the future. As well as the 11 submitted papers presented at the workshop, this volume also contains 4 invited papers on the following topics: the impact of active databases on commercial practice; the optimization of active database transactions; the need for better language, compiler and tool support for real-time databases; and the origin of time constraints associated with data, events and actions. Together the papers give a comprehensive overview of current research, and will provide invaluable reading for academic and industrial researchers and students at both undergraduate and postgraduate level. COMPUTERS,System Administration,Storage & Retrieval

Datenbanksysteme in Büro, Technik und Wissenschaft AngestoBen durch den Einsatz von Datenbanken in der Praxis sind in den vergange nen Jahren zahlreiche Forschungsprobleme und herausfordernde Entwicklungsaufgaben erkannt worden, fur deren Losung sich die derzeit auf dem Markt befindlichen Datenbank systeme nur bedingt geeignet zeigen. Datenbanken werden seit vielen Jahren erfolgreich in Anwendungen eingesetzt, die durch groBe Bestiinde einfach strukturierter Daten ge kennzeichnet sind. 1m Gegensatz dazu finden beispielsweise Hypertext-Anwendungen im Burobereich, die Verwaltung von Entwurfsdaten in ingenieurwissenschaftlichen Anwen dungen oder auch die Entwicklung von datenbankbasierten Expertensystemen durch Da tenbanken keine befriedigende Unterstutzung. Es werden deshalb zunehmend Konzepte diskutiert und prototypmiiBig implementiert, mittels denen sogenannte Nicht-Standard Datenbanken realisiert werden konnen, die den Einsatzbereich bisheriger Datenbanken in die neuen Anwendungsgebiete ausdehnen. Die 1985 in Karlsruhe begonnene im zweijiihrigen Turnus veranstaltete Tagungsreihe "BTW" hat es sich zum Anliegen gemacht, vor einem Forum von Datenbank-Forschern und -Praktikern den Enwicklungsstand und die Perspektiven neuer Datenbank-Technolgie in aktuellen Einsatzgebieten zu diskutieren. Uber 70 Kurz- und Langbeitriige wurden zur Begutachtung eingereicht. Diese hohe Zahl zeigt, daB auch nach nunmehr zehn Jahren die "BTW" nichts von ihrer Attraktivitiit verloren hat und nach wie vor als die wichtigste Datenbanktagung im deutschsprachigen Raum gesehen wird. Das Programmkomitee war in der erfreulichen Lage, ein interessantes und qualitativ hochwertiges Tagungsprogramm, bestehend aus 18 Lang- und 8 Kurzbeitriigen, zusammenstellen zu konnen. COMPUTERS,System Administration,Storage & Retrieval

SIGIR ’94 Information retrieval (IR) is becoming an increasingly important area as scientific, business and government organisations take up the notion of "information superhighways" and make available their full text databases for searching. Containing a selection of 35 papers taken from the 17th Annual SIGIR Conference held in Dublin, Ireland in July 1994, the book addresses basic research and provides an evaluation of information retrieval techniques in applications. Topics covered include text categorisation, indexing, user modelling, IR theory and logic, natural language processing, statistical and probabilistic models of information retrieval systems, routing, passage retrieval, and implementation issues. COMPUTERS,System Administration,Storage & Retrieval

14th Information Retrieval Colloquium We hope that all readers will find the papers included in this volume of interest. All were presented at the 14th BCS IRSG Research Colloquium held at Lancaster University on 13th-14th April 1992. The papers display very well the scope and breadth of information retrieval, as indeed did the workshop ilself. They also present a good cross-section of current IR research, and as such provide a useful signpost for trends in information retrieval. Before we finish we must thank the following colleagues: Simon Botley, Paul Rayson and Paul Jones for their help in the organization of the conference. We would also like to extend a special message of thanks to Professor G.N. Leech of the Department of Linguistics at Lancaster and Roger Garside of the Department of Computing at Lancaster for their support during the conference period. Tony McEnery would also like to express his thanks and gratitude to Paul Baker for his help during the production of this book. September 1992 Tony McEnery Chris Paice Contents A Logical Model of Information Retrieval Based on Situation Theory M. La/mas and K. van Rijsbergen ........................................................ . COMPUTERS,System Administration,Storage & Retrieval

Metadata Management in Statistical Information Processing As the integration of statistical data collected in various subject matter domains becomes more and more important in several socio-economic etc. investigation areas the management of so-called metadata – a formal digital processing of information about data – gains tremendously increasing relevance. Unlike current information technologies (e.g., database systems, computer networks, ...) facilitating merely the technical side of data collation, a coherent integration of empirical data still remains cumbersome, and thus rather costly, very often because of a lack of powerful semantic data models capturing the very meaning and structure of statistical data sets. Recognizing this deficiency, "Metadata Management" proposes a general framework for the computer-aided integration and harmonization of distributed heterogeneous statistical data sources, aiming at a truly comprehensive statistical meta-information system. COMPUTERS,System Administration,Storage & Retrieval

Guide to Computer Network Security This important text/reference presents a comprehensive guide to the field of computing and information security and assurance. The book takes a broad view of computer network security, encompassing online social networks, and wireless and mobile systems. This fully updated new edition explores the security issues, vulnerabilities and dangers encountered by the users of modern computing and communication devices, highlighting the need to develop improved algorithms, protocols, and best practices to enhance the security of public, private and enterprise systems alike. Topics and features: introduces the fundamentals of traditional computer networks, the security threats they face, and the best practices currently in use; discusses the security challenges introduced by virtualization software, cloud computing and mobile systems; examines the security quagmire presented by the home computing environment and the growing number of home hotspots (NEW); raises important legislative, legal, social, technical and ethical security issues, including the tension between the needs of individual privacy and collective security; provides both quickly workable and more thought-provoking exercises at the end of each chapter, with one chapter devoted entirely to lab exercises; supplies additional support material for instructors at an associated website, including laboratory exercises and projects, answers to selected exercises, and course slides. This unique work is suitable as both a teaching and a reference tool for all those interested in learning about security in the evolving computing ecosystem. Computer network and data security personnel and policy makers will also find the guide to be a useful and unique source of ideas. COMPUTERS,System Administration,Storage & Retrieval

Declutter Your Data Technology makes things faster, and simpler. At the same time, with all the technology that surrounds us on a daily basis, everyone is awash in too much information. Our computers, phones, tablets, work projects, tax and other files, and various online accounts all store data. It’s a lot! Can anything be done? Yes! 'Declutter Your Data' is for anyone who is interested in making better use of technology, cleaning up their digital clutter, and coming up with an organized and efficient way to access their data going forward. This book guides readers step by step through the process of figuring out what data is important to them; wrestling with the information to clear out what’s not useful and organize what they want to keep; and dealing with the ongoing data maintenance aspect that is a necessity in this digital age. Following author Angela Crocker’s advice and putting these ideas into practice will reduce your digital clutter, make you more efficient, help you save time, and give you a happier relationship with your information, clearing your mind for more important things. COMPUTERS,System Administration,Storage & Retrieval

Mastering Ceph Discover the unified, distributed storage system and improve the performance of applications Key Features Explore the latest features of Ceph's Mimic release Get to grips with advanced disaster and recovery practices for your storage Harness the power of Reliable Autonomic Distributed Object Store (RADOS) to help you optimize storage systems Book Description Ceph is an open source distributed storage system that is scalable to Exabyte deployments. This second edition of Mastering Ceph takes you a step closer to becoming an expert on Ceph. You'll get started by understanding the design goals and planning steps that should be undertaken to ensure successful deployments. In the next sections, you'll be guided through setting up and deploying the Ceph cluster with the help of orchestration tools. This will allow you to witness Ceph's scalability, erasure coding (data protective) mechanism, and automated data backup features on multiple servers. You'll then discover more about the key areas of Ceph including BlueStore, erasure coding and cache tiering with the help of examples. Next, you'll also learn some of the ways to export Ceph into non-native environments and understand some of the pitfalls that you may encounter. The book features a section on tuning that will take you through the process of optimizing both Ceph and its supporting infrastructure. You'll also learn to develop applications, which use Librados and distributed computations with shared object classes. Toward the concluding chapters, you'll learn to troubleshoot issues and handle various scenarios where Ceph is not likely to recover on its own. By the end of this book, you'll be able to master storage management with Ceph and generate solutions for managing your infrastructure. What you will learn Plan, design and deploy a Ceph cluster Get well-versed with different features and storage methods Carry out regular maintenance and daily operations with ease Tune Ceph for improved ROI and performance Recover Ceph from a range of issues Upgrade clusters to BlueStore Who this book is for If you are a storage professional, system administrator, or cloud engineer looking for guidance on building powerful storage solutions for your cloud and on-premise infrastructure, this book is for you. COMPUTERS,System Administration,Storage & Retrieval

Principles of Data Mining This book explains and explores the principal techniques of Data Mining, the automatic extraction of implicit and potentially useful information from data, which is increasingly used in commercial, scientific and other application areas. It focuses on classification, association rule mining and clustering. Each topic is clearly explained, with a focus on algorithms not mathematical formalism, and is illustrated by detailed worked examples. The book is written for readers without a strong background in mathematics or statistics and any formulae used are explained in detail. It can be used as a textbook to support courses at undergraduate or postgraduate levels in a wide range of subjects including Computer Science, Business Studies, Marketing, Artificial Intelligence, Bioinformatics and Forensic Science.As an aid to self-study, it aims to help general readers develop the necessary understanding of what is inside the 'black box' so they can use commercial data mining packages discriminatingly, as well as enabling advanced readers or academic researchers to understand or contribute to future technical advances in the field. Each chapter has practical exercises to enable readers to check their progress. A full glossary of technical terms used is included. Principles of Data Mining includes descriptions of algorithms for classifying streaming data, both stationary data, where the underlying model is fixed, and data that is time-dependent, where the underlying model changes from time to time - a phenomenon known as concept drift. The expanded fourth edition gives a detailed description of a feed-forward neural network with backpropagation and shows how it can be used for classification. COMPUTERS,System Administration,Storage & Retrieval

The Semantic Web This book constitutes the refereed proceedings of the 17th International Semantic Web Conference, ESWC 2020, held in Heraklion, Crete, Greece.* The 39 revised full papers presented were carefully reviewed and selected from 166 submissions. The papers were submitted to three tracks: the research track, the resource track and the in-use track. These tracks showcase research and development activities, services and applications, and innovative research outcomes making their way into industry. The research track caters for both long standing and emerging research topics in the form of the following subtracks: ontologies and reasoning; natural language processing and information retrieval; semantic data management and data infrastructures; social and human aspects of the Semantic Web; machine learning; distribution and decentralization; science of science; security, privacy, licensing and trust; knowledge graphs; and integration, services and APIs. *The conference was held virtually due to the COVID-19 pandemic. Chapter ‘Piveau: A Large-scale Oopen Data Management Platform based on Semantic Web Technologies’ is available open access under a Creative Commons Attribution 4.0 International License via link.springer.com. COMPUTERS,System Administration,Storage & Retrieval

Understanding and Improving Information Search This edited book adopts a cognitive perspective to provide breadth and depth to state-of-the-art research related to understanding, analyzing, predicting and improving one of the most prominent and important classes of behavior of modern humans, information search. It is timely as the broader research area of cognitive computing and cognitive technology have recently attracted much attention, and there has been a surge in interest to develop systems and technology that are more compatible with human cognitive abilities. Divided into three interlocking sections, the first introduces the foundational concepts of information search from a cognitive computing perspective to highlight the research questions and approaches that are shared among the contributing authors. Relevant concepts from psychology, information and computing sciences are addressed. The second section discusses methods and tools that are used to understand and predict information search behavior and how the cognitive perspective can provide unique insights into the complexities of the behavior in various contexts. The final part highlights a number of areas of applications of which education and training, collaboration and conversational search interfaces are important ones. Understanding and Improving Information Search - A Cognitive Approach includes contributions from cognitive psychologists, information and computing scientists around the globe, including researchers from Europe (France, Netherlands, Germany), the US, and Asia (India, Japan), providing their unique but coherent perspectives to the core issues and questions most relevant to our current understanding of information search behavior and improving information search. COMPUTERS,System Administration,Storage & Retrieval

Data Security in Cloud Storage This book provides a comprehensive overview of data security in cloud storage, ranging from basic paradigms and principles, to typical security issues and practical security solutions. It also illustrates how malicious attackers benefit from the compromised security of outsourced data in cloud storage and how attacks work in real situations, together with the countermeasures used to ensure the security of outsourced data. Furthermore, the book introduces a number of emerging technologies that hold considerable potential – for example, blockchain, trusted execution environment, and indistinguishability obfuscation – and outlines open issues and future research directions in cloud storage security. The topics addressed are important for the academic community, but are also crucial for industry, since cloud storage has become a fundamental component in many applications. The book offers a general introduction for interested readers with a basic modern cryptography background, and a reference guide for researchers and practitioners in the fields of data security and cloud storage. It will also help developers and engineers understand why some current systems are insecure and inefficient, and move them to design and develop improved systems. COMPUTERS,System Administration,Storage & Retrieval

Guide to Computer Network Security This important text/reference presents a comprehensive guide to the field of computing and information security and assurance. The book takes a broad view of computer network security, encompassing online social networks, and wireless and mobile systems. This fully updated new edition explores the security issues, vulnerabilities and dangers encountered by the users of modern computing and communication devices, highlighting the need to develop improved algorithms, protocols, and best practices to enhance the security of public, private and enterprise systems alike. Topics and features: introduces the fundamentals of traditional computer networks, the security threats they face, and the best practices currently in use; discusses the security challenges introduced by virtualization software, cloud computing and mobile systems; examines the security quagmire presented by the home computing environment and the growing number of home hotspots (NEW); raises important legislative, legal, social, technical and ethical security issues, including the tension between the needs of individual privacy and collective security; provides both quickly workable and more thought-provoking exercises at the end of each chapter, with one chapter devoted entirely to lab exercises; supplies additional support material for instructors at an associated website, including laboratory exercises and projects, answers to selected exercises, and course slides. This unique work is suitable as both a teaching and a reference tool for all those interested in learning about security in the evolving computing ecosystem. Computer network and data security personnel and policy makers will also find the guide to be a useful and unique source of ideas. COMPUTERS,System Administration,Storage & Retrieval

Knowledge Discovery, Knowledge Engineering and Knowledge Management This book constitutes the thoroughly refereed proceedings of the 10th International Joint Conference on Knowledge Discovery, Knowledge Engineering and Knowledge Management, IC3K 2018, held in Seville, Spain, in September 2018.The 12 full papers presented were carefully reviewed and selected from 167 submissions. The papers are organized in topical sections on knowledge discovery and information retrieval; knowledge engineering and ontology development; and knowledge management and information sharing. COMPUTERS,System Administration,Storage & Retrieval

The Discipline of Organizing A framework for the theory and practice of organizing that integrates the concepts and methods of information organization and information retrieval. Organizing is such a common activity that we often do it without thinking much about it. In our daily lives we organize physical things—books on shelves, cutlery in kitchen drawers—and digital things—Web pages, MP3 files, scientific datasets. Millions of people create and browse Web sites, blog, tag, tweet, and upload and download content of all media types without thinking “I'm organizing now” or “I'm retrieving now.” This book offers a framework for the theory and practice of organizing that integrates information organization (IO) and information retrieval (IR), bridging the disciplinary chasms between Library and Information Science and Computer Science, each of which views and teaches IO and IR as separate topics and in substantially different ways. It introduces the unifying concept of an Organizing System—an intentionally arranged collection of resources and the interactions they support—and then explains the key concepts and challenges in the design and deployment of Organizing Systems in many domains, including libraries, museums, business information systems, personal information management, and social computing. Intended for classroom use or as a professional reference, the book covers the activities common to all organizing systems: identifying resources to be organized; organizing resources by describing and classifying them; designing resource-based interactions; and maintaining resources and organization over time. The book is extensively annotated with disciplinary-specific notes to ground it with relevant concepts and references of library science, computing, cognitive science, law, and business. COMPUTERS,System Administration,Storage & Retrieval

Big Data 2.0 Processing Systems This book provides readers the “big picture†and a comprehensive survey of the domain of big data processing systems. For the past decade, the Hadoop framework has dominated the world of big data processing, yet recently academia and industry have started to recognize its limitations in several application domains and thus, it is now gradually being replaced by a collection of engines that are dedicated to specific verticals (e.g. structured data, graph data, and streaming data). The book explores this new wave of systems, which it refers to as Big Data 2.0 processing systems. After Chapter 1 presents the general background of the big data phenomena, Chapter 2 provides an overview of various general-purpose big data processing systems that allow their users to develop various big data processing jobs for different application domains. In turn, Chapter 3 examines various systems that have been introduced to support the SQL flavor on top of the Hadoop infrastructure and provide competing and scalable performance in the processing of large-scale structured data. Chapter 4 discusses several systems that have been designed to tackle the problem of large-scale graph processing, while the main focus of Chapter 5 is on several systems that have been designed to provide scalable solutions for processing big data streams, and on other sets of systems that have been introduced to support the development of data pipelines between various types of big data processing jobs and systems. Next, Chapter 6 focuses on covering the emerging frameworks and systems in the domain of scalable machine learning and deep learning processing. Lastly, Chapter 7 shares conclusions and an outlook on future research challenges. This new and considerably enlarged second edition not only contains the completely new chapter 6, but also offers a refreshed content for the state-of-the-art in all domains of big data processing over the last years. Overall, the book offers a valuable reference guide for professional, students, and researchers in the domain of big data processing systems. Further, its comprehensive content will hopefully encourage readers to pursue further research on the subject. COMPUTERS,System Administration,Storage & Retrieval

Running Xen “This accessible and immediately useful book expertly provides the Xen community with everything it needs to know to download, build, deploy and manage Xen implementations.†—Ian Pratt, Xen Project Leader VP Advanced Technology, Citrix Systems The Real–World, 100% Practical Guide to Xen Virtualization in Production Environments Using free, open source Xen virtualization software, you can save money, gain new flexibility, improve utilization, and simplify everything from disaster recovery to software testing. Running Xen brings together all the knowledge you need to create and manage high–performance Xen virtual machines in any environment. Drawing on the unparalleled experience of a world–class Xen team, it covers everything from installation to administration—sharing field-tested insights, best practices, and case studies you can find nowhere else. The authors begin with a primer on virtualization: its concepts, uses, and advantages. Next, they tour Xen’s capabilities, explore the Xen LiveCD, introduce the Xen hypervisor, and walk you through configuring your own hard–disk–based Xen installation. After you’re running, they guide you through each leading method for creating “guests†and migrating existing systems to run as Xen guests. Then they offer comprehensive coverage of managing and securing Xen guests, devices, networks, and distributed resources. Whether you’re an administrator, data center manager, developer, system integrator, or ISP, Running Xen will help you achieve your goals with Xen–reliably, efficiently, with outstanding performance, and at a surprisingly low cost. •Understanding the Xen hypervisor: what it does, and how it works •Using pre-built system images, including compressed file systems •Managing domains with the xm console •Populating and storing guest images •Planning, designing, and configuring networks in Xen •Utilizing Xen security: special purpose VMs, virtual network segments, remote access, firewalls, network monitors, sHype access control, Xen Security Modules (XSM), and more •Managing guest resources: memory, CPU, and I/O •Employing Xen in the enterprise: tools, products, and techniques COMPUTERS,System Administration,Virtualization & Containerization

Virtualization What exactly is virtualization? As this concise book explains, virtualization is a smorgasbord of technologies that offer organizations many advantages, whether you're managing extremely large stores of rapidly changing data, scaling out an application, or harnessing huge amounts of computational power. With this guide, you get an overview of the five main types of virtualization technology, along with information on security, management, and modern use cases. Topics include: Access virtualization—Allows access to any application from any device Application virtualization—Enables applications to run on many different operating systems and hardware platforms Processing virtualization—Makes one system seem like many, or many seem like one Network virtualization—Presents an artificial view of the network that differs from the physical reality Storage virtualization—Allows many systems to share the same storage devices, enables concealing the location of storage systems, and more COMPUTERS,System Administration,Virtualization & Containerization

VMware vSphere PowerCLI Reference Master vSphere automation with this comprehensive reference VMware vSphere PowerCLI Reference, Automating vSphere Administration, 2nd Edition is a one-stop solution for vSphere automation. Fully updated to align with the latest vSphere and PowerCLI release, this detailed guide shows you how to get the most out of PowerCLI's handy cmdlets using real-world examples and a practical, task-based approach. You'll learn how to store, access, update, back up, and secure massive amounts of data quickly through the power of virtualization automation, and you'll get acquainted with PowerCLI as you learn how to automate management, monitoring, and life-cycle operations for vSphere. Coverage includes areas like the PowerCLI SDK, SRM, vCOPS, and vCloud Air. Plus guidance toward scheduling and viewing automation, using DevOps methodology and structured testing and source control of your PowerCLI scripts. Clear language and detailed explanations make this reference the manual you've been looking for. This book is your complete reference for managing vSphere in a Windows environment, with expert instruction and real-world application. Automate vCenter Server deployment and configuration Create and configure virtual machines, and utilize vApps Monitor, audit, and report the status of your vSphere environment Secure, back up, and restore your virtual machines Work with other vSphere components from your PowerCLI scripts Take control of your PowerCLI scripts through versioning and structured testing Don't spend another day slogging through routine systems management — automate it, with this invaluable guide. COMPUTERS,System Administration,Virtualization & Containerization

Building Data Centers with VXLAN BGP EVPN The complete guide to building and managing next-generation data center network fabrics with VXLAN and BGP EVPN This is the only comprehensive guide and deployment reference for building flexible data center network fabrics with VXLAN and BGP EVPN technologies. Writing for experienced network professionals, three leading Cisco experts address everything from standards and protocols to functions, configurations, and operations. The authors first explain why and how data center fabrics are evolving, and introduce Cisco’s fabric journey. Next, they review key switch roles, essential data center network fabric terminology, and core concepts such as network attributes, control plane details, and the associated data plane encapsulation. Building on this foundation, they provide a deep dive into fabric semantics, efficient creation and addressing of the underlay, multi-tenancy, control and data plane interaction, forwarding flows, external interconnectivity, and service appliance deployments. You’ll find detailed tutorials, descriptions, and packet flows that can easily be adapted to accommodate customized deployments. This guide concludes with a full section on fabric management, introducing multiple opportunities to simplify, automate, and orchestrate data center network fabrics. Learn how changing data center requirements have driven the evolution to overlays, evolved control planes, and VXLAN BGP EVPN spine-leaf fabrics Discover why VXLAN BGP EVPN fabrics are so scalable, resilient, and elastic Implement enhanced unicast and multicast forwarding of tenant traffic over the VXLAN BGP EVPN fabric Build fabric underlays to efficiently transport uni- and multi-destination traffic Connect the fabric externally via Layer 3 (VRF-Lite, LISP, MPLS L3VPN) and Layer 2 (VPC) Choose your most appropriate Multi-POD, multifabric, and Data Center Interconnect (DCI) options Integrate Layer 4-7 services into the fabric, including load balancers and firewalls Manage fabrics with POAP-based day-0 provisioning, incremental day 0.5 configuration, overlay day-1 configuration, or day-2 operations COMPUTERS,System Administration,Virtualization & Containerization

VMware vSphere 6.5 Cookbook Deploy and manage VMware vSphere 6.5 components with ease.About This BookSimplified and to-the-point theory and practical recipes to deploy and manage vSphere 6.5Discover the best ways to deploy stateless and stateful ESXi hosts and upgrade themStorage and network resource managementCertificate management using VMCAMonitor the performance of a vSphere environment.Who This Book Is ForIf you are a system administrator, support professional, or anyone interested in learning how to install, configure, and manage a vSphere environment, then this book is for you. This task-oriented reference guide will also benefit consultants or infrastructure architects who design and deploy vSphere 6.5 environments.What You Will LearnUpgrade your existing vSphere environment or perform a fresh deployment.Automate the deployment and management of large sets of ESXi hosts in your vSphere EnvironmentConfigure and manage FC, iSCSI, and NAS storage, and get more control over how storage resources are allocated and managedConfigure vSphere networking by deploying host-wide and data center-wide switches in your vSphere environmentConfigure high availability on a host cluster and learn how to enable the fair distribution and utilization of compute resourcesPatch and upgrade the vSphere environmentHandle certificate request generation and renew component certificatesMonitor performance of a vSphere environmentIn DetailVMware vSphere is a complete and robust virtualization product suite that helps transform data centers into simplified on-premises cloud infrastructures, providing for the automation and orchestration of workload deployment and life cycle management of the infrastructure. This book focuses on the latest release of VMware vSphere and follows a recipe-based approach, giving you hands-on instructions required to deploy and manage a vSphere environment.The book starts with the procedures involved in upgrading your existing vSphere infrastructure to vSphere 6.5, followed by deploying a new vSphere 6.5 environment. Then the book delves further into the procedures involved in managing storage and network access to the ESXi hosts and the virtual machines running on them. Moving on, the book covers high availability and fair distribution/utilization of clustered compute and storage resources.Finally, the book covers patching and upgrading the vSphere infrastructure using VUM, certificate management using VMCA, and finishes with a chapter covering the tools that can be used to monitor the performance of a vSphere infrastructure.Style and approachThis book will quickly get you started with managing VMware components. COMPUTERS,System Administration,Virtualization & Containerization

Mastering VMware vSphere 6.7 Master your virtual environment with the ultimate vSphere guide Mastering VMware vSphere 6.7 is the fully updated edition of the bestselling guide to VMware's virtualization solution. With comprehensive coverage of this industry-leading toolset, this book acts as an informative guide and valuable reference. Step-by-step instruction walks you through installation, configuration, operation, security processes, and much more as you conquer the management and automation of your virtual environment. Written by certified VMware vExperts, this indispensable guide provides hands-on instruction and detailed conceptual explanations, anchored by practical applications and real-world examples. This book is the ultimate guide to vSphere, helping administrators master their virtual environment. Learn to: Install, configure, and manage the vCenter Server components Leverage the Support Tools to provide maintenance and updates Create and configure virtual networks, storage devices, and virtual machines Implement the latest features to ensure compatibility and flexibility Manage resource allocation and utilization to meet application needs Monitor infrastructure performance and availability Automate and orchestrate routine administrative tasks Mastering VMware vSphere 6.7 is what you need to stay up-to-date on VMware's industry-leading software for the virtualized datacenter. COMPUTERS,System Administration,Virtualization & Containerization

Mastering VMware Horizon 7.8 Discover advanced virtualization techniques and strategies to deliver centralized desktop and application services Key Features Leverage advanced desktop virtualization techniques and strategies to transform your organization Build better virtualized services for your users with VMware Horizon 7.8 Develop and deploy end-to-end virtualized solutions Book Description Desktop virtualization can be tough, but VMware Horizon 7.8 changes all that. With a rich and adaptive UX, improved security,and a range of useful features for storage and networking optimization, there's plenty to love. But to properly fall in love with it, you need to know how to use it, and that means venturing deeper into the software and taking advantage of its extensive range of features, many of which are underused and underpromoted. This guide will take you through everything you need to know to not only successfully virtualize your desktop infrastructure, but also to maintain and optimize it to keep all your users happy. We'll show you how to assess and analyze your infrastructure, and how to use that analysis to design a solution that meets your organizational and user needs. Once you've done that, you'll find out how to build your virtualized environment, before deploying your virtualized solution. But more than that,we'll also make sure you know everything you need to know about the full range of features on offer, including the mobile cloud, so that you can use them to take full control of your virtualized infrastructure. What you will learn Successfully configure Horizon 7.8 for the needs of your users Deliver virtual desktops, session-based desktops, and hosted applications Become familiar with how to develop, and deploy, a complete, end-to-end solution Discover how to optimize desktop OS images for virtual desktops Build, optimize, and tune desktop operating systems to deliver a superior end user experience Explore the Horizon 7.8 infrastructure so that you can take full advantage of it Who this book is for This book is ideal for system admins, and solution architects interested in gaining hands-on experience with virtualization. It will take you to an advanced level, but at a pace that ensures you are always solving real-world problems. Some experience in desktop management using Windows and Microsoft Office (and familiarity with Active Directory, SQL, Windows Remote Desktop Session Hosting, and VMware vSphere technology) is necessary. COMPUTERS,System Administration,Virtualization & Containerization

The Kubernetes Book Understand the Kubernetes ecosystem and learn techniques to run fault-tolerant, scalable applications Key Features Gain insight into the inner workings of Kubernetes Learn how to deploy and manage applications on Kubernetes Explore ways to build and secure Kubernetes clusters Book Description Kubernetes is the leading orchestrator of cloud-native apps. With knowledge of how to work with Kubernetes, you can easily deploy and manage applications on the cloud or in your on-premises data center. The book begins by introducing you to Kubernetes and showing you how to install it. You'll learn how to use Kubernetes Services and bring stable and reliable networking to apps that are deployed on Kubernetes. You'll delve deep into the powerful storage subsystem of Kubernetes and learn how to leverage the variety of external storage backends in your applications. As the book progresses, it shows you how to use features such as DaemonSets, Helm, and RBAC to enhance your Kubernetes applications. You'll explore the six categories of identifying vulnerabilities and look at a few ways to prevent and mitigate them. You'll also look at ways to secure the software delivery pipeline by discussing some image-related best practices. The book ends by sharing with you some resources that'll help take your Kubernetes knowledge to the next level. By the end of the book, you'll have the confidence and skills to leverage all the features of Kubernetes to develop scalable applications. What you will learn Explore cluster-level and node-level isolation and runtime isolation options Use Kubernetes Deployments for self-healing, scaling, and updating apps Manage Kubernetes clusters with kubectl Write a Container Storage Interface (CSI) plugin to work across multiple orchestrators Use Kubernetes features such as Jons and CronJobs in your apps Identify vulnerabilities and learn measures to prevent and mitigate them Who this book is for If you want to be more comfortable using Kubernetes to orchestrate your containerized applications, this is the ideal book for you. To easily grasp the concepts explained in this book, you must be familiar with Docker and containers. COMPUTERS,System Administration,Virtualization & Containerization

Hands-On Linux Administration on Azure Develop a solid understanding of cloud computing, Linux virtual machine, container virtualization, and other fundamental concepts to create and manage your Linux workload in Azure Key Features Deploy and manage virtual machines in the Azure environment Explore open source tools to integrate automation and orchestration Implement Linux features to create and manage containers Book Description Thanks to its flexibility in delivering scalable cloud solutions, Microsoft Azure is a suitable platform for managing all your workloads. You can use it to implement Linux virtual machines and containers, and to create applications in open source languages with open APIs. This Linux administration book first takes you through the fundamentals of Linux and Azure to prepare you for the more advanced Linux features in later chapters. With the help of real-world examples, you'll learn how to deploy virtual machines (VMs) in Azure, expand their capabilities, and manage them efficiently. You will manage containers and use them to run applications reliably, and in the concluding chapter, you'll explore troubleshooting techniques using a variety of open source tools. By the end of this book, you'll be proficient in administering Linux on Azure and leveraging the tools required for deployment. What you will learn Grasp the fundamentals of virtualization and cloud computing Understand file hierarchy and mount new filesystems Maintain the life cycle of your application in Azure Kubernetes Service Manage resources with the Azure CLI and PowerShell Manage users, groups, and filesystem permissions Use Azure Resource Manager to redeploy virtual machines Implement configuration management to configure a VM correctly Build a container using Docker Who this book is for If you are a Linux administrator or a Microsoft professional looking to deploy and manage your workload in Azure, this book is for you. Although not necessary, knowledge of Linux and Azure will assist with understanding core concepts. COMPUTERS,System Administration,Virtualization & Containerization

Mastering VMware NSX for vSphere A clear, comprehensive guide to VMware ’ s latest virtualization solution Mastering VMware NSX for vSphere is the ultimate guide to VMware’s network security virtualization platform. Written by a rock star in the VMware community, this book offers invaluable guidance and crucial reference for every facet of NSX, with clear explanations that go far beyond the public documentation. Coverage includes NSX architecture, controllers, and edges; preparation and deployment; logical switches; VLANS and VXLANS; logical routers; virtualization; edge network services; firewall security; and much more to help you take full advantage of the platform’s many features. More and more organizations are recognizing both the need for stronger network security and the powerful solution that is NSX; usage has doubled in the past year alone, and that trend is projected to grow—and these organizations need qualified professionals who know how to work effectively with the NSX platform. This book covers everything you need to know to exploit the platform’s full functionality so you can: Step up security at the application level Automate security and networking services Streamline infrastructure for better continuity Improve compliance by isolating systems that handle sensitive data VMware’s NSX provides advanced security tools at a lower cost than traditional networking. As server virtualization has already become a de facto standard in many circles, network virtualization will follow quickly—and NSX positions VMware in the lead the way vSphere won the servers. NSX allows you to boost security at a granular level, streamline compliance, and build a more robust defense against the sort of problems that make headlines. Mastering VMware NSX for vSphere helps you get up to speed quickly and put this powerful platform to work for your organization. COMPUTERS,System Administration,Virtualization & Containerization

ACI Advanced Monitoring and Troubleshooting Advanced real-world Cisco Application Centric Infrastructure (ACI) monitoring and troubleshooting This expert guide and reference will help you confidently deploy, support, monitor, and troubleshoot ACI fabrics and components. It is also designed to help you prepare for your Cisco DCACIA (300-630) exam, earning Cisco Certified Specialist–ACI Advanced Implementation certification and credit toward CCNP Data Center certification if you choose. Authored by three leading Cisco ACI experts, it combines a solid conceptual foundation, in-depth technical knowledge, and practical techniques. It also contains proven features to help exam candidates prepare, including review questions in most chapters, and Key Topic icons highlighting concepts covered on the exam. The authors thoroughly introduce ACI functions, components, policies, command-line interfaces, connectivity, fabric design, virtualization and service integration, automation, orchestration, and more. Next, they introduce best practices for monitoring and management, including the use of faults, health scores, tools, the REST API, in-band and out-of-band management techniques, and monitoring protocols. Proven configurations are provided, with steps for verification. Finally, they present advanced forwarding and troubleshooting techniques for maximizing ACI performance and value. ACI Advanced Monitoring and Troubleshooting is an indispensable resource for every data center architect, engineer, developer, network or virtualization administrator, and operations team member working in ACI environments. Understand Cisco ACI core functions, components, and protocols Apply the ACI Policy-Based Object Model to develop overall application frameworks Use command-line interfaces to manage and monitor Cisco ACI systems Master proven options for ACI physical and logical fabric design Establish connectivity for compute, storage, and service devices, switches, and routers Gain visibility into virtualization layers through VMM, and integrate hypervisors from multiple vendors Seamlessly integrate Layer 4 to Layer 7 services such as load balancing and firewalling Automate and orchestrate for fast deployment with the REST API, scripting, and Ansible Minimize downtime and maximize ROI through more effective monitoring and configuration Thoroughly master concepts and techniques for advanced ACI and VXLAN forwarding Build deep practical expertise for quickly troubleshooting critical events Gain quick visibility into traffic flows and streamline problem isolation with the ACI Visibility & Troubleshooting Tool Walk through multiple real-world troubleshooting scenarios step-by-step Forewords written by Yusuf Bhaiji, Director of Certifications, Cisco Systems; and Ronak Desai, VP of Engineering for the Data Center Networking Business Unit, Cisco Systems. This book is part of the Networking Technology Series from Cisco Press, which offers networking professionals valuable information for constructing efficient networks, understanding new technologies, and building successful careers. COMPUTERS,System Administration,Virtualization & Containerization

Active Directory Organize your network resources by learning how to design, manage, and maintain Active Directory. Updated to cover Windows Server 2012, the fifth edition of this bestselling book gives you a thorough grounding in Microsoft’s network directory service by explaining concepts in an easy-to-understand, narrative style. You’ll negotiate a maze of technologies for deploying a scalable and reliable AD infrastructure, with new chapters on management tools, searching the AD database, authentication and security protocols, and Active Directory Federation Services (ADFS). This book provides real-world scenarios that let you apply what you’ve learned—ideal whether you’re a network administrator for a small business or a multinational enterprise. Upgrade Active Directory to Windows Server 2012 Learn the fundamentals, including how AD stores objects Use the AD Administrative Center and other management tools Learn to administer AD with Windows PowerShell Search and gather AD data, using the LDAP query syntax Understand how Group Policy functions Design a new Active Directory forest Examine the Kerberos security protocol Get a detailed look at the AD replication process COMPUTERS,System Administration,Windows Administration

Active Directory Cookbook Take the guesswork out of deploying, administering, and automating Active Directory. With hundreds of proven recipes, the updated edition of this popular cookbook provides quick, step-by-step solutions to common (and not so common) problems you might encounter when working with Microsoft’s network directory service. This fourth edition includes troubleshooting recipes for Windows Server 2012, Windows 8, and Exchange 2013, based on valuable input from Windows administrators. You’ll also find quick solutions for the Lightweight Directory Access Protocol (LDAP), Active Directory Lightweight Directory Services (AD LDS), multi-master replication, DNS, Group Policy, and many other features. Manage new AD features, such as the Recycle Bin, Group Managed Service Accounts, and fine-grained password policies Work with AD from the command line and use Windows PowerShell to automate tasks Remove and create forests, domains, and trusts Create groups, modify group scope and type, and manage membership Delegate control, view and modify permissions, and handle Kerberos tickets Import and export data with LDAP Data Interchange Format (LDIF) Synchronize multiple directories and enforce data integrity within a single or multiple stores Back up AD, and perform authoritative and non-authoritative restores COMPUTERS,System Administration,Windows Administration

System Center 2016 Virtual Machine Manager Cookbook Maximize your administration skills effectively and efficiently About This Book Implement cost-effective virtualization solutions for your organization with actionable recipes Explore the concepts of VMM with real-world use cases Use the latest features with VMM 2016 such as Cluster OS Rolling Upgrade, Guarded Fabric and Storage Spaces Direct Who This Book Is For If you are a solutions architect, technical consultant, administrator, or any other virtualization enthusiast who needs to use Microsoft System Center Virtual Machine Manager in a real-world environment, then this is the book for you. What You Will Learn Plan and design a VMM architecture for real-world deployment Configure fabric resources, including compute, networking, and storage Create and manage Storage Spaces Direct clusters in VMM Configure Guarded Fabric with Shielded VMs Create and deploy virtual machine templates and multi-tier services Manage Hyper-V and VMware environments from VMM Enhance monitoring and management capabilities Upgrade to VMM 2016 from previous versions In Detail Virtual Machine Manager (VMM) 2016 is part of the System Center suite to configure and manage datacenters and offers a unified management experience on-premises and Azure cloud. This book will be your best companion for day-to-day virtualization needs within your organization, as it takes you through a series of recipes to simplify and plan a highly scalable and available virtual infrastructure. You will learn the deployment tips, techniques, and solutions designed to show users how to improve VMM 2016 in a real-world scenario. The chapters are divided in a way that will allow you to implement the VMM 2016 and additional solutions required to effectively manage and monitor your fabrics and clouds. We will cover the most important new features in VMM 2016 across networking, storage, and compute, including brand new Guarded Fabric, Shielded VMs and Storage Spaces Direct. The recipes in the book provide step-by-step instructions giving you the simplest way to dive into VMM fabric concepts, private cloud, and integration with external solutions such as VMware, Operations Manager, and the Windows Azure Pack. By the end of this book, you will be armed with the knowledge you require to start designing and implementing virtual infrastructures in VMM 2016. Style and approach This book follows a recipe-based approach similar to our previous two successful editions, covering the practical application of the major features in VMM 2016. COMPUTERS,System Administration,Windows Administration

Docker on Windows Learn how to run new and old applications in Docker containers on Windows - modernizing the architecture, improving security and maximizing efficiency. Key Features Run .NET Framework and .NET Core apps in Docker containers for efficiency, security and portability Design distributed containerized apps, using enterprise-grade open source software from Docker Hub Build a CI/CD pipeline with Docker, going from source to a production Docker Swarm in the cloud Book Description Docker on Windows, Second Edition teaches you all you need to know about Docker on Windows, from the 101 to running highly-available workloads in production. You'll be guided through a Docker journey, starting with the key concepts and simple examples of .NET Framework and .NET Core apps in Docker containers on Windows. Then you'll learn how to use Docker to modernize the architecture and development of traditional ASP.NET and SQL Server apps. The examples show you how to break up legacy monolithic applications into distributed apps and deploy them to a clustered environment in the cloud, using the exact same artifacts you use to run them locally. You'll see how to build a CI/CD pipeline which uses Docker to compile, package, test and deploy your applications. To help you move confidently to production, you'll learn about Docker security, and the management and support options. The book finishes with guidance on getting started with Docker in your own projects. You'll walk through some real-world case studies for Docker implementations, from small-scale on-premises apps to very large-scale apps running on Azure. What you will learn Understand key Docker concepts: images, containers, registries and swarms Run Docker on Windows 10, Windows Server 2019, and in the cloud Deploy and monitor distributed solutions across multiple Docker containers Run containers with high availability and failover with Docker Swarm Master security in-depth with the Docker platform, making your apps more secure Build a Continuous Deployment pipeline, running Jenkins and Git in Docker Debug applications running in Docker containers using Visual Studio Plan the adoption of Docker in your organization Who this book is for If you want to modernize an old monolithic application without rewriting it, smooth the deployment to production, or move to DevOps or the cloud, then Docker is the enabler for you. This book gives you a solid grounding in Docker so you can confidently approach all of these scenarios. COMPUTERS,System Administration,Windows Administration

AWS SysOps Cookbook Become an AWS SysOps administrator and explore best practices to maintain a well-architected, resilient, and secure AWS environment Key Features Explore AWS Cloud functionalities through a recipe-based approach Get to grips with a variety of techniques for automating your infrastructure Discover industry-proven best practices for architecting reliable and efficient workloads Book Description AWS is an on-demand remote computing service providing cloud infrastructure over the internet with storage, bandwidth, and customized support for APIs. This updated second edition will help you implement these services and efficiently administer your AWS environment. You will start with the AWS fundamentals and then understand how to manage multiple accounts before setting up consolidated billing. The book will assist you in setting up reliable and fast hosting for static websites, sharing data between running instances and backing up data for compliance. By understanding how to use compute service, you will also discover how to achieve quick and consistent instance provisioning. You'll then learn to provision storage volumes and autoscale an app server. Next, you'll explore serverless development with AWS Lambda, and gain insights into using networking and database services such as Amazon Neptune. The later chapters will focus on management tools like AWS CloudFormation, and how to secure your cloud resources and estimate costs for your infrastructure. Finally, you'll use the AWS well-architected framework to conduct a technology baseline review self-assessment and identify critical areas for improvement in the management and operation of your cloud-based workloads. By the end of this book, you'll have the skills to effectively administer your AWS environment. What you will learn Secure your account by creating IAM users and avoiding the use of the root login Simplify the creation of a multi-account landing zone using AWS Control Tower Master Amazon S3 for unlimited, cost-efficient storage of data Explore a variety of compute resources on the AWS Cloud, such as EC2 and AWS Lambda Configure secure networks using Amazon VPC, access control lists, and security groups Estimate your monthly bill by using cost estimation tools Learn to host a website with Amazon Route 53, Amazon CloudFront, and S3 Who this book is for If you are an administrator, DevOps engineer, or an IT professional interested in exploring administrative tasks on the AWS Cloud, then this book is for you. Familiarity with cloud computing platforms and some understanding of virtualization, networking, and other administration-related tasks is assumed. COMPUTERS,System Administration,Windows Administration

MCA Modern Desktop Administrator Complete Study Guide The ultimate study guide for Microsoft 365 Certified Associate (MCA) Modern Desktop certification—covers the new Exam MD-100 and the new Exam MD-101 in one book! Referred to as the Modern Desktop, Microsoft 365 is Microsoft’s new suite of modern workplace services comprising Windows 10, Office 365, and Enterprise Mobility & Security. IT administrators tasked with deploying and implementing Modern Desktop are required to configure, secure, manage, and monitor devices and applications in enterprise environments. Success on the MCA Modern Desktop Administrator certification exam is essential for IT professionals seeking to expand their job opportunities and advance their careers. The MCA Modern Desktop Administrator Complete Study Guide is an indispensable resource for candidates preparing for certification. This guide covers 100% of all exam objectives for the new Exam MD-100: Windows 10 and the new Exam-101: Managing Modern Desktops. All aspects of both new exams are covered, including in-depth information on advanced topics and technologies. Included is access to Sybex's comprehensive online learning environment—offering an assessment test, bonus practice exams, electronic flashcards, a searchable glossary, and videos for many of the chapter exercises (ONLY available for Exam MD-100). This must-have guide enables users to: Configure devices, core services, networking, storage, users, updates, and system and data recovery Implement, install, maintain, manage, and monitor Windows 10 Plan desktop deployment and Microsoft Intune device management solutions Manage identities, applications, remote access, and data access and protection Review real-world scenarios, hands-on exercises, and challenging practice questions The MCA Modern Desktop Administrator Complete Study Guide: Exam MD-100 and Exam MD-101 is an essential tool for anyone preparing for the exams and students and IT professionals looking to learn new skills or upgrade their existing skills. COMPUTERS,System Administration,Windows Administration

Handbook of Usability Testing Whether it's software, a cell phone, or a refrigerator, your customer wants - no, expects - your product to be easy to use. This fully revised handbook provides clear, step-by-step guidelines to help you test your product for usability. Completely updated with current industry best practices, it can give you that all-important marketplace advantage: products that perform the way users expect. You'll learn to recognize factors that limit usability, decide where testing should occur, set up a test plan to assess goals for your product's usability, and more. COMPUTERS,User Interfaces

Usable Usability The A-to-Z guide to spotting and fixing usability problems Frustrated by pop-ups? Forms that make you start over if you miss a field? Nonsensical error messages? You're not alone! This book helps you simply get it right the first time (or fix what's broken). Boasting a full-color interior packed with design and layout examples, this book teaches you how to understand a user's needs, divulges techniques for exceeding a user's expectations, and provides a host of hard won advice for improving the overall quality of a user's experience. World-renowned UX guru Eric Reiss shares his knowledge from decades of experience making products useable for everyone...all in an engaging, easy-to-apply manner. Reveals proven tools that simply make products better, from the users' perspective Provides simple guidelines and checklists to help you evaluate and improve your own products Zeroes in on essential elements to consider when planning a product, such as its functionality and responsiveness, whether or not it is ergonomic, making it foolproof, and more Addresses considerations for product clarity, including its visibility, understandability, logicalness, consistency, and predictability Usable Usability walks you through numerous techniques that will help ensure happy customers and successful products! COMPUTERS,User Interfaces

User-Centered Design How do you design engaging applications that people love to use? This book demonstrates several ways to include valuable input from potential clients and customers throughout the process. With practical guidelines and insights from his own experience, author Travis Lowdermilk shows you how usability and user-centered design will dramatically change the way people interact with your application. Learn valuable strategies for conducting each stage of the design process—from interviewing likely users and discovering your application’s purpose to creating a rich user experience with sound design principles. User-Centered Design is invaluable no matter what platform you use or audience you target. Explore usability and how it relates to user-centered design Learn how to deal with users and their unique personalities Clarify your application’s purpose, using a simple narrative to describe its use Plan your project’s development with a software development life cycle Be creative within the context of your user experience goals Use visibility, consistency, and other design principles to enhance user experience Collect valuable user feedback on your prototype with surveys, interviews, and usability studies COMPUTERS,User Interfaces

Evil by Design How to make customers feel good about doing what you want Learn how companies make us feel good about doing what they want. Approaching persuasive design from the dark side, this book melds psychology, marketing, and design concepts to show why we’re susceptible to certain persuasive techniques. Packed with examples from every nook and cranny of the web, it provides easily digestible and applicable patterns for putting these design techniques to work. Organized by the seven deadly sins, it includes: Pride — use social proof to position your product in line with your visitors’ values Sloth — build a path of least resistance that leads users where you want them to go Gluttony — escalate customers’ commitment and use loss aversion to keep them there Anger — understand the power of metaphysical arguments and anonymity Envy — create a culture of status around your product and feed aspirational desires Lust — turn desire into commitment by using emotion to defeat rational behavior Greed — keep customers engaged by reinforcing the behaviors you desire Now you too can leverage human fallibility to create powerful persuasive interfaces that people will love to use — but will you use your new knowledge for good or evil? Learn more on the companion website, evilbydesign.info. COMPUTERS,User Interfaces

People and Computers XI Disciplines, including Human-Computer Interaction (HCI), consist of knowledge supporting practices which solve general problems (Long & Dowell, 1989). A disci pline thus requires knowledge to be acquired which can be applied by practitioners to solve problems within the scope of the discipline. In the case of HCI, such knowledge is being acquired through research and, less formally, through the description of successful system development practice. Some have argued that knowledge is further embodied in the artefacts. HCI knowledge is applied to solve user interface design problems. Such applica tion is facilitated if the knowledge is expressed in a conception which makes explicit the design problems of practitioners. A conception has been proposed by Dowell & Long (1989). The conception provides a framework within which to reason about the implications of designs for system performance. The framework is concordant with the trend towards design, discernible in recent HCI research. It is further compatible with notions of top-down design, fundamental to software engineering practice. 2 Teaching and the HeI Research and Development Gap 2.1 An Assessment of Current HCI Education Teaching is one means by which practitioners learn to specify discipline problems. It is also a means by which they acquire knowledge to enable the problems to be solved. COMPUTERS,User Interfaces

Auditory User Interfaces Auditory User Interfaces: Toward the Speaking Computer describes a speech-enabling approach that separates computation from the user interface and integrates speech into the human-computer interaction. The Auditory User Interface (AUI) works directly with the computational core of the application, the same as the Graphical User Interface. The author's approach is implemented in two large systems, ASTER - a computing system that produces high-quality interactive aural renderings of electronic documents - and Emacspeak - a fully-fledged speech interface to workstations, including fluent spoken access to the World Wide Web and many desktop applications. Using this approach, developers can design new high-quality AUIs. Auditory interfaces are presented using concrete examples that have been implemented on an electronic desktop. This aural desktop system enables applications to produce auditory output using the same information used for conventional visual output. Auditory User Interfaces: Toward the Speaking Computer is for the electrical and computer engineering professional in the field of computer/human interface design. It will also be of interest to academic and industrial researchers, and engineers designing and implementing computer systems that speak. Communication devices such as hand-held computers, smart telephones, talking web browsers, and others will need to incorporate speech-enabling interfaces to be effective. COMPUTERS,User Interfaces

Organized Activity and its Support by Computer Organized Human Activity and Its Support by Computer proposes an answer to the question: what are computers for? With technical expertise, Anatol Holt analyzes human activity and its relevance to computer use. Holt interleaves a theory about the universal aspect of social life with a vision of how to harness computer power. `This book is a culmination of a life of work that exemplifies two characteristics of the author: intellectual passion, and a concern for what matters to people. In the past thirty years, Holt has been a participant in the computing work at every level, from managing computer systems to developing commercial software to publishing theoretical articles in academic journals. His breadth of knowledge and experience makes possible the interweaving of theory and practice that shapes the fabric of this book. People often make a false opposition between theory and practice. In this case, it is a synergy: practice guides the theory, and the theory is grounded in its application.' Terry Winograd, Stanford University Organized Human Activity and Its Support by Computer will be of interest to those concerned with computers, especially those with and interest in `groupware'. Particular relevance to social scientists, management scientists, students of law, and philosophers are also addressed. Though technical in spirit and method, this book does not expect significant prior computer knowledge of the reader. COMPUTERS,User Interfaces

Design, Specification and Verification of Interactive Systems ’97 An increasing recognition of the role of the human-system interface is leading to new extensions and styles of specification. Techniques are being developed that facilitate the expression of user-oriented requirements and the refinement and checking of specifications of interactive systems. This book reflects the state of the art in this important area and also contains a summary of working group discussions about how the various techniques represented might be applied to a common case study. COMPUTERS,User Interfaces

Business Object Design and Implementation Over the past 10 years, object technology has gained widespread acceptance within the software industry. Within a wider context, however, it has made little impact on the core applications which support businesses in carrying out their tasks. This volume contains a collection of papers establishing the need for Business Objects, with particular reference to work undertaken by the Object Management Group (OMG). The emphasis is on defining an agenda for establishing Business Object standards and architectures, for developing software technology to support Business Objects applications and managing object oriented development projects. The wide variety of papers presented, and their authors' expertise, make this book a significant contribution to the development of Business Objects and their management. COMPUTERS,User Interfaces

People and Computers XII Most organisations try to protect their systems from unauthorised access, usually through passwords. Considerable resources are spent designing secure authentication mechanisms, but the number of security breaches and problems is still increasing (DeAlvare, 1990; Gordon, 1995; Hitchings, 1995). Unauthorised access to systems, and resulting theft of information or misuse of the system, is usually due to hackers "cracking" user passwords, or obtaining them through social engineering. System security, unlike other fields of system development, has to date been regarded as an entirely technical issue - little research has been done on usability or human factors related to use of security mechanisms. Hitchings (1995) concludes that this narrow perspective has produced security mechanisms which are much less effective than they are generally thought to be. Davis & Price (1987) point out that, since security is designed, implemented, used and breached by people, human factors should be considered in the design of security mechanism. It seems that currently hackers pay more attention to human factors than security designers do. The technique of social engineering, for instanc- obtaining passwords by deception and persuasion- exploits users' lack of security awareness. Hitchings (1995) also suggests that organisational factors ought to be considered when assessing security systems. The aim of the study described in this paper was to identify usability and organisational factors which affect the use of passwords. The following section provides a brief overview of authentication systems along with usability and organisational issues which have been identified to date. 1. COMPUTERS,User Interfaces

Proceedings of the Fifth European Conference on Computer Supported Cooperative Work The emergence of network facilities and the increased availability of personal computer systems over the last decade has seen the development of interest in the use of computers to support cooperative work. This volume presents the proceedings of the fifth European conference on Computer Supported Cooperative Work (CSCW). This is a multidisciplinary area which embraces both the development of new technologies and an understanding of the relationship between technology and society. This volume contains a collection of papers that encompass activities in the field. It includes papers addressing distribute virtual environments, the use of the Internet, studies of work and emerging models, theories and techniques to support the development of cooperative applications. The papers present emerging technologies alongside new methods and approaches to the development of this important class of applications. The work in this volume represents the best of the current research and practice within CSCW. The collection of papers presented here will appeal to both researchers and practitioners alike, as they combine an understanding of the nature of work with the possibilities offered by new technologies. COMPUTERS,User Interfaces

Kasparov versus Deep Blue In February 1996, a chess-playing computer known as Deep Blue made history by defeating the reigning world chess champion, Gary Kasparov, in a game played under match conditions. Kasparov went on to win the six-game match 4-2 and at the end of the match announced that he believed that chess computing had come of age. This book provides an enthralling account of the match and of the story that lies behind it: the evolution of chess-playing computers and the development of Deep Blue. The story of chess-playing computers goes back a long way and the author provides a whistlestop tour of the highlights of this history. As the development comes to its culmination in Philadelphia, we meet the Deep Blue team, Garry Kasparov and each of the historic six games is provided in full with a detailed commentary. Chess grandmaster Yasser Seirawan provided a lively commentary throughout the match and here provides a Foreword about the significance of this event. COMPUTERS,User Interfaces

Human Comfort and Security of Information Systems The Commission of the European Union, through its Fourth Framework R&D programme is committed to the development of the Information Society. There is no doubt that there will be many radical changes in all aspects of society caused by the far-reaching impact of continuing advances in information and communi cation technologies. Many of these changes cannot be predicted, but that uncer tainty must not stop us from moving forward. The challenge is to ensure that these technologies are put to use in the most beneficial manner, taking fully into account the rich cultural and linguistic backgrounds within the peoples of Europe. We have a duty to ensure that the ultimate end-users of the technology are involved in the development and application of that technology to help shape its use. Without this active involvement, designers will not understand the individual and organisational requirements of the users, and the users will not understand the impact and applicability of the new technology. Failure on either account will lead to a sense of resentment on the part of the users and a lost opportunity to improve the quality of human life. The work, sponsored by the Human Comfort & Security sub-domain of the ESPRIT programme, has a central part to play in the creation of the Information Society, lying as it does at the interface between the technology and the user. COMPUTERS,User Interfaces

Design, Specification and Verification of Interactive Systems ’96 Making systems easier to use implies an ever increasing complexity in managing communication between users and applications. Indeed an increasing part of the application code is devoted to the user interface portion. In order to manage this complexity, it is important to have tools, notations, and methodologies which support the designer’s work during the refinement process from specification to implementation. Selected revised papers from the Eurographics workshop in Namur review the state of the art in this area, comparing the different existing approaches to this field in order to identify the principle requirements and the most suitable notations, and indicate the meaningful results which can be obtained from them. COMPUTERS,User Interfaces

Remote Cooperation Computer supported work is increasingly being done out of the traditional office environment, for example whilst travelling or at home and there is a growing need to support the cooperative aspects of such work. Remote Cooperation looks at ways of improving the available communications, through the use of packet radio and compression techniques, in order to reduce the imbalance between office-based and mobile workers. It also assesses how the effectiveness of the existing communications infrastructure can be improved, by providing cooperative applications which fit within its limitations. Broadly divided into five sections - social and economic context, application domains, software technology and infrastructure, communications technology and infrastructure, working and learning from home - this volume contains contributions from both the research community and industry. COMPUTERS,User Interfaces

Human Machine Symbiosis There is now a serious discussion taking place about the moment at which human beings will be surpassed and replaced by the machine. On the one hand we are designing machines which embed more and more human intelligence, but at the same time we are in danger of becoming more and more like machines. In these circumstances, we all need to consider: • What can we do? • What should we do? • What are the alternatives of doing it? This book is about the human-centred alternative of designing systems and technologies. This alternative is rooted in the European tradition of human-centredness which emphasises the symbiosis of human capabilities and machine capacity. The human-centred tra dition celebrates the diversity of human skill and ingenuity and provides an alternative to the 'mechanistic' paradigm of 'one best way', the 'sameness of science' and the 'dream of the exact language'. This alternative vision has its origin in the founding European human-centred movements of the 1970s. These include the British movement of Socially Useful Technology, the Scandinavian move ment of Democratic Participation, and the German movement of Humanisation of Work and Technology. The present volume brings together various strands of human-centred systems philosophy which span the conceptual richness and cultural diversity of the human-centred movements. The core ideas of human-centredness include human-machine symbiosis, the tacit dimension of knowl edge, the system as a tool rather than a machine, dialogue, partici pation, social shaping and usability. COMPUTERS,User Interfaces

Industrial Cultures and Production This book contains a selection of articles on the subject of 'Culture and Production'. They are results of international conferences held in Tokyo, Washington and Bremen between 1991 and 1994. The International Research Network on Culture and Production (CAPIRN) carried out a 5-year joint research project examining the impact of different industrial cultures on the development and implementation, and above all on the international transfer of technology. The machine tools sector was selected for this international comparative study, because over the last 15 years this global market has undergone dramatic changes that cannot be adequately explained by traditional economic theories of international competition. The 'industrial culture' research concept permits an analysis and understanding of hitherto unrecognised interrelationships between the dimensions of different industrial cultures and the process of technological innovation in international competition. The special challenge faced by CAPIRN was to develop the theoretical concept of industrial culture further and to apply it within a large-scale international study. A considerable amount of work in this field has been published by CAPIRN members since 1990. This book is the first compilation of research findings in the field of industrial culture. We wish to express our thanks to the national research councils in the participant countries, the FORCE and FAST programmes of the European Union, the Japanese Ministry for Industry, MITI, and the Hans Bockler Foundation, to mention only some of the many bodies that have provided support. COMPUTERS,User Interfaces

Proceedings of the Fourth European Conference on Computer-Supported Cooperative Work ECSCW ’95 Computer Supported Cooperative Work (CSCW) is an interdisciplinary research area devoted to exploring the issues of designing computer-based systems that enhance the abilities to cooperate and integrate activities in an efficient and flexible manner for people in cooperative work situations. This volume is a rigorous selection of papers that represent both practical and theoretical approaches to CSCW from many leading researchers in the field. As an interdisciplinary area of research, CSCW brings together widely disparate research traditions and perspectives from computer, human, organisational and design sciences. The papers selected reflect a variety of approaches and cultures in the field. Audience: Of interest to a wide audience because of the huge practical impact of the issues and the interdisciplinary nature of the problems and solutions proposed. In particular: researchers and professionals in computing, sociology, cognitive science, human factors, and system design. COMPUTERS,User Interfaces

Multimedia Interface Design in Education Proceedings of the NATO Advanced Research Workshop on Multi-media Interface Design in Education, held at Castel Vecchio Pascoli, Lucca, Italy, September 20-24, 1989 COMPUTERS,User Interfaces

Mobile Design Pattern Gallery When you’re under pressure to produce a well-designed, easy-to-navigate mobile app, there’s no time to reinvent the wheel—and no need to. This handy reference provides more than 90 mobile app design patterns, illustrated by 1,000 screenshots from current Android, iOS, and Windows Phone apps. Much has changed since this book’s first edition. Mobile OSes have become increasingly different, driving their own design conventions and patterns, and many designers have embraced mobile-centric thinking. In this edition, user experience professional Theresa Neil walks product managers, designers, and developers through design patterns in 11 categories: Navigation: get patterns for primary and secondary navigation Forms: break industry-wide habits of bad form design Tables: display only the most important information Search, sort, and filter: make these functions easy to use Tools: create the illusion of direct interaction Charts: learn best practices for basic chart design Tutorials & Invitations: invite users to get started and discover features Social: help users connect and become part of the group Feedback & Affordance: provide users with timely feedback Help: integrate help pages into a smaller form factor Anti-Patterns: what not to do when designing a mobile app COMPUTERS,User Interfaces

Learning Responsive Web Design Deliver an optimal user experience to all devices—including tablets, smartphones, feature phones, laptops, and large screens—by learning the basics of responsive web design. In this hands-on guide, UX designer Clarissa Peterson explains how responsive web design works, and takes you through a responsive workflow from project kickoff to site launch. Ideal for anyone involved in the process of creating websites—not just developers—this book teaches you fundamental strategies and techniques for using HTML and CSS to design websites that not only adapt to any screen size, but also use progressive enhancement to provide a better user experience based on device capabilities such as touchscreens and retina displays. Start with content strategy before creating a visual design Learn why your default design should be for the narrowest screens Explore the HTML elements and CSS properties essential for responsive web design Use media queries to display different CSS styles based on a device’s viewport width Handle elements such as images, typography, and navigation Use performance optimization techniques to make your site lighter and faster COMPUTERS,User Interfaces

About Face The essential interaction design guide, fully revised and updated for the mobile age About Face: The Essentials of Interaction Design, Fourth Edition is the latest update to the book that shaped and evolved the landscape of interaction design. This comprehensive guide takes the worldwide shift to smartphones and tablets into account. New information includes discussions on mobile apps, touch interfaces, screen size considerations, and more. The new full-color interior and unique layout better illustrate modern design concepts. The interaction design profession is blooming with the success of design-intensive companies, priming customers to expect "design" as a critical ingredient of marketplace success. Consumers have little tolerance for websites, apps, and devices that don't live up to their expectations, and the responding shift in business philosophy has become widespread. About Face is the book that brought interaction design out of the research labs and into the everyday lexicon, and the updated Fourth Edition continues to lead the way with ideas and methods relevant to today's design practitioners and developers. Updated information includes: Contemporary interface, interaction, and product design methods Design for mobile platforms and consumer electronics State-of-the-art interface recommendations and up-to-date examples Updated Goal-Directed Design methodology Designers and developers looking to remain relevant through the current shift in consumer technology habits will find About Face to be a comprehensive, essential resource. COMPUTERS,User Interfaces

Designing Mobile Payment Experiences Now that consumer purchases with mobile phones are on the rise, how do you design a payment app that’s safe, easy to use, and compelling? With this practical book, interaction and product designer Skip Allums provides UX best practices and recommendations to help you create familiar, friendly, and trustworthy experiences. Consumers want mobile transactions to be as fast and reliable as cash or bank cards. This book shows designers, developers, and product managers—from startups to financial institutions—how to design mobile payments that not only safeguard identity and financial data, but also provide value-added features that exceed customer expectations. Learn about the major mobile payment frameworks: NFC, cloud, and closed loop Examine the pros and cons of Google Wallet, Isis, Square, PayPal, and other payment apps Provide walkthroughs, demos, and easy registration to quickly gain a new user’s trust Design efficient point-of-sale interactions, using NFC, QR, barcodes, or geolocation Add peripheral services such as points, coupons and offers, and money management COMPUTERS,User Interfaces

UX Strategy User experience (UX) strategy requires a careful blend of business strategy and UX design, but until now, there hasn’t been an easy-to-apply framework for executing it. This hands-on guide introduces lightweight strategy tools and techniques to help you and your team craft innovative multi-device products that people want to use. Whether you’re an entrepreneur, UX/UI designer, product manager, or part of an intrapreneurial team, this book teaches simple-to-advanced strategies that you can use in your work right away. Along with business cases, historical context, and real-world examples throughout, you’ll also gain different perspectives on the subject through interviews with top strategists. Define and validate your target users through provisional personas and customer discovery techniques Conduct competitive research and analysis to explore a crowded marketplace or an opportunity to create unique value Focus your team on the primary utility and business model of your product by running structured experiments using prototypes Devise UX funnels that increase customer engagement by mapping desired user actions to meaningful metrics COMPUTERS,User Interfaces

Workflow Management Systems for Process Organisations As the business environment has become more and more turbulent over the past decade, information technology has begun to run into the danger of becoming an impediment rather than a motor of progress. In order to deal with the need for rapid, continuous change, computer science is challenged to develop novel interrelated information and communication technologies, and to align them with the social needs of co-operating user groups, as well as the management requirements of formal organisations. Workflow systems are among the most advertised technologies addressing this trend, but they mean different things to different people. Computer scientists understand workflows as a way to extract control from application programs, thus making them more flexible. Bureaucratic organisations (and most commercial products) perceive them as supporting a linear or branching flow of documents from one workplace to another - the next try after the failure cf office automation. This book takes another perspective, that of the modem customer-driven and groupwork-oriented process organisation. Extending the language-action perspective from the CSCW field, its customer-oriented view of workflows enables novel kinds of business process analysis, and leads to interesting new combinations of information and co-operation technologies. Schal's empirical studies show some of the pitfalls resulting from a naive use of these technologies, and exemplify ways to get around these pitfalls. COMPUTERS,User Interfaces

Verification and Validation of Complex Systems Prodeecings of the NATO Advanced Study Institute on Verification and Validation of Complex and Integrated Human-Machine Systems, held in Vimeiro, Portugal, July 6-17, 1992 COMPUTERS,User Interfaces

Design Leadership What does it take to be the leader of a design firm or group? We often assume they have all the answers, but in this rapidly evolving industry they’re forced to find their way like the rest of us. So how do good design leaders manage? If you lead a design group, or want to understand the people who do, this insightful book explores behind-the-scenes strategies and tactics from leaders of top design companies throughout North America. Based on scores of interviews he conducted over a two-year period—from small companies to massive corporations like ESPN—author Richard Banfield covers a wide range of topics, including: How design leaders create a healthy company culture Innovative ways for attracting and nurturing talent Creating productive workspaces, and handling remote employees Staying on top of demands while making time for themselves Consistent patterns among vastly different leadership styles Techniques and approaches for keeping the work pipeline full Making strategic and tactical plans for the future Mistakes that design leaders made—and how they bounced back COMPUTERS,User Interfaces

Understanding Industrial Design With the coming flood of connected products, many UX and interaction designers are looking into hardware design, a discipline largely unfamiliar to them. If you’re among those who want to blend digital and physical design concepts successfully, this practical book helps you explore seven long-standing principles of industrial design. Two present and former design directors at IDEO, the international design and innovation firm, use real-world examples to describe industrial designs that are sensorial, simple, enduring, playful, thoughtful, sustainable, and beautiful. You’ll learn how to approach, frame, and evaluate your designs as they extend beyond the screen and into the physical world. Sensorial: create experiences that fully engage our human senses Simple: design simple products that provide overall clarity in relation to their purpose Enduring: build products that wear well and live on as classics Playful: use playful design to go beyond functionality and create emotional connections Thoughtful: observe people’s struggles and anticipate their needs Sustainable: design products that reduce environmental impact Beautiful: elevate the experience of everyday products through beauty COMPUTERS,User Interfaces

Mapping Experiences Customers who have inconsistent, broken experiences with products and services are understandably frustrated. But it’s worse when people inside these companies can’t pinpoint the problem because they’re too focused on business processes. This practical book shows your company how to use alignment diagrams to turn valuable customer observations into actionable insight. With this unique tool, you can visually map your existing customer experience and envision future solutions. Product and brand managers, marketing specialists, and business owners will learn how experience diagramming can help determine where business goals and customer perspectives intersect. Once you’re armed with this data, you can provide users with real value. Mapping Experiences is divided into three parts: Understand the underlying principles of diagramming, and discover how these diagrams can inform strategy Learn how to create diagrams with the four iterative modes in the mapping process: setting up a mapping initiative, investigating the evidence, visualizing the process, and using diagrams in workshops and experiments See key diagrams in action, including service blueprints, customer journey maps, experience maps, mental models, and spatial maps and ecosystem models COMPUTERS,User Interfaces

Designing Voice User Interfaces Voice user interfaces (VUIs) are becoming all the rage today. But how do you build one that people can actually converse with? Whether you’re designing a mobile app, a toy, or a device such as a home assistant, this practical book guides you through basic VUI design principles, helps you choose the right speech recognition engine, and shows you how to measure your VUI’s performance and improve upon it. Author Cathy Pearl also takes product managers, UX designers, and VUI designers into advanced design topics that will help make your VUI not just functional, but great. Understand key VUI design concepts, including command-and-control and conversational systems Decide if you should use an avatar or other visual representation with your VUI Explore speech recognition technology and its impact on your design Take your VUI above and beyond the basic exchange of information Learn practical ways to test your VUI application with users Monitor your app and learn how to quickly improve performance Get real-world examples of VUIs for home assistants, smartwatches, and car systems COMPUTERS,User Interfaces

Designing with Data On the surface, design practices and data science may not seem like obvious partners. But these disciplines actually work toward the same goal, helping designers and product managers understand users so they can craft elegant digital experiences. While data can enhance design, design can bring deeper meaning to data. This practical guide shows you how to conduct data-driven A/B testing for making design decisions on everything from small tweaks to large-scale UX concepts. Complete with real-world examples, this book shows you how to make data-driven design part of your product design workflow. Understand the relationship between data, business, and design Get a firm grounding in data, data types, and components of A/B testing Use an experimentation framework to define opportunities, formulate hypotheses, and test different options Create hypotheses that connect to key metrics and business goals Design proposed solutions for hypotheses that are most promising Interpret the results of an A/B test and determine your next move COMPUTERS,User Interfaces

Hands-On Android UI Development Master the art of creating impressive and reactive UIs for mobile applications on the latest version of Android Oreo. About This Book A comprehensive guide to designing and developing highly interactive user interfaces for your app. Design responsive and agile applications targeting multiple Android devices (up to Android Oreo) using Android Studio 3.0 Write reactive user interfaces with minimal effort by leveraging the latest Android technologies, such as Architecture components and the Lifecycle API Avoid common design problems and pitfalls with the help of shared UI design patterns and best practices. Who This Book Is For This book is for novice Android and Java developers who have a basic knowledge of Android development and want to start developing stunning user interfaces. What You Will Learn Create effective and efficient user interfaces that allow users to carry out tasks smoothly Understand the fundamentals of Android UI design, and take a look at the basic layouts, Inputs, and controls Learn about various UI components provided by Android, which include structured layout objects and UI controls that allow you to build the graphical user interface for your app Explore various styles and themes that allow you to customize the look and feel of your app Leverage the animation and graphics APIs to improve user experience and draw custom 2D graphics In Detail A great user interface (UI) can spell the difference between success and failure for any new application. This book will show you not just how to code great UIs, but how to design them as well. It will take novice Android developers on a journey, showing them how to leverage the Android platform to produce stunning Android applications. Begin with the basics of creating Android applications and then move on to topics such as screen and layout design. Next, learn about techniques that will help improve performance for your application. Also, explore how to create reactive applications that are fast, animated, and guide the user toward their goals with minimal distraction. Understand Android architecture components and learn how to build your application to automatically respond to changes made by the user. Great platforms are not always enough, so this book also focuses on creating custom components, layout managers, and 2D graphics. Also, explore many tips and best practices to ease your UI development process. By the end, you'll be able to design and build not only amazing UIs, but also systems that provide the best possible user experience. Style and approach This book takes an easy tutorial approach to help you learn how to create consistent and efficient user interfaces for your apps. The book first takes you through the basics of user interfaces such as basic layouts, inputs, and controls, and also covers animations and graphics. By the end of the book, you will have learned best practices and will be able to develop inspired interfaces that look good and also work subtly in the background. COMPUTERS,User Interfaces

Designed for Use This book is for designers, developers, and product managers who are charged with what sometimes seems like an impossible task: making sure products work the way your users expect them to. You'll find out how to design applications and websites that people will not only use, but will absolutely love. The second edition brings the book up to date and expands it with three completely new chapters. Interaction design - the way the apps on our phones work, the way we enter a destination into our car's GPS - is becoming more and more important. Identify and fix bad software design by making usability the cornerstone of your design process. Lukas weaves together hands-on techniques and fundamental concepts. Each technique chapter explains a specific approach you can use to make your product more user friendly, such as storyboarding, usability tests, and paper prototyping. Idea chapters are concept-based: how to write usable text, how realistic your designs should look, when to use animations. This new edition is updated and expanded with new chapters covering requirements gathering, how the design of data structures influences the user interface, and how to do design work as a team. Through copious illustrations and supporting psychological research, expert developer and user interface designer Lukas Mathis gives you a deep dive into research, design, and implementation--the essential stages in designing usable interfaces for applications and websites. Lukas inspires you to look at design in a whole new way, explaining exactly what to look for - and what to avoid - in creating products that get people excited. COMPUTERS,User Interfaces

Storytelling for User Experience We all tell stories. It's one of the most natural ways to share information, as old as the human race. This book is not about a new technique, but how to use something we already know in a new way. Stories help us gather and communicate user research, put a human face on analytic data, communicate design ideas, encourage collaboration and innovation, and create a sense of shared history and purpose. This book looks across the full spectrum of user experience design to discover when and how to use stories to improve our products. Whether you are a researcher, designer, analyst or manager, you will find ideas and techniques you can put to use in your practice. COMPUTERS,User Interfaces

UX Fundamentals for Non-UX Professionals What can a WWII-era tank teach us about design? What does a small, blue flower tell us about audiences? What do drunk, French marathon-runners show us about software? In 40+ chapters and stories, you will learn the ways in which UX has influenced history and vice versa, and how it continues to change our daily lives. This book enables you to participate fully in discussions about UX, as you discover the fundamentals of user experience design and research. Rather than grasp concepts through a barrage of facts and figures, you will learn through stories. Poisonous blowfish, Russian playwrights, tiny angels, Texas sharpshooters, and wilderness wildfires all make an appearance. From Chinese rail workers to UFOs, you will cover a lot of territory, because the experiences that surround you are as broad and varied as every age, culture, and occupation. You will start by covering the principles of UX before going into more diverse topics, including: being human, the art of persuasion, and the murky waters of process. Every day, people gather around conference tables, jump onto phone calls, draw on whiteboards, stare at computer monitors, and try to build things — we all create. Increasingly, what we create is something digital. From apps to web sites, and from emails to video games, often the sole evidence of an experience appears on an illuminated screen. We design tiny worlds that thrive or perish at the whim of a device’s on/off button. With this book you will be ready. What You'll Learn Master the fundamentals of UX Acquire the skills to participate intelligently in discussions about UX design and research Understand how UX impacts business, including product, pricing, placement, and promotion as well as security, speed, and privacy Who This Book Is For Professionals who work alongside UX designers and researchers, including but not limited to: project managers, graphic designers, copyeditors, developers, and human resource professionals; and business, marketing, and computer science students seeking to understand how UX affects human cognition and memory, product pricing and promotion, and software security and privacy. COMPUTERS,User Interfaces

Interaction Design A new edition of the #1 text in the human computer Interaction field! Hugely popular with students and professionals alike, the Fifth Edition of Interaction Design is an ideal resource for learning the interdisciplinary skills needed for interaction design, human-computer interaction, information design, web design, and ubiquitous computing. New to the fifth edition: a chapter on data at scale, which covers developments in the emerging fields of 'human data interaction' and data analytics. The chapter demonstrates the many ways organizations manipulate, analyze, and act upon the masses of data being collected with regards to human digital and physical behaviors, the environment, and society at large. Revised and updated throughout, this edition offers a cross-disciplinary, practical, and process-oriented, state-of-the-art introduction to the field, showing not just what principles ought to apply to interaction design, but crucially how they can be applied. Explains how to use design and evaluation techniques for developing successful interactive technologies Demonstrates, through many examples, the cognitive, social and affective issues that underpin the design of these technologies Provides thought-provoking design dilemmas and interviews with expert designers and researchers Uses a strong pedagogical format to foster understanding and enjoyment An accompanying website contains extensive additional teaching and learning material including slides for each chapter, comments on chapter activities, and a number of in-depth case studies written by researchers and designers. COMPUTERS,User Interfaces

Learn React Hooks Create large-scale web applications with code that is extensible and easy to understand using React Hooks Key Features Explore effective strategies for migrating your state management from Redux and MobX to React Hooks Integrate Hooks with React features such as Context and Suspense to add advanced functionality to your web apps Create complex applications by combining multiple hooks Book Description React Hooks revolutionize how you manage state and effects in your web applications. They enable you to build simple and concise React.js applications, along with helping you avoid using wrapper components in your applications, making it easy to refactor code. This React book starts by introducing you to React Hooks. You will then get to grips with building a complex UI in React while keeping the code simple and extensible. Next, you will quickly move on to building your first applications with React Hooks. In the next few chapters, the book delves into various Hooks, including the State and Effect Hooks. After covering State Hooks and understanding how to use them, you will focus on the capabilities of Effect Hooks for adding advanced functionality to React apps. You will later explore the Suspense and Context APIs and how they can be used with Hooks. Toward the concluding chapters, you will learn how to integrate Redux and MobX with React Hooks. Finally, the book will help you develop the skill of migrating your existing React class components, and Redux and MobX web applications to Hooks. By the end of this book, you will be well-versed in building your own custom Hooks and effectively refactoring your React applications. What you will learn Understand the fundamentals of React Hooks and how they modernize state management in React apps Build your own custom Hooks and learn how to test them Use community Hooks for implementing responsive design and more Learn the limitations of Hooks and what you should and shouldn't use them for Get to grips with implementing React context using Hooks Refactor your React-based web application, replacing existing React class components with Hooks Use state management solutions such as Redux and MobX with React Hooks Who this book is for This book is for React developers who want to learn how to build applications with Hooks. Developers who are looking to migrate to React for its advanced feature set and capabilities will also find the book useful. COMPUTERS,User Interfaces

Storytelling in Design With the wide variety of devices, touch points, and channels in use, your ability to control how people navigate your well-crafted experiences is fading. Yet it’s still important to understand where people are in their journey if you’re to deliver the right content and interactions atthe right time and on the right device. This practical guide shows you how storytelling can make a powerful difference in product design. Author Anna Dahlström details the many ways you can use storytelling in your projects and throughout your organization. By applying tried-and-tested principles from film and fiction to the context of design and business, you’ll learn to create great product experiences. Learn how the anatomy of a great story can make a difference in product design Explore how traditional storytelling principles, tools, and methods relate to key product design aspects Understand how purposeful storytelling helps tell the right story and move people into action Use storytelling principles to tell, sell, and present your work COMPUTERS,User Interfaces

Beyond Interactions This book contains revised selected papers presented at 3 workshops held at the 17th IFIP TC 13 International Conference on Human-Computer Interaction, INTERACT 2019, which was held in September 2019 in Paphos, Cyprus. The workshops are: - Beyond Computers: Wearables, Humans, And Things - WHAT! - User Experiences and Wellbeing at Work (UX@Work) - Workshop on Handling Security, Usability, User Experience and Reliability in User-Centered Development Processes. The 12 papers included in this volume were carefully reviewed and selected from numerous submissions. They show advances in the field of HCI dealing with topics such as wearables, user experience and wellbeing at work, security, usability, user experience and reliability in user-centered development processes. COMPUTERS,User Interfaces

Augmented Reality in Education This is the first comprehensive research monograph devoted to the use of augmented reality in education. It is written by a team of 58 world-leading researchers, practitioners and artists from 15 countries, pioneering in employing augmented reality as a new teaching and learning technology and tool. The authors explore the state of the art in educational augmented reality and its usage in a large variety of particular areas, such as medical education and training, English language education, chemistry learning, environmental and special education, dental training, mining engineering teaching, historical and fine art education. Augmented Reality in Education: A New Technology for Teaching and Learning is essential reading not only for educators of all types and levels, educational researchers and technology developers, but also for students (both graduates and undergraduates) and anyone who is interested in the educational use of emerging augmented reality technology. COMPUTERS,User Interfaces

From Chaos to Concept This book is written for product design, software development, graphic design, and UX professionals with a focus on creating measurably better user experiences. If you want to design solutions to meet business goals and delight your users, you can look to this resource which covers the following areas: Creating and documenting goals, strategies, objectives, and tactics Defining or refining personas based on your measurable objectives (OKRs) Creating and iterating on scenarios based your prioritized personas A team approach to defining the product and roadmap to address critical use cases Team based divergent ideation and solution exploration Team based convergent solution definition Wireframing potential solutions for rapid research and iteration Using quantitative and qualitative methods to understand usage and test with users Exploring approaches to taxonomy and information architecture Using psychology and human factors to drive your design decisions Developing performant, accessible, maintainable experiences Using analytics to measure the results and inform the next iteration How this process differs based on the size of the company or team that is employing it COMPUTERS,User Interfaces

Human-Computer Interaction. Design and User Experience The three-volume set LNCS 12181, 12182, and 12183 constitutes the refereed proceedings of the Human Computer Interaction thematic area of the 22nd International Conference on Human-Computer Interaction, HCII 2020, which took place in Copenhagen, Denmark, in July 2020.* A total of 1439 papers and 238 posters have been accepted for publication in the HCII 2020 proceedings from a total of 6326 submissions. The 145 papers included in this HCI 2020 proceedings were organized in topical sections as follows:Part I: design theory, methods and practice in HCI; understanding users; usability, user experience and quality; and images, visualization and aesthetics in HCI. Part II: gesture-based interaction; speech, voice, conversation and emotions; multimodal interaction; and human robot interaction. Part III: HCI for well-being and Eudaimonia; learning, culture and creativity; human values, ethics, transparency and trust; and HCI in complex environments. *The conference was held virtually due to the COVID-19 pandemic. COMPUTERS,User Interfaces

Engineering Psychology and Cognitive Ergonomics. Cognition and Design This book constitutes the proceedings of the 17th International Conference on Engineering Psychology and Cognitive Ergonomics, EPCE 2020, held as part of the 22nd International Conference, HCI International 2020, which took place in Copenhagen, Denmark, in July 2020. The total of 1439 papers and 238 posters included in the 37 HCII 2020 proceedings volumes was carefully reviewed and selected from 6326 submissions.EPCE 2020 includes a total of 60 regular papers; they were organized in topical sections named: mental workload and performance; human physiology, human energy and cognition; cognition and design of complex and safety critical systems; human factors in human autonomy teaming and intelligent systems; cognitive psychology in aviation and automotive. As a result of the Danish Government's announcement, dated April 21, 2020, to ban all large events (above 500 participants) until September 1, 2020, the HCII 2020 conference was held virtually. COMPUTERS,User Interfaces

Human-Computer Interaction. Multimodal and Natural Interaction The three-volume set LNCS 12181, 12182, and 12183 constitutes the refereed proceedings of the Human Computer Interaction thematic area of the 22nd International Conference on Human-Computer Interaction, HCII 2020, which took place in Copenhagen, Denmark, in July 2020.* A total of 1439 papers and 238 posters have been accepted for publication in the HCII 2020 proceedings from a total of 6326 submissions. The 145 papers included in these HCI 2020 proceedings were organized in topical sections as follows: Part I: design theory, methods and practice in HCI; understanding users; usability, user experience and quality; and images, visualization and aesthetics in HCI. Part II: gesture-based interaction; speech, voice, conversation and emotions; multimodal interaction; and human robot interaction. Part III: HCI for well-being and Eudaimonia; learning, culture and creativity; human values, ethics, transparency and trust; and HCI in complex environments. *The conference was held virtually due to the COVID-19 pandemic. COMPUTERS,User Interfaces

Universal Access in Human-Computer Interaction. Applications and Practice This two-volume set of LNCS 12188 and 12189 constitutes the refereed proceedings of the 14th International Conference on Universal Access in Human-Computer Interaction, UAHCI 2020, held as part of the 22nd International Conference, HCI International 2020, which took place in Copenhagen, Denmark, in July 2020. The conference was held virtually due to the COVID-19 pandemic. The total of 1439 papers and 238 posters have been accepted for publication in the HCII 2020 proceedings from a total of 6326 submissions. UAHCI 2020 includes a total of 80 regular papers which are organized in topical sections named: Design for All Theory, Methods and Practice; User Interfaces and Interaction Techniques for Universal Access; Web Accessibility; Virtual and Augmented Reality for Universal Access; Robots in Universal Access; Technologies for Autism Spectrum Disorders; Technologies for Deaf Users; Universal Access to Learning and Education; Social Media, Digital Services, Inclusion and Innovation; Intelligent Assistive Environments. COMPUTERS,User Interfaces

Social Computing and Social Media. Participation, User Experience, Consumer Experience, and Applications of Social Computing This two-volume set LNCS 12194 and 12195 constitutes the refereed proceedings of the 12th International Conference on Social Computing and Social Media, SCSM 2020, held as part of the 22nd International Conference, HCI International 2020, which was planned to be held in Copenhagen, Denmark, in July 2020. The conference was held virtually due to the COVID-19 pandemic. The total of 1439 papers and 238 posters have been accepted for publication in the HCII 2020 proceedings from a total of 6326 submissions. SCSM 2020 includes a total of 93 papers which are organized in topical sections named: Design Issues in Social Computing, Ethics and Misinformation in Social Media, User Behavior and Social Network Analysis, Participation and Collaboration in Online Communities, Social Computing and User Experience, Social Media Marketing and Consumer Experience, Social Computing for Well-Being, Learning, and Entertainment. COMPUTERS,User Interfaces

Virtual, Augmented and Mixed Reality. Design and Interaction The 2 volume-set of LNCS 12190 and 12191 constitutes the refereed proceedings of the 12th International Conference on Virtual, Augmented and Mixed Reality, VAMR 2020, which was due to be held in July 2020 as part of HCI International 2020 in Copenhagen, Denmark. The conference was held virtually due to the COVID-19 pandemic. A total of 1439 papers and 238 posters have been accepted for publication in the HCII 2020 proceedings from a total of 6326 submissions. The 71 papers included in these HCI 2020 proceedings were organized in topical sections as follows: Part I: design and user experience in VAMR; gestures and haptic interaction in VAMR; cognitive, psychological and health aspects in VAMR; robots in VAMR. Part II: VAMR for training, guidance and assistance in industry and business; learning, narrative, storytelling and cultural applications of VAMR; VAMR for health, well-being and medicine. COMPUTERS,User Interfaces

Universal Access in Human-Computer Interaction. Design Approaches and Supporting Technologies This two-volume set of LNCS 12188 and 12189 constitutes the refereed proceedings of the 14th International Conference on Universal Access in Human-Computer Interaction, UAHCI 2020, held as part of the 22nd International Conference, HCI International 2020, which took place in Copenhagen, Denmark, in July 2020. The conference was held virtually due to the COVID-19 pandemic. The total of 1439 papers and 238 posters have been accepted for publication in the HCII 2020 proceedings from a total of 6326 submissions. UAHCI 2020 includes a total of 80 regular papers which are organized in topical sections named: Design for All Theory, Methods and Practice; User Interfaces and Interaction Techniques for Universal Access; Web Accessibility; Virtual and Augmented Reality for Universal Access; Robots in Universal Access; Technologies for Autism Spectrum Disorders; Technologies for Deaf Users; Universal Access to Learning and Education; Social Media, Digital Services, eInclusion and Innovation; Intelligent Assistive Environments. COMPUTERS,User Interfaces

Human-Computer Interaction. Human Values and Quality of Life The three-volume set LNCS 12181, 12182, and 12183 constitutes the refereed proceedings of the Human Computer Interaction thematic area of the 22nd International Conference on Human-Computer Interaction, HCII 2020, which took place in Copenhagen, Denmark, in July 2020.* A total of 1439 papers and 238 posters have been accepted for publication in the HCII 2020 proceedings from a total of 6326 submissions. The 145 papers included in these HCI 2020 proceedings were organized in topical sections as follows: Part I: design theory, methods and practice in HCI; understanding users; usability, user experience and quality; and images, visualization and aesthetics in HCI. Part II: gesture-based interaction; speech, voice, conversation and emotions; multimodal interaction; and human robot interaction. Part III: HCI for well-being and Eudaimonia; learning, culture and creativity; human values, ethics, transparency and trust; and HCI in complex environments. *The conference was held virtually due to the COVID-19 pandemic. COMPUTERS,User Interfaces

Virtual, Augmented and Mixed Reality. Industrial and Everyday Life Applications The 2 volume-set of LNCS 12190 and 12191 constitutes the refereed proceedings of the 12th International Conference on Virtual, Augmented and Mixed Reality, VAMR 2020, which was due to be held in July 2020 as part of HCI International 2020 in Copenhagen, Denmark. The conference was held virtually due to the COVID-19 pandemic. A total of 1439 papers and 238 posters have been accepted for publication in the HCII 2020 proceedings from a total of 6326 submissions. The 71 papers included in these HCI 2020 proceedings were organized in topical sections as follows: Part I: design and user experience in VAMR; gestures and haptic interaction in VAMR; cognitive, psychological and health aspects in VAMR; robots in VAMR. Part II: VAMR for training, guidance and assistance in industry and business; learning, narrative, storytelling and cultural applications of VAMR; VAMR for health, well-being and medicine. COMPUTERS,User Interfaces

Social Computing and Social Media. Design, Ethics, User Behavior, and Social Network Analysis This two-volume set LNCS 12194 and 12195 constitutes the refereed proceedings of the 12th International Conference on Social Computing and Social Media, SCSM 2020, held as part of the 22nd International Conference, HCI International 2020, which was planned to be held in Copenhagen, Denmark, in July 2020. The conference was held virtually due to the COVID-19 pandemic. The total of 1439 papers and 238 posters have been accepted for publication in the HCII 2020 proceedings from a total of 6326 submissions. SCSM 2020 includes a total of 93 papers which are organized in topical sections named: Design Issues in Social Computing, Ethics and Misinformation in Social Media, User Behavior and Social Network Analysis, Participation and Collaboration in Online Communities, Social Computing and User Experience, Social Media Marketing and Consumer Experience, Social Computing for Well-Being, Learning, and Entertainment. COMPUTERS,User Interfaces

Digital Human Modeling and Applications in Health, Safety, Ergonomics and Risk Management. Human Communication, Organization and Work This two-volume set LNCS 12198 and 12199 constitutes the thoroughly refereed proceedings of the 11th International Conference on Digital Human Modeling and Applications in Health, Safety, Ergonomics and Risk Management, DHM 2020, which was supposed to be held as part of the 22st HCI International Conference, HCII 2020, in Copenhagen, Denmark, in July 2020. The conference was held virtually due to the COVID-19 pandemic. A total of 1439 papers and 238 posters have been carefully reviewed and accepted for publication in HCII 2020. DHM 2020 includes a total of 77 papers; they were organized in topical sections named:Part I, Posture, Motion and Health: Posture and motion modelling in design; ergonomics and occupational health; applications for exercising, physical therapy and rehabilitation; health services; DHM for aging support. Part II, Human Communication, Organization and Work: Modelling human communication; modelling work, collaboration and the human environment; addressing ethical and societal challenges; new research issues and approaches in digital human modelling. COMPUTERS,User Interfaces

Cross-Cultural Design. User Experience of Products, Services, and Intelligent Environments This two-volume set LNCS 12192 and 12193 constitutes the refereed proceedings of the 12th International Conference on Cross-Cultural Design, CCD 2020, held as part of HCI International 2020 in Copenhagen, Denmark in July 2020.The conference was held virtually due to the corona pandemic. The total of 1439 papers and 238 posters included in the 40 HCII 2020 proceedings volumes was carefully reviewed and selected from 6326 submissions. The regular papers of Cross-Cultural Design CCD 2020 presented in this volume were organized in topical sections named: Cross-Cultural User Experience Design; Culture-Based Design, Cross-Cultural Behaviour and Attitude, and Cultural Facets of Interactions with Autonomous Agents and Intelligent Environments. COMPUTERS,User Interfaces

Design, User Experience, and Usability. Interaction Design This book constitutes the refereed proceedings of the 9th International Conference on Design, User Experience, and Usability, DUXU 2020, held as part of the 22nd International Conference on Human-Computer Interaction, HCII 2020, in Copenhagen, Denmark, in July 2020. The conference was held virtually due to the COVID-19 pandemic.From a total of 6326 submissions, a total of 1439 papers and 238 posters has been accepted for publication in the HCII 2020 proceedings. The 40 papers included in this volume were organized in topical sections on UX design methods, tools and guidelines, interaction design and information visualization, and emotional design. COMPUTERS,User Interfaces

Cross-Cultural Design. Applications in Health, Learning, Communication, and Creativity This two-volume set LNCS 12192 and 12193 constitutes the refereed proceedings of the 12th International Conference on Cross-Cultural Design, CCD 2020, held as part of HCI International 2020 in Copenhagen, Denmark in July 2020.The conference was held virtually due to the corona pandemic. The total of 1439 papers and 238 posters included in the 40 HCII 2020 proceedings volumes was carefully reviewed and selected from 6326 submissions. The regular papers of Cross-Cultural Design CCD 2020 presented in this volume were organized in topical sections named: Health, Well-being and Social Design Across Cultures, Culture, Learning and Communication, and Culture and Creativity. COMPUTERS,User Interfaces

Digital Human Modeling and Applications in Health, Safety, Ergonomics and Risk Management. Posture, Motion and Health This two-volume set LNCS 12198 and 12199 constitutes the thoroughly refereed proceedings of the 11th International Conference on Digital Human Modeling and Applications in Health, Safety, Ergonomics and Risk Management, DHM 2020, which was supposed to be held as part of the 22st HCI International Conference, HCII 2020, in Copenhagen, Denmark, in July 2020. The conference was held virtually due to the COVID-19 pandemic. A total of 1439 papers and 238 posters have been carefully reviewed and accepted for publication in HCII 2020. DHM 2020 includes a total of 77 papers; they were organized in topical sections named:Part I, Posture, Motion and Health: Posture and motion modelling in design; ergonomics and occupational health; applications for exercising, physical therapy and rehabilitation; health services; DHM for aging support. Part II, Human Communication, Organization and Work: Modelling human communication; modelling work, collaboration and the human environment; addressing ethical and societal challenges; new research issues and approaches in digital human modelling. COMPUTERS,User Interfaces

Human Interface and the Management of Information. Designing Information This two-volume set LNCS 12184 and 12185 constitutes the refereed proceedings of the Thematic Area on Human Interface and the Management of Information, HIMI 2020, held as part of HCI International 2020 in Copenhagen, Denmark.* HCII 2020 received a total of 6326 submissions, of which 1439 papers and 238 posters were accepted for publication after a careful reviewing process. The 72 papers presented in the two volumes were organized in the following topical sections: Part I: information presentation and visualization; service design and management; and information in VR and AR. Part II: recommender and decision support systems; information, communication, relationality and learning; supporting work, collaboration and creativity; and information in intelligent systems and environments. *The conference was held virtually due to the COVID-19 pandemic. COMPUTERS,User Interfaces

Human Aspects of IT for the Aged Population. Technology and Society This three volume set of LNCS 12207, 12208 and 12209 constitutes the refereed proceedings of the 6th International Conference on Human Aspects of IT for the Aged Population, ITAP 2020, held as part of the 22nd International Conference, HCI International 2020, which took place in Copenhagen, Denmark, in July 2020. The conference was held virtually due to the COVID-19 pandemic. The total of 1439 papers and 238 posters have been accepted for publication in the HCII 2020 proceedings from a total of 6326 submissions. ITAP 2020 includes a total of 104 regular papers which are organized in topical sections named: Involving Older Adults in HCI Methodology , User Experience and Aging, Aging and Mobile and Wearable Devices, Health and Rehabilitation Technologies, Well-being, Persuasion, Health Education and Cognitive Support, Aging in Place, Cultural and Entertainment Experiences for Older Adults, Aging and Social Media, Technology Acceptance and Societal Impact. COMPUTERS,User Interfaces

Human Interface and the Management of Information. Interacting with Information This two-volume set LNCS 12184 and 12185 constitutes the refereed proceedings of the Thematic Area on Human Interface and the Management of Information, HIMI 2020, held as part of HCI International 2020 in Copenhagen, Denmark.* HCII 2020 received a total of 6326 submissions, of which 1439 papers and 238 posters were accepted for publication after a careful reviewing process. The 72 papers presented in the two volumes were organized in the following topical sections: Part I: information presentation and visualization; service design and management; and information in VR and AR. Part II: recommender and decision support systems; information, communication, relationality and learning; supporting work, collaboration and creativity; and information in intelligent systems and environments. *The conference was held virtually due to the COVID-19 pandemic. COMPUTERS,User Interfaces

Artificial Intelligence in HCI This book constitutes the refereed proceedings of the First International Conference on Artificial Intelligence in HCI, AI-HCI 2020, held as part of the 22nd International Conference on Human-Computer Interaction, HCII 2020, in July 2020. The conference was planned to be held in Copenhagen, Denmark, but had to change to a virtual conference mode due to the COVID-19 pandemic. The conference presents results from academic and industrial research, as well as industrial experiences, on the use of Artificial Intelligence technologies to enhance Human-Computer Interaction. From a total of 6326 submissions, a total of 1439 papers and 238 posters has been accepted for publication in the HCII 2020 proceedings. The 30 papers presented in this volume were organized in topical sections as follows: Human-Centered AI; and AI Applications in HCI.pical sections as follows: Human-Centered AI; and AI Applications in HCI. COMPUTERS,User Interfaces

Design, User Experience, and Usability. Design for Contemporary Interactive Environments This book constitutes the refereed proceedings of the 9th International Conference on Design, User Experience, and Usability, DUXU 2020, held as part of the 22nd International Conference on Human-Computer Interaction, HCII 2020, in Copenhagen, Denmark, in July 2020. The conference was held virtually due to the COVID-19 pandemic. From a total of 6326 submissions, a total of 1439 papers and 238 posters has been accepted for publication in the HCII 2020 proceedings. The 50 papers included in this volume were organized in topical sections on interactions in intelligent and IoT environments, usability aspects of handheld and mobile devices, designing games and immersive experiences, and UX studies in automotive and transport. COMPUTERS,User Interfaces

Human Aspects of IT for the Aged Population. Healthy and Active Aging This three volume set of LNCS 12207, 12208 and 12209 constitutes the refereed proceedings of the 6th International Conference on Human Aspects of IT for the Aged Population, ITAP 2020, held as part of the 22nd International Conference, HCI International 2020, which took place in Copenhagen, Denmark, in July 2020. The conference was held virtually due to the COVID-19 pandemic. The total of 1439 papers and 238 posters have been accepted for publication in the HCII 2020 proceedings from a total of 6326 submissions. ITAP 2020 includes a total of 104 regular papers which are organized in topical sections named: Involving Older Adults in HCI Methodology , User Experience and Aging, Aging and Mobile and Wearable Devices, Health and Rehabilitation Technologies, Well-being, Persuasion, Health Education and Cognitive Support, Aging in Place, Cultural and Entertainment Experiences for Older Adults, Aging and Social Media, Technology Acceptance and Societal Impact. COMPUTERS,User Interfaces

Human Aspects of IT for the Aged Population. Technologies, Design and User Experience This three volume set of LNCS 12207, 12208 and 12209 constitutes the refereed proceedings of the 6th International Conference on Human Aspects of IT for the Aged Population, ITAP 2020, held as part of the 22nd International Conference, HCI International 2020, which took place in Copenhagen, Denmark, in July 2020. The conference was held virtually due to the COVID-19 pandemic. The total of 1439 papers and 238 posters have been accepted for publication in the HCII 2020 proceedings from a total of 6326 submissions. ITAP 2020 includes a total of 104 regular papers which are organized in topical sections named: Involving Older Adults in HCI Methodology , User Experience and Aging, Aging and Mobile and Wearable Devices, Health and Rehabilitation Technologies, Well-being, Persuasion, Health Education and Cognitive Support, Aging in Place, Cultural and Entertainment Experiences for Older Adults, Aging and Social Media, Technology Acceptance and Societal Impact. COMPUTERS,User Interfaces

HCI in Mobility, Transport, and Automotive Systems. Driving Behavior, Urban and Smart Mobility This two-volume set LNCS 12212 and 12213 constitutes the refereed proceedings of the Second International Conference on HCI in Mobility, Transport, and Automotive Systems, MobiTAS 2020, held as part of the 22nd International Conference on Human-Computer Interaction, HCII 2020, in Copenhagen, Denmark, in July, 2020.* A total of 1439 full papers and 238 posters have been carefully reviewed and accepted for publication in HCII 2020. The papers cover the entire field of human-computer interaction, addressing major advances in knowledge and effective use of computers in a variety of application areas. MobiTAS 2020 includes a total of 59 papers and they are organized in the following topical sections: Part I, Automated Driving and In-Vehicle Experience Design: UX topics in automated driving, and designing in-vehicle experiences. Part II, Driving Behavior, Urban and Smart Mobility: studies on driving behavior, and urban and smart mobility. *The conference was held virtually due to the COVID-19 pandemic. COMPUTERS,User Interfaces

Augmented Cognition. Human Cognition and Behavior This book constitutes the refereed proceedings of 14th International Conference on Augmented Cognition, AC 2020, held as part of the 22nd International Conference on Human-Computer Interaction, HCII 2020, in July 2020. The conference was planned to be held in Copenhagen, Denmark, but had to change to a virtual conference mode due to the COVID-19 pandemic.From a total of 6326 submissions, a total of 1439 papers and 238 posters has been accepted for publication in the HCII 2020 proceedings. The 21 papers presented in this volume were organized in topical sections as follows: cognitive modeling, perception, emotion and interaction; electroencephalography and BCI; and AI and augmented cognition. COMPUTERS,User Interfaces

Design, User Experience, and Usability. Case Studies in Public and Personal Interactive Systems This book constitutes the refereed proceedings of the 9th International Conference on Design, User Experience, and Usability, DUXU 2020, held as part of the 22nd International Conference on Human-Computer Interaction, HCII 2020, in Copenhagen, Denmark, in July 2020. The conference was held virtually due to the COVID-19 pandemic. From a total of 6326 submissions, a total of 1439 papers and 238 posters has been accepted for publication in the HCII 2020 proceedings. The 51 papers included in this volume were organized in topical sections on interactions in public, urban and rural contexts; UX design for health and well-being; DUXU for creativity, learning and collaboration; DUXU for culture and tourism. COMPUTERS,User Interfaces

HCI for Cybersecurity, Privacy and Trust This book constitutes the proceedings of the Second International Conference on HCI for Cybersecurity, Privacy and Trust, HCI-CPT 2020, held as part of the 22nd International Conference, HCI International 2020, which took place in Copenhagen, Denmark, in July 2020. The total of 1439 papers and 238 posters included in the 37 HCII 2020 proceedings volumes was carefully reviewed and selected from 6326 submissions. HCI-CPT 2020 includes a total of 45 regular papers; they were organized in topical sections named: human factors in cybersecurity; privacy and trust; usable security approaches. As a result of the Danish Government's announcement, dated April21, 2020, to ban all large events (above 500 participants) until September 1, 2020, the HCII 2020 conference was held virtually. COMPUTERS,User Interfaces

Culture and Computing This book constitutes the refereed proceedings of the First International Conference on Culture and Computing, C&C 2020, held as part of the 22nd International Conference on Human-Computer Interaction, HCII 2020, in July 2020. The conference was planned to be held in Copenhagen, Denmark, but had to change to a virtual conference mode due to the COVID-19 pandemic.From a total of 6326 submissions, a total of 1439 papers and 238 posters has been accepted for publication in the HCII 2020 proceedings. The 34 papers presented in this volume were organized in topical sections as follows: HCI and ethics in cultural contexts; interactive and immersive cultural heritage; and preservation of local cultures. COMPUTERS,User Interfaces

HCI in Mobility, Transport, and Automotive Systems. Automated Driving and In-Vehicle Experience Design This two-volume set LNCS 12212 and 12213 constitutes the refereed proceedings of the Second International Conference on HCI in Mobility, Transport, and Automotive Systems, MobiTAS 2020, held as part of the 22nd International Conference on Human-Computer Interaction, HCII 2020, in Copenhagen, Denmark, in July, 2020.* A total of 1439 full papers and 238 posters have been carefully reviewed and accepted for publication in HCII 2020. The papers cover the entire field of human-computer interaction, addressing major advances in knowledge and effective use of computers in a variety of application areas. MobiTAS 2020 includes a total of 59 papers and they are organized in the following topical sections: Part I, Automated Driving and In-Vehicle Experience Design: UX topics in automated driving, and designing in-vehicle experiences. Part II, Driving Behavior, Urban and Smart Mobility: studies on driving behavior, and urban and smart mobility. *The conference was held virtually due to the COVID-19 pandemic. COMPUTERS,User Interfaces

Adaptive Instructional Systems This volume constitutes the refereed proceedings of the Second International Conference on Adaptive Instructional Systems, AIS 2020, which was due to be held in July 2020 as part of HCI International 2020 in Copenhagen, Denmark. The conference was held virtually due to the COVID-19 pandemic. A total of 1439 papers and 238 posters have been accepted for publication in the HCII 2020 proceedings from a total of 6326 submissions. The 41 papers presented in this volume were organized in topical sections as follows: designing and developing adaptive instructional systems; learner modelling and methods of adaptation; evaluating the effectiveness of adaptive instructional systems. Chapter "Exploring Video Engagement in an Intelligent Tutoring System" is available open access under a Creative Commons Attribution 4.0 International License via link.springer.com. COMPUTERS,User Interfaces

Learning and Collaboration Technologies. Designing, Developing and Deploying Learning Experiences This two-volume set LNCS 12205 and LNCS 12206 constitutes the proceedings of the 7th International Conference on Learning and Collaboration Technologies, LCT 2020, held as part of the 22nd International Conference, HCI International 2020, which took place in Copenhagen, Denmark, in July 2020.The total of 1439 papers and 238 posters included in the 37 HCII 2020 proceedings volumes was carefully reviewed and selected from 6326 submissions.The papers in this volume are organized in the following topical sections: designing and evaluating learning experiences; learning analytics, dashboards and learners models; language learning and teaching; and technology in education: policies and practice. As a result of the Danish Government's announcement, dated April 21, 2020, to ban all large events (above 500 participants) until September 1, 2020, the HCII 2020 conference was held virtually. COMPUTERS,User Interfaces

Learning and Collaboration Technologies. Human and Technology Ecosystems This two-volume set LNCS 12205 and LNCS 12206 constitutes the proceedings of the 7th International Conference on Learning and Collaboration Technologies, LCT 2020, held as part of the 22nd International Conference, HCI International 2020, which took place in Copenhagen, Denmark, in July 2020.The total of 1439 papers and 238 posters included in the 37 HCII 2020 proceedings volumes was carefully reviewed and selected from 6326 submissions.The papers in this volume are organized in the following topical sections: communication and conversation in learning; cognition, emotions and learning; games and gamification in learning; VR, robot and IoT in learning; and collaboration technology and collaborative learning. As a result of the Danish Government's announcement, dated April 21, 2020, to ban all large events (above 500 participants) until September 1, 2020, the HCII 2020 conference was held virtually. COMPUTERS,User Interfaces

HCI International 2020 - Posters The three-volume set CCIS 1224, CCIS 1225, and CCIS 1226 contains the extended abstracts of the posters presented during the 21st International Conference on Human-Computer Interaction, HCII 2020, which took place in Copenhagen, Denmark, in July 2020.* HCII 2020 received a total of 6326 submissions, of which 1439 papers and 238 posters were accepted for publication in the pre-conference proceedings after a careful reviewing process. The 238 papers presented in these three volumes are organized in topical sections as follows: Part I: design and evaluation methods and tools; user characteristics, requirements and preferences; multimodal and natural interaction; recognizing human psychological states; user experience studies; human perception and cognition. -AI in HCI. Part II: virtual, augmented and mixed reality; virtual humans and motion modelling and tracking; learning technology. Part III: universal access, accessibility and design for the elderly; smartphones, social media and human behavior; interacting with cultural heritage; human-vehicle interaction; transport, safety and crisis management; security, privacy and trust; product and service design. *The conference was held virtually due to the COVID-19 pandemic. COMPUTERS,User Interfaces

HCI International 2020 - Posters The three-volume set CCIS 1224, CCIS 1225, and CCIS 1226 contains the extended abstracts of the posters presented during the 21st International Conference on Human-Computer Interaction, HCII 2020, which took place in Copenhagen, Denmark, in July 2020.* HCII 2020 received a total of 6326 submissions, of which 1439 papers and 238 posters were accepted for publication in the pre-conference proceedings after a careful reviewing process. The 238 papers presented in these three volumes are organized in topical sections as follows: Part I: design and evaluation methods and tools; user characteristics, requirements and preferences; multimodal and natural interaction; recognizing human psychological states; user experience studies; human perception and cognition. -AI in HCI. Part II: virtual, augmented and mixed reality; virtual humans and motion modelling and tracking; learning technology. Part III: universal access, accessibility and design for the elderly; smartphones, social media and human behavior; interacting with cultural heritage; human-vehicle interaction; transport, safety and crisis management; security, privacy and trust; product and service design. *The conference was held virtually due to the COVID-19 pandemic. COMPUTERS,User Interfaces

HCI International 2020 - Posters The three-volume set CCIS 1224, CCIS 1225, and CCIS 1226 contains the extended abstracts of the posters presented during the 21st International Conference on Human-Computer Interaction, HCII 2020, which took place in Copenhagen, Denmark, in July 2020.* HCII 2020 received a total of 6326 submissions, of which 1439 papers and 238 posters were accepted for publication in the pre-conference proceedings after a careful reviewing process. The 238 papers presented in these three volumes are organized in topical sections as follows: Part I: design and evaluation methods and tools; user characteristics, requirements and preferences; multimodal and natural interaction; recognizing human psychological states; user experience studies; human perception and cognition. -AI in HCI. Part II: virtual, augmented and mixed reality; virtual humans and motion modelling and tracking; learning technology. Part III: universal access, accessibility and design for the elderly; smartphones, social media and human behavior; interacting with cultural heritage; human-vehicle interaction; transport, safety and crisis management; security, privacy and trust; product and service design. *The conference was held virtually due to the COVID-19 pandemic.The chapter "“Developing an Interactive Tabletop Mediated Activity to Induce Collaboration by Implementing Design Considerations Based on Cooperative Learning Principles†is available open access under a Creative Commons Attribution 4.0 International License via link.springer.com. COMPUTERS,User Interfaces

Augmented Cognition. Theoretical and Technological Approaches This book constitutes the refereed proceedings of 14th International Conference on Augmented Cognition, AC 2020, held as part of the 22nd International Conference on Human-Computer Interaction, HCII 2020, in July 2020. The conference was planned to be held in Copenhagen, Denmark, but had to change to a virtual conference mode due to the COVID-19 pandemic.From a total of 6326 submissions, a total of 1439 papers and 238 posters has been accepted for publication in the HCII 2020 proceedings. The 21 papers presented in this volume were organized in topical sections as follows: cognitive modeling, perception, emotion and interaction; electroencephalography and BCI; and AI and augmented cognition. COMPUTERS,User Interfaces

HCI and Design in the Context of Dementia Old age is currently the greatest risk factor for developing dementia. Since older people make up a larger portion of the population than ever before, the resulting increase in the incidence of dementia presents a major challenge for society. Dementia is complex and multifaceted and impacts not only the person with the diagnosis but also those caring for them and society as a whole. Human-Computer Interaction (HCI) design and development are pivotal in enabling people with dementia to live well and be supported in the communities around them. HCI is increasingly addressing the need for inclusivity and accessibility in the design and development of new technologies, interfaces, systems, services, and tools. Using interdisciplinary approaches HCI engages with the complexities and ‘messiness’ of real-world design spaces to provide novel perspectives and new ways of addressing the challenge of dementia and multi-stakeholder needs. HCI and Design in the Context of Dementia brings together the work of international experts, designers and researchers working across disciplines. It provides methodologies, methods and frameworks, approaches to participatory engagement and case studies showing how technology can impact the lives of people living with dementia and those around them. It includes examples of how to conduct dementia research and design in-context in the field of HCI, ethically and effectively and how these issues transcend the design space of dementia to inform HCI design and technology development more broadly. The book is valuable for and aimed at designers, researchers, scholars and caregivers that work with vulnerable groups like people with dementia, and those directly impacted. COMPUTERS,User Interfaces

The History of the Future The dramatic, larger-than-life true story behind the founding of Oculus and its quest for virtual reality, by the bestselling author of Console Wars. Drawing on over a hundred interviews with the key players driving this revolution, The History of the Future weaves together a rich, cinematic narrative that captures the breakthroughs, breakdowns and human drama of trying to change the world. The result is a super accessible and supremely entertaining look at the birth of a game-changing new industry. From iconic books like Neuromancer to blockbuster films like The Matrix, virtual reality has long been hailed as the ultimate technology. But outside of a few research labs and military training facilities, this tantalizing vision of the future was nothing but science fiction. Until 2012, when Oculus founder Palmer Luckey—then just a rebellious teenage dreamer living alone in a camper trailer—invents a device that has the potential to change everything. With the help of a videogame legend, a serial entrepreneur and many other colorful characters, Luckey’s scrappy startup kickstarts a revolution and sets out to bring VR to the masses. As with most underdog stories, things don’t quite go according to plan. But what happens next turns out to be the ultimate entrepreneurial journey: a tale of battles won and lost, lessons learned and neverending twists and turns—including an unlikely multi-billion-dollar acquisition by Facebook’s Mark Zuckerberg, which shakes up the landscape in Silicon Valley and gives Oculus the chance to forever change our reality. Drawing on over a hundred interviews with the key players driving this revolution, The History of the Future weaves together a rich, cinematic narrative that captures the breakthroughs, breakdowns and human drama of trying to change the world. The result is a super accessible and supremely entertaining look at the birth of a game-changing new industry. COMPUTERS,Virtual & Augmented Reality

Dawn of the New Everything Named one of the best books of 2017 by The Economist, The Wall Street Journal, & Vox The father of virtual reality explains its dazzling possibilities by reflecting on his own lifelong relationship with technology Bridging the gap between tech mania and the experience of being inside the human body, Dawn of the New Everything is a look at what it means to be human at a moment of unprecedented technological possibility. Through a fascinating look back over his life in technology, Jaron Lanier, an interdisciplinary scientist and father of the term “virtual reality,†exposes VR’s ability to illuminate and amplify our understanding of our species, and gives readers a new perspective on how the brain and body connect to the world. An inventive blend of autobiography, science writing, philosophy and advice, this book tells the wild story of his personal and professional life as a scientist, from his childhood in the UFO territory of New Mexico, to the loss of his mother, the founding of the first start-up, and finally becoming a world-renowned technological guru. Understanding virtual reality as being both a scientific and cultural adventure, Lanier demonstrates it to be a humanistic setting for technology. While his previous books offered a more critical view of social media and other manifestations of technology, in this book he argues that virtual reality can actually make our lives richer and fuller. COMPUTERS,Virtual & Augmented Reality

Virtual & Augmented Reality For Dummies An easy-to-understand primer on Virtual Reality and Augmented Reality Virtual Reality (VR) and Augmented Reality (AR) are driving the next technological revolution. If you want to get in on the action, this book helps you understand what these technologies are, their history, how they’re being used, and how they’ll affect consumers both personally and professionally in the very near future. With VR and AR poised to become mainstream within the next few years, an accessible book to bring users up to speed on the subject is sorely needed—and that’s where this handy reference comes in! Rather than focusing on a specific piece of hardware (HTC Vive, Oculus Rift, iOS ARKit) or software (Unity, Unreal Engine), Virtual & Augmented Reality For Dummies offers a broad look at both VR and AR, giving you a bird’s eye view of what you can expect as they continue to take the world by storm. * Keeps you up-to-date on the pulse of this fast-changing technology * Explores the many ways AR/VR are being used in fields such as healthcare, education, and entertainment * Includes interviews with designers, developers, and technologists currently working in the fields of VR and AR Perfect for both potential content creators and content consumers, this book will change the way you approach and contribute to these emerging technologies. COMPUTERS,Virtual & Augmented Reality

Gaming and the Virtual Sublime Gaming and the Virtual Sublime considers the ‘virtual sublime’ as a conceptual toolbox for understanding our affective engagement with contemporary interactive entertainment. COMPUTERS,Virtual & Augmented Reality

Communities of Play The odyssey of a group of “refugees” from a closed-down online game and an exploration of emergent fan cultures in virtual worlds. Play communities existed long before massively multiplayer online games; they have ranged from bridge clubs to sports leagues, from tabletop role-playing games to Civil War reenactments. With the emergence of digital networks, however, new varieties of adult play communities have appeared, most notably within online games and virtual worlds. Players in these networked worlds sometimes develop a sense of community that transcends the game itself. In Communities of Play, game researcher and designer Celia Pearce explores emergent fan cultures in networked digital worlds—actions by players that do not coincide with the intentions of the game's designers. Pearce looks in particular at the Uru Diaspora—a group of players whose game, Uru: Ages Beyond Myst, closed. These players (primarily baby boomers) immigrated into other worlds, self-identifying as “refugees”; relocated in There.com, they created a hybrid culture integrating aspects of their old world. Ostracized at first, they became community leaders. Pearce analyzes the properties of virtual worlds and looks at the ways design affects emergent behavior. She discusses the methodologies for studying online games, including a personal account of the sometimes messy process of ethnography. Pearce considers the “play turn” in culture and the advent of a participatory global playground enabled by networked digital games every bit as communal as the global village Marshall McLuhan saw united by television. Countering the ludological definition of play as unproductive and pointing to the long history of pre-digital play practices, Pearce argues that play can be a prelude to creativity. COMPUTERS,Virtual & Augmented Reality

Virtual Reality A comprehensive overview of developments in augmented reality, virtual reality, and mixed reality—and how they could affect every part of our lives. After years of hype, extended reality—augmented reality (AR), virtual reality (VR), and mixed reality (MR)—has entered the mainstream. Commercially available, relatively inexpensive VR headsets transport wearers to other realities—fantasy worlds, faraway countries, sporting events—in ways that even the most ultra-high-definition screen cannot. AR glasses receive data in visual and auditory forms that are more useful than any laptop or smartphone can deliver. Immersive MR environments blend physical and virtual reality to create a new reality. In this volume in the MIT Press Essential Knowledge series, technology writer Samuel Greengard offers an accessible overview of developments in extended reality, explaining the technology, considering the social and psychological ramifications, and discussing possible future directions. Greengard describes the history and technological development of augmented and virtual realities, including the latest research in the field, and surveys the various shapes and forms of VR, AR, and MR, including head-mounted displays, mobile systems, and goggles. He examines the way these technologies are shaping and reshaping some professions and industries, and explores how extended reality affects psychology, morality, law, and social constructs. It's not a question of whether extended reality will become a standard part of our world, he argues, but how, when, and where these technologies will take hold. Will extended reality help create a better world? Will it benefit society as a whole? Or will it merely provide financial windfalls for a select few? Greengard's account equips us to ask the right questions about a transformative technology. COMPUTERS,Virtual & Augmented Reality

Experience on Demand “If you want to understand the most immersive new communications medium to come along since cinema… I’d suggest starting with Mr. Bailenson’s [book].†—Wall Street Journal Virtual reality is able to effectively blur the line between reality and illusion, granting us access to any experience imaginable. These experiences, ones that the brain is convinced are real, will soon be available everywhere. In Experience on Demand, Jeremy Bailenson draws upon two decades spent researching the psychological effects of VR to help readers understand its upsides and possible downsides. He offers expert guidelines for interacting with VR, and describes the profound ways this technology can be put to use to hone our performance, help us recover from trauma, improve our learning, and even enhance our empathic and imaginative capacities so that we treat others and ourselves better. COMPUTERS,Virtual & Augmented Reality

Using Google Spreadsheets (Digital Short Cut) Google Spreadsheets is the new web-based spreadsheet application that's giving Microsoft Excel a run for its money. With Google Spreadsheets, you can create complex spreadsheets online, using any web browser, complete with sophisticated formulas and functions. You can even share spreadsheets online and perform collaborative editing on those spreadsheets with other users anywhere in the world. And the best thing is, Google Spreadsheets is completely free! Using Google Spreadsheets is the first e-book to cover Google's innovative online spreadsheet program. You learn how to create new web-based spreadsheets, upload and work with existing Excel spreadsheets, create complex formulas, apply a variety of formatting effects, and let other users share and edit their spreadsheets. Delivered in Adobe PDF format for quick and easy access, Using Google Spreadsheets includes everything you need to create your own sophisticated online spreadsheets. It also includes a detailed reference to the more than 200 functions included in the program, and a great cheatsheet you can print off and refer to for quick reference. Introducing Google Spreadsheets Migrating from Excel to Google Spreadsheets Navigating the Google Spreadsheets Workspace Creating, Opening, and Saving Google Spreadsheets Entering and Editing Data Working with Ranges Sorting Data Inserting, Deleting, Moving, and Copying Data Changing Column Width and Row Height Formatting Google Spreadsheets Entering and Editing Formulas Using Functions Working with Multiple Sheets Printing Google Spreadsheets Sharing and Collaborating with Google Spreadsheets A Final Word COMPUTERS,Web,General

Build Your Own Combat Robot Create your own powerful battling robot from start to finish using this easy-to-follow manual. Robotics experts Pete Miles and Tom Carroll explain the science and technology behind robots, and show you what materials you need to build and program a robot for home, school, and competition. COMPUTERS,Web,General

Web Design Complete Reference Design, build, and maintain dynamic Web sites that balance form and function. You’ll find thorough explanations of effective site architecture, layout, and navigational features, and discover how to add graphics, links, and multimedia. Also learn to handle privacy and security issues with respect to site design, and program dynamic Web applications. COMPUTERS,Web,General

Ace the IT Interview Proven strategies for getting hired as an IT professional This practical guide for developing winning interviewing skills has been fully updated and revised to focus on today's most sought-after IT jobs. Go behind the scenes of the IT interview process and get inside the mind of potential employers. You'll find out how to make a great first impression and stand out from the competition. Ace the IT Interview features hundreds of questions that are likely to come up on your next technical interview along with key points to include in your answers so you can practice your responses based on your strengths and experience. Present yourself as a truly valuable IT professional and get a great job with help from this real-world guide. Understand the hiring manager's perspective Create a first-rate resume that highlights your skills Get past gatekeepers and get the interviews you want Make a great first impression and stand out in the crowd Master sticky questions about your work history Prepare for different types of interview settings, including telephone and video-conference interviews Ask intelligent, relevant questions Ace the interview follow-up Evaluate your offers, negotiate salary, and close the deal COMPUTERS,Web,General

Learning PHP and MySQL The PHP scripting language and MySQL open source database are quite effective independently, but together they make a simply unbeatable team. When working hand-in-hand, they serve as the standard for the rapid development of dynamic, database-driven websites. This combination is so popular, in fact, that it's attracting manyprogramming newbies who come from a web or graphic design background and whose first language is HTML. If you fall into this ever-expanding category, then this book is for you. Learning PHP and MySQL starts with the very basics of the PHP language, including strings and arrays, pattern matching and a detailed discussion of the variances in different PHP versions. Next, it explains how to work with MySQL, covering information on SQL data access for language and data fundamentals like tables and statements.Finally, after it's sure that you've mastered these separate concepts, the book shows you how to put them together to generate dynamic content. In the process, you'll also learn about error handling, security, HTTP authentication, and more. If you're a hobbyist who is intimidated by thick, complex computer books, then this guide definitely belongs on your shelf. Learning PHP and MySQL explains everything--from basic concepts to the nuts and bolts of performing specific tasks--in plain English. Part of O'Reilly's bestselling Learning series, the book is an easy-to-use resource designed specifically for newcomers. It's also a launching pad for future learning, providing you with a solid foundation for more advanced development. COMPUTERS,Web,General

How to Do Everything Netbook Get the most out of your netbook! Now that you've got a netbook, it's time to find out how to maximize all of its capabilities. This hands-on guide explains how you can keep your netbook running at peak performance by limiting how many programs you run concurrently and what you download. Learn the best ways to connect to the Internet, secure your system, install software, use web-based programs from Microsoft, Google, and others, add memory, and troubleshoot your netbook. You'll also get helpful tips for working with Windows and Linux operating systems. Secure your netbook, set up a firewall, and protect it from viruses, malware, and other threats Connect to public wireless networks, Wi-Fi hotspots, and wired networks Configure your web browser to run quickly and cleanly Connect to printers, USB drives, backup devices, and other hardware Install software stored on a CD or DVD Configure and use the built-in web cam Expand your netbook with accessories Take advantage of Office Live Workspace, Google Apps, and other free web-based applications Use Open Office on a Linux-based netbook Learn how to use Windows 7 About the author: Joli Ballew, MCSE, MCTS, MCDST, is a technical writer, technology trainer, and website manager. She is the author of How to Do Everything with Windows Vista Media Center, Hardcore Windows XP, and other books. COMPUTERS,Web,General

WordPress WordPress: Visual QuickStart Guide, 2E uses a visual approach to teach the essential elements of WordPress, one of the world's most popular publishing platforms. This book gives readers the tools they need to create beautiful, functional WordPress-powered sites with minimal hassle. Using plenty of screenshots and a clear, organized format, authors Jessica Neuman Beck and Matt Beck walk new users through the installation and setup process while providing valuable tips and tricks for more experienced users. With no other resource but this guide, readers can set up a fully-functional and well-designed WordPress site that takes advantage of all the features WordPress has to offer. This new, fully updated version covers all the key new features of WordPress 3, including an improved welcome screen with enhanced security and usability; internal linking to articles on one's own blog; support for individual author templates; improved menu interface allowing for changes to be made from inside the WordPress dashboard; and the new, easily customizable Default Theme, Twenty Eleven, with support for child themes and header and background adjustments. It also covers more advanced features, such as improved content management with Custom Post types, which allow WordPress theme developers to create custom content types outside of pages and posts; and integration of the WordPress Multi-User into the WordPress core so that users can create and manage hundreds of blogs. COMPUTERS,Web,General

Writing for the Web With Writing for the Web, you’ll learn everything you need to know to create effective Web content using words, pictures, and sound. Follow along as instructor and writer Lynda Felder combines easy-to-follow guidelines with photographs, lists, and tables to illustrate the key concepts behind writing nonlinear, interactive stories; creating succinct and clear copy; and working compelling images, motion graphics, and sound into your content. Many books offer instruction on how to use software programs to build Web sites, podcasts, and illustrations. But only Writing for the Web explains when and why an author might choose an illustration over a photograph, motion graphics over text, or a slice of Beethoven’s Fifth over the sound of a bubbling brook. Focusing on storytelling techniques that work best for digital media, this book describes the essential skills and tools in a Web author’s toolbox, including a thorough understanding of grammar and style, a critical eye for photography, and an ear for just the right sound byte for a podcast. This clearly written guide provides a fun and practical approach to Web writing that busy students and writers will be eager to learn and explore. Uses concise, straight-to-the-point style to illustrate techniques for writing sharp and focused Web copy, coupled with compelling visuals and sound Focuses on writing practices and guidelines, with exercises and prompts developed and tested by the author Features clear design, with plenty of pictures and visual elements, and a friendly and knowledgeable voice Take your learning even further with Lynda's companion book: The Web Writer's Toolkit: 365 prompts, collaborative exercises, games, and challenges for effective online content. For more tips, exercises, and suggestions for teachers, check out the book’s Web site at www.write4web.com. COMPUTERS,Web,General

Display Advertising A complete guide to developing, implementing, monitoring, and optimizing an online display ad campaign The display business is online advertising's fastest growing field. Google and others are starting to provide easy tools to enable small- and medium-sized businesses to take advantage of this opportunity. This guide provides marketers, consultants, and small-business owners with the knowledge and skills to create and optimize a display advertising campaign. It covers concepts, trends, and best practices, and presents a day-to-day plan for developing, managing, and measuring a successful campaign. Online display advertising is a hot topic, and this hands-on guide helps marketing professionals and small-business owners gain the skills to create and manage their own campaigns Provides an overview of display advertising concepts, including types, formats, and how they're placed on websites Explains how to plan a campaign, including defining goals and planning resources, contextual and placement targeting, and keyword use Covers campaign launch and measurement, ad creation, social media advertising, how to optimize a campaign, and much more Display Advertising: An Hour a Day helps anyone promote a business successfully with effective online display ad campaigns. COMPUTERS,Web,General

Multimedia Demystified Learn cutting-edge MULTIMEDIA skills! Discover how to create impressive multimedia projects using state-of-the-art tools and techniques. Multimedia Demystified is filled with information on the latest technologies, as well as design and production guidelines. This practical guide provides a background on multimedia and then delves into the elements that make up a successful multimedia project. You'll learn about software and hardware tools, digital photography, sound editing, web authoring with HTML, vector graphics, file formats, computer animation, and much more. Detailed examples and concise explanations make it easy to understand the material, and end-of-chapter quizzes and a final exam help reinforce key concepts. It's a no-brainer! You'll learn about: Graphics, images, text, and typography 2D and 3D animation Music, sound effects, and video Authoring for multimedia functionality Software and hardware Delivering the final project to the intended audience Simple enough for a beginner, but challenging enough for an advanced student, Multimedia Demystified helps you master this marketable skill. COMPUTERS,Web,General

Microsoft® Excel® 2013 QuickSteps Full-color, step-by-step guide to the new release of the world’s most popular spreadsheet application Get up and running with Excel 2013 right away--the QuickSteps way. Full-color screenshots on every page with clear instructions make it easy to use the latest release of Microsoft's powerful spreadsheet application. Follow along and quickly learn how to create workbooks, enter and edit data, use formulas and functions, create charts and tables, analyze data, extend Excel, and more. This practical, fast-paced guide gets you started in no time! Use these handy guideposts: Shortcuts for accomplishing common tasks Need-to-know facts in concise narrative Helpful reminders or alternate ways of doing things Bonus information related to the topic being covered Errors and pitfalls to avoid The unique, landscape-oriented layout of the QuickSteps series mimics your computer screen, displays graphics and explanations side by side, and lays flat so you can easily refer to the book while working on your computer. COMPUTERS,Web,General

Python in 24 Hours, Sams Teach Yourself In just 24 sessions of one hour or less, Sams Teach Yourself Python in 24 Hours will help you get started fast, master all the core concepts of programming, and build anything from websites to games. Using this book’s straightforward, step-by-step approach, you’ll move from the absolute basics through functions, objects, classes, modules, database integration, and more. Every lesson and case study application builds on what you’ve already learned, giving you a rock-solid foundation for real-world success! Step-by-step instructions carefully walk you through the most common Python development tasks. Quizzes and Exercises at the end of each chapter help you test your knowledge. Notes present interesting information related to the discussion. Tips offer advice or show you easier ways to perform tasks. Warnings alert you to possible problems and give you advice on how to avoid them. Learn how to… Install and run the right version of Python for your operating system Store, manipulate, reformat, combine, and organise information Create logic to control how programs run and what they do Interact with users or other programs, wherever they are Save time and improve reliability by creating reusable functions Master Python data types: numbers, text, lists, and dictionaries Write object-oriented programs that work better and are easier to improve Expand Python classes to make them even more powerful Use third-party modules to perform complex tasks without writing new code Split programs to make them more maintainable and reusable Clearly document your code so others can work with it Store data in SQLite databases, write queries, and share data via JSON Simplify Python web development with the Flask framework Quickly program Python games with PyGame Avoid, troubleshoot, and fix problems with your code The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. COMPUTERS,Web,General

How to Do Everything Written by a renowned genealogy expert, this fully updated bestseller shows you how to use both traditional and online genealogy research methods. Thoroughly revised for the latest tools and techniques, How to Do Everything: Genealogy, Fourth Edition uniquely addresses all the different genealogical record types, explaining traditional and digital research strategies. It defines the basic rules of genealogical evidence, explains how to evaluate source materials, and describes proven research methods. This practical guide shows you how to research your family history using the most current websites, social networking sites, record archives, newly released and forthcoming census data, digital records, new frontiers in DNA research, and more. The latest technological tools such as hardware and software are also covered. Featuring global resources from the U.S., Canada, the U.K., and Australia in a single volume, this book reveals how to: Organize and create your family tree Research census documents, military service records, and land and property rolls Locate difficult-to-find records Use the most efficient internet search techniques Plan a successful genealogy research trip Evaluate sources for authenticity Research and verify ancestors using genetic genealogy (DNA) Get past brick walls and dead ends in your research Use social networking sites and collaboration techniques COMPUTERS,Web,General

Internet of Things, The The Internet of Things (IoT) won’t just connect people: It will connect “smart†homes, appliances, cars, offices, factories, cities… the world. You need to know what’s coming: It might just transform your life. Now, the world’s #1 author of beginning technology books has written the perfect introduction to IoT for everyone. Michael Miller shows how connected smart devices will help people do more, do it smarter, do it faster. He also reveals the potential risks—to your privacy, your freedom, and maybe your life. Make no mistake: IoT is coming quickly. Miller explains why you care, helps you use what’s already here, and prepares you for the world that’s hurtling toward you. COMPUTERS,Web,General

My Google Apps My Google Apps Full-color, step-by-step tasks walk you through doing exactly what you want with Google Apps. Learn how to: Use Google Apps to reduce technology expenses and grow your business Choose the best Google Apps version for your needs Quickly activate and customize your account Give your users customized email that uses your domain, not gmail.com Connect Gmail to your smartphone so your email and schedule always go with you Create, format, edit, print, and collaborate on documents with Docs Track and analyze your data with Sheets Create presentations with Slides and present anywhere via the Internet Cut travel costs: run video meetings online with Google Hangouts Improve project collaboration with a shared Sites workspace Efficiently manage and share your schedule with Calendar Store and share your files for secure anytime/anywhere access Sync your files between your PC or Mac and Google Drive in the cloud Use Vault to archive content and activity for compliance or other legal reasons COVERS: Gmail, Calendar, Drive, Docs, Sheets, Slides, Hangouts, Sites, Vault Step-by-step instructions with callouts to new Google Apps screenshots that show you exactly what to do. Help when you run into Google Apps problems or limitations. Tips and Notes to help you get the most from Google Apps. COMPUTERS,Web,General

Quicken 2016 The Official Guide Fully authorized by Intuit, this practical volume has been revised to cover the latest release of the #1 bestselling personal finance software. You will learn how to manage finances, save money, and find current balances—even via mobile devices. The book provides professional advice that will help you reduce debt, stay on budget, save money, and plan for a secure financial future. Quicken 2016: The Official Guide offers complete coverage of setting up and balancing personal banking and credit accounts, paying bills and viewing accounts online, and tracking and managing investments. Readers will get step-by-step instructions, examples, and illustrations. This comprehensive guide contains full details on all-new investment tools and updated loan and budgeting features. Covers mobile use on both Apple and Android platforms, including banking, credit card, and investment sync online “In My Experience†sidebars highlight the benefits of specific features Written in a no-nonsense, practical style by Intuit Certified Professional Advisor Bobbi Sandberg COMPUTERS,Web,General

Grid Layout in CSS CSS has had a layout-shaped hole at its center since the beginning. Designers have bent features such as float and clear to help fill that hole, but nothing has quite done the job. Now that’s about to change. With this concise guide, you’ll learn how to use CSS grid layout, a generalized system that lets you lay out pieces of your design independent of their document source order and with full awareness of the overall design. Short and deep, this book is an excerpt from the upcoming fourth edition of CSS: The Definitive Guide. When you purchase either the print or the ebook edition of Grid Layout in CSS, you’ll receive a discount on the entire Definitive Guide once it’s released. Why wait? Learn how to make your web pages come alive today. Explore the differences between grid boxes and block containers Create block-level grids, inline grids, and even nest grids inside grids Learn best practices for attaching elements to your layout, using explicitly defined grid lines or grid area Understand how the implicit grid automatically adjusts for oversized elements Create gutters between grid elements, and align and justify individual items Eric A. Meyer is an author, speaker, blogger, sometime teacher, and co-founder of An Event Apart. He’s a two-decade veteran of the Web and web standards, a past member of the W3C’s Cascading Style Sheets Working Group, and the author of O’Reilly’s CSS: The Definitive Guide. COMPUTERS,Web,General

Python Web Scraping Successfully scrape data from any website with the power of Python 3.x About This Book A hands-on guide to web scraping using Python with solutions to real-world problems Create a number of different web scrapers in Python to extract information This book includes practical examples on using the popular and well-maintained libraries in Python for your web scraping needs Who This Book Is For This book is aimed at developers who want to use web scraping for legitimate purposes. Prior programming experience with Python would be useful but not essential. Anyone with general knowledge of programming languages should be able to pick up the book and understand the principals involved. What You Will Learn Extract data from web pages with simple Python programming Build a concurrent crawler to process web pages in parallel Follow links to crawl a website Extract features from the HTML Cache downloaded HTML for reuse Compare concurrent models to determine the fastest crawler Find out how to parse JavaScript-dependent websites Interact with forms and sessions In Detail The Internet contains the most useful set of data ever assembled, most of which is publicly accessible for free. However, this data is not easily usable. It is embedded within the structure and style of websites and needs to be carefully extracted. Web scraping is becoming increasingly useful as a means to gather and make sense of the wealth of information available online. This book is the ultimate guide to using the latest features of Python 3.x to scrape data from websites. In the early chapters, you'll see how to extract data from static web pages. You'll learn to use caching with databases and files to save time and manage the load on servers. After covering the basics, you'll get hands-on practice building a more sophisticated crawler using browsers, crawlers, and concurrent scrapers. You'll determine when and how to scrape data from a JavaScript-dependent website using PyQt and Selenium. You'll get a better understanding of how to submit forms on complex websites protected by CAPTCHA. You'll find out how to automate these actions with Python packages such as mechanize. You'll also learn how to create class-based scrapers with Scrapy libraries and implement your learning on real websites. By the end of the book, you will have explored testing websites with scrapers, remote scraping, best practices, working with images, and many other relevant topics. Style and approach This hands-on guide is full of real-life examples and solutions starting simple and then progressively becoming more complex. Each chapter in this book introduces a problem and then provides one or more possible solutions. COMPUTERS,Web,General

Mastering Kali Linux for Web Penetration Testing Master the art of exploiting advanced web penetration techniques with Kali Linux 2016.2 About This Book Make the most out of advanced web pen-testing techniques using Kali Linux 2016.2 Explore how Stored (a.k.a. Persistent) XSS attacks work and how to take advantage of them Learn to secure your application by performing advanced web based attacks. Bypass internet security to traverse from the web to a private network. Who This Book Is For This book targets IT pen testers, security consultants, and ethical hackers who want to expand their knowledge and gain expertise on advanced web penetration techniques. Prior knowledge of penetration testing would be beneficial. What You Will Learn Establish a fully-featured sandbox for test rehearsal and risk-free investigation of applications Enlist open-source information to get a head-start on enumerating account credentials, mapping potential dependencies, and discovering unintended backdoors and exposed information Map, scan, and spider web applications using nmap/zenmap, nikto, arachni, webscarab, w3af, and NetCat for more accurate characterization Proxy web transactions through tools such as Burp Suite, OWASP's ZAP tool, and Vega to uncover application weaknesses and manipulate responses Deploy SQL injection, cross-site scripting, Java vulnerabilities, and overflow attacks using Burp Suite, websploit, and SQLMap to test application robustness Evaluate and test identity, authentication, and authorization schemes and sniff out weak cryptography before the black hats do In Detail You will start by delving into some common web application architectures in use, both in private and public cloud instances. You will also learn about the most common frameworks for testing, such as OWASP OGT version 4, and how to use them to guide your efforts. In the next section, you will be introduced to web pentesting with core tools and you will also see how to make web applications more secure through rigorous penetration tests using advanced features in open source tools. The book will then show you how to better hone your web pentesting skills in safe environments that can ensure low-risk experimentation with the powerful tools and features in Kali Linux that go beyond a typical script-kiddie approach. After establishing how to test these powerful tools safely, you will understand how to better identify vulnerabilities, position and deploy exploits, compromise authentication and authorization, and test the resilience and exposure applications possess. By the end of this book, you will be well-versed with the web service architecture to identify and evade various protection mechanisms that are used on the Web today. You will leave this book with a greater mastery of essential test techniques needed to verify the secure design, development, and operation of your customers' web applications. Style and approach An advanced-level guide filled with real-world examples that will help you take your web application's security to the next level by using Kali Linux 2016.2. COMPUTERS,Web,General

Expert Hadoop Administration The Comprehensive, Up-to-Date Apache Hadoop Administration Handbook and Reference “Sam Alapati has worked with production Hadoop clusters for six years. His unique depth of experience has enabled him to write the go-to resource for all administrators looking to spec, size, expand, and secure production Hadoop clusters of any size.†–Paul Dix, Series Editor In Expert Hadoop® Administration, leading Hadoop administrator Sam R. Alapati brings together authoritative knowledge for creating, configuring, securing, managing, and optimizing production Hadoop clusters in any environment. Drawing on his experience with large-scale Hadoop administration, Alapati integrates action-oriented advice with carefully researched explanations of both problems and solutions. He covers an unmatched range of topics and offers an unparalleled collection of realistic examples. Alapati demystifies complex Hadoop environments, helping you understand exactly what happens behind the scenes when you administer your cluster. You’ll gain unprecedented insight as you walk through building clusters from scratch and configuring high availability, performance, security, encryption, and other key attributes. The high-value administration skills you learn here will be indispensable no matter what Hadoop distribution you use or what Hadoop applications you run. Understand Hadoop’s architecture from an administrator’s standpoint Create simple and fully distributed clusters Run MapReduce and Spark applications in a Hadoop cluster Manage and protect Hadoop data and high availability Work with HDFS commands, file permissions, and storage management Move data, and use YARN to allocate resources and schedule jobs Manage job workflows with Oozie and Hue Secure, monitor, log, and optimize Hadoop Benchmark and troubleshoot Hadoop COMPUTERS,Web,General

Learning C# 7 By Developing Games with Unity 2017 Develop your first interactive 2D and 3D platform game by learning the fundamentals of C# About This Book Learn the fundamentals of C# 7 scripting to develop GameObjects and master the basics of the new UI system in Unity 2017 Build and develop your 2D game right from scratch and extend it to 3D while implementing the principles of object-oriented programming and coding in C# 7 Get to grips with the fundamentals of optimizing your game using the latest features of Unity 2017 Who This Book Is For This book is for game developers and enthusiasts who want to get started with game development with Unity 2017. No prior experience of C# is required. What You Will Learn Create your first 2D and 3D games in Unity Understand the fundamentals of variables, methods, and code syntax in C# Use loops and collections efficiently in Unity to reduce the amount of code Develop a game using object-oriented programming principles Implement simple enemy characters into the game to learn point-to-point movement and Tree behaviors Avoid performance mistakes by implementing different optimization techniques Export 3D models and animations and import them inside a Unity project In Detail Do you want to learn C# programming by creating fun and interactive games using the latest Unity 2017 platform? If so, look no further; this is the right book for you. Get started with programming C# so you can create 2D and 3D games in Unity. We will walk you through the basics to get you started with C# 7 and its latest features. Then, explore the use of C# 7 and its latest functional programming capabilities to create amazing games with Unity 2017. You will create your first C# script for Unity, add objects into it, and learn how to create game elements with it. Work with the latest functional programming features of C# and leverage them for great game scripting. Throughout the book, you will learn to use the new Unity 2017 2D tool set and create an interactive 2D game with it. You will make enemies appear to challenge your player, and discover some optimization techniques for great game performance. At the end, you will learn how to transform a 2D game into 3D, and you will be able to skill up to become a pro C# programmer with Unity 2017! Style and approach The book takes a practical, step-by-step approach where you learn C# coding while developing fun and interactive games. COMPUTERS,Web,General

Django RESTful Web Services Design, build and test RESTful web services with the Django framework and Python About This Book Create efficient real-world RESTful web services with the latest Django framework Authenticate, secure, and integrate third-party packages efficiently in your Web Services Leverage the power of Python for faster Web Service development Who This Book Is For This book is for Python developers who want to create RESTful web services with Django; you need to have a basic working knowledge of Django but no previous experience with RESTful web services is required. What You Will Learn The best way to build a RESTful Web Service or API with Django and the Django REST Framework Develop complex RESTful APIs from scratch with Django and the Django REST Framework Work with either SQL or NoSQL data sources Design RESTful Web Services based on application requirements Use third-party packages and extensions to perform common tasks Create automated tests for RESTful web services Debug, test, and profile RESTful web services with Django and the Django REST Framework In Detail Django is a Python web framework that makes the web development process very easy. It reduces the amount of trivial code, which simplifies the creation of web applications and results in faster development. It is very powerful and a great choice for creating RESTful web services. If you are a Python developer and want to efficiently create RESTful web services with Django for your apps, then this is the right book for you. The book starts off by showing you how to install and configure the environment, required software, and tools to create RESTful web services with Django and the Django REST framework. We then move on to working with advanced serialization and migrations to interact with SQLite and non-SQL data sources. We will use the features included in the Django REST framework to improve our simple web service. Further, we will create API views to process diverse HTTP requests on objects, go through relationships and hyperlinked API management, and then discover the necessary steps to include security and permissions related to data models and APIs. We will also apply throttling rules and run tests to check that versioning works as expected. Next we will run automated tests to improve code coverage. By the end of the book, you will be able to build RESTful web services with Django. Style and approach The book takes a straightforward approach, giving you the techniques and best use cases to build great web services with Django and Python COMPUTERS,Web,General

Hands-On Full-Stack Development with Swift Build full-stack shopping list applications from scratch for web and mobile platforms using Xcode, Vapor, and Swift About This Book Build, package, and deploy an end-to-end app solution for mobile and web with Swift 4 Increase developer productivity by creating reusable client and server components Develop backend services for your apps and websites using Vapor framework Who This Book Is For This book is for developers who are looking to build full-stack web and native mobile applications using Swift. An understanding of HTML, CSS, and JavaScript would be beneficial when building server-rendered pages with Vapor. What You Will Learn Get accustomed to server-side programming as well as the Vapor framework Learn how to build a RESTful API Make network requests from your app and handle error states when a network request fails Deploy your app to Heroku using the CLI command Write a test for the Vapor backend Create a tvOS version of your shopping list app and explore code-sharing with an iOS platform Add registration and authentication so that users can have their own shopping lists In Detail Making Swift an open-source language enabled it to share code between a native app and a server. Building a scalable and secure server backend opens up new possibilities, such as building an entire application written in one language—Swift. This book gives you a detailed walk-through of tasks such as developing a native shopping list app with Swift and creating a full-stack backend using Vapor (which serves as an API server for the mobile app). You'll also discover how to build a web server to support dynamic web pages in browsers, thereby creating a rich application experience. You'll begin by planning and then building a native iOS app using Swift. Then, you'll get to grips with building web pages and creating web views of your native app using Vapor. To put things into perspective, you'll learn how to build an entire full-stack web application and an API server for your native mobile app, followed by learning how to deploy the app to the cloud, and add registration and authentication to it. Once you get acquainted with creating applications, you'll build a tvOS version of the shopping list app and explore how easy is it to create an app for a different platform with maximum code shareability. Towards the end, you'll also learn how to create an entire app for different platforms in Swift, thus enhancing your productivity. Style and approach A step-by-step tutorial-based approach that teaches you full-stack Swift through the development of a single application on several platforms. COMPUTERS,Web,General

Full-Stack React Projects Unleash the power of MERN stack by building diverse web applications using React, Node.js, Express, and MongoDB About This Book Create dynamic web applications with the MERN stack Leverage the power of React in building interactive and complex user interfaces Unlock the potential of Node, Express, and MongoDB to build modern full-stack applications Who This Book Is For Full-Stack React Web Development Projects is for JavaScript developers who have some experience with React, but no previous experience with full-stack development involving Node, Express, and MongoDB, and who want practical guidelines to start building different types of real-world web applications with this stack. What You Will Learn Set up your development environment and develop a MERN application Implement user authentication and authorization using JSON Web Tokens Build a social media application by extending the basic MERN application Create an online marketplace application with shopping cart and Stripe payments Develop a media streaming application using MongoDB GridFS Implement server-side rendering with data to improve SEO Set up and use React 360 to develop user interfaces with VR capabilities Learn industry best practices to make MERN stack applications reliable and scalable In Detail The benefits of using a full JavaScript stack for web development are undeniable, especially when robust and widely adopted technologies such as React, Node, and Express and are available. Combining the power of React with industry-tested, server-side technologies, such as Node, Express, and MongoDB, creates a diverse array of possibilities when developing real-world web applications. This book guides you through preparing the development environment for MERN stack-based web development, to creating a basic skeleton application and extending it to build four different web applications. These applications include a social media, an online marketplace, a media streaming, and a web-based game application with virtual reality features. While learning to set up the stack and developing a diverse range of applications with this book, you will grasp the inner workings of the MERN stack, extend its capabilities for complex features, and gain actionable knowledge of how to prepare MERN-based applications to meet the growing demands of real-world web applications. Style and approach This book provides practical guidelines on setting up and building MERN stack based applications, while providing further explanations on key concepts and implementations. COMPUTERS,Web,General

Node.js Web Development Create real-time applications using Node.js 10, Docker, MySQL, MongoDB, and Socket.IO with this practical guide and go beyond the developer's laptop to cover live deployment, including HTTPS and hardened security. About This Book Learn server-side JavaScript coding through the most up-to-date book on Node.js Explore the latest JavaScript features, and EcmaScript modules Walk through different stages of developing robust applications using Node.js 10 Who This Book Is For This book is for anybody looking for an alternative to the "P" languages (Perl, PHP, and Python), or anyone looking for a new paradigm of server-side application development. You should have at least a rudimentary understanding of JavaScript and web application development. What You Will Learn Install and use Node.js 10 for both development and deployment Use the Express 4.16 application framework Work with REST service development using the Restify framework Use data storage engines such as MySQL, SQLITE3, and MongoDB Use User authentication methods with OAuth2 Perform Real-time communication with the front-end using Socket.IO Implement Docker microservices in development, testing and deployment Perform unit testing with Mocha 5.x, and functional testing with Puppeteer 1.1.x Work with HTTPS using Let's Encrypt, and application security with Helmet In Detail Node.js is a server-side JavaScript platform using an event-driven, non-blocking I/O model allowing users to build fast and scalable data-intensive applications running in real time. This book gives you an excellent starting point, bringing you straight to the heart of developing web applications with Node.js. You will progress from a rudimentary knowledge of JavaScript and server-side development to being able to create, maintain, deploy and test your own Node.js application.You will understand the importance of transitioning to functions that return Promise objects, and the difference between fs, fs/promises and fs-extra. With this book you'll learn how to use the HTTP Server and Client objects, data storage with both SQL and MongoDB databases, real-time applications with Socket.IO, mobile-first theming with Bootstrap, microservice deployment with Docker, authenticating against third-party services using OAuth, and use some well known tools to beef up security of Express 4.16 applications. Style and approach Benefit from an easy, step-by-step approach that really works. COMPUTERS,Web,General

Moodle 3 E-Learning Course Development A complete guide on course development and delivery using Moodle 3.x About This Book Get the best out of the latest Moodle 3 framework to ensure successful learning Gain experience in creating different kinds of courses Create your first Moodle VR app using the Moodle VR toolset Who This Book Is For This book is for anyone who wants to get the best out of Moodle. As a beginner, this is a thorough guide for you to understand how the software works, with great ideas for getting off to a good start with your first course. Some experience of working with e-learning systems will be beneficial. Experienced Moodle users will find powerful insights into developing successful and educational courses. What You Will Learn Know what Moodle does and how it supports your teaching strategies Install Moodle on your computer and navigate your way around it Understand all of Moodle's learning features Monitor how learners interact with your site using site statistics Add multimedia content to your site Allow students to enroll themselves or invite other students to join a course In Detail Moodle is a learning platform or Course Management System (CMS) that is easy to install and use, but the real challenge is in developing a learning process that leverages its power and maps the learning objectives to content and assessments for an integrated and effective course. Moodle 3 E-Learning Course Development guides you through meeting that challenge in a practical way. This latest edition will show you how to add static learning material, assessments, and social features such as forum-based instructional strategy, a chat module, and forums to your courses so that students reach their learning potential. Whether you want to support traditional class teaching or lecturing, or provide complete online and distance e-learning courses, this book will prove to be a powerful resource throughout your use of Moodle. You'll learn how to create and integrate third-party plugins and widgets in your Moodle app, implement site permissions and user accounts, and ensure the security of content and test papers. Further on, you'll implement PHP scripts that will help you create customized UIs for your app. You'll also understand how to create your first Moodle VR e-learning app using the latest VR learning experience that Moodle 3 has to offer. By the end of this book, you will have explored the decisions, design considerations, and thought processes that go into developing a successful course. Style and approach Packed with clear step-by-step instructions, plenty of screenshots, and thorough explanations, this book guides you through the many features and options that you have to choose from when using Moodle 3. COMPUTERS,Web,General

Content Chemistry The result of thousands of conversations about web marketing with hundreds of companies, this handbook is a compilation of the most important and effective lessons and advice about the power of search engine optimization, social media, and email marketing. The first and only comprehensive guide to content marketing, this book explains the social, analytical, and creative aspects of modern marketing that are necessary to succeed on the web. By first covering the theory behind web and content marketing and then detailing it in practice, it shows how it is not only critical to modern business but is also a lot of fun. This edition has been updated to reflect new technology and marketing trends. COMPUTERS,Web,General

Web 2.0 Web 2.0 makes headlines, but how does it make money? This concise guide explains what's different about Web 2.0 and how those differences can improve your company's bottom line. Whether you're an executive plotting the next move, a small business owner looking to expand, or an entrepreneur planning a startup, Web 2.0: A Strategy Guide illustrates through real-life examples how businesses, large and small, are creating new opportunities on today's Web. This book is about strategy. Rather than focus on the technology, the examples concentrate on its effect. You will learn that creating a Web 2.0 business, or integrating Web 2.0 strategies with your existing business, means creating places online where people like to come together to share what they think, see, and do. When people come together over the Web, the result can be much more than the sum of the parts. The customers themselves help build the site, as old-fashioned "word of mouth" becomes hypergrowth. Web 2.0: A Strategy Guide demonstrates the power of this new paradigm by examining how: Flickr, a classic user-driven business, created value for itself by helping users create their own value Google made money with a model based on free search, and changed the rules for doing business on the Web-opening opportunities you can take advantage of Social network effects can support a business-ever wonder how FaceBook grew so quickly? Businesses like Amazon tap into the Web as a source of indirect revenue, using creative new approaches to monetize the investments they've made in the Web Written by Amy Shuen, an authority on Silicon Valley business models and innovation economics, Web 2.0: A Strategy Guide explains how to transform your business by looking at specific practices for integrating Web 2.0 with what you do. If you're executing business strategy and want to know how the Web is changing business, this book is for you. COMPUTERS,Web,General

Mastering React Test-Driven Development Implement TDD for your React applications using Jest, React Router, Redux, and GraphQL/Relay. Learn BDD and end-to-end acceptance testing with CucumberJS and Puppeteer. Key Features Learn the TDD process using the React framework Build complex, real-world applications with a pragmatic approach to TDD Use Cucumber for acceptance and BDD testing, bringing TDD to the wider team Book Description Many programmers are aware of TDD but struggle to apply it beyond basic examples. This book teaches how to build complex, real-world applications using Test-Driven Development (TDD). It takes a first principles approach to the TDD process using plain Jest and includes test-driving the integration of libraries including React Router, Redux, and Relay (GraphQL). Readers will practice systematic refactoring while building out their own test framework, gaining a deep understanding of TDD tools and techniques. They will learn how to test-drive features such as client- and server-side form validation, data filtering and searching, navigation and user workflow, undo/redo, animation, LocalStorage access, WebSocket communication, and querying GraphQL endpoints. The book covers refactoring codebases to use the React Router and Redux libraries. via TDD. Redux is explored in depth, with reducers, middleware, sagas, and connected React components. The book also covers acceptance testing using Cucumber and Puppeteer. The book is fully up to date with React 16.9 and has in-depth coverage of hooks and the 'act' test helper. What you will learn Build test-driven applications using React 16.9+ and Jest Build complete web applications using a variety of HTML input elements Understand the different types of test double and when to apply them Test-drive the Integration of libraries such as React Router, Redux, and Relay (GraphQL) Learn when to be pragmatic and how to apply TDD shortcuts Test-drive interaction with browser APIs including fetch and WebSockets Use Cucumber.js and Puppeteer to build BDD-style acceptance tests for your applications Build and test async Redux code using redux-saga and expect-redux Who this book is for The target audience for this book is JavaScript developers who are looking to implement test-driven and behavior-driven approaches for their React applications. COMPUTERS,Web,General

Making the Move to eLearning This book proposes a radical truth_that online education, when taught using the methodology perfected by successful veterans of distance learning, surpasses traditional face-to-face teaching and learning. EDUCATION,Computers & Technology

Instructional Design The Analyze, Design, Develop, Implement, and Evaluate (ADDIE) process is used to introduce an approach to instruction design that has a proven record of success. Instructional Design: The ADDIE Approach is intended to serve as an overview of the ADDIE concept. The primary rationale for this book is to respond to the need for an instruction design primer that addresses the current proliferation of complex educational development models, particularly non-traditional approaches to learning, multimedia development and online learning environments. Many entry level instructional designers and students enrolled in related academic programs indicate they are better prepared to accomplish the challenging work of creating effective training and education materials after they have a thorough understanding of the ADDIE principles. However, a survey of instructional development applications indicate that the overwhelming majority of instructional design models are based on ADDIE, often do not present the ADDIE origins as part of their content, and are poorly applied by people unfamiliar with the ADDIE paradigm. The purpose of this book is to focus on fundamental ADDIE principles, written with a minimum of professional jargon. This is not an attempt to debate scholars or other educational professionals on the finer points of instructional design, however, the book's content is based on sound doctrine and supported by valid empirical research. The only bias toward the topic is that generic terms will be used as often as possible in order to make it easy for the reader to apply the concepts in the book to other specific situations. EDUCATION,Computers & Technology

The Socially Networked Classroom Incorporate social networking into instruction, no matter your level of technological expertise or Internet access! With appropriate guidance, students’ social networking skills can be harnessed for teaching and learning in the 21st century. William Kist demonstrates how pioneering teachers have successfully integrated screen-based literacies into instruction and provides: Real-world activities and lesson examples for Grades 5–12, with assignment sheets, assessments, and rubrics Ideas on fostering collaborative learning using blogs, wikis, nings, and other interactive media. Tips on Internet safety, blogging etiquette, protected blogging sites, and more Blog entries from classroom teachers EDUCATION,Computers & Technology

The Anti-Education Era One of the first champions of the positive effects of gaming reveals the dark side of today's digital and social media Today's schools are eager to use the latest technology in the classroom, but rather than improving learning, the new e-media can just as easily narrow students' horizons. Education innovator James Paul Gee first documented the educational benefits of gaming a decade ago in his classic What Video Games Have to Teach Us About Learning and Literacy. Now, with digital and social media at the center of modern life, he issues an important warning that groundbreaking new technologies, far from revolutionizing schooling, can stymie the next generation's ability to resolve deep global challenges. The solution-and perhaps our children's future-lies in what Gee calls synchronized intelligence, a way of organizing people and their digital tools to solve problems, produce knowledge, and allow people to count and contribute. Gee explores important strategies and tools for today's parents, educators, and policy makers, including virtual worlds, artificial tutors, and ways to create collective intelligence where everyday people can solve hard problems. By harnessing the power of human creativity with interactional and technological sophistication we can finally overcome the limitations of today's failing educational system and solve problems in our high-risk global world. The Anti-Education Era is a powerful and important call to reshape digital learning, engage children in a meaningful educational experience, and bridge inequality. EDUCATION,Computers & Technology

Blended Learning in Grades 4–12 Use technology to focus on your students! In this step-by-step guide, teacher and education blogger Catlin Tucker outlines the process for integrating online discussion with face-to-face instruction in a way that empowers teachers to focus their energies where they’re most needed. With concrete strategies, ready-to-use resources, and sample rubrics grounded in the Common Core State Standards, this book shows teachers how to: Increase engagement and drive higher-order thinking Prepare students for high-stakes exams without sacrificing class time Assess online work Personalize learning and differentiate lessons Move toward flipped instruction to create a student-centered classroom EDUCATION,Computers & Technology

Advanced Educational Technology Proceedings of the NATO Advanced Research Workshop on Advanced Educational Technology - Research Issues and Future Potential, held in Grenoble, France, September 25-28, 1993 EDUCATION,Computers & Technology

Automating Instructional Design Proceedings of the NATO Advanced Study Institute on Automating Instructional Design: Computer-Based Development and Delivery Tools, held in Grimstad, Norway, July 12-23, 1993 EDUCATION,Computers & Technology

Educational Innovation in Economics and Business Administration During the last few years economics and business education have emerged as one of the largest fields of study in higher education. At the same time, the pressing concern for improving the quality of higher education has led to a definite need for more knowledge about effective instruction and innovation in economics and business education. The book brings together many examples of reform in economics and business education. Special attention is paid to the problem-based learning approach, which over the past ten years, has developed as a very important innovation in higher education. The book contains contributions from a variety of institutions on the necessity of curriculum reform, the choice of instructional methods, assessment and testing, and management of change. It is of interest for teachers in higher education, educational psychologists, and any person interested in educational innovation in economics and business administration. EDUCATION,Computers & Technology

Design and Production of Multimedia and Simulation-based Learning Material This volume results from a meeting that was held in Barcelona, Spain, April 1993, under the auspices of the DELTA programme of the European Commission. DELTA (Developing European Learning through Technological Advance) is the commission's technology R&D programme that concentrates on "Telematic Systems for Flexible and Distance Learning". The overarching goal of this programme is to contribute through information technology to more efficient and effective design, production, and delivery of learning material. The DELTA programme started its main phase in 1992 with a total of 22 projects and a total budget of 92. 4 million ECU. In the meanwhile an extension of the programme has resulted in 8 extensions of existing projects and 8 new projects, bringing the number of projects to 30, with a corresponding total budget of 99. 9 million ECU. The programme has three main areas: telecommunication, delivery information systems, and design and production. In the projects, in total 201 organisations (industrial, commercial, and universities) from 12 European Union member states and 5 EFTA countries are represented. The DELTA programme pays much attention to the exchange of ideas and dissemination of information both between individual DELTA projects and between DELTA projects and other initiatives in the EU. Meetings in which DELTA projects are involved are held several times a year as so-called 'concertation meetings', meetings where also non-DELTA projects participate are called 'concerted actions'. EDUCATION,Computers & Technology

Advanced Educational Technologies for Mathematics and Science This book is the outgrowth of a NATO Advanced Research Workshop, held in Milton Keynes (United Kingdom) in the summer of 1990. The workshop brought together about 30 world leaders in the use of advanced technologies in the teaching of mathematics and science. Many of these participants commented that the workshop was one of the more productive and exciting workshops that they had attended. It was not uncommon to see participants engaged in informal discussion far into the evenings and early mornings, long after formal sessions had ended. It is my hope that this book captures the substance and excitement of many of the ideas that were presented at the workshop. Indeed, the process by which this book has come about has given every opportunity for the best thinking to get reflected here. Participants wrote papers prior to the workshop. After the workshop, participants revised the papers at least once. In a few instances, three versions of papers were written. Some participants could not resist the urge to incorporate descriptions of some of the newer developments in their projects. The papers in this book demonstrate how technology is impacting our view of what should be taught, what can be taught, and how we should go about teaching in the various disciplines. As such, they offer great insight into the central issues of teaching and learning in a wide range of disciplines and across many grade levels (ranging from elementary school through undergraduate college education). EDUCATION,Computers & Technology

Control Technology in Elementary Education Proceedings of the NATO Advanced Research Workshop on Control Technology in Elementary Education, held in Liege, Belgium, November 17-21, 1992 EDUCATION,Computers & Technology

New Directions in Educational Technology Proceedings of the NATO Advanced Research Workshop on New Directions in Advanced Educational Technology, held in Milton Keynes, UK, 10-13 November, 1988 EDUCATION,Computers & Technology

Planning for Technology Stay a step ahead of technological change so that every student can flourish! Students and classrooms are growing more technologically savvy every semester, and falling behind is not an option. This new edition of an essential text shows educational leaders how to equip their students for the future, with updates such as: Digital developments of the past decade that school leaders must address New content covering the Common Core, distributed leadership, adult learning theory, digital citizenship, cybersecurity, cloud computing, and more A new chapter on creating a “culture of technology†that goes beyond mere user manuals to create responsible, tech-savvy students EDUCATION,Computers & Technology

What Video Games Have to Teach Us About Learning and Literacy. Second Edition The definitive look at all that can be learned from video games EDUCATION,Computers & Technology

Deeper Learning Through Technology Use the Cloud to Individualize Your Instruction and Watch Your Students Thrive! Cloud-based technology offers massive benefits to the classroom. But technology tools require conscientious implementation by educators. This book is the all-in-one resource you need to be sure your students reap the fullest rewards of how cloud-based tools can facilitate learning. In Deeper Learning Through Technology, teacher and top ed-blogger Ken Halla explains: How to implement new tech tools to create a self-paced, learner-centered classroom Strategies for leveraging cloud technology to ensure that students have access to an individualized, personalized education Real-life case studies and activities that will make applying the book’s strategies to your classroom enjoyable and achievable EDUCATION,Computers & Technology

Creatively Teach the Common Core Literacy Standards With Technology Let technology pave the way to Common Core success. Engage your students by delving into the Common Core ELA standards with the tools they use the most. As you explore the creative road to academic success, with the Common Core ELA and literacy standards—you will turn your classroom into a student-centered learning environment that fosters collaboration, individualizes instruction, and cultivates technological literacy. Features include: Specific recommendations for free apps and tech tools that support the Common Core Step-by-step guidelines to breaking down standards by grade and subject Teacher-tested, research-supported lesson ideas and strategies Replicable resources, including prewriting activities and writing templates Real-life examples EDUCATION,Computers & Technology

Technology Handbook for School Librarians Both theoretical and practical, this book will provide you with a strong introduction to a variety of technologies that will serve you—and your patrons—well. Each chapter addresses a different aspect or kind of technology. You'll learn essential skills, planning and funding techniques, and what hardware and software you'll need. You'll find plenty of information on creating or maintaining your library's web presence through websites, blogs, and social networking, as well as on various tools that you can use and apply to your curriculum. Many state standards include technology components, and this guide shows you how to meet them and stay up to date. You'll also learn what you should watch for in the future so you remain essential to your school. EDUCATION,Computers & Technology

Using Social Media in the Classroom ‘A book for every teacher’s bookshelf. This book gives a comprehensive overview of the tools and apps that can be used to help turn a mediocre teaching session into an outstanding one.’ - Cheryl Hine, Leeds City College EDUCATION,Computers & Technology

The Online Teaching Survival Guide Essential reading for online instructors, updated to cover new and emerging issues and technologies The Online Teaching Survival Guide provides a robust overview of theory-based techniques for teaching online or technology-enhanced courses. Covering all aspects of online teaching, this book reviews the latest research in cognitive processing and related learning outcomes while retaining a focus on the practical. A simple framework of instructional strategies mapped across a four-phase timeline provides a concrete starting point for both new online teachers and experienced teachers designing or revamping an online course. Essential technologies are explored in their basic and expanded forms, and traditional pedagogy serves as the foundation for tips and practices customized for online learning. The tips cover course management, social presence, community building, integration of new technologies, discussion and questioning techniques, assessment, and debriefing, along with new coverage of intensive or accelerated courses, customizing learning strategies, developing expertise, advanced course design, and assessment techniques exclusive to this new second edition. The theory and techniques of successful online teaching can be significantly different from those used face-to-face. With more and more classes being offered online, this book provides a valuable resource for taking your course to the next level. Understand the technology used in online teaching Learn specialized pedagogical tips and practices Examine new research on cognition and learning Adopt a clear framework of instructional strategies The explosion of online learning has created a demand for great online teachers. Increasingly, faculty who normally teach face-to-face are being asked to cover online courses—yet comprehensive pedagogical resources are scarce. The learning curve is huge, and faculty need a practical approach to course design and management that can be quickly and easily implemented. The Online Teaching Survival Guide provides that essential resource, with a customizable framework and deeper exploration of effective online teaching. EDUCATION,Computers & Technology

Redesigning Learning Spaces Bring hope, joy, and positive energy back into the daily work of the classroom. In this book, learn to design brain-friendly learning environments that foster engagement, productivity, and achievement while allowing for seamless integration of educational technology. Discover how flexible, welcoming, and comfortable learning spaces can prepare students for the future. In this book you’ll: Find resources for redesigning spaces on a sustainable budget Support technology integration through blended and virtual learning Hear from teachers and schools whose successfully transformed spaces have increased student achievement EDUCATION,Computers & Technology

Foundation of Digital Badges and Micro-Credentials This edited volume provides insight into how digital badgesmay enhance formal, non-formal and informal education by focusing on technicaldesign issues including organizational requirements, learning and instructionaldesign, as well as deployment. It features current research exploring thetheoretical foundation and empirical evidence of the utilization of digitalbadges as well as case studies that describe current practices and experiencesin the use of digital badges for motivation, learning, and instruction in K-12,higher education, workplace learning, and further education settings. EDUCATION,Computers & Technology

Going Google Unique ideas for authentic, 21st-century learning! Use this easy-access guide to discover exactly how and why Google’s latest internet tools can help prepare your students for the modern workplace! Quickly scan for detailed guidance and learn: Which tools help you meet 21st century learning skills and the new ISTE Standards for Students of Google Classroom, Google Drive, Google Earth, YouTube, and more 5 major points to consider before using each tool Includes a handy glossary of tech terms, a new companion website, teacher vignettes, screen casts, project tutorials, and classroom management tips. EDUCATION,Computers & Technology

Blended Learning in Action Shift to blended learning to transform education Blended learning has the power to reinvent education, but the transition requires a new approach to learning and a new skillset for educators. Loaded with research and examples, Blended Learning in Action demonstrates the advantages a blended model has over traditional instruction when technology is used to engage students both inside the classroom and online. Readers will find: Breakdowns of the most effective classroom setups for blended learning Tips for leaders Ideas for personalizing and differentiating instruction using technology Strategies for managing devices in schools Questions to facilitate professional development and deeper learning EDUCATION,Computers & Technology

Computational Thinking and Coding for Every Student Empower tomorrow’s tech innovators Our students are avid users and consumers of technology. Isn’t it time that they see themselves as the next technological innovators, too? Computational Thinking and Coding for Every Student is the beginner’s guide for K-12 educators who want to learn to integrate the basics of computer science into their curriculum. Readers will find Strategies and activities for teaching computational thinking and coding inside and outside of school, at any grade level, across disciplines Instruction-ready lessons for every grade A discussion guide and companion website with videos, activities, and other resources EDUCATION,Computers & Technology

Disruptive Classroom Technologies Timely and powerful, this book offers a new framework to elevate instructional practices with technology and maximize student learning. The T3 Framework helps teachers categorize students’ learning as translational, transformational, or transcendent, sorting through the low-impact applications to reach high-impact usage of technologies. Teachers and leaders will find: Examples of technology use at the translational, transformational, and transcendent levels Activities, guides, and prompts for deeper learning that move technology use to higher levels of the T3 Framework Evaluative rubrics to self-assess current technology use, establish meaningful goals, and track progress towards those goals EDUCATION,Computers & Technology

Best Practices for Teaching with Emerging Technologies As social media and Web 2.0 technologies continue to transform the learning trends and preferences of students, educators need to understand the applicability of these new tools in all types of learning environments. The second edition of Best Practices for Teaching with Emerging Technologies provides new and experienced instructors with practical examples of how low-cost and free technologies can be used to support student learning as well as best practices for integrating web-based tools into a course management system and managing student privacy in a Web 2.0 environment. "Showcase" spotlights throughout exemplify how the tools described in the book are already being used effectively in educational settings. This thoroughly revised second edition includes: a new chapter that explores how and why faculty are using the public web and open educational resources in place of a learning management system (LMS) and an expensive textbook additional tips and showcases in every chapter that illustrate faculty use of particular technologies the inclusion of new tools to replace technologies that no longer exist a revamped website featuring expanded online resources. This practical, easy-to-use guide will serve the needs of educators seeking to refresh or transform their instruction. Readers will be rewarded with an ample yet manageable collection of proven emerging technologies that can be leveraged for generating content, enhancing communications with and between students, and cultivating participatory, student-centered learning activities. EDUCATION,Computers & Technology

Teaching Computational Thinking and Coding in Primary Schools This core text for trainee primary teachers is a guide to the teaching of computing and coding, and provides an exploration of how children develop their computational thinking. EDUCATION,Computers & Technology

Design of Technology-Enhanced Learning This book explains how educational research can inform the design of technology-enhanced learning environments. After laying pedagogical, technological and content foundations, it analyses learning in Web 2.0, Social Networking, Mobile Learning and Virtual Worlds to derive nuanced principles for technology-enhanced learning design. EDUCATION,Computers & Technology

Remixing the Curriculum Remixing the Curriculum suggests that the way to develop curriculum to maximize student access and engagement is to employ essential elements of traditional pedagogy, but infuse it with technology to create new features through the Technology Fitness , Proactive Teaching , Universal Design for Learning , and Assistive Technology. EDUCATION,Computers & Technology

Machine Learning and Human Intelligence Intelligence is at the heart of what makes us human, but we invest artificial intelligence (AI) with qualities it does not have. Rosemary Luckin proposes a way to understand the complexity of human intelligence, offering clear-sighted recommendations for how educators can draw on what AI does best to nurture and expand our human capabilities. EDUCATION,Computers & Technology

ICT Strategies for Schools Recognizing the potential of ICTs to make taught curriculum significantly more relevant and purposeful, principals and school administrators in India have to design appropriate IT strategies and oversee the entire implementation process in their schools. This book is a guide to the use of ICT in schools, covering issues of pedagogy, curriculum, and learning. In brief, it deals with educational uses of IT; criteria for selection of hardware and software; designing an IT-assisted curriculum; teacher recruitment, training and desired competencies; management and financial issues; and possible problem areas: plagiarism, privacy, hacking. EDUCATION,Computers & Technology

Postphenomenological Methodologies This volume contributes to postphenomenological research into human-technology relations with essays reflecting on methodological issues through empirical studies of education, digital media, biohacking, health, robotics, and skateboarding. This work provides new perspectives that call for a comprehensive postphenomenological research methodology. EDUCATION,Computers & Technology

Teaching AI For many, artificial intelligence, or AI, may seem like a new, and possibly overwhelming concept. The reality is that AI is already being applied in industry and, for many of us, in our daily lives as well. A better understanding of AI can help you make informed decisions now, that will impact the future of your learners. This book explores what AI is, how it works and how educators can use it to better prepare students in a world with increased human-computer interaction. This book features perspectives from educators and industry experts on how they are using AI; approaches to teaching about AI including design thinking, project based learning and STEM connections; tools for exploring AI and sharing it with your students; and activities to introduce AI concepts, reflection questions and lesson ideas. EDUCATION,Computers & Technology

Technologies to Lead Schools In this book, we share perspectives on how education leaders can use computer technologies to enhance their effectiveness in working with other adults. EDUCATION,Computers & Technology

Reclaiming Personalized Learning Where exactly did personalized learning go so wrong? For teacher and consultant Paul France, at first technology-powered personalized learning seemed like a panacea. But after three years spent at a personalized learning start-up and network of microschools, he soon realized that such corporate-driven individualized learning initiatives do more harm than good, especially among our most vulnerable students. The far-superior alternative? A human-centered pedagogy that prioritizes children over technology. First, let’s be clear: Reclaiming Personalized Learning is not yet-another ed tech book. Instead it’s a user’s guide to restoring equity and humanity to our classrooms and schools through personalization. One part polemical, eleven parts practical, the book describes how to: Shape whole-class instruction, leverage small-group interactions, and nurture a student’s inner-dialogue Cultivate awareness within and among students, and build autonomy and authority Design curriculum with a flexible frame and where exactly the standards fit Humanize assessment and instruction, including the place of responsive teaching Create a sense of belonging, humanize technology integration, and effect socially just teaching and learning—all central issues in equity The truth is this: there’s no one framework, there’s no one tool that makes learning personalized–what personalized learning companies with a vested interest in profits might tempt you to believe. It’s people who personalize learning, and people not technology must be at the center of education. The time is now for all of us teachers to reclaim personalized learning, and this all-important book is our very best resource for getting started. “This is a compelling and critically important book for our time. With rich stories of teaching and learning Paul France considers ways to create the most positive learning experiences possible.†- JO BOALER, Nomellini & Olivier Professor of Education , Stanford Graduate School of Education “This brilliant book is a major contribution to the re-imagination of learning and teaching for the twenty-first century and should be essential reading for new and experienced teachers alike." - TONY WAGNER, Senior Research Fellow, Learning Policy Institute “In these troubled times, this book is more than a breath of fresh air, it is a call to action. Paul gives us an accessible and sophisticated book that explains how and why we should celebrate the humanity of every single student.†- JIM KNIGHT, Senior Partner of the Instructional Coaching Group (ICG) and Author of The Impact Cycle EDUCATION,Computers & Technology

The School in the Cloud The Science and the Story of the Future of Learning In 1999, Sugata Mitra conducted the famous "Hole in the Wall" experiment that inspired three TED Talks and earned him the first million-dollar TED prize for research in 2013. Since then, he has conducted new research around self-organized learning environments (SOLE), building "Schools in the Cloud" all over the world. This new book shares the results of this research and offers • Examples of thriving Schools in the Cloud in unlikely places • Mitra’s predictions on the future of learning • How to design assessments for self-organizing learning • How to build your own School in the Cloud • Clips from the documentary, The School in the Cloud EDUCATION,Computers & Technology

Coding in the Classroom A book for anyone teaching computer science, from elementary school teachers and coding club coaches to parents looking for some guidance. Computer science opens more doors for today's youth than any other discipline - which is why Coding in the Classroom is your key to unlocking students' future potential. Author Ryan Somma untangles the current state of CS education standards; describes the cognitive, academic, and professional benefits of learning CS; and provides numerous strategies to promote computational thinking and get kids coding! Whether you're a teacher, an after-school coach, or a parent seeking accessible ways to boost your kid's computer savvy, Coding in the Classroom is here to help. With quick-start programming strategies, scaffolded exercises for every grade level, and ideas for designing CS events that promote student achievement, this book is a rock-solid roadmap to CS integration from a wide variety of on-ramps. You'll learn: • tips and resources for teaching programming concepts via in-class activities and games, without a computer • development environments that make coding and sharing web apps a breeze • lesson plans for the software lifecycle process and techniques for facilitating long-term projects • ways to craft interdisciplinary units that bridge CS and computational thinking with other content areas Coding in the Classroom does more than make CS less formidable - it makes it more fun! From learning computational thinking via board games to building their own websites, students are offered a variety of entry points for acquiring the skills they need to succeed in the 21st-century workforce. Moreover, Somma understands how schools operate - and he's got your back. You'll be empowered to advocate for the value of implementing CS across the curriculum, get stakeholder buy-in, and build the supportive, equitable coding community that your school deserves. EDUCATION,Computers & Technology

Digital and Media Literacy in the Age of the Internet This book serves as a comprehensive guide for educators looking to make informed decisions and navigate digital spaces with their students. The author sets the stage for educators who may not be familiar with the digital world that their students live in, including the complexities of online identities, digital communities and social media. EDUCATION,Computers & Technology

Teach Boldly Transformational education leader Jennifer Williams offers design- and empathy-driven practices to help teachers activate positive change in student learning. Today’s students are ready to design, dream and MAKE the future. Teach Boldly: Using Edtech for Social Good is a guide for educators ready to apply innovative practices, meaningful technology use and global collaboration to drive the change they want to see in the world. Readers will learn how to create a customized plan for education innovation, with strategies for constructing agile classroom environments, digital storytelling and communicating across lines of difference, and prioritizing feedback and active listening. This book: Showcases the power of narrative and bringing focus to the need for storytelling in education. Offers direction for seeking out authentic feedback and steps for iterating on ideas, emphasizing preservation of voice and creative expression. Discusses learning space design through the lens of empathy and amplification of student voice. Provides easy-to-implement ideas for transforming learning and classroom culture through space. With inspiration from real-world peaceMAKERS in education, Teach Boldly invites readers to create ready-to-go action plans for themselves as educators, for classroom communities and for the global community. EDUCATION,Computers & Technology

OCR GCSE Computer Science, Second Edition Written by leading Computer Science teachers, this brand-new textbook will guide students through the updated OCR GCSE Computer Science specification topic by topic, and provide them with standalone recap and review sections, worked examples and clear explanations of complex topics. This Student Book: >> develops computational thinking skills in line with the new Practical Programming element of Component 02>> provides differentiated material with the 'beyond the spec' feature>> includes standalone recap and review sections at the end of each chapter>> provides definitions of technical terms, along with a glossary of words that will be needed for assessment. Look out for a free set of practice questions on the Hodder Education website. Please note, these questions are not endorsed by OCR and have not been subject to any OCR quality assurance processes. George Rouse, Lorne Pearcey and Gavin Craddock are highly respected and widely published authors of resources. EDUCATION,Computers & Technology

AQA GCSE Computer Science, Second Edition Updated specification; first teaching September 2020. Specification code: 8525 Written by leading Computer Science teachers, this textbook will guide students through the updated AQA GCSE Computer Science specification topic by topic, and provide them with standalone recap and review sections, practice questions, worked examples and clear explanations of complex topics. This textbook:>> Prepares students for assessment with numerous practice questions for all topics>> Develops computational thinking skills>> Provides differentiated material with the 'beyond the spec' feature>> Includes standalone recap and review sections at the end of each chapter>> Provides definitions of technical terms, along with a glossary of words to ensure students feel confident with the assessment. Authors George Rouse, Lorne Pearcey and Gavin Craddock are highly respected and widely published authors of resources. EDUCATION,Computers & Technology

Learning Disabilities and e-Information Digital Technology is becoming ever more used by people with learning disabilities for information, entertainment, to socialise and enjoy self-expression. This book explores these important issues, establishing how page design, use of images and other factors facilitate or inhibit information access and information behaviour more generally. EDUCATION,Computers & Technology

Peer Pedagogies on Digital Platforms How a popular entertainment genre on YouTube--Let's Play videos created by Minecraft players--offers opportunities for children to learn from their peers. Every day millions of children around the world watch video gameplay on YouTube in the form of a popular entertainment genre known as Let's Play videos. These videos, which present a player's gameplay and commentary, offer children opportunities for interaction and learning not available in traditional television viewing or solo video gameplay. In this book, Michael Dezuanni examines why Let's Play videos are so appealing to children, looking in particular at videos of Minecraft gameplay. He finds that a significant aspect of the popularity of these videos is the opportunity for knowledge and skill exchange. EDUCATION,Computers & Technology
Algorithms In the tradition of Real World Algorithms: A Beginner's Guide, Panos Louridas is back to introduce algorithms in an accessible manner, utilizing various examples to explain not just what algorithms are but how they work. Digital technology runs on algorithms, sets of instructions that describe how to do something efficiently. Application areas range from search engines to tournament scheduling, DNA sequencing, and machine learning. Arguing that every educated person today needs to have some understanding of algorithms and what they do, in this volume in the MIT Press Essential Knowledge series, Panos Louridas offers an introduction to algorithms that is accessible to the nonspecialist reader. Louridas explains not just what algorithms are but also how they work, offering a wide range of examples and keeping mathematics to a minimum. EDUCATION,Computers & Technology

Radical Solutions and Learning Analytics Learning Analytics become the key for Personalised Learning and Teaching thanks to the storage, categorisation and smart retrieval of Big Data. Thousands of user data can be tracked online via Learning Management Systems, instant messaging channels, social networks and other ways of communication. Always with the explicit authorisation from the end user, being a student, a teacher, a manager or a persona in a different role, an instructional designer can design a way to produce a practical dashboard that helps him improve that very user’s performance, interaction, motivation or just grading. This book provides a thorough approach on how education, as such, from teaching to learning through management, is improved by a smart analysis of available data, making visible and useful behaviours, predictions and patterns that are hinder to the regular eye without the process of massive data. EDUCATION,Computers & Technology

Applied Degree Education and the Future of Work This edited volume sets the stage for discussion on Education 4.0, with a focus on applied degree education and the future of work. Education 4.0 refers to the shifts in the education sector in response to Industry 4.0 where digital transformation is impacting the ways in which the world of work and our everyday lives are becoming increasingly automated. In the applied degree sector, significant change and transformation is occurring as leaders, educators and partners evolve smart campus environments to include blended learning, artificial intelligence, data analytics, BYOD devices, process automation and engage in curriculum renewal for and with industries and professions. This volume aims to profile and enhance the contribution of applied educational practice and research particularly in the applied degree sector and includes contributions that show case real world outcomes with students and industry as partners. This edited volume includes a wide range of topics, such as rethinking the role of education and educators; curriculum and the future of work; industrial partnership, collaboration and work integrated learning; vocational and professional practices; students, industry and professions as partners; employability skills and qualities for the 21st century world of work; innovative pedagogy and instructional design; adaptive learning technologies; and data analytics, assessment and feedback. The contributors come from different parts of the world in higher education, including, Canada, China, Finland, Germany, Hong Kong, Italy, Macau, Singapore and the United Kingdom. EDUCATION,Computers & Technology

Radical Solutions and eLearning Educational Technology is the right couple to a radical innovation. Thanks to the appropriate technology in the right context with the best fit to the target audience, education can be drastically improved, meaning a better performance, competence achievement, match with the user’s expectations and with the market needs. Serious games, Virtual reality, Augmented reality, Remote labs, Online learning, Blockchain, Mobile learning and many other key technologies allow for a better explanation of so many subjects, and even more: for a complete student involvement and a full teacher engagement into the educational system. Technology gives another angle to the same content, provides the user with a personalised experience and pushes the limits of knowledge a little further, every time. This book presents a number of radical innovations through technology, from experienced cases studies, to be replicated and inspired by; a powerful resource handbook for cutting-edge education. EDUCATION,Computers & Technology

Intelligent Tutoring Systems This volume constitutes the proceedings of the 16th International Conference on Intelligent Tutoring Systems, ITS 2020, held in Athens, Greece, in June 2020. The 23 full papers and 31 short papers presented in this volume were carefully reviewed and selected from 85 submissions. They reflect a variety of new techniques, including multimodal affective computing, explainable AI, mixed-compensation multidimensional item response, ensemble deep learning, cohesion network analysis, spiral of silence, conversational agent, semantic web, computer-supported collaborative learning, and social network analysis. EDUCATION,Computers & Technology

Student Data Privacy Attai removes the fear around what could go wrong when it comes to protecting student data privacy and provides the guidance and support needed to build strong protections in place from the start. EDUCATION,Computers & Technology

Connected Code Why every child needs to learn to code: the shift from “computational thinking” to computational participation. Coding, once considered an arcane craft practiced by solitary techies, is now recognized by educators and theorists as a crucial skill, even a new literacy, for all children. Programming is often promoted in K-12 schools as a way to encourage “computational thinking”—which has now become the umbrella term for understanding what computer science has to contribute to reasoning and communicating in an ever-increasingly digital world. In Connected Code, Yasmin Kafai and Quinn Burke argue that although computational thinking represents an excellent starting point, the broader conception of “computational participation” better captures the twenty-first-century reality. Computational participation moves beyond the individual to focus on wider social networks and a DIY culture of digital “making.” Kafai and Burke describe contemporary examples of computational participation: students who code not for the sake of coding but to create games, stories, and animations to share; the emergence of youth programming communities; the practices and ethical challenges of remixing (rather than starting from scratch); and the move beyond stationary screens to programmable toys, tools, and textiles. EDUCATION,Computers & Technology

Education and Social Media Leading scholars from a variety of disciplines explore the future of education, including social media usage, new norms of knowledge, privacy, copyright, and MOOCs. How are widely popular social media such as Facebook, Twitter, and Instagram transforming how teachers teach, how kids learn, and the very foundations of education? What controversies surround the integration of social media in students' lives? The past decade has brought increased access to new media, and with this new opportunities and challenges for education. In this book, leading scholars from education, law, communications, sociology, and cultural studies explore the digital transformation now taking place in a variety of educational contexts. The contributors examine such topics as social media usage in schools, online youth communities, and distance learning in developing countries; the disruption of existing educational models of how knowledge is created and shared; privacy; accreditation; and the tension between the new ease of sharing and copyright laws. Case studies examine teaching media in K–12 schools and at universities; tuition-free, open education powered by social media, as practiced by the University of the People; new financial models for higher education; the benefits and challenges of MOOCS (Massive Open Online Courses); social media and teacher education; and the civic and individual advantages of teens' participatory play. Contributors Colin Agur, Jack M. Balkin, Valerie Belair-Gagnon, danah boyd, Nicholas Bramble, David Buckingham, Chris Dede, Benjamin Gleason, Christine Greenhow, Daniel J. H. Greenwood, Jiahang Li, Yite John Lu, Minhtuyen Mai, John Palfrey, Ri Pierce-Grove, Adam Poppe, Shai Reshef, Julia Sonnevend, Mark Warschauer EDUCATION,Computers & Technology

Connected Gaming How making and sharing video games offer educational benefits for coding, collaboration, and creativity. Over the last decade, video games designed to teach academic content have multiplied. Students can learn about Newtonian physics from a game or prep for entry into the army. An emphasis on the instructionist approach to gaming, however, has overshadowed the constructionist approach, in which students learn by designing their own games themselves. In this book, Yasmin Kafai and Quinn Burke discuss the educational benefits of constructionist gaming—coding, collaboration, and creativity—and the move from “computational thinking” toward “computational participation.” Kafai and Burke point to recent developments that support a shift to game making from game playing, including the game industry's acceptance, and even promotion, of “modding” and the growth of a DIY culture. Kafai and Burke show that student-designed games teach not only such technical skills as programming but also academic subjects. Making games also teaches collaboration, as students frequently work in teams to produce content and then share their games with in class or with others online. Yet Kafai and Burke don't advocate abandoning instructionist for constructionist approaches. Rather, they argue for a more comprehensive, inclusive idea of connected gaming in which both making and gaming play a part. EDUCATION,Computers & Technology
Families at Play How family video game play promotes intergenerational communication, connection, and learning. Video games have a bad reputation in the mainstream media. They are blamed for encouraging social isolation, promoting violence, and creating tensions between parents and children. In this book, Sinem Siyahhan and Elisabeth Gee offer another view. They show that video games can be a tool for connection, not isolation, creating opportunities for families to communicate and learn together. Like smartphones, Skype, and social media, games help families stay connected. Siyahhan and Gee offer examples: One family treats video game playing as a regular and valued activity, and bonds over Halo. A father tries to pass on his enthusiasm for Star Wars by playing Lego Star Wars with his young son. Families express their feelings and share their experiences and understanding of the world through playing video games like The Sims, Civilization, and Minecraft. Some video games are designed specifically to support family conversations around such real-world issues and sensitive topics as bullying and peer pressure. Siyahhan and Gee draw on a decade of research to look at how learning and teaching take place when families play video games together. With video games, they argue, the parents are not necessarily the teachers and experts; all family members can be both teachers and learners. They suggest video games can help families form, develop, and sustain their learning culture as well as develop skills that are valued in the twenty-first century workplace. Educators and game designers should take note. EDUCATION,Computers & Technology
Playful Visions The kaleidoscope, the stereoscope, and other nineteenth-century optical toys analyzed as “new media” of their era, provoking anxieties similar to our own about children and screens. In the nineteenth century, the kaleidoscope, the thaumatrope, the zoetrope, the stereoscope, and other optical toys were standard accessories of a middle-class childhood, used both at home and at school. In Playful Visions, Meredith Bak argues that the optical toys of the nineteenth century were the “new media” of their era, teaching children to be discerning consumers of media—and also provoking anxieties similar to contemporary worries about children's screen time. Bak shows that optical toys—which produced visual effects ranging from a moving image to the illusion of depth—established and reinforced a new understanding of vision as an interpretive process. At the same time, the expansion of the middle class as well as education and labor reforms contributed to a new notion of childhood as a time of innocence and play. Modern media culture and the emergence of modern Western childhood are thus deeply interconnected. Drawing on extensive archival research, Bak discusses, among other things, the circulation of optical toys, and the wide visibility gained by their appearance as printed templates and textual descriptions in periodicals; expanding conceptions of literacy, which came to include visual acuity; and how optical play allowed children to exercise a sense of visual mastery. She examines optical toys alongside related visual technologies including chromolithography—which inspired both chromatic delight and chromophobia. Finally, considering the contemporary use of optical toys in advertising, education, and art, Bak analyzes the endurance of nineteenth-century visual paradigms. EDUCATION,Computers & Technology

Engineering Play How the influential industry that produced such popular games as Oregon Trail and KidPix emerged from experimental efforts to use computers as tools in child-centered learning. Today, computers are part of kids' everyday lives, used both for play and for learning. We envy children's natural affinity for computers, the ease with which they click in and out of digital worlds. Thirty years ago, however, the computer belonged almost exclusively to business, the military, and academia. In Engineering Play, Mizuko Ito describes the transformation of the computer from a tool associated with adults and work to one linked to children, learning, and play. Ito gives an account of a pivotal period in the 1980s and 1990s, which saw the rise of a new category of consumer software designed specifically for elementary school-aged children. “Edutainment” software sought to blend various educational philosophies with interactive gaming and entertainment, and included such titles as Number Munchers, Oregon Trail, KidPix, and Where in the World Is Carmen Sandiego?. The children's software boom (and the bust that followed), says Ito, can be seen as a microcosm of the negotiations surrounding new technology, children, and education. The story she tells is both a testimonial to the transformative power of innovation and a cautionary tale about its limitations. EDUCATION,Computers & Technology

Handbook of Game-Based Learning A comprehensive introduction to the latest research and theory on learning and instruction with computer games. This book offers a comprehensive introduction to the latest research on learning and instruction with computer games. Unlike other books on the topic, which emphasize game development or best practices, Handbook of Game-Based Learning is based on empirical findings and grounded in psychological and learning sciences theory. The contributors, all leading researchers in the field, offer a range of perspectives, including cognitive, motivational, affective, and sociocultural. They explore research on whether (and how) computer games can help students learn educational content and academic skills; which game features (including feedback, incentives, adaptivity, narrative theme, and game mechanics) can improve the instructional effectiveness of these games; and applications, including games for learning in STEM disciplines, for training cognitive skills, for workforce learning, and for assessment. The Handbook offers an indispensable reference both for readers with practical interests in designing or selecting effective game-based learning environments and for scholars who conduct or evaluate research in the field. It can also be used in courses related to play, cognition, motivation, affect, instruction, and technology. Contributors Roger Azevedo, Ryan S. Baker, Daphne Bavelier, Amanda E. Bradbury, Ruth C. Clark, Michele D. Dickey, Hamadi Henderson, Bruce D. Homer, Fengfeng Ke, Younsu Kim, Charles E. Kinzer, Eric Klopfer, James C. Lester, Kristina Loderer, Richard E. Mayer, Bradford W. Mott, Nicholas V. Mudrick, Brian Nelson, Frank Nguyen, V. Elizabeth Owen, Shashank Pawar, Reinhard Pekrun, Jan L. Plass, Charles Raffale, Jonathon Reinhardt, C. Scott Rigby, Jonathan P. Rowe, Richard M. Ryan, Ruth N. Schwartz, Quinnipiac Valerie J. Shute, Randall D. Spain, Constance Steinkuehler, Frankie Tam, Michelle Taub, Meredith Thompson, Steven L. Thorne, A. M. Tsaasan EDUCATION,Computers & Technology

Online Predators, an Internet Insurgency The key to preventing online child predation is Stakeholder Involvement. Parents and guardians need to place themselves in the forefront of their kids’ minds when it comes to their devices. Educational professionals need to use their unique positions to educate their students and detect online predation and problems in their schools. EDUCATION,Computers & Technology

Evolving Perspectives on ICTs in Global Souths This book constitutes the refereed proceedings of the 11th International Development Informatics Association Conference, IDIA 2020, held in Macau, China, in March 2020.* The 14 revised full papers presented were carefully reviewed and selected from 43 submissions. The papers are organized in topical sections on ICT4D: taking stock; harnessing frontier technologies for sustainable development; ICT4D discourse, methodologies, and theoretical reflections; the evolving Global Souths. *The conference was held virtually due to the COVID-19 pandemic. EDUCATION,Computers & Technology

Blended Learning. Education in a Smart Learning Environment This book constitutes the refereed proceedings of the 13th International Conference on Blended Learning, ICBL 2020, held in Bangkok, in August 2020. The 33 papers presented were carefully reviewed and selected from 70 submissions. The conference theme of ICBL 2020 is Blended Learning : Education in a Smart Learning Environment. The papers are organized in topical sections named: Blended Learning, Hybrid Learning, Online Learning, Enriched and Smart Learning, Learning Management System and Content and Instructional Design. EDUCATION,Computers & Technology

Hello Ruby Welcome back to the world's most whimsical way to learn about technology and coding as a programming superstar introduces kids to the basic components of a computer through storytelling and imaginative activities. JUVENILE FICTION,Computers & Digital Media

Adventures of a Creeper In this humorous, illustrated chapter-book diary, you’ll find out that life is not always a blast—even if you’re an exploding Minecraft creeper! Minecraft creeper Mervyn Miles has just one goal: to win the annual Creeper Combustion and Confusion Competition so his father will finally be proud of him. But, between family and school pressures and bullying by arch-rival Wesley, things turn out to be more difficult than Mervyn could have ever imagined. Read all about this little green monster’s quest to become the biggest exploder in the entire Overworld in this humorous, unofficial Minecraft chapter-book diary with black-and-white illustrations. JUVENILE FICTION,Computers & Digital Media

Battle Royale Paul’s a normal teenager: he likes sports, junk food, and action movies—he even wants to be in one someday. But what seems like Paul’s big break, his very first acting role, quickly takes a turn for the worse. One minute he’s on a festive bus heading for a new life of stardom, and the next, he’s hurtling toward the ground and certain death. Though saved at the last minute by an unexplained parachute, things don’t get any easier when Paul lands: he’s lost on an unknown island, he’s unable to speak, and every time he sees someone else, he hears strange noises and then blacks out . . . before falling from the sky again. But when a girl inexplicably saves him (and spray paints him) instead of attacking, Paul starts to learn the survival basics. Bit by bit, he must explore his surroundings, build structures, evade violent storms, unlock the mysteries of his strange island prison, and maybe—just maybe—find a way out. JUVENILE FICTION,Computers & Digital Media

Chicken Clicking One night Chick hops onto the farmer's house and has a browse on his computer - CLICK - soon she's shopping online for the whole farm! But when she arranges to meet up with a friend she's made online, she discovers all is not as it seems... Little Red Riding Hood for the iPad generation, this is the perfect book for teaching children how to stay safe online. JUVENILE FICTION,Computers & Digital Media

How to Code a Rollercoaster Pearl and Pascal take their coding adventures to the amusement park in this follow-up picture book from our Girls Who Code program! Pearl and her trusty rust-proof robot, Pascal, are enjoying a day out at the amusement park. Spinning teacups, ice cream, and of course: rollercoasters! Through the use of code, Pearl and Pascal can keep track of their ride tokens and calculate when the line is short enough to get a spot on the biggest ride of them all--the Python Coaster. Variables, if-then-else sequences, and a hunt for a secret hidden code make this a humorous, code-tastic day at the amusement park! JUVENILE FICTION,Computers & Digital Media

How to Code a Sandcastle From the computer science nonprofit Girls Who Code comes this lively and funny story introducing kids to computer coding concepts. All summer, Pearl has been trying to build the perfect sandcastle, but out-of-control Frisbees and mischievous puppies keep getting in the way! Pearl and her robot friend Pascal have one last chance, and this time, they’re going to use code to get the job done. Using fundamental computer coding concepts like sequences and loops, Pearl and Pascal are able to break down their sandcastle problem into small, manageable steps. If they can create working code, this could turn out to be the best beach day ever! With renowned computer science nonprofit Girls Who Code, Josh Funk and Sara Palacios use humor, relatable situations, and bright artwork to introduce kids to the fun of coding. JUVENILE FICTION,Computers & Digital Media

Everything You Need to Master Minecraft Earth Minecraft Earth is the latest worldwide mobile gaming phenomenon. Now you can get ahead of the game with Everything You Need to Master Minecraft Earth, the essential guide to the Augmented Reality spin-off. You don't have to travel far to take your on-screen builds into the real world--learn how to craft amazing structures in your own living room, backyard, and beyond. This unofficial book contains everything you need to master the game, including: Tips on how to build up your collection of blocks, mobs, and rare items by finding Tappables. Build Plate ideas that will help you to craft incredible small-scale Augmented Reality structures with your friends—before placing them life-size into the real world. Hints on how to master Minecraft Earth Adventures, in which you can explore a Minecraft AR structure, solve tricky puzzles, or battle hordes of Minecraft mobs in the world around you. A complete guide to all the mobs you'll meet, including the new types developed specifically for Minecraft Earth. JUVENILE NONFICTION,Computers,Entertainment & Games

Hacks for TikTok Become a Pro at TikTok with This Tell-All Guide! From getting started to getting famous, Hacks for TikTok is the perfect hands-on guide for learning how to use Tiktok for your own personal enjoyment as well as for getting noticed, getting likes, and getting followed. This book covers the ins and outs of the app, providing practical advice so that you can master creating and managing content and grow your following. With this comprehensive guide, learn how to: • Navigate the TikTok app • Edit and post videos • Add special effects and sound clips • Interact and engage with your audience • Go viral and get famous • Keep your fans happy • Make money • And learn hacks for duets, skits, lip-syncing, challenges, and more! Including simple step-by-step instructions and screenshots for visual aid, this book is the perfect resource for beginners looking to learn the ropes and experts to brush up on their knowledge. JUVENILE NONFICTION,Computers,Entertainment & Games

Guide to Minecraft Dungeons With insider info and tips from the experts at Mojang, this is the definitive guide to Minecraft Dungeons. It is a dark and dangerous time. Corrupted by the Orb of Dominance, the evil Arch-Illager has gathered a loyal following of Illagers. Together they have ravaged the land, enslaving the peaceful Villagers and forcing them to do their bidding. The Villagers are in desperate need of a hero, and you are their only hope. Within the pages of this valuable book, you will find strategies for fighting malicious mobs, observations about the perils of each dungeon and advice about how to get your hands on rare and powerful items. You will also learn how to work as part of a team to vanquish the Arch-Illager once and for all. The fate of us all lies in your hands, brave hero. The Arch-Illager’s reign of terror ends now. JUVENILE NONFICTION,Computers,Entertainment & Games

Minecraft The official Minecraft: Guide to Ocean Survival will teach you how to breathe underwater, find valuable sunken loot and fight off guardians and other menacing mobs of the deep. Minecraft’s oceans are teeming with colorful life and rare treasures, but new dangers lurk beneath the water and survival can prove difficult. With insider info and tips from the experts at Mojang, this is the definitive guide to underwater survival. This ebook is best viewed on a color device with a larger screen. Collect all of the official Minecraft books: Minecraft: The Island Minecraft: The CrashMinecraft: The Lost Journals Minecraft: The Survivors’ Book of Secrets Minecraft: Exploded Builds: Medieval Fortress Minecraft: Guide to Exploration Minecraft: Guide to Creative Minecraft: Guide to the Nether & the End Minecraft: Guide to Redstone Minecraft: Mobestiary Minecraft: Guide to Enchantments & Potions Minecraft: Guide to PVP Minigames Minecraft: Guide to Farming Minecraft: Let’s Build! Theme Park Adventure Minecraft for Beginners Minecraft: Guide to Ocean Survival JUVENILE NONFICTION,Computers,Entertainment & Games

Minecraft The official Minecraft: Guide to Creative will teach you all you need to know to create builds more impressive than you could’ve dreamed of. The world of Minecraft is so varied and limitless that incredible creations can often be daunting to think about, never mind to build. With insider info and tips from the experts at Mojang, this is the definitive guide to creation in Minecraft. This ebook is best viewed on a color device with a larger screen. Collect all of the official Minecraft books: Minecraft: The Island Minecraft: The CrashMinecraft: The Lost Journals Minecraft: The Survivors’ Book of Secrets Minecraft: Exploded Builds: Medieval Fortress Minecraft: Guide to Exploration Minecraft: Guide to Creative Minecraft: Guide to the Nether & the End Minecraft: Guide to Redstone Minecraft: Mobestiary Minecraft: Guide to Enchantments & Potions Minecraft: Guide to PVP Minigames Minecraft: Guide to Farming Minecraft: Let’s Build! Theme Park Adventure Minecraft for Beginners JUVENILE NONFICTION,Computers,Entertainment & Games

The Unofficial Guide to Minecraft Maps Explore the ins and outs of making and using maps in the super popular game Minecraft. Tips and tricks help game-lovers master the craft while sidebars that highlight STEM and coding round out the experience. JUVENILE NONFICTION,Computers,Entertainment & Games

The Unofficial Guide to Minecraft Redstone Discover the different uses for redstone ore in the hit game Minecraft. Readers will learn all kinds of tips and tricks! STEM sidebars connect game play to real-world applications. JUVENILE NONFICTION,Computers,Entertainment & Games

The Unofficial Guide to Minecraft Enchantments Enchanted tools, weapons, and armor in the hit game Minecraft make playing more fun. Learn how to create them in this overview. Sidebars highlight elements of game play related to STEM and coding concepts. JUVENILE NONFICTION,Computers,Entertainment & Games

The Unofficial Guide to Minecraft Creative Mode Flying around and building without having to worry about zombie mobs? It's all fun and games when you play Minecraft in Creative mode! Fun tips, STEM content, and a fun coding feature will have players enthralled. JUVENILE NONFICTION,Computers,Entertainment & Games

Become a YouTuber GET EYES ON YOUR VIDS If you're the type who goes to YouTube for everything from entertainment to information to a way to communicate with your friends, this is the book you need to build a channel worth subscribing to. Packed with the advice of a video production teacher who's created her own channel, this book offers step-by-step advice for building a YouTube audience. Launch your channel – establish a home on YouTube where people can find your work Create your videos – apply production tricks to create videos that viewers watch over and over again Collaborate with your audience – build a relationship with your viewers that helps your audience grow JUVENILE NONFICTION,Computers,General

Ultimate Unofficial Survival Tactics for Fortniters The Essential Guide to Maximizing Your Settings in Fortnite Battle Royale! Unlock a plethora of gaming tips and strategies to achieve victory! Ultimate Unofficial Survival Tactics for Fortnite Battle Royale: Mastering Game Settings for Victory explains to readers what each customizable setting within the game is used for and helps gamers fine-tune these settings to meet their unique needs. This full-color, unofficial guide will focus on customizing the game’s options and settings when playing on a PC or Mac, console-based gaming system, and/or on a mobile device. Using easy-to-understand explanations, along with hundreds of full-color screenshots, Ultimate Unofficial Survival Tactices for Fortnite Battle Royale: Mastering Game Settings for Victory will quickly become an indispensable resource for gamers looking to enhance and fully personalize their gaming experience. Learn the best uses for the 100+ user-customizable options in the game Fine-tune the game’s settings to enhance your gaming style, experience, and strengths as a player Improve your performance by mastering the settings that fit your game-play JUVENILE NONFICTION,Computers,Internet & Social Media

Minecraft The official Minecraft: Guide to Farming will teach you about everything form basic crop farming and animal breeding to hostile mob and block farming. In Survival mode you’re constantly in need of food and other useful items, and true survivors knows the importance of setting up their own farming systems. With insider info and tips from the experts at Mojang, this is the definitive guide to becoming self-sufficient in Minecraft. This ebook is best viewed on a color device with a larger screen. Collect all of the official Minecraft books: Minecraft: The Island Minecraft: The CrashMinecraft: The Lost Journals Minecraft: The Survivors’ Book of Secrets Minecraft: Exploded Builds: Medieval Fortress Minecraft: Guide to Exploration Minecraft: Guide to Creative Minecraft: Guide to the Nether & the End Minecraft: Guide to Redstone Minecraft: Mobestiary Minecraft: Guide to Enchantments & Potions Minecraft: Guide to PVP Minigames Minecraft: Guide to Farming Minecraft: Let’s Build! Theme Park Adventure Minecraft for Beginners JUVENILE NONFICTION,Computers,Internet & Social Media

Garfield's ® Guide to Digital Citizenship Nermal may be the world's cutest kitten, but he's got a thing or two to learn about being the best little cat he can be online! Follow along as Garfield and the gang teach Nermal about online friends, being kind, thinking before you post, and avoiding download disasters in full-color comic book style. Activities after each story let you test your internet IQ with fun activities and quizzes. You're a great cyber citizen! JUVENILE NONFICTION,Computers,Internet & Social Media

Adventures in Raspberry Pi Build cool Raspberry Pi projects with no experience required! Adventures in Raspberry Pi, 3rd Edition is the fun guide to learning programming. Starting from the very basics and building skill upon skill, you'll learn developing fundamentals—even if you've never programmed before. Learning is exciting when you're working your way through cool projects, but the concepts you learn and the skills you master will take you further than you ever thought possible. You'll learn how your Raspberry Pi 3 works and what it can do as you create stories and games, program shapes, code music, and even build Minecraft worlds with projects designed specifically for kids 11 to 15. Author Carrie Anne Philbin is a former high school teacher, and she showcases her skills with clear, easy to follow instructions and explanations every step of the way. If you're interested in programming but find other books hard to understand, this book is your ideal starting point for mastering the Raspberry Pi. Inexpensive, non-intimidating, yet surprisingly versatile, the Raspberry Pi 3 is an ideal way to learn programming. Updated to align with the newest board, this book will teach you fundamental programming skills while having a ton of fun! Get acquainted with your Raspberry Pi's bits and pieces Take control of your Pi's "insides" with simple commands Program games, code music, and build a jukebox Discover where your new skills can take you next The tiny, credit-card sized Raspberry Pi has become a huge hit among kids—and adults—interested in programming. It does everything your desktop can do, but with a few basic programming skills, you can make it do so much more. With simple instructions, fun projects, and solid skills, Adventures in Raspberry Pi is the ultimate kids' programming guide! JUVENILE NONFICTION,Computers,Programming

Coding Projects in Scratch A perfect introduction to coding for young minds! This updated step-by-step visual guide teaches children to create their own projects using Scratch 3.0. Suitable for complete beginners, this educational book for kids gives readers a solid understanding of programming. Teach them to create their own projects from scratch, preparing them for more complex programming languages like Python. Techy kids will familiarize themselves with Scratch 3.0 using this beginner's guide to scratch coding. Difficult coding concepts become fun and easy to understand, as budding programmers build their own projects using the latest release of the world's most popular programming language for beginners. Make a Dino Dance Party or create your own electronic birthday cards for friends and family. Build games, simulations, and mind-bending graphics as you discover the awesome things computer programmers can do with Scratch 3.0. This second edition of Coding Projects in Scratch uses a visual step-by-step approach to split complicated code into manageable, easy-to-digest chunks. Even the most impressive projects become possible. This book is an impressive guide that is perfect for anyone who wants to learn to code. Follow Simple Steps, Improve Your Skills & Share Your Creations! Follow the simple steps to become an expert coder using the latest version of the popular programming language Scratch 3.0 in this new edition. Create mind-bending illusions, crazy animations, and interactive artwork with this amazing collection of Scratch projects. Suitable for beginners and experts alike, this fabulous introduction to programming for kids has everything you need to learn how to code. You'll improve your coding skills and learn to create and customize your own projects, then you can share your games online and challenge friends and family to beat each other's scores! What's inside this kids' coding book? - Simulations, mind-benders, music, and sounds- Algorithms, virtual snow, and interactive features- Different devices, operating systems, programming languages and more Computer coding teaches kids how to think creatively, work collaboratively, and reason systematically, and is quickly becoming a necessary and sought-after skill. DK's computer coding books for kids are full of fun exercises with step-by-step guidance, making them the perfect introductory tools for building vital skills in computer programming. Coding Projects in Scratch is one of three brilliant coding books for kids. Add Coding Games in Scratch and Coding Projects in Python to your collection. JUVENILE NONFICTION,Computers,Programming

Writing Computer Code A technology book for kids! Learning how to code can be like learning a foreign language.This book serves as an excellent guide to help you start writing in the odd-looking languages that make the web work. Follow simple steps as you work with real code to build your own web robots. Create your robot—write code that builds your robot's body and structure Give your bot some style—add code lines that customize your robot's color and shape Get your robot moving—finish off your robot with code that teaches it how to dance Technology Requirements: Hardware – PC or tablet with Internet connection running Windows 7 or higher or Mac with Internet connection running Mac OS X 10.7 or higher Software – Web browser to access JSFiddle.net: Google Chrome™, Mozilla Firefox, Apple Safari, Microsoft Edge, or Microsoft Internet Explorer version 9.0 or higher JUVENILE NONFICTION,Computers,Programming

Girls Who Code NEW YORK TIMES BESTSELLER! Part how-to, part girl-empowerment, and all fun, from the leader of the movement championed by Sheryl Sandberg, Malala Yousafzai, and John Legend. Since 2012, the organization Girls Who Code has taught computing skills to and inspired over 40,000 girls across America. Now its founder, and author Brave Not Perfect, Reshma Saujani, wants to inspire you to be a girl who codes! Bursting with dynamic artwork, down-to-earth explanations of coding principles, and real-life stories of girls and women working at places like Pixar and NASA, this graphically animated book shows what a huge role computer science plays in our lives and how much fun it can be. No matter your interest—sports, the arts, baking, student government, social justice—coding can help you do what you love and make your dreams come true. Whether you’re a girl who’s never coded before, a girl who codes, or a parent raising one, this entertaining book, printed in bold two-color and featuring art on every page, will have you itching to create your own apps, games, and robots to make the world a better place. JUVENILE NONFICTION,Computers,Programming

DKfindout! Coding Supporting STEM-based learning, this fun, fact-filled book for kids ages 6-9 explores the programming that makes our world work, in everyday objects from traffic lights to vending machines. Educating young readers through a combination of close-up images, quirky trivia facts, quiz questions, and fascinating tidbits, it's the perfect book for any reader who can't get enough of coding. How much did the first laptop weigh? What exactly is a computer bug? How many calculations can the world's fastest computer perform in a single second? Find out the answers to these questions and more in DKfindout! Coding, which features photographs and illustrations of gadgets, games, and coding geniuses like Ada Lovelace and Alan Turing. Beginning in the mid-1800s, readers can trace the path of coding pioneers from the birth of the first computer all the way to today's tech boom. Along the way, they'll learn about the fundamentals of coding languages like Java and Python-including their application in everything from cars to calculators-and how coding continues to revolutionize tech, gaming, medicine, space travel, and more. Vetted by educational consultants, the DKfindout! series drives kids ages 6-9 to become experts on more than 30 of their favorite STEM- and history-related subjects, whether Vikings, volcanoes, or robots. This series covers the subjects that kids really want to learn about-ones that have a direct impact on the world around them, like climate change, space exploration, and rapidly evolving technology-making learning fun through amazing images, stimulating quizzes, and cutting-edge information. The DKfindout! series is one that kids will want to turn to again and again. JUVENILE NONFICTION,Computers,Programming

Super Scratch Programming Adventure! (Scratch 3) Comics! Games! Programming! Now updated to cover Scratch 3. Scratch is the wildly popular educational programming language used by millions of first-time learners in classrooms and homes worldwide. By dragging together colorful blocks of code, kids can learn computer programming concepts and make cool games and animations. The latest version, Scratch 3, features an updated interface, new sprites and programming blocks, and extensions that let you program things like the micro:bit. In Super Scratch Programming Adventure!, kids learn programming fundamentals as they make their very own playable video games. They'll create projects inspired by classic arcade games that can be programmed (and played!) in an afternoon. Patient, step-by-step explanations of the code and fun programming challenges will have kids creating their own games in no time. This full-color comic book makes programming concepts like variables, flow control, and subroutines effortless to absorb. Packed with ideas for games that kids will be proud to show off, Super Scratch Programming Adventure! is the perfect first step for the budding programmer. Covers Scratch 3 JUVENILE NONFICTION,Computers,Programming

25 Scratch 3 Games for Kids Build your own computer games with Scratch 3! Learn how to make fun games with Scratch--a free, beginner-friendly programming language from the MIT Media Lab. Create mazes, road-crossing games, and two-player games that keep score. Colorful pictures and easy-to-follow instructions show you how to add cool animations and sound effects to your games. You'll have hours of fun catching snowflakes, gobbling up tacos, and dodging donuts in space--while learning how to code along the way! Covers Scratch 3 JUVENILE NONFICTION,Computers,Programming

Everything You Need to Ace Computer Science and Coding in One Big Fat Notebook The newest addition to the wildly successful Big Fat Notebook series, with 3.99 million copies in print: a lively, information-packed, and fully illustrated guide to Computer Science and Coding for middle schoolers. JUVENILE NONFICTION,Computers,Programming

I Can Code JUVENILE NONFICTION,Computers,Programming

¡Al bebé le encanta codificar! / Baby Loves Coding! Now available in Spanish bilingual editions, this best-selling series offers big, brainy science for the littlest listeners. Accurate enough to satisfy an expert, yet simple enough for baby, this clever board book showcases the use of logic, sequence, and patterns to solve problems. Can Baby think like a coder to fix her train? Beautiful, visually stimulating illustrations complement age-appropriate language to encourage baby's sense of wonder. Parents and caregivers may learn a thing or two, as well! Author's Note:The goal of the Baby Loves Science books is to introduce STEM topics in a developmentally appropriate way. As a precursor to learning programming languages and syntax, Baby Loves Coding presents the concepts of sequencing, problem solving, cause and effect, and thinking step-by-step. Practicing these skills early creates a solid foundation for reading, writing, math and eventually, programming. JUVENILE NONFICTION,Computers,Programming

Baby Loves Coding! Big, brainy science for the littlest listeners. Accurate enough to satisfy an expert, yet simple enough for baby, this clever board book showcases the use of logic, sequence, and patterns to solve problems. Can Baby think like a coder to fix her train? Beautiful, visually stimulating illustrations complement age-appropriate language to encourage baby's sense of wonder. Parents and caregivers may learn a thing or two, as well! Author's Note:The goal of the Baby Loves Science books is to introduce STEM topics in a developmentally appropriate way. As a precursor to learning programming languages and syntax, Baby Loves Coding presents the concepts of sequencing, problem solving, cause and effect, and thinking step-by-step. Practicing these skills early creates a solid foundation for reading, writing, math and eventually, programming. JUVENILE NONFICTION,Computers,Programming

Baby Code! Music It's never too early to get little ones interested in computer coding with this unique series of board books! How do you explain coding in music to a baby? By showing how it's all around them, and how they can take part in it, of course! By using experiences common in a baby's world, like hearing a melody from a mobile or tapping on an electronic xylophone, this charming board book full of bright, colorful illustrations is the perfect introduction to coding in music for babies and their caregivers--and is sure to leave them wanting to learn more! JUVENILE NONFICTION,Computers,Programming

Baby Code! Play It's never too early to get little ones interested in computer coding with this unique series of board books! How do you explain coding in playtime to a baby? By showing how it's all around them, and how they can take part in it, of course! By using items and experiences in a baby's world, like an electric swing or a ride at the amusement park, this charming board book full of bright, colorful illustrations is the perfect introduction to coding in active play for babies and their caregivers--and is sure to leave them wanting to learn more! JUVENILE NONFICTION,Computers,Programming

Baby Code! Art It's never too early to get little ones interested in computer coding with this unique series of board books! How do you explain coding in art to a baby? By showing how it's all around them, and how they can take part in it, of course! By using items in a baby's world, like a camera or a block made from a 3D printer, this charming board book full of bright, colorful illustrations is the perfect introduction to coding in art for babies and their caregivers--and is sure to leave them wanting to learn more! JUVENILE NONFICTION,Computers,Programming

Baby Code! It's never too early to get little ones interested in computer coding with this unique series of board books! How do you explain coding to a baby? By showing how it's all around them, and how they can take part in it, of course! By using items common in a baby's world, like a teddy bear and electric train, this charming board book full of bright, colorful illustrations is the perfect introduction to coding for babies and their caregivers--and is sure to leave them wanting to learn more! JUVENILE NONFICTION,Computers,Programming

I Can Code Introduce your little computer scientist to the essential coding basics and turn their everyday world into an extraordinary learning adventure! Written by an expert, I Can Code: AND/OR uses simple text, colorful illustrations, and interactive flaps to help little ones discover the building blocks of coding all around them! As kids follow along with an adorable story about sharing, they'll explore fundamental concepts like logical operators and true/false statements—and have fun doing it. Educators are saying every child needs to know the basics of coding—this is the book to get them started as early as possible! JUVENILE NONFICTION,Computers,Programming

20-Minute (Or Less) Animation Hacks Beginning coders can build their skill set with step-by-step instructions and animation projects. Start with stop-motion, add text and emoji, and finish with a few special effects! Page Plus links to hands-on coding activities are included. These project-based titles are created in partnership with Vidcode, an online coding platform for grades 4 and up. JUVENILE NONFICTION,Computers,Programming

20-Minute (Or Less) Meme Hacks With customizable projects, readers learn to combine pictures and text to create hilarious memes! Page Plus links to hands-on coding activities are included. These project-based titles are created in partnership with Vidcode, a rigorous and creative online coding platform designed for grades 4 and up that appeals as strongly to girls as to boys. JUVENILE NONFICTION,Computers,Programming

20-Minute (Or Less) Filter Hacks Create a filter, dress up a photo, share it with your friends! Beginning coders learn solid skills while they build their own filters. Page Plus links to hands-on coding activities are included. These project-based titles are created in partnership with Vidcode, a rigorous and creative online coding platform designed for grades 4 and up that appeals as strongly to girls as to boys. JUVENILE NONFICTION,Computers,Programming

20-Minute (Or Less) Digital Storytelling Hacks By completing these story-based projects, readers will gain a solid baseline in coding and have fun while learning. Build a slideshow, design a flag, create headlines that scroll across the bottom of newscasts, and more! Page Plus links to hands-on coding activities are included. These project-based titles are created in partnership with Vidcode, a rigorous and creative online coding platform designed for grades 4 and up that appeals as strongly to girls as to boys. JUVENILE NONFICTION,Computers,Programming

Blockchain for Babies Help your future genius become the smartest baby in the room by introducing them to cryptology technology with the next installment of the Baby University board book series! Full of scientific information from notable experts, this is the perfect book to teach complex concepts in a simple, engaging way. Blockchain for Babies is a colorfully simple introduction to the technology behind Bitcoin for cryptologists of all ages. It's never too early to become a scientist! JUVENILE NONFICTION,Computers,Software

Cyberspace Law This book explores what the American Civil Liberties Union calls the "third era" in cyberspace, in which filters "fundamentally alter the architectural structure of the Internet, with significant implications for free speech." Although courts and nongovernmental organizations increasingly insist upon constitutional and other legal guarantees of a freewheeling Internet, multi-national corporations compete to produce tools and strategies for making it more predictable. When Google attempted to improve our access to information containing in books and the World Wide Web, copyright litigation began to tie up the process of making content searchable, and resulted in the wrongful removal of access to thousands if not millions of works. Just as the courts were insisting that using trademarks online to criticize their owners is First Amendment-protected, corporations and trade associations accelerated their development of ways to make Internet companies liable for their users’ infringing words and actions, potentially circumventing free speech rights. And as social networking and content-sharing sites have proliferated, so have the terms of service and content-detecting tools for detecting, flagging, and deleting content that makes one or another corporation or trade association fear for its image or profits. The book provides a legal history of Internet regulation since the mid-1990s, with a particular focus on efforts by patent, trademark, and copyright owners to compel Internet firms to monitor their online offerings and remove or pay for any violations of the rights of others. This book will be of interest to students of law, communications, political science, government and policy, business, and economics, as well as anyone interested in free speech and commerce on the internet. LAW,Computer & Internet

EU General Data Protection Regulation (GDPR) - An Implementation and Compliance Guide All organisations – wherever they are in the world – that process the personally identifiable information (PII) of EU residents must comply with the Regulation. Failure to do so could result in fines of up to €20 million or 4% of annual global turnover. This book provides a detailed commentary on the GDPR, explains the changes you need to make to your data protection and information security regimes, and tells you exactly what you need to do to avoid severe financial penalties. LAW,Computer & Internet

EU General Data Protection Regulation (GDPR), third edition EU GDPR – An Implementation and Compliance Guide is a perfect companion for anyone managing a GDPR compliance project. It explains the changes you need to make to your data protection and information security regimes and tells you exactly what you need to do to avoid severe financial penalties. LAW,Computer & Internet

ISO/IEC 27701 ISO/IEC 27701:2019: An introduction to privacy information management offers a concise introduction to the Standard, aiding those organisations looking to improve their privacy information management regime, particularly where ISO/IEC 27701:2019 is involved. LAW,Computer & Internet

Nash Editions This is the magnum opus on digital printing and the book to read before color calibrating your monitor or wondering about differences in pigmented and dye-based inks. With little in the way of “how-to,†the book focuses more on why and showcases eloquent photographs, including a heartbreakingly beautiful portrait of Marilyn Monroe, a naked World War II bomber tail gunner, and the inevitable “Emperor’s New Clothes†work. Equally heartbreaking for far different reasons is Henry Wilhelm’s essay “A History of Permanence†that includes a section called “The Totally Lost Kodacolor Era†that will leave you stunned by the corporate callousness that’s described. This book not only deserves to be on the bookshelf of anybody who cares about photography, it deserves to be read. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Basic Critical Theory for Photographers Basic Critical Theory for Photographers generates discussion, thought and practical assignments around key debates in photography. Ashley la Grange avoids the trap of an elitist and purely academic approach to critical theory, taking a dual theoretical and practical approach when considering the issues. Key critical theory texts (such as Sontag's 'On Photography' and Barthes' 'Camera Lucida') are clarified and shortened. La Grange avoids editorilising, letting the arguments develop as the writers had intended; it is the assignments which call into question each writer's approach and promote debate. This is the ideal book if you want to understand key debates in photography and have a ready-made structure within which to discuss and explore these fascinating issues. It is accessible to students, from high school to university level, but will also be of interest to the general reader and to those photographers whose training and work is concerned with the practical aspects of photography. Also includes invaluable glossary of terms and a substantial index that incorporates the classic texts, helping you to navigate your way through these un-indexed works. The book also contains useful information on photo-mechanical processes, explaining how a photograph can appear very differently, and as a result be interpreted in a range of ways, in a variety of books. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Hot Shoe Diaries, The When it comes to photography, it’s all about the light. After spending more than thirty years behind the lens—working for National Geographic, Time, Life, and Sports Illustrated—Joe McNally knows about light. He knows how to talk about it, shape it, color it, control it, and direct it. Most importantly, he knows how to create it...using small hot shoe flashes. In The Hot Shoe Diaries, Joe brings you behind the scenes to candidly share his lighting solutions for a ton of great images. Using Nikon Speedlights, Joe lets you in on his uncensored thought process—often funny, sometimes serious, always fascinating—to demonstrate how he makes his pictures with these small flashes. Whether he’s photographing a gymnast on the Great Wall, an alligator in a swamp, or a fire truck careening through Times Square, Joe uses these flashes to create great light that makes his pictures sing. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Nikon D300s For Dummies The know-how you need to get the most out of your Nikon D300s The Nikon D300s is packed with pro features at a consumer price of less than $2,000, making it a camera both pro and beginning photographers will be looking to scoop up. Newcomers to the D300s can rely on this easy-to-understand book to guide them through the essentials of the camera's controls and how to adjust them in order to get results you want. Assuming no previous dSLR experience, veteran author Julie Adair King helps familiarize you with the features of the D300s and provides you with an overview of the camera body and automatic settings. You'll quickly learn to apply what you've learned to any shooting situation. Serves as ideal reading for newcomers to the Nikon D300s Veteran author Julie Adair King provides you with an overview of the camera body and its controls and features Looks at the camera's exposure, lighting, focus, automatic settings, and color controls Covers the retouch menu, as well as lesser-known features, so that you can get a final product worth sharing Set your focus on learning the essentials of the Nikon D300s with this friendly guide by your side! PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Photographing New York City Digital Field Guide Take memorable photos of the most popular attractions in the Big Apple! Whether using a point-and-shoot or a high-end dSLR, this companion guide provides you with detailed information for taking amazing shots of one of one of the world's most photographed cities. Whether you aim to capture the regal Empire State Building, vibrant Times Square, historic Grand Central Station, massive Central Park, or one of New York City's many other landmarks, this portable resource goes where you go and walks you through valuable tips and techniques for taking the best shot possible. You'll discover suggested locations for taking photos, recommended equipment, what camera settings to use, best times of day to photograph specific attractions, how to handle weather challenges, and more. In addition, beautiful images of New York City's most breathtaking attractions and recognizable landmarks serve to both inspire and assist you as you embark on an amazing photographic adventure! Elevates your photography skills to a new level with photography secrets from professional photographer and SmugMug COO, Andy Williams Presents clear, understandable tips and techniques that span all skill levels, using all types of digital cameras, from full-featured compact cameras to high end DSLRs Features New York City's main attractions in alphabetical order as well as thumb tabs on the pages so you can quickly and easily access the information you are looking for Shares detailed information and insight on critical topics, such as ideal locations to photograph from, the best time of day to shoot, camera equipment to have handy, weather conditions, and optimal camera settings to consider Whether you're a local familiar with the territory or a visitor seeing the Big Apple for the first time, this handy guide will help you capture fantastic photos! PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Digital Photography for the Older and Wiser Helpful, easy-to-follow guide for new digital photographers over the age of 50 Digital photography is a fun and exciting hobby, but digital cameras can be overwhelming and daunting to a newcomer. If you're entering the digital photography world as an older adult—and wondering about which digital camera will meet your needs—this straightforward, helpful book is for you. Written in full colour with lots of screenshots and clear, easy-to-read type, this friendly guide assumes no previous experience in digital photography and walks you through the subject of digital photography from start to finish: selecting which type of digital camera is right for you, understanding the seemingly endless jargon, benefiting from valuable photograph tips, and much more. Provides guidance for purchasing your digital camera and deciphers the common jargon that is used in the field Walks you through all the features and functions of a digital camera Reveals top photography tips Explains how to retouch, enhance, and print your photos Demonstrates easy ways to share photos with friends and family Prepare properly, enjoy the freedom, and maybe even show the family a thing or two with this fun and practical guide! PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Photographic Composition "Those of you who follow this blog know that Dr. Richard Zakia, former RIT professor, is one of my all time favorite photo gurus. We send each other pictures. We talk about looking into pictures - and not just looking at them. Big difference.. Dr. Richard Zakia, a.k.a. Dick, is the co-author, along with David Page, of Photographic Composition: A Visual Guide. These two dudes are also two of my favorite people."---Rick Sammon's blog "Covers all the tips needed to help photographers construct their own unique, outstanding images and is an outstanding 'must' for any collection."--CA Bookwatch PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Nikon D7000 This book is for anyone upgrading from their Nikon D90 or current DSLR to the highly anticipated Nikon D7000. There's the manual, of course, as well as competing books, and while they all explain, often in 400+ pages, what the camera can do, none of them shows exactly how to use the camera to create great images! This book has one goal: to teach D7000 owners how to make great shots using their new Nikon camera. Users learn how to use the D7000 to create the type of photos that inspired them to buy the camera in the first place. Everything in the book is in service of creating a great image. Starting with the top ten things users needed to know about the camera, photographer John Batdorff carefully guides readers through the operating features. Owners get practical advice from a pro on which settings to use when, great shooting tips, and even end of chapter assignments. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Canon EOS 60D This book has one goal: to teach you how to make great shots using your Canon EOS 60D. Starting with the top ten things you need to know about the camera—charging your battery, setting your ISO, reviewing your photos, and more—photography pro Nicole Young then carefully guides you through the modes of the camera, offering practical advice on choosing your settings, expert shooting tips, and end-of-chapter “challenges†to get you up and running with your EOS 60D. This book is for anyone who wants to upgrade from a point-and-shoot, or who wants to jump right into photography with the control and capabilities of a powerful DSLR. Canon EOS 60D: From Snapshots to Great Shots shows not only what makes a great shot work—but how to get that shot using your EOS 60D. Follow along with your friendly and knowledgeable guide, and you will: Learn the top ten things you need to know about shooting with the EOS 60D Use the EOS 60D’s advanced camera settings to gain full control over the look and feel of your images Master the photographic basics of composition, focus, depth of field, and much more Learn all the best tricks and techniques for getting great action shots, landscapes, and portraits Find out how to get great shots in low light Learn the basics of shooting video with your EOS 60D and start making movies of your own Fully grasp all the concepts and techniques as you go, with challenges at the end of every chapter And once you’ve got the shot, show it off! Join the book’s Flickr group, share your photos, and discuss how you use your EOS 60D to get great shots at http://www.flickr.com/groups/canon60dfromsnapshotstogreatshots. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Wedding Photography Take control of your digital photography and learn the skills and techniques required to record once-in-a-lifetime events–weddings. This beautifully illustrated guide by pro photographer Suzy Clement will help you conquer the fundamentals and take authentic and memorable shots that capture the essence of the day. Clement starts with the basics–exposure, metering, composition, lighting, depth of field, and motion blur and panning–and covers the key camera features that affect your image. She provides expert advice and techniques for each stage of the day, breaking down the demands into manageable portions, with advice on moments to watch for, must-have shots, and how to bring your own unique artistic expression to the event. Follow along with this friendly and knowledgeable guide and you will: Understand how to create a schedule for the day’s photography, prepare for the shoot, and effectively scout the site before the wedding Learn tips for packing your bag, lens choices, lighting options, and working in black and white or color Find the story of the wedding day as it unfolds–getting dressed, the ceremony, bride and groom and group portraits, the reception, wedding details, guests, departure–and use your limited time effectively Master the techniques for organizing and presenting your images to the couple after the wedding, including editing down, categorizing images, and using online versus hard copy proofs And once you’ve got the shot, show it off! Join the book’s Flickr group, share your wedding photos, and discuss how you used your camera at flickr.com/groups/weddingsfromsnapshotstogreatshots. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Wildlife Photography In Wildlife Photography: From Snapshots to Great Shots, author and wildlife photographer Laurie Excell shows you how to get the best shots of birds, bears, and bugs–whether you’re on safari, on vacation, or on a nature walk around your own backyard. Starting with the basics of equipment, camera settings, and exposure, Laurie covers the fundamentals of lighting and composition in capturing (in-camera!) a menagerie’s worth of animals, with a particular focus on mammals and birds. The book is packed with details on what seasons are best for photographing different animals, tips on the best locations to photograph them, and techniques for how to approach even the wiliest subjects. Beautifully illustrated with large, vibrant photos, this book teaches you how to take control of your photography to get the wildlife photo you want every time you pick up the camera. Follow along with your friendly and knowledgeable guide, photographer and author Laurie Excell, and you will: Use your camera’s settings to gain full control over the look and feel of your images Master the photographic basics of composition, focus, depth of field, and much more Get tips on research, including field ethics and the best locations for photographing your subjects Learn key techniques for photographing various animals, such as how to approach your subject without disturbing it and how to interpret behavior so that you can anticipate action Fully grasp all the concepts and techniques as you go, with assignments at the end of every chapter And once you’ve got the shot, show it off! Join the book’s Flickr group to share your photos, recipes, and tips at flickr.com/groups/wildlifephotographyfromsnapshotstogreatshots. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Photographing Flowers Capture stunning macro floral images with this gorgeous guide by acclaimed photographer Harold Davis. You'll learn about different types of flowers, macro equipment basics, and the intricacies of shooting different floral varieties in the field and in the studio. Harold also shows you techniques in the Photoshop darkroom that can be applied to flower photography to help you get the most out of your images. Beautiful and authoritative, this guide to photographing flowers is a must-read for every photographer interested in flower photography. Photographing Flowers will also win a place in the hearts of those who simply love striking floral imagery. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Storytellers It's amazing how many images the world's photographers produce! Professional or not, images surround us in our everyday lives. What makes successful photographers stand out? What drives us to revisit the same images over and over? All images tell a story. Whether they're produced as works of art, on assignment for National Geographic, or as part of a family vacation, images say more than just a shutter speed, ISO, or aperture setting. We make images for a reason. Storytellers, by photographer/teacher Jerod Foster, focuses on visual storytelling and how a deep knowledge of your process and your personal vision can create stronger images. Storytelling often requires the use of certain lenses, apertures, or light modifiers, but the story is what holds everything together. To become a better storyteller you will explore: Composition, light, depth of field, and motion and how to properly use your camera technically to dig deeper. Visual themes and how they provide stories with interest and depth Types of shots and shooting styles and what they convey in your images Research and ways to conceptualize your story before shooting Strategies for developing your own effective storytelling workflow during and after the shoot. This beautifully written and illustrated guide will help you connect the how-tos of digital photography with the who, what, when, where and why of storytelling to bring your vision and your images to life! PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Nikon D3300 For Dummies Take your best shot with your new Nikon D3300 Congratulations on your new Nikon D3300 DSLR! You probably want to get shooting right away, but first you need to know some basics about the controls and functions. Nikon D3300 For Dummies is your ultimate guide to your new camera, packed with everything you need to know to start taking beautiful photographs right out of the gate. Author Julie Adair King draws on a decade of experience in photography instruction, specifically Nikon and Canon, to walk you through the basics and get you started off on the right foot. Your new Nikon D3300 offers full control over exposure settings, but it also includes pre-sets and auto mode options for beginners. Nikon D3300 For Dummies guides you through the specifics of each setting, and teaches you how to determine what controls work best in a given situation. Written specifically for the Nikon D3300, the book discusses only the controls and capabilities available on your model, and shows you where to find them and how to use them. Topics include: Shooting in auto mode, playback options, and basic troubleshooting Working with light, focus, and color, and conquering video mode Picture organization, including file transfer and sharing Tips on photo editing and select features This full-color book includes a variety of photos that demonstrate the effects of different settings, allowing you to develop an eye for matching controls to situations. If you want to get the most out of your new DSLR, Nikon D3300 For Dummies is the best, most complete guide on the market. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Photo Inspiration The inspiration you need to help improve your photography skills Well-known for their stunning world-class photography, 1x.com has worked with their most talented photographers to handpick 100 awe-inspiring images and provided the back-story and photographer's secrets that helped capture them. This book presents you with inspiration as well as underlying techniques that can help improve your photography skills immediately. Shares behind-the-scene stories of the featured photos from the photographers themselves, from their artistic vision to the technical details that went into each shot Offers clear, concise, and accessible descriptions for the ideas, vision, performance, setup, location, equipment, camera settings, lighting diagrams, and image editing methods of each amazing photo Photo Inspiration provides a unique combination of the final photograph with the tools and knowledge that made it possible, all of which are aimed at helping you meet your photographic potential. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Travel Photography In A Day For Dummies Take better travel shots on your next vacation with this terrific, 100-page e-book! From pro to hobbyist, from short weekends to dream vacations, every photographer wants to be able to capture memorable and compelling travel photos. Now you can hit the road with this fast-paced, In A Day For Dummies e-book that really zeros in on how to best capture eye-popping travel photos. Find out how to set your camera, make adjustments on the fly, prepare for all kinds of light--even get great shots with your smartphone. You'll go through this handy e-book in a day, and capture photos for a lifetime. Focuses on techniques for capturing fantastic travel photos, no matter where you are or what kind of camera Covers setting the camera for the shot, making adjustments on the fly, lighting and composition, using a smartphone camera, and editing and sharing your photos Includes a "Beyond the book" online component, where you can find step-by-step tutorials, videos, and a bonus lesson on creating a high-dynamic range travel photo Online extras also include a photo book, how to make money selling your photos, and a gallery of unique travel photos to inspire you Get Travel Photography In A Day For Dummies, grab your camera, and hit the road! PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Adobe Photoshop CS6 Book for Digital Photographers ARE YOU READY FOR AN AMAZING NEW VERSION OF THE PHOTOSHOP BOOK THAT BREAKS ALL THE RULES? Scott Kelby, Editor and Publisher of Photoshop User magazine – and the best-selling Photoshop author in the world today – once again takes this book to a whole new level as he uncovers more of the latest, most important, and most useful Adobe Photoshop CS6 techniques for digital photographers. This major update to his award-winning, record-breaking book does something for digital photographers that’s never been done before – it cuts through the bull and shows you exactly “how to do it.†It’s not a bunch of theory; it doesn’t challenge you to come up with your own settings or figure it out on your own. Instead, Scott shows you step by step the exact techniques used by today’s cutting-edge digital photographers, and best of all, he shows you flat-out exactly which settings to use, when to use them, and why. That’s why the previous editions of this book are widely used as the official study guides in photography courses at colleges and universities around the world. LEARN HOW THE PROS DO IT Each year, Scott trains thousands of professional photographers on how to use Photoshop, and almost without exception they have the same questions, the same problems, and the same challenges – and that’s exactly what he covers in this book. You’ll learn: The sharpening techniques the pros really use. The pros’ tricks for fixing the most common digital photo problems fast! The step-by-step setup for getting what comes out of your printer to match exactly what you see onscreen. How to process HDR (High Dynamic Range) images using CS6’s Merge to HDR Pro. How to master CS6’s Content-Aware features. How to use Photoshop CS6’s new video editing features to make movies from your DSLR videos. How to process RAW images like a pro (plus how to take advantage of all the new Camera Raw features in CS6!). The latest Photoshop special effects for photographers (there’s a whole chapter just on these!). A host of shortcuts, workarounds, and slick “insider†tricks to send your productivity through the roof! Plus, Scott includes a special bonus chapter with his own CS6 workflow, from start to finish, and each chapter ends with a Photoshop Killer Tips section, packed with timesaving, job-saving tips that make all the difference. If you’re a digital photographer, and if you’re ready to learn all the “tricks of the trade†– the same ones that today’s leading pros use to correct, edit, sharpen, retouch, and present their work—then you’re holding the book that will do just that. Note from the publisher: August 9, 2012: All binding issues mentioned in our July 31, 2012 note below have been resolved. Thank you. July 31, 2012: We have encountered issues with the binding in our initial print run of this book. If you have purchased a copy of the book you are not happy with, please return it to the store where you made your purchase to request a replacement copy right away. We apologize for the inconvenience and appreciate your patience. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Bird Photography In Bird Photography: From Snapshots to Great Shots, author and wildlife photographer Laurie Excell teaches you key techniques for capturing images of birds–whether you spot them in your own backyard or in a faraway, exotic location. Laurie starts by discussing various camera setups and basic settings and why she uses them, as well as the fundamentals of exposure and how it relates to real-world bird photography. She then covers practicing at home, planning your trip, and selecting the best locations and times to shoot. Finally, she explains how to interpret behavior to determine how to approach your subject–so that you can maximize the time you have on your next big photography adventure. Filled with dozens of beautiful images, this short ebook will show you how to get the bird photo you want every time you pick up your camera. Follow along with your friendly and knowledgeable guide, photographer and author Laurie Excell, and you will: Use your camera’s settings to gain full control over the look and feel of your images Master the photographic basics of composition, focus, depth of field, and much more Get tips on the best seasons and locations for photographing your subjects Develop an understanding of your subjects' behavior, increasing your chances of getting great shots Fully grasp all the concepts and techniques as you go, with assignments at the end of every chapter PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Photographer's MBA, The If you have finally taken the leap with your photography and gone into business–or if you are considering it– The Photographer’s MBA will prove a helpful guide in navigating the often confusing and occasionally frustrating territories of business, marketing, pricing, and contracts. Photographer Sal Cincotta, who runs a highly successful portrait, senior, and wedding photography business, deftly leads you through “the other 90%†of the job of a photographer. In this book, you will: Consider what kind of business entity is best suited for you, such as a sole proprietorship, S-Corp, or LLC Learn about the critical importance of both business plans and marketing plans, and how they will help you reach your short-term and long-term goals Understand branding’s elements and how to define your own brand so that you stand out from the crowd Assess your social media strategy to optimize your presence online, and learn about search engine optimization (SEO) to increase your findability Tackle costs, pricing, and contracts (including copyright and model releases) At the end of each chapter, Sal offers a Next Steps section, containing exercises that challenge you to actively implement the overall lessons in the book. By helping you create a solid plan, a strategy you can implement, and a vision for your business, The Photographer’s MBA gets you well on your way to creating and sustaining a photography business that will grow and succeed for years to come. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Digital Wildlife Photography Using a combination of artistic approach and impeccable technique, professional photographers John and Barbara Gerlach will guide you through the field as you photograph the most intriguing and captivating subjects out in the wild. A sampling of what you'll learn: How to integrate equipment with technique to capture superb wildlife images of birds, mammals, amphibians, and more with an emphasis on precision and speed Where and how animals can be approached closely enough to photograph well How not to disturb the critters around you, depending on environment (den vs. tree and everything in-between) When (and when-not) to feed the animals Technical info like cropping, frames per second for capture, pixels/enlarging, and even HDR Where to focus on various types of wildlife Lighting depending on which animals have high contrast Ethics Traveling with your gear The "top 10" places in the world to shoot and how to find the best location for your interests PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

GIMP 2.8 for Photographers Image editing is a crucial element in the photographic workflow. Image editing tools, most notably Photoshop, are usually sophisticated and deep applications, and are fairly expensive. The only open source tool in this market is the GIMP, which has developed into a powerful, multiplatform system running on Linux, Mac OS X, and Microsoft Windows. GIMP 2.8 for Photographers is a beginner's guide to the only open source image editing tool that provides a no-cost alternative to expensive programs such as Photoshop. Topics include the new user interface and tools, the basics of image editing and simple adjustments, advanced techniques using layers and masks, developing RAW images, working with the improved text tool, and preparing high-quality black-and-white images. The most important editing functions are presented in individual, easy-to-follow workshops. A bonus section on the included DVD describes special techniques for web graphics. GIMP 2.8 for Photographers has evolved from classroom materials that the author developed and taught in courses and workshops on image editing with the GIMP. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Nikon D5200 For Dummies Invaluable photography advice for D5200 beginners The Nikon D5200 is one of Nikon's most advanced cameras offered in the entry-level line of dSLRs. This book goes beyond the user's manual to deliver a helpful introduction to the basic photo skills needed in order to get great shots from the D5200. Assuming no prior dSLR knowledge, veteran author Julie Adair King offers you a tour of the camera body with this full-color book as she presents you with a hands-on how-to on all the features of the D5200. Packed with pics, this fun and friendly guide offers unique inspiration for capturing your own memorable images. Helps you get an accurate feel for the camera, shooting in Auto mode, and managing playback options Walks you through adjusting settings to get better results from exposure, lighting, focus, and color Includes a full chapter on video mode Addresses sending images to a computer for organizing, editing, and sharing Demonstrates how to put the pieces together to get better portraits, action shots, and outdoor shots in any sort of light. Shares tips on the most common edits needed to improve shots Featuring an abundance of useful tips, this helpful guide encourages you to take control of your Nikon 5200 to get the photos you want. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Digital Photography Book, The This is it—the #1 best-selling digital photography book ever! It’s the award winning, worldwide smash hit, written by Scott Kelby, that’s been translated into dozens of different languages, because it’s the one book that really shows you how to take professional-quality shots using the same tricks today’s top digital pros use (and surprisingly, it’s easier than you’d think). This updated, second edition of the bestselling digital photography book of all time includes many new images; up-to-date information on gear, pricing, and links; and a new chapter from the author on the "Ten Things I Wish Someone Had Told Me When I Was First Starting Out in Photography." Here’s how Scott describes this book’s brilliant premise: “If you and I were out on a shoot, and you asked me, ‘Hey, how do I get this flower to be in focus, with the background out of focus?,’ I wouldn’t stand there and give you a photography lecture. In real life, I’d just say, ‘Put on your zoom lens, set your f-stop to f/2.8, focus on the flower, and fire away.’ That’s what this book is all about: you and I out shooting where I answer questions, give you advice, and share the secrets I’ve learned just like I would with a friend—without all the technical explanations and techie photo speak.†This isn’t a book of theory—full of confusing jargon and detailed concepts. This is a book on which button to push, which setting to use, and when to use it. With over 200 of the most closely guarded photographic “tricks of the trade,†this book gets you shooting dramatically better-looking, sharper, more colorful, more professional-looking photos every time. Each page covers a single concept that makes your photography better. Every time you turn the page, you’ll learn another pro setting, tool, or trick to transform your work from snapshots into gallery prints. If you’re tired of taking shots that look “okay,†and if you’re tired of looking in photography magazines and thinking, “Why don’t my shots look like that?†then this is the book for you. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Speedlights & Speedlites Canon Speedlites and Nikon Speedlights are small, off-camera flashguns that can provide big results - if you know how to use them properly. Acclaimed Boston photographers Lou Jones, Bob Keenan and Steve Ostrowski guide you through the technical and creative aspects of how to get the most out of these powerful tools in this indispensable guide, packed full of inspirational images and comprehensive diagrams of the lighting set ups used to capture them. They are significantly more advanced, lighter and considerably cheaper than a standard flashgun, and have many advantages. They are small (and cheap) enough that a number can be carried in your kit, and they can be used in combination, triggered wirelessly. They use through-the-lens (TTL) metering, which allows you to use the in-camera LCD and histograms to calculate the required power/direction, rather than havng to use a light meter or trial and error. They use proprietary, dedicated technology (from Canon and Nikon) that means there are no compatability issues. Getting the most out of them, however, remains a mystery - most photographers still just use their speedlights in the same way as a standard flash gun. This is where this book comes in. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Nikon D7100 Now that you’ve bought the amazing Nikon D7100, you need a book that goes beyond a tour of the camera’s features to show you exactly how to use the D7100 to take great pictures. With Nikon D7100: From Snapshots to Great Shots, you get the perfect blend of photography instruction and camera reference that will take your images to the next level. Beautifully illustrated with large, vibrant photos, this book teaches you how to take control of your photography to get the image you want every time you pick up the camera. Follow along with your friendly and knowledgeable guide, pro photographer John Batdorff, and you will: Learn the top ten things you need to get up and running with the D7100 Use the D7100’s automatic scene modes to get better shots right away Take full control over the look and feel of your images with professional modes Master the photographic basics of composition, focus, depth of field, and much more Learn all the best tricks and techniques for getting great action shots, landscapes, and portraits Find out how to get great shots in low light Use spot white balance in Live View and other new D7100 features And once you’ve got the shot, show it off! Join the book’s Flickr group, share your photos, and discuss how you use your camera to get great shots at flickr.com/groups/nikond7100_fromsnapshotstogreatshots. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Canon EOS Rebel SL1/100D For Dummies Get up to speed on your Canon SL1/100D and enter the world of dSLR photography! Canon's EOS Rebel SL1/100D is for photographers who prefer a smaller, lightweight camera that still offers heavyweight features. This full-color guide explains how to get better photos from an SL1. Written by professional photographer Doug Sahlin, this book explains the camera?s controls and shooting modes. It also shows how to take creative control by moving out of auto mode. You'll also learn how to manage and edit your images, shoot video, use autofocus, and get troubleshooting advice. Features a full-color format that shows you the camera controls and menus, explaining what each is for and how to use them all Demonstrates how to use the new autofocus feature, manage playback options, and shoot video Helps you graduate to manual mode and learn to control exposure, lighting, focus, and color Covers downloading, organizing, editing, and sharing photos Canon EOS Rebel SL1/100D For Dummies gives you the knowledge and confidence to make the move to dSLR photography using the Canon EOS Rebel SL1/100D, which is perfect for photographers who've been waiting for a smaller dSLR with big features. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Learning to Photograph - Volume 2 The two volumes of the Learning to Photograph series give students and interested amateur photographers essential information about technique and design as well as an understanding of the big concepts of photography. Beginning and advanced photographers alike will find the content instructive, thoroughly explained, and effectively illustrated, making this book a useful resource for readers to develop their own craft. This second volume addresses the topics of visual design and composition. The authors describe various methods of visual design and how you can use these methods effectively. You will learn which techniques to use to design your images while at the same time training your photographic eye. You will develop the ability to support the message of your subject purposefully, hone your photographic style, and analyze your own work and the work of others competently. The striking images and informational graphics not only illustrate the concepts at hand, but also make the lessons visually pleasing and offer useful examples for readers to mimic in their own work. Topics include: Visual perception Composition, shapes, and lines Managing light Color and its effects Sharpness, blur, and movement The interplay of visual design elements Image analysis and evaluation The previous volume in the Learning to Photograph series addresses cameras, equipment, and basic photographic techniques. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Digital Photography Masterclass Join Tom Ang's masterclass for a one-on-one guide to every aspect of digital photography. You'll improve your skills, develop your eye and learn to take control of your camera in Digital Photography Masterclass . Learn to be a better photographer; find out how to imagine the results you want before achieving them. Discover how to master the complexities of lighting, composition and timing. Enhance your pictures with image manipulation, then start to specialise in what interests you; from sport to portrait, following Tom's tips on taking genre photos. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Digital Photography Idiot's Guides®: Digital Photography is not a book on using Photoshop to fix bad photos, nor is it a book loaded down with technical data telling readers which camera to buy. Instead, it's the simplest guide to becoming a better photographer and taking better pictures with any DSLR. Instead of focusing on complicated and quickly outdated discussions of things like gear or retouching software, readers learn the timeless principles of good photography, the essentials of every camera and lens, and how to use all that knowledge to take the shots they previously thought were only achievable by professional photographers. Readers learn how to set up every shot, avoid common mistakes, and do more with their pictures through unique and creative photography projects. Focused on making people better photographers, this full-color guide finally simplifies the process of taking great pictures by focusing on what people really need to know to take better pictures. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Beyond the Zone System This fourth edition of Beyond the Zone System makes the science of photographic sensitometry both accessible and useful to interested photographers. It will appeal to any serious photographer interested in knowing how the materials and processes of black-and-white photography work. Instead of describing rote procedures to be followed blindly, this book provides the basis for understanding what needs to be done and why. This book relates theory to practice in a way that promotes a true partnership of science and art. Beyond the Zone System bridges the gap between the more theoretical aspects of the photographic process and the popular empirical procedures used by many photographers in the attempt to predict and control the quality of their photographs in practice. This book is intended primarily for photographers who use large-format cameras and black-and-white sheet film, but the basic information about how the B&W photographic materials and processes work will be useful to users of any B&W film format. Beyond the Zone System, 4th ed. will appeal to any serious photographer interested in knowing how the materials and processes of black-and-white photography work. Instead of describing rote procedures to be followed blindly, this book provides the basis for understanding what needs to be done and why. This book relates theory to practice in a way that promotes a true partnership of science and art. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Night Photography In Night Photography: From Snapshots to Great Shots , photographer Gabriel Biderman brings you the basics of digital night photography—exposure, composition, and light—and how to scout and capture different nocturnal locations once the sun goes down. Gabriel will help you understand the fundamentals and bring your unique artistic expression to any night situation. In this beautifully illustrated guide you will: Focus in the dark and master basic composition rules—and know when to break them Understand metering and switch to manual mode for more control over your exposure Set white balance, understand color temperature, and add flash or slow sync Explore colour, light painting, and creative ways to play with light in your images Learn what gear works best for your style of shooting and strategies for operating your equipment in the dark Discover expert techniques for post-processing your nighttime images in Lightroom and Photoshop Beautifully illustrated with large, compelling photos, this book teaches you how to take control of your photography to get the image you want every time. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

The Art and Style of Product Photography High quality images sell products. Here's how you do it. From cereal boxes to billboards to photos on Amazon, product photos have a strong impact on viewers. Now you can master the secrets of effective product photography with this essential guide. Author J. Dennis Thomas guides you through the basics, from selecting the right equipment and practicing different lighting techniques to controlling exposure, using backgrounds and props, and much more. Whether it's jewelry, food, fashion, or other products, learn how to photograph for effective selling, while building the skills and tools you need for a career. Explains how to produce quality photos for product or commercial photography, including fashion, food, jewelry, technology, and more The author is a professional photographer whose work has been published in major U.S. magazines including Rolling Stone, Elle, W Magazine, and US Weekly Covers choosing the right equipment, practicing different lighting techniques, controlling exposure, using backgrounds and props, and more Gives new and even experienced photographers the tools they need to build careers in product photography Take photographs that impress, intrigue, dazzle, and sell with The Art and Style of Product Photography. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Mastering the Nikon D610 Mastering the Nikon D610 by Darrell Young provides a wealth of experience-based information and insights for owners of the new D610 camera. Darrell is determined to help the user navigate past the confusion that often comes with complex and powerful professional camera equipment. This book explores the features and capabilities of the camera in a way that far surpasses the user's manual. It guides readers through the camera features with step-by-step setting adjustments; color illustrations; and detailed how, when, and why explanations for each option. Every button, dial, switch, and menu configuration setting is explored in a user-friendly manner, with suggestions for setup according to various shooting styles. Darrell's friendly and informative writing style allows readers to easily follow directions while feeling as if a friend dropped in to share his knowledge. The learning experience for new D610 users goes beyond just the camera itself and covers basic photography technique. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Picture Perfect Posing Photographer, author, and educator Roberto Valenzuela has a proven track record for teaching and explaining difficult concepts to photographers of all skill levels. His remarkable ability to break down complicated ideas into understandable, approachable elements that photographers can truly grasp–and then use their newfound knowledge to improve their photography–made his first book, Picture Perfect Practice, a breakout success. In Picture Perfect Posing, Roberto takes on the art of posing. For many photographers, after learning to compose an image and even light it properly, a portrait can still easily be a failure if the pose is not natural, elegant, and serving the needs of both the subject and the photographer. Instead of just showing page after page of poses–like most posing books on the market–Roberto actually breaks down the concept of posing by examining the anatomy, starting with the core foundation: the spinal chord and neck. Building from there, Roberto discusses every component of what makes poses work, as well as fail. How should the model hold her hands? Bend her elbows? Position her fingers? Should the model look toward or away from the camera, and why? It all depends on what the photographer wants for the shot, and Roberto discusses the entire process, from the intent of the photographer through the execution of the pose. For those who have been discouraged by an inability to pose their subjects, or who have simply not known where to start in order to "figure it out," Picture Perfect Posing is the essential resource they need to learn how posing truly works, and how they can learn to direct the exact pose they need for the shot they want. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Primitive Photography Primitive Photography considers the hand-made photographic process in its entirety, showing the reader how to make box-cameras, lenses, paper negatives and salt prints, using inexpensive tools and materials found in most hardware and art-supply stores. Step-by-step procedures are presented alongside theoretical explanations and historical background. Streamlined calotype procedures are demonstrated, featuring different paper negative processes and overlooked, developing-out printing methods. Primitive Photography combines the simplicity of pinhole photography, the handmade quality of alternative processes, and the precision of large-format. For those seeking alternatives to commercially prepared material as well as digital photography, it provides the instructions for creating the entire photographic process from the ground up. Given its scope and treatment of the photographic process as a whole, this may be the first book of its kind to appear in over a century. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Nikon D5300 For Dummies See the world differently through your new Nikon D5300 Your new Nikon D5300 digital SLR camera represents something about you. It shows that you want something more than a point-and-shoot camera has to offer. You want to take better photos. You want more control. You don't want to rely on editing to make beautiful photographs. Well, there's good news-you now have the right tool to make that happen! Now you need to learn how to use it. The Nikon D5300 has more features and expanded capabilities, and offers you more options for shooting in different situations. Taking advantage of the full complement of controls and settings gives you the power to capture images in new and imaginative ways. Nikon D5300 For Dummies is your ultimate guide to using your new DSLR to its utmost capability. Author Julie Adair King brings her vast experience both as a veteran photographer and a photography teacher to you in this full-color, easy to follow Nikon D5300 guide. Nikon D5300 For Dummies contains more information that you would typically get in a basic photography course, plus information specific to the camera. Over 200 full-color images help illustrate concepts and apply them to the Nikon D5300, making this the ultimate reference for the beginning or veteran photographer. Master controls, basic photography principles, and shooting in auto Get creative with advanced settings and video functions Take charge with manual controls, and understand camera functionality Find tips on editing and sharing photos You have an excellent camera. Don't be content with shooting in auto mode forever! Master your DSLR and learn your way around the settings for the most gorgeous photographs you've ever taken. Nikon D5300 For Dummies is your guide to making it all happen. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Composition Now that you’ve bought an amazing new DSLR, you need a book that goes beyond the camera manual to teach you how to take great shots. That’s where Composition: From Snapshots to Great Shots, Second Edition, comes in, teaching you the fundamentals of composition—the creative arrangement of elements in the shot, and the way a viewer’s eye travels through an image—so you can get great shots no matter what gear you use. In this book, author and professional photographer Laurie Excell starts with the basics of composition—such as the popular rule of thirds—and illustrates how elements like color, shape, angles, and contrast work to create compelling images. In the process, she covers all key camera features that affect composition (regardless of what type of DSLR you have), including the ability to freeze and convey motion depending on what shutter speed you choose, and the correlation between aperture and depth of field. In addition to dozens of brand-new images and more in-depth coverage on topics such as patterns and textures and arranging elements in a frame, this revised edition features several completely new chapters. These will include a chapter of step-by-step examples that highlight the compositional technique used to get just the right shot; a new chapter on black-and-white photography; and a chapter on what to do after the shot—enhancing and editing the images in post-processing. Beautifully illustrated with large, vibrant photos, this book will help you bring your own unique artistic expression to any situation whether taking portraits, action shots, landscapes, or events, teaching you how to take control of your photography to get the image you want every time you pick up the camera. The book includes coverage of Lightroom for image management; Nikon Capture NX2 for RAW processing; Photoshop for image processing; and NIK and OnOne software for creative effects. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Photographing Rivers, Lakes, and Falling Water Whether you are photographing a local lake, a decorative fountain, or an enchanting waterfall, capturing high-quality images of water can be a challenge. In this ebook, photographer and author Robert Correll walks you through everything you need to know to get those elusive great shots. Starting with an overview of all the gear you need, he explains how to protect your equipment amid the elements, as well as how to configure your camera so you can take the pictures you want to take. Next he shows you how to consider issues such as time of day, light, and weather in planning your shoots. Then he takes you through the specific techniques to capture images of rivers and lakes, and falling water such as waterfalls, splash pads, and fountains. Follow along with Robert and you will: • Explore how time affects your lighting and determine what time of day and conditions are best for shooting water • Find the best locations for photographing rivers and lakes and learn how to shoot from various positions such as from the shore and in the water • Learn techniques to capture special effects with shutter speed by stopping motion and encouraging motion blur PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Digital SLR Cameras & Photography For Dummies The perennial DSLR bestseller—now expanded with more photography tips Digital SLR Cameras & Photography For Dummies has remained the top-selling book on DSLR photography since the first edition was published. Now in its Fifth Edition, itcovers the latest technologies in the world of DSLR cameras and photography to help you master the techniques that will take your digital photography skills to the next level. Written in plain English and complemented with full-color photos, this hands-on, friendly guide covers the mechanics of the camera; exposure, lenses, and composition; how to capture action, portrait, and low-light shots; editing and sharing images; tips for improving your digital photography skills; and much more. Digital SLR cameras offer the mechanisms and flexibility of traditional pro-level cameras with the instant results and output of digital cameras. If you're a proud owner of a DSLR camera and want to take stunning shots that were once only achievable by the pros, this is the guide you need. Written by one of the most recognized authors in digital photography, this accessible resource makes it fast and easy to start capturing professional-quality photos. Full-color format helps bring the information to life Includes coverage of the latest DSLR cameras to hit the market Provides a foundation on exposure settings, file formats, and editing photos Offers expanded content on capturing the portraits, action shots, nature shots, and night shots photographers love to take If you're interested in capturing more than just a "selfie" and truly want to hone the craft of digital SLR photography, Digital SLR Cameras and Photography For Dummies sets you up for success. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Travel and Street Photography Whether you’re heading to Paris or San Francisco, Patagonia or Yosemite, you need a book that goes beyond the camera manual to teach you how to take great shots. This guide by pro photographer John Batdorff will help you conquer the fundamentals of travel and street photography and capture stunning pictures. Batdorff starts with the basics–composition, light, and exposure–and how to plan and pack the right equipment for different types of shooting conditions. He also covers all the key camera features that affect your image. Once you’ve captured those shots, John takes you step-by-step through an effective workflow in Lightroom to organize your images and develop your own personal style. This guide is for beginning-to-intermediate digital photographers to understand the basics and bring their own unique artistic expression to any situation whether you’re taking landscapes, cityscapes, portraits, or food and drink shots. Beautifully illustrated with large, compelling photos, this book teaches you how to take control of your photography to get the image you want every time you pack up your camera and take it on the road. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Learning to See Creatively, Third Edition Completely revised and updated throughout, Bryan Peterson's classic guide to creativity helps photographers visualize their work, and the world, in a whole new light by developing their photographic vision. Fully revised with all new photography, this best-selling guide takes a radical approach to creativity by explaining that it is not an inherent ability but a skill that can be learned and applied. Using inventive photos from his own stunning portfolio, author and veteran photographer Bryan Peterson deconstructs creativity for photographers. He details the basic techniques that go into not only taking a particular photo, but also provides insights on how to improve upon it--helping readers avoid the visual pitfalls and technical dead ends that can lead to dull, uninventive photographs. This revised edition features a complete section on color as a design element and all new photographs to illustrate Peterson's points. Learning to See Creatively is the definitive reference for any photographer looking for a fresh perspective on their work. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Nikon D750 Now that you’ve bought the amazing Nikon D750, you need a book that goes beyond a tour of the camera’s features to show you exactly how to use the camera to take great pictures. With Nikon D750: From Snapshots to Great Shots, you get the perfect blend of photography instruction and camera reference that will take your images to the next level! Beautifully illustrated with large, vibrant photos, this book teaches you how to take control of your photography to get the image you want every time you pick up the camera. Follow along with your friendly and knowledgeable guide, photographer and author Rob Sylvan, and you will: Learn the top ten things you need to know about shooting with the D750 Use the D750’s advanced camera settings to gain full control over the look and feel of your images Master the photographic basics of composition, focus, depth of field, and much more Learn all the best tricks and techniques for getting great action shots, landscapes, and portraits Find out how to get great photos in low light Learn the basics behind shooting video with your D750 and start making movies of your own Fully grasp all the concepts and techniques as you go, with assignments at the end of every chapter And once you’ve got the shot, show it off! Join the book’s Flickr group, share your photos, and discuss how you use your D750 to get great shots at flickr.com/group /nikond750_fromsnapshotstogreatshots. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Macro Photography Close-up and macro photography is one of the most popular types of photography among digital photographers today. After the big-range zoom, a macro lens is typically one of the next purchases considered by serious outdoor photographers and amateur photographers looking for close-up capability in all zoom lenses. Yet hobbyist photographers struggle. Many macro shots just don’t make it–not sharp, confusing backgrounds, muddled compositions, misplaced sharpness, and distracting light. Even more advanced photographers find challenges working with depth of field, dealing with light, and using different focal lengths up close. You need a book that goes beyond the camera manuals to teach you how to select and use various lenses to take great macro shots. This guide by pro photographer Rob Sheppard will help you conquer the fundamentals and capture stunning pictures. Sheppard starts with the basics. He discusses factors such as depth of field, perspective, and compression and which types of lenses are right for your style of shooting. You will have a better understanding of your equipment and understand your choices for investing in lenses. Beautifully illustrated with large, compelling photos, this book teaches you how to take control of your photography to get the image you want every time you pick up the camera. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Understanding Exposure, Fourth Edition This newly revised edition of Bryan Peterson's most popular book demystifies the complex concepts of exposure in photography, allowing readers to capture the images they want. Understanding Exposure has taught generations of photographers how to shoot the images they want by demystifying the complex concepts of exposure in photography. In this newly updated edition, veteran photographer Bryan Peterson explains the fundamentals of light, aperture, and shutter speed and how they interact with and influence one another. With an emphasis on finding the right exposure even in tricky situations, Understanding Exposure shows you how to get (or lose) sharpness and contrast in images, freeze action, and take the best meter readings, while also exploring filters, flash, and light. With all new images, as well as an expanded section on flash, tips for using colored gels, and advice on shooting star trails, this revised edition will clarify exposure for photographers of all levels. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Digital Photography Complete Course Why be a good photographer when you can be a great one! This guide will help you use your digital camera to its full potential in just 20 weeks. This modular photography course is the ultimate master class in digital photography. Using a combination of tutorials, step-by-step demonstrations, practical assignments, and fun Q&As, you'll go from photography novice to pro in no time. Build your photography and image-editing skills with this comprehensive course that guides you through every aspect of digital photography. From conveying movement and using natural light, to understanding exposure and mastering composition, this book will teach you how to take professional-looking pictures you'll be proud to display. Packed with helpful advice and stunning images, this one-on-one learning program is a great resource for people who want to take photography more seriously. Learn about the different modes on bridge and system cameras (DSLR or mirrorless), and demystify digital photography jargon such as aperture, exposure, shutter speed, and depth-of-field. This photography book will show you how to control and understand every element of your camera. With the aid of simple text and innovative graphics, you'll explore a wide variety of photography skills and genres. Find out how to create landscapes, portraits, still life, and action shots as you discover the full range of your camera. Master the Art of Photography in As Little As 20 Weeks Digital Photography Complete Course teaches you everything you need to know about photography in 20 weeks through easy-to-understand tutorials. The program is completely customizable to your schedule, so you can work through the modules at your own pace. It's also an especially thoughtful gift for aspiring photographers. This digital photography course will guide you through every aspect of digital photography: - Interactive and user-friendly with 20 different modules.- Combines practical demonstrations, step-by-step tutorials, and creative assignments.- Packed with no-nonsense advice and stunning images. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Headshot, The It used to be that the only people that needed professional-looking headshots were actors and models, but now thanks to Facebook, Twitter, LinkedIn, and social media in general, headshots are hot! They've never been more in demand than they are today, and Peter Hurley's unique headshot style and trademark look have made him the most sought-after headshot photographer in the world today. Here's your chance to learn exactly how to create "the look" that everybody's after. This is bankable stuff! If you're not adding headshots to what you offer as a photographer, you're leaving a lot of money on the table. Peter knows first-hand the secrets to not only lighting your headshots like a pro (there's a whole chapter on that alone), but in this book he reveals, in the very same fashion that made him a famous name with photographers everywhere, how he gets authentic expressions and incredibly flattering positioning that will make your clients look better than they ever have in any photo—period! It's all here: he shows you his positioning techniques, his secrets for getting genuine smiles and images that look so natural you won't believe they're posed (but of course, they are), and you'll learn the very same techniques that Peter uses to create amazing headshots for everyone from execs at top Fortune 500 companies, to Silicon Valley startups, to actors and public figures who know all too well how important a great-looking headshot really is. Peter doesn't hold anything back. He reveals all his tricks of the trade, from his trademark lighting look, to how to create good-looking backgrounds on location, to positioning tricks you won't hear anywhere else, and it's all written in Peter's fun, quirky, inspiring style that lets you know, right from the beginning, you can do this, and you can do this big! These are the techniques that Peter has crafted from years in front of the lens, as a model for top brands like Abercrombie & Fitch and Guess, and years behind the lens, giving him an insight few photographers will ever possess, and he's willing to share every bit of it—every trick, every technique, and every nuance—in this book that will pay for itself at your very next shoot. Yes, it's that good. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Surreal Photography Ever since Man Ray imposed the sound holes of a violin onto his model's back, photographers have been enthusiastic practitioners of surreal art. Now with the advent of high-quality digital photo-manipulation the possibilities for creativity have become infinite. This book reveals the latest techniques in the field of surreal photography and features art from a host of the very best modern surreal photographers. - Breaks down the shooting and editing process so any photographer can make their own impossible images - With processing walkthroughs from contributing artists including Natalie Dybisz, Julie de Waroquier and Sarolta Bán - Step-by-step instructions for creating extraordinary scenes - Covers many different styles, from impossible landscapes to unsettling portraits PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Photographer's Guide to Focus and Autofocus, A Autofocus changed the way photos are taken, making it easier to capture and keep the subject in sharp focus. Since autofocus was first introduced, it has become much more complicated, offering different focus modes, focus types, and focus points. What started out as a way to simplify the photo-making process has turned into a complicated endeavor with numerous choices and settings. A Photographer’s Guide to Focus and Autofocus: From Snapshots to Great Shots is here to answer all your questions about the focusing system in today’s cameras and their various autofocus modes. Photographer Alan Hess covers the simple basics of focus: manual focus versus autofocus, the best focus modes to use, and how focus works in both DSLRs and mirrorless cameras. Then he discusses more advanced topics, including autofocus sensor types, back-button autofocus, and focus for DSLR video. There is much more to autofocus, and focus in general, than just pushing the shutter release button and hoping the image is sharp and in focus. With this book, you’ll learn how to get the right focus in your images, no matter what the occasion. Follow along with your friendly and knowledgeable guide, and you will: Learn the top ten things to know about focus, including how to use the focus controls on the camera, how to pick the autofocus point, and when to use pre-focus in your images Address common autofocus issues such as dealing with low contrast or low light, or shooting through obstacles like glass or a fence Develop troubleshooting techniques for what to do when the autofocus doesn’t work properly Work with both manual focus and autofocus and learn tricks to achieve better focus in video And once you’ve got the shot, show it off! Join the book’s Flickr group to share your photos and tips at flickr.com/groups/focusandautofocusfromsnapshotstogreatshots PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Creative Workflow in Lightroom Adobe’s Lightroom has emerged as a must-have software due to its powerful editing tools and time saving organizational capabilities but how you establish a personalized, creative workflow that optimizes this technology, your time, and your art eludes most photographers. Jason Bradley, award-winning photographer and Lightroom pro, shares the answers to these questions in this practical and easy to follow guide that taps into the "how" and the "why" of a professional photographer’s creative workflow in Lightroom. Bradley will show you how all workflows can be simplified into three steps: establishing, managing, and rendering the file, alongside stunning photographs and explanations from his own experiences. This book will not only teach you how to work within Lightroom but, ultimately, how to make Lightroom work for you. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Capture Your Style New York Times Bestseller From Instagram star Aimee Song, creator of the popular fashion blog Song of Style, comes the very first how-to Instagram guide, breaking down the essentials to taking gorgeous photos and building your brand and following. With over three million Instagram fans, Aimee Song knows a thing or two about taking the perfect Instagram photo. And Instagram is so much more than a platform for pretty pictures. It’s the fastest-growing social media network with an engaged community, a major marketing tool for brands, a place where Beyoncé drops her albums, and a hub where products can be bought with a simple double tap. Including everything from fashion, travel, food, décor, and more, Aimee includes insider tips on curating a gorgeous feed and growing an audience. In this ultimate how-to Instagram guide, you’ll learn: · How to brighten, sharpen, and filter your photos · The best apps and filters · How to prop and style food and fashion photos · Ways to craft your voice and story on Instagram · How to gain more Instagram followers · Secrets behind building a top Instagram brand · How to transform an Instagram hobby into a successful business · Tips for driving revenue based on your following Capture Your Style will empower you to become your own master mobile photographer, whether you’re looking to launch an e-commerce business or simply sharing a gorgeous meal with your friends, turning even the most mundane moment into Instagold. This is a must-have reference for anyone interested in the ins and outs of stylish personal branding. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Digital Restoration from Start to Finish This third edition of Digital Restoration from Start to Finish walks you step-by-step through the entire process of restoring old photographs and repairing new ones using Adobe Photoshop, Photoshop Elements, GIMP and more. This best-selling guide is now updated with the latest software advancements, and new techniques including hand-tinting in lab, repairing water damaged photos, and tips for the spot healing brush and masked layers. No process detail is overlooked, from choosing the right hardware and software, getting the photographs into the computer, getting the finished photo out of the computer and preserving it for posterity. LEARN HOW TO: Scan faded and damaged prints or films Improve snapshots with Shadow/Highlight adjustment Correct uneven exposure Fix color and skin tones quickly with Curves, plug-ins, and Hue/Saturation adjustment layers Correct uneven exposure and do dodging and burning-in with adjustment layers Hand-tint your photographs easily Correct skin tones with airbrush layers Clean up dust and scratches speedily and effectively Repair small and large cracks with masks and filters Eliminate tarnish and silvered-out spots from a photograph in just a few steps Minimize unwanted print surface textures Erase mildew spots Eliminate dots from newspaper photographs Increase sharpness and fine detail Maximize print quality PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Time Lapse Photography, Long Exposure & Other Tricks of Time In the newest entry in Peachpit's popular From Snapshots to Great Shots series, photographer John Carucci shares amazing techniques for creative time-related photography techniques, including long-exposure, time-lapse, and high-speed photography. Carucci starts by reviewing your equipment needs, including filters, image stabilizers (tripods, monopods, beanbags, etc.), software, and more. Next, he explains the basics of long-exposure photography, demonstrating how to effectively capture time in nighttime cityscapes, photos of the night sky, and in brighter light using neutral density filters. Along the way, you'll learn the fundamentals of blurring, shooting in RAW, and balancing flash and ambient light. He then walks through the essentials of time-lapse photography: how to regulate your camera's motion, determine the best duration to use, and use software to perfect your images. Carucci's time-lapse section is complemented with a complete online video tutorial on capturing effective time-lapse sequences. You'll also find expert coverage of high-speed photography, including choosing shutter speed, stopping action with flash, shooting sports, and more. Carucci concludes by helping you develop and perfect your own aesthetic, with tips on properly framing your scenes, creative composition, and effective use of color and tone. Time Lapse, Long Exposure, and Other Tricks of Time features beautiful full-color images, clear design, and John Carucci's friendly, knowledgeable voice. It's a pleasure to learn from - and if you've ever wanted to master any of these techniques, it's the guide you've been waiting for. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Adobe Photoshop CC Classroom in a Book (2017 release) This is the eBook of the printed book and may not include any media, website access codes, or print supplements that may come packaged with the bound book. Creative professionals seeking the fastest, easiest, most comprehensive way to learn Adobe Photoshop choose Adobe Photoshop CC Classroom in a Book (2017 release) from Adobe Press. The 15 project-based lessons in this book show users step-by-step the key techniques for working in Photoshop and how to correct, enhance, and distort digital images, create image composites, and prepare images for print and the web. In addition to learning the key elements of the Photoshop interface, this completely revised CC (2017 release) edition covers features like new and improved search capabilities, Content-Aware Crop, Select and Mask, Face-Aware Liquify, designing with multiple artboards, and much more! The online companion files include all the necessary assets for readers to complete the projects featured in each chapter as well as ebook updates when Adobe releases new features for Creative Cloud customers. All buyers of the book get full access to the Web Edition: a Web-based version of the complete ebook enhanced with video and interactive multiple-choice quizzes. As always with the Classroom in a Book, Instructor Notes are available for teachers to download. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

The Adobe Photoshop Lightroom Classic CC Book Adobe Photoshop Lightroom Classic CC is one of the most powerful tools a digital photographer has in their toolset, offering powerful editing features in a streamlined interface that lets photographers import, sort, and organize images. In this completely updated bestseller, author Martin Evening describes Lightroom Classic CC features in detail, covering library organization, develop image processing, output modules, and the latest Lightroom CC/mobile features. As an established commercial and landscape photographer, Martin knows firsthand what photographers need for an efficient workflow. He has been working with Lightroom from the beginning, and as a result, knows the software inside and out. In this book, he’ll teach you how to: · Work efficiently with images shot in raw or JPEG formats · Import photographs with ease and sort them according to your workflow · Create and manage a personal image and video library · Integrate Lightroom with Adobe Photoshop · Prepare images for print, slideshows, or to create a book · Make the most of new features, such as the ability to migrate and sync photos via the cloud Photographers will find Lightroom Classic CC–and The Adobe Photoshop Lightroom Classic CC Book–indispensable tools in their digital darkrooms. “With Martin’s expert guidance, you’ll soon find that you have precisely the tools you need to turn your concentration back where it belongs—on making better pictures!†—George Jardine, digital photography consultant “As a photographer himself, Martin Evening knows what tools photographers need to realize their creative vision. In this book, he shows not only how Adobe Photoshop Lightroom works but also why it will become an essential part of any photographer’s workflow.†—Greg Gorman, photographer PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Adobe Photoshop Elements 2018 Classroom in a Book Adobe Photoshop Elements 2018 Classroom in a Book is the most thorough and comprehensive way for you to master Adobe’s industry-leading consumer-targeted photo-editing software. Each chapter in this step-by-step, lesson-based guide contains a project that builds on your growing knowledge of the program, while end-of-chapter review questions reinforce each lesson. You will learn the basics of editing your images with Photoshop Elements and learn how to best use the program's many new features. This edition covers many new and improved features in Adobe Photoshop Elements 2018, from the Auto Curate feature that makes it easier than ever to organize and find your photos by analyzing your library to present just the best images, to a revamped slide show, and new tools that will help you make complex selections in moments or improve a portrait by opening closed eyes. New exercises explore enhancements in the Organizer, an improved selection workflow, and several of the latest guided edits. You’ll discover new tools that let you expand your creativity. And you’ll learn how to print, export, and share your images. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Adobe Photoshop CC Classroom in a Book (2018 release) Creative professionals seeking the fastest, easiest, most comprehensive way to learn Adobe Photoshop choose Adobe Photoshop CC Classroom in a Book (2018 release) from Adobe Press. The 15 project-based lessons show key step-by-step techniques for working in Photoshop, including how to correct, enhance, and distort digital images, create image composites, and prepare images for print and the web. In addition to learning the essential elements of the Photoshop interface, this revised edition for the 2018 release covers features like search capabilities, Content-Aware Crop, Select and Mask, Face-Aware Liquify, designing with multiple artboards, creating and organizing enhanced brush presets, and much more! The online companion files include all the necessary assets for readers to complete the projects featured in each chapter as well as ebook updates when Adobe releases relevant new features for Creative Cloud customers. All buyers of the book get full access to the Web Edition: a Web-based version of the complete ebook enhanced with video and multiple-choice quizzes. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Adobe Photoshop CC for Photographers 2018 Adobe Photoshop CC for Photographers by acclaimed digital imaging professional Martin Evening has been revamped to include detailed instruction for all of the updates to Photoshop CC on Adobe’s Creative Cloud, including significant new features, such as the painting tool and Pen path tool refinements and Range Masking in Camera Raw. This guide covers all the tools and techniques photographers and professional image editors need to know when using Photoshop, from workflow guidance to core skills to advanced techniques for professional results. Using clear, succinct instruction and real world examples, this guide is the essential reference for Photoshop users. The accompanying website has been updated with new sample images, tutorial videos, and bonus chapters. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Light and Lens The new edition of this pioneering book allows students to acquire an essential foundation for digital photography. Fully updated, it clearly and concisely covers the fundamental concepts of imagemaking, how to use digital technology to create compelling images, and how to output and preserve images in the digital world. Exploring history, methods, and theory, this text offers classroom-tested assignments and exercises from leading photographic educators, approaches for analyzing, discussing, and writing about photographs, and tools to critically explore and make images with increased visual literacy. New to this edition: New larger page format Revised and renewed to reflect technological advances Expanded coverage of smartphone/mobile photography Extended coverage of the careers section More than 100 new images PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Tiny Worlds Successful nature photographer and lecturer Charles Needle often asks students in his workshops if they understand the difference between looking†and seeingâ€. The difference he is pointing out is that while we are constantly looking†at countless people, places and things, we might not be actually seeing what is right in front of us. Being tuned into this difference can elevate your art as a photographer, allowing you to be more in tune with your surroundings. Needle has applied this concept to his work and it shows. Utilizing macro photography to capture the nuances of the nature all around us. In this extensive handbook, Needle covers not only his philosophy for seeing and capturing nature photography but delves into the equipment he uses. Needle covers composition, flash techniques, the fundamentals of macro photography and so much more. The book features many set-up shots, equipment shots and sequential shots detailing the progression towards creating the final images. This essential text provides both the inspiration and the technique required to beautifully capture the wonders of nature. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Storytelling for Photojournalists Learn what it takes to shoot reportagephotojournalistic imagesfrom developing an idea, to making travel plans, to gathering the requisite information about the subject/scene and locale, to packing the appropriate gear and nailing the technical aspects of the shoot. Success in photojournalism is predicated on having a firm understanding of the business. Conceiving of a suitable reportage concept and getting a technically sound image may seem a simple task for photographers well-versed in photographing other subjects, but the truth is, photojournalism requires a special skill-set and understanding of what it is that such jobs entail. In this book, you’ll learn what to shoot, how to shoot it, how and where to socialize and determine cultural basics that may impact how and what you can photograph, how to get your images onto editors’ desks and in front of the eyes of the wider world audience, and how to make sales. STORYTELLING PHOTOJOURNALISTS is designed to help professional photographers and inspire photography novices who want to learn how to get the most out of a shooting trip. 128 pages of shooting strategies made clear in behind-the-scenes episodes illustrated with pictures from the Enzo Dal Verme's archive. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Garage Glamour Nude and beauty photographers can find the invaluable highimpact techniques in this exhaustively illustrated manual that covers everything from compositional tips for clothing, accessories, and poses to more technical challenges such as lighting, lens selection, and exposure, demonstrating how to produce stunning, worldclass images using minimal equipment without accruing a burdening investment. Beginning with the Four S's of glamour photography (sexiness, sultriness, sensuality, and seductiveness), amateurs and professionals alike are shown new ways to achieve beautiful shots, with additional tips on working with models that include methods for accentuating assets while minimizing flaws and initiating comfortable working relationships. Photographers are also shown how to turn their hobby into a successful career, or enhance the productivity and income of an existing business by honing marketing and advertising skills and mastering the art of generating business by referral. Based on the author's popular website (garageglamour.com), this guide offers helpful instruction to creating glamorous, sexy images like those seen in Playboy, Maxim, and other men's magazines. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Advancing Your Photography One of America's top photographers, shows how everyone can take top quality photographs they love. Whether you are a professional looking to advance your skills, a beginner, or a budding Instagrammer, this book will help you learn more fast and have fun in the process. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Mastering the Nikon D750 Mastering the Nikon D750 by Darrell Young provides a wealth of experience-based information and insights for owners of the new D750 camera. Darrell is determined to help the user navigate past the confusion that often comes with complex and powerful professional camera equipment. This book explores the features and capabilities of the camera in a way that far surpasses the user's manual. It guides readers through the camera features with step-by-step setting adjustments; color illustrations; and detailed how, when, and why explanations for each option. Every button, dial, switch, and menu configuration setting is explored in a user-friendly manner, with suggestions for setup according to various shooting styles. Darrell's friendly and informative writing style allows readers to easily follow directions while feeling as if a friend dropped in to share his knowledge. The information in this book goes beyond the camera itself and also covers basic photography technique. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Mastering the Nikon D500 Mastering the Nikon D500 by Darrell Young provides a wealth of experience-based information and insights for owners of the new D500 camera. Darrell is determined to help the user navigate past the confusion that often comes with complex and powerful professional camera equipment.This book explores the features and capabilities of the camera in a way that far surpasses the user’s manual. It guides readers through the camera features with step-by-step setting adjustments; color illustrations; and detailed how, when, and why explanations for each option. Every button, dial, switch, and menu configuration setting is explored in a user-friendly manner, with suggestions for setup according to various shooting styles.Darrell’s friendly and informative writing style allows readers to easily follow directions while feeling as if a friend dropped in to share his knowledge. The information in this book goes beyond the camera itself and also covers basic photography technique. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

The Film Photography Handbook In recent years, film photography has witnessed a significant renaissance—and not just among those who have previously shot with film. Interest in film photography has also grown enormously among those who only have experience shooting digitally. In The Film Photography Handbook, authors Chris Marquardt and Monika Andrae speak to both kinds of film photographer as they offer an easy-to-understand, complete resource to shooting film. They also address today’s working climate, including such topics as the hybrid film/digital workflow, the digitization of negatives, and working with smartphones for light metering and to assist in film processing.This book is intended for anyone who is curious about film, whether you need a refresher course or are discovering this wonderful format for the first time. You’ll learn how easy it is to shoot and process black-and-white film at home, and how little special equipment you need to get into film photography. You’ll learn all about: the important differences between film and digital photography numerous film cameras, as well as how to buy a second-hand camera film formats, from 35 mm to medium format and large format exposure settings, tonal values, and tonal representations in different types of film, from color negatives and slides to the enormous spectrum of black-and-white films processing film, covering everything you need to know: equipment, chemicals, and workflow scanning negatives to bring your film into a digital workflow both presenting and archiving your prints and negatives Working in such an “analog†medium requires a unique approach to photography, and it fosters a completely different form of creativity. Working in film can also prove to be a great inspiration for your own digital photography, as well. The Film Photography Handbook covers it all, from the technical to the creative, and will have you shooting film in no time, whether it’s with an old rangefinder, an inexpensive Holga, or a medium-format Rolleiflex or Hasselblad. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

David Busch’s Sony Alpha a6300/ILCE-6300 Guide to Digital Photography David Busch’s Sony Alpha a6300/ILCE-6300 Guide to Digital Photography is the most comprehensive reference and guide book available for Sony’s advanced APS-C mirrorless camera. This eagerly-anticipated enthusiast/professional digital camera features a new 24 megapixel sensor with 425 embedded phase-detect pixels for lightning-fast autofocus at up to 11 frames per second. With an electronic shutter that provides a silent shooting option, stunning 4K/UHD video capabilities, and ISO sensitivities up to ISO 51,200, the a6300/ILCE-6300 is a versatile digital camera that’s simple to use, yet boasts features demanded by the most avid photo buff. With this book in hand, you will discover all the capabilities of the Sony Alpha a6300/ILCE-6300 as you explore the world of digital photography, develop your creativity, and capture the best photographs you’ve ever taken.Filled with detailed how-to steps and full-color illustrations, David Busch’s Sony Alpha a6300/ILCE-6300 Guide to Digital Photography describes every feature of this sophisticated camera in depth, from taking your first photos through advanced details of setup, exposure, lens selection, lighting, and more. It relates each feature to specific photographic techniques and situations. Also included is the handy camera “roadmap,†an easy-to-use visual guide to the a6300/ILCE-6300’s features and controls. Learn when to use every option and, more importantly, when not to use them, by following the author’s recommended settings for every menu entry. With best-selling photographer and mentor David Busch as your guide, you’ll quickly have full creative mastery of your camera’s capabilities, whether you’re shooting on the job, taking pictures as an advanced enthusiast pushing the limits of your imagination, or are just out for fun. Start building your knowledge and confidence, while bringing your vision to light with the Sony Alpha a6300/ILCE-6300. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

David Busch’s Sony Alpha a6000/ILCE-6000 Guide to Digital Photography The best-selling and universally-praised bible for the Sony Alpha a6000 is finally back in print! David Busch's Sony a6000 Guide to Digital Photography is your all-in-one resource and reference for the Sony Alpha a6000, and now it’s available in both printed and ebook form from Rocky Nook. The top-ranking a6000 mirrorless camera features expanded ISO settings to 25,600, a high-resolution 24MP sensor, fast 11 fps maximum shooting rate, and a high resolution electronic viewfinder. With this book in hand, you will explore the world of digital photography, develop your creativity, and take great photographs with the Sony a6000. With clear how-to steps and full-color illustrations, David Busch's Sony a6000 Guide to Digital Photography covers all the camera's features in depth, from taking your first photos through advanced details of setup, exposure, lenses, lighting, and more, and relates each feature to specific photographic techniques and situations. Also included is the handy a6000 "roadmap," an easy-to-use visual guide to the camera's features and controls. With David Busch as your guide and mentor, you'll be in full creative control, whether you're shooting on the job, as an advanced hobbyist, or are just out for fun. Start building your knowledge, creativity, and confidence with the Sony a6000 today. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Photograph Like a Thief No photographer works in a vacuum. Photographers, like all artists, stand on the shoulders of those who came before them, and they are informed and influenced by those working around them. If you are striving to find your own style, one of the most powerful exercises you can practice is to find influence and inspiration in the work of those around you, and then emulate that work in an effort to define, shape, and grow your own photographic voice. By collecting, imitating, and eventually reshaping and combining the work of those around you, your unique voice can be found and the quality of your work can soar.In Photograph Like a Thief, photographer, author, and retoucher Glyn Dewis embraces the idea of “stealing†and recreating others’ work in order to improve as an artist. By stepping inside others’ images, you can learn to reverse engineer their creation, then build an image that simultaneously pays homage to that work and is also an original creation itself.Glyn begins by covering the process of "stealing ideas" and finding inspiration. He shares the gear he uses as well as his retouching and post-processing workflow. In a chapter on how to reverse engineer a photograph, Glyn discusses how to read an image by looking at the catch lights, shadow and highlight positions, and the hardness or softness of the shadows. This is a crucial skill to acquire if you want to recreate a specific look.Glyn then works through a series of images—inspired by movies, books, history, and a few legendary photographers—from the initial concept and influence to the final result. For each image, he reverse engineers the shot to describe how it was created, then works through the gear he used, the lighting for the image, and the post-processing of the image in Photoshop—from the RAW out-of-camera shot to the finished piece. While Glyn's work primarily focuses on portraiture, he finds inspiration and influence from a wide variety of work.By working alongside Glyn (he makes all the files available for download), you too can learn to find inspiration all around you, discover how others’ work can influence you, improve your photographic and post-processing skill set, and begin your own journey to defining your unique style. Who knows? Soon, others may be stealing from you. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

The Dramatic Portrait Without light, there is no photograph. As almost every photographer knows, the word “photograph†has its roots in two Greek words that, together, mean “drawing with light.†But what is less commonly acknowledged and understood is the role that shadow plays in creating striking, expressive imagery, especially in portraiture. It is through deft, nuanced use of both light and shadow that you can move beyond shooting simply ordinary, competent headshots into the realm of creating dramatic portraiture that can so powerfully convey a subject’s inner essence, communicate a personal narrative, and express your photographic vision. In The Dramatic Portrait: The Art of Crafting Light and Shadow, Chris Knight addresses portraiture with a unique approach to both light and shadow that allows you to improve and elevate your own portraiture. He begins with the history of portraiture, from the early work of Egyptians and Greeks to the sublime treatment of light and subject by artists such as Caravaggio, Rembrandt, and Vermeer. Chris then dives into a deep, hands-on exploration of light, shadow, and portraiture, offering numerous lessons and takeaways. He covers: • The qualities of light: hard, soft, and the spectrum in between • The relationships between light, subject, and background, and how to control them • Lighting patterns such as Paramount, Rembrandt, loop, and split • Lighting ratios and how they affect contrast in your image • Equipment: from big and small modifiers to grids, snoots, barn doors, flags, and gels • Multiple setups for portrait shoots, including those that utilize one, two, and three lights • How color contributes to drama and mood, eliciting an emotional response from the viewer • How to approach styling your portrait, from wardrobe to background • The post-processing workflow, including developing the RAW file, maximizing contrast, color grading, retouching, and dodging and burning for heightened drama and effect • How all of these elements culminate to help you define your personal style and create your own narrative PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

David Busch’s Canon EOS 5D Mark IV Guide to Digital SLR Photography David Busch’s Canon EOS 5D Mark IV Guide to Digital SLR Photography is your essential reference and guide book for Canon’s ground-breaking 30.4 megapixel full frame dSLR. Canon’s most versatile professional/enthusiast camera is adept at still photography, combining a high-resolution sensor with 7 fps continuous shooting, blazing fast autofocus, and excellent high-ISO performance. Those shooting video will be equally impressed with its 4K Ultra High Definition movie mode and Dual Pixel AF that allows continuous autofocus even when capturing video. Touch screen access to features, a 150,000-pixel RGB+infrared exposure sensor, and built-in Wi-Fi and GPS add to the 5D Mark IV’s appeal.With this book in hand, you will discover all the capabilities of the Canon EOS 5D Mark IV as you explore the world of digital photography, develop your creativity, and capture the best photographs you’ve ever taken. Filled with detailed how-to steps and full-color illustrations, David Busch’s Canon EOS 5D Mark IV Guide to Digital SLR Photography describes every feature of this sophisticated camera in depth, from taking your first photos through advanced details of setup, exposure, lens selection, lighting, and more. It relates each feature to specific photographic techniques and situations. Also included is the handy camera “roadmap,†an easy-to-use visual guide to the Mark IV’s features and controls. Learn when to use every option and, more importantly, when not to use them, by following the author’s recommended settings for every menu entry. With best-selling photographer and mentor David Busch as your guide, you’ll quickly have full creative mastery of your camera’s capabilities, whether you’re shooting on the job, taking pictures as an advanced enthusiast exploring photography for the first time, or are just out for fun. Start building your knowledge and confidence, while bringing your vision to light with the Canon 5D Mark IV. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

The Photographer's Guide to Posing When photographing people, you can have a great composition, perfect light, and the right camera settings, but if your subject doesn’t look right—if the pose is off—the shot will not be a keeper. Posing is truly a crucial skill that photographers need to have in order to create great photographs. If you’re looking to improve your ability to pose your subjects—whether they’re men, women, couples, or groups—best-selling author and photographer Lindsay Adler’s The Photographer’s Guide to Posing: Techniques to Flatter Everyone is the perfect resource for you.In the first half of The Photographer’s Guide to Posing, Lindsay discusses how the camera sees, and thus how camera angle, lens choice, and perspective all affect the appearance of your subject. Lindsay then covers the five most important things that ruin a pose—such as placement of the hands, and your subject’s expression and posture. If you can look out for and avoid these five things, your skills (and your images) will quickly improve. Next, Lindsay dives into “posing essentials,†outlining her approach to start with a “base pose,†then build on that to create endless posing opportunities. She also discusses posing the face—with specific sections dedicated to the chin, jaw, eyes, and forehead—as well as posing hands. In the second half of the book, Lindsay dedicates entire chapters to posing specific subject matter: women, men, couples, curvy women, families and small groups, and large groups. In each chapter, Lindsay addresses that subject matter’s specific challenges, provides five “go-to poses†you can always use, and covers how to train the eye to determine the best pose for your subject(s). In the final chapter of the book, Lindsay brings it all together as she teaches you how to analyze a pose so that you can create endless posing opportunities and continuously improve your work PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

The Fujifilm X-T20 In this book, popular Fuji Rumors "X-Pert Corner" columnist Rico Pfirstinger teaches about the little-known capabilities of the X-T20, which he’s discovered through months of in-depth research and experimentation with the camera. After a brief overview of the camera’s basic functions, Rico cuts to the chase and provides a plethora of tips and practical instructions not found in the user's manual. With this knowledge, you will be able to fully exploit the capabilities of the X-T20. The Fujifilm X-series cameras have amazing features but may require an adjustment period for those new to using these cameras, even photographers who have been lifetime DSLR shooters. This guide will help you to quickly feel comfortable using your camera so that you can achieve excellent results. Topics covered include: •Menu shortcuts •Long exposures •Firmware upgrades •Hybrid autofocus system •Auto and manual focusing •Face detection •ISOless sensor •Dynamic Range expansion •Film simulations •Custom settings •RAW conversion •Panoramas •Movies •Self-timer •Flash •Adapted lenses •And much more… PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

David Busch's Nikon D5600 Guide to Digital SLR Photography David Busch's Nikon D5600 Guide to Digital Photography is your all-in-one comprehensive resource and reference for the Nikon D5600 camera. This ultracompact and light weight Nikon digital SLR has new SnapBridge wireless Bluetooth communication so you can use your iOS or Android device to control the camera. Nikon has also added an easy-to-use time-lapse feature to its impressive capabilities, which include a swiveling touch screen LCD that makes taking photos or changing settings quick and easy. The D5600 captures 24-megapixel still images and 1080p 60 fps high-definition movies with stereo sound, too. With this book in hand, you can fine tune your camera skills as you explore the world of digital photography, develop your creativity, and take great photographs with your D5600.Filled with detailed how-to steps and full-color illustrations, David Busch's Nikon D5600 Guide to Digital Photography covers all the camera's features in depth, from taking your first photos through advanced details of setup, exposure, lens selection, lighting, and more, and relates each feature to specific photographic techniques and situations. Also included is the handy visual guide to the D5600, with close-up photos and descriptions of the camera's essential features and controls, including the versatile LCD touch screen. Learn when to use each option and, more importantly, when not to use them, by following the author’s recommended settings for every menu entry. With best-selling photographer and mentor David Busch as your guide, you'll quickly have full creative mastery of your camera’s capabilities, whether you're shooting on the job, as an advanced enthusiast, or are just out for fun. Start building your knowledge and confidence, while bringing your vision to light with the Nikon D5600 today. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

The Fujifilm X100F In this book, popular Fuji Rumors "X-Pert Corner" columnist Rico Pfirstinger teaches about the little-known capabilities of the X100F, which he’s discovered through months of in-depth research and experimentation with the camera. After a brief overview of the camera’s basic functions, Rico cuts to the chase and provides a plethora of tips and practical instructions not found in the user's manual. With this knowledge, you will be able to fully exploit the capabilities of the X100F. The Fujifilm X-series cameras have amazing features but may require an adjustment period for those new to using these cameras, even photographers who have been lifetime DSLR shooters. This guide will help you to quickly feel comfortable using your camera so that you can achieve excellent results. Topics covered include: •Menu shortcuts •Long exposures •Firmware upgrades •Hybrid autofocus system •Auto and manual focusing •Face detection •Dynamic Range expansion •Film simulations •Custom settings •RAW conversion •Panoramas •Movies •Self-timer •Flash •Conversion lenses •And much more… PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

David Busch's Sony Alpha a7R III Guide to Digital Photography David Busch's Sony Alpha a7R III Guide to Digital Photography is most comprehensive resource and reference for Sony’s high-speed, high-resolution full frame mirrorless camera. Capable of 10 frame-per-second bursts even at 42 megapixels, the a7R III is fast enough for sports photography with the image quality that the most demanding landscape photographer demands. Coupled with remarkable low-light performance, fast sensor-based phase detect autofocus, and improved 5-axis in-body image stabilization, it gives you all the tools needed to take incredible images. This book will show you how to master those features as you explore the world of digital photography and hone your creativity with your a7R III.Filled with detailed how-to steps and full-color illustrations, David Busch's Sony Alpha a7R III Guide to Digital Photography covers every feature of this camera in depth, from taking your first photos through advanced details of setup, exposure, lens selection, lighting, and more, and relates each feature to specific photographic techniques and situations. Also included is the handy camera "roadmap," an easy-to-use visual guide to the camera's features and controls. Learn when to use every option and, more importantly, when not to use them, by following the author’s recommended settings for each menu entry. With best-selling photographer and mentor David Busch as your guide, you'll quickly have full creative mastery of your camera’s capabilities, whether you're shooting on the job, as an advanced enthusiast exploring full frame photography for the first time, or are just out for fun. Start building your knowledge and confidence, while bringing your vision to light with the Sony a7R III. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

David Busch's Nikon D7500 Guide to Digital SLR Photography David Busch's Nikon D7500 Guide to Digital Photography is your all-in-one comprehensive resource and reference for the Nikon D7500 camera. Built around the same 20.9 megapixel sensor as the D500, this mid-level Nikon model has BlueTooth and Wi-Fi wireless control with the SnapBridge smart phone/tablet app. A swiveling screen, 4K video, 8 fps continuous shooting, and ISO speeds up to 1.6 million make the D7500 a significant enthusiast-oriented upgrade. With this book in hand, you can fine tune your camera skills as you explore the world of digital photography, develop your creativity, and take great photographs with your D7500.Filled with detailed how-to steps and full-color illustrations, David Busch's Nikon D7500 Guide to Digital Photography covers all the camera's features in depth, from taking your first photos through advanced details of setup, exposure, lens selection, lighting, and more, and relates each feature to specific photographic techniques and situations. Also included is the handy visual guide to the D7500, with close-up photos and descriptions of the camera's essential features and controls. Learn when to use each option and, more importantly, when not to use them, by following the author’s recommended settings for every menu entry. With best-selling photographer and mentor David Busch as your guide, you'll quickly have full creative mastery of your camera’s capabilities, whether you're shooting on the job, as an advanced enthusiast, or are just out for fun. Start building your knowledge and confidence, while bringing your vision to light with the Nikon D7500 today. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

David Busch's Canon EOS Rebel SL2/200D Guide to Digital SLR Photography David Busch's Canon EOS Rebel SL2/200D Guide to Digital SLR Photography is your complete all-in-one comprehensive resource and reference for the versatile Canon EOS Rebel SL2/200D. An ultra-compact 24-megapixel model aimed at budding photo enthusiasts seeking to improve their photographic skills, the SL2/200D is a budget-priced digital SLR with an impressive range of features. These include Wi-Fi/NFC/Bluetooth communications to link your camera to your iOS or Android smart device, a fully articulated touch screen, and high definition move-making capabilities. With this book in hand, the camera is remarkably easy to master, too. Even new users will quickly master the full range of semi-automatic modes, scene options, and creative filters that make this newest Rebel ready to explore the world of photography.With clear how-to steps and full-color illustrations, David Busch's Canon EOS Rebel SL2/200D Guide to Digital SLR Photography covers all the camera's capabilities in depth, from taking your first photos through advanced details of setup, exposure, lenses, lighting, and more. Also included is a handy Canon Rebel SL2/200D "roadmap," an easy-to-use visual guide to the camera's features and controls. With best-selling author and mentor David Busch as your guide, you'll be in full creative control, whether you're shooting on the job, as an advanced hobbyist, or are just out for fun. Start building your knowledge and confidence, while bringing your vision to light with the Canon EOS Rebel SL2/200D today. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

FUJIFILM X Series Unlimited FUJIFILM X Series Unlimited teaches you everything you need to know in order to achieve mastery with your FUJIFILM camera, gaining maximum performance and total creative liberation with your photography…no matter what FUJIFILM X Series camera you use. Written by professional photographer, expert Fuji user, and X Series ambassador Dan Bailey, you'll learn every feature and every menu item, button, and function of the FUJIFILM X Series lineup. More importantly, you'll learn how to use these features and settings in actual shooting situations out in the world in order to capture great photographs. Dan has shot with X Series cameras for nearly six years, and he’s worked closely with the FUJIFILM tech reps and product managers. He knows these cameras inside and out. He knows how they function out in the real world, and he's tested them with a wide range of subject matter, often in extremely challenging conditions, environments, and shooting situations. FUJIFILM X Series Unlimited teaches you everything he’s learned along the way. In this book, you'll learn all the camera settings, how to use autofocus, how to use and customize the film simulations to create your own “look,†how to set up the camera for maximum image quality and performance, and many other features such as bracketing, exposure modes, the ADV mode filters, how to update firmware, and how to optimize your Fuji to match your style and subject matter. The book is organized into the following chapters: • Chapter 1: The Really Important Stuff • Chapter 2: Image Quality (I.Q.) Settings • Chapter 3: Focus Menus—AF/MF (Autofocus/Manual Focus) Settings • Chapter 4: Shooting Settings • Chapter 5: Flash Settings • Chapter 6: Movie Settings • Chapter 7: Set Up Menus • Chapter 8: Playback Menu • Online References This book is absolutely packed with tons of great recommendations, advice, and insight. If you take the time to learn and master just a few of the features covered in this guide, you'll be able to take your creative and technical skills to a whole new level. Whether you have a “MY MENU†camera model (the X-Pro2, X-T2, X-T20, X-E3, and X100F) or one of the “RED/BLUE†camera models (the X-Pro1, X-T1, X-T10, X100 models prior to the “F†model, the X-E1, X-E2, X-E2S, X70, and the X-A series, as well as the X10, X20, and X30), you’re certain to learn the ins and outs of your Fuji camera in order to improve your photography. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

David Busch's Canon EOS 6D Mark II Guide to Digital SLR Photography David Busch's Canon EOS 6D Mark II Guide to Digital SLR Photography is your all-in-one comprehensive resource and reference for the long-awaited Canon EOS 6D Mark II camera, the company’s most affordable full-frame camera. This upgraded 26.2 megapixel model features an enhanced autofocus system with 45 as many focus points as its predecessor. The Dual Pixel CMOS hybrid autofocus brings lightning-fast phase detect AF to live view and high-definition movie modes, too. The 6D Mark II has Wi-Fi/NFC connectivity to allow linking the camera to a computer and iOS or Android smart devices, and a fully articulated touch screen LCD. With this book in hand, you can quickly apply all these advanced features to your digital photography, while boosting your creativity to take great photographs with your Canon EOS 6D Mark II.Filled with detailed how-to steps and full-color illustrations, David Busch's Canon EOS 6D Mark II Guide to Digital SLR Photography covers all this upscale full-frame camera's features in depth, from taking your first photos through advanced details of setup, exposure, lens selection, lighting, and more, and relates each feature to specific photographic techniques and situations. Also included is the handy 6D Mark II "roadmap," an easy-to-use visual guide to the camera's features and controls. Learn when to use each option and, more importantly, when not to use them, by following the author’s recommended settings for every menu entry. With best-selling photographer and mentor David Busch as your guide, you'll quickly have full creative mastery of your camera’s capabilities, whether you're shooting on the job, as an advanced enthusiast, or are just out for fun. Start building your knowledge and confidence, while bringing your vision to light with the Canon EOS 6D Mark II today. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

David Busch's Nikon D850 Guide to Digital SLR Photography David Busch's Nikon D850 Guide to Digital SLR Photography is your all-in-one comprehensive resource and reference for the feature-packed Nikon D850 camera. Built around a ground-breaking 45.7 megapixel back-illuminated sensor, this pro/enthusiast model offers incredible image quality and high ISO performance, along with 4K movie shooting capabilities. With continuous shooting up to 9 fps with optional battery grip, the Nikon D850 is one of the most versatile cameras the company has ever offered. With this book in hand, you master all the camera’s impressive features, and fine tune your skills as you develop your creativity taking great photographs with your D850.Filled with detailed how-to steps and full-color illustrations, David Busch's Nikon D850 Guide to Digital SLR Photography covers all the camera's capabilities in depth, from taking your first photos through advanced details of setup, exposure, lens selection, lighting, and more. It relates each feature to specific photographic techniques and situations. Also included is a handy visual guide to the D850, with close-up photos and descriptions of the camera's essential features and controls. Learn when to use each option and, more importantly, when not to use them, by following the author’s recommended settings for every menu entry. With best-selling photographer and mentor David Busch as your guide, you'll quickly have full creative mastery of your camera’s capabilities, whether you're shooting on the job, as an advanced enthusiast, or are just out for fun. Start building your knowledge and confidence, while bringing your vision to light with the Nikon D850 today. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Wide-Angle Photography The very thing that makes wide-angle photography so compelling also makes it a challenge: While you’re sure to capture a vast scene using a wide-angle lens, it can be difficult to direct the viewer’s attention when so many elements are included in an image. For many photographers, the results of their wide-angle attempts are a disappointment and they just can’t seem to achieve that “Wow†they are hoping for in their images. Whether you’re new to wide-angle lenses or you’ve been frustrated by them for a long time, expert photographer, teacher, and author Chris Marquardt is here to help. Wide-Angle Photography is packed with information—as well as beautiful and inspiring photography—that will help you take your wide-angle image making to the next level. In a friendly, accessible manner Chris walks you through in-depth discussions of both the advantages and the pitfalls of wide-angle photography, the fundamentals you need to know, composition and design principles, and the specific genres in which wide-angle lenses can be used to create outstanding images—not only for landscape photography, but for portrait, street, architectural, and interior photography, as well. Throughout the book, Chris offers hands-on exercises that drive home the concepts being taught so you can learn by doing. Chris also dedicates two full chapters to tilt-shift lenses for those who are interested in exploring and maximizing the fascinating capabilities these kinds of lenses offer. Topics include: Types of lenses and filters Understanding depth of field Angles of view, crop factors, and focal lengths Handling distortion and aberrations Composition, design, and context Point of view and perspective Wide-angle for various genres Panoramas and stitching images Tilt-shift lenses Hands-on exercises And much more… PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

David Busch's Sony Alpha a7 III Guide to Digital Photography David Busch's Sony Alpha a7 III Guide to Digital Photography is most comprehensive resource and reference for Sony’s affordable 24MP full-frame mirrorless camera. With advanced 693-point phase detect autofocus, 5-axis in-body image stabilization, 10 frames-per-second continuous shooting, and 4K video capture, the a7 III offers enthusiasts a versatile combination of advanced features. This book shows you how to master those capabilities as you explore the world of digital photography and hone your creativity with the a7 III.Filled with detailed how-to steps and full-color illustrations, David Busch's Sony Alpha a7 III Guide to Digital Photography covers every feature of this camera in depth, from taking your first photos through advanced details of setup, exposure, lens selection, lighting, and more, and relates each feature to specific photographic techniques and situations. Also included is the handy camera "roadmap," an easy-to-use visual guide to the camera's features and controls. Learn when to use every option and, more importantly, when not to use them, by following the author’s recommended settings for each menu entry. With best-selling photographer and mentor David Busch as your guide, you'll quickly have full creative mastery of your camera’s capabilities, whether you're shooting on the job, as an advanced enthusiast exploring full frame photography for the first time, or are just out for fun. Start building your knowledge and confidence, while bringing your vision to light with the Sony a7 III. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Mastering the Nikon D850 Mastering the Nikon D850 by Darrell Young provides a wealth of experience-based information and insights for owners of the new D850 camera. Darrell is determined to help the user navigate past the confusion that often comes with complex and powerful professional camera equipment. This book explores the features and capabilities of the camera in a way that far surpasses the user’s manual. It guides readers through the camera features with step-by-step setting adjustments; color illustrations; and detailed how, when, and why explanations for each option. Every button, dial, switch, and menu configuration setting is explored in a user-friendly manner, with suggestions for setup according to various shooting styles. Darrell’s friendly and informative writing style allows readers to easily follow directions, while feeling as if a friend dropped in to share his knowledge. The information in this book goes beyond the camera itself and also covers basic photography technique. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Underwater Photography This is a step-by-step guide to taking professional quality underwater photos with a point-and-shoot camera. _x000D_Modern compact cameras are capable of capturing fantastic underwater images – and this book shows you how. Easy-to-follow techniques are accompanied by hundreds of photographs that show you how it is done and the results you can achieve. _x000D_There is advice for both beginners and more advanced compact camera users, covering topics such as what camera to buy and how to look after it, how to master settings for different cameras and how to compose great underwater photographs. _x000D_Perfect for divers and snorkelers, this book will take your photography to a new level. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

How Do I Do That In Lightroom Classic? Lightroom has become the photographer’s tool because it just has so much power and so much depth, but because it has so much power and depth, sometimes the things you need are…well…kinda hidden or not really obvious. There will be a lot of times when you need to get something done in Lightroom, but you have no idea where Adobe hid that feature, or what the “secret handshake†is to do that thing you need now so you can get back to working on your images. That’s why this book was created: to get you to the technique, the shortcut, or exactly the right setting, right now. How Do I Do That In Lightroom Classic? (2nd Edition) is a fully updated version of the bestselling first edition, and here's how it works: When you need to know how to do a particular thing, you turn to the chapter where it would be found (Print, Slideshow, Organizing, Importing, etc.), find the thing you need to do (it’s easy—each page covers just one single topic), and Scott tells you exactly how to do it just like he was sitting there beside you, using the same casual style as if he were telling a friend. That way, you get back to editing your images fast. This isn’t a book of theory, full of confusing jargon and detailed multi-step concepts. This is a book on which button to click, which setting to use, and exactly how and when to use it, so you’re never “stuck†in Lightroom again. This will be your “go to†book that sits within reach any time you’re working in Lightroom, and you are going to love having this type of help right at your fingertips. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

The Enthusiast's Guide to iPhone Photography If you’re a passionate photographer and you’re ready to take your work to the next level, The Enthusiast’s Guide book series was created just for you. Whether you’re diving head first into a new topic or exploring a classic theme, Enthusiast’s Guides are designed to help you quickly learn more about a topic or subject so that you can improve your photography. The Enthusiast’s Guide to iPhone Photography: 63 Photographic Principles You Need to Know teaches you what you need to know in order to shoot great images with your iPhone. Chapters are broken down into numbered lessons, with each lesson providing all you need to improve your photography. Photographer and author Seán Duggan covers the iPhone's basic and advanced camera controls, the apps you need most for shooting and processing your images, and the principles you need to know in order to capture and share great, creative, beautiful images with your mobile device. Lessons include: 4. Five Essential Apps You Need 11. Capture Action with Burst Mode 13. Portrait Mode 34. Night Photography 38. Double Exposures and Composites 43. The Video Settings 59. Share on Social Media Written in a friendly and approachable manner, and illustrated with examples that drive home each lesson, The Enthusiast’s Guide to iPhone Photography is designed to be effective and efficient, friendly and fun. Read an entire chapter at once, or read just one topic at a time. With either approach, you’ll quickly learn a lot so you can head out with your camera to capture great shots. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Mastering Bird Photography In Mastering Bird Photography: The Art, Craft, and Technique of Photographing Birds and Their Behavior, acclaimed bird photographer and author Marie Read shares techniques and stories behind her compelling images, offering fresh insights into making successful bird photographs, whether you’re out in the field or in the comfort of your own backyard. In this richly illustrated book, you’ll learn how to be in the right place at the right time and how to obtain tack sharp portraits, and then take your skills to the next level in order to capture action shots, illustrate birds in their habitats, and portray birds in evocative and artistic ways. Building on basic technical topics such as camera choice, lens choice, and camera settings, Marie reveals how fieldcraft, compositional decisions, and knowledge of bird behavior contribute greatly to a successful bird photograph. Captions for the over 400 images contained in the book provide details on the equipment used, as well as camera settings. Throughout the book, bird behavior insights provide bird photographers of all skill levels a wealth of essential insider information that will help you produce images that stand out from the crowd. Topics include: Equipment and accessoriesFocus, exposure, and lightComposition and creativityBird photography ethicsCapturing bird behaviorStorytelling imagesAction and in-flight shotsBackyard photo studioWeather, water, and moodTop bird photo sites in North AmericaBasic image editing…and much more PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

David Busch's Nikon Z7 Guide to Digital Photography David Busch's Nikon Z7 Guide to Digital Photography is your all-in-one comprehensive resource and reference for the exciting Nikon Z7 compact mirrorless camera. This ground-breaking pro/enthusiast camera is built around a 45.7 megapixel back-illuminated sensor, that offers incredible image quality, especially when coupled with a new line of ultra-sharp S-series, Z-mount lenses. The affordable FTZ adapter allows you to use more than 300 different lenses in Nikon’s F-mount lineup, too. Five-axis in-body image stabilization provides up to five stops of anti-shake performance so you can hand-hold the camera at slower shutter speeds. With 493 phase-detect AF focus points, covering 90 percent of the frame, and the next-generation EXPEED 6 processing chip, the Z7 offers lightning fast focus for stills and both 4K and Full HD movie-shooting. The stunning 3.7 megapixel Quad VGA electronic viewfinder presents a crystal-clear image as you shoot. With this book in hand, you’ll master all the camera’s impressive features, and fine tune your camera skills as develop your creativity taking great photographs with your new Z7.Filled with detailed how-to steps and full-color illustrations, David Busch's Nikon Z7 Guide to Digital Photography covers all the camera's capabilities in depth, from taking your first photos through advanced details of setup, exposure, lens selection, lighting, and more, and relates each feature to specific photographic techniques and situations. Also included is the handy visual guide to the Z7, with close-up photos and descriptions of the camera's essential features and controls. Learn when to use each option and, more importantly, when not to use them, by following the author’s recommended settings for every menu entry. With best-selling photographer and mentor David Busch as your guide, you'll quickly have full creative mastery of your camera’s capabilities, whether you're shooting on the job, as an advanced enthusiast, or are just out for fun. Start building your knowledge and confidence, while bringing your vision to light with the Nikon Z7 today. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

David Busch's Nikon Z6 Guide to Digital Photography David Busch's Nikon Z6 Guide to Digital Photography is your all-in-one comprehensive resource and reference for the exciting and affordable Nikon Z6 compact mirrorless camera. This ground-breaking enthusiast camera is built around a 24.5 megapixel sensor, that offers excellent image quality and ISO speeds from ISO 100-51200. The Z6 can be fitted with any of the new ultra-sharp S-series, Z-mount lenses, or mount a full line of Nikon’s existing F-mount lenses, with the optional FTZ adapter. Five-axis in-body image stabilization provides up to five stops of anti-shake performance so you can hand-hold the camera at slower shutter speeds. With 273 phase-detect AF focus points, covering 90 percent of the frame, and the next-generation EXPEED 6 processing chip, the Z6 can shoot sports and action at up to 12 frames per second, with lightning fast focus. The Z6 can capture both 4K and Full HD movies, too. With this book in hand, you’ll master all the camera’s impressive features, and fine tune your camera skills as develop your creativity taking great photographs with your new Z6.Filled with detailed how-to steps and full-color illustrations, David Busch's Nikon Z6 Guide to Digital Photography covers all the camera's capabilities in depth, from taking your first photos through advanced details of setup, exposure, lens selection, lighting, and more, and relates each feature to specific photographic techniques and situations. Also included is the handy visual guide to the Z6, with close-up photos and descriptions of the camera's essential features and controls. Learn when to use each option and, more importantly, when not to use them, by following the author’s recommended settings for every menu entry. With best-selling photographer and mentor David Busch as your guide, you'll quickly have full creative mastery of your camera’s capabilities, whether you're shooting on the job, as an advanced enthusiast, or are just out for fun. Start building your knowledge and confidence, while bringing your vision to light with the Nikon Z6 today. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Adobe Photoshop and Lightroom Classic CC Classroom in a Book (2019 release) Adobe Lightroom CC and Photoshop CC for Photographers Classroom in a Book contains lessons that cover the basics and beyond, providing countless tips and techniques to help you become more productive with the programs. You can follow the book from start to finish or choose only those lessons that interest you. Using Lightroom CC and Photoshop CC together can dramatically speed your workflow and decrease editing time. This book teaches you exactly when to use each program and how to pass images back and forth between them at the highest possible quality. You'll learn how to import, organize, correct and add creative color effects in Lightroom using global and local editing tools, as well as how to merge multiple exposures and stitch panoramas. In Photoshop, you'll learn practical techniques for combining photos, pro-level retouching, creating precise selections, masking, turning a photo into a painting and pencil sketch, and adding creative blur effects. Back in Lightroom, you'll learn how to show off your masterpieces by exporting them en masse, sharing via social media, creating fine art-style signed print layouts, slideshows, photo book, and web gallery projects. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

The Landscape Photography Book Have you ever dreamed of taking such incredible landscape photos that your friends and family say, “Wait a minute, this is your photo?! You took this?†Well, you’re in luck. Right here, in this book, pro photographer and award-winning author Scott Kelby teaches you how to shoot and edit jaw-dropping landscape photographs. Scott shares all his secrets and time-tested techniques, as he discusses everything from his go-to essential gear and camera settings to the landscape photography techniques you need to create absolutely stunning images. From epic scenes at sunrise to capturing streams and waterfalls with that smooth, silky look, and from photographing the night sky or the Milky Way to creating breathtaking, sweeping panoramas, Scott has got you covered. Among many other topics, you’ll learn: • The secrets to getting super-sharp, crisp images (without having to buy a new lens). • Exactly which camera settings work best for landscape photography and why (and which ones you should avoid). • Where to focus your camera for tack-sharp images from foreground to background. • How to shoot beautiful high dynamic range images and stunning panoramas (and even HDR panos!), along with how to post-process them like a pro. • How to create captivating long-exposure landscape shots that wow your viewers. • What gear you need, what gear you can skip, which accessories work best, and a ton of killer tips that will not only help you create better images, but make the entire experience thatmuch more fun. It’s all here, from the planning, to the shoot, to the post-processing—taking your images from flat to fabulous—and best of all, it’s just one topic per page, so you’ll get straight to the info you need fast. There has never been a landscape book like it! TABLE OF CONTENTSChapter 1: Essential GearChapter 2: Camera Settings & LensesChapter 3: Before Your ShootChapter 4: CompositionChapter 5: HDR & PanosChapter 6: Long ExposuresChapter 7: Starry Skies & the Milky WayChapter 8: Post-ProcessingChapter 9: Even More TipsChapter 10: Landscape Recipes PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

David Busch's Canon EOS R Guide to Digital Photography David Busch's Canon EOS R Guide to Digital Photography is your all-in-one comprehensive resource and reference for the exciting new Canon EOS R full-frame mirrorless camera. It sports a high-resolution 30 MP sensor embedded with 5,655 Dual-Pixel phase detection AF points for lightning-fast, precise autofocus. The EOS R’s 3.69 million dot electronic viewfinder provides a bright, clear view. Three available mount adapters make it easy to supplement your R-mount lenses with a broad selection of legacy Canon EF and EF-S optics. The EOS R has Wi-Fi/ NFC connectivity to allow linking the camera to a computer and iOS or Android smart devices, high-definition movie-making capabilities, and a versatile swiveling touch screen LCD. With this book in hand, you can quickly apply all these advanced features to your digital photography, while boosting your creativity to take great photographs with your Canon EOS R.Filled with detailed how-to steps and full-color illustrations, David Busch's Canon EOS R Guide to Digital Photography covers all this upscale camera's features in depth, from taking your first photos through advanced details of setup, exposure, lens selection, lighting, and more, and relates each feature to specific photographic techniques and situations. Also included is the handy EOS R "roadmap" chapter, an easy-to-use visual guide to the camera's features and controls. Learn when to use each option and, more importantly, when not to use them, by following the author’s recommended settings for every menu entry. With best-selling photographer and mentor David Busch as your guide, you'll quickly have full creative mastery of your camera’s capabilities, whether you're shooting on the job, as an advanced enthusiast, or are just out for fun. Start building your knowledge and confidence, while bringing your vision to light with the Canon EOS R today. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Creative Black and White Black-and-white photography poses unique challenges; without color to guide the eye, contrast, lighting, and composition take on even more importance. In Creative Black and White, 2nd Edition, renowned photographer Harold Davis explains these elements and demonstrates the basic rules of black and white photography, as well as when and how to break them. He breaks through the complexity of this photographic medium, explores opportunities for black-and-white imagery, and shows how to capitalize on each and every one of them. This new, revised, and expanded edition brings the tools up to date with extended sections on monochrome in Lightroom, Photoshop, and related plugins. TABLE OF CONTENTS THE MONOCHROMATIC VISION Past, Present, and Future Thinking in Black and White Contrast Color Implied The Tonal Landscape Visual Implication Seeing in Black and White Pre-Visualization Techniques Black and White Composition Framing Patterns and Lines Shape and Form High Key Low Key Shades of Gray Finding Monochromatic Subjects Black and White at Night Photographing People Portraiture in Black and White BLACK AND WHITE IN THE DIGITAL ERA Digital Black and White Roadmap The RAW Advantage Black and White in Adobe Camera RAW Black and White in Lightroom Grayscale Conversion Using Presets HSL Conversion Exposure Gradients and Adjustments Exporting Virtual Copies into Photoshop as Layers Multiple Layers and Masking in Photoshop Multi-RAW Processing in Photoshop Black and White in Photoshop Blending with Black Using the Channel Mixer Black & White Adjustment Layers Silver Efex Pro Topaz B&W Effects OnOne Perfect B&W The Digital Analog to the Analog Zone System Combining Conversions in Photoshop CREATIVE BLACK AND WHITE OPPORTUNITIES Lighting and Monochromatic Photos Creating High-Key Effects Creating Low-Key Effects HDR in Black and White Shooting for HDR Using HDR Software Toning and Tinting Tinting with a Black & White Adjustment Layer Split Toning The Ansel Adams Effect Selective Color Hand Coloring Using LAB Color Inverting the L Channel Equalizing LAB Channels Swapping Tonalities Using Blending Modes LAB Inversions Soft Focus Adding Soft Focus Pinhole Effect Solarization Using Curves to Solarize an Image Simulating the Blossfeldt Effect Duotone and Tritone Effects Adding and Reducing Noise Film Effects Infrared Camera Conversions Infrared Conversion without an IR Camera Creating X-Ray Images MOBILE BLACK AND WHITE Black and White using a Cell Phone Camera Working with Snapseed Toward a Monochromatic Mobile Workflow Notes and Resources Glossary Index PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

50 Things Photographers Need to Know About Focus While focusing your camera seems like it should be a no-brainer—there’s autofocus, after all!—it’s often not a simple task. Depending on the shooting situation, your camera, and the countless scenarios that can “throw off†the focus, the task of achieving sharp images with great focus can be deceptively challenging. If you’re a passionate photographer eager to learn the best ways to achieve tack-sharp focus in your images, these 50 focus-based principles are exactly what you need to take your work to the next level. With photographer and author John Greengo as your guide, you’ll quickly learn nearly four dozen techniques for achieving focus in every shooting situation. You’ll learn: • How to optimize autofocus no matter what kind of camera you have (DSLR or mirrorless) • How to master manual focus • Which focus modes and focus areas work best for different situations • How to use your camera’s autofocus aids, such as magnification and focus peaking • Techniques to keep your camera stable, either handheld or on a tripod • How shutter speed and aperture affect sharpness Written in the author’s friendly and approachable style, and illustrated with examples that clearly show how each technique can help you capture great photos, 50 Things Photographers Need to Know About Focus is designed to be an effective, fast, and fun way to learn how to achieve great focus in your images—no matter what situation. TABLE OF CONTENTS Chapter 1: Focus Basics Chapter 2: Autofocus Chapter 3: Mirrorless Autofocus Chapter 4: DSLR Autofocus Chapter 5: Customized Autofocus Controls Chapter 6: Autofocus Aids Chapter 7: Autofocus and Lenses Chapter 8: Manual Focus and Lenses Chapter 9: Exposure Control for Focus Chapter 10: Advanced Focusing Techniques Chapter 11: Other Focus Topics PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Adobe Photoshop Lightroom Classic CC Classroom in a Book (2019 Release) Classroom in a Book, the best-selling series of hands-on software training workbooks, offers what no other book or training program does—an official training series from Adobe, developed with the support of Adobe product experts. Adobe Photoshop Lightroom Classic CC Classroom in a Book contains lessons that cover the basics and beyond, providing countless tips and techniques to help you become more productive with the program. You can follow the book from start to finish or choose only those lessons that interest you. The full text downloaded to your computer With eBooks you can: search for key concepts, words and phrases make highlights and notes as you study share your notes with friends eBooks are downloaded to your computer and accessible either offline through the Bookshelf (available as a free download), available online and also via the iPad and Android apps. Upon purchase, you will receive via email the code and instructions on how to access this product. Time limit The eBooks products do not have an expiry date. You will continue to access your digital ebook products whilst you have your Bookshelf installed. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

David Busch’s Sony Alpha a6400/ILCE-6400 Guide to Digital Photography David Busch’s Sony Alpha a6400/ILCE-6400 Guide to Digital Photography is the most comprehensive reference and guide book available for Sony’s advanced APS-C mirrorless camera. This enthusiast digital camera has a more powerful processor and upgraded autofocus with enhanced real-time tracking and advanced Eye AF. Its new LCD swivels to face forward, making the camera excellent for self-portraits, vlogging, and other applications. The a6400 features a 24 megapixel sensor with 425 embedded phase-detect pixels for lightning-fast autofocus at up to 11 frames per second. With an electronic shutter that provides a silent shooting option, stunning 4K/UHD video capabilities, and new time-lapse photography features, the a6400/ILCE-6400 is a versatile digital camera that’s simple to use, yet boasts features demanded by the most avid photo buff. With this book in hand, you will discover all the capabilities of the Sony Alpha a6400/ILCE-6400 as you explore the world of digital photography, develop your creativity, and capture the best photographs you’ve ever taken.Filled with detailed how-to steps and full-color illustrations, David Busch’s Sony Alpha a6400/ILCE-6400 Guide to Digital Photography describes every feature of this sophisticated camera in depth, from taking your first photos through advanced details of setup, exposure, lens selection, lighting, and more. It relates each feature to specific photographic techniques and situations. Also included is the handy camera “roadmap,†an easy-to-use visual guide to the a6400/ILCE-6400’s features and controls. Learn when to use every option and, more importantly, when not to use them, by following the author’s recommended settings for every menu entry. With best-selling photographer and mentor David Busch as your guide, you’ll quickly have full creative mastery of your camera’s capabilities, whether you’re shooting on the job, taking pictures as an advanced enthusiast pushing the limits of your imagination, or are just out for fun. Start building your knowledge and confidence, while bringing your vision to light with the Sony Alpha a6400/ILCE-6400. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Mastering the Nikon Z6 Mastering the Nikon Z6 by Darrell Young provides a wealth of experience-based information and insights for owners of Nikon's new mirrorless full-frame Z6 camera. Darrell is determined to help the user navigate past the confusion that often comes with complex and powerful professional camera equipment. This book explores the features and capabilities of the camera in a way that far surpasses the user’s manual. It guides readers through the camera features with step-by-step setting adjustments; color illustrations; and detailed how, when, and why explanations for each option. Every button, dial, switch, and menu configuration setting is explored in a user-friendly manner, with suggestions for setup according to various shooting styles. Darrell’s friendly and informative writing style allows readers to easily follow directions, while feeling as if a friend dropped in to share his knowledge. The information in this book goes beyond the camera itself and also covers basic photography technique. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Basic Photographic Materials and Processes Basic Photographic Materials and Processes describes the three crucial stages of creating the perfect photograph—capture, processing and output—by providing a thorough technical investigation of modern, applied photographic technologies. This new edition has been fully revised and updated to explore digital image capture, processing and output. It covers a wide range of topics including: the scientific principles of measuring and recording light, the inner workings of digital cameras, image processing concepts, color management and photographic output to screen and print media. With these topics come in-depth discussions of extending dynamic range, image histograms, camera characterization, display capabilities, printer and paper technologies. It also includes applied exercises that provide the reader with a deeper understanding of the material through hands-on experiments and demonstrations, connecting theoretical concepts to real-world use. This comprehensive text provides photography students, educators and working professionals with the technical knowledge required to successfully create images and manage digital photographic assets. It is an essential resource for mastering the technical craft of photography. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

The Fujifilm X-T3 In this book, popular Fuji Rumors "X-Pert Corner" columnist Rico Pfirstinger teaches you about the little-known capabilities of the Fujifilm X-T3, which he’s discovered through months of in-depth research and experimentation with the camera. After a brief overview of the camera’s basic functions, Rico cuts to the chase and provides a plethora of tips and practical instructions not found in the user's manual. With this knowledge, you will be able to take full advantage of the capabilities of the X-T3. The Fujifilm X-series cameras have amazing features but may require an adjustment period for those new to using these cameras, even photographers who have been lifetime shooters. This guide will help you to quickly feel comfortable using your camera so that you can achieve excellent results. Topics covered include: •Menu shortcuts •Long exposures •Firmware upgrades •Hybrid autofocus system •Auto and manual focusing •Face detection •ISOless sensor •Dynamic Range expansion •Film simulations •Custom settings •RAW conversion •Movies •Self-timer •Flash •Adapted lenses •Taking Videos •And much more… PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Adobe Photoshop Classroom in a Book (2020 release) Creative professionals seeking the fastest, easiest, most comprehensive way to learn Adobe Photoshop choose Adobe Photoshop Classroom in a Book (2020 release) from Adobe Press. The 15 project-based lessons show key step-by-step techniques for working in Photoshop, including how to correct, enhance, and distort digital images, create image composites, and prepare images for print and the web. In addition to learning the essential elements of the Photoshop interface, this revised edition for the 2020 release covers features like the new Object Selection tool, saving Cloud Documents for easy access from Photoshop on other devices such as the Apple iPad, removing objects with upgraded Content-Aware Fill, applying styles and objects such as gradients and shapes, instantly using redesigned Presets panels, and much more! The online companion files include all the necessary assets for readers to complete the projects featured in each chapter. All buyers of the book get full access to the Web Edition: A Web-based version of the complete ebook enhanced with video and multiple-choice quizzes PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

David Busch's Sony Alpha a7R IV Guide to Digital Photography David Busch's Sony Alpha a7R IV Guide to Digital Photography is the most comprehensive resource and reference for Sony’s innovative 61-megapixel full frame mirrorless camera. Capable of 10 frame-per-second bursts even at full resolution, the a7R IV is fast enough for action photography, and its 15-stop enhanced dynamic range delivers the image quality that the most demanding landscape or fine-art photographer requires. This camera’s remarkable low-light performance, fast sensor-based 567-point phase detect autofocus (with real-time face and eye tracking in both still and movie modes), and improved 5-axis in-body image stabilization, the a7R IV has all the tools needed to take incredible images. This book will show you how to master those features as you explore the world of digital photography and hone your creativity with your a7R IV.Filled with detailed how-to steps and full-color illustrations, David Busch's Sony Alpha a7R IV Guide to Digital Photography covers every feature of this camera in depth, from taking your first photos through advanced details of setup, exposure, lens selection, lighting, and more, and relates each feature to specific photographic techniques and situations. Also included is the handy camera "roadmap" chapter, an easy-to-use visual guide to the camera's features and controls. Learn when to use every option and, more importantly, when not to use them, by following the author’s recommended settings for each menu entry. With best-selling photographer and mentor David Busch as your guide, you'll quickly have full creative mastery of your camera’s capabilities, whether you're shooting on the job, as an advanced enthusiast exploring full frame photography for the first time, or are just out for fun. Start building your knowledge and confidence, while bringing your vision to light with the Sony a7R IV. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Adobe Photoshop Elements 2020 Classroom in a Book Adobe Photoshop Elements 2020 Classroom in a Book is the most thorough and comprehensive way for you to master Adobe’s industry-leading consumer-targeted photo-editing software. Each chapter in this step-by-step, lesson-based guide contains a project that builds on your growing knowledge of the program, while end-of-chapter review questions reinforce each lesson. You will learn the basics of editing your images with Photoshop Elements and learn how to best use the program's many new features. This edition covers many new and improved features in Adobe Photoshop Elements 2020, including two tools based on Adobe Sensei AI technology that smooth skin to improve people’s appearance while still looking natural, and colorize black and white photos or give a new look to color images. The revolutionary Select Subject feature makes complex selections in one click that would normally take much longer to create. And, of course, this edition includes Auto Creations delivered to your Home Screen and some of the latest guided edits, such as a fun way to paint patterns onto any photo. You’ll discover new techniques that let you expand your creativity and improve your images from the other side of the photography process. And you’ll learn how to print, export, and share your images. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

The Off-Camera Flash Handbook If your past attempts at learning flash have all ended in failure (not to mention tears and/or blind rage), then The Off-Camera Flash Handbook is about to change everything for you. For years, photographer Vanessa Joy has been using off-camera flash to create gorgeous portraits that look like they were shot in the most beautiful natural light at the perfect time of day. Well, guess what? That consistent look was not created thanks to the most amazing luck with the weather. No. It was created by a pro photographer who mastered her use of off-camera flash. And with her down-to-earth and practical explanations, that’s exactly what Vanessa teaches you in this book. Vanessa breaks down off-camera flash into an easy-to-understand approach, and instead of focusing on the gear and the settings (which are also included, of course), she focuses on the kinds of shots you want to make. This book is about learning to use off-camera flash easily and quickly so that you can create beautiful, natural-looking light in any situation, at any time you need it…regardless of the weather or time of day. The book is divided into three parts. Part One covers the fundamentals of off-camera flash, and it does so without blasting you with a firehose of information. Instead, Vanessa gives you the basics you need so that you can start shooting right away without becoming overwhelmed with technical jargon. Once you’re set up and ready to go, Vanessa jumps right into Part Two with specific photo scenarios and real-world situations where you’ll learn key techniques for using your flash to create consistent, beautiful photographs. For each scenario, Vanessa provides the goal for the shoot, a gear list, the step-by-step shooting instructions, and images that show both the progress of the shoot and the behind-the-scenes shots or lighting diagrams of the setup. She also discusses problems you may encounter, variations on the shot, and additional practical scenarios for each situation. Just a few examples include: • Recreating the golden hour at any time • Shooting groups • Making indoors look like outdoors • Enhancing natural light • Using flash at events • Working in harsh sunlight • Creating silhouettes • Shooting at sunset • Fixing an ugly-light room • And much more Finally, Part Three tackles the questions you’ll likely have once you’ve got the basics under your belt and you’re already creating great photos with your off-camera flash—things like high-speed sync, sync speed, a practical understanding of the inverse square law, etc. There is also a helpful FAQ section at the end of the book. TABLE OF CONTENTS PART 1: GETTING STARTED WITH OFF-CAMERA FLASH You Already Know This Getting Your Flash Off Camera The Fourth Point of the Exposure Triangle Light Positions and Modifiers How to Add More Lights PART 2: SCENARIOS Golden Haze Golden Hour Creating Twilight Photographing at Sunset Making a Magenta Sunset Groups with One Light Individual Portraits Couple Portraits Enhancing Natural Light Making Indoors Look Like Outdoors Super Soft Portrait Light Creating a Fiery Sky Keeping the Sky Blue Lighting a Dark Room Creating a Silhouette Turning Day into Night Tiny Little Details Table Details Event Speeches In Harsh Sunlight Shooting with Reflectors Event Bounce Flash Using Gels for Fun Color Effects Using Gels to Color Correct Lighting a Dark Room Turn a Rainy Day Sunny Lighting to Look Like Window Light Making Front Bokeh To Fill in Shadows Wow, This Indoor Light Sucks Rim Lighting PART 3: FACTS AND FAQS What Are You Talking About? But Light Doesn’t Do That FAQs about OCF PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

David Busch’s Sony Alpha a6100/ILCE-6100 Guide to Digital Photography David Busch’s Sony Alpha a6100/ILCE-6100 Guide to Digital Photography is your essential handbook for learning all the powerful – but easy to use -- features of Sony's most advanced entry-level APS-C mirrorless camera. Its new LCD swivels to face forward, making the camera excellent for self-portraits, vlogging, and other applications. The a6100 features a 24 megapixel sensor with 425 embedded phase-detect pixels for lightning-fast autofocus at up to 11 frames per second. With an electronic shutter that provides a silent shooting option, stunning 4K/UHD video capabilities, and new time-lapse photography features, the a6100/ILCE-6100 is a versatile digital camera that has simple operation yet boasts all the features you need to take great photos. With this book in hand, you will discover all the capabilities of the Sony Alpha a6100/ILCE-6100 as you explore the world of digital photography, develop your creativity, and capture the best photographs you’ve ever taken.Filled with detailed how-to steps and full-color illustrations, David Busch’s Sony Alpha a6100/ILCE-6100 Guide to Digital Photography describes every feature of this sophisticated camera in depth, from taking your first photos through advanced details of setup, exposure, lens selection, lighting, and more. It relates each feature to specific photographic techniques and situations. Also included is the handy camera “roadmap,†an easy-to-use visual guide to the a6100/ILCE-6100’s features and controls. Learn when to use every option and, more importantly, when not to use them, by following the author’s recommended settings for every menu entry. With best-selling photographer and mentor David Busch as your guide, you’ll quickly have full creative mastery of your camera’s capabilities, whether you’re shooting on the job, taking pictures as an advanced enthusiast pushing the limits of your imagination, or are just out for fun. Start building your knowledge and confidence, while bringing your vision to light with the Sony Alpha a6100/ILCE-6100. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Adobe Photoshop Lightroom Classic Classroom in a Book (2020 release) The fastest, easiest, most comprehensive way to learn Adobe Photoshop Lightroom Classic! Classroom in a Book®, the best-selling series of hands-on software training workbooks, offers what no other book or training program does–an official training series from Adobe, developed with the support of Adobe product experts. Adobe Photoshop Lightroom Classic Classroom in a Book (2020 release) contains 12 lessons that cover the basics and beyond, providing countless tips and techniques to help you become more productive with the program. You can follow the book from start to finish or choose only those lessons that interest you. Purchase of this book includes valuable online features. Follow the instructions in the book’s Getting Started section to unlock access to: Downloadable lesson files you need to work through the projects in the book Web Edition containing the complete text of the book, interactive quizzes, and videos that walk you through the lessons step by step PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Digital Photographer's Handbook Discover how to get the very best from your photography with clear step-by-step guidance from expert photographer, Tom Ang. In this fully comprehensive photography companion, renowned photographer and teacher Tom Ang teaches you how to capture, enhance, and transform your photographs. The first half of the book explains all of the essential techniques that every photographer needs to learn - from how to handle your camera correctly and understand its features, to composing a successful shot. The second half develops your understanding of photography, guiding you through a range of projects that focus on different photographic genres and subjects, including landscapes, cityscapes, and live events. It explains how to digitally enhance your images, not only to improve the original shot, but also to apply creative techniques that will take your image to a new level. This section also gives advice on the best way to share your work, to choosing the most suitable equipment, and should you wish, how to develop a career in photography. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

The Underwater Photographer In this long-awaited fifth edition of the best-selling book, Martin Edge continues to provide the definitive guide to underwater photography. The book covers everything from the basic principles, the equipment and approaches to composition and lighting through to creating an individual style. The book features over 400 updated colour images - taken on numerous dives around the world - with an accompanying narrative that provides detailed information on how the shots were taken, their strengths and weaknesses and how to fix mistakes. Practical examples take you step-by-step through the basic techniques: photographing shipwrecks, divers, marine life, macro images and taking photographs at night. New chapters cover the latest equipment, processes and techniques including SLR Cameras, water contact lenses, mirrorless interchangeable lens cameras, micro four third systems, super macro techniques, motion blur, LED lighting and more. Packed with inspiring examples from global diving destinations and speciality chapters written by professionals in the field, this book is an indispensable masterclass for both the novice and seasoned underwater photographer. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

David Busch’s Sony Alpha a6600/ILCE-6600 Guide to Digital Photography David Busch’s Sony Alpha a6600/ILCE-6600 Guide to Digital Photography is the most comprehensive reference and guide book available for Sony’s flagship APS-C mirrorless camera. This enthusiast digital camera has a more powerful processor and upgraded autofocus with enhanced real-time tracking and advanced Eye AF. Built-in 5-axis image stabilization allows sharp images hand-held even with slower shutter speeds. The a6600’s new LCD swivels to face forward, making the camera excellent for self-portraits, vlogging, and other applications. The a6600 features a 24 megapixel sensor with 425 embedded phase-detect pixels for lightning-fast autofocus at up to 11 frames per second, and a more powerful battery to extend shooting life. With an electronic shutter that provides a silent shooting option, stunning 4K/UHD video capabilities, and new time-lapse photography features, the a6600/ILCE-6600 is a versatile digital camera that’s simple to use, yet boasts features demanded by the most avid photo buff. With this book in hand, you will discover all the capabilities of the Sony Alpha a6600/ILCE-6600 as you explore the world of digital photography, develop your creativity, and capture the best photographs you’ve ever taken.Filled with detailed how-to steps and full-color illustrations, David Busch’s Sony Alpha a6600/ILCE-6600 Guide to Digital Photography describes every feature of this sophisticated camera in depth, from taking your first photos through advanced details of setup, exposure, lens selection, lighting, and more. It relates each feature to specific photographic techniques and situations. Also included is the handy camera “roadmap,†an easy-to-use visual guide to the a6600/ILCE-6600’s features and controls. Learn when to use every option and, more importantly, when not to use them, by following the author’s recommended settings for every menu entry. With best-selling photographer and mentor David Busch as your guide, you’ll quickly have full creative mastery of your camera’s capabilities, whether you’re shooting on the job, taking pictures as an advanced enthusiast pushing the limits of your imagination, or are just out for fun. Start building your knowledge and confidence, while bringing your vision to light with the Sony Alpha a6600/ILCE-6600. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Digital Photography Through the Year Discover how to capture the moods and moments of each season to stunning effect with renowned photographer Tom Ang. From photographing a dewdrop in spring to a beautiful frost in winter, you can now follow your hobby throughout the year with Digital Photography Through the Year. Whatever your level of expertise or type of camera, from the best digital SLRs on the market right down to camera phones, you'll find tips and tricks to help you get the most out of your shot. Fully updated for this third edition with the latest developments in technology and equipment, you'll learn how to take great photographs that convey a sense of time, place, and atmosphere. Packed with "how-to" advice and projects to keep you snapping throughout the year, Digital Photography Through the Year is an inspiring and practical guide to taking beautiful photos in every season. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

Mastering the Nikon Z50 Mastering the Nikon Z50 by Darrell Young provides a wealth of experience-based information and insights for owners of Nikon's new mirrorless Z50 camera. Darrell is determined to help the user navigate past the confusion that often comes with complex and powerful professional camera equipment. This book explores the features and capabilities of the camera in a way that far surpasses the user’s manual. It guides readers through the camera features with step-by-step setting adjustments; color illustrations; and detailed how, when, and why explanations for each option. Every button, dial, switch, and menu configuration setting is explored in a user-friendly manner, with suggestions for setup according to various shooting styles. Darrell’s friendly and informative writing style allows readers to easily follow directions, while feeling as if a friend dropped in to share his knowledge. The information in this book goes beyond the camera itself and also covers basic photography technique. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

The Digital Photography Book Learn how to take professional-quality photographs using the same tricks today’s top photographers use (surprisingly, it’s easier than you’d think)! This is a completely, totally updated version of the #1 best-selling digital photography book of all time! It’s the award winning, worldwide smash hit, written by Scott Kelby, that’s been translated into dozens of different languages. Here’s how Scott describes this book’s brilliant premise: “If you and I were out on a shoot, and you asked me, ‘Hey, how do I get this flower to be in focus, with the background out of focus?,’ I wouldn’t stand there and give you a photography lecture. In real life, I’d just say, ‘Put on your zoom lens, set your f-stop to f/2.8, focus on the flower, and fire away.’ That’s what this book is all about: you and I out shooting where I answer questions, give you advice, and share the secrets I’ve learned just like I would with a friend—without all the technical explanations and techie photo speak.†This isn’t a book of theory—full of confusing jargon and detailed concepts. This is a book on which button to push, which setting to use, and when to use it. With over 200 of the most closely guarded photographic “tricks of the trade,†this book gets you shooting dramatically better-looking, sharper, more colorful, more professional-looking photos every time. Each page covers a single concept that makes your photography better. Every time you turn the page, you’ll learn another pro setting, tool, or trick to transform your work from snapshots into gallery prints. If you’re tired of taking shots that look “okay,†and if you’re tired of looking in photography magazines and thinking, “Why don’t my shots look like that?†then this is the book for you.TABLE OF CONTENTSChapter 1: Pro Tips for Getting Sharp PhotosChapter 2: The Scoop on LensesChapter 3: Shooting Landscapes Like a ProChapter 4: Shooting Travel Like a ProChapter 5: Making Portraits Like a ProChapter 6: Making Portraits with Flash Like a ProChapter 7: Shooting Weddings Like a ProChapter 8: Shooting Sports Like a ProChapter 9: Shooting Other Stuff Like a ProChapter 10: Pro Tips for Getting Better PhotosChapter 11: How to Print Like a ProChapter 12: Photo Recipes to Help You Get the Shot PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

David Busch's Canon EOS 90D Guide to Digital Photography David Busch's Canon EOS 90D Guide to Digital Photography is your all-in-one comprehensive resource and reference for the advanced Canon EOS 90D camera. This upgraded 32.5 megapixel APS-C model features a 45-point autofocus system. The Dual Pixel CMOS hybrid autofocus brings lightning-fast phase detect AF to live view and high-definition movie modes, too. The 90D’s metering system includes a 220,000-pixel RGB+Infrared sensor with Face Detection for accurate exposure control. The 90D has Wi-Fi/ Bluetooth connectivity to allow linking the camera to a computer and iOS or Android smart devices, and an improved swiveling touch screen LCD. With this book in hand, you can quickly apply all these advanced features to your digital photography, while boosting your creativity to take great photographs with your Canon EOS 90D.Filled with detailed how-to steps and full-color illustrations, David Busch's Canon EOS 90D Guide to Digital Photography covers all this upscale camera's features in depth, from taking your first photos through advanced details of setup, exposure, lens selection, lighting, and more, and relates each feature to specific photographic techniques and situations. Also included is the handy 90D "roadmap," an easy-to-use visual guide to the camera's features and controls. Learn when to use each option and, more importantly, when not to use them, by following the author’s recommended settings for every menu entry. With best-selling photographer and mentor David Busch as your guide, you'll quickly have full creative mastery of your camera’s capabilities, whether you're shooting on the job, as an advanced enthusiast, or are just out for fun. Start building your knowledge and confidence, while bringing your vision to light with the Canon EOS 90D today. PHOTOGRAPHY,Techniques,Digital (see also COMPUTERS,Design,Graphics & Media,Photography)

The Rule of Thoughts (The Mortality Doctrine, Book Two) Reality just became a virtual nightmare in book two of the bestselling Mortality Doctrine series, the next phenomenon from the author of the Maze Runner series, James Dashner. Includes a sneak peek of The Fever Code, the highly-anticipated conclusion to the Maze Runner series—the novel that finally reveals how the maze was built! Michael thought he understood the VirtNet, but the truth he discovered is more terrifying than anyone at VirtNet Security could have anticipated. The cyber terrorist Kaine isn’t human. It’s a Tangent, a computer program that has become sentient. And Michael just completed the first step in turning Kaine’s master plan, the Mortality Doctrine, into a reality. The Mortality Doctrine will populate Earth entirely with human bodies harboring Tangent minds. The VNS would like to pretend the world is perfectly safe, but Michael and his friends know that the takeover has already begun. And if they don’t stop Kaine soon, it will be game over for humanity. The author who brought you the #1 New York Times bestselling MAZE RUNNER series and two #1 movies—The Maze Runner and The Scorch Trials—now brings you an electrifying cyber-adventure trilogy that takes you into a world of hyperadvanced technology, cyber terrorists, and gaming beyond your wildest dreams . . . and your worst nightmares. Praise for the Bestselling MORTALITY DOCTRINE series: “Dashner takes full advantage of the Matrix-esque potential for asking ‘what is real.’†—io9.com “Set in a world taken over by virtual reality gaming, the series perfectly capture[s] Dashner’s hallmarks for inventiveness, teen dialogue and an ability to add twists and turns like no other author.†—MTV.com “A brilliant, visceral, gamified mash-up of The Matrix and Inception, guaranteed to thrill even the non-gaming crowd.†—Christian Science Monitor YOUNG ADULT FICTION,Computers & Digital Media

Problems With A Point 'Points, questions, stories, and occasional rants introduce the 24 chapters of this engaging volume. With a focus on mathematics and peppered with a scattering of computer science settings, the entries range from lightly humorous to curiously thought-provoking. Each chapter includes sections and sub-sections that illustrate and supplement the point at hand. Most topics are self-contained within each chapter, and a solid high school mathematics background is all that is needed to enjoy the discussions. There certainly is much to enjoy here.'CHOICEEver notice how people sometimes use math words inaccurately? Or how sometimes you instinctively know a math statement is false (or not known)?Each chapter of this book makes a point like those above and then illustrates the point by doing some real mathematics through step-by-step mathematical techniques.This book gives readers valuable information about how mathematics and theoretical computer science work, while teaching them some actual mathematics and computer science through examples and exercises. Much of the mathematics could be understood by a bright high school student. The points made can be understood by anyone with an interest in math, from the bright high school student to a Field's medal winner. YOUNG ADULT NONFICTION,Computers,Programming

Cryptocurrencies and the Blockchain Revolution In January 2009, a mysterious software developer, Satoshi Nakamoto, exchanged a specially designed code with another developer. The code was a digital currency that Nakamoto had proposed several months before in a paper titled “Bitcoin: A Peer-to-Peer Electronic Cash System.†This was the first Bitcoin transaction. Since then, Bitcoin has become the face of a tech revolution in digital cryptocurrencies based on blockchain technology. Its success has sparked a tech revolution that could fundamentally change global economics. Author Brendan January delves into the world of coders, libertarians, criminals, financial regulators, and crypto-detectives to understand what digital cryptocurrencies have to offer, their limitations and potential pitfalls, security issues, and how they may affect government and financial regulations in the future. YOUNG ADULT NONFICTION,Computers,Programming
compteur pour site
































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































